├── .gitattributes
├── .gitignore
├── roles
├── jenkins
│ ├── templates
│ │ ├── jenkins.lastExecVersion
│ │ ├── set_jnlp_port.groovy
│ │ ├── basic-security.groovy
│ │ └── proxy.groovy
│ ├── tasks
│ │ ├── install_packages.yml
│ │ ├── plugins.yml
│ │ ├── main.yml
│ │ └── settings.yml
│ └── vars
│ │ └── jenkins.yml
├── placeflag
│ ├── templates
│ │ ├── flag1.txt
│ │ ├── flag2.txt
│ │ ├── flag3.txt
│ │ └── flag4.txt
│ └── tasks
│ │ └── main.yml
├── java
│ ├── defaults
│ │ └── main.yml
│ └── tasks
│ │ └── main.yml
├── impacket
│ └── tasks
│ │ └── main.yml
├── joindomain
│ └── tasks
│ │ ├── enable_rdp.yml
│ │ ├── firewall_3389.yml
│ │ ├── firewall_445.yml
│ │ └── main.yml
├── tomcat
│ ├── tasks
│ │ ├── firewall_8080.yml
│ │ ├── firewall_8009.yml
│ │ └── main.yml
│ └── templates
│ │ ├── context.xml
│ │ ├── tomcat-users.xml
│ │ └── server.xml
├── private
│ └── tasks
│ │ └── main.yml
├── mssql
│ ├── tasks
│ │ ├── accounts.yml
│ │ ├── pre_reqs.yml
│ │ ├── main.yml
│ │ ├── firewall.yml
│ │ ├── configure.yml
│ │ ├── prepare_install.yml
│ │ └── install.yml
│ └── defaults
│ │ └── main.yml
├── pentest
│ └── tasks
│ │ └── main.yml
├── docker
│ └── tasks
│ │ └── main.yml
└── promotedc
│ └── tasks
│ ├── main.yml
│ └── accounts.yml
├── anpt
└── bli_2018.jpg
├── ansible
├── pentest.yml
├── goku.yml
├── dcpromo.yml
└── dcpromo2.yml
├── pentest.yml
├── ssh
├── capsulecorp_id_rsa.pub
└── capsulecorp_id_rsa
├── kowalski.yml
├── raditz.yml
├── vegeta.yml
├── tien.yml
├── skipper.yml
├── private.yml
├── rico.yml
├── dvwa.yml
├── Vagrantfile
└── README.md
/.gitattributes:
--------------------------------------------------------------------------------
1 | *.groovy linguist-detectable=false
2 |
--------------------------------------------------------------------------------
/.gitignore:
--------------------------------------------------------------------------------
1 | .DS_Store
2 | /tmp
3 | /.vagrant
4 | /.git
5 |
--------------------------------------------------------------------------------
/roles/jenkins/templates/jenkins.lastExecVersion:
--------------------------------------------------------------------------------
1 | 2.16
2 |
--------------------------------------------------------------------------------
/roles/placeflag/templates/flag1.txt:
--------------------------------------------------------------------------------
1 | wvyo9zdZskXJhOfqYejWB8ERmgIUHrpC
2 |
--------------------------------------------------------------------------------
/roles/placeflag/templates/flag2.txt:
--------------------------------------------------------------------------------
1 | TMYRDQVmhov0ulOngKa5N8CSPHcGwUpy
2 |
--------------------------------------------------------------------------------
/roles/placeflag/templates/flag3.txt:
--------------------------------------------------------------------------------
1 | FzqUDLeiQ6Kjdk5wyg2rYcHtaN1slW40
2 |
--------------------------------------------------------------------------------
/roles/placeflag/templates/flag4.txt:
--------------------------------------------------------------------------------
1 | DQVHcGwUpymhOa5N8CTMYRngKSPov0ul
2 |
--------------------------------------------------------------------------------
/anpt/bli_2018.jpg:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/NetPenguins/pentest-lab/HEAD/anpt/bli_2018.jpg
--------------------------------------------------------------------------------
/roles/java/defaults/main.yml:
--------------------------------------------------------------------------------
1 | ---
2 | jdk_package: jdk8
3 | java_major_version: 8.0
4 | java_minor_version: 242
5 |
--------------------------------------------------------------------------------
/roles/impacket/tasks/main.yml:
--------------------------------------------------------------------------------
1 | ---
2 | - name: Pip install impacket
3 | become: true
4 | pip:
5 | name: impacket
6 |
7 |
--------------------------------------------------------------------------------
/roles/placeflag/tasks/main.yml:
--------------------------------------------------------------------------------
1 | ---
2 | - name: Place exercise flag
3 | template:
4 | src: "{{ anpt_flag }}"
5 | dest: "C:\\flag.txt"
6 | register: anpt_flag_placed
7 |
--------------------------------------------------------------------------------
/ansible/pentest.yml:
--------------------------------------------------------------------------------
1 | ---
2 | - hosts: pentest
3 | become: false
4 | roles:
5 | - role: crackmapexec
6 | - role: nmap
7 | - role: rvm
8 | - role: metasploit
9 |
10 |
--------------------------------------------------------------------------------
/roles/joindomain/tasks/enable_rdp.yml:
--------------------------------------------------------------------------------
1 | ---
2 | - name: Enable Remote Desktop
3 | raw: reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f
4 |
--------------------------------------------------------------------------------
/pentest.yml:
--------------------------------------------------------------------------------
1 | ---
2 | - hosts: pentest
3 | become: false
4 | roles:
5 | # - role: crackmapexec
6 | # - role: nmap
7 | # - role: rvm
8 | # - role: metasploit
9 | - role: pentest
10 | # - role: xrdp
11 | - role: impacket
12 |
13 |
--------------------------------------------------------------------------------
/roles/joindomain/tasks/firewall_3389.yml:
--------------------------------------------------------------------------------
1 | ---
2 | - name: Open up port 3389 on Windows firewall
3 | win_firewall_rule:
4 | name: RDP
5 | localport: 3389
6 | action: allow
7 | direction: in
8 | protocol: tcp
9 | state: present
10 | enabled: yes
11 |
--------------------------------------------------------------------------------
/roles/joindomain/tasks/firewall_445.yml:
--------------------------------------------------------------------------------
1 | ---
2 | - name: Open up port 445 on Windows firewall
3 | win_firewall_rule:
4 | name: CIFS
5 | localport: 445
6 | action: allow
7 | direction: in
8 | protocol: tcp
9 | state: present
10 | enabled: yes
11 |
--------------------------------------------------------------------------------
/roles/tomcat/tasks/firewall_8080.yml:
--------------------------------------------------------------------------------
1 | ---
2 | - name: Open up port 8080 on Windows firewall
3 | win_firewall_rule:
4 | name: Tomcat
5 | localport: 8080
6 | action: allow
7 | direction: in
8 | protocol: tcp
9 | state: present
10 | enabled: yes
11 |
--------------------------------------------------------------------------------
/roles/jenkins/templates/set_jnlp_port.groovy:
--------------------------------------------------------------------------------
1 |
2 | import hudson.model.*;
3 | import jenkins.model.*;
4 |
5 |
6 | Thread.start {
7 | sleep 10000
8 | println "--> setting agent port for jnlp"
9 | Jenkins.instance.setSlaveAgentPort({{jenkins_jnlp_port}})
10 | }
11 |
--------------------------------------------------------------------------------
/roles/tomcat/tasks/firewall_8009.yml:
--------------------------------------------------------------------------------
1 | ---
2 | - name: Open up port 8009 on Windows firewall
3 | win_firewall_rule:
4 | name: Tomcat AJP
5 | localport: 8009
6 | action: allow
7 | direction: in
8 | protocol: tcp
9 | state: present
10 | enabled: yes
11 |
--------------------------------------------------------------------------------
/roles/tomcat/templates/context.xml:
--------------------------------------------------------------------------------
1 |
2 |
3 |
4 |
5 |
--------------------------------------------------------------------------------
/roles/private/tasks/main.yml:
--------------------------------------------------------------------------------
1 | ---
2 | - name: Set the logon user to a domain account
3 | community.windows.win_auto_logon:
4 | username: WADDLECORP\private
5 | password: PasW0rd543#
6 |
7 | - name: Set Service startup mode to Automatic
8 | ansible.windows.win_service:
9 | name: spooler
10 | start_mode: auto
11 | state: started
12 |
13 |
--------------------------------------------------------------------------------
/ansible/goku.yml:
--------------------------------------------------------------------------------
1 | ---
2 | - hosts: skipper
3 | gather_facts: True
4 | vars:
5 | dc_address: 172.28.128.100
6 | dc_netmask_cidr: 24
7 | dc_gateway: 172.28.128.2
8 | dc_hostname: skipper
9 | domain_Name: waddlecorp.local
10 | ansible_winrm_transport: plaintext
11 | ansible_winrm_scheme: http
12 | roles:
13 | - role: promotedc
14 |
--------------------------------------------------------------------------------
/ansible/dcpromo.yml:
--------------------------------------------------------------------------------
1 | - hosts: skipper
2 | gather_facts: no
3 | tasks:
4 | - win_domain_controller:
5 | dns_domain_name: waddlecorp.local
6 | domain_admin_user: skipper@waddlecorp.local
7 | domain_admin_password: PassW0rd432!
