├── Docs
├── README
└── Screenshot from 2019-09-22 22-49-57.png
├── SAST
├── .codeql
│ └── code-query.codeql
└── README.md
├── releases
└── changelog.md
├── SANS-2021
├── README.md
└── SEC760.md
├── Books
└── README.md
├── Web-Application-Hacking
└── README.md
├── CodeInjectionVulnerablities
└── FRIDA
│ └── README.md
├── fintech-infrastructure-security
└── README.md
├── Seccoms
└── README.md
├── .github
└── workflows
│ └── github-actions.yaml
├── web3-security
├── README.md
└── polkastarter.md
├── Malware_Analysis
└── README.md
├── Essentials
├── README.md
└── ReverseEngineering-CTF
│ ├── README.md
│ └── Nexmon.md
├── Protocols
└── README.md
├── Cloud-Security
└── README.md
├── AppleOsSecurity
└── README.md
├── Machine_Learning_In_Cyber_Security
└── README.md
├── DevSecOps
└── README.md
├── RE-Competition
└── README.md
├── Network_Security_Course
└── README.md
├── README.md
├── Black_Hat_Attacks
└── README.md
└── LICENSE
/Docs/README:
--------------------------------------------------------------------------------
1 | documents
2 |
--------------------------------------------------------------------------------
/SAST/.codeql/code-query.codeql:
--------------------------------------------------------------------------------
1 | - queries
--------------------------------------------------------------------------------
/releases/changelog.md:
--------------------------------------------------------------------------------
1 | ## Version 0.0.1 .
2 |
3 | - writing the documentation for diffrent cybersecurity tools and the SANS courses .
--------------------------------------------------------------------------------
/Docs/Screenshot from 2019-09-22 22-49-57.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/GrandGarcon/Complete_Cybersecurity_Path/HEAD/Docs/Screenshot from 2019-09-22 22-49-57.png
--------------------------------------------------------------------------------
/SANS-2021/README.md:
--------------------------------------------------------------------------------
1 |
2 | ## Starting with the SANS courses pathways
3 |
4 | 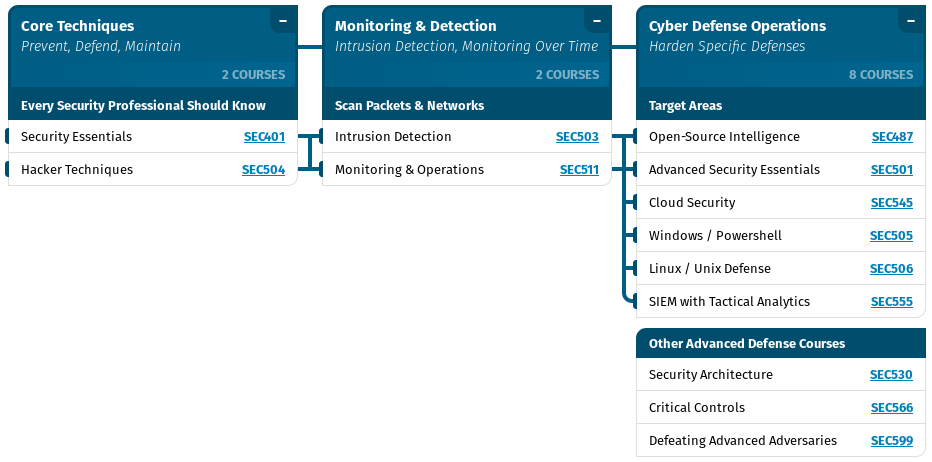
5 |
6 | 1. [SEC760]()
7 | 2. [SEC660]()
8 |
9 |
10 |
11 |
12 |
--------------------------------------------------------------------------------
/Books/README.md:
--------------------------------------------------------------------------------
1 | # the ultimate course bundle of cybersecurity books
2 |
3 | 1. malware Analysis:- an awesome book on teaching the doctorate in the field of commputer science. how to dissect , understand and re-engineer the malware.
4 | will be adding the implementation and other additional notes.
5 |
6 |
7 |
--------------------------------------------------------------------------------
/Web-Application-Hacking/README.md:
--------------------------------------------------------------------------------
1 | ## Capture the web 😈
2 | this repository will rather than practical implementation of scripts , tricks that will be breaking the nascent web3.0 framework by
3 | taking the reference (from https://github.com/qazbnm456/awesome-web-security#saml , awesome infosec and IppSec ).
