165 |
249 |
166 |
167 |
168 |
248 |
169 |
181 |
182 | Get started with Intercom
170 |
171 |
172 | Chat with visitors to your website in real-time, capture them as leads, and convert them to customers. Install Intercom on your WordPress site in a couple of clicks.
173 |
174 |
175 |
176 |
177 |  178 |
179 |
178 |
179 |
180 |  178 |
179 |
178 |
179 | Intercom setup
183 | Intercom app ID saved
184 |
185 |
186 |
187 |
247 |
188 |
199 |
200 |
246 |
201 |
204 |
245 | 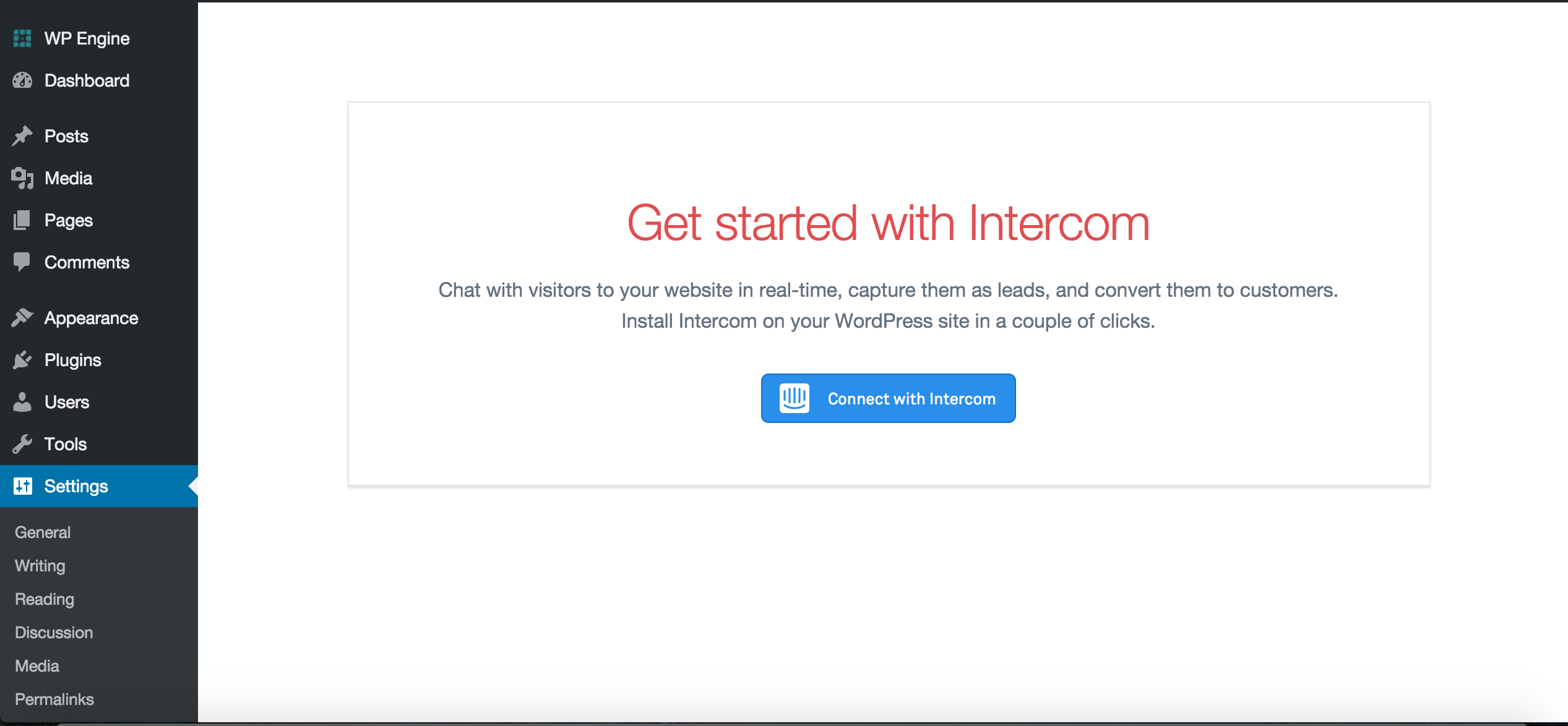 22 |
23 | Once authenticated, the Intercom widget will automatically appear on your site.
24 |
25 |
22 |
23 | Once authenticated, the Intercom widget will automatically appear on your site.
24 |
25 | 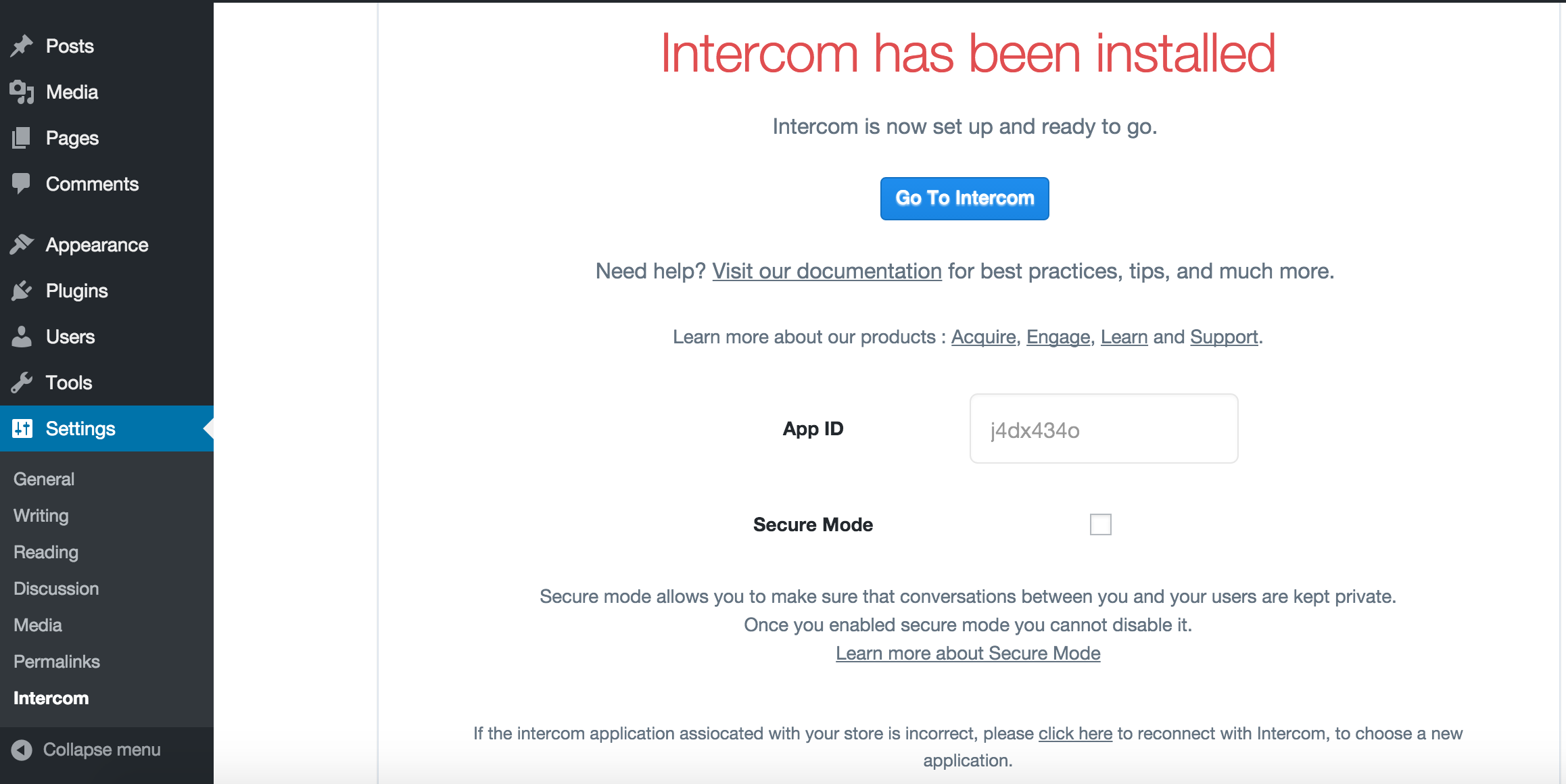 26 |
27 | NB: This plugin injects a Javascript snippet on your website frontend containing dynamic user data. Some caching solutions will cache entire pages and should not be used with this plugin. Doing so may cause conversations to be delivered to the wrong user.
