├── Xpath.txt
├── windows-rdp-auth-fail.json
├── mssql-auth-fail.json
├── nsg-malicious-allowed-in.json
├── linux-ssh-auth-fail.json
├── README.md
└── Sentinel-Analytics-Rules(KQL Alert Queries).json
/Xpath.txt:
--------------------------------------------------------------------------------
1 | // Windows Defender Malware Detection XPath Query
2 | Microsoft-Windows-Windows Defender/Operational!*[System[(EventID=1116 or EventID=1117)]]
3 |
4 | // Windows Firewall Tampering Detection XPath Query
5 | Microsoft-Windows-Windows Firewall With Advanced Security/Firewall!*[System[(EventID=2003)]]
6 |
--------------------------------------------------------------------------------
/windows-rdp-auth-fail.json:
--------------------------------------------------------------------------------
1 | {
2 | "type": 3,
3 | "content": {
4 | "version": "KqlItem/1.0",
5 | "query": "let GeoIPDB_FULL = _GetWatchlist(\"geoip\");\nlet WindowsEvents = SecurityEvent;\nWindowsEvents | where EventID == 4625\n| order by TimeGenerated desc\n| evaluate ipv4_lookup(GeoIPDB_FULL, IpAddress, network)\n| project TimeGenerated, Account, AccountType, Computer, EventID, Activity, IpAddress, LogonTypeName, network, latitude, longitude, city = cityname, country = countryname, friendly_location = strcat(cityname, \" (\", countryname, \")\");\n",
6 | "size": 3,
7 | "timeContext": {
8 | "durationMs": 2592000000
9 | },
10 | "queryType": 0,
11 | "resourceType": "microsoft.operationalinsights/workspaces",
12 | "visualization": "map",
13 | "mapSettings": {
14 | "locInfo": "LatLong",
15 | "locInfoColumn": "countryname",
16 | "latitude": "latitude",
17 | "longitude": "longitude",
18 | "sizeSettings": "EventID",
19 | "sizeAggregation": "Count",
20 | "opacity": 0.8,
21 | "labelSettings": "friendly_location",
22 | "legendMetric": "EventID",
23 | "legendAggregation": "Count",
24 | "itemColorSettings": {
25 | "nodeColorField": "EventID",
26 | "colorAggregation": "Sum",
27 | "type": "heatmap",
28 | "heatmapPalette": "greenRed"
29 | }
30 | }
31 | },
32 | "name": "query - 0"
33 | }
34 |
--------------------------------------------------------------------------------
/mssql-auth-fail.json:
--------------------------------------------------------------------------------
1 | {
2 | "type": 3,
3 | "content": {
4 | "version": "KqlItem/1.0",
5 | "query": "let GeoIPDB_FULL = _GetWatchlist(\"geoip\");\nlet IpAddress_REGEX_PATTERN = @\"\\b\\d{1,3}\\.\\d{1,3}\\.\\d{1,3}\\.\\d{1,3}\\b\";\n// Brute Force Attempt MS SQL Server\nEvent\n| where EventLog == \"Application\"\n| where EventID == 18456\n| project TimeGenerated, AttackerIP = extract(IpAddress_REGEX_PATTERN, 0, RenderedDescription), DestinationHostName = Computer, RenderedDescription\n| evaluate ipv4_lookup(GeoIPDB_FULL, AttackerIP, network)\n| project TimeGenerated, AttackerIP, DestinationHostName, RenderedDescription, latitude, longitude, city = cityname, country = countryname, friendly_location = strcat(cityname, \" (\", countryname, \")\");",
6 | "size": 3,
7 | "timeContext": {
8 | "durationMs": 2592000000
9 | },
10 | "queryType": 0,
11 | "resourceType": "microsoft.operationalinsights/workspaces",
12 | "visualization": "map",
13 | "mapSettings": {
14 | "locInfo": "LatLong",
15 | "locInfoColumn": "countryname",
16 | "latitude": "latitude",
17 | "longitude": "longitude",
18 | "sizeSettings": "latitude",
19 | "sizeAggregation": "Count",
20 | "opacity": 0.8,
21 | "labelSettings": "friendly_location",
22 | "legendMetric": "friendly_location",
23 | "legendAggregation": "Count",
24 | "itemColorSettings": {
25 | "nodeColorField": "latitude",
26 | "colorAggregation": "Sum",
27 | "type": "heatmap",
28 | "heatmapPalette": "greenRed"
29 | }
30 | }
31 | },
32 | "name": "query - 0"
33 | }
34 |
--------------------------------------------------------------------------------
/nsg-malicious-allowed-in.json:
--------------------------------------------------------------------------------
1 | {
2 | "type": 3,
3 | "content": {
4 | "version": "KqlItem/1.0",
5 | "query": "let GeoIPDB_FULL = _GetWatchlist(\"geoip\");\nlet MaliciousFlows = AzureNetworkAnalytics_CL \n| where FlowType_s == \"MaliciousFlow\"\n| order by TimeGenerated desc\n| project TimeGenerated, FlowType = FlowType_s, IpAddress = SrcIP_s, DestinationIpAddress = DestIP_s, DestinationPort = DestPort_d, Protocol = L7Protocol_s, NSGRuleMatched = NSGRules_s;\nMaliciousFlows\n| evaluate ipv4_lookup(GeoIPDB_FULL, IpAddress, network)\n| project TimeGenerated, FlowType, IpAddress, DestinationIpAddress, DestinationPort, Protocol, NSGRuleMatched, latitude, longitude, city = cityname, country = countryname, friendly_location = strcat(cityname, \" (\", countryname, \")\")",
6 | "size": 3,
7 | "timeContext": {
8 | "durationMs": 2592000000
9 | },
10 | "queryType": 0,
11 | "resourceType": "microsoft.operationalinsights/workspaces",
12 | "visualization": "map",
13 | "mapSettings": {
14 | "locInfo": "LatLong",
15 | "locInfoColumn": "countryname",
16 | "latitude": "latitude",
17 | "longitude": "longitude",
18 | "sizeSettings": "city",
19 | "sizeAggregation": "Count",
20 | "opacity": 0.8,
21 | "labelSettings": "friendly_location",
22 | "legendMetric": "IpAddress",
23 | "legendAggregation": "Count",
24 | "itemColorSettings": {
25 | "nodeColorField": "city",
26 | "colorAggregation": "Count",
27 | "type": "heatmap",
28 | "heatmapPalette": "greenRed"
29 | }
30 | }
31 | },
32 | "name": "query - 0"
33 | }
34 |
--------------------------------------------------------------------------------
/linux-ssh-auth-fail.json:
--------------------------------------------------------------------------------
1 | {
2 | "type": 3,
3 | "content": {
4 | "version": "KqlItem/1.0",
5 | "query": "let GeoIPDB_FULL = _GetWatchlist(\"geoip\");\nlet IpAddress_REGEX_PATTERN = @\"\\b\\d{1,3}\\.\\d{1,3}\\.\\d{1,3}\\.\\d{1,3}\\b\";\nSyslog\n| where Facility == \"auth\"\n| where SyslogMessage startswith \"Failed password for\"\n| order by TimeGenerated desc\n| project TimeGenerated, SourceIP = extract(IpAddress_REGEX_PATTERN, 0, SyslogMessage), DestinationHostName = HostName, DestinationIP = HostIP, Facility, SyslogMessage, ProcessName, SeverityLevel, Type\n| evaluate ipv4_lookup(GeoIPDB_FULL, SourceIP, network)\n| project TimeGenerated, SourceIP, DestinationHostName, DestinationIP, Facility, SyslogMessage, ProcessName, SeverityLevel, Type, latitude, longitude, city = cityname, country = countryname, friendly_location = strcat(cityname, \" (\", countryname, \")\");",
6 | "size": 3,
7 | "timeContext": {
8 | "durationMs": 2592000000
9 | },
10 | "queryType": 0,
11 | "resourceType": "microsoft.operationalinsights/workspaces",
12 | "visualization": "map",
13 | "mapSettings": {
14 | "locInfo": "LatLong",
15 | "locInfoColumn": "countryname",
16 | "latitude": "latitude",
17 | "longitude": "longitude",
18 | "sizeSettings": "latitude",
19 | "sizeAggregation": "Count",
20 | "opacity": 0.8,
21 | "labelSettings": "friendly_location",
22 | "legendMetric": "friendly_location",
23 | "legendAggregation": "Count",
24 | "itemColorSettings": {
25 | "nodeColorField": "latitude",
26 | "colorAggregation": "Count",
27 | "type": "heatmap",
28 | "heatmapPalette": "greenRed"
29 | }
30 | }
31 | },
32 | "name": "query - 0"
33 | }
34 |
--------------------------------------------------------------------------------
/README.md:
--------------------------------------------------------------------------------
1 |
2 | # Building a SOC + Honeynet in Azure (Live Traffic)
3 | 
4 |
5 | Video Demonstration
6 |
7 | - ### [YouTube: How To Build a SOC + Honeynet in Azure](https://youtu.be/mOjbD7FkUUI)
8 |
9 | [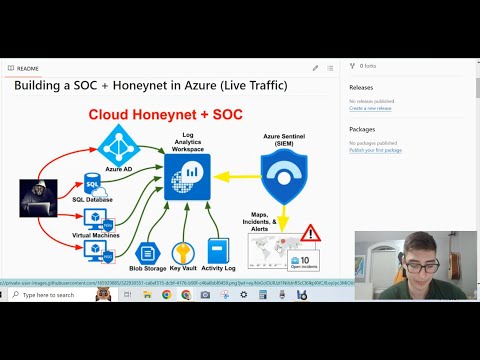](https://www.youtube.com/watch?v=mOjbD7FkUUI)
10 |
11 |
12 | ## Introduction
13 |
14 | In this project, I build a mini honeynet in Azure and ingest logs from various resources into a Log Analytics Workspace, which is then used by Microsoft Sentinel to build attack maps, trigger alerts, and create incidents. I measured some security metrics in the insecure environment for 24 hours, applied security controls to harden the environment, measured metrics for another 24 hours, and then shared the results below. The metrics we will collect are:
15 |
16 | - SecurityEvent (Windows Event Logs)
17 | - Syslog (Linux Event Logs)
18 | - SecurityAlert (Log Analytics Alerts Triggered)
19 | - SecurityIncident (Incidents created by Sentinel)
20 | - AzureNetworkAnalytics_CL (Malicious Flows allowed into our honeynet)
21 |
22 | ## Architecture Before Hardening / Security Controls
23 | 
24 |
25 |
26 | ## Architecture After Hardening / Security Controls
27 | 
28 |
29 |
30 | The architecture of the mini honeynet in Azure consists of the following components:
31 |
32 | - Virtual Network (VNet)
33 | - Network Security Group (NSG)
34 | - Virtual Machines (2 windows, 1 linux)
35 | - Log Analytics Workspace
36 | - Azure Key Vault
37 | - Azure Storage Account
38 | - Microsoft Sentinel
39 |
40 |
41 | ## Attack Maps Before Hardening / Security Controls
42 |  43 |
43 |
44 |  45 |
45 |
46 |  47 |
47 |
48 |
49 | ## Metrics Before Hardening / Security Controls
50 |
51 | The following table shows the metrics we measured in our insecure environment for 24 hours:
52 |
53 | | Start Time 2024-04-13 13:53:48
54 |
55 | | Stop Time 2024-04-14 13:53:48
56 |
57 | | Metric | Count
58 | | ------------------------ | -----
59 | | SecurityEvent | 7671
60 | | Syslog | 833
61 | | SecurityAlert | 4
62 | | SecurityIncident | 59
63 | | AzureNetworkAnalytics_CL | 620
64 |
65 | ## Attack Maps After Hardening / Security Controls
66 |
67 |  68 |
68 |
69 |
70 | ```All map queries actually returned no results due to no instances of malicious activity for the 24 hour period after hardening.```
71 |
72 | ## Metrics After Hardening / Security Controls
73 |
74 | The following table shows the metrics we measured in our environment for another 24 hours, but after we have applied security controls:
75 |
76 | | Start Time 2024-04-15 11:50:28
77 |
78 | | Stop Time 2024-04-16 11:50:28
79 |
80 | | Metric | Count
81 | | ------------------------ | -----
82 | | SecurityEvent | 3894
83 | | Syslog | 6
84 | | SecurityAlert | 0
85 | | SecurityIncident | 0
86 | | AzureNetworkAnalytics_CL | 0
87 |
88 | 
89 |
90 |
91 | ## Summary
92 |
93 | In this project, a mini honeynet was constructed in Microsoft Azure and the logs were pushed into a Log Analytics Workspace for analysis. Microsoft Sentinel was also employed to trigger alerts and create incidents based on the ingested logs. Additionally, metrics were measured in the insecure environment before security controls were applied, and then again after implementing security measures. The number of security events and incidents were drastically reduced after the security controls were applied, demonstrating their effectiveness.
94 |
95 | It is worth noting that if the resources within the network were heavily utilized by regular users, it is likely that more security events and alerts may have been generated within the 24-hour period following the implementation of the security controls.
