| Hostname | 12 |Status | 13 |IP | 14 |Owner | 15 |Description | 16 |Up | 17 |Down | 18 ||
|---|---|---|---|---|---|---|---|
| {{ .Hostname }} | 28 | 29 | {{ if .Online }} 30 |online | 31 | 32 | {{ else }} 33 |offline | 34 | 35 | {{ end }} 36 | 37 | 38 |{{ .IP }} | 39 |{{ .Owner }} | 40 |{{ .Description }} | 41 |{{ .ReceiveBytesSI }} | 42 |{{ .TransmitBytesSI }} | 43 |
50 |
51 | /etc/dsnetreport.json not found or empty
52 |
53 |
54 | {{ end }}
55 |
--------------------------------------------------------------------------------
/lib/lib.go:
--------------------------------------------------------------------------------
1 | package lib
2 |
3 | import (
4 | "fmt"
5 |
6 | "golang.zx2c4.com/wireguard/wgctrl"
7 | "golang.zx2c4.com/wireguard/wgctrl/wgtypes"
8 | )
9 |
10 | func (s *Server) Up() error {
11 | if err := s.CreateLink(); err != nil {
12 | return err
13 | }
14 | return s.ConfigureDevice()
15 | }
16 |
17 | // ConfigureDevice sets up the WG interface
18 | func (s *Server) ConfigureDevice() error {
19 | wg, err := wgctrl.New()
20 | if err != nil {
21 | return err
22 | }
23 | defer wg.Close()
24 |
25 | dev, err := wg.Device(s.InterfaceName)
26 |
27 | if err != nil {
28 | return fmt.Errorf("could not retrieve device '%s' (%v)", s.InterfaceName, err)
29 | }
30 |
31 | peers := s.GetPeers()
32 |
33 | // compare peers to see if any exist on the device and not the config. If
34 | // so, they should be removed by appending a dummy peer with Remove:true + pubkey.
35 | knownKeys := make(map[wgtypes.Key]bool)
36 |
37 | for _, peer := range peers {
38 | knownKeys[peer.PublicKey] = true
39 | }
40 |
41 | // find deleted peers, and append dummy "remove" peers
42 | for _, peer := range dev.Peers {
43 | if !knownKeys[peer.PublicKey] {
44 | peers = append(peers, wgtypes.PeerConfig{
45 | PublicKey: peer.PublicKey,
46 | Remove: true,
47 | })
48 | }
49 | }
50 |
51 | wgConfig := wgtypes.Config{
52 | PrivateKey: &s.PrivateKey.Key,
53 | ListenPort: &s.ListenPort,
54 | // ReplacePeers with the same peers results in those peers losing
55 | // connection, so it's not possible to do declarative configuration
56 | // idempotently with ReplacePeers like I had assumed. Instead, peers
57 | // must be removed imperatively with Remove:true. Peers can still be
58 | // added/updated with ConfigureDevice declaratively.
59 | ReplacePeers: false,
60 | Peers: peers,
61 | }
62 |
63 | err = wg.ConfigureDevice(s.InterfaceName, wgConfig)
64 |
65 | if err != nil {
66 | return fmt.Errorf("could not configure device '%s' (%v)", s.InterfaceName, err)
67 | }
68 | return nil
69 | }
70 |
--------------------------------------------------------------------------------
/cmd/cli/regenerate.go:
--------------------------------------------------------------------------------
1 | package cli
2 |
3 | import (
4 | "fmt"
5 | "os"
6 |
7 | "github.com/naggie/dsnet/lib"
8 | "github.com/spf13/viper"
9 | )
10 |
11 | func Regenerate(hostname string, confirm bool) error {
12 | config, err := LoadConfigFile()
13 | if err != nil {
14 | return fmt.Errorf("%w - failure to load config file", err)
15 | }
16 | server := GetServer(config)
17 |
18 | found := false
19 |
20 | if !confirm {
21 | ConfirmOrAbort("This will invalidate current configuration. Regenerate config for %s?", hostname)
22 | }
23 |
24 | for _, peer := range server.Peers {
25 | if peer.Hostname == hostname {
26 | privateKey, err := lib.GenerateJSONPrivateKey()
27 | if err != nil {
28 | return fmt.Errorf("%w - failed to generate private key", err)
29 | }
30 |
31 | preshareKey, err := lib.GenerateJSONKey()
32 | if err != nil {
33 | return fmt.Errorf("%w - failed to generate preshared key", err)
34 | }
35 |
36 | peer.PrivateKey = privateKey
37 | peer.PublicKey = privateKey.PublicKey()
38 | peer.PresharedKey = preshareKey
39 |
40 | err = config.RemovePeer(hostname)
41 | if err != nil {
42 | return fmt.Errorf("%w - failed to regenerate peer", err)
43 | }
44 |
45 | peerType := viper.GetString("output")
46 |
47 | peerConfigBytes, err := lib.AsciiPeerConfig(peer, peerType, *server)
48 | if err != nil {
49 | return fmt.Errorf("%w - failed to get peer configuration", err)
50 | }
51 | os.Stdout.Write(peerConfigBytes.Bytes())
52 | found = true
53 | if err = config.AddPeer(peer); err != nil {
54 | return fmt.Errorf("%w - failure to add peer", err)
55 | }
56 |
57 | break
58 | }
59 | }
60 |
61 | if !found {
62 | return fmt.Errorf("unknown hostname: %s", hostname)
63 | }
64 |
65 | // Get a new server configuration so we can update the wg interface with the new peer details
66 | server = GetServer(config)
67 | if err = config.Save(); err != nil {
68 | return fmt.Errorf("%w - failure saving config", err)
69 | }
70 | server.ConfigureDevice()
71 | return nil
72 | }
73 |
--------------------------------------------------------------------------------
/cmd/cli/util.go:
--------------------------------------------------------------------------------
1 | package cli
2 |
3 | // FIXME every function in this file has public scope, but only private references
4 |
5 | import (
6 | "bufio"
7 | "fmt"
8 | "os"
9 | "strings"
10 |
11 | "github.com/naggie/dsnet/lib"
12 | )
13 |
14 | func jsonPeerToDsnetPeer(peers []PeerConfig) []lib.Peer {
15 | libPeers := make([]lib.Peer, 0, len(peers))
16 | for _, p := range peers {
17 | libPeers = append(libPeers, lib.Peer{
18 | Hostname: p.Hostname,
19 | Owner: p.Owner,
20 | Description: p.Description,
21 | IP: p.IP,
22 | IP6: p.IP6,
23 | Added: p.Added,
24 | PublicKey: p.PublicKey,
25 | PrivateKey: p.PrivateKey,
26 | PresharedKey: p.PresharedKey,
27 | Networks: p.Networks,
28 | })
29 | }
30 | return libPeers
31 | }
32 |
33 | func PromptString(prompt string, required bool) (string, error) {
34 | reader := bufio.NewReader(os.Stdin)
35 | var text string
36 | var err error
37 |
38 | for text == "" {
39 | fmt.Fprintf(os.Stderr, "%s: ", prompt)
40 | text, err = reader.ReadString('\n')
41 | if err != nil {
42 | return "", fmt.Errorf("%w - error getting input", err)
43 | }
44 | text = strings.TrimSpace(text)
45 | }
46 | return text, nil
47 | }
48 |
49 | // FIXME is it critical for this to panic, or can we cascade the errors?
50 | func ConfirmOrAbort(format string, a ...interface{}) {
51 | fmt.Fprintf(os.Stderr, format+" [y/n] ", a...)
52 |
53 | reader := bufio.NewReader(os.Stdin)
54 |
55 | input, err := reader.ReadString('\n')
56 | if err != nil {
57 | panic(err)
58 | }
59 |
60 | if input == "y\n" {
61 | return
62 | } else {
63 | fmt.Fprintf(os.Stderr, "\033[31mAborted.\033[0m\n")
64 | os.Exit(1)
65 | }
66 | }
67 |
68 | func BytesToSI(b uint64) string {
69 | const unit = 1000
70 | if b < unit {
71 | return fmt.Sprintf("%d B", b)
72 | }
73 | div, exp := int64(unit), 0
74 | for n := b / unit; n >= unit; n /= unit {
75 | div *= unit
76 | exp++
77 | }
78 | return fmt.Sprintf("%.1f %cB",
79 | float64(b)/float64(div), "kMGTPE"[exp])
80 | }
81 |
--------------------------------------------------------------------------------
/lib/types.go:
--------------------------------------------------------------------------------
1 | package lib
2 |
3 | import (
4 | "fmt"
5 | "net"
6 | "strings"
7 |
8 | "golang.zx2c4.com/wireguard/wgctrl/wgtypes"
9 | )
10 |
11 | type JSONIPNet struct {
12 | IPNet net.IPNet
13 | }
14 |
15 | func (n JSONIPNet) MarshalJSON() ([]byte, error) {
16 | if len(n.IPNet.IP) == 0 {
17 | return []byte("\"\""), nil
18 | } else {
19 | return []byte("\"" + n.IPNet.String() + "\""), nil
20 | }
21 | }
22 |
23 | func (n *JSONIPNet) UnmarshalJSON(b []byte) error {
24 | cidr := strings.Trim(string(b), "\"")
25 |
26 | if cidr == "" {
27 | // Leave as empty/uninitialised IPNet. A bit like omitempty behaviour,
28 | // but we can leave the field there and blank which is useful if the
29 | // user wishes to add the cidr manually.
