├── .github
├── ISSUE_TEMPLATE
│ ├── bug-report.yaml
│ ├── config.yml
│ └── feature-request.yaml
├── dependabot.yaml
└── workflows
│ ├── artifacthub.yaml
│ ├── e2e.yaml
│ ├── go.yaml
│ ├── helm.yaml
│ └── release.yaml
├── .gitignore
├── .golangci.yaml
├── .goreleaser.yaml
├── CHANGELOG.md
├── CONTRIBUTING.md
├── Dockerfile
├── LICENSE
├── Makefile
├── README.md
├── charts
└── spegel
│ ├── .helmignore
│ ├── Chart.yaml
│ ├── README.md
│ ├── README.md.gotmpl
│ ├── artifacthub-repo.yml
│ ├── monitoring
│ └── grafana-dashboard.json
│ ├── templates
│ ├── _helpers.tpl
│ ├── daemonset.yaml
│ ├── grafana-dashboard.yaml
│ ├── post-delete-hook.yaml
│ ├── rbac.yaml
│ ├── service.yaml
│ ├── servicemonitor.yaml
│ └── verticalpodautoscaler.yaml
│ └── values.yaml
├── go.mod
├── go.sum
├── internal
├── channel
│ └── channel.go
├── cleanup
│ ├── cleanup.go
│ └── cleanup_test.go
└── web
│ ├── templates
│ ├── index.html
│ ├── measure.html
│ └── stats.html
│ ├── web.go
│ └── web_test.go
├── main.go
├── pkg
├── httpx
│ ├── httpx.go
│ ├── metrics.go
│ ├── mux.go
│ ├── mux_test.go
│ ├── response.go
│ ├── response_test.go
│ ├── status.go
│ └── status_test.go
├── metrics
│ ├── metrics.go
│ └── metrics_test.go
├── oci
│ ├── client.go
│ ├── client_test.go
│ ├── containerd.go
│ ├── containerd_test.go
│ ├── distribution.go
│ ├── distribution_test.go
│ ├── image.go
│ ├── image_test.go
│ ├── memory.go
│ ├── oci.go
│ ├── oci_test.go
│ └── testdata
│ │ ├── blobs
│ │ └── sha256
│ │ │ ├── 0ad7c556c55464fa44d4c41e5236715e015b0266daced62140fb5c6b983c946b
│ │ │ ├── 3caa2469de2a23cbcc209dd0b9d01cd78ff9a0f88741655991d36baede5b0996
│ │ │ ├── 44cb2cf712c060f69df7310e99339c1eb51a085446f1bb6d44469acff35b4355
│ │ │ ├── 68b8a989a3e08ddbdb3a0077d35c0d0e59c9ecf23d0634584def8bdbb7d6824f
│ │ │ ├── 9430beb291fa7b96997711fc486bc46133c719631aefdbeebe58dd3489217bfe
│ │ │ ├── 9506c8e7a2d0a098d43cadfd7ecdc3c91697e8188d3a1245943b669f717747b4
│ │ │ ├── addc990c58744bdf96364fe89bd4aab38b1e824d51c688edb36c75247cd45fa9
│ │ │ ├── aec8273a5e5aca369fcaa8cecef7bf6c7959d482f5c8cfa2236a6a16e46bbdcf
│ │ │ ├── b6d6089ca6c395fd563c2084f5dd7bc56a2f5e6a81413558c5be0083287a77e9
│ │ │ ├── d8df04365d06181f037251de953aca85cc16457581a8fc168f4957c978e1008b
│ │ │ └── dce623533c59af554b85f859e91fc1cbb7f574e873c82f36b9ea05a09feb0b53
│ │ └── images.json
├── registry
│ ├── registry.go
│ └── registry_test.go
├── routing
│ ├── bootstrap.go
│ ├── bootstrap_test.go
│ ├── memory.go
│ ├── memory_test.go
│ ├── p2p.go
│ ├── p2p_test.go
│ └── routing.go
└── state
│ ├── state.go
│ └── state_test.go
└── test
└── e2e
├── e2e_test.go
└── testdata
├── conformance-job.yaml
└── test-nginx.yaml
/.github/ISSUE_TEMPLATE/bug-report.yaml:
--------------------------------------------------------------------------------
1 | name: Bug Report
2 | description: Create a report to help improve Spegel
3 | labels: ["bug"]
4 | body:
5 | - type: markdown
6 | attributes:
7 | value: |
8 | Thank you for taking the time to fill ot this bug report! Please read the [FAQ](https://spegel.dev/docs/faq/) and check existing issues before submitting a new issue.
9 | - type: input
10 | attributes:
11 | label: Spegel version
12 | placeholder: eg. v0.0.16
13 | validations:
14 | required: true
15 | - type: input
16 | attributes:
17 | label: Kubernetes distribution
18 | placeholder: eg. AKS, EKS, K3S, Kubeadm...
19 | validations:
20 | required: true
21 | - type: input
22 | attributes:
23 | label: Kubernetes version
24 | placeholder: eg. v1.29.0
25 | validations:
26 | required: true
27 | - type: input
28 | attributes:
29 | label: CNI
30 | placeholder: eg. Calico, Cilium, Azure CNI...
31 | validations:
32 | required: true
33 | - type: textarea
34 | attributes:
35 | label: Describe the bug
36 | description: A clear description of what the bug is.
37 | validations:
38 | required: true
39 |
--------------------------------------------------------------------------------
/.github/ISSUE_TEMPLATE/config.yml:
--------------------------------------------------------------------------------
1 | blank_issues_enabled: true
2 |
--------------------------------------------------------------------------------
/.github/ISSUE_TEMPLATE/feature-request.yaml:
--------------------------------------------------------------------------------
1 | name: Feature Request
2 | description: Suggest a new feature for Spegel
3 | labels: ["enhancement"]
4 | body:
5 | - type: markdown
6 | attributes:
7 | value: |
8 | Thank you for creating a feature request! Please check existing issues before submitting.
9 | - type: textarea
10 | attributes:
11 | label: Describe the problem to be solved
12 | description: A clear description of the problem that needs to be addressed by this feature request.
13 | validations:
14 | required: true
15 | - type: textarea
16 | attributes:
17 | label: Proposed solution to the problem
18 | description: A clear description of the solution or multiple possible solutions to implement this feature request.
19 | validations:
20 | required: false
21 |
--------------------------------------------------------------------------------
/.github/dependabot.yaml:
--------------------------------------------------------------------------------
1 | version: 2
2 | updates:
3 | - package-ecosystem: "github-actions"
4 | directory: "/"
5 | schedule:
6 | interval: "daily"
7 | open-pull-requests-limit: 15
8 | - package-ecosystem: "gomod"
9 | directory: "/"
10 | schedule:
11 | interval: "daily"
12 | open-pull-requests-limit: 15
13 | groups:
14 | k8s:
15 | patterns:
16 | - "k8s.io/*"
17 |
--------------------------------------------------------------------------------
/.github/workflows/artifacthub.yaml:
--------------------------------------------------------------------------------
1 | name: artifacthub
2 | on:
3 | push:
4 | branches: ["main"]
5 | paths:
6 | - "charts/spegel/artifacthub-repo.yml"
7 | permissions:
8 | contents: read
9 | packages: write
10 | defaults:
11 | run:
12 | shell: bash
13 | jobs:
14 | release:
15 | runs-on: ubuntu-latest
16 | steps:
17 | - name: Clone repo
18 | uses: actions/checkout@11bd71901bbe5b1630ceea73d27597364c9af683 #v4.2.2
19 | with:
20 | submodules: true
21 | - name: Login to GitHub Container Registry
22 | uses: docker/login-action@74a5d142397b4f367a81961eba4e8cd7edddf772 #v3.4.0
23 | with:
24 | registry: ghcr.io
25 | username: ${{ github.repository_owner }}
26 | password: ${{ secrets.GITHUB_TOKEN }}
27 | - name: Setup ORAS
28 | uses: oras-project/setup-oras@8d34698a59f5ffe24821f0b48ab62a3de8b64b20 #v1.2.3
29 | - name: Push Artifact Hub metadata
30 | run: oras push ghcr.io/spegel-org/helm-charts/spegel:artifacthub.io --config /dev/null:application/vnd.cncf.artifacthub.config.v1+yaml charts/spegel/artifacthub-repo.yml:application/vnd.cncf.artifacthub.repository-metadata.layer.v1.yaml
31 |
--------------------------------------------------------------------------------
/.github/workflows/e2e.yaml:
--------------------------------------------------------------------------------
1 | name: e2e
2 | on:
3 | pull_request:
4 | permissions:
5 | contents: read
6 | defaults:
7 | run:
8 | shell: bash
9 | jobs:
10 | test:
11 | runs-on: ubuntu-latest
12 | strategy:
13 | matrix:
14 | include:
15 | - proxy-mode: iptables
16 | ip-family: ipv4
17 | - proxy-mode: iptables
18 | ip-family: ipv6
19 | - proxy-mode: ipvs
20 | ip-family: ipv4
21 | steps:
22 | - name: Checkout
23 | uses: actions/checkout@11bd71901bbe5b1630ceea73d27597364c9af683 #v4.2.2
24 | - name: Setup Go
25 | uses: actions/setup-go@d35c59abb061a4a6fb18e82ac0862c26744d6ab5 #v5.5.0
26 | with:
27 | go-version-file: go.mod
28 | - name: Setup GoReleaser
29 | uses: goreleaser/goreleaser-action@v6
30 | with:
31 | install-only: true
32 | - name: Setup Kind
33 | uses: helm/kind-action@a1b0e391336a6ee6713a0583f8c6240d70863de3 #v1.12.0
34 | with:
35 | version: v0.29.0
36 | install_only: true
37 | - name: Run e2e
38 | run: make test-e2e E2E_PROXY_MODE=${{ matrix.proxy-mode }} E2E_IP_FAMILY=${{ matrix.ip-family }}
39 |
--------------------------------------------------------------------------------
/.github/workflows/go.yaml:
--------------------------------------------------------------------------------
1 | name: go
2 | on:
3 | pull_request:
4 | permissions:
5 | contents: read
6 | defaults:
7 | run:
8 | shell: bash
9 | jobs:
10 | lint:
11 | runs-on: ubuntu-latest
12 | steps:
13 | - name: Checkout
14 | uses: actions/checkout@11bd71901bbe5b1630ceea73d27597364c9af683 #v4.2.2
15 | - name: Setup Go
16 | uses: actions/setup-go@d35c59abb061a4a6fb18e82ac0862c26744d6ab5 #v5.5.0
17 | with:
18 | go-version-file: go.mod
19 | - name: Setup golangci-lint
20 | uses: golangci/golangci-lint-action@4afd733a84b1f43292c63897423277bb7f4313a9 #v8.0.0
21 | unit:
22 | runs-on: ubuntu-latest
23 | steps:
24 | - name: Checkout
25 | uses: actions/checkout@11bd71901bbe5b1630ceea73d27597364c9af683 #v4.2.2
26 | - name: Setup Go
27 | uses: actions/setup-go@d35c59abb061a4a6fb18e82ac0862c26744d6ab5 #v5.5.0
28 | with:
29 | go-version-file: go.mod
30 | - name: Run tests
31 | run: go test -race -coverprofile=coverage.txt -covermode=atomic ./...
