├── img
├── beacon_spam.png
└── networkscanner.jpg
├── .gitignore
├── LICENSE
├── README.md
└── esp8266_beaconSpam
└── esp8266_beaconSpam.ino
/img/beacon_spam.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/spacehuhn/esp8266_beaconSpam/HEAD/img/beacon_spam.png
--------------------------------------------------------------------------------
/img/networkscanner.jpg:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/spacehuhn/esp8266_beaconSpam/HEAD/img/networkscanner.jpg
--------------------------------------------------------------------------------
/.gitignore:
--------------------------------------------------------------------------------
1 | # Object files
2 | *.o
3 | *.ko
4 | *.obj
5 | *.elf
6 |
7 | # Precompiled Headers
8 | *.gch
9 | *.pch
10 |
11 | # Libraries
12 | *.lib
13 | *.a
14 | *.la
15 | *.lo
16 |
17 | # Shared objects (inc. Windows DLLs)
18 | *.dll
19 | *.so
20 | *.so.*
21 | *.dylib
22 |
23 | # Executables
24 | *.exe
25 | *.out
26 | *.app
27 | *.i*86
28 | *.x86_64
29 | *.hex
30 |
31 | # Debug files
32 | *.dSYM/
33 | *.su
34 |
--------------------------------------------------------------------------------
/LICENSE:
--------------------------------------------------------------------------------
1 | MIT License
2 |
3 | Copyright (c) 2017 Stefan Kremser
4 |
5 | Permission is hereby granted, free of charge, to any person obtaining a copy
6 | of this software and associated documentation files (the "Software"), to deal
7 | in the Software without restriction, including without limitation the rights
8 | to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
9 | copies of the Software, and to permit persons to whom the Software is
10 | furnished to do so, subject to the following conditions:
11 |
12 | The above copyright notice and this permission notice shall be included in all
13 | copies or substantial portions of the Software.
14 |
15 | THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
16 | IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
17 | FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
18 | AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
19 | LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
20 | OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
21 | SOFTWARE.
22 |
--------------------------------------------------------------------------------
/README.md:
--------------------------------------------------------------------------------
1 | # ESP8266 Beacon Spam
2 |
3 |
4 | 
5 |
6 |
7 | 🐦 Twitter
8 | | 📺 YouTube
9 | | 🌍 spacehuhn.de
10 |
11 | pAdvertise hundreds of WiFi access points with custom SSIDs.
12 |
13 | Support the development of this project by purchasing one of the official deauther boards.
Or become a patron on patreon.com/spacehuhn.
14 |
15 |
16 | ESP32 version by [@Tnze](https://github.com/Tnze): [esp32_beaconSpam](https://github.com/Tnze/esp32_beaconSpam).
17 |
18 | ## Changes
19 |
20 | I wrote the initial sketch in 2017 and it had some flaws.
21 | Here are the latest changes (06/2018):
22 | - Now works with ESP8266 Arduino Core v2.0.0 or newer without **any** further modification
23 | - Fixed the bug that the SSIDs are not shown correctly on IOS
24 | - No need for a SD card anymore to save hundrets of SSIDs, they are all stored in the PROGMEM now
25 |
26 | Using the SD card might be useful for some people... but thanks to the magic of git, you can still view the old repository [here](https://github.com/spacehuhn/esp8266_beaconSpam/tree/v1.0).
27 |
28 | I didn't publish a .bin file on purpose. This project is easy to create with Arduino and everyone should be able to get it working!
