├── .github
├── ISSUE_TEMPLATE
│ ├── bug_report.md
│ └── feature_request.md
└── release.yml
├── .gitignore
├── AtomicESClient
├── README.md
├── eula.txt
└── src
│ ├── AtomicESClient.swift
│ └── atomic_es_ents.plist
├── Iconography
├── GoldCardinal-1-0-3.md
├── GoldCardinal-1-0-4.md
└── README.md
├── Mute sets
├── GoldCardinal_1_0_1_mute_set.json
├── GoldCardinal_1_0_5_mute_set.json
└── es_default_mute_set_13_3_1.json
├── README.md
├── Resources
├── ArtifactFilteringOverview.png
├── DistributionChart.png
├── EventFactsOverview.png
├── FeatureSummary.png
├── GoldCardinal-1-0-1-event-iconography.png
├── GoldCardinal-1-0-5-event-iconography.png
├── Install.png
├── MuteSubscriptionsOverview.png
├── build-phases.png
├── run-as.png
└── signing-capabilities.png
├── Telemetry reports
├── GoldCardinal-1-0-3.md
├── GoldCardinal-1-0-4.md
└── README.md
└── eula.txt
/.github/ISSUE_TEMPLATE/bug_report.md:
--------------------------------------------------------------------------------
1 | ---
2 | name: Bug report
3 | about: Let us know of any bugs, crashes, performance, or any other issues you come
4 | across!
5 | title: ''
6 | labels: rc-mac-bug
7 | assignees: Brandon7CC
8 |
9 | ---
10 |
11 | **Describe the bug**
12 | A clear and concise description of what the bug is.
13 |
14 | **Expected behavior**
15 | A clear and concise description of what you expected to happen.
16 |
17 | **To Reproduce**
18 | Steps to reproduce the behavior:
19 | 1. Start system trace
20 | 2. Exercise some behavior
21 | 3. See error
22 |
23 | **Crash report (if applicable)**
24 | * Go to `Console.app`
25 | * Click on `Crash Reports` in the left side bar
26 | * Find the relevant crash report. For us, these will correspond to:
27 | * `com.redcanary.agent.securityextension` for the Security Extension process
28 | * and `Red Canary Mac Monitor" largely for the SwiftUI front-end
29 | * PLEASE attach the crash report to this bug report if applicable.
30 |
31 | **Screenshots**
32 | If applicable, add screenshots to help explain your problem.
33 |
34 | **Platform specifics (please complete the following information):**
35 | - macOS version [e.g. `13.3.1`]
36 | - Architecture [e.g. Apple Silicon]
37 | - Version [e.g. `Roadrunner version 2`]
38 |
39 | **Additional context**
40 | Add any other context about the problem here.
41 |
--------------------------------------------------------------------------------
/.github/ISSUE_TEMPLATE/feature_request.md:
--------------------------------------------------------------------------------
1 | ---
2 | name: Feature request
3 | about: Want something to improve your day-to-day? Let us know!
4 | title: ''
5 | labels: rc-mac-feature-request
6 | assignees: Brandon7CC
7 |
8 | ---
9 |
10 | **At a high level -- can you summarize your request?**
11 | (E.g.) For any given process execute event, pull the entitlements, and display them graphically within the "Event facts" window.
12 |
13 | **What is the current alternative solution?**
14 | (E.g.) Use of the `codesign` command line tool.
15 |
16 | **Are there "In-the-Wild" threats or corresponding ATT&CK techniques that exist for which this telemetry would be helpful?**
17 | (E.g.) For `T1553.001 Gatekeeper Bypass` -- File Quarantine information at the process and file level is very helpful.
18 |
19 | **Anything else?**
20 | Please list anything else that might help us implement the feature you're requesting. This could include marked-up screenshots, telemetry traces, mockups, etc.
21 |
--------------------------------------------------------------------------------
/.github/release.yml:
--------------------------------------------------------------------------------
1 | name: Release
2 | on:
3 | release:
4 | types: [created]
5 | jobs:
6 | build:
7 | name: Build
8 | runs-on: ubuntu-latest
9 | steps:
10 | - name: Create release
11 | uses: actions/create-release@v1
12 | env:
13 | GITHUB_TOKEN: ${{ secrets.GITHUB_TOKEN }}
14 | with:
15 | tag_name: ${{ github.ref }}
16 | release_name: Release ${{ github.ref }}
17 | draft: false
18 | prerelease: false
19 | body: |
20 | This is a new release.
21 | commitish: ${{ github.sha }}
22 | additional_files:
23 | - "!source code.zip"
--------------------------------------------------------------------------------
/.gitignore:
--------------------------------------------------------------------------------
1 | *.DS_Store
--------------------------------------------------------------------------------
/AtomicESClient/README.md:
--------------------------------------------------------------------------------
1 | # So you want to build an Endpoint Security app?
2 | > Author: [Brandon Dalton](https://redcanary.com/authors/brandon-dalton/)
3 |
4 | ## **Overview**
5 | AtomicESClient (a very small Endpoint Security (ES) client). AtomicESClient's goal is to provide an easy to follow example for quickly getting up and going with Apple's Endpoint Security APIs. This code should only be used as if it were written on a chalkboard -- in other words, purely for example. AtomicESClient is the very distilled version of an ES client with one event subscription.
6 |
7 | ## **Why?**
8 | We have received lots of requests to open source the "Red Canary Mac Monitor"! While this is not something I can do on my own -- we're always an open book when it comes to helping people learn and get familiar with complex security topics like ES. As a result of this feedback:
9 |
10 | We're releasing simple Swift program of just over 200 lines of code which (for educational use) shows the basics of how to:
11 | * Create an "entry point" and logger callback function
12 | * Model a basic `es_message_t` and process execution event `ES_EVENT_TYPE_NOTIFY_EXEC`.
13 | * A new ES client
14 | * Handle appropriate errors
15 | * Subscribe to events
16 | * Compile and sign your `Mach-O` to be free of any holes with pre-defined entitlements.
17 |
18 | ES is simply a public `C` API with extensive documentation and sample code release not just by Apple, but also by others. For more information on complete implementations please checkout these incredible resources:
19 | * ES documentation: https://developer.apple.com/documentation/endpointsecurity
20 | * ES sample code: ["Monitoring System Events with Endpoint Security"](https://developer.apple.com/documentation/endpointsecurity/monitoring_system_events_with_endpoint_security)
21 | * Filtering Network Traffic [(this sample code will be invaluable for understanding XPC)](https://developer.apple.com/documentation/networkextension/filtering_network_traffic)!
22 | * ProcessMonitor by Patrick Wardle: https://objective-see.org/blog/blog_0x47.html
23 | * FileMonitor by Patrick Wardle: https://objective-see.org/blog/blog_0x48.html
24 | * ESFang by Connor Morley: https://github.com/WithSecureLabs/ESFang
25 |
26 | > **The goal of AtomicESClient is simply to provide individuals with a *very* clear place to start -- nothing more or less.**
27 |
28 | ## **Getting going!**
29 | * Join the Apple Developer Program: cost $99/year (I had to pay too): https://developer.apple.com/programs/enroll/
30 | * Request the Endpoint Security entitlement: https://developer.apple.com/contact/request/system-extension/
31 | * Download the Swift file (purely for educational use)
32 |
33 | ### Option #1 (without Xcode)
34 | * Download the Swift and entitlements property list files
35 | * Compile the source:
36 | * You need to link with `libbsm.tbd` for `audit_token_to_pid`
37 | * and with `libEndpointSecurity.tbd` for ES functionality like `es_new_client` and `es_exec_arg`
38 | * Something like:
39 |
40 | `swiftc AtomicESClient.swift -L /Applications/Xcode.app/.../MacOSX.sdk/usr/lib/ -lEndpointSecurity -lbsm -o AtomicESClient`
41 | * Sign the Mach-O with your developer certificate and entitlements:
42 |
43 | `codesign -s $CERT --entitlements $ENT_PLIST --force --timestamp --options hard,kill,library-validation $ATOMIC_ES_CLIENT`
44 | * `$CERT` is the environment variable representing your Apple Developer certificate stored in Keychain. For me it's `Developer ID Application: Brandon Dalton (UA6JCQGF3F)`.
45 | * `$ENT_PLIST` is the environment variable representing the **path** to your entitlements property list file (XML formatted):
46 | ```xml
47 |
48 |
49 |
50 |
51 | com.apple.developer.endpoint-security.client
52 |
53 |
54 |
55 | ```
56 | * `$ATOMIC_ES_CLIENT` is the environment variable representing the **path** to your compiled `AtomicESClient` code.
57 |
58 | ### Option #2 (with Xcode)
59 | * Make a new Xcode "Command Line Tool" project and name it `AtomicESClient`
60 | * Replace the code in `main.swift` with the `AtomicESClient.swift` code
61 | * Add the Endpoint Security Entitlement to your target's `AtomicESClient.entitlements` file.
62 | * Key by the name of: `com.apple.developer.endpoint-security.client`
63 | * Next, under "Signing & Capabilities" ensure that "Automatically manage signing" is not enabled.
64 | * Give your target an appropriate bundle identifier e.g. for me I'd use something like `com.redcanary.atomicESClient`
65 | * Ensure that your development team is selected along with your signing certificate (e.g. `Developer ID: Application`)
66 | * If App Sandboxing is enabled remove it (can also be done from the `.entitlements` file)
67 | * Under your project's "Build Phases" tab go to the "Link Binaries With Libraries" section:
68 | * You need to link with `libbsm.tbd` for `audit_token_to_pid`
69 | * and with `libEndpointSecurity.tbd` for ES functionality like `es_new_client` and `es_exec_arg`
70 | * Ensure that Xcode is able to execute the `AtomicESClient` Mach-O as `root` by going to:
71 | * "Product" > "Scheme" > "Edit Scheme..."
72 | * Under "Run" > "Info" > "Debug Process As": `root`
73 |
74 | 
75 | 
76 | 
77 |
78 | ### **Running**
79 | * Endpoint Security **requires** Full Disk Access. This is a defined requirement in the API. Even if you use Apple's `/usr/bin/eslogger` tool you'll still need to enable Full Disk Access (part of TCC) for the host application. Likely something like `Terminal.app` or `iTerm2.app`.
80 | * To make this *even more clear* please refer to `es_new_client_result_t` which has the following enumeration:
81 | * `ES_NEW_CLIENT_RESULT_ERR_NOT_PERMITTED`: "This error indicates the app lacks Transparency, Consent, and Control (TCC) approval from the user."
82 | * Similarly, you *need* to run any ES client with elevation -- this makes sense right? See:
83 | * `ES_NEW_CLIENT_RESULT_ERR_NOT_PRIVILEGED`: "The caller isn’t running as root."
84 | * You also do *NEED* the ES entitlement in a *vast* majority of cases (without lowering macOS' security posture). See:
85 | * `ES_NEW_CLIENT_RESULT_ERR_NOT_ENTITLED`: "The caller isn’t properly entitled to connect to Endpoint Security."
86 | * **Optional**: Disabling System Integrity Protection (SIP) will aid you during the development process: using `lldb` to debug your Security Extension. I did most development with SIP enabled and then used it to debug more difficult to identify problems at the end of development. **PLEASE** do not forget to re-enable SIP on your development machine after you’re done!
87 |
88 | ### Did you do it right?
89 | > When all is said and done you should see output like the following!
90 | ```shell
91 | > sudo ./AtomicESClient
92 | Password:
93 | [ES CLIENT SUCCESS] We successfully created a new Endpoint Security client!
94 | {"initiating_process_signing_id":"com.apple.xpc.launchd","id":"07B2FB1B-39FD-447F-95C3-17A352B8418E","initiating_pid":1,"es_event_type":"ES_EVENT_TYPE_NOTIFY_EXEC","initiating_process_path":"/sbin/launchd","exec_event":{"process_path":"/usr/libexec/xpcproxy","process_name":"xpcproxy","pid":43459,"id":"321EEBC4-6753-45CA-ACFD-B75C633AA873","signing_id":"com.apple.xpc.proxy","is_platform_binary":true,"is_adhoc_signed":false,"command_line":"xpcproxy application.com.apple.iCal.1152921500311882688.1152921500311882957"},"mach_time":655266102521,"initiating_process_name":"launchd"}
95 | ```
--------------------------------------------------------------------------------
/AtomicESClient/eula.txt:
--------------------------------------------------------------------------------
1 | BSD 3-Clause License
2 |
3 | Copyright (c) 2023, Red Canary
4 | All rights reserved.
5 |
6 | Redistribution and use in source and binary forms, with or without
7 | modification, are permitted provided that the following conditions are met:
8 |
9 | 1. Redistributions of source code must retain the above copyright notice, this
10 | list of conditions and the following disclaimer.
11 |
12 | 2. Redistributions in binary form must reproduce the above copyright notice,
13 | this list of conditions and the following disclaimer in the documentation
14 | and/or other materials provided with the distribution.
15 |
16 | 3. Neither the name of the copyright holder nor the names of its
17 | contributors may be used to endorse or promote products derived from
18 | this software without specific prior written permission.
19 |
20 | THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS"
21 | AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
22 | IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
23 | DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT HOLDER OR CONTRIBUTORS BE LIABLE
24 | FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
25 | DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR
26 | SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER
27 | CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY,
28 | OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
29 | OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
--------------------------------------------------------------------------------
/AtomicESClient/src/AtomicESClient.swift:
--------------------------------------------------------------------------------
1 | //
2 | // AtomicESClient.swift
3 | // AtomicESClient
4 | //
5 | // Created by Brandon Dalton on 4/19/23.
6 | //
7 | // BSD 3-Clause License: ../eula.txt
8 | //
9 | // Discussion:
10 | // AtomicESClient (a very small Endpoint Security (ES) client). AtomicESClient's goal is to provide an easy
11 | // to follow example for quickly getting up and going with Apple's Endpoint Security APIs. This code should
12 | // only be used as if it were written on a chalkboard -- in other words, purely for example. AtomicESClient
13 | // is the very distilled version of an ES client with one event subscription. Much more complete examples
14 | // exist. Please see the README for a few of those references!
15 | //
16 | // Swift compile: `swiftc AtomicESClient.swift -L /Applications/Xcode.app/.../MacOSX.sdk/usr/lib/ -lEndpointSecurity -lbsm -o AtomicESClient`
17 | // Codesign: `codesign -s $CERT --entitlements atomic_es_ents.plist --force --timestamp --options hard,kill,library-validation AtomicESClient`
18 | //
19 | // Usage: `sudo ./AtomicESClient`
20 | //
21 |
22 | import Foundation
23 | import EndpointSecurity
24 |
25 |
26 | // @note: reference: `kern/cs_blobs.h`
27 | // Use a Swift module to expose the Kernel/kern/cs_blobs.h header file
28 | let CS_ADHOC: UInt32 = 0x00000002 /* ad hoc signed */
29 |
30 | // @discussion: This ES event will give you basic *high level* process execution information.
31 | public var esEventSubs: [es_event_type_t] = [
32 | ES_EVENT_TYPE_NOTIFY_EXEC
33 | ]
34 |
35 | // MARK: - Process Execution event
36 | // @note: we'll give you a *very* basic model here.
37 | public struct ExampleProcessExecEvent: Identifiable, Codable {
38 | public var id: UUID = UUID()
39 |
40 | public var is_platform_binary, is_adhoc_signed: Bool
41 | public var process_name, process_path, signing_id, command_line, team_id: String?
42 | public var pid: Int?
43 |
44 | private func parseCommandLine(execEvent: inout es_event_exec_t) -> String {
45 | let commandLineProducer = (0 ..< Int(es_exec_arg_count(&execEvent))).map {
46 | String(cString: es_exec_arg(&execEvent, UInt32($0)).data)
47 | }.joined(separator: " ")
48 |
49 | return commandLineProducer.trimmingCharacters(in: .whitespaces)
50 | }
51 |
52 | init(fromRawEvent rawEvent: UnsafePointer) {
53 | var processExecEvent: es_event_exec_t = rawEvent.pointee.event.exec
54 |
55 | self.pid = Int(audit_token_to_pid(rawEvent.pointee.process.pointee.audit_token))
56 | let processURL: NSURL = NSURL(fileURLWithPath: String(cString: processExecEvent.target.pointee.executable.pointee.path.data))
57 | self.process_name = processURL.lastPathComponent
58 | self.process_path = String(cString: processExecEvent.target.pointee.executable.pointee.path.data)
59 | self.is_platform_binary = processExecEvent.target.pointee.is_platform_binary
60 | self.is_adhoc_signed = (processExecEvent.target.pointee.codesigning_flags) & CS_ADHOC == CS_ADHOC
61 | self.command_line = parseCommandLine(execEvent: &processExecEvent)
62 |
63 | // @note: basic code signing information
64 | self.signing_id = String(cString: processExecEvent.target.pointee.signing_id.data)
65 |
66 | if processExecEvent.target.pointee.team_id.length > 0 {
67 | self.team_id = String(cString: processExecEvent.target.pointee.team_id.data)
68 | }
69 | }
70 | }
71 |
72 | public struct ExampleESEvent: Identifiable, Codable {
73 | public var id = UUID()
74 |
75 | // Top level "ES message" information. Here we're also including the `es_process_t`.
76 | public var es_event_type, initiating_process_name, initiating_process_path, initiating_process_signing_id: String?
77 | public var initiating_pid: Int?
78 | public var mach_time: Int
79 |
80 | // Add each event you've modeled here.
81 | public var exec_event: ExampleProcessExecEvent?
82 |
83 | init(fromRawEvent rawEvent: UnsafePointer) {
84 | // MARK: - Top-level `es_message_t` / `es_process_t`
85 | // Reference: https://developer.apple.com/documentation/endpointsecurity/message
86 | self.mach_time = Int(rawEvent.pointee.mach_time)
87 | self.initiating_pid = Int(audit_token_to_pid(rawEvent.pointee.process.pointee.parent_audit_token))
88 |
89 | let executableURL: NSURL = NSURL(fileURLWithPath: String(cString: rawEvent.pointee.process.pointee.executable.pointee.path.data))
90 | self.initiating_process_path = String(cString: rawEvent.pointee.process.pointee.executable.pointee.path.data)
91 | self.initiating_process_name = executableURL.lastPathComponent ?? "Unknown"
92 |
93 | // @note: basic code signing information
94 | self.initiating_process_signing_id = String(cString: rawEvent.pointee.process.pointee.signing_id.data)
95 |
96 | // MARK: - ES event switch
97 | switch (rawEvent.pointee.event_type) {
98 | case ES_EVENT_TYPE_NOTIFY_EXEC:
99 | self.es_event_type = "ES_EVENT_TYPE_NOTIFY_EXEC"
100 | self.exec_event = ExampleProcessExecEvent(fromRawEvent: rawEvent)
101 | break
102 | default:
103 | self.es_event_type = "NOT MAPPED"
104 | break
105 | }
106 | }
107 | }
108 |
109 | // MARK: - Manage your Endpoint Security (ES) client
110 | public class EndpointSecurityClientManager: NSObject {
111 | public var esClient: OpaquePointer?
112 |
113 | // A simple function to convert an `Encodable` event to JSON.
114 | public static func eventToJSON(value: Encodable) -> String {
115 | let encoder = JSONEncoder()
116 | encoder.outputFormatting = .withoutEscapingSlashes
117 |
118 | let encodedData = try? encoder.encode(value)
119 | return String(data: encodedData!, encoding: .utf8)!
120 | }
121 |
122 | public func bootupESClient(completion: @escaping (_: String) -> Void) -> OpaquePointer? {
123 | var client: OpaquePointer?
124 |
125 | // MARK: - New ES client
126 | // Reference: https://developer.apple.com/documentation/endpointsecurity/client
127 | let result: es_new_client_result_t = es_new_client(&client){ _, event in
128 | // Here is where the ES client will "send" events to be handled by our app -- this is the "callback".
129 | completion(EndpointSecurityClientManager.eventToJSON(value: ExampleESEvent(fromRawEvent: event)))
130 | }
131 |
132 | // Check the result of your `es_new_client_result_t` operation. Here is where you'll run into issues like:
133 | // - Not having the ES entitlement signed to your app.
134 | // - Not running as `root`, etc.
135 | switch result {
136 | case ES_NEW_CLIENT_RESULT_ERR_TOO_MANY_CLIENTS:
137 | print("[ES CLIENT ERROR] There are too many Endpoint Security clients!")
138 | break
139 | case ES_NEW_CLIENT_RESULT_ERR_NOT_ENTITLED:
140 | print("[ES CLIENT ERROR] Failed to create new Endpoint Security client! The endpoint security entitlement is required.")
141 | break
142 | case ES_NEW_CLIENT_RESULT_ERR_NOT_PERMITTED:
143 | print("[ES CLIENT ERROR] Lacking TCC permissions!")
144 | break
145 | case ES_NEW_CLIENT_RESULT_ERR_NOT_PRIVILEGED:
146 | print("[ES CLIENT ERROR] Caller is not running as root!")
147 | break
148 | case ES_NEW_CLIENT_RESULT_ERR_INTERNAL:
149 | print("[ES CLIENT ERROR] Error communicating with ES!")
150 | break
151 | case ES_NEW_CLIENT_RESULT_ERR_INVALID_ARGUMENT:
152 | print("[ES CLIENT ERROR] Incorrect arguments creating a new ES client!")
153 | break
154 | case ES_NEW_CLIENT_RESULT_SUCCESS:
155 | print("[ES CLIENT SUCCESS] We successfully created a new Endpoint Security client!")
156 | break
157 | default:
158 | print("An unknown error occured while creating a new Endpoint Security client!")
159 | }
160 |
161 | // Validate that we have a valid reference to a client
162 | if client == nil {
163 | print("[ES CLIENT ERROR] After atempting to make a new ES client we failed.")
164 | return nil
165 | }
166 |
167 | // MARK: - Event subscriptions
168 | // Reference: https://developer.apple.com/documentation/endpointsecurity/3228854-es_subscribe
169 | if es_subscribe(client!, esEventSubs, UInt32(esEventSubs.count)) != ES_RETURN_SUCCESS {
170 | print("[ES CLIENT ERROR] Failed to subscribe to core events! \(result.rawValue)")
171 | es_delete_client(client)
172 | exit(EXIT_FAILURE)
173 | }
174 |
175 | self.esClient = client
176 | return client
177 | }
178 | }
179 |
180 | // Implement a very simple logger -- here is where your events will be printed.
181 | func logger(jsonEvent: String) {
182 | print(jsonEvent)
183 | }
184 |
185 | func bootupESClientWithLogger() -> OpaquePointer? {
186 | let esClientManager = EndpointSecurityClientManager()
187 | let esClient = esClientManager.bootupESClient(completion: logger)
188 |
189 | if esClient == nil {
190 | print("[ES CLIENT ERROR] Error creating the endpoint security client!")
191 | exit(EXIT_FAILURE)
192 | }
193 |
194 | return esClient
195 | }
196 |
197 | func waitForExit() {
198 | let waitForCTRLC = DispatchSource.makeSignalSource(signal: SIGINT, queue: .main)
199 | waitForCTRLC.setEventHandler {
200 | exit(EXIT_SUCCESS)
201 | }
202 |
203 | waitForCTRLC.resume()
204 | dispatchMain()
205 | }
206 |
207 | let esClient = bootupESClientWithLogger()
208 |
209 | // Simple `ctrl+c` to exit
210 | waitForExit()
211 |
--------------------------------------------------------------------------------
/AtomicESClient/src/atomic_es_ents.plist:
--------------------------------------------------------------------------------
1 |
2 |
3 |
4 |
5 | com.apple.developer.endpoint-security.client
6 |
7 |
8 |
--------------------------------------------------------------------------------
/Iconography/GoldCardinal-1-0-3.md:
--------------------------------------------------------------------------------
1 | # **Event Iconography**
2 | ## **Distribution details**
3 | - Build name: `GoldCardinal`
4 | - App versions: `1.0.1` - `1.0.3`
5 |
6 | ## **Overview**
7 | Utilizing **[SF Symbols](https://developer.apple.com/sf-symbols/)** we've assigned each ES event a symbol and colors which correspond to facts about any given event. To follow along, please download `SF Symbols`! *This guide will include pictures in the future*.
8 |
9 | ## **Color summary**
10 | * `Blue`: Login of some kind (e.g. login window unlock)
11 | * `Orange`: Generally speaking, a low volume "security relevant" event (e.g. background tasks being added)
12 | * `Red`: Something to potentially look into. For example, `com.apple.quarantine` extended attribute deletion -- [generally not a problem on its own](https://redcanary.com/blog/gatekeeper/).
13 | * `Purple`: Something you should *definitely* look at. Some heuristics developed include [Gatekeeper bypass](https://redcanary.com/threat-detection-report/techniques/gatekeeper-bypass/#:~:text=creating%20this%20file-,Detection%20opportunities,-While%20it%20might) at the File Quarantine level. XProtect detection events are also colored purple.
14 | * `Green`: A remediation action / setting a security policy occurred -- right now just XProtect Remediator / setting the quarantine flag.
15 |
16 | ## **Event breakdown detailed**
17 | Please note. In most cases, we've included "help" / "tooltip" text for each symbol which you can see by hovering the cursor over any given symbol.
18 |
19 | ## **Process events**
20 | ### `ES_EVENT_TYPE_NOTIFY_EXEC`
21 | - **Event symbol: "checkmark.seal"** or
22 | - **event symbol: "xmark.seal"**
23 |
24 | - **Code signing**
25 | - **Event symbol: "checkmark.seal"** represents `process_exec` events with a valid code signature (and not adhoc).
26 | - If the process is adhoc signed the event will be colored in `orange` with the **event symbol: "xmark.seal"** and a `yellow` "exclamationmark.triangle.fill" symbol proceeding it.
27 | - If the process is not signed at all it will be colored in `red` with the **event symbol: "xmark.seal"** and a `red` "exclamationmark.triangle.fill" symbol proceeding it.
28 |
29 | - **Dylib injection**
30 | - If we've observed this target process having `dyld_insert_libraries` in its environment variables we'll prefix the event symbol with a: "bookmark.slash".
31 |
32 | - **File Quarantine-aware processes**
33 | - If we've identified that this process is "File Quarantine-aware" then we'll prefix the event symbol with a: "lock.icloud".
34 |
35 | ### `ES_EVENT_TYPE_NOTIFY_FORK`
36 | - **Event symbol: "point.topleft.down.curvedto.point.bottomright.up".**
37 |
38 | ### `ES_EVENT_TYPE_NOTIFY_SIGNAL`
39 | - **Event symbol: "dot.radiowaves.forward".**
40 |
41 | ### `ES_EVENT_TYPE_NOTIFY_PROC_SUSPEND_RESUME`
42 | - **Event symbol: "autostartstop.trianglebadge.exclamationmark".**
43 |
44 | ### `ES_EVENT_TYPE_NOTIFY_CS_INVALIDATED`
45 | - **Event symbol: "signature"** and we'll color this event `red` / prefix the event symbol with a `yellow`: "exclamationmark.triangle.
46 |
47 | ### `ES_EVENT_TYPE_NOTIFY_REMOTE_THREAD_CREATE`
48 | - **Event symbol: bolt.horizontal.fill"** and we'll color this event `red` / prefix the event symbol with a `yellow`: "exclamationmark.triangle.fill" symbol.
49 |
50 | ### `ES_EVENT_TYPE_NOTIFY_TRACE`
51 | - **Event symbol: "stethoscope"** and we'll color this event `orange`.
52 |
53 | ### `ES_EVENT_TYPE_NOTIFY_GET_TASK`
54 | - **Event symbol: "creditcard.trianglebadge.exclamationmark"** and we'll color this event `orange`.
55 |
56 | ### `ES_EVENT_TYPE_NOTIFY_PROC_CHECK`
57 | - **Event symbol: "barcode.viewfinder".**
58 |
59 | ### `ES_EVENT_TYPE_NOTIFY_EXIT`
60 | - **Event symbol: "eject.fill".**
61 |
62 | - **Non-zero exit codes**
63 | - If this event is representing a non-zero exit code then we'll prefix the event symbol with an: "info.square".
64 |
65 |
66 |
67 | ## **Memory events**
68 | ### `ES_EVENT_TYPE_NOTIFY_MMAP`
69 | - **Event symbol: "memorychip".**
70 |
71 | - **OSA (Open Scripting Architecture)**
72 | - If this event is mapping an OSA component into memory then we'll add a `yellow`: "exclamationmark.triangle.fill" symbol proceeding it.
73 |
74 |
75 |
76 | ## **File events**
77 | ### `ES_EVENT_TYPE_NOTIFY_CREATE`
78 | - **Event symbol: "doc.plaintext".**
79 |
80 | - **File Quarantine**
81 | - If we've identified a potential "File Quarantine violation" (see our Gatekeeper blogs) we'll color the event `red` (unquarantined file downloaded by a File Quarantine-aware app).
82 | - Additionally, if the file was found on disk to be quarantined we'll prefix the event symbol with: "lock.shield".
83 |
84 | ### `ES_EVENT_TYPE_NOTIFY_DUP`
85 | - **Event symbol: "folder.badge.plus".**
86 |
87 | ### `ES_EVENT_TYPE_NOTIFY_RENAME`
88 | - **Event symbol: filemenu.and.cursorarrow".**
89 |
90 | - **File Quarantine**
91 | - If we've identified a potential "File Quarantine violation" (see our [Gatekeeper bypass](https://redcanary.com/threat-detection-report/techniques/gatekeeper-bypass/#:~:text=creating%20this%20file-,Detection%20opportunities,-While%20it%20might) blogs) we'll color the event:
92 | - `purple`: As the result of a deep search on an inflated archive by `Archive Utility.app` we found that a file was not quarantined, but its parent directory was. The quarantine flag should *always* propagate. **This heuristic should be high fidelity.** Additionally, we'll prefix the event symbol with: "bolt.trianglebadge.exclamationmark.fill".
93 | - `red`: We noticed that an app bundle was unarchived with `Archive Utility.app` and it's not quarantined, but, on the surface we have no way to tell "which" process ordered the unarchive operation. This means that **false positives are more likely** due to the missing "File Quarantine-aware" artifact. Additionally, we'll prefix the event symbol with: "hand.raised.app".
94 |
95 | ### `ES_EVENT_TYPE_NOTIFY_UNLINK`
96 | - **Event symbol: "trash".**
97 |
98 | ### `ES_EVENT_TYPE_NOTIFY_OPEN`
99 | - **Event symbol: "envelope.open.fill".**
100 |
101 | ### `ES_EVENT_TYPE_NOTIFY_WRITE`
102 | - **Event symbol: "square.and.pencil".**
103 |
104 | ### `ES_EVENT_TYPE_NOTIFY_LINK`
105 | - **Event symbol: "link.badge.plus".**
106 |
107 | ### `ES_EVENT_TYPE_NOTIFY_CLOSE`
108 | - **Event symbol: "xmark.square".**
109 |
110 |
111 |
112 | ## **File metadata events**
113 | ### `ES_EVENT_TYPE_NOTIFY_DELETEEXTATTR`
114 | - **Event symbol: "delete.backward.fill".**
115 |
116 | - **File Quarantine**
117 | - If this event is deleting the quarantine flag then we'll color this event `red`.
118 |
119 | ### `ES_EVENT_TYPE_NOTIFY_SETEXTATTR`
120 | - **Event symbol: "filemenu.and.selection".**
121 |
122 | - **File Quarantine**
123 | - If this event is setting the quarantine flag then we'll color this event `green`.
124 |
125 |
126 |
127 | ## **File system events**
128 | ### `ES_EVENT_TYPE_NOTIFY_MOUNT`
129 | - **Event symbol: "mount".**
130 |
131 |
132 |
133 | ## **Background Task events**
134 | ### `ES_EVENT_TYPE_NOTIFY_BTM_LAUNCH_ITEM_ADD`
135 | - **Event symbol: "lock.doc"** and we'll color this event `orange` / prefix the event symbol with a `yellow`: "exclamationmark.triangle.fill" symbol.
136 |
137 | ### `ES_EVENT_TYPE_NOTIFY_BTM_LAUNCH_ITEM_REMOVE`
138 | - **Event symbol: "lock.doc"** and we'll color this event `orange` / prefix the event symbol with a `yellow`: "exclamationmark.triangle.fill" symbol.
139 |
140 |
141 |
142 | ## **Login events**
143 | ### `ES_EVENT_TYPE_NOTIFY_OPENSSH_LOGIN`
144 | - **Event symbol: "network"** and we'll color this event `blue`
145 |
146 | ### `ES_EVENT_TYPE_NOTIFY_OPENSSH_LOGOUT`
147 | - **Event symbol: "network"** and we'll color this event `blue`
148 |
149 | ### `ES_EVENT_TYPE_NOTIFY_LOGIN_LOGIN`
150 | - **Event symbol: "person.fill.checkmark".**
151 |
152 | ### `ES_EVENT_TYPE_NOTIFY_LW_SESSION_LOGIN`
153 | - **Event symbol: "macwindow.badge.plus".**
154 |
155 | ### `ES_EVENT_TYPE_NOTIFY_LW_SESSION_UNLOCK`
156 | - **Event symbol: "lock.open".**
157 |
158 |
159 |
160 | ## **XProtect events**
161 | ### `ES_EVENT_TYPE_NOTIFY_XP_MALWARE_DETECTED`
162 | - **Event symbol: "bolt.shield"** and we'll color this event `purple`
163 |
164 | ### `ES_EVENT_TYPE_NOTIFY_XP_MALWARE_REMEDIATED`
165 | - **Event symbol: "checkmark.shield"** and we'll color this event `green`
166 |
167 |
168 |
169 | ## **Kernel events**
170 | ### `ES_EVENT_TYPE_NOTIFY_IOKIT_OPEN`
171 | - **Event symbol: "captions.bubble".**
172 |
173 |
174 | 
--------------------------------------------------------------------------------
/Iconography/GoldCardinal-1-0-4.md:
--------------------------------------------------------------------------------
1 | # **Event Iconography**
2 | ## **Distribution details**
3 | - Build name: `GoldCardinal`
4 | - App versions: `1.0.4`
5 |
6 | ## **Overview**
7 | Utilizing **[SF Symbols](https://developer.apple.com/sf-symbols/)** we've assigned each ES event a symbol and colors which correspond to facts about any given event. To follow along, please download `SF Symbols`! *This guide will include pictures in the future*.
8 |
9 | ## **Color summary**
10 | * `Blue`: Login of some kind (e.g. login window unlock)
11 | * `Orange`: Generally speaking, a low volume "security relevant" event (e.g. background tasks being added)
12 | * `Red`: Something to potentially look into. For example, `com.apple.quarantine` extended attribute deletion -- [generally not a problem on its own](https://redcanary.com/blog/gatekeeper/).
13 | * `Purple`: Something you should *definitely* look at. Some heuristics developed include [Gatekeeper bypass](https://redcanary.com/threat-detection-report/techniques/gatekeeper-bypass/#:~:text=creating%20this%20file-,Detection%20opportunities,-While%20it%20might) at the File Quarantine level. XProtect detection events are also colored purple.
14 | * `Green`: A remediation action / setting a security policy occurred -- right now just XProtect Remediator / setting the quarantine flag.
15 |
16 | ## **Event breakdown detailed**
17 | Please note. In most cases, we've included "help" / "tooltip" text for each symbol which you can see by hovering the cursor over any given symbol.
18 |
19 | ## **Process events**
20 | ### `ES_EVENT_TYPE_NOTIFY_EXEC`
21 | - **Event symbol: "checkmark.seal"** or
22 | - **event symbol: "xmark.seal"**
23 |
24 | - **Code signing**
25 | - **Event symbol: "checkmark.seal"** represents `process_exec` events with a valid code signature (and not adhoc).
26 | - If the process is adhoc signed the event will be colored in `orange` with the **event symbol: "xmark.seal"** and a `yellow` "exclamationmark.triangle.fill" symbol proceeding it.
27 | - If the process is not signed at all it will be colored in `red` with the **event symbol: "xmark.seal"** and a `red` "exclamationmark.triangle.fill" symbol proceeding it.
28 |
29 | - **Dynamic Loader**
30 | - If we've observed this target process having `dyld_insert_libraries` in its environment variables we'll prefix the event symbol with a: "bookmark.slash".
31 | - Additionally, if the `dyld_exec_path` does not match the `process_path` we'll prefix the event symbol with a: "curlybraces.square".
32 |
33 | - **File Quarantine-aware processes**
34 | - If we've identified that this process is "File Quarantine-aware" then we'll prefix the event symbol with a: "lock.icloud".
35 |
36 | ### `ES_EVENT_TYPE_NOTIFY_FORK`
37 | - **Event symbol: "point.topleft.down.curvedto.point.bottomright.up".**
38 |
39 | ### `ES_EVENT_TYPE_NOTIFY_SIGNAL`
40 | - **Event symbol: "dot.radiowaves.forward".**
41 |
42 | ### `ES_EVENT_TYPE_NOTIFY_PROC_SUSPEND_RESUME`
43 | - **Event symbol: "autostartstop.trianglebadge.exclamationmark".**
44 |
45 | ### `ES_EVENT_TYPE_NOTIFY_CS_INVALIDATED`
46 | - **Event symbol: "signature"** and we'll color this event `red` / prefix the event symbol with a `yellow`: "exclamationmark.triangle.
47 |
48 | ### `ES_EVENT_TYPE_NOTIFY_REMOTE_THREAD_CREATE`
49 | - **Event symbol: bolt.horizontal.fill"** and we'll color this event `red` / prefix the event symbol with a `yellow`: "exclamationmark.triangle.fill" symbol.
50 |
51 | ### `ES_EVENT_TYPE_NOTIFY_TRACE`
52 | - **Event symbol: "stethoscope"** and we'll color this event `orange`.
53 |
54 | ### `ES_EVENT_TYPE_NOTIFY_GET_TASK`
55 | - **Event symbol: "creditcard.trianglebadge.exclamationmark"** and we'll color this event `orange`.
56 |
57 | ### `ES_EVENT_TYPE_NOTIFY_PROC_CHECK`
58 | - **Event symbol: "barcode.viewfinder".**
59 |
60 | ### `ES_EVENT_TYPE_NOTIFY_EXIT`
61 | - **Event symbol: "eject.fill".**
62 |
63 | - **Non-zero exit codes**
64 | - If this event is representing a non-zero exit code then we'll prefix the event symbol with an: "info.square".
65 |
66 |
67 |
68 | ## **Memory events**
69 | ### `ES_EVENT_TYPE_NOTIFY_MMAP`
70 | - **Event symbol: "memorychip".**
71 |
72 | - **OSA (Open Scripting Architecture)**
73 | - If this event is mapping an OSA component into memory then we'll add a `yellow`: "exclamationmark.triangle.fill" symbol proceeding it.
74 |
75 |
76 |
77 | ## **File events**
78 | ### `ES_EVENT_TYPE_NOTIFY_CREATE`
79 | - **Event symbol: "doc.plaintext".**
80 |
81 | - **File Quarantine**
82 | - If we've identified a potential "File Quarantine violation" (see our Gatekeeper blogs) we'll color the event `red` (unquarantined file downloaded by a File Quarantine-aware app).
83 | - Additionally, if the file was found on disk to be quarantined we'll prefix the event symbol with: "lock.shield".
84 |
85 | ### `ES_EVENT_TYPE_NOTIFY_DUP`
86 | - **Event symbol: "folder.badge.plus".**
87 |
88 | ### `ES_EVENT_TYPE_NOTIFY_RENAME`
89 | - **Event symbol: filemenu.and.cursorarrow".**
90 |
91 | - **File Quarantine**
92 | - If we've identified a potential "File Quarantine violation" (see our [Gatekeeper bypass](https://redcanary.com/threat-detection-report/techniques/gatekeeper-bypass/#:~:text=creating%20this%20file-,Detection%20opportunities,-While%20it%20might) blogs) we'll color the event:
93 | - `purple`: As the result of a deep search on an inflated archive by `Archive Utility.app` we found that a file was not quarantined, but its parent directory was. The quarantine flag should *always* propagate. **This heuristic should be high fidelity.** Additionally, we'll prefix the event symbol with: "bolt.trianglebadge.exclamationmark.fill".
94 | - `red`: We noticed that an app bundle was unarchived with `Archive Utility.app` and it's not quarantined, but, on the surface we have no way to tell "which" process ordered the unarchive operation. This means that **false positives are more likely** due to the missing "File Quarantine-aware" artifact. Additionally, we'll prefix the event symbol with: "hand.raised.app".
95 |
96 | ### `ES_EVENT_TYPE_NOTIFY_UNLINK`
97 | - **Event symbol: "trash".**
98 |
99 | ### `ES_EVENT_TYPE_NOTIFY_OPEN`
100 | - **Event symbol: "envelope.open.fill".**
101 |
102 | ### `ES_EVENT_TYPE_NOTIFY_WRITE`
103 | - **Event symbol: "square.and.pencil".**
104 |
105 | ### `ES_EVENT_TYPE_NOTIFY_LINK`
106 | - **Event symbol: "link.badge.plus".**
107 |
108 | ### `ES_EVENT_TYPE_NOTIFY_CLOSE`
109 | - **Event symbol: "xmark.square".**
110 |
111 |
112 |
113 | ## **File metadata events**
114 | ### `ES_EVENT_TYPE_NOTIFY_DELETEEXTATTR`
115 | - **Event symbol: "delete.backward.fill".**
116 |
117 | - **File Quarantine**
118 | - If this event is deleting the quarantine flag then we'll color this event `red`.
119 |
120 | ### `ES_EVENT_TYPE_NOTIFY_SETEXTATTR`
121 | - **Event symbol: "filemenu.and.selection".**
122 |
123 | - **File Quarantine**
124 | - If this event is setting the quarantine flag then we'll color this event `green`.
125 |
126 |
127 |
128 | ## **File system events**
129 | ### `ES_EVENT_TYPE_NOTIFY_MOUNT`
130 | - **Event symbol: "mount".**
131 |
132 |
133 |
134 | ## **Background Task events**
135 | ### `ES_EVENT_TYPE_NOTIFY_BTM_LAUNCH_ITEM_ADD`
136 | - **Event symbol: "lock.doc"** and we'll color this event `orange` / prefix the event symbol with a `yellow`: "exclamationmark.triangle.fill" symbol.
137 |
138 | ### `ES_EVENT_TYPE_NOTIFY_BTM_LAUNCH_ITEM_REMOVE`
139 | - **Event symbol: "lock.doc"** and we'll color this event `orange` / prefix the event symbol with a `yellow`: "exclamationmark.triangle.fill" symbol.
140 |
141 |
142 |
143 | ## **Login events**
144 | ### `ES_EVENT_TYPE_NOTIFY_OPENSSH_LOGIN`
145 | - **Event symbol: "network"** and we'll color this event `blue`
146 |
147 | ### `ES_EVENT_TYPE_NOTIFY_OPENSSH_LOGOUT`
148 | - **Event symbol: "network"** and we'll color this event `blue`
149 |
150 | ### `ES_EVENT_TYPE_NOTIFY_LOGIN_LOGIN`
151 | - **Event symbol: "person.fill.checkmark".**
152 |
153 | ### `ES_EVENT_TYPE_NOTIFY_LW_SESSION_LOGIN`
154 | - **Event symbol: "macwindow.badge.plus".**
155 |
156 | ### `ES_EVENT_TYPE_NOTIFY_LW_SESSION_UNLOCK`
157 | - **Event symbol: "lock.open".**
158 |
159 |
160 |
161 | ## **XProtect events**
162 | ### `ES_EVENT_TYPE_NOTIFY_XP_MALWARE_DETECTED`
163 | - **Event symbol: "bolt.shield"** and we'll color this event `purple`
164 |
165 | ### `ES_EVENT_TYPE_NOTIFY_XP_MALWARE_REMEDIATED`
166 | - **Event symbol: "checkmark.shield"** and we'll color this event `green`
167 |
168 |
169 |
170 | ## **Kernel events**
171 | ### `ES_EVENT_TYPE_NOTIFY_IOKIT_OPEN`
172 | - **Event symbol: "captions.bubble".**
173 |
174 |
175 | 
--------------------------------------------------------------------------------
/Iconography/README.md:
--------------------------------------------------------------------------------
1 | # **Event Iconography**
2 | ## **Distribution details**
3 | - Build name: `GoldCardinal`
4 | - App versions: `1.0.5`
5 |
6 | ## **Overview**
7 | Utilizing **[SF Symbols](https://developer.apple.com/sf-symbols/)** we've assigned each ES event a symbol and colors which correspond to facts about any given event. To follow along, please download `SF Symbols`! *This guide will include pictures in the future*.
8 |
9 | ## **Color summary**
10 | * `Blue`: Login of some kind (e.g. login window unlock)
11 | * `Orange`: Generally speaking, a low volume "security relevant" event (e.g. background tasks being added)
12 | * `Red`: Something to potentially look into. For example, `com.apple.quarantine` extended attribute deletion -- [generally not a problem on its own](https://redcanary.com/blog/gatekeeper/).
13 | * `Purple`: Something you should *definitely* look at. Some heuristics developed include [Gatekeeper bypass](https://redcanary.com/threat-detection-report/techniques/gatekeeper-bypass/#:~:text=creating%20this%20file-,Detection%20opportunities,-While%20it%20might) at the File Quarantine level. XProtect detection events are also colored purple.
14 | * `Green`: A remediation action / setting a security policy occurred -- right now just XProtect Remediator / setting the quarantine flag.
15 |
16 | ## **Event breakdown detailed**
17 | Please note. In most cases, we've included "help" / "tooltip" text for each symbol which you can see by hovering the cursor over any given symbol.
18 |
19 | ## **Process events**
20 | ### `ES_EVENT_TYPE_NOTIFY_EXEC`
21 | - **Event symbol: "checkmark.seal"** or
22 | - **event symbol: "xmark.seal"**
23 |
24 | - **Code signing**
25 | - **Event symbol: "checkmark.seal"** represents `process_exec` events with a valid code signature (and not adhoc).
26 | - If the process is adhoc signed the event will be colored in `orange` with the **event symbol: "xmark.seal"** and a `yellow` "exclamationmark.triangle.fill" symbol proceeding it.
27 | - If the process is not signed at all it will be colored in `red` with the **event symbol: "xmark.seal"** and a `red` "exclamationmark.triangle.fill" symbol proceeding it.
28 |
29 | - **Dynamic Loader**
30 | - If we've observed this target process having `dyld_insert_libraries` in its environment variables we'll prefix the event symbol with a: "bookmark.slash".
31 | - Additionally, if the `dyld_exec_path` does not match the `process_path` we'll prefix the event symbol with a: "curlybraces.square".
32 |
33 | - **File Quarantine-aware processes**
34 | - If we've identified that this process is "File Quarantine-aware" then we'll prefix the event symbol with a: "lock.icloud".
35 |
36 | ### `ES_EVENT_TYPE_NOTIFY_FORK`
37 | - **Event symbol: "point.topleft.down.curvedto.point.bottomright.up".**
38 |
39 | ### `ES_EVENT_TYPE_NOTIFY_SIGNAL`
40 | - **Event symbol: "dot.radiowaves.forward".**
41 |
42 | ### `ES_EVENT_TYPE_NOTIFY_PROC_SUSPEND_RESUME`
43 | - **Event symbol: "autostartstop.trianglebadge.exclamationmark".**
44 |
45 | ### `ES_EVENT_TYPE_NOTIFY_CS_INVALIDATED`
46 | - **Event symbol: "signature"** and we'll color this event `red` / prefix the event symbol with a `yellow`: "exclamationmark.triangle.
47 |
48 | ### `ES_EVENT_TYPE_NOTIFY_REMOTE_THREAD_CREATE`
49 | - **Event symbol: bolt.horizontal.fill"** and we'll color this event `red` / prefix the event symbol with a `yellow`: "exclamationmark.triangle.fill" symbol.
50 |
51 | ### `ES_EVENT_TYPE_NOTIFY_TRACE`
52 | - **Event symbol: "stethoscope"** and we'll color this event `orange`.
53 |
54 | ### `ES_EVENT_TYPE_NOTIFY_GET_TASK`
55 | - **Event symbol: "creditcard.trianglebadge.exclamationmark"** and we'll color this event `orange`.
56 |
57 | ### `ES_EVENT_TYPE_NOTIFY_PROC_CHECK`
58 | - **Event symbol: "barcode.viewfinder".**
59 |
60 | ### `ES_EVENT_TYPE_NOTIFY_EXIT`
61 | - **Event symbol: "eject.fill".**
62 |
63 | - **Non-zero exit codes**
64 | - If this event is representing a non-zero exit code then we'll prefix the event symbol with an: "info.square".
65 |
66 |
67 |
68 | ## **Memory events**
69 | ### `ES_EVENT_TYPE_NOTIFY_MMAP`
70 | - **Event symbol: "memorychip".**
71 |
72 | - **OSA (Open Scripting Architecture)**
73 | - If this event is mapping an OSA component into memory then we'll add a `yellow`: "exclamationmark.triangle.fill" symbol proceeding it.
74 |
75 |
76 |
77 | ## **File events**
78 | ### `ES_EVENT_TYPE_NOTIFY_CREATE`
79 | - **Event symbol: "doc.plaintext".**
80 |
81 | - **File Quarantine**
82 | - If we've identified a potential "File Quarantine violation" (see our Gatekeeper blogs) we'll color the event `red` (unquarantined file downloaded by a File Quarantine-aware app).
83 | - Additionally, if the file was found on disk to be quarantined we'll prefix the event symbol with: "lock.shield".
84 |
85 | ### `ES_EVENT_TYPE_NOTIFY_DUP`
86 | - **Event symbol: "folder.badge.plus".**
87 |
88 | ### `ES_EVENT_TYPE_NOTIFY_RENAME`
89 | - **Event symbol: filemenu.and.cursorarrow".**
90 |
91 | - **File Quarantine**
92 | - If we've identified a potential "File Quarantine violation" (see our [Gatekeeper bypass](https://redcanary.com/threat-detection-report/techniques/gatekeeper-bypass/#:~:text=creating%20this%20file-,Detection%20opportunities,-While%20it%20might) blogs) we'll color the event:
93 | - `purple`: As the result of a deep search on an inflated archive by `Archive Utility.app` we found that a file was not quarantined, but its parent directory was. The quarantine flag should *always* propagate. **This heuristic should be high fidelity.** Additionally, we'll prefix the event symbol with: "bolt.trianglebadge.exclamationmark.fill".
94 | - `red`: We noticed that an app bundle was unarchived with `Archive Utility.app` and it's not quarantined, but, on the surface we have no way to tell "which" process ordered the unarchive operation. This means that **false positives are more likely** due to the missing "File Quarantine-aware" artifact. Additionally, we'll prefix the event symbol with: "hand.raised.app".
95 |
96 | ### `ES_EVENT_TYPE_NOTIFY_UNLINK`
97 | - **Event symbol: "trash".**
98 |
99 | ### `ES_EVENT_TYPE_NOTIFY_OPEN`
100 | - **Event symbol: "envelope.open.fill".**
101 |
102 | ### `ES_EVENT_TYPE_NOTIFY_WRITE`
103 | - **Event symbol: "square.and.pencil".**
104 |
105 | ### `ES_EVENT_TYPE_NOTIFY_LINK`
106 | - **Event symbol: "link.badge.plus".**
107 |
108 | ### `ES_EVENT_TYPE_NOTIFY_CLOSE`
109 | - **Event symbol: "xmark.square".**
110 |
111 |
112 |
113 | ## **File metadata events**
114 | ### `ES_EVENT_TYPE_NOTIFY_DELETEEXTATTR`
115 | - **Event symbol: "delete.backward.fill".**
116 |
117 | - **File Quarantine**
118 | - If this event is deleting the quarantine flag then we'll color this event `red`.
119 |
120 | ### `ES_EVENT_TYPE_NOTIFY_SETEXTATTR`
121 | - **Event symbol: "filemenu.and.selection".**
122 |
123 | - **File Quarantine**
124 | - If this event is setting the quarantine flag then we'll color this event `green`.
125 |
126 |
127 |
128 | ## **File system events**
129 | ### `ES_EVENT_TYPE_NOTIFY_MOUNT`
130 | - **Event symbol: "mount".**
131 |
132 |
133 |
134 | ## **Background Task events**
135 | ### `ES_EVENT_TYPE_NOTIFY_BTM_LAUNCH_ITEM_ADD`
136 | - **Event symbol: "lock.doc"** and we'll color this event `orange` / prefix the event symbol with a `yellow`: "exclamationmark.triangle.fill" symbol.
137 |
138 | ### `ES_EVENT_TYPE_NOTIFY_BTM_LAUNCH_ITEM_REMOVE`
139 | - **Event symbol: "lock.doc"** and we'll color this event `orange` / prefix the event symbol with a `yellow`: "exclamationmark.triangle.fill" symbol.
140 |
141 |
142 |
143 | ## **Login events**
144 | ### `ES_EVENT_TYPE_NOTIFY_OPENSSH_LOGIN`
145 | - **Event symbol: "network"** and we'll color this event `blue`
146 |
147 | ### `ES_EVENT_TYPE_NOTIFY_OPENSSH_LOGOUT`
148 | - **Event symbol: "network"** and we'll color this event `blue`
149 |
150 | ### `ES_EVENT_TYPE_NOTIFY_LOGIN_LOGIN`
151 | - **Event symbol: "person.fill.checkmark".**
152 |
153 | ### `ES_EVENT_TYPE_NOTIFY_LW_SESSION_LOGIN`
154 | - **Event symbol: "macwindow.badge.plus".**
155 |
156 | ### `ES_EVENT_TYPE_NOTIFY_LW_SESSION_UNLOCK`
157 | - **Event symbol: "lock.open".**
158 |
159 |
160 |
161 | ## **XProtect events**
162 | ### `ES_EVENT_TYPE_NOTIFY_XP_MALWARE_DETECTED`
163 | - **Event symbol: "bolt.shield"** and we'll color this event `purple`
164 |
165 | ### `ES_EVENT_TYPE_NOTIFY_XP_MALWARE_REMEDIATED`
166 | - **Event symbol: "checkmark.shield"** and we'll color this event `green`
167 |
168 |
169 |
170 | ## **Kernel events**
171 | ### `ES_EVENT_TYPE_NOTIFY_IOKIT_OPEN`
172 | - **Event symbol: "captions.bubble".**
173 |
174 |
175 |
176 | ## **Open Directory events**
177 | ### `ES_EVENT_TYPE_NOTIFY_OD_CREATE_USER`
178 | - **Event symbol: "person.fill.badge.plus"** and we'll color this event `orange`
179 |
180 | ### `ES_EVENT_TYPE_NOTIFY_OD_CREATE_GROUP`
181 | - **Event symbol: "person.3.fill"** and we'll color this event `orange`
182 |
183 | ### `ES_EVENT_TYPE_NOTIFY_OD_GROUP_ADD`
184 | - **Event symbol: "person.3.fill"** and we'll color this event `orange`
185 |
186 | ### `ES_EVENT_TYPE_NOTIFY_OD_ATTRIBUTE_VALUE_ADD`
187 | - **Event symbol: "text.badge.plus"** and we'll color this event `orange`
188 |
189 | ### `ES_EVENT_TYPE_NOTIFY_OD_MODIFY_PASSWORD`
190 | - **Event symbol: "rectangle.and.pencil.and.ellipsis"** and we'll color this event `orange`
191 |
192 |
193 |
194 | ## **Profile / MDM events**
195 | ### `ES_EVENT_TYPE_NOTIFY_PROFILE_ADD`
196 | - **Event symbol: "magazine".**
197 |
198 |
199 |
200 | ## **Authorization events**
201 | ### `ES_EVENT_TYPE_NOTIFY_AUTHORIZATION_PETITION`
202 | - **Event symbol: "questionmark.diamond".**
203 | ### `ES_EVENT_TYPE_NOTIFY_AUTHORIZATION_JUDGEMENT`
204 | - **Event symbol: "arrowshape.right.fill".**
205 |
206 |
207 |
208 | ## **XPC events**
209 | ### `ES_EVENT_TYPE_NOTIFY_XPC_CONNECT`
210 | - **Event symbol: "magazine".**
211 |
212 |
213 |
214 | 
--------------------------------------------------------------------------------
/Mute sets/GoldCardinal_1_0_1_mute_set.json:
--------------------------------------------------------------------------------
1 | {"path":"/Applications/Xcode.app","id":"104C82DD-E19E-42B9-9C43-9898976C885A","eventCount":1,"type":"ES_MUTE_PATH_TYPE_PREFIX","events":["ES_EVENT_TYPE_NOTIFY_PROC_CHECK"]}
2 | {"path":"/Applications/Xcode.app/Contents/Developer/Toolchains/XcodeDefault.xctoolchain","id":"724177B4-A6EF-4503-A00A-A8C013DE4C0D","eventCount":126,"type":"ES_MUTE_PATH_TYPE_PREFIX","events":["ES_EVENT_TYPE_AUTH_EXEC","ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_KEXTLOAD","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_MOUNT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_NOTIFY_EXEC","ES_EVENT_TYPE_NOTIFY_OPEN","ES_EVENT_TYPE_NOTIFY_FORK","ES_EVENT_TYPE_NOTIFY_CLOSE","ES_EVENT_TYPE_NOTIFY_CREATE","ES_EVENT_TYPE_NOTIFY_EXCHANGEDATA","ES_EVENT_TYPE_NOTIFY_EXIT","ES_EVENT_TYPE_NOTIFY_GET_TASK","ES_EVENT_TYPE_NOTIFY_KEXTLOAD","ES_EVENT_TYPE_NOTIFY_KEXTUNLOAD","ES_EVENT_TYPE_NOTIFY_LINK","ES_EVENT_TYPE_NOTIFY_MMAP","ES_EVENT_TYPE_NOTIFY_MPROTECT","ES_EVENT_TYPE_NOTIFY_MOUNT","ES_EVENT_TYPE_NOTIFY_UNMOUNT","ES_EVENT_TYPE_NOTIFY_IOKIT_OPEN","ES_EVENT_TYPE_NOTIFY_RENAME","ES_EVENT_TYPE_NOTIFY_SETATTRLIST","ES_EVENT_TYPE_NOTIFY_SETEXTATTR","ES_EVENT_TYPE_NOTIFY_SETFLAGS","ES_EVENT_TYPE_NOTIFY_SETMODE","ES_EVENT_TYPE_NOTIFY_SETOWNER","ES_EVENT_TYPE_NOTIFY_SIGNAL","ES_EVENT_TYPE_NOTIFY_UNLINK","ES_EVENT_TYPE_NOTIFY_WRITE","ES_EVENT_TYPE_AUTH_FILE_PROVIDER_MATERIALIZE","ES_EVENT_TYPE_NOTIFY_FILE_PROVIDER_MATERIALIZE","ES_EVENT_TYPE_AUTH_FILE_PROVIDER_UPDATE","ES_EVENT_TYPE_NOTIFY_FILE_PROVIDER_UPDATE","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_NOTIFY_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_NOTIFY_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_NOTIFY_LOOKUP","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_NOTIFY_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_NOTIFY_GETATTRLIST","ES_EVENT_TYPE_NOTIFY_STAT","ES_EVENT_TYPE_NOTIFY_ACCESS","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_NOTIFY_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_NOTIFY_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_NOTIFY_CLONE","ES_EVENT_TYPE_NOTIFY_FCNTL","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_NOTIFY_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_NOTIFY_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_NOTIFY_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_NOTIFY_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_NOTIFY_FSGETPATH","ES_EVENT_TYPE_NOTIFY_DUP","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_NOTIFY_SETTIME","ES_EVENT_TYPE_NOTIFY_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_NOTIFY_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_NOTIFY_SETACL","ES_EVENT_TYPE_NOTIFY_PTY_GRANT","ES_EVENT_TYPE_NOTIFY_PTY_CLOSE","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_NOTIFY_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_NOTIFY_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_NOTIFY_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_NOTIFY_CS_INVALIDATED","ES_EVENT_TYPE_NOTIFY_GET_TASK_NAME","ES_EVENT_TYPE_NOTIFY_TRACE","ES_EVENT_TYPE_NOTIFY_REMOTE_THREAD_CREATE","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_NOTIFY_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_NOTIFY_GET_TASK_READ","ES_EVENT_TYPE_NOTIFY_GET_TASK_INSPECT","ES_EVENT_TYPE_NOTIFY_SETUID","ES_EVENT_TYPE_NOTIFY_SETGID","ES_EVENT_TYPE_NOTIFY_SETEUID","ES_EVENT_TYPE_NOTIFY_SETEGID","ES_EVENT_TYPE_NOTIFY_SETREUID","ES_EVENT_TYPE_NOTIFY_SETREGID","ES_EVENT_TYPE_AUTH_COPYFILE","ES_EVENT_TYPE_NOTIFY_COPYFILE","ES_EVENT_TYPE_NOTIFY_AUTHENTICATION","ES_EVENT_TYPE_NOTIFY_XP_MALWARE_DETECTED","ES_EVENT_TYPE_NOTIFY_XP_MALWARE_REMEDIATED","ES_EVENT_TYPE_NOTIFY_LW_SESSION_LOGIN","ES_EVENT_TYPE_NOTIFY_LW_SESSION_LOGOUT","ES_EVENT_TYPE_NOTIFY_LW_SESSION_LOCK","ES_EVENT_TYPE_NOTIFY_LW_SESSION_UNLOCK","ES_EVENT_TYPE_NOTIFY_SCREENSHARING_ATTACH","ES_EVENT_TYPE_NOTIFY_SCREENSHARING_DETACH","ES_EVENT_TYPE_NOTIFY_OPENSSH_LOGIN","ES_EVENT_TYPE_NOTIFY_OPENSSH_LOGOUT","ES_EVENT_TYPE_NOTIFY_LOGIN_LOGIN","ES_EVENT_TYPE_NOTIFY_LOGIN_LOGOUT","ES_EVENT_TYPE_NOTIFY_BTM_LAUNCH_ITEM_ADD","ES_EVENT_TYPE_NOTIFY_BTM_LAUNCH_ITEM_REMOVE"]}
3 | {"path":"/Applications/Xcode.app/Contents/SharedFrameworks","id":"03BA0B08-B061-4074-9CD6-E98B7698DD1E","eventCount":1,"type":"ES_MUTE_PATH_TYPE_PREFIX","events":["ES_EVENT_TYPE_NOTIFY_MMAP"]}
4 | {"path":"/Library/Caches/","id":"541E1A61-0E16-4776-B6A2-04DA38ADE073","eventCount":1,"type":"ES_MUTE_PATH_TYPE_TARGET_PREFIX","events":["ES_EVENT_TYPE_NOTIFY_MMAP"]}
5 | {"path":"/Library/SystemExtensions/","id":"FA259A81-D2FA-4930-848E-54C679B155A6","eventCount":3,"type":"ES_MUTE_PATH_TYPE_PREFIX","events":["ES_EVENT_TYPE_NOTIFY_OPEN","ES_EVENT_TYPE_NOTIFY_CLOSE","ES_EVENT_TYPE_NOTIFY_WRITE"]}
6 | {"path":"/System/Library/CoreServices/Diagnostics Reporter.app/Contents/MacOS/Diagnostics Reporter","id":"8DC0729C-3B3F-4D13-97AC-59C6CC5A91A5","eventCount":126,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_AUTH_EXEC","ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_KEXTLOAD","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_MOUNT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_NOTIFY_EXEC","ES_EVENT_TYPE_NOTIFY_OPEN","ES_EVENT_TYPE_NOTIFY_FORK","ES_EVENT_TYPE_NOTIFY_CLOSE","ES_EVENT_TYPE_NOTIFY_CREATE","ES_EVENT_TYPE_NOTIFY_EXCHANGEDATA","ES_EVENT_TYPE_NOTIFY_EXIT","ES_EVENT_TYPE_NOTIFY_GET_TASK","ES_EVENT_TYPE_NOTIFY_KEXTLOAD","ES_EVENT_TYPE_NOTIFY_KEXTUNLOAD","ES_EVENT_TYPE_NOTIFY_LINK","ES_EVENT_TYPE_NOTIFY_MMAP","ES_EVENT_TYPE_NOTIFY_MPROTECT","ES_EVENT_TYPE_NOTIFY_MOUNT","ES_EVENT_TYPE_NOTIFY_UNMOUNT","ES_EVENT_TYPE_NOTIFY_IOKIT_OPEN","ES_EVENT_TYPE_NOTIFY_RENAME","ES_EVENT_TYPE_NOTIFY_SETATTRLIST","ES_EVENT_TYPE_NOTIFY_SETEXTATTR","ES_EVENT_TYPE_NOTIFY_SETFLAGS","ES_EVENT_TYPE_NOTIFY_SETMODE","ES_EVENT_TYPE_NOTIFY_SETOWNER","ES_EVENT_TYPE_NOTIFY_SIGNAL","ES_EVENT_TYPE_NOTIFY_UNLINK","ES_EVENT_TYPE_NOTIFY_WRITE","ES_EVENT_TYPE_AUTH_FILE_PROVIDER_MATERIALIZE","ES_EVENT_TYPE_NOTIFY_FILE_PROVIDER_MATERIALIZE","ES_EVENT_TYPE_AUTH_FILE_PROVIDER_UPDATE","ES_EVENT_TYPE_NOTIFY_FILE_PROVIDER_UPDATE","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_NOTIFY_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_NOTIFY_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_NOTIFY_LOOKUP","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_NOTIFY_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_NOTIFY_GETATTRLIST","ES_EVENT_TYPE_NOTIFY_STAT","ES_EVENT_TYPE_NOTIFY_ACCESS","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_NOTIFY_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_NOTIFY_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_NOTIFY_CLONE","ES_EVENT_TYPE_NOTIFY_FCNTL","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_NOTIFY_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_NOTIFY_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_NOTIFY_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_NOTIFY_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_NOTIFY_FSGETPATH","ES_EVENT_TYPE_NOTIFY_DUP","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_NOTIFY_SETTIME","ES_EVENT_TYPE_NOTIFY_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_NOTIFY_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_NOTIFY_SETACL","ES_EVENT_TYPE_NOTIFY_PTY_GRANT","ES_EVENT_TYPE_NOTIFY_PTY_CLOSE","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_NOTIFY_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_NOTIFY_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_NOTIFY_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_NOTIFY_CS_INVALIDATED","ES_EVENT_TYPE_NOTIFY_GET_TASK_NAME","ES_EVENT_TYPE_NOTIFY_TRACE","ES_EVENT_TYPE_NOTIFY_REMOTE_THREAD_CREATE","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_NOTIFY_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_NOTIFY_GET_TASK_READ","ES_EVENT_TYPE_NOTIFY_GET_TASK_INSPECT","ES_EVENT_TYPE_NOTIFY_SETUID","ES_EVENT_TYPE_NOTIFY_SETGID","ES_EVENT_TYPE_NOTIFY_SETEUID","ES_EVENT_TYPE_NOTIFY_SETEGID","ES_EVENT_TYPE_NOTIFY_SETREUID","ES_EVENT_TYPE_NOTIFY_SETREGID","ES_EVENT_TYPE_AUTH_COPYFILE","ES_EVENT_TYPE_NOTIFY_COPYFILE","ES_EVENT_TYPE_NOTIFY_AUTHENTICATION","ES_EVENT_TYPE_NOTIFY_XP_MALWARE_DETECTED","ES_EVENT_TYPE_NOTIFY_XP_MALWARE_REMEDIATED","ES_EVENT_TYPE_NOTIFY_LW_SESSION_LOGIN","ES_EVENT_TYPE_NOTIFY_LW_SESSION_LOGOUT","ES_EVENT_TYPE_NOTIFY_LW_SESSION_LOCK","ES_EVENT_TYPE_NOTIFY_LW_SESSION_UNLOCK","ES_EVENT_TYPE_NOTIFY_SCREENSHARING_ATTACH","ES_EVENT_TYPE_NOTIFY_SCREENSHARING_DETACH","ES_EVENT_TYPE_NOTIFY_OPENSSH_LOGIN","ES_EVENT_TYPE_NOTIFY_OPENSSH_LOGOUT","ES_EVENT_TYPE_NOTIFY_LOGIN_LOGIN","ES_EVENT_TYPE_NOTIFY_LOGIN_LOGOUT","ES_EVENT_TYPE_NOTIFY_BTM_LAUNCH_ITEM_ADD","ES_EVENT_TYPE_NOTIFY_BTM_LAUNCH_ITEM_REMOVE"]}
7 | {"path":"/System/Library/CoreServices/ManagedClient.app","id":"4BC85CA2-7009-4E7B-B774-E0121FD2115D","eventCount":1,"type":"ES_MUTE_PATH_TYPE_PREFIX","events":["ES_EVENT_TYPE_NOTIFY_CLOSE"]}
8 | {"path":"/System/Library/CoreServices/NotificationCenter.app","id":"D9613BEA-D40B-460C-9529-2E5E69FDCC7D","eventCount":1,"type":"ES_MUTE_PATH_TYPE_PREFIX","events":["ES_EVENT_TYPE_NOTIFY_CLOSE"]}
9 | {"path":"/System/Library/CoreServices/Spotlight.app","id":"229F3E9C-C10C-49EB-BCFA-7E94FB7E9BCA","eventCount":3,"type":"ES_MUTE_PATH_TYPE_PREFIX","events":["ES_EVENT_TYPE_NOTIFY_OPEN","ES_EVENT_TYPE_NOTIFY_CLOSE","ES_EVENT_TYPE_NOTIFY_WRITE"]}
10 | {"path":"/System/Library/CoreServices/diagnostics_agent","id":"A4B9A19A-C6BA-4826-8BDA-E49C42B30878","eventCount":1,"type":"ES_MUTE_PATH_TYPE_PREFIX","events":["ES_EVENT_TYPE_NOTIFY_CLOSE"]}
11 | {"path":"/System/Library/Frameworks/Accounts.framework","id":"94A4988D-12FA-4EDD-B554-552B9274374B","eventCount":1,"type":"ES_MUTE_PATH_TYPE_PREFIX","events":["ES_EVENT_TYPE_NOTIFY_PROC_CHECK"]}
12 | {"path":"/System/Library/Frameworks/ApplicationServices.framework/Versions/A/Frameworks/ATS.framework","id":"8A3E6CC4-1C9E-495A-A2CD-37FB0241877C","eventCount":1,"type":"ES_MUTE_PATH_TYPE_PREFIX","events":["ES_EVENT_TYPE_NOTIFY_PROC_CHECK"]}
13 | {"path":"/System/Library/Frameworks/AudioToolbox.framework","id":"D081140C-545B-4E83-9F1D-29C3ACBFEABF","eventCount":2,"type":"ES_MUTE_PATH_TYPE_PREFIX","events":["ES_EVENT_TYPE_NOTIFY_OPEN","ES_EVENT_TYPE_NOTIFY_CLOSE"]}
14 | {"path":"/System/Library/Frameworks/Contacts.framework","id":"A92A2BEF-B1FC-425B-8C37-0B71E39ED586","eventCount":2,"type":"ES_MUTE_PATH_TYPE_PREFIX","events":["ES_EVENT_TYPE_NOTIFY_CLOSE","ES_EVENT_TYPE_NOTIFY_PROC_CHECK"]}
15 | {"path":"/System/Library/Frameworks/CoreServices.framework/Versions/A/Frameworks/Metadata.framework","id":"A4EBCB8F-9CEC-4BA3-A3AC-8B583131A4DD","eventCount":1,"type":"ES_MUTE_PATH_TYPE_TARGET_PREFIX","events":["ES_EVENT_TYPE_NOTIFY_MMAP"]}
16 | {"path":"/System/Library/Frameworks/CoreServices.framework/Versions/A/Frameworks/Metadata.framework","id":"D550BBE7-E292-4492-831F-66CB945085F5","eventCount":1,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_NOTIFY_PROC_CHECK"]}
17 | {"path":"/System/Library/Frameworks/CoreServices.framework/Versions/A/Frameworks/Metadata.framework","id":"FDAD2434-566B-4382-BA21-D05314A51F84","eventCount":126,"type":"ES_MUTE_PATH_TYPE_PREFIX","events":["ES_EVENT_TYPE_AUTH_EXEC","ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_KEXTLOAD","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_MOUNT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_NOTIFY_EXEC","ES_EVENT_TYPE_NOTIFY_OPEN","ES_EVENT_TYPE_NOTIFY_FORK","ES_EVENT_TYPE_NOTIFY_CLOSE","ES_EVENT_TYPE_NOTIFY_CREATE","ES_EVENT_TYPE_NOTIFY_EXCHANGEDATA","ES_EVENT_TYPE_NOTIFY_EXIT","ES_EVENT_TYPE_NOTIFY_GET_TASK","ES_EVENT_TYPE_NOTIFY_KEXTLOAD","ES_EVENT_TYPE_NOTIFY_KEXTUNLOAD","ES_EVENT_TYPE_NOTIFY_LINK","ES_EVENT_TYPE_NOTIFY_MMAP","ES_EVENT_TYPE_NOTIFY_MPROTECT","ES_EVENT_TYPE_NOTIFY_MOUNT","ES_EVENT_TYPE_NOTIFY_UNMOUNT","ES_EVENT_TYPE_NOTIFY_IOKIT_OPEN","ES_EVENT_TYPE_NOTIFY_RENAME","ES_EVENT_TYPE_NOTIFY_SETATTRLIST","ES_EVENT_TYPE_NOTIFY_SETEXTATTR","ES_EVENT_TYPE_NOTIFY_SETFLAGS","ES_EVENT_TYPE_NOTIFY_SETMODE","ES_EVENT_TYPE_NOTIFY_SETOWNER","ES_EVENT_TYPE_NOTIFY_SIGNAL","ES_EVENT_TYPE_NOTIFY_UNLINK","ES_EVENT_TYPE_NOTIFY_WRITE","ES_EVENT_TYPE_AUTH_FILE_PROVIDER_MATERIALIZE","ES_EVENT_TYPE_NOTIFY_FILE_PROVIDER_MATERIALIZE","ES_EVENT_TYPE_AUTH_FILE_PROVIDER_UPDATE","ES_EVENT_TYPE_NOTIFY_FILE_PROVIDER_UPDATE","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_NOTIFY_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_NOTIFY_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_NOTIFY_LOOKUP","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_NOTIFY_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_NOTIFY_GETATTRLIST","ES_EVENT_TYPE_NOTIFY_STAT","ES_EVENT_TYPE_NOTIFY_ACCESS","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_NOTIFY_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_NOTIFY_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_NOTIFY_CLONE","ES_EVENT_TYPE_NOTIFY_FCNTL","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_NOTIFY_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_NOTIFY_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_NOTIFY_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_NOTIFY_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_NOTIFY_FSGETPATH","ES_EVENT_TYPE_NOTIFY_DUP","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_NOTIFY_SETTIME","ES_EVENT_TYPE_NOTIFY_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_NOTIFY_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_NOTIFY_SETACL","ES_EVENT_TYPE_NOTIFY_PTY_GRANT","ES_EVENT_TYPE_NOTIFY_PTY_CLOSE","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_NOTIFY_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_NOTIFY_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_NOTIFY_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_NOTIFY_CS_INVALIDATED","ES_EVENT_TYPE_NOTIFY_GET_TASK_NAME","ES_EVENT_TYPE_NOTIFY_TRACE","ES_EVENT_TYPE_NOTIFY_REMOTE_THREAD_CREATE","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_NOTIFY_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_NOTIFY_GET_TASK_READ","ES_EVENT_TYPE_NOTIFY_GET_TASK_INSPECT","ES_EVENT_TYPE_NOTIFY_SETUID","ES_EVENT_TYPE_NOTIFY_SETGID","ES_EVENT_TYPE_NOTIFY_SETEUID","ES_EVENT_TYPE_NOTIFY_SETEGID","ES_EVENT_TYPE_NOTIFY_SETREUID","ES_EVENT_TYPE_NOTIFY_SETREGID","ES_EVENT_TYPE_AUTH_COPYFILE","ES_EVENT_TYPE_NOTIFY_COPYFILE","ES_EVENT_TYPE_NOTIFY_AUTHENTICATION","ES_EVENT_TYPE_NOTIFY_XP_MALWARE_DETECTED","ES_EVENT_TYPE_NOTIFY_XP_MALWARE_REMEDIATED","ES_EVENT_TYPE_NOTIFY_LW_SESSION_LOGIN","ES_EVENT_TYPE_NOTIFY_LW_SESSION_LOGOUT","ES_EVENT_TYPE_NOTIFY_LW_SESSION_LOCK","ES_EVENT_TYPE_NOTIFY_LW_SESSION_UNLOCK","ES_EVENT_TYPE_NOTIFY_SCREENSHARING_ATTACH","ES_EVENT_TYPE_NOTIFY_SCREENSHARING_DETACH","ES_EVENT_TYPE_NOTIFY_OPENSSH_LOGIN","ES_EVENT_TYPE_NOTIFY_OPENSSH_LOGOUT","ES_EVENT_TYPE_NOTIFY_LOGIN_LOGIN","ES_EVENT_TYPE_NOTIFY_LOGIN_LOGOUT","ES_EVENT_TYPE_NOTIFY_BTM_LAUNCH_ITEM_ADD","ES_EVENT_TYPE_NOTIFY_BTM_LAUNCH_ITEM_REMOVE"]}
18 | {"path":"/System/Library/Frameworks/CoreServices.framework/Versions/A/Frameworks/Metadata.framework/Versions/A/Support/mdworker_shared","id":"B961C2FA-9E8C-4836-B1D1-21A33E13D007","eventCount":1,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_NOTIFY_MMAP"]}
19 | {"path":"/System/Library/Frameworks/VideoToolbox.framework","id":"A301E0C6-757C-42D4-8F4F-5B85AF85CDEC","eventCount":1,"type":"ES_MUTE_PATH_TYPE_PREFIX","events":["ES_EVENT_TYPE_NOTIFY_CLOSE"]}
20 | {"path":"/System/Library/PrivateFrameworks/AXAssetLoader.framework","id":"D9FEF985-A461-417C-80C2-98F6FFC492D6","eventCount":2,"type":"ES_MUTE_PATH_TYPE_PREFIX","events":["ES_EVENT_TYPE_NOTIFY_OPEN","ES_EVENT_TYPE_NOTIFY_CLOSE"]}
21 | {"path":"/System/Library/PrivateFrameworks/BiomeStreams.framework","id":"062CE2A0-E239-4662-97D6-180AD8F40460","eventCount":2,"type":"ES_MUTE_PATH_TYPE_PREFIX","events":["ES_EVENT_TYPE_NOTIFY_CLOSE","ES_EVENT_TYPE_NOTIFY_DUP"]}
22 | {"path":"/System/Library/PrivateFrameworks/BiomeStreams.framework","id":"374081FD-FF66-46BD-967A-DEE24C99F29A","eventCount":1,"type":"ES_MUTE_PATH_TYPE_TARGET_PREFIX","events":["ES_EVENT_TYPE_NOTIFY_CREATE"]}
23 | {"path":"/System/Library/PrivateFrameworks/BiomeStreams.framework/Support/BiomeAgent","id":"C8C4CF41-4FE7-453C-8419-6C3EECB1AA16","eventCount":1,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_NOTIFY_MMAP"]}
24 | {"path":"/System/Library/PrivateFrameworks/CalendarDaemon.framework","id":"E7A79242-780C-49FF-83D3-80AEE4501478","eventCount":1,"type":"ES_MUTE_PATH_TYPE_PREFIX","events":["ES_EVENT_TYPE_NOTIFY_PROC_CHECK"]}
25 | {"path":"/System/Library/PrivateFrameworks/CoreAnalytics.framework","id":"BB5C5E71-E74B-45A4-9307-2F285980F3B2","eventCount":1,"type":"ES_MUTE_PATH_TYPE_PREFIX","events":["ES_EVENT_TYPE_NOTIFY_PROC_CHECK"]}
26 | {"path":"/System/Library/PrivateFrameworks/CoreDuetContext.framework","id":"89BB0C38-A745-4E1B-AC75-02FB94306FE0","eventCount":2,"type":"ES_MUTE_PATH_TYPE_PREFIX","events":["ES_EVENT_TYPE_NOTIFY_CLOSE","ES_EVENT_TYPE_NOTIFY_PROC_CHECK"]}
27 | {"path":"/System/Library/PrivateFrameworks/DataAccess.framework","id":"6B4CED66-FF47-4E16-9DCD-46F4C2F967E0","eventCount":1,"type":"ES_MUTE_PATH_TYPE_PREFIX","events":["ES_EVENT_TYPE_NOTIFY_PROC_CHECK"]}
28 | {"path":"/System/Library/PrivateFrameworks/HelpData.framework/Versions/A/Resources/helpd","id":"C14EA3B6-84F6-4A0B-B6CA-39C84AC99C27","eventCount":1,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_NOTIFY_MMAP"]}
29 | {"path":"/System/Library/PrivateFrameworks/PackageKit.framework/Versions/A/Resources/system_installd","id":"CE7F2EBC-E77E-4F64-83E7-6E1DC2D903C5","eventCount":1,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_NOTIFY_CREATE"]}
30 | {"path":"/System/Library/PrivateFrameworks/SiriTTSService.framework","id":"D8B902AF-EFBD-4881-898E-DE6FC65355A8","eventCount":3,"type":"ES_MUTE_PATH_TYPE_PREFIX","events":["ES_EVENT_TYPE_NOTIFY_OPEN","ES_EVENT_TYPE_NOTIFY_CLOSE","ES_EVENT_TYPE_NOTIFY_PROC_CHECK"]}
31 | {"path":"/System/Library/PrivateFrameworks/SkyLight.framework","id":"FA19D1ED-9145-4B38-84DE-98B6EF87AEE3","eventCount":2,"type":"ES_MUTE_PATH_TYPE_PREFIX","events":["ES_EVENT_TYPE_NOTIFY_OPEN","ES_EVENT_TYPE_NOTIFY_CLOSE"]}
32 | {"path":"/System/Library/PrivateFrameworks/SkyLight.framework/Versions/A/Resources/WindowServer","id":"B8688BDC-1235-4DCC-AC11-E68F73AB857D","eventCount":39,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_AUTH_COPYFILE"]}
33 | {"path":"/System/Library/PrivateFrameworks/TCC.framework","id":"83AB6F75-D94B-4EBA-82B0-C9DDBEE7694E","eventCount":2,"type":"ES_MUTE_PATH_TYPE_PREFIX","events":["ES_EVENT_TYPE_NOTIFY_OPEN","ES_EVENT_TYPE_NOTIFY_CLOSE"]}
34 | {"path":"/System/Library/PrivateFrameworks/TCC.framework/Support/tccd","id":"BB083BA0-C57F-4EBB-9CBA-62F7AE695953","eventCount":39,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_AUTH_COPYFILE"]}
35 | {"path":"/System/Library/PrivateFrameworks/TCC.framework/Versions/A/Resources/tccd","id":"27FD2F65-399C-4CDA-90E9-69B6564F43A4","eventCount":39,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_AUTH_COPYFILE"]}
36 | {"path":"/System/Volumes/Preboot/Cryptexes/OS/System/Library/dyld/","id":"2244622F-2DFE-40E1-920C-2FBC83F21235","eventCount":1,"type":"ES_MUTE_PATH_TYPE_TARGET_PREFIX","events":["ES_EVENT_TYPE_NOTIFY_MMAP"]}
37 | {"path":"/Users/brandondalton/Library/Caches","id":"D7A984D3-6ABD-4A65-B4E4-57C1D6B1C13C","eventCount":2,"type":"ES_MUTE_PATH_TYPE_TARGET_PREFIX","events":["ES_EVENT_TYPE_NOTIFY_CREATE","ES_EVENT_TYPE_NOTIFY_RENAME"]}
38 | {"path":"/dev/console","id":"B8D50BCE-2A6A-4102-8765-EA099B96B46B","eventCount":1,"type":"ES_MUTE_PATH_TYPE_TARGET_LITERAL","events":["ES_EVENT_TYPE_NOTIFY_DUP"]}
39 | {"path":"/dev/null","id":"1C192EB1-798C-407A-BF97-09475572A03B","eventCount":79,"type":"ES_MUTE_PATH_TYPE_TARGET_LITERAL","events":["ES_EVENT_TYPE_AUTH_EXEC","ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_NOTIFY_EXEC","ES_EVENT_TYPE_NOTIFY_OPEN","ES_EVENT_TYPE_NOTIFY_CLOSE","ES_EVENT_TYPE_NOTIFY_CREATE","ES_EVENT_TYPE_NOTIFY_EXCHANGEDATA","ES_EVENT_TYPE_NOTIFY_GET_TASK","ES_EVENT_TYPE_NOTIFY_LINK","ES_EVENT_TYPE_NOTIFY_MMAP","ES_EVENT_TYPE_NOTIFY_RENAME","ES_EVENT_TYPE_NOTIFY_SETATTRLIST","ES_EVENT_TYPE_NOTIFY_SETEXTATTR","ES_EVENT_TYPE_NOTIFY_SETFLAGS","ES_EVENT_TYPE_NOTIFY_SETMODE","ES_EVENT_TYPE_NOTIFY_SETOWNER","ES_EVENT_TYPE_NOTIFY_SIGNAL","ES_EVENT_TYPE_NOTIFY_UNLINK","ES_EVENT_TYPE_NOTIFY_WRITE","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_NOTIFY_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_NOTIFY_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_NOTIFY_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_NOTIFY_GETATTRLIST","ES_EVENT_TYPE_NOTIFY_STAT","ES_EVENT_TYPE_NOTIFY_ACCESS","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_NOTIFY_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_NOTIFY_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_NOTIFY_CLONE","ES_EVENT_TYPE_NOTIFY_FCNTL","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_NOTIFY_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_NOTIFY_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_NOTIFY_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_NOTIFY_DELETEEXTATTR","ES_EVENT_TYPE_NOTIFY_DUP","ES_EVENT_TYPE_NOTIFY_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_NOTIFY_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_NOTIFY_SETACL","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_NOTIFY_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_NOTIFY_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_NOTIFY_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_NOTIFY_GET_TASK_NAME","ES_EVENT_TYPE_NOTIFY_TRACE","ES_EVENT_TYPE_NOTIFY_REMOTE_THREAD_CREATE","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_NOTIFY_GET_TASK_READ","ES_EVENT_TYPE_NOTIFY_GET_TASK_INSPECT","ES_EVENT_TYPE_AUTH_COPYFILE","ES_EVENT_TYPE_NOTIFY_COPYFILE"]}
40 | {"path":"/private/var/db/","id":"A7233327-FF6D-4D98-AB1D-F18DFE6B6844","eventCount":1,"type":"ES_MUTE_PATH_TYPE_TARGET_PREFIX","events":["ES_EVENT_TYPE_NOTIFY_MMAP"]}
41 | {"path":"/private/var/db/KernelExtensionManagement/KernelCollections/BootKernelCollection.kc","id":"B8C08D12-8450-4F89-9E18-4267887D9333","eventCount":1,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_NOTIFY_MMAP"]}
42 | {"path":"/usr/bin/heap","id":"B852EC4E-3F61-41A3-8B4B-9CE5254FA6DE","eventCount":39,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_AUTH_COPYFILE"]}
43 | {"path":"/usr/bin/sample","id":"4D4873C3-6822-469E-AB93-417889C6CED3","eventCount":39,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_AUTH_COPYFILE"]}
44 | {"path":"/usr/bin/tailspin","id":"82754108-5716-420D-8ED8-BE534CD7AA3E","eventCount":40,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_NOTIFY_MMAP","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_AUTH_COPYFILE"]}
45 | {"path":"/usr/libexec/ReportMemoryException","id":"90F0800E-FCA6-463F-A0EF-B3CBBF060AA9","eventCount":126,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_AUTH_EXEC","ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_KEXTLOAD","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_MOUNT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_NOTIFY_EXEC","ES_EVENT_TYPE_NOTIFY_OPEN","ES_EVENT_TYPE_NOTIFY_FORK","ES_EVENT_TYPE_NOTIFY_CLOSE","ES_EVENT_TYPE_NOTIFY_CREATE","ES_EVENT_TYPE_NOTIFY_EXCHANGEDATA","ES_EVENT_TYPE_NOTIFY_EXIT","ES_EVENT_TYPE_NOTIFY_GET_TASK","ES_EVENT_TYPE_NOTIFY_KEXTLOAD","ES_EVENT_TYPE_NOTIFY_KEXTUNLOAD","ES_EVENT_TYPE_NOTIFY_LINK","ES_EVENT_TYPE_NOTIFY_MMAP","ES_EVENT_TYPE_NOTIFY_MPROTECT","ES_EVENT_TYPE_NOTIFY_MOUNT","ES_EVENT_TYPE_NOTIFY_UNMOUNT","ES_EVENT_TYPE_NOTIFY_IOKIT_OPEN","ES_EVENT_TYPE_NOTIFY_RENAME","ES_EVENT_TYPE_NOTIFY_SETATTRLIST","ES_EVENT_TYPE_NOTIFY_SETEXTATTR","ES_EVENT_TYPE_NOTIFY_SETFLAGS","ES_EVENT_TYPE_NOTIFY_SETMODE","ES_EVENT_TYPE_NOTIFY_SETOWNER","ES_EVENT_TYPE_NOTIFY_SIGNAL","ES_EVENT_TYPE_NOTIFY_UNLINK","ES_EVENT_TYPE_NOTIFY_WRITE","ES_EVENT_TYPE_AUTH_FILE_PROVIDER_MATERIALIZE","ES_EVENT_TYPE_NOTIFY_FILE_PROVIDER_MATERIALIZE","ES_EVENT_TYPE_AUTH_FILE_PROVIDER_UPDATE","ES_EVENT_TYPE_NOTIFY_FILE_PROVIDER_UPDATE","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_NOTIFY_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_NOTIFY_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_NOTIFY_LOOKUP","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_NOTIFY_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_NOTIFY_GETATTRLIST","ES_EVENT_TYPE_NOTIFY_STAT","ES_EVENT_TYPE_NOTIFY_ACCESS","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_NOTIFY_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_NOTIFY_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_NOTIFY_CLONE","ES_EVENT_TYPE_NOTIFY_FCNTL","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_NOTIFY_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_NOTIFY_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_NOTIFY_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_NOTIFY_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_NOTIFY_FSGETPATH","ES_EVENT_TYPE_NOTIFY_DUP","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_NOTIFY_SETTIME","ES_EVENT_TYPE_NOTIFY_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_NOTIFY_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_NOTIFY_SETACL","ES_EVENT_TYPE_NOTIFY_PTY_GRANT","ES_EVENT_TYPE_NOTIFY_PTY_CLOSE","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_NOTIFY_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_NOTIFY_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_NOTIFY_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_NOTIFY_CS_INVALIDATED","ES_EVENT_TYPE_NOTIFY_GET_TASK_NAME","ES_EVENT_TYPE_NOTIFY_TRACE","ES_EVENT_TYPE_NOTIFY_REMOTE_THREAD_CREATE","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_NOTIFY_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_NOTIFY_GET_TASK_READ","ES_EVENT_TYPE_NOTIFY_GET_TASK_INSPECT","ES_EVENT_TYPE_NOTIFY_SETUID","ES_EVENT_TYPE_NOTIFY_SETGID","ES_EVENT_TYPE_NOTIFY_SETEUID","ES_EVENT_TYPE_NOTIFY_SETEGID","ES_EVENT_TYPE_NOTIFY_SETREUID","ES_EVENT_TYPE_NOTIFY_SETREGID","ES_EVENT_TYPE_AUTH_COPYFILE","ES_EVENT_TYPE_NOTIFY_COPYFILE","ES_EVENT_TYPE_NOTIFY_AUTHENTICATION","ES_EVENT_TYPE_NOTIFY_XP_MALWARE_DETECTED","ES_EVENT_TYPE_NOTIFY_XP_MALWARE_REMEDIATED","ES_EVENT_TYPE_NOTIFY_LW_SESSION_LOGIN","ES_EVENT_TYPE_NOTIFY_LW_SESSION_LOGOUT","ES_EVENT_TYPE_NOTIFY_LW_SESSION_LOCK","ES_EVENT_TYPE_NOTIFY_LW_SESSION_UNLOCK","ES_EVENT_TYPE_NOTIFY_SCREENSHARING_ATTACH","ES_EVENT_TYPE_NOTIFY_SCREENSHARING_DETACH","ES_EVENT_TYPE_NOTIFY_OPENSSH_LOGIN","ES_EVENT_TYPE_NOTIFY_OPENSSH_LOGOUT","ES_EVENT_TYPE_NOTIFY_LOGIN_LOGIN","ES_EVENT_TYPE_NOTIFY_LOGIN_LOGOUT","ES_EVENT_TYPE_NOTIFY_BTM_LAUNCH_ITEM_ADD","ES_EVENT_TYPE_NOTIFY_BTM_LAUNCH_ITEM_REMOVE"]}
46 | {"path":"/usr/libexec/amfid","id":"8DB8719E-7285-468C-8EA8-68AC8DDF747E","eventCount":39,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_AUTH_COPYFILE"]}
47 | {"path":"/usr/libexec/knowledge-agent","id":"9ACD829D-CC59-4841-93D2-8834887C95DA","eventCount":1,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_NOTIFY_MMAP"]}
48 | {"path":"/usr/libexec/locationd","id":"C8B6DA50-D896-4CB8-A267-908C6FFC13AB","eventCount":1,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_NOTIFY_MMAP"]}
49 | {"path":"/usr/libexec/logd","id":"57C311EA-B6A7-40CC-8D79-1B9B982BF2CE","eventCount":126,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_AUTH_EXEC","ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_KEXTLOAD","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_MOUNT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_NOTIFY_EXEC","ES_EVENT_TYPE_NOTIFY_OPEN","ES_EVENT_TYPE_NOTIFY_FORK","ES_EVENT_TYPE_NOTIFY_CLOSE","ES_EVENT_TYPE_NOTIFY_CREATE","ES_EVENT_TYPE_NOTIFY_EXCHANGEDATA","ES_EVENT_TYPE_NOTIFY_EXIT","ES_EVENT_TYPE_NOTIFY_GET_TASK","ES_EVENT_TYPE_NOTIFY_KEXTLOAD","ES_EVENT_TYPE_NOTIFY_KEXTUNLOAD","ES_EVENT_TYPE_NOTIFY_LINK","ES_EVENT_TYPE_NOTIFY_MMAP","ES_EVENT_TYPE_NOTIFY_MPROTECT","ES_EVENT_TYPE_NOTIFY_MOUNT","ES_EVENT_TYPE_NOTIFY_UNMOUNT","ES_EVENT_TYPE_NOTIFY_IOKIT_OPEN","ES_EVENT_TYPE_NOTIFY_RENAME","ES_EVENT_TYPE_NOTIFY_SETATTRLIST","ES_EVENT_TYPE_NOTIFY_SETEXTATTR","ES_EVENT_TYPE_NOTIFY_SETFLAGS","ES_EVENT_TYPE_NOTIFY_SETMODE","ES_EVENT_TYPE_NOTIFY_SETOWNER","ES_EVENT_TYPE_NOTIFY_SIGNAL","ES_EVENT_TYPE_NOTIFY_UNLINK","ES_EVENT_TYPE_NOTIFY_WRITE","ES_EVENT_TYPE_AUTH_FILE_PROVIDER_MATERIALIZE","ES_EVENT_TYPE_NOTIFY_FILE_PROVIDER_MATERIALIZE","ES_EVENT_TYPE_AUTH_FILE_PROVIDER_UPDATE","ES_EVENT_TYPE_NOTIFY_FILE_PROVIDER_UPDATE","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_NOTIFY_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_NOTIFY_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_NOTIFY_LOOKUP","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_NOTIFY_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_NOTIFY_GETATTRLIST","ES_EVENT_TYPE_NOTIFY_STAT","ES_EVENT_TYPE_NOTIFY_ACCESS","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_NOTIFY_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_NOTIFY_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_NOTIFY_CLONE","ES_EVENT_TYPE_NOTIFY_FCNTL","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_NOTIFY_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_NOTIFY_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_NOTIFY_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_NOTIFY_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_NOTIFY_FSGETPATH","ES_EVENT_TYPE_NOTIFY_DUP","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_NOTIFY_SETTIME","ES_EVENT_TYPE_NOTIFY_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_NOTIFY_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_NOTIFY_SETACL","ES_EVENT_TYPE_NOTIFY_PTY_GRANT","ES_EVENT_TYPE_NOTIFY_PTY_CLOSE","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_NOTIFY_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_NOTIFY_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_NOTIFY_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_NOTIFY_CS_INVALIDATED","ES_EVENT_TYPE_NOTIFY_GET_TASK_NAME","ES_EVENT_TYPE_NOTIFY_TRACE","ES_EVENT_TYPE_NOTIFY_REMOTE_THREAD_CREATE","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_NOTIFY_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_NOTIFY_GET_TASK_READ","ES_EVENT_TYPE_NOTIFY_GET_TASK_INSPECT","ES_EVENT_TYPE_NOTIFY_SETUID","ES_EVENT_TYPE_NOTIFY_SETGID","ES_EVENT_TYPE_NOTIFY_SETEUID","ES_EVENT_TYPE_NOTIFY_SETEGID","ES_EVENT_TYPE_NOTIFY_SETREUID","ES_EVENT_TYPE_NOTIFY_SETREGID","ES_EVENT_TYPE_AUTH_COPYFILE","ES_EVENT_TYPE_NOTIFY_COPYFILE","ES_EVENT_TYPE_NOTIFY_AUTHENTICATION","ES_EVENT_TYPE_NOTIFY_XP_MALWARE_DETECTED","ES_EVENT_TYPE_NOTIFY_XP_MALWARE_REMEDIATED","ES_EVENT_TYPE_NOTIFY_LW_SESSION_LOGIN","ES_EVENT_TYPE_NOTIFY_LW_SESSION_LOGOUT","ES_EVENT_TYPE_NOTIFY_LW_SESSION_LOCK","ES_EVENT_TYPE_NOTIFY_LW_SESSION_UNLOCK","ES_EVENT_TYPE_NOTIFY_SCREENSHARING_ATTACH","ES_EVENT_TYPE_NOTIFY_SCREENSHARING_DETACH","ES_EVENT_TYPE_NOTIFY_OPENSSH_LOGIN","ES_EVENT_TYPE_NOTIFY_OPENSSH_LOGOUT","ES_EVENT_TYPE_NOTIFY_LOGIN_LOGIN","ES_EVENT_TYPE_NOTIFY_LOGIN_LOGOUT","ES_EVENT_TYPE_NOTIFY_BTM_LAUNCH_ITEM_ADD","ES_EVENT_TYPE_NOTIFY_BTM_LAUNCH_ITEM_REMOVE"]}
50 | {"path":"/usr/libexec/lsd","id":"0D46B279-F739-4819-AA9A-E45756520A62","eventCount":2,"type":"ES_MUTE_PATH_TYPE_PREFIX","events":["ES_EVENT_TYPE_NOTIFY_CLOSE","ES_EVENT_TYPE_NOTIFY_WRITE"]}
51 | {"path":"/usr/libexec/mobileassetd","id":"C95C0476-5C6A-47F2-A51D-9FA4514D35CC","eventCount":2,"type":"ES_MUTE_PATH_TYPE_PREFIX","events":["ES_EVENT_TYPE_NOTIFY_CLOSE","ES_EVENT_TYPE_NOTIFY_PROC_CHECK"]}
52 | {"path":"/usr/libexec/opendirectoryd","id":"7F02FBF2-75D4-446A-B6DF-F70D82778495","eventCount":40,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_NOTIFY_MMAP","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_AUTH_COPYFILE"]}
53 | {"path":"/usr/libexec/runningboardd","id":"D0746540-6ED3-43F3-8CE8-27A2C8B4124C","eventCount":39,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_AUTH_COPYFILE"]}
54 | {"path":"/usr/libexec/sandboxd","id":"A86432E5-C093-4E75-BC46-C46A877B422E","eventCount":39,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_AUTH_COPYFILE"]}
55 | {"path":"/usr/libexec/spindump","id":"C721DAD2-FFD8-4F5A-BF87-00B17E291A40","eventCount":1,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_NOTIFY_MMAP"]}
56 | {"path":"/usr/libexec/sysmond","id":"29678B96-0C02-49B6-999C-6D7A42A2FA10","eventCount":1,"type":"ES_MUTE_PATH_TYPE_PREFIX","events":["ES_EVENT_TYPE_NOTIFY_PROC_CHECK"]}
57 | {"path":"/usr/libexec/syspolicyd","id":"EC967963-859F-4D96-8099-EE1EB741EB41","eventCount":39,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_AUTH_COPYFILE"]}
58 | {"path":"/usr/libexec/tailspind","id":"AA0CCCDC-2C13-4F88-B06E-E52592C43F28","eventCount":79,"type":"ES_MUTE_PATH_TYPE_TARGET_LITERAL","events":["ES_EVENT_TYPE_AUTH_EXEC","ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_NOTIFY_EXEC","ES_EVENT_TYPE_NOTIFY_OPEN","ES_EVENT_TYPE_NOTIFY_CLOSE","ES_EVENT_TYPE_NOTIFY_CREATE","ES_EVENT_TYPE_NOTIFY_EXCHANGEDATA","ES_EVENT_TYPE_NOTIFY_GET_TASK","ES_EVENT_TYPE_NOTIFY_LINK","ES_EVENT_TYPE_NOTIFY_MMAP","ES_EVENT_TYPE_NOTIFY_RENAME","ES_EVENT_TYPE_NOTIFY_SETATTRLIST","ES_EVENT_TYPE_NOTIFY_SETEXTATTR","ES_EVENT_TYPE_NOTIFY_SETFLAGS","ES_EVENT_TYPE_NOTIFY_SETMODE","ES_EVENT_TYPE_NOTIFY_SETOWNER","ES_EVENT_TYPE_NOTIFY_SIGNAL","ES_EVENT_TYPE_NOTIFY_UNLINK","ES_EVENT_TYPE_NOTIFY_WRITE","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_NOTIFY_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_NOTIFY_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_NOTIFY_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_NOTIFY_GETATTRLIST","ES_EVENT_TYPE_NOTIFY_STAT","ES_EVENT_TYPE_NOTIFY_ACCESS","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_NOTIFY_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_NOTIFY_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_NOTIFY_CLONE","ES_EVENT_TYPE_NOTIFY_FCNTL","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_NOTIFY_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_NOTIFY_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_NOTIFY_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_NOTIFY_DELETEEXTATTR","ES_EVENT_TYPE_NOTIFY_DUP","ES_EVENT_TYPE_NOTIFY_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_NOTIFY_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_NOTIFY_SETACL","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_NOTIFY_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_NOTIFY_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_NOTIFY_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_NOTIFY_GET_TASK_NAME","ES_EVENT_TYPE_NOTIFY_TRACE","ES_EVENT_TYPE_NOTIFY_REMOTE_THREAD_CREATE","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_NOTIFY_GET_TASK_READ","ES_EVENT_TYPE_NOTIFY_GET_TASK_INSPECT","ES_EVENT_TYPE_AUTH_COPYFILE","ES_EVENT_TYPE_NOTIFY_COPYFILE"]}
59 | {"path":"/usr/libexec/trustd","id":"B25B9F73-2143-47BC-AD36-12613072DAD0","eventCount":1,"type":"ES_MUTE_PATH_TYPE_PREFIX","events":["ES_EVENT_TYPE_NOTIFY_PROC_CHECK"]}
60 | {"path":"/usr/libexec/trustd","id":"ECB8118D-D0C2-4DB3-BB29-05253B844617","eventCount":39,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_AUTH_COPYFILE"]}
61 | {"path":"/usr/libexec/watchdogd","id":"87F865EC-ACDF-4DDA-80BD-49265390D111","eventCount":39,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_AUTH_COPYFILE"]}
62 | {"path":"/usr/libexec/xpcproxy","id":"1E14FE05-A376-4180-96CF-16DBE51235BE","eventCount":3,"type":"ES_MUTE_PATH_TYPE_PREFIX","events":["ES_EVENT_TYPE_NOTIFY_OPEN","ES_EVENT_TYPE_NOTIFY_CLOSE","ES_EVENT_TYPE_NOTIFY_PROC_CHECK"]}
63 | {"path":"/usr/libexec/xpcproxy","id":"DEF7AB1D-7D2E-4BBD-A9FE-6261D161CC34","eventCount":2,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_NOTIFY_MMAP","ES_EVENT_TYPE_NOTIFY_DUP"]}
64 | {"path":"/usr/sbin/cfprefsd","id":"0CE5DAB8-14F7-44B0-B1AD-D256873088B7","eventCount":4,"type":"ES_MUTE_PATH_TYPE_PREFIX","events":["ES_EVENT_TYPE_NOTIFY_OPEN","ES_EVENT_TYPE_NOTIFY_CLOSE","ES_EVENT_TYPE_NOTIFY_WRITE","ES_EVENT_TYPE_NOTIFY_PROC_CHECK"]}
65 | {"path":"/usr/sbin/cfprefsd","id":"B6C2CC9F-F698-47FF-B7D4-391492AD2041","eventCount":42,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_NOTIFY_CREATE","ES_EVENT_TYPE_NOTIFY_RENAME","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_NOTIFY_DUP","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_AUTH_COPYFILE"]}
66 | {"path":"/usr/sbin/distnoted","id":"E84810EA-23BB-4FF3-8EE9-C978F5BC87B5","eventCount":1,"type":"ES_MUTE_PATH_TYPE_PREFIX","events":["ES_EVENT_TYPE_NOTIFY_PROC_CHECK"]}
67 | {"path":"/usr/sbin/mDNSResponder","id":"1492ECD9-2B0E-4FE0-867B-BC6F4ED6D46D","eventCount":1,"type":"ES_MUTE_PATH_TYPE_PREFIX","events":["ES_EVENT_TYPE_NOTIFY_PROC_CHECK"]}
68 | {"path":"/usr/sbin/securityd","id":"ABCA7C48-4185-4D05-B17B-AC2C47226357","eventCount":39,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_AUTH_COPYFILE"]}
69 | {"path":"/usr/sbin/spindump","id":"62FE6D26-1148-4994-B939-31063C630327","eventCount":79,"type":"ES_MUTE_PATH_TYPE_TARGET_LITERAL","events":["ES_EVENT_TYPE_AUTH_EXEC","ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_NOTIFY_EXEC","ES_EVENT_TYPE_NOTIFY_OPEN","ES_EVENT_TYPE_NOTIFY_CLOSE","ES_EVENT_TYPE_NOTIFY_CREATE","ES_EVENT_TYPE_NOTIFY_EXCHANGEDATA","ES_EVENT_TYPE_NOTIFY_GET_TASK","ES_EVENT_TYPE_NOTIFY_LINK","ES_EVENT_TYPE_NOTIFY_MMAP","ES_EVENT_TYPE_NOTIFY_RENAME","ES_EVENT_TYPE_NOTIFY_SETATTRLIST","ES_EVENT_TYPE_NOTIFY_SETEXTATTR","ES_EVENT_TYPE_NOTIFY_SETFLAGS","ES_EVENT_TYPE_NOTIFY_SETMODE","ES_EVENT_TYPE_NOTIFY_SETOWNER","ES_EVENT_TYPE_NOTIFY_SIGNAL","ES_EVENT_TYPE_NOTIFY_UNLINK","ES_EVENT_TYPE_NOTIFY_WRITE","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_NOTIFY_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_NOTIFY_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_NOTIFY_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_NOTIFY_GETATTRLIST","ES_EVENT_TYPE_NOTIFY_STAT","ES_EVENT_TYPE_NOTIFY_ACCESS","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_NOTIFY_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_NOTIFY_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_NOTIFY_CLONE","ES_EVENT_TYPE_NOTIFY_FCNTL","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_NOTIFY_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_NOTIFY_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_NOTIFY_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_NOTIFY_DELETEEXTATTR","ES_EVENT_TYPE_NOTIFY_DUP","ES_EVENT_TYPE_NOTIFY_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_NOTIFY_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_NOTIFY_SETACL","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_NOTIFY_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_NOTIFY_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_NOTIFY_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_NOTIFY_GET_TASK_NAME","ES_EVENT_TYPE_NOTIFY_TRACE","ES_EVENT_TYPE_NOTIFY_REMOTE_THREAD_CREATE","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_NOTIFY_GET_TASK_READ","ES_EVENT_TYPE_NOTIFY_GET_TASK_INSPECT","ES_EVENT_TYPE_AUTH_COPYFILE","ES_EVENT_TYPE_NOTIFY_COPYFILE"]}
70 | {"path":"/usr/sbin/spindump","id":"7A09BD41-394A-438D-AE51-F34E100A23F2","eventCount":126,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_AUTH_EXEC","ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_KEXTLOAD","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_MOUNT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_NOTIFY_EXEC","ES_EVENT_TYPE_NOTIFY_OPEN","ES_EVENT_TYPE_NOTIFY_FORK","ES_EVENT_TYPE_NOTIFY_CLOSE","ES_EVENT_TYPE_NOTIFY_CREATE","ES_EVENT_TYPE_NOTIFY_EXCHANGEDATA","ES_EVENT_TYPE_NOTIFY_EXIT","ES_EVENT_TYPE_NOTIFY_GET_TASK","ES_EVENT_TYPE_NOTIFY_KEXTLOAD","ES_EVENT_TYPE_NOTIFY_KEXTUNLOAD","ES_EVENT_TYPE_NOTIFY_LINK","ES_EVENT_TYPE_NOTIFY_MMAP","ES_EVENT_TYPE_NOTIFY_MPROTECT","ES_EVENT_TYPE_NOTIFY_MOUNT","ES_EVENT_TYPE_NOTIFY_UNMOUNT","ES_EVENT_TYPE_NOTIFY_IOKIT_OPEN","ES_EVENT_TYPE_NOTIFY_RENAME","ES_EVENT_TYPE_NOTIFY_SETATTRLIST","ES_EVENT_TYPE_NOTIFY_SETEXTATTR","ES_EVENT_TYPE_NOTIFY_SETFLAGS","ES_EVENT_TYPE_NOTIFY_SETMODE","ES_EVENT_TYPE_NOTIFY_SETOWNER","ES_EVENT_TYPE_NOTIFY_SIGNAL","ES_EVENT_TYPE_NOTIFY_UNLINK","ES_EVENT_TYPE_NOTIFY_WRITE","ES_EVENT_TYPE_AUTH_FILE_PROVIDER_MATERIALIZE","ES_EVENT_TYPE_NOTIFY_FILE_PROVIDER_MATERIALIZE","ES_EVENT_TYPE_AUTH_FILE_PROVIDER_UPDATE","ES_EVENT_TYPE_NOTIFY_FILE_PROVIDER_UPDATE","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_NOTIFY_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_NOTIFY_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_NOTIFY_LOOKUP","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_NOTIFY_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_NOTIFY_GETATTRLIST","ES_EVENT_TYPE_NOTIFY_STAT","ES_EVENT_TYPE_NOTIFY_ACCESS","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_NOTIFY_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_NOTIFY_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_NOTIFY_CLONE","ES_EVENT_TYPE_NOTIFY_FCNTL","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_NOTIFY_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_NOTIFY_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_NOTIFY_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_NOTIFY_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_NOTIFY_FSGETPATH","ES_EVENT_TYPE_NOTIFY_DUP","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_NOTIFY_SETTIME","ES_EVENT_TYPE_NOTIFY_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_NOTIFY_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_NOTIFY_SETACL","ES_EVENT_TYPE_NOTIFY_PTY_GRANT","ES_EVENT_TYPE_NOTIFY_PTY_CLOSE","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_NOTIFY_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_NOTIFY_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_NOTIFY_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_NOTIFY_CS_INVALIDATED","ES_EVENT_TYPE_NOTIFY_GET_TASK_NAME","ES_EVENT_TYPE_NOTIFY_TRACE","ES_EVENT_TYPE_NOTIFY_REMOTE_THREAD_CREATE","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_NOTIFY_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_NOTIFY_GET_TASK_READ","ES_EVENT_TYPE_NOTIFY_GET_TASK_INSPECT","ES_EVENT_TYPE_NOTIFY_SETUID","ES_EVENT_TYPE_NOTIFY_SETGID","ES_EVENT_TYPE_NOTIFY_SETEUID","ES_EVENT_TYPE_NOTIFY_SETEGID","ES_EVENT_TYPE_NOTIFY_SETREUID","ES_EVENT_TYPE_NOTIFY_SETREGID","ES_EVENT_TYPE_AUTH_COPYFILE","ES_EVENT_TYPE_NOTIFY_COPYFILE","ES_EVENT_TYPE_NOTIFY_AUTHENTICATION","ES_EVENT_TYPE_NOTIFY_XP_MALWARE_DETECTED","ES_EVENT_TYPE_NOTIFY_XP_MALWARE_REMEDIATED","ES_EVENT_TYPE_NOTIFY_LW_SESSION_LOGIN","ES_EVENT_TYPE_NOTIFY_LW_SESSION_LOGOUT","ES_EVENT_TYPE_NOTIFY_LW_SESSION_LOCK","ES_EVENT_TYPE_NOTIFY_LW_SESSION_UNLOCK","ES_EVENT_TYPE_NOTIFY_SCREENSHARING_ATTACH","ES_EVENT_TYPE_NOTIFY_SCREENSHARING_DETACH","ES_EVENT_TYPE_NOTIFY_OPENSSH_LOGIN","ES_EVENT_TYPE_NOTIFY_OPENSSH_LOGOUT","ES_EVENT_TYPE_NOTIFY_LOGIN_LOGIN","ES_EVENT_TYPE_NOTIFY_LOGIN_LOGOUT","ES_EVENT_TYPE_NOTIFY_BTM_LAUNCH_ITEM_ADD","ES_EVENT_TYPE_NOTIFY_BTM_LAUNCH_ITEM_REMOVE"]}
71 | {"path":"/usr/sbin/systemstats","id":"655C554B-61B7-410E-9AF4-A2BBA7171D9C","eventCount":3,"type":"ES_MUTE_PATH_TYPE_PREFIX","events":["ES_EVENT_TYPE_NOTIFY_CLOSE","ES_EVENT_TYPE_NOTIFY_WRITE","ES_EVENT_TYPE_NOTIFY_PROC_CHECK"]}
--------------------------------------------------------------------------------
/Mute sets/es_default_mute_set_13_3_1.json:
--------------------------------------------------------------------------------
1 | {"path":"/System/Library/PrivateFrameworks/SkyLight.framework/Versions/A/Resources/WindowServer","id":"926D9832-06B4-43CF-9D91-921EE6E9D6C4","eventCount":39,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_AUTH_COPYFILE"]}
2 | {"path":"/System/Library/PrivateFrameworks/TCC.framework/Support/tccd","id":"4B4553B8-A78B-42C7-A8A1-F962EFE55292","eventCount":39,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_AUTH_COPYFILE"]}
3 | {"path":"/System/Library/PrivateFrameworks/TCC.framework/Versions/A/Resources/tccd","id":"2F780C1B-2B9B-4679-BAAB-C212AC9F7B8F","eventCount":39,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_AUTH_COPYFILE"]}
4 | {"path":"/usr/bin/heap","id":"7BD387C4-77AB-417D-97C6-963A22F7B60A","eventCount":39,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_AUTH_COPYFILE"]}
5 | {"path":"/usr/bin/sample","id":"E37C223F-4F2E-44AB-A4FA-0C48C4842E78","eventCount":39,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_AUTH_COPYFILE"]}
6 | {"path":"/usr/bin/tailspin","id":"B48C470D-6531-4428-A316-E42B24CD7725","eventCount":39,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_AUTH_COPYFILE"]}
7 | {"path":"/usr/libexec/amfid","id":"8C7B7265-D58D-4885-BAA1-861D1EC299A8","eventCount":39,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_AUTH_COPYFILE"]}
8 | {"path":"/usr/libexec/opendirectoryd","id":"7448172F-FCFE-4A87-B096-C9C0166D5904","eventCount":39,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_AUTH_COPYFILE"]}
9 | {"path":"/usr/libexec/runningboardd","id":"062878A6-46F8-4B8D-8553-DE632430B978","eventCount":39,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_AUTH_COPYFILE"]}
10 | {"path":"/usr/libexec/sandboxd","id":"A230ED5F-AE7C-4FC0-9446-22DC3257F98E","eventCount":39,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_AUTH_COPYFILE"]}
11 | {"path":"/usr/libexec/syspolicyd","id":"24FBC55F-E89A-4BAC-9CC8-65B0705DAC78","eventCount":39,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_AUTH_COPYFILE"]}
12 | {"path":"/usr/libexec/trustd","id":"40712A7C-8C29-41DD-B806-F5A4BAE2B20D","eventCount":39,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_AUTH_COPYFILE"]}
13 | {"path":"/usr/libexec/watchdogd","id":"BAC2C3FA-52B7-4358-A8EB-2C1F32379AC5","eventCount":39,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_AUTH_COPYFILE"]}
14 | {"path":"/usr/sbin/cfprefsd","id":"7900EB4E-4C03-4F4A-BA3A-432A98C0AABC","eventCount":39,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_AUTH_COPYFILE"]}
15 | {"path":"/usr/sbin/securityd","id":"92715395-DE45-4CDC-9DA7-3F12853C54C1","eventCount":39,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_AUTH_COPYFILE"]}
16 | {"path":"/usr/sbin/spindump","id":"EA68013B-B292-4D17-8F09-BB29DDB086AE","eventCount":39,"type":"ES_MUTE_PATH_TYPE_LITERAL","events":["ES_EVENT_TYPE_AUTH_OPEN","ES_EVENT_TYPE_AUTH_MMAP","ES_EVENT_TYPE_AUTH_MPROTECT","ES_EVENT_TYPE_AUTH_RENAME","ES_EVENT_TYPE_AUTH_SIGNAL","ES_EVENT_TYPE_AUTH_UNLINK","ES_EVENT_TYPE_AUTH_READLINK","ES_EVENT_TYPE_AUTH_TRUNCATE","ES_EVENT_TYPE_AUTH_LINK","ES_EVENT_TYPE_AUTH_CREATE","ES_EVENT_TYPE_AUTH_SETATTRLIST","ES_EVENT_TYPE_AUTH_SETEXTATTR","ES_EVENT_TYPE_AUTH_SETFLAGS","ES_EVENT_TYPE_AUTH_SETMODE","ES_EVENT_TYPE_AUTH_SETOWNER","ES_EVENT_TYPE_AUTH_CHDIR","ES_EVENT_TYPE_AUTH_GETATTRLIST","ES_EVENT_TYPE_AUTH_CHROOT","ES_EVENT_TYPE_AUTH_UTIMES","ES_EVENT_TYPE_AUTH_CLONE","ES_EVENT_TYPE_AUTH_GETEXTATTR","ES_EVENT_TYPE_AUTH_LISTEXTATTR","ES_EVENT_TYPE_AUTH_READDIR","ES_EVENT_TYPE_AUTH_DELETEEXTATTR","ES_EVENT_TYPE_AUTH_FSGETPATH","ES_EVENT_TYPE_AUTH_SETTIME","ES_EVENT_TYPE_AUTH_UIPC_BIND","ES_EVENT_TYPE_AUTH_UIPC_CONNECT","ES_EVENT_TYPE_AUTH_EXCHANGEDATA","ES_EVENT_TYPE_AUTH_SETACL","ES_EVENT_TYPE_AUTH_PROC_CHECK","ES_EVENT_TYPE_AUTH_GET_TASK","ES_EVENT_TYPE_AUTH_SEARCHFS","ES_EVENT_TYPE_AUTH_FCNTL","ES_EVENT_TYPE_AUTH_IOKIT_OPEN","ES_EVENT_TYPE_AUTH_PROC_SUSPEND_RESUME","ES_EVENT_TYPE_AUTH_REMOUNT","ES_EVENT_TYPE_AUTH_GET_TASK_READ","ES_EVENT_TYPE_AUTH_COPYFILE"]}
--------------------------------------------------------------------------------
/README.md:
--------------------------------------------------------------------------------
1 | ## Welcome to Red Canary Mac Monitor
2 | 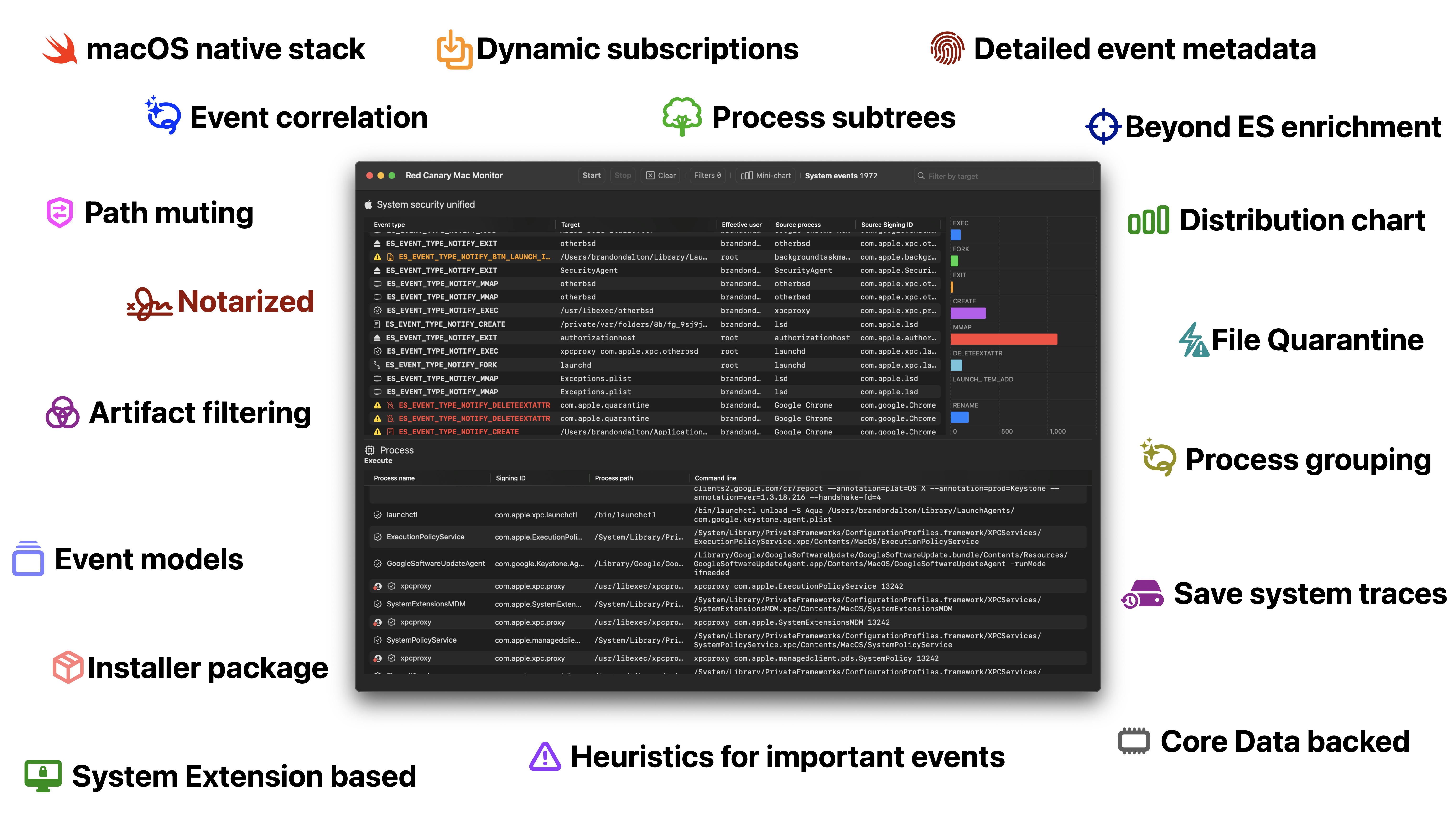
3 |
4 | Red Canary Mac Monitor is an **advanced, stand-alone system monitoring tool tailor-made for macOS security research, malware triage, and system troubleshooting**. Harnessing Apple Endpoint Security (ES), it collects and enriches system events, displaying them graphically, with an expansive feature set designed to surface only the events that are relevant to you. The telemetry collected includes process, interprocess, and file events in addition to rich metadata, allowing users to contextualize events and tell a story with ease. With an intuitive interface and a rich set of analysis features, Red Canary Mac Monitor was designed for a wide range of skill levels and backgrounds to detect macOS threats that would otherwise go unnoticed. As part of Red Canary’s commitment to the research community, the Mac Monitor distribution package is available to download for free.
5 |
6 | ## Requirements
7 | - Processor: We recommend an `Apple Silicon` machine, but `Intel` works too!
8 | - System memory: `4GB+` is recommended
9 | - macOS version: `13.1+` (Ventura)
10 |
11 | ## How can I install this thing?
12 | > **Homebrew?** `brew install --cask red-canary-mac-monitor`
13 | * Go to the releases section and download the latest installer: https://github.com/redcanaryco/mac-monitor/releases
14 | * Open the app: `Red Canary Mac Monitor.app`
15 | * You'll be prompted to "Open System Settings" to "Allow" the System Extension.
16 | * Next, System Settings will automatically open to `Full Disk Access` -- you'll need to flip the switch to enable this for the `Red Canary Security Extension`. Full Disk Access is a [*requirement* of Endpoint Security](https://developer.apple.com/documentation/endpointsecurity/3259700-es_new_client#:~:text=The%20user%20does%20this%20in%20the%20Security%20and%20Privacy%20pane%20of%20System%20Preferences%2C%20by%20adding%20the%20app%20to%20Full%20Disk%20Access.).
17 | * 🏎️ Click the "Start" button in the app and you'll be prompted to reopen the app. Done!
18 |
19 | 
20 |
21 | ### Install footprint
22 | - Event monitor app which establishes an XPC connection to the Security Extension: `/Applications/Red Canary Mac Monitor.app` w/signing identifier of `com.redcanary.agent`.
23 | - Security Extension: `/Library/SystemExtensions/../com.redcanary.agent.securityextension.systemextension` w/signing identifier of `com.redcanary.agent.securityextension.systemextension`.
24 |
25 |
26 | ## Uninstall
27 | > **Homebrew?** `brew uninstall red-canary-mac-monitor`. When using this option you will likely be prompted to authenticate to remove the System Extension.
28 | * **From the Finder** delete the app and authenticate to remove the System Extension. You can't do this from the Dock. It's that easy!
29 | * You can also *just* remove the Security Extension if you want in the app's menu bar or by going into the app settings.
30 | * (`1.0.3`) Supports removal using the `../Contents/SharedSupport/uninstall.sh` script.
31 |
32 |
33 | ## How are updates handled?
34 | > **Homebrew?** `brew update && brew upgrade red-canary-mac-monitor`. When using this option you will likely be prompted to authenticate to remove the System Extension.
35 | * When a new version is available for you to download we'll make a new [release](https://github.com/redcanaryco/mac-monitor/releases/).
36 | * We'll include updated notes and telemetry summaries (if applicable) for each release.
37 | * All you, as the end user, will need to do is download the update and run the installer. We'll take care of the rest 😉.
38 |
39 |
40 | ## How to use this repository
41 | Here we'll be hosting:
42 | * The distribution package for easy install. See the [`Releases` section](https://github.com/redcanaryco/mac-monitor/releases/). Each major build corresponds to a code name. The first of these builds is `GoldCardinal`.
43 | * Telemetry reports in `Telemetry reports/` (i.e. all the artifacts that can be collected by the Security Extension).
44 | * Iconography (what the symbols and colors mean) in `Iconography/`
45 | * Updated mute set summaries in `Mute sets/`
46 | * `AtomicESClient` is a seperate, but very closely related project showing the ropes of Endpoint Security check it out in: `AtomicESClient/`
47 |
48 | Additionally, you can submit feature requests and bug reports here as well. When creating a new Issue you'll be able to use one of the two provided templates. Both of these options are also accessible from the in-app "Help" menu.
49 | * [Feature request](https://github.com/redcanaryco/mac-monitor/issues/new?assignees=Brandon7CC&labels=rc-mac-feature-request&template=feature_request.md&title=)
50 | * [Bug report](https://github.com/redcanaryco/mac-monitor/issues/new?assignees=Brandon7CC&labels=rc-mac-bug&template=bug_report.md&title=)
51 |
52 |
53 | ## How are releases structured?
54 | Each release of Red Canary Mac Monitor has a corresponding build name and version number. The first release has the build name of: `GoldCardinal` and version number `1.0.1`.
55 |
56 |
57 | ## What are some standout features?
58 | - **High fidelity ES events modeled and enriched** with some events containing further enrichment. For example, a process being File Quarantine-aware, a file being quarantined, code signing certificates, etc.
59 | - **Dynamic runtime ES event subscriptions**. You have the ability to on-the-fly modify your event subscriptions -- enabling you to cut down on noise while you're working through traces.
60 | - **Path muting at the API level** -- Apple's Endpoint Security team has put a lot of work recently into enabling advanced path muting / inversion capabilities. Here, we cover the majority of the API features: `es_mute_path` and `es_mute_path_events` along with the types of `ES_MUTE_PATH_TYPE_PREFIX`, `ES_MUTE_PATH_TYPE_LITERAL`, `ES_MUTE_PATH_TYPE_TARGET_PREFIX`, and `ES_MUTE_PATH_TYPE_TARGET_LITERAL`. Right now we do not support inversion. **I'd love it if the ES team added inversion on a per-event basis instead of per-client**.
61 | 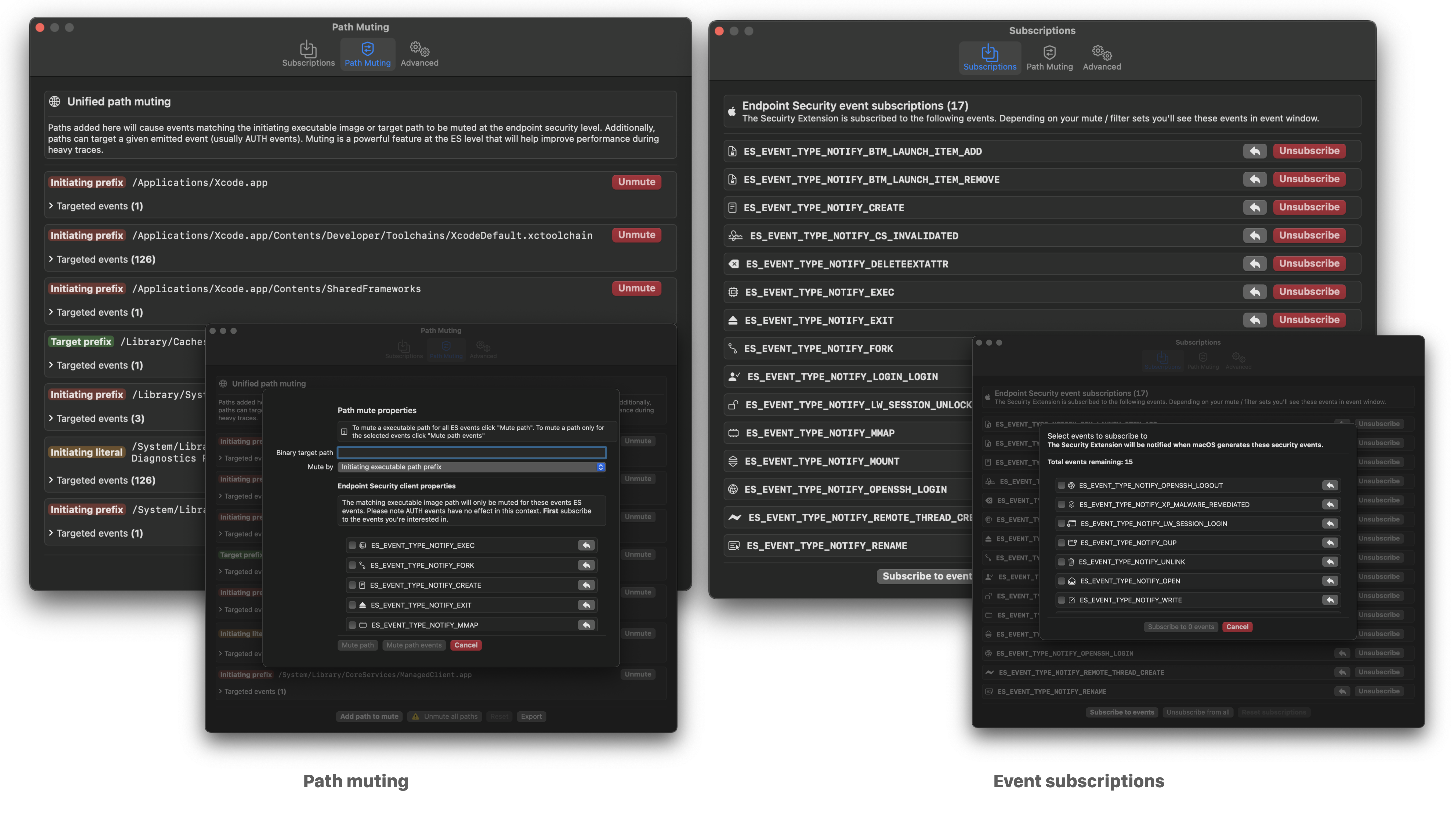
62 |
63 | - **Detailed event facts**. **Right click on any event** in a table row to access event metadata, filtering, muting, and unsubscribe options. Core to the user experience is the ability to drill down into any given event or set of events. To enable this functionality we’ve developed “Event facts” windows which contain metadata / additional enrichment about any given event. Each event has a curated set metadata that is displayed. For example, process execution events will generally contain code signing information, environment variables, correlated events, etc. Below you see examples of file creation and BTM launch item added event facts.
64 | 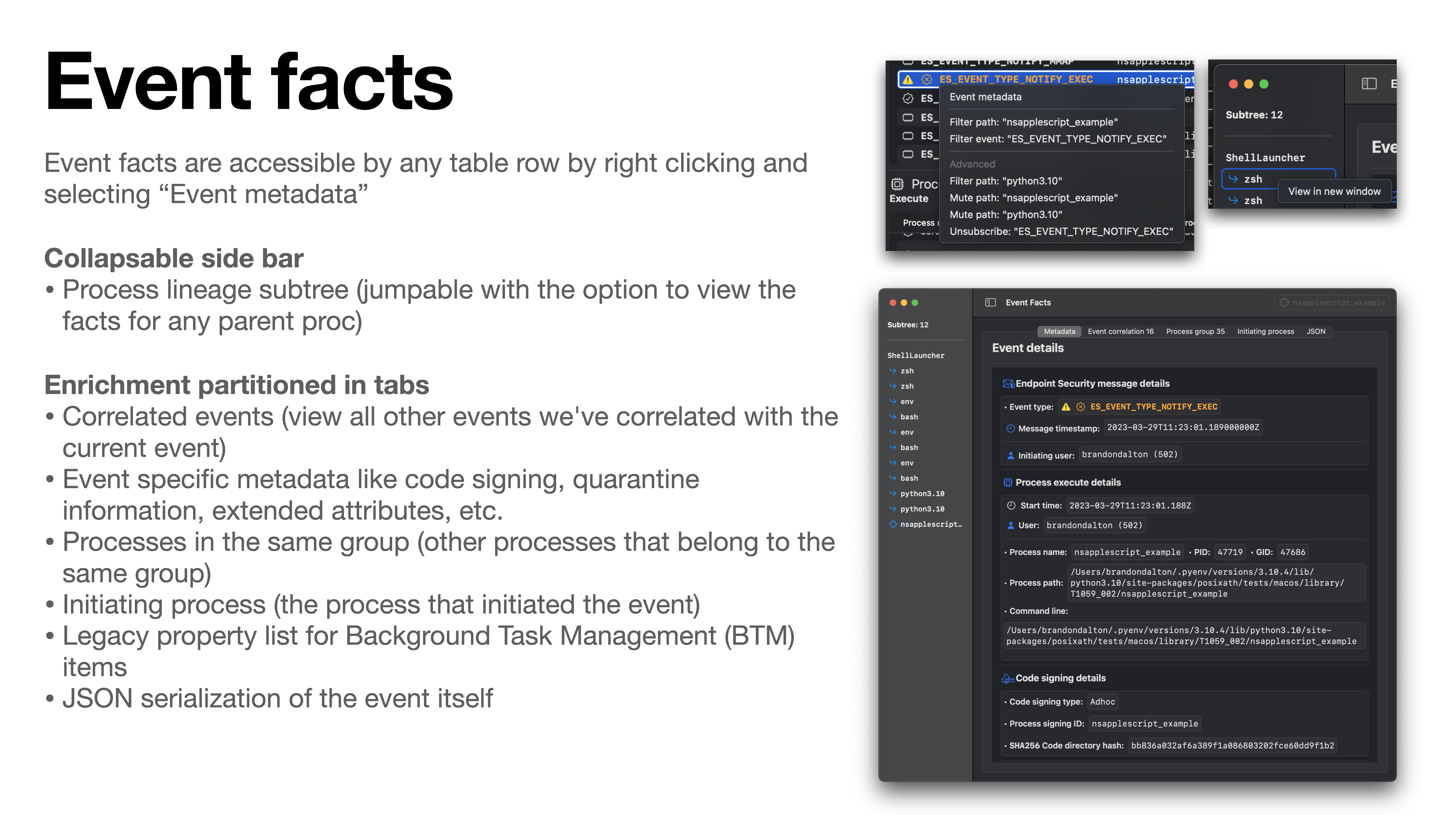
65 |
66 | - **Event correlation** is an *exceptionally* important component in any analyst's tool belt. The ability to see which events are "related" to one-another enables you to manipulate the telemetry in a way that makes sense (other than simply dumping to JSON or representing an individual event). We perform event correlation at the process level -- this means that for any given event (which have an initiating and/or target process) we can deeply link events that any given process instigated.
67 | - **Process grouping** is another helpful way to represent process telemetry around a given `ES_EVENT_TYPE_NOTIFY_EXEC` or `ES_EVENT_TYPE_NOTIFY_FORK` event. By grouping processes in this way you can easily identify the chain of activity.
68 | - **Artifact filtering** enabled users to remove (but not destroy) events from view based on: event type, initiating process path, or target process path. This standout feature enables analysts to cut through the noise quickly while still retaining all data.
69 | - Lossy filtering (i.e. events that are dropped from the trace) is also available in the form of "dropping platform binaries" -- another useful technique to cut through the noise.
70 |
71 | 
72 |
73 | - **Telemetry export**. Right now we support pretty JSON and JSONL (one JSON object per-line) for the full or partial system trace (keyboard shortcuts too). You can access these options in the menu bar under "Export Telemetry".
74 | - **Process subtree generation**. When viewing the event facts window for any given event we’ll attempt to generate a process lineage subtree in the left hand sidebar. This tree is intractable – click on any process and you’ll be taken to its event facts. **Similarly, you can right click on any process in the tree to pop out the facts for that event**.
75 | - **Dynamic event distribution chart**. This is a fun one enabled by the SwiftUI team. The graph shows the distribution of events you're subscribed to, currently in-scope (i.e. not filtered), and have a count of more than nothing. This enables you to *very* quickly identify noisy events. The chart auto-shows/hides itself, but you can bring it back with the: "Mini-chart" button in the toolbar.
76 |
77 | 
78 |
79 |
80 | ## Some other features
81 | - Another very important feature of any dynamic analysis tool is to not let an event limiter or memory inefficient implementation get in the way of the user experience. To address this (the best we currently can) we’ve implemented an asynchronous parent / child-like **Core Data stack** which stores our events as “entities” in-memory. This enables us to store virtually unlimited events with Mac Monitor. Although, the time of insertions does become more taxing as the event limit gets very large.
82 | - Since Mac Monitor is based on a Security Extension which is always running in the background (like an EDR sensor) we baked in functionality such that it **does not process events when a system trace is not occurring**. This means that the Red Canary Security Extension (`com.redcanary.agent.securityextension`) will not needlessly utilize resources / battery power when a trace is not occurring.
83 | - Distribution package: **The install process is often overlooked**. However, if users do not have a good understanding of what’s being installed or if it’s too complex to install the barrier to entry might be just high enough to dissuade people from using it. This is why we ship Mac Monitor as a notarized distribution package.
84 |
85 |
86 | ## Can you open source Mac Monitor?
87 |
88 | We know how much you would love to learn from the source code and/or build tools or commercial products on top of this. Currently, however, Mac Monitor will be distributed as a free, closed-source tool. Enjoy what's being offered and please continue to provide your great feedback. Additionally, never hesitate to reach out if there's one aspect of the implementation you'd love to learn more about. We're an open book when it comes to geeking out about all things implementation, usage, and research methodology.
89 |
--------------------------------------------------------------------------------
/Resources/ArtifactFilteringOverview.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/redcanaryco/mac-monitor/14b5b8b7021ea9bda9906ef4f00b89cd3b110652/Resources/ArtifactFilteringOverview.png
--------------------------------------------------------------------------------
/Resources/DistributionChart.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/redcanaryco/mac-monitor/14b5b8b7021ea9bda9906ef4f00b89cd3b110652/Resources/DistributionChart.png
--------------------------------------------------------------------------------
/Resources/EventFactsOverview.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/redcanaryco/mac-monitor/14b5b8b7021ea9bda9906ef4f00b89cd3b110652/Resources/EventFactsOverview.png
--------------------------------------------------------------------------------
/Resources/FeatureSummary.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/redcanaryco/mac-monitor/14b5b8b7021ea9bda9906ef4f00b89cd3b110652/Resources/FeatureSummary.png
--------------------------------------------------------------------------------
/Resources/GoldCardinal-1-0-1-event-iconography.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/redcanaryco/mac-monitor/14b5b8b7021ea9bda9906ef4f00b89cd3b110652/Resources/GoldCardinal-1-0-1-event-iconography.png
--------------------------------------------------------------------------------
/Resources/GoldCardinal-1-0-5-event-iconography.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/redcanaryco/mac-monitor/14b5b8b7021ea9bda9906ef4f00b89cd3b110652/Resources/GoldCardinal-1-0-5-event-iconography.png
--------------------------------------------------------------------------------
/Resources/Install.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/redcanaryco/mac-monitor/14b5b8b7021ea9bda9906ef4f00b89cd3b110652/Resources/Install.png
--------------------------------------------------------------------------------
/Resources/MuteSubscriptionsOverview.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/redcanaryco/mac-monitor/14b5b8b7021ea9bda9906ef4f00b89cd3b110652/Resources/MuteSubscriptionsOverview.png
--------------------------------------------------------------------------------
/Resources/build-phases.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/redcanaryco/mac-monitor/14b5b8b7021ea9bda9906ef4f00b89cd3b110652/Resources/build-phases.png
--------------------------------------------------------------------------------
/Resources/run-as.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/redcanaryco/mac-monitor/14b5b8b7021ea9bda9906ef4f00b89cd3b110652/Resources/run-as.png
--------------------------------------------------------------------------------
/Resources/signing-capabilities.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/redcanaryco/mac-monitor/14b5b8b7021ea9bda9906ef4f00b89cd3b110652/Resources/signing-capabilities.png
--------------------------------------------------------------------------------
/Telemetry reports/GoldCardinal-1-0-3.md:
--------------------------------------------------------------------------------
1 | # Red Canary Mac Monitor Telemetry Summary
2 | ## Distribution details
3 | - Build name: `GoldCardinal`
4 | - App versions: `1.0.1` - `1.0.3`
5 |
6 | # Overview
7 | The following is an in-depth look behind the "Red Canary Security Extension" telemetry curtain. While this information is readily viewable to users at any time by exporting telemetry or selecting the "JSON" tab in any "Event Facts" window these report(s) will serve as a "snapshot" of telemetry capabilities over time.
8 | - Total Endpoint Security (ES) events collected: `32`
9 | - Covering the following telemetry classes (abridged)
10 | * Process
11 | * Interprocess
12 | * File
13 | * File metadata
14 | * File system
15 | * Memory mapping
16 | * Login
17 | * Background Task Management (BTM)
18 | * XProtect
19 |
20 | ## Telemetry record structure
21 | Each event is delivered in a record which can be modeled in JSON in the following way:
22 | ```
23 | {
24 | // Initiating process metadata (responsible for the target event)
25 | {
26 | // Target event metadata (e.g. OpenSSH login, etc)
27 | }
28 | }
29 | ```
30 |
31 | Each event has a process which was responsible for it. In terms of process execute events this is the “parent” process, for XProtect detect events it’ll be Gatekeeper (aka syspolicyd), for file creation events it’ll be the process which created the file, etc. A sample telemetry object is shown below:
32 |
33 | ```json
34 | {
35 | "initiating_ruid" : 502,
36 | "responsible_audit_token" : "502-502-20-502-20-12327-100019-1883731",
37 | "initiating_is_platform_binary" : false,
38 | "parent_audit_token" : "502-502-20-502-20-13018-100019-1885461",
39 | "target" : "AppleScript",
40 | "initiating_process_cdhash" : "bb836a032af6a389f1a086803202fce60dd9f1b2",
41 | "initiating_process_file_quarantine_type" : 0,
42 | "macOS" : "13.2.1 (Build 22D68)",
43 | "sensor_id" : "bf169d19f3e7bea1b61c00db1bc9c98318007ae5f7a2b6c15e3f64f9ed5760c7cd8a49268472e75e0f916fe8acd503d9f9580a030d7d021582271813b6a3ff38",
44 | "initiating_process_path" : "/Users/brandondalton/.pyenv/versions/3.10.4/lib/python3.10/site-packages/posixath/tests/macos/library/T1059_002/nsapplescript_example",
45 | "initiating_process_name" : "nsapplescript_example",
46 | "initiating_euid_human" : "brandondalton",
47 | "initiating_ruid_human" : "brandondalton",
48 | "initiating_euid" : 502,
49 | "initiating_process_group_id" : 13018,
50 | "es_event_type" : "ES_EVENT_TYPE_NOTIFY_MMAP",
51 | "initiating_process_signing_id" : "nsapplescript_example",
52 | "path_is_truncated" : false,
53 | "audit_token" : "502-502-20-502-20-13051-100019-1885479",
54 | "initiating_pid" : 13018,
55 | "mmap_event" : {
56 | "path" : "/System/Library/Components/AppleScript.component/Contents/MacOS/AppleScript"
57 | },
58 | "activity_at_ts" : "2023-03-13T22:08:37.569Z"
59 | }
60 | ```
61 |
62 | # Endpoint Security event listing
63 | The following ES events are supported by the Red Canary Security Extension. Users can utilize the dynamic event subscriptions feature to subscribe to any supported event.
64 | - `ES_EVENT_TYPE_NOTIFY_EXEC`
65 | - `ES_EVENT_TYPE_NOTIFY_FORK`
66 | - `ES_EVENT_TYPE_NOTIFY_EXIT`
67 | - `ES_EVENT_TYPE_NOTIFY_CREATE`
68 | - `ES_EVENT_TYPE_NOTIFY_DELETEEXTATTR`
69 | - `ES_EVENT_TYPE_NOTIFY_MMAP`
70 | - `ES_EVENT_TYPE_NOTIFY_BTM_LAUNCH_ITEM_ADD`
71 | - `ES_EVENT_TYPE_NOTIFY_BTM_LAUNCH_ITEM_REMOVE`
72 | - `ES_EVENT_TYPE_NOTIFY_OPENSSH_LOGIN`
73 | - `ES_EVENT_TYPE_NOTIFY_OPENSSH_LOGOUT`
74 | - `ES_EVENT_TYPE_NOTIFY_XP_MALWARE_DETECTED`
75 | - `ES_EVENT_TYPE_NOTIFY_XP_MALWARE_REMEDIATED`
76 | - `ES_EVENT_TYPE_NOTIFY_MOUNT`
77 | - `ES_EVENT_TYPE_NOTIFY_LOGIN_LOGIN`
78 | - `ES_EVENT_TYPE_NOTIFY_LW_SESSION_LOGIN`
79 | - `ES_EVENT_TYPE_NOTIFY_LW_SESSION_UNLOCK`
80 | - `ES_EVENT_TYPE_NOTIFY_DUP`
81 | - `ES_EVENT_TYPE_NOTIFY_RENAME`
82 | - `ES_EVENT_TYPE_NOTIFY_UNLINK`
83 | - `ES_EVENT_TYPE_NOTIFY_OPEN`
84 | - `ES_EVENT_TYPE_NOTIFY_WRITE`
85 | - `ES_EVENT_TYPE_NOTIFY_LINK`
86 | - `ES_EVENT_TYPE_NOTIFY_CLOSE`
87 | - `ES_EVENT_TYPE_NOTIFY_SIGNAL`
88 | - `ES_EVENT_TYPE_NOTIFY_REMOTE_THREAD_CREATE`
89 | - `ES_EVENT_TYPE_NOTIFY_IOKIT_OPEN`
90 | - `ES_EVENT_TYPE_NOTIFY_CS_INVALIDATED`
91 | - `ES_EVENT_TYPE_NOTIFY_SETEXTATTR`
92 | - `ES_EVENT_TYPE_NOTIFY_PROC_SUSPEND_RESUME`
93 | - `ES_EVENT_TYPE_NOTIFY_TRACE`
94 | - `ES_EVENT_TYPE_NOTIFY_GET_TASK`
95 | - `ES_EVENT_TYPE_NOTIFY_PROC_CHECK`
96 |
97 |
98 | # Initiating process metadata
99 | Each component of our initiating process structure is listed below along with its type. Types which are suffixed with a question mark are optional. This means that any given telemetry object can have any given event we have modeled.
100 | - `audit_token: String`
101 | - `es_event_type: String`
102 | - `initiating_pid: Int32`
103 | - `initiating_process_name: String`
104 | - `initiating_process_signing_id: String`
105 | - `initiating_process_path: String`
106 | - `initiating_ruid: Int64`
107 | - `initiating_euid: Int64`
108 | - `initiating_ruid_human: String`
109 | - `initiating_euid_human: String`
110 | - `initiating_process_cdhash: String`
111 | - `parent_audit_token: String`
112 | - `path_is_truncated: Bool`
113 | - `responsible_audit_token: String`
114 | - `macOS: String`
115 | - `sensor_id: String`
116 | - `activity_at_ts: String`
117 | - `initiating_process_file_quarantine_type: Int16`
118 | - We attempt to read the app’s bundled property list for this information
119 | - `0`: The process is not File Quarantine-aware
120 | - `1`: The process has opted-into File Quarantine
121 | - `2`: The process has been forced into File Quarantine
122 | - `initiating_process_group_id: Int32`
123 | - `initiating_is_platform_binary: Bool`
124 | - `btm_launch_item_add_event: RCESLaunchItemAddEvent?`
125 | - `delete_xattr_event: RCESXattrEvent?`
126 | - `set_xattr_event: RCESXattrSetEvent?`
127 | - `exec_event: RCESProcessExecEvent?`
128 | - `code_signature_invalidated_event: RCESCodeSignatureInvalidatedEvent?`
129 | - `process_socket_event: RCESProcessSocketEvent?`
130 | - `process_trace_event: RCESProcessTraceEvent?`
131 | - `get_task_event: RCESGetTaskEvent?`
132 | - `process_check_event: RCESProcessCheckEvent?`
133 | - `process_signal_event: RCESProcessSignalEvent?`
134 | - `remote_thread_create_event: RCESRemoteThreadCreateEvent?`
135 | - `exit_event: RCESProcessExitEvent?`
136 | - `file_event: RCESFileEvent?`
137 | - `fork_event: RCESProcessForkEvent?`
138 | - `mmap_event: RCESMMapEvent?`
139 | - `btm_launch_item_remove_event: RCESLaunchItemRemoveEvent?`
140 | - `openssh_login_event: RCESOpenSSHLoginEvent?`
141 | - `openssh_logout_event: RCESOpenSSHLogoutEvent?`
142 | - `xprotect_detect_event: RCESXProtectDetect?`
143 | - `xprotect_remediate_event: RCESXProtectRemediate?`
144 | - `mount_event: RCESMountEvent?`
145 | - `login_login_event: RCESLoginLoginEvent?`
146 | - `lw_login_event: RCESLWLoginEvent?`
147 | - `lw_unlock_event: RCESLWUnlockEvent?`
148 | - `fd_duplicate_event: RCESFDDuplicateEvent?`
149 | - `file_rename_event: RCESFileRenameEvent?`
150 | - `file_delete_event: RCESFileDeleteEvent?`
151 | - `file_open_event: RCESFileOpenEvent?`
152 | - `file_write_event: RCESFileWriteEvent?`
153 | - `link_event: RCESLinkEvent?`
154 | - `file_close_event: RCESFileCloseEvent?`
155 | - `iokit_open_event: RCESIOKitOpenEvent?`
156 |
157 | # **Process events**
158 | ## Process execute target event metadata (`exec_event`): `ES_EVENT_TYPE_NOTIFY_EXEC`
159 | - `allow_jit: Bool`
160 | - `audit_token: String`
161 | - `command_line: String`
162 | - `get_task_allow: Bool`
163 | - `pid: Int32`
164 | - `is_adhoc_signed: Bool`
165 | - `is_es_client: Bool`
166 | - `is_platform_binary: Bool`
167 | - `parent_audit_token: String`
168 | - `process_name: String`
169 | - `process_path: String`
170 | - `ruid: Int64`
171 | - `euid: Int64`
172 | - `ruid_human: String`
173 | - `euid_human: String`
174 | - `responsible_audit_token: String`
175 | - `rootless: Bool`
176 | - `signing_id: String`
177 | - `cdhash: String`
178 | - `skip_lv: Bool`
179 | - `team_id: String?`
180 | - `start_time: String`
181 | - `certificate_chain: String?`
182 | - `env_variables: String`
183 | - `file_quarantine_type: Int16`
184 | - We attempt to read the app’s bundled property list for this information
185 | - `0`: The process is not File Quarantine-aware
186 | - `1`: The process has opted-into File Quarantine
187 | - `2`: The process has been forced into File Quarantine
188 | - `cs_type: String`
189 | - `group_id: Int32`
190 |
191 | ## Process fork target event metadata (`fork_event`): `ES_EVENT_TYPE_NOTIFY_FORK`
192 | - `audit_token: String`
193 | - `pid: Int32`
194 | - `ruid: Int64`
195 | - `euid: Int64`
196 | - `ruid_human: String`
197 | - `euid_human: String`
198 | - `parent_audit_token: String`
199 | - `process_name: String`
200 | - `process_path: String`
201 | - `responsible_audit_token: String`
202 | - `signing_id: String`
203 | - `cdhash: String`
204 | - `start_time: String`
205 | - `group_id: Int32`
206 | - `is_platform_binary: Bool`
207 |
208 | ## Process code signature invalidated target event metadata (`code_signature_invalidated_event`): `ES_EVENT_TYPE_NOTIFY_CS_INVALIDATED`
209 | - Note: This target event specifies that the initiating process's code signature was invalidated in-memory.
210 |
211 | ## Process socket target event metadata (`process_socket_event`): `ES_EVENT_TYPE_NOTIFY_PROC_SUSPEND_RESUME`
212 | - `target_process_name: String`
213 | - `target_process_path: String`
214 | - `target_process_signing_id: String`
215 | - `target_process_audit_token: String`
216 | - `type: String`
217 |
218 | ## Process trace target event metadata (`process_trace_event`): `ES_EVENT_TYPE_NOTIFY_TRACE`
219 | - `process_name: String`
220 | - `process_path: String`
221 | - `process_signing_id: String`
222 | - `process_audit_token: String`
223 |
224 | ## Process task port target event (`get_task_event`): `ES_EVENT_TYPE_NOTIFY_GET_TASK`
225 | - `process_path: String`
226 | - `process_name: String`
227 | - `process_audit_token: String`
228 | - `process_signing_id: String`
229 | - `type: String`
230 |
231 | ## Process check target event metadata (`process_check_event`): `ES_EVENT_TYPE_NOTIFY_PROC_CHECK`
232 | - `process_name: String`
233 | - `process_signing_id: String`
234 | - `process_path: String`
235 | - `process_audit_token: String`
236 | - `flavor: Int32`
237 | - `type: String`
238 |
239 | ## Process signal target event metadata (`process_signal_event`): `ES_EVENT_TYPE_NOTIFY_SIGNAL`
240 | - `signal_id: Int32`
241 | - `process_name: String`
242 | - `process_path: String`
243 | - `audit_token: String`
244 | - `signing_id: String`
245 | - `signal_name: String`
246 |
247 | ## Process remote thread created target event metadata (`remote_thread_create_event`): `ES_EVENT_TYPE_NOTIFY_REMOTE_THREAD_CREATE`
248 | - `target_process_name: String`
249 | - `target_process_path: String`
250 | - `target_process_signing_id: String`
251 | - `target_process_audit_token: String`
252 | - `thread_state: String`
253 |
254 | ## Process exit target event metadata (`exit_event`): `ES_EVENT_TYPE_NOTIFY_EXIT`
255 | - `exit_code: Int32`
256 |
257 |
258 |
259 | # **Memory events**
260 | ## Memory map target event metadata (`mmap_event`): `ES_EVENT_TYPE_NOTIFY_MMAP`
261 | - `path: String`
262 |
263 |
264 |
265 | # **File events**
266 | ## File creation target event metadata (`file_event`): `ES_EVENT_TYPE_NOTIFY_CREATE`
267 | - `destination_path: String`
268 | - `file_name: String`
269 | - `is_quarantined: Int16`
270 | - We attempt to determine if the file being created is quarantined. If a file is deleted / delete `xattr` event occurs too too quickly the file cannot be found.
271 | - `0`: The file is not quarantined
272 | - `1`: The file is quarantined
273 | - `2`: The file could not be found
274 |
275 | ## File rename target event metadata (`file_rename_event`): `ES_EVENT_TYPE_NOTIFY_RENAME`
276 | - `file_name: String`
277 | - `destination_path: String`
278 | - `source_path: String`
279 | - `archive_files_not_quarantined: String?`
280 | - If this file rename event is moving an inflated archive we perform a deep search of the destination file path to determine if any files are not quarantined.
281 | - `type: String`
282 | - `is_quarantined: Int16`
283 | - We attempt to determine if the file being created is quarantined. If a file is deleted / delete `xattr` event occurs too too quickly the file cannot be found.
284 | - `0`: The file is not quarantined
285 | - `1`: The file is quarantined
286 | - `2`: The file could not be found
287 |
288 | ## File delete target event metadata (`file_delete_event`): `ES_EVENT_TYPE_NOTIFY_UNLINK`
289 | - `file_path: String`
290 | - `file_name: String`
291 | - `parent_directory: String`
292 |
293 | ## File open target event metadata (`file_open_event`): `ES_EVENT_TYPE_NOTIFY_OPEN`
294 | - `file_path: String`
295 | - `file_name: String`
296 |
297 | ## File write target event metadata (`file_write_event`): `ES_EVENT_TYPE_NOTIFY_WRITE`
298 | - `file_path: String`
299 | - `file_name: String`
300 |
301 | ## File link target event metadata (`link_event`): `ES_EVENT_TYPE_NOTIFY_LINK`
302 | - `source_file_path: String`
303 | - `source_file_name: String`
304 | - `target_file_path: String`
305 | - `target_file_name: String`
306 |
307 | ## File close target event metadata (`file_close_event`): `ES_EVENT_TYPE_NOTIFY_CLOSE`
308 | - `file_path: String`
309 | - `file_name: String`
310 |
311 | ## File duplicate target event metadata (`fd_duplicate_event`): `ES_EVENT_TYPE_NOTIFY_DUP`
312 | - `file_path: String`
313 | - `file_name: String`
314 |
315 |
316 |
317 | # **File metadata events**
318 | ## Extended attribute (xattr) delete target event metadata (`delete_xattr_event`): `ES_EVENT_TYPE_NOTIFY_DELETEEXTATTR`
319 | - `file_name: String`
320 | - `file_path: String`
321 | - `operation: String`
322 | - `xattr: String`
323 |
324 |
325 | ## Extended attribute (xattr) set target event metadata (`set_xattr_event`): `ES_EVENT_TYPE_AUTH_SETEXTATTR`
326 | - `file_name: String`
327 | - `file_path: String`
328 | - `operation: String`
329 | - `xattr: String`
330 |
331 |
332 |
333 | # **File system events**
334 | ## File system mount target event metadata (`mount_event`): `ES_EVENT_TYPE_NOTIFY_MOUNT`
335 | - `total_files: Int64`
336 | - `mount_flags: Int64`
337 | - `type_name: String`
338 | - `source_name: String`
339 | - `mount_directory: String`
340 | - `owner_uid: Int64`
341 | - `fs_id: String`
342 | - `owner_uid_human: String`
343 |
344 |
345 |
346 | # **Background Task events**
347 | ## Background Task Management (BTM) add target event metadata (`btm_launch_item_add_event`): `ES_EVENT_TYPE_NOTIFY_BTM_LAUNCH_ITEM_ADD`
348 | - `file_name: String`
349 | - `file_path: String`
350 | - `uid: Int64`
351 | - `uid_human: String`
352 | - `is_legacy: Bool`
353 | - `is_managed: Bool`
354 | - `type: String`
355 | - `plist_contents: String`
356 | - We pull the legacy property list for the BTM item added if the property list is not in the Apple Binary Property List
357 | - `app_process_path: String`
358 | - `app_process_signing_id: String`
359 | - `app_process_team_id: String`
360 | - `instigating_process_path: String`
361 | - `instigating_process_signing_id: String`
362 | - `instigating_process_team_id: String?`
363 |
364 | ## Background Task Management (BTM) remove target event metadata (`btm_launch_item_remove_event`): `ES_EVENT_TYPE_NOTIFY_BTM_LAUNCH_ITEM_REMOVE`
365 | - `app_process_path: String?`
366 | - `app_process_signing_id: String?`
367 | - `app_process_team_id: String?`
368 | - `instigating_process_path: String?`
369 | - `instigating_process_signing_id: String?`
370 | - `instigating_process_team_id: String?`
371 | - `file_path: String?`
372 | - `file_name: String?`
373 | - `is_legacy: Bool`
374 | - `type: String?`
375 | - `uid: Int64`
376 | - `uid_human: String?`
377 | - `is_managed: Bool`
378 |
379 |
380 |
381 | # **Login events**
382 | ## LoginWindow login target event metadata (`lw_login_event`): `ES_EVENT_TYPE_NOTIFY_LW_SESSION_LOGIN`
383 | - `username: String`
384 | - `graphical_session_id: Int32`
385 |
386 | ## LoginWindow unlock target event metadata (`lw_unlock_event`): `ES_EVENT_TYPE_NOTIFY_LW_SESSION_UNLOCK`
387 | - `username: String`
388 | - `graphical_session_id: Int32`
389 |
390 | ## Login login target event metadata (`login_login_event`): `ES_EVENT_TYPE_NOTIFY_LOGIN_LOGIN`
391 | - `success: Bool`
392 | - `failure_message: String`
393 | - `username: String`
394 | - `uid: Int64`
395 | - `uid_human: String`
396 |
397 | ## OpenSSH login target event metadata (`openssh_login_event`): `ES_EVENT_TYPE_NOTIFY_OPENSSH_LOGIN`
398 | - `result_type: String?`
399 | - `source_address: String?`
400 | - `source_address_type: String?`
401 | - `success: Bool`
402 | - `user_name: String?`
403 |
404 | ## OpenSSH logout target event metadata (`openssh_logout_event`): `ES_EVENT_TYPE_NOTIFY_OPENSSH_LOGOUT`
405 | - `source_address_type: String`
406 | - `source_address: String`
407 | - `username: String`
408 |
409 |
410 |
411 | # **XProtect events**
412 | ## XProtect Malware detected target event metadata (`xprotect_detect_event`): `ES_EVENT_TYPE_NOTIFY_XP_MALWARE_DETECTED`
413 | - `signature_version: String`
414 | - `malware_identifier: String`
415 | - `incident_identifier: String`
416 | - `detected_path: String`
417 |
418 | ## XProtect Malware remediated target event metadata (`xprotect_remediate_event`): `ES_EVENT_TYPE_NOTIFY_XP_MALWARE_REMEDIATED`
419 | - `signature_version: String`
420 | - `malware_identifier: String`
421 | - `incident_identifier: String`
422 | - `action_type: String`
423 | - `success: Bool`
424 | - `result_description: String`
425 | - `remediated_path: String`
426 | - `remediated_process_audit_token: String`
427 |
428 |
429 |
430 | # **Kernel events**
431 | ## IOKit open target event metadata (`iokit_open_event`): `ES_EVENT_TYPE_NOTIFY_IOKIT_OPEN`
432 | - `user_client_class: String`
433 | - `user_client_type: Int32`
434 |
435 |
436 |
--------------------------------------------------------------------------------
/Telemetry reports/GoldCardinal-1-0-4.md:
--------------------------------------------------------------------------------
1 | # Red Canary Mac Monitor Telemetry Summary
2 | ## Distribution details
3 | - Build name: `GoldCardinal`
4 | - App versions: `1.0.4`
5 |
6 | # Overview
7 | The following is an in-depth look behind the "Red Canary Security Extension" telemetry curtain. While this information is readily viewable to users at any time by exporting telemetry or selecting the "JSON" tab in any "Event Facts" window these report(s) will serve as a "snapshot" of telemetry capabilities over time.
8 | - Total Endpoint Security (ES) events collected: `32`
9 | - Covering the following telemetry classes (abridged)
10 | * Process
11 | * Interprocess
12 | * File
13 | * File metadata
14 | * File system
15 | * Memory mapping
16 | * Login
17 | * Background Task Management (BTM)
18 | * XProtect
19 |
20 | ## Telemetry record structure
21 | Each event is delivered in a record which can be modeled in JSON in the following way:
22 | ```
23 | {
24 | // Initiating process metadata (responsible for the target event)
25 | {
26 | // Target event metadata (e.g. OpenSSH login, etc)
27 | }
28 | }
29 | ```
30 |
31 | Each event has a process which was responsible for it. In terms of process execute events this is the “parent” process, for XProtect detect events it’ll be Gatekeeper (aka syspolicyd), for file creation events it’ll be the process which created the file, etc. A sample telemetry object is shown below:
32 |
33 | ```json
34 | {
35 | "initiating_ruid" : 502,
36 | "responsible_audit_token" : "502-502-20-502-20-12327-100019-1883731",
37 | "initiating_is_platform_binary" : false,
38 | "parent_audit_token" : "502-502-20-502-20-13018-100019-1885461",
39 | "context" : "AppleScript",
40 | "target_path" : "/System/Library/Components/AppleScript.component/Contents/MacOS/AppleScript",
41 | "initiating_process_cdhash" : "bb836a032af6a389f1a086803202fce60dd9f1b2",
42 | "initiating_process_file_quarantine_type" : 0,
43 | "macOS" : "13.2.1 (Build 22D68)",
44 | "sensor_id" : "bf169d19f3e7bea1b61c00db1bc9c98318007ae5f7a2b6c15e3f64f9ed5760c7cd8a49268472e75e0f916fe8acd503d9f9580a030d7d021582271813b6a3ff38",
45 | "initiating_process_path" : "/Users/brandondalton/.pyenv/versions/3.10.4/lib/python3.10/site-packages/posixath/tests/macos/library/T1059_002/nsapplescript_example",
46 | "initiating_process_name" : "nsapplescript_example",
47 | "initiating_euid_human" : "brandondalton",
48 | "initiating_ruid_human" : "brandondalton",
49 | "initiating_euid" : 502,
50 | "initiating_process_group_id" : 13018,
51 | "es_event_type" : "ES_EVENT_TYPE_NOTIFY_MMAP",
52 | "initiating_process_signing_id" : "nsapplescript_example",
53 | "path_is_truncated" : false,
54 | "audit_token" : "502-502-20-502-20-13051-100019-1885479",
55 | "initiating_pid" : 13018,
56 | "mmap_event" : {
57 | "path" : "/System/Library/Components/AppleScript.component/Contents/MacOS/AppleScript"
58 | },
59 | "activity_at_ts" : "2023-03-13T22:08:37.569Z"
60 | }
61 | ```
62 |
63 | # Endpoint Security event listing
64 | The following ES events are supported by the Red Canary Security Extension. Users can utilize the dynamic event subscriptions feature to subscribe to any supported event.
65 | - `ES_EVENT_TYPE_NOTIFY_EXEC`
66 | - `ES_EVENT_TYPE_NOTIFY_FORK`
67 | - `ES_EVENT_TYPE_NOTIFY_EXIT`
68 | - `ES_EVENT_TYPE_NOTIFY_CREATE`
69 | - `ES_EVENT_TYPE_NOTIFY_DELETEEXTATTR`
70 | - `ES_EVENT_TYPE_NOTIFY_MMAP`
71 | - `ES_EVENT_TYPE_NOTIFY_BTM_LAUNCH_ITEM_ADD`
72 | - `ES_EVENT_TYPE_NOTIFY_BTM_LAUNCH_ITEM_REMOVE`
73 | - `ES_EVENT_TYPE_NOTIFY_OPENSSH_LOGIN`
74 | - `ES_EVENT_TYPE_NOTIFY_OPENSSH_LOGOUT`
75 | - `ES_EVENT_TYPE_NOTIFY_XP_MALWARE_DETECTED`
76 | - `ES_EVENT_TYPE_NOTIFY_XP_MALWARE_REMEDIATED`
77 | - `ES_EVENT_TYPE_NOTIFY_MOUNT`
78 | - `ES_EVENT_TYPE_NOTIFY_LOGIN_LOGIN`
79 | - `ES_EVENT_TYPE_NOTIFY_LW_SESSION_LOGIN`
80 | - `ES_EVENT_TYPE_NOTIFY_LW_SESSION_UNLOCK`
81 | - `ES_EVENT_TYPE_NOTIFY_DUP`
82 | - `ES_EVENT_TYPE_NOTIFY_RENAME`
83 | - `ES_EVENT_TYPE_NOTIFY_UNLINK`
84 | - `ES_EVENT_TYPE_NOTIFY_OPEN`
85 | - `ES_EVENT_TYPE_NOTIFY_WRITE`
86 | - `ES_EVENT_TYPE_NOTIFY_LINK`
87 | - `ES_EVENT_TYPE_NOTIFY_CLOSE`
88 | - `ES_EVENT_TYPE_NOTIFY_SIGNAL`
89 | - `ES_EVENT_TYPE_NOTIFY_REMOTE_THREAD_CREATE`
90 | - `ES_EVENT_TYPE_NOTIFY_IOKIT_OPEN`
91 | - `ES_EVENT_TYPE_NOTIFY_CS_INVALIDATED`
92 | - `ES_EVENT_TYPE_NOTIFY_SETEXTATTR`
93 | - `ES_EVENT_TYPE_NOTIFY_PROC_SUSPEND_RESUME`
94 | - `ES_EVENT_TYPE_NOTIFY_TRACE`
95 | - `ES_EVENT_TYPE_NOTIFY_GET_TASK`
96 | - `ES_EVENT_TYPE_NOTIFY_PROC_CHECK`
97 |
98 |
99 | # Initiating process metadata
100 | Each component of our initiating process structure is listed below along with its type. Types which are suffixed with a question mark are optional. This means that any given telemetry object can have any given event we have modeled.
101 | - `audit_token: String`
102 | - `es_event_type: String`
103 | - `initiating_pid: Int32`
104 | - `initiating_process_name: String`
105 | - `initiating_process_signing_id: String`
106 | - `initiating_process_path: String`
107 | - `initiating_ruid: Int64`
108 | - `initiating_euid: Int64`
109 | - `initiating_ruid_human: String`
110 | - `initiating_euid_human: String`
111 | - `initiating_process_cdhash: String`
112 | - `context: String?`
113 | - `target_path: String?`
114 | - `parent_audit_token: String`
115 | - `path_is_truncated: Bool`
116 | - `responsible_audit_token: String`
117 | - `macOS: String`
118 | - `sensor_id: String`
119 | - `activity_at_ts: String`
120 | - `initiating_process_file_quarantine_type: Int16`
121 | - We attempt to read the app’s bundled property list for this information
122 | - `0`: The process is not File Quarantine-aware
123 | - `1`: The process has opted-into File Quarantine
124 | - `2`: The process has been forced into File Quarantine
125 | - `initiating_process_group_id: Int32`
126 | - `initiating_is_platform_binary: Bool`
127 | - `btm_launch_item_add_event: RCESLaunchItemAddEvent?`
128 | - `delete_xattr_event: RCESXattrEvent?`
129 | - `set_xattr_event: RCESXattrSetEvent?`
130 | - `exec_event: RCESProcessExecEvent?`
131 | - `code_signature_invalidated_event: RCESCodeSignatureInvalidatedEvent?`
132 | - `process_socket_event: RCESProcessSocketEvent?`
133 | - `process_trace_event: RCESProcessTraceEvent?`
134 | - `get_task_event: RCESGetTaskEvent?`
135 | - `process_check_event: RCESProcessCheckEvent?`
136 | - `process_signal_event: RCESProcessSignalEvent?`
137 | - `remote_thread_create_event: RCESRemoteThreadCreateEvent?`
138 | - `exit_event: RCESProcessExitEvent?`
139 | - `file_event: RCESFileEvent?`
140 | - `fork_event: RCESProcessForkEvent?`
141 | - `mmap_event: RCESMMapEvent?`
142 | - `btm_launch_item_remove_event: RCESLaunchItemRemoveEvent?`
143 | - `openssh_login_event: RCESOpenSSHLoginEvent?`
144 | - `openssh_logout_event: RCESOpenSSHLogoutEvent?`
145 | - `xprotect_detect_event: RCESXProtectDetect?`
146 | - `xprotect_remediate_event: RCESXProtectRemediate?`
147 | - `mount_event: RCESMountEvent?`
148 | - `login_login_event: RCESLoginLoginEvent?`
149 | - `lw_login_event: RCESLWLoginEvent?`
150 | - `lw_unlock_event: RCESLWUnlockEvent?`
151 | - `fd_duplicate_event: RCESFDDuplicateEvent?`
152 | - `file_rename_event: RCESFileRenameEvent?`
153 | - `file_delete_event: RCESFileDeleteEvent?`
154 | - `file_open_event: RCESFileOpenEvent?`
155 | - `file_write_event: RCESFileWriteEvent?`
156 | - `link_event: RCESLinkEvent?`
157 | - `file_close_event: RCESFileCloseEvent?`
158 | - `iokit_open_event: RCESIOKitOpenEvent?`
159 | - `profile_add_event: RCESProfileAddEvent`
160 | - `od_create_user_event: RCESODCreateUserEvent`
161 | - `od_modify_password_event: RCESODModifyPasswordEvent`
162 | - `od_group_add_event: RCESODGroupAddEvent`
163 | - `od_create_group_event: RCESODCreateGroupEvent`
164 | - `od_attribute_add_event: RCESODAttributeValueAddEvent`
165 | - `xpc_connect_event: RCESXPCConnectEvent`
166 | - `authorization_petition_event: RCESAuthorizationPetitionEvent`
167 | - `authorization_judgement_event: RCESAuthorizationJudgementEvent`
168 |
169 |
170 | # **Process events**
171 | ## Process execute target event metadata (`exec_event`): `ES_EVENT_TYPE_NOTIFY_EXEC`
172 | - `allow_jit: Bool`
173 | - `audit_token: String`
174 | - `command_line: String`
175 | - `get_task_allow: Bool`
176 | - `pid: Int32`
177 | - `is_adhoc_signed: Bool`
178 | - `is_es_client: Bool`
179 | - `is_platform_binary: Bool`
180 | - `parent_audit_token: String`
181 | - `process_name: String`
182 | - `process_path: String`
183 | - `ruid: Int64`
184 | - `euid: Int64`
185 | - `ruid_human: String`
186 | - `euid_human: String`
187 | - `responsible_audit_token: String`
188 | - `rootless: Bool`
189 | - `signing_id: String`
190 | - `cdhash: String`
191 | - `skip_lv: Bool`
192 | - `team_id: String?`
193 | - `start_time: String`
194 | - `certificate_chain: String?`
195 | - `env_variables: String`
196 | - `file_quarantine_type: Int16`
197 | - We attempt to read the app’s bundled property list for this information
198 | - `0`: The process is not File Quarantine-aware
199 | - `1`: The process has opted-into File Quarantine
200 | - `2`: The process has been forced into File Quarantine
201 | - `cs_type: String`
202 | - `group_id: Int32`
203 | - `dyld_exec_path: String?`
204 |
205 | ## Process fork target event metadata (`fork_event`): `ES_EVENT_TYPE_NOTIFY_FORK`
206 | - `audit_token: String`
207 | - `pid: Int32`
208 | - `ruid: Int64`
209 | - `euid: Int64`
210 | - `ruid_human: String`
211 | - `euid_human: String`
212 | - `parent_audit_token: String`
213 | - `process_name: String`
214 | - `process_path: String`
215 | - `responsible_audit_token: String`
216 | - `signing_id: String`
217 | - `cdhash: String`
218 | - `start_time: String`
219 | - `group_id: Int32`
220 | - `is_platform_binary: Bool`
221 |
222 | ## Process code signature invalidated target event metadata (`code_signature_invalidated_event`): `ES_EVENT_TYPE_NOTIFY_CS_INVALIDATED`
223 | - Note: This target event specifies that the initiating process's code signature was invalidated in-memory.
224 |
225 | ## Process socket target event metadata (`process_socket_event`): `ES_EVENT_TYPE_NOTIFY_PROC_SUSPEND_RESUME`
226 | - `target_process_name: String`
227 | - `target_process_path: String`
228 | - `target_process_signing_id: String`
229 | - `target_process_audit_token: String`
230 | - `type: String`
231 |
232 | ## Process trace target event metadata (`process_trace_event`): `ES_EVENT_TYPE_NOTIFY_TRACE`
233 | - `process_name: String`
234 | - `process_path: String`
235 | - `process_signing_id: String`
236 | - `process_audit_token: String`
237 |
238 | ## Process task port target event (`get_task_event`): `ES_EVENT_TYPE_NOTIFY_GET_TASK`
239 | - `process_path: String`
240 | - `process_name: String`
241 | - `process_audit_token: String`
242 | - `process_signing_id: String`
243 | - `type: String`
244 |
245 | ## Process check target event metadata (`process_check_event`): `ES_EVENT_TYPE_NOTIFY_PROC_CHECK`
246 | - `process_name: String`
247 | - `process_signing_id: String`
248 | - `process_path: String`
249 | - `process_audit_token: String`
250 | - `flavor: Int32`
251 | - `type: String`
252 |
253 | ## Process signal target event metadata (`process_signal_event`): `ES_EVENT_TYPE_NOTIFY_SIGNAL`
254 | - `signal_id: Int32`
255 | - `process_name: String`
256 | - `process_path: String`
257 | - `audit_token: String`
258 | - `signing_id: String`
259 | - `signal_name: String`
260 |
261 | ## Process remote thread created target event metadata (`remote_thread_create_event`): `ES_EVENT_TYPE_NOTIFY_REMOTE_THREAD_CREATE`
262 | - `target_process_name: String`
263 | - `target_process_path: String`
264 | - `target_process_signing_id: String`
265 | - `target_process_audit_token: String`
266 | - `thread_state: String`
267 |
268 | ## Process exit target event metadata (`exit_event`): `ES_EVENT_TYPE_NOTIFY_EXIT`
269 | - `exit_code: Int32`
270 |
271 |
272 |
273 | # **Memory events**
274 | ## Memory map target event metadata (`mmap_event`): `ES_EVENT_TYPE_NOTIFY_MMAP`
275 | - `path: String`
276 |
277 |
278 |
279 | # **File events**
280 | ## File creation target event metadata (`file_event`): `ES_EVENT_TYPE_NOTIFY_CREATE`
281 | - `destination_path: String`
282 | - `file_name: String`
283 | - `is_quarantined: Int16`
284 | - We attempt to determine if the file being created is quarantined. If a file is deleted / delete `xattr` event occurs too too quickly the file cannot be found.
285 | - `0`: The file is not quarantined
286 | - `1`: The file is quarantined
287 | - `2`: The file could not be found
288 |
289 | ## File rename target event metadata (`file_rename_event`): `ES_EVENT_TYPE_NOTIFY_RENAME`
290 | - `file_name: String`
291 | - `destination_path: String`
292 | - `source_path: String`
293 | - `archive_files_not_quarantined: String?`
294 | - If this file rename event is moving an inflated archive we perform a deep search of the destination file path to determine if any files are not quarantined.
295 | - `type: String`
296 | - `is_quarantined: Int16`
297 | - We attempt to determine if the file being created is quarantined. If a file is deleted / delete `xattr` event occurs too too quickly the file cannot be found.
298 | - `0`: The file is not quarantined
299 | - `1`: The file is quarantined
300 | - `2`: The file could not be found
301 |
302 | ## File delete target event metadata (`file_delete_event`): `ES_EVENT_TYPE_NOTIFY_UNLINK`
303 | - `file_path: String`
304 | - `file_name: String`
305 | - `parent_directory: String`
306 |
307 | ## File open target event metadata (`file_open_event`): `ES_EVENT_TYPE_NOTIFY_OPEN`
308 | - `file_path: String`
309 | - `file_name: String`
310 |
311 | ## File write target event metadata (`file_write_event`): `ES_EVENT_TYPE_NOTIFY_WRITE`
312 | - `file_path: String`
313 | - `file_name: String`
314 |
315 | ## File link target event metadata (`link_event`): `ES_EVENT_TYPE_NOTIFY_LINK`
316 | - `source_file_path: String`
317 | - `source_file_name: String`
318 | - `target_file_path: String`
319 | - `target_file_name: String`
320 |
321 | ## File close target event metadata (`file_close_event`): `ES_EVENT_TYPE_NOTIFY_CLOSE`
322 | - `file_path: String`
323 | - `file_name: String`
324 |
325 | ## File duplicate target event metadata (`fd_duplicate_event`): `ES_EVENT_TYPE_NOTIFY_DUP`
326 | - `file_path: String`
327 | - `file_name: String`
328 |
329 |
330 |
331 | # **File metadata events**
332 | ## Extended attribute (xattr) delete target event metadata (`delete_xattr_event`): `ES_EVENT_TYPE_NOTIFY_DELETEEXTATTR`
333 | - `file_name: String`
334 | - `file_path: String`
335 | - `operation: String`
336 | - `xattr: String`
337 |
338 |
339 | ## Extended attribute (xattr) set target event metadata (`set_xattr_event`): `ES_EVENT_TYPE_AUTH_SETEXTATTR`
340 | - `file_name: String`
341 | - `file_path: String`
342 | - `operation: String`
343 | - `xattr: String`
344 |
345 |
346 |
347 | # **File system events**
348 | ## File system mount target event metadata (`mount_event`): `ES_EVENT_TYPE_NOTIFY_MOUNT`
349 | - `total_files: Int64`
350 | - `mount_flags: Int64`
351 | - `type_name: String`
352 | - `source_name: String`
353 | - `mount_directory: String`
354 | - `owner_uid: Int64`
355 | - `fs_id: String`
356 | - `owner_uid_human: String`
357 |
358 |
359 |
360 | # **Background Task events**
361 | ## Background Task Management (BTM) add target event metadata (`btm_launch_item_add_event`): `ES_EVENT_TYPE_NOTIFY_BTM_LAUNCH_ITEM_ADD`
362 | - `file_name: String`
363 | - `file_path: String`
364 | - `uid: Int64`
365 | - `uid_human: String`
366 | - `is_legacy: Bool`
367 | - `is_managed: Bool`
368 | - `type: String`
369 | - `plist_contents: String`
370 | - We pull the legacy property list for the BTM item added if the property list is not in the Apple Binary Property List
371 | - `app_process_path: String`
372 | - `app_process_signing_id: String`
373 | - `app_process_team_id: String`
374 | - `instigating_process_path: String`
375 | - `instigating_process_signing_id: String`
376 | - `instigating_process_team_id: String?`
377 |
378 | ## Background Task Management (BTM) remove target event metadata (`btm_launch_item_remove_event`): `ES_EVENT_TYPE_NOTIFY_BTM_LAUNCH_ITEM_REMOVE`
379 | - `app_process_path: String?`
380 | - `app_process_signing_id: String?`
381 | - `app_process_team_id: String?`
382 | - `instigating_process_path: String?`
383 | - `instigating_process_signing_id: String?`
384 | - `instigating_process_team_id: String?`
385 | - `file_path: String?`
386 | - `file_name: String?`
387 | - `is_legacy: Bool`
388 | - `type: String?`
389 | - `uid: Int64`
390 | - `uid_human: String?`
391 | - `is_managed: Bool`
392 |
393 |
394 |
395 | # **Login events**
396 | ## LoginWindow login target event metadata (`lw_login_event`): `ES_EVENT_TYPE_NOTIFY_LW_SESSION_LOGIN`
397 | - `username: String`
398 | - `graphical_session_id: Int32`
399 |
400 | ## LoginWindow unlock target event metadata (`lw_unlock_event`): `ES_EVENT_TYPE_NOTIFY_LW_SESSION_UNLOCK`
401 | - `username: String`
402 | - `graphical_session_id: Int32`
403 |
404 | ## Login login target event metadata (`login_login_event`): `ES_EVENT_TYPE_NOTIFY_LOGIN_LOGIN`
405 | - `success: Bool`
406 | - `failure_message: String`
407 | - `username: String`
408 | - `uid: Int64`
409 | - `uid_human: String`
410 |
411 | ## OpenSSH login target event metadata (`openssh_login_event`): `ES_EVENT_TYPE_NOTIFY_OPENSSH_LOGIN`
412 | - `result_type: String?`
413 | - `source_address: String?`
414 | - `source_address_type: String?`
415 | - `success: Bool`
416 | - `user_name: String?`
417 |
418 | ## OpenSSH logout target event metadata (`openssh_logout_event`): `ES_EVENT_TYPE_NOTIFY_OPENSSH_LOGOUT`
419 | - `source_address_type: String`
420 | - `source_address: String`
421 | - `username: String`
422 |
423 |
424 |
425 | # **XProtect events**
426 | ## XProtect Malware detected target event metadata (`xprotect_detect_event`): `ES_EVENT_TYPE_NOTIFY_XP_MALWARE_DETECTED`
427 | - `signature_version: String`
428 | - `malware_identifier: String`
429 | - `incident_identifier: String`
430 | - `detected_path: String`
431 |
432 | ## XProtect Malware remediated target event metadata (`xprotect_remediate_event`): `ES_EVENT_TYPE_NOTIFY_XP_MALWARE_REMEDIATED`
433 | - `signature_version: String`
434 | - `malware_identifier: String`
435 | - `incident_identifier: String`
436 | - `action_type: String`
437 | - `success: Bool`
438 | - `result_description: String`
439 | - `remediated_path: String`
440 | - `remediated_process_audit_token: String`
441 |
442 |
443 |
444 | # **Kernel events**
445 | ## IOKit open target event metadata (`iokit_open_event`): `ES_EVENT_TYPE_NOTIFY_IOKIT_OPEN`
446 | - `user_client_class: String`
447 | - `user_client_type: Int32`
448 |
449 |
450 |
--------------------------------------------------------------------------------
/Telemetry reports/README.md:
--------------------------------------------------------------------------------
1 | # Red Canary Mac Monitor Telemetry Summary
2 | ## Distribution details
3 | - Build name: `GoldCardinal`
4 | - App versions: `1.0.5`
5 |
6 | # Overview
7 | The following is an in-depth look behind the "Red Canary Security Extension" telemetry curtain. While this information is readily viewable to users at any time by exporting telemetry or selecting the "JSON" tab in any "Event Facts" window these report(s) will serve as a "snapshot" of telemetry capabilities over time.
8 | - Total Endpoint Security (ES) events collected: `41` on macOS 14 Sonoma and `32` on macOS 13 Ventura.
9 | - Covering the following telemetry classes (abridged)
10 | * Process
11 | * Interprocess
12 | * File
13 | * File metadata
14 | * File system
15 | * Memory mapping
16 | * Login
17 | * Background Task Management (BTM)
18 | * XProtect
19 | * Profiles
20 | * Open Directory
21 | * XPC
22 | * Authorization
23 |
24 | ## Telemetry record structure
25 | Each event is delivered in a record which can be modeled in JSON in the following way:
26 | ```
27 | {
28 | // Initiating process metadata (responsible for the target event)
29 | {
30 | // Target event metadata (e.g. OpenSSH login, etc)
31 | }
32 | }
33 | ```
34 |
35 | Each event has a process which was responsible for it. In terms of process execute events this is the “parent” process, for XProtect detect events it’ll be Gatekeeper (aka syspolicyd), for file creation events it’ll be the process which created the file, etc. A sample telemetry object is shown below:
36 |
37 | ```json
38 | {
39 | "initiating_ruid" : 502,
40 | "responsible_audit_token" : "502-502-20-502-20-12327-100019-1883731",
41 | "initiating_is_platform_binary" : false,
42 | "parent_audit_token" : "502-502-20-502-20-13018-100019-1885461",
43 | "target" : "AppleScript",
44 | "initiating_process_cdhash" : "bb836a032af6a389f1a086803202fce60dd9f1b2",
45 | "initiating_process_file_quarantine_type" : 0,
46 | "macOS" : "13.2.1 (Build 22D68)",
47 | "sensor_id" : "bf169d19f3e7bea1b61c00db1bc9c98318007ae5f7a2b6c15e3f64f9ed5760c7cd8a49268472e75e0f916fe8acd503d9f9580a030d7d021582271813b6a3ff38",
48 | "initiating_process_path" : "/Users/brandondalton/.pyenv/versions/3.10.4/lib/python3.10/site-packages/posixath/tests/macos/library/T1059_002/nsapplescript_example",
49 | "initiating_process_name" : "nsapplescript_example",
50 | "initiating_euid_human" : "brandondalton",
51 | "initiating_ruid_human" : "brandondalton",
52 | "initiating_euid" : 502,
53 | "initiating_process_group_id" : 13018,
54 | "es_event_type" : "ES_EVENT_TYPE_NOTIFY_MMAP",
55 | "initiating_process_signing_id" : "nsapplescript_example",
56 | "path_is_truncated" : false,
57 | "audit_token" : "502-502-20-502-20-13051-100019-1885479",
58 | "initiating_pid" : 13018,
59 | "mmap_event" : {
60 | "path" : "/System/Library/Components/AppleScript.component/Contents/MacOS/AppleScript"
61 | },
62 | "activity_at_ts" : "2023-03-13T22:08:37.569Z"
63 | }
64 | ```
65 |
66 | # Endpoint Security event listing
67 | The following ES events are supported by the Red Canary Security Extension. Users can utilize the dynamic event subscriptions feature to subscribe to any supported event.
68 | - `ES_EVENT_TYPE_NOTIFY_EXEC`
69 | - `ES_EVENT_TYPE_NOTIFY_FORK`
70 | - `ES_EVENT_TYPE_NOTIFY_EXIT`
71 | - `ES_EVENT_TYPE_NOTIFY_CREATE`
72 | - `ES_EVENT_TYPE_NOTIFY_DELETEEXTATTR`
73 | - `ES_EVENT_TYPE_NOTIFY_MMAP`
74 | - `ES_EVENT_TYPE_NOTIFY_BTM_LAUNCH_ITEM_ADD`
75 | - `ES_EVENT_TYPE_NOTIFY_BTM_LAUNCH_ITEM_REMOVE`
76 | - `ES_EVENT_TYPE_NOTIFY_OPENSSH_LOGIN`
77 | - `ES_EVENT_TYPE_NOTIFY_OPENSSH_LOGOUT`
78 | - `ES_EVENT_TYPE_NOTIFY_XP_MALWARE_DETECTED`
79 | - `ES_EVENT_TYPE_NOTIFY_XP_MALWARE_REMEDIATED`
80 | - `ES_EVENT_TYPE_NOTIFY_MOUNT`
81 | - `ES_EVENT_TYPE_NOTIFY_LOGIN_LOGIN`
82 | - `ES_EVENT_TYPE_NOTIFY_LW_SESSION_LOGIN`
83 | - `ES_EVENT_TYPE_NOTIFY_LW_SESSION_UNLOCK`
84 | - `ES_EVENT_TYPE_NOTIFY_DUP`
85 | - `ES_EVENT_TYPE_NOTIFY_RENAME`
86 | - `ES_EVENT_TYPE_NOTIFY_UNLINK`
87 | - `ES_EVENT_TYPE_NOTIFY_OPEN`
88 | - `ES_EVENT_TYPE_NOTIFY_WRITE`
89 | - `ES_EVENT_TYPE_NOTIFY_LINK`
90 | - `ES_EVENT_TYPE_NOTIFY_CLOSE`
91 | - `ES_EVENT_TYPE_NOTIFY_SIGNAL`
92 | - `ES_EVENT_TYPE_NOTIFY_REMOTE_THREAD_CREATE`
93 | - `ES_EVENT_TYPE_NOTIFY_IOKIT_OPEN`
94 | - `ES_EVENT_TYPE_NOTIFY_CS_INVALIDATED`
95 | - `ES_EVENT_TYPE_NOTIFY_SETEXTATTR`
96 | - `ES_EVENT_TYPE_NOTIFY_PROC_SUSPEND_RESUME`
97 | - `ES_EVENT_TYPE_NOTIFY_TRACE`
98 | - `ES_EVENT_TYPE_NOTIFY_GET_TASK`
99 | - `ES_EVENT_TYPE_NOTIFY_PROC_CHECK`
100 | - `ES_EVENT_TYPE_NOTIFY_PROFILE_ADD`
101 | - `ES_EVENT_TYPE_NOTIFY_OD_CREATE_USER`
102 | - `ES_EVENT_TYPE_NOTIFY_OD_CREATE_GROUP`
103 | - `ES_EVENT_TYPE_NOTIFY_OD_GROUP_ADD`
104 | - `ES_EVENT_TYPE_NOTIFY_OD_MODIFY_PASSWORD`
105 | - `ES_EVENT_TYPE_NOTIFY_OD_ATTRIBUTE_VALUE_ADD`
106 | - `ES_EVENT_TYPE_NOTIFY_XPC_CONNECT`
107 | - `ES_EVENT_TYPE_NOTIFY_AUTHORIZATION_PETITION`
108 | - `ES_EVENT_TYPE_NOTIFY_AUTHORIZATION_JUDGEMENT`
109 |
110 |
111 | # Initiating process metadata
112 | Each component of our initiating process structure is listed below along with its type. Types which are suffixed with a question mark are optional. This means that any given telemetry object can have any given event we have modeled.
113 | - `audit_token: String`
114 | - `es_event_type: String`
115 | - `initiating_pid: Int32`
116 | - `initiating_process_name: String`
117 | - `initiating_process_signing_id: String`
118 | - `initiating_process_path: String`
119 | - `initiating_ruid: Int64`
120 | - `initiating_euid: Int64`
121 | - `initiating_ruid_human: String`
122 | - `initiating_euid_human: String`
123 | - `initiating_process_cdhash: String`
124 | - `parent_audit_token: String`
125 | - `path_is_truncated: Bool`
126 | - `responsible_audit_token: String`
127 | - `macOS: String`
128 | - `sensor_id: String`
129 | - `activity_at_ts: String`
130 | - `initiating_process_file_quarantine_type: Int16`
131 | - We attempt to read the app’s bundled property list for this information
132 | - `0`: The process is not File Quarantine-aware
133 | - `1`: The process has opted-into File Quarantine
134 | - `2`: The process has been forced into File Quarantine
135 | - `initiating_process_group_id: Int32`
136 | - `initiating_is_platform_binary: Bool`
137 | - `btm_launch_item_add_event: RCESLaunchItemAddEvent?`
138 | - `delete_xattr_event: RCESXattrEvent?`
139 | - `set_xattr_event: RCESXattrSetEvent?`
140 | - `exec_event: RCESProcessExecEvent?`
141 | - `code_signature_invalidated_event: RCESCodeSignatureInvalidatedEvent?`
142 | - `process_socket_event: RCESProcessSocketEvent?`
143 | - `process_trace_event: RCESProcessTraceEvent?`
144 | - `get_task_event: RCESGetTaskEvent?`
145 | - `process_check_event: RCESProcessCheckEvent?`
146 | - `process_signal_event: RCESProcessSignalEvent?`
147 | - `remote_thread_create_event: RCESRemoteThreadCreateEvent?`
148 | - `exit_event: RCESProcessExitEvent?`
149 | - `file_event: RCESFileEvent?`
150 | - `fork_event: RCESProcessForkEvent?`
151 | - `mmap_event: RCESMMapEvent?`
152 | - `btm_launch_item_remove_event: RCESLaunchItemRemoveEvent?`
153 | - `openssh_login_event: RCESOpenSSHLoginEvent?`
154 | - `openssh_logout_event: RCESOpenSSHLogoutEvent?`
155 | - `xprotect_detect_event: RCESXProtectDetect?`
156 | - `xprotect_remediate_event: RCESXProtectRemediate?`
157 | - `mount_event: RCESMountEvent?`
158 | - `login_login_event: RCESLoginLoginEvent?`
159 | - `lw_login_event: RCESLWLoginEvent?`
160 | - `lw_unlock_event: RCESLWUnlockEvent?`
161 | - `fd_duplicate_event: RCESFDDuplicateEvent?`
162 | - `file_rename_event: RCESFileRenameEvent?`
163 | - `file_delete_event: RCESFileDeleteEvent?`
164 | - `file_open_event: RCESFileOpenEvent?`
165 | - `file_write_event: RCESFileWriteEvent?`
166 | - `link_event: RCESLinkEvent?`
167 | - `file_close_event: RCESFileCloseEvent?`
168 | - `iokit_open_event: RCESIOKitOpenEvent?`
169 |
170 | # **Process events**
171 | ## Process execute target event metadata (`exec_event`): `ES_EVENT_TYPE_NOTIFY_EXEC`
172 | - `allow_jit: Bool`
173 | - `audit_token: String`
174 | - `command_line: String`
175 | - `get_task_allow: Bool`
176 | - `pid: Int32`
177 | - `is_adhoc_signed: Bool`
178 | - `is_es_client: Bool`
179 | - `is_platform_binary: Bool`
180 | - `parent_audit_token: String`
181 | - `process_name: String`
182 | - `process_path: String`
183 | - `ruid: Int64`
184 | - `euid: Int64`
185 | - `ruid_human: String`
186 | - `euid_human: String`
187 | - `responsible_audit_token: String`
188 | - `rootless: Bool`
189 | - `signing_id: String`
190 | - `cdhash: String`
191 | - `skip_lv: Bool`
192 | - `team_id: String?`
193 | - `start_time: String`
194 | - `certificate_chain: String?`
195 | - `env_variables: String`
196 | - `file_quarantine_type: Int16`
197 | - We attempt to read the app’s bundled property list for this information
198 | - `0`: The process is not File Quarantine-aware
199 | - `1`: The process has opted-into File Quarantine
200 | - `2`: The process has been forced into File Quarantine
201 | - `cs_type: String`
202 | - `group_id: Int32`
203 | - `dyld_exec_path: String?`
204 |
205 | ## Process fork target event metadata (`fork_event`): `ES_EVENT_TYPE_NOTIFY_FORK`
206 | - `audit_token: String`
207 | - `pid: Int32`
208 | - `ruid: Int64`
209 | - `euid: Int64`
210 | - `ruid_human: String`
211 | - `euid_human: String`
212 | - `parent_audit_token: String`
213 | - `process_name: String`
214 | - `process_path: String`
215 | - `responsible_audit_token: String`
216 | - `signing_id: String`
217 | - `cdhash: String`
218 | - `start_time: String`
219 | - `group_id: Int32`
220 | - `is_platform_binary: Bool`
221 |
222 | ## Process code signature invalidated target event metadata (`code_signature_invalidated_event`): `ES_EVENT_TYPE_NOTIFY_CS_INVALIDATED`
223 | - Note: This target event specifies that the initiating process's code signature was invalidated in-memory.
224 |
225 | ## Process socket target event metadata (`process_socket_event`): `ES_EVENT_TYPE_NOTIFY_PROC_SUSPEND_RESUME`
226 | - `target_process_name: String`
227 | - `target_process_path: String`
228 | - `target_process_signing_id: String`
229 | - `target_process_audit_token: String`
230 | - `type: String`
231 |
232 | ## Process trace target event metadata (`process_trace_event`): `ES_EVENT_TYPE_NOTIFY_TRACE`
233 | - `process_name: String`
234 | - `process_path: String`
235 | - `process_signing_id: String`
236 | - `process_audit_token: String`
237 |
238 | ## Process task port target event (`get_task_event`): `ES_EVENT_TYPE_NOTIFY_GET_TASK`
239 | - `process_path: String`
240 | - `process_name: String`
241 | - `process_audit_token: String`
242 | - `process_signing_id: String`
243 | - `type: String`
244 |
245 | ## Process check target event metadata (`process_check_event`): `ES_EVENT_TYPE_NOTIFY_PROC_CHECK`
246 | - `process_name: String`
247 | - `process_signing_id: String`
248 | - `process_path: String`
249 | - `process_audit_token: String`
250 | - `flavor: Int32`
251 | - `type: String`
252 |
253 | ## Process signal target event metadata (`process_signal_event`): `ES_EVENT_TYPE_NOTIFY_SIGNAL`
254 | - `signal_id: Int32`
255 | - `process_name: String`
256 | - `process_path: String`
257 | - `audit_token: String`
258 | - `signing_id: String`
259 | - `signal_name: String`
260 |
261 | ## Process remote thread created target event metadata (`remote_thread_create_event`): `ES_EVENT_TYPE_NOTIFY_REMOTE_THREAD_CREATE`
262 | - `target_process_name: String`
263 | - `target_process_path: String`
264 | - `target_process_signing_id: String`
265 | - `target_process_audit_token: String`
266 | - `thread_state: String`
267 |
268 | ## Process exit target event metadata (`exit_event`): `ES_EVENT_TYPE_NOTIFY_EXIT`
269 | - `exit_code: Int32`
270 |
271 |
272 |
273 | # **Memory events**
274 | ## Memory map target event metadata (`mmap_event`): `ES_EVENT_TYPE_NOTIFY_MMAP`
275 | - `path: String`
276 |
277 |
278 |
279 | # **File events**
280 | ## File creation target event metadata (`file_event`): `ES_EVENT_TYPE_NOTIFY_CREATE`
281 | - `destination_path: String`
282 | - `file_name: String`
283 | - `is_quarantined: Int16`
284 | - We attempt to determine if the file being created is quarantined. If a file is deleted / delete `xattr` event occurs too too quickly the file cannot be found.
285 | - `0`: The file is not quarantined
286 | - `1`: The file is quarantined
287 | - `2`: The file could not be found
288 |
289 | ## File rename target event metadata (`file_rename_event`): `ES_EVENT_TYPE_NOTIFY_RENAME`
290 | - `file_name: String`
291 | - `destination_path: String`
292 | - `source_path: String`
293 | - `archive_files_not_quarantined: String?`
294 | - If this file rename event is moving an inflated archive we perform a deep search of the destination file path to determine if any files are not quarantined.
295 | - `type: String`
296 | - `is_quarantined: Int16`
297 | - We attempt to determine if the file being created is quarantined. If a file is deleted / delete `xattr` event occurs too too quickly the file cannot be found.
298 | - `0`: The file is not quarantined
299 | - `1`: The file is quarantined
300 | - `2`: The file could not be found
301 |
302 | ## File delete target event metadata (`file_delete_event`): `ES_EVENT_TYPE_NOTIFY_UNLINK`
303 | - `file_path: String`
304 | - `file_name: String`
305 | - `parent_directory: String`
306 |
307 | ## File open target event metadata (`file_open_event`): `ES_EVENT_TYPE_NOTIFY_OPEN`
308 | - `file_path: String`
309 | - `file_name: String`
310 |
311 | ## File write target event metadata (`file_write_event`): `ES_EVENT_TYPE_NOTIFY_WRITE`
312 | - `file_path: String`
313 | - `file_name: String`
314 |
315 | ## File link target event metadata (`link_event`): `ES_EVENT_TYPE_NOTIFY_LINK`
316 | - `source_file_path: String`
317 | - `source_file_name: String`
318 | - `target_file_path: String`
319 | - `target_file_name: String`
320 |
321 | ## File close target event metadata (`file_close_event`): `ES_EVENT_TYPE_NOTIFY_CLOSE`
322 | - `file_path: String`
323 | - `file_name: String`
324 |
325 | ## File duplicate target event metadata (`fd_duplicate_event`): `ES_EVENT_TYPE_NOTIFY_DUP`
326 | - `file_path: String`
327 | - `file_name: String`
328 |
329 |
330 |
331 | # **File metadata events**
332 | ## Extended attribute (xattr) delete target event metadata (`delete_xattr_event`): `ES_EVENT_TYPE_NOTIFY_DELETEEXTATTR`
333 | - `file_name: String`
334 | - `file_path: String`
335 | - `operation: String`
336 | - `xattr: String`
337 |
338 |
339 | ## Extended attribute (xattr) set target event metadata (`set_xattr_event`): `ES_EVENT_TYPE_AUTH_SETEXTATTR`
340 | - `file_name: String`
341 | - `file_path: String`
342 | - `operation: String`
343 | - `xattr: String`
344 |
345 |
346 |
347 | # **File system events**
348 | ## File system mount target event metadata (`mount_event`): `ES_EVENT_TYPE_NOTIFY_MOUNT`
349 | - `total_files: Int64`
350 | - `mount_flags: Int64`
351 | - `type_name: String`
352 | - `source_name: String`
353 | - `mount_directory: String`
354 | - `owner_uid: Int64`
355 | - `fs_id: String`
356 | - `owner_uid_human: String`
357 |
358 |
359 |
360 | # **Background Task events**
361 | ## Background Task Management (BTM) add target event metadata (`btm_launch_item_add_event`): `ES_EVENT_TYPE_NOTIFY_BTM_LAUNCH_ITEM_ADD`
362 | - `file_name: String`
363 | - `file_path: String`
364 | - `uid: Int64`
365 | - `uid_human: String`
366 | - `is_legacy: Bool`
367 | - `is_managed: Bool`
368 | - `type: String`
369 | - `plist_contents: String`
370 | - We pull the legacy property list for the BTM item added if the property list is not in the Apple Binary Property List
371 | - `app_process_path: String`
372 | - `app_process_signing_id: String`
373 | - `app_process_team_id: String`
374 | - `instigating_process_path: String`
375 | - `instigating_process_signing_id: String`
376 | - `instigating_process_team_id: String?`
377 |
378 | ## Background Task Management (BTM) remove target event metadata (`btm_launch_item_remove_event`): `ES_EVENT_TYPE_NOTIFY_BTM_LAUNCH_ITEM_REMOVE`
379 | - `app_process_path: String?`
380 | - `app_process_signing_id: String?`
381 | - `app_process_team_id: String?`
382 | - `instigating_process_path: String?`
383 | - `instigating_process_signing_id: String?`
384 | - `instigating_process_team_id: String?`
385 | - `file_path: String?`
386 | - `file_name: String?`
387 | - `is_legacy: Bool`
388 | - `type: String?`
389 | - `uid: Int64`
390 | - `uid_human: String?`
391 | - `is_managed: Bool`
392 |
393 |
394 |
395 | # **Login events**
396 | ## LoginWindow login target event metadata (`lw_login_event`): `ES_EVENT_TYPE_NOTIFY_LW_SESSION_LOGIN`
397 | - `username: String`
398 | - `graphical_session_id: Int32`
399 |
400 | ## LoginWindow unlock target event metadata (`lw_unlock_event`): `ES_EVENT_TYPE_NOTIFY_LW_SESSION_UNLOCK`
401 | - `username: String`
402 | - `graphical_session_id: Int32`
403 |
404 | ## Login login target event metadata (`login_login_event`): `ES_EVENT_TYPE_NOTIFY_LOGIN_LOGIN`
405 | - `success: Bool`
406 | - `failure_message: String`
407 | - `username: String`
408 | - `uid: Int64`
409 | - `uid_human: String`
410 |
411 | ## OpenSSH login target event metadata (`openssh_login_event`): `ES_EVENT_TYPE_NOTIFY_OPENSSH_LOGIN`
412 | - `result_type: String?`
413 | - `source_address: String?`
414 | - `source_address_type: String?`
415 | - `success: Bool`
416 | - `user_name: String?`
417 |
418 | ## OpenSSH logout target event metadata (`openssh_logout_event`): `ES_EVENT_TYPE_NOTIFY_OPENSSH_LOGOUT`
419 | - `source_address_type: String`
420 | - `source_address: String`
421 | - `username: String`
422 |
423 |
424 |
425 | # **XProtect events**
426 | ## XProtect Malware detected target event metadata (`xprotect_detect_event`): `ES_EVENT_TYPE_NOTIFY_XP_MALWARE_DETECTED`
427 | - `signature_version: String`
428 | - `malware_identifier: String`
429 | - `incident_identifier: String`
430 | - `detected_path: String`
431 |
432 | ## XProtect Malware remediated target event metadata (`xprotect_remediate_event`): `ES_EVENT_TYPE_NOTIFY_XP_MALWARE_REMEDIATED`
433 | - `signature_version: String`
434 | - `malware_identifier: String`
435 | - `incident_identifier: String`
436 | - `action_type: String`
437 | - `success: Bool`
438 | - `result_description: String`
439 | - `remediated_path: String`
440 | - `remediated_process_audit_token: String`
441 |
442 |
443 |
444 | # **Kernel events**
445 | ## IOKit open target event metadata (`iokit_open_event`): `ES_EVENT_TYPE_NOTIFY_IOKIT_OPEN`
446 | - `user_client_class: String`
447 | - `user_client_type: Int32`
448 |
449 |
450 |
451 | # **Open Directory events**
452 | ## Create user target event metadata (`od_create_user_event`): `ES_EVENT_TYPE_NOTIFY_OD_CREATE_USER`
453 | - `instigator_process_name: String`
454 | - `instigator_process_path: String`
455 | - `instigator_process_audit_token: String`
456 | - `instigator_process_signing_id: String`
457 | - `user_name: String`
458 | - `node_name: String`
459 | - `db_path: String`
460 | - `error_code: Int32`
461 | - `error_code_human: String`
462 |
463 | ## Create group target event metadata (`od_create_group_event`): `ES_EVENT_TYPE_NOTIFY_OD_CREATE_GROUP`
464 | - `instigator_process_name: String`
465 | - `instigator_process_path: String`
466 | - `instigator_process_audit_token: String`
467 | - `instigator_process_signing_id: String`
468 | - `group_name: String`
469 | - `node_name: String`
470 | - `db_path: String`
471 | - `error_code: Int32`
472 | - `error_code_human: String`
473 |
474 | ## Password modification target event metadata (`od_modify_password_event`): `ES_EVENT_TYPE_NOTIFY_OD_MODIFY_PASSWORD`
475 | - `instigator_process_name: String`
476 | - `instigator_process_path: String`
477 | - `instigator_process_audit_token: String`
478 | - `instigator_process_signing_id: String`
479 | - `account_type: String`
480 | - `account_name: String`
481 | - `node_name: String`
482 | - `db_path: String`
483 | - `error_code: Int32`
484 | - `error_code_human: String`
485 |
486 | ## Group add target event metadata (`od_group_add_event`): `ES_EVENT_TYPE_NOTIFY_OD_GROUP_ADD`
487 | - `instigator_process_name: String`
488 | - `instigator_process_path: String`
489 | - `instigator_process_audit_token: String`
490 | - `instigator_process_signing_id: String`
491 | - `group_name: String`
492 | - `member: String`
493 | - `node_name: String`
494 | - `error_code: Int32`
495 | - `db_path: String`
496 | - `error_code_human: String`
497 |
498 | ## Attribute value add target event metadata (`od_attribute_add_event`): `ES_EVENT_TYPE_NOTIFY_OD_ATTRIBUTE_VALUE_ADD`
499 | - `instigator_process_name: String`
500 | - `instigator_process_path: String`
501 | - `instigator_process_audit_token: String`
502 | - `instigator_process_signing_id: String`
503 | - `error_code: Int32`
504 | - `record_type: String`
505 | - `record_name: String`
506 | - `attribute_name: String`
507 | - `attribute_value: String`
508 | - `node_name: String`
509 | - `db_path: String`
510 | - `error_code_human: String`
511 |
512 |
513 |
514 |
515 | # **Profile / MDM events**
516 | ## Profile added target event metadata (`profile_add_event`): `ES_EVENT_TYPE_NOTIFY_PROFILE_ADD`
517 | - `instigator_process_name: String`
518 | - `instigator_process_path: String`
519 | - `instigator_process_audit_token: String`
520 | - `instigator_process_signing_id: String`
521 | - `is_update: Bool`
522 | - `profile_identifier: String`
523 | - `profile_uuid: String`
524 | - `profile_organization: String`
525 | - `profile_display_name: String`
526 | - `profile_scope: String`
527 | - `profile_source_type: String`
528 |
529 |
530 |
531 |
532 | # **Authorization events**
533 | ## Petition for rights target event metadata (`authorization_petition_event`): `ES_EVENT_TYPE_NOTIFY_AUTHORIZATION_PETITION`
534 | - `instigator_process_name: String`
535 | - `instigator_process_path: String`
536 | - `instigator_process_audit_token: String`
537 | - `instigator_process_signing_id: String`
538 | - `petitioner_process_name: String`
539 | - `petitioner_process_path: String`
540 | - `petitioner_process_audit_token: String`
541 | - `petitioner_process_signing_id: String`
542 | - `flags: String`
543 | - `right_count: Int32`
544 | - `rights: String`
545 |
546 | ## Authorization rights judgement target event metadata (`authorization_judgement_event`): `ES_EVENT_TYPE_NOTIFY_AUTHORIZATION_JUDGEMENT`
547 | - `instigator_process_name: String`
548 | - `instigator_process_path: String`
549 | - `instigator_process_audit_token: String`
550 | - `instigator_process_signing_id: String`
551 | - `petitioner_process_name: String`
552 | - `petitioner_process_path: String`
553 | - `petitioner_process_audit_token: String`
554 | - `petitioner_process_signing_id: String`
555 | - `return_code: Int32`
556 | - `result_count: Int32`
557 | - `results: String`
558 |
559 |
560 |
561 |
562 | # **XPC events**
563 | ## Connection established to an XPC service target event metadata (`xpc_connect_event`): `ES_EVENT_TYPE_NOTIFY_XPC_CONNECT`
564 | - `service_name: String`
565 | - `service_domain_type: String`
566 |
567 |
--------------------------------------------------------------------------------
/eula.txt:
--------------------------------------------------------------------------------
1 | Software License Agreement
2 |
3 | This License Agreement (the "License") is provided by Red Canary, Inc. ("Red Canary," "us," and "our") and
4 | covers your installation and use of the Red Canary Mac Monitor (the "Software") and related documentation
5 | provided by Red Canary (the "Documentation"). This License does not apply to the use of any other Red Canary
6 | products, services, or software, which would be covered under a separate agreement between you and Red Canary.
7 | By clicking "AGREE" you acknowledge that you have read, understood, and agree to be legally bound by this
8 | License. In this License we refer to "you" ("your") as the individual or company that accepts this License.
9 |
10 | 1. License
11 | Subject to, and conditioned on your compliance with all terms and conditions herein, Red Canary grants you a
12 | limited, non-exclusive, non-transferable, and non-sublicenseable license to install and use the Software and
13 | Documentation solely for your own internal business purposes, and not for any commercial use or purpose.
14 |
15 | 2. Restrictions on Use
16 | You shall not (and shall not permit any authorized user or third party to) make any use or disclosure of the
17 | Software or Documentation that is not expressly permitted under this License. Without limiting the
18 | foregoing, You shall not (and shall not permit any authorized user or third party to): (i) reverse engineer,
19 | decompile, disassemble, or otherwise attempt to discern the source code, object code, underlying structures,
20 | algorithms, ideas, know-how or any other information of or related to the Services; (ii) modify, translate,
21 | adapt or create derivative works based on the Software or Documentation; (iii) make any copies of the
22 | Software or Documentation; (iv) resell, distribute, or sublicense the Software or Documentation; (v) make
23 | the Software available on a timesharing or "service bureau" basis, or otherwise allow any third party to use
24 | or access the Software or Documentation; (vi) remove or modify any proprietary marking or restrictive
25 | legends placed on the Software or Documentation; or (vii) use the Software in violation of applicable law.
26 | In addition, you shall not transfer or assign this agreement to any third party.
27 |
28 | 3. Ownership of Intellectual Property
29 | With the exception of any open-source and/or other licensed-in components contained or incorporated therein,
30 | Red Canary is and shall remain the sole and exclusive owner of all right, title, and interest in and to the
31 | Software and Documentation, including all source code, object code, operating instructions, and all
32 | interfaces developed for or relating to the same, together with all modifications, enhancements, revisions,
33 | changes, copies, partial copies, translations, compilations, improvements, and derivative works thereof,
34 | including all intellectual property rights therein. If you or any of your employees or contractors
35 | communicates suggestions or recommendations regarding the Software or Documentation, including without
36 | limitation, new features or functionality relating thereto, or any comments, questions, suggestions, or the
37 | like ("Feedback"), Red Canary is free to use such Feedback irrespective of any other obligation or
38 | limitation between you and Red Canary governing such Feedback.
39 |
40 | 4. Warranty Disclaimer
41 | RED CANARY WILL NOT PROVIDE YOU WITH ANY MAINTENANCE, SUPPORT, OR PROFESSIONAL SERVICES RELATED TO YOUR
42 | INSTALLATION OR USE OF THE SOFTWARE OR DOCUMENTATION. THE SOFTWARE, DOCUMENTATION, AND ALL OTHER MATERIALS
43 | PROVIDED HEREUNDER ARE PROVIDED "AS IS" AND "AS AVAILABLE." RED CANARY MAKES NO WARRANTY WITH RESPECT TO THE
44 | SOFTWARE, THE DOCUMENTATION, OR OTHERWISE IN CONNECTION WITH THIS LICENSE AND HEREBY DISCLAIMS ANY AND ALL
45 | EXPRESS, IMPLIED, OR STATUTORY WARRANTIES, INCLUDING, WITHOUT LIMITATION, ANY WARRANTIES OF MERCHANTABILITY,
46 | FITNESS FOR A PARTICULAR PURPOSE, AVAILABILITY, ERROR-FREE OR UNINTERRUPTED OPERATION, AND ANY WARRANTIES
47 | ARISING FROM A COURSE OF DEALING, COURSE OF PERFORMANCE, OR USAGE OF TRADE. TO THE EXTENT THAT A PARTY MAY
48 | NOT AS A MATTER OF APPLICABLE LAW DISCLAIM ANY IMPLIED WARRANTY, THE SCOPE AND DURATION OF SUCH WARRANTY
49 | WILL BE THE MINIMUM PERMITTED UNDER SUCH LAW.
50 |
51 | 5. Limitation of Liability
52 | RED CANARY WILL NOT BE LIABLE TO YOU (NOR TO ANY PERSON CLAIMING RIGHTS DERIVED FROM YOUR RIGHTS) FOR
53 | CONSEQUENTIAL, INCIDENTAL, INDIRECT, PUNITIVE, OR EXEMPLARY DAMAGES OF ANY KIND (INCLUDING WITHOUT
54 | LIMITATION LOST REVENUES OR PROFITS, OR LOSS OF GOODWILL OR REPUTATION) ARISING OUT OF OR RELATING TO THE
55 | SOFTWARE, THE DOCUMENTATION, OR OTHERWISE ARISING OUT OF OR RELATING TO THIS LICENSE, REGARDLESS OF WHETHER
56 | THE PARTY LIABLE OR ALLEGEDLY LIABLE WAS ADVISED, HAD OTHER REASON TO KNOW, OR IN FACT KNEW OF THE
57 | POSSIBILITY THEREOF. IN NO EVENT WILL RED CANARY'S AGGREGATE LIABILITY UNDER THIS LICENSE EXCEED ONE HUNDRED
58 | U.S. DOLLARS ($100). BECAUSE SOME JURISDICTIONS DO NOT ALLOW THE EXCLUSION OR LIMITATION OF LIABILITY FOR
59 | NEGLIGENCE, CONSEQUENTIAL, INCIDENTAL OR OTHER DAMAGES, IN SUCH JURISDICTIONS RED CANARY'S LIABILITY IS
60 | LIMITED TO THE GREATEST EXTENT PERMITTED BY APPLICABLE LAW.
61 |
62 | 6. Governing Law
63 | This Agreement shall be governed and construed in accordance with the laws of the State of Colorado without
64 | regard to the application of conflict of laws principles. The United Nations Convention on Contracts for the
65 | International Sale of Goods shall not apply. The exclusive venue for any dispute relating to or arising out
66 | of this Agreement, including without limitation its construction, effect, the performance, breach,
67 | rescission or termination, shall be in the federal or state courts for Denver, Colorado, and the parties
68 | consent to personal jurisdiction in such courts.
69 |
70 | 7. Severability
71 | No failure or delay by either party in exercising any right under this Agreement shall constitute a waiver
72 | of that right. If a court of competent jurisdiction holds any provision of this Agreement invalid or
73 | unenforceable the remaining provisions of will remain in full force and effect, and the provision affected
74 | will be construed so as to be enforceable to the maximum extent permissible by law. The headings of this
75 | Agreement are for convenience only. In case of any difficulty in the interpretation of one or more of the
76 | headings, the headings shall have no meaning and no effect.
77 |
78 | 8. Complete Understanding
79 | This Agreement shall be the entire agreement between the parties and supersedes all prior or present
80 | proposals, representations, undertakings, agreements or warranties, expressed or implied, written or oral,
81 | concerning its subject matter. You agree that in agreeing to this License and in using the Software, you
82 | have not relied on any promises, warranties, or representations except those expressed in this agreement.
--------------------------------------------------------------------------------