30 | return nil
31 | }
32 |
33 | IP, IPNet, err := net.ParseCIDR(cidr)
34 |
35 | if err == nil {
36 | IPNet.IP = IP
37 | n.IPNet = *IPNet
38 | }
39 |
40 | return err
41 | }
42 |
43 | func (n *JSONIPNet) String() string {
44 | return n.IPNet.String()
45 | }
46 |
47 | type JSONKey struct {
48 | Key wgtypes.Key
49 | }
50 |
51 | func (k JSONKey) MarshalJSON() ([]byte, error) {
52 | return []byte("\"" + k.Key.String() + "\""), nil
53 | }
54 |
55 | func (k JSONKey) PublicKey() JSONKey {
56 | return JSONKey{
57 | Key: k.Key.PublicKey(),
58 | }
59 | }
60 |
61 | func (k *JSONKey) UnmarshalJSON(b []byte) error {
62 | b64Key := strings.Trim(string(b), "\"")
63 | key, err := wgtypes.ParseKey(b64Key)
64 | k.Key = key
65 | return err
66 | }
67 |
68 | func GenerateJSONPrivateKey() (JSONKey, error) {
69 | privateKey, err := wgtypes.GeneratePrivateKey()
70 |
71 | if err != nil {
72 | return JSONKey{}, fmt.Errorf("failed to generate private key: %s", err)
73 | }
74 |
75 | return JSONKey{
76 | Key: privateKey,
77 | }, nil
78 | }
79 |
80 | func GenerateJSONKey() (JSONKey, error) {
81 | privateKey, err := wgtypes.GenerateKey()
82 |
83 | if err != nil {
84 | return JSONKey{}, fmt.Errorf("failed to generate key: %s", err)
85 | }
86 |
87 | return JSONKey{
88 | Key: privateKey,
89 | }, nil
90 | }
91 |
92 | func ParseJSONIPNet(cidr string) (JSONIPNet, error) {
93 | _, ipnet, err := net.ParseCIDR(cidr)
94 | if err != nil {
95 | return JSONIPNet{}, fmt.Errorf("failed to parse CIDR %s: %w", cidr, err)
96 | }
97 | return JSONIPNet{IPNet: *ipnet}, nil
98 | }
99 |
--------------------------------------------------------------------------------
/cmd/cli/add.go:
--------------------------------------------------------------------------------
1 | package cli
2 |
3 | import (
4 | "fmt"
5 | "os"
6 |
7 | "github.com/naggie/dsnet/lib"
8 | "github.com/spf13/viper"
9 | )
10 |
11 | // Add prompts for the required information and creates a new peer
12 | func Add(hostname string, privKey, pubKey bool, owner, description string, confirm bool) error {
13 | config, err := LoadConfigFile()
14 | if err != nil {
15 | return fmt.Errorf("%w - failed to load configuration file", err)
16 | }
17 | server := GetServer(config)
18 |
19 | var private, public string
20 | if privKey {
21 | if private, err = PromptString("private key", true); err != nil {
22 | return err
23 | }
24 | }
25 | if pubKey {
26 | if public, err = PromptString("public key", true); err != nil {
27 | return err
28 | }
29 | }
30 | if owner == "" {
31 | owner, err = PromptString("owner", true)
32 | if err != nil {
33 | return fmt.Errorf("%w - invalid input for owner", err)
34 | }
35 | }
36 | if description == "" {
37 | description, err = PromptString("Description", true)
38 | if err != nil {
39 | return fmt.Errorf("%w - invalid input for Description", err)
40 | }
41 | }
42 |
43 | // publicKey := MustPromptString("PublicKey (optional)", false)
44 | if !confirm {
45 | ConfirmOrAbort("\nDo you want to add the above configuration?")
46 | }
47 |
48 | // newline (not on stdout) to separate config
49 | fmt.Fprintln(os.Stderr)
50 |
51 | peer, err := lib.NewPeer(server, private, public, owner, hostname, description)
52 | if err != nil {
53 | return fmt.Errorf("%w - failed to get new peer", err)
54 | }
55 |
56 | // TODO Some kind of recovery here would be nice, to avoid
57 | // leaving things in a potential broken state
58 |
59 | if err = config.AddPeer(peer); err != nil {
60 | return fmt.Errorf("%w - failed to add new peer", err)
61 | }
62 |
63 | peerType := viper.GetString("output")
64 |
65 | peerConfigBytes, err := lib.AsciiPeerConfig(peer, peerType, *server)
66 | if err != nil {
67 | return fmt.Errorf("%w - failed to get peer configuration", err)
68 | }
69 | os.Stdout.Write(peerConfigBytes.Bytes())
70 |
71 | if err = config.Save(); err != nil {
72 | return fmt.Errorf("%w - failed to save config file", err)
73 | }
74 |
75 | server = GetServer(config)
76 | if err = server.ConfigureDevice(); err != nil {
77 | return fmt.Errorf("%w - failed to configure device", err)
78 | }
79 | return nil
80 | }
81 |
--------------------------------------------------------------------------------
/lib/generator.go:
--------------------------------------------------------------------------------
1 | package lib
2 |
3 | import (
4 | "bytes"
5 | "errors"
6 | "fmt"
7 | "text/template"
8 | )
9 |
10 | func getPeerConfTplString(peerType PeerType) (string, error) {
11 | switch peerType {
12 | case WGQuick:
13 | return wgQuickPeerConf, nil
14 | case Vyatta:
15 | return vyattaPeerConf, nil
16 | case NixOS:
17 | return nixosPeerConf, nil
18 | case RouterOS:
19 | return routerosPeerConf, nil
20 | default:
21 | return "", fmt.Errorf("unrecognized peer type")
22 | }
23 | }
24 |
25 | func (p *Peer) getIfName() string {
26 | // derive deterministic interface name
27 | wgifSeed := 0
28 | for _, b := range p.IP {
29 | wgifSeed += int(b)
30 | }
31 |
32 | for _, b := range p.IP6 {
33 | wgifSeed += int(b)
34 | }
35 | return fmt.Sprintf("wg%d", wgifSeed%999)
36 | }
37 |
38 | // GetWGPeerTemplate returns a template string to be used when
39 | // configuring a peer
40 | func GetWGPeerTemplate(peer Peer, peerType PeerType, server Server) (*bytes.Buffer, error) {
41 | peerConf, err := getPeerConfTplString(peerType)
42 | if err != nil {
43 | return nil, fmt.Errorf("failed to get wg template: %s", err)
44 | }
45 |
46 | // See DsnetConfig type for explanation
47 | var endpoint string
48 |
49 | if server.ExternalHostname != "" {
50 | endpoint = server.ExternalHostname
51 | } else if len(server.ExternalIP) > 0 {
52 | endpoint = server.ExternalIP.String()
53 | } else if len(server.ExternalIP6) > 0 {
54 | endpoint = server.ExternalIP6.String()
55 | } else {
56 | return nil, errors.New("server config requires at least one of ExternalIP, ExternalIP6 or ExternalHostname")
57 | }
58 |
59 | t := template.Must(template.New("peerConf").Parse(peerConf))
60 | cidrSize, _ := server.Network.IPNet.Mask.Size()
61 | cidrSize6, _ := server.Network6.IPNet.Mask.Size()
62 |
63 | var templateBuff bytes.Buffer
64 | err = t.Execute(&templateBuff, map[string]interface{}{
