Error handling magic link {{ link }}: {{ error }}.
104 | ``` 105 | 106 | ### 1. Create a new login link 107 | 108 | The first step in managing magic links is to create one. Links are bound 109 | to a user, and can have a custom post-login redirect URL. 110 | 111 | ```python 112 | # create a link with the default expiry and redirect 113 | link = MagicLink.objects.create(user=user) 114 | 115 | # create a link with a specific redirect 116 | link = MagicLink.objects.create(user=user, redirect_to="/foo") 117 | 118 | # construct a full URL from a MagicLink object and a Django HttpResponse 119 | url = request.build_absolute_uri(link.get_absolute_url()) 120 | ``` 121 | 122 | ### 2. Send the link to the user 123 | 124 | This package does not handle the sending on your behalf - it is your 125 | responsibility to ensure that you send the link to the correct user. If 126 | you send the link to the wrong user, they will have full access to the 127 | link user's account. **YOU HAVE BEEN WARNED**. 128 | 129 | ## Auditing 130 | 131 | A core requirement of this package is to be able to audit the use of 132 | links - for monitoring and analysis. To enable this we have a second 133 | model, `MagicLinkUse`, and we create a new object for every request to a 134 | link URL, _regardless of outcome_. Questions that we want to have 135 | answers for include: 136 | 137 | - How long does it take for users to click on a link? 138 | - How many times is a link used before the POST login? 139 | - How often is a link used _after_ a successful login? 140 | - How often does a link expire before a successful login? 141 | - Can we identify common non-user client requests (email caches, bots, etc)? 142 | - Should we disable links after X non-POST requests? 143 | 144 | In order to facilitate this analysis we denormalise a number of 145 | timestamps from the `MagicLinkUse` object back onto the `MagicLink` 146 | itself: 147 | 148 | - `created_at` - when the record was created in the database 149 | - `accessed_at` - the first GET request to the link URL 150 | - `logged_in_at` - the successful POST 151 | - `expires_at` - the link expiry, set when the link is created. 152 | 153 | Note that the expiry timestamp is **not** updated when the link is used. 154 | This is by design, to retain the original expiry timestamp. 155 | 156 | ### Link validation 157 | 158 | In addition to the timestamp fields, there is a separate boolean flag, 159 | `is_active`. This acts as a "kill switch" that overrides any other 160 | attribute, and it allows a link to be disabled without having to edit 161 | (or destroy) existing timestamp values. You can deactivate all links in 162 | one hit by calling `MagicLink.objects.deactivate()`. 163 | 164 | A link's `is_valid` property combines both `is_active` and timestamp 165 | data to return a bool value that defines whether a link can used, based 166 | on the following criteria: 167 | 168 | 1. The link is active (`is_active`) 169 | 2. The link has not expired (`expires_at`) 170 | 3. The link has not already been used (`logged_in_at`) 171 | 172 | In addition to checking the property `is_valid`, the `validate()` method 173 | will raise an exception based on the specific condition that failed. 