71 |
72 |
167 |
168 | Options not demonstrated: 169 | 170 |
176 |
177 |
184 |
185 |
--------------------------------------------------------------------------------
/README.md:
--------------------------------------------------------------------------------
1 | ---
2 | page_type: sample
3 | description: A leafletjs plugin that makes it easy to overlay tile layers from the Azure Maps tile services.
4 | languages:
5 | - javascript
6 | - typescript
7 | products:
8 | - azure
9 | - azure-maps
10 | ---
11 |
12 | # Azure Maps Leaflet plugin
13 |
14 | A [leafletjs](https://leafletjs.com/) plugin that makes it easy to overlay tile layers from the [Azure Maps tile services](https://docs.microsoft.com/rest/api/maps/renderv2/getmaptilepreview).
15 |
16 | **Features:**
17 |
18 | - Authenticate using an Azure Maps subscription key or Azure Active Directory.
19 | - Works with with Azure Public and Government clouds.
20 | - [Supports over 30 languages](https://docs.microsoft.com/azure/azure-maps/supported-languages)
21 | - Supported layers:
22 | - **Road maps**
23 | - Main (`microsoft.base.road`) - All layers with our main style.
24 | - Labels (`microsoft.base.labels.road`) - Label data in our main style.
25 | - Hybrid (`microsoft.base.hybrid.road`) - Road, boundary and label data in our main style.
26 | - Dark grayscale (`microsoft.base.darkgrey`) - All layers with our dark grayscale style.
27 | - **Imagery** (`microsoft.imagery`)
28 | - **Traffic Flow**
29 | - absolute (`microsoft.traffic.flow.absolute`)
30 | - reduced-sensitivity (`microsoft.traffic.flow.reduced-sensitivity`)
31 | - relative (`microsoft.traffic.flow.relative`)
32 | - relative-delay (microsoft.traffic.flow.relative-delay`)
33 | - **Traffic Incident**
34 | - night (`microsoft.traffic.incident.night`)
35 | - s1 (`microsoft.traffic.incident.s1`)
36 | - s2 (`microsoft.traffic.incident.s2`)
37 | - s3 (`microsoft.traffic.incident.s3`)
38 | - **Weather**
39 | - Infrared (`microsoft.weather.infrared.main`) - Latest Infrared Satellite images shows clouds by their temperature.
40 | - Radar (`microsoft.weather.radar.main`) - Latest weather radar images including areas of rain, snow, ice and mixed conditions.
41 | - Use time stamps with weather layers to get recent and forecast data.
42 | - Adjust the line thickness in traffic flow layers.
43 |
44 | Currently supports raster (i.e PNG) tiles, support for vector tiles is planned.
45 |
46 | **Samples**
47 |
48 | [Render Azure Maps in Leaflet](https://azuremapscodesamples.azurewebsites.net/index.html?sample=Render%20Azure%20Maps%20in%20Leaflet)
49 | | Tileset ID: | 74 |75 | 92 | | 93 |
| Language: | 96 |97 | 155 | | 156 |
| Traffic flow thickness: | 159 |160 | 164 | | 165 |
168 | Options not demonstrated: 169 | 170 |
-
171 |
- authOptions 172 |
- timeStamp 173 |
- view 174 |
[
 ](https://azuremapscodesamples.azurewebsites.net/index.html?sample=Render%20Azure%20Maps%20in%20Leaflet)
50 |
51 | [Show Azure Maps in Leaflet layer control](https://azuremapscodesamples.azurewebsites.net/index.html?sample=Show%20Azure%20Maps%20in%20Leaflet%20layer%20control)
52 |
](https://azuremapscodesamples.azurewebsites.net/index.html?sample=Render%20Azure%20Maps%20in%20Leaflet)
50 |
