 ](https://www.patreon.com/spacehuhn)
8 |
9 |
10 | ## Contents
11 | - [Introduction](#introduction)
12 | - [What it is](#what-it-is)
13 | - [How it works](#how-it-works)
14 | - [What an ENC28J60 is](#what-an-enc28j60-is)
15 | - [How to protect against it](#how-to-protect-against-it)
16 | - [Disclaimer](#disclaimer)
17 | - [Installation](#installation)
18 | - [How to use it](#how-to-use-it)
19 | - [License](#license)
20 | - [Sources and additional links](#sources-and-additional-links)
21 |
22 | ## Introduction ##
23 |
24 |
25 | ### What it is
26 |
27 | Using an Arduino with an ethernet controller, this device will perform an [ARP spoofing](https://en.wikipedia.org/wiki/ARP_spoofing) attack to block the communication from every client device in your LAN to the gateway.
28 |
29 | ### How it works
30 |
31 | It will constanly send ARP replies to every device in the LAN and tell them that the gateway is at a random MAC adress.
32 | The gateway is the link between your local network and the internet. By telling everyone it's at an adress that doesn't exist, nobody will be able to communicate to it anymore and by that, lose the connection.
33 |
34 | ### What an ENC28J60 is
35 |
36 | The ENC28J60 is a cheap 10mbit SPI ethernet controller for Arduino. Because it has a very open and easy hackable library, it's perfect for this project and you could even programm a man-in-the-middle attack or other funny stuff with it.
37 |
38 | 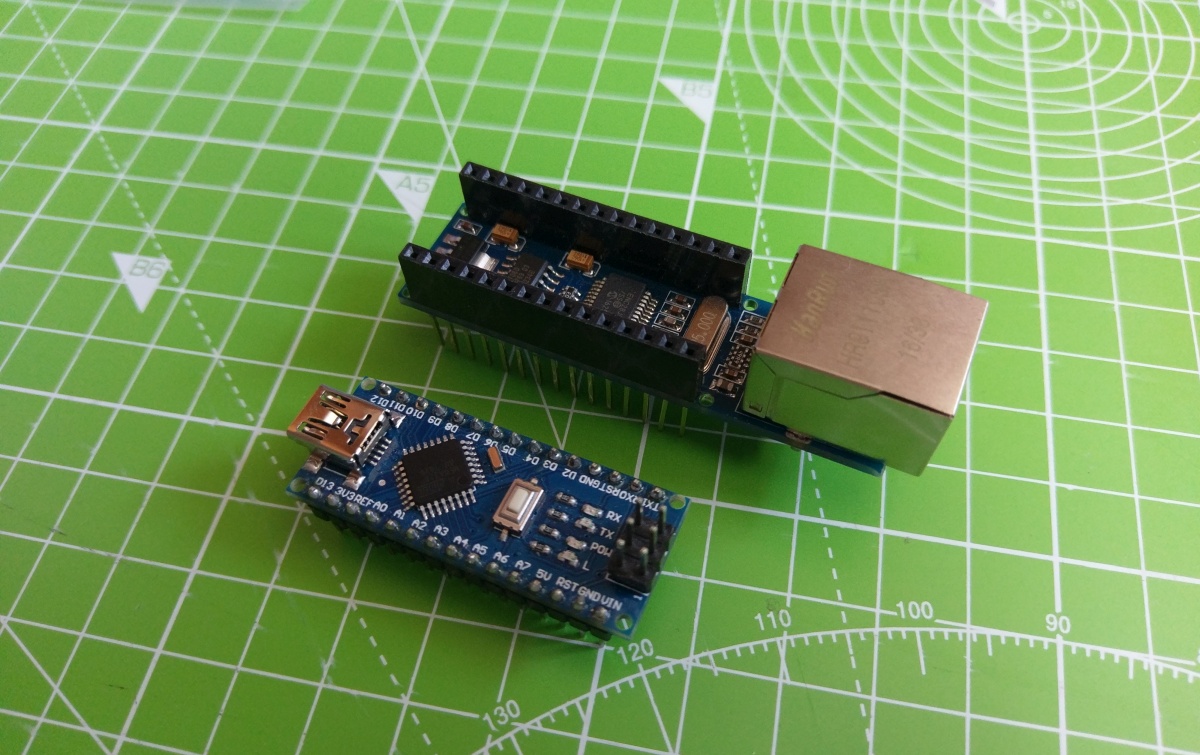
39 |
40 | ### How to protect against it
41 |
42 | Use a router, network switch or software that provides you protection against ARP spoofing.
43 | Note: I haven't tested it on such protected hardware yet.
44 |
45 | ## Disclaimer
46 |
47 | **Use it only for testing purposes on your own network!**
48 |
49 | ## Installation
50 |
51 | You will need an Arduino and an ENC28J60.
