39 |
41 |
46 |
47 |
48 |
59 |
92 |
93 |
114 |
115 |
116 |
117 |
118 |
119 |
120 |
121 |
122 |
123 |
124 |
125 |
126 |
127 |
128 |
129 |
130 |
132 |
133 |
134 |
135 |
136 |
143 |
144 |
145 |
--------------------------------------------------------------------------------
/OAuth/99~参考资料/2022~Sheng~OAuth 2.0 协议.md:
--------------------------------------------------------------------------------
1 | # OAuth2.0 协议
2 |
3 | OAuth 2.0 定义了四种授权方式:
4 |
5 | - 授权码模式(authorization code)
6 | - 简化模式(implicit)
7 | - 密码模式(resource owner password credentials)
8 | - 客户端模式(client credentials)
9 |
10 | ## 1. 授权码模式
11 |
12 | 授权码模式(authorization code)是功能最完整、流程最严密的授权模式。它的特点就是通过客户端的后台服务器,与"服务提供商"的认证服务器进行互动。
13 |
14 | 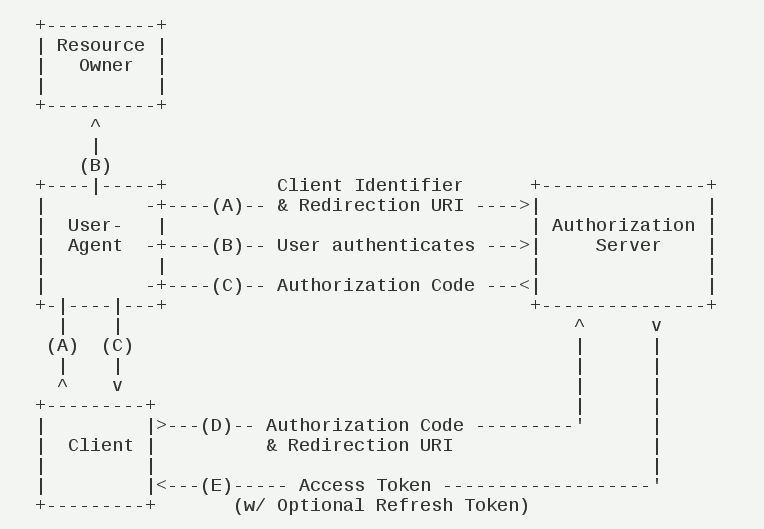
15 |
16 | 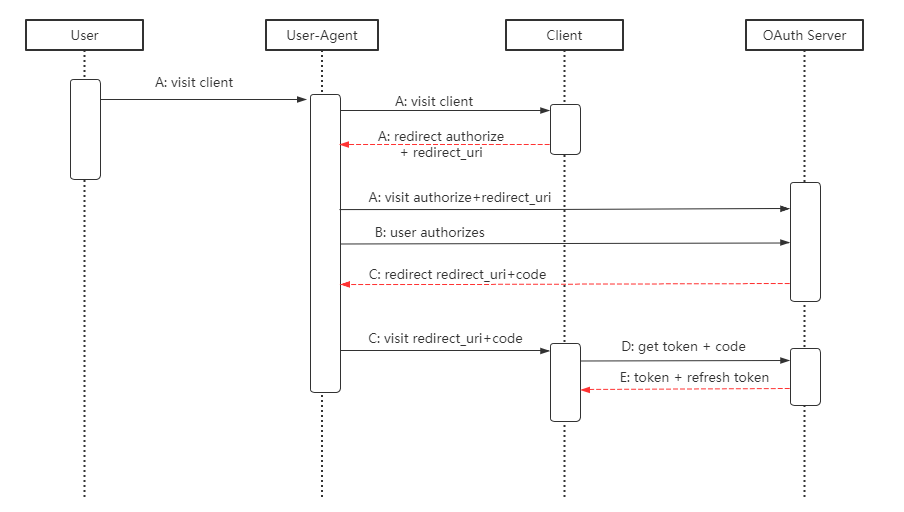
17 |
18 | 它的步骤如下:
19 |
20 | ```text
21 | (A)用户访问客户端,后者将前者导向认证服务器,并指定"重定向URI"(redirection URI)redirect_uri。
22 |
23 | (B)用户选择是否给予客户端授权。
24 |
25 | (C)假设用户给予授权,认证服务器将用户导向客户端事先指定的redirect_uri,同时附上一个授权码Code。
26 |
27 | (D)客户端收到授权码,向认证服务器申请令牌。这一步是在客户端的后台的服务器上完成的,对用户不可见。
28 |
29 | (E)认证服务器核对了授权码,确认无误后,向客户端发送访问令牌(access token)和更新令牌(refresh token)。
30 | ```
31 |
32 | A 步骤中,客户端申请认证的 URI,包含以下参数:
33 |
34 | - response_type:表示授权类型,必选项,此处的值固定为"code"
35 | - client_id:表示客户端的 ID,必选项
36 | - redirect_uri:表示重定向 URI,可选项
37 | - scope:表示申请的权限范围,可选项
38 | - state:表示客户端的当前状态,可以指定任意值,认证服务器会原封不动地返回这个值。
39 |
40 | ```http
41 | GET /oauth.sample.com/authorize
42 | ?response_type=code
43 | &client_id=s6BhdRkqt3
44 | &redirect_uri=http%3A%2F%2Fclient.sample.com%2Fsignin-oauth
45 | &scope=sns_login token
46 | &state=xyz
47 | ```
48 |
49 | C 步骤中,服务器回应客户端的 URI,包含以下参数:
50 |
51 | - code:表示授权码,必选项。该码的有效期应该很短,通常设为 10 分钟,客户端只能使用该码一次,否则会被授权服务器拒绝。该码与客户端 ID 和重定向 URI,是一一对应关系。
52 | - state:如果客户端的请求中包含这个参数,认证服务器的回应也必须一模一样包含这个参数。
53 |
54 | ```http
55 | HTTP/1.1 302 Found
56 | Location: https://client.example.com/signin-oauth
57 | ?code=SplxlOBeZQQYbYS6WxSbIA
58 | &state=xyz
59 | ```
60 |
61 | D 步骤中,客户端向认证服务器申请令牌的 HTTP 请求,包含以下参数:
62 |
63 | - grant_type:表示使用的授权模式,必选项,此处的值固定为"authorization_code"。
64 | - code:表示上一步获得的授权码,必选项。
65 | - redirect_uri:表示重定向 URI,必选项,且必须与 A 步骤中的该参数值保持一致。
66 | - client_id:表示客户端 ID,必选项。
67 |
68 | ```http
69 | POST /token HTTP/1.1
70 | Host: oauth.example.com
71 | Content-Type: application/x-www-form-urlencoded
72 |
73 | grant_type=authorization_code
74 | &code=SplxlOBeZQQYbYS6WxSbIA
75 | &redirect_uri=http%3A%2F%2Fclient.sample.com%2Fsignin-oauth
76 | &client_id=s6BhdRkqt3
77 | ```
78 |
79 | E 步骤中,认证服务器发送的 HTTP 回复,包含以下参数:
80 |
81 | - access_token:表示访问令牌,必选项。
82 | - token_type:表示令牌类型,该值大小写不敏感,必选项,可以是 bearer 类型或 mac 类型。
83 | - expires_in:表示过期时间,单位为秒。如果省略该参数,必须其他方式设置过期时间。
84 | - refresh_token:表示更新令牌,用来获取下一次的访问令牌,可选项。
85 | - scope:表示权限范围,如果与客户端申请的范围一致,此项可省略。
86 |
87 | ```http
88 | HTTP/1.1 200 OK
89 | Content-Type: application/json;charset=UTF-8
90 | Cache-Control: no-store
91 | Pragma: no-cache
92 |
93 | {
94 | "access_token":"2YotnFZFEjr1zCsicMWpAA",
95 | "token_type":"bearer",
96 | "expires_in":3600,
97 | "refresh_token":"tGzv3JOkF0XG5Qx2TlKWIA"
98 | }
99 | ```
100 |
101 | ## 2. 简化模式
102 |
103 | 简化模式(implicit grant type)不通过第三方应用程序的服务器,直接在浏览器中向认证服务器申请令牌,跳过了"授权码"这个步骤,因此得名。所有步骤在浏览器中完成,令牌对访问者是可见的,且客户端不需要认证。
104 |
105 | 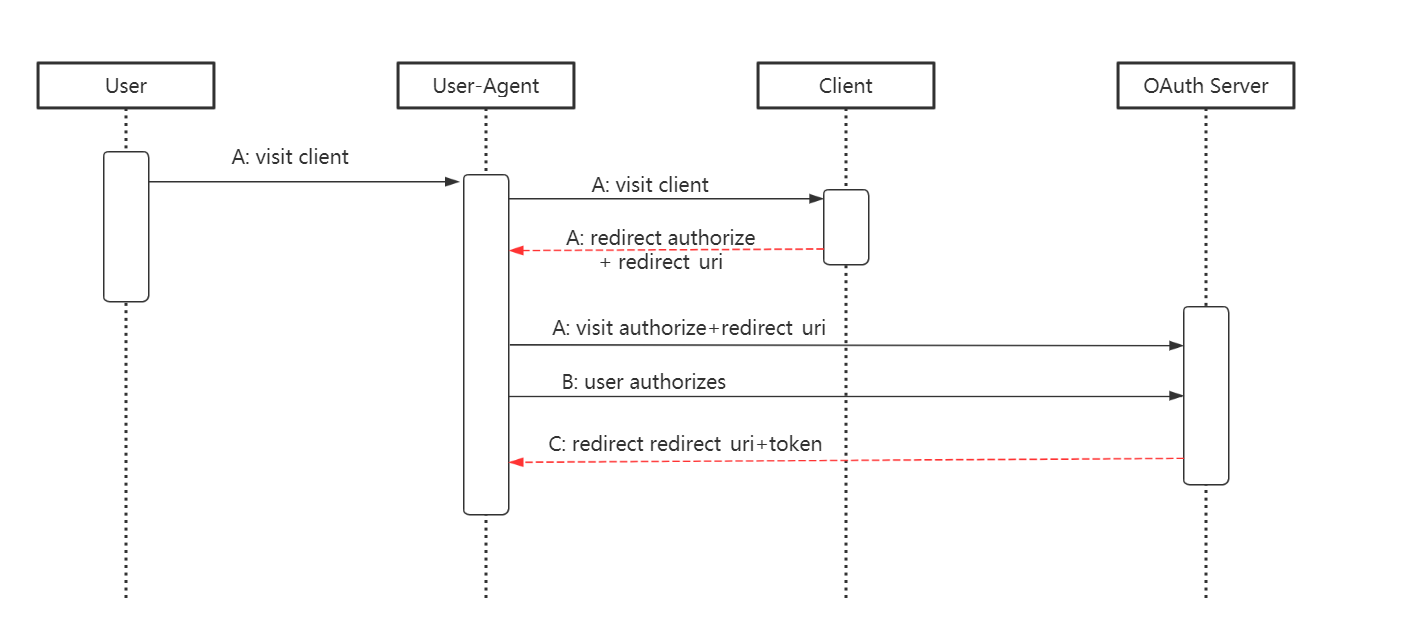
106 |
107 | ```text
108 | (A)客户端将用户导向认证服务器。
109 |
110 | (B)用户决定是否给于客户端授权。
111 |
112 | (C)假设用户给予授权,认证服务器向浏览器回应重定向,并在URI的Hash部分包含了访问令牌,将客户端导向“重定向URI”。
113 |
114 | (D)浏览器向资源服务器的“重定向URI”地址发出请求,其中不包括上一步收到的Hash值。
115 | ```
116 |
117 | A 步骤中,客户端发出的 HTTP 请求,包含以下参数:
118 |
119 | - response_type:表示授权类型,此处的值固定为"token",必选项。
120 | - client_id:表示客户端的 ID,必选项。
121 | - redirect_uri:表示重定向的 URI,可选项。
122 | - scope:表示权限范围,可选项。
123 | - state:表示客户端的当前状态,可以指定任意值,认证服务器会原封不动地返回这个值。
124 |
125 | ```http
126 | GET /oauth.sample.com/authorize
127 | ?response_type=token
128 | &client_id=s6BhdRkqt3
129 | &redirect_uri=http%3A%2F%2Fclient.sample.com%2Fcallback
130 | &scope=token
131 | &state=xyz
132 | ```
133 |
134 | C 步骤中,服务器回应客户端的 URI,包含以下参数:
135 |
136 | - access_token:表示访问令牌,必选项。
137 | - token_type:表示令牌类型,该值大小写不敏感,必选项。
138 | - expires_in:表示过期时间,单位为秒。如果省略该参数,必须其他方式设置过期时间。
139 | - scope:表示权限范围,如果与客户端申请的范围一致,此项可省略。
140 | - state:如果客户端的请求中包含这个参数,认证服务器的回应也必须一模一样包含这个参数。
141 |
142 | ```http
143 | HTTP/1.1 302 Found
144 | Location: http://client.sample.com/callback#access_token=2YotnFZFEjr1zCsicMWpAA
145 | &token_type=bearer
146 | &expires_in=3600
147 | &scope=token
148 | &state=xyz
149 | ```
150 |
151 | 在这个网址的 Hash 部分包含了令牌。
152 |
153 | 根据上面的 D 步骤,下一步浏览器会访问 Location 指定的网址,但是 Hash 部分不会发送。
154 |
155 | ## 3. 密码模式
156 |
157 | 密码模式(Resource Owner Password Credentials Grant)中,用户向客户端提供自己的用户名和密码。客户端使用这些信息,向"服务商提供商"索要授权。
158 |
159 | 在这种模式中,用户必须把自己的密码给客户端,但是客户端不得储存密码。这通常用在用户对客户端高度信任的情况下,比如客户端是操作系统的一部分。而认证服务器只有在其他授权模式无法执行的情况下,才能考虑使用这种模式。
160 |
161 | 它的步骤如下:
162 |
163 | ```text
164 | (A)用户向客户端提供用户名和密码。
165 |
166 | (B)客户端将用户名和密码发给认证服务器,向后者请求令牌。
167 |
168 | (C)认证服务器确认无误后,向客户端提供访问令牌。
169 | ```
170 |
171 | B 步骤中,客户端发出的 HTTP 请求,包含以下参数:
172 |
173 | - grant_type:表示授权类型,此处的值固定为"password",必选项。
174 | - username:表示用户名,必选项。
175 | - password:表示用户的密码,必选项。
176 | - scope:表示权限范围,可选项。
177 |
178 | 下面是一个例子。
179 |
180 | ```http
181 | POST /token HTTP/1.1
182 | Host: oauth.example.com
183 | Content-Type: application/x-www-form-urlencoded
184 |
185 | grant_type=password&username=johndoe&password=A3ddj3w
186 | ```
187 |
188 | ## 4. 客户端模式
189 |
190 | 客户端模式(Client Credentials Grant)指客户端以自己的名义,而不是以用户的名义,向"服务提供商"进行认证。严格地说,客户端模式并不属于 OAuth 框架所要解决的问题。在这种模式中,用户直接向客户端注册,客户端以自己的名义要求"服务提供商"提供服务,其实不存在授权问题。
191 |
192 | ```text
193 | (A)客户端向认证服务器进行身份认证,并要求一个访问令牌。
194 |
195 | (B)认证服务器确认无误后,向客户端提供访问令牌。
196 | ```
197 |
198 | A 步骤中,客户端发出的 HTTP 请求,包含以下参数:
199 |
200 | - grant*type:表示授权类型,此处的值固定为"client*credentials",必选项。
201 | - scope:表示权限范围,可选项。
202 |
203 | ```http
204 | POST /token HTTP/1.1
205 | Host: server.example.com
206 | Content-Type: application/x-www-form-urlencoded
207 |
208 | grant_type=client_credentials
209 | ```
210 |
211 | ## [#](https://thinking.renzhansheng.cn/pages/7459f3/#_5-更新令牌)5. 更新令牌
212 |
213 | 如果用户访问的时候,客户端的"访问令牌"已经过期,则需要使用"更新令牌"申请一个新的访问令牌。
214 |
215 | 客户端发出更新令牌的 HTTP 请求,包含以下参数:
216 |
217 | - grant*type:表示使用的授权模式,此处的值固定为"refresh*token",必选项。
218 | - refresh_token:表示早前收到的更新令牌,必选项。
219 | - scope:表示申请的授权范围,不可以超出上一次申请的范围,如果省略该参数,则表示与上一次一致。
220 |
221 | ```http
222 | POST /token HTTP/1.1
223 | Host: oauth.example.com
224 | Content-Type: application/x-www-form-urlencoded
225 |
226 | grant_type=refresh_token&refresh_token=tGzv3JOkF0XG5Qx2TlKWIA
227 | ```
228 |
--------------------------------------------------------------------------------
/_sidebar.md:
--------------------------------------------------------------------------------
1 | - 1 01~服务化架构 [5]
2 | - [1.1 01~架构变迁 [4]](/01~服务化架构/01~架构变迁/README.md)
3 | - [1.1.1 SOA](/01~服务化架构/01~架构变迁/SOA.md)
4 | - [1.1.2 云原生](/01~服务化架构/01~架构变迁/云原生.md)
5 | - [1.1.3 单体架构](/01~服务化架构/01~架构变迁/单体架构.md)
6 | - 1.1.4 微服务 [2]
7 | - [1.1.4.1 单体架构到分布式应用](/01~服务化架构/01~架构变迁/微服务/单体架构到分布式应用.md)
8 | - [1.1.4.2 微服务](/01~服务化架构/01~架构变迁/微服务/微服务.md)
9 | - [1.2 02~服务基础 [3]](/01~服务化架构/02~服务基础/README.md)
10 | - [1.2.1 中间件](/01~服务化架构/02~服务基础/中间件.md)
11 | - [1.2.2 服务视图](/01~服务化架构/02~服务基础/服务视图.md)
12 | - [1.2.3 服务间通信](/01~服务化架构/02~服务基础/服务间通信.md)
13 | - [1.3 03~微服务治理 [3]](/01~服务化架构/03~微服务治理/README.md)
14 | - [1.3.1 OpenSergo 规范](/01~服务化架构/03~微服务治理/OpenSergo%20规范/README.md)
15 |
16 | - [1.3.2 分布式应用治理](/01~服务化架构/03~微服务治理/分布式应用治理.md)
17 | - [1.3.3 微服务设计模式](/01~服务化架构/03~微服务治理/微服务设计模式.md)
18 | - [1.4 04~云原生 [4]](/01~服务化架构/04~云原生/README.md)
19 | - [1.4.1 Factor 应用原则](/01~服务化架构/04~云原生/12-Factor%20应用原则.md)
20 | - 1.4.2 99~参考资料 [2]
21 | - [1.4.2.1 一文简述:云原生架构的四个特征六个原则](/01~服务化架构/04~云原生/99~参考资料/2022-一文简述:云原生架构的四个特征六个原则.md)
22 | - [1.4.2.2 容器、K8s、微服务、云原生](/01~服务化架构/04~云原生/99~参考资料/容器、K8s、微服务、云原生.md)
23 | - [1.4.3 Distributionless](/01~服务化架构/04~云原生/Distributionless.md)
24 | - [1.4.4 Serverless [3]](/01~服务化架构/04~云原生/Serverless/README.md)
25 | - [1.4.4.1 BaaS](/01~服务化架构/04~云原生/Serverless/BaaS.md)
26 | - [1.4.4.2 FaaS](/01~服务化架构/04~云原生/Serverless/FaaS.md)
27 | - [1.4.4.3 Serverless 发展历程](/01~服务化架构/04~云原生/Serverless/Serverless%20发展历程.md)
28 | - [1.5 99~参考资料](/01~服务化架构/99~参考资料/README.md)
29 |
30 | - 2 02~微服务 RPC [6]
31 | - 2.1 00~框架对比 [1]
32 | - [2.1.1 微服务框架比较](/02~微服务%20RPC/00~框架对比/微服务框架比较.md)
33 | - [2.2 01~RPC 基础 [6]](/02~微服务%20RPC/01~RPC%20基础/README.md)
34 | - [2.2.1 RPC 安全性](/02~微服务%20RPC/01~RPC%20基础/RPC%20安全性.md)
35 | - [2.2.2 RPC 应用](/02~微服务%20RPC/01~RPC%20基础/RPC%20应用.md)
36 | - [2.2.3 RPC 简史](/02~微服务%20RPC/01~RPC%20基础/RPC%20简史.md)
37 | - [2.2.4 性能对比](/02~微服务%20RPC/01~RPC%20基础/性能对比.md)
38 | - [2.2.5 服务发现](/02~微服务%20RPC/01~RPC%20基础/服务发现/README.md)
39 |
40 | - [2.2.6 服务调用](/02~微服务%20RPC/01~RPC%20基础/服务调用/README.md)
41 |
42 | - 2.3 02~序列化协议 [1]
43 | - [2.3.1 Protobuf](/02~微服务%20RPC/02~序列化协议/Protobuf/README.md)
44 |
45 | - 2.4 03~RPC 框架 [5]
46 | - [2.4.1 Dapr [4]](/02~微服务%20RPC/03~RPC%20框架/Dapr/README.md)
47 | - [2.4.1.1 Components](/02~微服务%20RPC/03~RPC%20框架/Dapr/Components/README.md)
48 |
49 | - 2.4.1.2 应用开发 [4]
50 | - [2.4.1.2.1 Actor [1]](/02~微服务%20RPC/03~RPC%20框架/Dapr/应用开发/Actor/README.md)
51 | - [2.4.1.2.1.1 注册与调用](/02~微服务%20RPC/03~RPC%20框架/Dapr/应用开发/Actor/注册与调用.md)
52 | - [2.4.1.2.2 PubSub [1]](/02~微服务%20RPC/03~RPC%20框架/Dapr/应用开发/PubSub/README.md)
53 | - [2.4.1.2.2.1 消息发布与订阅](/02~微服务%20RPC/03~RPC%20框架/Dapr/应用开发/PubSub/消息发布与订阅.md)
54 | - [2.4.1.2.3 服务调用](/02~微服务%20RPC/03~RPC%20框架/Dapr/应用开发/服务调用.md)
55 | - [2.4.1.2.4 状态管理](/02~微服务%20RPC/03~RPC%20框架/Dapr/应用开发/状态管理.md)
56 | - [2.4.1.3 生产配置](/02~微服务%20RPC/03~RPC%20框架/Dapr/生产配置/README.md)
57 |
58 | - 2.4.1.4 部署案例 [2]
59 | - [2.4.1.4.1 Hello World](/02~微服务%20RPC/03~RPC%20框架/Dapr/部署案例/Hello%20World.md)
60 | - [2.4.1.4.2 K8s](/02~微服务%20RPC/03~RPC%20框架/Dapr/部署案例/K8s.md)
61 | - [2.4.2 Dubbo [3]](/02~微服务%20RPC/03~RPC%20框架/Dubbo/README.md)
62 | - [2.4.2.1 K8s [1]](/02~微服务%20RPC/03~RPC%20框架/Dubbo/K8s/README.md)
63 | - [2.4.2.1.1 K8s 与 Dubbo](/02~微服务%20RPC/03~RPC%20框架/Dubbo/K8s/K8s%20与%20Dubbo.md)
64 | - [2.4.2.2 架构机制](/02~微服务%20RPC/03~RPC%20框架/Dubbo/架构机制/README.md)
65 |
66 | - [2.4.2.3 踩坑汇总](/02~微服务%20RPC/03~RPC%20框架/Dubbo/踩坑汇总.md)
67 | - 2.4.3 Rpcx [2]
68 | - [2.4.3.1 Go RPC 框架](/02~微服务%20RPC/03~RPC%20框架/Rpcx/Go%20RPC%20框架.md)
69 | - [2.4.3.2 REAMDE](/02~微服务%20RPC/03~RPC%20框架/Rpcx/REAMDE.md)
70 | - [2.4.4 ServiceComb](/02~微服务%20RPC/03~RPC%20框架/ServiceComb/README.md)
71 |
72 | - [2.4.5 gRPC [2]](/02~微服务%20RPC/03~RPC%20框架/gRPC/README.md)
73 | - 2.4.5.1 99~参考资料 [1]
74 | - [2.4.5.1.1 李文周 gRPC 教程](/02~微服务%20RPC/03~RPC%20框架/gRPC/99~参考资料/2019-李文周-gRPC%20教程.md)
75 | - [2.4.5.2 开发环境](/02~微服务%20RPC/03~RPC%20框架/gRPC/开发环境.md)
76 | - 2.5 10~实践案例 [1]
77 | - [2.5.1 爱奇艺微服务标准技术架构实践](/02~微服务%20RPC/10~实践案例/爱奇艺微服务标准技术架构实践.md)
78 | - 2.6 99~参考资料 [2]
79 | - 2.6.1 RPC 服务治理框架实战 [1]
80 | - [2.6.1.1 Java RPC 框架](/02~微服务%20RPC/99~参考资料/2019-RPC%20服务治理框架实战/Java%20RPC%20框架.md)
81 | - [2.6.2 RPC 从零开始](/02~微服务%20RPC/99~参考资料/2020-RPC%20从零开始/README.md)
82 |
83 | - [3 03~微服务模式 [6]](/03~微服务模式/README.md)
84 | - [3.1 N + 1 查询](/03~微服务模式/N%20+%201%20查询/README.md)
85 |
86 | - [3.2 分布式追踪 [3]](/03~微服务模式/分布式追踪/README.md)
87 | - [3.2.1 OpenTelemetry](/03~微服务模式/分布式追踪/OpenTelemetry/README.md)
88 |
89 | - [3.2.2 OpenTracing](/03~微服务模式/分布式追踪/OpenTracing/README.md)
90 |
91 | - 3.2.3 系统设计 [2]
92 | - [3.2.3.1 框架对比](/03~微服务模式/分布式追踪/系统设计/框架对比.md)
93 | - [3.2.3.2 系统设计](/03~微服务模式/分布式追踪/系统设计/系统设计.md)
94 | - [3.3 协议编码 [4]](/03~微服务模式/协议编码/README.md)
95 | - [3.3.1 Avro [2]](/03~微服务模式/协议编码/Avro/README.md)
96 | - [3.3.1.1 Java](/03~微服务模式/协议编码/Avro/Java.md)
97 | - [3.3.1.2 模式演变](/03~微服务模式/协议编码/Avro/模式演变.md)
98 | - [3.3.2 Json [2]](/03~微服务模式/协议编码/Json/README.md)
99 | - [3.3.2.1 JSONSchema](/03~微服务模式/协议编码/Json/JSONSchema.md)
100 | - [3.3.2.2 二进制编码](/03~微服务模式/协议编码/Json/二进制编码.md)
101 | - [3.3.3 Protobuf [2]](/03~微服务模式/协议编码/Protobuf/README.md)
102 | - [3.3.3.1 快速开始](/03~微服务模式/协议编码/Protobuf/快速开始.md)
103 | - [3.3.3.2 类型定义](/03~微服务模式/协议编码/Protobuf/类型定义.md)
104 | - [3.3.4 Thrift](/03~微服务模式/协议编码/Thrift/README.md)
105 |
106 | - [3.4 发布订阅](/03~微服务模式/发布订阅/README.md)
107 |
108 | - [3.5 消息传递 [1]](/03~微服务模式/消息传递/README.md)
109 | - [3.5.1 数据流的类型](/03~微服务模式/消息传递/数据流的类型.md)
110 | - [3.6 消息队列](/03~微服务模式/消息队列/README.md)
111 |
112 | - [4 04~接入网关 [4]](/04~接入网关/README.md)
113 | - [4.1 02~负载均衡 [4]](/04~接入网关/02~负载均衡/README.md)
114 | - [4.1.1 LVS](/04~接入网关/02~负载均衡/LVS/README.md)
115 |
116 | - [4.1.2 Scratch [1]](/04~接入网关/02~负载均衡/Scratch/README.md)
117 | - [4.1.2.1 基于 Go 的简单负载均衡](/04~接入网关/02~负载均衡/Scratch/基于%20Go%20的简单负载均衡.md)
118 | - [4.1.3 分流算法](/04~接入网关/02~负载均衡/分流算法.md)
119 | - [4.1.4 负载分层](/04~接入网关/02~负载均衡/负载分层.md)
120 | - 4.2 04~接入网关 [1]
121 | - 4.2.1 Kong [1]
122 | - [4.2.1.1 Kong](/04~接入网关/04~接入网关/Kong/Kong.md)
123 | - [4.3 05~长连接服务 [3]](/04~接入网关/05~长连接服务/README.md)
124 | - 4.3.1 DeepStream [1]
125 | - [4.3.1.1 DeepStream](/04~接入网关/05~长连接服务/DeepStream/DeepStream.md)
126 | - [4.3.2 WebSocket 网关](/04~接入网关/05~长连接服务/WebSocket%20网关/README.md)
127 |
128 | - [4.3.3 多机房多网络](/04~接入网关/05~长连接服务/多机房多网络.md)
129 | - 4.4 10~实践案例 [4]
130 | - [4.4.1 喜马拉雅 自研网关架构演进过程](/04~接入网关/10~实践案例/2021-喜马拉雅-自研网关架构演进过程.md)
131 | - [4.4.2 爱奇艺 基于 Netty 的长连接网关](/04~接入网关/10~实践案例/2021-爱奇艺-基于%20Netty%20的长连接网关.md)
132 | - [4.4.3 How Tinder Built Their Own API Gateway](/04~接入网关/10~实践案例/2022-How%20Tinder%20Built%20Their%20Own%20API%20Gateway.md)
133 | - [4.4.4 Scratch [2]](/04~接入网关/10~实践案例/Scratch/README.md)
134 | - [4.4.4.1 基于 Netty 与 Webflux 的网关](/04~接入网关/10~实践案例/Scratch/基于%20Netty%20与%20Webflux%20的网关/README.md)
135 |
136 | - [4.4.4.2 网关特性](/04~接入网关/10~实践案例/Scratch/网关特性.md)
137 | - [5 05~服务网格 [6]](/05~服务网格/README.md)
138 | - [5.1 Envoy [1]](/05~服务网格/Envoy/README.md)
139 | - [5.1.1 Kuma](/05~服务网格/Envoy/Kuma/README.md)
140 |
141 | - [5.2 Istio](/05~服务网格/Istio/README.md)
142 |
143 | - [5.3 Linkerd](/05~服务网格/Linkerd/README.md)
144 |
145 | - [5.4 Serverless [3]](/05~服务网格/Serverless/README.md)
146 | - [5.4.1 函数模式](/05~服务网格/Serverless/函数模式.md)
147 | - [5.4.2 设计模式](/05~服务网格/Serverless/设计模式.md)
148 | - [5.4.3 阿里云](/05~服务网格/Serverless/阿里云.md)
149 | - 5.5 可视化 [1]
150 | - [5.5.1 Kiali](/05~服务网格/可视化/Kiali/README.md)
151 |
152 | - 5.6 设计与对比 [4]
153 | - [5.6.1 Sidecar](/05~服务网格/设计与对比/Sidecar.md)
154 | - [5.6.2 应用场景](/05~服务网格/设计与对比/应用场景.md)
155 | - [5.6.3 框架对比](/05~服务网格/设计与对比/框架对比.md)
156 | - [5.6.4 背景分析](/05~服务网格/设计与对比/背景分析.md)
157 | - 6 10~系统案例 [1]
158 | - [6.1 其他案例 [2]](/10~系统案例/其他案例/README.md)
159 | - [6.1.1 System Design Primer [8]](/10~系统案例/其他案例/System%20Design%20Primer/README.md)
160 | - [6.1.1.1 AWS 上设计一个百万用户级别的系统](/10~系统案例/其他案例/System%20Design%20Primer/AWS%20上设计一个百万用户级别的系统.md)
161 | - [6.1.1.2 Mint](/10~系统案例/其他案例/System%20Design%20Primer/Mint.md)
162 | - [6.1.1.3 Twitter 时间线和搜索](/10~系统案例/其他案例/System%20Design%20Primer/Twitter%20时间线和搜索.md)
163 | - [6.1.1.4 按类别分类的 Amazon 销售排名](/10~系统案例/其他案例/System%20Design%20Primer/按类别分类的%20Amazon%20销售排名.md)
164 | - [6.1.1.5 搜索引擎的 KV 存储](/10~系统案例/其他案例/System%20Design%20Primer/搜索引擎的%20KV%20存储.md)
165 | - [6.1.1.6 社交网络设计数据结构](/10~系统案例/其他案例/System%20Design%20Primer/社交网络设计数据结构.md)
166 | - [6.1.1.7 网页爬虫](/10~系统案例/其他案例/System%20Design%20Primer/网页爬虫.md)
167 | - [6.1.1.8 设计 Pastebin.com (或者 Bit.ly)](/10~系统案例/其他案例/System%20Design%20Primer/设计%20Pastebin.com%20(或者%20Bit.ly).md)
168 | - [6.1.2 刚果商城](/10~系统案例/其他案例/刚果商城/README.md)
169 |
170 | - [7 INTRODUCTION](/INTRODUCTION.md)
--------------------------------------------------------------------------------
/认证基础/99~参考资料/2023-Password, Session, Cookie, Token, JWT, SSO, OAuth - Authentication Explained.md:
--------------------------------------------------------------------------------
1 | > [原文地址](https://blog.bytebytego.com/p/password-session-cookie-token-jwt)
2 |
3 | # Password, Session, Cookie, Token, JWT, SSO, OAuth - Authentication Explained
4 |
5 | When we use various applications and websites, three essential security steps are continuously at play:
6 |
7 | - Identity
8 | - Authentication
9 | - Authorization
10 |
11 | The diagram below shows where these methods apply in a typical website architecture and their meanings.
12 |
13 | [](https://substackcdn.com/image/fetch/f_auto,q_auto:good,fl_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2Fced6562d-3be6-4dd4-a141-fed9e6b02182_1600x1226.png)
14 |
15 | In this 2-part series, we dive into different authentication methods, including passwords, sessions, cookies, tokens, JWTs (JSON Web Tokens), SSO (Single Sign-On), and OAuth2. We discuss the problems each method solves and how to choose the right authentication method for our needs.
16 |
17 | # Password Authentication
18 |
19 | Password authentication is a fundamental and widely used mechanism for verifying a user's identity on websites and applications. In this method, users enter their unique username and password combination to gain access to protected resources. The entered credentials are checked against stored user information in the system, and if they match, the user is granted access.