8 | safe_mode_password: PassW0rd432!
9 | state: domain_controller
10 | log_path: c:\capsulecorp_win_domain_controller.txt
11 |
--------------------------------------------------------------------------------
/ssh/capsulecorp_id_rsa.pub:
--------------------------------------------------------------------------------
1 | ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDFf6YidKyHViUNpxxMcCXmryVzBcryOiXyn8NizrpfliQJsxGlv0Q/9aCA5fYMwxelFGdFEcnYIRVQ4jPE4mpfFlcbtqOhss6nXgpP3yv4F04yHzX8WiXr7v2v2SWD3qITmloMBrYwuI00OFMiIZDAh8G2/xvDc1ipLlvmw6WBgeV8VHuss8Hi9/VOn8YxHkIh4EHS5EpTs7M3bDdXn2pedqsNEtX6RWk10i5YXmVBfxEe0D0QNLmRz980jLyiW16WJs/DQvbqebRCFYCHAQXNIRDKm+m84JIYe1fXejaNmA7PBrwvmJWKGiWdSX+3++CGkZ7R3y42P/IUyeWV3mCh
2 |
--------------------------------------------------------------------------------
/roles/mssql/tasks/accounts.yml:
--------------------------------------------------------------------------------
1 | ---
2 | # Setup service accounts
3 | - name: Ensure user sa is present
4 | win_user:
5 | name: sa
6 | password: Password1
7 | state: present
8 | groups:
9 | - Administrators
10 |
11 | - name: Ensure user sqlagent is present
12 | win_user:
13 | name: sqlagent
14 | password: Password2
15 | state: present
16 | groups:
17 | - Administrators
18 |
--------------------------------------------------------------------------------
/roles/jenkins/tasks/install_packages.yml:
--------------------------------------------------------------------------------
1 | ---
2 | - name: Ensure cUrl is installed.
3 | win_chocolatey:
4 | name: curl
5 | state: present
6 |
7 | - name: Ensure Java is installed
8 | win_chocolatey:
9 | name: jre8
10 | state: present
11 |
12 | - name: Ensure Jenkins is installed.
13 | win_chocolatey:
14 | name: jenkins
15 | state: present
16 | register: jenkins_install_package_win
17 |
--------------------------------------------------------------------------------
/roles/jenkins/vars/jenkins.yml:
--------------------------------------------------------------------------------
1 | ---
2 | jenkins_hostname: localhost
3 | jenkins_home: "C:\\Program Files (x86)\\Jenkins"
4 | jenkins_http_port_param: --httpPort
5 | jenkins_http_port: 8080
6 | jenkins_admin_username: admin
7 | jenkins_admin_password: admin
8 | jenkins_java_options: "-Djenkins.install.runSetupWizard=false"
9 | jenkins_url_prefix: ""
10 | jenkins_jar_location: "{{ jenkins_home }}\\jenkins-cli.jar"
11 | jenkins_plugins: []
12 |
--------------------------------------------------------------------------------
/kowalski.yml:
--------------------------------------------------------------------------------
1 | ---
2 | - hosts: kowalski
3 | gather_facts: True
4 | vars:
5 | ansible_winrm_transport: plaintext
6 | ansible_winrm_scheme: http
7 | waddlecorp_domain_hostname: "kowalski"
8 | ethernet_adapter: "Ethernet 2"
9 | tasks:
10 | - name: Activate windows
11 | win_shell: cscript slmgr.vbs /rearm
12 | args:
13 | chdir: C:\Windows\System32\
14 | roles:
15 | - role: mssql
16 | - role: joindomain
17 |
--------------------------------------------------------------------------------
/raditz.yml:
--------------------------------------------------------------------------------
1 | ---
2 | - hosts: raditz
3 | gather_facts: True
4 | vars:
5 | ansible_winrm_transport: plaintext
6 | ansible_winrm_scheme: http
7 | capsulecorp_domain_hostname: "raditz"
8 | ethernet_adapter: "Ethernet 2"
9 | anpt_flag: "flag3.txt"
10 | tasks:
11 | - name: Activate windows
12 | win_shell: cscript slmgr.vbs /rearm
13 | args:
14 | chdir: C:\Windows\System32\
15 | roles:
16 | #- role: joindomain
17 | - role: placeflag
18 |
--------------------------------------------------------------------------------
/vegeta.yml:
--------------------------------------------------------------------------------
1 | ---
2 | - hosts: vegeta
3 | gather_facts: True
4 | vars:
5 | ansible_winrm_transport: plaintext
6 | ansible_winrm_scheme: http
7 | waddlecorp_domain_hostname: "vegeta"
8 | jenkins_hostname: vegeta.waddlecorp.local
9 | ethernet_adapter: "Ethernet 2"
10 | tasks:
11 | - name: Activate windows
12 | win_shell: cscript slmgr.vbs /rearm
13 | args:
14 | chdir: C:\Windows\System32\
15 | roles:
16 | - role: jenkins
17 | - role: joindomain
18 |
--------------------------------------------------------------------------------
/tien.yml:
--------------------------------------------------------------------------------
1 | ---
2 | - hosts: tien
3 | gather_facts: False
4 | vars:
5 | ansible_winrm_transport: plaintext
6 | ansible_winrm_scheme: http
7 | waddlecorp_domain_hostname: "tien"
8 | ethernet_adapter: "Local Area Connection 2"
9 | ansible_user: vagrant
10 | ansible_password: vagrant
11 | ansible_connection: winrm
12 | ansible_winrm_server_cert_validation: ignore
13 | anpt_flag: "flag2.txt"
14 | roles:
15 | - role: joindomain
16 | - role: placeflag
17 |
--------------------------------------------------------------------------------
/skipper.yml:
--------------------------------------------------------------------------------
1 | ---
2 | - hosts: skipper
3 | gather_facts: True
4 | vars:
5 | dc_address: 172.28.128.100
6 | dc_netmask_cidr: 24
7 | dc_gateway: 172.28.128.2
8 | dc_hostname: skipper
9 | domain_Name: waddlecorp.local
10 | ansible_winrm_transport: plaintext
11 | ansible_winrm_scheme: http
12 | tasks:
13 | - name: Activate windows
14 | win_shell: cscript slmgr.vbs /rearm
15 | args:
16 | chdir: C:\Windows\System32\
17 | roles:
18 | - role: promotedc
19 |
--------------------------------------------------------------------------------
/private.yml:
--------------------------------------------------------------------------------
1 | ---
2 | - hosts: private
3 | gather_facts: True
4 | vars:
5 | ansible_winrm_transport: plaintext
6 | ansible_winrm_scheme: http
7 | waddlecorp_domain_hostname: "private"
8 | ethernet_adapter: "Ethernet 2"
9 | anpt_flag: "flag4.txt"
10 | tasks:
11 | - name: Activate windows
12 | win_shell: cscript slmgr.vbs /rearm
13 | args:
14 | chdir: C:\Windows\System32\
15 | roles:
16 | - role: private
17 | - role: placeflag
18 | - role: joindomain
19 |
--------------------------------------------------------------------------------
/rico.yml:
--------------------------------------------------------------------------------
1 | ---
2 | - hosts: trunks
3 | gather_facts: True
4 | vars:
5 | ansible_winrm_transport: plaintext
6 | ansible_winrm_scheme: http
7 | waddlecorp_domain_hostname: "trunks"
8 | ethernet_adapter: "Ethernet 2"
9 | anpt_flag: "flag1.txt"
10 | tasks:
11 | - name: Activate windows
12 | win_shell: cscript slmgr.vbs /rearm
13 | args:
14 | chdir: C:\Windows\System32\
15 | roles:
16 | - role: java
17 | - role: tomcat
18 | - role: placeflag
19 | - role: joindomain
20 |
--------------------------------------------------------------------------------
/roles/java/tasks/main.yml:
--------------------------------------------------------------------------------
1 | ---
2 | - name: Set Java_home
3 | win_environment:
4 | state: present
5 | name: JAVA_HOME
6 | value: 'c:\program files\java\jdk1.8.0_211'
7 | level: machine
8 | register: java_home
9 |
10 | - name: Add Java to path
11 | win_path:
12 | elements:
13 | - 'c:\program files\java\jdk1.8.0_211\bin'
14 | when: java_home.changed
15 |
16 | - name: Install Java JDK
17 | win_chocolatey:
18 | name: jdk8
19 | state: present
20 | when: java_home.changed
21 |
22 |
--------------------------------------------------------------------------------
/roles/jenkins/templates/basic-security.groovy:
--------------------------------------------------------------------------------
1 | #!groovy
2 | import hudson.security.*
3 | import jenkins.model.*
4 |
5 | def instance = Jenkins.getInstance()
6 |
7 | println "--> creating local user 'admin'"
8 |
9 | def hudsonRealm = new HudsonPrivateSecurityRealm(false)
10 | hudsonRealm.createAccount('{{ jenkins_admin_username }}', '{{ jenkins_admin_password }}')
11 | instance.setSecurityRealm(hudsonRealm)
12 |
13 | def strategy = new FullControlOnceLoggedInAuthorizationStrategy()
14 | instance.setAuthorizationStrategy(strategy)
15 | instance.save()
16 |
--------------------------------------------------------------------------------
/roles/tomcat/templates/tomcat-users.xml:
--------------------------------------------------------------------------------
1 |
2 |
3 |
7 |
8 |
9 |
10 |
11 |
12 |
13 |
14 |
15 |
16 |
--------------------------------------------------------------------------------
/roles/jenkins/templates/proxy.groovy:
--------------------------------------------------------------------------------
1 | mport jenkins.model.*
2 | import hudson.*
3 |
4 | def instance = Jenkins.getInstance()
5 | // Use Corporate HPE proxy link.
6 | def proxy_name = "{{ jenkins_web_proxy }}"
7 | def proxy_port = {{ jenkins_web_proxy_port }}
8 |
9 | def proxy = instance.proxy
10 |
11 | if ( proxy == null )
12 | {
13 | proxy = new ProxyConfiguration(proxy_name, proxy_port)
14 | instance.proxy = proxy
15 | }
16 | else
17 | {
18 | proxy.name = proxy_name
19 | proxy.port = proxy_port
20 | }
21 |
22 | println('proxy.groovy -- Proxy set to ' + proxy_name + ':' + proxy_port)
23 | instance.save()
24 |
--------------------------------------------------------------------------------
/roles/mssql/tasks/pre_reqs.yml:
--------------------------------------------------------------------------------
1 | ---
2 | # Setup SQL Server Pre-Reqs
3 | - name: Windows | Install .NET Framework Core
4 | win_feature:
5 | name: NET-Framework-Core
6 | state: present
7 |
8 | - name: Windows | Install .NET Framework 3.5
9 | win_feature:
10 | name: NET-Framework-Features
11 | state: present
12 |
13 | - name: Windows | Install .NET Framework 4.5 Features
14 | win_feature:
15 | name: NET-Framework-45-Features
16 | state: present
17 | include_sub_features: True
18 |
19 | - name: Windows | Install Windows Process Activation Service
20 | win_feature:
21 | name: WAS
22 | state: present
23 | include_sub_features: True
24 |
--------------------------------------------------------------------------------
/roles/joindomain/tasks/main.yml:
--------------------------------------------------------------------------------
1 | ---
2 | - name: Point dns to Skipper
3 | win_dns_client:
4 | adapter_names: "{{ ethernet_adapter }}"
5 | ipv4_addresses:
6 | - 172.28.128.100
7 | - 8.8.8.8
8 | register: dns_setup
9 |
10 | # Make sure RDP is on
11 | - include: enable_rdp.yml
12 |
13 | # Setup the firewall
14 | - include: firewall_445.yml
15 |
16 | - include: firewall_3389.yml
17 |
18 | - name: Join the waddlecorp.local domain
19 | win_domain_membership:
20 | dns_domain_name: waddlecorp.local
21 | hostname: "{{ waddlecorp_domain_hostname }}"
22 | domain_admin_user: skipper@waddlecorp.local
23 | domain_admin_password: PassW0rd432!
24 | state: domain
25 | register: domain_state
26 |
27 | - name: Reboot the server
28 | raw: shutdown /r
29 |
30 |
--------------------------------------------------------------------------------
/roles/pentest/tasks/main.yml:
--------------------------------------------------------------------------------
1 | ---
2 | - name: Update packages
3 | become: true
4 | shell:
5 | cmd: apt update
6 |
7 | - name: Initialize msfdb
8 | become: true
9 | shell:
10 | cmd: msfdb init
11 |
12 | - name: Setup Microsoft keys
13 | become: true
14 | shell:
15 | cmd: wget -q https://packages.microsoft.com/keys/microsoft.asc -O- | apt-key add -
16 |
17 | - name: Add repository for VSCode
18 | become: true
19 | shell:
20 | cmd: echo "deb [arch=amd64] https://packages.microsoft.com/repos/vscode stable main" | tee /etc/apt/sources.list.d/vscode.list
21 |
22 | - name: Install VSCode
23 | become: true
24 | shell:
25 | cmd: apt update -y && apt install code -y
26 |
27 | - name: Install Jupyter NoteBook
28 | become: true
29 | shell:
30 | cmd: apt install jupyter -y
31 |
--------------------------------------------------------------------------------
/roles/jenkins/tasks/plugins.yml:
--------------------------------------------------------------------------------
1 | ---
2 | # Jenkins doesn't allow updates via CLI, though that is required before plugins
3 | # can be installed via CLI. See: https://gist.github.com/rowan-m/1026918
4 | - name: Create Jenkins updates folder.
5 | win_file:
6 | path: "{{ jenkins_home }}/updates"
7 | state: directory
8 | register: jenkins_plugins_folder_create
9 |
10 | # Install plugins using the CLI. Should write a ps script to make things a bit cleaner...
11 | # TODO: Need to investigate how to use ssh keys instead of user/password
12 | - name: Install Jenkins plugins using password.
13 | raw: >
14 | java -jar {{ jenkins_jar_location }} -s http://{{ jenkins_hostname }}:{{ jenkins_http_port }}{{ jenkins_url_prefix | default('') }}/
15 | install-plugin {{ item }}
16 | --username {{ jenkins_admin_username }}
17 | --password {{ jenkins_admin_password }}
18 | with_items: "{{ jenkins_plugins }}"
19 | notify: restart jenkins
20 |
--------------------------------------------------------------------------------
/roles/docker/tasks/main.yml:
--------------------------------------------------------------------------------
1 | ---
2 | - name: Install Dependencies
3 | apt:
4 | name: "{{item}}"
5 | state: present
6 | update_cache: yes
7 | loop:
8 | - apt-transport-https
9 | - ca-certificates
10 | - curl
11 | - software-properties-common
12 | - gnupg-agent
13 | - name: Add GPG key
14 | apt_key:
15 | url: https://download.docker.com/linux/ubuntu/gpg
16 | state: present
17 | - name: Add Docker repository
18 | apt_repository:
19 | repo: "deb [arch=amd64] https://download.docker.com/linux/ubuntu bionic stable"
20 | state: present
21 | - name: Install Docker
22 | apt:
23 | name: "{{item}}"
24 | state: latest
25 | update_cache: yes
26 | loop:
27 | - docker-ce
28 | - docker-ce-cli
29 | - containerd.io
30 | - name: Check docker started
31 | service:
32 | name: docker
33 | state: started
34 | enabled: yes
35 | - name: Run DVWA in docker
36 | shell: docker run --rm -it -p 80:80 vulnerables/web-dvwa
37 |
38 |
--------------------------------------------------------------------------------
/roles/mssql/tasks/main.yml:
--------------------------------------------------------------------------------
1 | ---
2 | # Load required powershell modules
3 | - name: Powershell | Check for SQLServer DSC Powershell module
4 | win_psmodule:
5 | name: SQLServerDsc
6 | state: present
7 |
8 | - name: Powershell | Check for Storage DSC Powershell module
9 | win_psmodule:
10 | name: StorageDsc
11 | state: present
12 |
13 | - name: Powershell | Check for ServerManager Powershell module
14 | win_psmodule:
15 | name: ServerManager
16 | state: present
17 |
18 | - name: Powershell | Ensure that DBA Tools module is present
19 | win_psmodule:
20 | name: dbatools
21 | state: present
22 |
23 | - name: Powershell | Check for xNetworking Powershell module
24 | win_psmodule:
25 | name: xNetworking
26 | state: present
27 | register: powershell_modules
28 |
29 | - include: pre_reqs.yml
30 | when: powershell_modules.changed
31 |
32 | - include: accounts.yml
33 | - include: prepare_install.yml
34 | - include: install.yml
35 | - include: firewall.yml
36 | #- include: configure.yml
37 |
--------------------------------------------------------------------------------
/roles/jenkins/tasks/main.yml:
--------------------------------------------------------------------------------
1 | ---
2 | # Load up the vars file
3 | - name: Include variables
4 | include_vars: "jenkins.yml"
5 |
6 | # Setup/Install tasks.