65 | "Peer": peer,
66 | "Server": server,
67 | "CidrSize": cidrSize,
68 | "CidrSize6": cidrSize6,
69 | // vyatta requires an interface in range/format wg0-wg999
70 | // deterministically choosing one in this range will probably allow use
71 | // of the config without a colliding interface name
72 | "Wgif": peer.getIfName(),
73 | "Endpoint": endpoint,
74 | })
75 | if err != nil {
76 | return nil, err
77 | }
78 | return &templateBuff, nil
79 | }
80 |
81 | func AsciiPeerConfig(peer Peer, peerType string, server Server) (*bytes.Buffer, error) {
82 | switch peerType {
83 | case "wg-quick":
84 | return GetWGPeerTemplate(peer, WGQuick, server)
85 | case "vyatta":
86 | return GetWGPeerTemplate(peer, Vyatta, server)
87 | case "nixos":
88 | return GetWGPeerTemplate(peer, NixOS, server)
89 | case "routeros":
90 | return GetWGPeerTemplate(peer, RouterOS, server)
91 | default:
92 | return nil, errors.New("unrecognised OUTPUT type")
93 | }
94 | }
95 |
--------------------------------------------------------------------------------
/contrib/report_rendering/php/dsnetreport.php:
--------------------------------------------------------------------------------
1 |
16 |
17 |
18 |
19 |
20 |
70 |
71 | 76 | WireGuard 77 |
78 |WireGuard Peers
80 || Hostname | 84 |Status | 85 |IP | 86 |Owner | 87 |Description | 88 |Up | 89 |Down | 90 |
|---|---|---|---|---|---|---|
| '.($value['Online'] ? '' : '').' | '; 100 | echo ''.$value['IP'].' | '; 101 | echo ''.$value['Owner'].' | '; 102 | echo ''.$value['Description'].' | '; 103 | echo ''.$value['ReceiveBytesSI'].' | '; 104 | echo ''.$value['TransmitBytesSI'].' | '; 105 | ?> 106 |
116 | 117 | $value) { 119 | $date_str = substr($value['LastHandshakeTime'], 0, 19); 120 | $d2 = new DateTime($date_str); 121 | echo '
'; 122 | } 123 | ?> 124 | 125 | 126 | 127 | -------------------------------------------------------------------------------- /etc/logo/with-safe-area.svg: -------------------------------------------------------------------------------- 1 | 9 | -------------------------------------------------------------------------------- /etc/logo/without-safe-area.svg: -------------------------------------------------------------------------------- 1 | 9 | -------------------------------------------------------------------------------- /lib/peer.go: -------------------------------------------------------------------------------- 1 | package lib 2 | 3 | import ( 4 | "errors" 5 | "fmt" 6 | "net" 7 | "strings" 8 | "time" 9 | 10 | "golang.zx2c4.com/wireguard/wgctrl/wgtypes" 11 | ) 12 | 13 | // PeerType is what configuration to use when generating 14 | // peer config files 15 | type PeerType int 16 | 17 | const ( 18 | // WGQuick is used by wg-quick to set up a peer 19 | // https://manpages.debian.org/unstable/wireguard-tools/wg-quick.8.en.html 20 | WGQuick PeerType = iota 21 | // Vyatta is used by Ubiquiti routers 22 | // https://github.com/WireGuard/wireguard-vyatta-ubnt/ 23 | Vyatta 24 | // NixOS is a declartive linux distro 25 | // https://nixos.wiki/wiki/Wireguard 26 | NixOS 27 | // RouterOS is proprietary Linux based OS by MikroTik 28 | // https://help.mikrotik.com/docs/display/ROS/WireGuard 29 | RouterOS 30 | ) 31 | 32 | type Peer struct { 33 | Hostname string 34 | Owner string 35 | Description string 36 | IP net.IP 37 | IP6 net.IP 38 | Added time.Time 39 | PublicKey JSONKey 40 | PrivateKey JSONKey 41 | PresharedKey JSONKey 42 | Networks []JSONIPNet 43 | PersistentKeepalive int 44 | } 45 | 46 | // NewPeer generates a peer from the supplied arguments and generates keys if needed. 47 | // - server is required and provides network information 48 | // - private is a base64-encoded private key; if the empty string, a new key will be generated 49 | // - public is a base64-encoded public key. If empty, it will be generated from the private key. 50 | // If **not** empty, the private key will be included IFF a private key was provided. 51 | // - owner is the owner name (required) 52 | // - hostname is the name of the peer (required) 53 | // - description is the annotation for the peer 54 | func NewPeer(server *Server, private, public, owner, hostname, description string) (Peer, error) { 55 | if owner == "" { 56 | return Peer{}, errors.New("missing owner") 57 | } 58 | if hostname == "" { 59 | return Peer{}, errors.New("missing hostname") 60 | } 61 | 62 | var privateKey JSONKey 63 | if private != "" { 64 | userKey := &JSONKey{} 65 | userKey.UnmarshalJSON([]byte(private)) 66 | privateKey = *userKey 67 | } else { 68 | var err error 69 | privateKey, err = GenerateJSONPrivateKey() 70 | if err != nil { 71 | return Peer{}, fmt.Errorf("failed to generate private key: %s", err) 72 | } 73 | } 74 | 75 | var publicKey JSONKey 76 | if public != "" { 77 | b64Key := strings.Trim(string(public), "\"") 78 | key, err := wgtypes.ParseKey(b64Key) 79 | if err != nil { 80 | return Peer{}, err 81 | } 82 | publicKey = JSONKey{Key: key} 83 | if private == "" { 84 | privateKey = JSONKey{Key: wgtypes.Key([wgtypes.KeyLen]byte{})} 85 | } else { 86 | pubK := privateKey.PublicKey() 87 | ascK := pubK.Key.String() 88 | if ascK != public { 89 | return Peer{}, fmt.Errorf("user-supplied private and public keys are not related") 90 | } 91 | } 92 | } else { 93 | publicKey = privateKey.PublicKey() 94 | } 95 | 96 | presharedKey, err := GenerateJSONKey() 97 | if err != nil { 98 | return Peer{}, fmt.Errorf("failed to generate private key: %s", err) 99 | } 100 | 101 | newPeer := Peer{ 102 | Owner: owner, 103 | Hostname: hostname, 104 | Description: description, 105 | Added: time.Now(), 106 | PublicKey: publicKey, 107 | PrivateKey: privateKey, 108 | PresharedKey: presharedKey, 109 | Networks: []JSONIPNet{}, 110 | // inherit from server setting, which is derived from config 111 | PersistentKeepalive: server.PersistentKeepalive, 112 | } 113 | 114 | if len(server.Network.IPNet.Mask) > 0 { 115 | newIP, err := server.AllocateIP() 116 | if err != nil { 117 | return Peer{}, fmt.Errorf("failed to allocate ipv4 address: %s", err) 118 | } 119 | newPeer.IP = newIP 120 | } 121 | 122 | if len(server.Network6.IPNet.Mask) > 0 { 123 | newIPV6, err := server.AllocateIP6() 124 | if err != nil { 125 | return Peer{}, fmt.Errorf("failed to allocate ipv6 address: %s", err) 126 | } 127 | newPeer.IP6 = newIPV6 128 | } 129 | 130 | if len(server.IP) == 0 && len(server.IP6) == 0 { 131 | return Peer{}, fmt.Errorf("no IPv4 or IPv6 network defined in config") 132 | } 133 | return newPeer, nil 134 | } 135 | -------------------------------------------------------------------------------- /lib/server.go: -------------------------------------------------------------------------------- 1 | package lib 2 | 3 | import ( 4 | "fmt" 5 | "math/rand" 6 | "net" 7 | "time" 8 | 9 | "golang.zx2c4.com/wireguard/wgctrl/wgtypes" 10 | ) 11 | 12 | type Server struct { 13 | ExternalHostname string 14 | ExternalIP net.IP 15 | ExternalIP6 net.IP 16 | ListenPort int 17 | Domain string 18 | InterfaceName string 19 | Network JSONIPNet 20 | Network6 JSONIPNet 21 | IP net.IP 22 | IP6 net.IP 23 | DNS net.IP 24 | PrivateKey JSONKey 25 | PostUp string 26 | PostDown string 27 | FallbackWGBin string 28 | Peers []Peer 29 | Networks []JSONIPNet 30 | PersistentKeepalive int 31 | MTU int 32 | } 33 | 34 | func (s *Server) GetPeers() []wgtypes.PeerConfig { 35 | wgPeers := make([]wgtypes.PeerConfig, 0, len(s.Peers)) 36 | 37 | for _, peer := range s.Peers { 38 | // create a new PSK in memory to avoid passing the same value by 39 | // pointer to each peer (d'oh) 40 | presharedKey := peer.PresharedKey.Key 41 | 42 | // AllowedIPs = private IP + defined networks 43 | allowedIPs := make([]net.IPNet, 0, len(peer.Networks)+2) 44 | 45 | if len(peer.IP) > 0 { 46 | allowedIPs = append( 47 | allowedIPs, 48 | net.IPNet{ 49 | IP: peer.IP, 50 | Mask: net.IPMask{255, 255, 255, 255}, 51 | }, 52 | ) 53 | } 54 | 55 | if len(peer.IP6) > 0 { 56 | allowedIPs = append( 57 | allowedIPs, 58 | net.IPNet{ 59 | IP: peer.IP6, 60 | Mask: net.IPMask{0xff, 0xff, 0xff, 0xff, 0xff, 0xff, 0xff, 0xff, 0xff, 0xff, 0xff, 0xff, 0xff, 0xff, 0xff, 0xff}, 61 | }, 62 | ) 63 | } 64 | 65 | for _, net := range peer.Networks { 66 | allowedIPs = append(allowedIPs, net.IPNet) 67 | } 68 | 69 | wgPeers = append(wgPeers, wgtypes.PeerConfig{ 70 | PublicKey: peer.PublicKey.Key, 71 | Remove: false, 72 | UpdateOnly: false, 73 | PresharedKey: &presharedKey, 74 | Endpoint: nil, 75 | ReplaceAllowedIPs: true, 76 | AllowedIPs: allowedIPs, 77 | }) 78 | } 79 | 80 | return wgPeers 81 | } 82 | 83 | // AllocateIP finds a free IPv4 for a new Peer (sequential allocation) 84 | func (s *Server) AllocateIP() (net.IP, error) { 85 | network := s.Network.IPNet 86 | ones, bits := network.Mask.Size() 87 | zeros := bits - ones 88 | 89 | // avoids network addr 90 | min := 1 91 | // avoids broadcast addr + overflow 92 | max := (1 << zeros) - 2 93 | 94 | IP := make(net.IP, len(network.IP)) 95 | 96 | for i := min; i <= max; i++ { 97 | // dst, src! 98 | copy(IP, network.IP) 99 | 100 | // OR the host part with the network part 101 | for j := 0; j < len(IP); j++ { 102 | shift := (len(IP) - j - 1) * 8 103 | IP[j] = IP[j] | byte(i>>shift) 104 | } 105 | 106 | if !s.IPAllocated(IP) { 107 | return IP, nil 108 | } 109 | } 110 | 111 | return nil, fmt.Errorf("IP range exhausted") 112 | } 113 | 114 | // AllocateIP6 finds a free IPv6 for a new Peer (pseudorandom allocation) 115 | func (s *Server) AllocateIP6() (net.IP, error) { 116 | network := s.Network6.IPNet 117 | ones, bits := network.Mask.Size() 118 | zeros := bits - ones 119 | 120 | rbs := make([]byte, zeros) 121 | rand.Seed(time.Now().UTC().UnixNano()) 122 | 123 | IP := make(net.IP, len(network.IP)) 124 | 125 | for i := 0; i <= 10000; i++ { 126 | rand.Read(rbs) 127 | // dst, src! Copy prefix of IP 128 | copy(IP, network.IP) 129 | 130 | // OR the host part with the network part 131 | for j := ones / 8; j < len(IP); j++ { 132 | IP[j] = IP[j] | rbs[j] 133 | } 134 | 135 | if !s.IPAllocated(IP) { 136 | return IP, nil 137 | } 138 | } 139 | 140 | return nil, fmt.Errorf("Could not allocate random IPv6 after 10000 tries. This was highly unlikely!") 141 | } 142 | 143 | // IPAllocated checks the existing used ips and returns bool 144 | // depending on if the IP is in use 145 | func (s *Server) IPAllocated(IP net.IP) bool { 146 | if IP.Equal(s.IP) || IP.Equal(s.IP6) { 147 | return true 148 | } 149 | 150 | for _, peer := range s.Peers { 151 | if IP.Equal(peer.IP) || IP.Equal(peer.IP6) { 152 | return true 153 | } 154 | 155 | for _, peerIPNet := range peer.Networks { 156 | if IP.Equal(peerIPNet.IPNet.IP) { 157 | return true 158 | } 159 | } 160 | } 161 | 162 | return false 163 | } 164 | -------------------------------------------------------------------------------- /lib/link.go: -------------------------------------------------------------------------------- 1 | package lib 2 | 3 | import ( 4 | "errors" 5 | "fmt" 6 | "net" 7 | 8 | "github.com/naggie/dsnet/utils" 9 | "github.com/vishvananda/netlink" 10 | ) 11 | 12 | // IPExists checks if the given IP address already exists on the specified link 13 | func IPExists(link netlink.Link, ipNet *net.IPNet, family int) (bool, error) { 14 | addrs, err := netlink.AddrList(link, family) 15 | if err != nil { 16 | return false, fmt.Errorf("failed to list addresses for interface: %v", err) 17 | } 18 | for _, addr := range addrs { 19 | if addr.IPNet.String() == ipNet.String() { 20 | return true, nil 21 | } 22 | } 23 | return false, nil 24 | } 25 | 26 | // CreateLink sets up the WG interface and link with the correct 27 | // address 28 | func (s *Server) CreateLink() error { 29 | if len(s.IP) == 0 && len(s.IP6) == 0 { 30 | return errors.New("no IPv4 or IPv6 ip defined in config") 31 | } 32 | 33 | linkAttrs := netlink.NewLinkAttrs() 34 | linkAttrs.Name = s.InterfaceName 35 | 36 | link := &netlink.GenericLink{ 37 | LinkAttrs: linkAttrs, 38 | LinkType: "wireguard", 39 | } 40 | 41 | err := netlink.LinkAdd(link) 42 | if err != nil && s.FallbackWGBin != "" { 43 | // return fmt.Errorf("could not add interface '%s' (%v), falling back to the userspace implementation", s.InterfaceName, err) 44 | cmdStr := fmt.Sprintf("%s %s", s.FallbackWGBin, s.InterfaceName) 45 | if err = utils.ShellOut(cmdStr, "Userspace