18 |
30 | );
31 | }
32 | }
33 |
34 | function mapStateToProps(state) {
35 | const { user } = state.auth;
36 | return {
37 | user,
38 | };
39 | }
40 |
41 | export default connect(mapStateToProps)(Profile);
--------------------------------------------------------------------------------
/react-redux-jwt/src/reducers/auth.js:
--------------------------------------------------------------------------------
1 | import {
2 | REGISTER_SUCCESS,
3 | REGISTER_FAIL,
4 | LOGIN_SUCCESS,
5 | LOGIN_FAIL,
6 | LOGOUT,
7 | } from "../actions/types";
8 |
9 | const user = JSON.parse(localStorage.getItem("user"));
10 |
11 | const initialState = user
12 | ? { isLoggedIn: true, user }
13 | : { isLoggedIn: false, user: null };
14 |
15 | export default function (state = initialState, action) {
16 | const { type, payload } = action;
17 |
18 | switch (type) {
19 | case REGISTER_SUCCESS:
20 | return {
21 | ...state,
22 | isLoggedIn: false,
23 | };
24 | case REGISTER_FAIL:
25 | return {
26 | ...state,
27 | isLoggedIn: false,
28 | };
29 | case LOGIN_SUCCESS:
30 | return {
31 | ...state,
32 | isLoggedIn: true,
33 | user: payload.user,
34 | };
35 | case LOGIN_FAIL:
36 | return {
37 | ...state,
38 | isLoggedIn: false,
39 | user: null,
40 | };
41 | case LOGOUT:
42 | return {
43 | ...state,
44 | isLoggedIn: false,
45 | user: null,
46 | };
47 | default:
48 | return state;
49 | }
50 | }
51 |
--------------------------------------------------------------------------------
/react-redux-jwt/package.json:
--------------------------------------------------------------------------------
1 | {
2 | "name": "react-redux-jwt",
3 | "version": "0.1.0",
4 | "private": true,
5 | "dependencies": {
6 | "@testing-library/jest-dom": "^4.2.4",
7 | "@testing-library/react": "^9.3.2",
8 | "@testing-library/user-event": "^7.1.2",
9 | "bootstrap": "^4.5.2",
10 | "react": "^17.0.1",
11 | "react-dom": "^17.0.1",
12 | "react-redux": "^7.2.1",
13 | "react-router-dom": "^5.2.0",
14 | "react-scripts": "3.4.3",
15 | "react-validation": "^3.0.7",
16 | "redux": "^4.0.5",
17 | "redux-thunk": "^2.3.0",
18 | "axios": "^0.27.2",
19 | "validator": "^13.1.1"
20 | },
21 | "scripts": {
22 | "start": "react-scripts start",
23 | "build": "react-scripts build",
24 | "test": "react-scripts test",
25 | "eject": "react-scripts eject"
26 | },
27 | "eslintConfig": {
28 | "extends": "react-app"
29 | },
30 | "browserslist": {
31 | "production": [
32 | ">0.2%",
33 | "not dead",
34 | "not op_mini all"
35 | ],
36 | "development": [
37 | "last 1 chrome version",
38 | "last 1 firefox version",
39 | "last 1 safari version"
40 | ]
41 | },
42 | "devDependencies": {
43 | "redux-devtools-extension": "^2.13.8"
44 | }
45 | }
--------------------------------------------------------------------------------
/spring-boot-security-jwt/src/main/java/com/knf/dev/response/JwtResponse.java:
--------------------------------------------------------------------------------
1 | package com.knf.dev.response;
2 |
3 | public class JwtResponse {
4 | private String token;
5 | private String type = "Bearer";
6 | private Long id;
7 | private String username;
8 | private String email;
9 |
10 | public JwtResponse(String accessToken, Long id, String username, String email) {
11 | this.token = accessToken;
12 | this.id = id;
13 | this.username = username;
14 | this.email = email;
15 |
16 | }
17 |
18 | public String getAccessToken() {
19 | return token;
20 | }
21 |
22 | public void setAccessToken(String accessToken) {
23 | this.token = accessToken;
24 | }
25 |
26 | public String getTokenType() {
27 | return type;
28 | }
29 |
30 | public void setTokenType(String tokenType) {
31 | this.type = tokenType;
32 | }
33 |
34 | public Long getId() {
35 | return id;
36 | }
37 |
38 | public void setId(Long id) {
39 | this.id = id;
40 | }
41 |
42 | public String getEmail() {
