├── .github
└── CONTRIBUTING.md
├── .travis.yml
├── README.md
└── docs
├── DockerCheatSheet.pdf
├── Metasploit-CheatSheet.pdf
├── Metasploit-CheatSheet.png
├── PowerShellCheatSheet_v41.pdf
├── Wireshark_Display_Filters.pdf
├── js-in-one-pic.png
├── nmap.md
├── pentest-exploit-dev-cheatsheet.jpg
├── py3-in-one-pic.png
├── python-3-in-one-pic.png
├── python-snippets.md
├── shodan.md
└── sqlmap-cheatsheet-1.0-SDB.pdf
/.github/CONTRIBUTING.md:
--------------------------------------------------------------------------------
1 | # Contribution Guidelines
2 |
3 | ## Table of Contents
4 |
5 | - [Adding to this list](#adding-to-this-list)
6 | - [Updating your Pull Request](#updating-your-pull-request)
7 |
8 | ## Adding to this list
9 |
10 | Please ensure your pull request adheres to the following guidelines:
11 |
12 | - Search previous suggestions before making a new one, as yours may be a duplicate.
13 | - Make sure the submission is useful before submitting.
14 | - Make an individual pull request for each suggestion.
15 | - Use [title-casing](http://titlecapitalization.com) (AP style).
16 | - Use the following format: `[List Name](link) - Optional Description`.
17 | - Optional descriptions are useful when the name itself is not descriptive.
18 | - Link additions should be added to the bottom of the relevant category.
19 | - New categories or improvements to the existing categorization are welcome.
20 | - Check your spelling and grammar.
21 | - Make sure your text editor is set to remove trailing whitespace.
22 | - The pull request and commit should have a useful title.
23 | - The body of your commit message should contain a link to the repository.
24 |
25 | ## Updating your Pull Request
26 |
27 | Sometimes, a maintainer of an awesome list will ask you to edit your Pull Request before it is included. This is normally due to spelling errors or because your PR didn't make any useful addition.
28 |
29 | [Here](https://github.com/RichardLitt/knowledge/blob/master/github/amending-a-commit-guide.md) is a write up on how to change a Pull Request, and the different ways you can do that.
30 |
--------------------------------------------------------------------------------
/.travis.yml:
--------------------------------------------------------------------------------
1 | language: ruby
2 | rvm:
3 | - 2.2
4 | before_script:
5 | - gem install awesome_bot
6 | script:
7 | - awesome_bot README.md --allow-redirect
--------------------------------------------------------------------------------
/README.md:
--------------------------------------------------------------------------------
1 | **THIS REPOSITORY IS DEPRECATED.**
2 |
3 | **ALL OF ITS CONTENT HAS BEEN UPDATED AND MOVED TO [awesome-pentest-cheat-sheets](https://github.com/ByteSnipers/awesome-pentest-cheat-sheets)**
4 |
5 | # Awesome Pentest Cheat Sheets [](https://github.com/sindresorhus/awesome)
6 |
7 | Collection of cheat sheets useful for pentesting
8 |
9 | ### Contribution
10 | Your contributions and suggestions are heartily welcome. Please check the [Contributing Guidelines](.github/CONTRIBUTING.md) for more details.
11 |
12 |
13 | ## Security Talks and Videos
14 |
15 | * [InfoCon - Hacking Conference Archive](https://infocon.org/cons/)
16 | * [Curated list of Security Talks and Videos](https://github.com/PaulSec/awesome-sec-talks)
17 |
18 | ## General
19 |
20 | * [Docker Cheat Sheet](https://github.com/wsargent/docker-cheat-sheet)
21 | * [Mobile App Pentest Cheat Sheet](https://github.com/tanprathan/MobileApp-Pentest-Cheatsheet)
22 | * [OSX Command Line Cheat Sheet](https://github.com/herrbischoff/awesome-osx-command-line)
23 | * [PowerShell Cheat Sheet](https://pen-testing.sans.org/blog/2016/05/25/sans-powershell-cheat-sheet) - SANS PowerShell Cheat Sheet from SEC560 Course [(PDF version)](docs/PowerShellCheatSheet_v41.pdf)
24 | * [Rawsec's CyberSecurity Inventory](https://inventory.raw.pm/) - An open-source inventory of tools, resources, CTF platforms and Operating Systems about CyberSecurity. ([Source](https://gitlab.com/rawsec/rawsec-cybersecurity-list))
25 | * [Regexp Security Cheat Sheet](https://github.com/attackercan/regexp-security-cheatsheet)
26 | * [Security Cheat Sheets](https://github.com/teamghsoftware/security-cheatsheets) - A collection of security cheat sheets
27 | * [Unix / Linux Cheat Sheet](http://cheatsheetworld.com/programming/unix-linux-cheat-sheet/)
28 |
29 | ## Discovery
30 |
31 | * [Google Dorks](https://www.exploit-db.com/google-hacking-database) - Google Dorks Hacking Database (Exploit-DB)
32 | * [Shodan](docs/shodan.md) - Shodan is a search engine for finding specific devices, and device types, that exist online
33 | * [ZoomEye](http://zoomeye.org) - Zoomeye is a Cyberspace Search Engine recording information of devices, websites, services and components etc.
34 | * [Amass](https://github.com/OWASP/Amass) - OWASP Network mapping of attack surfaces and external asset discovery using open source information
35 |
36 | ## Enumeration
37 | * [enum4linux-ng](https://github.com/cddmp/enum4linux-ng) - Python tool for enumerating information from Windows/Samba systems
38 |
39 | ## Exploitation
40 | * [Empire Cheat Sheet](https://github.com/HarmJ0y/CheatSheets/blob/master/Empire.pdf) - [Empire](http://www.powershellempire.com) is a PowerShell and Python post-exploitation framework
41 | * [Exploit Development Cheat Sheet](docs/pentest-exploit-dev-cheatsheet.jpg) - [@ovid](https://twitter.com/ovid)'s exploit development in one picture
42 | * [Java Deserialization Cheat Sheet](https://github.com/GrrrDog/Java-Deserialization-Cheat-Sheet) - A cheat sheet for pentesters about Java Native Binary Deserialization vulnerabilities
43 | * [Local File Inclusion (LFI) Cheat Sheet #1](https://highon.coffee/blog/lfi-cheat-sheet/) - Arr0way's LFI Cheat Sheet
44 | * [Local File Inclusion (LFI) Cheat Sheet #2](https://www.aptive.co.uk/blog/local-file-inclusion-lfi-testing/) - Aptive's LFI Cheat Sheet
45 | * [Metasploit Unleashed](https://www.offensive-security.com/metasploit-unleashed/) - The ultimate guide to the Metasploit Framework
46 | * [Metasploit Cheat Sheet](https://www.tunnelsup.com/metasploit-cheat-sheet/) - A quick reference guide [(PNG version)](docs/Metasploit-CheatSheet.png)[(PDF version)](docs/Metasploit-CheatSheet.pdf)
47 | * [PowerSploit Cheat Sheet](https://github.com/HarmJ0y/CheatSheets/blob/master/PowerSploit.pdf) - [PowerSploit](https://github.com/PowerShellMafia/PowerSploit) is a powershell post-exploitation framework
48 | * [PowerView 2.0 Tricks](https://gist.github.com/HarmJ0y/3328d954607d71362e3c)
49 | * [PowerView 3.0 Tricks](https://gist.github.com/HarmJ0y/184f9822b195c52dd50c379ed3117993)
50 | * [PHP htaccess Injection Cheat Sheet](https://github.com/sektioneins/pcc/wiki/PHP-htaccess-injection-cheat-sheet) - htaccess Injection Cheat Sheet by PHP Secure Configuration Checker
51 | * [Reverse Shell Cheat Sheet #1](http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet) - Pentestmonkey Reverse Shell Cheat Sheet
52 | * [Reverse Shell Cheat Sheet #2](https://highon.coffee/blog/reverse-shell-cheat-sheet) - Arr0way's Reverse Shell Cheat Sheet
53 | * [SQL Injection Cheat Sheet](https://www.netsparker.com/blog/web-security/sql-injection-cheat-sheet) - Netsparker's SQL Injection Cheat Sheet
54 | * [SQLite3 Injection Cheat Sheet](http://atta.cked.me/home/sqlite3injectioncheatsheet)
55 |
56 | ## Privilege Escalation
57 |
58 | ### Learn Privilege Escalation
59 |
60 | * [Windows / Linux Local Privilege Escalation Workshop](https://github.com/sagishahar/lpeworkshop) - The Privilege Escalation Workshop covers all known (at the time) attack vectors of local user privilege escalation on both Linux and Windows operating systems and includes slides, videos, test VMs.
