├── Binary
└── Hard
│ └── Cryptoversing
│ └── README.md
├── Cryptography
├── Easy
│ ├── BASE 2 2 THE 6
│ │ └── README.md
│ ├── BRUXOR
│ │ └── README.md
│ ├── HEXTROADINARY
│ │ └── README.md
│ ├── HYPERSTREAM TEST 2
│ │ └── README.md
│ ├── MORSE CODE
│ │ └── README.md
│ └── VIGENERE CIPHER
│ │ └── README.md
└── Medium
│ ├── 5x5 Crypto
│ ├── 5x5.py
│ └── README.md
│ ├── ALEXCTF CR2
│ └── README.md
│ ├── RSA Noob
│ ├── README.md
│ └── RSA_Noob.py
│ └── Substitution Cipher
│ └── README.md
├── Forensics
├── Easy
│ ├── A CAPTURE OF A FLAG
│ │ └── README.md
│ ├── BINWALK
│ │ └── README.md
│ ├── FORENSICS 101
│ │ └── README.md
│ ├── README.md
│ ├── TAKING LS
│ │ └── README.md
│ └── WOW.... SO META
│ │ └── README.md
└── Medium
│ ├── 07601
│ └── README.md
│ ├── DUMPSTER
│ ├── Dumpster_Soltuion_By_EdbR.java
│ └── README.md
│ ├── THE ADVENTURES OF BORIS IVANOV. PART 1
│ └── README.md
│ └── UP FOR A LITTLE CHALLENGE
│ └── README.md
├── Programming
├── Hard
│ ├── IS IT THE FLAG
│ │ ├── BruteForce_Solution_By_EdbR.py
│ │ ├── Is it the Flag.java
│ │ ├── Mathematical Solution_By_EdbR.py
│ │ └── README.md
│ └── THE ADVENTURES OF BORIS IVANOV PART 2
│ │ ├── README.md
│ │ └── Soultion_By_EdbR.py
└── Medium
│ └── Weird Android Calculator
│ ├── README.md
│ ├── Soultion_by_EdbR.py
│ └── SuspiciousCode.txt
├── README.md
└── Reverse Engineering
├── Hard
├── Lost In The Binary
│ ├── Lost.py
│ └── README.md
└── RE_verseDIS
│ └── README.md
└── Medium
├── Bite-code
├── C_soultion_by_EdbR.c
├── Python_solution_by_EdbR.py
├── README.md
└── bitecode_with_comments.txt
└── PIN
└── README.md
/Binary/Hard/Cryptoversing/README.md:
--------------------------------------------------------------------------------
1 | # Cryptoversing
2 |
3 | * **Category:** Binary
4 | * **Points:** 90
5 | * **level:** Hard
6 |
7 |
8 | ## [Challenge](https://ctflearn.com/challenge/667)
9 |
10 | > Hello! My manager sent me a file named xor.bin, and he wants from you to crack this program, and get the flag.
11 | > https://mega.nz/#!neYzjQQS!mKNcdADY8u_V0Iy1a57gQpjNGTni03l7lTKOZVaYNes
12 |
13 | ## Solution
14 | We get a bin file , Lets execute and see what we get.
15 |
16 | 
17 |
18 | So we need to guess the password and the password should be the flag.
19 | Take a look in IDA to see the flow of the program.
20 |
21 |  22 |
23 | Its look like after we enter the password the program store two important values-
24 | 1. strlen - len of our password
25 | 2. shr strlen , 1 = **shr - shift right = divide by 2** , **shl - shift left = mul by 2** so the second value is **strlen/2**
26 |
27 | keep forward...
28 |
29 |
22 |
23 | Its look like after we enter the password the program store two important values-
24 | 1. strlen - len of our password
25 | 2. shr strlen , 1 = **shr - shift right = divide by 2** , **shl - shift left = mul by 2** so the second value is **strlen/2**
26 |
27 | keep forward...
28 |
29 |  30 | Because of "mov [rbp+var_CC], 0" we will take the jump to the right side. In the end after some operations that we will see now
31 | we will visit in the left side where the important compare has been executed and decide if our password is the correct flag.
32 | This is the operations that been executed on our password and then the been compared.
33 |
34 |
30 | Because of "mov [rbp+var_CC], 0" we will take the jump to the right side. In the end after some operations that we will see now
31 | we will visit in the left side where the important compare has been executed and decide if our password is the correct flag.
32 | This is the operations that been executed on our password and then the been compared.
33 |
34 |  35 |
36 | As you can see we have in the for loop this instruction "v18[j] = *(&v8 + i) ^ s[j];"
37 | s - array of our password
38 | *(&v8 + i) - we need to check the value , we will see in gdb
39 | v18 - array where the xor result been saved
40 |
41 | After that we have this instruction "if ( v18[k] != v14[k] )" And if the value are not the same we message get a "Wrong Password"
42 | So, If all the values in **v18 will equal to v14** we will get the good message "Successful Login""
43 |
44 | We now that in xor operation:
45 | **if (a^b == c ) -------> a^c == b , b^c ==a**
46 | So we need to preform ""v14[k] ^ *(&v8 + i) == s[k]"" lets find the missing parts
47 | After debug the program in gdb i found that the first half of our password been xor with **0x10** , And for the rest of our password been xor with **0x18**
48 | xor 'a' with 0x10 -
49 | 
50 |
51 | xor 'a' (in the second half of our password) with 0x18 -
52 |
53 | 
54 |
55 | RDX is equal to "*(&v8 + i)" and RAX is equal to "s[j]" and the result stored in "v18[j]".
56 | So now we only need to find v14[k] that is need to be equal to "v18[j]" and xor with "*(&v8 + i)".
57 | We can find v14[k] in gdb -
58 | 
59 |
60 | Now all we have to do is : xor the first half of **"h_bO}EcDOR+G)uh(jl,vL"** with **0x10** and the second half with **0x18**
61 |
62 | #### First half
63 |
35 |
36 | As you can see we have in the for loop this instruction "v18[j] = *(&v8 + i) ^ s[j];"
37 | s - array of our password
38 | *(&v8 + i) - we need to check the value , we will see in gdb
39 | v18 - array where the xor result been saved
40 |
41 | After that we have this instruction "if ( v18[k] != v14[k] )" And if the value are not the same we message get a "Wrong Password"
42 | So, If all the values in **v18 will equal to v14** we will get the good message "Successful Login""
43 |
44 | We now that in xor operation:
45 | **if (a^b == c ) -------> a^c == b , b^c ==a**
46 | So we need to preform ""v14[k] ^ *(&v8 + i) == s[k]"" lets find the missing parts
47 | After debug the program in gdb i found that the first half of our password been xor with **0x10** , And for the rest of our password been xor with **0x18**
48 | xor 'a' with 0x10 -
49 | 
50 |
51 | xor 'a' (in the second half of our password) with 0x18 -
52 |
53 | 
54 |
55 | RDX is equal to "*(&v8 + i)" and RAX is equal to "s[j]" and the result stored in "v18[j]".
56 | So now we only need to find v14[k] that is need to be equal to "v18[j]" and xor with "*(&v8 + i)".
57 | We can find v14[k] in gdb -
58 | 
59 |
60 | Now all we have to do is : xor the first half of **"h_bO}EcDOR+G)uh(jl,vL"** with **0x10** and the second half with **0x18**
61 |
62 | #### First half
63 |  64 |
65 | #### Second half
66 |
64 |
65 | #### Second half
66 |  67 |
68 | And we get the flag :
69 |
70 | Flag : ```xOr_mUsT_B3_1mp0rt4nT```
71 |
72 |
--------------------------------------------------------------------------------
/Cryptography/Easy/BASE 2 2 THE 6/README.md:
--------------------------------------------------------------------------------
1 | # BASE 2 2 THE 6
2 |
3 | * **Category:** Cryptography
4 | * **Points:** 20
5 | * **level:** Easy
6 |
7 | ## [Challenge](https://ctflearn.com/problems/158)
8 |
9 | > There are so many different ways of encoding and decoding information nowadays... One of them will work! Q1RGe0ZsYWdneVdhZ2d5UmFnZ3l9
10 |
11 |
12 | ## Solution
13 | Its very easy challenge just use base64 decoder.
14 |
15 |
67 |
68 | And we get the flag :
69 |
70 | Flag : ```xOr_mUsT_B3_1mp0rt4nT```
71 |
72 |
--------------------------------------------------------------------------------
/Cryptography/Easy/BASE 2 2 THE 6/README.md:
--------------------------------------------------------------------------------
1 | # BASE 2 2 THE 6
2 |
3 | * **Category:** Cryptography
4 | * **Points:** 20
5 | * **level:** Easy
6 |
7 | ## [Challenge](https://ctflearn.com/problems/158)
8 |
9 | > There are so many different ways of encoding and decoding information nowadays... One of them will work! Q1RGe0ZsYWdneVdhZ2d5UmFnZ3l9
10 |
11 |
12 | ## Solution
13 | Its very easy challenge just use base64 decoder.
14 |
15 |  16 |
17 | Flag : ```CTF{FlaggyWaggyRaggy}```
18 |
19 |
--------------------------------------------------------------------------------
/Cryptography/Easy/BRUXOR/README.md:
--------------------------------------------------------------------------------
1 | # BRUXOR
2 |
3 | * **Category:** Cryptography
4 | * **Points:** 20
5 | * **level:** Easy
6 |
7 | ## [Challenge](https://ctflearn.com/problems/227)
8 |
9 | > There is a technique called bruteforce. Message: q{vpln'bH_varHuebcrqxetrHOXEj No key! Just brute .. brute .. brute ...
10 |
11 |
12 | ## Solution
13 | From the beginning we can notice to a big hint **"BRUXOR" - Bruteforce + XOR**.\
14 | So we need to do bruteforce xor on the Message: q{vpln'bH_varHuebcrqxetrHOXEj.\
15 | Notice that the flag start with - "flag{" , So we have part of the plaintext.\
16 | We will use [xor bruteforce online](https://gchq.github.io/CyberChef/#recipe=XOR_Brute_Force(1,100,0,'Standard',false,true,false,'flag%7B')&input=IHF7dnBsbidiSF92YXJIdWViY3JxeGV0ckhPWEVq)
17 |
18 |
16 |
17 | Flag : ```CTF{FlaggyWaggyRaggy}```
18 |
19 |
--------------------------------------------------------------------------------
/Cryptography/Easy/BRUXOR/README.md:
--------------------------------------------------------------------------------
1 | # BRUXOR
2 |
3 | * **Category:** Cryptography
4 | * **Points:** 20
5 | * **level:** Easy
6 |
7 | ## [Challenge](https://ctflearn.com/problems/227)
8 |
9 | > There is a technique called bruteforce. Message: q{vpln'bH_varHuebcrqxetrHOXEj No key! Just brute .. brute .. brute ...
10 |
11 |
12 | ## Solution
13 | From the beginning we can notice to a big hint **"BRUXOR" - Bruteforce + XOR**.\
14 | So we need to do bruteforce xor on the Message: q{vpln'bH_varHuebcrqxetrHOXEj.\
15 | Notice that the flag start with - "flag{" , So we have part of the plaintext.\
16 | We will use [xor bruteforce online](https://gchq.github.io/CyberChef/#recipe=XOR_Brute_Force(1,100,0,'Standard',false,true,false,'flag%7B')&input=IHF7dnBsbidiSF92YXJIdWViY3JxeGV0ckhPWEVq)
17 |
18 |  19 |
20 | Flag : ```7flag{y0u_Have_bruteforce_XOR}```
21 |
22 |
--------------------------------------------------------------------------------
/Cryptography/Easy/HEXTROADINARY/README.md:
--------------------------------------------------------------------------------
1 |
2 |
3 | # HEXTROADINARY
4 |
5 | * **Category:** Cryptography
6 | * **Points:** 30
7 | * **level:** Easy
8 |
9 | ## [Challenge](https://ctflearn.com/problems/158)
10 |
11 | > Meet ROXy, a coder obsessed with being exclusively the worlds best hacker. She specializes in short cryptic hard to decipher secret codes. The below hex values for example, she did something with them to generate a secret code, can you figure out what? Your answer should start with 0x. 0xc4115 0x4cf8
12 |
13 |
14 | ## Solution
15 | From the beginning we can notice to a big hint -"Meet **ROX**y" - **ROX** -> **XOR** , So probably we use xor operation.\
16 | Another hint is "a coder obsessed with being **exclusively** the worlds best hacker" , And if you remember XOR = **Exclusive or**.\
17 | So lets xor the hex value we get in the CTF, Using [xor calculator](http://xor.pw/).
18 |
19 |
19 |
20 | Flag : ```7flag{y0u_Have_bruteforce_XOR}```
21 |
22 |
--------------------------------------------------------------------------------
/Cryptography/Easy/HEXTROADINARY/README.md:
--------------------------------------------------------------------------------
1 |
2 |
3 | # HEXTROADINARY
4 |
5 | * **Category:** Cryptography
6 | * **Points:** 30
7 | * **level:** Easy
8 |
9 | ## [Challenge](https://ctflearn.com/problems/158)
10 |
11 | > Meet ROXy, a coder obsessed with being exclusively the worlds best hacker. She specializes in short cryptic hard to decipher secret codes. The below hex values for example, she did something with them to generate a secret code, can you figure out what? Your answer should start with 0x. 0xc4115 0x4cf8
12 |
13 |
14 | ## Solution
15 | From the beginning we can notice to a big hint -"Meet **ROX**y" - **ROX** -> **XOR** , So probably we use xor operation.\
16 | Another hint is "a coder obsessed with being **exclusively** the worlds best hacker" , And if you remember XOR = **Exclusive or**.\
17 | So lets xor the hex value we get in the CTF, Using [xor calculator](http://xor.pw/).
18 |
19 |  20 |
21 | Dont forget add "0x." in the beginning as write above.
22 |
23 | Flag : ```0xc0ded```
24 |
25 |
--------------------------------------------------------------------------------
/Cryptography/Easy/HYPERSTREAM TEST 2/README.md:
--------------------------------------------------------------------------------
1 | # HYPERSTREAM TEST #2
2 |
3 | * **Category:** Cryptography
4 | * **Points:** 30
5 | * **level:** Easy
6 |
7 | ## [Challenge](https://ctflearn.com/problems/443)
8 |
9 | > I love the smell of bacon in the morning!
10 | > ABAAAABABAABBABBAABBAABAAAAAABAAAAAAAABAABBABABBAAAAABBABBABABBAABAABABABBAABBABBAABB
11 |
12 | ## Solution
13 | Read again the challenge... which word may be suspecious ???.\
14 | Probably the word **bacon** becuase its not a simple word like "morning" , "love" , "smell" ,"the" ...
15 | So maybe there is a encryption with the strange name **bacon** ?.\
16 | Apparently there is - [Bacon's cipher](https://en.wikipedia.org/wiki/Bacon%27s_cipher).\
17 | Use bacon decode and get the flag - https://www.dcode.fr/bacon-cipher
18 |
19 |
20 |
21 | Dont forget add "0x." in the beginning as write above.
22 |
23 | Flag : ```0xc0ded```
24 |
25 |
--------------------------------------------------------------------------------
/Cryptography/Easy/HYPERSTREAM TEST 2/README.md:
--------------------------------------------------------------------------------
1 | # HYPERSTREAM TEST #2
2 |
3 | * **Category:** Cryptography
4 | * **Points:** 30
5 | * **level:** Easy
6 |
7 | ## [Challenge](https://ctflearn.com/problems/443)
8 |
9 | > I love the smell of bacon in the morning!
10 | > ABAAAABABAABBABBAABBAABAAAAAABAAAAAAAABAABBABABBAAAAABBABBABABBAABAABABABBAABBABBAABB
11 |
12 | ## Solution
13 | Read again the challenge... which word may be suspecious ???.\
14 | Probably the word **bacon** becuase its not a simple word like "morning" , "love" , "smell" ,"the" ...
15 | So maybe there is a encryption with the strange name **bacon** ?.\
16 | Apparently there is - [Bacon's cipher](https://en.wikipedia.org/wiki/Bacon%27s_cipher).\
17 | Use bacon decode and get the flag - https://www.dcode.fr/bacon-cipher
18 |
19 |  20 |
21 | Flag : ```ILOUEBACONDONTYOU```
22 |
23 |
--------------------------------------------------------------------------------
/Cryptography/Easy/MORSE CODE/README.md:
--------------------------------------------------------------------------------
1 | # MORSE CODE
2 |
3 | * **Category:** Cryptography
4 | * **Points:** 20
5 | * **level:** Easy
6 |
7 | ## [Challenge](https://ctflearn.com/problems/309)
8 |
9 | > ..-. .-.. .- --. ... .- -- ..- . .-.. -- --- .-. ... . .. ... -.-. --- --- .-.. -... -.-- - .... . .-- .- -.-- .. .-.. .. -.- . -.-. .... . . ...
10 |
11 |
12 |
13 | ## Solution
14 | The solution is very easy , Just look for morse decode. Use this site https://cryptii.com/pipes/morse-code-to-text.
15 |
16 |
20 |
21 | Flag : ```ILOUEBACONDONTYOU```
22 |
23 |
--------------------------------------------------------------------------------
/Cryptography/Easy/MORSE CODE/README.md:
--------------------------------------------------------------------------------
1 | # MORSE CODE
2 |
3 | * **Category:** Cryptography
4 | * **Points:** 20
5 | * **level:** Easy
6 |
7 | ## [Challenge](https://ctflearn.com/problems/309)
8 |
9 | > ..-. .-.. .- --. ... .- -- ..- . .-.. -- --- .-. ... . .. ... -.-. --- --- .-.. -... -.-- - .... . .-- .- -.-- .. .-.. .. -.- . -.-. .... . . ...
10 |
11 |
12 |
13 | ## Solution
14 | The solution is very easy , Just look for morse decode. Use this site https://cryptii.com/pipes/morse-code-to-text.