96 |
97 |
98 | ## KQL Queries
99 |
100 | | Metric | Query |
101 | |----------------------------------------------|--------------------------------------------------------------------------------------------------------------------------------------------------|
102 | | Start/Stop Time | range x from 1 to 1 step 1
\| project StartTime = ago(24h), StopTime = now() |
103 | | Security Events (Windows VMs) | SecurityEvent
\| where TimeGenerated>= ago(24h)
\| count |
104 | | Syslog (Linux VMs) | Syslog
\| where TimeGenerated >= ago(24h)
\| count |
105 | | SecurityAlert (Microsoft Defender for Cloud) | Security Alert
\| where DisplayName !startswith "CUSTOM" and DisplayName !startswith "TEST"
\| where TimeGenerated >= ago(24h)
\| count |
106 | | Security Incident (Sentinel Incidents) | SecurityIncident
\| where TimeGenerated >= ago(24h)
\| count |
107 | | NSG Inbound Malicious Flows Allowed | AzureNetworkAnalytics_CL
\| where FlowType_s == "MaliciousFlow" and AllowedInFlows_d > 0
\| where TimeGenerated >= ago(24h)
\| count |
108 |
--------------------------------------------------------------------------------
/Sentinel-Analytics-Rules(KQL Alert Queries).json:
--------------------------------------------------------------------------------
1 | {
2 | "$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
3 | "contentVersion": "1.0.0.0",
4 | "parameters": {
5 | "workspace": {
6 | "type": "String"
7 | }
8 | },
9 | "resources": [
10 | {
11 | "id": "[concat(resourceId('Microsoft.OperationalInsights/workspaces/providers', parameters('workspace'), 'Microsoft.SecurityInsights'),'/alertRules/c220acf2-b8bb-436d-ad4f-7e3174bbf5a1')]",
12 | "name": "[concat(parameters('workspace'),'/Microsoft.SecurityInsights/c220acf2-b8bb-436d-ad4f-7e3174bbf5a1')]",
13 | "type": "Microsoft.OperationalInsights/workspaces/providers/alertRules",
14 | "kind": "Scheduled",
15 | "apiVersion": "2022-09-01-preview",
16 | "properties": {
17 | "displayName": "CUSTOM: Possible Privilege Escalation (Azure Key Vault Critical Credential Retrieval or Update)",
18 | "description": "",
19 | "severity": "High",
20 | "enabled": true,
21 | "query": "// Updating a specific existing password Success\nlet CRITICAL_PASSWORD_NAME = \"Tenant-Global-Admin-Password\";\nAzureDiagnostics\n| where ResourceProvider == \"MICROSOFT.KEYVAULT\" \n| where OperationName == \"SecretGet\" or OperationName == \"SecretSet\"\n| where id_s contains CRITICAL_PASSWORD_NAME",
22 | "queryFrequency": "PT10M",
23 | "queryPeriod": "PT5H",
24 | "triggerOperator": "GreaterThan",
25 | "triggerThreshold": 0,
26 | "suppressionDuration": "PT5H",
27 | "suppressionEnabled": false,
28 | "startTimeUtc": null,
29 | "tactics": [
30 | "PrivilegeEscalation"
31 | ],
32 | "techniques": [],
33 | "alertRuleTemplateName": null,
34 | "incidentConfiguration": {
35 | "createIncident": true,
36 | "groupingConfiguration": {
37 | "enabled": true,
38 | "reopenClosedIncident": false,
39 | "lookbackDuration": "PT5H",
40 | "matchingMethod": "AllEntities",
41 | "groupByEntities": [],
42 | "groupByAlertDetails": [],
43 | "groupByCustomDetails": []
44 | }
45 | },
46 | "eventGroupingSettings": {
47 | "aggregationKind": "SingleAlert"
48 | },
49 | "alertDetailsOverride": null,
50 | "customDetails": null,
51 | "entityMappings": [
52 | {
53 | "entityType": "IP",
54 | "fieldMappings": [
55 | {
56 | "identifier": "Address",
57 | "columnName": "CallerIPAddress"
58 | }
59 | ]
60 | }
61 | ],
62 | "sentinelEntitiesMappings": null,
63 | "templateVersion": null
64 | }
65 | },
66 | {
67 | "id": "[concat(resourceId('Microsoft.OperationalInsights/workspaces/providers', parameters('workspace'), 'Microsoft.SecurityInsights'),'/alertRules/dbab268c-6906-4e22-a632-8fe263025f2b')]",
68 | "name": "[concat(parameters('workspace'),'/Microsoft.SecurityInsights/dbab268c-6906-4e22-a632-8fe263025f2b')]",
69 | "type": "Microsoft.OperationalInsights/workspaces/providers/alertRules",
70 | "kind": "Scheduled",
71 | "apiVersion": "2022-09-01-preview",
72 | "properties": {
73 | "displayName": "CUSTOM: Brute Force SUCCESS - Linux Syslog",
74 | "description": "",
75 | "severity": "High",
76 | "enabled": true,
77 | "query": "// Brute Force Success Linux\nlet FailedLogons = Syslog\n| where Facility == \"auth\" and SyslogMessage startswith \"Failed password for\"\n| where TimeGenerated > ago(1h)\n| project TimeGenerated, SourceIP = extract(@\"\\b\\d{1,3}\\.\\d{1,3}\\.\\d{1,3}\\.\\d{1,3}\\b\", 0, SyslogMessage), DestinationHostName = HostName, DestinationIP = HostIP, Facility, SyslogMessage, ProcessName, SeverityLevel, Type\n| summarize FailureCount = count() by AttackerIP = SourceIP, DestinationHostName\n| where FailureCount >= 5;\nlet SuccessfulLogons = Syslog\n| where Facility == \"auth\" and SyslogMessage startswith \"Accepted password for\"\n| where TimeGenerated > ago(1h)\n| project TimeGenerated, SourceIP = extract(@\"\\b\\d{1,3}\\.\\d{1,3}\\.\\d{1,3}\\.\\d{1,3}\\b\", 0, SyslogMessage), DestinationHostName = HostName, DestinationIP = HostIP, Facility, SyslogMessage, ProcessName, SeverityLevel, Type\n| summarize SuccessfulCount = count() by SuccessTime = TimeGenerated, AttackerIP = SourceIP, DestinationHostName\n| where SuccessfulCount >= 1\n| project DestinationHostName, SuccessfulCount, AttackerIP, SuccessTime;\nlet BruteForceSuccesses = SuccessfulLogons \n| join kind = inner FailedLogons on AttackerIP, DestinationHostName;\nBruteForceSuccesses",
78 | "queryFrequency": "PT59M",
79 | "queryPeriod": "PT1H",
80 | "triggerOperator": "GreaterThan",
81 | "triggerThreshold": 0,