4 |
--------------------------------------------------------------------------------
/CodeInjectionVulnerablities/FRIDA/README.md:
--------------------------------------------------------------------------------
1 | # FRIDA is a framework to inject your own code into native apps in order to find vulnerablities or to reverse engineer the application which has encrypted communication
2 |
3 | Link:- https://www.frida.re/docs/home/.
4 |
5 | # Sample Project:- making a Making a web app data collection service using frida.js:-
6 |
Coming soon
7 |
8 |
--------------------------------------------------------------------------------
/fintech-infrastructure-security/README.md:
--------------------------------------------------------------------------------
1 | ## general overview of the information about security of financial markets and security concerns
2 |
3 | 1 [Financial market attacks](https://www.swift.com/resource/how-cyber-attackers-could-target-worlds-financial-markets)
4 |
2. [security markets , having close to 2x the US gdp traded each year ](https://www.issanet.org/e/pdf/2018-10_ISSA_Cyber_Risk_in_Securities_Services.pdf)
5 |
--------------------------------------------------------------------------------
/Seccoms/README.md:
--------------------------------------------------------------------------------
1 | # Seccoms : the super shadoy coders starting the second phreaking wave in infosec ecosystem.
2 |
3 | sharing here are the list of the organisations / forums discussing on the diffrent concepts of infosec in real time scenario
4 |
5 | - https://0x00sec.org/.
6 | - [anarchoTech](https://github.com/AnarchoTechNYC).
7 | - [techCollective](https://techlearningcollective.com/) is their for paid (but decently priced) courses for the
--------------------------------------------------------------------------------
/.github/workflows/github-actions.yaml:
--------------------------------------------------------------------------------
1 | name: github actions for tutorial merge
2 | on: [push]
3 | jobs:
4 | GitHub-Actions-grammatical:
5 | runs-on: ubuntu-latest
6 | steps:
7 | - run: echo "🎉 The job was automatically triggered by a ${{ github.event_name }} event."
8 | - run: echo "TODO:grammatical corrections needed to be corrected"
9 | - name: Check spelling
10 | uses: check-spelling/check-spelling@v0.0.19
11 |
--------------------------------------------------------------------------------
/web3-security/README.md:
--------------------------------------------------------------------------------
1 | ## web3 ecosystem security : WAGMI
2 |
3 | here i will be going through auditing (mostly statically but if possible dynamically also) the repo's of the ecosystem , and then analysing the potential threat vectors that are being currently being neglected from the lens of the underlying web2 primitves being currently used in all of these ecosystems .
4 |
5 | - from Immunefi , following are the reports that i am currently researching
6 | - polkastarter
7 | - TheGraph
--------------------------------------------------------------------------------
/Malware_Analysis/README.md:
--------------------------------------------------------------------------------
1 | # learning the malware analysis the fast way
2 |
3 |
in this repo , i will be implementing practical excercises from the book :- Learning Malware Analysis with practical Examples.
4 |
5 | **Topics**
6 |
7 | *1. Static analysis
8 | *2. Dynamic analysis
9 | *3. reverse engineering
10 | *4. malware Obfuscation
11 |
12 |
13 | ## for beginners , this book will be sufficient to get started:- https://github.com/hija/MalwareDataScience
14 |
15 |
--------------------------------------------------------------------------------
/SAST/README.md:
--------------------------------------------------------------------------------
1 | # Static Analysis of security tests
2 |
3 | here we wil be discussing the state of the art tools being used in doing the automated static analysis on the codebase to avoid backdoors / vulnerablities ( specially the top 10) . there are multitude of tools in the space , from doing static analysis of the codebase ( Codeql) , to writing your own policies following the principles of devsecops .
4 |
5 | this will include the following documentation / tutorials :
6 |
7 | 1. codeql
8 | 2. workflows on github
9 | 3.
--------------------------------------------------------------------------------
/Essentials/README.md:
--------------------------------------------------------------------------------
1 | # working on binary level and get yourself acquited with unmanagable bugs is the most important step in the beginning. thus this folder consist on
2 |
3 | - [ ] Computer architecture and OS excercises from CMU's course with a awesome book
4 |
5 | - [ ] little bit of system based programming in Linux , Windows and Ios ( with example)
6 | - [ ] Binary reverse engineering , Buffer overflow attacks and other basic attacks situated in OWASP top 10 .
7 |
8 | - [ ] then System design and basic ML to make course more professional.
9 |
10 | - [ ] Networking essentials and tools of KALI Linux
11 |
--------------------------------------------------------------------------------
/Protocols/README.md:
--------------------------------------------------------------------------------
1 | this folder will check the implementation of the main protocls for the IOT space (unlike the pre-esthablished ones) with the emphasis on security
2 |
3 |
4 | 1. V2x:- this is standard protocol of IEEE poised to become the "IP stack" protocol in the field of connected cars.
