├── README.md
├── anveshan.sh
├── img
├── chart.jpg
├── dnsdumpsterAPI.png
├── googleAPI.png
└── logo.jpg
└── setup_linux.sh
/README.md:
--------------------------------------------------------------------------------
1 |
2 |  3 |
3 |
4 |
5 | anveshan is the all in one script for your recon process, It helps to find subdomains, urls, js files, parameters, screenshots, scan js files.
6 |
7 | ### Features :fire:
8 | - Finding subdomains from each service using tools [subdominator, bbot, amass etc.]
9 | - Filter live subdomains and capture screenshots
10 | - Finding open ports [naabu]
11 | - Finding URLs [waymore, getjs, xnlinkfinder, katana, paramspider]
12 | - Finding JS Files and scan them using nuclei and trufflehog
13 |
14 |
15 | ### Installation 📦
16 | ```bash
17 | git clone https://github.com/hackersthan/anveshan.git
18 | cd anveshan/
19 | bash setup_linux.sh
20 | ```
21 |
22 |
23 | ### Input 🧑🏻💻
24 | ```
25 | $HOME/$ bash anveshan.sh
26 | ,
27 | ███▓▄,,▄▄▄▓█████▓▄▄,
28 | ██████████▀ `█████████▌_
29 | █████████ ███████████
30 | "▀▀▀▀` ████████████
31 | ,,▄▄,,__ ▄████████████
32 | ▄███████████████████████████
33 | ████████████φ▓▓▓▓▓╚██████████
34 | ███████████╫ ╫█████████
35 | ╫██████████▒ ,▓█████████▌
36 | ▀████████ ╬█▄▄╔╔φ████████████
37 | ▀█████╬█████████████████████
38 | ╙▀▀▀▀▀▀▀`\@hackersthan/█▀
39 |
40 | Enter target domain name [ex. target.com] :
41 | ```
42 |
43 | ### Output :sound:
44 | ```bash
45 | $HOME/target.com-recon > tree
46 | .
47 | ├── subs-source/
48 | ├── screenshots/
49 | ├── ips.txt
50 | ├── naabu.txt
51 | ├── subdomains.txt
52 | ├── httpx.txt
53 | ├── webdomains.txt
54 | ├── js_nuclei.txt
55 | ├── trufflehog-src.txt
56 | ├── urls/
57 | ├── urls-source/
58 | ├── js-files-sourcecode/
59 | ├── urls.txt
60 | ├── jsfiles.txt
61 | ├── xnParams.txt
62 | └── parameters.txt
63 |
64 | 8 directories, 33 files
65 | ```
66 |
67 |
68 | 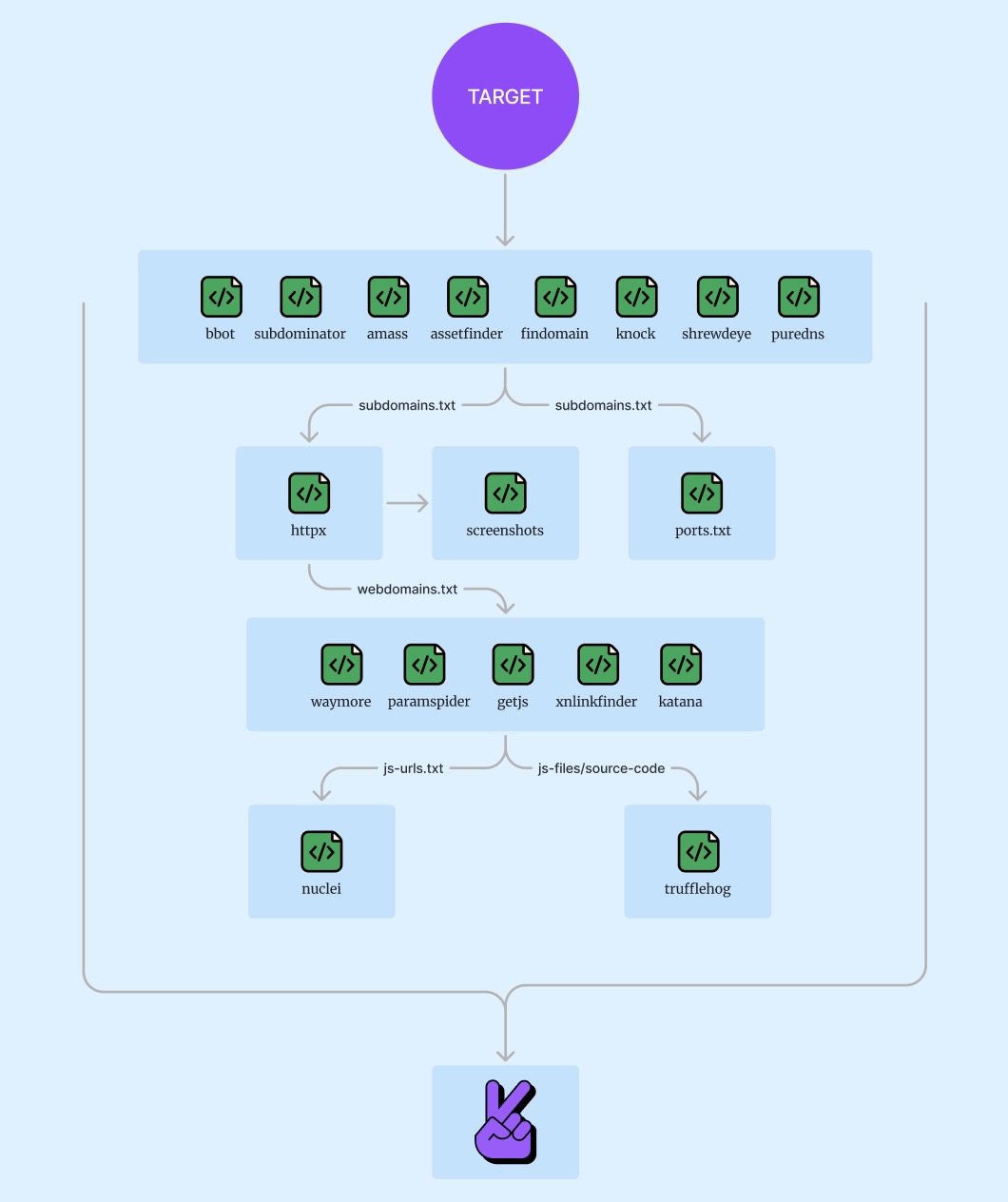 69 |
69 |
70 |
71 | ---
72 |
73 | ## Tools and Wordlists :flashlight:
74 |
75 | |SUBDOMAINS |URLS |WORDLISTS |SCANNERS |
76 | |------------|------------|----------------------|----------|
77 | |subdominator|waymore |six2dez.txt |naabu |
78 | |amass |getjs |dnscan-top10k.txt |nuclei |
79 | |bbot |xnlinkfinder|best-dns-wordlist.txt |trufflehog|
80 | |knock |paramspider |trickest-resolvers.txt| |
81 | |findomain |katana | | |
82 | |assetfinder | | | |
83 | |shrewdeye | | | |
84 | |dnsvalidator| | | |
85 | |puredns | | | |
86 | |httpx | | | |
87 |
88 | ---
89 |
90 | ## APIs :art:
91 | ### You need to setup API Keys for these tools
92 | ```
93 | amass : $HOME/.config/amass/datasources.yaml
94 | bbot : $HOME/.config/bbot/secrets.yml
95 | subdominator : $HOME/.config/Subdominator/provider-config.yaml
96 | waymore : $HOME/.config/waymore/config.yml
97 | ```
98 |
99 | ### DO NOT PUT API KEYS IN EVERY TOOL :pushpin:
100 | `Here is a list of API Services with tool name, Please add API Key in the provided tool only.`
101 | `Give some of your hour to get all of these free api keys, trust me it is worth it.`
102 | |SUBDOMINATOR|AMASS|BBOT|
103 | |------------|-----|----|
104 | |bevigil |360PassiveDNS|hunterio|
105 | |binaryedge |ASNLookup|ip2location|
106 | |bufferover |Ahrefs|credshed|
107 | |c99 |AlienVault|ipstack|
108 | |censys |BigDataCloud|dehashed|
109 | |certspotter |BuiltWith| |
110 | |chaos |CIRCL| |
111 | |dnsdumpster |CertCentral| |
112 | |facebook |DNSDB| |
113 | |fofa |DNSlytics| |
114 | |fullhunt |DNSRepo| |
115 | |google |Deepinfo| |
116 | |huntermap |Detectify| |
117 | |intelx |GitHub| |
118 | |leakix |GitLab| |
119 | |netlas |HackerTarget| |
120 | |quake |IPdata| |
121 | |rapidapi |IPinfo| |
122 | |redhuntlabs |ONYPHE| |
123 | |rsecloud |Pastebin| |
124 | |virustotal |PassiveTotal| |
