 7 |
8 | ### System call - Capability Mapping
9 | We performed a thorough investigation of all available Linux capabilities and the system calls they affect, to derive a detailed and complete mapping between all system calls related to privileged operations and their respective capabilities. The complete mapping can be found [here](https://hasanmdme.github.io/decap/website/syscall-capabilitymappingtable.html), and a visual representation of the mapping is available [here](https://hasanmdme.github.io/decap/website/syscall-capabilitymapping.html).
10 |
11 |
7 |
8 | ### System call - Capability Mapping
9 | We performed a thorough investigation of all available Linux capabilities and the system calls they affect, to derive a detailed and complete mapping between all system calls related to privileged operations and their respective capabilities. The complete mapping can be found [here](https://hasanmdme.github.io/decap/website/syscall-capabilitymappingtable.html), and a visual representation of the mapping is available [here](https://hasanmdme.github.io/decap/website/syscall-capabilitymapping.html).
10 |
11 | 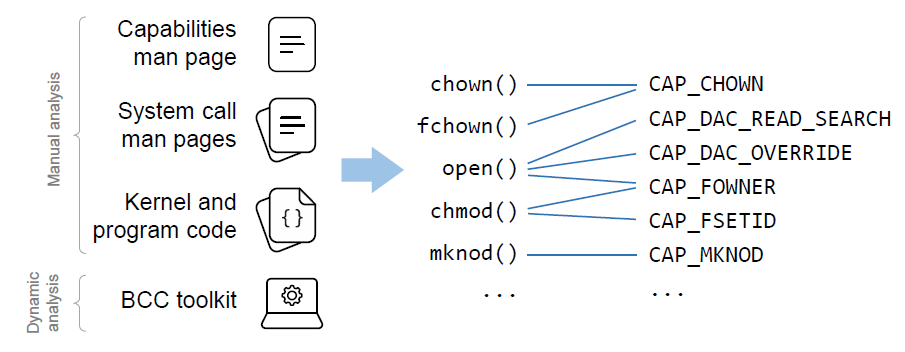 14 |
15 | ### System call Identification and Capability Enforcement
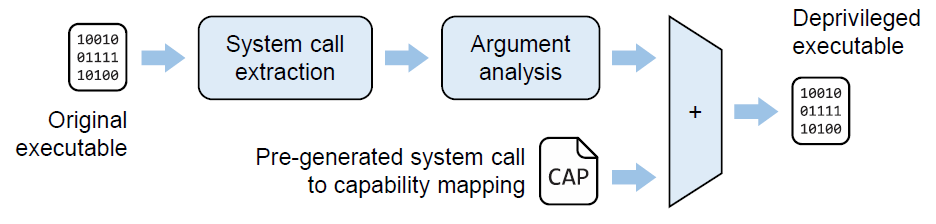
16 | The first step in deprivileging a setuid program is to identify its required system calls. Decap performs static binary code analysis of a target program and its libraries to extract the set of all possible system calls it may invoke, and then to derive and enforce the corresponding set of required capabilities. Decap relies on both [Confine](https://www3.cs.stonybrook.edu/~sghavamnia/papers/confine.raid20.pdf) and [Sysfilter](https://cs.brown.edu/~vpk/papers/sysfilter.raid20.pdf) to identify the system calls required by a given application. Also, CAP_SYS_ADMIN capability is required by multiple system calls but only when invoked with a limited set of specific argument values. Therefore, once the set of required system calls has been extracted, Decap performs argumentlevel analysis for those system calls that conditionally require CAP_SYS_ADMIN, and attempts to extract the concrete values passed to the arguments that determine whether CAP_SYS_ADMIN is required, across all their call sites. Decap identifies the required capabilities for an application based on the system call analysis and the previously generated mapping. Finally, it reduces the privileges by first deprivileging the target application entirely by removing its setuid bit, and then granting only the capabilities that the program actually requires.
17 |
18 | ## Step by Step Guide
19 | This section shows the step by step guide for running Decap to generate capability profile of setuid binaries. [Read more...](https://hasanmdme.github.io/decap/website/stepbystepguide.html)
20 |
21 | ## Academic Publication
22 | Please use the following citation for [Decap](https://www3.cs.stonybrook.edu/~mdhasan/papers/decap.raid22.pdf).
