142 |
143 | Colors
144 |
145 | Red - This security group has ports open and contains instances with public IP
146 | addresses. Those instances can accept traffic on those ports, and it should be
147 | verified that this is intended.
148 |
149 |
150 | Yellow - This security
151 | group is not ideal, but does not present an immediate risk. It is
152 | worth examining to see if it can be further locked down or removed,
153 | if unused.
154 |
155 |
156 | Green - No recommendations
157 | for this security group.
158 |
159 |
160 |
161 | Assumptions
162 |
163 | Default security groups should not be used, and should be locked down.
164 | This prevents instances from accidentally inheriting open ports when
165 | created.
166 |
167 |
168 | Unused security groups should be removed, as they represent surface area
169 | that doesn't need to exist.
170 |
171 |
172 | While we do list IP addresses alongside ports that are open, we do not
173 | verify whether any of the instances are actually listening on those ports.
174 | We recommend not relying only on instances not actively listening
175 | on a port. The principle of defense-in-depth suggests that if an instance
176 | does not need a port open, the firewall should also enforce that.
177 |
178 |
179 |
 51 |
52 | `nmap` results are in `output/nmap/` with a summary cross-referencing security groups found in nmap.html:
53 |
54 |
51 |
52 | `nmap` results are in `output/nmap/` with a summary cross-referencing security groups found in nmap.html:
53 |
54 | 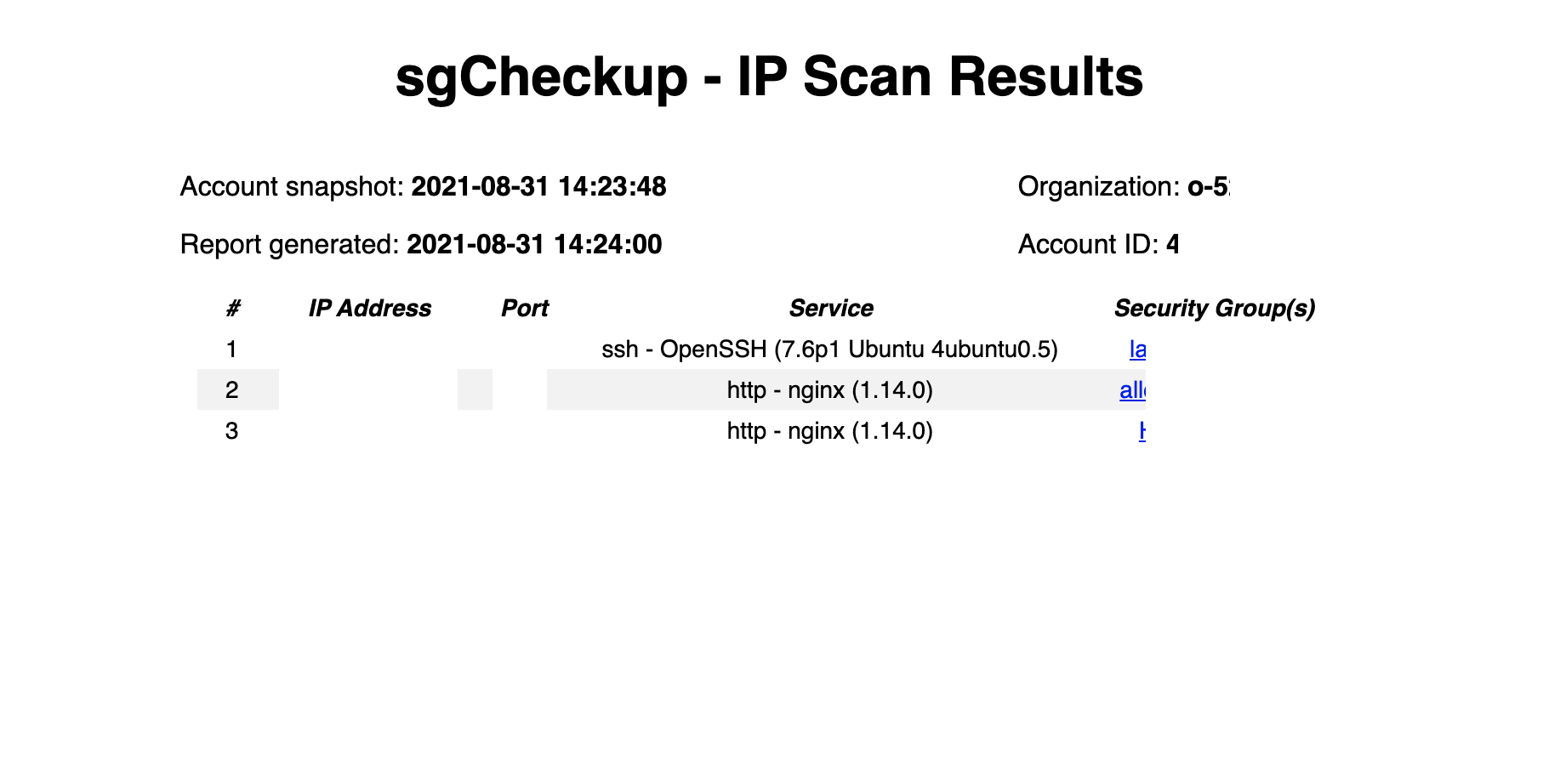 55 |
56 | ## Overview
57 |
58 | sgCheckup uses [goldfiglabs/introspector](https://github.com/goldfiglabs/introspector) to snapshot the Security Groups and Network Interfaces from your AWS Account into a Postgres database. sgCheckup then runs SQL queries to look for Security Groups with open ports and attached Network Interfaces. This list is then used to configure running `nmap` against the targeted list of IPs and ports. The output of nmap is used to determine if a) anything is listening and b) what software is listening on open ports.
59 |
60 | ## Notes
61 |
62 | 1. 2 HTML and CSV reports are provided: one each organized by Security Group, and one each organized by IP/Port combination.
63 |
64 | 1. By default, sgCheckup considers ports 22, 80, and 443 to be open intentionally. You can use the flag `-safePorts
55 |
56 | ## Overview
57 |
58 | sgCheckup uses [goldfiglabs/introspector](https://github.com/goldfiglabs/introspector) to snapshot the Security Groups and Network Interfaces from your AWS Account into a Postgres database. sgCheckup then runs SQL queries to look for Security Groups with open ports and attached Network Interfaces. This list is then used to configure running `nmap` against the targeted list of IPs and ports. The output of nmap is used to determine if a) anything is listening and b) what software is listening on open ports.
59 |
60 | ## Notes
61 |
62 | 1. 2 HTML and CSV reports are provided: one each organized by Security Group, and one each organized by IP/Port combination.
63 |
64 | 1. By default, sgCheckup considers ports 22, 80, and 443 to be open intentionally. You can use the flag `-safePorts