28 |
29 | # Pass custom data attributes to the Intercom Messenger
30 |
31 | Using the [add_filter](https://developer.wordpress.org/reference/functions/add_filter) method in your WordPress theme or custom plugin you can pass [custom data attributes](https://www.intercom.com/help/en/articles/179-create-and-track-custom-data-attributes-cdas) to the Intercom Messenger (see example below):
32 |
33 | ```php
34 | add_filter( 'intercom_settings', function( $settings ) {
35 | $settings['customer_type'] = $customer_type;
36 | return $settings;
37 | } );
38 | ```
39 |
40 |
41 | # Users
42 |
43 | If a `$current_user` is present, we use their email and ID as an identifier in the widget.
44 | We recommend enabling [Identity Verification](https://docs.intercom.com/configure-intercom-for-your-product-or-site/staying-secure/enable-identity-verification-on-your-web-product) in the settings page.
45 |
46 | # Contributing
47 |
48 | * Check out the latest master to make sure the feature hasn't been implemented or the bug hasn't been fixed yet.
49 | * Check out the issue tracker to make sure someone already hasn't requested it and/or contributed it.
50 | * Fork the project.
51 | * Start a feature/bugfix branch.
52 | * Commit and push until you are happy with your contribution.
53 | * Make sure to add tests for it. This is important so we don't break it in a future version unintentionally.
54 |
--------------------------------------------------------------------------------
/vendor/composer/installed.json:
--------------------------------------------------------------------------------
1 | {
2 | "packages": [
3 | {
4 | "name": "firebase/php-jwt",
5 | "version": "v6.4.0",
6 | "version_normalized": "6.4.0.0",
7 | "source": {
8 | "type": "git",
9 | "url": "https://github.com/firebase/php-jwt.git",
10 | "reference": "4dd1e007f22a927ac77da5a3fbb067b42d3bc224"
11 | },
12 | "dist": {
13 | "type": "zip",
14 | "url": "https://api.github.com/repos/firebase/php-jwt/zipball/4dd1e007f22a927ac77da5a3fbb067b42d3bc224",
15 | "reference": "4dd1e007f22a927ac77da5a3fbb067b42d3bc224",
16 | "shasum": ""
17 | },
18 | "require": {
19 | "php": "^7.1||^8.0"
20 | },
21 | "require-dev": {
22 | "guzzlehttp/guzzle": "^6.5||^7.4",
23 | "phpspec/prophecy-phpunit": "^1.1",
24 | "phpunit/phpunit": "^7.5||^9.5",
25 | "psr/cache": "^1.0||^2.0",
26 | "psr/http-client": "^1.0",
27 | "psr/http-factory": "^1.0"
28 | },
29 | "suggest": {
30 | "ext-sodium": "Support EdDSA (Ed25519) signatures",
31 | "paragonie/sodium_compat": "Support EdDSA (Ed25519) signatures when libsodium is not present"
32 | },
33 | "time": "2023-02-09T21:01:23+00:00",
34 | "type": "library",
35 | "installation-source": "dist",
36 | "autoload": {
37 | "psr-4": {
38 | "Firebase\\JWT\\": "src"
39 | }
40 | },
41 | "notification-url": "https://packagist.org/downloads/",
42 | "license": [
43 | "BSD-3-Clause"
44 | ],
45 | "authors": [
46 | {
47 | "name": "Neuman Vong",
48 | "email": "neuman+pear@twilio.com",
49 | "role": "Developer"
50 | },
51 | {
52 | "name": "Anant Narayanan",
53 | "email": "anant@php.net",
54 | "role": "Developer"
55 | }
56 | ],
57 | "description": "A simple library to encode and decode JSON Web Tokens (JWT) in PHP. Should conform to the current spec.",
58 | "homepage": "https://github.com/firebase/php-jwt",
59 | "keywords": [
60 | "jwt",
61 | "php"
62 | ],
63 | "support": {
64 | "issues": "https://github.com/firebase/php-jwt/issues",
65 | "source": "https://github.com/firebase/php-jwt/tree/v6.4.0"
66 | },
67 | "install-path": "../firebase/php-jwt"
68 | }
69 | ],
70 | "dev": true,
71 | "dev-package-names": []
72 | }
73 |
--------------------------------------------------------------------------------
/test/SnippetSettingsTest.php:
--------------------------------------------------------------------------------
1 | "bar"));
29 | $this->assertEquals("{\"app_id\":\"bar\",\"installation_type\":\"wordpress\",\"installation_version\":\"" . INTERCOM_PLUGIN_VERSION . "\"}", $snippet_settings->json());
30 | }
31 | public function testJSONRenderingWithIdentityVerification()
32 | {
33 | $snippet_settings = new IntercomSnippetSettings(array("app_id" => "bar"), "s3cre7", new FakeWordPressUserForSnippetTest());
34 | $jwt_data = array(
35 | "user_id" => "foo@bar.com",
36 | "email" => "foo@bar.com",
37 | "exp" => TimeProvider::getCurrentTime() + 3600
38 | );
39 | $jwt = JWT::encode($jwt_data, "s3cre7", 'HS256');
40 | $this->assertEquals('{"app_id":"bar","intercom_user_jwt":"'.$jwt.'","installation_type":"wordpress","installation_version":"' . INTERCOM_PLUGIN_VERSION . '"}', $snippet_settings->json());
41 | }
42 | public function testJSONRenderingWithIdentityVerificationAndNoSecret()
43 | {
44 | $snippet_settings = new IntercomSnippetSettings(array("app_id" => "bar"), NULL, new FakeWordPressUserForSnippetTest());
45 | $this->assertEquals("{\"app_id\":\"bar\",\"email\":\"foo@bar.com\",\"installation_type\":\"wordpress\",\"installation_version\":\"" . INTERCOM_PLUGIN_VERSION . "\"}", $snippet_settings->json());
46 | }
47 | public function testInstallationType()
48 | {
49 | $snippet_settings = new IntercomSnippetSettings(array("app_id" => "bar"));
50 | $this->assertEquals("{\"app_id\":\"bar\",\"installation_type\":\"wordpress\",\"installation_version\":\"" . INTERCOM_PLUGIN_VERSION . "\"}", $snippet_settings->json());
51 | }
52 | public function testIclLanguageConstant()
53 | {
54 | define('ICL_LANGUAGE_CODE', 'fr');
55 | $snippet_settings = new IntercomSnippetSettings(array("app_id" => "bar"));
56 | $this->assertEquals("{\"app_id\":\"bar\",\"language_override\":\"fr\",\"installation_type\":\"wordpress\",\"installation_version\":\"" . INTERCOM_PLUGIN_VERSION . "\"}", $snippet_settings->json());
57 | }
58 |
59 | public function testAppId()
60 | {
61 | $snippet_settings = new IntercomSnippetSettings(array("app_id" => "bar"));
62 | $this->assertEquals("bar", $snippet_settings->appId());
63 | }
64 |
65 | public function testValidation()
66 | {
67 | $this->expectException(\Exception::class);
68 | $snippet = new IntercomSnippetSettings(array("foo" => "bar"));
69 | }
70 | }
71 |
