├── .gitignore
├── Email-Rapportive.py
├── Heartbleed.py
├── License
├── README.md
├── Remote_TDS
├── Graph
│ └── CE-haveibeenpwned.mtgx
├── Images
│ ├── 1.Carbon-Import_Configuration.png
│ ├── 10.Carbon-Accept_Disclaimer.png
│ ├── 11.Carbon-Maltego_Graph.png
│ ├── 2.Carbon-Select_Configuration_File.png
│ ├── 3.Carbon-Select_Configuration.png
│ ├── 4.Carbon-Import_Complete.png
│ ├── 5.Carbon-Discover_Transforms.png
│ ├── 6.Carbon-Discovery_Complete.png
│ ├── 7.Carbon-Run_Machine.png
│ ├── 8.Carbon-Choose_Machine.png
│ └── 9.Carbon-Specify_Target.png
├── README.md
├── haveibeenpwned.mtz
└── machine_emailpwnedatdomain
├── canari
└── haveibeenpwned
│ ├── MANIFEST.in
│ ├── README.md
│ ├── setup.py
│ └── src
│ └── haveibeenpwned
│ ├── __init__.py
│ ├── resources
│ ├── __init__.py
│ ├── etc
│ │ ├── __init__.py
│ │ └── haveibeenpwned.conf
│ ├── external
│ │ └── __init__.py
│ ├── images
│ │ └── __init__.py
│ └── maltego
│ │ └── __init__.py
│ └── transforms
│ ├── __init__.py
│ ├── common
│ ├── __init__.py
│ └── entities.py
│ └── emailtoHIBP.py
├── domaintoemailfrommetadata
├── emailpwnedatdomain
├── emailtoHIBP.py
├── mtgxtocsv.py
├── phntocomp.py
└── reverseipdomain.py
/.gitignore:
--------------------------------------------------------------------------------
1 | *.py[cod]
2 |
3 | # C extensions
4 | *.so
5 |
6 | # Packages
7 | *.egg
8 | *.egg-info
9 | dist
10 | build
11 | eggs
12 | parts
13 | bin
14 | var
15 | sdist
16 | develop-eggs
17 | .installed.cfg
18 | lib
19 | lib64
20 | __pycache__
21 |
22 | # Installer logs
23 | pip-log.txt
24 |
25 | # Unit test / coverage reports
26 | .coverage
27 | .tox
28 | nosetests.xml
29 |
30 | # Translations
31 | *.mo
32 |
33 | # Mr Developer
34 | .mr.developer.cfg
35 | .project
36 | .pydevproject
37 |
--------------------------------------------------------------------------------
/Email-Rapportive.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/python
2 |
3 | #Email-Rapportive.py
4 | #Author: Sudhanshu Chauhan - @Sudhanshu_C
5 |
6 | #Based upon the service Rapportive: http://www.rapportive.com/
7 | #Credits: This code is based upon the research and code of Jordan Wright.
8 | #Blog Link: http://jordan-wright.github.io/blog/2013/10/14/automated-social-engineering-recon-using-rapportive/
9 | #Code Link: https://github.com/jordan-wright/rapportive
10 | #This code requires the Requests library: https://pypi.python.org/pypi/requests/
11 | #Rapportive Code: https://github.com/SudhanshuC/Rapportive/blob/master/rapportive.py
12 | #For MaltegoTransform library and Installation guidelines go to http://www.paterva.com/web6/documentation/developer-local.php
13 |
14 | from MaltegoTransform import *
15 | import sys
16 | import urllib2
17 | import requests
18 | mt = MaltegoTransform()
19 | mt.parseArguments(sys.argv)
20 | target_email=mt.getValue()
21 | mt = MaltegoTransform()
22 | random_email="random-email@gmail.com"
23 | response = requests.get('https://rapportive.com/login_status?user_email=' + random_email).json()
24 | profile = requests.get('https://profiles.rapportive.com/contacts/email/' + target_email, headers = {'X-Session-Token' : response['session_token']}).json()
25 |
26 | if profile['contact']['name']:
27 | mt.addEntity("maltego.Person", profile['contact']['name'])
28 |
29 | if profile['contact']['location']:
30 | mt.addEntity("maltego.Location", profile['contact']['location'])
31 |
32 | if profile['contact']['occupations']:
33 | for occupation in profile['contact']['occupations']:
34 | mt.addEntity("maltego.Phrase", "Job Title: " + occupation['job_title'] + " at " + occupation['company'])
35 |
36 | if profile['contact']['memberships']:
37 | for membership in profile['contact']['memberships']:
38 | purl=membership['profile_url']
39 | url=mt.addEntity("maltego.URL", membership['site_name'] + " profile: " + purl)
40 | url.addAdditionalFields("theurl","URL",True,purl)
41 |
42 | mt.returnOutput()
43 |
--------------------------------------------------------------------------------
/Heartbleed.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/python
2 | from MaltegoTransform import *
3 | import sys
4 | import urllib2
5 | import re
6 | mt = MaltegoTransform()
7 | mt.parseArguments(sys.argv)
8 | domain=mt.getValue()
9 | url="http://safeweb.norton.com/heartbleed?url=www."