82 | "suppressionDuration": "PT5H",
83 | "suppressionEnabled": false,
84 | "startTimeUtc": null,
85 | "tactics": [
86 | "CredentialAccess"
87 | ],
88 | "techniques": [
89 | "T1110"
90 | ],
91 | "alertRuleTemplateName": null,
92 | "incidentConfiguration": {
93 | "createIncident": true,
94 | "groupingConfiguration": {
95 | "enabled": true,
96 | "reopenClosedIncident": false,
97 | "lookbackDuration": "PT1H",
98 | "matchingMethod": "AllEntities",
99 | "groupByEntities": [],
100 | "groupByAlertDetails": [],
101 | "groupByCustomDetails": []
102 | }
103 | },
104 | "eventGroupingSettings": {
105 | "aggregationKind": "AlertPerResult"
106 | },
107 | "alertDetailsOverride": null,
108 | "customDetails": null,
109 | "entityMappings": [
110 | {
111 | "entityType": "IP",
112 | "fieldMappings": [
113 | {
114 | "identifier": "Address",
115 | "columnName": "AttackerIP"
116 | }
117 | ]
118 | },
119 | {
120 | "entityType": "Host",
121 | "fieldMappings": [
122 | {
123 | "identifier": "HostName",
124 | "columnName": "DestinationHostName"
125 | }
126 | ]
127 | }
128 | ],
129 | "sentinelEntitiesMappings": null,
130 | "templateVersion": null
131 | }
132 | },
133 | {
134 | "id": "[concat(resourceId('Microsoft.OperationalInsights/workspaces/providers', parameters('workspace'), 'Microsoft.SecurityInsights'),'/alertRules/2ba75994-1fbe-4ec0-b312-015b47e10576')]",
135 | "name": "[concat(parameters('workspace'),'/Microsoft.SecurityInsights/2ba75994-1fbe-4ec0-b312-015b47e10576')]",
136 | "type": "Microsoft.OperationalInsights/workspaces/providers/alertRules",
137 | "kind": "Scheduled",
138 | "apiVersion": "2022-09-01-preview",
139 | "properties": {
140 | "displayName": "CUSTOM: Brute Force ATTEMPT - Azure Key Vault",
141 | "description": "",
142 | "severity": "Medium",
143 | "enabled": true,
144 | "query": "// Failed access attempts\nAzureDiagnostics\n| where ResourceProvider == \"MICROSOFT.KEYVAULT\" \n| where ResultSignature == \"Forbidden\"\n\n",
145 | "queryFrequency": "PT10M",
146 | "queryPeriod": "PT5H",
147 | "triggerOperator": "GreaterThan",
148 | "triggerThreshold": 9,
149 | "suppressionDuration": "PT5H",
150 | "suppressionEnabled": false,
151 | "startTimeUtc": null,
152 | "tactics": [
153 | "CredentialAccess"
154 | ],
155 | "techniques": [
156 | "T1110"
157 | ],
158 | "alertRuleTemplateName": null,
159 | "incidentConfiguration": {
160 | "createIncident": true,
161 | "groupingConfiguration": {
162 | "enabled": true,
163 | "reopenClosedIncident": false,
164 | "lookbackDuration": "PT5H",
165 | "matchingMethod": "AllEntities",
166 | "groupByEntities": [],
167 | "groupByAlertDetails": [],
168 | "groupByCustomDetails": []
169 | }
170 | },
171 | "eventGroupingSettings": {
172 | "aggregationKind": "SingleAlert"
173 | },
174 | "alertDetailsOverride": null,
175 | "customDetails": null,
176 | "entityMappings": [
177 | {
178 | "entityType": "IP",
179 | "fieldMappings": [
180 | {
181 | "identifier": "Address",
182 | "columnName": "CallerIPAddress"
183 | }
184 | ]
185 | }
186 | ],
187 | "sentinelEntitiesMappings": null,
188 | "templateVersion": null
189 | }
190 | },
191 | {
192 | "id": "[concat(resourceId('Microsoft.OperationalInsights/workspaces/providers', parameters('workspace'), 'Microsoft.SecurityInsights'),'/alertRules/e5450d35-8fd2-47a8-b9cf-e8081d798e8b')]",
193 | "name": "[concat(parameters('workspace'),'/Microsoft.SecurityInsights/e5450d35-8fd2-47a8-b9cf-e8081d798e8b')]",
194 | "type": "Microsoft.OperationalInsights/workspaces/providers/alertRules",
195 | "kind": "Scheduled",
196 | "apiVersion": "2022-09-01-preview",
197 | "properties": {
198 | "displayName": "CUSTOM: Malware Detected",
199 | "description": "",
200 | "severity": "High",
201 | "enabled": true,
202 | "query": "Event\n| where EventLog == \"Microsoft-Windows-Windows Defender/Operational\"\n| where EventID == \"1116\" or EventID == \"1117\"",
203 | "queryFrequency": "PT10M",
204 | "queryPeriod": "PT1H",
205 | "triggerOperator": "GreaterThan",
206 | "triggerThreshold": 0,
207 | "suppressionDuration": "PT5H",
208 | "suppressionEnabled": false,
209 | "startTimeUtc": null,
210 | "tactics": [],
211 | "techniques": [],
212 | "alertRuleTemplateName": null,
213 | "incidentConfiguration": {
214 | "createIncident": true,
215 | "groupingConfiguration": {
216 | "enabled": true,
217 | "reopenClosedIncident": false,
218 | "lookbackDuration": "PT5H",
219 | "matchingMethod": "AllEntities",
220 | "groupByEntities": [],
221 | "groupByAlertDetails": [],
222 | "groupByCustomDetails": []
223 | }
224 | },
225 | "eventGroupingSettings": {
226 | "aggregationKind": "SingleAlert"
227 | },
228 | "alertDetailsOverride": null,
229 | "customDetails": null,
230 | "entityMappings": [
231 | {
232 | "entityType": "Host",
233 | "fieldMappings": [
234 | {
235 | "identifier": "HostName",
236 | "columnName": "Computer"
237 | }
238 | ]
239 | }
240 | ],
241 | "sentinelEntitiesMappings": null,
242 | "templateVersion": null
243 | }
244 | },
245 | {
246 | "id": "[concat(resourceId('Microsoft.OperationalInsights/workspaces/providers', parameters('workspace'), 'Microsoft.SecurityInsights'),'/alertRules/5b3b873a-3204-4983-9533-88b4a9c71c2d')]",
247 | "name": "[concat(parameters('workspace'),'/Microsoft.SecurityInsights/5b3b873a-3204-4983-9533-88b4a9c71c2d')]",
248 | "type": "Microsoft.OperationalInsights/workspaces/providers/alertRules",
249 | "kind": "Scheduled",
250 | "apiVersion": "2022-09-01-preview",
251 | "properties": {
252 | "displayName": "CUSTOM: Brute Force SUCCESS - Windows",