32 | - name: Upload coverage reports to Codecov
33 | uses: codecov/codecov-action@18283e04ce6e62d37312384ff67231eb8fd56d24 #v5.4.3
34 | with:
35 | token: ${{ secrets.CODECOV_TOKEN }}
36 |
--------------------------------------------------------------------------------
/.github/workflows/helm.yaml:
--------------------------------------------------------------------------------
1 | name: helm
2 | on:
3 | pull_request:
4 | permissions:
5 | contents: read
6 | defaults:
7 | run:
8 | shell: bash
9 | jobs:
10 | docs:
11 | runs-on: ubuntu-latest
12 | steps:
13 | - name: Checkout
14 | uses: actions/checkout@11bd71901bbe5b1630ceea73d27597364c9af683 #v4.2.2
15 | - name: Setup Go
16 | uses: actions/setup-go@d35c59abb061a4a6fb18e82ac0862c26744d6ab5 #v5.5.0
17 | with:
18 | go-version-file: go.mod
19 | - name: Run helm-docs
20 | run: make helm-docs
21 | - name: Check if working tree is dirty
22 | run: |
23 | if [[ $(git diff --stat) != '' ]]; then
24 | git diff
25 | echo 'run make helm-docs and commit changes'
26 | exit 1
27 | fi
28 |
--------------------------------------------------------------------------------
/.github/workflows/release.yaml:
--------------------------------------------------------------------------------
1 | name: release
2 | on:
3 | push:
4 | tags:
5 | - 'v*'
6 | permissions:
7 | contents: write
8 | packages: write
9 | id-token: write
10 | defaults:
11 | run:
12 | shell: bash
13 | jobs:
14 | release:
15 | runs-on: ubuntu-latest
16 | steps:
17 | - name: Clone repo
18 | uses: actions/checkout@11bd71901bbe5b1630ceea73d27597364c9af683 #v4.2.2
19 | - name: Setup Cosign
20 | uses: sigstore/cosign-installer@3454372f43399081ed03b604cb2d021dabca52bb #v3.8.2
21 | - name: Setup Helm
22 | uses: azure/setup-helm@b9e51907a09c216f16ebe8536097933489208112 #v4.3.0
23 | with:
24 | version: v3.17.3
25 | - name: Setup Docker Buildx
26 | id: buildx
27 | uses: docker/setup-buildx-action@b5ca514318bd6ebac0fb2aedd5d36ec1b5c232a2 #v3.10.0
28 | - name: Setup yq
29 | uses: frenck/action-setup-yq@c4b5be8b4a215c536a41d436757d9feb92836d4f #v1.0.2
30 | - name: Login to GitHub Container Registry
31 | uses: docker/login-action@74a5d142397b4f367a81961eba4e8cd7edddf772 #v3.4.0
32 | with:
33 | registry: ghcr.io
34 | username: ${{ github.repository_owner }}
35 | password: ${{ secrets.GITHUB_TOKEN }}
36 | - name: Prepare version
37 | id: prep
38 | run: |
39 | VERSION=sha-${GITHUB_SHA::8}
40 | if [[ $GITHUB_REF == refs/tags/* ]]; then
41 | VERSION=${GITHUB_REF/refs\/tags\//}
42 | fi
43 | echo "Refer to the [Changelog](https://github.com/spegel-org/spegel/blob/main/CHANGELOG.md#${VERSION//.}) for list of changes." > ${{ runner.temp }}/NOTES.txt
44 | echo "VERSION=${VERSION}" >> $GITHUB_OUTPUT
45 | - name: Run GoReleaser
46 | uses: goreleaser/goreleaser-action@v6
47 | with:
48 | args: release --clean --release-notes ${{ runner.temp }}/NOTES.txt
49 | env:
50 | GITHUB_TOKEN: ${{ secrets.GITHUB_TOKEN }}
51 | - name: Generate images meta
52 | id: meta
53 | uses: docker/metadata-action@902fa8ec7d6ecbf8d84d538b9b233a880e428804 #v5.7.0
54 | with:
55 | images: ghcr.io/${{ github.repository_owner }}/spegel
56 | tags: type=raw,value=${{ steps.prep.outputs.VERSION }}
57 | - name: Publish multi-arch image
58 | uses: docker/build-push-action@1dc73863535b631f98b2378be8619f83b136f4a0 #v6.17.0
59 | id: build
60 | with:
61 | push: true
62 | builder: ${{ steps.buildx.outputs.name }}
63 | context: .
64 | file: ./Dockerfile
65 | platforms: linux/amd64,linux/arm/v7,linux/arm64
66 | tags: ghcr.io/${{ github.repository_owner }}/spegel:${{ steps.prep.outputs.VERSION }}
67 | labels: ${{ steps.meta.outputs.labels }}
68 | - name: Sign the image with Cosign
69 | run: |
70 | cosign sign --yes ghcr.io/${{ github.repository_owner }}/spegel@${{ steps.build.outputs.DIGEST }}
71 | - name: Publish Helm chart to GHCR
72 | id: helm
73 | run: |
74 | HELM_VERSION=${{ steps.prep.outputs.VERSION }}
75 | HELM_VERSION=${HELM_VERSION#v}
76 | rm charts/spegel/artifacthub-repo.yml
77 | yq -i '.image.digest = "${{ steps.build.outputs.DIGEST }}"' charts/spegel/values.yaml
78 | helm package --app-version ${{ steps.prep.outputs.VERSION }} --version ${HELM_VERSION} charts/spegel
79 | helm push spegel-${HELM_VERSION}.tgz oci://ghcr.io/${{ github.repository_owner }}/helm-charts 2> .digest
80 | DIGEST=$(cat .digest | awk -F "[, ]+" '/Digest/{print $NF}')
81 | echo "DIGEST=${DIGEST}" >> $GITHUB_OUTPUT
82 | - name: Sign the Helm chart with Cosign
83 | run: |
84 | cosign sign --yes ghcr.io/${{ github.repository_owner }}/helm-charts/spegel@${{ steps.helm.outputs.DIGEST }}
85 |
--------------------------------------------------------------------------------
/.gitignore:
--------------------------------------------------------------------------------
1 | # If you prefer the allow list template instead of the deny list, see community template:
2 | # https://github.com/github/gitignore/blob/main/community/Golang/Go.AllowList.gitignore
3 | #
4 | # Binaries for programs and plugins
5 | *.exe
6 | *.exe~
7 | *.dll
8 | *.so
9 | *.dylib
10 |
11 | # Test binary, built with `go test -c`
12 | *.test
13 |
14 | # Output of the go coverage tool, specifically when used with LiteIDE
15 | *.out
16 |
17 | # Dependency directories (remove the comment below to include it)
18 | # vendor/
19 |
20 | # Go workspace file
21 | go.work
22 |
23 | # Added by goreleaser init:
24 | dist/
25 |
--------------------------------------------------------------------------------
/.golangci.yaml:
--------------------------------------------------------------------------------
1 | version: "2"
2 | linters:
3 | default: none
4 | enable:
5 | - bodyclose
6 | - errcheck
7 | - gocritic
8 | - govet
9 | - importas
10 | - ineffassign
11 | - ireturn
12 | - misspell
13 | - nolintlint
14 | - paralleltest
15 | - perfsprint
16 | - staticcheck
17 | - testifylint
18 | - unused
19 | settings:
20 | errcheck:
21 | disable-default-exclusions: true
22 | check-type-assertions: true
23 | check-blank: true
24 | gocritic:
25 | enable-all: true
26 | disabled-checks:
27 | - importShadow
28 | - hugeParam
29 | - rangeValCopy
30 | - whyNoLint
31 | - unnamedResult
32 | - httpNoBody
33 | govet:
34 | disable:
35 | - shadow
36 | enable-all: true
37 | importas:
38 | alias:
39 | - pkg: io/fs
40 | alias: iofs
41 | - pkg: github.com/go-logr/logr/testing
42 | alias: tlog
43 | - pkg: github.com/pelletier/go-toml/v2/unstable
44 | alias: tomlu
45 | - pkg: github.com/multiformats/go-multiaddr/net
46 | alias: manet
47 | - pkg: github.com/multiformats/go-multiaddr
48 | alias: ma
49 | - pkg: github.com/multiformats/go-multicodec
50 | alias: mc
51 | - pkg: github.com/multiformats/go-multihash
52 | alias: mh
53 | - pkg: github.com/ipfs/go-cid
54 | alias: cid
55 | - pkg: github.com/libp2p/go-libp2p-kad-dht
56 | alias: dht
57 | - pkg: github.com/libp2p/go-libp2p/p2p/net/mock
58 | alias: mocknet
59 | - pkg: go.etcd.io/bbolt
60 | alias: bolt
61 | - pkg: k8s.io/cri-api/pkg/apis/runtime/v1
62 | alias: runtimeapi
63 | - pkg: github.com/containerd/containerd/api/events
64 | alias: eventtypes
65 | - pkg: github.com/opencontainers/go-digest
66 | alias: digest
67 | - pkg: github.com/opencontainers/image-spec/specs-go/v1
68 | alias: ocispec
69 | - pkg: k8s.io/apimachinery/pkg/util/version
70 | alias: utilversion
71 | no-extra-aliases: true
72 | nolintlint:
73 | require-explanation: true
74 | require-specific: true
75 | perfsprint:
76 | strconcat: false
77 | testifylint:
78 | enable-all: true
79 | ireturn:
80 | allow:
81 | - anon
82 | - error
83 | - empty
84 | - stdlib
85 | - github.com/libp2p/go-libp2p/core/crypto.PrivKey
86 | exclusions:
87 | generated: lax
88 | presets:
89 | - comments
90 | - common-false-positives
91 | - legacy
92 | - std-error-handling
93 | paths:
94 | - third_party$
95 | - builtin$
96 | - examples$
97 | formatters:
98 | enable:
99 | - goimports
100 | exclusions:
101 | generated: lax
102 | paths:
103 | - third_party$
104 | - builtin$
105 | - examples$
106 |
--------------------------------------------------------------------------------
/.goreleaser.yaml:
--------------------------------------------------------------------------------
1 | version: 2
2 | project_name: spegel
3 | before:
4 | hooks:
5 | - go mod tidy
6 | builds:
7 | - goos:
8 | - linux
9 | goarch:
10 | - amd64
11 | - arm
12 | - arm64
13 | goarm:
14 | - 7
15 | env:
16 | - CGO_ENABLED=0
17 | flags:
18 | - -trimpath
19 | - -a
20 | no_unique_dist_dir: true
21 | binary: "{{ .ProjectName }}_{{ .Os }}_{{ .Arch }}/{{ .ProjectName }}"
22 | archives:
23 | - formats: [tar.gz]
24 | name_template: "{{ .ProjectName }}_{{ .Version }}_{{ .Os }}_{{ .Arch }}"
25 | files:
26 | - none*
27 |
--------------------------------------------------------------------------------
/CONTRIBUTING.md:
--------------------------------------------------------------------------------
1 | # Contributing
2 |
3 | Thank you for considering contributing to Spegel, hopefully this document will make this process easier.
4 |
5 | ## Running tests
6 |
7 | The following tools are required to run the tests properly.
8 |
9 | * go
10 | * [golangci-lint](https://github.com/golangci/golangci-lint)
11 | * [kind](https://github.com/kubernetes-sigs/kind)
12 | * [goreleaser](https://github.com/goreleaser/goreleaser)
13 | * [docker](https://docs.docker.com/get-started/get-docker/)
14 | * [helm](https://github.com/helm/helm)
15 | * [kubectl](https://kubernetes.io/docs/tasks/tools/#kubectl)
16 |
17 | Run the linter and the unit tests to quickly validate changes.
18 |
19 | ```shell
20 | make lint test
21 | ```
22 |
23 | Run the e2e tests which take a bit more time.
24 |
25 | ```shell
26 | make test-e2e
27 | ```
28 |
29 | There are e2e tests for the different CNIs iptables, iptables-v6, and ipvs.
30 |
31 | ```shell
32 | make test-e2e E2E_CNI=ipvs
33 | ```
34 |
35 | ## Building
36 |
37 | Build the Docker image locally.
38 |
39 | ```shell
40 | make build-image
41 | ```
42 |
43 | It is possible to specify a different image name and tag.
44 |
45 | ```shell
46 | make build-image IMG=example.com/spegel TAG=feature
47 | ```
48 |
49 | ### Local debugging
50 |
51 | Run the `dev-deploy` recipe which will create a Kind cluster with the proper configuration and deploy Spegel into it. If you run this command a second time the cluster will be kept but Spegel will be updated.
52 |
53 | ```shell
54 | make dev-deploy
55 | ```
56 |
57 | After the command has run you can get a kubeconfig file to access the cluster and do any debugging.
58 |
59 | ```shell
60 | kind get kubeconfig --name spegel-dev > kubeconfig
61 | export KUBECOONFIG=$(pwd)/kubeconfig
62 | kubectl -n spegel get pods
63 | ```
64 |
65 | ## Generate Helm documentation
66 |
67 | Changes to the Helm chart values will require the documentation to be regenerated.
68 |
69 | ```shell
70 | make helm-docs
71 | ```
72 |
73 | ## Acceptance policy
74 |
75 | Pull requests need to fulfill the following requirements to be accepted.
76 |
77 | * New code has tests where applicable.
78 | * The change has been added to the [changelog](./CHANGELOG.md).
79 | * Documentation has been generated if applicable.
80 | * The unit tests pass.
81 | * Linter does not report any errors.
82 | * All end to end tests pass.