--------------------------------------------------------------------------------
/composer.lock:
--------------------------------------------------------------------------------
1 | {
2 | "_readme": [
3 | "This file locks the dependencies of your project to a known state",
4 | "Read more about it at https://getcomposer.org/doc/01-basic-usage.md#installing-dependencies",
5 | "This file is @generated automatically"
6 | ],
7 | "content-hash": "f0ba7c25cd025ed8dd9b1c80e1eb2ef8",
8 | "packages": [
9 | {
10 | "name": "firebase/php-jwt",
11 | "version": "v6.4.0",
12 | "source": {
13 | "type": "git",
14 | "url": "https://github.com/firebase/php-jwt.git",
15 | "reference": "4dd1e007f22a927ac77da5a3fbb067b42d3bc224"
16 | },
17 | "dist": {
18 | "type": "zip",
19 | "url": "https://api.github.com/repos/firebase/php-jwt/zipball/4dd1e007f22a927ac77da5a3fbb067b42d3bc224",
20 | "reference": "4dd1e007f22a927ac77da5a3fbb067b42d3bc224",
21 | "shasum": ""
22 | },
23 | "require": {
24 | "php": "^7.1||^8.0"
25 | },
26 | "require-dev": {
27 | "guzzlehttp/guzzle": "^6.5||^7.4",
28 | "phpspec/prophecy-phpunit": "^1.1",
29 | "phpunit/phpunit": "^7.5||^9.5",
30 | "psr/cache": "^1.0||^2.0",
31 | "psr/http-client": "^1.0",
32 | "psr/http-factory": "^1.0"
33 | },
34 | "suggest": {
35 | "ext-sodium": "Support EdDSA (Ed25519) signatures",
36 | "paragonie/sodium_compat": "Support EdDSA (Ed25519) signatures when libsodium is not present"
37 | },
38 | "type": "library",
39 | "autoload": {
40 | "psr-4": {
41 | "Firebase\\JWT\\": "src"
42 | }
43 | },
44 | "notification-url": "https://packagist.org/downloads/",
45 | "license": [
46 | "BSD-3-Clause"
47 | ],
48 | "authors": [
49 | {
50 | "name": "Neuman Vong",
51 | "email": "neuman+pear@twilio.com",
52 | "role": "Developer"
53 | },
54 | {
55 | "name": "Anant Narayanan",
56 | "email": "anant@php.net",
57 | "role": "Developer"
58 | }
59 | ],
60 | "description": "A simple library to encode and decode JSON Web Tokens (JWT) in PHP. Should conform to the current spec.",
61 | "homepage": "https://github.com/firebase/php-jwt",
62 | "keywords": [
63 | "jwt",
64 | "php"
65 | ],
66 | "support": {
67 | "issues": "https://github.com/firebase/php-jwt/issues",
68 | "source": "https://github.com/firebase/php-jwt/tree/v6.4.0"
69 | },
70 | "time": "2023-02-09T21:01:23+00:00"
71 | }
72 | ],
73 | "packages-dev": [],
74 | "aliases": [],
75 | "minimum-stability": "stable",
76 | "stability-flags": {},
77 | "prefer-stable": false,
78 | "prefer-lowest": false,
79 | "platform": {},
80 | "platform-dev": {},
81 | "plugin-api-version": "2.6.0"
82 | }
83 |
--------------------------------------------------------------------------------
/readme.txt:
--------------------------------------------------------------------------------
1 | === Intercom ===
2 | Contributors: bobintercom, jacopointercom
3 | Tags: intercom, ai, customer, chat
4 | Requires at least: 4.7.0
5 | Tested up to: 6.7.2
6 | Requires PHP: 7.2
7 | License: Apache 2.0
8 | Stable tag: 3.0.2
9 |
10 | Official Intercom WordPress plugin: Engage visitors in real time, power growth with AI, and convert leads into loyal customers.
11 |
12 | == Description ==
13 |
14 | [Intercom](https://www.intercom.com/) is a next-generation customer communications platform that combines powerful live chat, proactive messaging, and advanced AI solutions — like our Fin AI chatbot — to help businesses instantly connect with customers.
15 |
16 | By installing the Intercom WordPress plugin, you can seamlessly add the Messenger to your site, track both logged-in users and visitors, and engage them right away. With Intercom’s industry-leading AI at your fingertips, you’ll deliver fast, personalized support and drive growth more effectively than ever before.
17 |
18 | == Installation ==
19 |
20 | Installing Intercom on your WordPress site takes just a few minutes.
21 |
22 | You can find full instructions on signing up and installing Intercom using the WordPress plugin [here](https://www.intercom.com/help/en/articles/173-install-intercom-on-your-wordpress-site).
23 |
24 | If you’re already an Intercom customer, you can also find instructions in the in-app [setup guide](https://app.intercom.com/a/apps/_/platform/guide) or [app store](https://app.intercom.com/a/apps/_/appstore?app_package_code=wordpress&search=wordpress).
25 |
26 | The first thing you’ll need to do is install and activate the plugin - you must be using WordPress v4.9.0 or higher and have the ability to install plugins in order to use this method.
27 |
28 | Note: This plugin injects a Javascript snippet on your website frontend containing dynamic user data. Some caching solutions will cache entire pages and should not be used with this plugin. Doing so may cause conversations to be delivered to the wrong user.
29 |
30 | == Screenshots ==
31 | 1. Plugin settings authenticate with Intercom settings_not_auth.png
32 | 2. Plugin settings successfully authenticated with Intercom settings_auth.png
33 | 3. Intercom widget used by customers to communicate with the business widget.png
34 | == Changelog ==
35 | = 3.0.2 =
36 |
37 | https://github.com/intercom/intercom-wordpress/pull/131
38 | * Updated version attribute to avoid it getting sent in the user data.
39 |
40 | = 3.0.1 =
41 |
42 | https://github.com/intercom/intercom-wordpress/pull/130
43 | * Added version tracking to help Intercom provide better support by identifying which plugin version is in use.
44 |
45 | https://github.com/intercom/intercom-wordpress/pull/88
46 | * Loads Intercom messenger last to ensure JQuery is present.
47 |
48 | = 3.0.0 =
49 |
50 | https://github.com/intercom/intercom-wordpress/pull/127
51 | * Replaced user_hash with intercom_user_jwt https://www.intercom.com/help/en/articles/10589769-authenticating-users-in-the-messenger-with-json-web-tokens-jwts.
52 | * Updated readme to follow guidelines.
53 | * Added missing tests.
54 |
55 | == Upgrade Notice ==
56 | = 3.0.1 =
57 | Updated version attribute name to avoid setting it as part of user data.
58 |
59 | = 3.0.1 =
60 | Help Intercom provide better support by sharing the plugin version is in use.