15 |
16 |  17 |
18 |
19 | Flag : ```flagsamuelmorseiscoolbythewayilikechees```
20 |
21 |
--------------------------------------------------------------------------------
/Cryptography/Easy/VIGENERE CIPHER/README.md:
--------------------------------------------------------------------------------
1 | # VIGENERE CIPHER
2 |
3 | * **Category:** Cryptography
4 | * **Points:** 30
5 | * **level:** 20
6 |
7 | ## [Challenge](https://ctflearn.com/problems/305)
8 |
9 | > The vignere cipher is a method of encrypting alphabetic text by using a series of interwoven Caesar ciphers based on the letters of a keyword.
17 |
18 |
19 | Flag : ```flagsamuelmorseiscoolbythewayilikechees```
20 |
21 |
--------------------------------------------------------------------------------
/Cryptography/Easy/VIGENERE CIPHER/README.md:
--------------------------------------------------------------------------------
1 | # VIGENERE CIPHER
2 |
3 | * **Category:** Cryptography
4 | * **Points:** 30
5 | * **level:** 20
6 |
7 | ## [Challenge](https://ctflearn.com/problems/305)
8 |
9 | > The vignere cipher is a method of encrypting alphabetic text by using a series of interwoven Caesar ciphers based on the letters of a keyword.
I’m not sure what this means, but it was left lying around: blorpy gwox{RgqssihYspOntqpxs}
10 |
11 | ## Solution
12 | Ok , So we have the solution in the title as you can see "**VIGENERE CIPHER**" we need to decrypt the cipher with **VIGENERE**.\
13 | As you can see in the site the flag start with "flag{" so we assume that **gwox** is encryption of **flag** so use this to find part of the key of the decryption , We will use this site - [VIGENERE CIPHER](https://www.dcode.fr/vigenere-cipher).
14 |
15 |  16 |
17 | As you cann see part of the decryption key is blor , Buy wait ... if you notice before the chiper we get the key:\
18 | "but it was left lying around: **blorpy** gwox{RgqssihYspOntqpxs}".So we also have the full key - **blorpy** , lets decrypt .
19 |
20 |
16 |
17 | As you cann see part of the decryption key is blor , Buy wait ... if you notice before the chiper we get the key:\
18 | "but it was left lying around: **blorpy** gwox{RgqssihYspOntqpxs}".So we also have the full key - **blorpy** , lets decrypt .
19 |
20 |  21 |
22 | Flag : ```flag{CiphersAreAwesome}```
23 |
24 |
--------------------------------------------------------------------------------
/Cryptography/Medium/5x5 Crypto/5x5.py:
--------------------------------------------------------------------------------
1 | import numpy as np
2 |
3 | arr = np.arange(65,90).reshape(5, 5) # Array of alphabet
4 | arr = np.where(arr <75, arr, arr+1) # Array without 'K'
5 |
6 | cells = ["1-3","4-4","2-1","{","4-4","2-3","4-5","3-2","1-2","4-3","_","4-5","3-5","}"]
7 | for i in cells:
8 | if(ord(i[0])>=48 and ord(i[0])<=57):
9 | x=int(i[0])-1
10 | y=int(i[2])-1
11 | print(chr(arr[x][y]),end="")
12 | else:
13 | print(i[0],end="")
14 |
15 |
16 |
--------------------------------------------------------------------------------
/Cryptography/Medium/5x5 Crypto/README.md:
--------------------------------------------------------------------------------
1 |
2 | # 5x5 Crypto
3 |
4 | * **Category:** Cryptography
5 | * **Points:** 60
6 | * **level:** Medium
7 |
8 | ## [Challenge](https://ctflearn.com/challenge/263)
9 |
10 | > Ever heard of the 5x5 secret message system? If not, basically it's a 5x5 grid with all letters of the alphabet in order, without k because c is represented to make the k sound only
11 | > Google it if you need to. A letter is identified by Row-Column. All values are in caps. Try: 1-3,4-4,2-1,{,4-4,2-3,4-5,3-2,1-2,4-3,_,4-5,3-5,}
12 |
13 | ## Solution
14 |
15 | So this is pretty easy , We simply need to create this 5x5 grid and take the letters in cells mention above.
16 |
17 |
21 |
22 | Flag : ```flag{CiphersAreAwesome}```
23 |
24 |
--------------------------------------------------------------------------------
/Cryptography/Medium/5x5 Crypto/5x5.py:
--------------------------------------------------------------------------------
1 | import numpy as np
2 |
3 | arr = np.arange(65,90).reshape(5, 5) # Array of alphabet
4 | arr = np.where(arr <75, arr, arr+1) # Array without 'K'
5 |
6 | cells = ["1-3","4-4","2-1","{","4-4","2-3","4-5","3-2","1-2","4-3","_","4-5","3-5","}"]
7 | for i in cells:
8 | if(ord(i[0])>=48 and ord(i[0])<=57):
9 | x=int(i[0])-1
10 | y=int(i[2])-1
11 | print(chr(arr[x][y]),end="")
12 | else:
13 | print(i[0],end="")
14 |
15 |
16 |
--------------------------------------------------------------------------------
/Cryptography/Medium/5x5 Crypto/README.md:
--------------------------------------------------------------------------------
1 |
2 | # 5x5 Crypto
3 |
4 | * **Category:** Cryptography
5 | * **Points:** 60
6 | * **level:** Medium
7 |
8 | ## [Challenge](https://ctflearn.com/challenge/263)
9 |
10 | > Ever heard of the 5x5 secret message system? If not, basically it's a 5x5 grid with all letters of the alphabet in order, without k because c is represented to make the k sound only
11 | > Google it if you need to. A letter is identified by Row-Column. All values are in caps. Try: 1-3,4-4,2-1,{,4-4,2-3,4-5,3-2,1-2,4-3,_,4-5,3-5,}
12 |
13 | ## Solution
14 |
15 | So this is pretty easy , We simply need to create this 5x5 grid and take the letters in cells mention above.
16 |
17 |  18 |
19 |
20 | Flag : ```CTF{THUMBS_UP} ```
21 |
22 |
--------------------------------------------------------------------------------
/Cryptography/Medium/ALEXCTF CR2/README.md:
--------------------------------------------------------------------------------
1 | # ALEXCTF CR2: Many time secrets
2 |
3 | * **Category:** Cryptography
4 | * **Points:** 60
5 | * **level:** Medium
6 |
7 | ## [Challenge](https://ctflearn.com/challenge/177)
8 |
9 | > This time Fady learned from his old mistake and decided to use onetime pad as his encryption
10 | > technique, but he never knew why people call it one time pad! Flag will start with ALEXCTF{.
11 | > https://mega.nz/#!DGxBjaDR!tMWkHf0s0svmkboGd-IASHsS9jACxSYx4zi_ETsyzyQ
12 |
13 |
14 | ## Solution
15 | In the description we see an encryption with the name - **onetime pad** https://www.tutorialspoint.com/cryptography_with_python/cryptography_with_python_one_time_pad_cipher.htm
16 | In this kind of encryption we use a key with the same size or longer of the plaintext that we want to encrypt.
17 | So is kind of Vigenère Cipher but the different is that for any letter we have a special shift.
18 | For example we have a msg with 10 letters like "plain text" so we need to execute 26^10 possibilities to find the plaintext.
19 |
20 | The is vulnerability in this encrpytion if the plaintext is small or there is **reused of the key**.
21 | In our challenge we can see 11 lines of numbers. Maybe each line is a cipher text and each line encrypted with the same key.
22 |
23 | We will use the tool **crib drag** to check that. https://github.com/SpiderLabs/cribdrag
24 | We know that part of the key is **ALEXCTF{** is a good start.
25 |
26 | 
27 |
28 | We will get a lot of possibilities for plain text , We need to make a calculate guess of the each line.
29 |
30 | 
31 |
32 | After a little work we can get the full key that reused again and again.
33 |
34 | 
35 |
36 |
37 |
38 |
39 | Flag : ```ALEXCTF{HERE_GOES_THE_KEY}```
40 |
41 |
--------------------------------------------------------------------------------
/Cryptography/Medium/RSA Noob/README.md:
--------------------------------------------------------------------------------
1 | # RSA Noob
2 |
3 | * **Category:** Cryptography
4 | * **Points:** 60
5 | * **level:** Medium
6 |
7 | ## [Challenge](https://ctflearn.com/challenge/120)
8 |
9 | > These numbers were scratched out on a prison wall. Can you help me decode them?
10 | > https://mega.nz/#!al8iDSYB!s5olEDK5zZmYdx1LZU8s4CmYqnynvU_aOUvdQojJPJQ
11 |
12 | ## Solution
13 |
14 | As you can guess , This CTF is about RSA Encryption. I extremely recommend explore and learn about RSA.
15 | You can read about RSA - https://simple.wikipedia.org/wiki/RSA_algorithm .
16 |
17 | So we have the variables :
18 | 1. 'e' and 'n' ----> public key.
19 | 2. 'c' cipher text.
20 |
21 |
18 |
19 |
20 | Flag : ```CTF{THUMBS_UP} ```
21 |
22 |
--------------------------------------------------------------------------------
/Cryptography/Medium/ALEXCTF CR2/README.md:
--------------------------------------------------------------------------------
1 | # ALEXCTF CR2: Many time secrets
2 |
3 | * **Category:** Cryptography
4 | * **Points:** 60
5 | * **level:** Medium
6 |
7 | ## [Challenge](https://ctflearn.com/challenge/177)
8 |
9 | > This time Fady learned from his old mistake and decided to use onetime pad as his encryption
10 | > technique, but he never knew why people call it one time pad! Flag will start with ALEXCTF{.
11 | > https://mega.nz/#!DGxBjaDR!tMWkHf0s0svmkboGd-IASHsS9jACxSYx4zi_ETsyzyQ
12 |
13 |
14 | ## Solution
15 | In the description we see an encryption with the name - **onetime pad** https://www.tutorialspoint.com/cryptography_with_python/cryptography_with_python_one_time_pad_cipher.htm
16 | In this kind of encryption we use a key with the same size or longer of the plaintext that we want to encrypt.
17 | So is kind of Vigenère Cipher but the different is that for any letter we have a special shift.
18 | For example we have a msg with 10 letters like "plain text" so we need to execute 26^10 possibilities to find the plaintext.
19 |
20 | The is vulnerability in this encrpytion if the plaintext is small or there is **reused of the key**.
21 | In our challenge we can see 11 lines of numbers. Maybe each line is a cipher text and each line encrypted with the same key.
22 |
23 | We will use the tool **crib drag** to check that. https://github.com/SpiderLabs/cribdrag
24 | We know that part of the key is **ALEXCTF{** is a good start.
25 |
26 | 
27 |
28 | We will get a lot of possibilities for plain text , We need to make a calculate guess of the each line.
29 |
30 | 
31 |
32 | After a little work we can get the full key that reused again and again.
33 |
34 | 
35 |
36 |
37 |
38 |
39 | Flag : ```ALEXCTF{HERE_GOES_THE_KEY}```
40 |
41 |
--------------------------------------------------------------------------------
/Cryptography/Medium/RSA Noob/README.md:
--------------------------------------------------------------------------------
1 | # RSA Noob
2 |
3 | * **Category:** Cryptography
4 | * **Points:** 60
5 | * **level:** Medium
6 |
7 | ## [Challenge](https://ctflearn.com/challenge/120)
8 |
9 | > These numbers were scratched out on a prison wall. Can you help me decode them?
10 | > https://mega.nz/#!al8iDSYB!s5olEDK5zZmYdx1LZU8s4CmYqnynvU_aOUvdQojJPJQ
11 |
12 | ## Solution
13 |
14 | As you can guess , This CTF is about RSA Encryption. I extremely recommend explore and learn about RSA.
15 | You can read about RSA - https://simple.wikipedia.org/wiki/RSA_algorithm .
16 |
17 | So we have the variables :
18 | 1. 'e' and 'n' ----> public key.
19 | 2. 'c' cipher text.
20 |
21 |  22 |
23 | ## Using RsaCtfTool
24 |
25 | We will use this tool - https://github.com/Ganapati/RsaCtfTool to find 'd' and decrypt the cipher- 'c'.
26 | Use this command and get the flag. ```./RsaCtfTool.py -n 245841236512478852752909734912575581815967630033049838269083 -e 1 --uncipher 9327565722767258308650643213344542404592011161659991421```
27 |
28 | 
29 |
30 | ## Using a script
31 |
32 | You can also do it manually by script.
33 | First get the initial two primes - **p** and **q** from http://factordb.com/index.php
34 |
35 |
22 |
23 | ## Using RsaCtfTool
24 |
25 | We will use this tool - https://github.com/Ganapati/RsaCtfTool to find 'd' and decrypt the cipher- 'c'.
26 | Use this command and get the flag. ```./RsaCtfTool.py -n 245841236512478852752909734912575581815967630033049838269083 -e 1 --uncipher 9327565722767258308650643213344542404592011161659991421```
27 |
28 | 
29 |
30 | ## Using a script
31 |
32 | You can also do it manually by script.
33 | First get the initial two primes - **p** and **q** from http://factordb.com/index.php
34 |
35 |  36 |
37 |
36 |
37 |  38 |
39 |
40 | Flag : ```abctf{b3tter_up_y0ur_e}```
41 |
42 |
--------------------------------------------------------------------------------
/Cryptography/Medium/RSA Noob/RSA_Noob.py:
--------------------------------------------------------------------------------
1 | from Crypto.Util.number import inverse
2 | import binascii
3 |
4 | e = 1
5 | c = 9327565722767258308650643213344542404592011161659991421
6 | n = 245841236512478852752909734912575581815967630033049838269083
7 |
8 | # From factordb
9 |
10 | p = 416064700201658306196320137931
11 | q = 590872612825179551336102196593
12 |
13 | phi = (p-1) * (q-1)
14 |
15 | d = inverse(e,phi)
16 | m = pow(c,d,n)
17 |
18 | hex_str = hex(m)[2:] # Removing '0x'
19 | print(binascii.unhexlify(hex_str))
20 |
--------------------------------------------------------------------------------
/Cryptography/Medium/Substitution Cipher/README.md:
--------------------------------------------------------------------------------
1 | # Substitution Cipher
2 |
3 | * **Category:** Cryptography
4 | * **Points:** 60
5 | * **level:** Medium
6 |
7 | ## [Challenge](https://ctflearn.com/challenge/238)
8 |
9 | > Someone gave me this, but I haven't the slightest idea as to what it says!
10 | > https://mega.nz/#!iCBz2IIL!B7292dJSx1PGXoWhd9oFLk2g0NFqGApBaItI_2Gsp9w Figure it out for me, will ya?
11 |
12 | ## Solution
13 |
14 | So as mentioned in the title thie is **Substitution cipher** - https://en.wikipedia.org/wiki/Substitution_cipher.
15 | For example ROT13 is a Caesar cipher, a type of substitution cipher. In ROT13, the alphabet is rotated 13 steps.
16 |
17 | 
18 |
19 | Lets use a online tool for the decryption - https://www.dcode.fr/monoalphabetic-substitution
20 |
21 |
38 |
39 |
40 | Flag : ```abctf{b3tter_up_y0ur_e}```
41 |
42 |
--------------------------------------------------------------------------------
/Cryptography/Medium/RSA Noob/RSA_Noob.py:
--------------------------------------------------------------------------------
1 | from Crypto.Util.number import inverse
2 | import binascii
3 |
4 | e = 1
5 | c = 9327565722767258308650643213344542404592011161659991421
6 | n = 245841236512478852752909734912575581815967630033049838269083
7 |
8 | # From factordb
9 |
10 | p = 416064700201658306196320137931
11 | q = 590872612825179551336102196593
12 |
13 | phi = (p-1) * (q-1)
14 |
15 | d = inverse(e,phi)
16 | m = pow(c,d,n)
17 |
18 | hex_str = hex(m)[2:] # Removing '0x'
19 | print(binascii.unhexlify(hex_str))
20 |
--------------------------------------------------------------------------------
/Cryptography/Medium/Substitution Cipher/README.md:
--------------------------------------------------------------------------------
1 | # Substitution Cipher
2 |
3 | * **Category:** Cryptography
4 | * **Points:** 60
5 | * **level:** Medium
6 |
7 | ## [Challenge](https://ctflearn.com/challenge/238)
8 |
9 | > Someone gave me this, but I haven't the slightest idea as to what it says!
10 | > https://mega.nz/#!iCBz2IIL!B7292dJSx1PGXoWhd9oFLk2g0NFqGApBaItI_2Gsp9w Figure it out for me, will ya?
11 |
12 | ## Solution
13 |
14 | So as mentioned in the title thie is **Substitution cipher** - https://en.wikipedia.org/wiki/Substitution_cipher.
15 | For example ROT13 is a Caesar cipher, a type of substitution cipher. In ROT13, the alphabet is rotated 13 steps.
16 |
17 | 
18 |
19 | Lets use a online tool for the decryption - https://www.dcode.fr/monoalphabetic-substitution
20 |
21 |  22 |
23 |
24 |
25 | Flag : ```IFONLYMODERNCRYPTOWASLIKETHIS```
26 |
27 |
--------------------------------------------------------------------------------
/Forensics/Easy/A CAPTURE OF A FLAG/README.md:
--------------------------------------------------------------------------------
1 |
2 | # A CAPTURE OF A FLAG
3 |
4 | * **Category:** Forensics
5 | * **Points:** 30
6 | * **level:** Easy
7 |
8 | ## [Challenge](https://ctflearn.com/problems/356)
9 |
10 | > This isn't what I had in mind, when I asked someone to capture a flag... can you help? You should check out WireShark.\
11 | > https://mega.nz/#!3WhAWKwR!1T9cw2srN2CeOQWeuCm0ZVXgwk-E2v-TrPsZ4HUQ_f4
12 |
13 | ## Solution
14 |
15 | We have a wireshark file with a lot of data.\
16 | In this case lets search for post and get request to find passwords or flags hidden.\
17 | Lets sort the file by the Protocol column, by a quick glance we noitce about somthing interesting.\
18 | You can see a get request with a msg and after that probably base64 encryption.