10 | getrequrl=url+domain
11 | try:
12 | response = urllib2.urlopen(getrequrl)
13 | ser=re.search(r'is vulnerable',response.read())
14 | if ser:
15 | print "a"
16 | mt.addEntity("maltego.Phrase","HeartBleed Vulnerable")
17 | except:
18 | print ""
19 | mt.returnOutput()
20 |
--------------------------------------------------------------------------------
/License:
--------------------------------------------------------------------------------
1 | The MIT License (MIT)
2 |
3 | Copyright (c) 2013 Jordan Wright
4 |
5 | Copyright (c) 2014 Sudhanshu Chauhan
6 |
7 | Permission is hereby granted, free of charge, to any person obtaining a copy
8 | of this software and associated documentation files (the "Software"), to deal
9 | in the Software without restriction, including without limitation the rights
10 | to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
11 | copies of the Software, and to permit persons to whom the Software is
12 | furnished to do so, subject to the following conditions:
13 |
14 | The above copyright notice and this permission notice shall be included in all
15 | copies or substantial portions of the Software.
16 |
17 | THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
18 | IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
19 | FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
20 | AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
21 | LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
22 | OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
23 | SOFTWARE.
24 |
--------------------------------------------------------------------------------
/README.md:
--------------------------------------------------------------------------------
1 | Maltego-Addons
2 | ==================
3 |
4 | Maltego Transforms, Machines and other Extensions
5 |
6 |
7 | Prerequisites:
8 | ==============
9 |
10 | 1. Python 2.7 installed in the system.
11 | 2. MaltegoTransform library: http://www.paterva.com/web6/documentation/MaltegoTransform-Python.zip
12 |
13 |
14 | How to use the script(s):
15 | ======================
16 |
17 | Installation guidelines: http://www.paterva.com/web6/documentation/developer-local.php
18 | ***
19 | # @haveibeenpwned - Remote TDS Configuration
20 |
21 | Instructions in the [`./TDS` directory](https://github.com/cmlh/Maltego-haveibeenpwned/blob/TDS/TDS/README.md)
22 |
--------------------------------------------------------------------------------
/Remote_TDS/Graph/CE-haveibeenpwned.mtgx:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/SudhanshuC/Maltego-Transforms/96693340e74dc40dea0cebd53a4e9dff0918edb3/Remote_TDS/Graph/CE-haveibeenpwned.mtgx
--------------------------------------------------------------------------------
/Remote_TDS/Images/1.Carbon-Import_Configuration.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/SudhanshuC/Maltego-Transforms/96693340e74dc40dea0cebd53a4e9dff0918edb3/Remote_TDS/Images/1.Carbon-Import_Configuration.png
--------------------------------------------------------------------------------
/Remote_TDS/Images/10.Carbon-Accept_Disclaimer.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/SudhanshuC/Maltego-Transforms/96693340e74dc40dea0cebd53a4e9dff0918edb3/Remote_TDS/Images/10.Carbon-Accept_Disclaimer.png
--------------------------------------------------------------------------------
/Remote_TDS/Images/11.Carbon-Maltego_Graph.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/SudhanshuC/Maltego-Transforms/96693340e74dc40dea0cebd53a4e9dff0918edb3/Remote_TDS/Images/11.Carbon-Maltego_Graph.png
--------------------------------------------------------------------------------