61 | 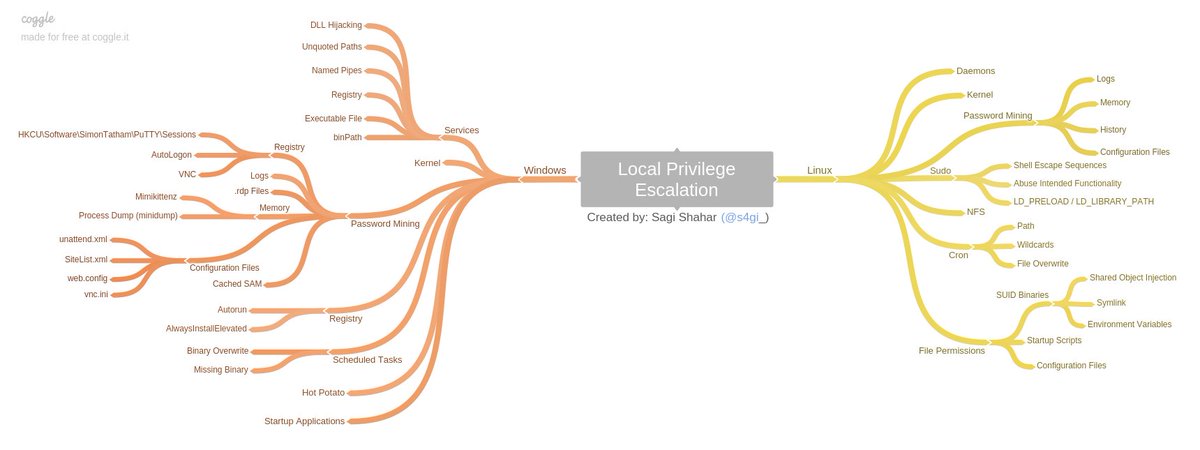 62 |
63 | ### Linux Privilege Escalation
64 |
65 | * [Basic Linux Privilege Escalation](https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/) - Linux Privilege Escalation by [@g0tmi1k](https://twitter.com/g0tmi1k)
66 | * [linux-exploit-suggester.sh](https://github.com/mzet-/linux-exploit-suggester) - Linux privilege escalation auditing tool written in bash (updated)
67 | * [Linux_Exploit_Suggester.pl](https://github.com/PenturaLabs/Linux_Exploit_Suggester) - Linux Exploit Suggester written in Perl (last update 3 years ago)
68 | * [Linux_Exploit_Suggester.pl v2](https://github.com/jondonas/linux-exploit-suggester-2) - Next-generation exploit suggester based on Linux_Exploit_Suggester (updated)
69 | * [Linux Soft Exploit Suggester](https://github.com/belane/linux-soft-exploit-suggester) - linux-soft-exploit-suggester finds exploits for all vulnerable software in a system helping with the privilege escalation. It focuses on software packages instead of Kernel vulnerabilities
70 | * [checksec.sh](https://github.com/slimm609/checksec.sh) - bash script to check the properties of executables (like PIE, RELRO, PaX, Canaries, ASLR, Fortify Source)
71 | * [linuxprivchecker.py](http://www.securitysift.com/download/linuxprivchecker.py) - This script is intended to be executed locally on a Linux box to enumerate basic system info and search for common privilege escalation vectors such as world writable files, misconfigurations, clear-text passwords and applicable exploits (@SecuritySift)
72 | * [LinEnum](https://github.com/rebootuser/LinEnum) - This tool is great at running through a heap of things you should check on a Linux system in the post exploit process. This include file permissions, cron jobs if visible, weak credentials etc.(@Rebootuser)
73 | * [linPEAS](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/tree/master/linPEAS) - LinPEAS - Linux Privilege Escalation Awesome Script. Check the Local Linux Privilege Escalation checklist from [book.hacktricks.xyz](https://book.hacktricks.xyz)
74 | * [MimiPenguin](https://github.com/huntergregal/mimipenguin) - A tool to dump the login password from the current linux desktop user. Adapted from the idea behind the popular Windows tool mimikatz.
75 |
76 |
77 | ### Windows Privilege Escalation
78 |
79 | * [PowerUp](https://github.com/PowerShellMafia/PowerSploit/tree/master/Privesc) - Excellent powershell script for checking of common Windows privilege escalation vectors. Written by [harmj0y](https://twitter.com/harmj0y) [(direct link)](https://raw.githubusercontent.com/PowerShellMafia/PowerSploit/master/Privesc/PowerUp.ps1)
80 | * [PowerUp Cheat Sheet](https://github.com/HarmJ0y/CheatSheets/blob/master/PowerUp.pdf)
81 | * [Windows Exploit Suggester](https://github.com/GDSSecurity/Windows-Exploit-Suggester) - Tool for detection of missing security patches on the windows operating system and mapping with the public available exploits
82 | * [Sherlock](https://github.com/rasta-mouse/Sherlock) - PowerShell script to quickly find missing software patches for local privilege escalation vulnerabilities
83 | * [Watson](https://github.com/rasta-mouse/Watson) - Enumerate missing KBs and suggest exploits for useful Privilege Escalation vulnerabilities
84 | * [Precompiled Windows Exploits](https://github.com/abatchy17/WindowsExploits) - Collection of precompiled Windows exploits
85 | * [Metasploit Modules](https://github.com/rapid7/metasploit-framework)
86 | * post/multi/recon/local_exploit_suggester - suggests local meterpreter exploits that can be used
87 | * post/windows/gather/enum_patches - helps to identify any missing patches
88 |
89 |
90 | ## Tools
91 |
92 | * [Nmap Cheat Sheet](docs/nmap.md)
93 | * [SQLmap Cheat Sheet](docs/sqlmap-cheatsheet-1.0-SDB.pdf)
94 | * [SQLmap Tamper Scripts](https://forum.bugcrowd.com/t/sqlmap-tamper-scripts-sql-injection-and-waf-bypass/423) - SQLmap Tamper Scripts General/MSSQL/MySQL
95 | * [VIM Cheatsheet](https://i.imgur.com/YLInLlY.png)
96 | * [Wireshark Display Filters](docs/Wireshark_Display_Filters.pdf) - Filters for the best sniffing tool
97 |
98 | # Tools Online
99 | * [XSS'OR Encoder/Decoder](http://xssor.io/#ende) - Online Decoder/Encoder for testing purposes (@evilcos)
100 | * [WebGun](https://brutelogic.com.br/webgun/) - WebGun, XSS Payload Creator (@brutelogic)
101 | * [Hackvertor](https://hackvertor.co.uk) - Tool to convert various encodings and generate attack vectors (@garethheyes)
102 | * [JSFiddle](https://jsfiddle.net) - Test and share XSS payloads, [Example PoC](https://jsfiddle.net/xqjpsh65/)
103 |
104 | ## Payloads
105 |
106 | ### Genaral
107 | * [Fuzzdb](https://github.com/fuzzdb-project/fuzzdb) - Dictionary of attack patterns and primitives for black-box application testing
108 | Polyglot Challenge with submitted solutions
109 | * [SecList](https://github.com/danielmiessler/SecLists) - A collection of multiple types of lists used during security assessments. List types include usernames, passwords, URLs, sensitive data grep strings, fuzzing payloads, and many more
110 |
111 | ### XSS
112 | * [XSS Polyglot Payloads #1](https://github.com/0xsobky/HackVault/wiki/Unleashing-an-Ultimate-XSS-Polyglot) - Unleashing an Ultimate XSS Polyglot list by 0xsobky
113 | * [XSS Polyglot Payloads #2](http://polyglot.innerht.ml/) - [@filedescriptor](https://twitter.com/filedescriptor)'s XSS
114 | * [Browser's-XSS-Filter-Bypass-Cheat-Sheet](https://github.com/masatokinugawa/filterbypass/wiki/Browser's-XSS-Filter-Bypass-Cheat-Sheet)- Excellent List of working XSS bypasses running on the latest version of Chrome / Safari, IE 11 / Edge created by Masato Kinugawa
115 |
116 | ## Write-Ups
117 |
118 | * [Bug Bounty Reference](https://github.com/ngalongc/bug-bounty-reference) - huge list of bug bounty write-up that is categorized by the bug type (SQLi, XSS, IDOR, etc.)