253 | "description": "If you see a SUCCESS but the Account is \"NT AUTHORITY\\ANONYMOUS LOGON\", check out this article: https://www.inversecos.com/2020/04/successful-4624-anonymous-logons-to.html",
254 | "severity": "High",
255 | "enabled": true,
256 | "query": "// Brute Force Success Windows\nlet FailedLogons = SecurityEvent\n| where EventID == 4625 and LogonType == 3\n| where TimeGenerated > ago(1h)\n| summarize FailureCount = count() by AttackerIP = IpAddress, EventID, Activity, LogonType, DestinationHostName = Computer\n| where FailureCount >= 5;\nlet SuccessfulLogons = SecurityEvent\n| where EventID == 4624 and LogonType == 3\n| where TimeGenerated > ago(1h)\n| summarize SuccessfulCount = count() by AttackerIP = IpAddress, LogonType, DestinationHostName = Computer, AuthenticationSuccessTime = TimeGenerated;\nSuccessfulLogons\n| join kind = inner FailedLogons on DestinationHostName, AttackerIP, LogonType\n| project AuthenticationSuccessTime, AttackerIP, DestinationHostName, FailureCount, SuccessfulCount\n",
257 | "queryFrequency": "PT59M",
258 | "queryPeriod": "PT1H",
259 | "triggerOperator": "GreaterThan",
260 | "triggerThreshold": 0,
261 | "suppressionDuration": "PT5H",
262 | "suppressionEnabled": false,
263 | "startTimeUtc": null,
264 | "tactics": [
265 | "CredentialAccess"
266 | ],
267 | "techniques": [
268 | "T1110"
269 | ],
270 | "alertRuleTemplateName": null,
271 | "incidentConfiguration": {
272 | "createIncident": true,
273 | "groupingConfiguration": {
274 | "enabled": true,
275 | "reopenClosedIncident": false,
276 | "lookbackDuration": "PT1H",
277 | "matchingMethod": "AllEntities",
278 | "groupByEntities": [],
279 | "groupByAlertDetails": [],
280 | "groupByCustomDetails": []
281 | }
282 | },
283 | "eventGroupingSettings": {
284 | "aggregationKind": "AlertPerResult"
285 | },
286 | "alertDetailsOverride": null,
287 | "customDetails": null,
288 | "entityMappings": [
289 | {
290 | "entityType": "IP",
291 | "fieldMappings": [
292 | {
293 | "identifier": "Address",
294 | "columnName": "AttackerIP"
295 | }
296 | ]
297 | },
298 | {
299 | "entityType": "Host",
300 | "fieldMappings": [
301 | {
302 | "identifier": "HostName",
303 | "columnName": "DestinationHostName"
304 | }
305 | ]
306 | }
307 | ],
308 | "sentinelEntitiesMappings": null,
309 | "templateVersion": null
310 | }
311 | },
312 | {
313 | "id": "[concat(resourceId('Microsoft.OperationalInsights/workspaces/providers', parameters('workspace'), 'Microsoft.SecurityInsights'),'/alertRules/c18a784d-5d2e-47bd-8203-bd4cc09b03d2')]",
314 | "name": "[concat(parameters('workspace'),'/Microsoft.SecurityInsights/c18a784d-5d2e-47bd-8203-bd4cc09b03d2')]",
315 | "type": "Microsoft.OperationalInsights/workspaces/providers/alertRules",
316 | "kind": "Scheduled",
317 | "apiVersion": "2022-09-01-preview",
318 | "properties": {
319 | "displayName": "CUSTOM: Brute Force ATTEMPT - MS SQL Server",
320 | "description": "",
321 | "severity": "Medium",
322 | "enabled": true,
323 | "query": "// Brute Force Attempt MS SQL Server\nlet IpAddress_REGEX_PATTERN = @\"\\b\\d{1,3}\\.\\d{1,3}\\.\\d{1,3}\\.\\d{1,3}\\b\";\nEvent\n| where EventLog == \"Application\"\n| where EventID == 18456\n| where TimeGenerated > ago(1hr)\n| project TimeGenerated, AttackerIP = extract(IpAddress_REGEX_PATTERN, 0, RenderedDescription), DestinationHostName = Computer, RenderedDescription\n| summarize FailureCount = count() by AttackerIP, DestinationHostName\n| where FailureCount >= 10",
324 | "queryFrequency": "PT10M",
325 | "queryPeriod": "PT1H",
326 | "triggerOperator": "GreaterThan",
327 | "triggerThreshold": 0,
328 | "suppressionDuration": "PT5H",
329 | "suppressionEnabled": false,
330 | "startTimeUtc": null,
331 | "tactics": [
332 | "CredentialAccess"
333 | ],
334 | "techniques": [
335 | "T1110"
336 | ],
337 | "alertRuleTemplateName": null,
338 | "incidentConfiguration": {
339 | "createIncident": true,
340 | "groupingConfiguration": {
341 | "enabled": true,
342 | "reopenClosedIncident": false,
343 | "lookbackDuration": "PT5H",
344 | "matchingMethod": "AllEntities",
345 | "groupByEntities": [],
346 | "groupByAlertDetails": [],
347 | "groupByCustomDetails": []
348 | }
349 | },
350 | "eventGroupingSettings": {
351 | "aggregationKind": "SingleAlert"
352 | },
353 | "alertDetailsOverride": null,
354 | "customDetails": null,
355 | "entityMappings": [
356 | {
357 | "entityType": "Host",
358 | "fieldMappings": [
359 | {
360 | "identifier": "HostName",
361 | "columnName": "DestinationHostName"
362 | }
363 | ]
364 | },
365 | {
366 | "entityType": "IP",
367 | "fieldMappings": [
368 | {
369 | "identifier": "Address",
370 | "columnName": "AttackerIP"
371 | }
372 | ]
373 | }
374 | ],
375 | "sentinelEntitiesMappings": null,
376 | "templateVersion": null
377 | }
378 | },
379 | {
380 | "id": "[concat(resourceId('Microsoft.OperationalInsights/workspaces/providers', parameters('workspace'), 'Microsoft.SecurityInsights'),'/alertRules/d333ea31-4077-48a4-ad0e-c43909edde93')]",
381 | "name": "[concat(parameters('workspace'),'/Microsoft.SecurityInsights/d333ea31-4077-48a4-ad0e-c43909edde93')]",
382 | "type": "Microsoft.OperationalInsights/workspaces/providers/alertRules",
383 | "kind": "Scheduled",
384 | "apiVersion": "2022-09-01-preview",
385 | "properties": {
386 | "displayName": "CUSTOM: Possible Privilege Escallation (Global Administrator Role Assignment)",
387 | "description": "",
388 | "severity": "High",
389 | "enabled": true,