43 | return email;
44 | }
45 |
46 | public void setEmail(String email) {
47 | this.email = email;
48 | }
49 |
50 | public String getUsername() {
51 | return username;
52 | }
53 |
54 | public void setUsername(String username) {
55 | this.username = username;
56 | }
57 |
58 | }
59 |
--------------------------------------------------------------------------------
/react-redux-jwt/src/components/user.component.js:
--------------------------------------------------------------------------------
1 | import React, { Component } from "react";
2 |
3 | import UserService from "../services/user.service";
4 | import EventBus from "../common/EventBus";
5 |
6 | export default class User extends Component {
7 | constructor(props) {
8 | super(props);
9 |
10 | this.state = {
11 | content: ""
12 | };
13 | }
14 |
15 | componentDidMount() {
16 | UserService.getGreetings().then(
17 | response => {
18 | this.setState({
19 | content: response.data.message
20 | });
21 | },
22 | error => {
23 | this.setState({
24 | content:
25 | (error.response &&
26 | error.response.data &&
27 | error.response.data.message) ||
28 | error.message ||
29 | error.toString()
30 | });
31 |
32 | if (error.response && error.response.status === 401) {
33 | EventBus.dispatch("logout");
34 | }
35 | }
36 | );
37 | }
38 |
39 | render() {
40 | return (
41 |
42 |
43 |
50 |
51 | );
52 | }
53 | }
--------------------------------------------------------------------------------
/spring-boot-security-jwt/src/main/java/com/knf/dev/models/User.java:
--------------------------------------------------------------------------------
1 | package com.knf.dev.models;
2 |
3 | import javax.persistence.Column;
4 | import javax.persistence.Entity;
5 | import javax.persistence.GeneratedValue;
6 | import javax.persistence.GenerationType;
7 | import javax.persistence.Id;
8 | import javax.persistence.Table;
9 |
10 | @Entity
11 | @Table(name = "auser")
12 | public class User {
13 |
14 | @Id
15 | @GeneratedValue(strategy = GenerationType.AUTO)
16 | private Long id;
17 | @Column(unique = true)
18 | private String username;
19 | @Column(unique = true)
20 | private String email;
21 | private String password;
22 |
23 | public User(String username, String email, String password) {
24 | this.username = username;
25 | this.email = email;
26 | this.password = password;
27 | }
28 |
29 | public Long getId() {
30 | return id;
31 | }
32 |
33 | public void setId(Long id) {
34 | this.id = id;
35 | }
36 |
37 | public String getUsername() {
38 | return username;
39 | }
40 |
41 | public void setUsername(String username) {
42 | this.username = username;
43 | }
44 |
45 | public String getEmail() {
46 | return email;
47 | }
48 |
49 | public void setEmail(String email) {
50 | this.email = email;
51 | }
52 |
53 | public String getPassword() {
54 | return password;
55 | }
56 |
57 | public void setPassword(String password) {
58 | this.password = password;
59 | }
60 |
61 | public User() {
62 | super();
63 | }
64 |
65 | }
66 |
--------------------------------------------------------------------------------
/README.md:
--------------------------------------------------------------------------------
1 | # springboot-reactjs-jwt-authentication
2 |
3 | # ReactJS - SpringBoot - JWT - Flow
4 | {currentUser.username}
19 |20 | Id: {currentUser.id} 21 |
22 |23 | Email: {currentUser.email} 24 |
25 | 26 | 27 | 28 | 29 |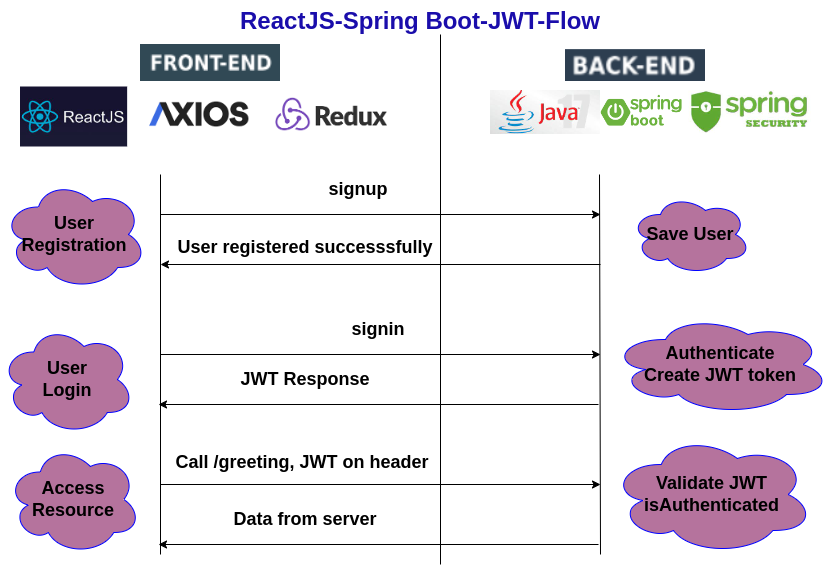 5 |
6 | # Local setup
7 |
8 | Step 1: Download or clone the source code from GitHub to a local machine
9 |
10 | # Backend
11 |
12 | Step 2: ```mvn clean install```
13 |
14 | Step 3: ```mvn spring-boot:run```
15 |
16 | # Frontend
17 |
18 | Step 4: ```npm install or yarn install```
19 |
20 | Step 5: ```npm start or yarn start```
21 |
22 | # From the browser call the endpoint http://localhost:9080/.