125 | |securitytrails|PentestTools| |
126 | |shodan |PublicWWW| |
127 | |whoisxmlapi |SOCRadar| |
128 | |zoomeyeapi |Spamhaus| |
129 | | |ThreatBook| |
130 | | |URLScan| |
131 | | |Yandex| |
132 | | |ZETAlytics| |
133 |
134 | - **VirusTotal**: [VirusTotal](https://www.virustotal.com)
135 | - **Chaos**: [Chaos](https://chaos.projectdiscovery.io)
136 | - **Dnsdumpter**: [Dnsdumpster](https://dnsdumpster.com)
137 | - **Whoisxml**: [WhoisXML](https://whois.whoisxmlapi.com)
138 | - **SecurityTrails**: [SecurityTrails](https://securitytrails.com)
139 | - **Bevigil**: [Bevigil](https://bevigil.com/)
140 | - **Binaryedge**: [BinaryEdge](https://binaryedge.io)
141 | - **Fullhunt**: [Fullhunt](https://fullhunt.io)
142 | - **Rapidapi**: [RapidAPI](https://rapidapi.com)
143 | - **Bufferover**: [Bufferover](https://tls.bufferover.run/)
144 | - **Certspotter**: [Certspotter](https://sslmate.com/certspotter)
145 | - **Censys**: [Censys](https://search.censys.io/)
146 | - **Fullhunt**: [Fullhunt](https://fullhunt.io/)
147 | - **Zoomeye**: [Zoomeye](https://www.zoomeye.org/)
148 | - **Netlas**: [Netlas](https://netlas.io/)
149 | - **Leakix**: [Leakix](https://leakix.net/)
150 | - **Redhunt**: [Redhunt](https://devportal.redhuntlabs.com/) [PAID]
151 | - **Shodan** : [Shodan](https://shodan.io)
152 | - **Huntermap** : [Hunter](https://hunter.how/)
153 | - **Google**: [Google](https://programmablesearchengine.google.com/controlpanel/create)
154 | - **Facebook**: [Facebook](https://developers.facebook.com/)
155 | - **Quake**: [Quake](https://quake.360.cn/)
156 | - **RapidFinder**: [RapidFinder](https://rapidapi.com/Glavier/api/subdomain-finder3/pricing)
157 | - **RapidScan**: [RapidScan](https://rapidapi.com/sedrakpc/api/subdomain-scan1/pricing)
158 | - **Fofa**: [Fofa](https://en.fofa.info/)
159 | - **CodeRog**: [CodeRog](https://rapidapi.com/coderog-coderog-default/api/subdomain-finder5/pricing)
160 | - **C99**: [C99](https://subdomainfinder.c99.nl/) [PAID]
161 | - **RSECloud**: [RSECloud](https://rsecloud.com/search)
162 | - **Myssl**: [Myssl](https://myssl.com)
163 | - **Racent**: [Racent](https://face.racent.com)
164 | - **Intelx**: [Intelx](intelx.io)
165 | - **IPData**: [IPData](https://ipdata.co)
166 | - **Gitlab**: [Gitlab](https://about.gitlab.com)
167 | - **Github**: [Github](https://github.com)
168 | - **Onyphe**: [Onyphe](http://Onyphe.io)
169 | - **Twitter**: [Twitter](https://twitter.com)
170 | - **Alienvault**: [Alienvault](https://otx.alienvault.com)
171 |
172 |
173 | #### Dnsdumpter and Google API Keys is tricky, here is the way to access it :
174 |
175 | - Dnsdumpter Setup:
176 |
177 | - Visit [Dnsdumpster](https://dnsdumpster.com)
178 | - Search any domain and view request using Burpsuite or Inspect tool.
179 | - Copy the `csrftoken from cookie header` and `csrfmiddlewaretoken from body` and paste in your yaml file like this
180 | ```
181 | dnsdumpster:
182 | - csrftoken:csrfmiddlewaretoken
183 | ```
184 |
185 |
186 |  187 |
187 |
188 |
189 |
190 | - Google Setup:
191 |
192 | - Visit [here](https://programmablesearchengine.google.com/controlpanel/create) and create a search engine [choose all web option].
193 | - copy your `CX ID`
194 | - Create your google api key [here](https://developers.google.com/custom-search/v1/introduction)
195 | - Click `Get a Key` button and create a new project with any name you want
196 | - After creating and completing your api key is generated and press show key then copy it
197 | - Paste CX API and Google API Keys like this
198 | ```
199 | google:
200 | - CXID:GOOGLEAPIKEY
201 | ```
202 |
203 |
204 |  205 |
205 |
206 |
207 |
208 | ---
209 |
210 | ### Credit 🙏🏻
211 | **Special thanks to the authers of these tools.