7 | - include: install_packages.yml
8 |
9 | # Configure Jenkins init settings.
10 | - include: settings.yml
11 | when: jenkins_install_package_win.changed
12 |
13 | # Make sure Jenkins starts and configures
14 | - name: Ensure Jenkins starts, then configure Jenkins.
15 | win_service: name=jenkins state=started enabled=yes
16 | when: jenkins_install_package_win.changed
17 |
18 | - name: Get the jenkins-cli jarfile from the Jenkins server.
19 | win_get_url:
20 | url: "http://{{ jenkins_hostname }}:{{ jenkins_http_port }}{{ jenkins_url_prefix }}/jnlpJars/jenkins-cli.jar"
21 | dest: "{{ jenkins_jar_location }}"
22 | when: jenkins_install_package_win.changed
23 |
24 | # Update Jenkins and install configured plugins.
25 | - include: plugins.yml
26 | when: jenkins_install_package_win.changed
27 |
28 | #and finaly restart jenkins
29 | - name: Ensure Jenkins is re-started.
30 | win_service: name=jenkins state=restarted enabled=yes
31 | when: jenkins_install_package_win.changed
32 |
--------------------------------------------------------------------------------
/roles/promotedc/tasks/main.yml:
--------------------------------------------------------------------------------
1 | ---
2 | - name: Change hostname to skipper
3 | win_hostname:
4 | name: skipper
5 |
6 | - name: Install Active Directory Services
7 | win_feature: >
8 | name=AD-Domain-Services
9 | include_management_tools=yes
10 | include_sub_features=yes
11 | state=present
12 |
13 | - name: Promote skipper to domain controller
14 | win_domain:
15 | create_dns_delegation: no
16 | dns_domain_name: waddlecorp.local
17 | domain_netbios_name: WADDLECORP
18 | safe_mode_password: PassW0rd432!
19 | register: domain_install
20 |
21 | - name: Reboot after promotion and wait for "Applying computer settings" to finish
22 | win_reboot:
23 | test_command: 'exit (Get-Service -Name Netlogon).Status -ne "Running"'
24 | post_reboot_delay: 200
25 | when: domain_install.reboot_required
26 |
27 | - name: Set DA user account information
28 | win_domain_user:
29 | name: skipper
30 | firstname: Skipper
31 | password: PassW0rd432!
32 | state: present
33 | groups:
34 | - Domain Admins
35 |
36 | - include: accounts.yml
37 |
38 |
--------------------------------------------------------------------------------
/dvwa.yml:
--------------------------------------------------------------------------------
1 | ---
2 | - hosts: dvwa
3 | become: true
4 | # tasks:
5 | # - name: Install Dependencies
6 | # apt:
7 | # name: "{{item}}"
8 | # state: present
9 | # update_cache: yes
10 | # loop:
11 | # - apt-transport-https
12 | # - ca-certificates
13 | # - curl
14 | # - software-properties-common
15 | # - gnupg-agent
16 | # - name: Add GPG key
17 | # apt_key:
18 | # url: https://download.docker.com/linux/ubuntu/gpg
19 | # state: present
20 | # - name: Add Docker repository
21 | # apt_repository:
22 | # repo: "deb [arch=amd64] https://download.docker.com/linux/ubuntu bionic stable"
23 | # state: present
24 | # - name: Install Docker
25 | # apt:
26 | # name: "{{item}}"
27 | # state: latest
28 | # update_cache: yes
29 | # loop:
30 | # - docker-ce
31 | # - docker-ce-cli
32 | # - containerd.io
33 | # - name: Check docker started
34 | # service:
35 | # name: docker
36 | # state: started
37 | # enabled: yes
38 | roles:
39 | - role: docker
40 |
41 |
--------------------------------------------------------------------------------
/roles/mssql/tasks/firewall.yml:
--------------------------------------------------------------------------------
1 | ---
2 | # Firewall configuration
3 | - name: Firewall | Allow Database Engine for instance
4 | win_dsc:
5 | resource_name: xFirewall
6 | Name: "SQL Server Database Engine instance {{ mssql_instance_name }}"
7 | Program: sqlservr.exe
8 | Ensure: present
9 | Enabled: True
10 | Profile: "Domain"
11 | Direction: "Inbound"
12 | Action: Allow
13 | Description: "Allows the Database Engine to access the network"
14 | tags: configure_firewall
15 |
16 | - name: Firewall | Allow SQLBrowser for instance
17 | win_dsc:
18 | resource_name: xFirewall
19 | Name: "SQL Server Browser instance {{ mssql_instance_name }}"
20 | Service: SQLBrowser
21 | Ensure: present
22 | Enabled: True
23 | Profile: "Domain"
24 | Direction: "Inbound"
25 | Action: Allow
26 | Description: "Allows the SQL Server Browser to access the network"
27 | tags: configure_firewall
28 |
29 | - name: Open up port 1433 on Windows firewall
30 | win_firewall_rule:
31 | name: MSSQL
32 | localport: 1433
33 | action: allow
34 | direction: in
35 | protocol: tcp
36 | state: present
37 | enabled: yes
38 |
--------------------------------------------------------------------------------
/roles/jenkins/tasks/settings.yml:
--------------------------------------------------------------------------------
1 | ---
2 | - name: bypass the security wizard
3 | template:
4 | src: jenkins.lastExecVersion
5 | dest: "{{ jenkins_home }}/jenkins.install.InstallUtil.lastExecVersion"
6 | register: jenkins_init
7 |
8 | - name: Create custom init scripts directory.
9 | win_file:
10 | path: "{{ jenkins_home }}/init.groovy.d"
11 | state: directory
12 |
13 | - name: Configure Jenkins default users.
14 | template:
15 | src: basic-security.groovy
16 | dest: "{{ jenkins_home }}/init.groovy.d/basic-security.groovy"
17 |
18 | - name: Set JNLP port for CLI access
19 | template:
20 | src: set_jnlp_port.groovy
21 | dest: "{{ jenkins_home }}/init.groovy.d/set_jnlp_port.groovy"
22 | register: jenkins_jnlp_port_config
23 | when: (jenkins_install_package_win is defined and jenkins_install_package_win.changed)
24 |
25 | - name: Immediately restart Jenkins after all changes.
26 | win_service: name=jenkins state=restarted
27 | register: jenkins_started
28 |
29 | #- name: Remove Jenkins security init scripts after first startup.
30 | # win_file:
31 | # path: "{{ jenkins_home }}/init.groovy.d/basic-security.groovy"
32 | # state: absent
33 | # when: jenkins_started is defined
34 |
--------------------------------------------------------------------------------
/ansible/dcpromo2.yml:
--------------------------------------------------------------------------------
1 | - hosts: skipper
2 | gather_facts: True
3 | vars:
4 | dc_address: 172.28.128.100
5 | dc_netmask_cidr: 24
6 | dc_gateway: 172.28.128.2
7 | dc_hostname: skipper
8 | domain_Name: waddlecorp.local
9 | ansible_winrm_transport: plaintext
10 | ansible_winrm_scheme: http
11 | tasks:
12 | - name: Set a static address to 172.28.128.100
13 | win_shell: "(new-netipaddress -InterfaceAlias \"Ethernet 2\" -IPAddress {{ dc_address }} -prefixlength {{dc_netmask_cidr}} -defaultgateway {{ dc_gateway }})"
14 |
15 | - name: Change hostname to skipper
16 | win_hostname:
17 | name: skipper
18 |
19 | - name: Install Active Directory Services
20 | win_feature: >
21 | name=AD-Domain-Services
22 | include_management_tools=yes
23 | include_sub_features=yes
24 | state=present
25 |
26 | - name: Promote skipper to domain controller
27 | win_domain:
28 | create_dns_delegation: no
29 | dns_domain_name: waddlecorp.local
30 | domain_netbios_name: WADDLECORP
31 | safe_mode_password: PassW0rd432!
32 | register: domain_install
33 |
34 | - name: Set DA user account information
35 | win_domain_user:
36 | name: skipper
37 | firstname: Skipper
38 | password: PassW0rd432!
39 | state: present
40 | groups:
41 | - Domain Admins
42 |
43 | - name: Reboot after promotion
44 | raw: shutdown /r
45 |
--------------------------------------------------------------------------------
/roles/tomcat/tasks/main.yml:
--------------------------------------------------------------------------------
1 | ---
2 | - name: Ensure cUrl is installed.
3 | win_chocolatey:
4 | name: curl
5 | state: present
6 |
7 | - name: Ensure Java RE is installed
8 | win_chocolatey:
9 | name: jre8
10 | state: present
11 |
12 | - name: Ensure Tomcat is installed.
13 | win_chocolatey:
14 | name: tomcat
15 | version: 9.0.30
16 | state: present
17 | register: tomcat_installed
18 |
19 | - name: Set the insecure tomcat-users.xml file in the right place
20 | template:
21 | src: tomcat-users.xml
22 | dest: "C:\\ProgramData\\Tomcat9\\conf\\tomcat-users.xml"
23 | register: tomcat_users
24 | when: tomcat_installed.changed
25 |
26 | - name: Set the server.xml file with AJP enabled
27 | template:
28 | src: server.xml
29 | dest: "C:\\ProgramData\\Tomcat9\\conf\\server.xml"
30 | register: tomcat_server_conf
31 | when: tomcat_installed.changed
32 |
33 | - name: Allow access to manager gui from anywhere
34 | template:
35 | src: context.xml
36 | dest: "C:\\ProgramData\\Tomcat9\\webapps\\manager\\META-INF\\context.xml"
37 | register: tomcat_context
38 | when: tomcat_installed.changed
39 |
40 | - name: Configure service to run as system
41 | win_service:
42 | name: Tomcat9
43 | start_mode: auto
44 | username: LocalSystem
45 | password: ""
46 | state: restarted
47 | when: tomcat_installed.changed
48 |
49 | - include: firewall_8080.yml
50 | when: tomcat_installed.changed
51 |
52 | - include: firewall_8009.yml
53 | when: tomcat_installed.changed
54 |
55 |
56 |
--------------------------------------------------------------------------------
/roles/mssql/tasks/configure.yml:
--------------------------------------------------------------------------------
1 | ---
2 | # Begin SQL Server configuration
3 | - name: Enable TCP Connectivity
4 | win_dsc:
5 | resource_name: SqlServerNetwork
6 | InstanceName: "{{ mssql_instance_name }}"
7 | ProtocolName: tcp
8 | TcpPort: "{{ mssql_port }}"
9 | IsEnabled: True
10 | RestartService: True
11 | tags: configure_sql
12 |
13 | - name: Adjust Max Server Memory to {{ mssql_max_server_memory }}
14 | when: mssql_max_server_memory is defined
15 | win_dsc:
16 | resource_name: SqlServerConfiguration
17 | InstanceName: "{{ mssql_instance_name }}"
18 | ServerName: "{{ ansible_hostname }}"
19 | OptionName: max server memory (MB)
20 | OptionValue: "{{ mssql_max_server_memory }}"
21 | RestartService: False
22 | tags: configure_sql
23 |
24 | - name: Adjust Min Server Memory to {{ mssql_min_server_memory }}
25 | when: mssql_min_server_memory is defined
26 | win_dsc:
27 | resource_name: SqlServerConfiguration
28 | ServerName: "{{ ansible_hostname }}"
29 | InstanceName: "{{ mssql_instance_name }}"
30 | OptionName: min server memory (MB)
31 | OptionValue: "{{ mssql_min_server_memory }}"
32 | tags: configure_sql
33 |
34 | - name: Adjust Max Degree of Parallelism
35 | when: mssql_max_degree_of_parallelism is defined
36 | win_dsc:
37 | resource_name: SqlServerConfiguration
38 | ServerName: "{{ ansible_hostname }}"
39 | InstanceName: "{{ mssql_instance_name }}"
40 | OptionName: max degree of parallelism
41 | OptionValue: "{{ mssql_max_degree_of_parallelism }}"
42 | tags: configure_sql
--------------------------------------------------------------------------------
/roles/mssql/tasks/prepare_install.yml:
--------------------------------------------------------------------------------
1 | ---
2 | # SQL install may fail if a pending reboot is detected
3 | # Assuming we are allowed to reboot this step will check for pending reboots
4 | # and execute a reboot, reboot activity can be controlled using the variable mssql_suppress_reboot
5 | - name: Ensure that a reboot is not pending
6 | when: ansible_reboot_pending
7 | debug:
8 | msg: 'Pending reboot detected'
9 | changed_when: true
10 | notify: reboot windows
11 |
12 | - meta: flush_handlers
13 |
14 | - name: Make sure Temp dir exists
15 | win_file:
16 | path: "{{ mssql_temp_download_path }}"
17 | state: directory
18 | register: sql_temp_dir
19 |
20 | - name: Fetch SQL Media Downloader
21 | win_get_url:
22 | url: "{{ mssql_installation_source }}"
23 | dest: "{{ mssql_temp_download_path }}\\SQLServer2017-SSEI-Dev.exe"
24 | when: sql_temp_dir.changed
25 |
26 | - name: Use Media Downloader to fetch SQL Installation CABs to {{ mssql_installation_path }}
27 | win_shell: "{{ mssql_temp_download_path }}\\SQLServer2017-SSEI-Dev.exe /Action=Download /MediaPath={{ mssql_installation_path }} /MediaType=CAB /Quiet"
28 | when: sql_temp_dir.changed
29 |
30 | # Job will fail if extracted media folder is not empty, quick step to ensure it's empty
31 | - name: Ensure installation media extraction path is empty
32 | win_file:
33 | path: "{{ mssql_installation_path }}\\Media"
34 | state: absent
35 |
36 | - name: Extract installation media
37 | win_shell: "{{ mssql_installation_path }}\\SQLServer2017-DEV-x64-ENU.exe /X:{{ mssql_installation_path }}\\Media /Q"
38 |
--------------------------------------------------------------------------------
/ssh/capsulecorp_id_rsa:
--------------------------------------------------------------------------------
1 | -----BEGIN RSA PRIVATE KEY-----
2 | MIIEowIBAAKCAQEAxX+mInSsh1YlDaccTHAl5q8lcwXK8jol8p/DYs66X5YkCbMR
3 | pb9EP/WggOX2DMMXpRRnRRHJ2CEVUOIzxOJqXxZXG7ajobLOp14KT98r+BdOMh81
4 | /Fol6+79r9klg96iE5paDAa2MLiNNDhTIiGQwIfBtv8bw3NYqS5b5sOlgYHlfFR7
5 | rLPB4vf1Tp/GMR5CIeBB0uRKU7OzN2w3V59qXnarDRLV+kVpNdIuWF5lQX8RHtA9
6 | EDS5kc/fNIy8oltelibPw0L26nm0QhWAhwEFzSEQypvpvOCSGHtX13o2jZgOzwa8
7 | L5iViholnUl/t/vghpGe0d8uNj/yFMnlld5goQIDAQABAoIBAHGLV8pLZb1RC3Bz
8 | +NMBTuj3HQKp++mTAKoiq8Qssf2uZf2lk6nE8soKv0Ib83+W0gs4Vb7h4Td+nbCo
9 | u7afrSQJxf7K2/xkvmZ+rFMLLU4up+gtBW6VrWOdPQBSST0tS+UVQlvTp/8Ouy+g
10 | ijr/LSdjZT1+IUoXEIwDeRaMuKRhM8HnOdqkDyvM7gPPEyk3rNOYXdAH8wQo2bMi
11 | dUo1HRQpTBKNP3EDr+iHj3jbgOJMRGyyloPSavnTdGmJerU9h3HcJP3G3S4wJpCb
12 | RLcg0ztiZkDqEjfxpwPjfGfLzOn3EiJO//q8E12+N1FyDfdeHjpERC+dxxPJh/fp
13 | XeLC+oECgYEA+crlOmHAB3vXxVhOw73/QGUKFD0p5+A3fXK8vEWM61BS9Y/LHeF3
14 | QRjZegnRZ9tcZfLRGvDAD5d1GzcljhC3p+nPaehnyHNKo41KzfieQxI5w16Pi96d
15 | qWsm9qI+MC9WU/aLLnFDnEXZp0PV0bnuYGgsluqANDD/Ui4QNFBxNCkCgYEAymgT
16 | TRNAhRhE4OI9A4jpc/Fxya1VXyX2OaCsiuya5+XjBkaoXOn/aPGq4Y4H+HQ4HtjW
17 | 9NsOidov1jughm3tK44N/7HRorl2DFbMiV2h1ms8FeqV1lHLY3uCcaDNYTmGuD2k
18 | zrMs1OP6Vz45X7z9JGsuiV2KK7s+V+XYuxFgF7kCgYAnZD638ThWNcp2HZH2Pl0l
19 | a4mmXWrhXTOC/fgTfKhXZ4hdnzp50Nd8lY2eODQku6wbi6o8JGE1VD4sd4rdl3dO
20 | 7Ik/+116d+v6VMrKJn3Wt+YSEDR06ztTv0katcU21hA4F3YlcckmuME1JnZup3KX
21 | E3aMqhhjoqJw9ECr70+a2QKBgG8DgDqQ6Z1WP0j8rSxIJosCDT/pQt7J6m+XEaus
22 | tBWmv8rMbEFx0jVT/z5w8SwzSiiZE+T+VM4FDqG42IWCu0ddRY5NkEZo5DdGUC6z
23 | XTVGYZE/tejzudMZheUepibCL4LTxJXeLiOh2seJCFzbQhh8dOzAki0EKOB631FS
24 | 6Vp5AoGBAPUFcEmpz+EX8hyn0u8fZJyh6ZjEobT5oBa6sgj4JOUI2wQTMhXkcPAD
25 | Q/pFh5Ua+WKqanOYjLhw60LXI/c/ClXuMmoyaiDQ5izjc5mVanMbKJugp0Gg1apq
26 | iv5hUQqTbMbcYDsn0a5vqMcDynQqwPoSW/sQmyv7z56I/DbKt/ab
27 | -----END RSA PRIVATE KEY-----
28 |
--------------------------------------------------------------------------------
/Vagrantfile:
--------------------------------------------------------------------------------
1 | # -*- mode: ruby -*-
2 | # vi: set ft=ruby :
3 |
4 | # All Vagrant configuration is done below. The "2" in Vagrant.configure
5 | # configures the configuration version (we support older styles for
6 | # backwards compatibility). Please don't change it unless you know what
7 | # you're doing.
8 | Vagrant.configure("2") do |config|
9 |
10 | winsrv = "royce/capsulecorp-winsrv"
11 | kali = "kalilinux/rolling"
12 | winwks = "royce/capsulecorp-win7"
13 | dcmem = "0.0.7-alpha-dc-member"
14 | vms = [{name: "skipper", ip: "172.28.128.100", box: winsrv, version: "0.0.5-alpha"},
15 | {name: "kowalski", ip: "172.28.128.101", box: winsrv, version: dcmem},
16 | {name: "vegeta", ip: "172.28.128.102", box: winsrv, version: dcmem},
17 | {name: "rico", ip: "172.28.128.103", box: winsrv, version: dcmem},
18 | {name: "tien", ip: "172.28.128.104", box: winwks, version: "0.0.2-alpha"},
19 | {name: "raditz", ip: "172.28.128.105", box: winsrv, version: dcmem},
20 | {name: "private", ip: "172.28.128.106", box: winsrv, version: dcmem}]
21 | vms.each do |vm|
22 | config.vm.define vm[:name] do |system|
23 | system.vm.network "private_network", ip: vm[:ip], name: "vboxnet1"
24 | system.vm.box = vm[:box]
25 | system.vm.box_version = vm[:version]
26 | system.vm.guest = :windows
27 | system.vm.communicator = "winrm"
28 | system.vm.network :forwarded_port, guest: 3389, host: 3389, auto_correct: true
29 | system.vm.provision "ansible" do |ansible|
30 | ansible.playbook = "#{vm[:name]}.yml"
31 | end
32 | end
33 | end
34 | config.vm.synced_folder ".", "/vagrant", id: "vagrant-root", disabled: true
35 | config.vm.define "pentest" do |box|
36 | box.vm.box = "kalilinux/rolling"
37 | box.vm.network "private_network", ip: "172.28.128.200", name: "vboxnet1"
38 | box.vm.network "private_network", ip: "10.10.10.3", name: "vboxnet5"
39 | box.vm.network :forwarded_port, guest: 3389, host: 3389, auto_correct: true
40 | box.vm.provision "ansible" do |ansible|
41 | ansible.playbook = "pentest.yml"
42 | end
43 | end
44 | config.vm.define "dvwa" do |box|
45 | box.vm.box = "kalilinux/rolling"
46 | box.vm.network "private_network", ip: "172.28.128.201", name: "vboxnet1"
47 | box.vm.network "private_network", ip: "10.10.10.3", name: "vboxnet5"
48 | box.vm.network :forwarded_port, guest: 3389, host: 3389, auto_correct: true
49 | box.vm.provision "ansible" do |ansible|
50 | ansible.playbook = "dvwa.yml"
51 | end
52 | end
53 | end
54 |
--------------------------------------------------------------------------------
/roles/promotedc/tasks/accounts.yml:
--------------------------------------------------------------------------------
1 | ---
2 | - name: Ensure AD account vegeta exists
3 | win_domain_user:
4 | name: vegeta
5 | firstname: Vegeta
6 | password: PasW0rd432#
7 | state: present
8 | groups:
9 | - Domain Users
10 |
11 | - name: Ensure AD account kowalski exists
12 | win_domain_user:
13 | name: kowalski
14 | firstname: Kowalski
15 | password: PasW0rd543#
16 | state: present
17 | groups:
18 | - Domain Users
19 |
20 | - name: Ensure AD account rico exists
21 | win_domain_user:
22 | name: rico
23 | firstname: Rico
24 | password: PasW0rd654#
25 | state: present
26 | groups:
27 | - Domain Users
28 |
29 | - name: Ensure AD account raditz exists
30 | win_domain_user:
31 | name: raditz
32 | firstname: Raditz
33 | password: PasW0rd765#
34 | state: present
35 | groups:
36 | - Domain Users
37 |
38 | - name: Ensure AD account tien exists
39 | win_domain_user:
40 | name: tien
41 | firstname: Tien
42 | password: PasW0rd876#
43 | state: present
44 | groups:
45 | - Domain Users
46 |
47 | - name: Ensure AD account private exists
48 | win_domain_user:
49 | name: private
50 | firstname: Private
51 | password: PasW0rd543#
52 | state: present
53 | groups:
54 | - Domain Users
55 |
56 | - name: Ensure AD account KowalskiADM exists
57 | win_domain_user:
58 | name: kowalski.adm
59 | firstname: KowalskiADM
60 | password: PassW0rd876#!
61 | state: present
62 | groups:
63 | - Domain Users
64 |
65 | - name: Ensure AD account PrivateADM exists
66 | win_domain_user:
67 | name: private.adm
68 | firstname: PrivateADM
69 | password: PassW0rd876#!
70 | state: present
71 | groups:
72 | - Domain Users
73 |
74 | - name: Ensure AD account Vegetaadm exists
75 | win_domain_user:
76 | name: vegeta.adm
77 | firstname: VegetaADM
78 | password: PassW0rd765#!
79 | state: present
80 | groups:
81 | - Domain Users
82 |
83 | - name: Ensure AD account RicoADM exists
84 | win_domain_user:
85 | name: rico.adm
86 | firstname: ricoADM
87 | password: PassW0rd654#!
88 | state: present
89 | groups:
90 | - Domain Users
91 |
92 | - name: Ensure AD account serveradmin exists
93 | win_domain_user:
94 | name: server.admin
95 | firstname: ServerAdmin
96 | password: P@ssW0rd123#_!
97 | state: present
98 | groups:
99 | - Domain Admins
100 |
--------------------------------------------------------------------------------
/roles/mssql/tasks/install.yml:
--------------------------------------------------------------------------------
1 | ---
2 | # If this step fails, logs are in C:\Program Files\Microsoft SQL Server\...\Setup Bootstrap\Log
3 | # it will often contain the actual error. If it shows everything passing, the issue is within the DSC logs.
4 | #
5 | # This module also typically throws this error fpr all failure conditions:
6 | # PowerShell DSC resource MSFT_SqlSetup failed to execute Set-TargetResource functionality with error message:
7 | # System.Exception: Test-TargetResource returned false after calling Set-TargetResource.