174 | This is used by the link view to give feedback to the user on the nature 175 | of the failure. 176 | 177 | ### Request authorization 178 | 179 | If the link's `is_valid` property returns `True`, then the link _can_ be 180 | used. However, this does not mean that the link can be used by anyone. 181 | We do not allow authenticated users to login using someone else's magic 182 | link. The `authorize()` method takes a `User` argument and determines 183 | whether they are authorized to use the link. If the user is 184 | authenticated, and does not match the `link.user`, then a 185 | `PermissionDenied` exception is raised. 186 | 187 | ### Putting it together 188 | 189 | Combining the validation, authorization and auditing, we get a 190 | simplified flow that looks something like this: 191 | 192 | ```python 193 | def get(request, token): 194 | """Render login page.""" 195 | link = get_object_or_404(MagicLink, token=token) 196 | link.validate() 197 | link.authorize(request.user) 198 | link.audit() 199 | return render("logmein.html") 200 | 201 | def post(request, token): 202 | """Handle the login POST.""" 203 | link = get_object_or_404(MagicLink, token=token) 204 | link.validate() 205 | link.authorize(request.user) 206 | link.login(request) 207 | link.disable() 208 | return redirect(link.redirect_to) 209 | ``` 210 | 211 | ## Settings 212 | 213 | Settings are read from a `django.conf.settings` settings dictionary called `MAGIC_LINK`. 214 | 215 | Default settings show below: 216 | 217 | ```python 218 | # settings.py 219 | MAGIC_LINK = { 220 | # link expiry, in seconds 221 | "DEFAULT_EXPIRY": 300, 222 | # default link redirect 223 | "DEFAULT_REDIRECT": "/", 224 | # the preferred authorization backend to use, in the case where you have more 225 | # than one specified in the `settings.AUTHORIZATION_BACKENDS` setting. 226 | "AUTHENTICATION_BACKEND": "django.contrib.auth.backends.ModelBackend", 227 | # SESSION_COOKIE_AGE override for magic-link logins - in seconds (default is 1 week) 228 | "SESSION_EXPIRY": 7 * 24 * 60 * 60 229 | } 230 | ``` 231 | 232 | ## Screenshots 233 | 234 | **Default landing page (`logmein.html`)** 235 | 236 |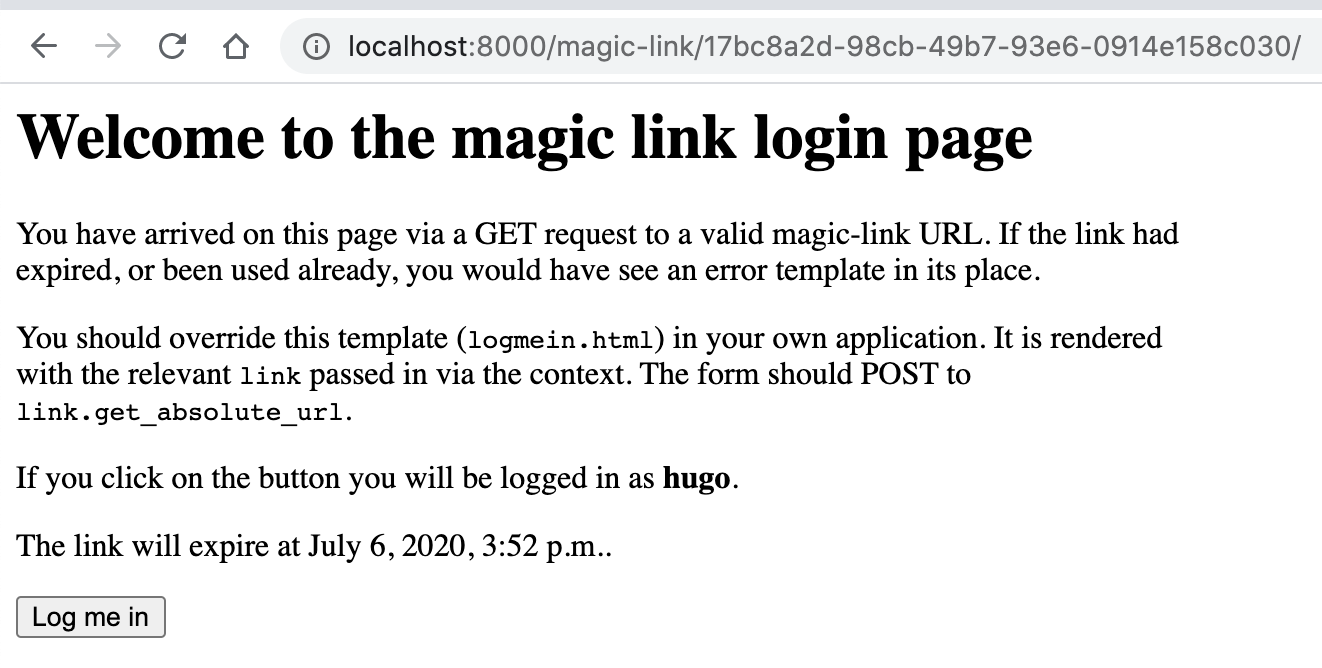 237 |
238 | **Default error page (`error.html`)**
239 |
240 |
237 |
238 | **Default error page (`error.html`)**
239 |
240 | 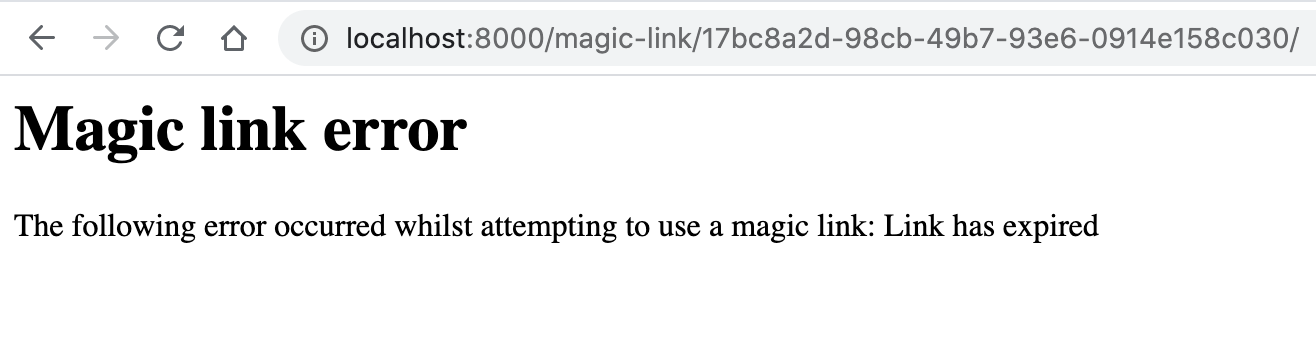 241 |
242 | **Admin view of magic link uses**
243 |
244 |
241 |
242 | **Admin view of magic link uses**
243 |
244 | 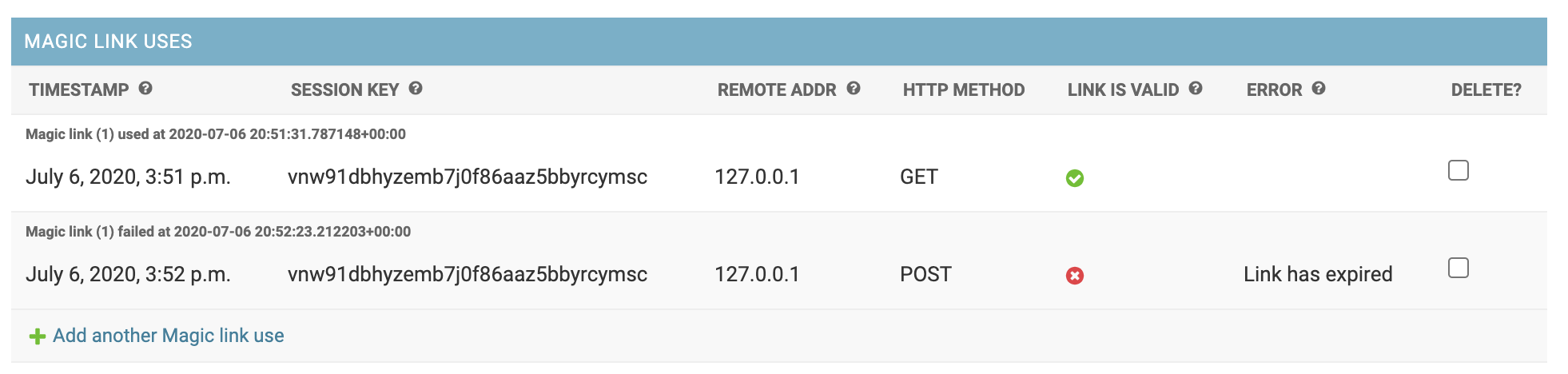 245 |
--------------------------------------------------------------------------------
/magic_link/__init__.py:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/yunojuno/django-magic-link/89b659b499a822102d548aceb6a73e3cfb2f0509/magic_link/__init__.py
