├── Ladon.go
├── README.md
├── WinrmCmd.go
├── WinrmCmd.ps1
├── WinrmCmd.py
├── goWinrmScan.ini
├── win7_nocli.PNG
└── winrm_dcom.PNG
/Ladon.go:
--------------------------------------------------------------------------------
1 | package main
2 | //Ladon Scanner for golang
3 | //Author: k8gege
4 | //K8Blog: http://k8gege.org/Ladon
5 | //Github: https://github.com/k8gege/LadonGo
6 | import (
7 | "fmt"
8 | //"github.com/k8gege/LadonGo/worker"
9 | //"github.com/k8gege/LadonGo/color" //Only Windows
10 | "github.com/k8gege/LadonGo/t3"
11 | "github.com/k8gege/LadonGo/icmp"
12 | "github.com/k8gege/LadonGo/ping"
13 | "github.com/k8gege/LadonGo/port"
14 | "github.com/k8gege/LadonGo/http"
15 | "github.com/k8gege/LadonGo/smb"
16 | "github.com/k8gege/LadonGo/ftp"
17 | "github.com/k8gege/LadonGo/ssh"
18 | "github.com/k8gege/LadonGo/mysql"
19 | "github.com/k8gege/LadonGo/winrm"
20 | "github.com/k8gege/LadonGo/rexec"
21 | "strings"
22 | "log"
23 | "time"
24 | "os"
25 | "runtime"
26 | "net"
27 | "sync"
28 | )
29 |
30 | func help() {
31 | if runtime.GOOS=="windows" {fmt.Println("\nHelp:")
32 | } else{fmt.Println("\033[32m\nHelp:\033[0m")}
33 | if runtime.GOOS=="windows" {
34 | //fmt.Println("Ladon Help")
35 | fmt.Println("Ladon FuncList")
36 | fmt.Println("Ladon Detection")
37 | fmt.Println("Ladon VulDetection")
38 | fmt.Println("Ladon BruteFor")
39 | fmt.Println("Ladon RemoteExec")
40 | fmt.Println("Ladon Example")
41 | } else{
42 | //fmt.Println("./Ladon Help")
43 | fmt.Println("./Ladon FuncList")
44 | fmt.Println("./Ladon Detection")
45 | fmt.Println("./Ladon VulDetection")
46 | fmt.Println("./Ladon BruteFor")
47 | fmt.Println("./Ladon RemoteExec")
48 | fmt.Println("./Ladon Example")
49 | }
50 | }
51 |
52 | func FuncList() {
53 | //help()
54 | Detection()
55 | VulDetection()
56 | BruteFor()
57 | RemoteExec()
58 | Example()
59 | }
60 |
61 | func Example() {
62 | if runtime.GOOS=="windows" {fmt.Println("\nExample:")
63 | } else{fmt.Println("\033[32m\nExample:\033[0m")}
64 | if runtime.GOOS=="windows" {
65 | fmt.Println("Ladon 192.168.1.8/24 MS17010")
66 | fmt.Println("Ladon 192.168.1/c MS17010")
67 | fmt.Println("Ladon 192.168/b MS17010")
68 | fmt.Println("Ladon 192/a MS17010")
69 | } else{
70 | fmt.Println("./Ladon 192.168.1.8/24 MS17010")
71 | fmt.Println("./Ladon 192.168.1/c MS17010")
72 | fmt.Println("./Ladon 192.168/b MS17010")
73 | fmt.Println("./Ladon 192/a MS17010")
74 | }
75 | fmt.Println("")
76 | }
77 |
78 | func Detection() {
79 | if runtime.GOOS=="windows" {fmt.Println("\nDetection:")
80 | } else{fmt.Println("\033[33m\nDetection:\033[0m")}
81 | fmt.Println("PingScan\t(Using system ping to detect Online hosts)")
82 | fmt.Println("IcmpScan\t(Using ICMP Protocol to detect Online hosts)")
83 | fmt.Println("HttpBanner\t(Using HTTP Protocol Scan Web Banner)")
84 | fmt.Println("HttpTitle\t(Using HTTP protocol Scan Web titles)")
85 | fmt.Println("T3Scan \t(Using T3 Protocol Scan Weblogic hosts)")
86 | fmt.Println("PortScan\t(Scan hosts open ports using TCP protocol)")
87 | }
88 |
89 | func VulDetection() {