20 |
21 | While password authentication is a foundational method for user verification, it has some limitations. Users may forget their passwords, and managing unique usernames and passwords for multiple websites can be challenging. Furthermore, password-based systems can be vulnerable to attacks, such as brute-force or dictionary attacks, if proper security measures aren't in place.
22 |
23 | To address these issues, modern systems often implement additional security measures, such as multi-factor authentication, or use other authentication mechanisms (e.g., session-cookie or token-based authentication) to complement or replace password-based authentication for subsequent access to protected resources.
24 |
25 | In this section, we will cover password-based authentication first to understand its history and how it functions.
26 |
27 | ## HTTP Basic Access Authentication
28 |
29 | HTTP basic access authentication requires a web browser to provide a username and a password when requesting a protected resource. The credentials are encoded using the Base64 algorithm and included in the HTTP header field _Authorization: Basic_.
30 |
31 | Here's how it typically works:
32 |
33 | 1. The client sends a request to access a protected resource on the server.
34 | 2. If the client has not yet provided any authentication credentials, the server responds with a 401 Unauthorized status code and includes the WWW-Authenticate: Basic header to indicate that it requires basic authentication.
35 | 3. The client then prompts the user to enter their username and password, which are combined into a single string in the format username:password.
36 | 4. The combined string is Base64 encoded and included in the "Authorization: Basic" header in the subsequent request to the server, e.g., Authorization: Basic dXNlcm5hbWU6cGFzc3dvcmQ=.
37 | 5. Upon receiving the request, the server decodes the Base64-encoded credentials and separates the username and password. The server then checks the provided credentials against its user database or authentication service.
38 | 6. If the credentials match, the server grants access to the requested resource. If not, the server responds with a 401 Unauthorized status code.
39 |
40 | HTTP Basic Access Authentication has limitations. The username and password, encoded using Base64, can be easily decoded. Most websites use TLS (Transport Layer Security) to encrypt data between the browser and server, improving security. However, users' credentials may still be exposed to interception or man-in-the-middle attacks.
41 |
42 | With HTTP Basic Access Authentication, the browser sends the Authorization header with the necessary credentials for each request to protected resources within the same domain. This provides a smoother user experience, without repeatedly entering the username and password. But, as each website maintains its own usernames and passwords, users may find it difficult to remember their credentials.
43 |
44 | This authentication mechanism is obsolete for modern websites.
45 |
46 | [](https://substackcdn.com/image/fetch/f_auto,q_auto:good,fl_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F10e83d0a-8fb5-42f6-abeb-a5e8980450c3_1600x1275.png)
47 |
48 | ## Session-Cookie Authentication
49 |
50 | Session-cookie authentication addresses HTTP basic access authentication's inability to track user login status. A session ID is generated to track the user's status during their visit. This session ID is recorded both server-side and in the client’s cookie, serving as an authentication mechanism. It is called a session-cookie because it is a cookie with the session ID stored inside. Users must still provide their username and password initially, after which the server creates a session for the user's visit. Subsequent requests include the cookie, allowing the server to compare client-side and server-side session IDs.
51 |
52 | Let’s see how it works:
53 |
54 | 1. The client sends a request to access a protected resource on the server. If the client has not yet authenticated, the server responds with a login prompt. The client submits their username and password to the server.
55 | 2. The server verifies the provided credentials against its user database or authentication service. If the credentials match, the server generates a unique session ID and creates a corresponding session in the server-side storage (e.g., server memory, database, or session server).
56 | 3. The server sends the session ID to the client as a cookie, typically with a Set-Cookie header.
57 | 4. The client stores the session cookie.
58 | 5. For subsequent requests, it sends the cookie along with the request headers.
59 | 6. The server checks the session ID in the cookie against the stored session data to authenticate the user.
60 | 7. If validated, the server grants access to the requested resource. When the user logs out or after a predetermined expiration time, the server invalidates the session, and the client deletes the session cookie.
61 |
62 | [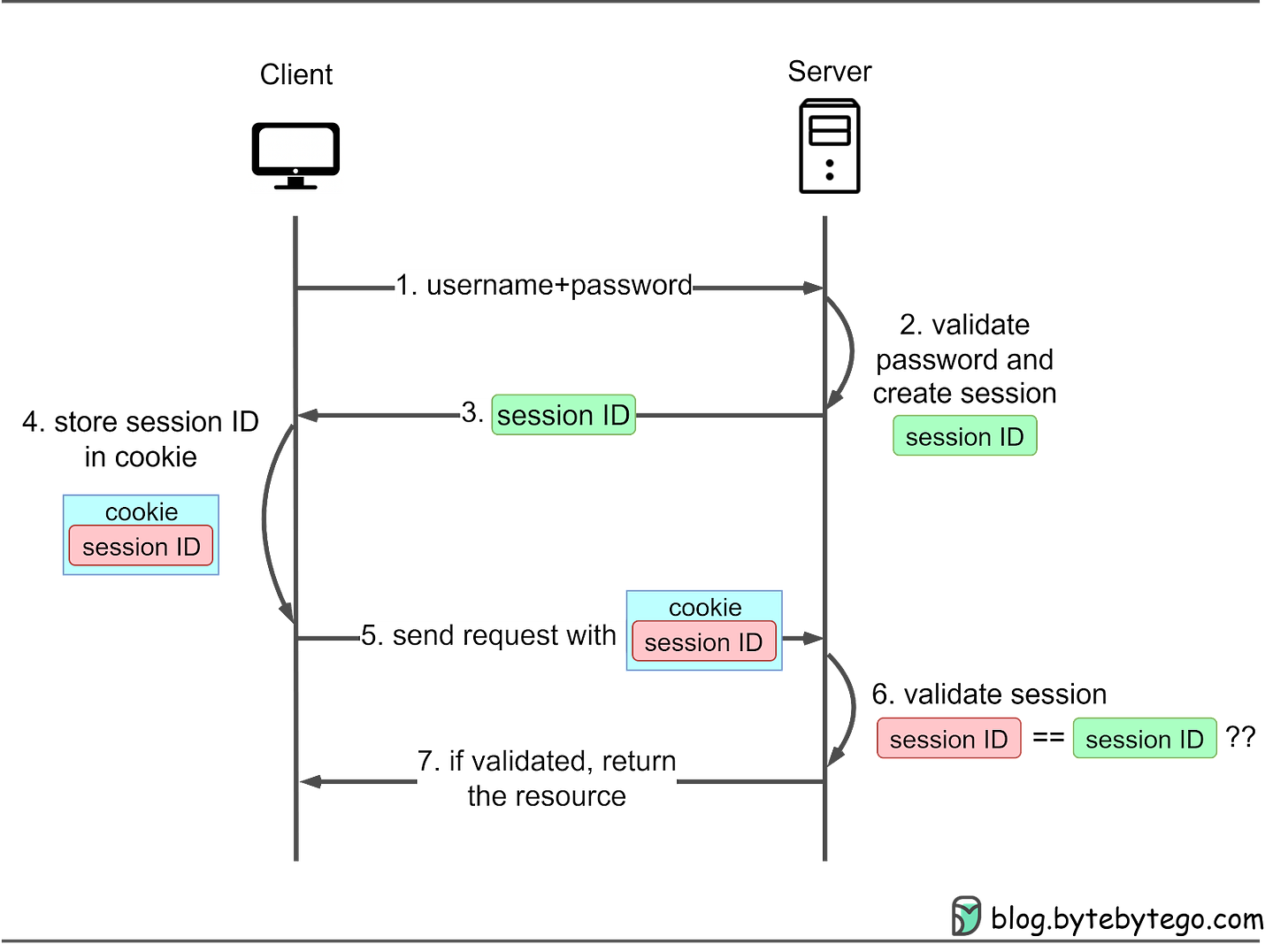](https://substackcdn.com/image/fetch/f_auto,q_auto:good,fl_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F9b3002be-d4f2-489c-99cd-f789012d76dc_1600x1173.png)
63 |
64 | # Passwordless Authentication
65 |
66 | We have covered three types of authentication so far: HTTP basic authentication, session-cookie authentication, and token-based authentication. They all require a password. However, there are other ways to prove your identity without a password.