23 | ```
24 | @inproceedings{decapraid22,
25 | title = {Decap: Deprivileging Programs by Reducing Their Capabilities},
26 | author = {Hasan, Md Mehedi and Ghavamnia, Seyedhamed and Polychronakis, Michalis},
27 | booktitle = {Proceedings of the International Conference on Research in Attacks,
28 | Intrusions, and Defenses (RAID)},
29 | year = {2022}
30 | }
31 | ```
32 |
--------------------------------------------------------------------------------
/sample-output/Output_Stat.csv:
--------------------------------------------------------------------------------
1 | ,app_name,syscalls_responsible_for_SYS_ADMIN,SYS_ADMIN removed?,total_capabilities,total_cap_count,number_of_syscalls_from_Confine,number_of_syscalls_from_Sysfilter,number_of_intersected_syscalls
2 | 0,nginx,"['ioctl', 'madvise', 'clone', 'prctl']",Yes,"{'CAP_SETGID', 'CAP_IPC_LOCK', 'CAP_SYS_RESOURCE', 'CAP_LEASE', 'CAP_BLOCK_SUSPEND', 'CAP_SYS_PTRACE', 'CAP_NET_RAW', 'CAP_SYS_NICE', 'CAP_KILL', 'CAP_CHOWN', 'CAP_SYS_TTY_CONFIG', 'CAP_MAC_OVERRIDE', 'CAP_LINUX_IMMUTABLE', 'CAP_SETUID', 'CAP_SETPCAP', 'CAP_NET_BIND_SERVICE', 'CAP_DAC_READ_SEARCH', 'CAP_FSETID', 'CAP_NET_ADMIN', 'CAP_AUDIT_CONTROL', 'CAP_SETFCAP', 'CAP_FOWNER', 'CAP_DAC_OVERRIDE'}",23,110,123,98
3 | 1,passwd,"['ioctl', 'madvise', 'clone', 'prctl']",Yes,"{'CAP_SETGID', 'CAP_IPC_LOCK', 'CAP_SYS_RESOURCE', 'CAP_LEASE', 'CAP_SYS_PTRACE', 'CAP_NET_RAW', 'CAP_SYS_NICE', 'CAP_KILL', 'CAP_CHOWN', 'CAP_SYS_TTY_CONFIG', 'CAP_MAC_OVERRIDE', 'CAP_SETUID', 'CAP_SETPCAP', 'CAP_NET_BIND_SERVICE', 'CAP_SYS_CHROOT', 'CAP_DAC_READ_SEARCH', 'CAP_FSETID', 'CAP_NET_ADMIN', 'CAP_DAC_OVERRIDE', 'CAP_AUDIT_CONTROL', 'CAP_SETFCAP', 'CAP_FOWNER', 'CAP_LINUX_IMMUTABLE'}",23,117,109,87
4 | 2,ping,"['ioctl', 'madvise', 'prctl']",Yes,"{'CAP_SETUID', 'CAP_SETPCAP', 'CAP_DAC_READ_SEARCH', 'CAP_NET_RAW', 'CAP_IPC_LOCK', 'CAP_SYS_RESOURCE', 'CAP_LINUX_IMMUTABLE', 'CAP_KILL', 'CAP_NET_ADMIN', 'CAP_SYS_TTY_CONFIG', 'CAP_LEASE', 'CAP_AUDIT_CONTROL', 'CAP_FOWNER', 'CAP_MAC_OVERRIDE', 'CAP_NET_BIND_SERVICE', 'CAP_DAC_OVERRIDE'}",16,67,60,50
5 | 3,dmcrypt-get-device,"['ioctl', 'madvise', 'clone', 'prctl']",No,"{'CAP_SETGID', 'CAP_IPC_LOCK', 'CAP_SYS_RESOURCE', 'CAP_LEASE', 'CAP_SYS_PTRACE', 'CAP_MKNOD', 'CAP_NET_RAW', 'CAP_SYS_NICE', 'CAP_KILL', 'CAP_CHOWN', 'CAP_SYS_TTY_CONFIG', 'CAP_MAC_OVERRIDE', 'CAP_LINUX_IMMUTABLE', 'CAP_SETUID', 'CAP_SETPCAP', 'CAP_NET_BIND_SERVICE', 'CAP_SYS_ADMIN', 'CAP_DAC_READ_SEARCH', 'CAP_NET_ADMIN', 'CAP_AUDIT_CONTROL', 'CAP_SETFCAP', 'CAP_FOWNER', 'CAP_DAC_OVERRIDE'}",23,115,104,83
6 | 4,lpr,['madvise'],Yes,"{'CAP_SETGID', 'CAP_SETUID', 'CAP_DAC_READ_SEARCH', 'CAP_FSETID', 'CAP_NET_RAW', 'CAP_IPC_LOCK', 'CAP_SYS_RESOURCE', 'CAP_SYS_NICE', 'CAP_KILL', 'CAP_NET_ADMIN', 'CAP_LEASE', 'CAP_DAC_OVERRIDE', 'CAP_AUDIT_CONTROL', 'CAP_FOWNER', 'CAP_MAC_OVERRIDE', 'CAP_NET_BIND_SERVICE', 'CAP_SYS_PTRACE'}",17,63,99,57
7 | 5,exim4,"['ioctl', 'madvise', 'shmctl', 'clone', 'prctl']",No,"{'CAP_SETGID', 'CAP_IPC_LOCK', 'CAP_SYS_RESOURCE', 'CAP_LEASE', 'CAP_SYS_PTRACE', 'CAP_NET_RAW', 'CAP_SYS_NICE', 'CAP_KILL', 'CAP_CHOWN', 'CAP_SYS_TTY_CONFIG', 'CAP_MAC_OVERRIDE', 'CAP_LINUX_IMMUTABLE', 'CAP_SETUID', 'CAP_SETPCAP', 'CAP_NET_BIND_SERVICE', 'CAP_SYS_ADMIN', 'CAP_DAC_READ_SEARCH', 'CAP_FSETID', 'CAP_NET_ADMIN', 'CAP_AUDIT_CONTROL', 'CAP_SETFCAP', 'CAP_FOWNER', 'CAP_IPC_OWNER', 'CAP_DAC_OVERRIDE'}",24,128,0,128