19 |
20 |
22 |
23 |
24 |
25 | Flag : ```IFONLYMODERNCRYPTOWASLIKETHIS```
26 |
27 |
--------------------------------------------------------------------------------
/Forensics/Easy/A CAPTURE OF A FLAG/README.md:
--------------------------------------------------------------------------------
1 |
2 | # A CAPTURE OF A FLAG
3 |
4 | * **Category:** Forensics
5 | * **Points:** 30
6 | * **level:** Easy
7 |
8 | ## [Challenge](https://ctflearn.com/problems/356)
9 |
10 | > This isn't what I had in mind, when I asked someone to capture a flag... can you help? You should check out WireShark.\
11 | > https://mega.nz/#!3WhAWKwR!1T9cw2srN2CeOQWeuCm0ZVXgwk-E2v-TrPsZ4HUQ_f4
12 |
13 | ## Solution
14 |
15 | We have a wireshark file with a lot of data.\
16 | In this case lets search for post and get request to find passwords or flags hidden.\
17 | Lets sort the file by the Protocol column, by a quick glance we noitce about somthing interesting.\
18 | You can see a get request with a msg and after that probably base64 encryption.
19 |
20 |  21 |
22 |
23 | So lets get in the packet with folow tcp stream ,Copy the message and try to decrypt the base64 encryption.
24 |
25 |
26 |
21 |
22 |
23 | So lets get in the packet with folow tcp stream ,Copy the message and try to decrypt the base64 encryption.
24 |
25 |
26 |  27 |
28 |
29 |
27 |
28 |
29 |  30 |
31 |
32 | Flag : ```flag{AFlagInPCAP} ```
33 |
34 |
--------------------------------------------------------------------------------
/Forensics/Easy/BINWALK/README.md:
--------------------------------------------------------------------------------
1 |
2 | # BINWALK
3 |
4 | * **Category:** Forensics
5 | * **Points:** 30
6 | * **level:** Easy
7 |
8 | ## [Challenge](https://ctflearn.com/problems/108)
9 |
10 | > Here is a file with another file hidden inside it. Can you extract it?\
11 | > https://mega.nz/#!qbpUTYiK!-deNdQJxsQS8bTSMxeUOtpEclCI-zpK7tbJiKV0tXYY
12 |
13 | ## Solution
14 |
15 | We have a huge hint to use **Binwalk**.\
16 | Binwalk is **very popular** tools for Forensics. Its a tool for searching a given binary image for embedded files and executable code.\
17 | I am very recommend to read and investigate about file signatures, and also on png and jpeg structre.\
18 | You can look here - [File Signatures](https://en.wikipedia.org/wiki/List_of_file_signatures)
19 |
20 | Ok , so lets use Binwalk to see if there are any hiddend files.
21 | We will use this command ```binwalk -b PurpleThing.jpeg ```
22 |
23 | 
24 |
25 |
26 | Binwalk recognize **two** Png files, But we only see **one jpeg file** !?!?\
27 | Lets use this command to extract the Png file - ```binwalk -D 'image:png' PurpleThing.jpeg ```
28 |
29 | We are done ! , We get a folder and inside him the original png file and the hidden png file that contain the **flag**.
30 |
31 | 
32 |
33 |
34 |
35 |
36 |
37 | Flag : ```ABCTF{b1nw4lk_is_us3ful} ```
38 |
39 |
--------------------------------------------------------------------------------
/Forensics/Easy/FORENSICS 101/README.md:
--------------------------------------------------------------------------------
1 |
2 | # FORENSICS 101
3 |
4 | * **Category:** Forensics
5 | * **Points:** 30
6 | * **level:** Easy
7 |
8 | ## [Challenge](https://ctflearn.com/problems/96)
9 |
10 | > Think the flag is somewhere in there. Would you help me find it?\
11 | > https://mega.nz/#!OHohCbTa!wbg60PARf4u6E6juuvK9-aDRe_bgEL937VO01EImM7c
12 |
13 | ## Solution
14 |
15 | The solution here is pretty easy. We are hit the flag in initial and basic check in Forensics , **Strings !!!**
16 | ```
17 | strings 95f6edfb66ef42d774a5a34581f19052.jpg
18 | ```
19 | 
20 |
21 | **scroll down and...**
22 |
23 | 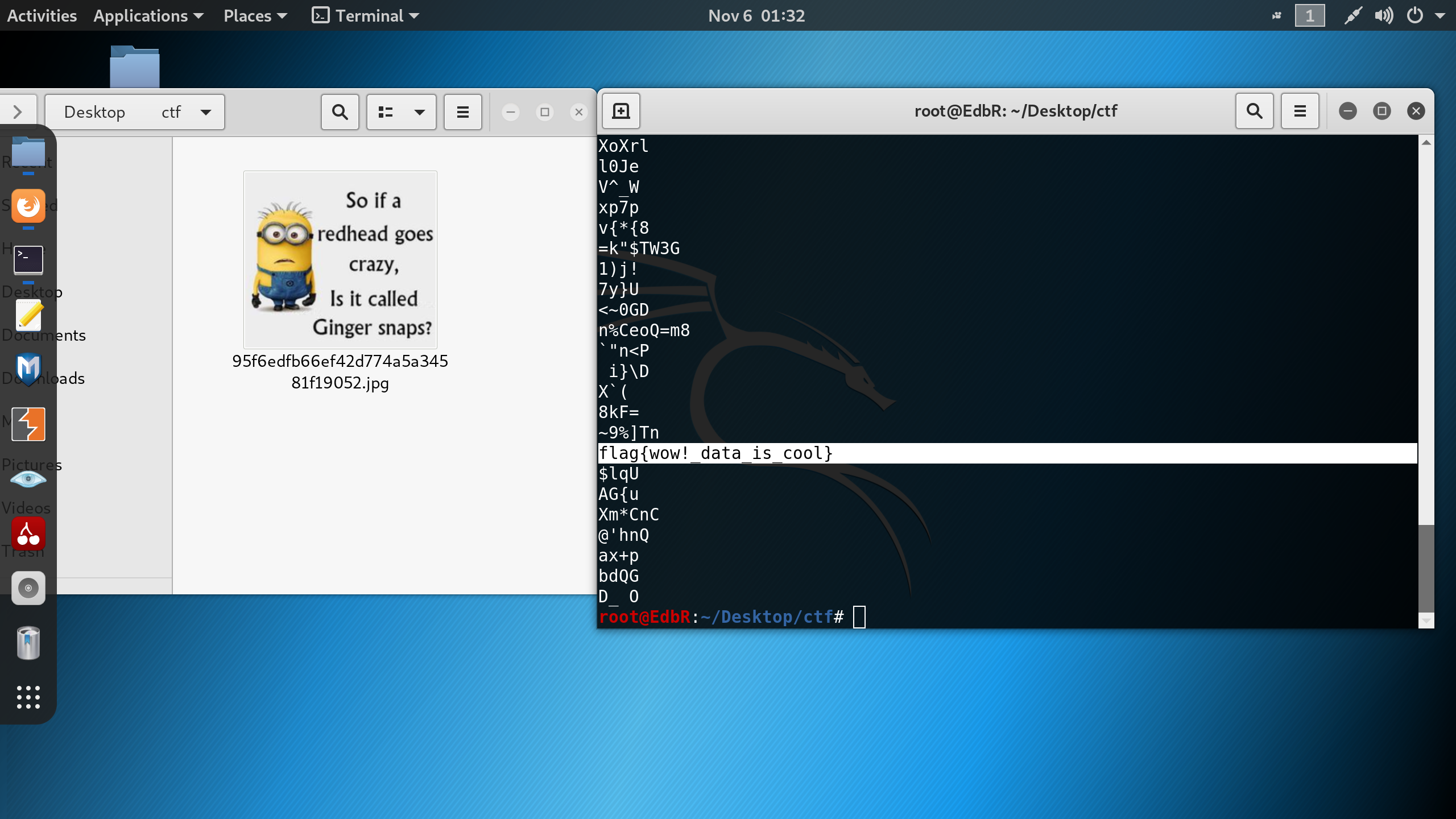
24 |
25 |
26 |
27 |
28 |
29 | Flag : ```flag{wow!_data_is_cool} ```
30 |
31 |
--------------------------------------------------------------------------------
/Forensics/Easy/README.md:
--------------------------------------------------------------------------------
1 |
2 | ### Hey everybody , In this folder you can find solution for the five CTFs above , from the website :
3 |
4 | ## [CTFlearn](https://ctflearn.com/problems)
5 |
6 | ### In addition i made a video of the solution of all the five Ctfs:
7 |
8 | ## [Forensics_Easy_Solution](https://www.youtube.com/watch?v=CwkcpJsHZfk)
9 |
10 | ### Enjoy !
11 |
--------------------------------------------------------------------------------
/Forensics/Easy/TAKING LS/README.md:
--------------------------------------------------------------------------------
1 |
2 |
3 | # TAKING LS
4 |
5 | * **Category:** Forensics
6 | * **Points:** 30
7 | * **level:** Easy
8 |
9 | ## [Challenge](https://ctflearn.com/problems/103)
10 |
11 | > Just take the Ls. Check out this zip file and I be the flag will remain hidden.\
12 | > https://mega.nz/#!mCgBjZgB!_FtmAm8s_mpsHr7KWv8GYUzhbThNn0I8cHMBi4fJQp8
13 |
14 | ## Solution
15 |
16 | After download the challenge we are getting a rar file, and inside him a pdf file with the name "The Flag.pdf".\
17 | But the pdf is protect by a password, So lets think.
18 |
19 | We are getting in this ctf 2 hints:
20 | 1. In the title - TAKING **LS**
21 | 2. In the description - the flag will remain **hidden** So lets look for hidden files with the help of ```ls-a```
22 |
23 |
24 | 
25 |
26 | Ok we are seeing a strange file start with a dot , with the name "ThePassword".\
27 | Hidden files and folder have names that start with a **.** (dot character). \
28 | To toggle show/hide hidden files or folders use the keyboard shortcut **Ctrl+H**.
29 |
30 | We are getting a folder and inside txt file - "ThePassword.txt".\
31 | When openning him we get the password for the pdf - ```Nice Job! The Password is "Im The Flag".```
32 |
33 |
34 | 
35 |
36 | Lets use the password to unlock the pdf and get the flag !
37 |
38 | 
39 |
40 |
41 |
42 | Flag : ```ABCTF{T3Rm1n4l_is_C00l} ```
43 |
44 |
--------------------------------------------------------------------------------
/Forensics/Easy/WOW.... SO META/README.md:
--------------------------------------------------------------------------------
1 |
2 | # WOW.... SO META
3 |
4 | * **Category:** Forensics
5 | * **Points:** 20
6 | * **level:** Easy
7 |
8 | ## [Challenge](https://ctflearn.com/problems/348)
9 |
10 | > This photo was taken by our target. See what you can find out about him from it.\
11 | > https://mega.nz/#!ifA2QAwQ!WF-S-MtWHugj8lx1QanGG7V91R-S1ng7dDRSV25iFbk
12 |
13 | ## Solution
14 |
15 | We are have a clue from the title - ""WOW.... SO **META**"" the META may be a short for Metadata.\
16 | Metadata is "data that provides information about other data".In short, it's data about data.\
17 | So we will use the tool - "**ExifTool**" , this tool we help us reading meta info about the file.\
18 | Use this command ```exiftool 3UWLBAUCb9Z2.jpg ``` and get the flag !.
19 |
20 | 
21 |
22 |
23 | Flag : ```flag{EEe_x_I_FFf} ```
24 |
25 |
--------------------------------------------------------------------------------
/Forensics/Medium/07601/README.md:
--------------------------------------------------------------------------------
1 |
2 |
3 | # 07601
4 |
5 | * **Category:** Forensics
6 | * **Points:** 60
7 | * **level:** Medium
8 |
9 | ## [Challenge](https://ctflearn.com/problems/97)
10 |
11 | > I think I lost my flag in there. Hopefully, it won't get attacked...\
12 | > https://mega.nz/#!CXYXBQAK!6eLJSXvAfGnemqWpNbLQtOHBvtkCzA7-zycVjhHPYQQ
13 |
14 | ## Solution
15 |
16 | With a quick use of strings command we get the flag **ABCTF{fooled_ya_dustin}** but its wrong flag...
17 | So lets use one of the famoust tools - **binwalk**.\
18 | By using this command ```binwalk -b AGT.png ``` we see alot of zip files hidden in the image.
19 |
20 | 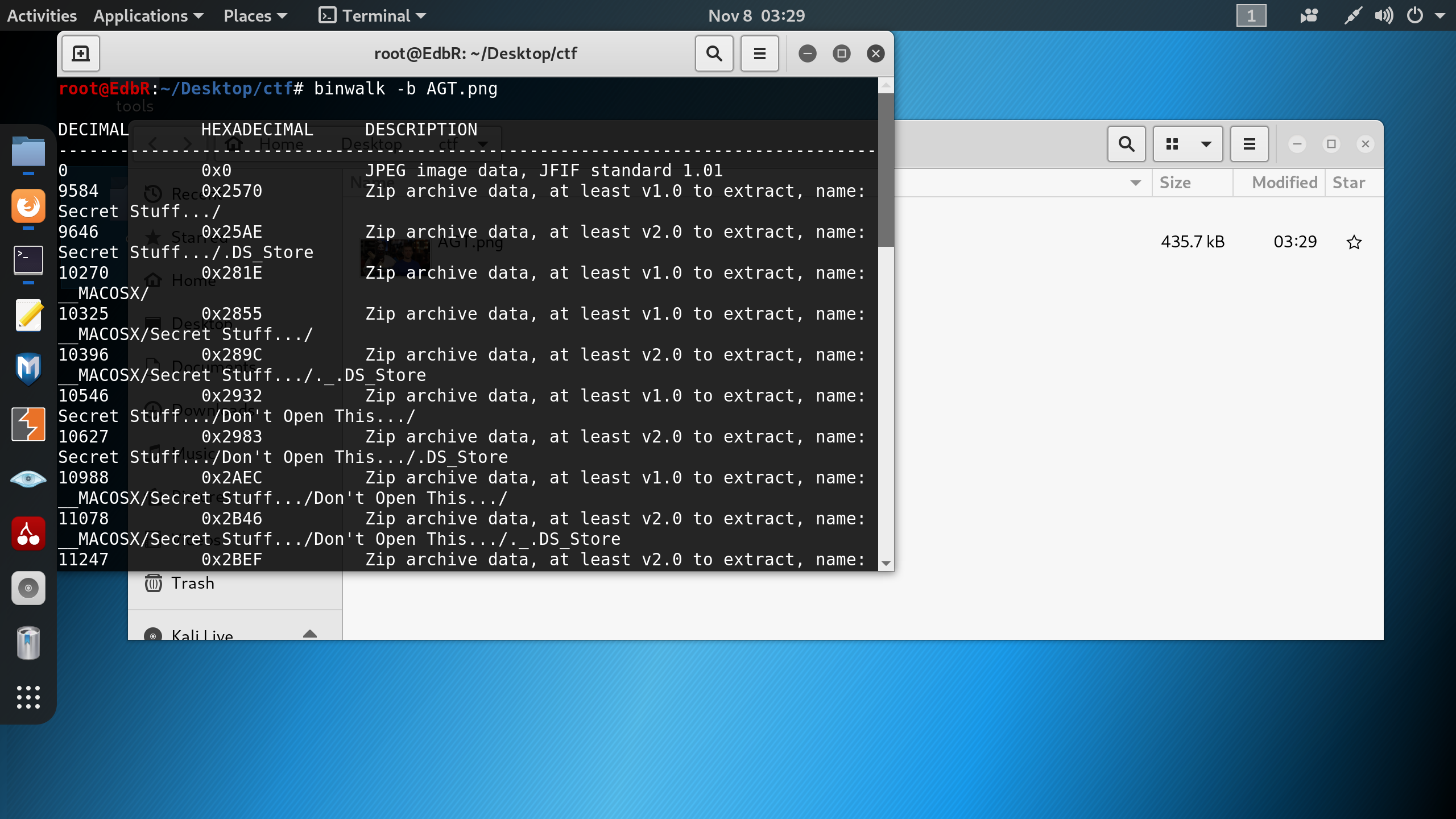
21 |
22 | Lets extract hidden data from the image using the command ```binwalk -e AGT.png ```\
23 | After extract the hidden data we see a folder with the name **Secret Stuff...** interesting..\
24 | When getting into this folders we meet **Don't Open This...** , enter to this folder we see image.\
25 | Using a simple strings command on the new image and we get the flag :
26 |
27 | 
28 |
29 |
30 | Flag : ```ABCTF{Du$t1nS_D0jo}1r ```
31 |
32 |
--------------------------------------------------------------------------------
/Forensics/Medium/DUMPSTER/Dumpster_Soltuion_By_EdbR.java:
--------------------------------------------------------------------------------
1 | import javax.crypto.Cipher;
2 | import javax.crypto.spec.SecretKeySpec;
3 | import java.util.Base64;
4 |
5 | public class Dumpster_Solution {
6 |
7 | public static final String FLAG = "S+kUZtaHEYpFpv2ixuTnqBdORNzsdVJrAxWznyOljEo=";
8 |
9 | public static byte [] decrypt(byte[] msg,byte [] passHash) throws Exception
10 | {
11 | SecretKeySpec spec = new SecretKeySpec(passHash, "AES");
12 | Cipher cipher = Cipher.getInstance("AES/ECB/PKCS5Padding");
13 | cipher.init(Cipher.DECRYPT_MODE, spec);
14 | return cipher.doFinal(msg);
15 | }
16 |
17 | public static void main(String[] args) throws Exception
18 | {
19 | byte [] passHash = {7, 95, -34, 16, -89, -86, 73, 108, -128, 71, 43, 41, 100, 40, 53, -24};
20 | System.out.println(new String(decrypt(Base64.getDecoder().decode(FLAG.getBytes()),passHash)));
21 | Thread.sleep(5000); //We did a heap dump right here.