67 |
68 | When it comes to authentication, there are three factors to consider:
69 |
70 | - Knowledge factors: something you know, such as a password
71 | - Ownership factors: something you own, such as a device or phone number
72 | - Inherence factors: something unique to you, such as your biometric features
73 |
74 | Passwords fall under “something you know”. One-Time Passwords (OTP) prove that the user owns a cell phone or a device, while biometric authentication proves "something unique to you".
75 |
76 | ## One-Time Passwords (OTP)
77 |
78 | One-Time Passwords (OTP) are widely used as a more secure method of authentication. Unlike static passwords, which can be reused, OTPs are valid for a limited time, typically a few minutes. This means that even if someone intercepts an OTP, they can’t use it to log in later. Additionally, OTPs require “something you own” as well as “something you know” to log in. This can be a cell phone number or email address that the user has access to, making it harder for hackers to steal.
79 |
80 | However, it's important to note that using SMS as the delivery method for OTPs can be less secure than other methods. This is because SMS messages can be intercepted or redirected by hackers, particularly if the user's phone number has been compromised. In some cases, attackers have been able to hijack phone numbers by convincing the mobile carrier to transfer the number to a new SIM card. Once the attacker has control of the number, they can intercept any OTPs sent via SMS. For this reason, it's recommended to use alternative delivery methods, such as email or mobile apps, whenever possible.
81 |
82 | Here’s how OTPs work in more detail:
83 |
84 | Step 1: The user wants to log in to a website and is asked to enter a username, cell phone number, or email.
85 |
86 | Step 2: The server generates an OTP with an expiration time.
87 |
88 | Step 3: The server sends the OTP to the user’s device via SMS or email.
89 |
90 | Step 4: The user enters the OTP received in the login box.
91 |
92 | Step 5-6: The server compares the generated OTP with the one the user entered. If they match, login is granted.
93 |
94 | [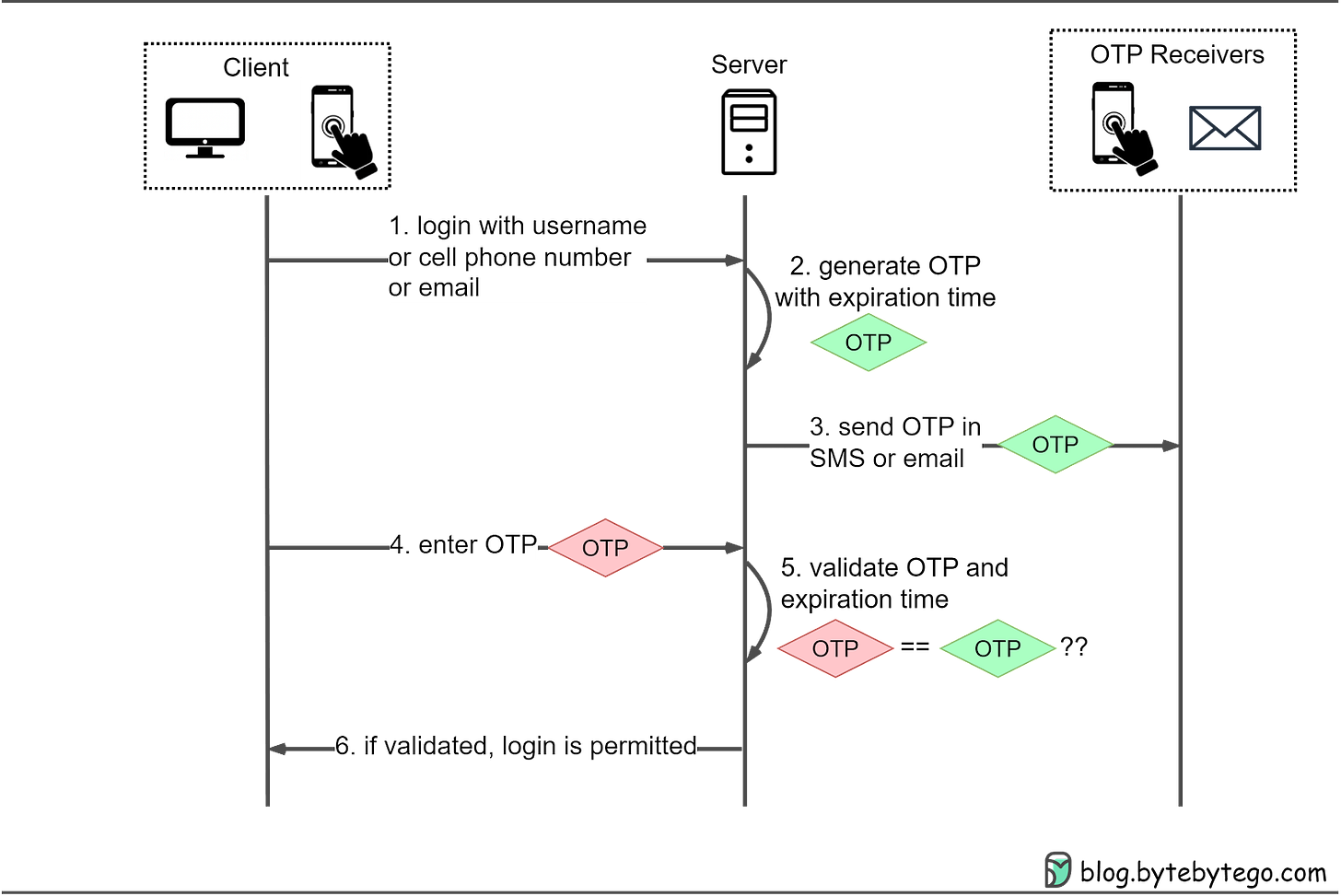](https://substackcdn.com/image/fetch/f_auto,q_auto:good,fl_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2Fb27865df-e833-47c8-9340-cba5510a90a0_1600x1069.png)
95 |
96 | Alternatively, a hardware or software key can be used to generate OTPs for multi-factor authentication (MFA). For example, Google 2FA uses a software key that generates a new OTP every 30 seconds. When logging in, users enter their password and the current OTP displayed on their device. This adds an extra layer of security as hackers would need access to the user’s device to steal the OTP. More on MFA later.
97 |
98 | ## SSO (Single Sign-On)
99 |
100 | Single Sign-On (SSO) is a user authentication method that allows us to access multiple systems or applications with a single set of credentials. SSO streamlines the login process, providing a seamless user experience across various platforms.
101 |
102 | The SSO process mainly relies on a Central Authentication Service (CAS) server. Here's a step-by-step breakdown of the SSO process:
103 |
104 | - When we attempt to log in to an application, such as Gmail, we're redirected to the CAS server.
105 | - The CAS server verifies our login credentials and creates a Ticket Granting Ticket (TGT). This TGT is then stored in a Ticket Granting Cookie (TGC) on our browser, representing our global session.
106 | - CAS generates a Service Ticket (ST) for our visit to Gmail and redirects us back to Gmail with the ST.
107 | - Gmail uses the ST to validate our login with the CAS server. After validation, we can access Gmail.
108 |
109 | When we want to access another application, like YouTube, the process is simplified:
110 |
111 | - Since we already have a TGC from our Gmail login, CAS recognizes our authenticated status.
112 | - CAS generates a new ST for YouTube access, and we can use YouTube without inputting our credentials again.
113 |
114 | This process reduces the need to remember and enter multiple sets of credentials for different applications.