61 |
62 | = 3.0.0 =
63 | Upgrade the security of your messenger with the introduction of JWT - https://www.intercom.com/help/en/articles/10589769-authenticating-users-in-the-messenger-with-json-web-tokens-jwts
64 |
--------------------------------------------------------------------------------
/test/SecureModeCalculatorTest.php:
--------------------------------------------------------------------------------
1 | "abcdef", "email" => "test@intercom.io");
24 | $calculator = new MessengerSecurityCalculator($data, "s3cre7");
25 | $jwt_data = array(
26 | "user_id" => "test@intercom.io",
27 | "email" => "test@intercom.io",
28 | "exp" => TimeProvider::getCurrentTime() + 3600
29 | );
30 | $jwt = JWT::encode($jwt_data, "s3cre7", 'HS256');
31 | $this->assertEquals(
32 | array(
33 | "app_id" => "abcdef",
34 | "intercom_user_jwt" => $jwt
35 | ),
36 | $calculator->messengerSecurityComponent()
37 | );
38 | }
39 |
40 | public function testUserIdEmailJWT()
41 | {
42 | $data = array("app_id" => "abcdef", "user_id" => "abcdef", "email" => "test@intercom.io");
43 | $calculator = new MessengerSecurityCalculator($data, "s3cre7");
44 | $jwt_data = array(
45 | "user_id" => "abcdef",
46 | "email" => "test@intercom.io",
47 | "exp" => TimeProvider::getCurrentTime() + 3600
48 | );
49 | $jwt = JWT::encode($jwt_data, "s3cre7", 'HS256');
50 | $this->assertEquals(
51 | array(
52 | "app_id" => "abcdef",
53 | "intercom_user_jwt" => $jwt
54 | ),
55 | $calculator->messengerSecurityComponent()
56 | );
57 | }
58 |
59 | public function testUserIdEmailNameJWT()
60 | {
61 | $data = array("app_id" => "abcdef", "user_id" => "abcdef", "email" => "test@intercom.io", "name" => "John Doe");
62 | $calculator = new MessengerSecurityCalculator($data, "s3cre7");
63 | $jwt_data = array(
64 | "user_id" => "abcdef",
65 | "email" => "test@intercom.io",
66 | "name" => "John Doe",
67 | "exp" => TimeProvider::getCurrentTime() + 3600
68 | );
69 | $jwt = JWT::encode($jwt_data, "s3cre7", 'HS256');
70 | $this->assertEquals(
71 | array(
72 | "app_id" => "abcdef",
73 | "intercom_user_jwt" => $jwt
74 | ),
75 | $calculator->messengerSecurityComponent()
76 | );
77 | }
78 |
79 | public function testEmpty()
80 | {
81 | $data = array("app_id" => "abcdef");
82 | $calculator = new MessengerSecurityCalculator($data, "s3cre7");
83 | $this->assertEquals(
84 | array(
85 | "app_id" => "abcdef",
86 | ),
87 | $calculator->messengerSecurityComponent()
88 | );
89 | }
90 |
91 | public function testExtraJWTData()
92 | {
93 | putenv('INTERCOM_PLUGIN_TEST_JWT_DATA=' . json_encode(array("custom_data" => "custom_value")));
94 |
95 | $data = array("app_id" => "abcdef", "user_id" => "abcdef", "email" => "test@intercom.io", "name" => "John Doe");
96 | $calculator = new MessengerSecurityCalculator($data, "s3cre7");
97 | $jwt_data = array(
98 | "user_id" => "abcdef",
99 | "email" => "test@intercom.io",
100 | "name" => "John Doe",
101 | "custom_data" => "custom_value",
102 | "exp" => TimeProvider::getCurrentTime() + 3600
103 | );
104 | $jwt = JWT::encode($jwt_data, "s3cre7", 'HS256');
105 | $this->assertEquals(
106 | array(
107 | "app_id" => "abcdef",
108 | "intercom_user_jwt" => $jwt
109 | ),
110 | $calculator->messengerSecurityComponent()
111 | );
112 | putenv('INTERCOM_PLUGIN_TEST_JWT_DATA=');
113 | }
114 | }
115 |
--------------------------------------------------------------------------------
/vendor/firebase/php-jwt/CHANGELOG.md:
--------------------------------------------------------------------------------
1 | # Changelog
2 |
3 | ## [6.4.0](https://github.com/firebase/php-jwt/compare/v6.3.2...v6.4.0) (2023-02-08)
4 |
5 |
6 | ### Features
7 |
8 | * add support for W3C ES256K ([#462](https://github.com/firebase/php-jwt/issues/462)) ([213924f](https://github.com/firebase/php-jwt/commit/213924f51936291fbbca99158b11bd4ae56c2c95))
9 | * improve caching by only decoding jwks when necessary ([#486](https://github.com/firebase/php-jwt/issues/486)) ([78d3ed1](https://github.com/firebase/php-jwt/commit/78d3ed1073553f7d0bbffa6c2010009a0d483d5c))
10 |
11 | ## [6.3.2](https://github.com/firebase/php-jwt/compare/v6.3.1...v6.3.2) (2022-11-01)
12 |
13 |
14 | ### Bug Fixes
15 |
16 | * check kid before using as array index ([bad1b04](https://github.com/firebase/php-jwt/commit/bad1b040d0c736bbf86814c6b5ae614f517cf7bd))
17 |
18 | ## [6.3.1](https://github.com/firebase/php-jwt/compare/v6.3.0...v6.3.1) (2022-11-01)
19 |
20 |
21 | ### Bug Fixes
22 |
23 | * casing of GET for PSR compat ([#451](https://github.com/firebase/php-jwt/issues/451)) ([60b52b7](https://github.com/firebase/php-jwt/commit/60b52b71978790eafcf3b95cfbd83db0439e8d22))
24 | * string interpolation format for php 8.2 ([#446](https://github.com/firebase/php-jwt/issues/446)) ([2e07d8a](https://github.com/firebase/php-jwt/commit/2e07d8a1524d12b69b110ad649f17461d068b8f2))
25 |
26 | ## 6.3.0 / 2022-07-15
27 |
28 | - Added ES256 support to JWK parsing ([#399](https://github.com/firebase/php-jwt/pull/399))
29 | - Fixed potential caching error in `CachedKeySet` by caching jwks as strings ([#435](https://github.com/firebase/php-jwt/pull/435))
30 |
31 | ## 6.2.0 / 2022-05-14
32 |
33 | - Added `CachedKeySet` ([#397](https://github.com/firebase/php-jwt/pull/397))
34 | - Added `$defaultAlg` parameter to `JWT::parseKey` and `JWT::parseKeySet` ([#426](https://github.com/firebase/php-jwt/pull/426)).
35 |
36 | ## 6.1.0 / 2022-03-23
37 |
38 | - Drop support for PHP 5.3, 5.4, 5.5, 5.6, and 7.0
39 | - Add parameter typing and return types where possible
40 |
41 | ## 6.0.0 / 2022-01-24
42 |
43 | - **Backwards-Compatibility Breaking Changes**: See the [Release Notes](https://github.com/firebase/php-jwt/releases/tag/v6.0.0) for more information.
44 | - New Key object to prevent key/algorithm type confusion (#365)
45 | - Add JWK support (#273)
46 | - Add ES256 support (#256)
47 | - Add ES384 support (#324)
48 | - Add Ed25519 support (#343)
49 |
50 | ## 5.0.0 / 2017-06-26
51 | - Support RS384 and RS512.
52 | See [#117](https://github.com/firebase/php-jwt/pull/117). Thanks [@joostfaassen](https://github.com/joostfaassen)!
53 | - Add an example for RS256 openssl.
54 | See [#125](https://github.com/firebase/php-jwt/pull/125). Thanks [@akeeman](https://github.com/akeeman)!
55 | - Detect invalid Base64 encoding in signature.
56 | See [#162](https://github.com/firebase/php-jwt/pull/162). Thanks [@psignoret](https://github.com/psignoret)!
57 | - Update `JWT::verify` to handle OpenSSL errors.
58 | See [#159](https://github.com/firebase/php-jwt/pull/159). Thanks [@bshaffer](https://github.com/bshaffer)!
59 | - Add `array` type hinting to `decode` method
60 | See [#101](https://github.com/firebase/php-jwt/pull/101). Thanks [@hywak](https://github.com/hywak)!
61 | - Add all JSON error types.
62 | See [#110](https://github.com/firebase/php-jwt/pull/110). Thanks [@gbalduzzi](https://github.com/gbalduzzi)!
63 | - Bugfix 'kid' not in given key list.