22 | }
23 | }
24 |
--------------------------------------------------------------------------------
/Forensics/Medium/DUMPSTER/README.md:
--------------------------------------------------------------------------------
1 |
2 | # DUMPSTER
3 |
4 | * **Category:** Forensics
5 | * **Points:** 60
6 | * **level:** Medium
7 |
8 |
9 | ## [Challenge](https://ctflearn.com/problems/355)
10 |
11 | > I found a flag, but it was encrypted! Our systems have detected that someone has successfully decrypted this flag, and we stealthily took a heap dump of the program (in Java). Can you recover the flag for me? Here's the source code of the Java program and the heap dump:
12 | > https://mega.nz/#!rHYGlAQT!48DlH2pSZg10Ei3f-Ivm7RoNBbV16Qw0wN4cWxANUwY
13 |
14 | ## Solution
15 | Ok , so we have two files:
16 | 1. Decryptor.java.
17 | 2. Heapdump.hprof - The heap dump of the Decryptor.
18 |
19 | By looking on the Decrypt file we can see the encrypted flag stored in the variable **FLAG**.
20 |
21 |
30 |
31 |
32 | Flag : ```flag{AFlagInPCAP} ```
33 |
34 |
--------------------------------------------------------------------------------
/Forensics/Easy/BINWALK/README.md:
--------------------------------------------------------------------------------
1 |
2 | # BINWALK
3 |
4 | * **Category:** Forensics
5 | * **Points:** 30
6 | * **level:** Easy
7 |
8 | ## [Challenge](https://ctflearn.com/problems/108)
9 |
10 | > Here is a file with another file hidden inside it. Can you extract it?\
11 | > https://mega.nz/#!qbpUTYiK!-deNdQJxsQS8bTSMxeUOtpEclCI-zpK7tbJiKV0tXYY
12 |
13 | ## Solution
14 |
15 | We have a huge hint to use **Binwalk**.\
16 | Binwalk is **very popular** tools for Forensics. Its a tool for searching a given binary image for embedded files and executable code.\
17 | I am very recommend to read and investigate about file signatures, and also on png and jpeg structre.\
18 | You can look here - [File Signatures](https://en.wikipedia.org/wiki/List_of_file_signatures)
19 |
20 | Ok , so lets use Binwalk to see if there are any hiddend files.
21 | We will use this command ```binwalk -b PurpleThing.jpeg ```
22 |
23 | 
24 |
25 |
26 | Binwalk recognize **two** Png files, But we only see **one jpeg file** !?!?\
27 | Lets use this command to extract the Png file - ```binwalk -D 'image:png' PurpleThing.jpeg ```
28 |
29 | We are done ! , We get a folder and inside him the original png file and the hidden png file that contain the **flag**.
30 |
31 | 
32 |
33 |
34 |
35 |
36 |
37 | Flag : ```ABCTF{b1nw4lk_is_us3ful} ```
38 |
39 |
--------------------------------------------------------------------------------
/Forensics/Easy/FORENSICS 101/README.md:
--------------------------------------------------------------------------------
1 |
2 | # FORENSICS 101
3 |
4 | * **Category:** Forensics
5 | * **Points:** 30
6 | * **level:** Easy
7 |
8 | ## [Challenge](https://ctflearn.com/problems/96)
9 |
10 | > Think the flag is somewhere in there. Would you help me find it?\
11 | > https://mega.nz/#!OHohCbTa!wbg60PARf4u6E6juuvK9-aDRe_bgEL937VO01EImM7c
12 |
13 | ## Solution
14 |
15 | The solution here is pretty easy. We are hit the flag in initial and basic check in Forensics , **Strings !!!**
16 | ```
17 | strings 95f6edfb66ef42d774a5a34581f19052.jpg
18 | ```
19 | 
20 |
21 | **scroll down and...**
22 |
23 | 
24 |
25 |
26 |
27 |
28 |
29 | Flag : ```flag{wow!_data_is_cool} ```
30 |
31 |
--------------------------------------------------------------------------------
/Forensics/Easy/README.md:
--------------------------------------------------------------------------------
1 |
2 | ### Hey everybody , In this folder you can find solution for the five CTFs above , from the website :
3 |
4 | ## [CTFlearn](https://ctflearn.com/problems)
5 |
6 | ### In addition i made a video of the solution of all the five Ctfs:
7 |
8 | ## [Forensics_Easy_Solution](https://www.youtube.com/watch?v=CwkcpJsHZfk)
9 |
10 | ### Enjoy !
11 |
--------------------------------------------------------------------------------
/Forensics/Easy/TAKING LS/README.md:
--------------------------------------------------------------------------------
1 |
2 |
3 | # TAKING LS
4 |
5 | * **Category:** Forensics
6 | * **Points:** 30
7 | * **level:** Easy
8 |
9 | ## [Challenge](https://ctflearn.com/problems/103)
10 |
11 | > Just take the Ls. Check out this zip file and I be the flag will remain hidden.\
12 | > https://mega.nz/#!mCgBjZgB!_FtmAm8s_mpsHr7KWv8GYUzhbThNn0I8cHMBi4fJQp8
13 |
14 | ## Solution
15 |
16 | After download the challenge we are getting a rar file, and inside him a pdf file with the name "The Flag.pdf".\
17 | But the pdf is protect by a password, So lets think.
18 |
19 | We are getting in this ctf 2 hints:
20 | 1. In the title - TAKING **LS**
21 | 2. In the description - the flag will remain **hidden** So lets look for hidden files with the help of ```ls-a```
22 |
23 |
24 | 
25 |
26 | Ok we are seeing a strange file start with a dot , with the name "ThePassword".\
27 | Hidden files and folder have names that start with a **.** (dot character). \
28 | To toggle show/hide hidden files or folders use the keyboard shortcut **Ctrl+H**.
29 |
30 | We are getting a folder and inside txt file - "ThePassword.txt".\
31 | When openning him we get the password for the pdf - ```Nice Job! The Password is "Im The Flag".```
32 |
33 |
34 | 
35 |
36 | Lets use the password to unlock the pdf and get the flag !
37 |
38 | 
39 |
40 |
41 |
42 | Flag : ```ABCTF{T3Rm1n4l_is_C00l} ```
43 |
44 |
--------------------------------------------------------------------------------
/Forensics/Easy/WOW.... SO META/README.md:
--------------------------------------------------------------------------------
1 |
2 | # WOW.... SO META
3 |
4 | * **Category:** Forensics
5 | * **Points:** 20
6 | * **level:** Easy
7 |
8 | ## [Challenge](https://ctflearn.com/problems/348)
9 |
10 | > This photo was taken by our target. See what you can find out about him from it.\
11 | > https://mega.nz/#!ifA2QAwQ!WF-S-MtWHugj8lx1QanGG7V91R-S1ng7dDRSV25iFbk
12 |
13 | ## Solution
14 |
15 | We are have a clue from the title - ""WOW.... SO **META**"" the META may be a short for Metadata.\
16 | Metadata is "data that provides information about other data".In short, it's data about data.\
17 | So we will use the tool - "**ExifTool**" , this tool we help us reading meta info about the file.\
18 | Use this command ```exiftool 3UWLBAUCb9Z2.jpg ``` and get the flag !.
19 |
20 | 
21 |
22 |
23 | Flag : ```flag{EEe_x_I_FFf} ```
24 |
25 |
--------------------------------------------------------------------------------
/Forensics/Medium/07601/README.md:
--------------------------------------------------------------------------------
1 |
2 |
3 | # 07601
4 |
5 | * **Category:** Forensics
6 | * **Points:** 60
7 | * **level:** Medium
8 |
9 | ## [Challenge](https://ctflearn.com/problems/97)
10 |
11 | > I think I lost my flag in there. Hopefully, it won't get attacked...\
12 | > https://mega.nz/#!CXYXBQAK!6eLJSXvAfGnemqWpNbLQtOHBvtkCzA7-zycVjhHPYQQ
13 |
14 | ## Solution
15 |
16 | With a quick use of strings command we get the flag **ABCTF{fooled_ya_dustin}** but its wrong flag...
17 | So lets use one of the famoust tools - **binwalk**.\
18 | By using this command ```binwalk -b AGT.png ``` we see alot of zip files hidden in the image.
19 |
20 | 
21 |
22 | Lets extract hidden data from the image using the command ```binwalk -e AGT.png ```\
23 | After extract the hidden data we see a folder with the name **Secret Stuff...** interesting..\
24 | When getting into this folders we meet **Don't Open This...** , enter to this folder we see image.\
25 | Using a simple strings command on the new image and we get the flag :
26 |
27 | 
28 |
29 |
30 | Flag : ```ABCTF{Du$t1nS_D0jo}1r ```
31 |
32 |
--------------------------------------------------------------------------------
/Forensics/Medium/DUMPSTER/Dumpster_Soltuion_By_EdbR.java:
--------------------------------------------------------------------------------
1 | import javax.crypto.Cipher;
2 | import javax.crypto.spec.SecretKeySpec;
3 | import java.util.Base64;
4 |
5 | public class Dumpster_Solution {
6 |
7 | public static final String FLAG = "S+kUZtaHEYpFpv2ixuTnqBdORNzsdVJrAxWznyOljEo=";
8 |
9 | public static byte [] decrypt(byte[] msg,byte [] passHash) throws Exception
10 | {
11 | SecretKeySpec spec = new SecretKeySpec(passHash, "AES");
12 | Cipher cipher = Cipher.getInstance("AES/ECB/PKCS5Padding");
13 | cipher.init(Cipher.DECRYPT_MODE, spec);
14 | return cipher.doFinal(msg);
15 | }
16 |
17 | public static void main(String[] args) throws Exception
18 | {
19 | byte [] passHash = {7, 95, -34, 16, -89, -86, 73, 108, -128, 71, 43, 41, 100, 40, 53, -24};
20 | System.out.println(new String(decrypt(Base64.getDecoder().decode(FLAG.getBytes()),passHash)));
21 | Thread.sleep(5000); //We did a heap dump right here.
22 | }
23 | }
24 |
--------------------------------------------------------------------------------
/Forensics/Medium/DUMPSTER/README.md:
--------------------------------------------------------------------------------
1 |
2 | # DUMPSTER
3 |
4 | * **Category:** Forensics
5 | * **Points:** 60
6 | * **level:** Medium
7 |
8 |
9 | ## [Challenge](https://ctflearn.com/problems/355)
10 |
11 | > I found a flag, but it was encrypted! Our systems have detected that someone has successfully decrypted this flag, and we stealthily took a heap dump of the program (in Java). Can you recover the flag for me? Here's the source code of the Java program and the heap dump:
12 | > https://mega.nz/#!rHYGlAQT!48DlH2pSZg10Ei3f-Ivm7RoNBbV16Qw0wN4cWxANUwY
13 |
14 | ## Solution
15 | Ok , so we have two files:
16 | 1. Decryptor.java.
17 | 2. Heapdump.hprof - The heap dump of the Decryptor.
18 |
19 | By looking on the Decrypt file we can see the encrypted flag stored in the variable **FLAG**.
20 |
21 |  22 |
23 |
24 |
25 | ## How to decrypt the flag ???
26 | We need to write some **pass** that will be encrypted with SHA-256, And the first 16 bytes will stored in variable **passHash**.
27 |
28 |
22 |
23 |
24 |
25 | ## How to decrypt the flag ???
26 | We need to write some **pass** that will be encrypted with SHA-256, And the first 16 bytes will stored in variable **passHash**.
27 |
28 |  29 |
30 | The variable **passHash** would be the **key** in the AES decryption of FLAG after that.
31 |
32 |
29 |
30 | The variable **passHash** would be the **key** in the AES decryption of FLAG after that.
31 |
32 |  33 |
34 | Ok, After we understood all the process , we only have one missing piece in the puzzle - how we get the **pass** !?
35 | The answer is the second file - **Heapdump.hpro**
36 |
37 | ## Heap dump memory analyzer
38 | The second file is a dump of the heap from the program as you can notice here:
39 |
40 |
33 |
34 | Ok, After we understood all the process , we only have one missing piece in the puzzle - how we get the **pass** !?
35 | The answer is the second file - **Heapdump.hpro**
36 |
37 | ## Heap dump memory analyzer
38 | The second file is a dump of the heap from the program as you can notice here:
39 |
40 |  41 |
42 | So we need to analyze the dump to catch where the user input the pass.\
43 | We will use the program **visualvm**.
44 | Before we start i recommend to you to explore the dump by yourself and do a full analyze and exploring for good understanding.
45 |
46 | ## Analyze
47 | After analyze all the dump i have notice a problem to find the pass... But i find the **passHash** !!!
48 | By going to the main thread -> Decryptor$Password -> **passHash**
49 |
50 | 
51 |
52 | Now that we have the passHash we can wirte a short program that would be decrypt the flag.
53 |
54 |
41 |
42 | So we need to analyze the dump to catch where the user input the pass.\
43 | We will use the program **visualvm**.
44 | Before we start i recommend to you to explore the dump by yourself and do a full analyze and exploring for good understanding.
45 |
46 | ## Analyze
47 | After analyze all the dump i have notice a problem to find the pass... But i find the **passHash** !!!
48 | By going to the main thread -> Decryptor$Password -> **passHash**
49 |
50 | 
51 |
52 | Now that we have the passHash we can wirte a short program that would be decrypt the flag.
53 |
54 |  55 |
56 | You can find the code here - https://pastebin.com/5vXTpVEN
57 |
58 | Run the program and get the flag :)
59 |
60 |
61 |
62 | Flag : ```stCTF{h34p_6ump5_r_c00l!11!!}```
63 |
64 |
--------------------------------------------------------------------------------
/Forensics/Medium/THE ADVENTURES OF BORIS IVANOV. PART 1/README.md:
--------------------------------------------------------------------------------
1 |
2 |
3 | # THE ADVENTURES OF BORIS IVANOV. PART 1.
4 |
5 | * **Category:** Forensics
6 | * **Points:** 60
7 | * **level:** Medium
8 |
9 |
10 | ## [Challenge](https://ctflearn.com/problems/373)
11 |
12 | > The KGB agent Boris Ivanov got information about an attempt to sell classified data. He quickly reacted and intercepted the correspondence. Help Boris understand what exactly they were trying to sell. Here is the interception data:
13 | > https://mega.nz/#!HfAHmKQb!zg6EPqfwes1bBDCjx7-ZFR_0O0-GtGg2Mrn56l5LCkE
14 |
15 | ## Solution
16 | Ok , From first look we dont have any idea from where to start. After trying set of tools still get nothing...\
17 | In this case when we get stuck , I recommend to read again the challenge and his files.
18 |
19 | 
20 |
21 |
22 | After reading the challenge again and again we can notice the word **KGB** may bay relate to stegnograpy by **RGB**.\
23 | So after play with some tools with rgb values and lsb , I found the solution in relation of rgb **offsets**.\
24 | I use the tool stegslove , One of his option is **Stereogram Solver** and in this option there are 1000 offsets possible.
25 |
26 | 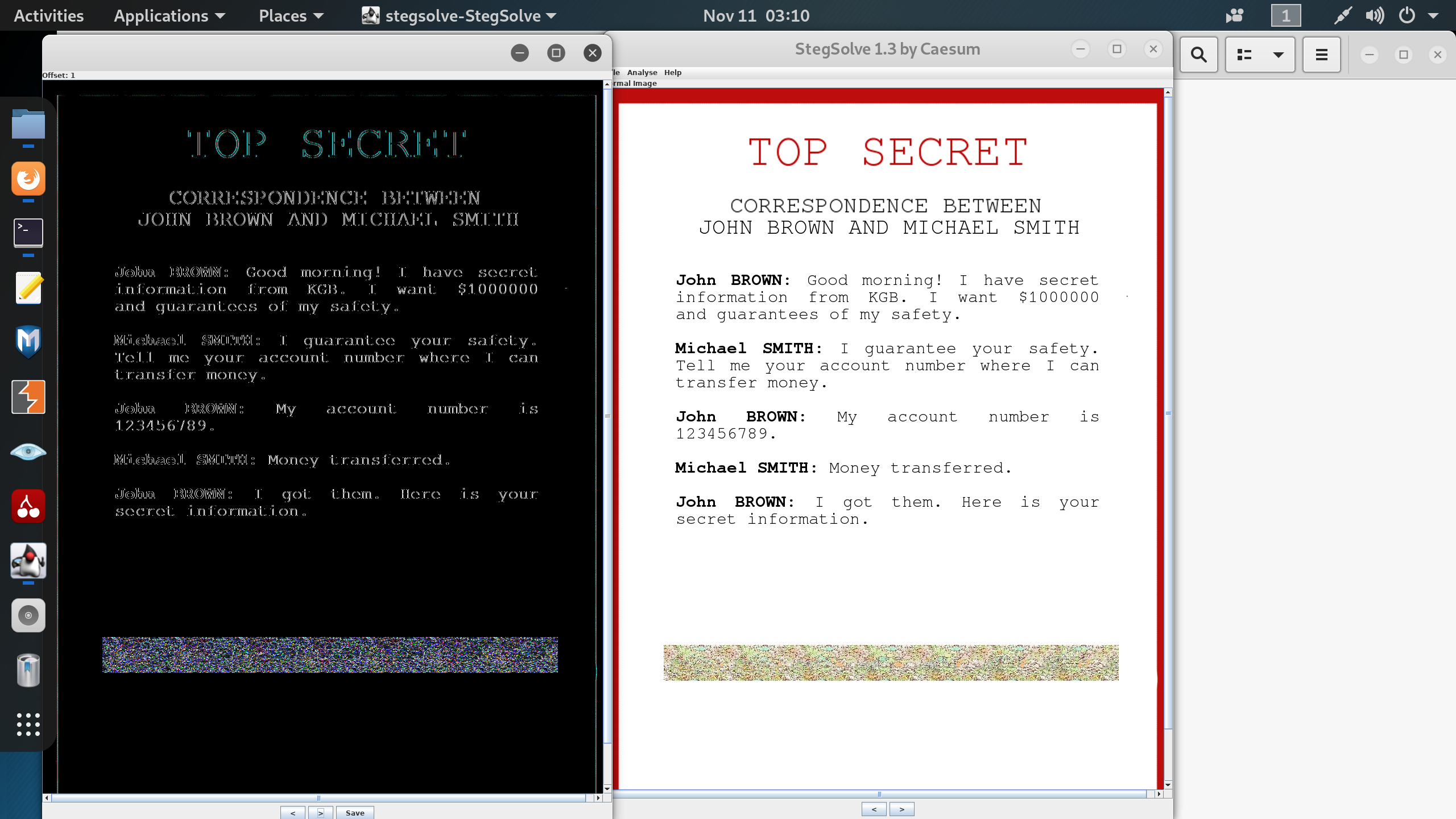
27 |
28 | After a little hard work i found the flag in offset **898**.