23 |
24 | # User Registration
25 |
5 |
6 | # Local setup
7 |
8 | Step 1: Download or clone the source code from GitHub to a local machine
9 |
10 | # Backend
11 |
12 | Step 2: ```mvn clean install```
13 |
14 | Step 3: ```mvn spring-boot:run```
15 |
16 | # Frontend
17 |
18 | Step 4: ```npm install or yarn install```
19 |
20 | Step 5: ```npm start or yarn start```
21 |
22 | # From the browser call the endpoint http://localhost:9080/.
23 |
24 | # User Registration
25 | ) 26 |
27 | # User Signin
28 |
26 |
27 | # User Signin
28 |  29 |
30 | # Profile View:
31 |
29 |
30 | # Profile View:
31 |  32 |
33 | # Access Resource:
34 |
32 |
33 | # Access Resource:
34 |  35 |
--------------------------------------------------------------------------------
/react-redux-jwt/src/actions/auth.js:
--------------------------------------------------------------------------------
1 | import {
2 | REGISTER_SUCCESS,
3 | REGISTER_FAIL,
4 | LOGIN_SUCCESS,
5 | LOGIN_FAIL,
6 | LOGOUT,
7 | SET_MESSAGE,
8 | } from "./types";
9 |
10 | import AuthService from "../services/auth.service";
11 |
12 | export const register = (username, email, password) => (dispatch) => {
13 | return AuthService.register(username, email, password).then(
14 | (response) => {
15 | dispatch({
16 | type: REGISTER_SUCCESS,
17 | });
18 |
19 | dispatch({
20 | type: SET_MESSAGE,
21 | payload: response.data.message,
22 | });
23 |
24 | return Promise.resolve();
25 | },
26 | (error) => {
27 | const message =
28 | (error.response &&
29 | error.response.data &&
30 | error.response.data.message) ||
31 | error.message ||
32 | error.toString();
33 |
34 | dispatch({
35 | type: REGISTER_FAIL,
36 | });
37 |
38 | dispatch({
39 | type: SET_MESSAGE,
40 | payload: message,
41 | });
42 |
43 | return Promise.reject();
44 | }
45 | );
46 | };
47 |
48 | export const login = (username, password) => (dispatch) => {
49 | return AuthService.login(username, password).then(
50 | (data) => {
51 | dispatch({
52 | type: LOGIN_SUCCESS,
53 | payload: { user: data },
54 | });
55 |
56 | return Promise.resolve();
57 | },
58 | (error) => {
59 | const message =
60 | (error.response &&
61 | error.response.data &&
62 | error.response.data.message) ||
63 | error.message ||
64 | error.toString();
65 |
66 | dispatch({
67 | type: LOGIN_FAIL,
68 | });
69 |
70 | dispatch({
71 | type: SET_MESSAGE,
72 | payload: message,
73 | });
74 |
75 | return Promise.reject();
76 | }
77 | );
78 | };
79 |
80 | export const logout = () => (dispatch) => {
81 | AuthService.logout();
82 |
83 | dispatch({
84 | type: LOGOUT,
85 | });
86 | };
87 |
--------------------------------------------------------------------------------
/spring-boot-security-jwt/src/main/java/com/knf/dev/security/jwt/JwtUtils.java:
--------------------------------------------------------------------------------
1 | package com.knf.dev.security.jwt;
2 |
3 | import java.util.Date;
4 |
5 | import org.slf4j.Logger;
6 | import org.slf4j.LoggerFactory;
7 | import org.springframework.beans.factory.annotation.Value;
8 | import org.springframework.security.core.Authentication;
9 | import org.springframework.stereotype.Component;
10 |
11 | import com.knf.dev.security.services.UserDetailsImpl;
12 |
13 | import io.jsonwebtoken.*;
14 |
15 | @Component
16 | public class JwtUtils {
17 | private static final Logger logger = LoggerFactory.getLogger(JwtUtils.class);
18 | @Value("${knf.app.jwtExpirationMs}")
19 | private int jwtExpirationMs;
20 | @Value("${knf.app.jwtSecret}")
21 | private String jwtSecret;
22 |
23 | public boolean validateJwtToken(String authToken) {
24 | try {
25 | Jwts.parser().setSigningKey(jwtSecret).parseClaimsJws(authToken);
26 | return true;
27 | } catch (SignatureException e) {
28 | logger.error("Invalid JWT signature: {}", e.getMessage());
29 | } catch (MalformedJwtException e) {
30 | logger.error("Invalid JWT token: {}", e.getMessage());
31 | } catch (ExpiredJwtException e) {
32 | logger.error("JWT token is expired: {}", e.getMessage());