--------------------------------------------------------------------------------
/magic_link/admin.py:
--------------------------------------------------------------------------------
1 | from django.contrib import admin
2 |
3 | from .models import MagicLink, MagicLinkUse
4 |
5 |
6 | class LoggedInMixin:
7 | """Mixin used to provide a logged_in method for display purposes."""
8 |
9 | def logged_in(self, obj: MagicLinkUse) -> bool:
10 | """Return True if the object was the one used to login."""
11 | return obj.timestamp == obj.link.logged_in_at
12 |
13 | logged_in.boolean = True # type: ignore
14 | logged_in.short_description = "Used for login" # type: ignore
15 |
16 |
17 | class MagicLinkUseInline(LoggedInMixin, admin.TabularInline):
18 | model = MagicLinkUse
19 | readonly_fields = (
20 | "link",
21 | "timestamp",
22 | "session_key",
23 | "remote_addr",
24 | "http_method",
25 | "logged_in",
26 | "error",
27 | )
28 | exclude = ("ua_string",)
29 | extra = 0
30 |
31 |
32 | class MagicLinkAdmin(admin.ModelAdmin):
33 | list_display = (
34 | "token",
35 | "user",
36 | "expires_at",
37 | "accessed_at",
38 | "logged_in_at",
39 | "valid",
40 | )
41 | search_fields = (
42 | "user__first_name",
43 | "user__last_name",
44 | "user__username",
45 | "token",
46 | )
47 | raw_id_fields = ("user",)
48 | readonly_fields = (
49 | "token",
50 | "created_at",
51 | "expires_at",
52 | "accessed_at",
53 | "logged_in_at",
54 | "has_expired",
55 | "has_been_used",
56 | )
57 | ordering = ("-created_at",)
58 | inlines = (MagicLinkUseInline,)
59 |
60 | def valid(self, obj: MagicLink) -> bool:
61 | # convenience method to enable pretty bool icons
62 | return obj.is_valid
63 |
64 | valid.short_description = "Valid" # type: ignore
65 | valid.boolean = True # type: ignore
66 |
67 |
68 | admin.site.register(MagicLink, MagicLinkAdmin)
69 |
70 |
71 | class MagicLinkUseAdmin(LoggedInMixin, admin.ModelAdmin):
72 | list_display = ("link", "http_method", "session_key", "logged_in")
73 | search_fields = (
74 | "session_key",
75 | "link__token",
76 | )
77 | raw_id_fields = ("link",)
78 | readonly_fields = (
79 | "link",
80 | "timestamp",
81 | "session_key",
82 | "remote_addr",
83 | "http_method",
84 | "ua_string",
85 | "error",
86 | "logged_in",
87 | )
88 | ordering = ("-timestamp",)
89 |
90 |
91 | admin.site.register(MagicLinkUse, MagicLinkUseAdmin)
92 |
--------------------------------------------------------------------------------
/magic_link/apps.py:
--------------------------------------------------------------------------------
1 | from django.apps import AppConfig
2 |
3 |
4 | class MagicLinkAppConfig(AppConfig):
5 | name = "magic_link"
6 | verbose_name = "Magic links"
7 | default_auto_field = "django.db.models.AutoField"
8 |
--------------------------------------------------------------------------------
/magic_link/exceptions.py:
--------------------------------------------------------------------------------
1 | class InvalidLink(Exception):
2 | """Generic base exception for invalid link errors."""
