├── README.md
├── blackarch
├── .gitignore
├── README.md
├── mate-desktop
│ ├── .gitignore
│ └── mygtkmenu
│ │ ├── README.md
│ │ ├── blackarch-tools.desktop
│ │ ├── blackarch.items
│ │ └── mygtkitems.sh
├── webgoat
│ ├── PKGBUILD
│ ├── README.md
│ ├── webgoat.service
│ └── webgoat.sh
└── zaproxy-systemd
│ ├── PKGBUILD
│ ├── README.md
│ └── zaproxy.service
├── exercises
├── course_feedback.md
├── h1.md
├── h2.md
├── h3.md
├── h4.md
├── h5.md
├── h6.md
└── h7.md
├── images
├── attack_principle-1.png
├── attack_principle-2.png
└── linux_hypervisor_rootkit.png
└── random
├── linux-backdoor.md
└── linux-rootkit-realcase.md
/README.md:
--------------------------------------------------------------------------------
1 | # Offensive penetration testing
2 |
3 | Aim of this repository is to present and simulate multiple attack types against web applications and various OSes, including Microsoft Windows.
4 |
5 | ---------------
6 |
7 | ## About
8 |
9 | **NOTE: Applying and carrying out the practices described below _can be considered as a criminal act_**. Instructions described on this website have been carried out in a precisely limited scope/environment, in accordance with the terms of use, and accepted by all relevant parties beforehand without affecting outside parties. The hostile practices defined here are not directed to any innocent third parties.
10 |
11 | Before utilizing these instructions in your environment, make sure that your actions will be legal and authorized, carried out in a limited scope and with transparency so that every affected party is aware of your actions and accepted them in full scale beforehand. In addition, any affected party must know consequences and risks involved in your actions.
12 |
13 | **DISCLAIMER:** Author of the instructions neither encourage or take responsibility of any misuse or criminal actions which are based on the instructions below!
14 |
15 | ---------------
16 |
17 | **This repository...**
18 |
19 | - ...utilizes [OWASP top 10 list of the most common attack types](https://owasp.org/www-pdf-archive/OWASP_Top_10-2017_%28en%29.pdf.pdf)
20 |
21 | - ...utilizes multiple penetration methods with various tools, including [Kali Linux](https://www.kali.org) and [Metasploit Framework](https://www.metasploit.com)
22 |
23 | The repository is mainly set up as a requirement by a school cource in Haaga-Helia University of Applied Sciences, Helsinki, Finland. It contains various exercises, translated to English.
24 |
25 | ## Table of Contents
26 |
27 | - [Exercise 1](exercises/h1.md) - OWASP Top 10, OWASP WebGoat
28 |
29 | - [Exercise 2](exercises/h2.md) - HackTheBox Environment, Nmap (port scanning), Metasploit Framework, OWASP WebGoat
30 |
31 | - [Exercise 3](exercises/h3.md) - Vulnerability Scanners (passwords, directories, ports etc.), Source Code Analysis of a Malicious Program, Authentication Bypass
32 |
33 | - [Exercise 4](exercises/h4.md) - CTF Hacking Challenges, Stuxnet
34 |
35 | - [Exercise 5](exercises/h5.md) - Trojan Horse (docx, pdf, GZDoom), Conficker Worm, Security Blogs/Articles, DHCP Starvation Attack (Denial of Service)
36 |
37 | - [Exercise 6](exercises/h6.md) - Android Backdoor, Trojan Horse (SteamSetup.exe), OSINT Techniques
38 |
39 | - [Exercise 7](exercises/h7.md) - Unicorn/Powershell Attack (docx), HTTP Server Hacking Challenge, Google Project Zero (Exploitation of Linux kernel vulnerability)
40 |
41 | - [Course feedback (in Finnish)](exercises/course_feedback.md)
42 |
43 | - [BlackArch Linux - Personal configurations](#blackarch-linux---personal-configurations)
44 |
45 | - [Iptables ruleset for a simple server](#iptables-ruleset-for-a-simple-server)
46 |
47 | - [Fake Apache server HTTP response codes](#fake-apache-server-http-response-codes)
48 |
49 | - [Find old package versions at high risk on Arch Linux using updated CVE data](#find-old-package-versions-at-high-risk-on-arch-linux-using-updated-cve-data)
50 |
51 | ## Other contents
52 |
53 | ### [Linux backdoor](random/linux-backdoor.md)
54 |
55 | - Create backdoor for Linux victim machine(s). Does not require server environment, applies to Linux clients, too. Requires social engineering tactics.