8 | 6,unix_chkpwd,"['ioctl', 'madvise', 'clone', 'prctl']",Yes,"{'CAP_SETGID', 'CAP_IPC_LOCK', 'CAP_SYS_RESOURCE', 'CAP_LEASE', 'CAP_SYS_PTRACE', 'CAP_NET_RAW', 'CAP_SYS_NICE', 'CAP_KILL', 'CAP_SYS_TTY_CONFIG', 'CAP_MAC_OVERRIDE', 'CAP_SETUID', 'CAP_SETPCAP', 'CAP_NET_BIND_SERVICE', 'CAP_DAC_READ_SEARCH', 'CAP_NET_ADMIN', 'CAP_DAC_OVERRIDE', 'CAP_AUDIT_CONTROL', 'CAP_SETFCAP', 'CAP_FOWNER', 'CAP_LINUX_IMMUTABLE'}",20,108,96,73
9 | 7,tcpdump,"['ioctl', 'madvise', 'clone', 'prctl']",No,"{'CAP_SETGID', 'CAP_IPC_LOCK', 'CAP_SYS_RESOURCE', 'CAP_LEASE', 'CAP_SYS_PTRACE', 'CAP_NET_RAW', 'CAP_SYS_NICE', 'CAP_KILL', 'CAP_SYS_TTY_CONFIG', 'CAP_MAC_OVERRIDE', 'CAP_LINUX_IMMUTABLE', 'CAP_SETUID', 'CAP_SETPCAP', 'CAP_NET_BIND_SERVICE', 'CAP_SYS_ADMIN', 'CAP_DAC_READ_SEARCH', 'CAP_FSETID', 'CAP_NET_ADMIN', 'CAP_AUDIT_CONTROL', 'CAP_SETFCAP', 'CAP_FOWNER', 'CAP_DAC_OVERRIDE'}",22,94,120,79
10 | 8,httpd,"['ioctl', 'madvise', 'shmctl', 'clone', 'prctl']",No,"{'CAP_SETGID', 'CAP_IPC_LOCK', 'CAP_SYS_RESOURCE', 'CAP_LEASE', 'CAP_BLOCK_SUSPEND', 'CAP_SYS_PTRACE', 'CAP_NET_RAW', 'CAP_SYS_NICE', 'CAP_KILL', 'CAP_CHOWN', 'CAP_SYS_TTY_CONFIG', 'CAP_MAC_OVERRIDE', 'CAP_LINUX_IMMUTABLE', 'CAP_SETUID', 'CAP_SETPCAP', 'CAP_NET_BIND_SERVICE', 'CAP_SYS_ADMIN', 'CAP_DAC_READ_SEARCH', 'CAP_FSETID', 'CAP_NET_ADMIN', 'CAP_AUDIT_CONTROL', 'CAP_SETFCAP', 'CAP_FOWNER', 'CAP_IPC_OWNER', 'CAP_DAC_OVERRIDE'}",25,124,133,106
11 | 9,lighttpd,"['ioctl', 'madvise', 'clone', 'prctl']",Yes,"{'CAP_SETGID', 'CAP_IPC_LOCK', 'CAP_SYS_RESOURCE', 'CAP_LEASE', 'CAP_BLOCK_SUSPEND', 'CAP_SYS_PTRACE', 'CAP_NET_RAW', 'CAP_SYS_NICE', 'CAP_KILL', 'CAP_SYS_TTY_CONFIG', 'CAP_MAC_OVERRIDE', 'CAP_LINUX_IMMUTABLE', 'CAP_SETUID', 'CAP_SETPCAP', 'CAP_NET_BIND_SERVICE', 'CAP_SYS_CHROOT', 'CAP_DAC_READ_SEARCH', 'CAP_FSETID', 'CAP_NET_ADMIN', 'CAP_AUDIT_CONTROL', 'CAP_SETFCAP', 'CAP_FOWNER', 'CAP_DAC_OVERRIDE'}",23,121,130,96
12 |
--------------------------------------------------------------------------------
/website/about.html:
--------------------------------------------------------------------------------
1 |
2 |
3 |
4 |
5 |
6 |
7 |
14 |
15 | ### System call Identification and Capability Enforcement
16 | The first step in deprivileging a setuid program is to identify its required system calls. Decap performs static binary code analysis of a target program and its libraries to extract the set of all possible system calls it may invoke, and then to derive and enforce the corresponding set of required capabilities. Decap relies on both [Confine](https://www3.cs.stonybrook.edu/~sghavamnia/papers/confine.raid20.pdf) and [Sysfilter](https://cs.brown.edu/~vpk/papers/sysfilter.raid20.pdf) to identify the system calls required by a given application. Also, CAP_SYS_ADMIN capability is required by multiple system calls but only when invoked with a limited set of specific argument values. Therefore, once the set of required system calls has been extracted, Decap performs argumentlevel analysis for those system calls that conditionally require CAP_SYS_ADMIN, and attempts to extract the concrete values passed to the arguments that determine whether CAP_SYS_ADMIN is required, across all their call sites. Decap identifies the required capabilities for an application based on the system call analysis and the previously generated mapping. Finally, it reduces the privileges by first deprivileging the target application entirely by removing its setuid bit, and then granting only the capabilities that the program actually requires.