119 | * [Write-Ups for CTF challenges](https://ctftime.org/writeups)
120 | * [Facebook Bug Bounties](https://www.facebook.com/notes/phwd/facebook-bug-bounties/707217202701640) - Categorized Facebook Bug Bounties write-ups
121 |
122 |
123 | ## Learning Platforms
124 |
125 | ### Online
126 | * [Hack The Box :: Penetration Testing Labs](https://www.hackthebox.eu)
127 | * [OWASP Vulnerable Web Applications Directory Project (Online)](https://www.owasp.org/index.php/OWASP_Vulnerable_Web_Applications_Directory_Project#tab=On-Line_apps) - List of online available vulnerable applications for learning purposes
128 | * [Pentestit labs](https://lab.pentestit.ru) - Hands-on Pentesting Labs (OSCP style)
129 | * [Root-me.org](https://www.root-me.org) - Hundreds of challenges are available to train yourself in different and not simulated environments
130 | * [Vulnhub.com](https://www.vulnhub.com) - Vulnerable By Design VMs for practical 'hands-on' experience in digital security
131 |
132 | ### Off-Line
133 | * [Damn Vulnerable Xebia Training Environment](https://github.com/davevs/dvxte) - Docker Container including several vurnerable web applications (DVWA,DVWServices, DVWSockets, WebGoat, Juiceshop, Railsgoat, django.NV, Buggy Bank, Mutilidae II and more)
134 | * [OWASP Vulnerable Web Applications Directory Project (Offline)](https://www.owasp.org/index.php/OWASP_Vulnerable_Web_Applications_Directory_Project#tab=Off-Line_apps) - List of offline available vulnerable applications for learning purposes
135 | * [Vulnerable SOAP Web Service](https://github.com/anil-yelken/Vulnerable-Soap-Service) - a vulnerable SOAP web service lab environment
136 | * [Vulnerable Flask Web App](https://github.com/anil-yelken/Vulnerable-Flask-App) - vulnerable Flask Web App lab environment
137 |
138 | ## Wireless Hacking
139 |
140 | ### Tools
141 |
142 | * [wifite2](https://github.com/coreb1t/wifite2) - Full automated WiFi security testing script
143 |
144 | ## Defence Topics
145 |
146 | * [Docker Security Cheat Sheet](https://container-solutions.com/content/uploads/2015/06/15.06.15_DockerCheatSheet_A2.pdf) - The following tips should help you to secure a container based system [(PDF version)](docs/DockerCheatSheet.pdf)
147 | * [Windows Domain Hardening](https://github.com/PaulSec/awesome-windows-domain-hardening) - A curated list of awesome Security Hardening techniques for Windows
148 |
149 | ## Programming
150 |
151 | * [JavaScript Cheat Sheet](https://github.com/coodict/javascript-in-one-pic) - Learn javascript in one picture [(Online version)](https://git.io/Js-pic) [(PNG version)](docs/js-in-one-pic.png)
152 | * [Python Cheat Sheet #1](https://github.com/siyuanzhao/python3-in-one-pic) - Learn python3 in one picture [(PNG version)](docs/python-3-in-one-pic.png)
153 | * [Python Cheat Sheet #2 ](https://github.com/coodict/python3-in-one-pic) - Learn python3 in one picture [(Online version)](https://git.io/Coo-py3) [(PNG version)](docs/py3-in-one-pic.png)
154 | * [Python Snippets Cheat Sheet](docs/python-snippets.md) - List of helpful re-usable code snippets in Python
155 |
156 |
157 |
--------------------------------------------------------------------------------
/docs/DockerCheatSheet.pdf:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/coreb1t/awesome-pentest-cheat-sheets/ab0b4405674dced49f4e1e49bb7cebe4245f5782/docs/DockerCheatSheet.pdf
--------------------------------------------------------------------------------
/docs/Metasploit-CheatSheet.pdf:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/coreb1t/awesome-pentest-cheat-sheets/ab0b4405674dced49f4e1e49bb7cebe4245f5782/docs/Metasploit-CheatSheet.pdf
--------------------------------------------------------------------------------
/docs/Metasploit-CheatSheet.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/coreb1t/awesome-pentest-cheat-sheets/ab0b4405674dced49f4e1e49bb7cebe4245f5782/docs/Metasploit-CheatSheet.png
--------------------------------------------------------------------------------
/docs/PowerShellCheatSheet_v41.pdf:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/coreb1t/awesome-pentest-cheat-sheets/ab0b4405674dced49f4e1e49bb7cebe4245f5782/docs/PowerShellCheatSheet_v41.pdf
--------------------------------------------------------------------------------
/docs/Wireshark_Display_Filters.pdf:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/coreb1t/awesome-pentest-cheat-sheets/ab0b4405674dced49f4e1e49bb7cebe4245f5782/docs/Wireshark_Display_Filters.pdf
--------------------------------------------------------------------------------
/docs/js-in-one-pic.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/coreb1t/awesome-pentest-cheat-sheets/ab0b4405674dced49f4e1e49bb7cebe4245f5782/docs/js-in-one-pic.png
--------------------------------------------------------------------------------
/docs/nmap.md:
--------------------------------------------------------------------------------
1 | # Nmap Cheat Sheet
2 |
3 | ## DNS Brute Force
4 |
5 | nmap -p 80 --script dns-brute
6 |
7 | ## Find virtual hosts on an IP address
8 |
9 | nmap -p 80 --script hostmap-bfk
10 |
11 | ## Traceroute Geolocation
12 |
13 | nmap -p 80 --traceroute --script traceroute-geolocation.nse
14 |
15 | ## HTTP Scripts
16 |
17 | + ### HTTP Enum - web path brute force
18 |
19 | nmap -p 80 --script http-enum
20 |
21 | + ### HTTP Title
22 |
23 | nmap -p 80 -sV --script http-title
24 |
--------------------------------------------------------------------------------
/docs/pentest-exploit-dev-cheatsheet.jpg:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/coreb1t/awesome-pentest-cheat-sheets/ab0b4405674dced49f4e1e49bb7cebe4245f5782/docs/pentest-exploit-dev-cheatsheet.jpg
--------------------------------------------------------------------------------
/docs/py3-in-one-pic.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/coreb1t/awesome-pentest-cheat-sheets/ab0b4405674dced49f4e1e49bb7cebe4245f5782/docs/py3-in-one-pic.png
--------------------------------------------------------------------------------
/docs/python-3-in-one-pic.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/coreb1t/awesome-pentest-cheat-sheets/ab0b4405674dced49f4e1e49bb7cebe4245f5782/docs/python-3-in-one-pic.png
--------------------------------------------------------------------------------
/docs/python-snippets.md:
--------------------------------------------------------------------------------
1 | # Python Snippets
2 |
3 | ## File Operations
4 |
5 | * read a file line by line into a list
6 |
7 | * If you want the \n included:
8 |
9 | ```python
10 | with open(fname) as f:
11 | content = f.readlines()
12 | ```
13 |
14 | * If you do not want \n included:
15 |
16 | ```python
17 | with open(fname) as f:
18 | content = f.read().splitlines()
19 | ```
20 |
21 | * move file to the dist_dir folder
22 |
23 | os.rename(, dist_dir + os.path.sep + )
24 |
25 | * get working directory
26 |
27 | PWD = os.getcwd()
28 |
29 | * write file
30 |
31 | RESOURCE = "filename.txt"
32 | fd = open(RESOURCE, 'w')
33 | fd.write("first line\n")
34 | fd.close()
35 |
36 |
37 | ## Parsing Arguments
38 |
39 | ```python
40 | parser = argparse.ArgumentParser()
41 |
42 | parser.add_argument("-p", dest="payload", help=payloads, required=True)
43 | parser.add_argument("-i", dest="interface", help="use interface - default: eth0", default="eth0")
44 | args = parser.parse_args()
45 |
46 | payload_type = args.payload
47 | ```
