├── Browser HTML render research.docx
├── .DS_Store
├── Account Hijacking.docx
├── Arbitrary File Uploaded - HTML File Uploading Led to XSS Vulnerability.pdf
├── Brute Force Attack on WP Background Account.docx
├── Command Execution Summary.pdf
├── Command Execution Vulnerability Exists on the User Login interface of Tuniu.docx
├── Deserialization of ws interface fastjson.pdf
├── Improper Bucket Configuration - Improper Configuration of S3Bucket Policy Led to the Leakage of Sensitive Information.pdf
├── Improper Cors Configuration - Improper Cors Policy Configuration Led to User API Key Leakage.pdf
├── Instruct Verification Led to Unauthorized Login.docx
├── Logical Vulnerability - Incomplete Verification Code Led to Arbitrary Registration.pdf
├── Logical Vulnerability - the Leakage of Credentials Led to Arbitrary Registration.pdf
├── Nodejs in CTF.pdf
├── PushGateway have a question.docx
├── README.md
├── S3_Security_Configuration_Risks--Leaky_S3_Buckets.pdf
├── SQL Injection Led By Mybatis-plus.docx
├── SQL Injection Vulnerability Exists on Peking University Website.doc
├── SSRF in BEKE Can Lead to Unauthorized Detection on the Internal network.docx
├── Tools
├── Behinder.md
├── Godzilla.md
├── Nuclei.md
├── Xray.md
└── amass.md
├── Unauthorized Components - Unauthorized Access to Alibaba Druid.pdf
├── Unauthorized Components - Unauthorized Spring Actuator Component Led to the Leakage of Sensitive Information.pdf
├── Unauthorized Deletion of Others’ Read-only Interface .pdf
├── Unauthorized_Access--Alibaba_Druid_unauthorized_access_vulnerability.pdf
├── Weak Passwords Exist on Peking University Website.doc
└── how-i-hacked-companies-related-to-the-crypto-currency-and-earned.pdf
/ Browser HTML render research.docx:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/DVPNET/Report_Public/278061bee41584dda3dfe080f3f93c09a86e3a9f/ Browser HTML render research.docx
--------------------------------------------------------------------------------
/.DS_Store:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/DVPNET/Report_Public/278061bee41584dda3dfe080f3f93c09a86e3a9f/.DS_Store
--------------------------------------------------------------------------------
/Account Hijacking.docx:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/DVPNET/Report_Public/278061bee41584dda3dfe080f3f93c09a86e3a9f/Account Hijacking.docx
--------------------------------------------------------------------------------
/Arbitrary File Uploaded - HTML File Uploading Led to XSS Vulnerability.pdf:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/DVPNET/Report_Public/278061bee41584dda3dfe080f3f93c09a86e3a9f/Arbitrary File Uploaded - HTML File Uploading Led to XSS Vulnerability.pdf
--------------------------------------------------------------------------------
/Brute Force Attack on WP Background Account.docx:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/DVPNET/Report_Public/278061bee41584dda3dfe080f3f93c09a86e3a9f/Brute Force Attack on WP Background Account.docx
--------------------------------------------------------------------------------
/Command Execution Summary.pdf:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/DVPNET/Report_Public/278061bee41584dda3dfe080f3f93c09a86e3a9f/Command Execution Summary.pdf
--------------------------------------------------------------------------------
/Command Execution Vulnerability Exists on the User Login interface of Tuniu.docx:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/DVPNET/Report_Public/278061bee41584dda3dfe080f3f93c09a86e3a9f/Command Execution Vulnerability Exists on the User Login interface of Tuniu.docx
--------------------------------------------------------------------------------
/Deserialization of ws interface fastjson.pdf:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/DVPNET/Report_Public/278061bee41584dda3dfe080f3f93c09a86e3a9f/Deserialization of ws interface fastjson.pdf