390 | "query": "AuditLogs\n| where OperationName == \"Add member to role\" and Result == \"success\"\n| where TargetResources[0].modifiedProperties[1].newValue == '\"Global Administrator\"' or TargetResources[0].modifiedProperties[1].newValue == '\"Company Administrator\"' and TargetResources[0].type == \"User\"\n| where TimeGenerated > ago(60m)\n| project\n TimeGenerated,\n OperationName,\n AssignedRole = TargetResources[0].modifiedProperties[1].newValue,\n Status = Result,\n TargetResources,\n InitiatorID = InitiatedBy[\"user\"][\"id\"],\n TargetID = TargetResources[0][\"id\"]",
391 | "queryFrequency": "PT5M",
392 | "queryPeriod": "PT1H",
393 | "triggerOperator": "GreaterThan",
394 | "triggerThreshold": 0,
395 | "suppressionDuration": "PT5H",
396 | "suppressionEnabled": false,
397 | "startTimeUtc": null,
398 | "tactics": [
399 | "PrivilegeEscalation"
400 | ],
401 | "techniques": [],
402 | "alertRuleTemplateName": null,
403 | "incidentConfiguration": {
404 | "createIncident": true,
405 | "groupingConfiguration": {
406 | "enabled": true,
407 | "reopenClosedIncident": false,
408 | "lookbackDuration": "PT5H",
409 | "matchingMethod": "AllEntities",
410 | "groupByEntities": [],
411 | "groupByAlertDetails": [],
412 | "groupByCustomDetails": []
413 | }
414 | },
415 | "eventGroupingSettings": {
416 | "aggregationKind": "SingleAlert"
417 | },
418 | "alertDetailsOverride": null,
419 | "customDetails": null,
420 | "entityMappings": [
421 | {
422 | "entityType": "Account",
423 | "fieldMappings": [
424 | {
425 | "identifier": "AadUserId",
426 | "columnName": "InitiatorID"
427 | }
428 | ]
429 | },
430 | {
431 | "entityType": "Account",
432 | "fieldMappings": [
433 | {
434 | "identifier": "AadUserId",
435 | "columnName": "TargetID"
436 | }
437 | ]
438 | }
439 | ],
440 | "sentinelEntitiesMappings": null,
441 | "templateVersion": null
442 | }
443 | },
444 | {
445 | "id": "[concat(resourceId('Microsoft.OperationalInsights/workspaces/providers', parameters('workspace'), 'Microsoft.SecurityInsights'),'/alertRules/4891fd6a-75e3-4b43-a5ae-33dbaaf2342e')]",
446 | "name": "[concat(parameters('workspace'),'/Microsoft.SecurityInsights/4891fd6a-75e3-4b43-a5ae-33dbaaf2342e')]",
447 | "type": "Microsoft.OperationalInsights/workspaces/providers/alertRules",
448 | "kind": "Scheduled",
449 | "apiVersion": "2022-09-01-preview",
450 | "properties": {
451 | "displayName": "CUSTOM: Brute Force ATTEMPT - Azure Active Directory",
452 | "description": "",
453 | "severity": "Medium",
454 | "enabled": true,
455 | "query": "SigninLogs\n| where ResultDescription == \"Invalid username or password or Invalid on-premise username or password.\"\n| project TimeGenerated, ResultDescription, UserPrincipalName, UserId, AppDisplayName, IPAddress, IPAddressFromResourceProvider, City = LocationDetails.city, State = LocationDetails.state, Country = LocationDetails.country, Latitude = LocationDetails.geoCoordinates.latitude, Longitude = LocationDetails.geoCoordinates.longitude",
456 | "queryFrequency": "PT10M",
457 | "queryPeriod": "PT1H",
458 | "triggerOperator": "GreaterThan",
459 | "triggerThreshold": 9,
460 | "suppressionDuration": "PT5H",
461 | "suppressionEnabled": false,
462 | "startTimeUtc": null,
463 | "tactics": [
464 | "CredentialAccess"
465 | ],
466 | "techniques": [
467 | "T1110"
468 | ],
469 | "alertRuleTemplateName": null,
470 | "incidentConfiguration": {
471 | "createIncident": true,
472 | "groupingConfiguration": {
473 | "enabled": true,
474 | "reopenClosedIncident": false,
475 | "lookbackDuration": "PT1H",
476 | "matchingMethod": "AllEntities",
477 | "groupByEntities": [],
478 | "groupByAlertDetails": [],
479 | "groupByCustomDetails": []
480 | }
481 | },
482 | "eventGroupingSettings": {
483 | "aggregationKind": "SingleAlert"
484 | },
485 | "alertDetailsOverride": null,
486 | "customDetails": null,
487 | "entityMappings": [
488 | {
489 | "entityType": "Account",
490 | "fieldMappings": [
491 | {
492 | "identifier": "AadUserId",
493 | "columnName": "UserId"
494 | }
495 | ]
496 | },
497 | {
498 | "entityType": "IP",
499 | "fieldMappings": [
500 | {
501 | "identifier": "Address",
502 | "columnName": "IPAddress"
503 | }
504 | ]
505 | }
506 | ],
507 | "sentinelEntitiesMappings": null,
508 | "templateVersion": null
509 | }
510 | },
511 | {
512 | "id": "[concat(resourceId('Microsoft.OperationalInsights/workspaces/providers', parameters('workspace'), 'Microsoft.SecurityInsights'),'/alertRules/b1cafe38-aa17-49a4-ac62-99198caeb3fb')]",
513 | "name": "[concat(parameters('workspace'),'/Microsoft.SecurityInsights/b1cafe38-aa17-49a4-ac62-99198caeb3fb')]",
514 | "type": "Microsoft.OperationalInsights/workspaces/providers/alertRules",
515 | "kind": "Scheduled",
516 | "apiVersion": "2022-09-01-preview",
517 | "properties": {
518 | "displayName": "CUSTOM: Possible Lateral Movement (Excessive Password Resets)",
519 | "description": "",
520 | "severity": "Medium",
521 | "enabled": true,
522 | "query": "AuditLogs\n| where OperationName startswith \"Change\" or OperationName startswith \"Reset\"\n| order by TimeGenerated\n| summarize count() by tostring(InitiatedBy)\n| project Count = count_, InitiatorId = parse_json(InitiatedBy).user.id, InitiatorUpn = parse_json(InitiatedBy).user.userPrincipalName, InitiatorIpAddress = parse_json(InitiatedBy).user.ipAddress \n| where Count >= 10\n",
523 | "queryFrequency": "PT5M",
524 | "queryPeriod": "PT5H",
525 | "triggerOperator": "GreaterThan",
526 | "triggerThreshold": 0,
527 | "suppressionDuration": "PT5H",
528 | "suppressionEnabled": false,
529 | "startTimeUtc": null,
530 | "tactics": [
531 | "CredentialAccess",
532 | "PrivilegeEscalation"
533 | ],
534 | "techniques": [
535 | "T1555",