83 |
--------------------------------------------------------------------------------
/Dockerfile:
--------------------------------------------------------------------------------
1 | FROM gcr.io/distroless/static:nonroot
2 | ARG TARGETOS
3 | ARG TARGETARCH
4 | COPY ./dist/spegel_${TARGETOS}_${TARGETARCH}/spegel /
5 | USER root:root
6 | ENTRYPOINT ["/spegel"]
7 |
--------------------------------------------------------------------------------
/LICENSE:
--------------------------------------------------------------------------------
1 | MIT License
2 |
3 | Copyright (c) 2024 The Spegel Authors
4 |
5 | Permission is hereby granted, free of charge, to any person obtaining a copy
6 | of this software and associated documentation files (the "Software"), to deal
7 | in the Software without restriction, including without limitation the rights
8 | to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
9 | copies of the Software, and to permit persons to whom the Software is
10 | furnished to do so, subject to the following conditions:
11 |
12 | The above copyright notice and this permission notice shall be included in all
13 | copies or substantial portions of the Software.
14 |
15 | THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
16 | IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
17 | FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
18 | AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
19 | LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
20 | OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE
21 | SOFTWARE.
22 |
--------------------------------------------------------------------------------
/Makefile:
--------------------------------------------------------------------------------
1 | TAG = $$(git rev-parse --short HEAD)
2 | IMG_NAME ?= ghcr.io/spegel-org/spegel
3 | IMG_REF = $(IMG_NAME):$(TAG)
4 | E2E_PROXY_MODE ?= iptables
5 | E2E_IP_FAMILY ?= ipv4
6 |
7 | lint:
8 | golangci-lint run ./...
9 |
10 | build:
11 | goreleaser build --snapshot --clean --single-target --skip before
12 |
13 | build-image: build
14 | docker build -t ${IMG_REF} .
15 |
16 | test-unit:
17 | go test ./...
18 |
19 | test-e2e: build-image
20 | IMG_REF=${IMG_REF} \
21 | E2E_PROXY_MODE=${E2E_PROXY_MODE} \
22 | E2E_IP_FAMILY=${E2E_IP_FAMILY} \
23 | go test ./test/e2e -v -timeout 200s -tags e2e -count 1 -run TestE2E
24 |
25 | dev-deploy: build-image
26 | IMG_REF=${IMG_REF} go test ./test/e2e -v -timeout 200s -tags e2e -count 1 -run TestDevDeploy
27 |
28 | tools:
29 | GO111MODULE=on go install github.com/norwoodj/helm-docs/cmd/helm-docs
30 |
31 | helm-docs: tools
32 | cd ./charts/spegel && helm-docs
33 |
--------------------------------------------------------------------------------
/README.md:
--------------------------------------------------------------------------------
1 | > [!NOTE]
2 | > We’ve started hosting community meetings every Tuesday at 17:00 CET. Find out how to participate at https://spegel.dev/project/community/#meeting.
3 |
4 | # Spegel
5 |
6 | Spegel, mirror in Swedish, is a stateless cluster local OCI registry mirror.
7 |
8 |
9 | 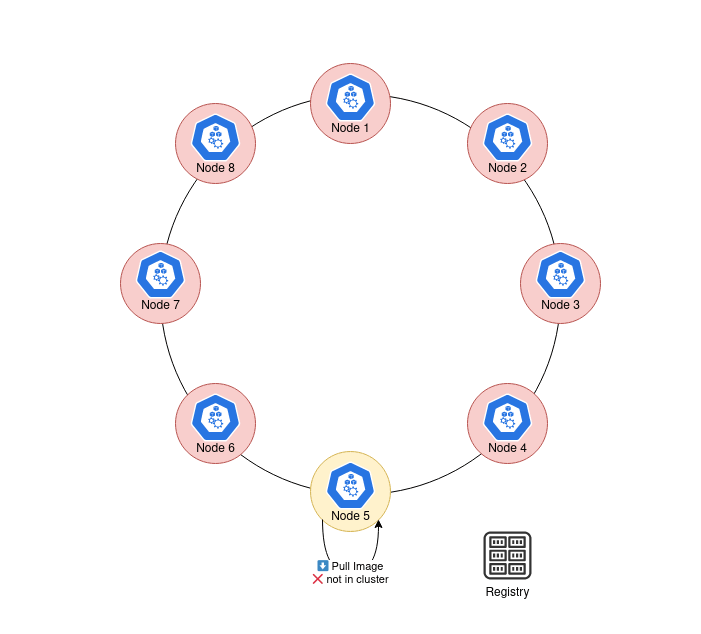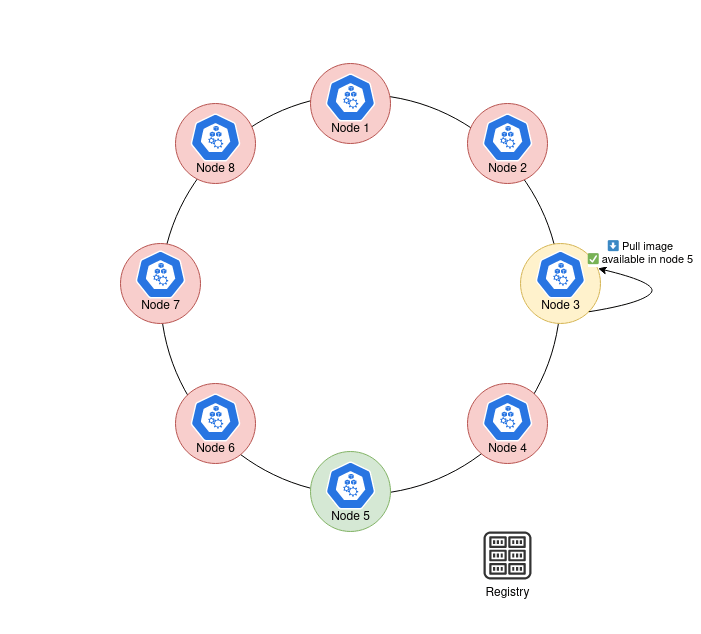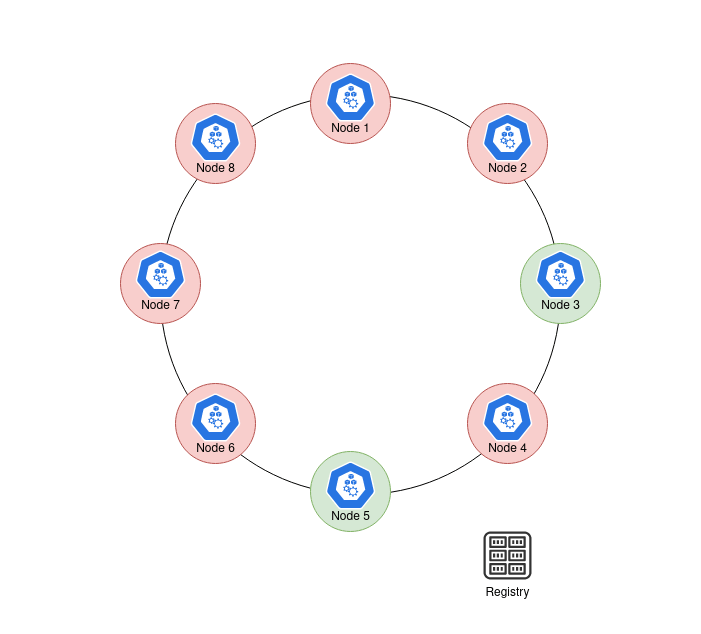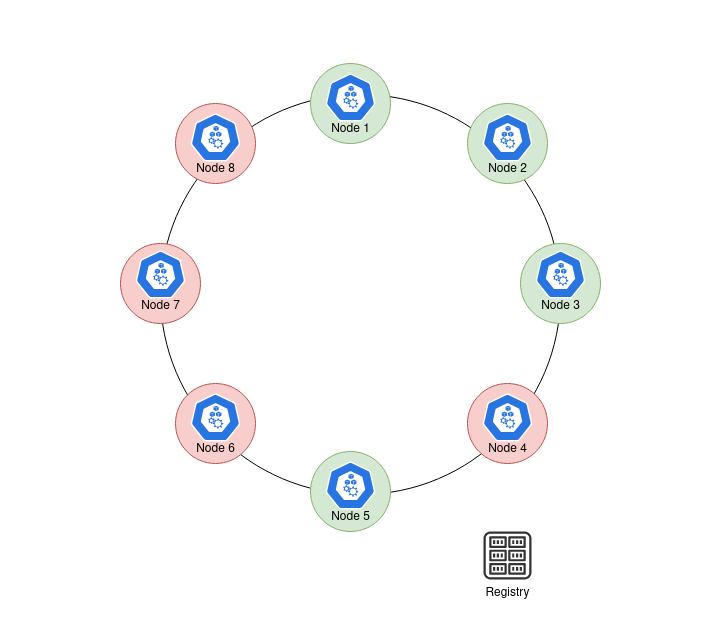 10 |
10 |
11 |
12 | ## Features
13 |
14 | Spegel is for you if you are looking to do any of the following.
15 |
16 | * Locally cache images from external registries with no explicit configuration.
17 | * Avoid cluster failure during external registry downtime.
18 | * Improve image pull speed and pod startup time by pulling images from the local cache first.
19 | * Avoid rate-limiting when pulling images from external registries (e.g. Docker Hub).
20 | * Decrease egressing traffic outside of the clusters network.
21 | * Increase image pull efficiency in edge node deployments.
22 |
23 | ## Getting Started
24 |
25 | Read the [getting started](https://spegel.dev/docs/getting-started/) guide to deploy Spegel.
26 |
27 | ## Contributing
28 |
29 | Read [contribution guidelines](./CONTRIBUTING.md) for instructions on how to build and test Spegel.
30 |
31 | ## Acknowledgements
32 |
33 | Spegel was initially developed at [Xenit AB](https://xenit.se/).
34 |
35 | ## License
36 |
37 | This project is licensed under the MIT License - see the [LICENSE](LICENSE) file for details.
38 |
--------------------------------------------------------------------------------
/charts/spegel/.helmignore:
--------------------------------------------------------------------------------
1 | # Patterns to ignore when building packages.
2 | # This supports shell glob matching, relative path matching, and
3 | # negation (prefixed with !). Only one pattern per line.
4 | .DS_Store
5 | # Common VCS dirs
6 | .git/
7 | .gitignore
8 | .bzr/
9 | .bzrignore
10 | .hg/
11 | .hgignore
12 | .svn/
13 | # Common backup files
14 | *.swp
15 | *.bak
16 | *.tmp
17 | *.orig
18 | *~
19 | # Various IDEs
20 | .project
21 | .idea/
22 | *.tmproj
23 | .vscode/
24 |
--------------------------------------------------------------------------------
/charts/spegel/Chart.yaml:
--------------------------------------------------------------------------------
1 | apiVersion: v2
2 | name: spegel
3 | description: Stateless cluster local OCI registry mirror.
4 | type: application
5 | version: v0.0.1
6 | appVersion: v0.0.1
7 | annotations:
8 | artifacthub.io/category: "integration-delivery"
9 | artifacthub.io/license: "MIT"
10 | artifacthub.io/operator: "false"
11 | artifacthub.io/prerelease: "false"
12 |
--------------------------------------------------------------------------------
/charts/spegel/README.md:
--------------------------------------------------------------------------------
1 | # Spegel
2 |
3 | Stateless cluster local OCI registry mirror.
4 |
5 | Read the [getting started](https://spegel.dev/docs/getting-started/) guide to deploy Spegel.