51 | [Show Azure Maps in Leaflet layer control](https://azuremapscodesamples.azurewebsites.net/index.html?sample=Show%20Azure%20Maps%20in%20Leaflet%20layer%20control)
52 | [
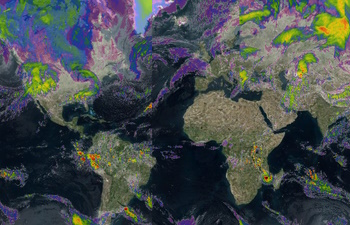 ](https://azuremapscodesamples.azurewebsites.net/index.html?sample=Show%20Azure%20Maps%20in%20Leaflet%20layer%20control)
53 |
54 | [Azure Maps Leaflet options](https://azuremapscodesamples.azurewebsites.net/index.html?sample=Azure%20Maps%20Leaflet%20options)
55 |
](https://azuremapscodesamples.azurewebsites.net/index.html?sample=Show%20Azure%20Maps%20in%20Leaflet%20layer%20control)
53 |
54 | [Azure Maps Leaflet options](https://azuremapscodesamples.azurewebsites.net/index.html?sample=Azure%20Maps%20Leaflet%20options)
55 | [
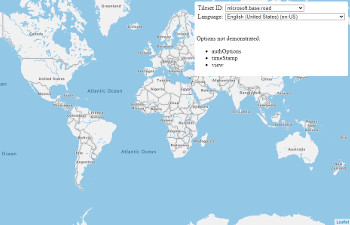 ](https://azuremapscodesamples.azurewebsites.net/index.html?sample=Azure%20Maps%20Leaflet%20options)
56 |
57 | ## Getting started
58 |
59 | Download the project and copy the `azure-maps-leaflet` JavaScript file from the `dist` folder into your project.
60 |
61 | **Usage**
62 |
63 | ```html
64 |
65 |
66 |
67 |
](https://azuremapscodesamples.azurewebsites.net/index.html?sample=Azure%20Maps%20Leaflet%20options)
56 |
57 | ## Getting started
58 |
59 | Download the project and copy the `azure-maps-leaflet` JavaScript file from the `dist` folder into your project.
60 |
61 | **Usage**
62 |
63 | ```html
64 |
65 |
66 |
67 | `'microsoft.base.road',`
`'microsoft.base.darkgrey'`
`'microsoft.imagery'`
`'microsoft.weather.infrared.main'`
`'microsoft.weather.radar.main'`
`'microsoft.base.hybrid.road'`
`'microsoft.base.labels.road'`
`'microsoft.traffic.incident.night'`
`'microsoft.traffic.incident.s1'`
`'microsoft.traffic.incident.s2'`
`'microsoft.traffic.incident.s3'`
`'microsoft.traffic.flow.absolute'`
`'microsoft.traffic.flow.reduced-sensitivity'`
`'microsoft.traffic.flow.relative'`
`'microsoft.traffic.flow.relative-delay'` Custom tileset ID's that return raster tiles that are 256x256 pixels in size can also be specified as a string. Default `'microsoft.base.road'` | 219 | | `timeStamp` | `string` \| `Date` | The desired date and time of the requested tile. This parameter must be specified in the standard date-time format (e.g. 2019-11-14T16:03:00-08:00), as defined by ISO 8601. This parameter is only supported when tilesetId parameter is set to `microsoft.weather.infrared.main` or `microsoft.weather.radar.main`. | 220 | | `trafficFlowThickness` | `number` | The thickness of lines when using the traffic flow tilesets. Default: `5` | 221 | | `view` | `string` | Geopolitical view of the map. [Supported views](https://docs.microsoft.com/en-us/azure/azure-maps/supported-languages#sdks) Default: `'Auto'` | 222 | 223 | ### Alternative Option for Leaflet 224 | 225 | This Leaflet plugin makes it easy to overlay tile layers from Azure Maps using any of the supported authentication methods available in Azure Maps; subscription key or Azure Active Directory (recommended). If you are only using a subscription key and don't plan to use Azure Active Directory, the following code can be used instead to easily overlay Azure Maps tile layers on a leaflet map without having to use this plugin. 226 | 227 | ```html 228 | 229 | 230 | 231 |