90 | if runtime.GOOS=="windows" {fmt.Println("\nVulDetection:")
91 | } else{fmt.Println("\033[33m\nVulDetection:\033[0m")}
92 | fmt.Println("MS17010 \t(Using SMB Protocol to detect MS17010 hosts))")
93 | fmt.Println("SmbGhost\t(Using SMB Protocol to detect SmbGhost hosts))")
94 |
95 | }
96 |
97 | func BruteFor() {
98 | if runtime.GOOS=="windows" {fmt.Println("\nBruteForce:")
99 | } else{fmt.Println("\033[35m\nBruteForce:\033[0m")}
100 | fmt.Println("SmbScan \t(Using SMB Protocol to Brute-For 445 Port))")
101 | fmt.Println("SshScan \t(Using SSH Protocol to Brute-For 22 Port))")
102 | fmt.Println("FtpScan \t(Using FTP Protocol to Brute-For 21 Port))")
103 | fmt.Println("MysqlScan \t(Using Mysql Protocol to Brute-For 3306 Port))")
104 | fmt.Println("WinrmScan \t(Using Winrm Protocol to Brute-For 5985 Port))")
105 | }
106 |
107 | func RemoteExec() {
108 | if runtime.GOOS=="windows" {fmt.Println("\nRemoteExec:")
109 | } else{fmt.Println("\033[35m\nRemoteExec:\033[0m")}
110 | fmt.Println("SshCmd \t(SSH Remote command execution Default 22 Port))")
111 | fmt.Println("WinrmCmd \t(Winrm Remote command execution Default 5985 Port))")
112 | }
113 |
114 |
115 | func incIP(ip net.IP) {
116 | for j := len(ip) - 1; j >= 0; j-- {
117 | ip[j]++
118 | if ip[j] > 0 {
119 | break
120 | }
121 | }
122 | }
123 | var debugLog *log.Logger
124 | func main() {
125 | fmt.Println("LadonGo 2.0 by k8gege")
126 | fmt.Println("Arch: "+runtime.GOARCH+" OS: "+runtime.GOOS)
127 | fmt.Println("")
128 | ParLen := len(os.Args)
129 | if ParLen==1 {
130 | help()
131 | os.Exit(0)
132 | }
133 |
134 | if ParLen==2 {
135 | SecPar := strings.ToUpper(os.Args[1])
136 | //fmt.Println(SecPar)
137 | if SecPar=="HELP"||SecPar=="/HELP"||SecPar=="-H"||SecPar=="-H" {
138 | help()
139 | os.Exit(0)
140 | }
141 | if SecPar=="HELPLIST"||SecPar=="FUNCLIST" {
142 | FuncList()
143 | os.Exit(0)
144 | }
145 | if SecPar=="BRUTEFOR"||SecPar=="BRUTE"||SecPar=="BRUTEFORCE" {
146 | BruteFor()
147 | os.Exit(0)
148 | }
149 | if SecPar=="DETECTION" {
150 | Detection()
151 | os.Exit(0)
152 | }
153 | if SecPar=="VULDETECTION" {
154 | VulDetection()
155 | os.Exit(0)
156 | }
157 | if SecPar=="EXAMPLE"||SecPar=="USAGE" {
158 | Example()
159 | os.Exit(0)
160 | }
161 | if SecPar == "WINRMCMD" || SecPar == "WINRMEXEC"|| SecPar == "SSHSHELL" {
162 | rexec.WinrmHelp()
163 | os.Exit(0)
164 | }
165 | if SecPar == "SSHCMD" || SecPar == "SSHEXEC" || SecPar == "SSHSHELL" {
166 | ssh.SshHelp()
167 | os.Exit(0)
168 | }
169 | }
170 |
171 | if ParLen>4 {
172 | SecPar := strings.ToUpper(os.Args[1])
173 | if SecPar == "WINRMCMD" || SecPar == "WINRMEXEC" || SecPar == "WINRMSHELL"{
174 | rexec.WinrmCmd(os.Args[2],os.Args[3],os.Args[4],os.Args[5],os.Args[6])
175 | os.Exit(0)
176 | }
177 | if SecPar == "SSHCMD" || SecPar == "SSHEXEC" || SecPar == "SSHSHELL" {
178 | ssh.ExecCmd(os.Args[2],os.Args[3],os.Args[4],os.Args[5],os.Args[6])
179 | os.Exit(0)
180 | }
181 | }
182 |
183 | EndPar := os.Args[ParLen-1]
184 | Target := os.Args[ParLen-2]
185 |
186 | fmt.Println("Targe: "+Target)
187 | fmt.Println("Load "+EndPar)
188 | //log.Println("Start...")
