├── README.md
├── access.lua
├── config.lua
├── init.lua
├── other
├── 20180503174007.png
├── 20180503174354.png
├── WAF.png
├── nginx.conf
├── socket.lua
├── usertime.c
├── usertime.so
└── 编译命令.txt
├── rules
├── args.rule
├── blackip.rule
├── cookie.rule
├── frequency.rule
├── post.rule
├── re.txt
├── url.rule
├── useragent.rule
├── whiteip.rule
└── whiteurl.rule
├── util.lua
└── waf.lua
/README.md:
--------------------------------------------------------------------------------
1 | # Nginx-Lua-WAF概述
2 | Nginx-Lua-WAF是一款基于Nginx的使用Lua语言开发的灵活高效的Web应用层防火墙。Lua语言的灵活和不亚于C语言的执行效率,保证了在做为网站应用层防火墙时,功能和性能之间完美的平衡,整个防火墙系统对性能的消耗几乎可以忽略不计。
3 |
4 | Nginx-Lua-WAF完全可以放心在生产环境中使用,整个防火墙仅由5个lua程序文件组成,逻辑清晰,代码简单易懂,并配有较为详细的注释。整个代码全部读完也不会超过半个小时。强列建议先看下代码,相信你能很容易看懂。
5 |
6 | 本项目推荐使用由春哥(章亦春)维护的基于Nginx和LuaJIT的Web平台OpenResty作为Web服务器。OpenResty可以看作是在Nginx中添加了Lua的支持,并集成了常用的各类Lua库。当然,也可以手动编译Nginx,在编译中添加lua-nginx-module。
7 |
8 | # 主要特性
9 | 防火墙只是一个框架,核心是rule规则文件,源码中规则文件仅供参考,在实际的使用过程中,接合自己的业务特点,可以灵活开关各项功能,以及增添各种规则。
10 | - 支持对特定站点特定IP和特定URL组合的访问频率控制,即可以通过配置的百分比控制返回真实数据或预先配置的JSON字符串,该功能通常用于希望控制访问频率的接口,不希望客户端高频访问,以优雅的方式减少服务端不必要的性能开销
11 | - Nginx工作于web服务器模式,可以有多个不同的站点,仅需要配置hostname就可以对不同的站点应用不同的规则,或者使用全局的规则
12 | - 规则使用正则匹配,灵活性高
13 | - 支持IP白名单、IP黑名单、UserAgent、URL白名单、URL、Cookie、请求参数、POST级别的过滤,每个功能均有独立开关,可以自由启用需要的过滤功能,并且在规则层面都是可以基于站点的
14 | - 支持对CC攻击的防护
15 | - 完整的日志记录功能,JSON格式日志,方便后期通过ELK集中管理
16 | - 匹配规则后,支持回显html字符串、跳转到指定URL和不处理三种模式,其不设置为不处理后,仅记录日志,并不真正执行拦截动作,方便在生产环境中调试,不影响业务
17 | - 安装、部署和维护非常简单
18 | - 重载规则不会中断正常业务
19 | - 跨平台,Nginx可以运行在哪里,WAF就可以运行在哪里
20 |
21 | # 性能测试
22 | Nginx-Lua-WAF拥有非常高的性能,在虚拟机中测试结果如下:
23 | - 系统:CentOS Linux release 7.3.1611 (Core)
24 | - 内核:3.10.0-514.el7.x86_64
25 | - 内存:1G
26 | - CPU:1核心 Intel(R) Core(TM) i7-4600U CPU @ 2.10GHz
27 | - 测试命令:ab -n 10000 -c 50 http://127.0.0.1/index.html
28 |
29 | ### 关闭waf时测试
30 | 每秒处理14806次请求,处理单个请求平均3毫秒