212 | They have worked very hard and dedicated a lot of their time, we should thank them.**
213 |
214 | - [subdominator](https://github.com/RevoltSecurities/Subdominator)
215 | - [bbot](https://github.com/blacklanternsecurity/bbot)
216 | - [amass](https://github.com/owasp-amass/amass)
217 | - [knock](https://github.com/guelfoweb/knock)
218 | - [findomain](https://github.com/Findomain/Findomain)
219 | - [assetfinder](https://github.com/tomnomnom/assetfinder)
220 | - [shrewdeye-bash (shrewdeye.app)](https://github.com/tess-ss/shrewdeye-bash)
221 | - [dnsvalidator](https://github.com/vortexau/dnsvalidator)
222 | - [trickest-resolvers](https://github.com/trickest/resolvers)
223 | - [puredns](https://github.com/d3mondev/puredns)
224 | - [httpx](https://github.com/projectdiscovery/httpx)
225 | - [naabu](https://github.com/projectdiscovery/naabu)
226 | - [waymore](https://github.com/xnl-h4ck3r/waymore)
227 | - [getjs](https://github.com/003random/getJS)
228 | - [xnlinkfinder](https://github.com/xnl-h4ck3r/xnLinkFinder)
229 | - [katana](https://github.com/projectdiscovery/katana)
230 | - [paramspider](https://github.com/0xKayala/ParamSpider)
231 | - [nuclei](https://github.com/projectdiscovery/nuclei)
232 | - [trufflehog](https://github.com/trufflesecurity/truffleHog)
233 |
234 |
235 | ### Issues 📬
236 | If you encounter any errors please report them [here](https://github.com/hackersthan/anveshan/issues). I will try to fix it immediately.
237 |
238 |
239 | ### Disclaimer ❗️
240 | 1. The User is solely responsible for the misuse or unlawful use of any Content. Hacking and cybersecurity laws vary by jurisdiction. By engaging with the Content, you agree to take full responsibility for your actions
241 | 2. Some Content may include or link to third-party materials. The User agrees to respect all applicable intellectual property laws, including copyrights and trademarks, when engaging with this Content.
242 | 3. Always read full script before runnnig it, Never run any script blindly.
243 |
244 | ❤️🇮🇳
245 |
--------------------------------------------------------------------------------
/anveshan.sh:
--------------------------------------------------------------------------------
1 | #!/bin/bash
2 | # shree_hari
3 |
4 | # Basic recon script
5 | # Usecase : Finding subdomains, urls, js files, parameters
6 |
7 | # Current version
8 | current_version="v1.0.0"
9 |
10 | # colors
11 | blue=$'\e[34m'
12 | cyan=$'\e[36m'
13 | red=$'\e[91m'
14 | green=$'\e[92m'
15 | yellow=$'\e[93m'
16 | magenta=$'\e[95m'
17 | reset=$'\e[0m'
18 |
19 | # print logo
20 | logo() {
21 | echo -e "${green} , ${reset}"
22 | echo -e "${green} ███▓▄,,▄▄▄▓█████▓▄▄, ${reset}"
23 | echo -e "${green} ██████████▀ \`█████████▌_ ${reset}"
24 | echo -e "${green} █████████ ███████████ ${reset}"
25 | echo -e "${green} \"▀▀▀▀\` ████████████ ${reset}"
26 | echo -e "${green} ,,▄▄,,__ ▄████████████ ${reset}"
27 | echo -e "${green} ▄███████████████████████████ ${reset}"
28 | echo -e "${green} ████████████${red}φ▓▓▓▓▓╚${green}██████████ ${reset}"
29 | echo -e "${green} ███████████${red}╫ ╫${green}█████████ ${reset}"
30 | echo -e "${green} ╫██████████${red}▒ ,▓${green}█████████▌ ${reset}"
31 | echo -e "${green} ▀████████ ${red}╬█▄▄╔╔φ${green}████████████ ${reset}"
32 | echo -e "${green} ▀█████${red}╬█${green}████████████████████ ${reset}"
33 | echo -e "${green} ${red}╙▀${green}▀▀▀▀▀▀\`\@hackersthan/█▀ ${red}${current_version} ${reset}"
34 | }
35 |
36 | logo
37 |
38 |
39 | # check for latest version
40 | check_for_updates() {
41 | echo -e "${yellow}Checking for updates...${reset}"
42 |
43 | local latest_file_version
44 | latest_file_version=$(curl -s https://raw.githubusercontent.com/hackersthan/anveshan/refs/heads/main/anveshan.sh | grep 'current_version' | cut -d '=' -f2 | tr -d ' "')
45 |
46 | # Compare versions
47 | if [ "$latest_file_version" != "$current_version" ]; then
48 | if printf '%s\n' "$latest_file_version" "$current_version" | sort -V | head -n1 | grep -q "$current_version"; then
49 | echo -e "${red}A newer version ($latest_file_version) is available!${reset}"
50 | read -p "${red}Would you like to update? [y/n]: ${reset}" update_choice
51 | if [[ "$update_choice" == [Yy] ]]; then
52 | curl -o "$0" https://raw.githubusercontent.com/hackersthan/anveshan/refs/heads/main/anveshan.sh
53 | echo -e "${green}Updated to version $latest_file_version. Please re-run the script.${reset}"
54 | exit 0
55 | else
56 | echo -e "${yellow}Proceeding with the current version.${reset}"
57 | fi
58 | fi
59 | else
60 | echo -e "${green}You are using the latest version: $current_version${reset}"
61 | fi
62 | }
63 |
64 | check_for_updates
65 |
66 |
67 | # screen clear
68 | scrclr() {
69 | clear && logo && echo
70 | }
71 |
72 | #adding help section
73 | if [[ $1 == "--help" ]] | [[ $1 == "-h" ]]; then
74 | echo "Usage:"
75 | echo "${green} bash anveshan.sh${reset}"
76 | echo "Options:"
77 | echo "${green} --help Show this help message${reset}"
78 | exit 0
79 | fi
80 |
81 |
82 | # wordlist for DNS Brute-Forcing
83 | choose_wordlist() {
84 | printf "${magenta}Select a wordlist for DNS Brute-Forcing:${reset}\n"
85 | printf "${yellow}1) dns.txt [best-dns-wordlist ++] [Size: 9M, Takes longer time]${reset}\n"
86 | printf "${yellow}2) dns2.txt [six2dez + dnscan-top10k] [Size: 112K, Takes less time]${reset}\n"
87 | read -p "${green}Enter your choice [1/2]: ${reset}" choice
88 |
89 | case $choice in
90 | 1)
91 | wordlist="$HOME/anveshan/wordlists/dns.txt"
92 | ;;
93 | 2)
94 | wordlist="$HOME/anveshan/wordlists/dns2.txt"
95 | ;;
96 | *)
97 | printf "${red}Invalid choice. Exiting.${reset}\n"
98 | exit 1
99 | ;;
100 | esac
101 |
102 | printf "${green}Using wordlist: $wordlist${reset}\n"
103 | }
104 |
105 |
106 | # reading domain name
107 | read -p "${magenta}Enter target domain name [ex. target.com] : ${reset}" domain
108 | echo ""
109 |
110 | if [[ -d "$domain-recon" ]]
111 | then
112 | cd "$domain-recon"
113 | else
114 | mkdir "$domain-recon" && cd "$domain-recon"
115 | fi
116 |
117 |
118 | # choosing wordlist
119 | choose_wordlist
120 | scrclr
121 |
122 |
123 | # Activating the virtual python environment
124 | VENV_PATH="$HOME/anveshan/venv"
125 |
126 | if [[ -d "$VENV_PATH" ]]; then
127 | source "$VENV_PATH/bin/activate"
128 | echo "Virtual environment activated."