5 | [link for a vendor](http://www.redpinesignals.com/Products/802.11p_V2X_Connectivity/)
6 |
7 |
8 |
9 | 2. [a paper showing the Embedded supplychain hardware attacks ](https://arxiv.org/abs/1812.02770)
10 |
11 | 3. [Attacks on Air gapped Networks from Negev university ](https://i.blackhat.com/us-18/Wed-August-8/us-18-Guri-AirGap.pdf)
12 |
--------------------------------------------------------------------------------
/Essentials/ReverseEngineering-CTF/README.md:
--------------------------------------------------------------------------------
1 | #Deep dive into the basic block of traning of the hacker . this is the minimal info that is enough for the programmer to break into systems ( although in real case we use on during analysing close sources system like MacOS or any obfuscated malware).
2 |
3 | 1.Basic Resource :- https://yurichev.com/writings/RE4B-EN.pdf .
4 | 2.Operating Systems Book :- introduction to the programmers persepective ( by richard Bryant). [https://www.amazon.com/Computer-Systems-Programmers-Perspective-3rd/dp/013409266X] .
5 |
6 | 3. Notes on the [Nexmon project](./Nexmon.md) , allowing the Injection in the Wifi and network devices.
7 |
--------------------------------------------------------------------------------
/Cloud-Security/README.md:
--------------------------------------------------------------------------------
1 | # learning cloud-security
2 | # the ultimate guide for entry into the entry job for cloud security
3 |
4 | in this repo , i will be introducing the ecosystem of the 4 top cloud services in the world ( AWS , Azure , GCP and alibaba / tencent / huawei cloud ).
5 | along with this , i will explain the architecture that they currently use .also relative comparison and the possiblity of creating the open source solution on top of their offerings so as to
6 | avoid hugh unnecessary costs and making robust SIEM and monitoring center.
7 |
8 | # 1. Amazon cloud service :
9 | thanks to the book [aws security - packt publications]() i have highlighted some tutorials and notes on the aws security and how to generalise for the other cloud.
10 |
--------------------------------------------------------------------------------
/AppleOsSecurity/README.md:
--------------------------------------------------------------------------------
1 |
2 |
3 | # this folder will consist of links , implementation of recent exploits on the latest Mac-Os and Icloud
4 |
5 | some links to get you interested :-
1. Apple file system :-https://developer.apple.com/support/apple-file-system/Apple-File-System-Reference.pdf
6 |
2. some cool blogs ( at your own risk , implement these techniques) :- https://null-byte.wonderhowto.com/how-to/hacking-macos-break-into-macbook-encrypted-with-filevault-0185177/
7 |
8 |
9 | 3. [An Extensive attack for priviledge escalation on exploit-db](https://www.exploit-db.com/exploits/46914) :- this creates an executed payload in disguise of the feedback pushup notification of the service.
10 | ### to do
11 | - [ ] Do an awesome CVE type work and then do the MITRE ATTA&K analysis .
12 | - [X] work on exhaustively as many projects you may get on this .
13 |
14 |
--------------------------------------------------------------------------------
/Machine_Learning_In_Cyber_Security/README.md:
--------------------------------------------------------------------------------
1 | ## MLSecurity resources
2 |
3 | Implementing the excercises and code of the latest book working on using machine learning in cybersecurity :- Machine learning and cybersecurity ( by oreilly publications ).
4 |
5 |
6 | Work to do
7 | - [ ] implement all the excercises when yo uget time
8 | - [ ] try to beautify and focus your work only on specific area.
9 | - [ ] work on big data + cybersecurity + data Engg projects.
10 | - [ ] working on complementing the book resources.
11 |
12 |
13 |
14 | ### great book for entry level projects for getting theb
15 | https://mlsec.net
16 |
17 |
18 |
19 | ## some miscenallenous contracts for understanding the diffrent .
20 | 1. [a nice paper on using crypto for avoiding adversarial attacks on dnn](https://arxiv.org/pdf/1809.01715.pdf)
21 | - [X] some papers on adversarial Machine learning from the arxiv and their code
22 |
--------------------------------------------------------------------------------
/DevSecOps/README.md:
--------------------------------------------------------------------------------
1 | # devsecops 101 and current trends
2 |
3 | 1. understanding the concept of [extreme programming and devops](https://blog.yourlabs.org/posts/2020-02-08-bigsudo-extreme-devops-hacking-operations/ .
