9 | ```
10 |
11 | Build all markdown files with:
12 |
13 | ```
14 | pipenv run python bbig.py *.md
15 | ```
16 |
17 | ---
18 |
19 | Under the hood this really just combines a bunch of bigger utilities:
20 |
21 | - [big](https://github.com/tmcw/big/) to power the presentation
22 | - [mistune](https://mistune.lepture.com/en/latest/) for Markdown parsing
23 | - [highlight.js](https://highlightjs.org/) for syntax highlighting
24 | - [Twemoji](https://twemoji.twitter.com/) to ensure emoji are consistent and scalable
25 | - [thttp](https://github.com/sesh/thttp) as a lightweight HTTP client
26 |
27 | ---
28 |
29 | The Markdown files in this repository are presentations.
30 |
31 | Processed examples:
32 |
33 | - [This README](https://sesh.github.io/quick-presentations/README.html)
34 | - [Lighting TDD Introduction](https://sesh.github.io/quick-presentations/tdd-general.html)
35 | - [Estimation Challenge](https://sesh.github.io/quick-presentations/pragprog-challenges.html)
36 | - [OWASP Top 10](https://sesh.github.io/quick-presentations/owasp-top10/top10.html)
37 |
38 | The `docs` folder is generated locally (i.e. not with Github Actions) and deployed with Github Pages.
39 |
40 | ---
41 |
42 | The `screenshots.py` script is a simple utility to generate screenshots from a hosted presentation:
43 |
44 | ```
45 | python3 screenshots.py http://localhost:8000/top10.html --num-slides=62
46 | ```
47 |
48 | ---
49 |
50 | Licence
51 |
52 | - Code: MIT
53 | - Presentations: CC-BY-SA
54 |
--------------------------------------------------------------------------------
/bbig.py:
--------------------------------------------------------------------------------
1 | import sys
2 | import mistune
3 | import thttp
4 | import os
5 | from pathlib import Path
6 | import hashlib
7 |
8 | # TODO:
9 | # Single image of a slide gets wrapped with and breaks layout
10 | # Image slide with footnote
11 |
12 |
13 | SCRIPTS = [
14 | "https://cdnjs.cloudflare.com/ajax/libs/highlight.js/11.7.0/highlight.min.js",
15 | "https://unpkg.com/twemoji@latest/dist/twemoji.min.js",
16 | "https://raw.githubusercontent.com/sesh/big/master/big.js",
17 | ]
18 |
19 | STYLES = [
20 | "https://cdnjs.cloudflare.com/ajax/libs/highlight.js/11.7.0/styles/default.min.css",
21 | "https://cdnjs.cloudflare.com/ajax/libs/highlight.js/11.7.0/styles/tokyo-night-dark.min.css",
22 | "https://raw.githubusercontent.com/sesh/big/master/big.css",
23 | "https://raw.githubusercontent.com/sesh/big/master/themes/light.css",
24 | ]
25 |
26 |
27 | def cached_get(url, enable_cache=True):
28 | m = hashlib.sha256()
29 | m.update(url.encode())
30 | fn = m.hexdigest()
31 |
32 | cache_dir = Path('.cache')
33 | cache_dir.mkdir(exist_ok=True)
34 | cached_file = cache_dir / fn
35 |
36 | if enable_cache and cached_file.exists():
37 | with open(cached_file, 'r') as f:
38 | return f.read()
39 | else:
40 | content = thttp.request(url).content.decode()
41 |
42 | with open(cached_file, 'w') as f:
43 | f.write(content)
44 |
45 | return content
46 |
47 |
48 | def parse_args(args):
49 | result = {
50 | a.split("=")[0]: int(a.split("=")[1])
51 | if "=" in a and a.split("=")[1].isnumeric()
52 | else a.split("=")[1]
53 | if "=" in a
54 | else True
55 | for a in args
56 | if "--" in a
57 | }
58 | result["[]"] = [a for a in args if not a.startswith("--")]
59 | return result
60 |
61 |
62 | def parse_slides(slides_fn):
63 | with open(slides_fn) as f:
64 | text = f.read()
65 | slides = text.split("\n---\n")
66 | return slides
67 |
68 |
69 | def process_slide(slide):
70 | # If the slide is wrapped in
then just return the slide
71 | # the author knows better than us :)
72 | if slide.strip().startswith('
')[0].strip()
79 |
80 | body_style = ''
81 | if "')[0].strip()
83 |
84 | slide_html = f" " + mistune.html(slide).strip() + "
\n"
85 | return slide_html
86 |
87 |
88 | if __name__ == "__main__":
89 | args = parse_args(sys.argv[1:])
90 |
91 | slides_fns = args.get("[]")
92 |
93 | if not slides_fns:
94 | print("Slide filenames must be provided as arguments")
95 | sys.exit(1)
96 |
97 | for slides_fn in slides_fns:
98 | print(f"Processing {slides_fn}...")