129 | else
130 | echo "Virtual environment not found. Please run setup_linux.sh first."
131 | exit 1
132 | fi
133 |
134 |
135 |
136 |
137 | #=====================================#
138 | #=============SUBDOMAINS==============#
139 | #=====================================#
140 |
141 |
142 | #\\\\\\\\\\\\ subdominator ///////////#
143 | printf "${magenta}[+] running subdominator...${reset}\n" | pv -qL 23
144 | subdominator -d $domain -o subdominator.txt
145 | echo
146 |
147 |
148 | #\\\\\\\\\\\\\\\ amass ///////////////#
149 | printf "${magenta}[+] running amass ...${reset}\n" | pv -qL 23
150 | timeout 1200 amass enum -passive -d $domain -norecursive -nocolor -config $HOME/anveshan/.config/amass/datasources.yaml -o amassP
151 | timeout 1200 amass enum -active -d $domain -nocolor -config $HOME/anveshan/.config/amass/datasources.yaml -o amassA
152 | cat amassP amassA | cut -d " " -f1 | grep "$domain" | anew amass.txt
153 | echo
154 |
155 |
156 | #\\\\\\\\\\\\\\\ knock ///////////////#
157 | printf "${magenta}[+] running knock${reset}\n" | pv -qL 23
158 | mkdir knockpy/
159 | knockpy -d $domain --recon --save knockpy
160 | cat knockpy/*.json | grep '"domain"' | cut -d '"' -f4 | anew knockpy.txt
161 | echo
162 |
163 |
164 | #\\\\\\\\\\\\\ findomain /////////////#
165 | printf "${magenta}[+] running findomain${reset}\n" | pv -qL 23
166 | findomain -t $domain -u findomain.txt
167 | echo
168 |
169 |
170 | #\\\\\\\\\\\\ assetfinder ////////////#
171 | printf "${magenta}[+] running assetfinder${reset}\n" | pv -qL 23
172 | assetfinder -subs-only $domain | anew assetfinder.txt
173 | echo
174 |
175 |
176 | #\\\\\\\\\\\\\\\ bbot ////////////////#
177 | printf "${magenta}[+] running bbot${reset}\n" | pv -qL 23
178 | sudo bbot -t $domain -f subdomain-enum -rf passive -o output -n bbot -y
179 | cp output/bbot/subdomains.txt bbot.txt
180 | echo
181 |
182 |
183 | #\\\\\\\\\\\\\ shrewdeye /////////////#
184 | printf "${magenta}[+] running shrewdeye${reset}\n" | pv -qL 23
185 | bash $HOME/anveshan/shrewdeye-bash/shrewdeye.sh -d $domain
186 | echo
187 |
188 | #\\\\\\\\\\\\\\ combine //////////////#
189 | printf "${yellow}[*] combine all the result${reset}\n" | pv -qL 23
190 | sed "s/\x1B\[[0-9;]*[mK]//g" *.txt | sed 's/\*\.//g' | anew psubdomains.txt
191 |
192 |
193 |
194 | #\\\\\\\\\\\\ screen clear ///////////#
195 | scrclr
196 | printf "${yellow}[+] dns bruteforce${reset}\n" | pv -qL 23
197 | puredns bruteforce "$wordlist" $domain -r $HOME/anveshan/wordlists/resolvers.txt -w bruteforce.txt
198 | echo
199 |
200 | printf "${yellow}[+] resolving subdomains${reset}\n" | pv -qL 23
201 | cat psubdomains.txt bruteforce.txt | anew lets-resolve.txt
202 | puredns resolve lets-resolve.txt -r $HOME/anveshan/wordlists/resolvers.txt -w resolved.txt
203 | cat resolved.txt | anew subdomains.txt
204 | echo "$domain" | anew subdomains.txt
205 |
206 | #\\\\\\\\\\\\\\ cleanup //////////////#
207 | mkdir subs-source/
208 | mv subdominator.txt subs-source/
209 | mv amass.txt subs-source/
210 | mv amassA subs-source/
211 | mv amassP subs-source/
212 | mv knockpy subs-source/
213 | mv knockpy.txt subs-source/
214 | mv findomain.txt subs-source/
215 | mv assetfinder.txt subs-source
216 | mv bbot.txt subs-source/
217 | mv output/ subs-source/bbot-output/
218 | mv *output.txt subs-source/
219 | rm lets-resolve.txt
220 | rm resolved.txt
221 | rm bruteforce.txt
222 |
223 |
224 | #\\\\\\\\\\\\ screen clear ///////////#
225 | scrclr
226 | printf "${yellow}[$] Found $(cat subdomains.txt | wc -l) subdomains${reset}\n" | pv -qL 23
227 | sleep 2 && echo
228 |
229 | #\\\\\\\\\\\\\\\ httpx ///////////////#
230 | printf "${magenta}[*] getting webdomains using httpx ${reset}\n" | pv -qL 23
231 | $HOME/go/bin/httpx -l subdomains.txt -ss -pa -sc -fr -title -td -location -retries 3 -silent -nc -o httpx.txt
232 | cat httpx.txt | cut -d " " -f1 | anew webdomains.txt
233 | mv output/ screenshots/
234 |
235 | #\\\\\\\\\\\\\\\\ ips ////////////////#
236 | cat httpx.txt | grep -E -o '\b([0-9]{1,3}\.){3}[0-9]{1,3}\b' | anew ips.txt
237 | cat subs-source/knockpy/*.json | jq '.[] .ip[]' | cut -d '"' -f2 | anew ips.txt
238 |
239 |
240 | #\\\\\\\\\\\\ screen clear ///////////#
241 | scrclr
242 | printf "${yellow}[$] Found $(cat subdomains.txt | wc -l) subdomains${reset}\n" | pv -qL 23
243 | printf "${yellow}[$] Found $(cat webdomains.txt | wc -l) webdomains${reset}\n" | pv -qL 23
244 | sleep 3 && echo
245 |
246 | #\\\\\\\\\\\\ port scanning //////////#
247 | printf "${magenta}[+] port scanning using naabu : top 1000 ports ${reset}\n" | pv -qL 23
248 | naabu -list subdomains.txt -tp 1000 -rate 2000 -o naabu.txt
249 | #cat ips.txt | cf-check | naabu -tp 1000 -rate 2000 -o naabu-ip.txt
250 | echo && echo
251 | printf "${yellow}[$] Found $(cat naabu.txt | wc -l) open web_ports${reset}\n" | pv -qL 23
252 | #printf "${yellow}[$] Found $(cat naabu-ip.txt | wc -l) open ports on IPs${reset}\n" | pv -qL 23
253 | sleep 3
254 |
255 |
256 |
257 | #=====================================#
258 | #================URLS=================#
259 | #=====================================#