4 | )( Ci + CD + testing + code formatting / reviewing in real time)
5 |
6 |
7 | ## Cyber threat intelligence :
8 | 1. MISP : getting the collaboration information sharing for malware analysis and threat intelligence . check its compatiblity and diffrence with the TAXII and other protocols .
9 |
10 |
11 | ## patch deployment and devops
12 |
13 | 1. the automated patching management system on the scales of thousands of servers ( like oracle autonomous linux service) is a great start to really check the Linux admin stuff and the principles of site reliablity engineering so as to work on the automating the patch management and also checking the file systems by the automation of the file reverse engineering .
14 |
15 |
--------------------------------------------------------------------------------
/RE-Competition/README.md:
--------------------------------------------------------------------------------
1 |
2 |
3 | ## resources from some of the competitions /tools on the rev engineering and obfuscation.
4 |
5 | ### competition :- completing the codebreaker competition :-
6 | this is the competition started by the NSA to crack the apps by getting the information about the network packets using the reverse engineering the associateion with the android based application and the access . the frameworks and tech stacks being referenced here are follows
7 | - radare.
8 | - Gidra
9 | - wireshark
10 |
11 | Given below the tutorials can help in understanding the diffrent concepts of the frameworks and the analysis of the payload :
12 |
13 | - wireless packet analysis using wireshark :- [book on the tutorial](http://index-of.es/Varios-2/Practical%20Packet%20Analysis%20Using%20Wireshark%20to%20Solve%20Real%20World%20Problems.pdf)
14 |
15 | - understanding the python libraries like scapy for defining the payload of the TCP/IP , IoT protocols and other formats from scratch
16 |
17 | -
--------------------------------------------------------------------------------
/Network_Security_Course/README.md:
--------------------------------------------------------------------------------
1 | This folder will consist of the sample excercises of the course taught in my univ . it has examples of running IDS , create your own payload of packets using scapy and working out on VM's to create a virtual network and do the attacks.
2 |
3 | ## INF 586 :- securite reseaux :-
4 | an intresting research subject with topics covering the every aspect from analysing the filtering of packets on each layer to checking the case studies of cybersecurity attacks. in order to practice , we will be using tools like wireshark , snaort and kernel network programming to create compartmentalised & secured network (INF586)[https://moodle.polytechnique.fr/course/view.php?id=5646].
5 |
6 | ## CNIT sanfrancisco network security and advance hacking course :-
7 | protocol dissector and using bioinformatics for reverse engineering proprietary protocols for getting THE ARCHITECTURE BUT ALSO TESTING SOME OF THE MOST DEVASTATING ATTACKS ON COMPLETE NETWORK " . here are the following links of my writeups from the infosec and the course :-
8 |
--------------------------------------------------------------------------------
/Essentials/ReverseEngineering-CTF/Nexmon.md:
--------------------------------------------------------------------------------
1 | # Nexmon 101.
2 |
3 | An C based patching framework for Wifi chips and enabling monitor mode with radiotap headers / frame injection.
4 |
5 | allows to scan and doing following operations on network packets :
6 | - Monitor Mode : an more efficient version of wireshark but with less energy transfer
7 | - Monitor Mode with RadioTap headers.
8 | - frame injection : can be an stateless attacks on the wifi ( can either be cryptanalysis for the wifi wpa3 standards or the simply ).