33 | } catch (UnsupportedJwtException e) {
34 | logger.error("JWT token is unsupported: {}", e.getMessage());
35 | } catch (IllegalArgumentException e) {
36 | logger.error("JWT claims string is empty: {}", e.getMessage());
37 | }
38 |
39 | return false;
40 | }
41 |
42 | public String generateJwtToken(Authentication authentication) {
43 |
44 | UserDetailsImpl userPrincipal = (UserDetailsImpl) authentication.getPrincipal();
45 |
46 | return Jwts.builder().setSubject((userPrincipal.getUsername())).setIssuedAt(new Date())
47 | .setExpiration(new Date((new Date()).getTime() + jwtExpirationMs))
48 | .signWith(SignatureAlgorithm.HS512, jwtSecret).compact();
49 | }
50 |
51 | public String getUserNameFromJwtToken(String token) {
52 | return Jwts.parser().setSigningKey(jwtSecret).parseClaimsJws(token).getBody().getSubject();
53 | }
54 |
55 | }
56 |
--------------------------------------------------------------------------------
/spring-boot-security-jwt/src/main/java/com/knf/dev/security/services/UserDetailsImpl.java:
--------------------------------------------------------------------------------
1 | package com.knf.dev.security.services;
2 |
3 | import java.util.Collection;
4 | import java.util.Objects;
5 |
6 | import org.springframework.security.core.GrantedAuthority;
7 | import org.springframework.security.core.userdetails.UserDetails;
8 |
9 | import com.fasterxml.jackson.annotation.JsonIgnore;
10 | import com.knf.dev.models.User;
11 |
12 | public class UserDetailsImpl implements UserDetails {
13 | private static final long serialVersionUID = 1L;
14 |
15 | private Long id;
16 |
17 | private String username;
18 |
19 | private String email;
20 |
21 | @JsonIgnore
22 | private String password;
23 |
24 | public UserDetailsImpl(Long id, String username, String email, String password) {
25 | this.id = id;
26 | this.username = username;
27 | this.email = email;
28 | this.password = password;
29 |
30 | }
31 |
32 | public static UserDetailsImpl build(User user) {
33 |
34 | return new UserDetailsImpl(user.getId(), user.getUsername(), user.getEmail(), user.getPassword());
35 | }
36 |
37 | public Long getId() {
38 | return id;
39 | }
40 |
41 | public String getEmail() {
42 | return email;
43 | }
44 |
45 | @Override
46 | public String getPassword() {
47 | return password;
48 | }
49 |
50 | @Override
51 | public String getUsername() {
52 | return username;
53 | }
54 |
55 | @Override
56 | public boolean isAccountNonExpired() {
57 | return true;
58 | }
59 |
60 | @Override
61 | public boolean isAccountNonLocked() {
62 | return true;
63 | }
64 |
65 | @Override
66 | public boolean isCredentialsNonExpired() {
67 | return true;
68 | }
69 |
70 | @Override
71 | public boolean isEnabled() {
72 | return true;
73 | }
74 |
75 | @Override
76 | public boolean equals(Object o) {
77 | if (this == o)
78 | return true;
79 | if (o == null || getClass() != o.getClass())
80 | return false;
81 | UserDetailsImpl user = (UserDetailsImpl) o;
82 | return Objects.equals(id, user.id);
83 | }
84 |
85 | @Override
86 | public Collection getAuthorities() {
87 | // TODO Auto-generated method stub
88 | return null;
89 | }
90 | }
91 |
--------------------------------------------------------------------------------
/spring-boot-security-jwt/pom.xml:
--------------------------------------------------------------------------------
1 |
2 |
35 |
--------------------------------------------------------------------------------
/react-redux-jwt/src/actions/auth.js:
--------------------------------------------------------------------------------
1 | import {
2 | REGISTER_SUCCESS,
3 | REGISTER_FAIL,
4 | LOGIN_SUCCESS,
5 | LOGIN_FAIL,
6 | LOGOUT,
7 | SET_MESSAGE,
8 | } from "./types";
9 |
10 | import AuthService from "../services/auth.service";
11 |
12 | export const register = (username, email, password) => (dispatch) => {
13 | return AuthService.register(username, email, password).then(
14 | (response) => {
15 | dispatch({
16 | type: REGISTER_SUCCESS,