260 |
261 | #\\\\\\\\\\\\ screen clear ///////////#
262 | scrclr
263 |
264 | printf "${magenta}[*] finding urls ${reset}\n" | pv -qL 23
265 | mkdir urls/ && cd urls/
266 |
267 | printf "${yellow} [+] waymore ${reset}\n" | pv -qL 23
268 | waymore -i $domain -mode U -c $HOME/anveshan/.config/waymore/config.yml -oU waymore.txt
269 |
270 | printf "${yellow} [+] getJS ${reset}\n" | pv -qL 23
271 | getJS --input ../webdomains.txt --output getjs.txt --complete
272 |
273 | printf "${yellow} [+] xnlinkfinder ${reset}\n" | pv -qL 23
274 | xnLinkFinder -i waymore.txt -d 3 -sf $domain -o xnUrls.txt -op xnParams.txt
275 |
276 | printf "${yellow} [+] finding parameters ${reset}\n" | pv -qL 23
277 | python3 $HOME/anveshan/tools/ParamSpider/paramspider.py --domain $domain --level high | uro | anew parameters.txt
278 |
279 | printf "${yellow} [+] Katan for js files ${reset}\n" | pv -qL 23
280 | katana -list ../webdomains.txt -jc -em js,json,jsp,jsx,ts,tsx,mjs -d 3 -nc -o katana.txt
281 |
282 | # combine
283 | sed "s/\x1B\[[0-9;]*[mK]//g" waymore.txt getjs.txt xnUrls.txt parameters.txt katana.txt | anew urls.txt
284 | mkdir urls-source/
285 | mv waymore.txt urls-source/
286 | mv getjs.txt urls-source/
287 | mv xnUrls.txt urls-source/
288 | mv katana.txt urls-source/
289 |
290 |
291 |
292 | #=====================================#
293 | #=================JS==================#
294 | #=====================================#
295 |
296 |
297 | #\\\\\\\\\\\\ screen clear ///////////#
298 | scrclr
299 |
300 | printf "${magenta}[*] extracting js files and finding secrets ${reset}\n" | pv -qL 23
301 | cat urls.txt | grep -Ei ".+\.js(?:on|p|x)?$" | $HOME/go/bin/httpx -mc 200 | anew jsurls.txt
302 |
303 | #\\\\\\\\getting live js files////////#
304 | $HOME/go/bin/httpx -l jsurls.txt -sr -sc -mc 200 -ct -nc | grep -v "text/html" | cut -d " " -f1 | anew jsfiles.txt
305 | mv output/ js-source/
306 |
307 | #\\\\\\\nuclei on live js files///////#
308 | scrclr
309 | printf "${magenta}[*] finding secrets inside $(cat jsfiles.txt | wc -l) js files${reset}\n" | pv -qL 23
310 | cat jsfiles.txt | nuclei -t $HOME/nuclei-templates/http/exposures/tokens/ | tee -a js_nuclei.txt
311 | mv js_nuclei.txt ../
312 |
313 |
314 | #\\\\\\\trufflehog on source code/////#
315 | printf "${magenta}[*] trufflehog scanning on webdomains source${reset}\n" | pv -qL 30
316 | trufflehog filesystem js-source/response | tee -a trufflehog-src.txt
317 | mv trufflehog-src.txt ../ && cd ../
318 |
319 |
320 |
321 |
322 | #=====================================#
323 | #==============HIGHLIGHT==============#
324 | #=====================================#
325 | scrclr
326 | logo
327 | printf "${magenta}[*] script executed successfully, here are the key highlights${reset}\n" | pv -qL 23
328 | echo
329 | printf "${red} [+] Subdomains${reset}\n" | pv -qL 23
330 | printf "${yellow} [$] Found %d subdomains${reset}\n" "$(cat subdomains.txt | wc -l)" | pv -qL 23
331 | printf "${yellow} [$] Found %d webdomains${reset}\n" "$(cat webdomains.txt | wc -l)" | pv -qL 23
332 | echo
333 | printf "${red} [+] Ports${reset}\n" | pv -qL 23
334 | printf "${yellow} [$] Found %d open web_ports${reset}\n" "$(cat naabu.txt | wc -l)" | pv -qL 23
335 | echo
336 | printf "${red} [+] URLs${reset}\n" | pv -qL 23
337 | printf "${yellow} [$] Found %d urls${reset}\n" "$(cat urls/urls.txt | wc -l)" | pv -qL 23
338 | echo
339 | printf "${red} [+] Scanning${reset}\n" | pv -qL 23
340 | printf "${yellow} [$] Found %d nuclei secrets in %d js files${reset}\n" "$(cat js_nuclei.txt | wc -l)" "$(cat urls/jsfiles.txt | wc -l)" | pv -qL 23
341 | printf "${yellow} [$] Found %d trufflehog secrets in js files source code${reset}\n" "$(cat trufflehog-src.txt | grep -i "raw" | wc -l)" | pv -qL 23
342 | echo
343 | printf "${red} [&] Happy Hacking ;D${reset}\n" | pv -qL 23
344 |
345 | # iti
346 |
--------------------------------------------------------------------------------
/img/chart.jpg:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/hackersthan/anveshan/2b46faf6708d86c158670cc9c31715fa4272ddda/img/chart.jpg
--------------------------------------------------------------------------------
/img/dnsdumpsterAPI.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/hackersthan/anveshan/2b46faf6708d86c158670cc9c31715fa4272ddda/img/dnsdumpsterAPI.png
--------------------------------------------------------------------------------
/img/googleAPI.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/hackersthan/anveshan/2b46faf6708d86c158670cc9c31715fa4272ddda/img/googleAPI.png
--------------------------------------------------------------------------------
/img/logo.jpg:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/hackersthan/anveshan/2b46faf6708d86c158670cc9c31715fa4272ddda/img/logo.jpg
--------------------------------------------------------------------------------
/setup_linux.sh:
--------------------------------------------------------------------------------
1 | #!/bin/bash
2 | # shree_hari
3 | # Usecase : setup your device to run anveshan without any errors.