29 |
30 | 
31 |
32 | Flag : ```flag{d0nt_m3s5_w1th_th3_KGB} ```
33 |
34 |
--------------------------------------------------------------------------------
/Forensics/Medium/UP FOR A LITTLE CHALLENGE/README.md:
--------------------------------------------------------------------------------
1 |
2 |
3 | # UP FOR A LITTLE CHALLENGE?
4 |
5 | * **Category:** Forensics
6 | * **Points:** 60
7 | * **level:** Medium
8 |
9 |
10 | ## [Challenge](https://ctflearn.com/problems/142)
11 |
12 | > https://mega.nz/#!LoABFK5K!0sEKbsU3sBUG8zWxpBfD1bQx_JY_MuYEWQvLrFIqWZ0 You Know What To Do ...\
13 |
14 | ## Solution
15 |
16 | As you probably know , The first thing we will check is **strings**.\
17 | When using strings we can notice to four suspecious strings:
18 | 1. **Url address - https://mega.nz/#!z8hACJbb!vQB569ptyQjNEoxIwHrUhwWu5WCj1JWmU-OFjf90Prg**
19 | 2. **Mp real_unlock_key: Nothing Is As It SeemsU**
20 | 3. **password: Really? Again**
21 | 4. **flag{Not_So_Simple...}**
22 |
23 | As you can see :
24 |
25 | 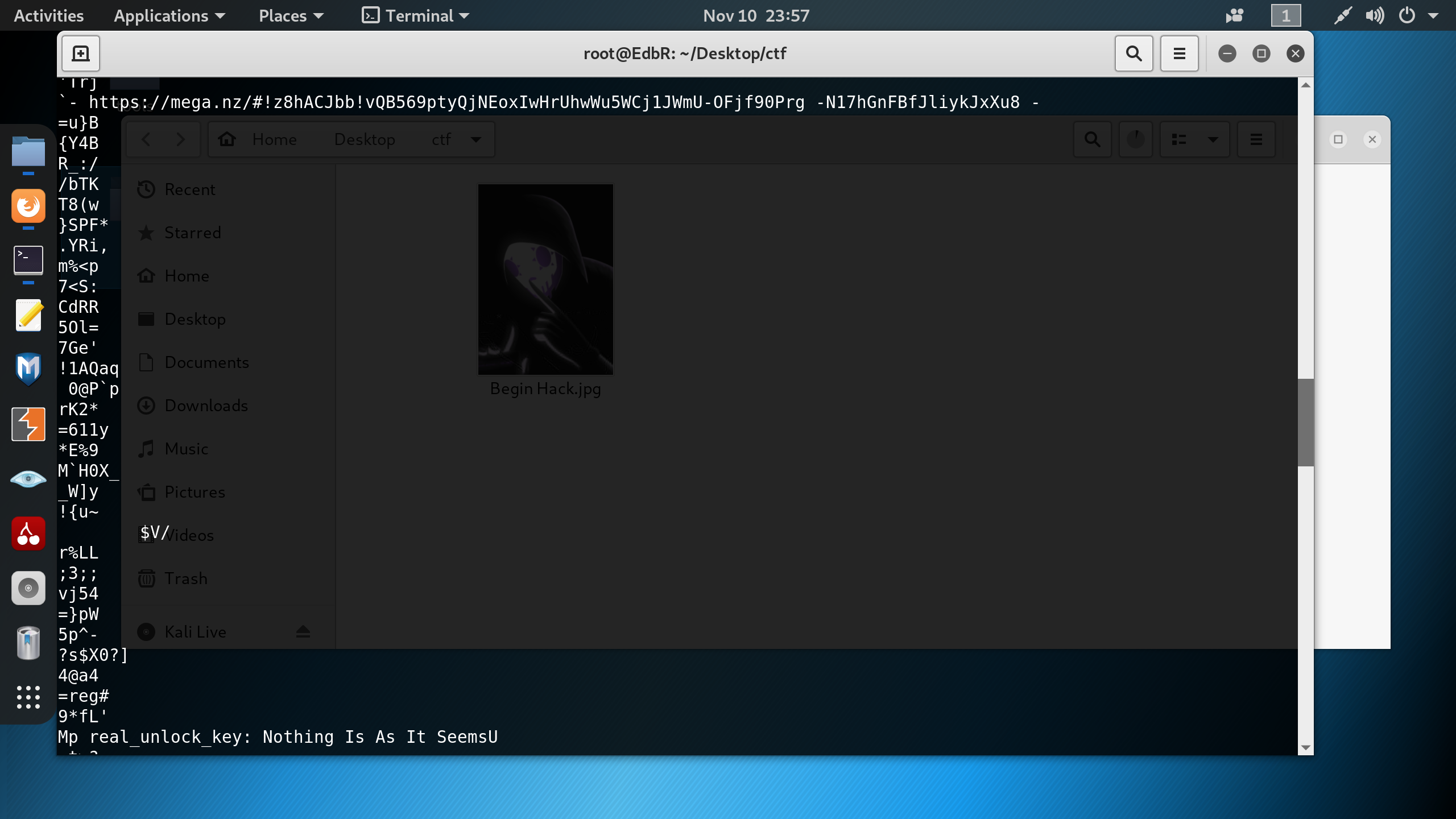
26 |
27 | 
28 |
29 |
30 | As you can assume... the flag is not correct :).\
31 | So , after trying few more tools we dont find something special, So lets use the URL.\
32 | We get a rar file , after extracting him and get inside the folder - "Did I Forget Again?" We see a jpeg file -"Loo Nothing Becomes Useless ack".\
33 | After trying a lot of tools that not bring nothing , lets think... , Maybe there is a hidden file that we forgot to check !?\
34 | Lets use ```ls -a```. YeS ! there is , So lets use ```ctrl+h```\
35 | We get a rar with a locked jpeg file inside , We need the password to unlock the jpeg.
36 |
37 | ## Moment to think...
38 |
39 | Where we can find this password ??? You remember the four strings we found from the original image ?\
40 | After try all of them we got a **hit** !!! **Nothing Is As It SeemsU** , but remove the last **U**.\
41 | The Password is - ```Nothing Is As It Seems```
42 | Unlock the jpeg file and if you notice we see a red string in the **bottom right corner**.
43 |
44 |
45 | 
46 |
47 |
48 | Flag : ```flag{hack_complete} ```
49 |
50 |
--------------------------------------------------------------------------------
/Programming/Hard/IS IT THE FLAG/BruteForce_Solution_By_EdbR.py:
--------------------------------------------------------------------------------
1 | # Solution By EdbR
2 | import sys
3 |
4 | def java_string_hashcode(s): # The hashCode function in java.
5 | h = 0
6 | for c in s:
7 | h = (31 * h + ord(c)) & 0xFFFFFFFF
8 | return ((h + 0x80000000) & 0xFFFFFFFF) - 0x80000000
9 |
10 | def isFlag(str):
11 | return java_string_hashcode(str) == 1471587914 and java_string_hashcode(str.lower) == 1472541258 # The function from the CTF.
12 |
13 | def main():
14 | list = []
15 | for i in range (48,58):
16 | list.append(i)
17 | for i in range (65,91):
18 | list.append(i)
19 | for i in range(97, 123):
20 | list.append(i)
21 | flag=""
22 | for i0 in list:
23 | if (i0 > 48):
24 | flag = flag[:-5]
25 | flag += chr(i0)
26 | for i1 in list:
27 | if (i1 > 48):
28 | flag = flag[:-4]
29 | flag += chr(i1)
30 | for i2 in list:
31 | if (i2 > 48):
32 | flag = flag[:-3]
33 | flag += chr(i2)
34 | for i3 in list:
35 | if (i3 > 48):
36 | flag = flag[:-2]
37 | flag += chr(i3)
38 | for i4 in list:
39 | if (i4 > 48):
40 | flag = flag[:-1]
41 | flag += chr(i4)
42 | for i5 in list:
43 | flag += chr(i5)
44 | if(java_string_hashcode(flag)==1471587914 and java_string_hashcode(flag.lower())==1472541258):
45 | print("The flag is:", flag)
46 | sys.exit()
47 | flag = flag[:-1]
48 | main()
49 |
--------------------------------------------------------------------------------
/Programming/Hard/IS IT THE FLAG/Is it the Flag.java:
--------------------------------------------------------------------------------
1 | public class IsItTheFlag {
2 |
3 | public static boolean isFlag(String str) {
4 | return str.hashCode() == 1471587914 && str.toLowerCase().hashCode() == 1472541258;
5 | }
6 |
7 | public static void main(String[] args) {
8 |
9 | String flag = "------";
10 |
11 | if (isFlag(flag))
12 | System.out.println("You found it!");
13 | else
14 | System.out.println("Try again :(");
15 |
16 | }
17 | }
18 |
--------------------------------------------------------------------------------
/Programming/Hard/IS IT THE FLAG/Mathematical Solution_By_EdbR.py:
--------------------------------------------------------------------------------
1 | # Solution By EdbR
2 | import sys
3 |
4 | def java_string_hashcode(s): # The hashCode function in java.
5 | h = 0
6 | for c in s:
7 | h = (31 * h + ord(c)) & 0xFFFFFFFF
8 | return ((h + 0x80000000) & 0xFFFFFFFF) - 0x80000000
9 |
10 | def isFlag(str):
11 | return java_string_hashcode(str) == 1471587914 and java_string_hashcode(str.lower) == 1472541258 # The function from the CTF.
12 |
13 | def main():
14 | sum=0
15 | max1 = pow(31, 4) * 122 # Max option of alphanumeric characters.
16 | min1 = pow(31, 4) * 48 # Min option of alphanumeric characters.
17 | max2 = pow(31, 3) * 122
18 | min2 = pow(31, 3) * 48
19 | max3 = pow(31, 2) * 122
20 | min3 = pow(31, 2) * 48
21 | max4 = pow(31, 1) * 122
22 | min4 = pow(31, 1) * 48
23 | max5 = 122
24 | min5 = 48
25 | list=[] # Make a list of alphanumeric characters.
26 | for i in range (48,58):
27 | list.append(i)
28 | for i in range (65,91):
29 | list.append(i)
30 | for i in range(97, 123):
31 | list.append(i)
32 |
33 | for i0 in list:
34 | x0 = pow(31, 5) * i0
35 | if (x0 + max1 + max2 + max3 + max4 + max5 >= 1471587914 and x0 + min1 + min2 + min3 + min4 + min5 <= 1472541258):
36 | print("flag[0] =", i0)
37 |
38 | for i1 in list:
39 | x1 = pow(31, 4) * i1
40 | if (x0 + x1 + max2 + max3 + max4 + max5 >= 1471587914 and x0 + x1 + min2 + min3 + min4 + min5 <= 1472541258):
41 | print("flag[1] = ", i1)
42 |
43 | for i2 in list:
44 | x2 = pow(31, 3) * i2
45 | if (x0 + x1 + x2 + max3 + max4 + max5 >= 1471587914 and x0 + x1 + x2 + min3 + min4 + min5 <= 1472541258):
46 | print("flag[2] = ", i2)
47 |
48 | for i3 in list:
49 | x3 = pow(31, 2) * i3
50 | if (x0 + x1 + x2 + x3 + max4 + max5 >= 1471587914 and x0 + x1 + x2 + x3 + min4 + min5 <= 1472541258):
51 | print("flag[3] = ", i3)
52 |
53 | for i4 in list:
54 | x4 = pow(31, 1) * i4
55 | if (x0 + x1 + x2 + x3 + x4 + max5 >= 1471587914 and x0 + x1 + x2 + x3 + x4 + min5 <= 1472541258):
56 | print("flag[4] = ", i4)
57 |
58 | for i5 in list:
59 | x5 = i5
60 | if (x0 + x1 + x2 + x3 + x4 + x5 == 1471587914 ):
61 | flag = ""
62 | flag += chr(i0) + chr(i1) + chr(i2) + chr(i3) + chr(i4) + chr(i5)
63 | if(java_string_hashcode(flag.lower())==1472541258): # Check for the lowercase condition.
64 | print("The flag is:", flag)
65 | sys.exit()
66 | main()
67 |
--------------------------------------------------------------------------------
/Programming/Hard/IS IT THE FLAG/README.md:
--------------------------------------------------------------------------------
1 |
2 | # IS IT THE FLAG? (JAVA)
3 |
4 | * **Category:** Programming
5 | * **Points:** 90
6 | * **level:** Hard
7 |
8 | ## [Challenge](https://ctflearn.com/problems/197)
9 |
10 | > Pedro was disappointed because he didn't speak Python well enough to capture some of the flags on CTFLearn. His plan for revenge was to create one in his native language (Java). The flag is a String of 6 alphanumeric characters. Capture it. https://mega.nz/#!SHp1xCAL!I9-Zy4kwu_JY019MiYZ6CzGey8sJ6UvqE-ML2idmkrs
11 |
12 |
13 | ## Solution
14 | The java file contain simple code that check a flag hash and compare the hash to a specific hash.\
15 | Using the java funcion hashCode.We need to find the correct flag that will give us the output **"You found it!"**.
16 |
17 |
55 |
56 | You can find the code here - https://pastebin.com/5vXTpVEN
57 |
58 | Run the program and get the flag :)
59 |
60 |
61 |
62 | Flag : ```stCTF{h34p_6ump5_r_c00l!11!!}```
63 |
64 |
--------------------------------------------------------------------------------
/Forensics/Medium/THE ADVENTURES OF BORIS IVANOV. PART 1/README.md:
--------------------------------------------------------------------------------
1 |
2 |
3 | # THE ADVENTURES OF BORIS IVANOV. PART 1.
4 |
5 | * **Category:** Forensics
6 | * **Points:** 60
7 | * **level:** Medium
8 |
9 |
10 | ## [Challenge](https://ctflearn.com/problems/373)
11 |
12 | > The KGB agent Boris Ivanov got information about an attempt to sell classified data. He quickly reacted and intercepted the correspondence. Help Boris understand what exactly they were trying to sell. Here is the interception data:
13 | > https://mega.nz/#!HfAHmKQb!zg6EPqfwes1bBDCjx7-ZFR_0O0-GtGg2Mrn56l5LCkE
14 |
15 | ## Solution
16 | Ok , From first look we dont have any idea from where to start. After trying set of tools still get nothing...\
17 | In this case when we get stuck , I recommend to read again the challenge and his files.
18 |
19 | 
20 |
21 |
22 | After reading the challenge again and again we can notice the word **KGB** may bay relate to stegnograpy by **RGB**.\
23 | So after play with some tools with rgb values and lsb , I found the solution in relation of rgb **offsets**.\
24 | I use the tool stegslove , One of his option is **Stereogram Solver** and in this option there are 1000 offsets possible.
25 |
26 | 
27 |
28 | After a little hard work i found the flag in offset **898**.
29 |
30 | 
31 |
32 | Flag : ```flag{d0nt_m3s5_w1th_th3_KGB} ```
33 |
34 |
--------------------------------------------------------------------------------
/Forensics/Medium/UP FOR A LITTLE CHALLENGE/README.md:
--------------------------------------------------------------------------------
1 |
2 |
3 | # UP FOR A LITTLE CHALLENGE?
4 |
5 | * **Category:** Forensics
6 | * **Points:** 60
7 | * **level:** Medium
8 |
9 |
10 | ## [Challenge](https://ctflearn.com/problems/142)
11 |
12 | > https://mega.nz/#!LoABFK5K!0sEKbsU3sBUG8zWxpBfD1bQx_JY_MuYEWQvLrFIqWZ0 You Know What To Do ...\
13 |
14 | ## Solution
15 |
16 | As you probably know , The first thing we will check is **strings**.\
17 | When using strings we can notice to four suspecious strings:
18 | 1. **Url address - https://mega.nz/#!z8hACJbb!vQB569ptyQjNEoxIwHrUhwWu5WCj1JWmU-OFjf90Prg**
19 | 2. **Mp real_unlock_key: Nothing Is As It SeemsU**
20 | 3. **password: Really? Again**
21 | 4. **flag{Not_So_Simple...}**
22 |
23 | As you can see :
24 |
25 | 
26 |
27 | 
28 |
29 |
30 | As you can assume... the flag is not correct :).\
31 | So , after trying few more tools we dont find something special, So lets use the URL.\
32 | We get a rar file , after extracting him and get inside the folder - "Did I Forget Again?" We see a jpeg file -"Loo Nothing Becomes Useless ack".\
33 | After trying a lot of tools that not bring nothing , lets think... , Maybe there is a hidden file that we forgot to check !?\
34 | Lets use ```ls -a```. YeS ! there is , So lets use ```ctrl+h```\
35 | We get a rar with a locked jpeg file inside , We need the password to unlock the jpeg.
36 |
37 | ## Moment to think...
38 |
39 | Where we can find this password ??? You remember the four strings we found from the original image ?\
40 | After try all of them we got a **hit** !!! **Nothing Is As It SeemsU** , but remove the last **U**.\
41 | The Password is - ```Nothing Is As It Seems```
42 | Unlock the jpeg file and if you notice we see a red string in the **bottom right corner**.
43 |
44 |
45 | 
46 |
47 |
48 | Flag : ```flag{hack_complete} ```
49 |
50 |
--------------------------------------------------------------------------------
/Programming/Hard/IS IT THE FLAG/BruteForce_Solution_By_EdbR.py:
--------------------------------------------------------------------------------
1 | # Solution By EdbR
2 | import sys
3 |
4 | def java_string_hashcode(s): # The hashCode function in java.
5 | h = 0
6 | for c in s:
7 | h = (31 * h + ord(c)) & 0xFFFFFFFF
8 | return ((h + 0x80000000) & 0xFFFFFFFF) - 0x80000000
9 |
10 | def isFlag(str):
11 | return java_string_hashcode(str) == 1471587914 and java_string_hashcode(str.lower) == 1472541258 # The function from the CTF.