--------------------------------------------------------------------------------
/Improper Bucket Configuration - Improper Configuration of S3Bucket Policy Led to the Leakage of Sensitive Information.pdf:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/DVPNET/Report_Public/278061bee41584dda3dfe080f3f93c09a86e3a9f/Improper Bucket Configuration - Improper Configuration of S3Bucket Policy Led to the Leakage of Sensitive Information.pdf
--------------------------------------------------------------------------------
/Improper Cors Configuration - Improper Cors Policy Configuration Led to User API Key Leakage.pdf:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/DVPNET/Report_Public/278061bee41584dda3dfe080f3f93c09a86e3a9f/Improper Cors Configuration - Improper Cors Policy Configuration Led to User API Key Leakage.pdf
--------------------------------------------------------------------------------
/Instruct Verification Led to Unauthorized Login.docx:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/DVPNET/Report_Public/278061bee41584dda3dfe080f3f93c09a86e3a9f/Instruct Verification Led to Unauthorized Login.docx
--------------------------------------------------------------------------------
/Logical Vulnerability - Incomplete Verification Code Led to Arbitrary Registration.pdf:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/DVPNET/Report_Public/278061bee41584dda3dfe080f3f93c09a86e3a9f/Logical Vulnerability - Incomplete Verification Code Led to Arbitrary Registration.pdf
--------------------------------------------------------------------------------
/Logical Vulnerability - the Leakage of Credentials Led to Arbitrary Registration.pdf:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/DVPNET/Report_Public/278061bee41584dda3dfe080f3f93c09a86e3a9f/Logical Vulnerability - the Leakage of Credentials Led to Arbitrary Registration.pdf
--------------------------------------------------------------------------------
/Nodejs in CTF.pdf:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/DVPNET/Report_Public/278061bee41584dda3dfe080f3f93c09a86e3a9f/Nodejs in CTF.pdf
--------------------------------------------------------------------------------
/PushGateway have a question.docx:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/DVPNET/Report_Public/278061bee41584dda3dfe080f3f93c09a86e3a9f/PushGateway have a question.docx
--------------------------------------------------------------------------------
/README.md:
--------------------------------------------------------------------------------
1 | # DVPNET 公开漏洞知识库
2 |
3 | `DVP官网`:https://dvpnet.io/
4 |
5 |
6 |
7 | `你可以从本项目中了解到一些典型的或是非常规的漏洞案例,也可以从漏洞技术细节中了解到其他白帽子对于厂商资产的各类收集方式。`
8 |
9 | `“知识面决定攻击面,知识深度决定攻击链” ————
10 | 本项目将长期更新,作为DVP社区的知识沉淀,供社区白帽子、厂商、安全从业人员不断扩展自身的知识面`
11 |
12 |
13 | 关于公开漏洞说明:
14 | 1. DVP选择对具备行业典型性的漏洞进行公开,旨在帮助社区的白帽子进行技术学习及厂商风险自检自查,避免损失。
15 | 2. DVP从核心价值观出发,公开漏洞的是已修复且经过脱敏处理的。
16 | 3. 在白帽子原有报告内容上,DVP可能会对漏洞信息做额外的补充及完善,方便白帽子理解更多的技术细节或是方便厂商了解到相关风险的规避方式。
17 |
18 | ***
19 | # DVPNET Public Vunerability Knowledge Base
20 |
21 | `DVP Official Website`:https://dvpnet.io/
22 |
23 |
24 |
25 | `You can learn some typical or unconventional vunerabilities from this project, as well as how other white hats collect vendor assets technical details through the technical details on the vulnerabilities.
26 | `
27 |
28 | `“What you know determines what the Attack Surface is; how deep your knowledge is determines which chain to attack” ————
29 | This project will keep updating to manage the accumulated knowledge for DVP community, so that white hats, vendors, and security practitioners can continuously expand their knowledge.
30 | `
31 |
32 |
33 | About the Public Vulnerability
34 | 1. DVP discloses the typical vulnerabilities in the industry to facilitate the technology learning of white hats in the community and the self-inspection of vendors, enabling loss prevention.