115 |
116 | [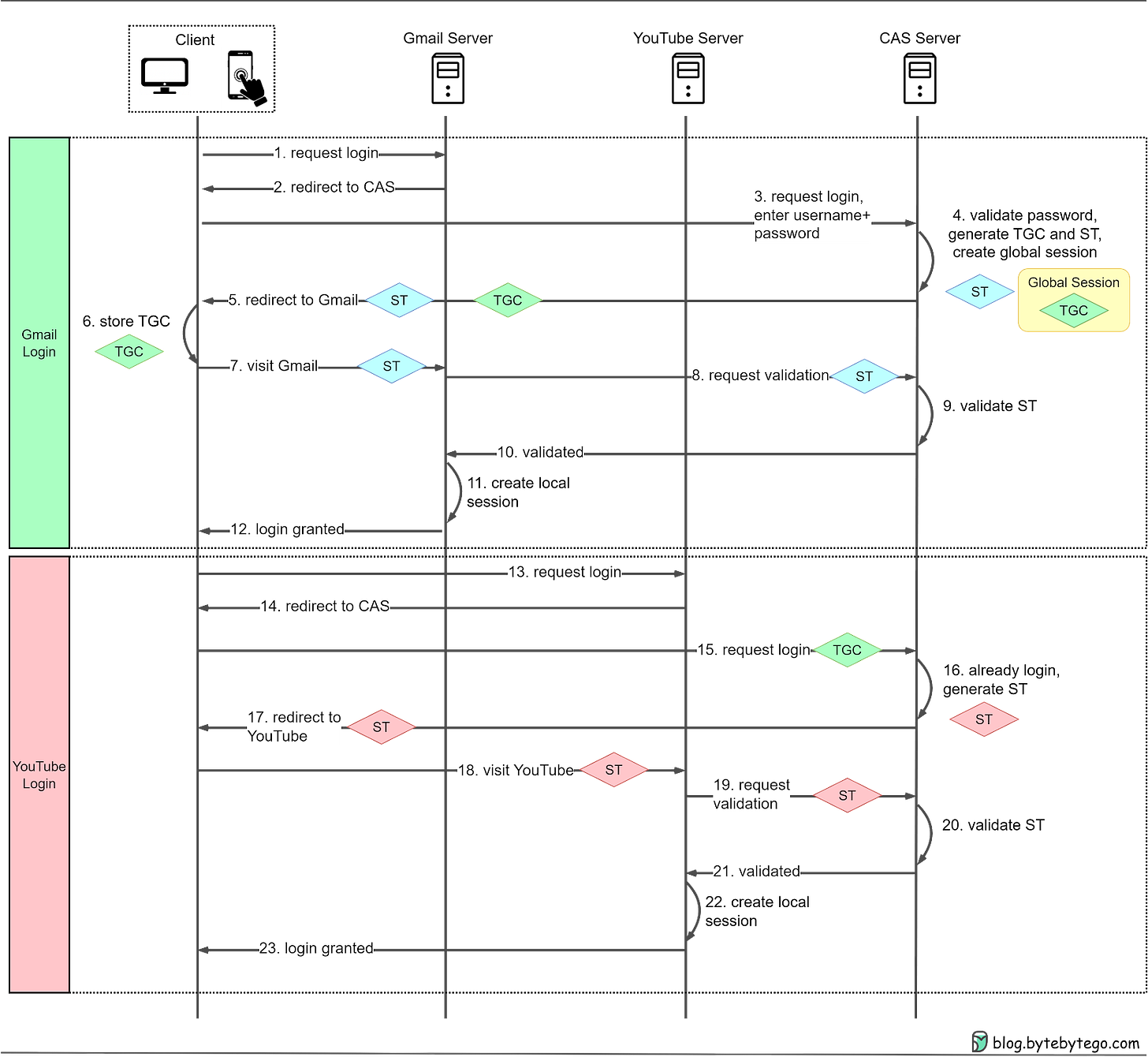](https://substackcdn.com/image/fetch/f_auto,q_auto:good,fl_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2Fff52780c-e94e-4d80-a083-7c9cbead8b6f_1600x1473.png)
117 |
118 | There are different protocols that facilitate SSO:
119 |
120 | - SAML (Security Assertion Markup Language) is widely used in enterprise applications. SAML communicates authentication and authorization data in an XML format.
121 | - OIDC (OpenID Connect) is popular in consumer applications. OIDC handles authentication through JSON Web Tokens (JWT) and builds on the OAuth 2.0 framework. More on this in the next section.
122 |
123 | For new applications, OIDC is the preferred choice. It supports various client types, including web-based, mobile, and [JavaScript clients](https://openid.net/connect/).
124 |
125 | SSO offers a streamlined and secure authentication method, providing a seamless user experience by requiring only one set of credentials for multiple applications. This approach enhances security through the use of strong, unique passwords and reduced phishing risks. It also minimizes administrative burdens for IT departments.
126 |
127 | ## OAuth 2.0 and OpenID Connect (OIDC)
128 |
129 | While OAuth 2.0 is primarily an authorization framework, it can be used in conjunction with OpenID Connect (OIDC) for authentication purposes. OIDC is an authentication layer built on top of OAuth 2.0, enabling the verification of a user's identity and granting controlled access to protected resources.
130 |
131 | When using "Sign in with Google" or similar features, OAuth 2.0 and OIDC work together to streamline the authentication process. OIDC provides user identity data in the form of a standardized JSON Web Token (JWT). This token contains information about the authenticated user, allowing the third-party application to create a user profile without requiring a separate registration process.
132 |
133 | In this setup, [OAuth 2.0](https://oauth.net/2/) provides "secure delegated access" by issuing short-lived tokens instead of passwords, allowing third-party services to access protected resources with the resource owner's permission. This method enhances security, as the third-party service does not handle or store the user's password directly.
134 |
135 | The diagram below shows how the protocol works in the “Sign in with Google” scenario.
136 |
137 | [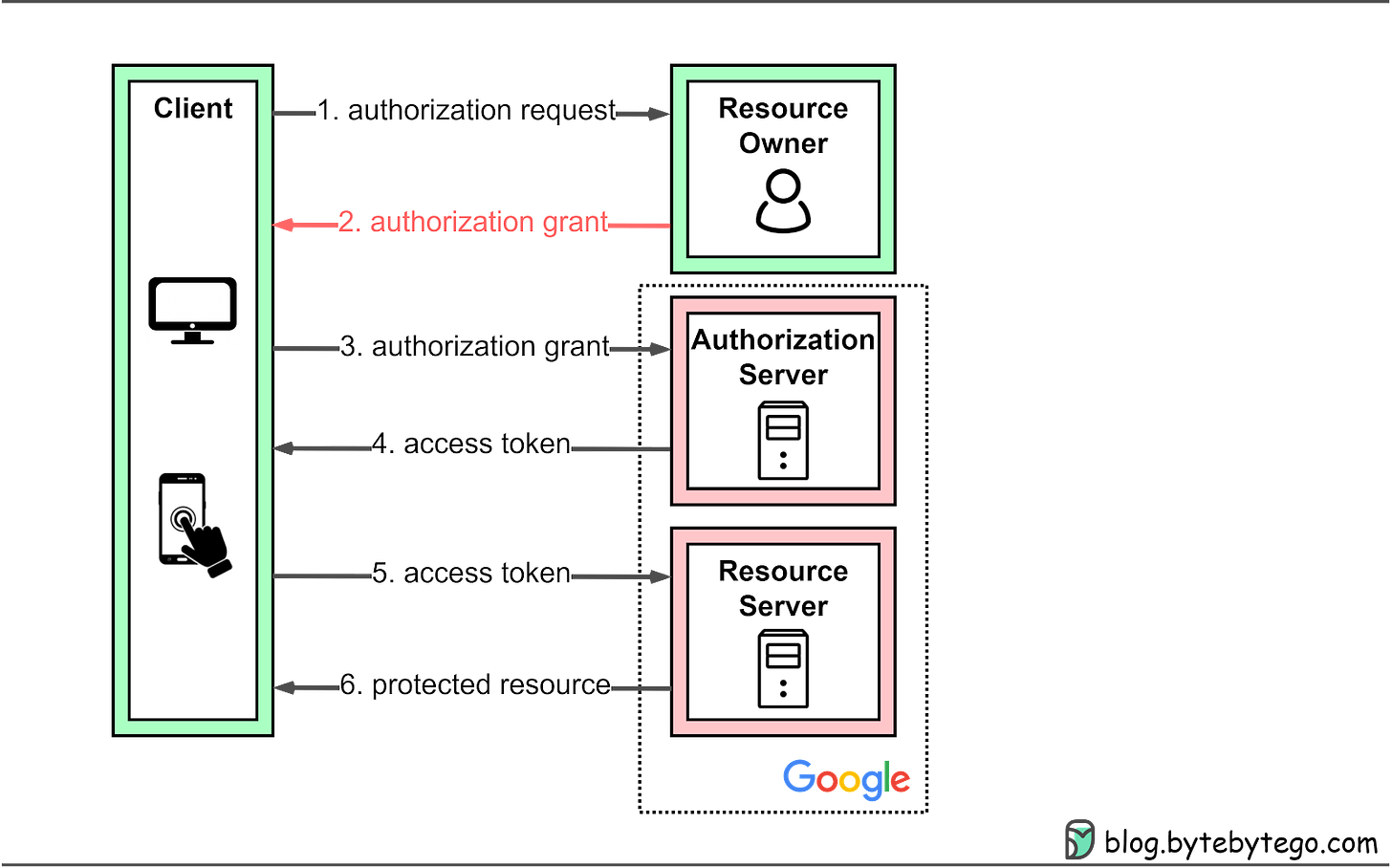](https://substackcdn.com/image/fetch/f_auto,q_auto:good,fl_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F75a1f3e9-7bad-410a-b059-66ccd6189f6b_1600x998.png)
138 |
139 | In the “Sign in with Google” example, OAuth 2.0 defines four roles:
140 |
141 | 1. Resource owner: The end user, who controls access to their personal data.
142 | 2. Resource server: The Google server hosting user profiles as protected resources. It uses access tokens to respond to protected resource requests, ensuring that only authorized services can access the data.
143 | 3. Client: The device (PC or smartphone) making requests on behalf of the resource owner. This device represents the third-party application seeking access to the user's data.
144 | 4. Authorization server: The Google authorization server that issues tokens to clients, managing the secure exchange of tokens between the resource server and the client.
145 |
146 | OAuth 2.0 offers four types of authorization grants to accommodate different situations:
147 |
148 | 1. Authorization code grant: The most complete and versatile mode, suitable for most application types. More details below.
149 | 2. Implicit grant: Designed for applications with only a frontend, such as single-page applications or mobile apps. This is no longer recommended. More details below.
150 | 3. Resource owner password credentials grant: Used when users trust a third-party application with their credentials, such as a trusted mobile app.
151 | 4. Client credentials grant: Suitable for cases without a frontend, like command-line tools or server-to-server communication, where resource owner interaction is not needed.