17 | });
18 |
19 | dispatch({
20 | type: SET_MESSAGE,
21 | payload: response.data.message,
22 | });
23 |
24 | return Promise.resolve();
25 | },
26 | (error) => {
27 | const message =
28 | (error.response &&
29 | error.response.data &&
30 | error.response.data.message) ||
31 | error.message ||
32 | error.toString();
33 |
34 | dispatch({
35 | type: REGISTER_FAIL,
36 | });
37 |
38 | dispatch({
39 | type: SET_MESSAGE,
40 | payload: message,
41 | });
42 |
43 | return Promise.reject();
44 | }
45 | );
46 | };
47 |
48 | export const login = (username, password) => (dispatch) => {
49 | return AuthService.login(username, password).then(
50 | (data) => {
51 | dispatch({
52 | type: LOGIN_SUCCESS,
53 | payload: { user: data },
54 | });
55 |
56 | return Promise.resolve();
57 | },
58 | (error) => {
59 | const message =
60 | (error.response &&
61 | error.response.data &&
62 | error.response.data.message) ||
63 | error.message ||
64 | error.toString();
65 |
66 | dispatch({
67 | type: LOGIN_FAIL,
68 | });
69 |
70 | dispatch({
71 | type: SET_MESSAGE,
72 | payload: message,
73 | });
74 |
75 | return Promise.reject();
76 | }
77 | );
78 | };
79 |
80 | export const logout = () => (dispatch) => {
81 | AuthService.logout();
82 |
83 | dispatch({
84 | type: LOGOUT,
85 | });
86 | };
87 |
--------------------------------------------------------------------------------
/spring-boot-security-jwt/src/main/java/com/knf/dev/security/jwt/JwtUtils.java:
--------------------------------------------------------------------------------
1 | package com.knf.dev.security.jwt;
2 |
3 | import java.util.Date;
4 |
5 | import org.slf4j.Logger;
6 | import org.slf4j.LoggerFactory;
7 | import org.springframework.beans.factory.annotation.Value;
8 | import org.springframework.security.core.Authentication;
9 | import org.springframework.stereotype.Component;
10 |
11 | import com.knf.dev.security.services.UserDetailsImpl;
12 |
13 | import io.jsonwebtoken.*;
14 |
15 | @Component
16 | public class JwtUtils {
17 | private static final Logger logger = LoggerFactory.getLogger(JwtUtils.class);
18 | @Value("${knf.app.jwtExpirationMs}")
19 | private int jwtExpirationMs;
20 | @Value("${knf.app.jwtSecret}")
21 | private String jwtSecret;
22 |
23 | public boolean validateJwtToken(String authToken) {
24 | try {
25 | Jwts.parser().setSigningKey(jwtSecret).parseClaimsJws(authToken);
26 | return true;
27 | } catch (SignatureException e) {
28 | logger.error("Invalid JWT signature: {}", e.getMessage());
29 | } catch (MalformedJwtException e) {
30 | logger.error("Invalid JWT token: {}", e.getMessage());
31 | } catch (ExpiredJwtException e) {
32 | logger.error("JWT token is expired: {}", e.getMessage());
33 | } catch (UnsupportedJwtException e) {
34 | logger.error("JWT token is unsupported: {}", e.getMessage());
35 | } catch (IllegalArgumentException e) {
36 | logger.error("JWT claims string is empty: {}", e.getMessage());
37 | }
38 |
39 | return false;
40 | }
41 |
42 | public String generateJwtToken(Authentication authentication) {
43 |
44 | UserDetailsImpl userPrincipal = (UserDetailsImpl) authentication.getPrincipal();
45 |
46 | return Jwts.builder().setSubject((userPrincipal.getUsername())).setIssuedAt(new Date())
47 | .setExpiration(new Date((new Date()).getTime() + jwtExpirationMs))
48 | .signWith(SignatureAlgorithm.HS512, jwtSecret).compact();
49 | }
50 |
51 | public String getUserNameFromJwtToken(String token) {
52 | return Jwts.parser().setSigningKey(jwtSecret).parseClaimsJws(token).getBody().getSubject();
53 | }
54 |
55 | }
56 |
--------------------------------------------------------------------------------
/spring-boot-security-jwt/src/main/java/com/knf/dev/security/services/UserDetailsImpl.java:
--------------------------------------------------------------------------------
1 | package com.knf.dev.security.services;
2 |
3 | import java.util.Collection;
4 | import java.util.Objects;
5 |
6 | import org.springframework.security.core.GrantedAuthority;