17 |
18 | ## Step by Step Guide
19 | This section shows the step by step guide for running Decap to generate capability profile of setuid binaries. [Read more...](https://hasanmdme.github.io/decap/website/stepbystepguide.html)
20 |
21 | ## Academic Publication
22 | Please use the following citation for [Decap](https://www3.cs.stonybrook.edu/~mdhasan/papers/decap.raid22.pdf).
23 | ```
24 | @inproceedings{decapraid22,
25 | title = {Decap: Deprivileging Programs by Reducing Their Capabilities},
26 | author = {Hasan, Md Mehedi and Ghavamnia, Seyedhamed and Polychronakis, Michalis},
27 | booktitle = {Proceedings of the International Conference on Research in Attacks,
28 | Intrusions, and Defenses (RAID)},
29 | year = {2022}
30 | }
31 | ```
32 |
--------------------------------------------------------------------------------
/sample-output/Output_Stat.csv:
--------------------------------------------------------------------------------
1 | ,app_name,syscalls_responsible_for_SYS_ADMIN,SYS_ADMIN removed?,total_capabilities,total_cap_count,number_of_syscalls_from_Confine,number_of_syscalls_from_Sysfilter,number_of_intersected_syscalls
2 | 0,nginx,"['ioctl', 'madvise', 'clone', 'prctl']",Yes,"{'CAP_SETGID', 'CAP_IPC_LOCK', 'CAP_SYS_RESOURCE', 'CAP_LEASE', 'CAP_BLOCK_SUSPEND', 'CAP_SYS_PTRACE', 'CAP_NET_RAW', 'CAP_SYS_NICE', 'CAP_KILL', 'CAP_CHOWN', 'CAP_SYS_TTY_CONFIG', 'CAP_MAC_OVERRIDE', 'CAP_LINUX_IMMUTABLE', 'CAP_SETUID', 'CAP_SETPCAP', 'CAP_NET_BIND_SERVICE', 'CAP_DAC_READ_SEARCH', 'CAP_FSETID', 'CAP_NET_ADMIN', 'CAP_AUDIT_CONTROL', 'CAP_SETFCAP', 'CAP_FOWNER', 'CAP_DAC_OVERRIDE'}",23,110,123,98
3 | 1,passwd,"['ioctl', 'madvise', 'clone', 'prctl']",Yes,"{'CAP_SETGID', 'CAP_IPC_LOCK', 'CAP_SYS_RESOURCE', 'CAP_LEASE', 'CAP_SYS_PTRACE', 'CAP_NET_RAW', 'CAP_SYS_NICE', 'CAP_KILL', 'CAP_CHOWN', 'CAP_SYS_TTY_CONFIG', 'CAP_MAC_OVERRIDE', 'CAP_SETUID', 'CAP_SETPCAP', 'CAP_NET_BIND_SERVICE', 'CAP_SYS_CHROOT', 'CAP_DAC_READ_SEARCH', 'CAP_FSETID', 'CAP_NET_ADMIN', 'CAP_DAC_OVERRIDE', 'CAP_AUDIT_CONTROL', 'CAP_SETFCAP', 'CAP_FOWNER', 'CAP_LINUX_IMMUTABLE'}",23,117,109,87
4 | 2,ping,"['ioctl', 'madvise', 'prctl']",Yes,"{'CAP_SETUID', 'CAP_SETPCAP', 'CAP_DAC_READ_SEARCH', 'CAP_NET_RAW', 'CAP_IPC_LOCK', 'CAP_SYS_RESOURCE', 'CAP_LINUX_IMMUTABLE', 'CAP_KILL', 'CAP_NET_ADMIN', 'CAP_SYS_TTY_CONFIG', 'CAP_LEASE', 'CAP_AUDIT_CONTROL', 'CAP_FOWNER', 'CAP_MAC_OVERRIDE', 'CAP_NET_BIND_SERVICE', 'CAP_DAC_OVERRIDE'}",16,67,60,50
5 | 3,dmcrypt-get-device,"['ioctl', 'madvise', 'clone', 'prctl']",No,"{'CAP_SETGID', 'CAP_IPC_LOCK', 'CAP_SYS_RESOURCE', 'CAP_LEASE', 'CAP_SYS_PTRACE', 'CAP_MKNOD', 'CAP_NET_RAW', 'CAP_SYS_NICE', 'CAP_KILL', 'CAP_CHOWN', 'CAP_SYS_TTY_CONFIG', 'CAP_MAC_OVERRIDE', 'CAP_LINUX_IMMUTABLE', 'CAP_SETUID', 'CAP_SETPCAP', 'CAP_NET_BIND_SERVICE', 'CAP_SYS_ADMIN', 'CAP_DAC_READ_SEARCH', 'CAP_NET_ADMIN', 'CAP_AUDIT_CONTROL', 'CAP_SETFCAP', 'CAP_FOWNER', 'CAP_DAC_OVERRIDE'}",23,115,104,83