9 |
10 |
11 | Also it supports most of the Android OS based firmwares . my major writeup will explain the reference implementations from the diffrent raspPi OS , specially extracting the
12 |
13 | in the patches/ channel check the patches.c and the other helper functions for the
14 |
15 |
16 |
17 |
18 |
19 |
20 |
21 |
22 |
23 |
24 |
25 |
26 |
27 |
28 |
29 |
30 | ## Tasks :
31 | - [ ]Getting firmware to be rewritten in Rust , specially the cargo pallets for packaging and implementing some sort of "metasploit for firmware "
32 |
33 | - [ ]
--------------------------------------------------------------------------------
/web3-security/polkastarter.md:
--------------------------------------------------------------------------------
1 | # polkastarter project
2 |
3 | TODO: index of the topics i will be writing about the potential bugs in the codebase :
4 |
5 | ## Smart Contracts and Blockchain
6 |
7 | Re-entrancy
8 | Logic errors
9 | including user authentication errors
10 | Solidity/EVM details not considered
11 | including integer over-/under-flow
12 | including rounding errors
13 | including unhandled exceptions
14 | Trusting trust/dependency vulnerabilities
15 | including composability vulnerabilities
16 | Oracle failure/manipulation
17 | Novel governance attacks
18 | Economic/financial attacks
19 | including flash loan attacks
20 | Congestion and scalability
21 | including running out of gas
22 | including block stuffing
23 | including susceptibility to frontrunning
24 | Consensus failures
25 | Cryptography problems
26 | Signature malleability
27 | Susceptibility to replay attacks
28 | Weak randomness
29 | Weak encryption
30 | Susceptibility to block timestamp manipulation
31 | Missing access controls / unprotected internal or debugging interfaces
32 |
33 | ## Websites and Apps
34 |
35 | Remote Code Execution
36 | Trusting trust/dependency vulnerabilities
37 | Vertical Privilege Escalation
38 | XML External Entities Injection
39 | SQL Injection
40 | LFI/RFI
41 | Horizontal Privilege Escalation
42 | Stored XSS
43 | Reflective XSS with impact
44 | CSRF with impact
45 | Direct object reference
46 | Internal SSRF
47 | Session fixation
48 | Insecure Deserialization
49 | DOM XSS
50 | SSL misconfigurations
51 | SSL/TLS issues (weak crypto, improper setup)
52 | URL redirect
53 | Clickjacking (must be accompanied with PoC)
54 | Misleading Unicode text (e.g. using right to left override characters)
55 |
--------------------------------------------------------------------------------
/README.md:
--------------------------------------------------------------------------------
1 | # Complete_Cybersecurity_Path
2 | The open source way to do the excercises to be a Full-Stack Cybersecurity Engineer. added with the recent research in the field of Machine learning and cybersecurity.
3 |
4 | The main objective of this repository , apart from the indexing the numerous "Awesome repo's for diffrent cybersec topics" is to give an glimpse to more unknown and recent challanges in the field of cybersecurity accross verticals , trying to create an open source alternative to these premium courses in the cybersecurity field , by able to connect the dots
5 |
6 |
7 | apart from the traditional verticals in the security (cloud audits , embedded systems security) , my foray into the web3 dapp development across EVM / non EVM ecosystems and adapting the diffrent general concepts concering the security practices in the traditional web2 world and how that can be integrated into the web3 ecosystem.
8 |
9 | Each of the folder defines the diffrent verticals into the given IT stacks (either being from cloud native , or from the web3 ecosystem).
10 |
11 |
12 |
13 |
14 | ## Status
15 | 'TODO'
16 | - stars and associated forks explanation .
17 | - indexing of the content .
18 | - [ ] writing the min viable details of each of the topics and resources
19 | - [ ] have an extensive web3 based security based content .
20 | - [ ] make it more OG (emoji use , well structured content).
21 |
22 |
23 |
24 | ## References (and credits).
25 |
26 | - [Starting with the impressive collection of course with syllabus for latest courses ](https://www.sans.org/cyber-security-courses/)
27 |
28 | - [rmusser , the umtimate infosec reference](https://github.com/rmusser01/Infosec_Reference).
29 |
30 |
31 | traditional security pentesting freelancing /professional websites
32 | - hackerone
33 | - synack
34 |
35 |
36 | for understanding the practical and sensational details of the security and web3 , the following courses /
37 | - [yacademy]()
38 | - [rekt news]().
39 | - [immunefi]().
40 | - [code42n34]().
41 | - [quarksLabs RE blog]().
42 | - [Kernel resources]().
43 |
44 |
45 |
46 |
47 |
--------------------------------------------------------------------------------
/Black_Hat_Attacks/README.md:
--------------------------------------------------------------------------------
1 | __here i will be posting the research on the latest attacks in the field of cybersecurity and also to show the viewpoint of how the actual APT attack is engineering
__
2 | **with precision as similar as that of actual harmful attacks**
3 |
4 |
5 | But before working head on more ambitious tasks , we will be first thinking on the building blocks (understanding the languagee of treasure trove of data generated by the machines , sensors in the form of assembly data , logs by sensors , processing units and like , thus following are the most important and unique tools to work on.
6 |
7 | 1. [splunk enterprise](http://docs.splunk.com/Documentation/Splunk/7.2.1/Overview/AboutSplunkEnterprise) :- the most prominent company which has developed enterprise level , multi facet parsing engine for pretty much every data format present in the field of computer science ( IoT data , computer , server and web generated logs , other standards of the web ) and show the results into clean web ui. But cons is that it is pricey.
