13 | {tags.map((tag, index) => (
14 |
23 | {tag}
24 |
25 | ))}
26 |
27 | )
28 | }
--------------------------------------------------------------------------------
/docs/pages/devsecops/index.mdx:
--------------------------------------------------------------------------------
1 | ---
2 | title: "Devsecops"
3 | ---
4 |
5 | {/* AUTOGENERATED: This file is generated by utils/generate-folder-indexes.js */}
6 |
7 | # Devsecops
8 |
9 | > _Note:_ This page is auto-generated. Please use the sidebar to explore the docs instead of
10 | > navigating directory paths directly.
11 |
12 | ## Pages
13 |
14 | - [Code Signing](/devsecops/code-signing)
15 | - [Continuous Integration Continuous Deployment](/devsecops/continuous-integration-continuous-deployment)
16 | - [DevSecOps](/devsecops/overview)
17 | - [Integrated Development Environments](/devsecops/integrated-development-environments)
18 | - [Repository Hardening](/devsecops/repository-hardening)
19 | - [Security Testing](/devsecops/security-testing)
20 |
--------------------------------------------------------------------------------
/docs/pages/dprk-it-workers/index.mdx:
--------------------------------------------------------------------------------
1 | ---
2 | title: "Dprk It Workers"
3 | ---
4 |
5 | {/* AUTOGENERATED: This file is generated by utils/generate-folder-indexes.js */}
6 |
7 | # Dprk It Workers
8 |
9 | > _Note:_ This page is auto-generated. Please use the sidebar to explore the docs instead of
10 | > navigating directory paths directly.
11 |
12 | ## Pages
13 |
14 | - [Case Studies](/dprk-it-workers/case-studies)
15 | - [General Information](/dprk-it-workers/general-information)
16 | - [Insider Threats (DPRK)](/dprk-it-workers/overview)
17 | - [Mitigating DPRK IT Workers](/dprk-it-workers/mitigating-dprk-it-workers)
18 | - [Summary](/dprk-it-workers/summary)
19 | - [Techniques, Tactics, and Procedures](/dprk-it-workers/techniques-tactics-and-procedures)
20 |
--------------------------------------------------------------------------------
/docs/pages/front-end-web-app/index.mdx:
--------------------------------------------------------------------------------
1 | ---
2 | title: "Front End Web App"
3 | ---
4 |
5 | {/* AUTOGENERATED: This file is generated by utils/generate-folder-indexes.js */}
6 |
7 | # Front End Web App
8 |
9 | > _Note:_ This page is auto-generated. Please use the sidebar to explore the docs instead of
10 | > navigating directory paths directly.
11 |
12 | ## Pages
13 |
14 | - [Common Vulnerabilities](/front-end-web-app/common-vulnerabilities)
15 | - [Front-End Web Application Security Best Practices](/front-end-web-app/overview)
16 | - [Mobile Application Security](/front-end-web-app/mobile-application-security)
17 | - [Security Tools Resources](/front-end-web-app/security-tools-resources)
18 | - [Web Application Security](/front-end-web-app/web-application-security)
19 |
--------------------------------------------------------------------------------
/.gitignore:
--------------------------------------------------------------------------------
1 | **/.DS_Store
2 | **/.DS_Store?
3 | **/.vscode
4 | **/.vscode?
5 | **/.obsidian
6 | **/.obsidian?
7 | **/.idea
8 | **/.idea?
9 | book
10 | bin
11 | *.code-workspace
12 | # Rust build artifacts
13 | **/target/
14 | **/*.rs.bk
15 | **/*.rmeta
16 | **/*.rlib
17 | Cargo.lock
18 |
19 | # Ignore contributors index file to prevent watch loops
20 | theme/contributors/contributorsindex.js
21 | theme/tags/tagsindex.js
22 |
23 | # Ignore claude-code installation
24 | claude-code
25 | @anthropic-ai/claude-code
26 |
27 | # Node.js dependencies
28 | node_modules/
29 | package-lock.json
30 | .pnpm-store/
31 |
32 | # pnpm artifacts
33 | pnpm-lock.yaml
34 | .pnpm-store/
35 |
36 | # Claude Code configuration
37 | CLAUDE.md
38 |
39 | # Build folder
40 | **/dist/
41 |
42 | .direnv
--------------------------------------------------------------------------------
/docs/pages/encryption/file-encryption.mdx:
--------------------------------------------------------------------------------
1 | ---
2 | title: "File Encryption"
3 | tags:
4 | - Engineer/Developer
5 | - Security Specialist
6 | ---
7 |
8 | import { TagList, AttributionList, TagProvider, TagFilter, ContributeFooter } from '../../../components'
9 |
10 |
19 |
31 | );
32 | });
33 |
34 | SectionProgress.displayName = "SectionProgress";
35 |
--------------------------------------------------------------------------------
/docs/pages/vulnerability-disclosure/overview.mdx:
--------------------------------------------------------------------------------
1 | ---
2 | title: "Vulnerability Disclosure"
3 | tags:
4 | - Engineer/Developer
5 | - Security Specialist
6 | - Devops
7 | ---
8 |
9 | import { TagList, AttributionList, TagProvider, TagFilter, ContributeFooter } from '../../../components'
10 |
11 |
20 |
24 |
28 |
29 | {completed + na}/{total}
30 | Error rendering Mermaid diagram: ${err.message}`;
29 | }
30 | console.error(err);
31 | }
32 | };
33 |
34 | renderMermaid();
35 | }, [code, id]);
36 |
37 | return ;
38 | };
39 |
40 | export default MermaidRenderer;
41 |
--------------------------------------------------------------------------------
/docs/pages/encryption/full-disk-encryption.mdx:
--------------------------------------------------------------------------------
1 | ---
2 | title: "Full Disk Encryption"
3 | tags:
4 | - Engineer/Developer
5 | - Security Specialist
6 | ---
7 |
8 | import { TagList, AttributionList, TagProvider, TagFilter, ContributeFooter } from '../../../components'
9 |
10 |
12 | {/* Tag filter in header area */}
13 |
22 |
14 |
16 |
17 | {/* Main content - no custom sidebar, just existing content */}
18 |
19 |
21 |
32 | {/* Tag filter in header area */}
33 |
42 |
34 |
36 |
37 | {/* Main content - existing Vocs sidebar will be highlighted */}
38 |
39 | {children}
40 |
41 |
24 |
45 | );
46 | }
47 |
48 |
--------------------------------------------------------------------------------
/docs/pages/devsecops/continuous-integration-continuous-deployment.mdx:
--------------------------------------------------------------------------------
1 | ---
2 | title: "Continuous Integration Continuous Deployment"
3 | tags:
4 | - Engineer/Developer
5 | - Security Specialist
6 | - Devops
7 | - SRE
8 | ---
9 |
10 | import { TagList, AttributionList, TagProvider, TagFilter, ContributeFooter } from '../../../components'
11 |
12 |
25 |
44 | Help us improve!
26 |27 | Spotted an error or have ideas to enhance this content? 28 |
29 |30 | Your contributions are valuable to us.{' '} 31 | 32 | Learn more 33 | 34 |
35 | 41 | ✏️ Contribute today! 42 | 43 |
35 |
36 |  37 |
37 |
54 | );
55 | }
56 |
57 | export function CertifiedProtocols({ protocols }: CertifiedProtocolsProps) {
58 | if (!protocols || protocols.length === 0) {
59 | return
60 | }
61 |
62 | return (
63 | {protocol.name}
38 | 39 |
40 | {protocol.certifications.map((cert, index) => (
41 |
49 | {cert.type.charAt(4)}
50 |
51 | ))}
52 |
53 |
64 | {protocols.map((protocol) => (
65 |
68 | );
69 | }
70 |
--------------------------------------------------------------------------------
/docs/pages/iam/access-management.mdx:
--------------------------------------------------------------------------------
1 | ---
2 | title: "Access Management"
3 | tags:
4 | - Engineer/Developer
5 | - Security Specialist
6 | - Operations & Strategy
7 | - Devops
8 | - HR
9 | ---
10 |
11 | import { TagList, AttributionList, TagProvider, TagFilter, ContributeFooter } from '../../../components'
12 |
13 | 30 |
31 | 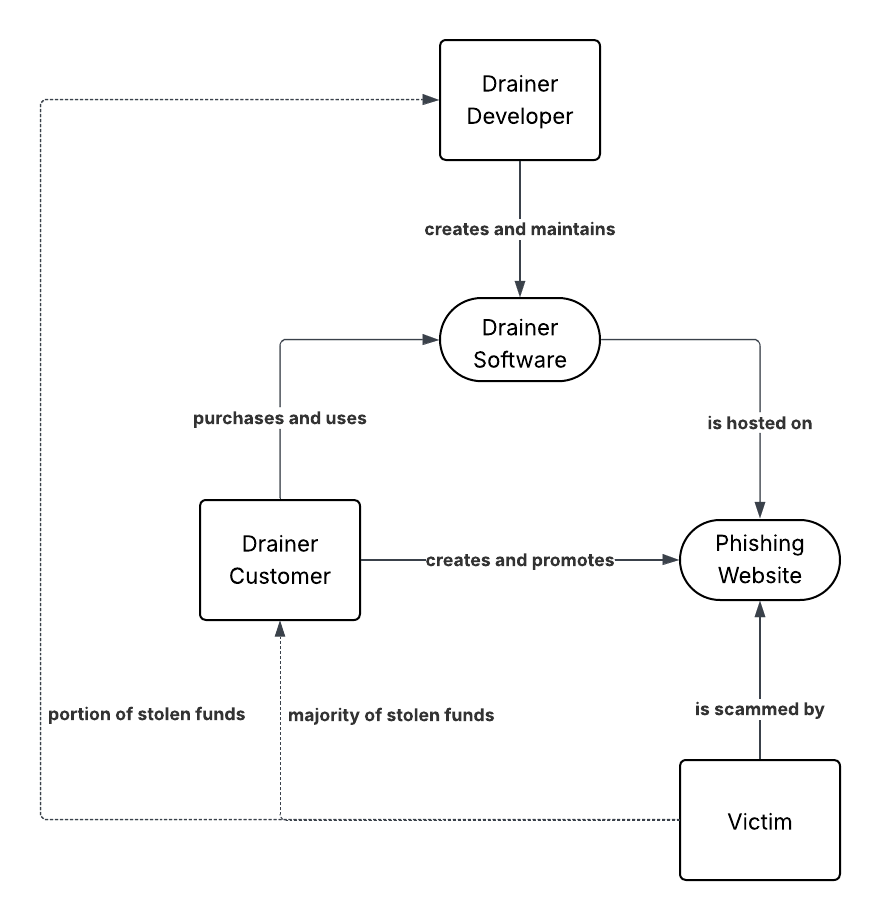 33 |
33 |
34 |  33 |
33 | 35 | 36 | Drainers use a variety of different tactics to gain control over your wallet and tokens. For example, drainers have been 37 | known to: 38 | 39 | - Request approval to spend your tokens directly 40 | - Request signatures to buy your tokens via a DEX that you’ve already approved 41 | - Request permission to upgrade your wallet to a 7702 wallet, which gives them full control 42 | - Request your private key or seed phrase directly, which gives them full control 43 | 44 | Depending which type of drainer you were impacted on, you might need to take different actions to recover control of 45 | your wallet. 46 | 47 | --- 48 | 49 |