536 | "T1078"
537 | ],
538 | "alertRuleTemplateName": null,
539 | "incidentConfiguration": {
540 | "createIncident": true,
541 | "groupingConfiguration": {
542 | "enabled": true,
543 | "reopenClosedIncident": false,
544 | "lookbackDuration": "PT1H",
545 | "matchingMethod": "AllEntities",
546 | "groupByEntities": [],
547 | "groupByAlertDetails": [],
548 | "groupByCustomDetails": []
549 | }
550 | },
551 | "eventGroupingSettings": {
552 | "aggregationKind": "SingleAlert"
553 | },
554 | "alertDetailsOverride": null,
555 | "customDetails": null,
556 | "entityMappings": [
557 | {
558 | "entityType": "Account",
559 | "fieldMappings": [
560 | {
561 | "identifier": "AadUserId",
562 | "columnName": "InitiatorId"
563 | }
564 | ]
565 | },
566 | {
567 | "entityType": "IP",
568 | "fieldMappings": [
569 | {
570 | "identifier": "Address",
571 | "columnName": "InitiatorIpAddress"
572 | }
573 | ]
574 | }
575 | ],
576 | "sentinelEntitiesMappings": null,
577 | "templateVersion": null
578 | }
579 | },
580 | {
581 | "id": "[concat(resourceId('Microsoft.OperationalInsights/workspaces/providers', parameters('workspace'), 'Microsoft.SecurityInsights'),'/alertRules/cf0df627-c9ba-4fa7-858d-265cd5cd3548')]",
582 | "name": "[concat(parameters('workspace'),'/Microsoft.SecurityInsights/cf0df627-c9ba-4fa7-858d-265cd5cd3548')]",
583 | "type": "Microsoft.OperationalInsights/workspaces/providers/alertRules",
584 | "kind": "Scheduled",
585 | "apiVersion": "2022-09-01-preview",
586 | "properties": {
587 | "displayName": "CUSTOM: Brute Force ATTEMPT - Linux Syslog",
588 | "description": "",
589 | "severity": "Medium",
590 | "enabled": true,
591 | "query": "// Brute Force Success Linux\nlet IpAddress_REGEX_PATTERN = @\"\\b\\d{1,3}\\.\\d{1,3}\\.\\d{1,3}\\.\\d{1,3}\\b\";\nSyslog\n| where Facility == \"auth\" and SyslogMessage startswith \"Failed password for\"\n| where TimeGenerated > ago(1h)\n| project TimeGenerated, AttackerIP = extract(IpAddress_REGEX_PATTERN, 0, SyslogMessage), DestinationHostName = HostName, DestinationIP = HostIP, Facility, SyslogMessage, ProcessName, SeverityLevel, Type\n| summarize FailureCount = count() by AttackerIP, DestinationHostName, DestinationIP\n| where FailureCount >= 10",
592 | "queryFrequency": "PT10M",
593 | "queryPeriod": "PT1H",
594 | "triggerOperator": "GreaterThan",
595 | "triggerThreshold": 0,
596 | "suppressionDuration": "PT5H",
597 | "suppressionEnabled": false,
598 | "startTimeUtc": null,
599 | "tactics": [
600 | "CredentialAccess"
601 | ],
602 | "techniques": [
603 | "T1110"
604 | ],
605 | "alertRuleTemplateName": null,
606 | "incidentConfiguration": {
607 | "createIncident": true,
608 | "groupingConfiguration": {
609 | "enabled": true,
610 | "reopenClosedIncident": false,
611 | "lookbackDuration": "PT5H",
612 | "matchingMethod": "AllEntities",
613 | "groupByEntities": [],
614 | "groupByAlertDetails": [],
615 | "groupByCustomDetails": []
616 | }
617 | },
618 | "eventGroupingSettings": {
619 | "aggregationKind": "SingleAlert"
620 | },
621 | "alertDetailsOverride": null,
622 | "customDetails": null,
623 | "entityMappings": [
624 | {
625 | "entityType": "Host",
626 | "fieldMappings": [
627 | {
628 | "identifier": "HostName",
629 | "columnName": "DestinationHostName"
630 | }
631 | ]
632 | },
633 | {
634 | "entityType": "IP",
635 | "fieldMappings": [
636 | {
637 | "identifier": "Address",
638 | "columnName": "AttackerIP"
639 | }
640 | ]
641 | }
642 | ],
643 | "sentinelEntitiesMappings": null,
644 | "templateVersion": null
645 | }
646 | },
647 | {
648 | "id": "[concat(resourceId('Microsoft.OperationalInsights/workspaces/providers', parameters('workspace'), 'Microsoft.SecurityInsights'),'/alertRules/c6099513-e6c6-492f-b81a-a66d14d84445')]",
649 | "name": "[concat(parameters('workspace'),'/Microsoft.SecurityInsights/c6099513-e6c6-492f-b81a-a66d14d84445')]",
650 | "type": "Microsoft.OperationalInsights/workspaces/providers/alertRules",
651 | "kind": "Scheduled",
652 | "apiVersion": "2022-09-01-preview",
653 | "properties": {
654 | "displayName": "CUSTOM: Windows Host Firewall Tampering",
655 | "description": "",
656 | "severity": "High",
657 | "enabled": true,
658 | "query": "Event\n| where EventLog == \"Microsoft-Windows-Windows Firewall With Advanced Security/Firewall\"\n| where EventID == 2003",
659 | "queryFrequency": "PT10M",
660 | "queryPeriod": "PT1H",
661 | "triggerOperator": "GreaterThan",
662 | "triggerThreshold": 0,
663 | "suppressionDuration": "PT5H",
664 | "suppressionEnabled": false,
665 | "startTimeUtc": null,
666 | "tactics": [
667 | "DefenseEvasion"
668 | ],
669 | "techniques": [],
670 | "alertRuleTemplateName": null,
671 | "incidentConfiguration": {
672 | "createIncident": true,
673 | "groupingConfiguration": {
674 | "enabled": true,
675 | "reopenClosedIncident": false,
676 | "lookbackDuration": "PT5H",
677 | "matchingMethod": "AllEntities",
678 | "groupByEntities": [],
679 | "groupByAlertDetails": [],
680 | "groupByCustomDetails": []
681 | }
682 | },
683 | "eventGroupingSettings": {
684 | "aggregationKind": "SingleAlert"
685 | },
686 | "alertDetailsOverride": null,
687 | "customDetails": null,
688 | "entityMappings": [
689 | {
690 | "entityType": "Host",
691 | "fieldMappings": [
692 | {
693 | "identifier": "HostName",
694 | "columnName": "Computer"
695 | }
696 | ]
697 | }
698 | ],
699 | "sentinelEntitiesMappings": null,
700 | "templateVersion": null
701 | }
702 | },
703 | {
704 | "id": "[concat(resourceId('Microsoft.OperationalInsights/workspaces/providers', parameters('workspace'), 'Microsoft.SecurityInsights'),'/alertRules/afe7b0a7-d84f-462d-b751-548861bc0c5d')]",