29 | The goal of this is to motivate people to get into hacking, electronics and Arduino, so don't be lazy and start making your own stuff! :D
30 |
31 | ## About
32 |
33 | 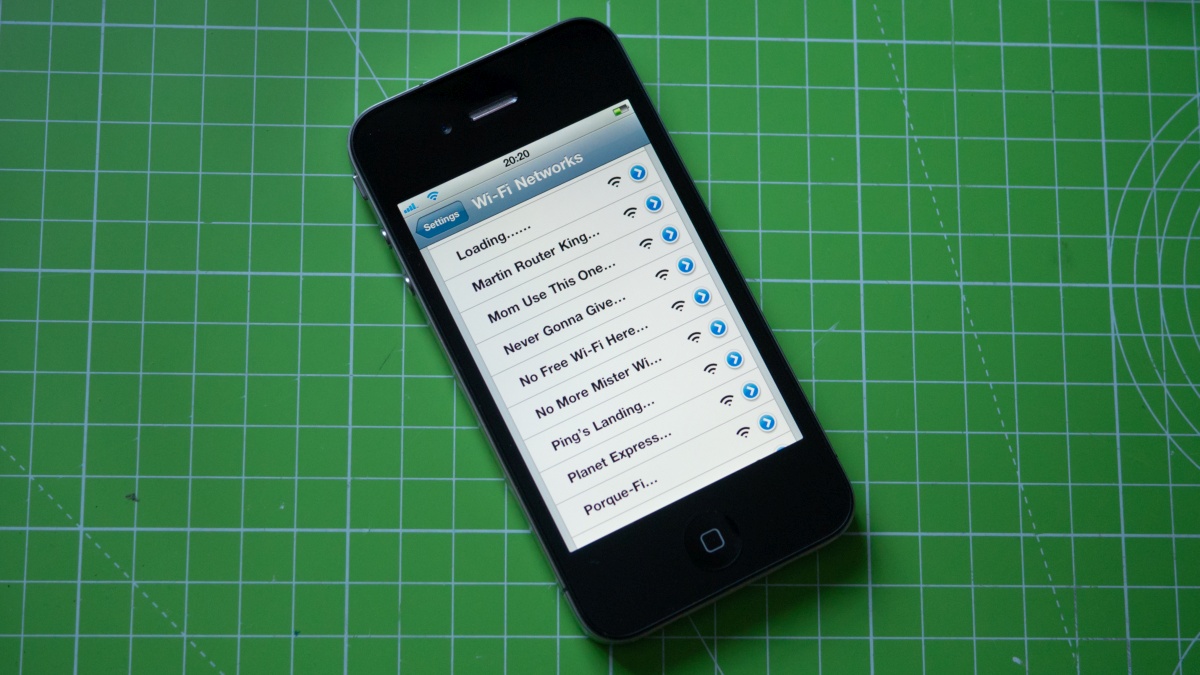
34 |
35 | This project emerged from the [ESP8266 Deauther](https://github.com/spacehuhn/esp8266_deauther) that also has this type of attack implemented.
36 | But while the Deauther is very complex and might seem intimidating to an Arduino beginner, this project is simple, hackable and easy get running!
37 |
38 | The Arduino sketch comes with 50 default SSID names, but you can edit that list easily in the source code :).
39 | By constantly broadcasting the so-called beacon frames, your standard WiFi scanner will think there are active networks nearby and adds them to the list.
40 | In reality though, it is just advertising these network names without actually creating them. So there is no way you could connect to one of the "created" networks.
41 |
42 | It is using the `wifi_send_pkt_freedom` function in the ESP8266 Arduino Core SDK. This function allows packet injection for specific Wi-Fi frames.
43 |
44 | ## Disclaimer
45 |
46 | Even if it is more of a fun party trick than something that could actually do any harm, **please use it respectfully!**
47 | Some people might interpret this as a "Jammer" and those are illegal. But this project is just sending a bunch of WiFi packets through the air and works within the 802.11 Wi-Fi standard.
48 |
49 | ## Installation
50 |
51 | - First get an ESP8266 development board! If you don't know which one, have a look at the [supported devices](https://github.com/spacehuhn/esp8266_deauther/wiki/Supported-Devices) page from the Deauther wiki. It's for a different project, but the requirements are the same.
52 | - Install [Arduino](https://www.arduino.cc/en/Main/software)
53 | - Install the [ESP8266 Arduino Core](https://github.com/esp8266/Arduino#installing-with-boards-manager) version 2.0.0 or newer (no more changes are required)
54 | - Download [this project](https://github.com/spacehuhn/esp8266_beaconSpam/archive/master.zip)
55 | - Extract the .zip file somewhere and open the `esp8266_beaconSpam/esp8266_beaconSpam.ino` file with Arduino
56 | - Edit the SSIDs if you want
57 | - Select the correct Board under Tools > Board, the serial (COM) port your device is using and hit upload!
58 |
59 | If you have trouble uploading, have a look at the [installation guide](https://github.com/spacehuhn/esp8266_deauther/wiki/Installation#drivers-and-com-port) on the Deauther Wiki. There you will also find drivers for the most common USB-Serial chips.