/Remote_TDS/Images/2.Carbon-Select_Configuration_File.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/SudhanshuC/Maltego-Transforms/96693340e74dc40dea0cebd53a4e9dff0918edb3/Remote_TDS/Images/2.Carbon-Select_Configuration_File.png
--------------------------------------------------------------------------------
/Remote_TDS/Images/3.Carbon-Select_Configuration.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/SudhanshuC/Maltego-Transforms/96693340e74dc40dea0cebd53a4e9dff0918edb3/Remote_TDS/Images/3.Carbon-Select_Configuration.png
--------------------------------------------------------------------------------
/Remote_TDS/Images/4.Carbon-Import_Complete.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/SudhanshuC/Maltego-Transforms/96693340e74dc40dea0cebd53a4e9dff0918edb3/Remote_TDS/Images/4.Carbon-Import_Complete.png
--------------------------------------------------------------------------------
/Remote_TDS/Images/5.Carbon-Discover_Transforms.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/SudhanshuC/Maltego-Transforms/96693340e74dc40dea0cebd53a4e9dff0918edb3/Remote_TDS/Images/5.Carbon-Discover_Transforms.png
--------------------------------------------------------------------------------
/Remote_TDS/Images/6.Carbon-Discovery_Complete.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/SudhanshuC/Maltego-Transforms/96693340e74dc40dea0cebd53a4e9dff0918edb3/Remote_TDS/Images/6.Carbon-Discovery_Complete.png
--------------------------------------------------------------------------------
/Remote_TDS/Images/7.Carbon-Run_Machine.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/SudhanshuC/Maltego-Transforms/96693340e74dc40dea0cebd53a4e9dff0918edb3/Remote_TDS/Images/7.Carbon-Run_Machine.png
--------------------------------------------------------------------------------
/Remote_TDS/Images/8.Carbon-Choose_Machine.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/SudhanshuC/Maltego-Transforms/96693340e74dc40dea0cebd53a4e9dff0918edb3/Remote_TDS/Images/8.Carbon-Choose_Machine.png
--------------------------------------------------------------------------------
/Remote_TDS/Images/9.Carbon-Specify_Target.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/SudhanshuC/Maltego-Transforms/96693340e74dc40dea0cebd53a4e9dff0918edb3/Remote_TDS/Images/9.Carbon-Specify_Target.png
--------------------------------------------------------------------------------
/Remote_TDS/README.md:
--------------------------------------------------------------------------------
1 | # Remote TDS
2 |
3 | ## Maltego Chlorine
4 |
5 | 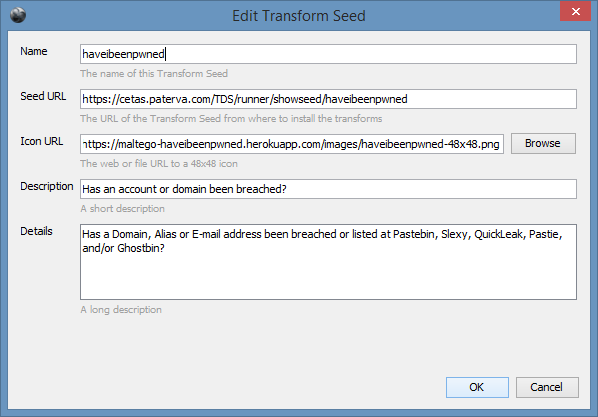
6 |
7 | ## Maltego Carbon
8 |
9 | 1.Click Import Configuration.
10 |
11 | 
12 |
13 | 2.Select the `Maltego-Configuration-haveibeenpwned.mtz` file.
14 |
15 | 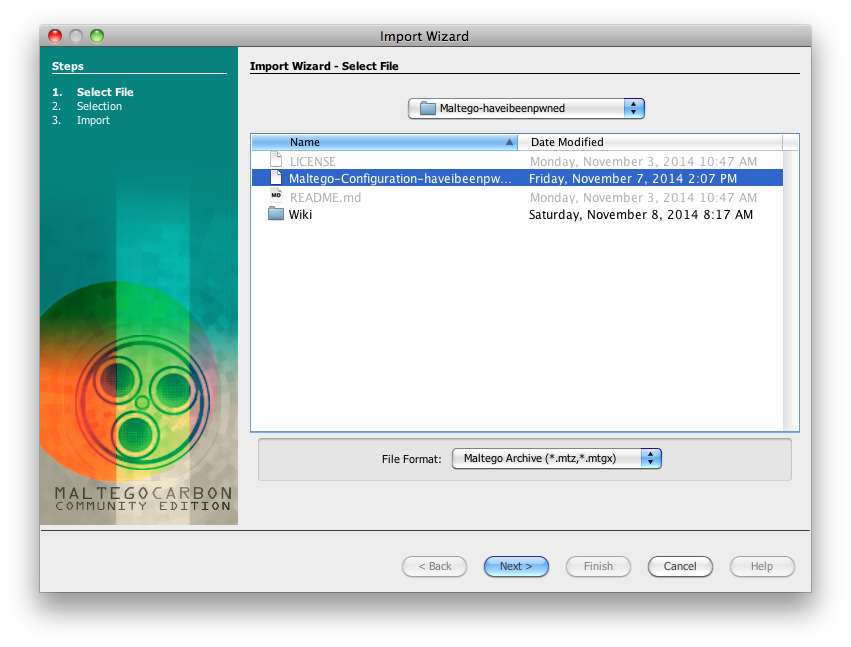
16 |
17 | 3.Ensure that the checkbox for Seeds, Transforms, Machines and all Transform Sets is checked
18 |
19 | 
20 |
21 | 4.Click Finish
22 |
23 | 
24 |
25 | 5.Click Discover Transforms
26 |
27 | 
28 |
29 | 6.Click Finish
30 |
31 | 
32 |
--------------------------------------------------------------------------------
/Remote_TDS/haveibeenpwned.mtz:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/SudhanshuC/Maltego-Transforms/96693340e74dc40dea0cebd53a4e9dff0918edb3/Remote_TDS/haveibeenpwned.mtz
--------------------------------------------------------------------------------
/Remote_TDS/machine_emailpwnedatdomain:
--------------------------------------------------------------------------------
1 | // A Maltego Machine which extracts emails for a domain and checks if any account related to that has been pwned (using HaveIBeenPwned: HIBP).