3 |
4 |
5 | class InactiveLink(InvalidLink):
6 | """Raised if link is marked as inactive."""
7 |
8 |
9 | class ExpiredLink(InvalidLink):
10 | """Raised if link has expired."""
11 |
12 |
13 | class UsedLink(InvalidLink):
14 | """Raised if the link has already been used."""
15 |
--------------------------------------------------------------------------------
/magic_link/migrations/0001_initial.py:
--------------------------------------------------------------------------------
1 | # Generated by Django 3.0.8 on 2020-07-06 18:01
2 | import uuid
3 |
4 | import django.db.models.deletion
5 | import django.utils.timezone
6 | from django.conf import settings
7 | from django.db import migrations, models
8 |
9 | import magic_link.models
10 | import magic_link.settings
11 |
12 |
13 | class Migration(migrations.Migration):
14 | initial = True
15 |
16 | dependencies = [
17 | migrations.swappable_dependency(settings.AUTH_USER_MODEL),
18 | ]
19 |
20 | operations = [
21 | migrations.CreateModel(
22 | name="MagicLink",
23 | fields=[
24 | (
25 | "id",
26 | models.AutoField(
27 | auto_created=True,
28 | primary_key=True,
29 | serialize=False,
30 | verbose_name="ID",
31 | ),
32 | ),
33 | (
34 | "token",
35 | models.UUIDField(
36 | default=uuid.uuid4,
37 | editable=False,
38 | help_text="Unique login token",
39 | unique=True,
40 | ),
41 | ),
42 | (
43 | "redirect_to",
44 | models.CharField(
45 | default=magic_link.settings.DEFAULT_REDIRECT,
46 | help_text="URL to which user will be redirected after logging in. ('/')",
47 | max_length=255,
48 | ),
49 | ),
50 | (
51 | "created_at",
52 | models.DateTimeField(
53 | default=django.utils.timezone.now,
54 | help_text="When the link was originally created",
55 | ),
56 | ),
57 | (
58 | "expires_at",
59 | models.DateTimeField(
60 | default=magic_link.models.link_expires_at,
61 | help_text="When the link is due to expire (uses DEFAULT_EXPIRY)",
62 | ),
63 | ),
64 | (
65 | "is_active",
66 | models.BooleanField(
67 | default=True, help_text="Set to False to deactivate the token"
68 | ),
69 | ),
70 | (
71 | "user",
72 | models.ForeignKey(
73 | on_delete=django.db.models.deletion.CASCADE,
74 | related_name="magic_links",
75 | to=settings.AUTH_USER_MODEL,
76 | ),
77 | ),
78 | ],
79 | ),
80 | migrations.CreateModel(
81 | name="MagicLinkUse",
82 | fields=[
83 | (
84 | "id",
85 | models.AutoField(
86 | auto_created=True,
87 | primary_key=True,
88 | serialize=False,
89 | verbose_name="ID",
90 | ),
91 | ),
92 | (
93 | "timestamp",
94 | models.DateTimeField(
95 | default=django.utils.timezone.now,
96 | help_text="When the token page was requested",
97 | ),
98 | ),
99 | ("http_method", models.CharField(max_length=10)),
100 | (
101 | "session_key",
102 | models.CharField(
103 | blank=True,
104 | help_text="The request session identifier",
105 | max_length=40,
106 | ),
107 | ),
108 | (
109 | "remote_addr",
110 | models.CharField(
111 | blank=True,
112 | help_text="The client IP address, extracted from HttpRequest",
113 | max_length=100,
114 | ),
115 | ),
116 | (
117 | "ua_string",
118 | models.TextField(
119 | blank=True,
120 | help_text="The client User-Agent, extracted from HttpRequest headers",
121 | ),
122 | ),
123 | (
124 | "link_is_valid",
125 | models.BooleanField(
126 | default=True,
127 | help_text="Snapshot of parent link is_valid property at the time of use",
128 | ),
129 | ),
130 | (
131 | "error",
132 | models.CharField(
133 | blank=True,
134 | help_text="If the link use failed the error will be recorded here",
135 | max_length=100,
136 | ),
137 | ),
138 | (
139 | "link",
140 | models.ForeignKey(
141 | on_delete=django.db.models.deletion.CASCADE,
142 | to="magic_link.MagicLink",
143 | ),
144 | ),
145 | ],
146 | options={
147 | "get_latest_by": ("timestamp",),
148 | },
149 | ),