99 | slides = parse_slides(slides_fn)
100 |
101 | html = """
102 |
103 |
104 |
105 |
106 |
107 |
108 | """
109 |
110 | for style_url in STYLES:
111 | content = cached_get(style_url)
112 | html += f"\n"
113 |
114 | for script_url in SCRIPTS:
115 | content = cached_get(script_url)
116 | html += f"\n"
117 |
118 | html += """
119 |
133 |
134 |
135 | """
136 |
137 | for slide in slides:
138 | html += process_slide(slide)
139 |
140 | html += """"""
144 | html += "\n"
145 | html += ""
146 |
147 | docs = Path("docs")
148 | out_fn = docs / slides_fn.replace(".md", ".html")
149 | Path(os.path.dirname(out_fn)).mkdir(parents=True, exist_ok=True)
150 |
151 | with open(out_fn, "w") as f:
152 | print(f"Saving to {out_fn}...")
153 | f.write(html)
154 |
--------------------------------------------------------------------------------
/tdd-general.md:
--------------------------------------------------------------------------------
1 | # Test Driven Development
2 |
3 | ---
4 |
5 | - I'll introduce TDD and some of its guidelines
6 | - We will run through a quick example together
7 | - Complete a TDD Kata in pairs
8 | - We'll have a quick chat about TDD
9 |
10 | ---
11 |
12 | So, what is TDD?
13 |
14 | ---
15 |
16 | > Test-Driven Development (TDD) is a technique for building software that guides software development by writing tests
17 |
18 | _- Martin Fowler_
19 |
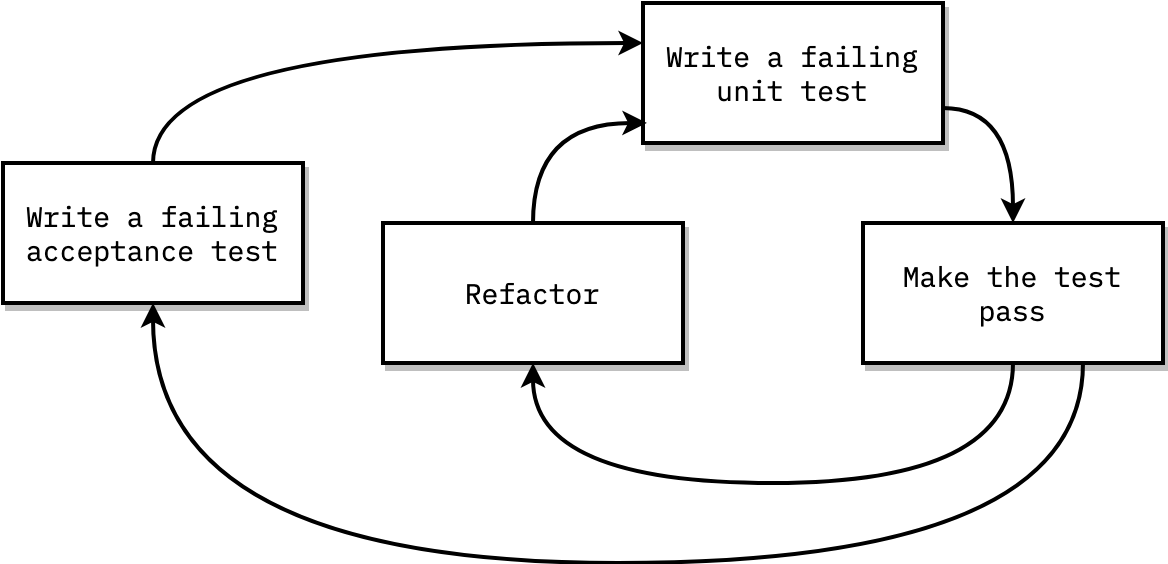
20 |
23 |
24 | ---
25 |
26 | 1. Write a failing test
27 | 2. Write code to make it pass
28 | 3. Refactor to ensure clean code
29 |
30 | ---
31 |
32 | 🔴💚🔁
33 |
34 | ---
35 |
36 | Refactor both your code and tests
37 |
38 | ---
39 |
40 | Rules, you say?