7 | import org.springframework.security.core.userdetails.UserDetails;
8 |
9 | import com.fasterxml.jackson.annotation.JsonIgnore;
10 | import com.knf.dev.models.User;
11 |
12 | public class UserDetailsImpl implements UserDetails {
13 | private static final long serialVersionUID = 1L;
14 |
15 | private Long id;
16 |
17 | private String username;
18 |
19 | private String email;
20 |
21 | @JsonIgnore
22 | private String password;
23 |
24 | public UserDetailsImpl(Long id, String username, String email, String password) {
25 | this.id = id;
26 | this.username = username;
27 | this.email = email;
28 | this.password = password;
29 |
30 | }
31 |
32 | public static UserDetailsImpl build(User user) {
33 |
34 | return new UserDetailsImpl(user.getId(), user.getUsername(), user.getEmail(), user.getPassword());
35 | }
36 |
37 | public Long getId() {
38 | return id;
39 | }
40 |
41 | public String getEmail() {
42 | return email;
43 | }
44 |
45 | @Override
46 | public String getPassword() {
47 | return password;
48 | }
49 |
50 | @Override
51 | public String getUsername() {
52 | return username;
53 | }
54 |
55 | @Override
56 | public boolean isAccountNonExpired() {
57 | return true;
58 | }
59 |
60 | @Override
61 | public boolean isAccountNonLocked() {
62 | return true;
63 | }
64 |
65 | @Override
66 | public boolean isCredentialsNonExpired() {
67 | return true;
68 | }
69 |
70 | @Override
71 | public boolean isEnabled() {
72 | return true;
73 | }
74 |
75 | @Override
76 | public boolean equals(Object o) {
77 | if (this == o)
78 | return true;
79 | if (o == null || getClass() != o.getClass())
80 | return false;
81 | UserDetailsImpl user = (UserDetailsImpl) o;
82 | return Objects.equals(id, user.id);
83 | }
84 |
85 | @Override
86 | public Collection getAuthorities() {
87 | // TODO Auto-generated method stub
88 | return null;
89 | }
90 | }
91 |
--------------------------------------------------------------------------------
/spring-boot-security-jwt/pom.xml:
--------------------------------------------------------------------------------
1 |
2 |
61 |
105 |
106 |
116 |
107 |
108 |
114 |
115 |
15 | This field is required!
16 |
17 | );
18 | }
19 | };
20 |
21 | class Login extends Component {
22 | constructor(props) {
23 | super(props);
24 | this.handleLogin = this.handleLogin.bind(this);
25 | this.onChangeUsername = this.onChangeUsername.bind(this);
26 | this.onChangePassword = this.onChangePassword.bind(this);
27 |
28 | this.state = {
29 | username: "",
30 | password: "",
31 | loading: false,
32 | };
33 | }
34 |
35 | onChangeUsername(e) {
36 | this.setState({
37 | username: e.target.value,
38 | });
39 | }
40 |
41 | onChangePassword(e) {
42 | this.setState({
43 | password: e.target.value,
44 | });
45 | }
46 |
47 | handleLogin(e) {
48 | e.preventDefault();
49 |
50 | this.setState({
51 | loading: true,
52 | });
53 |
54 | this.form.validateAll();
55 |
56 | const { dispatch, history } = this.props;
57 |
58 | if (this.checkBtn.context._errors.length === 0) {
59 | dispatch(login(this.state.username, this.state.password))
60 | .then(() => {
61 | history.push("/profile");
62 | window.location.reload();
63 | })
64 | .catch(() => {
65 | this.setState({
66 | loading: false
67 | });
68 | });
69 | } else {
70 | this.setState({
71 | loading: false,
72 | });
73 | }
74 | }
75 |
76 | render() {
77 | const { isLoggedIn, message } = this.props;
78 |
79 | if (isLoggedIn) {
80 | return
85 |
147 | );
148 | }
149 | }
150 |
151 | function mapStateToProps(state) {
152 | const { isLoggedIn } = state.auth;
153 | const { message } = state.message;
154 | return {
155 | isLoggedIn,
156 | message
157 | };
158 | }
159 |
160 | export default connect(mapStateToProps)(Login);
161 |
--------------------------------------------------------------------------------
/react-redux-jwt/src/serviceWorker.js:
--------------------------------------------------------------------------------
1 | // This optional code is used to register a service worker.