189 | fmt.Println("\nScanStart: "+time.Now().Format("2006-01-02 03:04:05"))
190 | ScanType := strings.ToUpper(EndPar)
191 | if strings.Contains(Target, "/c")||strings.Contains(Target, "/C") {
192 | CScan(ScanType,Target)
193 | } else if strings.Contains(Target, "/b")||strings.Contains(Target, "/B") {
194 | BScan(ScanType,Target)
195 | } else if strings.Contains(Target, "/a")||strings.Contains(Target, "/A") {
196 | AScan(ScanType,Target)
197 | } else if strings.Contains(Target, "/") {
198 | if Target != "" {
199 | ip, ipNet, err := net.ParseCIDR(Target)
200 | if err != nil {
201 | fmt.Println(Target +" invalid CIDR")
202 | return
203 | }
204 | var wg sync.WaitGroup
205 | for ip := ip.Mask(ipNet.Mask); ipNet.Contains(ip); incIP(ip) {
206 | wg.Add(1)
207 | go func(ip string) {
208 | defer wg.Done()
209 | LadonScan(ScanType,ip)
210 | }(ip.String())
211 | }
212 | wg.Wait()
213 | }
214 | } else {
215 | LadonScan(ScanType,Target)
216 | }
217 | //log.Println("Finished")
218 | fmt.Println(" Finished: "+time.Now().Format("2006-01-02 03:04:05"))
219 | }
220 | func End(){
221 | fmt.Println(" Finished: "+time.Now().Format("2006-01-02 03:04:05"))
222 | os.Exit(0)
223 | }
224 | func CScan(ScanType string,Target string){
225 | ip:=strings.Replace(Target, "/c", "", -1)
226 | ip = strings.Replace(ip, "/C", "", -1)
227 | var wg sync.WaitGroup
228 | for i:=1;i<256;i++ {
229 | ip:=fmt.Sprintf("%s.%d",ip,i)
230 | wg.Add(1)
231 | go func(ip string) {
232 | defer wg.Done()
233 | //fmt.Println("c: "+ip)
234 | LadonScan(ScanType,ip);
235 | }(ip)
236 | }
237 | wg.Wait()
238 | }
239 | func BScan(ScanType string,Target string){
240 | ip:=strings.Replace(Target, "/b", "", -1)
241 | ip = strings.Replace(ip, "/B", "", -1)
242 | for i:=1;i<256;i++ {
243 | ip:=fmt.Sprintf("%s.%d",ip,i)
244 | CScan(ScanType,ip)
245 | }
246 | }
247 | func AScan(ScanType string,Target string){
248 | ip:=strings.Replace(Target, "/a", "", -1)
249 | ip = strings.Replace(ip, "/A", "", -1)
250 | for i:=1;i<256;i++ {
251 | ip:=fmt.Sprintf("%s.%d",ip,i)
252 | BScan(ScanType,ip)
253 | }
254 | }
255 | func LadonScan(ScanType string,Target string) {
256 | if ScanType == "PINGSCAN" ||ScanType == "PING" {
257 | ping.PingName(Target)
258 | } else if ScanType == "ICMPSCAN" ||ScanType == "ICMP" {
259 | icmp.Icmp(Target,debugLog)
260 | } else if ScanType == "PORTSCAN" || ScanType == "SCANPORT" {
261 | port.ScanPort(Target)
262 | } else if ScanType == "HTTPBANNER" {
263 | http.HttpBanner(Target)
264 | } else if ScanType == "HTTPTITLE" || ScanType == "WEBTITLE" {
265 | http.ScanTitle(Target)
266 | } else if ScanType == "T3SCAN" || ScanType=="WEBLOGICSCAN" {
267 | t3.T3version(Target)
268 | } else if ScanType == "MS17010" {
269 | smb.MS17010(Target,3)
270 | } else if ScanType == "SMBSCAN" {
271 | smb.SmbScan(ScanType,Target)
272 | } else if ScanType == "FTPSCAN" {
273 | ftp.FtpScan(ScanType,Target)
274 | } else if ScanType == "SMBGHOST"||ScanType == "CVE-2020-0796" {
275 | smb.SmbGhost(Target,445)
276 | } else if ScanType == "SSHSCAN" {
277 | ssh.SshScan(ScanType,Target)
278 | } else if ScanType == "MYSQLSCAN" {
279 | mysql.MysqlScan(ScanType,Target)
280 | } else if ScanType == "WINRMSCAN" {
281 | winrm.WinrmScan(ScanType,Target)
282 | }
283 | }
--------------------------------------------------------------------------------
/README.md:
--------------------------------------------------------------------------------
1 | # WinrmCmd
2 | WinrmCmd For Golang (Winrm Remote Shell)
3 |
4 | wiki: http://k8gege.org/Ladon/WinrmScan.html
5 |
6 |
7 | ### WinrmScan (Brute-Force 5985 Port)
8 | ```Bash
9 | Ladon 192.168.1.8 WinrmScan
10 | Ladon 192.168.1.8/24 WinrmScan
11 | ```
12 |
13 | ### Ladon WinrmExec
14 | ```Bash