8 | #
9 | #
10 | # This document can also be useful to troubleshoot issues with DSC modules
11 | # https://docs.microsoft.com/en-us/powershell/dsc/troubleshooting
12 | #
13 | # In particular completing these steps:
14 | # https://docs.microsoft.com/en-us/powershell/dsc/troubleshooting#gathering-events-from-a-single-dsc-operation
15 | # then re-running a failing PowershellDSC job can help you find the source of your error
16 | - name: Install SQL Server
17 | win_dsc:
18 | resource_name: SQLSetup
19 | Action: Install
20 | UpdateEnabled: True
21 | SourcePath: "{{ mssql_installation_path }}\\Media"
22 | InstanceName: "{{ mssql_instance_name }}"
23 | InstallSharedDir: "{{ mssql_installshared_path }}"
24 | InstallSharedwowDir: "{{ mssql_installsharedwow_path }}"
25 | InstanceDir: "{{ mssql_instance_path }}"
26 | InstallSQLDataDir: "{{ mssql_sqlinstalldata_path }}"
27 | SQLUserDBDir: "{{ mssql_sqluserdata_path }}"
28 | SQLUserDBLogDir: "{{ mssql_sqluserlog_path }}"
29 | SQLTempDBDir: "{{ mssql_sqltempDB_path }}"
30 | SQLTempDBLogDir: "{{ mssql_sqltempDBlog_path }}"
31 | Features: "{{ mssql_features }}"
32 | SQLCollation: "{{ mssql_collation }}"
33 | BrowserSvcStartupType: "{{ mssql_browsersvc_mode }}"
34 | SuppressReboot: "{{ mssql_suppress_reboot }}"
35 | # Service Accounts
36 | #
37 | # If the type of the DSC resource option is a PSCredential then
38 | # there needs to be 2 options set in the Ansible task definition
39 | # suffixed with _username and _password. So we will be providing
40 | # two options for these normally single option items.
41 |
42 | # SQL Service Account
43 | SQLSvcAccount_username: "{{ mssql_sqlsvc_account }}"
44 | SQLSvcAccount_password: "{{ mssql_sqlsvc_account_pass }}"
45 | # SQL Agent Service Account
46 | AgtSvcAccount_username: "{{ mssql_agentsvc_account }}"
47 | AgtSvcAccount_password: "{{ mssql_agentsvc_account_pass }}"
48 | # SQL Analysis Services Account
49 | ASSvcAccount_username: "{{ mssql_assvc_account }}"
50 | ASSvcAccount_password: "{{ mssql_assvc_account_pass }}"
51 |
52 | # Used when installing on a network path, comment out
53 | # SourceCredential_username: "{{ ansible_user }}"
54 | # SourceCredential_password: "{{ ansible_password }}"
55 |
56 | # System Admins
57 | SQLSysAdminAccounts: "{{ mssql_sysadmin_accounts }}"
58 | # Analysis Services Admins (if installed)
59 | ASSysAdminAccounts: "{{ mssql_asadmin_accounts }}"
60 | tags: install_sql
--------------------------------------------------------------------------------
/roles/tomcat/templates/server.xml:
--------------------------------------------------------------------------------
1 |
2 |
3 |
4 |
5 |
8 |
9 |
10 |
11 |
12 |
13 |
14 |
15 |
18 |
19 |
22 |
27 |
28 |
29 |
34 |
35 |
36 |
37 |
40 |
41 |
42 |
43 |
47 |
48 |
49 |
50 |
51 |
54 |
57 |
58 |
60 |
61 |
65 |
67 |
68 |
69 |
71 |
72 |
74 |
77 |
78 |
81 |
84 |
85 |
86 |
87 |
88 |
89 |
--------------------------------------------------------------------------------
/roles/mssql/defaults/main.yml:
--------------------------------------------------------------------------------
1 | # installation files source
2 | mssql_installation_source: https://go.microsoft.com/fwlink/?linkid=853016
3 |
4 | # Path to download installation media to
5 | mssql_installation_path: C:\SQLInstall
6 |
7 | # Temporary path to store downloader
8 | mssql_temp_download_path: C:\temp
9 |
10 | # instance details
11 | mssql_instance_name: WaddleCorp
12 | mssql_drive: C
13 | mssql_userdbvol_name: waddlecorpdbvol01
14 | mssql_port: 1433
15 |
16 | ### Memory Configuration ###
17 | # memory in MB
18 | # values must be divisible by 512
19 |
20 | # Max memory to allocate to this instance
21 | mssql_max_server_memory: 1024
22 |
23 | # Memory to reserve to the OS
24 | mssql_os_memory_reservation: 512
25 |
26 | # Total system memory
27 | mssql_total_system_memory: "{{ mssql_max_server_memory + mssql_os_memory_reservation }}"
28 |
29 | # Suppress reboots that may occur during SQL Setup tasks
30 | # you will want to set this to True if working on a sensitive system:
31 | mssql_suppress_reboot: False
32 |
33 | ### Service Accounts ###
34 | #mssql_base_ldap_path: "cn=Users,dc=WADDLECORP,dc=local"
35 | #domain_controller: goku
36 |
37 | # SQL Service Account
38 | mssql_sqlsvc_account: sa
39 | mssql_sqlsvc_account_pass: Password1
40 |
41 | # SQL Agent Service Account
42 | mssql_agentsvc_account: sqlagent
43 | mssql_agentsvc_account_pass: Password2
44 |
45 | # SQL Analysis Services Account
46 | mssql_assvc_account: "{{ mssql_sqlsvc_account }}"
47 | mssql_assvc_account_pass: "{{ mssql_sqlsvc_account_pass }}"
48 |
49 | ### File and Folder Paths ###
50 |
51 | # volume paths
52 | mssql_userdbvol_path: "{{ mssql_drive }}:\\{{ mssql_userdbvol_name }}"
53 | mssql_db_accesspath: "{{ mssql_userdbvol_path }}\\DatabaseFiles"
54 | mssql_logs_accesspath: "{{ mssql_userdbvol_path }}\\DatabaseLogs"
55 |
56 | # shared files paths
57 | mssql_installshared_path: C:\Program Files\Microsoft SQL Server
58 | mssql_installsharedwow_path: C:\Program Files (x86)\Microsoft SQL Server
59 |
60 | # instance path
61 | mssql_instance_path: "C:\\Program Files\\Microsoft SQL Server\\{{ mssql_instance_name }}"
62 |
63 | # SQL DB and Logging Paths
64 | mssql_sqlinstalldata_path: "{{ mssql_db_accesspath }}\\{{mssql_instance_name }}"
65 | mssql_sqluserdata_path: "{{ mssql_db_accesspath }}\\{{mssql_instance_name }}"
66 | mssql_sqluserlog_path: "{{ mssql_logs_accesspath }}\\{{mssql_instance_name }}"
67 | mssql_sqltempDB_path: "C:\\TempDBFiles\\Data\\{{mssql_instance_name }}"
68 | mssql_sqltempDBlog_path: "C:\\TempDBFiles\\Log\\{{mssql_instance_name }}"
69 |
70 | # security mode - SQL indicates mixed-mode auth, while Windows indicates Windows Auth.
71 | mssql_security_mode: sql
72 |
73 | # SA user password, if security mode is set to 'SQL'
74 | # by default for testing we'll be lazy and use the service account password,
75 | # but on live systems you should use something else:
76 | mssql_sa_password: "{{ mssql_sqlsvc_account_pass }}"
77 |
78 |
79 | mssql_features: SQLENGINE,FULLTEXT,CONN
80 |
81 | # Collation
82 | mssql_collation: SQL_Latin1_General_CP1_CI_AS
83 |
84 | # Browser service startup mode
85 | # Specifies the startup mode for SQL Server Browser service. { Automatic | Disabled | 'Manual' }
86 | mssql_browsersvc_mode: Automatic
87 |
88 | # Default Account Access
89 | # Ansible_Admin must be included so that the playbook can make configuration changes post install
90 | mssql_sysadmin_accounts:
91 | - sa
92 |
93 | # Analysis Services Admins (if installed)
94 | mssql_asadmin_accounts: "{{ mssql_sysadmin_accounts }}"
95 |
96 | # Tuning options
97 |
98 | # When an instance of SQL Server runs on a computer that has more than one microprocessor or CPU,
99 | # it detects the best degree of parallelism, that is, the number of processors employed to run a single statement,
100 | # for each parallel plan execution. You can use the max degree of parallelism option to limit the number of processors
101 | # to use in parallel plan execution.
102 | #
103 | # If the affinity mask option is not set to the default, it may restrict the number of processors available to
104 | # SQL Server on symmetric multiprocessing (SMP) systems.
105 | #
106 | # To enable the server to determine the maximum degree of parallelism, set this option to 0, the default value.
107 | #
108 | # See: https://docs.microsoft.com/en-us/sql/database-engine/configure-windows/configure-the-max-degree-of-parallelism-server-configuration-option
109 | mssql_max_degree_of_parallelism: 0
110 | mssql_min_server_memory: 0
111 |
--------------------------------------------------------------------------------
/README.md:
--------------------------------------------------------------------------------
1 | > Credit to R3dy#23 for the establishment of this envirnoment.