2 | // Special thanks to Troy Hunt for https://haveibeenpwned.com/
3 |
4 | machine("sudhanshuchauhan.EmailPwnedatDomain",
5 | displayName:"Email Pwned at Domain",
6 | author:"Sudhanshu Chauhan",
7 | description: "Extracts Emails for the Domain and checks if account related to any one of them has been pwned.\
8 | ") {
9 |
10 | start {
11 |
12 |
13 | paths{
14 | path{
15 | run("paterva.v2.DomainToEmailAddress_AtDomain_SE")
16 | run("paterva.v2.PasswordCompromisedhaveibeenpwnedAPIv1")
17 | }
18 | path{
19 | run("paterva.v2.DomainToEmailAddress_SE")
20 | run("paterva.v2.PasswordCompromisedhaveibeenpwnedAPIv1")
21 | }
22 | path{
23 | run("paterva.v2.DomainToEmailAddress_Whois")
24 | run("paterva.v2.PasswordCompromisedhaveibeenpwnedAPIv1")
25 | }
26 | path{
27 | run("paterva.v2.DomainToEmailAddress_PGP")
28 | run("paterva.v2.PasswordCompromisedhaveibeenpwnedAPIv1")
29 | }
30 | }
31 | }
32 | }
33 |
34 |
--------------------------------------------------------------------------------
/canari/haveibeenpwned/MANIFEST.in:
--------------------------------------------------------------------------------
1 | include *.md
2 | recursive-include src *.py *.conf *.gif *.png *.mtz *.machine
3 | recursive-include maltego *.mtz
4 |
--------------------------------------------------------------------------------
/canari/haveibeenpwned/README.md:
--------------------------------------------------------------------------------
1 | # README - Haveibeenpwned
2 |
3 | Welcome to Canari. You might be wondering what all these files are about. Before you can use the power of
4 | `canari install-package` you needed to create a transform package and that's exactly what you did here! I've given you a
5 | directory structure to use in the following manner:
6 |
7 | * `src/haveibeenpwned` directory is where all your stuff goes in terms of auxiliary modules that you may need for your
8 | modules
9 | * `src/haveibeenpwned/transforms` directory is where all your transform modules should be placed. An example
10 | `helloworld` transform is there for your viewing pleasure.
11 | * `src/haveibeenpwned/transforms/common` directory is where you can put some common code for your transforms like result
12 | parsing, entities, etc.
13 | * `src/haveibeenpwned/transforms/common/entities.py` is where you define your custom entities. Take a look at the
14 | examples provided if you want to play around with custom entities.
15 | * `maltego/` is where you can store your Maltego entity exports.
16 | * `src/haveibeenpwned/resources/maltego` directory is where your `entities.mtz` and `*.machine` files can be stored for auto
17 | install and uninstall.
18 | * `src/haveibeenpwned/resources/external` directory is where you can place non-Python transforms written in other languages.
19 |
20 | If you're going to add a new transform in the transforms directory, remember to update the `__all__` variable in
21 | `src/haveibeenpwned/transforms/__init__.py`. Otherwise, `canari install-package` won't attempt to install the transform.
22 | Alternatively, `canari create-transform ` can be used within the `src/haveibeenpwned/transforms` directory
23 | to generate a transform module and have it automatically added to the `__init__.py` file, like so:
24 |
25 | To test your transform, simply `cd` into the src directory and run `canari debug-transform`, like so:
26 |
27 | ```bash
28 | $ canari debug-transform Haveibeenpwned.transforms.helloworld Phil
29 | %50
30 | D:This was pointless!
31 | %100
32 | `- MaltegoTransformResponseMessage:
33 | `- Entities:
34 | `- Entity: {'Type': 'test.MyTestEntity'}
35 | `- Value: Hello Phil!
36 | `- Weight: 1
37 | `- AdditionalFields:
38 | `- Field: 2 {'DisplayName': 'Field 1', 'Name': 'test.field1', 'MatchingRule': 'strict'}
39 | `- Field: test {'DisplayName': 'Field N', 'Name': 'test.fieldN', 'MatchingRule': 'strict'}
40 | ```
41 |
42 | Cool right? If you have any further questions don't hesitate to drop us a line;)
43 |
44 | Have fun!