152 |
153 | The standard provides multiple modes to cater to different application scenarios and requirements, ensuring flexibility and adaptability for diverse situations.
154 |
155 | The authorization code grant is one example worth examining. The specifications for the other three grant types are available in [RFC-6749](https://www.rfc-editor.org/rfc/rfc6749).
156 |
157 | [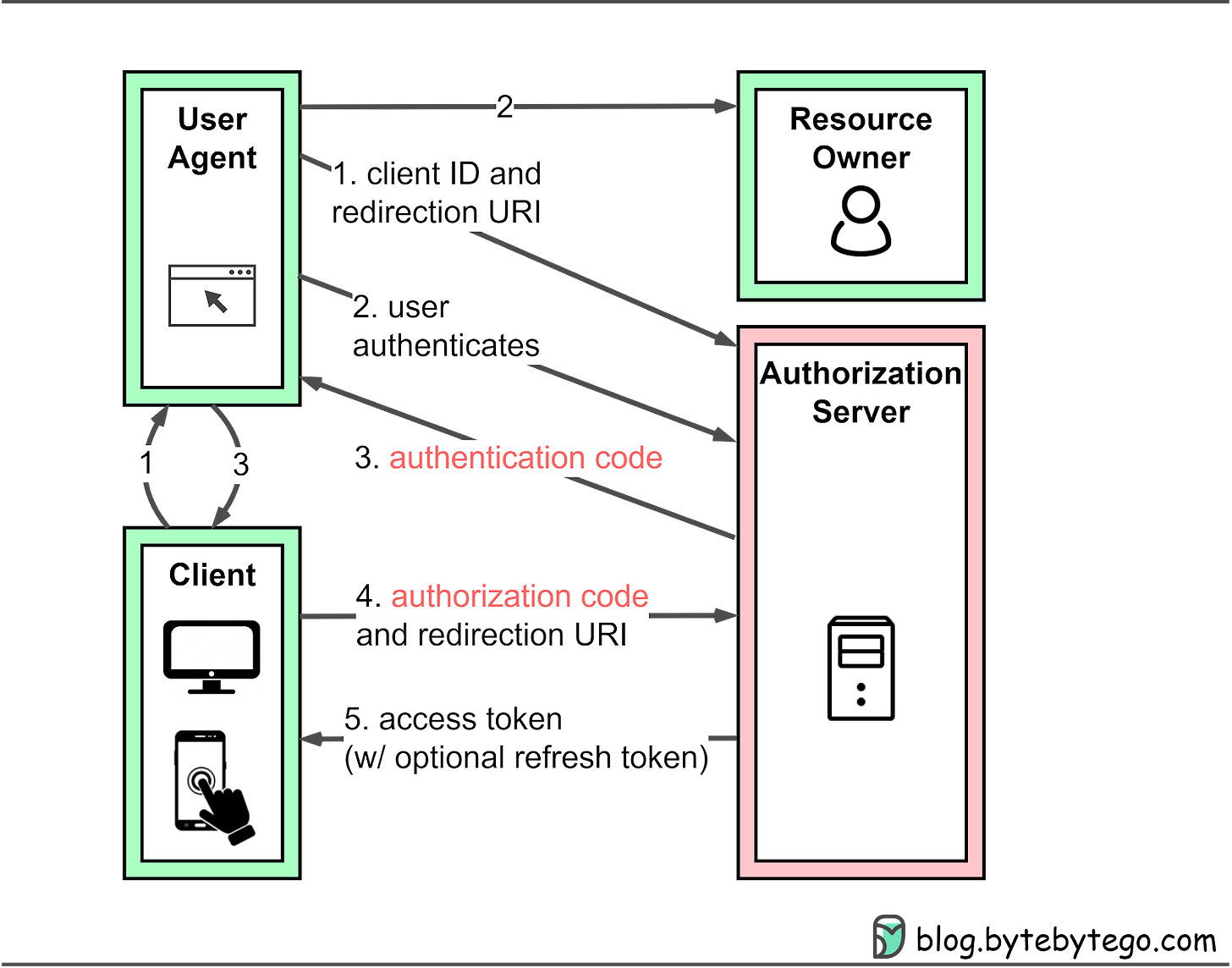](https://substackcdn.com/image/fetch/f_auto,q_auto:good,fl_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2Fce0b4f94-1fae-4d70-a71e-1f82ef93220c_1600x1257.png)
158 |
--------------------------------------------------------------------------------
/LICENSE:
--------------------------------------------------------------------------------
1 | Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International
2 | Public License
3 |
4 | By exercising the Licensed Rights (defined below), You accept and agree
5 | to be bound by the terms and conditions of this Creative Commons
6 | Attribution-NonCommercial-ShareAlike 4.0 International Public License
7 | ("Public License"). To the extent this Public License may be
8 | interpreted as a contract, You are granted the Licensed Rights in
9 | consideration of Your acceptance of these terms and conditions, and the
10 | Licensor grants You such rights in consideration of benefits the
11 | Licensor receives from making the Licensed Material available under
12 | these terms and conditions.
13 |
14 |
15 | Section 1 -- Definitions.
16 |
17 | a. Adapted Material means material subject to Copyright and Similar
18 | Rights that is derived from or based upon the Licensed Material
19 | and in which the Licensed Material is translated, altered,
20 | arranged, transformed, or otherwise modified in a manner requiring
21 | permission under the Copyright and Similar Rights held by the
22 | Licensor. For purposes of this Public License, where the Licensed
23 | Material is a musical work, performance, or sound recording,
24 | Adapted Material is always produced where the Licensed Material is
25 | synched in timed relation with a moving image.
26 |
27 | b. Adapter's License means the license You apply to Your Copyright
28 | and Similar Rights in Your contributions to Adapted Material in
29 | accordance with the terms and conditions of this Public License.
30 |
31 | c. BY-NC-SA Compatible License means a license listed at
32 | creativecommons.org/compatiblelicenses, approved by Creative
33 | Commons as essentially the equivalent of this Public License.
34 |
35 | d. Copyright and Similar Rights means copyright and/or similar rights
36 | closely related to copyright including, without limitation,
37 | performance, broadcast, sound recording, and Sui Generis Database
38 | Rights, without regard to how the rights are labeled or
39 | categorized. For purposes of this Public License, the rights
40 | specified in Section 2(b)(1)-(2) are not Copyright and Similar
41 | Rights.
42 |
43 | e. Effective Technological Measures means those measures that, in the
44 | absence of proper authority, may not be circumvented under laws
45 | fulfilling obligations under Article 11 of the WIPO Copyright
46 | Treaty adopted on December 20, 1996, and/or similar international
47 | agreements.
48 |
49 | f. Exceptions and Limitations means fair use, fair dealing, and/or
50 | any other exception or limitation to Copyright and Similar Rights
51 | that applies to Your use of the Licensed Material.
52 |
53 | g. License Elements means the license attributes listed in the name
54 | of a Creative Commons Public License. The License Elements of this
55 | Public License are Attribution, NonCommercial, and ShareAlike.
56 |
57 | h. Licensed Material means the artistic or literary work, database,
58 | or other material to which the Licensor applied this Public
59 | License.
60 |
61 | i. Licensed Rights means the rights granted to You subject to the
62 | terms and conditions of this Public License, which are limited to
63 | all Copyright and Similar Rights that apply to Your use of the
64 | Licensed Material and that the Licensor has authority to license.
65 |
66 | j. Licensor means the individual(s) or entity(ies) granting rights
67 | under this Public License.
68 |
69 | k. NonCommercial means not primarily intended for or directed towards
70 | commercial advantage or monetary compensation. For purposes of
71 | this Public License, the exchange of the Licensed Material for
72 | other material subject to Copyright and Similar Rights by digital
73 | file-sharing or similar means is NonCommercial provided there is
74 | no payment of monetary compensation in connection with the
75 | exchange.
76 |
77 | l. Share means to provide material to the public by any means or
78 | process that requires permission under the Licensed Rights, such
79 | as reproduction, public display, public performance, distribution,
80 | dissemination, communication, or importation, and to make material
81 | available to the public including in ways that members of the
82 | public may access the material from a place and at a time
83 | individually chosen by them.
84 |
85 | m. Sui Generis Database Rights means rights other than copyright
86 | resulting from Directive 96/9/EC of the European Parliament and of
87 | the Council of 11 March 1996 on the legal protection of databases,
88 | as amended and/or succeeded, as well as other essentially
89 | equivalent rights anywhere in the world.
90 |
91 | n. You means the individual or entity exercising the Licensed Rights
92 | under this Public License. Your has a corresponding meaning.
93 |
94 |
95 | Section 2 -- Scope.
96 |
97 | a. License grant.
98 |
99 | 1. Subject to the terms and conditions of this Public License,
100 | the Licensor hereby grants You a worldwide, royalty-free,
101 | non-sublicensable, non-exclusive, irrevocable license to
102 | exercise the Licensed Rights in the Licensed Material to:
103 |
104 | a. reproduce and Share the Licensed Material, in whole or
105 | in part, for NonCommercial purposes only; and
106 |
107 | b. produce, reproduce, and Share Adapted Material for
108 | NonCommercial purposes only.
109 |
110 | 2. Exceptions and Limitations. For the avoidance of doubt, where
111 | Exceptions and Limitations apply to Your use, this Public
112 | License does not apply, and You do not need to comply with
113 | its terms and conditions.
114 |
115 | 3. Term. The term of this Public License is specified in Section
116 | 6(a).
117 |
118 | 4. Media and formats; technical modifications allowed. The
119 | Licensor authorizes You to exercise the Licensed Rights in
120 | all media and formats whether now known or hereafter created,
121 | and to make technical modifications necessary to do so. The
122 | Licensor waives and/or agrees not to assert any right or
123 | authority to forbid You from making technical modifications
124 | necessary to exercise the Licensed Rights, including
125 | technical modifications necessary to circumvent Effective
126 | Technological Measures. For purposes of this Public License,
127 | simply making modifications authorized by this Section 2(a)
128 | (4) never produces Adapted Material.
129 |
130 | 5. Downstream recipients.
131 |
132 | a. Offer from the Licensor -- Licensed Material. Every
133 | recipient of the Licensed Material automatically
134 | receives an offer from the Licensor to exercise the
135 | Licensed Rights under the terms and conditions of this
136 | Public License.