2 | // register() is not called by default.
3 |
4 | // This lets the app load faster on subsequent visits in production, and gives
5 | // it offline capabilities. However, it also means that developers (and users)
6 | // will only see deployed updates on subsequent visits to a page, after all the
7 | // existing tabs open on the page have been closed, since previously cached
8 | // resources are updated in the background.
9 |
10 | // To learn more about the benefits of this model and instructions on how to
11 | // opt-in, read https://bit.ly/CRA-PWA
12 |
13 | const isLocalhost = Boolean(
14 | window.location.hostname === 'localhost' ||
15 | // [::1] is the IPv6 localhost address.
16 | window.location.hostname === '[::1]' ||
17 | // 127.0.0.0/8 are considered localhost for IPv4.
18 | window.location.hostname.match(
19 | /^127(?:\.(?:25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)){3}$/
20 | )
21 | );
22 |
23 | export function register(config) {
24 | if (process.env.NODE_ENV === 'production' && 'serviceWorker' in navigator) {
25 | // The URL constructor is available in all browsers that support SW.
26 | const publicUrl = new URL(process.env.PUBLIC_URL, window.location.href);
27 | if (publicUrl.origin !== window.location.origin) {
28 | // Our service worker won't work if PUBLIC_URL is on a different origin
29 | // from what our page is served on. This might happen if a CDN is used to
30 | // serve assets; see https://github.com/facebook/create-react-app/issues/2374
31 | return;
32 | }
33 |
34 | window.addEventListener('load', () => {
35 | const swUrl = `${process.env.PUBLIC_URL}/service-worker.js`;
36 |
37 | if (isLocalhost) {
38 | // This is running on localhost. Let's check if a service worker still exists or not.
39 | checkValidServiceWorker(swUrl, config);
40 |
41 | // Add some additional logging to localhost, pointing developers to the
42 | // service worker/PWA documentation.
43 | navigator.serviceWorker.ready.then(() => {
44 | console.log(
45 | 'This web app is being served cache-first by a service ' +
46 | 'worker. To learn more, visit https://bit.ly/CRA-PWA'
47 | );
48 | });
49 | } else {
50 | // Is not localhost. Just register service worker
51 | registerValidSW(swUrl, config);
52 | }
53 | });
54 | }
55 | }
56 |
57 | function registerValidSW(swUrl, config) {
58 | navigator.serviceWorker
59 | .register(swUrl)
60 | .then(registration => {
61 | registration.onupdatefound = () => {
62 | const installingWorker = registration.installing;
63 | if (installingWorker == null) {
64 | return;
65 | }
66 | installingWorker.onstatechange = () => {
67 | if (installingWorker.state === 'installed') {
68 | if (navigator.serviceWorker.controller) {
69 | // At this point, the updated precached content has been fetched,
70 | // but the previous service worker will still serve the older
71 | // content until all client tabs are closed.
72 | console.log(
73 | 'New content is available and will be used when all ' +
74 | 'tabs for this page are closed. See https://bit.ly/CRA-PWA.'
75 | );
76 |
77 | // Execute callback
78 | if (config && config.onUpdate) {
79 | config.onUpdate(registration);
80 | }
81 | } else {
82 | // At this point, everything has been precached.
83 | // It's the perfect time to display a
84 | // "Content is cached for offline use." message.
85 | console.log('Content is cached for offline use.');
86 |
87 | // Execute callback
88 | if (config && config.onSuccess) {
89 | config.onSuccess(registration);
90 | }
91 | }
92 | }
93 | };
94 | };
95 | })
96 | .catch(error => {
97 | console.error('Error during service worker registration:', error);
98 | });
99 | }
100 |
101 | function checkValidServiceWorker(swUrl, config) {
102 | // Check if the service worker can be found. If it can't reload the page.
103 | fetch(swUrl, {
104 | headers: { 'Service-Worker': 'script' },
105 | })
106 | .then(response => {
107 | // Ensure service worker exists, and that we really are getting a JS file.