--------------------------------------------------------------------------------
/docs/shodan.md:
--------------------------------------------------------------------------------
1 | # Shodan Cheat Sheet
2 |
3 | ## Filter
4 |
5 | Here are the basic search filters you can use:
6 |
7 | * `city`: find devices in a particular city
8 | * `country`: find devices in a particular country
9 | * `geo`: you can pass it coordinates
10 | * `hostname`: find values that match the hostname
11 | * `net`: search based on an IP or /x CIDR
12 | * `os`: search based on operating system
13 | * `port`: find particular ports that are open
14 | * `before/after`: find results within a timeframe
15 | * `org`: Search by organization
16 | * `hash`: Search based on banner hash
17 | * `has_screenshot:true`: Filter search based on a screenshot being present
18 | * `title`: Search based on text within the title
19 |
20 | ## Examples
21 |
22 | Find Apache servers in San Francisco:
23 |
24 | apache city:"San Francisco"
25 |
26 | Find Nginx servers in Germany:
27 |
28 | nginx country:"DE"
29 |
30 | Find GWS (Google Web Server) servers:
31 |
32 | "Server: gws" hostname:"google"
33 |
34 | Find Cisco devices on a particular subnet:
35 |
36 | cisco net:"216.219.143.0/24"
37 |
--------------------------------------------------------------------------------
/docs/sqlmap-cheatsheet-1.0-SDB.pdf:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/coreb1t/awesome-pentest-cheat-sheets/ab0b4405674dced49f4e1e49bb7cebe4245f5782/docs/sqlmap-cheatsheet-1.0-SDB.pdf
--------------------------------------------------------------------------------
62 |
63 | ### Linux Privilege Escalation
64 |
65 | * [Basic Linux Privilege Escalation](https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/) - Linux Privilege Escalation by [@g0tmi1k](https://twitter.com/g0tmi1k)
66 | * [linux-exploit-suggester.sh](https://github.com/mzet-/linux-exploit-suggester) - Linux privilege escalation auditing tool written in bash (updated)
67 | * [Linux_Exploit_Suggester.pl](https://github.com/PenturaLabs/Linux_Exploit_Suggester) - Linux Exploit Suggester written in Perl (last update 3 years ago)
68 | * [Linux_Exploit_Suggester.pl v2](https://github.com/jondonas/linux-exploit-suggester-2) - Next-generation exploit suggester based on Linux_Exploit_Suggester (updated)
69 | * [Linux Soft Exploit Suggester](https://github.com/belane/linux-soft-exploit-suggester) - linux-soft-exploit-suggester finds exploits for all vulnerable software in a system helping with the privilege escalation. It focuses on software packages instead of Kernel vulnerabilities
70 | * [checksec.sh](https://github.com/slimm609/checksec.sh) - bash script to check the properties of executables (like PIE, RELRO, PaX, Canaries, ASLR, Fortify Source)
71 | * [linuxprivchecker.py](http://www.securitysift.com/download/linuxprivchecker.py) - This script is intended to be executed locally on a Linux box to enumerate basic system info and search for common privilege escalation vectors such as world writable files, misconfigurations, clear-text passwords and applicable exploits (@SecuritySift)
72 | * [LinEnum](https://github.com/rebootuser/LinEnum) - This tool is great at running through a heap of things you should check on a Linux system in the post exploit process. This include file permissions, cron jobs if visible, weak credentials etc.(@Rebootuser)
73 | * [linPEAS](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/tree/master/linPEAS) - LinPEAS - Linux Privilege Escalation Awesome Script. Check the Local Linux Privilege Escalation checklist from [book.hacktricks.xyz](https://book.hacktricks.xyz)
74 | * [MimiPenguin](https://github.com/huntergregal/mimipenguin) - A tool to dump the login password from the current linux desktop user. Adapted from the idea behind the popular Windows tool mimikatz.
75 |
76 |
77 | ### Windows Privilege Escalation
78 |
79 | * [PowerUp](https://github.com/PowerShellMafia/PowerSploit/tree/master/Privesc) - Excellent powershell script for checking of common Windows privilege escalation vectors. Written by [harmj0y](https://twitter.com/harmj0y) [(direct link)](https://raw.githubusercontent.com/PowerShellMafia/PowerSploit/master/Privesc/PowerUp.ps1)
80 | * [PowerUp Cheat Sheet](https://github.com/HarmJ0y/CheatSheets/blob/master/PowerUp.pdf)
81 | * [Windows Exploit Suggester](https://github.com/GDSSecurity/Windows-Exploit-Suggester) - Tool for detection of missing security patches on the windows operating system and mapping with the public available exploits
82 | * [Sherlock](https://github.com/rasta-mouse/Sherlock) - PowerShell script to quickly find missing software patches for local privilege escalation vulnerabilities
83 | * [Watson](https://github.com/rasta-mouse/Watson) - Enumerate missing KBs and suggest exploits for useful Privilege Escalation vulnerabilities
84 | * [Precompiled Windows Exploits](https://github.com/abatchy17/WindowsExploits) - Collection of precompiled Windows exploits
85 | * [Metasploit Modules](https://github.com/rapid7/metasploit-framework)
86 | * post/multi/recon/local_exploit_suggester - suggests local meterpreter exploits that can be used
87 | * post/windows/gather/enum_patches - helps to identify any missing patches
88 |
89 |
90 | ## Tools
91 |
92 | * [Nmap Cheat Sheet](docs/nmap.md)
93 | * [SQLmap Cheat Sheet](docs/sqlmap-cheatsheet-1.0-SDB.pdf)
94 | * [SQLmap Tamper Scripts](https://forum.bugcrowd.com/t/sqlmap-tamper-scripts-sql-injection-and-waf-bypass/423) - SQLmap Tamper Scripts General/MSSQL/MySQL
95 | * [VIM Cheatsheet](https://i.imgur.com/YLInLlY.png)
96 | * [Wireshark Display Filters](docs/Wireshark_Display_Filters.pdf) - Filters for the best sniffing tool
97 |
98 | # Tools Online
99 | * [XSS'OR Encoder/Decoder](http://xssor.io/#ende) - Online Decoder/Encoder for testing purposes (@evilcos)
100 | * [WebGun](https://brutelogic.com.br/webgun/) - WebGun, XSS Payload Creator (@brutelogic)
101 | * [Hackvertor](https://hackvertor.co.uk) - Tool to convert various encodings and generate attack vectors (@garethheyes)
102 | * [JSFiddle](https://jsfiddle.net) - Test and share XSS payloads, [Example PoC](https://jsfiddle.net/xqjpsh65/)
103 |
104 | ## Payloads
105 |
106 | ### Genaral
107 | * [Fuzzdb](https://github.com/fuzzdb-project/fuzzdb) - Dictionary of attack patterns and primitives for black-box application testing
108 | Polyglot Challenge with submitted solutions
109 | * [SecList](https://github.com/danielmiessler/SecLists) - A collection of multiple types of lists used during security assessments. List types include usernames, passwords, URLs, sensitive data grep strings, fuzzing payloads, and many more
110 |
111 | ### XSS
112 | * [XSS Polyglot Payloads #1](https://github.com/0xsobky/HackVault/wiki/Unleashing-an-Ultimate-XSS-Polyglot) - Unleashing an Ultimate XSS Polyglot list by 0xsobky
113 | * [XSS Polyglot Payloads #2](http://polyglot.innerht.ml/) - [@filedescriptor](https://twitter.com/filedescriptor)'s XSS
114 | * [Browser's-XSS-Filter-Bypass-Cheat-Sheet](https://github.com/masatokinugawa/filterbypass/wiki/Browser's-XSS-Filter-Bypass-Cheat-Sheet)- Excellent List of working XSS bypasses running on the latest version of Chrome / Safari, IE 11 / Edge created by Masato Kinugawa
115 |
116 | ## Write-Ups
117 |
118 | * [Bug Bounty Reference](https://github.com/ngalongc/bug-bounty-reference) - huge list of bug bounty write-up that is categorized by the bug type (SQLi, XSS, IDOR, etc.)