150 | ]
151 |
--------------------------------------------------------------------------------
/magic_link/migrations/0002_magiclink_logged_in_at.py:
--------------------------------------------------------------------------------
1 | # Generated by Django 3.0.8 on 2020-07-06 22:25
2 |
3 | from django.db import migrations, models
4 |
5 |
6 | class Migration(migrations.Migration):
7 | dependencies = [
8 | ("magic_link", "0001_initial"),
9 | ]
10 |
11 | operations = [
12 | migrations.AddField(
13 | model_name="magiclink",
14 | name="logged_in_at",
15 | field=models.DateTimeField(
16 | blank=True, help_text="When the link was used to login", null=True
17 | ),
18 | ),
19 | ]
20 |
--------------------------------------------------------------------------------
/magic_link/migrations/0003_magiclink_accessed_at.py:
--------------------------------------------------------------------------------
1 | # Generated by Django 3.0.8 on 2020-07-07 09:34
2 |
3 | from django.db import migrations, models
4 |
5 |
6 | class Migration(migrations.Migration):
7 | dependencies = [
8 | ("magic_link", "0002_magiclink_logged_in_at"),
9 | ]
10 |
11 | operations = [
12 | migrations.AddField(
13 | model_name="magiclink",
14 | name="accessed_at",
15 | field=models.DateTimeField(
16 | blank=True, help_text="When the link was first used (GET)", null=True
17 | ),
18 | ),
19 | ]
20 |
--------------------------------------------------------------------------------
/magic_link/migrations/0004_remove_magiclinkuse_link_is_valid.py:
--------------------------------------------------------------------------------
1 | # Generated by Django 3.0.8 on 2020-07-07 11:06
2 |
3 | from django.db import migrations
4 |
5 |
6 | class Migration(migrations.Migration):
7 | dependencies = [
8 | ("magic_link", "0003_magiclink_accessed_at"),
9 | ]
10 |
11 | operations = [
12 | migrations.RemoveField(
13 | model_name="magiclinkuse",
14 | name="link_is_valid",
15 | ),
16 | ]
17 |
--------------------------------------------------------------------------------
/magic_link/migrations/__init__.py:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/yunojuno/django-magic-link/89b659b499a822102d548aceb6a73e3cfb2f0509/magic_link/migrations/__init__.py
--------------------------------------------------------------------------------
/magic_link/models.py:
--------------------------------------------------------------------------------
1 | from __future__ import annotations
2 |
3 | import datetime
4 | import uuid
5 |
6 | from django.conf import settings
7 | from django.contrib.auth import login
8 | from django.core.exceptions import PermissionDenied
9 | from django.db import models
10 | from django.http import HttpRequest
11 | from django.urls import reverse
12 | from django.utils import timezone
13 |
14 | from .exceptions import ExpiredLink, InactiveLink, InvalidLink, UsedLink
15 | from .settings import (
16 | AUTHENTICATION_BACKEND,
17 | DEFAULT_EXPIRY,
18 | DEFAULT_REDIRECT,
19 | SESSION_EXPIRY,
20 | )
21 |
22 |
23 | def parse_remote_addr(request: HttpRequest) -> str:
24 | """Extract client IP from request."""
25 | x_forwarded_for = request.headers.get("X-Forwarded-For", "")
26 | if x_forwarded_for:
27 | return x_forwarded_for.split(",")[0]
28 | return request.META.get("REMOTE_ADDR", "")
29 |
30 |
31 | def parse_ua_string(request: HttpRequest) -> str:
32 | """Extract client user-agent from request."""
33 | return request.headers.get("User-Agent", "")
34 |
35 |
36 | def link_expires_at(interval: int = DEFAULT_EXPIRY) -> datetime.datetime:
37 | """Return timestamp used as default link exires_at value."""
38 | return timezone.now() + datetime.timedelta(seconds=interval)
39 |
40 |
41 | class MagicLink(models.Model):
42 | """A unique token used for magic links."""