35 | 2. Adhering to the core values, DVP has conducted data desensitization before the vulnerability disclosure.
36 | 3. For White Hats' easier understanding on more technical details and Vendors' risk-avoidance learning, DVP may make supplements and improvements on the vulnerability data on the basis of the original report of White Hats.
37 |
38 |
--------------------------------------------------------------------------------
/S3_Security_Configuration_Risks--Leaky_S3_Buckets.pdf:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/DVPNET/Report_Public/278061bee41584dda3dfe080f3f93c09a86e3a9f/S3_Security_Configuration_Risks--Leaky_S3_Buckets.pdf
--------------------------------------------------------------------------------
/SQL Injection Led By Mybatis-plus.docx:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/DVPNET/Report_Public/278061bee41584dda3dfe080f3f93c09a86e3a9f/SQL Injection Led By Mybatis-plus.docx
--------------------------------------------------------------------------------
/SQL Injection Vulnerability Exists on Peking University Website.doc:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/DVPNET/Report_Public/278061bee41584dda3dfe080f3f93c09a86e3a9f/SQL Injection Vulnerability Exists on Peking University Website.doc
--------------------------------------------------------------------------------
/SSRF in BEKE Can Lead to Unauthorized Detection on the Internal network.docx:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/DVPNET/Report_Public/278061bee41584dda3dfe080f3f93c09a86e3a9f/SSRF in BEKE Can Lead to Unauthorized Detection on the Internal network.docx
--------------------------------------------------------------------------------
/Tools/Behinder.md:
--------------------------------------------------------------------------------
1 | [Behinder_v3.0] https://github.com/rebeyond/Behinder
2 |
3 | ## 工具介绍
4 |
5 | Behinder 是一款用于通过 WebShell 进行服务器管理的工具