119 | * [Write-Ups for CTF challenges](https://ctftime.org/writeups)
120 | * [Facebook Bug Bounties](https://www.facebook.com/notes/phwd/facebook-bug-bounties/707217202701640) - Categorized Facebook Bug Bounties write-ups
121 |
122 |
123 | ## Learning Platforms
124 |
125 | ### Online
126 | * [Hack The Box :: Penetration Testing Labs](https://www.hackthebox.eu)
127 | * [OWASP Vulnerable Web Applications Directory Project (Online)](https://www.owasp.org/index.php/OWASP_Vulnerable_Web_Applications_Directory_Project#tab=On-Line_apps) - List of online available vulnerable applications for learning purposes
128 | * [Pentestit labs](https://lab.pentestit.ru) - Hands-on Pentesting Labs (OSCP style)
129 | * [Root-me.org](https://www.root-me.org) - Hundreds of challenges are available to train yourself in different and not simulated environments
130 | * [Vulnhub.com](https://www.vulnhub.com) - Vulnerable By Design VMs for practical 'hands-on' experience in digital security
131 |
132 | ### Off-Line
133 | * [Damn Vulnerable Xebia Training Environment](https://github.com/davevs/dvxte) - Docker Container including several vurnerable web applications (DVWA,DVWServices, DVWSockets, WebGoat, Juiceshop, Railsgoat, django.NV, Buggy Bank, Mutilidae II and more)
134 | * [OWASP Vulnerable Web Applications Directory Project (Offline)](https://www.owasp.org/index.php/OWASP_Vulnerable_Web_Applications_Directory_Project#tab=Off-Line_apps) - List of offline available vulnerable applications for learning purposes
135 | * [Vulnerable SOAP Web Service](https://github.com/anil-yelken/Vulnerable-Soap-Service) - a vulnerable SOAP web service lab environment
136 | * [Vulnerable Flask Web App](https://github.com/anil-yelken/Vulnerable-Flask-App) - vulnerable Flask Web App lab environment
137 |
138 | ## Wireless Hacking
139 |
140 | ### Tools
141 |
142 | * [wifite2](https://github.com/coreb1t/wifite2) - Full automated WiFi security testing script
143 |
144 | ## Defence Topics
145 |
146 | * [Docker Security Cheat Sheet](https://container-solutions.com/content/uploads/2015/06/15.06.15_DockerCheatSheet_A2.pdf) - The following tips should help you to secure a container based system [(PDF version)](docs/DockerCheatSheet.pdf)
147 | * [Windows Domain Hardening](https://github.com/PaulSec/awesome-windows-domain-hardening) - A curated list of awesome Security Hardening techniques for Windows
148 |
149 | ## Programming
150 |
151 | * [JavaScript Cheat Sheet](https://github.com/coodict/javascript-in-one-pic) - Learn javascript in one picture [(Online version)](https://git.io/Js-pic) [(PNG version)](docs/js-in-one-pic.png)
152 | * [Python Cheat Sheet #1](https://github.com/siyuanzhao/python3-in-one-pic) - Learn python3 in one picture [(PNG version)](docs/python-3-in-one-pic.png)
153 | * [Python Cheat Sheet #2 ](https://github.com/coodict/python3-in-one-pic) - Learn python3 in one picture [(Online version)](https://git.io/Coo-py3) [(PNG version)](docs/py3-in-one-pic.png)
154 | * [Python Snippets Cheat Sheet](docs/python-snippets.md) - List of helpful re-usable code snippets in Python
155 |
156 |
157 |
--------------------------------------------------------------------------------
/docs/DockerCheatSheet.pdf:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/coreb1t/awesome-pentest-cheat-sheets/ab0b4405674dced49f4e1e49bb7cebe4245f5782/docs/DockerCheatSheet.pdf
--------------------------------------------------------------------------------
/docs/Metasploit-CheatSheet.pdf:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/coreb1t/awesome-pentest-cheat-sheets/ab0b4405674dced49f4e1e49bb7cebe4245f5782/docs/Metasploit-CheatSheet.pdf
--------------------------------------------------------------------------------
/docs/Metasploit-CheatSheet.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/coreb1t/awesome-pentest-cheat-sheets/ab0b4405674dced49f4e1e49bb7cebe4245f5782/docs/Metasploit-CheatSheet.png
--------------------------------------------------------------------------------
/docs/PowerShellCheatSheet_v41.pdf:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/coreb1t/awesome-pentest-cheat-sheets/ab0b4405674dced49f4e1e49bb7cebe4245f5782/docs/PowerShellCheatSheet_v41.pdf
--------------------------------------------------------------------------------
/docs/Wireshark_Display_Filters.pdf:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/coreb1t/awesome-pentest-cheat-sheets/ab0b4405674dced49f4e1e49bb7cebe4245f5782/docs/Wireshark_Display_Filters.pdf
--------------------------------------------------------------------------------
/docs/js-in-one-pic.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/coreb1t/awesome-pentest-cheat-sheets/ab0b4405674dced49f4e1e49bb7cebe4245f5782/docs/js-in-one-pic.png
--------------------------------------------------------------------------------
/docs/nmap.md:
--------------------------------------------------------------------------------
1 | # Nmap Cheat Sheet
2 |
3 | ## DNS Brute Force
4 |
5 | nmap -p 80 --script dns-brute
6 |
7 | ## Find virtual hosts on an IP address
8 |
9 | nmap -p 80 --script hostmap-bfk
10 |
11 | ## Traceroute Geolocation
12 |
13 | nmap -p 80 --traceroute --script traceroute-geolocation.nse
14 |
15 | ## HTTP Scripts
16 |
17 | + ### HTTP Enum - web path brute force
18 |
19 | nmap -p 80 --script http-enum
20 |
21 | + ### HTTP Title
22 |
23 | nmap -p 80 -sV --script http-title
24 |
--------------------------------------------------------------------------------
/docs/pentest-exploit-dev-cheatsheet.jpg:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/coreb1t/awesome-pentest-cheat-sheets/ab0b4405674dced49f4e1e49bb7cebe4245f5782/docs/pentest-exploit-dev-cheatsheet.jpg
--------------------------------------------------------------------------------
/docs/py3-in-one-pic.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/coreb1t/awesome-pentest-cheat-sheets/ab0b4405674dced49f4e1e49bb7cebe4245f5782/docs/py3-in-one-pic.png
--------------------------------------------------------------------------------
/docs/python-3-in-one-pic.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/coreb1t/awesome-pentest-cheat-sheets/ab0b4405674dced49f4e1e49bb7cebe4245f5782/docs/python-3-in-one-pic.png
--------------------------------------------------------------------------------
/docs/python-snippets.md:
--------------------------------------------------------------------------------
1 | # Python Snippets
2 |
3 | ## File Operations
4 |
5 | * read a file line by line into a list
6 |
7 | * If you want the \n included:
8 |
9 | ```python
10 | with open(fname) as f:
11 | content = f.readlines()
12 | ```
13 |
14 | * If you do not want \n included:
15 |
16 | ```python
17 | with open(fname) as f:
18 | content = f.read().splitlines()
19 | ```
20 |
21 | * move file to the dist_dir folder
22 |
23 | os.rename(, dist_dir + os.path.sep + )
24 |
25 | * get working directory
26 |
27 | PWD = os.getcwd()
28 |
29 | * write file
30 |
31 | RESOURCE = "filename.txt"
32 | fd = open(RESOURCE, 'w')
33 | fd.write("first line\n")
34 | fd.close()
35 |
36 |
37 | ## Parsing Arguments
38 |
39 | ```python
40 | parser = argparse.ArgumentParser()
41 |
42 | parser.add_argument("-p", dest="payload", help=payloads, required=True)
43 | parser.add_argument("-i", dest="interface", help="use interface - default: eth0", default="eth0")
44 | args = parser.parse_args()
45 |
46 | payload_type = args.payload
47 | ```