56 |
57 | ### [BlackArch Linux - Personal configurations](blackarch/)
58 |
59 | - [OWASP WebGoat](blackarch/webgoat) - Install [OWASP WebGoat](https://www.owasp.org/index.php/Category:OWASP_WebGoat_Project) as a systemd user service
60 |
61 | - [OWASP Zed Attack Proxy](blackarch/zaproxy-systemd) - Install [OWASP ZAP](https://www.owasp.org/index.php/OWASP_Zed_Attack_Proxy_Project) as a systemd user service
62 |
63 | - [MATE Desktop/myGtkMenu](blackarch/mate-desktop) - Convert BlackArch Openbox penetration tool menu entries into [myGtkMenu](https://sites.google.com/site/jvinla/mygtkmenu) compliant format, use these entries with myGtkMenu
64 |
65 | ------------------
66 |
67 | ### Iptables ruleset for a simple server
68 |
69 | Iptables firewall ruleset featuring the following:
70 |
71 | > 1) Do not respond to ping echoes by clients (possibly reduce spambots)
72 |
73 | > 2) Reject connection if too intense attempts. Useful against port scanners such as [Nmap](https://nmap.org/) and other brute force scanners such as [Dirbuster](https://www.owasp.org/index.php/Category:OWASP_DirBuster_Project).
74 |
75 | > 3) Drop all incoming connections, apply only SSH, HTTP and HTTPS
76 |
77 | - [[File] iptables.rules / Fincer - Linux server setup](https://github.com/Fincer/linux-server-setup/blob/master/other/iptables.rules)
78 |
79 | ------------------
80 |
81 | ### Fake Apache server HTTP response codes
82 |
83 | - [[Patch] Apache - Manipulate standard HTTP header response codes](https://github.com/Fincer/linux-server-setup/blob/master/patches/patch_apache_break_http_code_standard.patch)
84 |
85 | - Manipulate HTTP header response codes returned to a client by Apache HTTP server.
86 |
87 | > 1) Server HTTP response codes in range 402-451 are returned as error code 400 response instead.
88 |
89 | > 2) Server HTTP response codes in range 500-511 are returned as error code 400 response instead.
90 |
91 | > 3) Server HTTP response codes in range 100-308 are returned normally, including 200 OK message.
92 |
93 | - [[Patch] Apache - Remove default HTML error message from all error pages](https://github.com/Fincer/linux-server-setup/blob/master/patches/patch_apache_disable_html_errormsg.patch)
94 |
95 | - Remove default error pages returned by an erroneous HTTP client request.
96 |
97 | - Remove additional HTML error messages as well (such as ones generated by servers behind an Apache proxy, if [ProxyErrorOverride On](https://httpd.apache.org/docs/2.4/mod/mod_proxy.html#proxyerroroverride) directive is used)
98 |
99 | **NOTE:** These are experimental patches for Apache HTTP web server, use with caution. Feel free to modify them! The server configuration can easily break because we break very deep standards here, just be aware and proceed with care! Thanks!
100 |
101 | **NOTE:** This patchset is useful in some cases but it can bury underneath problems in server
102 | configuration. Thus, use discretion before implementing the patches in your Apache server.
103 |
104 | **NOTE:** Apache *will complain* about missing error codes after you have applied this patchset and if you have custom error redirections in your `.htaccess` or in other settings. This is why you need to adjust your custom `ErrorDocument` directives and equivalent settings (RewriteRules, for instance) in your VirtualHost/Page configuration file (`/etc/{apache2,httpd}/sites-available/*.conf`).