--------------------------------------------------------------------------------
/canari/haveibeenpwned/setup.py:
--------------------------------------------------------------------------------
1 | from setuptools import setup, find_packages
2 |
3 | setup(
4 | name='haveibeenpwned',
5 | author='Christian Heinrich',
6 | version='1.0',
7 | author_email='christian.heinrich@cmlh.id.au',
8 | description='cmlh.id.au',
9 | license='GPL',
10 | packages=find_packages('src'),
11 | package_dir={ '' : 'src' },
12 | zip_safe=False,
13 | package_data={
14 | '' : [ '*.gif', '*.png', '*.conf', '*.mtz', '*.machine' ] # list of resources
15 | },
16 | install_requires=[
17 | 'canari'
18 | ],
19 | dependency_links=[
20 | # custom links for the install_requires
21 | ]
22 | )
23 |
--------------------------------------------------------------------------------
/canari/haveibeenpwned/src/haveibeenpwned/__init__.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env python
2 |
3 | __author__ = 'Christian Heinrich'
4 | __copyright__ = 'Copyright 2014, Haveibeenpwned Project'
5 | __credits__ = []
6 |
7 | __license__ = 'GPL'
8 | __version__ = '0.1'
9 | __maintainer__ = 'Christian Heinrich'
10 | __email__ = 'christian.heinrich@cmlh.id.au'
11 | __status__ = 'Development'
12 |
13 | __all__ = [
14 | 'resources',
15 | 'transforms'
16 | ]
--------------------------------------------------------------------------------
/canari/haveibeenpwned/src/haveibeenpwned/resources/__init__.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env python
2 |
3 | __author__ = 'Christian Heinrich'
4 | __copyright__ = 'Copyright 2014, Haveibeenpwned Project'
5 | __credits__ = []
6 |
7 | __license__ = 'GPL'
8 | __version__ = '0.1'
9 | __maintainer__ = 'Christian Heinrich'
10 | __email__ = 'christian.heinrich@cmlh.id.au'
11 | __status__ = 'Development'
12 |
13 | __all__ = [
14 | 'etc',
15 | 'images',
16 | 'maltego',
17 | 'external'
18 | ]
--------------------------------------------------------------------------------
/canari/haveibeenpwned/src/haveibeenpwned/resources/etc/__init__.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env python
2 |
3 | __author__ = 'Christian Heinrich'
4 | __copyright__ = 'Copyright 2014, Haveibeenpwned Project'
5 | __credits__ = []
6 |
7 | __license__ = 'GPL'
8 | __version__ = '0.1'
9 | __maintainer__ = 'Christian Heinrich'
10 | __email__ = 'christian.heinrich@cmlh.id.au'
11 | __status__ = 'Development'
--------------------------------------------------------------------------------
/canari/haveibeenpwned/src/haveibeenpwned/resources/etc/haveibeenpwned.conf:
--------------------------------------------------------------------------------
1 | [section1]
2 |
3 | option1 = this, is, a, list
4 |
5 | option2 = this\, is\, a\, comma-separated string
6 |
7 |
8 | [section2]
9 |
10 | etc = etc
--------------------------------------------------------------------------------
/canari/haveibeenpwned/src/haveibeenpwned/resources/external/__init__.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env python
2 |
3 | __author__ = 'Christian Heinrich'
4 | __copyright__ = 'Copyright 2014, Haveibeenpwned Project'
5 | __credits__ = []
6 |
7 | __license__ = 'GPL'
8 | __version__ = '0.1'
9 | __maintainer__ = 'Christian Heinrich'
10 | __email__ = 'christian.heinrich@cmlh.id.au'
11 | __status__ = 'Development'
--------------------------------------------------------------------------------
/canari/haveibeenpwned/src/haveibeenpwned/resources/images/__init__.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env python
2 |
3 | __author__ = 'Christian Heinrich'
4 | __copyright__ = 'Copyright 2014, Haveibeenpwned Project'
5 | __credits__ = []
6 |
7 | __license__ = 'GPL'
8 | __version__ = '0.1'
9 | __maintainer__ = 'Christian Heinrich'
10 | __email__ = 'christian.heinrich@cmlh.id.au'
11 | __status__ = 'Development'
--------------------------------------------------------------------------------
/canari/haveibeenpwned/src/haveibeenpwned/resources/maltego/__init__.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env python
2 |
3 | __author__ = 'Christian Heinrich'
4 | __copyright__ = 'Copyright 2014, Haveibeenpwned Project'
5 | __credits__ = []
6 |
7 | __license__ = 'GPL'
8 | __version__ = '0.1'
9 | __maintainer__ = 'Christian Heinrich'
10 | __email__ = 'christian.heinrich@cmlh.id.au'
11 | __status__ = 'Development'
--------------------------------------------------------------------------------
/canari/haveibeenpwned/src/haveibeenpwned/transforms/__init__.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env python
2 |
3 | __author__ = 'Christian Heinrich'
4 | __copyright__ = 'Copyright 2014, Haveibeenpwned Project'
5 | __credits__ = []
6 |
7 | __license__ = 'GPL'
8 | __version__ = '0.1'
9 | __maintainer__ = 'Christian Heinrich'
10 | __email__ = 'christian.heinrich@cmlh.id.au'
11 | __status__ = 'Development'
12 |
13 | __all__ = [
14 | 'common',
15 | 'emailtoHIBP'
16 | ]
--------------------------------------------------------------------------------
/canari/haveibeenpwned/src/haveibeenpwned/transforms/common/__init__.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env python
2 |
3 | __author__ = 'Christian Heinrich'
4 | __copyright__ = 'Copyright 2014, Haveibeenpwned Project'
5 | __credits__ = []
6 |
7 | __license__ = 'GPL'
8 | __version__ = '0.1'
9 | __maintainer__ = 'Christian Heinrich'
10 | __email__ = 'christian.heinrich@cmlh.id.au'
11 | __status__ = 'Development'
12 |
13 | __all__ = [
14 | 'entities'
15 | ]
--------------------------------------------------------------------------------
/canari/haveibeenpwned/src/haveibeenpwned/transforms/common/entities.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env python
2 |
3 | from canari.maltego.message import Entity, EntityField, EntityFieldType, MatchingRule
4 |
5 | __author__ = 'Christian Heinrich'
6 | __copyright__ = 'Copyright 2014, Haveibeenpwned Project'
7 | __credits__ = []
8 |
9 | __license__ = 'GPL'
10 | __version__ = '0.1'
11 | __maintainer__ = 'Christian Heinrich'
12 | __email__ = 'christian.heinrich@cmlh.id.au'
13 | __status__ = 'Development'
14 |
15 | __all__ = [
16 | 'HaveibeenpwnedEntity',
17 | 'MyHaveibeenpwnedEntity'
18 | ]
19 |
20 | """
21 | DO NOT EDIT:
22 | The following entity is the base entity type from which all your entities will inherit from. This provides you with the
23 | default namespace that all your entities will use for their unique entity type in Maltego. For example, MyHaveibeenpwnedEntity will
24 | have an entity type name of haveibeenpwned.MyHaveibeenpwnedEntity. When adding a new entity in Maltego, you will have to specify this
25 | name (haveibeenpwned.MyHaveibeenpwnedEntity) in the 'Unique entity type' field.
26 | """
27 | class HaveibeenpwnedEntity(Entity):
28 | _namespace_ = 'haveibeenpwned'
29 |
30 |
31 | """
32 | You can specify as many entity fields as you want by just adding an extra @EntityField() decorator to your entities. The
33 | @EntityField() decorator takes the following parameters:
34 | - name: the name of the field without spaces or special characters except for dots ('.') (required)
35 | - propname: the name of the object's property used to get and set the value of the field (required, if name contains dots)
36 | - displayname: the name of the entity as it appears in Maltego (optional)
37 | - type: the data type of the field (optional, default: EntityFieldType.String)
38 | - required: whether or not the field's value must be set before sending back the message (optional, default: False)
39 | - choices: a list of acceptable field values for this field (optional)
40 | - matchingrule: whether or not the field should be loosely or strictly matched (optional, default: MatchingRule.Strict)
41 | - decorator: a function that is invoked each and everytime the field's value is set or changed.
42 | - is_value: a boolean value that determines whether the field is also the default value of the entity object.
43 | TODO: define as many custom fields and entity types as you wish:)
44 | """
45 | @EntityField(name='haveibeenpwned.fieldN', propname='fieldN', displayname='Field N', matchingrule=MatchingRule.Loose)
46 | @EntityField(name='haveibeenpwned.field1', propname='field1', displayname='Field 1', type=EntityFieldType.Integer)
47 | class MyHaveibeenpwnedEntity(HaveibeenpwnedEntity):
48 | """
49 | Uncomment the line below and comment out the pass if you wish to define a ridiculous entity type name like
50 | 'my.fancy.EntityType'
51 | """
52 | # _name_ = 'my.fancy.EntityType'
53 | pass
--------------------------------------------------------------------------------
/canari/haveibeenpwned/src/haveibeenpwned/transforms/emailtoHIBP.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env python
2 |
3 | import sys
4 | import urllib2
5 |
6 | from canari.maltego.entities import EmailAddress, Phrase
7 | from canari.maltego.utils import debug, progress
8 | from canari.framework import configure #, superuser
9 |
10 | __author__ = 'Christian Heinrich'
11 | __copyright__ = 'Copyright 2014, cmlh.id.au'
12 | __credits__ = ['Sudhanshu Chauhan']
13 |
14 | __license__ = 'GPL'
15 | __version__ = '0.2' # Incremented for canari
16 | __maintainer__ = 'Christian Heinrich'
17 | __email__ = 'christian.heinrich@cmlh.id.au'
18 | __status__ = 'Development'
19 |
20 | __all__ = [
21 | 'dotransform',
22 | 'onterminate'
23 | ]
24 |
25 | # Uncomment the line below if the transform needs to run as super-user
26 | #@superuser
27 |
28 | @configure(
29 | label='To Compromised Domains [haveibeenpwned]',
30 | description='Retrieves the Domain(s) at which the specified account has been compromised',
31 | uuids=[ 'cmlh.haveibeenpwned.emailtoHIBP' ],
32 | inputs=[ ( 'haveibeenpwned', EmailAddress ) ],
33 | remote=False,
34 | debug=False
35 | )
36 | def dotransform(request, response, config):
37 |
38 | HIBP = "https://haveibeenpwned.com/api/breachedaccount/" # http://legacy.python.org/dev/peps/pep-0008/#constants
39 |
40 | email = request.value
41 | getrequrl = HIBP + email
42 |
43 | progress(50)
44 |
45 | try:
46 | urllib2_response = urllib2.urlopen(getrequrl) # Renamed "response" due conflict within canari namespace
47 | for rep in urllib2_response:
48 | e = Phrase("Pwned at %s" % rep)
49 | response += e
50 | except:
51 | print ""
52 |
53 | progress(100)
54 |
55 | return response
56 |
57 |
58 | """
59 | Called if transform interrupted. It's presence is optional; you can remove this function if you don't need to do any
60 | resource clean up.
61 |
62 | TODO: Write your cleanup logic below or delete the onterminate function and remove it from the __all__ variable
63 | """
64 | def onterminate():
65 | debug('Caught signal... exiting.')
66 | exit(0)
--------------------------------------------------------------------------------
/domaintoemailfrommetadata:
--------------------------------------------------------------------------------
1 | //A Maltego Machine which extracts files from a DOmain and further extracts metadata from them. This metadata is used to extract related email IDs for the entities Person.
2 |
3 | machine("sudhanshuchauhan.DomaintoMetatoPersontoEmail",
4 | displayName:"DomaintoMetatoPersontoEmail",
5 | author:"Sudhanshu Chauhan",
6 | description: "DomaintoMetatoPersontoEmail") {
7 |
8 | start {
9 | paths{
10 | run("paterva.v2.DomainToDocumentOther_SE")
11 | run("paterva.v2.DomainToDocument_SE")
12 | }
13 | run("paterva.v2.DocumentToPersonEmail_Meta")
14 | type("maltego.Person")
15 | run("paterva.v2.PersonToEmailAddress_SamePGP")
16 | run("paterva.v2.PersonToEmailAddress_Common")
17 | run("paterva.v2.PersonToEmailAddress_SE")
18 | }
19 | }
20 |
--------------------------------------------------------------------------------
/emailpwnedatdomain:
--------------------------------------------------------------------------------
1 | // A Maltego Machine which extracts emails for a domain and checks if any account related to that has been pwned (using HaveIBeenPwned: HIBP).
2 | // Special thanks to Troy Hunt for https://haveibeenpwned.com/
3 | // It requires the local transform emailtoHIBP: https://github.com/SudhanshuC/Maltego-Transforms/blob/master/emailtoHIBP.py
4 |
5 | machine("sudhanshuchauhan.EmailPwnedatDomain",
6 | displayName:"Email Pwned at Domain",
7 | author:"Sudhanshu Chauhan",
8 | description: "Extracts Emails for the Domain and checks if account related to any one of them has been pwned.\
9 | ") {
10 |
11 | start {
12 |
13 |
14 | paths{
15 | path{
16 | run("paterva.v2.DomainToEmailAddress_AtDomain_SE")
17 | run("sudhanshuchauhan.emailtohibp")
18 | }
19 | path{
20 | run("paterva.v2.DomainToEmailAddress_SE")
21 | run("sudhanshuchauhan.emailtohibp")
22 | }
23 | path{
24 | run("paterva.v2.DomainToEmailAddress_Whois")
25 | run("sudhanshuchauhan.emailtohibp")
26 | }
27 | path{
28 | run("paterva.v2.DomainToEmailAddress_PGP")
29 | run("sudhanshuchauhan.emailtohibp")
30 | }
31 | }
32 | }
33 | }
34 |
35 |
--------------------------------------------------------------------------------
/emailtoHIBP.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/python
2 |
3 | #EmailtoHIBP.py
4 | #Author: Sudhanshu Chauhan - @Sudhanshu_C
5 |
6 | #This Script will retrieve the Domain(s) at which the specified account has been compromised
7 | #It uses the API provided by https://haveibeenpwned.com/
8 | #Special Thanks to Troy Hunt - http://www.troyhunt.com/
9 | #For MaltegoTransform library and Installation guidelines go to http://www.paterva.com/web6/documentation/developer-local.php
10 |
11 | import sys
12 | import urllib2
13 | import json
14 |
15 | from MaltegoTransform import *
16 |
17 | HIBP = "https://haveibeenpwned.com/api/breachedaccount/"
18 |
19 | mt = MaltegoTransform()
20 | mt.parseArguments(sys.argv)
21 | email = mt.getValue()
22 | mt = MaltegoTransform()
23 | getrequrl = HIBP + email
24 |
25 | try:
26 | response = urllib2.urlopen(getrequrl)
27 | data = json.load(response)
28 | response = data
29 | for rep in response:
30 | mt.addEntity("maltego.Phrase","Pwned at " + rep)
31 |
32 | except urllib2.URLError, e: # "Response Codes" within https://haveibeenpwned.com/API/v1
33 |
34 | if e.code == 400:
35 | mt.addUIMessage("The e-mail account does not comply with an acceptable format",messageType="PartialError")
36 |
37 | if e.code == 404:
38 | UIMessage = email + " could not be found and has therefore not been pwned"
39 | mt.addUIMessage(UIMessage,messageType="Inform")
40 |
41 | mt.returnOutput()
--------------------------------------------------------------------------------
/mtgxtocsv.py:
--------------------------------------------------------------------------------
1 | #! /usr/bin/python
2 | # This script can be used to generate a CSV file from the mtgx file. A mtgx file is a file created by saving the Maltego graph.