12 |
13 | def main():
14 | list = []
15 | for i in range (48,58):
16 | list.append(i)
17 | for i in range (65,91):
18 | list.append(i)
19 | for i in range(97, 123):
20 | list.append(i)
21 | flag=""
22 | for i0 in list:
23 | if (i0 > 48):
24 | flag = flag[:-5]
25 | flag += chr(i0)
26 | for i1 in list:
27 | if (i1 > 48):
28 | flag = flag[:-4]
29 | flag += chr(i1)
30 | for i2 in list:
31 | if (i2 > 48):
32 | flag = flag[:-3]
33 | flag += chr(i2)
34 | for i3 in list:
35 | if (i3 > 48):
36 | flag = flag[:-2]
37 | flag += chr(i3)
38 | for i4 in list:
39 | if (i4 > 48):
40 | flag = flag[:-1]
41 | flag += chr(i4)
42 | for i5 in list:
43 | flag += chr(i5)
44 | if(java_string_hashcode(flag)==1471587914 and java_string_hashcode(flag.lower())==1472541258):
45 | print("The flag is:", flag)
46 | sys.exit()
47 | flag = flag[:-1]
48 | main()
49 |
--------------------------------------------------------------------------------
/Programming/Hard/IS IT THE FLAG/Is it the Flag.java:
--------------------------------------------------------------------------------
1 | public class IsItTheFlag {
2 |
3 | public static boolean isFlag(String str) {
4 | return str.hashCode() == 1471587914 && str.toLowerCase().hashCode() == 1472541258;
5 | }
6 |
7 | public static void main(String[] args) {
8 |
9 | String flag = "------";
10 |
11 | if (isFlag(flag))
12 | System.out.println("You found it!");
13 | else
14 | System.out.println("Try again :(");
15 |
16 | }
17 | }
18 |
--------------------------------------------------------------------------------
/Programming/Hard/IS IT THE FLAG/Mathematical Solution_By_EdbR.py:
--------------------------------------------------------------------------------
1 | # Solution By EdbR
2 | import sys
3 |
4 | def java_string_hashcode(s): # The hashCode function in java.
5 | h = 0
6 | for c in s:
7 | h = (31 * h + ord(c)) & 0xFFFFFFFF
8 | return ((h + 0x80000000) & 0xFFFFFFFF) - 0x80000000
9 |
10 | def isFlag(str):
11 | return java_string_hashcode(str) == 1471587914 and java_string_hashcode(str.lower) == 1472541258 # The function from the CTF.
12 |
13 | def main():
14 | sum=0
15 | max1 = pow(31, 4) * 122 # Max option of alphanumeric characters.
16 | min1 = pow(31, 4) * 48 # Min option of alphanumeric characters.
17 | max2 = pow(31, 3) * 122
18 | min2 = pow(31, 3) * 48
19 | max3 = pow(31, 2) * 122
20 | min3 = pow(31, 2) * 48
21 | max4 = pow(31, 1) * 122
22 | min4 = pow(31, 1) * 48
23 | max5 = 122
24 | min5 = 48
25 | list=[] # Make a list of alphanumeric characters.
26 | for i in range (48,58):
27 | list.append(i)
28 | for i in range (65,91):
29 | list.append(i)
30 | for i in range(97, 123):
31 | list.append(i)
32 |
33 | for i0 in list:
34 | x0 = pow(31, 5) * i0
35 | if (x0 + max1 + max2 + max3 + max4 + max5 >= 1471587914 and x0 + min1 + min2 + min3 + min4 + min5 <= 1472541258):
36 | print("flag[0] =", i0)
37 |
38 | for i1 in list:
39 | x1 = pow(31, 4) * i1
40 | if (x0 + x1 + max2 + max3 + max4 + max5 >= 1471587914 and x0 + x1 + min2 + min3 + min4 + min5 <= 1472541258):
41 | print("flag[1] = ", i1)
42 |
43 | for i2 in list:
44 | x2 = pow(31, 3) * i2
45 | if (x0 + x1 + x2 + max3 + max4 + max5 >= 1471587914 and x0 + x1 + x2 + min3 + min4 + min5 <= 1472541258):
46 | print("flag[2] = ", i2)
47 |
48 | for i3 in list:
49 | x3 = pow(31, 2) * i3
50 | if (x0 + x1 + x2 + x3 + max4 + max5 >= 1471587914 and x0 + x1 + x2 + x3 + min4 + min5 <= 1472541258):
51 | print("flag[3] = ", i3)
52 |
53 | for i4 in list:
54 | x4 = pow(31, 1) * i4
55 | if (x0 + x1 + x2 + x3 + x4 + max5 >= 1471587914 and x0 + x1 + x2 + x3 + x4 + min5 <= 1472541258):
56 | print("flag[4] = ", i4)
57 |
58 | for i5 in list:
59 | x5 = i5
60 | if (x0 + x1 + x2 + x3 + x4 + x5 == 1471587914 ):
61 | flag = ""
62 | flag += chr(i0) + chr(i1) + chr(i2) + chr(i3) + chr(i4) + chr(i5)
63 | if(java_string_hashcode(flag.lower())==1472541258): # Check for the lowercase condition.
64 | print("The flag is:", flag)
65 | sys.exit()
66 | main()
67 |
--------------------------------------------------------------------------------
/Programming/Hard/IS IT THE FLAG/README.md:
--------------------------------------------------------------------------------
1 |
2 | # IS IT THE FLAG? (JAVA)
3 |
4 | * **Category:** Programming
5 | * **Points:** 90
6 | * **level:** Hard
7 |
8 | ## [Challenge](https://ctflearn.com/problems/197)
9 |
10 | > Pedro was disappointed because he didn't speak Python well enough to capture some of the flags on CTFLearn. His plan for revenge was to create one in his native language (Java). The flag is a String of 6 alphanumeric characters. Capture it. https://mega.nz/#!SHp1xCAL!I9-Zy4kwu_JY019MiYZ6CzGey8sJ6UvqE-ML2idmkrs
11 |
12 |
13 | ## Solution
14 | The java file contain simple code that check a flag hash and compare the hash to a specific hash.\
15 | Using the java funcion hashCode.We need to find the correct flag that will give us the output **"You found it!"**.
16 |
17 |  18 |
19 | Ok, By looking the hashCode we can see that is not a complicated mathematical function.
20 |
21 |
18 |
19 | Ok, By looking the hashCode we can see that is not a complicated mathematical function.
20 |
21 |  22 |
23 | Now when we understand the code , We have two option :
24 | #### 1. Brutefuce - You can notice that the flag is 6 alphanumeric characters so we have (26+26+10)^6 = 62^6 options.
25 | #### 2. Mathematical way - In this option we think about a more efficient way to get the flag.
26 |
27 | ## 1.Brutefuce
28 | In this option we will simply pass all the options - **62^6 = 56,800,235,584**.\
29 | This option is simply **but** takes a lot of time and less efficient from the Mathematical Solution.
30 |
31 |
22 |
23 | Now when we understand the code , We have two option :
24 | #### 1. Brutefuce - You can notice that the flag is 6 alphanumeric characters so we have (26+26+10)^6 = 62^6 options.
25 | #### 2. Mathematical way - In this option we think about a more efficient way to get the flag.
26 |
27 | ## 1.Brutefuce
28 | In this option we will simply pass all the options - **62^6 = 56,800,235,584**.\
29 | This option is simply **but** takes a lot of time and less efficient from the Mathematical Solution.
30 |
31 |  32 |
33 |
34 | ## 2.Mathematical Solution
35 | As you can notice , The isFlag function check the flag with some hash **but** check also the **lowercase flag** with some hash.
36 | So maybe the second check may some hint for the way of thinking...
37 | ## Moment to think...
38 | Lets take an example - We know that **flag.hashCode()==1471587914** so lets check from the start.
39 | Our option for each letter is : list=[alphanumeric](0-9 A-Z a-z).\
40 |
32 |
33 |
34 | ## 2.Mathematical Solution
35 | As you can notice , The isFlag function check the flag with some hash **but** check also the **lowercase flag** with some hash.
36 | So maybe the second check may some hint for the way of thinking...
37 | ## Moment to think...
38 | Lets take an example - We know that **flag.hashCode()==1471587914** so lets check from the start.
39 | Our option for each letter is : list=[alphanumeric](0-9 A-Z a-z).\
40 |  41 |
42 | So lets assume that the first letter is '0' , this mean that we need to **ensure** two things:\
43 | 1.Sum this letters with all the next letter at **maximum** value (122) , the hashcode of the flag will be **bigger or equal to 1471587914**.
44 | By that we can play with the next characters and to the same algorithm we just did.\
45 | Because if this **smaller** than 1471587914 , No matter what will be the next letter this will not be equal to 1471587914.
46 |
47 | 2.Sum this letters with all the next letter at **minimum** value (48) , the hashcode of the flag will be **smaller or equal to 1472541258**.
48 | By that we can play with the next characters and to the same algorithm we just did.\
49 | Because if this **bigger** than 1472541258 , No matter what will be the next letter this will not be equal to 1472541258.
50 |
51 |
41 |
42 | So lets assume that the first letter is '0' , this mean that we need to **ensure** two things:\
43 | 1.Sum this letters with all the next letter at **maximum** value (122) , the hashcode of the flag will be **bigger or equal to 1471587914**.
44 | By that we can play with the next characters and to the same algorithm we just did.\
45 | Because if this **smaller** than 1471587914 , No matter what will be the next letter this will not be equal to 1471587914.
46 |
47 | 2.Sum this letters with all the next letter at **minimum** value (48) , the hashcode of the flag will be **smaller or equal to 1472541258**.
48 | By that we can play with the next characters and to the same algorithm we just did.\
49 | Because if this **bigger** than 1472541258 , No matter what will be the next letter this will not be equal to 1472541258.
50 |
51 |  52 |
53 |
54 | Using this way of thinking we throw away all the option thats **not** stands in the conditions.\
55 | Doing that do next **valid** characters we are covering all the **valid** options.
56 |
57 |
58 |
59 | ### Now its matter of time (not much as the first option - full bruteforce) untill we hit the flag :)
60 |
61 |
52 |
53 |
54 | Using this way of thinking we throw away all the option thats **not** stands in the conditions.\
55 | Doing that do next **valid** characters we are covering all the **valid** options.
56 |
57 |
58 |
59 | ### Now its matter of time (not much as the first option - full bruteforce) untill we hit the flag :)
60 |
61 |  62 |
63 | ### The difference in time about the two soltuion is -
64 | **1.Brutefuce - 753.046875 seconds ----> 12.55 minutes**.\
65 | **2.Mathematical Solution - 1 second** !!!
66 |
67 |
68 | 
69 |
70 |
71 |
72 | Flag : ```0gHzxY```
73 |
74 |
--------------------------------------------------------------------------------
/Programming/Hard/THE ADVENTURES OF BORIS IVANOV PART 2/README.md:
--------------------------------------------------------------------------------
1 |
2 | # THE ADVENTURES OF BORIS IVANOV PART 2
3 |
4 | * **Category:** Programming
5 | * **Points:** 80
6 | * **level:** Hard
7 |
8 |
9 | ## [Challenge](https://ctflearn.com/problems/382)
10 |
11 | > The KGB agent Boris Ivanov found the place where one of the criminals was hiding for a long time. Unfortunately the criminal disappeared and more than that he shredded the piece of paper with important information. Help Boris to restore it. Here is a bin with the strips of paper: https://mega.nz/#!KLR3gaYD!6qvqvopHKjjzZZ0HC6pnWjXw0Pw5Z9kgKdGQCMXeUb0. Boris is an experienced agent and he instantly realized that the size of the sheet was 500x500
12 |
13 | ## Solution
14 | Ok , So we have **500** PNG files, This amount of photos may be suspecious.\
15 | In addition if you notice , each picture seems to be empty , Or with a thin line in some color.\
16 | Lets look for more data , You can notice that the dimension of all the pictures is **500 X 1** and we have **500** pictures :)
17 | Think about that , If we have **500** pictures with **widith=500 and height = 1** , The simple thought is to concatenate them vertically.
18 |
19 | #### This is vertically concatenate -
20 |
21 | 
22 |
23 | #### This is horizontally concatenate -
24 |
25 | 
26 |
27 | So , We need to make vertically concatenate to all of the 500 pictures...
28 | Using PIL , Its pretty simple.
29 |
30 |
62 |
63 | ### The difference in time about the two soltuion is -
64 | **1.Brutefuce - 753.046875 seconds ----> 12.55 minutes**.\
65 | **2.Mathematical Solution - 1 second** !!!
66 |
67 |
68 | 
69 |
70 |
71 |
72 | Flag : ```0gHzxY```
73 |
74 |
--------------------------------------------------------------------------------
/Programming/Hard/THE ADVENTURES OF BORIS IVANOV PART 2/README.md:
--------------------------------------------------------------------------------
1 |
2 | # THE ADVENTURES OF BORIS IVANOV PART 2
3 |
4 | * **Category:** Programming
5 | * **Points:** 80
6 | * **level:** Hard
7 |
8 |
9 | ## [Challenge](https://ctflearn.com/problems/382)
10 |
11 | > The KGB agent Boris Ivanov found the place where one of the criminals was hiding for a long time. Unfortunately the criminal disappeared and more than that he shredded the piece of paper with important information. Help Boris to restore it. Here is a bin with the strips of paper: https://mega.nz/#!KLR3gaYD!6qvqvopHKjjzZZ0HC6pnWjXw0Pw5Z9kgKdGQCMXeUb0. Boris is an experienced agent and he instantly realized that the size of the sheet was 500x500
12 |
13 | ## Solution
14 | Ok , So we have **500** PNG files, This amount of photos may be suspecious.\
15 | In addition if you notice , each picture seems to be empty , Or with a thin line in some color.\
16 | Lets look for more data , You can notice that the dimension of all the pictures is **500 X 1** and we have **500** pictures :)
17 | Think about that , If we have **500** pictures with **widith=500 and height = 1** , The simple thought is to concatenate them vertically.
18 |
19 | #### This is vertically concatenate -
20 |
21 | 
22 |
23 | #### This is horizontally concatenate -
24 |
25 | 
26 |
27 | So , We need to make vertically concatenate to all of the 500 pictures...
28 | Using PIL , Its pretty simple.
29 |
30 |  31 |
32 | After finishing the concatenate of all the pictures we get the final picture -
33 |
34 | 
35 |
36 | The digits in the middle is a simple hex code, Convert to ascii...
37 |
38 |
31 |
32 | After finishing the concatenate of all the pictures we get the final picture -
33 |
34 | 
35 |
36 | The digits in the middle is a simple hex code, Convert to ascii...
37 |
38 |  39 |
40 |
41 | Flag : ```flag{th3_KGB_l0v3s_CTF}```
42 |
43 |
--------------------------------------------------------------------------------
/Programming/Hard/THE ADVENTURES OF BORIS IVANOV PART 2/Soultion_By_EdbR.py:
--------------------------------------------------------------------------------
1 | # Solution By EdbR
2 | from PIL import Image
3 |
4 | listimages=[]
5 | for i in range(0,500):
6 | listimages.append(Image.open(str(i) + ".png")) # Make a list of pointers to the 500 pictures.
7 |
8 | concatenate=Image.new("RGB",(500,500)) # Size of the concatenate picture
9 | Y_offset=0
10 |
11 | for i in listimages:
12 | concatenate.paste(i,(0,Y_offset))
13 | Y_offset+=1 # Add 1 at a time , Because the height of each picture is 1.
14 | concatenate.save("concatenate.png")
15 |
16 | print(bytearray.fromhex("666c61677b7468335f4b47425f6c307633735f4354467d").decode())
17 |
--------------------------------------------------------------------------------
/Programming/Medium/Weird Android Calculator/README.md:
--------------------------------------------------------------------------------
1 |
2 | # Weird Android Calculator
3 |
4 | * **Category:** Programming
5 | * **Points:** 60
6 | * **level:** Medium
7 |
8 |
9 | ## [Challenge](https://ctflearn.com/challenge/290)
10 |
11 | > I've found this very weird android application.Seems to be some kind of calculator, but there is something strange with it. Can you find out what it is? https://mega.nz/#!qXIAgSKZ!u2QBlLV-3G8kmsr6yR0wqpQOFyv89e0WvBt45alBIRY
12 | > Flag is in Format: FLAG{...}
13 | > Note: You don't really need an android device to solve this. But it might be helpful :)
14 |
15 | ## Solution
16 | First lets run the app in android eumulator. I am using **BlueStacks** emulator.\
17 | As you can see its simple calculator...
18 |
19 |
39 |
40 |
41 | Flag : ```flag{th3_KGB_l0v3s_CTF}```
42 |
43 |
--------------------------------------------------------------------------------
/Programming/Hard/THE ADVENTURES OF BORIS IVANOV PART 2/Soultion_By_EdbR.py:
--------------------------------------------------------------------------------
1 | # Solution By EdbR
2 | from PIL import Image
3 |
4 | listimages=[]
5 | for i in range(0,500):
6 | listimages.append(Image.open(str(i) + ".png")) # Make a list of pointers to the 500 pictures.
7 |
8 | concatenate=Image.new("RGB",(500,500)) # Size of the concatenate picture
9 | Y_offset=0
10 |
11 | for i in listimages:
12 | concatenate.paste(i,(0,Y_offset))
13 | Y_offset+=1 # Add 1 at a time , Because the height of each picture is 1.
14 | concatenate.save("concatenate.png")
15 |
16 | print(bytearray.fromhex("666c61677b7468335f4b47425f6c307633735f4354467d").decode())
17 |
--------------------------------------------------------------------------------
/Programming/Medium/Weird Android Calculator/README.md:
--------------------------------------------------------------------------------
1 |
2 | # Weird Android Calculator
3 |
4 | * **Category:** Programming
5 | * **Points:** 60
6 | * **level:** Medium
7 |
8 |
9 | ## [Challenge](https://ctflearn.com/challenge/290)
10 |
11 | > I've found this very weird android application.Seems to be some kind of calculator, but there is something strange with it. Can you find out what it is? https://mega.nz/#!qXIAgSKZ!u2QBlLV-3G8kmsr6yR0wqpQOFyv89e0WvBt45alBIRY
12 | > Flag is in Format: FLAG{...}
13 | > Note: You don't really need an android device to solve this. But it might be helpful :)
14 |
15 | ## Solution
16 | First lets run the app in android eumulator. I am using **BlueStacks** emulator.\
17 | As you can see its simple calculator...