60 | Again, this is for the Deauther and not for this project, but the hardware (ESP8266) is the same and you will find a lot of trouble-shooting info on the Wiki there! :)
61 |
62 | Additionally, here's a video tutorial :)
63 | [](https://www.youtube.com/watch?v=Zq7QNpPxCqE)
64 |
65 | ## License
66 |
67 | This project is licensed under the MIT License - see the [license file](LICENSE) file for details
68 |
69 | ## Sources
70 |
71 | The 50 default SSIDs are from: http://www.makeuseof.com/tag/50-funny-wi-fi-names-network-ssid/
72 | More info about beacon frames: https://mrncciew.com/2014/10/08/802-11-mgmt-beacon-frame/
73 |
--------------------------------------------------------------------------------
/esp8266_beaconSpam/esp8266_beaconSpam.ino:
--------------------------------------------------------------------------------
1 | /*
2 | ===========================================
3 | Copyright (c) 2018 Stefan Kremser
4 | github.com/spacehuhn
5 | ===========================================
6 | */
7 |
8 | // ===== Settings ===== //
9 | const uint8_t channels[] = {1, 6, 11}; // used Wi-Fi channels (available: 1-14)
10 | const bool wpa2 = false; // WPA2 networks
11 | const bool appendSpaces = true; // makes all SSIDs 32 characters long to improve performance
12 |
13 | /*
14 | SSIDs:
15 | - don't forget the \n at the end of each SSID!
16 | - max. 32 characters per SSID
17 | - don't add duplicates! You have to change one character at least
18 | */
19 | const char ssids[] PROGMEM = {
20 | "Mom Use This One\n"
21 | "Abraham Linksys\n"
22 | "Benjamin FrankLAN\n"
23 | "Martin Router King\n"
24 | "John Wilkes Bluetooth\n"
25 | "Pretty Fly for a Wi-Fi\n"
26 | "Bill Wi the Science Fi\n"
27 | "I Believe Wi Can Fi\n"
28 | "Tell My Wi-Fi Love Her\n"
29 | "No More Mister Wi-Fi\n"
30 | "LAN Solo\n"
31 | "The LAN Before Time\n"
32 | "Silence of the LANs\n"
33 | "House LANister\n"
34 | "Winternet Is Coming\n"
35 | "Ping’s Landing\n"
36 | "The Ping in the North\n"
37 | "This LAN Is My LAN\n"
38 | "Get Off My LAN\n"
39 | "The Promised LAN\n"
40 | "The LAN Down Under\n"
41 | "FBI Surveillance Van 4\n"
42 | "Area 51 Test Site\n"
43 | "Drive-By Wi-Fi\n"
44 | "Planet Express\n"
45 | "Wu Tang LAN\n"
46 | "Darude LANstorm\n"
47 | "Never Gonna Give You Up\n"
48 | "Hide Yo Kids, Hide Yo Wi-Fi\n"
49 | "Loading…\n"
50 | "Searching…\n"
51 | "VIRUS.EXE\n"
52 | "Virus-Infected Wi-Fi\n"
53 | "Starbucks Wi-Fi\n"
54 | "Text ###-#### for Password\n"
55 | "Yell ____ for Password\n"
56 | "The Password Is 1234\n"
57 | "Free Public Wi-Fi\n"
58 | "No Free Wi-Fi Here\n"
59 | "Get Your Own Damn Wi-Fi\n"
60 | "It Hurts When IP\n"
61 | "Dora the Internet Explorer\n"
62 | "404 Wi-Fi Unavailable\n"
63 | "Porque-Fi\n"
64 | "Titanic Syncing\n"
65 | "Test Wi-Fi Please Ignore\n"
66 | "Drop It Like It’s Hotspot\n"
67 | "Life in the Fast LAN\n"
68 | "The Creep Next Door\n"
69 | "Ye Olde Internet\n"
70 | };
71 | // ==================== //
72 |
73 | // ===== Includes ===== //
74 | #include
75 |
76 | extern "C" {
77 | #include "user_interface.h"
78 | typedef void (*freedom_outside_cb_t)(uint8 status);
79 | int wifi_register_send_pkt_freedom_cb(freedom_outside_cb_t cb);
80 | void wifi_unregister_send_pkt_freedom_cb(void);