31 |
32 | 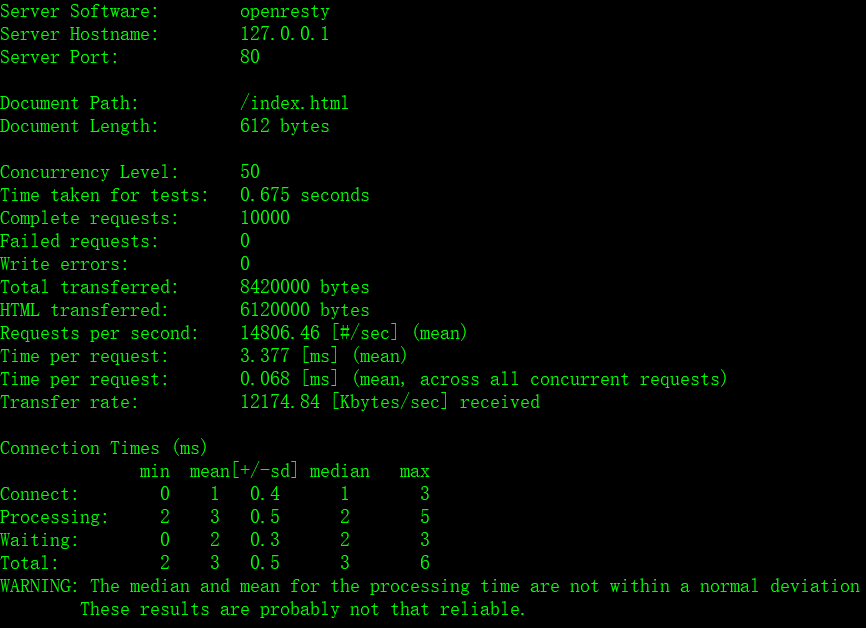
33 | ### 开启waf时测试
34 | (开启所有功能,因为有cc检测,将cc阈值设置为20000/60防止压测时被拦截)
35 | 每秒处理9581次请求,处理单个请求平均5毫秒
36 |
37 | 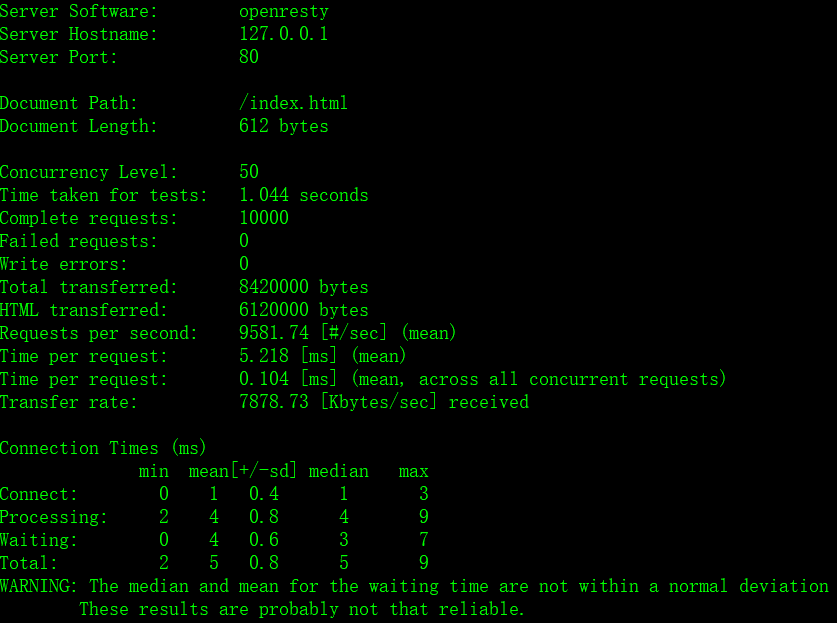
38 | ##### 可以看出启用waf后,Nginx性能依然非常高,近10k次的处理能力,能够满足任何业务场景的需要
39 |
40 | # Nginx-Lua-WAF处理流程
41 | 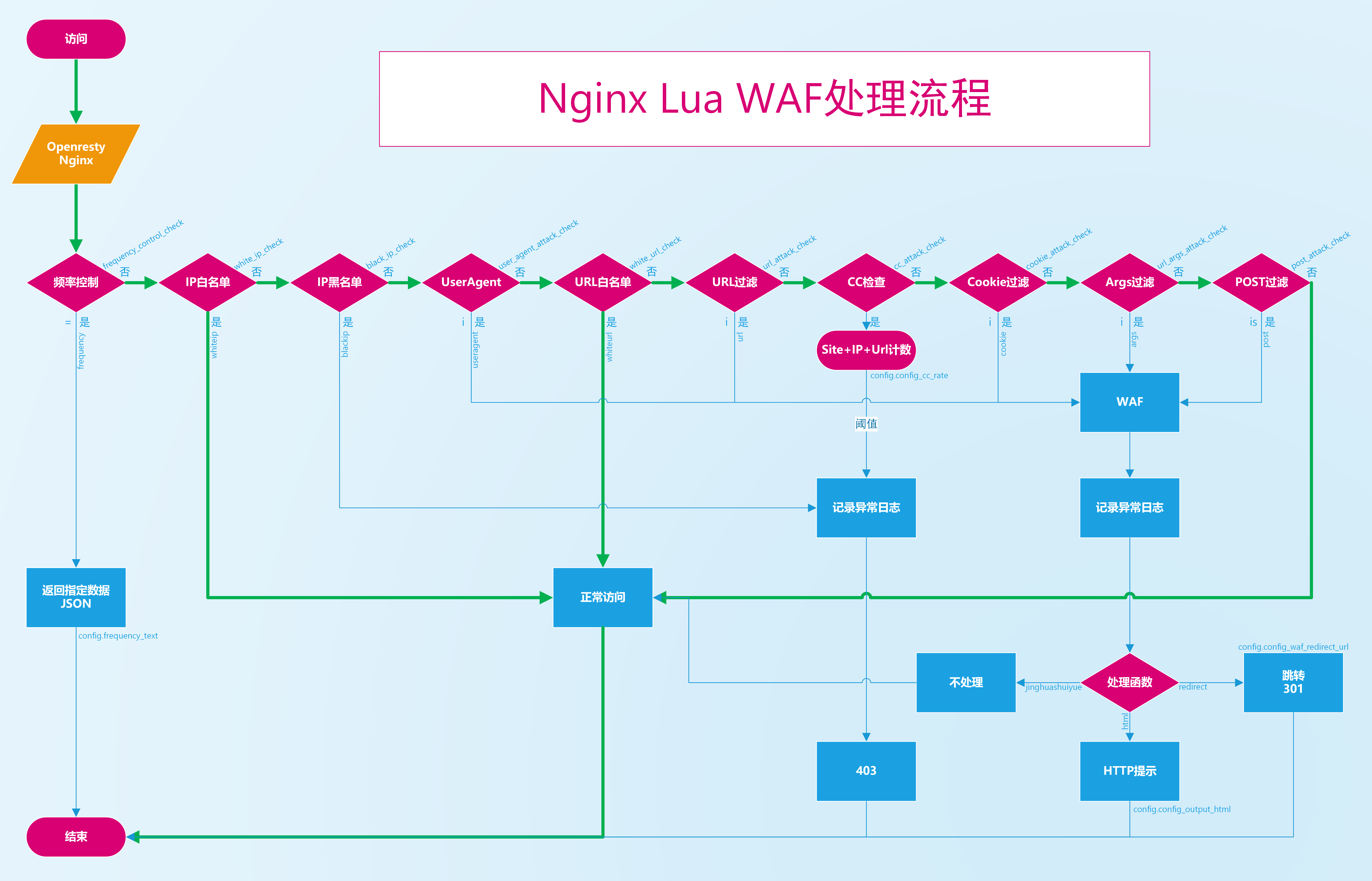
42 |
43 | # 安装部署
44 | ## 以CentOS 7为例
45 | ### 编译安装openresty
46 |
47 | 从[openresty](http://openresty.org/cn/download.html)官方下载最新版本的源码包。
48 |
49 | 01、编译安装openresty:
50 |
51 | ```bash
52 | #安装工具
53 | yum -y install wget
54 | #准备编译环境
55 | yum -y install gcc
56 | #准备依赖包
57 | yum -y install install perl openssl openssl-devel
58 | #下载并解压源码包
59 | wget https://openresty.org/download/openresty-1.13.6.1.tar.gz
60 | tar zxf openresty-1.13.6.1.tar.gz
61 | #编译安装
62 | cd openresty-1.13.6.1
63 | ./configure
64 | make
65 | make install
66 | #默认openresty会安装到/usr/local/openresty目录
67 | #nginx配置文件位置:/usr/local/openresty/nginx/conf/nginx.conf
68 | #nginx站点目录:/usr/local/openresty/nginx/html
69 | #nginx可执行文件位置:/usr/local/openresty/nginx/sbin/nginx
70 | #后续工作
71 | #临时关闭selinux
72 | setenforce 0
73 | #开启防火墙
74 | #开启80端口的两种方式
75 | firewall-cmd --permanent --zone=public --add-port=80/tcp
76 | firewall-cmd --permanent --zone=public --add-service=http
77 | firewall-cmd --reload #重载防火墙,使配置生效
78 | #启动nginx
79 | /usr/local/openresty/nginx/sbin/nginx -t #检查配置文件语法是否正确
80 | /usr/local/openresty/nginx/sbin/nginx #启动nginx
81 | ```
82 |
83 | 02、编译模块usertime.so
84 |
85 | ```bash
86 | #usertime.c文件位于nginx-lua-waf/other/usertime.c
87 | #编译好的usertime.so位于nginx-lua-waf/other/usertime.so
88 | #如果平台和我的不一样建议自己编译usertime.so模块
89 | #安装依赖包
90 | yum -y install lua-devel
91 | #编译模块usertime.so
92 | cc -g -O2 -Wall -fPIC --shared usertime.c -o usertime.so
93 | #将模块复制到lualib目录
94 | cp usertime.so /usr/local/openresty/lualib
