├── .gitignore
├── LICENSE
├── README.md
├── Rewind.sln
├── Rewind
├── App.xaml
├── App.xaml.cs
├── AssemblyInfo.cs
├── MainWindow.xaml
├── MainWindow.xaml.cs
└── Rewind.csproj
└── screens
└── poc1.png
/.gitignore:
--------------------------------------------------------------------------------
1 | ## Ignore Visual Studio temporary files, build results, and
2 | ## files generated by popular Visual Studio add-ons.
3 | ##
4 | ## Get latest from https://github.com/github/gitignore/blob/master/VisualStudio.gitignore
5 |
6 | # User-specific files
7 | *.rsuser
8 | *.suo
9 | *.user
10 | *.userosscache
11 | *.sln.docstates
12 |
13 | # User-specific files (MonoDevelop/Xamarin Studio)
14 | *.userprefs
15 |
16 | # Mono auto generated files
17 | mono_crash.*
18 |
19 | # Build results
20 | [Dd]ebug/
21 | [Dd]ebugPublic/
22 | [Rr]elease/
23 | [Rr]eleases/
24 | x64/
25 | x86/
26 | [Aa][Rr][Mm]/
27 | [Aa][Rr][Mm]64/
28 | bld/
29 | [Bb]in/
30 | [Oo]bj/
31 | [Ll]og/
32 | [Ll]ogs/
33 |
34 | # Visual Studio 2015/2017 cache/options directory
35 | .vs/
36 | # Uncomment if you have tasks that create the project's static files in wwwroot
37 | #wwwroot/
38 |
39 | # Visual Studio 2017 auto generated files
40 | Generated\ Files/
41 |
42 | # MSTest test Results
43 | [Tt]est[Rr]esult*/
44 | [Bb]uild[Ll]og.*
45 |
46 | # NUnit
47 | *.VisualState.xml
48 | TestResult.xml
49 | nunit-*.xml
50 |
51 | # Build Results of an ATL Project
52 | [Dd]ebugPS/
53 | [Rr]eleasePS/
54 | dlldata.c
55 |
56 | # Benchmark Results
57 | BenchmarkDotNet.Artifacts/
58 |
59 | # .NET Core
60 | project.lock.json
61 | project.fragment.lock.json
62 | artifacts/
63 |
64 | # StyleCop
65 | StyleCopReport.xml
66 |
67 | # Files built by Visual Studio
68 | *_i.c
69 | *_p.c
70 | *_h.h
71 | *.ilk
72 | *.meta
73 | *.obj
74 | *.iobj
75 | *.pch
76 | *.pdb
77 | *.ipdb
78 | *.pgc
79 | *.pgd
80 | *.rsp
81 | *.sbr
82 | *.tlb
83 | *.tli
84 | *.tlh
85 | *.tmp
86 | *.tmp_proj
87 | *_wpftmp.csproj
88 | *.log
89 | *.vspscc
90 | *.vssscc
91 | .builds
92 | *.pidb
93 | *.svclog
94 | *.scc
95 |
96 | # Chutzpah Test files
97 | _Chutzpah*
98 |
99 | # Visual C++ cache files
100 | ipch/
101 | *.aps
102 | *.ncb
103 | *.opendb
104 | *.opensdf
105 | *.sdf
106 | *.cachefile
107 | *.VC.db
108 | *.VC.VC.opendb
109 |
110 | # Visual Studio profiler
111 | *.psess
112 | *.vsp
113 | *.vspx
114 | *.sap
115 |
116 | # Visual Studio Trace Files
117 | *.e2e
118 |
119 | # TFS 2012 Local Workspace
120 | $tf/
121 |
122 | # Guidance Automation Toolkit
123 | *.gpState
124 |
125 | # ReSharper is a .NET coding add-in
126 | _ReSharper*/
127 | *.[Rr]e[Ss]harper
128 | *.DotSettings.user
129 |
130 | # TeamCity is a build add-in
131 | _TeamCity*
132 |
133 | # DotCover is a Code Coverage Tool
134 | *.dotCover
135 |
136 | # AxoCover is a Code Coverage Tool
137 | .axoCover/*
138 | !.axoCover/settings.json
139 |
140 | # Visual Studio code coverage results
141 | *.coverage
142 | *.coveragexml
143 |
144 | # NCrunch
145 | _NCrunch_*
146 | .*crunch*.local.xml
147 | nCrunchTemp_*
148 |
149 | # MightyMoose
150 | *.mm.*
151 | AutoTest.Net/
152 |
153 | # Web workbench (sass)
154 | .sass-cache/
155 |
156 | # Installshield output folder
157 | [Ee]xpress/
158 |
159 | # DocProject is a documentation generator add-in
160 | DocProject/buildhelp/
161 | DocProject/Help/*.HxT
162 | DocProject/Help/*.HxC