6 |
7 | ## 工具下载
8 |
9 | https://github.com/rebeyond/Behinder/releases/download/Behinder_v3.0_Beta_7/Behinder_v3.0_Beta_7.zip
10 |
11 | 下载并将其解压到本地即可,server 目录的文件都是用于放置到目标服务器上的 WebShell
12 |
13 | ## 运行环境
14 |
15 | 客户端:jre8+
16 | 服务端:.net 2.0+;php 5.3-7.4;java 6+
17 |
18 | 工具在最近更新了如下功能:
19 |
20 | ## 工具优势
21 |
22 | 1. 流量加密
23 | 2. 插件众多,比如可以直接将 Shell 反弹至 MSF
24 | 3. 数据库连接,白名单状态下可通过目标机连接数据库
25 | 4. GUI 可视化
26 |
27 | ### 2021.4.8 v3.0 Beta 7 更新日志
28 |
29 | 修复:
30 | 1.数据库查询内容显示不正常;
31 | 2.关闭主界面后,虚拟终端后台线程继续请求;
32 | 3.某些场景下中文路径显示乱码;
33 | 4.优麒麟系统无法弹出窗口;
34 | 5.备忘录不能自动保存;
35 | 6.某些场景下提示数据库被锁定;
36 | 7.目标https证书过期连接问题;
37 | 8.Jar包体积缩小,Jar包执行不再区分操作系统平台,提供跨平台版本;
38 | 9.去除了一些特征;
39 | 10.其他一些问题;
40 |
41 | 新增:
42 | 1.反弹shell中增加CobaltStrike一键上线;
43 | 2.新增Java内存马注入功能,支持多种Web容器,包括但不限于Tomact、jboss、weblogic;
44 | 3.新增反向DMZ功能,可以将VPS或本地局域网监听端口映射进目标内网,在目标内网不出网的情况下,实现目标内网反向木马回连;
45 | 4.反弹Shell支持一键穿透,在目标内网不能出网的情况下,可以实现将meterpreter、shell、CobaltStrike直接上线至本地、本地局域网主机、远程VPS。msfconsole、CobaltStrike Server不再需要部署在公网;
46 | 5.新增Shell关键字搜索功能;
47 | 6.新增shell批量存活检测功能;
48 | 7.新增Shell多选删除;
49 | 8.新增老版本数据库Shell批量导入;
50 | 9.新增文件时间戳修改功能;
51 | 10.文件管理UI细节优化;
52 | 11.增加基于端口映射的的Socks代理;内网直接将Socks代理服务开到远程VPS;
53 | 12.命令行优化,支持命令历史记录;
54 |
55 | 补充:beta7版本客户端不再内置JavaFX库,请使用Java8运行;Java 11及以后的版本,需要下载JavaFX库;
56 |
--------------------------------------------------------------------------------
/Tools/Godzilla.md:
--------------------------------------------------------------------------------
1 | [Godzilla] https://github.com/BeichenDream/Godzilla
2 |
3 | # Godzilla
4 |
5 | ## 运行环境
6 | 1. JavaDynamicPayload -> jre5及以上
7 | 2. CShapDynamicPayload -> .net2.0及以上
8 | 3. PhpDynamicPayload -> php5.0及以上
9 |
10 | ## 简介
11 |
12 | ### 使用指南
13 |
14 | 具备 Java 运行环境(JDK1.8即可)
15 |
16 | 打开 Godzilla-xx.jar,程序会在当前目录生成一个用于存储数据的 data.db 文件,点击管理标签生成所需的 WebShell,保存生成所用的密钥等信息,将 WebShell 放置到目标服务器,使用 Godzilla 添加连接即可使用
17 |
18 | ### 工具特性
19 |
20 | 1. 工具自身插件强大