64 | See [#129](https://github.com/firebase/php-jwt/pull/129). Thanks [@stampycode](https://github.com/stampycode)!
65 | - Miscellaneous cleanup, documentation and test fixes.
66 | See [#107](https://github.com/firebase/php-jwt/pull/107), [#115](https://github.com/firebase/php-jwt/pull/115),
67 | [#160](https://github.com/firebase/php-jwt/pull/160), [#161](https://github.com/firebase/php-jwt/pull/161), and
68 | [#165](https://github.com/firebase/php-jwt/pull/165). Thanks [@akeeman](https://github.com/akeeman),
69 | [@chinedufn](https://github.com/chinedufn), and [@bshaffer](https://github.com/bshaffer)!
70 |
71 | ## 4.0.0 / 2016-07-17
72 | - Add support for late static binding. See [#88](https://github.com/firebase/php-jwt/pull/88) for details. Thanks to [@chappy84](https://github.com/chappy84)!
73 | - Use static `$timestamp` instead of `time()` to improve unit testing. See [#93](https://github.com/firebase/php-jwt/pull/93) for details. Thanks to [@josephmcdermott](https://github.com/josephmcdermott)!
74 | - Fixes to exceptions classes. See [#81](https://github.com/firebase/php-jwt/pull/81) for details. Thanks to [@Maks3w](https://github.com/Maks3w)!
75 | - Fixes to PHPDoc. See [#76](https://github.com/firebase/php-jwt/pull/76) for details. Thanks to [@akeeman](https://github.com/akeeman)!
76 |
77 | ## 3.0.0 / 2015-07-22
78 | - Minimum PHP version updated from `5.2.0` to `5.3.0`.
79 | - Add `\Firebase\JWT` namespace. See
80 | [#59](https://github.com/firebase/php-jwt/pull/59) for details. Thanks to
81 | [@Dashron](https://github.com/Dashron)!
82 | - Require a non-empty key to decode and verify a JWT. See
83 | [#60](https://github.com/firebase/php-jwt/pull/60) for details. Thanks to
84 | [@sjones608](https://github.com/sjones608)!
85 | - Cleaner documentation blocks in the code. See
86 | [#62](https://github.com/firebase/php-jwt/pull/62) for details. Thanks to
87 | [@johanderuijter](https://github.com/johanderuijter)!
88 |
89 | ## 2.2.0 / 2015-06-22
90 | - Add support for adding custom, optional JWT headers to `JWT::encode()`. See
91 | [#53](https://github.com/firebase/php-jwt/pull/53/files) for details. Thanks to
92 | [@mcocaro](https://github.com/mcocaro)!
93 |
94 | ## 2.1.0 / 2015-05-20
95 | - Add support for adding a leeway to `JWT:decode()` that accounts for clock skew
96 | between signing and verifying entities. Thanks to [@lcabral](https://github.com/lcabral)!
97 | - Add support for passing an object implementing the `ArrayAccess` interface for
98 | `$keys` argument in `JWT::decode()`. Thanks to [@aztech-dev](https://github.com/aztech-dev)!
99 |
100 | ## 2.0.0 / 2015-04-01
101 | - **Note**: It is strongly recommended that you update to > v2.0.0 to address
102 | known security vulnerabilities in prior versions when both symmetric and
103 | asymmetric keys are used together.
104 | - Update signature for `JWT::decode(...)` to require an array of supported
105 | algorithms to use when verifying token signatures.
106 |
--------------------------------------------------------------------------------
/vendor/firebase/php-jwt/src/CachedKeySet.php:
--------------------------------------------------------------------------------
1 |
18 | */
19 | class CachedKeySet implements ArrayAccess
20 | {
21 | /**
22 | * @var string
23 | */
24 | private $jwksUri;
25 | /**
26 | * @var ClientInterface
27 | */
28 | private $httpClient;
29 | /**
30 | * @var RequestFactoryInterface
31 | */
32 | private $httpFactory;
33 | /**
34 | * @var CacheItemPoolInterface
35 | */
36 | private $cache;
37 | /**
38 | * @var ?int
39 | */
40 | private $expiresAfter;
41 | /**
42 | * @var ?CacheItemInterface
43 | */
44 | private $cacheItem;
45 | /**
46 | * @var array
26 |
27 | NB: This plugin injects a Javascript snippet on your website frontend containing dynamic user data. Some caching solutions will cache entire pages and should not be used with this plugin. Doing so may cause conversations to be delivered to the wrong user.
28 |
29 | # Pass custom data attributes to the Intercom Messenger
30 |
31 | Using the [add_filter](https://developer.wordpress.org/reference/functions/add_filter) method in your WordPress theme or custom plugin you can pass [custom data attributes](https://www.intercom.com/help/en/articles/179-create-and-track-custom-data-attributes-cdas) to the Intercom Messenger (see example below):
32 |
33 | ```php
34 | add_filter( 'intercom_settings', function( $settings ) {
35 | $settings['customer_type'] = $customer_type;
36 | return $settings;
37 | } );
38 | ```
39 |
40 |
41 | # Users
42 |
43 | If a `$current_user` is present, we use their email and ID as an identifier in the widget.
44 | We recommend enabling [Identity Verification](https://docs.intercom.com/configure-intercom-for-your-product-or-site/staying-secure/enable-identity-verification-on-your-web-product) in the settings page.
45 |
46 | # Contributing
47 |
48 | * Check out the latest master to make sure the feature hasn't been implemented or the bug hasn't been fixed yet.
49 | * Check out the issue tracker to make sure someone already hasn't requested it and/or contributed it.
50 | * Fork the project.
51 | * Start a feature/bugfix branch.
52 | * Commit and push until you are happy with your contribution.
53 | * Make sure to add tests for it. This is important so we don't break it in a future version unintentionally.