15 | Usage:
16 | Ladon WinrmExec [Port] [Domain] [Username] [Password]
17 | Default Port is 5985
18 | Example:
19 | Ladon WinrmExec 192.168.1.116 . k8gege K8test520!@# calc.exe
20 | Ladon WinrmExec 192.168.1.116 80 . k8gege K8test520!@# calc.exe
21 | Ladon WinrmExec 192.168.1.116 5985 . k8gege K8test520!@# calc.exe
22 | ```
23 |
24 | ### LadonGo WinrmCmd
25 |
26 | ```Bash
27 | Ladon SshCmd host port user pass cmd
28 | Ladon WinrmCmd host port user pass cmd
29 | ```
30 |
31 | 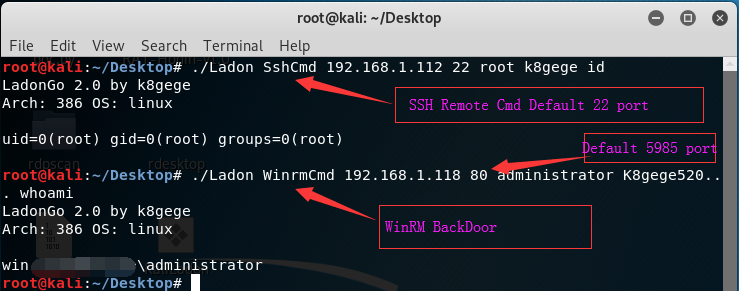
32 |
--------------------------------------------------------------------------------
/WinrmCmd.go:
--------------------------------------------------------------------------------
1 | package main
2 | import (
3 | "github.com/masterzen/winrm"
4 | "fmt"
5 | "os"
6 | "strconv"
7 | )
8 | //Winrm Remote Shell by k8gege
9 | //http://k8gege.org/Ladon/WinrmScan.html
10 | #C:\Users\k8gege\Desktop\>winrmcmd.exe 192.168.1.116 5985 k8gege k8gege520 whoami
11 | #k8gege
12 |
13 | var help = func () {
14 | fmt.Println("Winrm Shell by k8gege")
15 | fmt.Println("====================================================")
16 | fmt.Println("winrmcmd host port user pass cmd")
17 | }
18 |
19 | func main() {
20 |
21 | args := os.Args
22 | if len(args) < 5 || args == nil {
23 | help()
24 | return
25 | }
26 | host := args[1]
27 | port,err := strconv.Atoi(args[2])
28 | user := args[3]
29 | pass := args[4]
30 | cmd := args[5]
31 |
32 | endpoint := winrm.NewEndpoint(host, port, false, false, nil, nil, nil, 0)
33 | client, err := winrm.NewClient(endpoint, user, pass)
34 | if err != nil {
35 | panic(err)
36 | }
37 | client.Run(cmd, os.Stdout, os.Stderr)
38 | }
--------------------------------------------------------------------------------
/WinrmCmd.ps1:
--------------------------------------------------------------------------------
1 | #WIN7: 1.20 fail win7-server
2 | #2012: 1.116 isok 2020-server
3 | $ip="192.168.1.116"
4 | #$ip="192.168.1.20"
5 | Set-Item WSMan:\localhost\Client\TrustedHosts -Value $ip -Force
6 | $securePassword = ConvertTo-SecureString -AsPlainText -Force 'k8gege520'
7 | $cred = New-Object System.Management.Automation.PSCredential 'k8gege', $securePassword
8 | $cmd = {ls C:\users\public}
9 | Invoke-Command -ComputerName $ip -Credential $cred -ScriptBlock $cmd
--------------------------------------------------------------------------------
/WinrmCmd.py:
--------------------------------------------------------------------------------
1 |
2 | #C:\Users\null\Desktop\pywinrm>python test1.py
3 | #win-\k8gege
4 | import winrm
5 | s=winrm.Session('http://192.168.1.116',auth=('k8gege','k8gege520'))#2012 ok
6 | #s=winrm.Session('http://192.168.1.20',auth=('k8gege','k8gege520'))#win7 fail
7 | r=s.run_ps('dir')
8 | r=s.run_cmd('whoami')
9 | print r.std_out
10 | print r.std_err
--------------------------------------------------------------------------------
/goWinrmScan.ini:
--------------------------------------------------------------------------------
1 | [Ladon]
2 | #Brute-Force WinRM
3 | exe=winrmcmd.exe
4 | arg=$ip$ 5985 $user$ $pass$ "echo isok""
5 | #exe=WinrmScan.exe
6 | #arg=$ip$ $user$ $pass$
7 | isok=isok
8 | log=true
--------------------------------------------------------------------------------
/win7_nocli.PNG:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/k8gege/WinrmCmd/9de36931135148fd6d015e6e68637f585feb4015/win7_nocli.PNG
--------------------------------------------------------------------------------
/winrm_dcom.PNG:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/k8gege/WinrmCmd/9de36931135148fd6d015e6e68637f585feb4015/winrm_dcom.PNG
--------------------------------------------------------------------------------