--------------------------------------------------------------------------------
/docs/shodan.md:
--------------------------------------------------------------------------------
1 | # Shodan Cheat Sheet
2 |
3 | ## Filter
4 |
5 | Here are the basic search filters you can use:
6 |
7 | * `city`: find devices in a particular city
8 | * `country`: find devices in a particular country
9 | * `geo`: you can pass it coordinates
10 | * `hostname`: find values that match the hostname
11 | * `net`: search based on an IP or /x CIDR
12 | * `os`: search based on operating system
13 | * `port`: find particular ports that are open
14 | * `before/after`: find results within a timeframe
15 | * `org`: Search by organization
16 | * `hash`: Search based on banner hash
17 | * `has_screenshot:true`: Filter search based on a screenshot being present
18 | * `title`: Search based on text within the title
19 |
20 | ## Examples
21 |
22 | Find Apache servers in San Francisco:
23 |
24 | apache city:"San Francisco"
25 |
26 | Find Nginx servers in Germany:
27 |
28 | nginx country:"DE"
29 |
30 | Find GWS (Google Web Server) servers:
31 |
32 | "Server: gws" hostname:"google"
33 |
34 | Find Cisco devices on a particular subnet:
35 |
36 | cisco net:"216.219.143.0/24"
37 |
--------------------------------------------------------------------------------
/docs/sqlmap-cheatsheet-1.0-SDB.pdf:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/coreb1t/awesome-pentest-cheat-sheets/ab0b4405674dced49f4e1e49bb7cebe4245f5782/docs/sqlmap-cheatsheet-1.0-SDB.pdf
--------------------------------------------------------------------------------
 62 |
63 | ### Linux Privilege Escalation
64 |
65 | * [Basic Linux Privilege Escalation](https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/) - Linux Privilege Escalation by [@g0tmi1k](https://twitter.com/g0tmi1k)
66 | * [linux-exploit-suggester.sh](https://github.com/mzet-/linux-exploit-suggester) - Linux privilege escalation auditing tool written in bash (updated)
67 | * [Linux_Exploit_Suggester.pl](https://github.com/PenturaLabs/Linux_Exploit_Suggester) - Linux Exploit Suggester written in Perl (last update 3 years ago)
68 | * [Linux_Exploit_Suggester.pl v2](https://github.com/jondonas/linux-exploit-suggester-2) - Next-generation exploit suggester based on Linux_Exploit_Suggester (updated)
69 | * [Linux Soft Exploit Suggester](https://github.com/belane/linux-soft-exploit-suggester) - linux-soft-exploit-suggester finds exploits for all vulnerable software in a system helping with the privilege escalation. It focuses on software packages instead of Kernel vulnerabilities
70 | * [checksec.sh](https://github.com/slimm609/checksec.sh) - bash script to check the properties of executables (like PIE, RELRO, PaX, Canaries, ASLR, Fortify Source)
71 | * [linuxprivchecker.py](http://www.securitysift.com/download/linuxprivchecker.py) - This script is intended to be executed locally on a Linux box to enumerate basic system info and search for common privilege escalation vectors such as world writable files, misconfigurations, clear-text passwords and applicable exploits (@SecuritySift)
72 | * [LinEnum](https://github.com/rebootuser/LinEnum) - This tool is great at running through a heap of things you should check on a Linux system in the post exploit process. This include file permissions, cron jobs if visible, weak credentials etc.(@Rebootuser)
73 | * [linPEAS](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/tree/master/linPEAS) - LinPEAS - Linux Privilege Escalation Awesome Script. Check the Local Linux Privilege Escalation checklist from [book.hacktricks.xyz](https://book.hacktricks.xyz)
74 | * [MimiPenguin](https://github.com/huntergregal/mimipenguin) - A tool to dump the login password from the current linux desktop user. Adapted from the idea behind the popular Windows tool mimikatz.
75 |
76 |
77 | ### Windows Privilege Escalation
78 |
79 | * [PowerUp](https://github.com/PowerShellMafia/PowerSploit/tree/master/Privesc) - Excellent powershell script for checking of common Windows privilege escalation vectors. Written by [harmj0y](https://twitter.com/harmj0y) [(direct link)](https://raw.githubusercontent.com/PowerShellMafia/PowerSploit/master/Privesc/PowerUp.ps1)
80 | * [PowerUp Cheat Sheet](https://github.com/HarmJ0y/CheatSheets/blob/master/PowerUp.pdf)
81 | * [Windows Exploit Suggester](https://github.com/GDSSecurity/Windows-Exploit-Suggester) - Tool for detection of missing security patches on the windows operating system and mapping with the public available exploits
82 | * [Sherlock](https://github.com/rasta-mouse/Sherlock) - PowerShell script to quickly find missing software patches for local privilege escalation vulnerabilities
83 | * [Watson](https://github.com/rasta-mouse/Watson) - Enumerate missing KBs and suggest exploits for useful Privilege Escalation vulnerabilities
84 | * [Precompiled Windows Exploits](https://github.com/abatchy17/WindowsExploits) - Collection of precompiled Windows exploits
85 | * [Metasploit Modules](https://github.com/rapid7/metasploit-framework)
86 | * post/multi/recon/local_exploit_suggester - suggests local meterpreter exploits that can be used
87 | * post/windows/gather/enum_patches - helps to identify any missing patches
88 |
89 |
90 | ## Tools
91 |
92 | * [Nmap Cheat Sheet](docs/nmap.md)
93 | * [SQLmap Cheat Sheet](docs/sqlmap-cheatsheet-1.0-SDB.pdf)
94 | * [SQLmap Tamper Scripts](https://forum.bugcrowd.com/t/sqlmap-tamper-scripts-sql-injection-and-waf-bypass/423) - SQLmap Tamper Scripts General/MSSQL/MySQL
95 | * [VIM Cheatsheet](https://i.imgur.com/YLInLlY.png)
96 | * [Wireshark Display Filters](docs/Wireshark_Display_Filters.pdf) - Filters for the best sniffing tool
97 |
98 | # Tools Online
99 | * [XSS'OR Encoder/Decoder](http://xssor.io/#ende) - Online Decoder/Encoder for testing purposes (@evilcos)
100 | * [WebGun](https://brutelogic.com.br/webgun/) - WebGun, XSS Payload Creator (@brutelogic)
101 | * [Hackvertor](https://hackvertor.co.uk) - Tool to convert various encodings and generate attack vectors (@garethheyes)
102 | * [JSFiddle](https://jsfiddle.net) - Test and share XSS payloads, [Example PoC](https://jsfiddle.net/xqjpsh65/)
103 |
104 | ## Payloads
105 |
106 | ### Genaral
107 | * [Fuzzdb](https://github.com/fuzzdb-project/fuzzdb) - Dictionary of attack patterns and primitives for black-box application testing
108 | Polyglot Challenge with submitted solutions
109 | * [SecList](https://github.com/danielmiessler/SecLists) - A collection of multiple types of lists used during security assessments. List types include usernames, passwords, URLs, sensitive data grep strings, fuzzing payloads, and many more
110 |
111 | ### XSS
112 | * [XSS Polyglot Payloads #1](https://github.com/0xsobky/HackVault/wiki/Unleashing-an-Ultimate-XSS-Polyglot) - Unleashing an Ultimate XSS Polyglot list by 0xsobky
113 | * [XSS Polyglot Payloads #2](http://polyglot.innerht.ml/) - [@filedescriptor](https://twitter.com/filedescriptor)'s XSS
114 | * [Browser's-XSS-Filter-Bypass-Cheat-Sheet](https://github.com/masatokinugawa/filterbypass/wiki/Browser's-XSS-Filter-Bypass-Cheat-Sheet)- Excellent List of working XSS bypasses running on the latest version of Chrome / Safari, IE 11 / Edge created by Masato Kinugawa
115 |
116 | ## Write-Ups
117 |
118 | * [Bug Bounty Reference](https://github.com/ngalongc/bug-bounty-reference) - huge list of bug bounty write-up that is categorized by the bug type (SQLi, XSS, IDOR, etc.)