163 | DocProject/Help/*.hhc
164 | DocProject/Help/*.hhk
165 | DocProject/Help/*.hhp
166 | DocProject/Help/Html2
167 | DocProject/Help/html
168 |
169 | # Click-Once directory
170 | publish/
171 |
172 | # Publish Web Output
173 | *.[Pp]ublish.xml
174 | *.azurePubxml
175 | # Note: Comment the next line if you want to checkin your web deploy settings,
176 | # but database connection strings (with potential passwords) will be unencrypted
177 | *.pubxml
178 | *.publishproj
179 |
180 | # Microsoft Azure Web App publish settings. Comment the next line if you want to
181 | # checkin your Azure Web App publish settings, but sensitive information contained
182 | # in these scripts will be unencrypted
183 | PublishScripts/
184 |
185 | # NuGet Packages
186 | *.nupkg
187 | # NuGet Symbol Packages
188 | *.snupkg
189 | # The packages folder can be ignored because of Package Restore
190 | **/[Pp]ackages/*
191 | # except build/, which is used as an MSBuild target.
192 | !**/[Pp]ackages/build/
193 | # Uncomment if necessary however generally it will be regenerated when needed
194 | #!**/[Pp]ackages/repositories.config
195 | # NuGet v3's project.json files produces more ignorable files
196 | *.nuget.props
197 | *.nuget.targets
198 |
199 | # Microsoft Azure Build Output
200 | csx/
201 | *.build.csdef
202 |
203 | # Microsoft Azure Emulator
204 | ecf/
205 | rcf/
206 |
207 | # Windows Store app package directories and files
208 | AppPackages/
209 | BundleArtifacts/
210 | Package.StoreAssociation.xml
211 | _pkginfo.txt
212 | *.appx
213 | *.appxbundle
214 | *.appxupload
215 |
216 | # Visual Studio cache files
217 | # files ending in .cache can be ignored
218 | *.[Cc]ache
219 | # but keep track of directories ending in .cache
220 | !?*.[Cc]ache/
221 |
222 | # Others
223 | ClientBin/
224 | ~$*
225 | *~
226 | *.dbmdl
227 | *.dbproj.schemaview
228 | *.jfm
229 | *.pfx
230 | *.publishsettings
231 | orleans.codegen.cs
232 |
233 | # Including strong name files can present a security risk
234 | # (https://github.com/github/gitignore/pull/2483#issue-259490424)
235 | #*.snk
236 |
237 | # Since there are multiple workflows, uncomment next line to ignore bower_components
238 | # (https://github.com/github/gitignore/pull/1529#issuecomment-104372622)
239 | #bower_components/
240 |
241 | # RIA/Silverlight projects
242 | Generated_Code/
243 |
244 | # Backup & report files from converting an old project file
245 | # to a newer Visual Studio version. Backup files are not needed,
246 | # because we have git ;-)
247 | _UpgradeReport_Files/
248 | Backup*/
249 | UpgradeLog*.XML
250 | UpgradeLog*.htm
251 | ServiceFabricBackup/
252 | *.rptproj.bak
253 |
254 | # SQL Server files
255 | *.mdf
256 | *.ldf
257 | *.ndf
258 |
259 | # Business Intelligence projects
260 | *.rdl.data
261 | *.bim.layout
262 | *.bim_*.settings
263 | *.rptproj.rsuser
264 | *- [Bb]ackup.rdl
265 | *- [Bb]ackup ([0-9]).rdl
266 | *- [Bb]ackup ([0-9][0-9]).rdl
267 |
268 | # Microsoft Fakes
269 | FakesAssemblies/
270 |
271 | # GhostDoc plugin setting file
272 | *.GhostDoc.xml
273 |
274 | # Node.js Tools for Visual Studio
275 | .ntvs_analysis.dat
276 | node_modules/
277 |
278 | # Visual Studio 6 build log
279 | *.plg
280 |
281 | # Visual Studio 6 workspace options file
282 | *.opt
283 |
284 | # Visual Studio 6 auto-generated workspace file (contains which files were open etc.)
285 | *.vbw
286 |
287 | # Visual Studio LightSwitch build output
288 | **/*.HTMLClient/GeneratedArtifacts
289 | **/*.DesktopClient/GeneratedArtifacts
290 | **/*.DesktopClient/ModelManifest.xml
291 | **/*.Server/GeneratedArtifacts
292 | **/*.Server/ModelManifest.xml
293 | _Pvt_Extensions
294 |
295 | # Paket dependency manager
296 | .paket/paket.exe
297 | paket-files/
298 |
299 | # FAKE - F# Make
300 | .fake/
301 |
302 | # CodeRush personal settings
303 | .cr/personal
304 |
305 | # Python Tools for Visual Studio (PTVS)
306 | __pycache__/
307 | *.pyc
308 |
309 | # Cake - Uncomment if you are using it
310 | # tools/**
311 | # !tools/packages.config
312 |
313 | # Tabs Studio
314 | *.tss
315 |
316 | # Telerik's JustMock configuration file
317 | *.jmconfig
318 |
319 | # BizTalk build output
320 | *.btp.cs
321 | *.btm.cs
322 | *.odx.cs
323 | *.xsd.cs
324 |
325 | # OpenCover UI analysis results
326 | OpenCover/
327 |
328 | # Azure Stream Analytics local run output
329 | ASALocalRun/
330 |
331 | # MSBuild Binary and Structured Log
332 | *.binlog
333 |
334 | # NVidia Nsight GPU debugger configuration file
335 | *.nvuser
336 |
337 | # MFractors (Xamarin productivity tool) working folder
338 | .mfractor/
339 |
340 | # Local History for Visual Studio
341 | .localhistory/
342 |
343 | # BeatPulse healthcheck temp database
344 | healthchecksdb
345 |
346 | # Backup folder for Package Reference Convert tool in Visual Studio 2017
347 | MigrationBackup/
348 |
349 | # Ionide (cross platform F# VS Code tools) working folder
350 | .ionide/
351 | dist/
--------------------------------------------------------------------------------
/LICENSE:
--------------------------------------------------------------------------------
1 | MIT License
2 |
3 | Copyright (c) 2021 Florian Roth
4 |
5 | Permission is hereby granted, free of charge, to any person obtaining a copy
6 | of this software and associated documentation files (the "Software"), to deal
7 | in the Software without restriction, including without limitation the rights
8 | to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
9 | copies of the Software, and to permit persons to whom the Software is
10 | furnished to do so, subject to the following conditions:
11 |
12 | The above copyright notice and this permission notice shall be included in all
13 | copies or substantial portions of the Software.
14 |
15 | THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
16 | IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
17 | FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
18 | AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
19 | LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
20 | OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
21 | SOFTWARE.
22 |
--------------------------------------------------------------------------------
/README.md:
--------------------------------------------------------------------------------
1 | # Rewind
2 | Immediate Virus Infection Counter Measures
3 |
4 | ## The Idea
5 |
6 | Users that have opened a weaponized document are often aware that something is wrong with that document. In many cases they notice suspicious activity or aspects like
7 |
8 | - a command line window pops up for a fraction of a second
9 | - no contents show up after clicking "Enable Content"
10 | - a ransom note appears on the desktop
11 | - another program gets started without their interaction (e.g. browser window)
12 | - the attached document doesn't open at all (.docx.exe extensions)
13 |
14 | We can use these moments of realization to prevent further damage caused by malicious code by providing an emergency button that users can press when they believe that sh++ just hit the fan.
15 |
16 | Rewind tries to kill or undo changes that occured recently by ending all recently spawned processes and removing all recently created files of certain types, as well as removing recently modified registry keys used for persistence (e.g. RUN key entries) regardless of their actual values.
17 |
18 | This generic appreach doesn't recognize a specific type of threat but radically removes every process, file or registry key created within a very short time frame after a potential infection.
19 |
20 | ## The Effect
21 |
22 | During an infection the following things happen:
23 |
24 | - new processes spawn
25 | - executed code downloads further stages
26 | - files are written to (temporary) folders on disk
27 | - registry values are written to persist the threat
28 |
29 | By providing the user with a panic button, we can try to interfere and try to stop some of the malicious activity before it is able to cause more damage in form of:
30 |
31 | - disk encryption (Ransomware)
32 | - propagation (Worms)
33 | - dump and steal credentials (Credential Stealer)
34 | - load further stages (Beacons)
35 |
36 | ## The Side Effects
37 |
38 | There are obvious side effects of these counter measures. Since it kills all processes accessible within the user context, removes files and registry keys, it could lead to the following situation:
39 |
40 | - programs started within the selected time frame get killed (work is lost)
41 | - legitimate files written to disk get removed
42 | - program installations executed within the selected time frame may be broken
43 |
44 | **BUT:**
45 |
46 | 1. Since the time frame is rather short, we limit the effect of the measures to the most recent moments. It is unlikely that someone notices the suspicious activity and then starts to work on a Word document of Excel spreadsheet before pressing the panic button.
47 | 2. We limit the file actions to certain file types often used by second stages or dropped by malicious documents.
48 | 3. We limit the counter measures on the Registry to certain keys that are frequently used for persistence
49 |
50 | ## The Limitation
51 |
52 | All activity by Rewind is limited to the user's context. It is unable to kill important systems processes spawned within the targeted time frame.
53 |
54 | It is therefore unable to kill processes that used local privilege escalation vulnerabilities to spawn processes in a privileged context.
55 |
56 | ## Features
57 |
58 | - Kills all processes started within the last X minutes and accessible from the current user context
59 |
60 | Not yet implemented in the POC
61 | - Removes all files written to disk within the last X minutes if extension is in the predefined blacklist (.exe, .dll, .ps1,.vbs, .hta, .bat, .js)
62 | - Removes values from certain registry keys used for persitence if modified within the last X minutes
63 |
64 | ## Screenshots
65 |
66 | 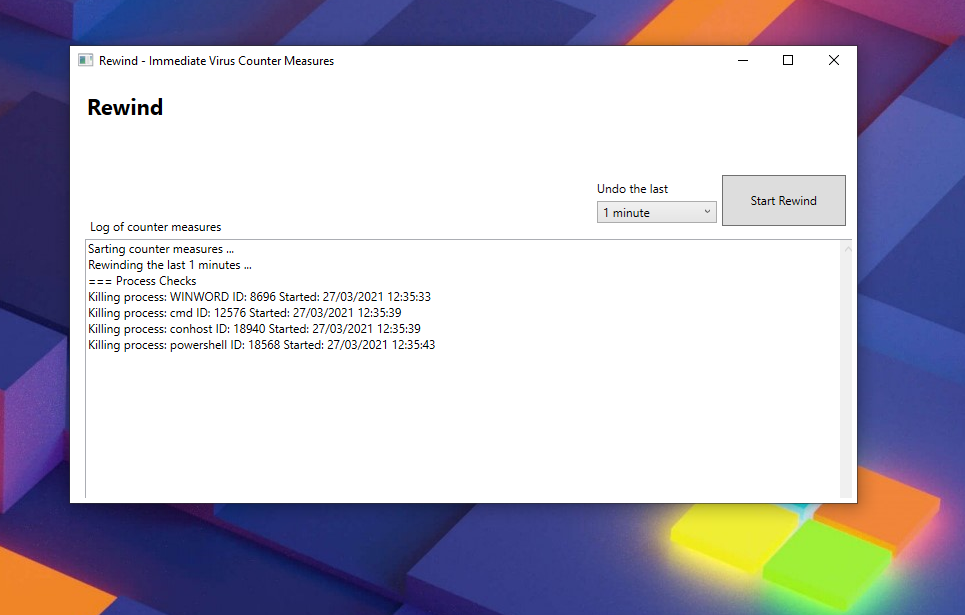
67 |
68 | ## Further Ideas
69 |
70 | - I would combine it with a "ping" (webhook, email, ticket etc.) to a local SOC or MDR provider, so that users can actively point out suspicious activity on their desktops to the analysts and they can search for threats on that endpoint within the indicated time frame (why not include the end user in the threat hunting activity?)
71 |
--------------------------------------------------------------------------------
/Rewind.sln:
--------------------------------------------------------------------------------
1 |
2 | Microsoft Visual Studio Solution File, Format Version 12.00
3 | # Visual Studio Version 16
4 | VisualStudioVersion = 16.0.30709.132
5 | MinimumVisualStudioVersion = 10.0.40219.1
6 | Project("{FAE04EC0-301F-11D3-BF4B-00C04F79EFBC}") = "Rewind", "Rewind\Rewind.csproj", "{6E3B9697-793F-4BCF-905A-3C09F29138D3}"
7 | EndProject
8 | Global
9 | GlobalSection(SolutionConfigurationPlatforms) = preSolution
10 | Debug|Any CPU = Debug|Any CPU
11 | Release|Any CPU = Release|Any CPU
12 | EndGlobalSection
13 | GlobalSection(ProjectConfigurationPlatforms) = postSolution
14 | {6E3B9697-793F-4BCF-905A-3C09F29138D3}.Debug|Any CPU.ActiveCfg = Debug|Any CPU
15 | {6E3B9697-793F-4BCF-905A-3C09F29138D3}.Debug|Any CPU.Build.0 = Debug|Any CPU
16 | {6E3B9697-793F-4BCF-905A-3C09F29138D3}.Release|Any CPU.ActiveCfg = Release|Any CPU
17 | {6E3B9697-793F-4BCF-905A-3C09F29138D3}.Release|Any CPU.Build.0 = Release|Any CPU
18 | EndGlobalSection
19 | GlobalSection(SolutionProperties) = preSolution
20 | HideSolutionNode = FALSE
21 | EndGlobalSection
22 | GlobalSection(ExtensibilityGlobals) = postSolution
23 | SolutionGuid = {B5FDB9C2-7C35-4E4B-AEDF-B8F0DB234150}
24 | EndGlobalSection
25 | EndGlobal
26 |
--------------------------------------------------------------------------------
/Rewind/App.xaml:
--------------------------------------------------------------------------------
1 |
6 |
7 |
8 |
9 |
10 |
--------------------------------------------------------------------------------
/Rewind/App.xaml.cs:
--------------------------------------------------------------------------------
1 | using System;
2 | using System.Collections.Generic;
3 | using System.Configuration;
4 | using System.Data;
5 | using System.Linq;
6 | using System.Threading.Tasks;
7 | using System.Windows;
8 |
9 | namespace Rewind
10 | {
11 | ///
12 | /// Interaction logic for App.xaml
13 | ///
14 | public partial class App : Application
15 | {
16 | }
17 | }
18 |
--------------------------------------------------------------------------------
/Rewind/AssemblyInfo.cs:
--------------------------------------------------------------------------------
1 | using System.Windows;
2 |
3 | [assembly: ThemeInfo(
4 | ResourceDictionaryLocation.None, //where theme specific resource dictionaries are located
5 | //(used if a resource is not found in the page,
6 | // or application resource dictionaries)
7 | ResourceDictionaryLocation.SourceAssembly //where the generic resource dictionary is located
8 | //(used if a resource is not found in the page,
9 | // app, or any theme specific resource dictionaries)
10 | )]
11 |
--------------------------------------------------------------------------------
/Rewind/MainWindow.xaml:
--------------------------------------------------------------------------------
1 |
9 |
10 |
11 |
12 |
13 |
14 |
15 |
16 |
17 |
18 |
19 | 1 minute
20 | 2 minutes
21 | 5 minutes
22 |
23 |
24 |
25 |
26 |
27 |
28 |
29 |
--------------------------------------------------------------------------------
/Rewind/MainWindow.xaml.cs:
--------------------------------------------------------------------------------
1 | using System;
2 | using System.Collections.Generic;
3 | using System.Linq;
4 | using System.Text;
5 | using System.Threading.Tasks;
6 | using System.Windows;
7 | using System.Windows.Controls;
8 | using System.Windows.Data;
9 | using System.Windows.Documents;
10 | using System.Windows.Input;
11 | using System.Windows.Media;
12 | using System.Windows.Media.Imaging;
13 | using System.Windows.Navigation;
14 | using System.Windows.Shapes;
15 | using System.Diagnostics;
16 |
17 | namespace Rewind
18 | {
19 | ///
20 | /// Interaction logic for MainWindow.xaml
21 | ///
22 | public partial class MainWindow : Window
23 | {
24 | public MainWindow()
25 | {
26 | InitializeComponent();
27 | }
28 |
29 | private void Start_Rewind(object sender, RoutedEventArgs e)
30 | {
31 | TextOutput.Text += String.Format("Starting countermeasures ...\n");
32 |
33 | ComboBoxItem typeItem = (ComboBoxItem)ComboTimeFrame.SelectedItem;
34 | var TimeFrame = typeItem.Content.ToString();
35 | TextOutput.Text += String.Format("Rewinding the last {0} minutes ...\n", TimeFrame[0]);
36 | int NumMinutes = Int32.Parse(TimeFrame[0].ToString());
37 |
38 | // ##################################################################################################################
39 | // Process Checks and Kills -----------------------------------------------------------------------------------------
40 | TextOutput.Text += String.Format("=== Process Checks\n");
41 | // Exceptions
42 | List exceptions = new List(new string[] { "Rewind", "msvsmon", "ScriptedSandbox64" });
43 | var allProcesses = Process.GetProcesses();
44 | var numberKilled = 0;
45 | foreach (Process proc in allProcesses)
46 | {
47 | try
48 | {
49 | //TextOutput.Text += String.Format("Process: {0} ID: {1} Started: {2}\n", theprocess.ProcessName, theprocess.Id, theprocess.StartTime);
50 | // Kill all processes younger than 5 minutes and accessible in this user context
51 | if (proc.StartTime.AddMinutes(NumMinutes) > DateTime.Now)
52 | {
53 | if (!exceptions.Any(proc.ProcessName.Contains)) {
54 | proc.Kill(true);
55 | if (proc.HasExited)
56 | {
57 | TextOutput.Text += String.Format("Killing process: {0} ID: {1} Started: {2}\n", proc.ProcessName, proc.Id, proc.StartTime);
58 | } else
59 | {
60 | TextOutput.Text += String.Format("Killing process FAILED: {0} ID: {1} Started: {2}\n", proc.ProcessName, proc.Id, proc.StartTime);
61 | }
62 | numberKilled += 1;
63 | }
64 | }
65 | }
66 | catch (System.ComponentModel.Win32Exception)
67 | {
68 | // pass
69 | }
70 | }
71 | // not a single process killed
72 | if (numberKilled == 0)
73 | {
74 | TextOutput.Text += String.Format("Not a single process has been killed by Rewind\n");
75 | }
76 |
77 |
78 | }
79 | }
80 | }
81 |
--------------------------------------------------------------------------------
/Rewind/Rewind.csproj:
--------------------------------------------------------------------------------
1 |
2 |
3 |
4 | WinExe
5 | netcoreapp3.1
6 | true
7 | 0.1.0
8 |
9 |
10 |
11 |
--------------------------------------------------------------------------------
/screens/poc1.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/Neo23x0/Rewind/2c5f756e135dfd11ae8cc0f351fc0d2faf765703/screens/poc1.png
--------------------------------------------------------------------------------