4 | # Usage: Run `bash setup_linux.sh`. [if you have bash shell]
5 | # Usage: Run `zsh setup_linux.sh`. [if you have zsh shell]
6 | # Logs: Logs actions and errors to setup_log.txt
7 |
8 | # Current version
9 | current_version="v1.2.0"
10 |
11 | # colors
12 | blue=$'\e[34m'
13 | cyan=$'\e[36m'
14 | red=$'\e[91m'
15 | green=$'\e[92m'
16 | yellow=$'\e[93m'
17 | magenta=$'\e[95m'
18 | reset=$'\e[0m'
19 |
20 | # print logo
21 | logo() {
22 | echo -e "${green} , ${reset}"
23 | echo -e "${green} ███▓▄,,▄▄▄▓█████▓▄▄, ${reset}"
24 | echo -e "${green} ██████████▀ \`█████████▌_ ${reset}"
25 | echo -e "${green} █████████ ███████████ ${reset}"
26 | echo -e "${green} \"▀▀▀▀\` ████████████ ${reset}"
27 | echo -e "${green} ,,▄▄,,__ ▄████████████ ${reset}"
28 | echo -e "${green} ▄███████████████████████████ ${reset}"
29 | echo -e "${green} ████████████${red}φ▓▓▓▓▓╚${green}██████████ ${reset}"
30 | echo -e "${green} ███████████${red}╫ ╫${green}█████████ ${reset}"
31 | echo -e "${green} ╫██████████${red}▒ ,▓${green}█████████▌ ${reset}"
32 | echo -e "${green} ▀████████ ${red}╬█▄▄╔╔φ${green}████████████ ${reset}"
33 | echo -e "${green} ▀█████${red}╬█${green}████████████████████ ${reset}"
34 | echo -e "${green} ${red}╙▀${green}▀▀▀▀▀▀\`\@hackersthan/█▀ setup_version : ${current_version} ${reset}"
35 | }
36 |
37 | # log file to check errors
38 | log_file="setup_log.txt"
39 | exec > >(tee -a "$log_file") 2>&1
40 |
41 | logo
42 |
43 | # check for latest version
44 | check_for_updates() {
45 | echo -e "${yellow}Checking for updates...${reset}"
46 |
47 | local latest_file_version
48 | latest_file_version=$(curl -s https://raw.githubusercontent.com/hackersthan/anveshan/main/setup_linux.sh | grep 'current_version\=' | cut -d '=' -f2 | tr -d ' "')
49 |
50 | # Compare versions
51 | if [ "$latest_file_version" != "$current_version" ]; then
52 | if printf '%s\n' "$latest_file_version" "$current_version" | sort -V | head -n1 | grep -q "$current_version"; then
53 | echo -e "${red}A newer version ($latest_file_version) is available!${reset}"
54 | read -p "${red}Would you like to update? [y/n]: ${reset}" update_choice
55 | if [[ "$update_choice" == [Yy] ]]; then
56 | curl -o "$0" https://raw.githubusercontent.com/hackersthan/anveshan/main/setup_linux.sh
57 | echo -e "${green}Updated to version $latest_file_version. Please re-run the script.${reset}"
58 | exit 0
59 | else
60 | echo -e "${yellow}Proceeding with the current version.${reset}"
61 | fi
62 | else
63 | echo -e "${green}You are using the latest version: $current_version${reset}"
64 | echo
65 | fi
66 | else
67 | echo -e "${green}You are using the latest version: $current_version${reset}"
68 | echo
69 | fi
70 | }
71 |
72 | check_for_updates
73 |
74 | # screen clear
75 | scrclr() {
76 | clear && logo && echo
77 | }
78 |
79 | #adding help section
80 | if [[ "$1" == "--help" ]] || [[ "$1" == "-h" ]]; then
81 | echo "Usage:"
82 | echo -e "${green} bash setup_linux.sh${reset}"
83 | echo "Options:"
84 | echo -e "${green} --help Show this help message${reset}"
85 | exit 0
86 | fi
87 |
88 | #* run with sudo
89 | if [ "$(whoami)" != 'root' ]; then
90 |
91 | printf "${red}[!] Manually enter your password when asked.${reset}\n"
92 | fi
93 |
94 | # function to check golang installed or not
95 | if ! command -v go &>/dev/null; then
96 | printf "${red}[!] GO language is not installed. Installing via apt.${reset}\n"
97 | sudo add-apt-repository ppa:longsleep/golang-backports
98 | sudo apt install golang-go
99 | fi
100 |
101 | #check GOPATH abd GOROOT
102 | if [ -f ~/.bashrc ]; then
103 | if ! grep -q "export GOPATH=" ~/.bashrc && ! grep -q "export GOROOT=" ~/.bashrc; then
104 | echo "export GOROOT=/usr/local/go" >>~/.bashrc
105 | echo "export GOPATH=\$HOME/go" >>~/.bashrc
106 | echo "export PATH=\$PATH:\$GOROOT/bin:\$GOPATH/bin" >>~/.bashrc
107 | fi
108 | source ~/.bashrc
109 | elif [ -f ~/.zshrc ]; then
110 | if ! grep -q "export GOPATH=" ~/.zshrc && ! grep -q "export GOROOT=" ~/.zshrc; then
111 | echo "export GOROOT=/usr/local/go" >>~/.zshrc
112 | echo "export GOPATH=\$HOME/go" >>~/.zshrc
113 | echo "export PATH=\$PATH:\$GOROOT/bin:\$GOPATH/bin" >>~/.zshrc
114 | fi
115 | source ~/.zshrc
116 | else
117 | echo "~/.bashrc or ~/.zshrc not found"
118 | fi
119 |
120 | # creating anveshan directory
121 | if [[ -d $HOME/anveshan ]]; then
122 | cd "$HOME/anveshan"
123 | else
124 | mkdir "$HOME/anveshan" && cd "$HOME/anveshan"
125 | fi
126 |
127 | # Creating a virtual python environment
128 | sudo apt install -y python3 python3-pip python3-venv || {
129 | echo -e "${red} Failed to install python3-venv. Exiting${reset}"
130 | exit 1
131 | }
132 | VENV_PATH="$HOME/anveshan/venv"
133 | python3 -m venv "$VENV_PATH"
134 | source "$VENV_PATH/bin/activate"
135 |
136 | echo "[+] Upgrading pip in the virtual environment..."
137 | pip3 install --upgrade pip
138 |
139 | # Check if --break-system-packages is required or not
140 | if pip3 install --help | grep -q -- '--break-system-packages'; then
141 | bsp="--break-system-packages"
142 | else
143 | bsp=""
144 | fi
145 |
146 | #Fix `urllib3` and `six` package errors
147 | read -p "removing 'urllib3' and 'six' packages from apt and installing from pip, Confirm? (Y/n): " confirm_uninstall
148 | if [[ "$confirm_uninstall" == "y" || "$confirm_uninstall" == "Y" ]]; then
149 | echo "Uninstalling 'urllib3' and 'six' from apt..."
150 | sudo apt remove -y python3-urllib3 python3-six
151 |
152 | echo "Uninstalling 'urllib3' and 'six' from pip3..."
153 | sudo pip3 uninstall -y urllib3 six $bsp
154 |
155 | echo "Installing 'urllib3' and 'six' from pip3"
156 | sudo pip3 install urllib3 six $bsp
157 |
158 | echo "Packages uninstalled and reinstalled successfully."
159 | else
160 | echo "Skipping uninstallation and installation of urllib3 and six."
161 | fi
162 |
163 | # function to upgrade pip packages
164 | echo -e "${magenta}You have $(pip3 list --outdated | grep '[0-9\.[0-9]' | wc -l) outdated pip packages.${reset}"
165 | read -p "${yellow}Do you want to upgrade all of them? (Y/n): ${reset}" answer
166 |
167 | if [[ "$answer" == "y" || "$answer" == "Y" ]]; then
168 | printf "${green}[*] Upgrading all pip packages${reset}\n"
169 | pip3 list --outdated | grep "[0-9\.[0-9]" | cut -d " " -f1 | xargs pip3 install --upgrade $bsp
170 | else
171 | printf "${red}[*] Not upgrading.${reset}\n"
172 | fi
173 |
174 | # installing basic tools
175 | scrclr
176 | printf "${green}[*] apt update, upgrade and basic tools${reset}\n"
177 | sudo apt -y update
178 | sudo apt -y upgrade
179 | sudo apt -y install pv curl net-tools build-essential
180 | sudo apt -y install python3 python3-pip python3-setuptools python3-dnspython python-dev-is-python3
181 | sudo apt -y install software-properties-common nmap npm parallel ruby-full rename findutils
182 | sudo apt -y install libpcap-dev libcurl4-openssl-dev libxml2 libxml2-dev libxslt1-dev ruby-dev libgmp-dev zlib1g-dev libssl-dev libffi-dev libldns-dev
183 | sudo apt -y install jq git chromium-bsu
184 |
185 | #\\\\\\ installing tools //////#
186 | scrclr
187 | printf "${magenta}[*] Installing tools ${reset}\n" | pv -qL 23
188 | sleep 2
189 |
190 | #basics
191 | pip3 install uro pipx urless $bsp
192 | go install -v github.com/tomnomnom/anew@latest
193 |
194 | #subdomains
195 | pip3 install bbot git+https://github.com/guelfoweb/knock.git $bsp
196 | go install github.com/tomnomnom/assetfinder@latest
197 | go install -v github.com/owasp-amass/amass/v4/...@master
198 |
199 | #findomain
200 | if ! command -v findomain &>/dev/null; then
201 | curl -LO https://github.com/findomain/findomain/releases/latest/download/findomain-linux.zip
202 | unzip findomain-linux.zip
203 | chmod +x findomain
204 | sudo mv findomain /usr/bin/findomain
205 | else
206 | echo "[*] findomain is already installed."
207 | fi
208 |
209 | #subdomainator
210 | pipx install git+https://github.com/RevoltSecurities/Subdominator
211 |
212 | #shrewdeye
213 | if [ ! -d "shrewdeye-bash" ]; then
214 | git clone https://github.com/tess-ss/shrewdeye-bash.git
215 | cd shrewdeye-bash
216 | chmod +x shrewdeye.sh
217 | cd ../
218 | else
219 | echo -e "${red}[*] shrewdeye already installed ${reset}"
220 | fi
221 |
222 | #dnsvalidator
223 | if ! command -v dnsvalidator &>/dev/null; then
224 | git clone https://github.com/vortexau/dnsvalidator.git
225 | cd dnsvalidator
226 | pip3 install -r requirements.txt $bsp
227 | python3 setup.py install
228 | cd ../
229 | else
230 | echo -e "${red}[*] dnsvalidator is already installed ${reset}"
231 | fi
232 |
233 | #puredns
234 | go install github.com/d3mondev/puredns/v2@latest
235 | #cf-check
236 | go install github.com/dwisiswant0/cf-check@latest
237 |
238 | #massdns
239 | if ! command -v massdns &>/dev/null; then
240 | git clone https://github.com/blechschmidt/massdns.git
241 | cd massdns
242 | sudo make
243 | sudo make install
244 | cd ../
245 | else
246 | echo -e "${red}[*] massdns is already installed.${reset}"
247 | fi
248 |
249 | #chrome
250 | if ! command -v google-chrome &>/dev/null; then
251 | wget https://dl.google.com/linux/direct/google-chrome-stable_current_amd64.deb
252 | sudo apt install ./google-chrome-stable_current_amd64.deb -y
253 | rm google-chrome-stable_current_amd64.deb
254 | else
255 | echo "[*] Chrome is already installed."
256 | fi
257 |
258 | #urls
259 | pip3 install waymore $bsp
260 | pip3 install xnLinkFinder $bsp
261 | go install github.com/003random/getJS/v2@latest
262 | go install github.com/hakluke/hakrawler@latest
263 | go install github.com/jaeles-project/gospider@latest
264 | go install github.com/projectdiscovery/katana/cmd/katana@latest
265 | go install -v github.com/projectdiscovery/httpx/cmd/httpx@latest
266 | go install -v github.com/projectdiscovery/naabu/v2/cmd/naabu@latest
267 | go install github.com/dwisiswant0/cf-check@latest
268 |
269 | #paramspider
270 | if [ ! -d "ParamSpider" ]; then
271 | git clone https://github.com/0xKayala/ParamSpider.git
272 | cd ParamSpider
273 | pip3 install -r requirements.txt $bsp
274 | cd ../
275 | else
276 | echo -e "${red}[*] ParamSpider already installed ${reset}"
277 | fi
278 |
279 | #nuclei
280 | go install -v github.com/projectdiscovery/nuclei/v3/cmd/nuclei@latest
281 | nuclei -ut
282 | #trufflehog
283 | if ! command -v google-chrome &>/dev/null; then
284 | curl -sSfL https://raw.githubusercontent.com/trufflesecurity/trufflehog/main/scripts/install.sh | sudo sh -s -- -b /usr/local/bin
285 | else
286 | echo "[*] trufflehog is already installed."