21 | 2. 流量加密
22 | 3. 支持内存Shell
23 |
24 | ### Payload以及加密器支持
25 |
26 | 哥斯拉内置了3种Payload以及6种加密器,6种支持脚本后缀,20个内置插件
27 |
28 | 1. JavaDynamicPayload
29 | 1. JAVA_AES_BASE64
30 | 1. jsp
31 | 2. jspx
32 | 2. JAVA_AES_RAW
33 | 1. jsp
34 | 2. jspx
35 |
36 | 2. CShapDynamicPayload
37 | 1. CSHAP_AES_BASE64
38 | 1. aspx
39 | 2. asmx
40 | 3. ashx
41 | 2. JAVA_AES_RAW
42 | 1. aspx
43 | 2. asmx
44 | 3. ashx
45 | 3. PhpDynamicPayload
46 | 1. PHP_XOR_BASE64
47 | 1. php
48 | 2. PHP_XOR_RAW
49 | 1. php
50 |
51 | ### Raw or Base64 加密器区别
52 |
53 | Raw : Raw是将加密后的数据直接发送或者输出
54 |
55 | 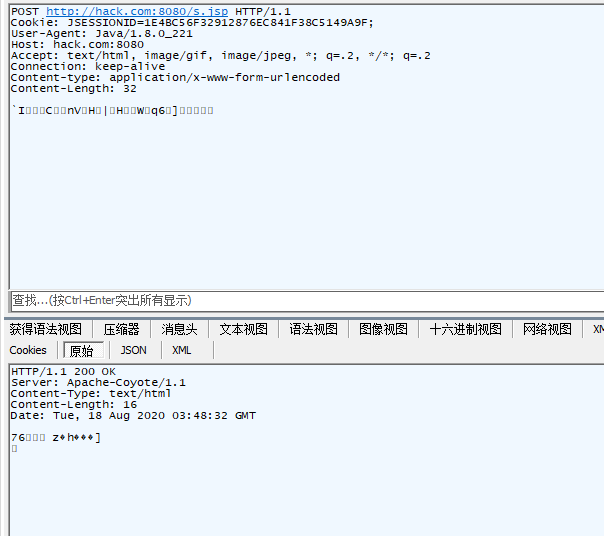
56 |
57 | Base64 : Base64是将加密后的数据再进行Base64编码
58 |
59 | 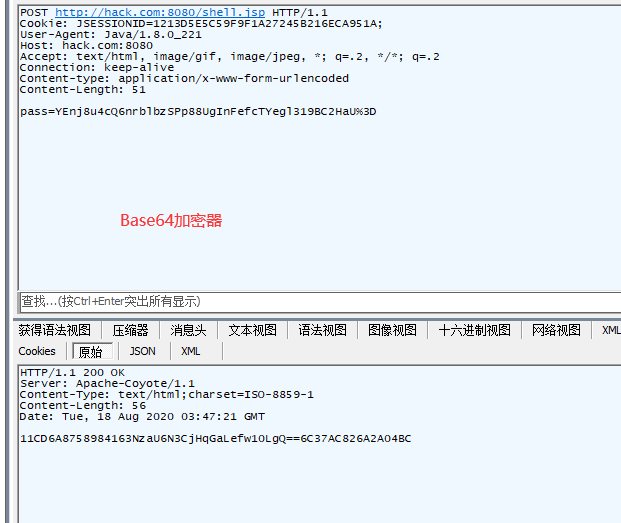
60 |
61 | ## 插件支持
62 |
63 | 1. JavaDynamicPayload
64 | 1. MemoryShell
65 |
66 | ```
67 | 支持 哥斯拉 冰蝎 菜刀 ReGeorg 的内存shell 并且支持卸载
68 | ```
69 |
70 | 2. Screen
71 |
72 | ```
73 | 屏幕截图
74 | ```
75 |
76 | 3. JRealCmd
77 |
78 | ```
79 | 虚拟终端 可以用netcat连接
80 | ```
81 |
82 | 4. JMeterpreter
83 |
84 | ```
85 | 与MSF联动
86 | ```
87 |
88 | 5. ServletManage
89 |
90 | ```
91 | Servlet管理 Servlet卸载
92 | ```
93 |
94 | 6. JarLoader
95 |
96 | ```
97 | 内存加载Jar 将Jar加载到 SystemClassLoader
98 | ```
99 |
100 | 7. JZip
101 |
102 | ```
103 | ZIP压缩 ZIP解压
104 | ```
105 | 2. CShapDynamicPayload
106 | 1. CZip
107 | ```
108 | ZIP压缩 ZIP解压
109 |
110 | ```
111 |
112 | 2. ShellcodeLoader
113 |
114 | ```
115 | Shellcode加载 与MSF联动
116 | ```
117 |
118 | 3. SafetyKatz
119 |
120 | ```
121 | Mimikatz
122 | ```
123 |
124 | 4. lemon
125 |
126 | ```
127 | 读取服务器 FileZilla navicat sqlyog Winscp xmangager 的配置信息以及密码
128 | ```
129 |
130 | 5. CRevlCmd
131 |
132 | ```
133 | 虚拟终端 可以用netcat连接
134 | ```
135 |
136 | 6. BadPotato
137 |
138 | ```
139 | Windows权限提升 2012-2019
140 | ```
141 |
142 | 7. ShapWeb
143 | ```
144 | 读取服务器 谷歌 IE 火狐 浏览器保存的账号密码
145 | ```
146 | 8. SweetPotato
147 |
148 | ```
149 | Windwos权限提升 烂土豆的C#版本 甜土豆
150 | ```
151 | 3. PhpDynamicPayload