81 | int wifi_send_pkt_freedom(uint8 *buf, int len, bool sys_seq);
82 | }
83 | // ==================== //
84 |
85 | // run-time variables
86 | char emptySSID[32];
87 | uint8_t channelIndex = 0;
88 | uint8_t macAddr[6];
89 | uint8_t wifi_channel = 1;
90 | uint32_t currentTime = 0;
91 | uint32_t packetSize = 0;
92 | uint32_t packetCounter = 0;
93 | uint32_t attackTime = 0;
94 | uint32_t packetRateTime = 0;
95 |
96 | // beacon frame definition
97 | uint8_t beaconPacket[109] = {
98 | /* 0 - 3 */ 0x80, 0x00, 0x00, 0x00, // Type/Subtype: managment beacon frame
99 | /* 4 - 9 */ 0xFF, 0xFF, 0xFF, 0xFF, 0xFF, 0xFF, // Destination: broadcast
100 | /* 10 - 15 */ 0x01, 0x02, 0x03, 0x04, 0x05, 0x06, // Source
101 | /* 16 - 21 */ 0x01, 0x02, 0x03, 0x04, 0x05, 0x06, // Source
102 |
103 | // Fixed parameters
104 | /* 22 - 23 */ 0x00, 0x00, // Fragment & sequence number (will be done by the SDK)
105 | /* 24 - 31 */ 0x83, 0x51, 0xf7, 0x8f, 0x0f, 0x00, 0x00, 0x00, // Timestamp
106 | /* 32 - 33 */ 0xe8, 0x03, // Interval: 0x64, 0x00 => every 100ms - 0xe8, 0x03 => every 1s
107 | /* 34 - 35 */ 0x31, 0x00, // capabilities Tnformation
108 |
109 | // Tagged parameters
110 |
111 | // SSID parameters
112 | /* 36 - 37 */ 0x00, 0x20, // Tag: Set SSID length, Tag length: 32
113 | /* 38 - 69 */ 0x20, 0x20, 0x20, 0x20,
114 | 0x20, 0x20, 0x20, 0x20,
115 | 0x20, 0x20, 0x20, 0x20,
116 | 0x20, 0x20, 0x20, 0x20,
117 | 0x20, 0x20, 0x20, 0x20,
118 | 0x20, 0x20, 0x20, 0x20,
119 | 0x20, 0x20, 0x20, 0x20,
120 | 0x20, 0x20, 0x20, 0x20, // SSID
121 |
122 | // Supported Rates
123 | /* 70 - 71 */ 0x01, 0x08, // Tag: Supported Rates, Tag length: 8
124 | /* 72 */ 0x82, // 1(B)
125 | /* 73 */ 0x84, // 2(B)
126 | /* 74 */ 0x8b, // 5.5(B)
127 | /* 75 */ 0x96, // 11(B)
128 | /* 76 */ 0x24, // 18
129 | /* 77 */ 0x30, // 24
130 | /* 78 */ 0x48, // 36
131 | /* 79 */ 0x6c, // 54
132 |
133 | // Current Channel
134 | /* 80 - 81 */ 0x03, 0x01, // Channel set, length
135 | /* 82 */ 0x01, // Current Channel
136 |
137 | // RSN information
138 | /* 83 - 84 */ 0x30, 0x18,
139 | /* 85 - 86 */ 0x01, 0x00,
140 | /* 87 - 90 */ 0x00, 0x0f, 0xac, 0x02,
141 | /* 91 - 92 */ 0x02, 0x00,
142 | /* 93 - 100 */ 0x00, 0x0f, 0xac, 0x04, 0x00, 0x0f, 0xac, 0x04, /*Fix: changed 0x02(TKIP) to 0x04(CCMP) is default. WPA2 with TKIP not supported by many devices*/
143 | /* 101 - 102 */ 0x01, 0x00,
144 | /* 103 - 106 */ 0x00, 0x0f, 0xac, 0x02,
145 | /* 107 - 108 */ 0x00, 0x00
146 | };
147 |
148 | // Shift out channels one by one
149 | void nextChannel() {
150 | if (sizeof(channels) > 1) {
151 | uint8_t ch = channels[channelIndex];
152 | channelIndex++;
153 | if (channelIndex > sizeof(channels)) channelIndex = 0;
154 |
155 | if (ch != wifi_channel && ch >= 1 && ch <= 14) {
156 | wifi_channel = ch;
157 | wifi_set_channel(wifi_channel);
158 | }
159 | }
160 | }
161 |
162 | // Random MAC generator
163 | void randomMac() {
164 | for (int i = 0; i < 6; i++){
165 | macAddr[i] = random(256);
166 | }
167 | }
168 |
169 | void setup() {
170 | // create empty SSID
171 | for (int i = 0; i < 32; i++)
172 | emptySSID[i] = ' ';
173 |
174 | // for random generator
175 | randomSeed(os_random());
176 |
177 | // set packetSize
178 | packetSize = sizeof(beaconPacket);