18 |
19 |  20 |
21 | After try some inputs in the calculator we get nothing interesting... , But in some cases i get this message:
22 | **"The number is too large. Please buy the full version!"**
23 |
24 | So, We need to do some **Reverse Engineering**. For that we will need 3 tools:
25 | #### 1. Apktool
26 | #### 2. dex2jar
27 | #### 3. jd-gui
28 | Im very recommend to read about the tools before you continue to read :)
29 | So, After read and install the tools lets create directory of the tools with out apk.
30 |
31 |
20 |
21 | After try some inputs in the calculator we get nothing interesting... , But in some cases i get this message:
22 | **"The number is too large. Please buy the full version!"**
23 |
24 | So, We need to do some **Reverse Engineering**. For that we will need 3 tools:
25 | #### 1. Apktool
26 | #### 2. dex2jar
27 | #### 3. jd-gui
28 | Im very recommend to read about the tools before you continue to read :)
29 | So, After read and install the tools lets create directory of the tools with out apk.
30 |
31 |  32 |
33 | First thing , using dex2jar - ```d2j-dex2jar WeirdCalculator.apk```
34 | We will get jar file of our apk.
35 | Now using jd-gui to read the code, Load ""WeirdCalculator-dex2jar.jar""
36 | After some exploring the code we can notice **two** things:
37 | 1. If the input is above 100 we get the message - **""The number is too large. Please buy the full version!""**
38 |
32 |
33 | First thing , using dex2jar - ```d2j-dex2jar WeirdCalculator.apk```
34 | We will get jar file of our apk.
35 | Now using jd-gui to read the code, Load ""WeirdCalculator-dex2jar.jar""
36 | After some exploring the code we can notice **two** things:
37 | 1. If the input is above 100 we get the message - **""The number is too large. Please buy the full version!""**
38 |  39 |
40 |
41 | 2. We can notice to an **array with 41** numbers that each value of the **xor with 0x539**
42 | Ok , This is very strange !!! Why a calculator need an array of 41 values and in addition, xor this values with **permanent value** ?!
43 |
39 |
40 |
41 | 2. We can notice to an **array with 41** numbers that each value of the **xor with 0x539**
42 | Ok , This is very strange !!! Why a calculator need an array of 41 values and in addition, xor this values with **permanent value** ?!
43 |  44 |
45 | So its pretty obvious with found somthing **jucy** !
46 |
47 | ### Python script
48 | Lets take the values of the array and copy to text file.
49 | After that writing a simple python script that will execute the Suspicious code, And we get the flag !!!
50 |
51 |
44 |
45 | So its pretty obvious with found somthing **jucy** !
46 |
47 | ### Python script
48 | Lets take the values of the array and copy to text file.
49 | After that writing a simple python script that will execute the Suspicious code, And we get the flag !!!
50 |
51 |  52 |
53 |
54 |
55 |
56 |
57 |
58 | Flag : ```FLAG{APK_4nalys1s_1s_r4th3r_3asy_1snt_1t}```
59 |
60 |
--------------------------------------------------------------------------------
/Programming/Medium/Weird Android Calculator/Soultion_by_EdbR.py:
--------------------------------------------------------------------------------
1 | #Soultion by EdbR
2 | import re
3 | f=open("SuspiciousCode.txt","r") # Txt file with the suspicious code
4 | str=f.read()
5 | p1="\s\d+"
6 | y=re.findall(p1,str) # Taking only the values in the array
7 | for i in y:
8 | print(chr(int(i)^1337),end="") # xor each value with 0x539 = 1337d
9 |
--------------------------------------------------------------------------------
/Programming/Medium/Weird Android Calculator/SuspiciousCode.txt:
--------------------------------------------------------------------------------
1 | arrayOfInt[0] = 1407;
2 | arrayOfInt[1] = 1397;
3 | arrayOfInt[2] = 1400;
4 | arrayOfInt[3] = 1406;
5 | arrayOfInt[4] = 1346;
6 | arrayOfInt[5] = 1400;
7 | arrayOfInt[6] = 1385;
8 | arrayOfInt[7] = 1394;
9 | arrayOfInt[8] = 1382;
10 | arrayOfInt[9] = 1293;
11 | arrayOfInt[10] = 1367;
12 | arrayOfInt[11] = 1368;
13 | arrayOfInt[12] = 1365;
14 | arrayOfInt[13] = 1344;
15 | arrayOfInt[14] = 1354;
16 | arrayOfInt[15] = 1288;
17 | arrayOfInt[16] = 1354;
18 | arrayOfInt[17] = 1382;
19 | arrayOfInt[18] = 1288;
20 | arrayOfInt[19] = 1354;
21 | arrayOfInt[20] = 1382;
22 | arrayOfInt[21] = 1355;
23 | arrayOfInt[22] = 1293;
24 | arrayOfInt[23] = 1357;
25 | arrayOfInt[24] = 1361;
26 | arrayOfInt[25] = 1290;
27 | arrayOfInt[26] = 1355;
28 | arrayOfInt[27] = 1382;
29 | arrayOfInt[28] = 1290;
30 | arrayOfInt[29] = 1368;
31 | arrayOfInt[30] = 1354;
32 | arrayOfInt[31] = 1344;
33 | arrayOfInt[32] = 1382;
34 | arrayOfInt[33] = 1288;
35 | arrayOfInt[34] = 1354;
36 | arrayOfInt[35] = 1367;
37 | arrayOfInt[36] = 1357;
38 | arrayOfInt[37] = 1382;
39 | arrayOfInt[38] = 1288;
40 | arrayOfInt[39] = 1357;
41 | arrayOfInt[40] = 1348;
42 |
--------------------------------------------------------------------------------
/README.md:
--------------------------------------------------------------------------------
1 |
2 | # Wellcome to my CTFlearn-Writeups Repository !
3 | In this Repository you will find writeups for CTFs from the website [CTFlearn](https://ctflearn.com/)
4 | You can also check the soultions on my YoTube channel -[EdbR yotube channel](https://www.youtube.com/channel/UCoD5lhTM5qtEKiFkhsDECkQ?view_as=subscriber)
5 |
--------------------------------------------------------------------------------
/Reverse Engineering/Hard/Lost In The Binary/Lost.py:
--------------------------------------------------------------------------------
1 | from z3 import *
2 |
3 | a = Int('a') # qword_602148
4 | b = Int('b') # qword_602150
5 | c = Int('c') # qword_602158
6 | d = Int('d') # qword_602160
7 |
8 | s = Solver()
9 | s.add(-24 * a + (-18 * b) + (-15 * c) + (-12 * d) == -18393)
10 | s.add(9 * c + 18 * (b + a) + -9 * d == 4419)
11 | s.add( 4 * c + 16 * a + 12 * b + 2 * d == 7300)
12 | s.add(-6 * (b + a) + -3 * c+ -11 * d == -8613)
13 | print(s.check())
14 | print(s.model())
15 |
--------------------------------------------------------------------------------
/Reverse Engineering/Hard/Lost In The Binary/README.md:
--------------------------------------------------------------------------------
1 | # Lost In The Binary
2 |
3 | * **Category:** Reverse Engineering
4 | * **Points:** 80
5 | * **level:** Hard
6 |
7 |
8 | ## [Challenge](https://ctflearn.com/challenge/285)
9 |
10 | > I lost a flag inside this binary, please help me to find it.
11 | > If you trigger certain anti-debugging techniques, you might get false flags….
12 | > flag format: FLAG-(str) https://mega.nz/#!ifgzQQCC!E1W0cSOFRvi7bE_v419rzwQB2jAHF0IsIRAWL6H1RNE
13 |
14 |
15 | ## Solution
16 |
17 | We have a clue in the description about **anti-debugging techniques** that this lead to a **false flag**
18 |
19 |
52 |
53 |
54 |
55 |
56 |
57 |
58 | Flag : ```FLAG{APK_4nalys1s_1s_r4th3r_3asy_1snt_1t}```
59 |
60 |
--------------------------------------------------------------------------------
/Programming/Medium/Weird Android Calculator/Soultion_by_EdbR.py:
--------------------------------------------------------------------------------
1 | #Soultion by EdbR
2 | import re
3 | f=open("SuspiciousCode.txt","r") # Txt file with the suspicious code
4 | str=f.read()
5 | p1="\s\d+"
6 | y=re.findall(p1,str) # Taking only the values in the array
7 | for i in y:
8 | print(chr(int(i)^1337),end="") # xor each value with 0x539 = 1337d
9 |
--------------------------------------------------------------------------------
/Programming/Medium/Weird Android Calculator/SuspiciousCode.txt:
--------------------------------------------------------------------------------
1 | arrayOfInt[0] = 1407;
2 | arrayOfInt[1] = 1397;
3 | arrayOfInt[2] = 1400;
4 | arrayOfInt[3] = 1406;
5 | arrayOfInt[4] = 1346;
6 | arrayOfInt[5] = 1400;
7 | arrayOfInt[6] = 1385;
8 | arrayOfInt[7] = 1394;
9 | arrayOfInt[8] = 1382;
10 | arrayOfInt[9] = 1293;
11 | arrayOfInt[10] = 1367;
12 | arrayOfInt[11] = 1368;
13 | arrayOfInt[12] = 1365;
14 | arrayOfInt[13] = 1344;
15 | arrayOfInt[14] = 1354;
16 | arrayOfInt[15] = 1288;
17 | arrayOfInt[16] = 1354;
18 | arrayOfInt[17] = 1382;
19 | arrayOfInt[18] = 1288;
20 | arrayOfInt[19] = 1354;
21 | arrayOfInt[20] = 1382;
22 | arrayOfInt[21] = 1355;
23 | arrayOfInt[22] = 1293;
24 | arrayOfInt[23] = 1357;
25 | arrayOfInt[24] = 1361;
26 | arrayOfInt[25] = 1290;
27 | arrayOfInt[26] = 1355;
28 | arrayOfInt[27] = 1382;
29 | arrayOfInt[28] = 1290;
30 | arrayOfInt[29] = 1368;
31 | arrayOfInt[30] = 1354;
32 | arrayOfInt[31] = 1344;
33 | arrayOfInt[32] = 1382;
34 | arrayOfInt[33] = 1288;
35 | arrayOfInt[34] = 1354;
36 | arrayOfInt[35] = 1367;
37 | arrayOfInt[36] = 1357;
38 | arrayOfInt[37] = 1382;
39 | arrayOfInt[38] = 1288;
40 | arrayOfInt[39] = 1357;
41 | arrayOfInt[40] = 1348;
42 |
--------------------------------------------------------------------------------
/README.md:
--------------------------------------------------------------------------------
1 |
2 | # Wellcome to my CTFlearn-Writeups Repository !
3 | In this Repository you will find writeups for CTFs from the website [CTFlearn](https://ctflearn.com/)
4 | You can also check the soultions on my YoTube channel -[EdbR yotube channel](https://www.youtube.com/channel/UCoD5lhTM5qtEKiFkhsDECkQ?view_as=subscriber)
5 |
--------------------------------------------------------------------------------
/Reverse Engineering/Hard/Lost In The Binary/Lost.py:
--------------------------------------------------------------------------------
1 | from z3 import *
2 |
3 | a = Int('a') # qword_602148
4 | b = Int('b') # qword_602150
5 | c = Int('c') # qword_602158
6 | d = Int('d') # qword_602160
7 |
8 | s = Solver()
9 | s.add(-24 * a + (-18 * b) + (-15 * c) + (-12 * d) == -18393)
10 | s.add(9 * c + 18 * (b + a) + -9 * d == 4419)
11 | s.add( 4 * c + 16 * a + 12 * b + 2 * d == 7300)
12 | s.add(-6 * (b + a) + -3 * c+ -11 * d == -8613)
13 | print(s.check())
14 | print(s.model())
15 |
--------------------------------------------------------------------------------
/Reverse Engineering/Hard/Lost In The Binary/README.md:
--------------------------------------------------------------------------------
1 | # Lost In The Binary
2 |
3 | * **Category:** Reverse Engineering
4 | * **Points:** 80
5 | * **level:** Hard
6 |
7 |
8 | ## [Challenge](https://ctflearn.com/challenge/285)
9 |
10 | > I lost a flag inside this binary, please help me to find it.
11 | > If you trigger certain anti-debugging techniques, you might get false flags….
12 | > flag format: FLAG-(str) https://mega.nz/#!ifgzQQCC!E1W0cSOFRvi7bE_v419rzwQB2jAHF0IsIRAWL6H1RNE
13 |
14 |
15 | ## Solution
16 |
17 | We have a clue in the description about **anti-debugging techniques** that this lead to a **false flag**
18 |
19 |  20 |
21 | In the main we can notice immediately the function **ptrace**
22 |
23 | `The ptrace() system call provides a means by which one process (the
24 | "tracer") may observe and control the execution of another process
25 | (the "tracee"), and examine and change the tracee's memory and
26 | registers. It is primarily used to implement breakpoint debugging
27 | and system call tracing. On error, all requests return -1`
28 |
29 |
20 |
21 | In the main we can notice immediately the function **ptrace**
22 |
23 | `The ptrace() system call provides a means by which one process (the
24 | "tracer") may observe and control the execution of another process
25 | (the "tracee"), and examine and change the tracee's memory and
26 | registers. It is primarily used to implement breakpoint debugging
27 | and system call tracing. On error, all requests return -1`
28 |
29 |  30 |
31 | ### Conclusions
32 |
33 | So its pretty clear that this is our **anti-debugging technique** that leads to **LABEL_2**.
34 | We will avoid from that by changing **jnz** to **jmp** in IDA.
35 |
36 |
30 |
31 | ### Conclusions
32 |
33 | So its pretty clear that this is our **anti-debugging technique** that leads to **LABEL_2**.
34 | We will avoid from that by changing **jnz** to **jmp** in IDA.
35 |
36 |  37 |
38 | The next compare is if a1 > 4. a1 is our **argc**.
39 | So we need to provide 4 arguments - (argv[1] ,argv[2] ,argv[3] argv[4]) + argv[0] (our path) = 5 > 4.
40 |
41 | ### The question is which arguments ?
42 |
43 | `The strtol() function converts the initial part of the string in nptr to a long integer value according to the given base, which must be between 2 and 36 inclusive, or be the special value 0.`
44 |
45 | So we need to provide 4 numbers that will confirm the equations :
46 |
47 | `
37 |
38 | The next compare is if a1 > 4. a1 is our **argc**.
39 | So we need to provide 4 arguments - (argv[1] ,argv[2] ,argv[3] argv[4]) + argv[0] (our path) = 5 > 4.
40 |
41 | ### The question is which arguments ?
42 |
43 | `The strtol() function converts the initial part of the string in nptr to a long integer value according to the given base, which must be between 2 and 36 inclusive, or be the special value 0.`
44 |
45 | So we need to provide 4 numbers that will confirm the equations :
46 |
47 | ` 48 |
49 | ### Z3
50 |
51 | We will use Z3 library to calculate this.
52 |
53 |
48 |
49 | ### Z3
50 |
51 | We will use Z3 library to calculate this.
52 |
53 |  54 |
55 | ### Final Stage
56 |
57 | Lets put the valus and run the program.
58 |
59 | 
60 |
61 |
62 |
63 |
64 | Flag : ```FLAG-21a84f2c7c7fd432edf1686215db05ea```
65 |
66 |
--------------------------------------------------------------------------------
/Reverse Engineering/Hard/RE_verseDIS/README.md:
--------------------------------------------------------------------------------
1 | # RE_verseDIS
2 |
3 | * **Category:** Reverse Engineering
4 | * **Points:** 90
5 | * **level:** Hard
6 |
7 |
8 | ## [Challenge](https://ctflearn.com/challenge/188)
9 |
10 | > Could you find the hidden password?
11 | >https://mega.nz/#!XOwVmCSC!ut_5r6b32j2kD6EvlvsvJhmm58pbswusUXF08yI93Zo
12 |
13 |
14 | ## Solution
15 | Lets open the file in IDA.
16 |
17 |
54 |
55 | ### Final Stage
56 |
57 | Lets put the valus and run the program.
58 |
59 | 
60 |
61 |
62 |
63 |
64 | Flag : ```FLAG-21a84f2c7c7fd432edf1686215db05ea```
65 |
66 |
--------------------------------------------------------------------------------
/Reverse Engineering/Hard/RE_verseDIS/README.md:
--------------------------------------------------------------------------------
1 | # RE_verseDIS
2 |
3 | * **Category:** Reverse Engineering
4 | * **Points:** 90
5 | * **level:** Hard
6 |
7 |
8 | ## [Challenge](https://ctflearn.com/challenge/188)
9 |
10 | > Could you find the hidden password?
11 | >https://mega.nz/#!XOwVmCSC!ut_5r6b32j2kD6EvlvsvJhmm58pbswusUXF08yI93Zo
12 |
13 |
14 | ## Solution
15 | Lets open the file in IDA.
16 |
17 |  18 |
19 | As you can see there is output "Input password" and our input go to the variable **input**
20 | After that the value in key that is "IdontKnowWhatsGoingOn" mov to key2.
21 | In the next instruction we put in **msg** the result of "str[4 * i] ^ LOBYTE(key2[i]);".
22 | Later we are going through every letter in out **input** and checking if this equal to the letter ing **msg**
23 | So our only job is to break before the check and see what in **msg** :)
24 |
25 | First thing find our address to break.
26 |
27 | 
28 |
29 | Execute and look the data stored in RAX.
30 |
31 | 
32 |
33 | Flag : ```AbCTF{r3vers1ng_dud3}```
34 |
35 |
--------------------------------------------------------------------------------
/Reverse Engineering/Medium/Bite-code/C_soultion_by_EdbR.c:
--------------------------------------------------------------------------------
1 | #include
2 | #include
3 | #pragma warning (disable : 4146)
4 |
5 |
6 | void BruteForce()
7 | {
8 | int flag , x1, x2, x3;
9 | flag = -2147483648; // The biggest negative value of 32bit.