152 | 1. PMeterpreter
153 |
154 | ```
155 | 与MSF联动
156 | ```
157 |
158 | 2. ByPassOpenBasedir
159 |
160 | ```
161 | 绕过OpenBasedir
162 | ```
163 |
164 | 3. PZip
165 |
166 | ```
167 | ZIP压缩 ZIP解压
168 | ```
169 |
170 | 4. P_Eval_Code
171 |
172 | ```
173 | 代码执行
174 | ```
175 |
176 | 5. BypassDisableFunctions
177 |
178 | ```
179 | 绕过 DisableFunctions
180 | ```
181 |
182 |
--------------------------------------------------------------------------------
/Tools/Nuclei.md:
--------------------------------------------------------------------------------
1 | [Nuclei] https://github.com/projectdiscovery/nuclei
2 |
3 | Nuclei 是一款基于模板向目标发送请求的工具,它提供对大量主机的快速扫描功能。 Nuclei提供扫描各种协议的功能,包括TCP,DNS,HTTP,文件等。借助强大灵活的模板,可以使用Nuclei对各种安全检查进行建模。
4 |
5 | Nuclei 有一个专用的存储库,其中包含由数名安全研究员和工程师提供的各种类型的漏洞模板。 可以使用 -update-templates 标志预加载了随时可以使用的模板。
6 |
7 | 安装步骤:
8 |
9 | go get -v github.com/projectdiscovery/nuclei/v2/cmd/nuclei
10 |
11 | 使用方法:
12 |
13 | PoC 基于 .yaml 格式进行编写
14 |
15 |
16 | 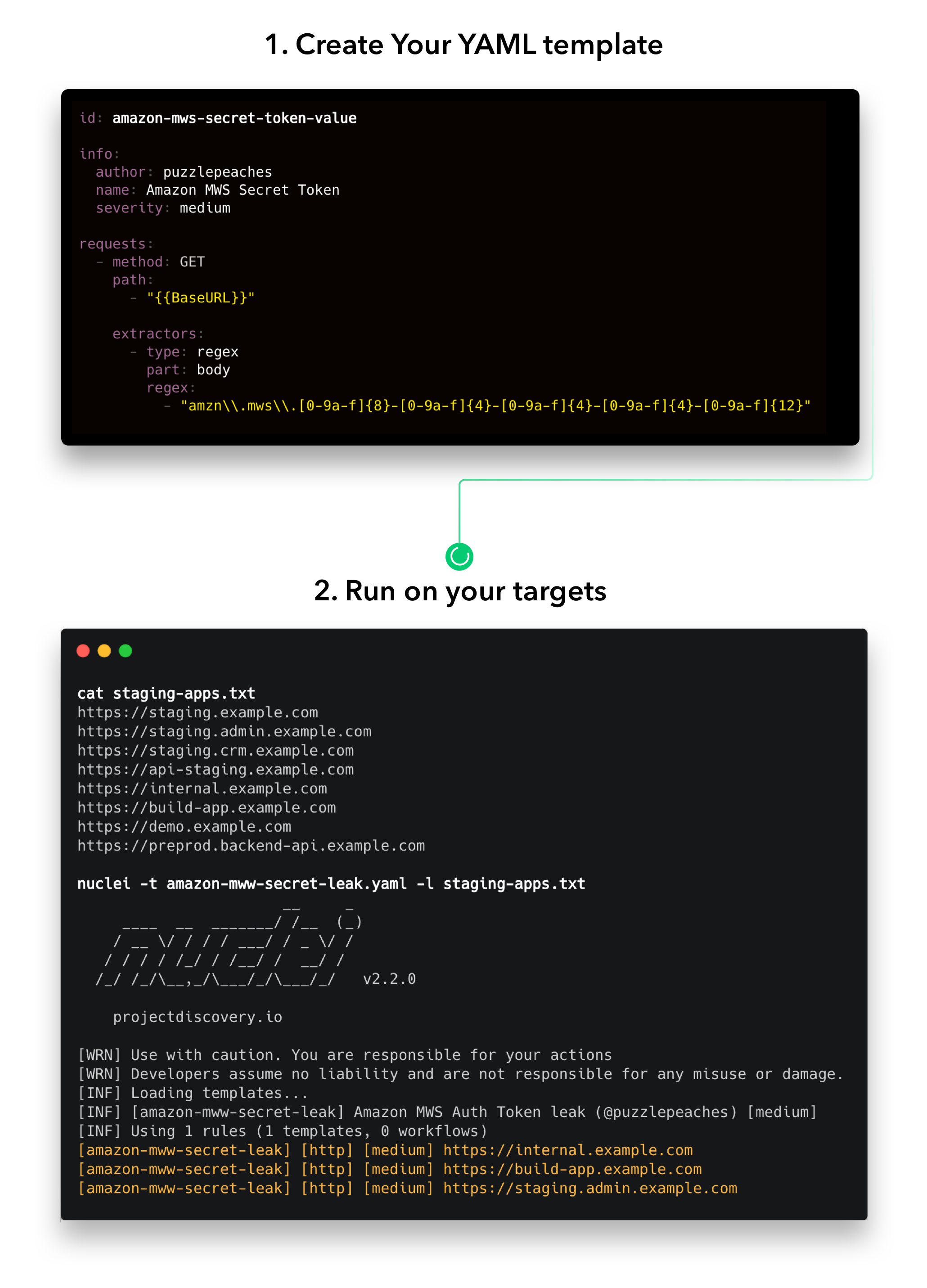 17 |
17 |
18 |
19 | 官方提供了一些模板供社区白帽子使用与学习
20 |
21 | https://github.com/projectdiscovery/nuclei-templates
22 |
23 | 
24 |
25 | 使用如下这条指令可以下载公开库中的最新模板
26 |
27 | > nuclei -update-templates
28 |
29 | 举例说明使用方法 (调用 cves 这个模板库对目标URL列表进行漏洞检测)
30 |
31 | > nuclei -l target_urls.txt -t cves/
32 |
--------------------------------------------------------------------------------
/Tools/Xray.md:
--------------------------------------------------------------------------------
1 | [Xray] https://github.com/chaitin/xray
2 |
3 | ## 工具介绍
4 |
5 | Xray 是一款功能强大的安全评估工具,共有三种版本,社区版,社区高级版以及企业版,通常来说白帽子自用的无非就是社区版和社区高级版两种版本
6 |
7 | 社区版免费向公众开放使用,社区高级版的这一版本需要对社区做出做出一定贡献才可获得
8 |
9 | ## 工具下载
10 |
11 | 根据自身运行环境选择其所需对应版本即可
12 |
13 | https://github.com/chaitin/xray/releases/tag/1.7.1
14 |
15 | ## 工具指南
16 |
17 | > ./xray_linux_amd64 webscan --listen 127.0.0.1:7777 --html-output xray-testphp.html
18 |
19 | 指令含义: 监听本地 7777 端口,将报告以 html 格式输出为 xray-testphp.html 文件
20 |
21 | 当然也可以搭配一些像 BurpSuite 之类的工具查看 Xray 发包情况
22 |
23 | https://tricksongs.com/BurpSuite_And_Xray/
24 |
25 | ## 工具优势
26 |
27 | 集众多令人惊异的特性于一身,常见 Web 漏洞检测,内置 10+ 通用 Web 漏洞检测模块,支持 SQL 注入、XSS、命令执行、文件包含等通用漏洞的精准检测
28 |
29 | 众多内置 PoC,社区提交的 200+ 高质量 POC,覆盖近三年实战高危 Web 漏洞,而且统统免费使用
30 |
31 | 专项检测能力,高级版支持 struts、fastjson、thinkphp、shiro 等框架的高危历史漏洞一键检测
32 |
33 | NG 检测算法,融合安全专家多年攻防经验,利用独有的高效检测方法表达出来,智能检测不再空谈
34 |
35 | 深度定制化支持,在配置文件中开放众多配置项,通过调整相关参数可以极大的自定义引擎的能力
36 |
37 | 多源扫描方式,支持被动代理、基础爬虫、浏览器爬虫、单 URL 等多种输入源可选,并可以使用代理自行拓展
38 |
39 | 浏览器爬虫,rad 爬虫可以动态渲染各种框架的网站并进行请求抓取,不放过漏洞存在的 "隐秘的角落"
40 |
41 | 高交互页面访问,模拟人的行为进行单击、输入等操作时,做到智能停止、返回、继续深入点击等操作
42 |
43 | 持续迭代更新,重要问题快速修复,重大漏洞持续添加,保持生命活力
44 |
45 | 社区活跃且强大
46 |
47 | https://blog.xray.cool/
48 |
--------------------------------------------------------------------------------
/Tools/amass.md:
--------------------------------------------------------------------------------
1 | [Amass] https://github.com/OWASP/Amass
2 |
3 | ## 工具介绍
4 |
5 | OWASP Amass项目使用开源信息收集和主动侦察技术执行攻击面的网络映射和外部资产发现。
6 |
7 | ## 工具下载
8 |
9 | ## Homebrew
10 |
11 | brew tap caffix/amass
12 | brew install amass
13 |
14 | ## Snapcraft
15 |
16 | ## 命令安装
17 |
18 | 有go环境的前提下
19 | go get -v github.com/OWASP/Amass/cmd/amass
20 |
21 |
22 | ## 工具指南
23 |
24 | 简单实用方法
25 | amass enum -d example.com
26 |
27 | 该命令是能够枚举子域名,是最基本的用途。
28 |
29 | 也可以根据需求设置其他的参数。
30 |
31 | https://github.com/OWASP/Amass/blob/master/doc/user_guide.md
32 |
33 | ## 工具优势
34 |
35 | Amass得到OWASP的支持,OWASP应该为结果提供声望和信心。它会得到积极维护,并且很可能会得到长期支持,这意味着将来的任何错误都将得到解决。此外,Amass的采用率很高,这可能意味着更好的数据一致性以及与其他工具的集成。因此,它可以构成一个更好和更值得信赖的工具,以用于概念和参与度的证明,并且可能更容易说服您的客户或经理使用它来定期绘制组织的攻击面。
36 |
37 |
--------------------------------------------------------------------------------
/Unauthorized Components - Unauthorized Access to Alibaba Druid.pdf:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/DVPNET/Report_Public/278061bee41584dda3dfe080f3f93c09a86e3a9f/Unauthorized Components - Unauthorized Access to Alibaba Druid.pdf
--------------------------------------------------------------------------------
/Unauthorized Components - Unauthorized Spring Actuator Component Led to the Leakage of Sensitive Information.pdf:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/DVPNET/Report_Public/278061bee41584dda3dfe080f3f93c09a86e3a9f/Unauthorized Components - Unauthorized Spring Actuator Component Led to the Leakage of Sensitive Information.pdf
--------------------------------------------------------------------------------
/Unauthorized Deletion of Others’ Read-only Interface .pdf:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/DVPNET/Report_Public/278061bee41584dda3dfe080f3f93c09a86e3a9f/Unauthorized Deletion of Others’ Read-only Interface .pdf
--------------------------------------------------------------------------------
/Unauthorized_Access--Alibaba_Druid_unauthorized_access_vulnerability.pdf:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/DVPNET/Report_Public/278061bee41584dda3dfe080f3f93c09a86e3a9f/Unauthorized_Access--Alibaba_Druid_unauthorized_access_vulnerability.pdf
--------------------------------------------------------------------------------
/Weak Passwords Exist on Peking University Website.doc:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/DVPNET/Report_Public/278061bee41584dda3dfe080f3f93c09a86e3a9f/Weak Passwords Exist on Peking University Website.doc
--------------------------------------------------------------------------------
/how-i-hacked-companies-related-to-the-crypto-currency-and-earned.pdf:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/DVPNET/Report_Public/278061bee41584dda3dfe080f3f93c09a86e3a9f/how-i-hacked-companies-related-to-the-crypto-currency-and-earned.pdf
--------------------------------------------------------------------------------
 17 |
17 |  17 |
17 |