179 | if (wpa2) {
180 | beaconPacket[34] = 0x31;
181 | } else {
182 | beaconPacket[34] = 0x21;
183 | packetSize -= 26;
184 | }
185 |
186 | // generate random mac address
187 | randomMac();
188 |
189 | // start serial
190 | Serial.begin(115200);
191 | Serial.println();
192 |
193 | // get time
194 | currentTime = millis();
195 |
196 | // start WiFi
197 | WiFi.mode(WIFI_OFF);
198 | wifi_set_opmode(STATION_MODE);
199 |
200 | // Set to default WiFi channel
201 | wifi_set_channel(channels[0]);
202 |
203 | // Display all saved WiFi SSIDs
204 | Serial.println("SSIDs:");
205 | int i = 0;
206 | int len = sizeof(ssids);
207 | while (i < len) {
208 | Serial.print((char)pgm_read_byte(ssids + i));
209 | i++;
210 | }
211 |
212 | Serial.println();
213 | Serial.println("Started \\o/");
214 | Serial.println();
215 | }
216 |
217 | void loop() {
218 | currentTime = millis();
219 |
220 | // send out SSIDs
221 | if (currentTime - attackTime > 100) {
222 | attackTime = currentTime;
223 |
224 | // temp variables
225 | int i = 0;
226 | int j = 0;
227 | int ssidNum = 1;
228 | char tmp;
229 | int ssidsLen = strlen_P(ssids);
230 | bool sent = false;
231 |
232 | // Go to next channel
233 | nextChannel();
234 |
235 | while (i < ssidsLen) {
236 | // Get the next SSID
237 | j = 0;
238 | do {
239 | tmp = pgm_read_byte(ssids + i + j);
240 | j++;
241 | } while (tmp != '\n' && j <= 32 && i + j < ssidsLen);
242 |
243 | uint8_t ssidLen = j - 1;
244 |
245 | // set MAC address
246 | macAddr[5] = ssidNum;
247 | ssidNum++;
248 |
249 | // write MAC address into beacon frame
250 | memcpy(&beaconPacket[10], macAddr, 6);
251 | memcpy(&beaconPacket[16], macAddr, 6);
252 |
253 | // reset SSID
254 | memcpy(&beaconPacket[38], emptySSID, 32);
255 |
256 | // write new SSID into beacon frame
257 | memcpy_P(&beaconPacket[38], &ssids[i], ssidLen);
258 |
259 | // set channel for beacon frame
260 | beaconPacket[82] = wifi_channel;
261 |
262 | // send packet
263 | if (appendSpaces) {
264 | for (int k = 0; k < 3; k++) {
265 | packetCounter += wifi_send_pkt_freedom(beaconPacket, packetSize, 0) == 0;
266 | delay(1);
267 | }
268 | }
269 |
270 | // remove spaces
271 | else {
272 |
273 | uint16_t tmpPacketSize = (packetSize - 32) + ssidLen; // calc size
274 | uint8_t* tmpPacket = new uint8_t[tmpPacketSize]; // create packet buffer
275 | memcpy(&tmpPacket[0], &beaconPacket[0], 38 + ssidLen); // copy first half of packet into buffer
276 | tmpPacket[37] = ssidLen; // update SSID length byte
277 | memcpy(&tmpPacket[38 + ssidLen], &beaconPacket[70], wpa2 ? 39 : 13); // copy second half of packet into buffer
278 |
279 | // send packet
280 | for (int k = 0; k < 3; k++) {
281 | packetCounter += wifi_send_pkt_freedom(tmpPacket, tmpPacketSize, 0) == 0;
282 | delay(1);
283 | }
284 |
285 | delete tmpPacket; // free memory of allocated buffer
286 | }
287 |
288 | i += j;
289 | }
290 | }
291 |
292 | // show packet-rate each second
293 | if (currentTime - packetRateTime > 1000) {
294 | packetRateTime = currentTime;
295 | Serial.print("Packets/s: ");
296 | Serial.println(packetCounter);
297 | packetCounter = 0;
298 | }
299 | }
300 |
--------------------------------------------------------------------------------
![]()