54 |
--------------------------------------------------------------------------------
/vendor/composer/installed.json:
--------------------------------------------------------------------------------
1 | {
2 | "packages": [
3 | {
4 | "name": "firebase/php-jwt",
5 | "version": "v6.4.0",
6 | "version_normalized": "6.4.0.0",
7 | "source": {
8 | "type": "git",
9 | "url": "https://github.com/firebase/php-jwt.git",
10 | "reference": "4dd1e007f22a927ac77da5a3fbb067b42d3bc224"
11 | },
12 | "dist": {
13 | "type": "zip",
14 | "url": "https://api.github.com/repos/firebase/php-jwt/zipball/4dd1e007f22a927ac77da5a3fbb067b42d3bc224",
15 | "reference": "4dd1e007f22a927ac77da5a3fbb067b42d3bc224",
16 | "shasum": ""
17 | },
18 | "require": {
19 | "php": "^7.1||^8.0"
20 | },
21 | "require-dev": {
22 | "guzzlehttp/guzzle": "^6.5||^7.4",
23 | "phpspec/prophecy-phpunit": "^1.1",
24 | "phpunit/phpunit": "^7.5||^9.5",
25 | "psr/cache": "^1.0||^2.0",
26 | "psr/http-client": "^1.0",
27 | "psr/http-factory": "^1.0"
28 | },
29 | "suggest": {
30 | "ext-sodium": "Support EdDSA (Ed25519) signatures",
31 | "paragonie/sodium_compat": "Support EdDSA (Ed25519) signatures when libsodium is not present"
32 | },
33 | "time": "2023-02-09T21:01:23+00:00",
34 | "type": "library",
35 | "installation-source": "dist",
36 | "autoload": {
37 | "psr-4": {
38 | "Firebase\\JWT\\": "src"
39 | }
40 | },
41 | "notification-url": "https://packagist.org/downloads/",
42 | "license": [
43 | "BSD-3-Clause"
44 | ],
45 | "authors": [
46 | {
47 | "name": "Neuman Vong",
48 | "email": "neuman+pear@twilio.com",
49 | "role": "Developer"
50 | },
51 | {
52 | "name": "Anant Narayanan",
53 | "email": "anant@php.net",
54 | "role": "Developer"
55 | }
56 | ],
57 | "description": "A simple library to encode and decode JSON Web Tokens (JWT) in PHP. Should conform to the current spec.",
58 | "homepage": "https://github.com/firebase/php-jwt",
59 | "keywords": [
60 | "jwt",
61 | "php"
62 | ],
63 | "support": {
64 | "issues": "https://github.com/firebase/php-jwt/issues",
65 | "source": "https://github.com/firebase/php-jwt/tree/v6.4.0"
66 | },
67 | "install-path": "../firebase/php-jwt"
68 | }
69 | ],
70 | "dev": true,
71 | "dev-package-names": []
72 | }
73 |
--------------------------------------------------------------------------------
/test/SnippetSettingsTest.php:
--------------------------------------------------------------------------------
1 | "bar"));
29 | $this->assertEquals("{\"app_id\":\"bar\",\"installation_type\":\"wordpress\",\"installation_version\":\"" . INTERCOM_PLUGIN_VERSION . "\"}", $snippet_settings->json());
30 | }
31 | public function testJSONRenderingWithIdentityVerification()
32 | {
33 | $snippet_settings = new IntercomSnippetSettings(array("app_id" => "bar"), "s3cre7", new FakeWordPressUserForSnippetTest());
34 | $jwt_data = array(
35 | "user_id" => "foo@bar.com",
36 | "email" => "foo@bar.com",
37 | "exp" => TimeProvider::getCurrentTime() + 3600
38 | );
39 | $jwt = JWT::encode($jwt_data, "s3cre7", 'HS256');
40 | $this->assertEquals('{"app_id":"bar","intercom_user_jwt":"'.$jwt.'","installation_type":"wordpress","installation_version":"' . INTERCOM_PLUGIN_VERSION . '"}', $snippet_settings->json());
41 | }
42 | public function testJSONRenderingWithIdentityVerificationAndNoSecret()
43 | {
44 | $snippet_settings = new IntercomSnippetSettings(array("app_id" => "bar"), NULL, new FakeWordPressUserForSnippetTest());
45 | $this->assertEquals("{\"app_id\":\"bar\",\"email\":\"foo@bar.com\",\"installation_type\":\"wordpress\",\"installation_version\":\"" . INTERCOM_PLUGIN_VERSION . "\"}", $snippet_settings->json());
46 | }
47 | public function testInstallationType()
48 | {
49 | $snippet_settings = new IntercomSnippetSettings(array("app_id" => "bar"));
50 | $this->assertEquals("{\"app_id\":\"bar\",\"installation_type\":\"wordpress\",\"installation_version\":\"" . INTERCOM_PLUGIN_VERSION . "\"}", $snippet_settings->json());
51 | }
52 | public function testIclLanguageConstant()
53 | {
54 | define('ICL_LANGUAGE_CODE', 'fr');
55 | $snippet_settings = new IntercomSnippetSettings(array("app_id" => "bar"));
56 | $this->assertEquals("{\"app_id\":\"bar\",\"language_override\":\"fr\",\"installation_type\":\"wordpress\",\"installation_version\":\"" . INTERCOM_PLUGIN_VERSION . "\"}", $snippet_settings->json());
57 | }
58 |
59 | public function testAppId()
60 | {
61 | $snippet_settings = new IntercomSnippetSettings(array("app_id" => "bar"));
62 | $this->assertEquals("bar", $snippet_settings->appId());
63 | }
64 |
65 | public function testValidation()
66 | {
67 | $this->expectException(\Exception::class);
68 | $snippet = new IntercomSnippetSettings(array("foo" => "bar"));
69 | }
70 | }
71 |
--------------------------------------------------------------------------------
/composer.lock:
--------------------------------------------------------------------------------
1 | {
2 | "_readme": [
3 | "This file locks the dependencies of your project to a known state",
4 | "Read more about it at https://getcomposer.org/doc/01-basic-usage.md#installing-dependencies",
5 | "This file is @generated automatically"
6 | ],
7 | "content-hash": "f0ba7c25cd025ed8dd9b1c80e1eb2ef8",
8 | "packages": [
9 | {
10 | "name": "firebase/php-jwt",
11 | "version": "v6.4.0",
12 | "source": {
13 | "type": "git",
14 | "url": "https://github.com/firebase/php-jwt.git",
15 | "reference": "4dd1e007f22a927ac77da5a3fbb067b42d3bc224"
16 | },
17 | "dist": {
18 | "type": "zip",
19 | "url": "https://api.github.com/repos/firebase/php-jwt/zipball/4dd1e007f22a927ac77da5a3fbb067b42d3bc224",
20 | "reference": "4dd1e007f22a927ac77da5a3fbb067b42d3bc224",
21 | "shasum": ""
22 | },
23 | "require": {
24 | "php": "^7.1||^8.0"
25 | },
26 | "require-dev": {
27 | "guzzlehttp/guzzle": "^6.5||^7.4",
28 | "phpspec/prophecy-phpunit": "^1.1",
29 | "phpunit/phpunit": "^7.5||^9.5",
30 | "psr/cache": "^1.0||^2.0",
31 | "psr/http-client": "^1.0",
32 | "psr/http-factory": "^1.0"
33 | },
34 | "suggest": {
35 | "ext-sodium": "Support EdDSA (Ed25519) signatures",
36 | "paragonie/sodium_compat": "Support EdDSA (Ed25519) signatures when libsodium is not present"
37 | },
38 | "type": "library",
39 | "autoload": {
40 | "psr-4": {
41 | "Firebase\\JWT\\": "src"
42 | }
43 | },
44 | "notification-url": "https://packagist.org/downloads/",
45 | "license": [
46 | "BSD-3-Clause"
47 | ],
48 | "authors": [
49 | {
50 | "name": "Neuman Vong",
51 | "email": "neuman+pear@twilio.com",
52 | "role": "Developer"
53 | },
54 | {
55 | "name": "Anant Narayanan",
56 | "email": "anant@php.net",
57 | "role": "Developer"
58 | }
59 | ],
60 | "description": "A simple library to encode and decode JSON Web Tokens (JWT) in PHP. Should conform to the current spec.",
61 | "homepage": "https://github.com/firebase/php-jwt",
62 | "keywords": [
63 | "jwt",
64 | "php"
65 | ],
66 | "support": {
67 | "issues": "https://github.com/firebase/php-jwt/issues",
68 | "source": "https://github.com/firebase/php-jwt/tree/v6.4.0"
69 | },
70 | "time": "2023-02-09T21:01:23+00:00"
71 | }
72 | ],
73 | "packages-dev": [],
74 | "aliases": [],
75 | "minimum-stability": "stable",
76 | "stability-flags": {},
77 | "prefer-stable": false,
78 | "prefer-lowest": false,
79 | "platform": {},
80 | "platform-dev": {},
81 | "plugin-api-version": "2.6.0"
82 | }
83 |
--------------------------------------------------------------------------------
/readme.txt:
--------------------------------------------------------------------------------
1 | === Intercom ===
2 | Contributors: bobintercom, jacopointercom
3 | Tags: intercom, ai, customer, chat
4 | Requires at least: 4.7.0
5 | Tested up to: 6.7.2
6 | Requires PHP: 7.2
7 | License: Apache 2.0
8 | Stable tag: 3.0.2
9 |
10 | Official Intercom WordPress plugin: Engage visitors in real time, power growth with AI, and convert leads into loyal customers.
11 |
12 | == Description ==
13 |
14 | [Intercom](https://www.intercom.com/) is a next-generation customer communications platform that combines powerful live chat, proactive messaging, and advanced AI solutions — like our Fin AI chatbot — to help businesses instantly connect with customers.
15 |
16 | By installing the Intercom WordPress plugin, you can seamlessly add the Messenger to your site, track both logged-in users and visitors, and engage them right away. With Intercom’s industry-leading AI at your fingertips, you’ll deliver fast, personalized support and drive growth more effectively than ever before.
17 |
18 | == Installation ==
19 |
20 | Installing Intercom on your WordPress site takes just a few minutes.
21 |
22 | You can find full instructions on signing up and installing Intercom using the WordPress plugin [here](https://www.intercom.com/help/en/articles/173-install-intercom-on-your-wordpress-site).
23 |
24 | If you’re already an Intercom customer, you can also find instructions in the in-app [setup guide](https://app.intercom.com/a/apps/_/platform/guide) or [app store](https://app.intercom.com/a/apps/_/appstore?app_package_code=wordpress&search=wordpress).
25 |
26 | The first thing you’ll need to do is install and activate the plugin - you must be using WordPress v4.9.0 or higher and have the ability to install plugins in order to use this method.
27 |
28 | Note: This plugin injects a Javascript snippet on your website frontend containing dynamic user data. Some caching solutions will cache entire pages and should not be used with this plugin. Doing so may cause conversations to be delivered to the wrong user.
29 |
30 | == Screenshots ==
31 | 1. Plugin settings authenticate with Intercom settings_not_auth.png
32 | 2. Plugin settings successfully authenticated with Intercom settings_auth.png
33 | 3. Intercom widget used by customers to communicate with the business widget.png
34 | == Changelog ==
35 | = 3.0.2 =
36 |
37 | https://github.com/intercom/intercom-wordpress/pull/131
38 | * Updated version attribute to avoid it getting sent in the user data.
39 |
40 | = 3.0.1 =
41 |
42 | https://github.com/intercom/intercom-wordpress/pull/130
43 | * Added version tracking to help Intercom provide better support by identifying which plugin version is in use.
44 |
45 | https://github.com/intercom/intercom-wordpress/pull/88
46 | * Loads Intercom messenger last to ensure JQuery is present.
47 |
48 | = 3.0.0 =
49 |
50 | https://github.com/intercom/intercom-wordpress/pull/127
51 | * Replaced user_hash with intercom_user_jwt https://www.intercom.com/help/en/articles/10589769-authenticating-users-in-the-messenger-with-json-web-tokens-jwts.
52 | * Updated readme to follow guidelines.
53 | * Added missing tests.
54 |
55 | == Upgrade Notice ==
56 | = 3.0.1 =
57 | Updated version attribute name to avoid setting it as part of user data.
58 |
59 | = 3.0.1 =
60 | Help Intercom provide better support by sharing the plugin version is in use.
61 |
62 | = 3.0.0 =
63 | Upgrade the security of your messenger with the introduction of JWT - https://www.intercom.com/help/en/articles/10589769-authenticating-users-in-the-messenger-with-json-web-tokens-jwts
64 |
--------------------------------------------------------------------------------
/test/SecureModeCalculatorTest.php:
--------------------------------------------------------------------------------
1 | "abcdef", "email" => "test@intercom.io");
24 | $calculator = new MessengerSecurityCalculator($data, "s3cre7");
25 | $jwt_data = array(
26 | "user_id" => "test@intercom.io",
27 | "email" => "test@intercom.io",
28 | "exp" => TimeProvider::getCurrentTime() + 3600
29 | );
30 | $jwt = JWT::encode($jwt_data, "s3cre7", 'HS256');
31 | $this->assertEquals(
32 | array(
33 | "app_id" => "abcdef",
34 | "intercom_user_jwt" => $jwt
35 | ),
36 | $calculator->messengerSecurityComponent()
37 | );
38 | }
39 |
40 | public function testUserIdEmailJWT()
41 | {
42 | $data = array("app_id" => "abcdef", "user_id" => "abcdef", "email" => "test@intercom.io");
43 | $calculator = new MessengerSecurityCalculator($data, "s3cre7");
44 | $jwt_data = array(
45 | "user_id" => "abcdef",
46 | "email" => "test@intercom.io",
47 | "exp" => TimeProvider::getCurrentTime() + 3600
48 | );
49 | $jwt = JWT::encode($jwt_data, "s3cre7", 'HS256');
50 | $this->assertEquals(
51 | array(
52 | "app_id" => "abcdef",
53 | "intercom_user_jwt" => $jwt
54 | ),
55 | $calculator->messengerSecurityComponent()
56 | );
57 | }
58 |
59 | public function testUserIdEmailNameJWT()
60 | {
61 | $data = array("app_id" => "abcdef", "user_id" => "abcdef", "email" => "test@intercom.io", "name" => "John Doe");
62 | $calculator = new MessengerSecurityCalculator($data, "s3cre7");
63 | $jwt_data = array(
64 | "user_id" => "abcdef",
65 | "email" => "test@intercom.io",
66 | "name" => "John Doe",
67 | "exp" => TimeProvider::getCurrentTime() + 3600
68 | );
69 | $jwt = JWT::encode($jwt_data, "s3cre7", 'HS256');
70 | $this->assertEquals(
71 | array(
72 | "app_id" => "abcdef",
73 | "intercom_user_jwt" => $jwt
74 | ),
75 | $calculator->messengerSecurityComponent()
76 | );
77 | }
78 |
79 | public function testEmpty()
80 | {
81 | $data = array("app_id" => "abcdef");
82 | $calculator = new MessengerSecurityCalculator($data, "s3cre7");
83 | $this->assertEquals(
84 | array(
85 | "app_id" => "abcdef",
86 | ),
87 | $calculator->messengerSecurityComponent()
88 | );
89 | }
90 |
91 | public function testExtraJWTData()
92 | {
93 | putenv('INTERCOM_PLUGIN_TEST_JWT_DATA=' . json_encode(array("custom_data" => "custom_value")));
94 |
95 | $data = array("app_id" => "abcdef", "user_id" => "abcdef", "email" => "test@intercom.io", "name" => "John Doe");
96 | $calculator = new MessengerSecurityCalculator($data, "s3cre7");
97 | $jwt_data = array(
98 | "user_id" => "abcdef",
99 | "email" => "test@intercom.io",
100 | "name" => "John Doe",
101 | "custom_data" => "custom_value",
102 | "exp" => TimeProvider::getCurrentTime() + 3600
103 | );
104 | $jwt = JWT::encode($jwt_data, "s3cre7", 'HS256');
105 | $this->assertEquals(
106 | array(
107 | "app_id" => "abcdef",
108 | "intercom_user_jwt" => $jwt
109 | ),
110 | $calculator->messengerSecurityComponent()
111 | );
112 | putenv('INTERCOM_PLUGIN_TEST_JWT_DATA=');
113 | }
114 | }
115 |
--------------------------------------------------------------------------------
/vendor/firebase/php-jwt/CHANGELOG.md:
--------------------------------------------------------------------------------
1 | # Changelog
2 |
3 | ## [6.4.0](https://github.com/firebase/php-jwt/compare/v6.3.2...v6.4.0) (2023-02-08)
4 |
5 |
6 | ### Features
7 |
8 | * add support for W3C ES256K ([#462](https://github.com/firebase/php-jwt/issues/462)) ([213924f](https://github.com/firebase/php-jwt/commit/213924f51936291fbbca99158b11bd4ae56c2c95))
9 | * improve caching by only decoding jwks when necessary ([#486](https://github.com/firebase/php-jwt/issues/486)) ([78d3ed1](https://github.com/firebase/php-jwt/commit/78d3ed1073553f7d0bbffa6c2010009a0d483d5c))
10 |
11 | ## [6.3.2](https://github.com/firebase/php-jwt/compare/v6.3.1...v6.3.2) (2022-11-01)
12 |
13 |
14 | ### Bug Fixes
15 |
16 | * check kid before using as array index ([bad1b04](https://github.com/firebase/php-jwt/commit/bad1b040d0c736bbf86814c6b5ae614f517cf7bd))
17 |
18 | ## [6.3.1](https://github.com/firebase/php-jwt/compare/v6.3.0...v6.3.1) (2022-11-01)
19 |
20 |
21 | ### Bug Fixes
22 |
23 | * casing of GET for PSR compat ([#451](https://github.com/firebase/php-jwt/issues/451)) ([60b52b7](https://github.com/firebase/php-jwt/commit/60b52b71978790eafcf3b95cfbd83db0439e8d22))
24 | * string interpolation format for php 8.2 ([#446](https://github.com/firebase/php-jwt/issues/446)) ([2e07d8a](https://github.com/firebase/php-jwt/commit/2e07d8a1524d12b69b110ad649f17461d068b8f2))
25 |
26 | ## 6.3.0 / 2022-07-15
27 |
28 | - Added ES256 support to JWK parsing ([#399](https://github.com/firebase/php-jwt/pull/399))
29 | - Fixed potential caching error in `CachedKeySet` by caching jwks as strings ([#435](https://github.com/firebase/php-jwt/pull/435))
30 |
31 | ## 6.2.0 / 2022-05-14
32 |
33 | - Added `CachedKeySet` ([#397](https://github.com/firebase/php-jwt/pull/397))
34 | - Added `$defaultAlg` parameter to `JWT::parseKey` and `JWT::parseKeySet` ([#426](https://github.com/firebase/php-jwt/pull/426)).
35 |
36 | ## 6.1.0 / 2022-03-23
37 |
38 | - Drop support for PHP 5.3, 5.4, 5.5, 5.6, and 7.0
39 | - Add parameter typing and return types where possible
40 |
41 | ## 6.0.0 / 2022-01-24
42 |
43 | - **Backwards-Compatibility Breaking Changes**: See the [Release Notes](https://github.com/firebase/php-jwt/releases/tag/v6.0.0) for more information.
44 | - New Key object to prevent key/algorithm type confusion (#365)
45 | - Add JWK support (#273)
46 | - Add ES256 support (#256)
47 | - Add ES384 support (#324)
48 | - Add Ed25519 support (#343)
49 |
50 | ## 5.0.0 / 2017-06-26
51 | - Support RS384 and RS512.
52 | See [#117](https://github.com/firebase/php-jwt/pull/117). Thanks [@joostfaassen](https://github.com/joostfaassen)!
53 | - Add an example for RS256 openssl.
54 | See [#125](https://github.com/firebase/php-jwt/pull/125). Thanks [@akeeman](https://github.com/akeeman)!
55 | - Detect invalid Base64 encoding in signature.
56 | See [#162](https://github.com/firebase/php-jwt/pull/162). Thanks [@psignoret](https://github.com/psignoret)!
57 | - Update `JWT::verify` to handle OpenSSL errors.
58 | See [#159](https://github.com/firebase/php-jwt/pull/159). Thanks [@bshaffer](https://github.com/bshaffer)!
59 | - Add `array` type hinting to `decode` method
60 | See [#101](https://github.com/firebase/php-jwt/pull/101). Thanks [@hywak](https://github.com/hywak)!
61 | - Add all JSON error types.
62 | See [#110](https://github.com/firebase/php-jwt/pull/110). Thanks [@gbalduzzi](https://github.com/gbalduzzi)!
63 | - Bugfix 'kid' not in given key list.
64 | See [#129](https://github.com/firebase/php-jwt/pull/129). Thanks [@stampycode](https://github.com/stampycode)!
65 | - Miscellaneous cleanup, documentation and test fixes.
66 | See [#107](https://github.com/firebase/php-jwt/pull/107), [#115](https://github.com/firebase/php-jwt/pull/115),
67 | [#160](https://github.com/firebase/php-jwt/pull/160), [#161](https://github.com/firebase/php-jwt/pull/161), and
68 | [#165](https://github.com/firebase/php-jwt/pull/165). Thanks [@akeeman](https://github.com/akeeman),
69 | [@chinedufn](https://github.com/chinedufn), and [@bshaffer](https://github.com/bshaffer)!
70 |
71 | ## 4.0.0 / 2016-07-17
72 | - Add support for late static binding. See [#88](https://github.com/firebase/php-jwt/pull/88) for details. Thanks to [@chappy84](https://github.com/chappy84)!
73 | - Use static `$timestamp` instead of `time()` to improve unit testing. See [#93](https://github.com/firebase/php-jwt/pull/93) for details. Thanks to [@josephmcdermott](https://github.com/josephmcdermott)!
74 | - Fixes to exceptions classes. See [#81](https://github.com/firebase/php-jwt/pull/81) for details. Thanks to [@Maks3w](https://github.com/Maks3w)!
75 | - Fixes to PHPDoc. See [#76](https://github.com/firebase/php-jwt/pull/76) for details. Thanks to [@akeeman](https://github.com/akeeman)!
76 |
77 | ## 3.0.0 / 2015-07-22
78 | - Minimum PHP version updated from `5.2.0` to `5.3.0`.
79 | - Add `\Firebase\JWT` namespace. See
80 | [#59](https://github.com/firebase/php-jwt/pull/59) for details. Thanks to
81 | [@Dashron](https://github.com/Dashron)!
82 | - Require a non-empty key to decode and verify a JWT. See
83 | [#60](https://github.com/firebase/php-jwt/pull/60) for details. Thanks to
84 | [@sjones608](https://github.com/sjones608)!
85 | - Cleaner documentation blocks in the code. See
86 | [#62](https://github.com/firebase/php-jwt/pull/62) for details. Thanks to
87 | [@johanderuijter](https://github.com/johanderuijter)!
88 |
89 | ## 2.2.0 / 2015-06-22
90 | - Add support for adding custom, optional JWT headers to `JWT::encode()`. See
91 | [#53](https://github.com/firebase/php-jwt/pull/53/files) for details. Thanks to
92 | [@mcocaro](https://github.com/mcocaro)!
93 |
94 | ## 2.1.0 / 2015-05-20
95 | - Add support for adding a leeway to `JWT:decode()` that accounts for clock skew
96 | between signing and verifying entities. Thanks to [@lcabral](https://github.com/lcabral)!
97 | - Add support for passing an object implementing the `ArrayAccess` interface for
98 | `$keys` argument in `JWT::decode()`. Thanks to [@aztech-dev](https://github.com/aztech-dev)!
99 |
100 | ## 2.0.0 / 2015-04-01
101 | - **Note**: It is strongly recommended that you update to > v2.0.0 to address
102 | known security vulnerabilities in prior versions when both symmetric and
103 | asymmetric keys are used together.
104 | - Update signature for `JWT::decode(...)` to require an array of supported
105 | algorithms to use when verifying token signatures.
106 |
--------------------------------------------------------------------------------
/vendor/firebase/php-jwt/src/CachedKeySet.php:
--------------------------------------------------------------------------------
1 |
18 | */
19 | class CachedKeySet implements ArrayAccess
20 | {
21 | /**
22 | * @var string
23 | */
24 | private $jwksUri;
25 | /**
26 | * @var ClientInterface
27 | */
28 | private $httpClient;
29 | /**
30 | * @var RequestFactoryInterface
31 | */
32 | private $httpFactory;
33 | /**
34 | * @var CacheItemPoolInterface
35 | */
36 | private $cache;
37 | /**
38 | * @var ?int
39 | */
40 | private $expiresAfter;
41 | /**
42 | * @var ?CacheItemInterface
43 | */
44 | private $cacheItem;
45 | /**
46 | * @var array