implementation"); err != nil { 46 | return fmt.Errorf("failed to start userspace wireguard: %s", err) 47 | } 48 | } 49 | 50 | if len(s.IP) != 0 { 51 | addr := &netlink.Addr{ 52 | IPNet: &net.IPNet{ 53 | IP: s.IP, 54 | Mask: s.Network.IPNet.Mask, 55 | }, 56 | } 57 | 58 | exists, err := IPExists(link, addr.IPNet, netlink.FAMILY_V4) 59 | if err != nil { 60 | return err 61 | } 62 | 63 | if !exists { 64 | err = netlink.AddrAdd(link, addr) 65 | if err != nil { 66 | return fmt.Errorf("could not add ipv4 addr %s to interface %s: %v", addr.IP, s.InterfaceName, err) 67 | } 68 | } 69 | 70 | // remove any other IPs on the interface 71 | addrs, err := netlink.AddrList(link, netlink.FAMILY_V4) 72 | if err != nil { 73 | return fmt.Errorf("failed to list addresses for interface: %v", err) 74 | } 75 | for _, addr := range addrs { 76 | if addr.IPNet.String() != addr.IPNet.String() { 77 | err := netlink.AddrDel(link, &addr) 78 | if err != nil { 79 | return fmt.Errorf("failed to delete address %s from interface %s: %v", addr.IP, s.InterfaceName, err) 80 | } 81 | } 82 | } 83 | } 84 | 85 | if len(s.IP6) != 0 { 86 | addr6 := &netlink.Addr{ 87 | IPNet: &net.IPNet{ 88 | IP: s.IP6, 89 | Mask: s.Network6.IPNet.Mask, 90 | }, 91 | } 92 | 93 | exists, err := IPExists(link, addr6.IPNet, netlink.FAMILY_V6) 94 | if err != nil { 95 | return err 96 | } 97 | 98 | if !exists { 99 | err = netlink.AddrAdd(link, addr6) 100 | if err != nil { 101 | return fmt.Errorf("could not add ipv6 addr %s to interface %s: %v. Do you have IPv6 enabled?", addr6.IP, s.InterfaceName, err) 102 | } 103 | } 104 | 105 | // remove any other IPs on the interface 106 | addrs, err := netlink.AddrList(link, netlink.FAMILY_V6) 107 | if err != nil { 108 | return fmt.Errorf("failed to list v6 addresses for interface: %v", err) 109 | } 110 | 111 | for _, addr := range addrs { 112 | if addr.IPNet.String() != addr6.IPNet.String() { 113 | err := netlink.AddrDel(link, &addr) 114 | if err != nil { 115 | return fmt.Errorf("failed to delete address %s from interface %s: %v", addr.IP, s.InterfaceName, err) 116 | } 117 | } 118 | } 119 | } 120 | 121 | // set MTU 122 | err = netlink.LinkSetMTU(link, s.MTU) 123 | if err != nil { 124 | return fmt.Errorf("failed to set MTU %d on interface %s: %v", s.MTU, s.InterfaceName, err) 125 | } 126 | 127 | // bring up interface (UNKNOWN state instead of UP, a wireguard quirk) 128 | err = netlink.LinkSetUp(link) 129 | 130 | if err != nil { 131 | return fmt.Errorf("could not bring up device '%s' (%v)", s.InterfaceName, err) 132 | } 133 | return nil 134 | } 135 | 136 | // DeleteLink removes the Netlink interface if it exists 137 | func (s *Server) DeleteLink() error { 138 | link, err := netlink.LinkByName(s.InterfaceName) 139 | if err != nil { 140 | // If the error is because the link doesn't exist, just return nil 141 | if _, ok := err.(netlink.LinkNotFoundError); ok { 142 | return nil 143 | } 144 | return fmt.Errorf("failed to get interface(%s): %v", s.InterfaceName, err) 145 | } 146 | 147 | err = netlink.LinkDel(link) 148 | if err != nil { 149 | return fmt.Errorf("failed to delete interface(%s): %v", s.InterfaceName, err) 150 | } 151 | return nil 152 | } 153 | -------------------------------------------------------------------------------- /etc/logo/square-brand-dark.svg: -------------------------------------------------------------------------------- 1 | 18 | -------------------------------------------------------------------------------- /etc/logo/square-brand-light.svg: -------------------------------------------------------------------------------- 1 | 18 | -------------------------------------------------------------------------------- /contrib/report_rendering/README.md: -------------------------------------------------------------------------------- 1 | This directory contains scripts and templates that can be used to render 2 | `/var/lib/dsnetreport.json`. They are useful for integrating a peer overview 3 | into an existing website or web application. 4 | 5 | Most are contributions from other users. If you have a useful addition, please 6 | do a PR. 7 | 8 | Most look something like this: 9 | 10 | ## Hugo shortcode template 11 | 12 | * `hugo/dsnetreport.html`: A hugo shortcode for rendering a report. 13 | 14 | 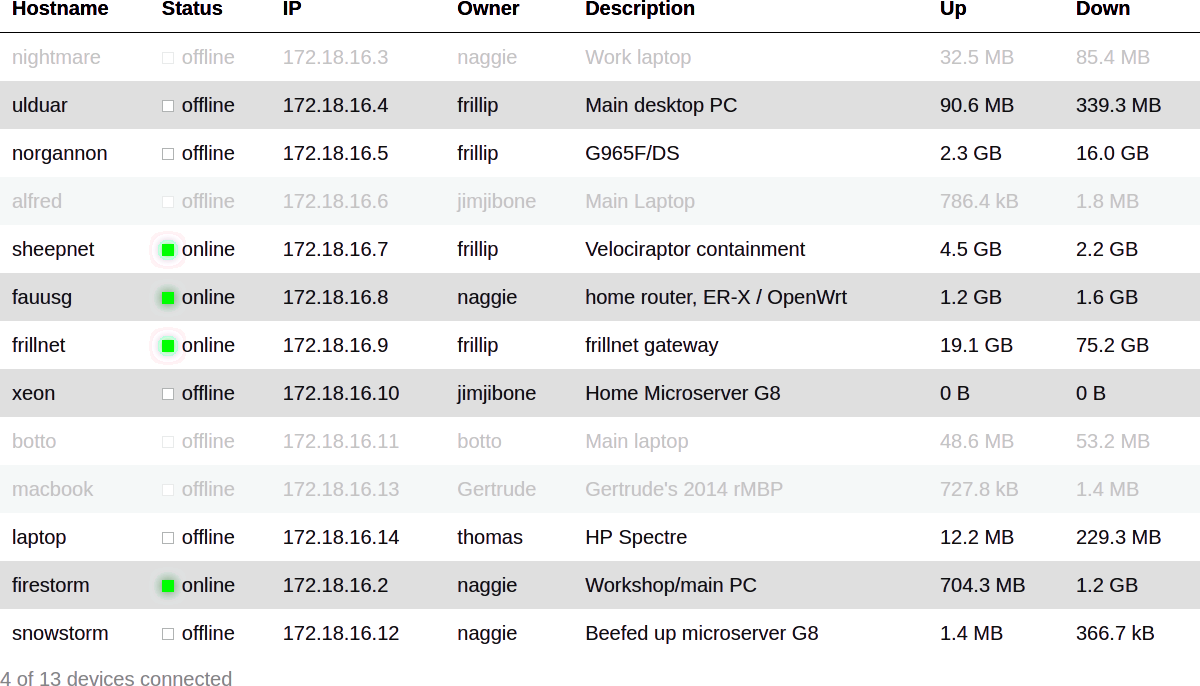 15 | 16 | # PHP template 17 | See https://github.com/naggie/dsnet/issues/4#issuecomment-632928158 for background. Courtesy of [@Write](https://github.com/Write) 18 | 19 | * `php/dsnetreport.php`: A php file to render a report. 20 | 21 |  22 |  23 | 24 | # Clientside JavaScript 25 | 26 | Courtesy of [@frillip](https://github.com/frillip/) 27 | 28 | * `js/dsnetreport.html`: Basic HTML with a `div` to place the table in. 29 | * `js/dsnetreport.js`: Fetches `dsnetreport.json` and renders table. 30 | * `js/dsnetreport.css`: CSS to render the table as per screenshot. 31 | 32 | 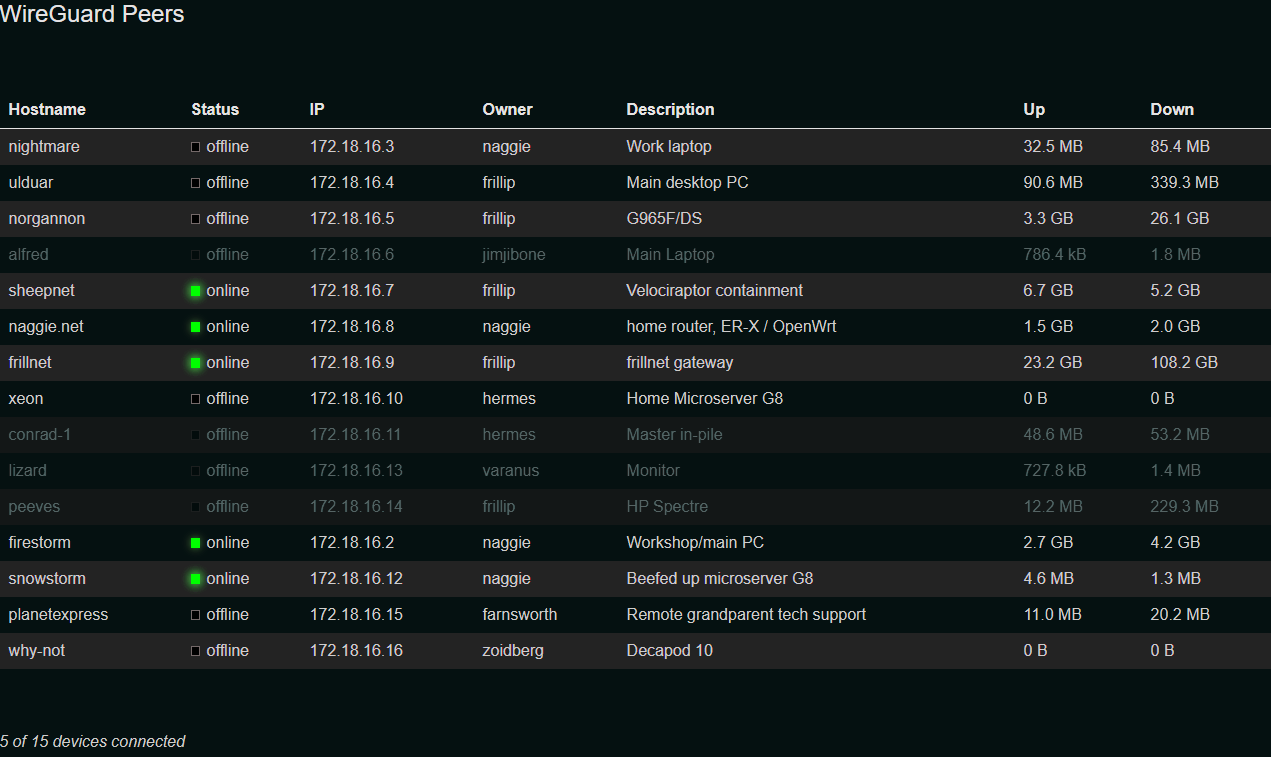 33 | 34 | # CLI (bash) 35 | 36 | On the command line, you can use [jtbl](https://github.com/kellyjonbrazil/jtbl) (and [jq](https://stedolan.github.io/jq/)) for a nice table rendering with this snippet: 37 | 38 | ```bash 39 | sudo dsnet report | jq '.Peers' | jtbl 40 | ``` 41 | 42 | The output looks like: 43 | ``` 44 | ╒═════════╤═══════╤══════════╤══════════╤══════════╤══════════╤═════════╤════════╤══════════╤══════════╤══════════╤══════════╤══════════╤══════════╤══════════╕ 45 | │ Owner │ IP6 │ Hostna │ Descri │ Online │ Dorman │ Added │ IP │ Extern │ Networ │ LastHa │ Receiv │ Transm │ Receiv │ Transm │ 46 | │ │ │ me │ ption │ │ t │ │ │ alIP │ ks │ ndshak │ eBytes │ itByte │ eBytes │ itByte │ 47 | │ │ │ │ │ │ │ │ │ │ │ eTime │ │ s │ SI │ sSI │ 48 | ╞═════════╪═══════╪══════════╪══════════╪══════════╪══════════╪═════════╪════════╪══════════╪══════════╪══════════╪══════════╪══════════╪══════════╪══════════╡ 49 | │ xyz │ │ eaetl │ eaetl. │ True │ False │ 2222-0 │ 99.99. │ dddd:d │ [] │ 1111-1 │ 175995 │ 447007 │ 175.9 │ 32.7 M │ 50 | │ │ │ │ fooo │ │ │ 2-22T1 │ 99.9 │ dd:ddd │ │ 1-11T1 │ 424 │ 28 │ MB │ B │ 51 | │ │ │ │ │ │ │ 2:22:5 │ │ d:dddd │ │ 1:11:1 │ │ │ │ │ 52 | │ │ │ │ │ │ │ 2.2274 │ │ :dddd: │ │ 1.1111 │ │ │ │ │ 53 | │ │ │ │ │ │ │ 22222- │ │ dddd:d │ │ 11111- │ │ │ │ │ 54 | │ │ │ │ │ │ │ 22:20 │ │ ddd:dd │ │ 11:11 │ │ │ │ │ 55 | │ │ │ │ │ │ │ │ │ dd │ │ │ │ │ │ │ 56 | ├─────────┼───────┼──────────┼──────────┼──────────┼──────────┼─────────┼────────┼──────────┼──────────┼──────────┼──────────┼──────────┼──────────┼──────────┤ 57 | │ xyz │ │ ammedu │ ammedu │ True │ False │ 2222-0 │ 88.88. │ eeee:e │ [] │ 1111-1 │ 751670 │ 759741 │ 6.7 GB │ 727.7 │ 58 | │ │ │ │ .mymy. │ │ │ 2-22T1 │ 88.8 │ eee:ee │ │ 1-11T1 │ 2852 │ 076 │ │ MB │ 59 | │ │ │ │ com │ │ │ 2:22:4 │ │ ee:eee │ │ 1:11:1 │ │ │ │ │ 60 | │ │ │ │ │ │ │ 2.2292 │ │ e::e │ │ 1.1111 │ │ │ │ │ 61 | │ │ │ │ │ │ │ 22226- │ │ │ │ 11111- │ │ │ │ │ 62 | │ │ │ │ │ │ │ 22:20 │ │ │ │ 11:11 │ │ │ │ │ 63 | ├─────────┼───────┼──────────┼──────────┼──────────┼──────────┼─────────┼────────┼──────────┼──────────┼──────────┼──────────┼──────────┼──────────┼──────────┤ 64 | ... 65 | ``` 66 | 67 | To tighten up the table, use JQ to remove columns you're not interested in: 68 | 69 | ``` 70 | sudo dsnet report | jq '.Peers | map(del(.Added,.Networks,.IP6,.Owner))' | jtbl 71 | ``` -------------------------------------------------------------------------------- /cmd/cli/init.go: -------------------------------------------------------------------------------- 1 | package cli 2 | 3 | import ( 4 | "errors" 5 | "fmt" 6 | "io/ioutil" 7 | "math/rand" 8 | "net" 9 | "net/http" 10 | "os" 11 | "strings" 12 | "time" 13 | 14 | "github.com/naggie/dsnet/lib" 15 | "github.com/spf13/viper" 16 | ) 17 | 18 | func Init() error { 19 | listenPort := viper.GetInt("listen_port") 20 | MTU := viper.GetInt("mtu") 21 | configFile := viper.GetString("config_file") 22 | interfaceName := viper.GetString("interface_name") 23 | 24 | _, err := os.Stat(configFile) 25 | 26 | if !os.IsNotExist(err) { 27 | return fmt.Errorf("Refusing to overwrite existing %s", configFile) 28 | } 29 | 30 | privateKey, err := lib.GenerateJSONPrivateKey() 31 | if err != nil { 32 | return fmt.Errorf("%w - failed to generate private key", err) 33 | } 34 | 35 | externalIPV4, err := getExternalIP() 36 | if err != nil { 37 | return err 38 | } 39 | 40 | externalIPV6, err := getExternalIP6() 41 | if err != nil { 42 | return err 43 | } 44 | 45 | conf := &DsnetConfig{ 46 | PrivateKey: privateKey, 47 | ListenPort: listenPort, 48 | Network: getPrivateNet(), 49 | Network6: getULANet(), 50 | Peers: []PeerConfig{}, 51 | Domain: "dsnet", 52 | ExternalIP: externalIPV4, 53 | ExternalIP6: externalIPV6, 54 | InterfaceName: interfaceName, 55 | Networks: []lib.JSONIPNet{}, 56 | PersistentKeepalive: 25, 57 | MTU: MTU, 58 | } 59 | 60 | server := GetServer(conf) 61 | 62 | ipv4, err := server.AllocateIP() 63 | if err != nil { 64 | return fmt.Errorf("%w - failed to allocate ipv4 address", err) 65 | } 66 | 67 | ipv6, err := server.AllocateIP6() 68 | if err != nil { 69 | return fmt.Errorf("%w - failed to allocate ipv6 address", err) 70 | } 71 | 72 | conf.IP = ipv4 73 | conf.IP6 = ipv6 74 | 75 | if len(conf.ExternalIP) == 0 && len(conf.ExternalIP6) == 0 { 76 | return fmt.Errorf("Could not determine any external IP, v4 or v6") 77 | } 78 | 79 | if err := conf.Save(); err != nil { 80 | return fmt.Errorf("%w - failed to save config file", err) 81 | } 82 | 83 | fmt.Printf("Config written to %s. Please check/edit.\n", configFile) 84 | return nil 85 | } 86 | 87 | // get a random IPv4 /22 subnet on 10.0.0.0 (1023 hosts) (or /24?) 88 | func getPrivateNet() lib.JSONIPNet { 89 | rbs := make([]byte, 2) 90 | rand.Seed(time.Now().UTC().UnixNano()) 91 | rand.Read(rbs) 92 | 93 | return lib.JSONIPNet{ 94 | IPNet: net.IPNet{ 95 | IP: net.IP{10, rbs[0], rbs[1] << 2, 0}, 96 | Mask: net.IPMask{255, 255, 252, 0}, 97 | }, 98 | } 99 | } 100 | 101 | func getULANet() lib.JSONIPNet { 102 | rbs := make([]byte, 5) 103 | rand.Seed(time.Now().UTC().UnixNano()) 104 | rand.Read(rbs) 105 | 106 | // fd00 prefix with 40 bit global id and zero (16 bit) subnet ID 107 | return lib.JSONIPNet{ 108 | IPNet: net.IPNet{ 109 | IP: net.IP{0xfd, 0, rbs[0], rbs[1], rbs[2], rbs[3], rbs[4], 0, 0, 0, 0, 0, 0, 0, 0, 0}, 110 | Mask: net.IPMask{0xff, 0xff, 0xff, 0xff, 0xff, 0xff, 0xff, 0xff, 0, 0, 0, 0, 0, 0, 0, 0}, 111 | }, 112 | } 113 | } 114 | 115 | // TODO factor getExternalIP + getExternalIP6 116 | func getExternalIP() (net.IP, error) { 117 | var IP net.IP 118 | // arbitrary external IP is used (one that's guaranteed to route outside. 119 | // In this case, Google's DNS server. Doesn't actually need to be online.) 120 | conn, err := net.Dial("udp", "8.8.8.8:53") 121 | if err != nil { 122 | return nil, err 123 | } 124 | defer conn.Close() 125 | 126 | localAddr := conn.LocalAddr().String() 127 | IP = net.ParseIP(strings.Split(localAddr, ":")[0]) 128 | IP = IP.To4() 129 | 130 | if !(IP[0] == 10 || (IP[0] == 172 && IP[1] >= 16 && IP[1] <= 31) || (IP[0] == 192 && IP[1] == 168)) { 131 | // not private, so public 132 | return IP, nil 133 | } 134 | 135 | // detect private IP and use icanhazip.com instead 136 | client := http.Client{ 137 | Timeout: 5 * time.Second, 138 | } 139 | resp, err := client.Get("https://ipv4.icanhazip.com/") 140 | if err != nil { 141 | return nil, err 142 | } 143 | defer resp.Body.Close() 144 | 145 | if resp.StatusCode == http.StatusOK { 146 | body, err := ioutil.ReadAll(resp.Body) 147 | if err != nil { 148 | return nil, err 149 | } 150 | IP = net.ParseIP(strings.TrimSpace(string(body))) 151 | return IP.To4(), nil 152 | } 153 | 154 | return nil, errors.New("failed to determine external ip") 155 | } 156 | 157 | func getExternalIP6() (net.IP, error) { 158 | var IP net.IP 159 | conn, err := net.Dial("udp", "2001:4860:4860::8888:53") 160 | if err == nil { 161 | defer conn.Close() 162 | 163 | localAddr := conn.LocalAddr().String() 164 | IP = net.ParseIP(strings.Split(localAddr, ":")[0]) 165 | 166 | // check is not a ULA 167 | if IP[0] != 0xfd && IP[0] != 0xfc { 168 | return IP, nil 169 | } 170 | } 171 | 172 | client := http.Client{ 173 | Timeout: 5 * time.Second, 174 | } 175 | resp, err := client.Get("https://ipv6.icanhazip.com/") 176 | if err == nil { 177 | defer resp.Body.Close() 178 | 179 | if resp.StatusCode == http.StatusOK { 180 | body, err := ioutil.ReadAll(resp.Body) 181 | if err != nil { 182 | return nil, err 183 | } 184 | IP = net.ParseIP(strings.TrimSpace(string(body))) 185 | return IP, nil 186 | } 187 | } 188 | 189 | return net.IP{}, nil 190 | } 191 | -------------------------------------------------------------------------------- /lib/templates.go: -------------------------------------------------------------------------------- 1 | package lib 2 | 3 | const wgQuickPeerConf = `[Interface] 4 | {{ if gt (.Server.Network.IPNet.IP | len) 0 -}} 5 | Address={{ .Peer.IP }}/{{ .CidrSize }} 6 | {{ end -}} 7 | {{ if gt (.Server.Network6.IPNet.IP | len) 0 -}} 8 | Address={{ .Peer.IP6 }}/{{ .CidrSize6 }} 9 | {{ end -}} 10 | PrivateKey={{ .Peer.PrivateKey.Key }} 11 | {{- if .Server.DNS }} 12 | DNS={{ .Server.DNS }} 13 | {{ end }} 14 | 15 | [Peer] 16 | PublicKey={{ .Server.PrivateKey.PublicKey.Key }} 17 | PresharedKey={{ .Peer.PresharedKey.Key }} 18 | Endpoint={{ .Endpoint }}:{{ .Server.ListenPort }} 19 | PersistentKeepalive={{ .Server.PersistentKeepalive }} 20 | {{ if gt (.Server.Network.IPNet.IP | len) 0 -}} 21 | AllowedIPs={{ .Server.Network.IPNet.IP }}/{{ .CidrSize }} 22 | {{ end -}} 23 | {{ if gt (.Server.Network6.IPNet.IP | len) 0 -}} 24 | AllowedIPs={{ .Server.Network6.IPNet.IP }}/{{ .CidrSize6 }} 25 | {{ end -}} 26 | {{ range .Server.Networks -}} 27 | AllowedIPs={{ . }} 28 | {{ end -}} 29 | ` 30 | 31 | const vyattaPeerConf = `configure 32 | {{ if gt (.Server.Network.IPNet.IP | len) 0 -}} 33 | set interfaces wireguard wg0 address {{ .Peer.IP }}/{{ .CidrSize }} 34 | {{ end -}} 35 | {{ if gt (.Server.Network6.IPNet.IP | len) 0 -}} 36 | set interfaces wireguard wg0 address {{ .Peer.IP6 }}/{{ .CidrSize6 }} 37 | {{ end -}} 38 | set interfaces wireguard wg0 route-allowed-ips true 39 | set interfaces wireguard wg0 private-key {{ .Peer.PrivateKey.Key }} 40 | set interfaces wireguard wg0 description {{ .Server.InterfaceName }} 41 | {{- if .Server.DNS }} 42 | #set service dns forwarding name-server {{ .Server.DNS }} 43 | {{ end }} 44 | 45 | set interfaces wireguard wg0 peer {{ .Server.PrivateKey.PublicKey.Key }} endpoint {{ .Endpoint }}:{{ .Server.ListenPort }} 46 | set interfaces wireguard wg0 peer {{ .Server.PrivateKey.PublicKey.Key }} persistent-keepalive {{ .Server.PersistentKeepalive }} 47 | set interfaces wireguard wg0 peer {{ .Server.PrivateKey.PublicKey.Key }} preshared-key {{ .Peer.PresharedKey.Key }} 48 | {{ if gt (.Server.Network.IPNet.IP | len) 0 -}} 49 | set interfaces wireguard wg0 peer {{ .Server.PrivateKey.PublicKey.Key }} allowed-ips {{ .Server.Network.IPNet.IP }}/{{ .CidrSize }} 50 | {{ end -}} 51 | {{ if gt (.Server.Network6.IPNet.IP | len) 0 -}} 52 | set interfaces wireguard wg0 peer {{ .Server.PrivateKey.PublicKey.Key }} allowed-ips {{ .Server.Network6.IPNet.IP }}/{{ .CidrSize6 }} 53 | {{ end -}} 54 | {{ range .Server.Networks -}} 55 | set interfaces wireguard wg0 peer {{ .Server.PrivateKey.PublicKey.Key }} allowed-ips {{ . }} 56 | {{ end -}} 57 | commit; save 58 | ` 59 | 60 | const nixosPeerConf = `networking.wireguard.interfaces = {{ "{" }} 61 | dsnet = {{ "{" }} 62 | ips = [ 63 | {{ if gt (.Server.Network.IPNet.IP | len) 0 -}} 64 | "{{ .Peer.IP }}/{{ .CidrSize }}" 65 | {{ end -}} 66 | {{ if gt (.Server.Network6.IPNet.IP | len) 0 -}} 67 | "{{ .Peer.IP6 }}/{{ .CidrSize6 }}" 68 | {{ end -}} 69 | ]; 70 | privateKey = "{{ .Peer.PrivateKey.Key }}"; 71 | peers = [ 72 | {{ "{" }} 73 | publicKey = "{{ .Server.PrivateKey.PublicKey.Key }}"; 74 | presharedKey = "{{ .Peer.PresharedKey.Key }}"; 75 | allowedIPs = [ 76 | {{ if gt (.Server.Network.IPNet.IP | len) 0 -}} 77 | "{{ .Server.Network.IPNet.IP }}/{{ .CidrSize }}" 78 | {{ end -}} 79 | {{ if gt (.Server.Network6.IPNet.IP | len) 0 -}} 80 | "{{ .Server.Network6.IPNet.IP }}/{{ .CidrSize6 }}" 81 | {{ end -}} 82 | {{ range .Server.Networks -}} 83 | "{{ . }}" 84 | {{ end -}} 85 | ]; 86 | endpoint = "{{ .Endpoint }}:{{ .Server.ListenPort }}"; 87 | persistentKeepalive = {{ .Server.PersistentKeepalive }}; 88 | dynamicEndpointRefreshRestartSeconds = 5; # restart on failure (e.g. DNS issue) 89 | dynamicEndpointRefreshSeconds = 300; # refresh DNS periodically 90 | {{ "}" }} 91 | ]; 92 | {{ "};" }} 93 | {{ "};" }} 94 | ` 95 | 96 | const routerosPeerConf = `/interface wireguard 97 | add name=wg0 private-key="{{ .Peer.PrivateKey.Key }}"; 98 | /interface list member 99 | add interface=wg0 list=LAN 100 | /ip address 101 | {{ if gt (.Server.Network.IPNet.IP | len) 0 -}} 102 | add address={{ .Peer.IP }}/{{ .CidrSize }} interface=wg0 103 | {{ end -}} 104 | /ipv6 address 105 | {{ if gt (.Server.Network6.IPNet.IP | len) 0 -}} 106 | add address={{ .Peer.IP6 }}/{{ .CidrSize6 }} advertise=no interface=wg0 107 | {{ end -}} 108 | /interface wireguard peers 109 | {{/* MikroTik RouterOS does not like trailing commas in arrays */ -}} 110 | {{ $first := true -}} 111 | add interface=wg0 \ 112 | public-key="{{ .Server.PrivateKey.PublicKey.Key }}" \ 113 | preshared-key="{{ .Peer.PresharedKey.Key }}" \ 114 | endpoint-address={{ .Endpoint }} \ 115 | endpoint-port={{ .Server.ListenPort }} \ 116 | persistent-keepalive={{ .Server.PersistentKeepalive }}s \ 117 | allowed-address= 118 | {{- if gt (.Server.Network.IPNet.IP | len) 0 }} 119 | {{- if $first}}{{$first = false}}{{else}},{{end}} 120 | {{- .Server.Network.IPNet.IP }}/{{ .CidrSize }} 121 | {{- end }} 122 | {{- if gt (.Server.Network6.IPNet.IP | len) 0 }} 123 | {{- if $first}}{{$first = false}}{{else}},{{end}} 124 | {{- .Server.Network6.IPNet.IP }}/{{ .CidrSize6 }} 125 | {{- end }} 126 | {{- range .Server.Networks }} 127 | {{- if $first}}{{$first = false}}{{else}},{{end}} 128 | {{- . }} 129 | {{- end }} 130 | ` 131 | -------------------------------------------------------------------------------- /CONFIG.md: -------------------------------------------------------------------------------- 1 | Explanation of each field: 2 | 3 | { 4 | "ExternalHostname": "", 5 | 6 | The `ExternalHostname` is used for the client config server `Endpoint` if 7 | defined. It has precedence over `ExternalIP` and `ExternalIP6`. 