3 | # It extracts the entities, their type and entity parent(s).
4 | from BeautifulSoup import BeautifulSoup
5 | import csv
6 | import zipfile
7 | import sys
8 | file=sys.argv[1]
9 | zp=zipfile.ZipFile(file)
10 | path=str(zp.namelist()[0])
11 | data=zp.read(path)
12 | xmlbs=BeautifulSoup(data)
13 | psxml=xmlbs.graph.findAll("node")
14 | key=xmlbs.findAll("key")
15 | edge=xmlbs.findAll("edge")
16 | xkey=""
17 | el=[]
18 | edgelink=["Entity Parent(s)"]
19 | entity=["Entity Type"]
20 | entvalue=["Entity Value"]
21 | link=["Entity ID"]
22 | lnk=""
23 | file=file.split('.')
24 | opfilename=file[0]+".csv"
25 | outcsv=open(opfilename, 'wb')
26 | csvwriter = csv.writer(outcsv)
27 | print ""
28 |
29 | for k in key:
30 | if (k["for"]=="edge"):
31 | if (k["attr.name"]=="MaltegoLink"):
32 | xkey=k["id"]
33 | break
34 |
35 | for node in psxml:
36 | lnk=node["id"]
37 | link.append(lnk)
38 | for ed in edge:
39 | if ed["target"]==lnk:
40 | el.append(str(ed["source"]))
41 | edgelink.append(el)
42 | el=[]
43 | ent=node.findAll("mtg:maltegoentity")[0]["type"]
44 | entity.append(ent)
45 | nod=node.findAll("mtg:value")[0].contents
46 | for nd in nod:
47 | entvalue.append(nd)
48 |
49 | for val in (link, entity, entvalue, edgelink):
50 | csvwriter.writerow(val)
51 | outcsv.close()
52 |
--------------------------------------------------------------------------------
/phntocomp.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/python
2 |
3 | #phntocomp.py
4 | #Author: Sudhanshu Chauhan - @Sudhanshu_C
5 |
6 | #This Script will retrieve the Company name from the provided Phone Number
7 | #It uses the API provided by https://www.opencnam.com
8 | #For MaltegoTransform library and Installation guidelines go to http://www.paterva.com/web6/documentation/developer-local.php
9 |
10 | from MaltegoTransform import *
11 | import sys
12 | import urllib2
13 | mt = MaltegoTransform()
14 | mt.parseArguments(sys.argv)
15 | phn=mt.getValue()
16 | phn=phn.replace(' ','')
17 | mt = MaltegoTransform()
18 | opencnam="https://api.opencnam.com/v2/phone/"
19 | getrequrl=opencnam+phn
20 | response = urllib2.urlopen(getrequrl)
21 | mt.addEntity("maltego.Phrase", response.read())
22 | mt.returnOutput()
23 |
--------------------------------------------------------------------------------
/reverseipdomain.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/python
2 |
3 | #reverseipdomain.py
4 | #Author: Sudhanshu Chauhan - @Sudhanshu_C
5 |
6 | #This Script will perform a reverse IP domain check using http://www.yougetsignal.com
7 | #In case yougetsignal is down due to overload, we can also use: http://www.my-ip-neighbors.com/?domain=. Simply change the value of the parameter 'opencnam'.
8 |
9 | from MaltegoTransform import *
10 | import sys
11 | import urllib2
12 | import re
13 | mt = MaltegoTransform()
14 | mt.parseArguments(sys.argv)
15 | url=mt.getValue()
16 | mt = MaltegoTransform()
17 | opencnam="http://domains.yougetsignal.com/domains.php?remoteAddress="
18 | getrequrl=opencnam+url
19 | header={'User-Agent':'Mozilla',}
20 | req=urllib2.Request(getrequrl,None,header)
21 | response=urllib2.urlopen(req)
22 | domains=re.findall("((?:[0-9]*[a-z][a-z\\.\\d\\-]+)\\.(?:[0-9]*[a-z][a-z\\-]+))(?![\\w\\.])",response.read())
23 | for domain in domains:
24 | mt.addEntity("maltego.Domain", domain)
25 | mt.returnOutput()
26 |
--------------------------------------------------------------------------------