705 | "name": "[concat(parameters('workspace'),'/Microsoft.SecurityInsights/afe7b0a7-d84f-462d-b751-548861bc0c5d')]",
706 | "type": "Microsoft.OperationalInsights/workspaces/providers/alertRules",
707 | "kind": "Scheduled",
708 | "apiVersion": "2022-09-01-preview",
709 | "properties": {
710 | "displayName": "CUSTOM: Brute Force ATTEMPT - Windows",
711 | "description": "",
712 | "severity": "Medium",
713 | "enabled": true,
714 | "query": "// Failed logon \nSecurityEvent\n| where EventID == 4625\n| where TimeGenerated > ago(60m)\n| summarize FailureCount = count() by AttackerIP = IpAddress, EventID, Activity, DestinationHostName = Computer\n| where FailureCount >= 10",
715 | "queryFrequency": "PT15M",
716 | "queryPeriod": "PT1H",
717 | "triggerOperator": "GreaterThan",
718 | "triggerThreshold": 0,
719 | "suppressionDuration": "PT5H",
720 | "suppressionEnabled": false,
721 | "startTimeUtc": null,
722 | "tactics": [
723 | "CredentialAccess"
724 | ],
725 | "techniques": [
726 | "T1110"
727 | ],
728 | "alertRuleTemplateName": null,
729 | "incidentConfiguration": {
730 | "createIncident": true,
731 | "groupingConfiguration": {
732 | "enabled": true,
733 | "reopenClosedIncident": false,
734 | "lookbackDuration": "PT5H",
735 | "matchingMethod": "AllEntities",
736 | "groupByEntities": [],
737 | "groupByAlertDetails": [],
738 | "groupByCustomDetails": []
739 | }
740 | },
741 | "eventGroupingSettings": {
742 | "aggregationKind": "SingleAlert"
743 | },
744 | "alertDetailsOverride": null,
745 | "customDetails": null,
746 | "entityMappings": [
747 | {
748 | "entityType": "IP",
749 | "fieldMappings": [
750 | {
751 | "identifier": "Address",
752 | "columnName": "AttackerIP"
753 | }
754 | ]
755 | },
756 | {
757 | "entityType": "Host",
758 | "fieldMappings": [
759 | {
760 | "identifier": "HostName",
761 | "columnName": "DestinationHostName"
762 | }
763 | ]
764 | }
765 | ],
766 | "sentinelEntitiesMappings": null,
767 | "templateVersion": null
768 | }
769 | },
770 | {
771 | "id": "[concat(resourceId('Microsoft.OperationalInsights/workspaces/providers', parameters('workspace'), 'Microsoft.SecurityInsights'),'/alertRules/e95fd1bb-b03a-4046-843b-1453a0a95482')]",
772 | "name": "[concat(parameters('workspace'),'/Microsoft.SecurityInsights/e95fd1bb-b03a-4046-843b-1453a0a95482')]",
773 | "type": "Microsoft.OperationalInsights/workspaces/providers/alertRules",
774 | "kind": "Scheduled",
775 | "apiVersion": "2022-09-01-preview",
776 | "properties": {
777 | "displayName": "CUSTOM: Brute Force SUCCESS - Azure Active Directory",
778 | "description": "",
779 | "severity": "High",
780 | "enabled": true,
781 | "query": "// Failed AAD logon\nlet FailedLogons = SigninLogs\n| where Status.failureReason == \"Invalid username or password or Invalid on-premise username or password.\"\n| where TimeGenerated > ago(1h)\n| project TimeGenerated, Status = Status.failureReason, UserPrincipalName, UserId, UserDisplayName, AppDisplayName, AttackerIP = IPAddress, IPAddressFromResourceProvider, City = LocationDetails.city, State = LocationDetails.state, Country = LocationDetails.country, Latitude = LocationDetails.geoCoordinates.latitude, Longitude = LocationDetails.geoCoordinates.longitude\n| summarize FailureCount = count() by AttackerIP, UserPrincipalName;\nlet SuccessfulLogons = SigninLogs\n| where Status.errorCode == 0 \n| where TimeGenerated > ago(1h)\n| project TimeGenerated, Status = Status.errorCode, UserPrincipalName, UserId, UserDisplayName, AppDisplayName, AttackerIP = IPAddress, IPAddressFromResourceProvider, City = LocationDetails.city, State = LocationDetails.state, Country = LocationDetails.country, Latitude = LocationDetails.geoCoordinates.latitude, Longitude = LocationDetails.geoCoordinates.longitude\n| summarize SuccessCount = count() by AuthenticationSuccessTime = TimeGenerated, AttackerIP, UserPrincipalName, UserId, UserDisplayName;\nlet BruteForceSuccesses = SuccessfulLogons\n| join kind = inner FailedLogons on AttackerIP, UserPrincipalName;\nBruteForceSuccesses\n| project AttackerIP, TargetAccount = UserPrincipalName, UserId, FailureCount, SuccessCount, AuthenticationSuccessTime",
782 | "queryFrequency": "PT5M",
783 | "queryPeriod": "PT5H",
784 | "triggerOperator": "GreaterThan",
785 | "triggerThreshold": 0,
786 | "suppressionDuration": "PT5H",
787 | "suppressionEnabled": false,
788 | "startTimeUtc": null,
789 | "tactics": [],
790 | "techniques": [],
791 | "alertRuleTemplateName": null,
792 | "incidentConfiguration": {
793 | "createIncident": true,
794 | "groupingConfiguration": {
795 | "enabled": true,
796 | "reopenClosedIncident": false,
797 | "lookbackDuration": "PT5H",
798 | "matchingMethod": "AllEntities",
799 | "groupByEntities": [],
800 | "groupByAlertDetails": [],
801 | "groupByCustomDetails": []
802 | }
803 | },
804 | "eventGroupingSettings": {
805 | "aggregationKind": "AlertPerResult"
806 | },
807 | "alertDetailsOverride": null,
808 | "customDetails": null,
809 | "entityMappings": [
810 | {
811 | "entityType": "IP",
812 | "fieldMappings": [
813 | {
814 | "identifier": "Address",
815 | "columnName": "AttackerIP"
816 | }
817 | ]
818 | },
819 | {
820 | "entityType": "Account",
821 | "fieldMappings": [
822 | {
823 | "identifier": "AadUserId",
824 | "columnName": "UserId"
825 | }
826 | ]
827 | }
828 | ],
829 | "sentinelEntitiesMappings": null,
830 | "templateVersion": null
831 | }
832 | }
833 | ]
834 | }
--------------------------------------------------------------------------------