6 |
7 | ## Values
8 |
9 | | Key | Type | Default | Description |
10 | |-----|------|---------|-------------|
11 | | affinity | object | `{}` | Affinity settings for pod assignment. |
12 | | basicAuthSecretName | string | `""` | Name of secret containing basic authentication credentials for registry. |
13 | | clusterDomain | string | `"cluster.local."` | Domain configured for service domain names. |
14 | | commonLabels | object | `{}` | Common labels to apply to all rendered resources. |
15 | | fullnameOverride | string | `""` | Overrides the full name of the chart. |
16 | | grafanaDashboard.annotations | object | `{}` | Annotations that ConfigMaps can have to get configured in Grafana, See: sidecar.dashboards.folderAnnotation for specifying the dashboard folder. https://github.com/grafana/helm-charts/tree/main/charts/grafana |
17 | | grafanaDashboard.enabled | bool | `false` | If true creates a Grafana dashboard. |
18 | | grafanaDashboard.sidecarLabel | string | `"grafana_dashboard"` | Label that ConfigMaps should have to be loaded as dashboards. |
19 | | grafanaDashboard.sidecarLabelValue | string | `"1"` | Label value that ConfigMaps should have to be loaded as dashboards. |
20 | | image.digest | string | `""` | Image digest. |
21 | | image.pullPolicy | string | `"IfNotPresent"` | Image Pull Policy. |
22 | | image.repository | string | `"ghcr.io/spegel-org/spegel"` | Image repository. |
23 | | image.tag | string | `""` | Overrides the image tag whose default is the chart appVersion. |
24 | | imagePullSecrets | list | `[]` | Image Pull Secrets |
25 | | nameOverride | string | `""` | Overrides the name of the chart. |
26 | | namespaceOverride | string | `""` | Overrides the namespace where spegel resources are installed. |
27 | | nodeSelector | object | `{"kubernetes.io/os":"linux"}` | Node selector for pod assignment. |
28 | | podAnnotations | object | `{}` | Annotations to add to the pod. |
29 | | podSecurityContext | object | `{}` | Security context for the pod. |
30 | | priorityClassName | string | `"system-node-critical"` | Priority class name to use for the pod. |
31 | | resources | object | `{"limits":{"memory":"128Mi"},"requests":{"memory":"128Mi"}}` | Resource requests and limits for the Spegel container. |
32 | | revisionHistoryLimit | int | `10` | The number of old history to retain to allow rollback. |
33 | | securityContext | object | `{}` | Security context for the Spegel container. |
34 | | service.cleanup.port | int | `8080` | Port to expose cleanup probe on. |
35 | | service.metrics.port | int | `9090` | Port to expose the metrics via the service. |
36 | | service.registry.hostPort | int | `30020` | Local host port to expose the registry. |
37 | | service.registry.nodeIp | string | `""` | Override the NODE_ID environment variable. It defaults to the field status.hostIP |
38 | | service.registry.nodePort | int | `30021` | Node port to expose the registry via the service. |
39 | | service.registry.port | int | `5000` | Port to expose the registry via the service. |
40 | | service.registry.topologyAwareHintsEnabled | bool | `true` | If true adds topology aware hints annotation to node port service. |
41 | | service.router.port | int | `5001` | Port to expose the router via the service. |
42 | | serviceAccount.annotations | object | `{}` | Annotations to add to the service account |
43 | | serviceAccount.name | string | `""` | The name of the service account to use. If not set and create is true, a name is generated using the fullname template. |
44 | | serviceMonitor.enabled | bool | `false` | If true creates a Prometheus Service Monitor. |
45 | | serviceMonitor.interval | string | `"60s"` | Prometheus scrape interval. |
46 | | serviceMonitor.labels | object | `{}` | Service monitor specific labels for prometheus to discover servicemonitor. |
47 | | serviceMonitor.metricRelabelings | list | `[]` | List of relabeling rules to apply to the samples before ingestion. |
48 | | serviceMonitor.relabelings | list | `[]` | List of relabeling rules to apply the target’s metadata labels. |
49 | | serviceMonitor.scrapeTimeout | string | `"30s"` | Prometheus scrape interval timeout. |
50 | | spegel.additionalMirrorTargets | list | `[]` | Additional target mirror registries other than Spegel. |
51 | | spegel.containerdContentPath | string | `"/var/lib/containerd/io.containerd.content.v1.content"` | Path to Containerd content store.. |
52 | | spegel.containerdMirrorAdd | bool | `true` | If true Spegel will add mirror configuration to the node. |
53 | | spegel.containerdNamespace | string | `"k8s.io"` | Containerd namespace where images are stored. |
54 | | spegel.containerdRegistryConfigPath | string | `"/etc/containerd/certs.d"` | Path to Containerd mirror configuration. |
55 | | spegel.containerdSock | string | `"/run/containerd/containerd.sock"` | Path to Containerd socket. |
56 | | spegel.debugWebEnabled | bool | `false` | When true enables debug web page. |
57 | | spegel.logLevel | string | `"INFO"` | Minimum log level to output. Value should be DEBUG, INFO, WARN, or ERROR. |
58 | | spegel.mirrorResolveRetries | int | `3` | Max amount of mirrors to attempt. |
59 | | spegel.mirrorResolveTimeout | string | `"20ms"` | Max duration spent finding a mirror. |
60 | | spegel.mirroredRegistries | list | `[]` | Registries for which mirror configuration will be created. Empty means all registires will be mirrored. |
61 | | spegel.prependExisting | bool | `false` | When true existing mirror configuration will be kept and Spegel will prepend it's configuration. |
62 | | spegel.resolveLatestTag | bool | `true` | When true latest tags will be resolved to digests. |
63 | | spegel.resolveTags | bool | `true` | When true Spegel will resolve tags to digests. |
64 | | tolerations | list | `[{"key":"CriticalAddonsOnly","operator":"Exists"},{"effect":"NoExecute","operator":"Exists"},{"effect":"NoSchedule","operator":"Exists"}]` | Tolerations for pod assignment. |
65 | | updateStrategy | object | `{}` | An update strategy to replace existing pods with new pods. |
66 | | verticalPodAutoscaler.controlledResources | list | `[]` | List of resources that the vertical pod autoscaler can control. Defaults to cpu and memory |
67 | | verticalPodAutoscaler.controlledValues | string | `"RequestsAndLimits"` | Specifies which resource values should be controlled: RequestsOnly or RequestsAndLimits. |
68 | | verticalPodAutoscaler.enabled | bool | `false` | If true creates a Vertical Pod Autoscaler. |
69 | | verticalPodAutoscaler.maxAllowed | object | `{}` | Define the max allowed resources for the pod |
70 | | verticalPodAutoscaler.minAllowed | object | `{}` | Define the min allowed resources for the pod |
71 | | verticalPodAutoscaler.recommenders | list | `[]` | Recommender responsible for generating recommendation for the object. List should be empty (then the default recommender will generate the recommendation) or contain exactly one recommender. |
72 | | verticalPodAutoscaler.updatePolicy.minReplicas | int | `2` | Specifies minimal number of replicas which need to be alive for VPA Updater to attempt pod eviction |
73 | | verticalPodAutoscaler.updatePolicy.updateMode | string | `"Auto"` | Specifies whether recommended updates are applied when a Pod is started and whether recommended updates are applied during the life of a Pod. Possible values are "Off", "Initial", "Recreate", and "Auto". |
74 |
--------------------------------------------------------------------------------
/charts/spegel/README.md.gotmpl:
--------------------------------------------------------------------------------
1 | # Spegel
2 |
3 | {{ template "chart.description" . }}
4 |
5 | Read the [getting started](https://spegel.dev/docs/getting-started/) guide to deploy Spegel.
6 |
7 | {{ template "chart.valuesSection" . }}
8 |
--------------------------------------------------------------------------------
/charts/spegel/artifacthub-repo.yml:
--------------------------------------------------------------------------------
1 | repositoryID: 8122016b-c465-4eaf-be87-f51423aa76f1
2 | owners:
3 | - name: Philip Laine
4 | email: philip.laine@gmail.com
5 |
--------------------------------------------------------------------------------
/charts/spegel/templates/_helpers.tpl:
--------------------------------------------------------------------------------
1 | {{/*
2 | Expand the name of the chart.
3 | */}}
4 | {{- define "spegel.name" -}}
5 | {{- default .Chart.Name .Values.nameOverride | trunc 63 | trimSuffix "-" }}
6 | {{- end }}
7 |
8 | {{/*
9 | Create a default fully qualified app name.
10 | We truncate at 63 chars because some Kubernetes name fields are limited to this (by the DNS naming spec).
11 | If release name contains chart name it will be used as a full name.
12 | */}}
13 | {{- define "spegel.fullname" -}}
14 | {{- if .Values.fullnameOverride }}
15 | {{- .Values.fullnameOverride | trunc 63 | trimSuffix "-" }}
16 | {{- else }}
17 | {{- $name := default .Chart.Name .Values.nameOverride }}
18 | {{- if contains $name .Release.Name }}
19 | {{- .Release.Name | trunc 63 | trimSuffix "-" }}
20 | {{- else }}
21 | {{- printf "%s-%s" .Release.Name $name | trunc 63 | trimSuffix "-" }}
22 | {{- end }}
23 | {{- end }}
24 | {{- end }}
25 |
26 | {{/*
27 | Creates the namespace for the chart.
28 | Defaults to the Release namespace unless the namespaceOverride is defined.
29 | */}}
30 | {{- define "spegel.namespace" -}}
31 | {{- if .Values.namespaceOverride }}
32 | {{- printf "%s" .Values.namespaceOverride -}}
33 | {{- else }}
34 | {{- printf "%s" .Release.Namespace -}}
35 | {{- end }}
36 | {{- end }}
37 |
38 |
39 | {{/*
40 | Create chart name and version as used by the chart label.
41 | */}}
42 | {{- define "spegel.chart" -}}
43 | {{- printf "%s-%s" .Chart.Name .Chart.Version | replace "+" "_" | trunc 63 | trimSuffix "-" }}
44 | {{- end }}
45 |
46 | {{/*
47 | Common labels
48 | */}}
49 | {{- define "spegel.labels" -}}
50 | helm.sh/chart: {{ include "spegel.chart" . }}
51 | {{ include "spegel.selectorLabels" . }}
52 | {{- if .Chart.AppVersion }}
53 | app.kubernetes.io/version: {{ .Chart.AppVersion | quote }}
54 | {{- end }}
55 | app.kubernetes.io/managed-by: {{ .Release.Service }}
56 | {{- with .Values.commonLabels }}
57 | {{ toYaml . }}
58 | {{- end }}
59 | {{- end }}
60 |
61 | {{/*
62 | {{- end }}
63 | {{- end }}
64 |
65 | {{/*
66 | Selector labels
67 | */}}
68 | {{- define "spegel.selectorLabels" -}}
69 | app.kubernetes.io/name: {{ include "spegel.name" . }}
70 | app.kubernetes.io/instance: {{ .Release.Name }}
71 | {{- end }}
72 |
73 | {{/*
74 | Create the name of the service account to use
75 | */}}
76 | {{- define "spegel.serviceAccountName" -}}
77 | {{- default (include "spegel.fullname" .) .Values.serviceAccount.name }}
78 | {{- end }}
79 |
80 | {{/*
81 | Image reference
82 | */}}
83 | {{- define "spegel.image" -}}
84 | {{- if .Values.image.digest }}
85 | {{- .Values.image.repository }}@{{ .Values.image.digest }}
86 | {{- else }}
87 | {{- .Values.image.repository }}:{{ .Values.image.tag | default .Chart.AppVersion }}
88 | {{- end }}
89 | {{- end }}
90 |
91 | {{/*
92 | Host networking
93 | */}}
94 | {{- define "networking.nodeIp" -}}
95 | {{- if .Values.service.registry.nodeIp -}}
96 | value: {{ .Values.service.registry.nodeIp }}
97 | {{- else -}}
98 | valueFrom:
99 | fieldRef:
100 | fieldPath: status.hostIP
101 | {{- end -}}
102 | {{- end -}}
103 |
--------------------------------------------------------------------------------
/charts/spegel/templates/daemonset.yaml:
--------------------------------------------------------------------------------
1 | apiVersion: apps/v1
2 | kind: DaemonSet
3 | metadata:
4 | name: {{ include "spegel.fullname" . }}
5 | namespace: {{ include "spegel.namespace" . }}
6 | labels:
7 | {{- include "spegel.labels" . | nindent 4 }}
8 | spec:
9 | revisionHistoryLimit: {{ .Values.revisionHistoryLimit }}
10 | updateStrategy:
11 | {{- toYaml .Values.updateStrategy | nindent 4 }}
12 | selector:
13 | matchLabels:
14 | {{- include "spegel.selectorLabels" . | nindent 6 }}
15 | template:
16 | metadata:
17 | {{- with .Values.podAnnotations }}
18 | annotations:
19 | {{- toYaml . | nindent 8 }}
20 | {{- end }}
21 | labels:
22 | {{- include "spegel.selectorLabels" . | nindent 8 }}
23 | {{- with .Values.commonLabels }}
24 | {{- toYaml . | nindent 8 }}
25 | {{- end }}
26 | spec:
27 | {{- with .Values.imagePullSecrets }}
28 | imagePullSecrets:
29 | {{- toYaml . | nindent 8 }}
30 | {{- end }}
31 | serviceAccountName: {{ include "spegel.serviceAccountName" . }}
32 | securityContext:
33 | {{- toYaml .Values.podSecurityContext | nindent 8 }}
34 | priorityClassName: {{ .Values.priorityClassName }}
35 | {{- if .Values.spegel.containerdMirrorAdd }}
36 | initContainers:
37 | - name: configuration
38 | image: "{{ include "spegel.image" . }}"
39 | imagePullPolicy: {{ .Values.image.pullPolicy }}
40 | securityContext:
41 | {{- toYaml .Values.securityContext | nindent 12 }}
42 | args:
43 | - configuration
44 | - --log-level={{ .Values.spegel.logLevel }}
45 | - --containerd-registry-config-path={{ .Values.spegel.containerdRegistryConfigPath }}
46 | {{- with .Values.spegel.mirroredRegistries }}
47 | - --mirrored-registries
48 | {{- range . }}
49 | - {{ . | quote }}
50 | {{- end }}
51 | {{- end }}
52 | - --mirror-targets
53 | - http://$(NODE_IP):{{ .Values.service.registry.hostPort }}
54 | - http://$(NODE_IP):{{ .Values.service.registry.nodePort }}
55 | {{- with .Values.spegel.additionalMirrorTargets }}
56 | {{- range . }}
57 | - {{ . | quote }}
58 | {{- end }}
59 | {{- end }}
60 | - --resolve-tags={{ .Values.spegel.resolveTags }}
61 | - --prepend-existing={{ .Values.spegel.prependExisting }}
62 | env:
63 | - name: NODE_IP
64 | {{- include "networking.nodeIp" . | nindent 10 }}
65 | resources:
66 | {{- toYaml .Values.resources | nindent 10 }}
67 | volumeMounts:
68 | - name: containerd-config
69 | mountPath: {{ .Values.spegel.containerdRegistryConfigPath }}
70 | {{- if .Values.basicAuthSecretName }}
71 | - name: basic-auth
72 | mountPath: "/etc/secrets/basic-auth"
73 | readOnly: true
74 | {{- end }}
75 | {{- end }}
76 | containers:
77 | - name: registry
78 | image: "{{ include "spegel.image" . }}"
79 | imagePullPolicy: {{ .Values.image.pullPolicy }}
80 | securityContext:
81 | {{- toYaml .Values.securityContext | nindent 12 }}
82 | args:
83 | - registry
84 | - --log-level={{ .Values.spegel.logLevel }}
85 | - --mirror-resolve-retries={{ .Values.spegel.mirrorResolveRetries }}
86 | - --mirror-resolve-timeout={{ .Values.spegel.mirrorResolveTimeout }}
87 | - --registry-addr=:{{ .Values.service.registry.port }}
88 | - --router-addr=:{{ .Values.service.router.port }}
89 | - --metrics-addr=:{{ .Values.service.metrics.port }}
90 | {{- with .Values.spegel.mirroredRegistries }}
91 | - --mirrored-registries
92 | {{- range . }}
93 | - {{ . | quote }}
94 | {{- end }}
95 | {{- end }}
96 | - --containerd-sock={{ .Values.spegel.containerdSock }}
97 | - --containerd-namespace={{ .Values.spegel.containerdNamespace }}
98 | - --containerd-registry-config-path={{ .Values.spegel.containerdRegistryConfigPath }}
99 | - --bootstrap-kind=dns
100 | - --dns-bootstrap-domain={{ include "spegel.fullname" . }}-bootstrap.{{ include "spegel.namespace" . }}.svc.{{ .Values.clusterDomain }}
101 | - --resolve-latest-tag={{ .Values.spegel.resolveLatestTag }}
102 | {{- with .Values.spegel.containerdContentPath }}
103 | - --containerd-content-path={{ . }}
104 | {{- end }}
105 | - --debug-web-enabled={{ .Values.spegel.debugWebEnabled }}
106 | env:
107 | {{- if ((.Values.resources).limits).cpu }}
108 | - name: GOMAXPROCS
109 | valueFrom:
110 | resourceFieldRef:
111 | resource: limits.cpu
112 | divisor: 1
113 | {{- end }}
114 | {{- if ((.Values.resources).limits).memory }}
115 | - name: GOMEMLIMIT
116 | valueFrom:
117 | resourceFieldRef:
118 | resource: limits.memory
119 | divisor: 1
120 | {{- end }}
121 | - name: NODE_IP
122 | {{- include "networking.nodeIp" . | nindent 10 }}
123 | ports:
124 | - name: registry
125 | containerPort: {{ .Values.service.registry.port }}
126 | hostPort: {{ .Values.service.registry.hostPort }}
127 | protocol: TCP
128 | - name: router
129 | containerPort: {{ .Values.service.router.port }}
130 | protocol: TCP
131 | - name: metrics
132 | containerPort: {{ .Values.service.metrics.port }}
133 | protocol: TCP
134 | # Startup may take a bit longer on bootsrap as Pods need to find each other.
135 | # This is why the startup proben is a bit more forgiving, while hitting the endpoint more often.
136 | startupProbe:
137 | periodSeconds: 3
138 | failureThreshold: 60
139 | httpGet:
140 | path: /healthz
141 | port: registry
142 | readinessProbe:
143 | httpGet:
144 | path: /healthz
145 | port: registry
146 | volumeMounts:
147 | {{- if .Values.basicAuthSecretName }}
148 | - name: basic-auth
149 | mountPath: "/etc/secrets/basic-auth"
150 | readOnly: true
151 | {{- end }}
152 | - name: containerd-sock
153 | mountPath: {{ .Values.spegel.containerdSock }}
154 | {{- with .Values.spegel.containerdContentPath }}
155 | - name: containerd-content
156 | mountPath: {{ . }}
157 | readOnly: true
158 | {{- end }}
159 | resources:
160 | {{- toYaml .Values.resources | nindent 10 }}
161 | volumes:
162 | {{- with .Values.basicAuthSecretName }}
163 | - name: basic-auth
164 | secret:
165 | secretName: {{ . }}
166 | {{- end }}
167 | - name: containerd-sock
168 | hostPath:
169 | path: {{ .Values.spegel.containerdSock }}
170 | type: Socket
171 | {{- with .Values.spegel.containerdContentPath }}
172 | - name: containerd-content
173 | hostPath:
174 | path: {{ . }}
175 | type: Directory
176 | {{- end }}
177 | {{- if .Values.spegel.containerdMirrorAdd }}
178 | - name: containerd-config
179 | hostPath:
180 | path: {{ .Values.spegel.containerdRegistryConfigPath }}
181 | type: DirectoryOrCreate
182 | {{- end }}
183 | {{- with .Values.nodeSelector }}
184 | nodeSelector:
185 | {{- toYaml . | nindent 8 }}
186 | {{- end }}
187 | {{- with .Values.affinity }}
188 | affinity:
189 | {{- toYaml . | nindent 8 }}
190 | {{- end }}
191 | {{- with .Values.tolerations }}
192 | tolerations:
193 | {{- toYaml . | nindent 8 }}
194 | {{- end }}
195 |
--------------------------------------------------------------------------------
/charts/spegel/templates/grafana-dashboard.yaml:
--------------------------------------------------------------------------------
1 | {{- if .Values.grafanaDashboard.enabled }}
2 | apiVersion: v1
3 | kind: ConfigMap
4 | metadata:
5 | name: {{ include "spegel.fullname" . }}-dashboard
6 | namespace: {{ include "spegel.namespace" . }}
7 | labels:
8 | {{ .Values.grafanaDashboard.sidecarLabel }}: {{ .Values.grafanaDashboard.sidecarLabelValue | quote }}
9 | {{- include "spegel.labels" . | nindent 4 }}
10 | {{- with .Values.grafanaDashboard.annotations }}
11 | annotations:
12 | {{- toYaml . | nindent 4 }}
13 | {{- end }}
14 | data:
15 | spegel.json: |-
16 | {{ .Files.Get "monitoring/grafana-dashboard.json" | indent 6 }}
17 | {{- end }}
18 |
--------------------------------------------------------------------------------
/charts/spegel/templates/post-delete-hook.yaml:
--------------------------------------------------------------------------------
1 | {{- if .Values.spegel.containerdMirrorAdd }}
2 | apiVersion: apps/v1
3 | kind: DaemonSet
4 | metadata:
5 | name: {{ include "spegel.fullname" . }}-cleanup
6 | namespace: {{ include "spegel.namespace" . }}
7 | labels:
8 | app.kubernetes.io/component: cleanup
9 | {{- include "spegel.labels" . | nindent 4 }}
10 | annotations:
11 | helm.sh/hook: "post-delete"
12 | helm.sh/hook-delete-policy: "before-hook-creation, hook-succeeded"
13 | helm.sh/hook-weight: "0"
14 | spec:
15 | selector:
16 | matchLabels:
17 | app.kubernetes.io/component: cleanup
18 | {{- include "spegel.selectorLabels" . | nindent 6 }}
19 | template:
20 | metadata:
21 | labels:
22 | app.kubernetes.io/component: cleanup
23 | {{- include "spegel.selectorLabels" . | nindent 8 }}
24 | spec:
25 | {{- with .Values.imagePullSecrets }}
26 | imagePullSecrets:
27 | {{- toYaml . | nindent 8 }}
28 | {{- end }}
29 | securityContext:
30 | {{- toYaml .Values.podSecurityContext | nindent 8 }}
31 | priorityClassName: {{ .Values.priorityClassName }}
32 | containers:
33 | - name: cleanup
34 | image: "{{ include "spegel.image" . }}"
35 | imagePullPolicy: {{ .Values.image.pullPolicy }}
36 | args:
37 | - cleanup
38 | - --containerd-registry-config-path={{ .Values.spegel.containerdRegistryConfigPath }}
39 | - --addr=:{{ .Values.service.cleanup.port }}
40 | readinessProbe:
41 | httpGet:
42 | path: /healthz
43 | port: readiness
44 | ports:
45 | - name: readiness
46 | containerPort: {{ .Values.service.cleanup.port }}
47 | protocol: TCP
48 | volumeMounts:
49 | - name: containerd-config
50 | mountPath: {{ .Values.spegel.containerdRegistryConfigPath }}
51 | volumes:
52 | - name: containerd-config
53 | hostPath:
54 | path: {{ .Values.spegel.containerdRegistryConfigPath }}
55 | type: DirectoryOrCreate
56 | {{- with .Values.tolerations }}
57 | tolerations:
58 | {{- toYaml . | nindent 8 }}
59 | {{- end }}
60 | ---
61 | apiVersion: v1
62 | kind: Service
63 | metadata:
64 | name: {{ include "spegel.fullname" . }}-cleanup
65 | namespace: {{ include "spegel.namespace" . }}
66 | labels:
67 | app.kubernetes.io/component: cleanup
68 | {{- include "spegel.labels" . | nindent 4 }}
69 | annotations:
70 | helm.sh/hook: "post-delete"
71 | helm.sh/hook-delete-policy: "before-hook-creation, hook-succeeded"
72 | helm.sh/hook-weight: "0"
73 | spec:
74 | selector:
75 | app.kubernetes.io/component: cleanup