8 |
9 |
10 | *thus welcome the alternative open source version*
11 | [**Fluentdu**](https://www.fluentd.org/):- although not that much robust , but still in competition being having the latest stable release and also involves plugins from many cloud sources.
12 |
13 |
14 | now starting with our lists of most threatening malware that can paralyse the whole automation world.
15 |
16 |
17 | 1. [**Trition Malware**](https://www.nozominetworks.com/downloads/US/Nozomi-Networks-TRITON-The-First-SIS-Cyberattack.pdf) :- a recent malware which can take down last line of defense in the critical stations.
18 |
19 | 2. Xori :- an open source machine learning based awesome disassembler which makes professional and pricey disassemblers like IDA pro biting dust.
20 |
21 | 3. Using AI to obfuscate malware :- this terrifying reality is best shown in the following slides by an IBM researcher[link](https://i.blackhat.com/us-18/Thu-August-9/us-18-Kirat-DeepLocker-Concealing-Targeted-Attacks-with-AI-Locksmithing.pdf)
22 |
23 | 4. [a nice thesis for understanding the basics of the industrial automation systems] (http://www.academia.edu/37057227/Simulation_of_cyber_attacks_against_SCADA_systems)
24 |
--------------------------------------------------------------------------------
/SANS-2021/SEC760.md:
--------------------------------------------------------------------------------
1 | # Advanced Exploit Development for Penetration Testers :
2 |
3 | this intresting course will improve and curate the fundamental skills for exploit development and understand vulns at fundamental leval and leveraging the tools to work on the following tools for ex :
4 | - writing modern exploits on Windows family and Azure
5 | - Complex attacks on kernel / memory level including use-after-free , driver exploitation and one day exploitation via patch analysis .
6 | - utlising various automation frameworks via scripting ( debuggers , msf , plugins ).
7 | - scale your understanding on cloud level inrastructure security
8 | - dealing with modern exploit mitigation controls and come up with better alternatives .
9 |
10 |
11 | starting with the revision on the RE tools IDA / Gidhra and then considering their automation capablities for bug hunting and analysis.
12 |
13 |
14 | ## Section 1: Understanding IDA and some associaed plugins to do static and functional dynamics .
15 |
16 | - SDLC , threat modelling , tutorials on all the functionalities , extensiblity and automation of the functionality.
17 |
18 | - 1.1 [Starting from the page providing the genral purpose tutorial of the primitive datastructure and scaling up to major projects](https://www.hex-rays.com/products/ida/support/tutorials/)
19 |
20 | - IDA for owrking with packed executables.
21 | - issues starts with the files with headers and other ELF / other OS dependent file structure being corrupted to the level that paid tools cant even recognise them . and specially their issues concerning non resolution of the jmp addresses .
22 |
23 | - start with the manual loading of the library , this will be allowing to set the limits on the memory to be decompiled and checking some unusual coe ( like having jmp instruction in header ).
24 |
25 |
26 | - After esthablishing the relation between the address , we can define the procedure to define that the chunk will be defined as function.
27 |
28 |
29 | - define the break points , then recursively opening the maincontent , substituting the opcodes with the operation and the data to be considered for the reverse compilation .
30 |
31 | - IDC : an C like language for automating the testing predefined by the user.
32 | - it starts with the defining of the preprocessor symbol for defining the type of the executable file .
33 |
34 |
35 |
36 |
37 |
38 | - debugging for Ios applications
39 | - using the debugging enviornment for diffrent debuggers :GDB , XNU , iOS debugger .
40 | - start with the source level debugging by rebuilding the idatest application which is being given as the test template by the IDA .
41 |
42 | -
43 |
44 |
--------------------------------------------------------------------------------
/LICENSE:
--------------------------------------------------------------------------------
1 | Apache License
2 | Version 2.0, January 2004
3 | http://www.apache.org/licenses/
4 |
5 | TERMS AND CONDITIONS FOR USE, REPRODUCTION, AND DISTRIBUTION
6 |
7 | 1. Definitions.
8 |
9 | "License" shall mean the terms and conditions for use, reproduction,
10 | and distribution as defined by Sections 1 through 9 of this document.
11 |
12 | "Licensor" shall mean the copyright owner or entity authorized by
13 | the copyright owner that is granting the License.
14 |
15 | "Legal Entity" shall mean the union of the acting entity and all
16 | other entities that control, are controlled by, or are under common
17 | control with that entity. For the purposes of this definition,
18 | "control" means (i) the power, direct or indirect, to cause the
19 | direction or management of such entity, whether by contract or
20 | otherwise, or (ii) ownership of fifty percent (50%) or more of the
21 | outstanding shares, or (iii) beneficial ownership of such entity.
22 |
23 | "You" (or "Your") shall mean an individual or Legal Entity
24 | exercising permissions granted by this License.
25 |
26 | "Source" form shall mean the preferred form for making modifications,
27 | including but not limited to software source code, documentation
28 | source, and configuration files.
29 |
30 | "Object" form shall mean any form resulting from mechanical
31 | transformation or translation of a Source form, including but
32 | not limited to compiled object code, generated documentation,
33 | and conversions to other media types.
34 |
35 | "Work" shall mean the work of authorship, whether in Source or
36 | Object form, made available under the License, as indicated by a
37 | copyright notice that is included in or attached to the work
38 | (an example is provided in the Appendix below).
39 |
40 | "Derivative Works" shall mean any work, whether in Source or Object
41 | form, that is based on (or derived from) the Work and for which the
42 | editorial revisions, annotations, elaborations, or other modifications
43 | represent, as a whole, an original work of authorship. For the purposes
44 | of this License, Derivative Works shall not include works that remain
45 | separable from, or merely link (or bind by name) to the interfaces of,
46 | the Work and Derivative Works thereof.
47 |
48 | "Contribution" shall mean any work of authorship, including
49 | the original version of the Work and any modifications or additions
50 | to that Work or Derivative Works thereof, that is intentionally
51 | submitted to Licensor for inclusion in the Work by the copyright owner
52 | or by an individual or Legal Entity authorized to submit on behalf of
53 | the copyright owner. For the purposes of this definition, "submitted"
54 | means any form of electronic, verbal, or written communication sent
55 | to the Licensor or its representatives, including but not limited to
56 | communication on electronic mailing lists, source code control systems,
57 | and issue tracking systems that are managed by, or on behalf of, the
58 | Licensor for the purpose of discussing and improving the Work, but
59 | excluding communication that is conspicuously marked or otherwise
60 | designated in writing by the copyright owner as "Not a Contribution."
61 |
62 | "Contributor" shall mean Licensor and any individual or Legal Entity
63 | on behalf of whom a Contribution has been received by Licensor and
64 | subsequently incorporated within the Work.
65 |
66 | 2. Grant of Copyright License. Subject to the terms and conditions of
67 | this License, each Contributor hereby grants to You a perpetual,
68 | worldwide, non-exclusive, no-charge, royalty-free, irrevocable
69 | copyright license to reproduce, prepare Derivative Works of,
70 | publicly display, publicly perform, sublicense, and distribute the
71 | Work and such Derivative Works in Source or Object form.
72 |
73 | 3. Grant of Patent License. Subject to the terms and conditions of
74 | this License, each Contributor hereby grants to You a perpetual,
75 | worldwide, non-exclusive, no-charge, royalty-free, irrevocable
76 | (except as stated in this section) patent license to make, have made,
77 | use, offer to sell, sell, import, and otherwise transfer the Work,
78 | where such license applies only to those patent claims licensable
79 | by such Contributor that are necessarily infringed by their
80 | Contribution(s) alone or by combination of their Contribution(s)
81 | with the Work to which such Contribution(s) was submitted. If You
82 | institute patent litigation against any entity (including a
83 | cross-claim or counterclaim in a lawsuit) alleging that the Work
84 | or a Contribution incorporated within the Work constitutes direct
85 | or contributory patent infringement, then any patent licenses
86 | granted to You under this License for that Work shall terminate
87 | as of the date such litigation is filed.
88 |
89 | 4. Redistribution. You may reproduce and distribute copies of the
90 | Work or Derivative Works thereof in any medium, with or without
91 | modifications, and in Source or Object form, provided that You
92 | meet the following conditions:
93 |
94 | (a) You must give any other recipients of the Work or
95 | Derivative Works a copy of this License; and
96 |
97 | (b) You must cause any modified files to carry prominent notices
98 | stating that You changed the files; and
99 |
100 | (c) You must retain, in the Source form of any Derivative Works
101 | that You distribute, all copyright, patent, trademark, and
102 | attribution notices from the Source form of the Work,
103 | excluding those notices that do not pertain to any part of
104 | the Derivative Works; and
105 |
106 | (d) If the Work includes a "NOTICE" text file as part of its
107 | distribution, then any Derivative Works that You distribute must
108 | include a readable copy of the attribution notices contained
109 | within such NOTICE file, excluding those notices that do not
110 | pertain to any part of the Derivative Works, in at least one
111 | of the following places: within a NOTICE text file distributed
112 | as part of the Derivative Works; within the Source form or
113 | documentation, if provided along with the Derivative Works; or,
114 | within a display generated by the Derivative Works, if and
115 | wherever such third-party notices normally appear. The contents
116 | of the NOTICE file are for informational purposes only and
117 | do not modify the License. You may add Your own attribution
118 | notices within Derivative Works that You distribute, alongside
119 | or as an addendum to the NOTICE text from the Work, provided
120 | that such additional attribution notices cannot be construed
121 | as modifying the License.
122 |
123 | You may add Your own copyright statement to Your modifications and
124 | may provide additional or different license terms and conditions
125 | for use, reproduction, or distribution of Your modifications, or
126 | for any such Derivative Works as a whole, provided Your use,
127 | reproduction, and distribution of the Work otherwise complies with
128 | the conditions stated in this License.
129 |
130 | 5. Submission of Contributions. Unless You explicitly state otherwise,
131 | any Contribution intentionally submitted for inclusion in the Work
132 | by You to the Licensor shall be under the terms and conditions of
133 | this License, without any additional terms or conditions.
134 | Notwithstanding the above, nothing herein shall supersede or modify
135 | the terms of any separate license agreement you may have executed
136 | with Licensor regarding such Contributions.
137 |
138 | 6. Trademarks. This License does not grant permission to use the trade
139 | names, trademarks, service marks, or product names of the Licensor,
140 | except as required for reasonable and customary use in describing the
141 | origin of the Work and reproducing the content of the NOTICE file.
142 |
143 | 7. Disclaimer of Warranty. Unless required by applicable law or
144 | agreed to in writing, Licensor provides the Work (and each
145 | Contributor provides its Contributions) on an "AS IS" BASIS,
146 | WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or
147 | implied, including, without limitation, any warranties or conditions
148 | of TITLE, NON-INFRINGEMENT, MERCHANTABILITY, or FITNESS FOR A
149 | PARTICULAR PURPOSE. You are solely responsible for determining the
150 | appropriateness of using or redistributing the Work and assume any
151 | risks associated with Your exercise of permissions under this License.
152 |
153 | 8. Limitation of Liability. In no event and under no legal theory,
154 | whether in tort (including negligence), contract, or otherwise,
155 | unless required by applicable law (such as deliberate and grossly
156 | negligent acts) or agreed to in writing, shall any Contributor be
157 | liable to You for damages, including any direct, indirect, special,
158 | incidental, or consequential damages of any character arising as a
159 | result of this License or out of the use or inability to use the
160 | Work (including but not limited to damages for loss of goodwill,
161 | work stoppage, computer failure or malfunction, or any and all
162 | other commercial damages or losses), even if such Contributor
163 | has been advised of the possibility of such damages.
164 |
165 | 9. Accepting Warranty or Additional Liability. While redistributing
166 | the Work or Derivative Works thereof, You may choose to offer,
167 | and charge a fee for, acceptance of support, warranty, indemnity,
168 | or other liability obligations and/or rights consistent with this
169 | License. However, in accepting such obligations, You may act only
170 | on Your own behalf and on Your sole responsibility, not on behalf
171 | of any other Contributor, and only if You agree to indemnify,
172 | defend, and hold each Contributor harmless for any liability
173 | incurred by, or claims asserted against, such Contributor by reason
174 | of your accepting any such warranty or additional liability.
175 |
176 | END OF TERMS AND CONDITIONS
177 |
178 | APPENDIX: How to apply the Apache License to your work.
179 |
180 | To apply the Apache License to your work, attach the following
181 | boilerplate notice, with the fields enclosed by brackets "[]"
182 | replaced with your own identifying information. (Don't include
183 | the brackets!) The text should be enclosed in the appropriate
184 | comment syntax for the file format. We also recommend that a
185 | file or class name and description of purpose be included on the
186 | same "printed page" as the copyright notice for easier
187 | identification within third-party archives.
188 |
189 | Copyright [yyyy] [name of copyright owner]
190 |
191 | Licensed under the Apache License, Version 2.0 (the "License");
192 | you may not use this file except in compliance with the License.
193 | You may obtain a copy of the License at
194 |
195 | http://www.apache.org/licenses/LICENSE-2.0
196 |
197 | Unless required by applicable law or agreed to in writing, software
198 | distributed under the License is distributed on an "AS IS" BASIS,
199 | WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
200 | See the License for the specific language governing permissions and
201 | limitations under the License.
202 |
--------------------------------------------------------------------------------