95 | #如果是直接使用我编译的usertime.so,复制到lualib后需要授予可执行权限
96 | chmod a+x /usr/local/openresty/lualib/usertime.so
97 | ```
98 |
99 | 03、部署Nginx-Lua-WAF
100 |
101 | ```
102 | #安装工具
103 | yum -y install unzip
104 | #下载Nginx-Lua-WAF
105 | wget https://github.com/ddonline/nginx-lua-waf/archive/master.zip
106 | #解压缩
107 | unzip master.zip #解压后得到文件夹nginx-lua-waf-master
108 | #对文件夹重命名
109 | mv nginx-lua-waf-master nginx-lua-waf
110 | #将nginx-lua-waf文件夹复制到nginx/conf目录下
111 | cp -r nginx-lua-waf /usr/local/openresty/nginx/conf
112 |
113 | #在nginx.conf中添加配置
114 | vi /usr/local/openresty/nginx/conf/nginx.conf
115 | 在http级别添加以下内容:
116 | #nginx-lua-waf配置
117 | lua_package_path "/usr/local/openresty/nginx/conf/nginx-lua-waf/?.lua;";
118 | lua_shared_dict limit 100m;
119 | #开启lua代码缓存功能
120 | lua_code_cache on;
121 | lua_regex_cache_max_entries 4096;
122 | init_by_lua_file /usr/local/openresty/nginx/conf/nginx-lua-waf/init.lua;
123 | access_by_lua_file /usr/local/openresty/nginx/conf/nginx-lua-waf/access.lua;
124 | 在server级别修改server_name:
125 | #在每个vhost中(server级别)定义server_name时,建议设置一个以上的主机名,默认第一个将做为规则中的主机区别标志,例如
126 | server_name api api.test.com;
127 |
128 | #修改config.lua中日志文件和规则文件路径和其它需要配置的项目
129 | vi /usr/local/openresty/nginx/conf/nginx-lua-waf/config.lua
130 | config_log_dir = "/var/log/nginx",
131 | config_rule_dir = "/usr/local/openresty/nginx/conf/nginx-lua-waf/rules",
132 | #修改日志目录权限,使nginx对目录可写
133 | mkdir -p /var/log/nginx/
134 | chmod o+w /var/log/nginx/
135 | #重载nginx使配置生效
136 | /usr/local/openresty/nginx/sbin/nginx -t #检查配置文件语法是否正确
137 | /usr/local/openresty/nginx/sbin/nginx -s reload #重载nginx
138 | #测试waf是否工作正常
139 | curl http://127.0.0.1/test.zip
140 | #若返回 "规则过滤测试" 字样,则说明waf已生效,url.rule中定义有规则阻止下载zip文件,此时/var/log/nginx/目录中应有类似2018-05-04_waf.log的JSON格式日志文件
141 | #若返回 404 说明waf未生效
142 | ```
143 |
144 | # 使用中注意事项