52 | If you buy an Arduino ethernet shield be sure it **doesn't** use a wiznet controller (e.g. w5100 or w5500), **this project will only work with an ENC28J60!**
53 |
54 | **1. Wire everything up**
55 |
56 | To do this you need to connect both the Arduino and the controller via their SPI pins. If you're unsure how to do this, you can google for the pinout of your Arduino and the ethernet controller. There are different versions of the ENC28J60 out there. I'm using a shield for the Arduino nano.
57 |
58 | **2. Install library**
59 |
60 | You will need to add the ethercard library in Arduino.
61 | Ho to do that is explained here: https://github.com/jcw/ethercard
62 |
63 | **3. [Optional] Change some settings**
64 |
65 | In the beginning of the sketch are a few settings declared that you can change.
66 | ```
67 | // ===== Settings ===== //
68 | //#define webinterface /* <-- uncomment that if you want to use the webinterface */
69 | //#define debug /* <-- uncomment that if you want to use get a serial output */
70 | #define led 13
71 | #define auth_password "ARP"
72 | int packetRate = 20; //packets send per second
73 | static uint8_t mymac[] = { 0xc0, 0xab, 0x03, 0x22, 0x55, 0x99 };
74 | ```
75 |
76 | **4. Upload the code**
77 |
78 | Compile & upload the sketch to your Arduino and you are done :)
79 |
80 |
81 | ## How to use it
82 |
83 | Power it over USB and plug in an ethernet cable.
84 |
85 | **Using the WebInterface:**
86 | If you uncommented `webinterface` in the code, the Arduino won't start the attack by itself.
87 | You have to open its website and start the attack manually.
88 | The IP will be printed out in the serial monitor and the default password is `ARP`.
89 |
90 | 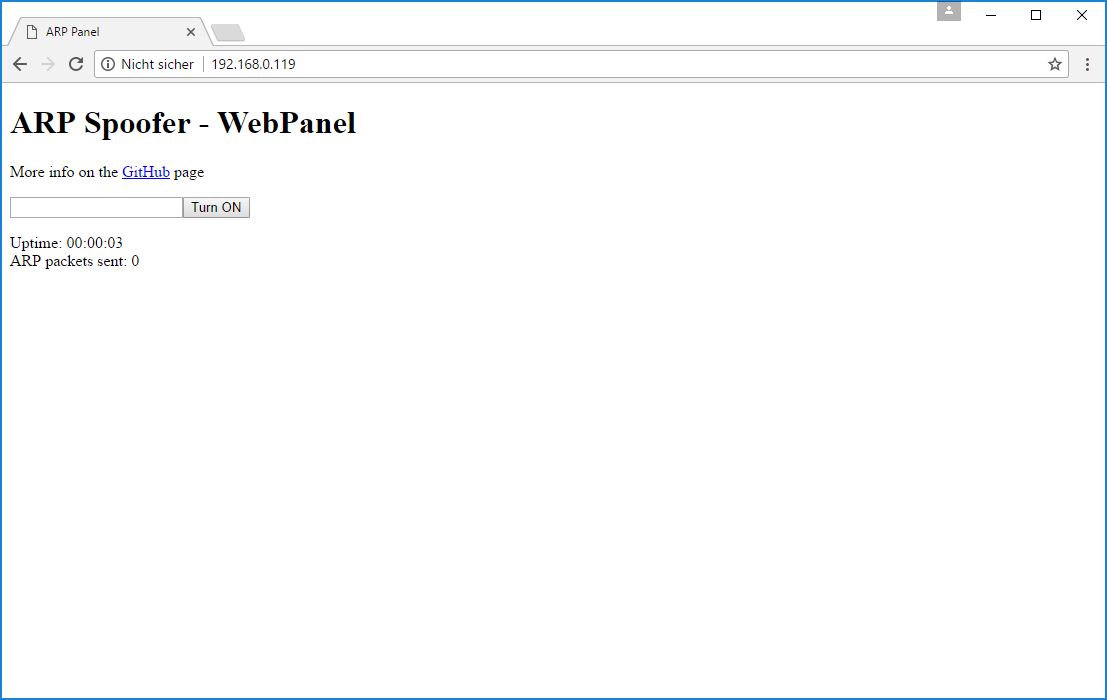
91 |
92 | ## License
93 |
94 | This project is licensed under the MIT License - see the [license file](LICENSE) for details.