119 | * [Write-Ups for CTF challenges](https://ctftime.org/writeups)
120 | * [Facebook Bug Bounties](https://www.facebook.com/notes/phwd/facebook-bug-bounties/707217202701640) - Categorized Facebook Bug Bounties write-ups
121 |
122 |
123 | ## Learning Platforms
124 |
125 | ### Online
126 | * [Hack The Box :: Penetration Testing Labs](https://www.hackthebox.eu)
127 | * [OWASP Vulnerable Web Applications Directory Project (Online)](https://www.owasp.org/index.php/OWASP_Vulnerable_Web_Applications_Directory_Project#tab=On-Line_apps) - List of online available vulnerable applications for learning purposes
128 | * [Pentestit labs](https://lab.pentestit.ru) - Hands-on Pentesting Labs (OSCP style)
129 | * [Root-me.org](https://www.root-me.org) - Hundreds of challenges are available to train yourself in different and not simulated environments
130 | * [Vulnhub.com](https://www.vulnhub.com) - Vulnerable By Design VMs for practical 'hands-on' experience in digital security
131 |
132 | ### Off-Line
133 | * [Damn Vulnerable Xebia Training Environment](https://github.com/davevs/dvxte) - Docker Container including several vurnerable web applications (DVWA,DVWServices, DVWSockets, WebGoat, Juiceshop, Railsgoat, django.NV, Buggy Bank, Mutilidae II and more)
134 | * [OWASP Vulnerable Web Applications Directory Project (Offline)](https://www.owasp.org/index.php/OWASP_Vulnerable_Web_Applications_Directory_Project#tab=Off-Line_apps) - List of offline available vulnerable applications for learning purposes
135 | * [Vulnerable SOAP Web Service](https://github.com/anil-yelken/Vulnerable-Soap-Service) - a vulnerable SOAP web service lab environment
136 | * [Vulnerable Flask Web App](https://github.com/anil-yelken/Vulnerable-Flask-App) - vulnerable Flask Web App lab environment
137 |
138 | ## Wireless Hacking
139 |
140 | ### Tools
141 |
142 | * [wifite2](https://github.com/coreb1t/wifite2) - Full automated WiFi security testing script
143 |
144 | ## Defence Topics
145 |
146 | * [Docker Security Cheat Sheet](https://container-solutions.com/content/uploads/2015/06/15.06.15_DockerCheatSheet_A2.pdf) - The following tips should help you to secure a container based system [(PDF version)](docs/DockerCheatSheet.pdf)
147 | * [Windows Domain Hardening](https://github.com/PaulSec/awesome-windows-domain-hardening) - A curated list of awesome Security Hardening techniques for Windows
148 |
149 | ## Programming
150 |
151 | * [JavaScript Cheat Sheet](https://github.com/coodict/javascript-in-one-pic) - Learn javascript in one picture [(Online version)](https://git.io/Js-pic) [(PNG version)](docs/js-in-one-pic.png)
152 | * [Python Cheat Sheet #1](https://github.com/siyuanzhao/python3-in-one-pic) - Learn python3 in one picture [(PNG version)](docs/python-3-in-one-pic.png)
153 | * [Python Cheat Sheet #2 ](https://github.com/coodict/python3-in-one-pic) - Learn python3 in one picture [(Online version)](https://git.io/Coo-py3) [(PNG version)](docs/py3-in-one-pic.png)
154 | * [Python Snippets Cheat Sheet](docs/python-snippets.md) - List of helpful re-usable code snippets in Python
155 |
156 |
157 |
--------------------------------------------------------------------------------
/docs/DockerCheatSheet.pdf:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/coreb1t/awesome-pentest-cheat-sheets/ab0b4405674dced49f4e1e49bb7cebe4245f5782/docs/DockerCheatSheet.pdf
--------------------------------------------------------------------------------
/docs/Metasploit-CheatSheet.pdf:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/coreb1t/awesome-pentest-cheat-sheets/ab0b4405674dced49f4e1e49bb7cebe4245f5782/docs/Metasploit-CheatSheet.pdf
--------------------------------------------------------------------------------
/docs/Metasploit-CheatSheet.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/coreb1t/awesome-pentest-cheat-sheets/ab0b4405674dced49f4e1e49bb7cebe4245f5782/docs/Metasploit-CheatSheet.png
--------------------------------------------------------------------------------
/docs/PowerShellCheatSheet_v41.pdf:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/coreb1t/awesome-pentest-cheat-sheets/ab0b4405674dced49f4e1e49bb7cebe4245f5782/docs/PowerShellCheatSheet_v41.pdf
--------------------------------------------------------------------------------
/docs/Wireshark_Display_Filters.pdf:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/coreb1t/awesome-pentest-cheat-sheets/ab0b4405674dced49f4e1e49bb7cebe4245f5782/docs/Wireshark_Display_Filters.pdf
--------------------------------------------------------------------------------
/docs/js-in-one-pic.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/coreb1t/awesome-pentest-cheat-sheets/ab0b4405674dced49f4e1e49bb7cebe4245f5782/docs/js-in-one-pic.png
--------------------------------------------------------------------------------
/docs/nmap.md:
--------------------------------------------------------------------------------
1 | # Nmap Cheat Sheet
2 |
3 | ## DNS Brute Force
4 |
5 | nmap -p 80 --script dns-brute
62 |
63 | ### Linux Privilege Escalation
64 |
65 | * [Basic Linux Privilege Escalation](https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/) - Linux Privilege Escalation by [@g0tmi1k](https://twitter.com/g0tmi1k)
66 | * [linux-exploit-suggester.sh](https://github.com/mzet-/linux-exploit-suggester) - Linux privilege escalation auditing tool written in bash (updated)
67 | * [Linux_Exploit_Suggester.pl](https://github.com/PenturaLabs/Linux_Exploit_Suggester) - Linux Exploit Suggester written in Perl (last update 3 years ago)
68 | * [Linux_Exploit_Suggester.pl v2](https://github.com/jondonas/linux-exploit-suggester-2) - Next-generation exploit suggester based on Linux_Exploit_Suggester (updated)
69 | * [Linux Soft Exploit Suggester](https://github.com/belane/linux-soft-exploit-suggester) - linux-soft-exploit-suggester finds exploits for all vulnerable software in a system helping with the privilege escalation. It focuses on software packages instead of Kernel vulnerabilities
70 | * [checksec.sh](https://github.com/slimm609/checksec.sh) - bash script to check the properties of executables (like PIE, RELRO, PaX, Canaries, ASLR, Fortify Source)
71 | * [linuxprivchecker.py](http://www.securitysift.com/download/linuxprivchecker.py) - This script is intended to be executed locally on a Linux box to enumerate basic system info and search for common privilege escalation vectors such as world writable files, misconfigurations, clear-text passwords and applicable exploits (@SecuritySift)
72 | * [LinEnum](https://github.com/rebootuser/LinEnum) - This tool is great at running through a heap of things you should check on a Linux system in the post exploit process. This include file permissions, cron jobs if visible, weak credentials etc.(@Rebootuser)
73 | * [linPEAS](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/tree/master/linPEAS) - LinPEAS - Linux Privilege Escalation Awesome Script. Check the Local Linux Privilege Escalation checklist from [book.hacktricks.xyz](https://book.hacktricks.xyz)
74 | * [MimiPenguin](https://github.com/huntergregal/mimipenguin) - A tool to dump the login password from the current linux desktop user. Adapted from the idea behind the popular Windows tool mimikatz.