105 |
106 | ------------------
107 |
108 | ### Find old package versions at high risk on Arch Linux using updated CVE data
109 |
110 | [[Bash script] archrisks.sh - Fincer/archtools](https://github.com/Fincer/archtools/blob/master/tools/archrisks.sh)
111 |
112 | Check packages on your system and find out number of potential CVE issues and evaluate generic risk of an outdated package on your Arch Linux system. **Does not give detailed information, just a basic summary**. Do further analysis for any package if needed on [Arch security database](https://security.archlinux.org/) and using [regular CVE databases](https://www.searx.me/?q=cve%20database)
113 |
114 | - Requires Arch Linux (core dependencies are: [pacman](https://www.archlinux.org/packages/core/x86_64/pacman/) and [arch-audit](https://www.archlinux.org/packages/community/x86_64/arch-audit/), [bc](https://www.archlinux.org/packages/extra/x86_64/bc/) and [bash](https://www.archlinux.org/packages/core/x86_64/bash/) version 4 or higher)
115 |
116 | - Simple **bash** shell script
117 |
118 | - CVE security information from [Arch security database](https://security.archlinux.org/)
119 |
120 | - **NOTE** `sudo` is required for package database updates retrieved by `pacman`. If in doubt, you can always check the script yourself ([link here](https://github.com/Fincer/archtools/blob/master/tools/archrisks.sh)).
121 |
122 | 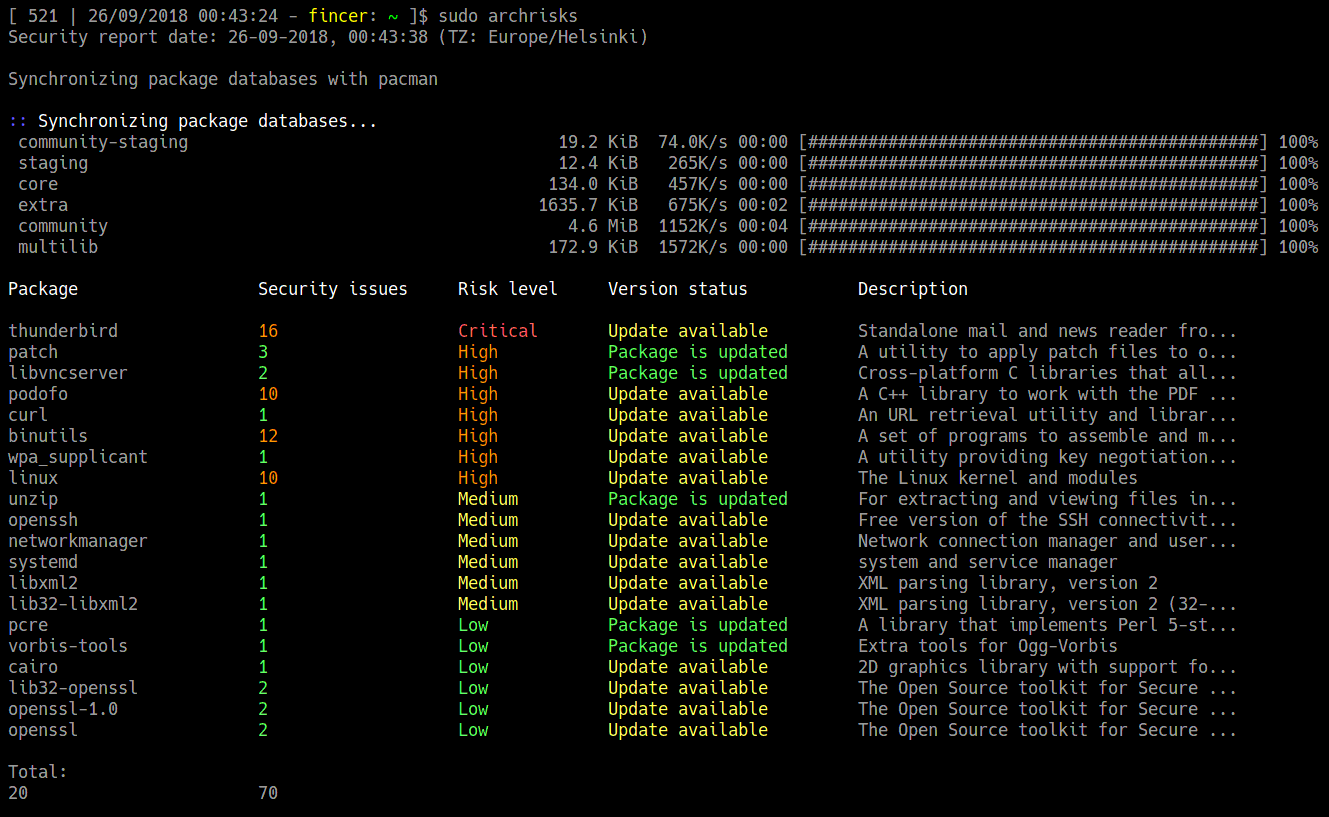
123 |
124 | ------------------
125 |
126 | ## Attack principle - unauthorized access to private intranet
127 |
128 | 
129 |
130 | _In this demonstration, I fired up a network environment with 1x Raspberry Pi, 1x strictly firewalled DD-WRT router, 1x physical computer & 1x virtual machine. Router established a LAN network for Raspberry Pi, whereas its WAN interface was connected to the physical computer, demonstrating common internet connection. Attack machine ran virtually inside the physical computer, with virtual network interface. Proper iptables & routing policy was applied both to the router and the physical computer, as seen in the image below._
131 |
132 | 
133 | _Sorry for this messy image: Just follow the numbers, and you may get the whole idea. This screenshot bundle is directly related to the first image above._
134 |
135 | As we can learn, human is the weakest factor here. If your users do not follow strict network policy, this scenario is possible. For attack purposes, I used basic TCP/443 (HTTPS) & TCP/80 (HTTP) ports in payloads, and these ports were used to establish outgoing connection to my rogue Metasploit reverse shell process. Basically, it is very difficult to block this connection type if you allow users to access basic HTTP(S)-based websites from intranet.
136 |
137 | ------------------
138 |
139 | ## Real life case - infected Arch Linux KVM hypervisor host
140 |
141 | Please see [Real life case: Hostile Linux rootkit on my system. How did I get infected by a real Linux rootkit first time in my life?](random/linux-rootkit-realcase.md) for details.
142 |
143 | ------------------
144 |
145 | ## Disclaimer
146 |
147 | Author of this repository is not responsible for any possible illegal or malicious usage of any files or instructions provided by this repository. The repository is provided as an act of good will and does not intend to encourage users to participate in any illegal activities. All exercises presented in this repository have been carried out in a pre-configured test environment, minimizing any possible attack vectors or unintended harm to outside parties.
148 |
149 | ------------------
150 |
151 | ## About this repository (update, 14th August 2020)
152 |
153 | Further development of this repository has been mainly halted. Additional + extended penetration testing, security testing & research is being done on a private repository for now. This policy may or may not change in the future.
154 |
--------------------------------------------------------------------------------
/blackarch/.gitignore:
--------------------------------------------------------------------------------
1 |
2 |
--------------------------------------------------------------------------------
/blackarch/README.md:
--------------------------------------------------------------------------------
1 | # Various settings & tools for BlackArch Linux
2 |
3 | -------------------
4 |
5 | ## CONTENTS
6 |
7 | ### mate-desktop
8 |
9 | - BlackArch penetration tools configuration for [MATE desktop](mate-desktop.org)
10 |
11 |
12 | ### webgoat
13 |
14 | - Installs [OWASP WebGoat](https://www.owasp.org/index.php/WebGoat_Installation) on BlackArch Linux with the official package manager `pacman`.
15 |
16 | - Adds WebGoat as a new Systemd user service which can be started during system boot-up.
17 |
18 |
19 | ### zaproxy-systemd
20 |
21 | - Adds [OWASP Zed Attack Proxy (ZAP)](https://www.owasp.org/index.php/OWASP_Zed_Attack_Proxy_Project) as a new Systemd user service which can be started during system boot-up.
22 |
23 | -------------------
24 |
25 | ## MISCELLANEOUS
26 |
27 | Start OpenVPN automatically during system boot-up:
28 |
29 | ```
30 | sudo systemctl enable openvpn-client@myuser.service
31 | ```
32 |
--------------------------------------------------------------------------------
/blackarch/mate-desktop/.gitignore:
--------------------------------------------------------------------------------
1 |
2 |
--------------------------------------------------------------------------------
/blackarch/mate-desktop/mygtkmenu/README.md:
--------------------------------------------------------------------------------
1 | # BlackArch - Openbox menu items for other desktops
2 |
3 | ## About
4 |
5 | Files in this directory aim to offer all BlackArch penetration tools for users who use unsupported desktop environments such as MATE, KDE/Plasma or Gnome.
6 |
7 | Normally, BlackArch penetration and hacking tools are available only for users of simple desktops (Openbox, i3, ... etc.)
8 |
9 | -----------------------
10 |
11 | ## myGtkmenu
12 |
13 | [myGtkmenu](https://sites.google.com/site/jvinla/mygtkmenu) provides a simple application launcher menu for user-defined commands. The menu can be used on multiple Linux desktop environments.
14 |
15 | ### mygtkitems.sh
16 |
17 | This script file aims to parse all Openbox XML menu entries to myGtkmenu compatible format. By default, it creates a valid `$HOME/blackarch.items` menu file for myGtkmenu.
18 |
19 | ### blackarch.items
20 |
21 | A sample menu/command list, parsed from default BlackArch Openbox menu.xml file (you can generate this file yourself by running `bash mygtkitems.sh`)
22 |
23 | ### blackarch-tools.desktop
24 |
25 | A sample desktop entry file for opening myGtkmenu program
26 |
27 | -----------------------
28 |
29 | ## Notes
30 |
31 | ### Not all Openbox menu entries are visible in myGtkmenu!
32 |
33 | As BlackArch Openbox menu.xml contains over 50 submenus, it seems that myGtkmenu has a limitation which limits visible submenu entries to around 20. Therefore, please be aware that not all Openbox menu entries are visible in myGtkmenu launcher!
34 |
--------------------------------------------------------------------------------
/blackarch/mate-desktop/mygtkmenu/blackarch-tools.desktop:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env xdg-open
2 | [Desktop Entry]
3 | Name=BlackArch Tools
4 |
5 | GenericName=BlackArch Tools
6 | Comment=Use BlackArch penetration tools
7 |
8 | TryExec=mygtkmenu
9 | Exec=bash -c 'mygtkmenu ~/blackarch.items'
10 | Icon=/home/black/blackarch-launcher.jpg
11 | Type=Application
12 | Categories=Utility;
13 | StartupNotify=true
14 |
--------------------------------------------------------------------------------
/blackarch/mate-desktop/mygtkmenu/mygtkitems.sh:
--------------------------------------------------------------------------------
1 | #!/bin/env bash
2 |
3 | # Simple Openbox to myGtkmenu menu items parser
4 | # Copyright (C) 2018 Pekka Helenius
5 | #
6 | # This program is free software: you can redistribute it and/or modify
7 | # it under the terms of the GNU General Public License as published by
8 | # the Free Software Foundation, either version 3 of the License, or
9 | # (at your option) any later version.
10 | #
11 | # This program is distributed in the hope that it will be useful,
12 | # but WITHOUT ANY WARRANTY; without even the implied warranty of
13 | # MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
14 | # GNU General Public License for more details.
15 | #
16 | # You should have received a copy of the GNU General Public License
17 | # along with this program. If not, see .
18 |
19 | ####################################################
20 |
21 | # Obenbox menu file
22 | # Default: /etc/xdg/openbox/menu.xml
23 |
24 | OB_MENUFILE="/etc/xdg/openbox/menu.xml"
25 |
26 | # myGtkMenu output menu file
27 | # Default: ${HOME}/mygtkmenu.items
28 |
29 | GTK_MENUFILE="${HOME}/mygtkmenu.items"
30 |
31 | # Icon for menu categories
32 | ICON_MENU="/usr/share/icons/Humanity/actions/24/stock_right.svg"
33 |
34 | # Icon for menu items
35 | ICON_CMD="/usr/share/icons/Humanity/apps/24/terminal.svg"
36 |
37 | ##########################
38 |
39 | # Slash conversion for sed stream:
40 |
41 | ICON_MENU=$(printf "${ICON_MENU}" | sed 's|/|\\/|g')
42 | ICON_CMD=$(printf "${ICON_CMD}" | sed 's|/|\\/|g')
43 |
44 | ##########################
45 |
46 | echo -e "\niconsize = 25\n" > "${GTK_MENUFILE}"
47 |
48 | [ $? -ne 0 ] && exit 1
49 |
50 | ##########################
51 |
52 | # Line count
53 | i_all=$(grep -E "|- $|
60 | *.*<\/command>$" "${OB_MENUFILE}"
61 | );
62 | do
63 | echo -en "Writing item line parameter $i of $i_all ( $(( (100 * $i / $i_all) ))% ) \r"
64 | echo $item | sed -E \
65 | "
66 | s/\"//g;
67 | s/=/ = /g;
68 | s/^(.*)/ cmd = \1\n icon = ${ICON_CMD}\n/g;
69 | s/<\/command>//g;
70 | s/