2 |
3 | # 1. WaddleCorp Pentest
4 | This project was based in part on [capsulecorp-pentest](https://github.com/R3dy/capsulecorp-pentest) and a huge shout out to [R3dy](https://github.com/R3dy) for the ground work!
5 |
6 | The WaddleCorp Pentest is a virtual network managed by Vagrant and Ansible.
7 | It contains virtual machines configured with various vulnerable services. This project can be used to learn penetration testing in a standalone environment. The primary differences between CapsuleCorp and WaddleCorp (aside from the change in theme from DBZ to Penguins) is that WaddleCorp is configured with a Kali linux machine and will be updated periodically to reflect exploits as they are researched and discovered.
8 |
9 | 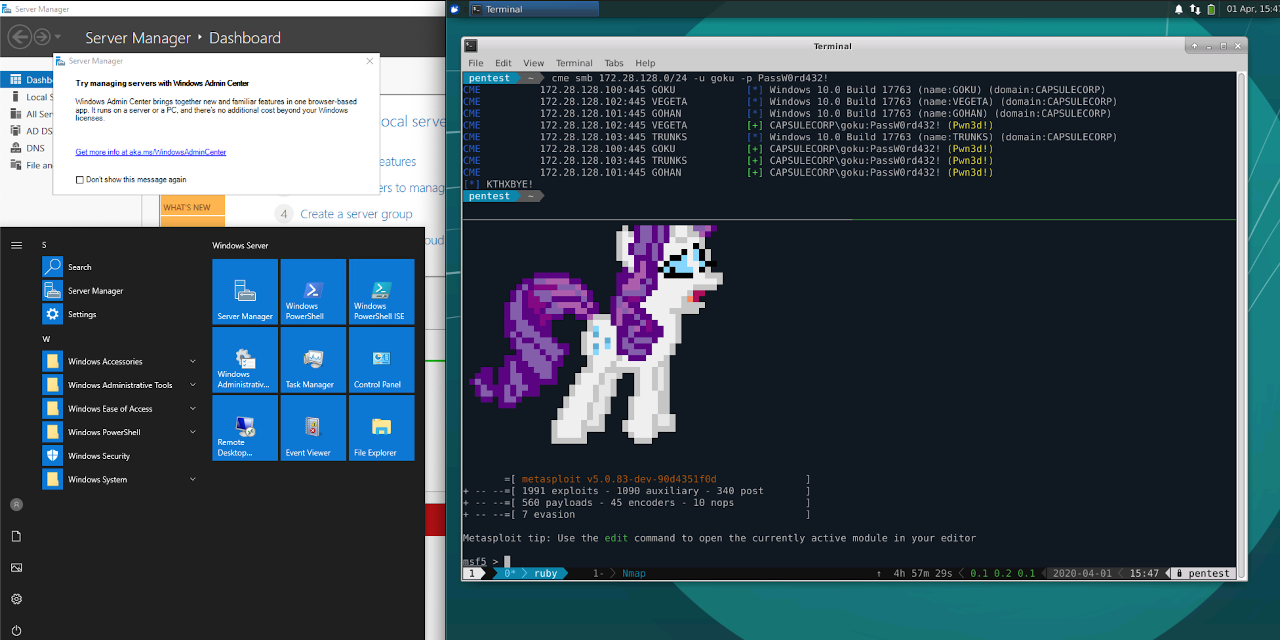
10 |
11 | ## Why is this cool?
12 | Setting up a virtual network to learn penetration testing can be tedious as well as time/resource consuming. Everything in the waddlecorp environment is pretty much done for you already. Once you get Vagrant, Ansible and VirtualBox installed on your machine you only need to run a couple of `vagrant` commands to have a fully functioning Active Directory domain that you can use for hacking/learning/pentesting etc.
13 |
14 | ## 1.1. Requirements
15 | In order to use the WaddleCorp Pentest network you must have the following:
16 |
17 | * VirtualBox
18 | * [https://www.virtualbox.org/wiki/Downloads](https://www.virtualbox.org/wiki/Downloads)
19 | * Vagrant
20 | * [https://www.vagrantup.com/downloads.html](https://www.vagrantup.com/downloads.html)
21 | * Ansible
22 | * [https://docs.ansible.com/ansible/latest/installation_guide/index.html](https://docs.ansible.com/ansible/latest/installation_guide/index.html)
23 |
24 | * Quad-core CPU with 16GB RAM is recommended.
25 | * With 8GB or less you could still use the project but ***only run 2 or 3 VMs at a time***.
26 | * For All VMs running at once 16GB is required.
27 |
28 | ## 1.2. Current Functionality
29 | * Active directory domain with one DC and 3 server members. All windows server have evaluation licenses, which are activated on installation (for 180 days)
30 | * Domain Controler: `skipper.waddlecorp.local`
31 | * Server 01: `vegeta.waddlecorp.local`
32 | * Server 02: `kowalski.waddlecorp.local`
33 | * Server 03: `rico.waddlecorp.local`
34 | * Wrkstn 01: `tien.waddlecorp.local`
35 | * Server 04: `private.waddlecorp.loca`
36 | * Print Nightmare server on `private`
37 | * Vulnerable Jenkins server on `vegeta`
38 | * Vulnerable Apache Tomcat server on `rico`
39 | * Vulnerable MSSQL server on `kowalski`
40 | * Vulnerable MS17-010 on `tien`
41 | * Kali Pentest Box
42 | * Impacket
43 |
44 | ## 1.3. OSX Configuration
45 | In order to manage Windows hosts you'll have to install `pywinrm` with pip inside the ansible virtual environment
46 |
47 | I prefer to run ansible in a virtualenv
48 | ```bash
49 | cd
50 | virtualenv ansible
51 | source ansible/bin/activate
52 | pip install ansible
53 | pip install pywinrm
54 | ```
55 |
56 | > If you receive the following error
57 | ```sh
58 | objc[3534]: +[__NSCFConstantString initialize] may have been in progress in another thread when fork() was called.
59 | objc[3534]: +[__NSCFConstantString initialize] may have been in progress in another thread when fork() was called. We cannot safely call it or ignore it in the fork() child process. Crashing instead. Set a breakpoint on objc_initializeAfterForkError to debug.
60 | ```
61 | > Apply the bandaid fix
62 |
63 | > `export OBJC_DISABLE_INITIALIZE_FORK_SAFETY=YES`
64 |
65 | # 2. Installation
66 | For a detailed installation walkthrough check out
67 |
68 | * [MacOS Setup Guide](https://github.com/R3dy/capsulecorp-pentest/wiki/MacOS-Setup-Guide)
69 |
70 | * [Windows Setup Guide](https://github.com/R3dy/capsulecorp-pentest/wiki/Windows-Setup-Guide)
71 |
72 | ## 2.1. Configure the windows hosts
73 | The first thing you should do is bring up and provision Skipper the domain controller. This system will likely take the longest to bring up because the dcpromo stuff just takes a while.
74 |
75 | ***Note***: if you are running vagrant with sudo. use ```sudo -E vagrant``` option to run vagrant
76 |
77 | Bring up the VM
78 |
79 | vagrant up skipper
80 |
81 | Provision the VM
82 |
83 | vagrant provision skipper
84 |
85 | Repeat the above two commands for the other boxes or you can simply leave out machine specification to run all of them.
86 |
87 | ***WARNING***: running all machines is resource intensive please make sure you understand your machines specifications before doing this!
88 |
89 | ***...WARNING...***
90 |
91 | This section of the provision is expected to take a while because after a dcpromo it takes a long time for the system to reboot.
92 |
93 | ```bash
94 | TASK [promotedc : Set a static address to 172.28.128.100] **********************
95 | changed: [skipper]
96 |
97 | TASK [promotedc : Change hostname to skipper] *************************************
98 | ok: [skipper]
99 |
100 | TASK [promotedc : Install Active Directory Services] ***************************
101 | ok: [skipper]
102 |
103 | TASK [promotedc : Promote skipper to domain controller] ***************************
104 | changed: [skipper]
105 |
106 | TASK [promotedc : Reboot after promotion] **************************************
107 | ```
108 |
109 | ## 2.2. Configure your pentest platform
110 |
111 | Bring up the virtual machines using Vagrant. First cd into the project directory, for example: `cd ~/waddlecorp-pentest`. Take note of the RDP port that gets forwarded to your localhost.
112 |
113 | vagrant up pentest
114 |
115 | Provision the pentest machine.
116 |
117 | vagrant provision pentest
118 |
119 | You can access your pentest machine either using your preferred RDP client to connect to the xrdp listener or via SSH with.
120 |
121 | vagrant ssh pentest
122 |
--------------------------------------------------------------------------------