43 |
44 | user = models.ForeignKey(
45 | settings.AUTH_USER_MODEL, on_delete=models.CASCADE, related_name="magic_links"
46 | )
47 | token = models.UUIDField(
48 | default=uuid.uuid4, editable=False, unique=True, help_text="Unique login token"
49 | )
50 | redirect_to = models.CharField(
51 | help_text="URL to which user will be redirected after logging in. ('/')",
52 | max_length=255,
53 | default=DEFAULT_REDIRECT,
54 | )
55 | created_at = models.DateTimeField(
56 | default=timezone.now, help_text="When the link was originally created"
57 | )
58 | expires_at = models.DateTimeField(
59 | help_text="When the link is due to expire (uses DEFAULT_EXPIRY)",
60 | default=link_expires_at,
61 | )
62 | accessed_at = models.DateTimeField(
63 | help_text="When the link was first used (GET)", blank=True, null=True
64 | )
65 | logged_in_at = models.DateTimeField(
66 | help_text="When the link was used to login", blank=True, null=True
67 | )
68 | is_active = models.BooleanField(
69 | default=True, help_text="Set to False to deactivate the token"
70 | )
71 |
72 | def __str__(self) -> str:
73 | return f"Magic link ({self.id}) for {self.user.username}"
74 |
75 | def __repr__(self) -> str:
76 | return f"
245 |
--------------------------------------------------------------------------------
/magic_link/__init__.py:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/yunojuno/django-magic-link/89b659b499a822102d548aceb6a73e3cfb2f0509/magic_link/__init__.py
--------------------------------------------------------------------------------
/magic_link/admin.py:
--------------------------------------------------------------------------------
1 | from django.contrib import admin
2 |
3 | from .models import MagicLink, MagicLinkUse
4 |
5 |
6 | class LoggedInMixin:
7 | """Mixin used to provide a logged_in method for display purposes."""
8 |
9 | def logged_in(self, obj: MagicLinkUse) -> bool:
10 | """Return True if the object was the one used to login."""
11 | return obj.timestamp == obj.link.logged_in_at
12 |
13 | logged_in.boolean = True # type: ignore
14 | logged_in.short_description = "Used for login" # type: ignore
15 |
16 |
17 | class MagicLinkUseInline(LoggedInMixin, admin.TabularInline):
18 | model = MagicLinkUse
19 | readonly_fields = (
20 | "link",
21 | "timestamp",
22 | "session_key",
23 | "remote_addr",
24 | "http_method",
25 | "logged_in",
26 | "error",
27 | )
28 | exclude = ("ua_string",)
29 | extra = 0
30 |
31 |
32 | class MagicLinkAdmin(admin.ModelAdmin):
33 | list_display = (
34 | "token",
35 | "user",
36 | "expires_at",
37 | "accessed_at",
38 | "logged_in_at",
39 | "valid",
40 | )
41 | search_fields = (
42 | "user__first_name",
43 | "user__last_name",
44 | "user__username",
45 | "token",
46 | )
47 | raw_id_fields = ("user",)
48 | readonly_fields = (
49 | "token",
50 | "created_at",
51 | "expires_at",
52 | "accessed_at",
53 | "logged_in_at",
54 | "has_expired",
55 | "has_been_used",
56 | )
57 | ordering = ("-created_at",)
58 | inlines = (MagicLinkUseInline,)
59 |
60 | def valid(self, obj: MagicLink) -> bool:
61 | # convenience method to enable pretty bool icons
62 | return obj.is_valid
63 |
64 | valid.short_description = "Valid" # type: ignore
65 | valid.boolean = True # type: ignore
66 |
67 |
68 | admin.site.register(MagicLink, MagicLinkAdmin)
69 |
70 |
71 | class MagicLinkUseAdmin(LoggedInMixin, admin.ModelAdmin):
72 | list_display = ("link", "http_method", "session_key", "logged_in")
73 | search_fields = (
74 | "session_key",
75 | "link__token",
76 | )
77 | raw_id_fields = ("link",)
78 | readonly_fields = (
79 | "link",
80 | "timestamp",
81 | "session_key",
82 | "remote_addr",
83 | "http_method",
84 | "ua_string",
85 | "error",
86 | "logged_in",
87 | )
88 | ordering = ("-timestamp",)
89 |
90 |
91 | admin.site.register(MagicLinkUse, MagicLinkUseAdmin)
92 |
--------------------------------------------------------------------------------
/magic_link/apps.py:
--------------------------------------------------------------------------------
1 | from django.apps import AppConfig
2 |
3 |
4 | class MagicLinkAppConfig(AppConfig):
5 | name = "magic_link"
6 | verbose_name = "Magic links"
7 | default_auto_field = "django.db.models.AutoField"
8 |
--------------------------------------------------------------------------------
/magic_link/exceptions.py:
--------------------------------------------------------------------------------
1 | class InvalidLink(Exception):
2 | """Generic base exception for invalid link errors."""
3 |
4 |
5 | class InactiveLink(InvalidLink):
6 | """Raised if link is marked as inactive."""
7 |
8 |
9 | class ExpiredLink(InvalidLink):
10 | """Raised if link has expired."""
11 |
12 |
13 | class UsedLink(InvalidLink):
14 | """Raised if the link has already been used."""