108 | const contentType = response.headers.get('content-type');
109 | if (
110 | response.status === 404 ||
111 | (contentType != null && contentType.indexOf('javascript') === -1)
112 | ) {
113 | // No service worker found. Probably a different app. Reload the page.
114 | navigator.serviceWorker.ready.then(registration => {
115 | registration.unregister().then(() => {
116 | window.location.reload();
117 | });
118 | });
119 | } else {
120 | // Service worker found. Proceed as normal.
121 | registerValidSW(swUrl, config);
122 | }
123 | })
124 | .catch(() => {
125 | console.log(
126 | 'No internet connection found. App is running in offline mode.'
127 | );
128 | });
129 | }
130 |
131 | export function unregister() {
132 | if ('serviceWorker' in navigator) {
133 | navigator.serviceWorker.ready
134 | .then(registration => {
135 | registration.unregister();
136 | })
137 | .catch(error => {
138 | console.error(error.message);
139 | });
140 | }
141 | }
142 |
--------------------------------------------------------------------------------
/react-redux-jwt/src/components/register.component.js:
--------------------------------------------------------------------------------
1 | import React, { Component } from "react";
2 | import Form from "react-validation/build/form";
3 | import Input from "react-validation/build/input";
4 | import CheckButton from "react-validation/build/button";
5 | import { isEmail } from "validator";
6 |
7 | import { connect } from "react-redux";
8 | import { register } from "../actions/auth";
9 |
10 | const required = (value) => {
11 | if (!value) {
12 | return (
13 |
86 |
87 |
88 |
89 |
145 |
146 | Login
87 |
88 |
89 |
145 |
14 | This field is required!
15 |
16 | );
17 | }
18 | };
19 |
20 | const email = (value) => {
21 | if (!isEmail(value)) {
22 | return (
23 |
24 | This is not a valid email.
25 |
26 | );
27 | }
28 | };
29 |
30 | const vusername = (value) => {
31 | if (value.length < 3 || value.length > 20) {
32 | return (
33 |
34 | The username must be between 3 and 20 characters.
35 |
36 | );
37 | }
38 | };
39 |
40 | const vpassword = (value) => {
41 | if (value.length < 6 || value.length > 40) {
42 | return (
43 |
44 | The password must be between 6 and 40 characters.
45 |
46 | );
47 | }
48 | };
49 |
50 | class Register extends Component {
51 | constructor(props) {
52 | super(props);
53 | this.handleRegister = this.handleRegister.bind(this);
54 | this.onChangeUsername = this.onChangeUsername.bind(this);
55 | this.onChangeEmail = this.onChangeEmail.bind(this);
56 | this.onChangePassword = this.onChangePassword.bind(this);
57 |
58 | this.state = {
59 | username: "",
60 | email: "",
61 | password: "",
62 | successful: false,
63 | };
64 | }
65 |
66 | onChangeUsername(e) {
67 | this.setState({
68 | username: e.target.value,
69 | });
70 | }
71 |
72 | onChangeEmail(e) {
73 | this.setState({
74 | email: e.target.value,
75 | });
76 | }
77 |
78 | onChangePassword(e) {
79 | this.setState({
80 | password: e.target.value,
81 | });
82 | }
83 |
84 | handleRegister(e) {
85 | e.preventDefault();
86 |
87 | this.setState({
88 | successful: false,
89 | });
90 |
91 | this.form.validateAll();
92 |
93 | if (this.checkBtn.context._errors.length === 0) {
94 | this.props
95 | .dispatch(
96 | register(this.state.username, this.state.email, this.state.password)
97 | )
98 | .then(() => {
99 | this.setState({
100 | successful: true,
101 | });
102 | })
103 | .catch(() => {
104 | this.setState({
105 | successful: false,
106 | });
107 | });
108 | }
109 | }
110 |
111 | render() {
112 | const { message } = this.props;
113 |
114 | return (
115 |
116 |
117 |
188 | );
189 | }
190 | }
191 |
192 | function mapStateToProps(state) {
193 | const { message } = state.message;
194 | return {
195 | message,
196 | };
197 | }
198 |
199 | export default connect(mapStateToProps)(Register);
200 |
--------------------------------------------------------------------------------
/LICENSE:
--------------------------------------------------------------------------------
1 | GNU GENERAL PUBLIC LICENSE
2 | Version 3, 29 June 2007
3 |
4 | Copyright (C) 2007 Free Software Foundation, Inc.
118 |
119 |
120 |
121 |
122 |
186 |
187 |