76 | {{- include "spegel.selectorLabels" . | nindent 4 }}
77 | clusterIP: None
78 | publishNotReadyAddresses: true
79 | ports:
80 | - name: readiness
81 | port: {{ .Values.service.cleanup.port }}
82 | protocol: TCP
83 | ---
84 | apiVersion: v1
85 | kind: Pod
86 | metadata:
87 | name: {{ include "spegel.fullname" . }}-cleanup-wait
88 | namespace: {{ include "spegel.namespace" . }}
89 | labels:
90 | app.kubernetes.io/component: cleanup-wait
91 | {{- include "spegel.labels" . | nindent 4 }}
92 | annotations:
93 | helm.sh/hook: "post-delete"
94 | helm.sh/hook-delete-policy: "before-hook-creation, hook-succeeded"
95 | helm.sh/hook-weight: "1"
96 | spec:
97 | containers:
98 | - name: cleanup-wait
99 | image: "{{ include "spegel.image" . }}"
100 | imagePullPolicy: {{ .Values.image.pullPolicy }}
101 | args:
102 | - cleanup-wait
103 | - --probe-endpoint={{ include "spegel.fullname" . }}-cleanup.{{ include "spegel.namespace" . }}.svc.{{ .Values.clusterDomain }}:{{ .Values.service.cleanup.port }}
104 | restartPolicy: Never
105 | terminationGracePeriodSeconds: 0
106 | {{- end }}
107 |
--------------------------------------------------------------------------------
/charts/spegel/templates/rbac.yaml:
--------------------------------------------------------------------------------
1 | apiVersion: v1
2 | kind: ServiceAccount
3 | metadata:
4 | name: {{ include "spegel.serviceAccountName" . }}
5 | namespace: {{ include "spegel.namespace" . }}
6 | labels:
7 | {{- include "spegel.labels" . | nindent 4 }}
8 | {{- with .Values.serviceAccount.annotations }}
9 | annotations:
10 | {{- toYaml . | nindent 4 }}
11 | {{- end }}
12 |
--------------------------------------------------------------------------------
/charts/spegel/templates/service.yaml:
--------------------------------------------------------------------------------
1 | apiVersion: v1
2 | kind: Service
3 | metadata:
4 | name: {{ include "spegel.fullname" . }}
5 | namespace: {{ include "spegel.namespace" . }}
6 | labels:
7 | app.kubernetes.io/component: metrics
8 | {{- include "spegel.labels" . | nindent 4 }}
9 | spec:
10 | selector:
11 | {{- include "spegel.selectorLabels" . | nindent 4 }}
12 | ports:
13 | - name: metrics
14 | port: {{ .Values.service.metrics.port }}
15 | targetPort: metrics
16 | protocol: TCP
17 | ---
18 | apiVersion: v1
19 | kind: Service
20 | metadata:
21 | name: {{ include "spegel.fullname" . }}-registry
22 | namespace: {{ include "spegel.namespace" . }}
23 | labels:
24 | {{- include "spegel.labels" . | nindent 4 }}
25 | {{- if .Values.service.registry.topologyAwareHintsEnabled }}
26 | annotations:
27 | service.kubernetes.io/topology-mode: "auto"
28 | {{- end }}
29 | spec:
30 | type: NodePort
31 | selector:
32 | {{- include "spegel.selectorLabels" . | nindent 4 }}
33 | ports:
34 | - name: registry
35 | port: {{ .Values.service.registry.port }}
36 | targetPort: registry
37 | nodePort: {{ .Values.service.registry.nodePort }}
38 | protocol: TCP
39 | ---
40 | apiVersion: v1
41 | kind: Service
42 | metadata:
43 | name: {{ include "spegel.fullname" . }}-bootstrap
44 | namespace: {{ include "spegel.namespace" . }}
45 | labels:
46 | {{- include "spegel.labels" . | nindent 4 }}
47 | spec:
48 | selector:
49 | {{- include "spegel.selectorLabels" . | nindent 4 }}
50 | clusterIP: None
51 | publishNotReadyAddresses: true
52 | ports:
53 | - name: router
54 | port: {{ .Values.service.router.port }}
55 | protocol: TCP
56 |
--------------------------------------------------------------------------------
/charts/spegel/templates/servicemonitor.yaml:
--------------------------------------------------------------------------------
1 | {{- if .Values.serviceMonitor.enabled }}
2 | apiVersion: monitoring.coreos.com/v1
3 | kind: ServiceMonitor
4 | metadata:
5 | name: {{ include "spegel.fullname" . }}
6 | namespace: {{ include "spegel.namespace" . }}
7 | labels:
8 | {{- include "spegel.labels" . | nindent 4 }}
9 | {{- if .Values.serviceMonitor.labels -}}
10 | {{ toYaml .Values.serviceMonitor.labels | nindent 4}}
11 | {{- end }}
12 | spec:
13 | selector:
14 | matchLabels:
15 | app.kubernetes.io/component: metrics
16 | {{- include "spegel.selectorLabels" . | nindent 6 }}
17 | endpoints:
18 | - port: metrics
19 | interval: {{ .Values.serviceMonitor.interval }}
20 | scrapeTimeout: {{ .Values.serviceMonitor.scrapeTimeout }}
21 | {{- with .Values.serviceMonitor.relabelings }}
22 | relabelings:
23 | {{- toYaml . | nindent 8 }}
24 | {{- end }}
25 | {{- with .Values.serviceMonitor.metricRelabelings }}
26 | metricRelabelings:
27 | {{- toYaml . | nindent 8 }}
28 | {{- end }}
29 | {{- end }}
30 |
--------------------------------------------------------------------------------
/charts/spegel/templates/verticalpodautoscaler.yaml:
--------------------------------------------------------------------------------
1 | {{- if and (.Capabilities.APIVersions.Has "autoscaling.k8s.io/v1") (.Values.verticalPodAutoscaler.enabled) }}
2 | apiVersion: autoscaling.k8s.io/v1
3 | kind: VerticalPodAutoscaler
4 | metadata:
5 | name: {{ include "spegel.fullname" . }}
6 | namespace: {{ include "spegel.namespace" . }}
7 | labels:
8 | {{- include "spegel.labels" . | nindent 4 }}
9 | spec:
10 | {{- with .Values.verticalPodAutoscaler.recommenders }}
11 | recommenders:
12 | {{- toYaml . | nindent 4 }}
13 | {{- end }}
14 | resourcePolicy:
15 | containerPolicies:
16 | - containerName: registry
17 | {{- with .Values.verticalPodAutoscaler.controlledResources }}
18 | controlledResources:
19 | {{- toYaml . | nindent 8 }}
20 | {{- end }}
21 | {{- if .Values.verticalPodAutoscaler.controlledValues }}
22 | controlledValues: {{ .Values.verticalPodAutoscaler.controlledValues }}
23 | {{- end }}
24 | {{- if .Values.verticalPodAutoscaler.maxAllowed }}
25 | maxAllowed:
26 | {{- toYaml .Values.verticalPodAutoscaler.maxAllowed | nindent 8 }}
27 | {{- end }}
28 | {{- if .Values.verticalPodAutoscaler.minAllowed }}
29 | minAllowed:
30 | {{- toYaml .Values.verticalPodAutoscaler.minAllowed | nindent 8 }}
31 | {{- end }}
32 | targetRef:
33 | apiVersion: apps/v1
34 | kind: DaemonSet
35 | name: {{ include "spegel.fullname" . }}
36 | {{- with .Values.verticalPodAutoscaler.updatePolicy }}
37 | updatePolicy:
38 | {{- toYaml . | nindent 4 }}
39 | {{- end }}
40 | {{- end }}
41 |
--------------------------------------------------------------------------------
/charts/spegel/values.yaml:
--------------------------------------------------------------------------------
1 | image:
2 | # -- Image repository.
3 | repository: ghcr.io/spegel-org/spegel
4 | # -- Image Pull Policy.
5 | pullPolicy: IfNotPresent
6 | # -- Overrides the image tag whose default is the chart appVersion.
7 | tag: ""
8 | # -- Image digest.
9 | digest: ""
10 |
11 | # -- Image Pull Secrets
12 | imagePullSecrets: []
13 | # -- Overrides the name of the chart.
14 | nameOverride: ""
15 | # -- Overrides the full name of the chart.
16 | fullnameOverride: ""
17 | # -- Overrides the namespace where spegel resources are installed.
18 | namespaceOverride: ""
19 |
20 | serviceAccount:
21 | # -- Annotations to add to the service account
22 | annotations: {}
23 | # -- The name of the service account to use.
24 | # If not set and create is true, a name is generated using the fullname template.
25 | name: ""
26 |
27 | # -- Annotations to add to the pod.
28 | podAnnotations: {}
29 |
30 | # -- Security context for the pod.
31 | podSecurityContext: {}
32 | # fsGroup: 2000
33 |
34 | # -- The number of old history to retain to allow rollback.
35 | revisionHistoryLimit: 10
36 |
37 | # -- Security context for the Spegel container.
38 | securityContext: {}
39 | # capabilities:
40 | # drop:
41 | # - ALL
42 | # readOnlyRootFilesystem: true
43 | # runAsNonRoot: true
44 | # runAsUser: 1000
45 |
46 | service:
47 | registry:
48 | # -- Override the NODE_ID environment variable. It defaults to the field status.hostIP
49 | nodeIp: ""
50 | # -- Port to expose the registry via the service.
51 | port: 5000
52 | # -- Node port to expose the registry via the service.
53 | nodePort: 30021
54 | # -- Local host port to expose the registry.
55 | hostPort: 30020
56 | # -- If true adds topology aware hints annotation to node port service.
57 | topologyAwareHintsEnabled: true
58 | router:
59 | # -- Port to expose the router via the service.
60 | port: 5001
61 | metrics:
62 | # -- Port to expose the metrics via the service.
63 | port: 9090
64 | cleanup:
65 | # -- Port to expose cleanup probe on.
66 | port: 8080
67 |
68 | # -- Resource requests and limits for the Spegel container.
69 | resources:
70 | requests:
71 | memory: 128Mi
72 | limits:
73 | memory: 128Mi
74 |
75 | # -- Node selector for pod assignment.
76 | nodeSelector:
77 | kubernetes.io/os: linux
78 |
79 | # -- An update strategy to replace existing pods with new pods.
80 | updateStrategy: {}
81 | # type: RollingUpdate
82 | # rollingUpdate:
83 | # maxSurge: 0
84 | # maxUnavailable: 1
85 |
86 | # -- Tolerations for pod assignment.
87 | tolerations:
88 | - key: CriticalAddonsOnly
89 | operator: Exists
90 | - effect: NoExecute
91 | operator: Exists
92 | - effect: NoSchedule
93 | operator: Exists
94 |
95 | # -- Affinity settings for pod assignment.
96 | affinity: {}
97 |
98 | # -- Common labels to apply to all rendered resources.
99 | commonLabels: {}
100 |
101 | # -- Domain configured for service domain names.
102 | clusterDomain: cluster.local.
103 |
104 | serviceMonitor:
105 | # -- If true creates a Prometheus Service Monitor.
106 | enabled: false
107 | # -- Prometheus scrape interval.
108 | interval: 60s
109 | # -- Prometheus scrape interval timeout.
110 | scrapeTimeout: 30s
111 | # -- Service monitor specific labels for prometheus to discover servicemonitor.
112 | labels: {}
113 | # -- List of relabeling rules to apply the target’s metadata labels.
114 | relabelings: []
115 | # -- List of relabeling rules to apply to the samples before ingestion.
116 | metricRelabelings: []
117 |
118 | grafanaDashboard:
119 | # -- If true creates a Grafana dashboard.
120 | enabled: false
121 | # -- Label that ConfigMaps should have to be loaded as dashboards.
122 | sidecarLabel: "grafana_dashboard"
123 | # -- Label value that ConfigMaps should have to be loaded as dashboards.
124 | sidecarLabelValue: "1"
125 | # -- Annotations that ConfigMaps can have to get configured in Grafana,
126 | # See: sidecar.dashboards.folderAnnotation for specifying the dashboard folder.
127 | # https://github.com/grafana/helm-charts/tree/main/charts/grafana
128 | annotations: {}
129 |
130 | # -- Priority class name to use for the pod.
131 | priorityClassName: system-node-critical
132 |
133 | # -- Name of secret containing basic authentication credentials for registry.
134 | basicAuthSecretName: ""
135 |
136 | spegel:
137 | # -- Minimum log level to output. Value should be DEBUG, INFO, WARN, or ERROR.
138 | logLevel: "INFO"
139 | # -- Registries for which mirror configuration will be created. Empty means all registires will be mirrored.
140 | mirroredRegistries: []
141 | # - https://docker.io
142 | # - https://ghcr.io
143 | # -- Additional target mirror registries other than Spegel.
144 | additionalMirrorTargets: []
145 | # -- Max amount of mirrors to attempt.
146 | mirrorResolveRetries: 3
147 | # -- Max duration spent finding a mirror.
148 | mirrorResolveTimeout: "20ms"
149 | # -- Path to Containerd socket.
150 | containerdSock: "/run/containerd/containerd.sock"
151 | # -- Containerd namespace where images are stored.
152 | containerdNamespace: "k8s.io"
153 | # -- Path to Containerd mirror configuration.
154 | containerdRegistryConfigPath: "/etc/containerd/certs.d"
155 | # -- Path to Containerd content store..
156 | containerdContentPath: "/var/lib/containerd/io.containerd.content.v1.content"
157 | # -- If true Spegel will add mirror configuration to the node.
158 | containerdMirrorAdd: true
159 | # -- When true Spegel will resolve tags to digests.