15 |
--------------------------------------------------------------------------------
/magic_link/migrations/0001_initial.py:
--------------------------------------------------------------------------------
1 | # Generated by Django 3.0.8 on 2020-07-06 18:01
2 | import uuid
3 |
4 | import django.db.models.deletion
5 | import django.utils.timezone
6 | from django.conf import settings
7 | from django.db import migrations, models
8 |
9 | import magic_link.models
10 | import magic_link.settings
11 |
12 |
13 | class Migration(migrations.Migration):
14 | initial = True
15 |
16 | dependencies = [
17 | migrations.swappable_dependency(settings.AUTH_USER_MODEL),
18 | ]
19 |
20 | operations = [
21 | migrations.CreateModel(
22 | name="MagicLink",
23 | fields=[
24 | (
25 | "id",
26 | models.AutoField(
27 | auto_created=True,
28 | primary_key=True,
29 | serialize=False,
30 | verbose_name="ID",
31 | ),
32 | ),
33 | (
34 | "token",
35 | models.UUIDField(
36 | default=uuid.uuid4,
37 | editable=False,
38 | help_text="Unique login token",
39 | unique=True,
40 | ),
41 | ),
42 | (
43 | "redirect_to",
44 | models.CharField(
45 | default=magic_link.settings.DEFAULT_REDIRECT,
46 | help_text="URL to which user will be redirected after logging in. ('/')",
47 | max_length=255,
48 | ),
49 | ),
50 | (
51 | "created_at",
52 | models.DateTimeField(
53 | default=django.utils.timezone.now,
54 | help_text="When the link was originally created",
55 | ),
56 | ),
57 | (
58 | "expires_at",
59 | models.DateTimeField(
60 | default=magic_link.models.link_expires_at,
61 | help_text="When the link is due to expire (uses DEFAULT_EXPIRY)",
62 | ),
63 | ),
64 | (
65 | "is_active",
66 | models.BooleanField(
67 | default=True, help_text="Set to False to deactivate the token"
68 | ),
69 | ),
70 | (
71 | "user",
72 | models.ForeignKey(
73 | on_delete=django.db.models.deletion.CASCADE,
74 | related_name="magic_links",
75 | to=settings.AUTH_USER_MODEL,
76 | ),
77 | ),
78 | ],
79 | ),
80 | migrations.CreateModel(
81 | name="MagicLinkUse",
82 | fields=[
83 | (
84 | "id",
85 | models.AutoField(
86 | auto_created=True,
87 | primary_key=True,
88 | serialize=False,
89 | verbose_name="ID",
90 | ),
91 | ),
92 | (
93 | "timestamp",
94 | models.DateTimeField(
95 | default=django.utils.timezone.now,
96 | help_text="When the token page was requested",
97 | ),
98 | ),
99 | ("http_method", models.CharField(max_length=10)),
100 | (
101 | "session_key",
102 | models.CharField(
103 | blank=True,
104 | help_text="The request session identifier",
105 | max_length=40,
106 | ),
107 | ),
108 | (
109 | "remote_addr",
110 | models.CharField(
111 | blank=True,
112 | help_text="The client IP address, extracted from HttpRequest",
113 | max_length=100,
114 | ),
115 | ),
116 | (
117 | "ua_string",
118 | models.TextField(
119 | blank=True,
120 | help_text="The client User-Agent, extracted from HttpRequest headers",
121 | ),
122 | ),
123 | (
124 | "link_is_valid",
125 | models.BooleanField(
126 | default=True,
127 | help_text="Snapshot of parent link is_valid property at the time of use",
128 | ),
129 | ),
130 | (
131 | "error",
132 | models.CharField(
133 | blank=True,
134 | help_text="If the link use failed the error will be recorded here",
135 | max_length=100,
136 | ),
137 | ),
138 | (
139 | "link",
140 | models.ForeignKey(
141 | on_delete=django.db.models.deletion.CASCADE,
142 | to="magic_link.MagicLink",
143 | ),
144 | ),
145 | ],
146 | options={
147 | "get_latest_by": ("timestamp",),
148 | },
149 | ),
150 | ]
151 |
--------------------------------------------------------------------------------
/magic_link/migrations/0002_magiclink_logged_in_at.py:
--------------------------------------------------------------------------------
1 | # Generated by Django 3.0.8 on 2020-07-06 22:25
2 |
3 | from django.db import migrations, models
4 |
5 |
6 | class Migration(migrations.Migration):
7 | dependencies = [
8 | ("magic_link", "0001_initial"),
9 | ]
10 |
11 | operations = [
12 | migrations.AddField(
13 | model_name="magiclink",
14 | name="logged_in_at",
15 | field=models.DateTimeField(
16 | blank=True, help_text="When the link was used to login", null=True
17 | ),
18 | ),
19 | ]
20 |
--------------------------------------------------------------------------------
/magic_link/migrations/0003_magiclink_accessed_at.py:
--------------------------------------------------------------------------------
1 | # Generated by Django 3.0.8 on 2020-07-07 09:34
2 |
3 | from django.db import migrations, models
4 |
5 |
6 | class Migration(migrations.Migration):
7 | dependencies = [
8 | ("magic_link", "0002_magiclink_logged_in_at"),
9 | ]
10 |
11 | operations = [
12 | migrations.AddField(
13 | model_name="magiclink",
14 | name="accessed_at",
15 | field=models.DateTimeField(
16 | blank=True, help_text="When the link was first used (GET)", null=True
17 | ),
18 | ),
19 | ]
20 |