75 |
76 |
77 | ### Windows Privilege Escalation
78 |
79 | * [PowerUp](https://github.com/PowerShellMafia/PowerSploit/tree/master/Privesc) - Excellent powershell script for checking of common Windows privilege escalation vectors. Written by [harmj0y](https://twitter.com/harmj0y) [(direct link)](https://raw.githubusercontent.com/PowerShellMafia/PowerSploit/master/Privesc/PowerUp.ps1)
80 | * [PowerUp Cheat Sheet](https://github.com/HarmJ0y/CheatSheets/blob/master/PowerUp.pdf)
81 | * [Windows Exploit Suggester](https://github.com/GDSSecurity/Windows-Exploit-Suggester) - Tool for detection of missing security patches on the windows operating system and mapping with the public available exploits
82 | * [Sherlock](https://github.com/rasta-mouse/Sherlock) - PowerShell script to quickly find missing software patches for local privilege escalation vulnerabilities
83 | * [Watson](https://github.com/rasta-mouse/Watson) - Enumerate missing KBs and suggest exploits for useful Privilege Escalation vulnerabilities
84 | * [Precompiled Windows Exploits](https://github.com/abatchy17/WindowsExploits) - Collection of precompiled Windows exploits
85 | * [Metasploit Modules](https://github.com/rapid7/metasploit-framework)
86 | * post/multi/recon/local_exploit_suggester - suggests local meterpreter exploits that can be used
87 | * post/windows/gather/enum_patches - helps to identify any missing patches
88 |
89 |
90 | ## Tools
91 |
92 | * [Nmap Cheat Sheet](docs/nmap.md)
93 | * [SQLmap Cheat Sheet](docs/sqlmap-cheatsheet-1.0-SDB.pdf)
94 | * [SQLmap Tamper Scripts](https://forum.bugcrowd.com/t/sqlmap-tamper-scripts-sql-injection-and-waf-bypass/423) - SQLmap Tamper Scripts General/MSSQL/MySQL
95 | * [VIM Cheatsheet](https://i.imgur.com/YLInLlY.png)
96 | * [Wireshark Display Filters](docs/Wireshark_Display_Filters.pdf) - Filters for the best sniffing tool
97 |
98 | # Tools Online
99 | * [XSS'OR Encoder/Decoder](http://xssor.io/#ende) - Online Decoder/Encoder for testing purposes (@evilcos)
100 | * [WebGun](https://brutelogic.com.br/webgun/) - WebGun, XSS Payload Creator (@brutelogic)
101 | * [Hackvertor](https://hackvertor.co.uk) - Tool to convert various encodings and generate attack vectors (@garethheyes)
102 | * [JSFiddle](https://jsfiddle.net) - Test and share XSS payloads, [Example PoC](https://jsfiddle.net/xqjpsh65/)
103 |
104 | ## Payloads
105 |
106 | ### Genaral
107 | * [Fuzzdb](https://github.com/fuzzdb-project/fuzzdb) - Dictionary of attack patterns and primitives for black-box application testing
108 | Polyglot Challenge with submitted solutions
109 | * [SecList](https://github.com/danielmiessler/SecLists) - A collection of multiple types of lists used during security assessments. List types include usernames, passwords, URLs, sensitive data grep strings, fuzzing payloads, and many more
110 |
111 | ### XSS
112 | * [XSS Polyglot Payloads #1](https://github.com/0xsobky/HackVault/wiki/Unleashing-an-Ultimate-XSS-Polyglot) - Unleashing an Ultimate XSS Polyglot list by 0xsobky
113 | * [XSS Polyglot Payloads #2](http://polyglot.innerht.ml/) - [@filedescriptor](https://twitter.com/filedescriptor)'s XSS
114 | * [Browser's-XSS-Filter-Bypass-Cheat-Sheet](https://github.com/masatokinugawa/filterbypass/wiki/Browser's-XSS-Filter-Bypass-Cheat-Sheet)- Excellent List of working XSS bypasses running on the latest version of Chrome / Safari, IE 11 / Edge created by Masato Kinugawa
115 |
116 | ## Write-Ups
117 |
118 | * [Bug Bounty Reference](https://github.com/ngalongc/bug-bounty-reference) - huge list of bug bounty write-up that is categorized by the bug type (SQLi, XSS, IDOR, etc.)
119 | * [Write-Ups for CTF challenges](https://ctftime.org/writeups)
120 | * [Facebook Bug Bounties](https://www.facebook.com/notes/phwd/facebook-bug-bounties/707217202701640) - Categorized Facebook Bug Bounties write-ups
121 |
122 |
123 | ## Learning Platforms
124 |
125 | ### Online
126 | * [Hack The Box :: Penetration Testing Labs](https://www.hackthebox.eu)
127 | * [OWASP Vulnerable Web Applications Directory Project (Online)](https://www.owasp.org/index.php/OWASP_Vulnerable_Web_Applications_Directory_Project#tab=On-Line_apps) - List of online available vulnerable applications for learning purposes
128 | * [Pentestit labs](https://lab.pentestit.ru) - Hands-on Pentesting Labs (OSCP style)
129 | * [Root-me.org](https://www.root-me.org) - Hundreds of challenges are available to train yourself in different and not simulated environments
130 | * [Vulnhub.com](https://www.vulnhub.com) - Vulnerable By Design VMs for practical 'hands-on' experience in digital security
131 |
132 | ### Off-Line
133 | * [Damn Vulnerable Xebia Training Environment](https://github.com/davevs/dvxte) - Docker Container including several vurnerable web applications (DVWA,DVWServices, DVWSockets, WebGoat, Juiceshop, Railsgoat, django.NV, Buggy Bank, Mutilidae II and more)
134 | * [OWASP Vulnerable Web Applications Directory Project (Offline)](https://www.owasp.org/index.php/OWASP_Vulnerable_Web_Applications_Directory_Project#tab=Off-Line_apps) - List of offline available vulnerable applications for learning purposes
135 | * [Vulnerable SOAP Web Service](https://github.com/anil-yelken/Vulnerable-Soap-Service) - a vulnerable SOAP web service lab environment
136 | * [Vulnerable Flask Web App](https://github.com/anil-yelken/Vulnerable-Flask-App) - vulnerable Flask Web App lab environment
137 |
138 | ## Wireless Hacking
139 |
140 | ### Tools
141 |
142 | * [wifite2](https://github.com/coreb1t/wifite2) - Full automated WiFi security testing script
143 |
144 | ## Defence Topics
145 |
146 | * [Docker Security Cheat Sheet](https://container-solutions.com/content/uploads/2015/06/15.06.15_DockerCheatSheet_A2.pdf) - The following tips should help you to secure a container based system [(PDF version)](docs/DockerCheatSheet.pdf)
147 | * [Windows Domain Hardening](https://github.com/PaulSec/awesome-windows-domain-hardening) - A curated list of awesome Security Hardening techniques for Windows
148 |
149 | ## Programming
150 |
151 | * [JavaScript Cheat Sheet](https://github.com/coodict/javascript-in-one-pic) - Learn javascript in one picture [(Online version)](https://git.io/Js-pic) [(PNG version)](docs/js-in-one-pic.png)
152 | * [Python Cheat Sheet #1](https://github.com/siyuanzhao/python3-in-one-pic) - Learn python3 in one picture [(PNG version)](docs/python-3-in-one-pic.png)
153 | * [Python Cheat Sheet #2 ](https://github.com/coodict/python3-in-one-pic) - Learn python3 in one picture [(Online version)](https://git.io/Coo-py3) [(PNG version)](docs/py3-in-one-pic.png)
154 | * [Python Snippets Cheat Sheet](docs/python-snippets.md) - List of helpful re-usable code snippets in Python
155 |
156 |
157 |
--------------------------------------------------------------------------------
/docs/DockerCheatSheet.pdf:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/coreb1t/awesome-pentest-cheat-sheets/ab0b4405674dced49f4e1e49bb7cebe4245f5782/docs/DockerCheatSheet.pdf
--------------------------------------------------------------------------------
/docs/Metasploit-CheatSheet.pdf:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/coreb1t/awesome-pentest-cheat-sheets/ab0b4405674dced49f4e1e49bb7cebe4245f5782/docs/Metasploit-CheatSheet.pdf
--------------------------------------------------------------------------------
/docs/Metasploit-CheatSheet.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/coreb1t/awesome-pentest-cheat-sheets/ab0b4405674dced49f4e1e49bb7cebe4245f5782/docs/Metasploit-CheatSheet.png
--------------------------------------------------------------------------------
/docs/PowerShellCheatSheet_v41.pdf:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/coreb1t/awesome-pentest-cheat-sheets/ab0b4405674dced49f4e1e49bb7cebe4245f5782/docs/PowerShellCheatSheet_v41.pdf
--------------------------------------------------------------------------------
/docs/Wireshark_Display_Filters.pdf:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/coreb1t/awesome-pentest-cheat-sheets/ab0b4405674dced49f4e1e49bb7cebe4245f5782/docs/Wireshark_Display_Filters.pdf
--------------------------------------------------------------------------------
/docs/js-in-one-pic.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/coreb1t/awesome-pentest-cheat-sheets/ab0b4405674dced49f4e1e49bb7cebe4245f5782/docs/js-in-one-pic.png
--------------------------------------------------------------------------------
/docs/nmap.md:
--------------------------------------------------------------------------------
1 | # Nmap Cheat Sheet
2 |
3 | ## DNS Brute Force
4 |
5 | nmap -p 80 --script dns-brute