41 |
42 | ---
43 |
44 | > ## The Three Laws of TDD
45 |
46 | _- Robert Martin_
47 |
48 |
51 |
52 | ---
53 |
54 | 1. You are not allowed to write any production code unless it is to make a failing unit test pass.
55 |
56 | ---
57 |
58 | 2. You are not allowed to write any more of a unit test than is sufficient to fail; and compilation failures are failures.
59 |
60 | ---
61 |
62 | 3. You are not allowed to write any more production code than is sufficient to pass the one failing unit test.
63 |
64 | ---
65 |
66 | Generalisation
67 |
68 | ---
69 |
70 | Avoid writing code for the "general" case when you don't have to
71 |
72 | ---
73 |
74 | ```javascript
75 | describe('isPrime', () => {
76 | it('should be prime', () => {
77 | expect(isPrime(3)).toBe(true);
78 | });
79 | });
80 | ```
81 |
82 | ---
83 |
84 | ```javascript
85 | const isPrime = (n) => {
86 | return n == 3;
87 | };
88 | ```
89 |
90 | ---
91 |
92 | Triangulation
93 |
94 | ---
95 |
96 | Use a second assertion to drive a safer creation of the generic version
97 |
98 |
101 |
102 | ---
103 |
104 | 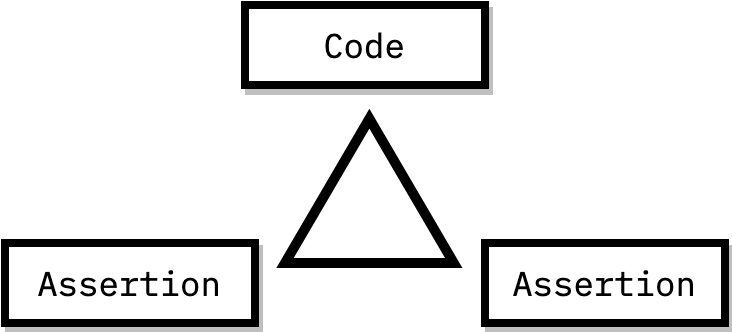
105 |
106 |
109 |
110 | ---
111 |
112 | ```javascript
113 | describe('isPrime', () => {
114 | it('should return true when prime', () => {
115 | expect(isPrime(3)).toBe(true);
116 | expect(isPrime(7)).toBe(true);
117 | });
118 | });
119 | ```
120 |
121 | ---
122 |
123 | ```javascript
124 | const isPrime = (n) => {
125 | for (let i = 2; i <= n/2; i++) {
126 | if (n % i === 0) {
127 | return;
128 | }
129 | }
130 | return true;
131 | };
132 | ```
133 |
134 | ---
135 |
136 | Refactor
137 |
138 | ---
139 |
140 | ```javascript
141 | const isPrime = (n) => {
142 | let max = Math.sqrt(n);
143 | for (let i = 2; i <= max; i++) {
144 | if (n % i === 0) {
145 | return;
146 | }
147 | }
148 | return true;
149 | };
150 | ```
151 |
152 | ---
153 |
154 | Once you're happy with the code, think about and test negative cases
155 |
156 | ---
157 |
158 | ```javascript
159 | describe('isPrime', () => {
160 | it('should return false when not prime', () => {
161 | expect(isPrime(22)).toBe(false);
162 | });
163 | });
164 | ```
165 |
166 | ---
167 |