137 |
138 | b. Additional offer from the Licensor -- Adapted Material.
139 | Every recipient of Adapted Material from You
140 | automatically receives an offer from the Licensor to
141 | exercise the Licensed Rights in the Adapted Material
142 | under the conditions of the Adapter's License You apply.
143 |
144 | c. No downstream restrictions. You may not offer or impose
145 | any additional or different terms or conditions on, or
146 | apply any Effective Technological Measures to, the
147 | Licensed Material if doing so restricts exercise of the
148 | Licensed Rights by any recipient of the Licensed
149 | Material.
150 |
151 | 6. No endorsement. Nothing in this Public License constitutes or
152 | may be construed as permission to assert or imply that You
153 | are, or that Your use of the Licensed Material is, connected
154 | with, or sponsored, endorsed, or granted official status by,
155 | the Licensor or others designated to receive attribution as
156 | provided in Section 3(a)(1)(A)(i).
157 |
158 | b. Other rights.
159 |
160 | 1. Moral rights, such as the right of integrity, are not
161 | licensed under this Public License, nor are publicity,
162 | privacy, and/or other similar personality rights; however, to
163 | the extent possible, the Licensor waives and/or agrees not to
164 | assert any such rights held by the Licensor to the limited
165 | extent necessary to allow You to exercise the Licensed
166 | Rights, but not otherwise.
167 |
168 | 2. Patent and trademark rights are not licensed under this
169 | Public License.
170 |
171 | 3. To the extent possible, the Licensor waives any right to
172 | collect royalties from You for the exercise of the Licensed
173 | Rights, whether directly or through a collecting society
174 | under any voluntary or waivable statutory or compulsory
175 | licensing scheme. In all other cases the Licensor expressly
176 | reserves any right to collect such royalties, including when
177 | the Licensed Material is used other than for NonCommercial
178 | purposes.
179 |
180 |
181 | Section 3 -- License Conditions.
182 |
183 | Your exercise of the Licensed Rights is expressly made subject to the
184 | following conditions.
185 |
186 | a. Attribution.
187 |
188 | 1. If You Share the Licensed Material (including in modified
189 | form), You must:
190 |
191 | a. retain the following if it is supplied by the Licensor
192 | with the Licensed Material:
193 |
194 | i. identification of the creator(s) of the Licensed
195 | Material and any others designated to receive
196 | attribution, in any reasonable manner requested by
197 | the Licensor (including by pseudonym if
198 | designated);
199 |
200 | ii. a copyright notice;
201 |
202 | iii. a notice that refers to this Public License;
203 |
204 | iv. a notice that refers to the disclaimer of
205 | warranties;
206 |
207 | v. a URI or hyperlink to the Licensed Material to the
208 | extent reasonably practicable;
209 |
210 | b. indicate if You modified the Licensed Material and
211 | retain an indication of any previous modifications; and
212 |
213 | c. indicate the Licensed Material is licensed under this
214 | Public License, and include the text of, or the URI or
215 | hyperlink to, this Public License.
216 |
217 | 2. You may satisfy the conditions in Section 3(a)(1) in any
218 | reasonable manner based on the medium, means, and context in
219 | which You Share the Licensed Material. For example, it may be
220 | reasonable to satisfy the conditions by providing a URI or
221 | hyperlink to a resource that includes the required
222 | information.
223 | 3. If requested by the Licensor, You must remove any of the
224 | information required by Section 3(a)(1)(A) to the extent
225 | reasonably practicable.
226 |
227 | b. ShareAlike.
228 |
229 | In addition to the conditions in Section 3(a), if You Share
230 | Adapted Material You produce, the following conditions also apply.
231 |
232 | 1. The Adapter's License You apply must be a Creative Commons
233 | license with the same License Elements, this version or
234 | later, or a BY-NC-SA Compatible License.
235 |
236 | 2. You must include the text of, or the URI or hyperlink to, the
237 | Adapter's License You apply. You may satisfy this condition
238 | in any reasonable manner based on the medium, means, and
239 | context in which You Share Adapted Material.
240 |
241 | 3. You may not offer or impose any additional or different terms
242 | or conditions on, or apply any Effective Technological
243 | Measures to, Adapted Material that restrict exercise of the
244 | rights granted under the Adapter's License You apply.
245 |
246 |
247 | Section 4 -- Sui Generis Database Rights.
248 |
249 | Where the Licensed Rights include Sui Generis Database Rights that
250 | apply to Your use of the Licensed Material:
251 |
252 | a. for the avoidance of doubt, Section 2(a)(1) grants You the right
253 | to extract, reuse, reproduce, and Share all or a substantial
254 | portion of the contents of the database for NonCommercial purposes
255 | only;
256 |
257 | b. if You include all or a substantial portion of the database
258 | contents in a database in which You have Sui Generis Database
259 | Rights, then the database in which You have Sui Generis Database
260 | Rights (but not its individual contents) is Adapted Material,
261 | including for purposes of Section 3(b); and
262 |
263 | c. You must comply with the conditions in Section 3(a) if You Share
264 | all or a substantial portion of the contents of the database.
265 |
266 | For the avoidance of doubt, this Section 4 supplements and does not
267 | replace Your obligations under this Public License where the Licensed
268 | Rights include other Copyright and Similar Rights.
269 |
270 |
271 | Section 5 -- Disclaimer of Warranties and Limitation of Liability.
272 |
273 | a. UNLESS OTHERWISE SEPARATELY UNDERTAKEN BY THE LICENSOR, TO THE
274 | EXTENT POSSIBLE, THE LICENSOR OFFERS THE LICENSED MATERIAL AS-IS
275 | AND AS-AVAILABLE, AND MAKES NO REPRESENTATIONS OR WARRANTIES OF
276 | ANY KIND CONCERNING THE LICENSED MATERIAL, WHETHER EXPRESS,
277 | IMPLIED, STATUTORY, OR OTHER. THIS INCLUDES, WITHOUT LIMITATION,
278 | WARRANTIES OF TITLE, MERCHANTABILITY, FITNESS FOR A PARTICULAR
279 | PURPOSE, NON-INFRINGEMENT, ABSENCE OF LATENT OR OTHER DEFECTS,
280 | ACCURACY, OR THE PRESENCE OR ABSENCE OF ERRORS, WHETHER OR NOT
281 | KNOWN OR DISCOVERABLE. WHERE DISCLAIMERS OF WARRANTIES ARE NOT
282 | ALLOWED IN FULL OR IN PART, THIS DISCLAIMER MAY NOT APPLY TO YOU.
283 |
284 | b. TO THE EXTENT POSSIBLE, IN NO EVENT WILL THE LICENSOR BE LIABLE
285 | TO YOU ON ANY LEGAL THEORY (INCLUDING, WITHOUT LIMITATION,
286 | NEGLIGENCE) OR OTHERWISE FOR ANY DIRECT, SPECIAL, INDIRECT,
287 | INCIDENTAL, CONSEQUENTIAL, PUNITIVE, EXEMPLARY, OR OTHER LOSSES,
288 | COSTS, EXPENSES, OR DAMAGES ARISING OUT OF THIS PUBLIC LICENSE OR
289 | USE OF THE LICENSED MATERIAL, EVEN IF THE LICENSOR HAS BEEN
290 | ADVISED OF THE POSSIBILITY OF SUCH LOSSES, COSTS, EXPENSES, OR
291 | DAMAGES. WHERE A LIMITATION OF LIABILITY IS NOT ALLOWED IN FULL OR
292 | IN PART, THIS LIMITATION MAY NOT APPLY TO YOU.
293 |
294 | c. The disclaimer of warranties and limitation of liability provided
295 | above shall be interpreted in a manner that, to the extent
296 | possible, most closely approximates an absolute disclaimer and
297 | waiver of all liability.
298 |
299 |
300 | Section 6 -- Term and Termination.
301 |
302 | a. This Public License applies for the term of the Copyright and
303 | Similar Rights licensed here. However, if You fail to comply with
304 | this Public License, then Your rights under this Public License
305 | terminate automatically.
306 |
307 | b. Where Your right to use the Licensed Material has terminated under
308 | Section 6(a), it reinstates:
309 |
310 | 1. automatically as of the date the violation is cured, provided
311 | it is cured within 30 days of Your discovery of the
312 | violation; or
313 |
314 | 2. upon express reinstatement by the Licensor.
315 |
316 | For the avoidance of doubt, this Section 6(b) does not affect any
317 | right the Licensor may have to seek remedies for Your violations
318 | of this Public License.
319 |
320 | c. For the avoidance of doubt, the Licensor may also offer the
321 | Licensed Material under separate terms or conditions or stop
322 | distributing the Licensed Material at any time; however, doing so
323 | will not terminate this Public License.
324 |
325 | d. Sections 1, 5, 6, 7, and 8 survive termination of this Public
326 | License.
327 |
328 |
329 | Section 7 -- Other Terms and Conditions.
330 |
331 | a. The Licensor shall not be bound by any additional or different
332 | terms or conditions communicated by You unless expressly agreed.
333 |
334 | b. Any arrangements, understandings, or agreements regarding the
335 | Licensed Material not stated herein are separate from and
336 | independent of the terms and conditions of this Public License.
337 |
338 |
339 | Section 8 -- Interpretation.
340 |
341 | a. For the avoidance of doubt, this Public License does not, and
342 | shall not be interpreted to, reduce, limit, restrict, or impose
343 | conditions on any use of the Licensed Material that could lawfully
344 | be made without permission under this Public License.
345 |
346 | b. To the extent possible, if any provision of this Public License is
347 | deemed unenforceable, it shall be automatically reformed to the
348 | minimum extent necessary to make it enforceable. If the provision
349 | cannot be reformed, it shall be severed from this Public License
350 | without affecting the enforceability of the remaining terms and
351 | conditions.
352 |
353 | c. No term or condition of this Public License will be waived and no
354 | failure to comply consented to unless expressly agreed to by the
355 | Licensor.
356 |
357 | d. Nothing in this Public License constitutes or may be interpreted
358 | as a limitation upon, or waiver of, any privileges and immunities
359 | that apply to the Licensor or You, including from the legal
360 | processes of any jurisdiction or authority.
361 |
--------------------------------------------------------------------------------