95 |
96 | ## Sources and additional links
97 |
98 | ARP spoofing: https://en.wikipedia.org/wiki/ARP_spoofing
99 | ENC28J60: http://www.microchip.com/wwwproducts/en/en022889
100 |
--------------------------------------------------------------------------------
/ARPspoofer/ARPspoofer.ino:
--------------------------------------------------------------------------------
1 | /*
2 | ===========================================
3 | Copyright (c) 2017 Stefan Kremser
4 | github.com/spacehuhn
5 | ===========================================
6 | */
7 |
8 | #include
](https://www.patreon.com/spacehuhn)
8 |
9 |
10 | ## Contents
11 | - [Introduction](#introduction)
12 | - [What it is](#what-it-is)
13 | - [How it works](#how-it-works)
14 | - [What an ENC28J60 is](#what-an-enc28j60-is)
15 | - [How to protect against it](#how-to-protect-against-it)
16 | - [Disclaimer](#disclaimer)
17 | - [Installation](#installation)
18 | - [How to use it](#how-to-use-it)
19 | - [License](#license)
20 | - [Sources and additional links](#sources-and-additional-links)
21 |
22 | ## Introduction ##
23 |
24 |
25 | ### What it is
26 |
27 | Using an Arduino with an ethernet controller, this device will perform an [ARP spoofing](https://en.wikipedia.org/wiki/ARP_spoofing) attack to block the communication from every client device in your LAN to the gateway.
28 |
29 | ### How it works
30 |
31 | It will constanly send ARP replies to every device in the LAN and tell them that the gateway is at a random MAC adress.
32 | The gateway is the link between your local network and the internet. By telling everyone it's at an adress that doesn't exist, nobody will be able to communicate to it anymore and by that, lose the connection.
33 |
34 | ### What an ENC28J60 is
35 |
36 | The ENC28J60 is a cheap 10mbit SPI ethernet controller for Arduino. Because it has a very open and easy hackable library, it's perfect for this project and you could even programm a man-in-the-middle attack or other funny stuff with it.
37 |
38 | 
39 |
40 | ### How to protect against it
41 |
42 | Use a router, network switch or software that provides you protection against ARP spoofing.
43 | Note: I haven't tested it on such protected hardware yet.
44 |
45 | ## Disclaimer
46 |
47 | **Use it only for testing purposes on your own network!**
48 |
49 | ## Installation
50 |
51 | You will need an Arduino and an ENC28J60.
52 | If you buy an Arduino ethernet shield be sure it **doesn't** use a wiznet controller (e.g. w5100 or w5500), **this project will only work with an ENC28J60!**
53 |
54 | **1. Wire everything up**
55 |
56 | To do this you need to connect both the Arduino and the controller via their SPI pins. If you're unsure how to do this, you can google for the pinout of your Arduino and the ethernet controller. There are different versions of the ENC28J60 out there. I'm using a shield for the Arduino nano.
57 |
58 | **2. Install library**
59 |
60 | You will need to add the ethercard library in Arduino.
61 | Ho to do that is explained here: https://github.com/jcw/ethercard
62 |
63 | **3. [Optional] Change some settings**
64 |
65 | In the beginning of the sketch are a few settings declared that you can change.
66 | ```
67 | // ===== Settings ===== //
68 | //#define webinterface /* <-- uncomment that if you want to use the webinterface */
69 | //#define debug /* <-- uncomment that if you want to use get a serial output */
70 | #define led 13
71 | #define auth_password "ARP"
72 | int packetRate = 20; //packets send per second
73 | static uint8_t mymac[] = { 0xc0, 0xab, 0x03, 0x22, 0x55, 0x99 };
74 | ```
75 |
76 | **4. Upload the code**
77 |
78 | Compile & upload the sketch to your Arduino and you are done :)
79 |
80 |
81 | ## How to use it
82 |
83 | Power it over USB and plug in an ethernet cable.
84 |
85 | **Using the WebInterface:**
86 | If you uncommented `webinterface` in the code, the Arduino won't start the attack by itself.
87 | You have to open its website and start the attack manually.
88 | The IP will be printed out in the serial monitor and the default password is `ARP`.
89 |
90 | 
91 |
92 | ## License
93 |
94 | This project is licensed under the MIT License - see the [license file](LICENSE) for details.
95 |
96 | ## Sources and additional links
97 |
98 | ARP spoofing: https://en.wikipedia.org/wiki/ARP_spoofing
99 | ENC28J60: http://www.microchip.com/wwwproducts/en/en022889
100 |
--------------------------------------------------------------------------------
/ARPspoofer/ARPspoofer.ino:
--------------------------------------------------------------------------------
1 | /*
2 | ===========================================
3 | Copyright (c) 2017 Stefan Kremser
4 | github.com/spacehuhn
5 | ===========================================
6 | */
7 |
8 | #include More info on the GitHub page
" 203 | ""));
212 |
213 | if(!password_valid) bfill.emit_p(PSTR("Wrong password!
"));
214 |
215 | long t = millis() / 1000;
216 | word h = t / 3600;
217 | byte m = (t / 60) % 60;
218 | byte s = t % 60;
219 | bfill.emit_p(PSTR("Uptime: $D$D:$D$D:$D$D
"), h / 10, h % 10, m / 10, m % 10, s / 10, s % 10);
220 | bfill.emit_p(PSTR("ARP packets sent: $D
"), arp_count);
221 |
222 | bfill.emit_p(PSTR("