168 | ```javascript
169 | const isPrime = (n) => {
170 | let max = Math.sqrt(n);
171 | for (let i = 2; i <= max; i++) {
172 | if (n % i === 0) {
173 | return false;
174 | }
175 | }
176 | return true;
177 | };
178 | ```
179 |
180 | ---
181 |
182 | Think about the edge cases
183 |
184 | ---
185 |
186 | ```javascript
187 | describe('isPrime', () => {
188 | it('should return false when passed one', () => {
189 | expect(isPrime(1)).toBe(false);
190 | });
191 | });
192 | ```
193 |
194 | ---
195 |
196 | ```javascript
197 | const isPrime = (n) => {
198 | let max = Math.sqrt(n);
199 | for (let i = 2; i <= max; i++) {
200 | if (n % i === 0) {
201 | return false;
202 | }
203 | }
204 | return n > 1;
205 | };
206 | ```
207 |
208 |
211 |
212 | ---
213 |
214 | Awesome-sauce 🍅
215 |
216 | ---
217 |
218 | Let's recap
219 |
220 | ---
221 |
222 | - Write a test
223 | - Write code
224 | - Refactor to make things 👍🏻
225 |
226 | ---
227 |
228 | Only write the code required to make your test pass
229 |
230 | ---
231 |
232 | Think about edge cases
233 |
234 | ---
235 |
236 | TDD is a discipline and takes practice
237 |
238 | ---
239 |
240 | Try using TDD on your next side project
241 |
242 | ---
243 |
244 | Thank you 🙏🏻
245 |
246 |
252 |
--------------------------------------------------------------------------------
/owasp-top10/top10.md:
--------------------------------------------------------------------------------
1 | OWASP Top 10
2 |
3 | ---
4 |
5 | A regularly updated list of the *most critical* security risks to web applications
6 |
7 |
10 |
11 | ---
12 |
13 | Open Worldwide Application Security Project (OWASP) is a community-led security project.
14 |
15 | The team is made up of security experts from around the world.
16 |
17 |
20 |
21 | ---
22 |
23 | # The 2021 Top 10
24 |
25 | 1. Broken Access Control
26 | 2. Cryptographic Failures
27 | 3. Injection
28 | 4. Insecure Design
29 | 5. Security Misconfiguration
30 | 6. Vulnerable and Outdated Components
31 | 7. Identification and Authentication Failures
32 | 8. Software and Data Integrity Failures
33 | 9. Security Logging and Monitoring Failures
34 | 10. Server-Side Request Forgery
35 |
36 | ---
37 |
38 |
39 |
40 | Broken Access Control
41 |
42 | ---
43 |
44 | Any situation where a user can access something that is outside their intended permissions
45 |
46 | ---
47 |
48 | Manipulating URLs, cookies or tokens
49 |
50 | ---
51 |
52 | Missing access controls on unexpected HTTP methods or routes
53 |
54 | ---
55 |
56 | ```
57 | /api/getCustomerInformation?id=123129112
58 | ```
59 |
60 | ---
61 |
62 |
63 |

64 |
109 |
110 |
132 |

133 |
152 |

153 |
180 |
181 |
204 |
205 |
228 |
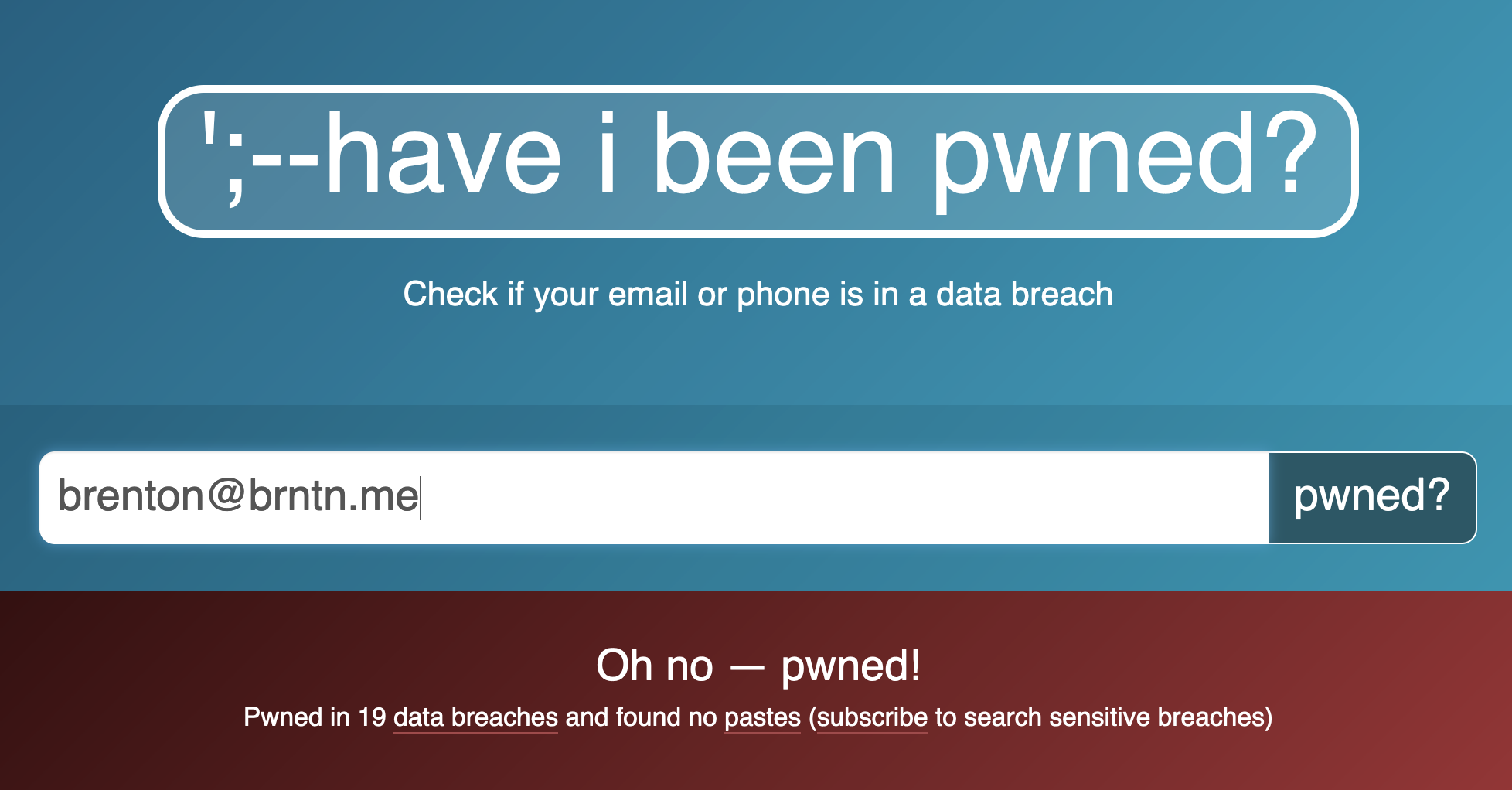
229 |
252 |
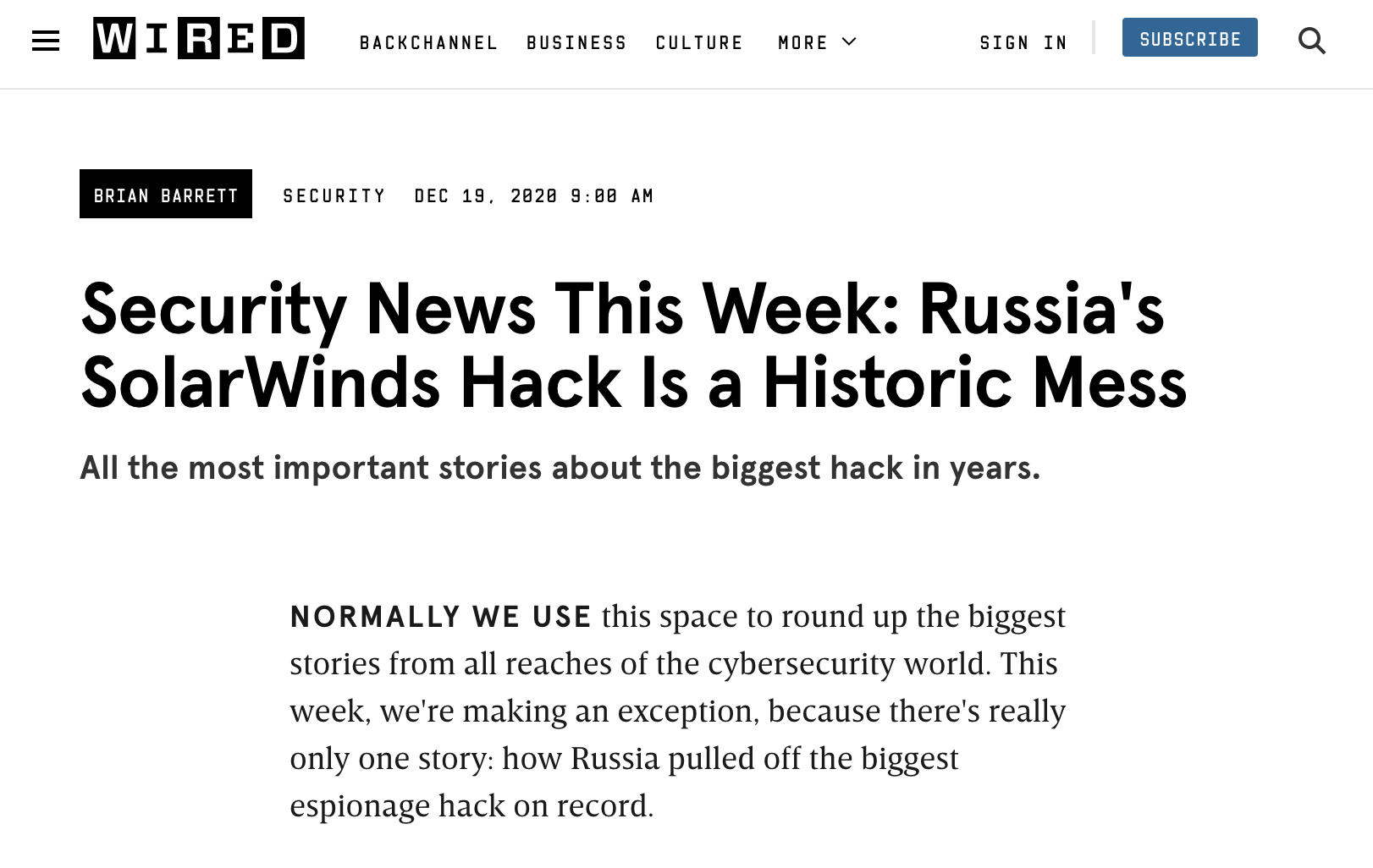
253 |
276 |

277 |
316 |
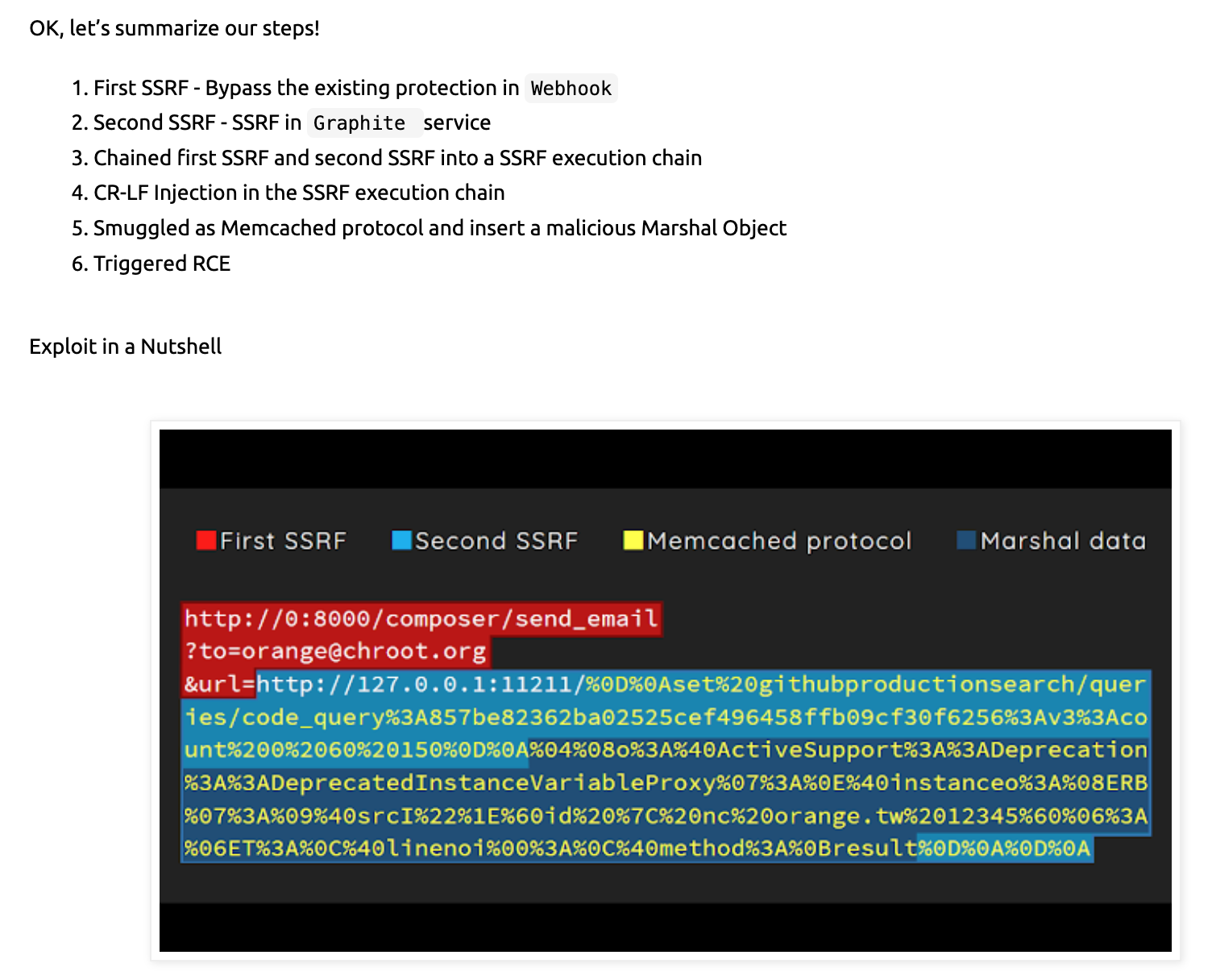
317 |
What do you call tests that aren’t unit tests?
1615 | - End to end tests
1616 | - Integration tests
1617 | - Acceptance tests
1618 | - Snapshot tests
1619 | - Fuzzing
1620 | - API tests
1621 | - Performance tests
1622 |
1624 |
What does your outer loop test look like?
Let's go write some code!
 64 |
64 |  110 |
110 |  133 |
133 |  153 |
153 |  181 |
181 |  205 |
205 |  229 |
229 |  253 |
253 |  277 |
277 |  317 |
317 | 