160 | resolveTags: true
161 | # -- When true latest tags will be resolved to digests.
162 | resolveLatestTag: true
163 | # -- When true existing mirror configuration will be kept and Spegel will prepend it's configuration.
164 | prependExisting: false
165 | # -- When true enables debug web page.
166 | debugWebEnabled: false
167 |
168 | verticalPodAutoscaler:
169 | # -- If true creates a Vertical Pod Autoscaler.
170 | enabled: false
171 |
172 | # -- Recommender responsible for generating recommendation for the object.
173 | # List should be empty (then the default recommender will generate the recommendation)
174 | # or contain exactly one recommender.
175 | recommenders: []
176 | # - name: custom-recommender-performance
177 |
178 | # -- List of resources that the vertical pod autoscaler can control. Defaults to cpu and memory
179 | controlledResources: []
180 | # -- Specifies which resource values should be controlled: RequestsOnly or RequestsAndLimits.
181 | controlledValues: RequestsAndLimits
182 |
183 | # -- Define the max allowed resources for the pod
184 | maxAllowed: {}
185 | # cpu: 100m
186 | # memory: 128Mi
187 | # -- Define the min allowed resources for the pod
188 | minAllowed: {}
189 | # cpu: 100m
190 | # memory: 128Mi
191 |
192 | updatePolicy:
193 | # -- Specifies minimal number of replicas which need to be alive for VPA Updater to attempt pod eviction
194 | minReplicas: 2
195 |
196 | # -- Specifies whether recommended updates are applied when a Pod is started and whether recommended updates
197 | # are applied during the life of a Pod. Possible values are "Off", "Initial", "Recreate", and "Auto".
198 | updateMode: Auto
199 |
--------------------------------------------------------------------------------
/go.mod:
--------------------------------------------------------------------------------
1 | module github.com/spegel-org/spegel
2 |
3 | go 1.24.2
4 |
5 | require (
6 | github.com/alexflint/go-arg v1.5.1
7 | github.com/containerd/containerd/api v1.9.0
8 | github.com/containerd/containerd/v2 v2.1.1
9 | github.com/containerd/errdefs v1.0.0
10 | github.com/containerd/typeurl/v2 v2.2.3
11 | github.com/go-logr/logr v1.4.2
12 | github.com/ipfs/go-cid v0.5.0
13 | github.com/libp2p/go-libp2p v0.41.1
14 | github.com/libp2p/go-libp2p-kad-dht v0.33.1
15 | github.com/multiformats/go-multiaddr v0.15.0
16 | github.com/multiformats/go-multicodec v0.9.0
17 | github.com/multiformats/go-multihash v0.2.3
18 | github.com/opencontainers/go-digest v1.0.0
19 | github.com/opencontainers/image-spec v1.1.1
20 | github.com/pelletier/go-toml/v2 v2.2.4
21 | github.com/prometheus/client_golang v1.22.0
22 | github.com/prometheus/common v0.64.0
23 | github.com/stretchr/testify v1.10.0
24 | go.etcd.io/bbolt v1.4.0
25 | golang.org/x/sync v0.14.0
26 | google.golang.org/grpc v1.72.1
27 | k8s.io/apimachinery v0.33.1
28 | k8s.io/cri-api v0.33.1
29 | k8s.io/klog/v2 v2.130.1
30 | )
31 |
32 | require (
33 | dario.cat/mergo v1.0.1 // indirect
34 | github.com/Masterminds/goutils v1.1.1 // indirect
35 | github.com/Masterminds/semver/v3 v3.3.1 // indirect
36 | github.com/Masterminds/sprig/v3 v3.3.0 // indirect
37 | github.com/Microsoft/go-winio v0.6.2 // indirect
38 | github.com/Microsoft/hcsshim v0.13.0 // indirect
39 | github.com/alexflint/go-scalar v1.2.0 // indirect
40 | github.com/benbjohnson/clock v1.3.5 // indirect
41 | github.com/beorn7/perks v1.0.1 // indirect
42 | github.com/cespare/xxhash/v2 v2.3.0 // indirect
43 | github.com/containerd/cgroups v1.1.0 // indirect
44 | github.com/containerd/cgroups/v3 v3.0.5 // indirect
45 | github.com/containerd/continuity v0.4.5 // indirect
46 | github.com/containerd/errdefs/pkg v0.3.0 // indirect
47 | github.com/containerd/fifo v1.1.0 // indirect
48 | github.com/containerd/log v0.1.0 // indirect
49 | github.com/containerd/platforms v1.0.0-rc.1 // indirect
50 | github.com/containerd/plugin v1.0.0 // indirect
51 | github.com/containerd/ttrpc v1.2.7 // indirect
52 | github.com/coreos/go-systemd/v22 v22.5.0 // indirect
53 | github.com/davecgh/go-spew v1.1.2-0.20180830191138-d8f796af33cc // indirect
54 | github.com/davidlazar/go-crypto v0.0.0-20200604182044-b73af7476f6c // indirect
55 | github.com/decred/dcrd/dcrec/secp256k1/v4 v4.4.0 // indirect
56 | github.com/distribution/reference v0.6.0 // indirect
57 | github.com/docker/go-units v0.5.0 // indirect
58 | github.com/elastic/gosigar v0.14.3 // indirect
59 | github.com/felixge/httpsnoop v1.0.4 // indirect
60 | github.com/flynn/noise v1.1.0 // indirect
61 | github.com/francoispqt/gojay v1.2.13 // indirect
62 | github.com/fsnotify/fsnotify v1.9.0 // indirect
63 | github.com/go-logr/stdr v1.2.2 // indirect
64 | github.com/go-task/slim-sprig/v3 v3.0.0 // indirect
65 | github.com/gobwas/glob v0.2.3 // indirect
66 | github.com/godbus/dbus/v5 v5.1.0 // indirect
67 | github.com/gogo/protobuf v1.3.2 // indirect
68 | github.com/golang/groupcache v0.0.0-20210331224755-41bb18bfe9da // indirect
69 | github.com/google/go-cmp v0.7.0 // indirect
70 | github.com/google/gopacket v1.1.19 // indirect
71 | github.com/google/pprof v0.0.0-20250208200701-d0013a598941 // indirect
72 | github.com/google/uuid v1.6.0 // indirect
73 | github.com/gorilla/websocket v1.5.3 // indirect
74 | github.com/hashicorp/golang-lru v1.0.2 // indirect
75 | github.com/hashicorp/hcl v1.0.0 // indirect
76 | github.com/huandu/xstrings v1.5.0 // indirect
77 | github.com/huin/goupnp v1.3.0 // indirect
78 | github.com/inconshreveable/mousetrap v1.1.0 // indirect
79 | github.com/ipfs/boxo v0.30.0 // indirect
80 | github.com/ipfs/go-datastore v0.8.2 // indirect
81 | github.com/ipfs/go-log/v2 v2.6.0 // indirect
82 | github.com/ipld/go-ipld-prime v0.21.0 // indirect
83 | github.com/jackpal/go-nat-pmp v1.0.2 // indirect
84 | github.com/jbenet/go-temp-err-catcher v0.1.0 // indirect
85 | github.com/klauspost/compress v1.18.0 // indirect
86 | github.com/klauspost/cpuid/v2 v2.2.10 // indirect
87 | github.com/koron/go-ssdp v0.0.5 // indirect
88 | github.com/kylelemons/godebug v1.1.0 // indirect
89 | github.com/libp2p/go-buffer-pool v0.1.0 // indirect
90 | github.com/libp2p/go-cidranger v1.1.0 // indirect
91 | github.com/libp2p/go-flow-metrics v0.2.0 // indirect
92 | github.com/libp2p/go-libp2p-asn-util v0.4.1 // indirect
93 | github.com/libp2p/go-libp2p-kbucket v0.7.0 // indirect
94 | github.com/libp2p/go-libp2p-record v0.3.1 // indirect
95 | github.com/libp2p/go-libp2p-routing-helpers v0.7.5 // indirect
96 | github.com/libp2p/go-msgio v0.3.0 // indirect
97 | github.com/libp2p/go-netroute v0.2.2 // indirect
98 | github.com/libp2p/go-reuseport v0.4.0 // indirect
99 | github.com/libp2p/go-yamux/v5 v5.0.0 // indirect
100 | github.com/magiconair/properties v1.8.7 // indirect
101 | github.com/marten-seemann/tcp v0.0.0-20210406111302-dfbc87cc63fd // indirect
102 | github.com/mattn/go-isatty v0.0.20 // indirect
103 | github.com/miekg/dns v1.1.66 // indirect
104 | github.com/mikioh/tcpinfo v0.0.0-20190314235526-30a79bb1804b // indirect
105 | github.com/mikioh/tcpopt v0.0.0-20190314235656-172688c1accc // indirect
106 | github.com/minio/sha256-simd v1.0.1 // indirect
107 | github.com/mitchellh/copystructure v1.2.0 // indirect
108 | github.com/mitchellh/mapstructure v1.5.0 // indirect
109 | github.com/mitchellh/reflectwalk v1.0.2 // indirect
110 | github.com/moby/locker v1.0.1 // indirect
111 | github.com/moby/sys/mountinfo v0.7.2 // indirect
112 | github.com/moby/sys/sequential v0.6.0 // indirect
113 | github.com/moby/sys/signal v0.7.1 // indirect
114 | github.com/moby/sys/user v0.4.0 // indirect
115 | github.com/moby/sys/userns v0.1.0 // indirect
116 | github.com/mr-tron/base58 v1.2.0 // indirect
117 | github.com/multiformats/go-base32 v0.1.0 // indirect
118 | github.com/multiformats/go-base36 v0.2.0 // indirect
119 | github.com/multiformats/go-multiaddr-dns v0.4.1 // indirect
120 | github.com/multiformats/go-multiaddr-fmt v0.1.0 // indirect
121 | github.com/multiformats/go-multibase v0.2.0 // indirect
122 | github.com/multiformats/go-multistream v0.6.0 // indirect
123 | github.com/multiformats/go-varint v0.0.7 // indirect
124 | github.com/munnerz/goautoneg v0.0.0-20191010083416-a7dc8b61c822 // indirect
125 | github.com/norwoodj/helm-docs v1.14.2 // indirect
126 | github.com/onsi/ginkgo/v2 v2.22.2 // indirect
127 | github.com/opencontainers/runtime-spec v1.2.1 // indirect
128 | github.com/opencontainers/selinux v1.12.0 // indirect
129 | github.com/pbnjay/memory v0.0.0-20210728143218-7b4eea64cf58 // indirect
130 | github.com/pion/datachannel v1.5.10 // indirect
131 | github.com/pion/dtls/v2 v2.2.12 // indirect
132 | github.com/pion/dtls/v3 v3.0.4 // indirect
133 | github.com/pion/ice/v4 v4.0.8 // indirect
134 | github.com/pion/interceptor v0.1.37 // indirect
135 | github.com/pion/logging v0.2.3 // indirect
136 | github.com/pion/mdns/v2 v2.0.7 // indirect
137 | github.com/pion/randutil v0.1.0 // indirect
138 | github.com/pion/rtcp v1.2.15 // indirect
139 | github.com/pion/rtp v1.8.11 // indirect
140 | github.com/pion/sctp v1.8.37 // indirect
141 | github.com/pion/sdp/v3 v3.0.10 // indirect
142 | github.com/pion/srtp/v3 v3.0.4 // indirect
143 | github.com/pion/stun v0.6.1 // indirect
144 | github.com/pion/stun/v3 v3.0.0 // indirect
145 | github.com/pion/transport/v2 v2.2.10 // indirect
146 | github.com/pion/transport/v3 v3.0.7 // indirect
147 | github.com/pion/turn/v4 v4.0.0 // indirect
148 | github.com/pion/webrtc/v4 v4.0.10 // indirect
149 | github.com/pkg/errors v0.9.1 // indirect
150 | github.com/pmezard/go-difflib v1.0.1-0.20181226105442-5d4384ee4fb2 // indirect
151 | github.com/polydawn/refmt v0.89.0 // indirect
152 | github.com/prometheus/client_model v0.6.2 // indirect
153 | github.com/prometheus/procfs v0.16.1 // indirect
154 | github.com/quic-go/qpack v0.5.1 // indirect
155 | github.com/quic-go/quic-go v0.50.1 // indirect
156 | github.com/quic-go/webtransport-go v0.8.1-0.20241018022711-4ac2c9250e66 // indirect