145 | - waf配置文件:nginx-lua-waf/config.lua,各项配置均有注释说明
146 | - 使用前请检查过滤规则是否符合自己实际情况,根据实际增删条目,防止误伤
147 | - 规则文件除frequency.rule外全部为正则表达式,除frequency.rule、whiteip.rule、blackip.rule、whiteurl.rule外全部不区分大小写
148 | - 规则文件中以"--"开头的为注释内容,除最后一行外,不能留有空行,且结尾字符应为LF
149 | - 在用于生产环境时,可先将模式设置为jinghuashuiyue并检查拦截日志,确认有无误伤,该模式仅记录日志,不实际进行拦截(对IP黑名单和CC攻击过滤不适用,详见处理流程图)
150 | - 更新规则文件后,使用reload命令(/usr/local/openresty/nginx/sbin/nginx -s reload)使用配置生效,该命令不会中断服务,不建议使用restart
151 | - 部署过程中对openresty的安装使用的是默认选项,如果需要自定义,可以参考我的博文:[编译Nginx(OpenResty)支持Lua扩展](http://pdf.us/2018/03/19/742.html)
152 |
153 |
154 | # 致谢
155 |
156 | 1. 感谢春哥开源的[openresty](https://openresty.org)
157 | 2. 开源项目:https://github.com/xsec-lab/x-waf
158 | 3. 开源项目:https://github.com/tluolovembtan/jsh_waf
159 | 4. 开源项目:https://github.com/loveshell/ngx_lua_waf
160 |
--------------------------------------------------------------------------------
/access.lua:
--------------------------------------------------------------------------------
1 | waf.check()
--------------------------------------------------------------------------------
/config.lua:
--------------------------------------------------------------------------------
1 | --[[
2 | 说明:
3 | 1、nginx配置:在http级别添加以下内容
4 | #nginx-lua-waf配置
5 | lua_package_path "/usr/local/openresty/nginx/conf/nginx-lua-waf/?.lua;";
6 | lua_shared_dict limit 100m;
7 | #开启lua代码缓存功能
8 | lua_code_cache on;
9 | lua_regex_cache_max_entries 4096;
10 | init_by_lua_file /usr/local/openresty/nginx/conf/nginx-lua-waf/init.lua;
11 | access_by_lua_file /usr/local/openresty/nginx/conf/nginx-lua-waf/access.lua;
12 | 2、vhost配置:server_name第一个名称为规则主机限制时的关键词
13 | server_name api api.test.com;
14 | 3、规则格式:
15 | 所有规则均可添加主机限制,如api-index.html 这会仅限制api站点的访问
16 | 如果不添加,则为全局限制
17 | 4、规则文件一行一条规则
18 | 5、规则文件可以使用"--"进行注释
19 | 6、规则文件需要LF行结尾 否则会发生问题
20 | 7、性能:
21 | ab -n 10000 -c 50 http://127.0.0.1/index.html
22 | 关闭waf Requests per second: 14806 [#/sec] (mean)
23 | 打开waf Requests per second: 9581 [#/sec] (mean)
24 | 8、日志存放文件夹需要有写放权限 chmod o+w /var/log/nginx/
25 | ]]
26 | -- enable = "on", disable = "off"
27 |
28 | local _M = {
29 | -- 防火墙开关
30 | config_waf_enable = "on",
31 | -- 日志文件存放目录 结尾不带/
32 | config_log_dir = "/var/log/nginx",
33 | -- 规则文件存放目录 结尾不带/
34 | config_rule_dir = "/usr/local/openresty/nginx/conf/nginx-lua-waf/rules",
35 |
36 | --01假数据时不进行后续流程,非正则匹配
37 | -- 频率控制开关
38 | frequency_control_check = "on",
39 | -- 频率控制中返回空数据内容
40 | frequency_text = [[{"status":"ok"}]],
41 |
42 | --02直接通过不进行后续流程
43 | -- IP白名单开关
44 | config_white_ip_check = "on",
45 |
46 | --03返回403
47 | -- IP黑名单开关
48 | config_black_ip_check = "on",
49 |
50 | --04WAF处理:跳转/html/仅日志
51 | -- UserAgent过滤开关
52 | config_user_agent_check = "on",
53 |
54 | --05直接通过不进行后续流程
55 | -- URL白名单开关
56 | config_white_url_check = "on",
57 |
58 | --06WAF处理:跳转/html/仅日志
59 | -- URL过滤开关
60 | config_url_check = "on",
61 |
62 | --07返回403记录limit
63 | -- CC攻击过滤开关
64 | config_cc_check = "on",
65 | -- 设置CC攻击检测依据 攻击阈值/检测时间段
66 | config_cc_rate = "3000/60",
67 |
68 | --08WAF处理:跳转/html/仅日志
69 | -- Cookie过滤开关
70 | config_cookie_check = "on",
71 |
72 | --09WAF处理:跳转/html/仅日志
73 | -- ARGS请求参数过滤开关
74 | config_url_args_check = "on",
75 |
76 | --10WAF处理:跳转/html/仅日志
77 | -- POST过滤开关
78 | config_post_check = "on",
79 | -- 处理方式 redirect/html/jinghuashuiyue jinghuashuiyue只记录日志
80 | config_waf_model = "html",
81 | -- 当配置为redirect时跳转到的URL
82 | config_waf_redirect_url = "http://www.baidu.com",
83 | -- bad_guys过期时间
84 | -- config_expire_time = 600,
85 | -- 当配置为html时 显示的内容
86 | config_output_html = [[
87 |
88 |
89 |
90 | LEPEI WAF
91 |
92 |
93 |
94 |
95 |
96 |
97 | 您的IP为: %s
98 |
99 |
100 | 已触发WAF规则
101 |
102 |
103 | 实际使用请修改此提示信息
104 |
105 |
106 |
107 |