10 | x3 = 0;
11 | while (x3 != -889275714)
12 | {
13 | x1 = flag << 3;
14 | x2 = flag ^ 525024598;
15 | x3 = x1 ^x2;
16 | flag += 1;
17 | }
18 | printf("%d \n", flag - 1);
19 | }
20 |
21 |
22 | void main()
23 | {
24 | BruteForce();
25 | system("pause");
26 | }
27 |
--------------------------------------------------------------------------------
/Reverse Engineering/Medium/Bite-code/Python_solution_by_EdbR.py:
--------------------------------------------------------------------------------
1 | from ctypes import *
2 |
3 | def BruteForce():
4 | flag = c_int(-2147483648) # Casting to int-32bit
5 | x3=0
6 | while (x3 != -889275714):
7 | x1 = c_int((flag.value) << 3)
8 | x2 = 525024598
9 | x2 = x2 ^ (flag.value)
10 | n3 = x2 ^ x1.value
11 | flag.value+=1
12 | print((flag.value)-1)
13 |
14 | BruteForce()
15 |
16 |
17 |
18 |
--------------------------------------------------------------------------------
/Reverse Engineering/Medium/Bite-code/README.md:
--------------------------------------------------------------------------------
1 |
2 | # Bite-code
3 |
4 | * **Category:** Reverse Engineering
5 | * **Points:** 60
6 | * **level:** Medium
7 |
8 |
9 | ## [Challenge](https://ctflearn.com/challenge/368)
10 |
11 | >I dunno what bytecode is. Could you tell me what input of 'checkNum' will return true? The flag is just a 32-bit signed integer as a decimal (nothing else.) https://mega.nz/#!qfATFaKR!zaTNExq3Bm1MjJnePjTGQyvnvLX_xZxhbGaMv_ypaxo
12 |
13 | ## Solution
14 | We get a txt file of java bytecode , For those who dont familiar wtih that, you have to read and explore before you continue.
15 | There are some good resources:
16 | 1.[Java Bytecode Crash Course](https://www.youtube.com/watch?v=e2zmmkc5xI0)
17 | 2.[A Java Programmer's Guide to Byte Code](https://www.beyondjava.net/java-programmers-guide-java-byte-code)
18 | 3.[Introduction to Java Bytecode](https://dzone.com/articles/introduction-to-java-bytecode)
19 |
20 | Ok , Now that we are pretty understood what is a bytecode and how the code executed i will show you some comments that i wrote for better understanding. I also upload the txt file with the comments.
21 |
22 |
18 |
19 | As you can see there is output "Input password" and our input go to the variable **input**
20 | After that the value in key that is "IdontKnowWhatsGoingOn" mov to key2.
21 | In the next instruction we put in **msg** the result of "str[4 * i] ^ LOBYTE(key2[i]);".
22 | Later we are going through every letter in out **input** and checking if this equal to the letter ing **msg**
23 | So our only job is to break before the check and see what in **msg** :)
24 |
25 | First thing find our address to break.
26 |
27 | 
28 |
29 | Execute and look the data stored in RAX.
30 |
31 | 
32 |
33 | Flag : ```AbCTF{r3vers1ng_dud3}```
34 |
35 |
--------------------------------------------------------------------------------
/Reverse Engineering/Medium/Bite-code/C_soultion_by_EdbR.c:
--------------------------------------------------------------------------------
1 | #include
2 | #include
3 | #pragma warning (disable : 4146)
4 |
5 |
6 | void BruteForce()
7 | {
8 | int flag , x1, x2, x3;
9 | flag = -2147483648; // The biggest negative value of 32bit.
10 | x3 = 0;
11 | while (x3 != -889275714)
12 | {
13 | x1 = flag << 3;
14 | x2 = flag ^ 525024598;
15 | x3 = x1 ^x2;
16 | flag += 1;
17 | }
18 | printf("%d \n", flag - 1);
19 | }
20 |
21 |
22 | void main()
23 | {
24 | BruteForce();
25 | system("pause");
26 | }
27 |
--------------------------------------------------------------------------------
/Reverse Engineering/Medium/Bite-code/Python_solution_by_EdbR.py:
--------------------------------------------------------------------------------
1 | from ctypes import *
2 |
3 | def BruteForce():
4 | flag = c_int(-2147483648) # Casting to int-32bit
5 | x3=0
6 | while (x3 != -889275714):
7 | x1 = c_int((flag.value) << 3)
8 | x2 = 525024598
9 | x2 = x2 ^ (flag.value)
10 | n3 = x2 ^ x1.value
11 | flag.value+=1
12 | print((flag.value)-1)
13 |
14 | BruteForce()
15 |
16 |
17 |
18 |
--------------------------------------------------------------------------------
/Reverse Engineering/Medium/Bite-code/README.md:
--------------------------------------------------------------------------------
1 |
2 | # Bite-code
3 |
4 | * **Category:** Reverse Engineering
5 | * **Points:** 60
6 | * **level:** Medium
7 |
8 |
9 | ## [Challenge](https://ctflearn.com/challenge/368)
10 |
11 | >I dunno what bytecode is. Could you tell me what input of 'checkNum' will return true? The flag is just a 32-bit signed integer as a decimal (nothing else.) https://mega.nz/#!qfATFaKR!zaTNExq3Bm1MjJnePjTGQyvnvLX_xZxhbGaMv_ypaxo
12 |
13 | ## Solution
14 | We get a txt file of java bytecode , For those who dont familiar wtih that, you have to read and explore before you continue.
15 | There are some good resources:
16 | 1.[Java Bytecode Crash Course](https://www.youtube.com/watch?v=e2zmmkc5xI0)
17 | 2.[A Java Programmer's Guide to Byte Code](https://www.beyondjava.net/java-programmers-guide-java-byte-code)
18 | 3.[Introduction to Java Bytecode](https://dzone.com/articles/introduction-to-java-bytecode)
19 |
20 | Ok , Now that we are pretty understood what is a bytecode and how the code executed i will show you some comments that i wrote for better understanding. I also upload the txt file with the comments.
21 |
22 |  23 |
24 | Now, its easy to under stand whats going on...
25 | **x1 = flag << 3**
26 | **x2 = flag ^ 525024598**
27 | **x3 = x1 ^ x2**
28 | **If (x3==-889275714) The flag is x3.**
29 |
30 | I also wirte for you in C language whats going on for better understanding.
31 |
32 |
23 |
24 | Now, its easy to under stand whats going on...
25 | **x1 = flag << 3**
26 | **x2 = flag ^ 525024598**
27 | **x3 = x1 ^ x2**
28 | **If (x3==-889275714) The flag is x3.**
29 |
30 | I also wirte for you in C language whats going on for better understanding.
31 |
32 |  33 |
34 | Ok , We understood perfectly the code but we need to notice somthing **very** important:
35 | The flag is **32 bit integer** , So its can be a **negative** and he most be between **-2,147,483,648 to 2,147,483,647**
36 | Now lets write bruteforce script to get the flag !
37 |
38 |
33 |
34 | Ok , We understood perfectly the code but we need to notice somthing **very** important:
35 | The flag is **32 bit integer** , So its can be a **negative** and he most be between **-2,147,483,648 to 2,147,483,647**
36 | Now lets write bruteforce script to get the flag !
37 |
38 |  39 |
40 | And we Get the flag.
41 |
42 |
39 |
40 | And we Get the flag.
41 |
42 |  43 |
44 |
45 | I wrote also python script for those who prefer , **But** notice - In default python numbers are up to **63 bit**
46 | So you must do casting to **int - 32bit** because of the **shifting that change the flag from negative to positive**
47 | The flag in binary is **10101111010111010001001010101000** = **-1352854872** int-32bit
48 | After shifting 3 is **01111010111010001001010101000000** = **2062062912** int 32bit
49 | So we can import ctypes in python and convert to 32bit.
50 |
51 |
43 |
44 |
45 | I wrote also python script for those who prefer , **But** notice - In default python numbers are up to **63 bit**
46 | So you must do casting to **int - 32bit** because of the **shifting that change the flag from negative to positive**
47 | The flag in binary is **10101111010111010001001010101000** = **-1352854872** int-32bit
48 | After shifting 3 is **01111010111010001001010101000000** = **2062062912** int 32bit
49 | So we can import ctypes in python and convert to 32bit.
50 |
51 |  52 |
53 |
54 |
55 |
56 |
57 | Flag : ```-1352854872```
58 |
59 |
--------------------------------------------------------------------------------
/Reverse Engineering/Medium/Bite-code/bitecode_with_comments.txt:
--------------------------------------------------------------------------------
1 | public static boolean checkNum(int);
2 | descriptor: (I)Z
3 | flags: ACC_PUBLIC, ACC_STATIC
4 | Code:
5 | stack=2, locals=3, args_size=1 # Comments by EdbR - Elad Beber :)
6 | 0: iload_0 # Load the int variable (our flag) into the stack.
7 | 1: iconst_3 # Load the value 3 to the top of the stack.The stack now looks like (int)-->(3) // 3 above int...
8 | 2: ishl # Shift left operation - int << 3 , In addition the stack been clear !!!
9 | 3: istore_1 # store the result of (int << 3) to variable_1
10 | 4: iload_0 # Load the int variable (our flag) into the stack.
11 | 5: ldc #2 # Load big number to the stack , In our the number is -----> 525024598 , As you can see -> // int 525024598
12 | 7: ixor # Xor operation of the two values in the stack ---> int xor 525024598
13 | 8: istore_2 # store the result of (int xor 525024598) to variable_2
14 | 9: iload_1 # Load variable_1 to the stack
15 | 10: iload_2 # Load variable_2 to the stack
16 | 11: ixor # Xor operation of the two values in the stack ---> variable_1 xor variable_2
17 | 12: ldc #3 # Load big number to the stack , In our the number is -----> -889275714 , As you can see -> // int -889275714
18 | 14: if_icmpne 21 # If compare not equal - If the result of variable_1 xor variable_2 not equals to -889275714 Jump to line 21 :(
19 | 17: iconst_1 # Load the value zero to the stack , Good for us :)
20 | 18: goto 22 # Return ...
21 | 21: iconst_0 # Load the value zero to the stack , Not good for us :(
22 | 22: ireturn # Return ...
23 | LineNumberTable:
24 | line 3: 0
25 | line 4: 4
26 | line 5: 9
27 | StackMapTable: number_of_entries = 2
28 | frame_type = 253 /* append */
29 | offset_delta = 21
30 | locals = [ int, int ]
31 | frame_type = 64 /* same_locals_1_stack_item */
32 | stack = [ int ]
33 |
--------------------------------------------------------------------------------
/Reverse Engineering/Medium/PIN/README.md:
--------------------------------------------------------------------------------
1 |
2 | # PIN
3 |
4 | * **Category:** Reverse Engineering
5 | * **Points:** 60
6 | * **level:** Medium
7 |
8 |
9 | ## [Challenge](https://ctflearn.com/challenge/379)
10 |
11 | > Can you crack my pin?
12 | >https://mega.nz/#!PXYjCKCY!F2gcs83XD6RxjOR-FNWGQZpyvUFvDbuT-PTnqRhBPGQ
13 |
14 |
15 |
16 |
17 | ## Solution
18 | We get a ELF file as you can see :
19 | 
20 |
21 | We need to guess the correct pin , The pin will be the flag.
22 |
23 |
24 | 
25 |
26 |
27 | Lets change the extenesion to exe and run it in IDA
28 | For those who dont familiar with IDA - https://www.hex-rays.com/products/ida/
29 |
30 | As You can see in the beginning we have the print to the screen **"Masukan PIN ="** this shows up before our input.
31 | After that we put our pin and the value going to --- > **[rbp+var4]** and **var = -4** Its mean our value stored in **[rbp-4]**
32 | And the most important thing is - **"call cek"** In this function the important check been executed.
33 | If eax==0 , We get the bad message **"PIN salah !"** Else - We get the good message **"PIN benar ! !"**
34 |
35 |
52 |
53 |
54 |
55 |
56 |
57 | Flag : ```-1352854872```
58 |
59 |
--------------------------------------------------------------------------------
/Reverse Engineering/Medium/Bite-code/bitecode_with_comments.txt:
--------------------------------------------------------------------------------
1 | public static boolean checkNum(int);
2 | descriptor: (I)Z
3 | flags: ACC_PUBLIC, ACC_STATIC
4 | Code:
5 | stack=2, locals=3, args_size=1 # Comments by EdbR - Elad Beber :)
6 | 0: iload_0 # Load the int variable (our flag) into the stack.
7 | 1: iconst_3 # Load the value 3 to the top of the stack.The stack now looks like (int)-->(3) // 3 above int...
8 | 2: ishl # Shift left operation - int << 3 , In addition the stack been clear !!!
9 | 3: istore_1 # store the result of (int << 3) to variable_1
10 | 4: iload_0 # Load the int variable (our flag) into the stack.
11 | 5: ldc #2 # Load big number to the stack , In our the number is -----> 525024598 , As you can see -> // int 525024598
12 | 7: ixor # Xor operation of the two values in the stack ---> int xor 525024598
13 | 8: istore_2 # store the result of (int xor 525024598) to variable_2
14 | 9: iload_1 # Load variable_1 to the stack
15 | 10: iload_2 # Load variable_2 to the stack
16 | 11: ixor # Xor operation of the two values in the stack ---> variable_1 xor variable_2
17 | 12: ldc #3 # Load big number to the stack , In our the number is -----> -889275714 , As you can see -> // int -889275714
18 | 14: if_icmpne 21 # If compare not equal - If the result of variable_1 xor variable_2 not equals to -889275714 Jump to line 21 :(
19 | 17: iconst_1 # Load the value zero to the stack , Good for us :)
20 | 18: goto 22 # Return ...
21 | 21: iconst_0 # Load the value zero to the stack , Not good for us :(
22 | 22: ireturn # Return ...
23 | LineNumberTable:
24 | line 3: 0
25 | line 4: 4
26 | line 5: 9
27 | StackMapTable: number_of_entries = 2
28 | frame_type = 253 /* append */
29 | offset_delta = 21
30 | locals = [ int, int ]
31 | frame_type = 64 /* same_locals_1_stack_item */
32 | stack = [ int ]
33 |
--------------------------------------------------------------------------------
/Reverse Engineering/Medium/PIN/README.md:
--------------------------------------------------------------------------------
1 |
2 | # PIN
3 |
4 | * **Category:** Reverse Engineering
5 | * **Points:** 60
6 | * **level:** Medium
7 |
8 |
9 | ## [Challenge](https://ctflearn.com/challenge/379)
10 |
11 | > Can you crack my pin?
12 | >https://mega.nz/#!PXYjCKCY!F2gcs83XD6RxjOR-FNWGQZpyvUFvDbuT-PTnqRhBPGQ
13 |
14 |
15 |
16 |
17 | ## Solution
18 | We get a ELF file as you can see :
19 | 
20 |
21 | We need to guess the correct pin , The pin will be the flag.
22 |
23 |
24 | 
25 |
26 |
27 | Lets change the extenesion to exe and run it in IDA
28 | For those who dont familiar with IDA - https://www.hex-rays.com/products/ida/
29 |
30 | As You can see in the beginning we have the print to the screen **"Masukan PIN ="** this shows up before our input.
31 | After that we put our pin and the value going to --- > **[rbp+var4]** and **var = -4** Its mean our value stored in **[rbp-4]**
32 | And the most important thing is - **"call cek"** In this function the important check been executed.
33 | If eax==0 , We get the bad message **"PIN salah !"** Else - We get the good message **"PIN benar ! !"**
34 |
35 |  36 |
37 | ### Verify with gdb-peda
38 |
39 | 
40 |
41 | I put the pin **65** and the scanf@plt function covert my value to hex and stored it in eax and in edi after that
42 | Now lets enter to the **cek function**
43 |
44 | 
45 |
46 | We can see a compare between the value **0x51615** and our value **0x41** that stored in **[rbp-0x4]**
47 | If they are same we will jump to mov **eax, 01** :)
48 | Else - jump to mov **eax, 00** :(
49 | So we just need to ensure that our pin will equal to **0x51615** in hex. Lets see that also in IDA
50 |
51 |
36 |
37 | ### Verify with gdb-peda
38 |
39 | 
40 |
41 | I put the pin **65** and the scanf@plt function covert my value to hex and stored it in eax and in edi after that
42 | Now lets enter to the **cek function**
43 |
44 | 
45 |
46 | We can see a compare between the value **0x51615** and our value **0x41** that stored in **[rbp-0x4]**
47 | If they are same we will jump to mov **eax, 01** :)
48 | Else - jump to mov **eax, 00** :(
49 | So we just need to ensure that our pin will equal to **0x51615** in hex. Lets see that also in IDA
50 |
51 |  52 |
53 | If you notice carefully you can see the eax will get the value of the variable **valid** , And guess what...
54 |
55 |
52 |
53 | If you notice carefully you can see the eax will get the value of the variable **valid** , And guess what...
54 |
55 |  56 |
57 | valid equal to **0x51615** like we see in gdb-peda :)
58 | So we need to convert **0x51615** to decimal value -
59 |
60 |
56 |
57 | valid equal to **0x51615** like we see in gdb-peda :)
58 | So we need to convert **0x51615** to decimal value -
59 |
60 |  61 |
62 | Lets check the flag - **"333333"**
63 |
64 | 
65 |
66 |
67 |
68 | Flag : ```333333```
69 |
70 |
--------------------------------------------------------------------------------
61 |
62 | Lets check the flag - **"333333"**
63 |
64 | 
65 |
66 |
67 |
68 | Flag : ```333333```
69 |
70 |
--------------------------------------------------------------------------------
 21 |
22 |
23 | So lets get in the packet with folow tcp stream ,Copy the message and try to decrypt the base64 encryption.
24 |
25 |
26 |
21 |
22 |
23 | So lets get in the packet with folow tcp stream ,Copy the message and try to decrypt the base64 encryption.
24 |
25 |
26 |  27 |
28 |
29 |
27 |
28 |
29 |