8 | 9 | 10 | "ExternalIP": "198.51.100.2", 11 | "ExternalIP6": "2001:0db8:85a3:0000:0000:8a2e:0370:7334", 12 | 13 | This is the external IPv4 and IPv6 that will be the value of Endpoint for the 14 | server peer in client configs. It is automatically detected by opening a socket 15 | or using an external IP discovery service -- the first to give a valid public 16 | IP will win. 17 | 18 | When generating configs, the `ExternalHostname` has precendence for the server 19 | `Endpoint`, followed by `ExternalIP` (IPv4) and `ExternalIP6` (IPv6) The IPs are 20 | discovered automatically on init. Define an `ExternalHostname` if you're using 21 | dynamic DNS, want to change IPs without updating configs, or want wireguard to 22 | be able to choose between IPv4/IPv6. It is only possible to specify one 23 | Endpoint per peer entry in wireguard. 24 | 25 | 26 | "ListenPort": 51820, 27 | 28 | The port wiregard should listen on. 29 | 30 | "Domain": "dsnet", 31 | 32 | The domain to copy to the report file. Not used for anything else; it's useful 33 | for DNS integration. At one site I have a script to add hosts to a zone upon 34 | connection by polling the report file. 35 | 36 | "InterfaceName": "dsnet", 37 | 38 | The wireguard interface name. 39 | 40 | "Network": "10.164.236.0/22", 41 | "Network6": "fd00:7b31:106a:ae00::/64", 42 | 43 | The CIDR network to use when allocating IPs to peers. This subnet, a `/22` in 44 | the `10.0.0.0/16` block is generated randomly to (probably) avoid collisions 45 | with other networks. There are 1022 addresses available. Addresses are 46 | allocated to peers when peers are added with `dsnet add` using the lowest 47 | available address. 48 | 49 | A random ULA network with a subnet of 0 is generated for IPv6. 50 | 51 | "IP": "10.164.236.1", 52 | "IP6": "fd00:7b31:106a:ae00:44c3:29c3:53b1:a6f9", 53 | 54 | This is the private VPN IP of the server peer. It is the first address in the 55 | above pool. 56 | 57 | "DNS": "", 58 | 59 | If defined, this IP address will be set in the generated peer wg-quick config 60 | files. 61 | 62 | "Networks": [], 63 | 64 | This is a list of additional CIDR-notated networks that can be routed through 65 | the server peer. They will be added under the server peer under `AllowedIPs` in 66 | addition to the private network defined in `Network` above. If you want to 67 | route the whole internet through the server peer, add `0.0.0.0/0` to the list 68 | before adding peers. For more advanced options and theory, see 69 |
6 |
18 |
19 |
20 | 21 | Set up a VPN in one minute: 22 | 23 | 24 | 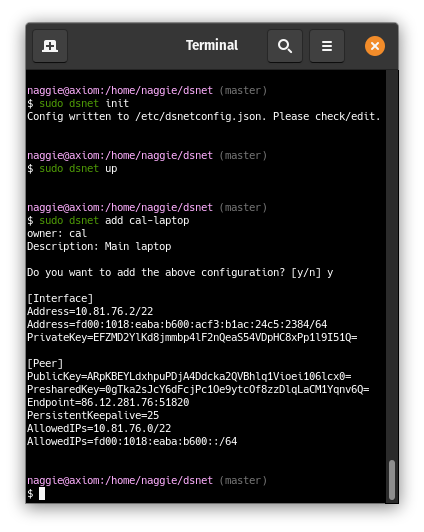 25 | 26 | The server peer is listening, and a client peer config has been generated and 27 | added to the server peer: 28 | 29 | 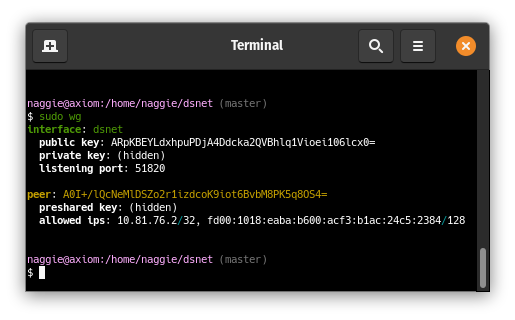 30 | 31 | More client peers can be added with `dsnet add`. They can connect immediately 32 | after! Don't forget to [enable IP forwarding](https://askubuntu.com/questions/311053/how-to-make-ip-forwarding-permanent) 33 | to allow peers to talk to one another. 34 | 35 | It works on AMD64 based linux and also ARMv5. 36 | 37 | Usage: 38 | dsnet [command] 39 | 40 | Available Commands: 41 | add Add a new peer + sync 42 | down Destroy the interface, run pre/post down 43 | help Help about any command 44 | init Create /etc/dsnetconfig.json containing default configuration + new keys without loading. Edit to taste. 45 | regenerate Regenerate keys and config for peer 46 | remove Remove a peer by hostname provided as argument + sync 47 | report Generate a JSON status report to stdout 48 | sync Update wireguard configuration from /etc/dsnetconfig.json after validating 49 | up Create the interface, run pre/post up, sync 50 | version Print version 51 | 52 | Flags: 53 | -h, --help help for this command 54 | --output string config file format: vyatta/wg-quick/nixos (default "wg-quick") 55 | 56 | Use "dsnet [command] --help" for more information about a command. 57 | 58 | 59 | Quick start (AMD64 linux) -- install wireguard, then, after making sure `/usr/local/bin` is in your path: 60 | 61 | sudo wget https://github.com/naggie/dsnet/releases/latest/download/dsnet-linux-amd64 -O /usr/local/bin/dsnet 62 | sudo chmod +x /usr/local/bin/dsnet 63 | sudo dsnet init 64 | # edit /etc/dsnetconfig.json to taste 65 | sudo dsnet up 66 | sudo dsnet add banana > dsnet-banana.conf 67 | sudo dsnet add apple > dsnet-apple.conf 68 | # enable IP forwarding to allow peers to talk to one another 69 | sudo sysctl -w net.ipv4.ip_forward=1 # edit /etc/sysctl.conf to make this persistent across reboots 70 | 71 | Copy the generated configuration file to your device and connect! 72 | 73 | To send configurations, here are a few suggestions. 74 | - [ffsend](https://github.com/timvisee/ffsend), the most straightforward option; 75 | - [magic wormhole](https://magic-wormhole.readthedocs.io/), a more advanced 76 | option, where the file never passes through another server; 77 | - [wormhole-william](https://github.com/psanford/wormhole-william), a Go 78 | implementation of the above. 79 | 80 | For the above options, one should transfer the password separately. 81 | 82 | A local QR code generator, such as the popular 83 | [qrencode](https://fukuchi.org/works/qrencode/) may also be used to generate a 84 | QR code of the configuration. For instance: `dsnet add | qrencode -t ansiutf8`. 85 | This works because the dsnet prompts are on STDERR and not passed to qrencode. 86 | 87 | The peer private key is generated on the server, which is technically not as 88 | secure as generating it on the client peer and then providing the server the 89 | public key; there is provision to specify a public key in the code when adding 90 | a peer to avoid the server generating the private key. The feature will be 91 | added when requested. 92 | 93 | Note that named arguments can be specified on the command line as well as 94 | entered by prompt; this allows for unattended usage. 95 | 96 | # GUI 97 | 98 | Dsnet does not include or require a GUI, however there is now a separate 99 | official monitoring GUI:

