2 |
3 | # Argo Compare
4 |
5 | A comparison tool for displaying the differences between applications in different Git branches
6 |
7 | 
8 | 
9 | 
10 | [](https://codecov.io/gh/shini4i/argo-compare)
11 | [](https://goreportcard.com/report/github.com/shini4i/argo-compare)
12 | 
13 |
14 |
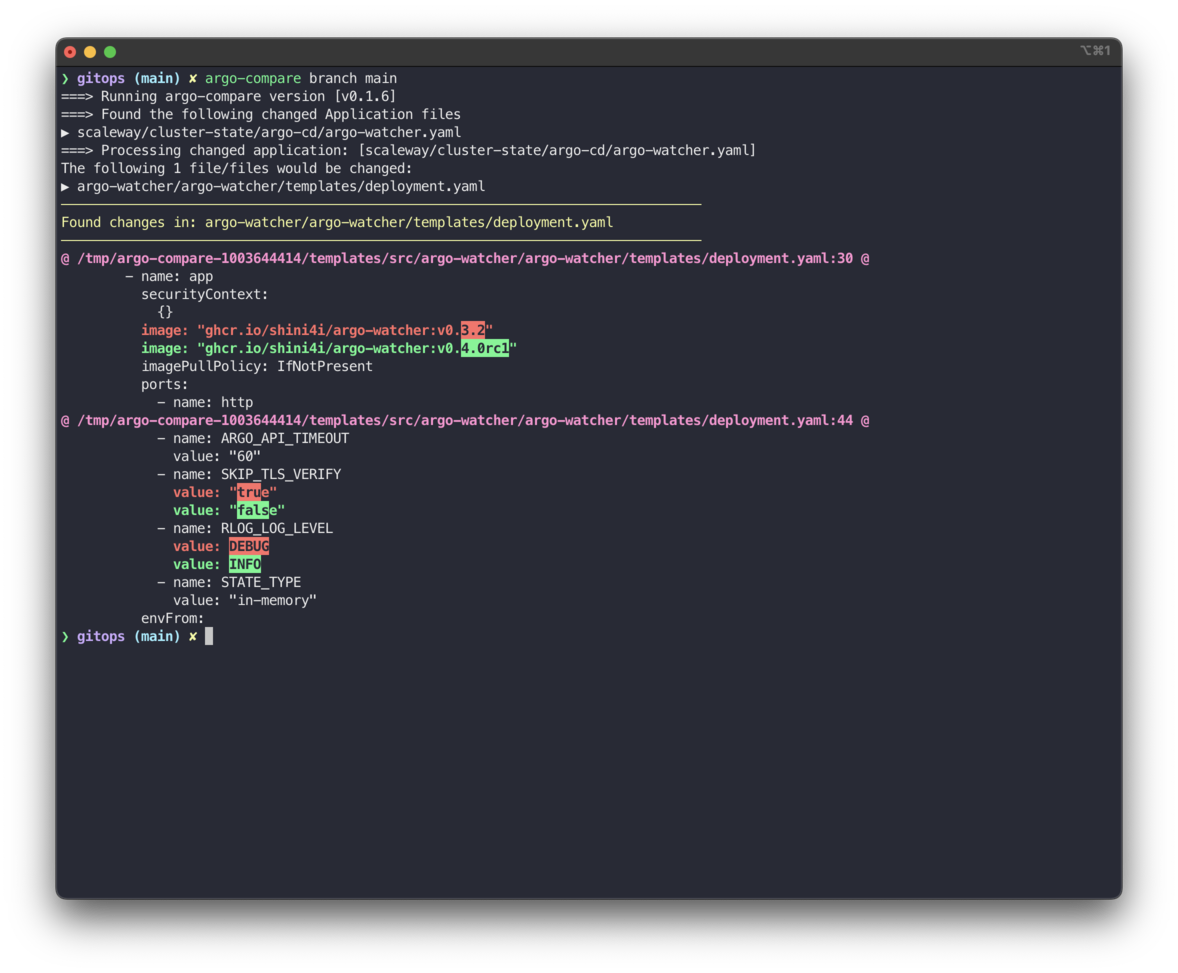
15 |
16 | Example output of `argo-compare` with `diff-so-fancy`
17 |
 15 |
16 | Example output of `argo-compare` with `diff-so-fancy`
17 |
15 |
16 | Example output of `argo-compare` with `diff-so-fancy`
17 |  15 |
16 | Example output of `argo-compare` with `diff-so-fancy`
17 |
15 |
16 | Example output of `argo-compare` with `diff-so-fancy`
17 |