6 | 4,lpr,['madvise'],Yes,"{'CAP_SETGID', 'CAP_SETUID', 'CAP_DAC_READ_SEARCH', 'CAP_FSETID', 'CAP_NET_RAW', 'CAP_IPC_LOCK', 'CAP_SYS_RESOURCE', 'CAP_SYS_NICE', 'CAP_KILL', 'CAP_NET_ADMIN', 'CAP_LEASE', 'CAP_DAC_OVERRIDE', 'CAP_AUDIT_CONTROL', 'CAP_FOWNER', 'CAP_MAC_OVERRIDE', 'CAP_NET_BIND_SERVICE', 'CAP_SYS_PTRACE'}",17,63,99,57
7 | 5,exim4,"['ioctl', 'madvise', 'shmctl', 'clone', 'prctl']",No,"{'CAP_SETGID', 'CAP_IPC_LOCK', 'CAP_SYS_RESOURCE', 'CAP_LEASE', 'CAP_SYS_PTRACE', 'CAP_NET_RAW', 'CAP_SYS_NICE', 'CAP_KILL', 'CAP_CHOWN', 'CAP_SYS_TTY_CONFIG', 'CAP_MAC_OVERRIDE', 'CAP_LINUX_IMMUTABLE', 'CAP_SETUID', 'CAP_SETPCAP', 'CAP_NET_BIND_SERVICE', 'CAP_SYS_ADMIN', 'CAP_DAC_READ_SEARCH', 'CAP_FSETID', 'CAP_NET_ADMIN', 'CAP_AUDIT_CONTROL', 'CAP_SETFCAP', 'CAP_FOWNER', 'CAP_IPC_OWNER', 'CAP_DAC_OVERRIDE'}",24,128,0,128
8 | 6,unix_chkpwd,"['ioctl', 'madvise', 'clone', 'prctl']",Yes,"{'CAP_SETGID', 'CAP_IPC_LOCK', 'CAP_SYS_RESOURCE', 'CAP_LEASE', 'CAP_SYS_PTRACE', 'CAP_NET_RAW', 'CAP_SYS_NICE', 'CAP_KILL', 'CAP_SYS_TTY_CONFIG', 'CAP_MAC_OVERRIDE', 'CAP_SETUID', 'CAP_SETPCAP', 'CAP_NET_BIND_SERVICE', 'CAP_DAC_READ_SEARCH', 'CAP_NET_ADMIN', 'CAP_DAC_OVERRIDE', 'CAP_AUDIT_CONTROL', 'CAP_SETFCAP', 'CAP_FOWNER', 'CAP_LINUX_IMMUTABLE'}",20,108,96,73
9 | 7,tcpdump,"['ioctl', 'madvise', 'clone', 'prctl']",No,"{'CAP_SETGID', 'CAP_IPC_LOCK', 'CAP_SYS_RESOURCE', 'CAP_LEASE', 'CAP_SYS_PTRACE', 'CAP_NET_RAW', 'CAP_SYS_NICE', 'CAP_KILL', 'CAP_SYS_TTY_CONFIG', 'CAP_MAC_OVERRIDE', 'CAP_LINUX_IMMUTABLE', 'CAP_SETUID', 'CAP_SETPCAP', 'CAP_NET_BIND_SERVICE', 'CAP_SYS_ADMIN', 'CAP_DAC_READ_SEARCH', 'CAP_FSETID', 'CAP_NET_ADMIN', 'CAP_AUDIT_CONTROL', 'CAP_SETFCAP', 'CAP_FOWNER', 'CAP_DAC_OVERRIDE'}",22,94,120,79
10 | 8,httpd,"['ioctl', 'madvise', 'shmctl', 'clone', 'prctl']",No,"{'CAP_SETGID', 'CAP_IPC_LOCK', 'CAP_SYS_RESOURCE', 'CAP_LEASE', 'CAP_BLOCK_SUSPEND', 'CAP_SYS_PTRACE', 'CAP_NET_RAW', 'CAP_SYS_NICE', 'CAP_KILL', 'CAP_CHOWN', 'CAP_SYS_TTY_CONFIG', 'CAP_MAC_OVERRIDE', 'CAP_LINUX_IMMUTABLE', 'CAP_SETUID', 'CAP_SETPCAP', 'CAP_NET_BIND_SERVICE', 'CAP_SYS_ADMIN', 'CAP_DAC_READ_SEARCH', 'CAP_FSETID', 'CAP_NET_ADMIN', 'CAP_AUDIT_CONTROL', 'CAP_SETFCAP', 'CAP_FOWNER', 'CAP_IPC_OWNER', 'CAP_DAC_OVERRIDE'}",25,124,133,106
11 | 9,lighttpd,"['ioctl', 'madvise', 'clone', 'prctl']",Yes,"{'CAP_SETGID', 'CAP_IPC_LOCK', 'CAP_SYS_RESOURCE', 'CAP_LEASE', 'CAP_BLOCK_SUSPEND', 'CAP_SYS_PTRACE', 'CAP_NET_RAW', 'CAP_SYS_NICE', 'CAP_KILL', 'CAP_SYS_TTY_CONFIG', 'CAP_MAC_OVERRIDE', 'CAP_LINUX_IMMUTABLE', 'CAP_SETUID', 'CAP_SETPCAP', 'CAP_NET_BIND_SERVICE', 'CAP_SYS_CHROOT', 'CAP_DAC_READ_SEARCH', 'CAP_FSETID', 'CAP_NET_ADMIN', 'CAP_AUDIT_CONTROL', 'CAP_SETFCAP', 'CAP_FOWNER', 'CAP_DAC_OVERRIDE'}",23,121,130,96
12 |
--------------------------------------------------------------------------------
/website/about.html:
--------------------------------------------------------------------------------
1 |
2 |
3 |
4 |
5 |
6 |
7 | About Decap
18 | 19 |Overview
21 |Decap is a binary code analysis tool that automatically deprivileges programs by identifying the subset of 25 | capabilities they require based on the system calls they may invoke. This is made possible by our systematic effort in deriving a complete 26 | mapping between all Linux system calls related to privileged operations and the corresponding capabilities on which they depend. We suggest reading our 27 | paper for more details. 28 |
29 | 32 |
32 | 34 | 35 | 36 | 37 |
System call - Capability Mapping
39 |We performed a thorough investigation 43 | of all available Linux capabilities and the system calls they affect, 44 | to derive a detailed and complete mapping between all system calls 45 | related to privileged operations and their respective capabilities. The complete mapping can be found 46 | here, 47 | and a visual representation of the mapping is available 48 | here. 49 |
50 | 53 |
53 | 55 | 56 | 57 |
System call Identification and Capability Enforcement
59 |The first step in deprivileging a setuid program is to identify its 63 | required system calls. Decap performs static binary code analysis of a target program and its libraries to extract the set 64 | of all possible system calls it may invoke, and then to derive and enforce the corresponding set of required capabilities. Decap relies on both 65 | Confine 66 | and 67 | Sysfilter 68 | to identify the system calls required by a given application. Also, CAP_SYS_ADMIN capability is 69 | required by multiple system calls but only when invoked with a 70 | limited set of specific argument values. Therefore, once the set of 71 | required system calls has been extracted, Decap performs argumentlevel 72 | analysis for those system calls that conditionally require 73 | CAP_SYS_ADMIN, and attempts to extract the concrete values passed 74 | to the arguments that determine whether CAP_SYS_ADMIN is required, across all their call sites. 75 | Decap identifies the required capabilities for an application based on the system call analysis and the 76 | previously generated mapping. Finally, it reduces the privileges by first deprivileging the target 77 | application entirely by removing its setuid bit, and then granting 78 | only the capabilities that the program actually requires. 79 | 80 |
81 |83 | 84 |
Academic Publication
86 |90 | Please use the following citation for Decap. 91 |
92 |
93 | @inproceedings{decapraid22,
94 | title = {Decap: Deprivileging Programs by Reducing Their Capabilities},
95 | author = {Hasan, Md Mehedi and Ghavamnia, Seyedhamed and Polychronakis, Michalis},
96 | booktitle = {Proceedings of the International Conference on Research in Attacks,
97 | Intrusions, and Defenses (RAID)},
98 | year = {2022}
99 | }
100 |
101 | Decap Step by Step Guide
17 |18 | In this page we will walk through the steps required to generate a capability 19 | profile for the ping application. 20 |
21 | 22 |Prerequisites
24 |Decap is mainly developed in python. You will need to install the python version 3.
30 |31 | sudo apt update 32 | sudo apt install -y python3 33 | sudo pip3 install pandas 34 |35 | 36 | As Decap uses sysfilter's system call extraction tool, you have to clone and build the sysfilter extraction tool from 37 | here. While running decap, you have to give the path of sysfilter_extract executable as a flag value. 38 | 39 |
40 | 41 |
System Validation
42 |Now we will check that we are running the correct 43 | kernel version required for completing the hands-on exercise. We tested Decap on Ubuntu 18.04 with kernel v5.4
44 |uname --kernel-release
45 | This should print the kernel version which should be as follows:
46 |5.4.0-48-lowlatency47 |
It is critical that you see the correct Linux kernel version.
48 |49 |
We can check the Ubuntu distribution using this command:
50 |cat /etc/issue
51 | This should print the Ubuntu version which should be as follows:
52 |Ubuntu 18.04.5 LTS \n \l53 |
54 |
Working with Decap
58 |Working with Decap
61 |1. Check where is binary ping
62 |whereis -b ping
63 | This should print the path of the binary like this:
64 |ping: /bin/ping65 | 66 |
2. Switch to the `src` directory.
67 |cd src
68 |
69 | 3. Open a new file, name it as you like. We will use myexample.json in the following examples.
70 |vim myexample.json
71 |
72 | 4. Copy the following text into the file and update the binary-path value from step 1.
73 |
74 | {
75 | "ping": {
76 | "binary-path": "/bin/ping"
77 | }
78 | }
79 |
80 | 5. Now run Decap:
81 |sudo python3 decap.py --input [full-path-of-myexample.json] --sysfilterpath [full-path-of-sysfilter_extraction-executable]
82 | The script will now start analyzing the binary for the required capability.
83 |Starting analysis for binary: ping ... 84 |85 | 86 |
System call extraction and argument analysis phase
87 |Starting system call extraction ... 88 | Extracting system calls using Confine and performing argument analysis for the system calls responsible for CAP_SYS_ADMIN ... 89 | Extracting system calls using Sysfilter ... 90 | Generating final system call list ... 91 | ... System call extraction done! 92 | Total number of extracted system calls : 50 93 |94 | 95 |
The script will now start finding the required capability based on extracted system calls.
96 |Finding required capabilities for the extracted system calls ... 97 | Checking if CAP_SYS_ADMIN is required based on the argument analysis ... 98 | ... removing CAP_SYS_ADMIN 99 | Total num of capabilties to add : 16 100 | Deprivileging setuid binary and enforcing only the required capabilities to the binary 101 | Done capability analysis for ping! 102 | ---------------------------------------------------------------- 103 |104 | 105 |
6. Now the analysis is done and we can check the capabilities of the binary
106 |getcap /bin/ping
107 | This should print the capabilities added to the binary like this:
108 |/bin/ping = cap_dac_override,cap_dac_read_search,cap_fowner,cap_kill,cap_setuid,cap_setpcap,cap_linux_immutable,cap_net_bind_service,cap_net_admin,cap_net_raw,cap_ipc_lock,cap_sys_resource,cap_sys_tty_config,cap_lease,cap_audit_control,cap_mac_override+ep109 |
110 | 111 |
Capability-System call Mapping
13 | 14 |As of Linux Kernel v5.17, 41 capabilities have been introduced. Our 15 | mapping includes 126 system calls, which depend on at least one of the 41 16 | available capabilities to perform some privileged operation. Visual 17 | representation of this mapping is also available 18 | here. 19 |
20 | 21 |The resulting mapping of our effort to identify the system calls that depend on each capability.
22 || Capability | 25 |System call(s) | 26 | 27 |
|---|---|
| CAP_AUDIT_CONTROL | 30 |sendto, recv, recvfrom, recvmsg | 31 |
| CAP_AUDIT_READ | 34 |bind | 35 |
| CAP_AUDIT_WRITE | 39 |sendto | 40 |
| CAP_BLOCK_SUSPEND | 44 |epoll_ctl | 45 |
| CAP_SYS_ADMIN | 49 |bpf, perf_event_open, syslog, mount, umount, pivot_root, swapon, swapoff, setdomainname, vm86, setns, 50 | fanotify_init, unshare, lookup_dcookie, io_submit, prctl, clone, quotactl, msgctl, setrlimit, shmctl, ioprio_set, keyctl, madvise, ioctl, seccomp, ptrace, sethostname | 51 |
| CAP_BPF | 55 |bpf | 56 |
| CAP_PERFMON | 60 |perf_event_open | 61 |
| CAP_SYSLOG | 65 |syslog | 66 |
| CAP_CHECKPOINT_RESTORE | 70 |clone | 71 |
| CAP_CHOWN | 75 |chown, fchown, lchown, fchownat | 76 |
| CAP_DAC_READ_SEARCH | 80 |open, openat, openat2, open_by_handle_at, linkat | 81 |
| CAP_DAC_OVERRIDE | 85 |utime, utimensat, utimes, open, openat, openat2 | 86 |
| CAP_FOWNER | 90 |chmod, fchmod, fchmodat, utime, utimes, utimensat, unlink, unlinkat, open, openat, openat2, fcntl, rename, renameat, renameat2, rmdir, ioctl | 91 |
| CAP_LEASE | 95 |fcntl | 96 |
| CAP_FSETID | 100 |chmod, fchmod, fchmodat | 101 |
| CAP_IPC_LOCK | 105 |mlock, mlock2, mlockall, mmap, memfd_create | 106 |
| CAP_IPC_OWNER | 110 |msgrcv, msgsnd, semop, semtimedop, shmat, shmdt, msgctl, msgget, shmctl | 111 |
| CAP_KILL | 115 |kill, ioctl | 116 |
| CAP_LINUX_IMMUTABLE | 120 |ioctl | 121 |
| CAP_MAC_ADMIN | 125 |setxattr, lsetxattr, fsetxattr | 126 |
| CAP_MAC_OVERRIDE | 130 |socket | 131 |
| CAP_MKNOD | 135 |mknod, mknodat, renameat2 | 136 |
| CAP_NET_ADMIN | 140 |setsockopt, ioctl | 141 |
| CAP_NET_BIND_SERVICE | 145 |bind | 146 |
| CAP_NET_BROADCAST | 150 |151 | |
| CAP_NET_RAW | 155 |socket | 156 |
| CAP_SETGID | 160 |setgroups, setfsgid, setgid, setregid, setresgid | 161 |
| CAP_SETFCAP | 165 |clone | 166 |
| CAP_SETPCAP | 170 |capset, prctl | 171 |
| CAP_SETUID | 175 |setuid, setreuid, setresuid, setfsuid, keyctl | 176 |
| CAP_SYS_BOOT | 180 |reboot, kexec_file_load, kexec_load | 181 |
| CAP_SYS_CHROOT | 185 |chroot, setns | 186 |
| CAP_SYS_MODULE | 190 |finit_module, init_module, create_module, delete_module | 191 |
| CAP_SYS_NICE | 195 |sched_setscheduler, sched_setparam, sched_setattr, migrate_pages, setpriority, sched_setaffinity, nice, ioprio_set, move_pages, spu_create, mbind | 196 |
| CAP_SYS_PACCT | 200 |acct | 201 |
| CAP_SYS_PTRACE | 205 |ptrace, userfaultfd, kcmp, set_robust_list, 206 | process_vm_readv, process_vm_writev | 207 |
| CAP_SYS_RAWIO | 211 |iopl, ioperm | 212 |
| CAP_SYS_RESOURCE | 216 |send, sendto, sendmsg, prctl, msgctl, setrlimit, fcntl, prlimit, mq_open, ioctl | 217 |
| CAP_SYS_TIME | 221 |settimeofday, stime, adjtimex, clock_adjtime, ntp_adjtime | 222 |
| CAP_SYS_TTY_CONFIG | 226 |vhangup, ioctl | 227 |
| CAP_WAKE_ALARM | 231 |timer_create, timerfd_create | 232 |
235 |
System calls that conditionally depend on CAP_SYS_ADMIN according to certain values of the highlighted arguments.
236 | 237 | 238 || System calls | 241 |
|---|
| int clone(int (*fn)(void *), void *child_stack, int flags, void *arg, 244 | ... /* pid_t *ptid, struct user_desc *tls, pid_t *ctid */); | 245 |
| int prctl(int option, unsigned long arg2, unsigned long 249 | arg3, unsigned long arg4, unsigned long arg5); | 250 |
| int quotactl(int cmd, const char *special, int id, caddr_t addr); | 254 |
| int msgctl(int msqid, int cmd, struct msqid_ds *buf); | 258 |
| int setrlimit(int resource, const struct rlimit *rlim); | 262 |
| int shmctl(int shmid, int cmd, struct shmid_ds *buf); | 266 |
| int syscall(SYS_ioprio_set, int which, int who, int ioprio); | 270 |
| long syscall(SYS_keyctl, int operation, unsigned long arg2, 274 | unsigned long arg3, unsigned long arg4, unsigned long arg5); | 275 |
| int madvise(void *addr, size_t length, int advice); | 279 |
| int ioctl(int fd, unsigned long request, ...); | 283 |
| int syscall(SYS_seccomp, unsigned int operation, unsigned 287 | int flags, void *args); | 288 |
| long ptrace(enum __ptrace_request request, pid_t pid,void *addr, void *data); | 292 |
295 |
296 |