157 | github.com/raulk/go-watchdog v1.3.0 // indirect
158 | github.com/shopspring/decimal v1.4.0 // indirect
159 | github.com/sirupsen/logrus v1.9.3 // indirect
160 | github.com/spaolacci/murmur3 v1.1.0 // indirect
161 | github.com/spf13/afero v1.14.0 // indirect
162 | github.com/spf13/cast v1.7.0 // indirect
163 | github.com/spf13/cobra v1.8.1 // indirect
164 | github.com/spf13/jwalterweatherman v1.1.0 // indirect
165 | github.com/spf13/pflag v1.0.6 // indirect
166 | github.com/spf13/viper v1.16.0 // indirect
167 | github.com/subosito/gotenv v1.4.2 // indirect
168 | github.com/whyrusleeping/go-keyspace v0.0.0-20160322163242-5b898ac5add1 // indirect
169 | github.com/wlynxg/anet v0.0.5 // indirect
170 | go.opencensus.io v0.24.0 // indirect
171 | go.opentelemetry.io/auto/sdk v1.1.0 // indirect
172 | go.opentelemetry.io/contrib/instrumentation/net/http/otelhttp v0.60.0 // indirect
173 | go.opentelemetry.io/otel v1.35.0 // indirect
174 | go.opentelemetry.io/otel/metric v1.35.0 // indirect
175 | go.opentelemetry.io/otel/trace v1.35.0 // indirect
176 | go.uber.org/dig v1.18.0 // indirect
177 | go.uber.org/fx v1.23.0 // indirect
178 | go.uber.org/mock v0.5.0 // indirect
179 | go.uber.org/multierr v1.11.0 // indirect
180 | go.uber.org/zap v1.27.0 // indirect
181 | golang.org/x/crypto v0.38.0 // indirect
182 | golang.org/x/exp v0.0.0-20250506013437-ce4c2cf36ca6 // indirect
183 | golang.org/x/mod v0.24.0 // indirect
184 | golang.org/x/net v0.40.0 // indirect
185 | golang.org/x/sys v0.33.0 // indirect
186 | golang.org/x/text v0.25.0 // indirect
187 | golang.org/x/tools v0.33.0 // indirect
188 | gonum.org/v1/gonum v0.16.0 // indirect
189 | google.golang.org/genproto/googleapis/rpc v0.0.0-20250218202821-56aae31c358a // indirect
190 | google.golang.org/protobuf v1.36.6 // indirect
191 | gopkg.in/ini.v1 v1.67.0 // indirect
192 | gopkg.in/yaml.v3 v3.0.1 // indirect
193 | helm.sh/helm/v3 v3.17.3 // indirect
194 | lukechampine.com/blake3 v1.4.1 // indirect
195 | )
196 |
197 | tool github.com/norwoodj/helm-docs/cmd/helm-docs
198 |
--------------------------------------------------------------------------------
/internal/channel/channel.go:
--------------------------------------------------------------------------------
1 | package channel
2 |
3 | import (
4 | "sync"
5 | )
6 |
7 | func Merge[T any](cs ...<-chan T) <-chan T {
8 | var wg sync.WaitGroup
9 | out := make(chan T)
10 |
11 | output := func(c <-chan T) {
12 | for n := range c {
13 | out <- n
14 | }
15 | wg.Done()
16 | }
17 | wg.Add(len(cs))
18 | for _, c := range cs {
19 | go output(c)
20 | }
21 |
22 | go func() {
23 | wg.Wait()
24 | close(out)
25 | }()
26 | return out
27 | }
28 |
--------------------------------------------------------------------------------
/internal/cleanup/cleanup.go:
--------------------------------------------------------------------------------
1 | package cleanup
2 |
3 | import (
4 | "context"
5 | "errors"
6 | "io"
7 | "net"
8 | "net/http"
9 | "net/url"
10 | "time"
11 |
12 | "github.com/go-logr/logr"
13 | "golang.org/x/sync/errgroup"
14 |
15 | "github.com/spegel-org/spegel/internal/channel"
16 | "github.com/spegel-org/spegel/pkg/httpx"
17 | "github.com/spegel-org/spegel/pkg/oci"
18 | )
19 |
20 | func Run(ctx context.Context, addr, configPath string) error {
21 | log := logr.FromContextOrDiscard(ctx)
22 |
23 | err := oci.CleanupMirrorConfiguration(ctx, configPath)
24 | if err != nil {
25 | return err
26 | }
27 |
28 | g, gCtx := errgroup.WithContext(ctx)
29 |
30 | mux := http.HandlerFunc(func(rw http.ResponseWriter, req *http.Request) {
31 | if req.Method != http.MethodGet && req.URL.Path != "/healthz" {
32 | log.Error(errors.New("unknown request"), "unsupported probe request", "path", req.URL.Path, "method", req.Method)
33 | rw.WriteHeader(http.StatusNotFound)
34 | return
35 | }
36 | rw.WriteHeader(http.StatusOK)
37 | })
38 | srv := &http.Server{
39 | Addr: addr,
40 | Handler: mux,
41 | }
42 | g.Go(func() error {
43 | if err := srv.ListenAndServe(); err != nil && !errors.Is(err, http.ErrServerClosed) {
44 | return err
45 | }
46 | return nil
47 | })
48 | g.Go(func() error {
49 | <-gCtx.Done()
50 | shutdownCtx, cancel := context.WithTimeout(context.Background(), 30*time.Second)
51 | defer cancel()
52 | return srv.Shutdown(shutdownCtx)
53 | })
54 |
55 | log.Info("waiting to be shutdown")
56 | err = g.Wait()
57 | if err != nil {
58 | return err
59 | }
60 | return nil
61 | }
62 |
63 | func Wait(ctx context.Context, probeEndpoint string, period time.Duration, threshold int) error {
64 | log := logr.FromContextOrDiscard(ctx)
65 | resolver := &net.Resolver{}
66 | client := &http.Client{}
67 |
68 | addr, port, err := net.SplitHostPort(probeEndpoint)
69 | if err != nil {
70 | return err
71 | }
72 |
73 | immediateCh := make(chan time.Time, 1)
74 | immediateCh <- time.Now()
75 | close(immediateCh)
76 | ticker := time.NewTicker(period)
77 | defer ticker.Stop()
78 | tickerCh := channel.Merge(immediateCh, ticker.C)
79 | thresholdCount := 0
80 | for {
81 | select {
82 | case <-ctx.Done():
83 | return ctx.Err()
84 | case <-tickerCh:
85 | start := time.Now()
86 |
87 | log.Info("running probe lookup", "host", addr)
88 | ips, err := resolver.LookupIPAddr(ctx, addr)
89 | if err != nil {
90 | log.Error(err, "cleanup probe lookup failed")
91 | thresholdCount = 0
92 | continue
93 | }
94 |
95 | log.Info("running probe request", "endpoints", len(ips))
96 | err = probeIPs(ctx, client, ips, port)
97 | if err != nil {
98 | log.Error(err, "cleanup probe request failed")
99 | thresholdCount = 0
100 | continue
101 | }
102 |
103 | thresholdCount += 1
104 | log.Info("probe ran successfully", "threshold", thresholdCount, "duration", time.Since(start).String())
105 | if thresholdCount == threshold {
106 | log.Info("probe threshold reached")
107 | return nil
108 | }
109 | }
110 | }
111 | }
112 |
113 | func probeIPs(ctx context.Context, client *http.Client, ips []net.IPAddr, port string) error {
114 | g, gCtx := errgroup.WithContext(ctx)
115 | g.SetLimit(10)
116 | for _, ip := range ips {
117 | g.Go(func() error {
118 | u := url.URL{
119 | Scheme: "http",
120 | Host: net.JoinHostPort(ip.String(), port),
121 | Path: "/healthz",
122 | }
123 | reqCtx, cancel := context.WithTimeout(gCtx, 1*time.Second)
124 | defer cancel()
125 | req, err := http.NewRequestWithContext(reqCtx, http.MethodGet, u.String(), nil)
126 | if err != nil {
127 | return err
128 | }
129 | resp, err := client.Do(req)
130 | if err != nil {
131 | return err
132 | }
133 | defer resp.Body.Close()
134 | _, err = io.Copy(io.Discard, resp.Body)
135 | if err != nil {
136 | return err
137 | }
138 | err = httpx.CheckResponseStatus(resp, http.StatusOK)
139 | if err != nil {
140 | return err
141 | }
142 | return nil
143 | })
144 | }
145 | err := g.Wait()
146 | if err != nil {
147 | return err
148 | }
149 | return nil
150 | }
151 |
--------------------------------------------------------------------------------
/internal/cleanup/cleanup_test.go:
--------------------------------------------------------------------------------
1 | package cleanup
2 |
3 | import (
4 | "context"
5 | "net"
6 | "net/http"
7 | "net/http/httptest"
8 | "net/url"
9 | "testing"
10 | "time"
11 |
12 | "github.com/stretchr/testify/require"
13 | "golang.org/x/sync/errgroup"
14 | )
15 |
16 | func TestCleanupFail(t *testing.T) {
17 | t.Parallel()
18 |
19 | srv := httptest.NewServer(http.HandlerFunc(func(rw http.ResponseWriter, req *http.Request) {
20 | rw.WriteHeader(http.StatusInternalServerError)
21 | }))
22 | defer srv.Close()
23 | u, err := url.Parse(srv.URL)
24 | require.NoError(t, err)
25 | timeoutCtx, timeoutCancel := context.WithTimeout(t.Context(), 1*time.Second)
26 | defer timeoutCancel()
27 | err = Wait(timeoutCtx, u.Host, 100*time.Millisecond, 3)
28 | require.EqualError(t, err, "context deadline exceeded")
29 | }
30 |
31 | func TestCleanupSucceed(t *testing.T) {
32 | t.Parallel()
33 |
34 | listener, err := net.Listen("tcp", ":0")
35 | if err != nil {
36 | panic(err)
37 | }
38 | addr := listener.Addr().String()
39 | err = listener.Close()
40 | require.NoError(t, err)
41 | timeoutCtx, timeoutCancel := context.WithTimeout(t.Context(), 1*time.Second)
42 | defer timeoutCancel()
43 | g, gCtx := errgroup.WithContext(timeoutCtx)
44 | g.Go(func() error {
45 | err := Run(gCtx, addr, t.TempDir())
46 | if err != nil {
47 | return err
48 | }
49 | return nil
50 | })
51 | g.Go(func() error {
52 | err := Wait(gCtx, addr, 100*time.Microsecond, 3)
53 | if err != nil {
54 | return err
55 | }
56 | return nil
57 | })
58 |
59 | err = g.Wait()
60 | require.NoError(t, err)
61 | }
62 |
--------------------------------------------------------------------------------
/internal/web/templates/index.html:
--------------------------------------------------------------------------------
1 |
2 |
3 |
4 |
5 |
6 |
7 | Spegel Debug
8 |
9 |
10 |
11 |
105 |
106 |
107 |
108 |
109 |
Spegel
110 |
111 |
112 |
113 |
114 |
Measure Image Pull
115 |
119 |
120 |
121 |
Resolved Peers
3 |
4 | Duration: {{ .PeerDuration | formatDuration }}
5 |
6 |
7 |
8 |
9 | | Peer |
10 | Duration |
11 |
12 |
13 | {{ range .PeerResults }}
14 |
15 | | {{ .Peer.Addr }} |
16 | {{ .Duration | formatDuration }} |
17 |
18 | {{ end }}
19 |
20 |
Result
23 |
24 | Duration: {{ .PullDuration | formatDuration }}
25 | Size: {{ .PullSize | formatBytes }}
26 |
27 |
28 |
29 |
30 | | Identifier |
31 | Type |
32 | Size |
33 | Duration |
34 |
35 |
36 | {{ range .PullResults }}
37 |
38 | | {{ .Identifier }} |
39 | {{ .Type }} |
40 | {{ .Size | formatBytes }} |
41 | {{ .Duration | formatDuration }} |
42 |
43 | {{ end }}
44 |
45 |
No peers found for image
48 | {{ end }}
--------------------------------------------------------------------------------
/internal/web/templates/stats.html:
--------------------------------------------------------------------------------
1 |
2 |
3 |
4 |
Images
5 |
{{ .ImageCount }}
6 |
7 |
8 |
Layers
9 |
{{ .LayerCount }}
10 |
11 |
12 |
 10 |
10 |  10 |
10 |