287 | fi
288 |
289 | #updating some golang tools
290 | ~/go/bin/httpx -up
291 | nuclei -up
292 | katana -up
293 |
294 | #\\\\\\\\\\ wordlists /////////#
295 | scrclr
296 | mkdir "wordlists" && cd "wordlists"
297 |
298 | # Download wordlists if they don't exist
299 | download_ifnotexist() {
300 | local file="$1"
301 | local url="$2"
302 |
303 | if [ ! -f "$file" ]; then
304 | echo -e "${green}[+] Downloading $file ${reset}"
305 | wget -q -O "$file" "$url"
306 | else
307 | echo -e "${red}[*] $file already exists, skipping download. ${reset}"
308 | fi
309 | }
310 |
311 | download_ifnotexist "trickest-resolvers.txt" "https://raw.githubusercontent.com/trickest/resolvers/refs/heads/main/resolvers.txt"
312 | download_ifnotexist "six2dez.txt" "https://gist.githubusercontent.com/six2dez/a307a04a222fab5a57466c51e1569acf/raw"
313 | download_ifnotexist "n0kovo-huge-subdomains.txt" "https://raw.githubusercontent.com/n0kovo/n0kovo_subdomains/refs/heads/main/n0kovo_subdomains_huge.txt"
314 | download_ifnotexist "dnscan-top10k.txt" "https://raw.githubusercontent.com/rbsec/dnscan/refs/heads/master/subdomains-10000.txt"
315 | download_ifnotexist "best-dns-wordlist.txt" "https://wordlists-cdn.assetnote.io/data/manual/best-dns-wordlist.txt"
316 | download_ifnotexist "assetfinder-httparchive-subdomains.txt" "https://wordlists-cdn.assetnote.io/data/automated/httparchive_subdomains_2024_05_28.txt"
317 |
318 | # Create DNS files if they don't exist
319 | if [ ! -f "dns.txt" ]; then
320 | echo -e "${green} [*] Creating dns.txt ${reset}"
321 | cat best-dns-wordlist.txt six2dez.txt dnscan-top10k.txt | anew dns.txt
322 | else
323 | echo -e "${red}[*] dns.txt already exists, skipping download. ${reset}"
324 | fi
325 |
326 | if [ ! -f "dns2.txt" ]; then
327 | echo -e "${green} [*] Creating dns2.txt ${reset}"
328 | cat six2dez.txt dnscan-top10k.txt | anew dns2.txt
329 | else
330 | echo -e "${red}[*] dns2.txt already exists, skipping download. ${reset}"
331 | fi
332 |
333 | # save
334 | echo "dns.txt contains best-dns-wordlist.txt, six2dez.txt, and dnscan-top10k.txt." >>readme
335 | echo "dns2.txt contains six2dez.txt and dnscan-top10k.txt." >>readme
336 | rm -f best-dns-wordlist.txt six2dez.txt dnscan-top10k.txt
337 |
338 | #\\ downloading config files //#
339 | AMASS_CONFIG_DIR="$HOME/anveshan/.config/amass"
340 | WAYMORE_CONFIG_DIR="$HOME/anveshan/.config/waymore"
341 |
342 | # Create directories if they don't exist
343 | mkdir -p "$AMASS_CONFIG_DIR"
344 | mkdir -p "$WAYMORE_CONFIG_DIR"
345 |
346 | # Function to download configuration files if they don't exist
347 | download_ifconfignotexist() {
348 | local configfile="$1"
349 | local configurl="$2"
350 |
351 | if [ ! -f "$configfile" ]; then
352 | echo -e "${green} [+] Downloading $(basename "$configfile") ${reset}"
353 | wget -q -O "$configfile" "$configurl"
354 | else
355 | echo -e "${red}[*] $(basename "$configfile") already exists, skipping download. ${reset}"
356 | fi
357 | }
358 |
359 | download_ifconfignotexist "$AMASS_CONFIG_DIR/datasources.yaml" "https://raw.githubusercontent.com/owasp-amass/amass/refs/heads/master/examples/datasources.yaml"
360 | download_ifconfignotexist "$AMASS_CONFIG_DIR/config.yaml" "https://raw.githubusercontent.com/owasp-amass/amass/refs/heads/master/examples/config.yaml"
361 | download_ifconfignotexist "$WAYMORE_CONFIG_DIR/config.yml" "https://raw.githubusercontent.com/xnl-h4ck3r/waymore/refs/heads/main/config.yml"
362 |
363 | #\\\\\\ getting resolvers /////#
364 | scrclr
365 | printf "${magenta}[*] getting fresh resolvers in 120 seconds ${reset}\n" | pv -qL 23
366 | timeout 120 dnsvalidator -tL trickest-resolvers.txt -threads 25 -o resolvers.txt
367 | printf "${yellow}[$] we got $(cat resolvers.txt | wc -l) fresh resolvers${reset}\n" | pv -qL 23
368 | cd ../
369 | sleep 2
370 |
371 | #\\\\\\\\\ screen clear ///////#
372 | scrclr
373 | printf "${magenta}You need to add API Keys for [AMASS] [BBOT] [SUBDOMINATOR] in these config files${reset}\n"
374 | printf "${yellow}amass: $HOME/anveshan/.config/amass/datasources.yaml${reset}\n"
375 | printf "${yellow}bbot: $HOME/.config/bbot/secrets.yml${reset}\n"
376 | printf "${yellow}subdominator: $HOME/.config/Subdominator/provider-config.yaml${reset}\n"
377 | echo
378 | printf "${magenta}Also add VIRUSTOTAL and URLSCAN API Keys in waymore config file to get more urls.${reset}\n"
379 | printf "${yellow}waymore: $HOME/anveshan/.config/waymore/config.yml${reset}\n"
380 | echo
381 | read -p "${red}You want to open these files in notepad? [Y/n] ${reset} " apianswer
382 | if [[ "$apianswer" == [Yy] ]]; then
383 | if command -v notepad &>/dev/null; then
384 | editor="notepad"
385 | elif command -v gedit &>/dev/null; then
386 | editor="gedit"
387 | elif command -v nano &>/dev/null; then
388 | editor="nano"
389 | else
390 | printf "${red}No text editor found. Please open these API config files manually.${reset}\n"
391 | exit 1
392 | fi
393 |
394 | $editor "$HOME/anveshan/.config/amass/datasources.yaml" \
395 | "$HOME/.config/bbot/secrets.yml" \
396 | "$HOME/.config/Subdominator/provider-config.yaml" \
397 | "$HOME/anveshan/.config/waymore/config.yml"
398 | else
399 | :
400 | fi
401 |
402 | echo
403 | printf "${red} script : setup.sh executed succesfully. ${reset}\n"
404 | printf "${yellow} check 'cd $HOME/anveshan' folder.${reset}\n"
405 | printf "${red} [&] Happy Hacking ;D${reset}\n"
406 |
407 | #deactivating the python virtual envirnment
408 | deactivate
409 |
410 | #iti
411 |
--------------------------------------------------------------------------------
 3 |
3 |  3 |
3 |  69 |
69 |  187 |
187 |  205 |
205 |