--------------------------------------------------------------------------------
/magic_link/migrations/0004_remove_magiclinkuse_link_is_valid.py:
--------------------------------------------------------------------------------
1 | # Generated by Django 3.0.8 on 2020-07-07 11:06
2 |
3 | from django.db import migrations
4 |
5 |
6 | class Migration(migrations.Migration):
7 | dependencies = [
8 | ("magic_link", "0003_magiclink_accessed_at"),
9 | ]
10 |
11 | operations = [
12 | migrations.RemoveField(
13 | model_name="magiclinkuse",
14 | name="link_is_valid",
15 | ),
16 | ]
17 |
--------------------------------------------------------------------------------
/magic_link/migrations/__init__.py:
--------------------------------------------------------------------------------
https://raw.githubusercontent.com/yunojuno/django-magic-link/89b659b499a822102d548aceb6a73e3cfb2f0509/magic_link/migrations/__init__.py
--------------------------------------------------------------------------------
/magic_link/models.py:
--------------------------------------------------------------------------------
1 | from __future__ import annotations
2 |
3 | import datetime
4 | import uuid
5 |
6 | from django.conf import settings
7 | from django.contrib.auth import login
8 | from django.core.exceptions import PermissionDenied
9 | from django.db import models
10 | from django.http import HttpRequest
11 | from django.urls import reverse
12 | from django.utils import timezone
13 |
14 | from .exceptions import ExpiredLink, InactiveLink, InvalidLink, UsedLink
15 | from .settings import (
16 | AUTHENTICATION_BACKEND,
17 | DEFAULT_EXPIRY,
18 | DEFAULT_REDIRECT,
19 | SESSION_EXPIRY,
20 | )
21 |
22 |
23 | def parse_remote_addr(request: HttpRequest) -> str:
24 | """Extract client IP from request."""
25 | x_forwarded_for = request.headers.get("X-Forwarded-For", "")
26 | if x_forwarded_for:
27 | return x_forwarded_for.split(",")[0]
28 | return request.META.get("REMOTE_ADDR", "")
29 |
30 |
31 | def parse_ua_string(request: HttpRequest) -> str:
32 | """Extract client user-agent from request."""
33 | return request.headers.get("User-Agent", "")
34 |
35 |
36 | def link_expires_at(interval: int = DEFAULT_EXPIRY) -> datetime.datetime:
37 | """Return timestamp used as default link exires_at value."""
38 | return timezone.now() + datetime.timedelta(seconds=interval)
39 |
40 |
41 | class MagicLink(models.Model):
42 | """A unique token used for magic links."""
43 |
44 | user = models.ForeignKey(
45 | settings.AUTH_USER_MODEL, on_delete=models.CASCADE, related_name="magic_links"
46 | )
47 | token = models.UUIDField(
48 | default=uuid.uuid4, editable=False, unique=True, help_text="Unique login token"
49 | )
50 | redirect_to = models.CharField(
51 | help_text="URL to which user will be redirected after logging in. ('/')",
52 | max_length=255,
53 | default=DEFAULT_REDIRECT,
54 | )
55 | created_at = models.DateTimeField(
56 | default=timezone.now, help_text="When the link was originally created"
57 | )
58 | expires_at = models.DateTimeField(
59 | help_text="When the link is due to expire (uses DEFAULT_EXPIRY)",
60 | default=link_expires_at,
61 | )
62 | accessed_at = models.DateTimeField(
63 | help_text="When the link was first used (GET)", blank=True, null=True
64 | )
65 | logged_in_at = models.DateTimeField(
66 | help_text="When the link was used to login", blank=True, null=True
67 | )
68 | is_active = models.BooleanField(
69 | default=True, help_text="Set to False to deactivate the token"
70 | )
71 |
72 | def __str__(self) -> str:
73 | return f"Magic link ({self.id}) for {self.user.username}"
74 |
75 | def __repr__(self) -> str:
76 | return f"4 | The following error occurred whilst attempting to use a magic link. 5 |
6 |
7 | error = {{ error }}
8 |
9 |
10 |
--------------------------------------------------------------------------------
/magic_link/templates/magic_link/logmein.html:
--------------------------------------------------------------------------------
1 |
2 |
3 |
8 |
9 |
10 | 12 | You have arrived on this page via a GET request to a valid magic-link URL. If the link 13 | had expired, or been used already, you would have see an error template in its place. 14 |
15 |
16 | You should override this template (logmein.html) in your own application.
17 | It is rendered with the relevant link passed in via the context. The form
18 | should POST to link.get_absolute_url.
19 |
21 | If you click on the button you will be logged in as 22 | {{ link.user.get_full_name|default:link.user.username }}. 23 |
24 |The link will expire at {{ link.expires_at }}.
25 | 29 | 30 | 31 | -------------------------------------------------------------------------------- /magic_link/urls.py: -------------------------------------------------------------------------------- 1 | from django.urls import path 2 | 3 | from . import views 4 | 5 | urlpatterns = [ 6 | path( 7 | "